Patents
Literature
192results about How to "Blocking in network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Anonymous location service for wireless networks
InactiveUS7069319B2Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
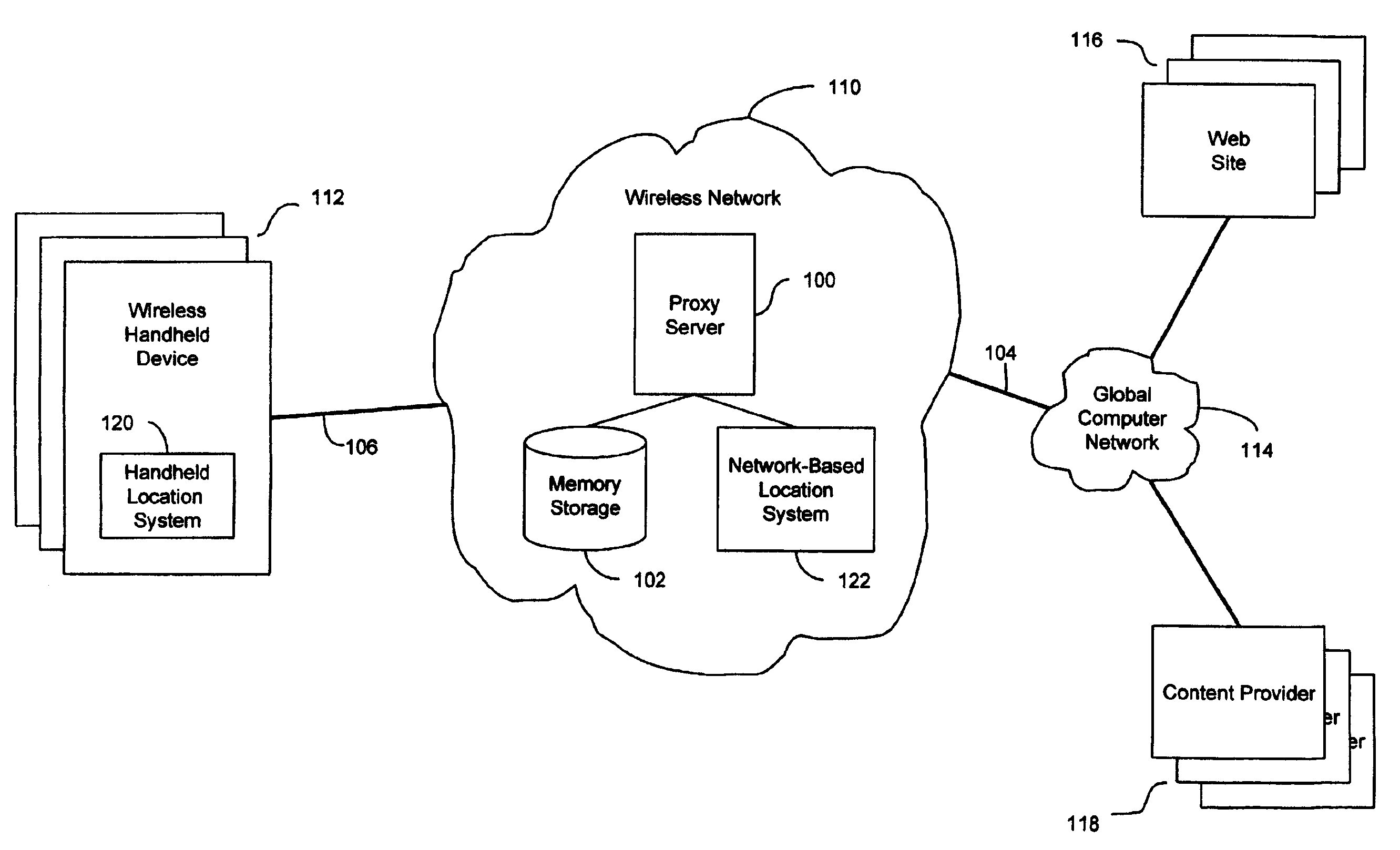
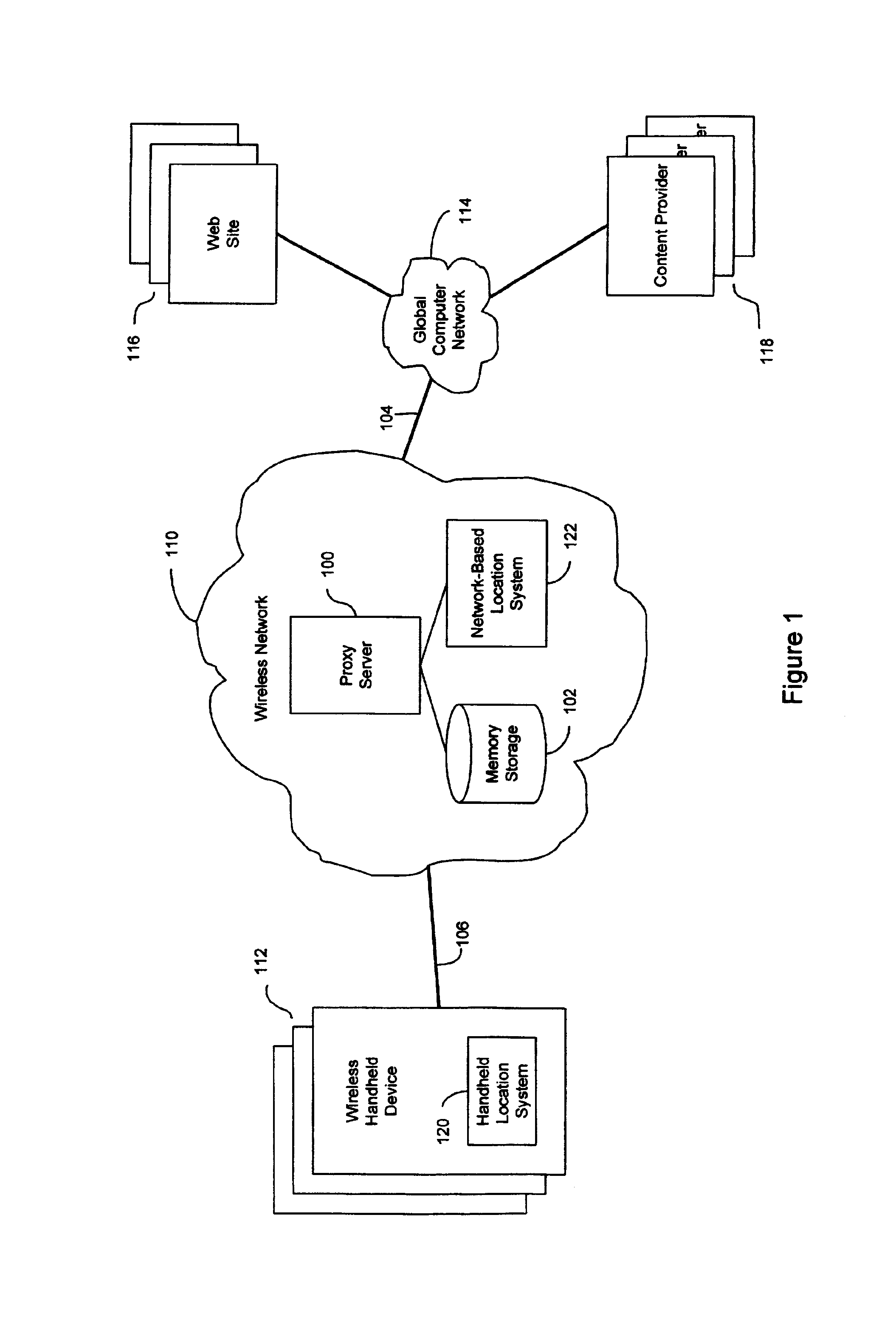
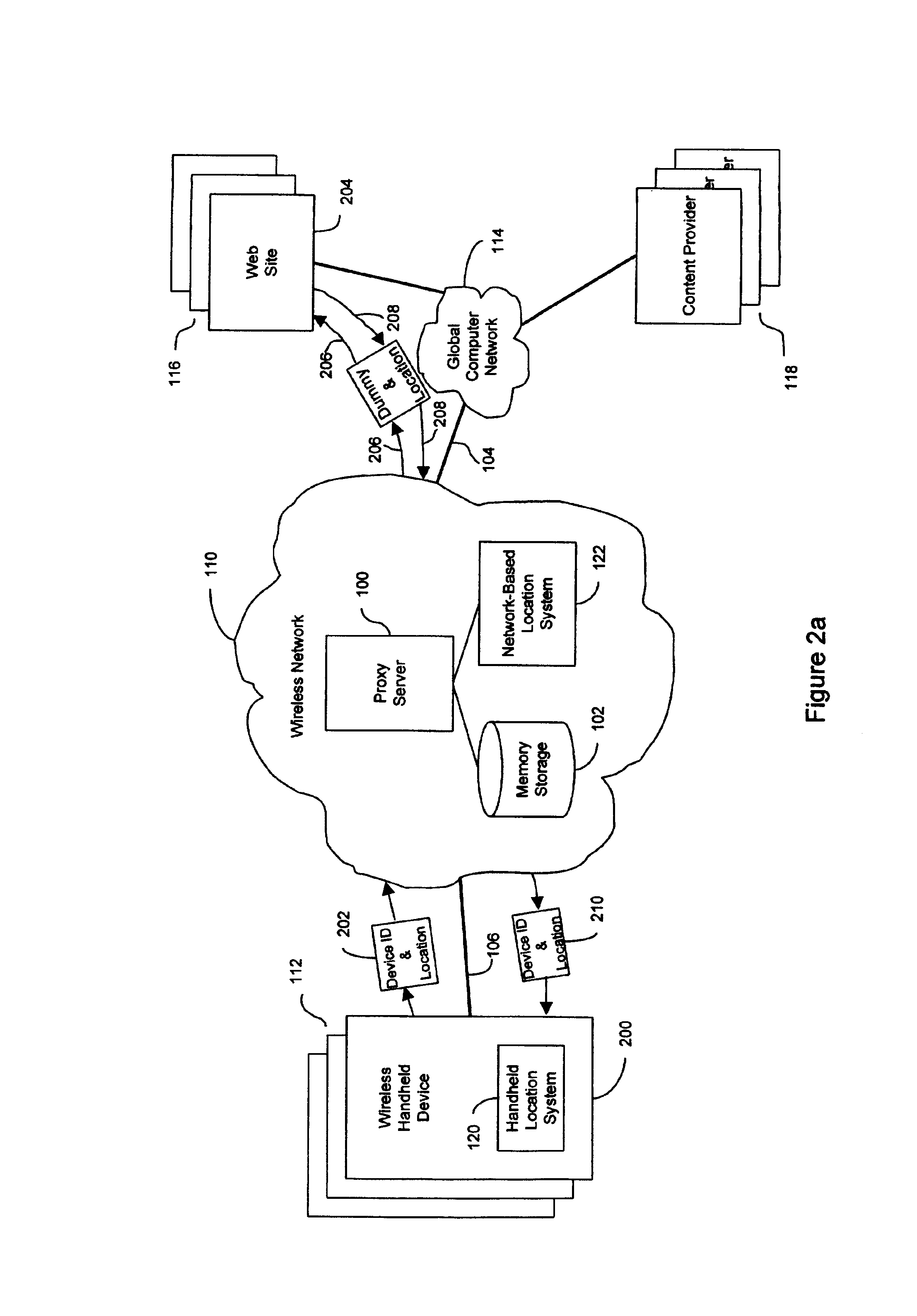
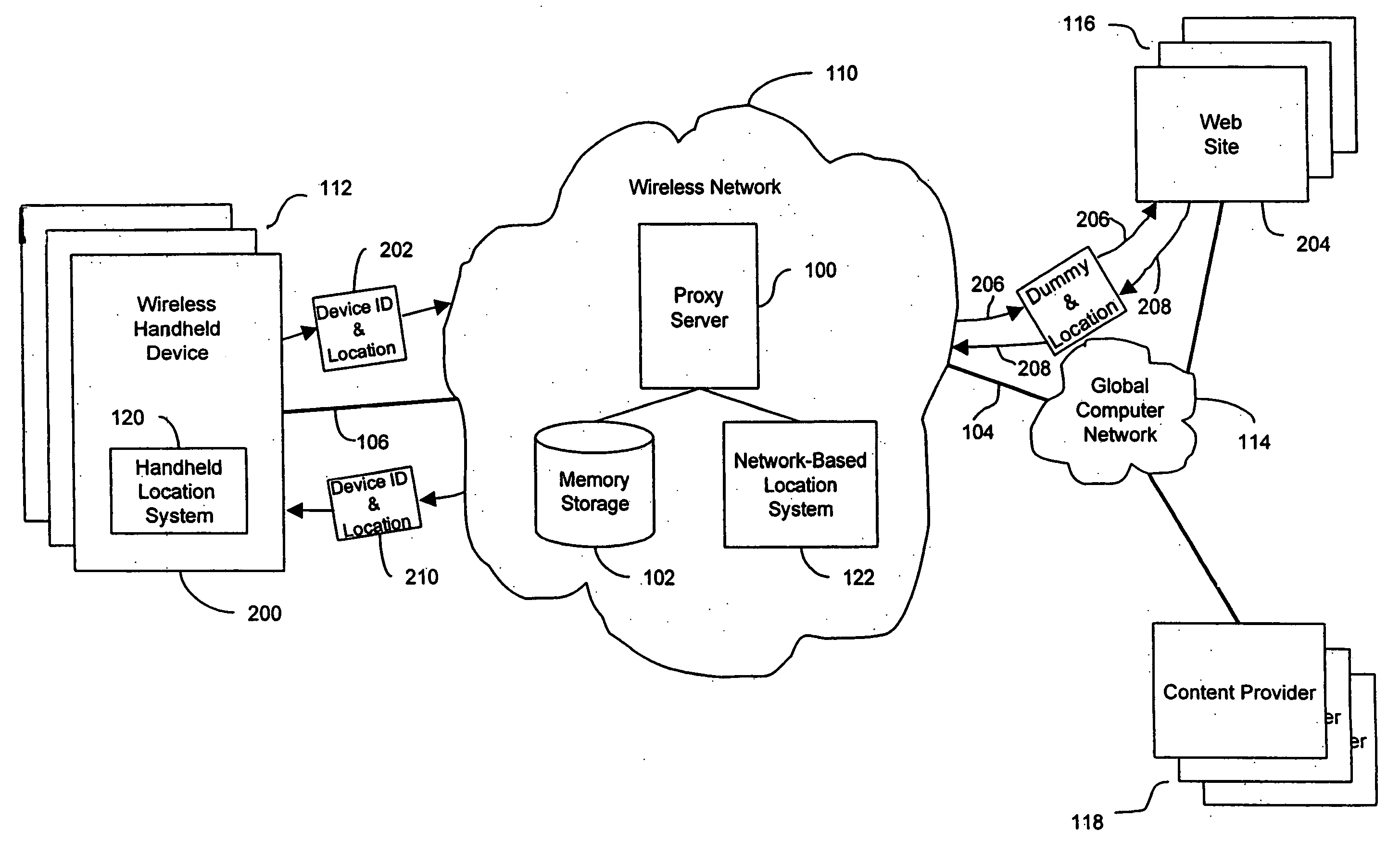
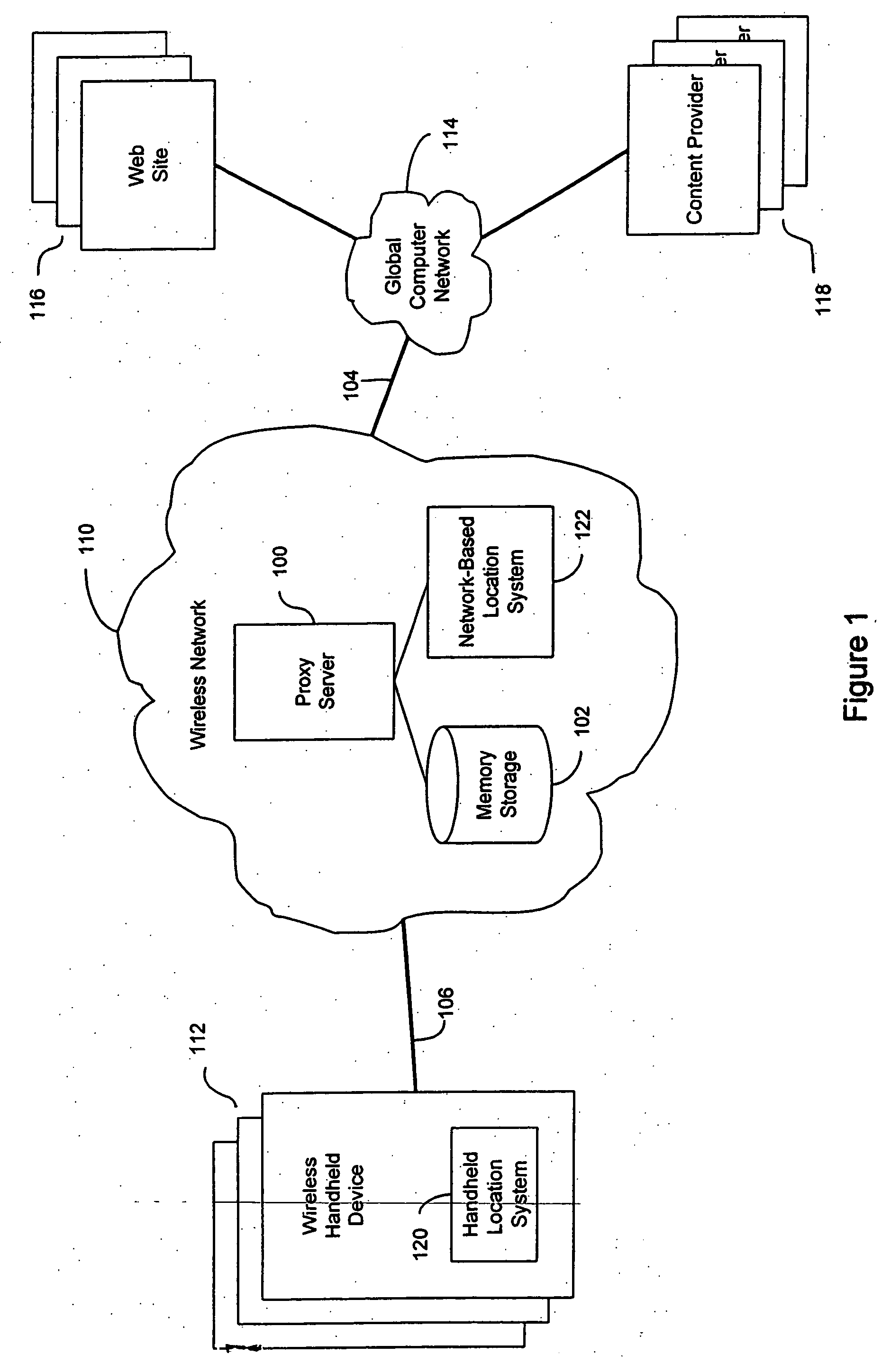
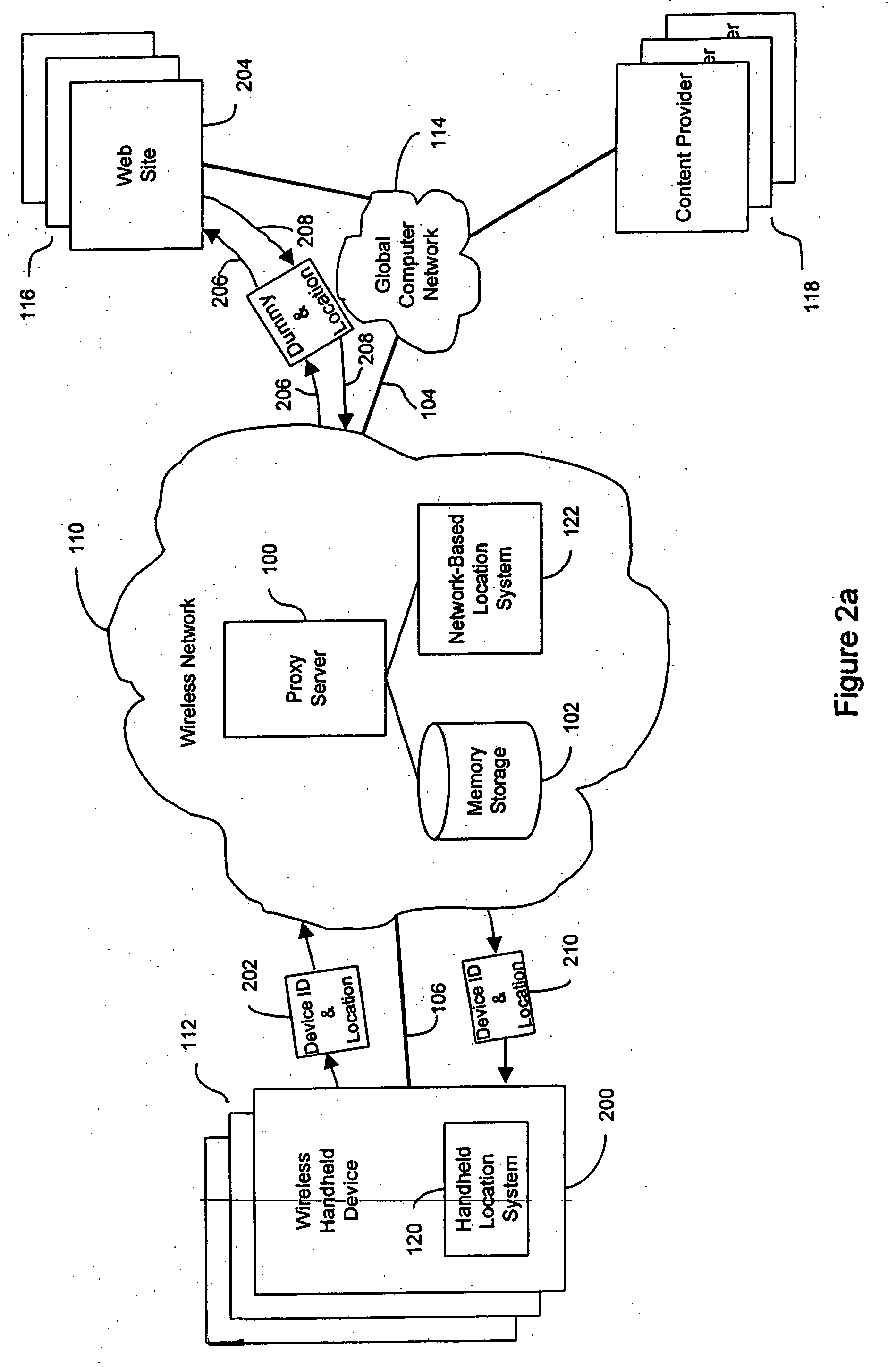
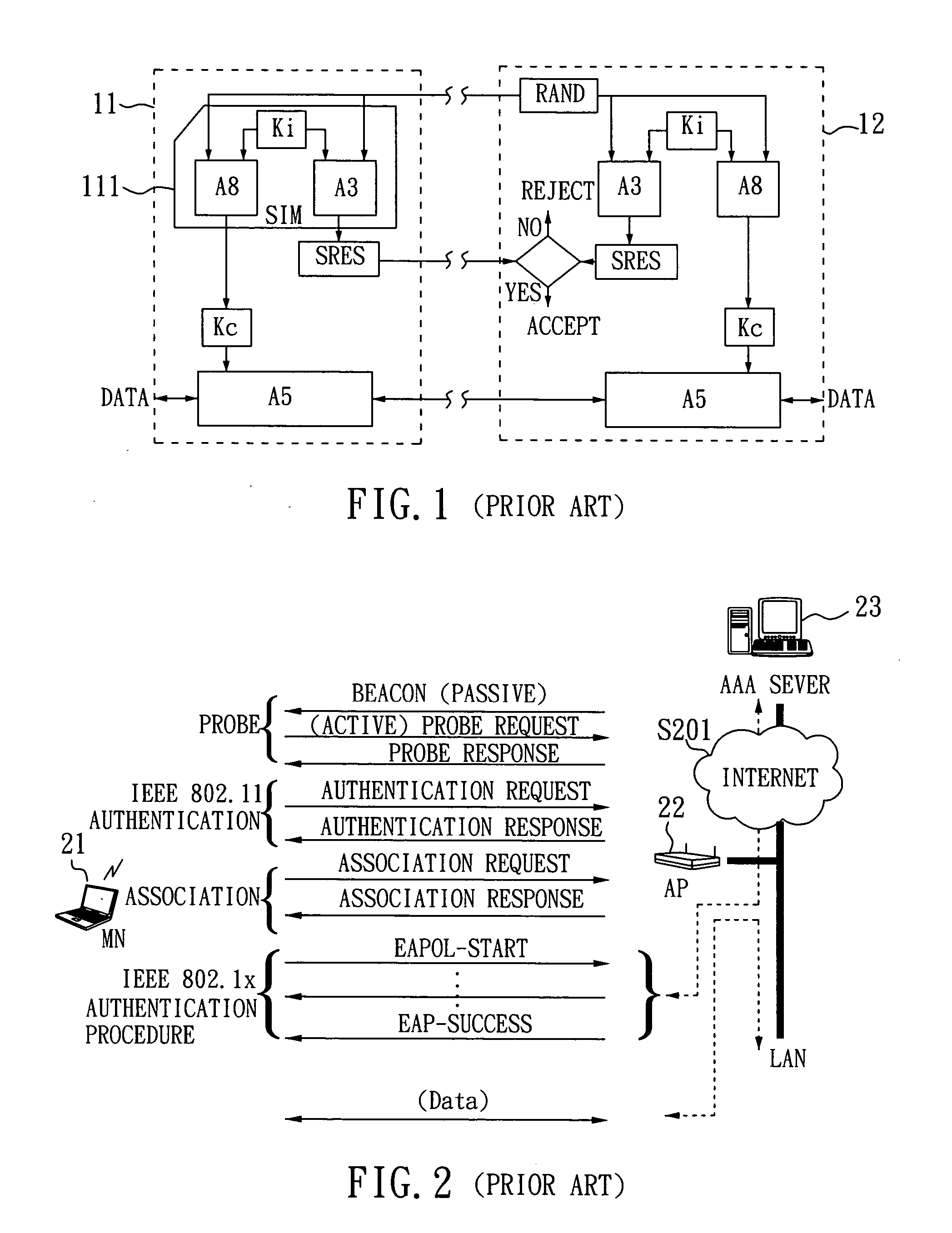
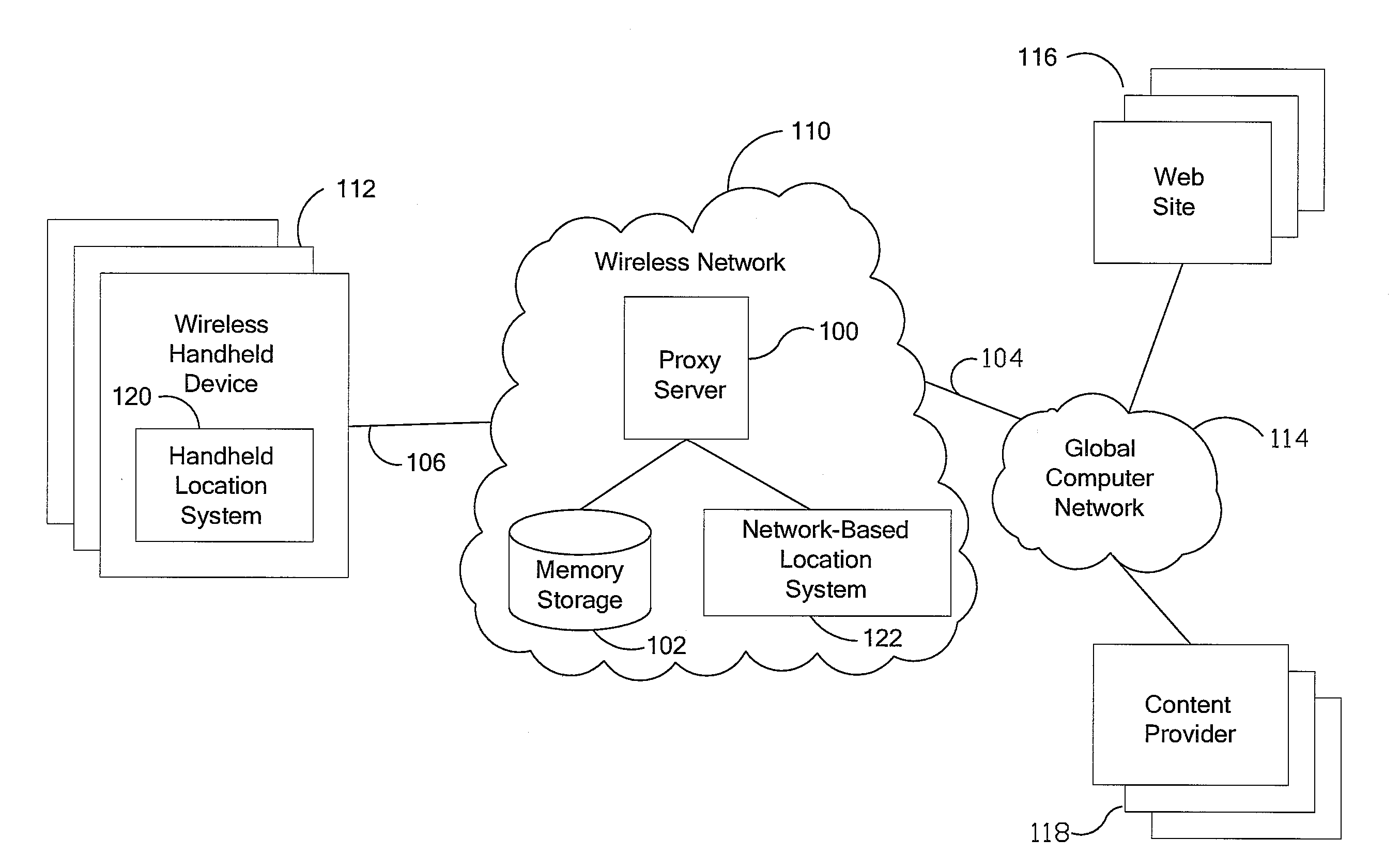
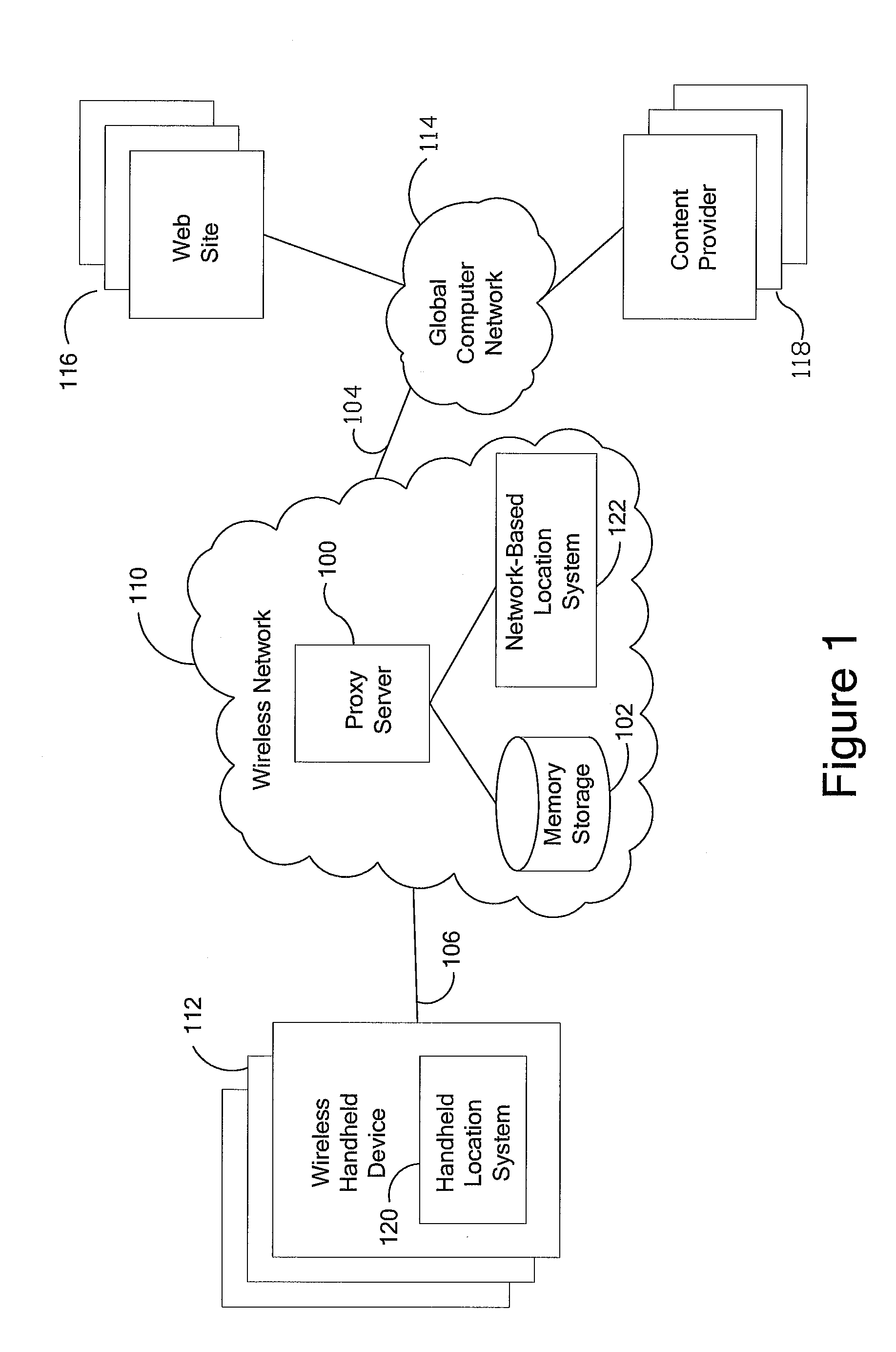
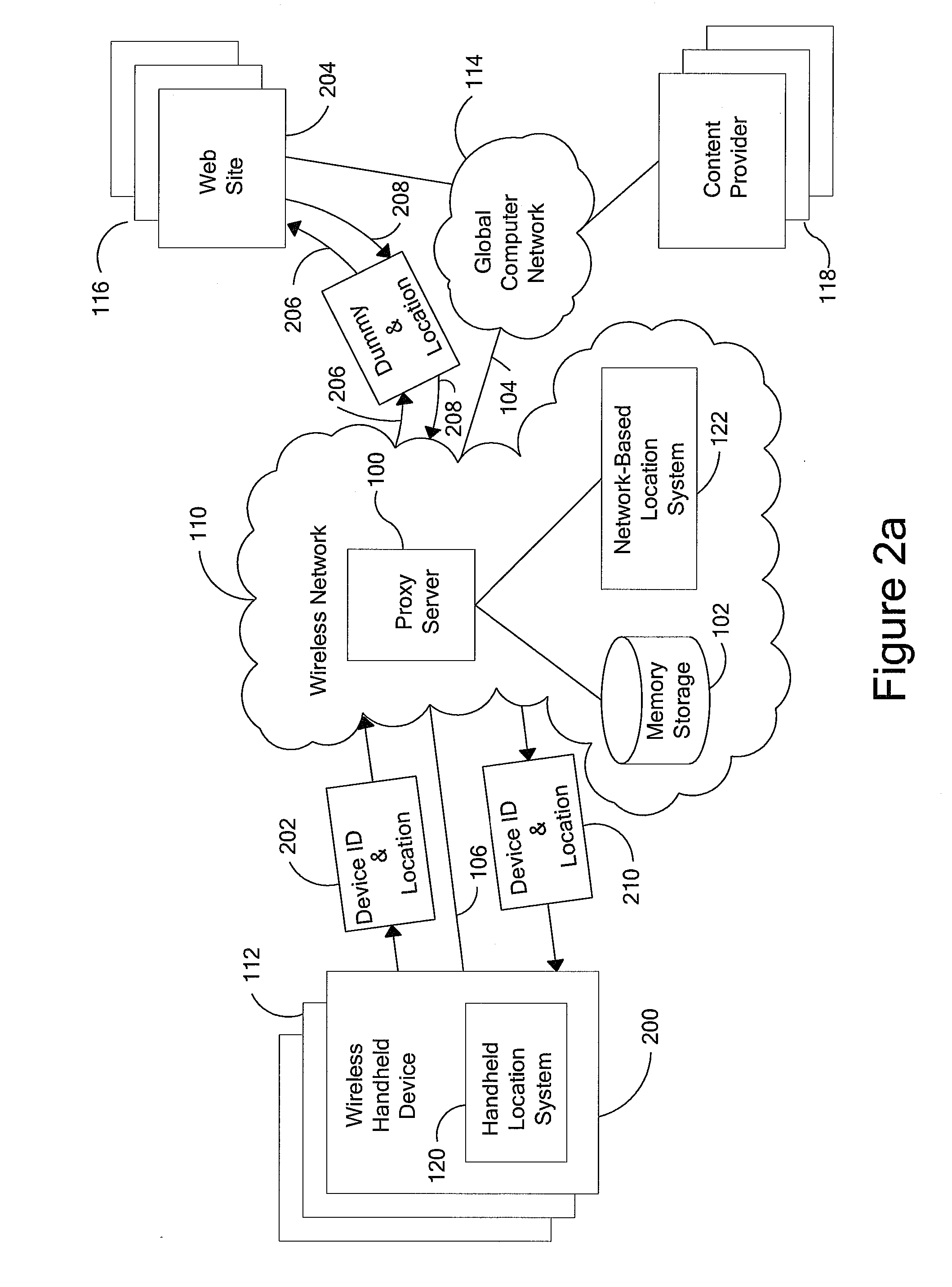
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
System and method for identifying nodes in a wireless network
InactiveUS7451365B2Blocking in networkAvoids a circular dependency on routing tablesElectronic circuit testingNetwork topologiesComputer hardwareWireless mesh network
Systems and methods for providing a boundary scan test of a wired or wireless network having a plurality of network nodes are presented. The system includes a test station communicatively coupled with the network. The test station creates a MAC layer scan test route sequence that includes each link in the network and is independent of the routing mechanism and protocol used for the network. The test station also creates a test agent that is configured to traverse each link in the scan test route sequence. The test agent is then deployed on the network and information about a link is reported back to the test station after the test agent examines the link. The scan test route sequence can be created by sending out a series of broadcast messages from one or more nodes in the network, sequentially applying a network tour to cover the entire network, or performing a depth first search on the entire network.
Owner:UNWIRED BROADBAND INC
Anonymous location service for wireless networks
InactiveUS20060195570A1Blocking in networkShorten access timeDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
Routing method in content-centric network
InactiveUS20130111063A1Avoid network bottlenecksFlexibly solving network congestionDigital computer detailsData switching by path configurationInformation repositoryTraffic capacity
