Method for realizing intra-mobile entity authentication and cipher key negotiation using short message
A technology of key agreement and mobile entity, which is applied in the direction of public key for secure communication, user identity/authority verification, radio/inductive link selection arrangement, etc. Message non-repudiation and anonymity, increase the processing delay of SMS system, etc., to achieve the effect of less communication overhead, easy operation, and broad application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
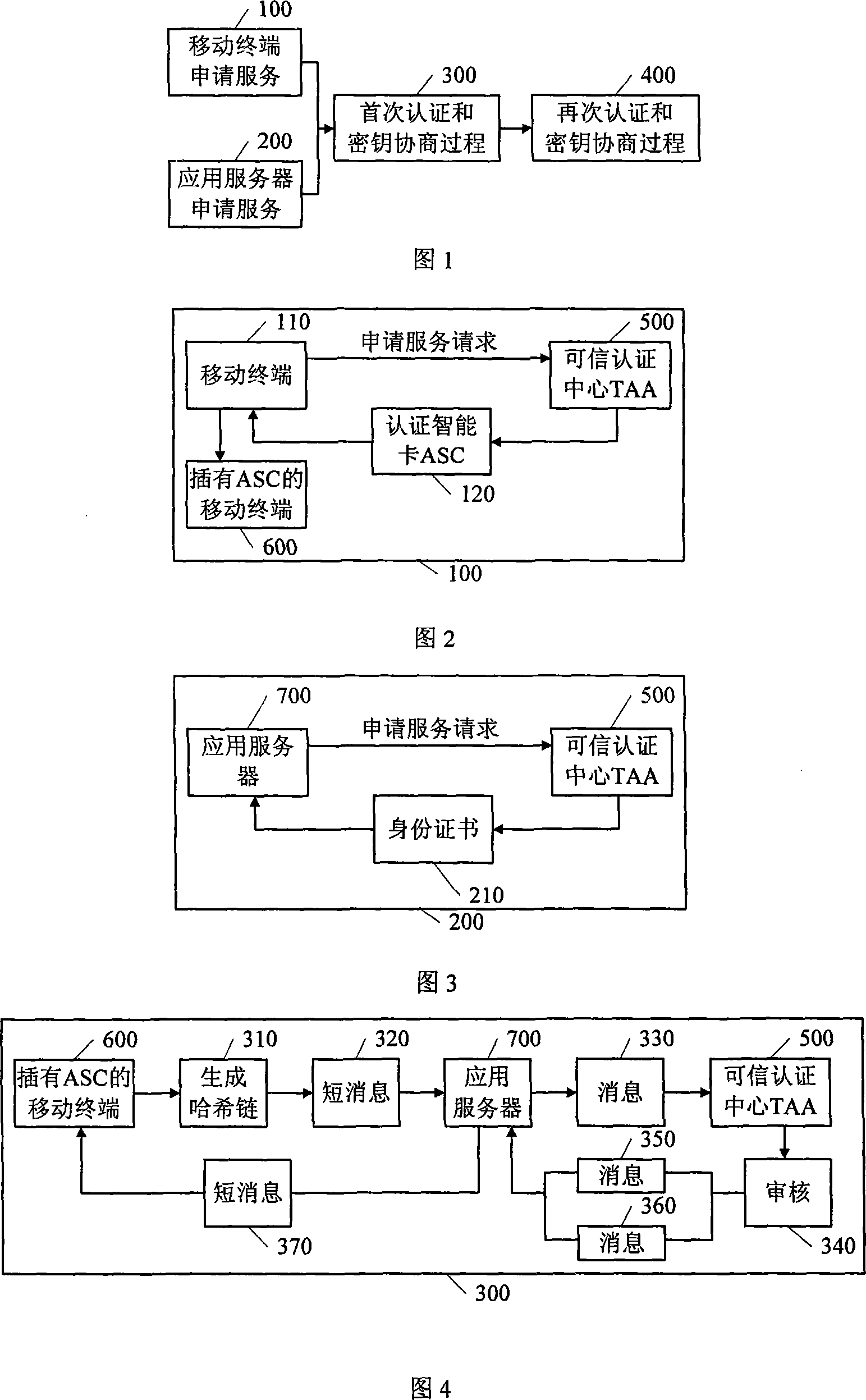
[0026] What Fig. 1 represented is the overall flow chart of the present invention. Firstly, the mobile terminal and the application server respectively submit service application requests 100 and 200 , then perform the first authentication and key agreement process 300 , and then perform the re-authentication and key agreement process 400 .
