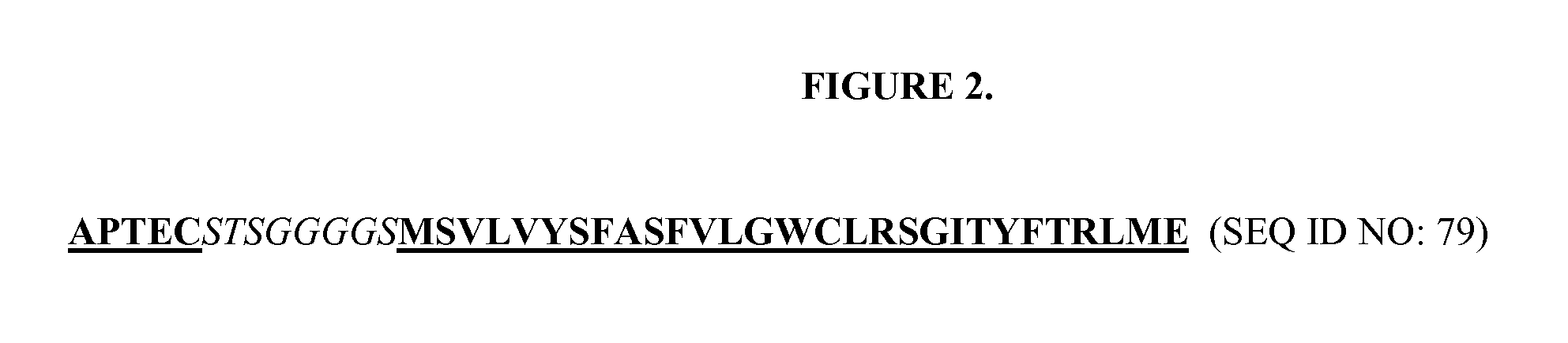Patents
Literature
312results about How to "Improve identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
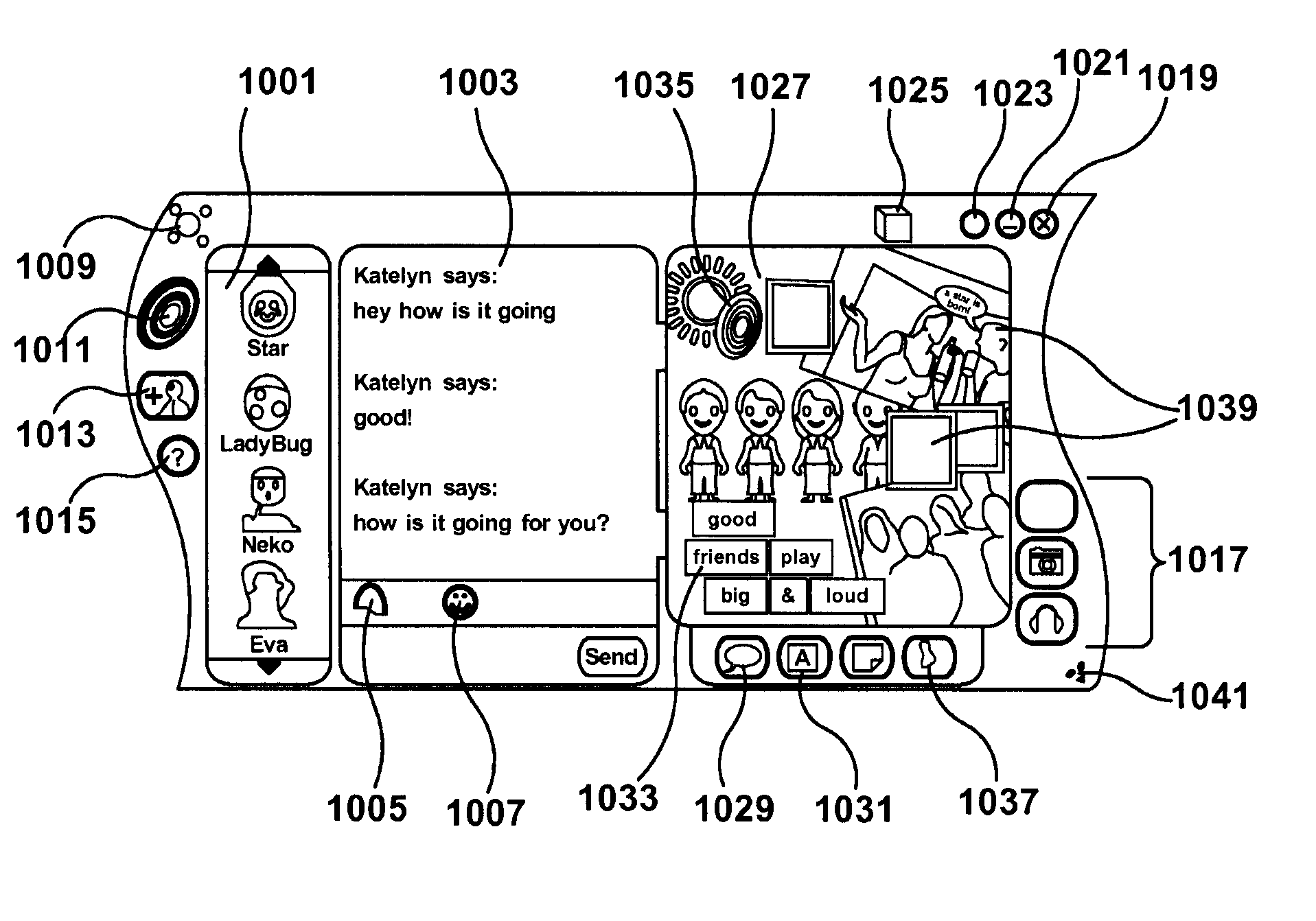
System and method for shared integrated online social interaction
InactiveUS7234117B2Enhanced interactionImprove identityOffice automationAnimationModularityNetwork communication
Owner:MICROSOFT TECH LICENSING LLC
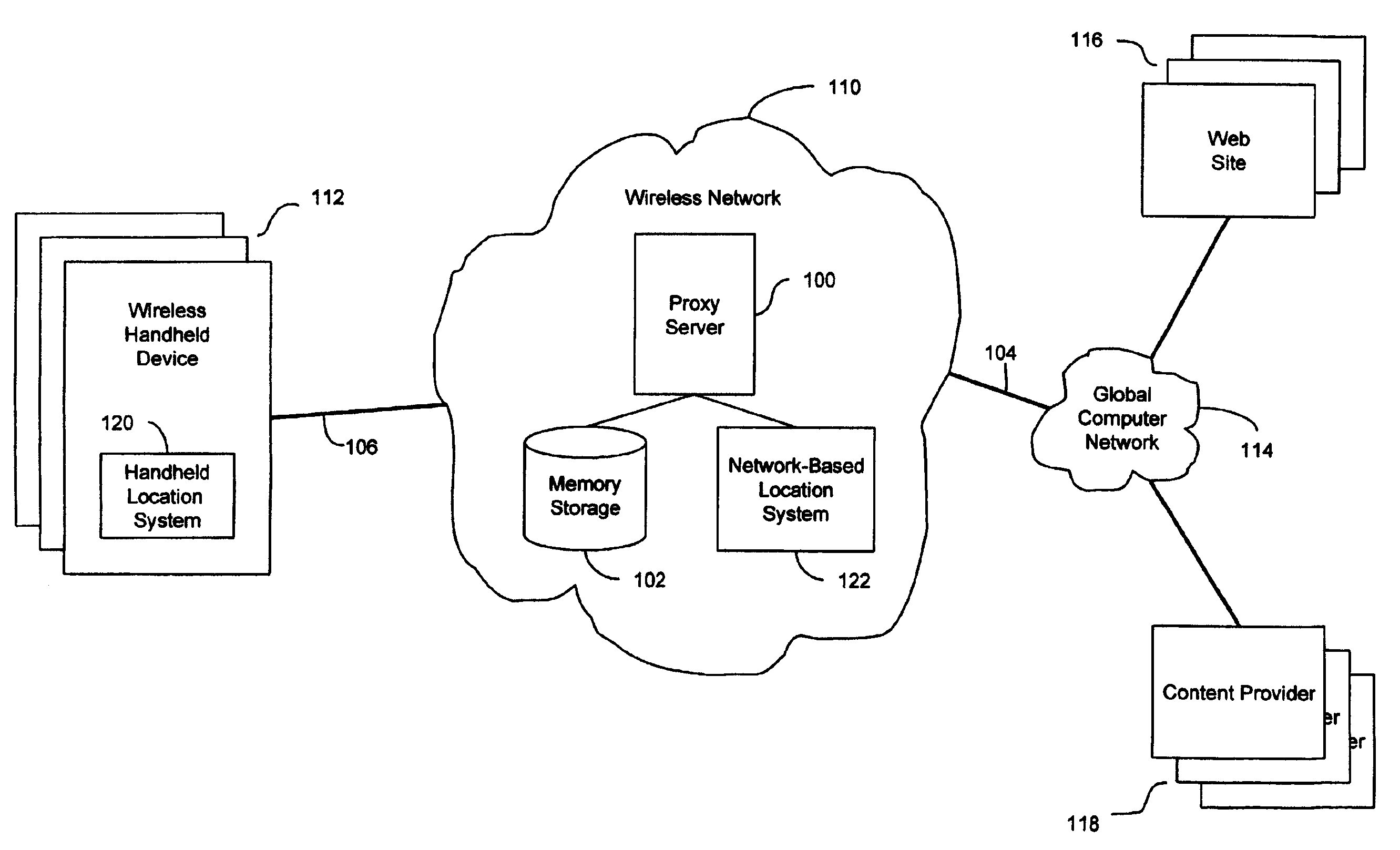
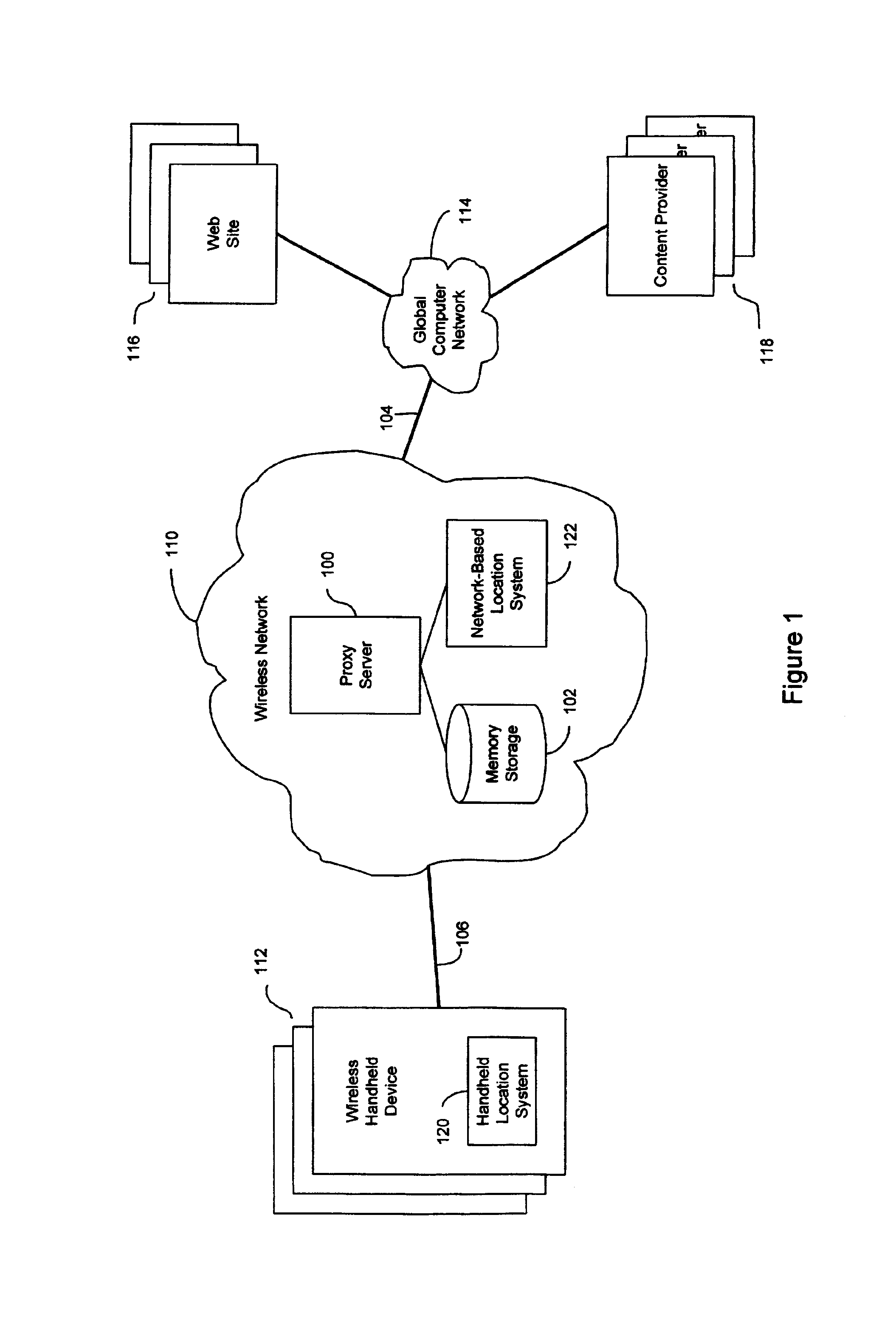
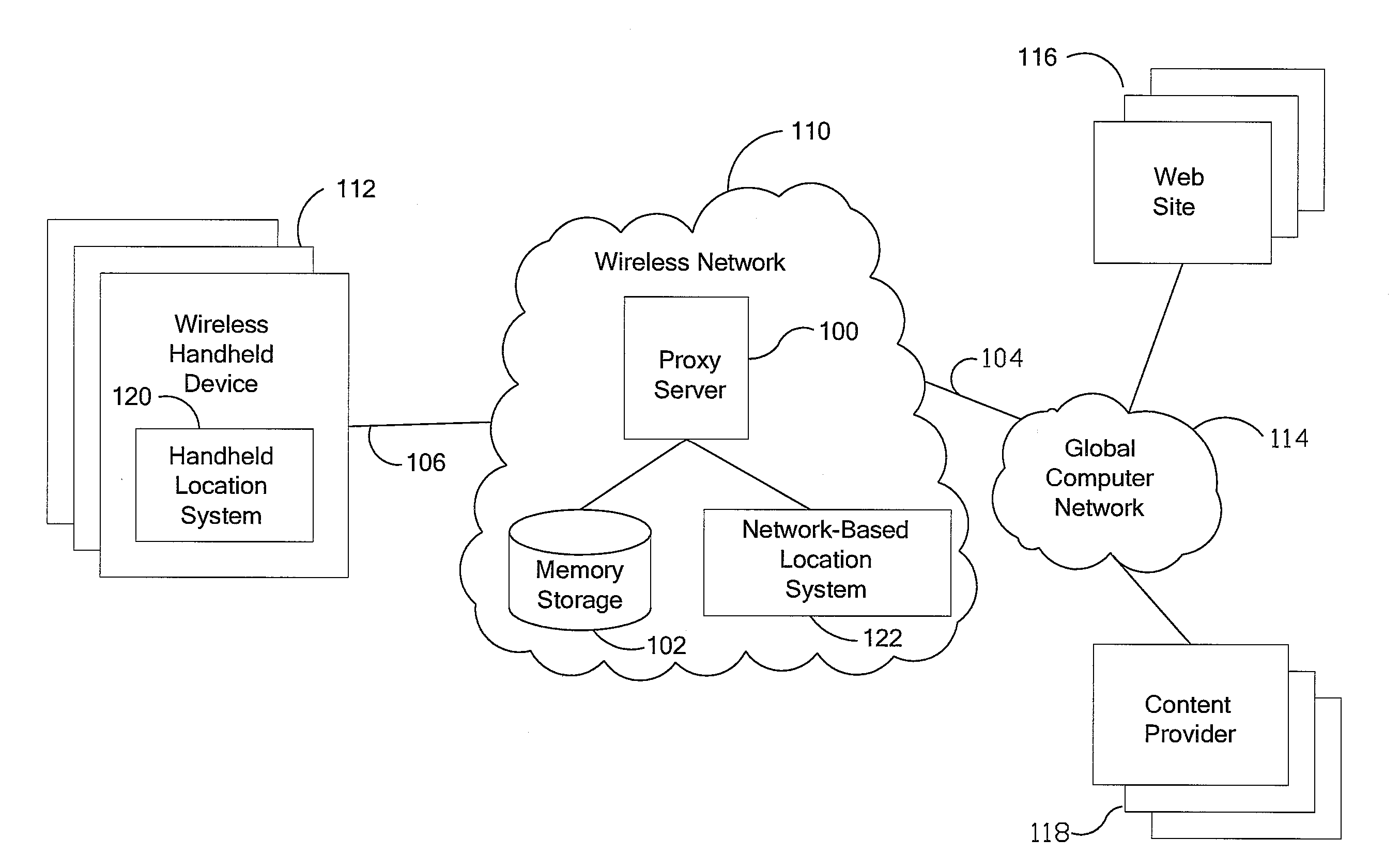
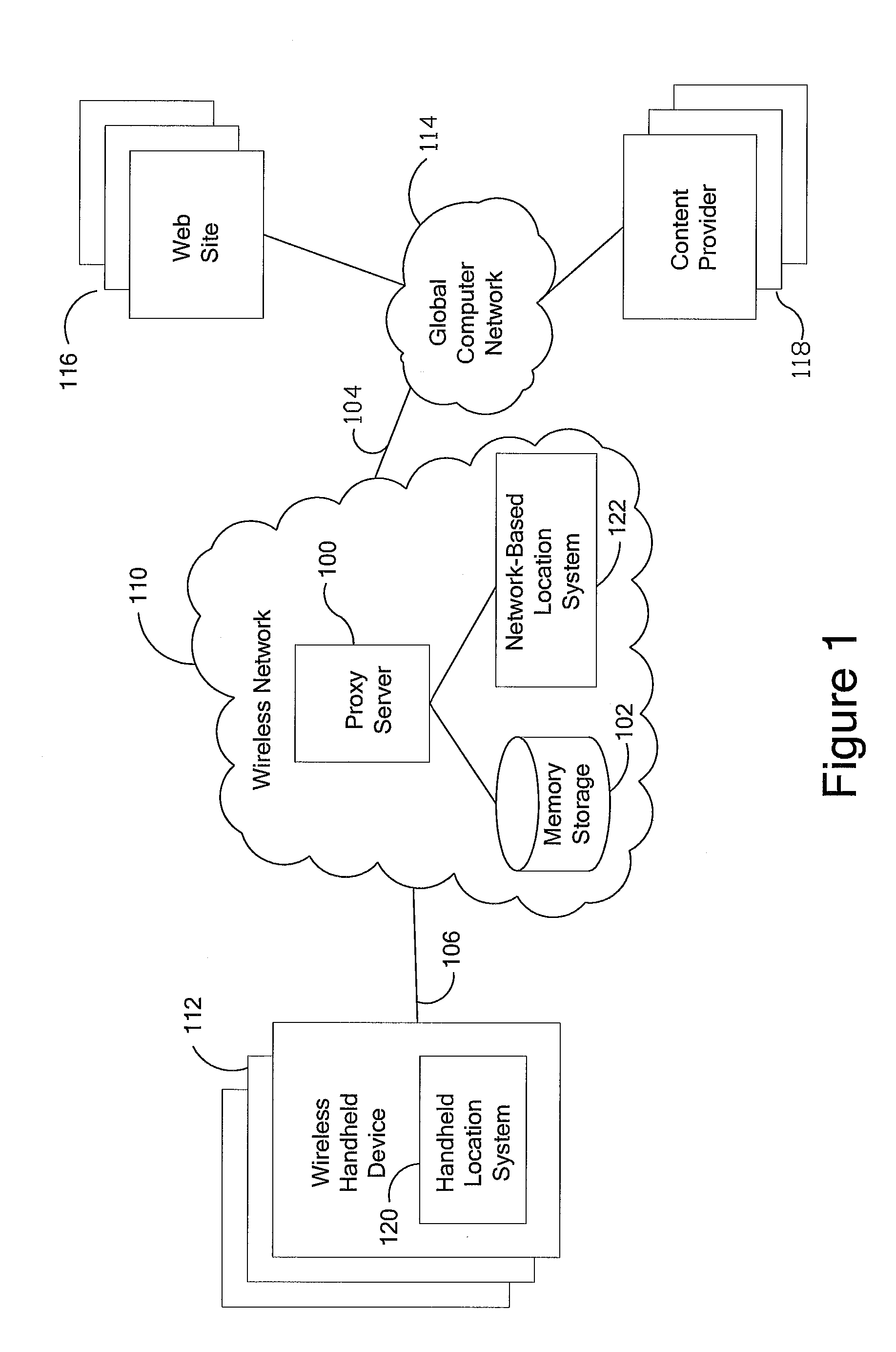
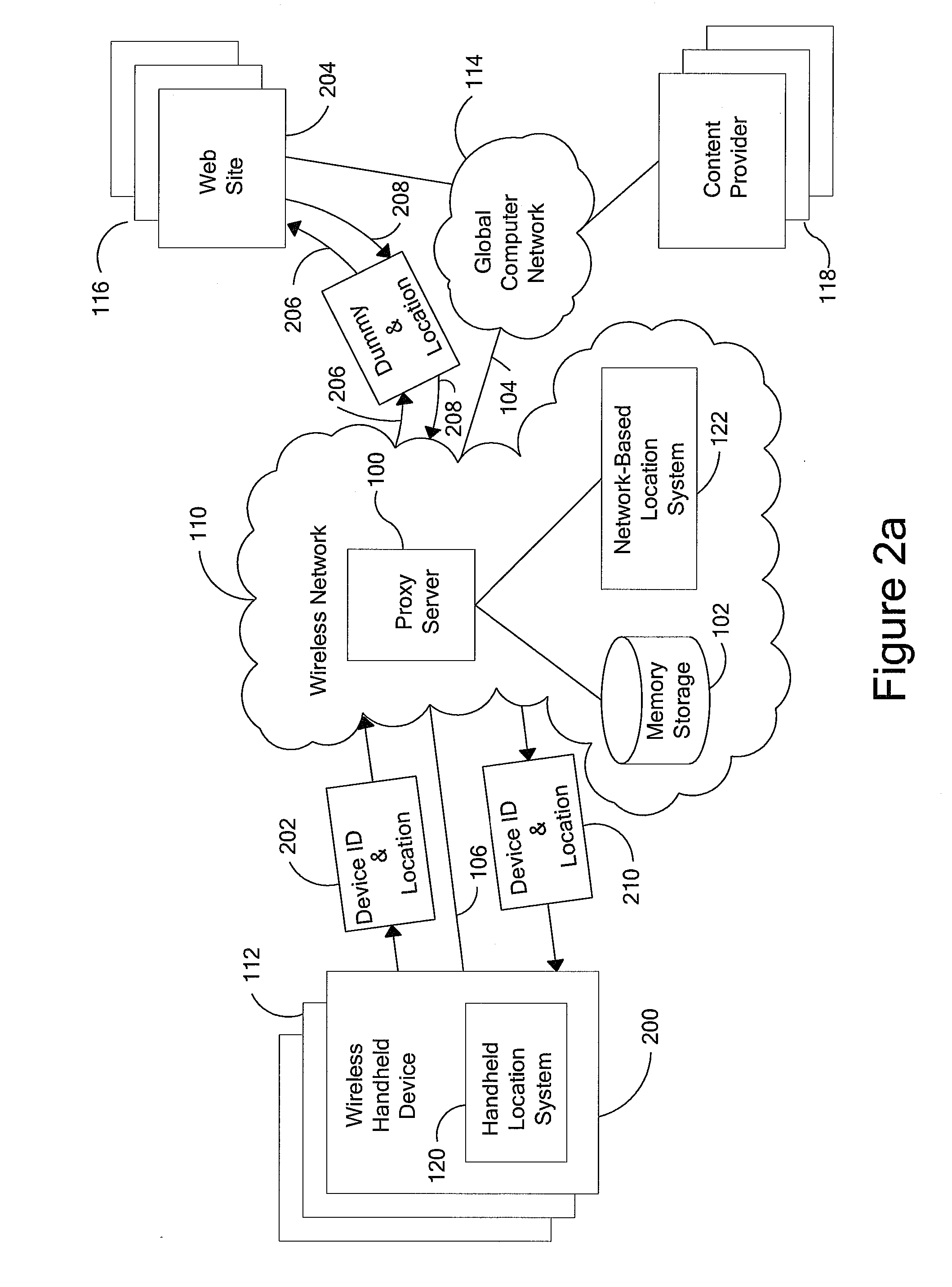
Anonymous location service for wireless networks
InactiveUS7069319B2Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
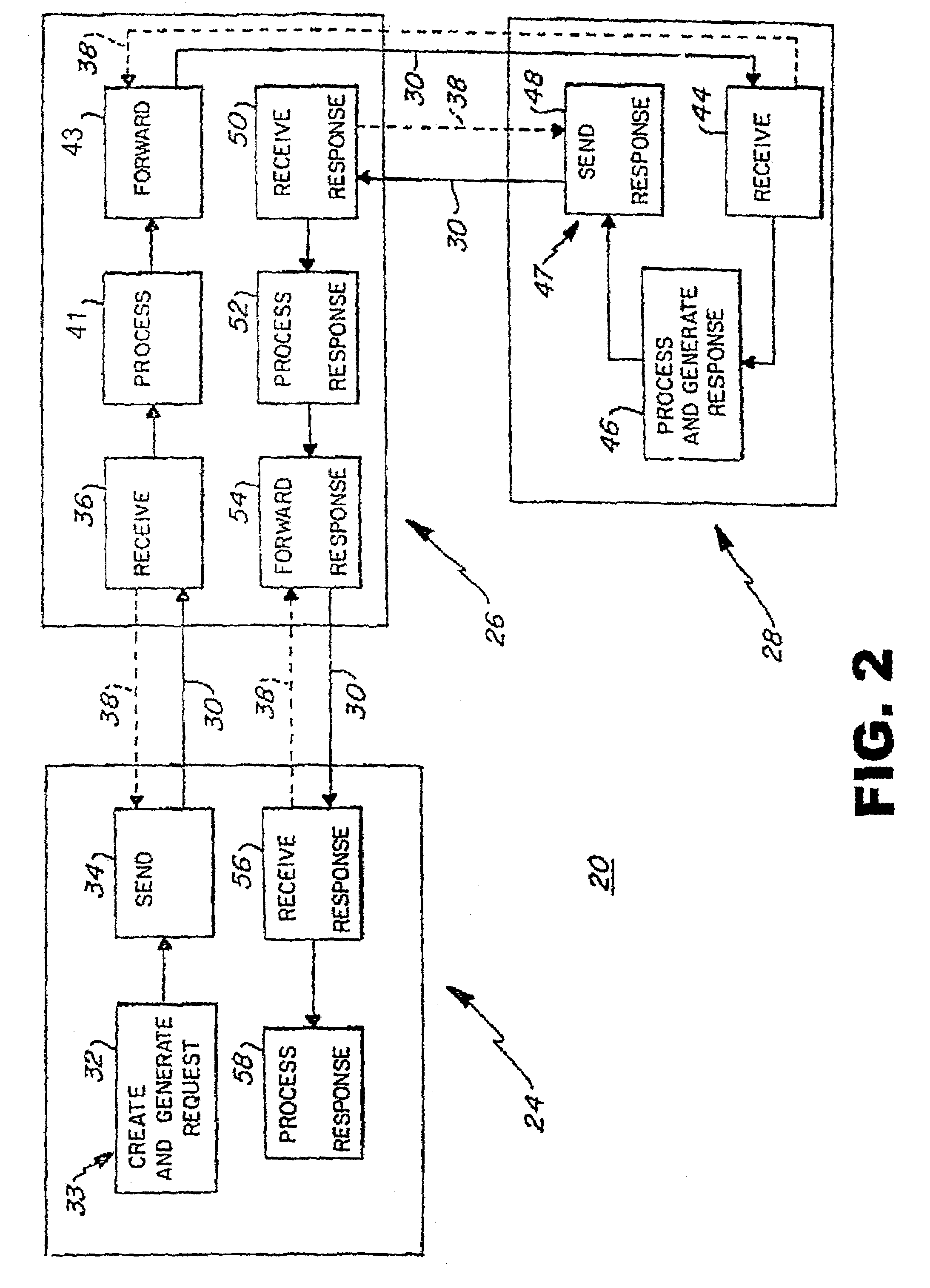
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
Smart Parking Meter
InactiveUS20060152349A1Improve complianceIncrease incomeTicket-issuing apparatusAnti-theft devicesPaymentMultiple forms
The present invention relates to a ‘smart parking system’ comprising of 1) ‘smart parking meter’ containing a radiofrequency reader (RF reader); 2) radiofrequency tag (RF tag) containing vehicle identification information, that is mounted on vehicles; 3) a central control station communicating with a multitude of ‘smart parking meters’ to form a network; 4) the said central control station having a central computer system programmed with parking enforcement instructions. RF reader is provided with means to interrogate the RF tag of a vehicle parked in the corresponding parking stall; and transmit information obtained thereby to a central control station. The central control station has means to identify the said vehicle and determine whether or not the said vehicle is legally parked. If a parking violation is detected, the central computer system remotely instructs the corresponding ‘smart parking meter’ to issue a parking ticket. Means are also provided in the ‘smart parking system’ to determine if a vehicle parked in a parking stall has previous unpaid parking tickets. The ‘smart parking system’ also has means to determine if a vehicle wanted by law enforcement personnel is present in a parking stall within its network. According to yet another aspect, the ‘smart parking system’ has means to determine if a parking stall in its network is vacant and to reserve the said vacant stall for an authorized driver. Further, means are provided in the ‘smart parking meter’ to accept multiple forms of payment.
