Patents
Literature
58 results about "Paper data storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Paper data storage refers to the use of paper as a data storage device. This includes writing, illustrating, and the use of data that can be interpreted by a machine or is the result of the functioning of a machine. A defining feature of paper data storage is the ability of humans to produce it with only simple tools and interpret it visually.
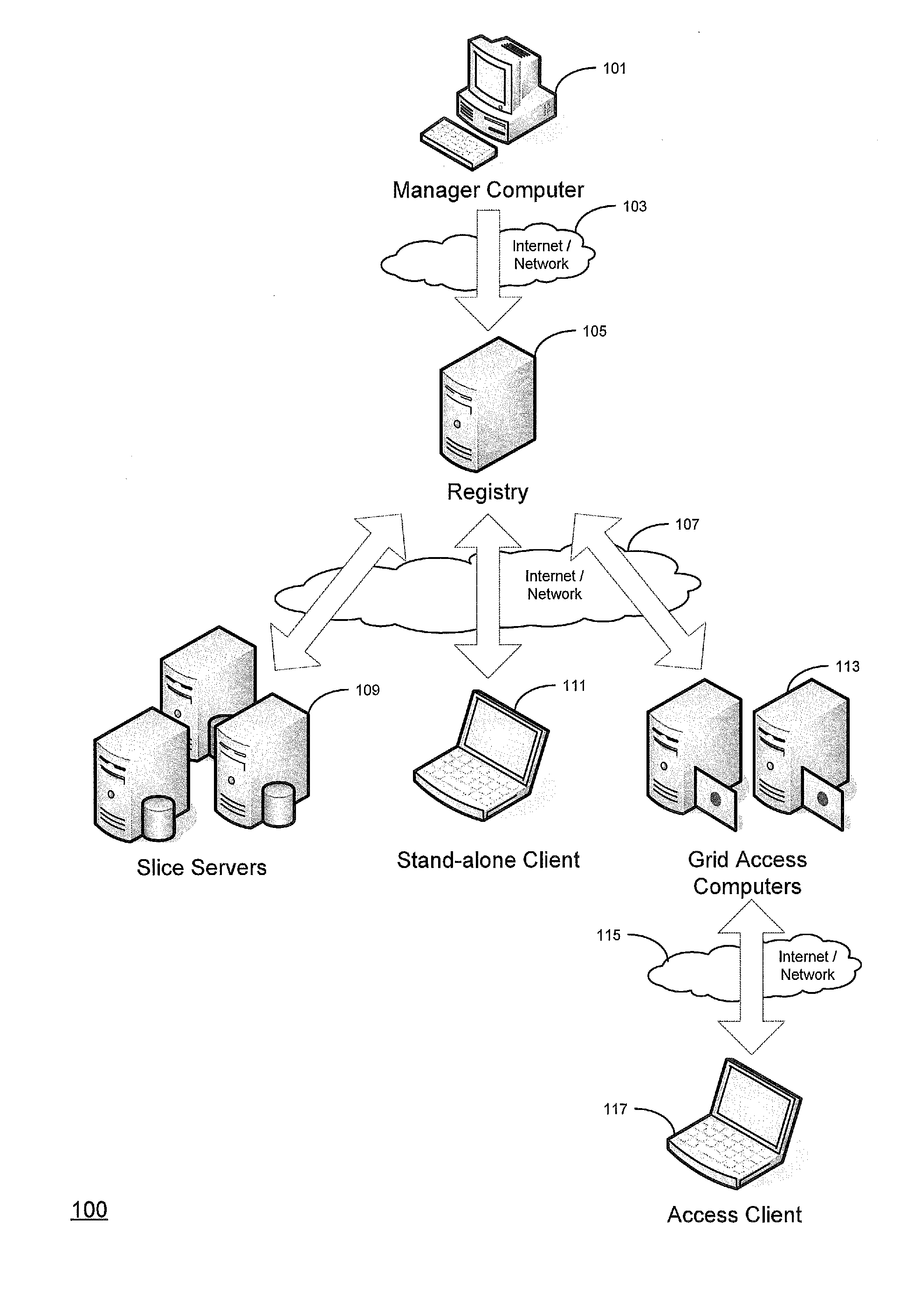
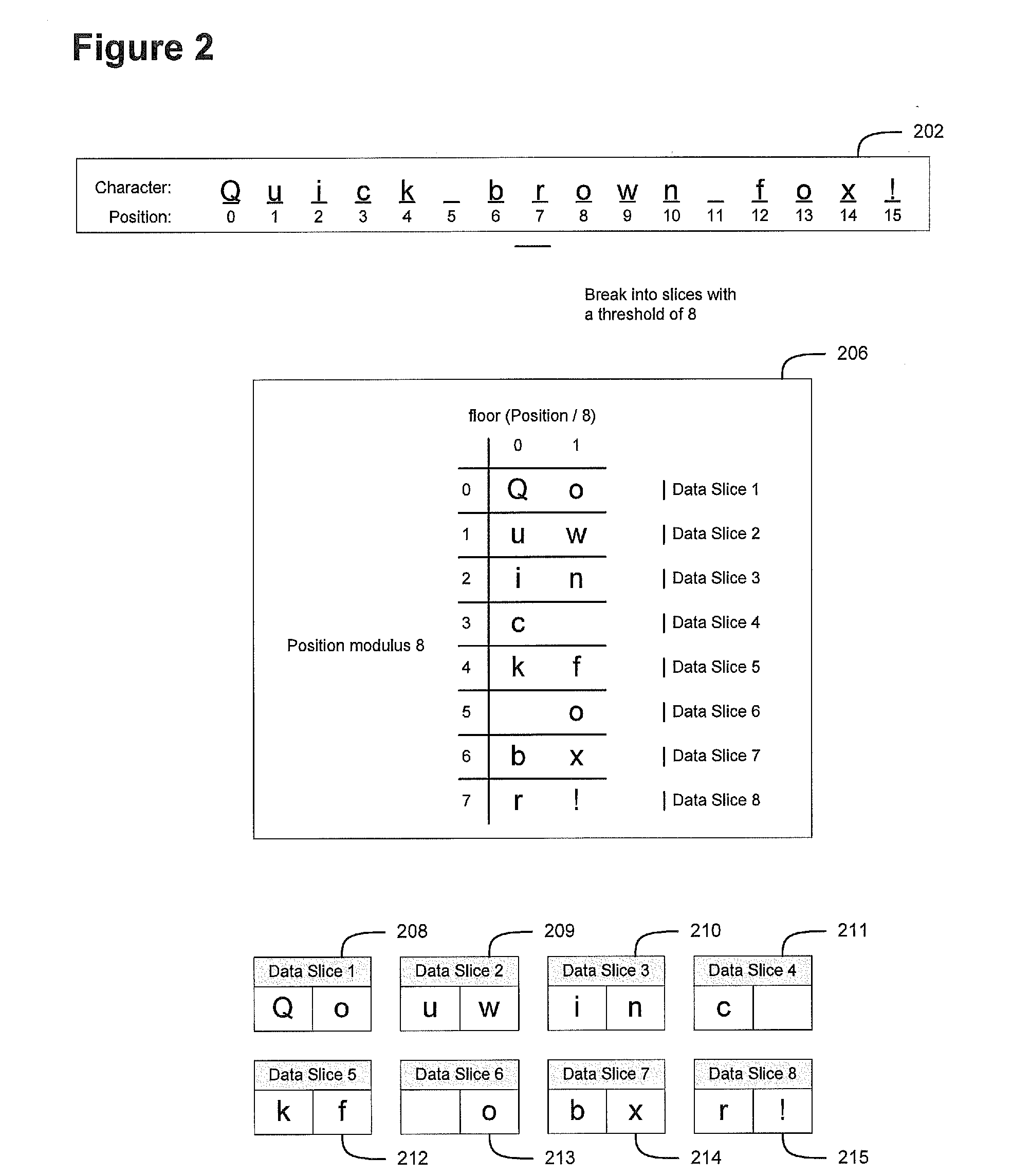
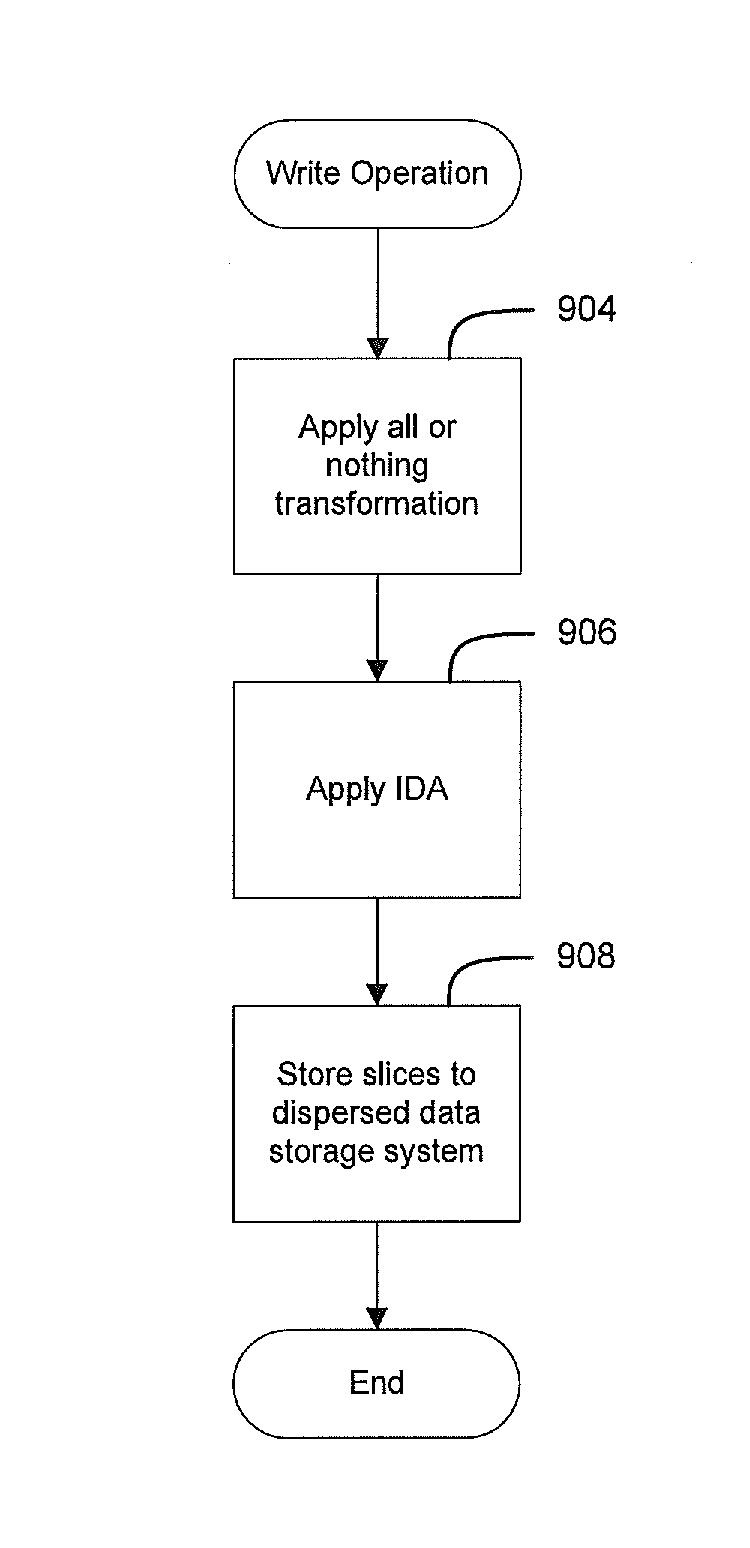
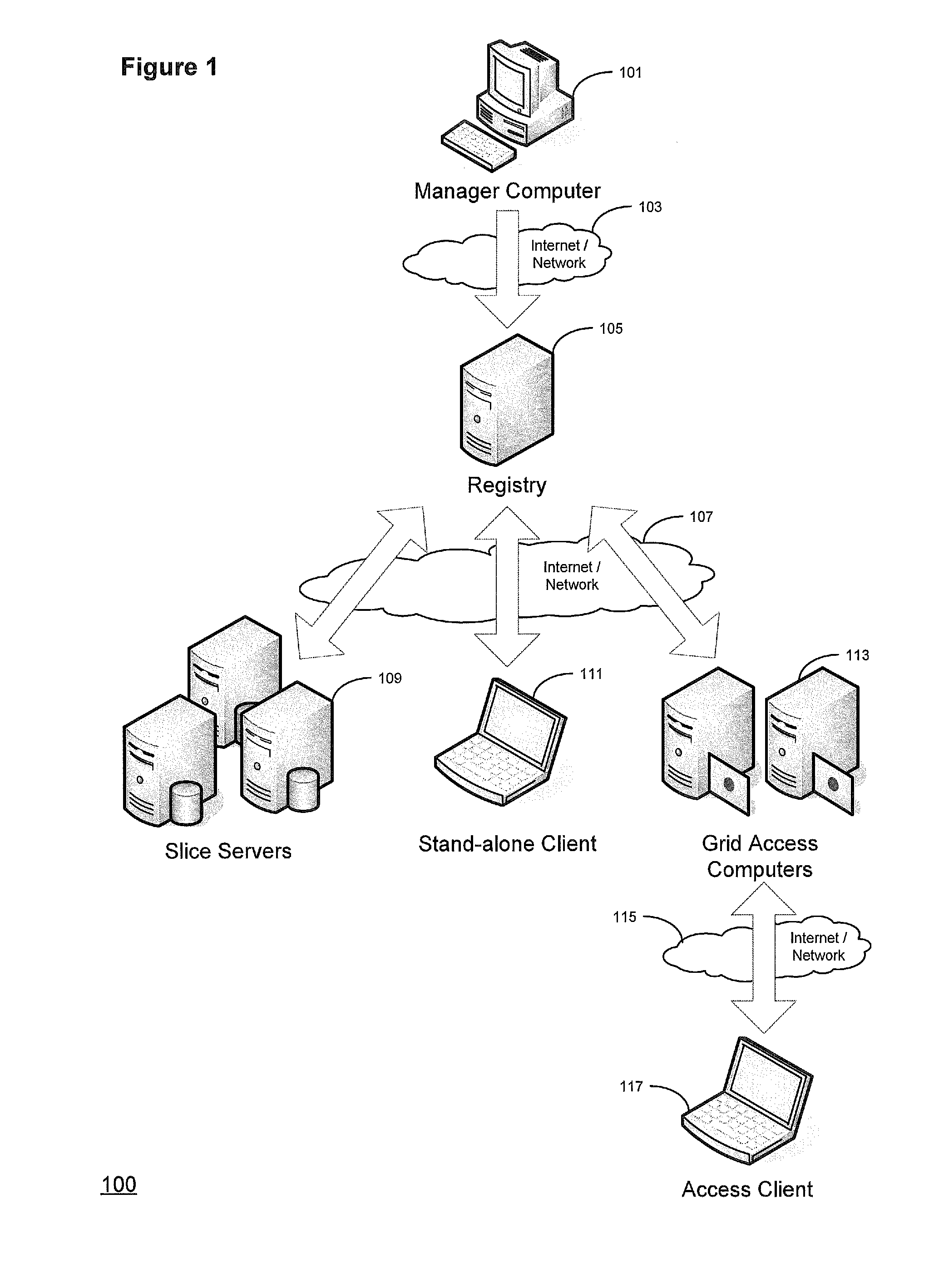
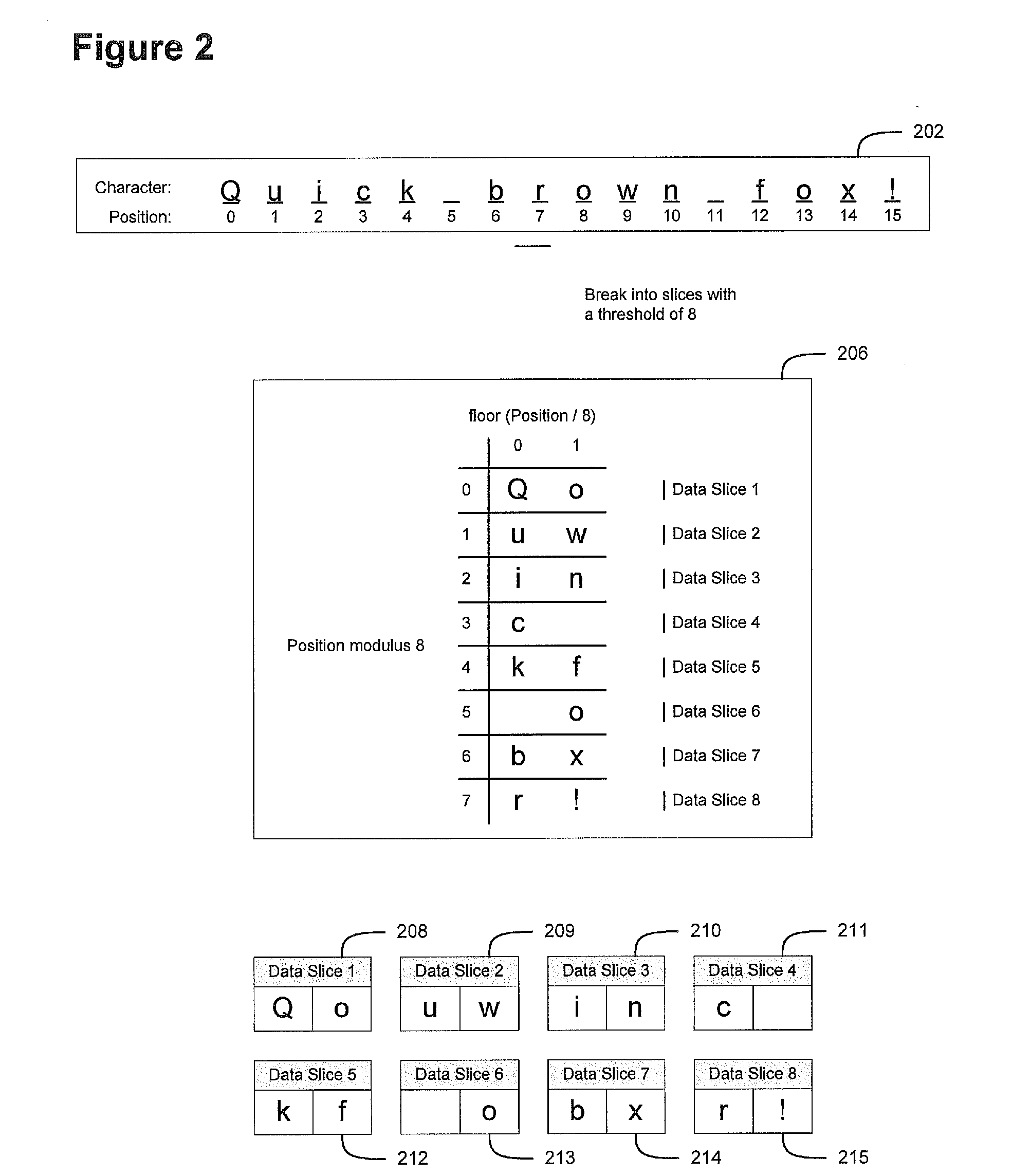
Efficient and secure data storage utilizing a dispersed data storage system
ActiveUS20100268966A1Efficient implementationReduce the amount of solutionUnauthorized memory use protectionHardware monitoringPaper data storageData segment
A method of securely storing data to a dispersed data storage system is disclosed. A data segment is arranged along the columns or rows of an appropriately sized matrix. Data slices are then created based on either the columns or the rows so that no consecutive data is stored in a data slice. Each data slice is then stored in a separate storage node.