[0027] Figure 2 shows the process of the mobile terminal applying for services from the TAA before the authentication and key agreement process officially starts. The mobile terminal 110 submits a service application request to the TAA 500 through the network or in written form. The application service request at least includes: mobile phone number, name of the owner of the mobile terminal, ID number and mailing address.
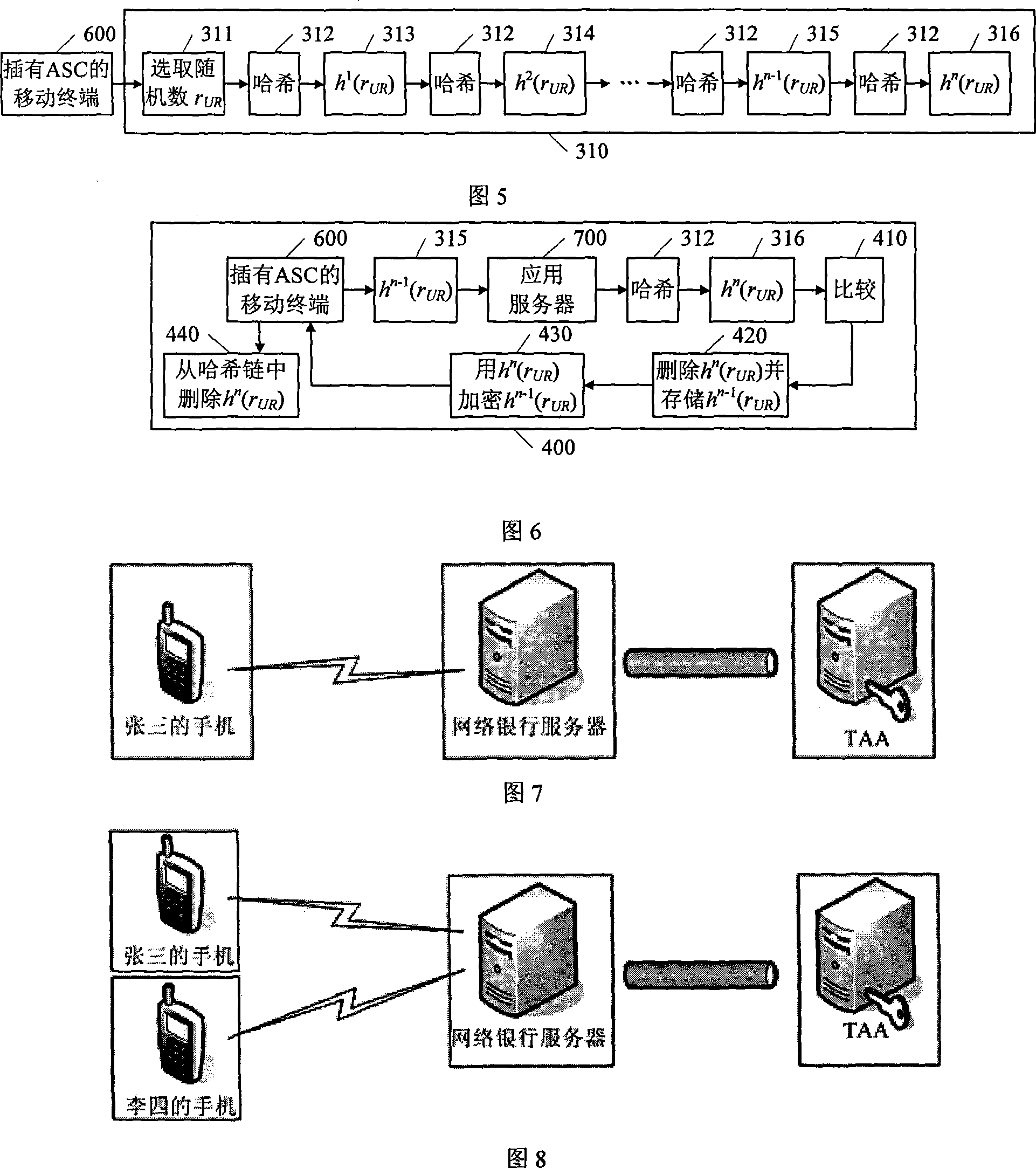
[0028] The TAA500 produces an authentication smart card (ASC, Authentication Smart Card) 120 that can represent the identity of the mobile terminal, and issues it to the mobile terminal. The mobile terminal 110 insert...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com