Owner:RATNAKAR NITESH
Relationship collaboration system
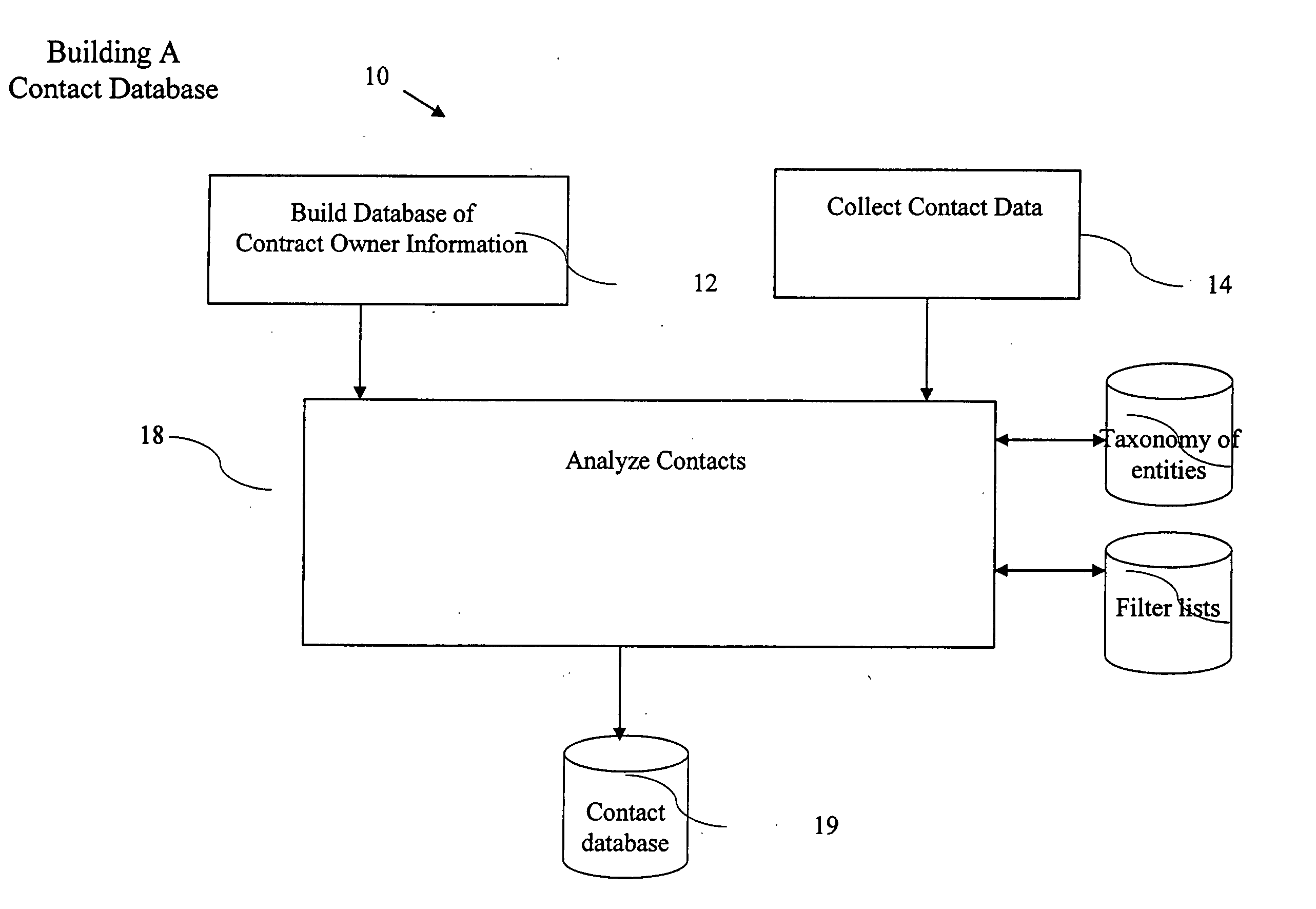
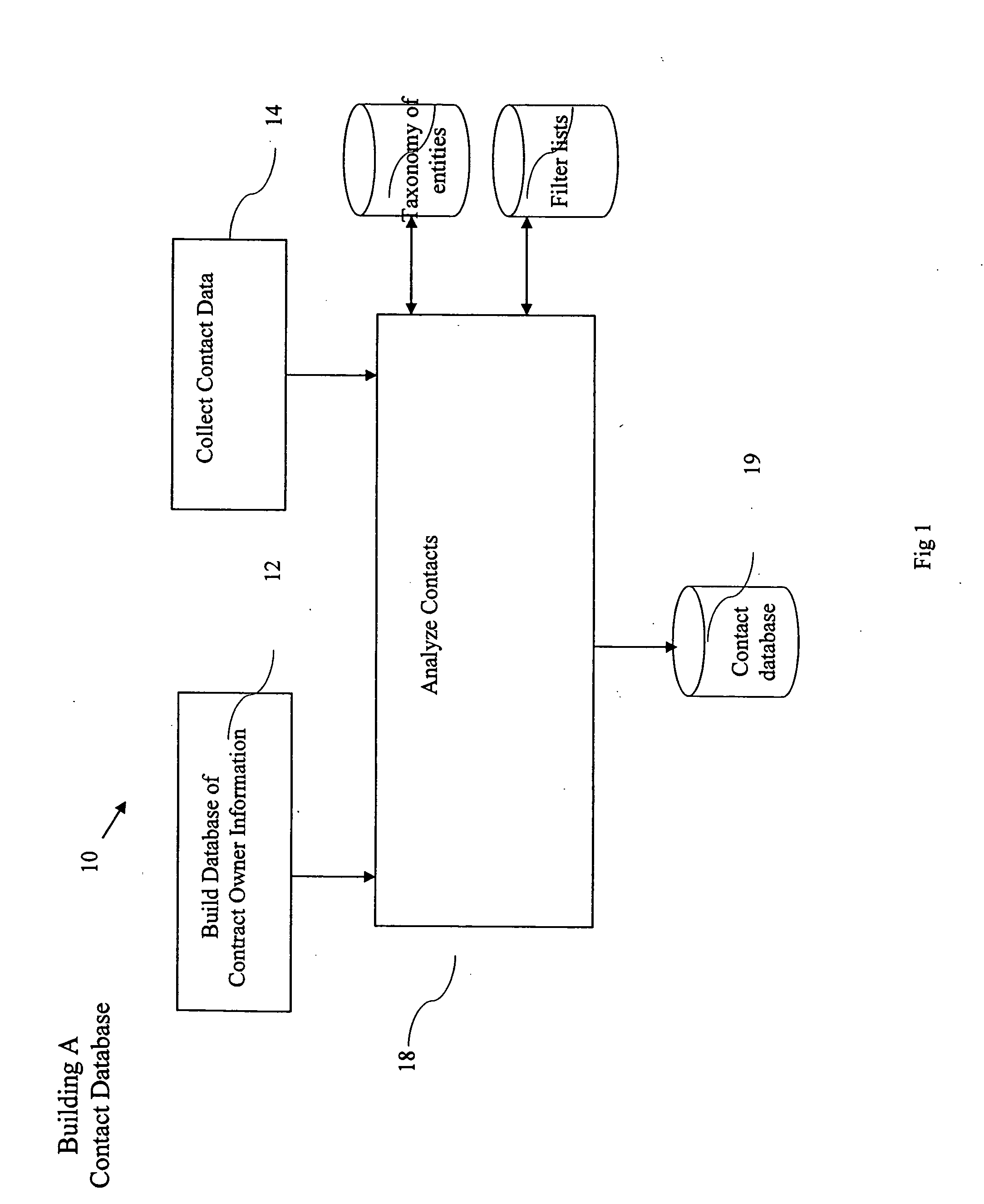
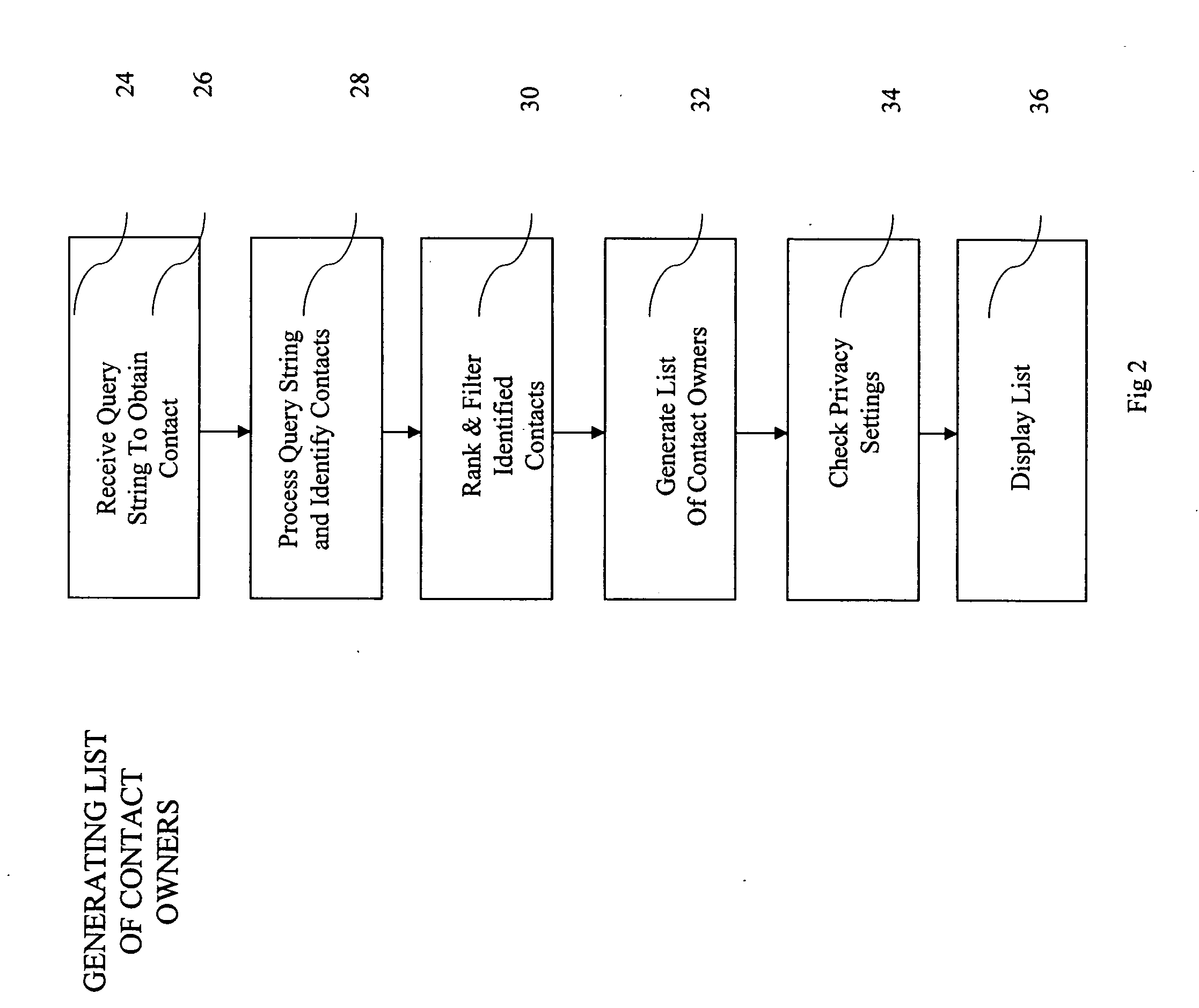
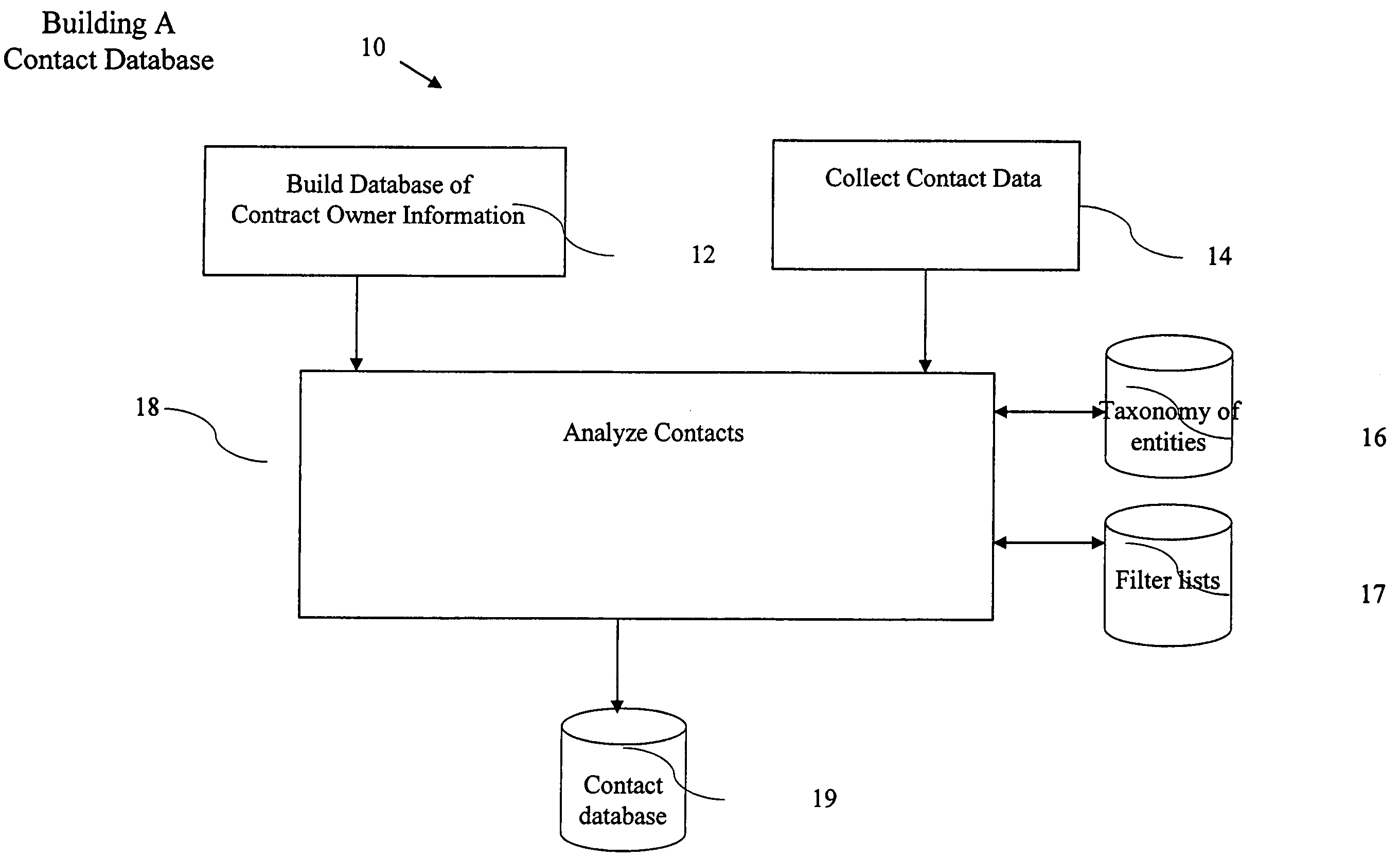
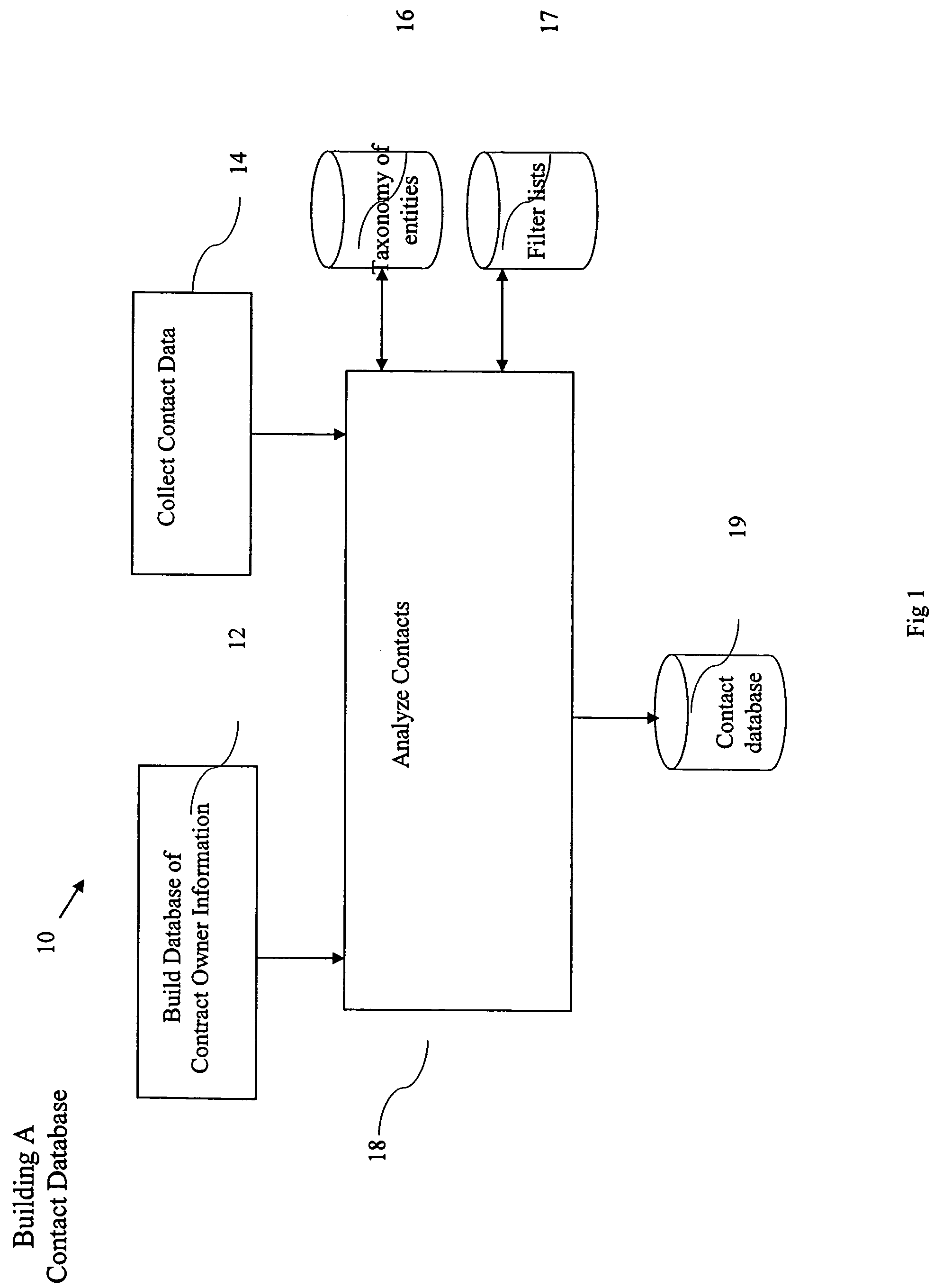
ActiveUS20050065980A1Improve identityData processing applicationsWeb data indexingDomain nameEmail address
A computer implemented method of processing data containing information about relationships between contacts and a community of contact owners, comprises: collecting data including contact information, contact owner information and one or more values related to strength of a relationship between the contact and the contact owner; evaluating the strength of the relationship based on the one or more values; and storing the collected data and evaluated strength in a computer database. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include a domain name field; and setting the domain name field as a key field; whereby a record for an entity is found by reference to a domain name. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include an email address field; and setting the email address field as a key field; whereby a record for an entity is found by reference to an email address. A method of keying a database, comprising: building a database of records, each containing information about an entity, and each of which includes a field holding an identifier uniquely associated with an entity by a convention of computer networking; and setting the field holding the identifier as a key field; whereby a record for an entity is found by reference to an identifier. A method of sharing relationship information, comprising: maintaining a database of relationship information records; selecting contact information according to a selection criterion; and returning selected relationship information also complying with restrictions set in a set of hierarchical privacy policies.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
Face sub-space determination
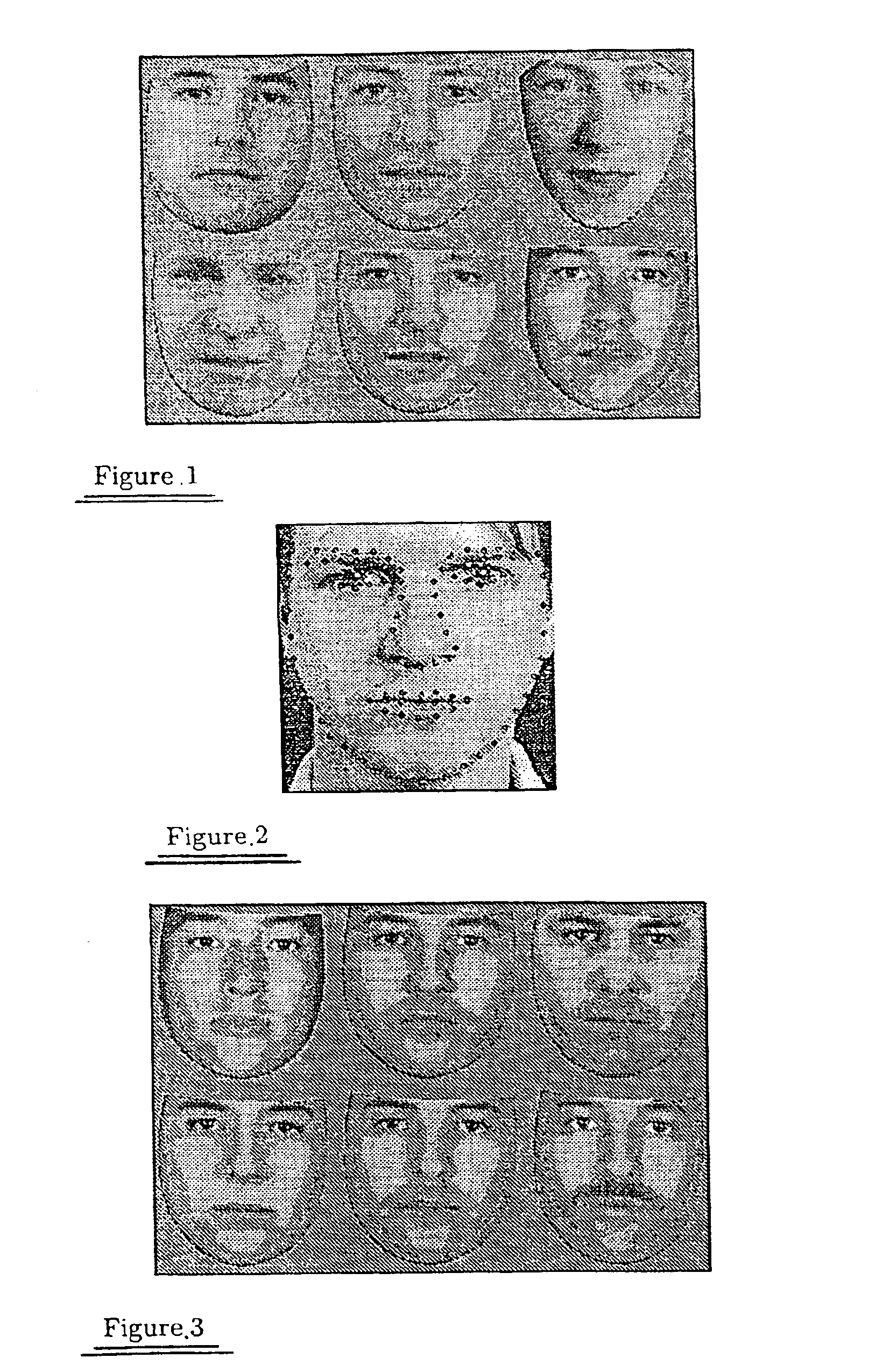
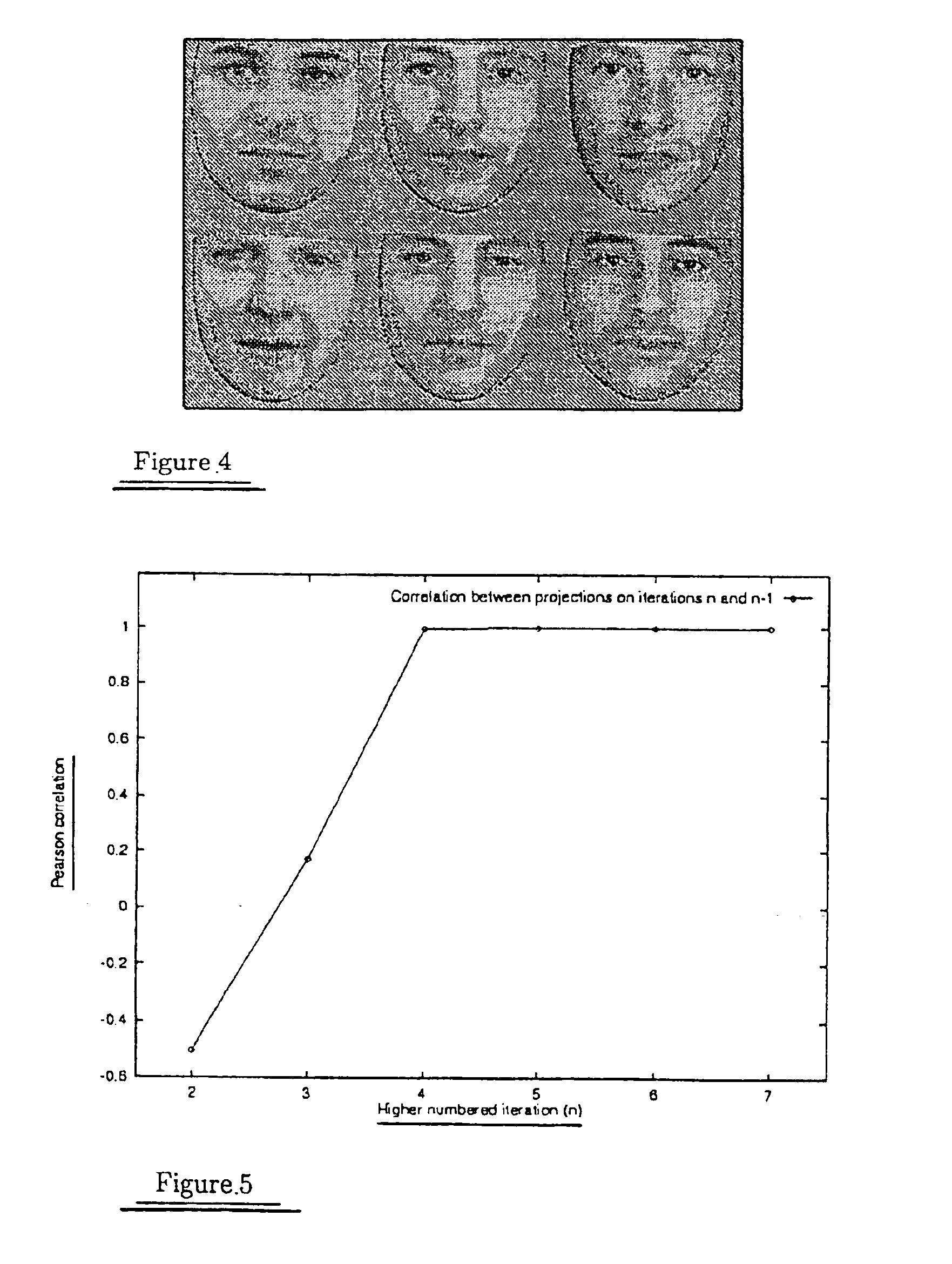
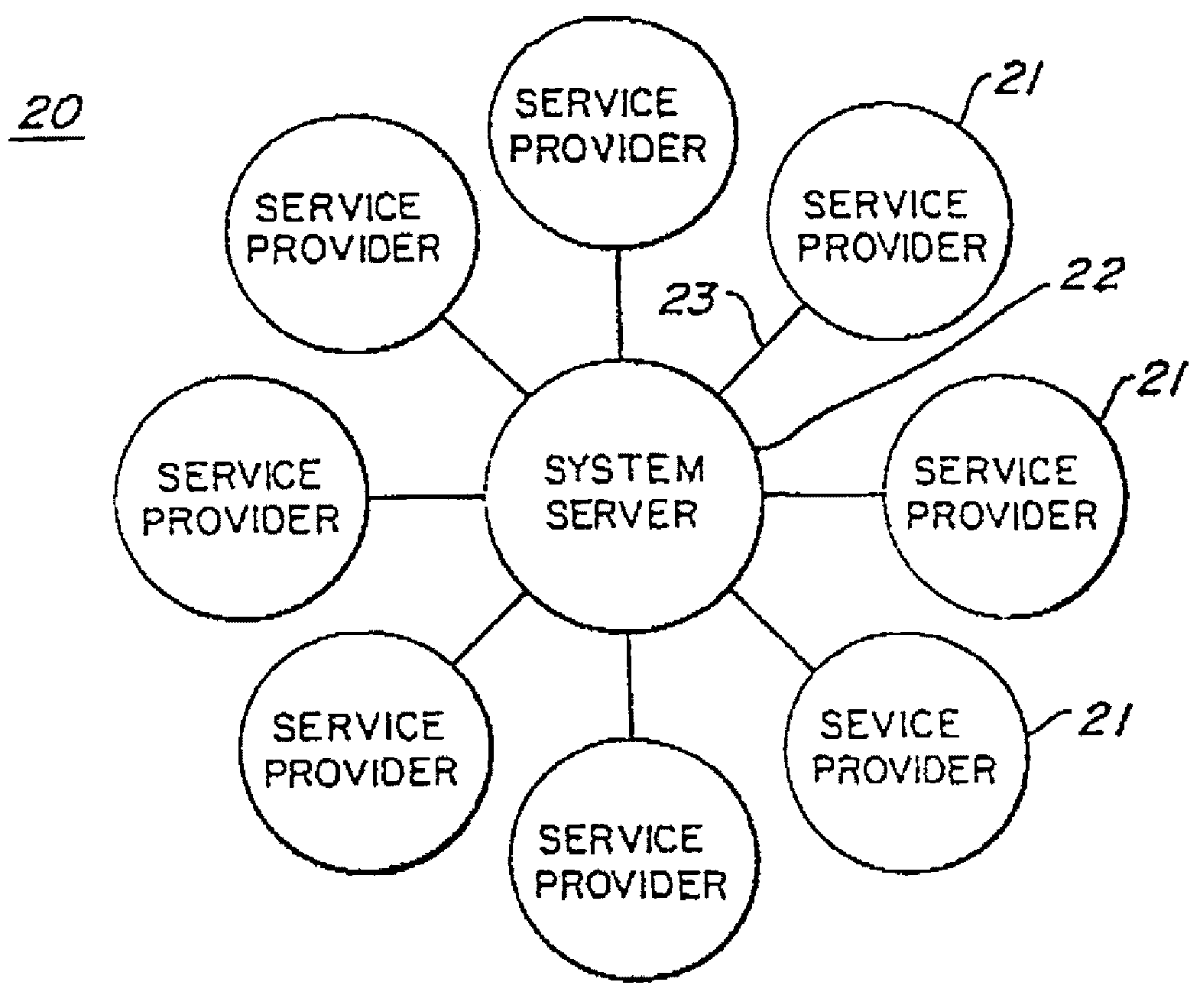
InactiveUS6876755B1Improve identityElectric signal transmission systemsImage analysisPrincipal component analysisComputer vision
A method of determining face sub-spaces includes making initial estimates of the sub-spaces, for example lighting, pose, identity and expression, using Principle Component Analysis on appropriate groups of faces. An iterative algorithm is applied to image codings to maximize the probability of coding across these non-orthogonal sub-spaces, obtaining the projection on each sub-space, and recalculating the spaces.
