Patents
Literature
134results about How to "Reduce the possibility of theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
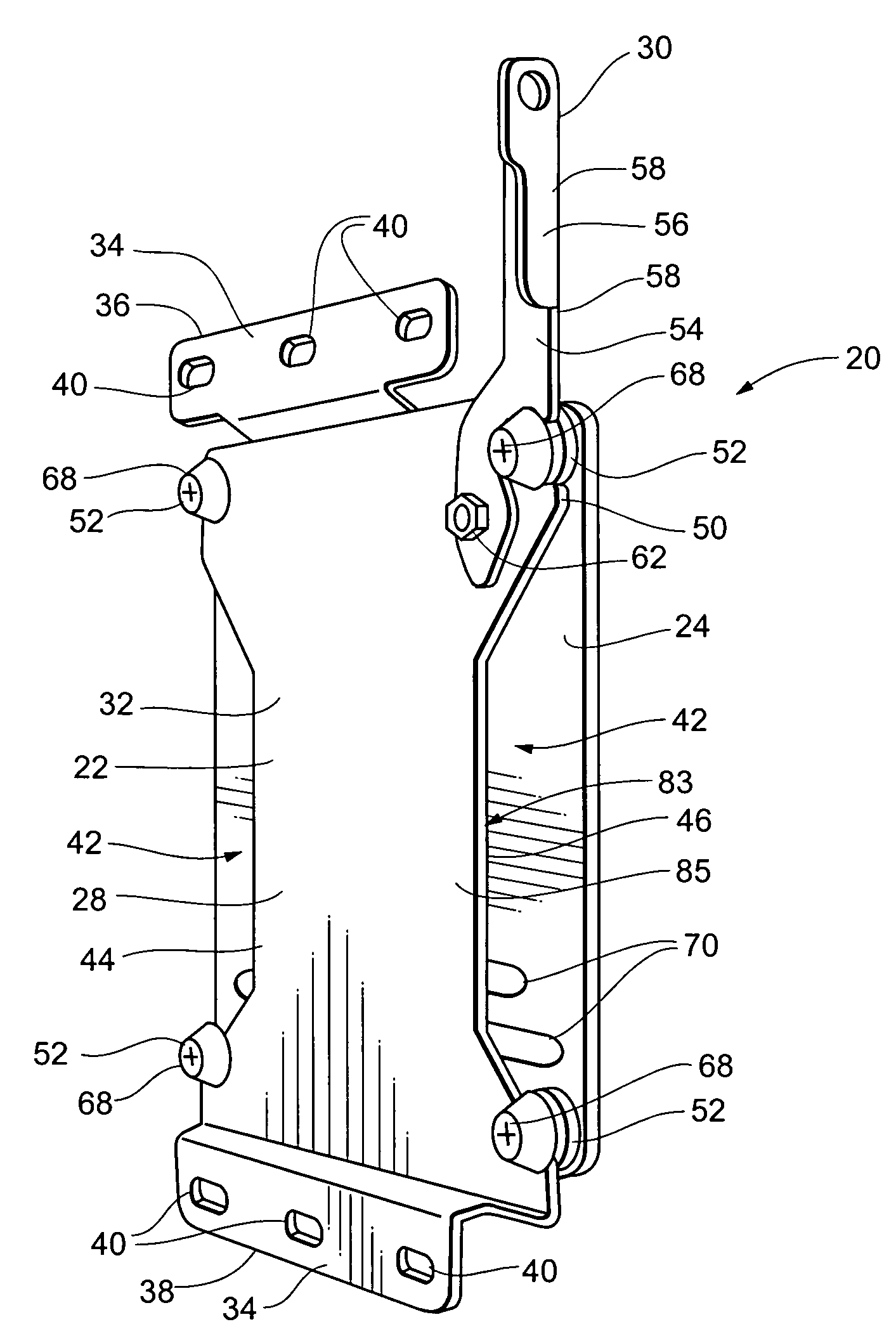
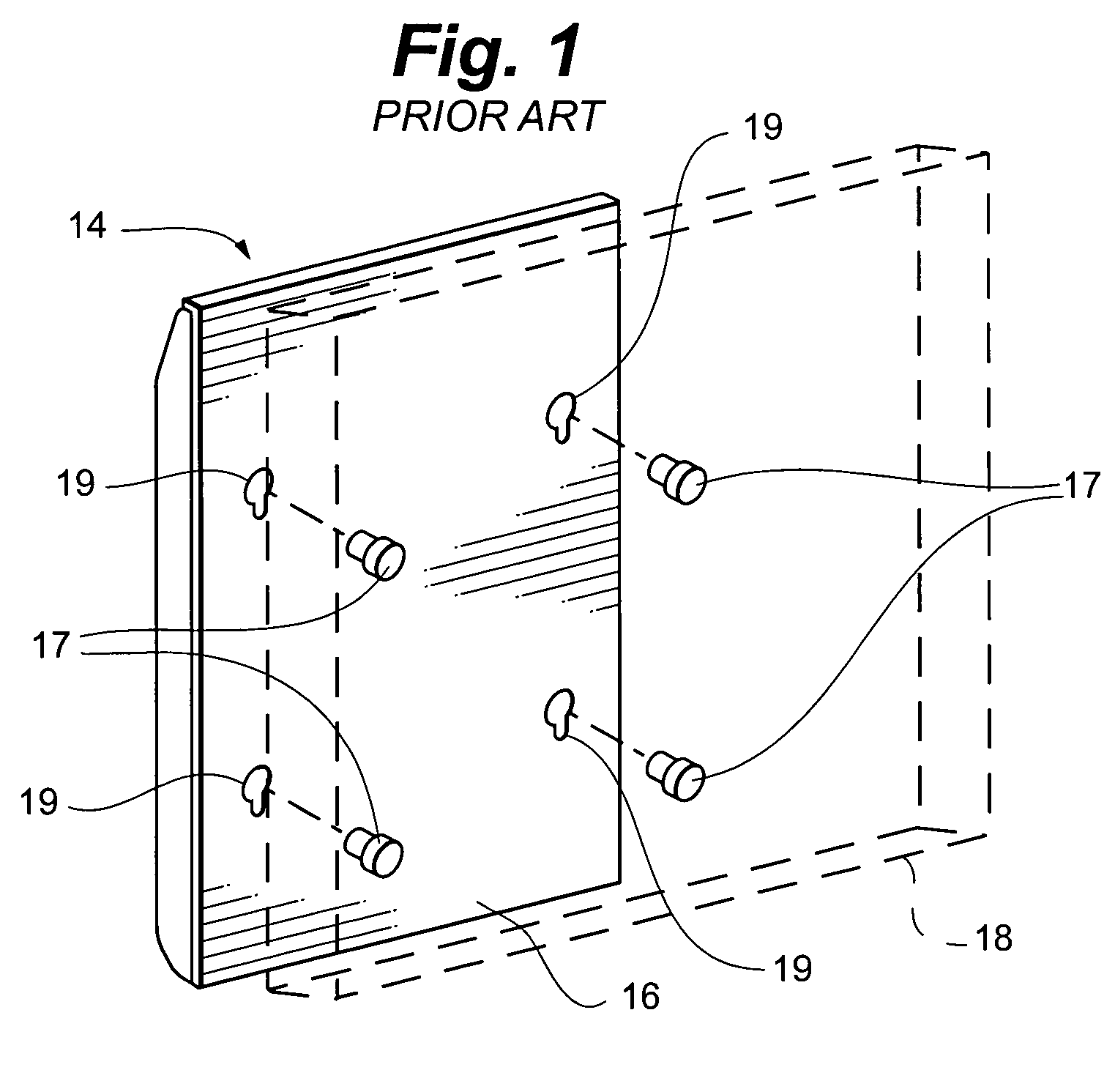
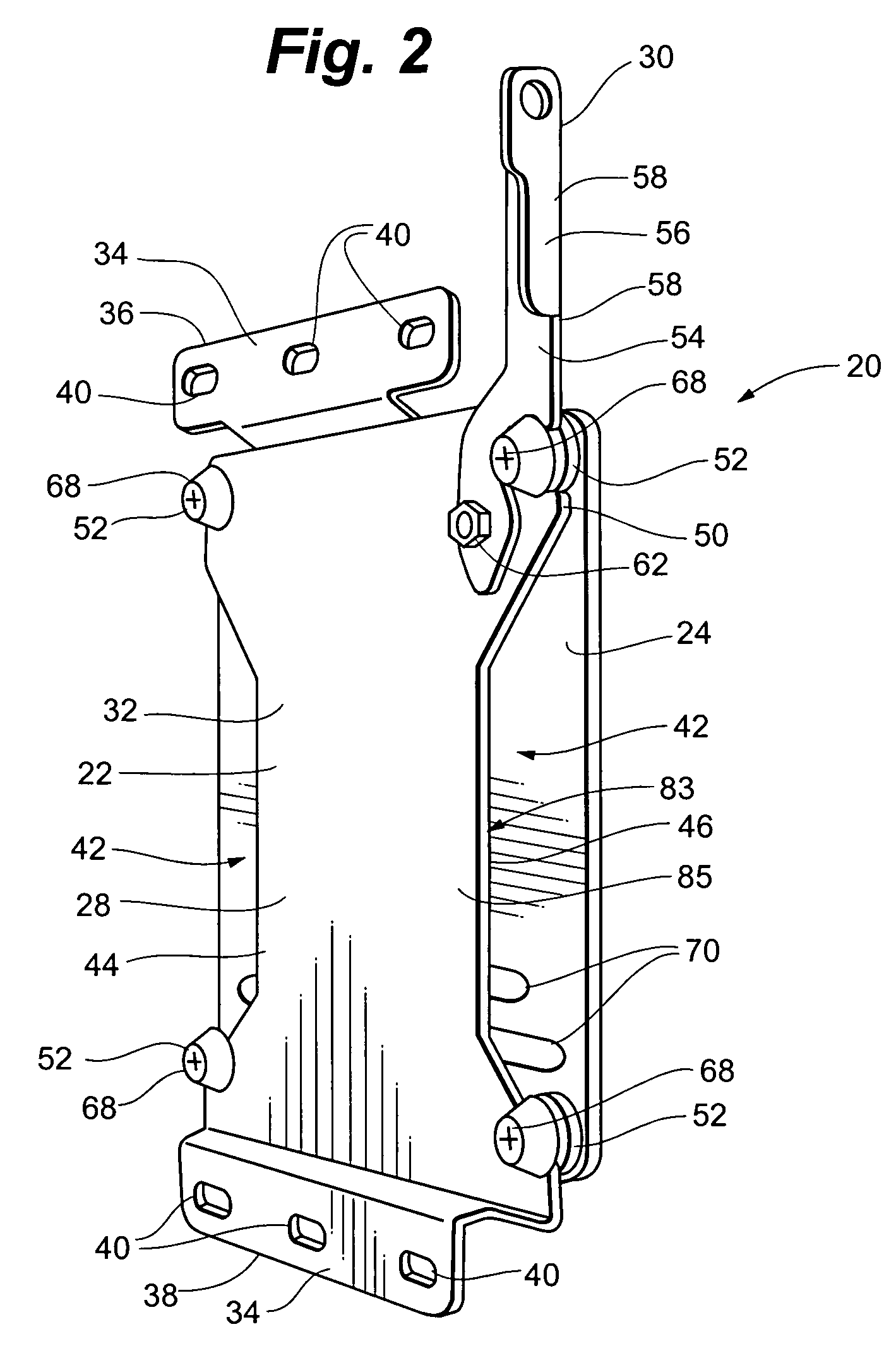
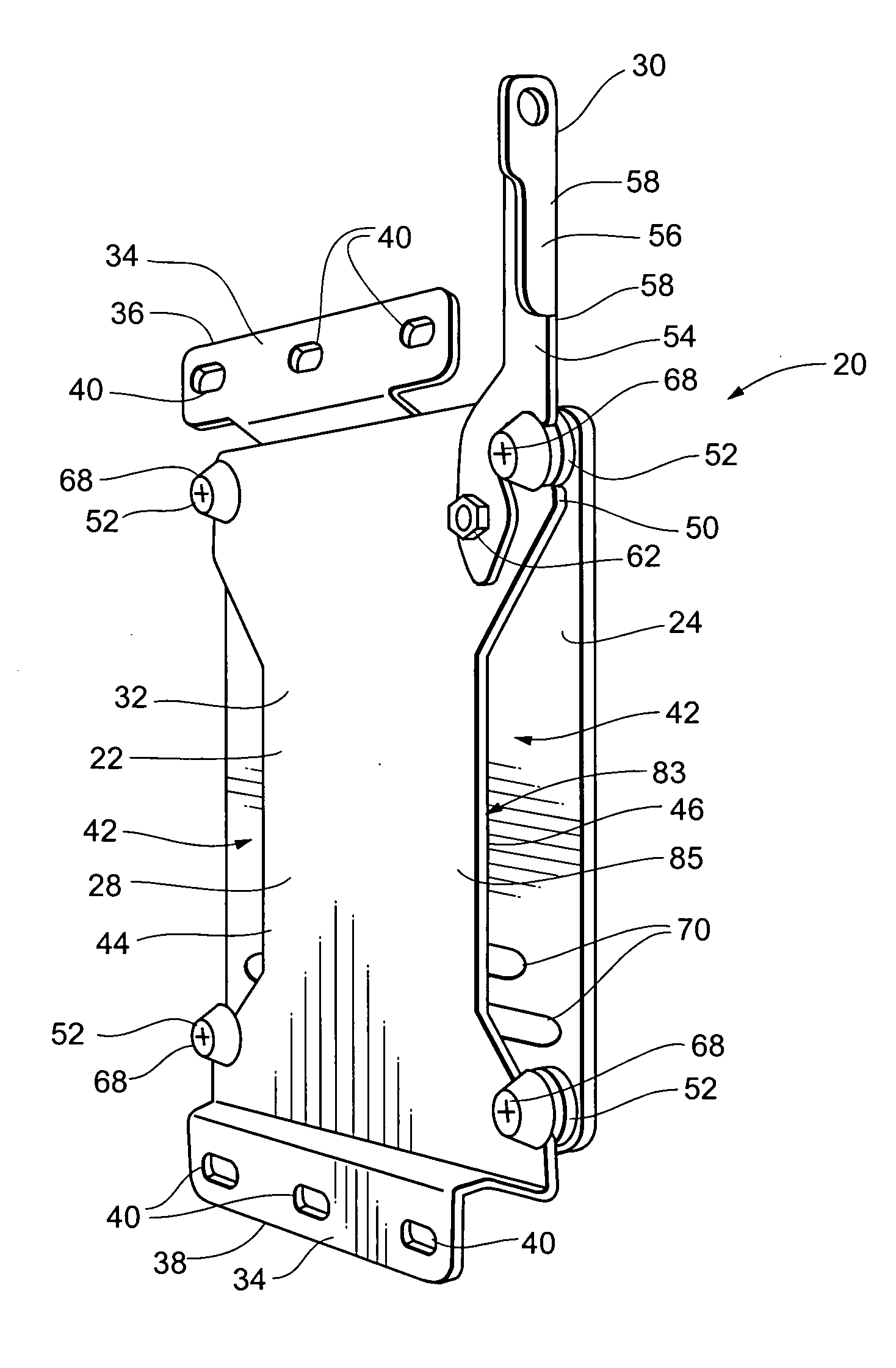
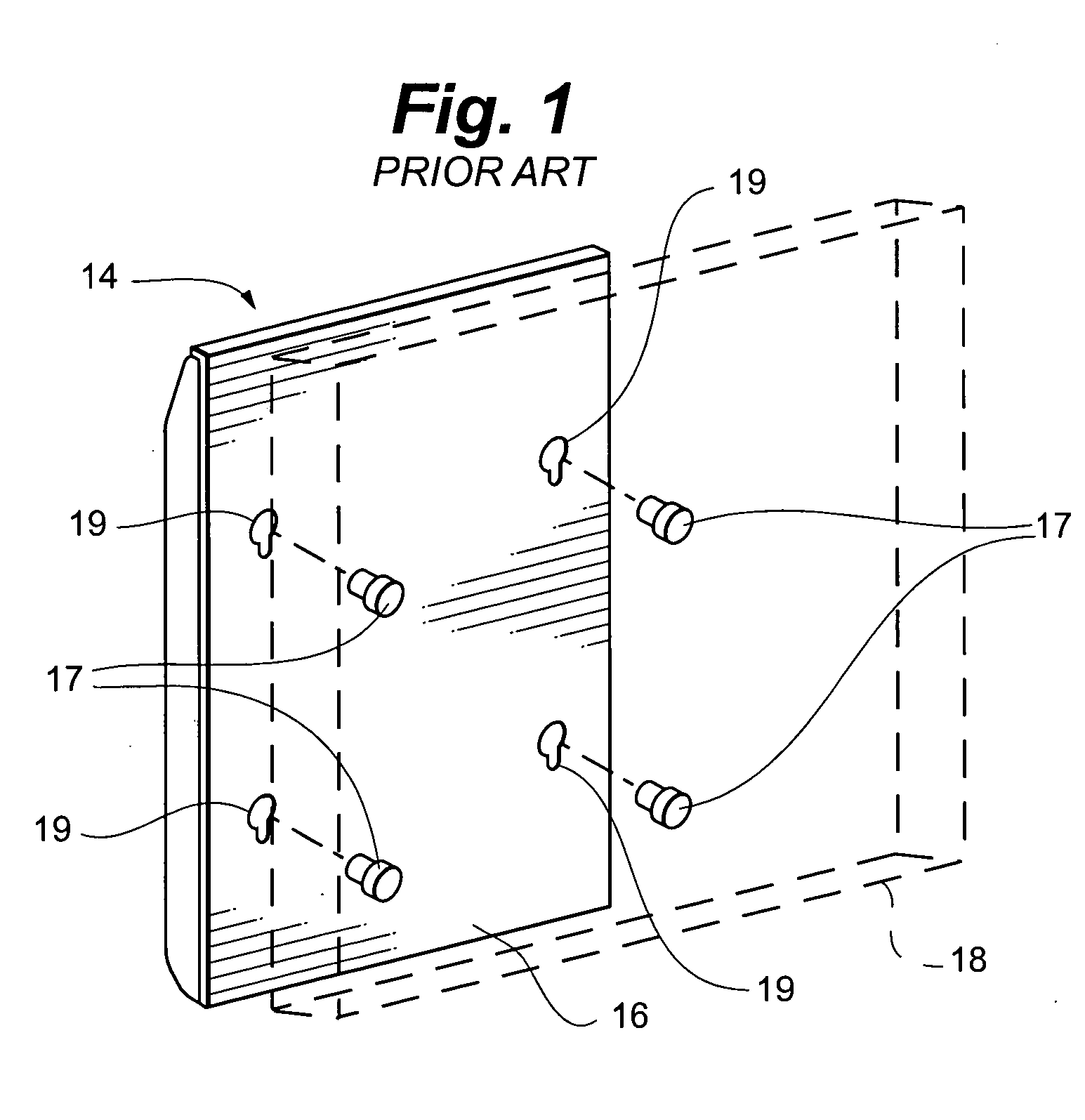
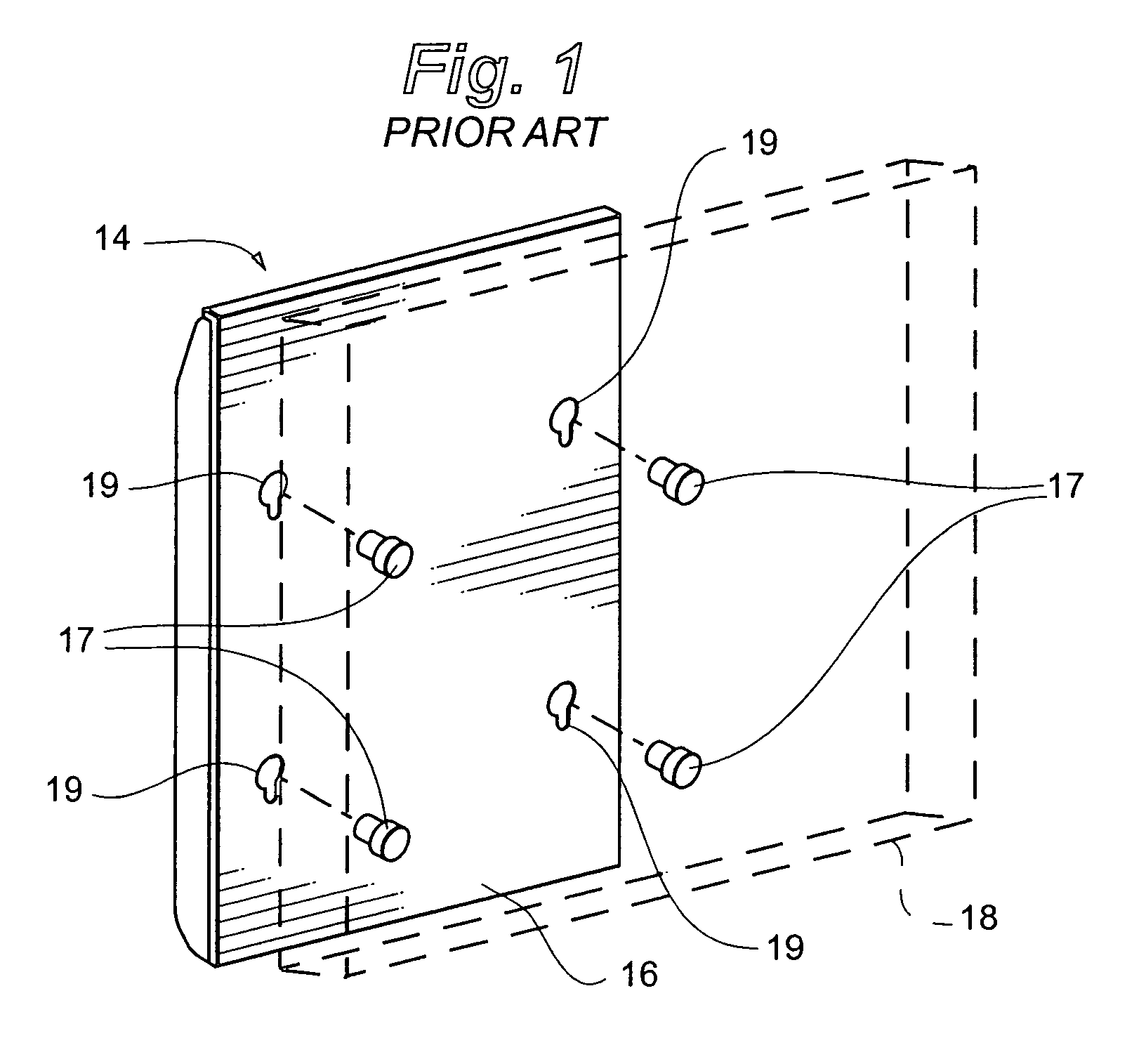
Display mounting device
ActiveUS7175152B2Quick installationEasy to repositionCandle holdersLighting support devicesDisplay deviceEngineering
A flat panel display mounting apparatus that enables quick and easy mounting and dismounting of the flat panel display. The system includes a first bracket having a periphery defining a plurality of spaced apart notches and a second bracket selectively removably receivable on the first bracket that includes a plurality of fastening buttons, each fastening button defining a slot. The fastening buttons are spaced apart and positioned correspondingly with the notches of the first bracket so that the slot of each fastening button receives the periphery of the first bracket at a separate one of the notches when the second bracket is received on the first bracket.
