Patents
Literature
249 results about "Hash chain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
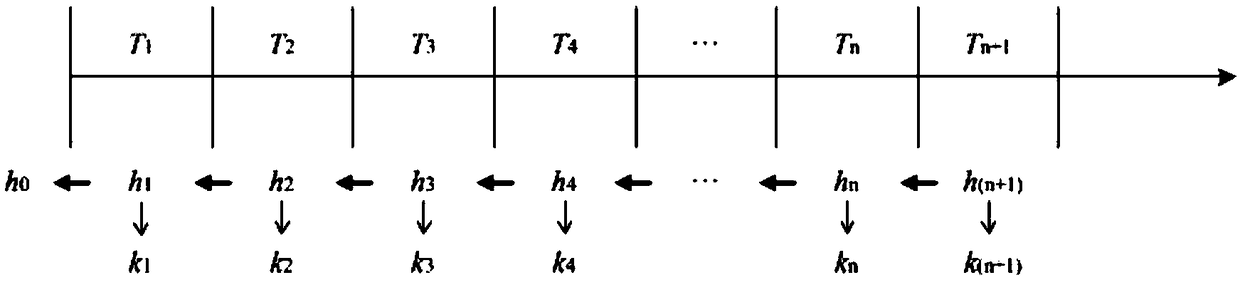
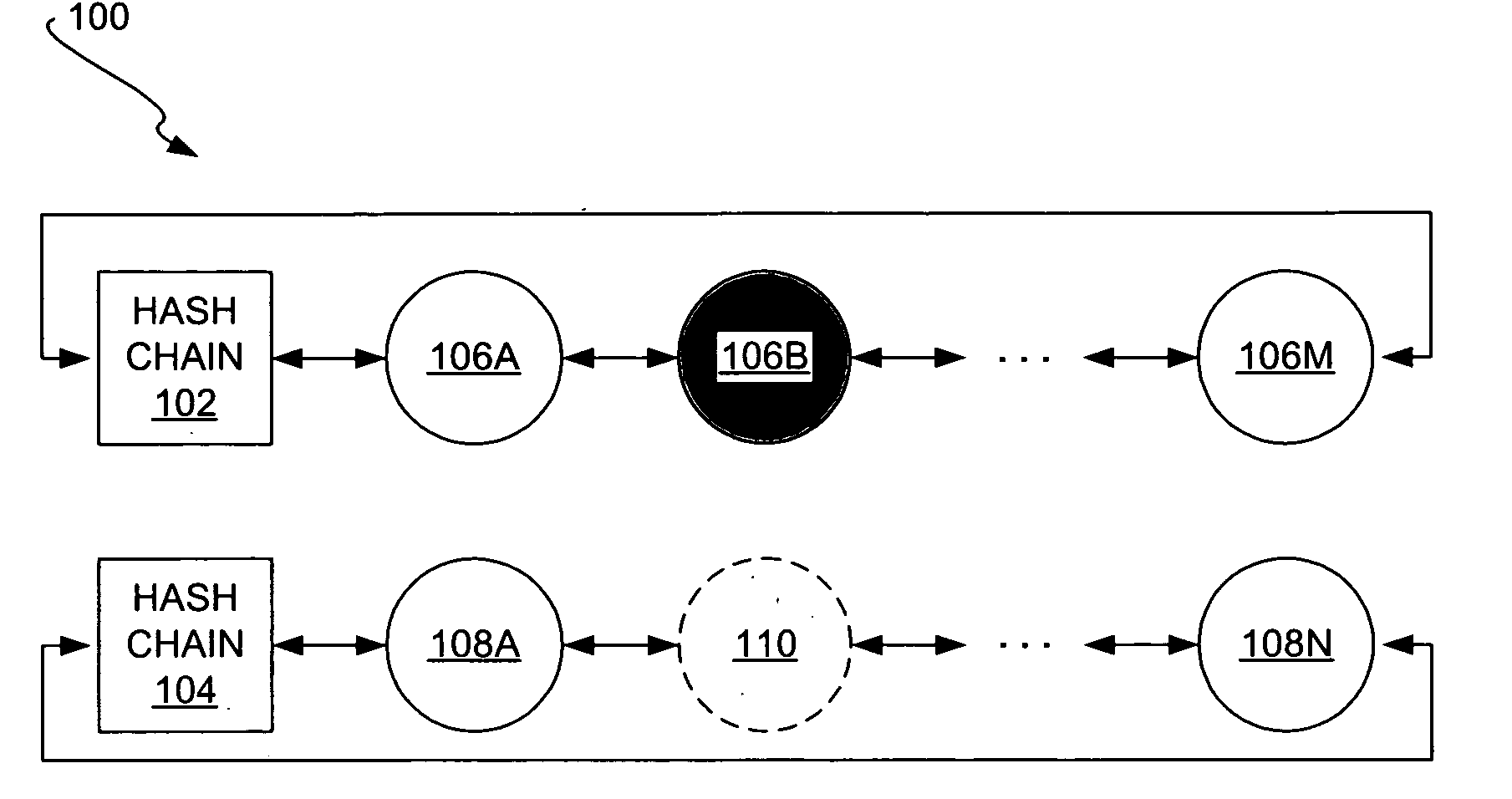
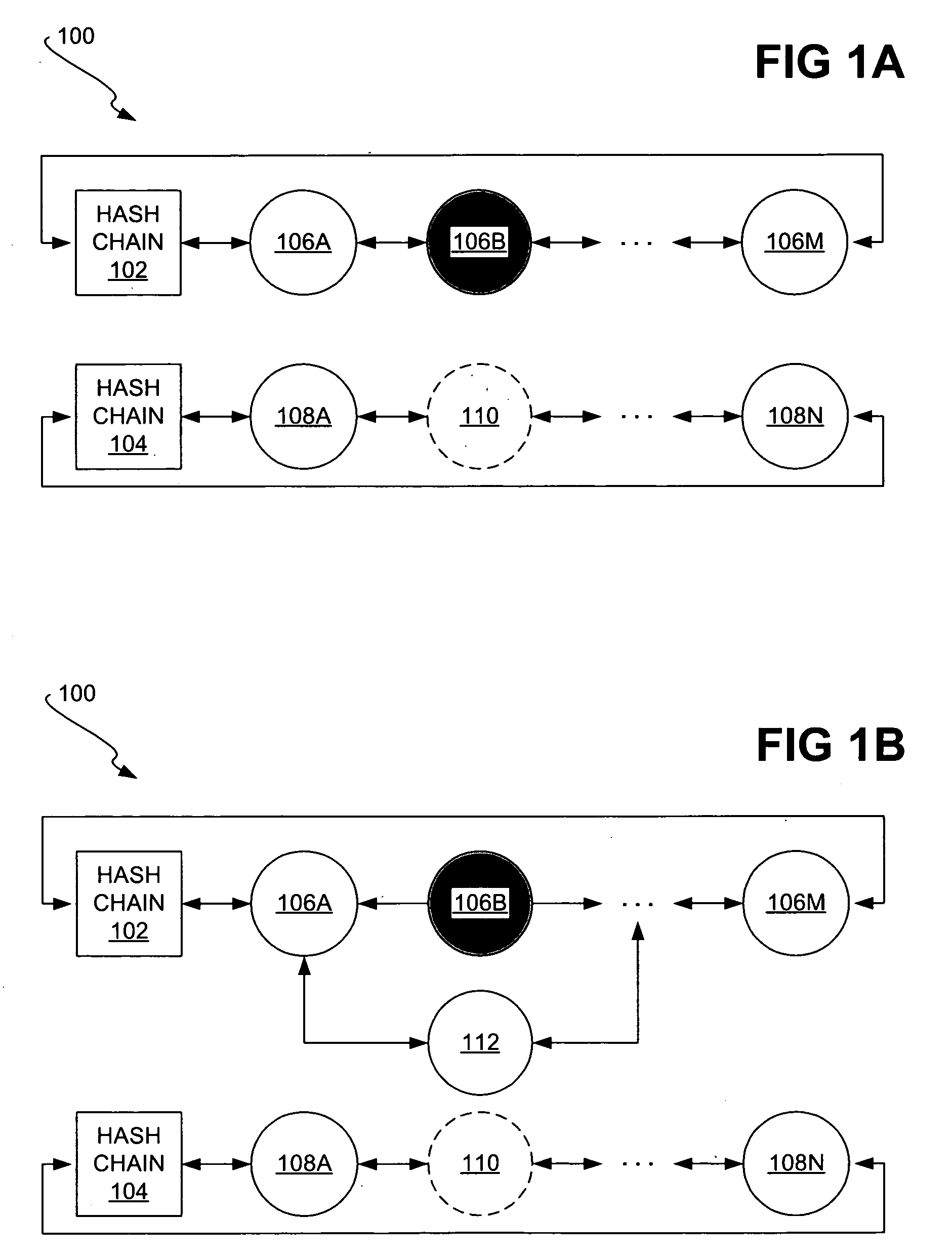
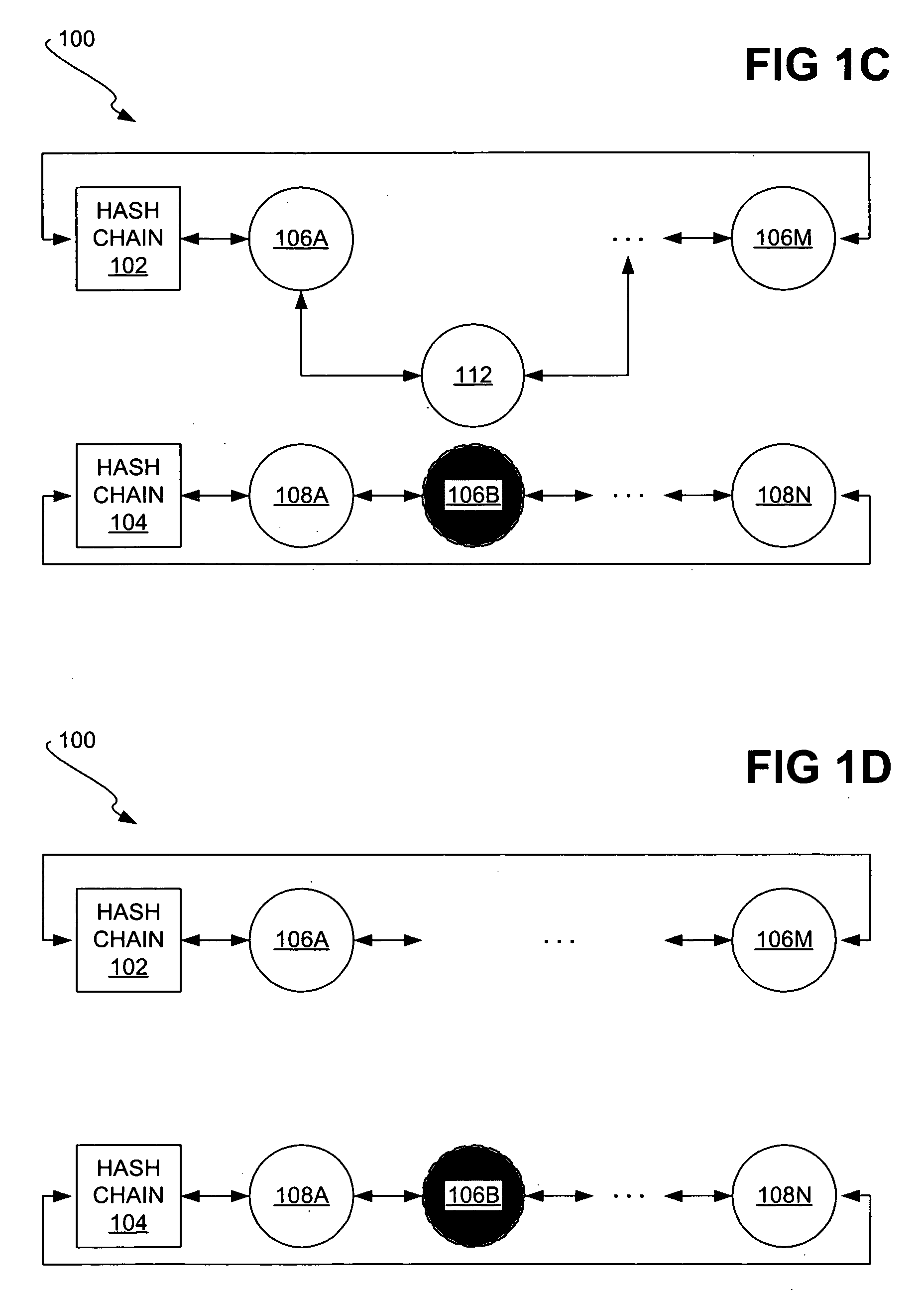
A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method to produce many one-time keys from a single key or password. For non-repudiation a hash function can be applied successively to additional pieces of data in order to record the chronology of data's existence.
Virtual currency transaction validation method based on block chain multi-factor cross-validation
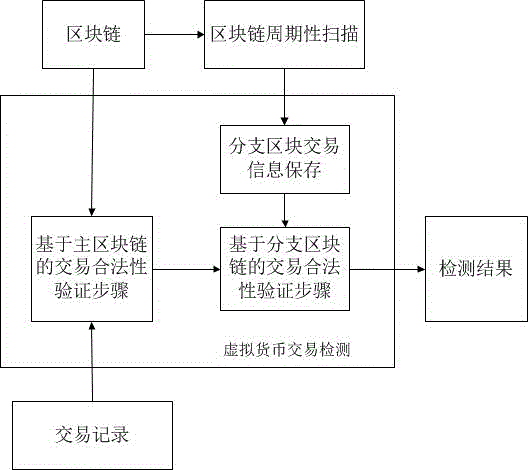
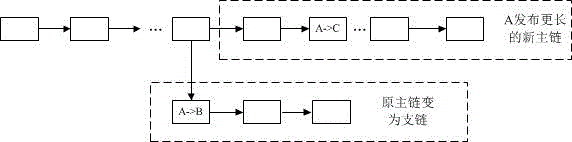
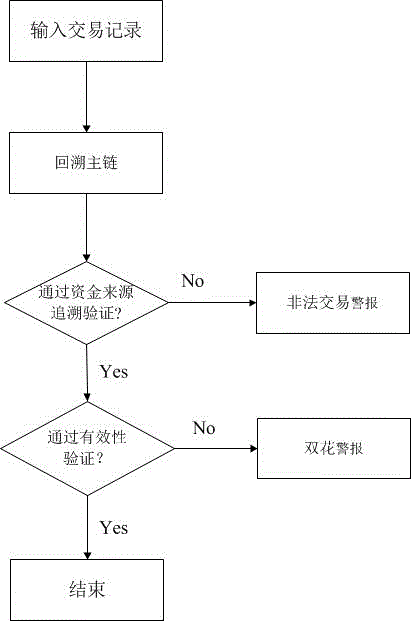
The invention provides a virtual currency transaction validation method based on block chain multi-factor cross-validation to solve the double-spending problem that virtual currency based on block chains are liable to 51% attacks and thus generates transactions. The method queries and backups a history block chain branch periodically, organizes confirmed transaction information into a hash chain list array which is easy for querying, and avoids branch transaction information losses induced by block chain evolution. During a virtual currency transaction, the method not only checks payer information, recipient information, a fund source, a currency transaction amount and the like recorded in a current main block chain, but also queries a backup branch block chain to check whether the current transaction and a history transaction on the branch block chain have the same fund source. If any transaction does not pass the check, a miner gives an alarm over the whole network about the transaction, so that the method can avoid the double-spending problem induced by illegal transactions.
Owner:SICHUAN UNIV
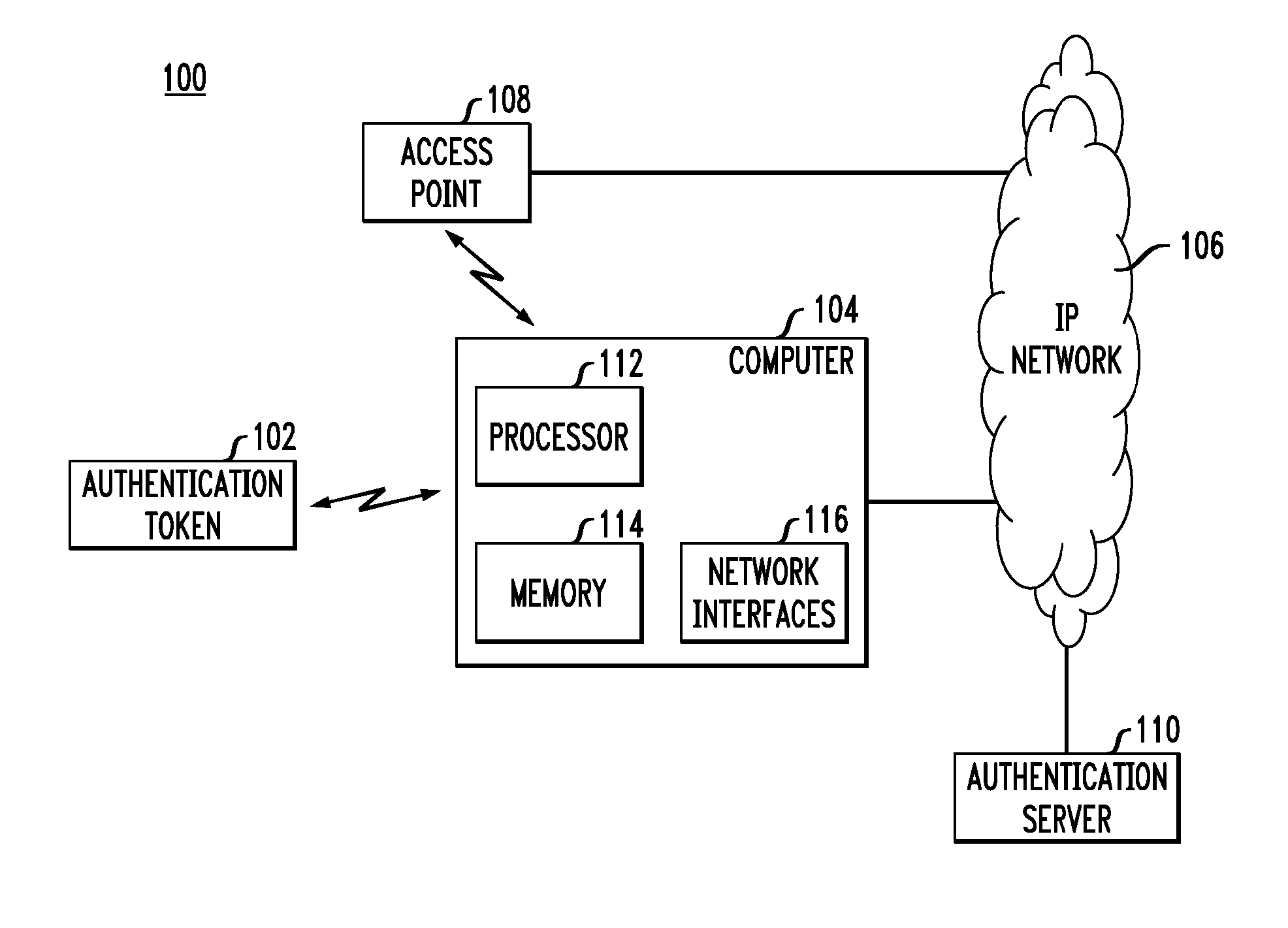
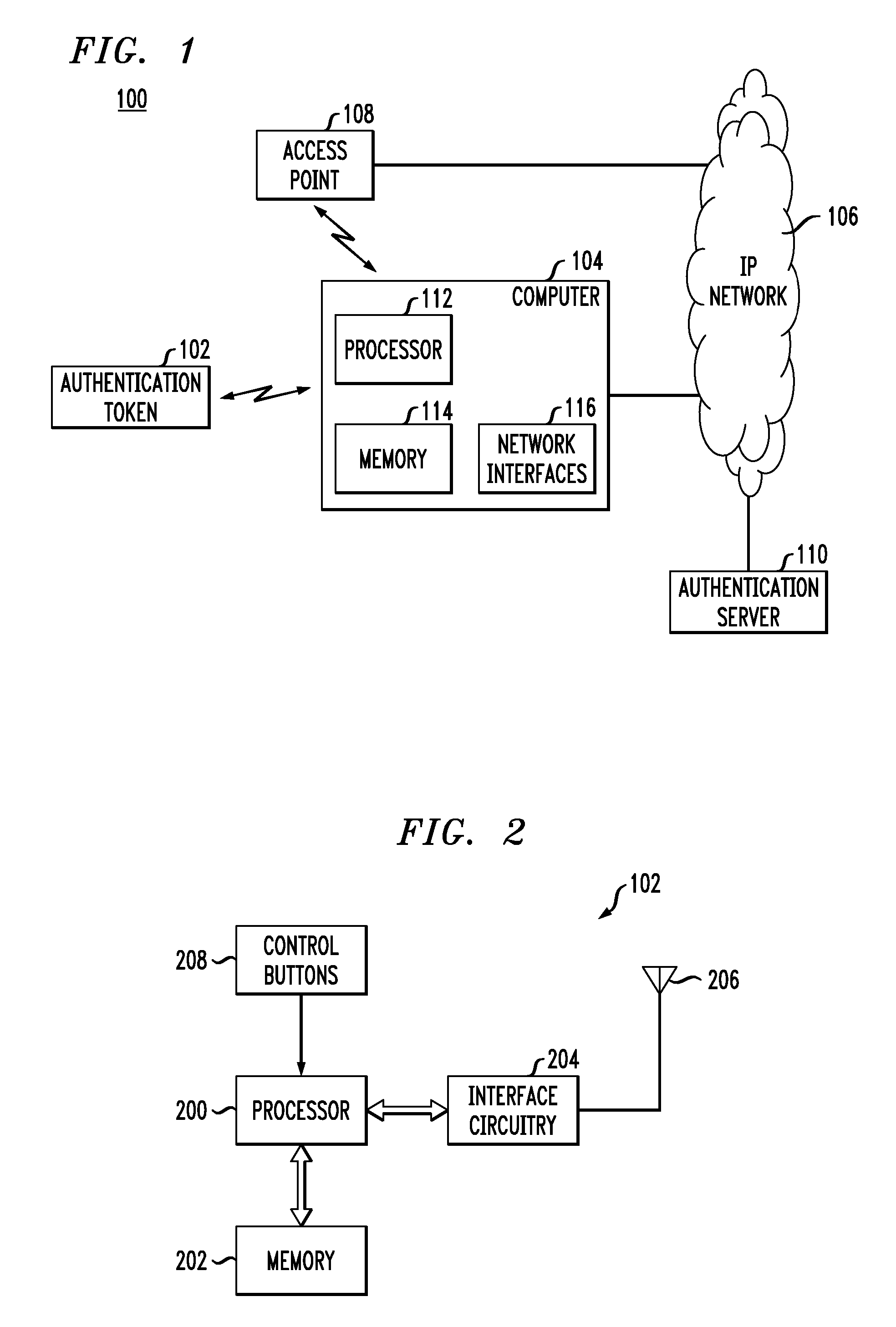
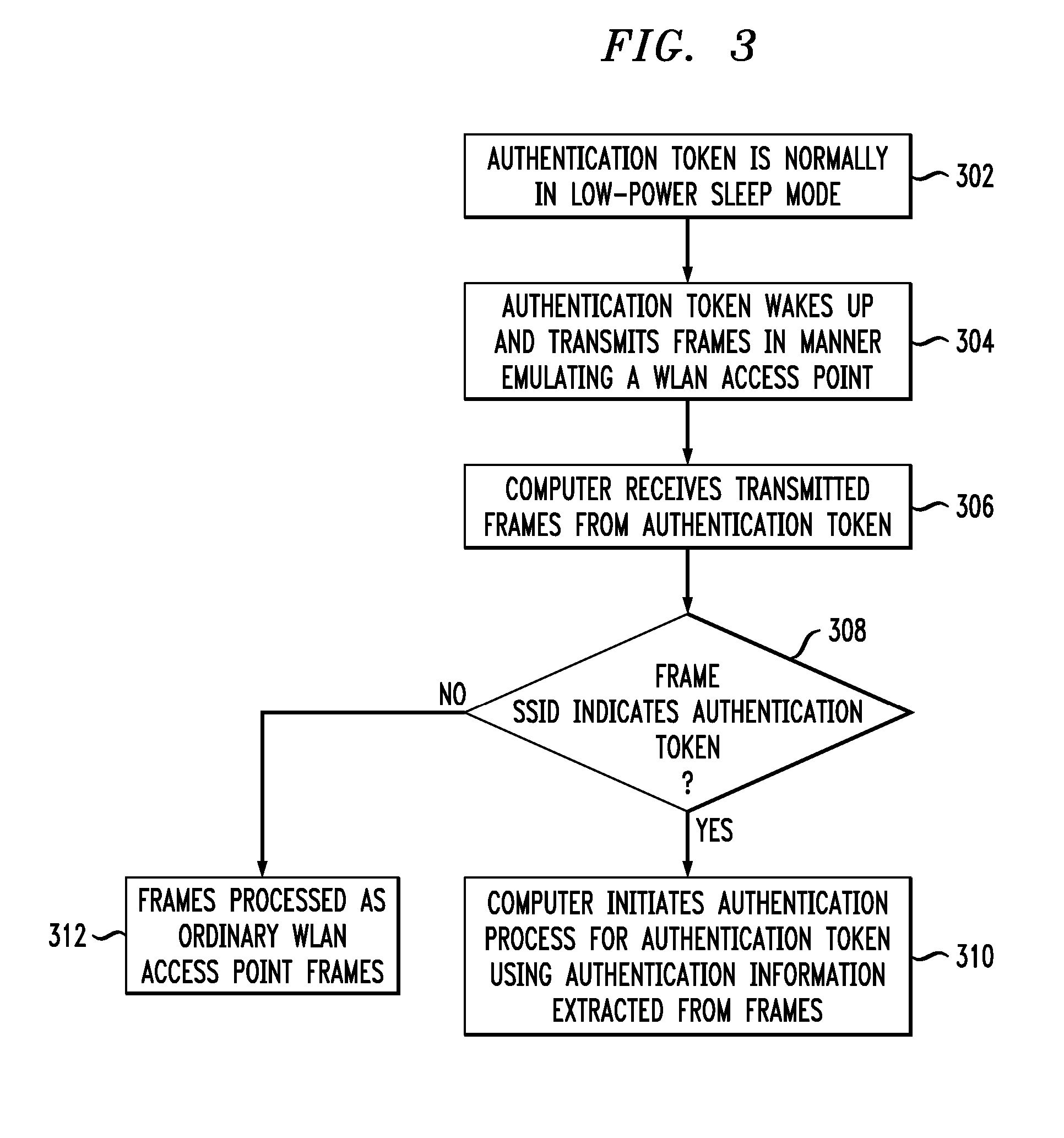
Authentication Methods and Apparatus Utilizing Hash Chains
ActiveUS20070279227A1Improve securitySuitable for operationUser identity/authority verificationUnauthorized memory use protectionComputer hardwareHash chain
A first processing device, which may be, for example, a wireless authentication token or an RFID tag, comprises a memory, a processor coupled to the memory, and interface circuitry coupled to the processor. The processor is operative to control the output of authentication information via the interface circuitry, where the authentication information comprises a sequence of values corresponding to images of a hash chain. A given one of the values of the sequence is utilized by a second processing device to generate a modified value suitable for providing joint authentication of the first and second processing devices.
Owner:EMC IP HLDG CO LLC
Electronic coin stick with potential for future added value
InactiveUS6341273B1Without incurring processing and communication overheadIncreased flexibility of useFinanceUser identity/authority verificationPayment transactionHash chain
In a digital payment transactions system, a broker generates and stores a secret number. The broker then generates a chain of hash values by successive operations of a hash function, using the secret number as the starting value. The broker then issues to the user a digitally encoded value from some way down the chain of hash values. The user generates a coin stick which comprises a chain of hash values starting with the value communicated by the broker. Subsequently, the broker can transfer further value to the user, without generating a new coin stick, by communicating a digitally encoded value from the broker's hash chain which precedes the value originally communicated to the user.