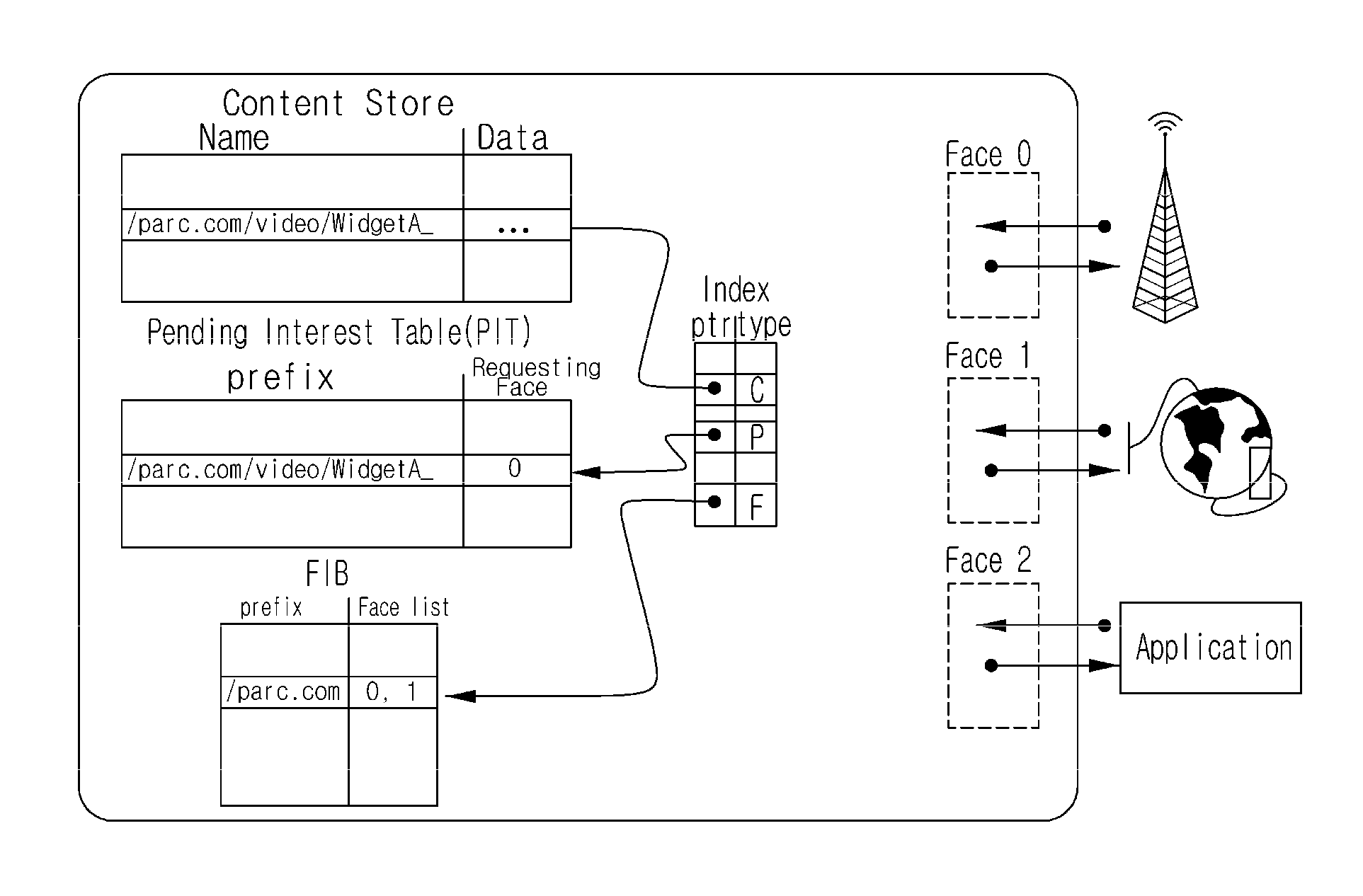
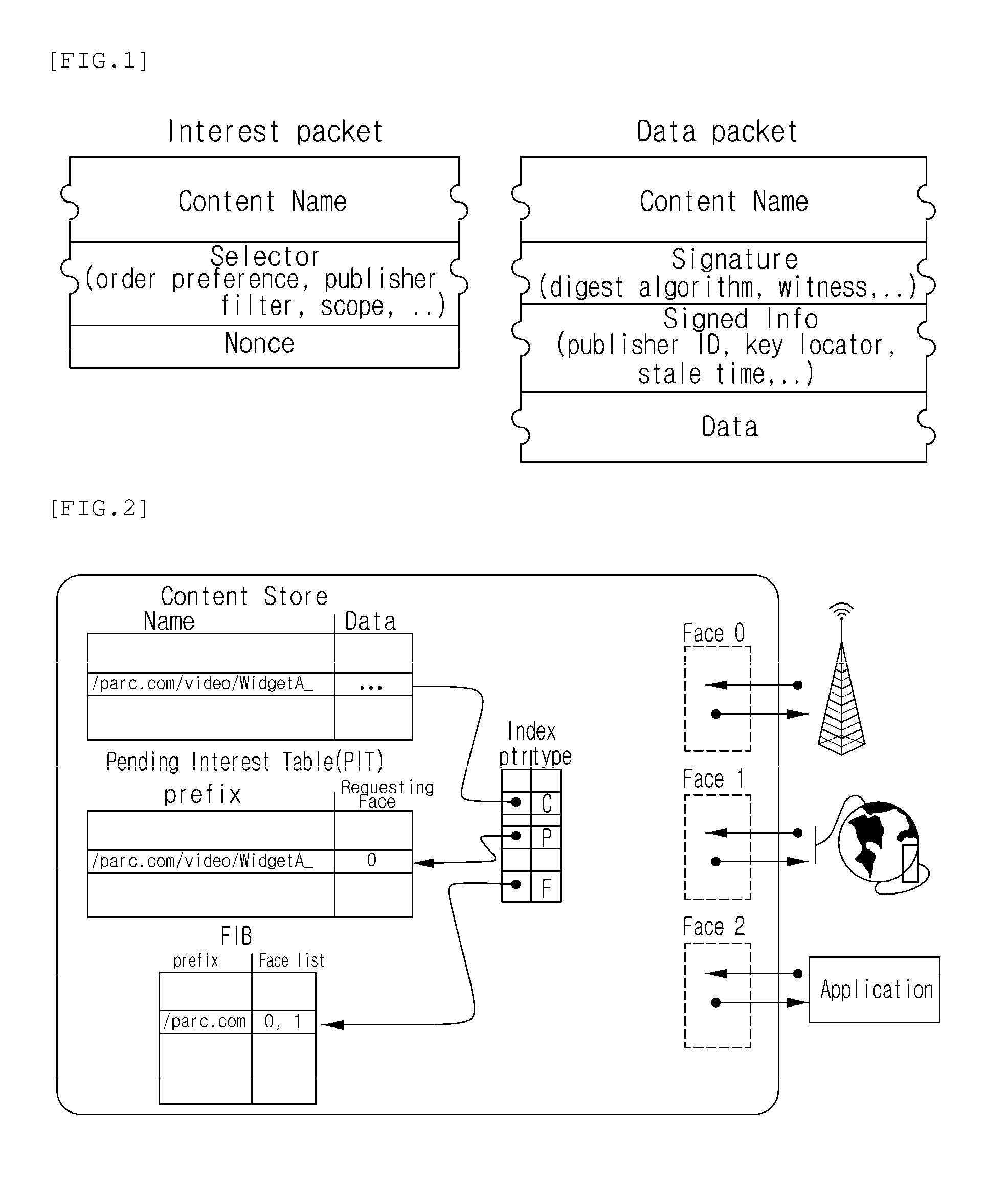
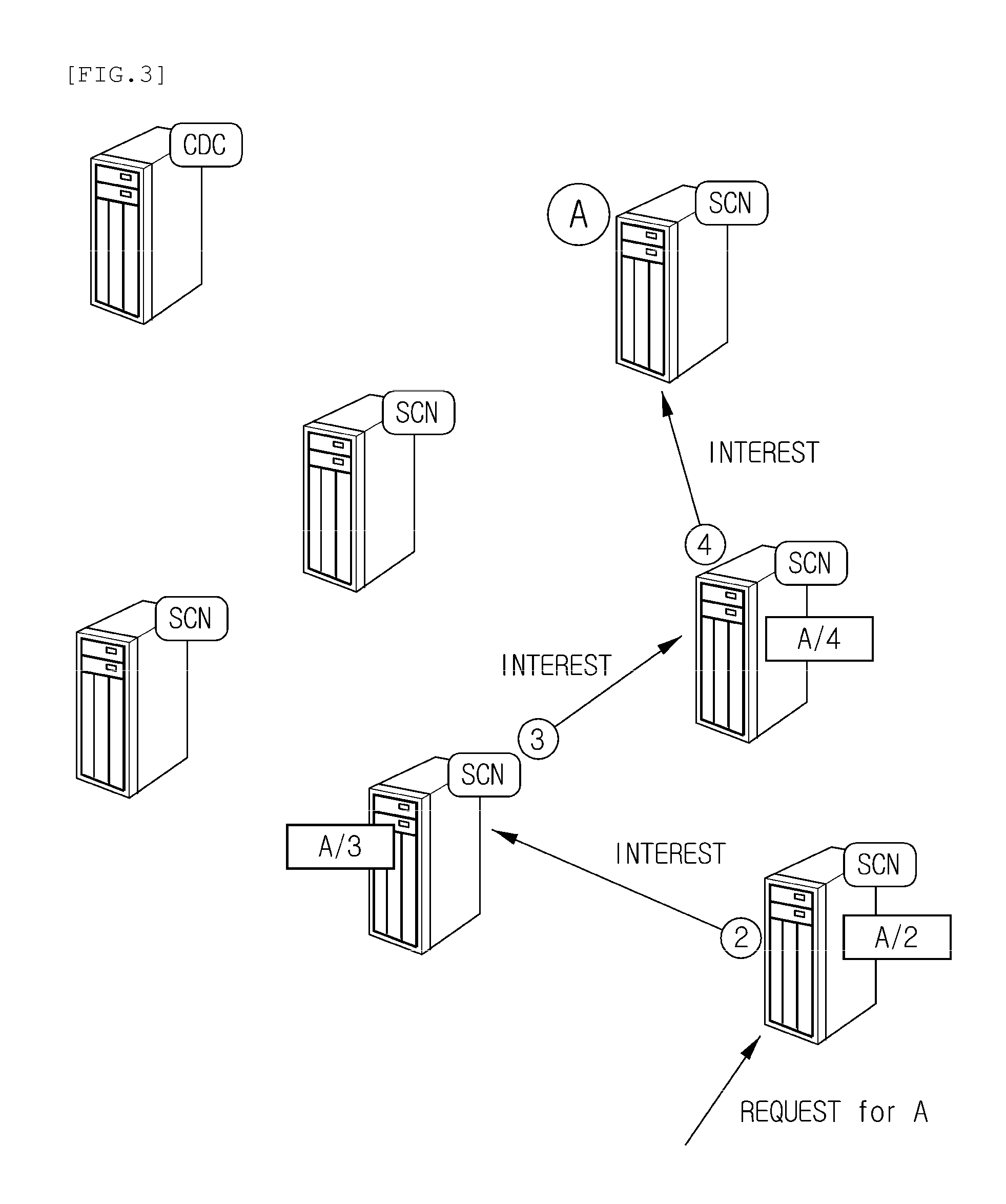
Disclosed is a centralized controlling method of the process of delivering a routing packet for content transmission in a content-centric network (CCN). The routing method in a content centric network according to the present invention includes: a content distribution controller in the content centric network receiving a request for specific-content distribution from a user, determining locations of routers storing the content, and finding one of the routers to which the request from the user will be transmitted; and the content distribution controller finding an optimal path in consideration of a traffic distribution status and then transmitting a forwarding information base (FIB) to routers included in the optimal path.
Owner:ELECTRONICS & TELECOMM RES INST
Home appliance network system and method for operating the same
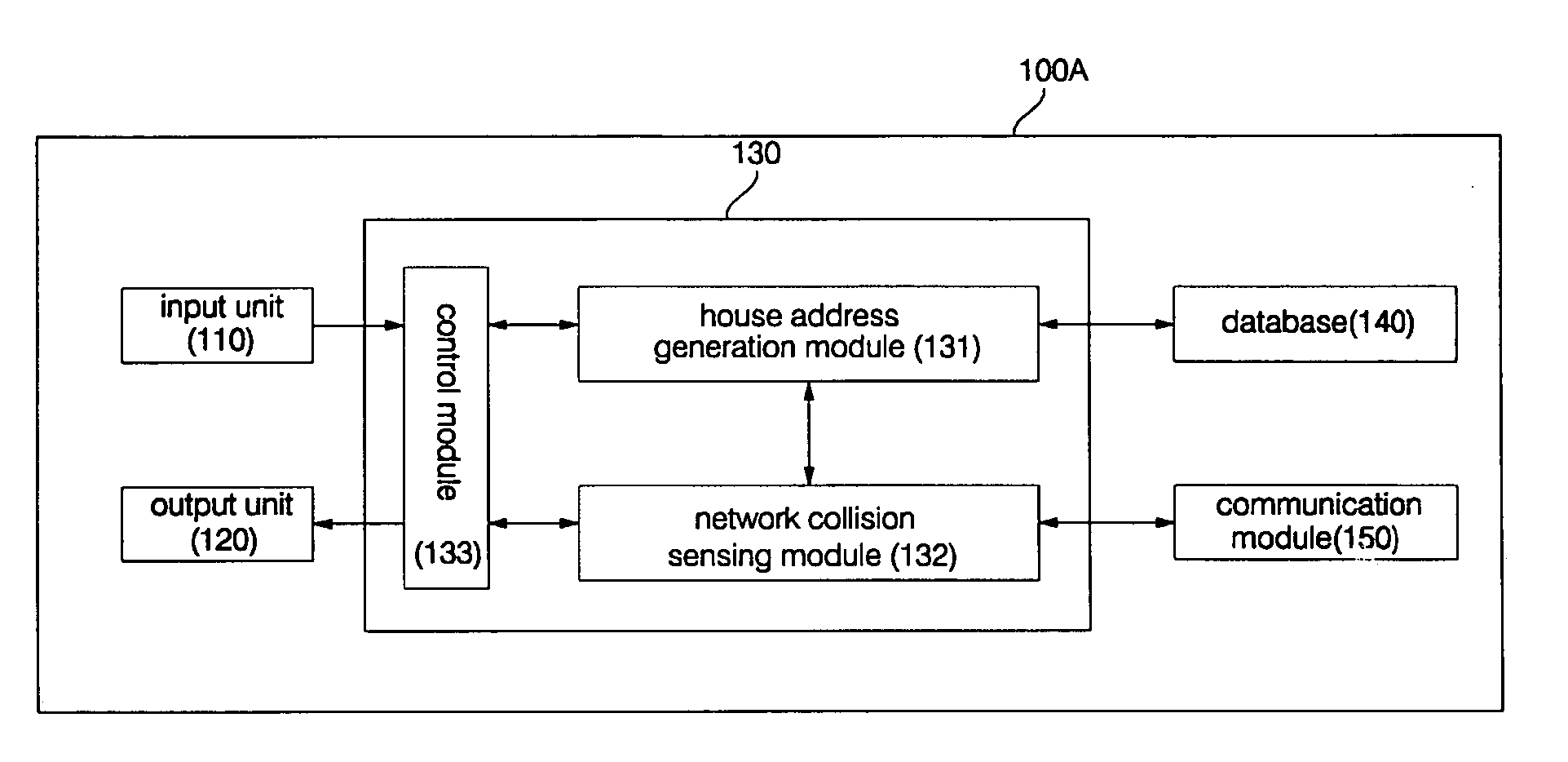
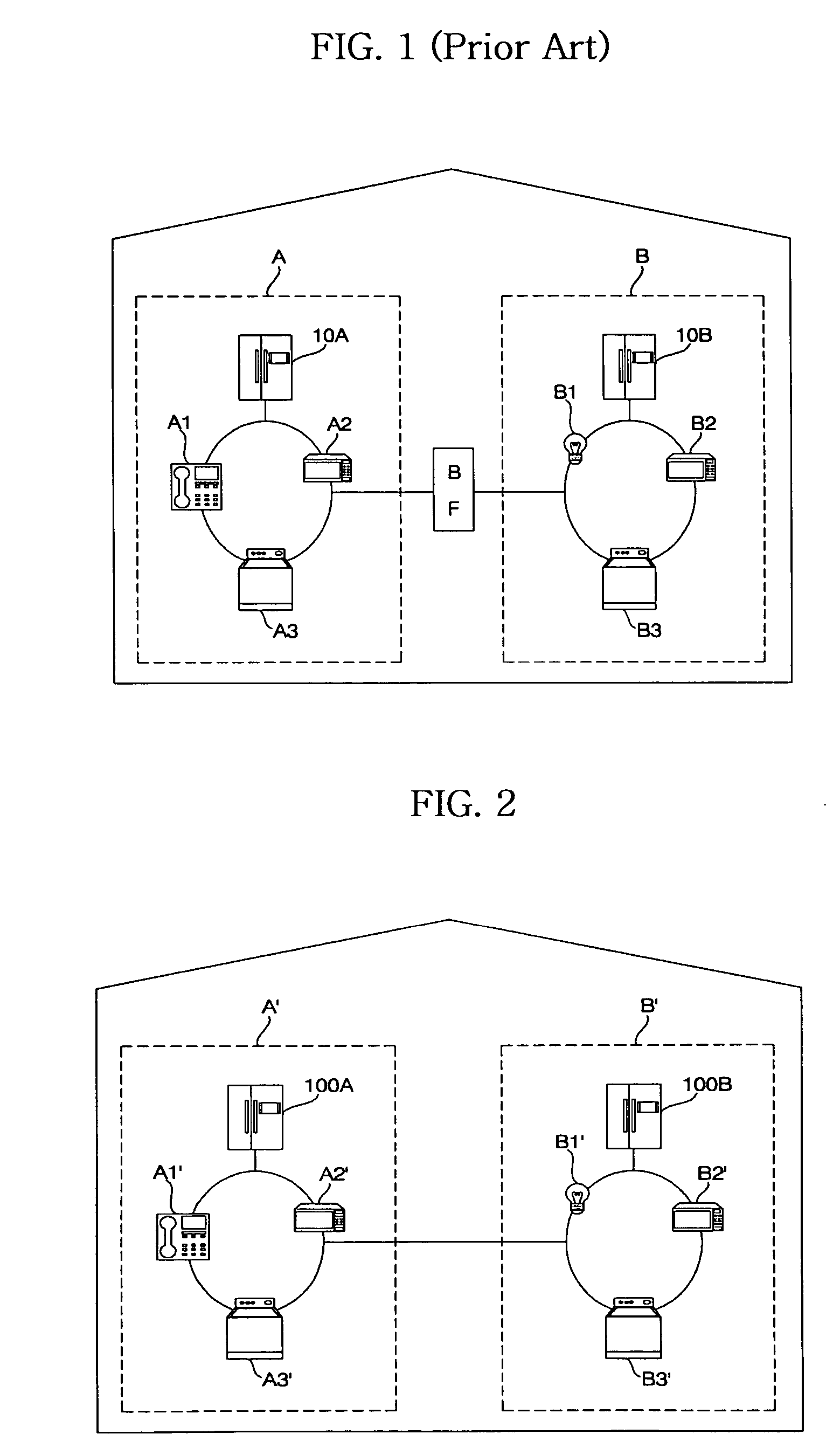
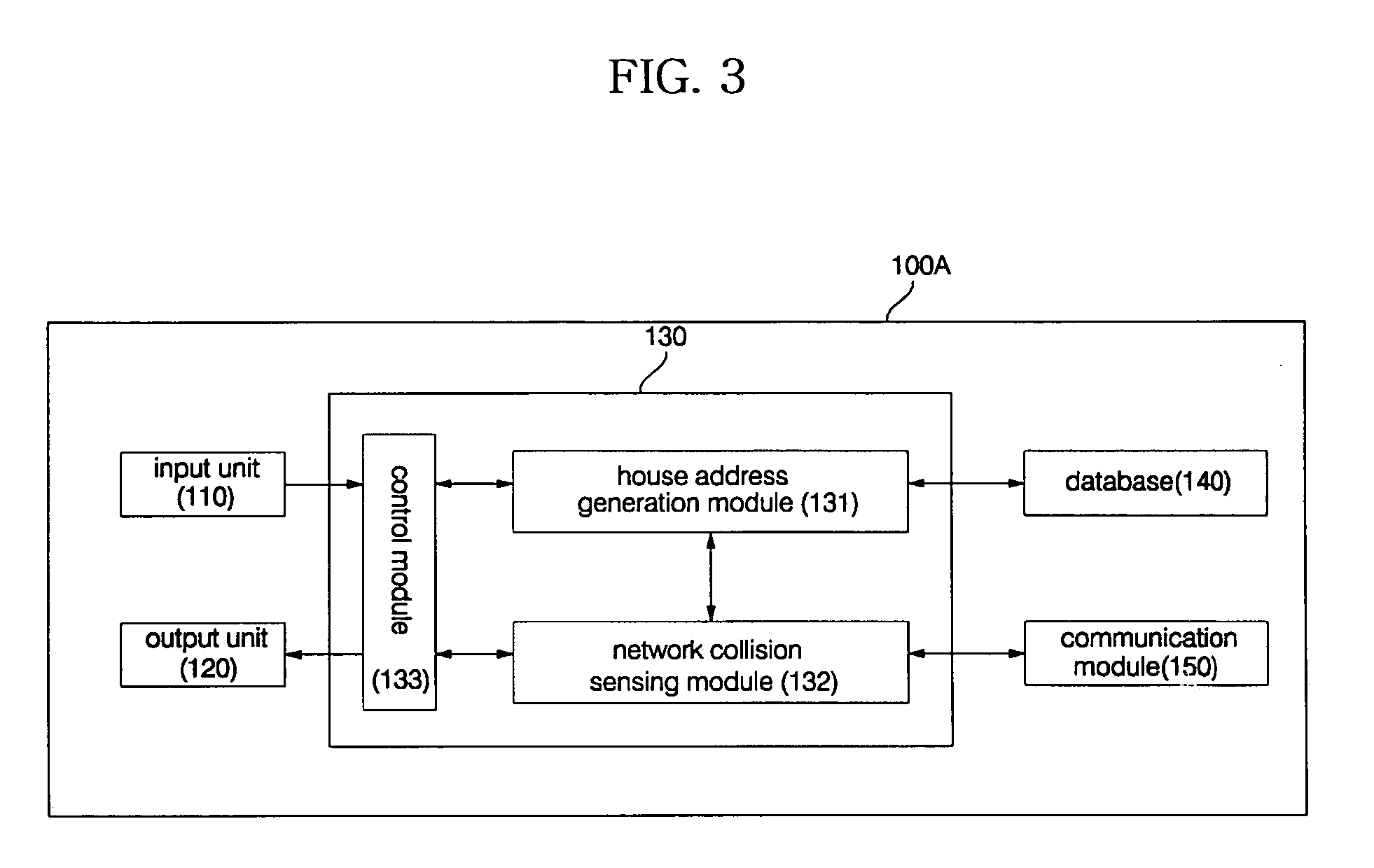
InactiveUS20050002408A1Blocking in networkImprove ease of useInterconnection arrangementsPower distribution line transmissionEngineeringHome appliance
A home appliance network system and a method for operating the same, wherein a network master can not only automatically generate a unique house address of a corresponding home, but also sense a network collision of the corresponding home with a neighboring home to maintain house address uniqueness. The network master manages / controls one or more home appliances connected to a network of the corresponding home and determines whether the generated house address collides with that of the neighboring home. If the generated house address is determined to collide with that of the neighboring home, the network master automatically changes the house address to a new one to maintain house address uniqueness. As a result, the network master can prevent a network interference / collision with the neighboring home, thereby increasing security and stability of the home appliance network system at low cost.
