Patents
Literature
648results about How to "Shorten access time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
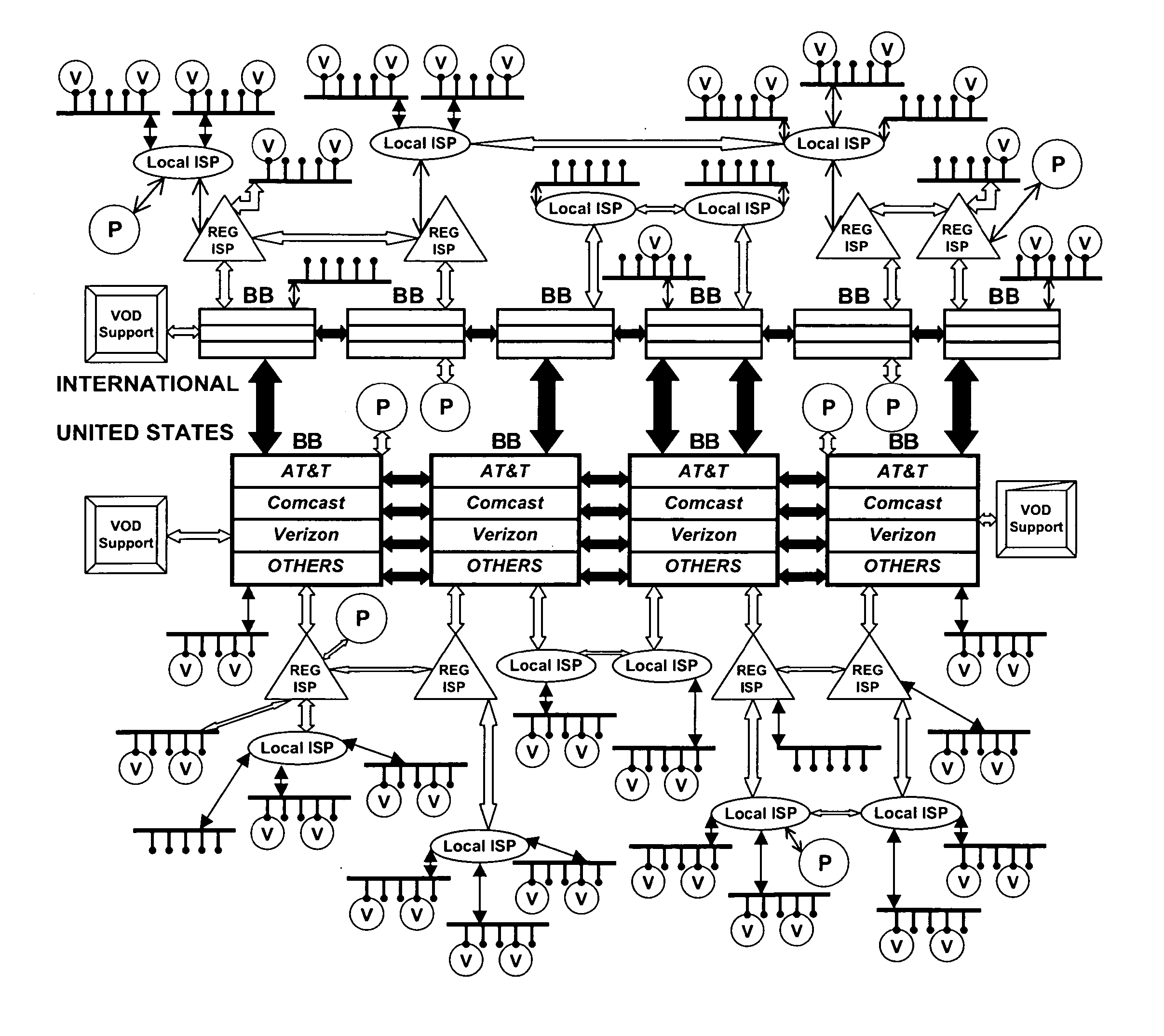
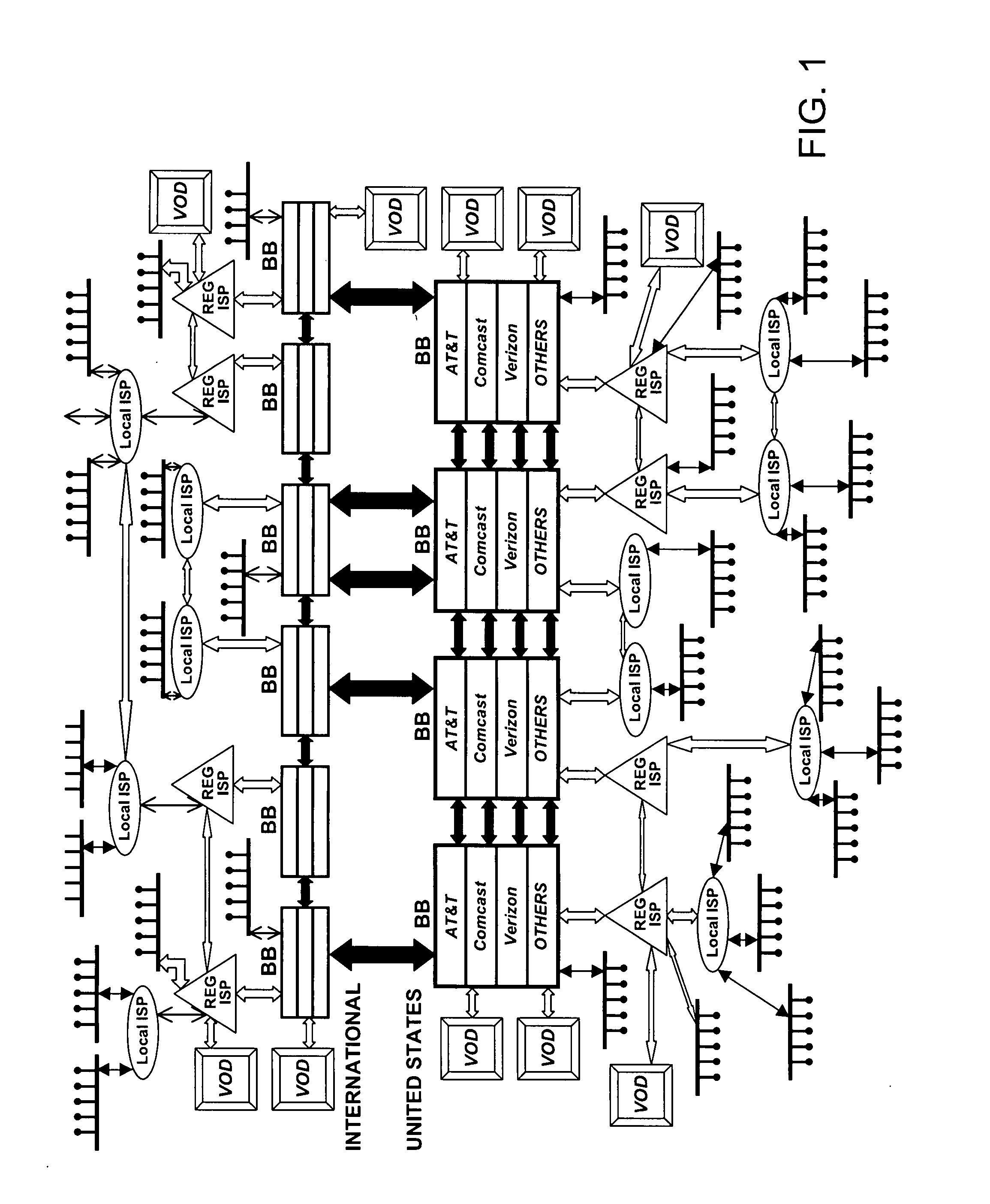
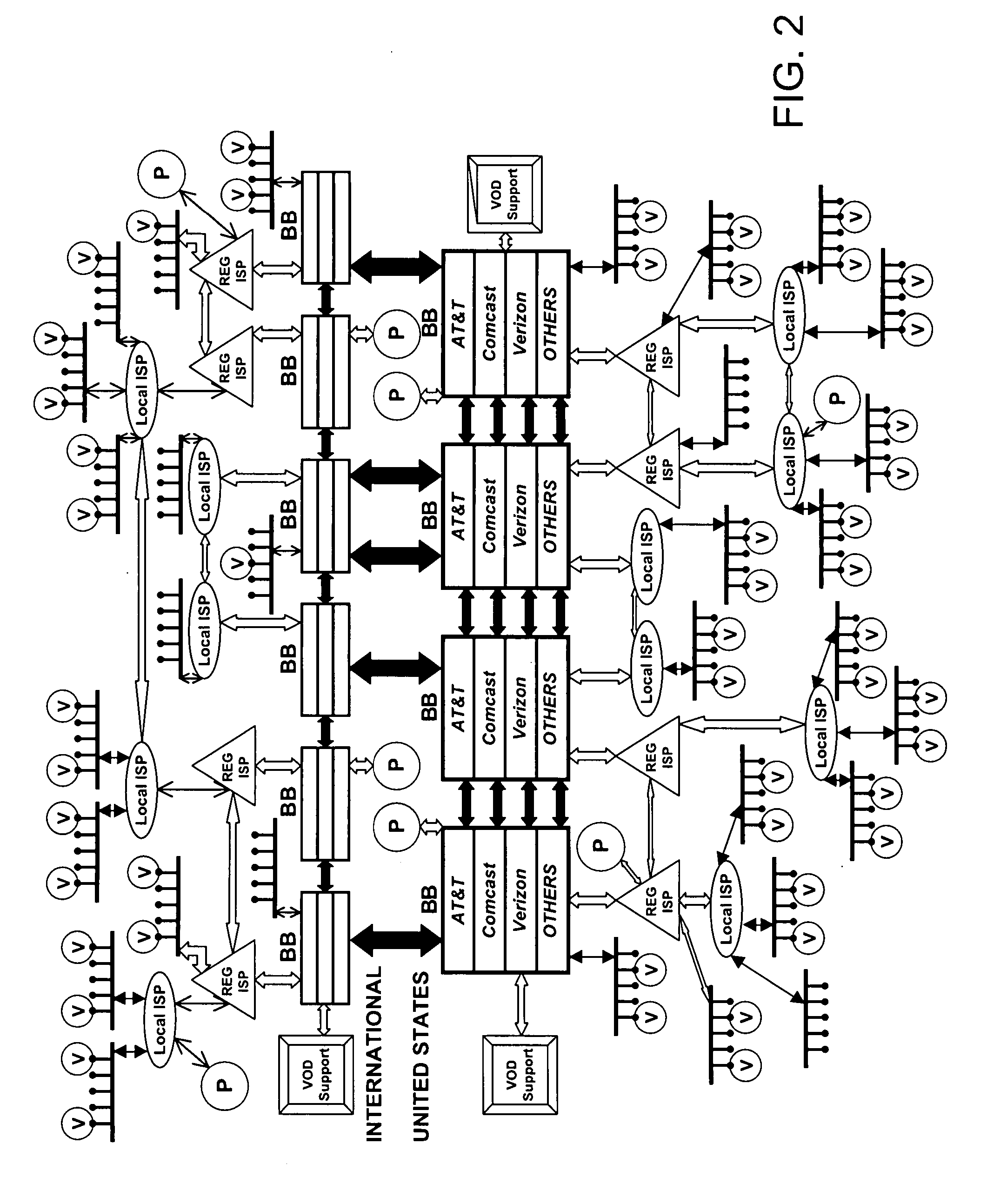
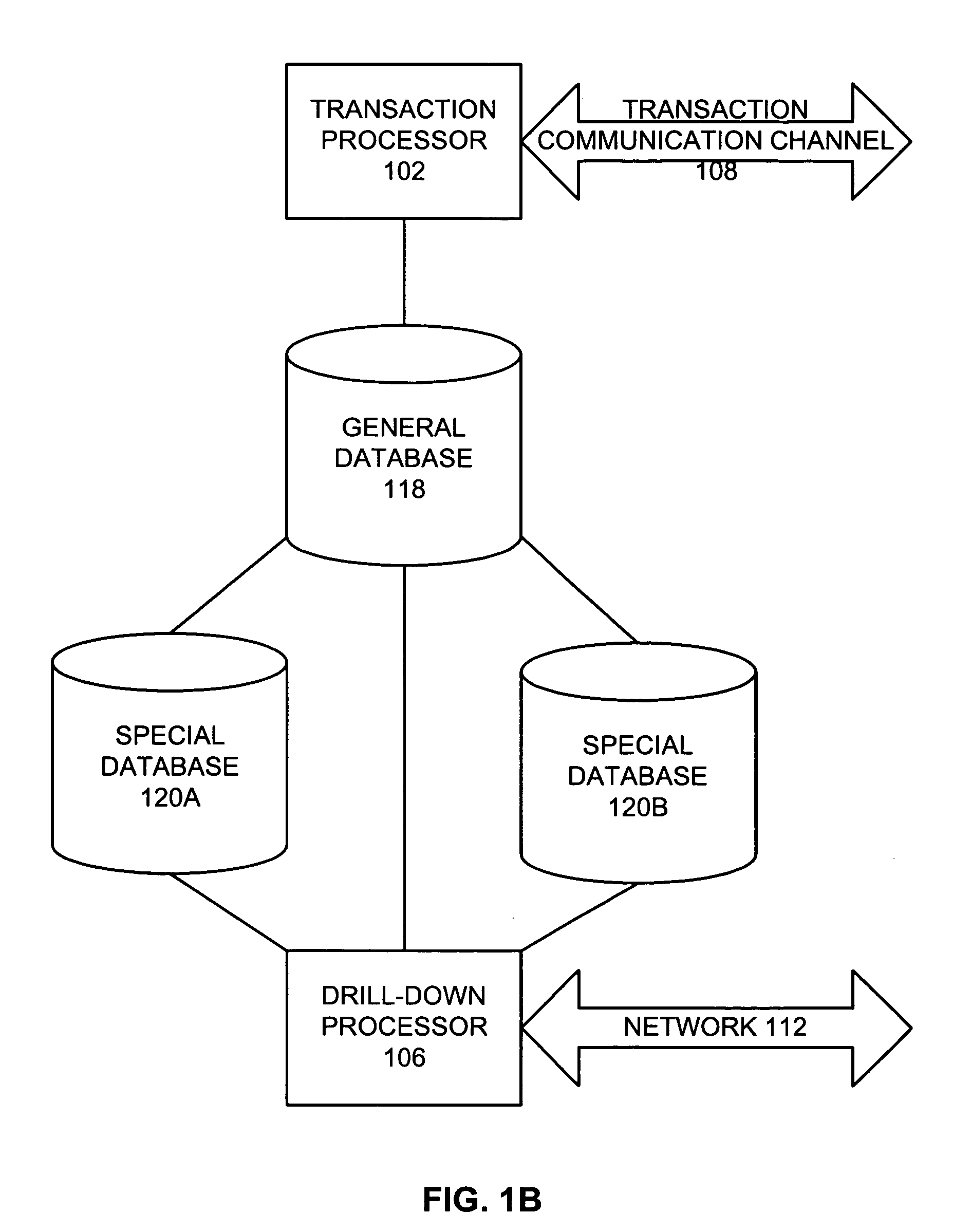
Push-Pull Based Content Delivery System
InactiveUS20080059631A1Maximize QoSImprove scalabilityDigital computer detailsTelevision systemsClosed loop feedbackPush pull
QoS is built into a peer network within existing Internet infrastructure itself lacking QoS, by enabling a network peer to continuously discern the network's ability to deliver to that peer a particular Content Object (distributed in groups of component Packages among neighboring VOD peers) within predetermined times. Content Objects are divided into groups of component Packages and distributed to Clusters of neighboring network peers, enhancing QoS upon subsequent retrieval. Tracking Files (lists of network peers storing Package groups) and Tracking Indexes (lists of network peers storing Tracking Files) are generated to facilitate “on demand” Content Objects retrieval. Dynamically monitoring network traffic (including VOD functionality, bandwidth and reliability) creates “distributed closed-loop feedback,” and in response, attributes of individual network peers (e.g., Trust Level and membership within a particular Cluster) are modified, and “content balancing” functions performed (e.g., redistribution of Package groups among network peers) enables maintaining high QoS.
Owner:VODDLER GRP
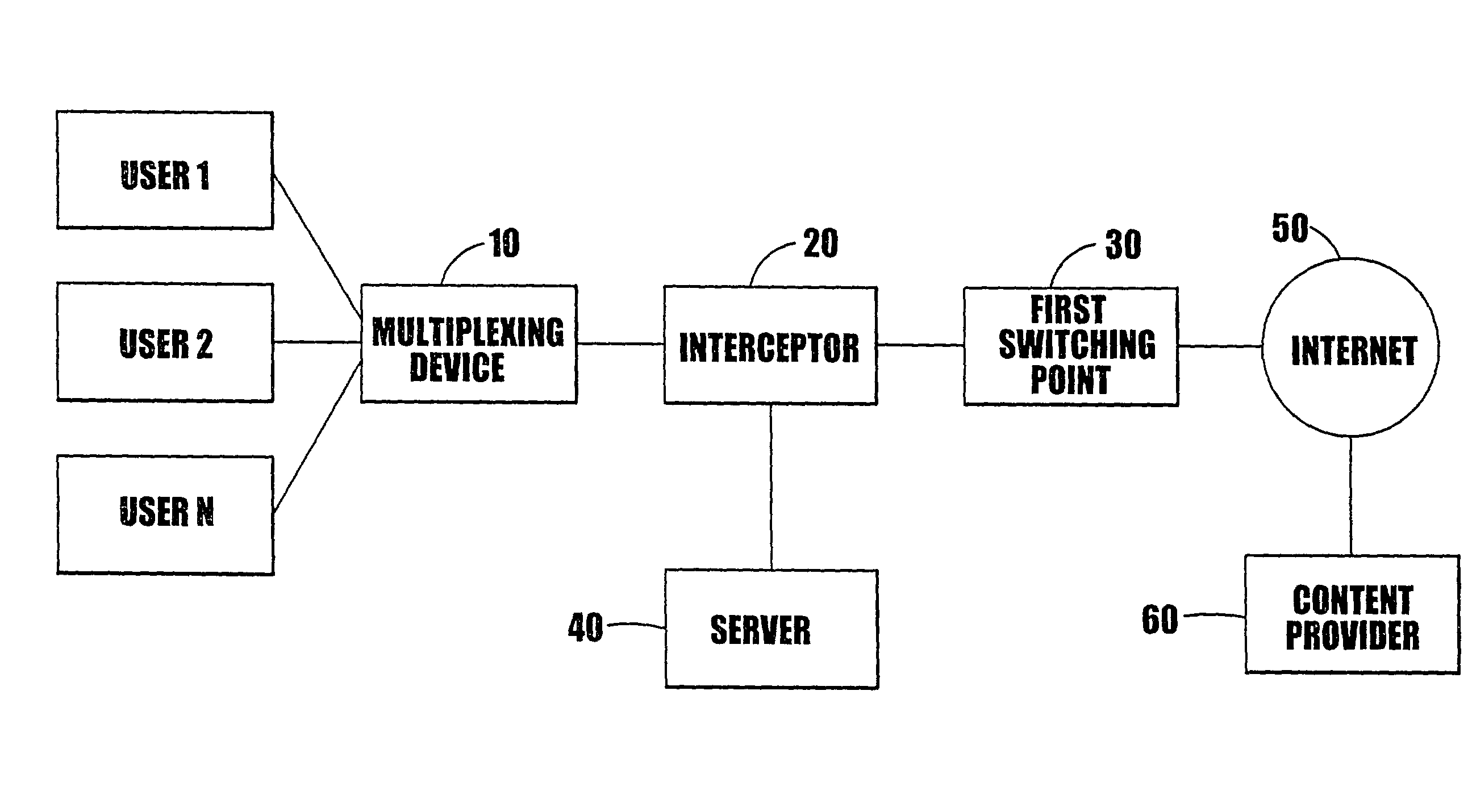
Internet communication system
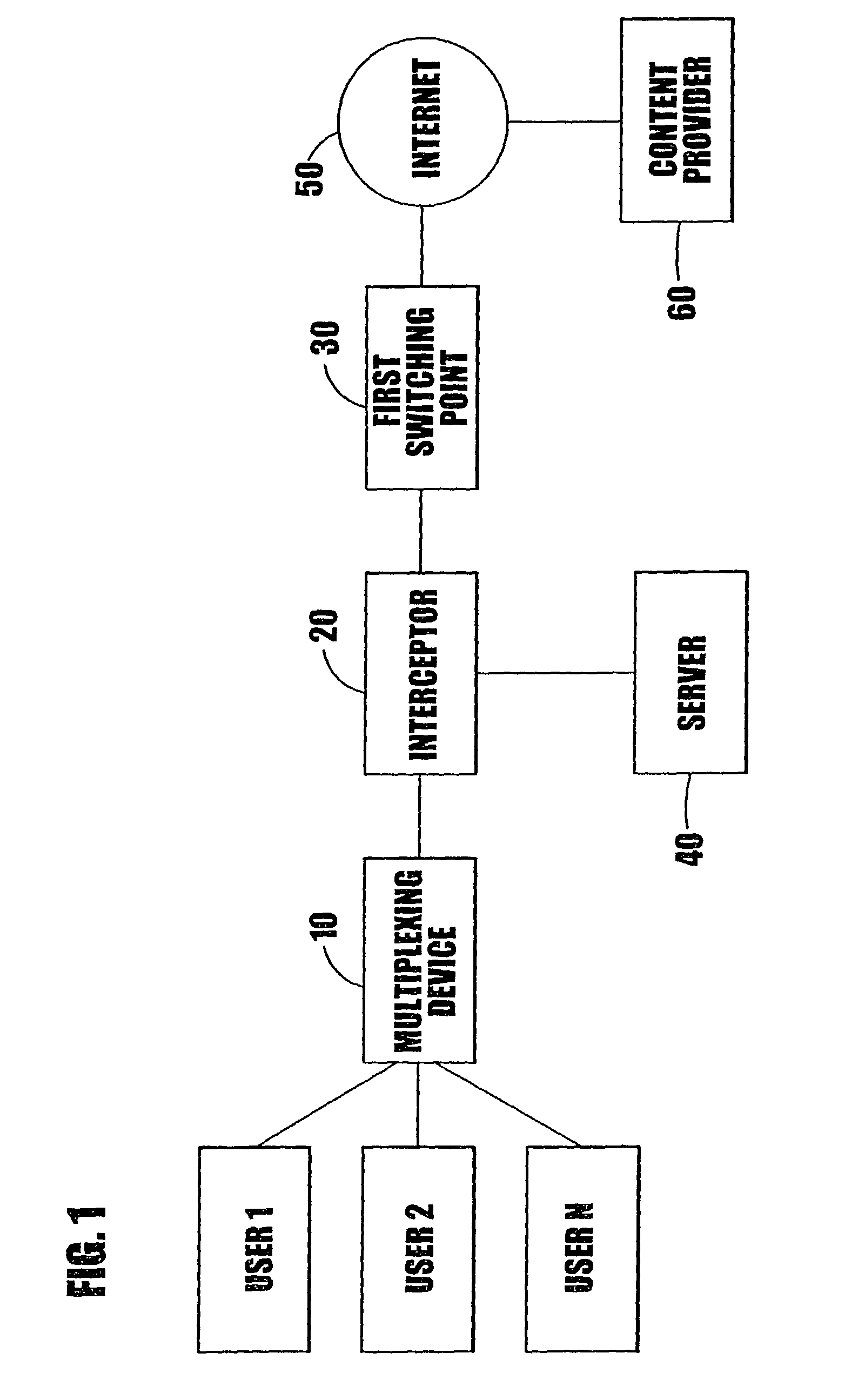
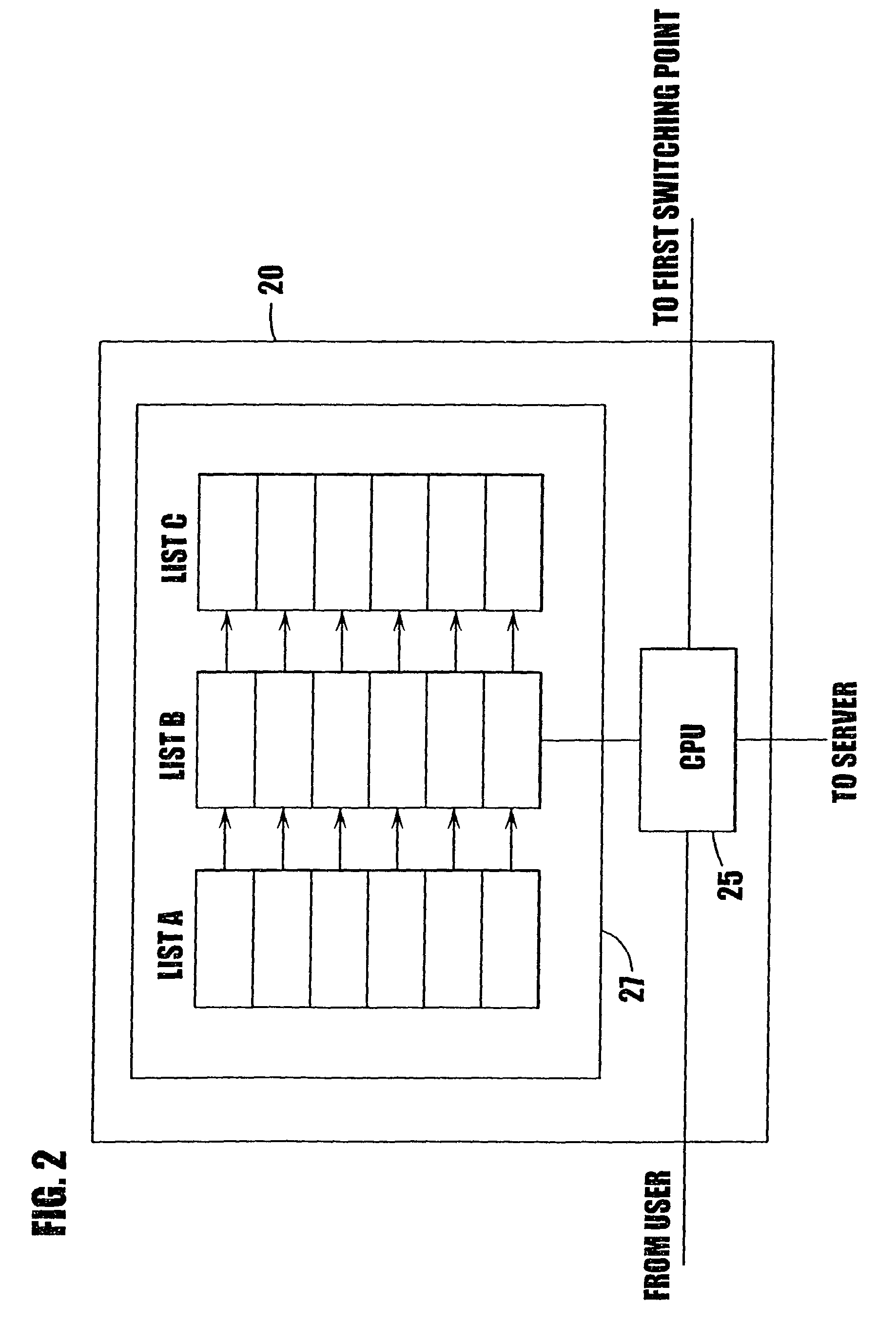
InactiveUS7739400B2Alleviate capacity constraintsShorten access timeMultiple digital computer combinationsElectric digital data processingInternet communicationInternet content
The present invention relates to the transferring of information on the Internet, comprising: means (40) for storing information, corresponding to information provided at an Internet content provider (60), at respective alternative addresses of said storing means; means (20) for intercepting an information request from an Internet user directed to an Internet content provider; means for determining whether or not the intercepted request is directed to an information content provider having an associated alternative address on said storing means (40); and means for directing the request to said alternative address if such an alternate address exists.
