Patents
Literature
404results about How to "Avoid sending" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multi-factor authentication and certification system for electronic transactions
InactiveUS20090172402A1Environment safetyImprove securityFinanceUser identity/authority verificationE-commerceOne-time password
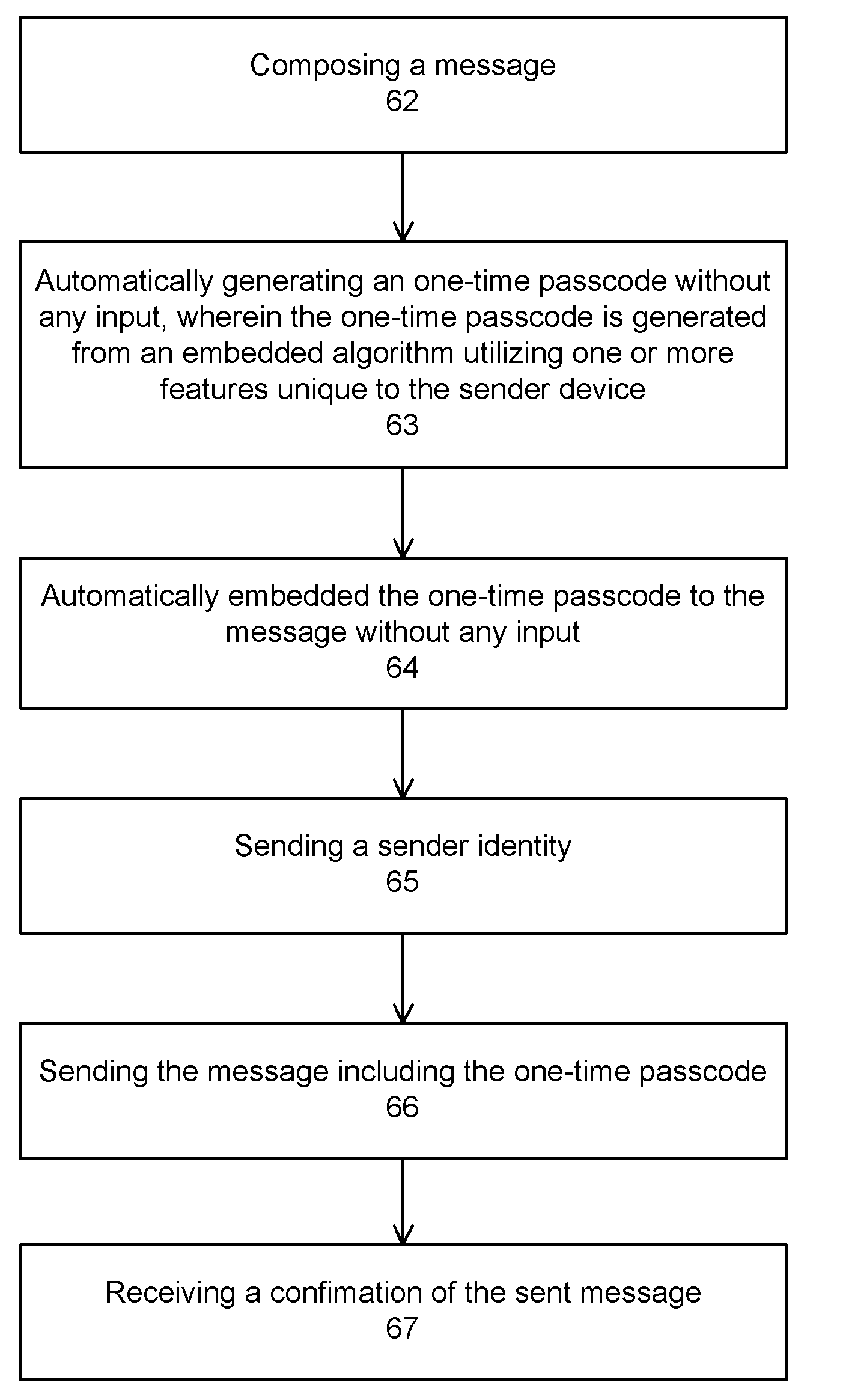
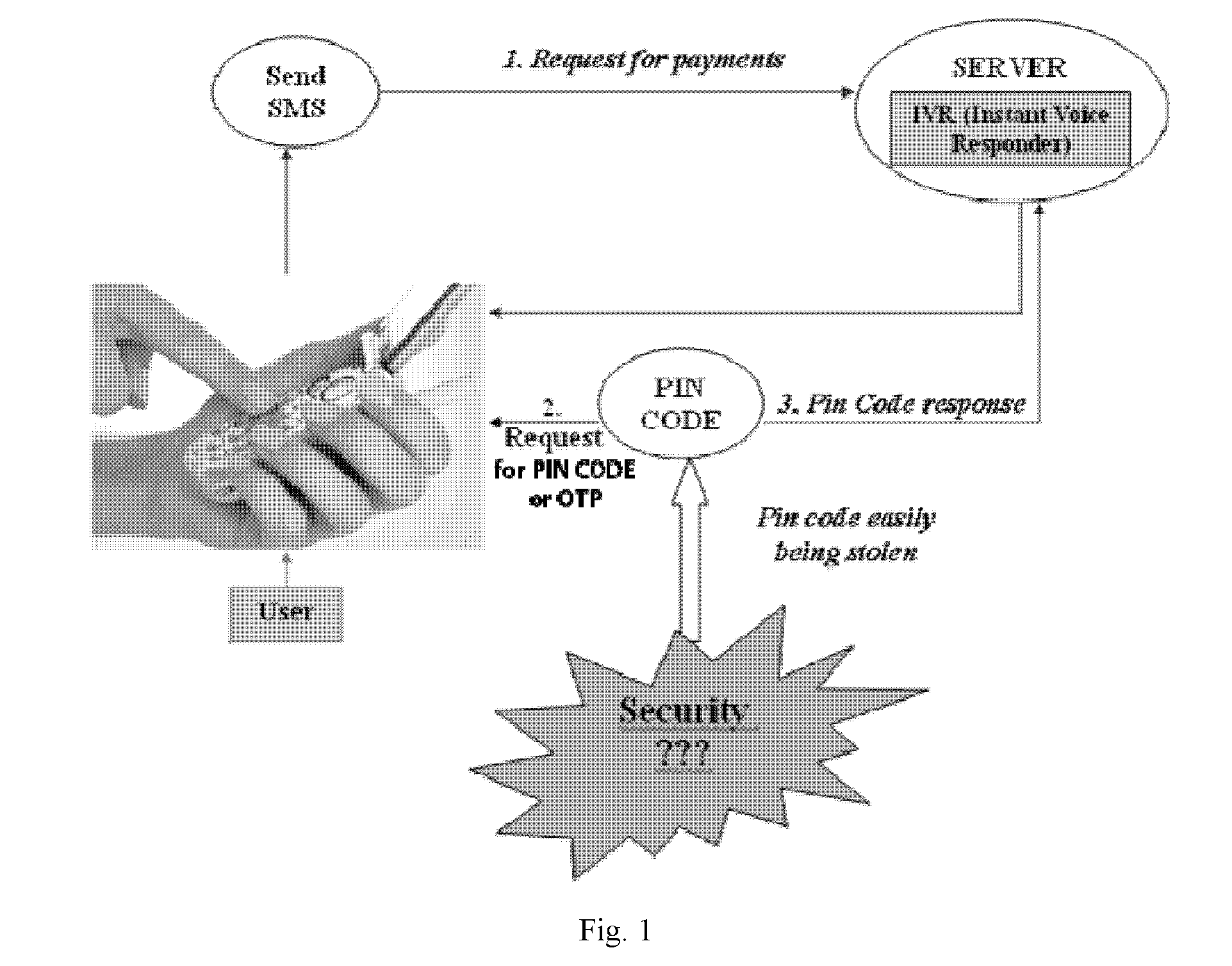
The present invention provides computer-enable certification and authentication in, for example, e-commerce with wireless and mobile devices. The present authentication method offers ease of operation by automatically embedding a one-time passcode to the message without the sender input. A one-time key can also be used to encrypt the message, further providing transmission security. In addition, sensitive information and one-time passcode generator are pre-arranged and stored at both sender and receiver devices, avoiding information comprising in wireless environment transmission.
Owner:TRAN NGUYEN THO
Address acquisition
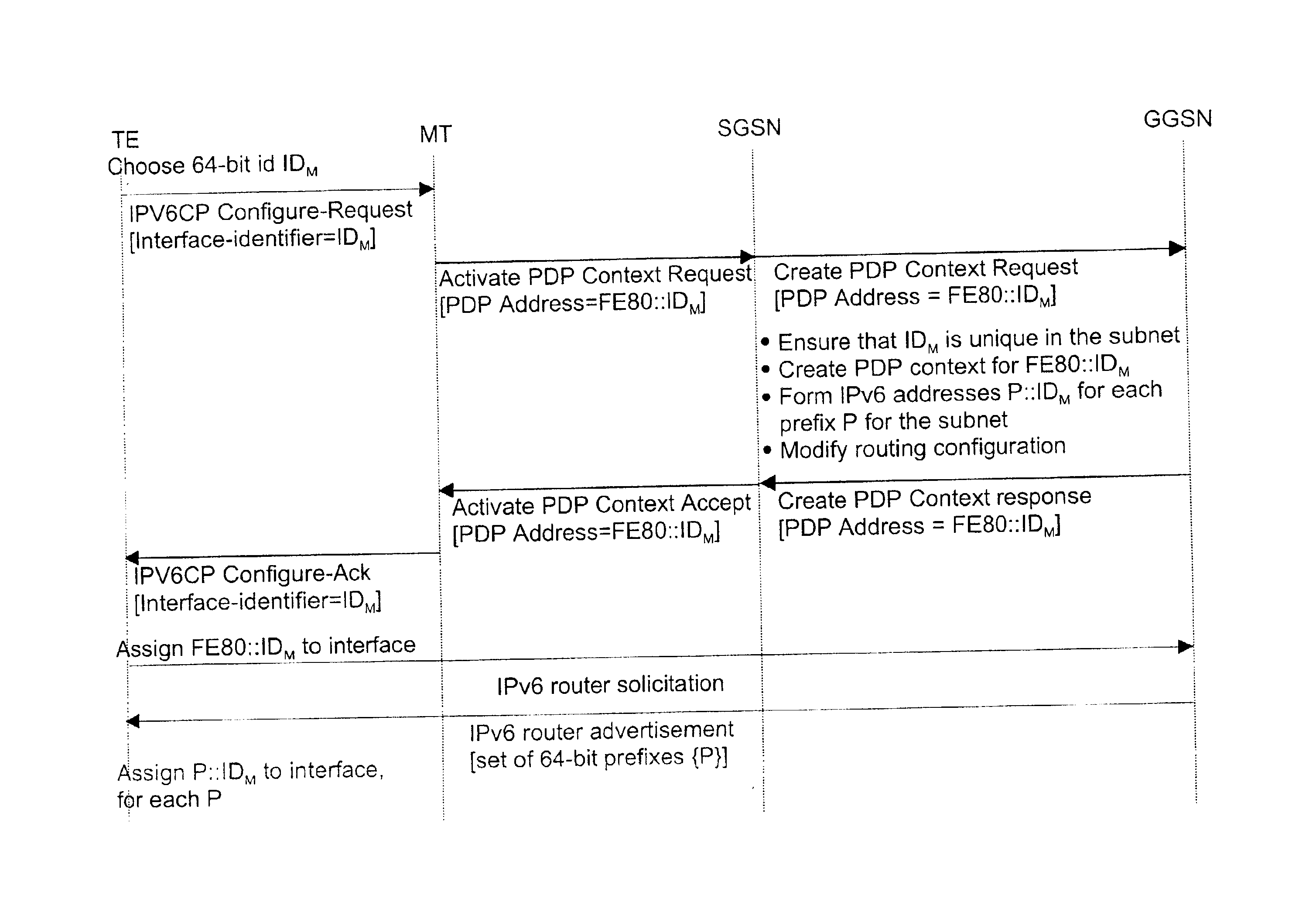
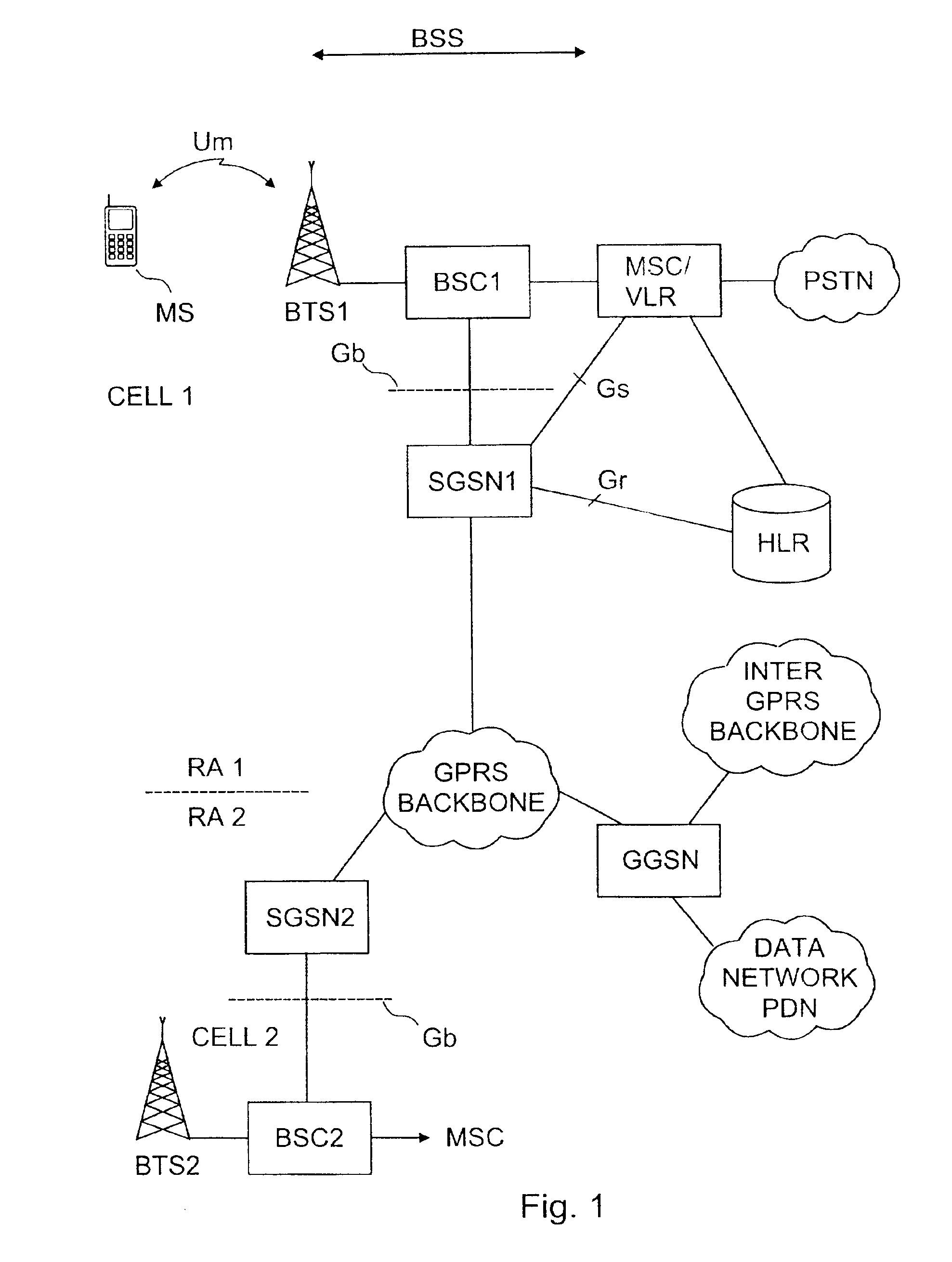
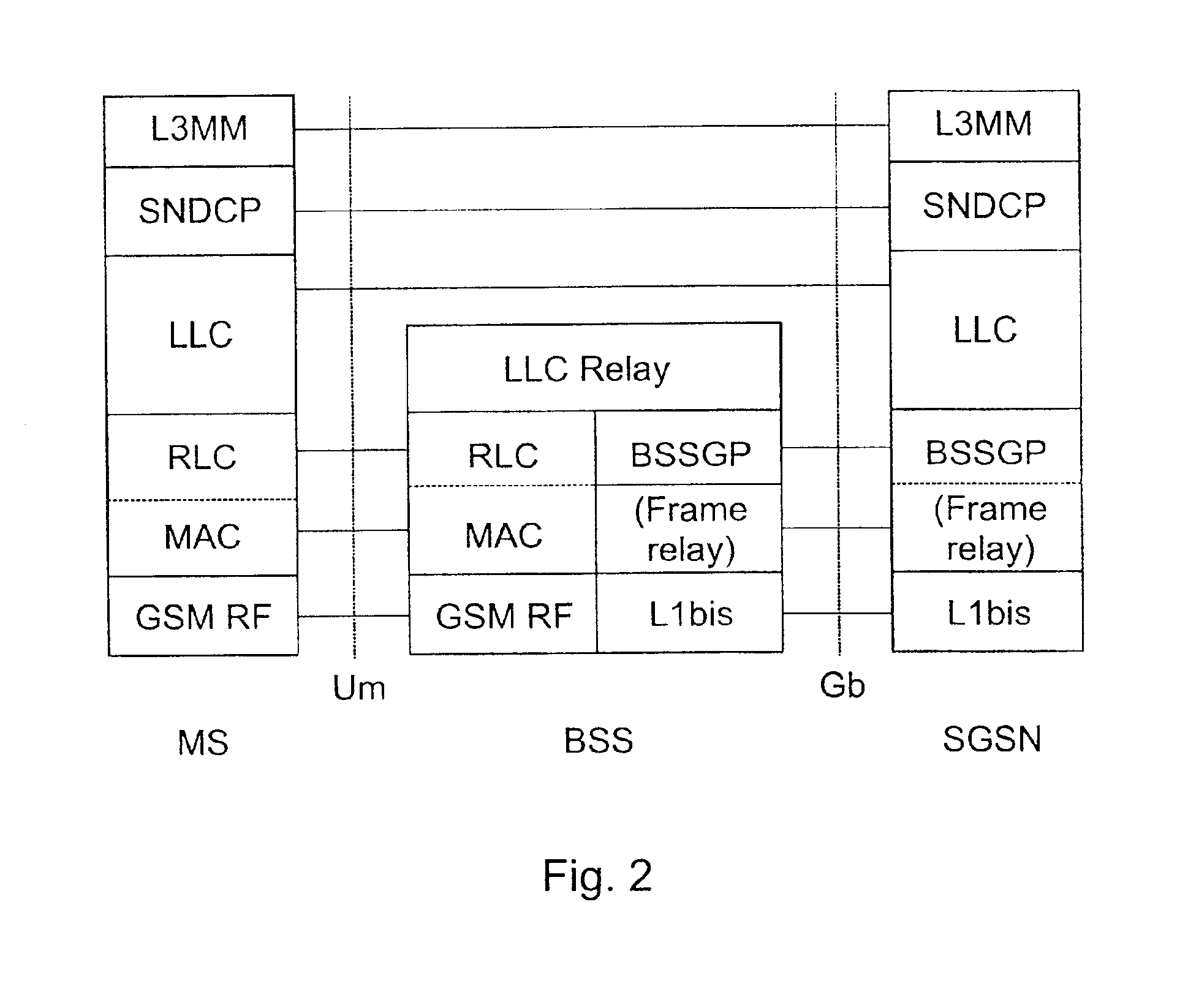
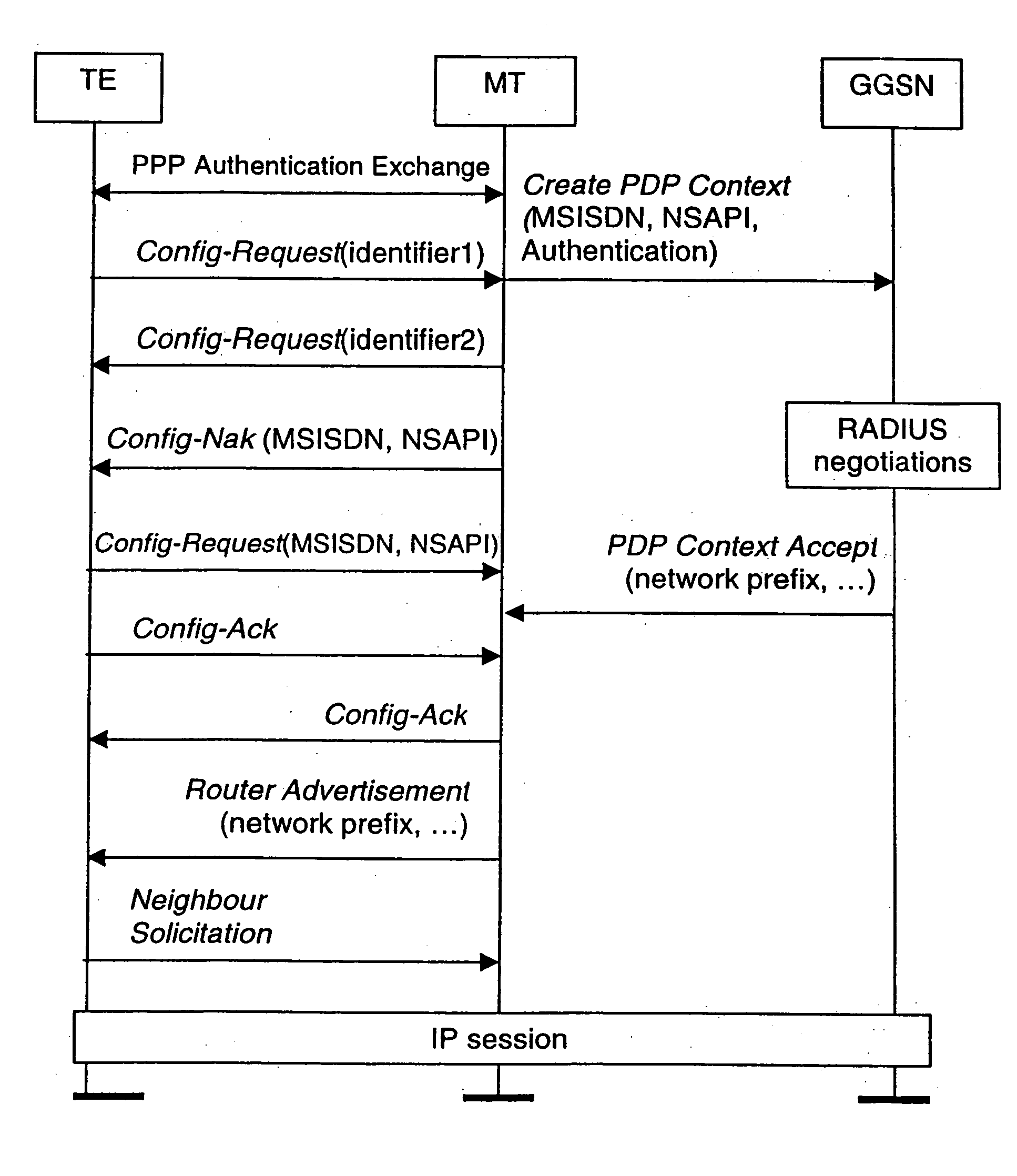
A method for a mobile station to acquire a IP network address from a gateway in GPRS system. First the mobile station generates a link identifier. Next the mobile requests a network address by sending a link identifier over a wireless to a gateway along with a request for the gateway to check to see if the link identifier is unique. Upon receiving the network address request the gateway checks to see if the link identifier is unique. The gateway responses by either confirming that the network link identifier is unique or by sending a different unique link identifier to the mobile station. The gateway also has the ability to respond by sending a network prefix to the mobile station. Upon receiving the network prefix the mobile station combines the network prefix with the interface identifier to generate a IP network address.