Owner:LG ELECTRONICS INC
Method and Apparatus for Ad Hoc Mesh Routing
ActiveUS20080002599A1Reduce probabilityBlocking in networkError prevention/detection by using return channelTransmission systemsSignal qualityMesh routing
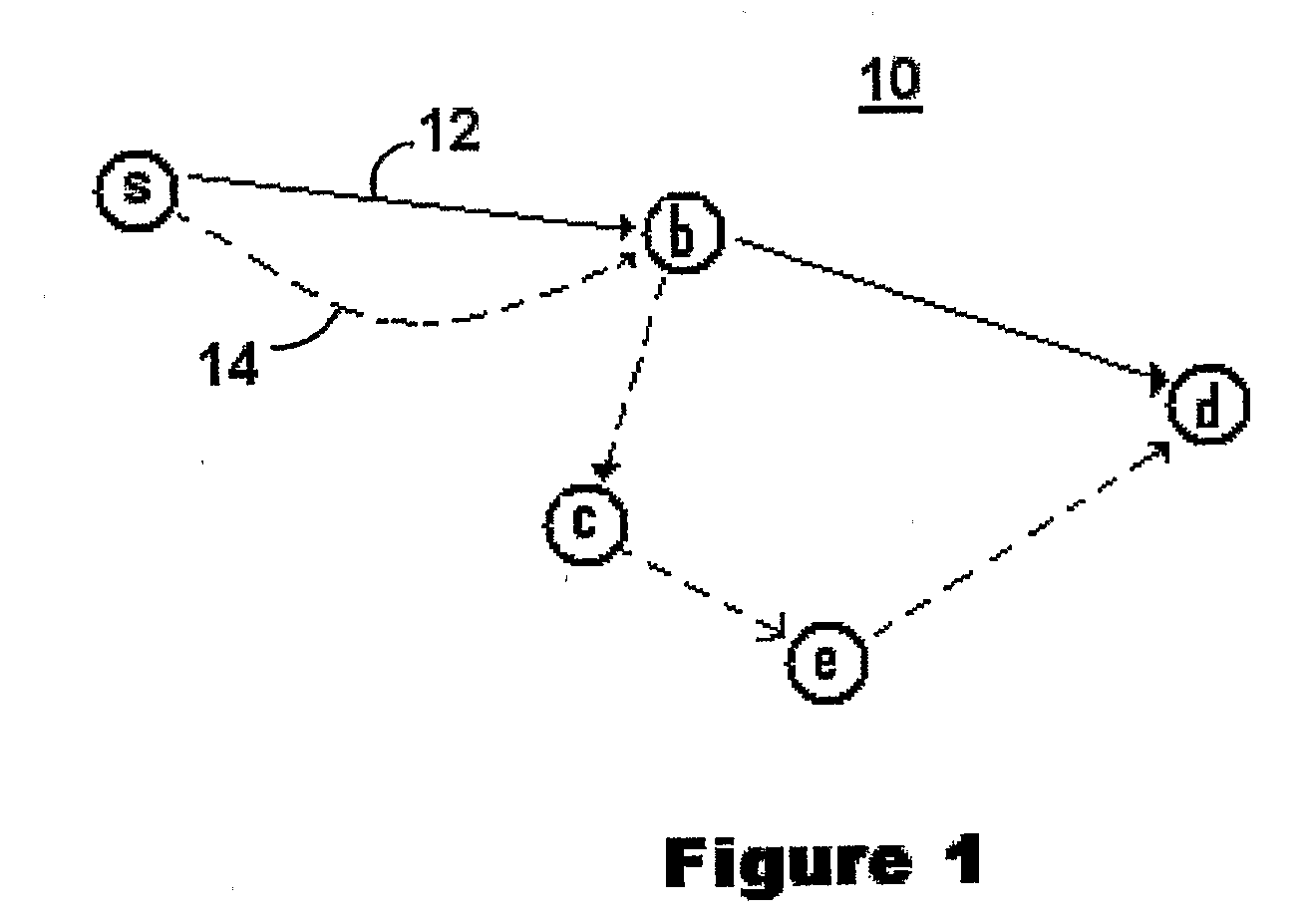
Packets are routed in a wireless mesh network by assigning a probability of packet retransmission based on certain factors which may include the number of hops the packet has made, whether the destination is within a certain number of known hops of the receiving node, the number of nearby nodes, whether the receiving node is a member of a past known route to the destination and / or whether a nearby neighbor of the receiving node is a member of a past known route to the destination. Once a probability is assigned, a random number generator may be used to make a decision between retransmitting the packet and dropping the packet. Signal quality may also be used as a factor in the probability of retransmission. In a preferred embodiment, Bloom filters are used to store information in the header of a data packet containing the identifiers of forwarding nodes and the identifiers of nodes on a previously-successful route from the source to the destination.
Owner:YAU JOHNNY +1
Method and system for enforcing secure network connection
InactiveUS20050278777A1Blocking in networkDigital data processing detailsUser identity/authority verificationNetwork connectionSecurity policy
The invention is a system and method for enforcing remote users to use secure network connections. Every time a user connects to the network, its network connection is verified for security vulnerabilities and a security policy applies to every network connection based on the number and severity of security vulnerabilities identified for this particular user on this particular network connection.
Owner:HACKERPROOF SECURITY
Virtual private networks and methods for their operation
InactiveUS6937574B1Economically feasibleLower acquisition costsNetworks interconnectionPrivate networkPhysical address
In methods and apparatus for routing packets through a communications network, a respective distinct broadcast address is assigned to each of a plurality of distinct sets of virtual ports. No virtual port belongs to more than one of the distinct sets. A respective egress address is assigned to each packet entering the network via an ingress virtual port. The respective egress address corresponds to a respective destination address of the entering packet when a correspondence between the destination address and an egress address is known. When no correspondence between the destination address and an egress address is known, the respective egress address is a broadcast egress address corresponding to the set comprising the ingress virtual port. The packet is routed according to the respective egress address. The routing is restricted to virtual ports belonging to the distinct set of virtual ports that includes the ingress virtual port. The distinct sets of virtual ports and their associated broadcast addresses define isolated virtual private networks within the network. Each physical port of the network may map one-to-one onto a corresponding virtual port, or may map onto a corresponding plurality of virtual ports, in which case the each virtual port of the plurality is associated with a respective distinct combination of a physical address of the physical port and a respective virtual network identifier.
Owner:RPX CLEARINGHOUSE
Expandable microspheres for foam insulation and methods
InactiveUS20050079352A1Use in some applicationHigh of encapsulationLiquid surface applicatorsGlass/slag layered productsPolymer scienceFoaming agent
Hollow thermoexpandable particles or microspheres are provided that contain hydrocarbon blowing agents and have a shell polymer that can be softened at the onset of the expansion temperature and solidified at a higher temperature (thermoset) in an expanded state. Preferably, the microspheres have a shell of thermally expandable and thermally crosslinkable polymer and a hollow interior that contains a hydrocarbon liquid that boils at a temperature below the heat activated crosslinking temperature of the polymer shell. The crosslinking of the shell polymer during or after expansion, which is heat activated at an elevated temperature, can solidify the shell polymer and, then, maintain the expanded volume of the microspheres. The thermoexpandable thermoset polymer particles are useful in insulation, packaging, for making foam materials such as polyurethane or polyisocyanurate rigid foams. The invented thermoset microspheres can substantially improve the close cell percentage and compressive strength of the foam materials and make the foam manufacturing less hazardous.
Owner:IP RIGHTS +1
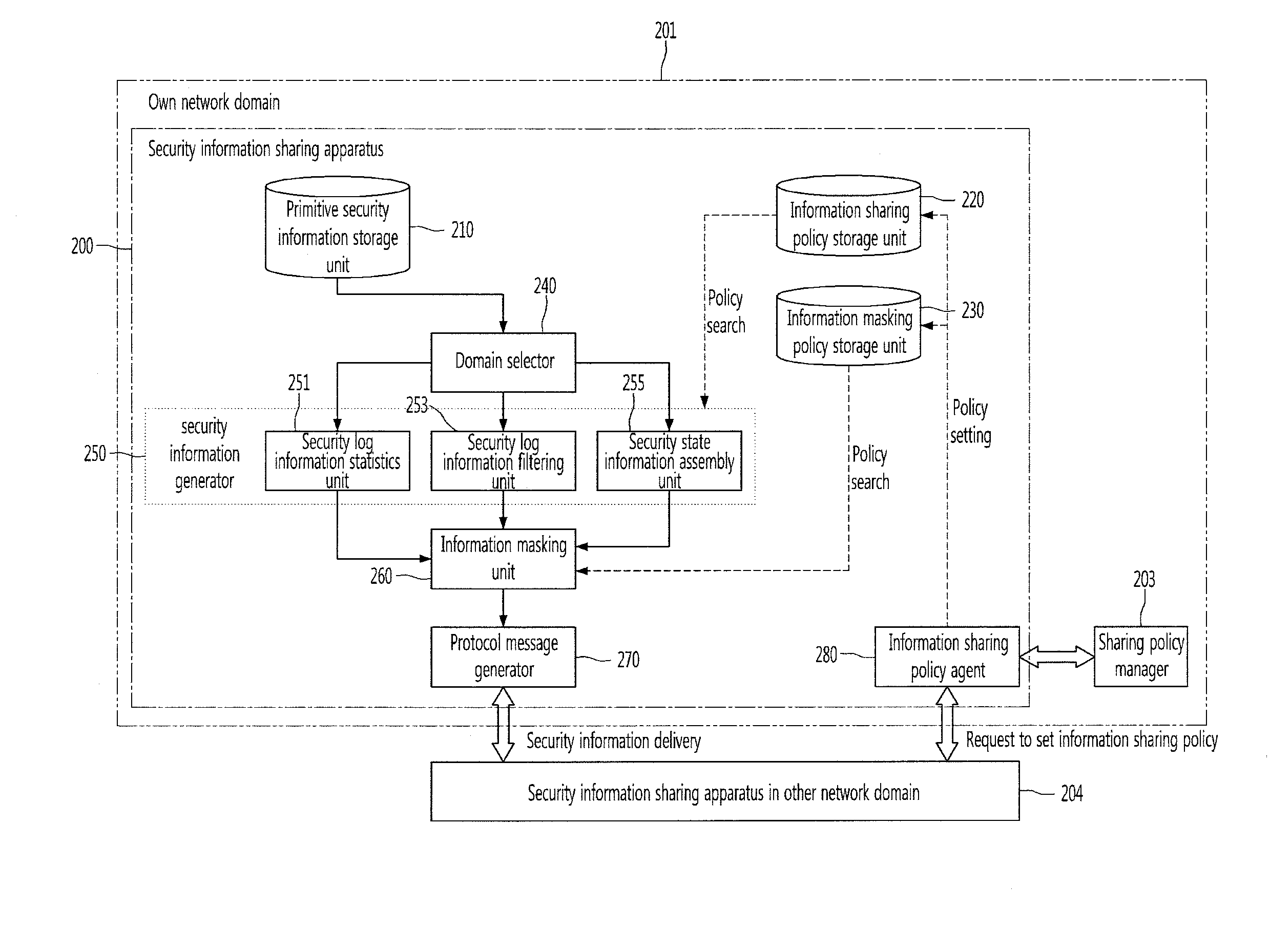
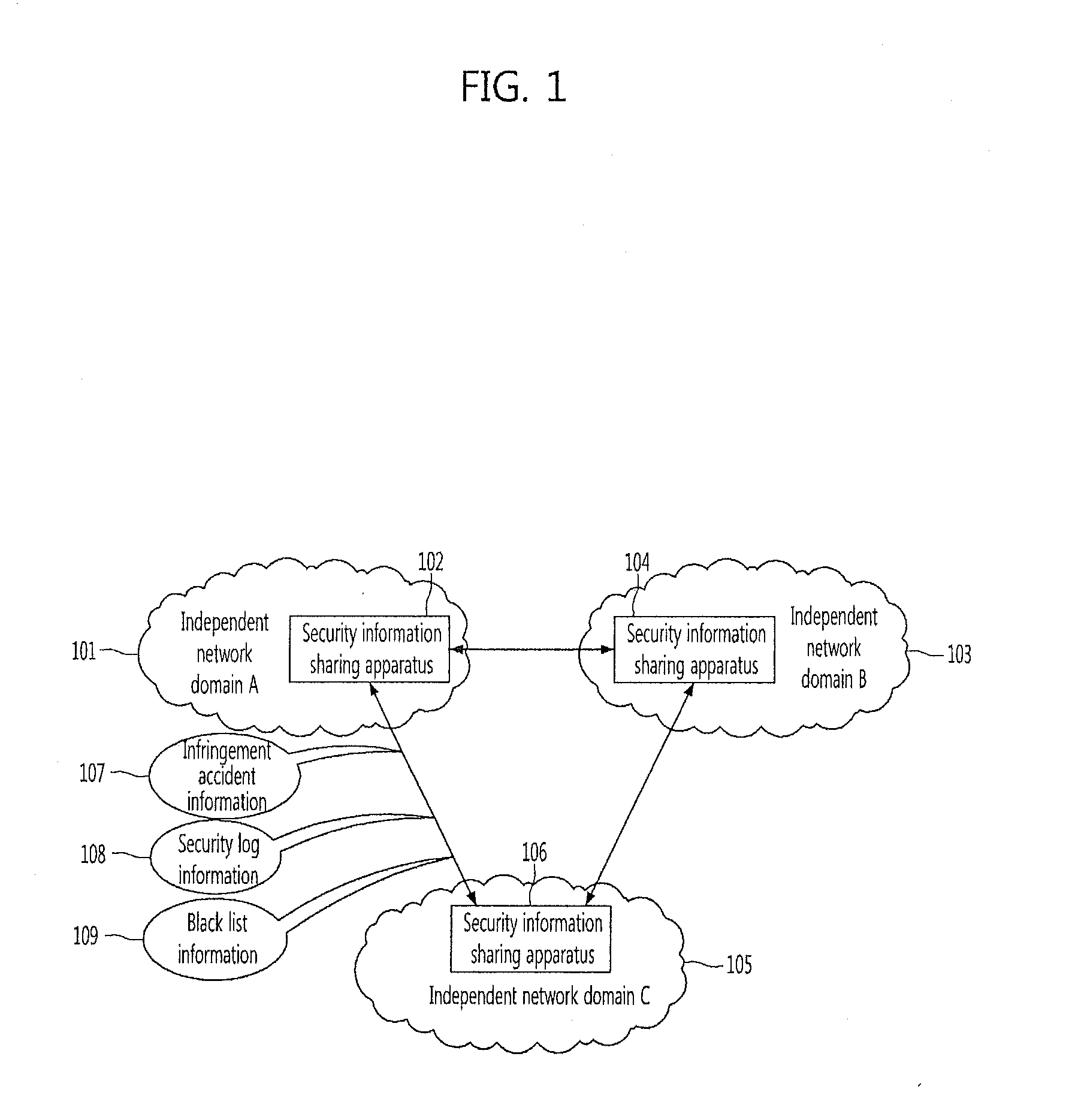
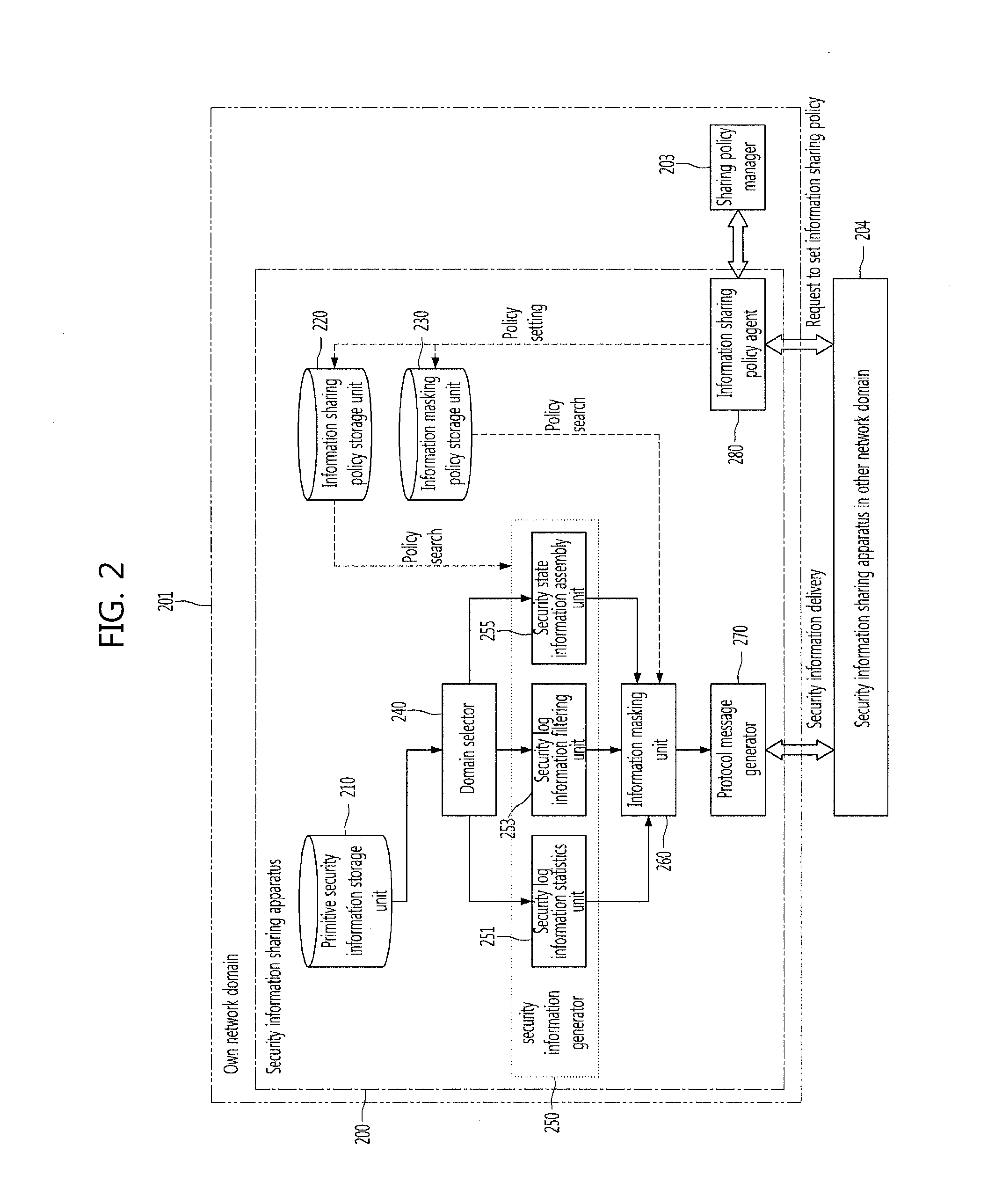
Apparatus for sharing security information among network domains and method thereof
InactiveUS20120110633A1Blocking in networkTransmissionSpecial data processing applicationsInformation sharingInternet privacy
Provided are a security information sharing apparatus capable of sharing security information among network domains and a method thereof. The security information sharing apparatus includes a primitive security information storage unit configured to store primitive security information to be shared with other network domains, an information sharing policy storage unit configured to store an information sharing policy for information to be shared, an information masking policy storage unit configured to store an information masking policy for information not to be opened to the other network domain, a domain selector configured to select the other network domain to receive the shared security information, a shared security information generator configured to generate shared security information for the selected other network domain by applying the information sharing policy to the primitive security information, an information masking unit configured to mask information not to be opened in the generated security information according to the information masking policy, a protocol message generator configured to generate a protocol message for the shared security information subjected to the information masking, to be transmitted, and a protocol message transmitter configured to transmit the protocol message to the selected other network domain.
Owner:ELECTRONICS & TELECOMM RES INST
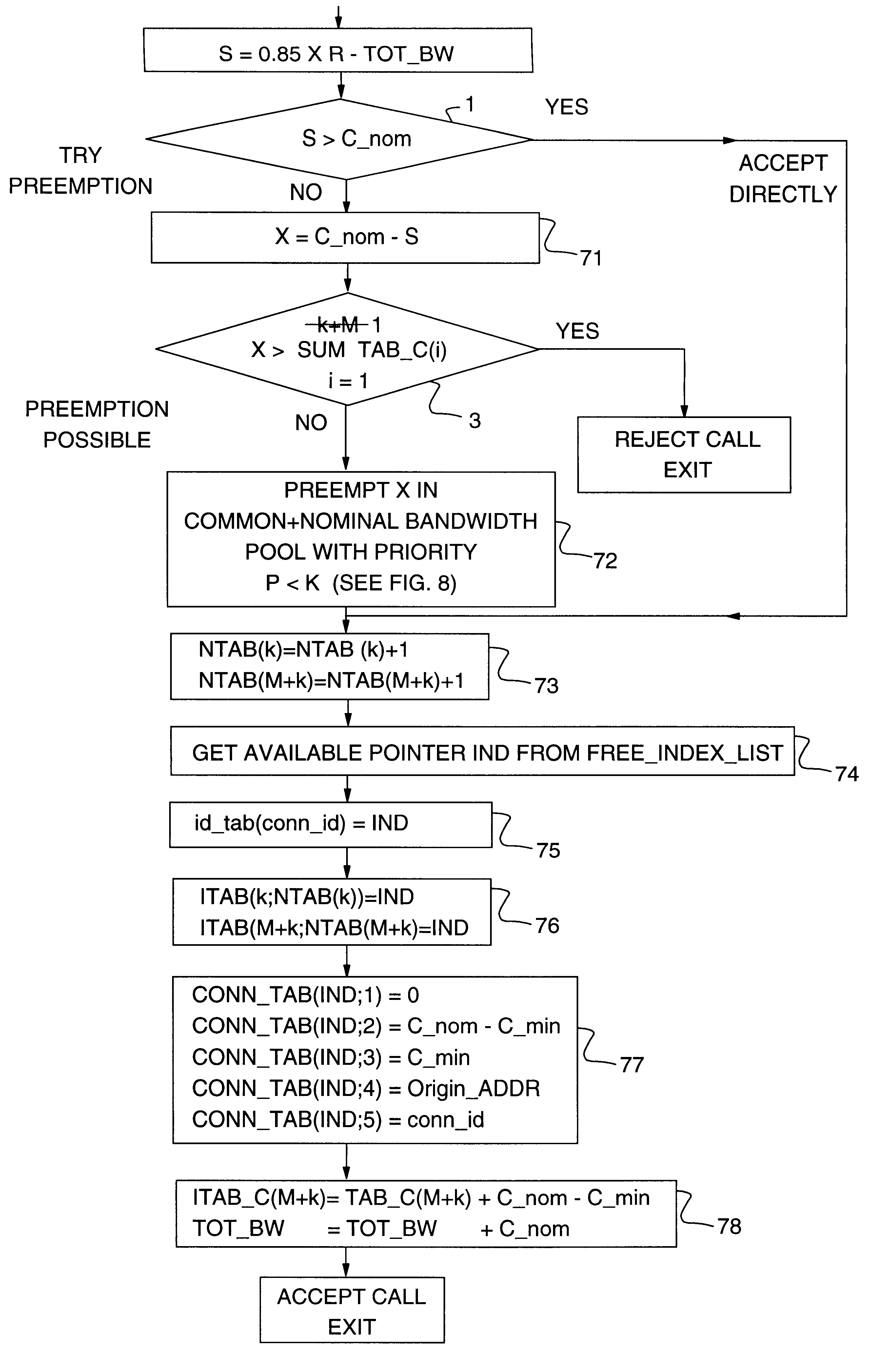
Method and system for non disruptively assigning link bandwidth to a user in a high speed digital network
InactiveUS6262974B1Blocking in networkAvoid disruptionError preventionFrequency-division multiplex detailsNetwork connectionHigh-speed link
A method based on predefined connection priorities for assigning link bandwidth to a requesting user in a high speed digital network interconnecting network users through a path including network nodes connected through high speed links.According to this method, a predefined reservable link bandwidth is split into so-called nominal bandwidth portions and common bandwidth portions, both assignable to the same connections on a priority basis. Each of the common bandwidth priorities is individually related to a nominal bandwidth priority through a predefined relationship, making the common bandwidth priorities always lower than any nominal priority. In this way the requested link connection bandwidth, whatever be its nominal priority, is made preemptable primarily on all common bandwidth, thus avoiding the disruption of any network connection which is already established.
Owner:IBM CORP
System and method for identifying nodes in a wireless mesh network
InactiveUS7069483B2Robust and simplifiedFind quicklyElectronic circuit testingNetwork topologiesComputer hardwareDepth-first search
Systems and methods for providing a boundary scan test of a wired or wireless network having a plurality of network nodes are presented. The system includes a test station communicatively coupled with the network. The test station creates a MAC layer scan test route sequence that includes each link in the network and is independent of the routing mechanism and protocol used for the network. The test station also creates a test agent that is configured to traverse each link in the scan test route sequence. The test agent is then deployed on the network and information about a link is reported back to the test station after the test agent examines the link. The scan test route sequence can be created by sending out a series of broadcast messages from one or more nodes in the network, sequentially applying a network tour to cover the entire network, or performing a depth first search on the entire network.