Owner:UNIV OF MANCHESTER
Anonymous transaction authentication
InactiveUS7264152B2Easy to centralizeMaintaining anonymityNon-ionic surface-active compoundsCredit registering devices actuationCredit cardPersonal details
An automated system for the confirmed efficient authentication of an anonymous subscriber's profile data. The system is comprised of software / hardware interface to facilitate centralized access and exchange to easily and inexpensively allow the confirmed authentication of subscriber profiles of customers wishing to blind their transactions, while maintaining current services. In one aspect the system allows a subscriber to anonymously accomplish credit card transactions without associating any aspect of the transaction with any information associated with the true identity of the subscriber.
Owner:FIRST DATA
Systems and Methods For Anonymity Protection
InactiveUS20110178943A1Improve identityAvoid spendingData processing applicationsComputer security arrangementsThird partyInternet privacy
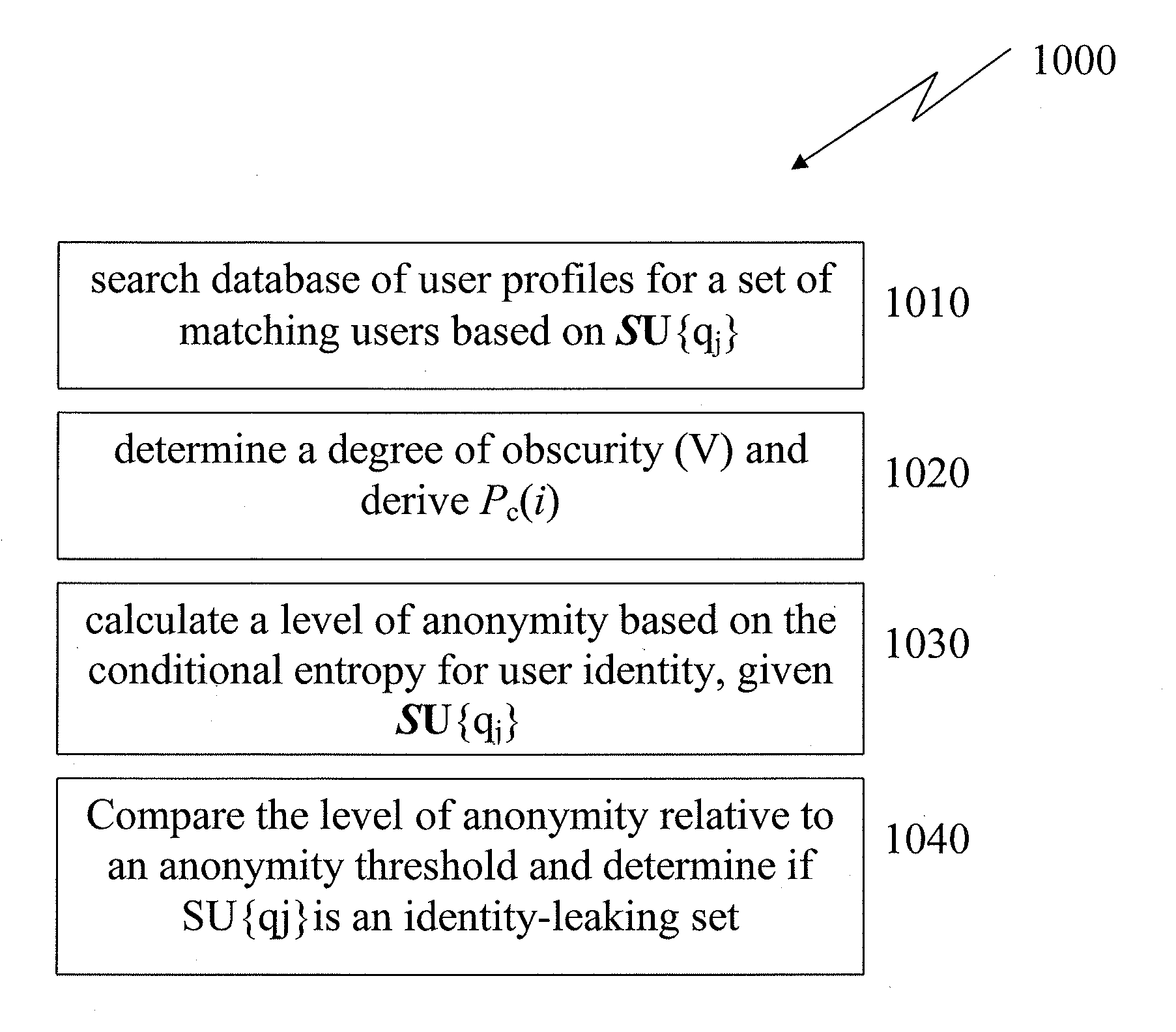
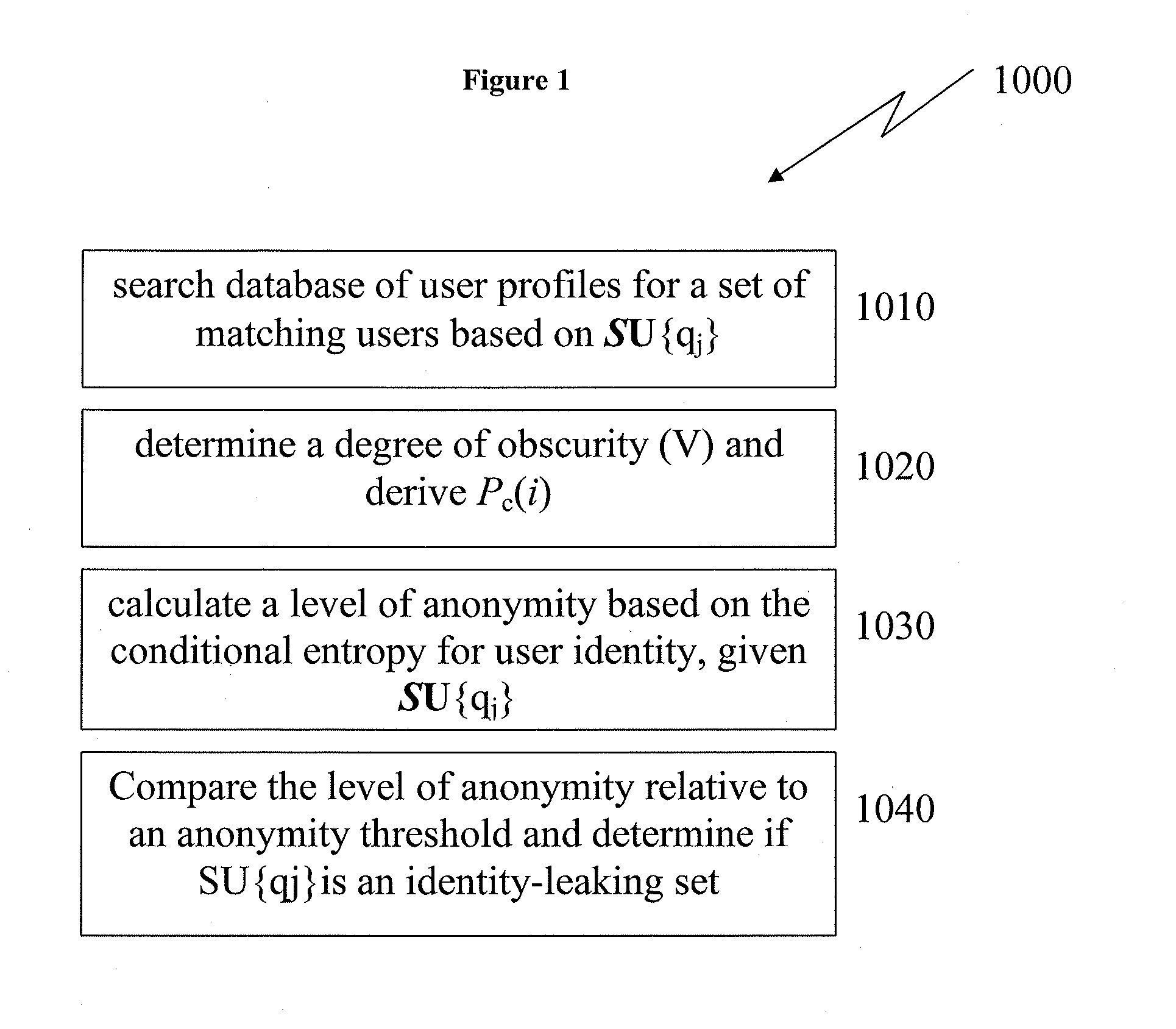
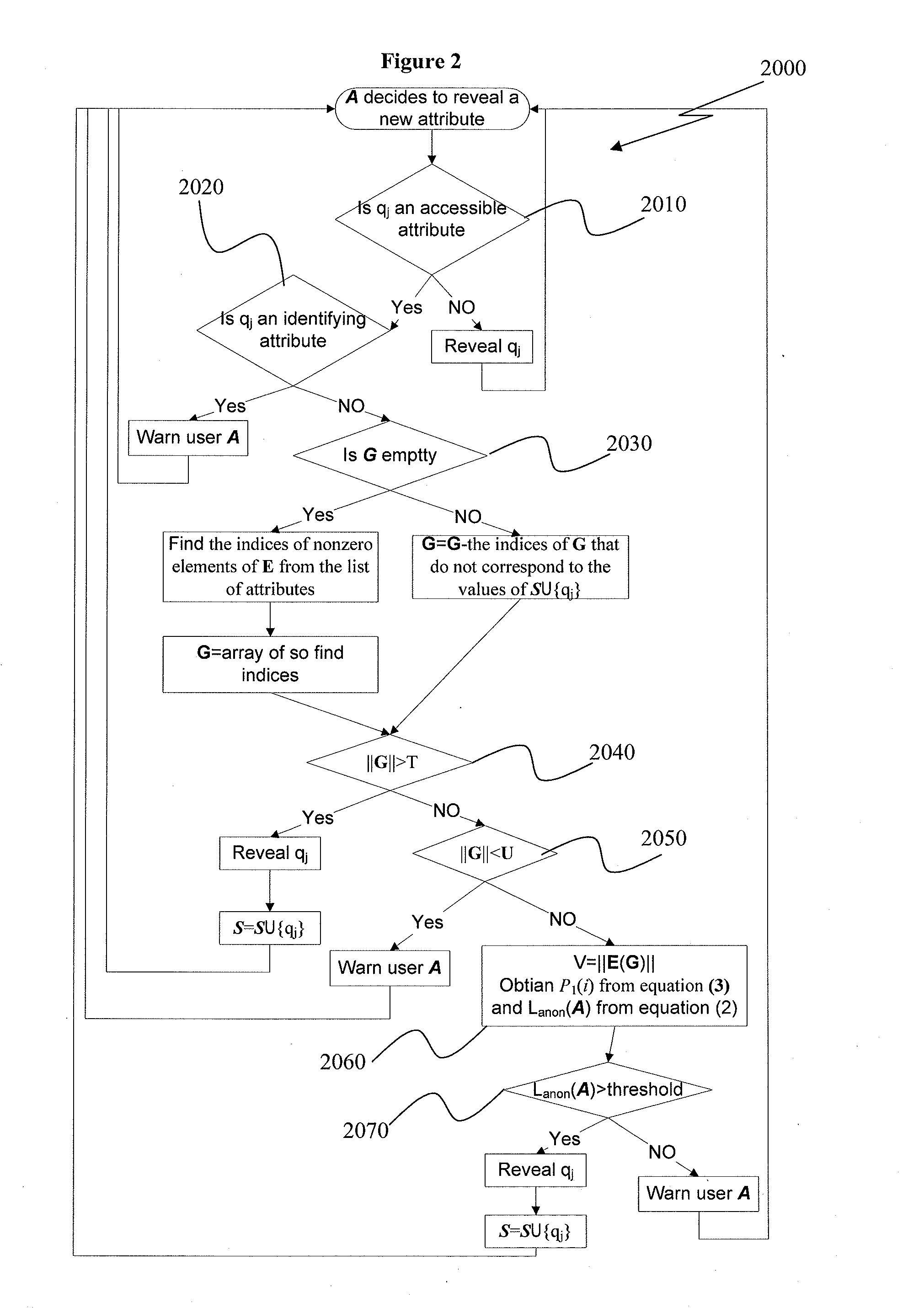
In any situation where an individual's personal attributes are at risk to be revealed or otherwise inferred by a third, there is a chance that such attributes may be linked back to the individual. Examples, of such situations include publishing user profile micro-data or information about social ties, sharing profile information on social networking sites or revealing personal information in computer-mediated communication. Measuring user anonymity is the first step to ensure that a users identity cannot be inferred. The systems and methods of the present disclosure, embrace an information-entropy-based estimation of the user anonymity level which may be used to predict identity inference risk. One important aspect of the present disclosure is complexity reduction with respect to the anonymity calculations.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
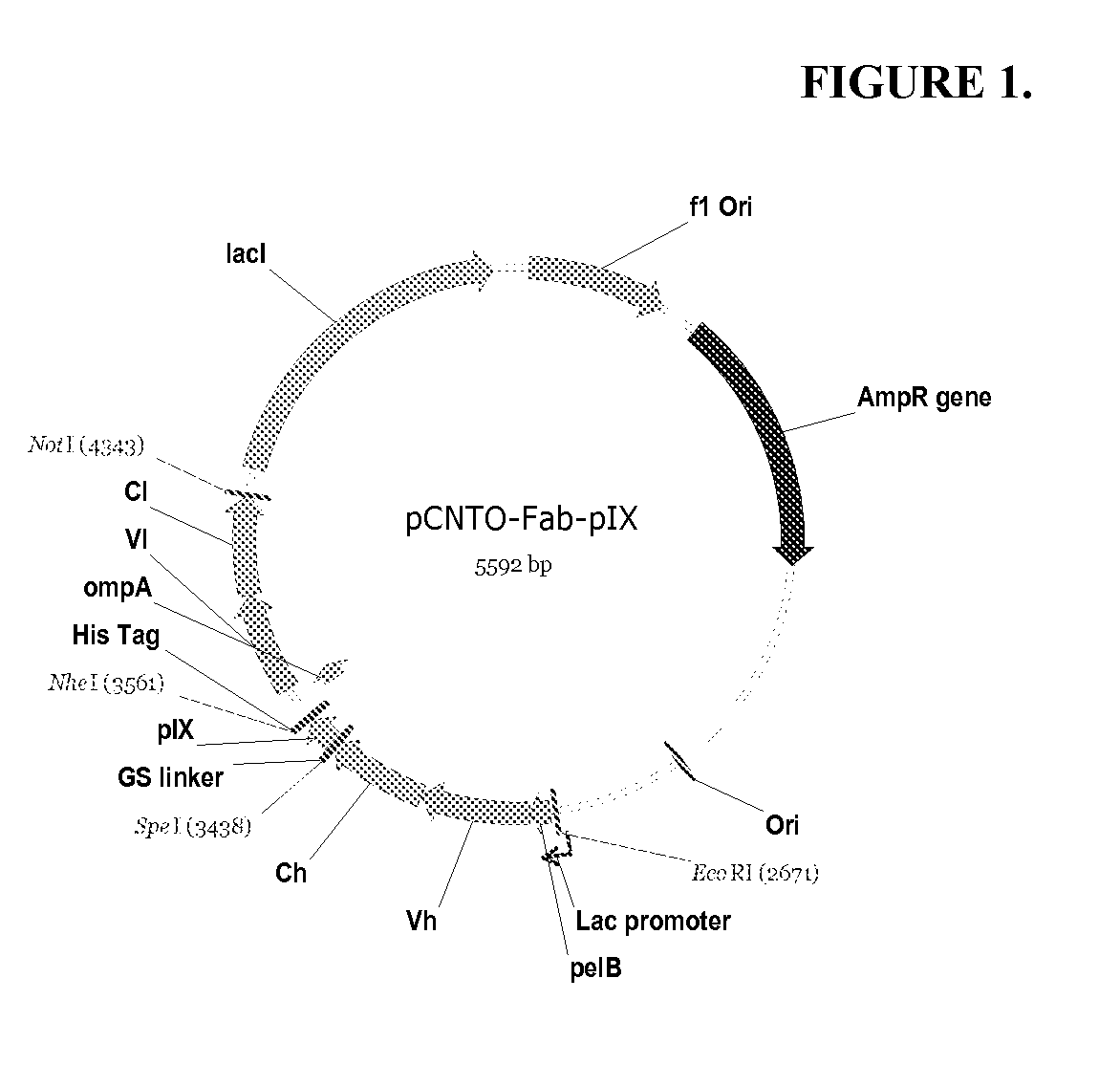
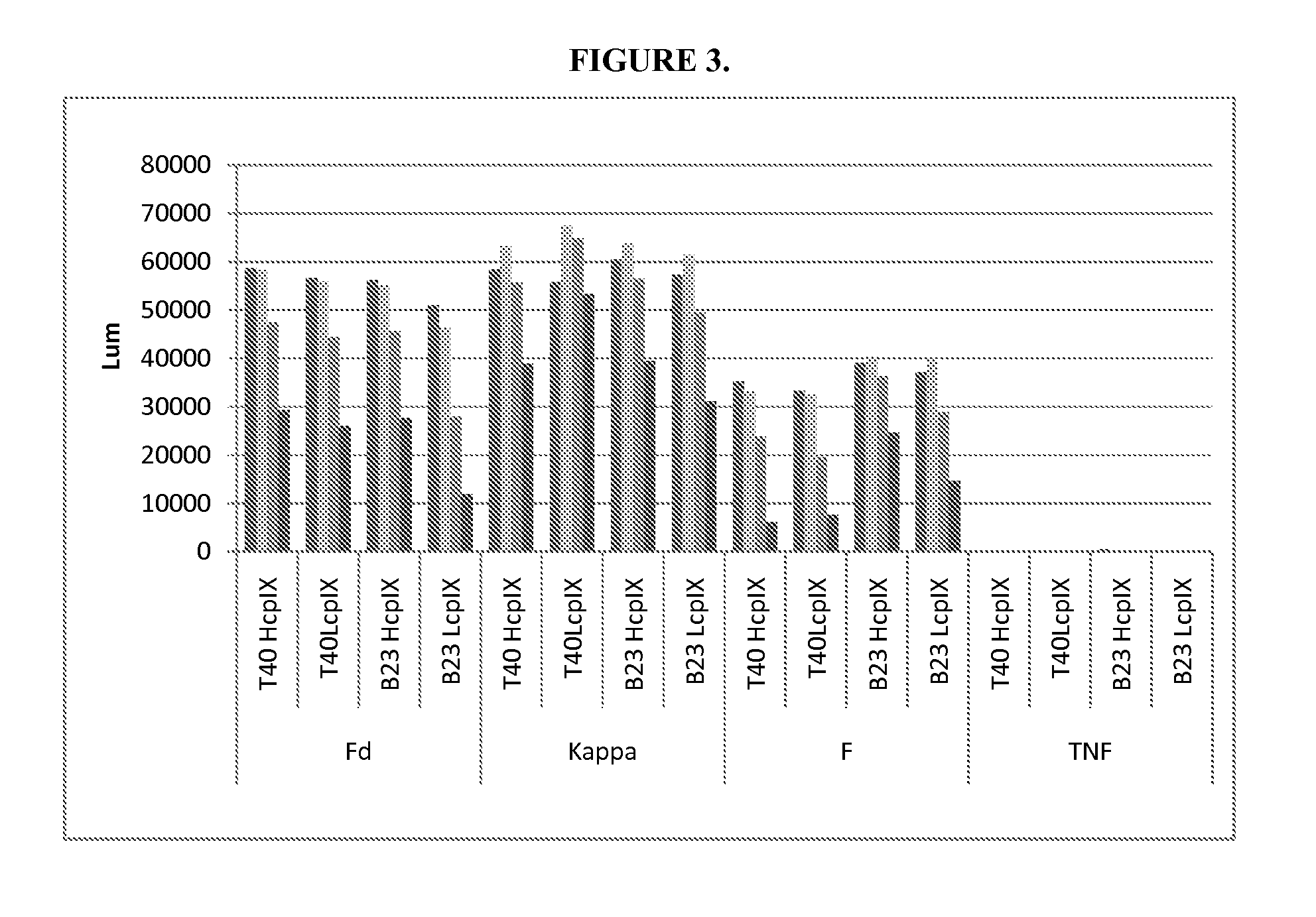
DESIGN AND GENERATION OF HUMAN DE NOVO pIX PHAGE DISPLAY LIBRARIES
InactiveUS20100021477A1Easy to understandIncrease diversityBacteriaLibrary screeningNatural antibodyStructure function
Described and claimed herein are combinatorial synthetic Fab libraries displayed on a phage pIX protein. The libraries were built on scaffolds representing the most frequently used genes in human antibodies, which were diversified to mirror the variability of natural antibodies. After selection using a diverse panel of proteins, numerous specific and high-affinity Fabs were isolated. By a process called in-line maturation the affinity of some antibodies was improved up to one hundred-fold yielding low pM binders suitable for in vivo use. This work thus demonstrates the feasibility of displaying complex Fab libraries as pIX-fusion proteins for antibody discovery and lays the foundations for studies on the structure-function relationship of antibodies.
Owner:JANSSEN BIOTECH INC
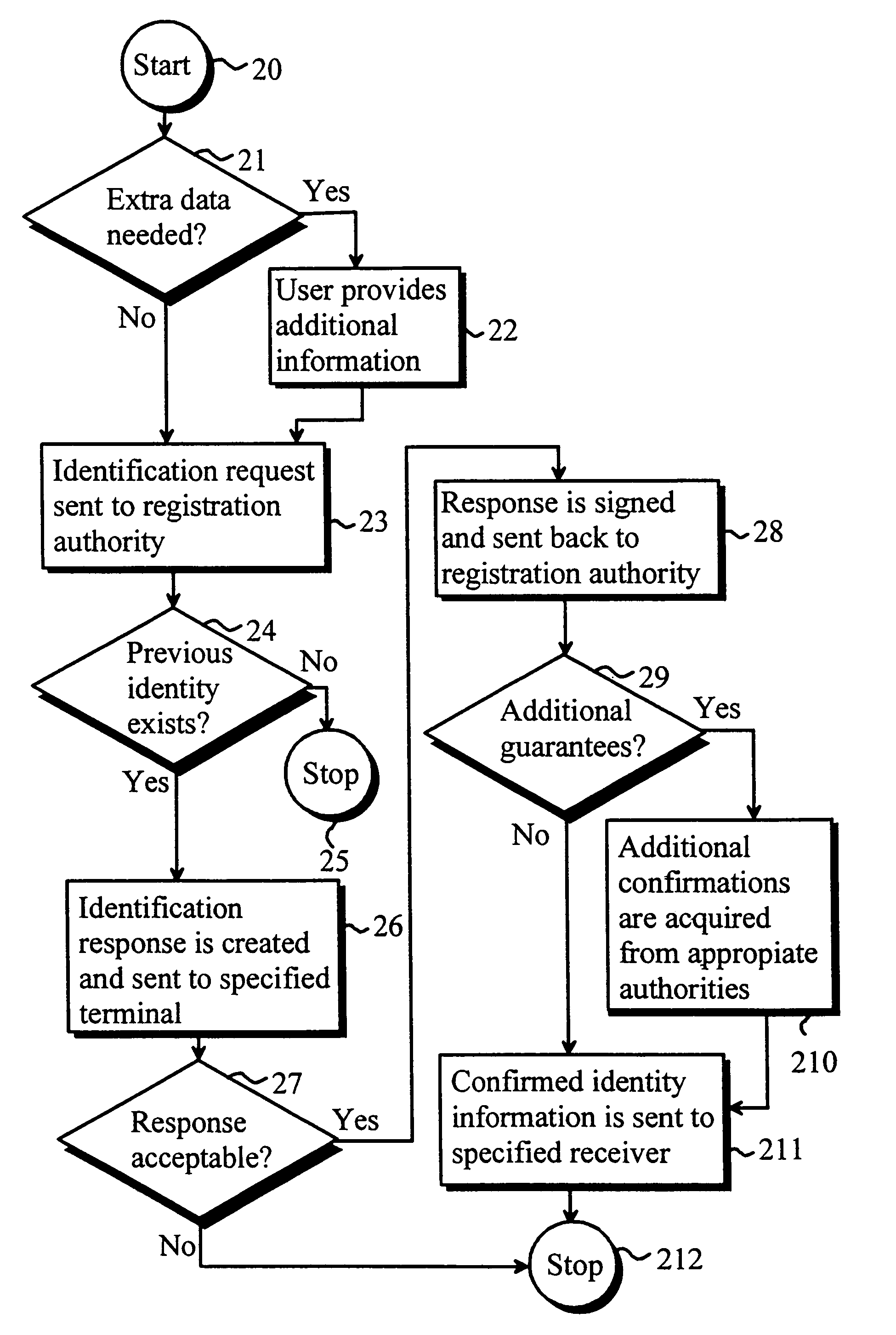
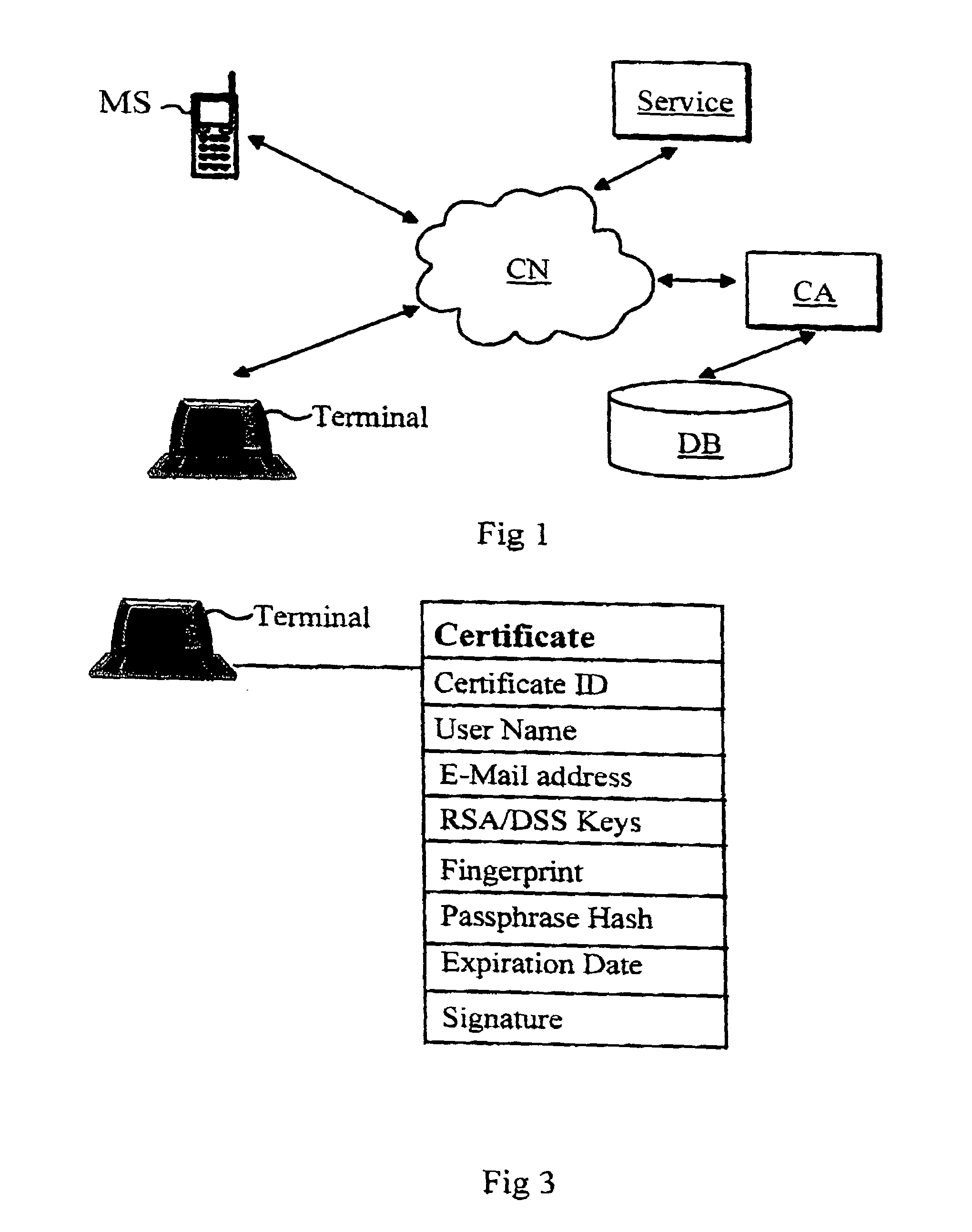
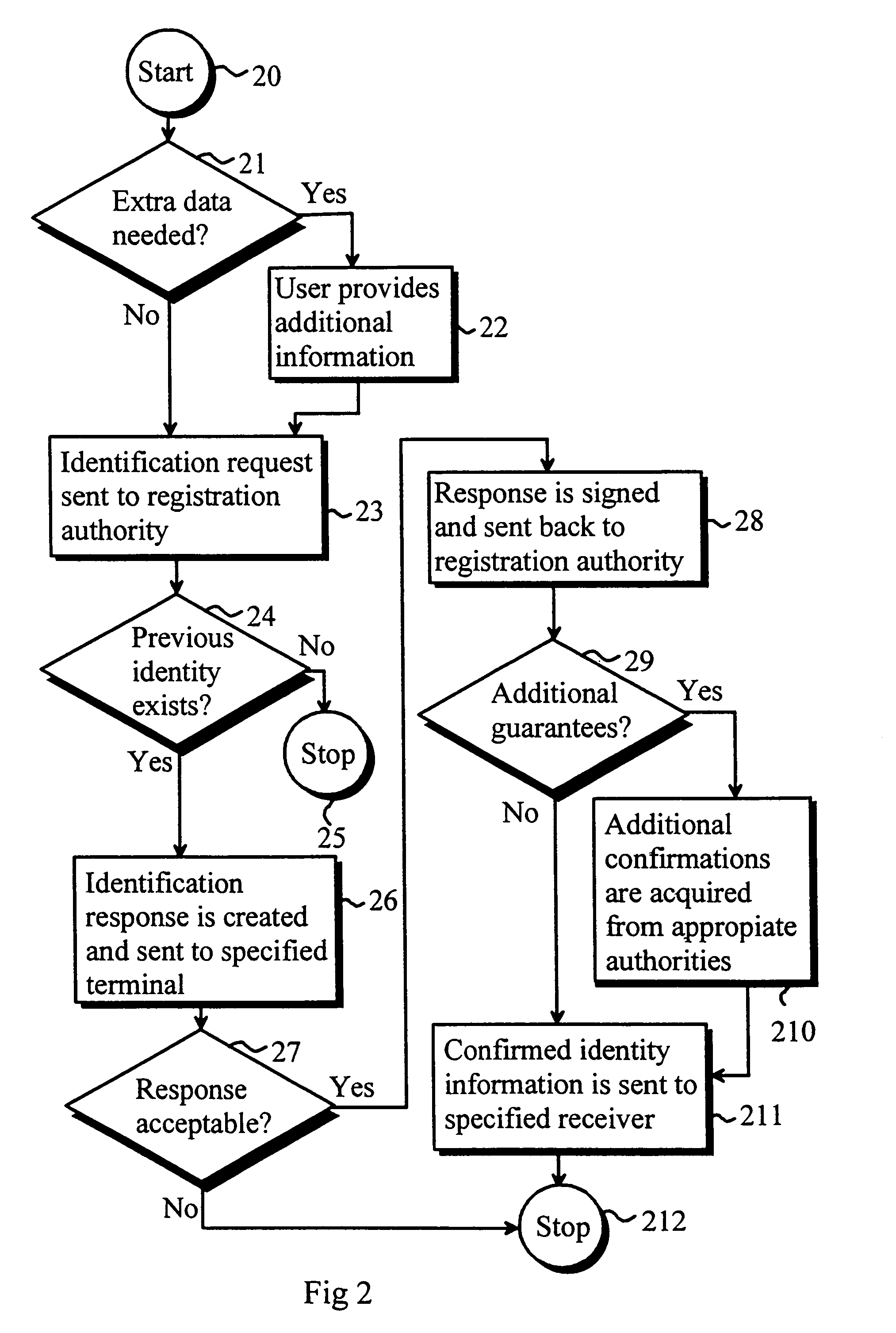
Method for issuing an electronic identity
InactiveUS7020778B1Improve identityData processing applicationsDigital data processing detailsDigital signatureComputer terminal
A method for issuing an electronic identity based on previously certified electronic identity. This is accomplished by providing a method to use a previously certified identity to create another representational form for the same identity. This way the holder of a certificate can extend his or her already verified identity for other uses. The previously certified identity can be for instance so called mobile identity which is associated to a person's mobile terminal such as mobile phone. The person can show to certificate be his / her own by using the digital signature feature of the mobile terminal.