Owner:BRITISH TELECOMM PLC
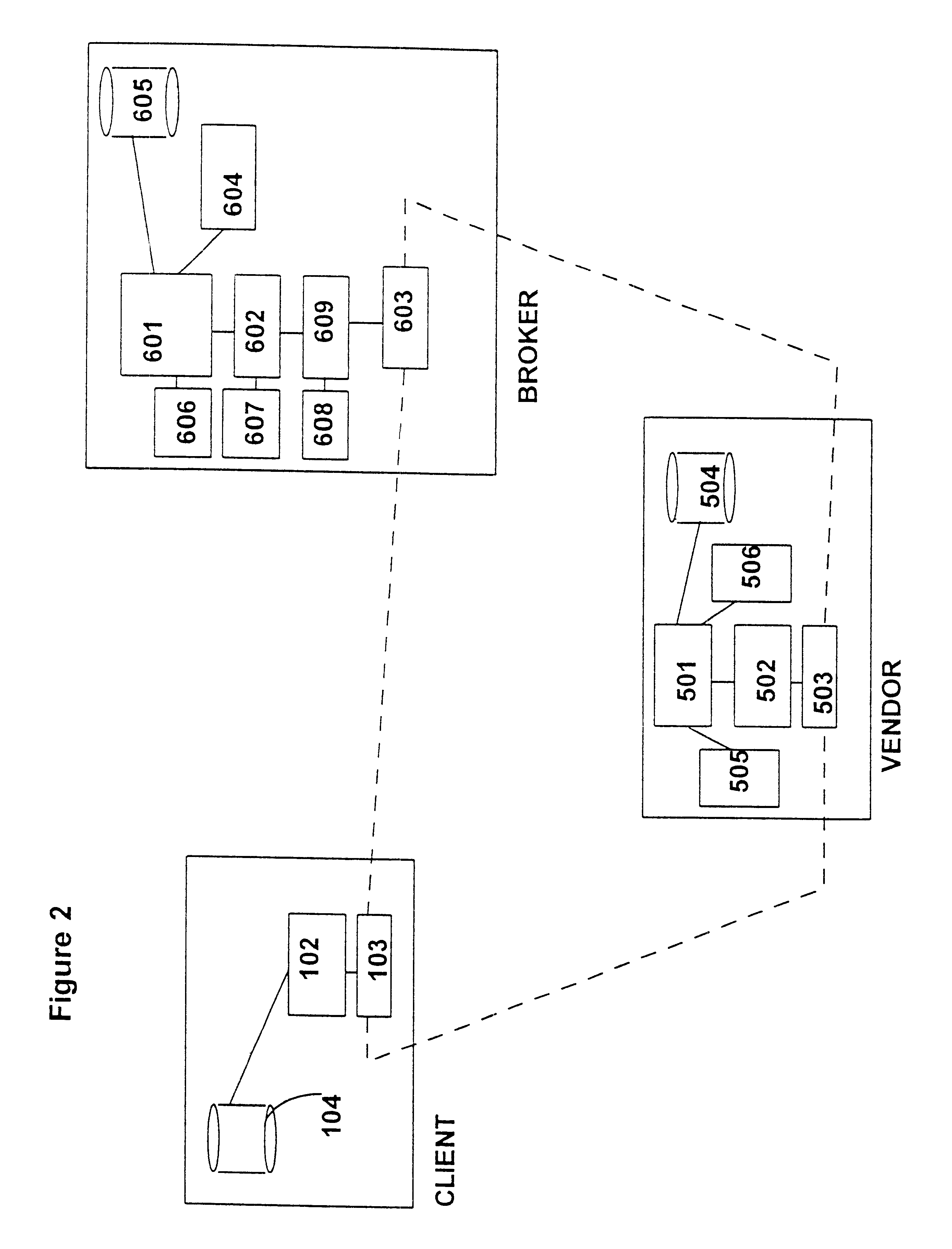
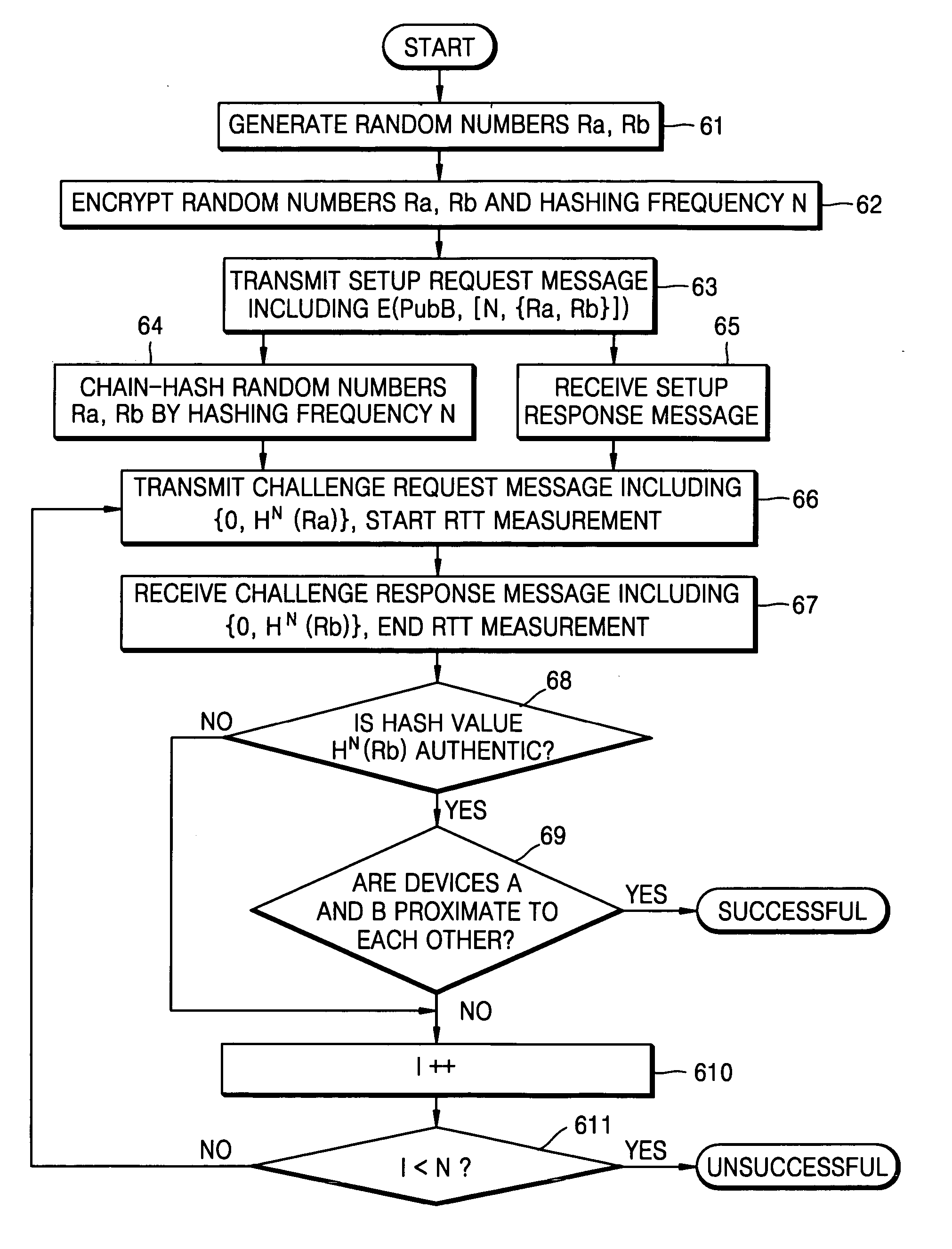
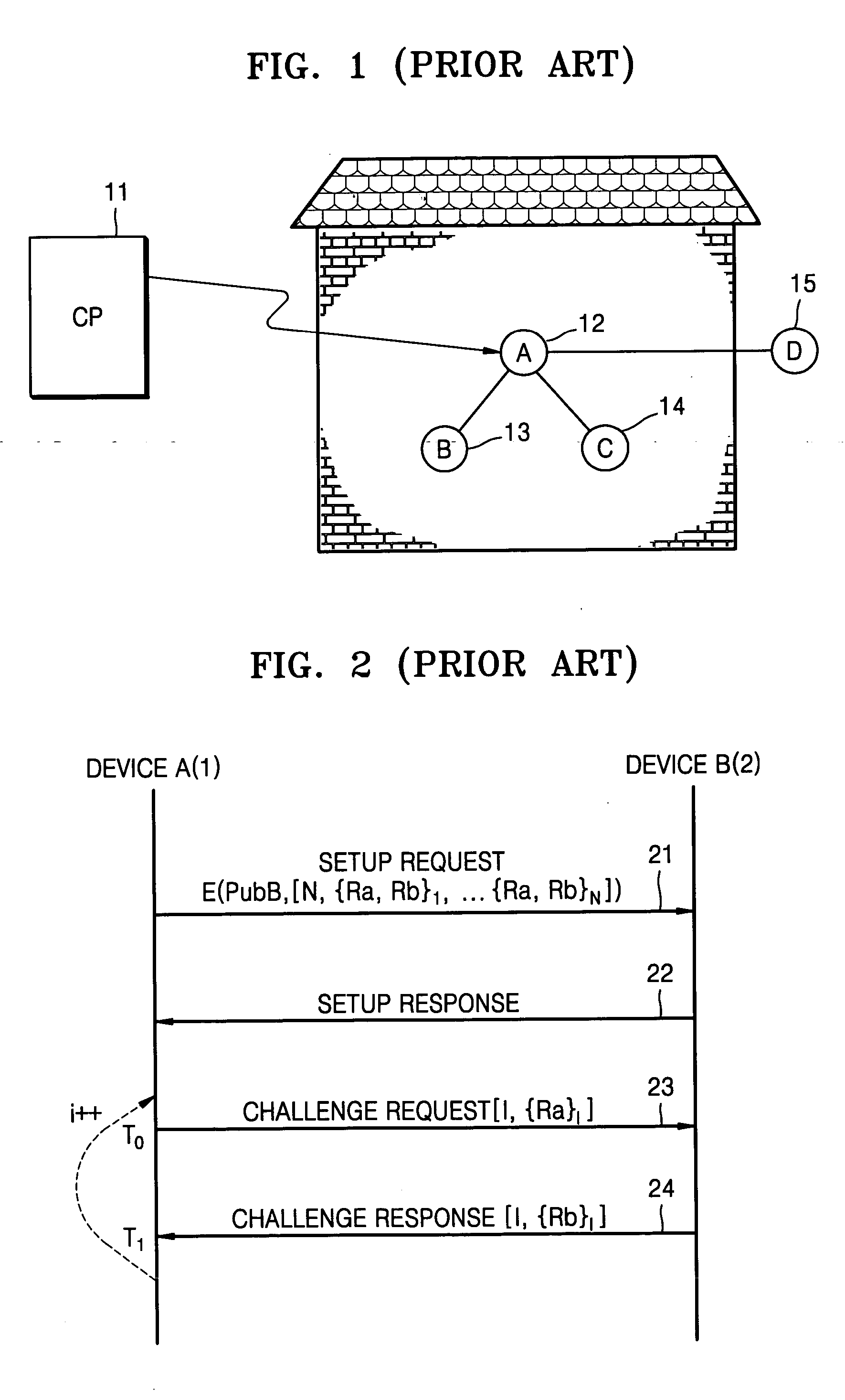
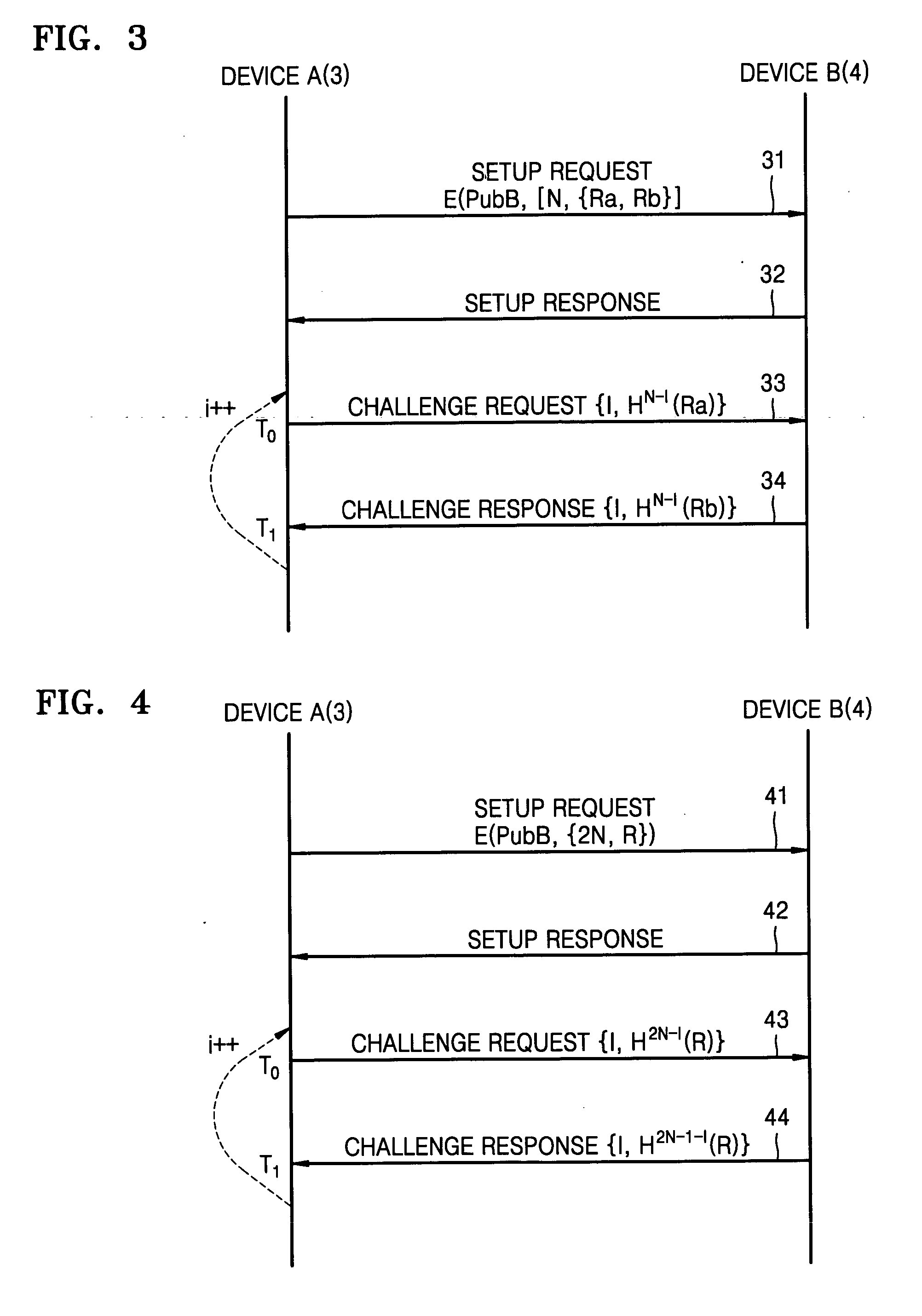
Method and apparatus for checking proximity between devices using hash chain
InactiveUS20060248340A1Checking proximity more effectivelyData taking preventionDigital data processing detailsComputer hardwareHash chain
Owner:SAMSUNG ELECTRONICS CO LTD
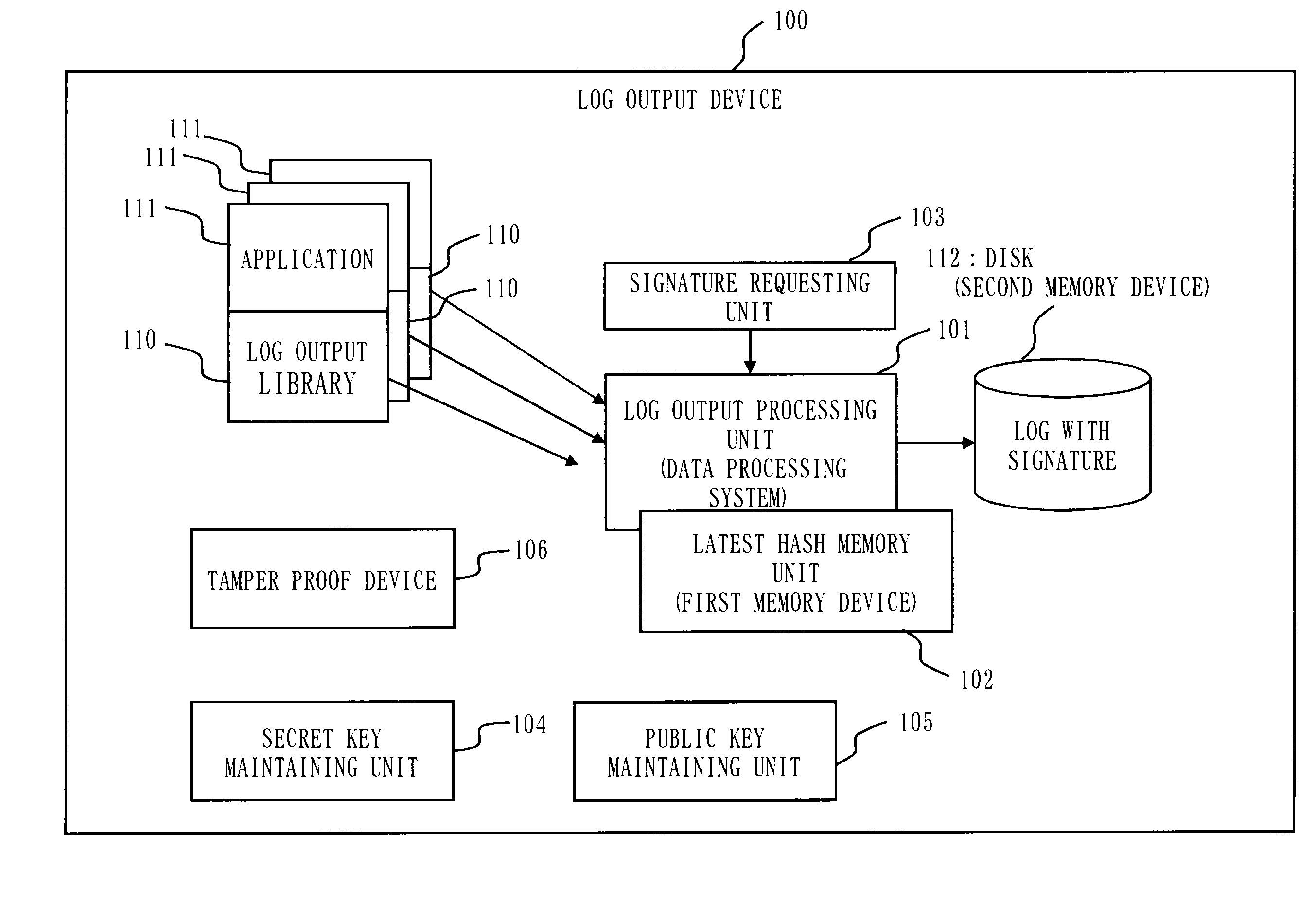
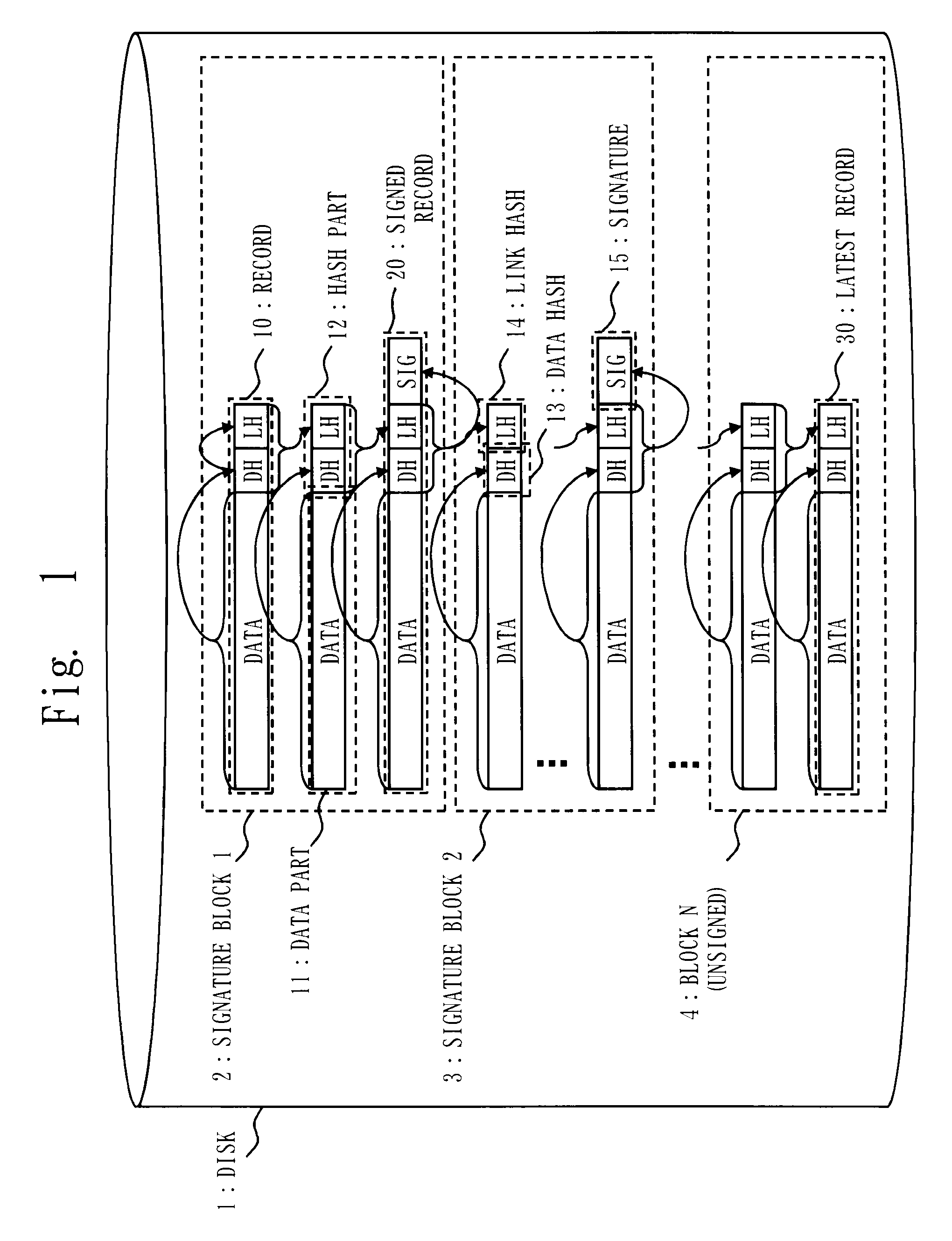
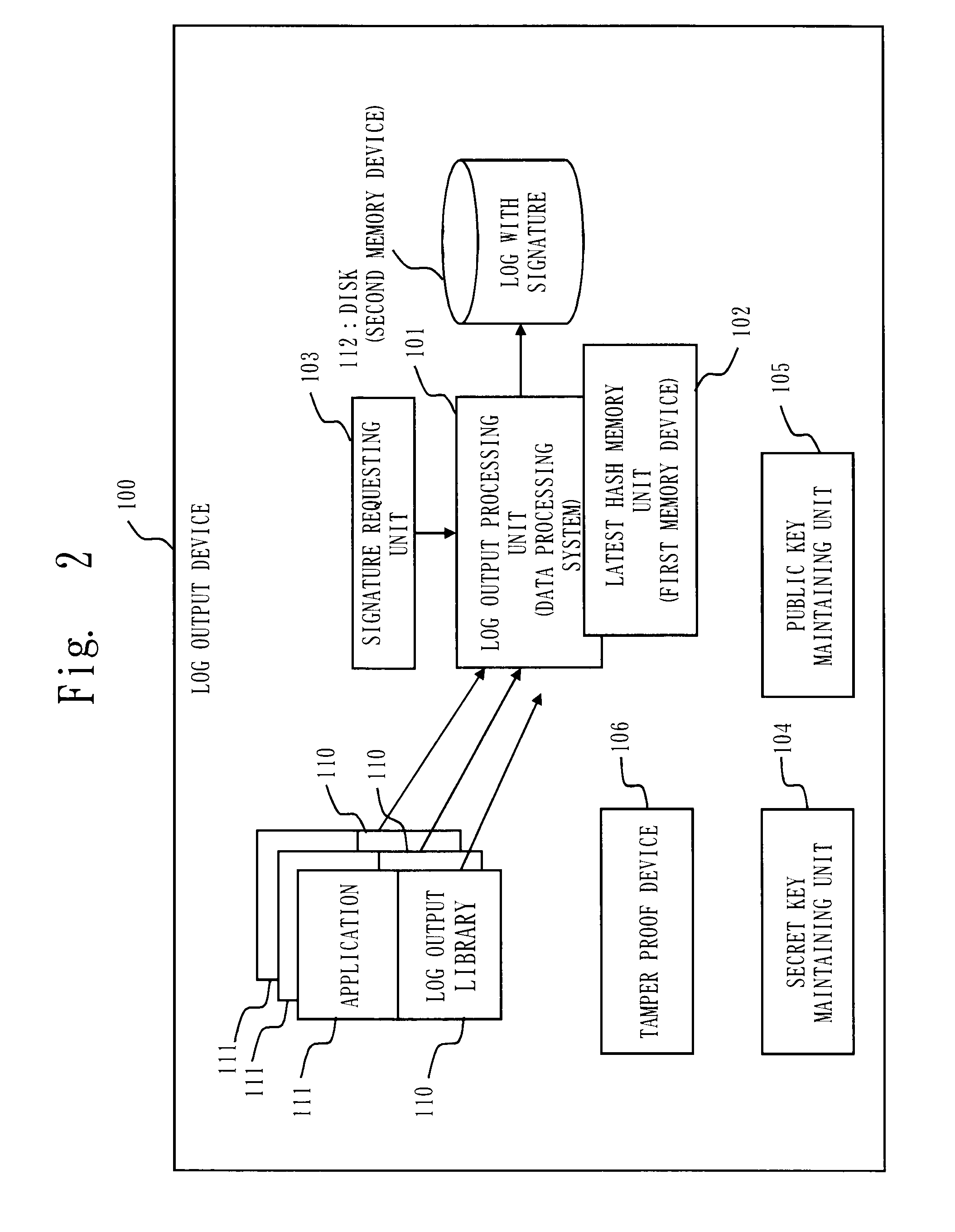
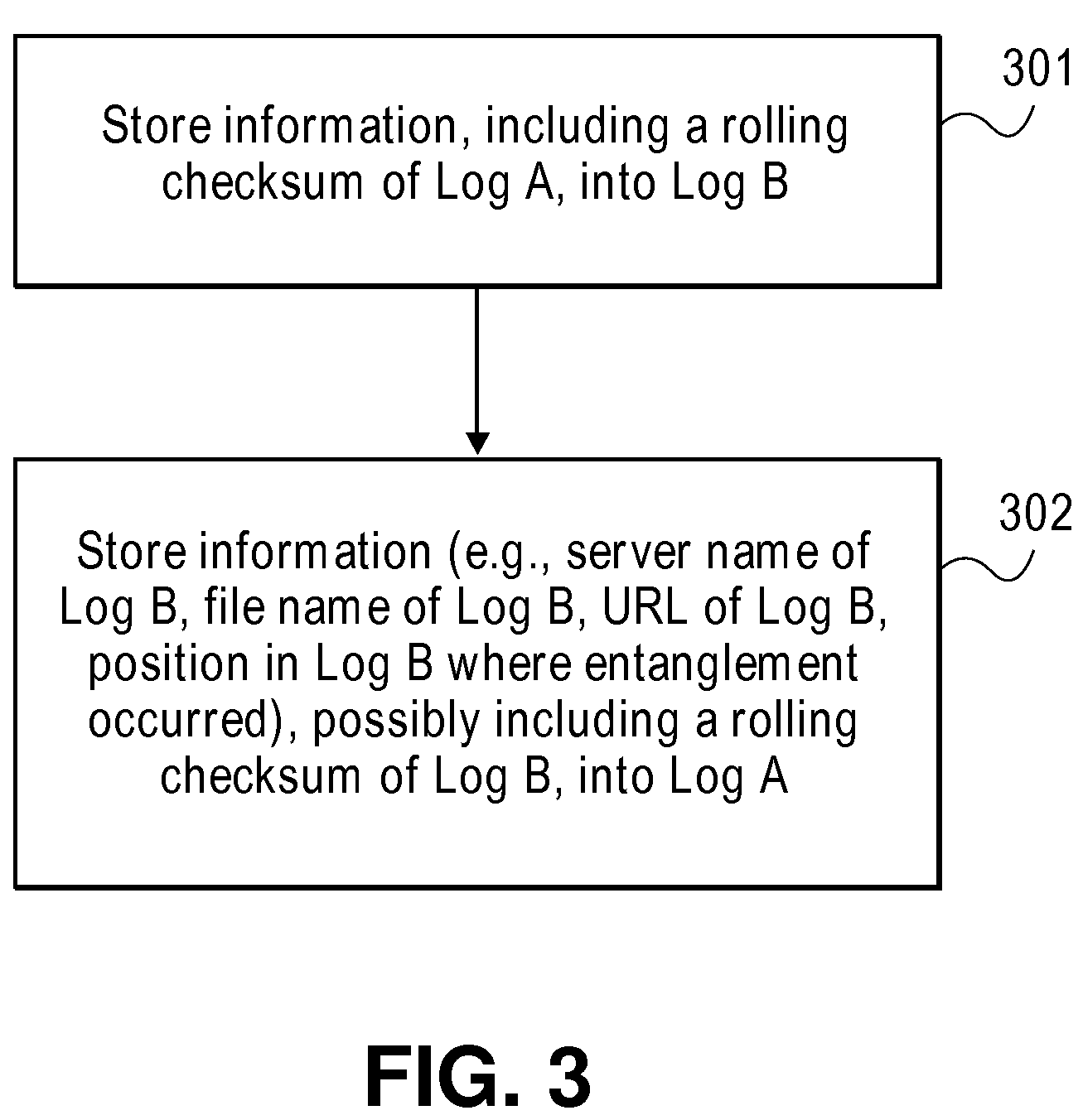
Data processing system, data processing method, and program
InactiveUS20090328218A1Reduce loadPrevent undetectable tamperingMemory loss protectionError detection/correctionData processing systemProcess memory
A log output device and a program are provided, which append a signature to a log, prevent an undetectable tampering (alteration, insertion, deletion, etc.), and are able to narrow tampered position if tampered. The log output device forms a log record including a data part and a hash part, and outputs to a disk; the hash part is formed by combining a hash of the data part (data hash) and a hash of the hash part of the previous record (link hash); a signature is appended to only a part of records of a hash chain; when outputting the record to the disk, a copy of the hash part of the record is maintained on a process memory; when outputting next record, the hash part of the latest record on the disk and the hash part maintained on the process memory are compared; if they are matched, the record on the disk is determined as not being tampered, and if mismatched, the record is determined as tampered.