Owner:UNWIRED BROADBAND INC
Expedited data transmission in packet based network
ActiveUS20050220097A1Blocking in networkImprove data throughputData switching by path configurationData transmissionDistributed computing
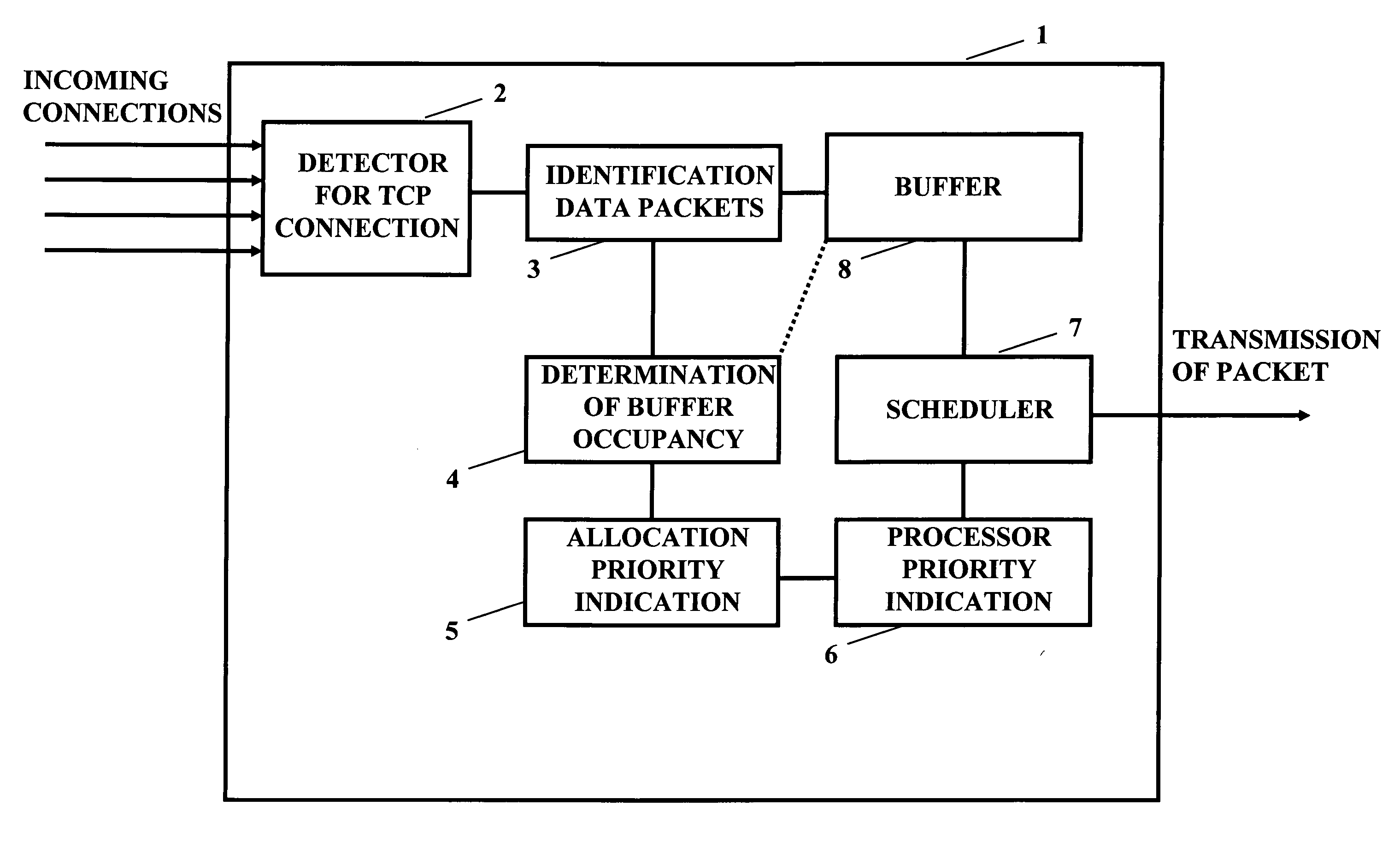
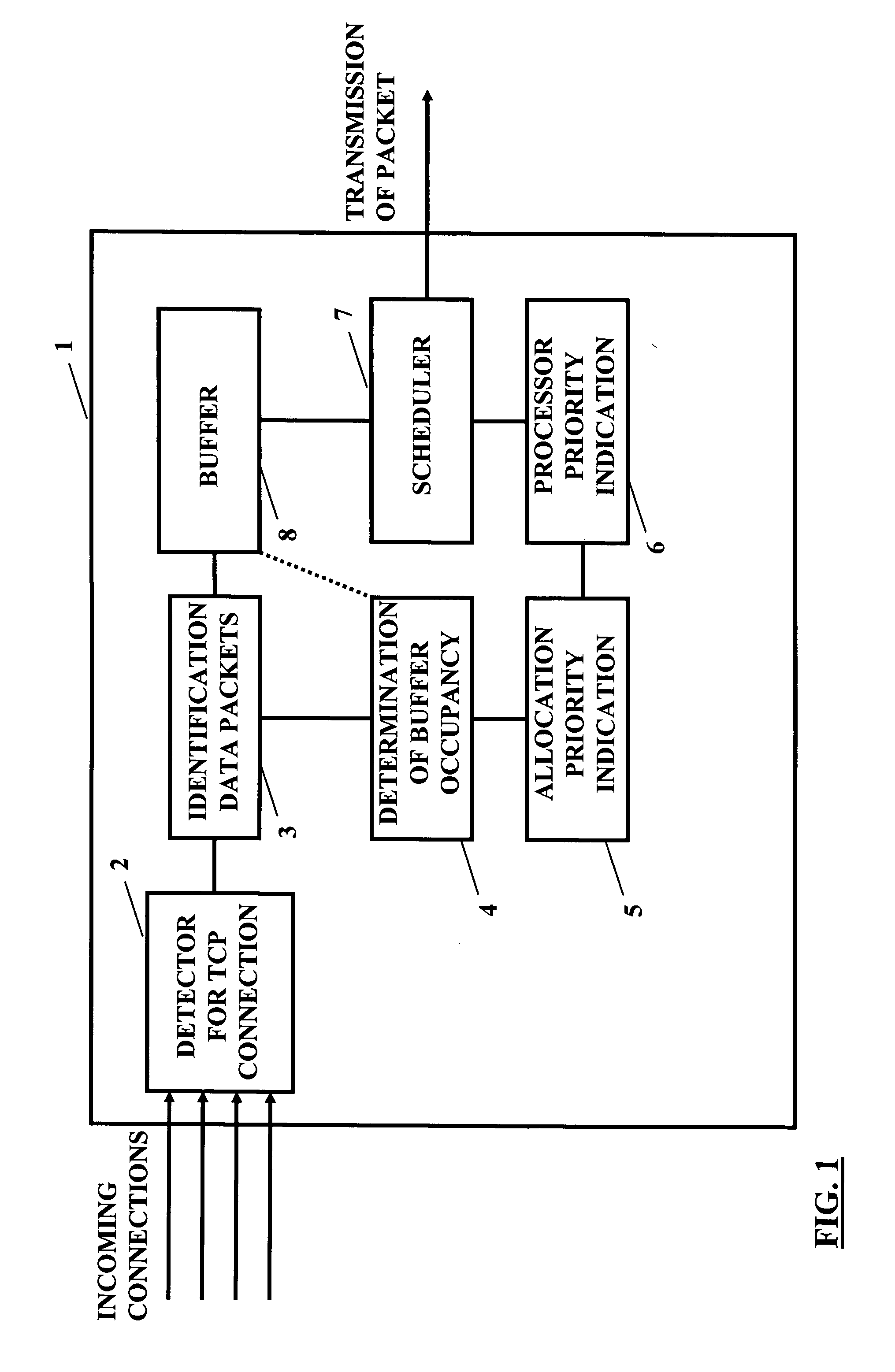
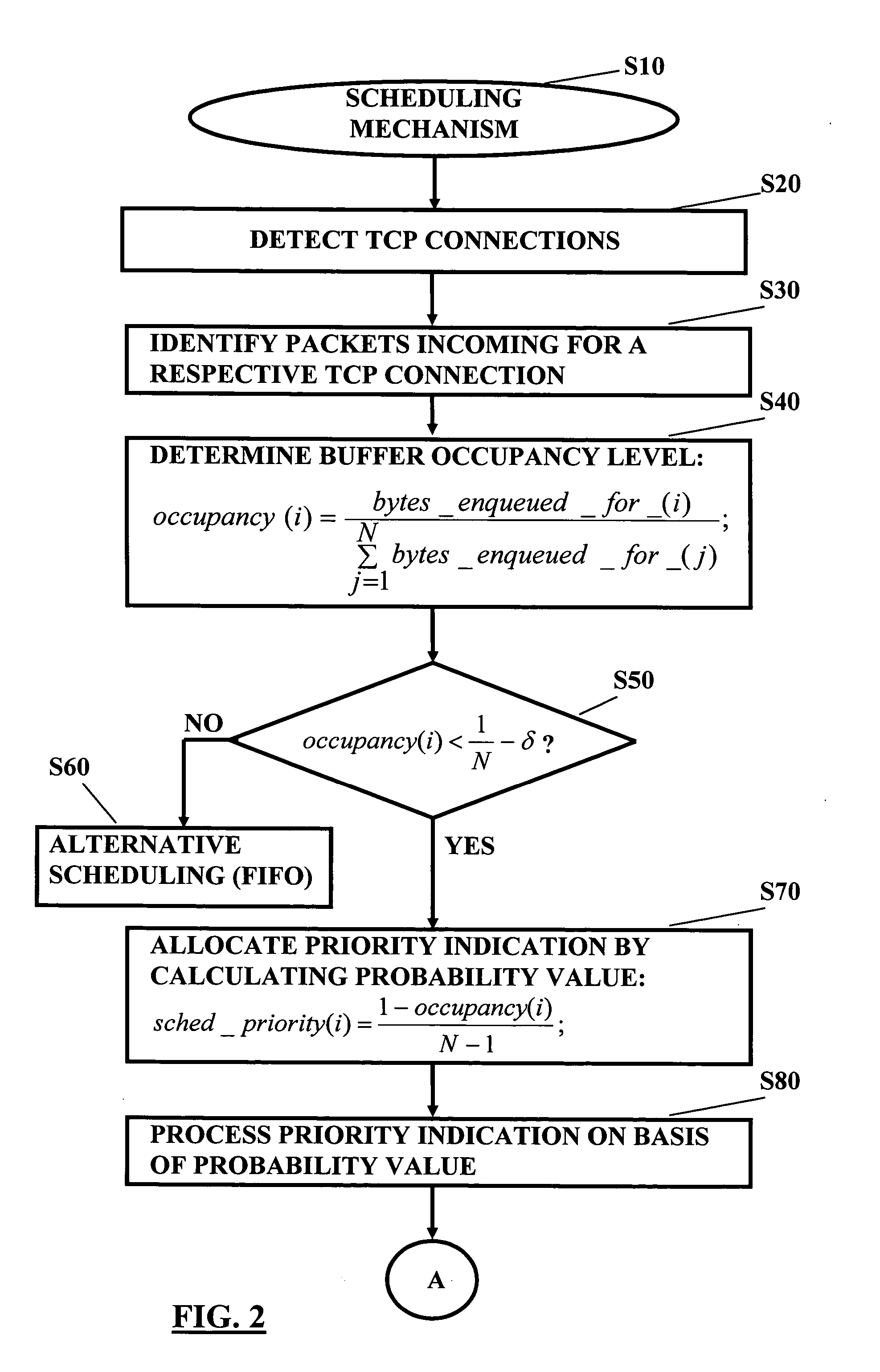
An improved scheduling mechanism usable for a data transmission in a packet based network is provided. A plurality of connections is detected, and for each of the connections, a buffer occupancy level is determined. Then, the connections having a smaller buffer occupancy level are prioritized in comparison to the other connections, and packets of the plurality of connections are scheduled on the basis of the result of the prioritizing. The scheduling mechanism is implemented in a network element of the packet based network or in a sender and receiver.
Owner:NOKIA TECHNOLOGLES OY
SIM-based authentication method capable of supporting inter-AP fast handover
ActiveUS20050177723A1Blocking in networkSafe WLAN environmentUnauthorised/fraudulent call preventionEavesdropping prevention circuitsFast handoverWireless lan
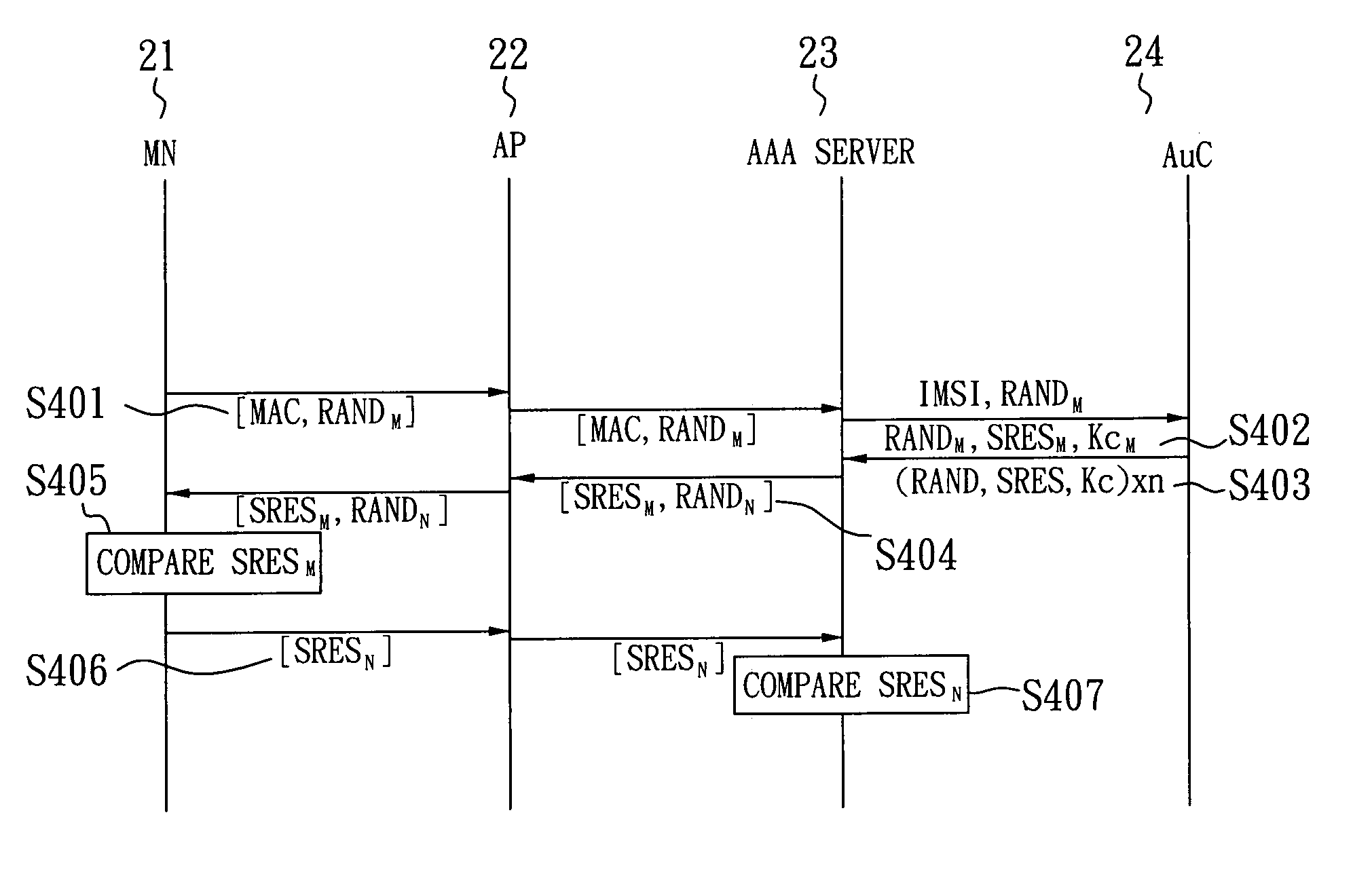
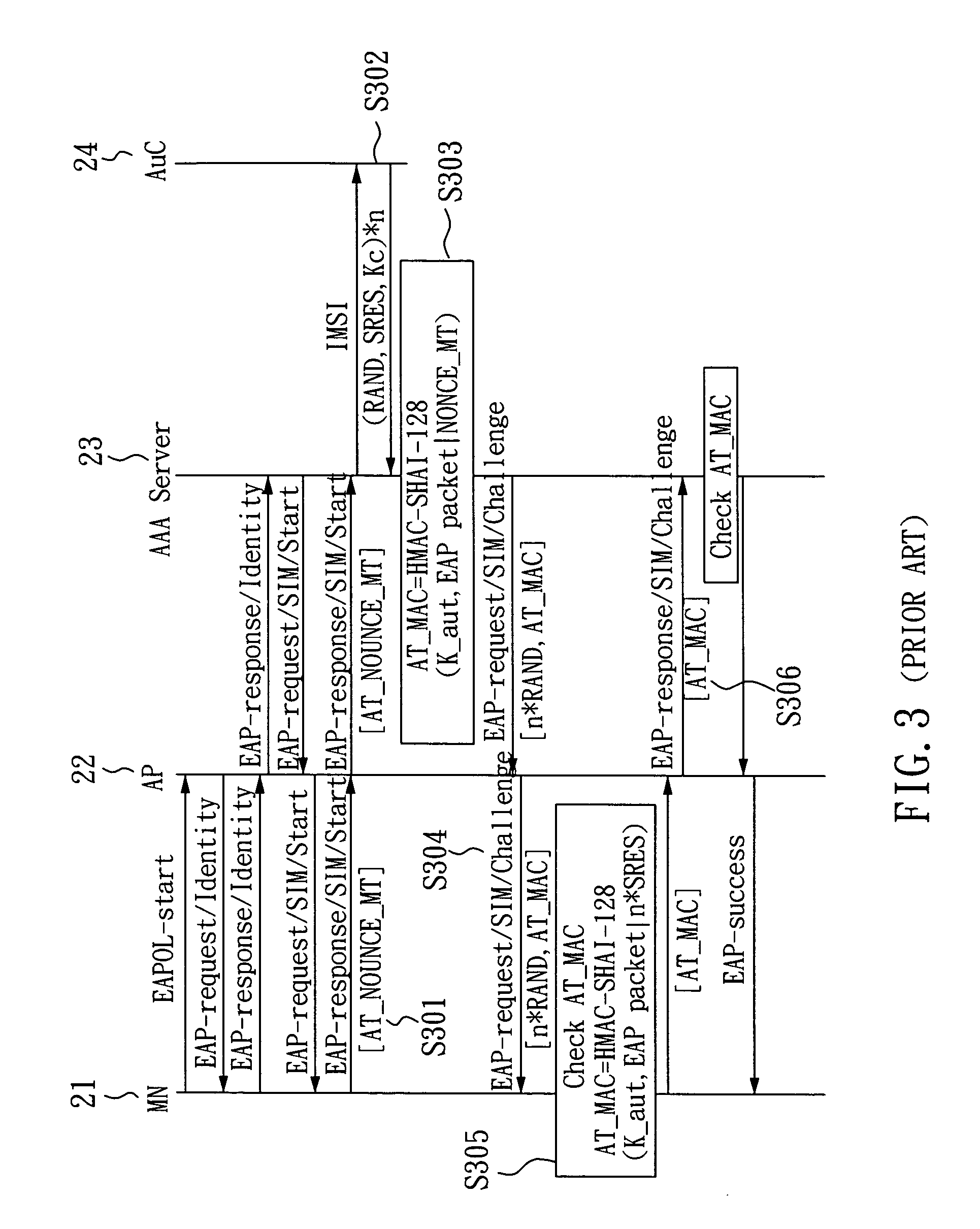
The invention relates to a SIM-based authentication method capable of supporting inter-AP fast handover, which can decrease the number of authentication procedures without negatively influencing the security of the wireless LAN by establishing an encrypted channel for each mobile node and using method 1: an aggressive key pre-distribution and method 2: probe request triggering passive key pre-query technique, thereby reducing the time of inter-AP handover for the mobile node. Furthermore, a re-authentication procedure is started to update the key after the key is used for a long time so as to ensure that the key is safe, thereby effectively achieving a fast and safe wireless LAN environment.
Owner:IND TECH RES INST
Anonymous location service for wireless networks
InactiveUS20090047937A1Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identification information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
Device triggering and apn-based congestion control
ActiveUS20140341041A1Avoid sendingEffective controlError preventionFrequency-division multiplex detailsData transmissionTimer
The present invention relates to device triggering in case of a congestion control. A triggering server transmits a device trigger request to a terminal over a communication network including a serving network node. The network node evaluates whether the connection can be established from the terminal to the server, including determining whether the network is congested and / or whether a back-off timer is running and / or the remaining time of the back-off timer at the terminal. Then the network node transmits a delivery delay indication to a device triggering control server to provide it with the delivery delay indication indicating at least one of impossibility of establishing the connection to the server after the trigger or a data transmission delay.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
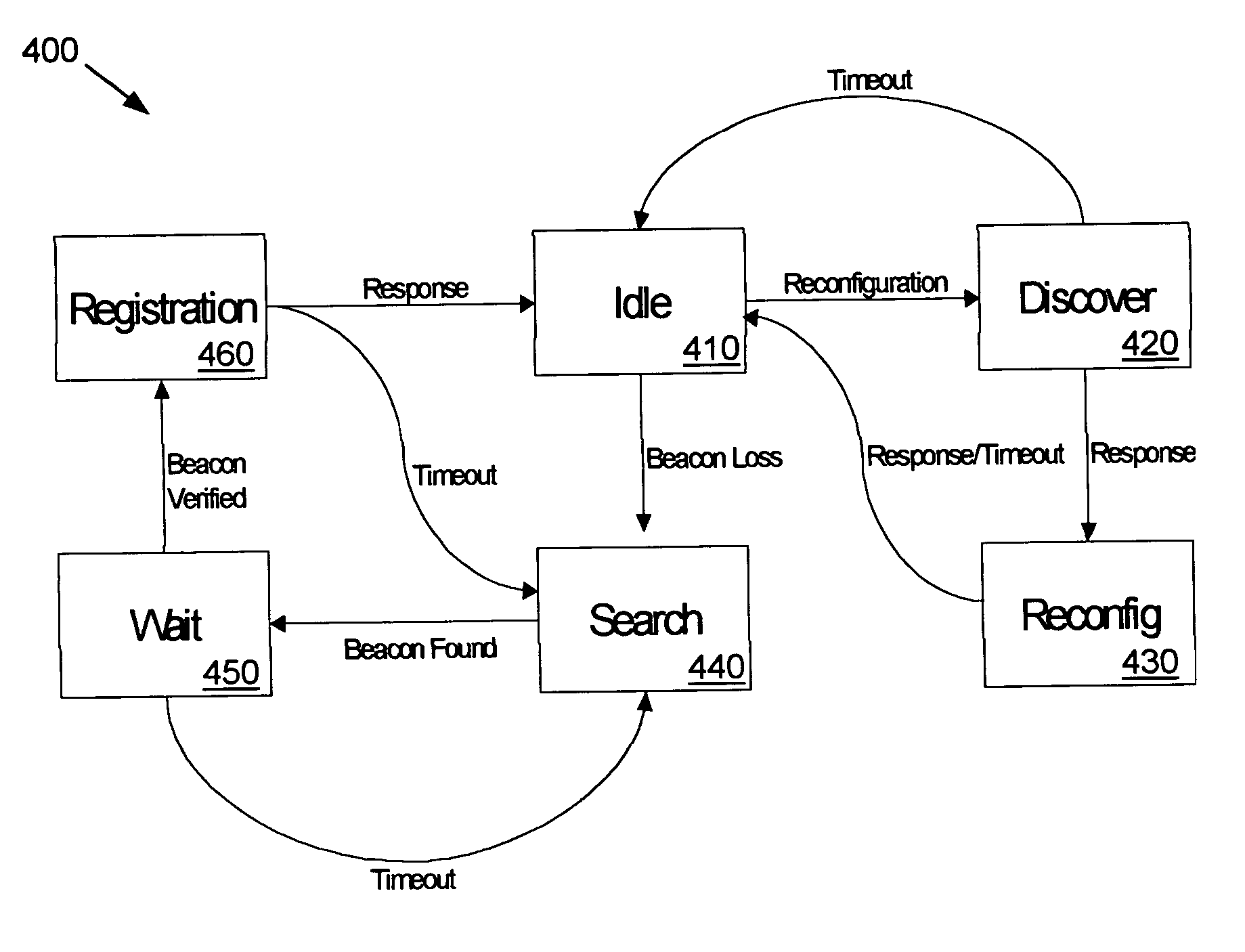
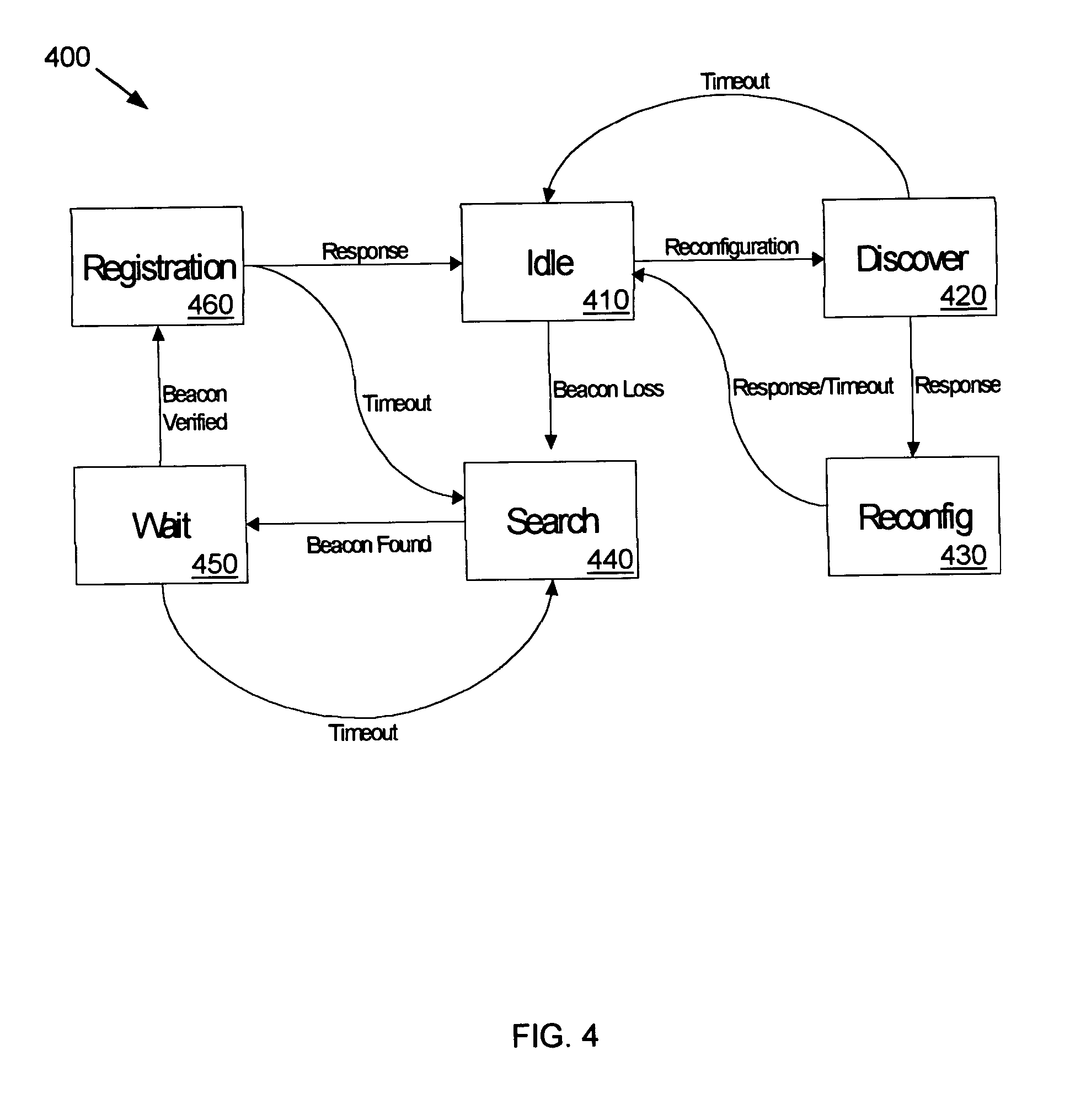
Self-healing tree network
InactiveUS7233991B2Blocking in networkAvoid creatingError detection/correctionData switching by path configurationSelf-healingNetwork isolation
A communications network is provided with a self-healing topological architecture. Each node in the network detects continuously transmitted beacon packets that are propagated through the network at regular intervals by a root node. Upon failure to detect a new beacon packet after a predetermined time from a parent node, a network node determines a network isolation condition and searches for another node that is still actively connected in the network. Algorithms are provided for registering with and identifying active parent node candidates during a network failure so as to prevent the creation of network loops.