Owner:LEGRAND AV INC
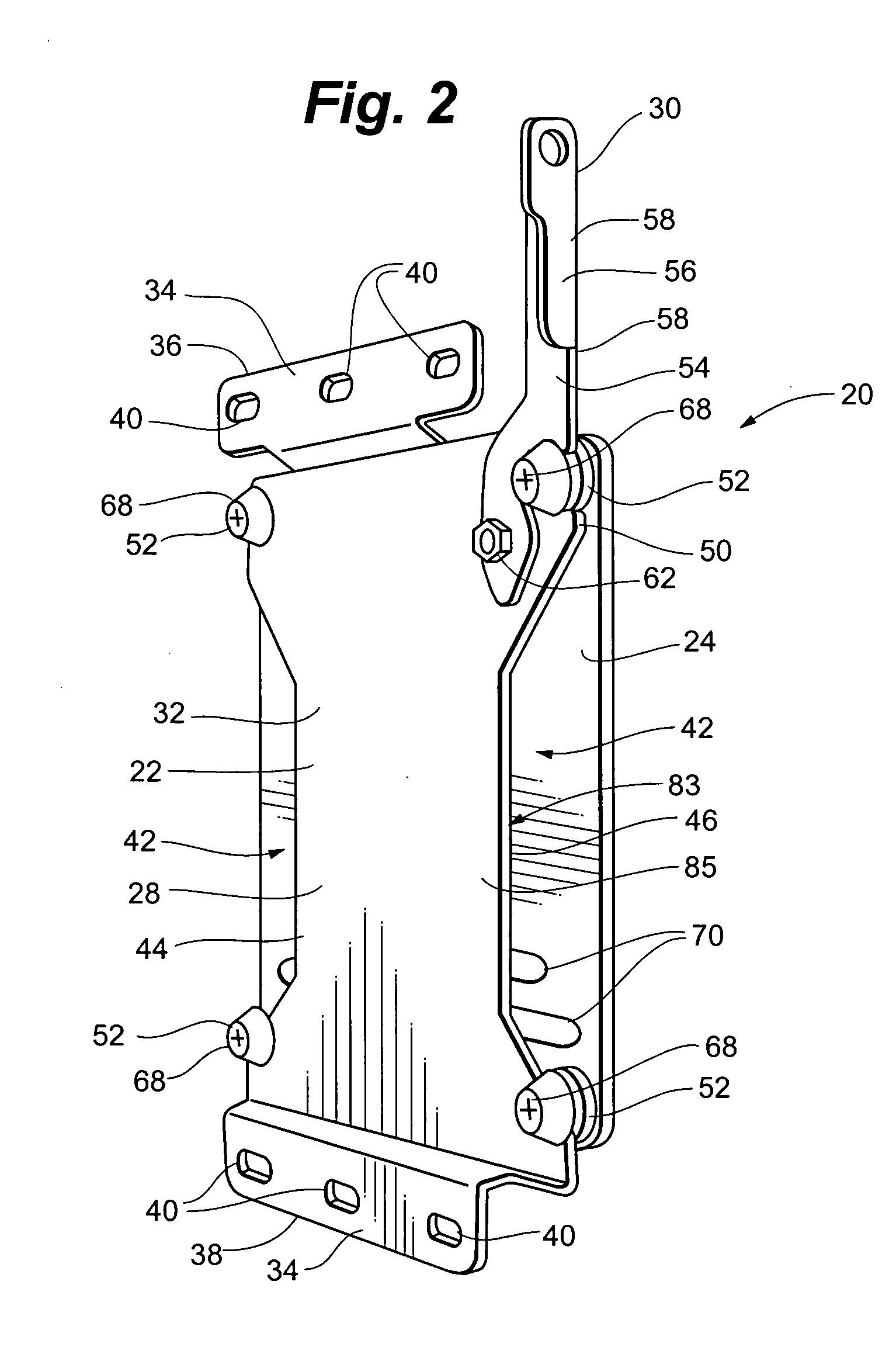
Display mounting device
ActiveUS20050127260A1Quick and easyReduce likelihood of theftCandle holdersLighting support devicesFlat panel displayEngineering
A flat panel display mounting apparatus that enables quick and easy mounting and dismounting of the flat panel display. The system includes a first bracket having a periphery defining a plurality of spaced apart notches and a second bracket selectively removably receivable on the first bracket that includes a plurality of fastening buttons, each fastening button defining a slot. The fastening buttons are spaced apart and positioned correspondingly with the notches of the first bracket so that the slot of each fastening button receives the periphery of the first bracket at a separate one of the notches when the second bracket is received on the first bracket.
Owner:LEGRAND AV INC
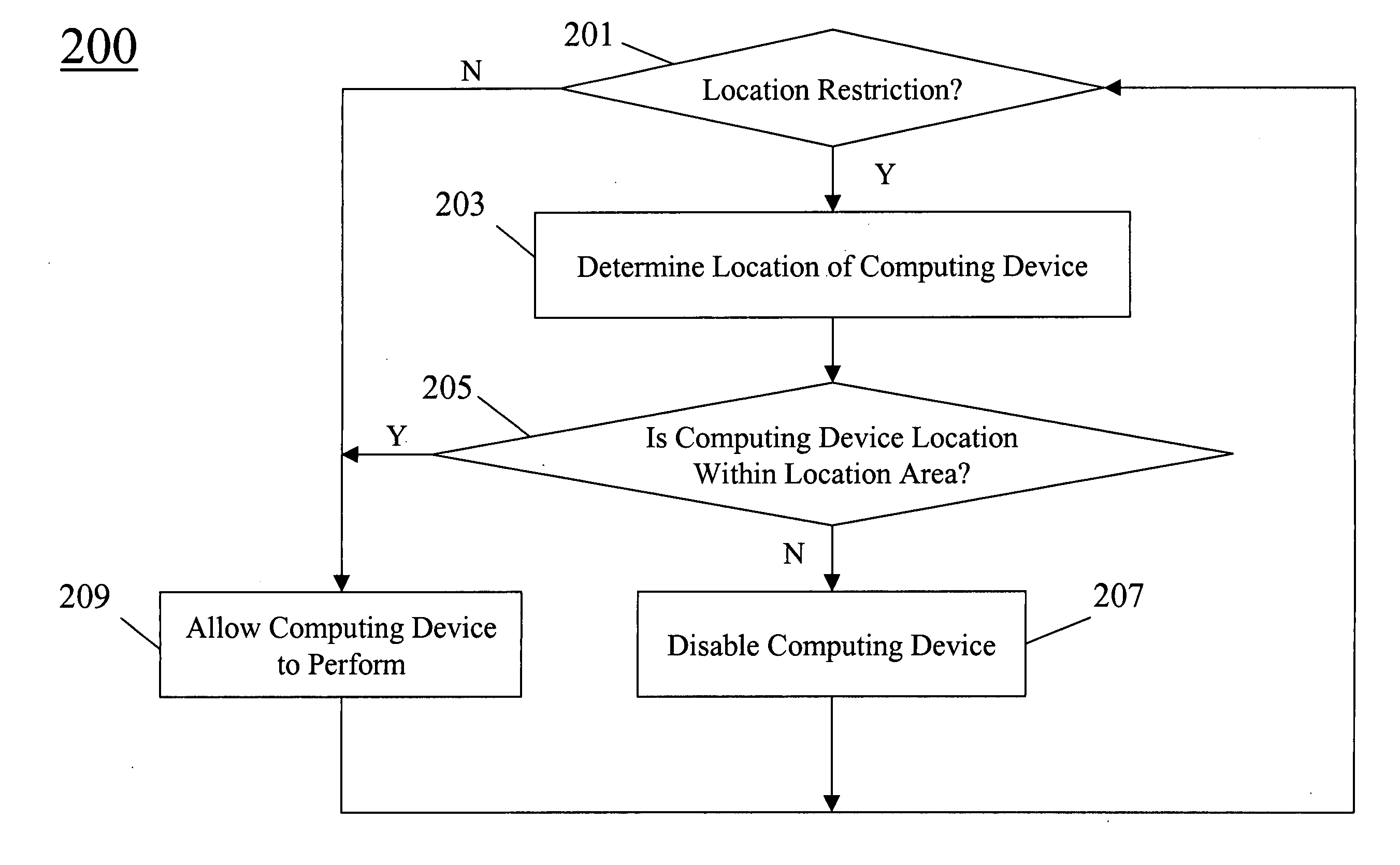
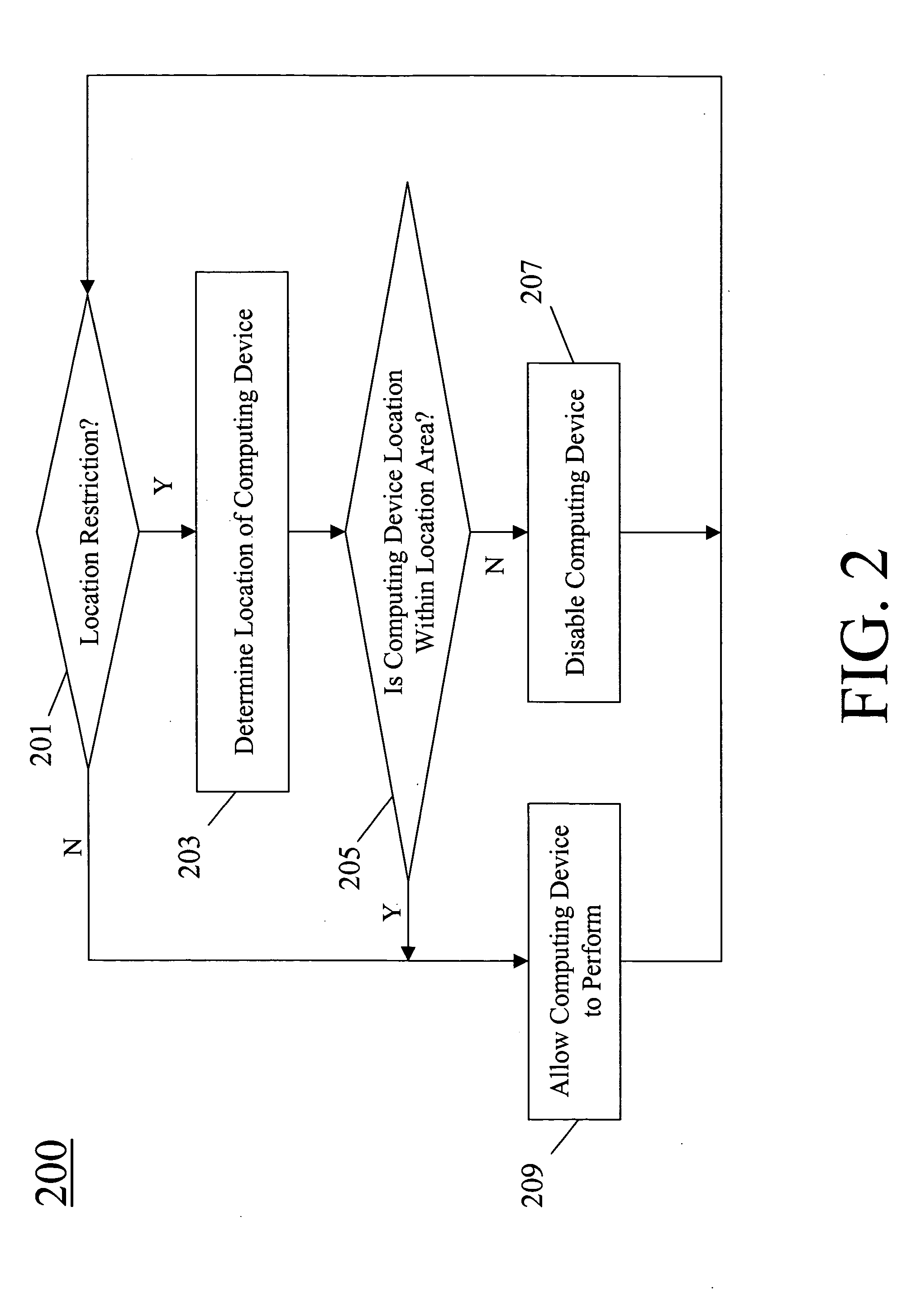
Method for disabling a computing device based on the location of the computing device
InactiveUS20060075487A1Reduce the possibility of theftReduce impactDigital data processing detailsUnauthorized memory use protectionBIOSGlobal Positioning System
The present invention provides a method for disabling a computing device based on the location of the computing device. The computing device, such as a computer or the like, determines if there is a location restriction for the computing device. This can be accomplished by checking the BIOS of the computing device, and is preferably accomplished during the powering up of the computing device. If so, the computing device determines its location. This can be accomplished utilizing a Global Positioning System (GPS). The computing device is disabled if there is a location restriction for the computing device for the current location of the computing device.
Owner:LUCENT TECH INC
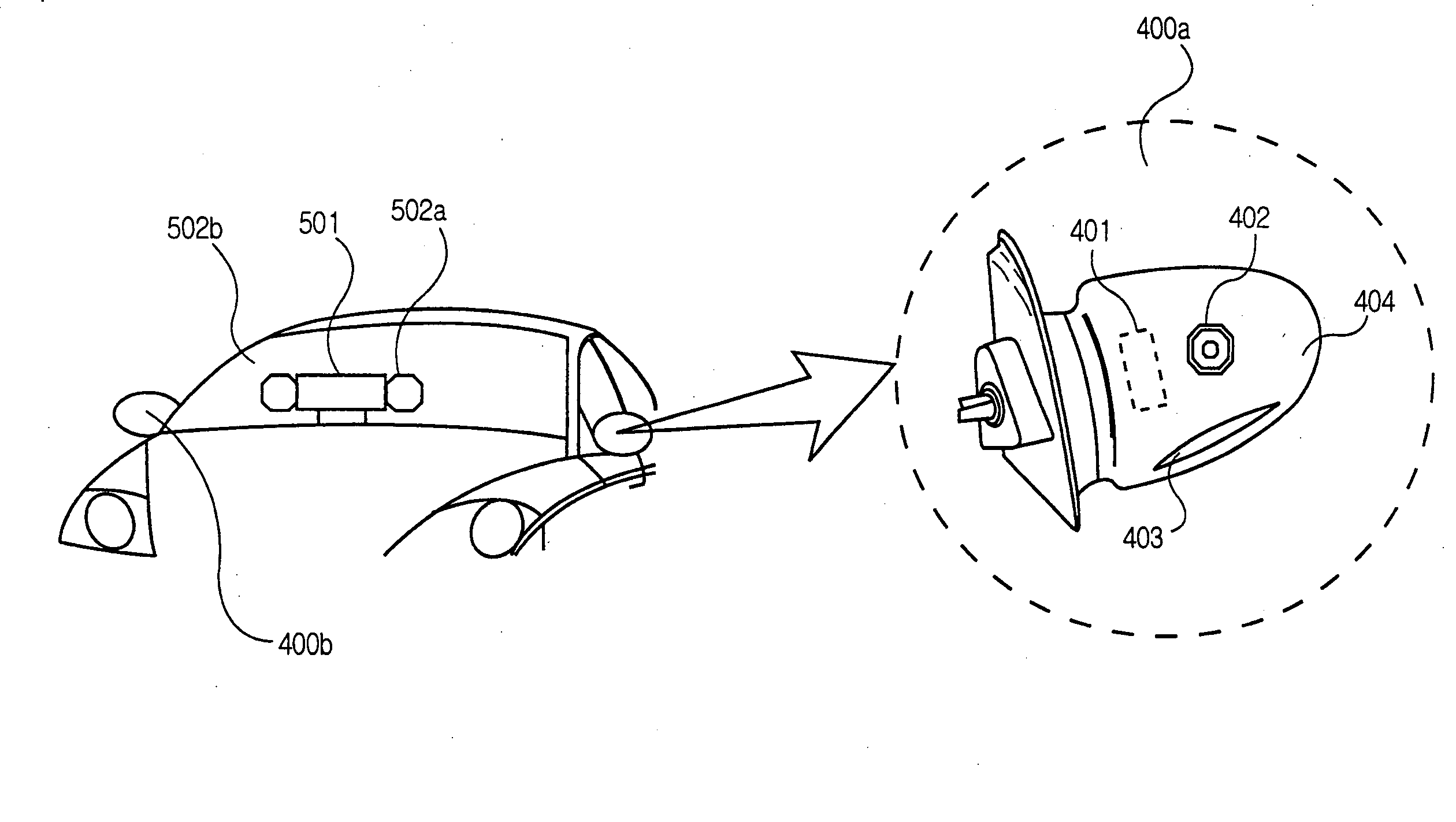
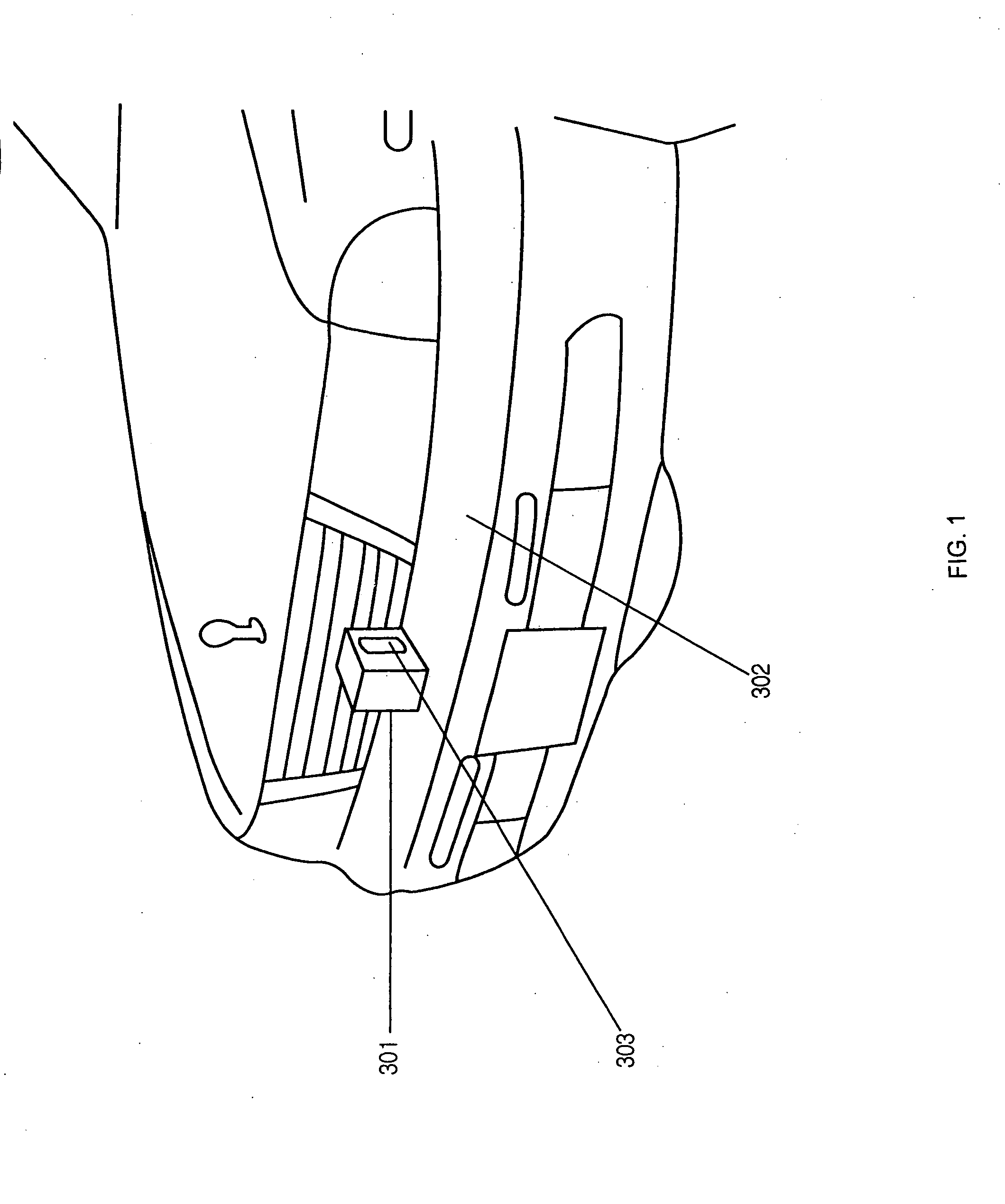
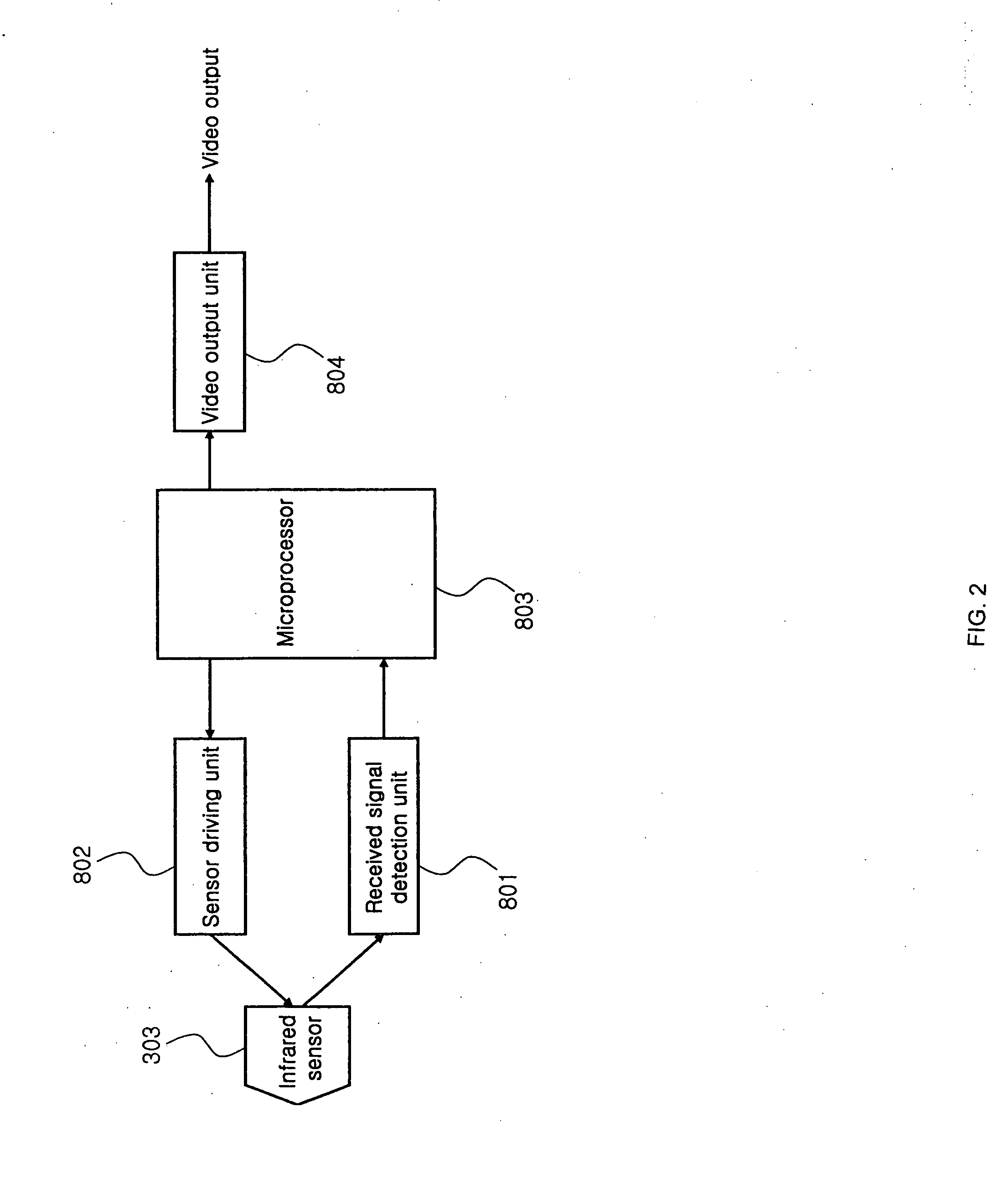
Car side mirror equipped with thermal infrared camera
InactiveUS20080203308A1Easily installedReduce expensesRadiation pyrometryPhotometryImage sensorElectronic circuit
Disclosed herein is a car side mirror equipped with a thermal infrared camera. The car side mirror includes a thermal infrared camera device, a video signal transmission device, a power unit. Associated with the side mirror device is a display device inside the car. The thermal infrared camera device includes a thermal image sensor for receiving infrared signals, an electronic circuit for determining whether an obstacle exists in front of a car, and containing an individual Identification (ID), and a video output unit for converting output signals into video signals. The thermal infrared camera device photographs one or more objects in a desired direction. The video signal transmission device transmits the video signals to a display device. The power unit supplies power to the thermal infrared camera device and the video signal transmission device. The display device identifies the individual ID of the thermal infrared camera and then receives the video signals.