Owner:NOKIA TECHNOLOGLES OY
Policy engine for modular generation of policy for a flat, per-device database
ActiveUS7159125B2Maintain independenceAvoid sendingUser identity/authority verificationUnauthorized memory use protectionThe InternetModularity
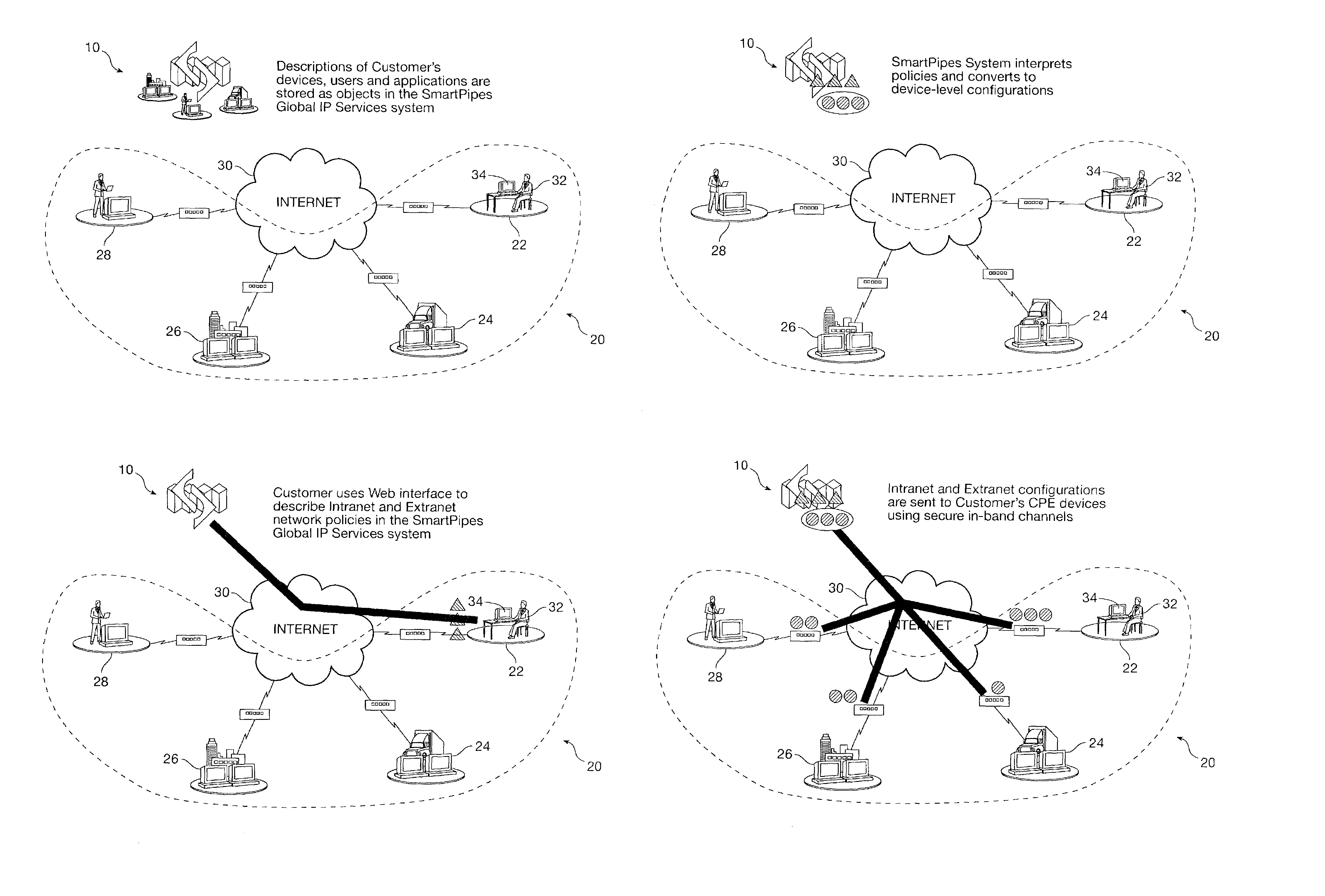
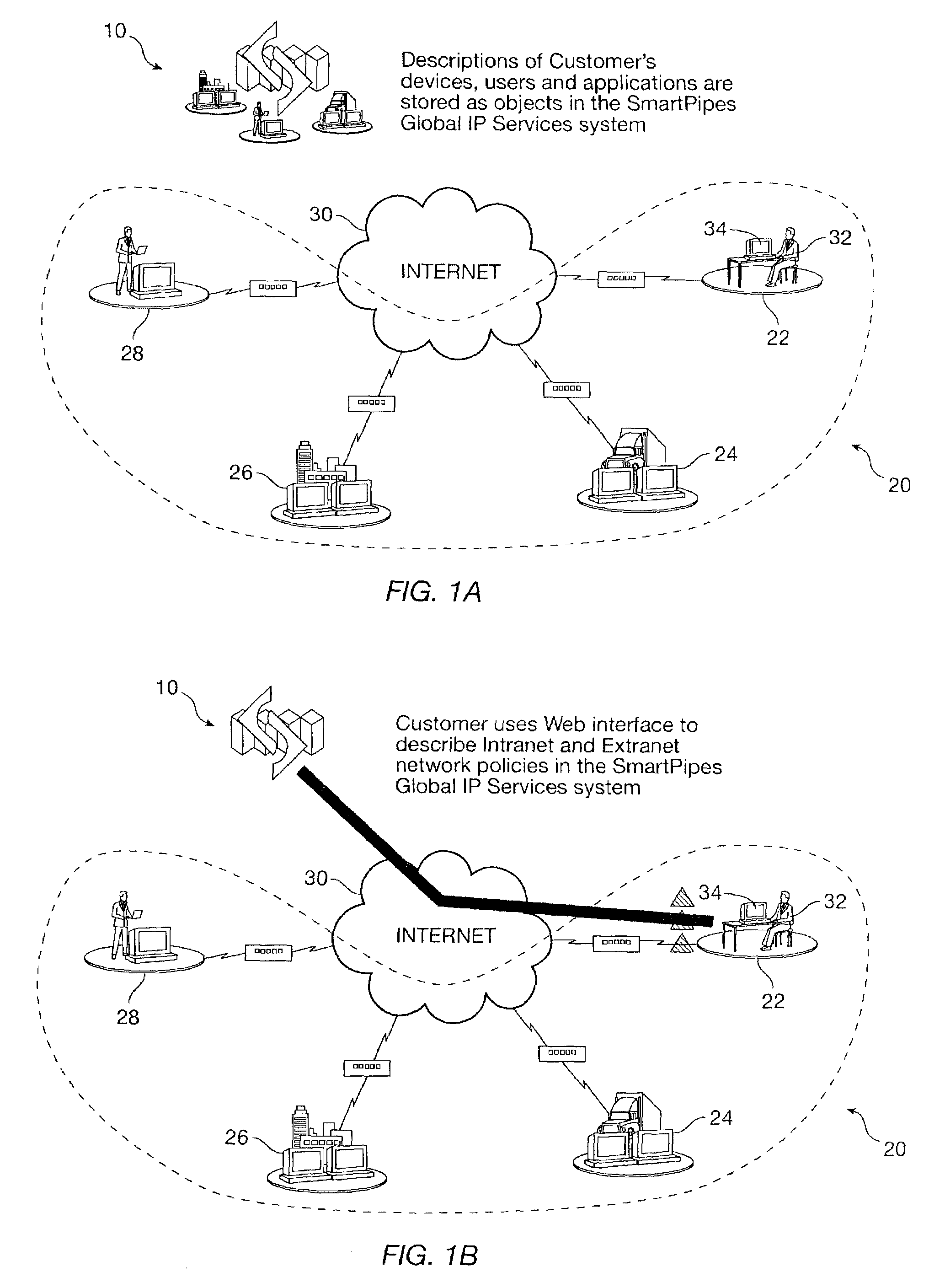
A policy engine in a policy-based, outsourced, network management system. In one embodiment, the management system is multi-layered, modular and stores device configuration data in non-device specific format, which are subsequently translated to device-specific format by lower layers of the management system. The non-device specific format is the same (e.g., XML) as that used to create the policies with the user GUI (e.g., browser) and transport them to the service center over the internet. A database stores a policy directory in a hierarchical format that is separate from a policy store (configuration store) for devices in a flat (non-hierarchical or parallel) format. In one embodiment, a policy engine develops policies in a hierarchical format, but then stores the device schema, or objects, in a low-level, flat database. Multiple hierarchical services which impact a single device have the characteristics related to that device knitted together, and then fed back to a policy store database as a flat file for that device, in a non-device specific format. Thus, instead of storing the policies separately, and in hierarchical linked format, the device descriptions are stored with the aspects of all policies that affect that device.
Owner:SOPHOS
Electronic mail control system
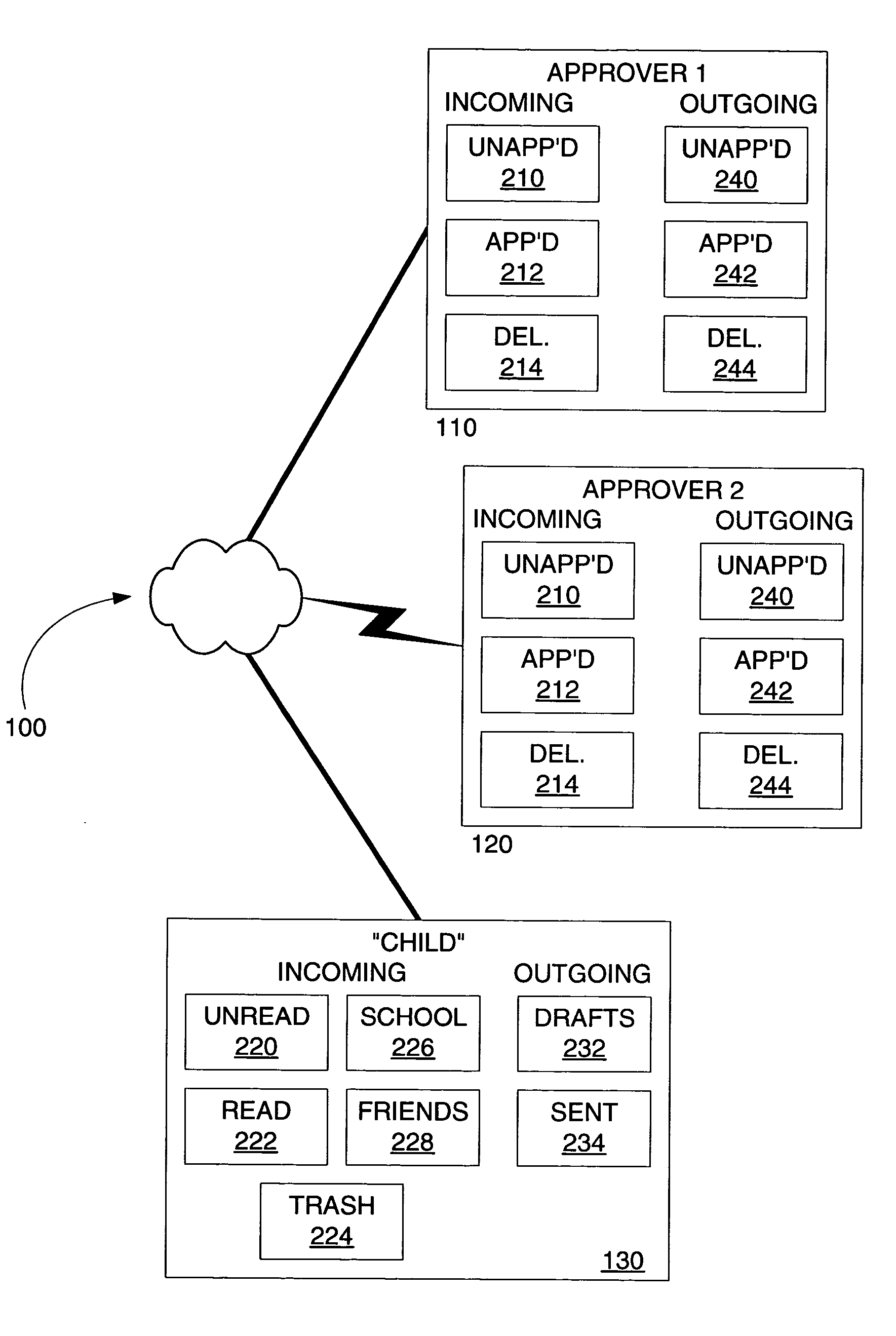
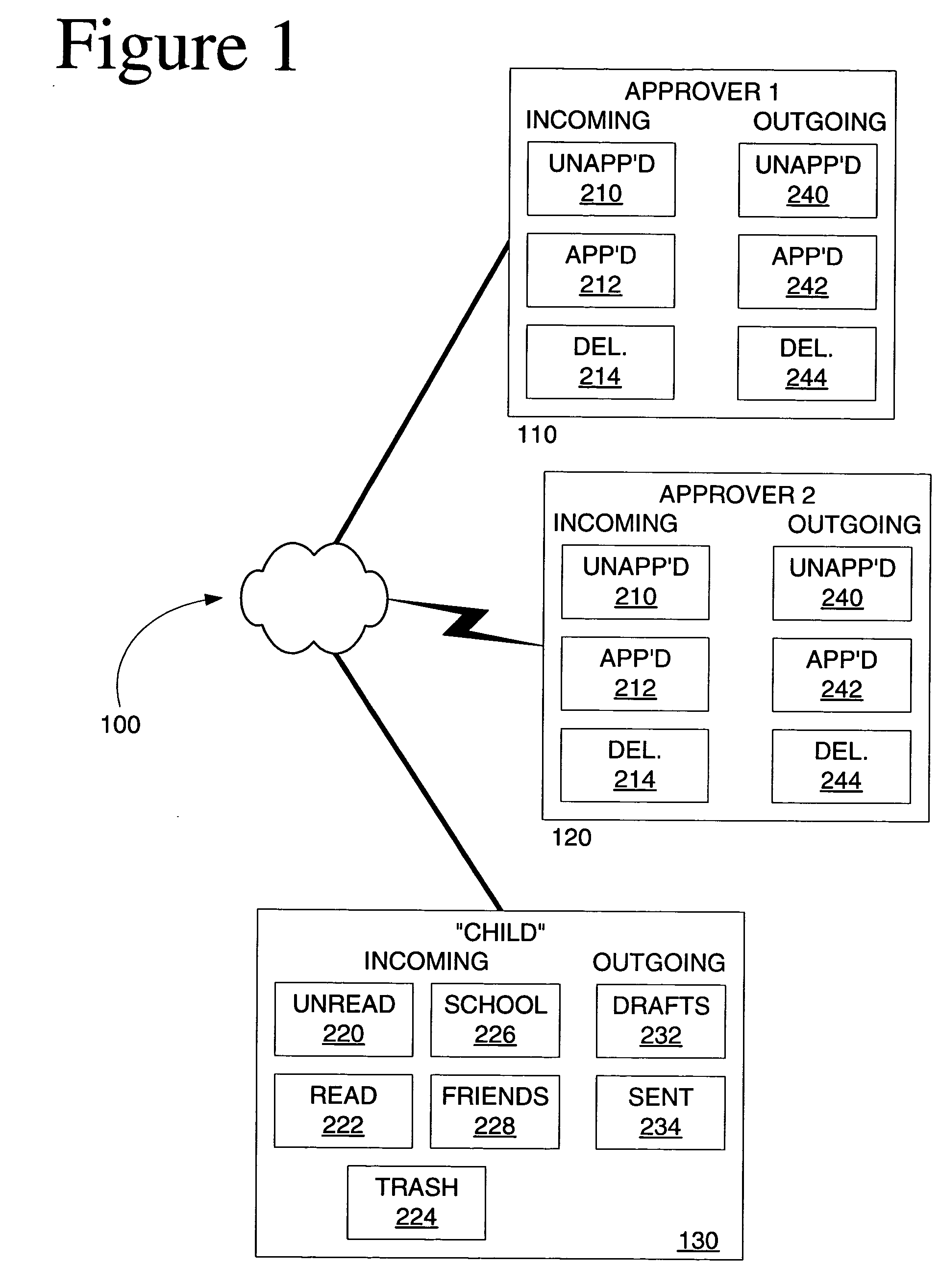
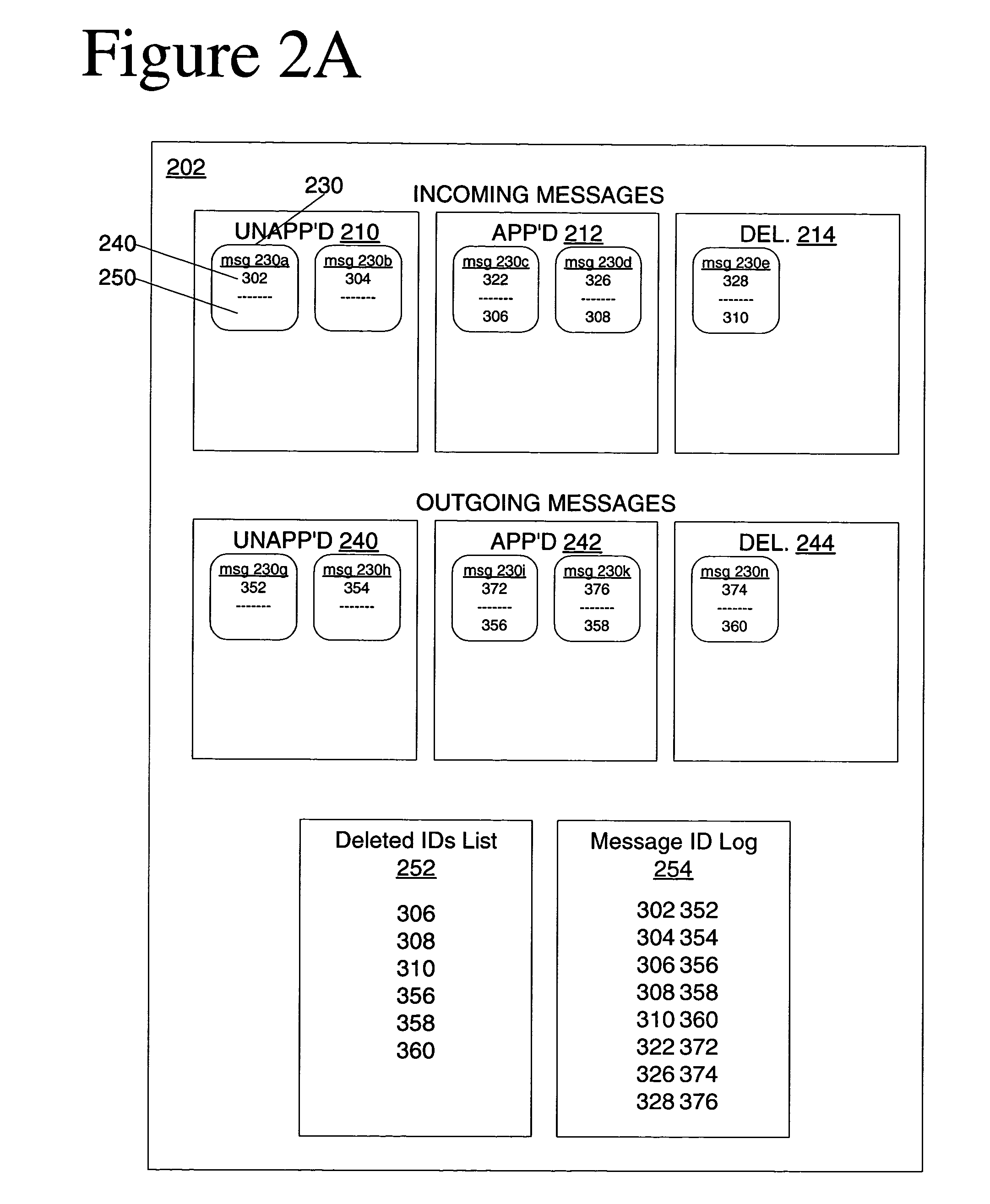
InactiveUS20050021637A1Sending of multiple copies of a message can be avoidedAvoid sendingMultiple digital computer combinationsElectric digital data processingControl systemMessage passing
An electronic mail system provides one or more approvers with approval authority over electronic mail of a user. The approvers have the opportunity to approve an incoming electronic mail message before the message is delivered to the user, and have the opportunity to approve an outgoing electronic mail message by the user before the message is sent to its intended recipient. Messages can be approved or rejected automatically, using filters, or through actions by an approver. Rejected incoming messages are not delivered to the user. Rejected outgoing messages are not sent to the intended recipient. Mail to be approved can be synchronized for consistency among multiple approvers. The user whose mail is to be approved can access the mail from multiple locations, with the mail at each location synchronized to appear in the same folders.
Owner:RED HAT
Pilot signal transmission method, signal measuring method, signal measuring system, pilot signal transmission equipment and signal measuring equipment
ActiveCN103840907AIncrease transmit powerImprove performanceSite diversitySpatial transmit diversityEngineeringData transmission
The embodiment of the invention relates to the technical field of wireless communication, particularly relates to a pilot signal transmission method, a signal measuring method, a signal measuring system, a piece of pilot signal transmission equipment and a piece of signal measuring equipment, and aims to solve the problem that each antenna unit transmits one pilot signal to result in very low transmission power of each antenna unit, and user equipment is high in complexity when the number of the antenna units is large in the prior art. The pilot signal transmission method of the embodiment of the invention comprises the step in which network side equipment sends determined CSI feedback configurations to user equipment, wherein one CSI feedback configuration corresponds to one CSI-RS resource, and a pilot signal corresponding to each port of one CSI-RS resource is sent through a set of antenna units corresponding to the port. By adopting the scheme provided by the embodiment of the invention, the transmission power of the antenna units can be increased to enable the user equipment to carry out signal measurement correctly, the performance of data transmission is improved, and the complexity of the user equipment is reduced when the number of the antenna units is large.
Owner:DATANG MOBILE COMM EQUIP CO LTD
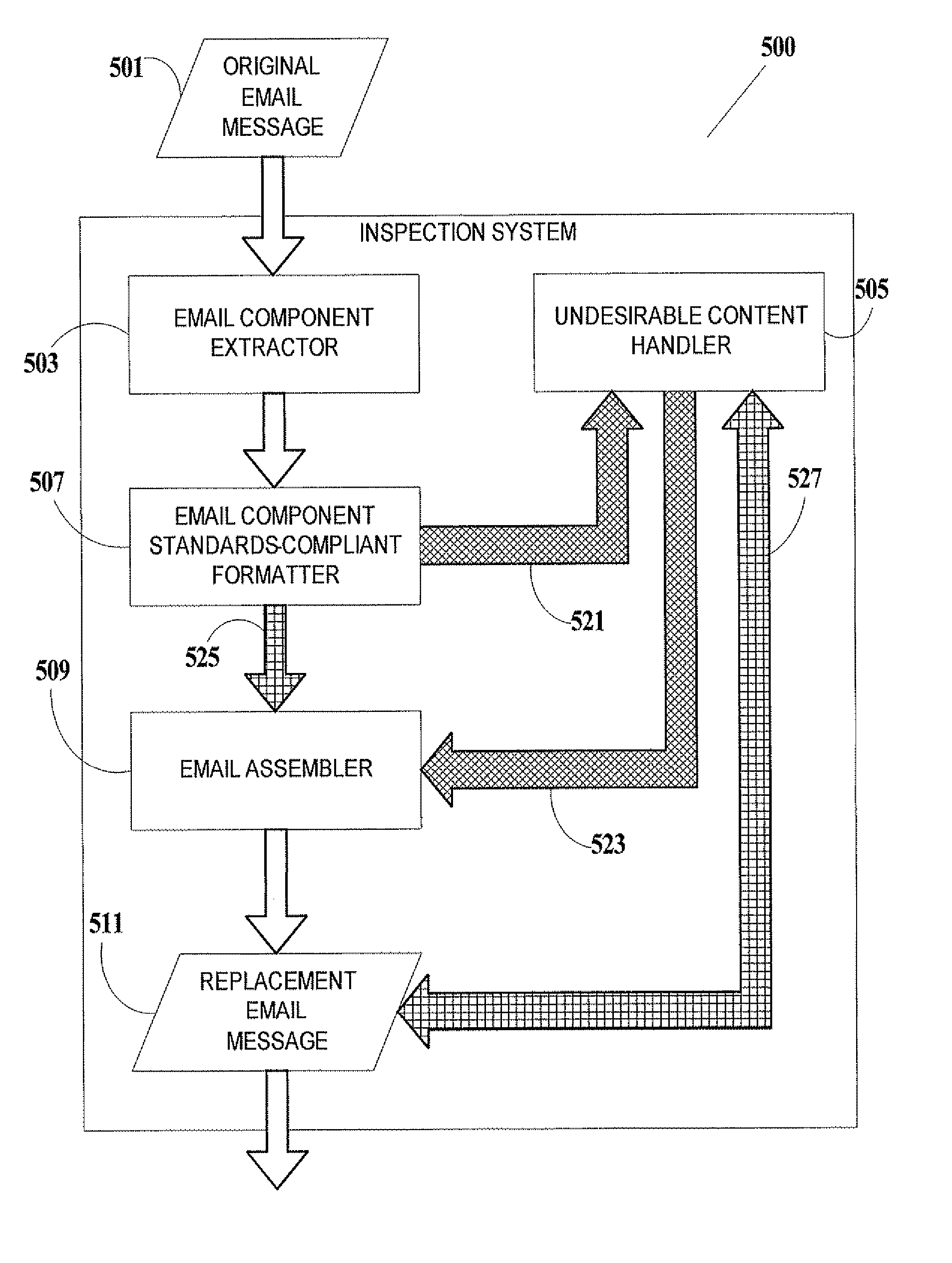
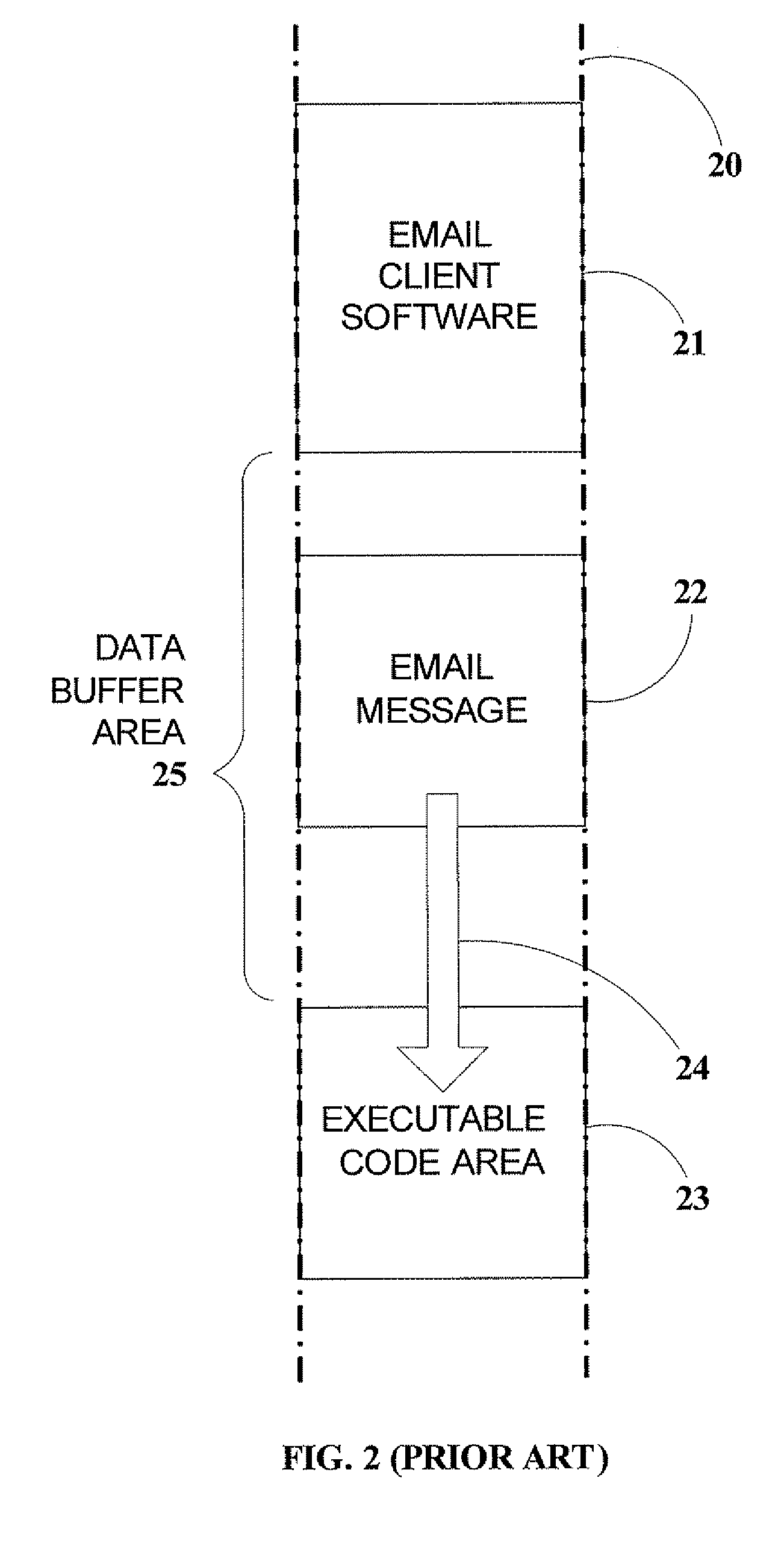
Method And System For Preventing Exploitation Of Email Messages
InactiveUS20070277238A1Prevent exploitationAvoid sendingMemory loss protectionUnauthorized memory use protectionInternet privacyFrequent use
A method and system for preventing the exploitation of email messages in attacks on computer systems. Invalid formatting is often used by attackers to introduce undesirable content into email, because email handling applications and utilities are often insensitive to deviations from the standards, and invalid formatting can allow undesirable content to go undetected. According to the present invention, an original email message is decomposed into component parts, which are formatted according to email message standards. Format-compliant components are inspected for undesirable content and reassembled into a replacement email message that is sent to the destination of the original email message. Components with undesirable content are sanitized.