Owner:GIESECKE & DEVRIENT MOBILE SECURITY GMBH
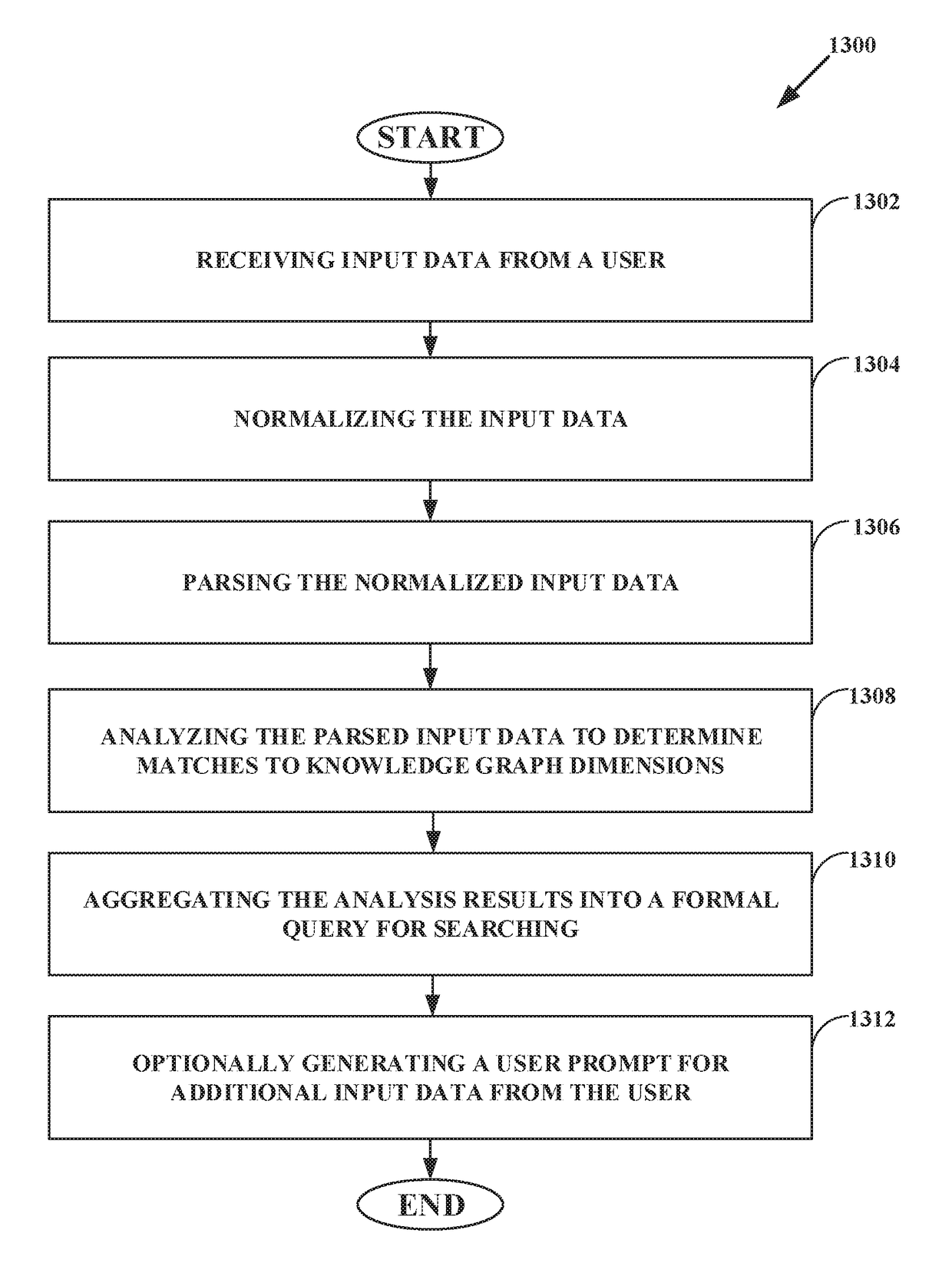
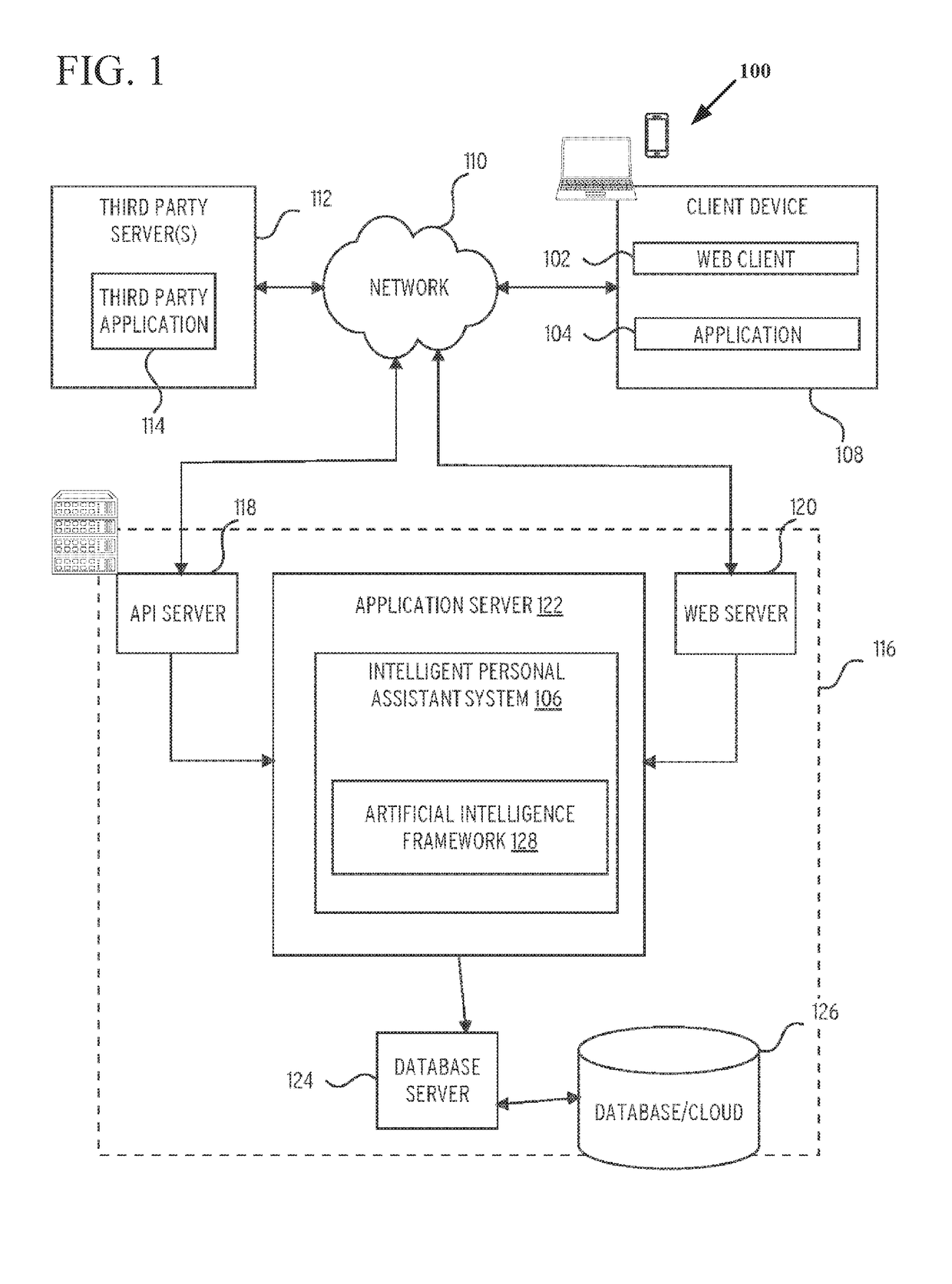
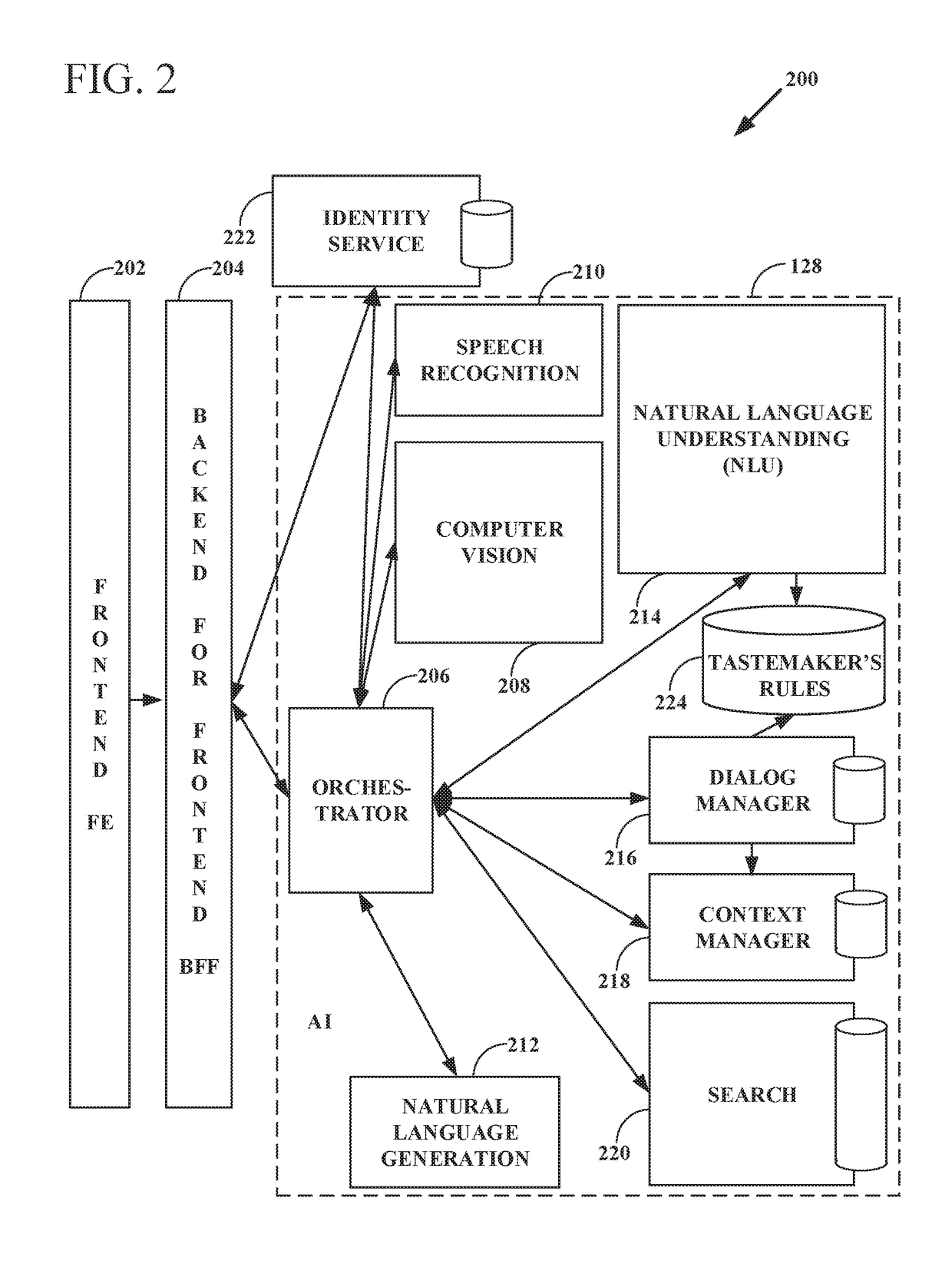
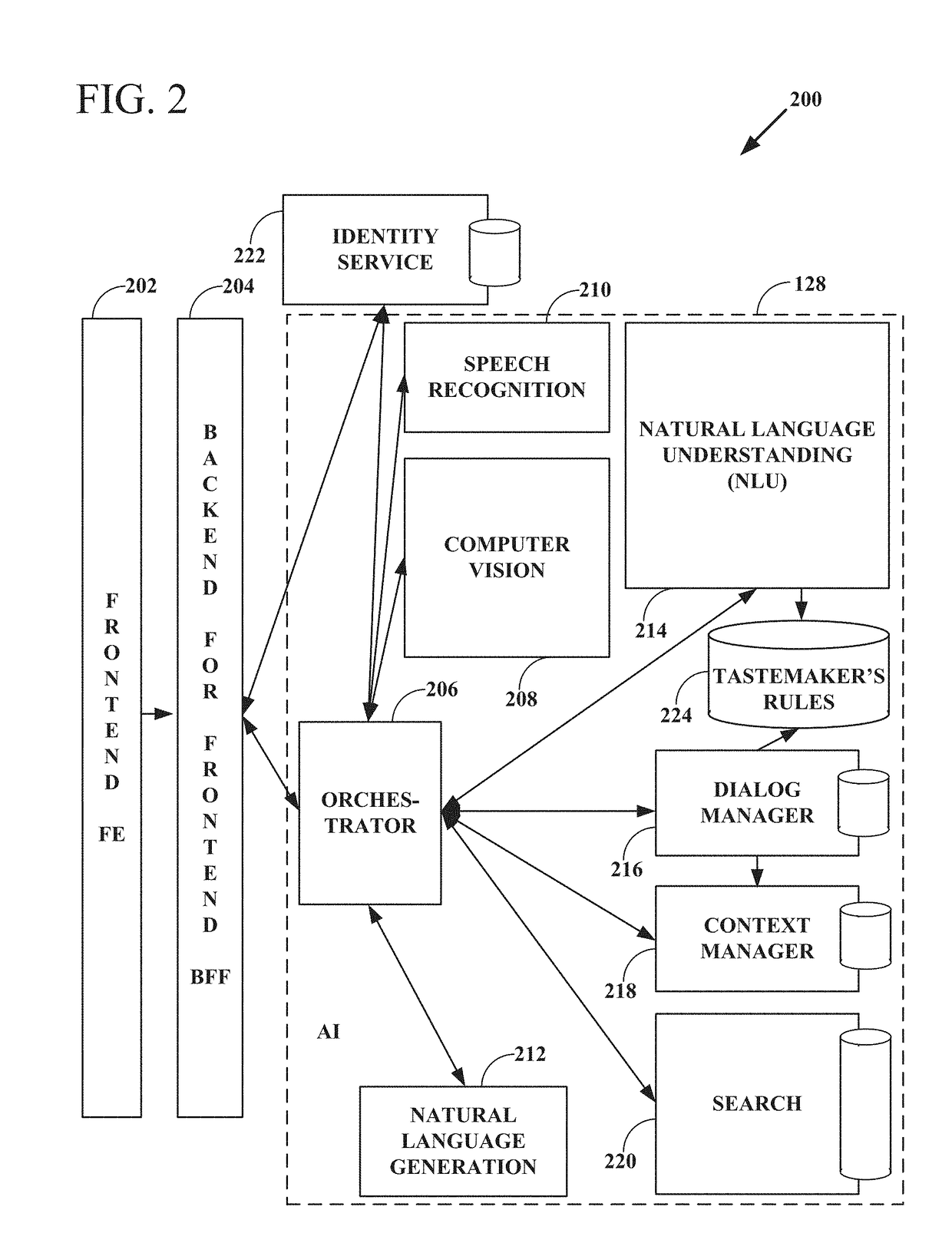
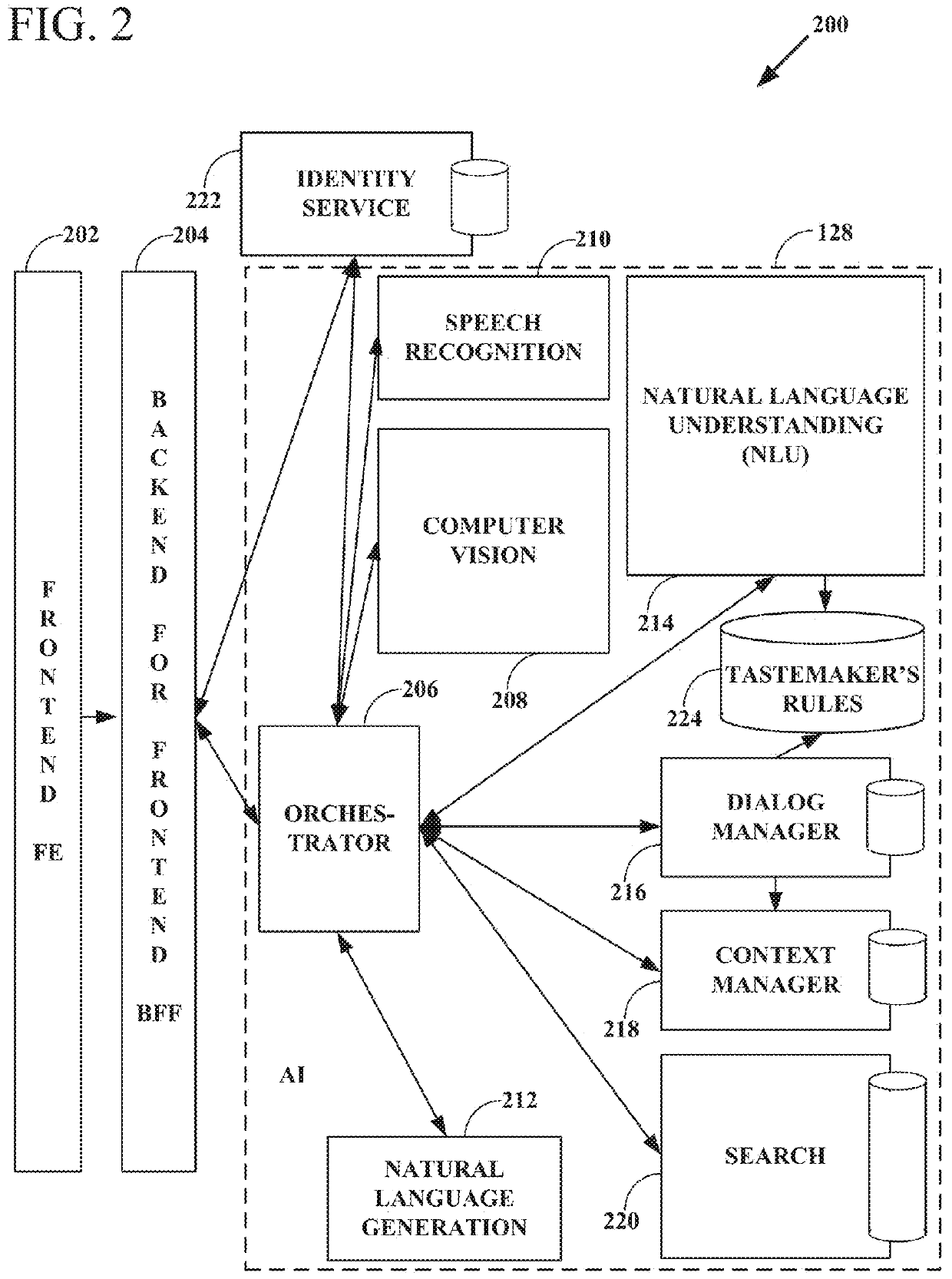
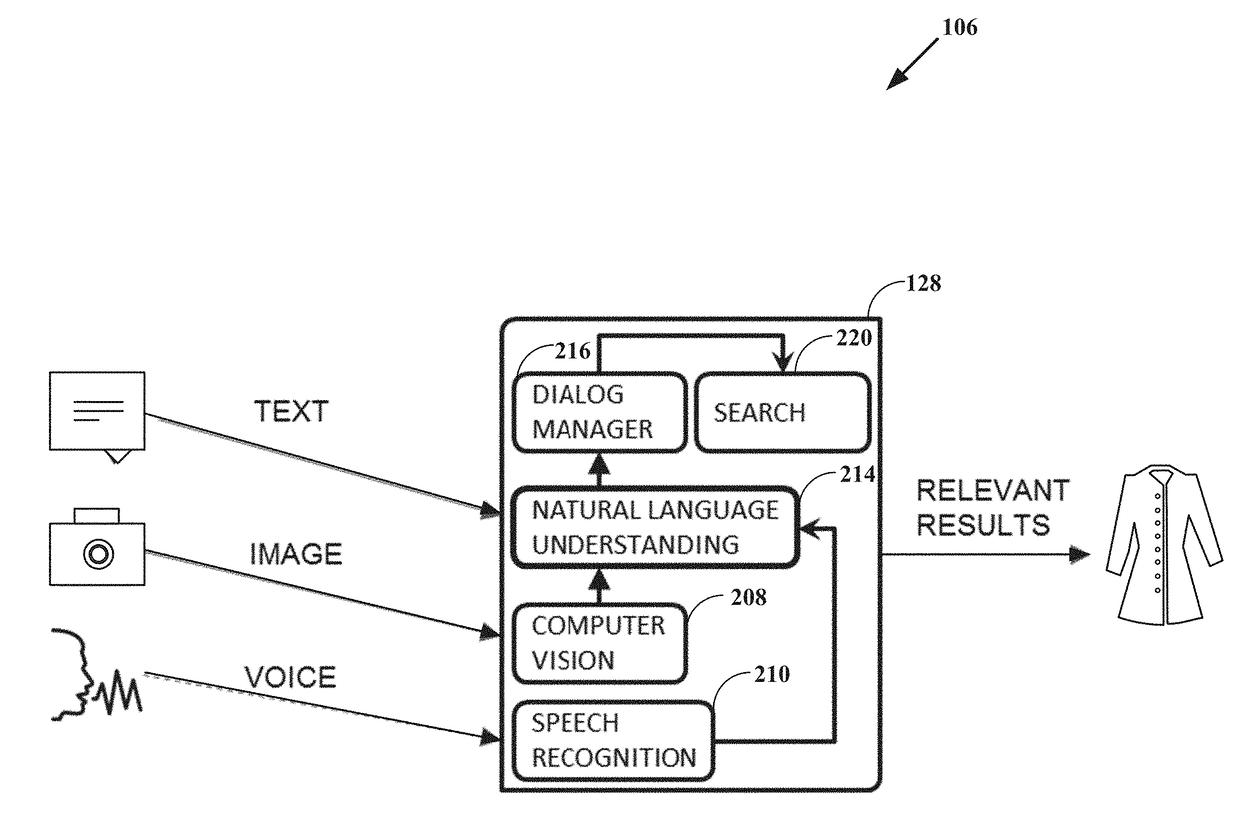
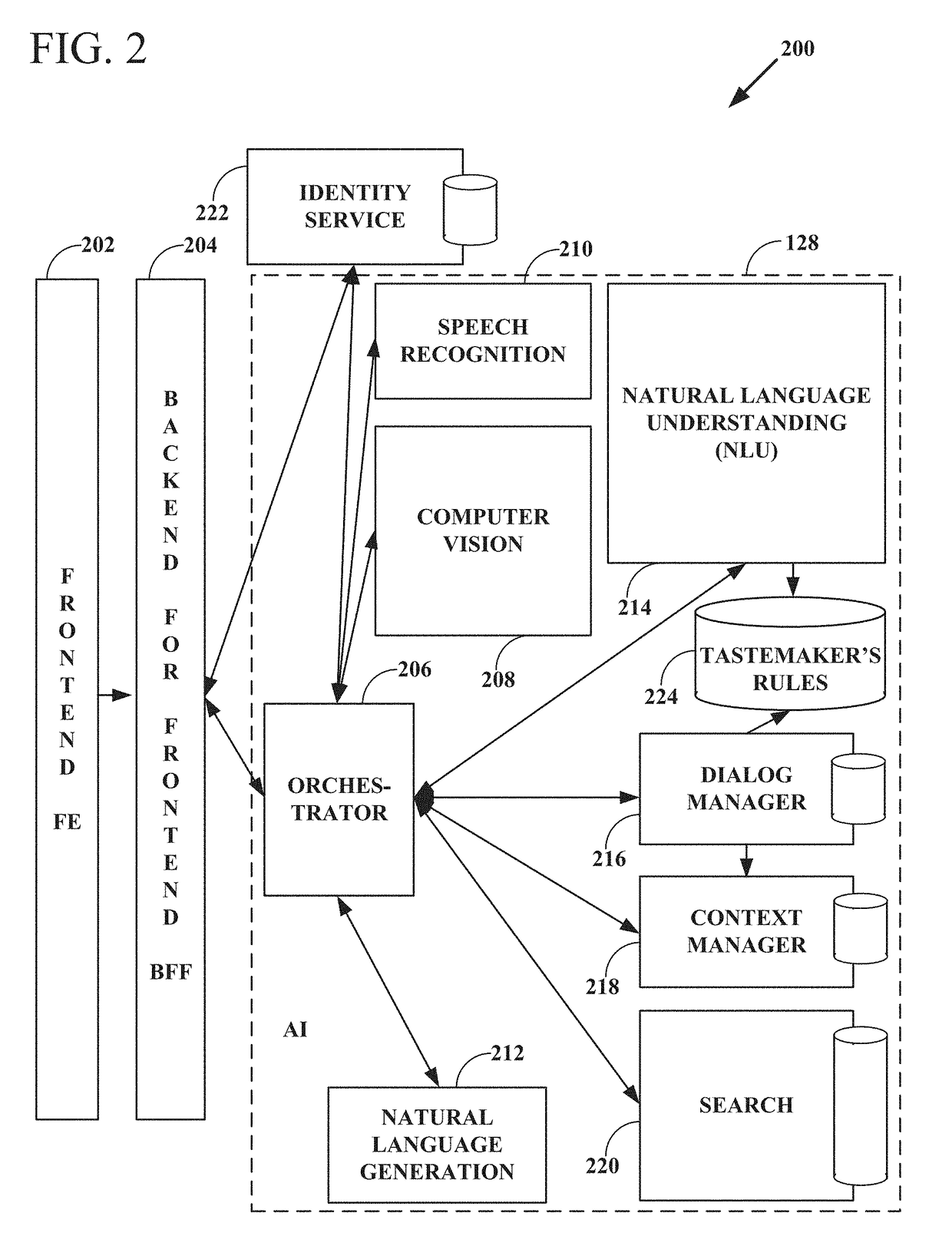
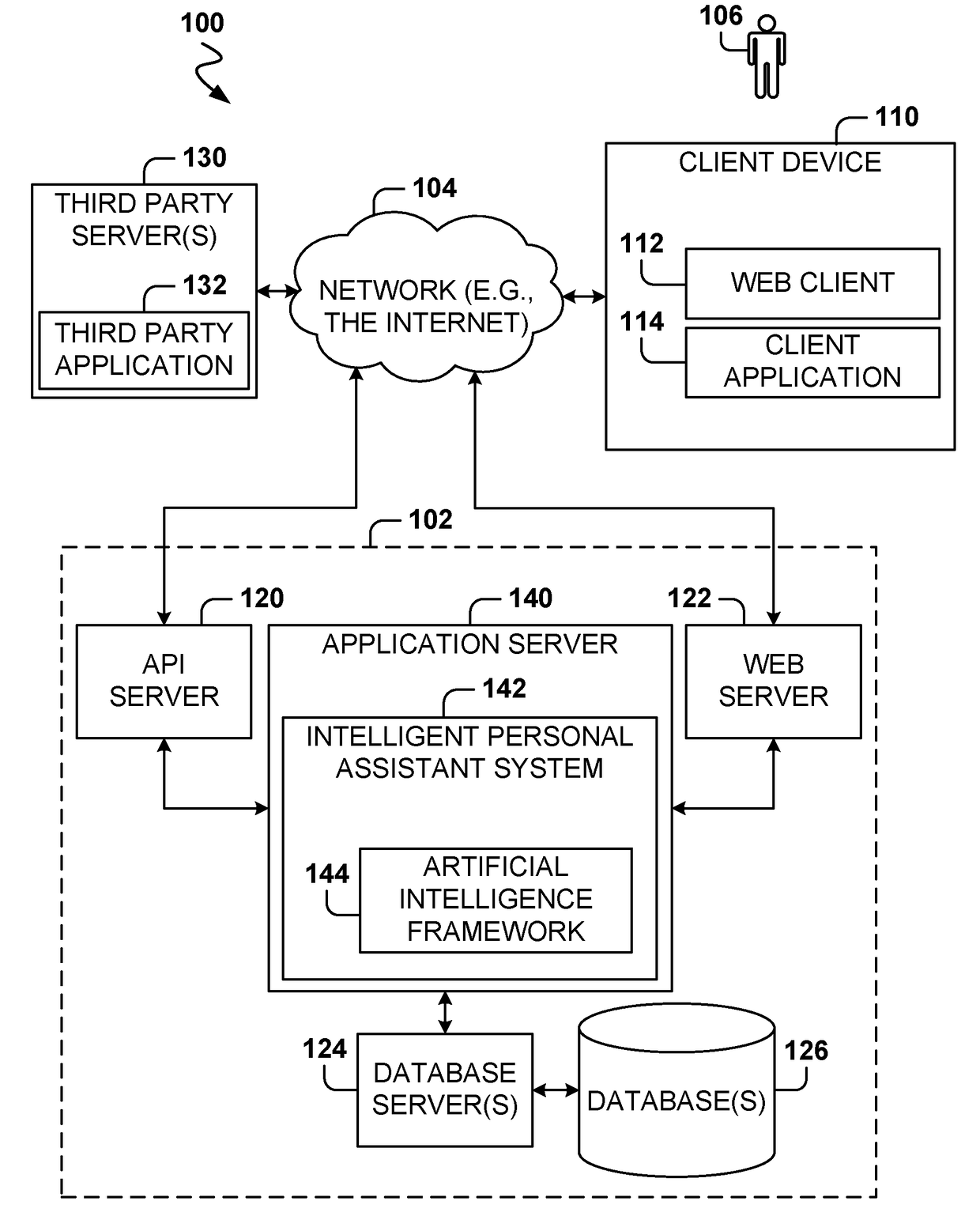
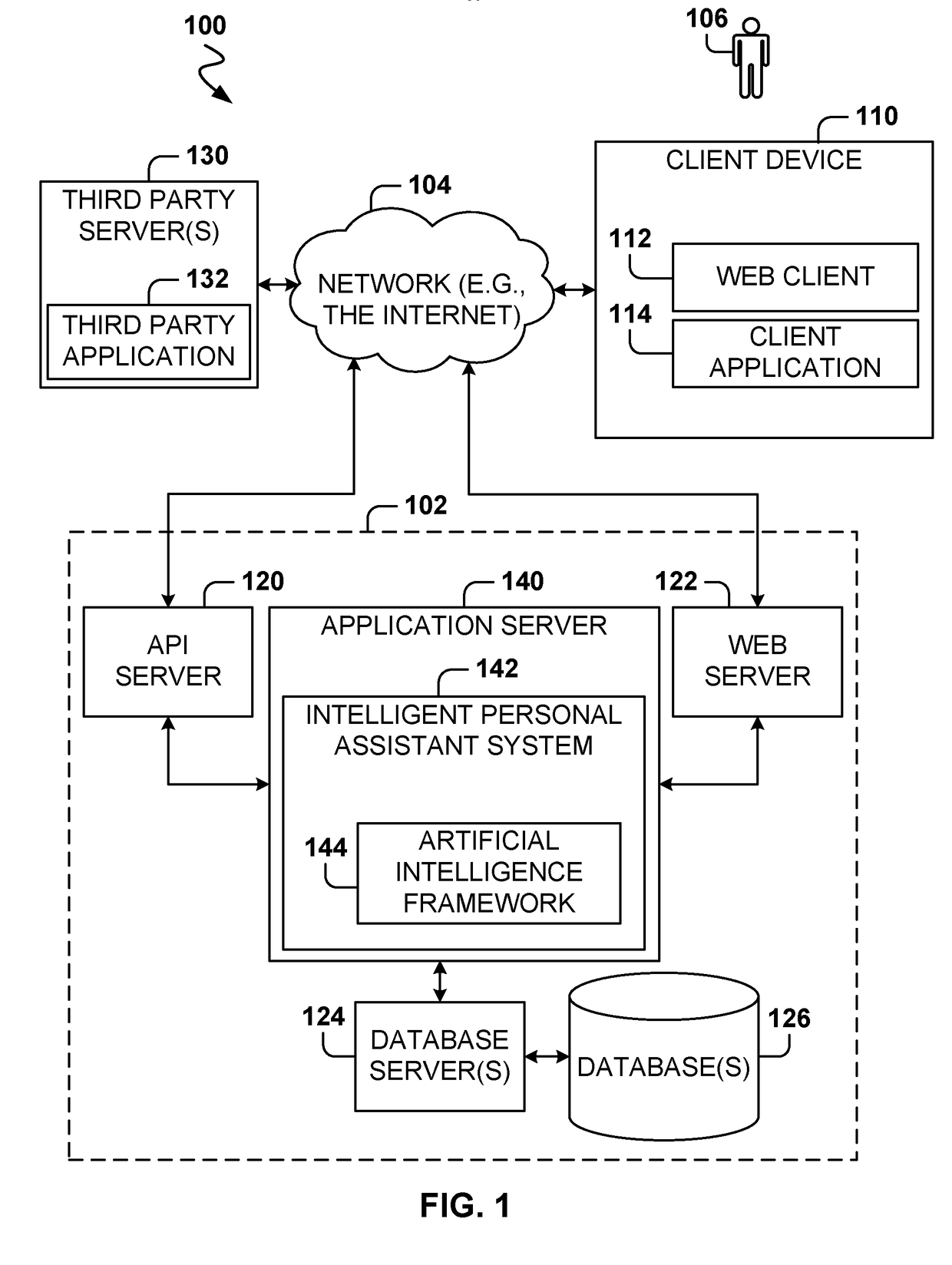
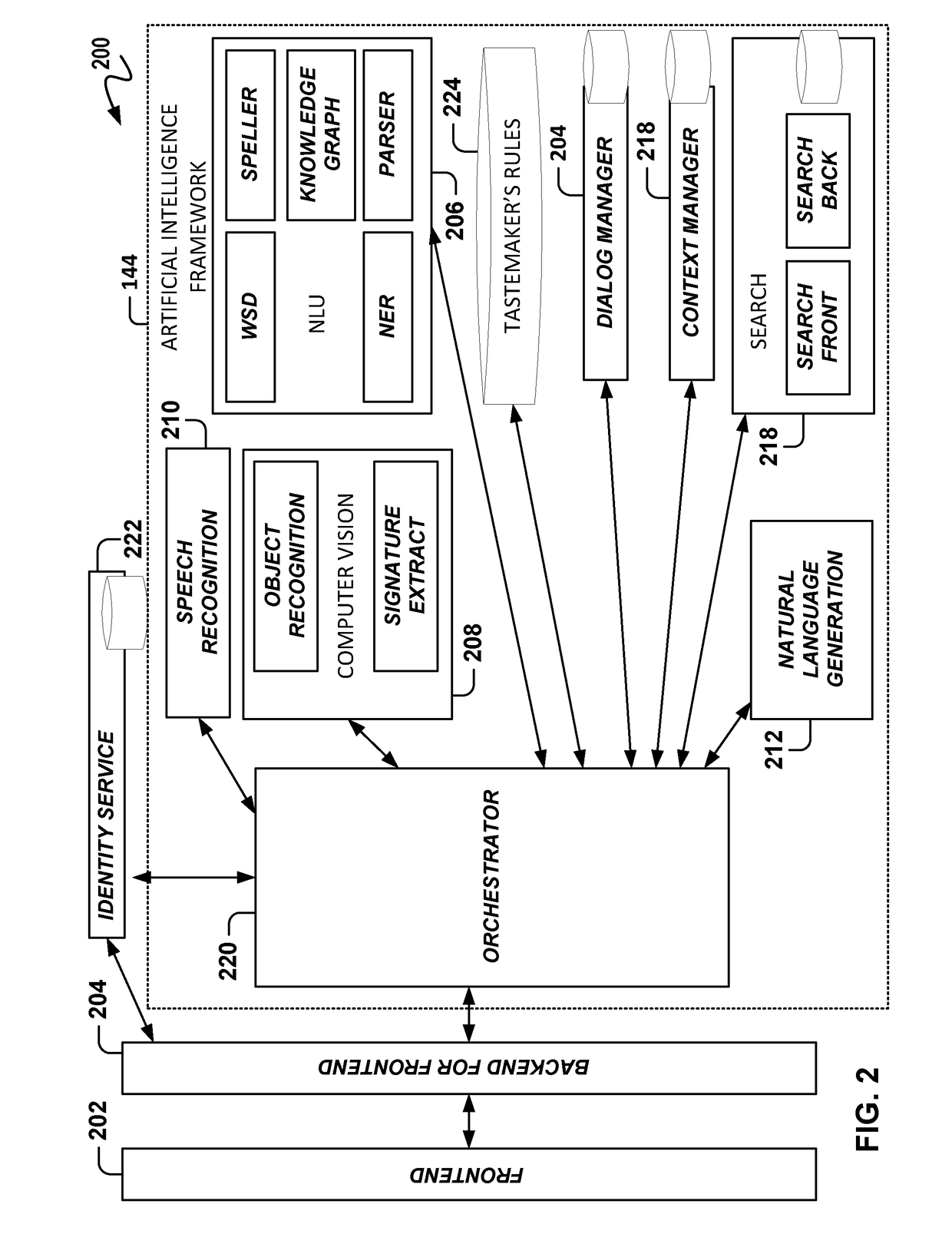
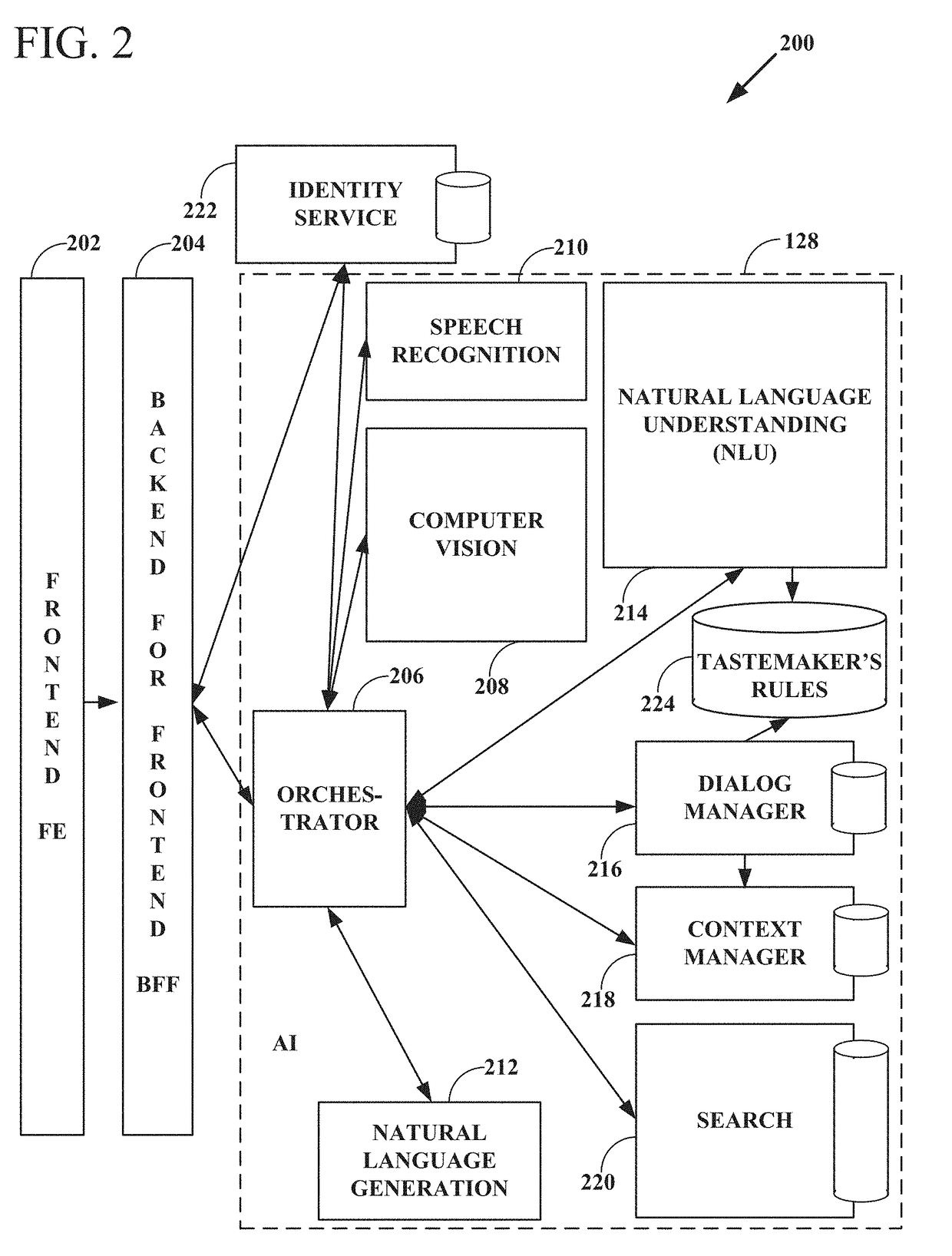
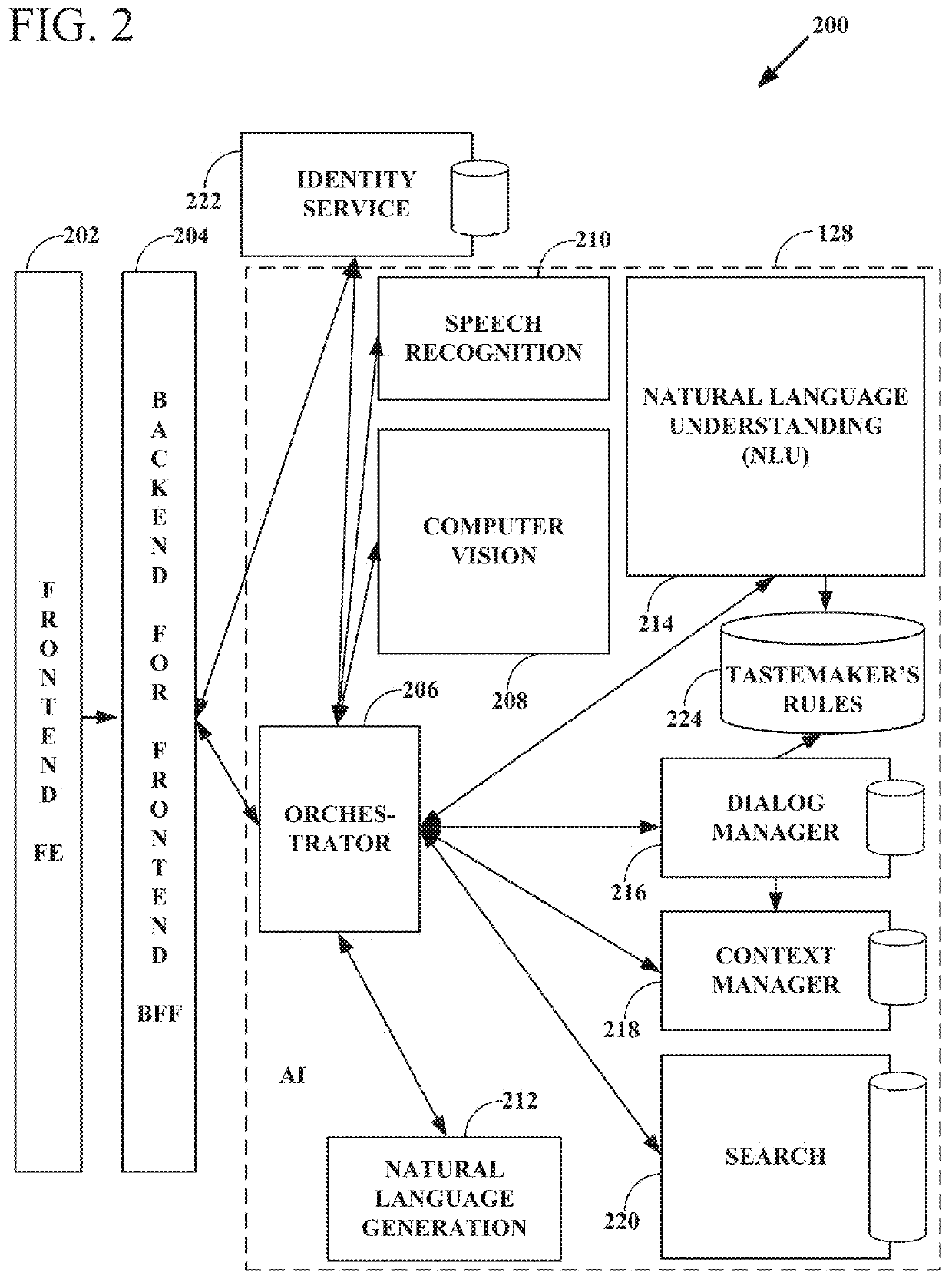
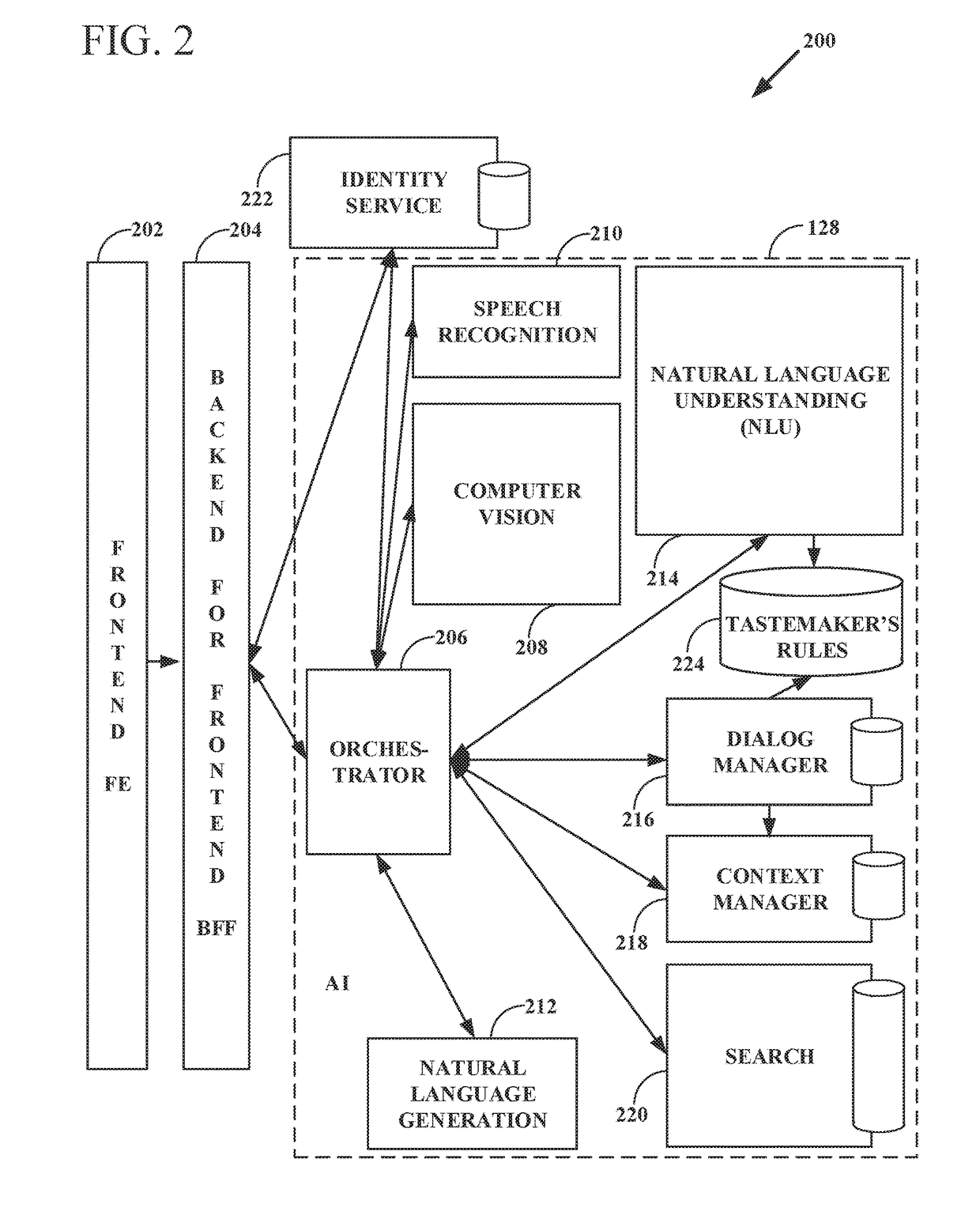
Intelligent online personal assistant with natural language understanding
InactiveUS20180052842A1Improve identityNatural language translationWeb data indexingNatural language understandingRelevant information
Systems and methods for transforming formal and informal natural language user inputs into a more formal, machine-readable, structured representation of a search query. In one scenario, a processed sequence of user inputs and machine-generated prompts for further data from a user in a multi-turn interactive dialog improves the efficiency and accuracy of automated searches for the most relevant items available for purchase in an electronic marketplace. Analysis of user inputs may discern user intent, user input type, a dominant object of user interest, item categories, item attributes, attribute values, and item recipients. Other inputs considered may include dialog context, item inventory-related information, and external knowledge to improve inference of user intent from user input. Different types of analyses of the inputs each yield results that are interpreted in aggregate and coordinated via a knowledge graph based on past users' interactions with the electronic marketplace and / or inventory-related data.
Owner:EBAY INC
Knowledge graph construction for intelligent online personal assistant
InactiveUS20180052884A1Improve identityDigital data information retrievalNatural language analysisMarket basedMetadata