Owner:MIRROR IMAGE INTERNET INC
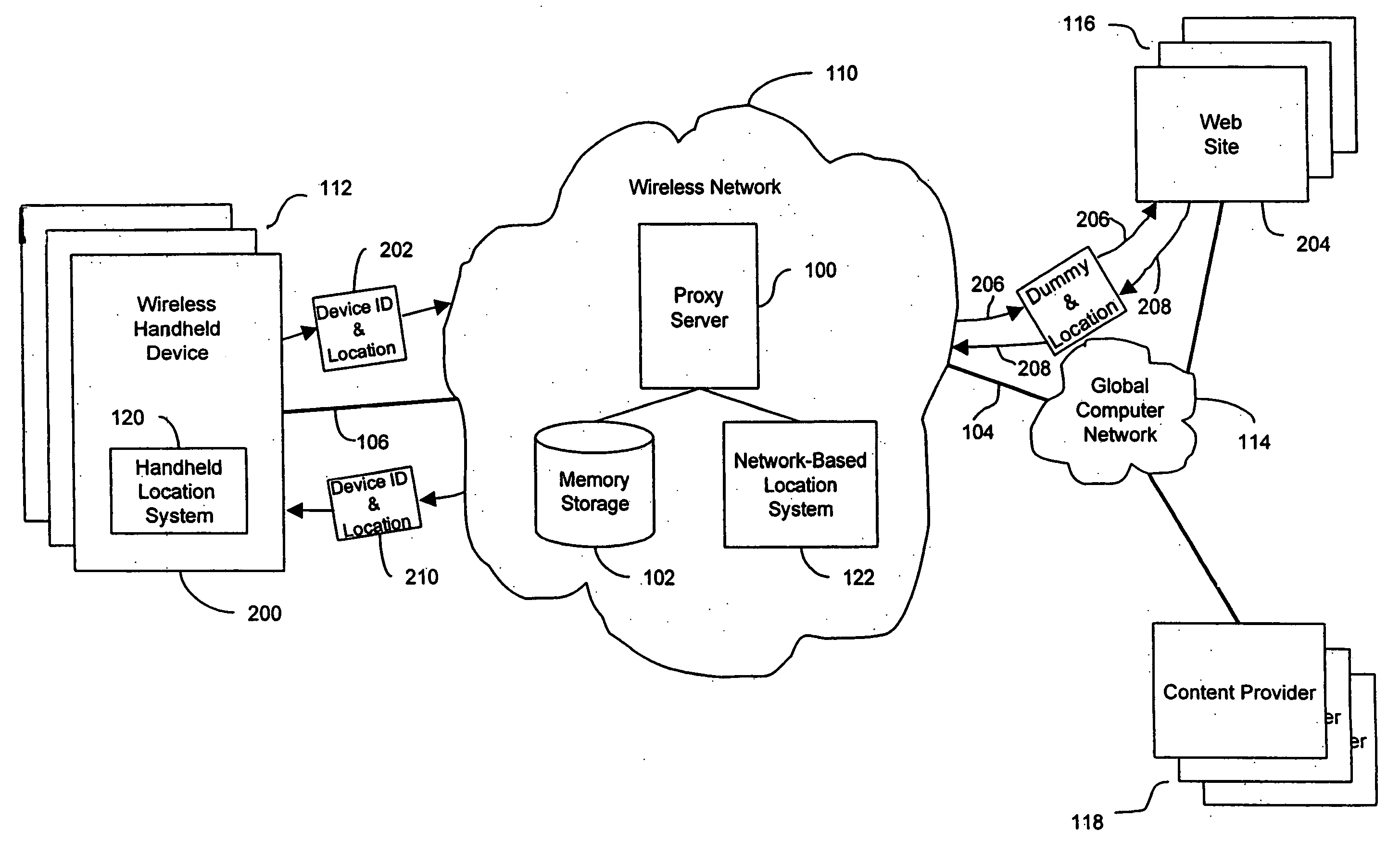
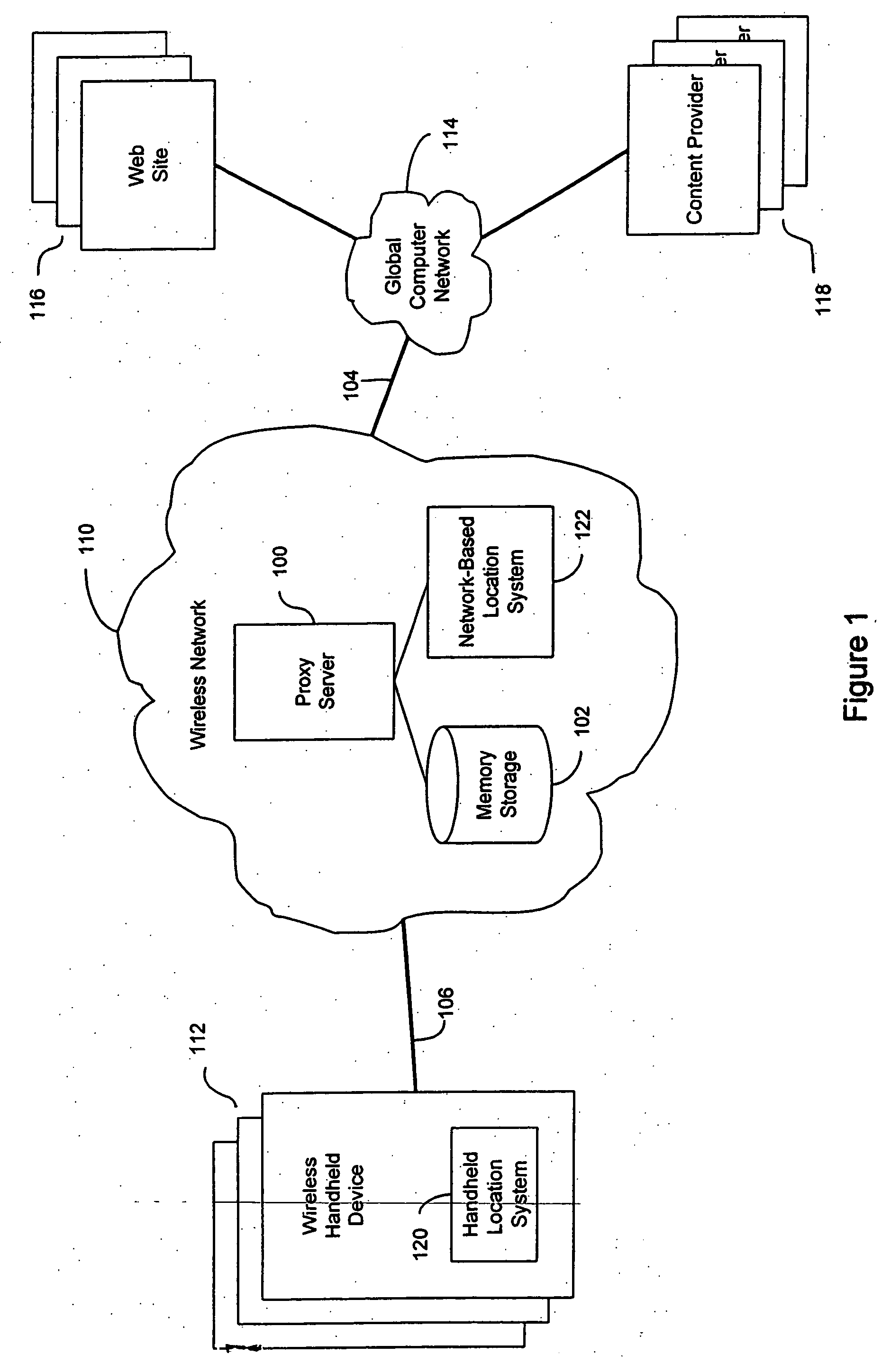
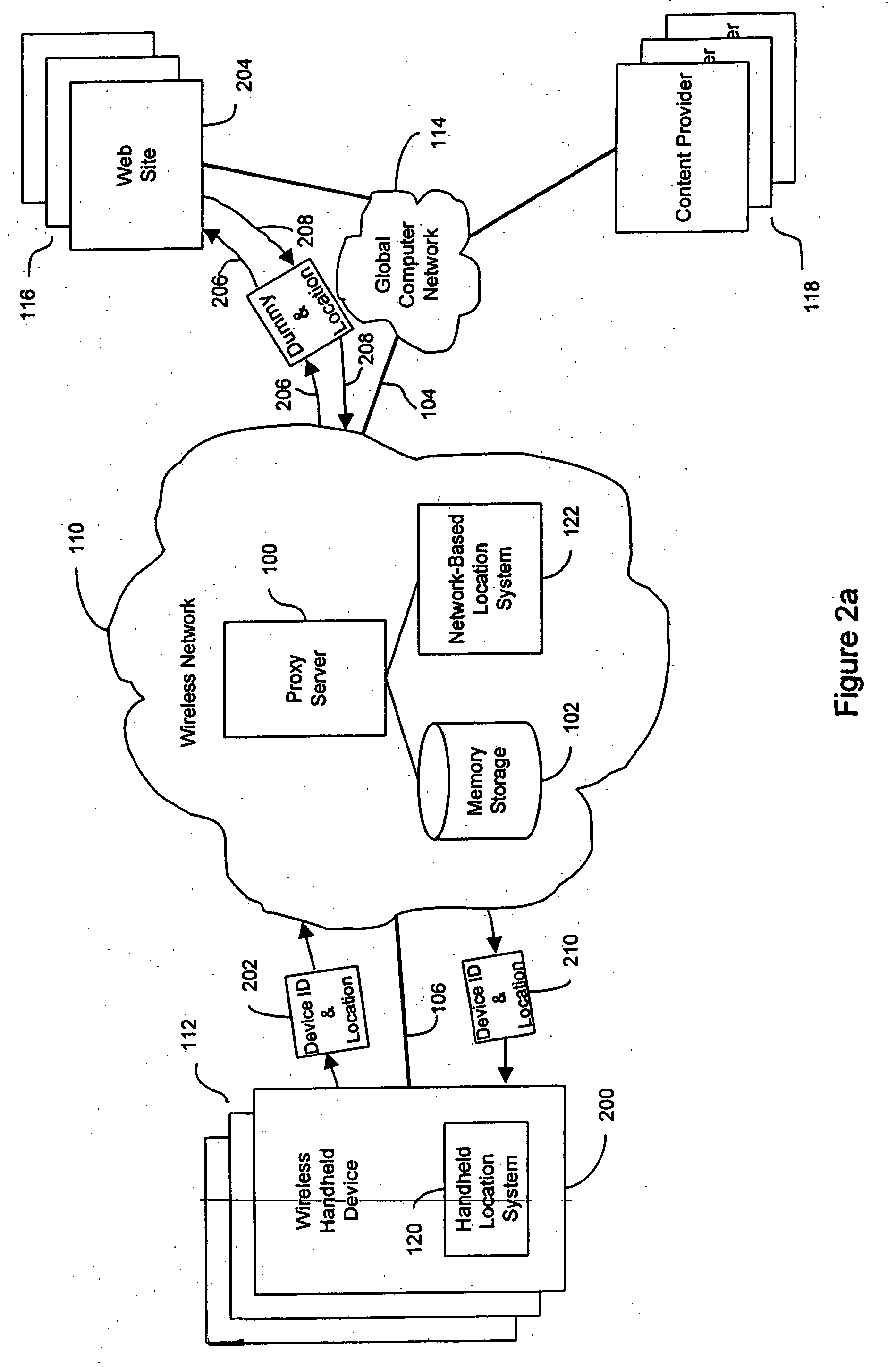
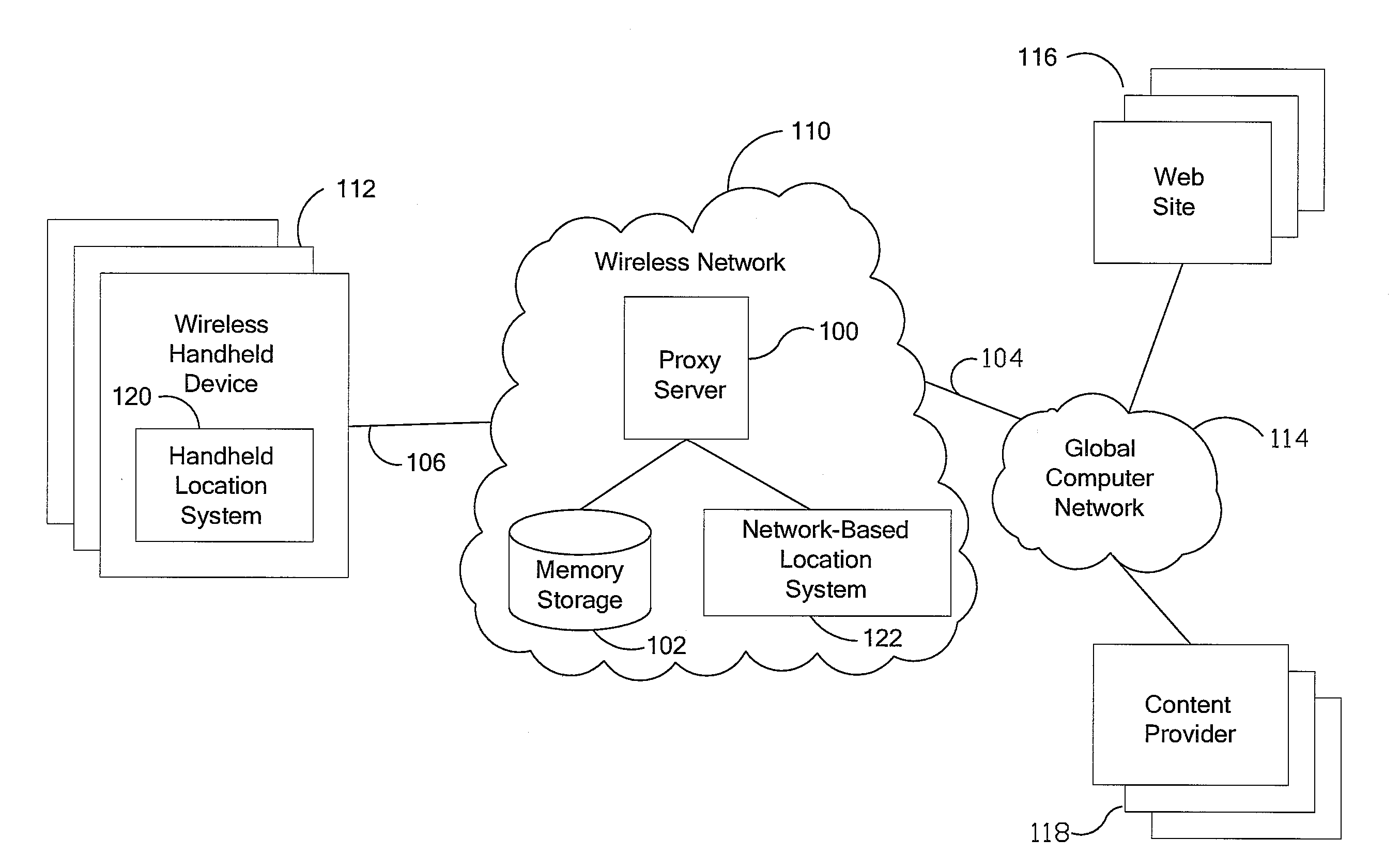
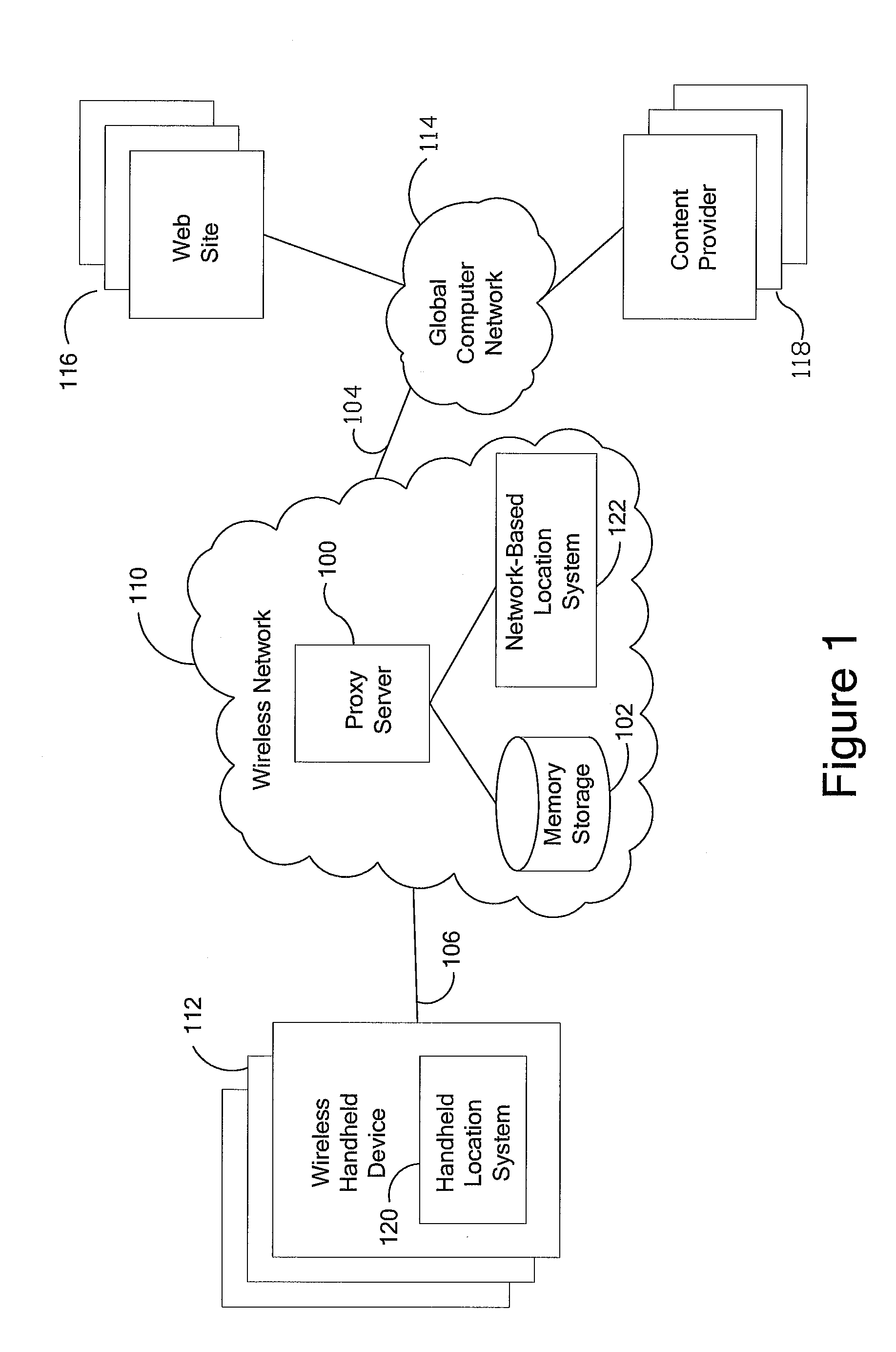
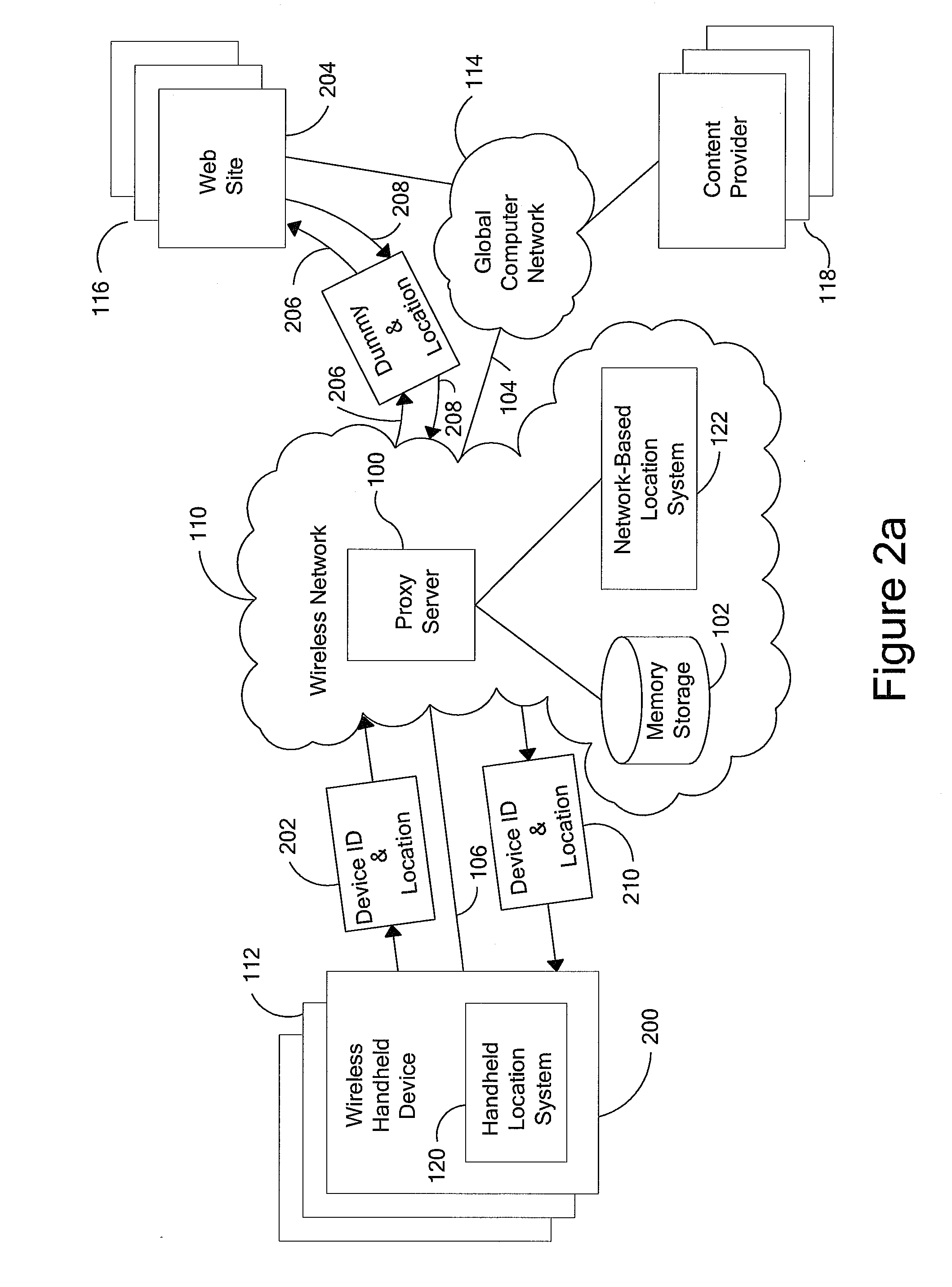
Anonymous location service for wireless networks
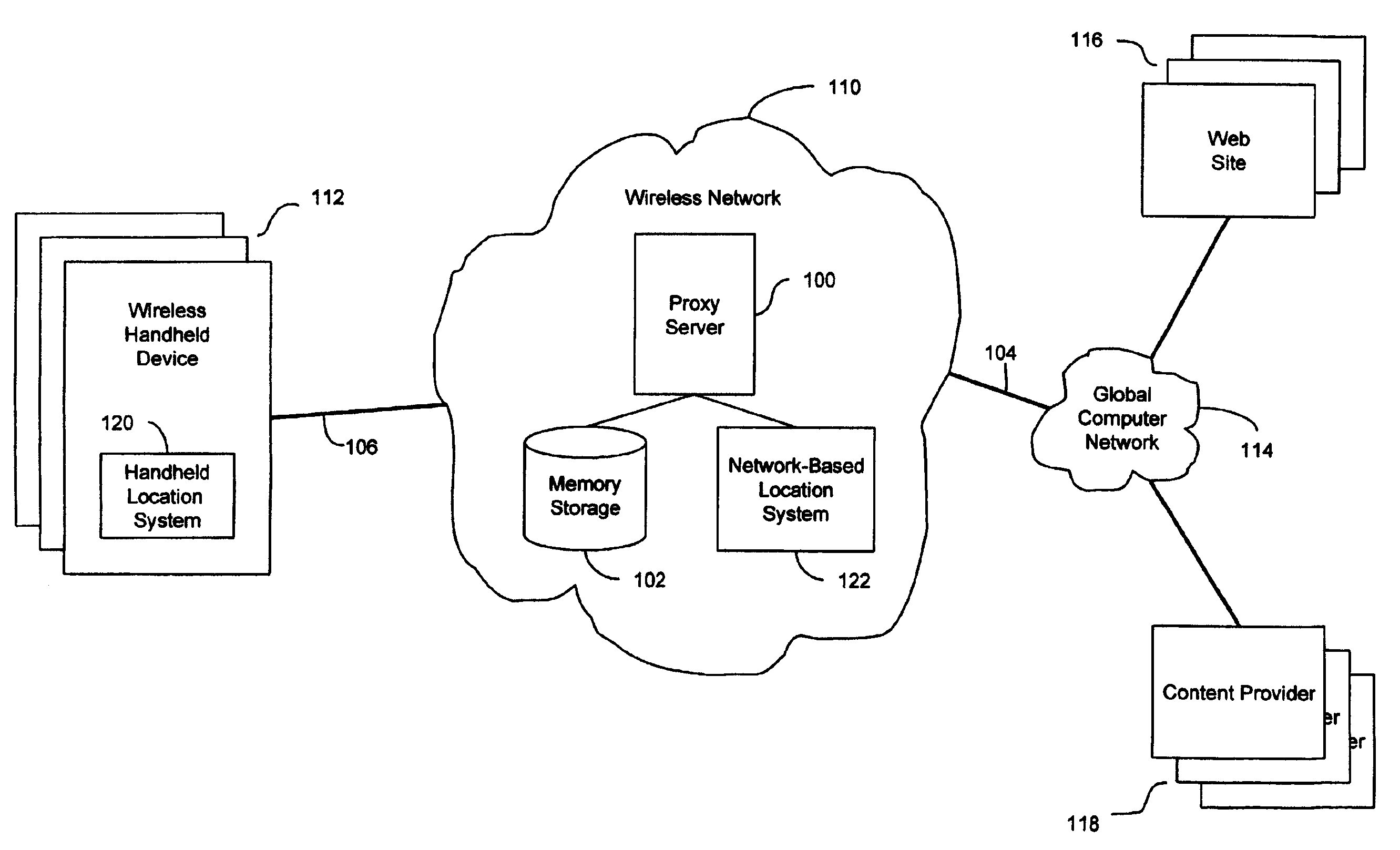
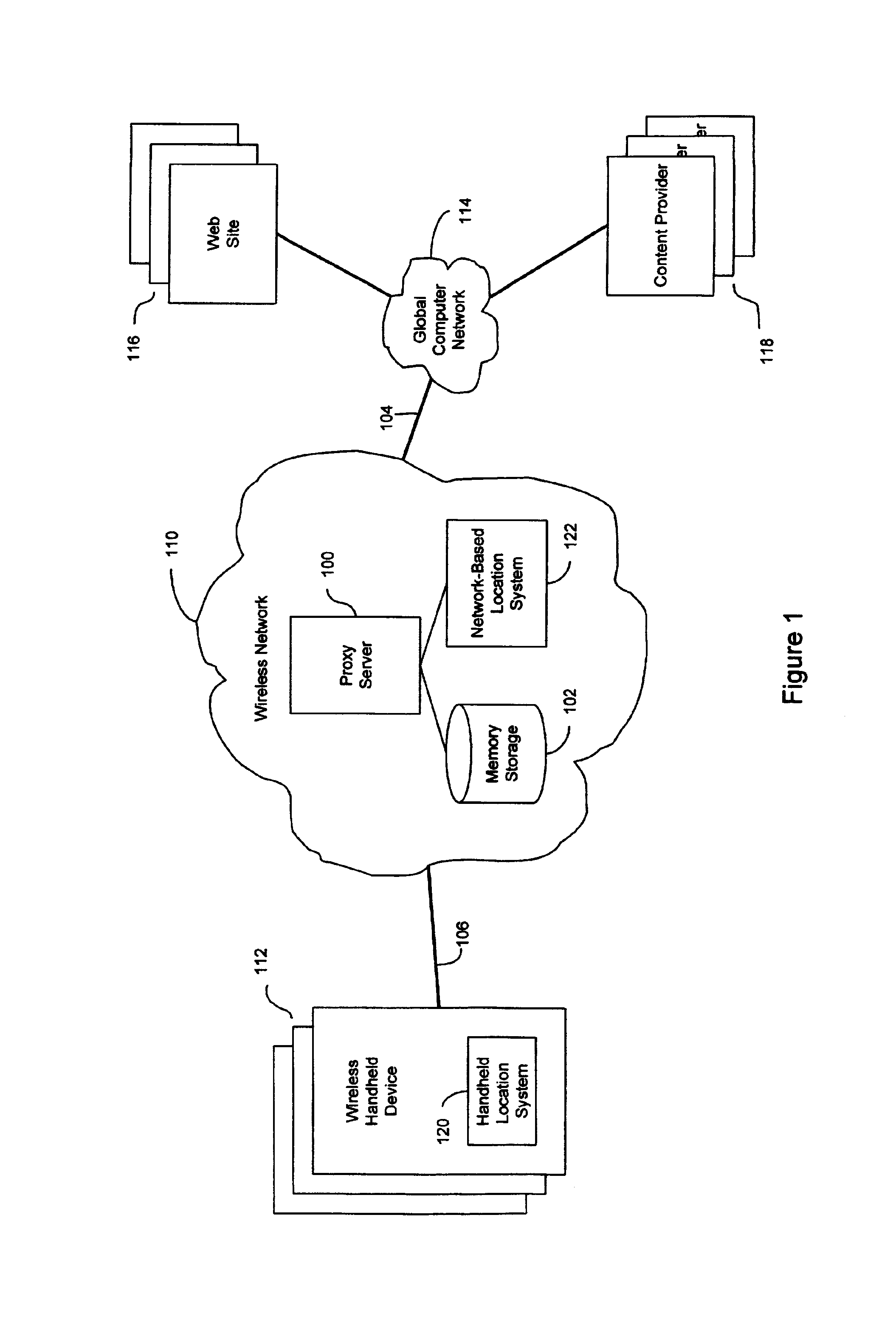
InactiveUS7069319B2Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
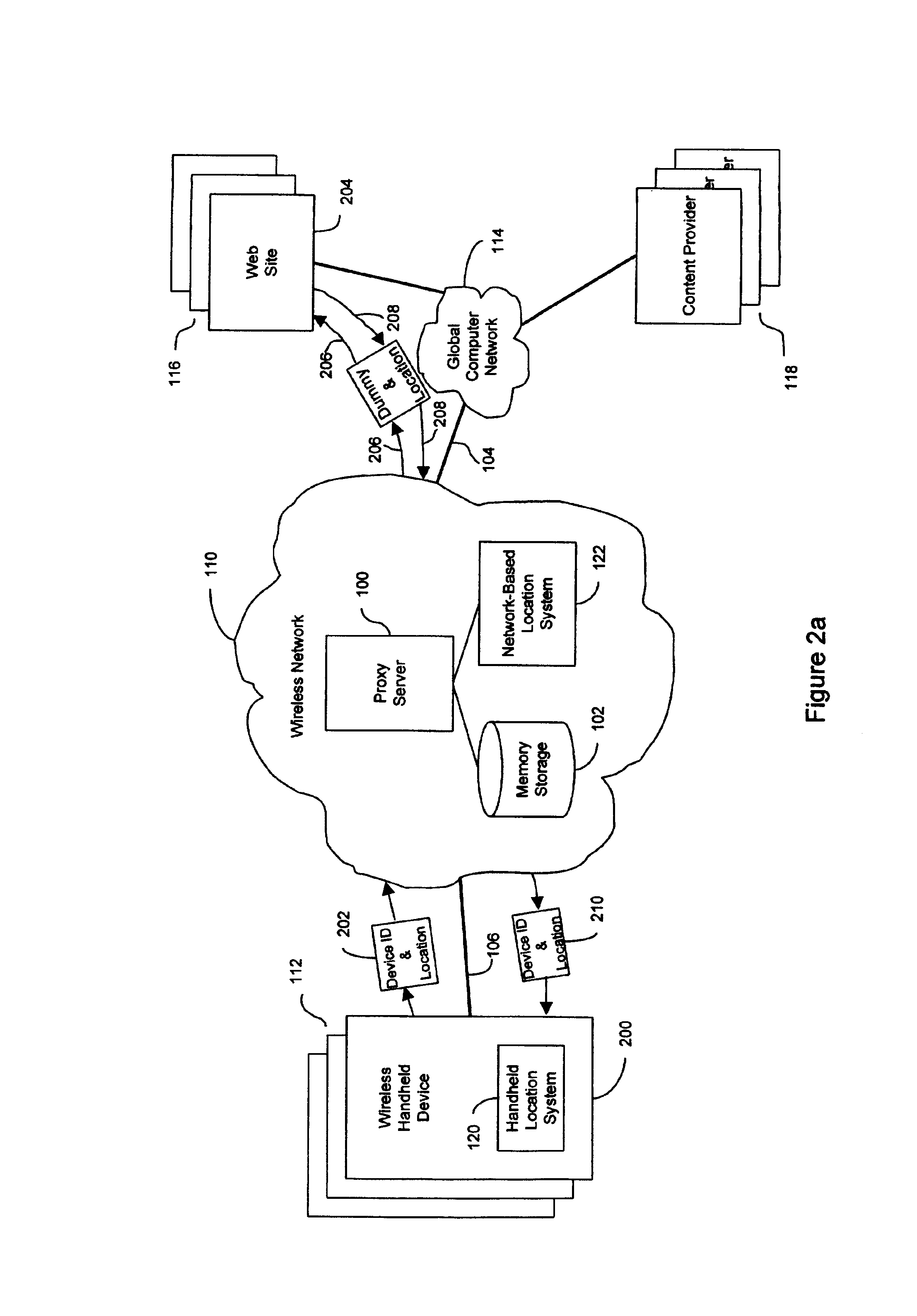
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
System and method for dynamically generating a customized menu page
InactiveUS20050108406A1Increase user friendlinessEliminate troubleDigital data information retrievalMultiple digital computer combinationsClient-sideSoftware
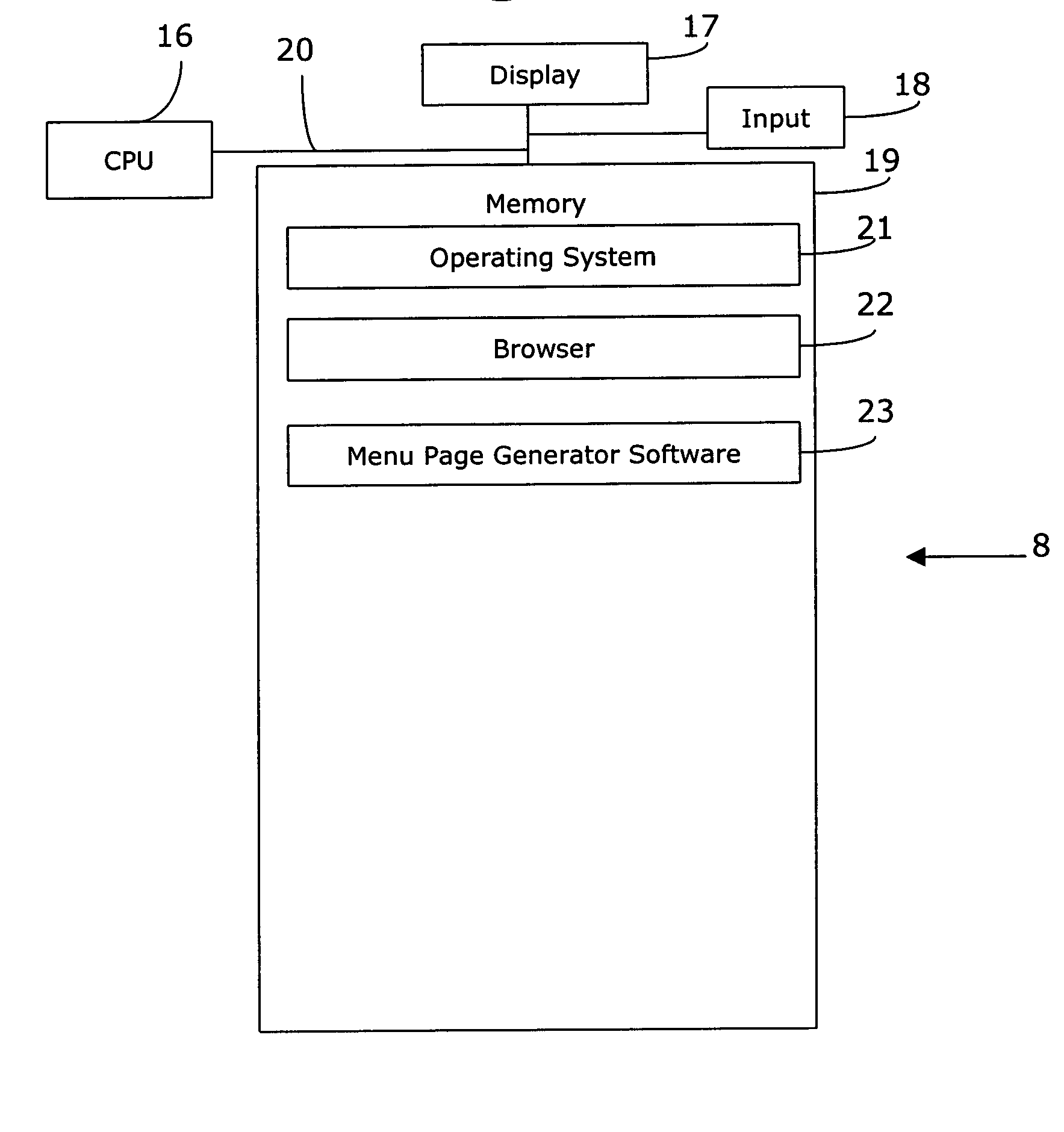
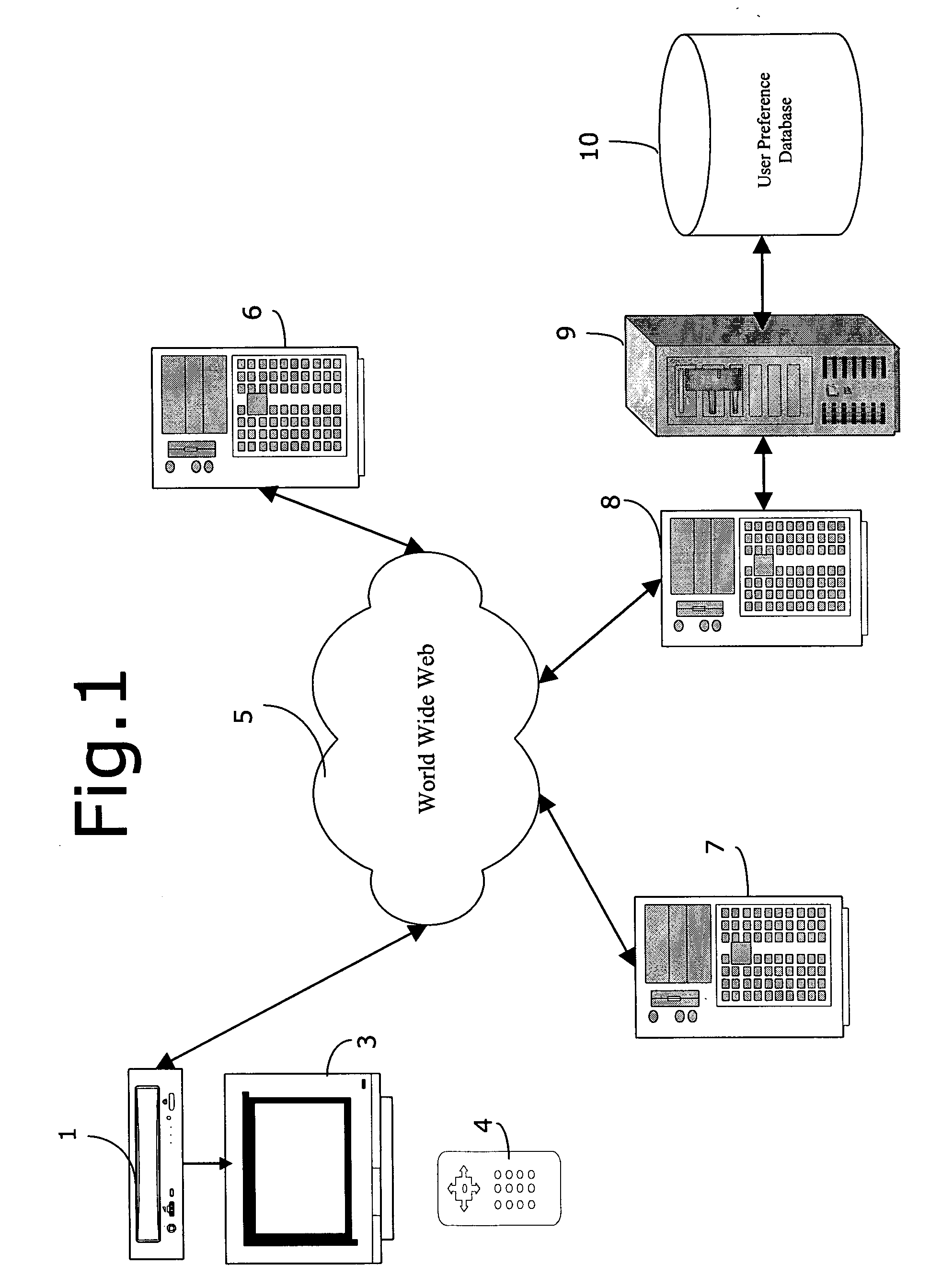
The present invention provides a method, system, and software for dynamically generating a customized menu page on a display of a client system coupled to a network, such as the Internet. The menu page includes a number of selectable icons, each associated with a particular Web site, service, Web guide channel, etc., that the user is likely to wish to access. The menu page is “customized” in the sense that each menu page is generated based on each user's network log history and preferences, as stored in a user preference database, so as to present only those information sources / services that he / she would want to access. The menu is “dynamically” generated in the sense that the user preference database is constantly updated so as to present a menu page that reflects the user's most recent preferences and history.
