Security chip, authentication method based on biological features and intelligent terminal
A security chip and biometric technology, applied in the field of information security, can solve problems such as the theft of fingerprint information by criminals, and achieve the effect of improving information security and reducing the possibility of theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
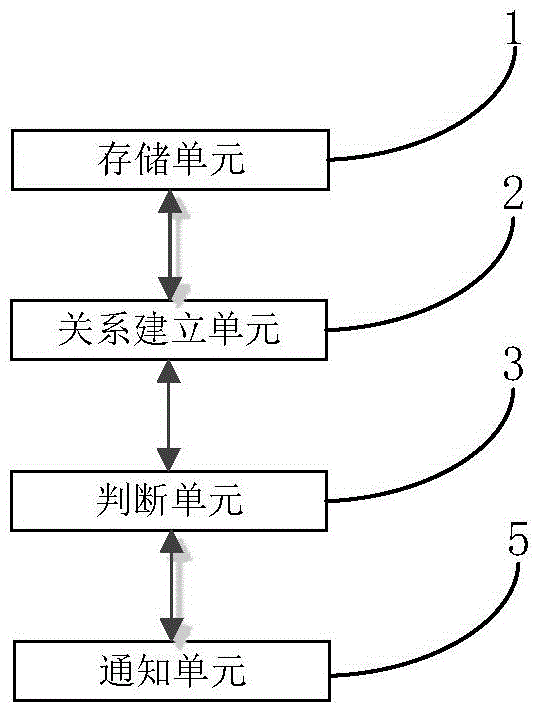
Image
Examples
Embodiment 1
[0039] A biometric-based authentication method comprising:
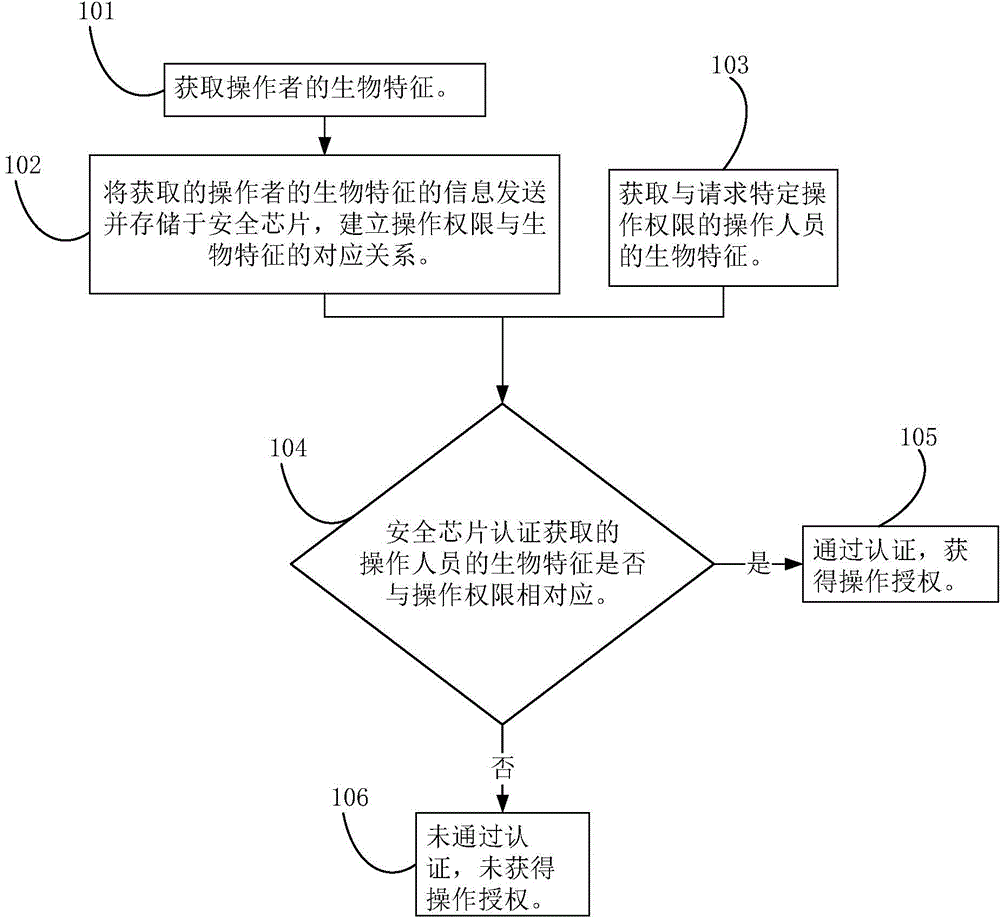
[0040] Step 101. Obtain the biometric feature of the operator corresponding to the operation authority.
[0041] Step 102. Sending and storing the acquired information of the operator's biometric feature in the security chip, and establishing a correspondence between the operation authority and the biometric feature.
[0042] Step 103. Obtain the biometrics of the operator requesting the operation authority.
