Method and device for sending and verifying cross-chain communication data
A technology of communication data and transmission method, applied in the field of cross-chain communication data transmission and verification, to achieve the effect of improving security and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
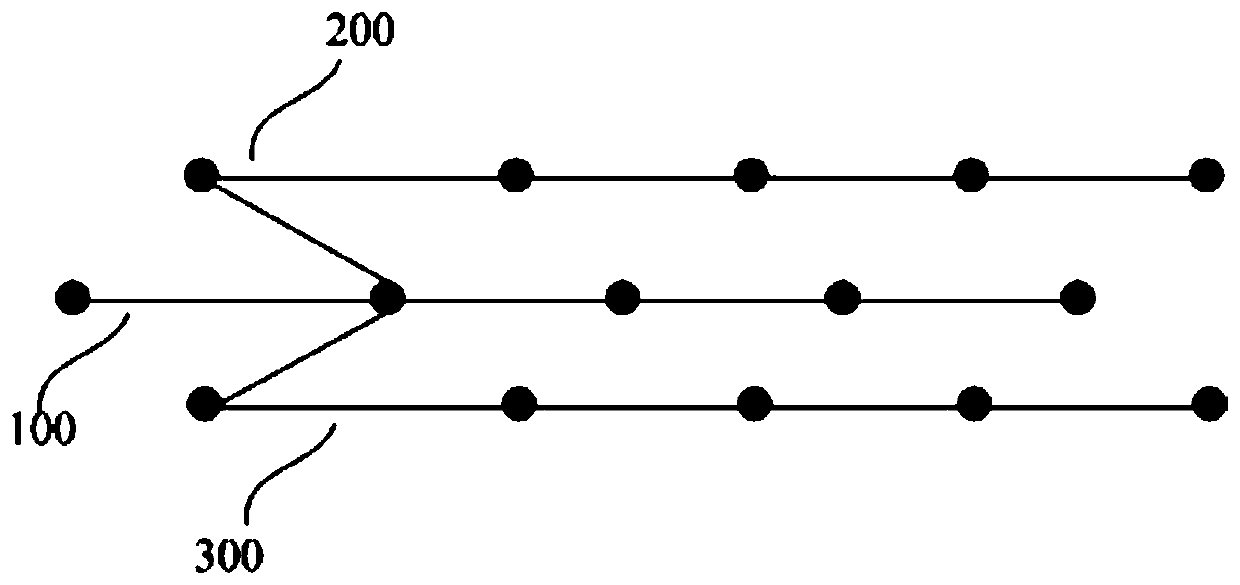
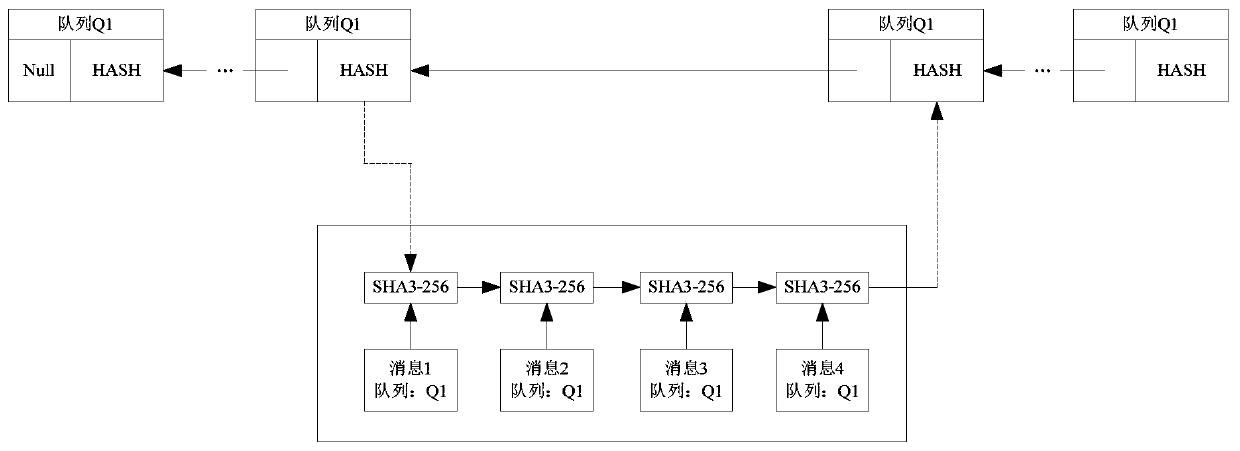
[0058] Such as figure 2 Shown is a schematic diagram of the verification of cross-chain transactions from the side chain to the main chain in the embodiment of this paper. In this figure, multiple nodes (user terminals) in the side chain are described to conduct transactions to the main chain (transaction data such as transaction requests) , these cross-chain transaction data form communication data, wherein the communication data includes multiple cross-chain transaction data, and the multiple cross-chain transaction data is used as a sequence (multiple cross-chain transaction data are stored in one cross-chain transaction block ), the hash value of the hash chain node corresponding to this sequence can also include the block header information of the block formed by the side chain for these transaction data, and the process of verifying the communication data at the relay node of the main chain.