Owner:DYNALAB
Anonymous location service for wireless networks
InactiveUS20060195570A1Blocking in networkShorten access timeDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
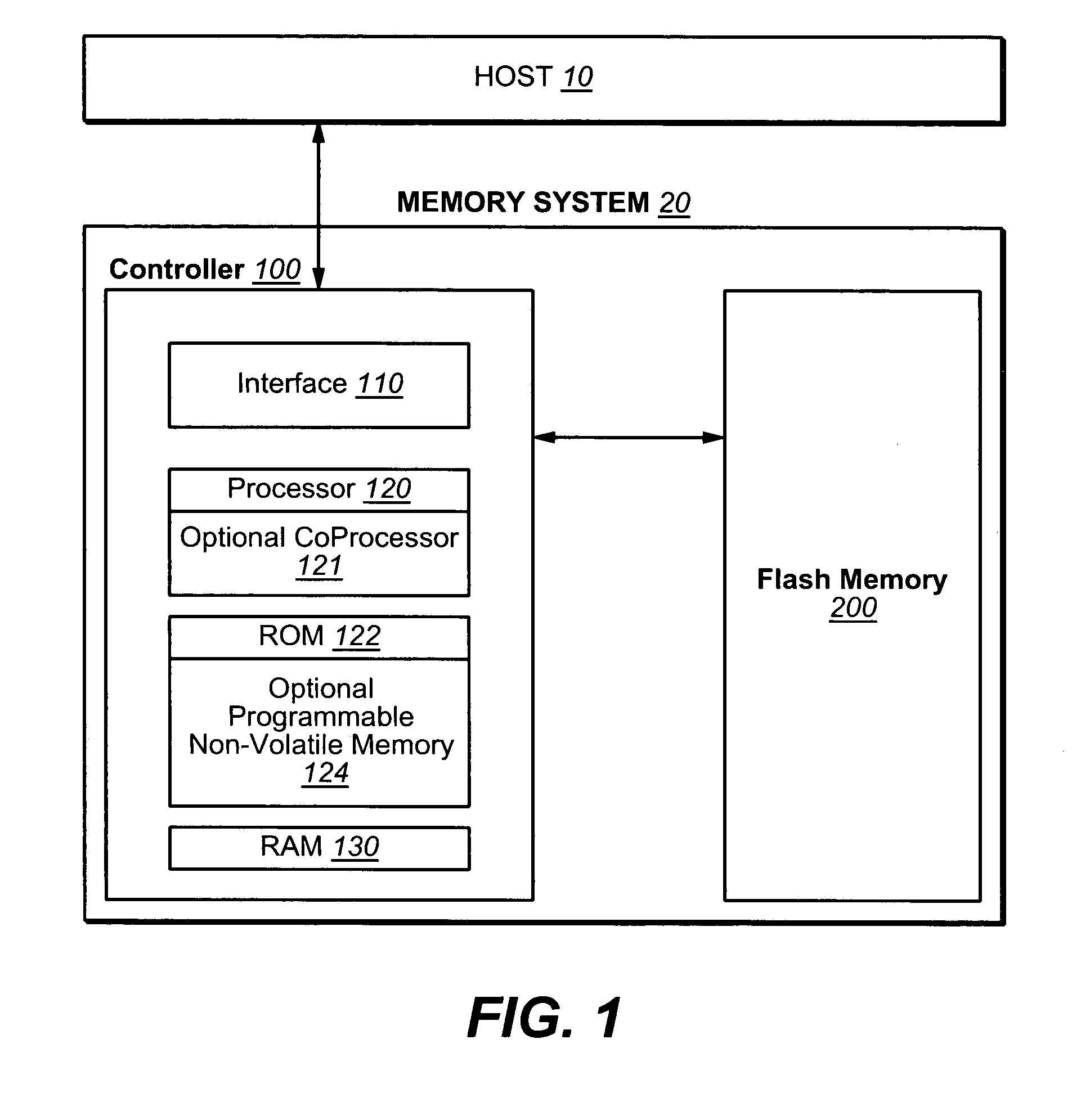
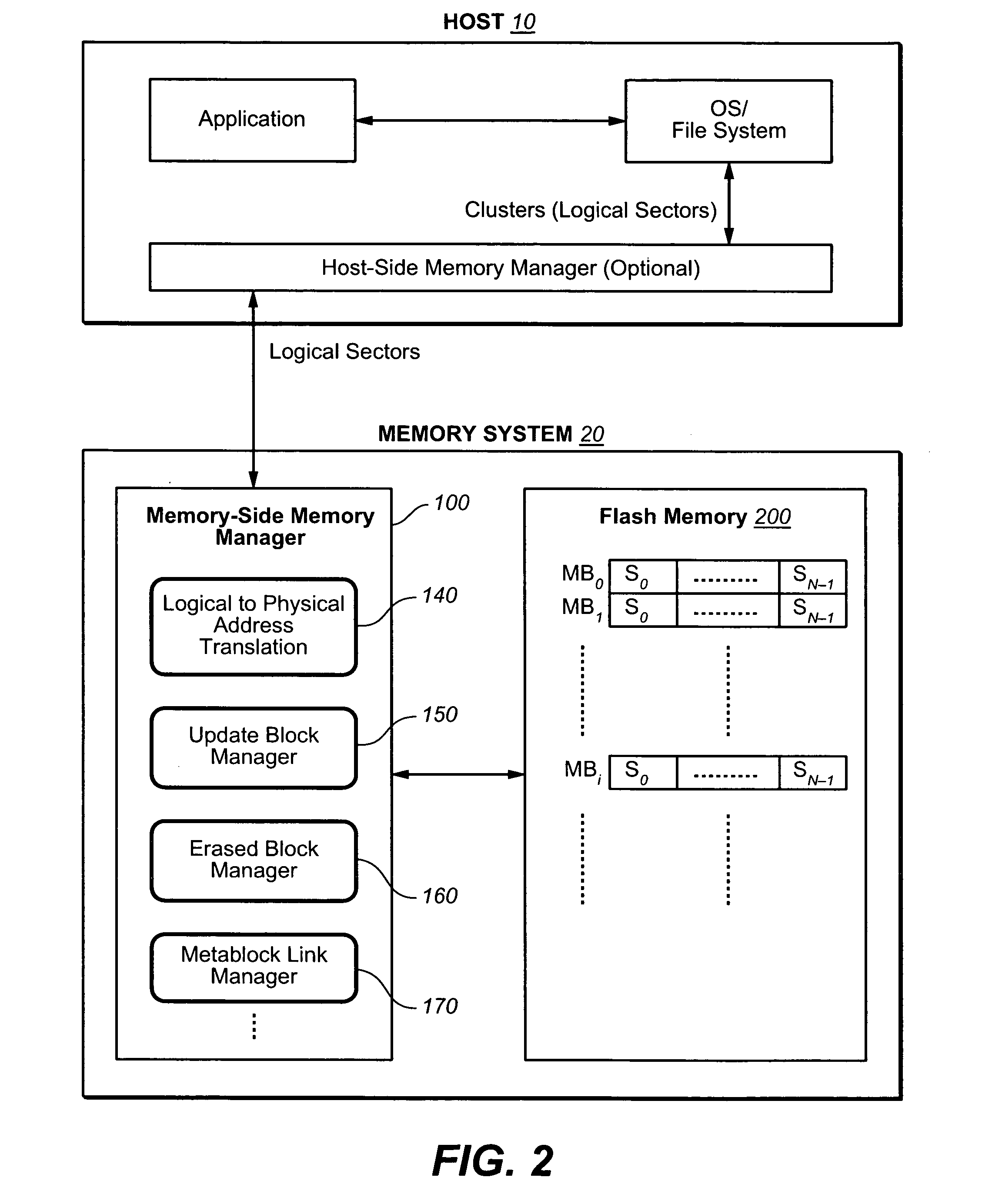
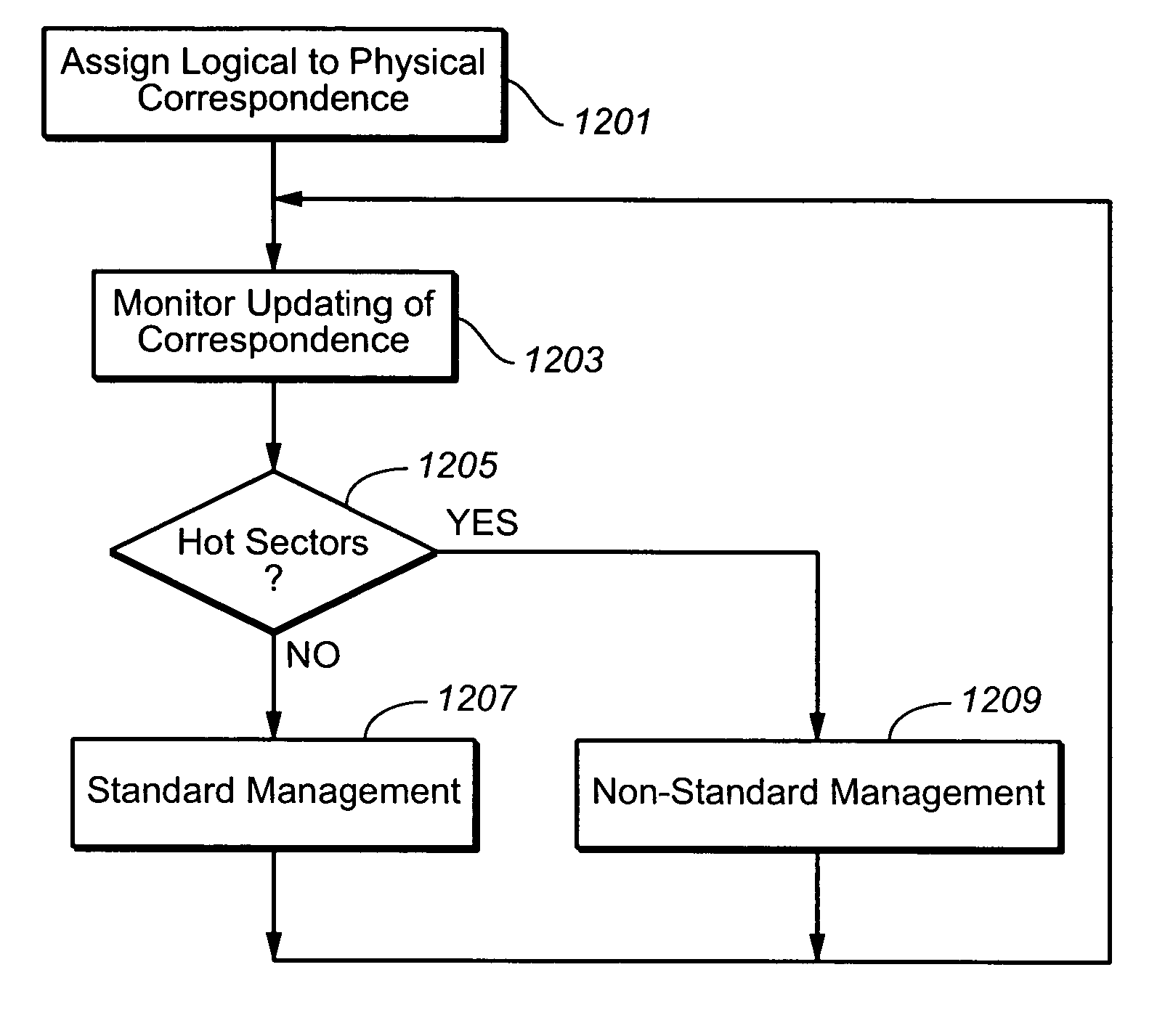
Non-volatile memory with adaptive handling of data writes
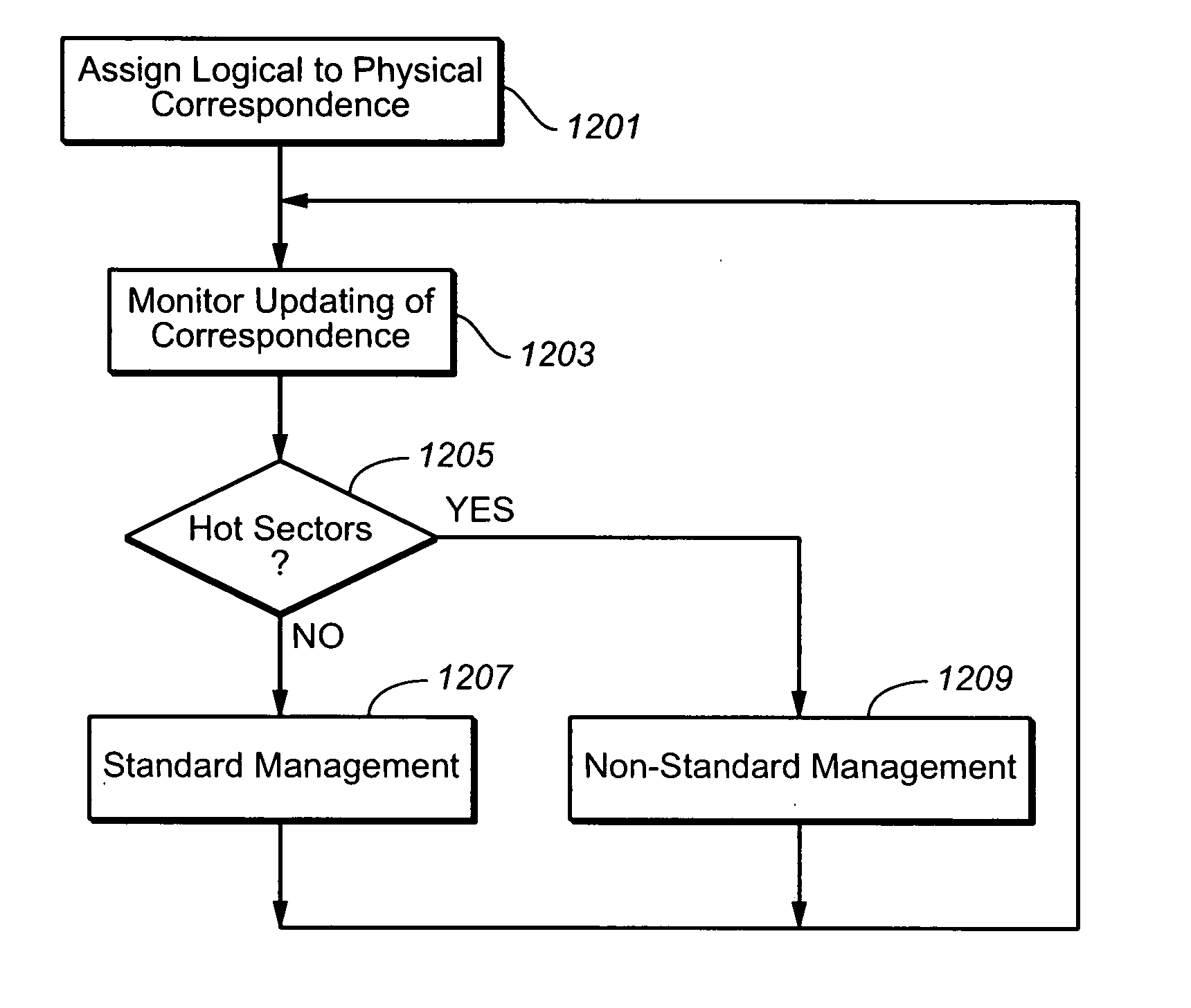
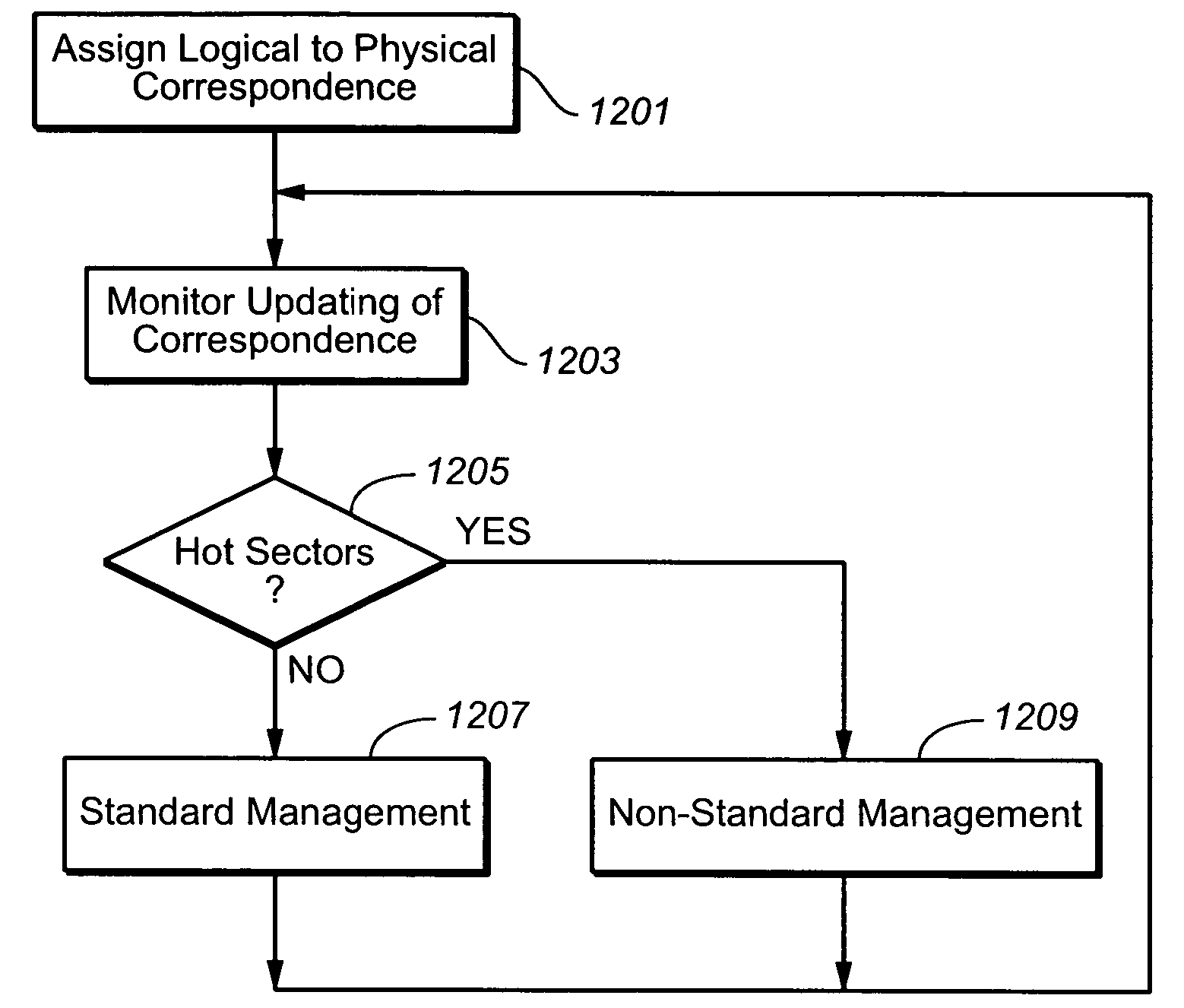
ActiveUS20070101096A1Reduce frequencyReduce the amount requiredMemory architecture accessing/allocationRead-only memoriesControl dataTerm memory
A memory system is presented where sectors are normally stored in logically contiguous groups. As repeated writes of the same small sector group can causes a massive garbage collection (data relocation), the pattern of host access is monitored by checking the sectors' update history and control data structures' update history. When repeated access patterns are detected and then expected again, the “hot” segments are separated into specially handled, non-standard zone in the memory. The non-standard zone has a sector management that is different from the logical groups and optimized for the repeated host accesses in order to reduce the frequency and amount of garbage collection operations.
Owner:SANDISK TECH LLC
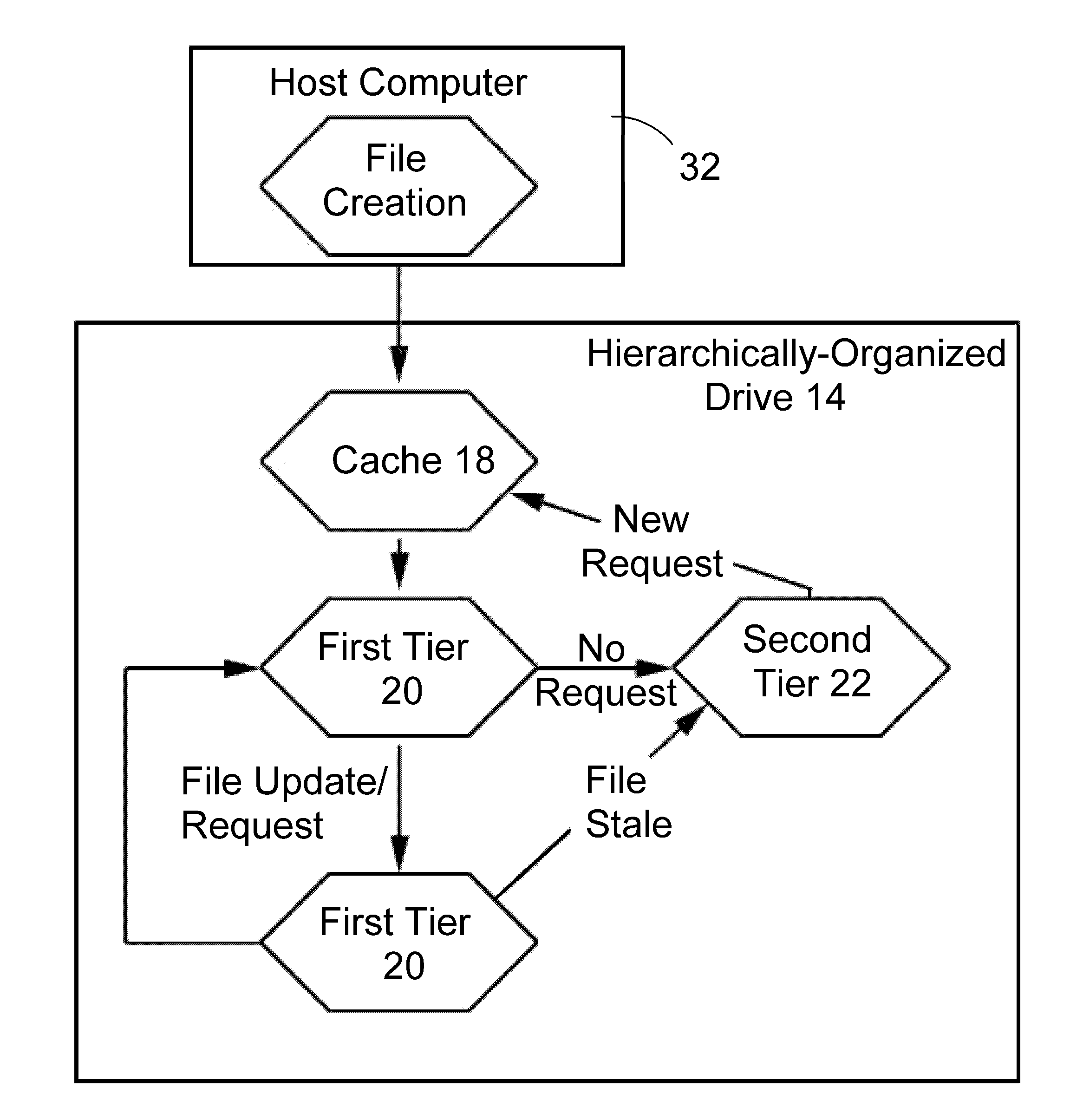
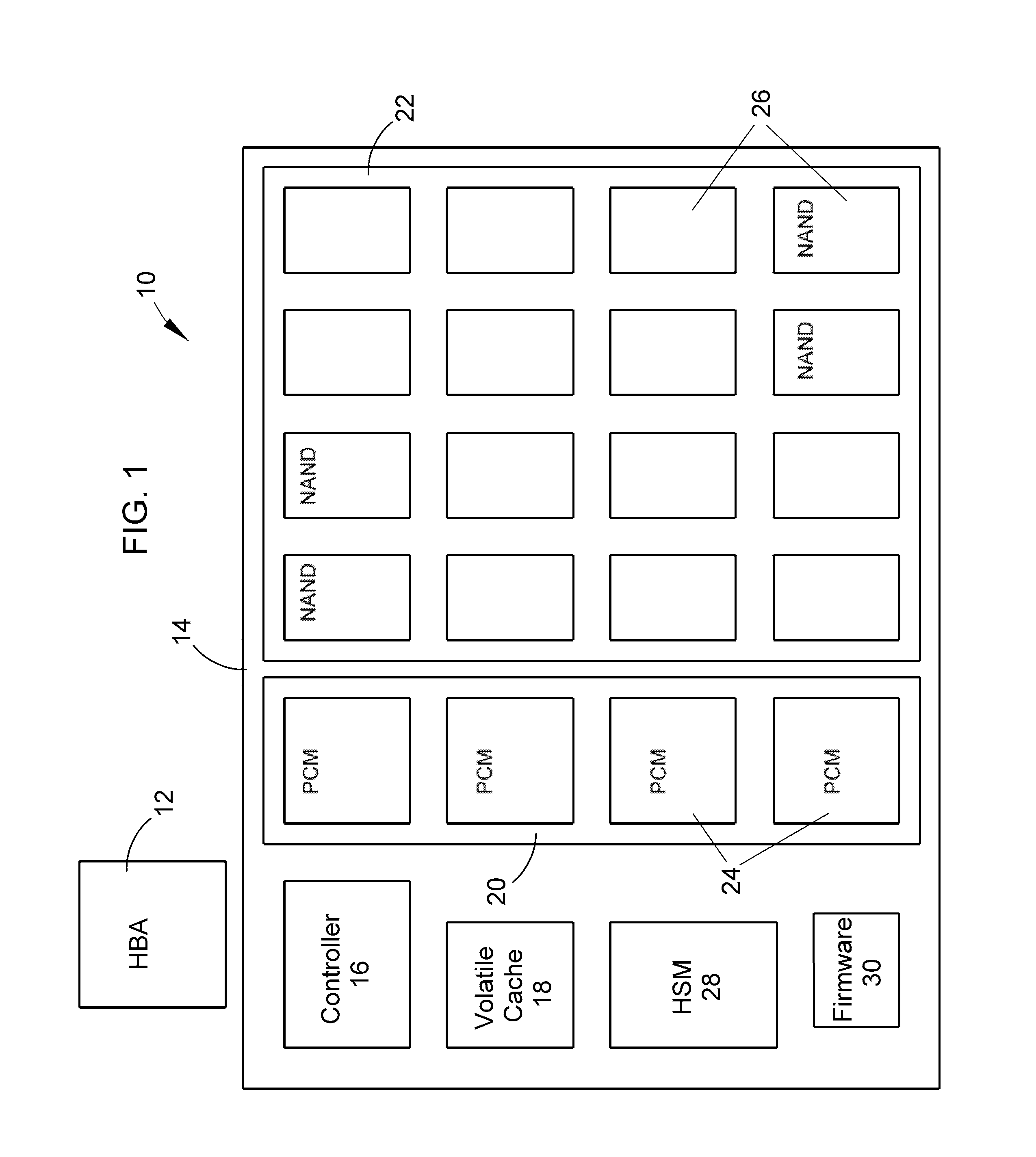
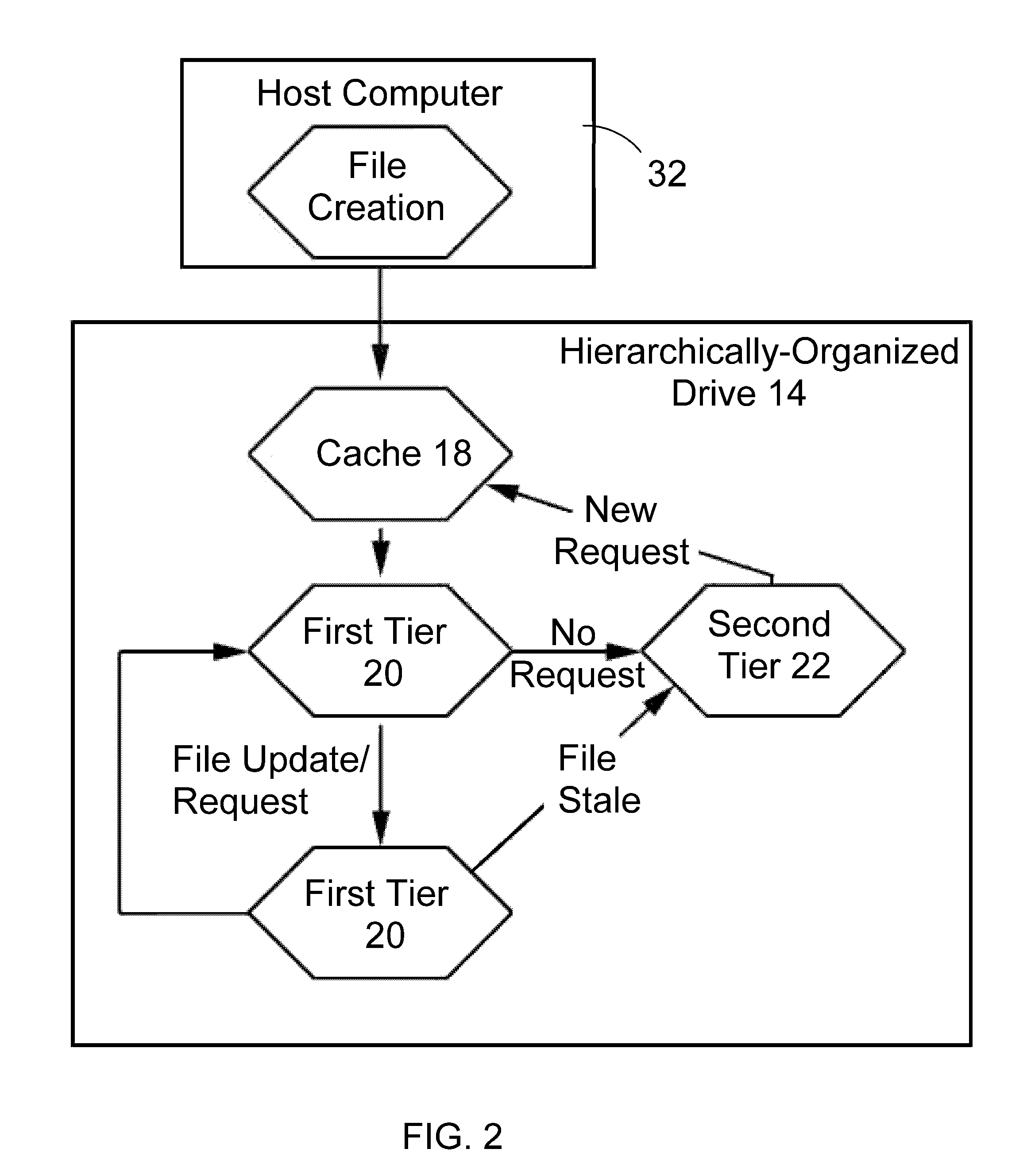
Hierarchically structured mass storage device and method
InactiveUS20100325352A1Faster access timeHigh write enduranceMemory architecture accessing/allocationMemory adressing/allocation/relocationAccess timeStorage management
A hierarchically-structured computer mass storage system and method. The mass storage system includes a mass storage memory drive, control logic on the mass storage memory drive that includes a controller and one or more devices for executing a hierarchical storage management technique, a volatile memory cache configured to be accessed by the control logic, and first and second non-volatile storage arrays on the mass storage memory drive and comprising, respectively, first and second non-volatile memory devices. The first and second non-volatile memory devices have properties including access times and write endurance, and at least one of the access time and the write endurance of the first non-volatile memory devices is faster or higher, respectively, than the second non-volatile memory devices. Desired data storage localities on the storage arrays are determined through access patterns and selectively utilizing the properties of the memory devices to match the data storage requirements.