Owner:ALADDIN KNOWLEDGE SYSTEMS
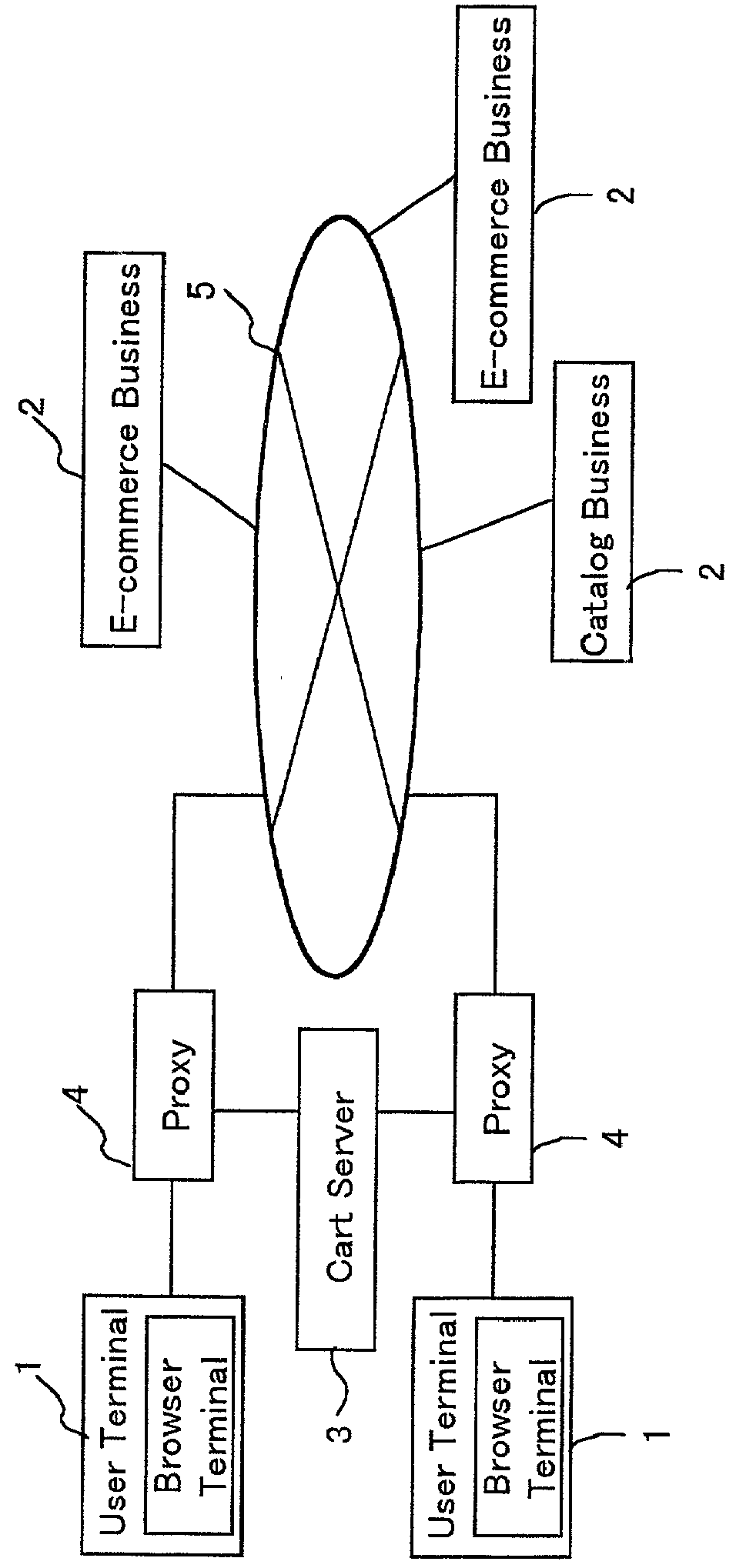
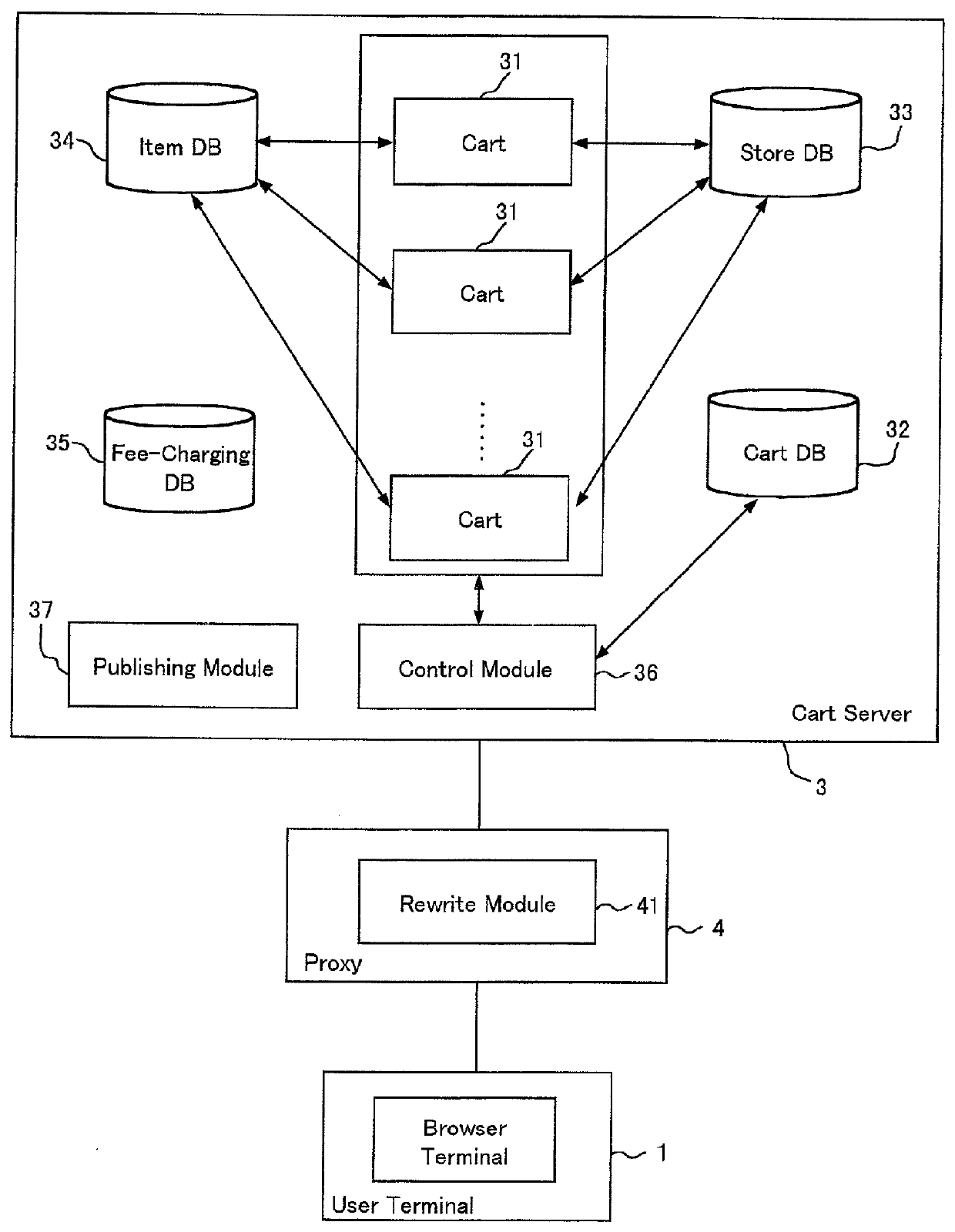
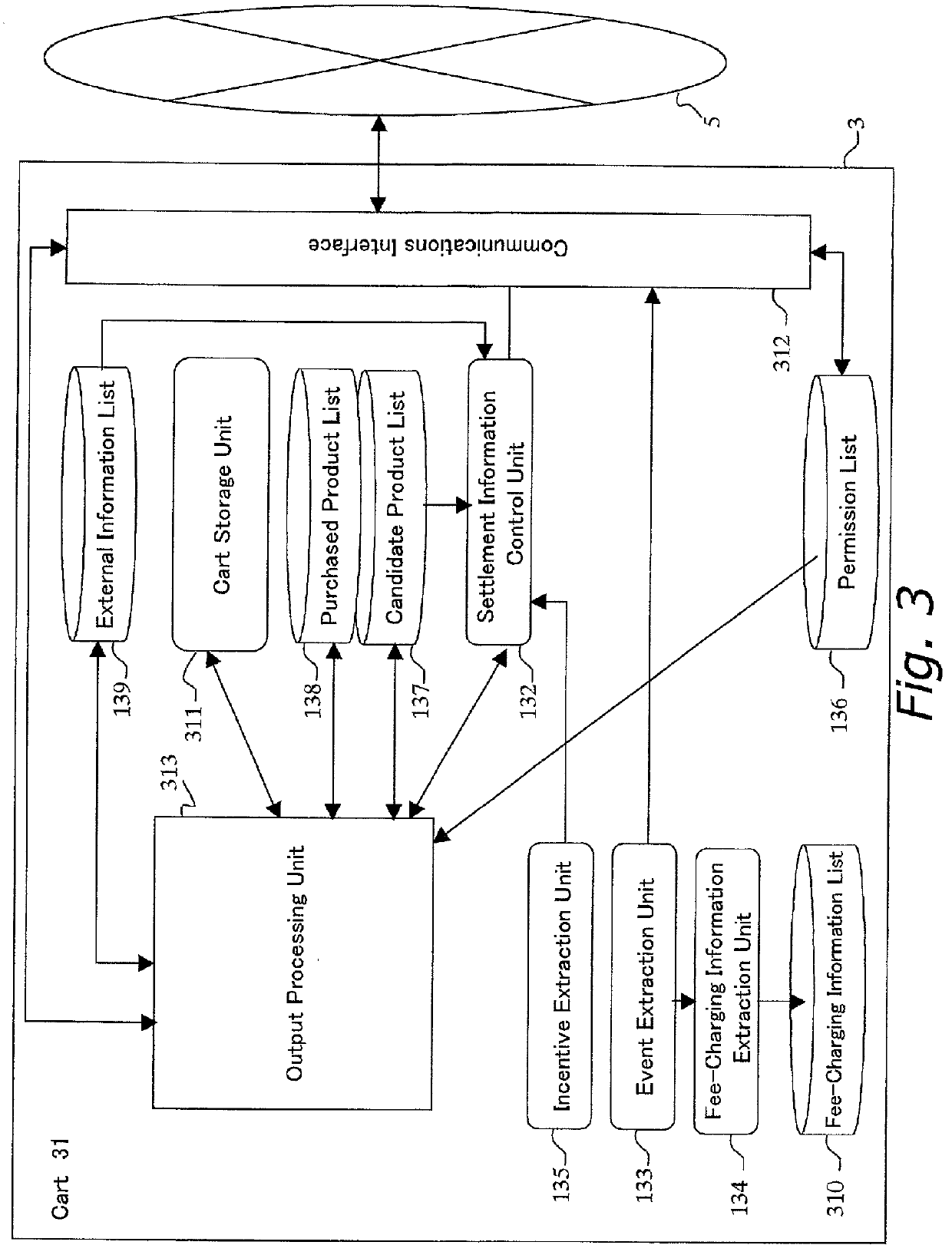
Online sales promotion method and device
InactiveUS20010053998A1Increase salesEffective marketing strategyAdvertisementsBilling/invoicingSales promotionExchange of information
The object of the invention is to perform a constructive exchange of information between a user and a provider of products in virtual reality. A user places a product 154 that he is considering buying in a cart, designates product providers, and gives notification thereto of the cart contents. A designated product provider 153, by seeing the cart contents, can learn in what products the user is interested. The product provider 153 can provide to the cart from which the designation arose additional information 155, such as advertisements for its products. The user, by receiving various types of additional information from a product provider that he trusts, can find products that meet his desires, and can enjoy more satisfactory network-based shopping.
Owner:FUJITSU LTD
Address acquisition
InactiveUS20050271034A1Avoid sendingInformation formatTime-division multiplexNetwork addressingNetwork address
In a GPRS system, a method of a mobile station acquiring an IP network address. The method comprises the steps of: the mobile station generating a link identifier and sending it to a gateway over a wireless link in a network address request together with a request to check if the link identifier is unique; the gateway receiving the network address request and checking if the link identifier is unique; the gateway responding with a network address request response including either the sending a unique link identifier confirmed as being unique or a different unique link identifier; the gateway sending a network prefix to the mobile station; the mobile station combining the interface identifier and the network prefix to generate the IP network address.
Owner:NOKIA CORP
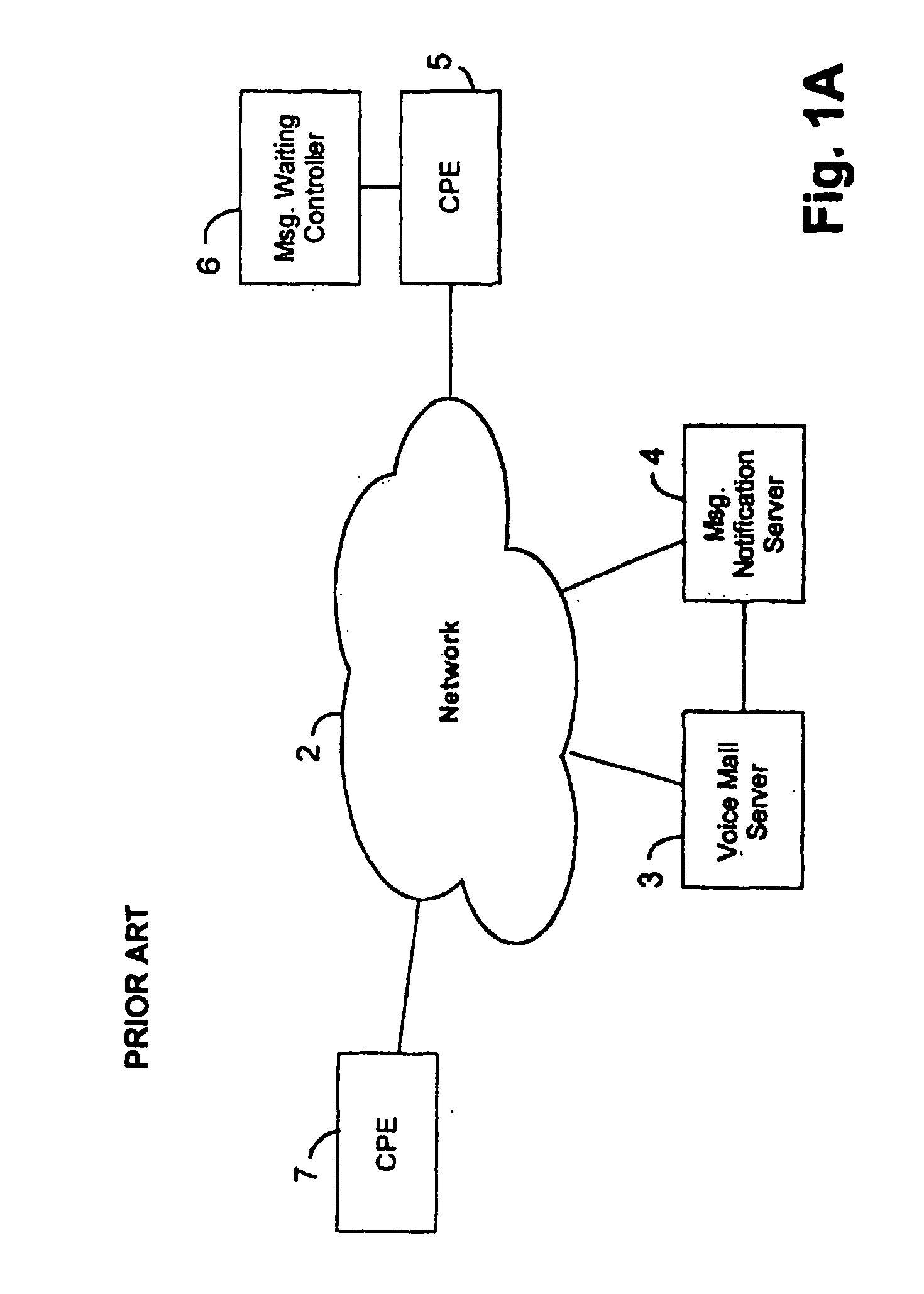
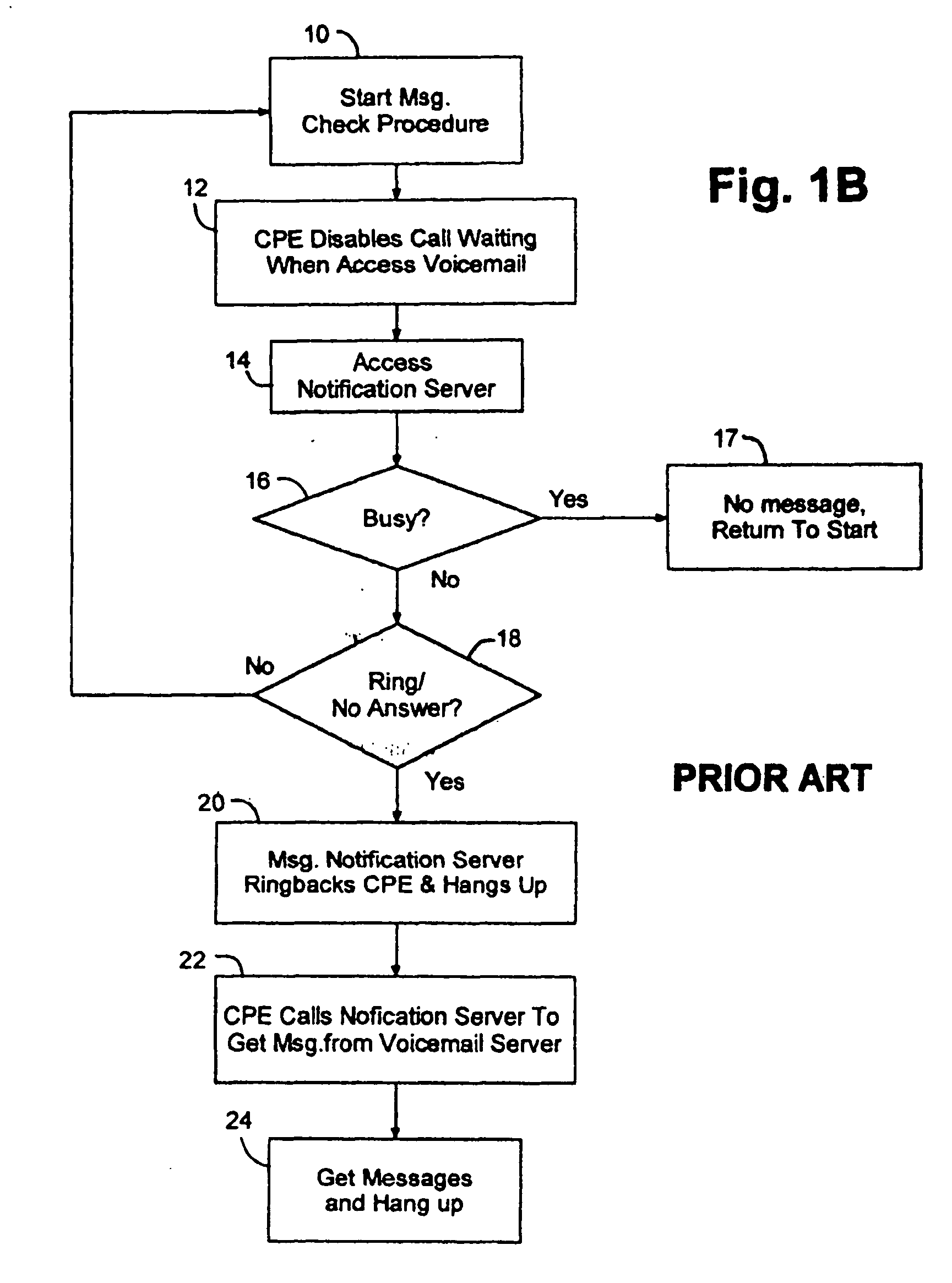
Intelligent voicemail message waiting system and method
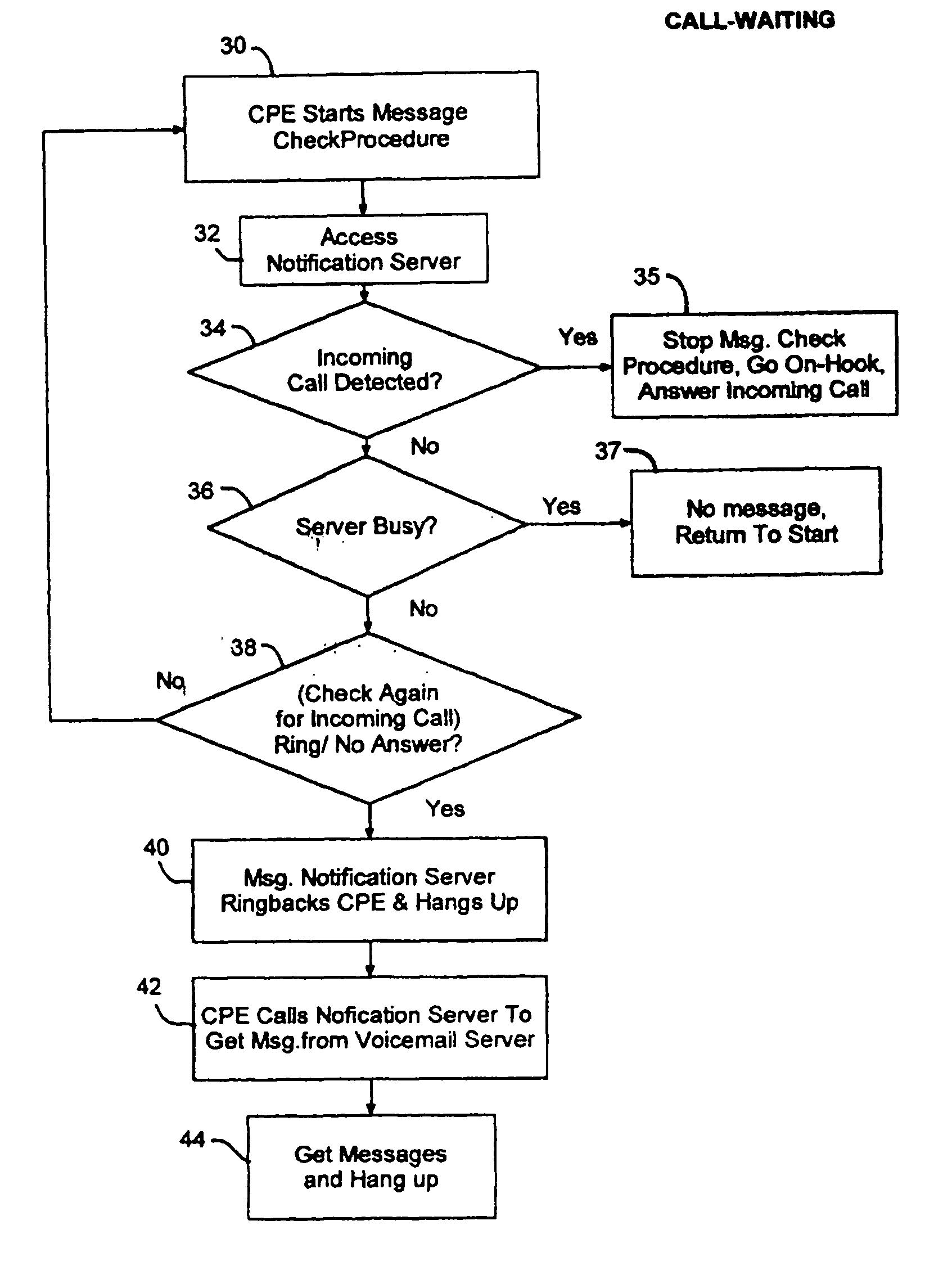
InactiveUS20040136505A1Avoid sendingAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesTelephone networkSpeech sound
An intelligent voice message status indication device for a single line of a telephone network includes a controller that responds to caller-ID signals to detect whether a mailbox contains a message, responds to a call-waiting signal to break communication with the voicemail system during message retrieval to capture an incoming call, and toggles multiple indicators associated with respective sub-mailboxes on a single line. The message waiting indicators may include respective unique audio, as well as respective unique, visual indication of message presence in one or more mailboxes. The voicemail servers of the network may be correspondingly partitioned to host multiple mailboxes and to provide unique outbound caller IDs to identify a mailbox having a message.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
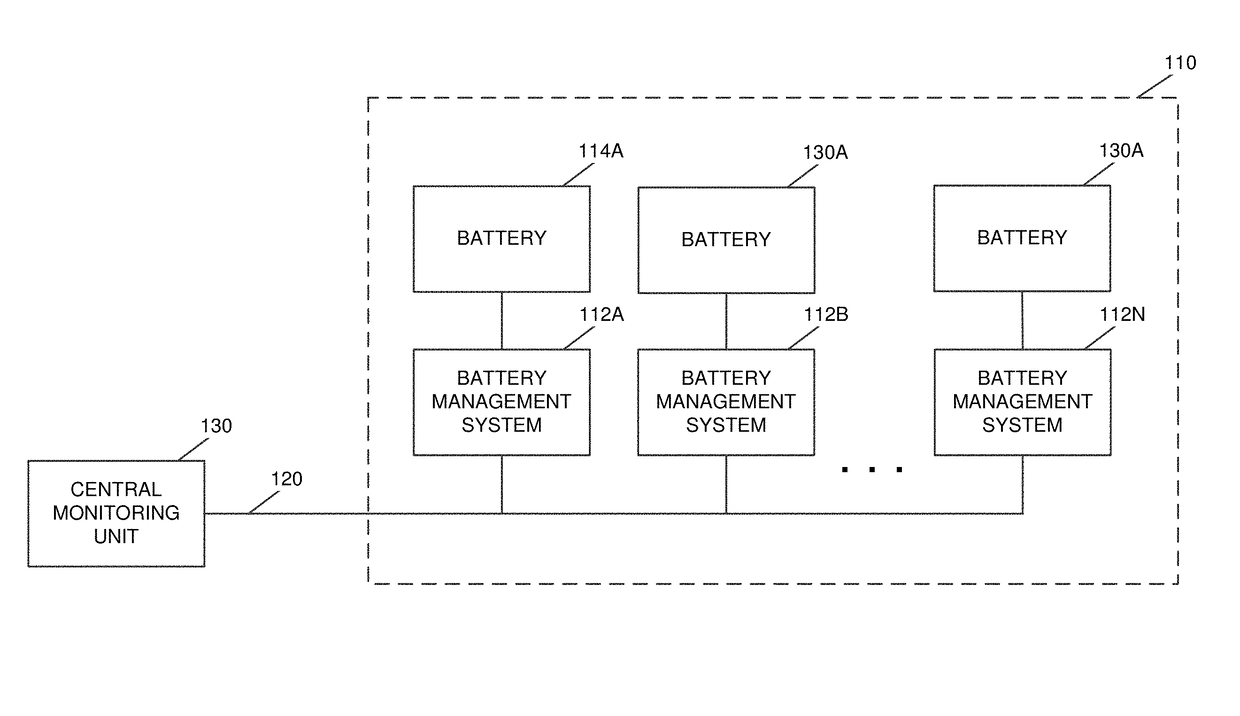
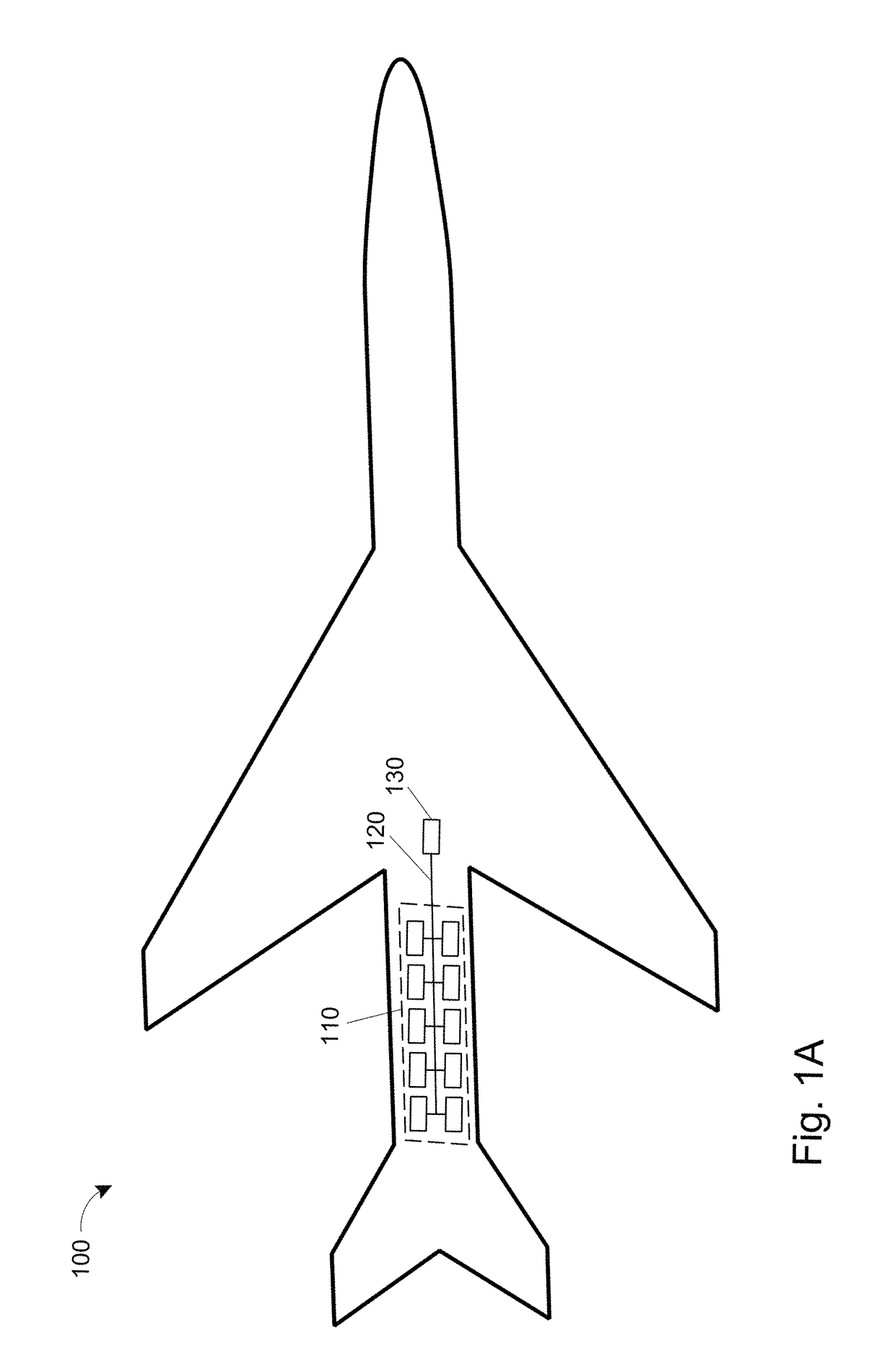
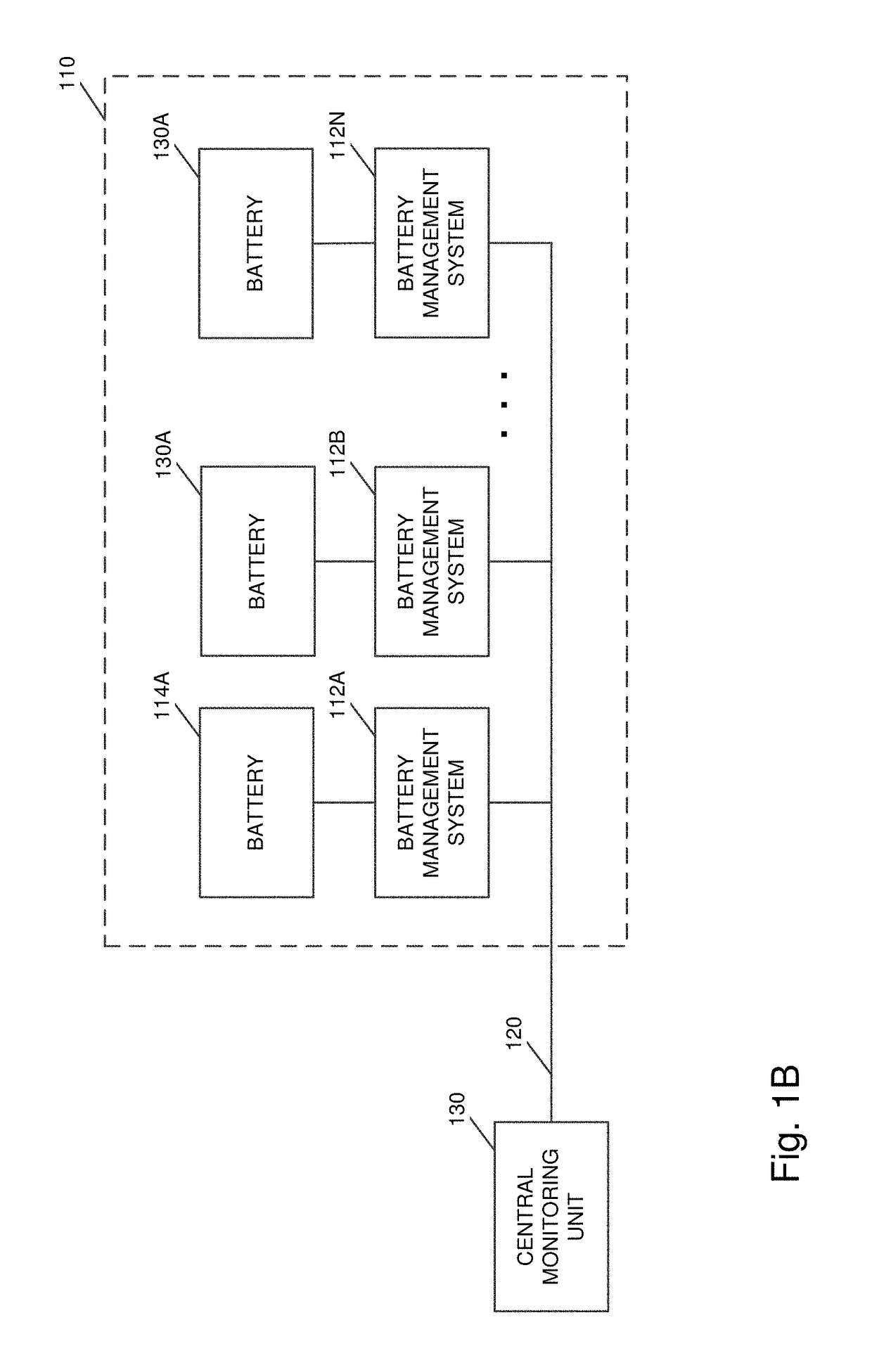
Communication system for battery management systems in electric or hybrid vehicles
ActiveUS10131246B2Avoid sendingCharge equalisation circuitCharging stationsCommunications systemElectrical battery
A circuit can include a CAN bus and multiple nodes. The multiple nodes can reboot at the same time so that a Time 0 is set at boot for each node. Each node can store an ID node and determine from its ID node one time slot of a plurality of periodic time slots starting from Time 0 in which to transmit on the CAN bus. Each node can transmit messages on the CAN bus in its determined time slot subsequent to Time 0.
Owner:H55 SA
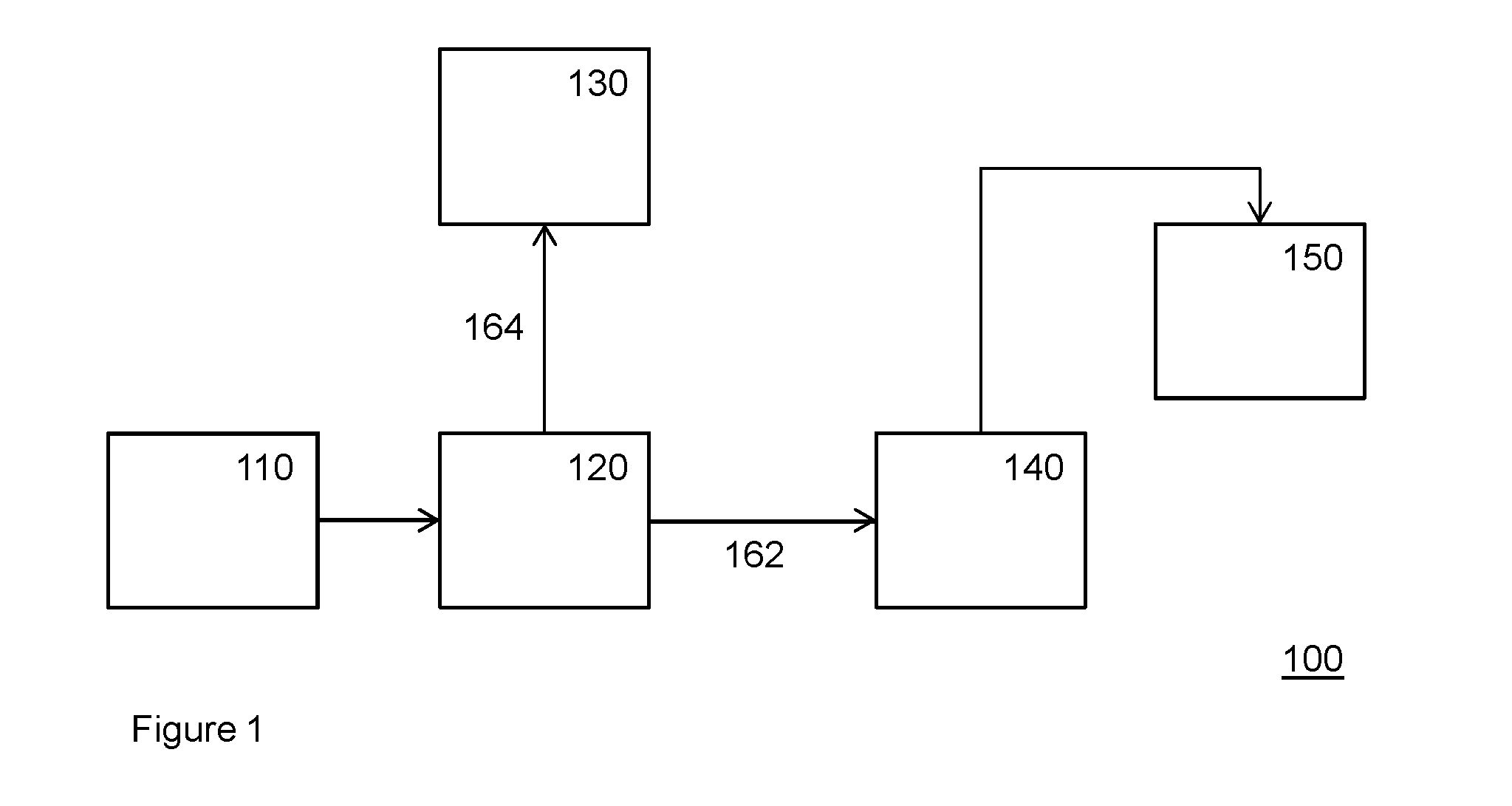
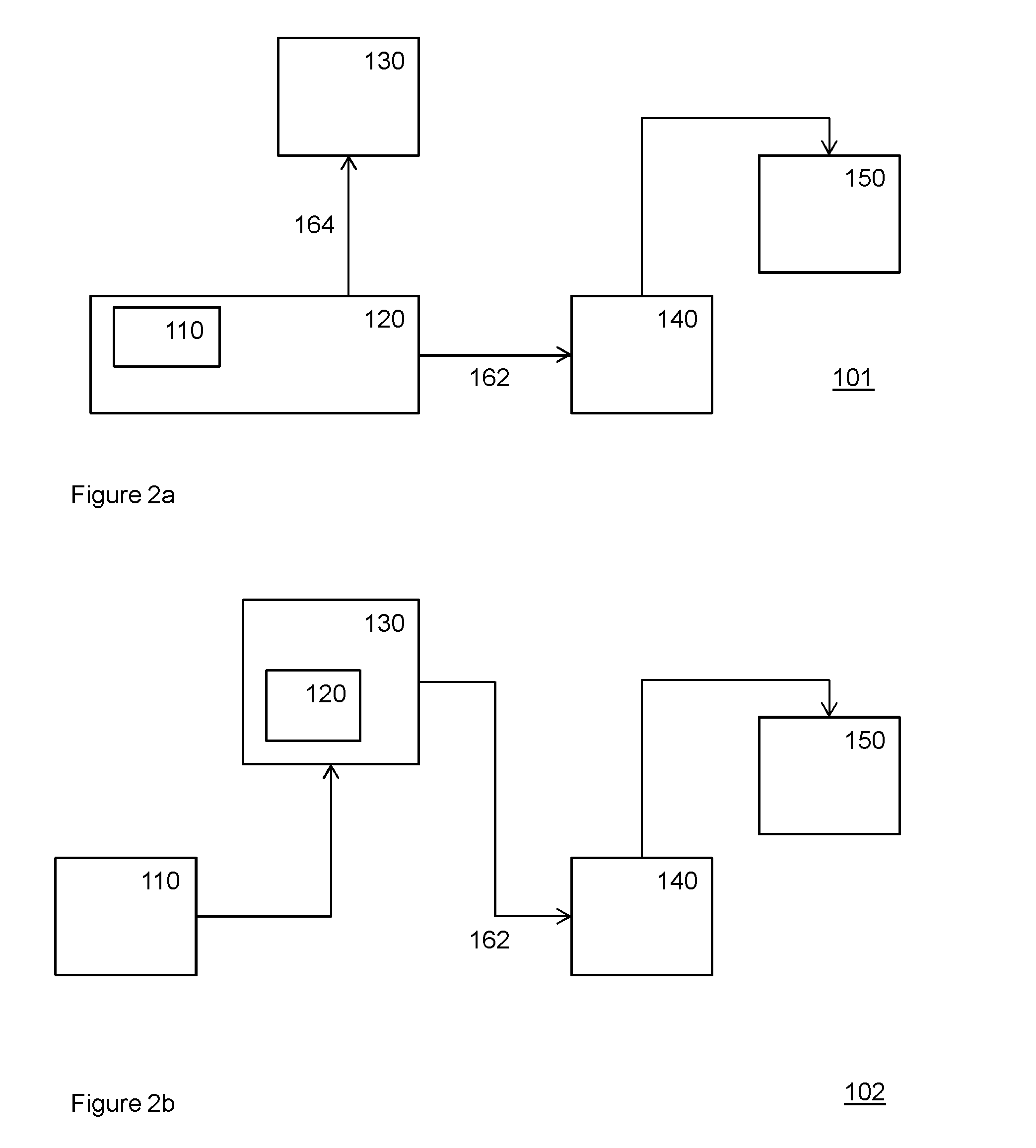
Audio forwarding device and corresponding method
ActiveUS20150208161A1Avoid playingHigh levelEarpiece/earphone attachmentsSelective content distributionDigital dataDisplay device