Owner:MITSUBISHI ELECTRIC CORP
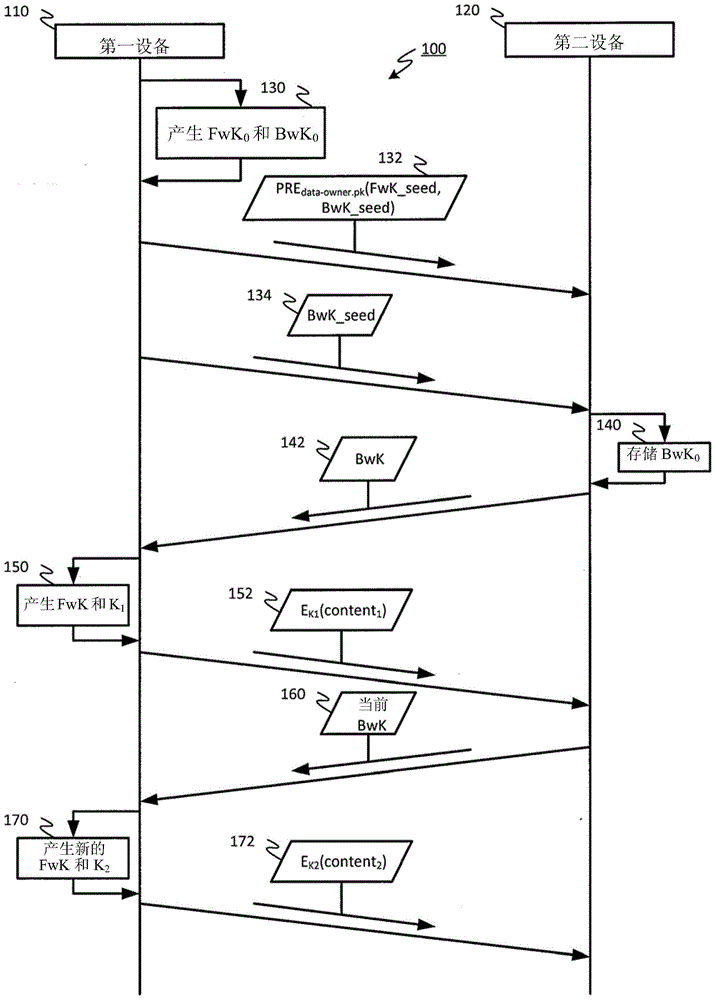
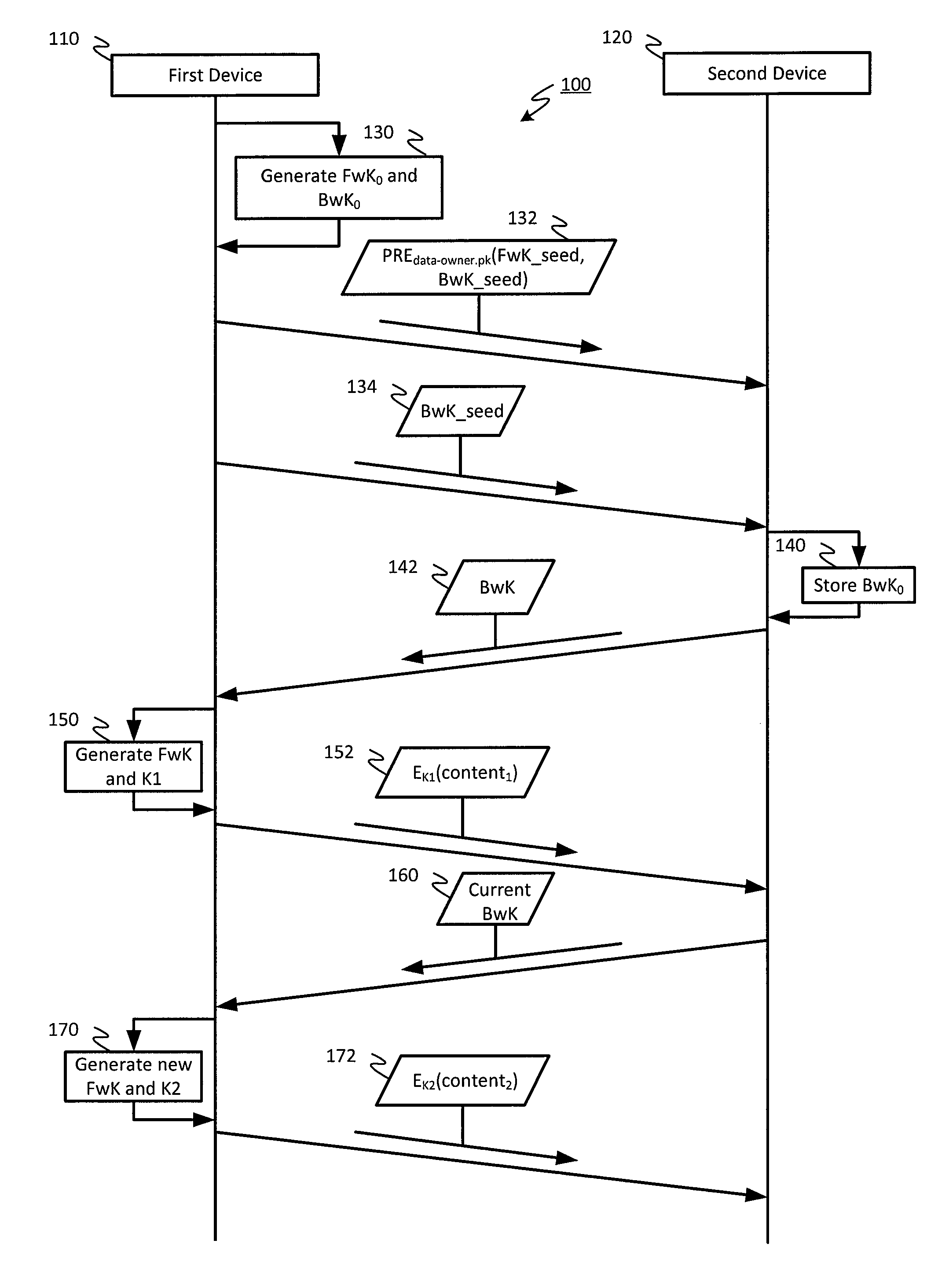
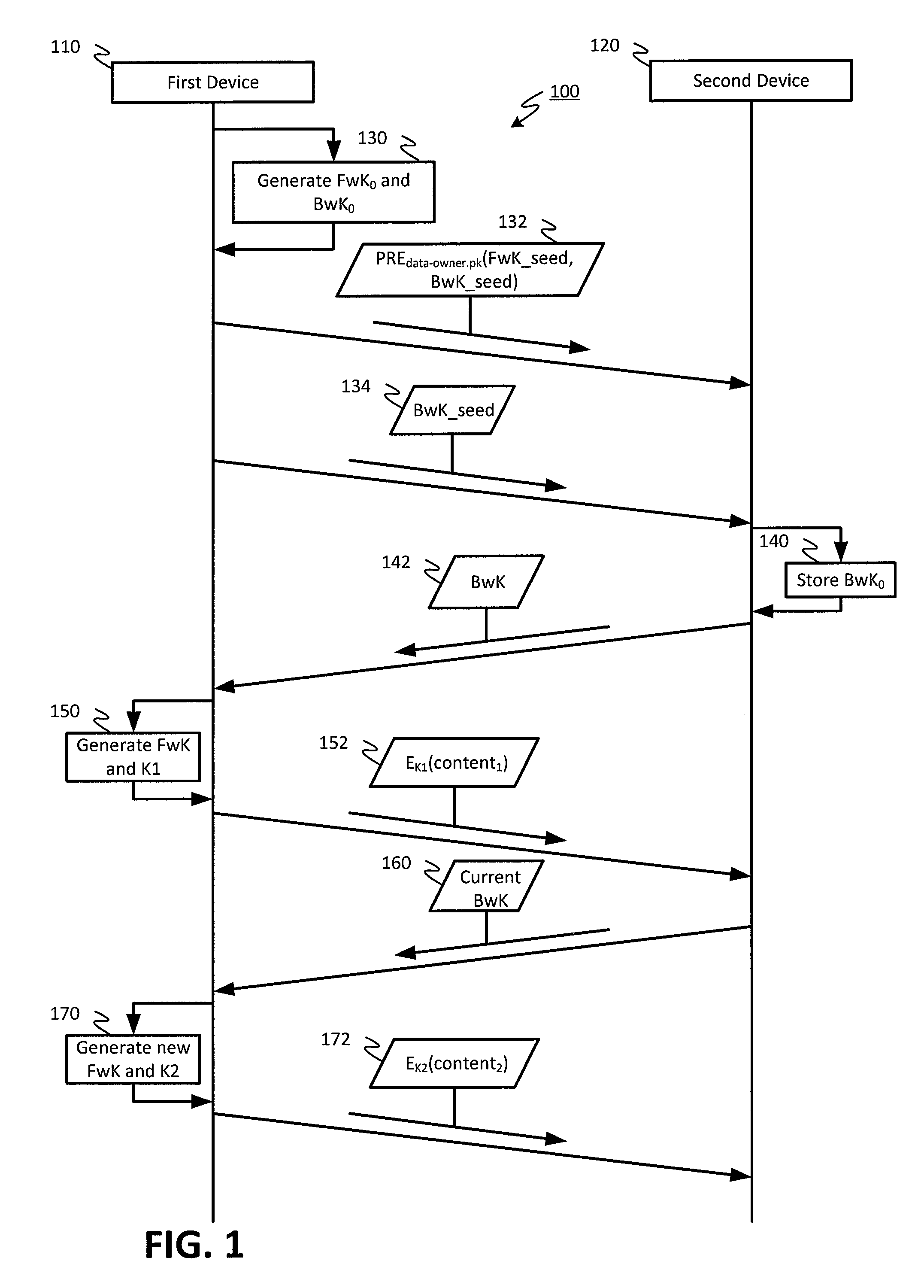
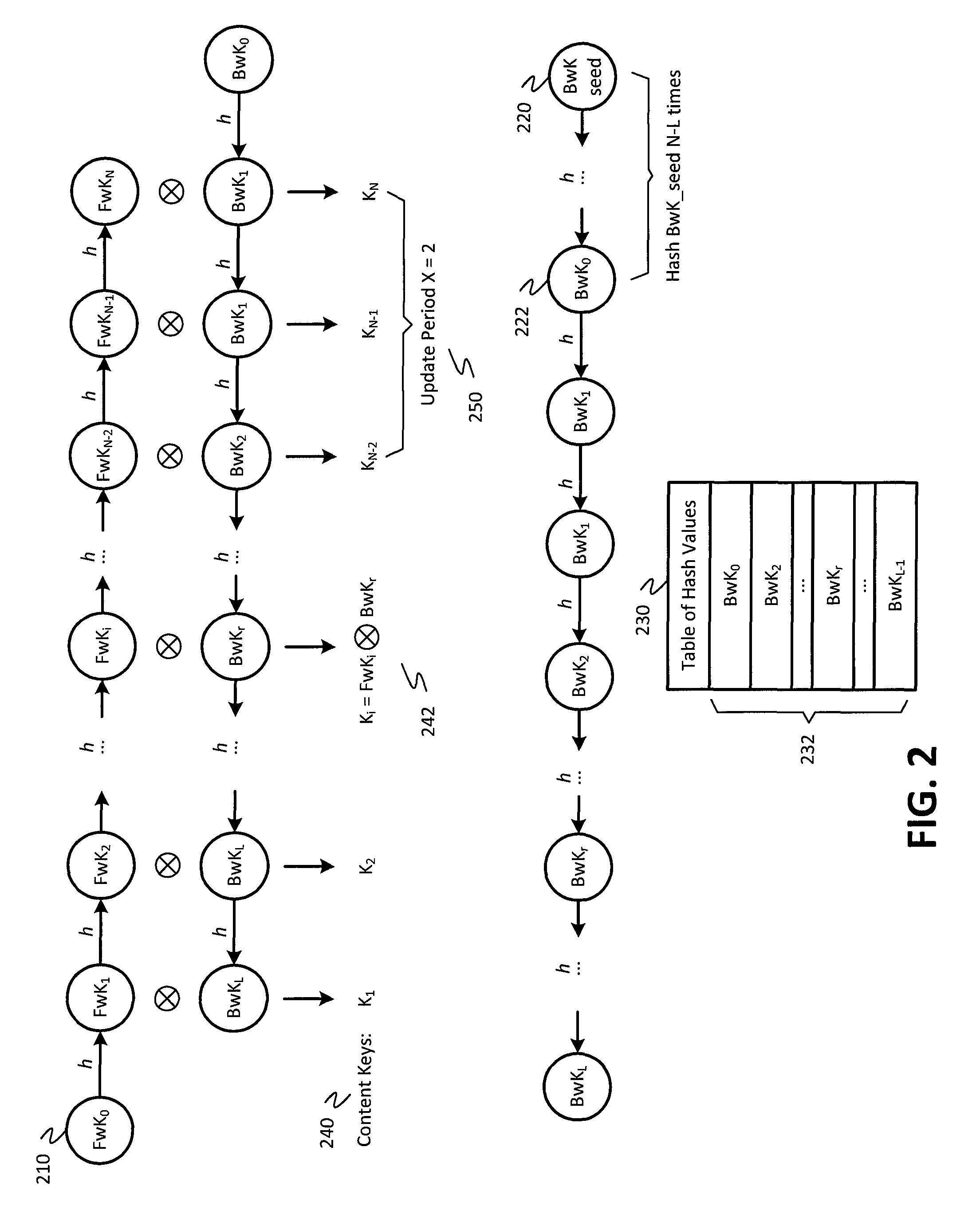
Improved encrypted/decrypted content, and method and apparatus for issuing encrypted content
ActiveCN104683099AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash chainProxy re-encryption
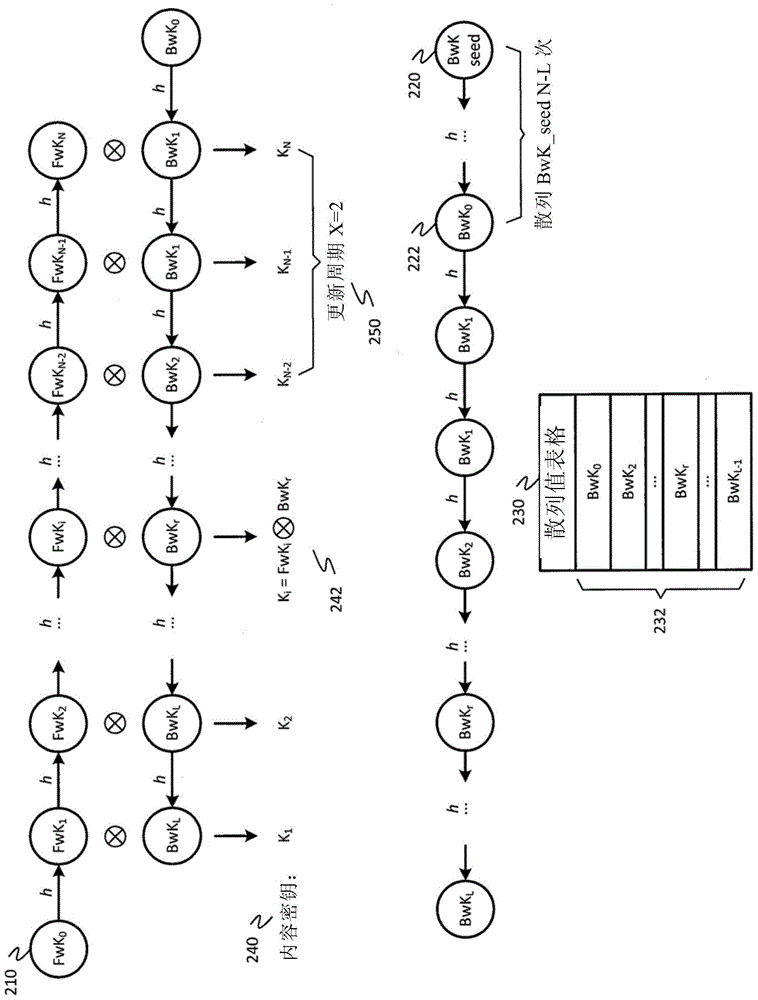
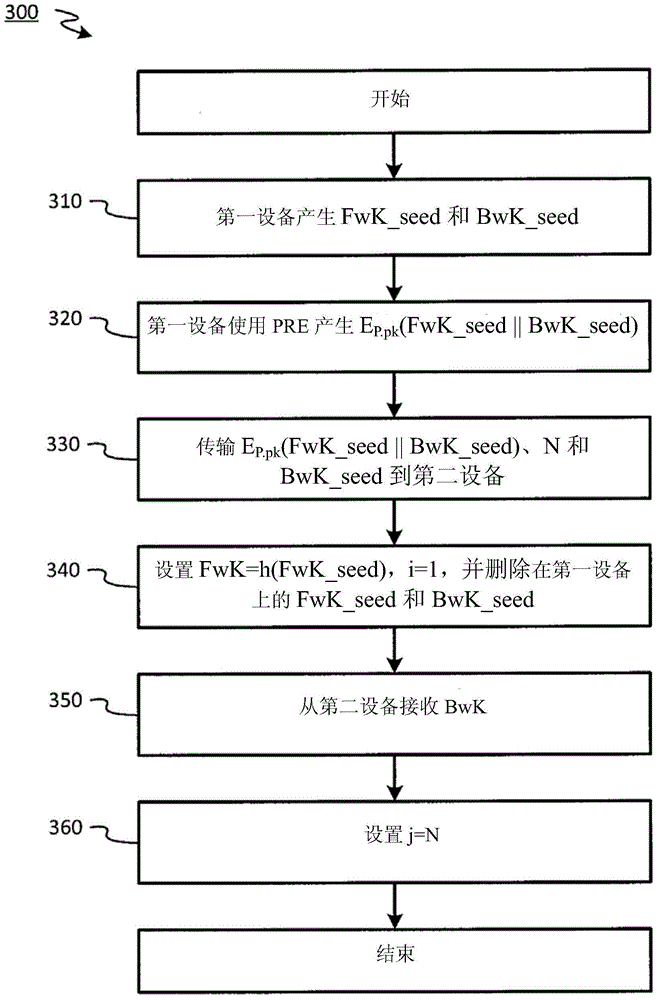
The invention discloses improved encrypted / decrypted contents, and a method and apparatus for issuing encrypted contents. In one embodiment, a first device encrypts contents by using a dual hash chain technology. The first device maintains forward hash chains. A second device maintains reverse hash chains. A content key for encrypting contents is guided out through forward and reverse hash chain values. The second device dose not know seeds used for generating forward hash chains and thus a content key cannot be produced, therefore, encrypted contents are less liable to leak. Moreover, the invention provides a technology for re-encrypting contents through a proxy re-encryption (PRE) technology. In this way, encrypted contents can be provided to a request device for decryption with need of forward and reverse hash chains. Furthermore, the invention provides a technology, having a fine-grained access control function, for issuing encrypted contents to the request device.
Owner:HONG KONG APPLIED SCI & TECH RES INST
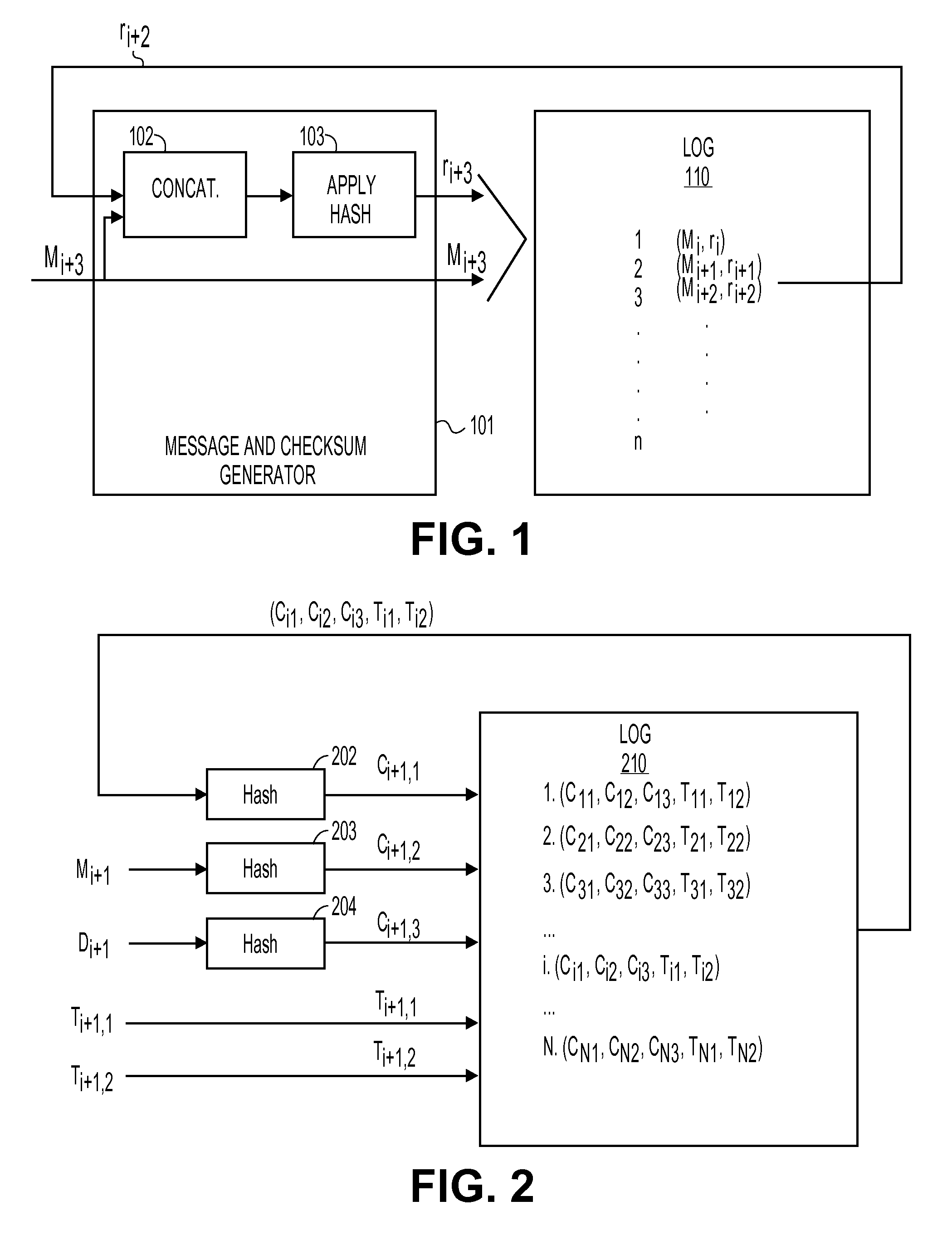
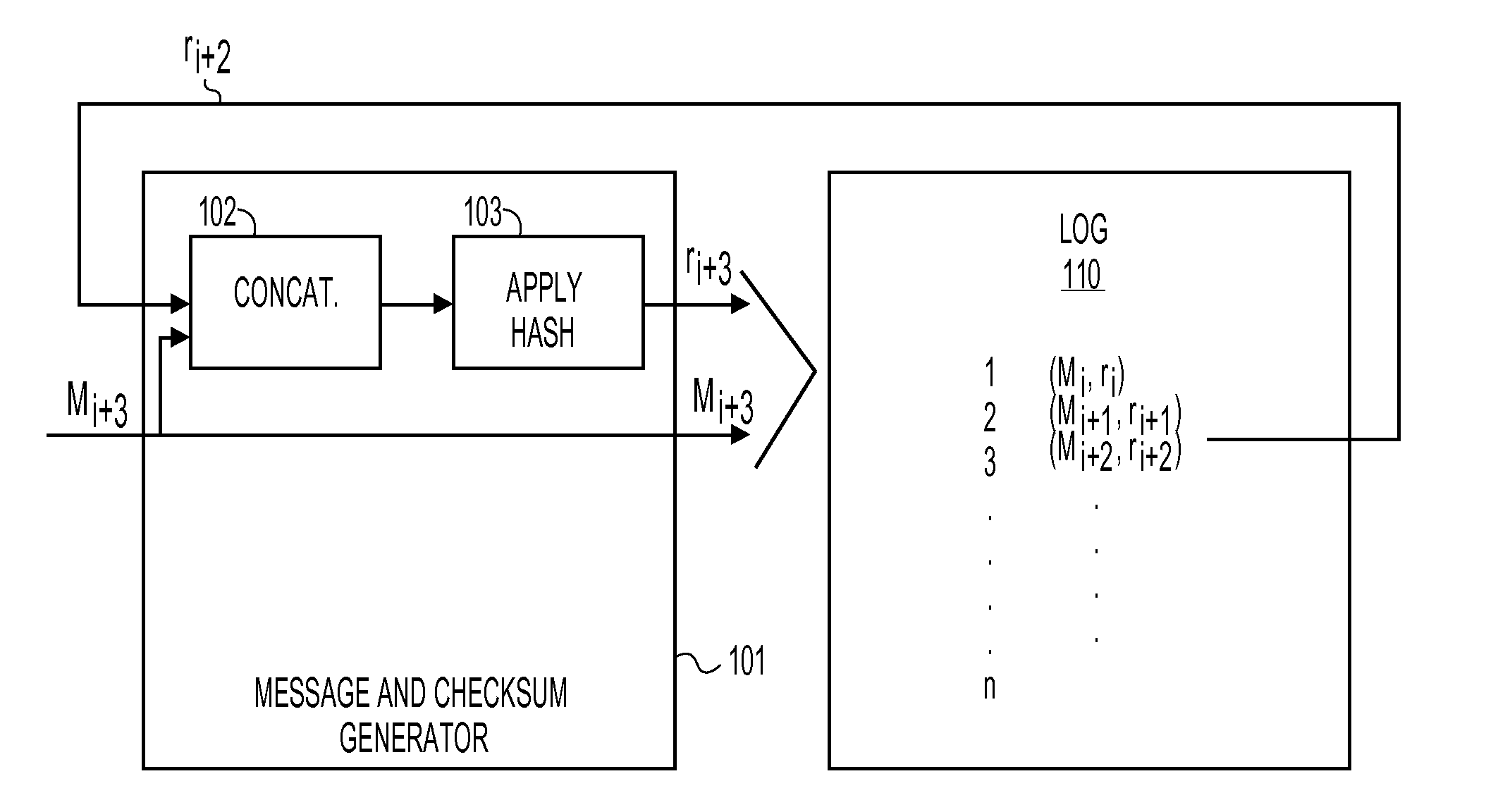
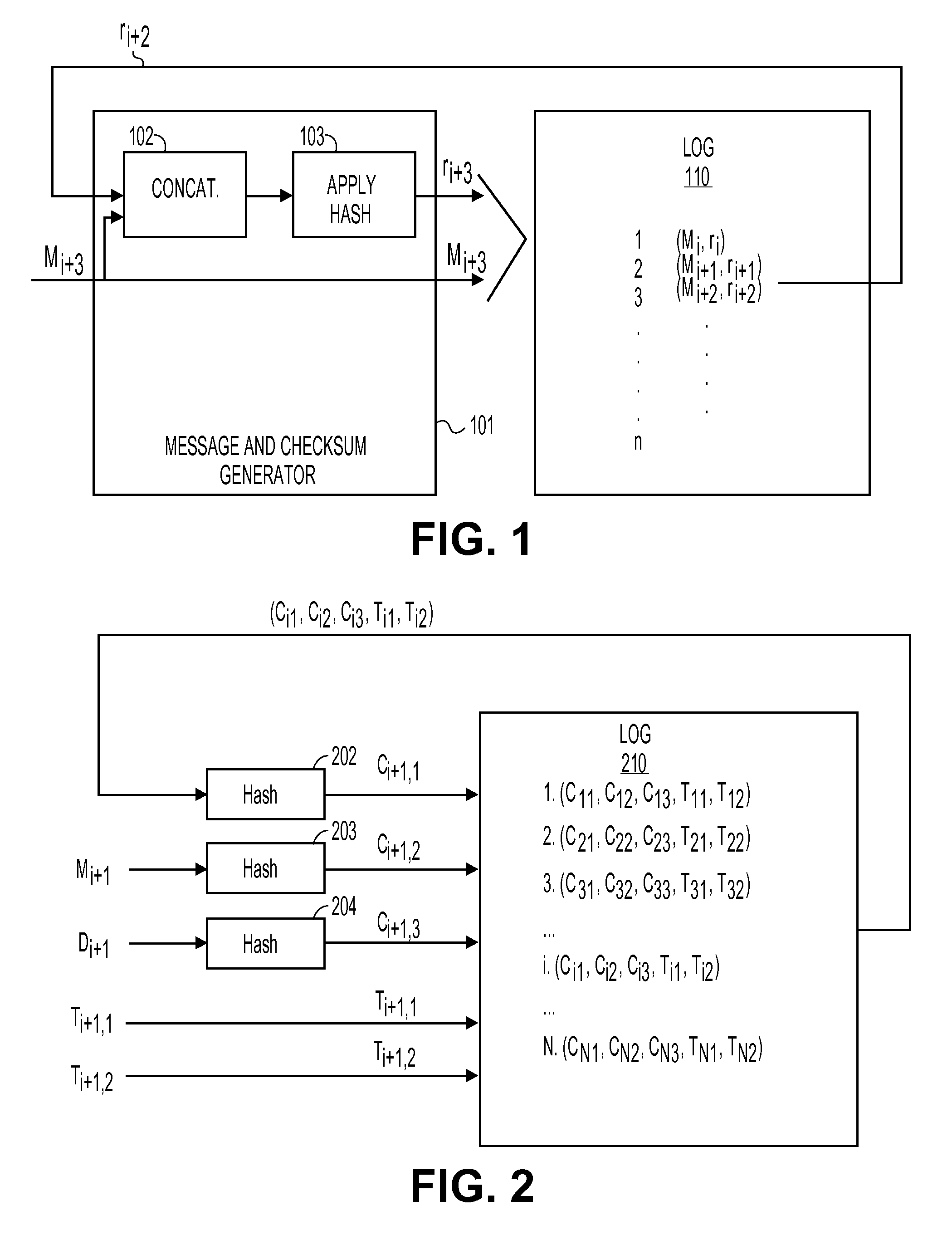
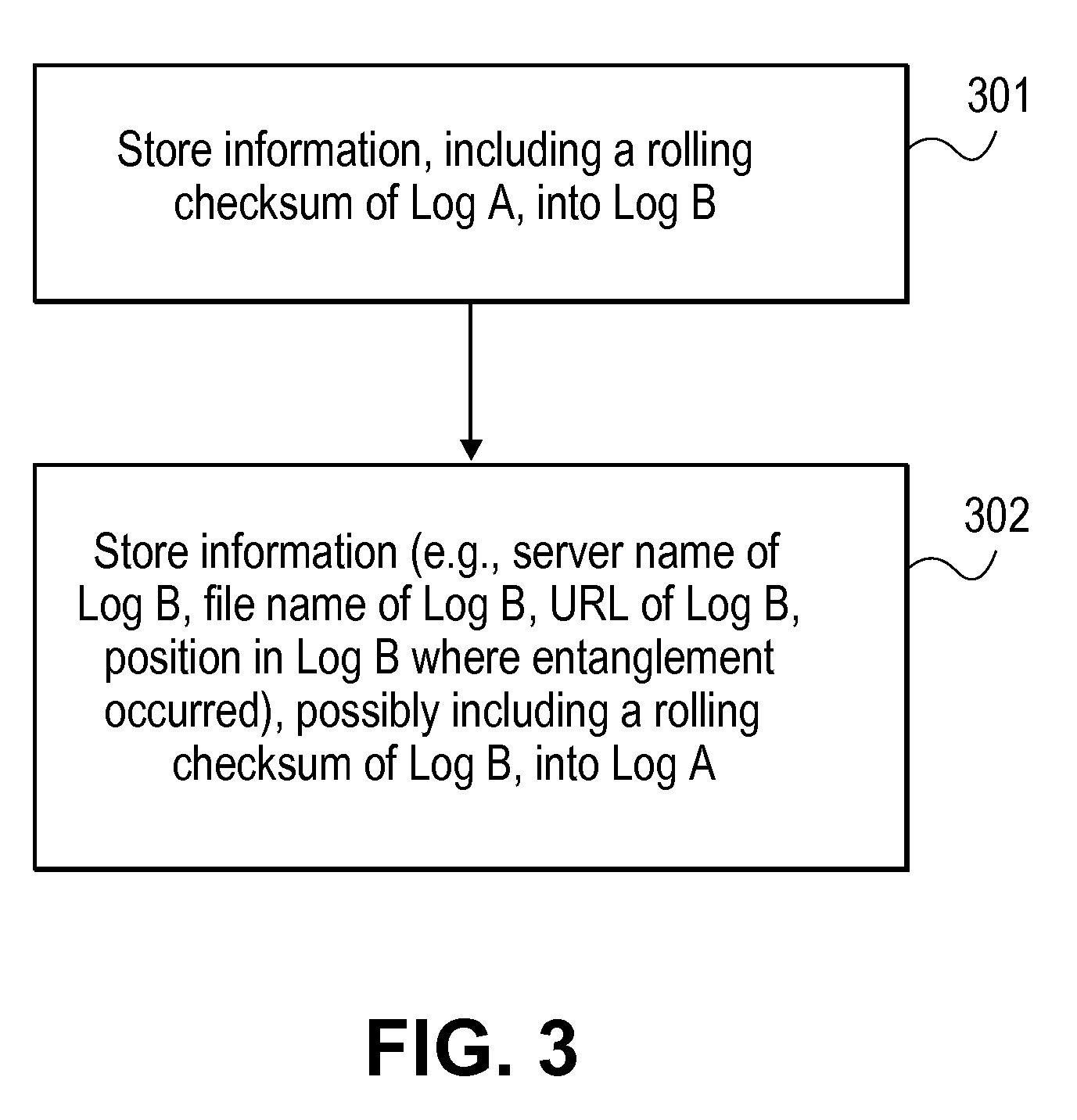
Method and Apparatus for Logging Based Identification
ActiveUS20100088517A1User identity/authority verificationStampingTheoretical computer scienceHash chain
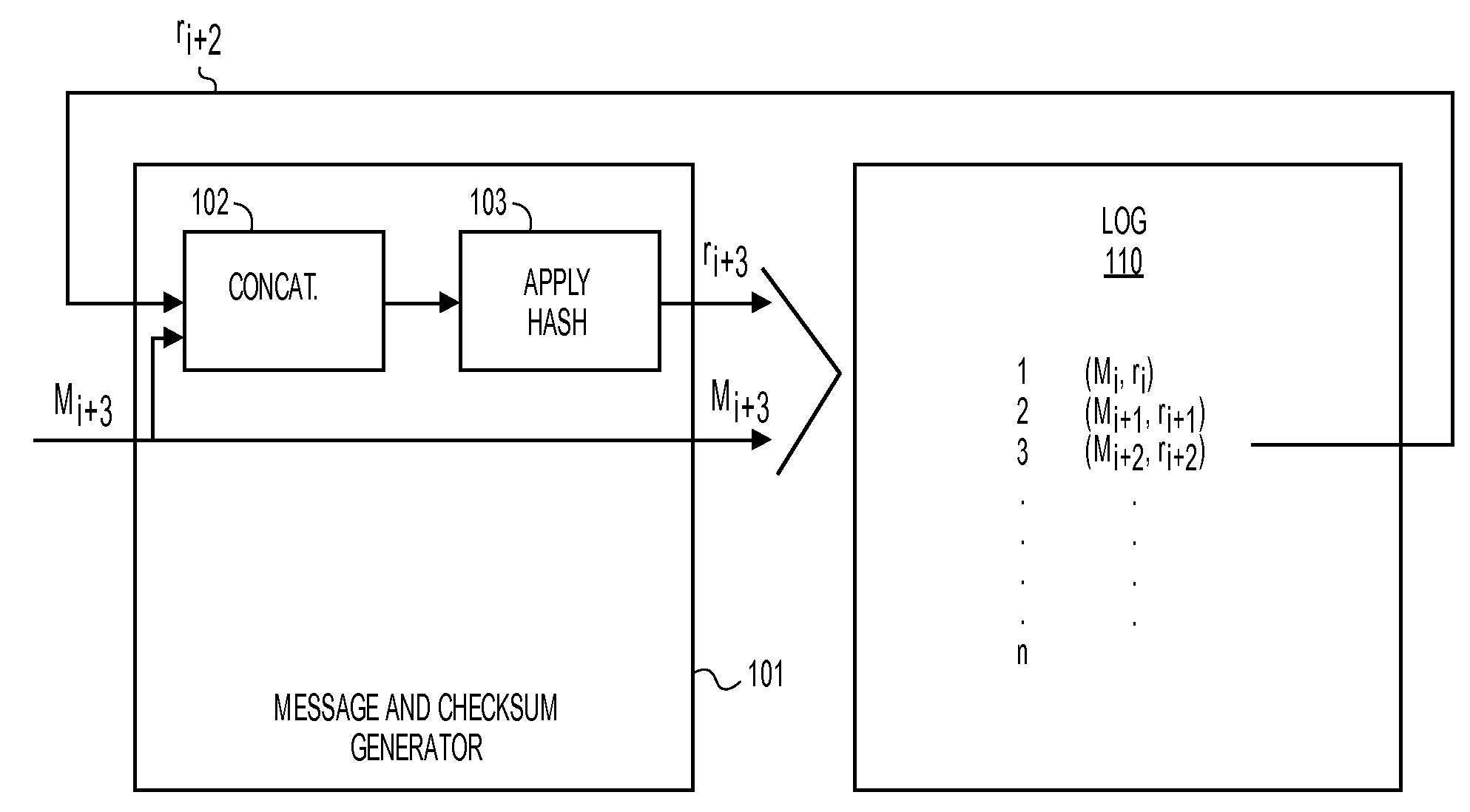
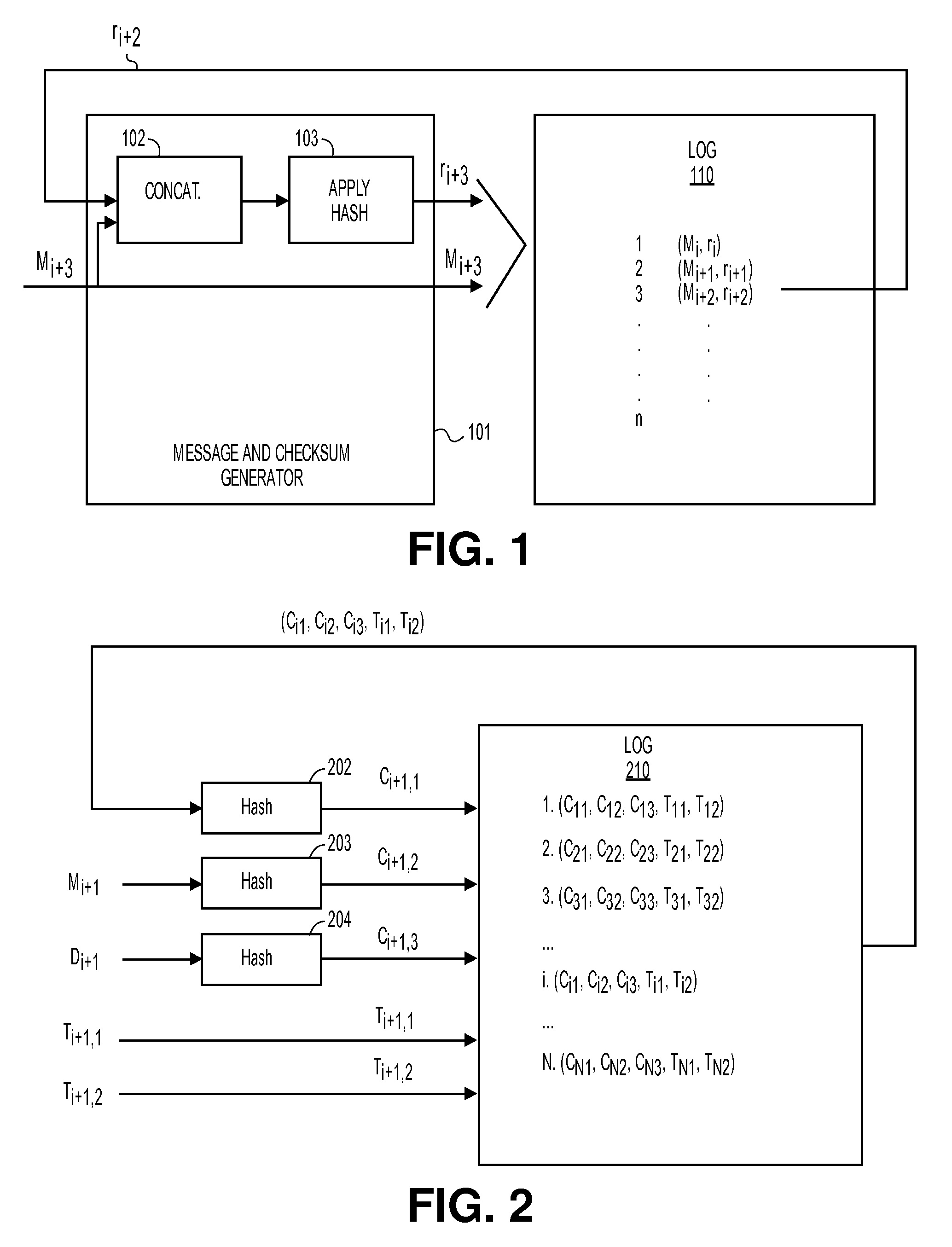
A method and apparatus for logging based identification are described. In one embodiment, the method comprises extracting entries of a hash chained log that represents a series of previous transactions. The method may also comprise ordering hash values of the entries extracted from the hash chained log into an ordered list. In one embodiment, the method may further comprise producing a cryptographic hash of the ordered list.
Owner:RICOH KK
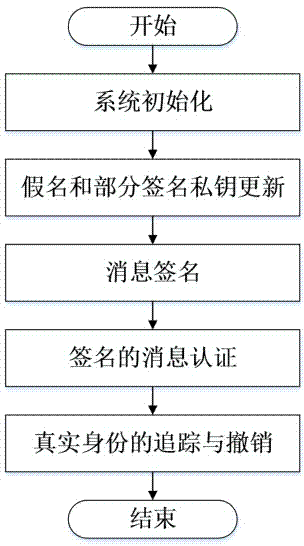
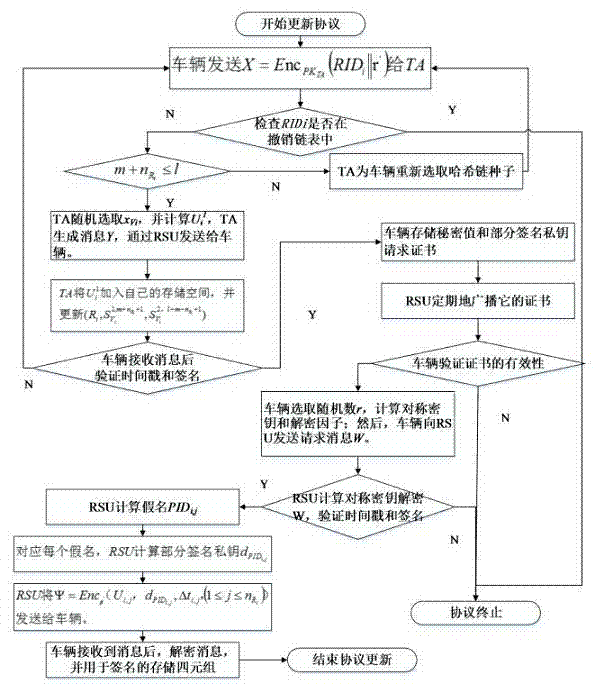
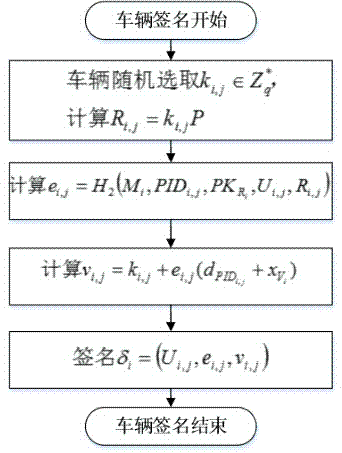
Internet of Vehicles distributed authentication method based on controllable privacy
InactiveCN104853351AReduce the burden onSolve the problem of non-repudiationSecurity arrangementTrusted authorityStructure of Management Information
The invention discloses an Internet of Vehicles distributed authentication method based on controllable privacy, relates to the field of vehicle network communication safety, and specifically relates to an Internet of Vehicles distributed authentication method based on controllable privacy. The method specifically includes five following steps: system initialization; private key update of fake names and a part of signatures; message signature; message authentication of signatures; and real identity tracking and revocation. According to the method, the double hash chain is employed to establish the fake names, the communication cost for invalidating a vehicle identity is irrelevant to the numbers of the fake names and a part of the signature private keys of the vehicle, a vehicle user can update multiple parts of signature private keys by the adoption of one authorization, and the burden of trusted authority (TA) and road-side units (RSU) is reduced; when a message with a controversial signature occurs, the TA can distinguish whether the signature is forged by the RSU according to re-signature of the message uploaded by the vehicle, and the problem of non-repudiation in the distributed environment is solved. According to the method, the security is high, the cost is low, and the method is applicable to node high-speed movement, topology structure volatility, and large-scale VANET network.