Owner:PURE STORAGE
Secure data storage for protecting digital content
InactiveUS8452988B2The implementation process is simpleConvenient for userKey distribution for secure communicationUnauthorized memory use protectionDigital dataPaper data storage
Owner:WANG MICHAEL SUJUE
Method, system, apparatus, and computer-readable medium for provisioning space in a data storage system
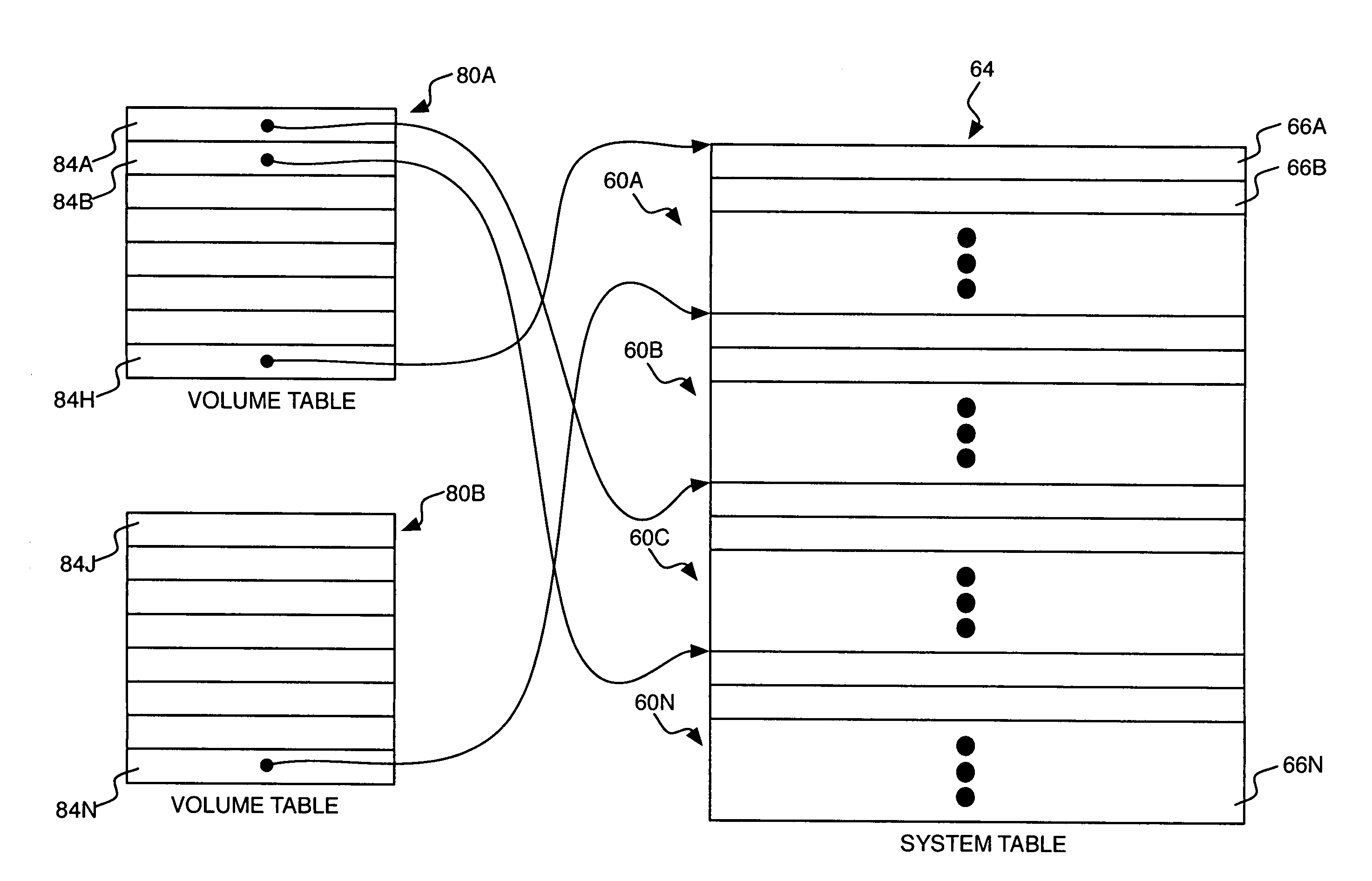
ActiveUS7536529B1Minimizes problemDifficult to allocateMemory architecture accessing/allocationMemory systemsPaper data storagePhysical space
A method, system, apparatus, and computer-readable medium are provided for dynamically provisioning available space in a data storage system without having to configure partitions at system startup. According to one method, a system table is maintained that includes entries corresponding to provisions within the available physical capacity of a data storage system. A volume table is also maintained that includes entries corresponding to territories within a logical data storage volume. When a data write operation is requested, a determination is made as to whether physical space has been allocated for the territory in the volume that is to be written. If physical space has not yet been allocated, the necessary physical space is allocated for the territory within the logical volume that is to receive the written data by creating a pointer to an available entry in the system table in an entry in the volume table corresponding to the territory to be written. Once the physical space has been allocated, the requested write operation is performed. Metadata is written to disk in a fashion that makes it easy to recover from system crashes and unclean shutdowns.
Owner:AMZETTA TECH LLC
Data storage method, inquiry method and system
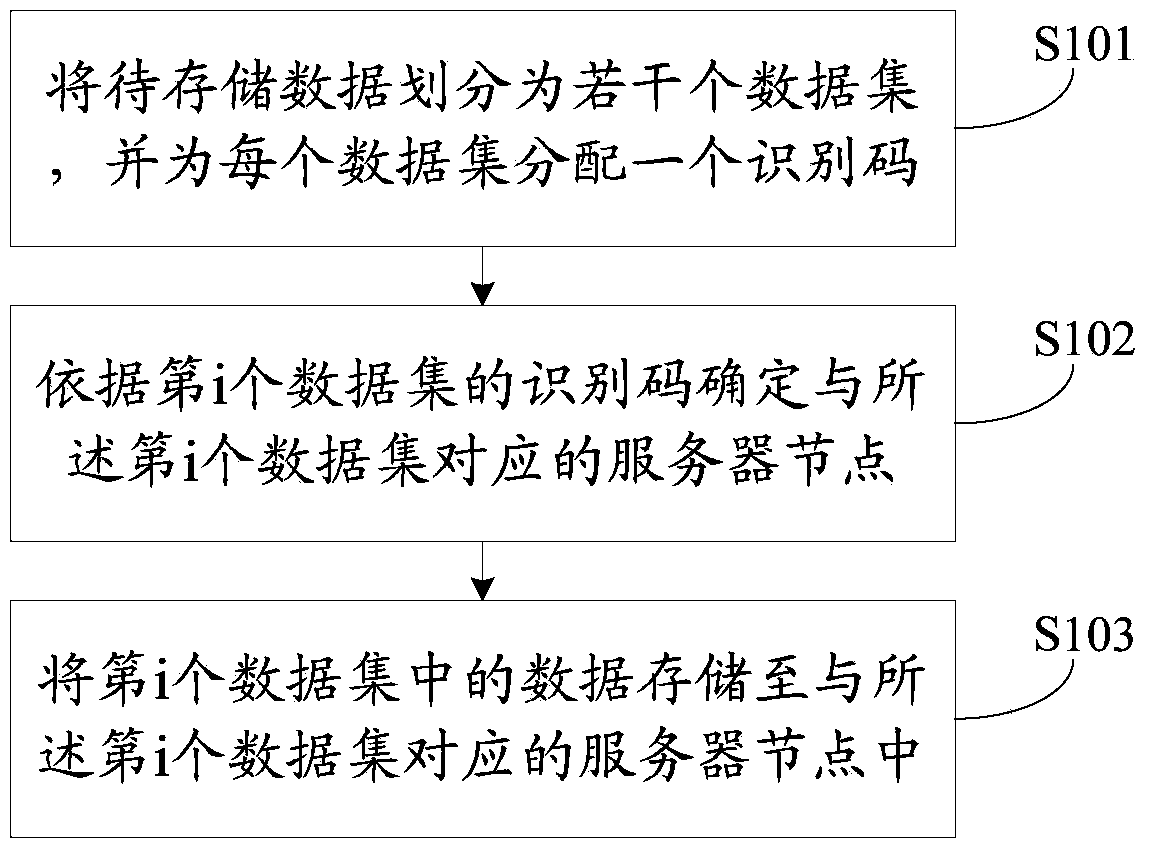
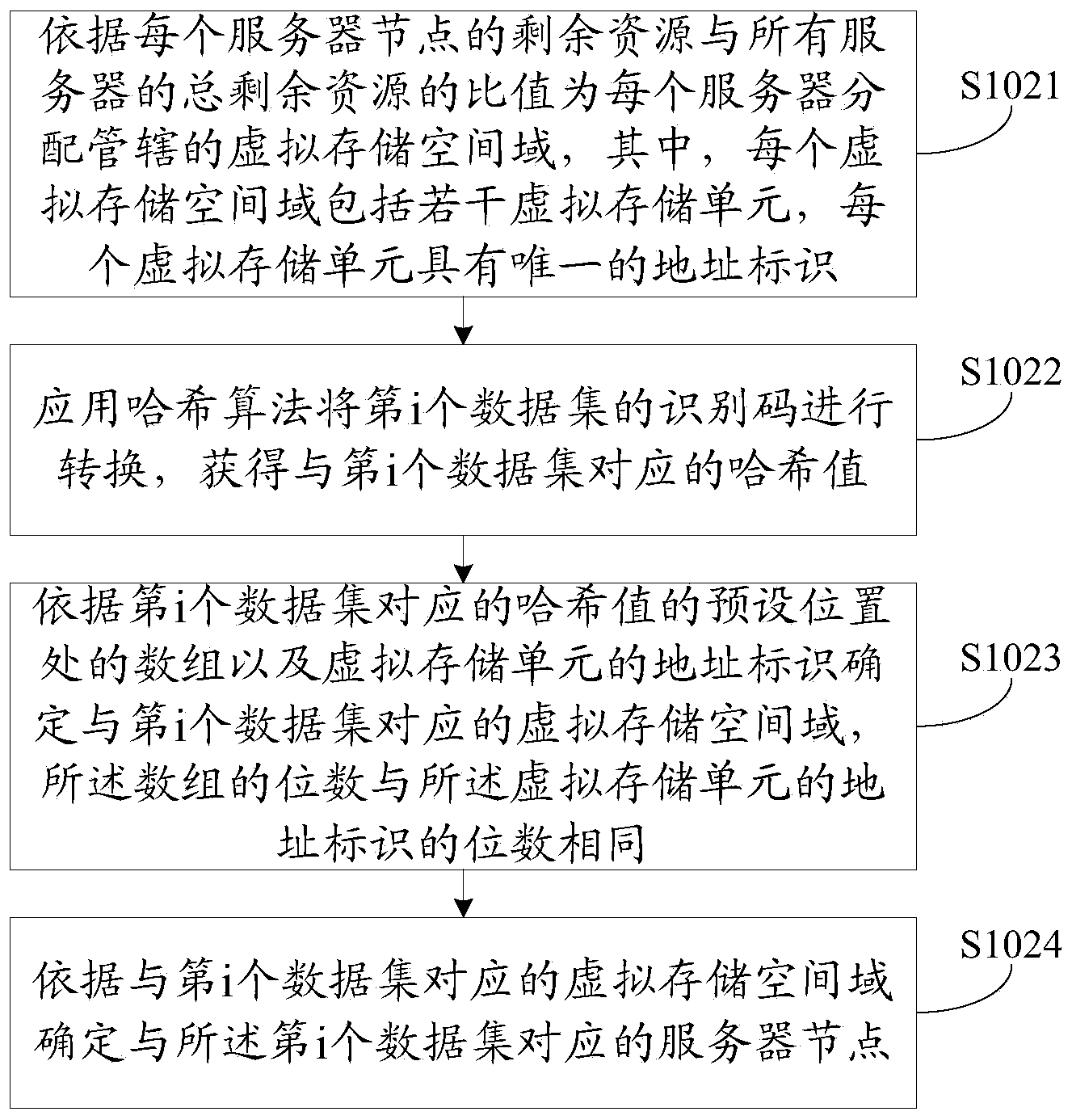
ActiveCN103473334AImprove distribution efficiencyImplement automatic storageMemory adressing/allocation/relocationTransmissionPaper data storageData set
The invention discloses a data storage method. The method comprises the following steps of dividing the to-be-stored data into a plurality of data sets; enabling each data set to establish a mapping relationship with a corresponding server node through a virtual storage space domain and a Harsh algorithm, namely storing each data set into the server node which has the mapping relationship with the data set. The automatic storage of massive data in a distributed real-time database system is realized, the data distribution workload of workers is reduced, and the distributing efficiency during data storage is improved. The invention also discloses a data inquiry method and a data storage system.
Owner:蓝卓数字科技有限公司
Method of exact repair of pairs of failed storage nodes in a distributed data storage system and corresponding device
InactiveUS20130073896A1Improve securityReduce computing costRedundant hardware error correctionPaper data storageDependability
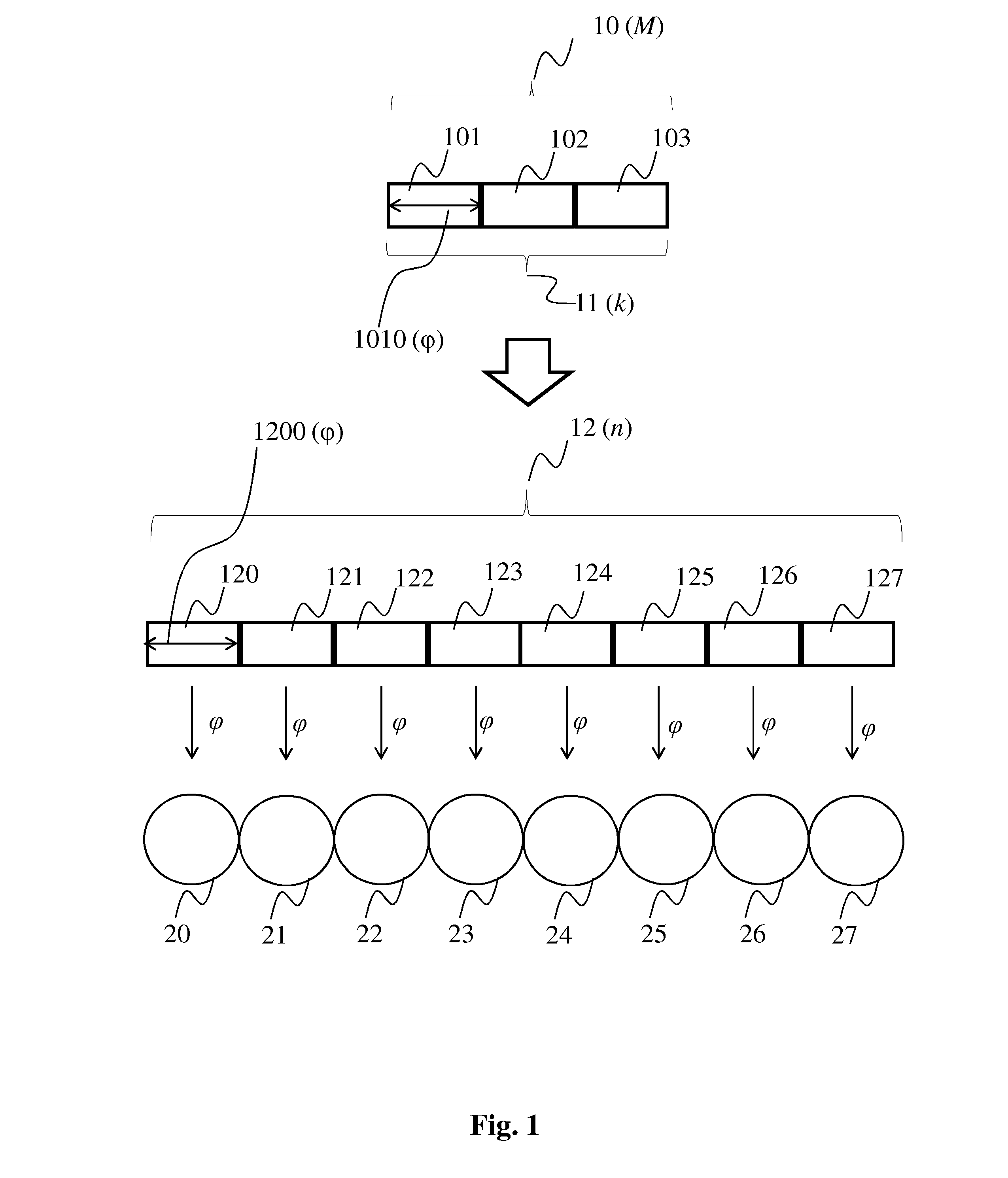
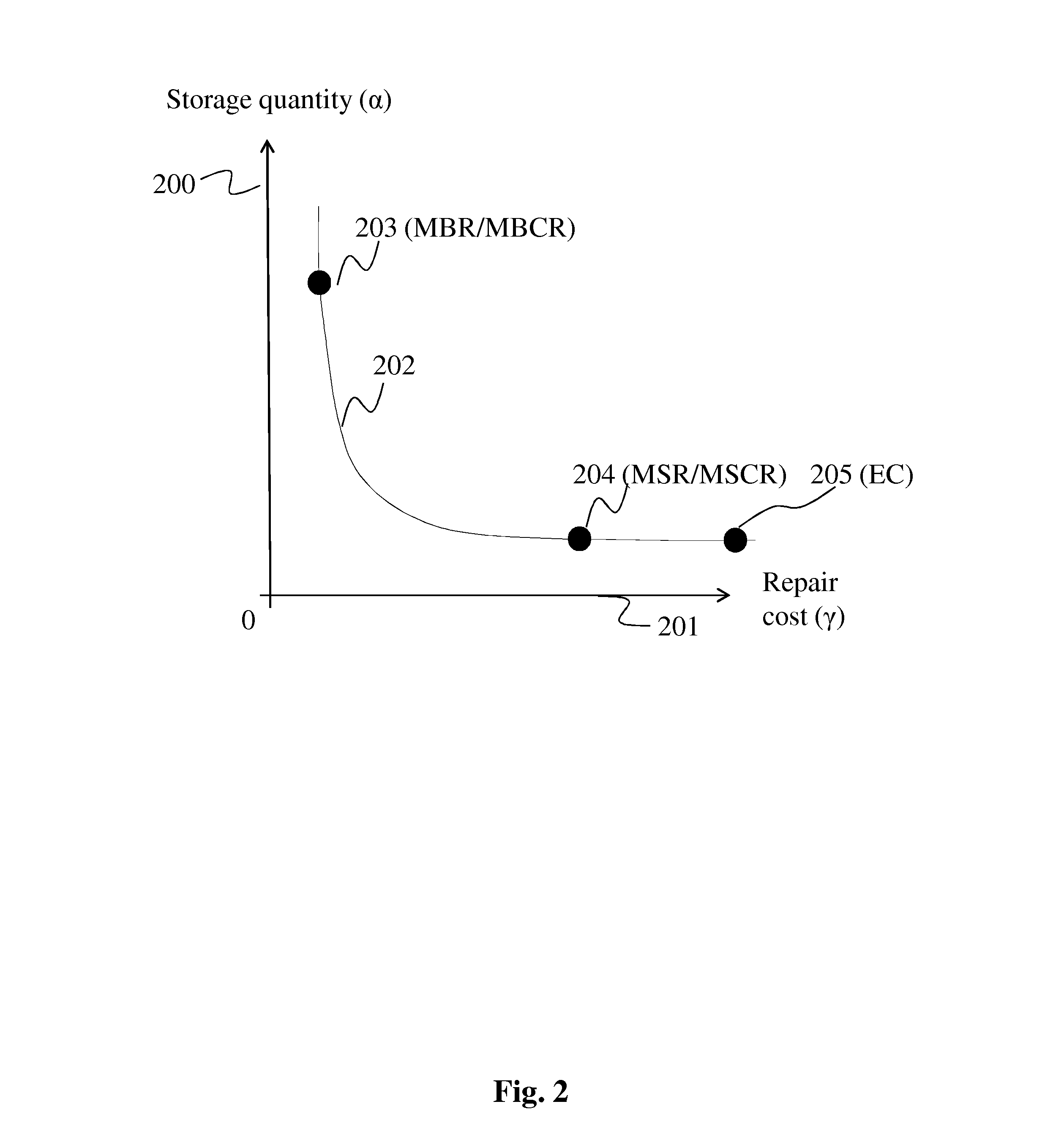
The invention proposes a method and corresponding device for exact repair of pairs of failed storage nodes interconnected in a distributed data storage system, which method and device are particularly efficient with respect to reliability while keeping the use of resources of the distributed storage network low.