Owner:OMNILUX
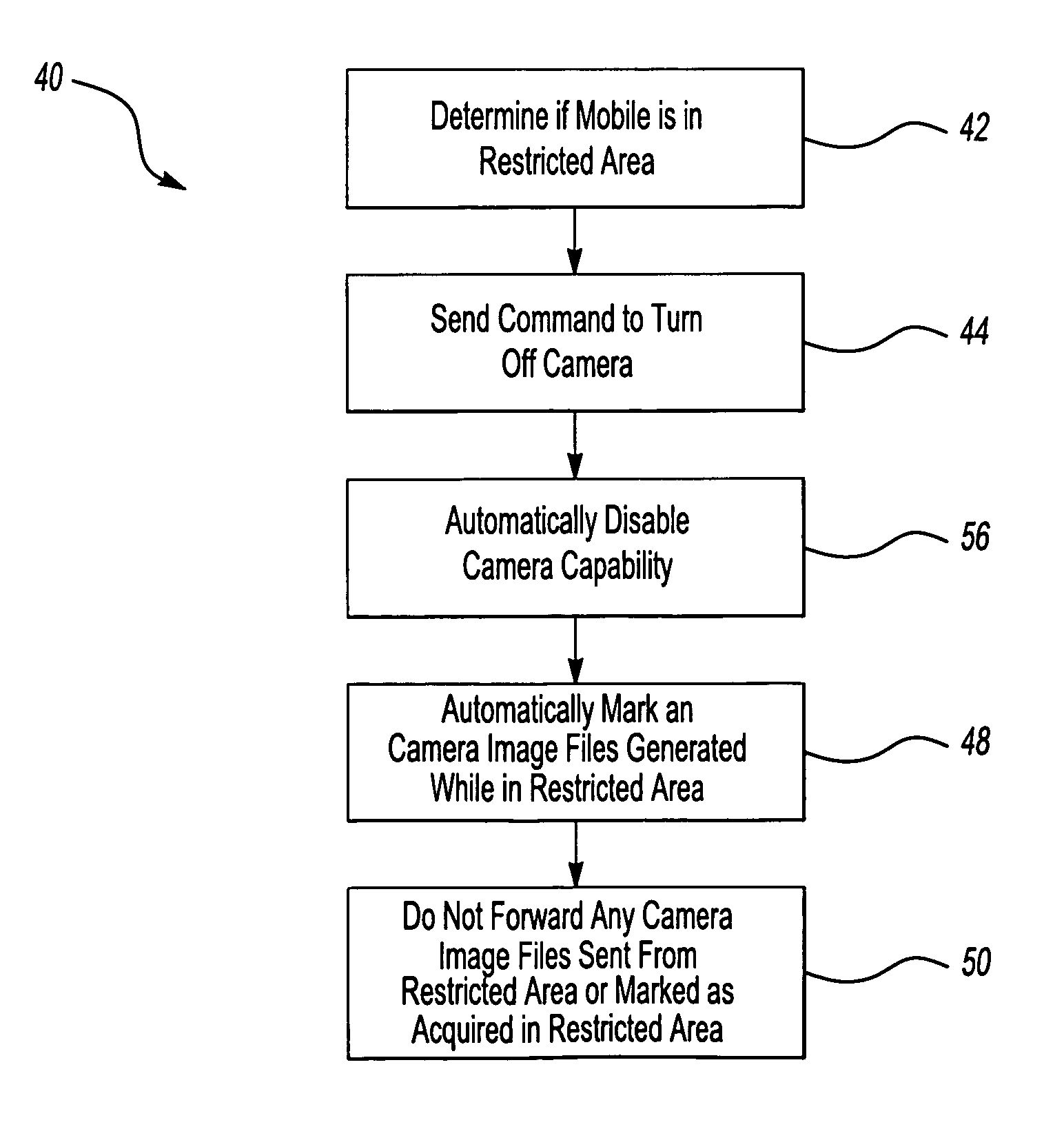
Controlling wireless communication devices with media recording capabilities
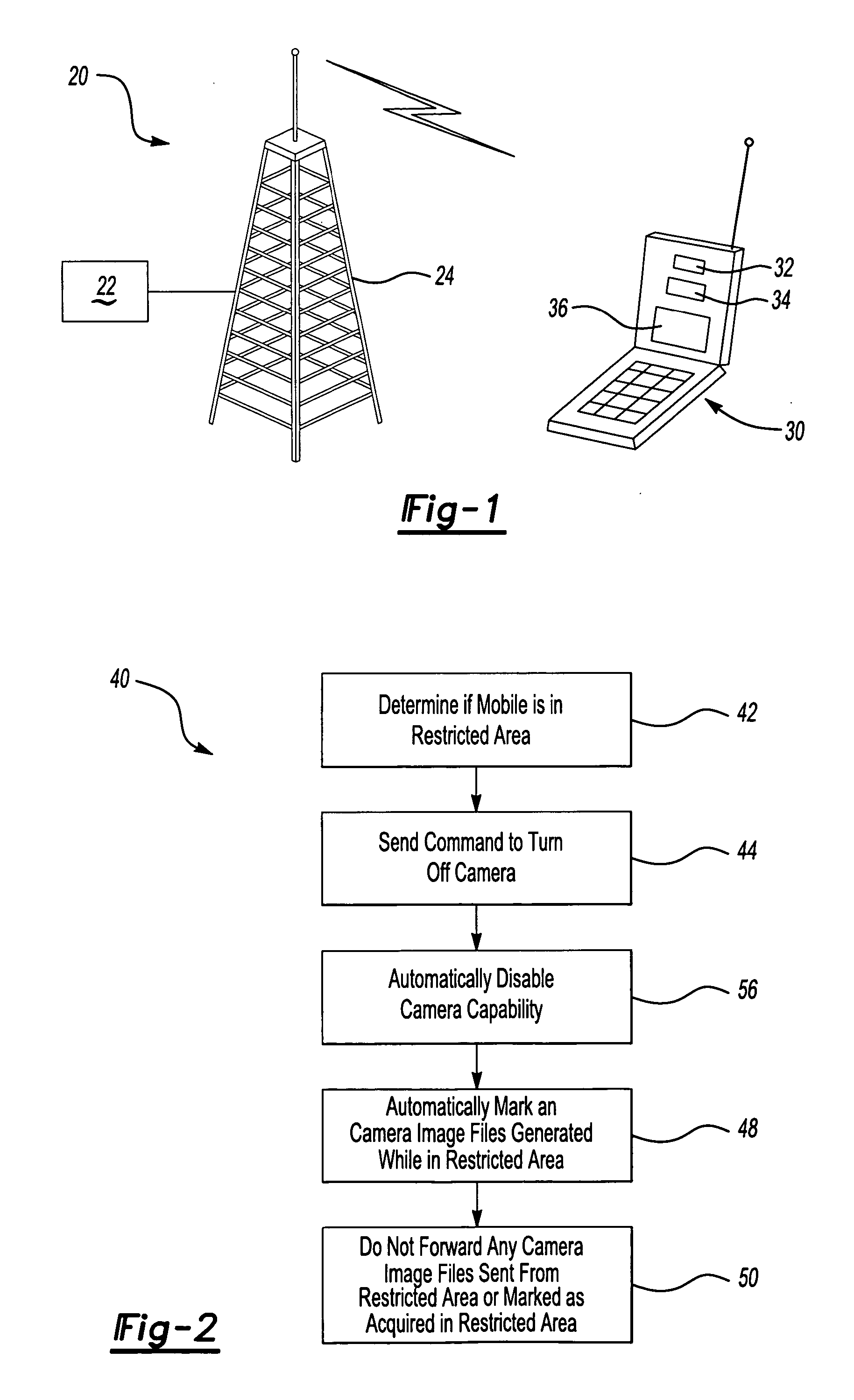
InactiveUS20070072598A1Inhibition of informationBlocking in networkAssess restrictionRadio/inductive link selection arrangementsCommunications systemMobile station
A wireless communication system (20) includes the capability of controlling when a media recording device such as a camera (32) associated with a mobile station (30) may be used. In a disclosed example, if the mobile station (30) is in a restricted area where audio recordings, photographs or video are not permitted, a controller (34) automatically disables the media recording device (32) responsive to an appropriate signal from a wireless network (22) or base station (24). In one example, a controller (34) automatically marks a file containing media data if that data was acquired in a restricted area. In a disclosed example, the wireless communication network (22) prevents forwarding any media files corresponding to media acquired in a restricted area.
Owner:LUCENT TECH INC
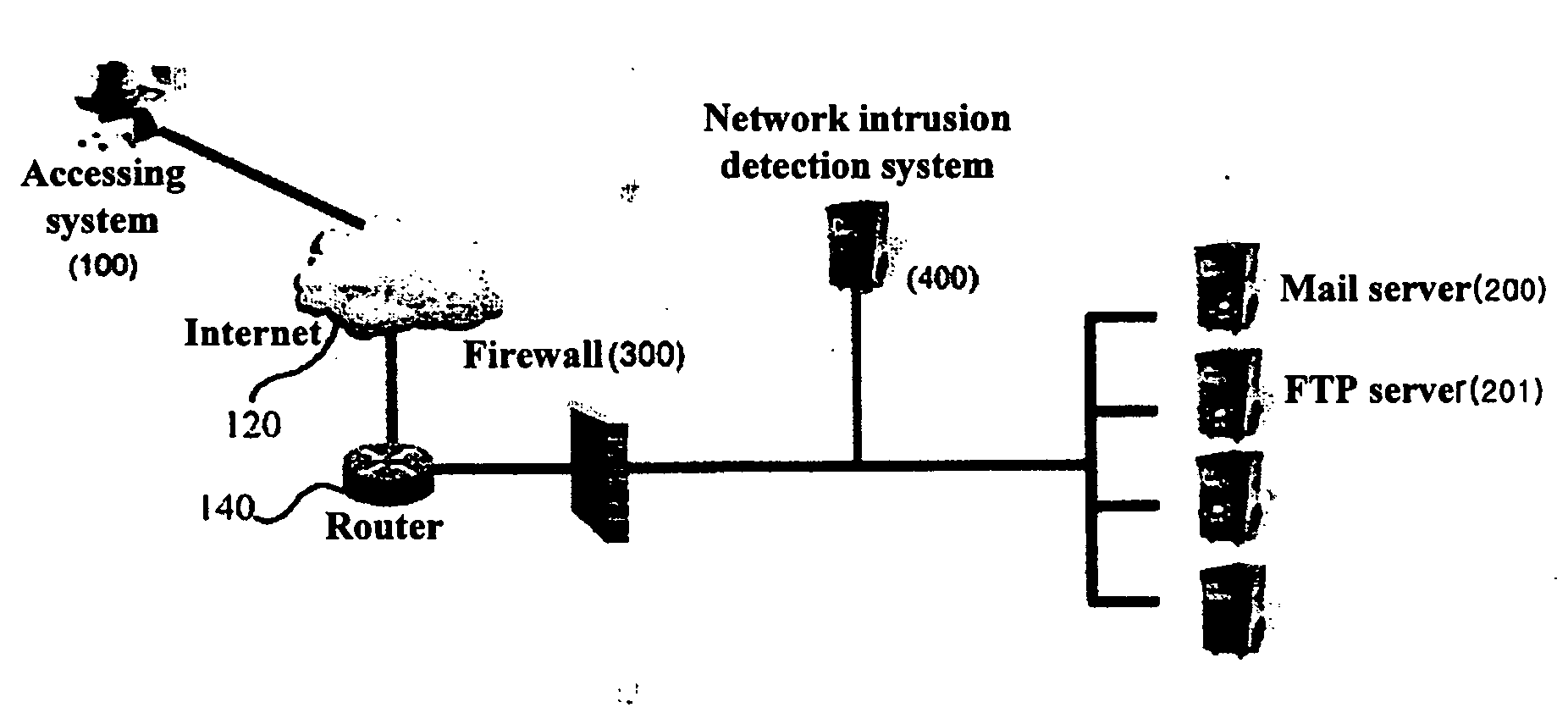
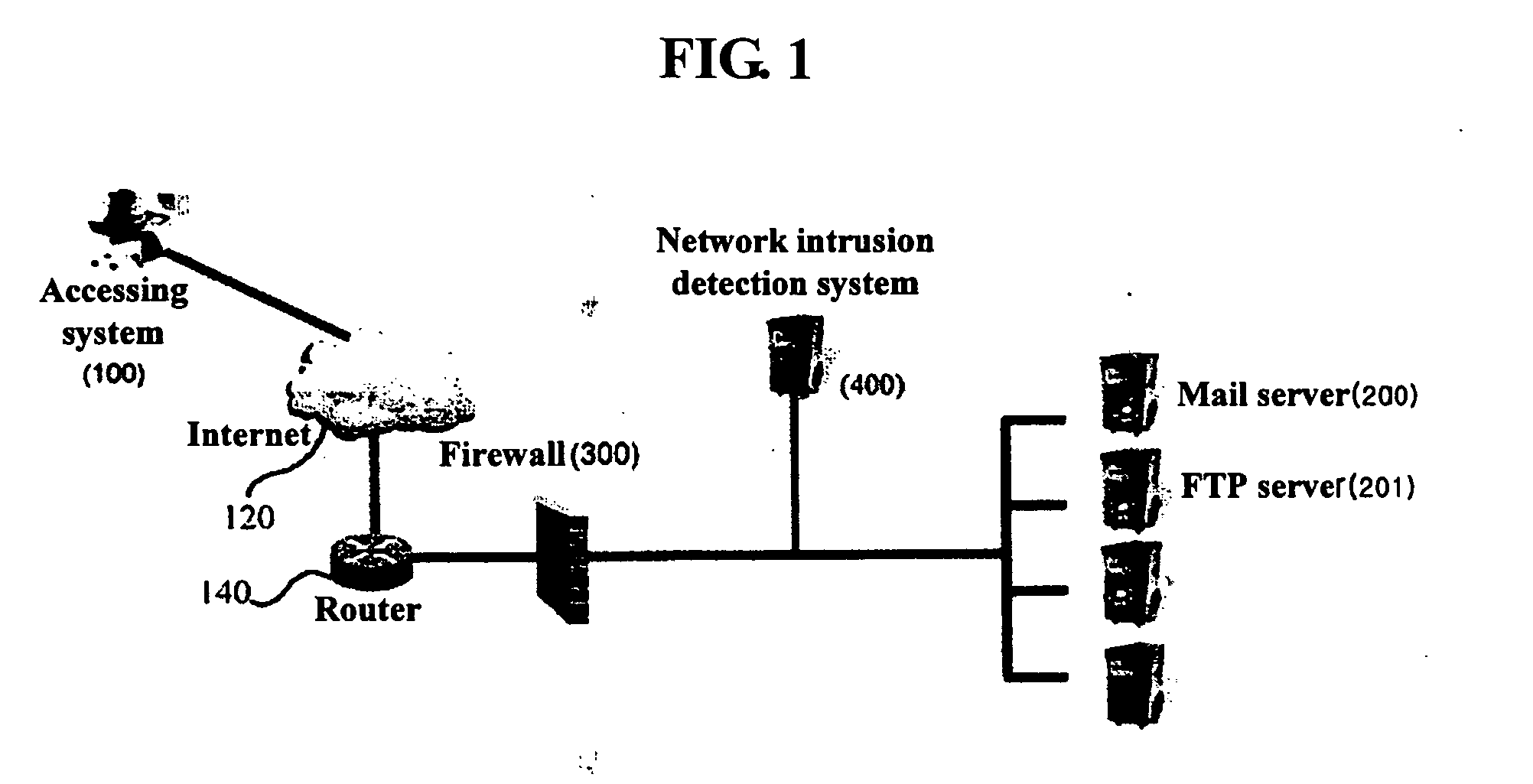
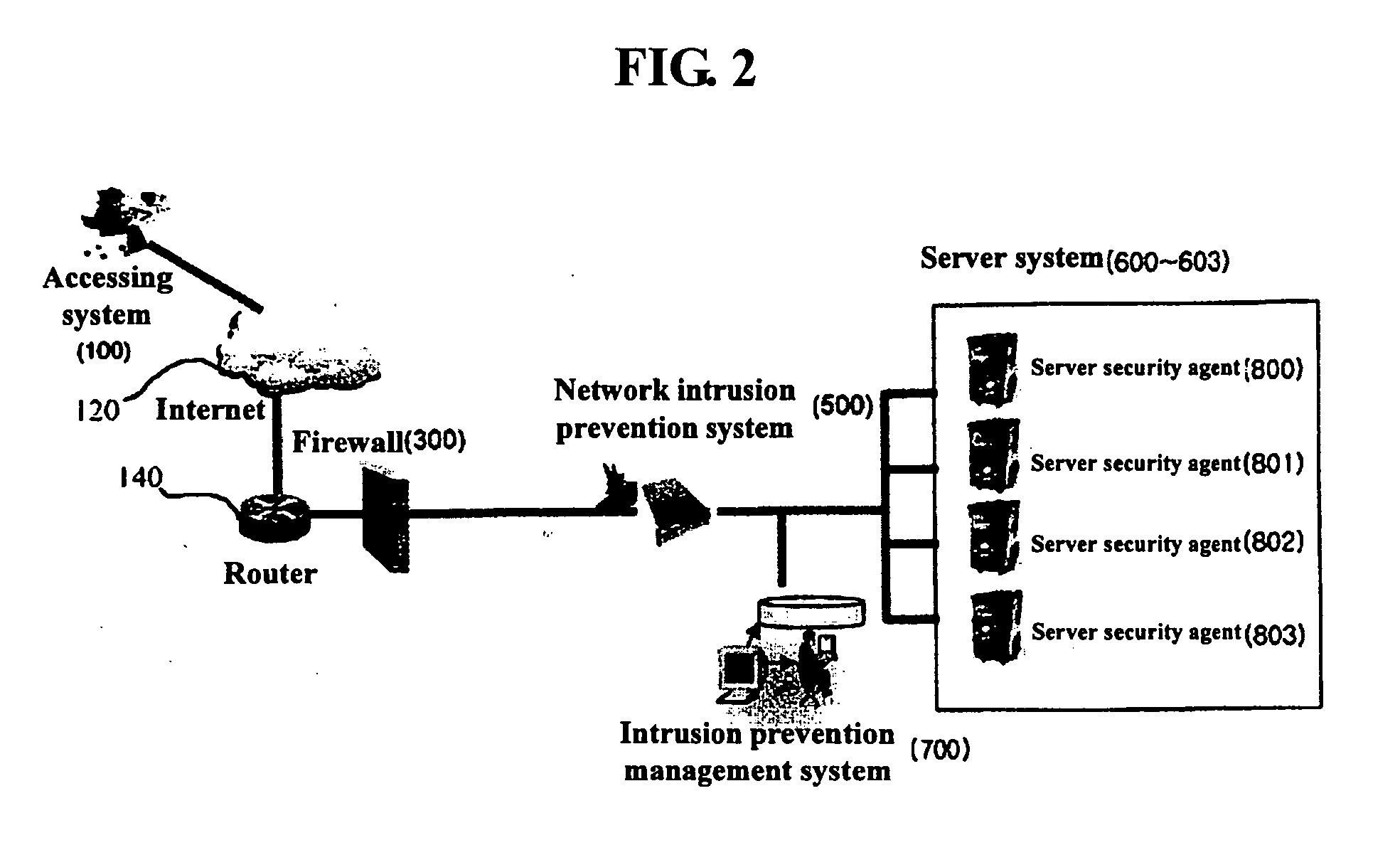
Security system and method using server security solution and network security solution
InactiveUS20050283831A1Blocking in networkImprove resource utilizationMultiple digital computer combinationsProgram controlTraffic volumeNetwork level
A security method and system using a server security solution and a network security solution is disclosed. In the security method based on the security system that has a firewall for blocking malicious access to a corresponding network, a network intrusion prevention system for blocking intrusion into the network and server systems including a mail server and a File Transfer Protocol (FTP) server, the server systems transmit information on an intruding system, which has transmitted harmful traffic, to the network intrusion prevention system at the time of detecting the harmful traffic. The network intrusion prevention system blocks the access of the harmful traffic based on the information transmitted from the server systems. According to the present invention, the server systems detect malicious intrusion attempts, and intrusion is blocked at a network level, so that the present invention is effective in that second and third malicious intrusion attempts can be fundamentally blocked and the consumption of network resources attributable to repeated intrusion attempts can be prevented.
Owner:LG CNS
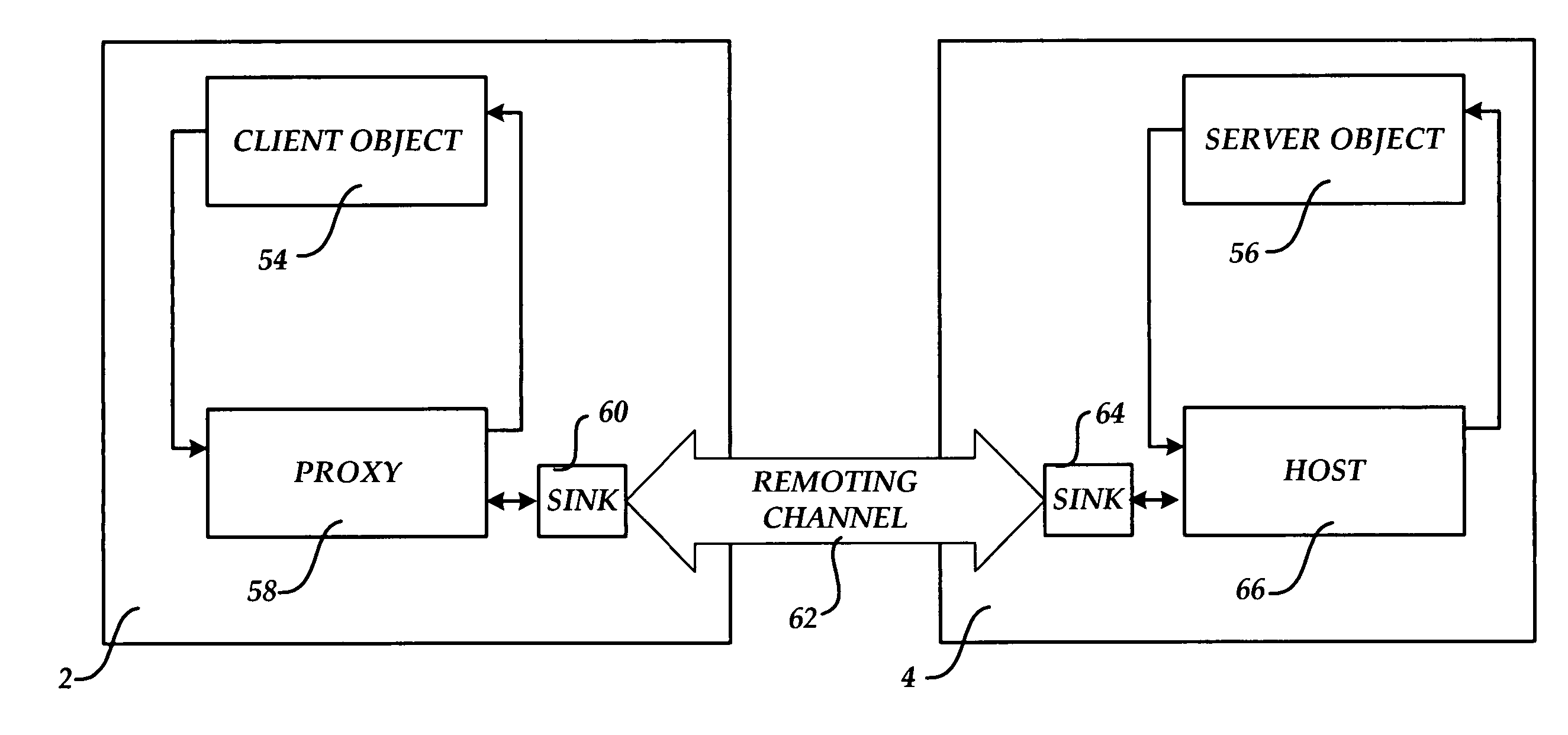
Instant messaging communications channel for transporting data between objects executing within a managed code environment
InactiveUS20050216594A1Facilitate information exchangeBlocking in networkMultiprogramming arrangementsMultiple digital computer combinationsManaged codeData transmission
A method, system, and apparatus for providing a communications channel for inter-object communication are provided. According to the method, a request may be received from a first object executing within a managed code environment to transmit data to a second object. In response thereto, an instant message (“IM”) including the data may be transmitted to an IM server computer. The IM may be forwarded to the managed code environment in which the second object is executing. The IM may then be received by the managed code environment, the data contained therein may be extracted, and the data may be presented to the second object. A reverse path may also be utilized for return communication between objects.