Owner:JIANGSU UNIV
Method for realizing intra-mobile entity authentication and cipher key negotiation using short message
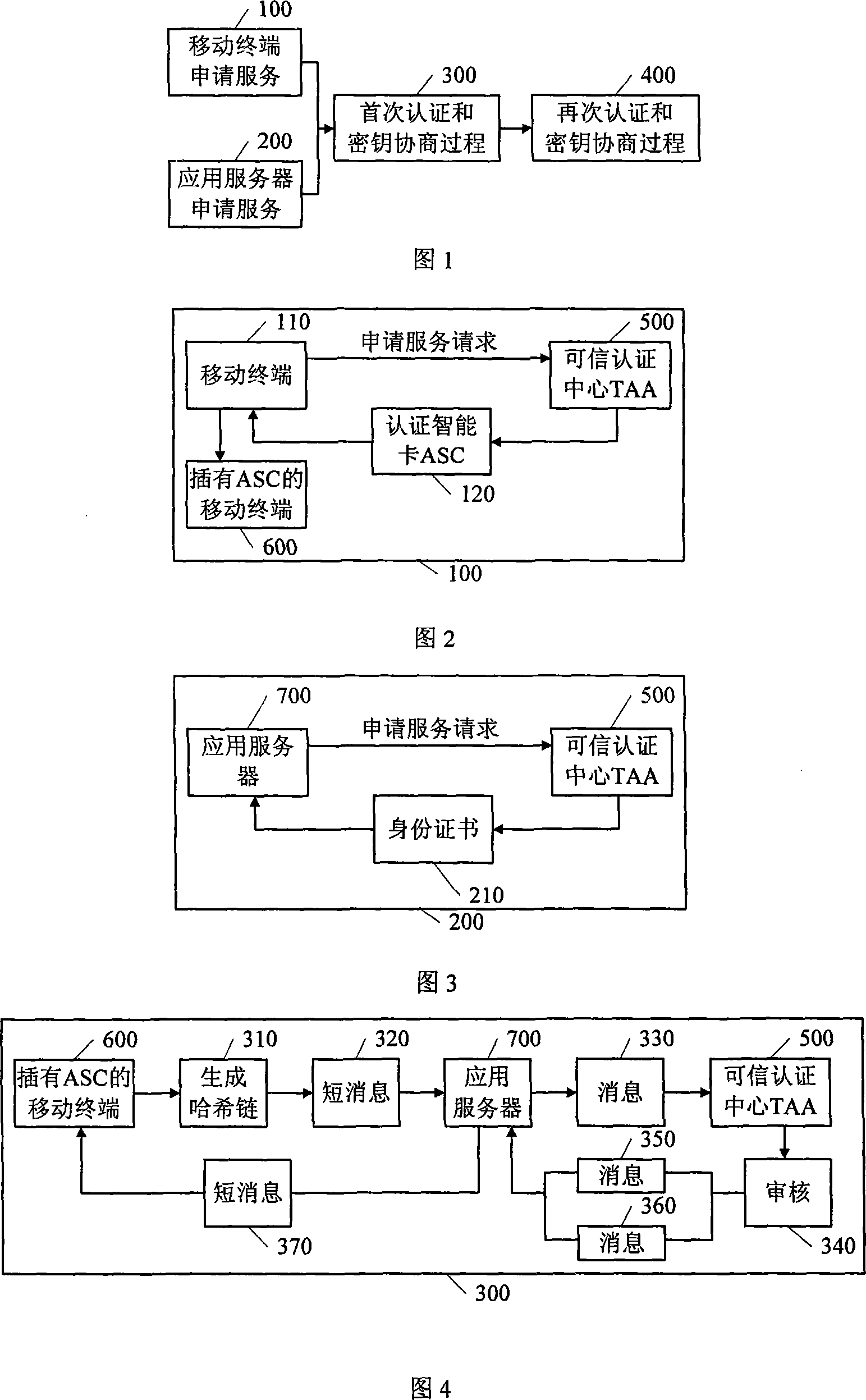
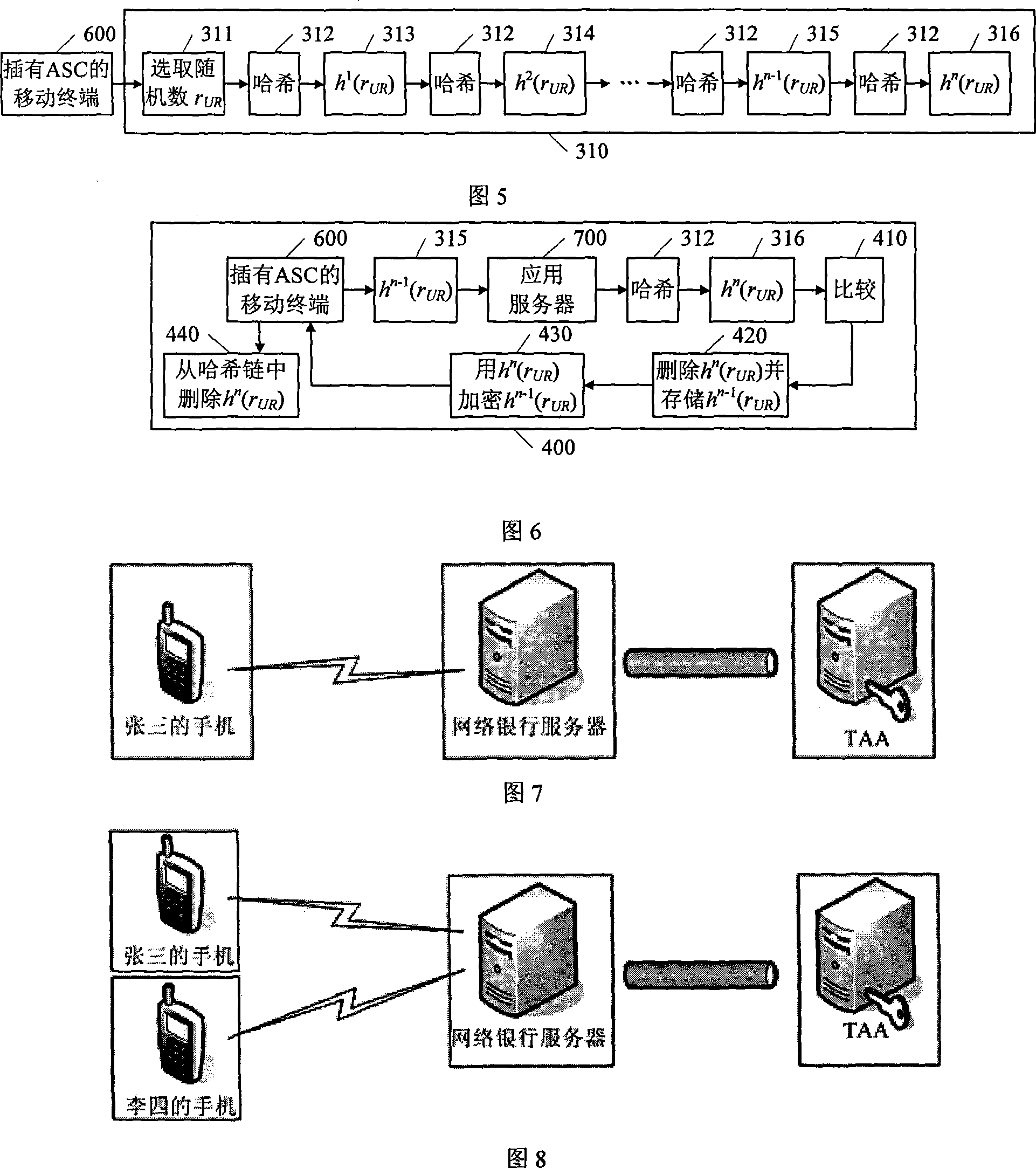
InactiveCN101083530AReduce overheadSimple and fast operationPublic key for secure communicationUser identity/authority verificationApplication serverMobile entity
The invention provides a method for entity authentication and key consultation by short message, which belongs to security domain of motion network. The characteristic is: using the identity information in the short message and the last value of the Hasche chain in the TAA public key encryption as the key when doing the fisrt certification and call between the mobile termination of the credible authentication center TAA and the application server. After that, can just shift the length of the Hasche chain to be bigger than 0 to do the Hasche operation once more by the short message. Verify the termination identity comparing with the former Hasche value as the new key for identity. The invention has few expenses, simple operation, without bottleneck, the support of anonymous and secure merit.
Owner:BEIJING UNIV OF TECH
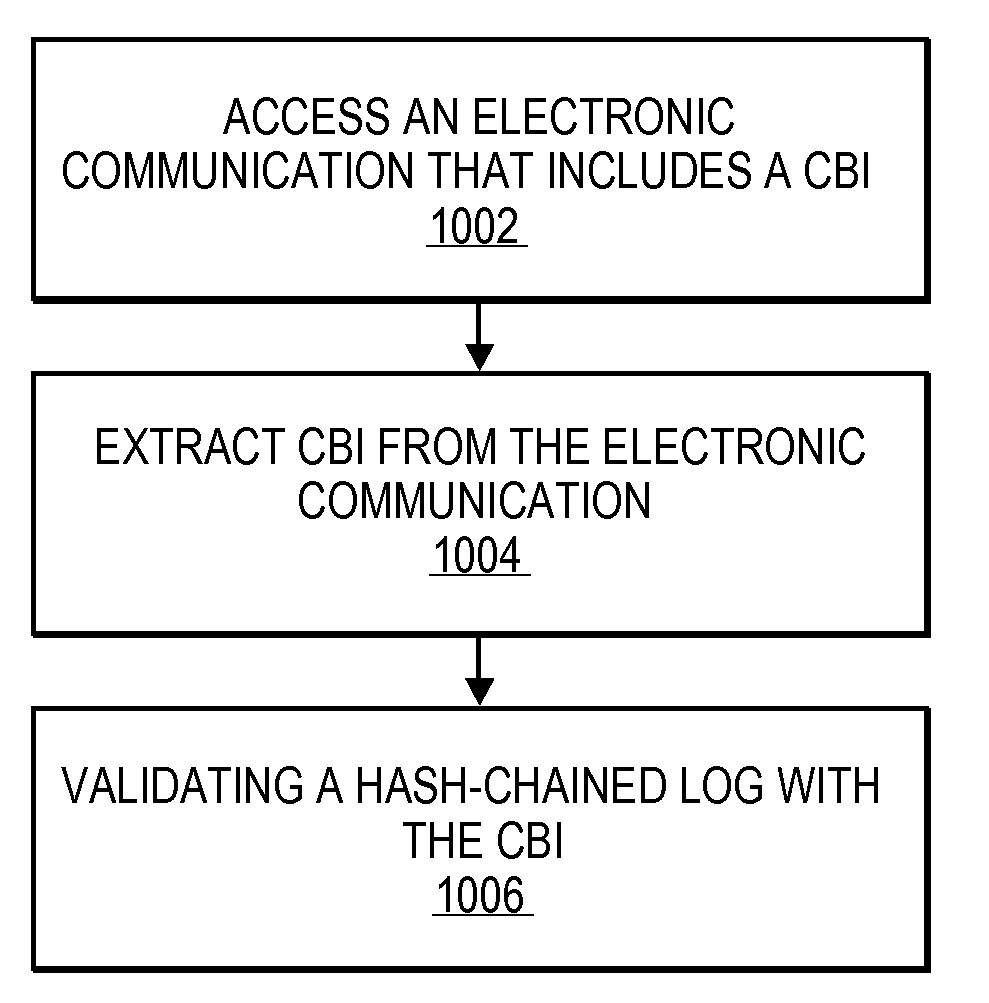
Method and Apparatus for Automatically Publishing Content Based Identifiers
ActiveUS20100088512A1User identity/authority verificationWebsite content managementElectronic communicationHash chain
A method and apparatus for automatically publishing content based identifiers are described. In one embodiment, the method comprises accessing an electronic communication to obtain a content based identifier (CBI) contained in the electronic communication. In one embodiment, the method may also comprise using the CBI to validate integrity of a hash chained log.
Owner:RICOH KK
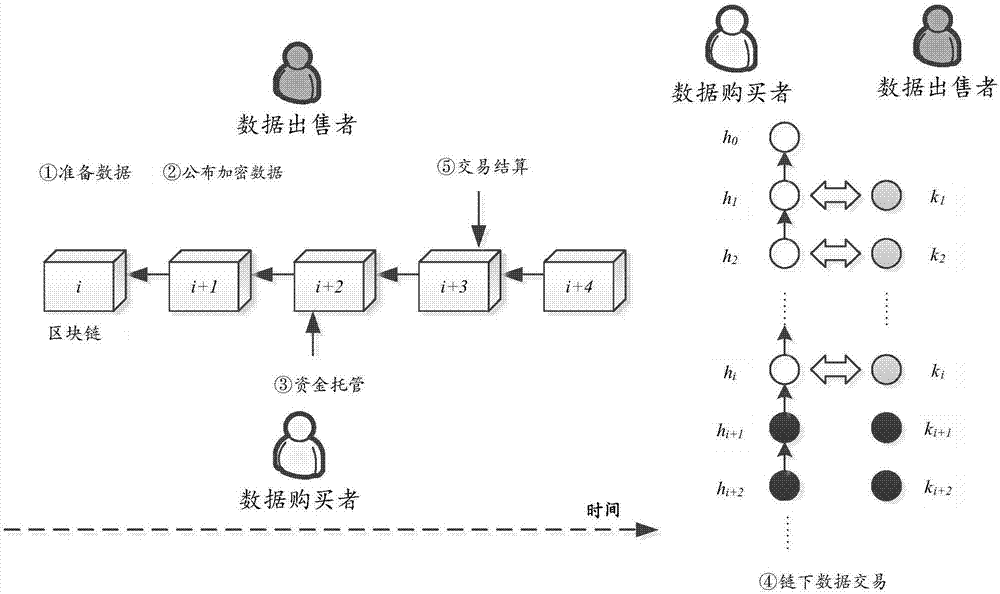
Block-chain-based fair data transaction method
PendingCN107169764APrevent leakageImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationPaymentHash chain
The invention relates to a block-chain-based fair data transaction method. The method comprises: step A, a data seller encrypts each piece of data by using different secret keys; step B, a data buyer buys one or more secret keys each time by using a Hash chain micro-payment technique to decrypt corresponding data and carry out verification, and repeated multi-times exchange is carried out until the transaction is completed; and step C, the data seller uses an obtained latest hash value to delock data purchasing expenses trusted at a block chain to obtain deserved data purchasing expenses and the remaining sum is returned to the data buyer in a forced manner. Therefore, on the basis of combination of block-chain-based encrypted currency with the hash chain micro payment technique, a fair data transaction is realized. Moreover, with the method, a problem that the lots of data bought by one time do not meet the requirement can be solved.
Owner:SHANDONG UNIV
Method and apparatus for automatically publishing content based identifiers
ActiveUS8185733B2User identity/authority verificationWebsite content managementElectronic communicationHash chain
A method and apparatus for automatically publishing content based identifiers are described. In one embodiment, the method comprises accessing an electronic communication to obtain a content based identifier (CBI) contained in the electronic communication. In one embodiment, the method may also comprise using the CBI to validate integrity of a hash chained log.