Owner:THOMSON LICENSING SA
Operating system independent, secure data storage system
ActiveUS20180082075A1Easy accessUnauthorized memory use protectionDigital data protectionPaper data storageOperational system
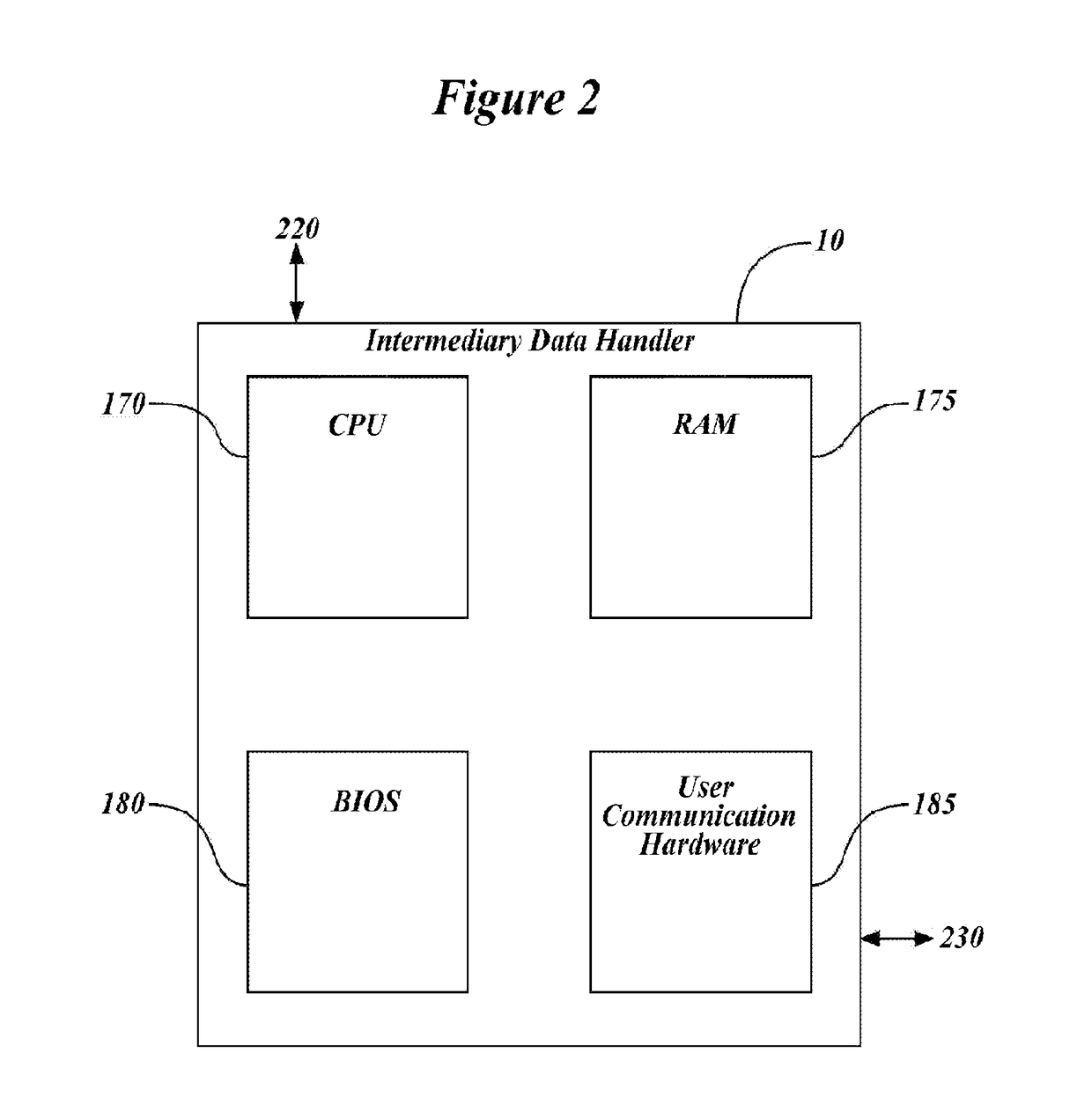
An intermediary data handler is used in a Secured Data Storage Subsystem (SDSS), to provide a host electrical computer system with security of certain data stored in memory of the computer system's static data storage device. The intermediary data handler is functionally disposed between the operating system (OS) and data storage device of the host computer. The data handler has Processor, Memory, and User Interface circuits, and resident software adapted to generate mocked-up response data in reply to an unauthorized read / write communication from the OS, the mock data response being automatically formatted to have a content and data-structure format acceptable by the host OS, while isolating and controlling the original communication from the OS. The SDSS includes host software adapted to integrate operation and function of the intermediary data handler with the host computer system to accomplish the security of data stored on the storage device.
Owner:SYRBAL LLC
Command queue loading
InactiveUS20090006606A1Improve washing effectDigital computer detailsTransmissionPaper data storageDepth dependent
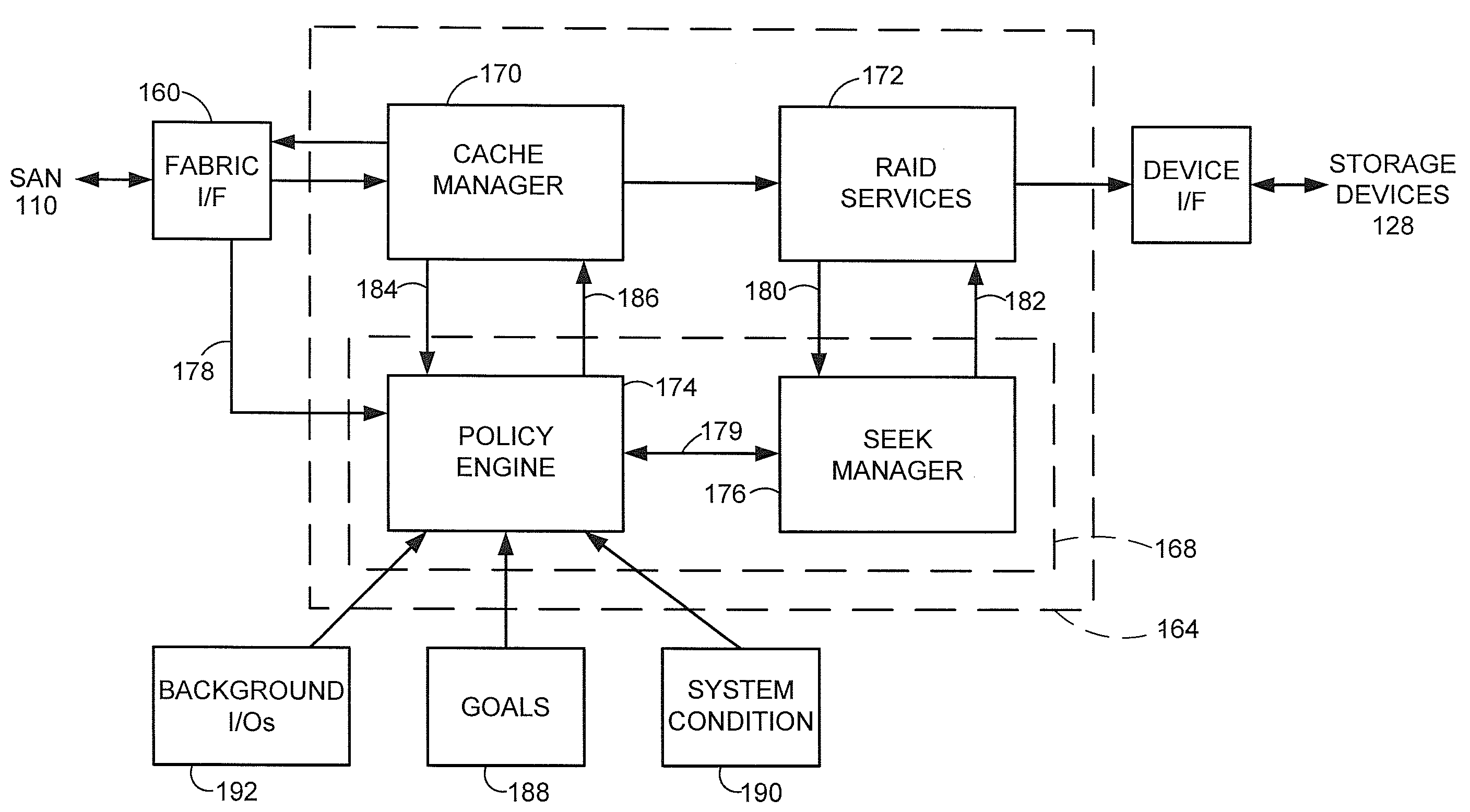
A data storage system and associated method are provided wherein a policy engine continuously collects qualitative information about a network load to the data storage system in order to dynamically characterize the load and continuously correlates the load characterization to a command queue depth of data transfer requests.
Owner:SEAGATE TECH LLC
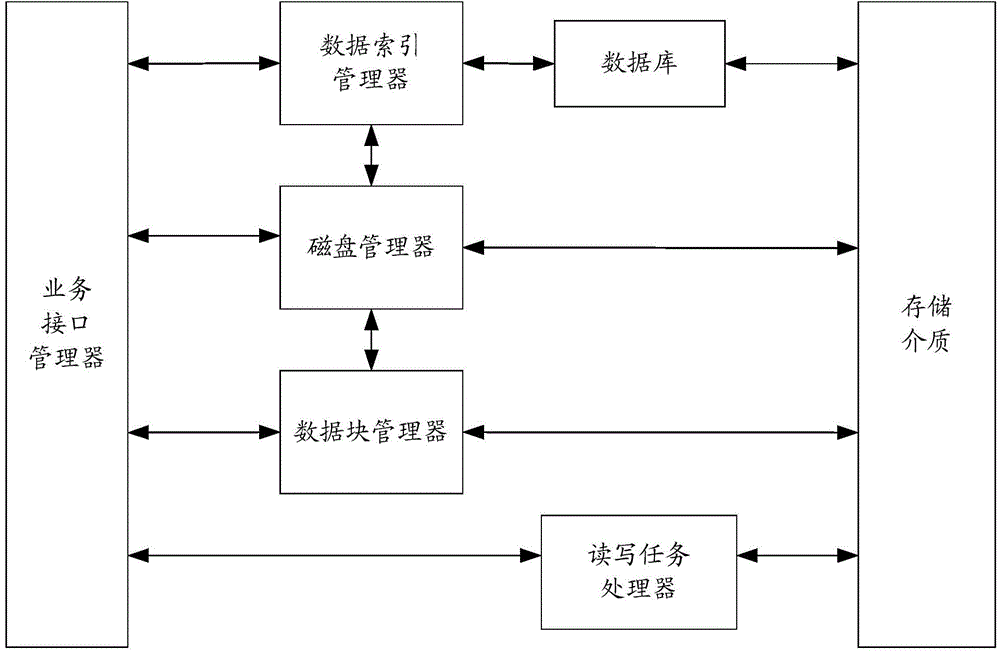
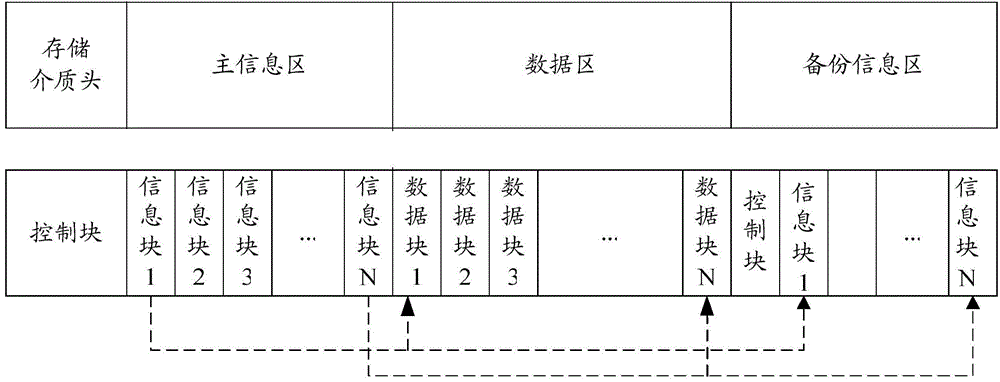
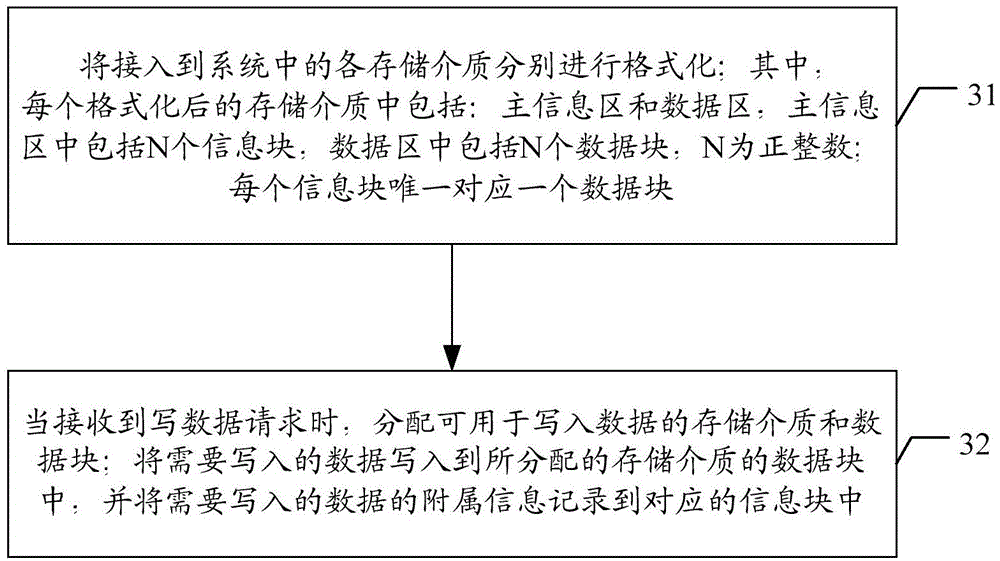
Data storage system and data storage method
ActiveCN104699416ASimple designReduce implementation complexityInput/output to record carriersPaper data storageData store
The invention discloses a data storage system and a data storage method. The data storage method comprises the following steps: respectively formatting various storage media connected into a system, wherein each formatted storage medium comprises a main information area and a data area, the main information area comprises N information blocks, the data area comprises N data blocks, N is a positive integer, and each information block corresponds to only one data block; when a data writing request is received, allocating the storage medium and the data blocks which can be written with data; writing the data to be written into the data blocks of the allocated storage medium, and recording subordinate information of the data to be written into the corresponding information blocks. After application of the scheme, the design can be simplified and the implementation complexity can be reduced.