Owner:HANVISION
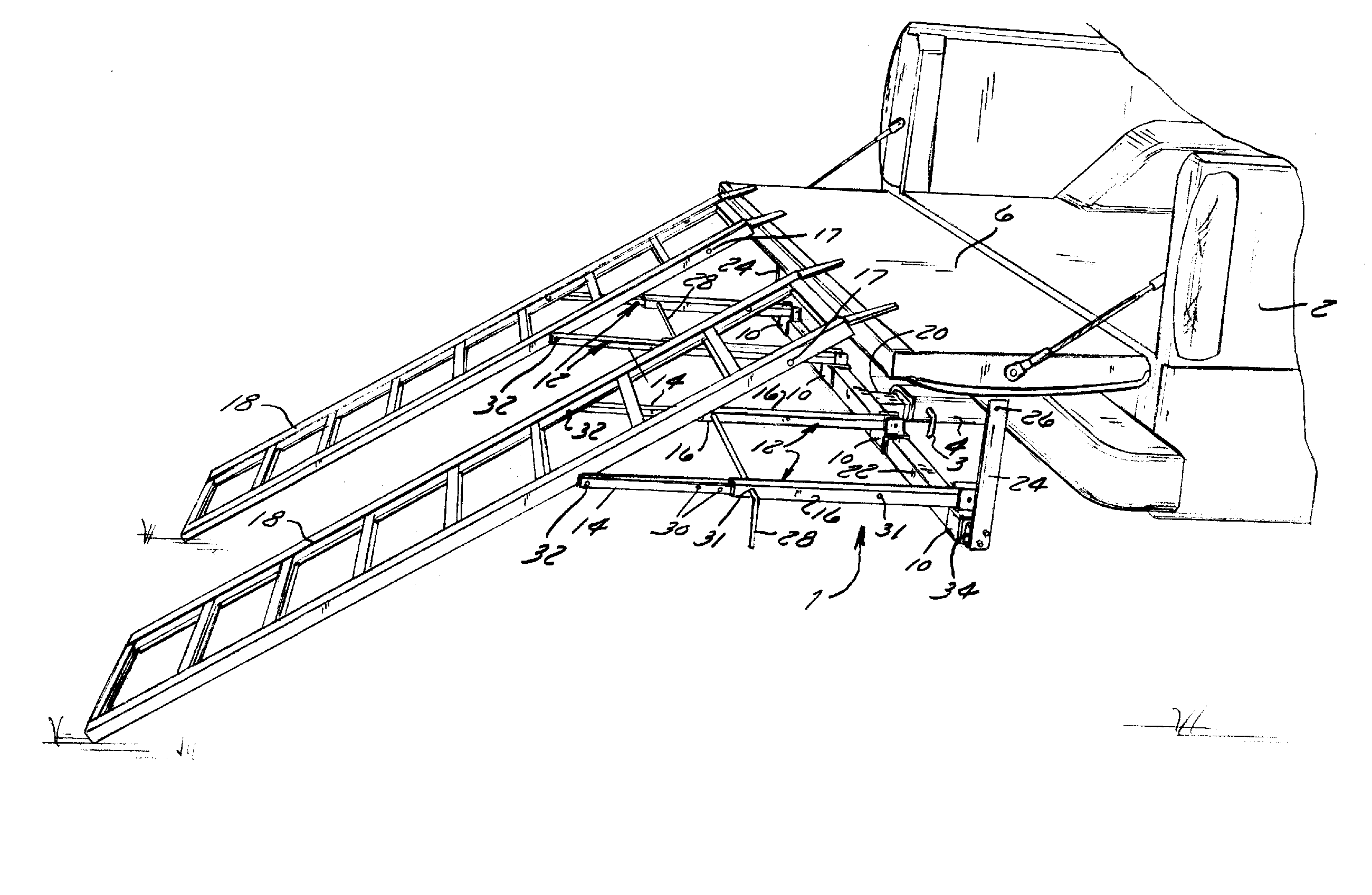
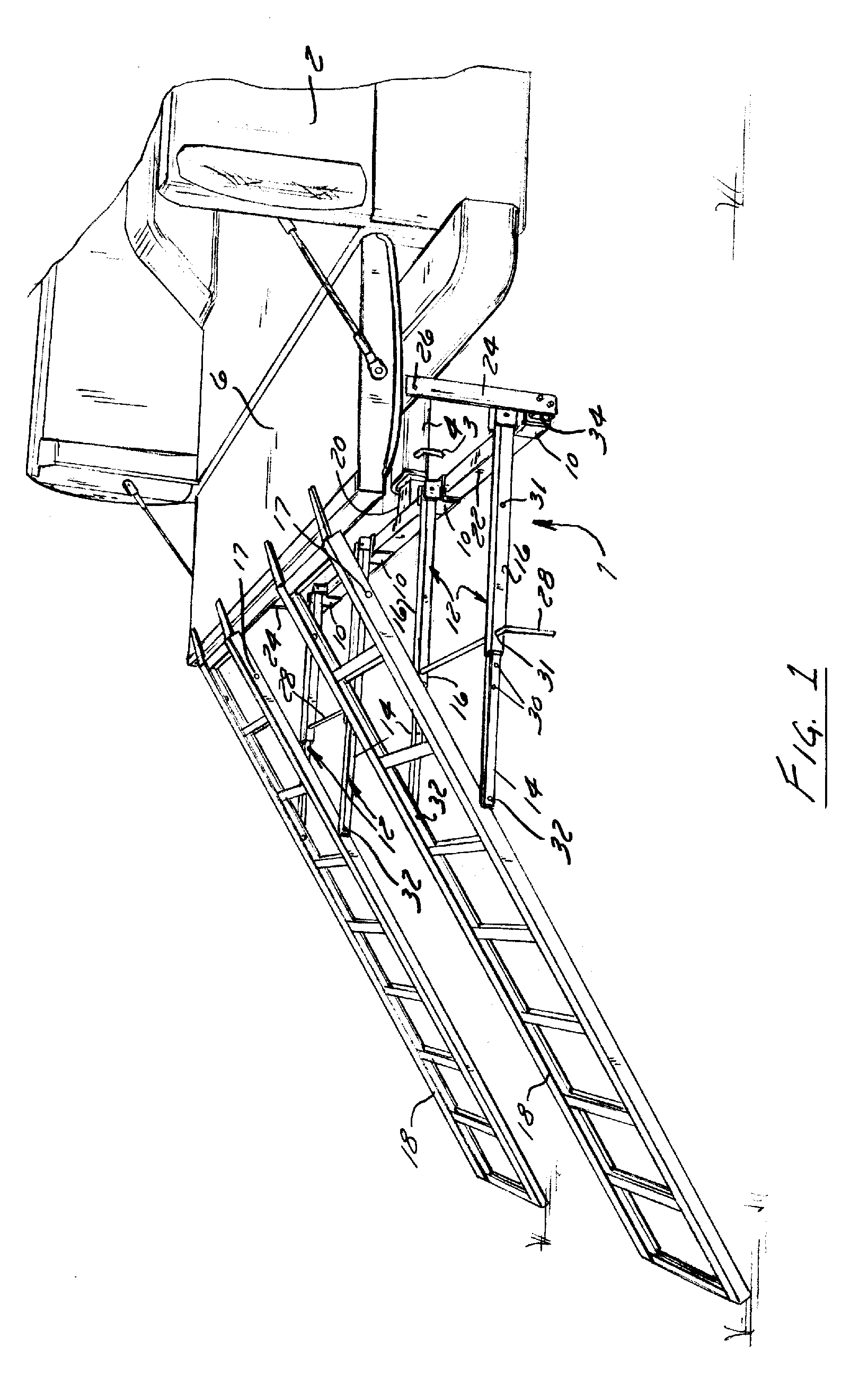
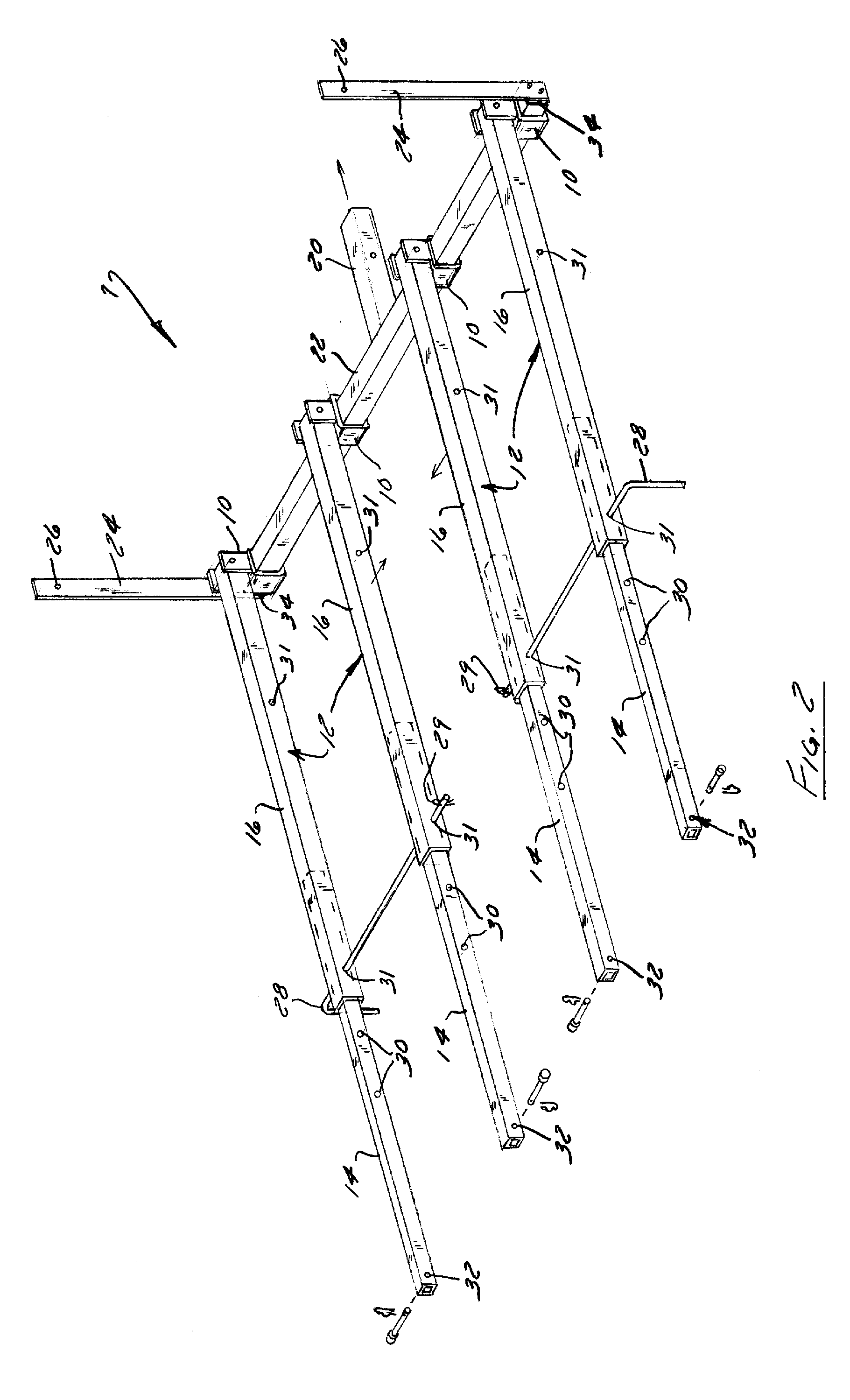
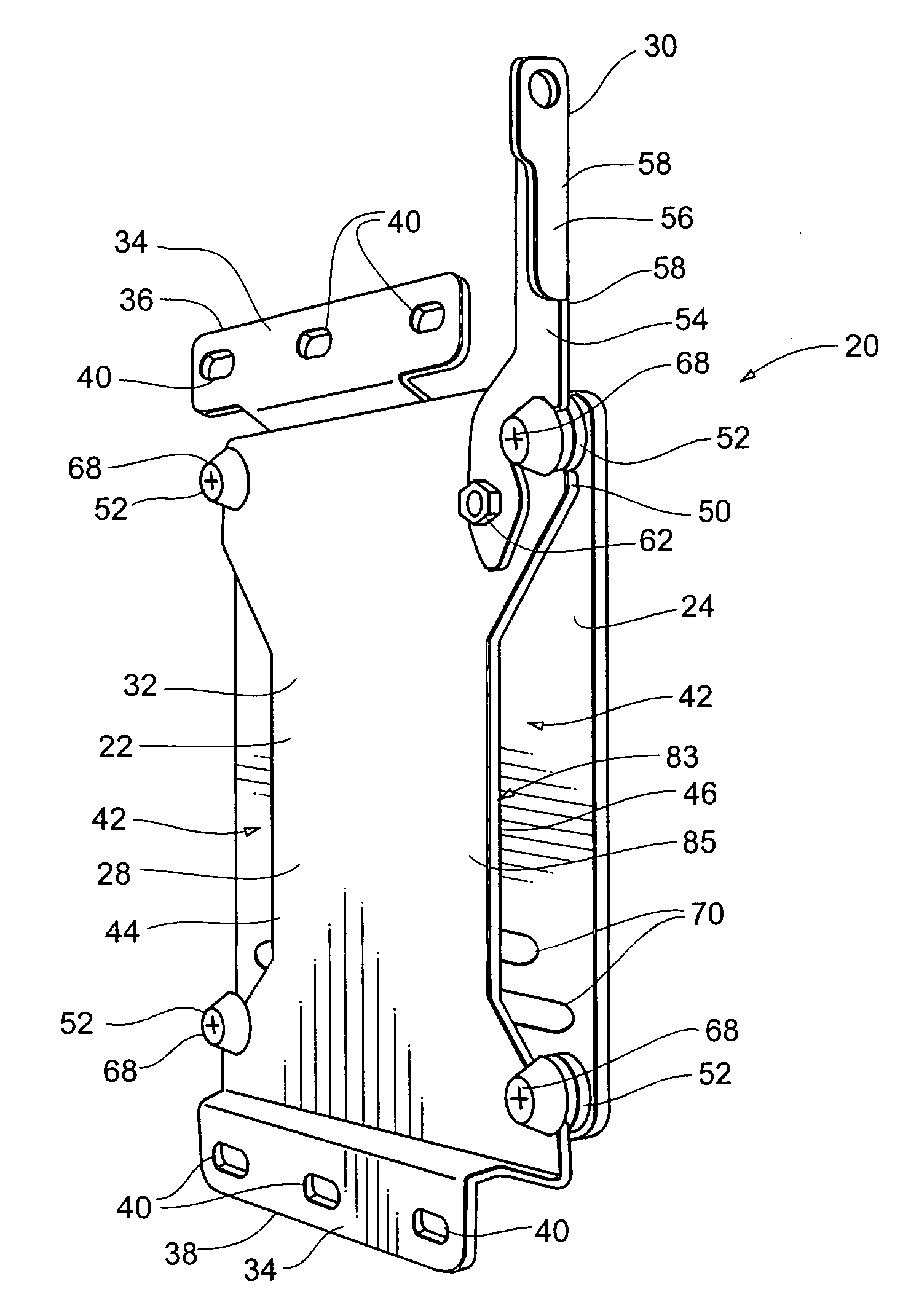
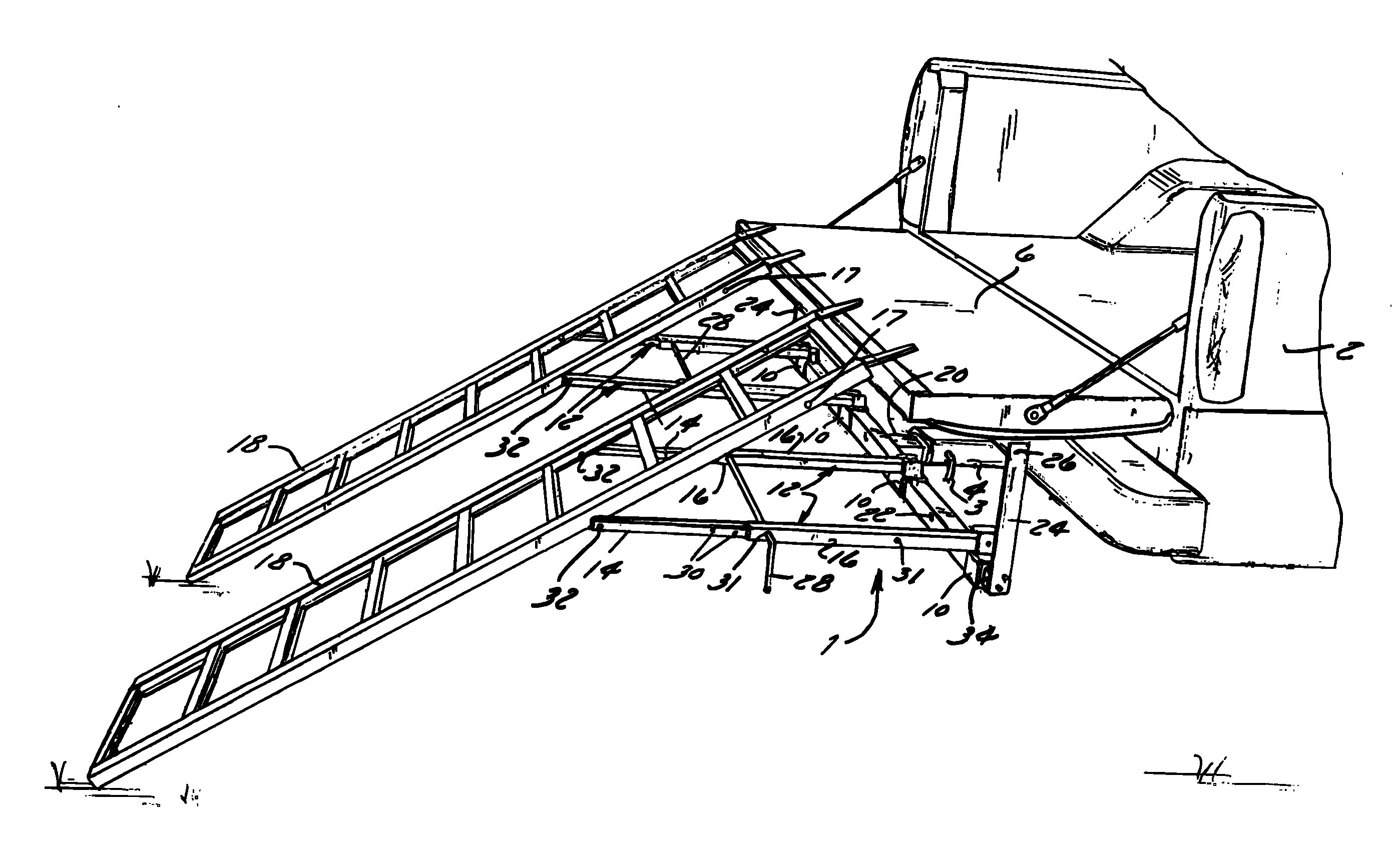
Apparatus and Method for Loading and Unloading Cargo
InactiveUS20060133915A1Unloading safetyStable positionRefuse receptaclesOther load carrying vehiclesMechanical engineering
An apparatus and method for securing a ramp to a cargo carrier having a receiver hitch and a loading surface are disclosed. The apparatus comprises an engaging member configured to engage the receiver hitch of the cargo carrier; a cross support attached to the engaging member, wherein the cross support has a plurality of mounting brackets mounted thereto; at least two locking members attached to opposite ends of the cross support and extend vertically therefrom, wherein each locking member has an aperture configured to slideably receive a ramp locking pin; and a plurality of telescopic arms attached to the mounting brackets, wherein each telescopic arm has an inner portion and an outer portion, wherein the outer portion and inner portion have at least one set of apertures for slideably receiving a ramp locking pin, wherein the inner portion is configured to attach to at least one ramp.
Owner:DAY JOHN P
Display mounting device
ActiveUS20070120030A1Quick installationEasy to repositionCandle holdersLighting support devicesDisplay deviceFlat panel display
A flat panel display mounting apparatus that enables quick and easy mounting and dismounting of the flat panel display. The system includes a first bracket having a periphery defining a plurality of spaced apart notches and a second bracket selectively removably receivable on the first bracket that includes a plurality of fastening buttons, each fastening button defining a slot. The fastening buttons are spaced apart and positioned correspondingly with the notches of the first bracket so that the slot of each fastening button receives the periphery of the first bracket at a separate one of the notches when the second bracket is received on the first bracket.
Owner:LEGRAND AV INC
Method and system for identifying service block
InactiveCN1946024AImprove experienceSimplify authentication operationsUser identity/authority verificationUser equipmentAuthentication information
This invention provides a method and a system for service packet authentication including storing packet information and authentication labels of users, who send access service requests and the authentication labels are checked after the requests are received, if they have passed the authentication, the service data are sent down and charged, otherwise, the authentication information of the user is got to ask a content provider to authenticate it, then said service data are sent down and charged and the label is set to be authenticated. This invention also provides a system for service packet authentication including UE and access devices.
Owner:HUAWEI TECH CO LTD
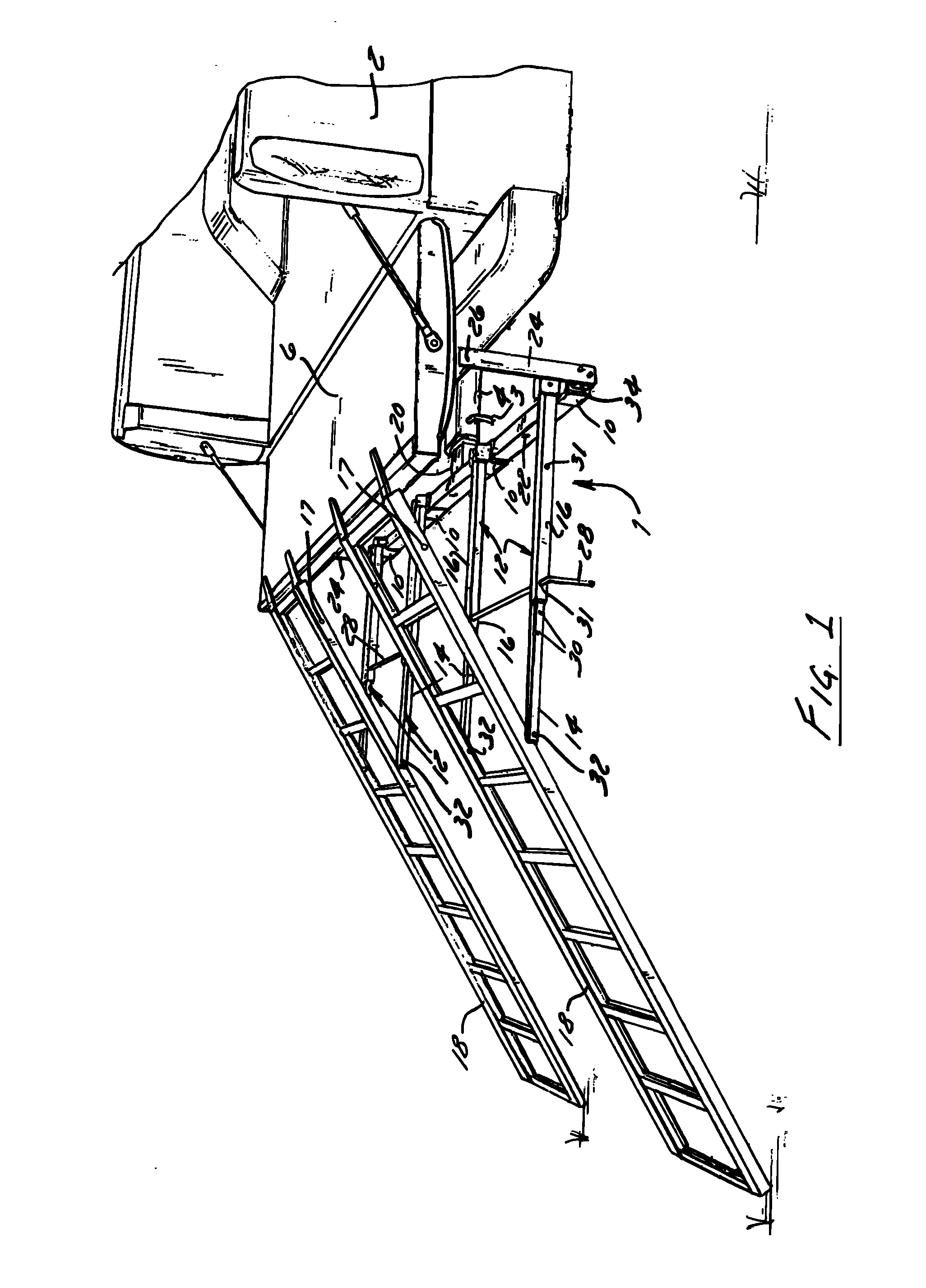
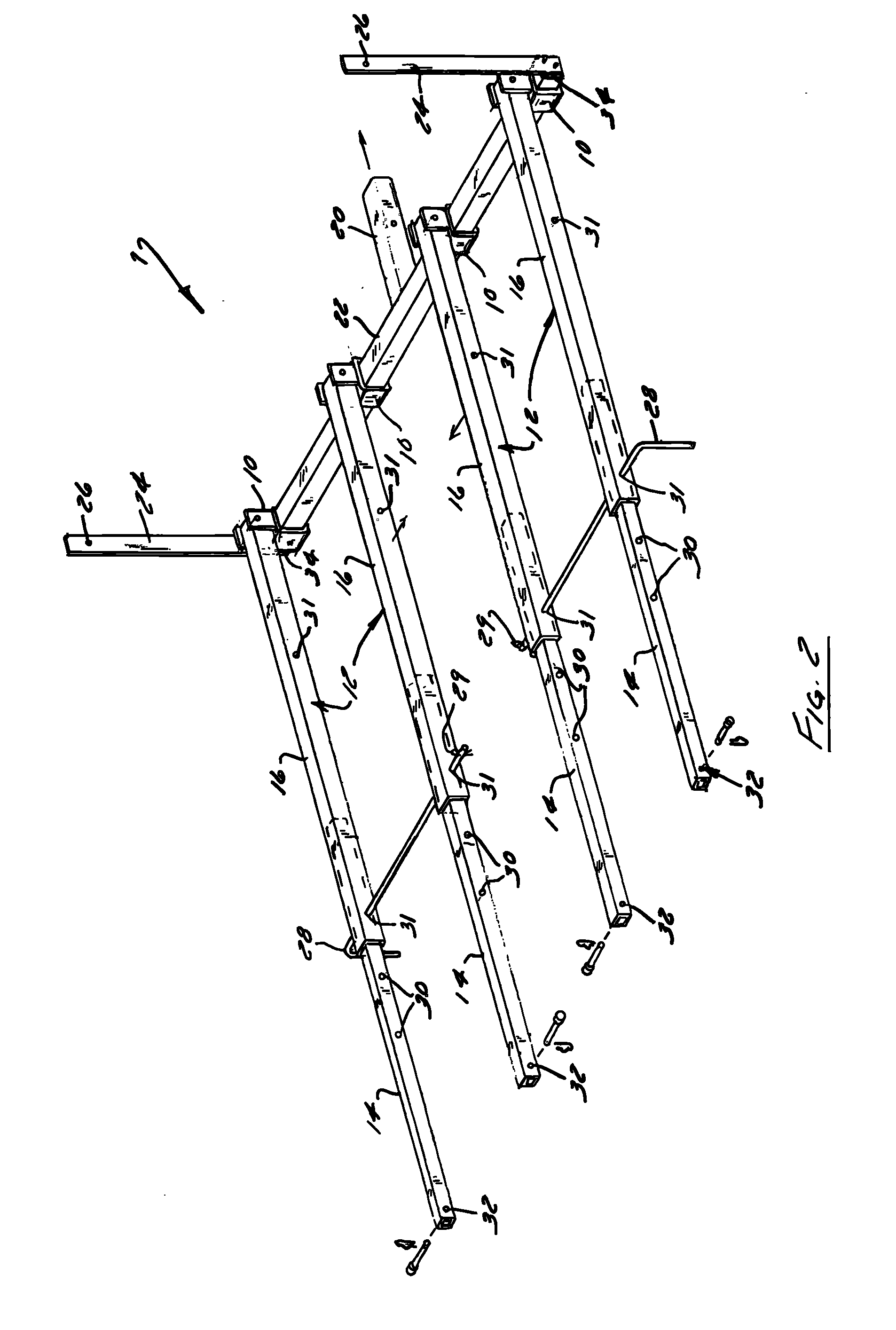
Apparatus and method for loading and unloading cargo
InactiveUS20130045069A1Unloading safetyStable positionRefuse receptaclesHand carts with one axisStructural engineeringMechanical engineering
An apparatus and method for securing a ramp to a cargo carrier having a receiver hitch and a loading surface are disclosed. The apparatus includes an engaging member configured to engage the receiver hitch of the cargo carrier; a cross support attached to the engaging member, wherein the cross support has a plurality of mounting brackets mounted thereto; at least two locking members attached to the cross support and on opposite sides of the engaging member extend vertically therefrom, wherein each locking member slideably receives a locking pin; and a plurality of telescopic arms attaching the ramp to the mounting brackets, wherein each telescopic arm has an inner portion and an outer portion, wherein the outer portion and inner portion have at least one set of apertures for slideably receiving a locking pin.