Owner:RICOH KK
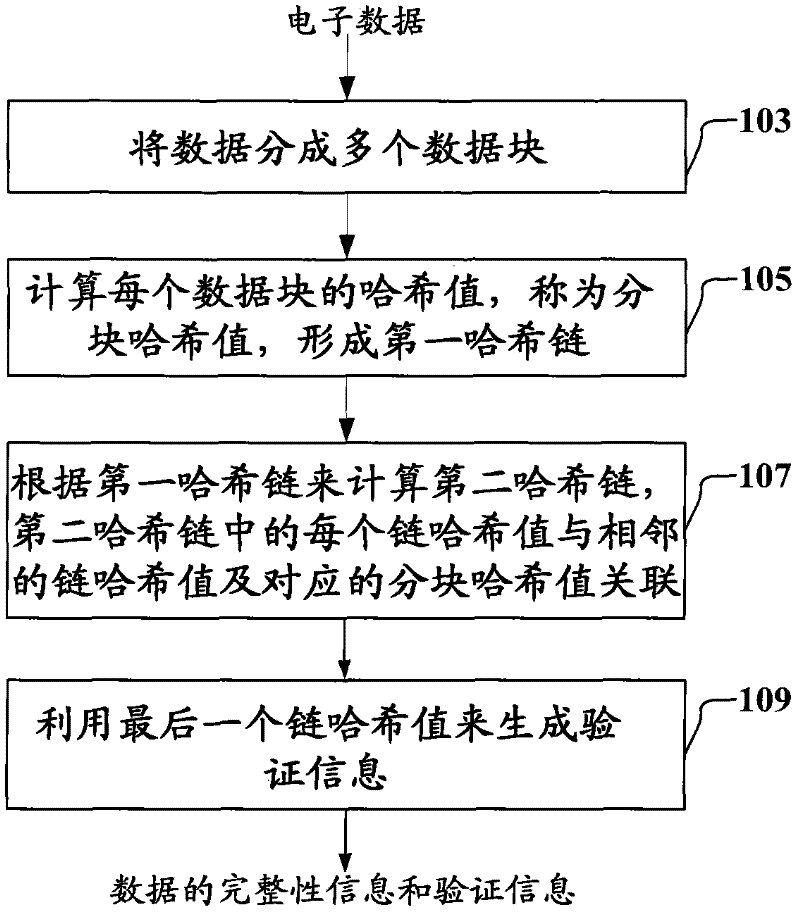
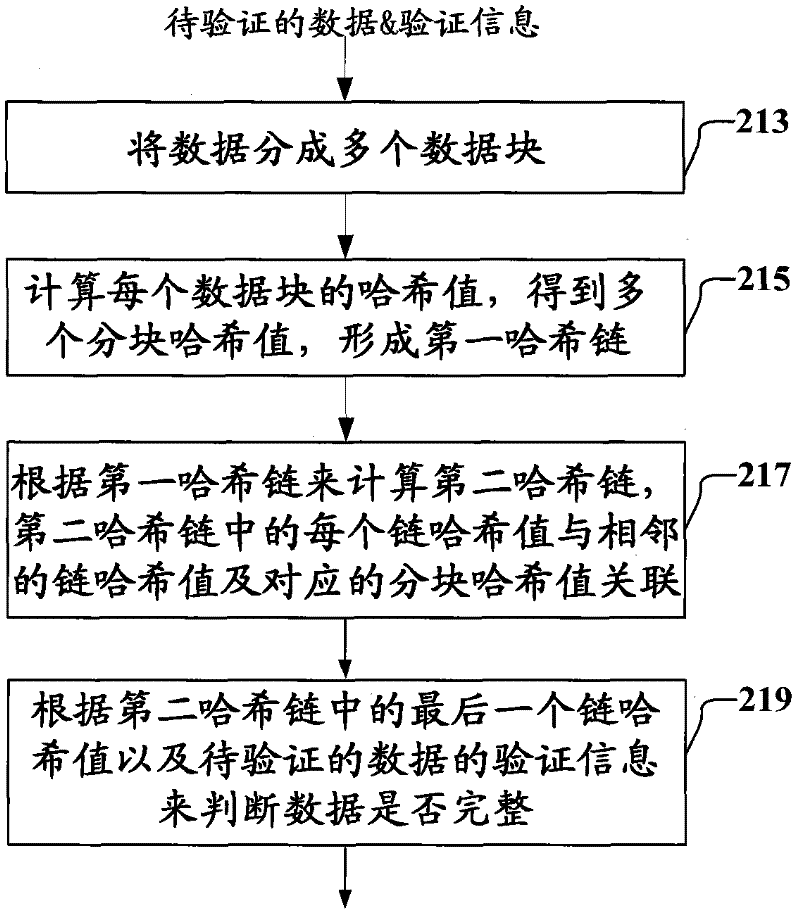
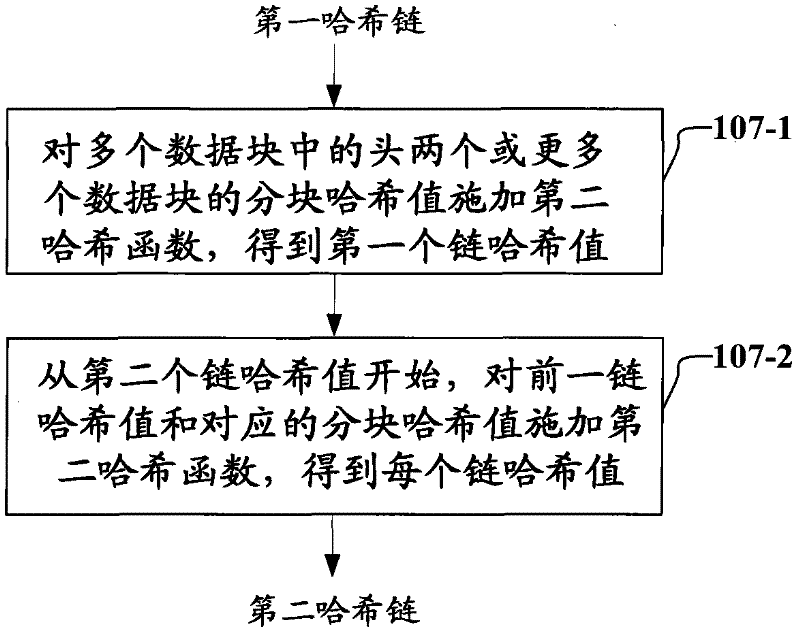
Methods, apparatuses and methods for protecting and verifying data integrity
The invention provides methods, apparatuses and methods for protecting and verifying data integrity. A method for protecting data integrity comprises the following steps of: dividing data into a plurality of data blocks; calculating the hash value of each data block by means of a first hash function, thereby obtaining a plurality of block hash values and forming a first hash chain; calculating a second hash chain by means of a second hash function according to the first hash chain, wherein the second hash chain comprises a plurality of chain hash values; each chain hash value is associated with the corresponding block hash value in the first hash chain, and associated with the adjacent chain hash value in the second hash chain, and wherein the first hash chain and the second hash chain serve as the integrity information of the data; and generating the verification information of the data by means of the last chain hash value in the second hash chain.
Owner:SONY CORP
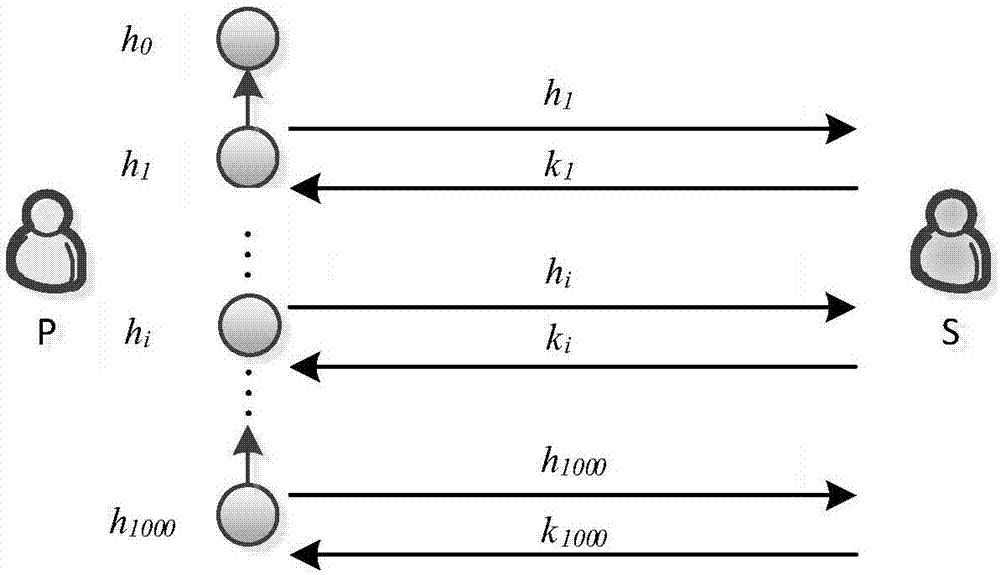
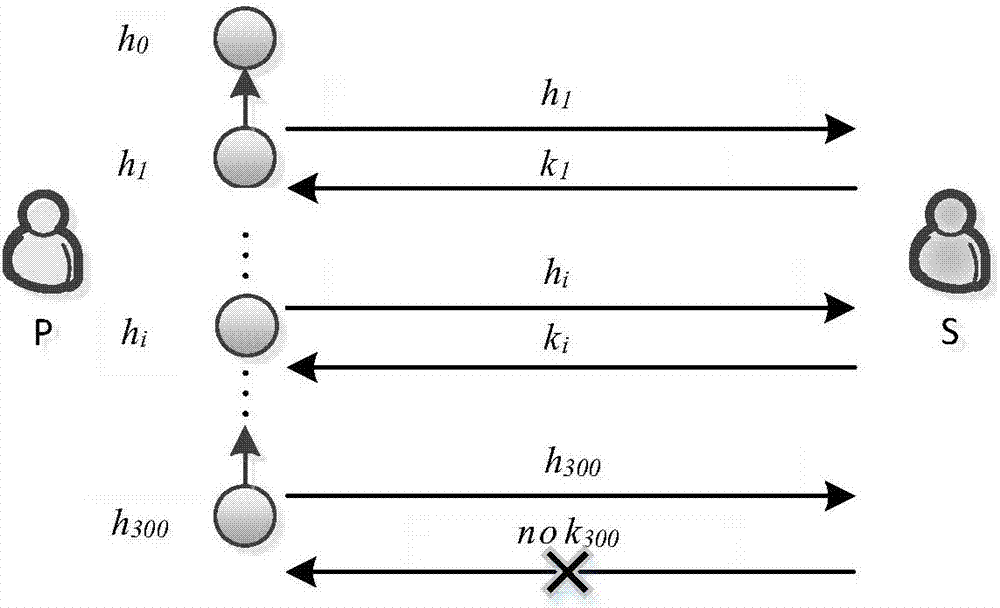
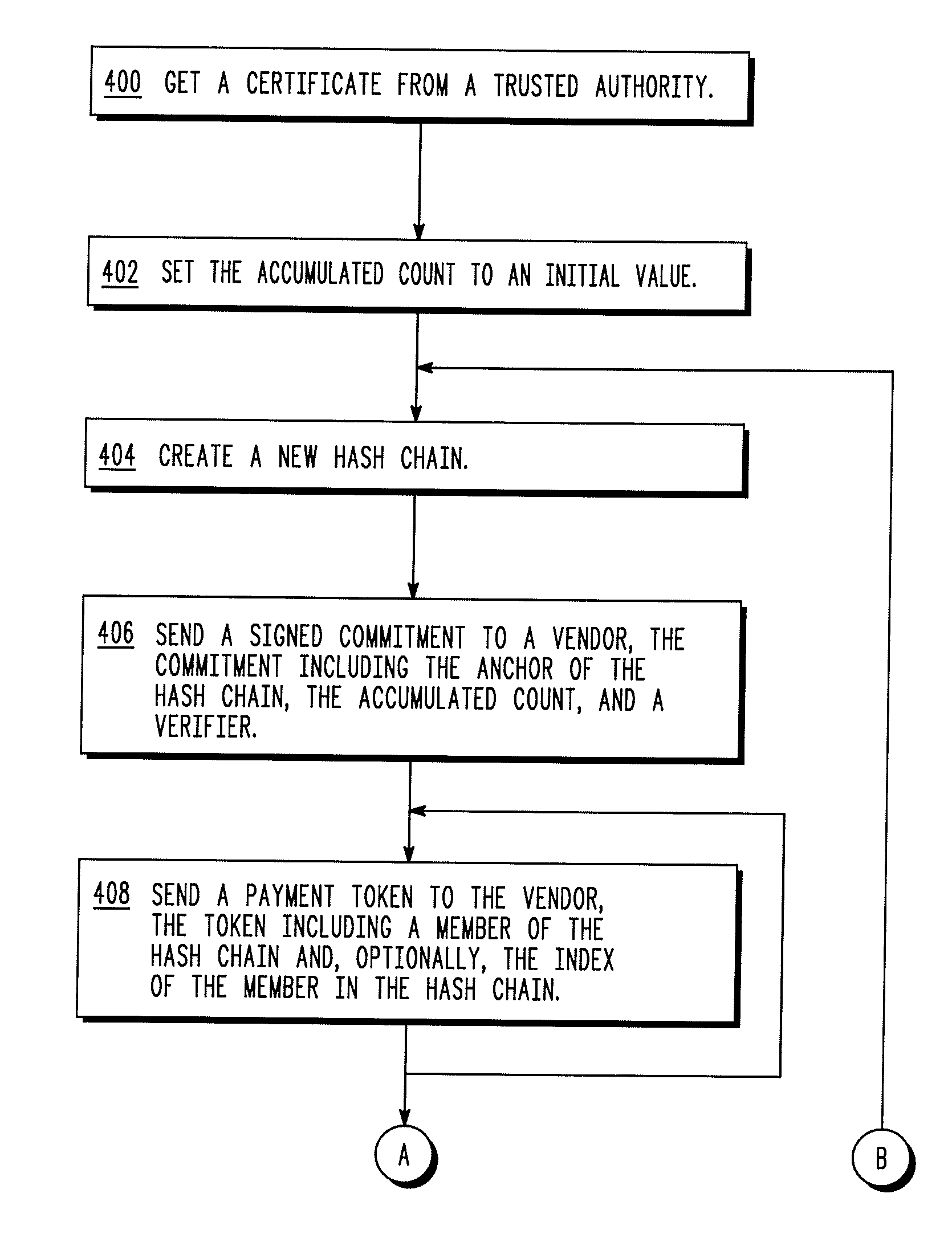
Aggregated hash-chain micropayment system
InactiveUS20090198619A1Reduce transmission costsFinanceUser identity/authority verificationPayment transactionMicropayment
Disclosed are a system and method for aggregating micropayment hash chains. An end user (the “payer”) cryptographically signs “commitments” and transmits then to a vendor. The commitments include an “accumulated count” field which tracks the total number of micropayments made thus far in the payment transaction between the payer and the vendor. The payer can also transmit payment tokens to the vendor. These payment tokens include micropayments verified by a hash chain. When the vendor seeks reimbursement from a broker, the vendor tells the broker the total number of micropayments in the payment transaction and sends verification information to the broker. The broker checks this information against a verification system established with the payer. If the information is verified to be correct, then the broker reimburses the vendor for the services provided and charges the payer. The verification information ensures that the payer and vendor cannot cheat each other.
Owner:MOTOROLA MOBILITY LLC
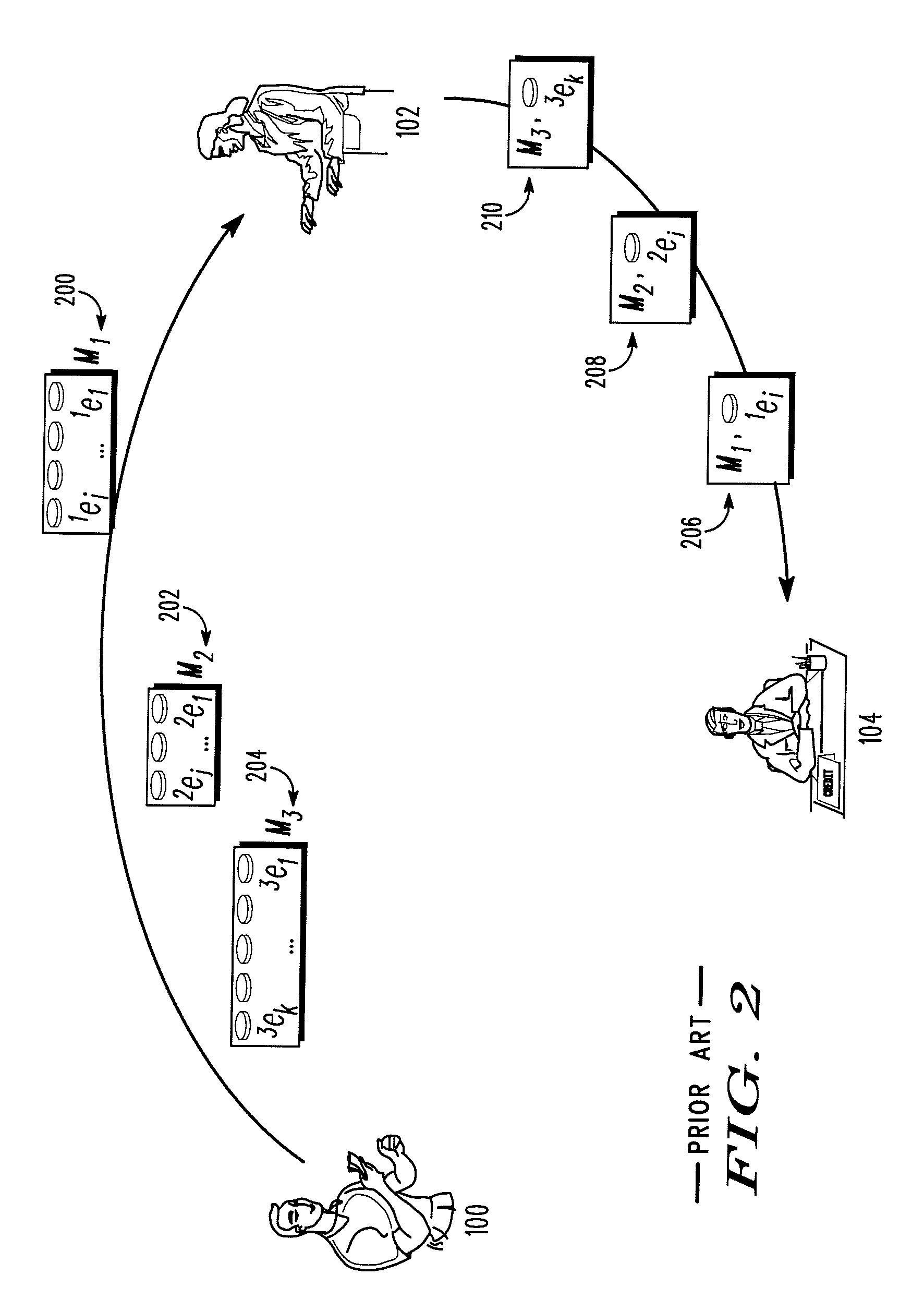
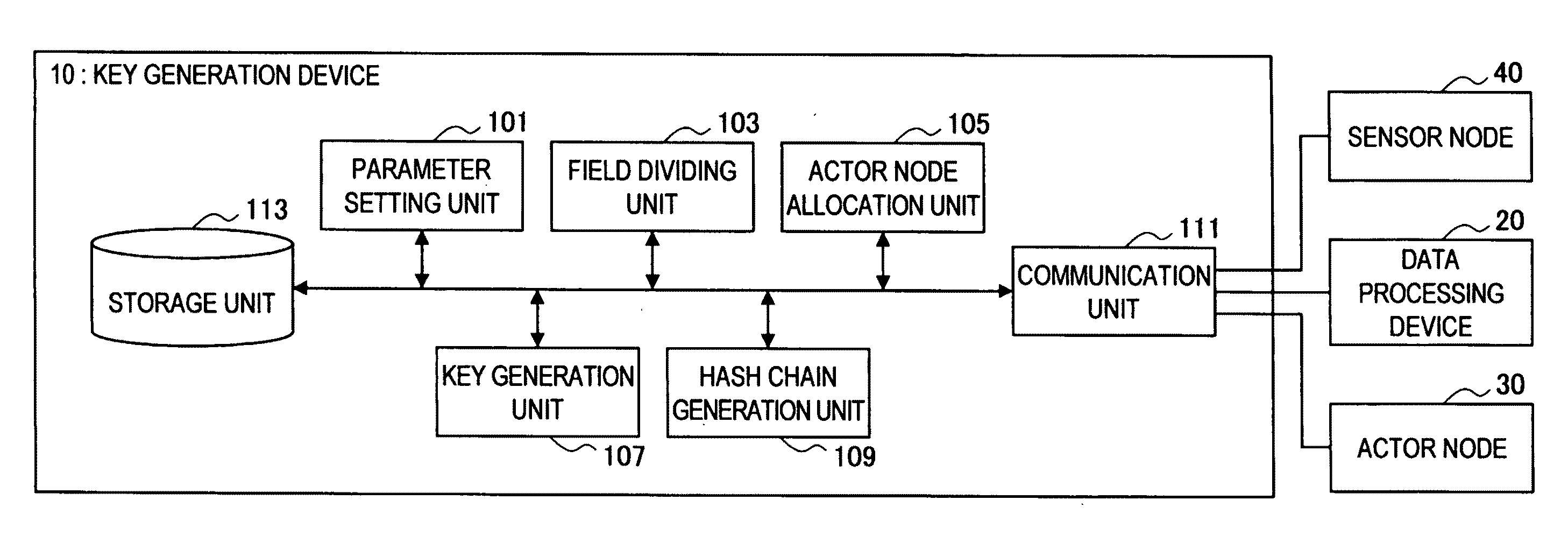
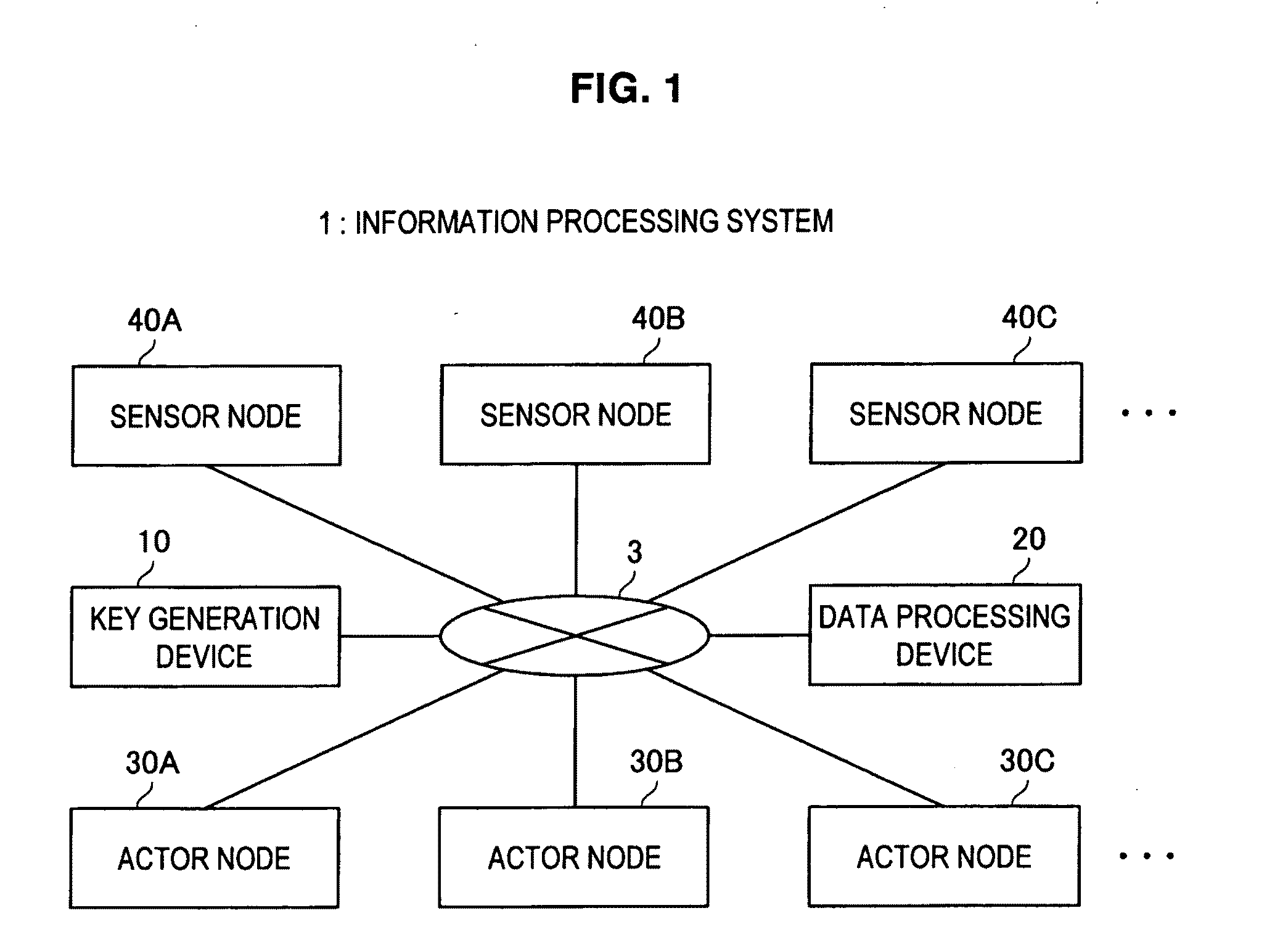
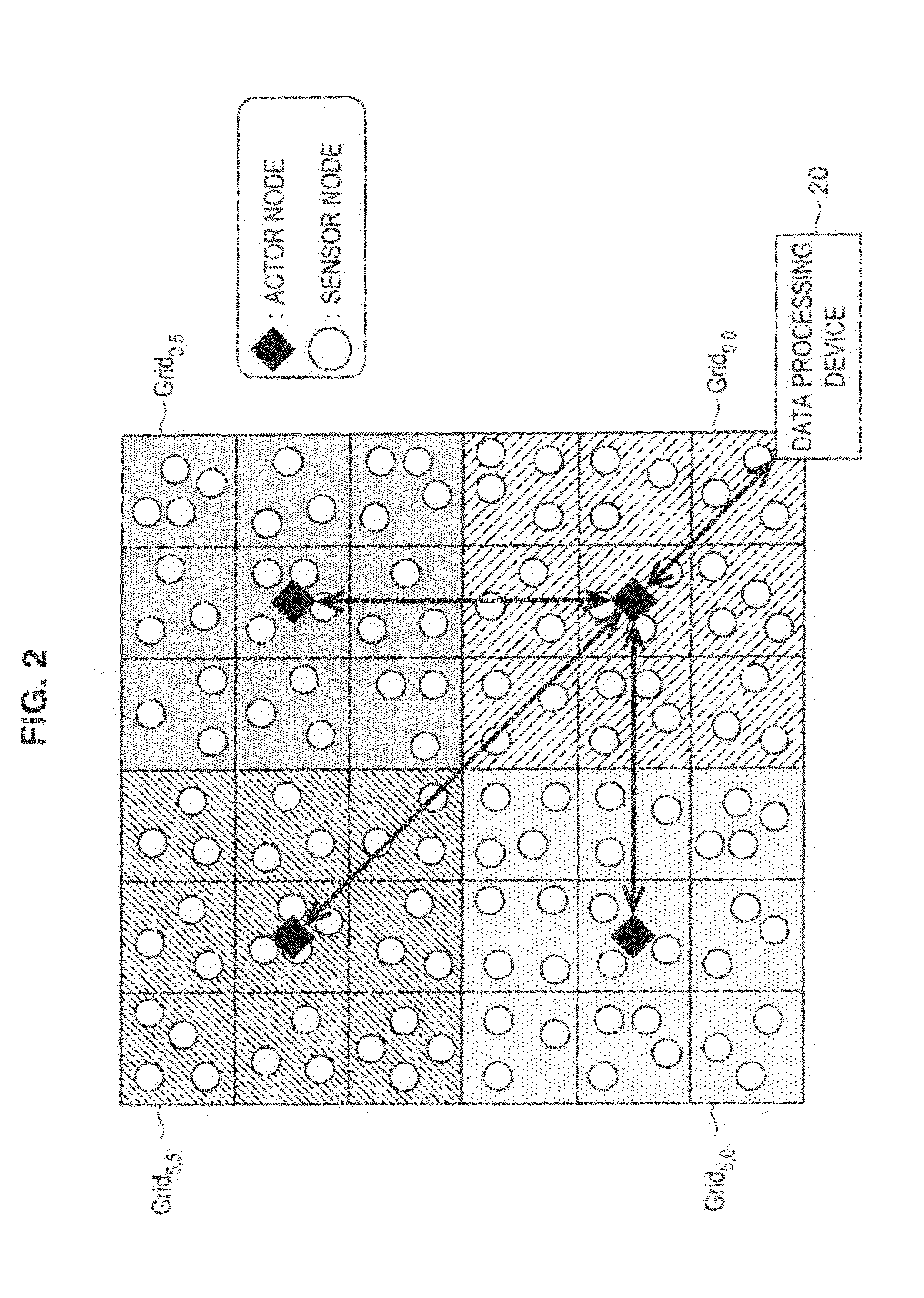
Actor node, sensor node, coverage block change method, parameter change method, program, and information processing system
InactiveUS20110145578A1Key distribution for secure communicationUser identity/authority verificationInformation processingSensor node
An actor node according to the present invention includes a dynamic change unit for temporarily changing a coverage block in which data are obtained from a sensor node and temporarily causing another actor node to obtain, on behalf of the actor node, data from the sensor node arranged in a partial region of at least a portion of the coverage blocks. The dynamic change unit obtains identification information unique to the another actor node from the another actor node. The dynamic change unit notifies, to the sensor node arranged in the partial region, the obtained identification information. The dynamic change unit notifies, to the another actor node, a portion of the hash chain and a temporary key generated using the obtained identification information and the key used for communication with the sensor node arranged in the partial region.
Owner:SONY CORP
Encryption techniques for improved sharing and distribution of encrypted content
In an embodiment, content may be encrypted by a first device using a dual hash chain technique, where the first device maintains a forward hash chain and a second device maintains a backward hash chain, and content keys for encrypting content are derived using values of the forward and backward hash chains. The second device may not have knowledge of a seed used to generate the forward hash chain, and therefore may be unable to generate the content keys, reducing a likelihood that the encrypted content becomes compromised. Additionally, embodiments provide for techniques for using proxy re-encryption (PRE) to re-encrypt content, such that the encrypted content may be provided to and decrypted by a requesting device without knowledge of the forward and backward hash chains. Additionally, embodiments provide techniques for distributing encrypted content to a requesting device with fine-grained access control.