Owner:OCZ STORAGE SOLUTIONS
Image display system
InactiveUS7607106B2Quickly and seamlessly navigateMassive in sizeCharacter and pattern recognitionStill image data indexingComputer graphics (images)Display device
An image display system is disclosed that enables users to navigate very large digital images quickly and seamlessly. The system is optimized to transmit image data from a disk drive to a display at high data rates. The image data is stored on the disk drive in a file format optimized for high speed retrieval, display, and seamless navigation. The image display system can be cascaded for showing two or more contiguous images on multiple displays.
Owner:PIXIA CORP
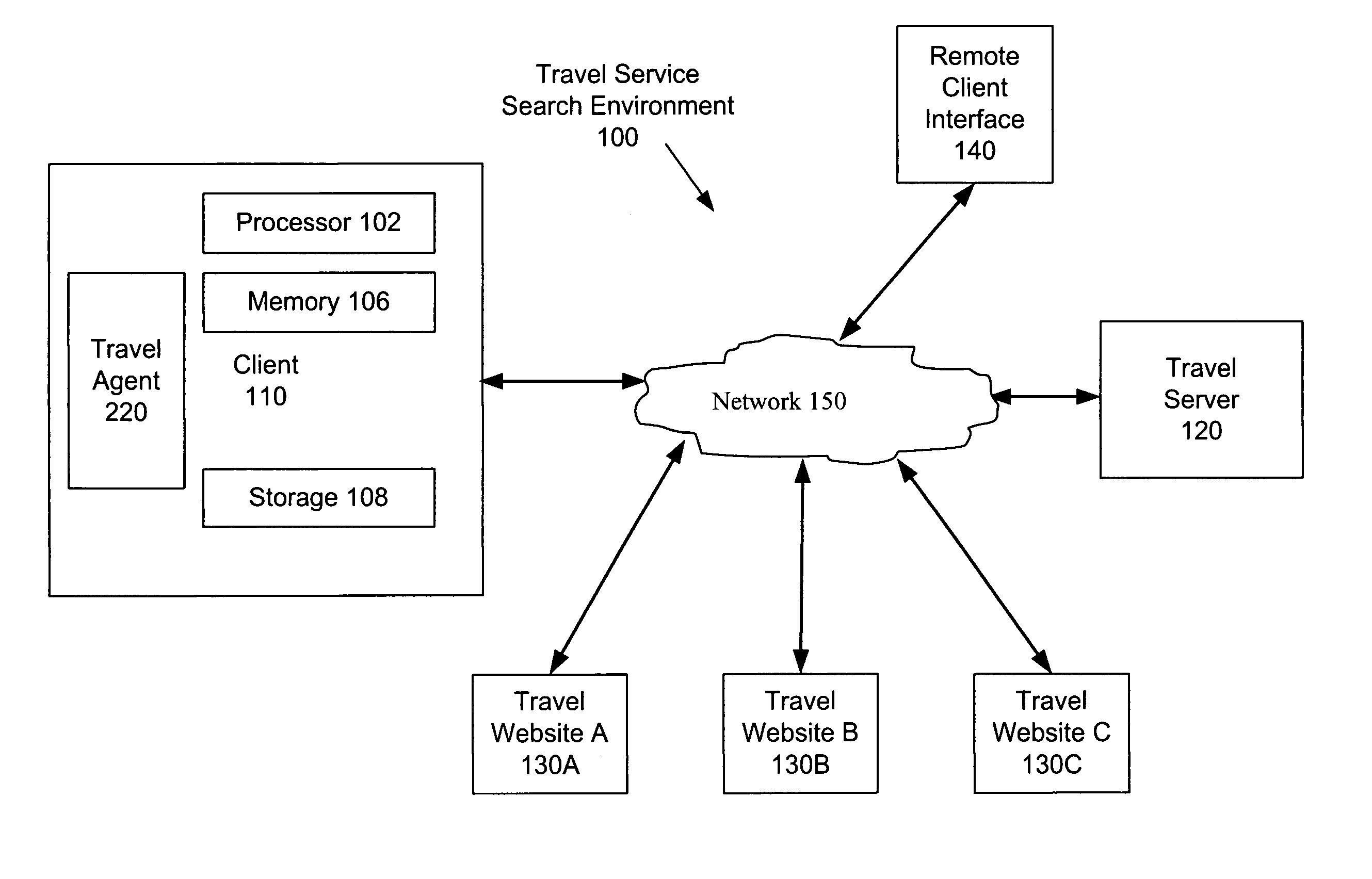
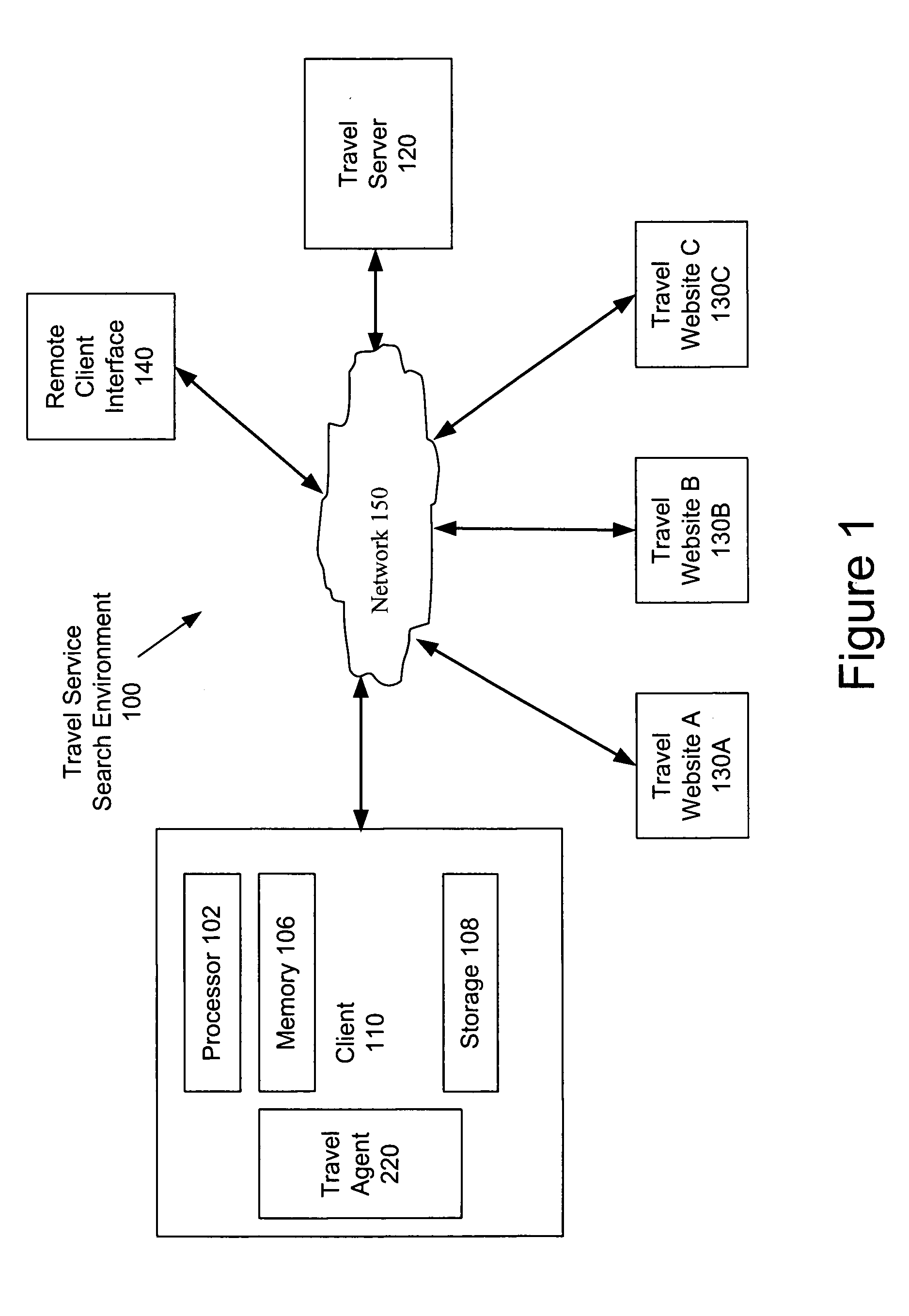
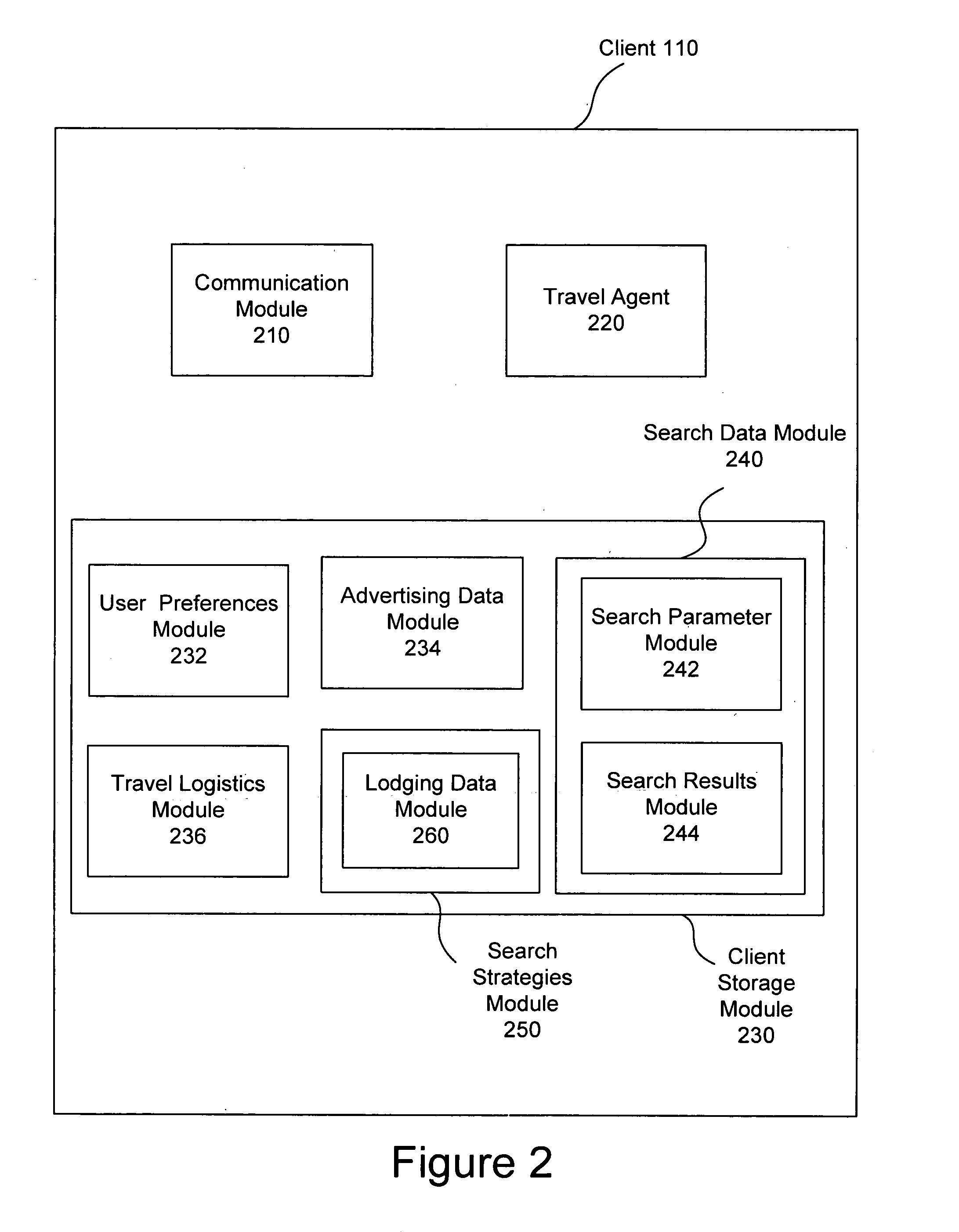
Intelligent search agent
InactiveUS20060265361A1Efficient searchShorten access timeDigital data information retrievalSpecial data processing applicationsAccess timeService provision
With the proliferation of travel websites, users must separately search competing travel websites to find a travel service that satisfies their travel preferences. A travel agent is provided for automatically searching multiple travel websites for travel services satisfying search criteria that are based on a user's travel preferences. The travel agent implements a search strategy to automatically access, navigate, and parse one or more travel websites, enter search parameters, and extract data associated with relevant travel services. The travel agent can execute on a user's personal computer to harness the computational power of the personal computer and reduce the burden on centralized servers that search for travel services. Moreover, by storing a user's travel preferences on the same personal computer, the travel agent reduces access times to user data and protects it from insecurities associated with transmission over a network.
Owner:ACQIS TECH
Storage and access method for an image retrieval system in a client/server environment
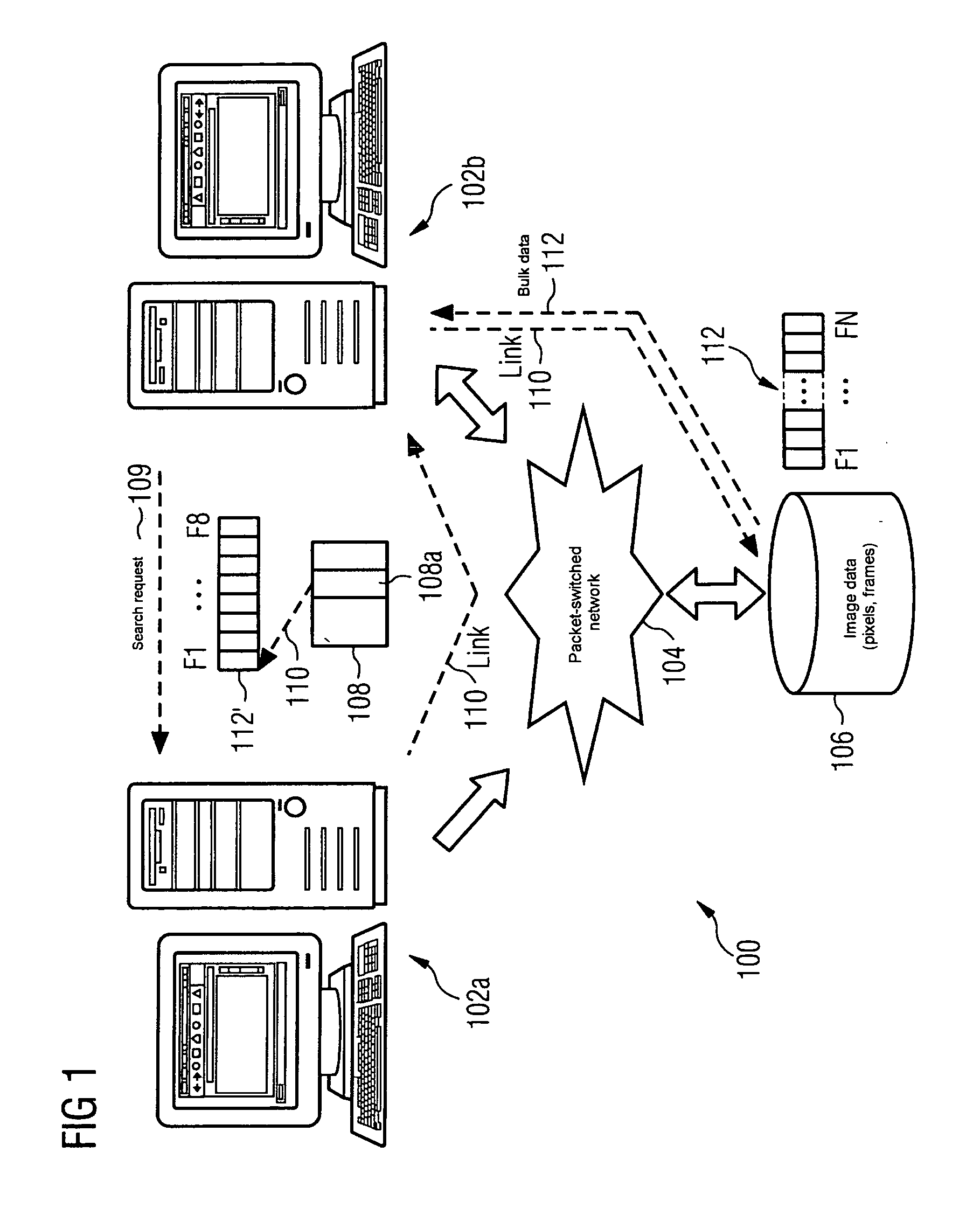
ActiveUS20050108365A1Reduce data volumeShorten access timeStill image data indexingMultiple digital computer combinationsData streamData field
An image retrieval system has a network server, at least one client terminal and a data archive of a multiuser file management system, spatially separated from server and client, of a file server. A reduced data stream is now transmitted between server and client and includes a header for transmitting address and meta information with an additional data field that includes an access key to the bulk data stored in the external data archive. This reduces the data volume to be transmitted during image retrieval, and thus reduces the network utilization in the transmission of the data stream occurring between server and client. As a result of this, the time period required to transfer the modified data stream between server and client terminal is correspondingly short.
Owner:SIEMENS HEALTHCARE GMBH
Systems and methods for managing and reporting financial information
ActiveUS20050222945A1Shorten access timeReduce the amount requiredComplete banking machinesFinanceTransaction dataLine item
Methods and system consistent with the present invention facilitate the management of financial information. Such methods and systems may receive transaction data, store the transaction data as a line item in a day ledger, receive a request for a report, the request indicating a financial figure, such as an average daily balance, to be generated over a specified time interval, and generate, substantially in real-time or during run-time per the request, a report with the financial figure over the specified time interval using data from the day ledger.
Owner:SAP AG
Methods for adaptively handling data writes in non-volatile memories
ActiveUS20070101095A1Reduce frequencyReduce the amount requiredMemory architecture accessing/allocationMemory systemsControl dataNon-volatile memory
A memory system is presented where sectors are normally stored in logically contiguous groups. As repeated writes of the same small sector group can causes a massive garbage collection (data relocation), the pattern of host access is monitored by checking the sectors' update history and control data structures' update history. When repeated access patterns are detected and then expected again, the “hot” segments are separated into specially handled, non-standard zone in the memory. The non-standard zone has a sector management that is different from the logical groups and optimized for the repeated host accesses in order to reduce the frequency and amount of garbage collection operations.
Owner:SANDISK TECH LLC
Methods for adaptively handling data writes in non-volatile memories
ActiveUS7509471B2Reduce frequencyReduce the amount requiredMemory architecture accessing/allocationMemory systemsControl dataWaste collection
A memory system is presented where sectors are normally stored in logically contiguous groups. As repeated writes of the same small sector group can causes a massive garbage collection (data relocation), the pattern of host access is monitored by checking the sectors' update history and control data structures' update history. When repeated access patterns are detected and then expected again, the “hot” segments are separated into specially handled, non-standard zone in the memory. The non-standard zone has a sector management that is different from the logical groups and optimized for the repeated host accesses in order to reduce the frequency and amount of garbage collection operations.
Owner:SANDISK TECH LLC
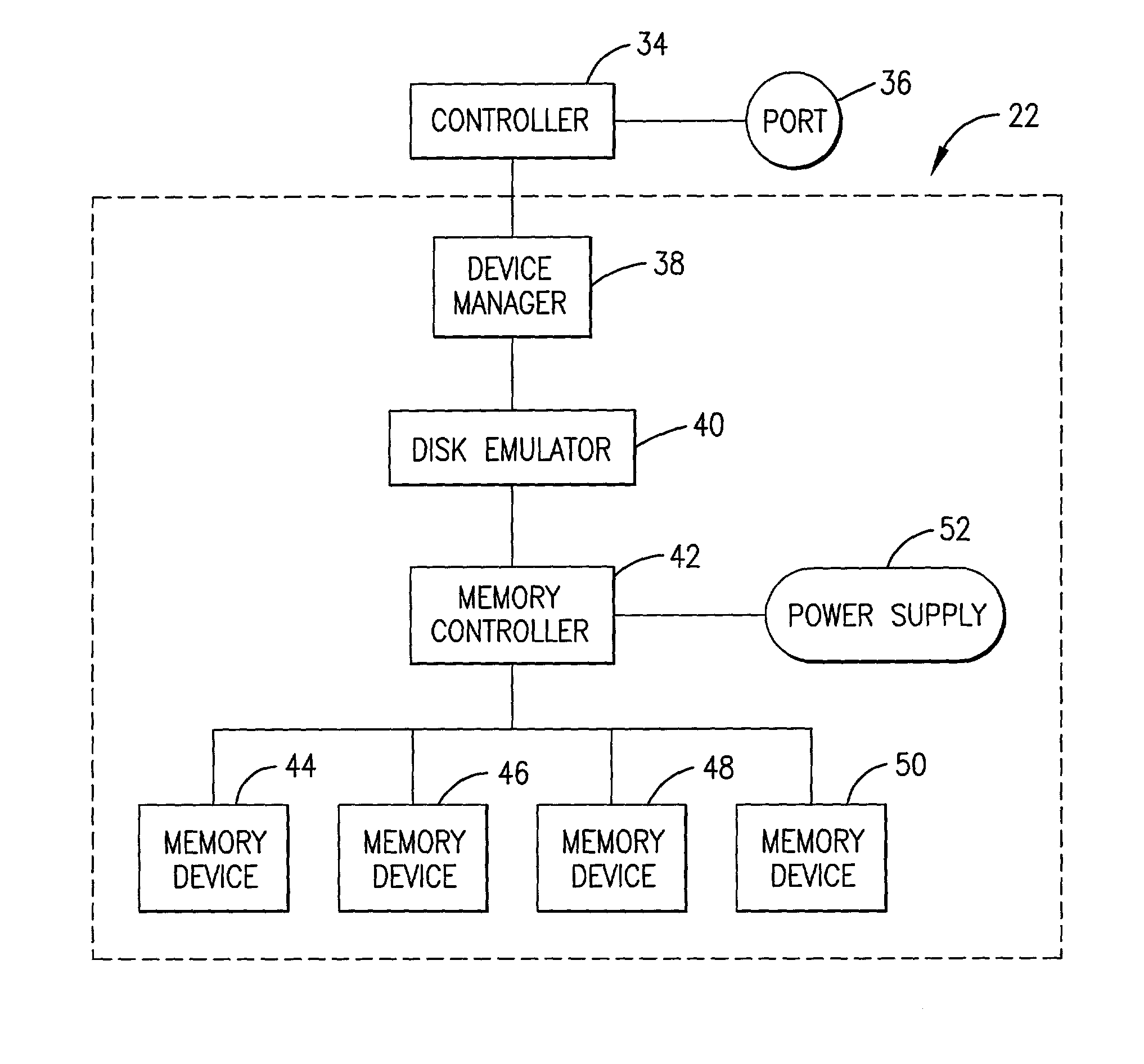
Hypercache RAM based disk emulation and method
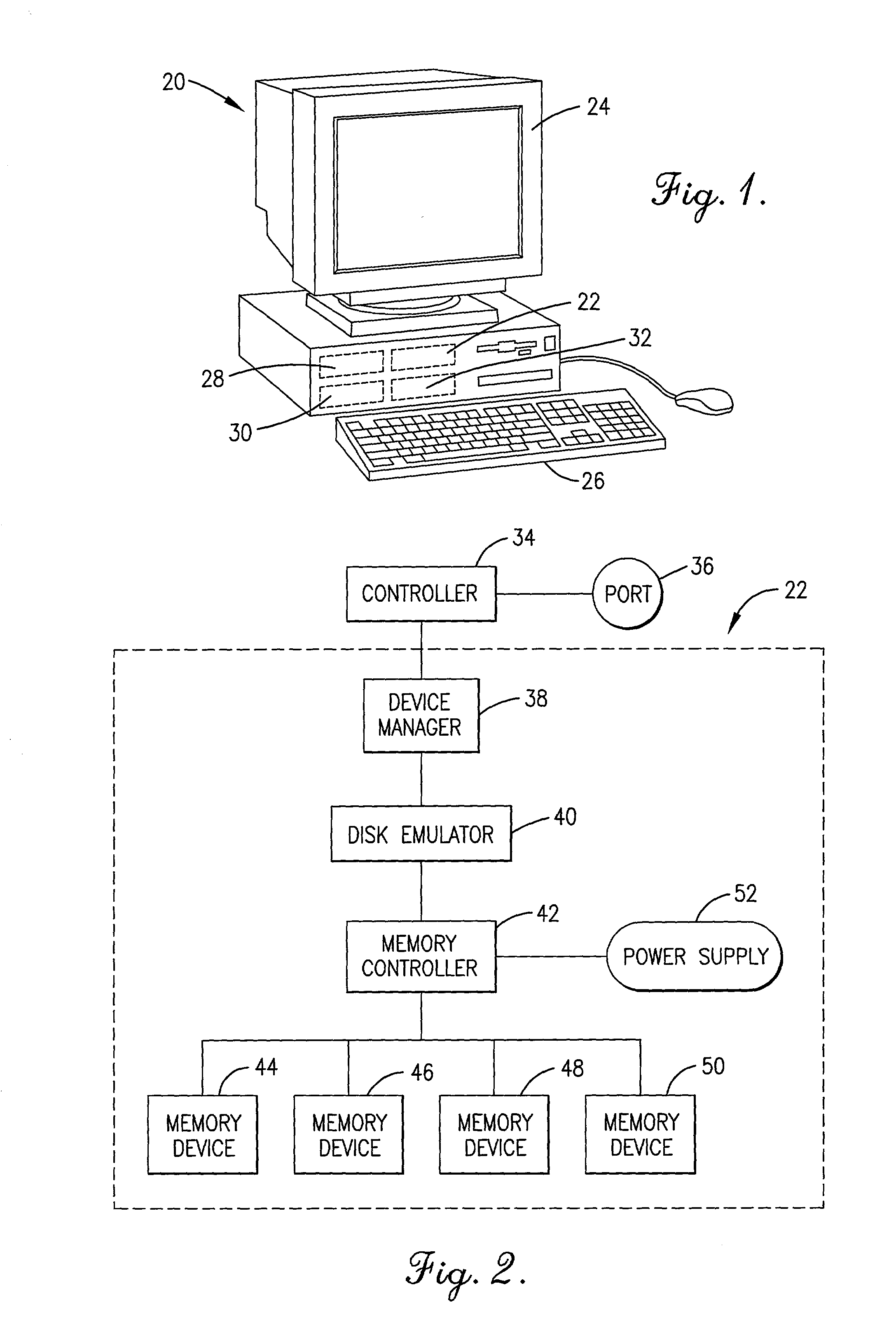
InactiveUS20020129204A1Shorten access timeImprove operationMemory architecture accessing/allocationInput/output to record carriersHard disc driveVirtual memory
A computer system (20) utilizes a monitor (24), keyboard (26), hard disk drive (28), processor (30), computer memory block (32), and memory based disk emulation device (22) to reduce access time for swap and paging files, thereby enhancing the computer system performance. The disk emulation device includes a device (22) manager (38) operable to select the number of logical drives, and a disk emulator (40) operable to cause actual memory devices (44-50) to appear as the virtual memory of the computer system disk drive (28). A memory controller (42) divides data bytes into data sets of two or four bits and saves the data sets simultaneously to the emulation memory devices (44-50). A backup battery (52) is provided to power the memory controller (42) and emulation memory devices (44-50) in the event of primary power supply failure.