Owner:DAY JOHN P
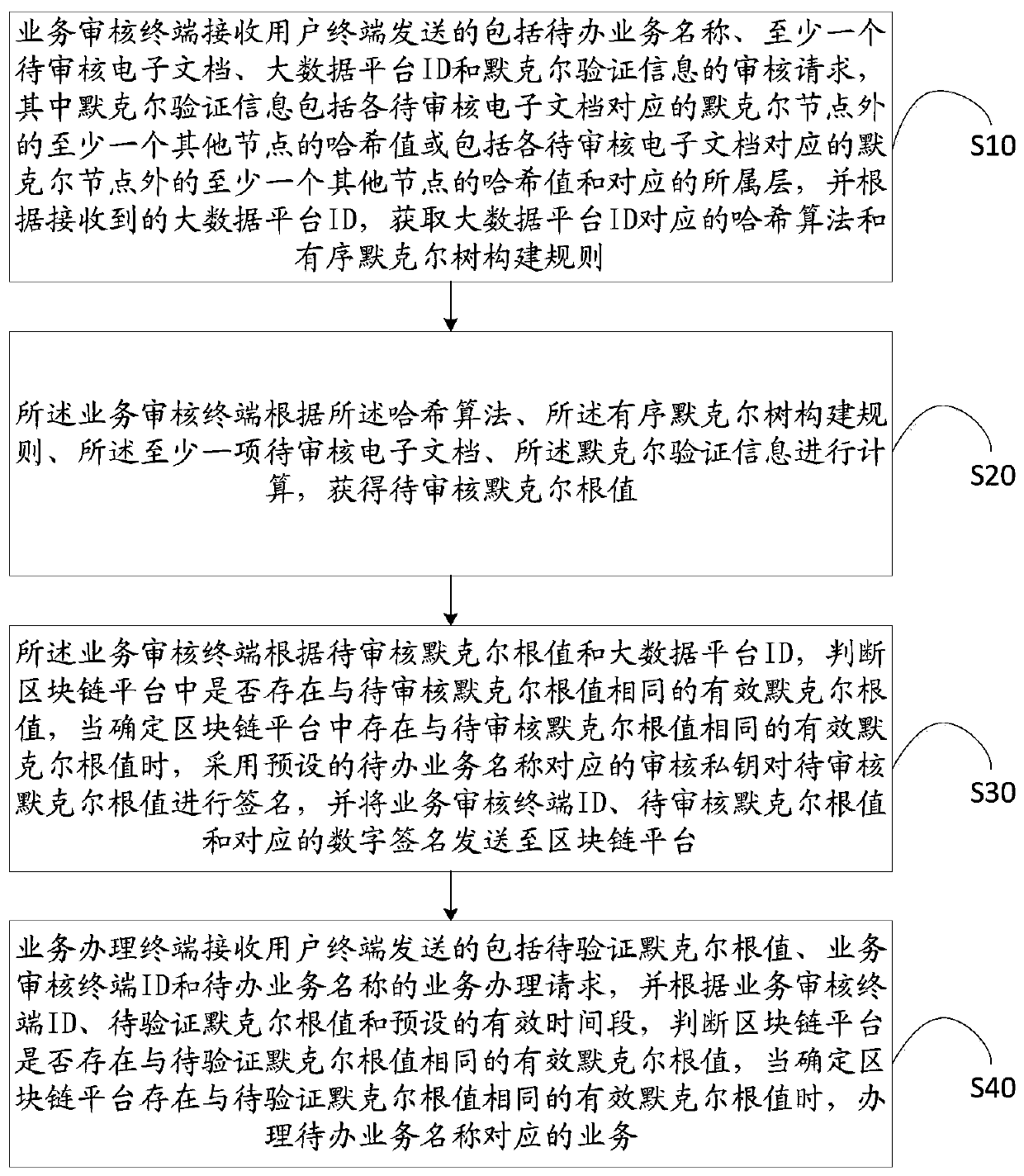
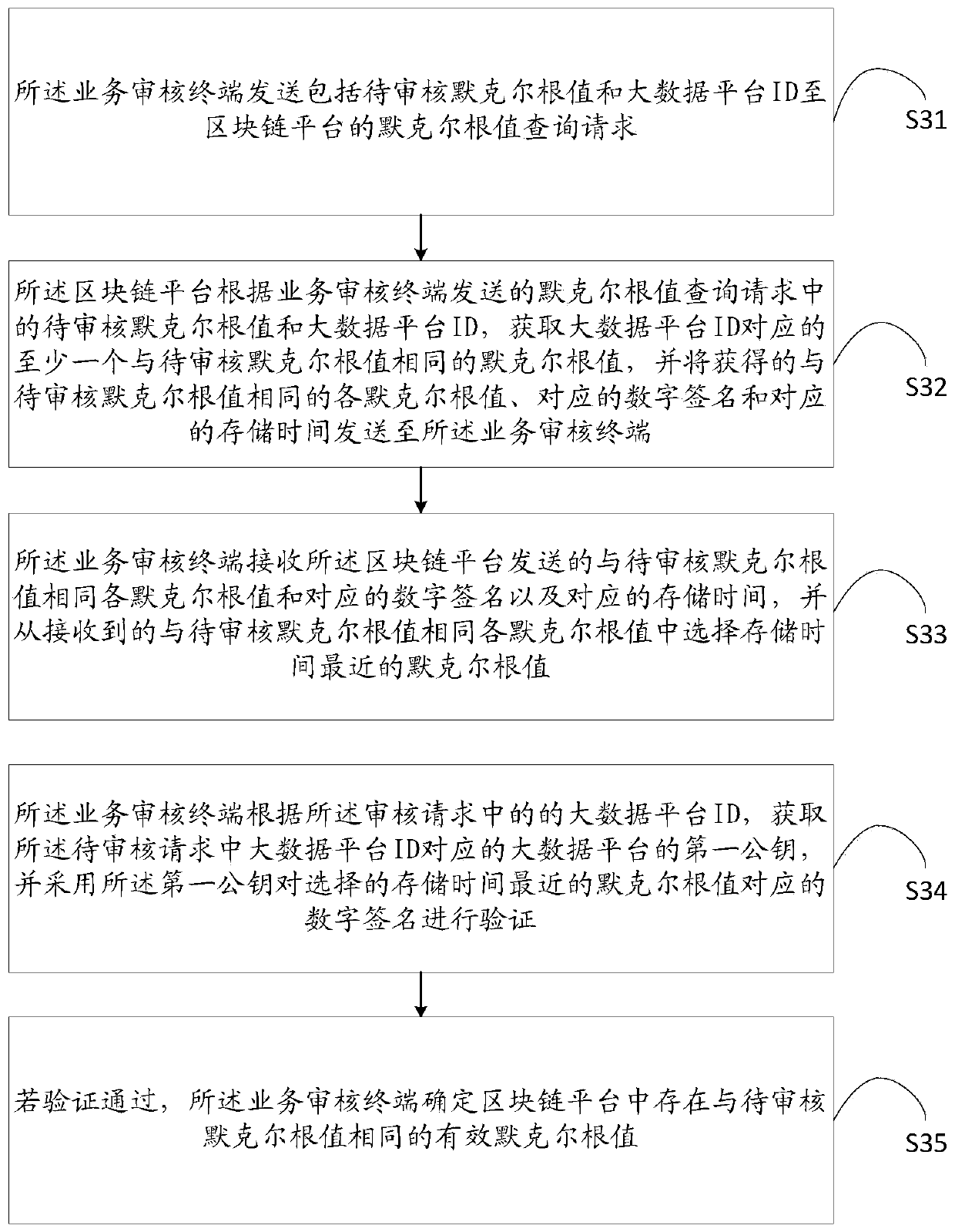
Business handling method and system based on zero knowledge proof, and storage medium
ActiveCN110321735AReduce the possibility of theftDigital data protectionElectronic documentPersonal details
The invention discloses a business handling method and system based on zero knowledge proof, and a storage medium. The method comprises the following steps: a service auditing terminal performing calculation according to the name of the to-do service, the to-be-audited electronic document, the big data platform ID, the Merkel verification information, the obtained hash algorithm and the ordered Merkel tree construction rule sent by the user terminal; obtaining a to-be-audited Merkel root value, signing the to-be-audited Merkel root value by adopting an auditing private key after determining that the to-be-audited Merkel root value is valid according to the to-be-audited Merkel root value, the big data platform ID and the block chain platform, and storing the signed to-be-audited Merkel root value to the block chain platform; and the business handling terminal handling related businesses after determining that the to-be-verified Merkel root value is valid according to the to-be-handledbusiness name, the to-be-verified Merkel root value and the auditing terminal ID sent by the blockchain platform and the user terminal. According to the invention, the technical problem of high possibility of stealing personal data provided in the business handling process is solved.
Owner:SHANDONG INST OF BUSINESS & TECH +1
Method for authorising a communication with a portable electronic device, such as access to a memory zone, corresponding electronic device and system
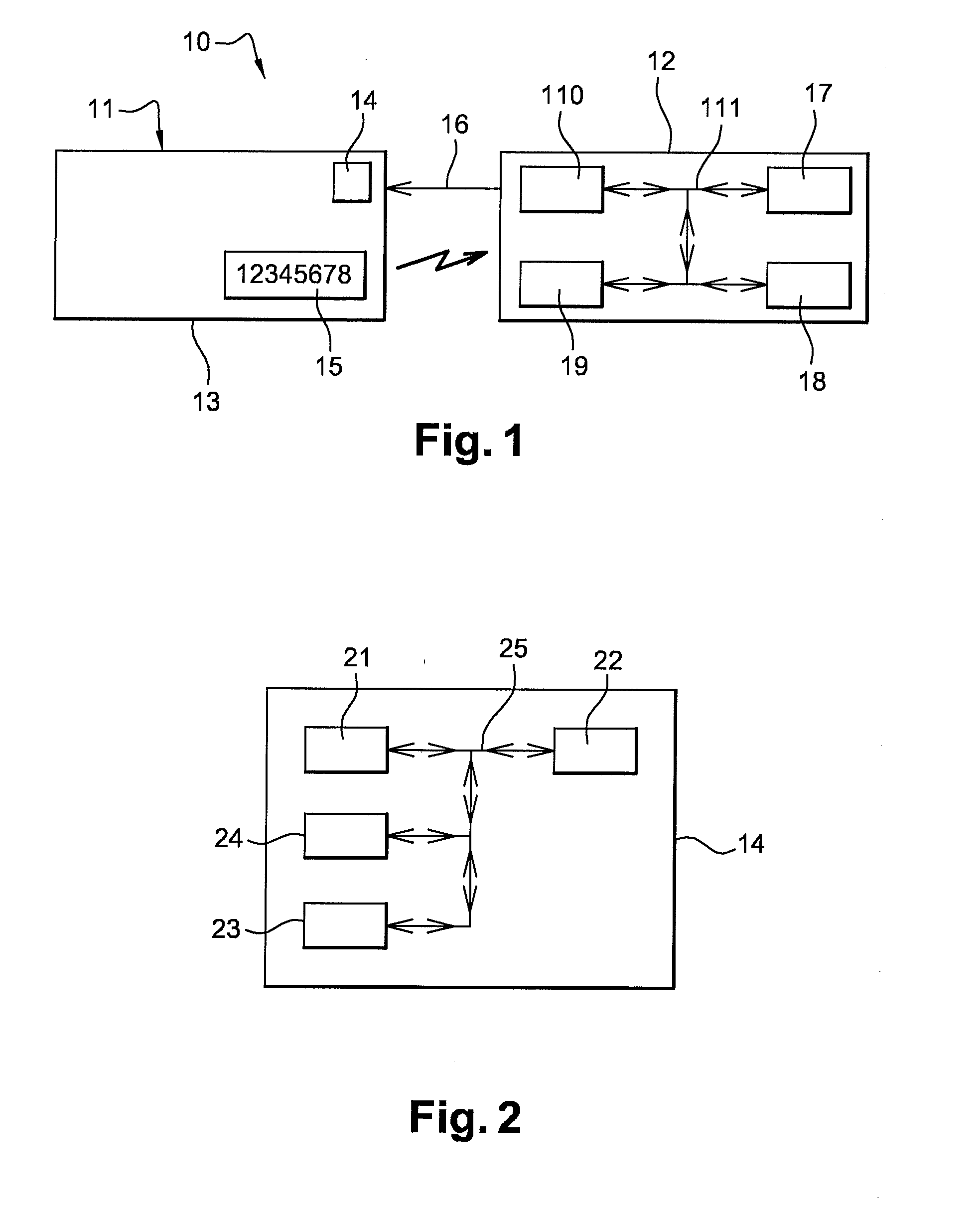
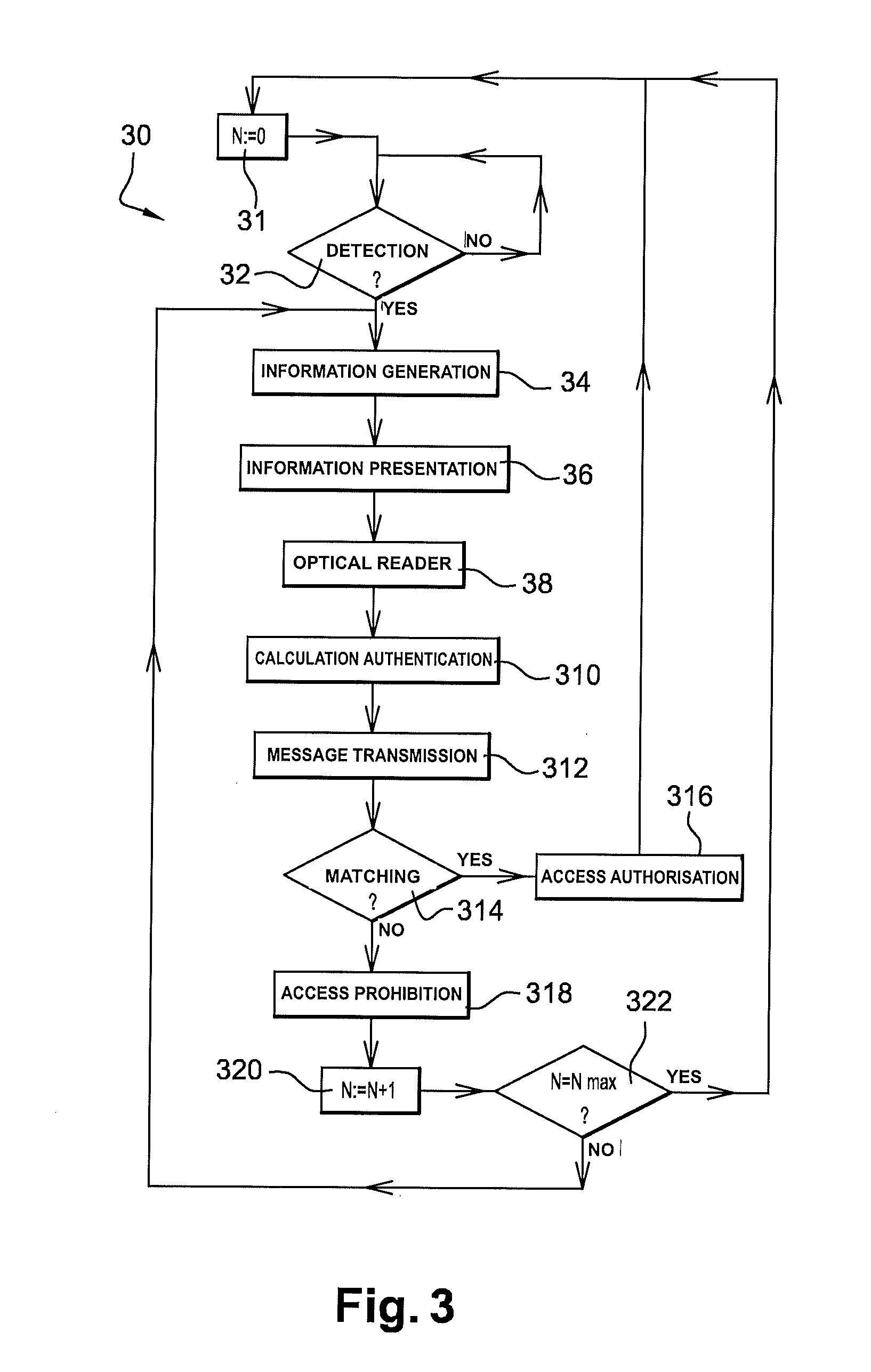
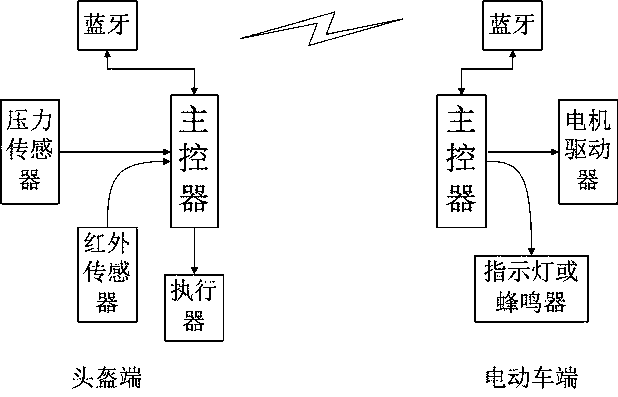
ActiveUS20100263034A1More accessIncrease the number ofDigital data processing detailsUser identity/authority verificationElectronic communicationDisplay device
The invention relates to a method for authorizing a communication with a portable electronic device, such as access to at least one memory area. The portable electronic device has a display for presenting an item of information visible to the outside and an interface for communication with the outside of the portable electronic device. The item of information is at least in part taken into account by the portable electronic device in order to authorize the communication. The method includes a step of optical reading of the item of information outside the portable electronic device. The method is distinguished in that it also includes a step of varying the item of information, the step of varying causing the item of information, termed the variable item of information, to vary at least in part. The invention also relates to the portable electronic device, and the system comprising the portable electronic device and an electronic communication or reading device.
Owner:THALES DIS FRANCE SA
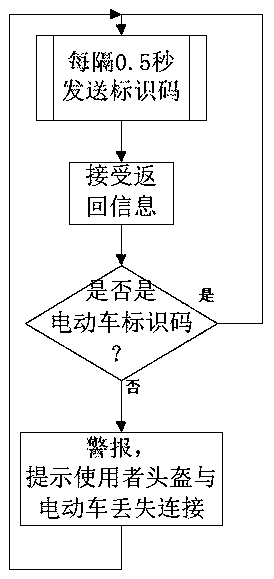
An electric vehicle driver and passenger helmet wearing system and a detection anti-theft method thereof
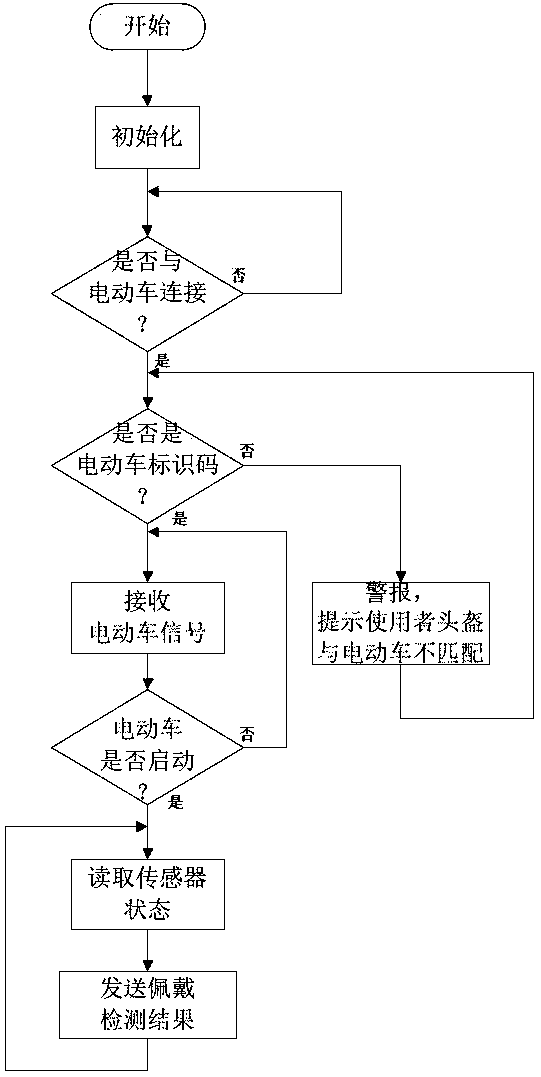
ActiveCN109703658ACultivate the habit of wearing a helmetReduce the possibility of theftAcoustic signalAnti-theft cycle devicesMotor driveActuator
The invention discloses an electric vehicle driver and passenger helmet wearing system and a detection anti-theft method thereof. The system comprises a helmet end, and an electric vehicle end matchedwith the helmet end; the helmet end comprises a helmet end main controller used for core control, a helmet end Bluetooth connected with the helmet end main controller, a pressure sensor connected with the helmet end main controller, an infrared sensor connected with the helmet end main controller, and an actuator connected with the helmet end main controller; the electric vehicle end comprises anelectric vehicle end main controller used for core control, an electric vehicle end Bluetooth connected with the electric vehicle end main controller, a motor driver connected with the electric vehicle end main controller, and an indicator lamp or a buzzer connected with the electric vehicle end main controller; the anti-theft effect is achieved through the structure of the system, and the accessconvenience is improved; in addition, a detection anti-theft method corresponding to the system is further set, the habit of drivers and passengers wearing the helmet can be effectively developed, and the possibility that the helmet is stolen is reduced.
Owner:陆宇超
Encrypted writing signing mobile terminal
InactiveCN101872420AReduce the possibility of theftReduce lossesNear-field transmissionCharacter and pattern recognitionComputer moduleComputer terminal
The invention relates to an encrypted writing signing mobile terminal, comprising a display module, a writing input module, a control operation module and a communication module for data exchange. The display module, the writing input module and the communication are respectively connected with the control operation module. The encrypted writing signing mobile terminal also comprises a data processing module which comprises writing signing software, wherein the writing signing software can be executed by the control operation module to realize the writing signing function, and the data processing module is connected with the control operation module. The invention improves the automatic office level and efficiency of governments and enterprises, realizes the purpose that office business can be handled anywhere at any time, and reduces the carbon emission.
