Universal authentication method for terminal equipment without identity in Internet-of-things
A terminal device, general authentication technology, applied in the field of information security, can solve the problems of privacy information leakage, low computational cost of symmetric encryption algorithm, protocol attack, etc., to achieve the effect of protecting identity information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings.
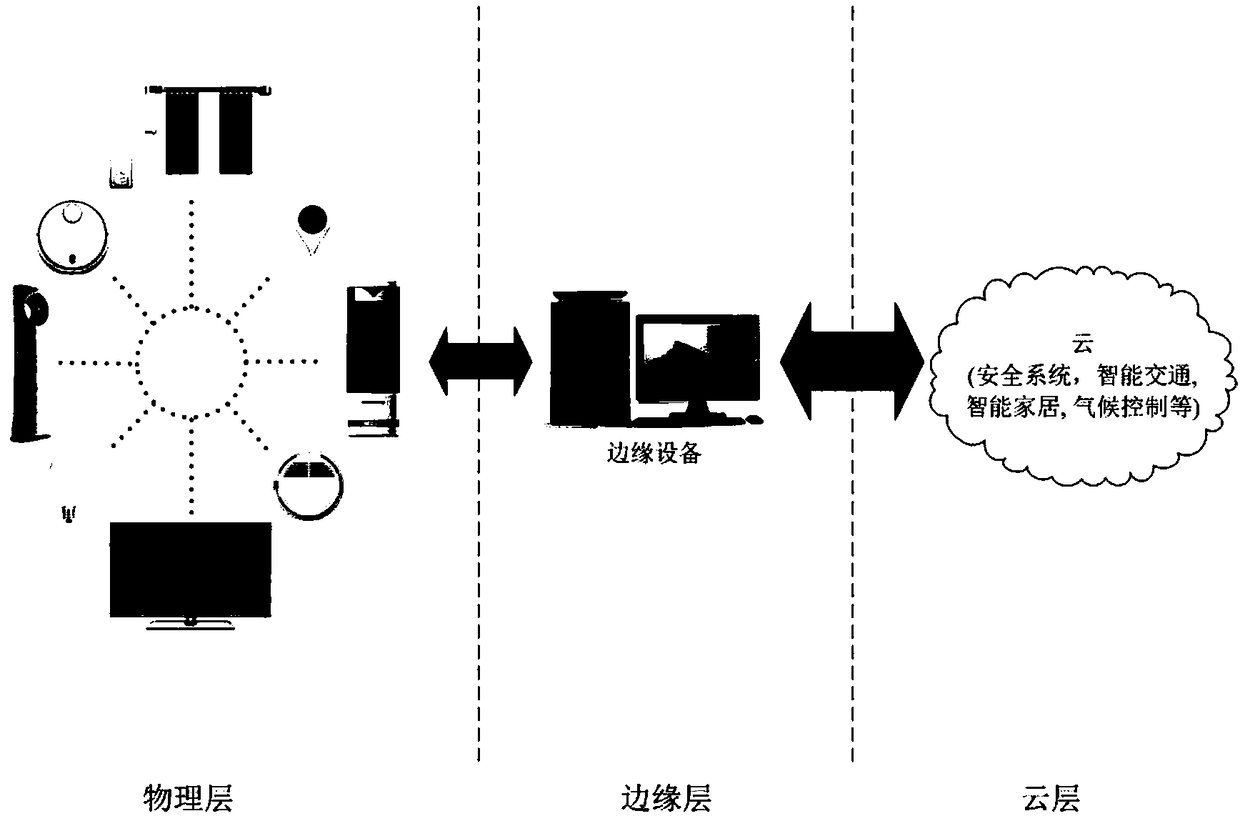
[0035] figure 1 It is a three-layer structural diagram of the Internet of Things in the present invention. Such as figure 1 As shown, the Internet of Things includes a three-layer structure, namely the physical layer, the edge layer and the cloud layer.
[0036] The first layer is the physical layer (Things Layer), used to collect data and control the physical world. Taking the smart home system as an example, assuming it is a physical layer, there are some terminal devices, such as heat detectors, cameras and smoke detectors, which have the ability to perceive the physical world and send key control commands. Most end devices in the physical layer are resource constrained, having as little as 64 bytes of memory and 2048 bytes of storage. Therefore, many conventional security mechanisms using asymmetric encryption algorithms are not suitable because they require hi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com