Owner:LEIGHNOR LANCE +1
Semiconductor memory device having a DRAM cell structure and handled as a SRAM
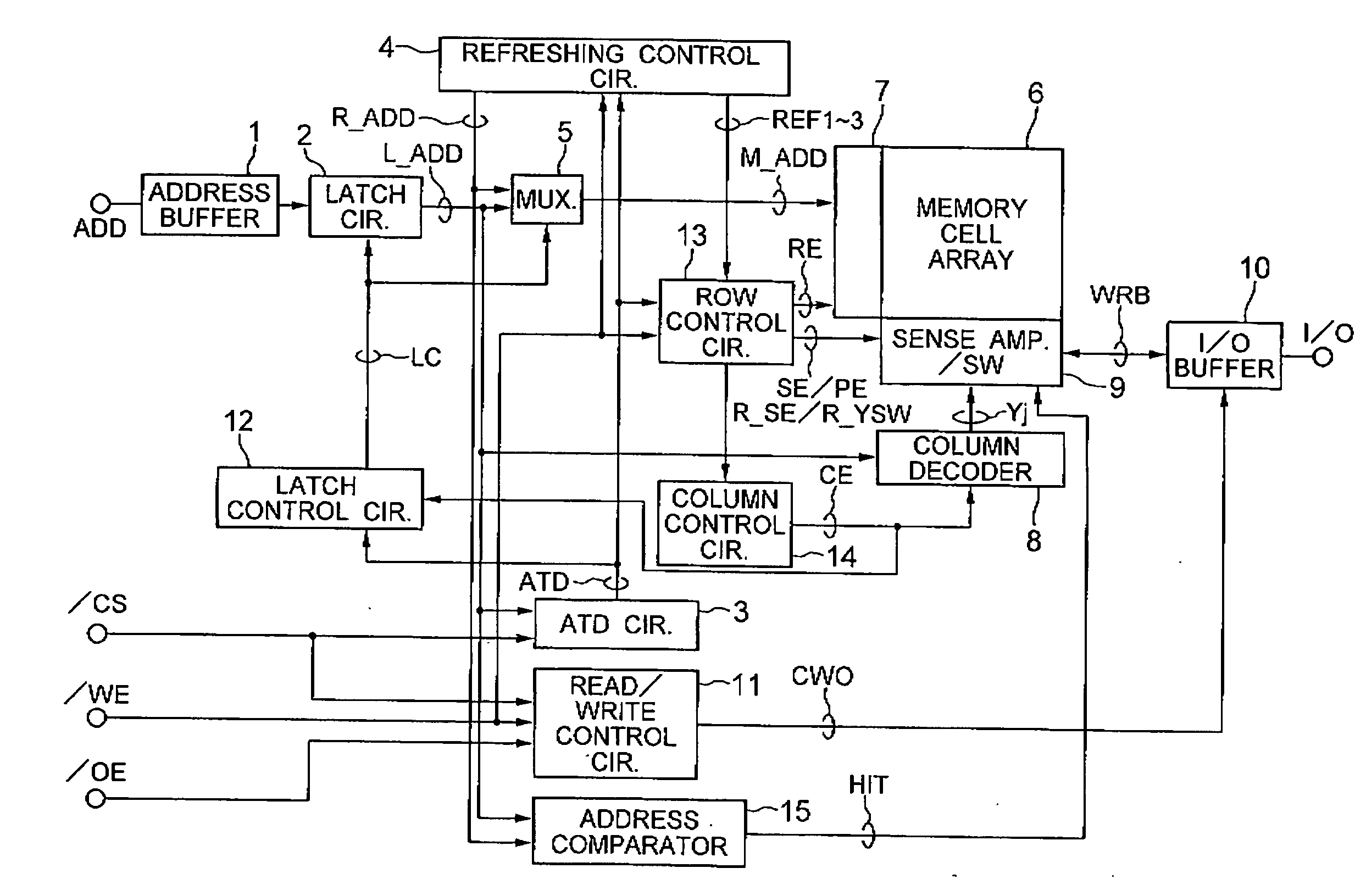
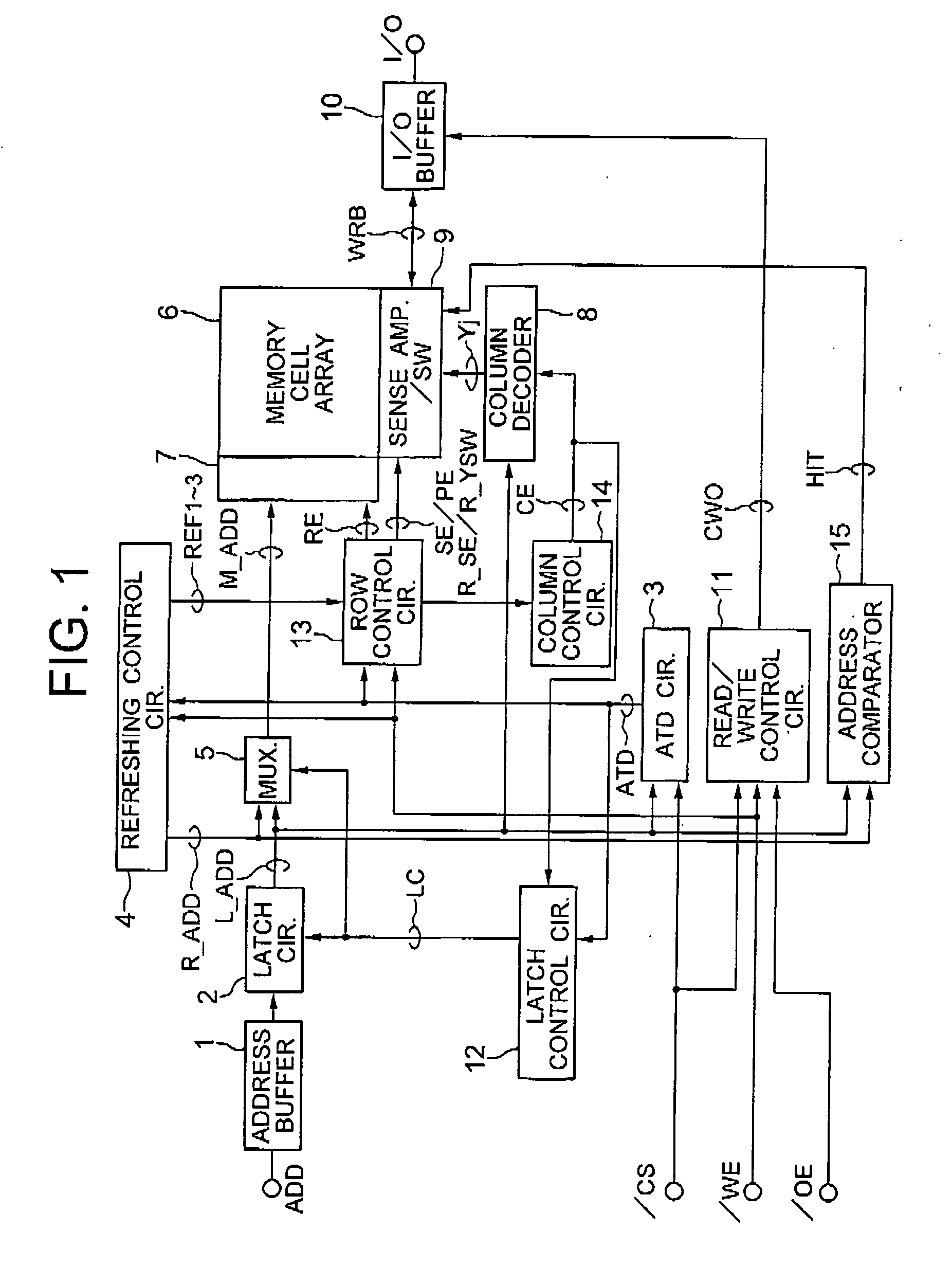
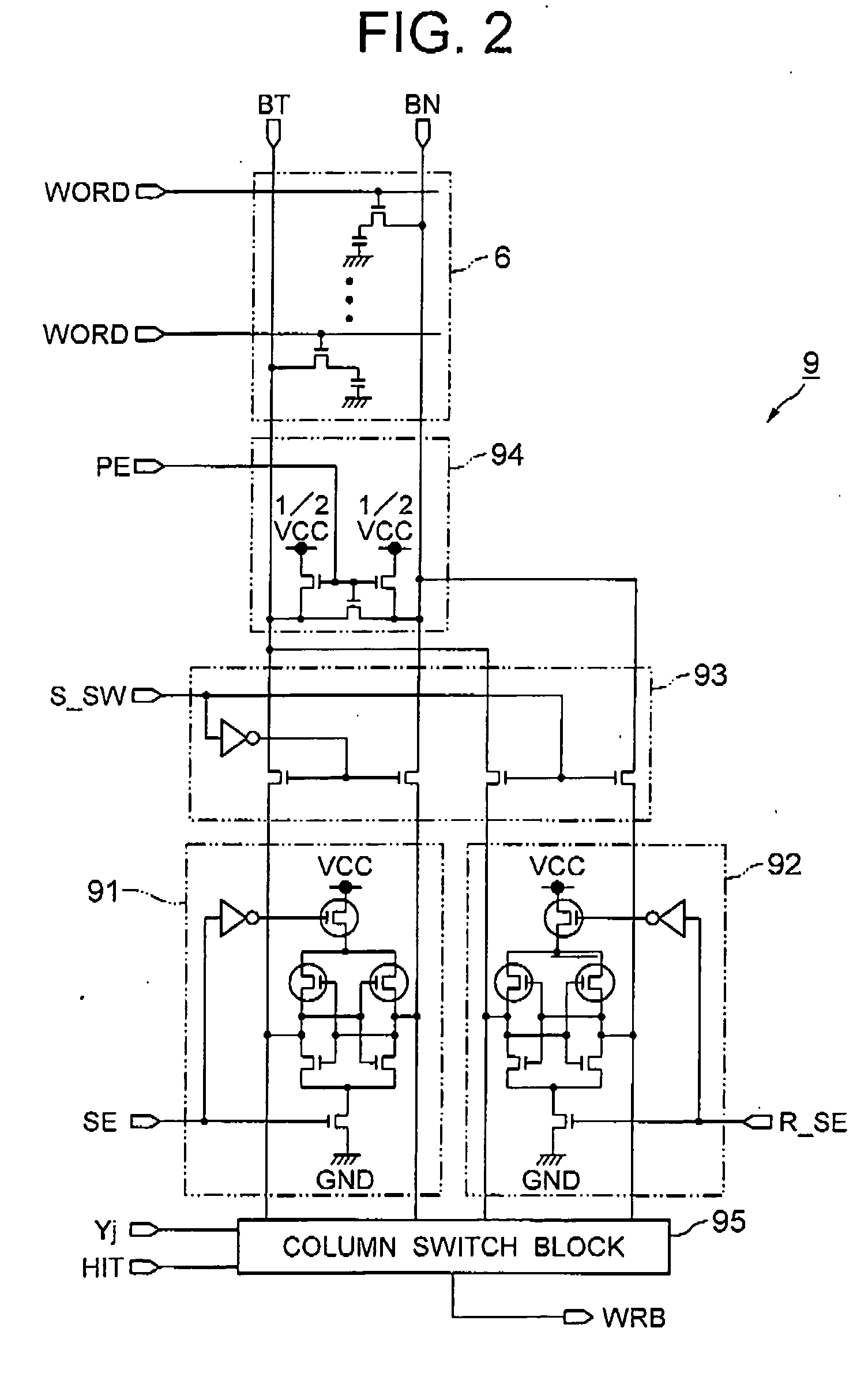
InactiveUS20040130959A1Access time of the read/write operation for the input address can be reducedShorten access timeSolid-state devicesDigital storageRefresh cycleComputer architecture
A semiconductor memory device includes a memory cell array including a plurality of memory cells having a DRAM cell structure and is treated as a SRAM memory device without controlling the data refreshing cycle for the memory cells. The refreshing cycle is separated into a read operation and a write operation, which sandwich therebetween a read / write operation for the input address of the memory cell. The data read in the refreshing cycle is saved in a refreshing sense amplifier during the read / write operation and stored in the memory cell after the read / write operation.
Owner:NEC ELECTRONICS CORP
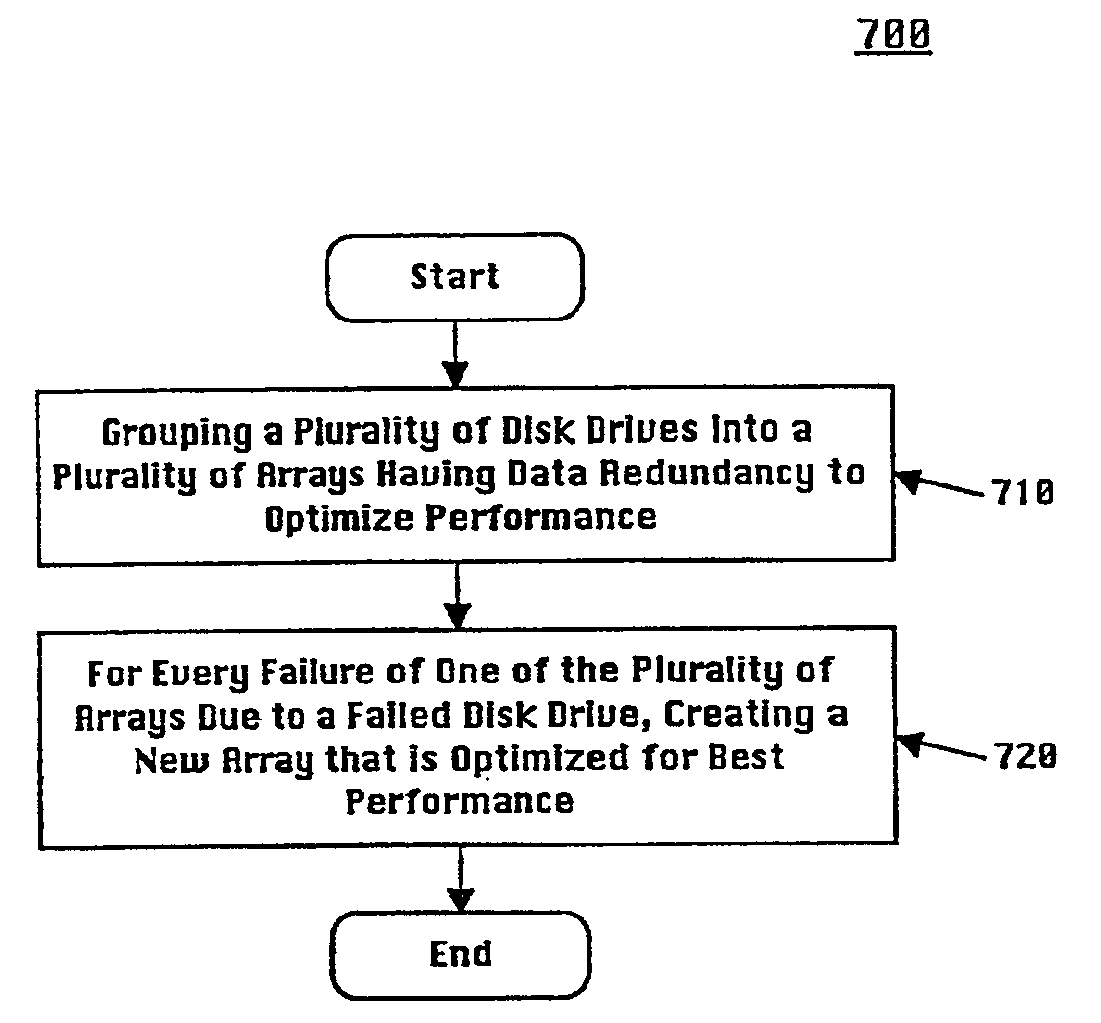
Method and system for leveraging spares in a data storage system including a plurality of disk drives
InactiveUS6845465B2Increase data efficiencyAccess time be reduceError preventionRedundant data error correctionMagnetic disksData storage system
Owner:ORACLE INT CORP
Self-contained processor subsystem as component for system-on-chip design
ActiveUS20050021871A1Processor speed be improveCache latency be reduceMultiple digital computer combinationsTransmissionLocal memoriesSwitched fabric
A System-on-Chip (SoC) component comprising a single independent multiprocessor subsystem core including a plurality of multiple processors, each multiple processor having a local memory associated therewith forming a processor cluster; and a switch fabric means connecting each processor cluster within an SoC integrated circuit (IC). The single SoC independent multiprocessor subsystem core is capable of performing multi-threading operation processing for SoC devices when configured as a DSP, coprocessor, Hybrid ASIC, or network processing arrangements. The switch fabric means additionally interconnects a SoC local system bus device with SoC processor components with the independent multiprocessor subsystem core.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for preemptive scanning of computer files
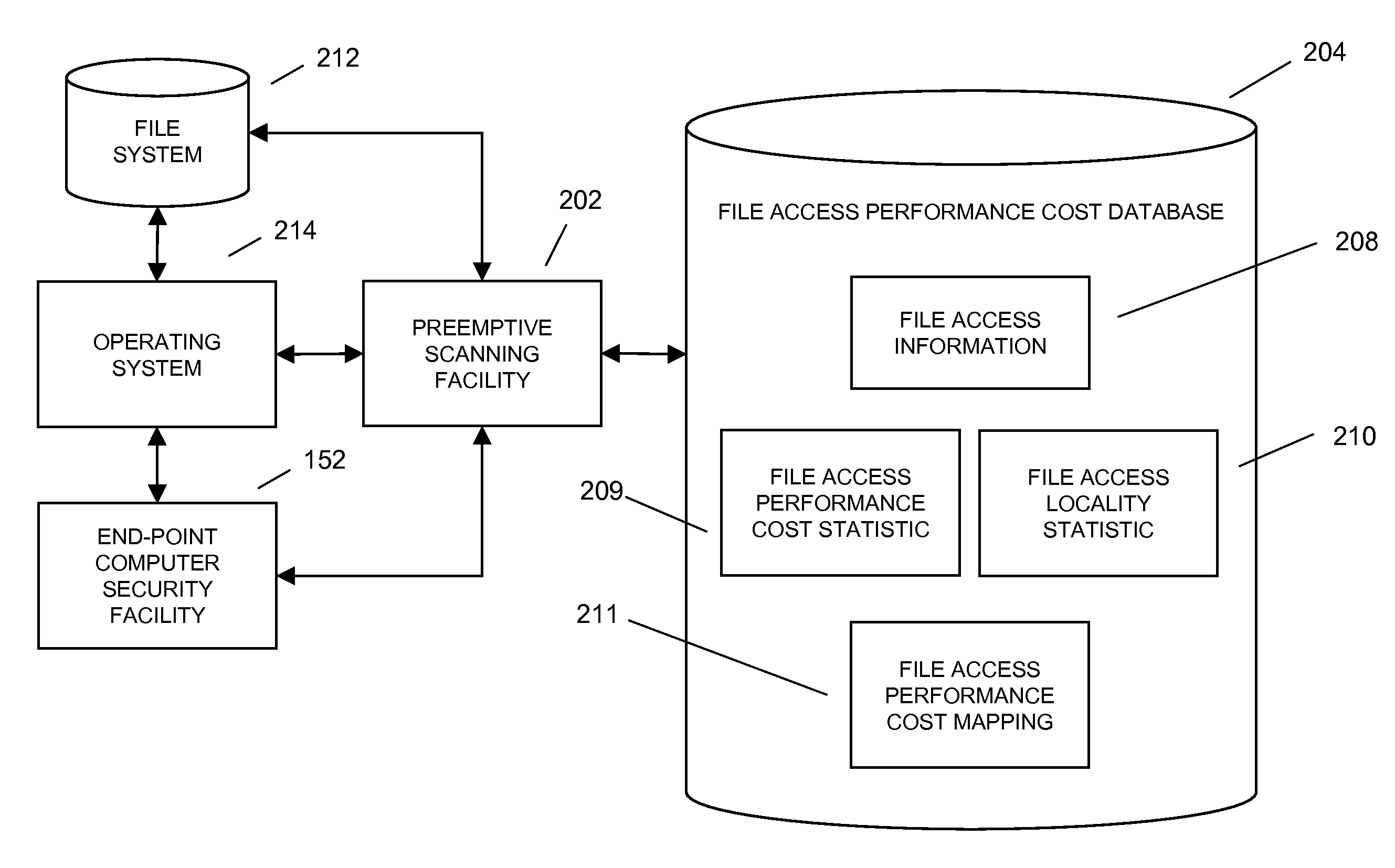
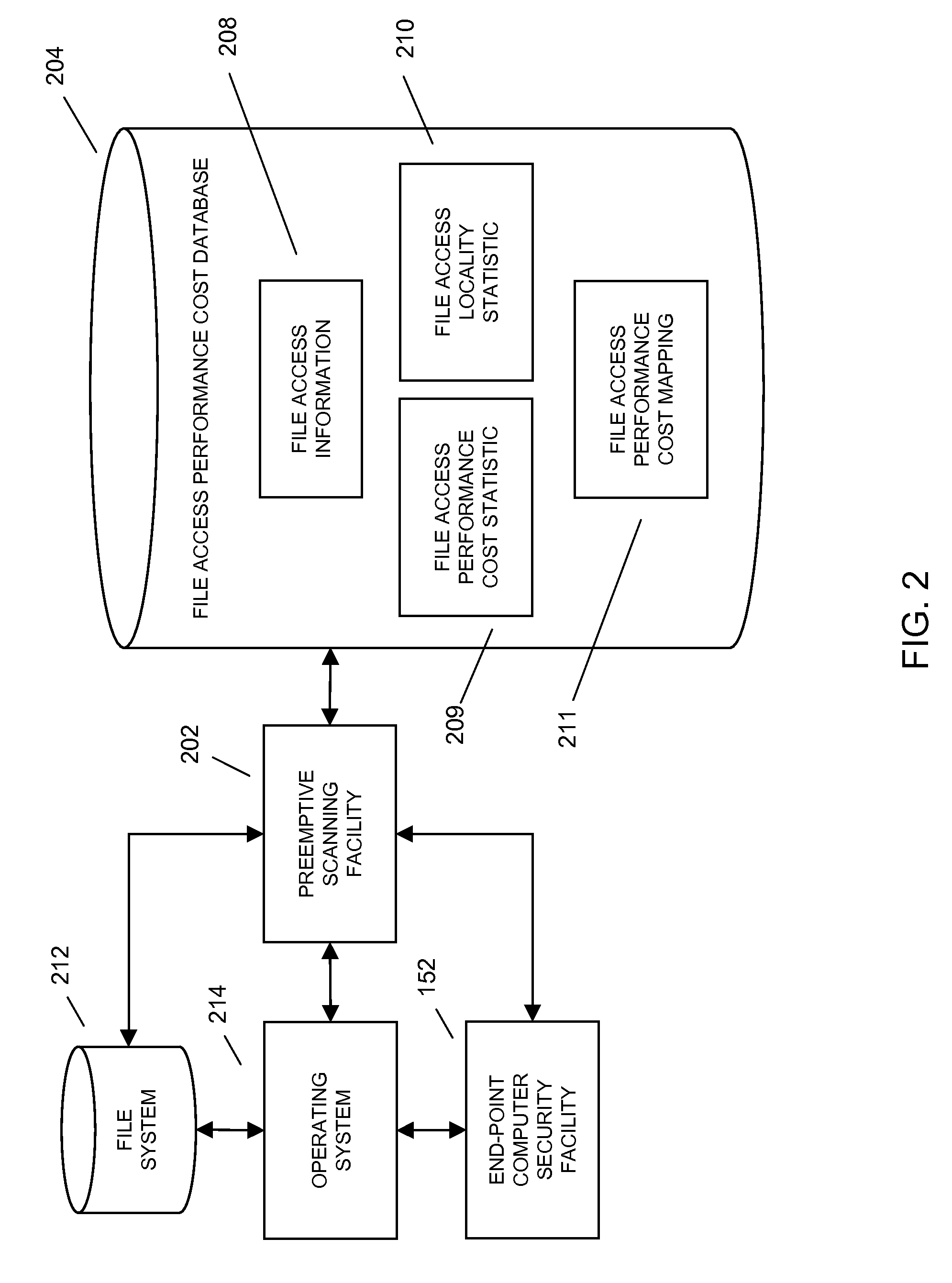
ActiveUS20100242109A1Extended file access delayShorten access timeDigital data information retrievalMemory loss protectionOperational systemFile system
In embodiments of the present invention improved capabilities are described for reducing computer file access time associated with on-access scanning through predictive preemptive scanning, where the prediction may be enabled through the development and use of a file access performance cost mapping of a computing facility's file system. In a first step, file access information describing a pattern of each of a plurality of computer files that have been accessed in a computer file system may be collected. In a second step, the file access information may be processed to generate a file access performance cost statistic for each of the plurality of computer files, where the file access performance cost statistic may be a measure of the time aggregate effect on the computing facility's system performance associated with the access of the file. In a third step, the file access performance cost statistic may be maintained for each of the plurality of files accessed by the computing facility. In a fourth step, the file access performance cost mapping of the computing facility's file system relating to the plurality of computer file may be generated, where the file access performance cost mapping may provide an indication of which of the plurality of files in the file system produce the greatest time aggregate file access effect based on the computing facility's system performance. Finally, in a fifth step, files from the computer file system may be pre-scanned based on the file access performance cost mapping. In embodiments, pre-scanning may access at least one of the plurality of files for scanning prior to the file being called for a use, such as by an operating system, an application, a utility program, and the like. The step of pre-scanning may be performed during periods of low computing facility processing activity, and may result in a reduced need to scan the computer file when the computer file is accessed for use.
Owner:SOPHOS
Efficiency of cache memory operations
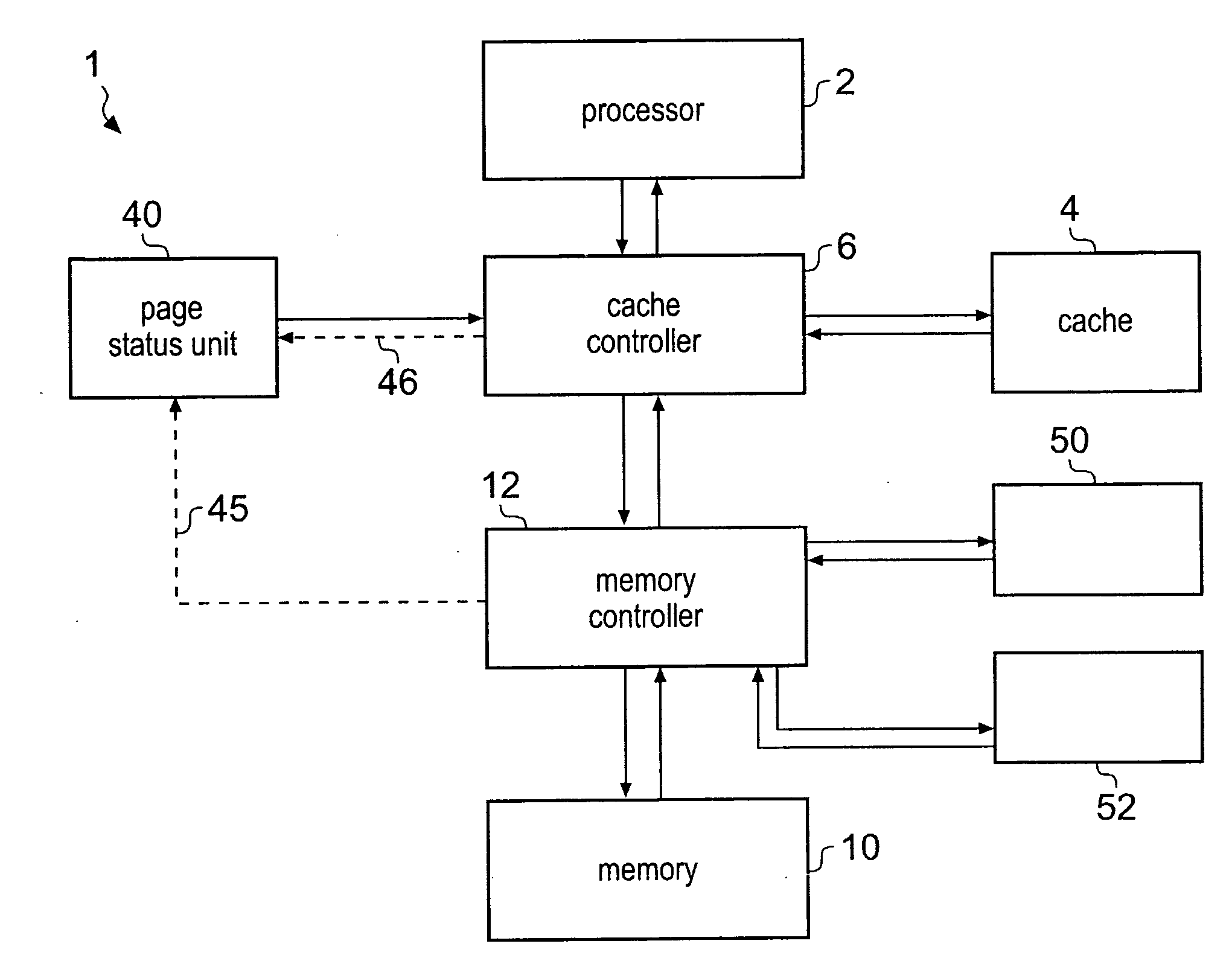
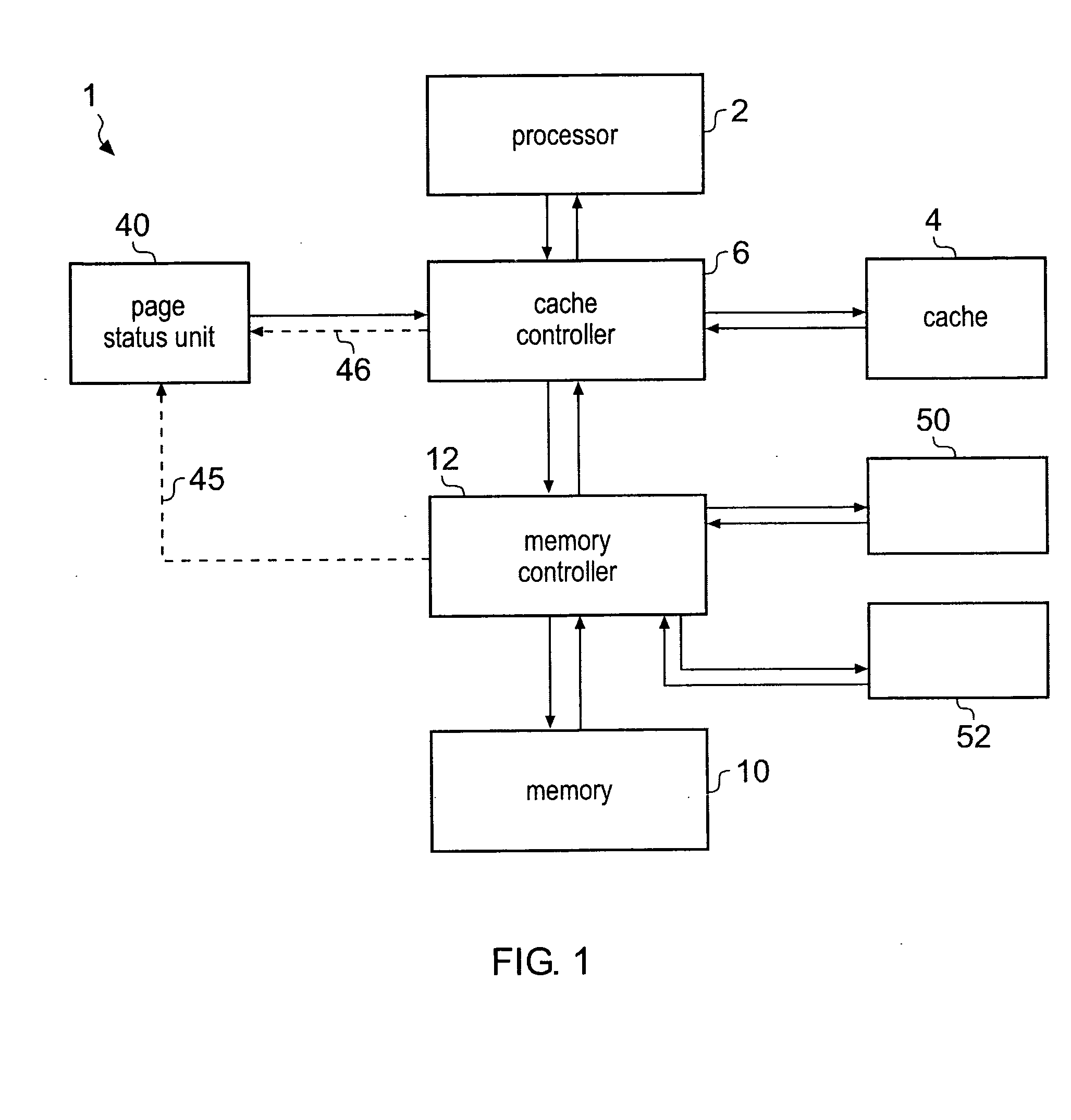
InactiveUS20090265514A1Improve caching efficiencyEasy accessMemory systemsParallel computingCache management
A processing system 1 including a memory 10 and a cache memory 4 is provided with a page status unit 40 for providing a cache controller with a page open indication indicating one or more open pages of data values in memory. At least one of one or more cache management operations performed by the cache controller is responsive to the page open indication so that the efficiency and / or speed of the processing system can be improved.