An audio forwarding device 120 comprising a media interface 122 configured to receive a media stream, the media stream comprising a video stream and an audio stream, the audio stream being synchronized with the video stream, a display interface 124 configured to transmit the video stream to a display 130 for display of the video stream, and a wireless data network interface 126 configured to stream the audio stream in the form of digital data to a mobile computing device 140 over a digital wireless data connection 162 for the mobile computing device to play the audio stream on a headphone interface.
Owner:KONINKLJIJKE PHILIPS NV
Method and system for preventing local area network ARP defection attacks
InactiveCN101635713AAvoid sendingBlocking deceptionData switching networksOperational systemAddress resolution
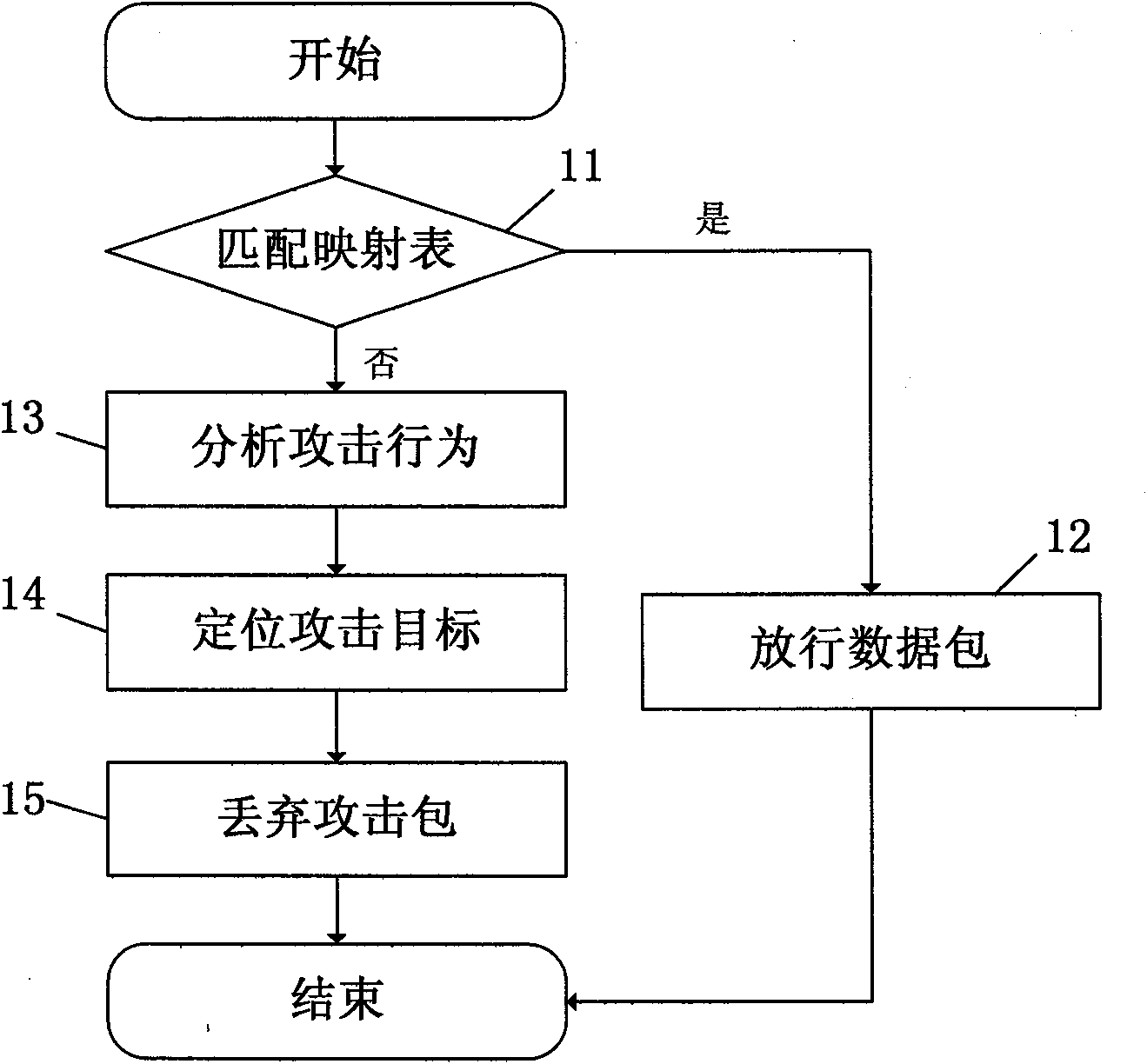
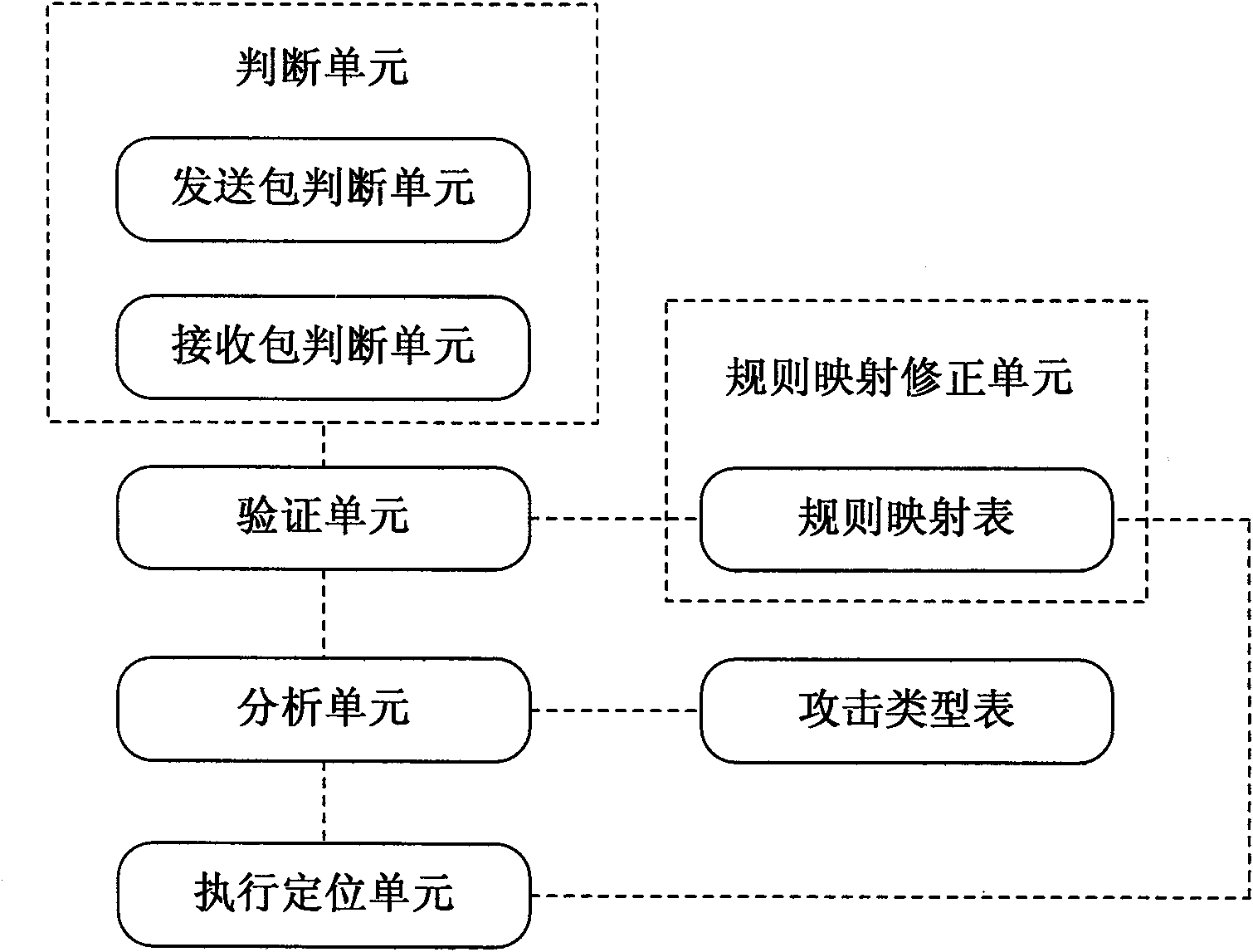
The invention discloses a method for preventing local area network ARP defection attacks, which mainly comprises the following steps: disposing a defined address resolution mapping table between a network card and an operating system of a terminal host in a local area network to ensure that each terminal only has one IP and MAC mapping relation; ensuring the correctness of the mapping table by a service program; and ensuring whether the ARP is reliable or not by matching ARP packs transmitted and received by the terminal host and the mapping table. The invention also discloses a system for preventing local area network ARP defection attacks; and the terminal host can defense the ARP attacks of a local host and the outside in the local area network.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
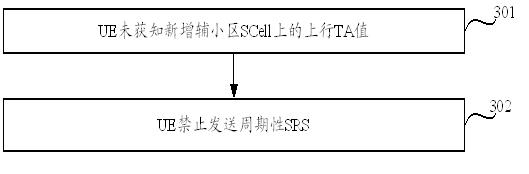
A kind of processing method and equipment of periodic SRS
ActiveCN102291837AAvoid sendingReduce distractionsWireless communicationSounding reference signalTiming advance
The invention discloses a method for processing a periodic sounding reference signal (SRS) and equipment. The method comprises the following steps of: forbidding user equipment to send the periodic SRS when an uplink timing advance (TA) value on a newly-added secondary cell (SCell) cannot be determined by the user equipment. By the embodiment of the invention, the unnecessary sending of the periodic SRS by the SCell is avoided, and the unnecessary interference of a system is reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
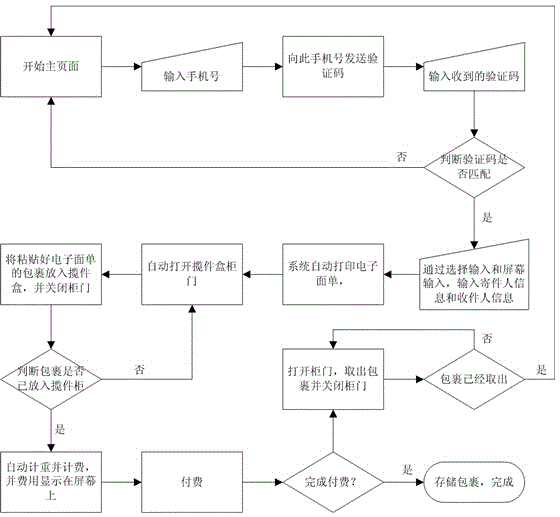
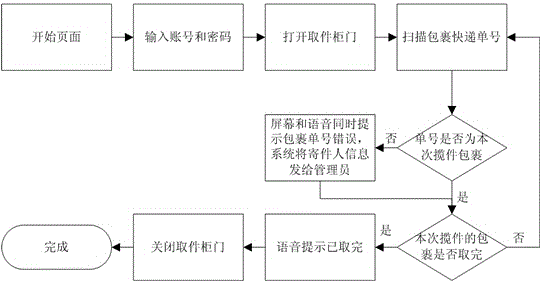
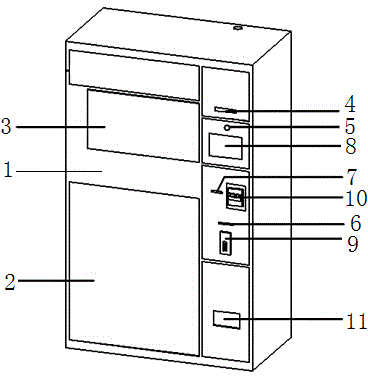
Collection type self-service express taking and pickup method and self-service express taking machine
InactiveCN104537773AImprove collection efficiencyReduce manpower expenditureApparatus for meter-controlled dispensingNetwork serviceMobile phone
The invention discloses a collection type self-service express taking and pickup method and a self-service express taking machine. The method is performed based on an express taking system, and the express taking system comprises a network background and a customer operation terminal, wherein the network background is arranged on a network server, and the customer operation terminal performs communication with the network background through a GPRS (general packet radio service) module or Ethernet. The customer operation terminal is placed in a place which needs to take expresses in the form of an express taking cabinet body, and an express receiving box, an express taking box, a bill printing and output module, an operation module, a scanning module and a money receiving and changing module are arranged on the express taking cabinet body; a sender can complete the process of sending an express by operating the customer operation terminal; and an express taking person can complete the process of taking the express by operating the customer operation terminal. By adopting the method disclosed by the invention, the express taking efficiency is greatly improved and the labor expense is reduced. The information of the sender is confirmed through a mobile phone verification code and a photographing means, thereby controlling the process flow of sending the express and being conductive to avoiding sending prohibited items.