Owner:石明霞
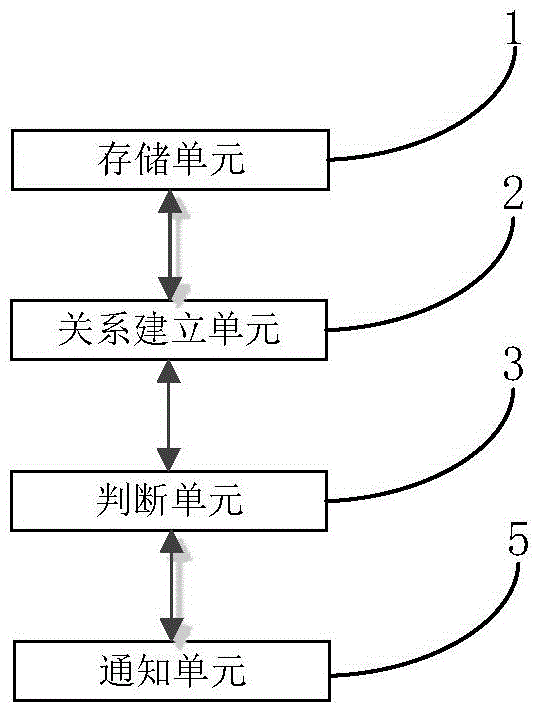
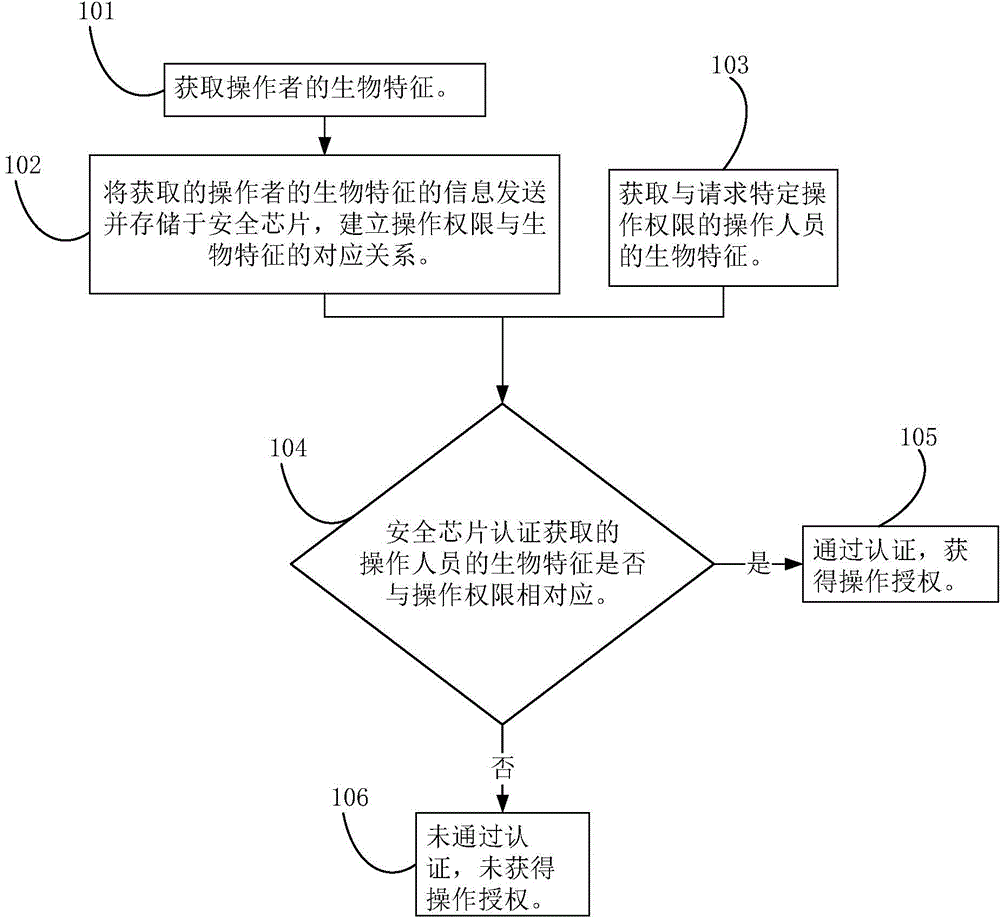
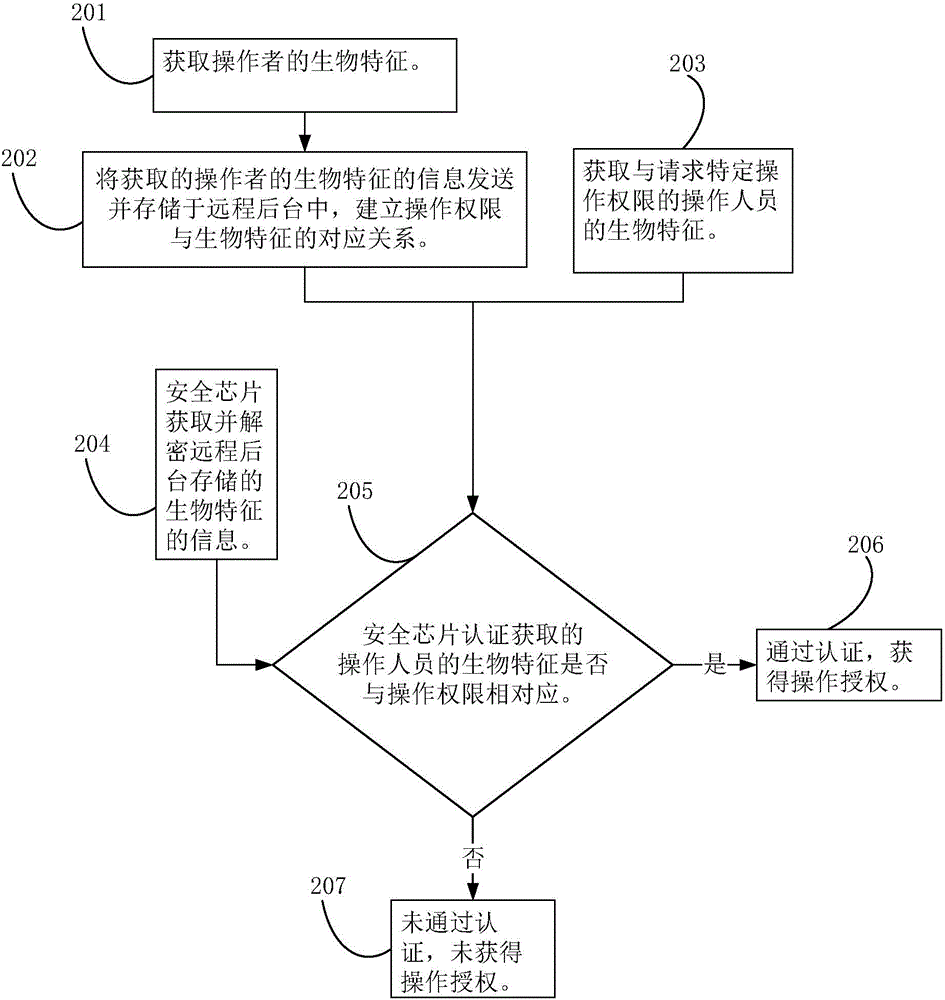
Security chip, authentication method based on biological features and intelligent terminal
PendingCN106156577AReduce the possibility of theftImprove securityDigital data authenticationInternet Authentication ServiceMalware
The invention provides a security chip which comprises a storage unit, a relation establishing unit and a judging unit. The storage unit is used for storing biological feature information of an operator with operation authority, the relation establishing unit is used for establishing the corresponding relation between the biological feature information and the operation authority of the operator, and the judging unit is used for judging whether the biological feature information for requesting for the operation authority corresponds to the operation authority or not. The security chip independently stores and verifies the corresponding relation between the biological feature information and the operation authority, an intelligent terminal process does not store the biological feature information, and the probability that the biological feature information is stolen by lawbreakers is greatly reduced; the security chip can independently carry out the authentication service of the biological features collected subsequently, the intelligent terminal process does not need to participate, the probability that an authentication system is damaged by malicious software, wooden horses and viruses is greatly reduced, and information security is greatly improved. The invention further provides an authentication method based on the biological features and an intelligent terminal capable of achieving authentication based on the biological features.
Owner:NATIONZ TECH INC
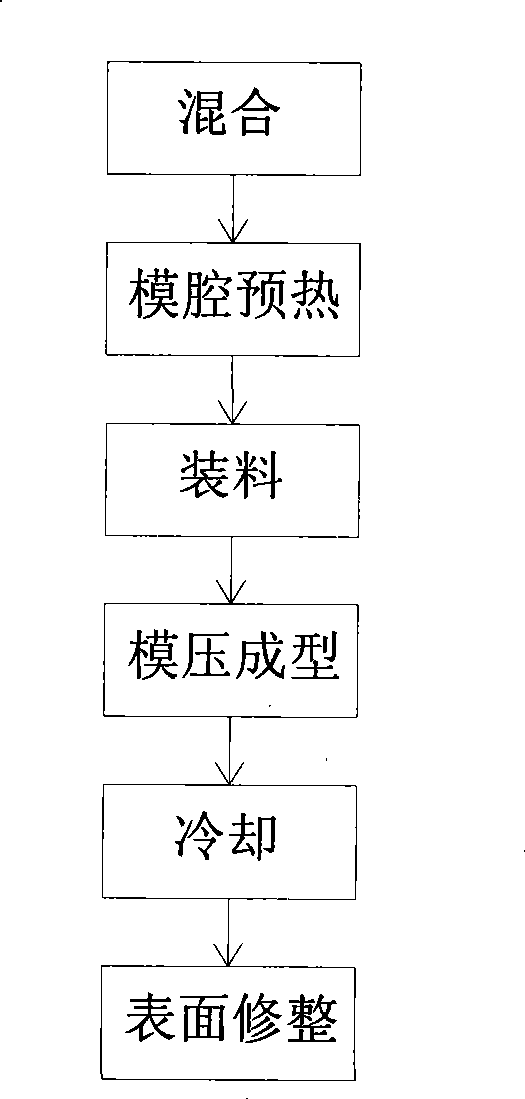
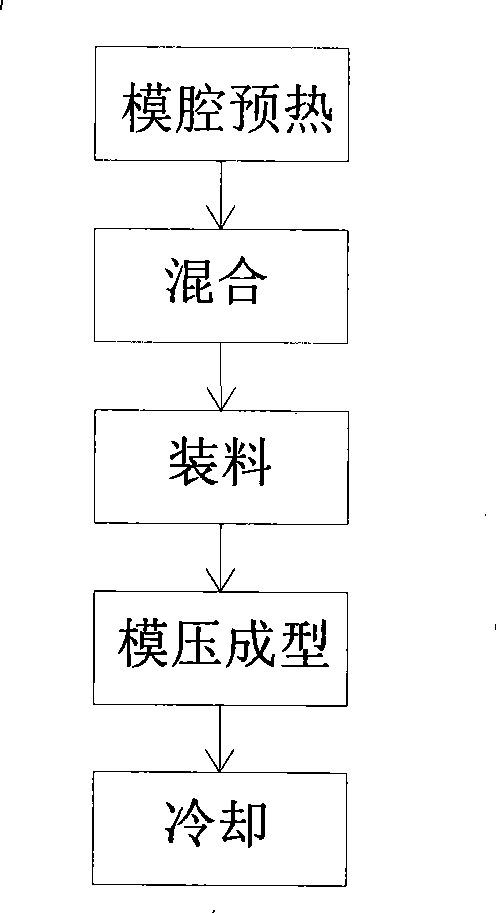
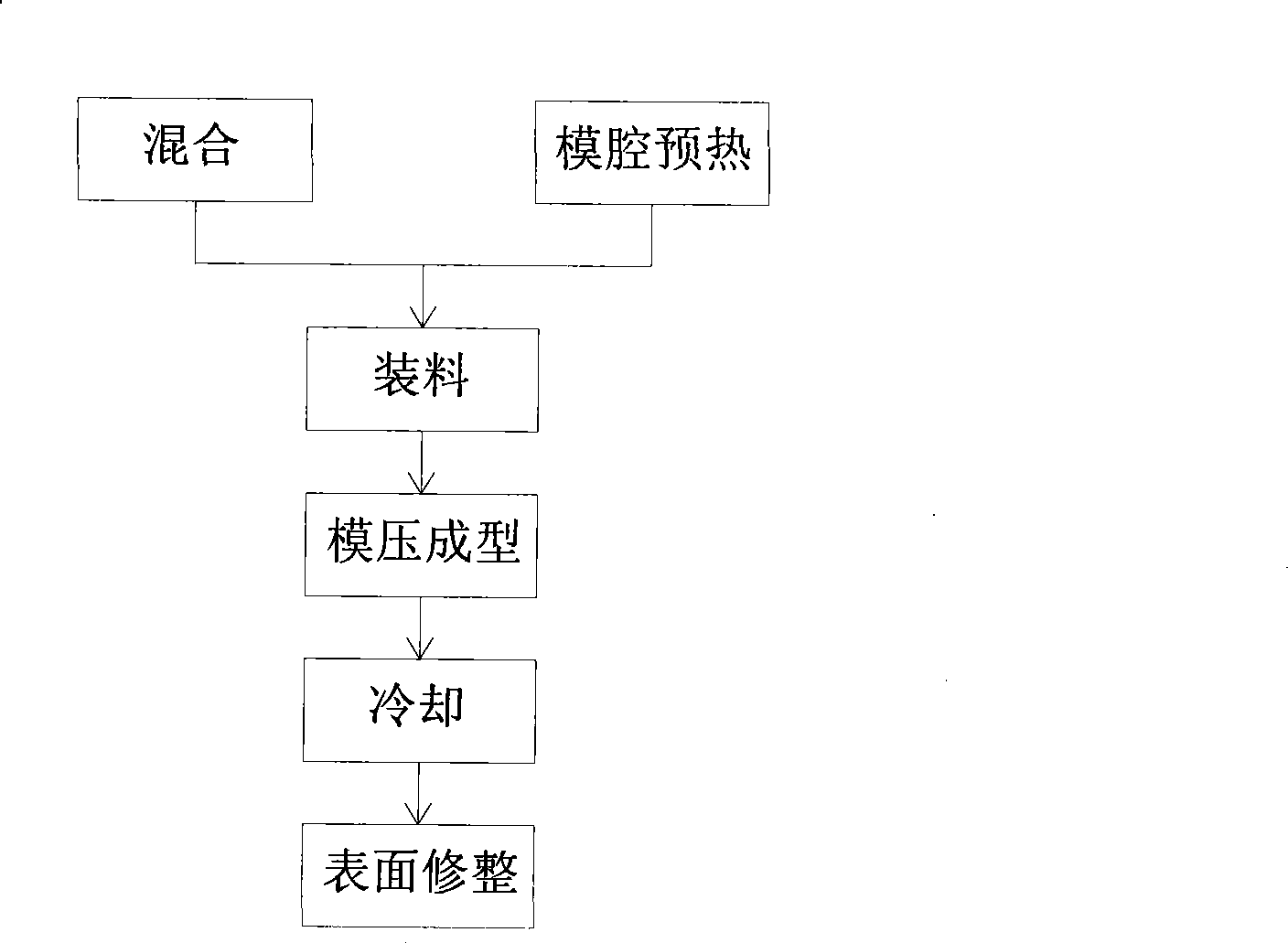
Process for manufacturing manhole cover
InactiveCN101367259ANo recycling valueShort holding timeDomestic articlesCompression moldingSheet moulding compound
The invention relates to a process for manufacturing inspection well covers. The method comprises the following: a step of mixing, which is to match and mix sheet molding compounds accounting for 1 to 99 percent of total weight, scattered molding compounds accounting for 1 to 99 percent of total weight and bulk molding compounds accounting for 1 to 99 percent of total weight; a step of preheating a mold cavity which is to preheat the mold cavity of a hydraulic press to be between 100 and 150 DEG C for 1 to 3 hours; a step of charging which is to put the mixed material into the mold cavity or lay profiles and then the residual mixed material; a step of carrying out compression molding which is to carry out compression molding under the pressure between 1,000 and 10,000 KN at the temperature between 100 and 150 DEG C, maintain pressure and preserve heat for 5 to 60 minutes; and a step of cooling. As the inspection well covers are made from sheet molding compounds and scattered molding compounds or bulk molding compounds through compression molding, the inspection well covers have the advantages of high strength, good anti-fracture toughness and the like. In addition, during manufacture, the time of compression molding and heat preservation is short, so as to save energy. As the inspection well covers have no recycling value, the possibility for stealing the inspection well covers is certainly reduced.
Owner:HANGZHOU JINMENG ROAD ESTAB CO LTD
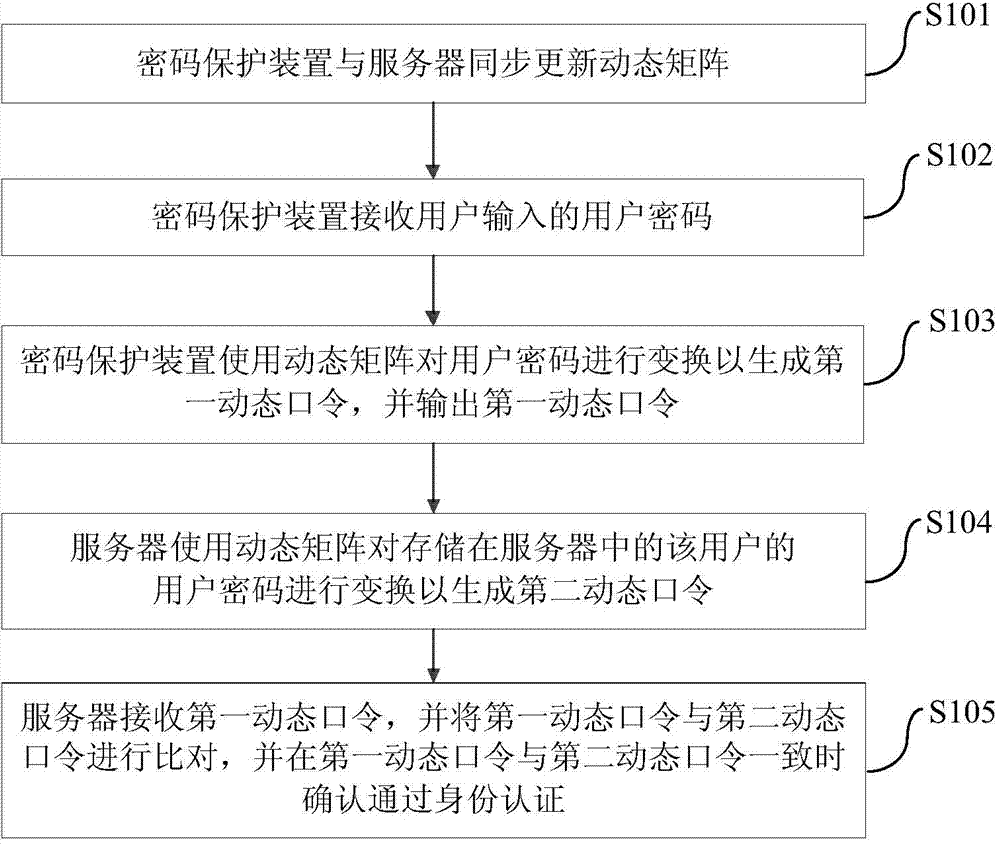
Identity authentication method and system and password protection device
InactiveCN103580873AReduce memory loadImprove experienceUser identity/authority verificationUser inputPassword protection
The invention provides an identity authentication method and system and a password protection device. The identity authentication method includes the steps that the password protection device and a server synchronously update dynamic matrixes; the password protection device receives a user password inputted by a user; the password protection device utilizes the dynamic matrix to carry out conversion on the user password so as to generate a first dynamic password, and then outputs the first dynamic password; the server utilizes the dynamic matrix to carry out conversion on the user password, stored in the server, of the user so as to generate a second dynamic password; the server receives the first dynamic password, compares the first dynamic password with the second dynamic password and then confirms that the user is authenticated when the first dynamic password accords with the second dynamic password. Through the identity authentication method, the burden of the user for remembering the password is effectively relieved, and the identity authentication efficiency and security of identity information of the user are improved.
Owner:TSINGHUA UNIV
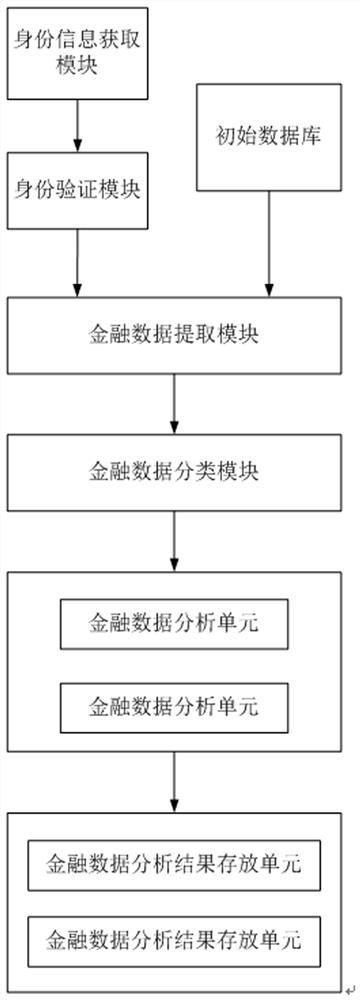
Financial big data analysis platform based on artificial intelligence
ActiveCN111861748AEnsure safetyReduce the possibility of theftFinanceTransmissionData ingestionData set
The invention relates to a financial big data analysis platform based on artificial intelligence. The system comprises an identity information acquisition module, an identity verification module, an initial database, a financial data extraction module, a financial data classification module, a financial data analysis module and a financial data analysis result storage module. The identity verification module analyzes the financial big data and starts the identity verification of the personnel; and the financial data classification module classifies the financial data extracted by the financialdata extraction module, and the financial data analysis module analyzes a financial data set obtained by classification and stores an analysis result in a corresponding financial data analysis resultstorage unit in the financial data analysis result storage module. According to the financial big data analysis platform based on artificial intelligence, the analysis process of financial big data is relatively regular, the analysis process of each type of financial data is not interfered with each other, and the analysis results are not interfered with each other, so that the financial data analysis efficiency and reliability are improved.