[0043] Step 104. Whether the biometrics of the operator acquired by the security chip authentication corresponds to the operation authority, if yes, go to step 105, if not, go to step 106.
[0044] Step 105. Obtain operation authorization through authentication.
[0045] Step 106. The authentication is not passed, and the operation authorization is not obtained.
[0046]The beneficial effects of the present invention are as follows: after the biometric feature is collected, it is directly sent to the securit...
Embodiment 2
[0057] A biometric-based authentication method comprising:
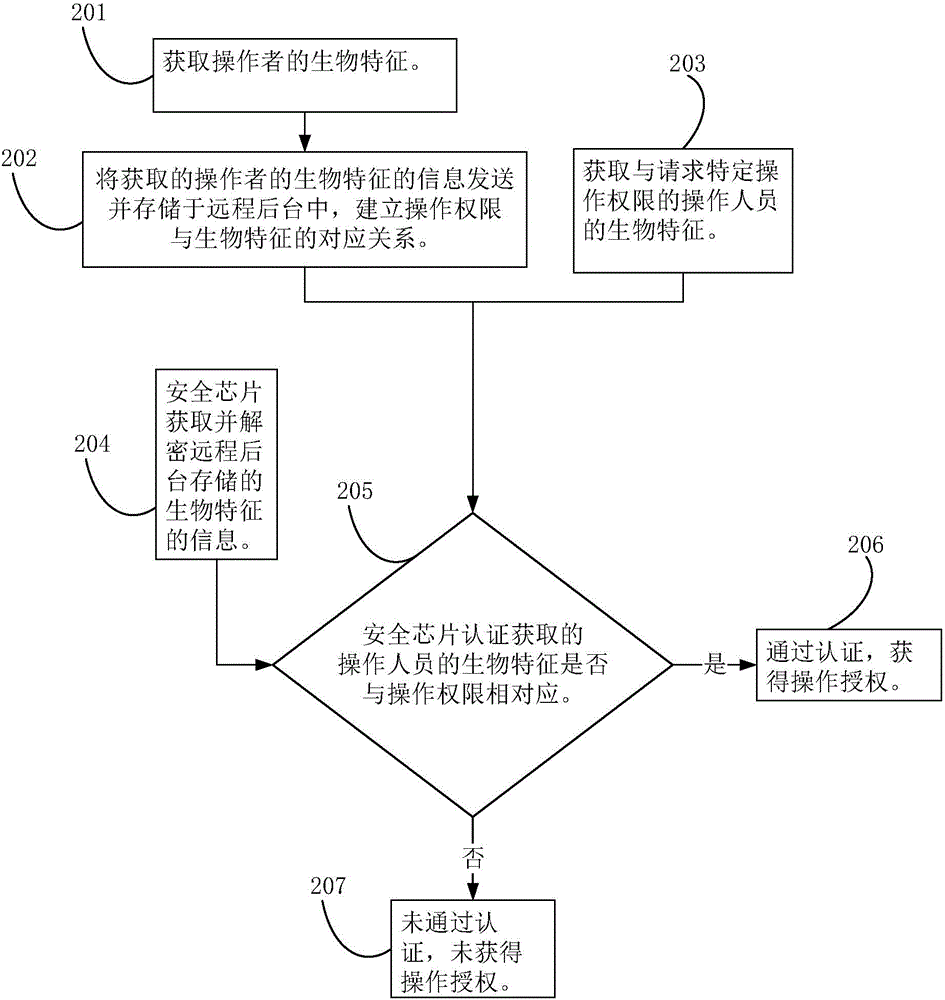
[0058] Step 201. Obtain the biometric feature of the operator corresponding to the operation authority.
[0059] Step 202. Send and store the obtained information of the operator's biometric feature in a third-party platform, and establish a correspondence between the operation authority and the biometric feature.
[0060] Step 203. Obtain the biometrics of the operator requesting the operation authority.
[0061] Step 204. The security chip acquires and decrypts the biometric information stored on the third-party platform.
[0062] Step 205. Whether the biometric feature of the operator acquired by the security chip authentication corresponds to the operation authority, if yes, go to step 206, if not, go to step 207.
[0063] Step 206. Obtain operation authorization through authentication.
[0064] Step 207. The authentication is not passed, and the operation authorization is not obtained.
[0065] The beneficia...
Embodiment 3
[0078] Embodiment 3 of an authentication method based on biometric features of the present invention is introduced.
[0079] In this embodiment, the smart terminal is a smart phone, and the biometric feature is a fingerprint feature. The smart terminal includes a fingerprint security authentication module, and the smart terminal completes the identity authentication of the operator through the fingerprint security authentication module.
[0080] In this embodiment, include:
[0081] Step 301: The mobile phone starts up and enters the operator registration module.
[0082] Step 302: The fingerprint security authentication module collects the fingerprint information of the operator through the fingerprint sensor.
[0083] Step 303. The fingerprint security authentication module or the fingerprint sensor itself extracts fingerprint feature data for the operator's fingerprint information collected by the fingerprint sensor.
[0084] Step 304. The fingerprint feature data is stor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com