Owner:廖友谊 +1
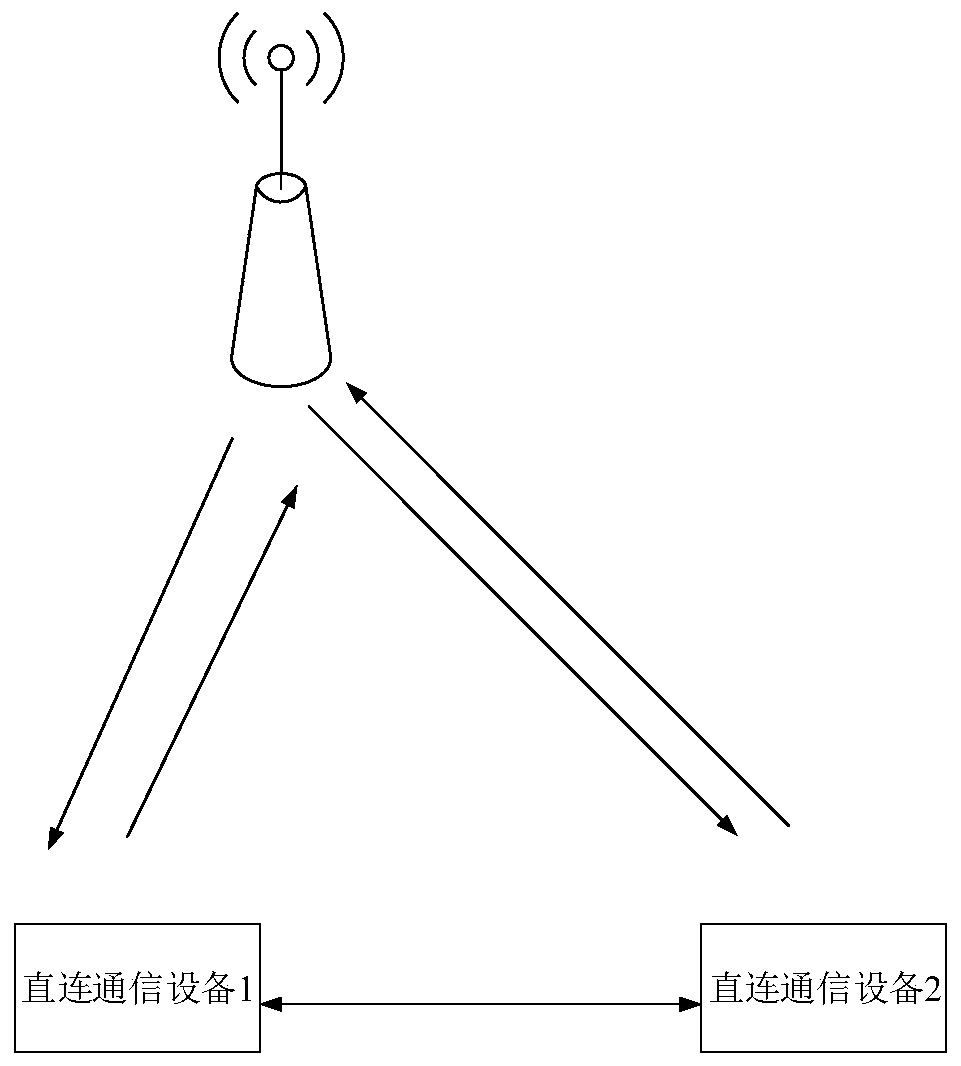
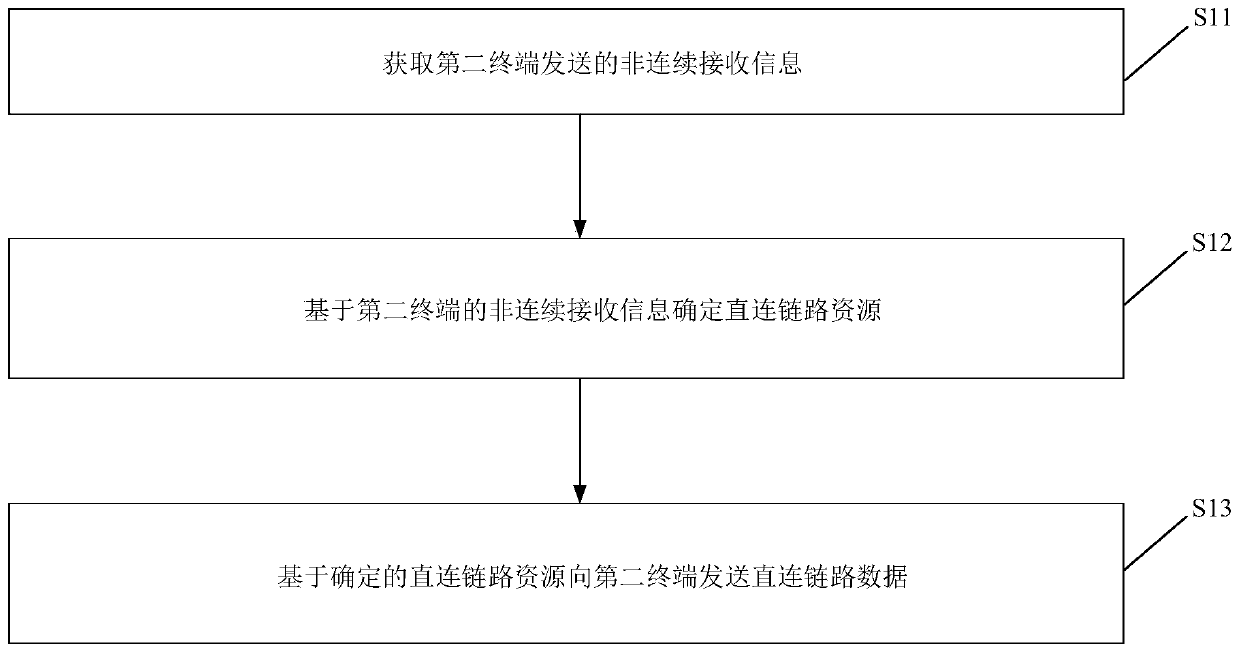
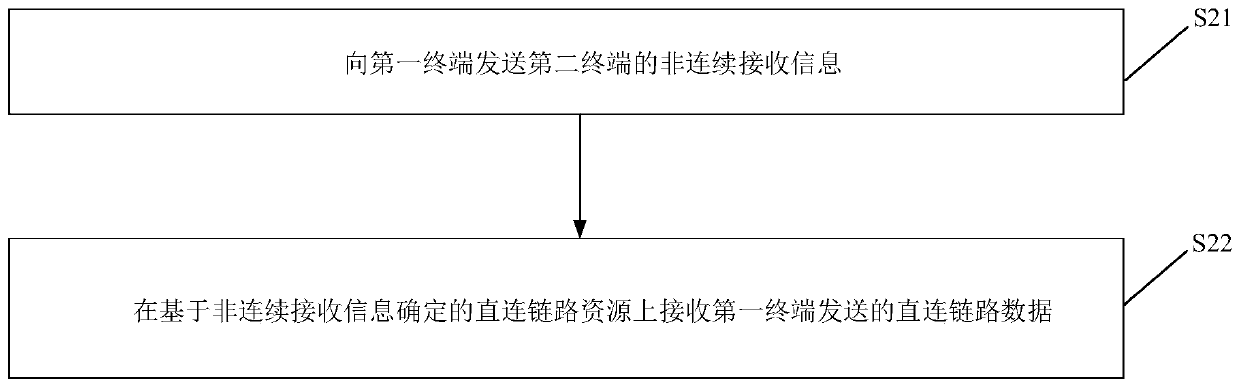
Direct link data transmission method and device, and storage medium
The invention relates to a direct link data transmission method and device, and a storage medium. The direct link data transmission method is applied to a first terminal and comprises the steps of acquiring non-continuous receiving DRX information transmitted from a second terminal; determining a direct link resource based on the DRX information, and transmitting direct link data to the second terminal based on the direct link resource. Through the method of the invention, data loss can be prevented.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
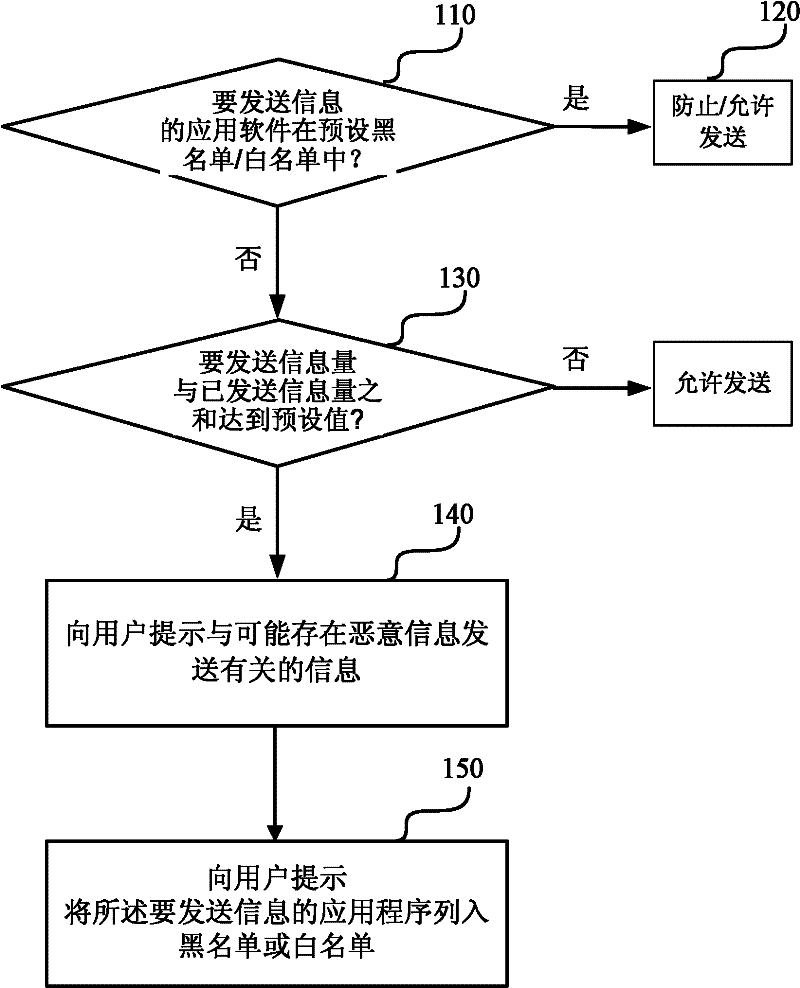
Malicious information transmission preventing method and system of mobile intelligent terminal
InactiveCN102395128AEfficiently prevent malicious information from being sentImprove real-time performancePlatform integrity maintainanceSecurity arrangementWhitelistApplication software
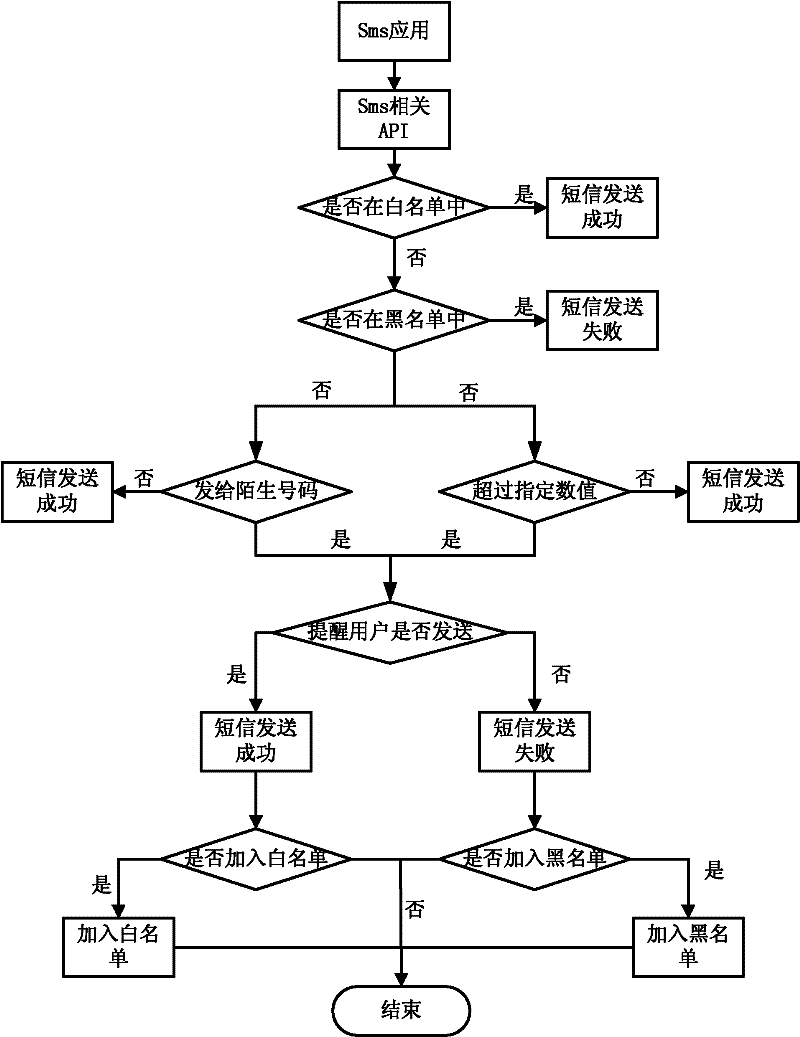
The invention discloses a malicious information transmission preventing method and system of a mobile intelligent terminal. The method comprises the following steps of: judging, namely judging whether an information transmission object is in a preset blacklist or whitelist or not when the application program of the mobile intelligent terminal is about to transmit information; and processing, stopping the transmission of the information if the information transmission object is in the preset blacklist and allowing the transmission of the information if the information transmission object is in the preset whitelist, wherein the blacklist is a list of application software untrusted by the mobile intelligent terminal, and the whitelist is a list of application software trusted by the mobile intelligent terminal. By applying the method and system disclosed by the invention, the transmission of the malicious information can be efficiently prevented.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method for measuring multimedia multicast service quality based on client
InactiveCN101674204ATimely measurementImprove friendlinessData switching networksActive measurementIPv6
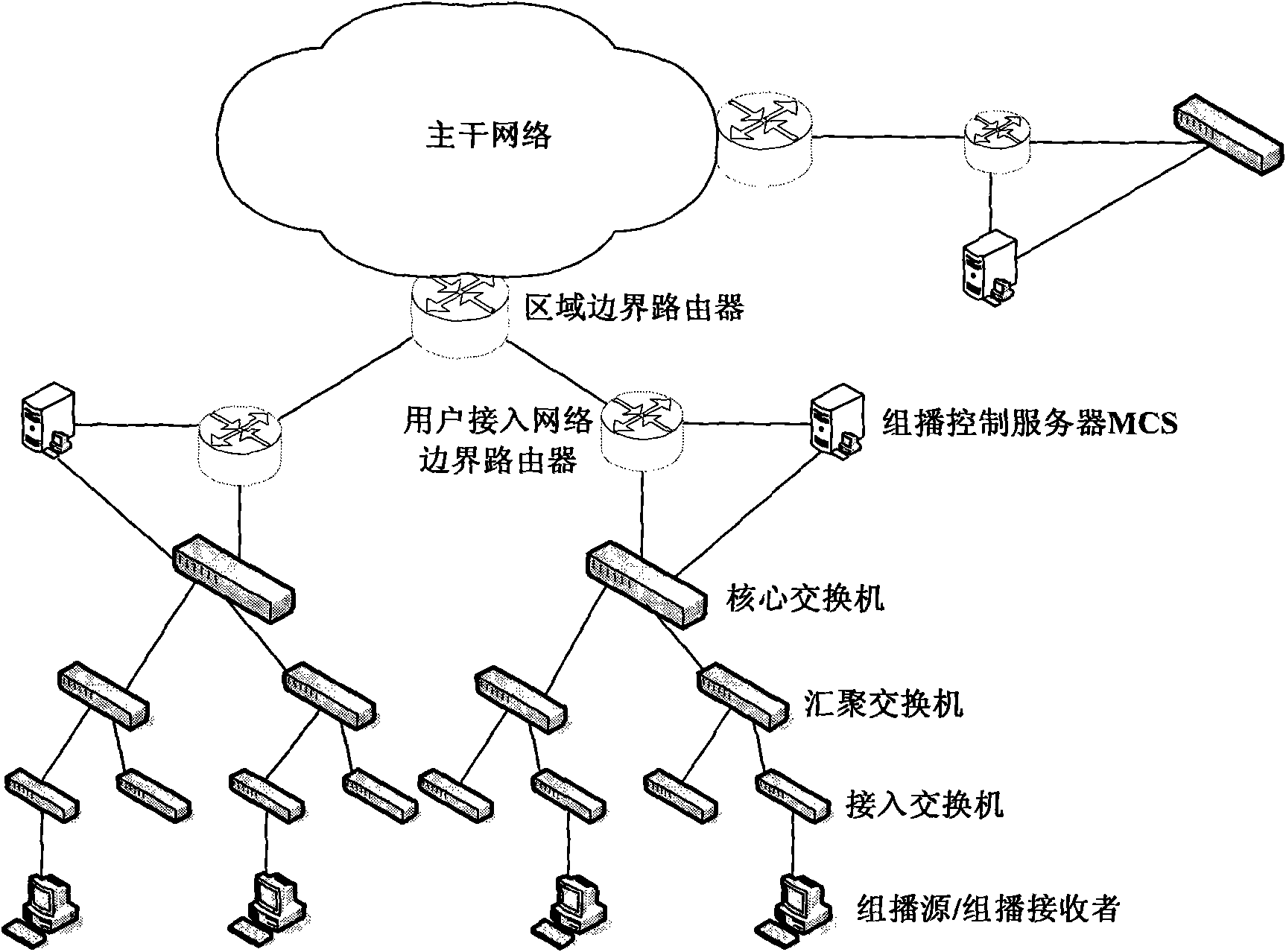
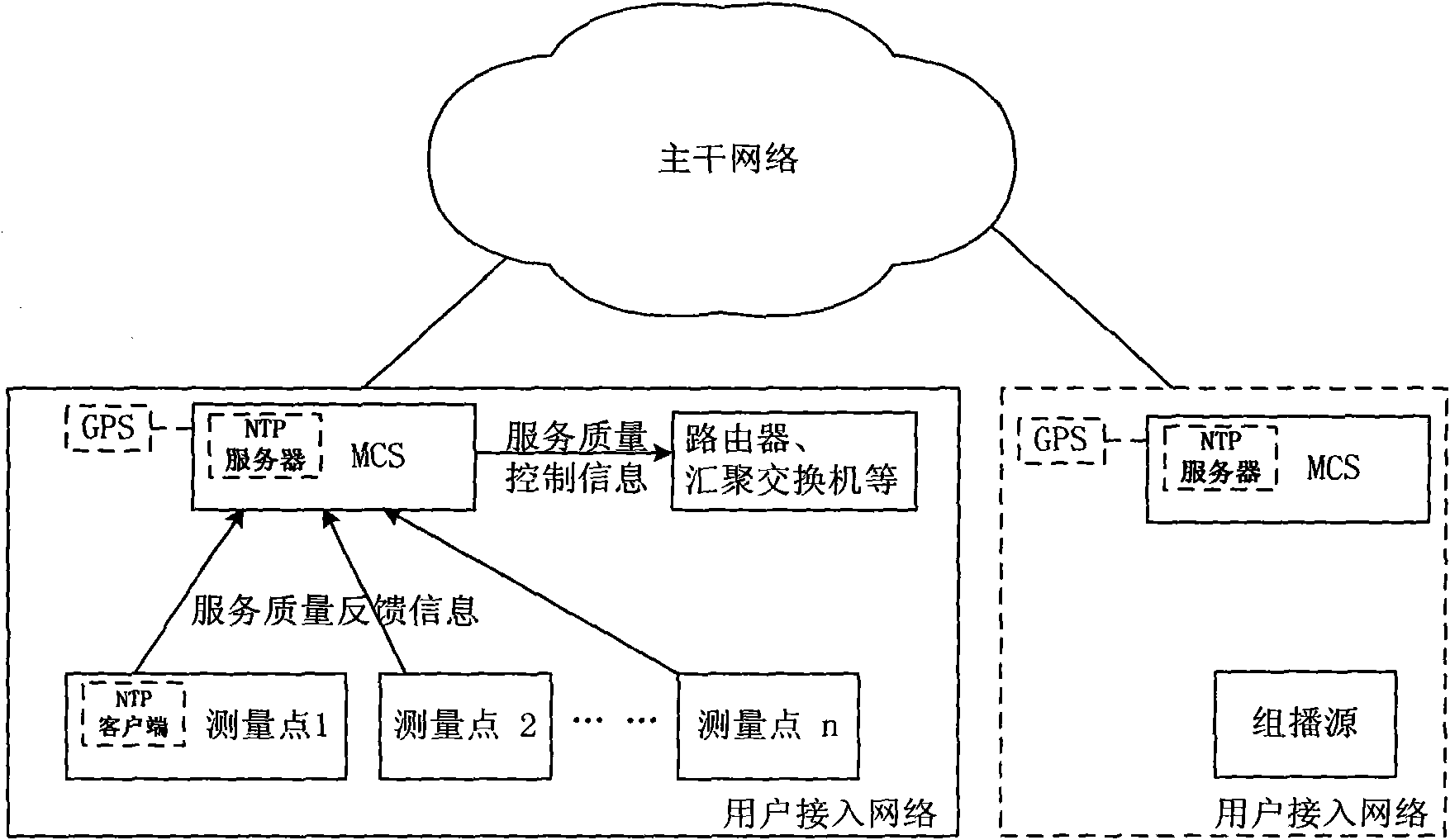
The invention discloses a method for measuring the multimedia multicast service quality based on a client under a large-scale IPv6 network environment. The method provides a whole set of schemes to solve the multimedia multicast service quality measurement, comprising the time synchronization of a closed system, the message sampling and time stamp adding of a multicast source end system, the selection of a dynamic measurement point, the measurement of multicast service quality parameters of a single measurement point, and the assessment and control of a multicast control server to the access network multimedia multicast service quality. The method not only can overcome the invasion and non-reliability of active measurement as well as the locality of passive measurement, but also can timelyand truly measure the multimedia multicast service quality, and has the advantages of convenient deployment, good expansibility and the like.
Owner:SOUTHEAST UNIV
Integrity of low bandwidth communications
InactiveUS8397151B2Reduce bandwidth consumptionQuick checkError preventionTransmission systemsSmart cardComputer science
The invention relates to a method for checking the integrity of a set of data packets received by a receiving communication device from a sending communication device, the data packets of the set being received in unpredictable order. The invention also relates to a communication device implementing a method according to the invention, in particular to a smart card.