Processing natural language user inputs into a more formal, machine-readable, structured query representation used for making an item recommendation. Analyses of user inputs are coordinated via a knowledge graph constructed from categories, attributes, and attribute values describing relatively frequently occurring prior interactions of various users with an electronic marketplace. The knowledge graph has directed edges each with a score value based on: the conditional probabilities of category / attribute / attribute value interactions calculated from user behavioral patterns, associations between user queries and structured data based on historical buyer behavioral patterns in the marketplace, metadata from items made available for purchase by sellers used to better define buyers' requirements, and / or world knowledge of weather, locations / places, occasions, and item recipients that map to inventory-related data, for generating relevant prompts for further user input. The knowledge graph may be dynamically updated during a multi-turn interactive dialog.
Owner:EBAY INC
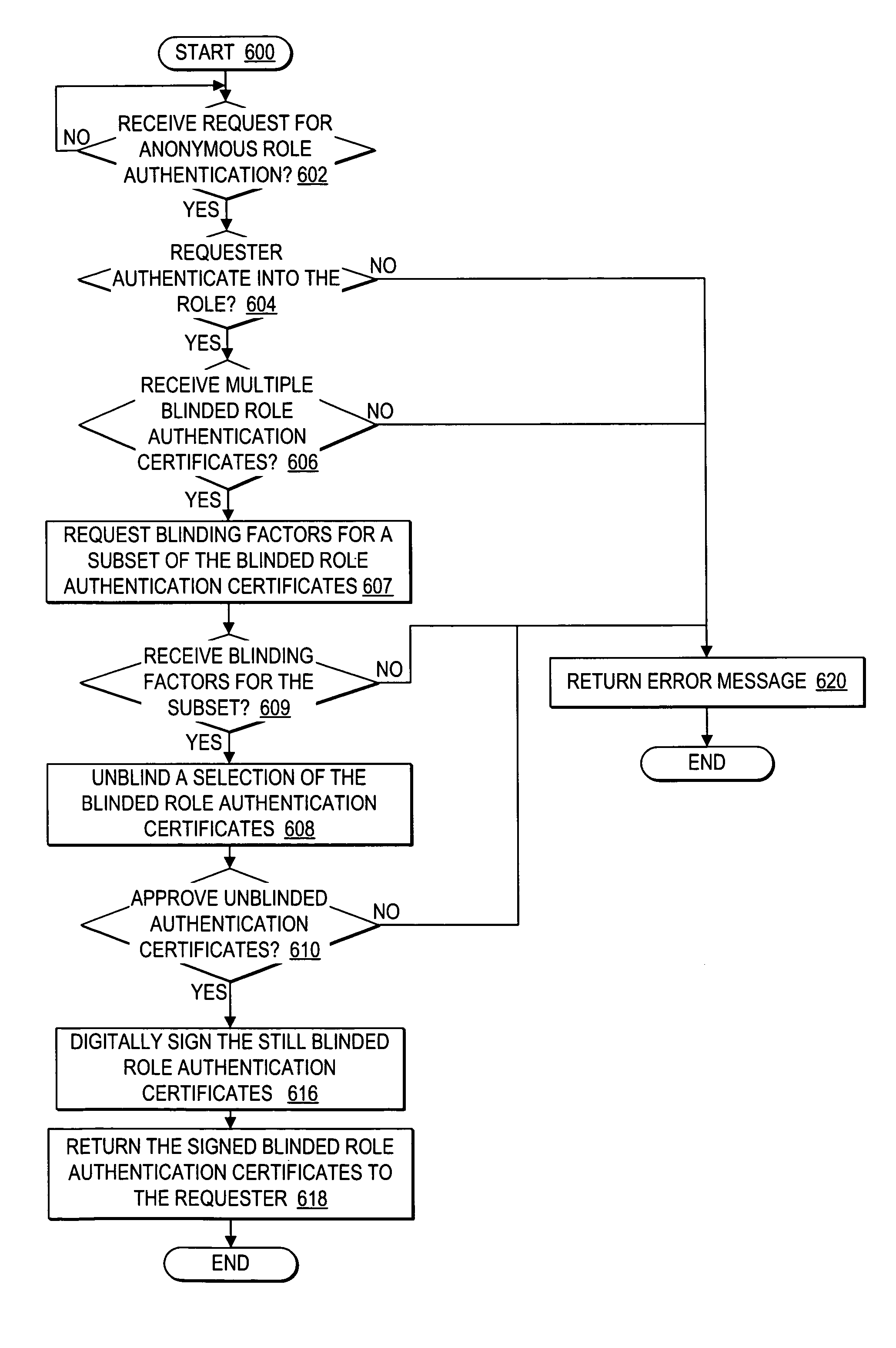
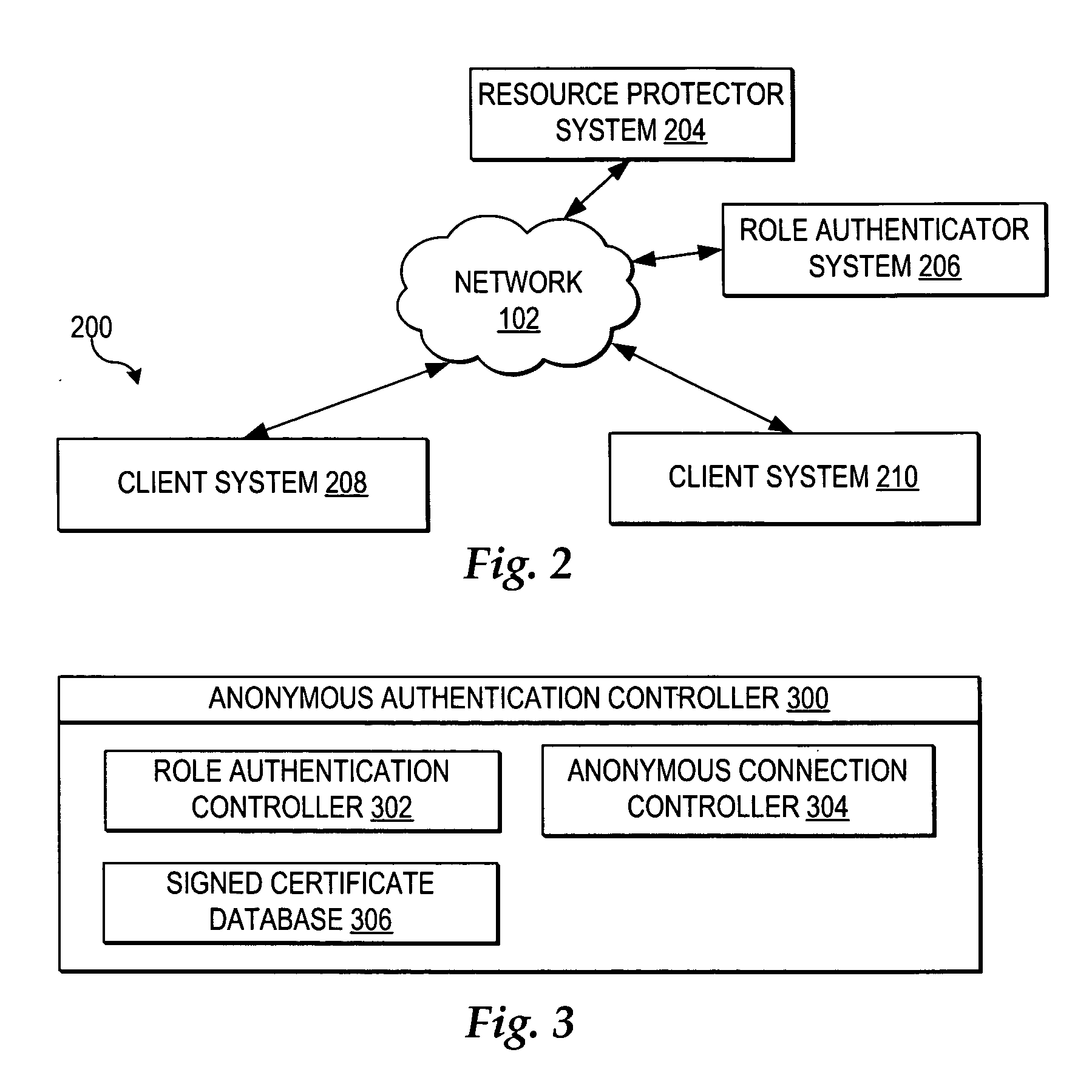
User controlled anonymity when evaluating into a role
InactiveUS20050283608A1Enhanced authenticationImprove identityDigital data processing detailsUser identity/authority verificationThird partyResource protection
A method, system, and program for user controlled anonymity when evaluating into a role are provided. An anonymous authentication controller enables a user to control anonymity of the user's identity for role based network accesses to resources, without requiring reliance on any single third party to maintain user anonymity. First, a role authentication certificate is received from a role authenticator, wherein the role authentication certificate certifies that the holder of the role authentication certificate is a member of a particular role without allowing the role authenticator issuing the role authentication certificate the ability to track an identity of a user holding the role authentication certificate. Next, an anonymous channel is established for anonymously presenting the role authentication certificate to a resource protector, wherein the resource protector requires the user to authenticate into the particular role to access a resource, wherein the role authentication certificate authenticates the user into the particular role without enabling the resource protector to ascertain the identity of the user, such that the user is in control of maintaining user anonymity for authenticated role-based accesses.
