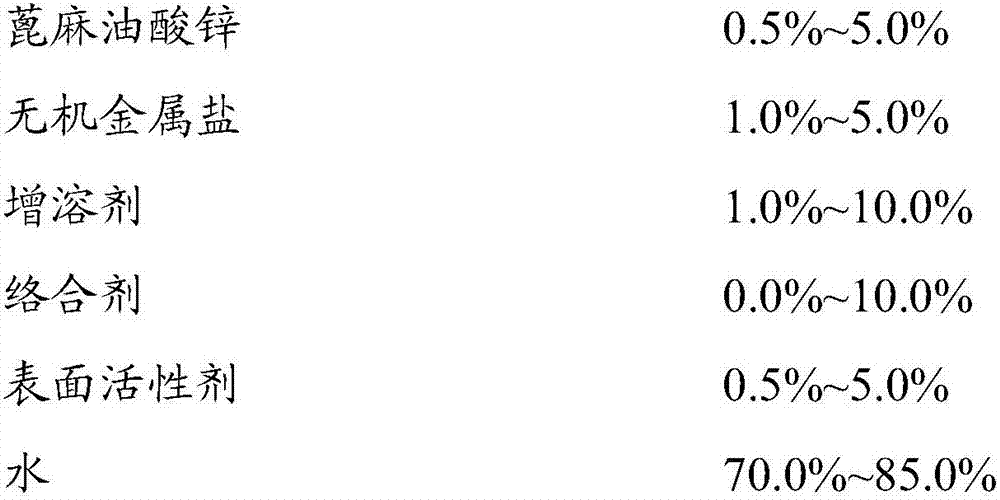Patents
Literature
64results about How to "High security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
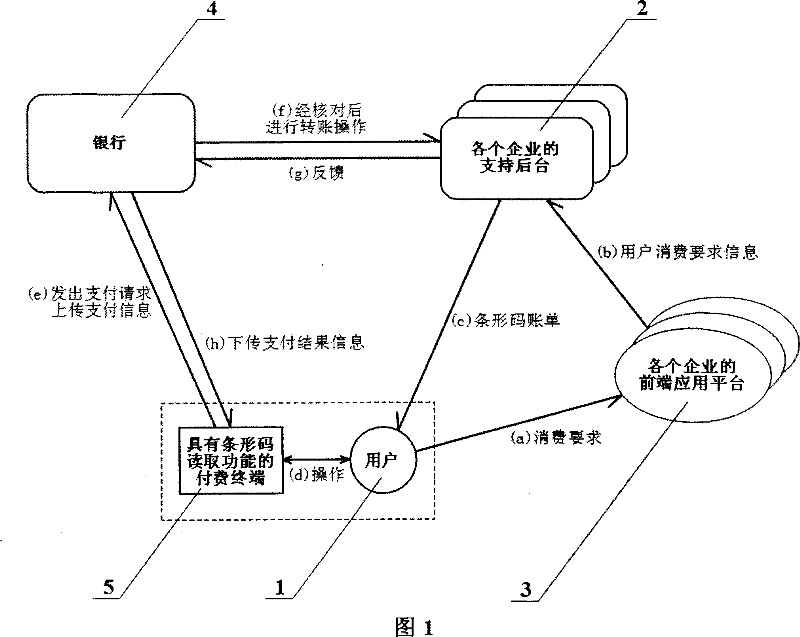
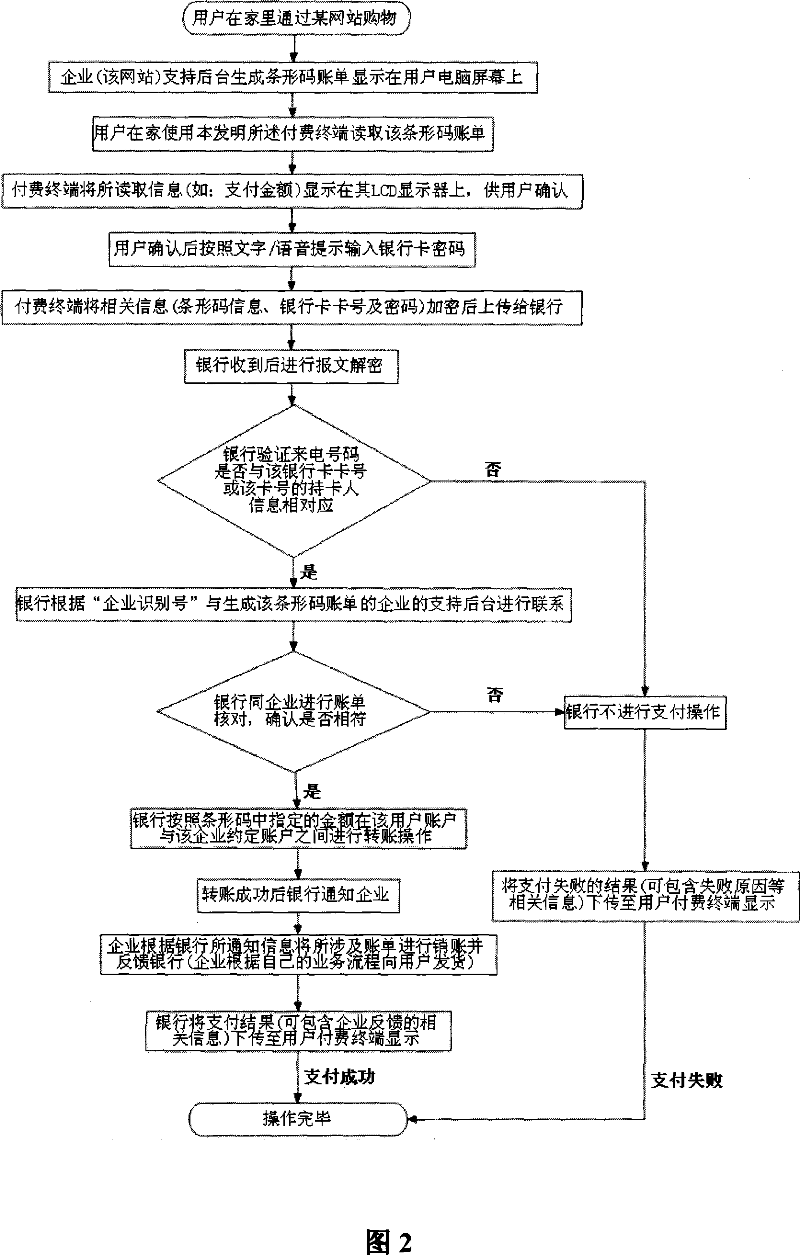
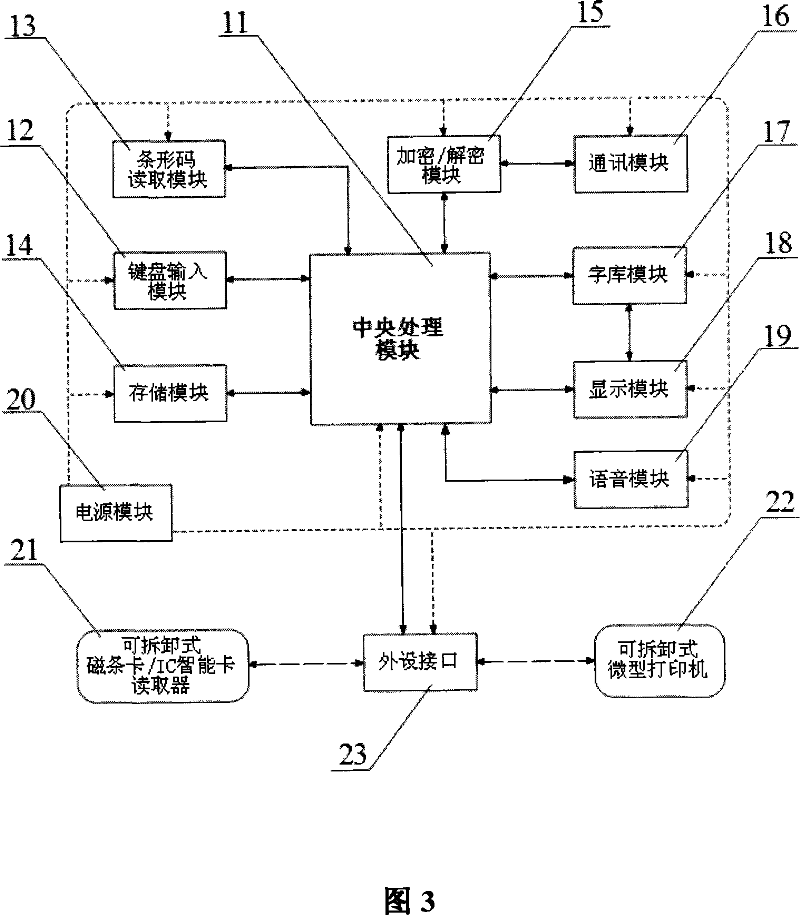
Individual paying method based on bar code and bar code scanner
InactiveCN101038642AHigh" securityImprove securityPayment architectureSensing record carriersPrivate networkPassword
The invention relates to a personal charging method based on the barcode and barcode scanning method comprising a user, an enterprise backup stage, an enterprise front end application platform, a bank and the charging terminal having barcode reading function for specified user, wherein the enterprise backup stage generated a barcode bill according to the consumption demand, the charging terminal having the barcode reading function at the client side reads the barcode bill and encrypts the barcode bill information, the bank card and password information to the bank by a specified bank, the bank receives, decrypts, and transfers the fund to the specified account designated by the enterprise, the bank and the enterprise backup stage communicates and the bank receives the returned information from the enterprise backup stage. The advantage of the invention is that the charging terminal is provided for specified user, which is safe, convenient and simple.
Owner:王亚东 +1
Chaotic optical network physical layer protection method and system, networking method and network
ActiveCN108964873AGood sync qualityHigh securityModulated-carrier systemsWavelength-division multiplex systemsComputer hardwarePhysical layer
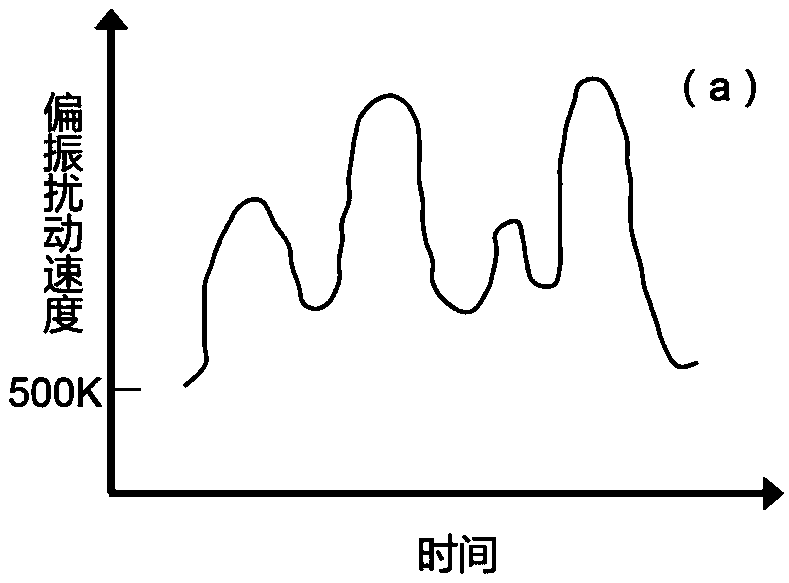
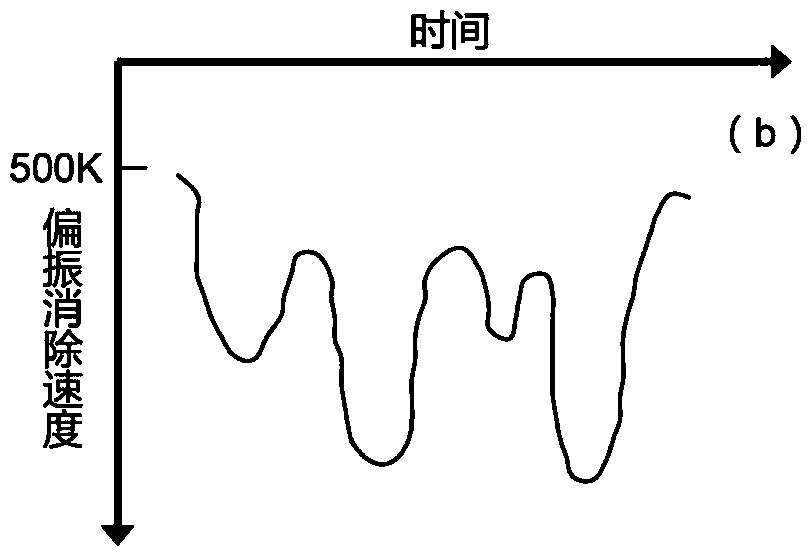
The invention discloses a chaotic optical network physical layer protection method and system, a networking method and a network, related to the physical layer protection field of a chaotic optical network. The multi-dimensional physical layer protection method comprises the following steps: a transmitting end performs digital chaotic encryption after performing optical chaotic phase modulation, so as to control the speed of polarization change and the change amount of each time, and realize two-level hardware encryption in the physical layer of the chaotic optical network; and a receiving endfirst performs digital chaos decryption, and then performs optical chaotic phase demodulation, so as to realize two-level hardware decryption in the physical layer of the chaotic optical network. Theinvention encrypts in three dimensions of time, frequency and polarization; the chaotic signal and polarization disturbance obviously enhance the secrecy; and the speed of polarization change and thechange amount of each time are controlled; so that the intercept probability is significantly reduced.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Information processing method and electronic device
ActiveCN104424432AAvoid exposureSolve the technical problem of poor confidentialityInternal/peripheral component protectionPlatform integrity maintainanceInformation processingOperating system
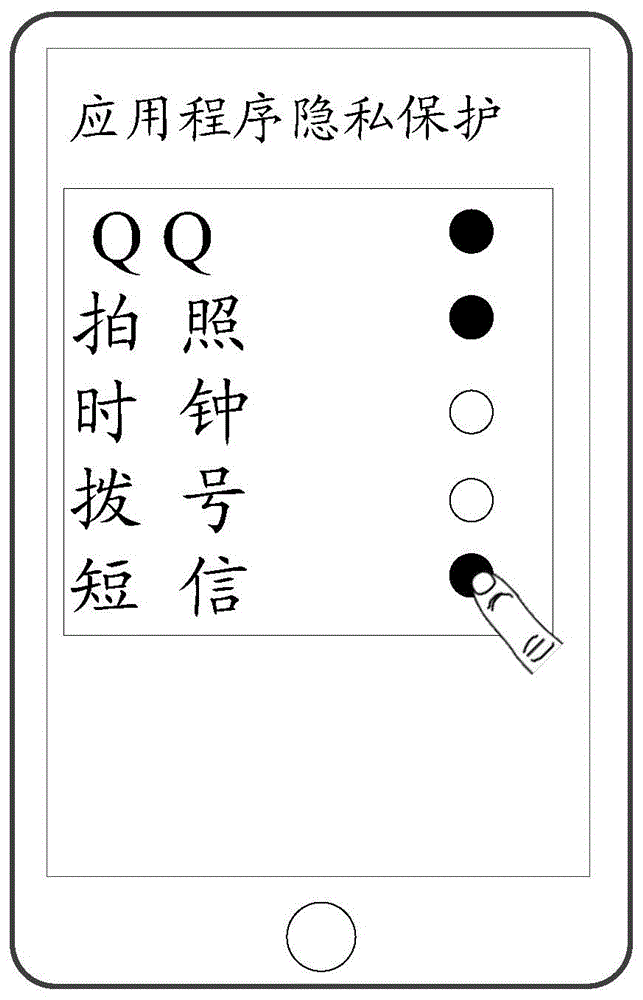
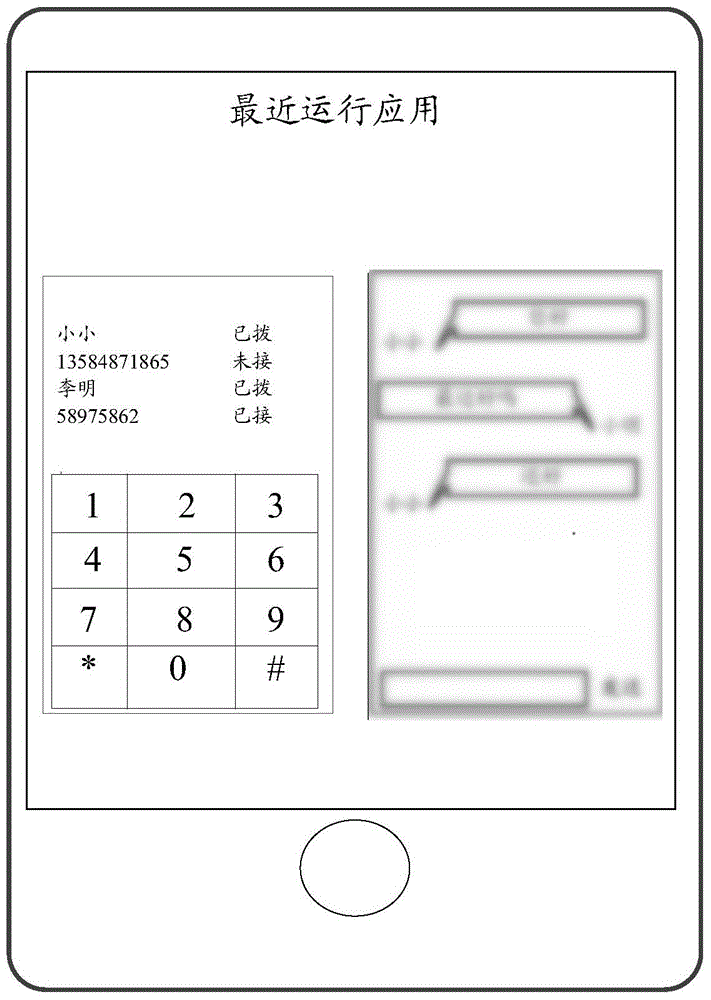
The present invention discloses an information processing method and an electronic device, the method being applicable to an electronic device capable of executing a first application, and the method including: detecting at an instance of time T1 whether there is a first predetermined operation, wherein the first predetermined operation is configured to control the electronic device to present a second interface for displaying a set of second applications satisfying a predetermined condition; determining whether the set of second applications includes the first application; and when it is determined that the set of second applications includes the first application, displaying the first application via a third interface in the second interface, wherein the difference between the third interface and a first interface is greater than or equal to a first threshold.
Owner:LENOVO (BEIJING) LTD
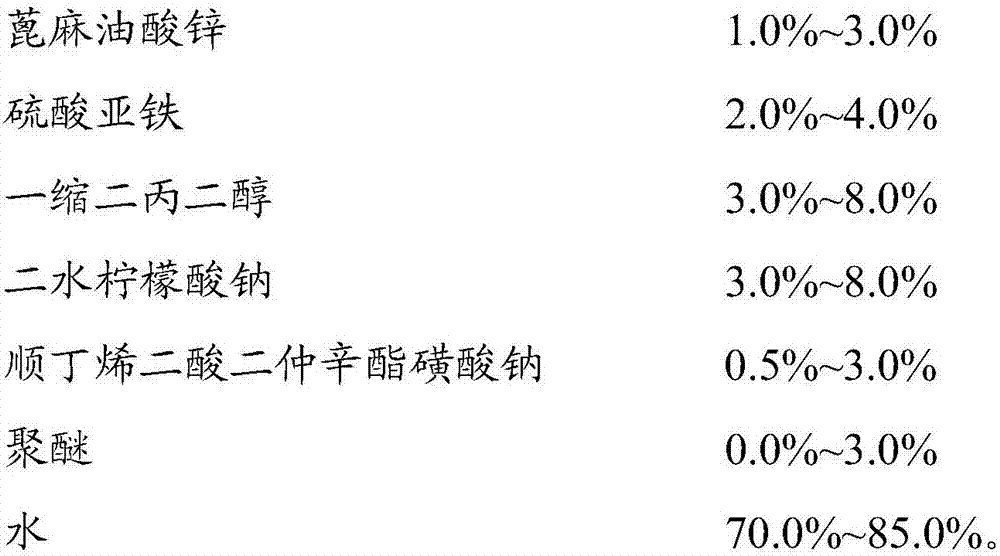
Deodorant composition and preparation method thereof
ActiveCN107281922ANo irritating smellHigh securityGas treatmentDispersed particle separationZinc ricinoleateSulfate
The invention discloses a deodorant composition and application thereof, and the deodorant composition is prepared from the following raw materials in parts by weight percent 1.5 to 2.0 parts of zinc diricinoleate, 2.0 to 3.5 parts of ferrous sulfate, 6.0 to 7.0 parts of dipropylene glycol, 5.0 to 6.0 parts of sodium citrate, 1.5 to 2.0 parts of sodium diethylhexyl sulfosuccinate, 0.5 to 1.0 parts of polyether, 3.0 to 4.0 parts of essence and 74.5 to 80.5 parts of water. The deodorant composition is prepared from components which are harmless to environment and safe to human body and biodegradable. The deodorant composition has advantages of safety, environment protection, good deodorant effect, no pungent smell and the like, and can be applied to deodorant of daily life and working environment, especially for deodorant of industrial production workshop.