Owner:GEMPLU
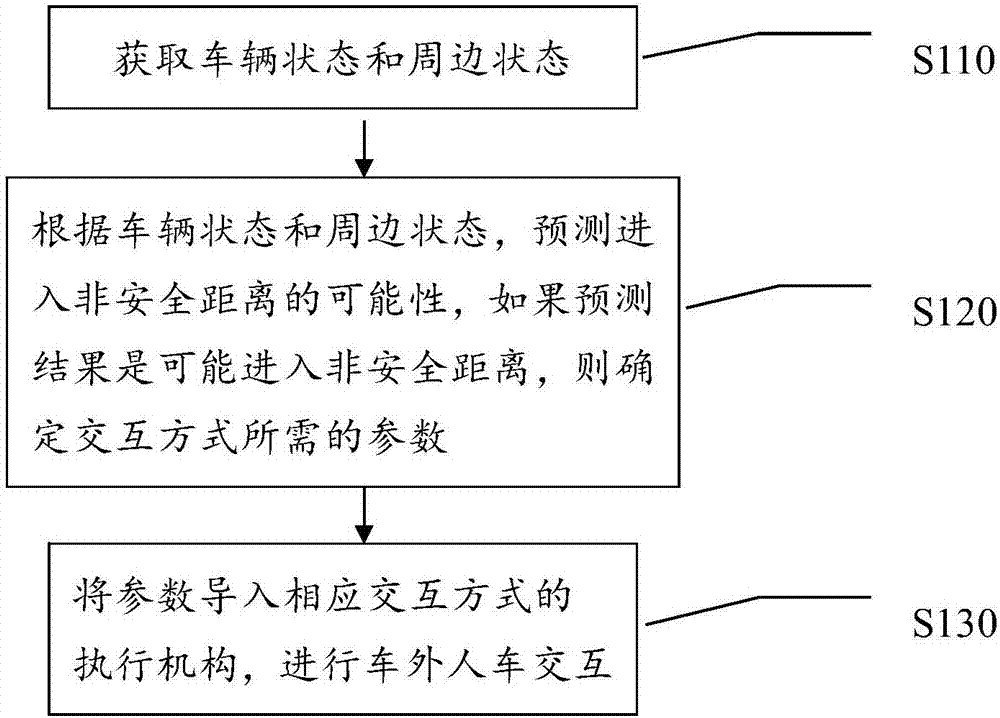
Method, system and device for human-vehicle interaction of vehicle and outside of vehicle and storage medium
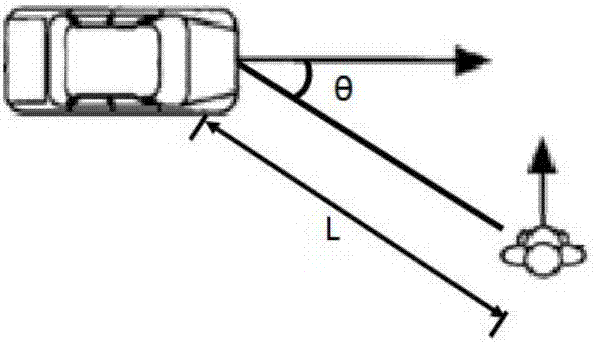
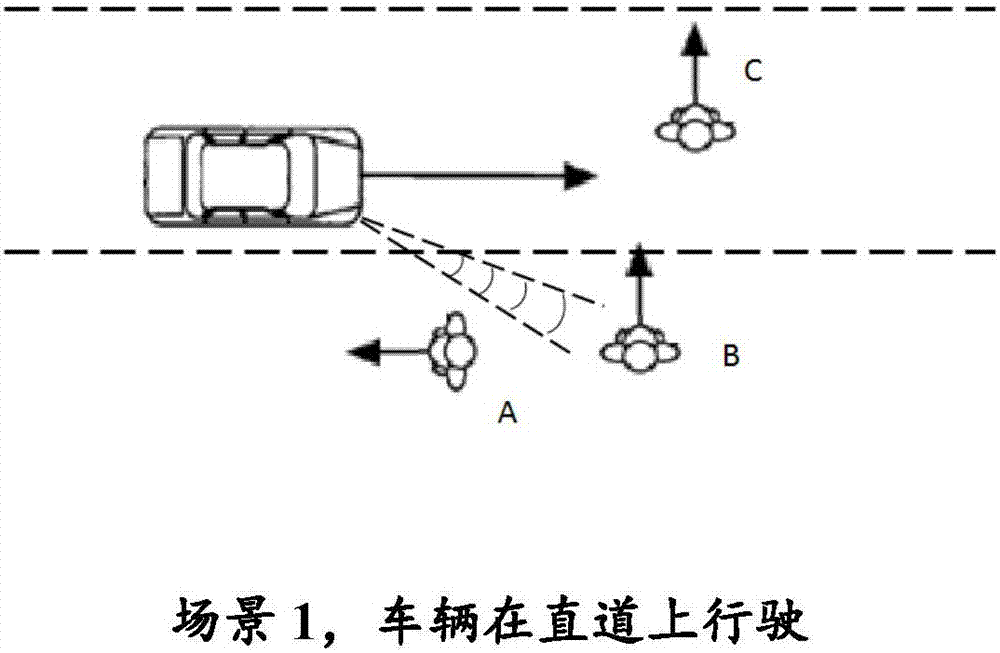
ActiveCN106864361AAvoid interferenceAvoid sendingAcoustic signal devicesPosition/course control in two dimensionsPedestrianAutomotive engineering
Disclosed are a method and device for human-vehicle interaction of a vehicle and the outside of the vehicle, a computer readable medium and a method for the human-vehicle interaction of a robot and the periphery. The method for the human-vehicle interaction of the vehicle and the outside the vehicle comprises the steps that the vehicle state and the peripheral state of the vehicle are obtained; and according to the obtained vehicle state and the peripheral state of the vehicle, the possibility of entering a non-safe distance is forecasted, and if the forecasting result is that entering the non-safe distance is possible, parameters needed by an interactive mode are determined. The situation that the vehicle sends invalid warning information outward is effectively avoided, and disturbance to a pedestrian / a vehicle in a non-interactive area is prevented.
Owner:UISEE TECH BEIJING LTD
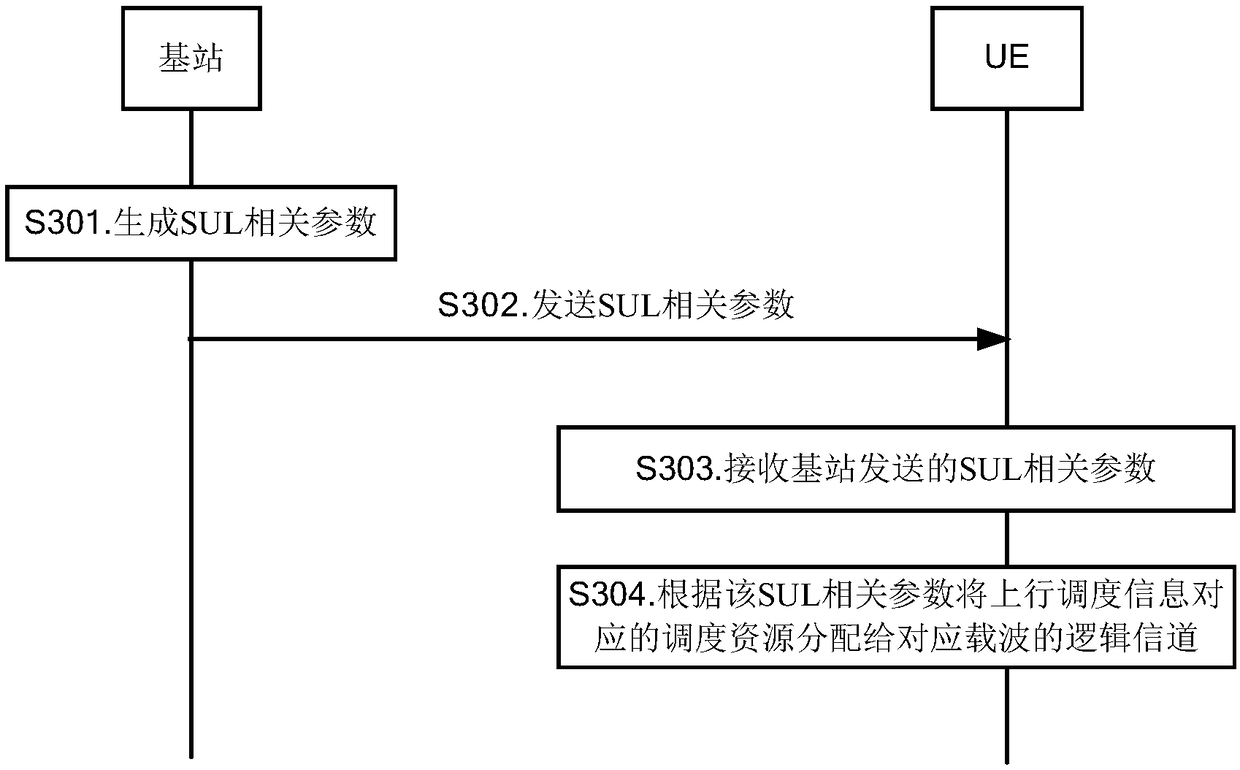
Supplementary uplink carrier configuration method and device, and scheduling resource allocation method and device
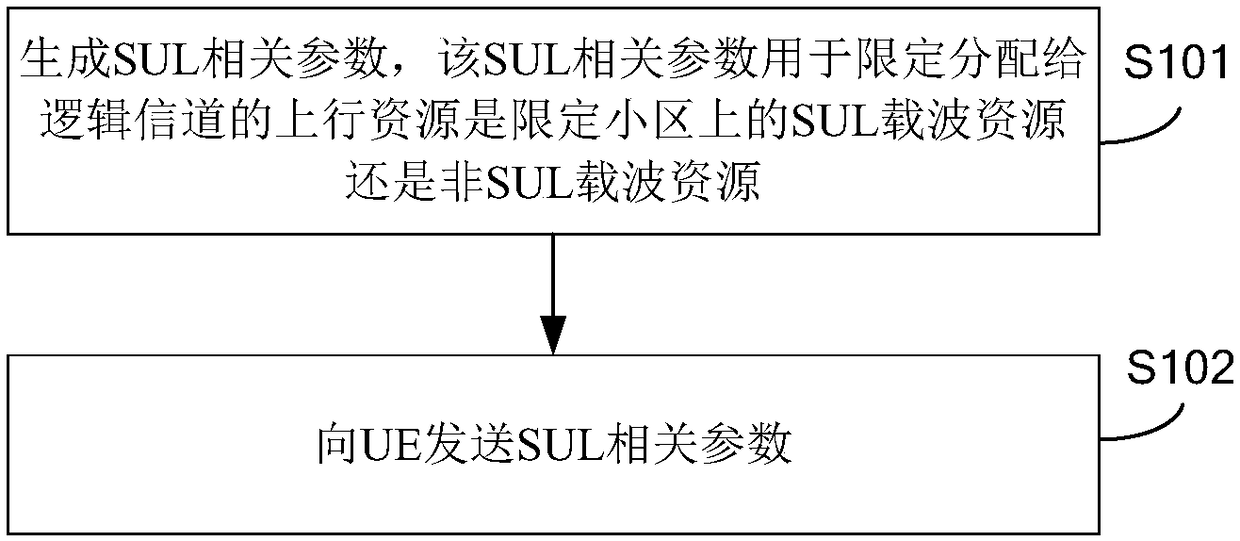
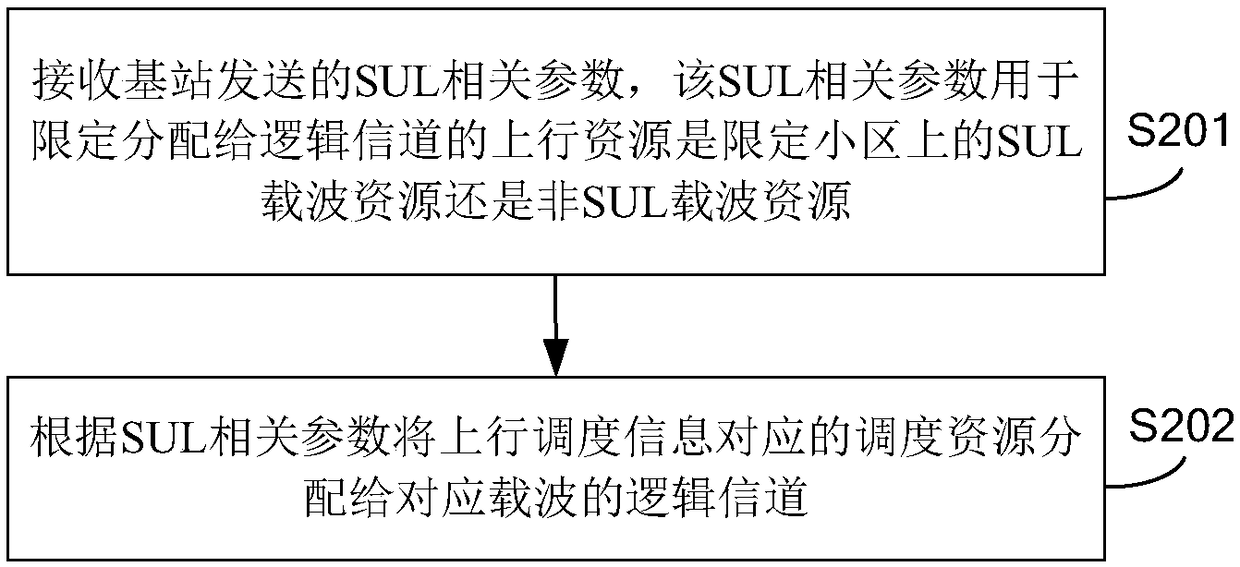
ActiveCN108353408AAvoid sendingReduce transmission delayConnection managementCarrier signalTransmission delay
The present disclosure relates to a supplementary uplink carrier SUL configuration method and device, a scheduling resource allocation method and device, a base station, user equipment, and a computerreadable storage medium. The SUL configuration method includes: generating a SUL related parameter, where the SUL related parameter is used to limit whether an uplink resource allocated to the logical channel is a SUL carrier resource or a non-SUL carrier resource on the qualified cell; sending the SUL related parameter to the UE. In the above embodiment, by generating and transmitting to the UE,the SUL related parameter for limiting whether the uplink resource allocated to the logical channel is the SUL carrier resource or the non-SUL carrier resource on the defined cell, whether the configuration logical channel adopts the SUL carrier resource or the non- SUL carrier resources to prevent data from being transmitted on carriers with poor channel, thereby reducing transmission delay andimproving service performance.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
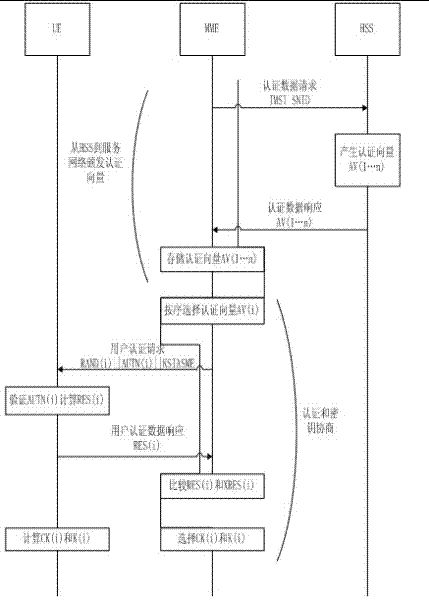
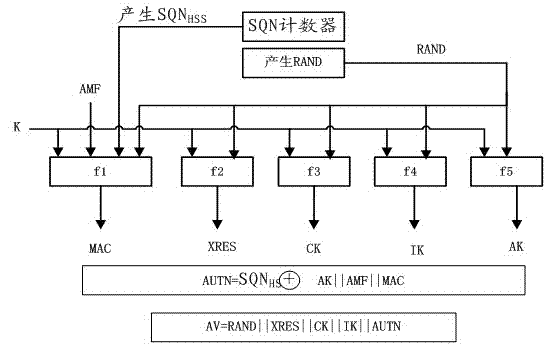
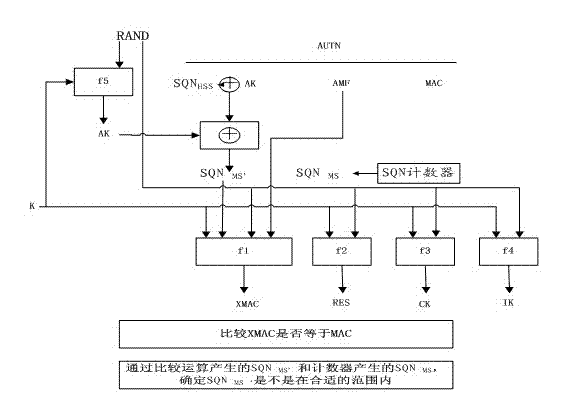
LTE authentication method
The invention discloses a new authentication method aiming at the safety problem of the present LTE network. The method comprises the following steps: since a core network is additionally arranged to authenticate an eNodeB and send the result of the authentication to an MME, illegal eNodeB which attacks the core network and users is avoided; and when UE is required to send an IMSI to the core network, the communication procedure is finished according to a distributed TMSI, then the identity of the UE issued by an ASE is used to encrypt the IMSI, so that the UE is prevented from sending the IMSI in a clear text way, and the IMSI is not easy to be intercepted. By adopting the steps provided by the invention, the communication link from the UE to the ASE is guaranteed to be safe, and a shared key K can be updated. In addition, the solution of the last two problems depends on a pre-established safe link.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
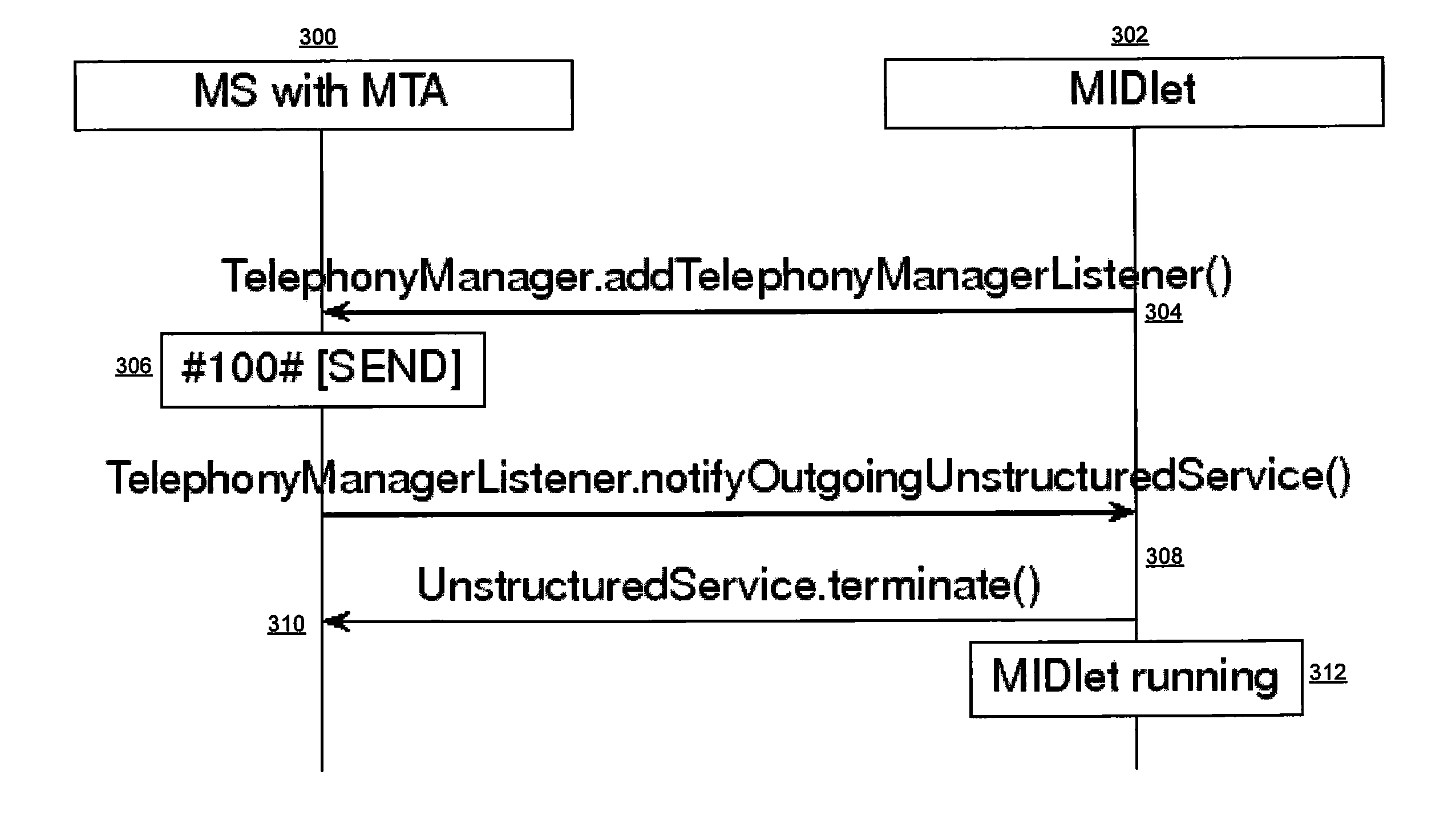
Method and system for executing applications in wireless telecommunication networks
InactiveUS20090270077A1Easy to rememberLow costSpecial service for subscribersMultiple digital computer combinationsTelecommunications networkMobile device
A method and system allow a mobile device user to automatically execute a service application to provide a requested service. The user may enter a USSD code or initiate a voice call to a special number. The wireless network recognizes the user's act as a request for a specific service and notifies the service provider. The service provider sends an activation command to the mobile device and may also initiate installing the service application.
Owner:MYRIAD GROUP
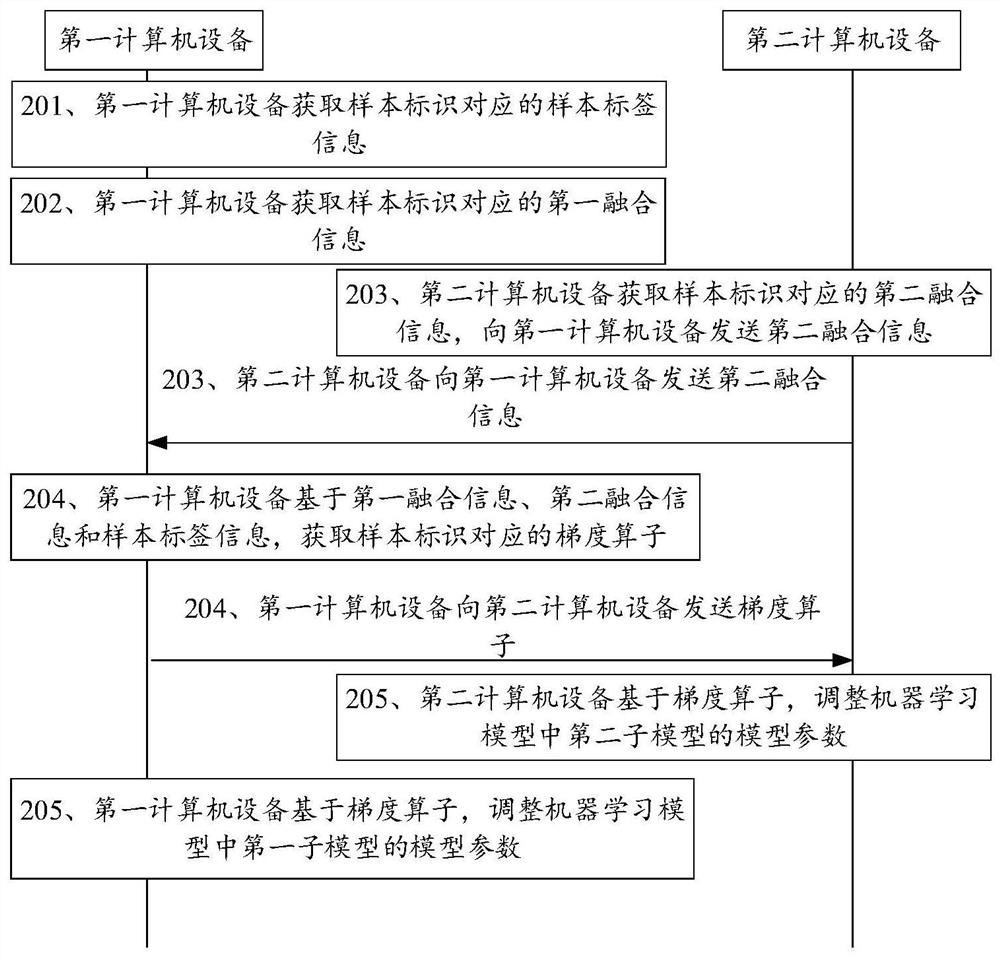
Federation learning method and device, computer equipment and medium
ActiveCN112257876AIncrease training speedImprove accuracyEnsemble learningAlgorithmInformation quantity
The embodiment of the invention discloses a federated learning method and device, computer equipment and a medium, and belongs to the technical field of computers. The method comprises the following steps that: first computer equipment acquires sample label information corresponding to a sample identifier, and acquires first fusion information corresponding to the sample identifier; the second computer equipment acquires second fusion information corresponding to the sample identifier and sends the second fusion information to the first computer equipment; the first computer equipment acquiresa gradient operator corresponding to the sample identifier based on the first fusion information, the second fusion information and the sample label information, and sends the gradient operator to the second computer equipment; and the first computer equipment and the second computer equipment respectively adjust model parameters of a first sub-model and model parameters of a second sub-model inthe machine learning model based on the gradient operator. According to the method, the training speed of the model is increased while the privacy of the user is ensured, the information amount of thecharacteristics of the sample is enriched, and the accuracy of the model is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
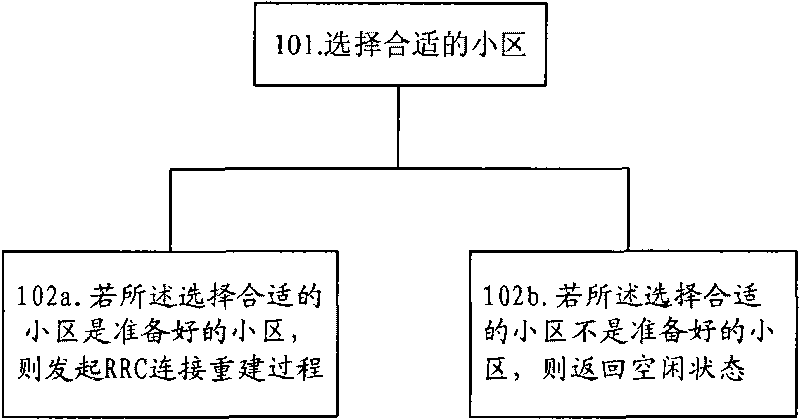
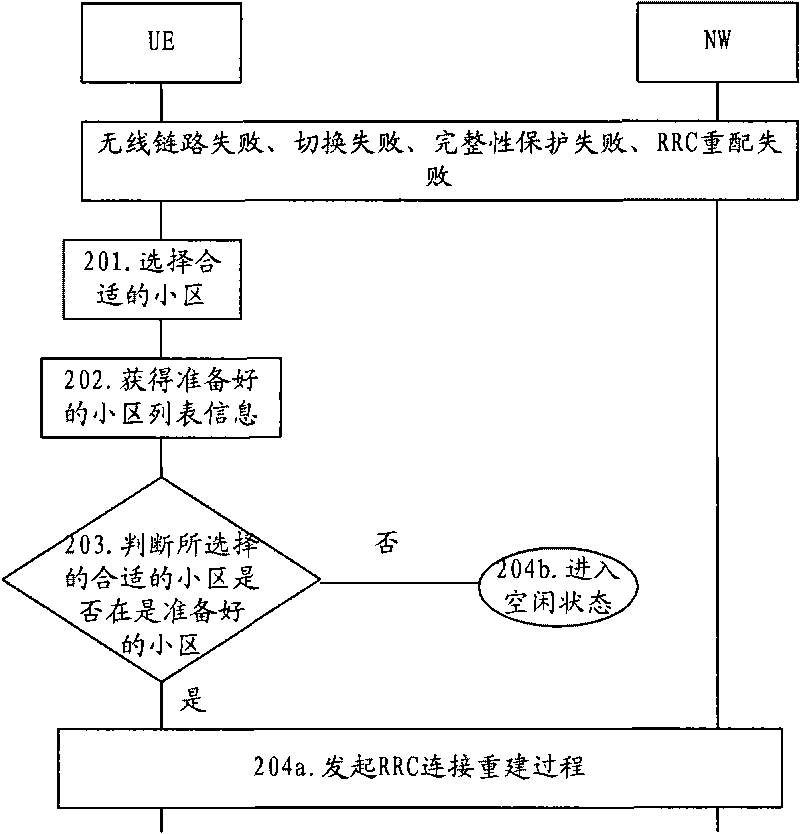
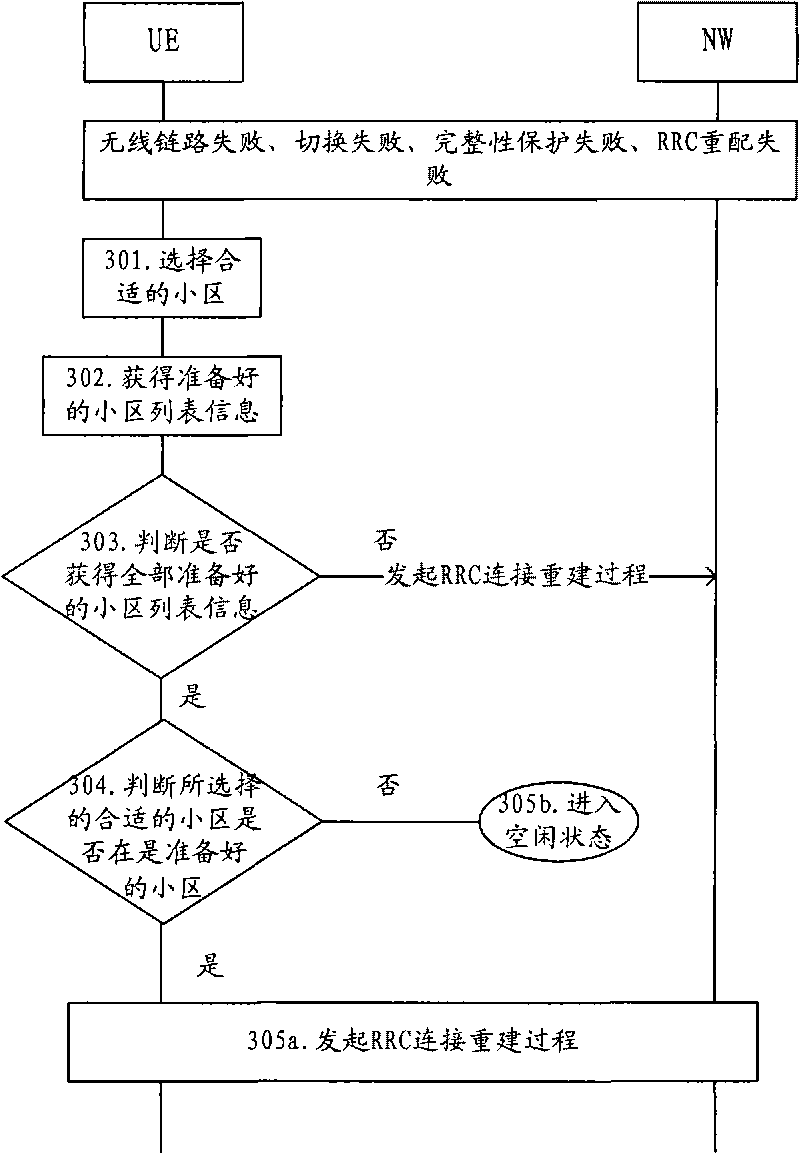
Method and device for RRC connection reestablishment
ActiveCN101754414AAvoid sendingReduced signaling processAssess restrictionConnection managementComputer networkWireless resources
The invention provides a method and a device for RRC connection reestablishment. The method is that a proper community is selected; the RRC connection reestablishment is initiated if the selected proper community is viewed as a prepared community; and idle state is returned if the selected proper community is viewed as an unprepared community. By adopting the method and the device for controlling the RRC connection reestablishment through wireless resources, the signaling flow is saved.