Owner:HANGZHOU HIKVISION SYST TECH
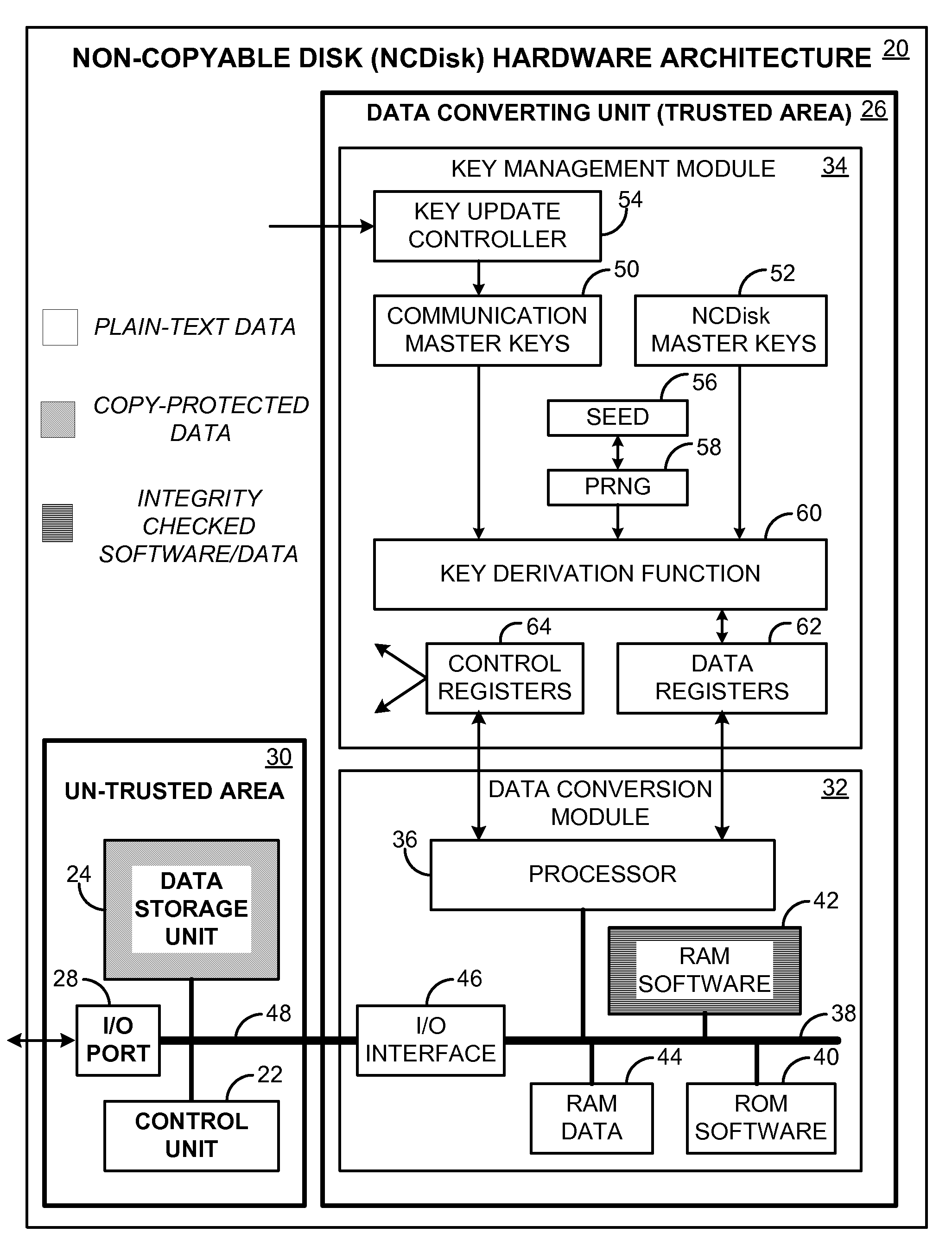
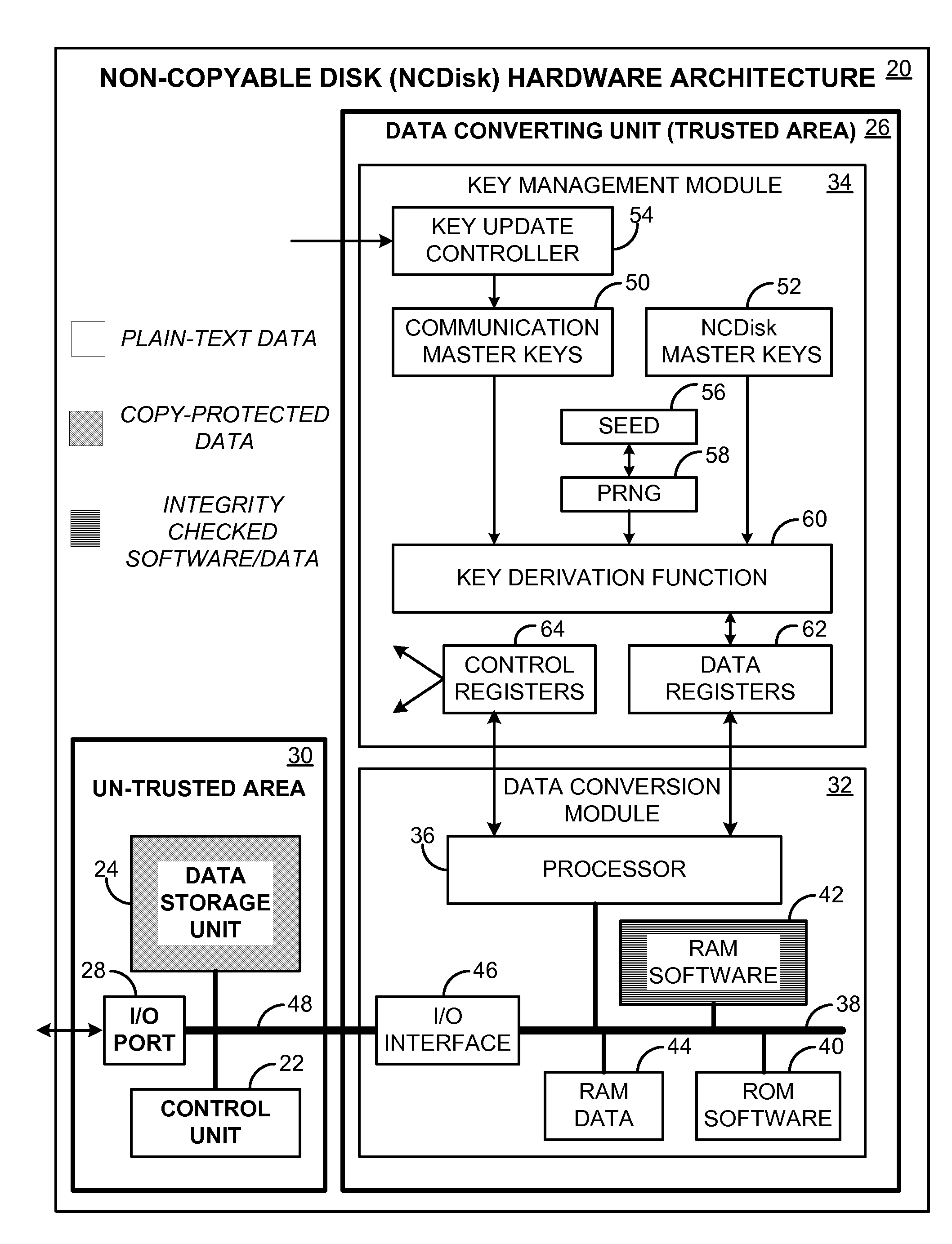
Secure Data Storage for Protecting Digital Content
InactiveUS20080022134A1Convenient typePrevent software attackUnauthorized memory use protectionHardware monitoringPaper data storageDigital data
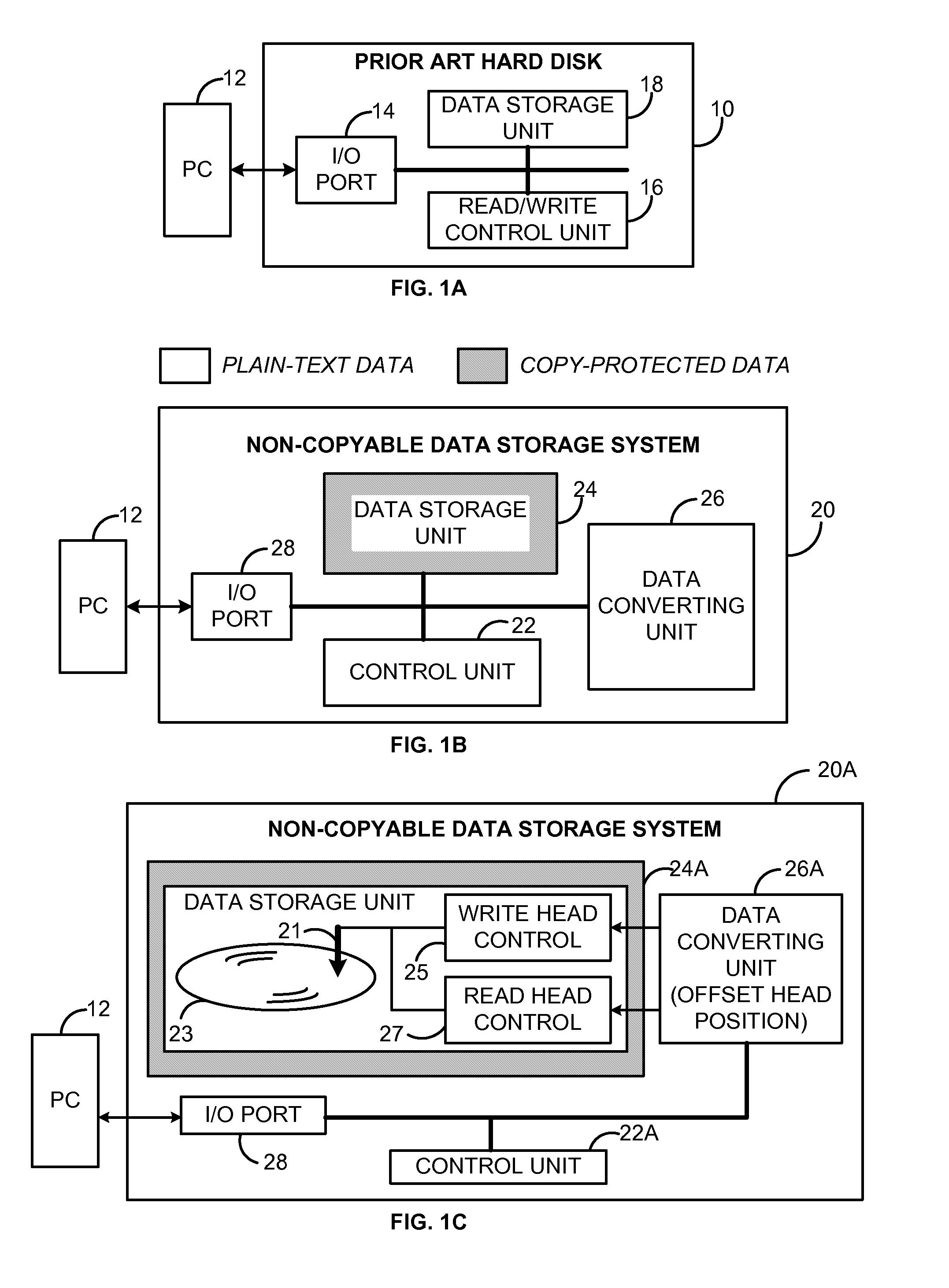
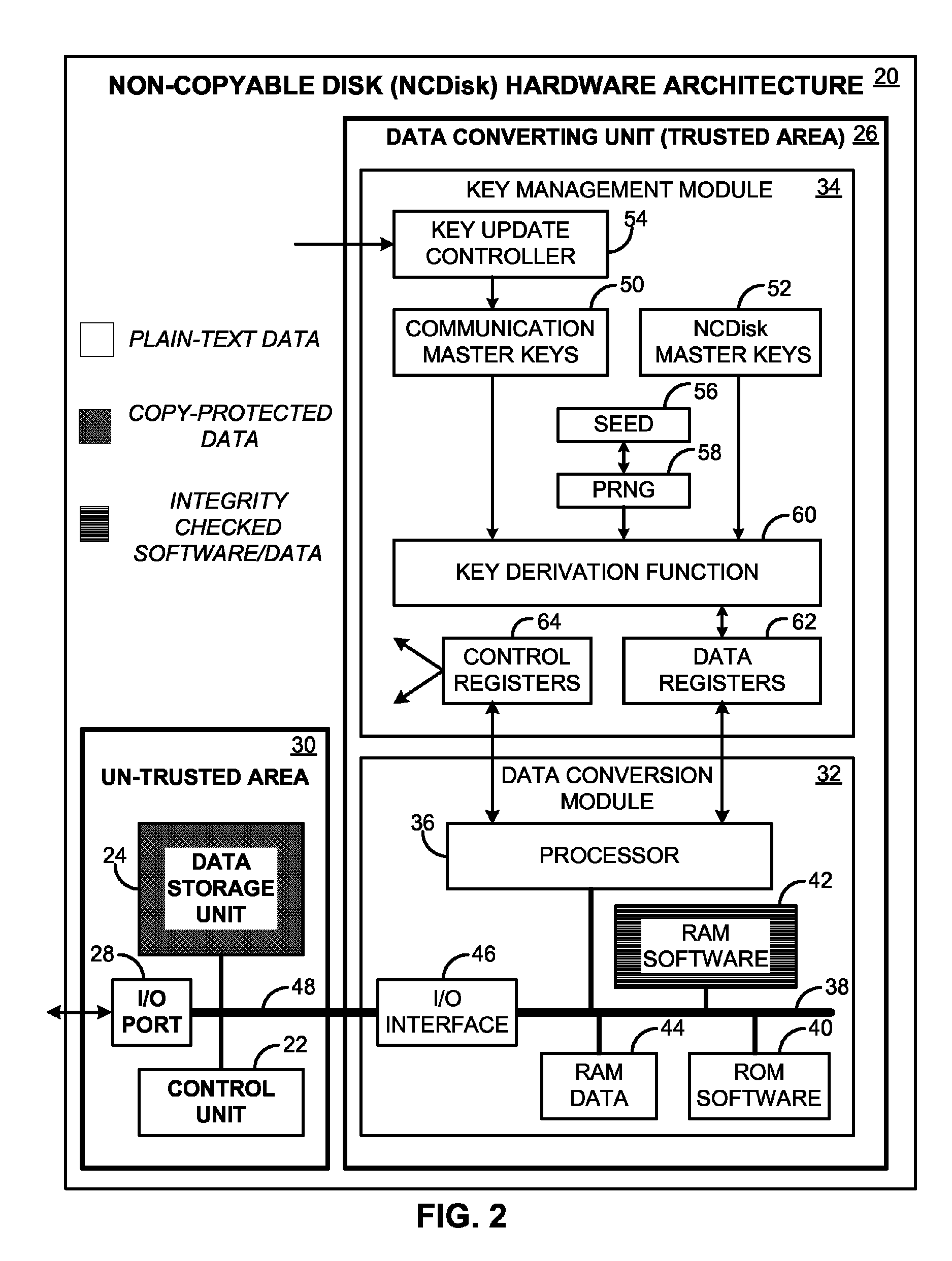
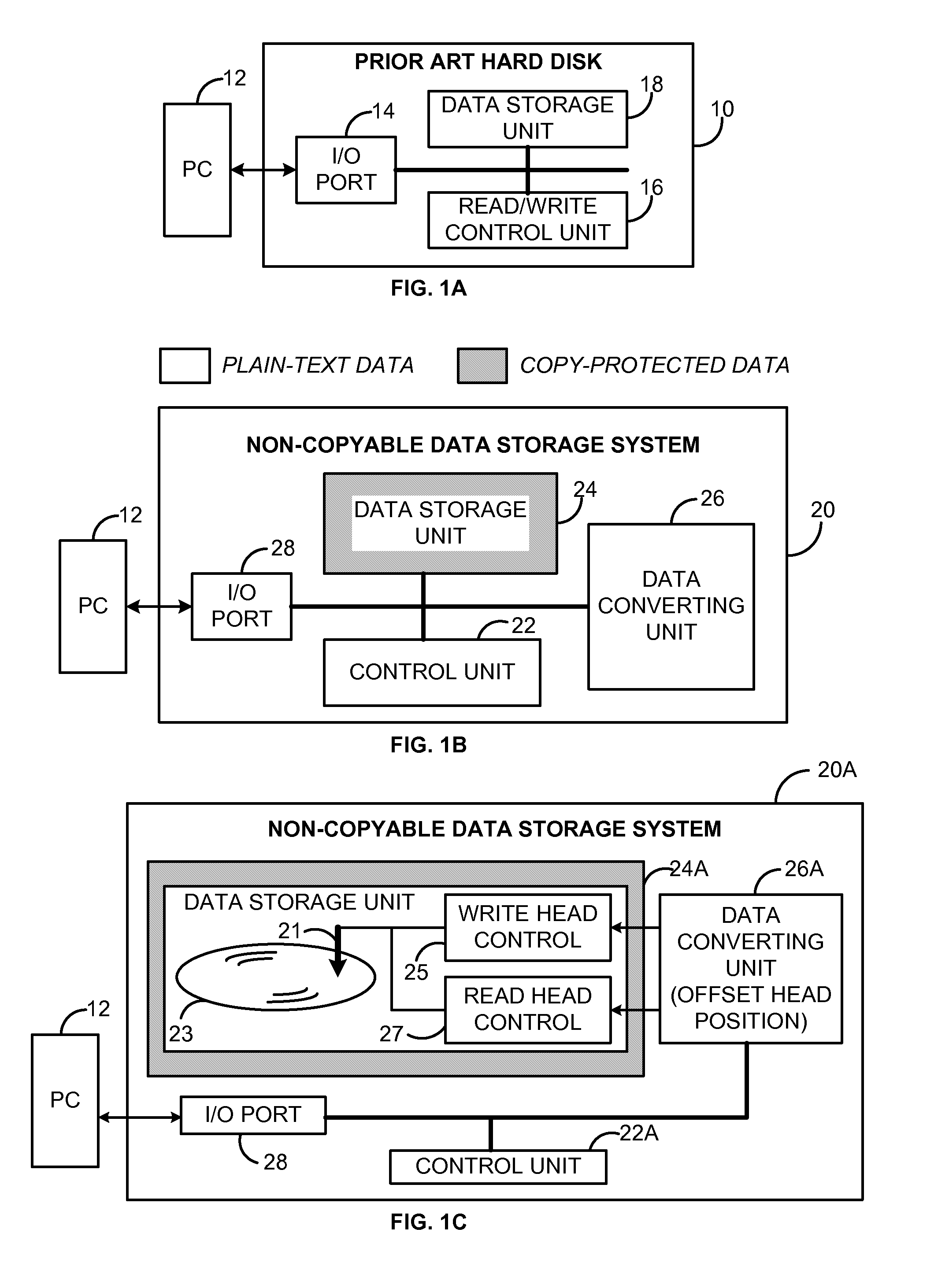
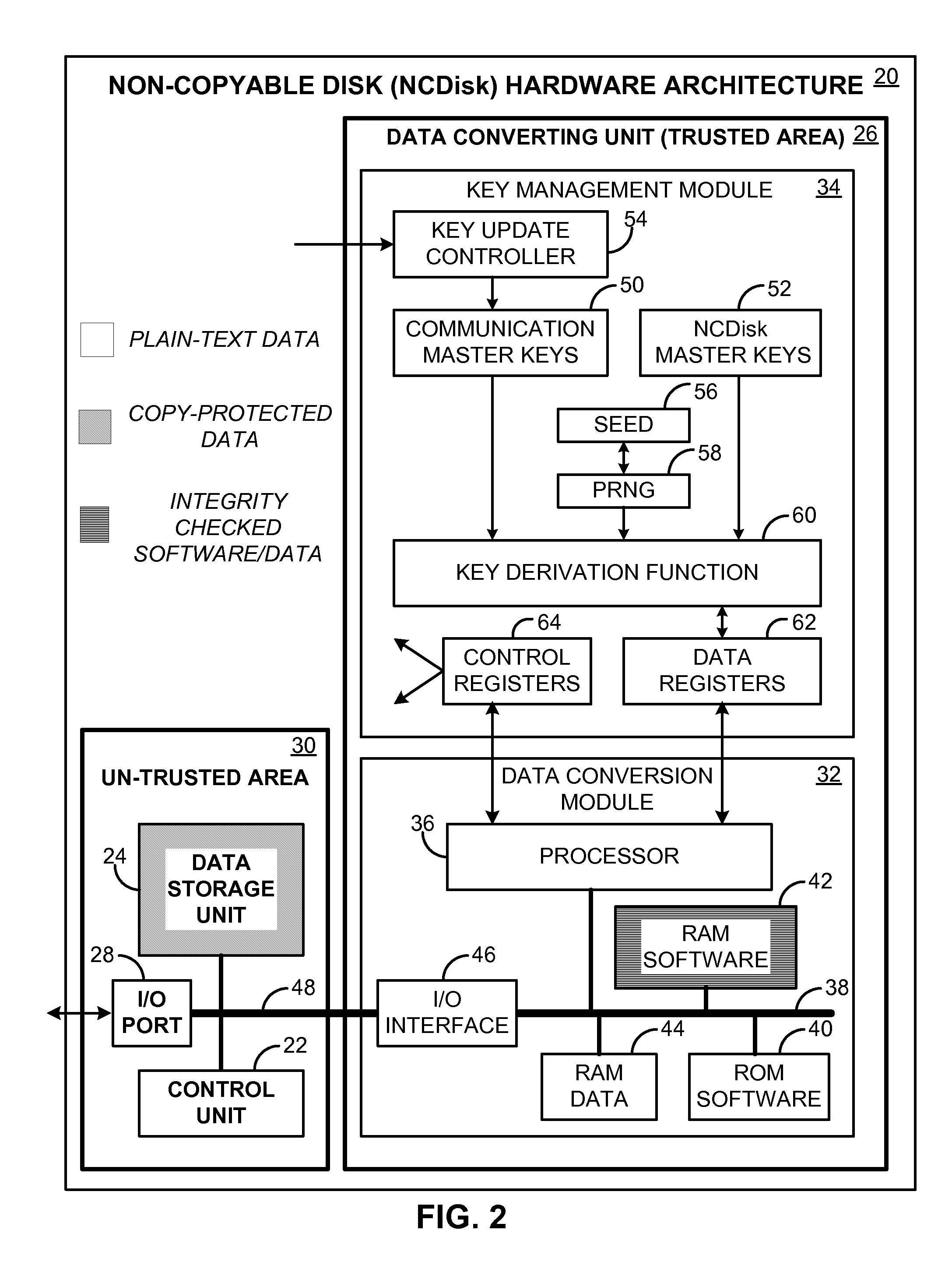
A non-copyable data storage disk (NCDisk) that may be used in a secure data storage system. Stored data items on the NCDisk may only be used through the data storage system, and cannot be copied to and used by any other devices. Digital data written to the NCDisk is automatically converted to a new format by the NCDisk itself before being stored on it. Similarly, when reading a data item out from the NCDisk, the NCDisk itself automatically converts the stored data item to a new data format that a reading device can recognize. Data conversion does not involve the computer operating system. The data conversion unit may include a chipset level 2 secure key management module that generates and manages the keys used for the data conversion.
Owner:WANG MICHAEL SUJUE
Data storage method
InactiveCN105471989AImprove sharing functionImplement snapshot managementTransmissionSpecial data processing applicationsPaper data storageClient-side
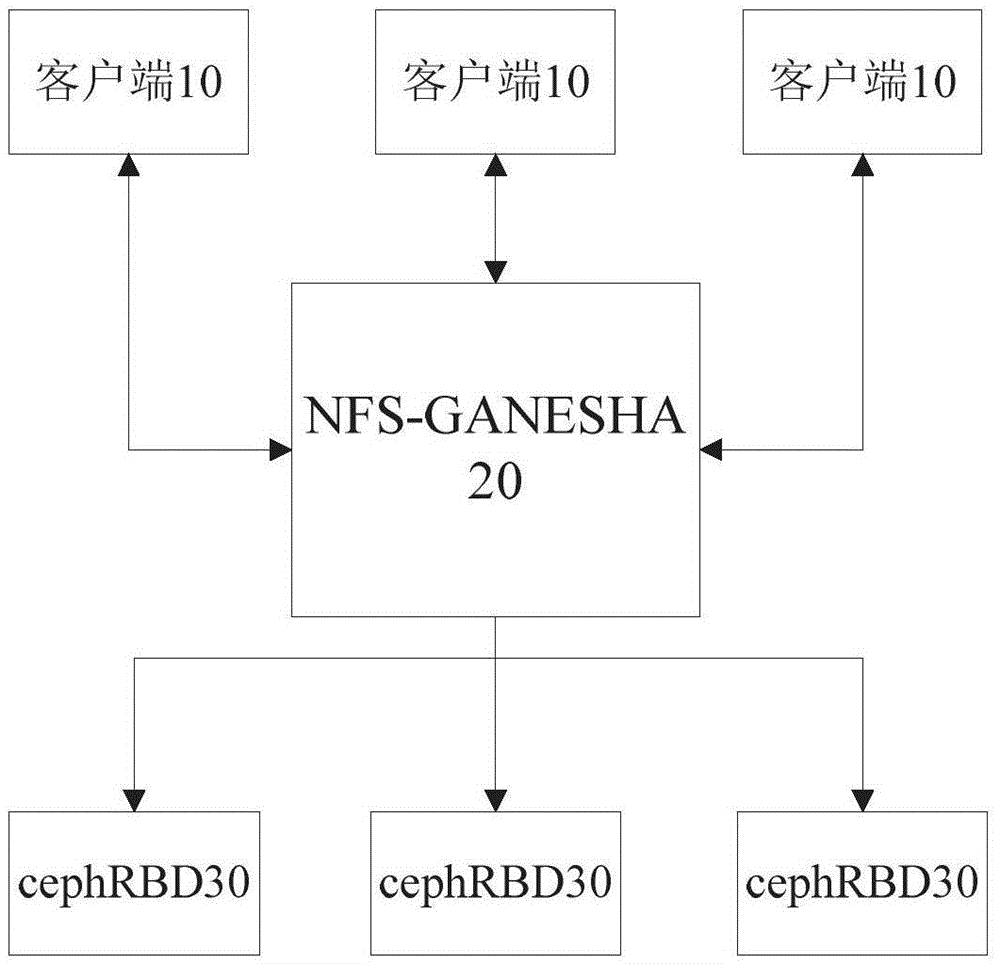
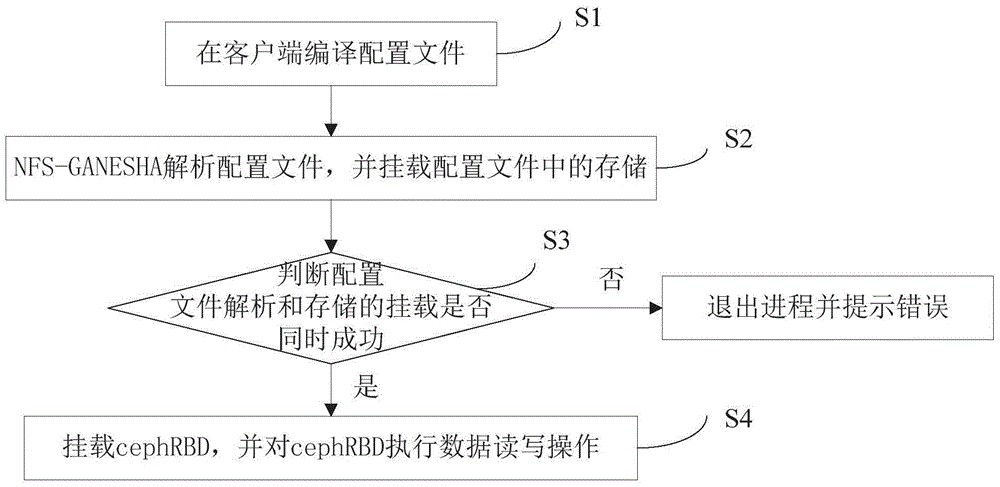
The invention provides a data storage method and relates to a data storage system. The data storage system comprises a client, NFS-GANESHA and Ceph RBD. The data storage method comprises the following steps that S1, an NFS-GANESHA server side compiles a configuration file; S2, the NFS-GANESHA analyzes the configuration file and mounts storage in the configuration file; S3, whether configuration file analysis and storage mounting are successful simultaneously is determined; if the configuration file analysis and storage mounting are not successful simultaneously, process exits and a fault is prompted; if the configuration file analysis and storage mounting are successful simultaneously, a step S4 is entered into; S4, the Ceph RBD is mounted and data reading and writing operation is performed on the Ceph RBD. The storage is connected to a customer service side, the Ceph RBD provides high performance storage and the NFS-GANESHA provides a high performance file sharing function so that high-efficient distributed storage is realized. The Ceph RBD which is taken as the storage is stable and the RBD can realize snapshot management. If the file is deleted by mistake or there is another problem, manual snapshot recovery can be achieved. And the Ceph RBD is used to store a VMware virtual machine so that domain division storage can be realized. According to importance of the virtual machine, different copy storage is realized.