Owner:IBM CORP
Intelligent online personal assistant with multi-turn dialog based on visual search
ActiveUS20180108066A1Improve identityMathematical modelsDigital data information retrievalUser inputVision based
Systems, methods, and computer program products for identifying a relevant candidate product in an electronic marketplace. Embodiments perform a visual similarity comparison between candidate product image visual content and input query image visual content, process formal and informal natural language user inputs, and coordinate aggregated past user interactions with the marketplace stored in a knowledge graph. Visually similar items and their corresponding product categories, aspects, and aspect values can determine suggested candidate products without discernible delay during a multi-turn user dialog. The user can then refine the search for the most relevant items available for purchase by providing responses to machine-generated prompts that are based on the initial search results from visual, voice, and / or text inputs. An intelligent online personal assistant can thus guide a user to the most relevant candidate product more efficiently than existing search tools.
Owner:EBAY INC
Generating next user prompts in an intelligent online personal assistant multi-turn dialog
InactiveUS20180052885A1Improve identityDigital data information retrievalSemantic analysisDialog systemUser input
Systems and methods for generating prompts for further data from a user in a multi-turn interactive dialog. Embodiments improve searches for the most relevant items available for purchase in an electronic marketplace via a processed sequence of user inputs and machine-generated prompts. Question type prompts, validating statement type prompts, and recommendation type prompts may be selectively generated based on whether a user query has been sufficiently specified, user intent is ambiguous, or a search mission has changed. Detection of a new dominant object denotes search mission change. Contextual associations between prompts and user replies are maintained, but a search mission change results in previous context data being disregarded. Prompts can be directed to unspecified knowledge graph dimensions based on data element association strength values, relative data element positions and depths in the knowledge graph, and generated following a predetermined order of data element knowledge graph dimension types.
Owner:EBAY INC
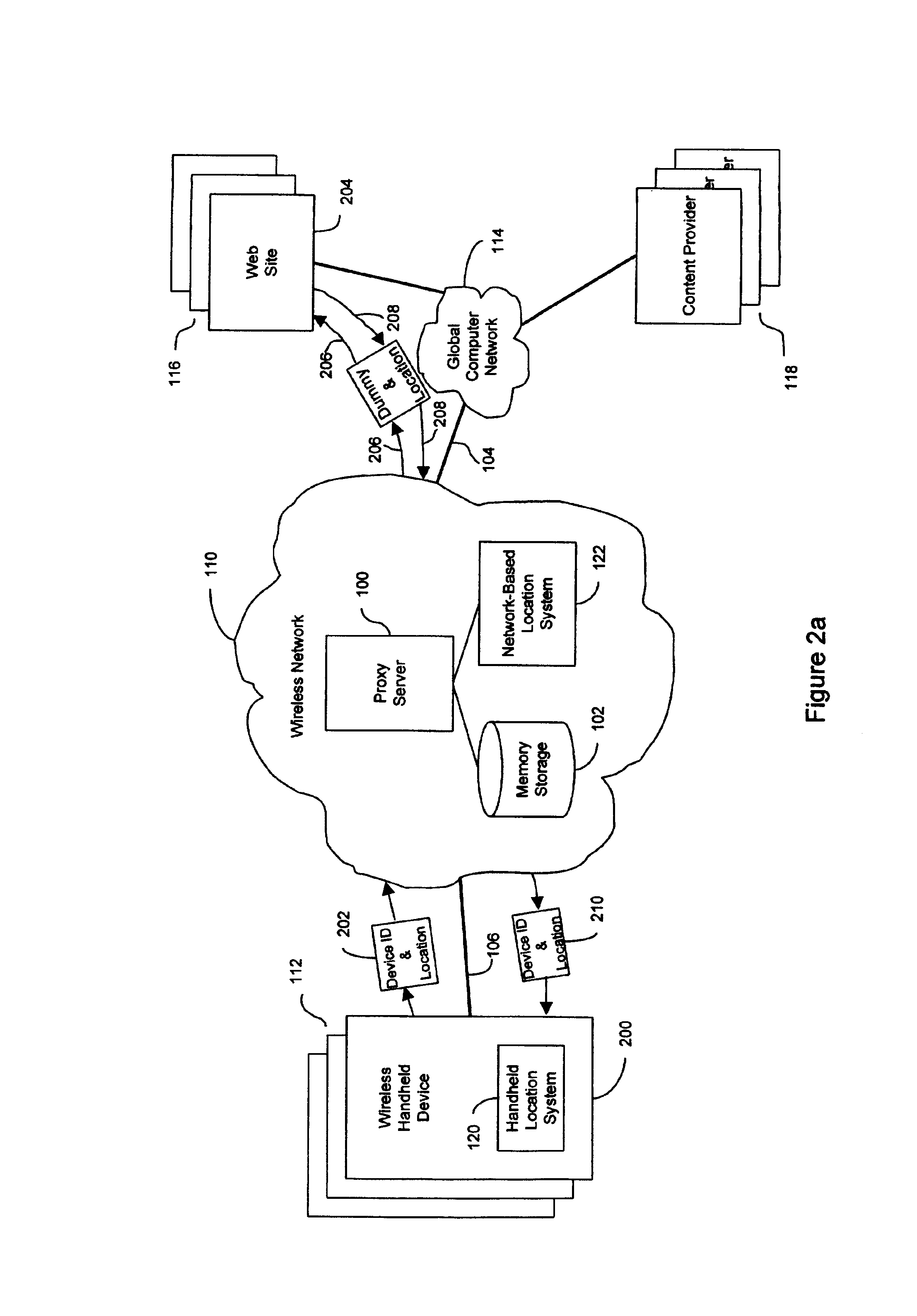
Anonymous location service for wireless networks
InactiveUS20090047937A1Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identification information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
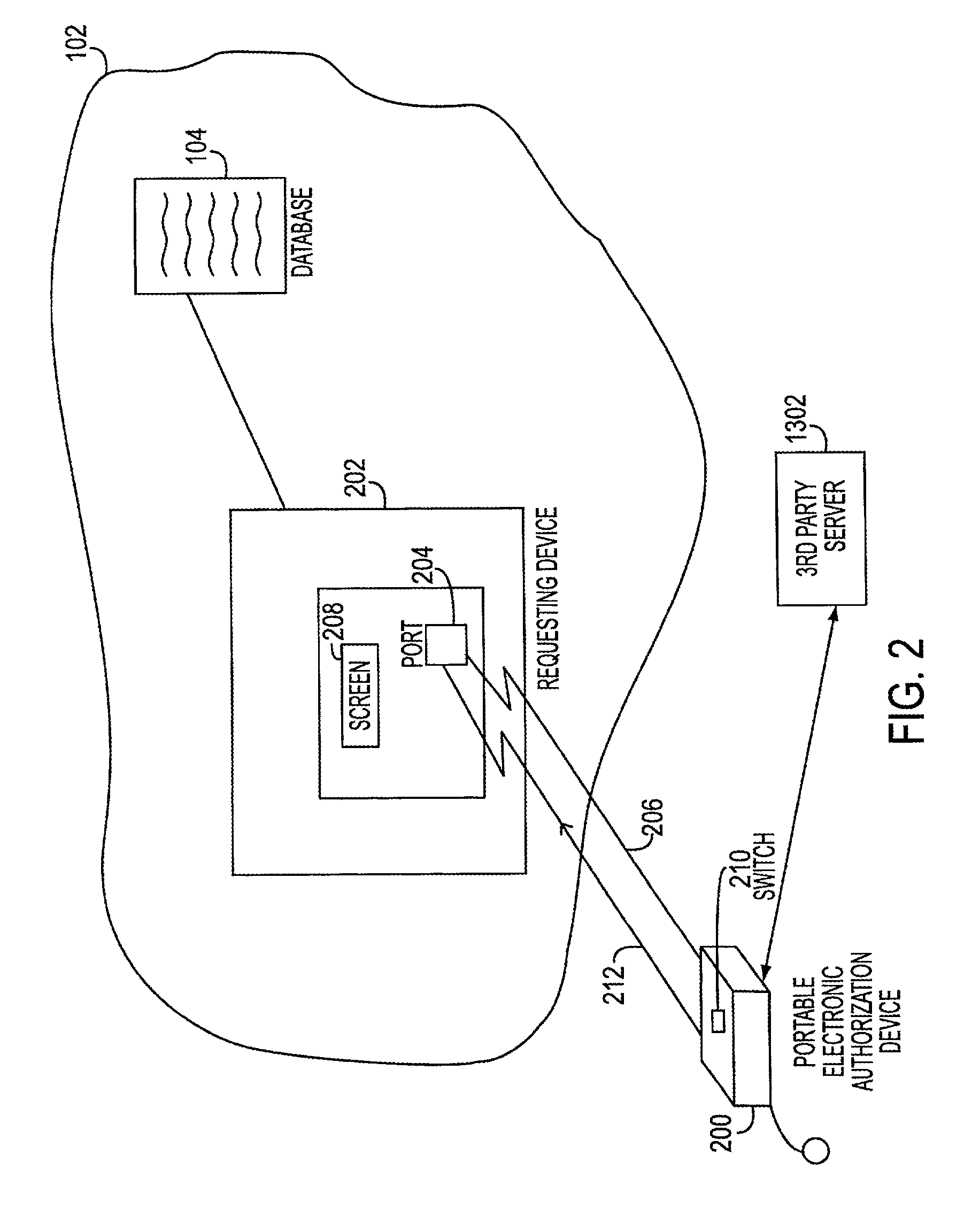
Electronic transaction systems and methods therfeor
InactiveUS20070089168A1Facilitates nonrepudiationImprove identityComplete banking machinesFinanceAuthorizationDigital data
The method includes the steps of receiving at the PEAD first digital data representing the transaction request. The PEAD provides information to the user regarding an ability to approve the transaction request. When the transaction request is approved by the user, the PEAD receives second digital data representing the electronic service authorization token. A remote agent server may provide a bridge between the electronic transaction system and the PEAD. In another embodiment, the private key is stored on the portable device, encrypted. The decryption key is stored outside of the device, at a trusted 3rd party location. When the user attempts to make a signature the software sends a request for the decryption key, along with the user's password or pass phrase keyed in at the keyboard of the PDA, smart phone, or cell phone, to a server belonging to the trusted 3rd party.
Owner:SERVSTOR TECHNOLOGIES LLC +1
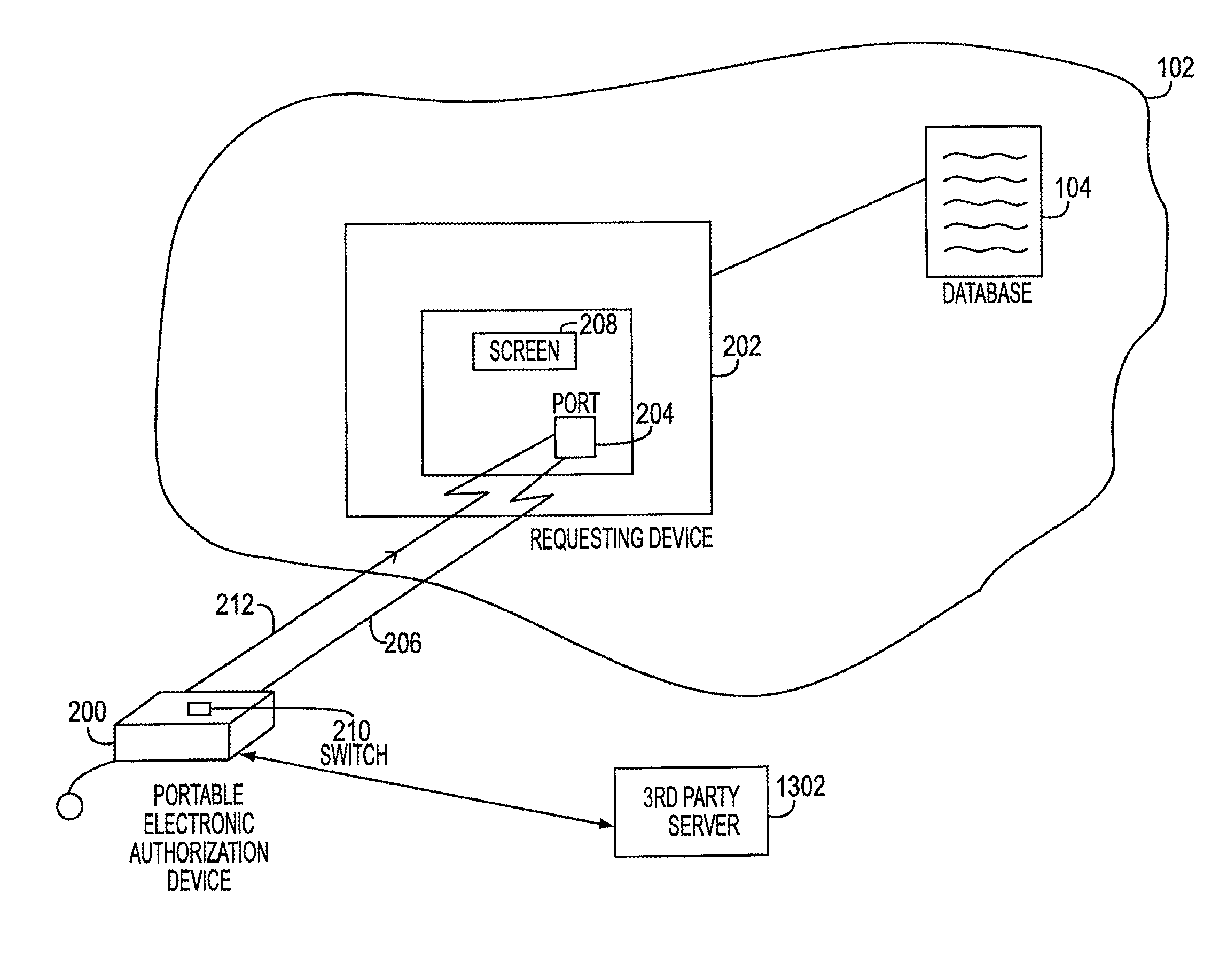
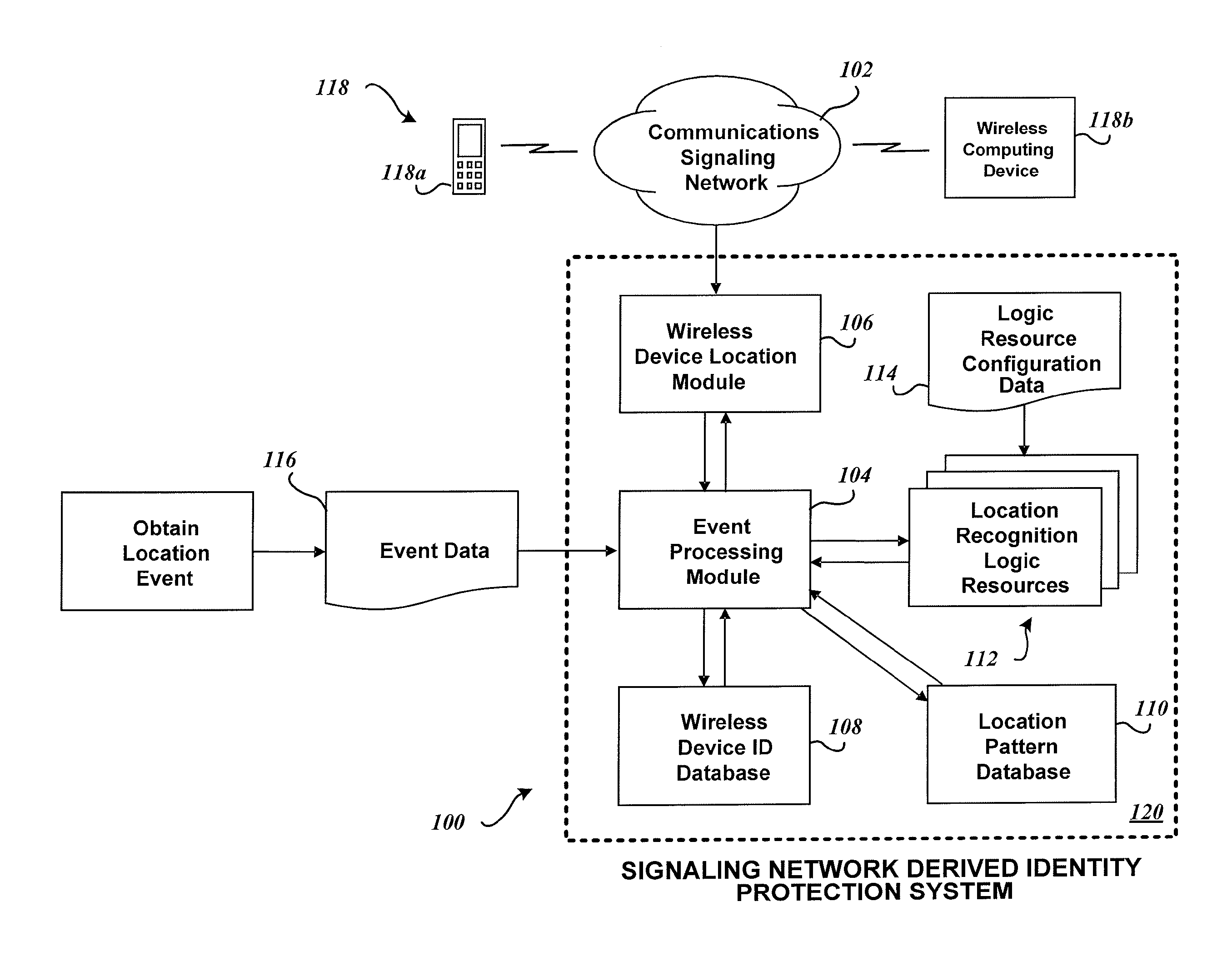
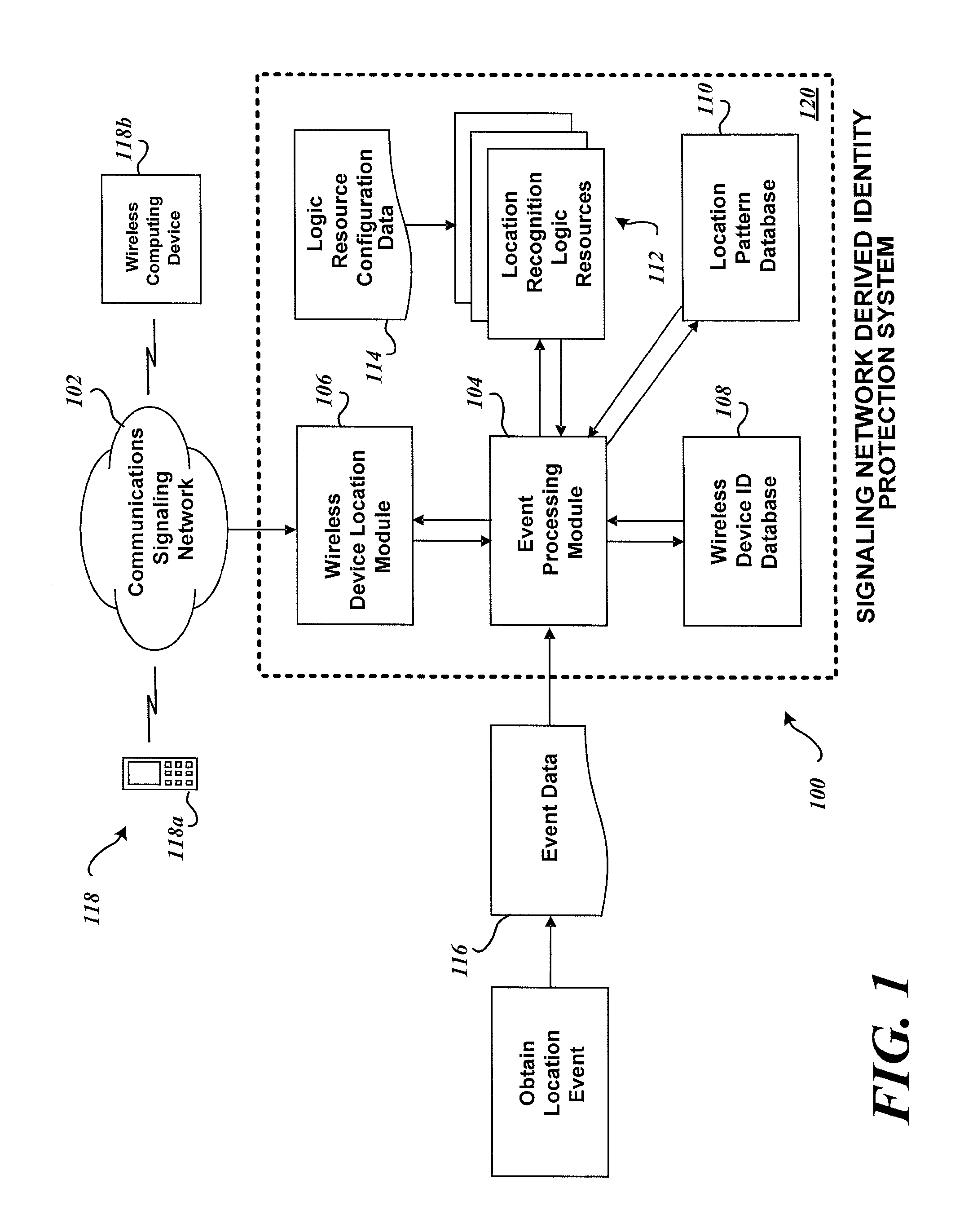
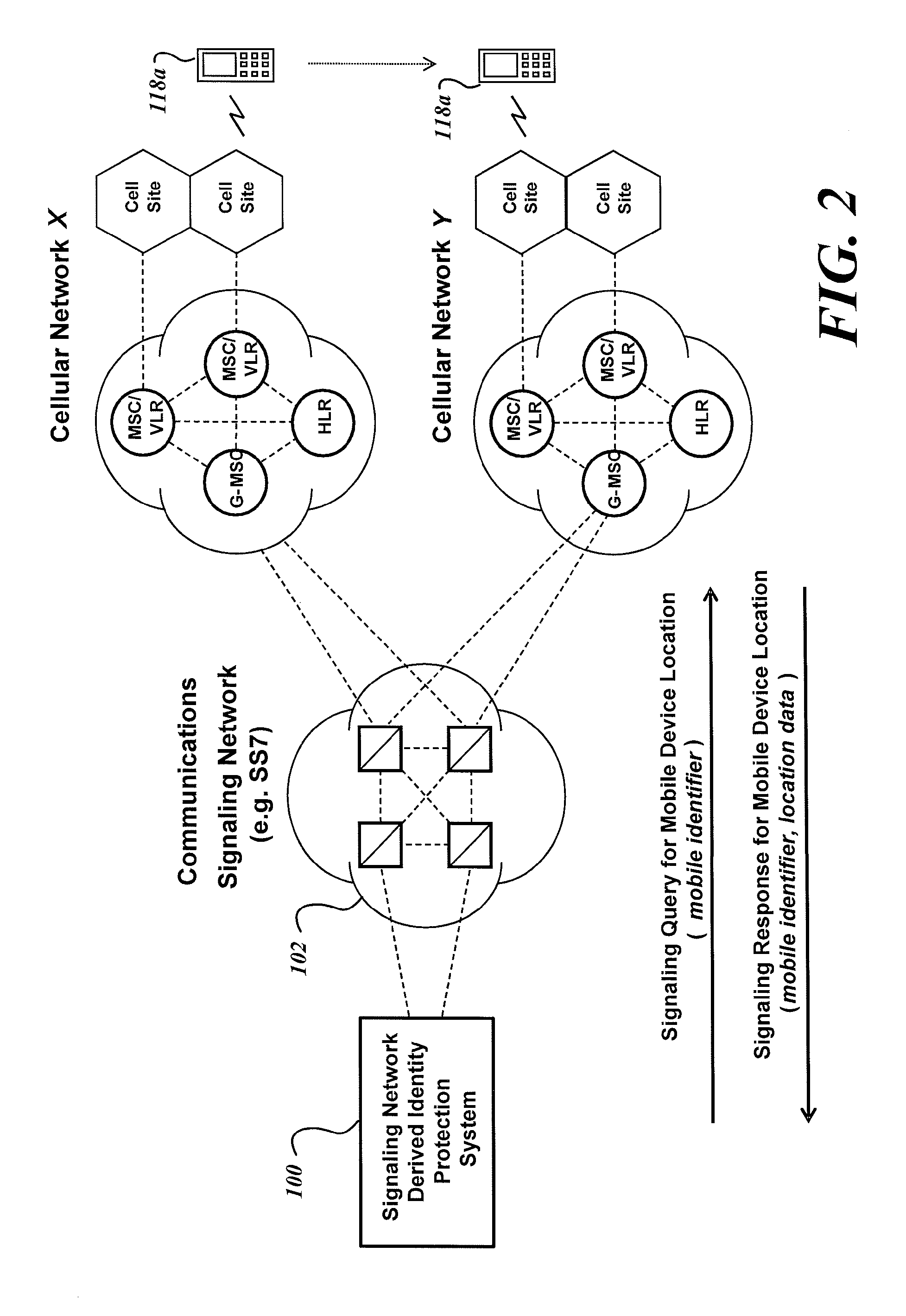
System and method for identity protection using mobile device signaling network derived location pattern recognition
ActiveUS20100130165A1Improve identityFinanceUnauthorised/fraudulent call preventionSignaling networkIdentity protection
A system and method for recognizing patterns in wireless device locations using wireless device location data derived from a communications signaling network is provided. By using wireless network supported signaling operations and messages, location data concerning the whereabouts of wireless devices, and hence wireless device users, may be obtained. The location data derived from the communications signaling network may be statistically analyzed to reveal potential geographic patterns that may indicate meaningful behaviors of the purported users of the wireless devices.
Owner:VISA INT SERVICE ASSOC
Enhancing user queries using implicit indicators
InactiveUS20180068031A1Improve identityNatural language translationSemantic analysisData miningData library
In various example embodiments, a system and method for balancing implicit and explicit indicators is presented. In one example, a method includes a user's utterance that includes a user query, extracting user intent parameters from the user query, constructing a structured query in a machine readable format using user intent parameters, determining whether the user query includes an implicit indicator, determining a confidence rating for the implicit indicator, updating the structured query to include the implicit indicator in response to the confidence rating for the implicit indicator being above a threshold value, and submitting the structured query to a database of items.