Owner:广州日之建生态环境科技有限公司
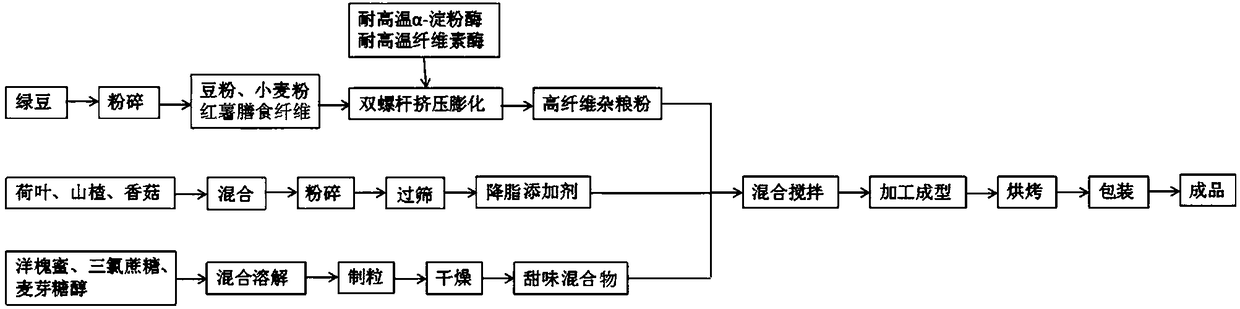
Making method of high-fiber bean crisp pastries
InactiveCN108391692AGreat tasteImprove digestibilityDough treatmentPre-baking dough treatmentMaltitolAlpha-amylase
The invention relates to a making method of high-fiber bean crisp pastries. The making method comprises the following steps of (1) preparing 60-80-mesh mung bean powder; (2) mixing the mung bean powder with wheat flour and sweet potato dietary fibers, adding high temperature resistant alpha-amylase and high temperature resistant cellulase, performing activation, adjusting the moisture content of materials to be 15-20%, pouring the treated materials into a twin-screw extrusion bulking machine to obtain bar-shaped semi-finished products, performing drying, and performing crushing to 100-120 meshto obtain puffed powder; (3) preparing an additive capable of reducing blood lipid from raw materials of dry products of lotus leaves, haws and shiitake mushrooms; (4) mixing robinia honey with sucralose and maltitol, performing dissolving, performing granulation, performing drying, and performing granule separation to obtain a sweet mixture; (5) mixing the puffed powder with the additive capableof reducing blood lipid and the sweet mixture, adding glutinous rice flour, eggs and olive oil, and performing uniform stirring to obtain dough; (6) performing baking to obtain pastries; and (7) encapsulating products. The invention provides the making method of high-fiber bean crisp pastries having the function of reducing blood lipid, the mouth feel of coarse cereals is significantly improved,and the digestibility is improved.
Owner:ZHEJIANG UNIV OF TECH
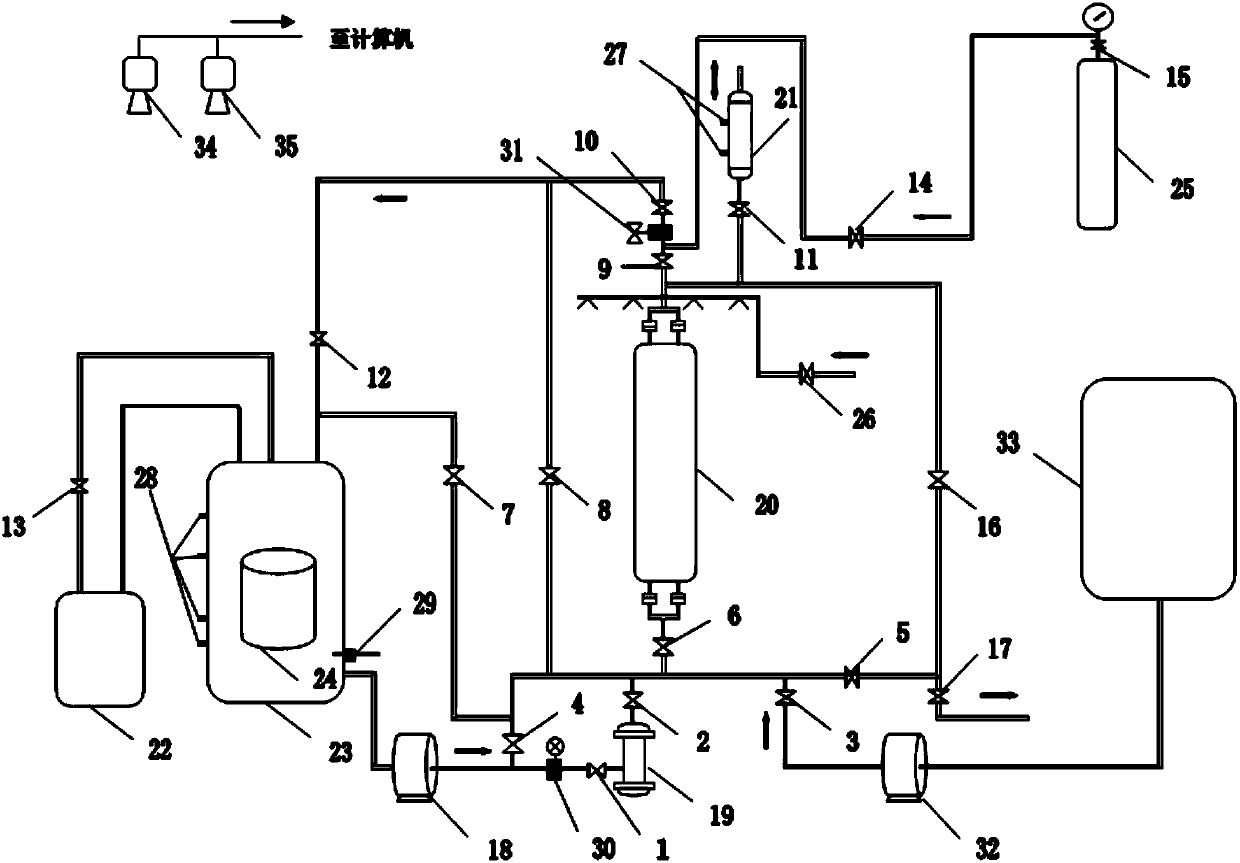
Full-automatic polishing system and method for whole superconducting cavity surface chemical buffering
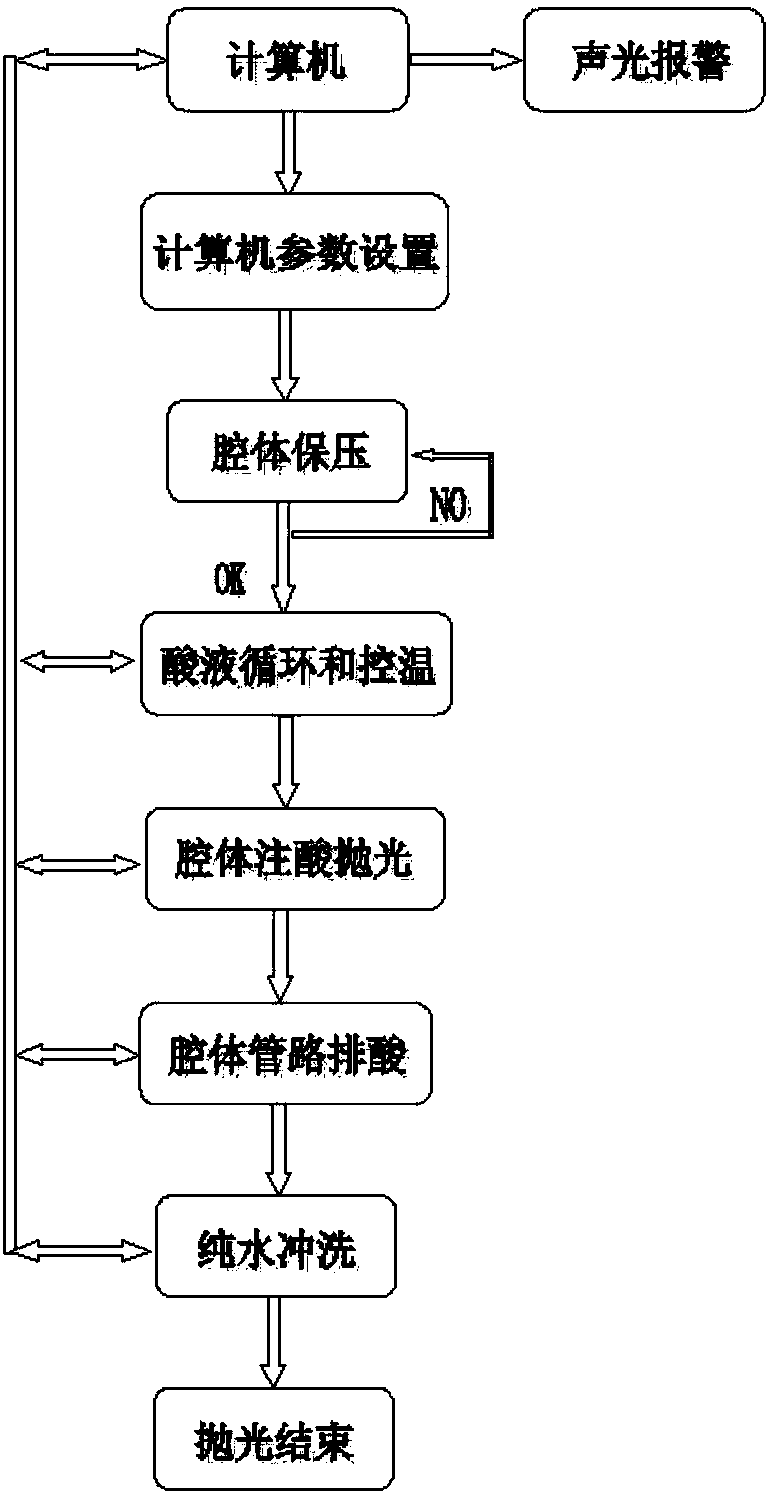
The invention relates to the technical field of ion accelerator superconducting cavity machining, in particular to a full-automatic polishing system and method for whole superconducting cavity surfacechemical buffering. The system is characterized by comprising an acid mixing tank, the upper end of the acid mixing tank is connected with a refrigeration unit through a pipeline, a heat exchanger isarranged in the acid mixing tank, and the lower end of the acid mixing tank is connected with an acid liquid conveying pump through a pipeline; the acid liquid conveying pump is connected with a filter through a pipeline, and the filter is connected with the lower end of a superconducting cavity and an ultrapure water pump through a pipeline; the ultrapure water pump is connected with an ultrapure water tank through a pipeline; the upper end of the superconducting cavity is connected with the upper end of the acid mixing tank and an observation window through a pipeline, and a high-purity nitrogen tank is connected with a pipeline between the acid mixing tank and the superconducting cavity through a pipeline; and a computer is adopted in the system for conducting strict control over flow,flow speed, temperature, pressure and time of acid liquid, and chemical buffering polishing of multiple types of superconducting cavities can be achieved. In addition, very high corrosion resistance,high safety, reliability, controllability and easy operability are achieved.
Owner:INST OF MODERN PHYSICS CHINESE ACADEMY OF SCI
Method and device for encrypting photos
ActiveCN102883268AHigh securityPrivacy protectionLocation information based serviceSecurity arrangementComputer hardwareReal-time data
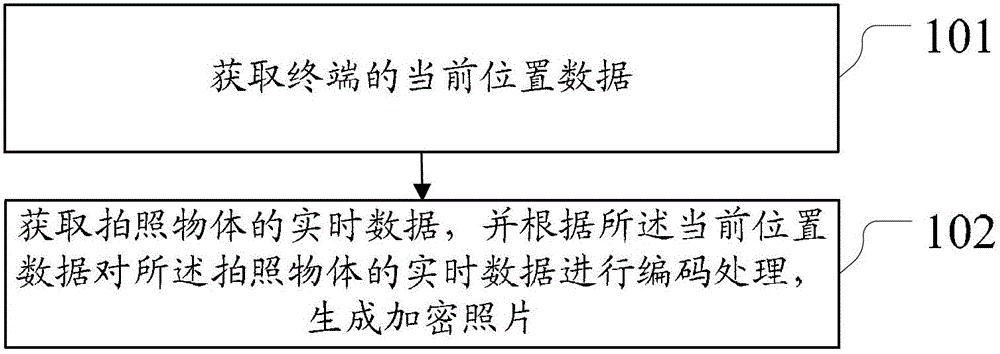
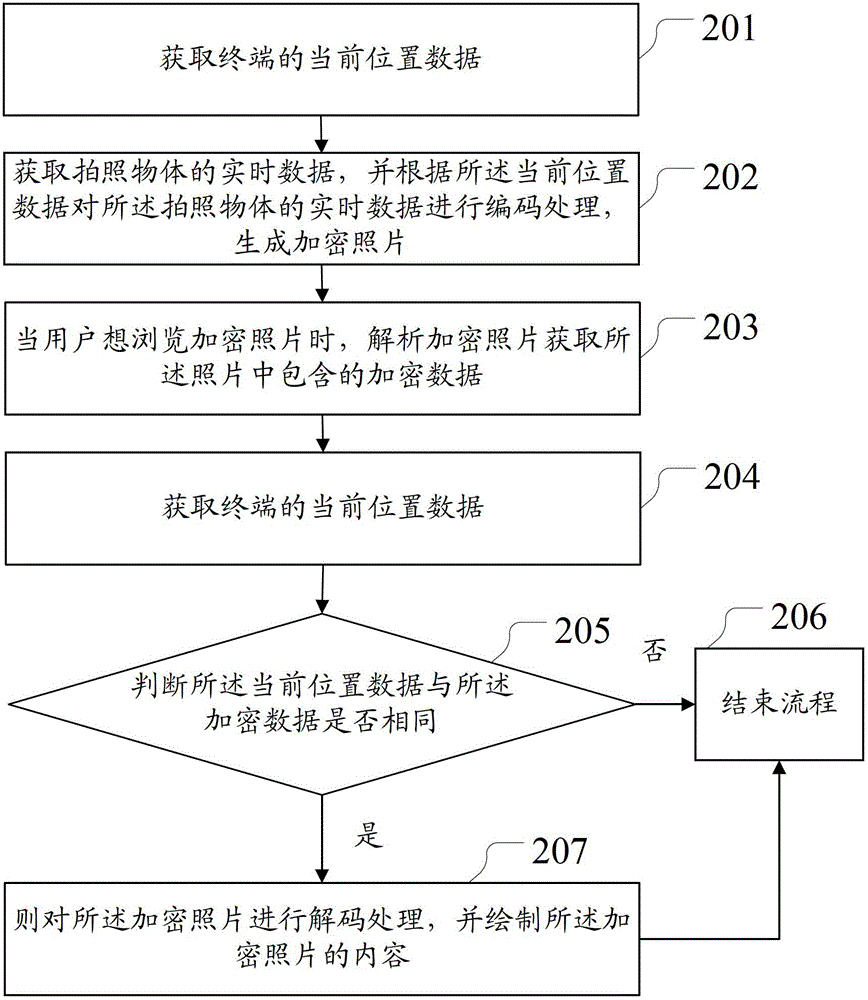
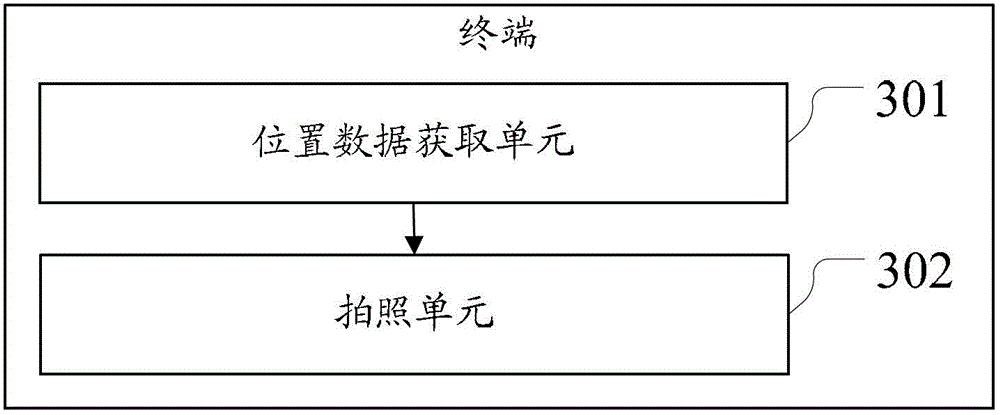
The invention discloses a method and device for encrypting photos and relates to the electronic technical field. The method and the device improve secrecy of photos, protect user privacy and improve use experience. The method includes acquiring real time data of a photo object by acquiring current position data of a terminal and coding the real time data of the photo object according to the current position data to generate the encrypted photos. The method and the device are suitable for encrypting the photos.
Owner:DONGGUAN YULONG COMM TECH +1
FPGA-based flat panel detector (FPD) with image correction function
ActiveCN105763818AHigh securityReduce complexityTelevision system detailsColor television detailsFlat panel detectorConfidentiality
The invention provides an FPGA-based flat panel detector (FPD) with an image correction function, which comprises an FPGA. The FPGA is internally provided with an original image acquisition module and an image correction module, wherein the original image acquisition module is used for acquiring an original image acquired by the FPD; and the image correction module is connected with the original image acquisition module for receiving the original image acquired by the original image acquisition module and correcting the original image. According to the FPGA-based FPD with the image correction function, the overall image correction process is completed inside the FPD, an image template does not need to be transmitted to a working station, the complexity of an interactive process between the FPD and the working station is reduced, and thus, the stability is improved, the image confidentiality is high, and the software development and integration difficulty of the working station is reduced; and meanwhile, the image correction speed is greatly enhanced, and the overall image acquisition process speed is enhanced.
Owner:SHANGHAI IRAY TECH
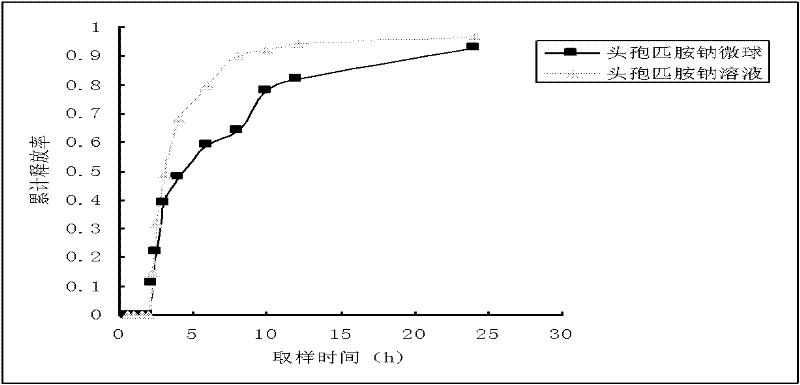
Cefpiramide sodium micro-spheres and preparing method thereof
InactiveCN102210655AHigh securitySolve the short biological half-lifeAntibacterial agentsOrganic active ingredientsChemistryWater soluble
The invention relates to cefpiramide sodium micro-spheres and a preparing method thereof, belonging to the technical field of medicaments. A carrier material of each cefpiramide sodium micro-sphere is carboxy methyl chitosan while a slow release medicament of each cefpiramide sodium micro-sphere is cefpiramide sodium, wherein the content of the cefpiramide sodium is 5.3% to 5.5% of mass of the overall micro-sphere; each micro-sphere is 17.920 mum to 20.749 mum in average grain diameter and 2.799 in span of the grain diameter. The preparing method comprises the following step of: with biodegradable high molecular material, i.e., carboxy methyl chitosan as the carrier material, preparing highly water-soluble antibiotic-medicament, i.e., cefpiramide sodium into the slow release micro-sphere by using an emulsifying and dispersing-curing cross-linking method, wherein the micro-sphere is taken orally. The cefpiramide sodium micro-spheres disclosed by the invention can be used for reducing damage of intravenous drip to skins and mucous membranes of a patient, improving absorption of oral taking, and increasing bioavailability of the medicament; meanwhile, the cefpiramide sodium micro-sphere can be used for prolonging action time of the medicament, reducing dosage and improving compliance of the patient. The preparing method disclosed by the invention has the advantages of simpleness in operation, gentle conditions and strong controllability and is suitable for large-scale industrial production.
