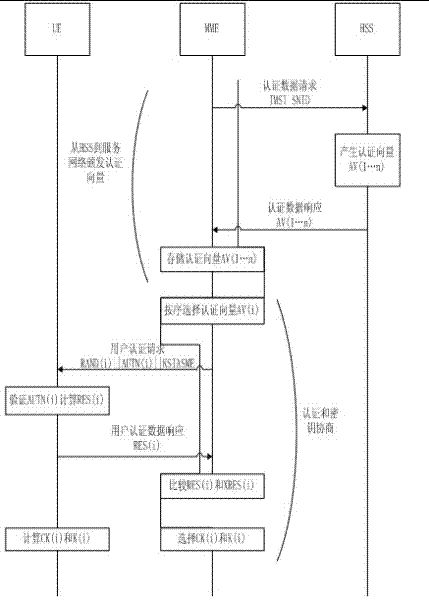
LTE authentication method
A technology of identity authentication and authentication request, which is applied in the field of authentication in LTE, and can solve problems such as loss and unrecoverable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
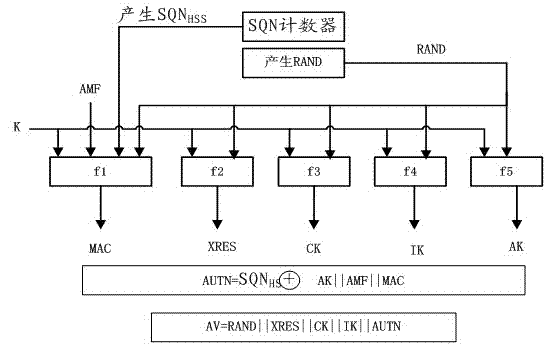
[0044] Embodiment 2, the generation process of authentication vector AV in LTE:
[0045] see image 3 , UE and HSS each maintain a counter, and the SQN generated by the counter MS and SQN HSS The initial value is 0. After HSS receives the authentication request, it generates random numbers RAND and SQN HSS . f in the figure 1 and f 2 is the authentication function, f 3 , f 4 , f 5 , S 10 function for key generation. Authentication token AUTN=SQN AK ||AMF ||MAC, authentication vector AV=(RAND ||XRES || KASME||AUTN), AK= f 5 (RAND, K), MAC = f 1 (SQN HSS ||RAND||AMF, K), XRES=f 2 (RAND, K), CK = f 3 (RAND, K), IK = f 4 (RAND, K), key K ASME The algorithm S is generated from the key by CK, IK and the service network number 10 get. (where "||" represents the concatenation of symbolic messages, " " identifies the XOR operator. f 1 -- f 5 , S 10 from the AKA protocol)
Embodiment 3
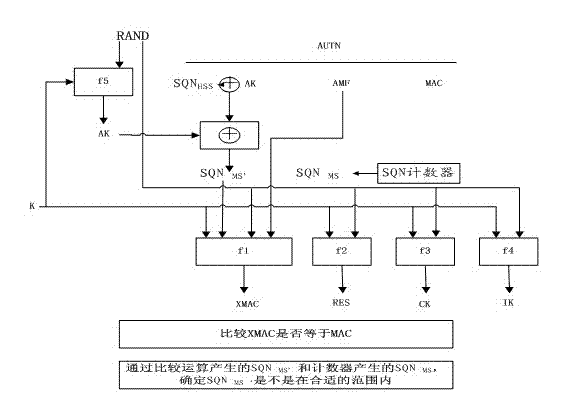
[0046] Embodiment 3, in LTE, UE's authentication function
[0047] see Figure 4 , after the UE receives the user authentication request b, it calculates the SQN MS′ After summing the SQN generated by the counter in the UE MS Compare and judge SQN MS′ Is it within the appropriate range. Among them, XMAC= (SQN|| RAND|| AMF, K), and the operation process of other parameters is the same as image 3 The operation process of each parameter in is the same. The UE will compare whether the XMAC and the MAC are equal, and will also verify whether the AMF separation flag is legal.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com