Owner:ARM LTD
Data storage and retrieval system and method
InactiveUS6912695B2Quickly and seamlessly navigateMassive in sizeStill image data indexingCharacter and pattern recognitionDigital imageData store
A data storage and retrieval system and method are disclosed that enable storage and retrieval of very large digital images. The image data is stored on a one-dimensional storage device in a format optimized for high speed retrieval, display, and seamless navigation.
Owner:PIXIA CORP
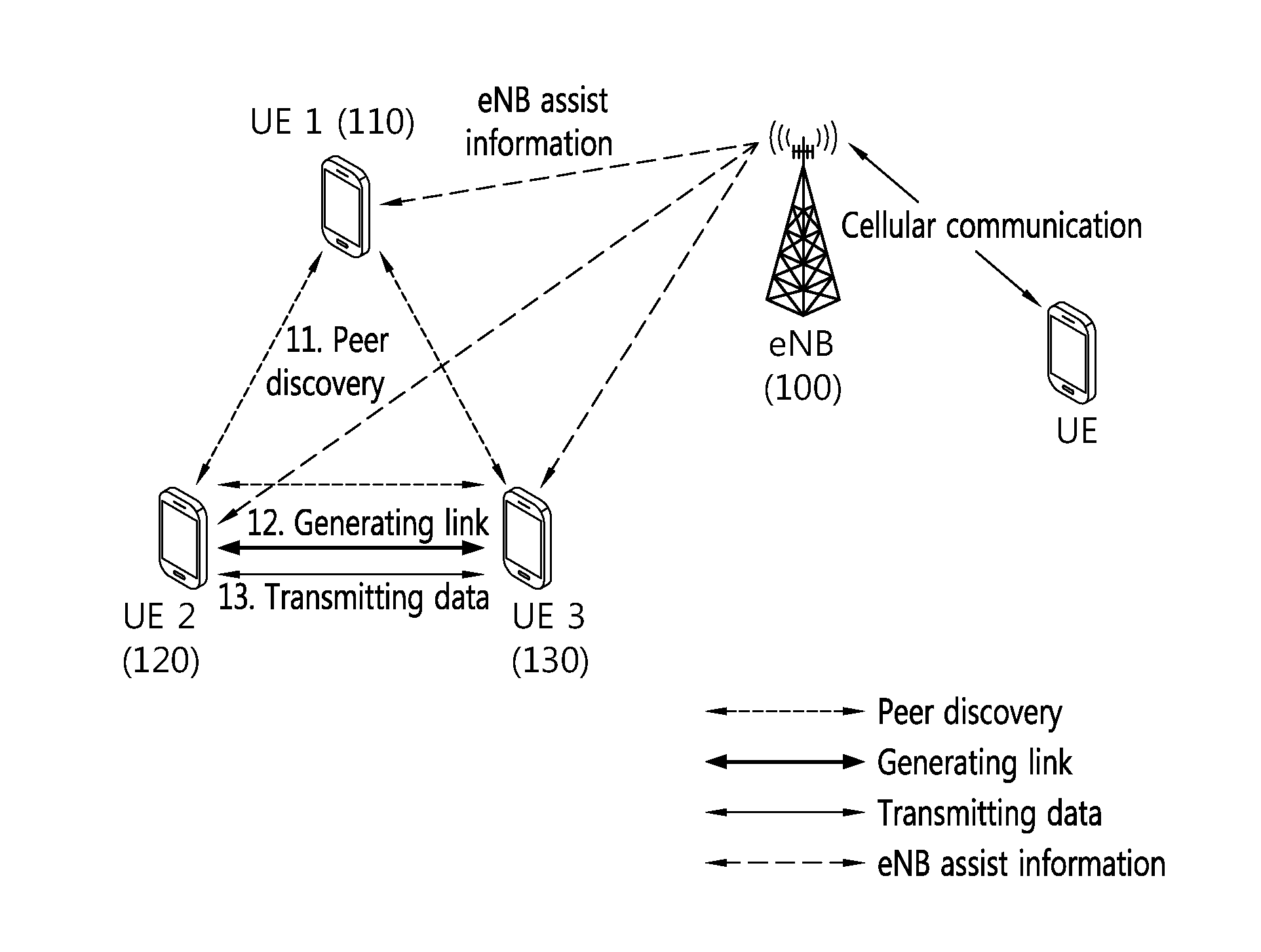
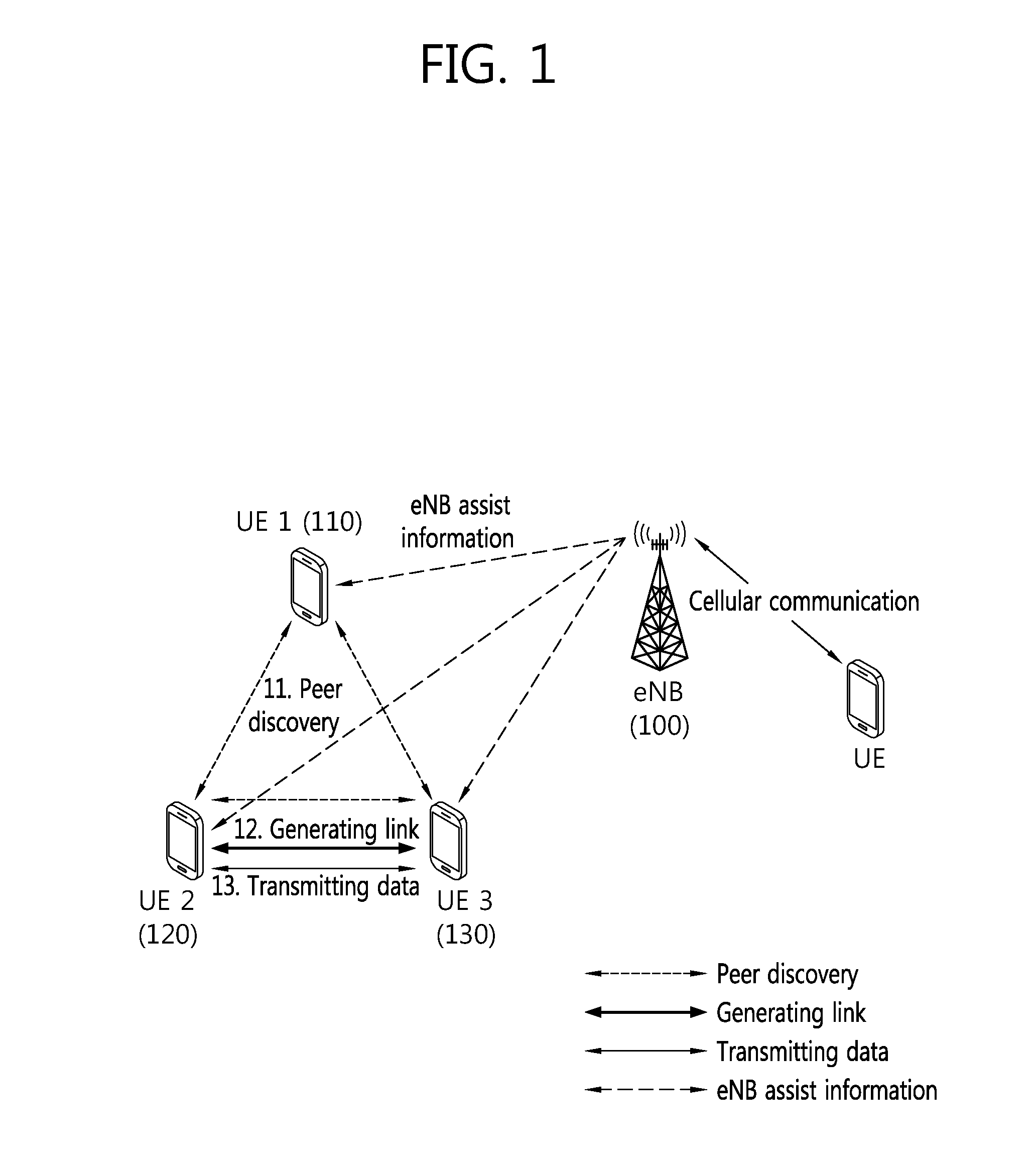
Method and apparatus for performing device-to-device communication in wireless communication system
ActiveUS20150282132A1System performanceSatisfied with the serviceAssess restrictionConnection managementTelecommunicationsCommunications system
The present invention provides a method and an apparatus for performing a device-to-device (D2D) communication service in a wireless communication system. More particularly, D2D terminals supporting D2D communication are identified, discovery groups are formed for the D2D terminals using the same application, and a discovery timing is established depending on the discovery group, wherein the D2D terminals belonging to the same discovery group are shifted to an active state during the discovery timing so as to transreceive signals by using time and frequency resources designated for D2D discovery, wherein the discovery timing is set so as to have a variable value depending on the discovery group.
Owner:LG ELECTRONICS INC +1
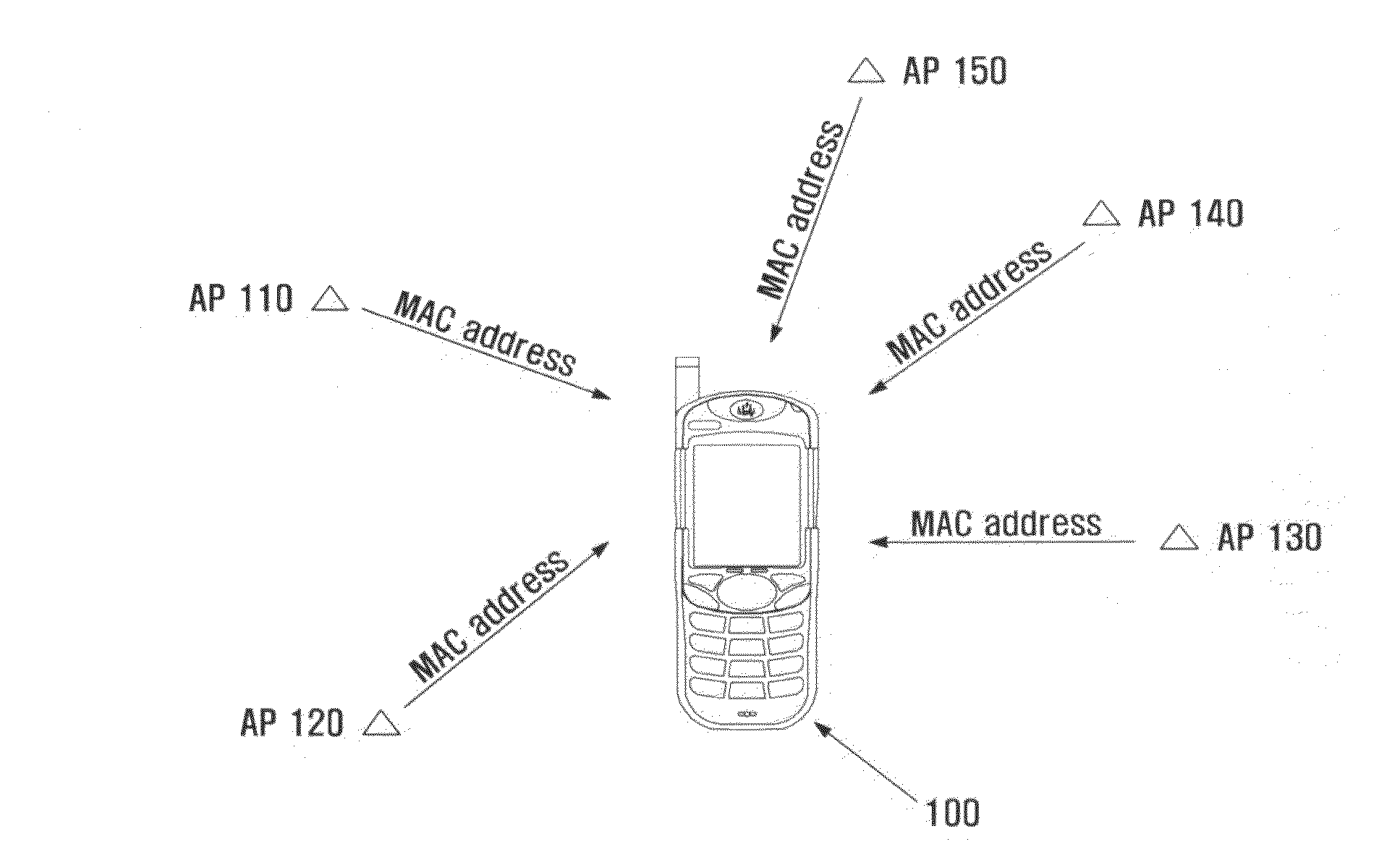
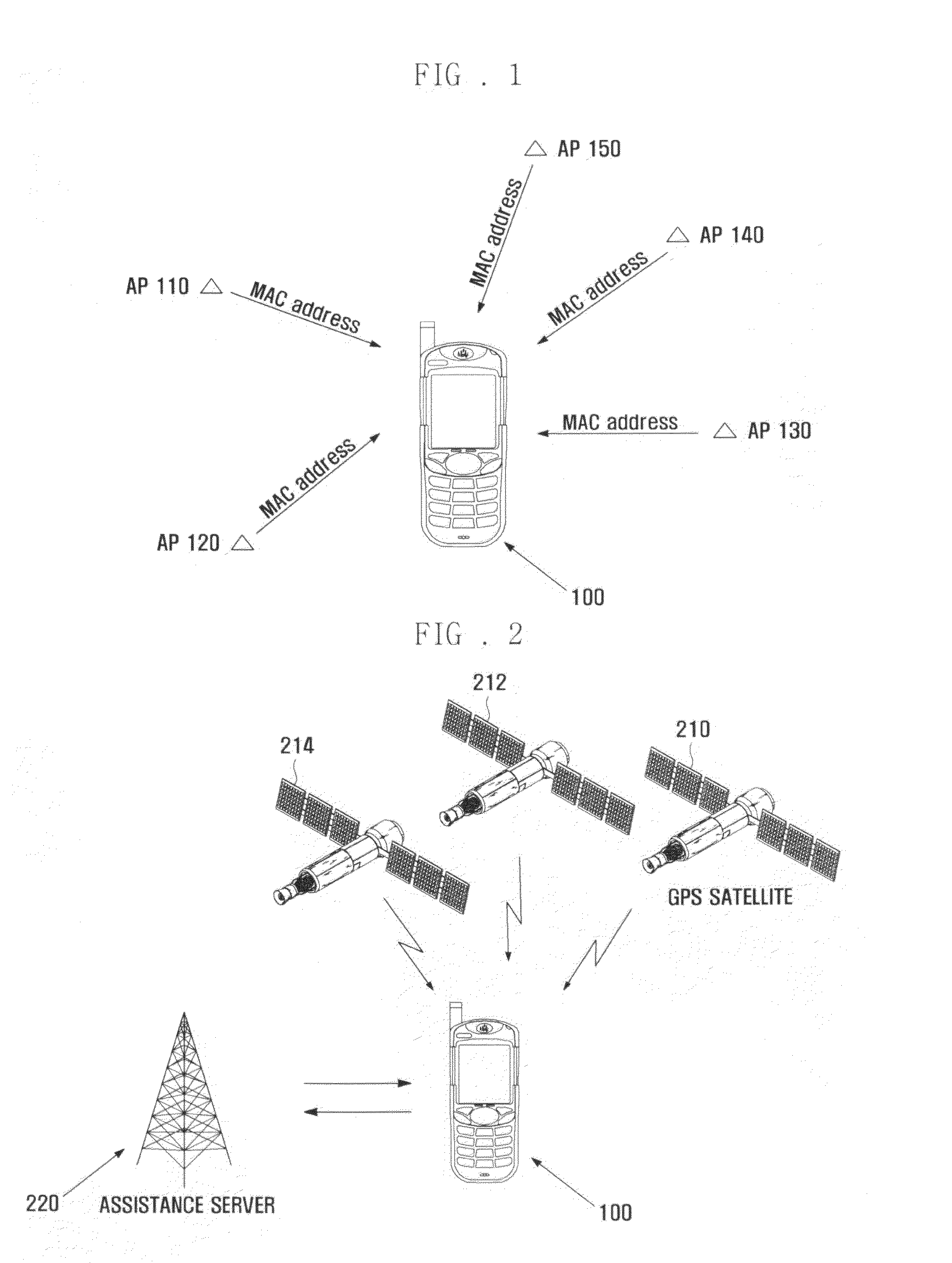
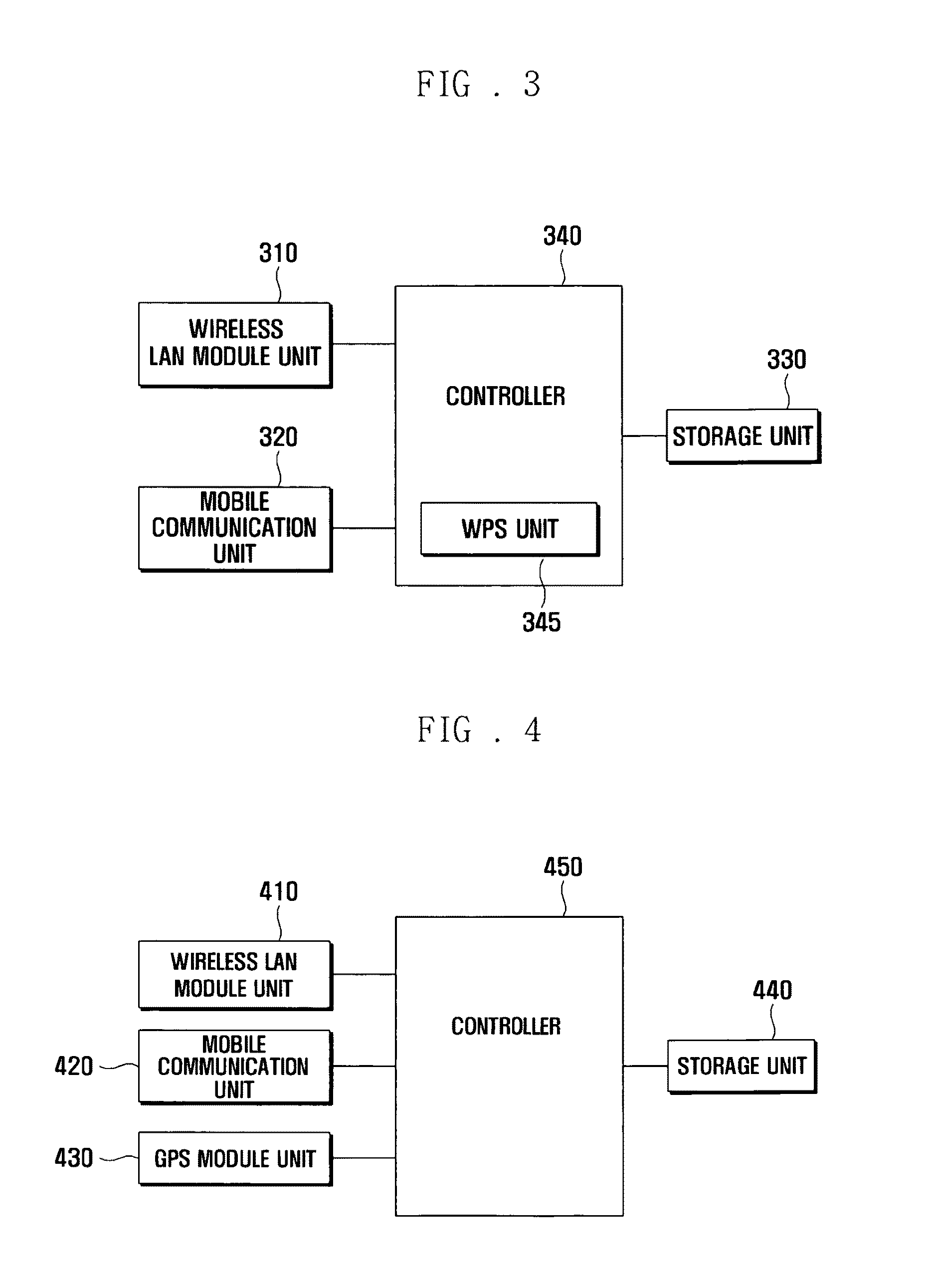
Method for connecting to wireless LAN access point and apparatus using the same
InactiveUS20100103844A1Reduce power consumptionShorten access timeEnergy efficient ICTAssess restrictionAccess timeWireless lan
A method and system for connecting to a wireless LAN Access Point (AP) using position information and an apparatus using the same. The method and system includes scanning APs in a preset period, determining a current position of an AP access apparatus based on the scanned APs, calculating distances between the current position of the AP access apparatus and each of positions of one or more user-designated APs, controlling a scan period in response to the calculated distances, and, when the user-designated APs are scanned, accessing the scanned user-designated APs. In scanning the nearby positioned wireless LAN AP and accessing the scanned AP, the power consumption can be reduced and the access time to AP can also be reduced.
Owner:SAMSUNG ELECTRONICS CO LTD
Anonymous location service for wireless networks
InactiveUS20090047937A1Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identification information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
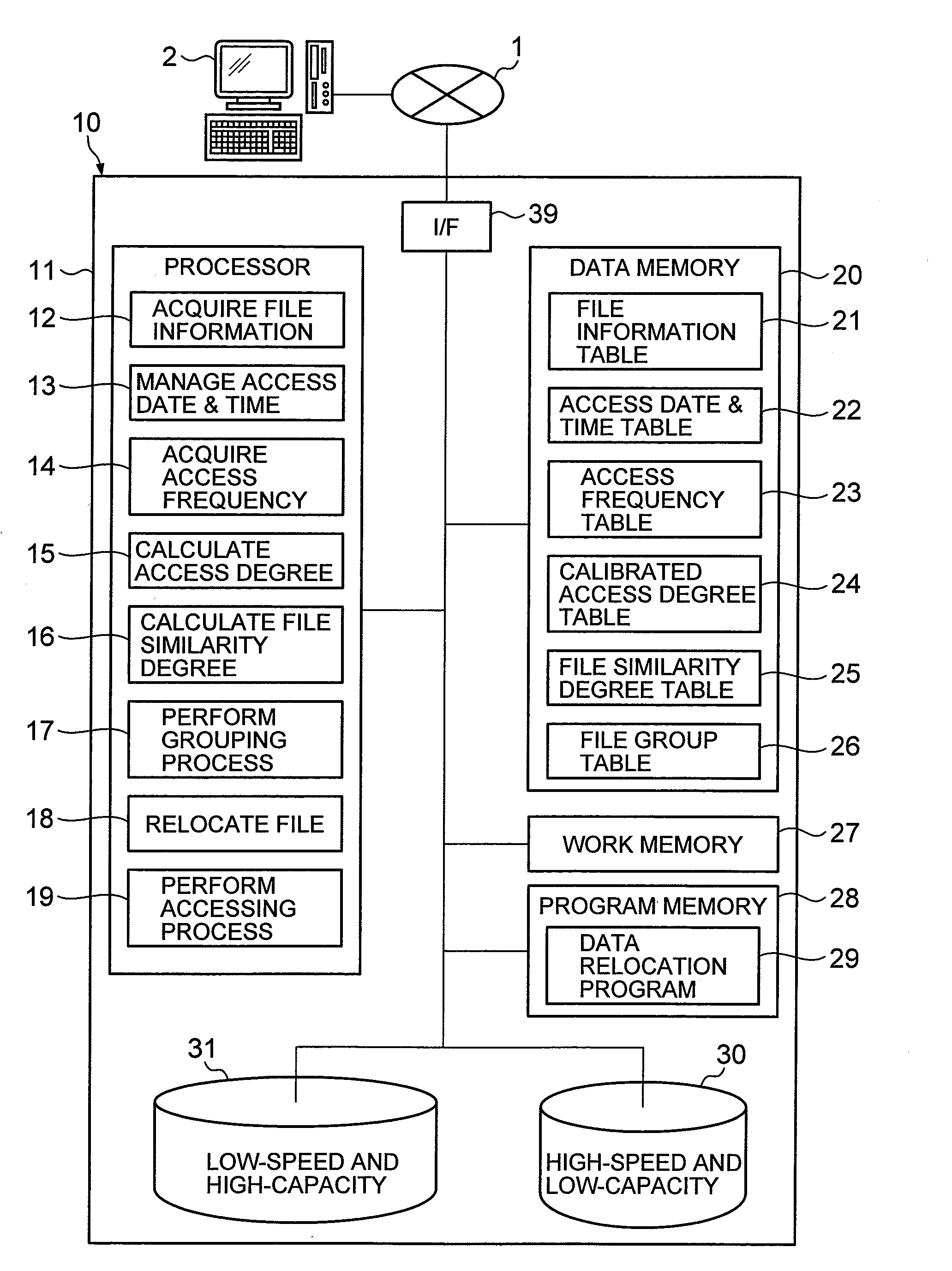
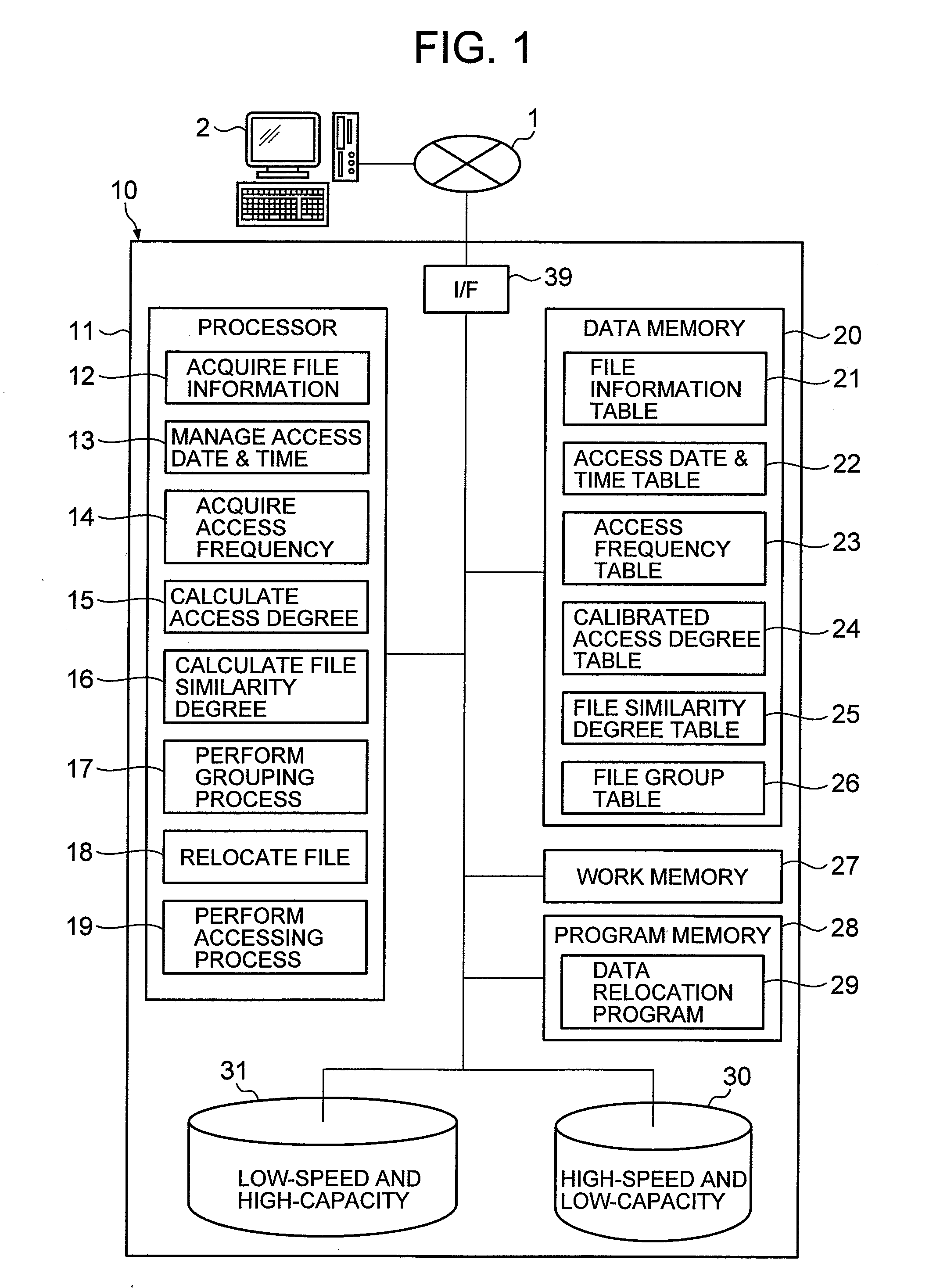
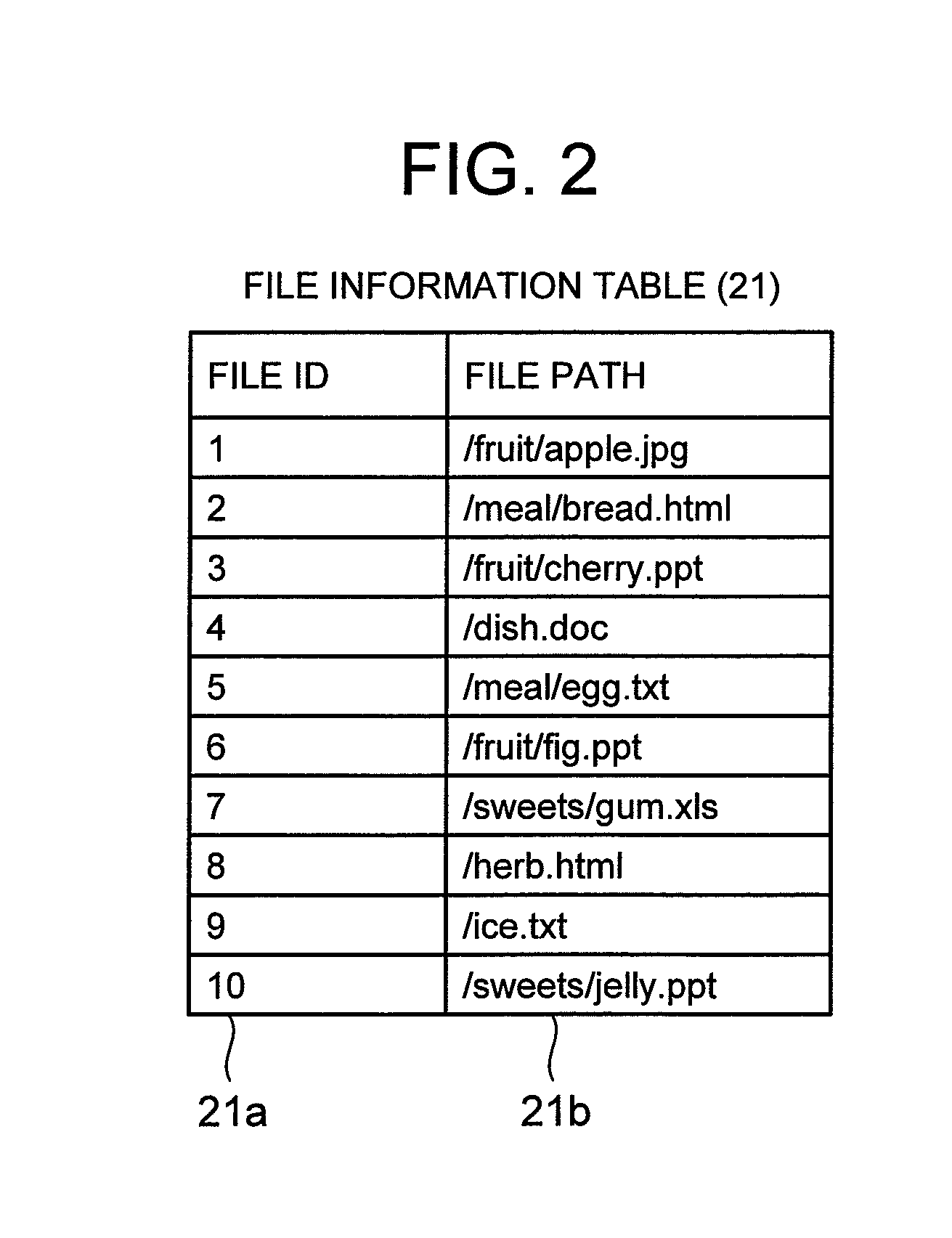
Storage system, data relocation method thereof, and recording medium that records data relocation program
InactiveUS20080059718A1Optimizes groupingShorten the timeMemory adressing/allocation/relocationInput/output processes for data processingData acquisitionAccess frequency
There is a need to improve access speed for a file in a storage system that is provided with multiple storage units having different access speeds.The storage system (10) includes an access frequency acquiring part (14) that divides a past constant accessed data acquisition period into multiple unit periods, and obtains an access frequency for file stored in any of the multiple storage units (30 and 31), a similarity degree calculating part (16) that obtains, for each file, a similarity degree between the access frequency to the file for each unit period, and the access frequency to every other file for each unit period, a grouping process part (17) that groups one or more other files having a similarity degree equal to or higher than a predetermined value, in an identical group, and a file relocation part (18) that places a file belonging to the identical group into a storage unit (30) having a high access speed, when the file stored in the storage units (30 and 31) is accessed and there exists any other file within the identical group to which the file belongs.