Owner:HONG KONG APPLIED SCI & TECH RES INST
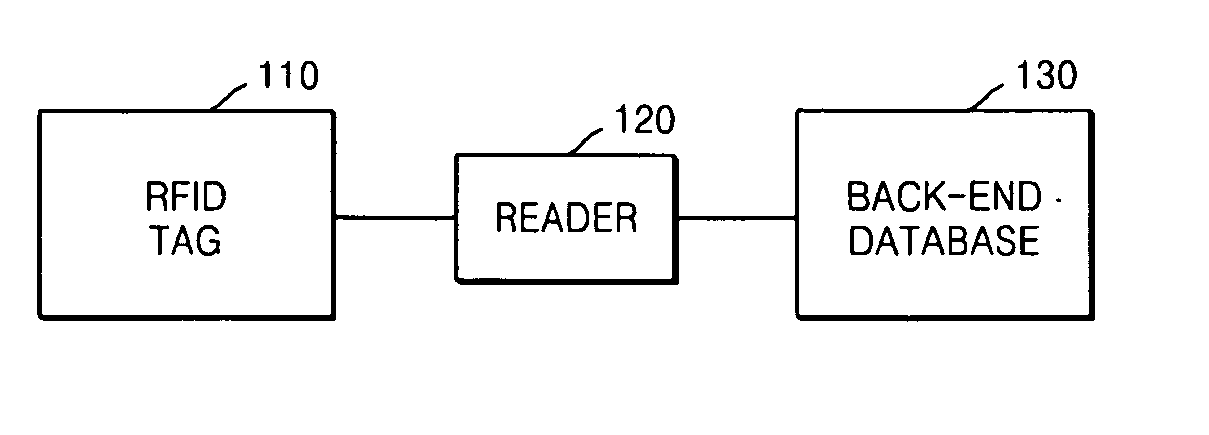
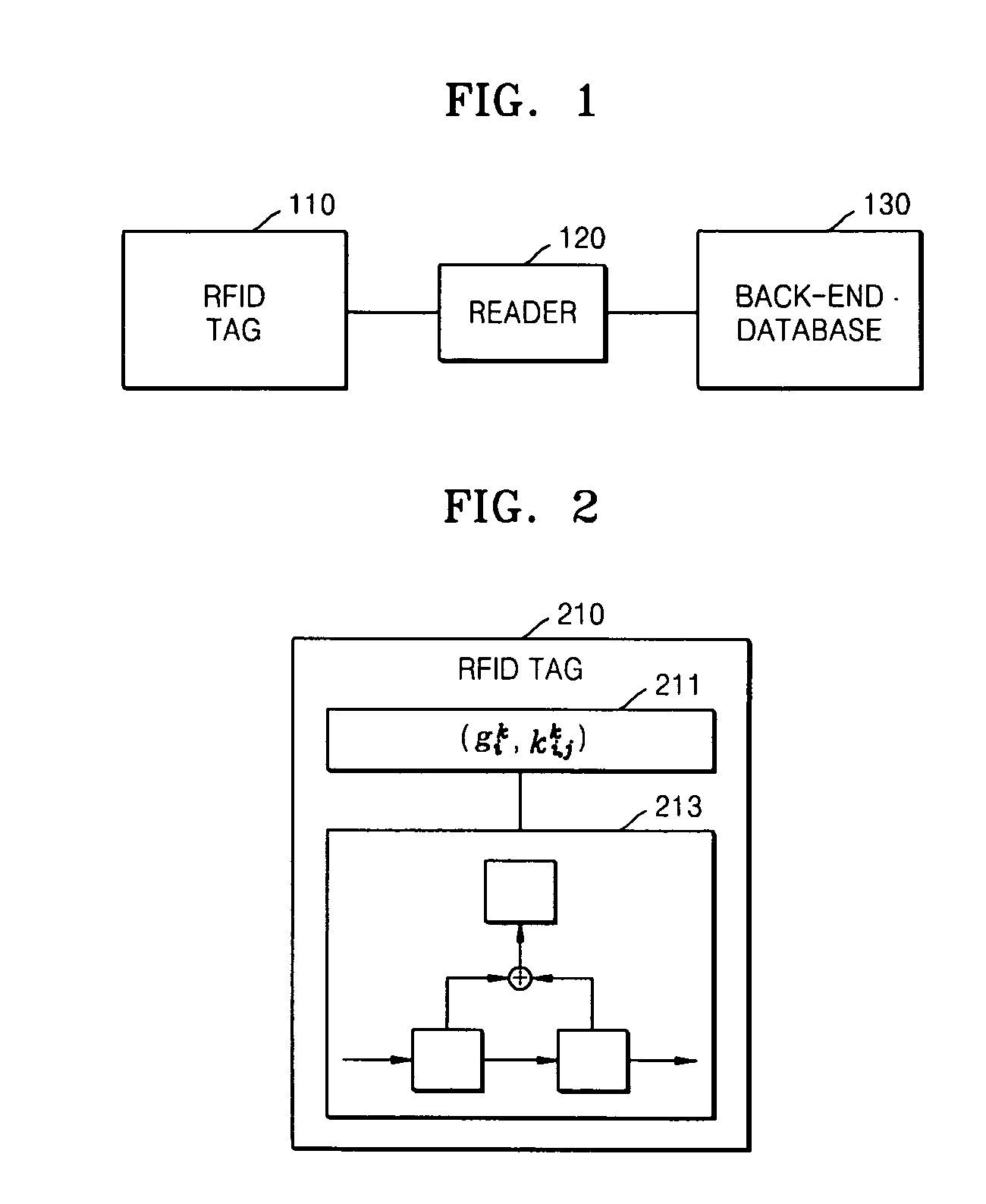
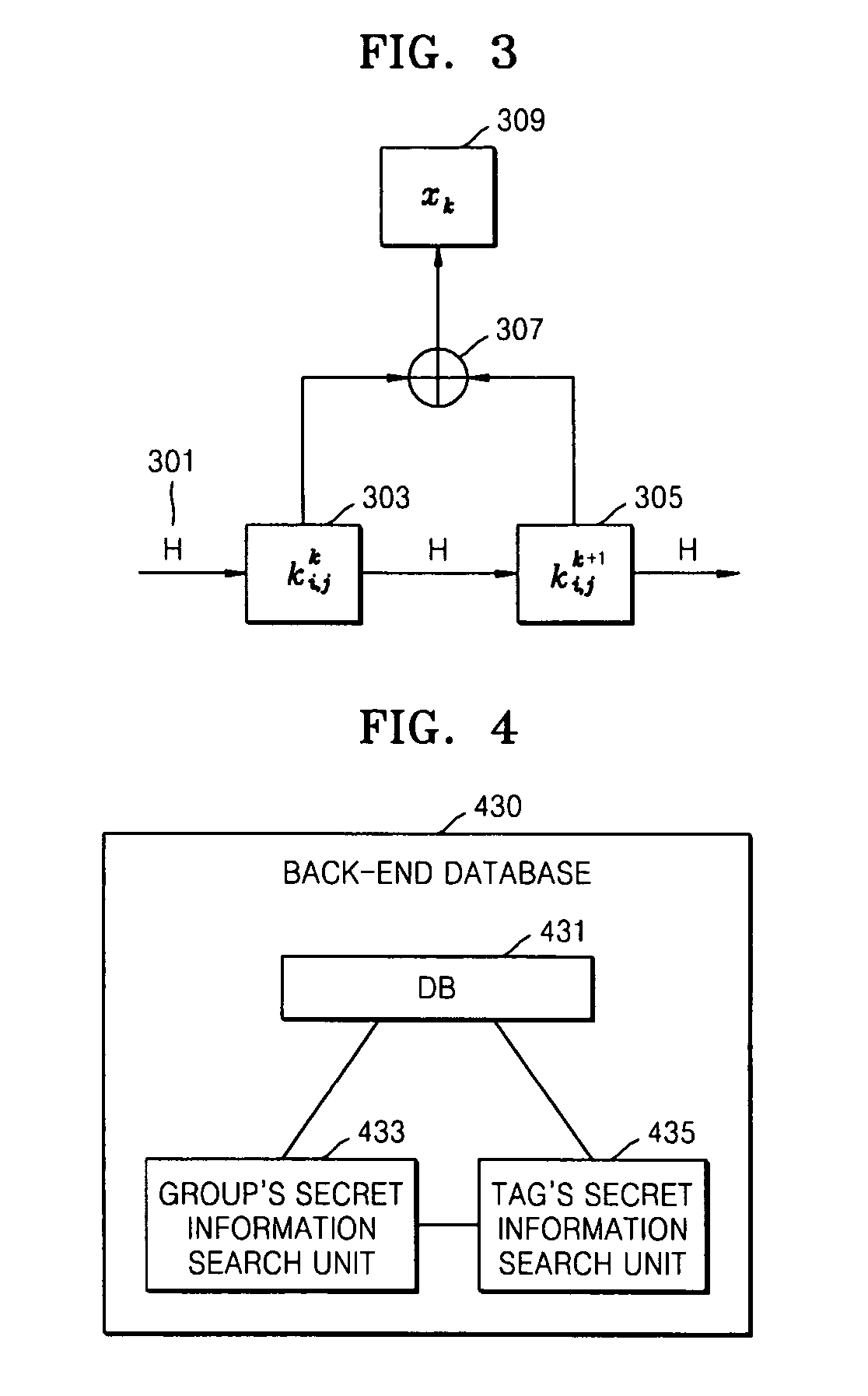
Tag authentication apparatus and method for radio frequency identification system
InactiveUS20070133807A1Reduce the amount of calculationKey distribution for secure communicationHash chainInformation searching
A radio frequency identification (RFID) tag authentication apparatus and method for accomplishing quick authentication and solving privacy problems using a hash algorithm are provided. An RFID tag includes a memory unit storing a tag's secret information and a group's secret information and a hash chain computation unit encrypting secret information based on a hash algorithm. The tag authentication apparatus includes a DB storing information about RFID tags, which is classified into groups and includes each group's secret information and each tag's secret information; a group's secret information search unit finding a group to which a tag to be authenticated belongs; and a tag's secret information search unit searching tags' secret information included in the found group.
Owner:ELECTRONICS & TELECOMM RES INST
Atomic renaming and moving of data files while permitting lock-free look-ups
InactiveUS20070198520A1Digital data processing detailsSpecial data processing applicationsData fileHash chain
Owner:INT BUSINESS MASCH CORP
Consistent hash based structural data storage, inquiry and migration method
ActiveCN104077423AEvenly dispersedImprove efficiencySpecial data processing applicationsDatabase indexingDistributed File SystemStorage model
The invention discloses a consistent hash based structural data storage, inquiry and migration method. The method comprises steps as follows: a consistent hash based HDFS (hadoop distributed file system) data storage model is established, data storage and data inquiry are performed on the basis of the model, and data migration is performed when a data node is added or fails; the data storage method is as follows: data blocks to be written into a file are subjected to consistent hash, Hash values of the data block are acquired, storage nodes of the data blocks are looked up in a node Hash chain according to the Hash values of the data blocks, and content of the data blocks is stored into the storage nodes of the data blocks. According to the method, on the basis of principal and subordinate structures of a HDFS cluster, structural data are uniformly dispersed onto the data nodes of the HDFS cluster by applying consistent hash, the data parallel traversing efficiency is effectively improved, when the number of data nodes changes, the number of nodes related to data migration and the total migration data amount can be greatly reduced, and the operating performance of the data storage system is improved.
Owner:SHANDONG UNIV
Universal authentication method for terminal equipment without identity in Internet-of-things
ActiveCN109167778AImprove identityRealize the function of privacy protectionKey distribution for secure communicationUser identity/authority verificationComputer hardwarePrivacy protection
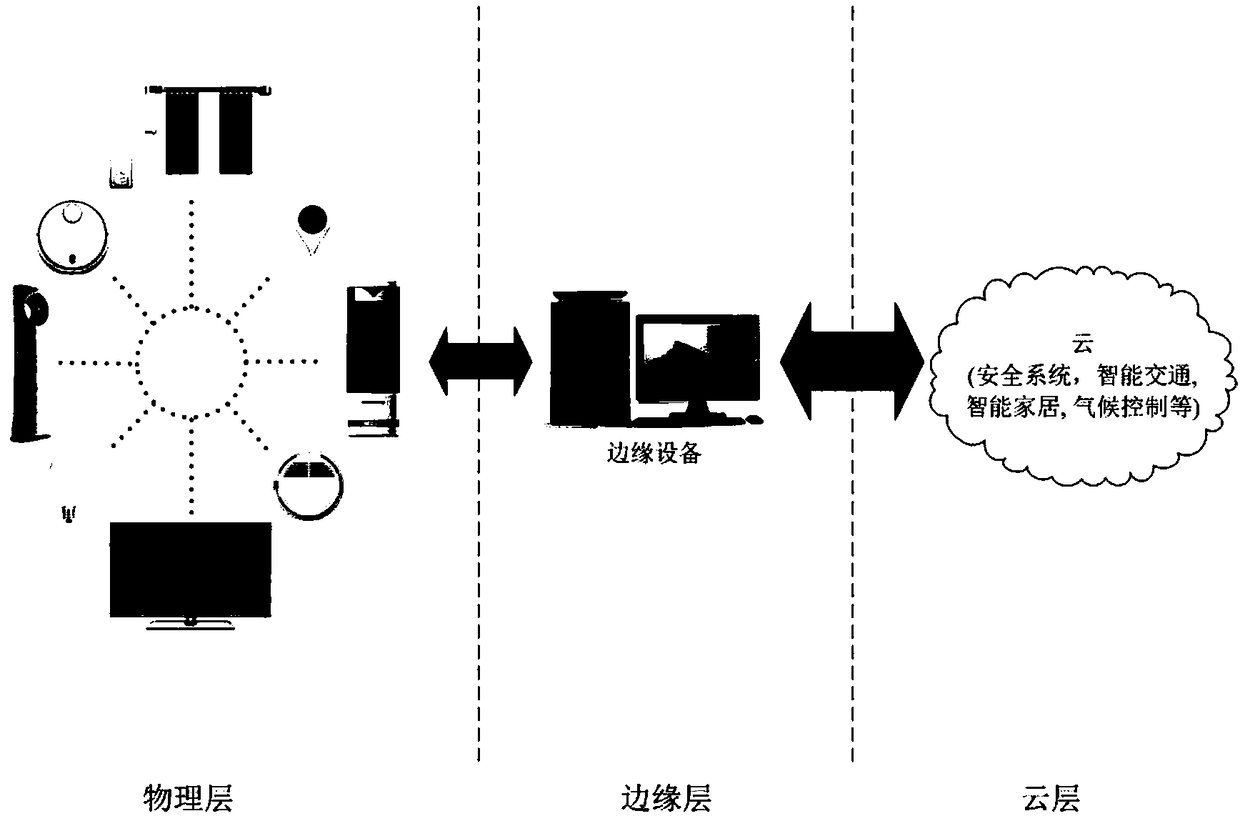
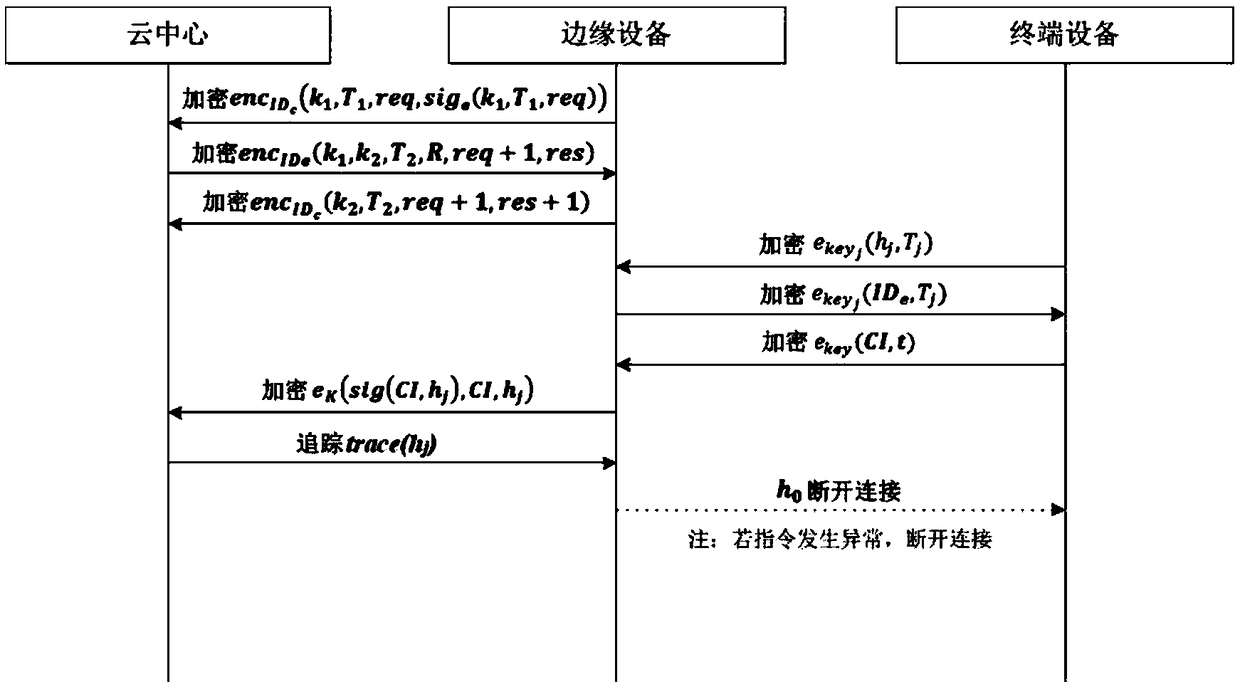
The invention discloses a universal authentication method for terminal equipment without identity in Internet-of-things, which is used for assisting the terminal equipment by introducing edge equipment, and delegates the authentication task to the edge equipment. The method includes a registration period, a session key generation phase, an instruction generation phase and an instruction verification and execution phase. The invention only according to the random identity of the terminal equipment, does not disclose any basic attribute thereof, protects the identity information of the equipmentwell, and realizes the function of privacy protection. Considering the limitation of computing power of Internet of Things devices, a lightweight authentication protocol based on hash chain technology is proposed for non-identifiable terminals.
Owner:NANJING UNIV OF POSTS & TELECOMM
Atomic renaming and moving of data files while permitting lock-free look-ups
InactiveUS20050223004A1Digital data processing detailsSpecial data processing applicationsData fileHash chain
Atomic renaming and moving of data files, while permitting lock-free look-ups to the data files, is disclosed. A temporary record may be created within a hash chain encompassing a record for a data file and corresponding to a location of the data file within a computer file system. The temporary record is linked within the hash chain so that the temporary record points to the same records to which the record for the data file points. The record for the data file is renamed with a new name, and / or moved to a new location within the computer file system, and the temporary record is removed from the hash chain. Before the temporary record is removed, look-ups of the data file resolve to the temporary record, the temporary record causing the look-ups to wait until the record for the data file has been renamed and / or moved and the temporary record removed.
Owner:IBM CORP
Partitioned type dynamic safety routing method for wireless sensor network on basis of hash chains
InactiveCN102244658AReduce loadImprove relevanceKey distribution for secure communicationData switching networksBalancing networkWireless mesh network
The invention discloses a partitioned type dynamic safety routing method of a wireless sensor network on the basis of hash chains, which belongs to the field of the computer communication network. According to the partitioned type dynamic safety routing method, a region concept is introduced according to characteristics of clustered routing algorithms and cycle circulation in the wireless sensor network, and a control message is broadcast to the entire network from converging nodes. The region of each node is determined according to the received signal strength, and direct communication among the nodes with larger distance can be avoided by the limitation of the region. After each cycle of cluster head is selected, q link keys are selected from a key pond composed of the hash chains by the node of each cluster head at random, and mutual communicating secret keys are derived according to oneway hash functions and fake random functions used for the chain keys by the other nodes so as to reduce the network communication load. According to the invention, the survival time of the network can be prolonged, the energy consumption of the nodes of the network is better balanced, the safety of the protocol is enhanced, the distribution of the nodes is made to be uniform, and the scope of networks where the protocol is applicable is enlarged.
Owner:NANJING UNIV OF TECH
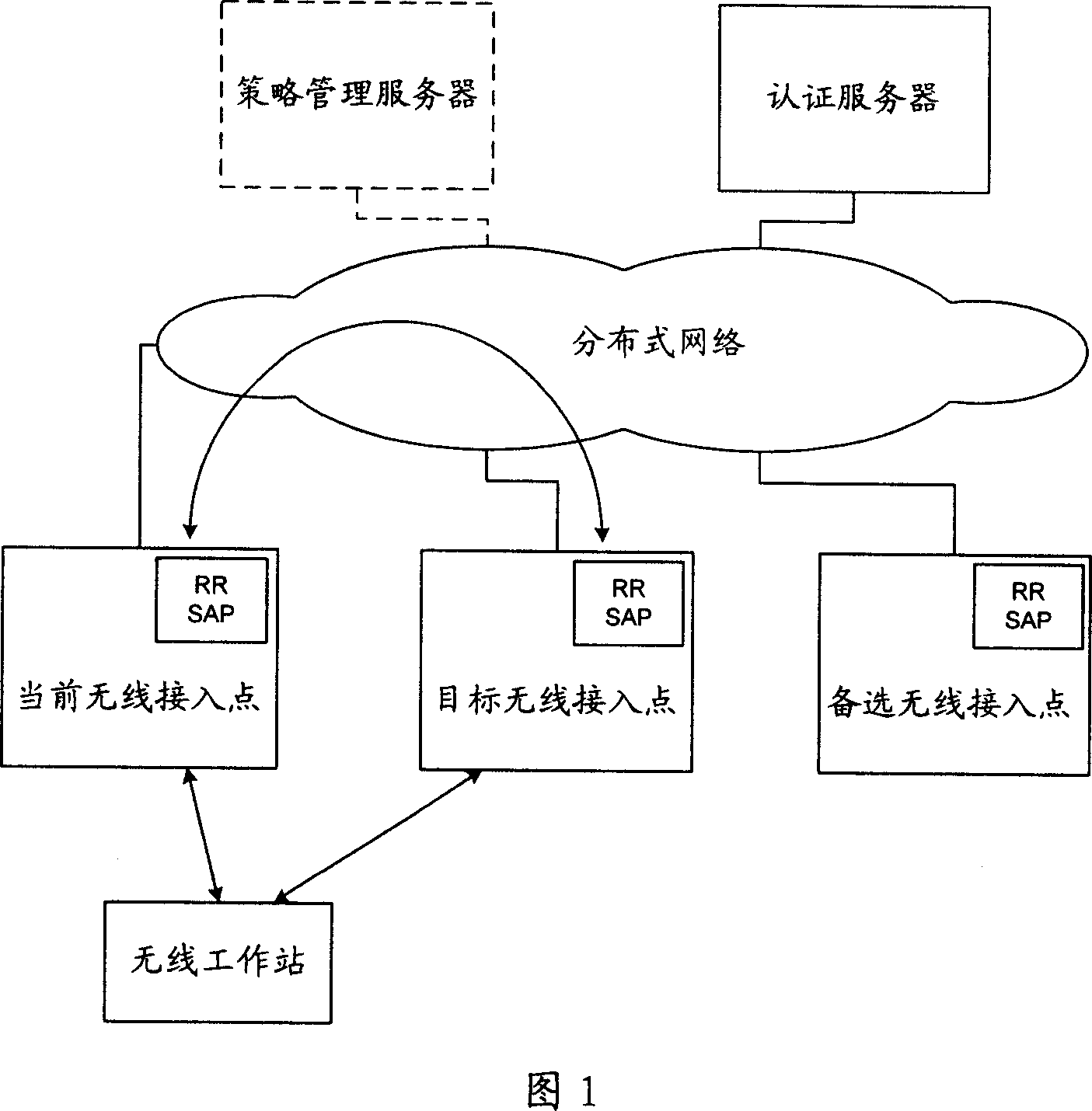
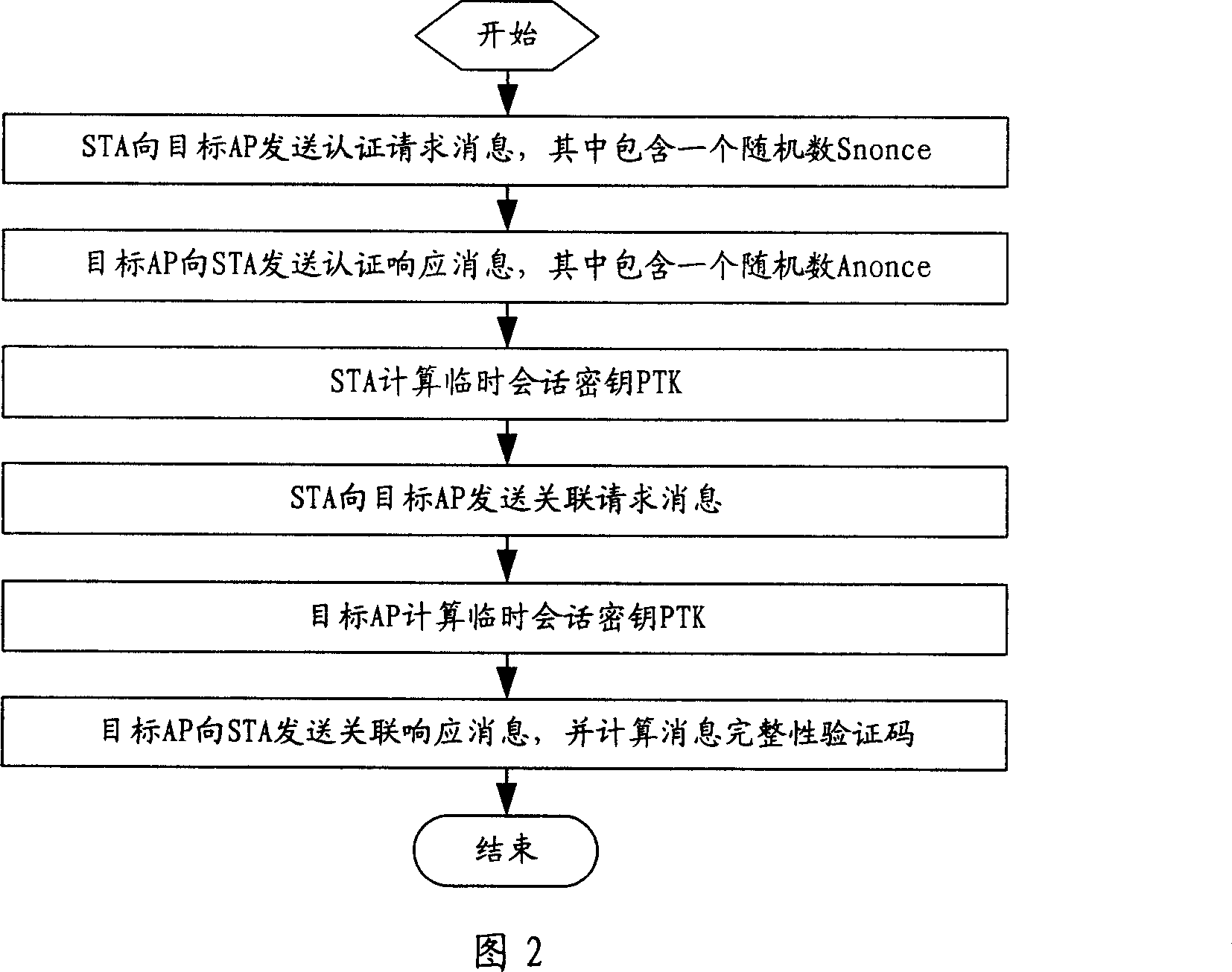
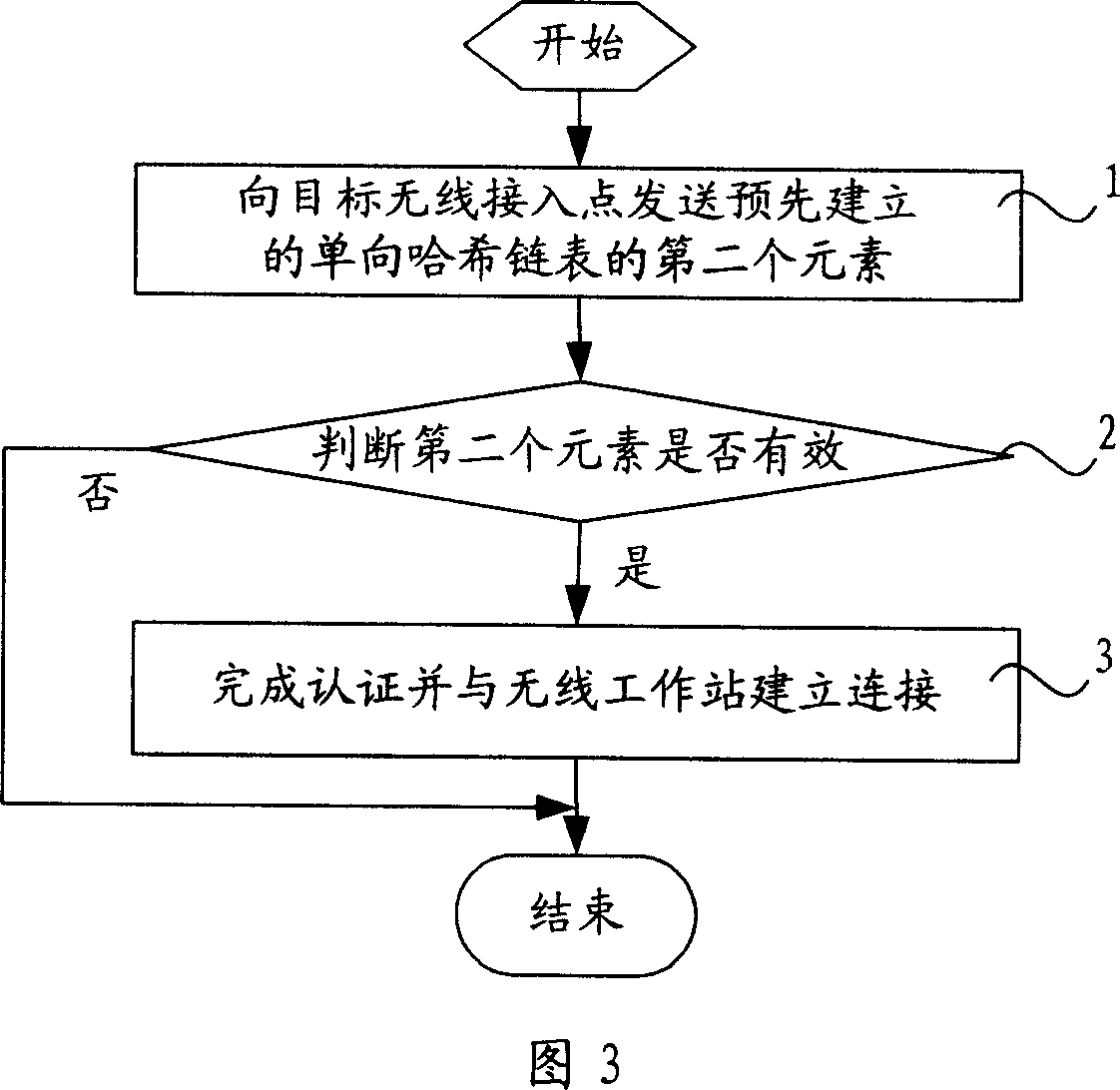
Fast switch method and system in wireless local area network
InactiveCN101114957AAvoid attackImprove securityData switching by path configurationRadio/inductive link selection arrangementsTelecommunicationsHash chain
A rapid-switching method in wireless local-area network includes the following steps: step 1, a wireless workstation sends a second element of a pre-constructed one-way hash chain table to a target wireless access point; step 2, whether the second element is effective or not is judged; if the second element is effective, step 3 is executed, otherwise the process is finished; step 3, connection between the target wireless access point and the wireless workstation is established. The rapid-switching method in wireless local-area network comprises a wireless access point, an authentication service unit, and a wireless workstation; the wireless workstation comprises a first communication module, which is connected with the wireless access point and the authentication service unit; the wireless access point comprises a second communication module, which is connected with the authentication service unit; a memory module, which is connected with the second communication module; an authentication module, which is connected with the memory module and the second communication module; the authentication service unit comprises a third communication module, which is connected with the wireless workstation and the wireless access point. The invention can realize one-way and / or two-way authentication between the wireless workstation and the wireless access point.