Owner:SHANDONG UNIV
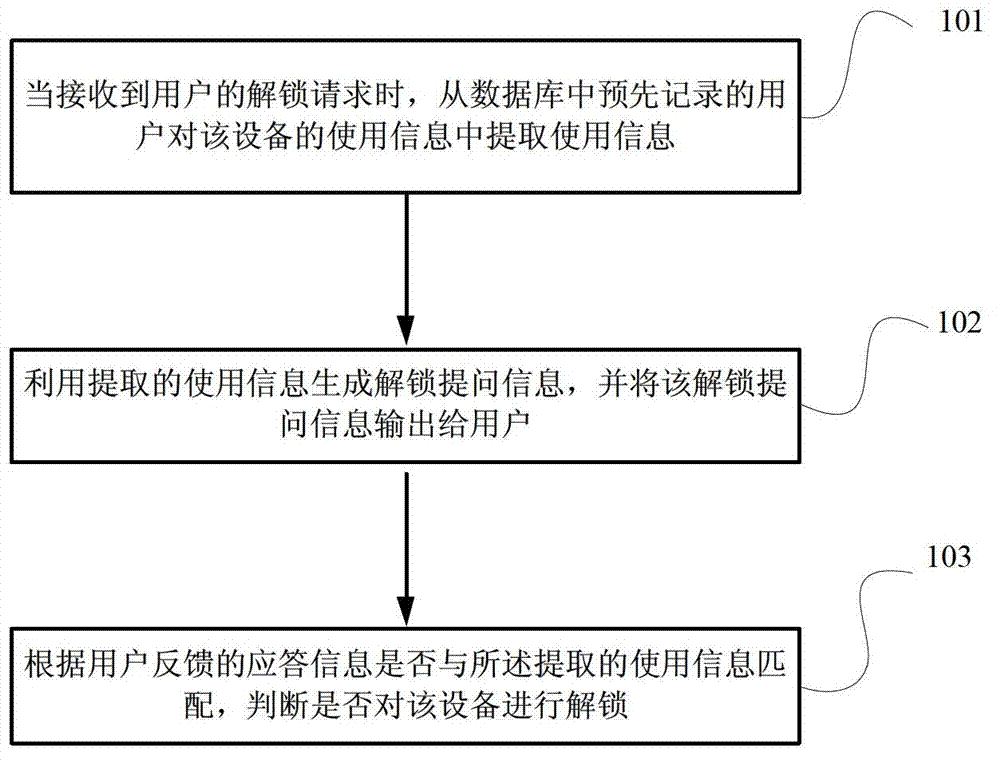
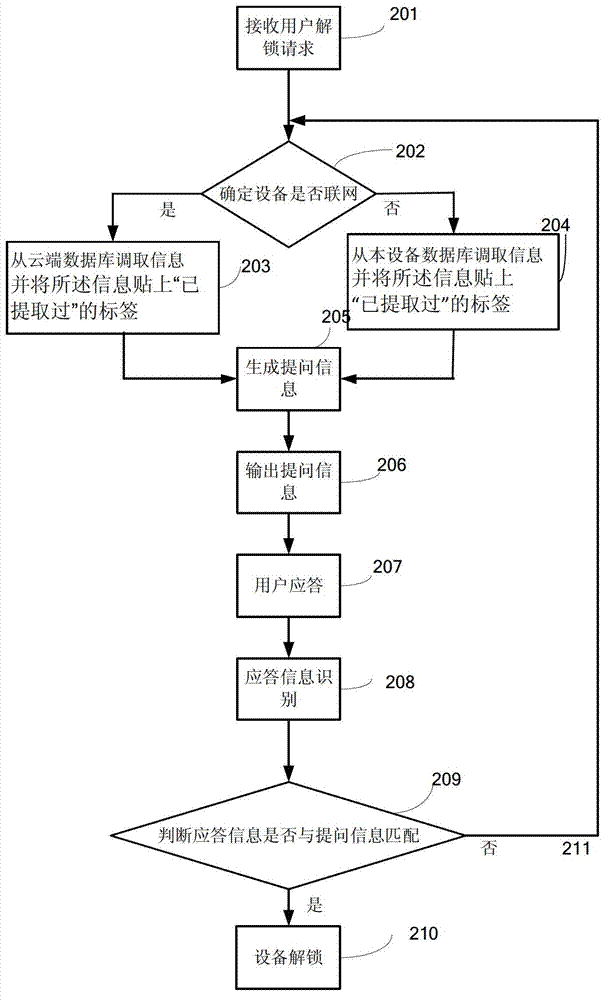
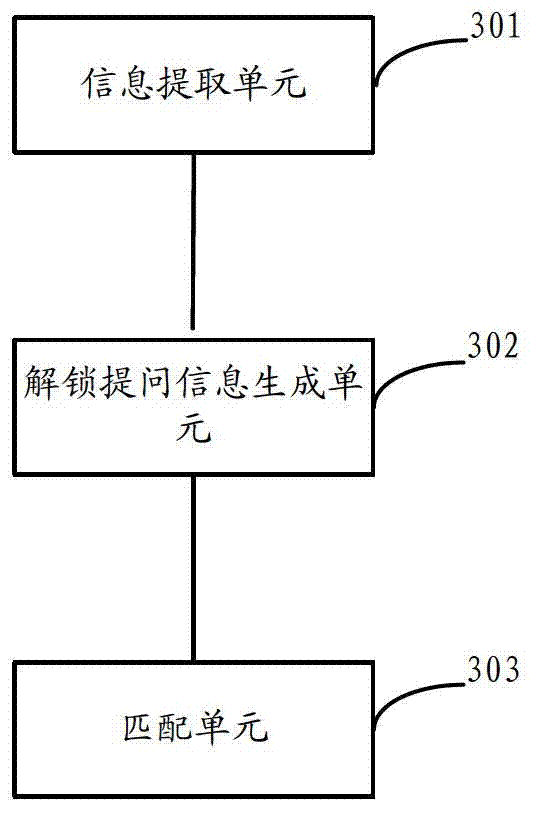
Method and device for unlocking equipment, and user equipment
ActiveCN102855427AHigh securityPrevent leakageDigital data protectionDigital data authenticationUser equipmentComputer science
The invention discloses a method and a device for unlocking equipment, and user equipment, and aims to improve the convenience and the safety of the equipment. The method for unlocking the equipment comprises the following steps of: when an unlocking request of a user is received, extracting use information from use information, which is pre-recorded in a database and executed by a user on the equipment; generating unlocking question information by using the extracted use information, and outputting the unlocking question information to the user; and judging whether response information fed back by the user is matched with the extracted use information, and then judging whether to unlock the equipment.
Owner:XIAOMI INC
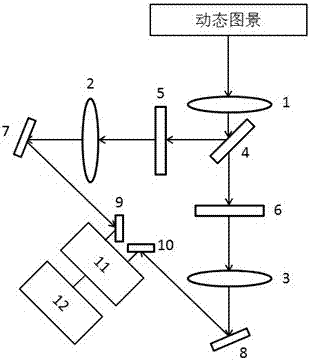
Ultrahigh-speed compression photographing device based on compression perception and streak camera principles
ActiveCN107205103AIncrease order of magnitudeImplement refactoringTelevision system detailsColor television detailsSpatial light modulatorBeam splitter
The invention provides an ultrahigh-speed compression photographing device based on compression perception and streak camera principles. The device comprises a lens, a beam splitter, a spatial light modulator, a flat mirror, a streak camera with a built-in CCD, and a decoder. Firstly, captured image information is coded through the spatial light modulator. Then the streak camera is utilized for superposing image information at different time points and performing compression sampling. Finally reconstruction is performed on the image based on a compression perception principle. According to the device, two-dimensional imaging can be performed on an ultrafast process on the condition of definite imaging speed of the streak camera; the image information is output to a decoder; a two-dimensional image dynamic process (x-y-t) is reconstructed through a TwIST algorithm; and the imaging speed can reach 10-12 frame / second. The ultrahigh-speed compression photographing device utilizes single-time photographing measuring technology which can measure un-repeated ultrafast events.
Owner:EAST CHINA NORMAL UNIV
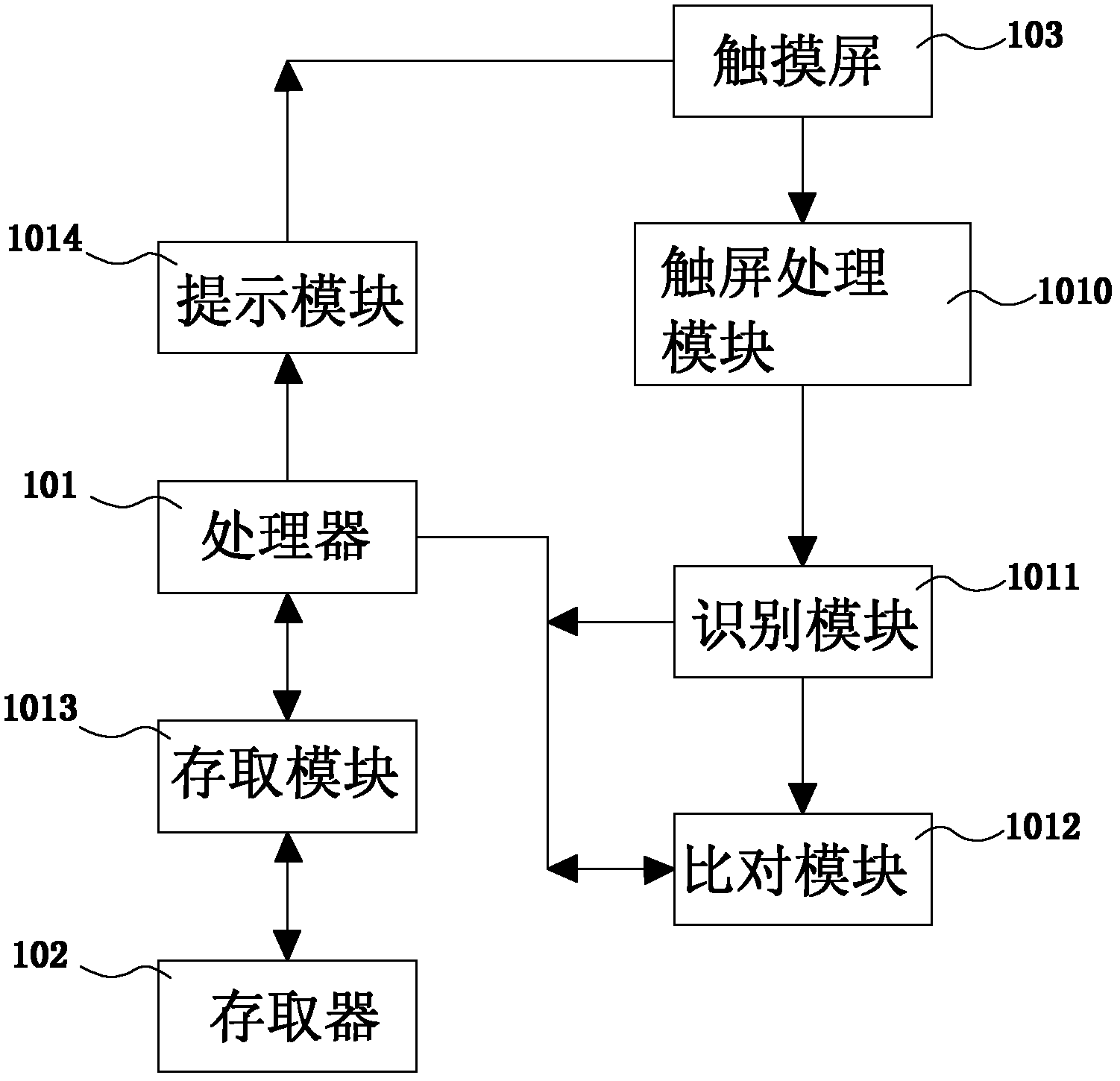
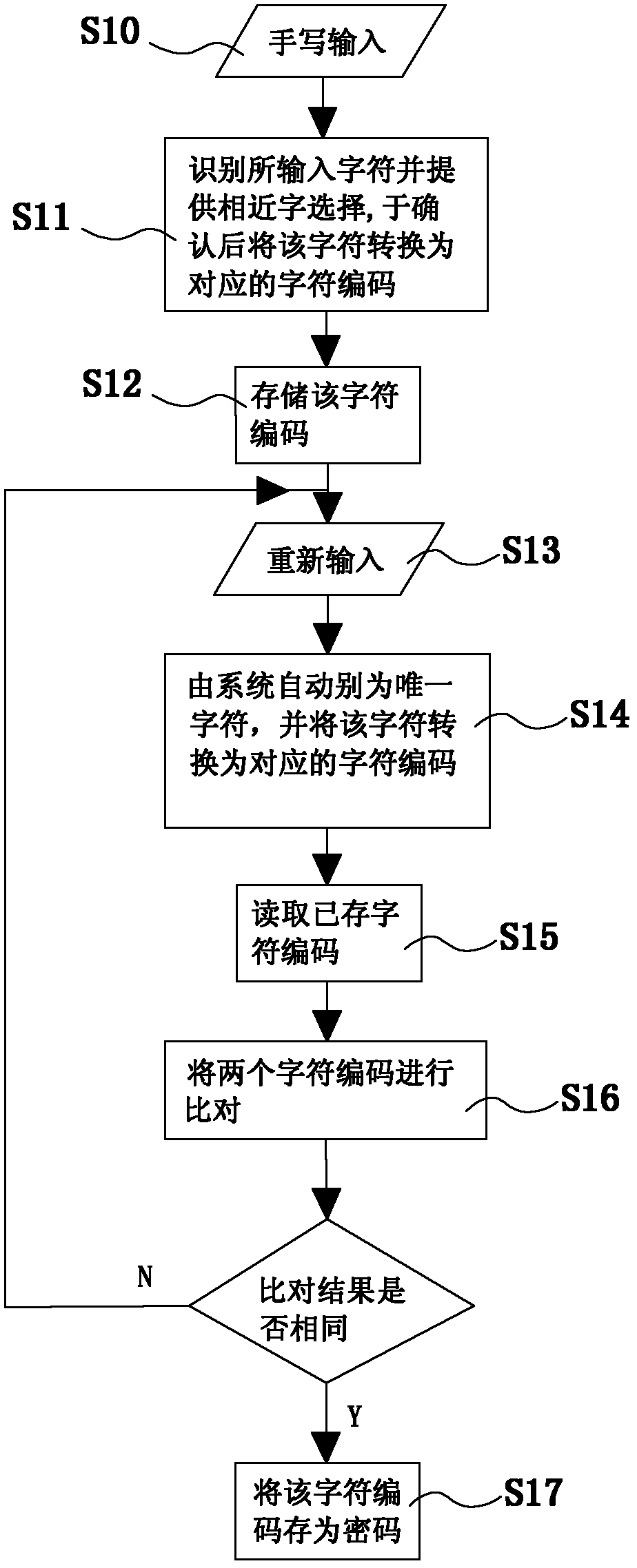
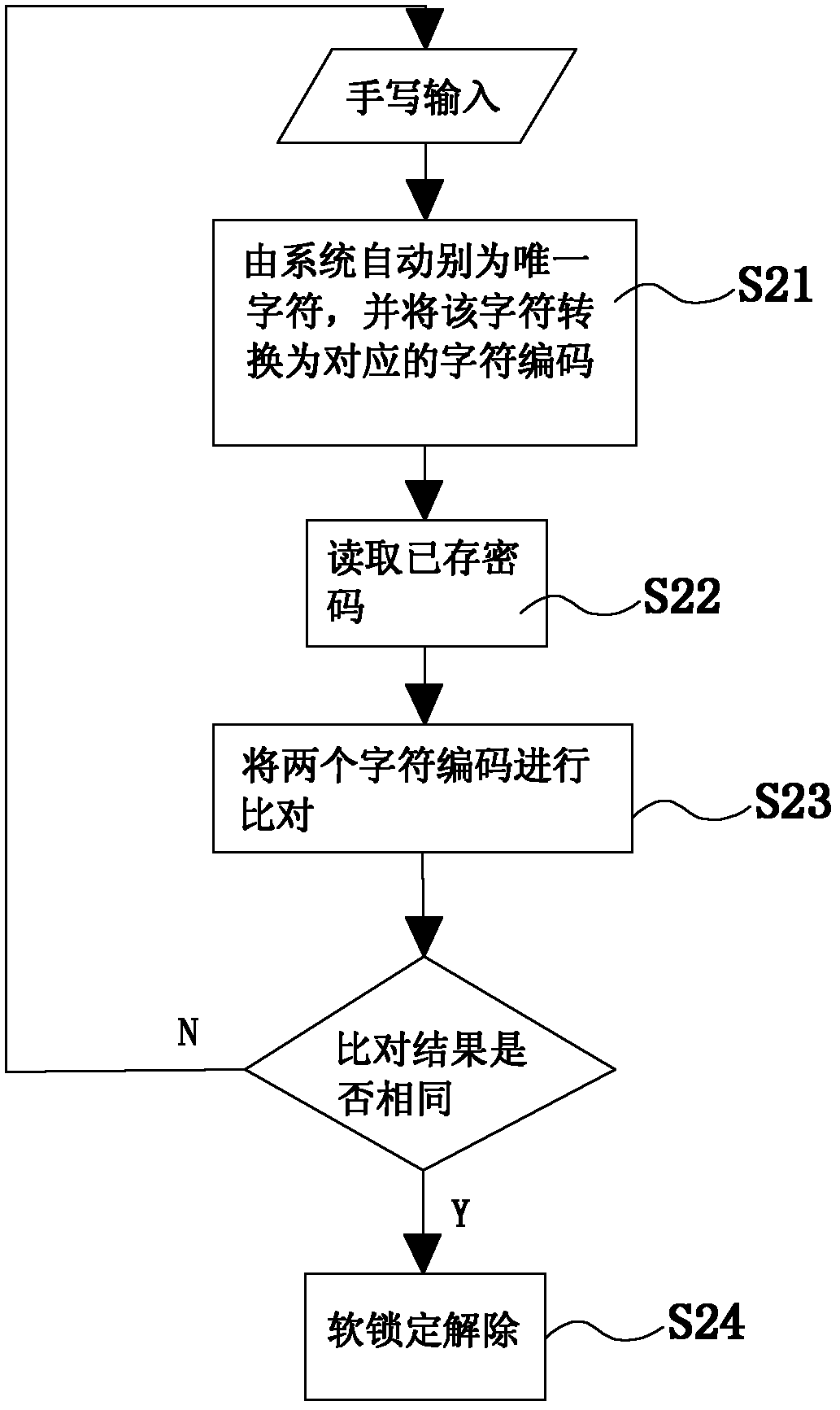
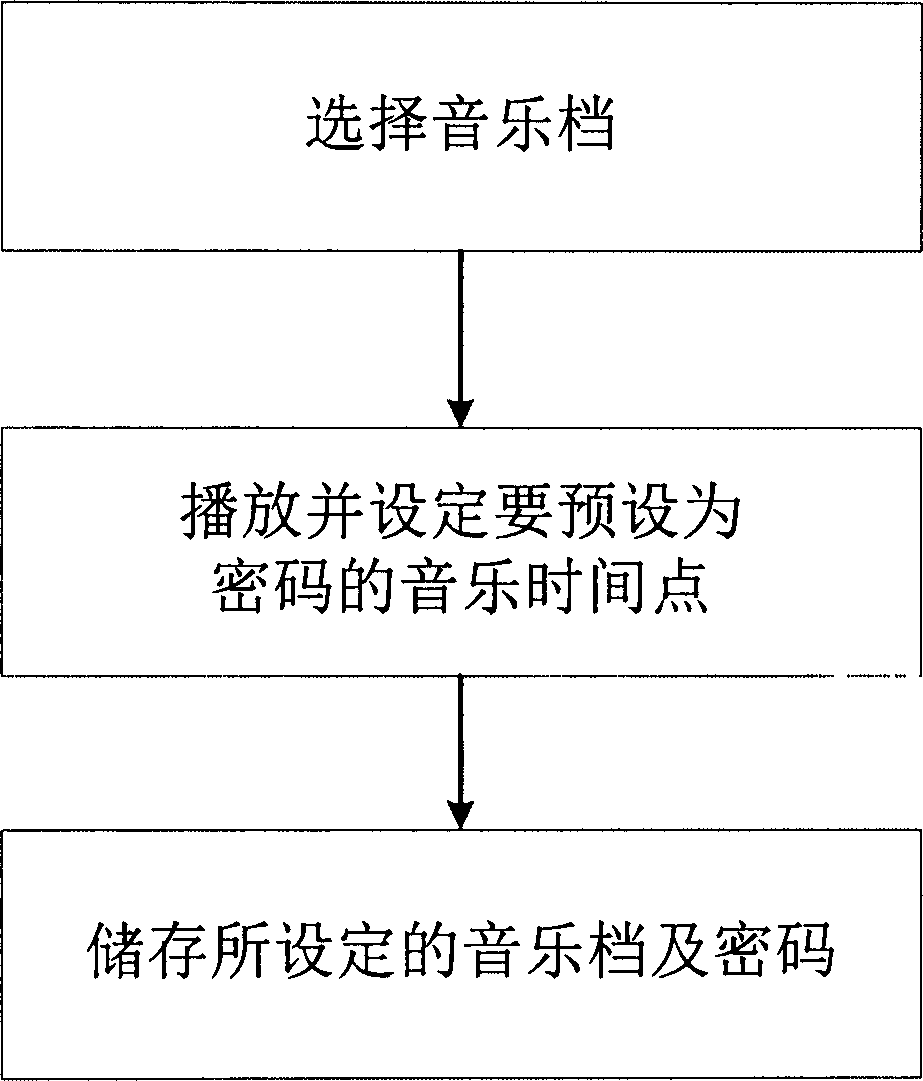
Touch screen mobile device, and method and system for soft locking password setup and unlocking for touch screen mobile device
InactiveCN102622554ASimple and efficient comparisonIncreased input freedomInternal/peripheral component protectionInput/output processes for data processingPasswordMobile device
The invention relates to a method for soft locking password setup for a touch screen mobile device and an unlocking method corresponding to the method for soft locking password setup. The method for soft locking password setup and the unlocking method are characterized in that hand input by a user is identified as a plurality of similar characters which are displayed from high to low according to similarity, and the character selected by the user can be stored via a corresponding character code; in password confirmation, the hand input is identified as the highest similar characters which are then converted into corresponding character codes, and the character codes are then compared with the stored character code; similarly, in unlocking, hand input by the user is recognized as the highest similar characters which are then converted into corresponding character codes, and the character codes are then compared with the stored character code. The invention further discloses a system for soft locking password setup and unlocking for the touch screen mobile device, which employs the methods and comprises a touch screen processing module, a recognition module, a comparison module, a storage and access module and a prompting module.
