Security outsourcing computing architecture suitable for power grid big data
A technology of secure outsourcing and computing architecture, applied in electrical digital data processing, computing, digital data authentication, etc., can solve problems such as data security that cannot be covered, and achieve the effect of improving social productivity, reducing operating costs, and promoting economic development.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The description of the following examples is a particular embodiment of the invention can be embodied in the following examples.
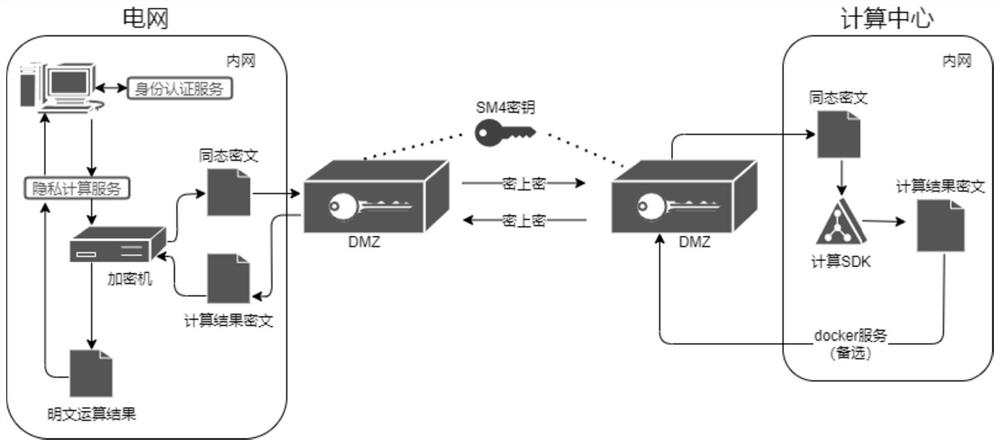
[0024] Outsourcing calculations can be understood as a cloud computing scenario, and the data owner has calculated data to the cloud by means of a powerful computing capacity of cloud platform. A typical safety outsourcing calculation role model consists of two parties: (1) Data Provonders: such as data companies, hospitals, individuals, and even Internet sensors, they have data, but due to severe computing resources, they cannot be calculated; 2) Calculation service providers: such as cloud computing platform, superior center, etc., this party may be with super integrated capacity, competing for special computing tasks, or have a certain advantage due to cost and reliability, thus Selected by customers to deploy computing services.
[0025] In response to this application scenario, embodiments of the present invention are intended to design a s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com