Owner:EISOO SOFTWARE
Data Storing system
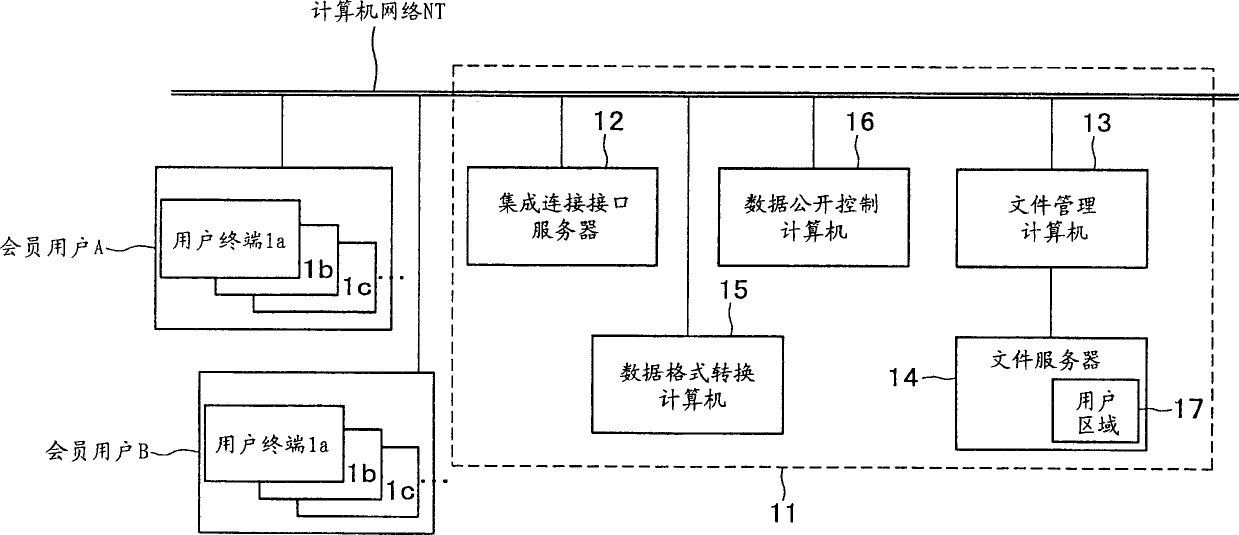
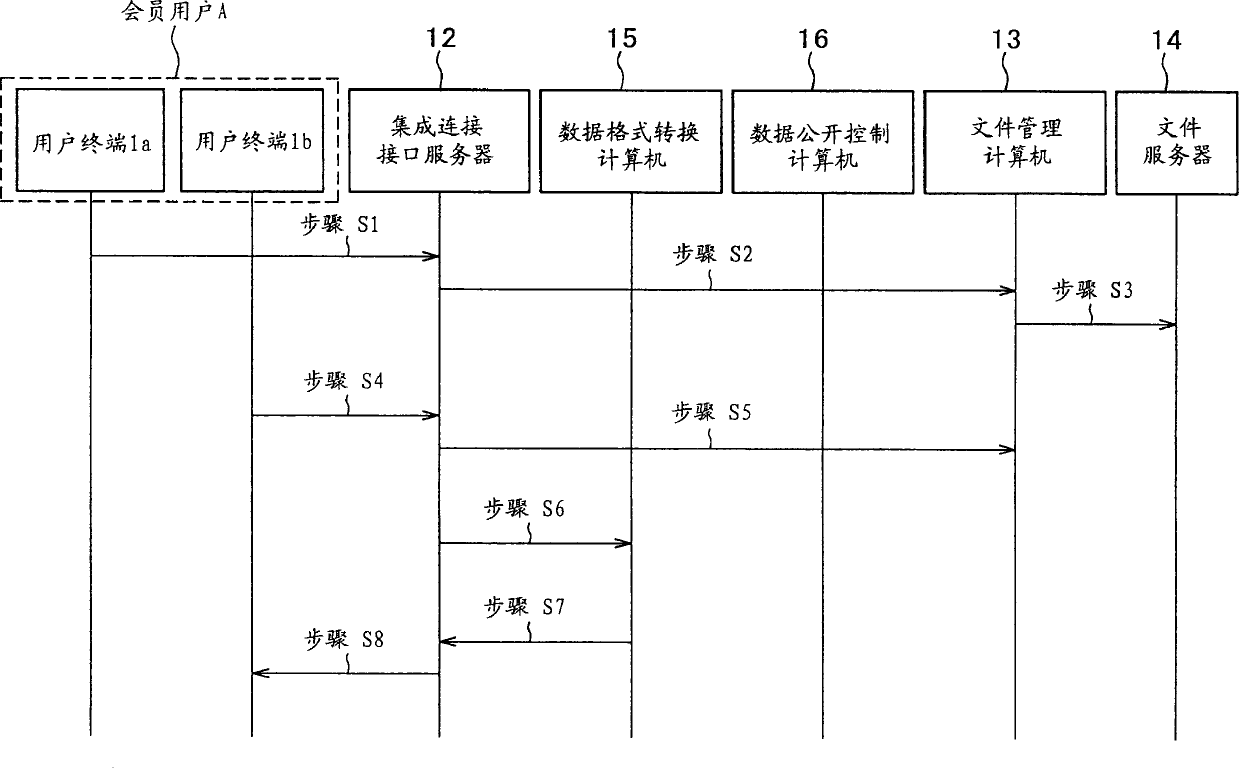
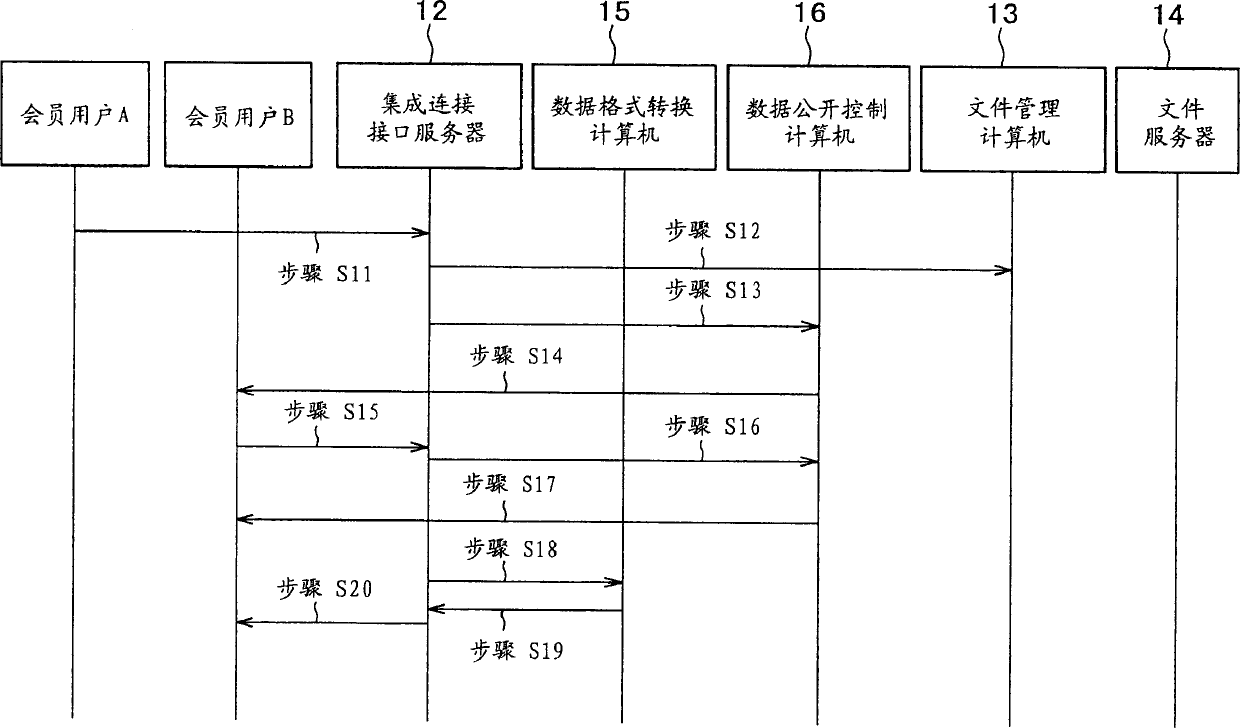
InactiveCN1494011AData processing applicationsDatabase management systemsPaper data storageNetwork connection
A data storage system is disclosed having a plurality of terminal apparatuses of users connected with a data storage unit of a service provider via a computer network, the data storage unit storing data from inside the terminal apparatuses so that the stored data are subsequently used by the users. The data storage unit includes a connecting element, a file storing element, a file managing element, and a data format converting element. In response to a use request from any one of the users, the data format converting element converts stored data in the file storing element into a format compatible with the type of the terminal apparatus used by the requesting user for connection to the system. The converted data is used by the terminal apparatus through which the requesting user has sent the use request.
Owner:SONY CORP
Efficient and secure data storage utilizing a dispersed data storage system
ActiveUS9483656B2Efficient implementationReduce the amount of solutionKey distribution for secure communicationInput/output to record carriersPaper data storageData segment
A method of securely storing data to a dispersed data storage system is disclosed. A data segment is arranged along the columns or rows of an appropriately sized matrix. Data slices are then created based on either the columns or the rows so that no consecutive data is stored in a data slice. Each data slice is then stored in a separate storage node.
Owner:PURE STORAGE
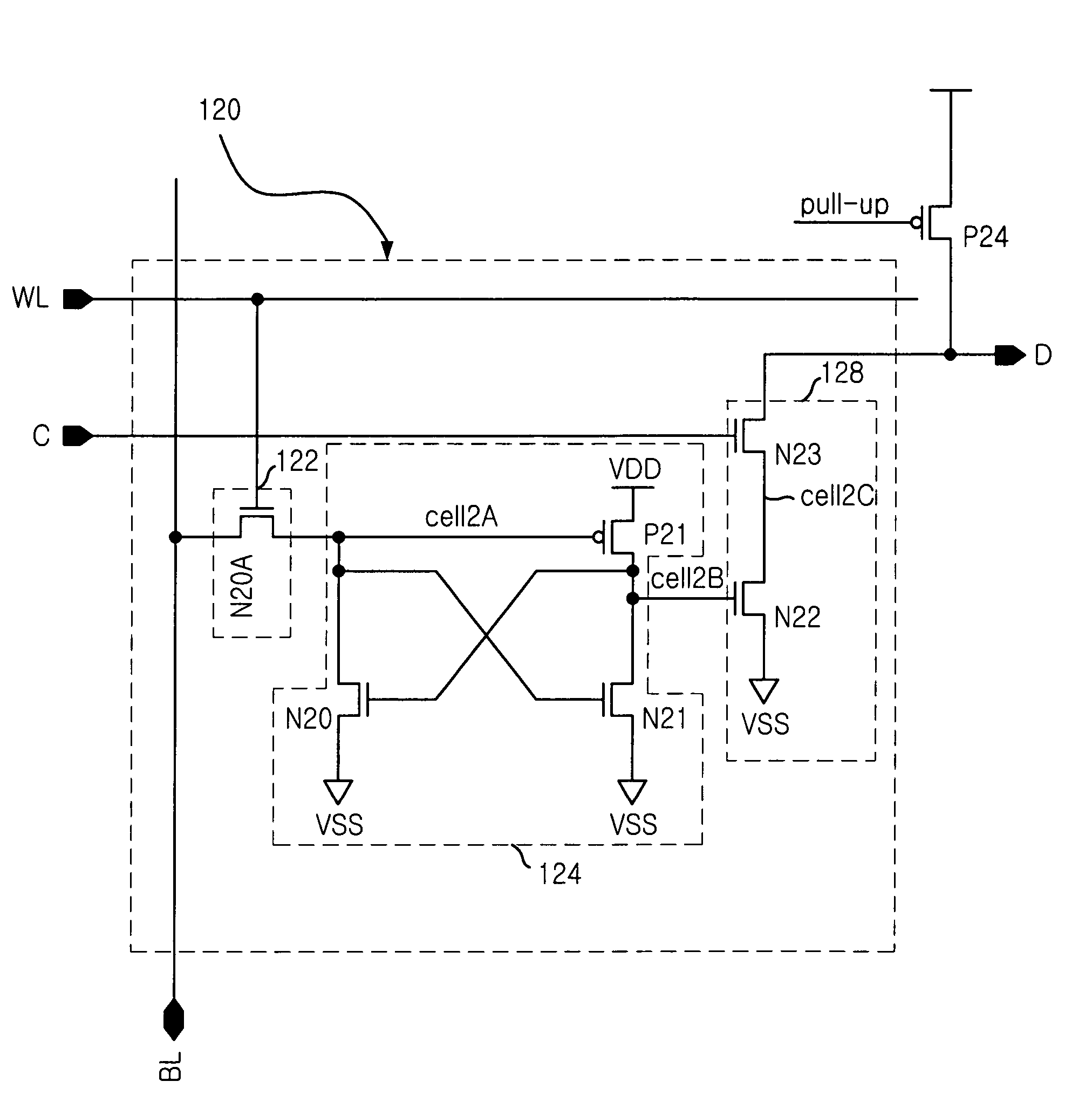
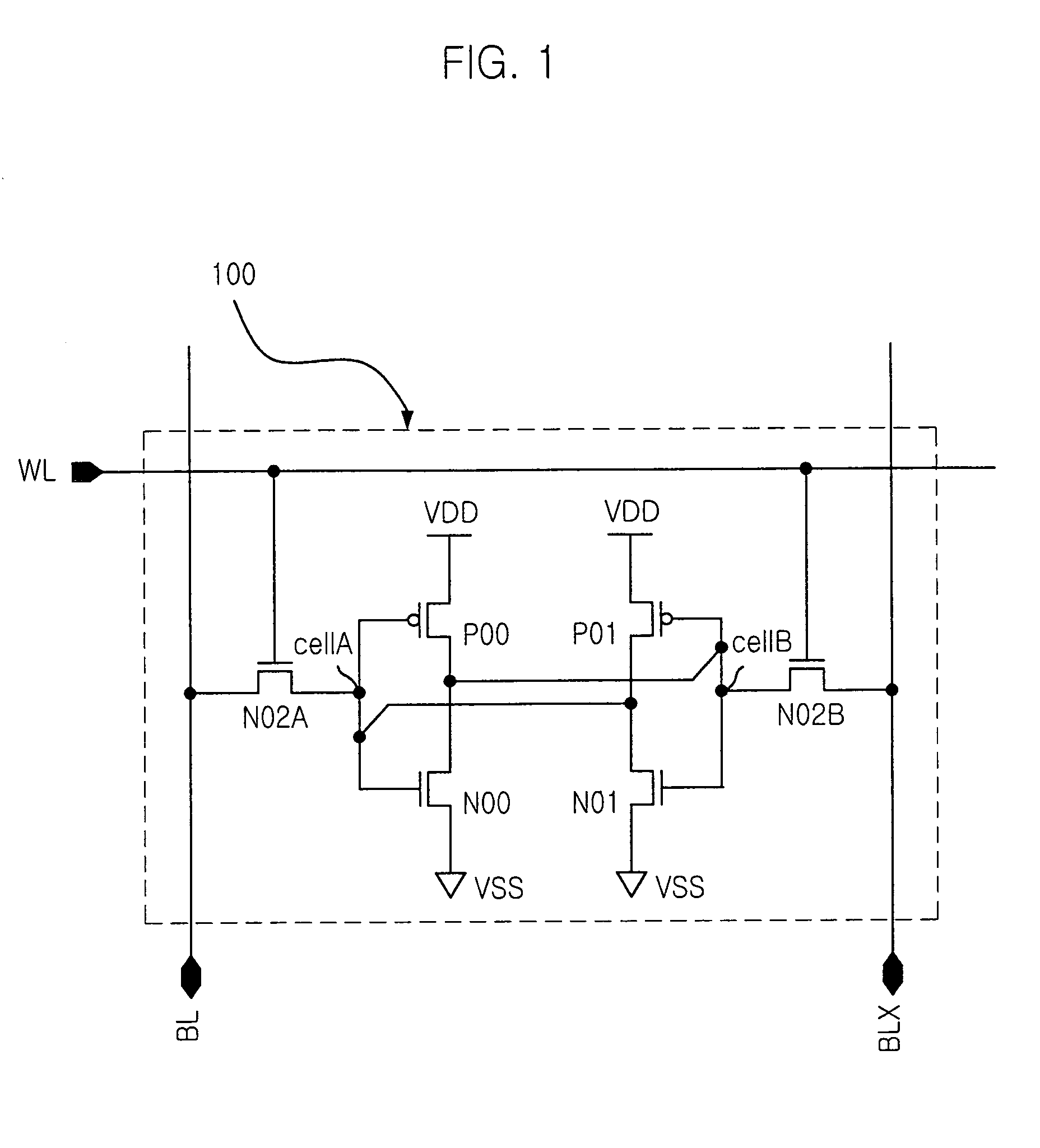
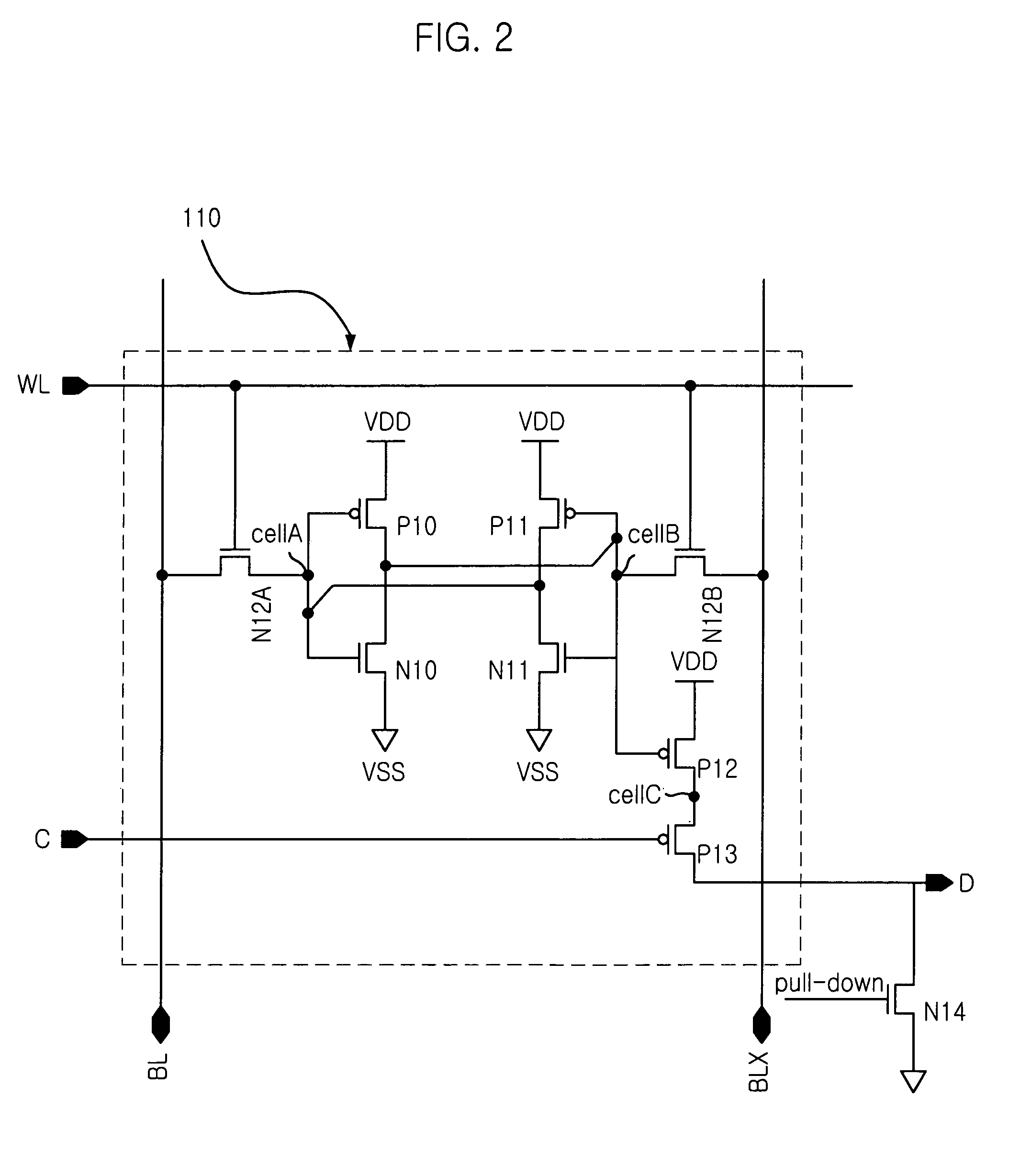
Dual port SRAM cell
The present invention provides a SRAM that is capable of performing a writing and reading operations simultaneously without collision while reducing size of cell, by providing a dual port SRAM cell. For this, the dual port SRAM cell, including: a writing section having a first transistor for inputting a data input signal from a bit line in response to a control signal from a word line; a data storage section having three transistors for storing the data input signal from the outside through the writing section; and a reading section having two transistors for reading the data input signal stored in the data storage section in response to control signal from a common line.
