Finger-print type port encipherizing device
An encryption device and port technology, applied in the direction of instruments, electrical digital data processing, digital data processing components, etc., can solve problems such as inconvenient use of computers, easy passwords to be stolen, and enterprise losses, etc., to reduce the risk of data theft Possibility, prevention of data leakage, and the effect of satisfying normal use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] Hereinafter, the present invention will be further described with reference to the accompanying drawings and the embodiments.
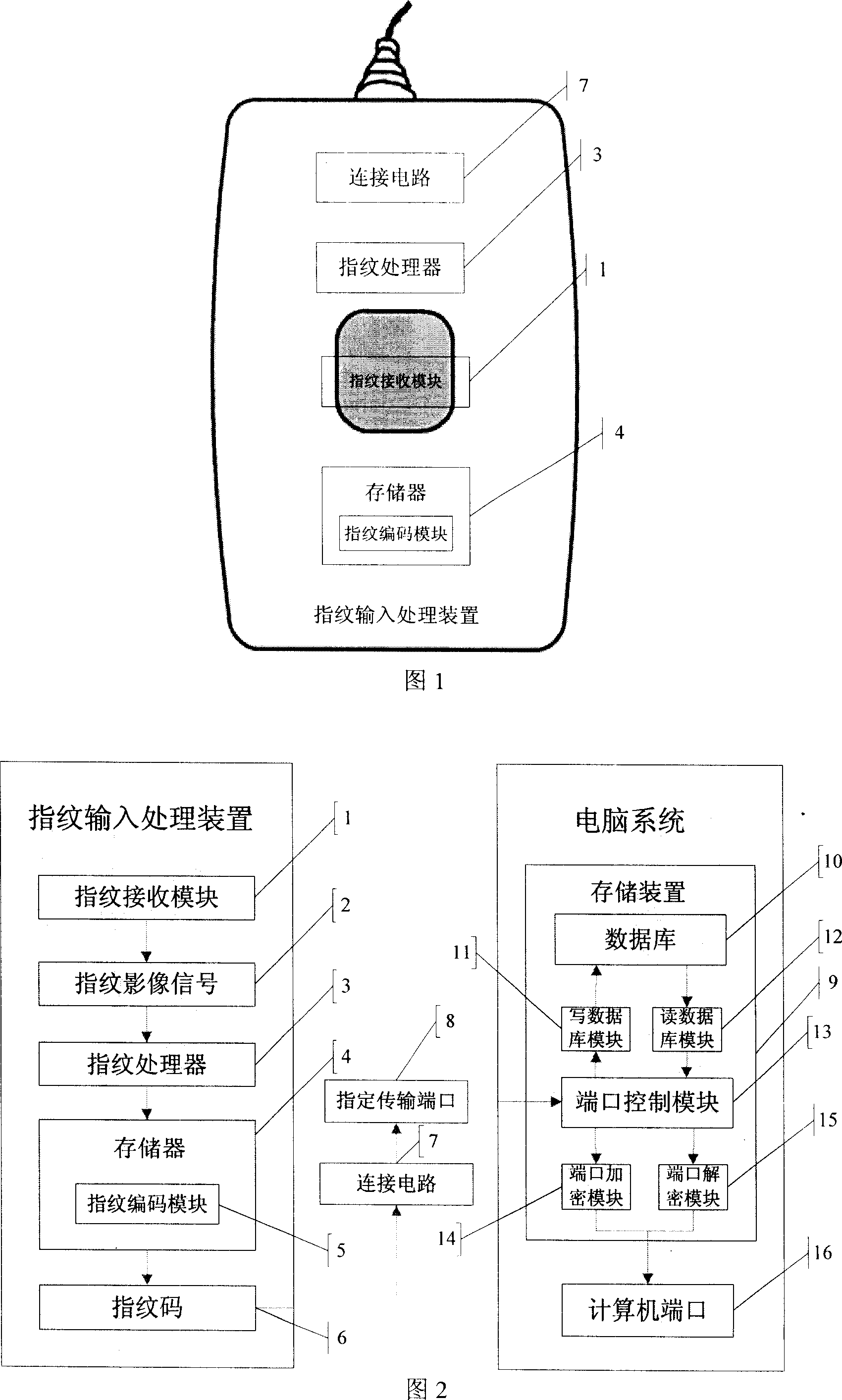
[0016] Please refer to FIGS. 1 and 2 together. The fingerprint-type port encryption device of the present invention includes a fingerprint input processing device, which is connected to a computer system, and includes a connection circuit 7, a fingerprint processor 3, a fingerprint receiving module 1 and a memory 4. The connection circuit 4 is used to connect the fingerprint input processing device to the computer system. The fingerprint receiving module 1 is used to receive a user's fingerprint to generate a fingerprint image signal 2. The memory 4 stores a fingerprint encoding module 5. The fingerprint processor 3 is used to execute the fingerprint encoding module 5 stored in the memory 3 to encode the fingerprint image signal 2 into the fingerprint code 6. The fingerprint code 6 can be transmitted to the designated transmission port 8 in the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com