Owner:GUANGDONG BUBUGAO ELECTRONICS IND
Moisturizing makeup removing mousse
InactiveCN111568827AEffective makeup removerNoble skinCosmetic preparationsMake-upCaprylyl GlycolGlycerol
The invention discloses moisturizing makeup removing mousse. The moisturizing makeup removing mousse is prepared from the following components in percentage by mass: 30 to 60 percent of water, 10 to 40 percent of grape hydrolat, 3 to 6 percent of PEG-6 caprylic / capric triglyceride, 2 to 5 percent of polyglycerol-10 laurate, 2 to 5 percent of glycerinum, 2 to 5 percent of 1, 3-butanediol, 0.5 to 2percent of betaine, 0.5 to 1.5 percent of grape seed extract, 0.3 to 0.5 percent of caprylyl glycol, 0.3 to 0.5 percent of preservative and 2 to 8 percent of acrylic acid (acrylate) cross-linked polymer. The moisturizing makeup removing mousse can effectively remove makeup, endows the product with dreamlike unique appearance, noble skin feeling, high safety and moist skin feeling, maintains the moist feeling, and avoids the discomfort of water loss, burning pain and the like caused by tight skin.
Owner:浙江欣妃化妆品有限公司
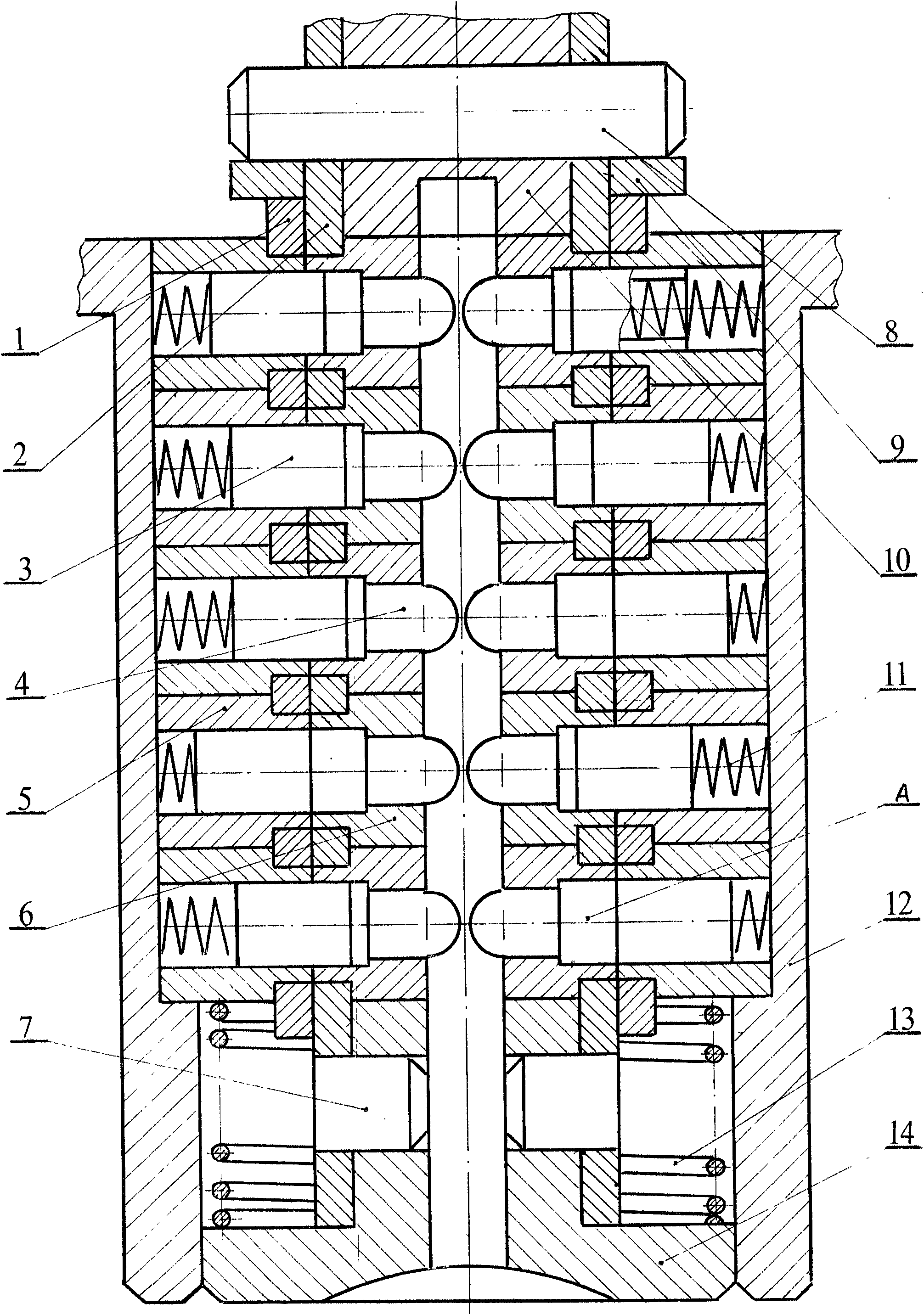
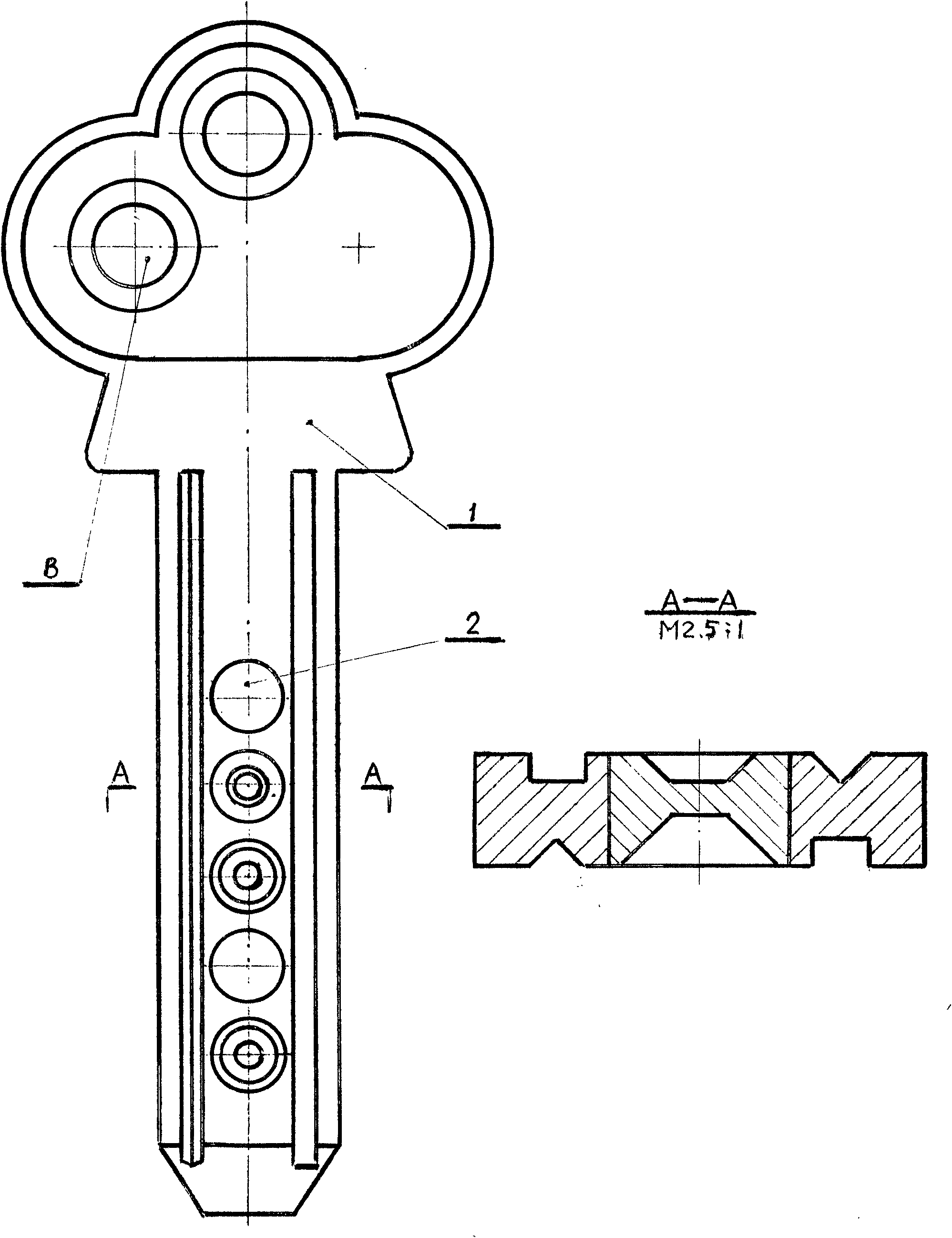
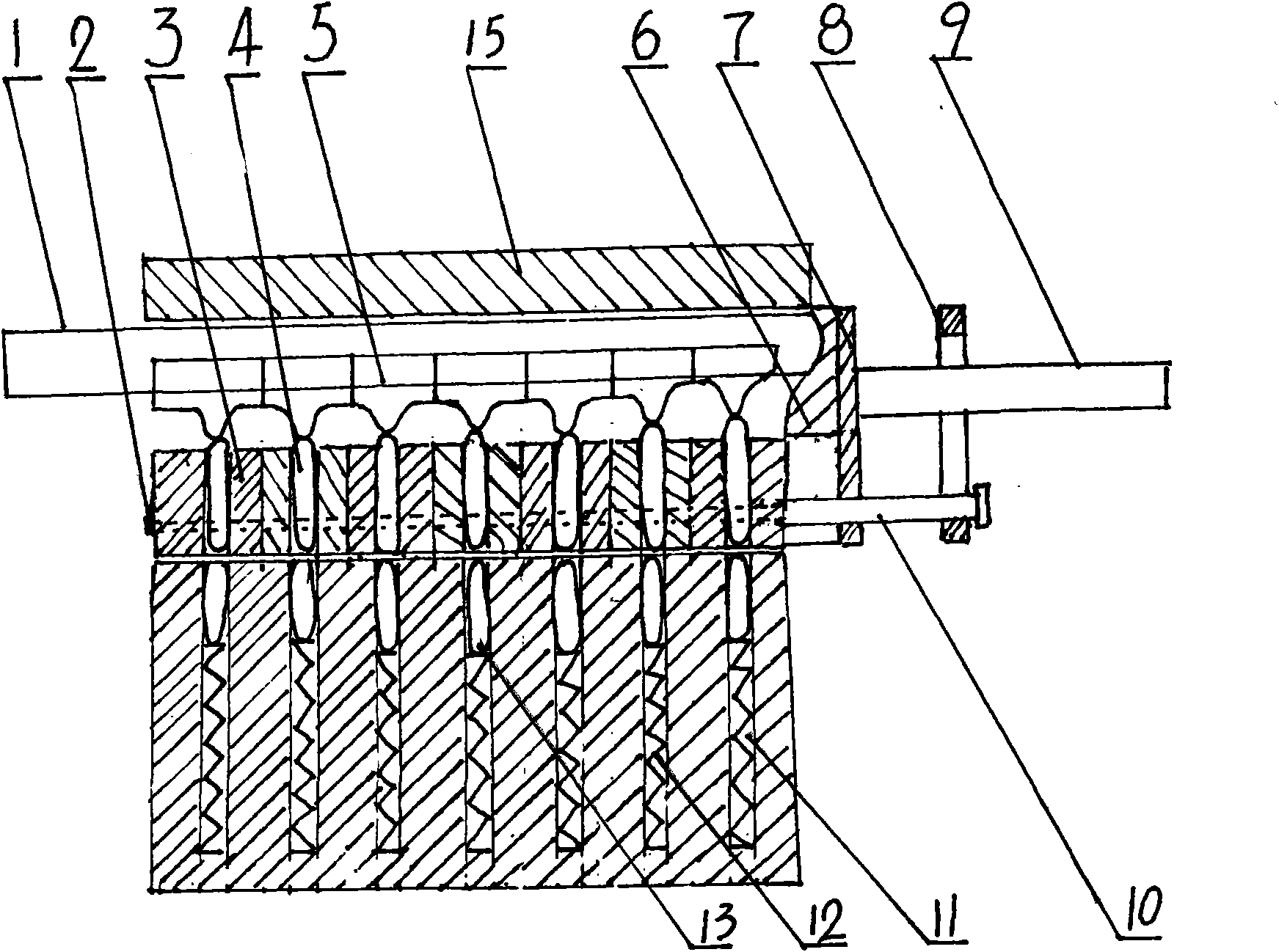
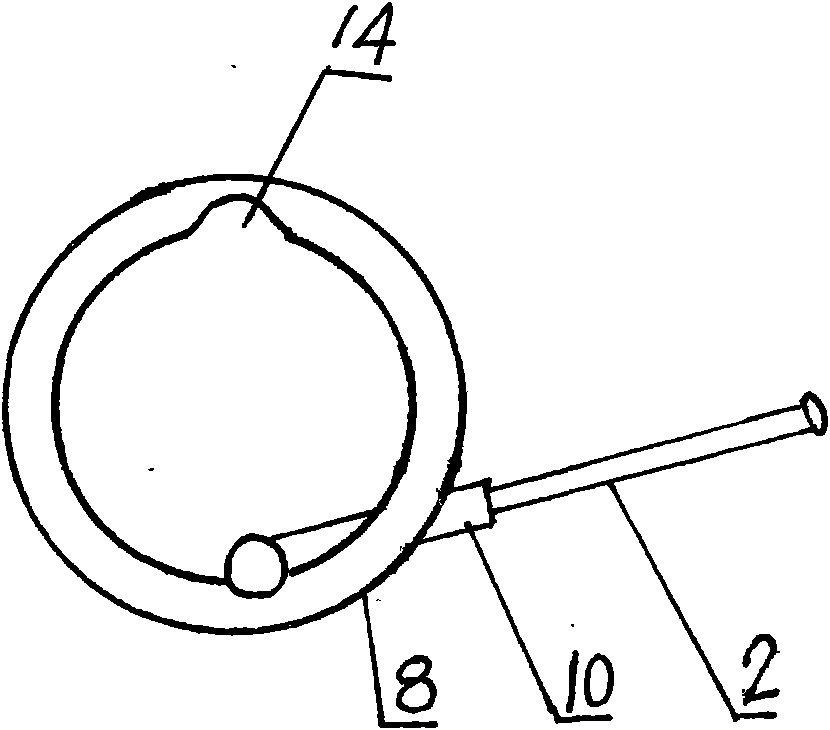
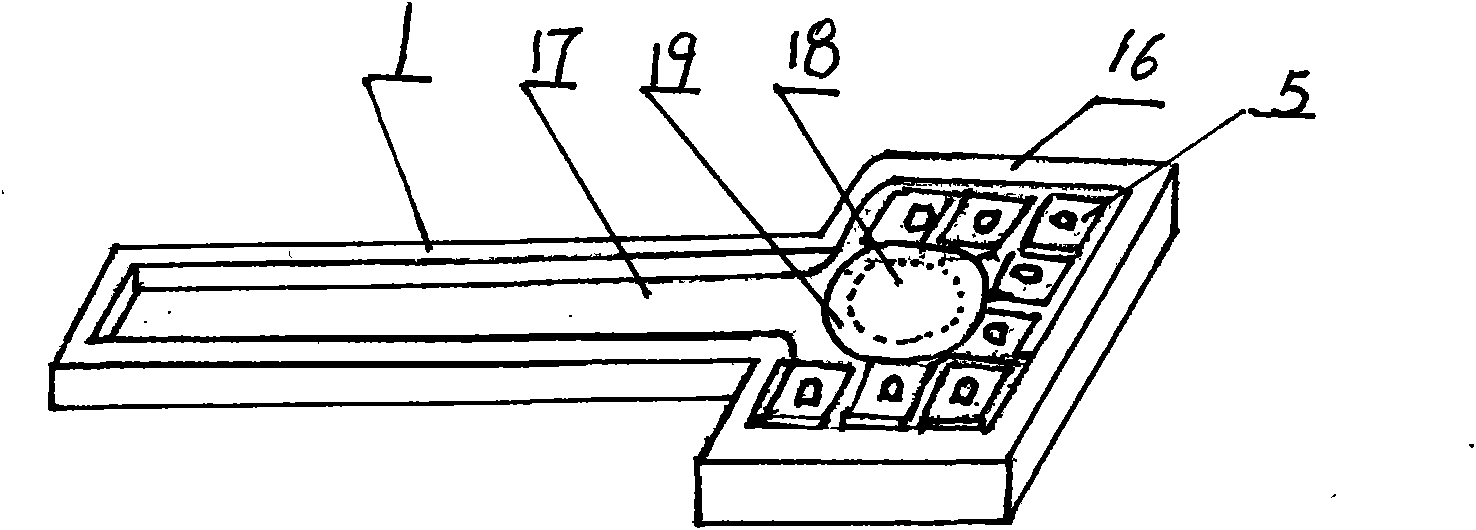
Anti-theft lock core with multi-gear marble structure and application thereof
The invention discloses an anti-theft lock core with a multi-gear marble structure and an application thereof on an anti-theft frame lock. The lock core structure comprises an upper clamping plate 1, a lower clamping plate 2, an upper marble 3, a lower marble 4, an upper clamping plate pipe 5, a lower clamping plate pipe 6, a short shaft pin 7, a long shaft pin 8, a positioning piece 9, a cushion block 10, an upper marble pressure spring 11, an upper clamping plate jacket 12, a pushing disk pressure spring 13 and a pushing disk 14. A is a sealed marble which is a go side in a normal state. Because the invention changes the traditional lock core structure and the traditional drilling process, the coaxiality accuracy of an upper marble hole and a lower marble hole of the lock core is ensured, so that the lock core can be designed into an anti-theft lock core with a 6-gear, 10-gear or 20-gear marble structure. The lock core can be unlocked in a linear pushing mode, and in order to adapt to the requirements of the related prior art, the lock core can be also designed for unlocking in a 360 degree rotating mode. Because the current anti-theft lock can not perform an anti-theft function, the invention can enable the anti-theft lock to really perform functions of guard against theft and security.