Owner:EBAY INC
Intelligent online personal assistant with image text localization
ActiveUS20180137551A1Improve identityImage enhancementMathematical modelsGround truthLocalization system
Owner:EBAY INC
Protein having affinity for immunoglobulin, and immunoglobulin-binding affinity ligand
ActiveUS20120208234A1Good chemical stabilityImprove identityBacteriaPeptide/protein ingredientsLow affinityADAMTS Proteins
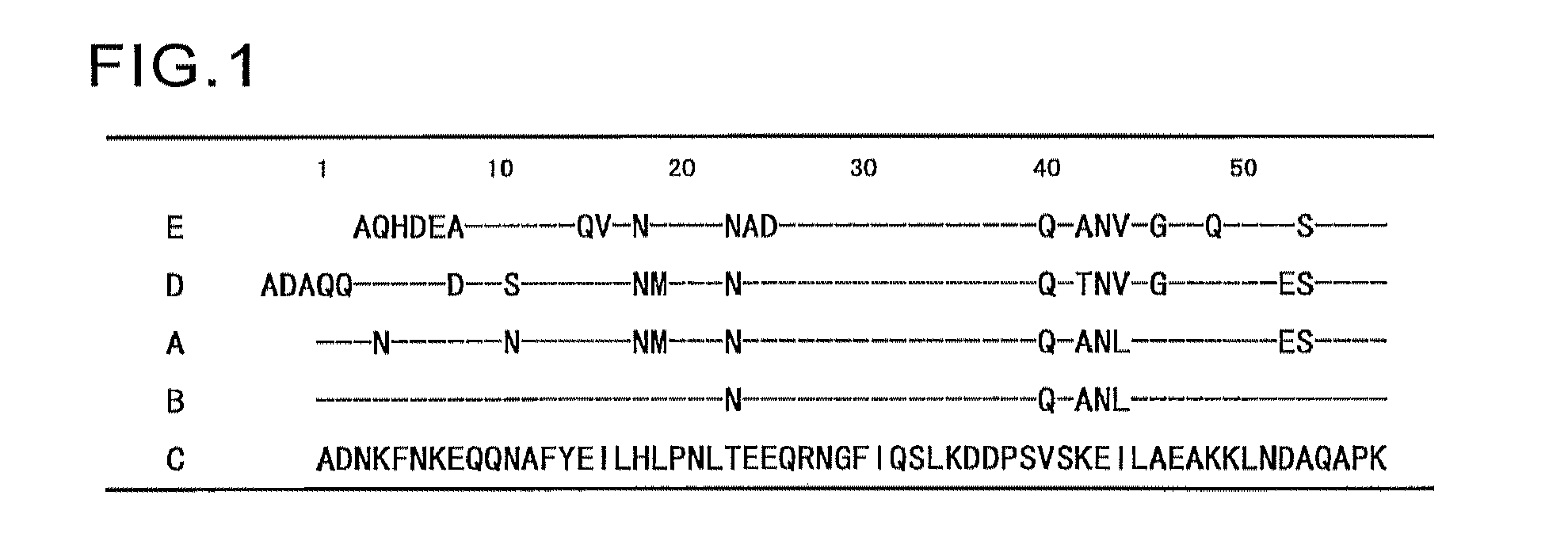
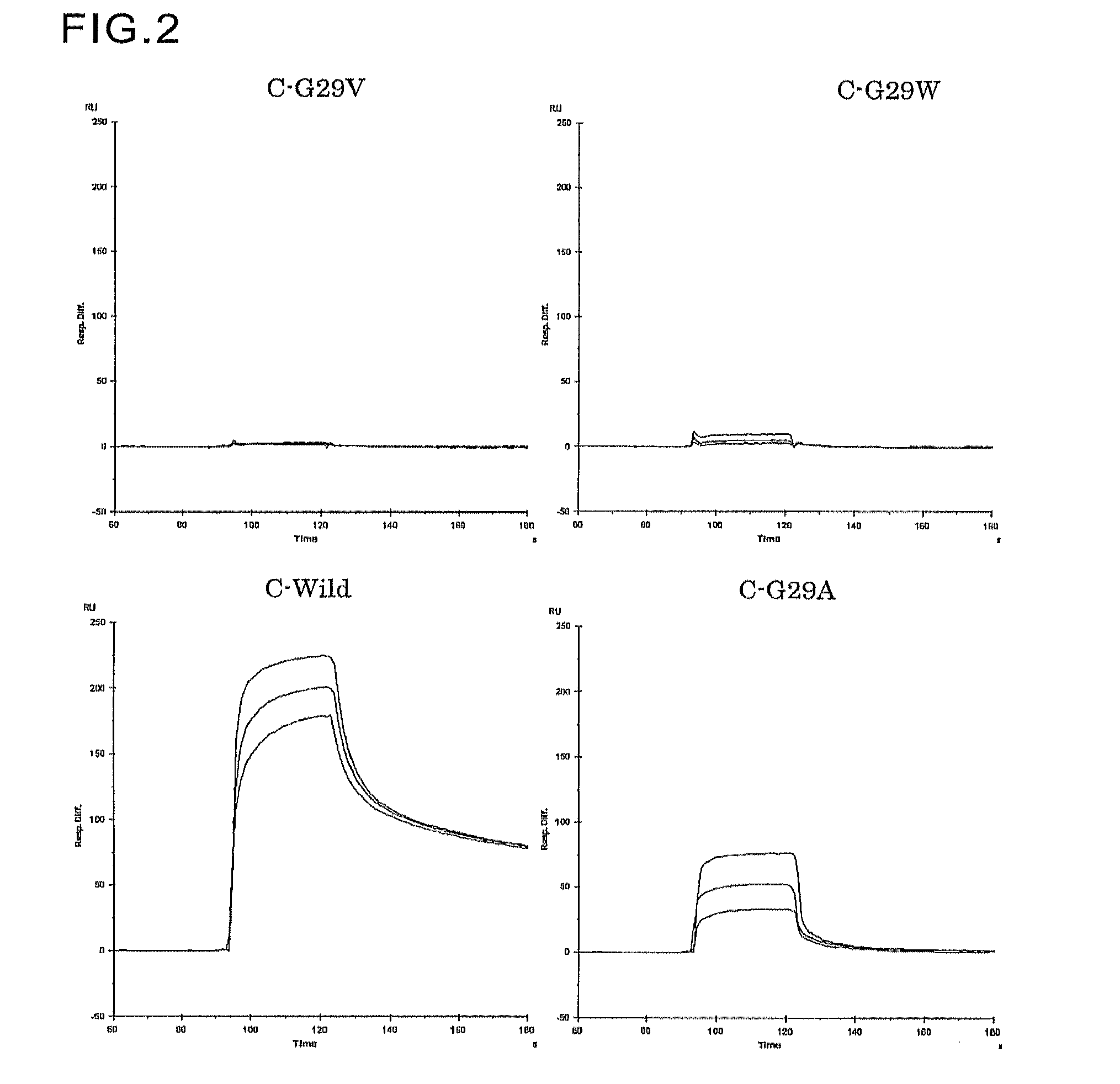
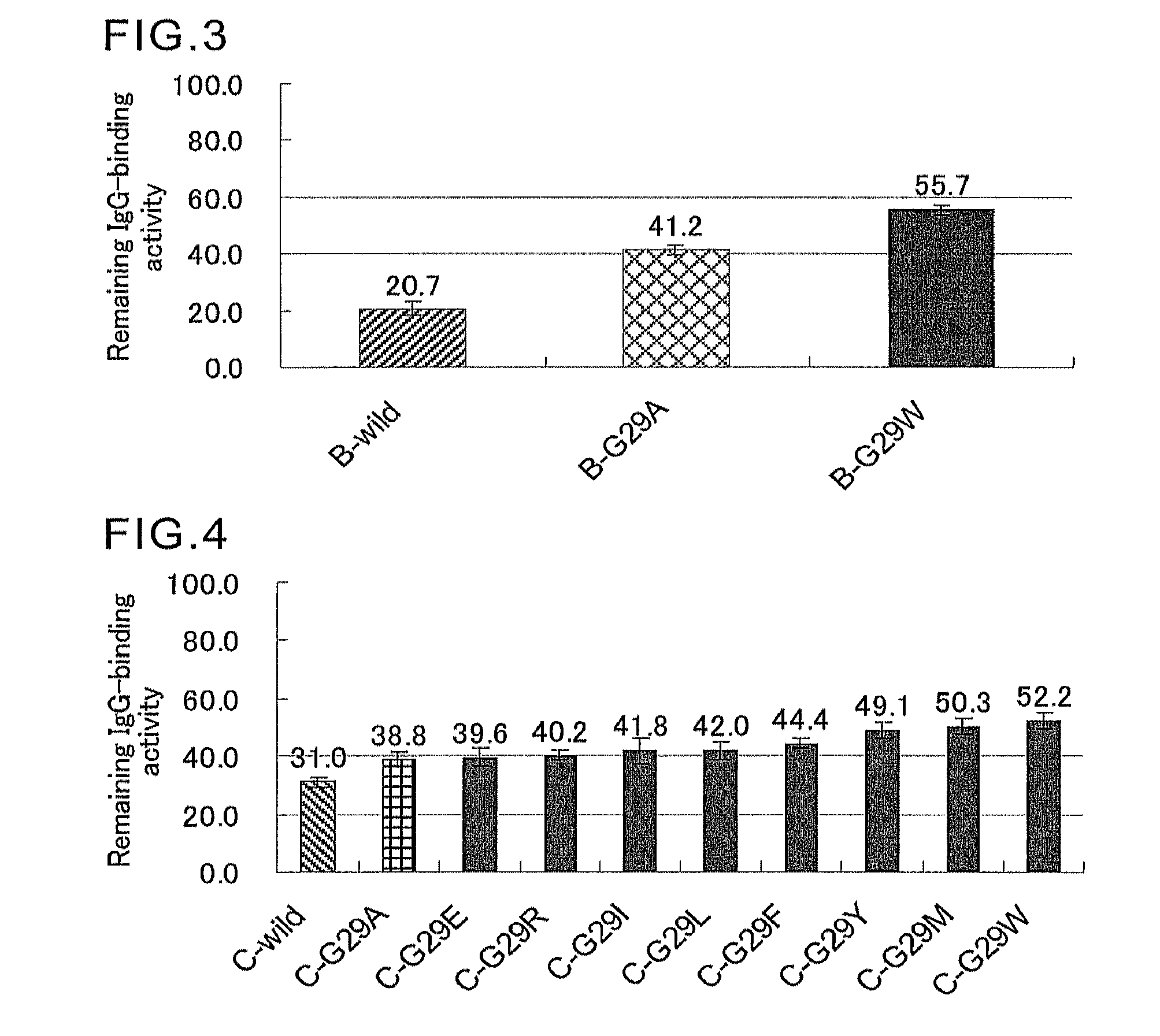
An object of the present invention is to create a novel engineered Protein A ligand having better antibody dissociation properties in the presence of an acid than conventional engineered Protein A ligands and a further object of the present invention is to create a novel engineered Protein A ligand having higher alkali resistance. The present invention is to provide a protein having an affinity for an immunoglobulin, including an amino acid sequence derived from any of E, D, A, B and C domains of Protein A, wherein at least one Gly residue in the amino acid sequence is replaced with an amino acid other than Ala, and the protein has a lower affinity for an Fab region of an immunoglobulin than a protein including an amino acid sequence in which the Gly residue is replaced with Ala. Also, the present invention is to provide the protein having an affinity for an immunoglobulin, which has improved chemical stability in an alkaline condition compared to the corresponding domain.
Owner:KANEKA CORP
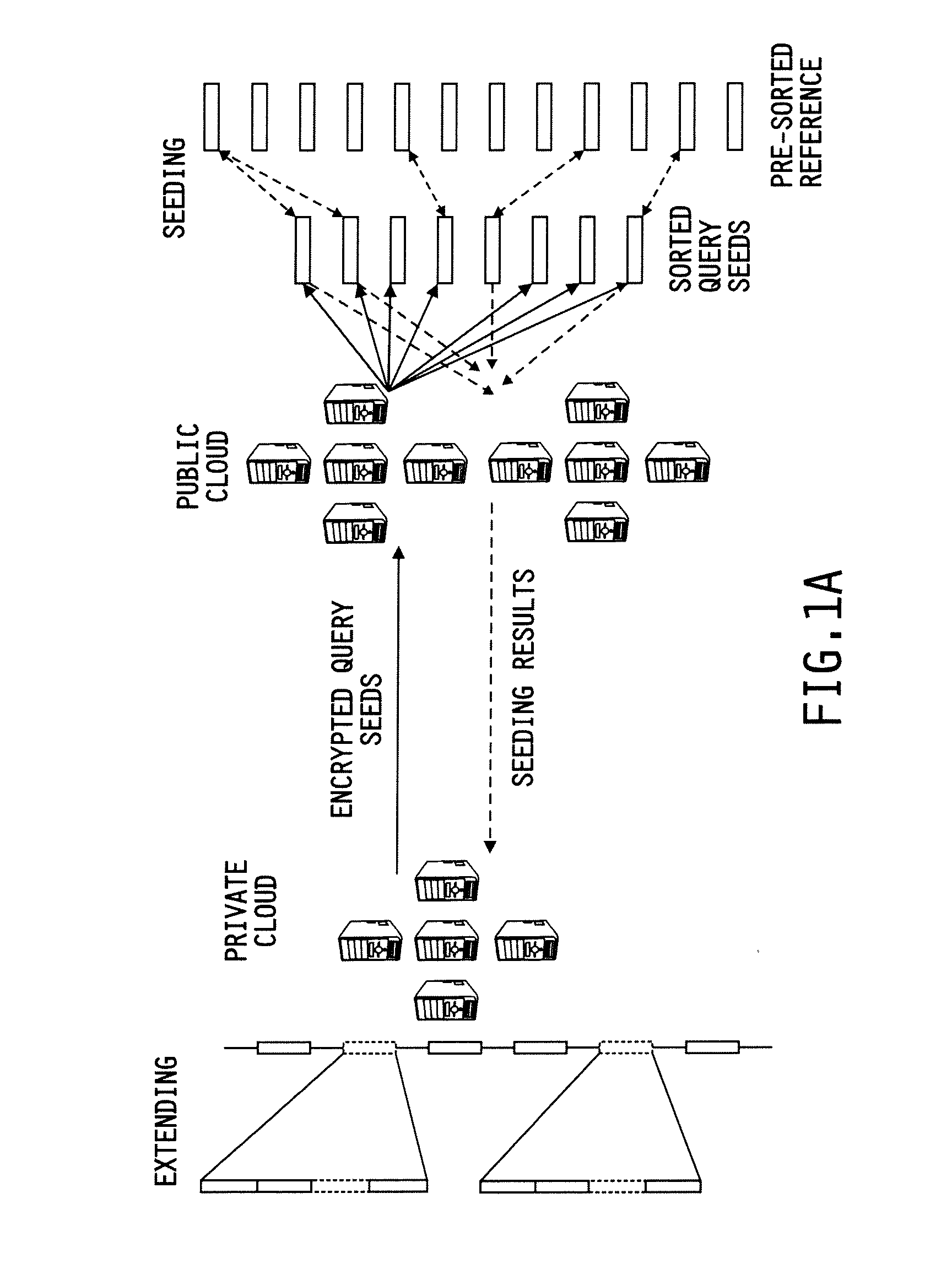
Secure and scalable mapping of human sequencing reads on hybrid clouds
ActiveUS20140075183A1Improve privacy protectionLow costSequence analysisSecuring communicationPhacusPrivacy protection
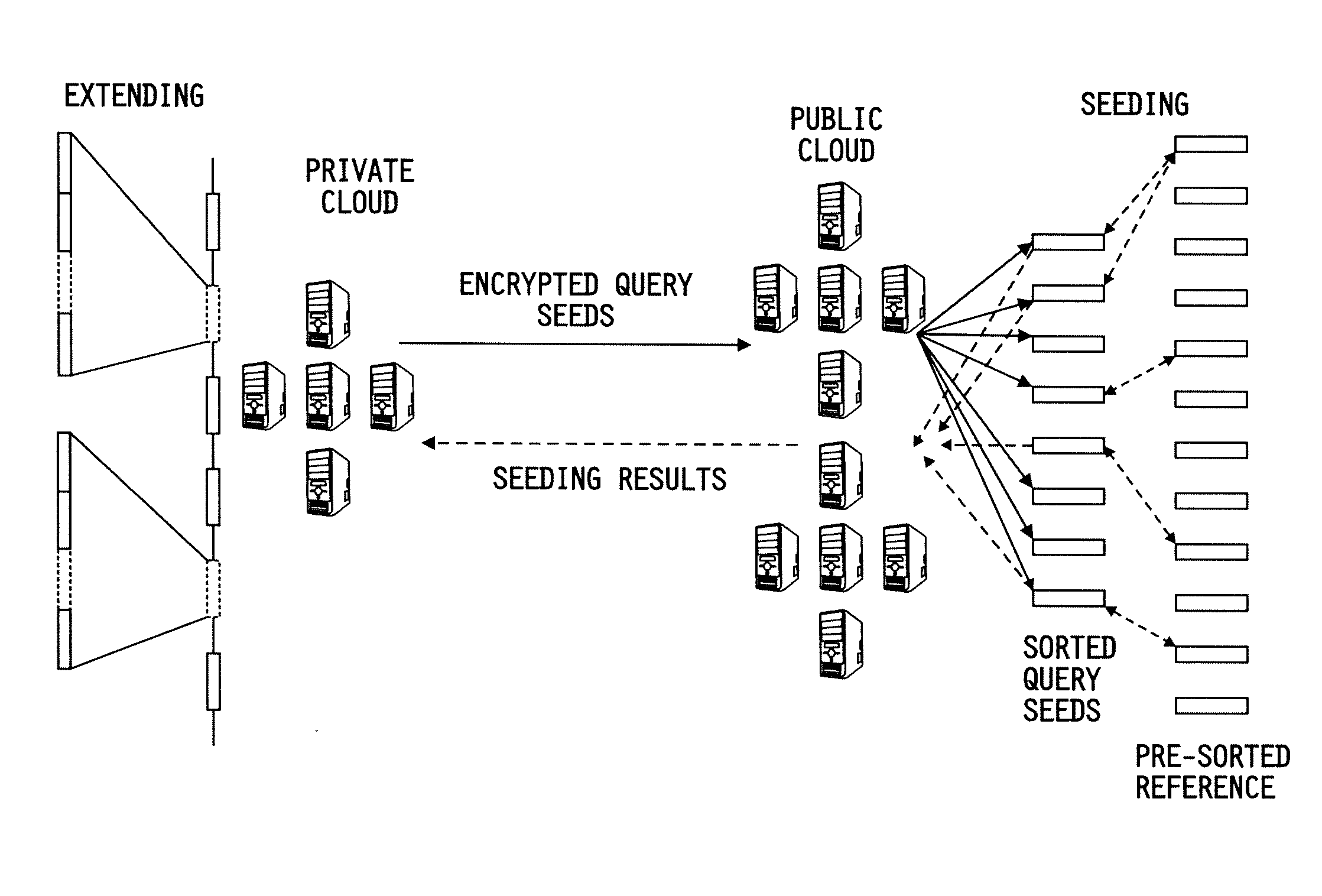
System and methods are provided for performing privacy-preserving, high-performance, and scalable DNA read mapping on hybrid clouds including a public cloud and a private cloud. The systems and methods offer strong privacy protection and have the capacity to process millions of reads and allocate most of the workload to the public cloud at a small overall cost. The systems and methods perform seeding on the public cloud using keyed hash values of individual sequencing reads' seeds and then extend matched seeds on the private cloud. The systems and methods are designed to move the workload of read mapping from the extension stage to the seeding stage, thereby ensuring that the dominant portion of the overhead is shouldered by the public cloud.
Owner:INDIANA UNIV RES & TECH CORP
Method and apparatus for intent prediction and proactive service offering
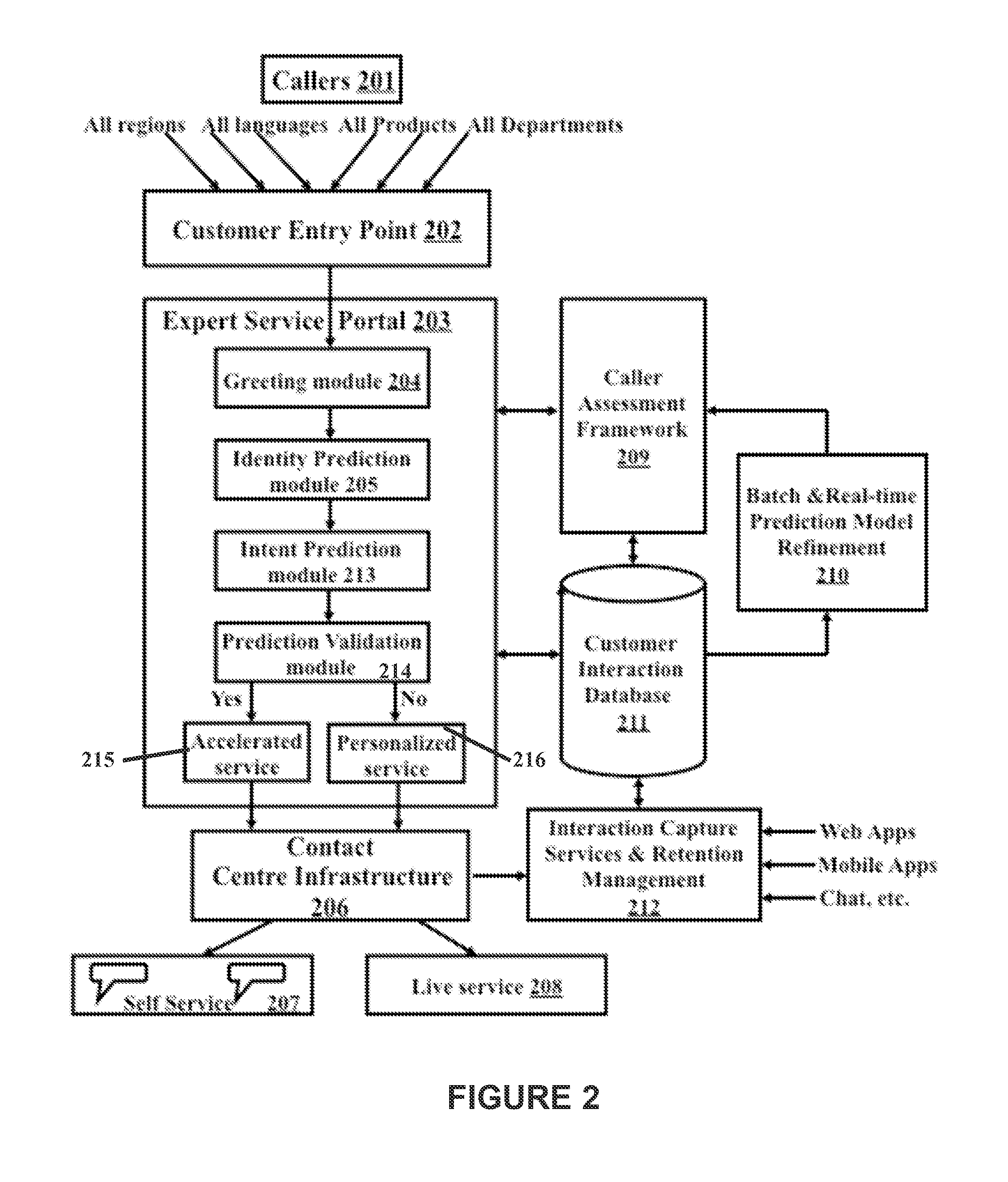
ActiveUS20140044243A1Improve identityPredict in advanceAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesPersonalization serviceCustomer engagement
An intelligent IVR system identifies a customer based on previous customer interactions. Customer intent is predicted for an ongoing interaction and personalized services are proactively offered to the customer. A self-optimizing algorithm improves intent prediction, customer identity, and customer willingness to engage and use IVR.
Owner:24 7 AI INC
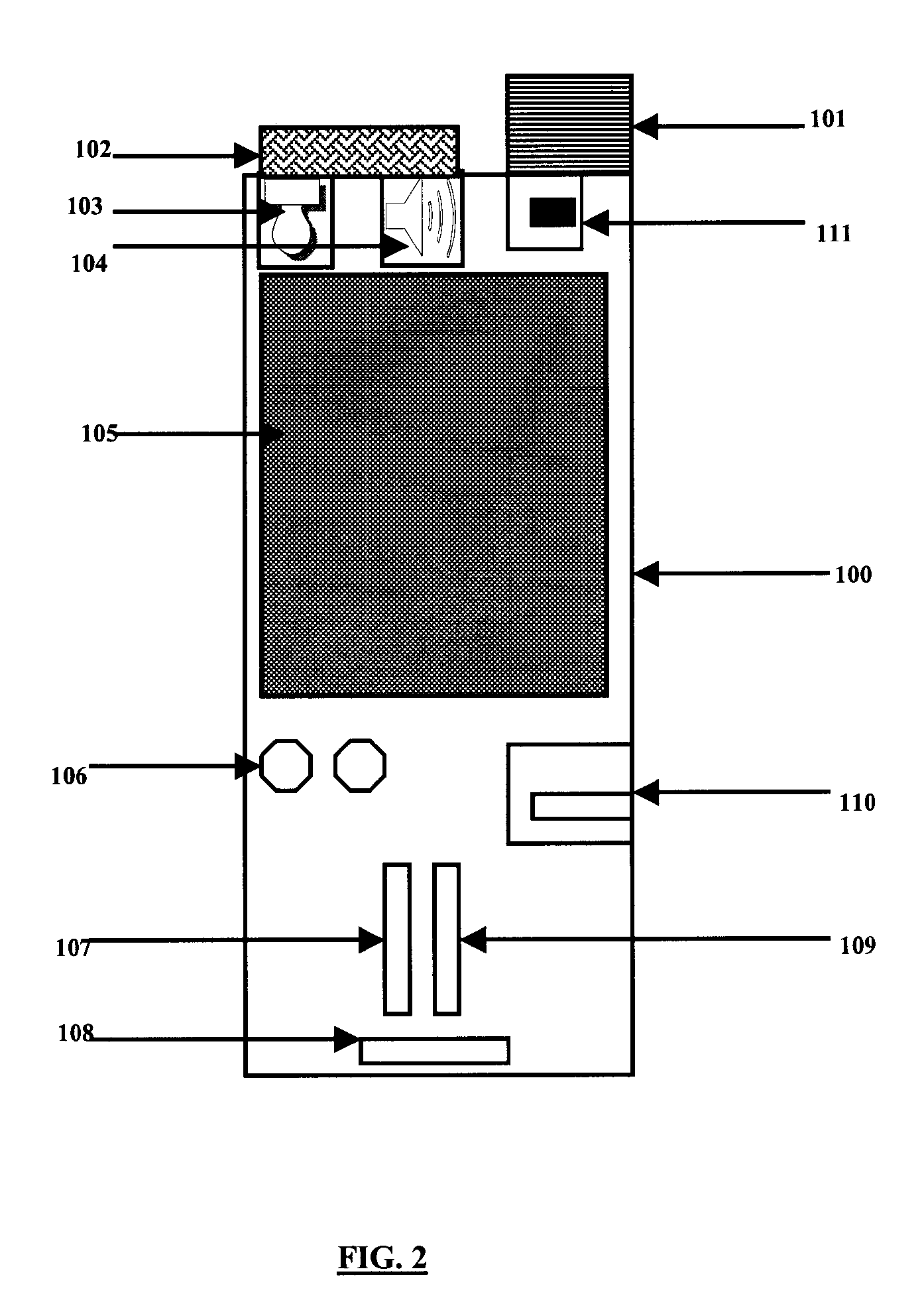
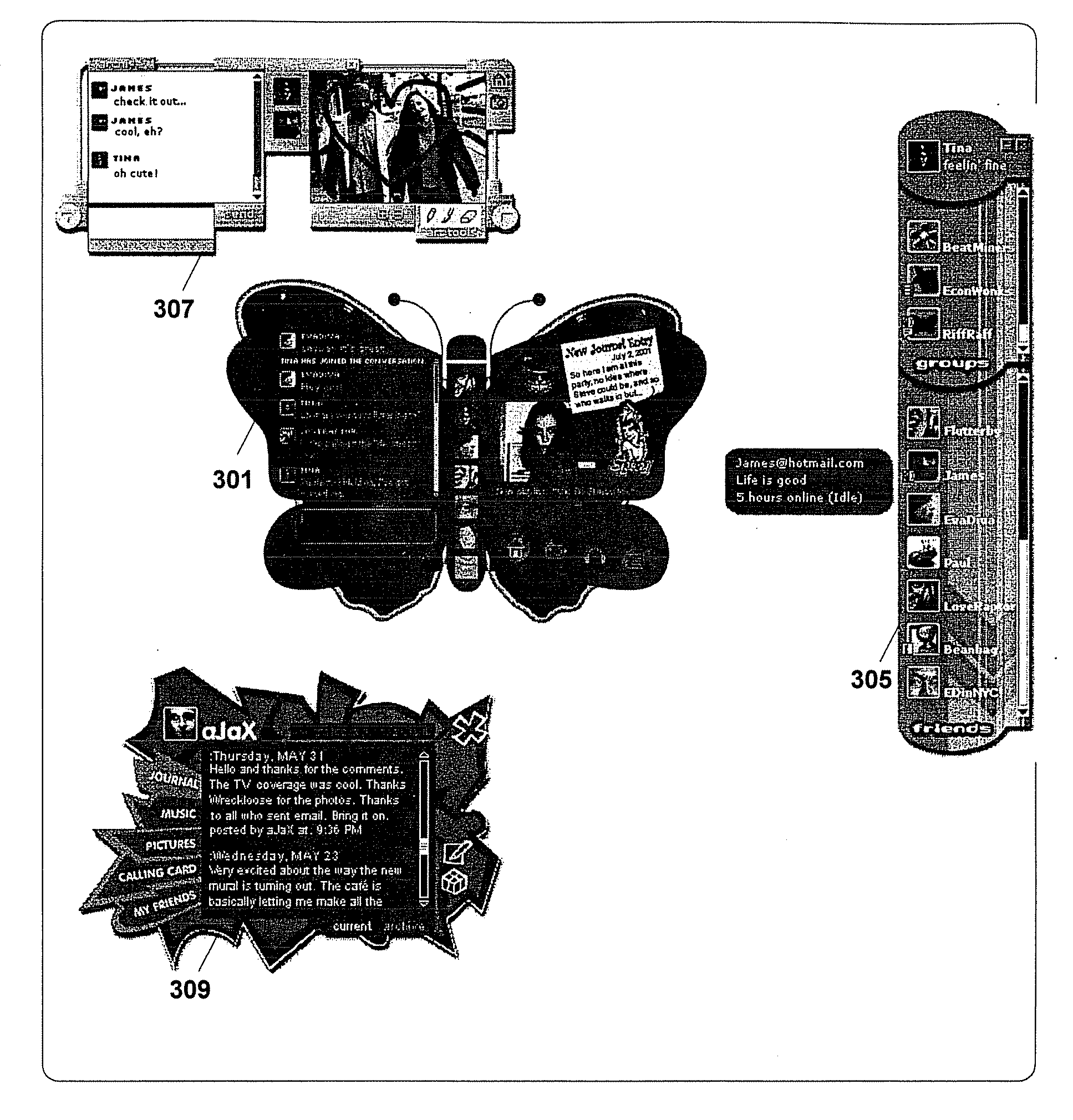
Intergrated experience of vogue system and method for shared intergrated online social interaction
InactiveUS20060190829A1Enhanced interactionImprove identityOffice automationAnimationModularityNetwork communication
A novel application and user interface for facilitating group interactions over a network integrates messaging, file sharing, media playing, journaling, profiles, and gaming into a cohesive environment. The groups facilitated by the invention are persistent and mobile in that a user does not have to recollect and reconfigure the group each time he or she wants to interact with the group online and, while online, the group may be taken from one activity to another without having to disband and reconnect at the second activity. The application is modular so as to be extensible to include other activities and functionalities. In an embodiment, the group interaction application utilizes a peer-to-peer network environment to facilitate network communications between group members.