Owner:MICROSOFT TECH LICENSING LLC
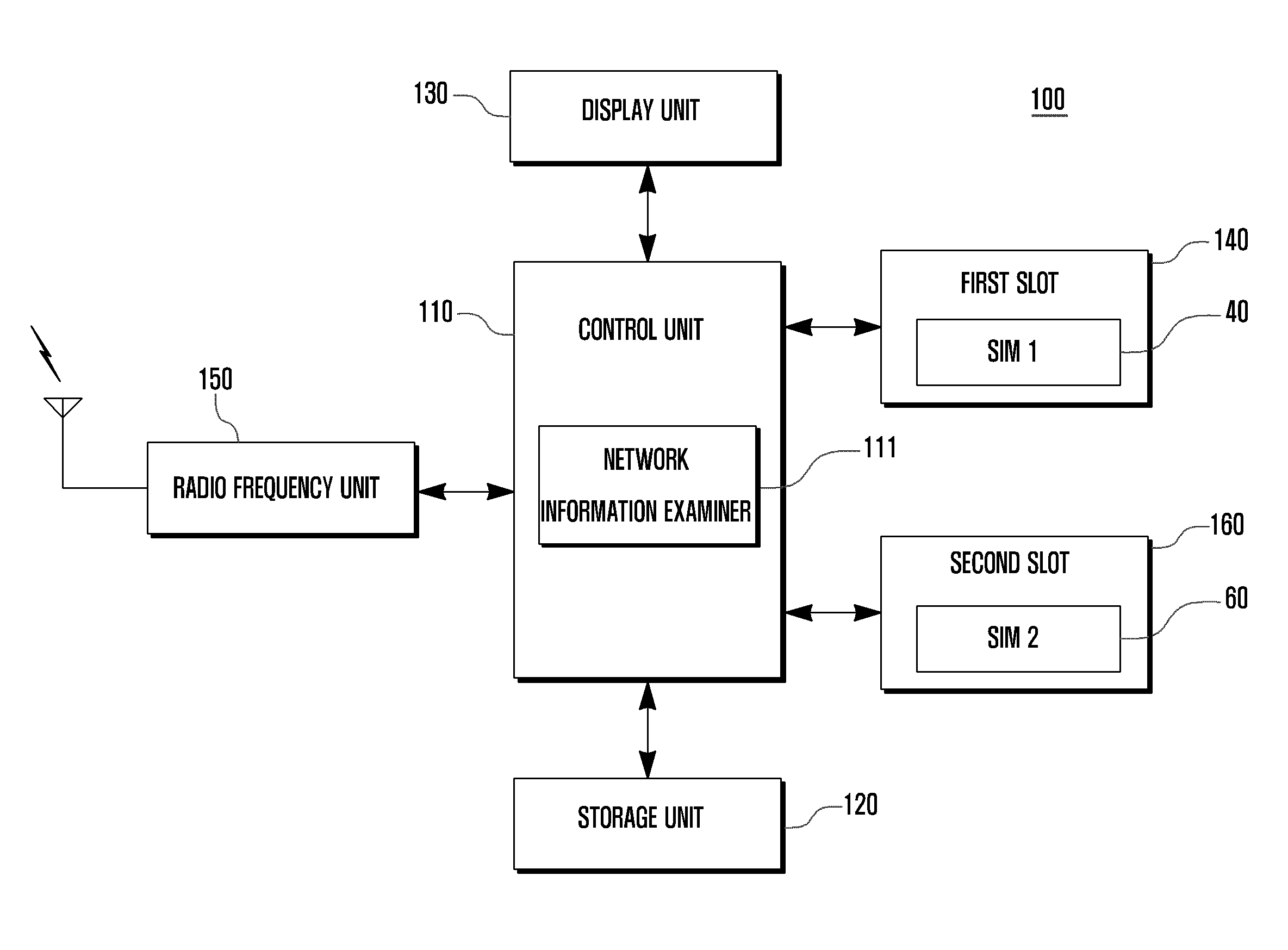
Protocol processing method and apparatus for multi-sim terminal
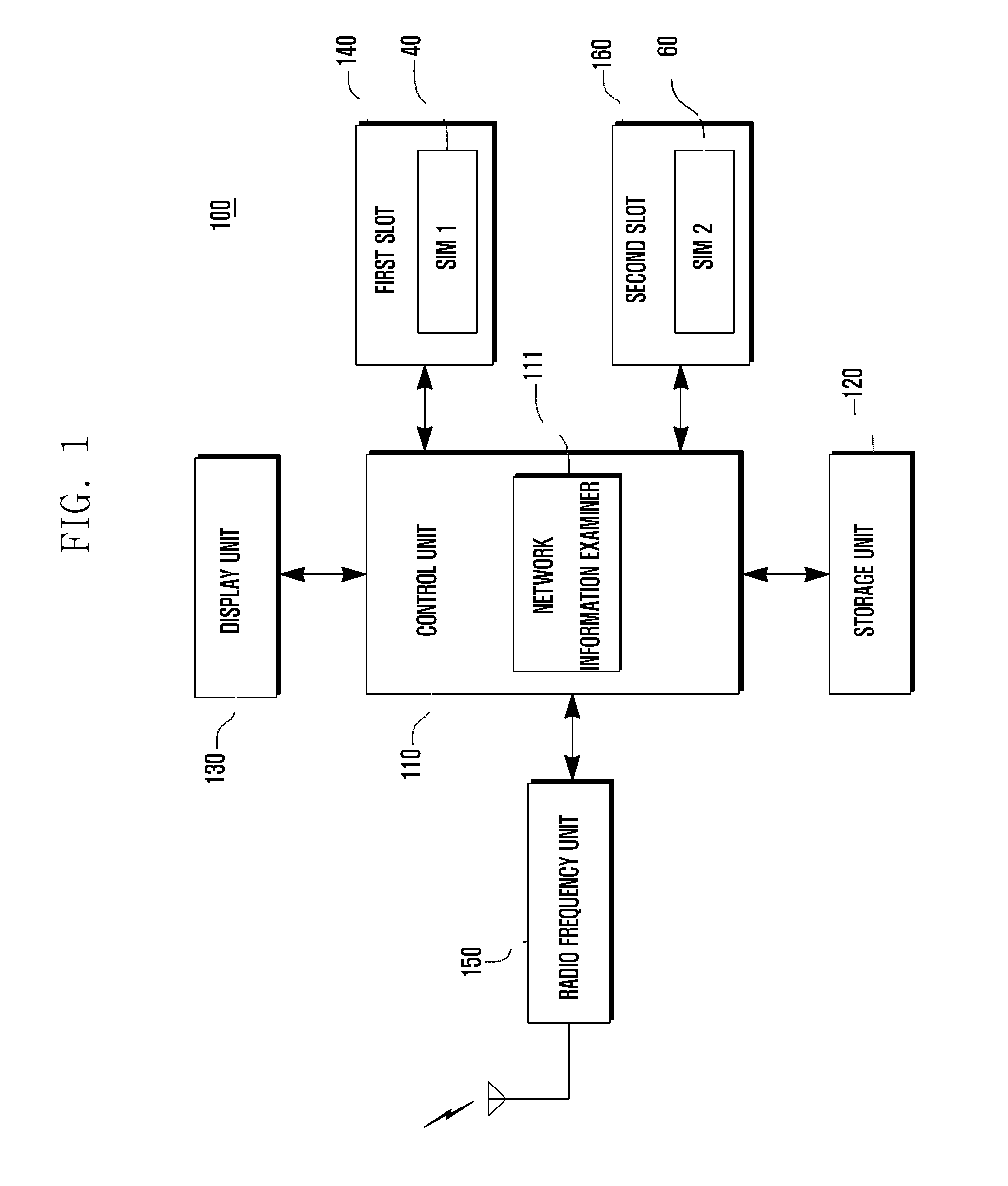
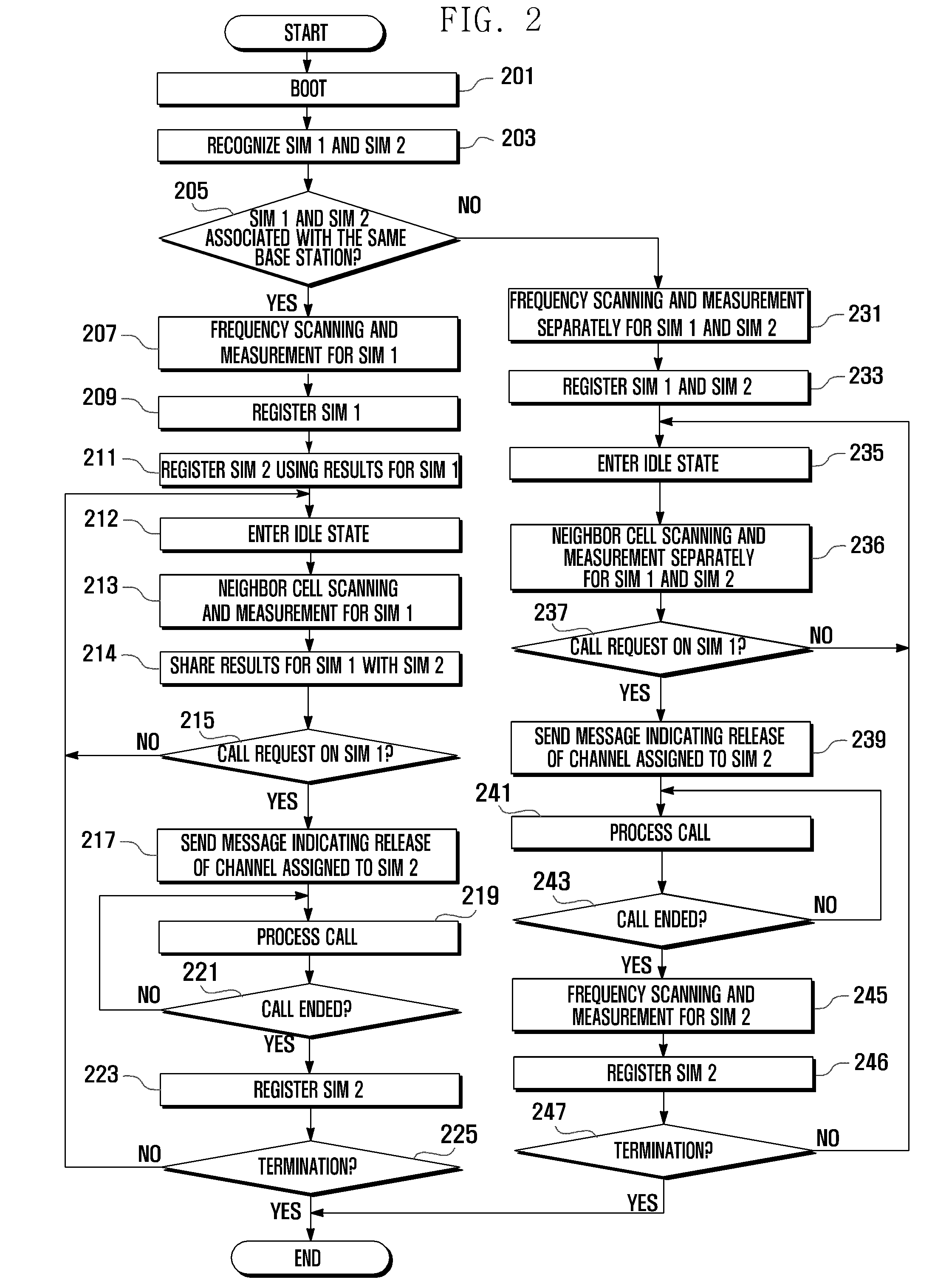
ActiveUS20110077003A1Reduce battery power consumptionBlocking in networkPower managementEnergy efficient ICTProtocol processingPublic land mobile network
A protocol processing method and apparatus are disclosed for a multi-SIM terminal holding multiple subscriber identification cards. The method includes: determining whether all the subscriber identification cards are associated with the same base station (e.g., a Public Land Mobile Network); and conducting, when all the subscriber identification cards are associated with the same base station, frequency scanning and measurement for a selected one of the subscriber identification cards, and sharing the results of frequency scanning and measurement with all the subscriber identification cards. Hence, the multi-SIM terminal may reduce battery power consumption without repeated frequency scanning and measurement for multiple subscriber identification cards.
Owner:SAMSUNG ELECTRONICS CO LTD
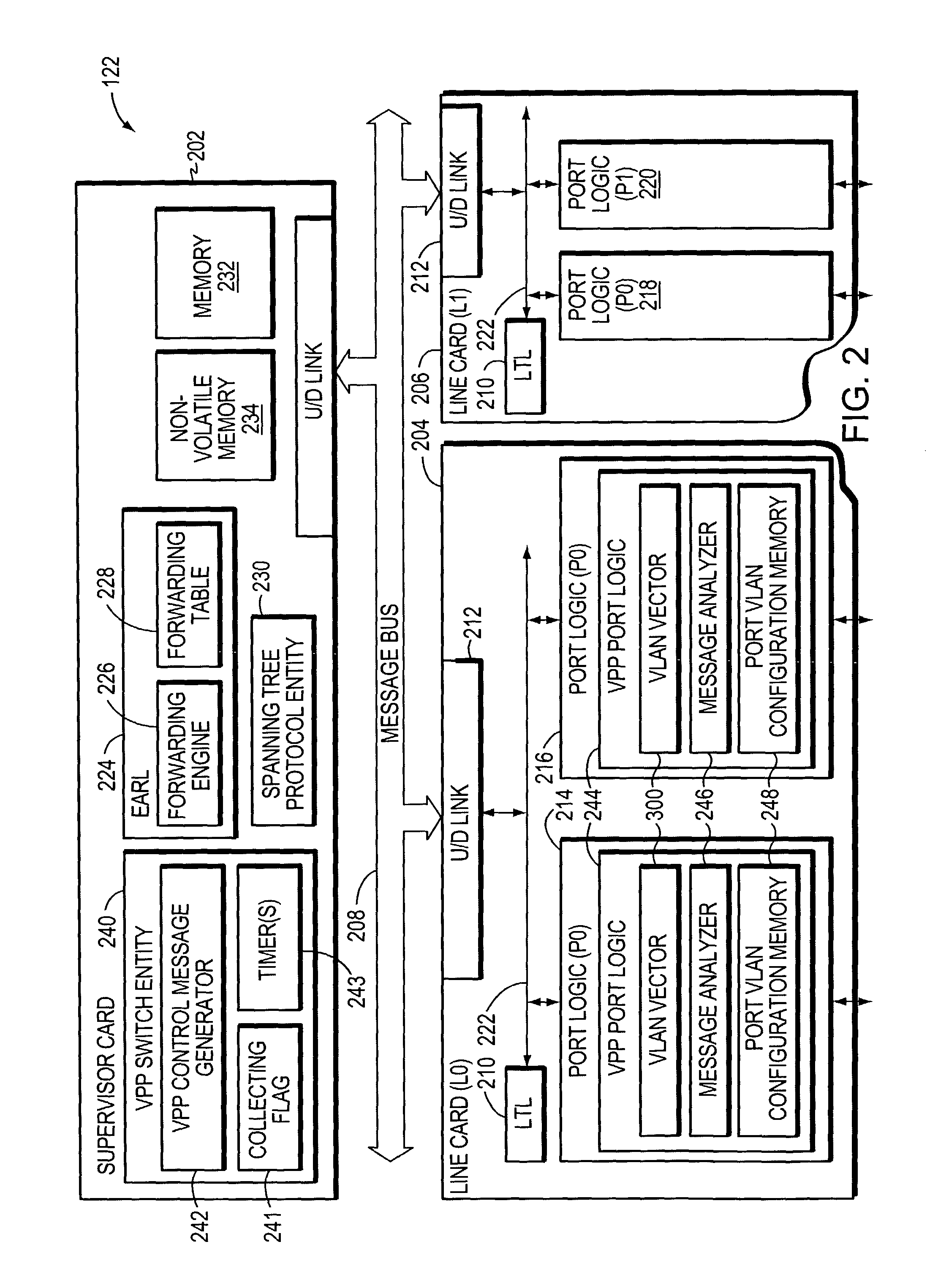
Virtual local area network pruning protocol
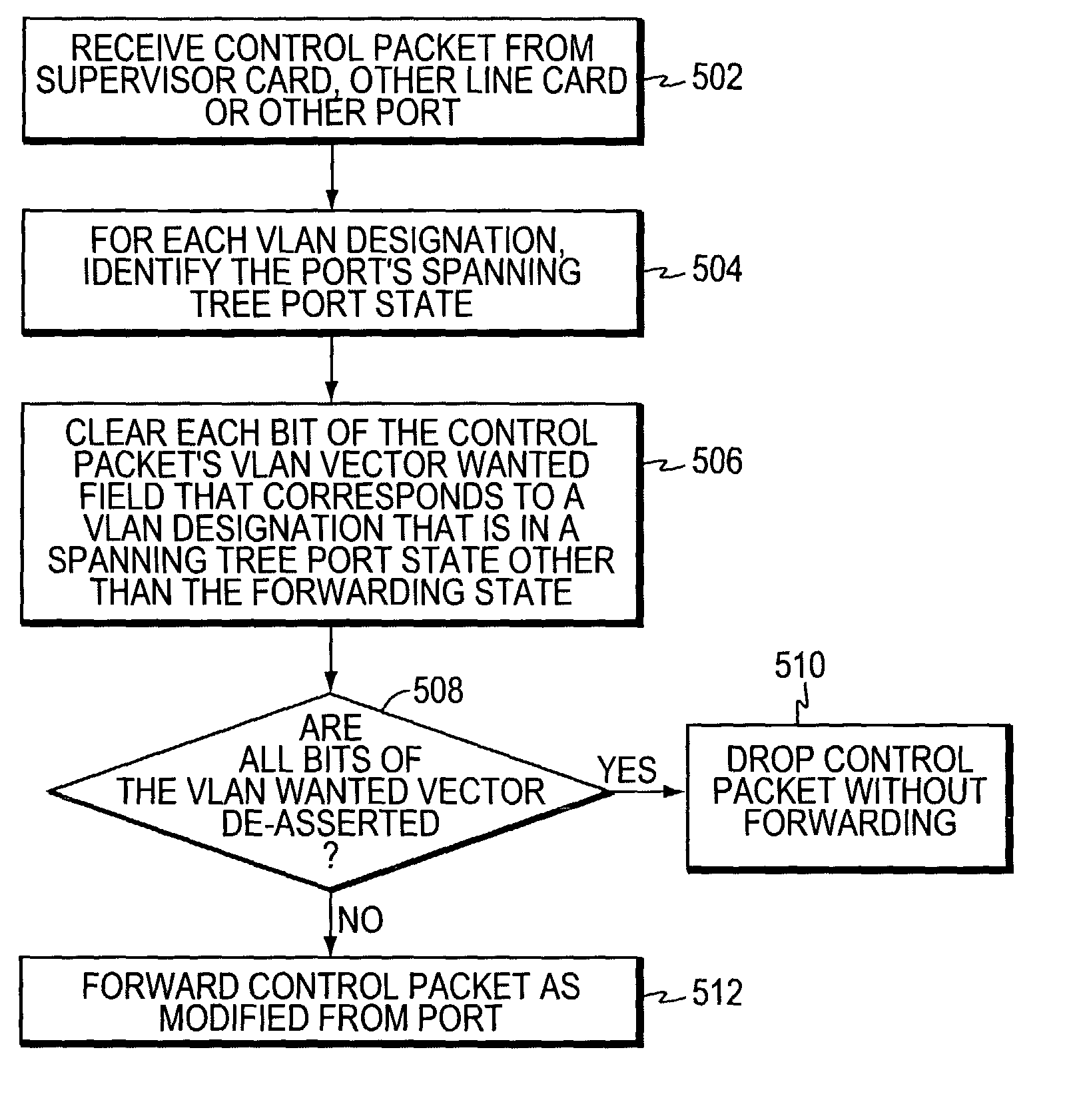
ActiveUS7877483B1Blocking in networkData switching by path configurationMultiple digital computer combinationsProtocol for Carrying Authentication for Network AccessSpanning Tree Protocol
In one embodiment, an intermediate network device has a plurality of ports, and at least some of the ports are associated with Virtual Local Area Network (VLAN) designations. A spanning tree entity executes a spanning tree protocol to transition the ports among a plurality of spanning tree states. A VLAN port logic circuit is disposed at one or more of the ports and processes control packets advertising VLAN memberships. The VLAN port logic circuit, in response to receiving a control packet broadcast by another intermediate network device, asserts bits in a VLAN wanted vector for which the spanning tree state of the selected port is in the forwarding state, signifying that network messages associated with such VLAN designations are to be forwarded from the respective port. The VLAN wanted vectors may later be transmitted in control messages from the intermediate network device.
Owner:CISCO TECH INC
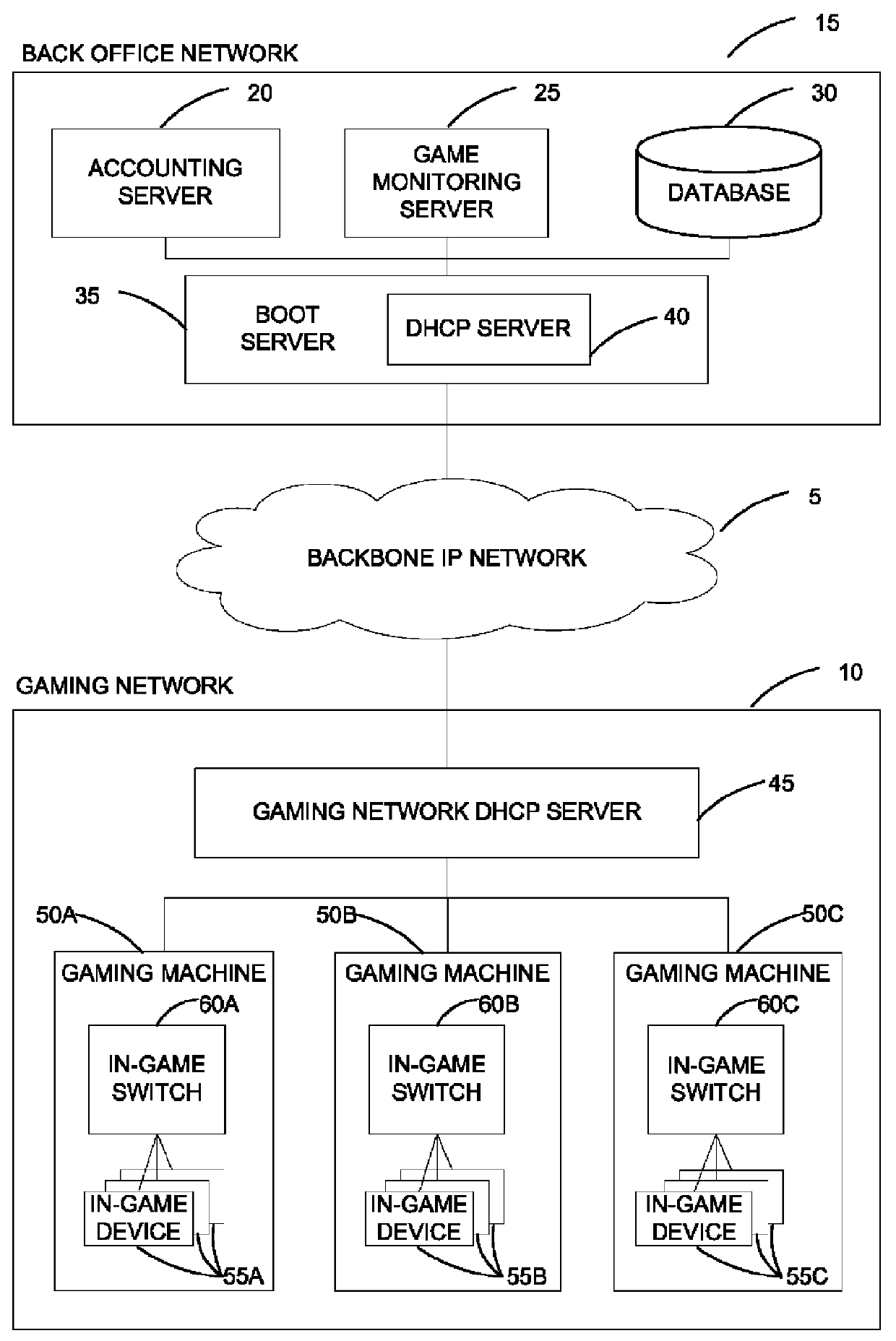
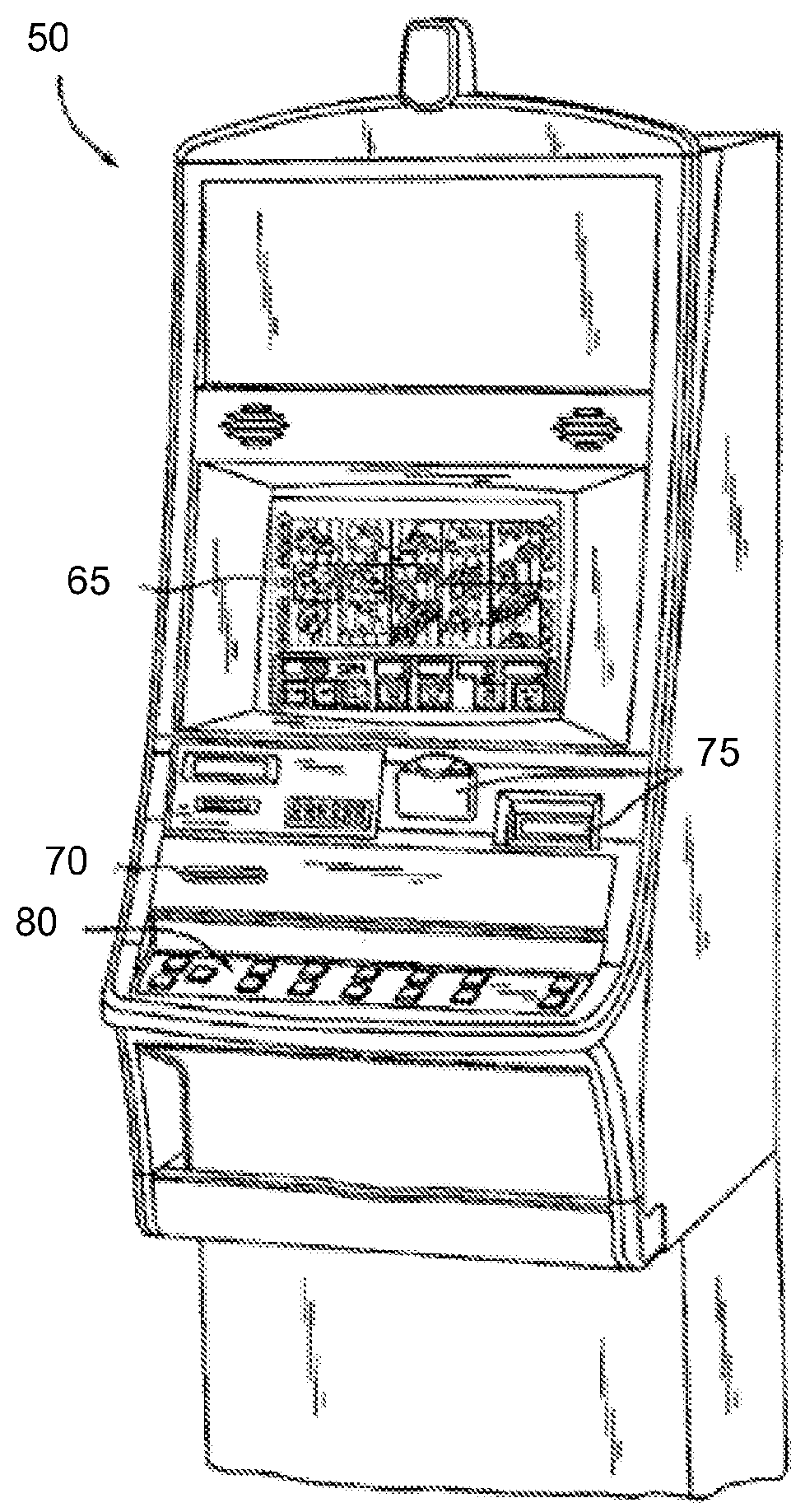
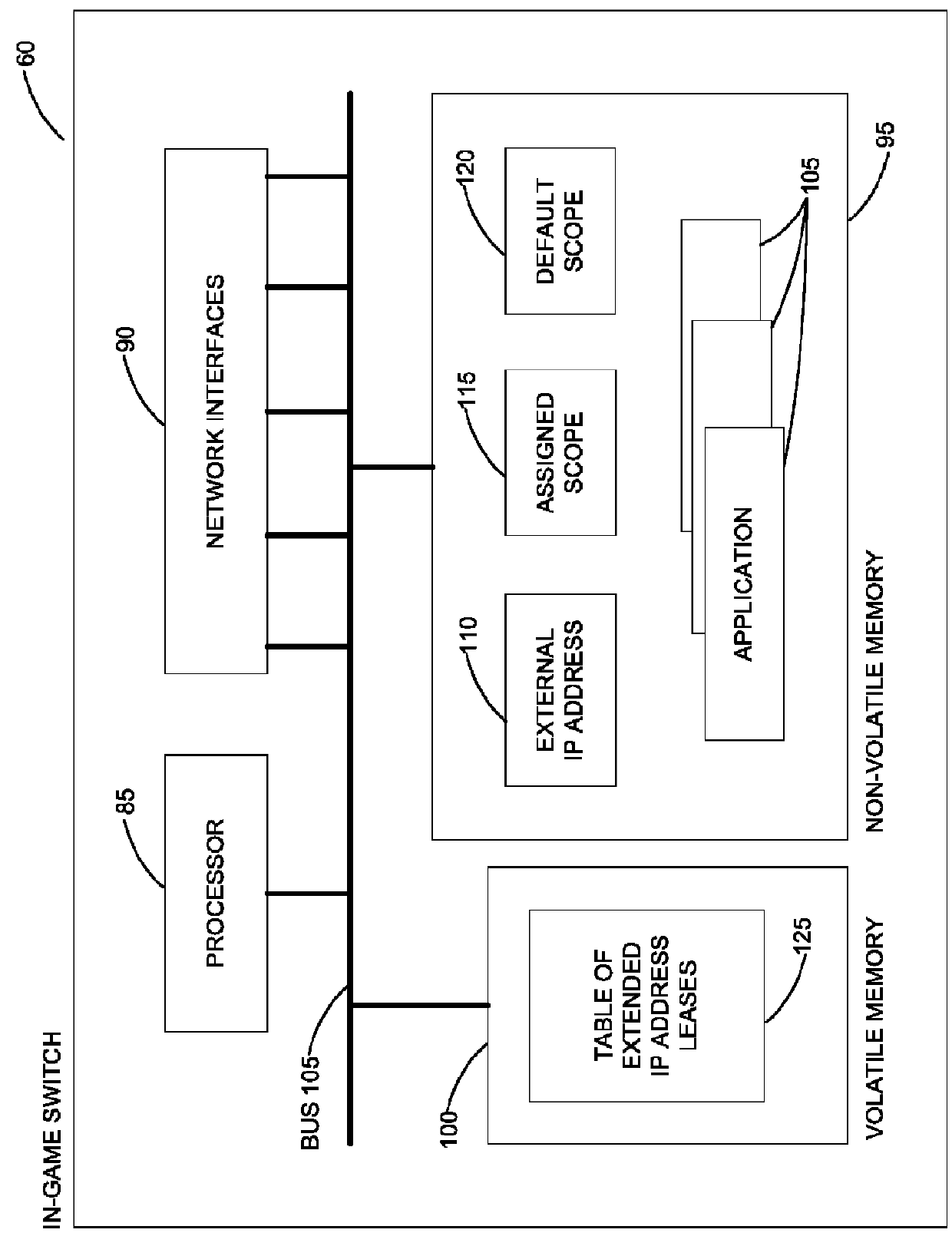
System for managing IP addresses in a network gaming environment
ActiveUS8259597B1Easy to manageBlocking in networkError preventionTransmission systemsIp addressProtocol for Carrying Authentication for Network Access
Disclosed are systems and methods for managing Internet Protocol (“IP”) addresses in a network gaming environment comprising a plurality of electronic gaming machines, having one or more in-game network devices. In particular an in-game switch is provided, which is configured to receiving an external IP address from a centrals DHCP server and to determine a scope of internal IP addresses associated with the one or more in-game network devices. Once the scope is determined, the in-game switch is configured to lease IP addresses from the address scope block to the associated in-game network devices.
