Cloud outsourcing computing security method based on SGX technology
A cloud computing and security technology, applied in the field of cloud outsourcing computing security based on SGX technology, which can solve the problems of unclear security protocols, eavesdropping, and inability to guarantee the credibility of cloud computing to users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
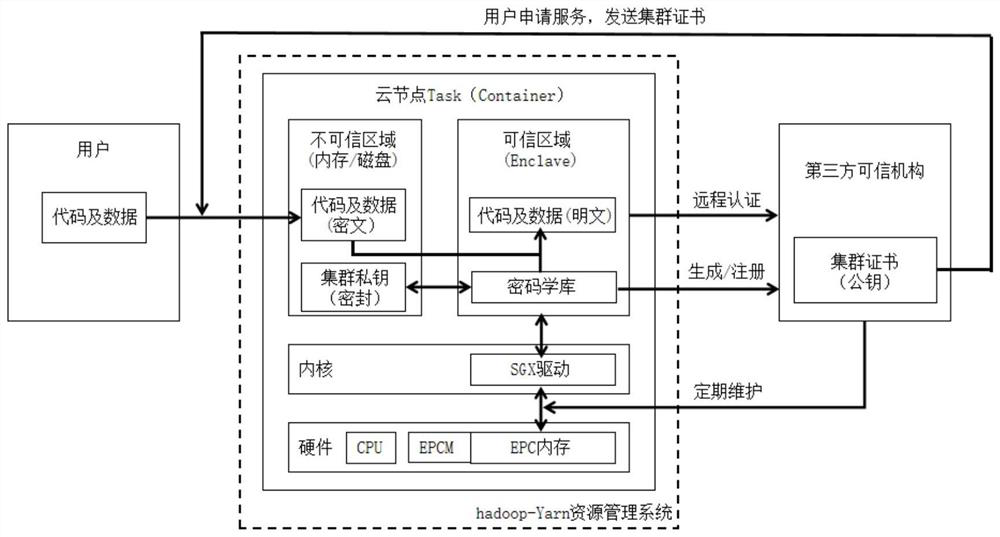
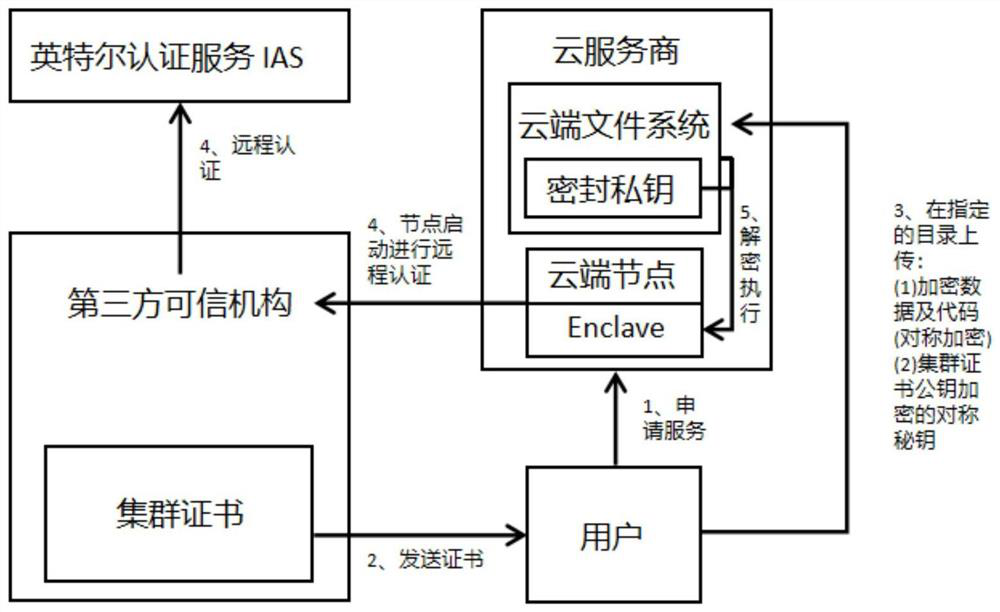
[0023] The purpose of the present invention is to provide a cloud outsourcing computing security method based on Intel SGX technology and a trusted third-party organization, thereby effectively ensuring the data security and personal privacy of users outsourced to cloud distributed computing services. The overall process of the program is mainly divided into the registration stage and the work stage. Next, the above two stages will be described in detail:
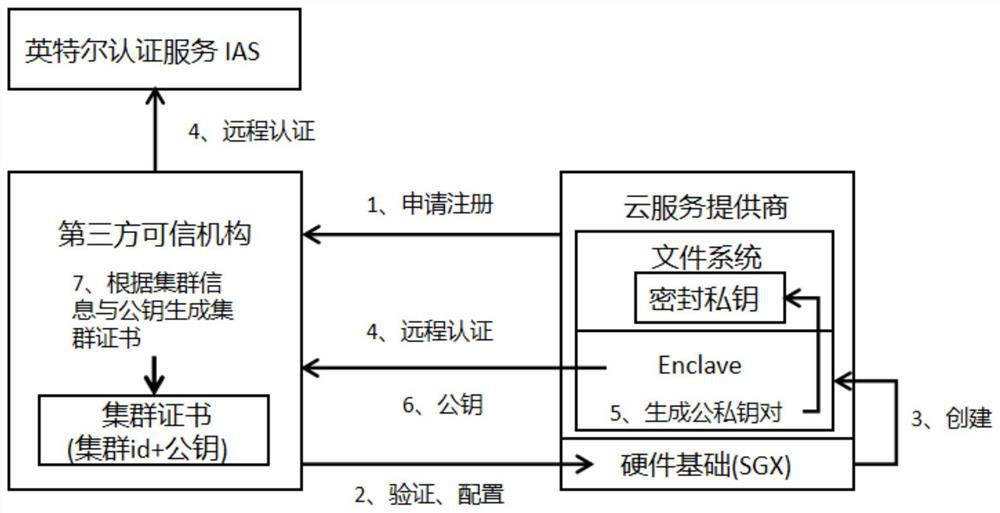
[0024] 1. Registration stage
[0025] (1-1): The cloud service provider applies to a third-party trusted organization to register the cluster.
[0026] (1-2): The third-party trusted organization inspects the hardware environment of the cloud service provider on the spot, generates an Enclave at each cloud node, and conducts remote authentication through the third-party trusted organization system.
[0027] (1-3): After the remote authentication is passed, the cloud computing node generates a public-private key pair in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com