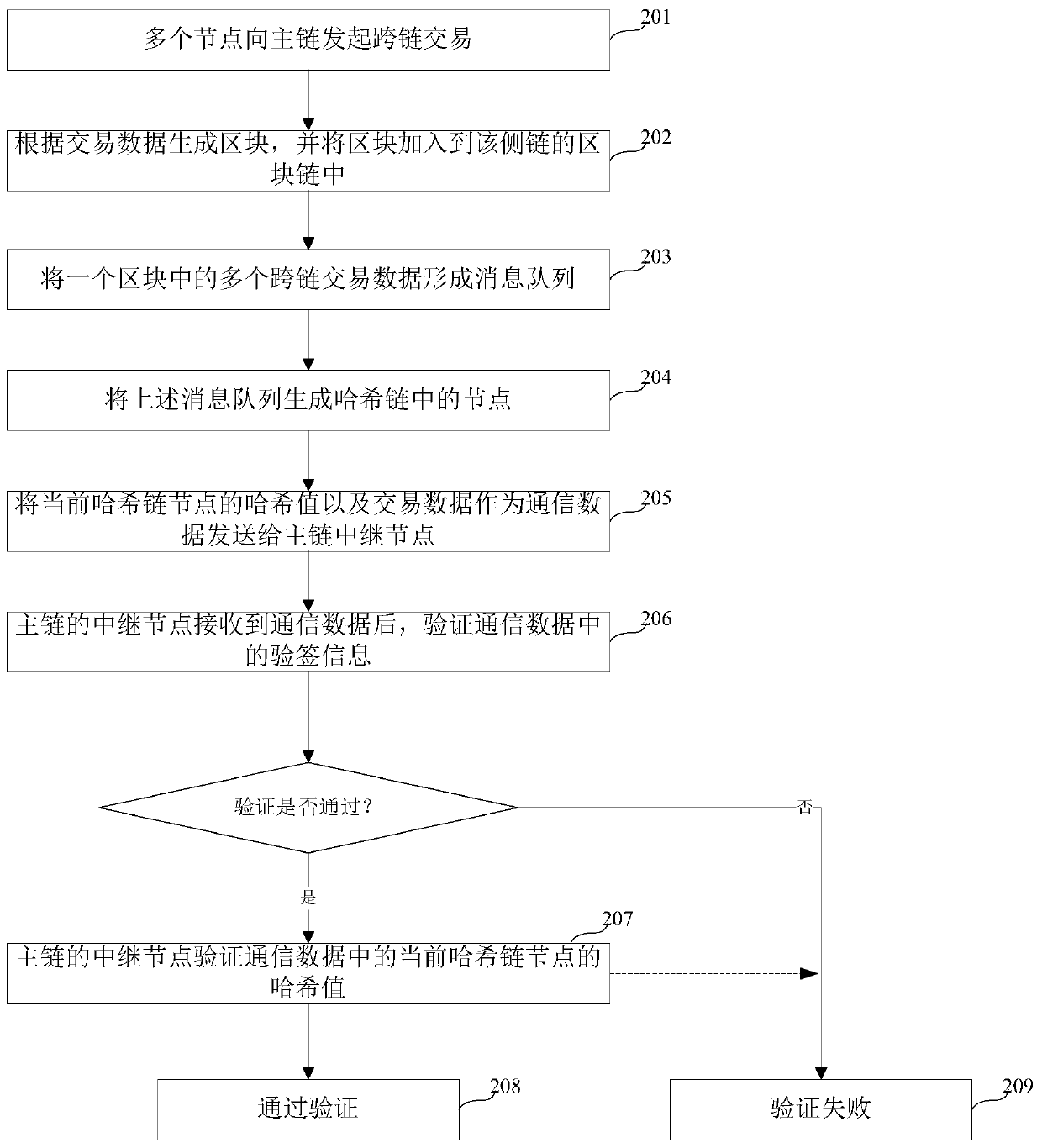
[0059] Step 201, multiple nodes initiate cross-chain transactions to the main...
no. 2 example
[0118] As another example of this paper, such as Figure 6 Shown is the verification flowchart of one side chain sending cross-chain transaction data to the other side chain in the embodiment of this article. In this example, the verification process of the first side chain sending cross-chain transaction data to the second side chain through the main chain is described ,details as follows:
[0119] Step 601, multiple nodes in the first side chain initiate cross-chain transactions to the main chain.
[0120] In this step, multiple nodes in the first side chain need to conduct cross-chain transactions to the second side chain, such as querying or storing data, but since the first side chain and the second side chain belong to two side chains, in this article In the technical solution, the two side chains cannot communicate directly, and need to be forwarded through the main chain. Therefore, in this embodiment, multiple nodes (computers, mobile phones, screen board computers o...
no. 3 example
[0140] In this example, refer to the attached Figure 8 The communication data structure, that is, in the block with a height of H+2, there are also information about the voting and signature of multiple decision-maker nodes in the side chain for the block with a height of H+1, and the main chain relay node or other Functional nodes (or side chain nodes that receive cross-chain transaction data) can follow the attached Figure 9 The flow chart of the method for verifying communication data shown in the verification process:
[0141] Step 901, after the main chain relay node receives the above-mentioned cross-chain communication data, the main chain relay node calculates the hash value of the block header according to the block header information whose block height is H+1.
[0142] In this step, the main chain relay node calculates the block header of the block with a height of H+1 through the block header information in the communication data (such as the hash value of the pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com