Owner:神州数码融信软件有限公司
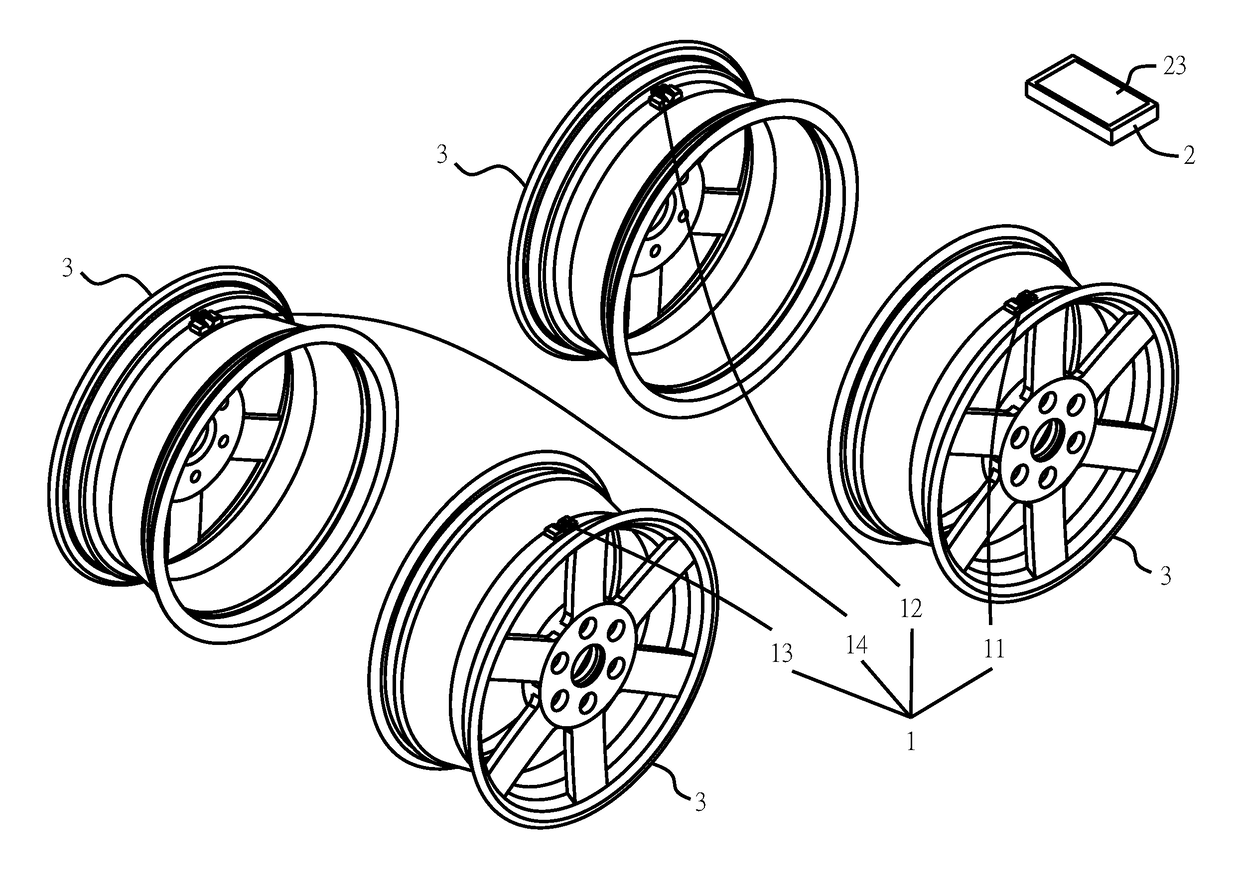
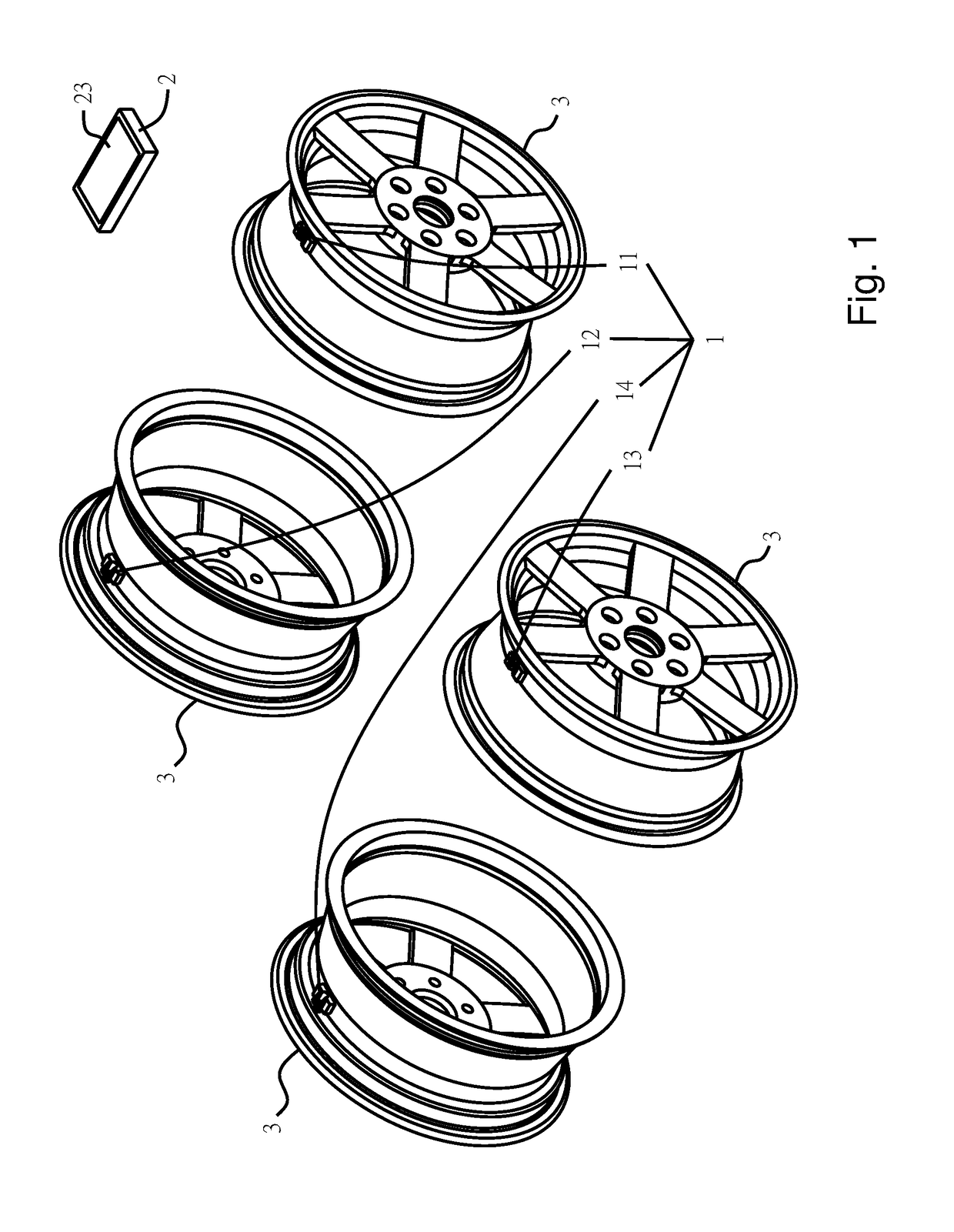
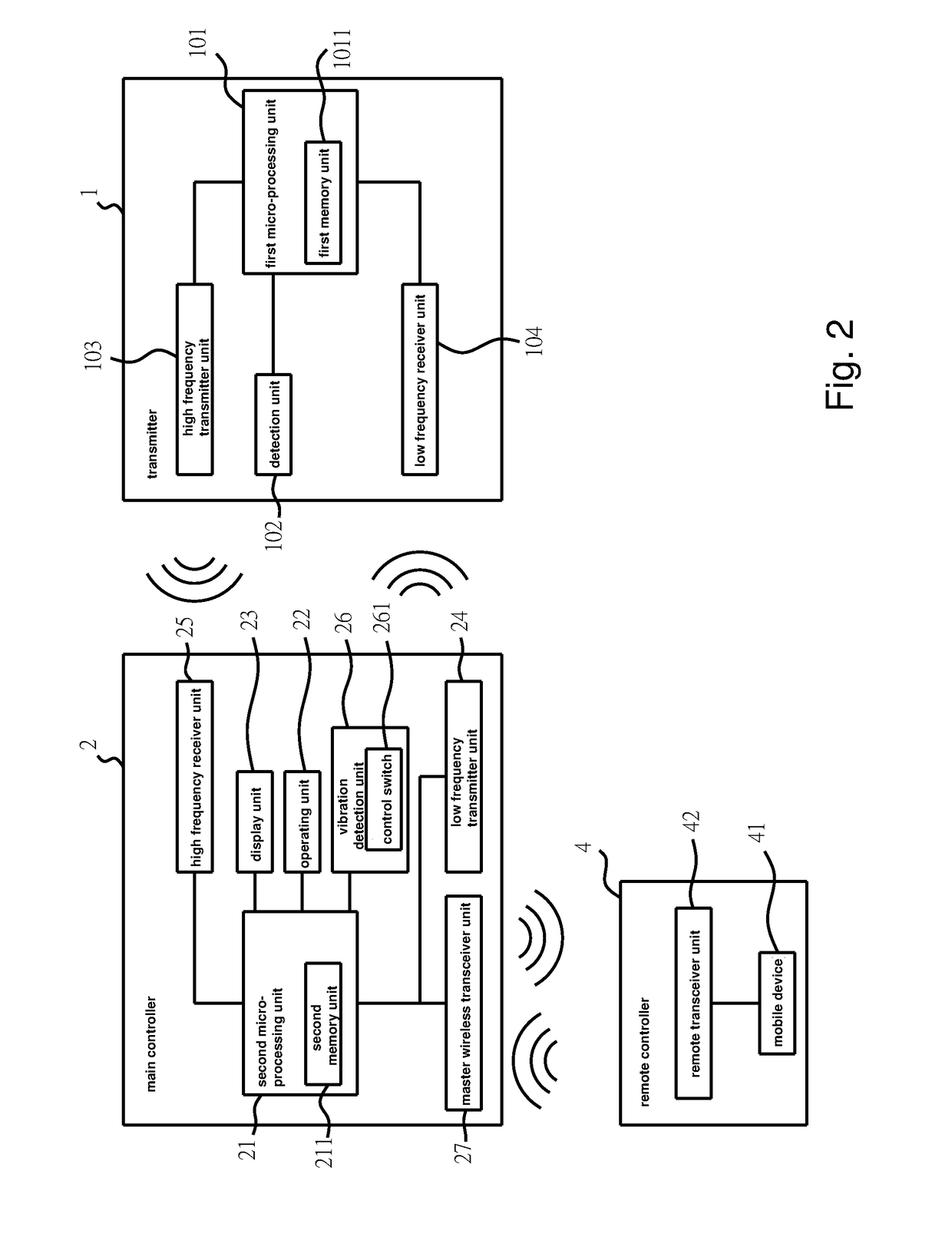
Method and system for tire pressure monitoring system (TPMS) with wireless tire condition sensing and warning
ActiveUS9649896B1Avoid signal interferenceReduce the possibility of theftAnti-theft devicesTyre measurementsEngineeringTire-pressure monitoring system
The present invention disclosed herein is a tire pressure monitoring system (TPMS) with a time encoded wireless tire condition sensing device and warning signal, wherein each transmitter ID is assigned its own timing parameter through the controlling device wherein each timing parameter has a different time delay to prevent any launch time transmission overlap. Furthermore, when the main controller receives data from a transmitter indicating abnormal tire condition, the vehicle velocity information is recorded and vibration detection is activated to determine whether there is abnormal vibration and, therefore, whether to transmit vibration warning signal to the display unit and / or to the mobile device of the driver.
Owner:LIN CHUNG I
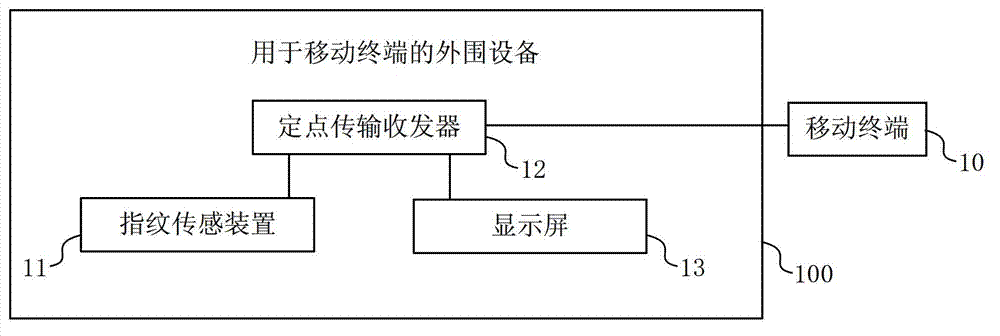
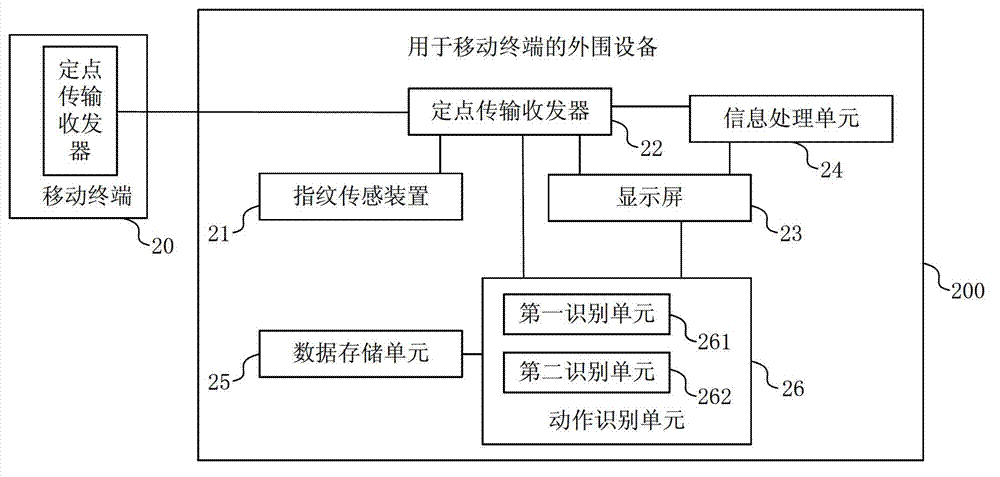
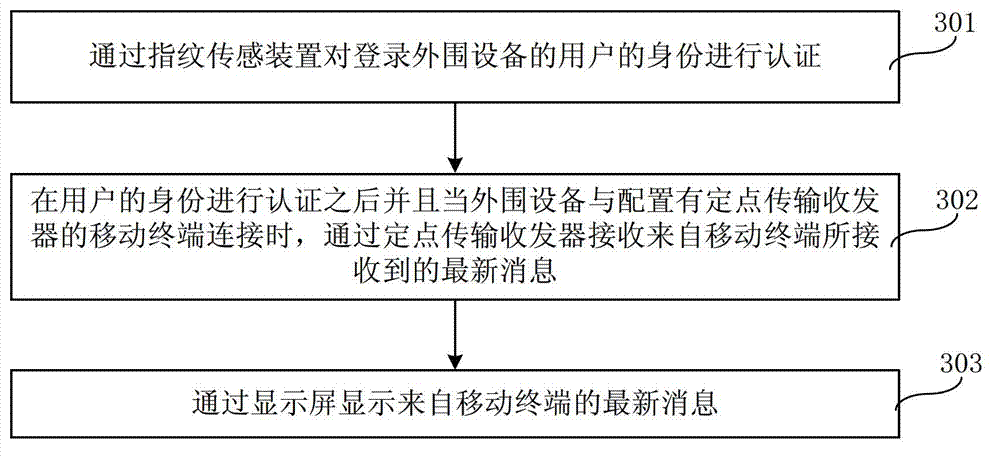
Peripheral device for mobile terminal and communication method for mobile terminal and peripheral device
InactiveCN103200325AReduce the possibility of theftProtection securityUser identity/authority verificationSubstation equipmentTransceiverComputer terminal
The invention discloses a peripheral device for a mobile terminal and a communication method for the mobile terminal and the peripheral device and belongs to the technical field of electrons. The peripheral device comprises a fingerprint sensing device, a fixed point transmission transceiver, a display screen, wherein the fingerprint sensing device is used for performing identity authentication of a user logging in the peripheral device, the fixed point transmission transceiver is used for receiving a newest message received by the mobile terminal after the identity authentication of the user is performed and when the peripheral device is connected with the mobile terminal configured with the fixed point transmission transceiver, and the display screen is used for displaying the newest message from the mobile terminal. Under the condition that the mobile terminal of the user does not expose, the newest message of the mobile terminal is obtained through the fixed point transmission transceiver on the peripheral device, accordingly the user obtains a newest state of the mobile terminal, the possibility that the mobile terminal is stolen is reduced, and the safety of the mobile terminal is achieved through external protection.
Owner:GOLDEN VAST MACAO COMML OFFSHORE
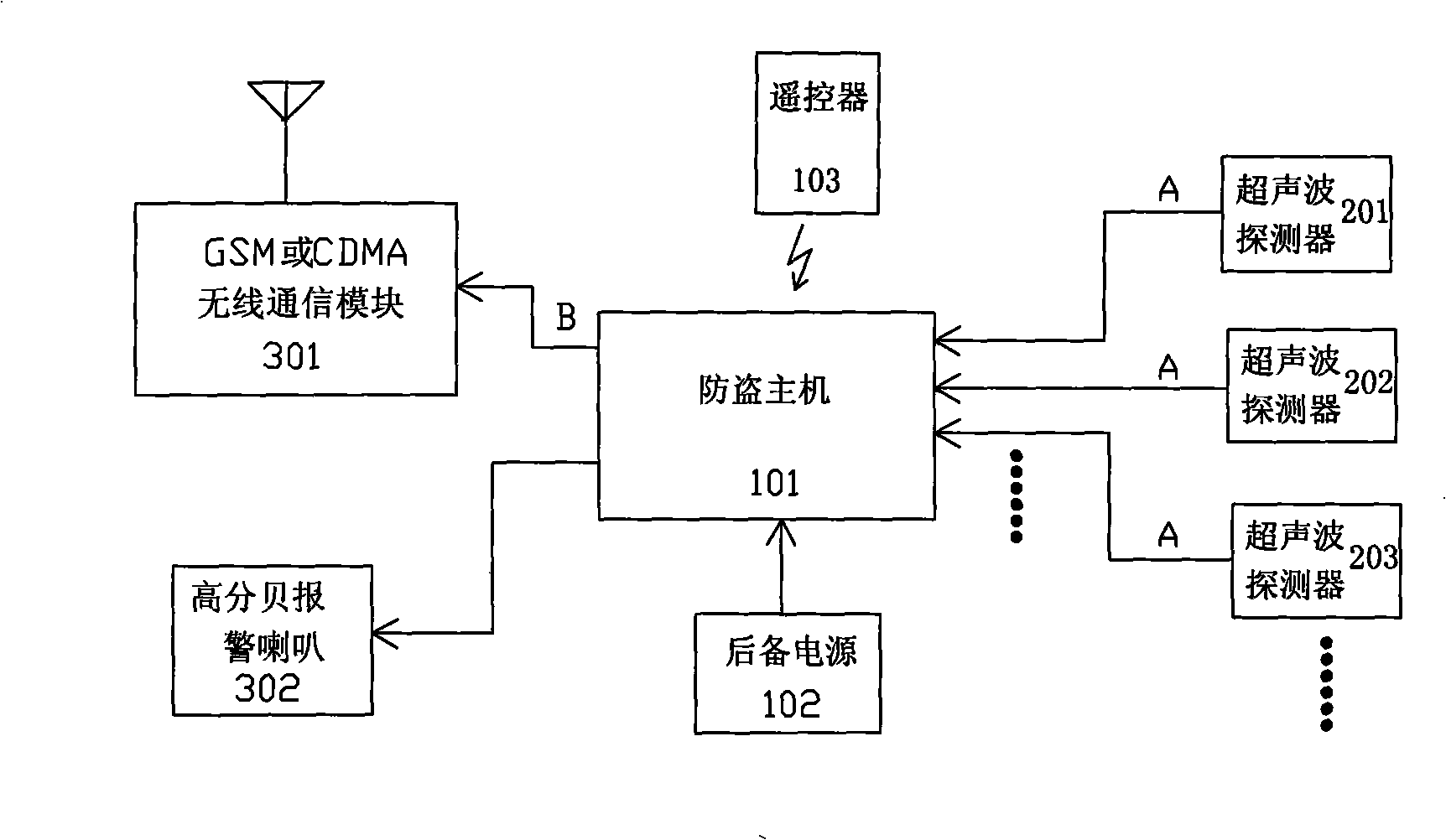
Ultrasonics induction type vehicle anti-stealing device
InactiveCN101337532AChange reflection distanceReduce the possibility of theftAnti-theft devicesFalse alarmGSM
The invention relates to an ultrasonic wave induction-type automobile anti-theft device, which comprises an automobile anti-theft host machine, at least one ultrasonic detector electrically connected with the automobile anti-theft host machine and at least one warning device electrically connected with the host machine. When a driver and passengers leave the automobile and start the device, then all the ultrasonic detectors respectively perform scanning to the reflected values of the ultrasonic waves in the positions corresponding to the ultrasonic detectors and preserve the reflected values in the host machine, if a person enters into the automobile or the glass of the automobile is broken, the change of the reflected values of the ultrasonic waves in the corresponding positions is caused respectively, the host machine responds to drive the warning device to send out warning after receiving the abnormal signal, and the warning device is provided with a high-decibel alarming horn and a GSM or CDMA mobile communication device which can be connected to the telephone of a vehicle owner. The invention also comprises a wireless remote controller used for controlling the starting and closing of the anti-theft function of the anti-theft device. By adopting the ultrasonic wave induction-type automobile anti-theft device with the structure, the false alarm phenomenon cannot occur, and the remote alarm can be realized.
Owner:佛山市顺德区骏达电子有限公司
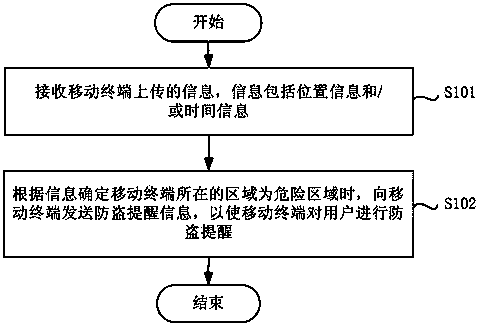
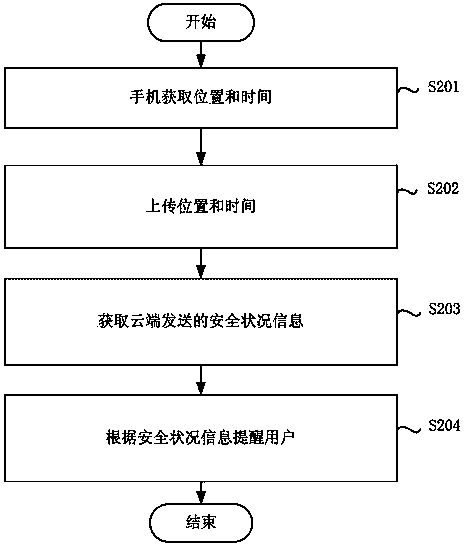
Antitheft prompting method and device
ActiveCN104023309AReduce the possibility of theftProtect against loss of personal propertyMessaging/mailboxes/announcementsLocation information based serviceTime informationComputer engineering
The invention provides an antitheft prompting method and a device. The antitheft prompting method comprises steps that: information uploaded by a mobile terminal is received, and the information comprises position information and / or time information; whether the located area of the mobile terminal is a dangerous area is determined according to the information, and antitheft prompting information is sent to the mobile terminal to make the mobile terminal carry out antitheft prompting for a user. According to the antitheft prompting method, when the located area of the mobile terminal is determined to be the dangerous area according to the information uploaded by the mobile terminal, antitheft prompting information in different grades is sent to the mobile terminal to make the mobile terminal carry out antitheft prompting for the user, so being-stolen possibility of the user is greatly reduced, and personal property loss because of theft is prevented.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
Cast stone manhole cover and its preparation method
InactiveCN1651349AGood flexural strength and fracture toughnessReduce the possibilityArtificial islandsSolid waste managementSmeltingFracture toughness
Owner:吕云南
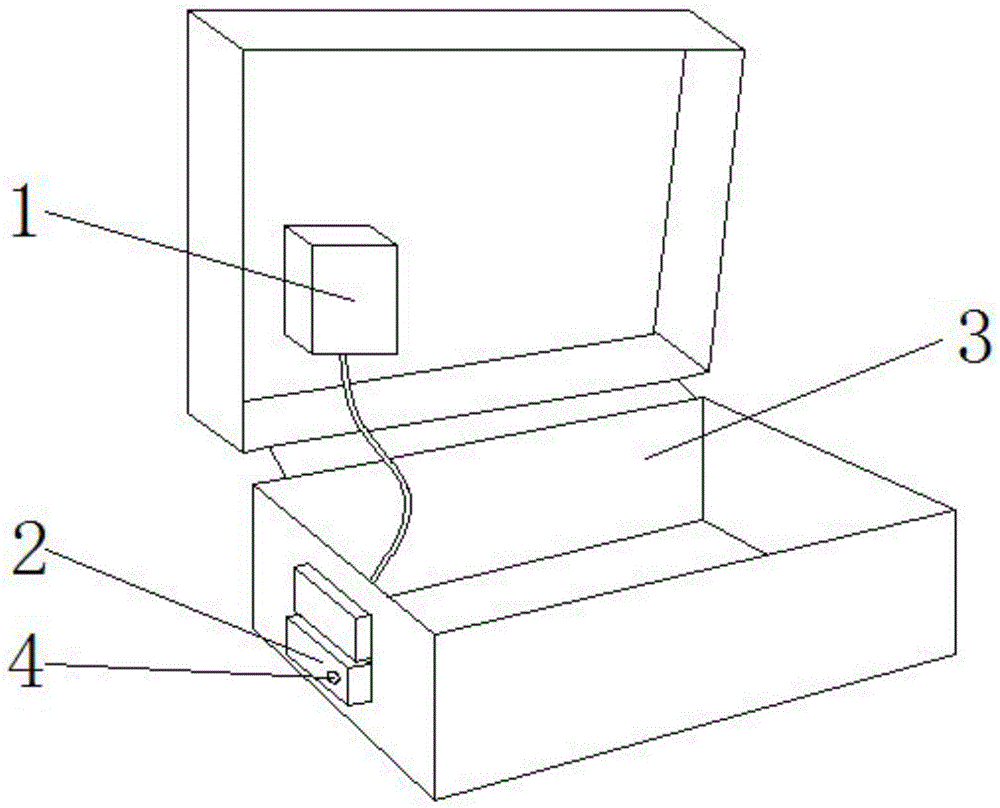
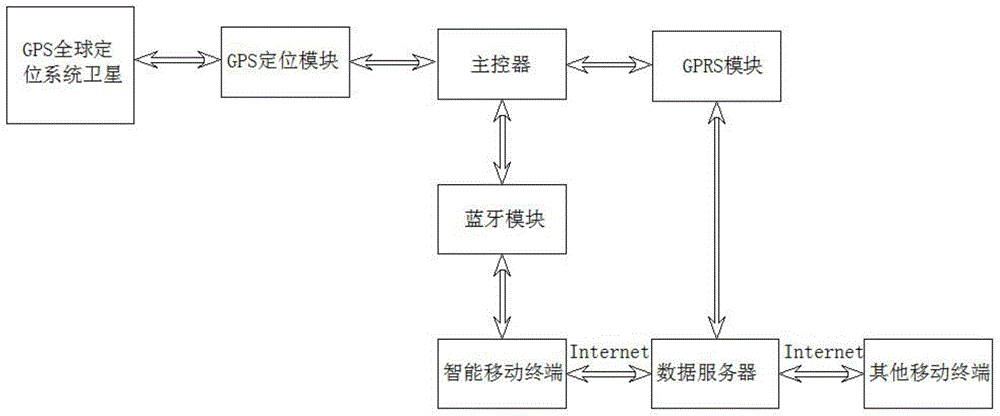
Intelligent luggage case based on STM32F407
InactiveCN104824942ARealize intelligenceDisplay location information in real timeLuggageOther accessoriesElectromagnetic lockComputer module
The invention discloses an intelligent luggage case based on STM32F407. The luggage case comprises an information collecting and controlling device, an electromagnetic lock, a box body, and a buzzer; wherein the information collecting and controlling device comprises a GPS positioning module, a GPRS data transmission module, a bluetooth module, and a M4 micro-controller module; the information collecting and collecting device is arranged in the box body, the electromagnetic lock is arranged on the lockset of the box body, the buzzer is arranged on the box body, the electromagnetic lock and the buzzer are connected to the information collecting and controlling device, and the bluetooth module is connected to the bluetooth module of a mobile intelligent terminal. The intellectualization of luggage case can be achieved by integrating a system to a luggage case; thus the time for finding the luggage case can be saved during the travelling process, the possibility that the luggage box is stolen or loss is reduced, furthermore, the system is suitable for various luggage cases, and the present luggage cases can be modified by the system.