Owner:LNW GAMING INC
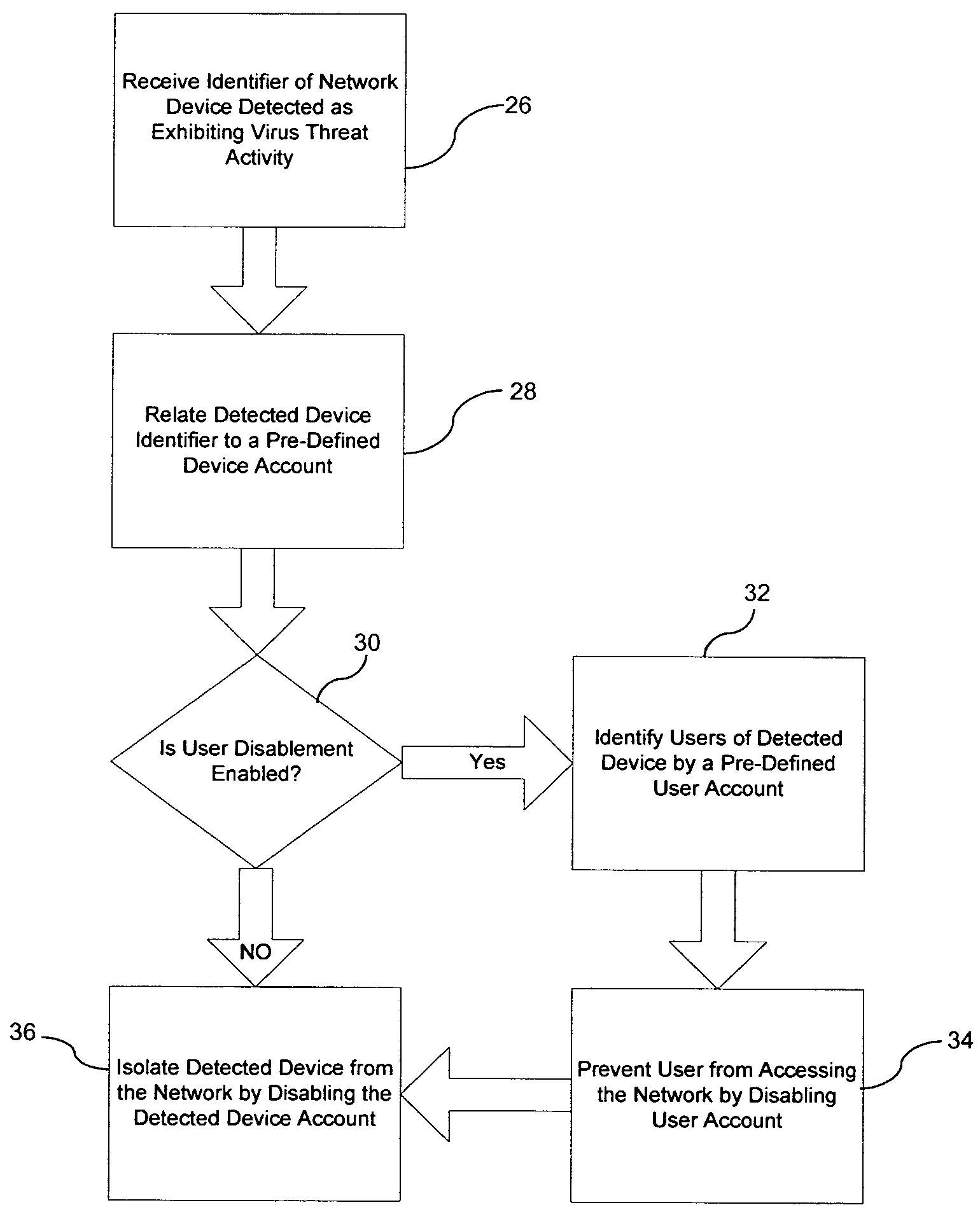
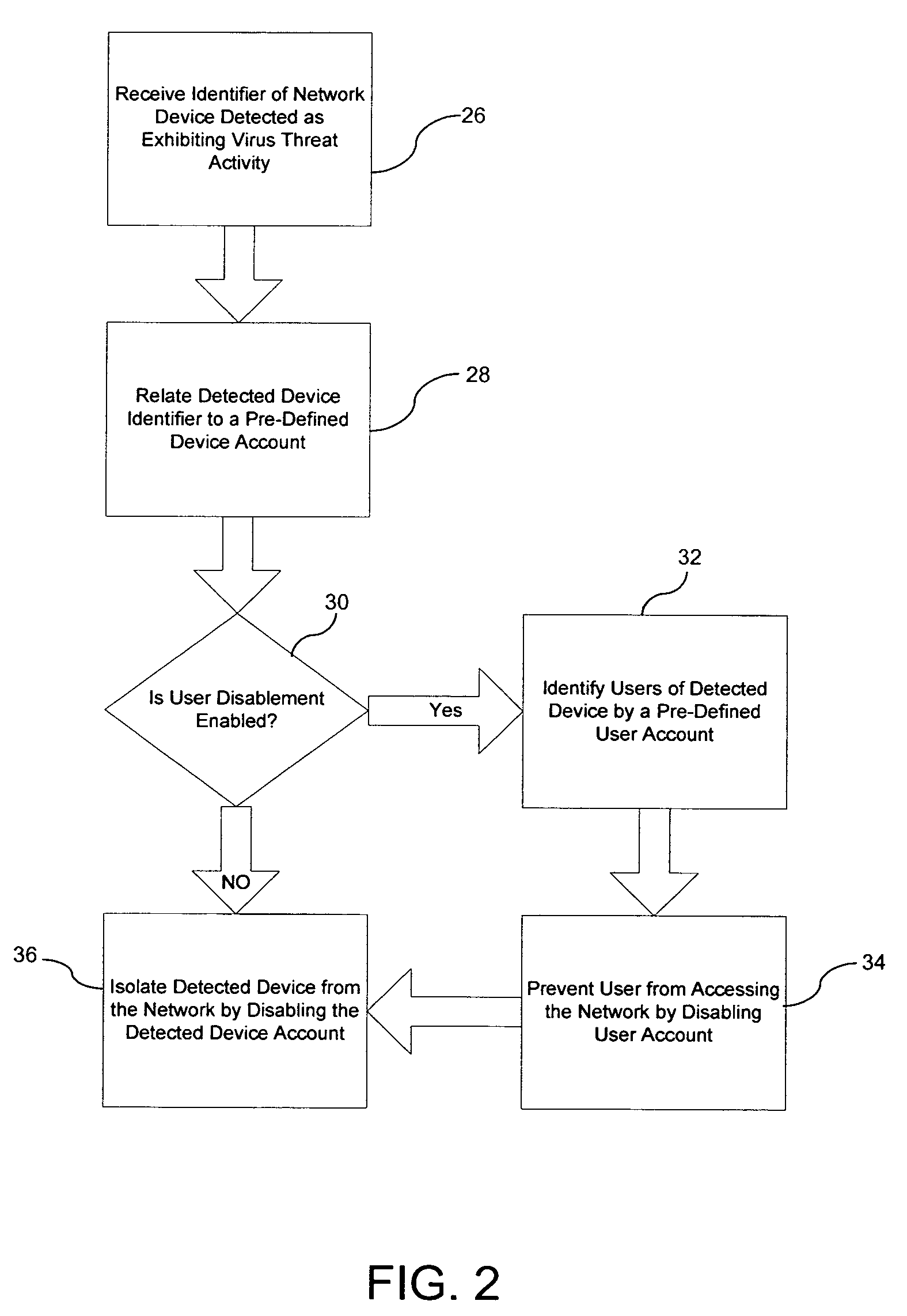
System and method for reducing the vulnerability of a computer network to virus threats
ActiveUS7571483B1Avoid infectionReduce vulnerabilityMemory loss protectionError detection/correctionNetwork isolationVirus
A method for reducing vulnerability of a computer network to a detected virus threat includes receiving an identifier of a network device detected as a source of virus activity. The method also includes relating the identifier to a predetermined account of the detected device and then automatically disabling the device account. Accordingly, the detected device is isolated from the network to prevent infection of the network by the detected device.
Owner:LOCKHEED MARTIN CORP
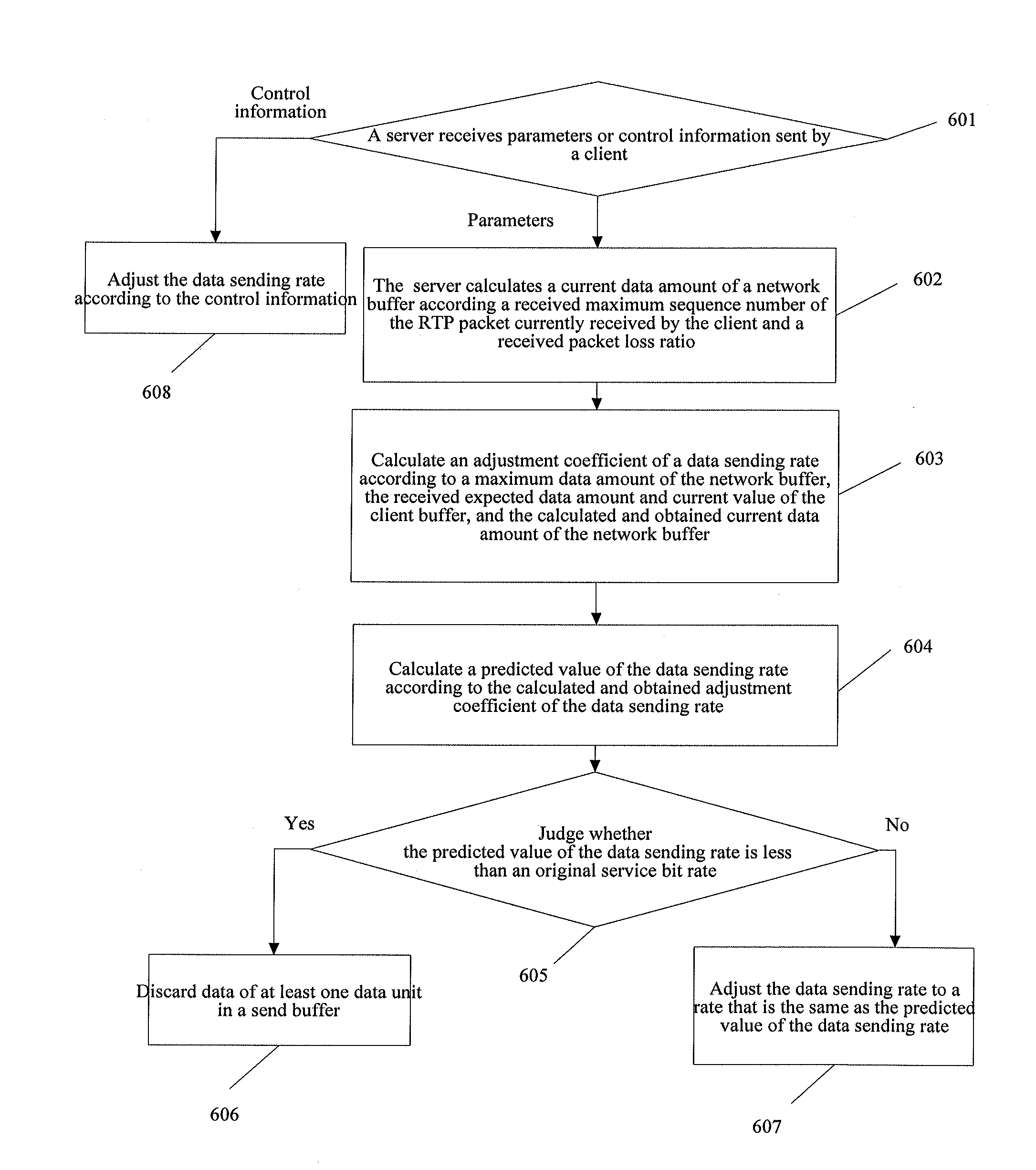
Method, device, and system for self-adaptively adjusting data transmission rate
ActiveUS20120079132A1Prevent overflowSolve the real problemEnergy efficient ICTMultiple digital computer combinationsData transmissionSelf adaptive
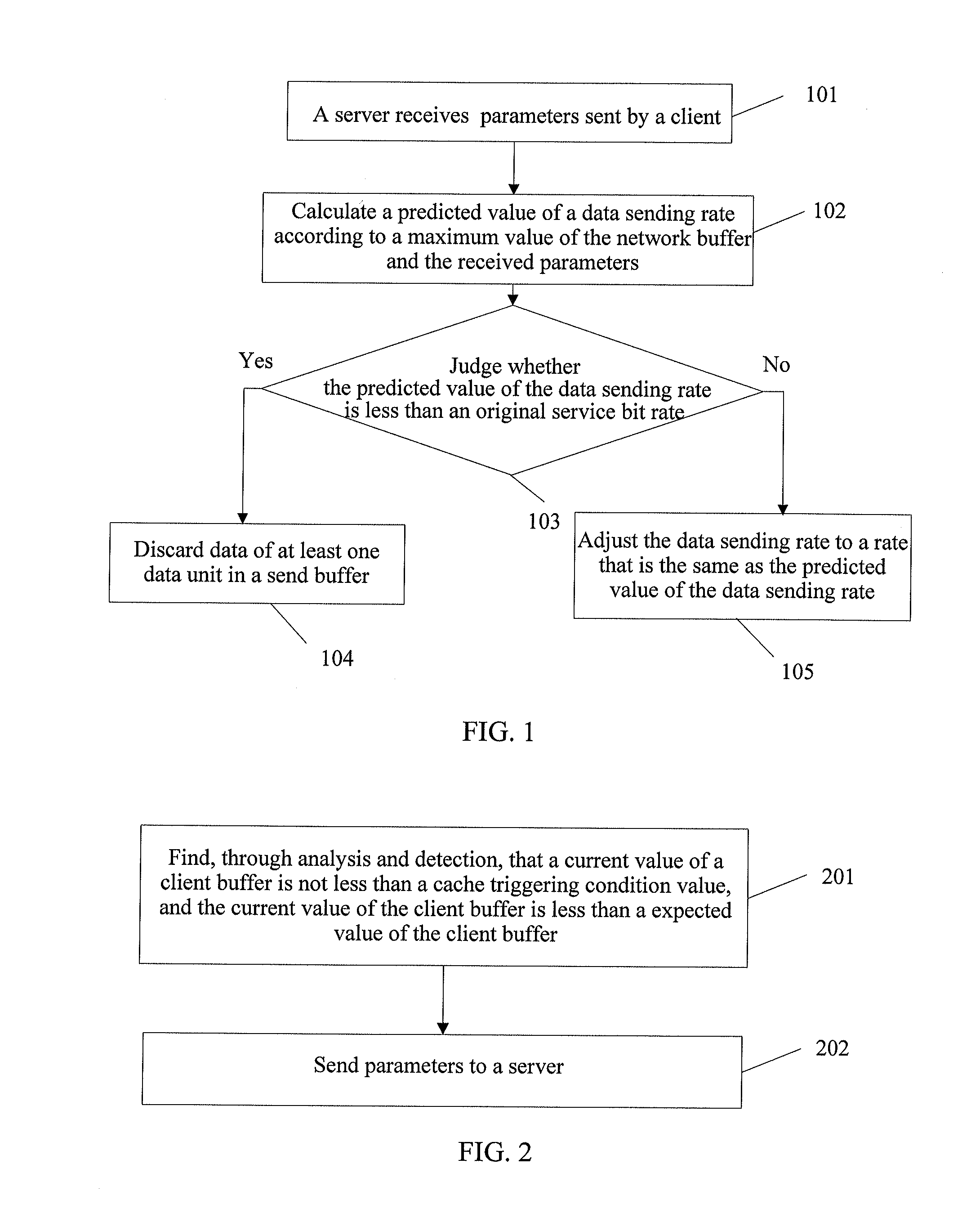
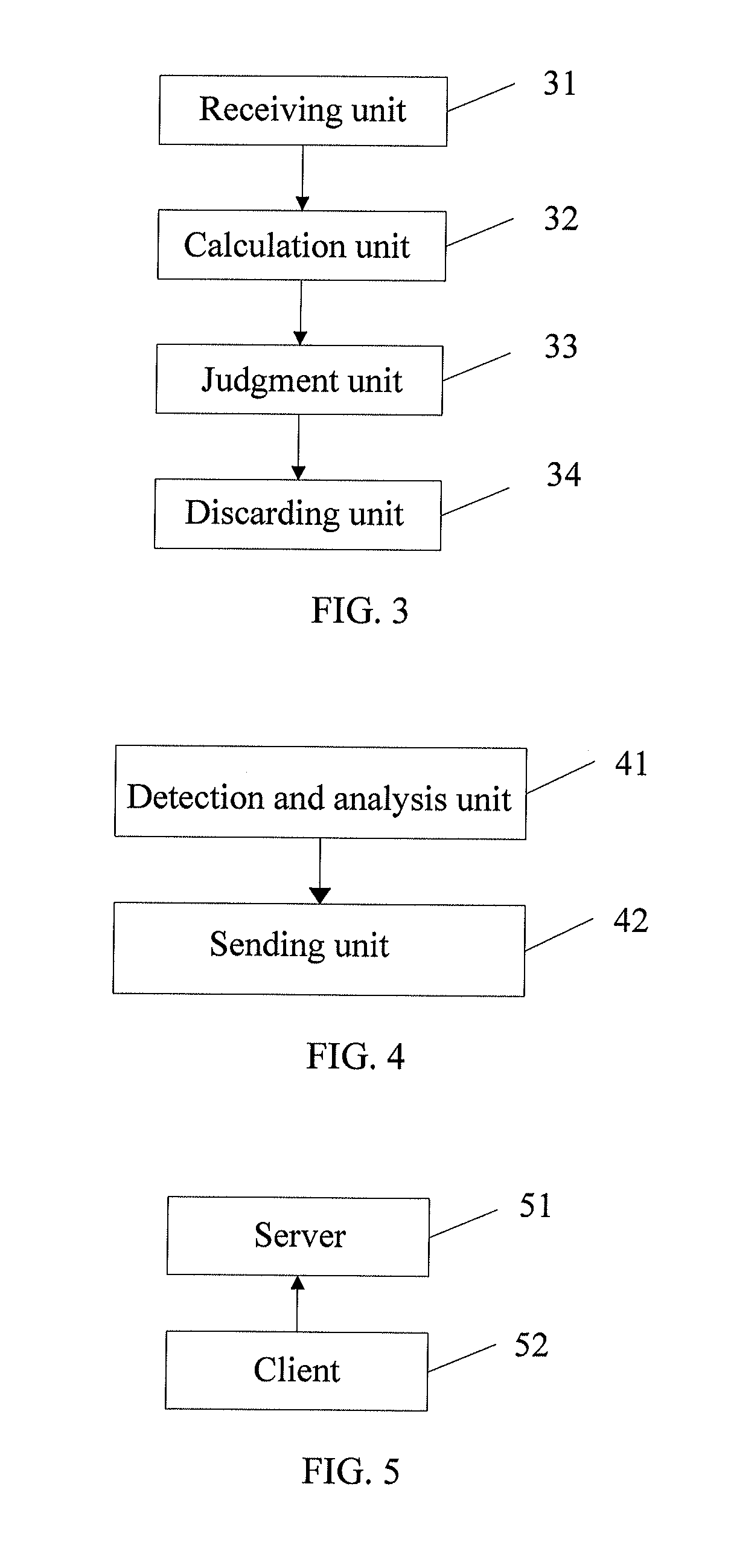
Embodiments of the present invention disclose a method, a device, and a system for self-adaptively adjusting a data transmission rate, which solve the problem of network buffer overflow. The method includes: receiving parameters sent by a client; calculating a predicted value of a data sending rate according to a maximum value of a network buffer and the received parameters; judging whether the predicted value of the data sending rate is less than an original service bit rate; and if the predicted value of the data sending rate is less than the original service bit rate, discarding data of at least one data unit in a send buffer. The method, the device, and the system are mainly applied to adjust the data transmission rate, and especially to adjust the data transmission rate in a time-varying network.
Owner:HUAWEI TECH CO LTD
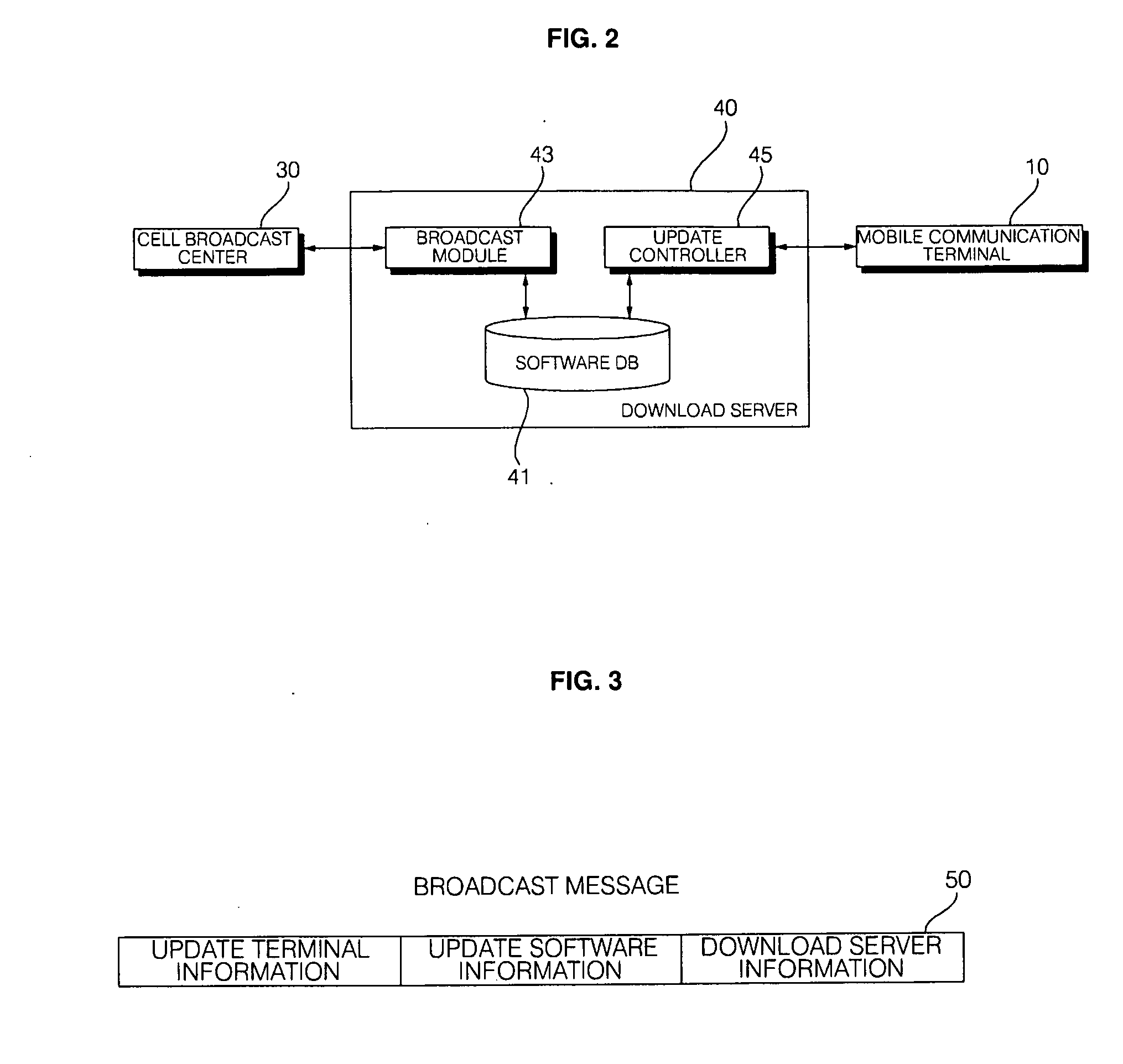
Mobile communication terminal and method of updating software thereof
InactiveUS20100070963A1Blocking in networkReduce ineffective useBroadcast service distributionTransmissionSoftware updateBroadcasting
There is provided mobile communication terminals and a method of updating software of the same. A method of updating software of mobile communication terminals includes, when software providers provide one or more pieces of update software for updating software of mobile communication terminals, creating a broadcast message including information about each piece of the update software, broadcasting the broadcast message to each of the mobile communication terminals over a wireless communication network, and, when a request to update the software of the mobile communication terminals is received from each of the mobile communication terminals that have received the broadcast message, providing a piece of corresponding update software to each of the corresponding mobile communication terminals over the wireless communication network. Accordingly, mobile communication terminals can be prevented from accessing a network unnecessarily, and ineffective use of wireless resources can be reduced.
Owner:ELECTRONICS & TELECOMM RES INST
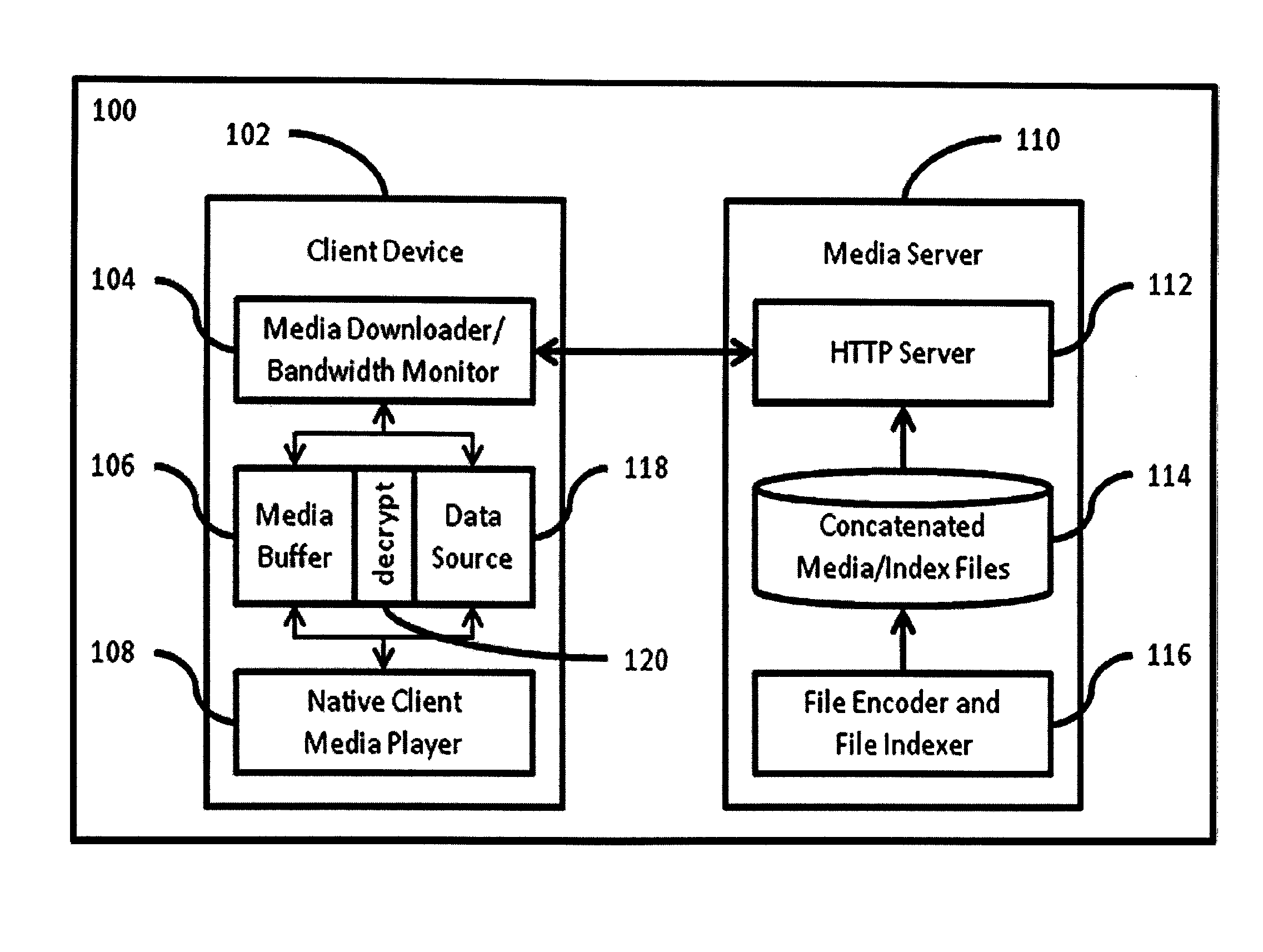
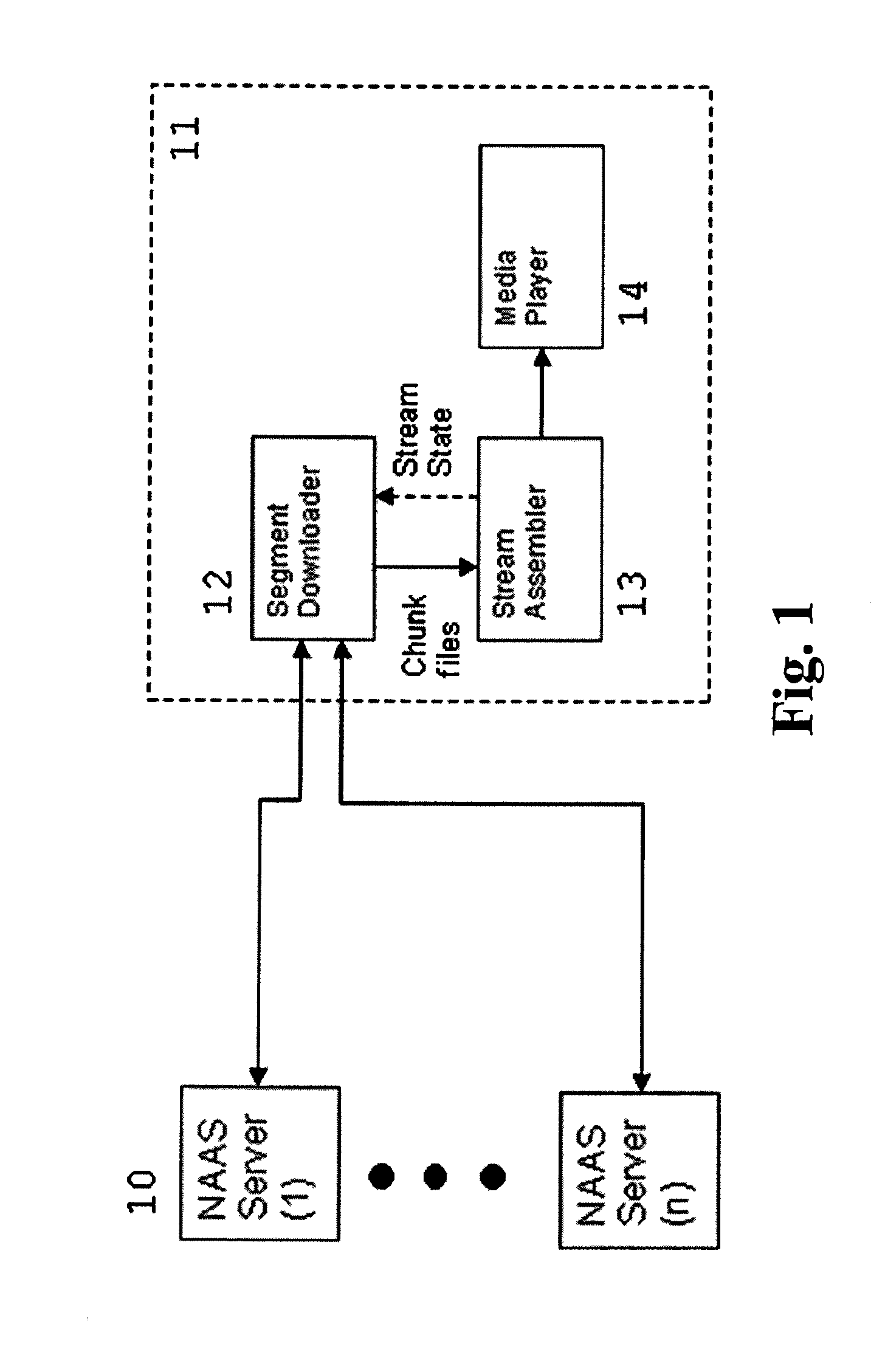
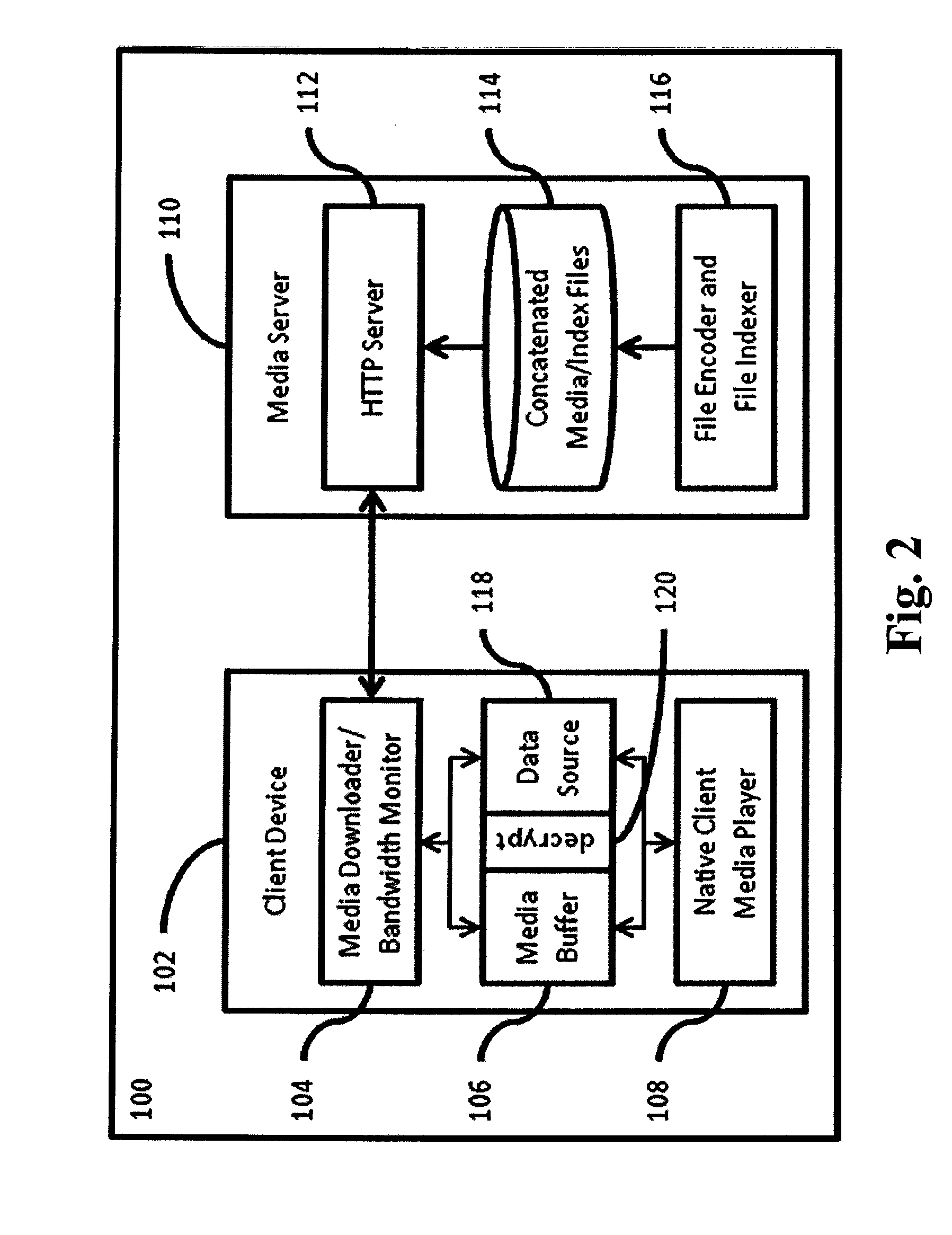
System and method for network aware adaptive streaming for nomadic endpoints
ActiveUS8959244B2Blocking in networkImprove throughputMultiple digital computer combinationsTwo-way working systemsBookmarkingStream data
In a system for streaming data over a network, the type and rate of streaming are automatically varied based on available network bandwidth. Video media is transcoded into different bit rate encodings that are divided into segment files. Segments are sent from a network-aware adaptive streaming (NAAS) server and reassembled and presented to a media player at a client device. The system may download additional segment files ahead of time from multiple NAAS servers to increase throughput. A playback status (“bookmark”) may be maintained to keep track of what the user has viewed and to allow the user to continue playing from where the user left off. The user may continue watching from the bookmark point on the same device or on a different device.