Owner:HITACHI LTD
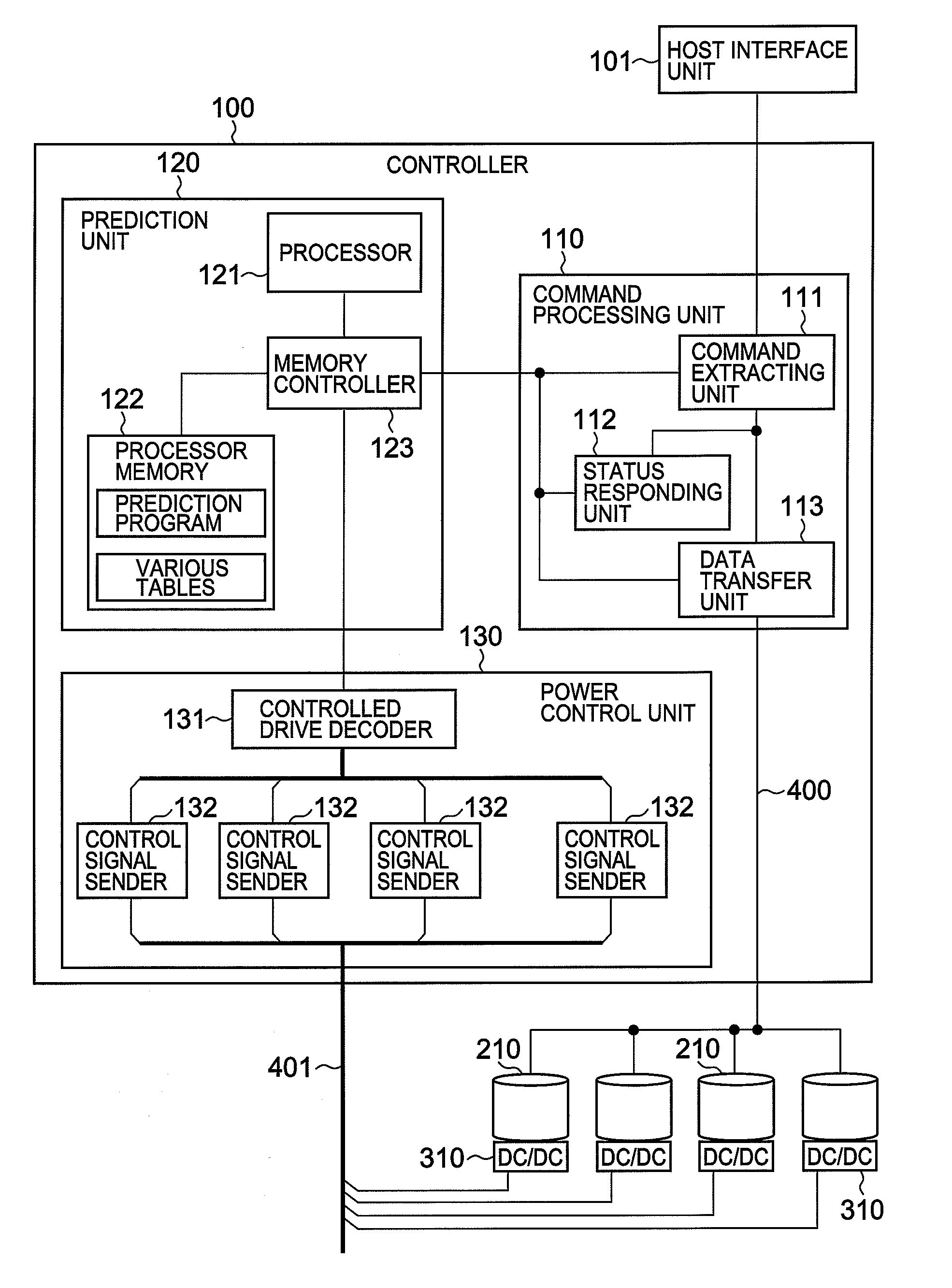
Storage system and method of controlling of feeding power to storage system
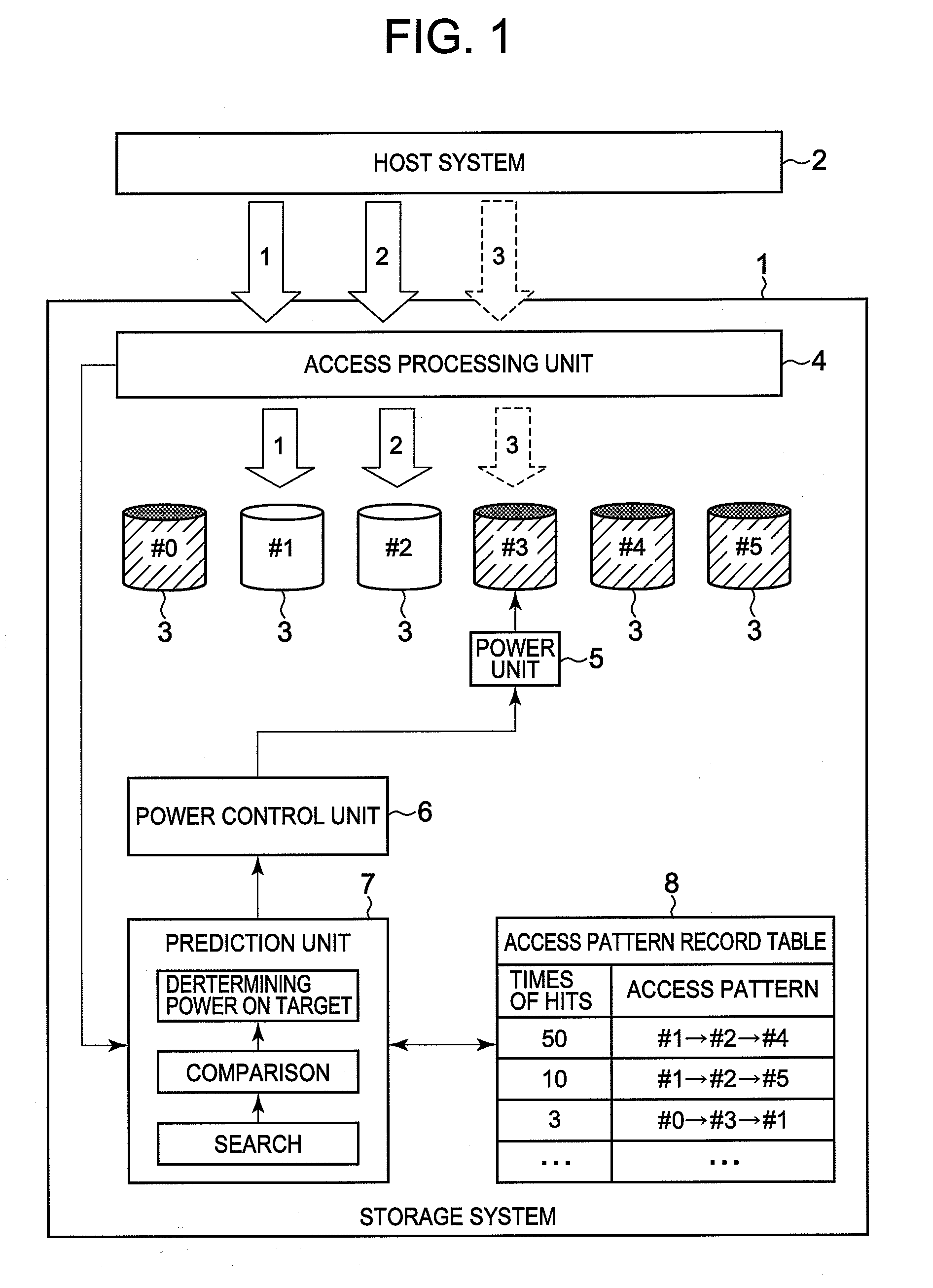
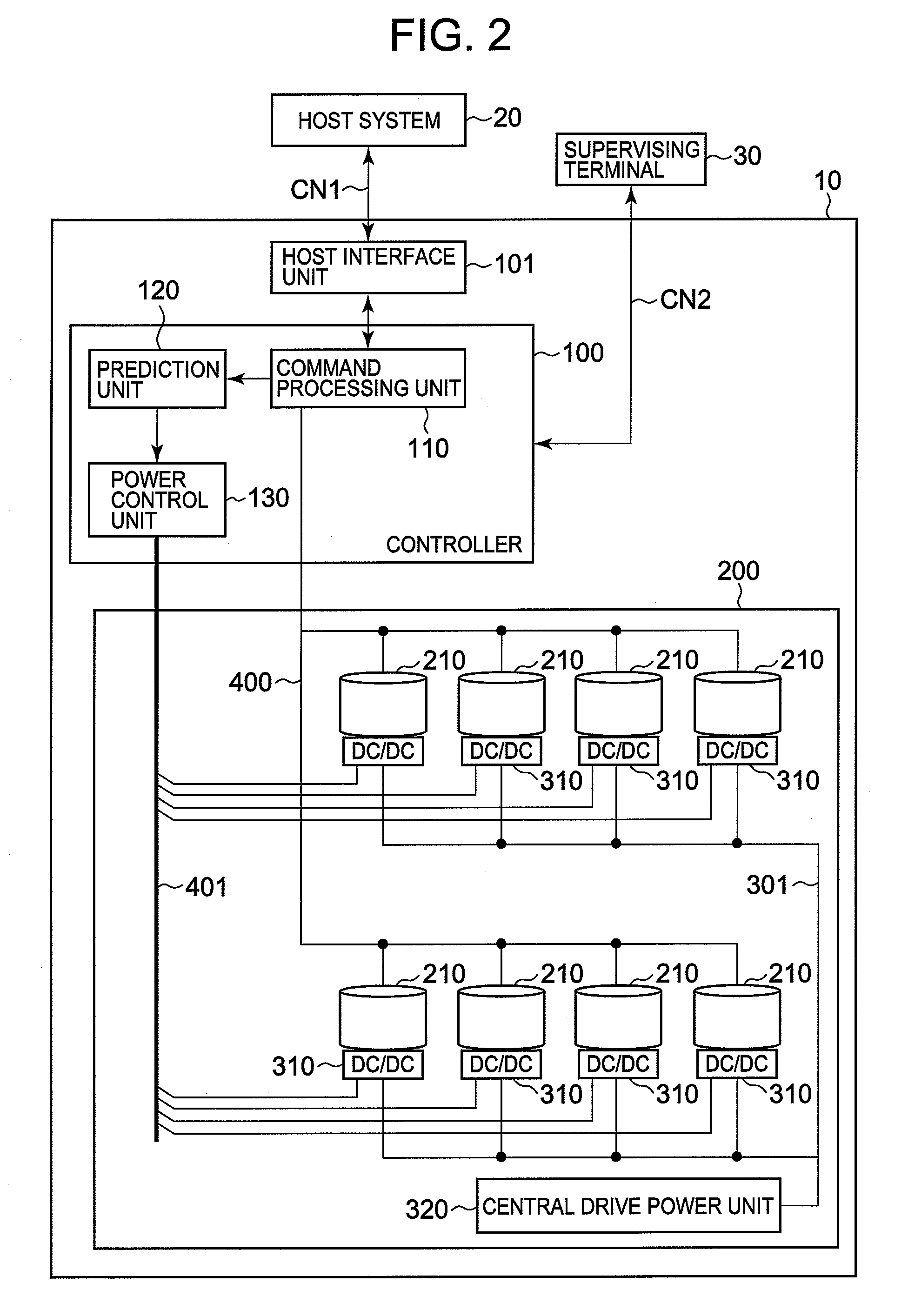
ActiveUS20080104431A1Shorten operation timeReduce the amount requiredEnergy efficient ICTVolume/mass flow measurementOperating systemPower unit
A storage system of the present invention saves power consumption of the storage system and enhances responsiveness by predicting a disk drive that is to be accessed next on the basis of an access request from a host system, and promptly feeding power to the predicted disk drive. A prediction unit predicts the disk drive which is to be accessed next by the host system, by comparing a recent access request from the host system against a past access pattern that is registered in an access pattern record table. A power control unit feeds power from a power unit to the disk drive predicted by the prediction unit.
Owner:RAKUTEN GRP INC
System for providing banking services by use of mobile communication
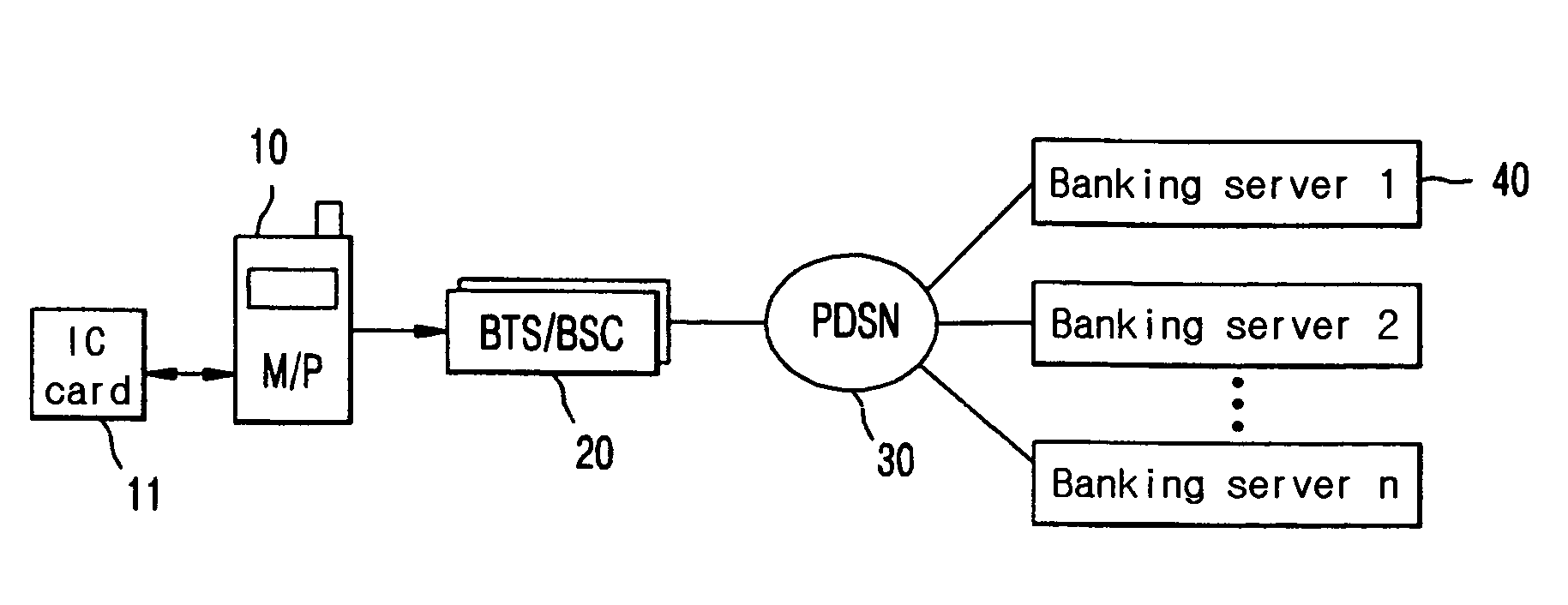
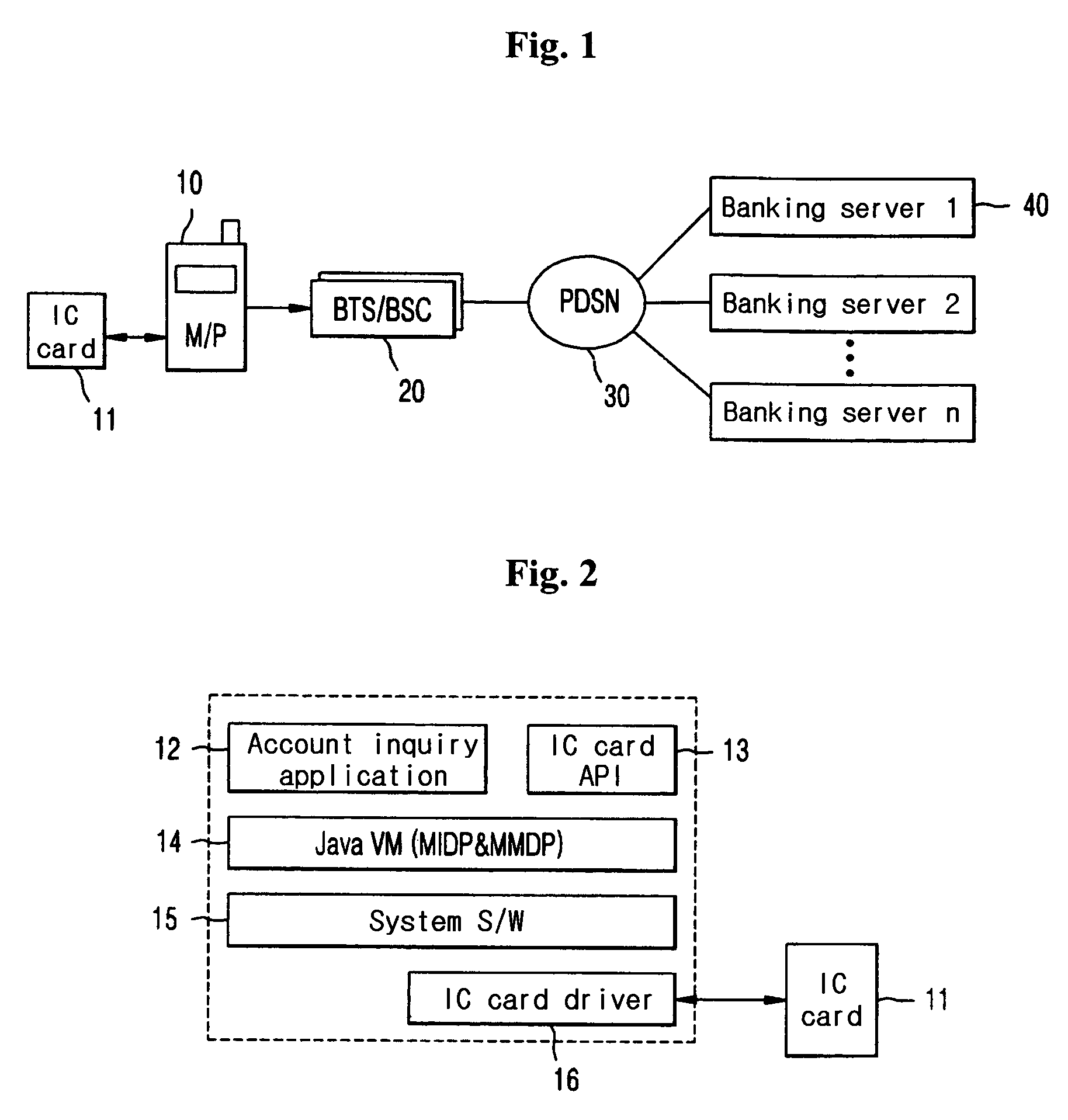
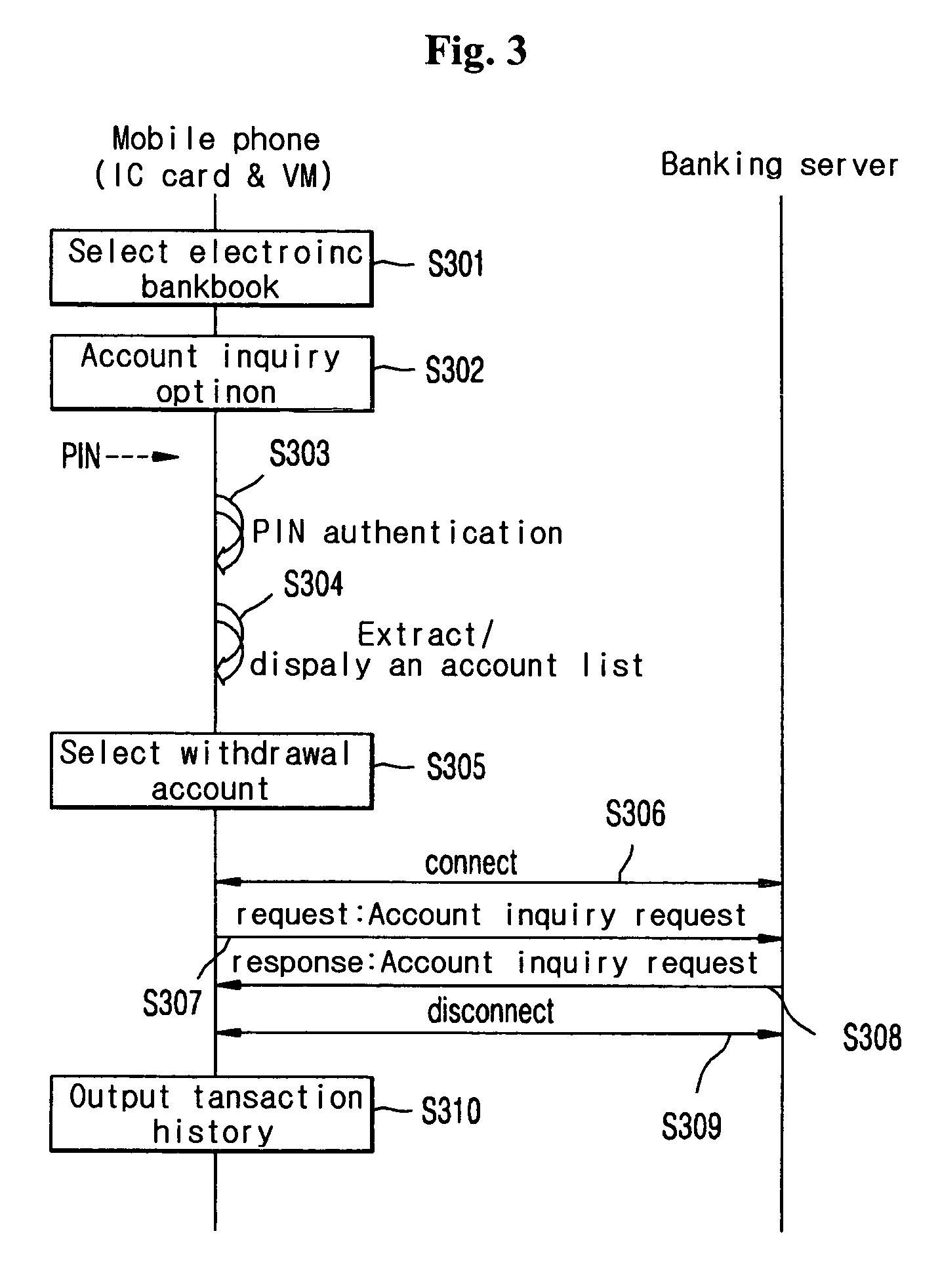
InactiveUS7885870B2Simple inputShorten access timeFinanceNetwork traffic/resource managementTransceiverFinancial transaction
A system for providing banking services by use of a mobile communication system, in which a variety of financial transactions including inquiry of at least one financial account of at least one financial institution, transfer and remittance, and loan and its interest payment are processed by the mobile communication system. The system includes: the mobile communication system, provided with an integrated circuit (IC) card and a memory device to which a banking application is installed, for transmitting and receiving data by wireless, the IC card being stored with information on a personal identification number (PIN) and information related to financial accounts including a loan account. The banking application processing the financial transactions including the financial account inquiry, the transfer and remittance, and the loan and its interest payment by mobile banking; a base station transceiver system (BTS) for executing a wireless interface with the mobile communication system and a base station controller (BSC) for performing call processing and for providing a core network interface with the BTS. A packet data switching network (PDSN) for providing a packet data transfer service using a transmission control protocol / Internet protocol (TCP / IP); and at least one banking server for, when being requested to process the financial transactions including the financial transactions including the financial account inquiry, the transfer and remittance, and the loan and its interest payment by the banking application of the mobile communication system.