Owner:靖江市悦达安防设备有限公司
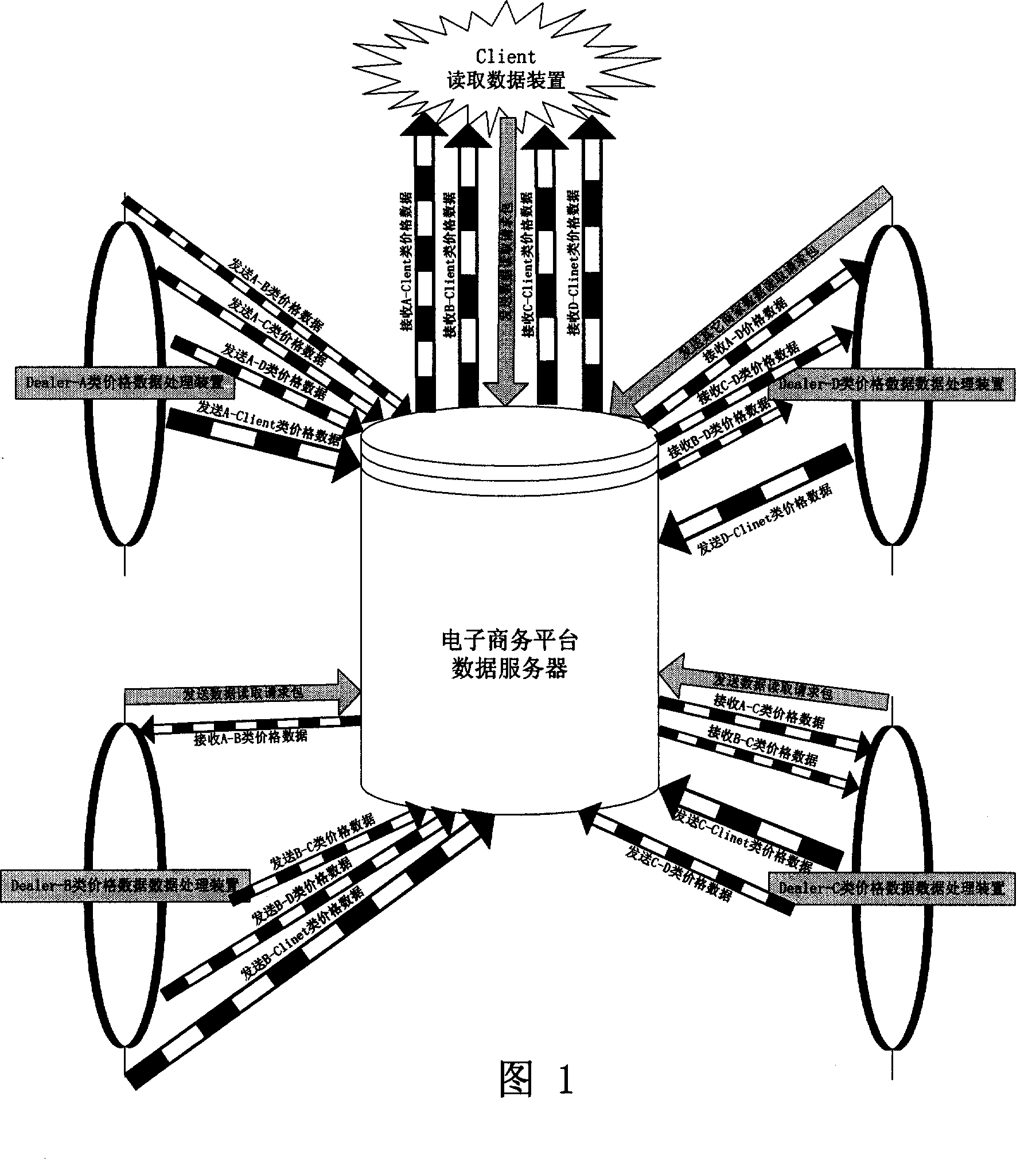
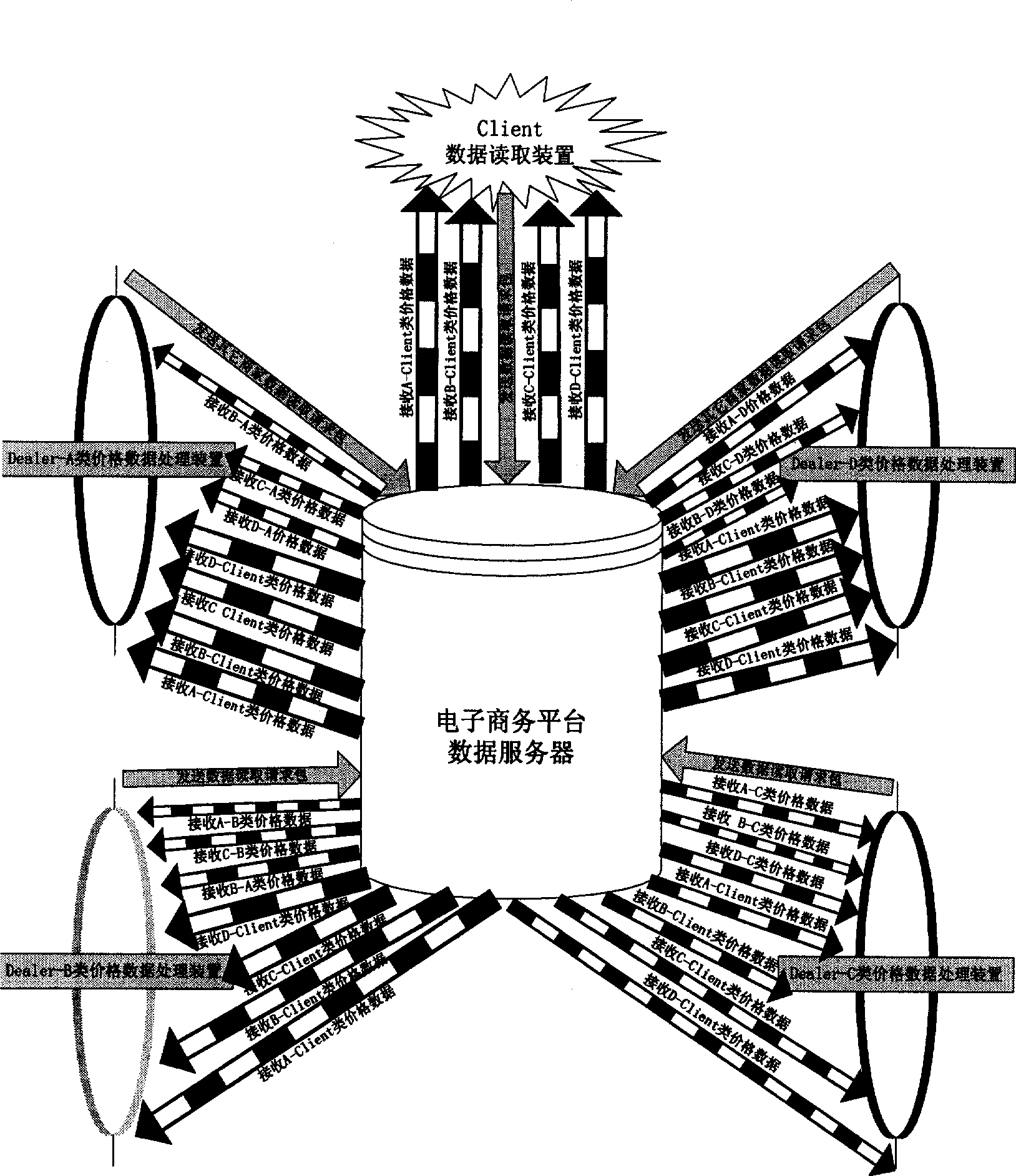
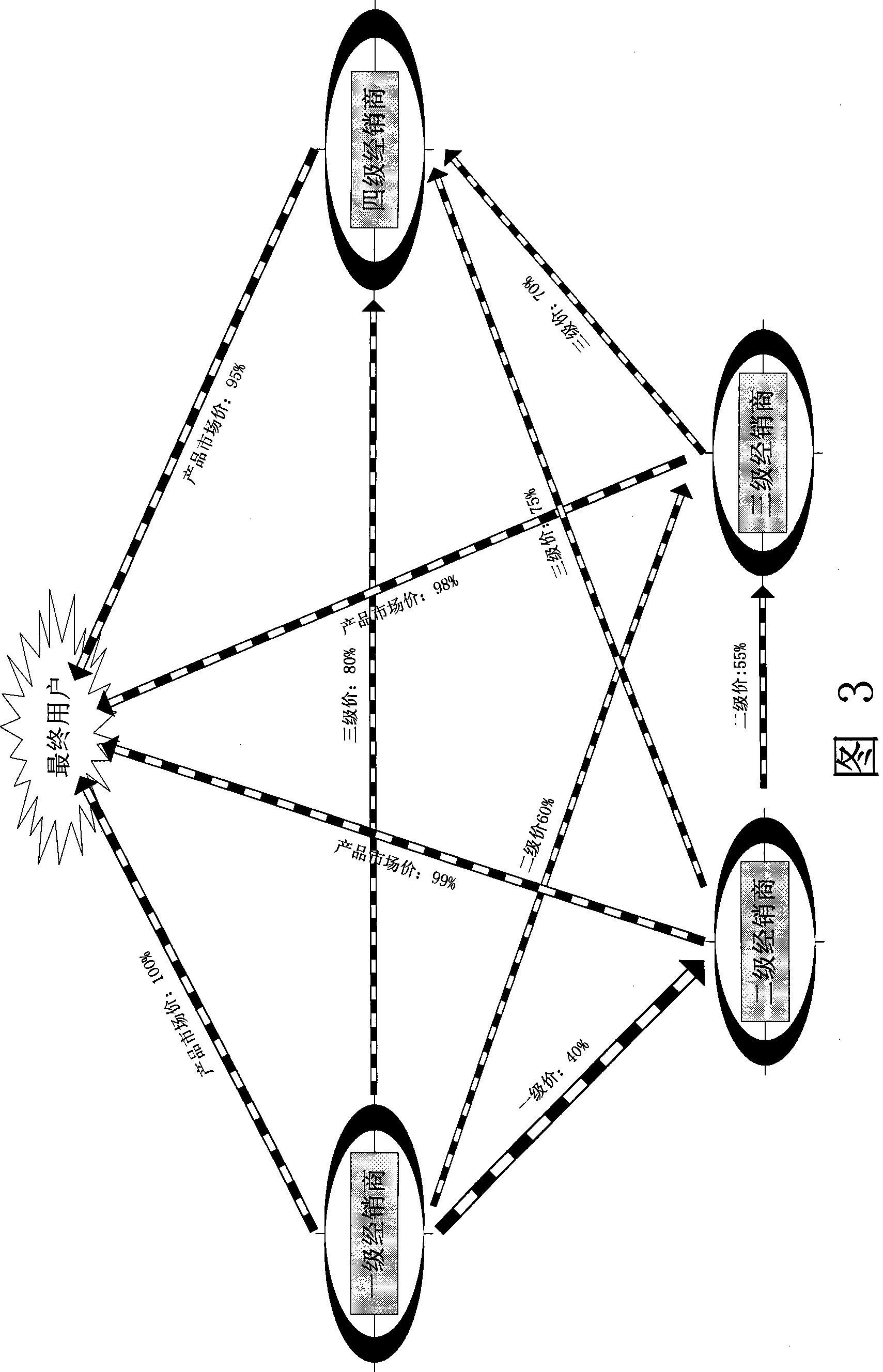
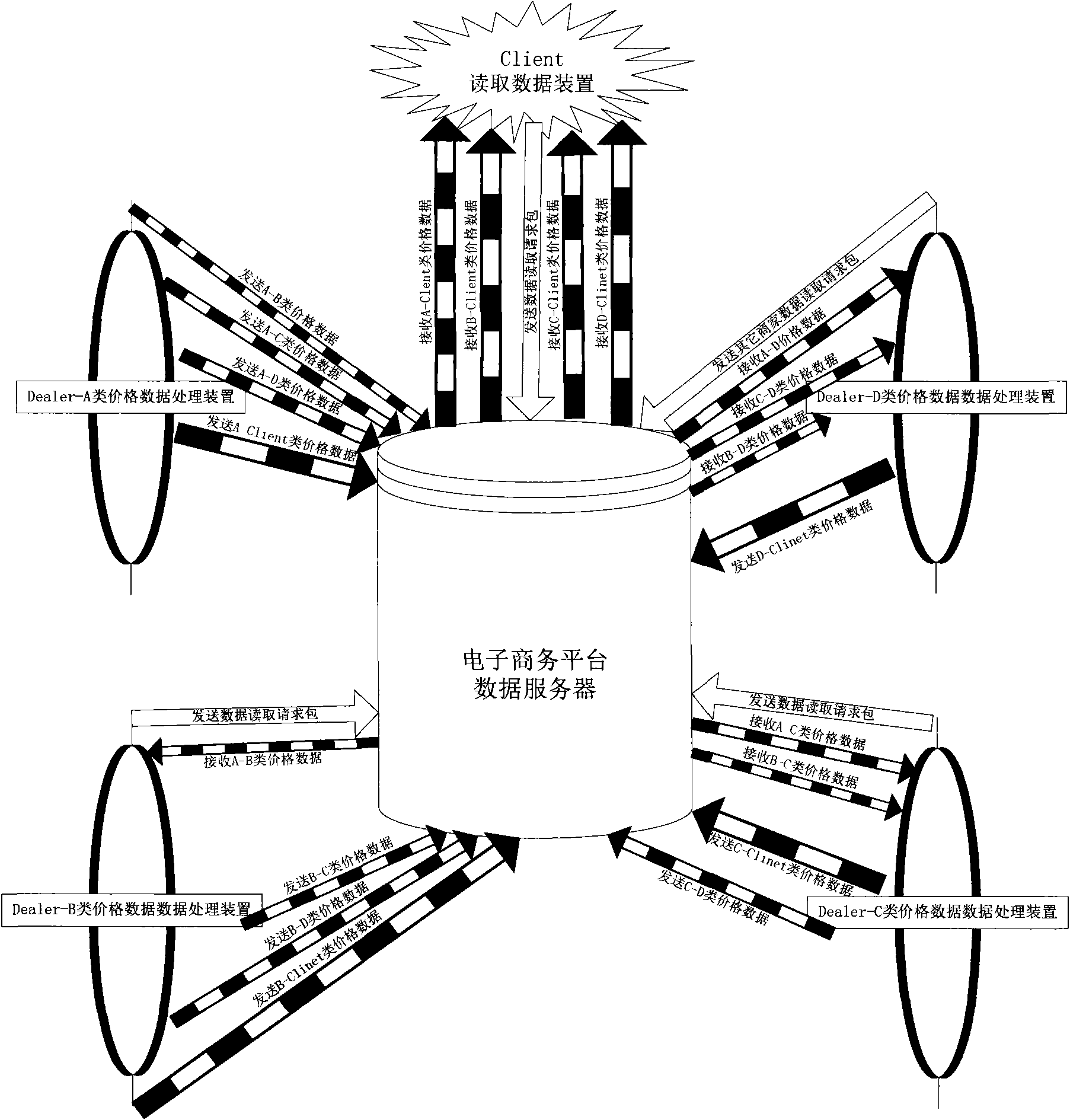
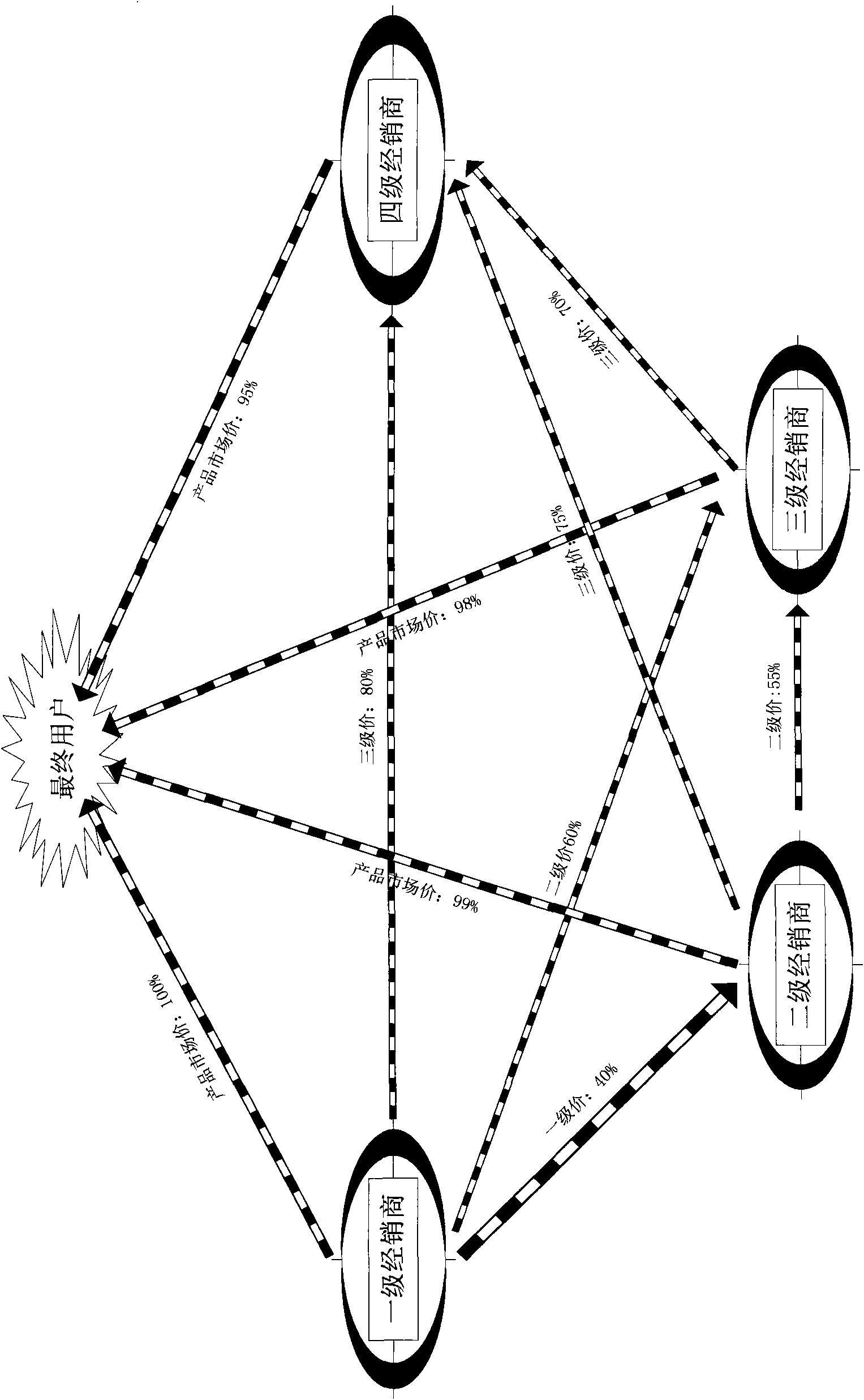
Method for implementing multi-stage price module structure by electronic commerce platform
The invention discloses a method for realizing multistage price module architecture on electronic commerce platform, which fully utilizes electronic commerce platform. The method comprises that a distributor sets itself as a first stage distributor according to its management mode, and classifies other distributors having trade with it into a plurality of stages or modules; the first stage distributor edits the price data for other lower stages and product users, and transmits the data via internet, the distributors not the first stage sends data read request packets to the electronic commerce platform to read and analyze price data, and edits the prices for other lower stages and product users to be transmitted to the electronic commerce platform to be stored, thereby forming multistage price module architecture. Via the method, in the product management of distributors and users, distributors can confirm the benefits of the distributors at each stage, confirm the marketing mode of multi dimensional market, and can avoid the vicious circle caused by competition of low price in market.
Owner:南宁柒柒壹电子科技有限公司
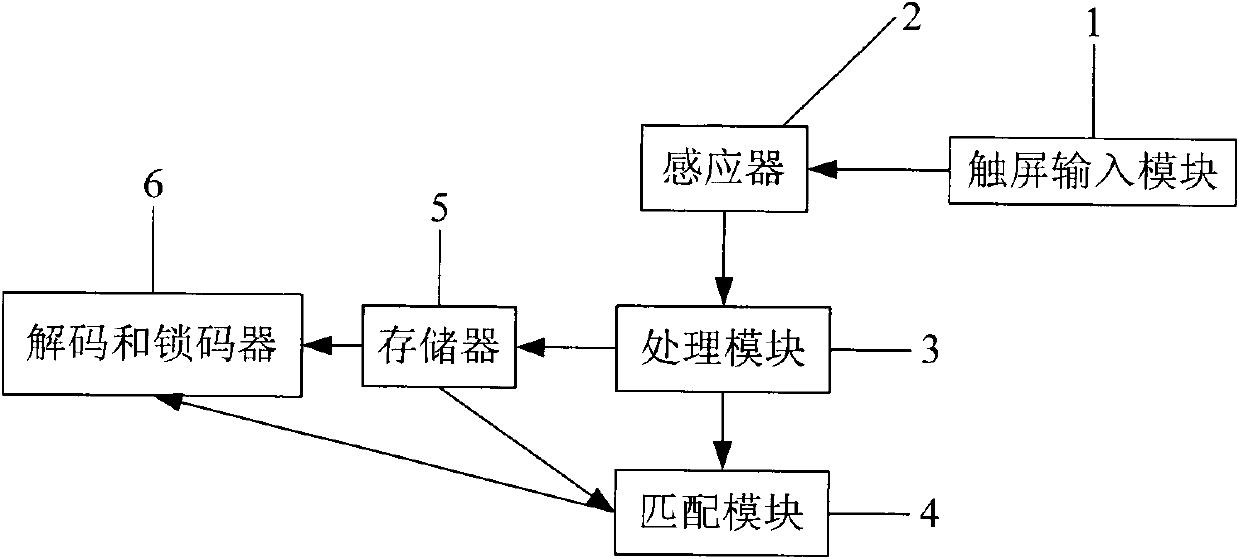
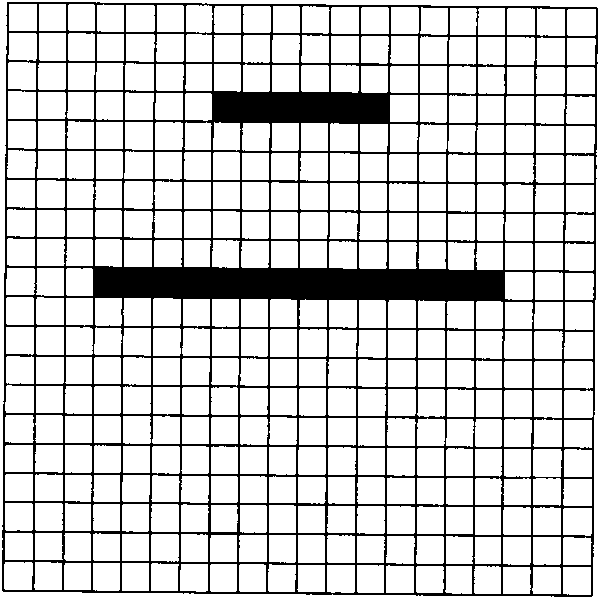
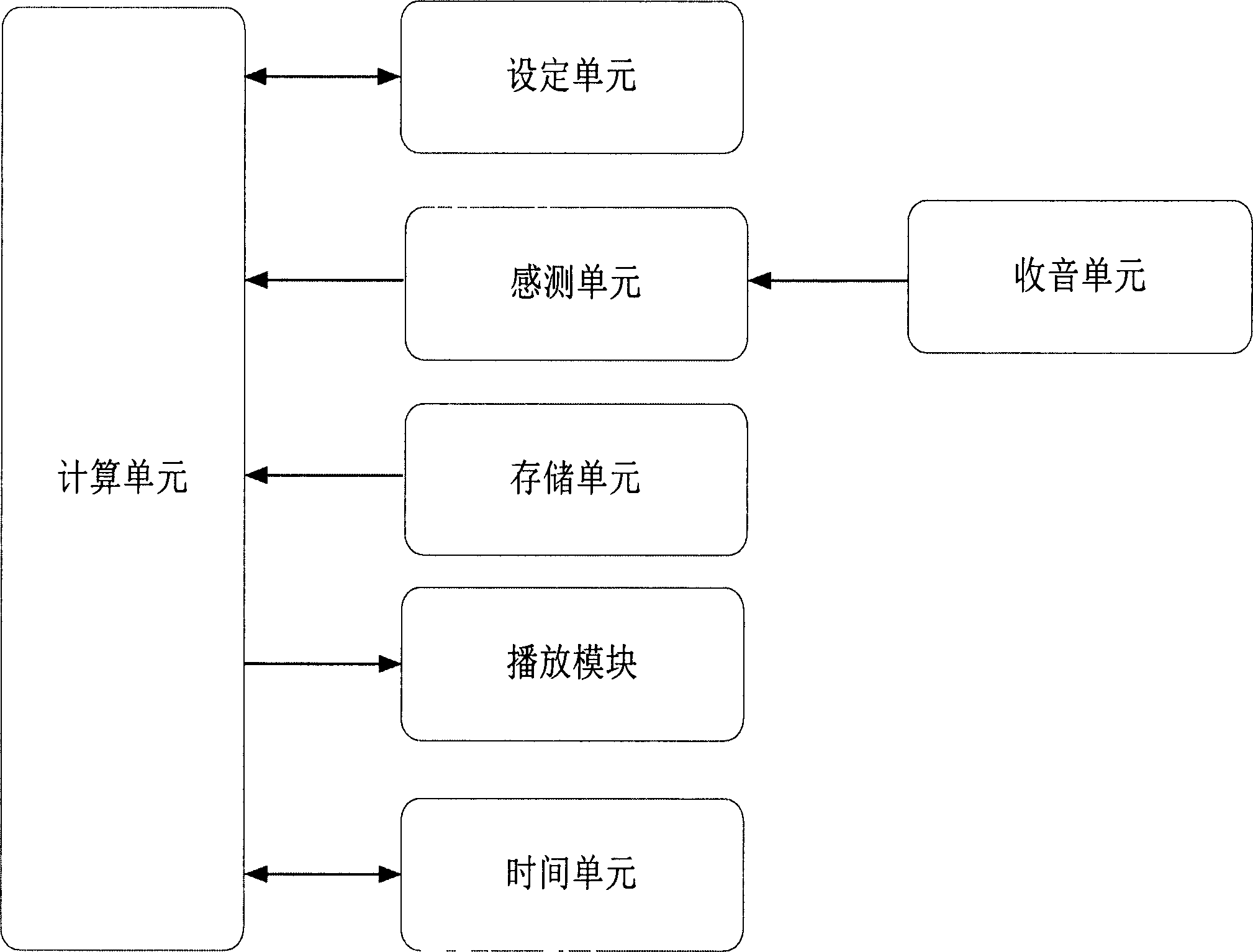
Handwriting privacy lock device and application method thereof
The invention discloses a handwriting privacy lock device, which comprises an inductor, a processing module and a matching module, which are sequentially connected, wherein the inductor is used for recording the position of each point, through which the handwriting input by a user passes; the processing module is used for carrying out value assignment on the handwriting, and recording in a corresponding current array; and the matching module is used for comparing contents of the current array and the privacy handwriting array to obtain a matching degree. According to the invention, handwriting of cipher character is recorded, so that the cipher character cannot duplicated; and the handwriting encryption treatment is carried out on the function requiring privacy, thus the function or electronic equipment is difficult to open even if the cipher character is leaked carelessly, and the privacy degree is remarkably improved.