Owner:HUAWEI TECH CO LTD
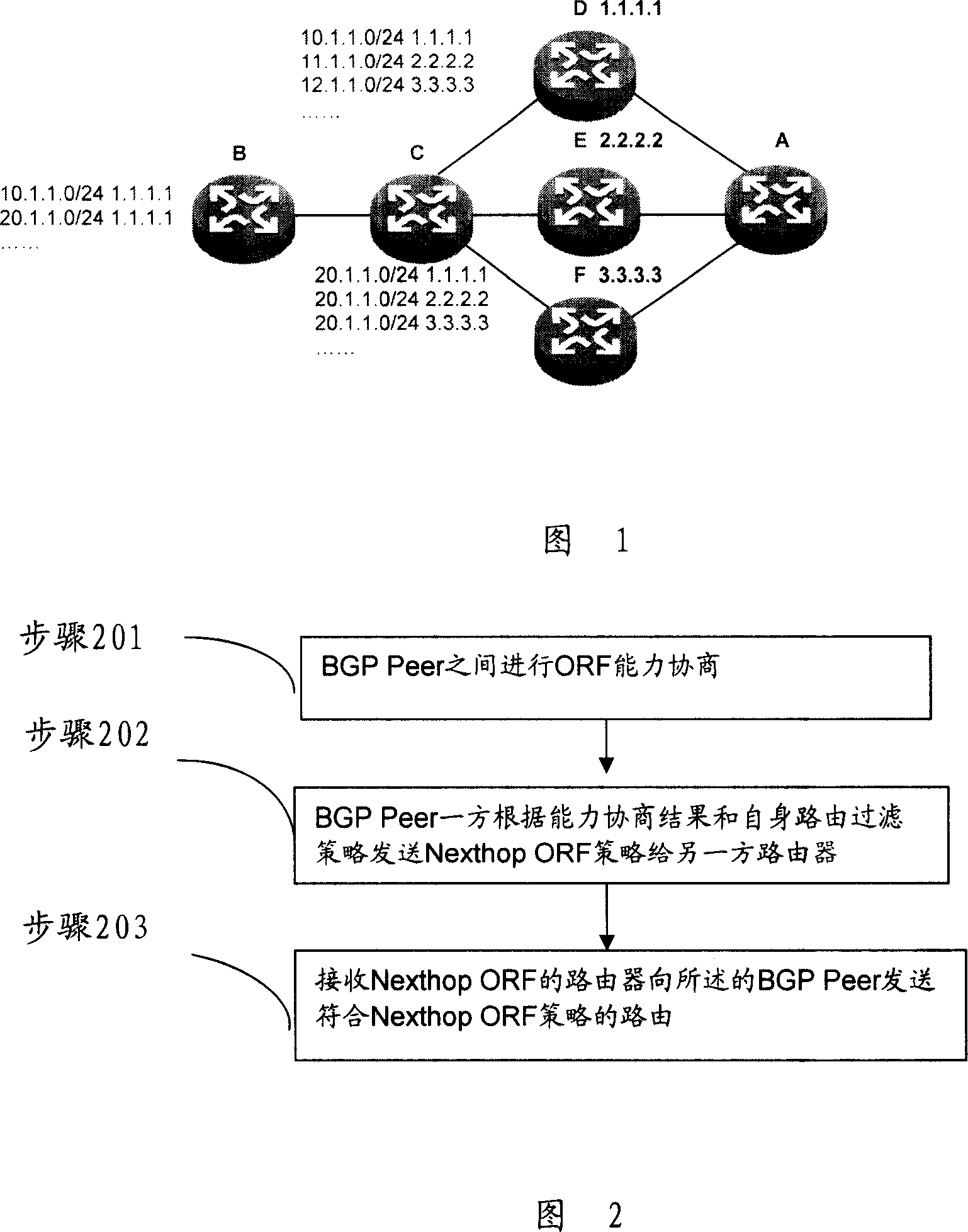
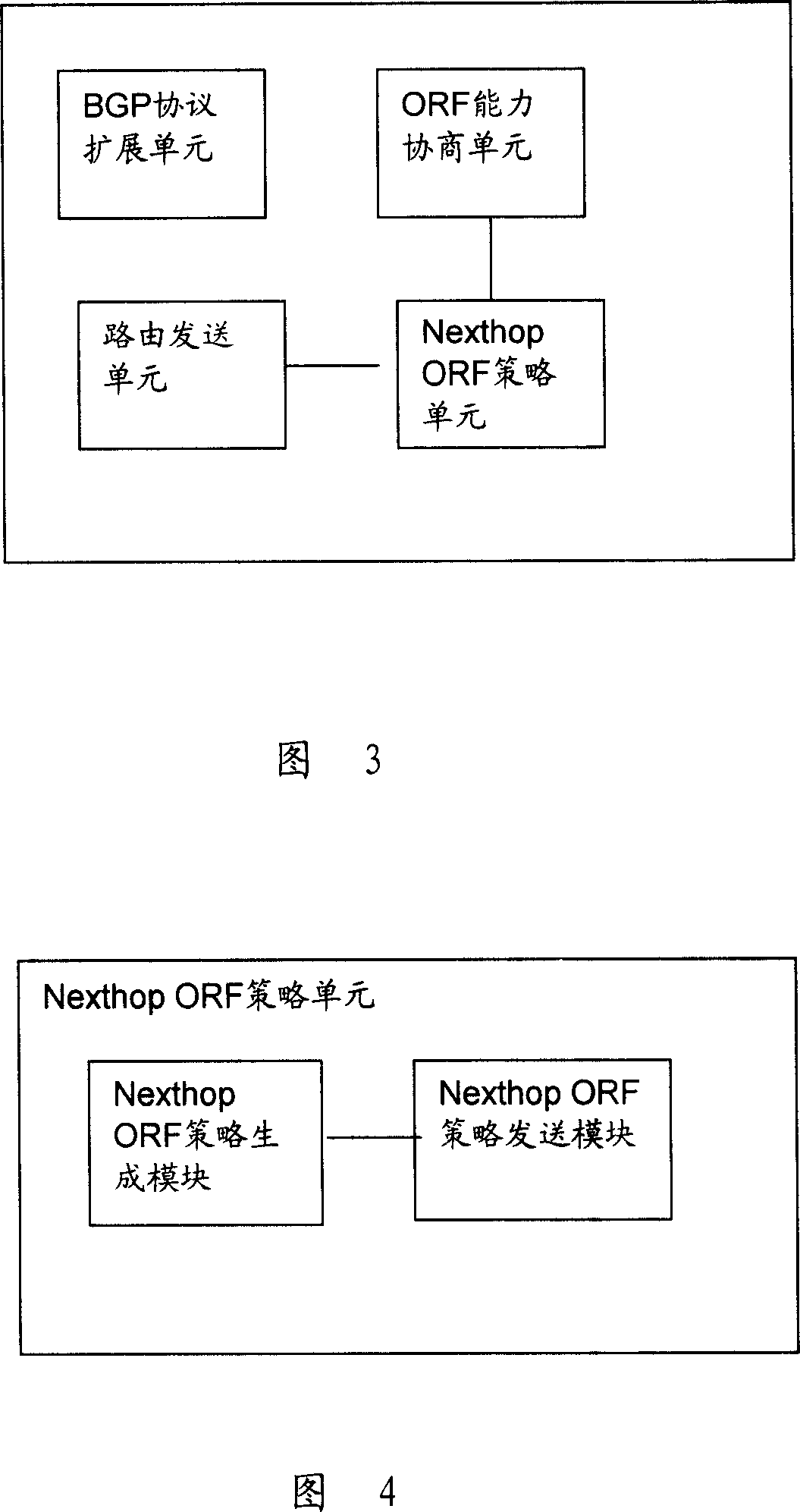
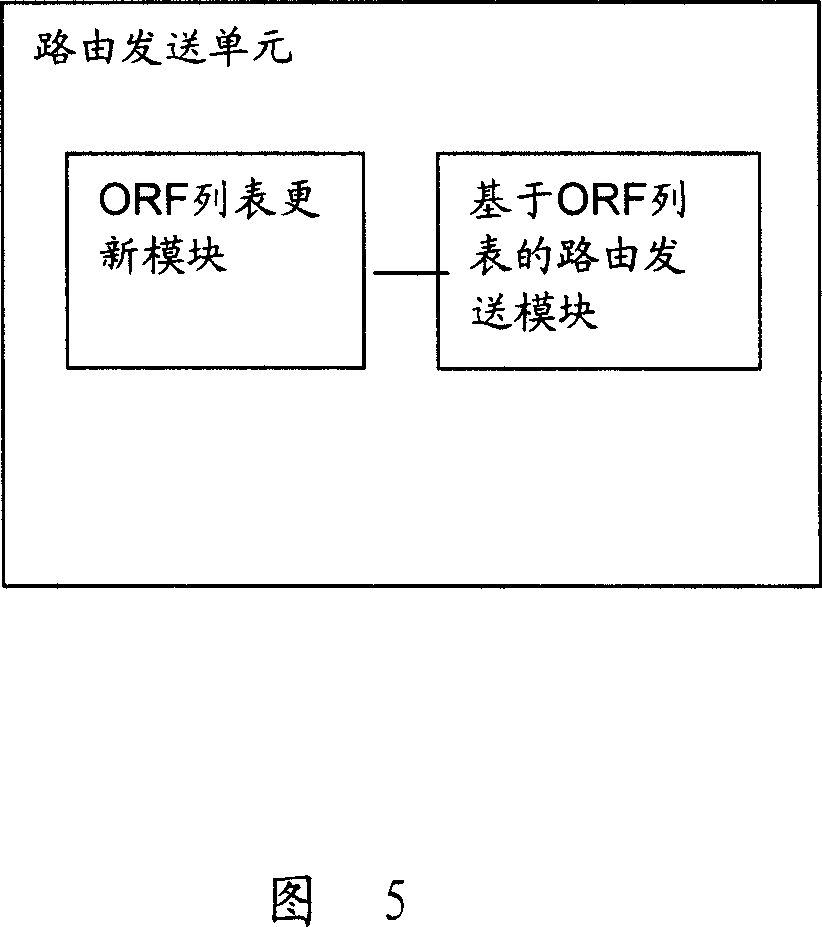
Method and device for routing filter based on BGP protocol
InactiveCN101155175ASimplify complexityIncrease in publishingData switching networksRoute filteringDistributed computing
The present invention relates to a method and an apparatus for filtering the out route based on BGP protocol. The kernel of the present invention is to carry the next hop outbound route filter information in BGP protocol, and to implement outbound route filter (ORF) ability negotiation between BGP Peer; then, to implement outbound filter processing according to the negotiatory result of ORF ability between the BGP Peer. By means of the present invention, the problem that the existing ORF can not filter according to the next hop of route, simplifying configuration greatly as well as complexity of BGP during the ORF processing.
Owner:HUAWEI TECH CO LTD
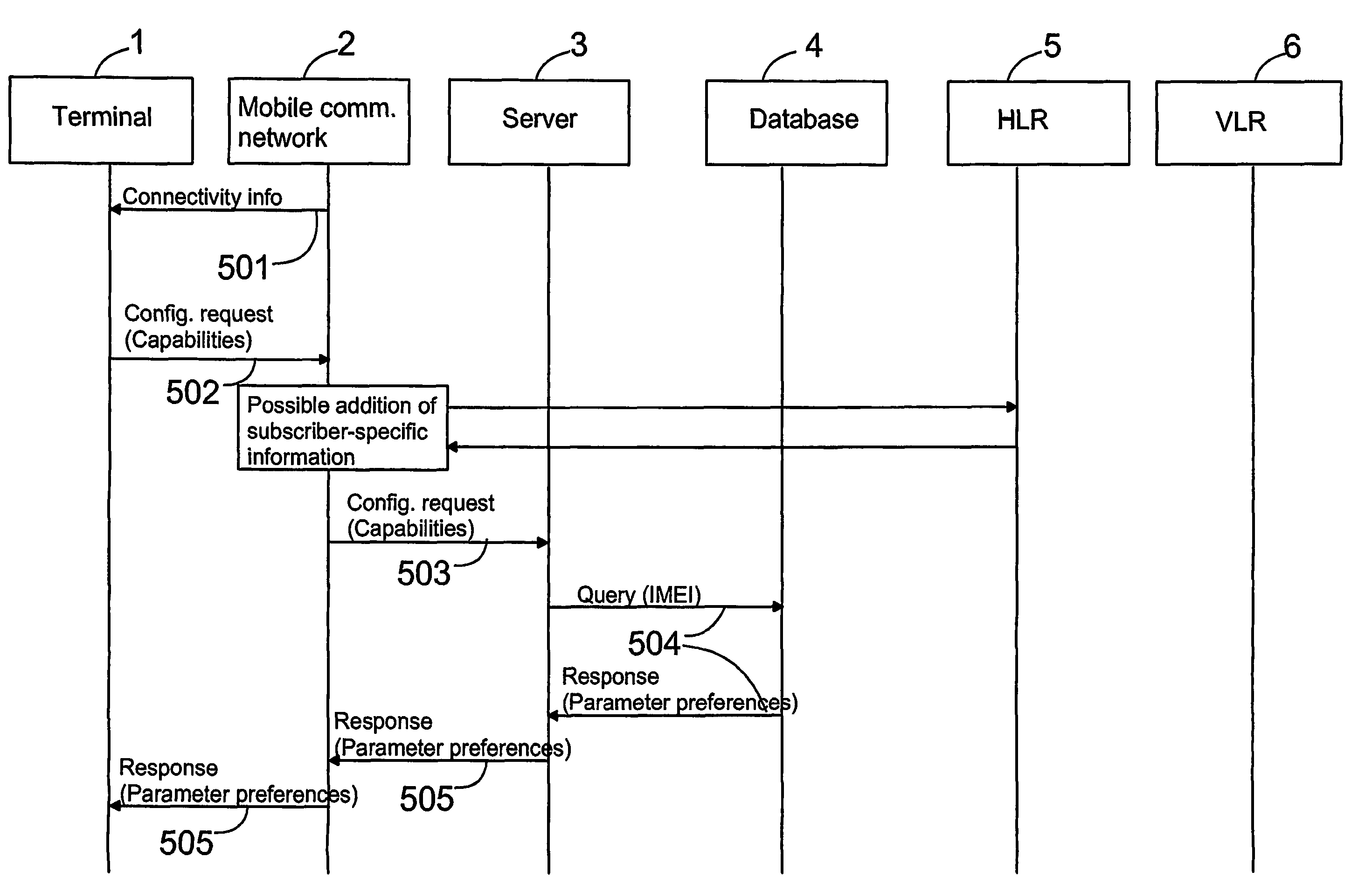
Configuration of a terminal
ActiveUS7818026B2Reduce deliveryAvoid sendingResonant long antennasDigital data information retrievalComputer terminalComputer software
The invention relates to a terminal to be used in a system, which comprises a device management server and a data transfer network for transmitting information used in association with configuration between the terminal and the device management server. The terminal comprises means for detecting change in the terminal capabilities, and means for transmitting information on the change in the terminal capabilities to the device management server. In addition, the invention relates to a system for transmitting information used in connection with the terminal configuration between the terminal and the device management server. Further, the invention relates to a method in the configuration of the terminal, to a method for providing configuration information to the terminal, as well as to a computer software product to be used in the terminal configuration.
Owner:NOKIA TECHNOLOGLES OY
Inland river hydrological and water administrative ship real-time location monitoring system and method
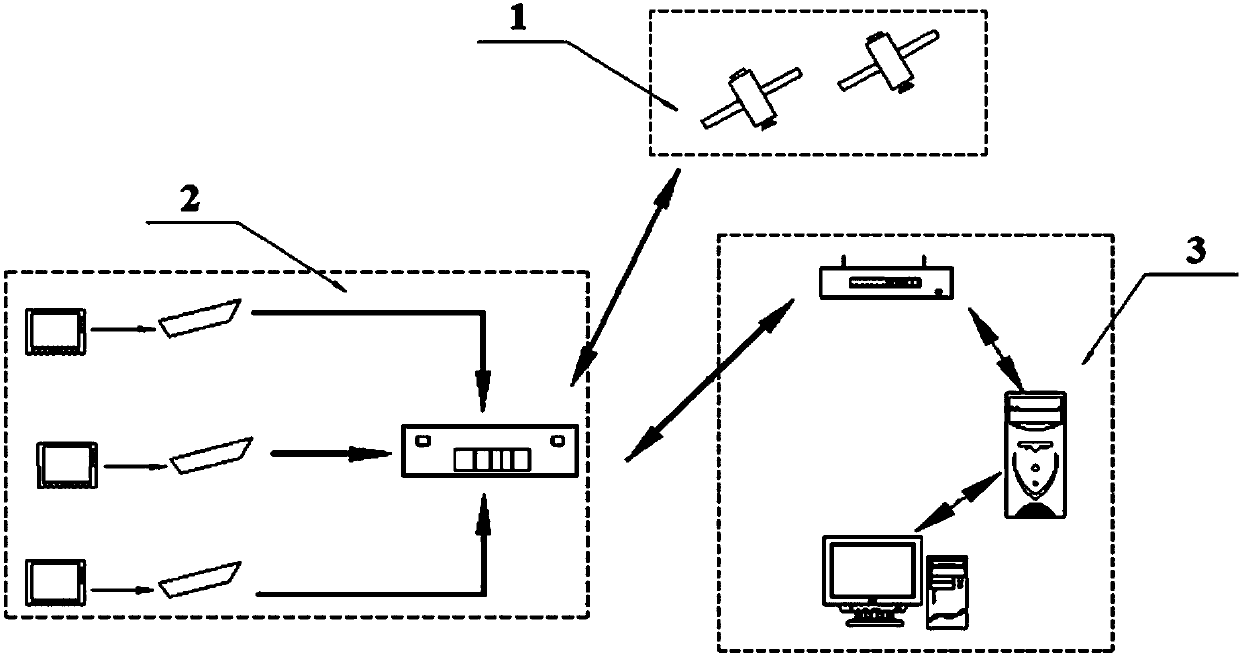
InactiveCN103778803AEfficient managementMaintain sand mining orderMarine craft traffic controlRiver sandDynamic monitoring
The invention discloses an inland river hydrological and water administrative ship real-time location monitoring system. The system comprises a satellite system (1), a terminal equipment system (2) and a background monitoring system (3). The real-time location monitoring system can realize real-time communication and location monitoring of the terminal equipment system (2) and the background monitoring system (3) through the satellite system (1). The invention further discloses an inland river hydrological and water administrative ship real-time location monitoring method. Through cooperation with an inland river sand excavation management method, the ideas that an early warning buffer zone with the width of 50 meters is established and the ship navigation line measurement allowable deviation range is displayed in two modes are put forward in the method for the first time, the early warning buffer zone and the line measurement allowable deviation range are displayed in a GIS visualized dynamic monitoring application platform of the background monitoring system (3), and the information recording precision can be measured in seconds. Through the inland river hydrological and water administrative ship real-time location monitoring system and method, the functions of locating and tracking, boundary violation alarm, monitoring and dispatching, yawing warning and trajectory analysis on monitored ships are achieved.