Owner:XIDIAN UNIV +1
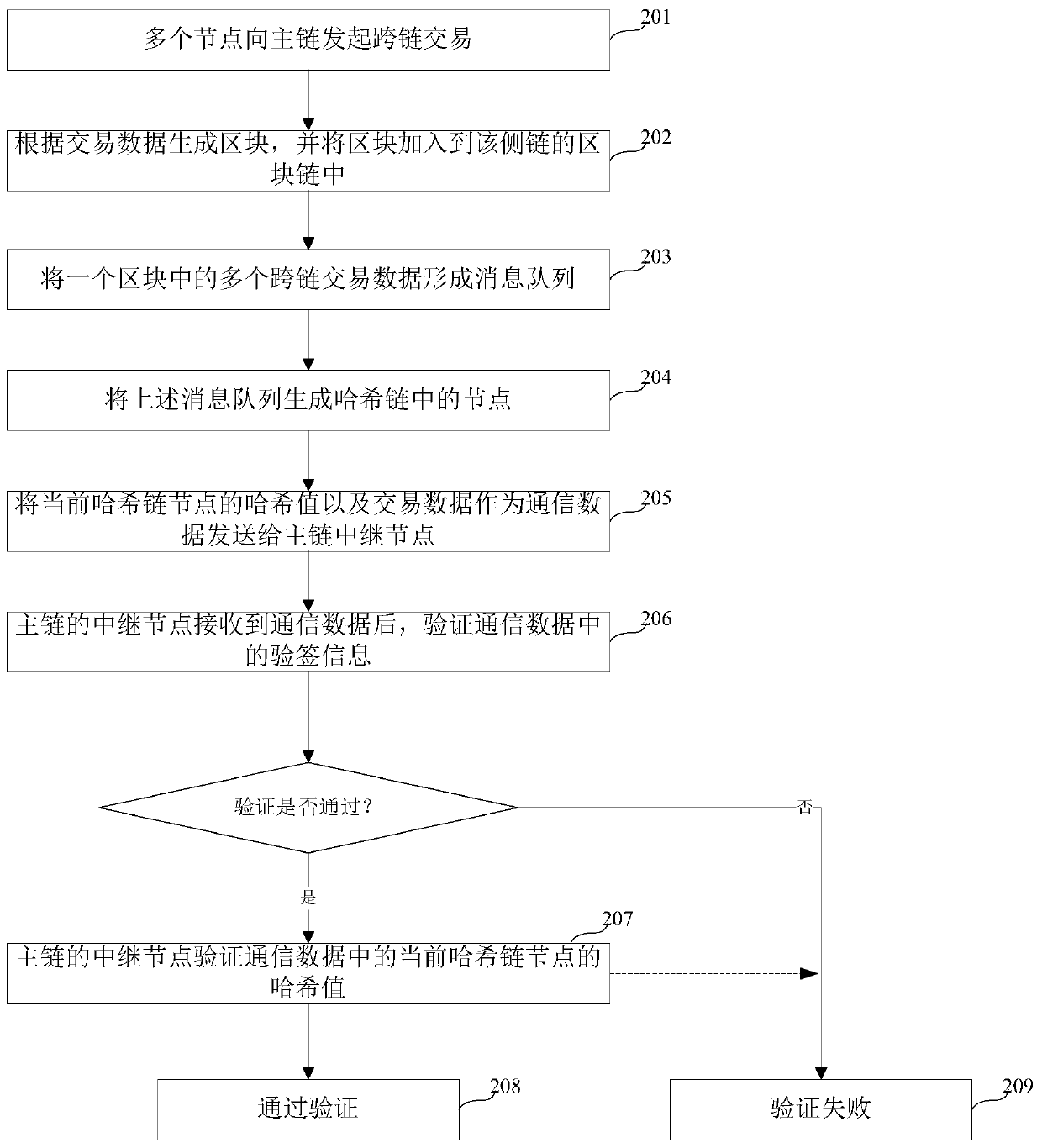
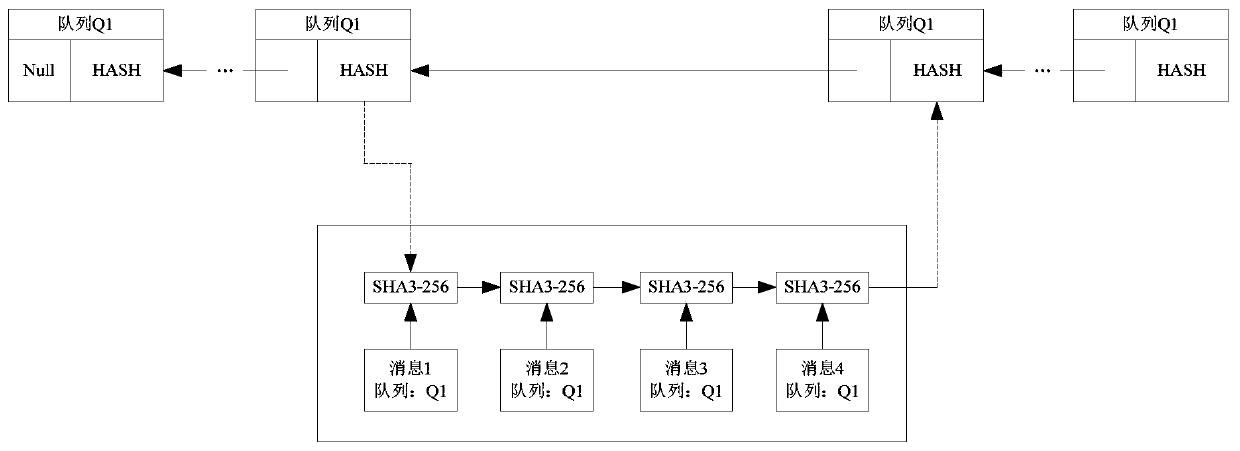
Method and device for sending and verifying cross-chain communication data
ActiveCN111464518AImprove securityEnsure safetyFinanceEncryption apparatus with shift registers/memoriesComputer networkTransaction data
The invention relates to the technical field of blockchain security, in particular to a method and device for sending and verifying cross-chain communication data. According to the scheme, hash operation is carried out on cross-chain transaction data to form a current hash chain node related to the front and back of a hash chain node; and the cross-chain transaction data and the hash value of thecurrent hash chain node are sent to a target block chain, operation is carried out on the cross-chain transaction data by using the same hash operation method in the target block chain, and a calculation result is compared with the hash value of the current hash chain node so as to verify the cross-chain communication data. The security of communication between a side chain and a main chain can beimproved.
Owner:北京新创智链科技有限公司
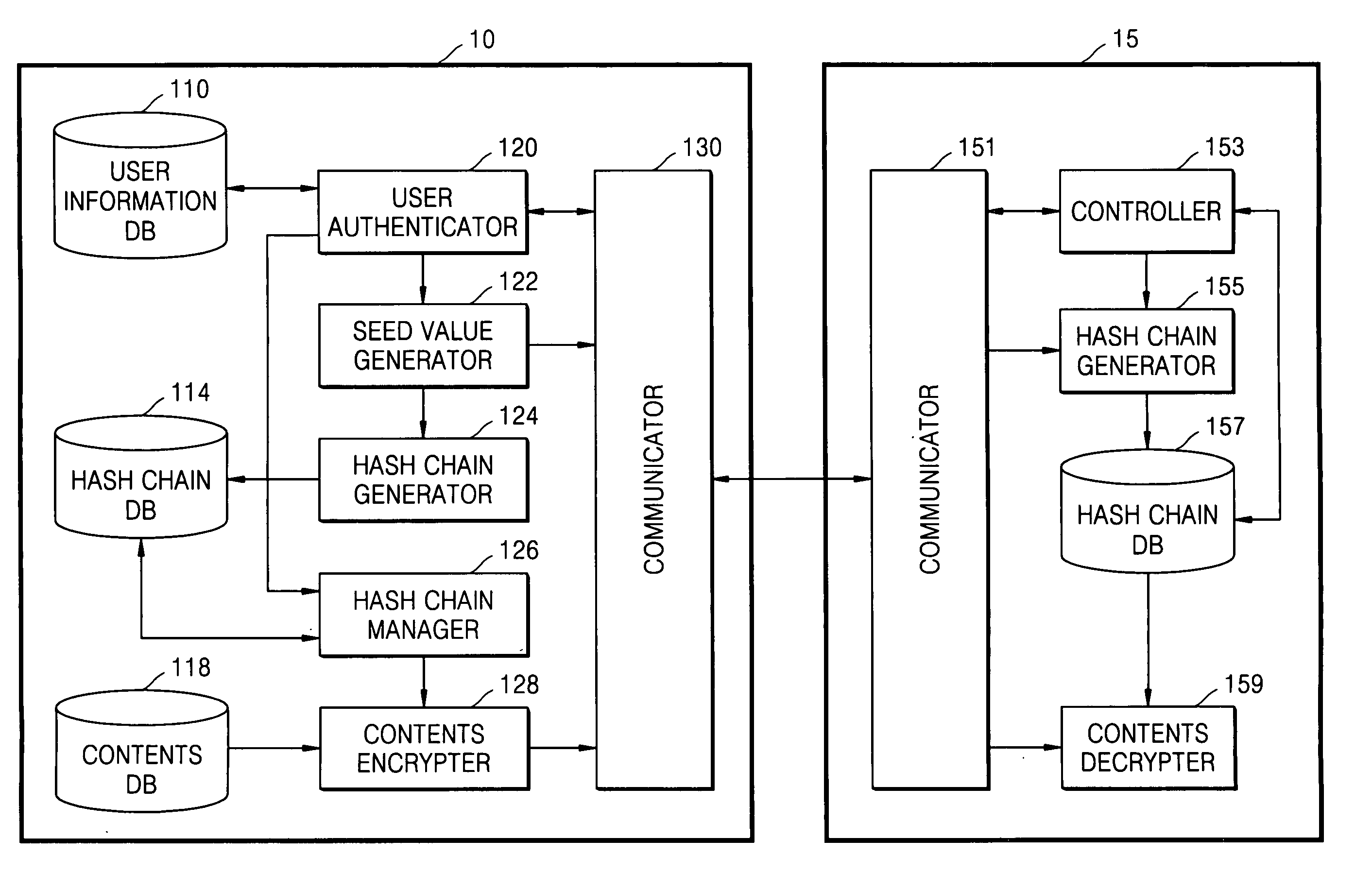
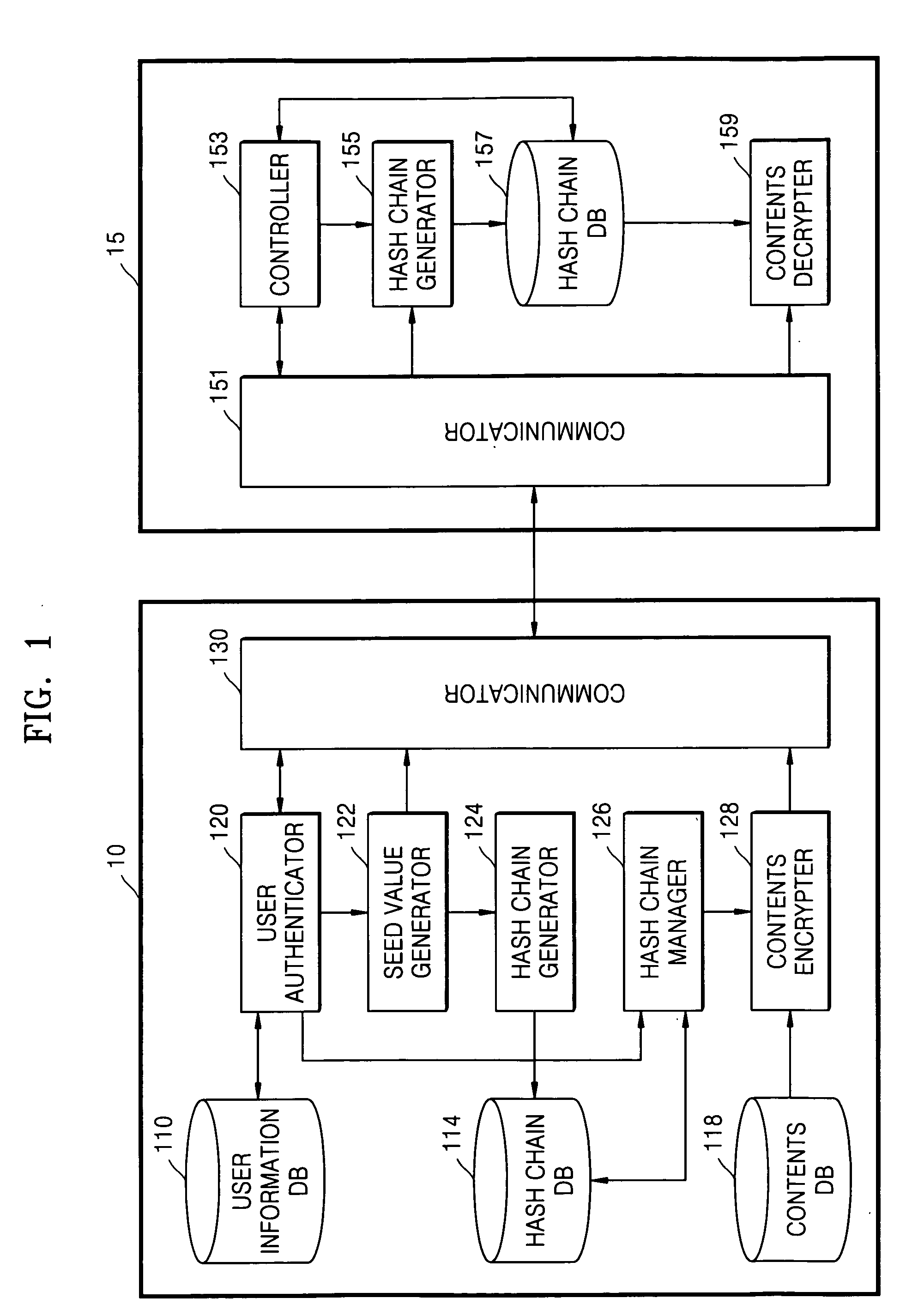
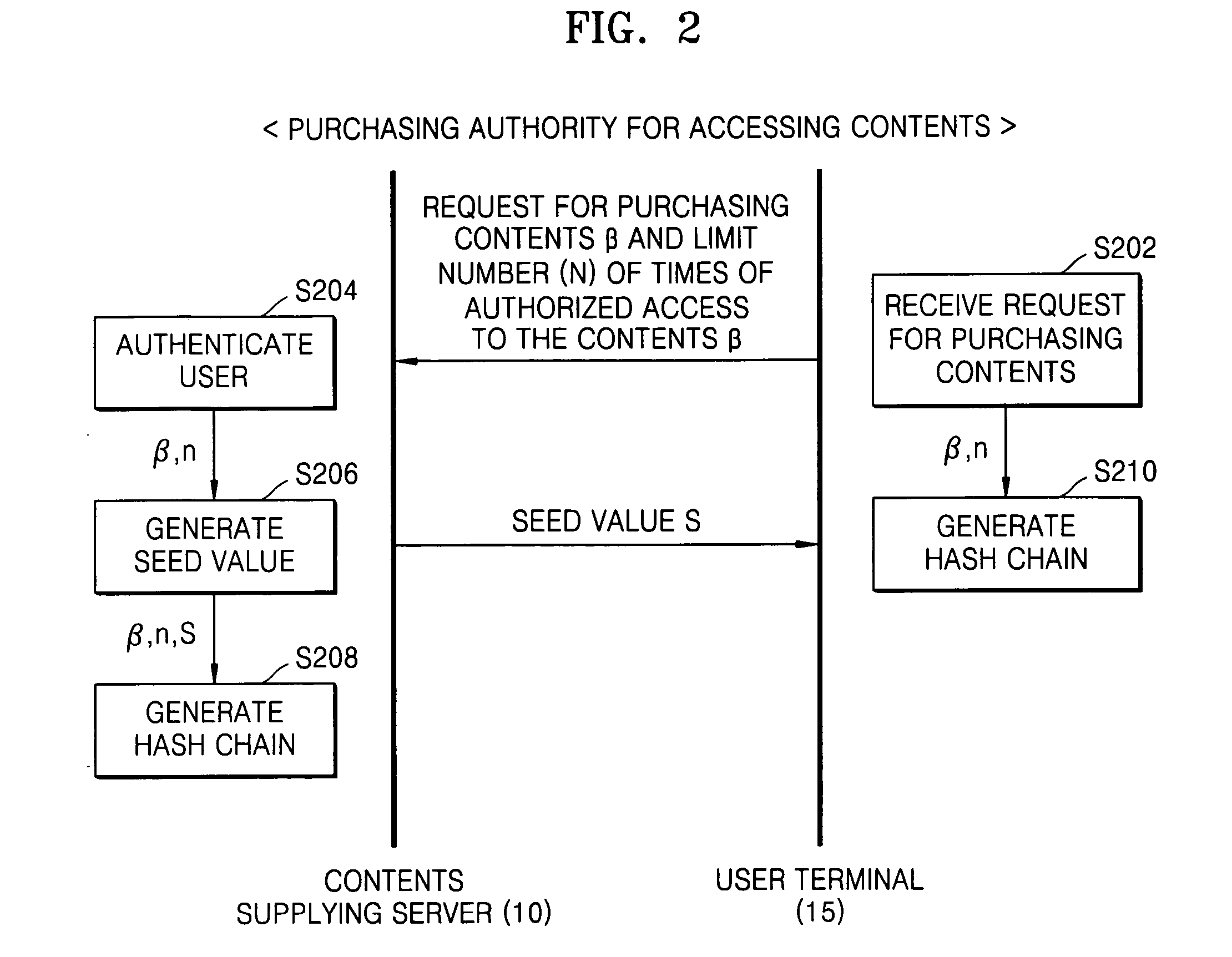
Method and apparatus for limiting number of times contents can be accessed using hash chain
ActiveUS20050256910A1Effectively managing copyrightSimply and securely limitingKey distribution for secure communicationDigital data processing detailsComputer networkHash chain
A method and apparatus are provided for simply and securely limiting a number of times that contents can be accessed using a hash chain. The apparatus limiting a number of times contents are accessed by a user terminal includes a hash chain generator receiving information indicating selected contents by the user terminal and information indicating how many times (n) the user terminal has authority to access the selected contents and generating a hash chain including n hash values derived from a seed value, and a contents access manager deleting the hash values one by one from the hash chain whenever the user terminal accesses the selected contents such that the number of times the contents can be accessed by the user terminal is decreased by the number of deleted hash values.
Owner:SAMSUNG ELECTRONICS CO LTD
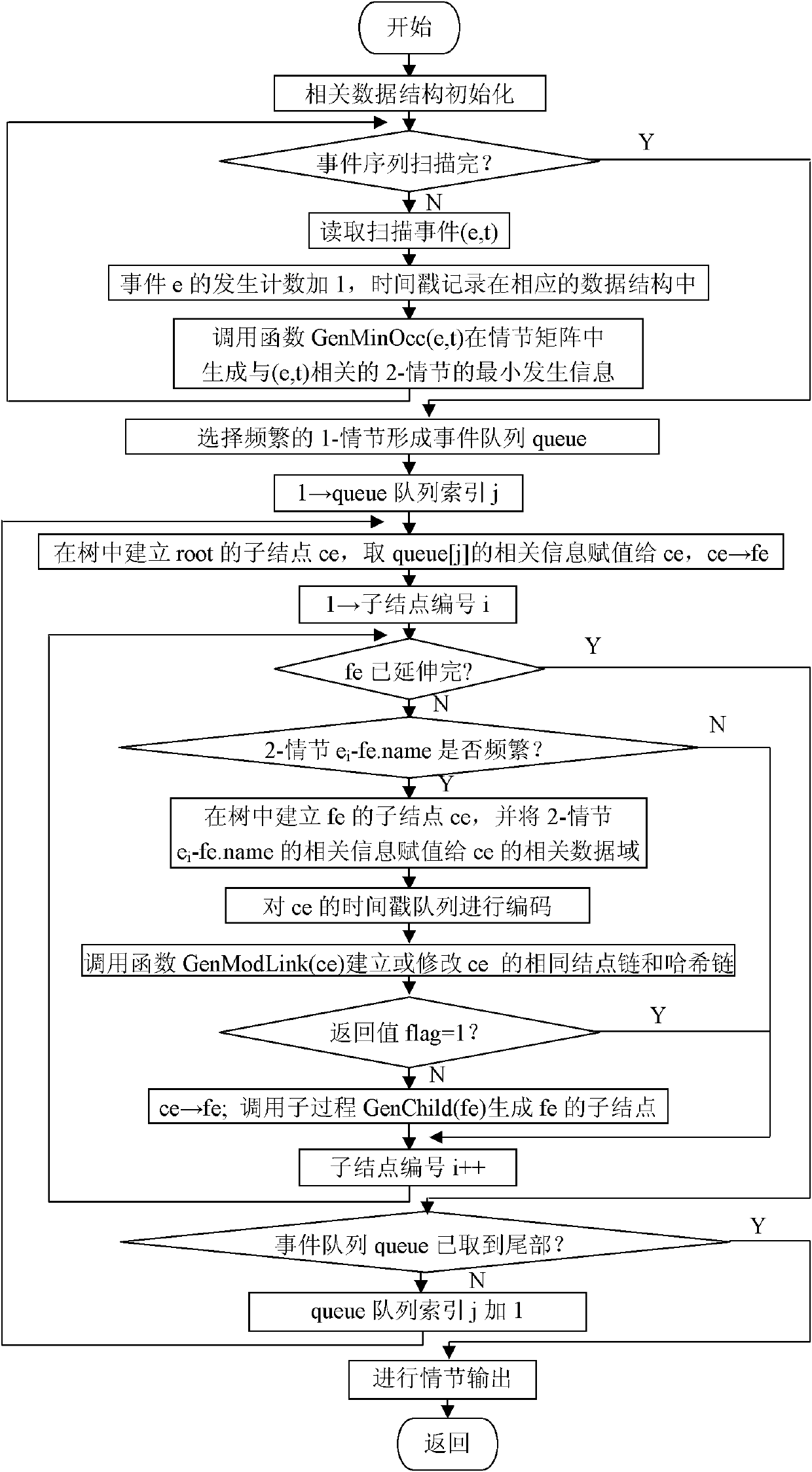
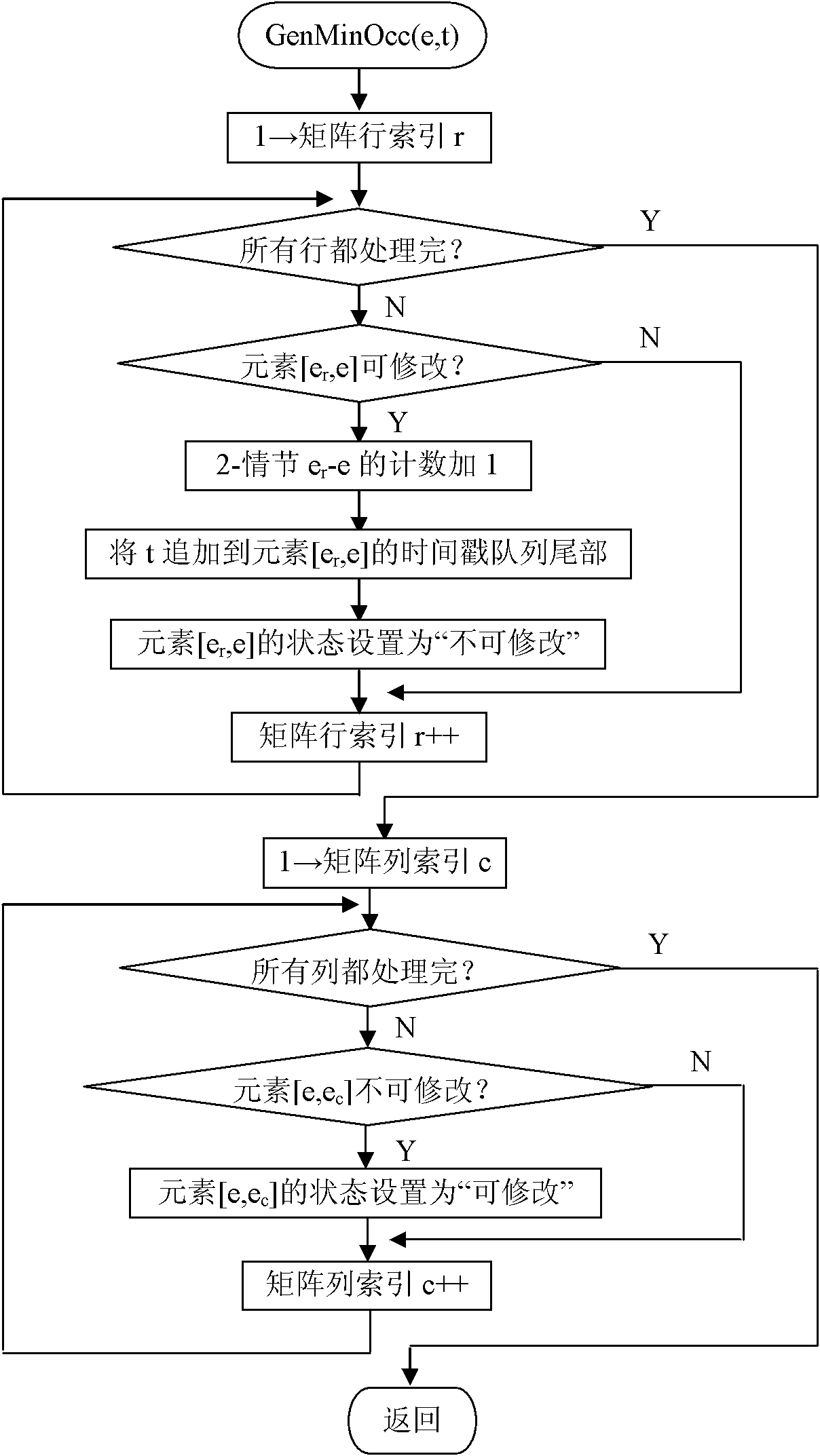
Method for mining frequency episode from event sequence by using same node chains and Hash chains
InactiveCN102073732AExtension of timeIncrease spaceSpecial data processing applicationsTimestampData needs
The invention relates to a method for mining the lowest occurrence frequency episode from an event sequence, which is characterized by extending the low-order frequency episode step by step so as to directly generate a high-order frequency episode. In the method for finding and counting the lowest occurrence frequency of an episode, the lowest occurrence frequency of a 2-episode is found and counted by establishing an episode matrix and setting corresponding modification states on episode matrix elements, and the lowest occurrence frequency of a k-episode is found and counted by carrying out the timestamp-queue based extension on a frequency 2-episode. In the method for mining the episode by establishing an episode tree and using same node chains and Hash chains, the episode extension time and the occupied memory space are saved, and data need to be scanned once in the process of mining without generating a candidate episode set so that the mining efficiency is high and the less memory space is occupied. The method for mining the episode by establishing the episode tree and using same node chains and Hash chains has good characteristic that the mining time and the mining cost do not change obviously along with the frequency number threshold and can be further used for mining the episode from an event flow.
Owner:NORTHEASTERN UNIV
Wireless sensor network key distribution and management protocol based on multiple hash chains
InactiveCN102131195AImprove survivabilityImprove securityAssess restrictionNetwork topologiesComputer hardwareWireless sensor networking
The invention provides a wireless sensor network key distribution and management protocol based on multiple hash chains. The protocol can overcome design defects of a traditional wireless sensor network key management algorithm, and provides confirmed safety for a network through pair-wise keys established by multiple hash chains while obviously reducing storage overhead. Based on factorization of polynomials, safe distribution and updating of cluster keys can be completed through primary broadcasting, and the problems which comprise low capability of physical capture attack resistance and large overheads for cluster key distribution and communication updating, and are generated on the basis of a clustering safety algorithm, are solved.