Owner:MICROSOFT TECH LICENSING LLC
Relationship collaboration system
ActiveUS7849103B2Improve identityData processing applicationsWeb data indexingComputer databaseData science
A computer implemented method of processing data containing information about relationships between contacts and a community of contact owners, includes: collecting data having contact information, contact owner information and one or more values related to the strength of a relationship between the contact and the contact owner; evaluating the strength of the relationship based on the one or more values; and storing the collected data and evaluated strength in a computer database.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
Intelligent online personal assistant with offline visual search database
ActiveUS20180107685A1Improve identityMathematical modelsCharacter and pattern recognitionVisual comparisonImaging analysis
Systems, methods, and computer program products for identifying a candidate product in an electronic marketplace based on a visual comparison between candidate product image visual content and input query image visual content. Embodiments generate and store descriptive image signatures from candidate product images or selected portions of such images. A subsequently calculated visual similarity measure serves as a visual search result score for the candidate product in comparison to an input query image. Any number of images of any number of candidate products may be analyzed, such as for items available for sale in an online marketplace. Image analysis results are stored in a database and made available for subsequent automated on-demand visual comparisons to an input query image. The embodiments enable substantially real time visual based product searching of a potentially vast catalog of items.
Owner:EBAY INC
Selecting next user prompt types in an intelligent online personal assistant multi-turn dialog
PendingUS20180052913A1Improve identityDigital data information retrievalKnowledge representationDialog systemUser input
Systems and methods for selecting types of generated prompts for further data from a user in a multi-turn interactive dialog. In one scenario, a processed sequence of user inputs and machine-generated prompts improves searches for the most relevant items available for purchase in an electronic marketplace. The number of prompts may be limited to a predetermined maximum value. Prompt generation is minimized by incorporating into a knowledge graph world knowledge that helps user intent inference. Prompt generation may be suppressed if a search indicates the reply to a prompt will not lead to any satisfactory search results. Prompts can provide suggestions for available search results that either meet all query constraints, or meet only some query constraints if a search indicates no search results are available that meet all query constraints. Prompts can provide suggested incisive reply phrasing likely to improve search results through an affirmation or negation reply.
Owner:EBAY INC
Equine herpesvirus glycoproteins
InactiveUS6193983B1Improve identityPeptide/protein ingredientsGenetic material ingredientsHerpes simplex virus DNAEquine herpesvirus
A vaccine for the selective immunization of horses against EHV4 and / or EHV1 is provided comprising at least one of (i) EHV4 virus wherein a portion of the gG gene of the EHV4 virus that elicits a type-specific response to EHV4 has been deleted and (ii) EHV1 virus wherein a portion of the gG gene of the EHV1 virus that elicits a type-specific response to EHV1 has been deleted. Antibodies which specifically bind to a epitopes of EHV4 gG or EHV1 also are provided.
Owner:UNIVERSITY OF MELBOURNE
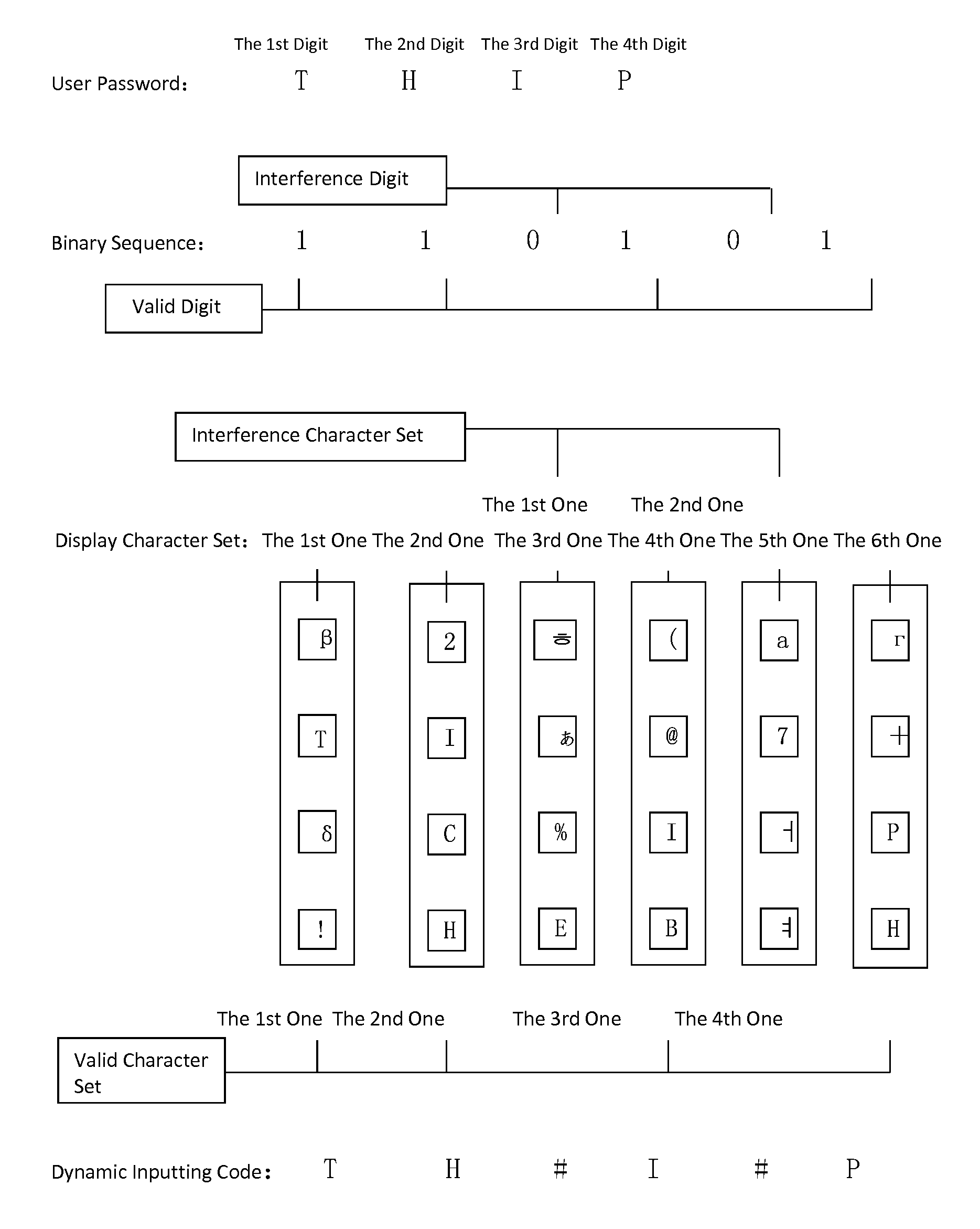
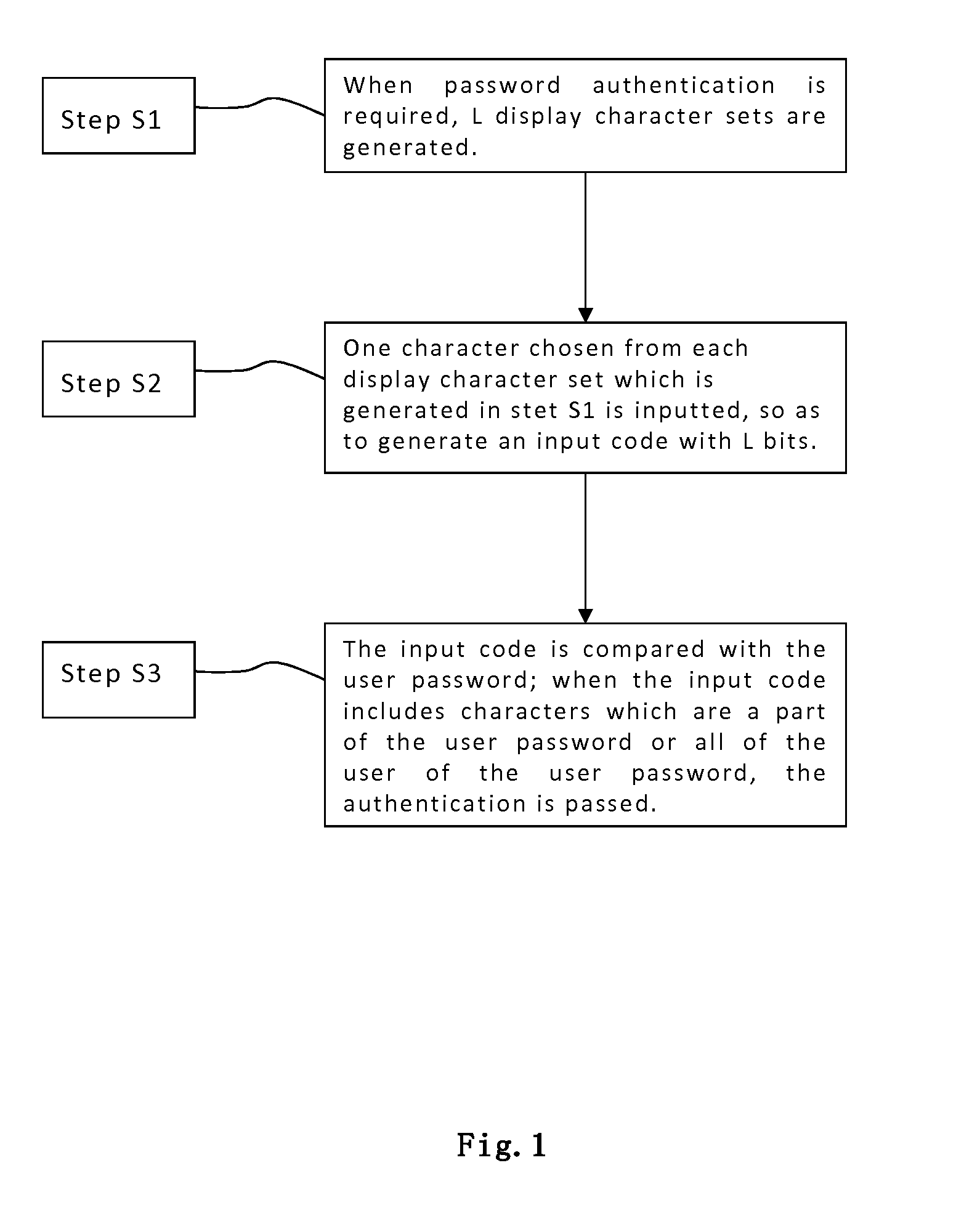
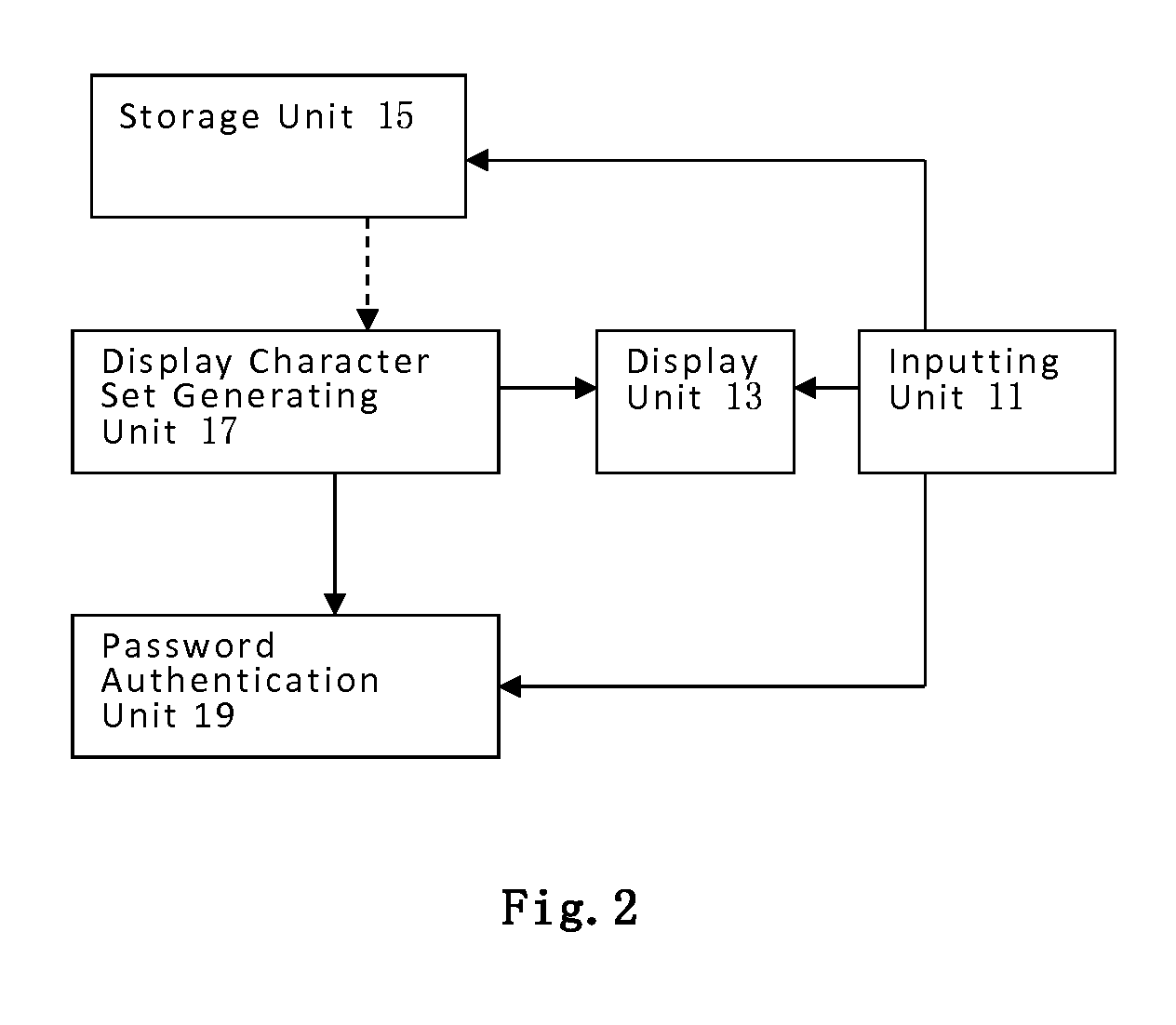
Dynamic interactive identity authentication method and system
ActiveUS20140101744A1Improve securityEasy to useDigital data processing detailsMultiple digital computer combinationsPasswordAuthentication system
An identity authentication system includes a storage unit, a display character set generation unit, a display unit and a password authentication unit. An identity authentication method includes the following steps: generating the dynamic display character sets; inputting a dynamic input code; and comparing the dynamic input code with the user password. This invention can improve the security of identity authentication and is convenient to use.
Owner:LIU YINGJIE
Mediated order management agent
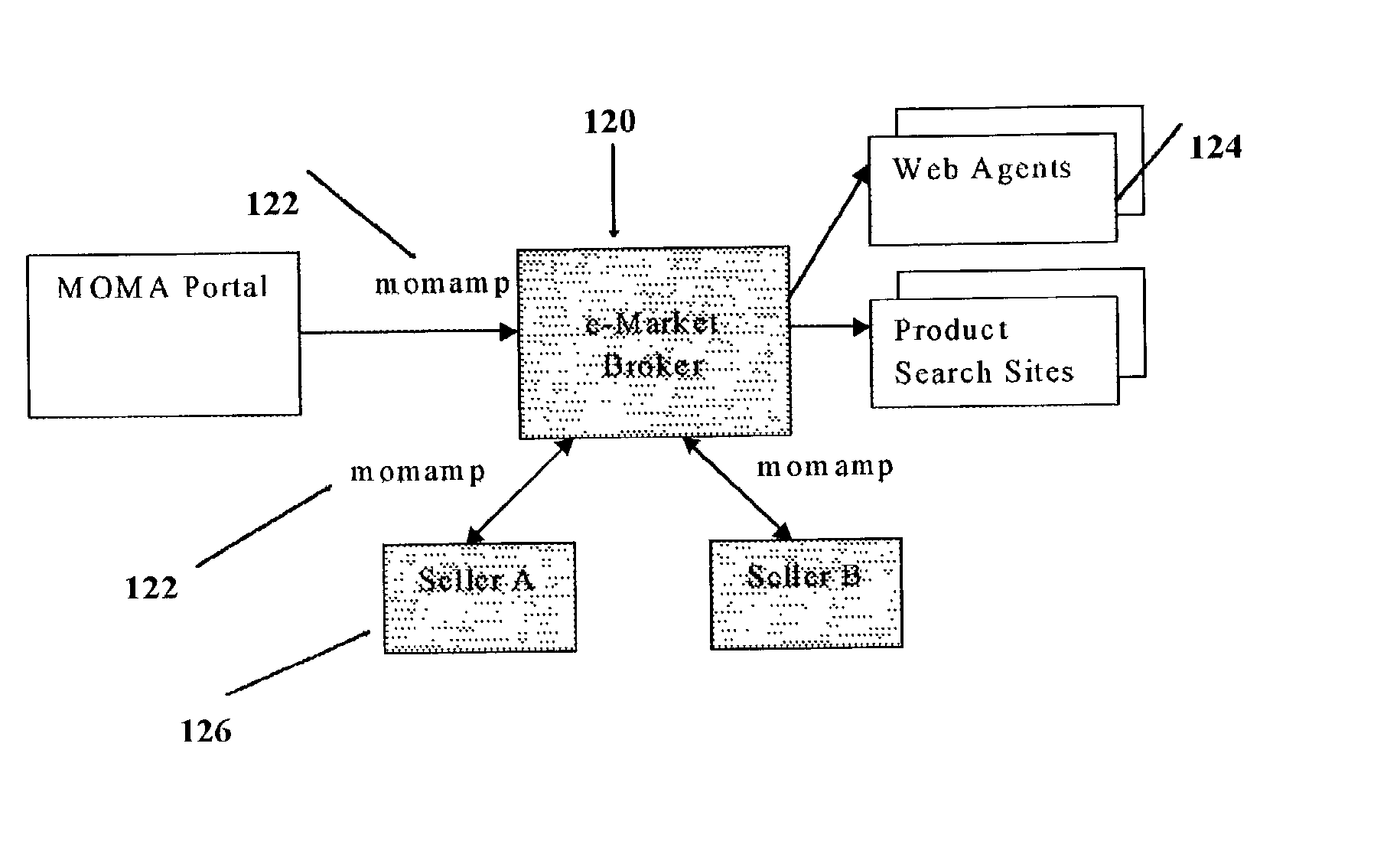
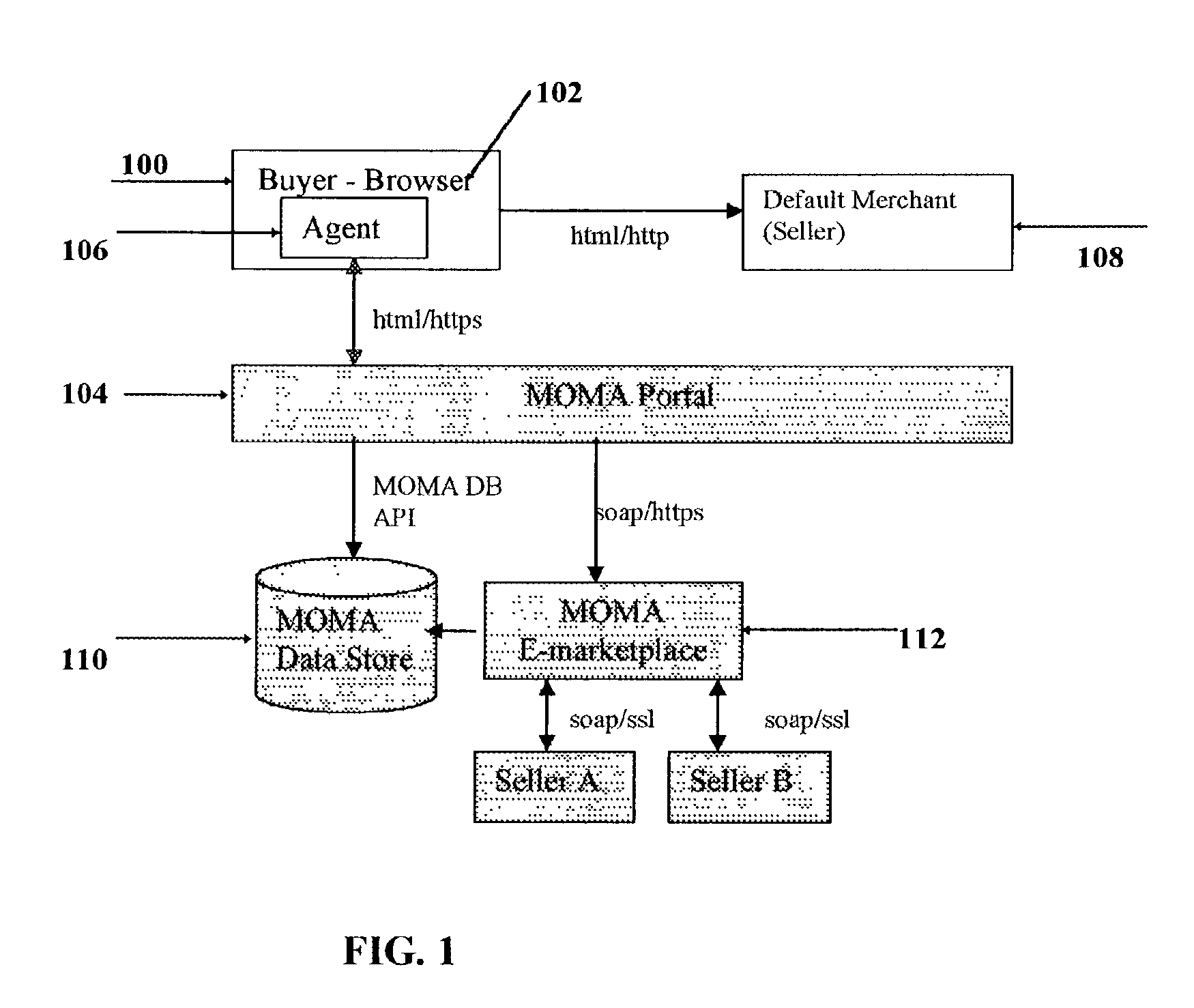
InactiveUS20030115111A1Low costImprove the environmentBuying/selling/leasing transactionsSpecial data processing applicationsThe InternetNetwork on
This invention pertains to a method, system, on-line service and software for on-line e-commerce. One preferred embodiment of the invention is a method, system, and on-line service, offered on a public network such as the Internet, for mediating a buyer's interaction with a first seller chosen by the buyer by observing when the buyer has indicated the intent to purchase an item at a first purchase price, seeking to obtain the item from alternative sellers at a lower price and obtaining one or more alternative bids, comparing the one or more alternative bids and the first purchase price according to pre-established rules, selecting a best offer, and completing the purchase of the best offer without further intervention of the buyer.
Owner:FISHER DOUGLAS C
Methods and systems for protection of identity
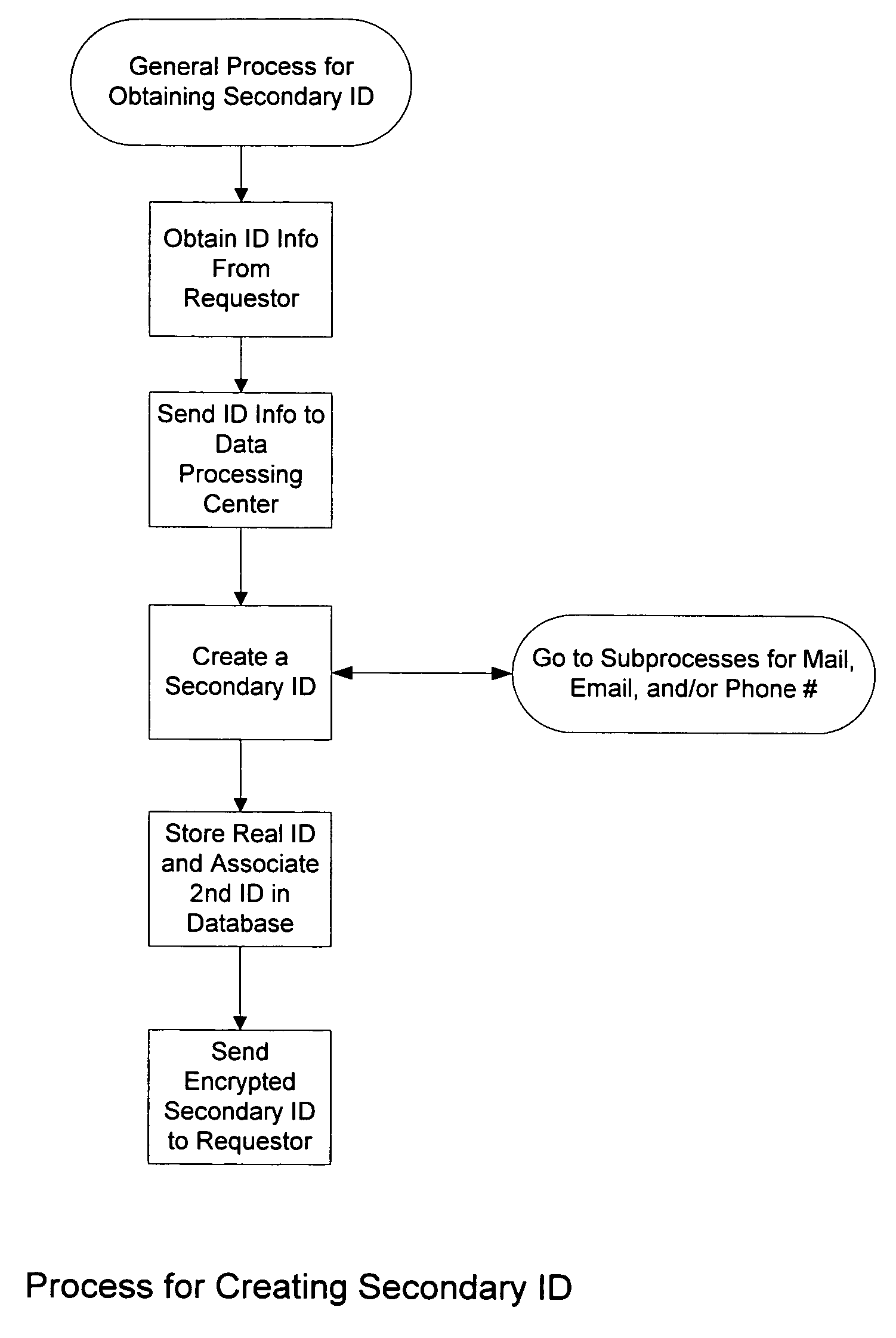
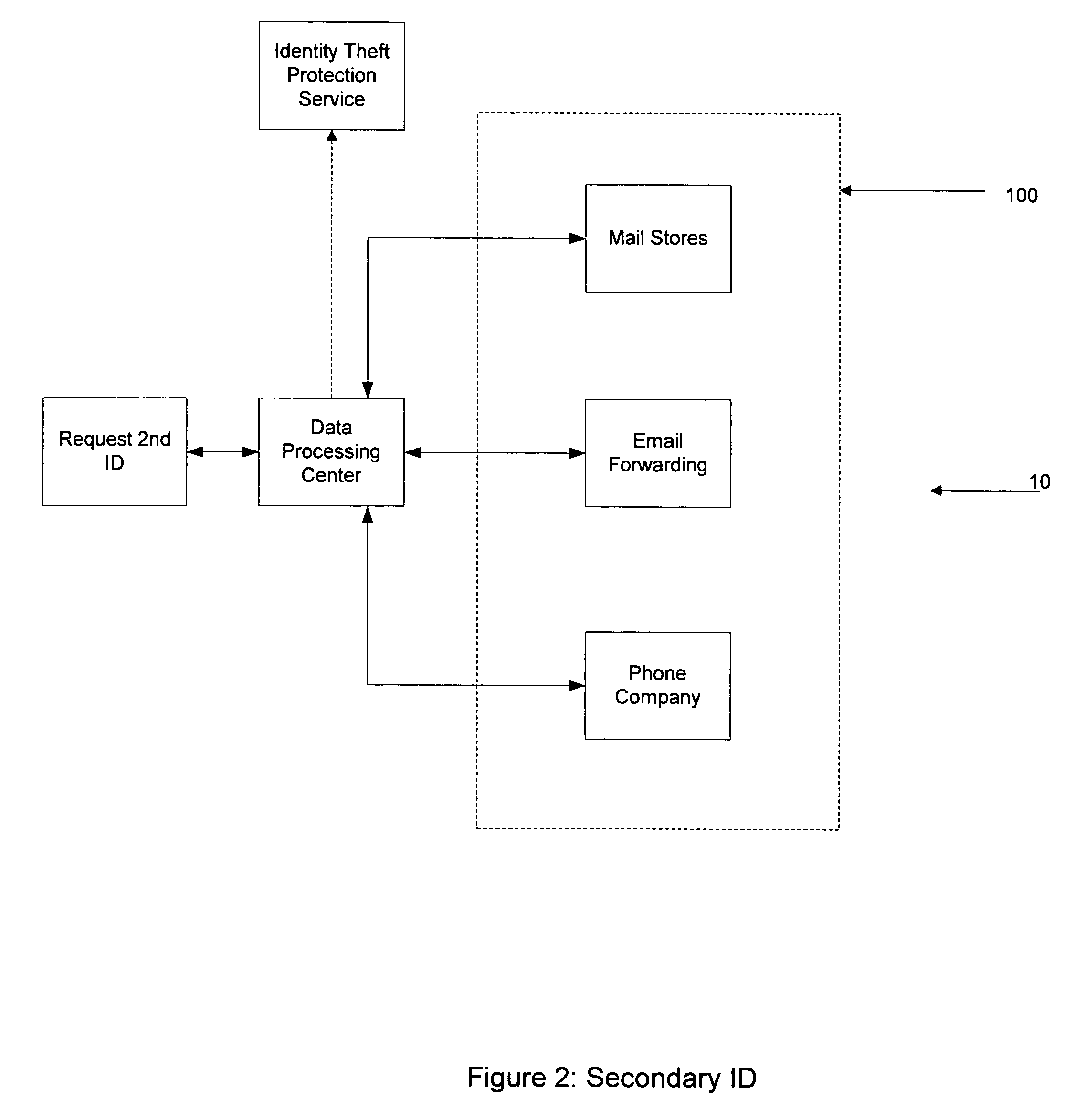
InactiveUS7689007B2Reduce harmImprove identityFinanceCharacter and pattern recognitionCredit cardEmail address
The present invention relates to a method to the creation and management of a secondary identification to avoid identify theft. Identity theft may occur over the internet, the purchase of goods and services by credit, and many other forms not yet known. The present invention creates a secondary identification for a person by creating one or more of the following secondary identifications which include a secondary email address, a secondary postal address, a secondary phone number, and any other identifying secondary information. The present invention describes methods and systems to create a secondary identification. Further, the present invention may be used to create a credit card containing the requestor's secondary identification.
Owner:SEAGATE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com