Owner:SHANGHAI CHENXING ELECTRONICS SCI & TECH CO LTD
Unlocking device and method thereof
InactiveCN104077005AHigh securityIncrease entertainmentInput/output processes for data processingEmbedded systemStorage cell
Owner:广东乐固智能科技有限公司
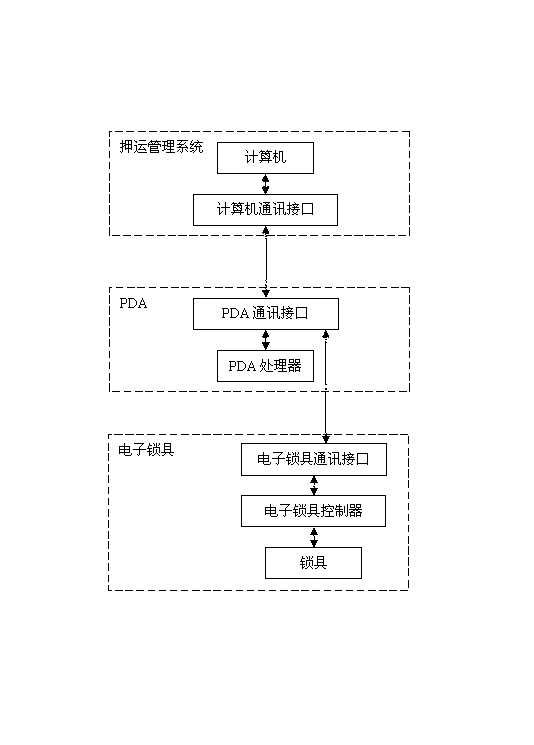
Identity recognition technology based escorting box management method
ActiveCN103236093ASolve security and confidentiality issuesHigh securityIndividual entry/exit registersIdentity recognitionKnowledge management
An identity recognition technology based escorting box management method comprises the following steps: a user sends an article escorting request to an escorting management system; the management system generates a random test key and escorting personnel information of the mission, and sends the random test key to the user; the escorting personnel carries PDA and an escorting box to the user's location, the identity authentication of the user is carried out in the PDA, the PDA can correctly display the random test key and the escorting personnel information after the authentication is successful, and the user identifies the random test key and the escorting personnel information; the user sends a box opening instruction to the escorting box through adopting the PDA; the article to be escorted is put in the box, and then the identity recognition is carried out to confirm that the box is correctly closed; and the escorting personnel returns to complete the escorting mission. The escorting box management method has the characteristics of high secrecy, safety and reliability, and effectively solves the safety and secrecy problems of the user and the escorted article.
Owner:NANJING EASTHOUSE ELECTRIC CO LTD
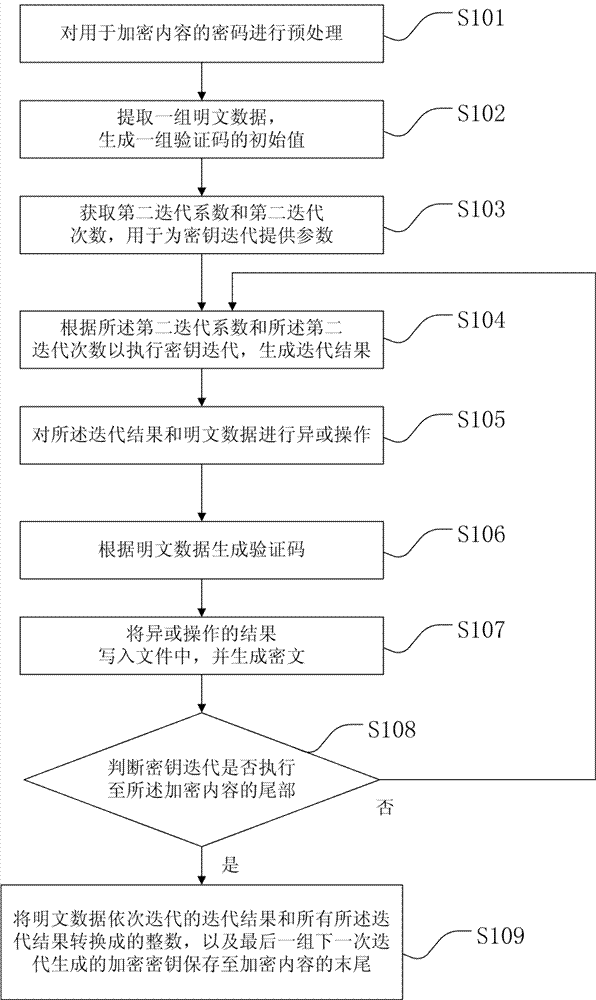
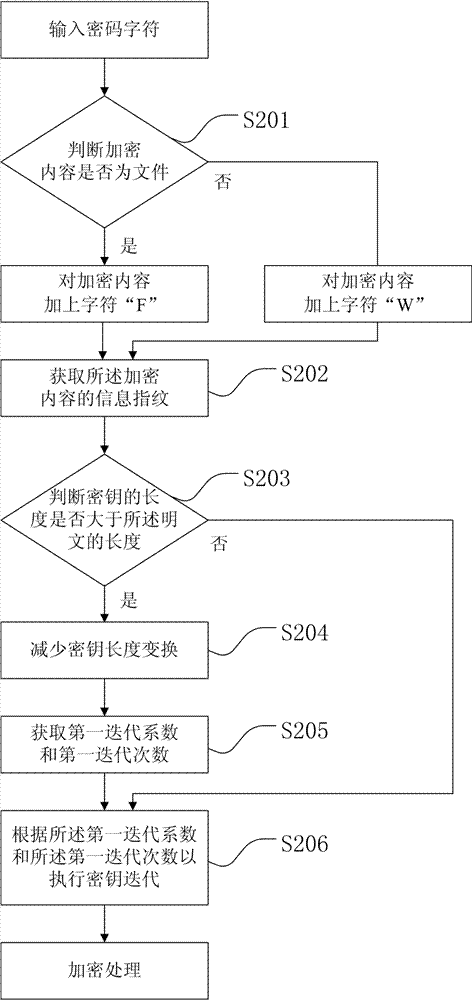
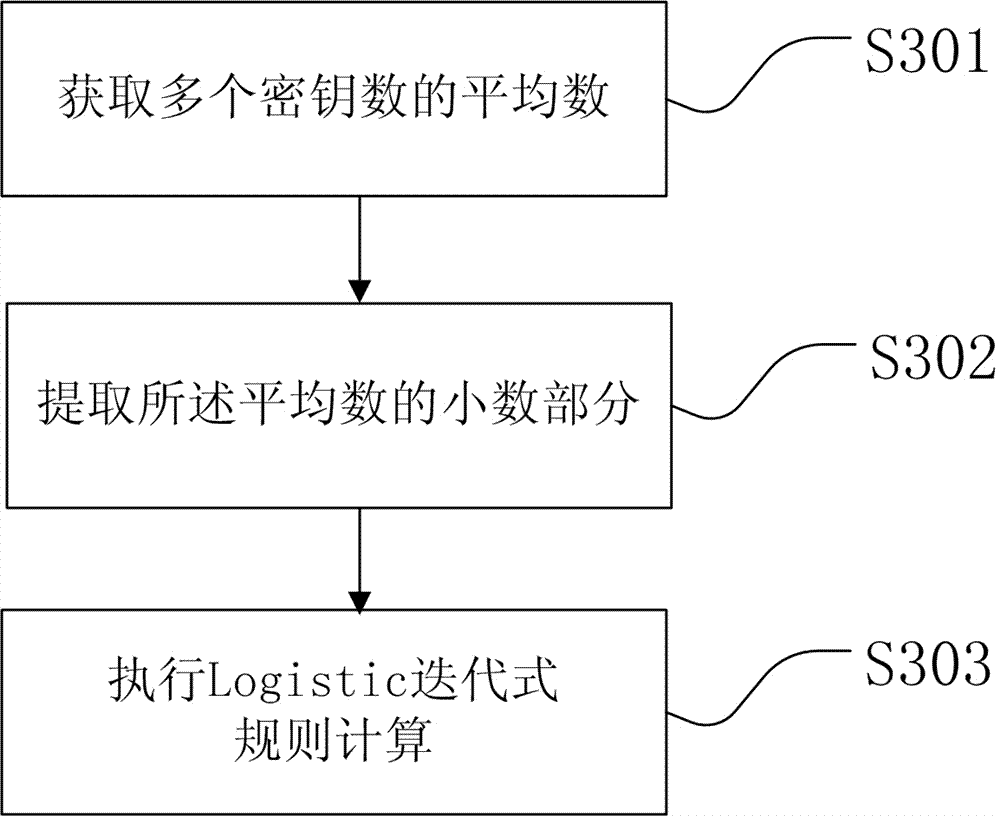
A file encryption method
InactiveCN103595523AIncrease the difficultyHigh securitySecuring communicationComputer hardwarePlaintext
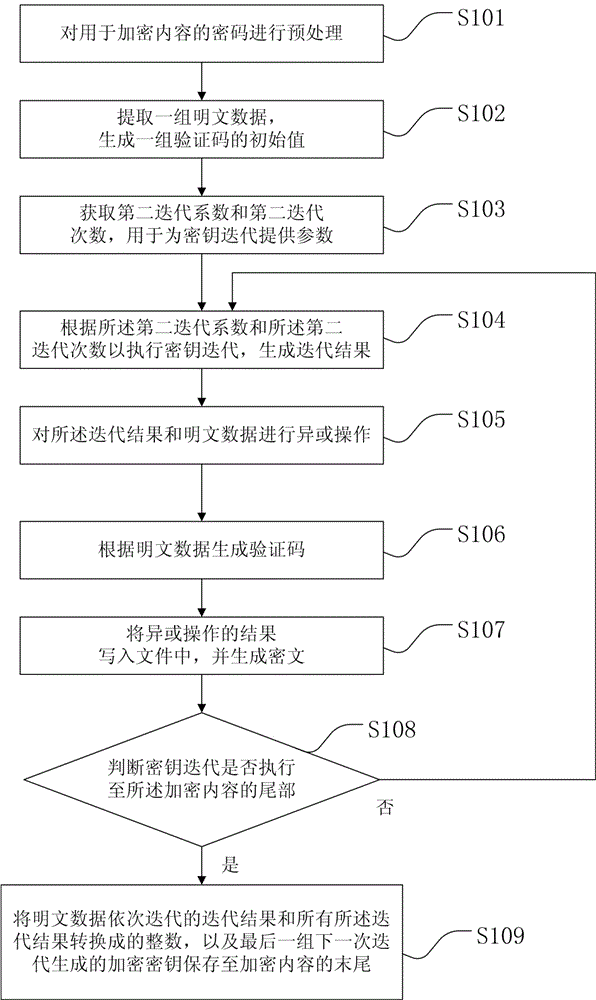
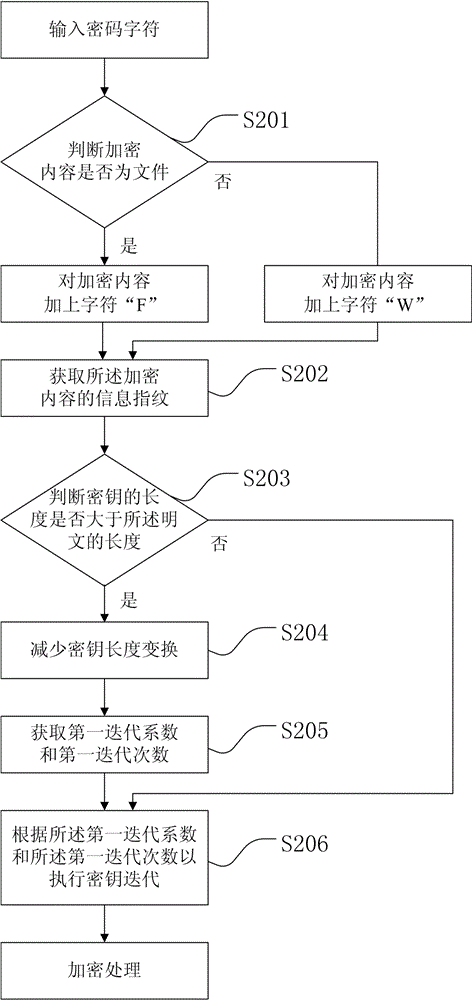
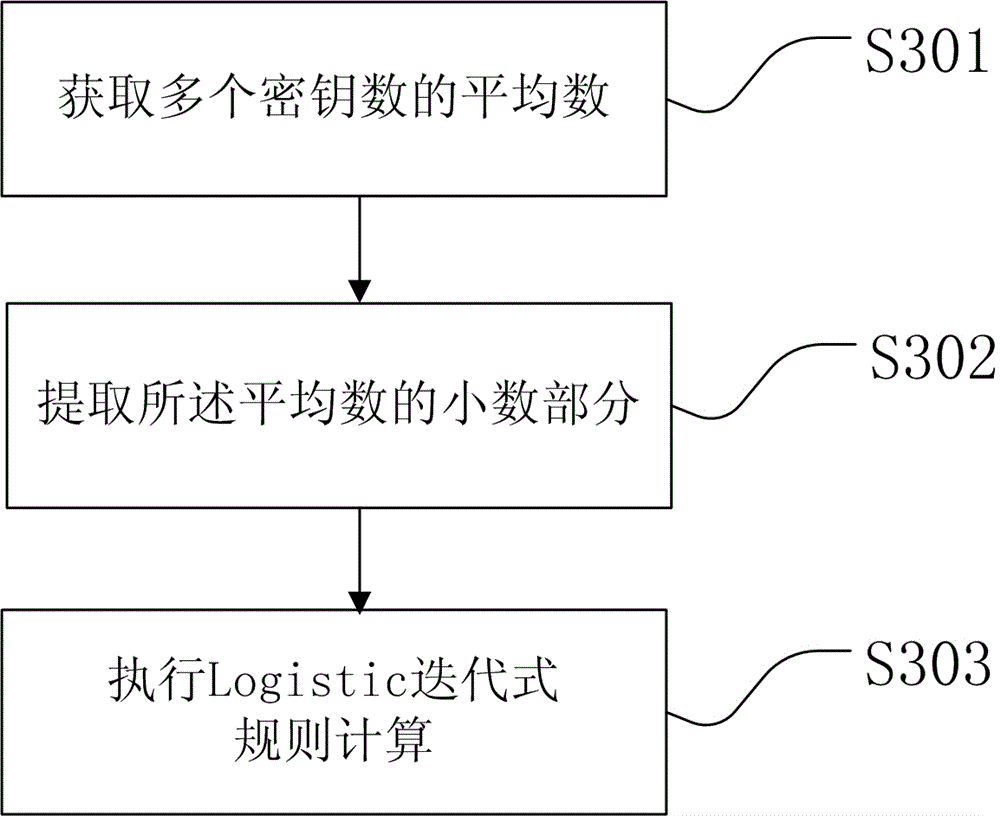
Provided is a file encryption method based on chaos transformation. The file encryption method comprises: (a1) preprocessing a password for encrypted content; (a2) extracting a group of plaintext data and generating the initial values of a group of vertificaiton codes; (a3) obtaining a second iteration coefficient and the number of second iteration times; (a4) executing secret key iteration and generating an iteration result according to the second iteration coefficient and the number of second iteration times; (a5) performing xor operation on the iteration result and the plaintext data; (a6) generating a verification code according to the plaintext data; (a7) writing the result of the xor operation in a file and generating a cryptograph; (a8) determining whether the secret key iteration is executed to the tail portion of the encrypted content, and executing a step (a9) if yes or continuously executing the step (a4) if not; (a9) the successive iteration result of the plaintext data and all the iteration results are converted into integers and the encryption key generated by the last next iteration is saved in the tail of the encrypted content.