Owner:SHANGHAI DIANJI UNIV
System, method, and computer readable medium for micropayment with varying denomination
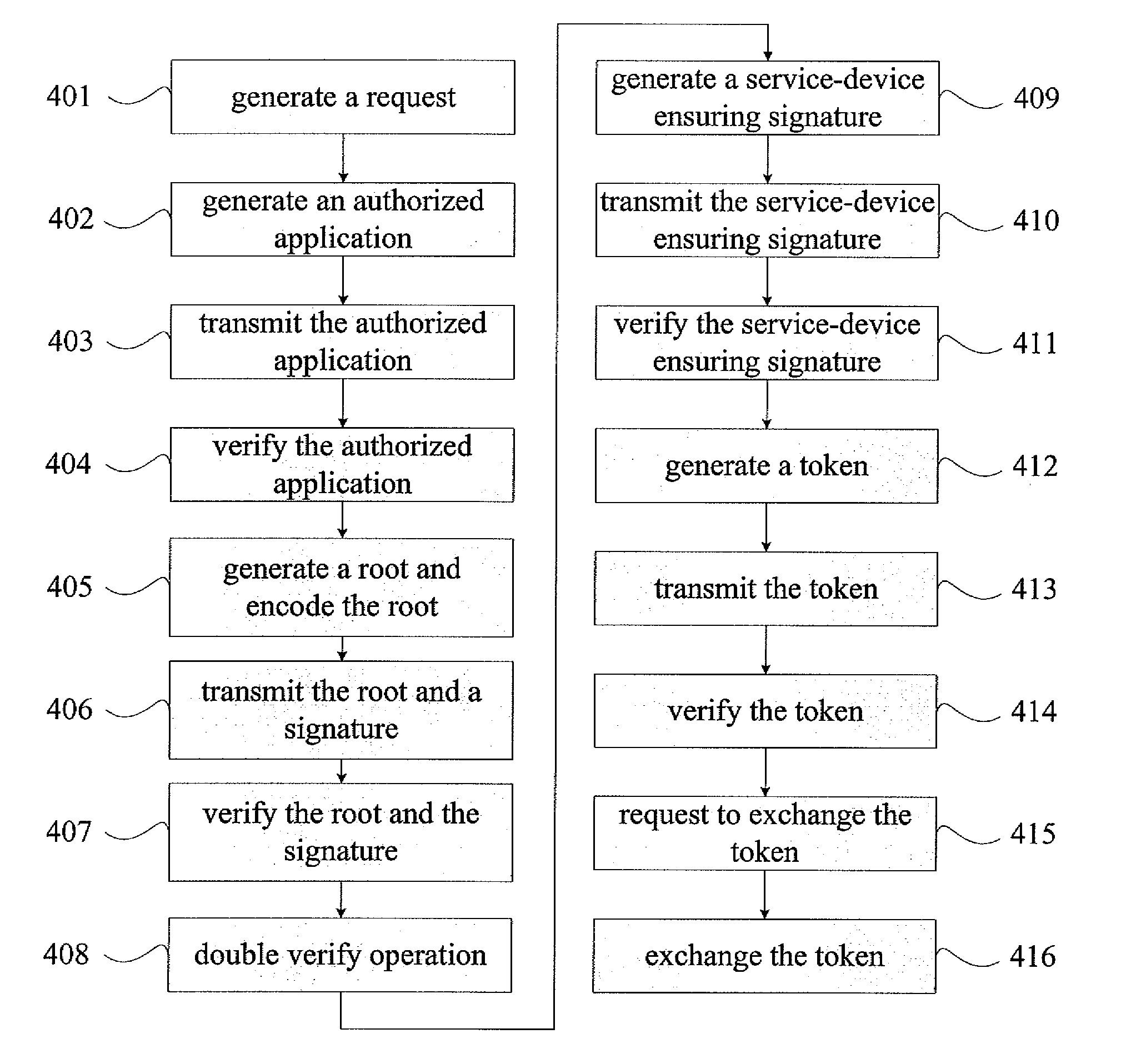
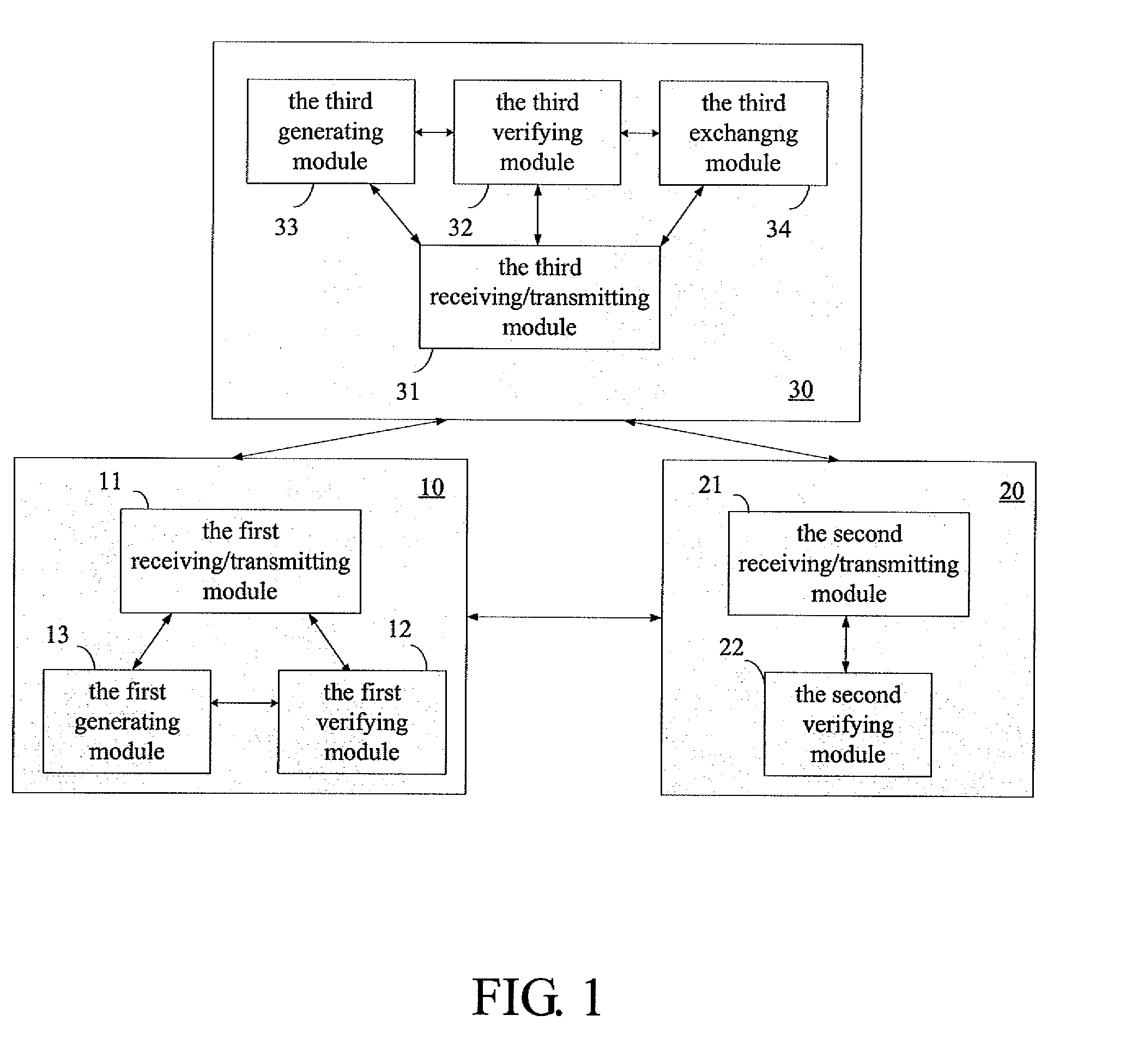
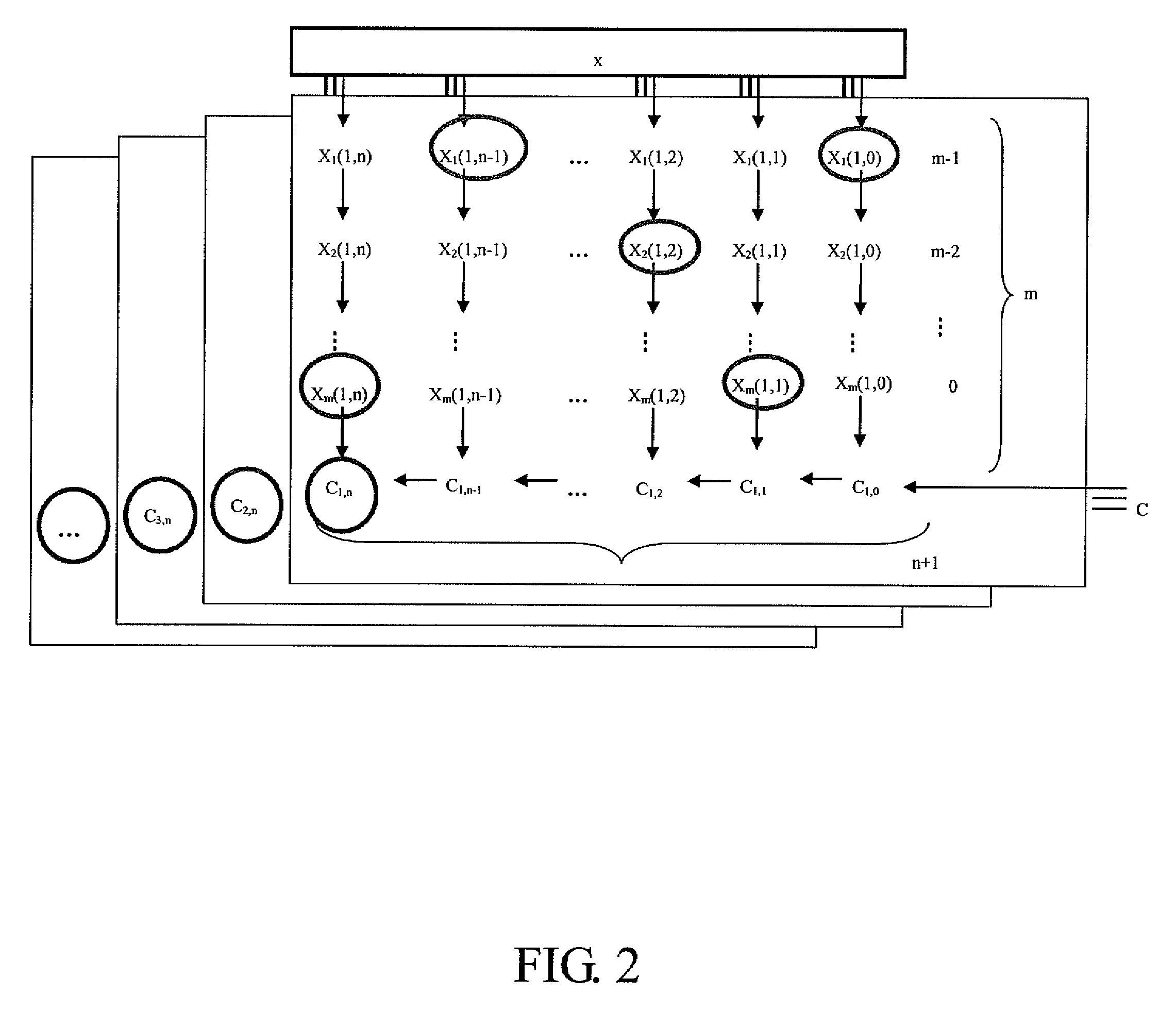
A system, a method, and a computer readable medium for micropayment with varying denomination are disclosed. The method utilizes a secret value, a public information, a number base parameter, a bit parameter, and merged one-way hash chains to calculate a root for providing a certificate of a transaction among a customer, a merchant and a service device. Therefore, the purpose of varying denomination for micropayment system can be achieved and the trade safety and the efficiency during the transaction process can be enhanced as well.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
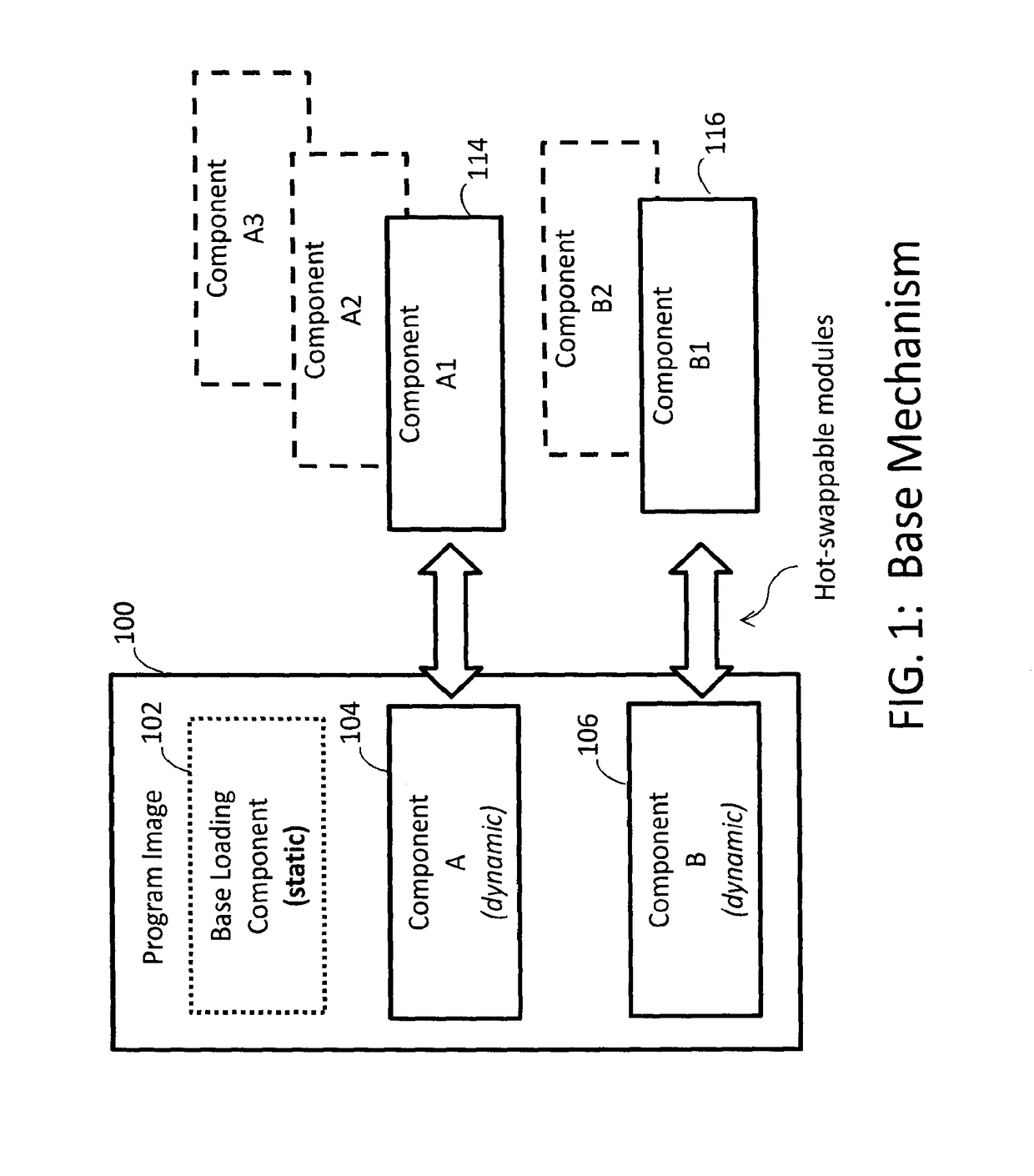
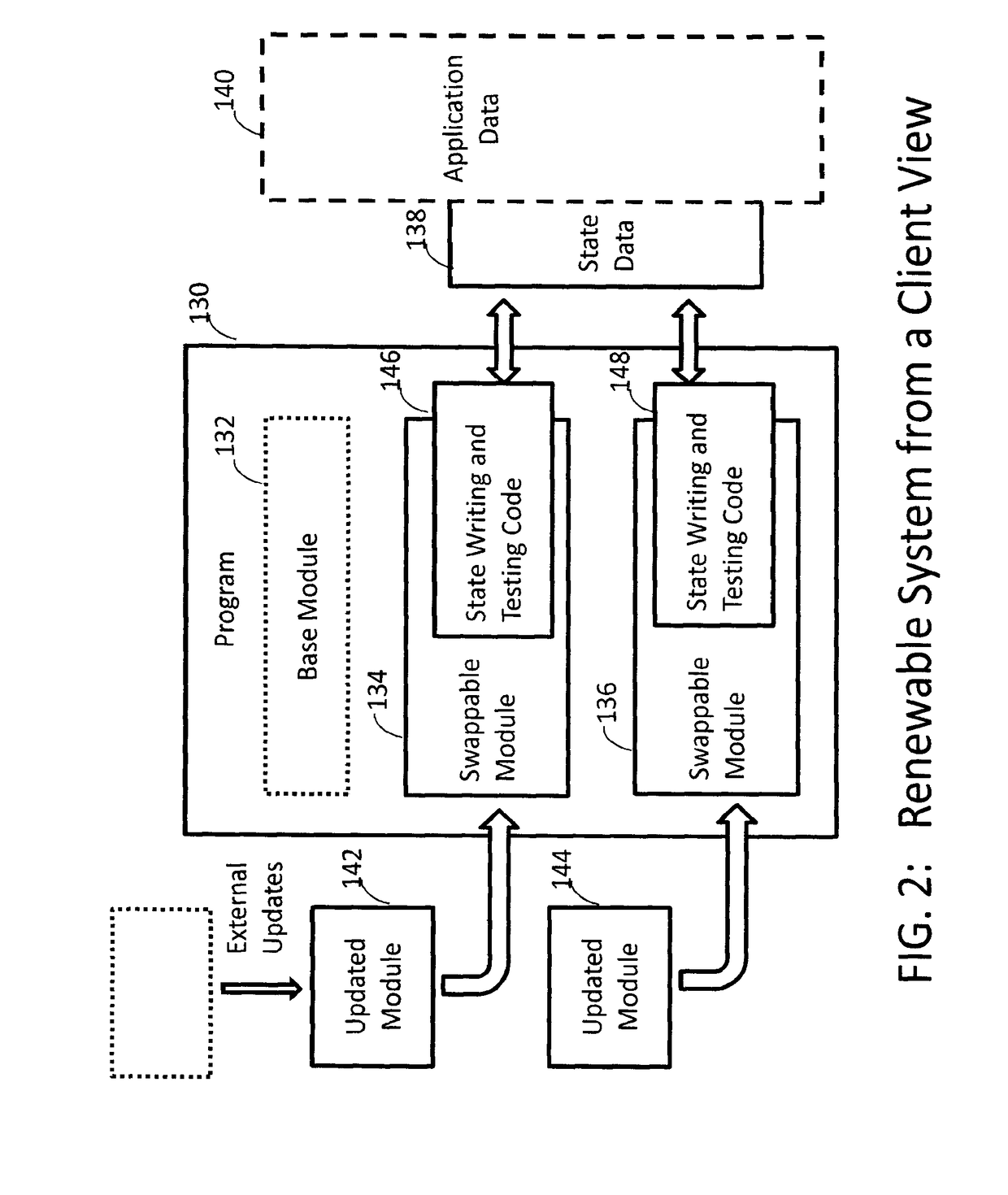
Updating software components
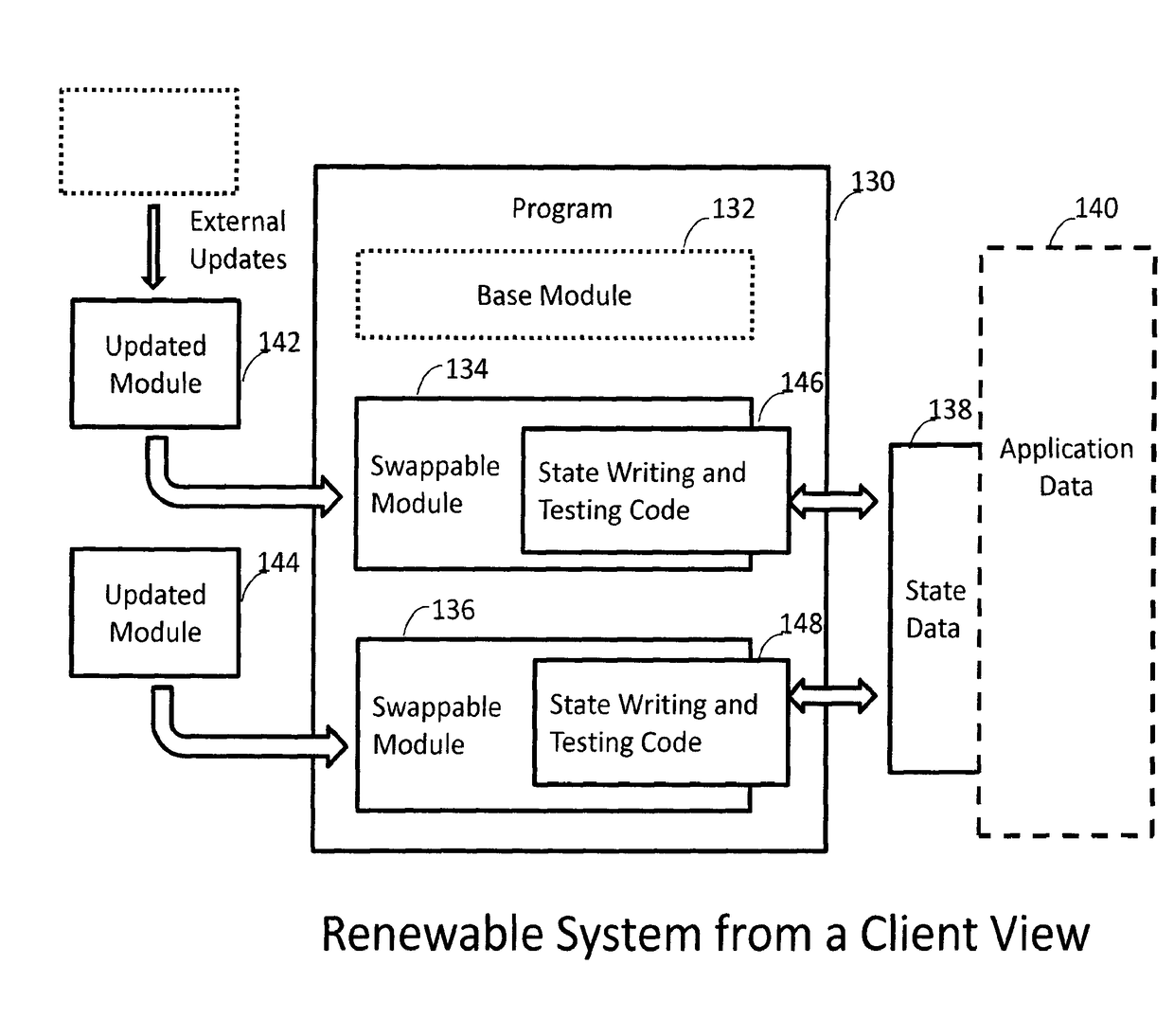
ActiveUS20170147331A1Platform integrity maintainanceProgram loading/initiatingSoftware updateGranularity
A method and system for renewing software at the component-level is provided. A client program includes a base component for loading a software component into at least one loadable region of the program to update the program. Code in the software component is for writing state data associating the state of the update in storage, upon execution of the software component, and testing the state data to verify condition of the updated program and disallowing rollback and roll-forward attacks, the state data comprising hash chain values. The state data for verifying the correctness of the updated program is entangled with application data used for the program functionality. A server includes: an update pool having a plurality of software updates deployed in each client, and a policy control for monitoring and controlling at least one of: the length of time the client runs until the software update is invoked, a chain of the updates; and the granularity of the update.
Owner:IRDETO ACCESS
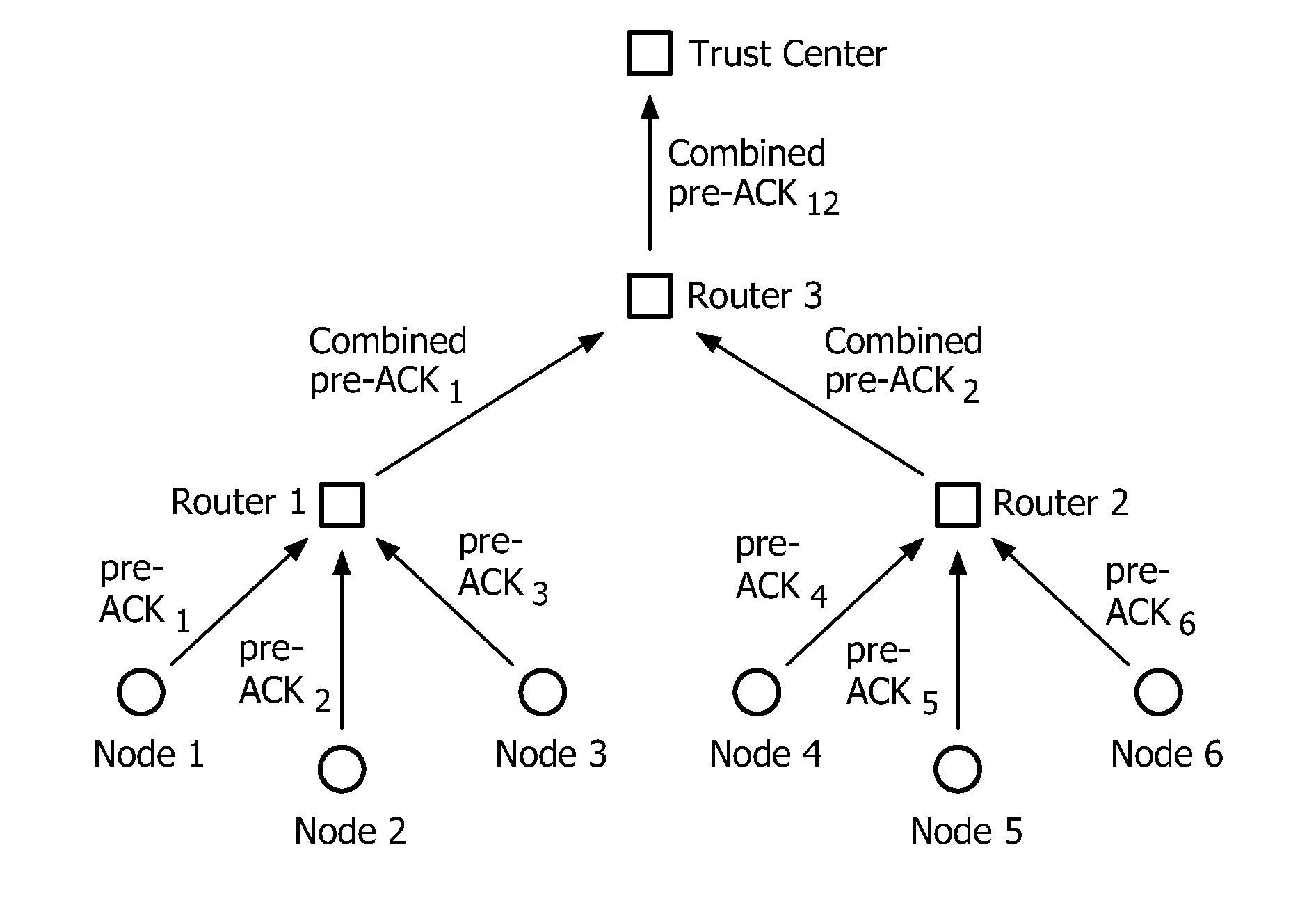
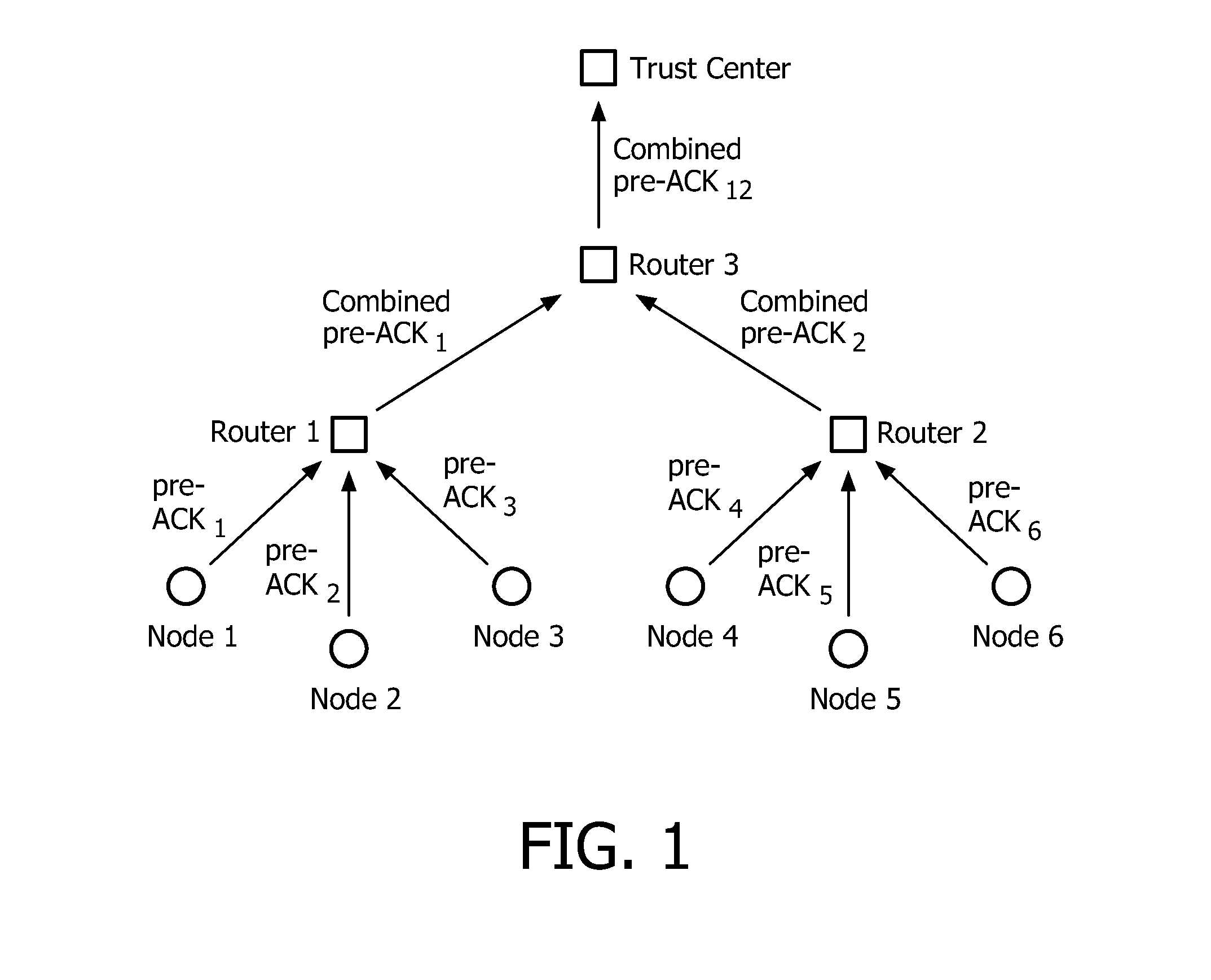
Method for securely broadcasting sensitive data in a wireless network
InactiveUS20120114123A1Secure performanceReduce storage requirementsNetwork topologiesSecret communicationComputer hardwareWireless sensor networking
The invention relates to a method for securely broadcasting sensitive data in a wireless sensor networks comprising a central device, called trust center, and a plurality of sensor nodes, the trust center being initialized with a cryptographic hash chain and each node being initialized with a node key and the anchor of the trust center hash chain, the method comprising the following steps: the trust center broadcasting a first secure message to the nodes, each node, after reception of the first message, creating a first acknowledgment message, and transmitting it back to the trust center, the trust center checking whether all the nodes have transmitted respective first acknowledgment message, and in case all messages have been received, the trust center securely broadcasting sensitive data in a third message, the nodes checking, based on elements included in the first message, whether sensitive data actually originates from the trust center.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com