Owner:MAGNACHIP SEMICONDUCTOR LTD
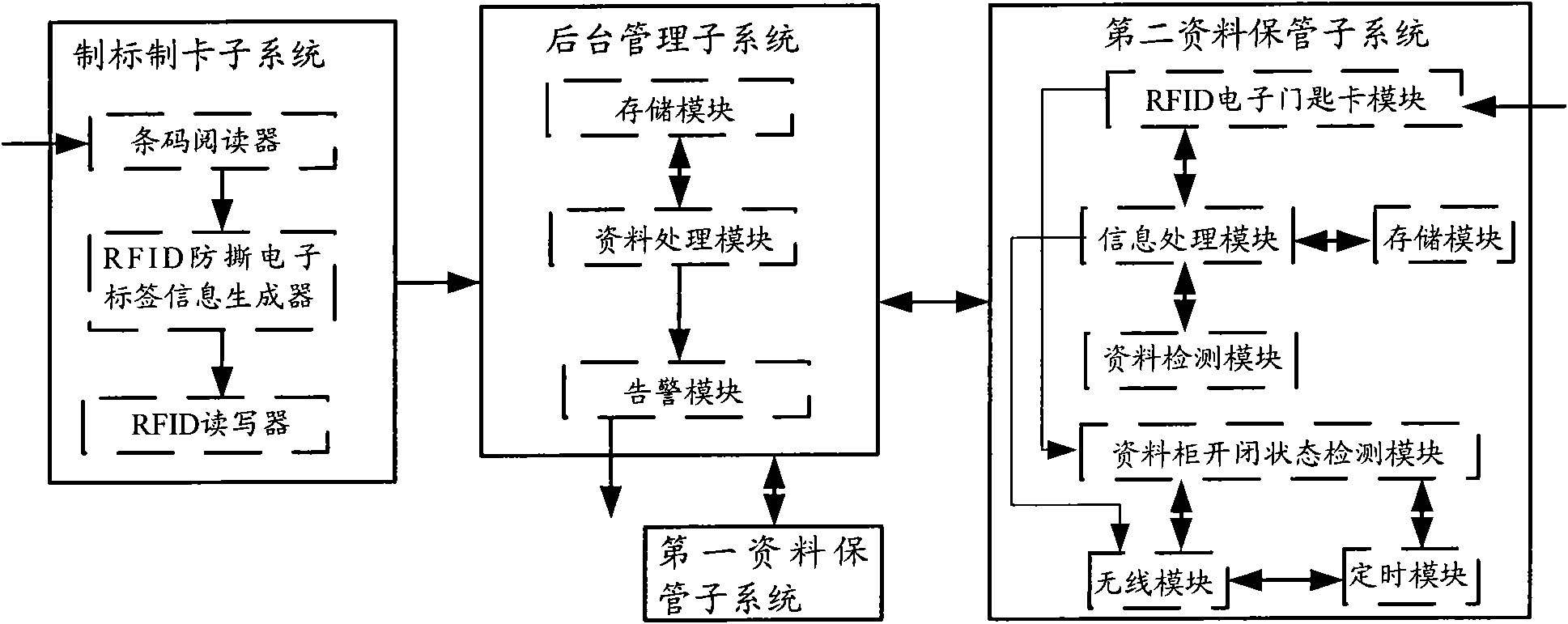
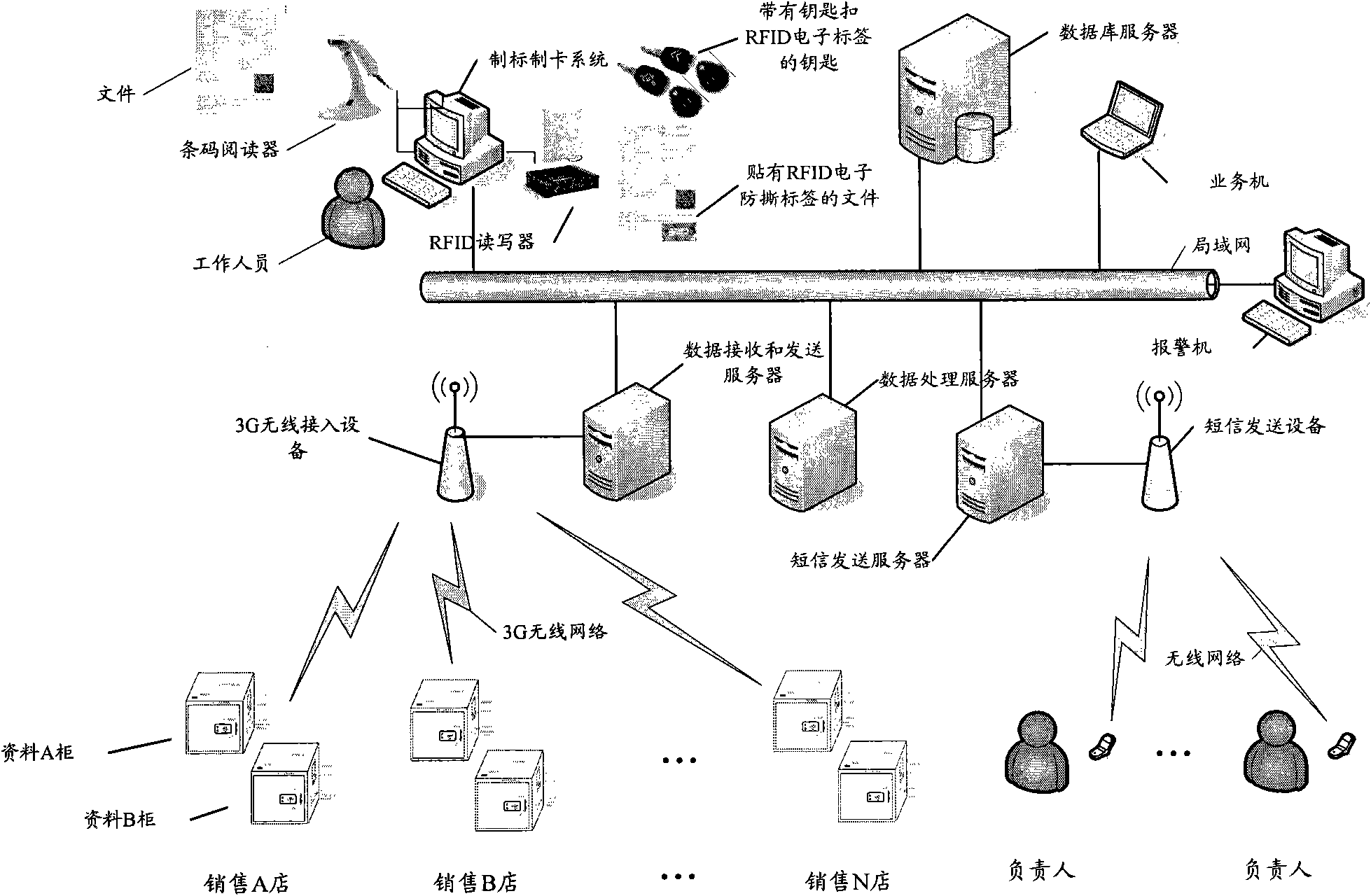
Data storage system and data storage method
InactiveCN101923677AImprove securityPrevent loan fraudCo-operative working arrangementsResourcesComputer hardwarePaper data storage
The invention discloses a data storage system and a data storage method. The system comprises a label and card manufacturing subsystem, a background management subsystem, a first data storage subsystem and a second data storage subsystem, wherein the first data storage subsystem and the second data storage subsystem are used for association control; different association data of the same object is respectively placed in different data storage subsystems; only one of the data storage subsystems for storing the different relative data of the same object can be opened at a time through setting; and moreover, as long as the data acquired from the data storage subsystems is authorized data, the other data storage subsystem for storing another association data of the object can be opened. By applying the invention, the safety of data storage can be improved.
Owner:BEIJING JUDUN TECH DEV
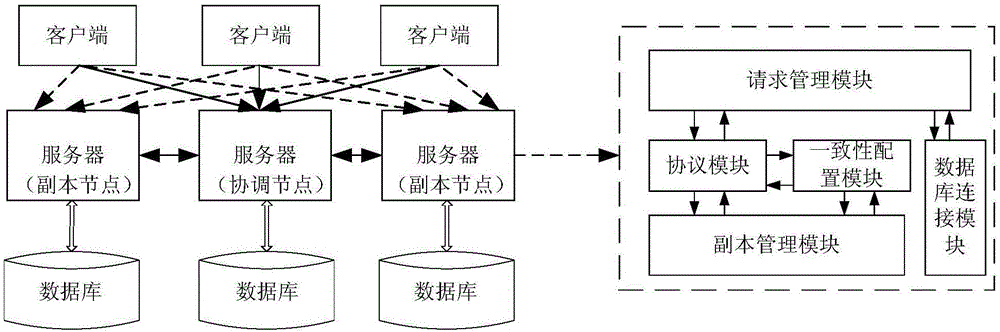
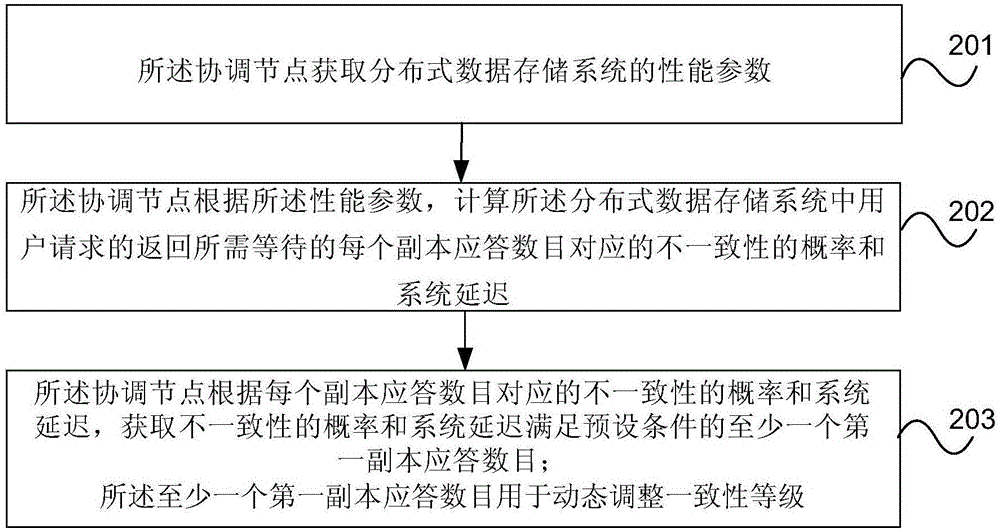
Consistency dynamic adjustment method and device in distributed data storage system
ActiveCN106375416ADatabase distribution/replicationTransmissionPaper data storageDistributed computing
The invention provides a consistency dynamic adjustment method and device in a distributed data storage system. The consistency dynamic adjustment method comprises the steps that a coordinating node obtains performance parameters of the distributed data storage system; the coordinating node calculates probability of inconsistency which corresponds to each copy response waiting to be returned of a user request in the distributed data storage system and a system delay; and the coordinating node obtains at least one first response number with the probability of inconsistency and the system delay meeting a preset condition based on the probability of inconsistency corresponding to each response number and the system delay. The at least one first response number is used for dynamic adjustment of the consistency level. According to the consistency dynamic adjustment method and device in the distributed data storage system, a consistency level meeting a delay requirement and a consistency requirement of a user can be selected in real time and automatically for a current running state of the distributed data storage system.
Owner:天航长鹰(江苏)科技有限公司
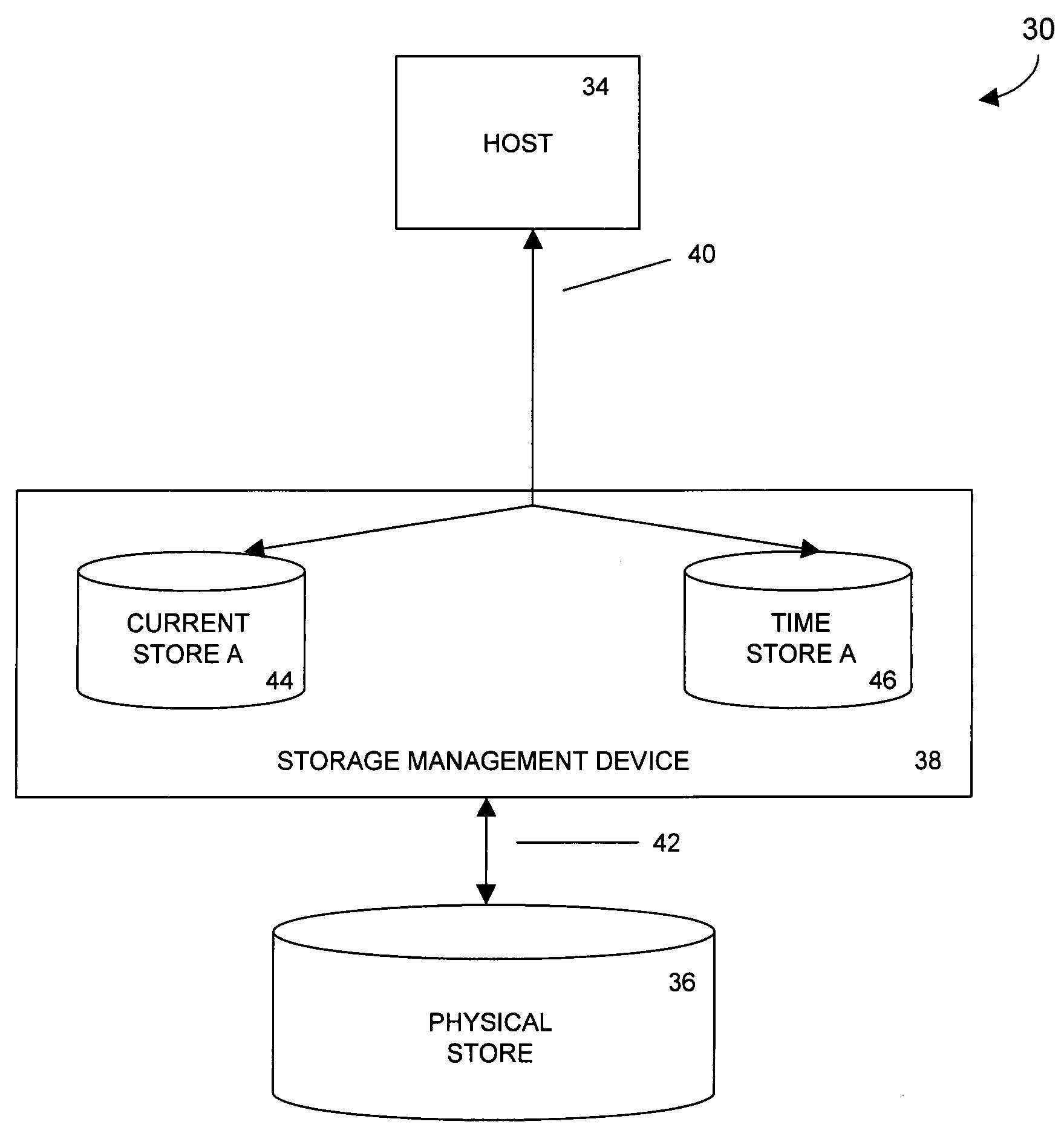
Data storage system
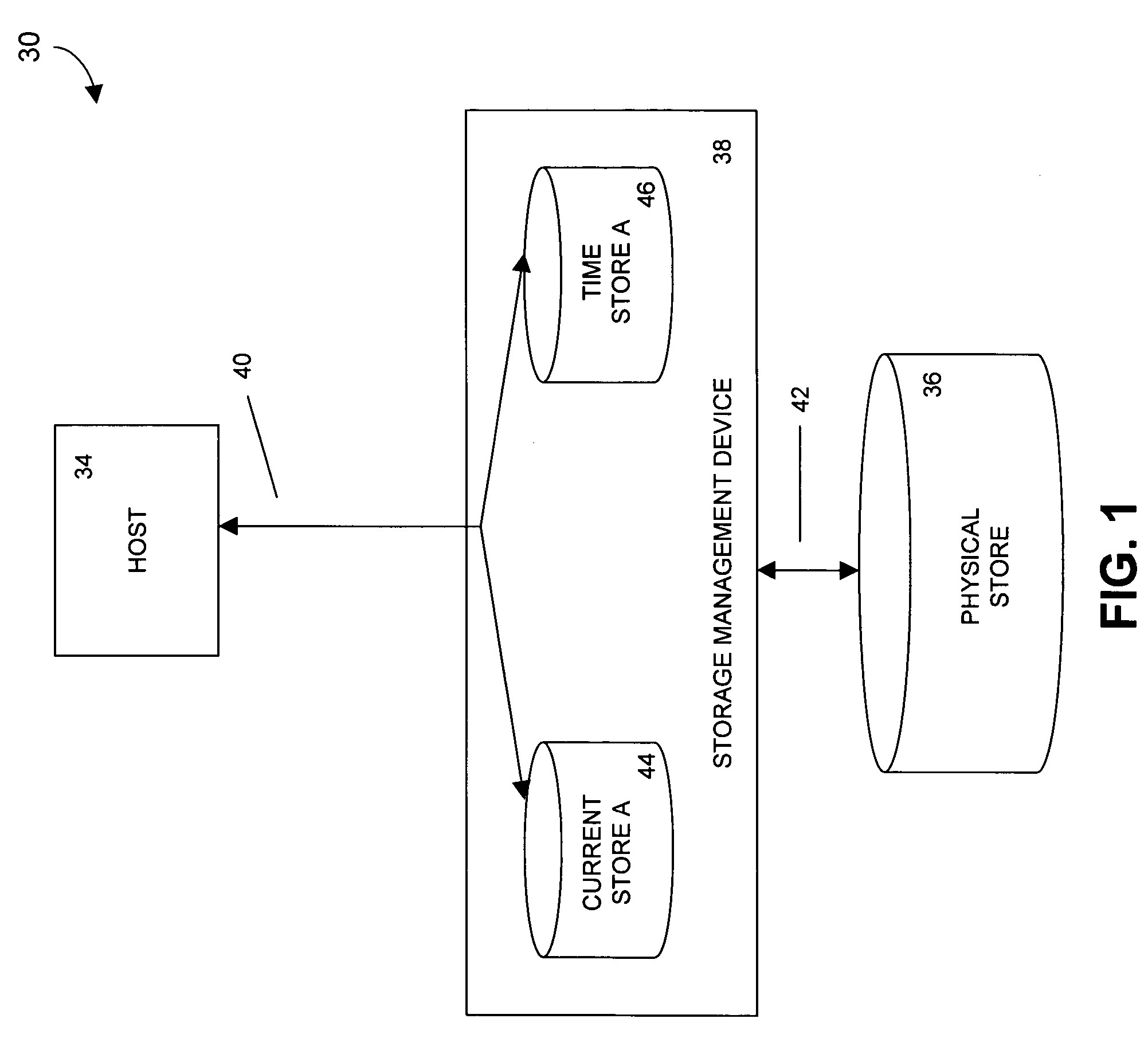
InactiveUS7725760B2Data storage is convenientMemory loss protectionError detection/correctionPaper data storageStorage management
In a data storage system, a storage management device includes at least a target mode driver, a data classifier in communication with the target mode driver, a plurality of storage buffers in communication with the target mode driver, a plurality of I / O managers in communication with the data classifier, and a physical store interface in communication with the plurality of I / O managers and with the plurality of storage buffers.