Owner:XIJING UNIV
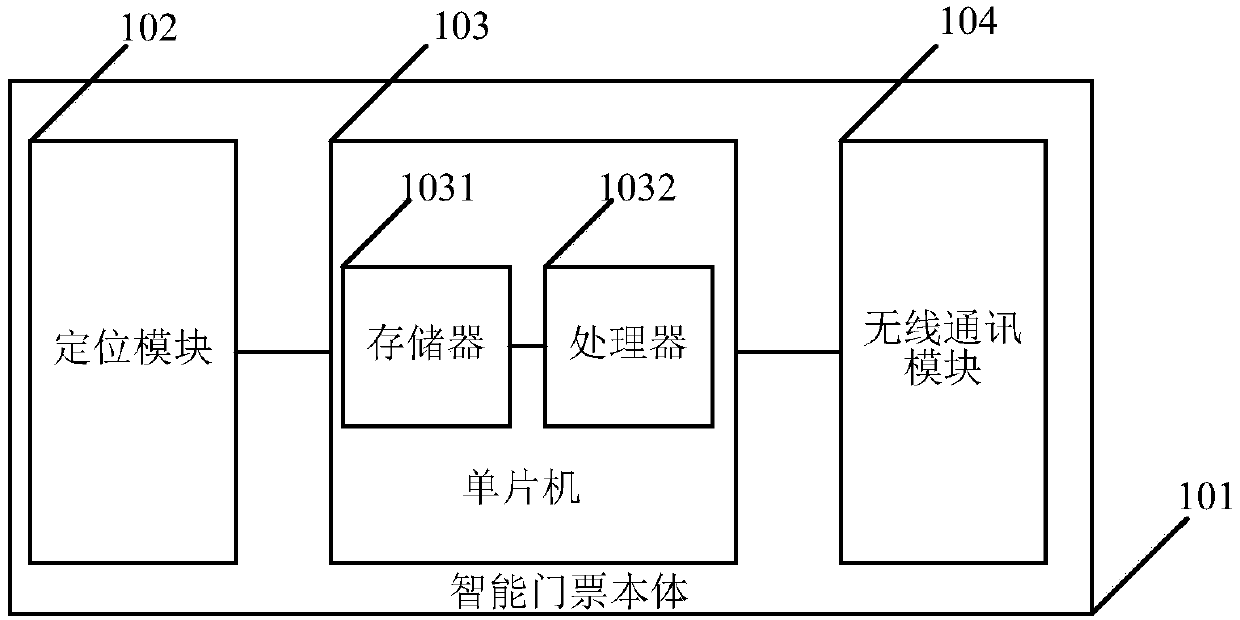
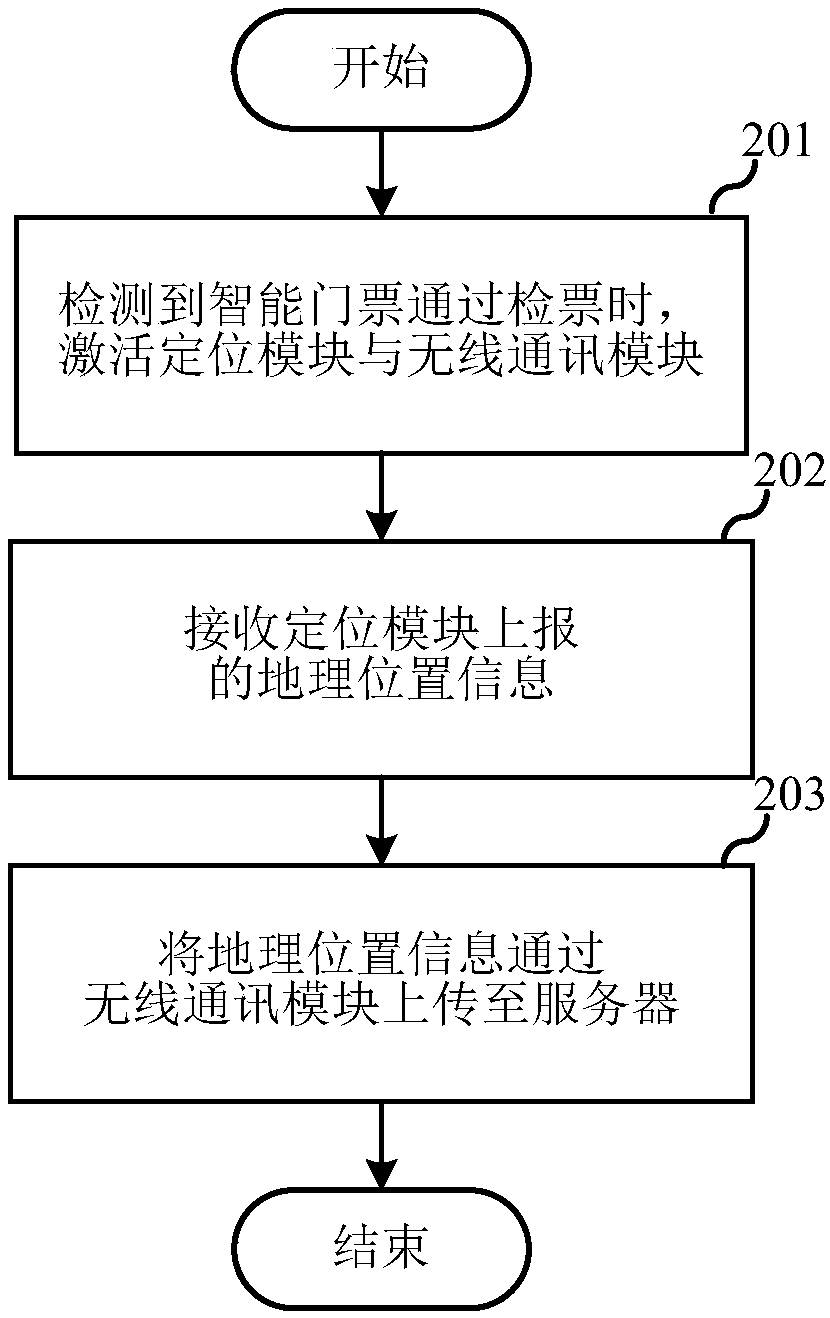
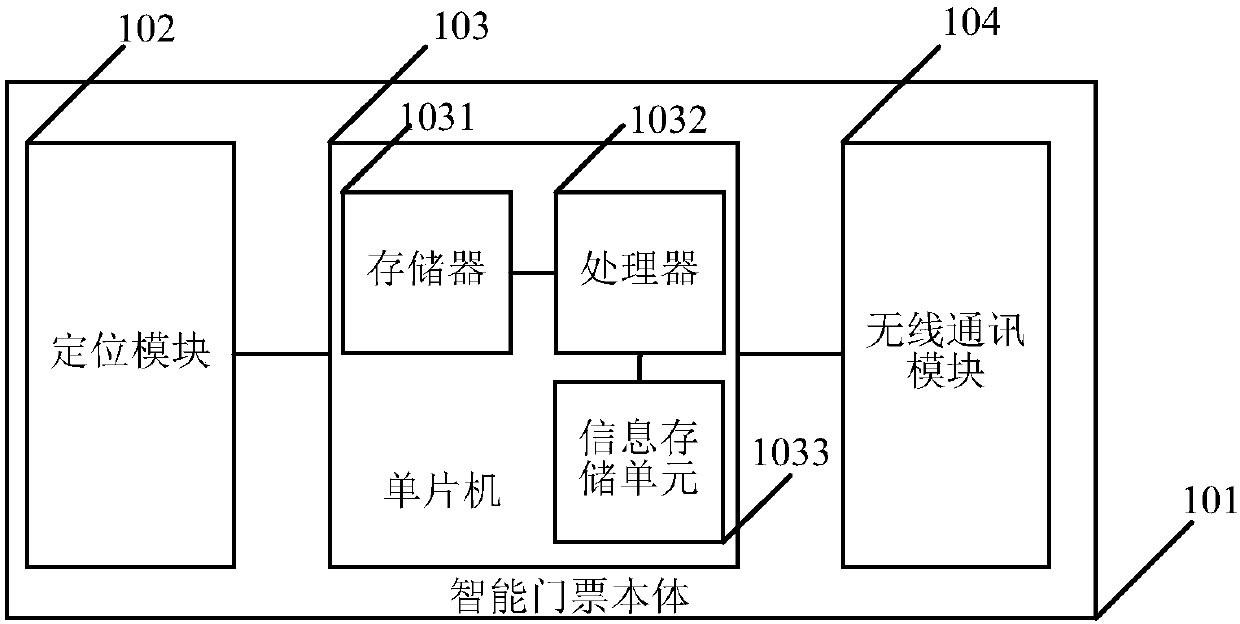
Intelligent ticket and intelligent ticket management system
InactiveCN107786945AReal-time trackingBe informed in timeTicket-issuing apparatusParticular environment based servicesMicrocomputerMicrocontroller
The embodiment of the invention relates to the technical field of communications, and discloses an intelligent ticket and an intelligent ticket management system. The intelligent ticket comprises an intelligent ticket body, a positioning module, a wireless communication module and a single chip microcomputer, wherein the positioning module, the wireless communication module and the single chip microcomputer are arranged in the intelligent ticket body; the positioning module and the wireless communication module are respectively connected with the single chip microcomputer; the single chip microcomputer includes a memory and a processor connected with the memory; the memory stores a computer program; and the program when being executed by the processor can implement the followings: activating the positioning module and the wireless communication module when detecting that the intelligent ticket passes through ticket checking, receiving geographical position information reported by the positioning module, and uploading the geographical position information to a server via the wireless communication module. Therefore, after the intelligent ticket passes through the ticket checking, position information of a tourist can be uploaded to the server; in this way, the position information of the tourist can be known timely, and the tracking of real-time position information is implemented.
Owner:博频(上海)科技股份有限公司
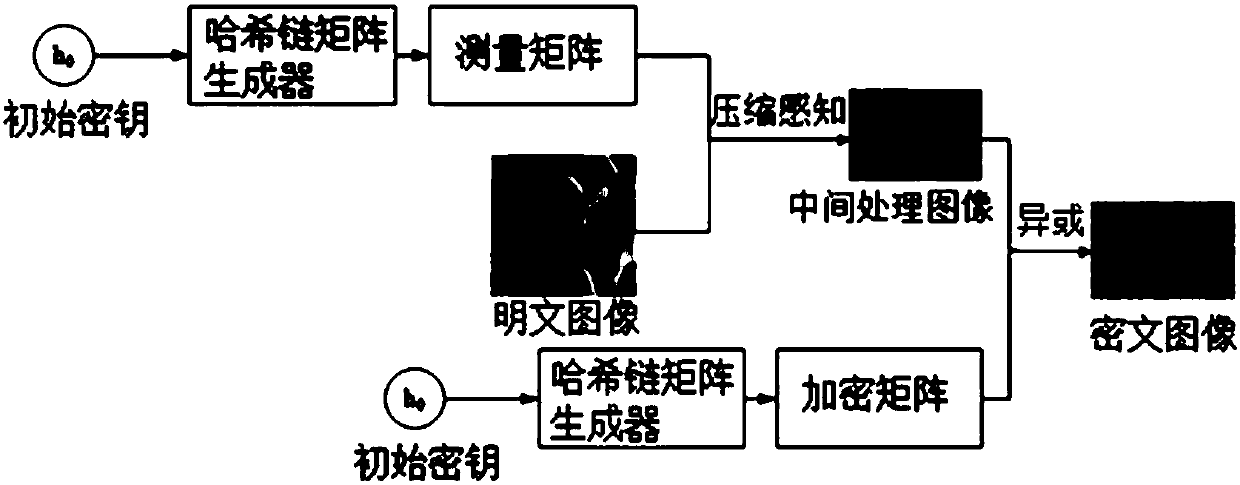
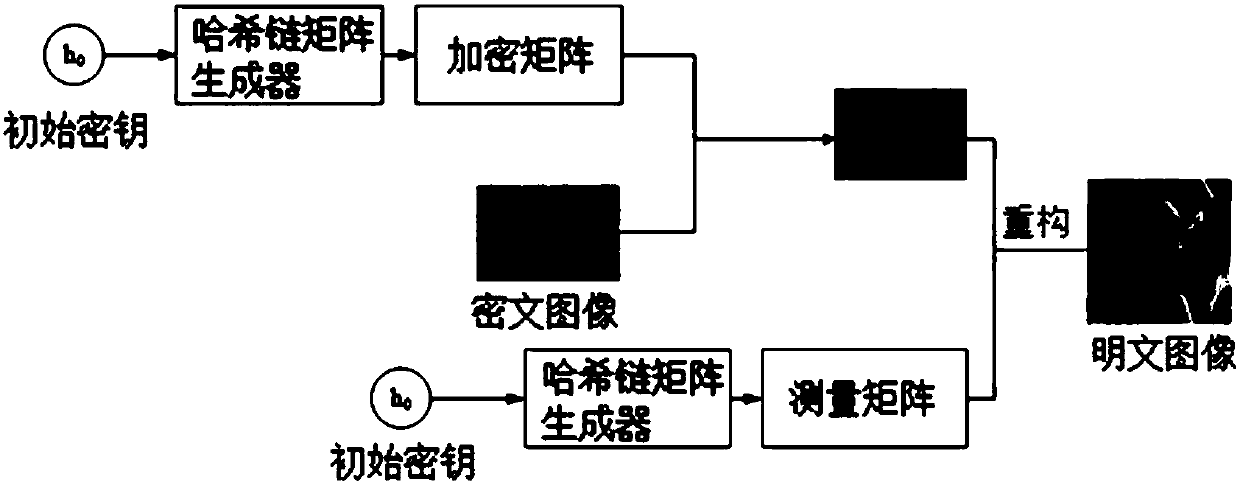
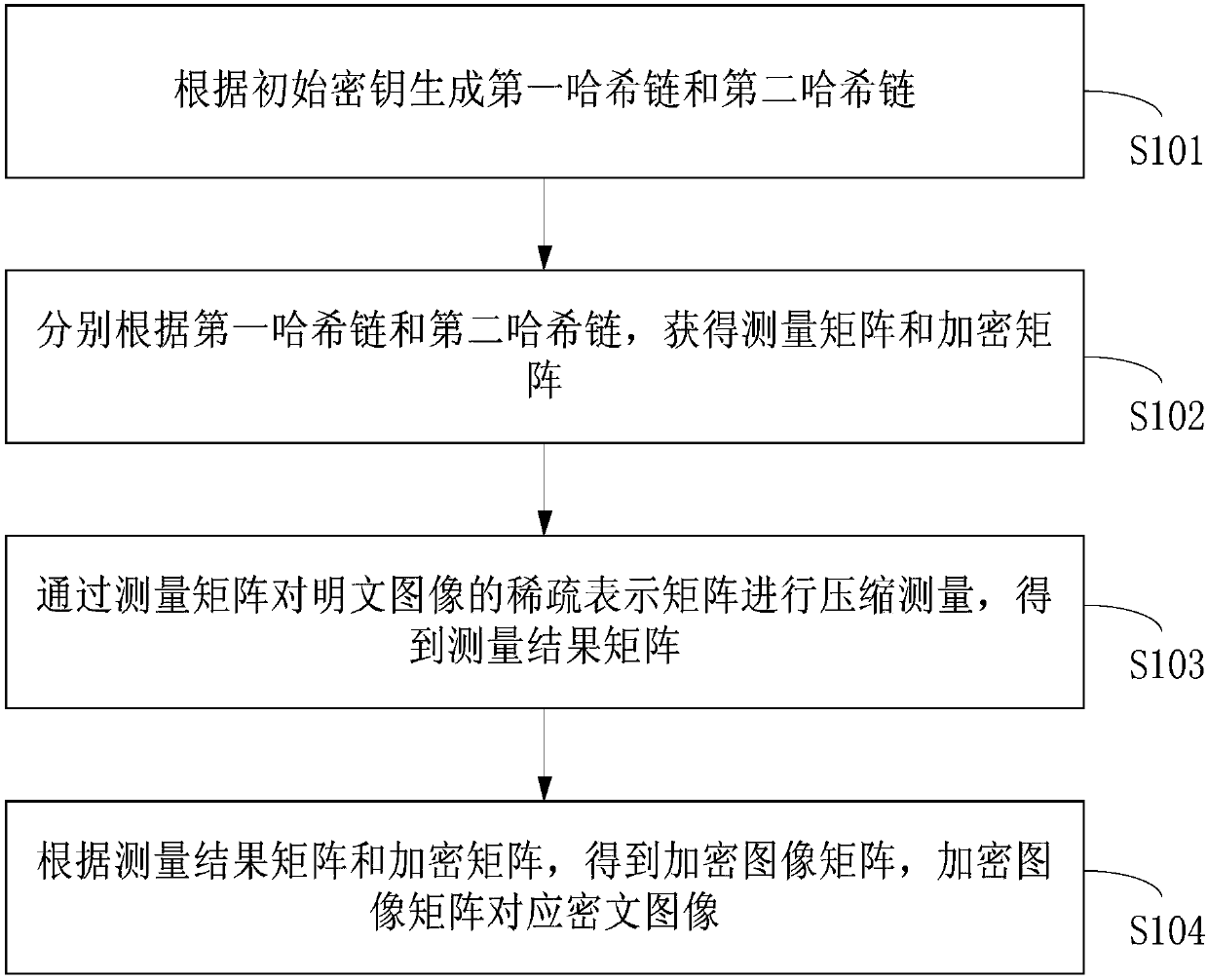
Image encryption method and decryption method based on Hash chain compressed sensing
ActiveCN108040191AReduce storage spaceReduce energy consumptionPictoral communicationComputer hardwareHash chain
The invention provides an image encryption method and decryption method based on Hash chain compressed sensing. According to the encryption method, a first Hash chain and a second Hash chain are generated according to an initial key; a measurement matrix and an encryption matrix are acquired according to the first Hash chain and the second Hash chain; compressed measurement is carried out on a sparse representation matrix of a plaintext image through the measurement matrix, thereby acquiring a measurement result matrix; and an encrypted image matrix is acquired according to the measurement result matrix and the encryption matrix. Only the initial key needs to be stored in a whole encryption process, so the key storage space and communication consumption are reduced. The key sensitivity ofa Hash function is very high, so completely different Hash sequences are generated due to small changes of an initial key value. The measurement matrix does not need to be stored at a position of a relay node, so the possibility that data is stolen at the position of the relay node is reduced, and the data transmission security is improved. The data security is ensured, and moreover, the key spaceoccupation quantity is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
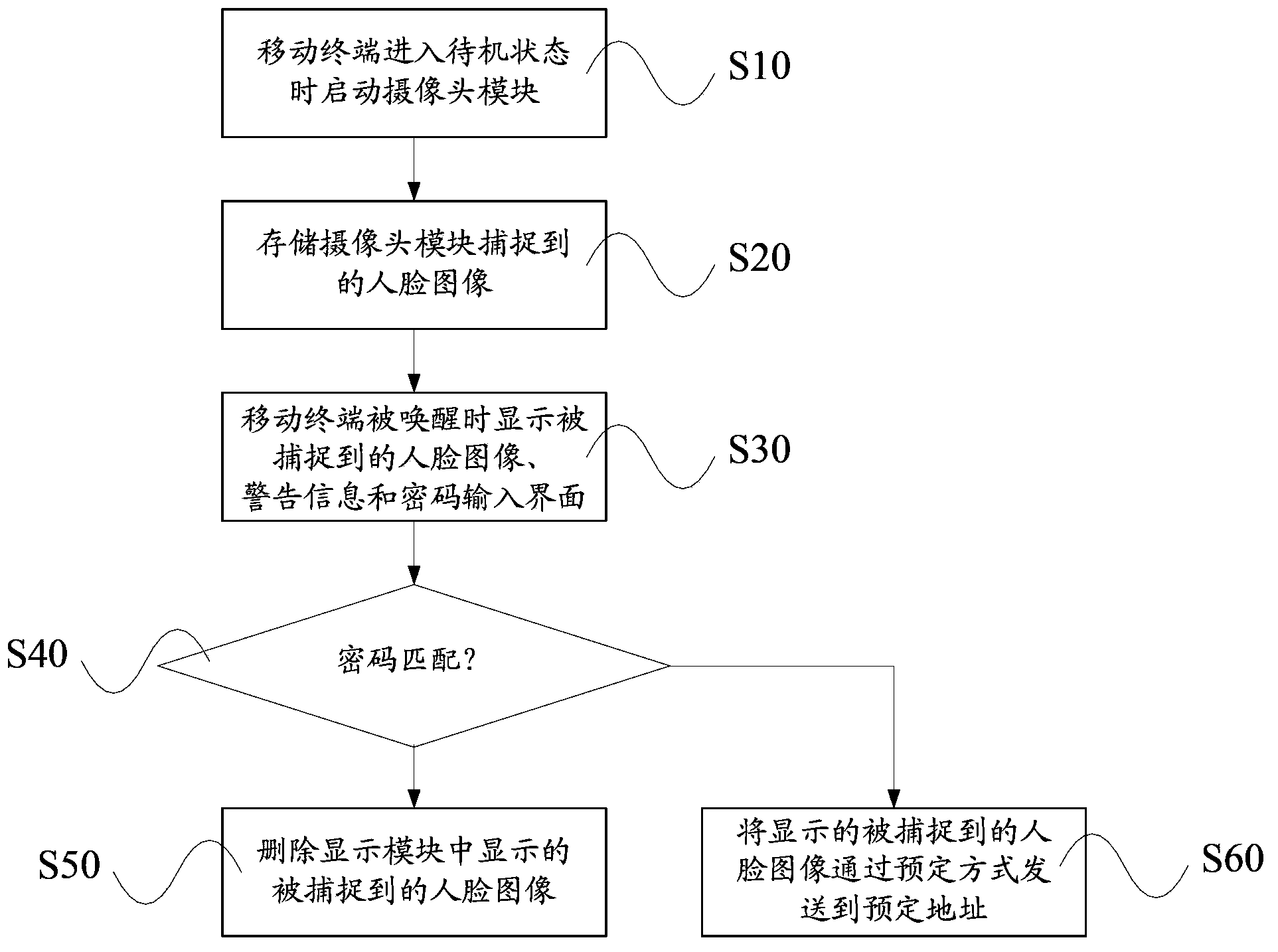
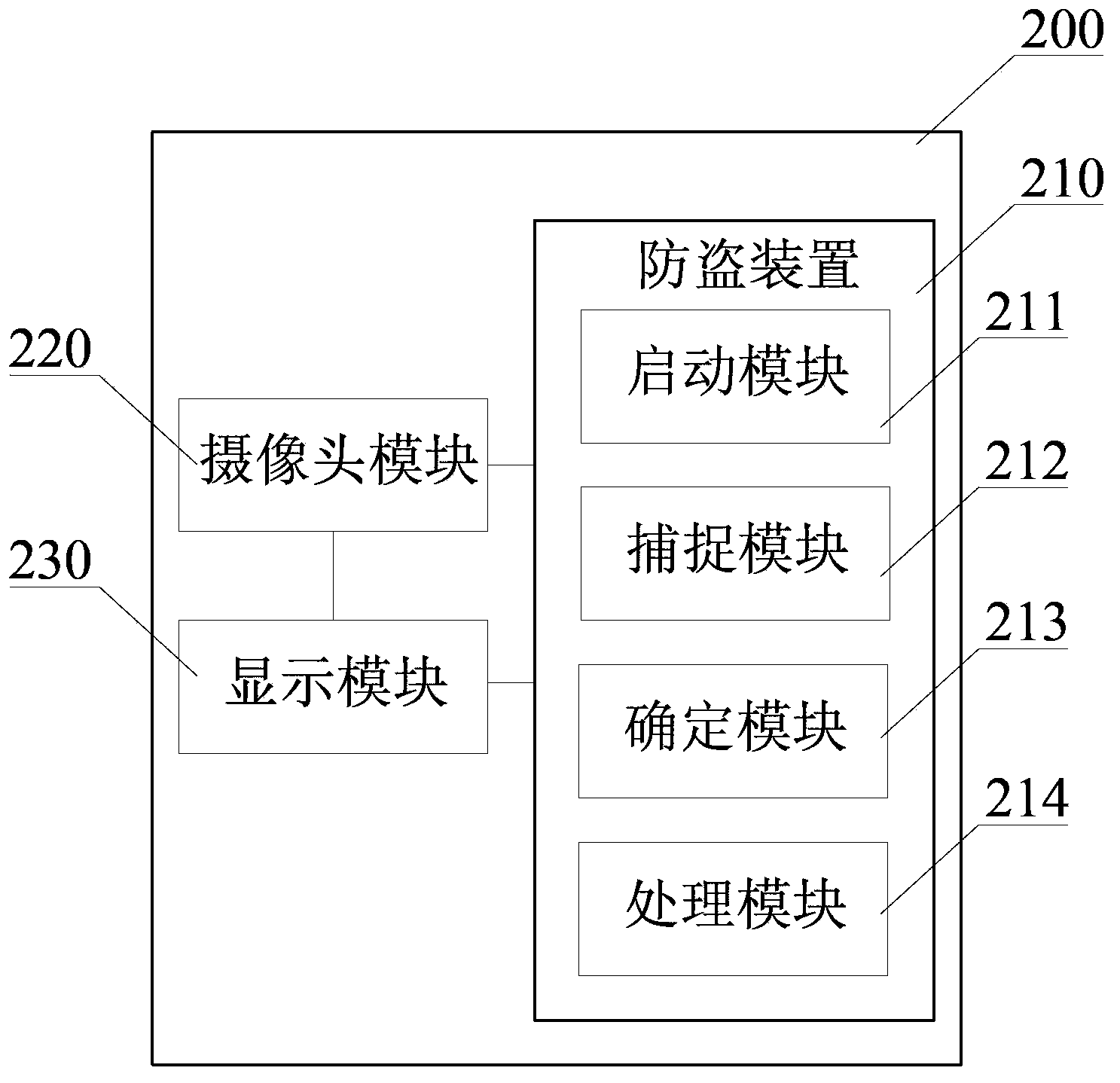
Mobile terminal theft prevention device and prevention method thereof
InactiveCN103581405AReduce the possibility of theftImprove securityCharacter and pattern recognitionSubstation equipmentTelecommunicationsComputer module
Provided in the present invention is an anti-theft method for a mobile terminal. The mobile terminal comprises a camera module and a display module. The method includes: a capturing step, in which the camera module is initiated to capture a facial image when the mobile terminal enters a stand-by state; and a determining step, in which the captured facial image and warning information are displayed on the display module when the mobile terminal is waked up. The anti-theft method of the mobile terminal provided in the present invention enables the mobile terminal to activate an alarm automatically before it can be stolen, therefore brings the effect of terminating a crime, greatly reduces the possibility of the mobile terminal being stolen, improves the safety of the mobile terminal, and satisfies needs of users.