Owner:SHANGHAI SIMCOM LTD
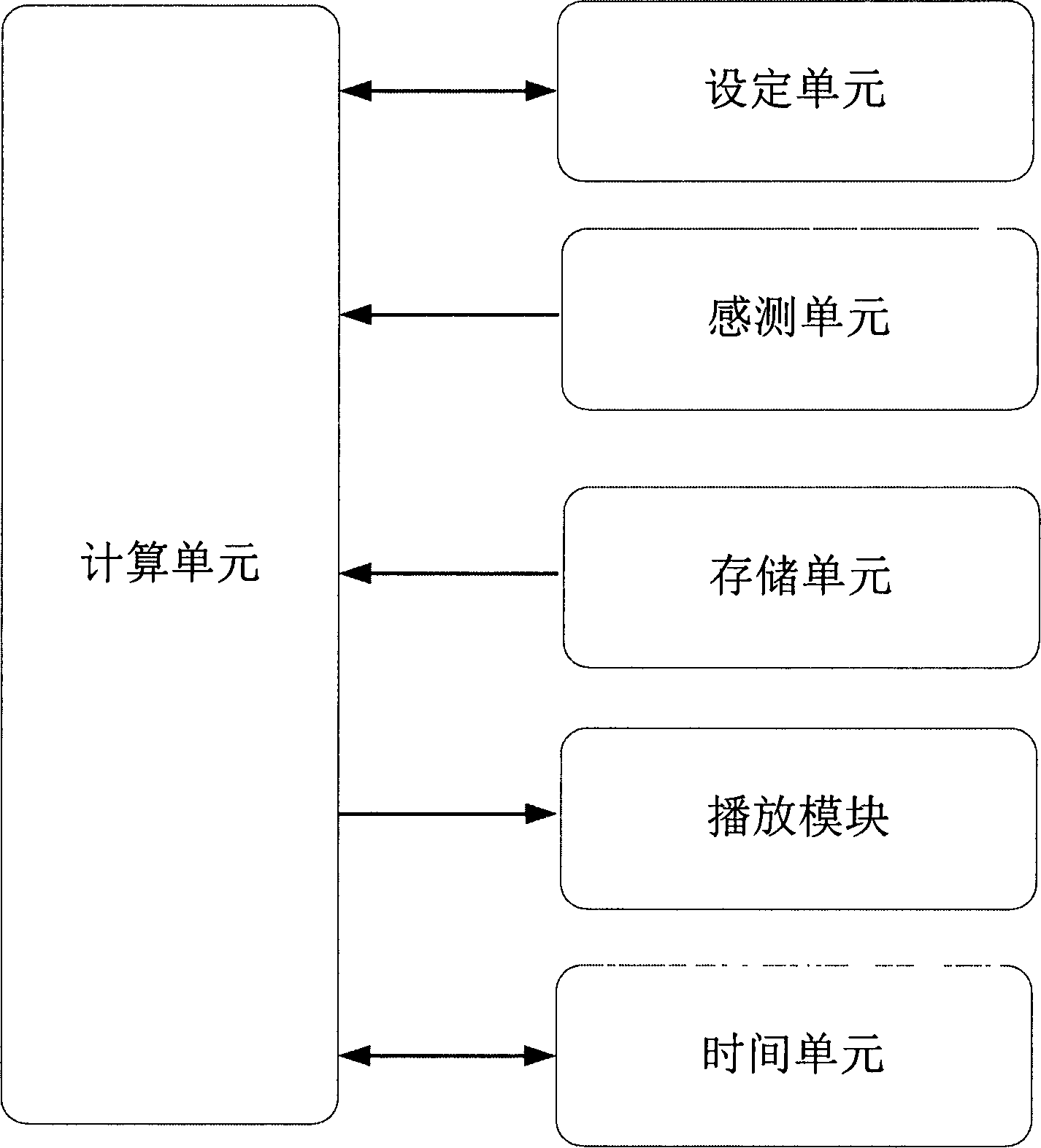
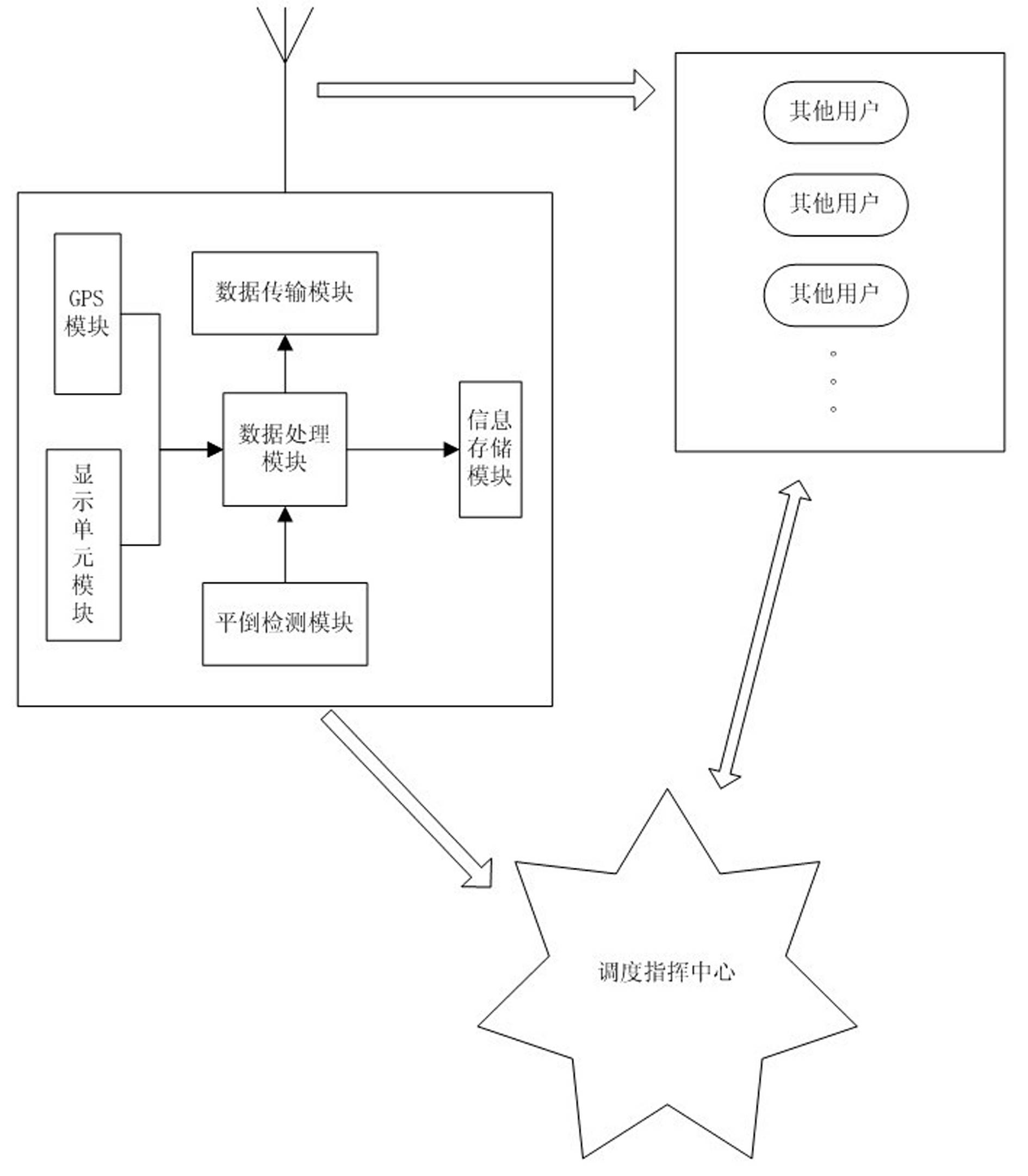
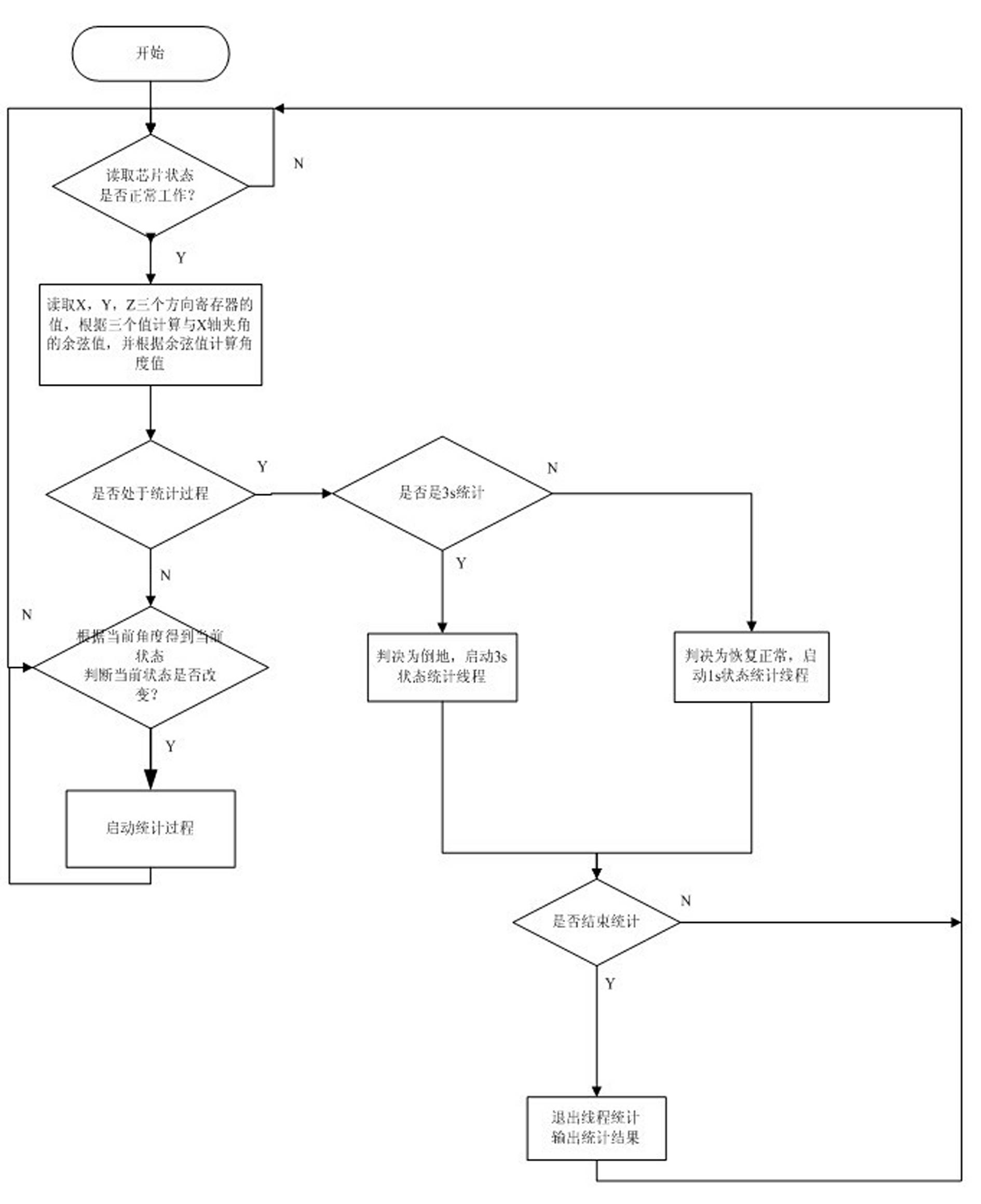
Digital interphone for intelligent standing and falling detection monitoring system
InactiveCN102595256AFacilitate search and rescue workGuaranteed stable workStations for two-party-line systemsInterference resistanceConfidentiality
The invention relates to a digital interphone for an intelligent standing and falling detection monitoring system. An interphone circuit mainly comprises a standing and falling detection module, a data processing module, an information storage module, a display unit module, a global positioning system (GPS) module and a data transmission module, wherein the standing and falling detection module mainly comprises a CMA3000 acceleration sensor of VastView technologies Inc. (VTI) and a signal output port; when a three-axis component of the CMA3000 acceleration sensor is changed, an interrupt signal is generated to notify the data processing module; and the data processing module acquires the three-axis component of the CMA3000 acceleration sensor of the VTI in the standing and falling detection module through a serial peripheral interface (SPI) bus, and judges the standing and falling state of the interphone according to threshold value data. The digital interphone adopts a digital private mobile ratio (DPMR) standard, and has the special performance of high anti-interference capability, high quality, long transmission distance, high confidentiality, high reliability, highly-flexible service adaptability and external interface connecting capability, and the like.
Owner:TIANJIN 712 COMM & BROADCASTING CO LTD
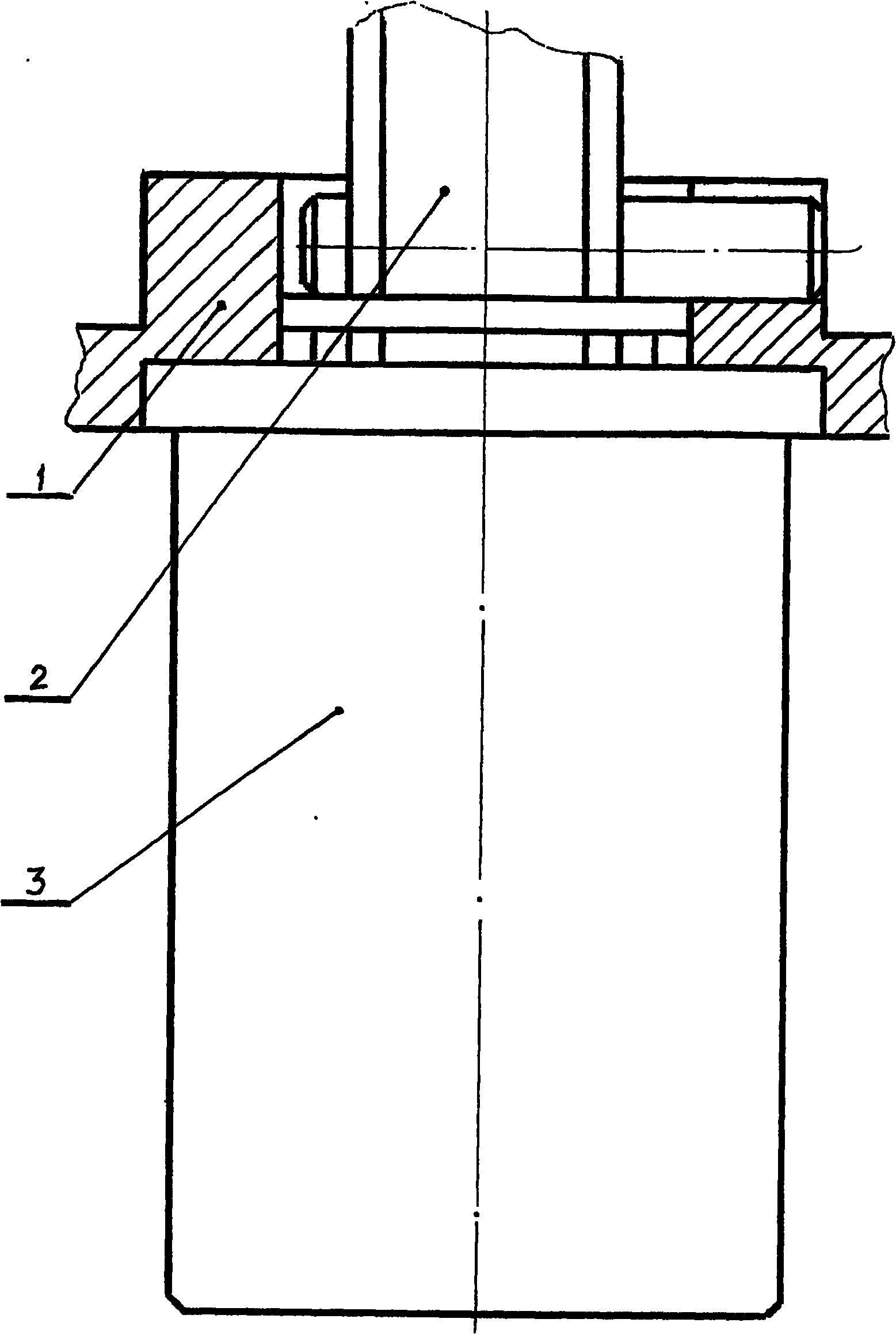
Lock key with changeable structure
InactiveCN101555739APlay the role of changing the passwordSave the trouble of carrying many keysKeysCylinder locksEngineeringMechanical engineering
The invention discloses a lock key with changeable structure. The lock key comprises a lock casing (15), a lock core (6), an inner lock bolt (9), a rotation disk (7), a bolt, a ball hole (11) and a ball and a spring (12) thereof. The lock key is characterized in that a primary marble (4) and the marble hole on the lock core (6) are connected in series by a split-type marble sleeve (3) via a sleeve fixing pin (2) and are then sheathed and positioned with a linkage skidproof rod; and a skidproof ring with cutting is fixed on the lock casing close to end of the skidproof rod behind the rotation disk. The lock key of the invention has high secrecy, flexible changeable lock key structure, low cost and convenient process; a single key can open a plurality of locks of the same size and the same type, thereby saving problems of bringing a great number of keys.
Owner:苟淋
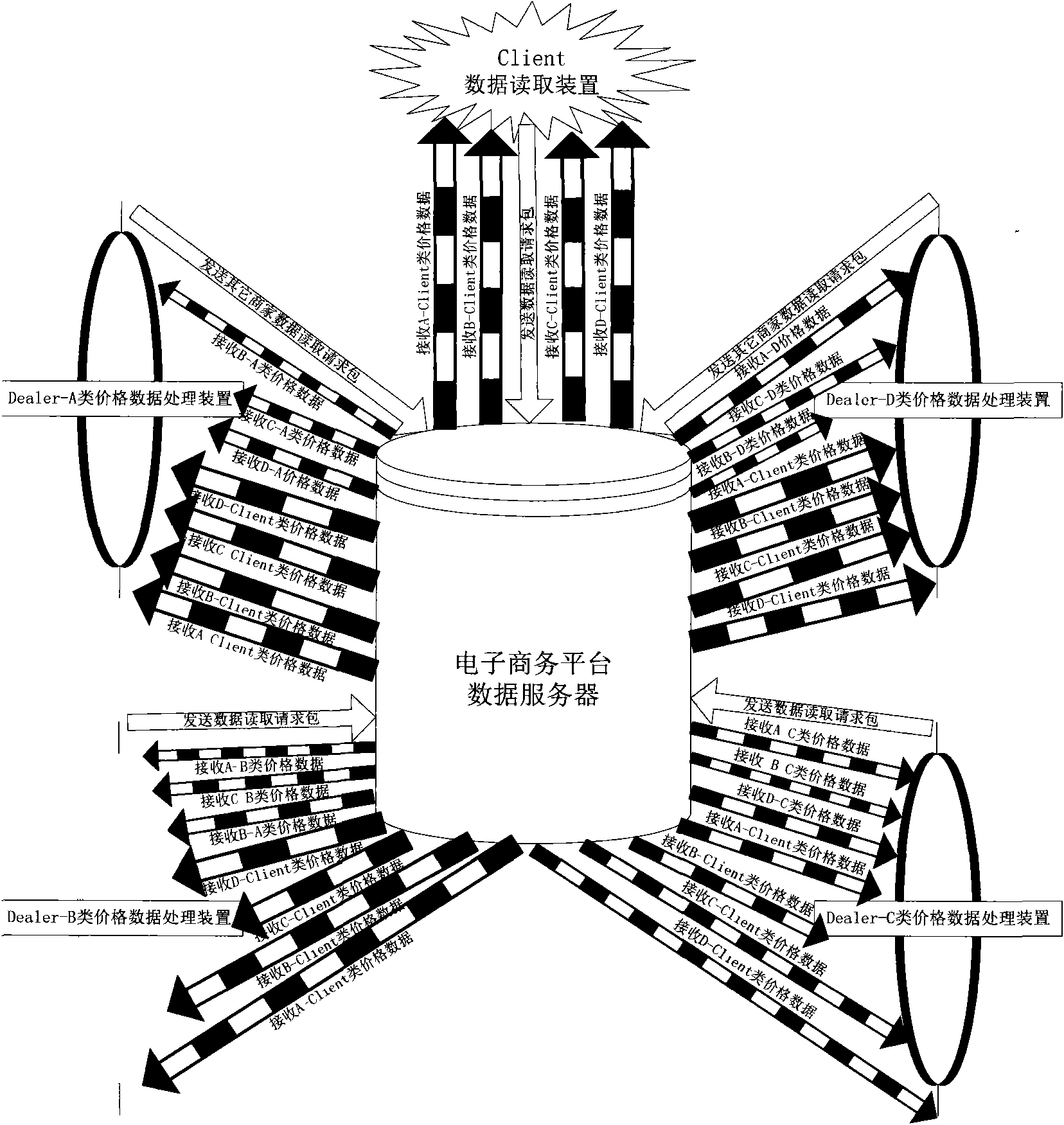
Network structure and method for realizing multi-level price module framework of e-commerce platform
The invention discloses a network structure and method for realizing a multi-level price module framework of an e-commerce platform. The network structure comprises an e-commerce platform data server, multiple price data processing devices at different levels and a data reading device, wherein the e-commerce platform data server comprises an information storage part for storing price data information, a control part for processing a reading request packet and a data providing part for providing price data information to the data reading device. The first-level price data processing device comprises a functional part which can respectively edit out price data information and a data transmission part for transmitting the price data information to the server. The price data processing devices at the lower levels are provided with reading request parts for sending a data reading request packet and reading the price data information, functional parts for editing out prices of the lower levels and product users, and data transmission parts for transmitting the price to the server; and the data reading device is provided with a reading part for reading price data of a product user.