Owner:SYMANTEC OPERATING CORP
Data storage apparatus and control method of data storage apparatus
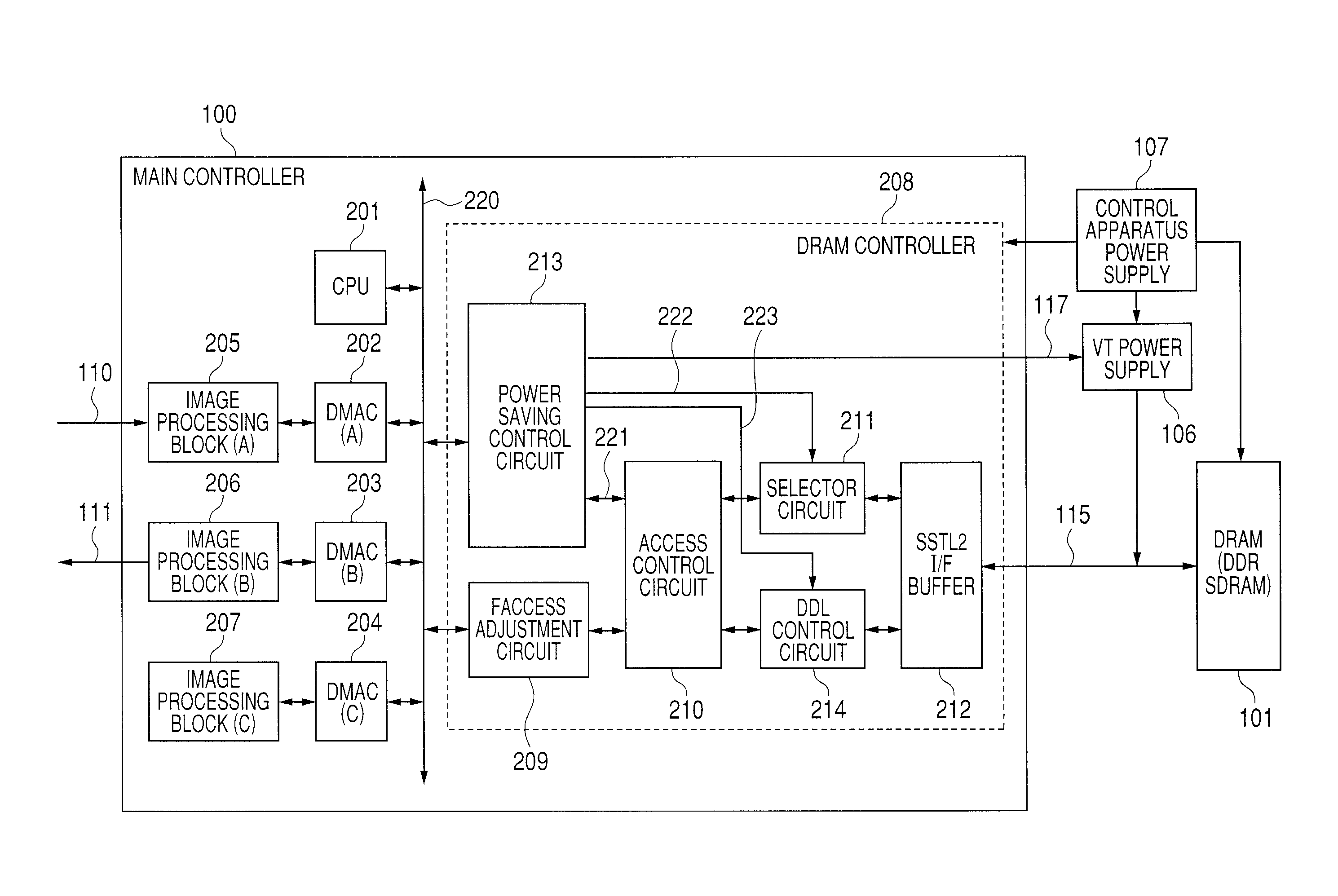
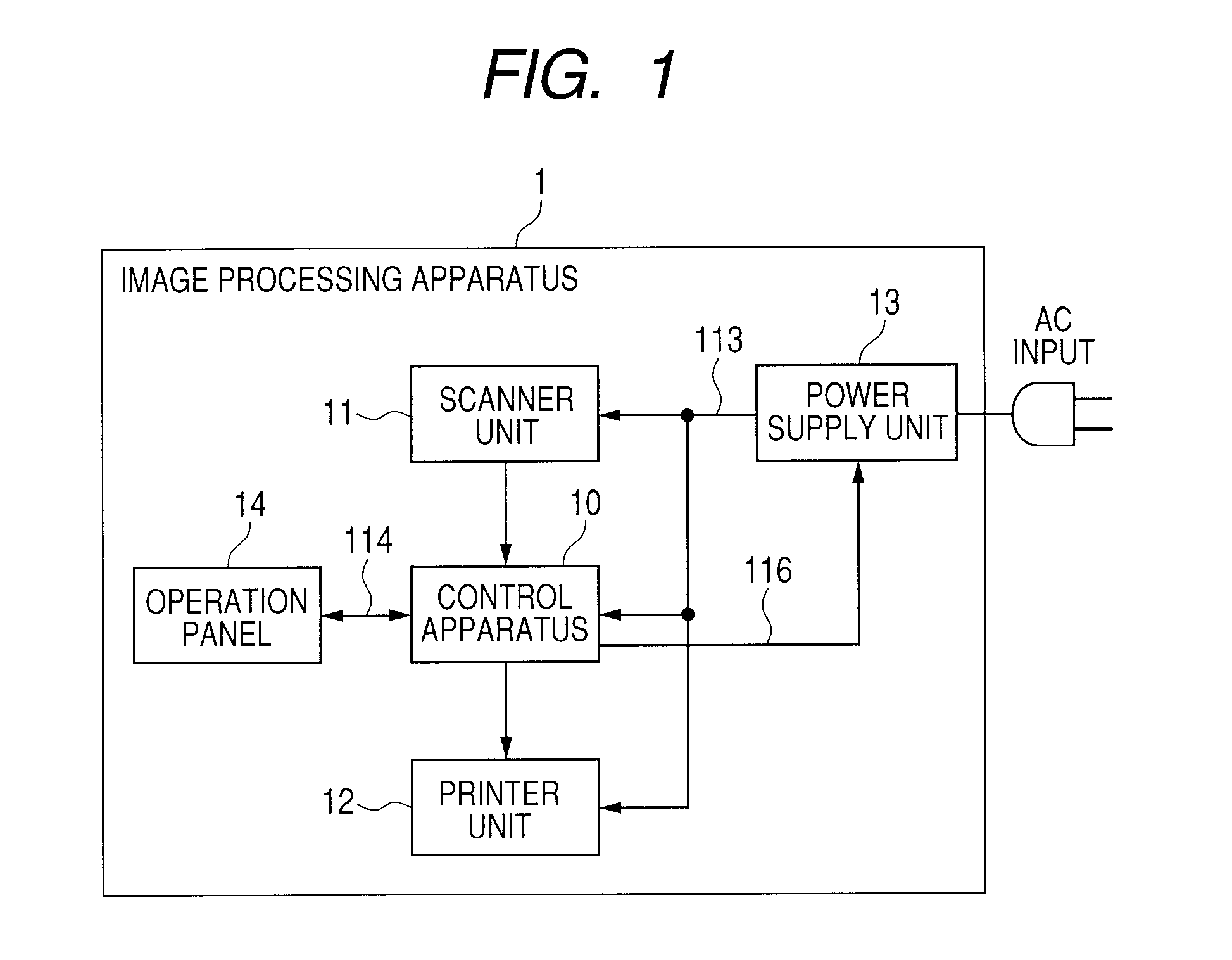
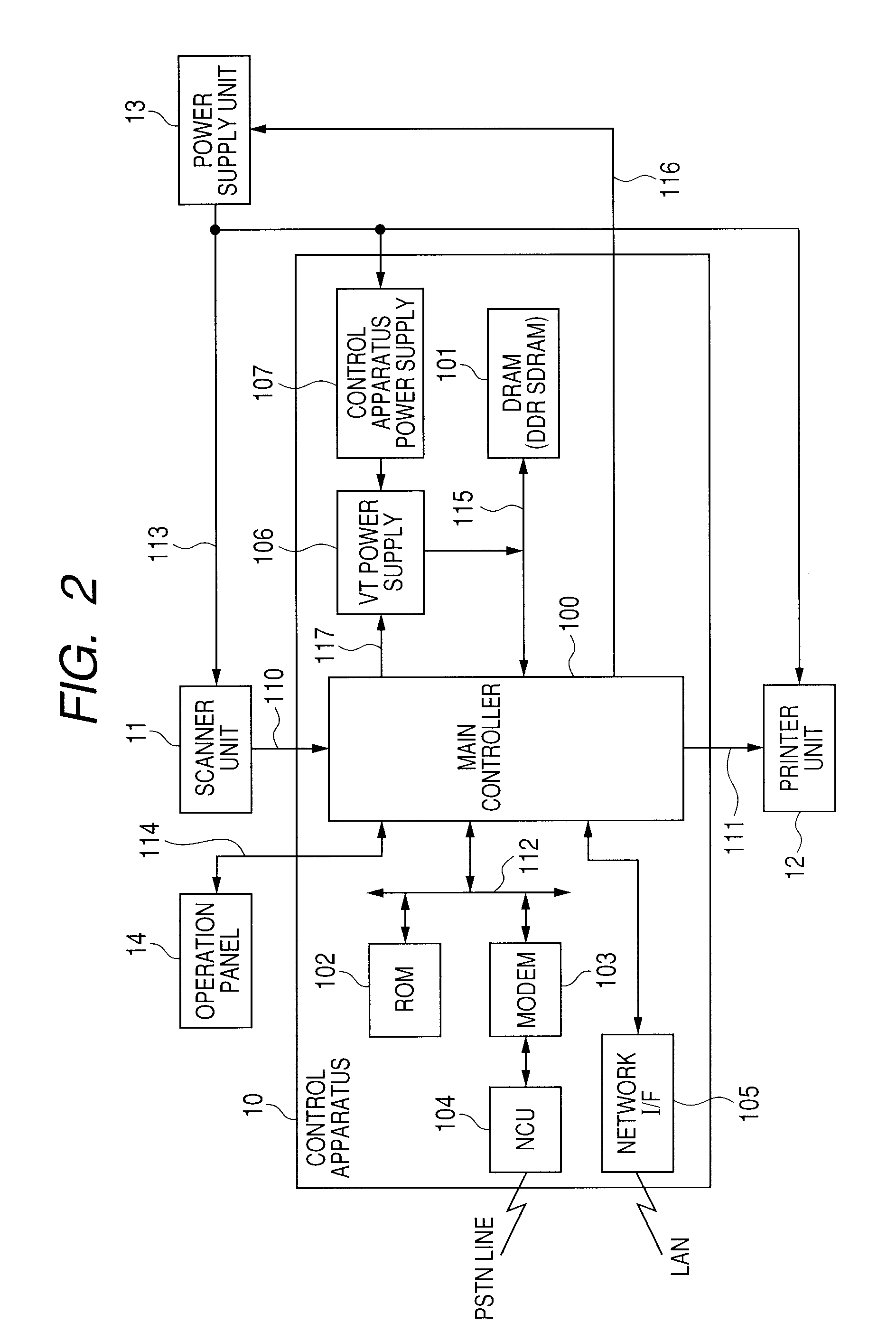
ActiveUS20100232247A1Reduce power consumptionEnergy efficient ICTDigital data processing detailsPaper data storageEngineering
Owner:CANON KK
Special printing quotation computing method and special printing quotation unit
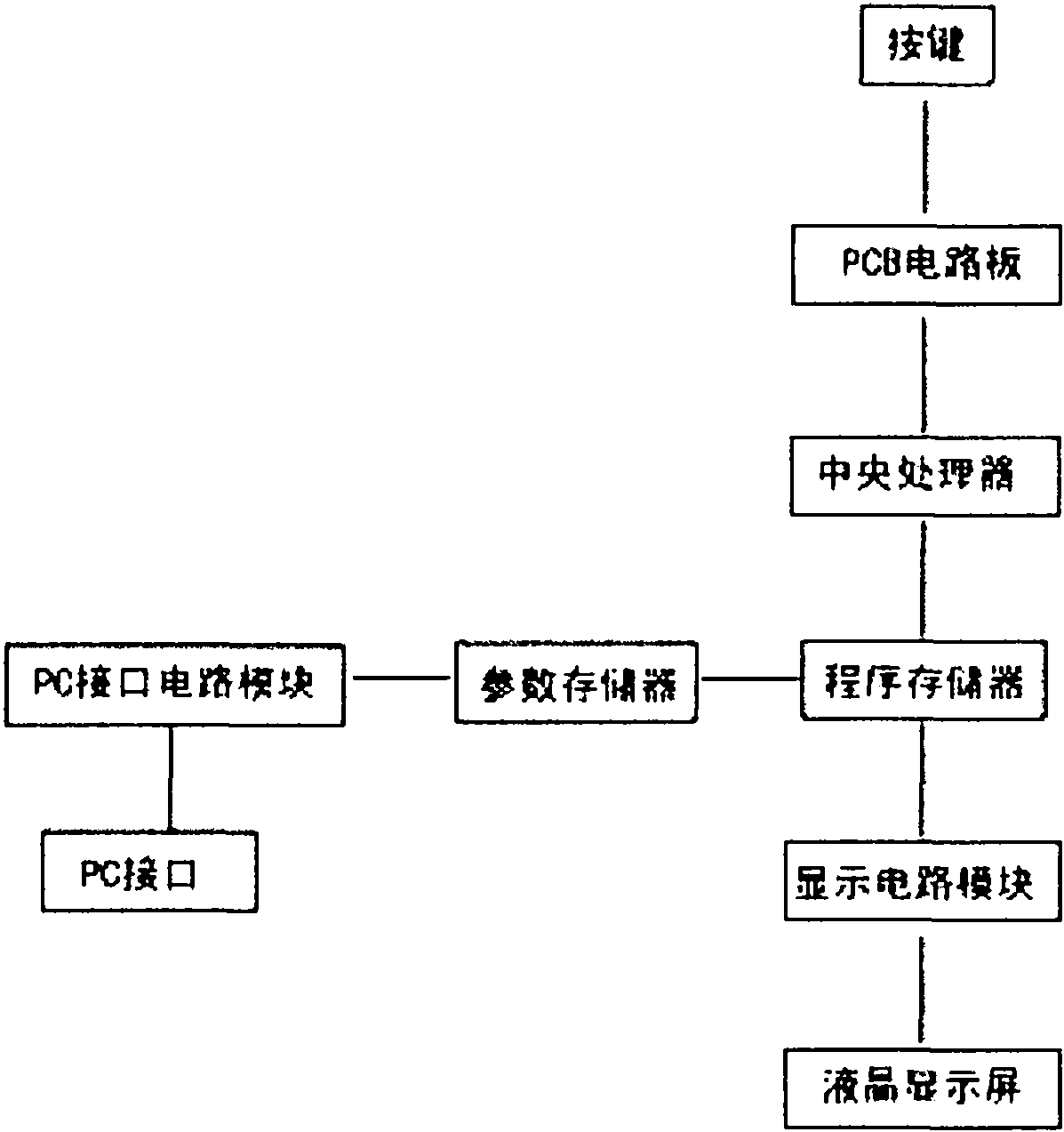
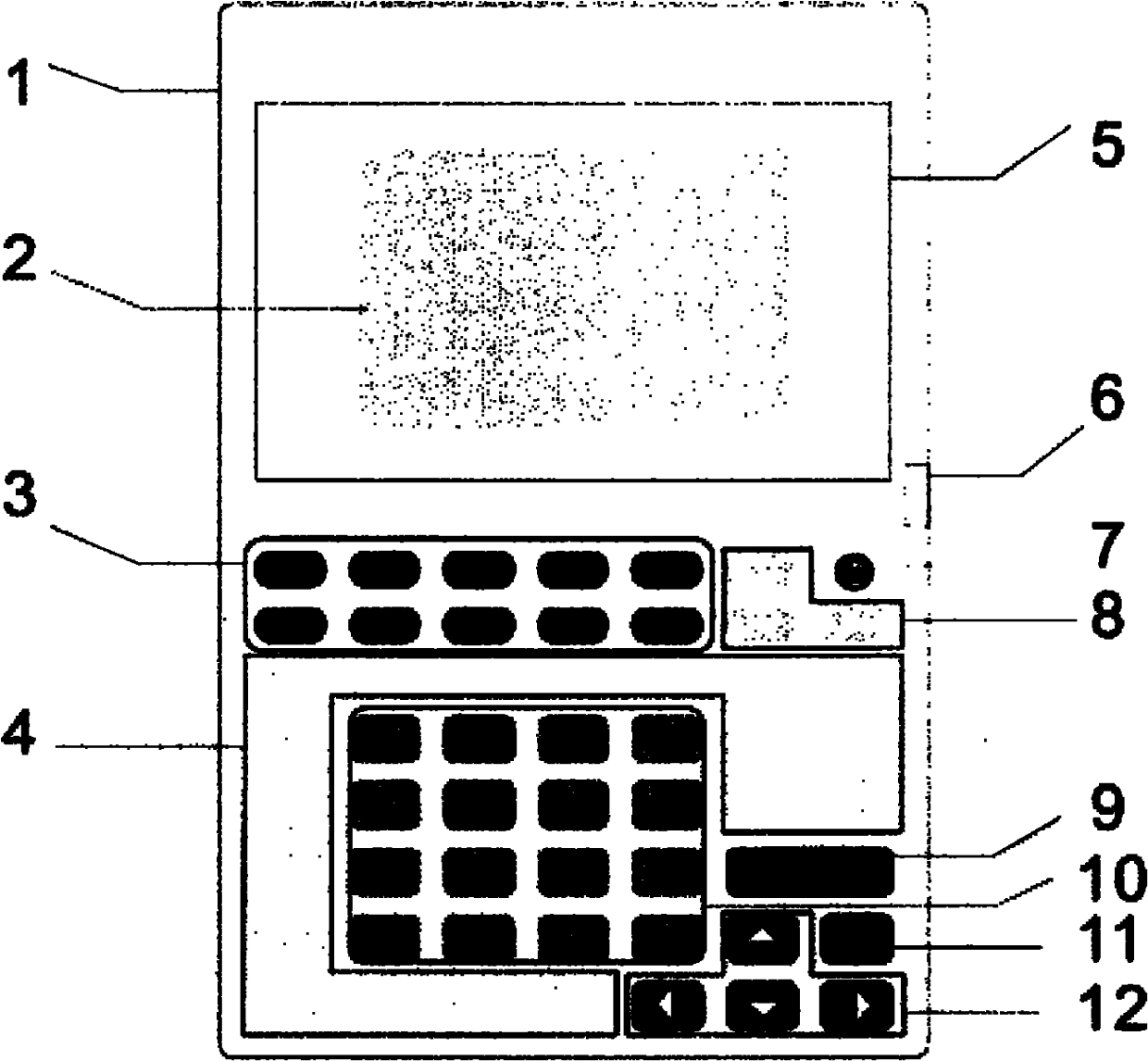
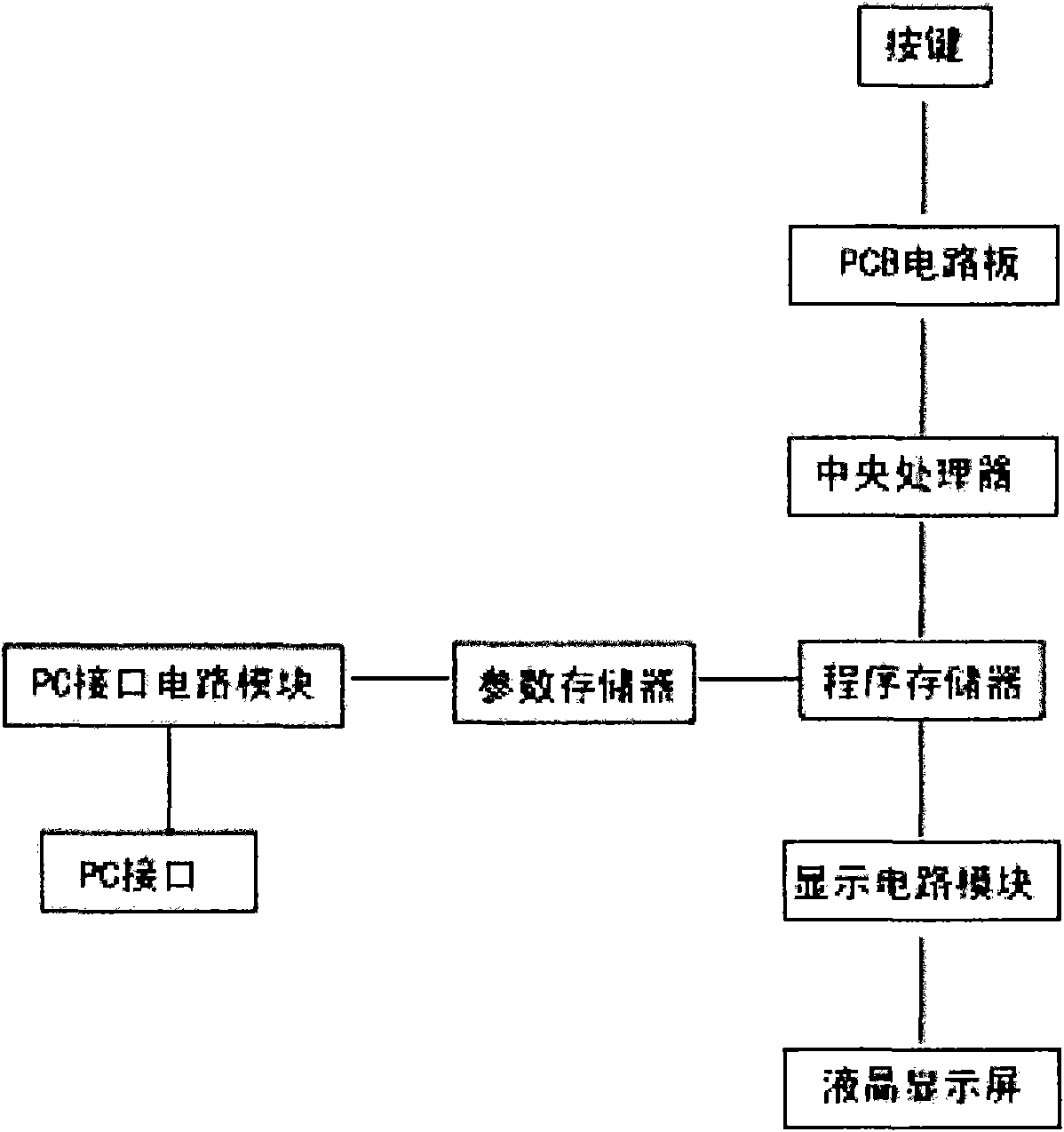
InactiveCN101996153ACalculation structure is clearCalculation speedDigital computer detailsElectric digital data processingPaper data storageControl signal
The invention relates to printing industry, in particular to the problem of the complicated quotation in the printing industry. The invention provides a computing method which utilizes a special quotation unit to directly compute the general expenses and make the general expenses clear. In order to achieve the goal, the special printing quotation unit comprises a display screen, a processor, number keys, symbolic keys, a storage, an item selector and a temporary data storage, wherein the processor is solidified on a circuit board and is connected with the display screen through a data line control signal; the storage is used for storing a data base and the attribute name and the corresponding numerical value of each item; the item selector is used for selecting items selected to be computed; and the temporary data storage is used for storing data which need to be temporarily stored. The computing method is used to compute the printing quotation conveniently, rapidly and accurately so as to make the cost and the profits clear at a glance. Meanwhile, the computing method has wide range of application and high universality rate and takes decisive action on quotation in the printing industry.