Owner:BEIJING NETQIN TECH
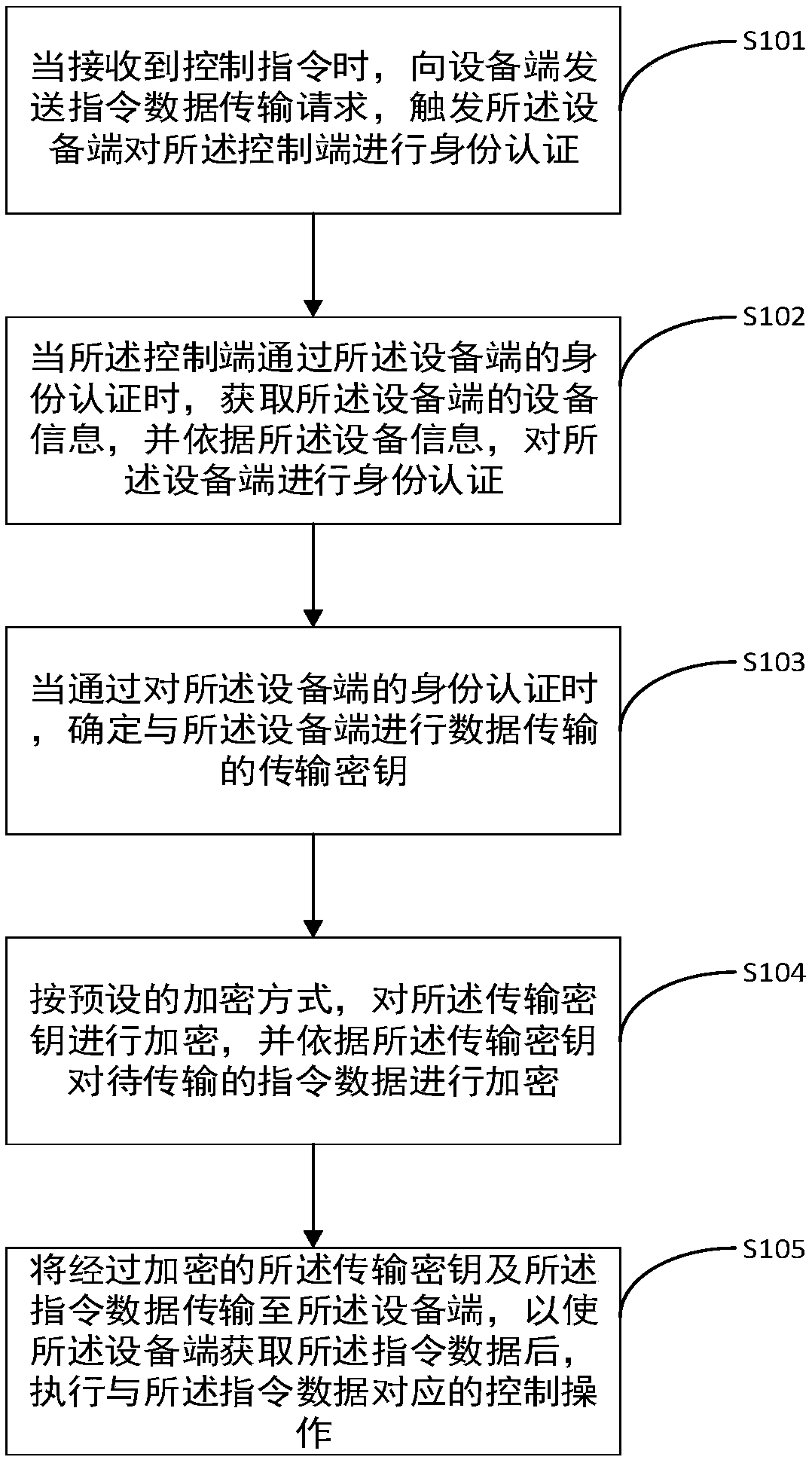
Control method and related equipment
ActiveCN109618334AImprove securityReduce the possibility of theftKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData transmissionData needs
The invention provides a control method. The control method comprises the steps that when a control end receives a control instruction, the control end sends an instruction data transmission request to an equipment end, and the equipment end is triggered to conduct identity authentication on the control end; when the control end passes identity authentication of the equipment end, the control endauthenticates the identity of the equipment end, and when identity authentication of the equipment end succeeds, a transmission key for achieving data transmission with the equipment is determined, and instruction data is encrypted according to the transmission key; and the equipment conducts decryption according to the transmission key, and a corresponding control operation is executed accordingto the instruction data obtained through decryption. By applying the control method, when the control end conducts instruction data transmission with the equipment end, the identities of the two parties are both authenticated, and after the identities pass authentication, the instruction data needing to be transmitted is encrypted, transmitted and decrypted according to the determined transmissionkey; and accordingly, the security of data information transmission is improved.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
A selling system for a self-service convenience store
InactiveCN107657769AIncrease incomeImprove purchasing efficiencyCoin-freed apparatus detailsCash registersPaymentSurveillance camera
The invention provides a selling system for a self-service convenience store. The selling system comprises a self-service convenience store body in which multiple selling shelves are arranged; the self-service convenience store body is inside provided with an entry / exit mechanism, a selling mechanism, an anti-theft mechanism and a light intelligent control mechanism; the entry / exit mechanism consists of an entrance, a round fixed plate, a unidirectional bearing, a rotary shaft, a revolving door, an induction lock, a square hole, a transverse stop rod, an exit and an automatic induction door; the selling mechanism is provided with a WiFi adapter, commodities, a cashier desk, an induction guard bar, an alarm light, an infrared sensor, a stop door, an electromagnet lock and a payment code scanner; the anti-theft mechanism comprises a placing stand, a two-dimensional code, software, wireless networking monitoring cameras, a management room, a display screen and a loudspeaker, wherein a control mechanism is arranged in the management room. The system is simple in structure and high in practicality.
Owner:深圳市小印相科技有限公司
Vehicular removable battery and antitheft system for vehicular removable battery
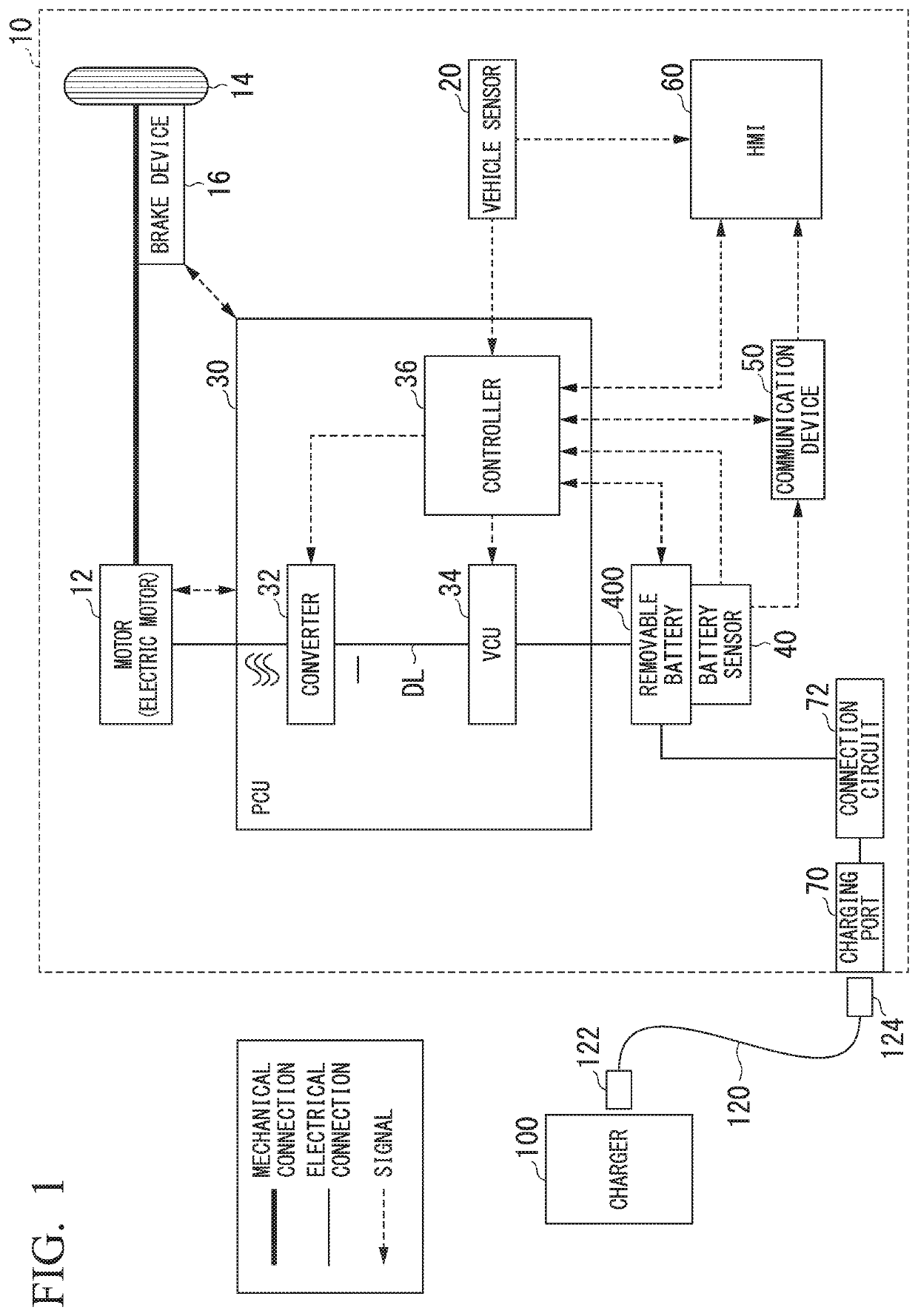
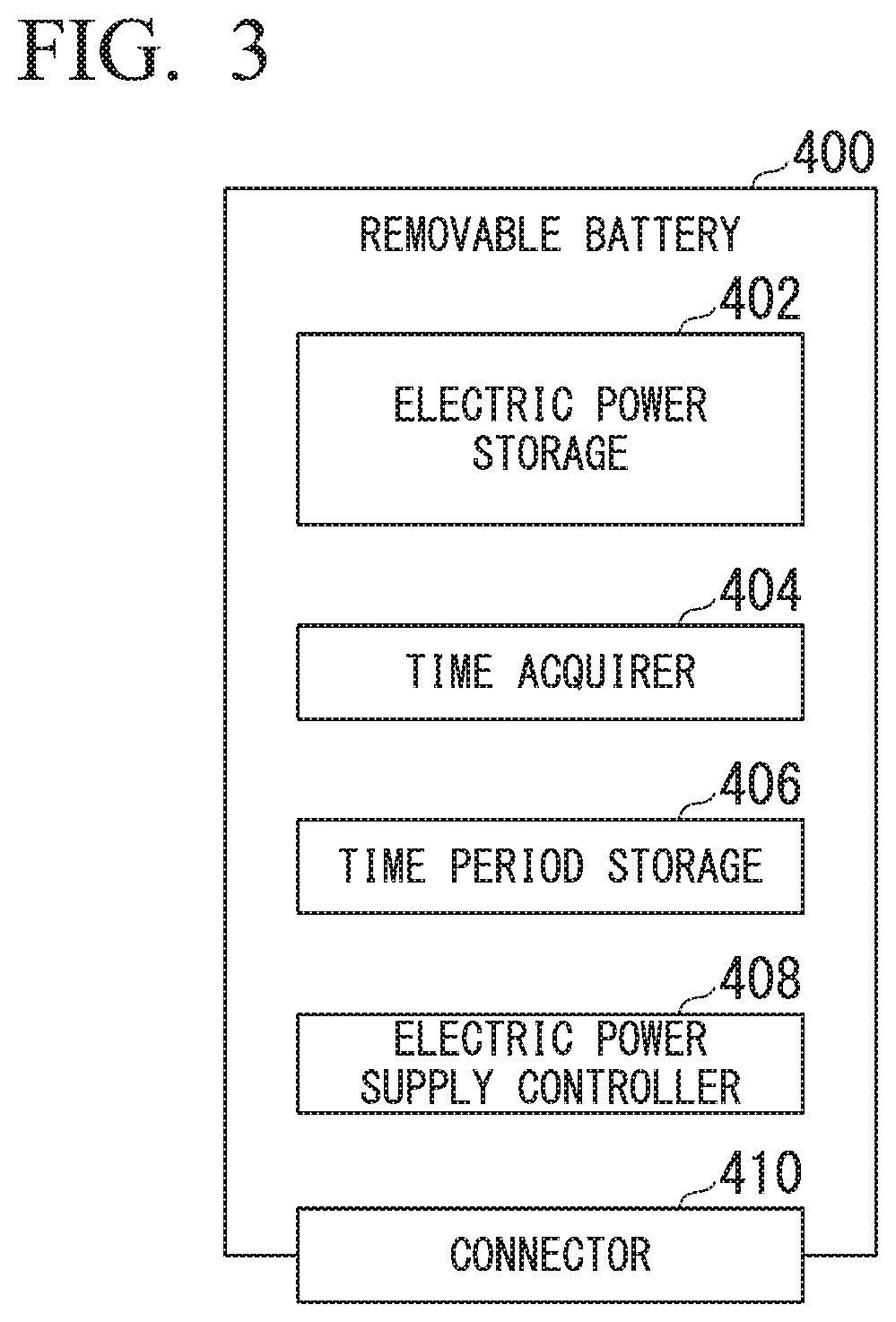
ActiveUS20210039595A1Reduce the possibilityReduce the possibility of theftBatteries circuit arrangementsCharging stationsElectrical batteryIn vehicle
A vehicular removable battery removably mountable in an electric vehicle includes a time acquirer configured to acquire a current time, a time period storage storing a time period in which electric power is supplied, and an electric power supply controller configured to control the supply of the electric power stored in an electric power storage to the electric vehicle. After the electric power supply controller detects that an activation instruction of the electric vehicle has been issued, the electric power supply controller is configured to enable the supply of the stored electric power to the electric vehicle in a case where the acquired current time is included in the stored time period. The electric power supply controller is configured to prohibit the supply of the electric power to the electric vehicle in a case where the acquired current time is not included in the stored time period.
Owner:HONDA MOTOR CO LTD
Cargo transportation monitoring method and system
ActiveCN107644309AReduce the possibility of theftGet it back in timeCo-operative working arrangementsLogisticsTransport engineeringMonitoring system
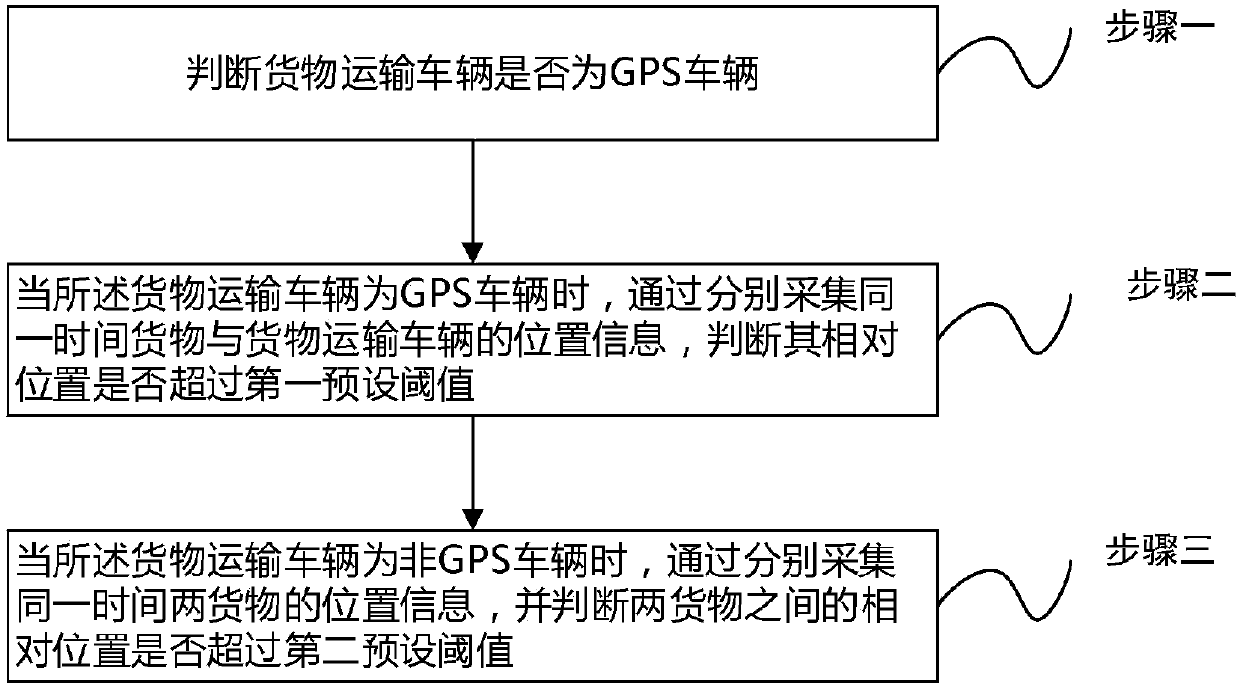
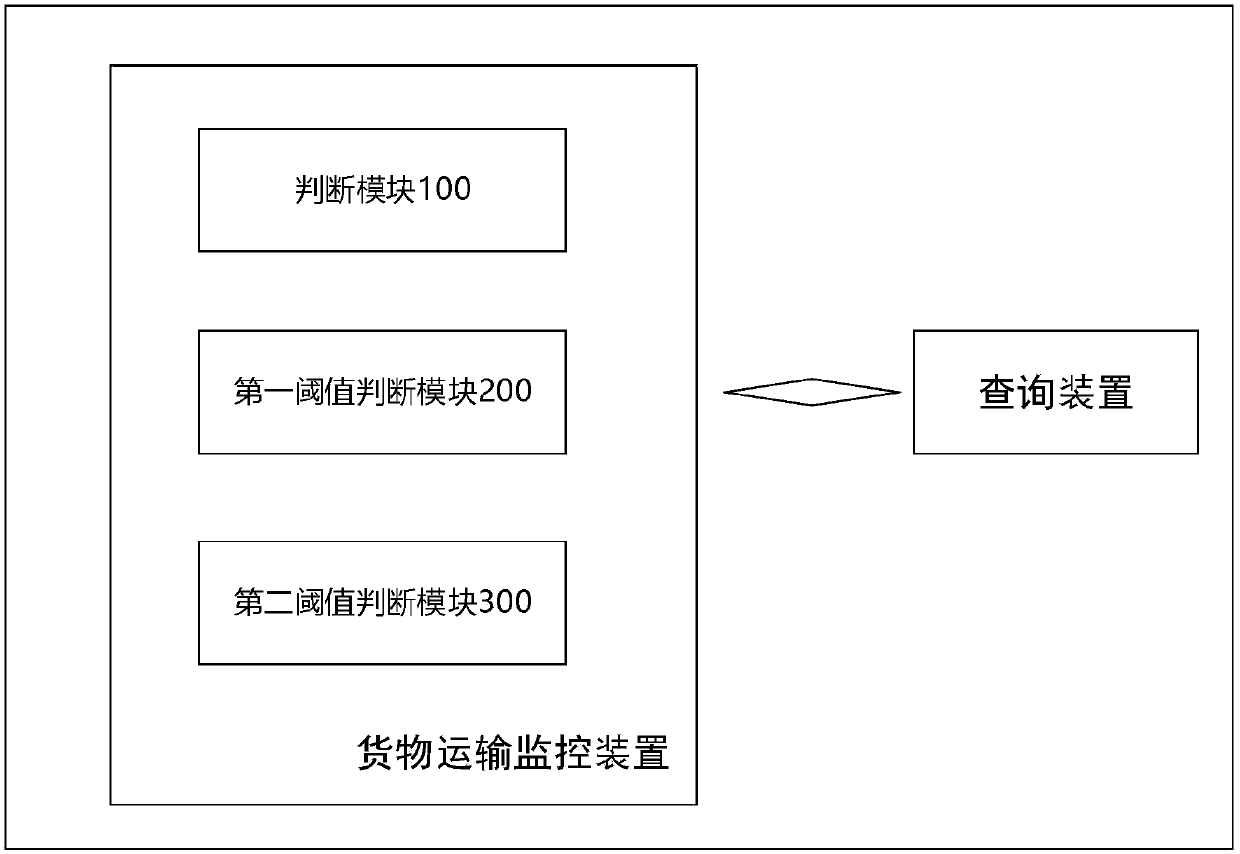
The invention discloses a cargo transportation monitoring method. Each cargo is provided with an electronic positioning label. The method comprises the steps that 1 whether a cargo transportation vehicle is a GPS vehicle is judged; 2 if the cargo transportation vehicle is a GPS vehicle, the position information of the cargo and the cargo transportation vehicle is separately collected at the same time to determine whether the relative position exceeds a first preset threshold; and 3 if the cargo transportation vehicle is not a GPS vehicle, the position information of two cargoes is separately collected at the same time to determine whether the relative position of two cargoes exceeds a second preset threshold. In addition, the invention further provides a cargo transportation monitoring system. The technical problem that cargoes are easily stolen during a transportation process and are difficultly taken back, which is caused by the fact that the transportation process of the cargoes cannot be continuously and comprehensively monitored in the prior art, is solved.
Owner:深圳市易流科技股份有限公司
Fingerprint lock
ActiveCN110454002AReduce traces of useLess chance of password compromiseCleaning using toolsElectric permutation locksFingerprintFixed frame
The invention belongs to the technical field of fingerprint locks, and particularly relates to a fingerprint lock. The fingerprint lock comprises a fingerprint lock body, the fingerprint lock body comprises a code keyboard and a fingerprint identification module, a fixed frame is fixed to the front face of the fingerprint lock body, sliding grooves are formed in the left and right inner side wallsof the fixed frame, sliding blocks are in sliding connection into the sliding grooves, baffles are fixed to the front faces of the sliding blocks, round rods are fixed to the bottom ends of the two sliding blocks, rectangular grooves are formed in the left and right inner side walls of the fixed frame, and a rectangular box is fixed in each rectangular groove. The fixed frame, the baffles and other structures e arranged, the baffles are used for protecting the fingerprint lock body, the surface of the fingerprint lock body is more clean, a pressing block is used, gas is sprayed out to the area of the code keyboard of the fingerprint lock, the area of the code keyboard of the fingerprint lock is kept clean, use traces left by a user are reduced, the password leakage probability is reduced,and safety of the fingerprint lock is improved.
Owner:龙南恩嘉智能科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com