Owner:南宁柒柒壹电子科技有限公司
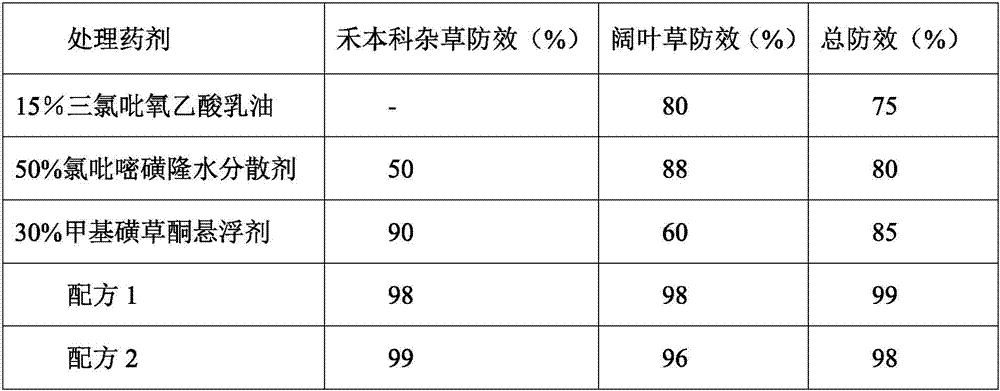
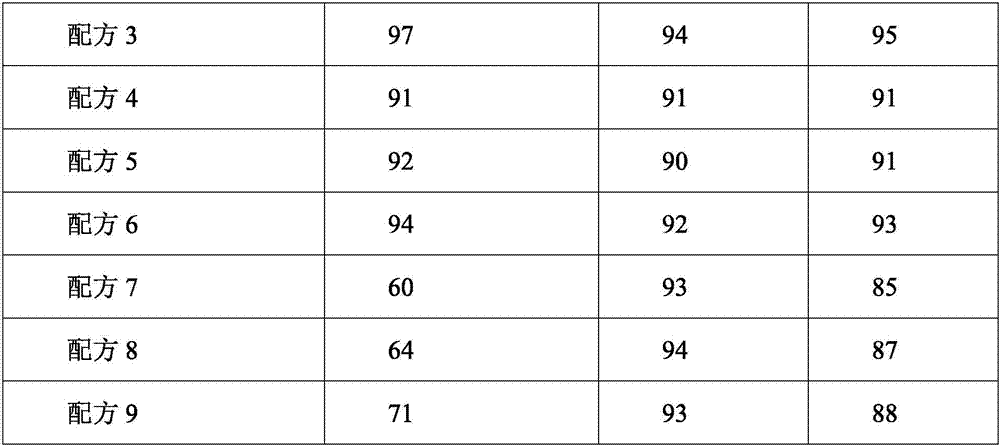
Novel method for prevention and control of older rice barnyard grass in paddy rice fields
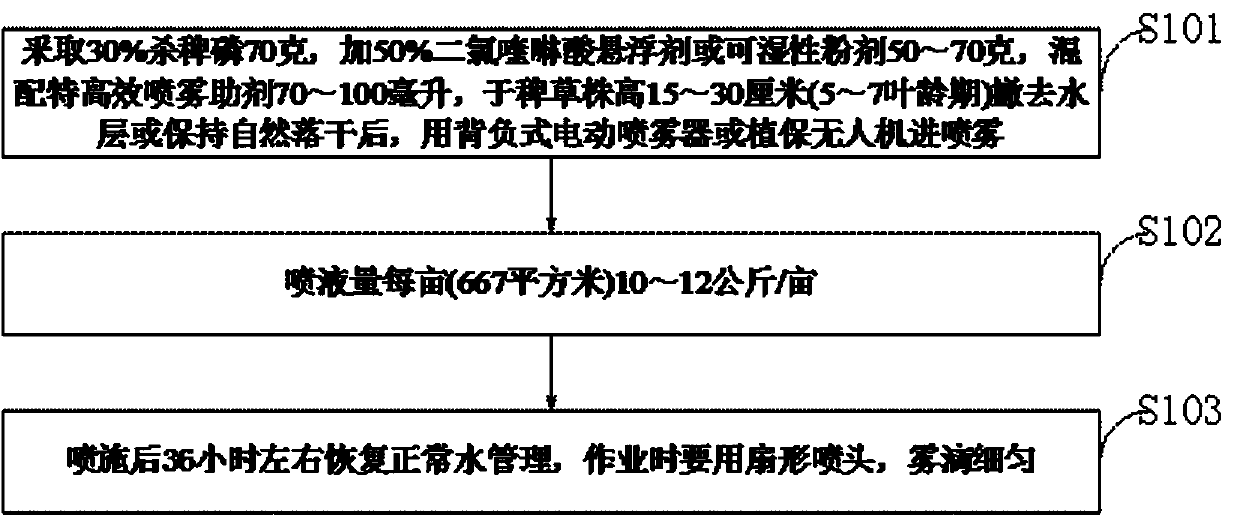
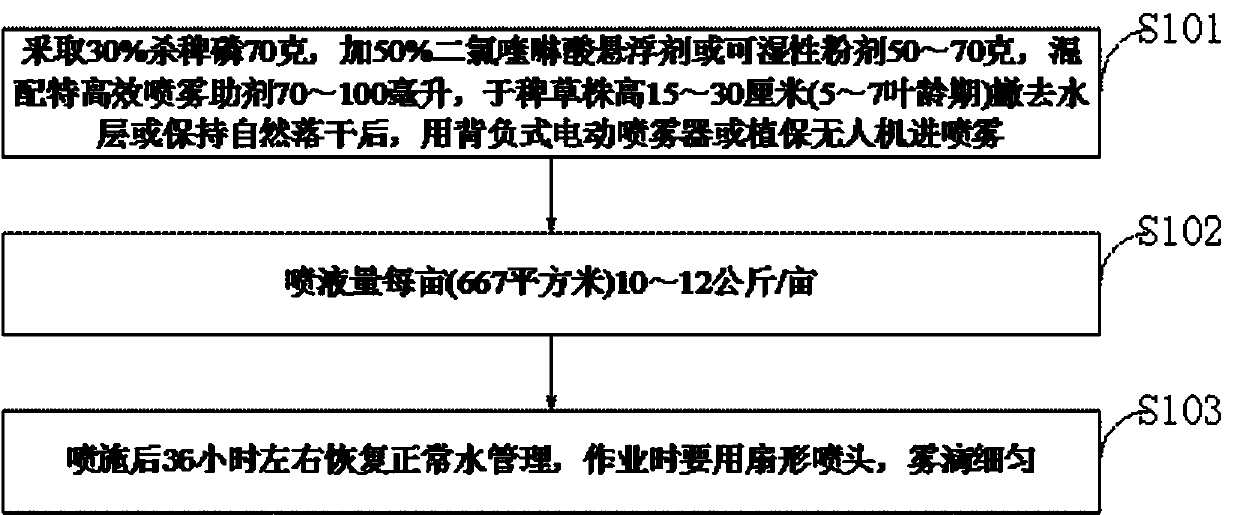
InactiveCN110037047ALower resistanceDelays resistance developmentBiocideAnimal repellantsPesticide residuePollution
The invention belongs to the technical field of prevention and control of barnyard grass in paddy rice fields, and discloses a novel method for prevention and control of older rice barnyard grass in paddy rice fields. When barnyard grass or echinochloa crusgalli has a plant height of 15-30 cm and is in a leaf age stage of 5-7, mixing 50-70 grams of 30% anilofos, 60-80 grams of a 50% quinclorac suspension or wettable powder and 70-100 ml of an alkyl ethyl sulfonate mixed efficient spray additive; and when the barnyard grass has a plant height of 15-30 cm, a water layer is removed or kept dry naturally, and then spraying is carried out. After the water layer is removed or kept dry naturally when the barnyard grass has a plant height of 15-30 cm, the amount of liquid spray is 10-12 kg / mu, andnormal water management is recovered about 36 hours after the spraying. The novel method of the invention is superior to paddy rice field post-emergence stem and leaf treatment herbicides ''molinate'' or ''penoxsulam'' imported from the United States, is highly safe to paddy rice, and has no obvious and hidden phytotoxicity, no pesticide residue to rice and no soil pollution.
Owner:王贵申
Process for producing novel growth regulator for pig
InactiveCN101429223AImprove growth performanceImprove qualitySugar derivativesAnimal feeding stuffDrug additiveSodium salt
The invention discloses a novel method for preparing a growth regulator used for pig. The method comprises the following steps: taking ATP as a raw material, adding Ba(OH)2 into the ATP to be dissolved in distilled water, distilling and heating the mixed solution at 96 DEG C for 40 minutes, and cooling and centrifugating the solution to obtain cAMP; preparing cAMP triethylamine salt by cAMP, 0.4mol / L triethylamine and absolute pyridine according to a proportion, and preparing DBC through acidylation and hydrolyzation; preparing DBC sodium salt by the DBC, sodium chloride, absolute ether and absolute ethanol according to a proportion; and mixing the DBC sodium salt and different assistant agents according to a proportion to prepare DBC growth regulator for feed addition and hypodermic injection. Animal experiments prove that the DBC growth regulator for the feed addition and the hypodermic injection can be effectively absorbed by animals with good stability, can remarkably improve the growth performance of pigs, can improve carcass quality without residue in animal body, and has higher safety compared with other chemical drug additives.
Owner:YUNNAN AGRICULTURAL UNIVERSITY
Trichlopyr containing herbicide composition and application thereof
InactiveCN106962353ABroad herbicidal spectrumImprove efficiencyBiocideDead animal preservationHalosulfuron methylAdditive ingredient
The invention relates to the field of pesticides and particularly relates to a trichlopyr containing herbicide composition and application of the trichlopyr containing herbicide composition. The herbicide composition comprises the effective ingredients of a component A and a component B, the component A is trichlopyr, the component B is one or two of halosulfuron-methyl and mesotrione, and the mass ratio of the component A to the component B is (1-50):(1-75). The herbicide composition is low in resistance risk, low in prevention and control costs, wide in herbicide controlling spectrum, good in pesticide effect, good in persistent effect and fast-acting property, and low in environmental pollution. The trichlopyr containing herbicide composition has excellent effects of preventing regenerated dayflower, piemarker, field bindweed, field horsetail, endive and cyperus rotundus hard to remove in a sugarcane field and a corn field.
Owner:江西正邦作物保护股份有限公司
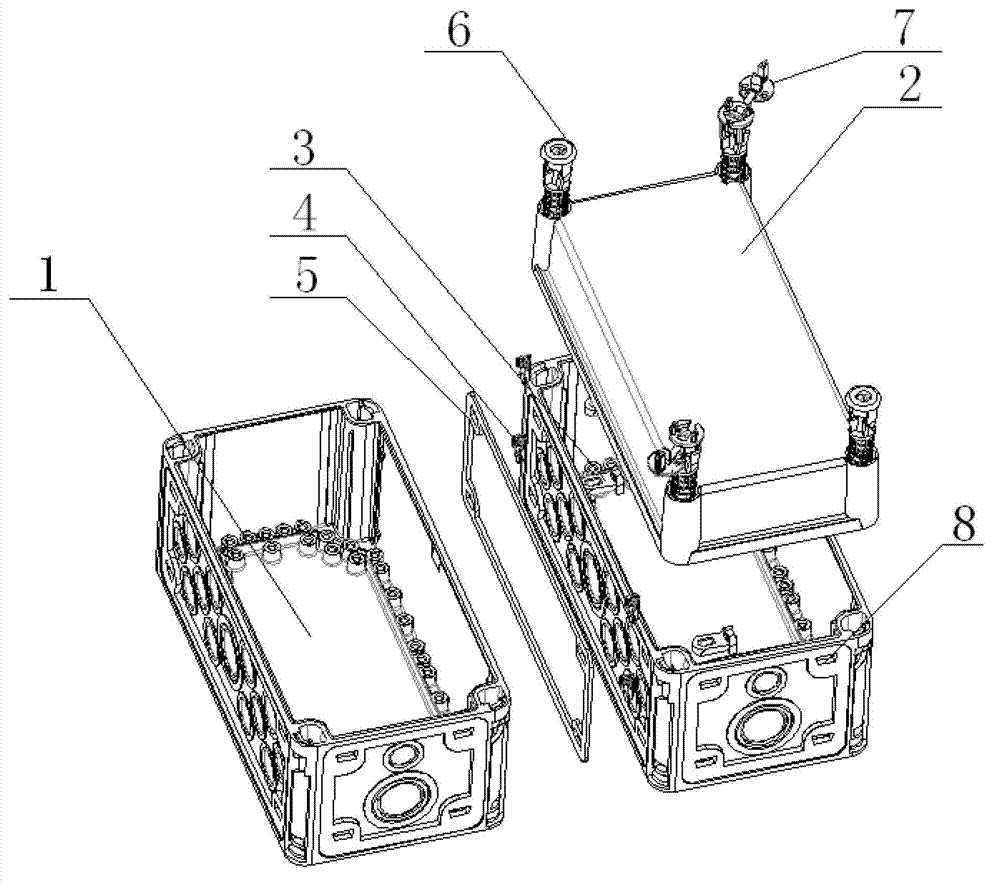
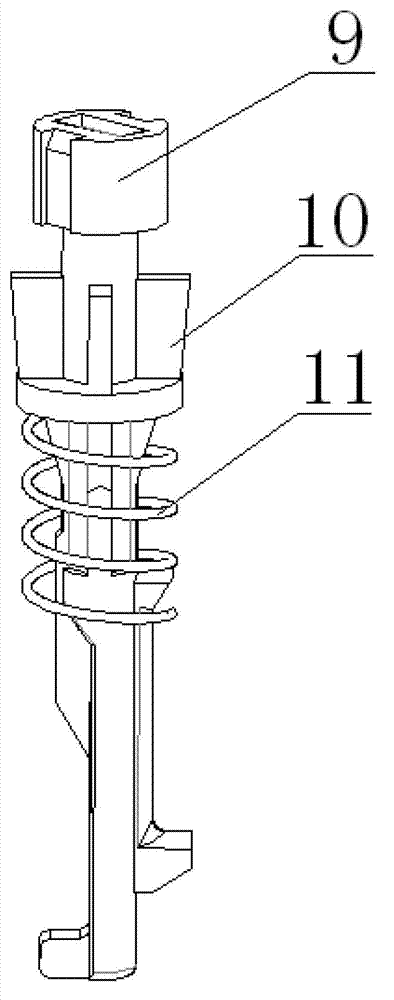
Connecting box
InactiveCN102882178AEasy to splitHigh securityCable junctionsEngineeringElectrical and Electronics engineering
Owner:JIANGSU JIANLONG ELECTRICAL
File Encryption and Decryption Method and System Based on Chaotic Transformation
InactiveCN103595523BIncrease the difficultyHigh securitySecuring communicationPlaintextComputer hardware
Provided is a file encryption method based on chaos transformation. The file encryption method comprises: (a1) preprocessing a password for encrypted content; (a2) extracting a group of plaintext data and generating the initial values of a group of vertificaiton codes; (a3) obtaining a second iteration coefficient and the number of second iteration times; (a4) executing secret key iteration and generating an iteration result according to the second iteration coefficient and the number of second iteration times; (a5) performing xor operation on the iteration result and the plaintext data; (a6) generating a verification code according to the plaintext data; (a7) writing the result of the xor operation in a file and generating a cryptograph; (a8) determining whether the secret key iteration is executed to the tail portion of the encrypted content, and executing a step (a9) if yes or continuously executing the step (a4) if not; (a9) the successive iteration result of the plaintext data and all the iteration results are converted into integers and the encryption key generated by the last next iteration is saved in the tail of the encrypted content.
Owner:SHANGHAI SIMCOM LTD
Grass lawn herbicide and its preparing method
The present invention relates to a lawn weedicide and its preparation method. The composition of said lawn weedicide includes (by wt%) 1-50% of alpha-bifluoropropanoic acid, 1-20% of fenchlorazole, 5-10% of synergistic agent and the rest is adjuvant. Its preparation method includes the following steps: synthesizing monofluoride, synthesizing bifluoride, dissolving three kinds of isomer compounds in acetylacetone, separating to obtain alpha-bifluroropropanoic acid solution, mixing alpha-bifluoropropanoic acid, fenchlorazole, bromoxynil and adjuvant, stirring them uniformly so as to obtain the invented weedicide.
Owner:张伟兴
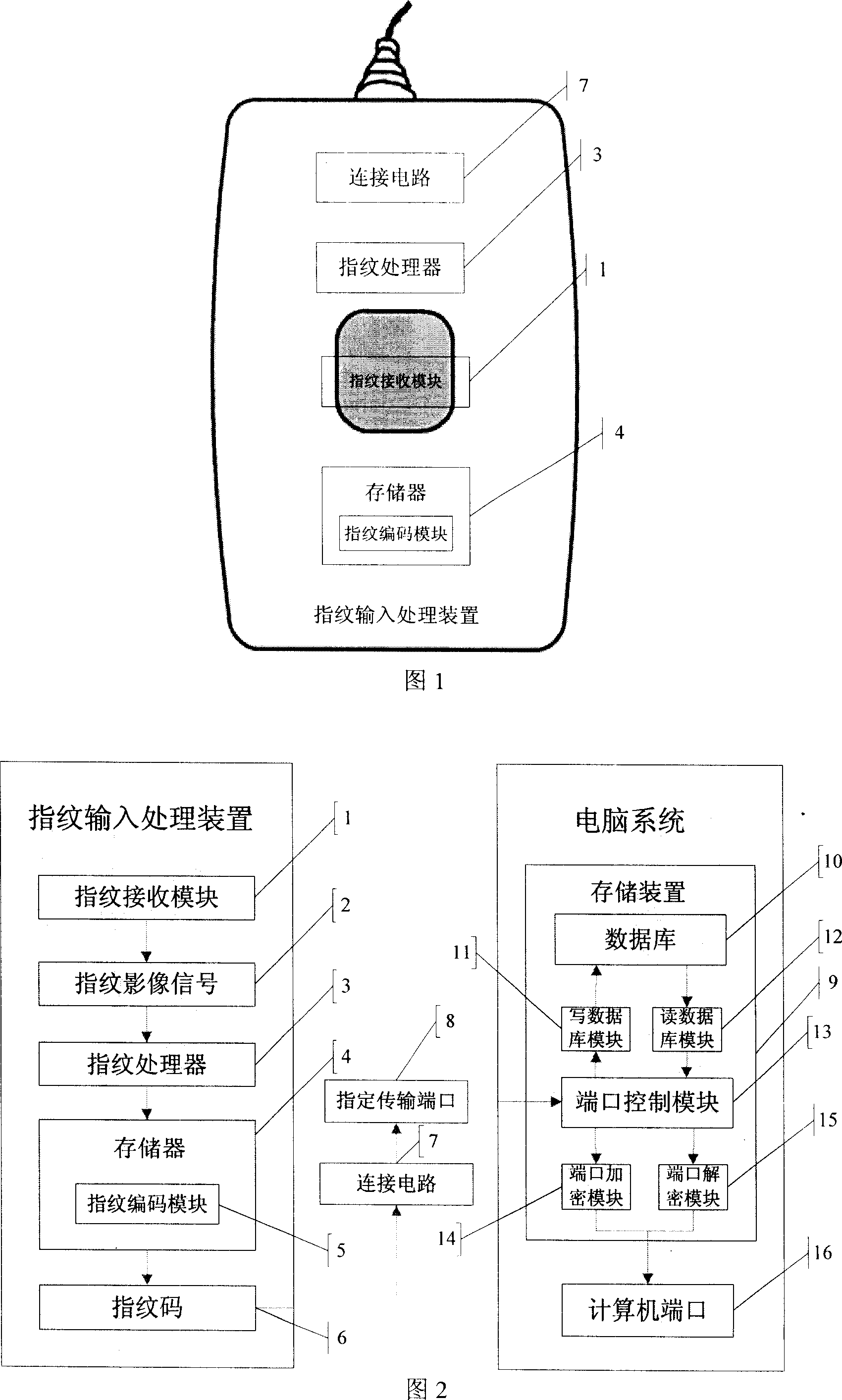
Finger-print type port encipherizing device
InactiveCN1936763APrevent leakageReduce the possibility of theftDigital data processing detailsComputer scienceEncryption
The invention is about an encryption device of fingerprint-port. It include: The treating device for the fingerprint input, which is used to input the fingerprint so as to output the fingerprint code, and the storage device. The treating device for the fingerprint input is connected to the storage device by assign the port for transmition, the following parts have been storaged in the storage device: The database used to storage the fingerprint code of the user. The control module of the port, it can be used to control the designate port and receive the fingerprint code of it and used to read and write the database and to encrypte or decrypte the port needed. This invention can not only avoid the leak of the database efficiently, but also retain the port not being encrypted, so as to meet the normal use of the legitimate users.
Owner:SHENZHEN TOPSTAR DIGITAL TECH
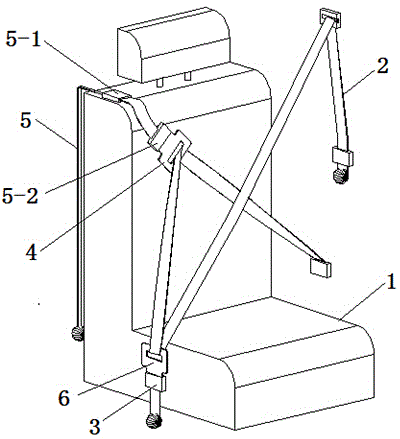
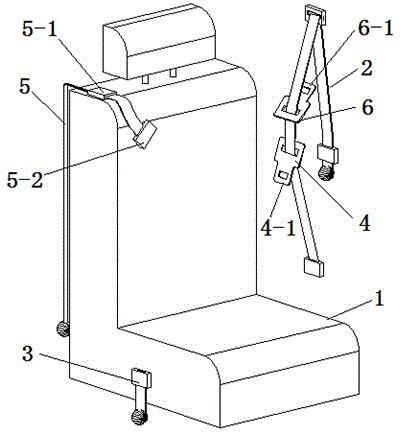
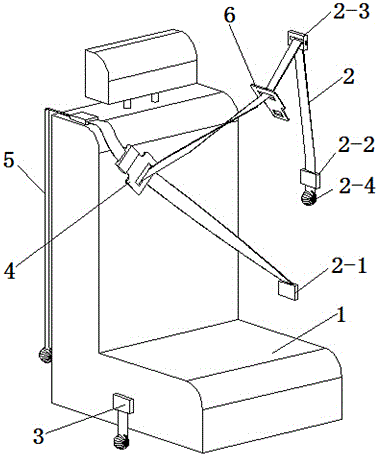
Four-point-type automobile safety belt and using method thereof
InactiveCN104554132AHigh securityUniform pressureBelt anchoring devicesAutomobile safetySafety harness
The invention relates to a four-point-type automobile safety belt and a using method thereof. The four-point-type automobile safety belt comprises a first safety belt, a first socket and a first plug, and also comprises a second safety belt and a second plug. During use, a driver sits on the automobile seat, a plugging head I of the first plug on the first safety belt is inserted into a second socket in a second safety belt retractor I, and a plugging head II of the second plug is inserted into the first socket, so that the first safety belt forms an X-shaped cross structure in front of the chest of the automobile driver. The four-point-type automobile safety belt disclosed by the invention has the beneficial effects that when an automobile suffers from front impact or rolls or meets with impact from the side surface, the shoulders of the automobile driver can be fixed by the safety belt, so that the body displacement of the driver is effectively avoided, an undue casualty accident caused by the body displacement of the driver is avoided, and the safety guarantee of passengers is greatly improved.
Owner:SUZHOU JISU SAFETY TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com