Owner:LG UPLUS
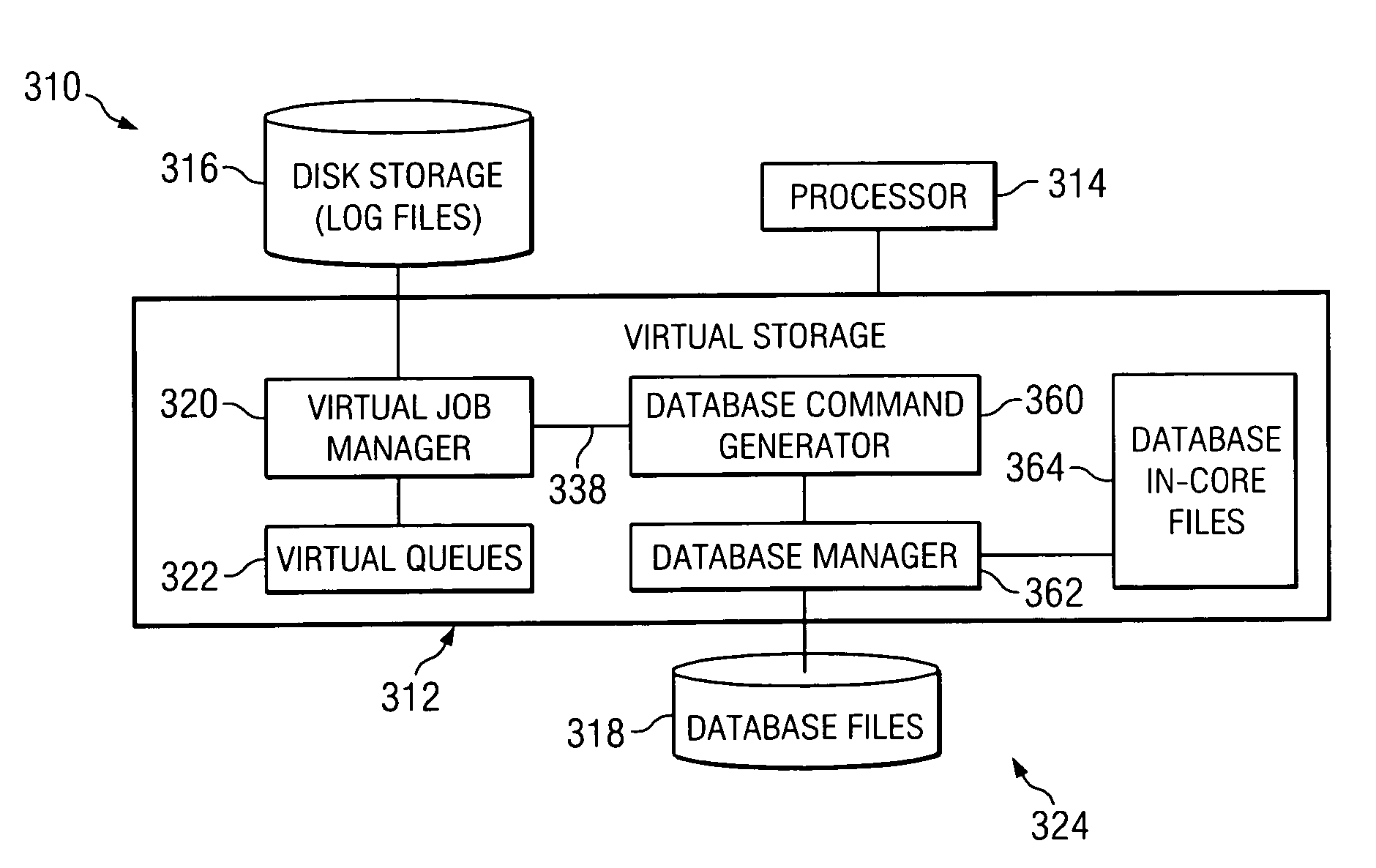
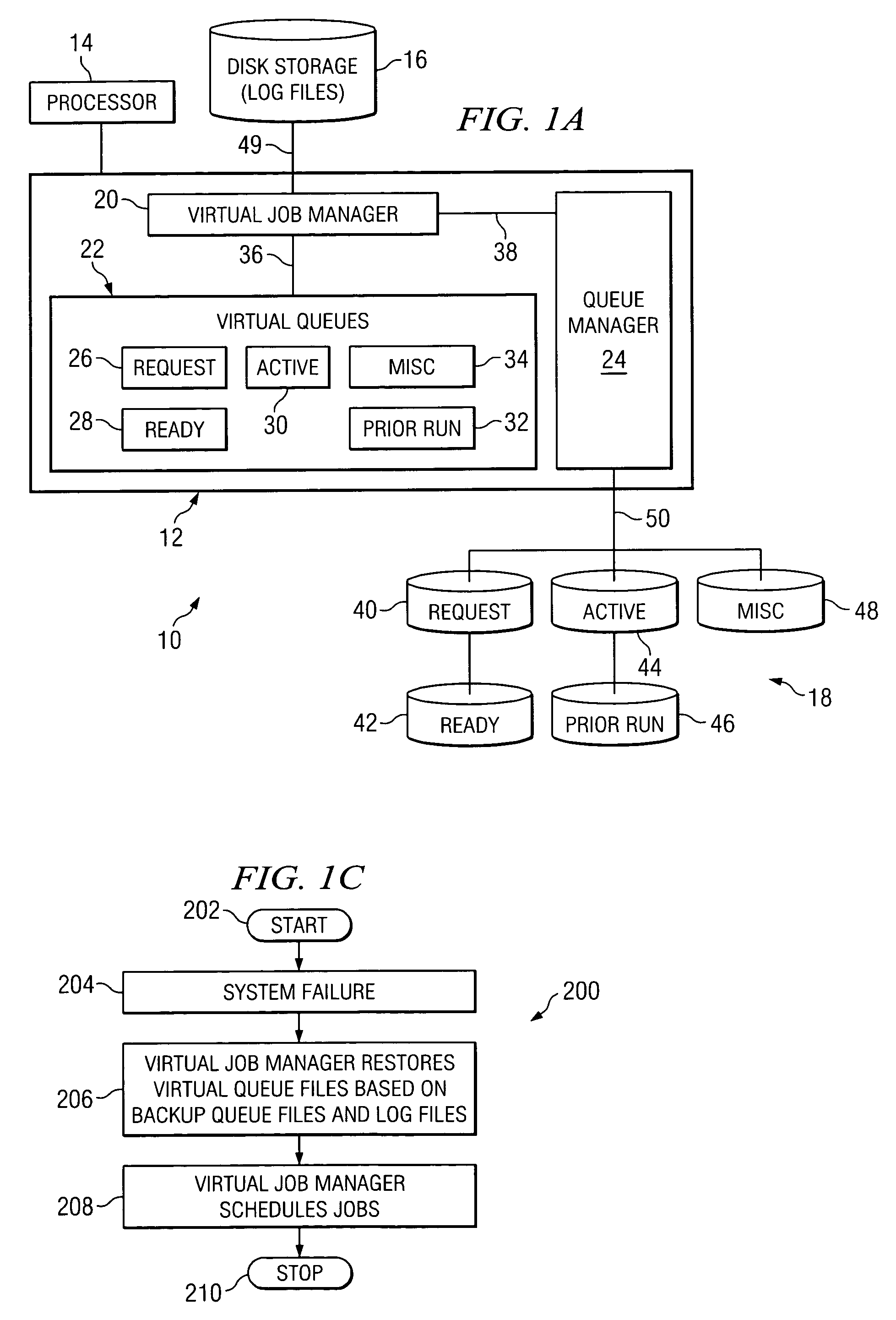
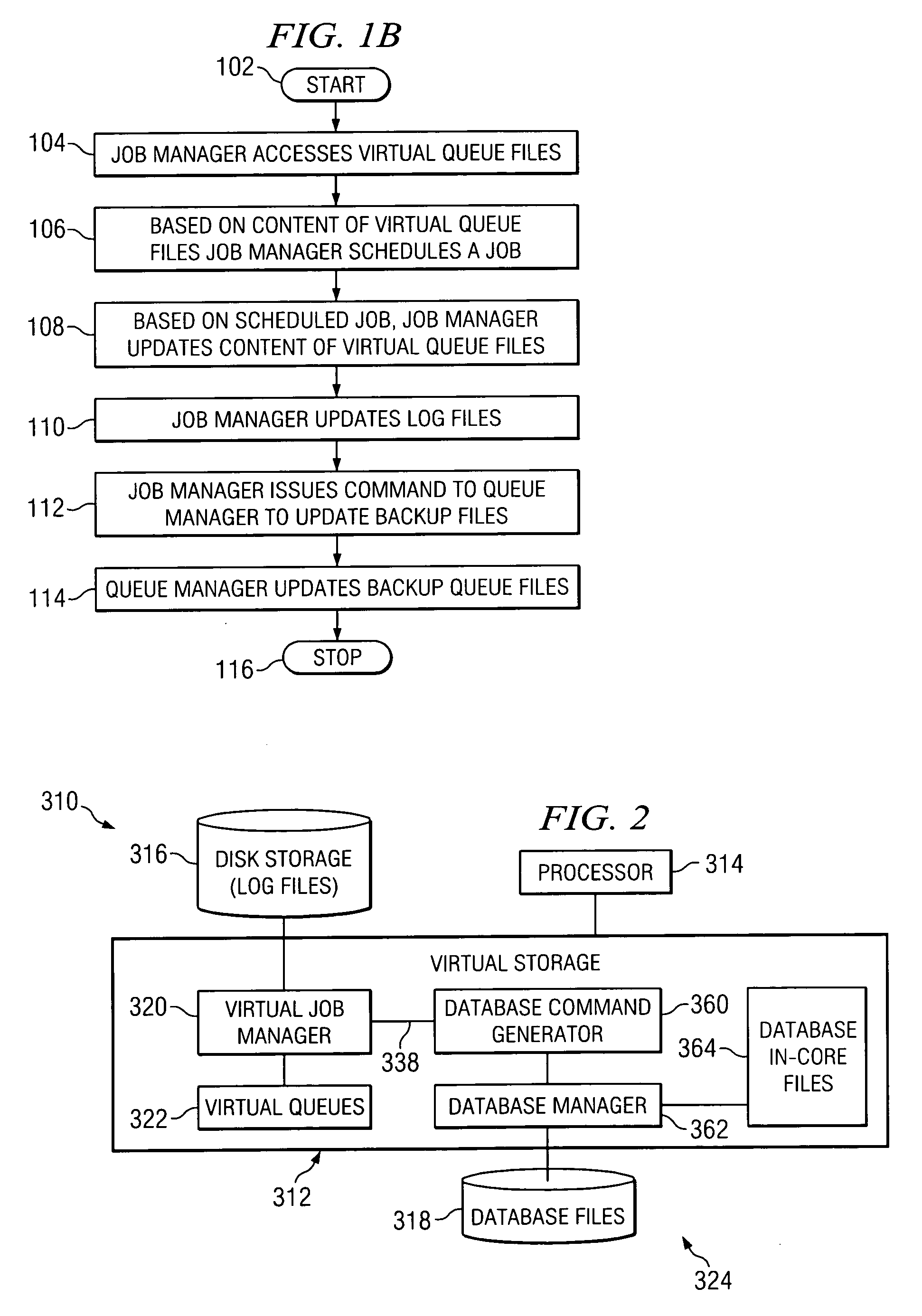
Method and system for scheduling jobs in a computer system
ActiveUS7898679B2Shorten access timeQuick dispatchMultiple digital computer combinationsProgram controlRandom access memoryComputerized system
A method for scheduling jobs in a computer system includes storing a plurality of job queue files in a random access memory, accessing at least one of the job queue files stored in random access memory, and scheduling, based in part on the at least one job queue file, execution of a job associated with the at least one job queue file. In a more particular embodiment, a method for scheduling jobs in a computer system include storing a plurality of job queue files in a random access memory. The plurality of job queue files include information associated with at least one job. The method also includes storing the information external to the random access memory and accessing at least one of the job queue files stored in the random access memory. The method also includes scheduling, based at least in part on the at least one job queue file, execution of a job associated with at least one job queue file. In response to the scheduling, the method includes updating the information stored in the job queue file and random access memory and the information stored external to the random access memory.
Owner:COMP ASSOC THINK INC
Method for software controllable dynamically lockable cache line replacement system
InactiveUS20060036811A1Shorten access timeSpeed up access timeMemory systemsParallel computingAccess line
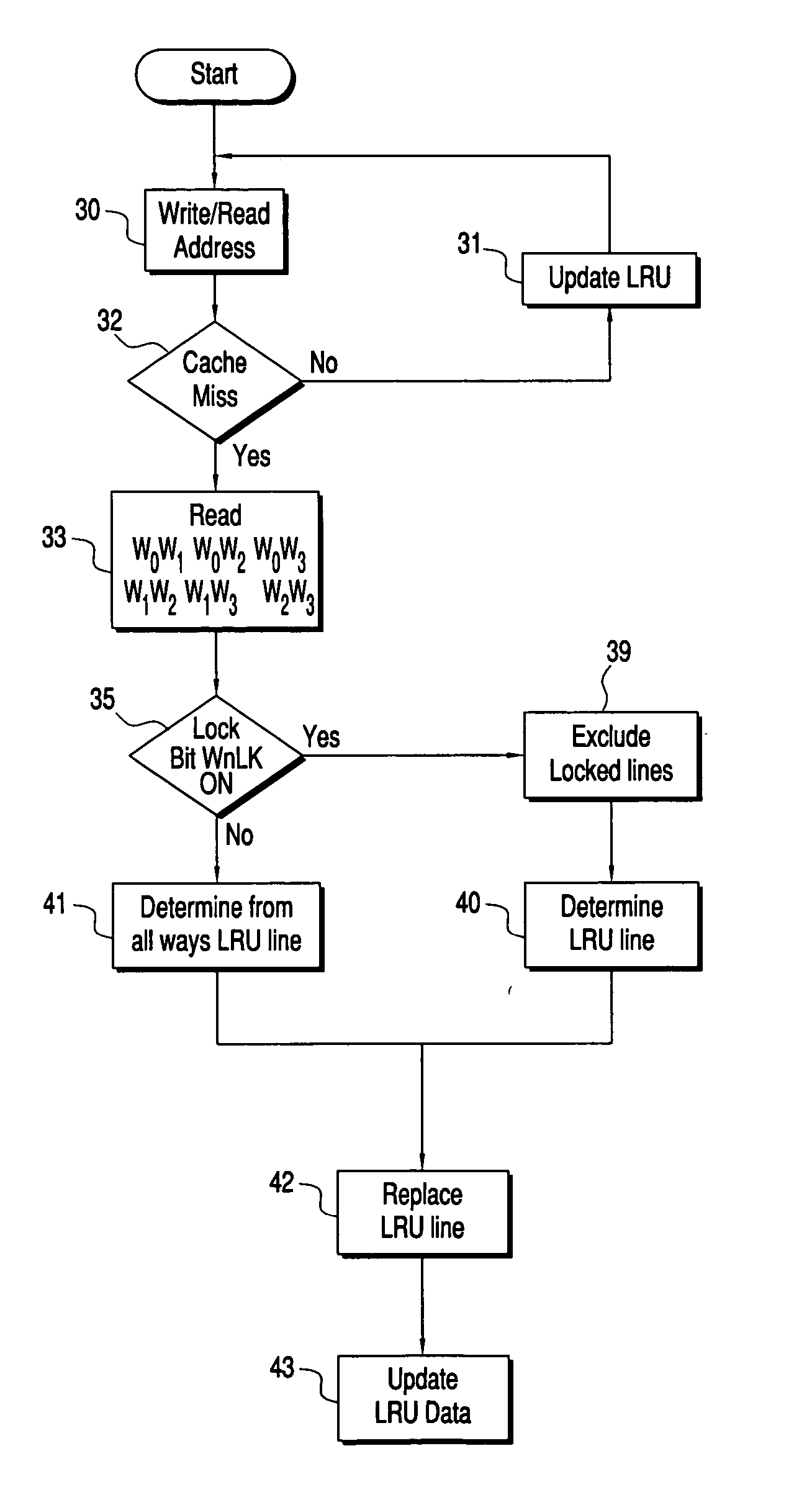
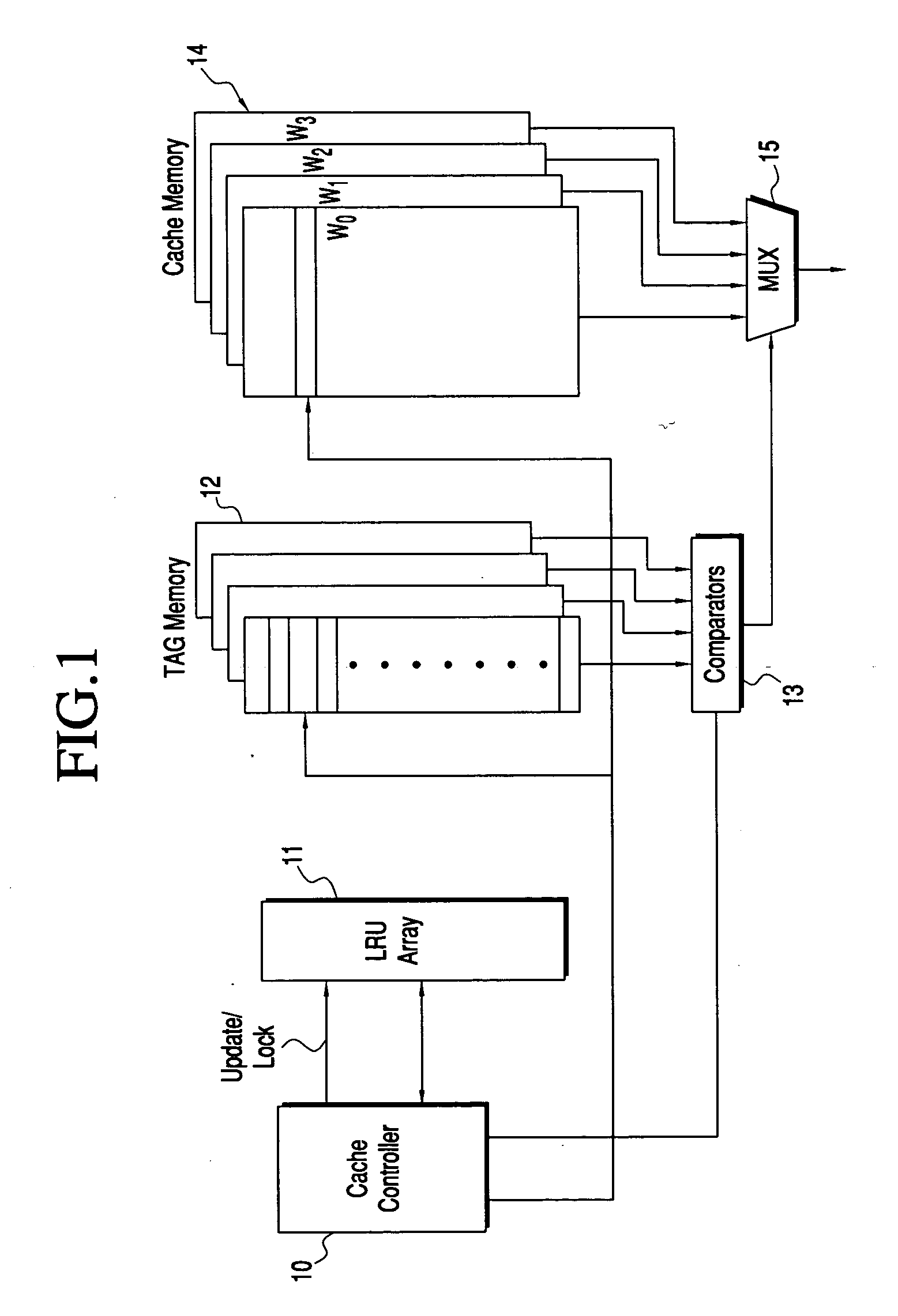
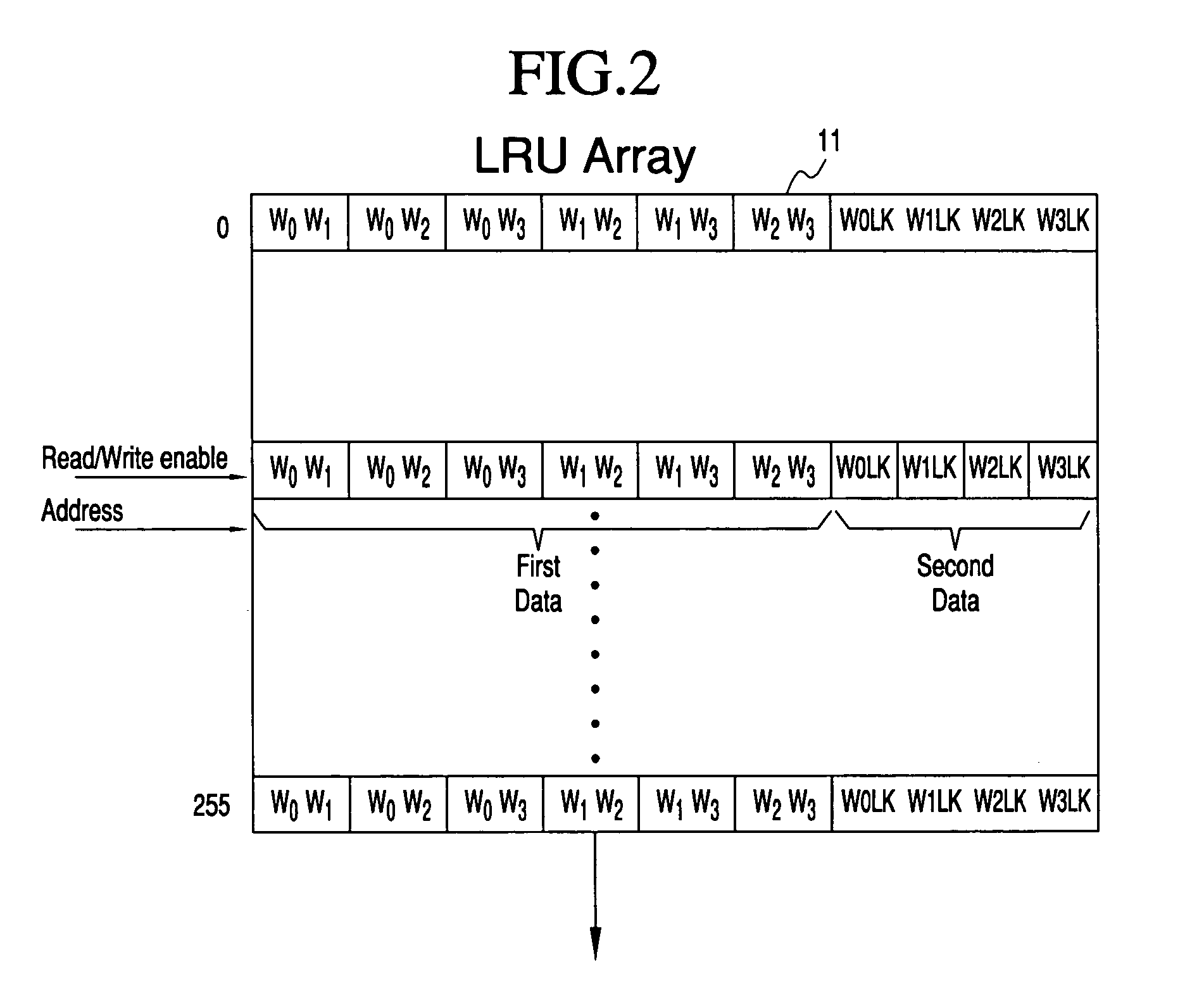
An LRU array and method for tracking the accessing of lines of an associative cache. The most recently accessed lines of the cache are identified in the table, and cache lines can be blocked from being replaced. The LRU array contains a data array having a row of data representing each line of the associative cache, having a common address portion. A first set of data for the cache line identifies the relative age of the cache line for each way with respect to every other way. A second set of data identifies whether a line of one of the ways is not to be replaced. For cache line replacement, the cache controller will select the least recently accessed line using contents of the LRU array, considering the value of the first set of data, as well as the value of the second set of data indicating whether or not a way is locked. Updates to the LRU occur after each pre-fetch or fetch of a line or when it replaces another line in the cache memory.
Owner:GOOGLE LLC
Method for booting a host device from an MMC/SD device, a host device bootable from an MMC/SD device and an MMC/SD device method a host device may booted from
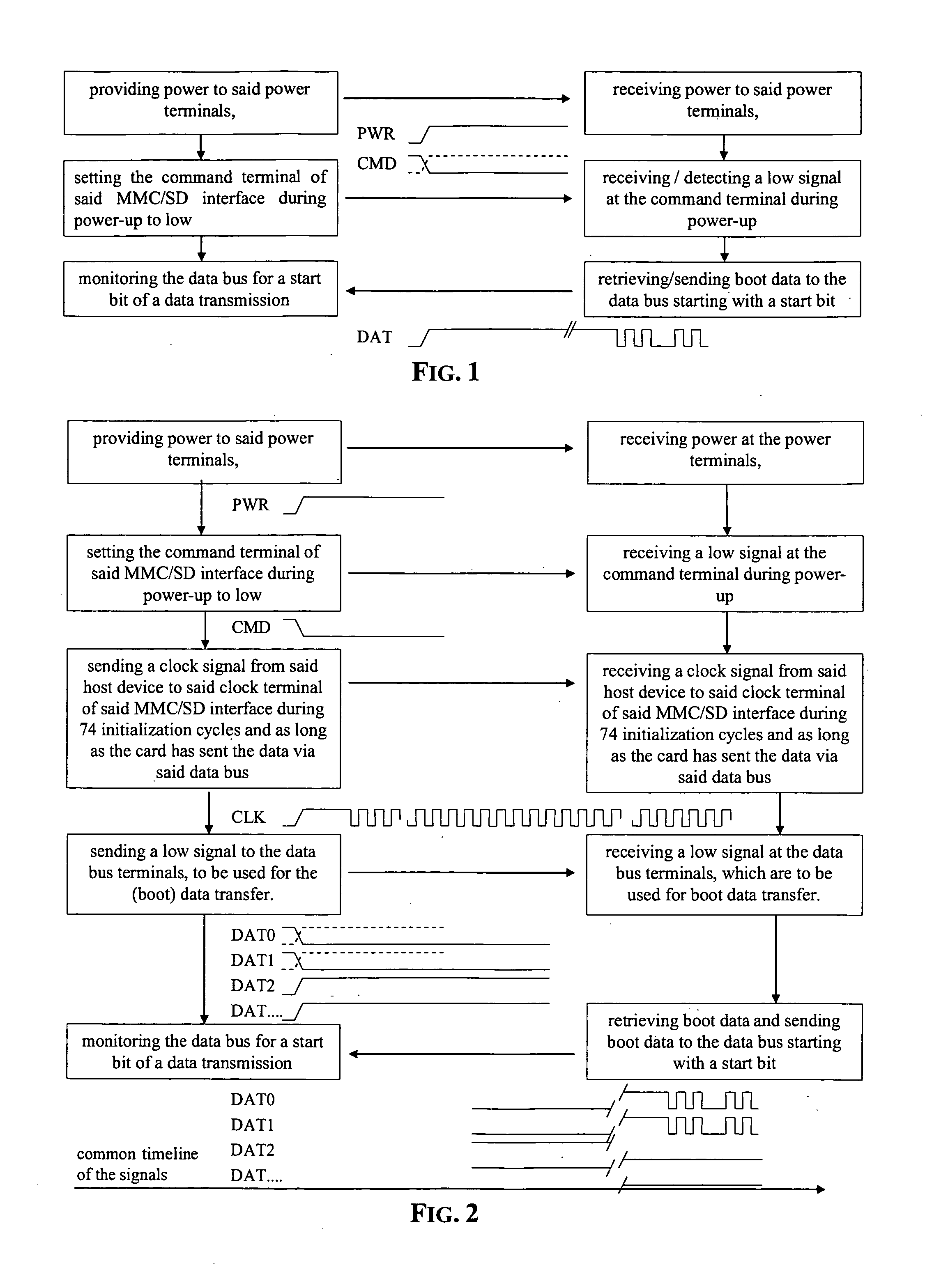
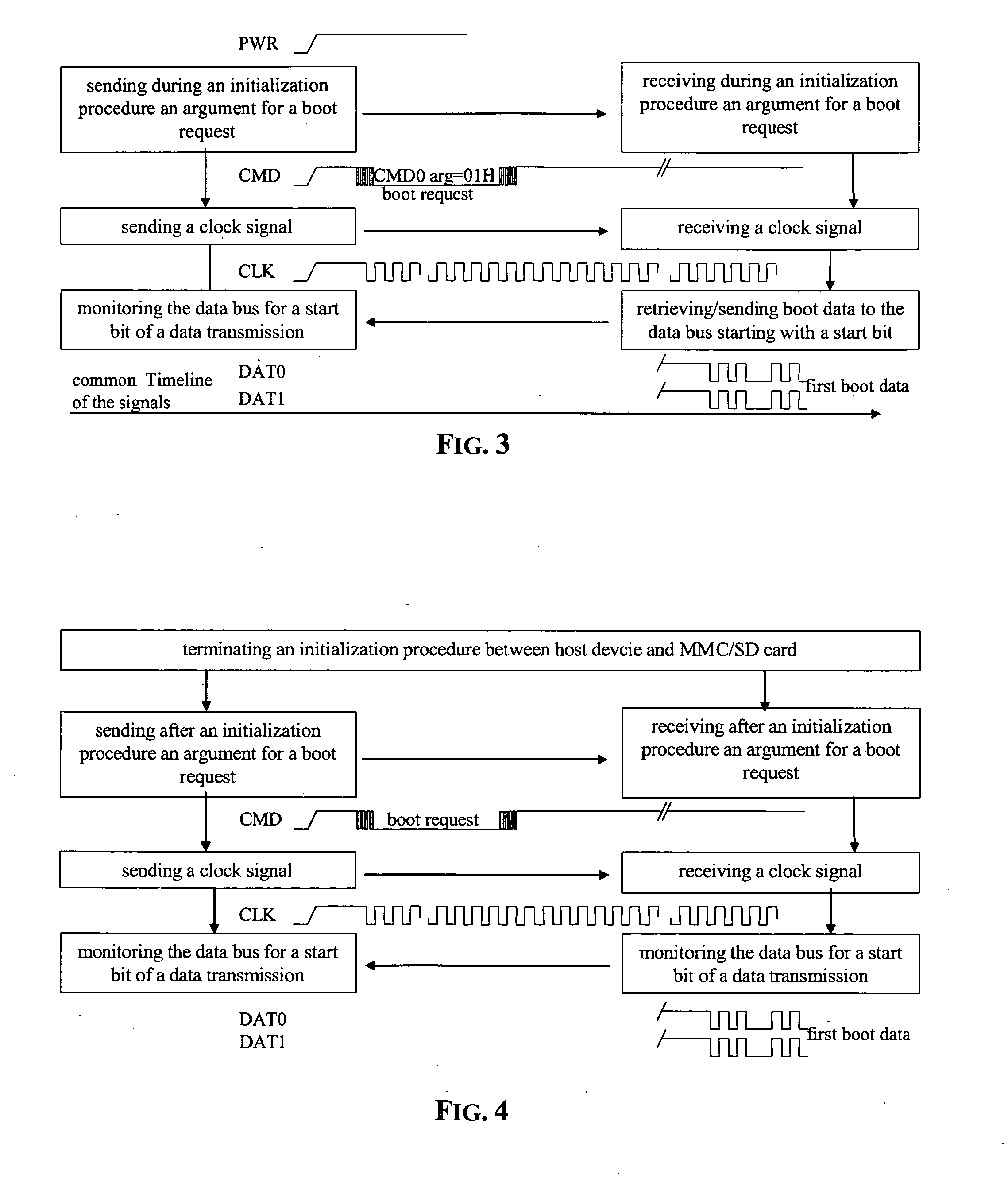
ActiveUS20070168652A1Data exchangeShorten access timeDigital computer detailsComponent plug-in assemblagesComputer hardwareElectricity
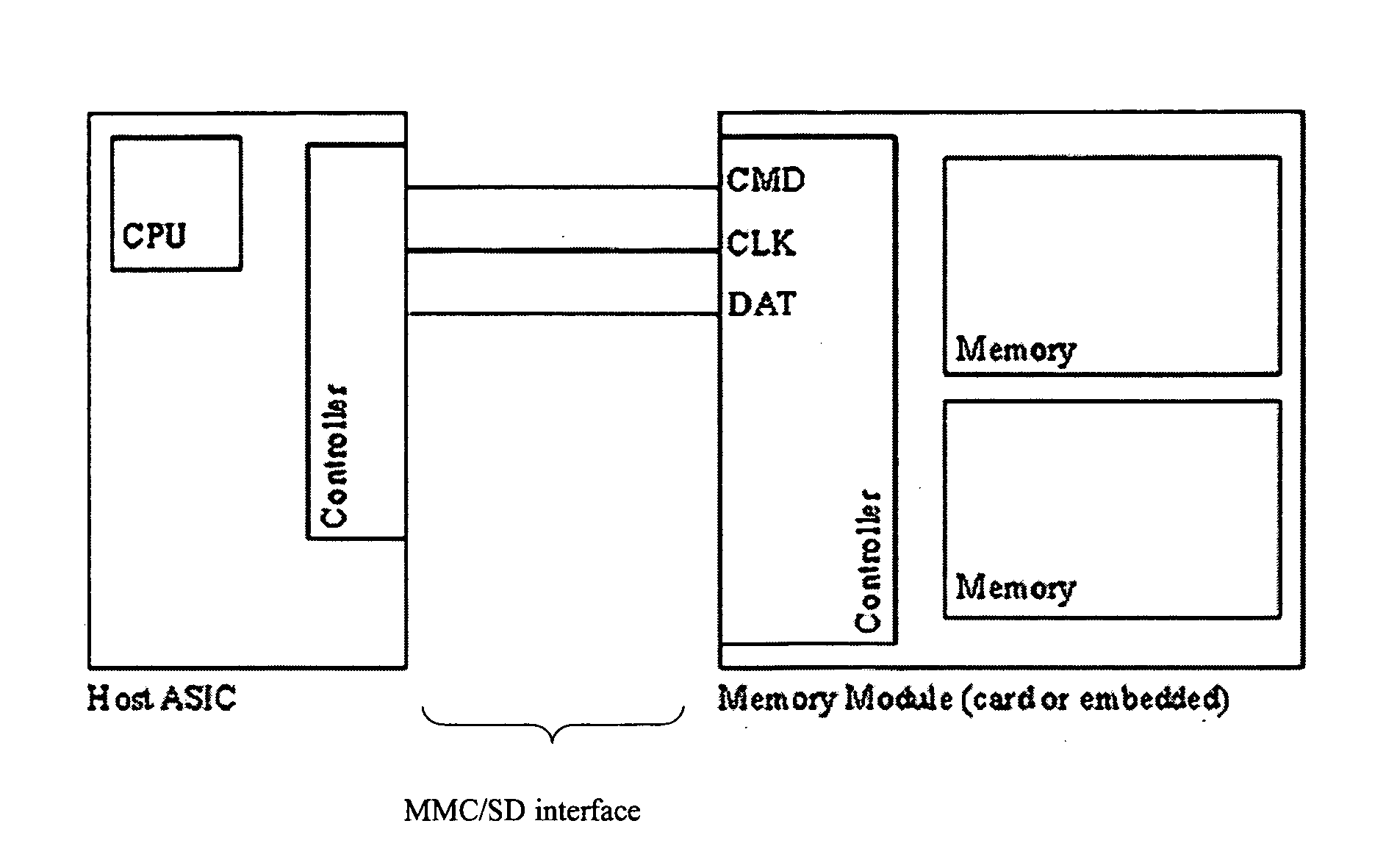
Systems and methods for booting a host device(s) from a peripheral device(s), via an interface, such as an MMC / SD interface, with power terminals, a data bus with data bus terminals, a clock line with a clock terminal and a command line with command terminal. Power is provided to the power terminals, and the command terminal of the MMC / SD or analogous interface is set during power-up to low. The data bus is monitored for a start bit of data transmission.
Owner:MEMORY TECHNOLOGIES LLC
System and method for providing virtual network attached storage using excess distributed storage capacity
ActiveUS7139809B2High access timeShorten access timeMultiple digital computer combinationsProgram loading/initiatingFailoverData storing
A system and method are disclosed for using free storage capacity on a plurality of storage media as a virtual storage device on a computer network comprising a plurality of computers. A first portion of each storage medium stores data. To implement Virtual Network Attached Storage (VNAS), the respective “free” second portions of each storage medium are aggregated into a shared storage volume. Computers on the network may mount the shared storage volume at one of a plurality of mount points and may store data on the shared storage volume. VNAS may be implemented in a peer-to-peer manner whereby each computer acts as a server for the data stored on its part of the shared storage volume (i.e., the second portion of its storage media). VNAS may be used to implement a system and method for managing data fail-over.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com