Owner:TELEFON AB LM ERICSSON (PUBL)
Radio Communication System and Radio Communication Method
ActiveUS20090052415A1Appropriate settingAvoid congestionConnection managementWireless network protocolsCommunications systemWireless lan
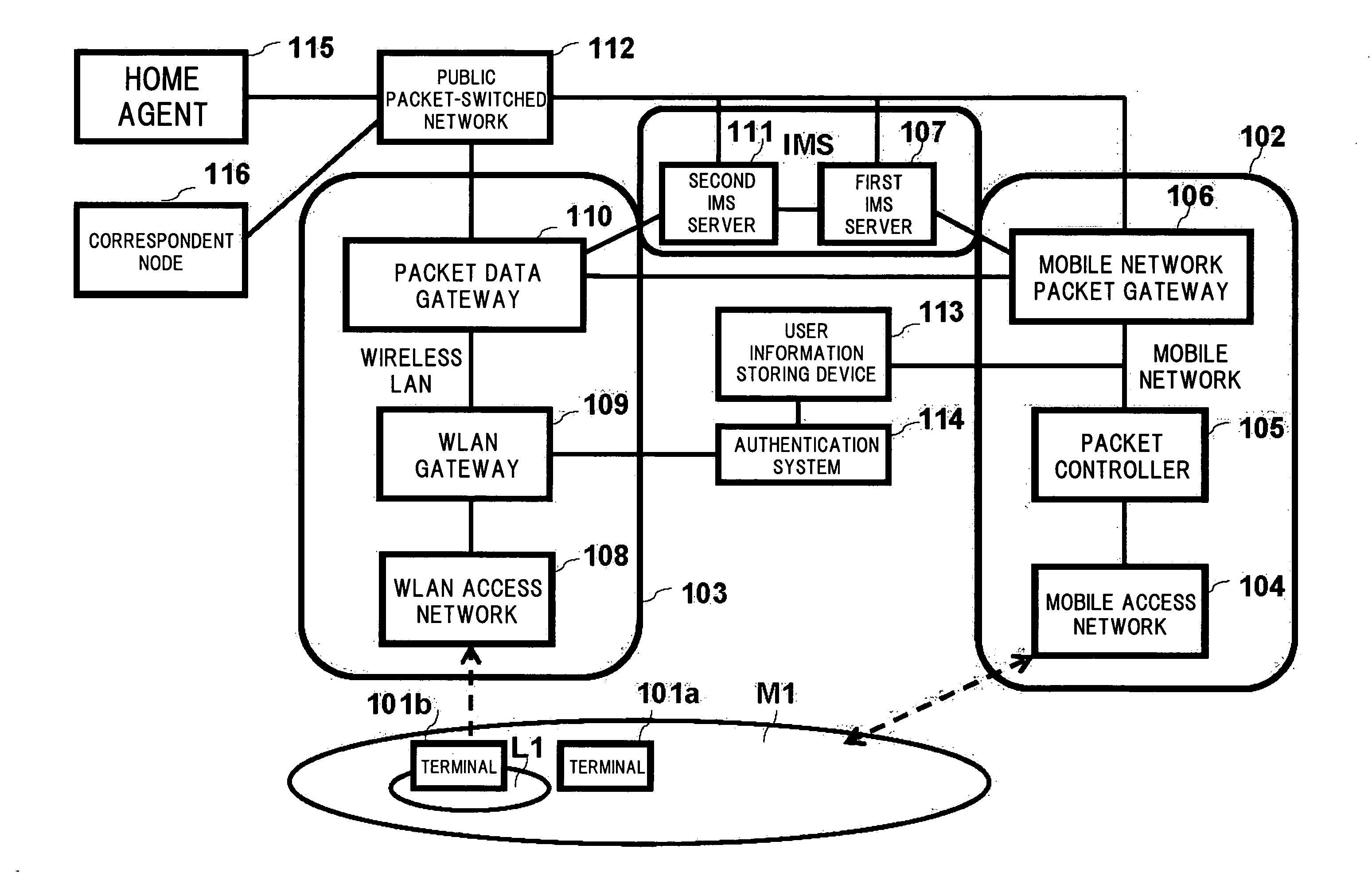
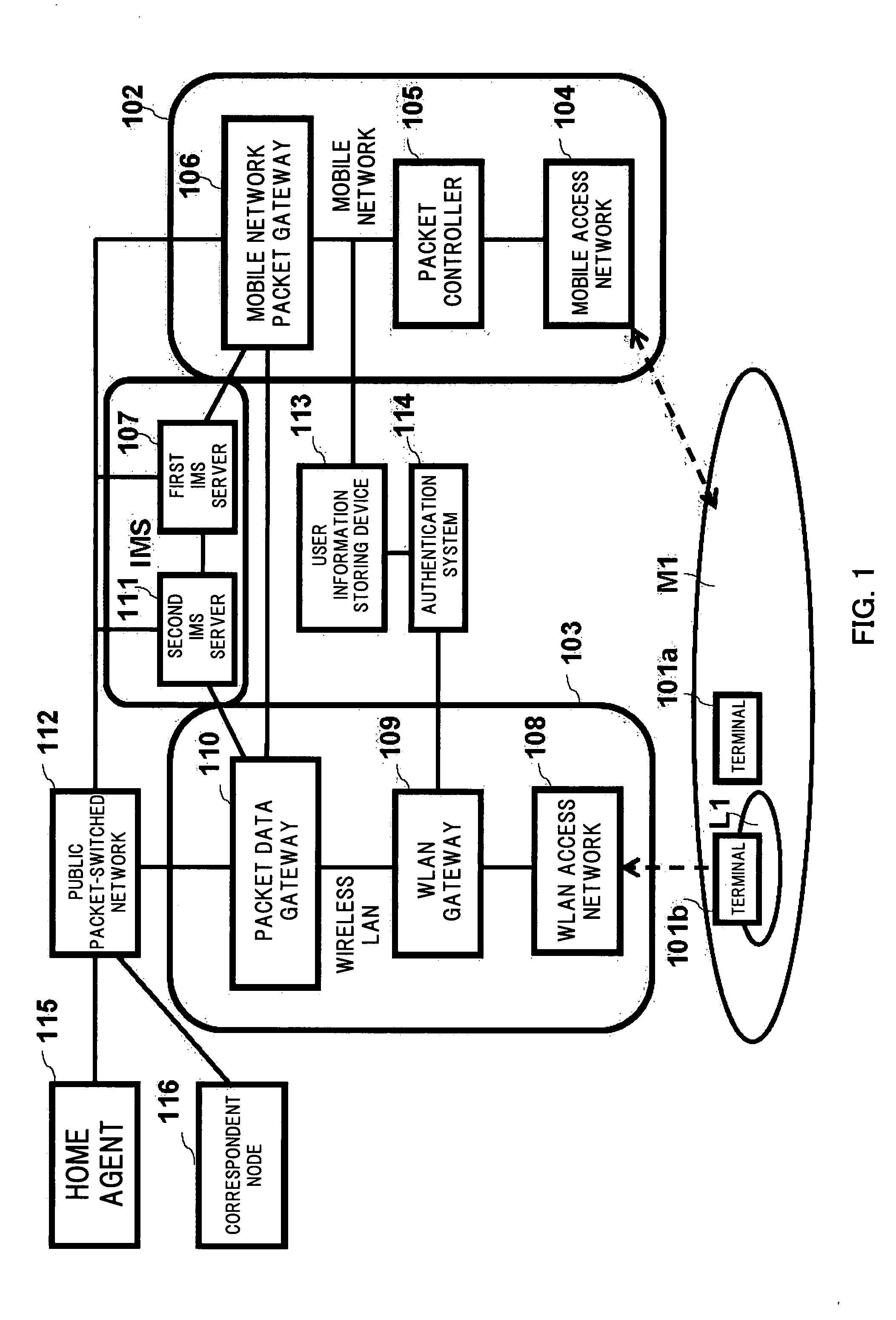
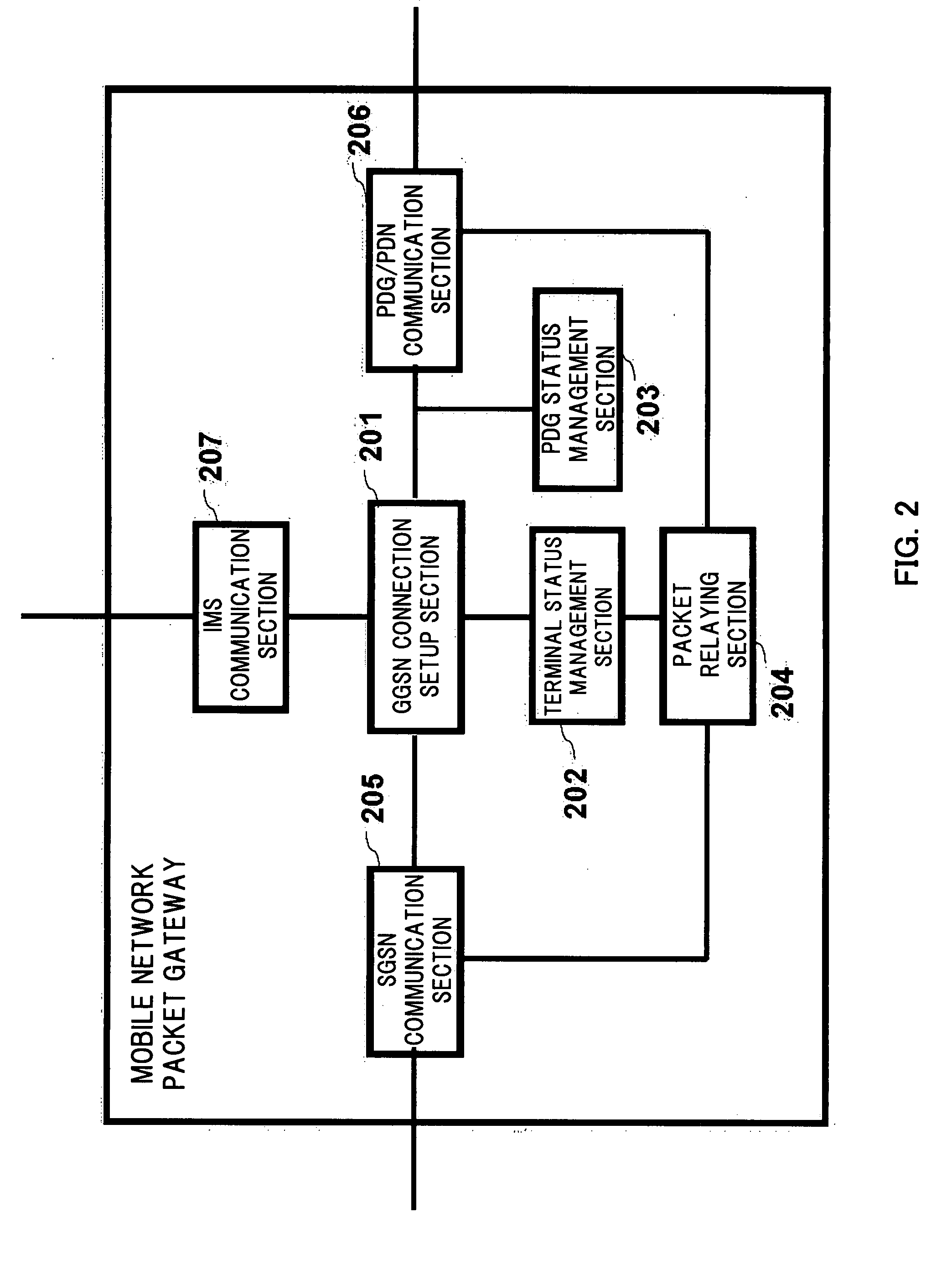
A terminal (101) includes interfaces for communication with a mobile network (102) and a wireless LAN (103). A first IMS server (107) performs IMS call control processing relating to terminals located in the mobile network (102) and a second IMS server (111) relays a signal relating to IMS call control processing concerning terminals located in the wireless LAN (103). These IMS servers search for a mobile network packet gateway (106), a packet data gateway (110), and a gateway to be controlled by a route change request for requesting change of a packet transmission path and relay the route change request. The route change request provided from the terminal (101) is relayed by the IMS servers to provide the change request to all networks specified. The packet transmission path is changed by the gateway in accordance with the request. Thus, the terminal having the interfaces for both of the mobile communication network and the wireless LAN can select a network to use for each communication port.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Block chain permission control method, device, and node apparatus
ActiveUS20190140822A1Ensure safetyImprove securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationAuthority controlBlockchain
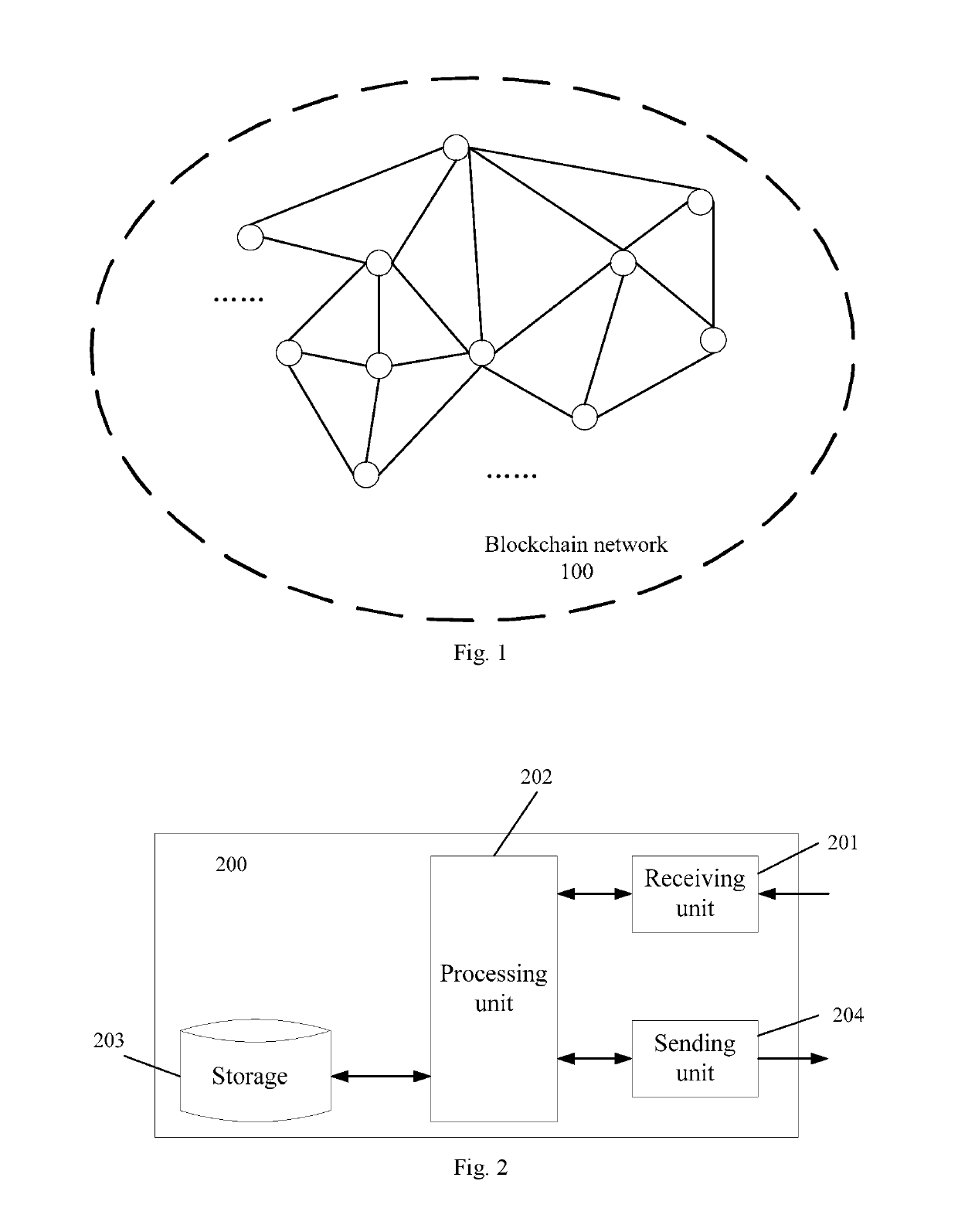
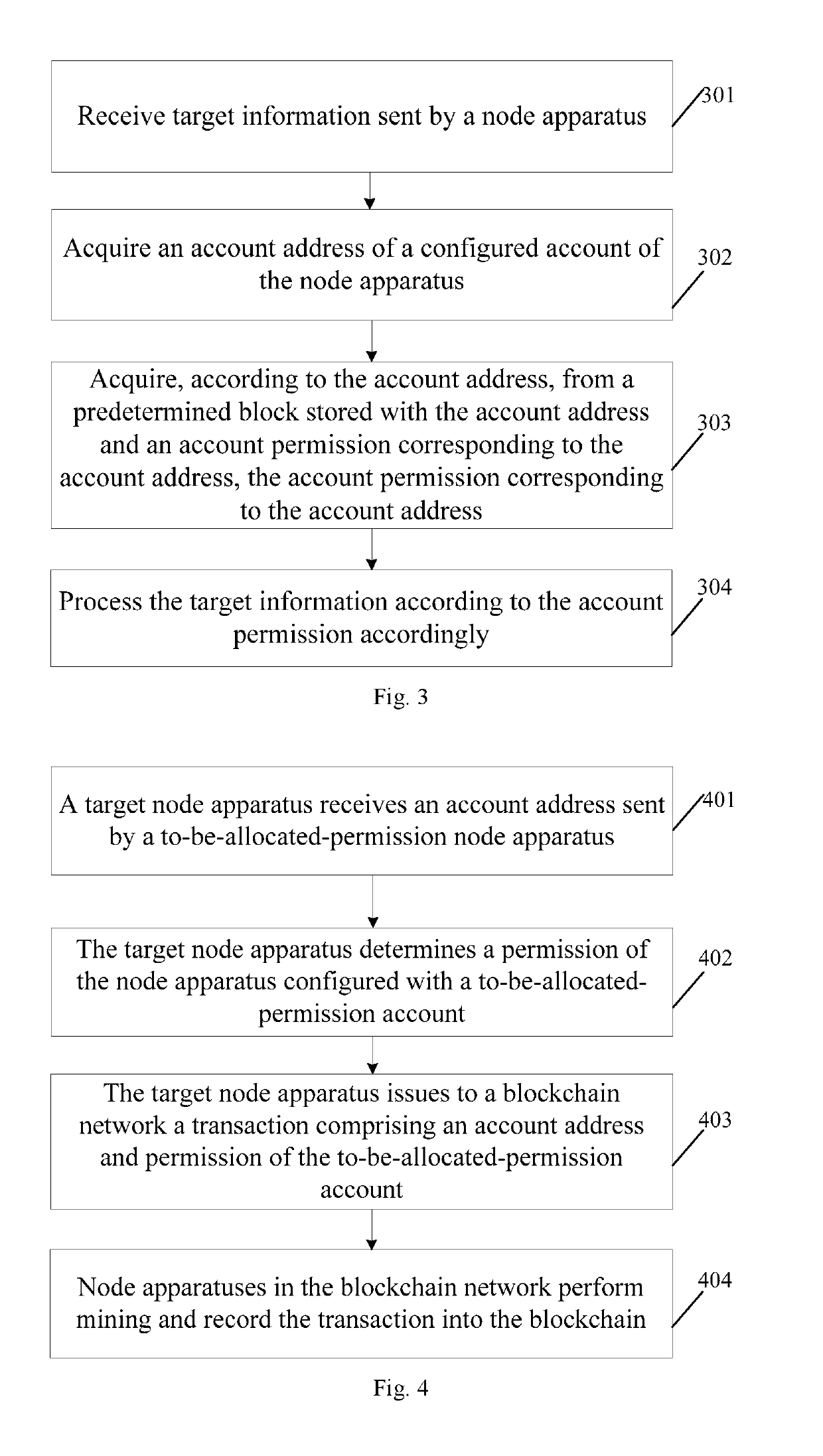
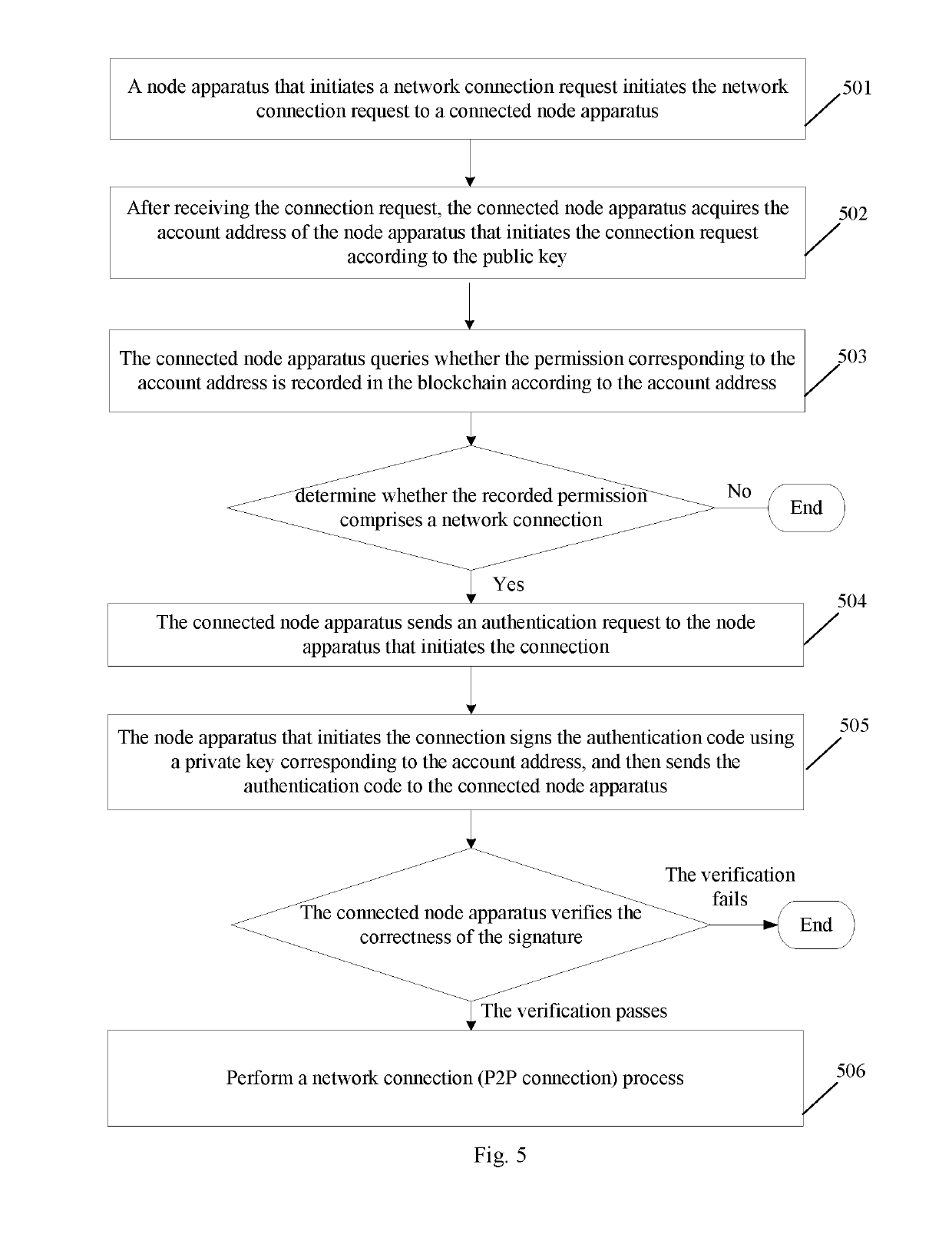
The present disclosure discloses a method, device and node apparatus for blockchain permission control. The method comprises: receiving target information sent by a node apparatus; acquiring an account address of a configured account of the node apparatus; acquiring, according to the account address, from a predetermined block stored with the account address and an account permission corresponding to the account address, the account permission corresponding to the account address; and processing the target information according to the account permission accordingly. In the present disclosure, node apparatuses are configured with corresponding accounts, and performing permission control on the accounts can restrict permissions of different node apparatuses so as to ensure security and privacy of blockchain data.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
Preventing network micro-congestion using send pacing based on end-to-end bandwidth
InactiveUS7616585B1Preventing network micro-congestionReduce suddennessError preventionTransmission systemsProgram instructionData transmission
A system for preventing network micro-congestion using send pacing based on end-to-end bandwidth. The system includes one or more processors and memory coupled to the processors, wherein the memory contains program instructions executable by the processors to obtain an estimate of end-to-end network bandwidth available to a particular application-level data transfer operation in progress over a network between a first endpoint and a second endpoint. Based at least in part on the estimate of end-to-end bandwidth, the instructions are further executable to introduce a delay between transmissions of two or more successive messages or packets of the particular application-level data transfer operation from the first endpoint.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com