Owner:YELLOW RIVER INST OF HYDRAULIC RES YELLOW RIVER CONSERVANCY COMMISSION
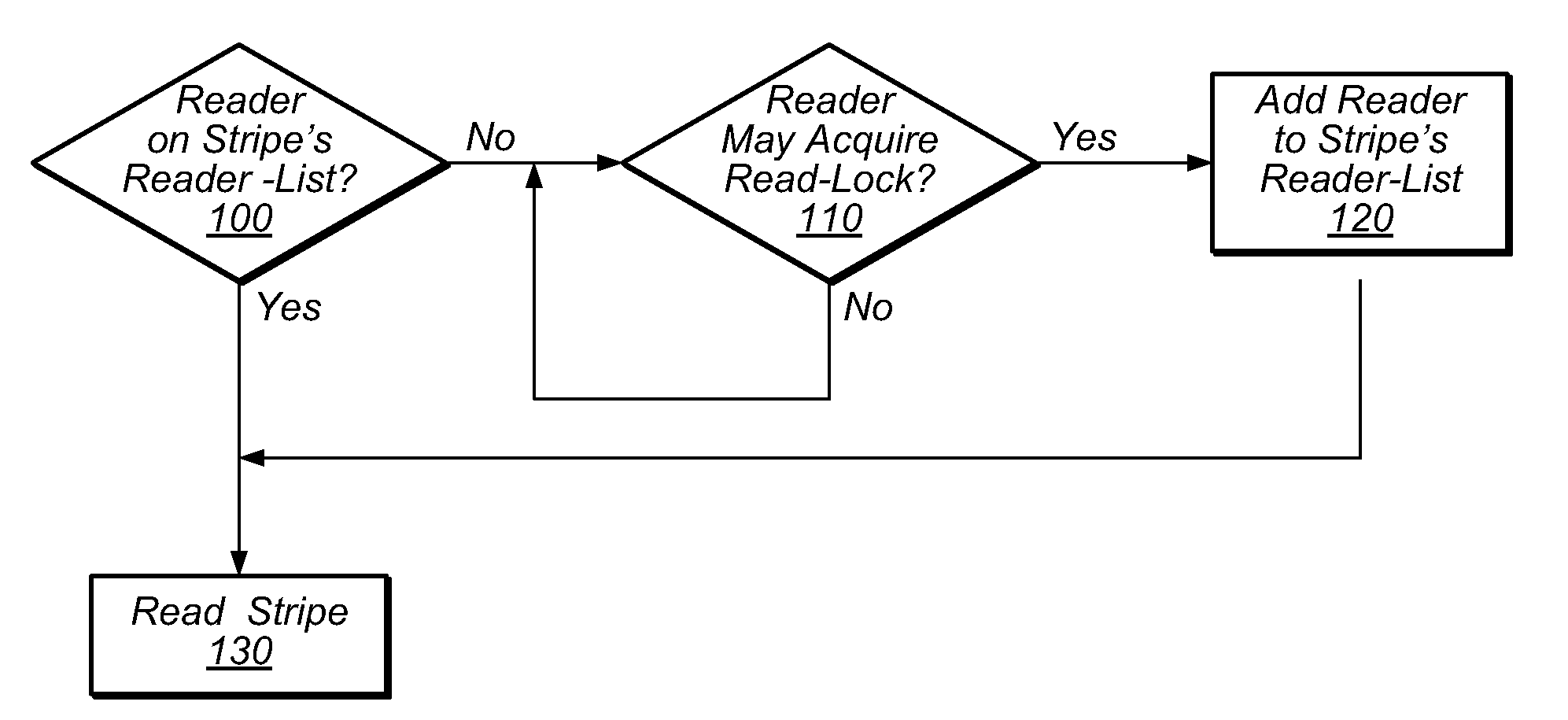
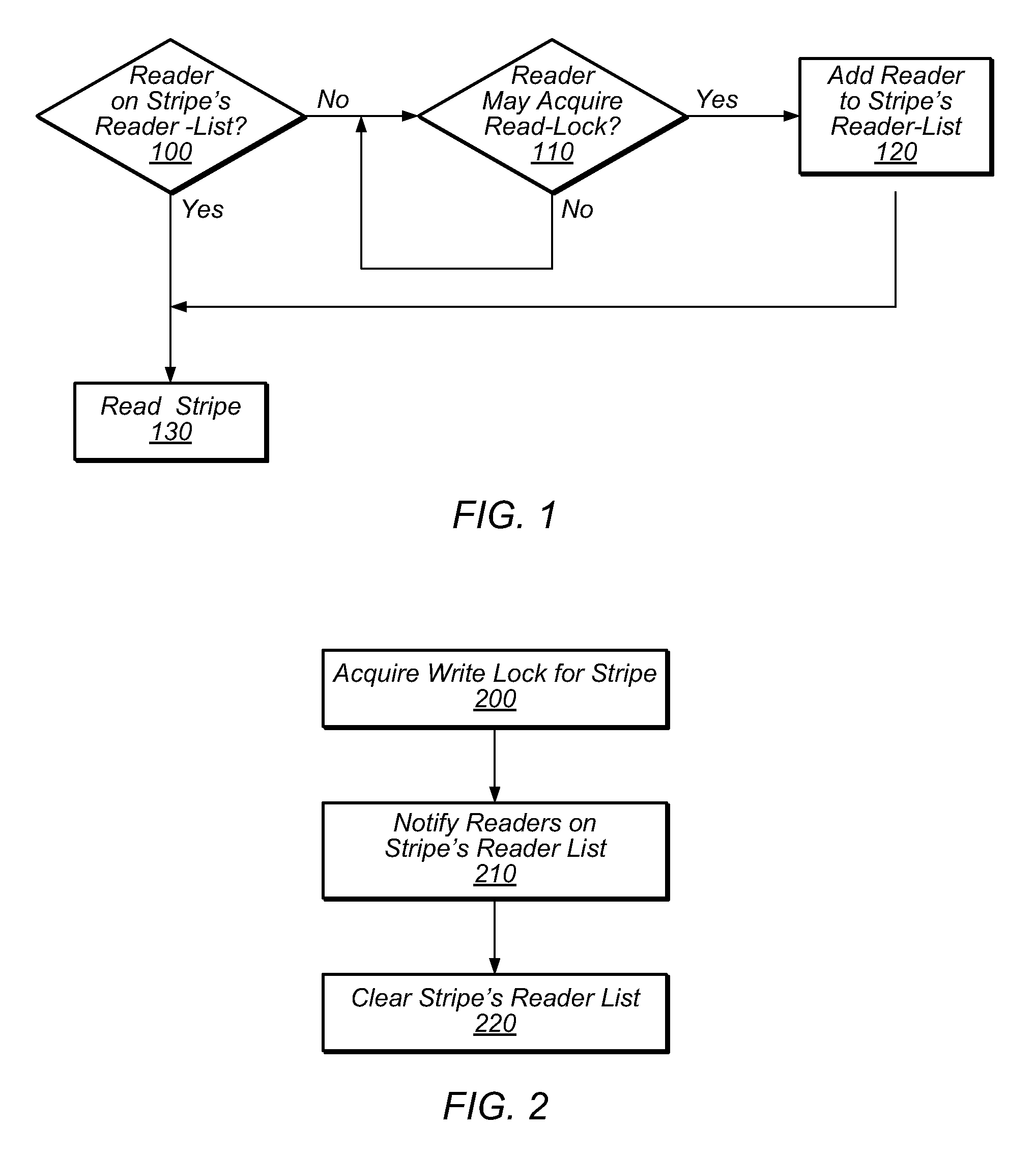
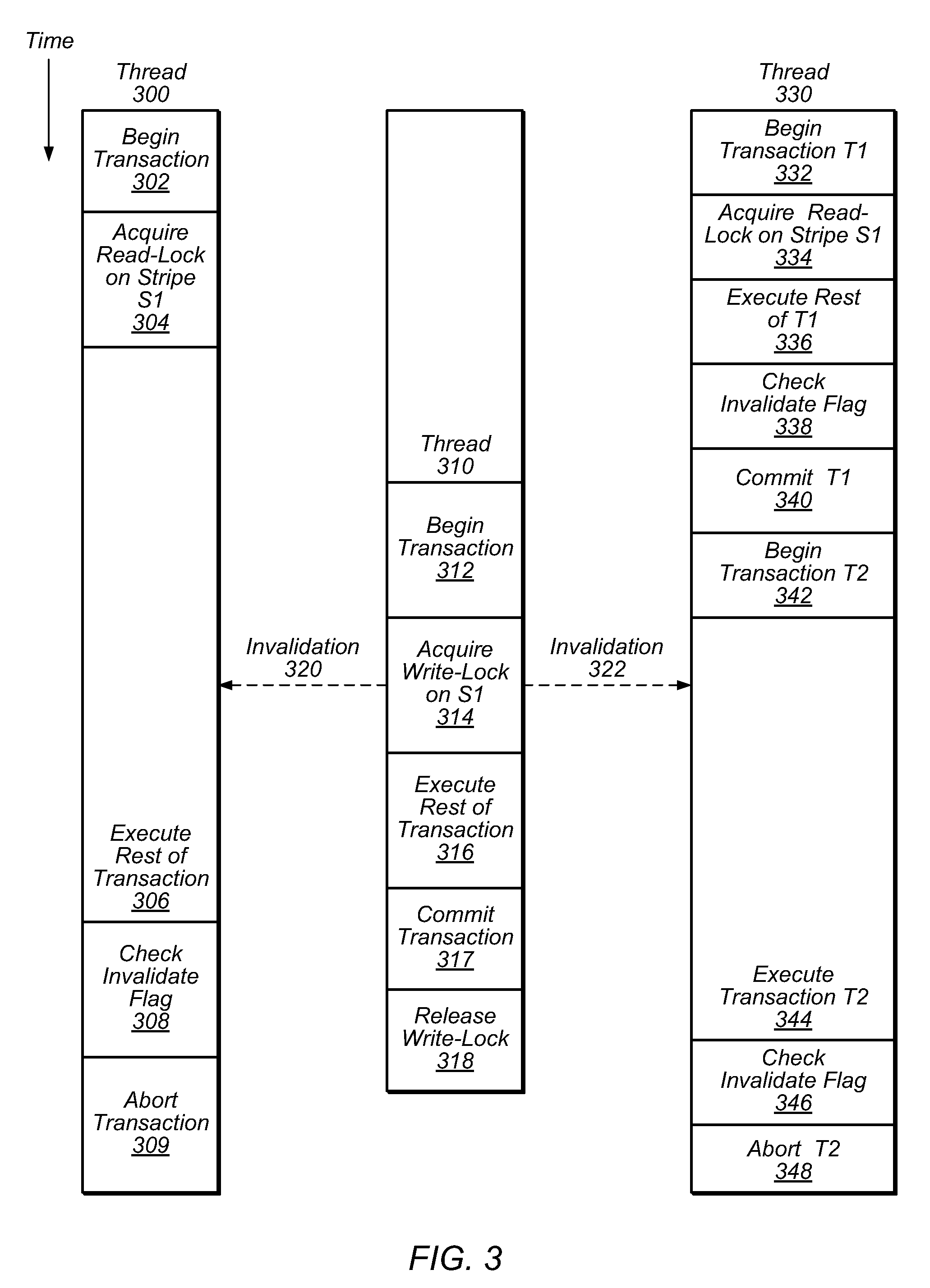
System and Method for Transactional Locking Using Reader-Lists
ActiveUS20100174875A1Avoid failureAvoid performanceProgram synchronisationMemory systemsMetadataShared memory
In traditional transactional locking systems, such as TLRW, threads may frequently update lock metadata, causing system performance degradation. A system and method for implementing transactional locking using reader-lists (TLRL) may associate a respective reader-list with each stripe of data in a shared memory system. Before reading a given stripe as part of a transaction, a thread may add itself to the stripe's reader-list, if the thread is not already on the reader-list. A thread may leave itself on a reader-list after finishing the transaction. Before a thread modifies a stripe, the modifying thread may acquire a write-lock for the stripe. The writer thread may indicate to each reader thread on the stripe's reader-list that if the reader thread is executing a transaction, the reader thread should abort. The indication may include setting an invalidation flag for the reader. The writer thread may clear the reader-list of a stripe it modified.
Owner:ORACLE INT CORP
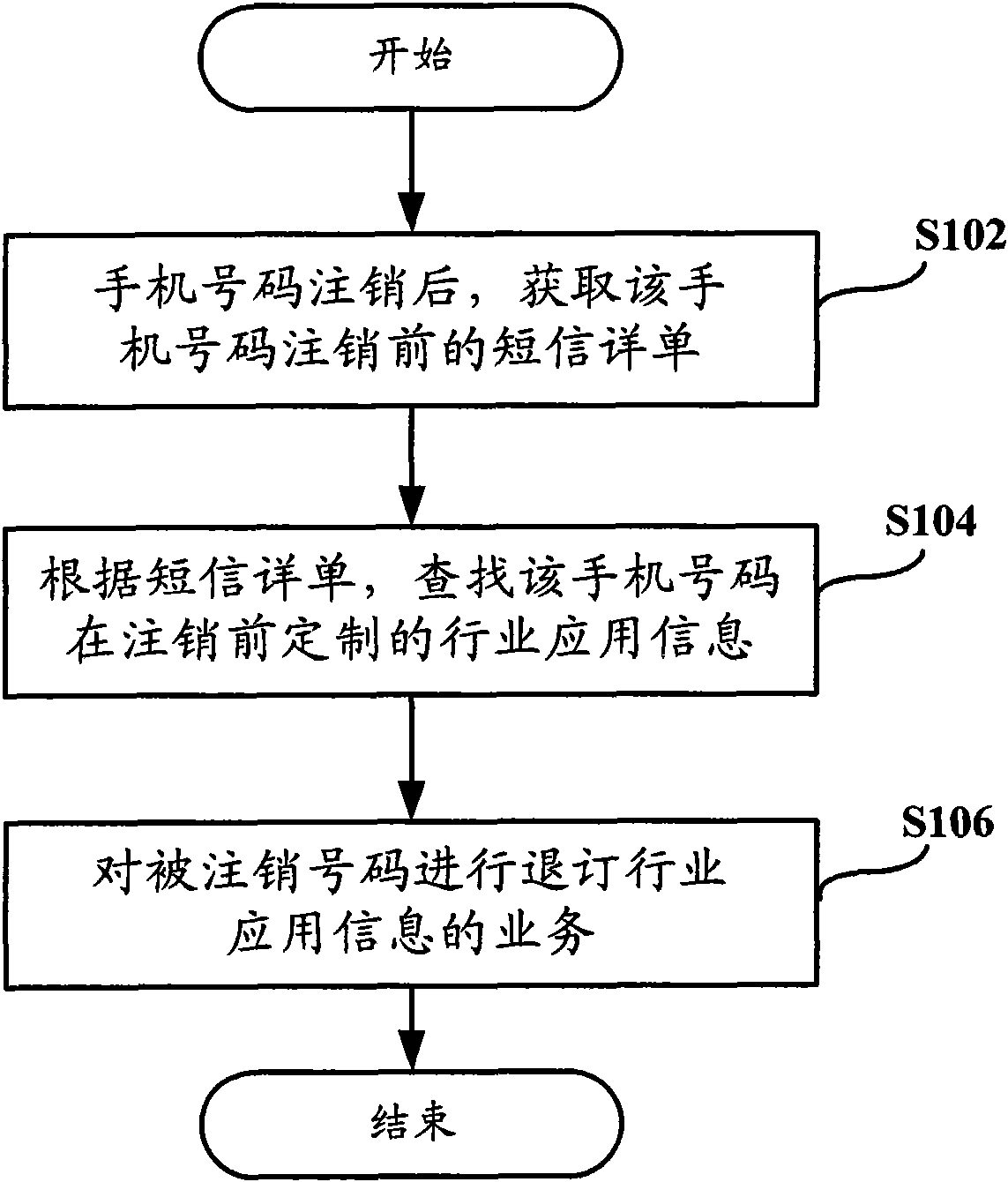
Spam message processing method, device and system
InactiveCN102036263AImprove user experienceReduce user complaintsWireless communicationText messagingMobile phone
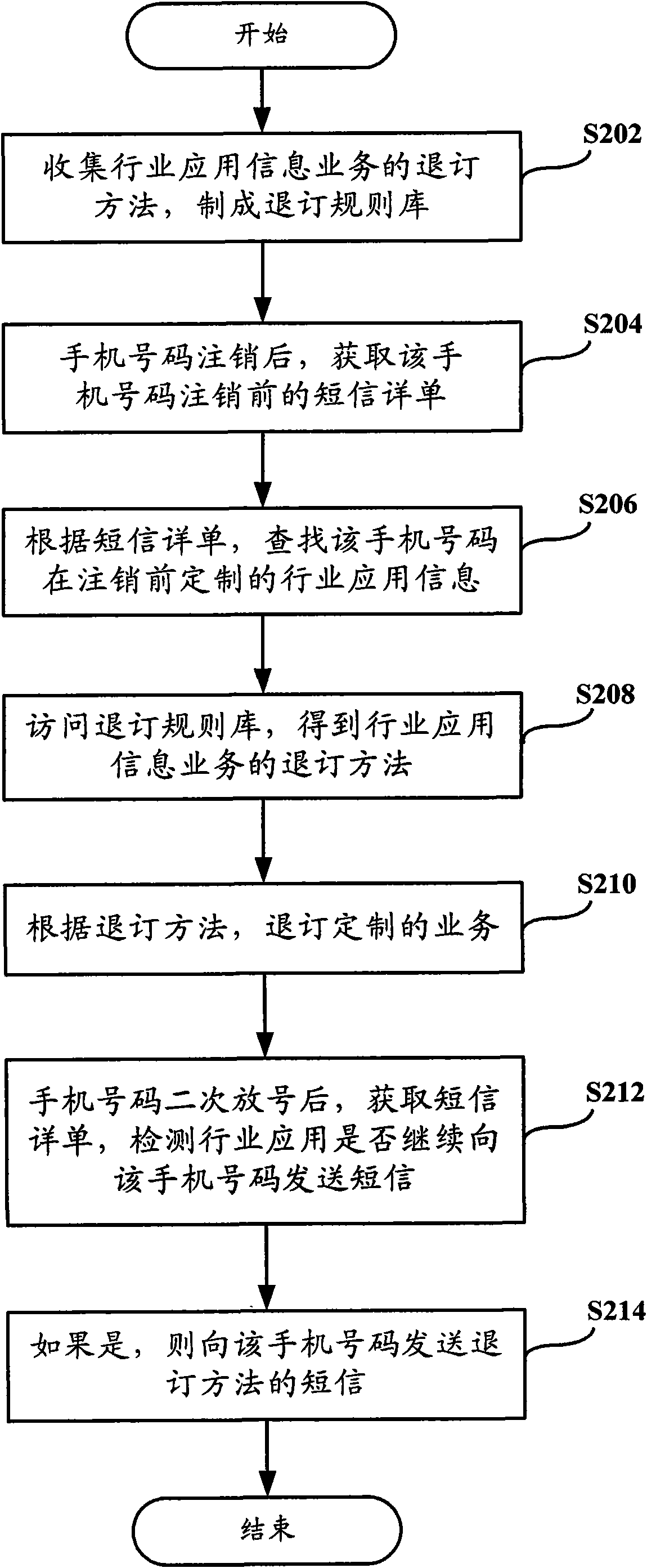
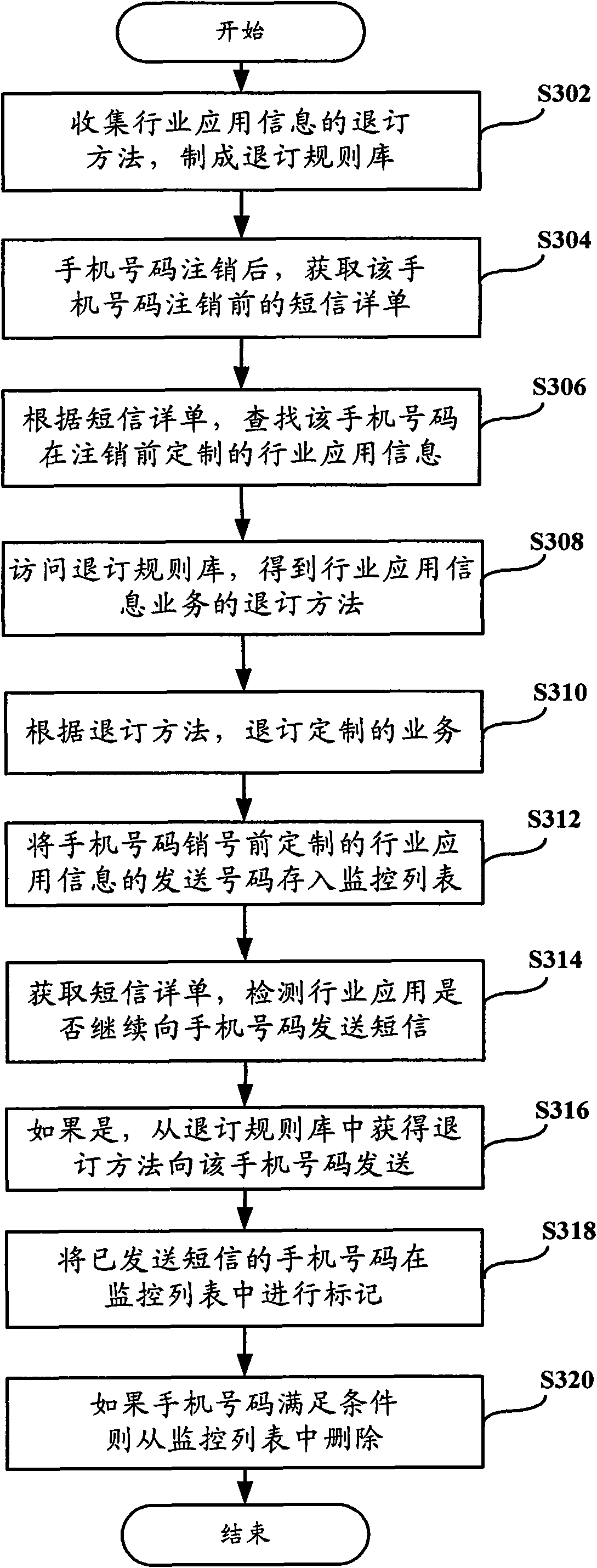
The invention provides a spam message processing method, device and system, aiming at overcoming the defect that a spam message is caused by cancelling of the number of a mobile terminal previously. The method comprises the steps: after the number of the mobile terminal is cancelled, acquiring a short message detail list before the mobile phone number is cancelled; according to the short message detail list, searching industrial application information subscribed by the number of the mobile terminal before being cancelled; and carrying out an industrial application information subscription cancellation service on the cancelled number. Preprocessing can be carried out on the spam message probably caused before or in the event, thus avoiding that spam message is sent to the number of the mobile terminal subscribing for the second time, improving user experience and reducing user complaint.
Owner:中国移动通信集团甘肃有限公司
3G (The Third Generation Telecommunication)-based method and equipment for guaranteeing service quality in real-time transmission service
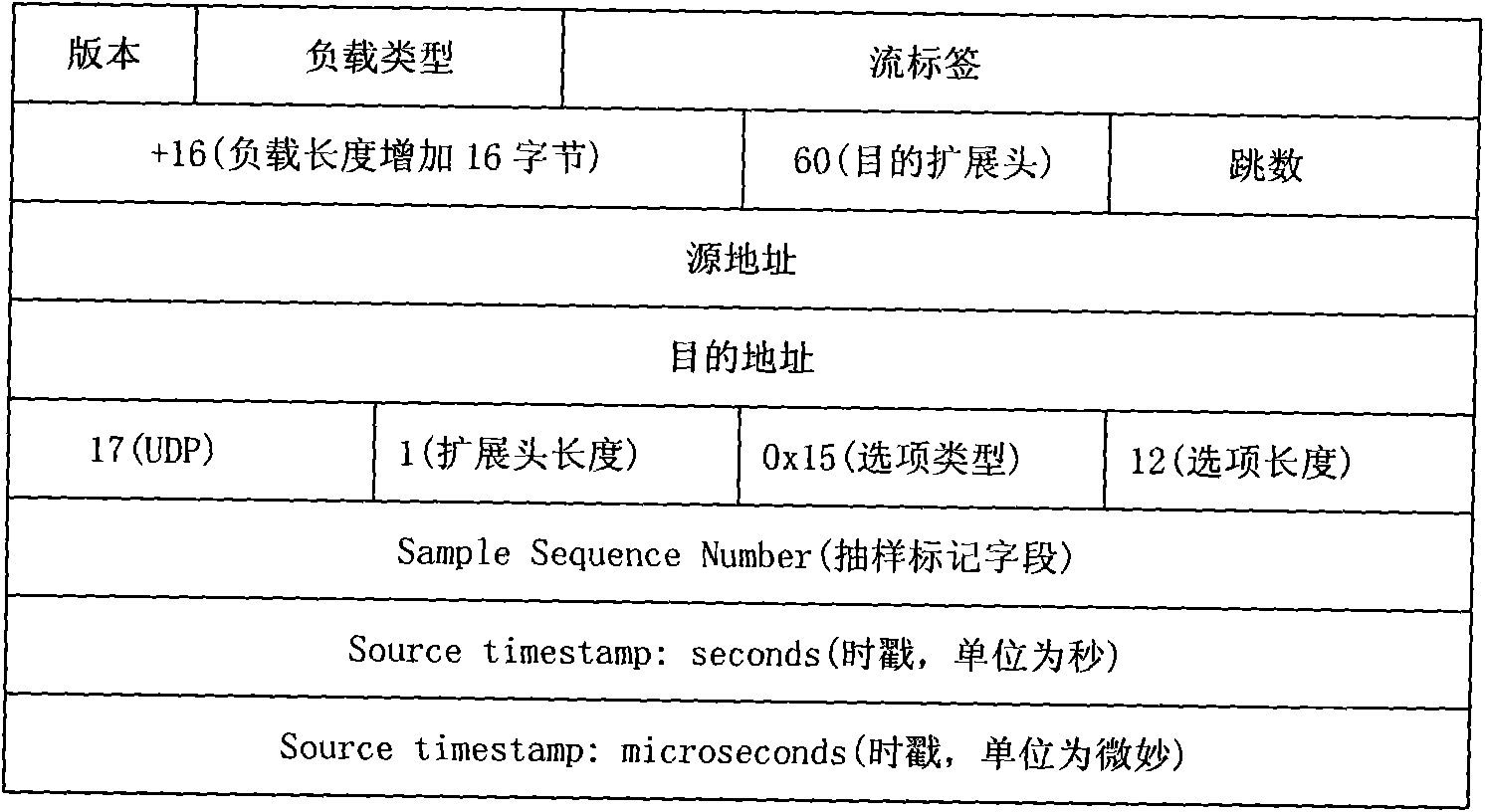
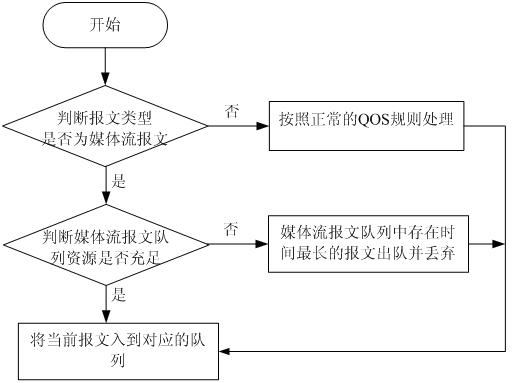
ActiveCN102170663ASolve the problem of excessive delayAvoid sendingNetwork traffic/resource managementQuality of serviceTimestamp
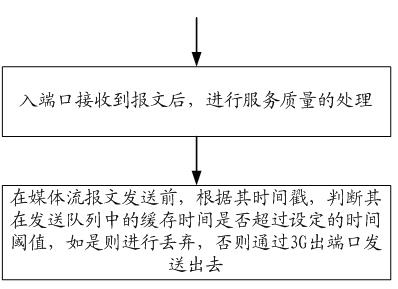
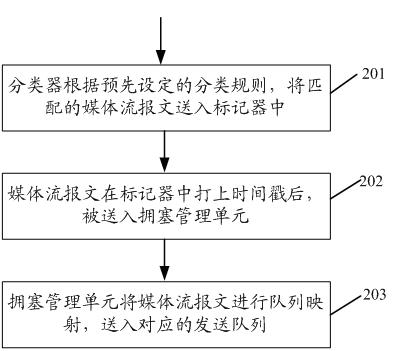
The invention discloses a 3G (The Third Generation Telecommunication)-based method and equipment for guaranteeing service quality in real-time transmission service. The method comprises the following steps: after an input port receives a message, carrying out service quality processing and merging into a queue; and before a media stream message is transmitted, according to a timestamp, judging whether the buffer time of the media stream message in a transmit queue is over a preset time threshold or not, if so, discarding media stream message, otherwise, transmitting the media stream message out through the destination port. The invention also discloses the 3G-based equipment for guaranteeing the service quality in real-time transmission service. The 3G-based method and the equipment for guaranteeing the service quality in the real-time transmission service can fully utilize network bandwidth to transmit the effective media stream message when the network bandwidth is fluctuated, and the condition that invalid media stream message is transmitted can be avoided.
Owner:MAIPU COMM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com