Owner:SHANGHAI YINLIAN NETWORK TECH
Validating objects in a data storage system
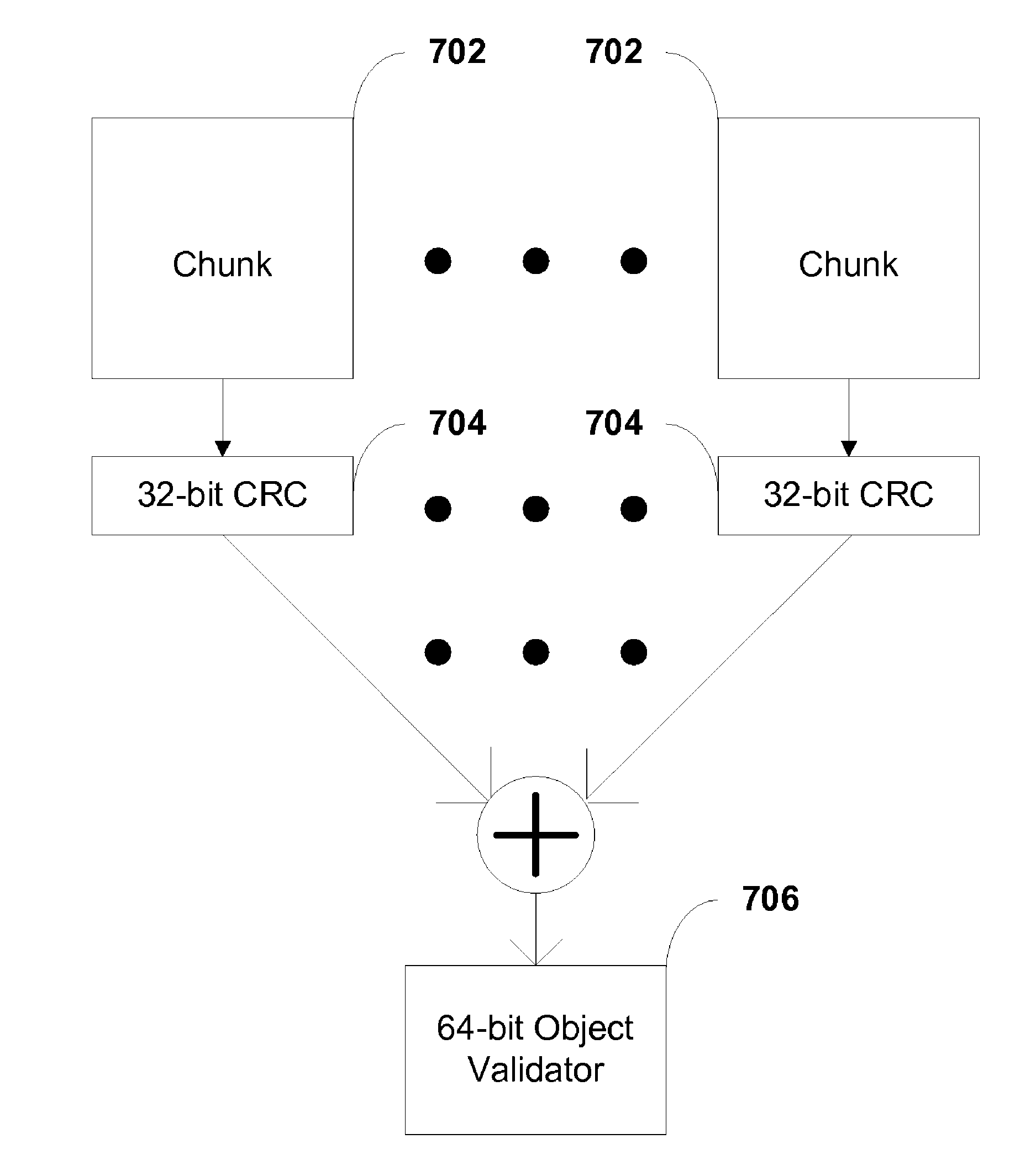
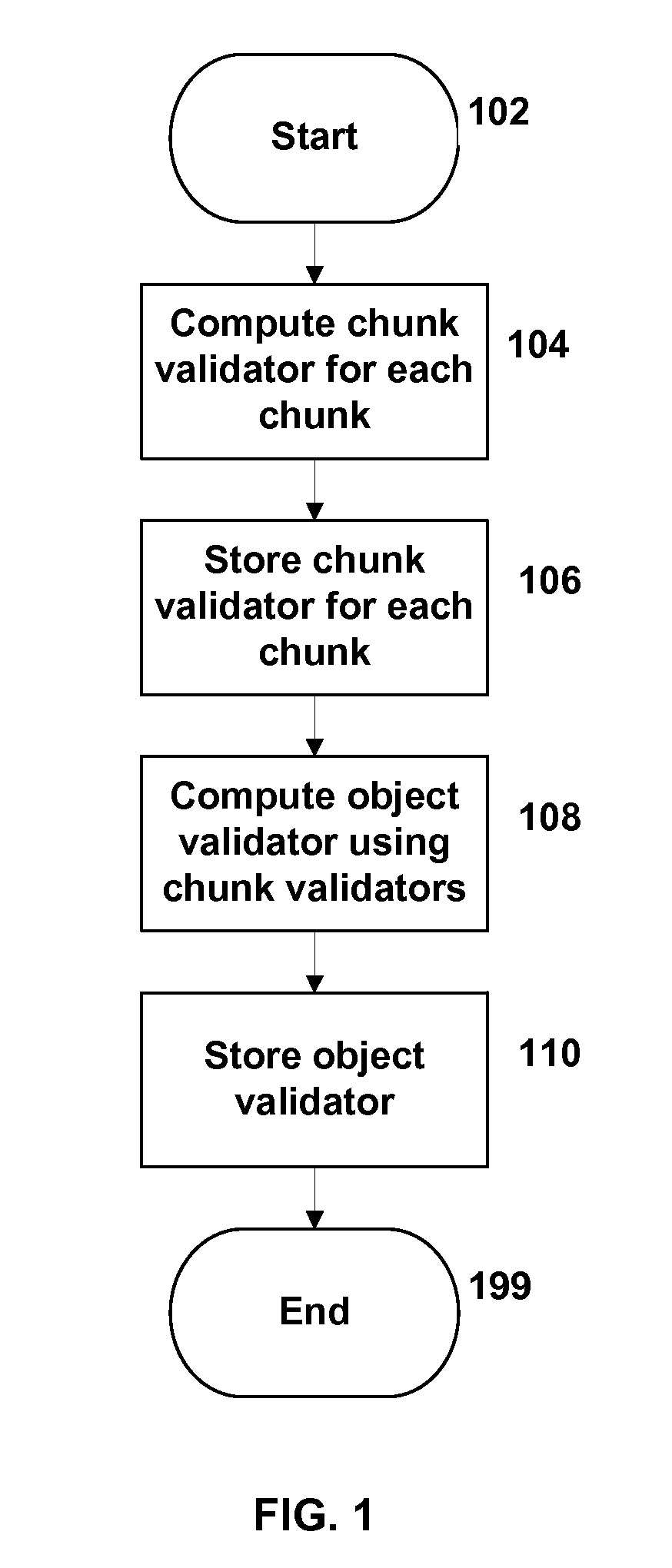
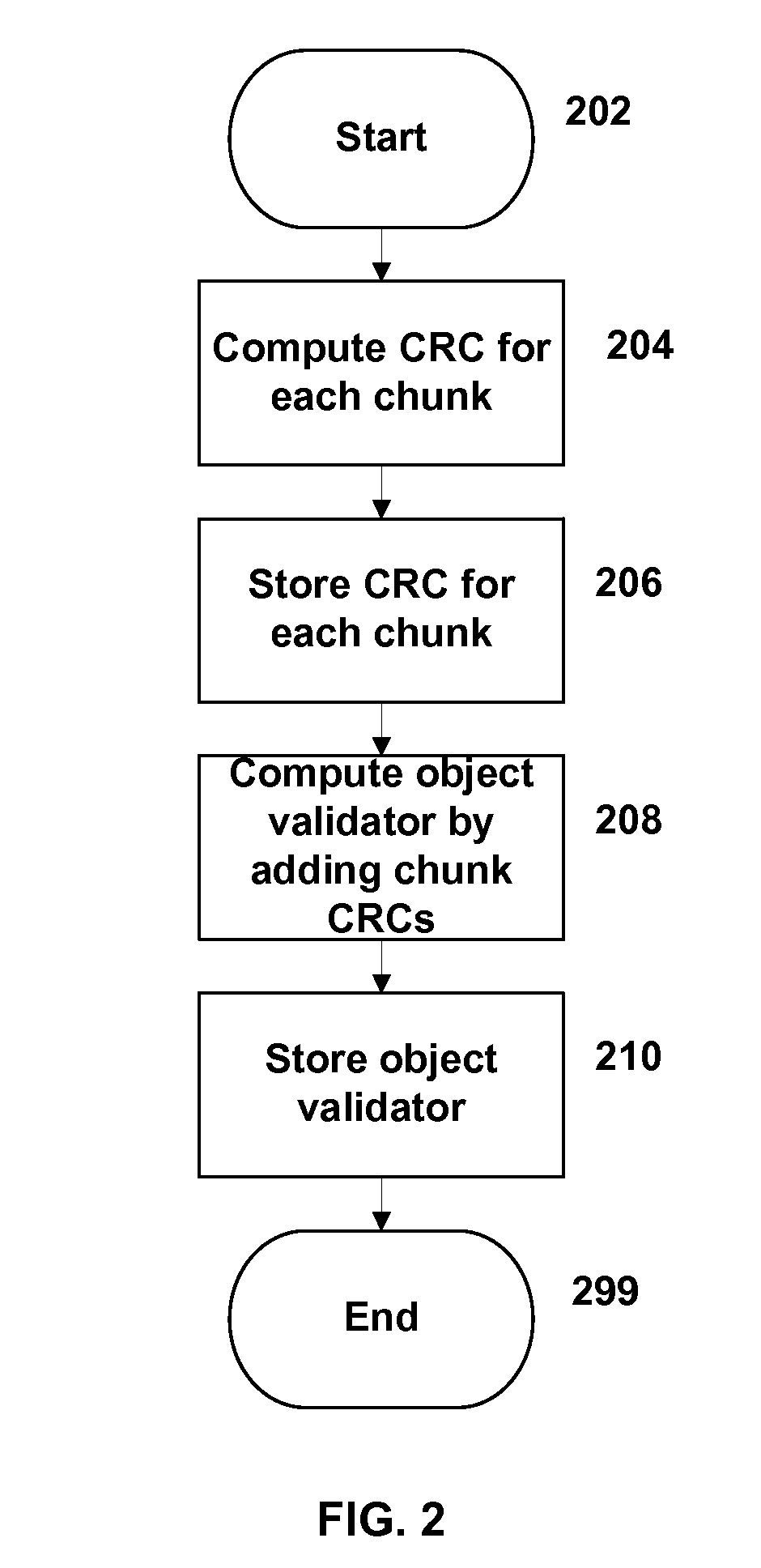
Objects stored in a storage system (such as a file server system) are protected by multiple levels of validation. Each chunk of an object is associated with a chunk validator, and an object validator is computed for the object based on the chunk validators. The object validator is stored in the storage system and may be used at various times to validate the object, for example, upon a startup of the storage system, upon taking a checkpoint or “snapshot” of the status of the storage system, or at other appropriate times.
Owner:HITACHI VANTARA LLC
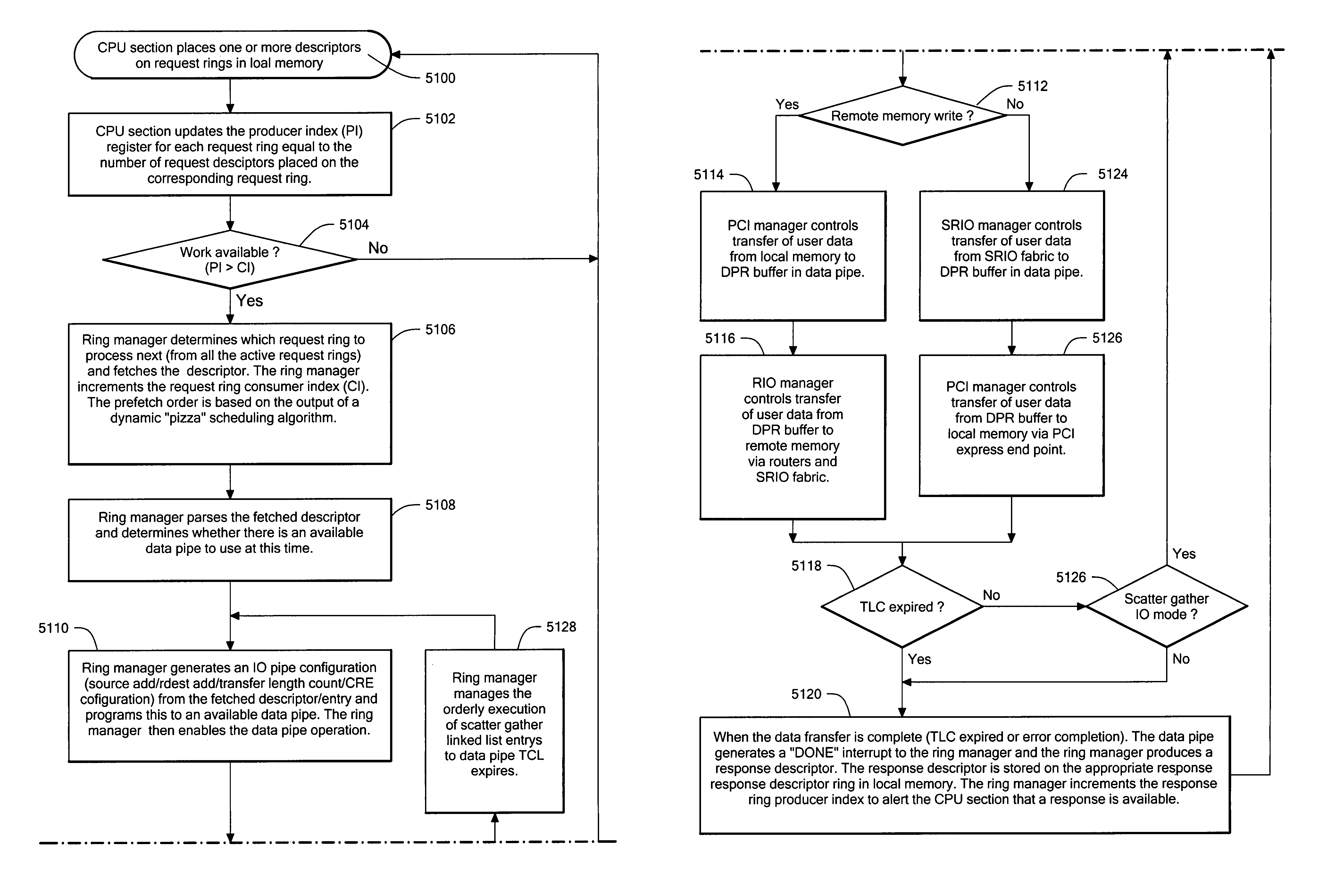
Method of operating a data storage system having plural data pipes
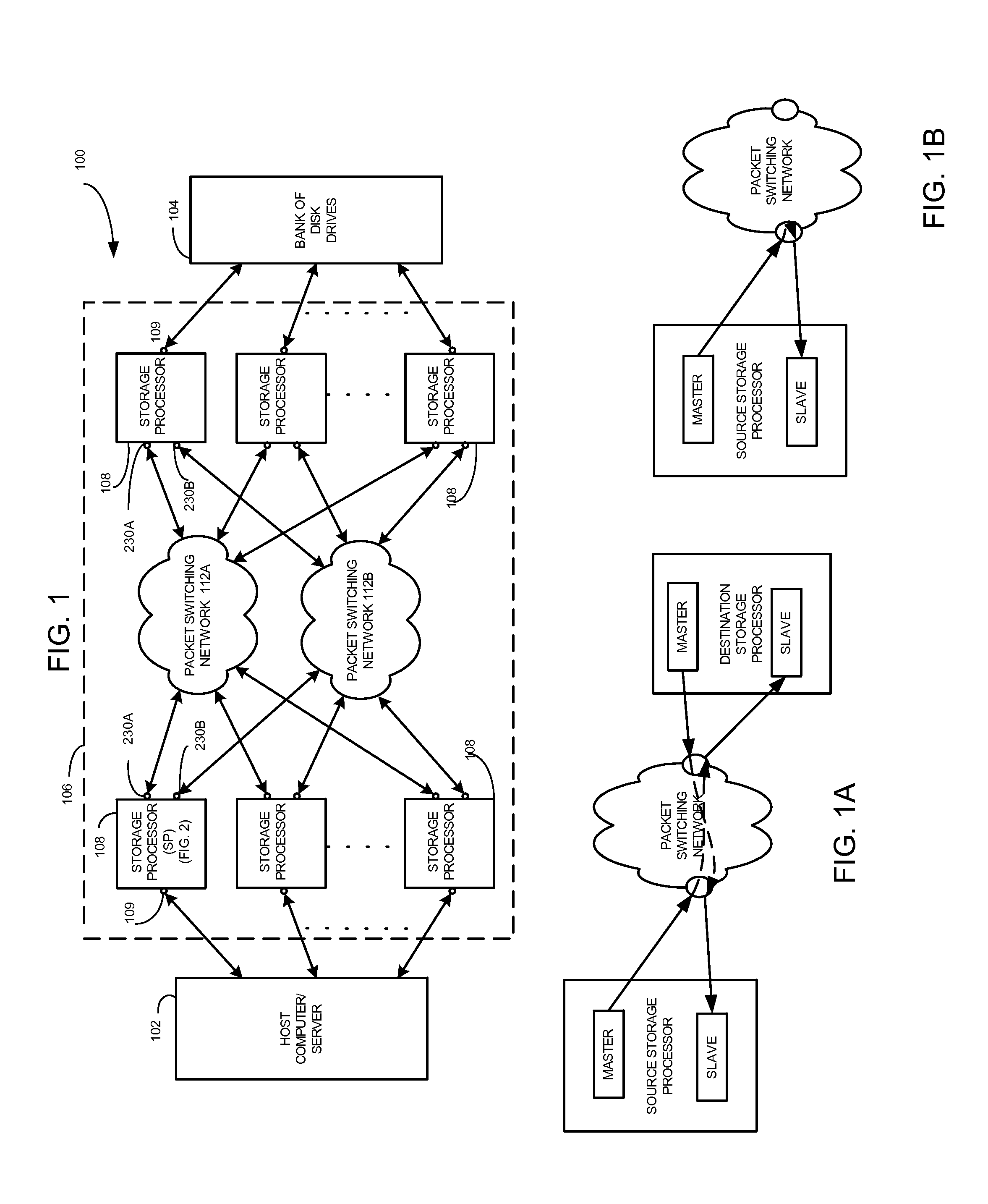
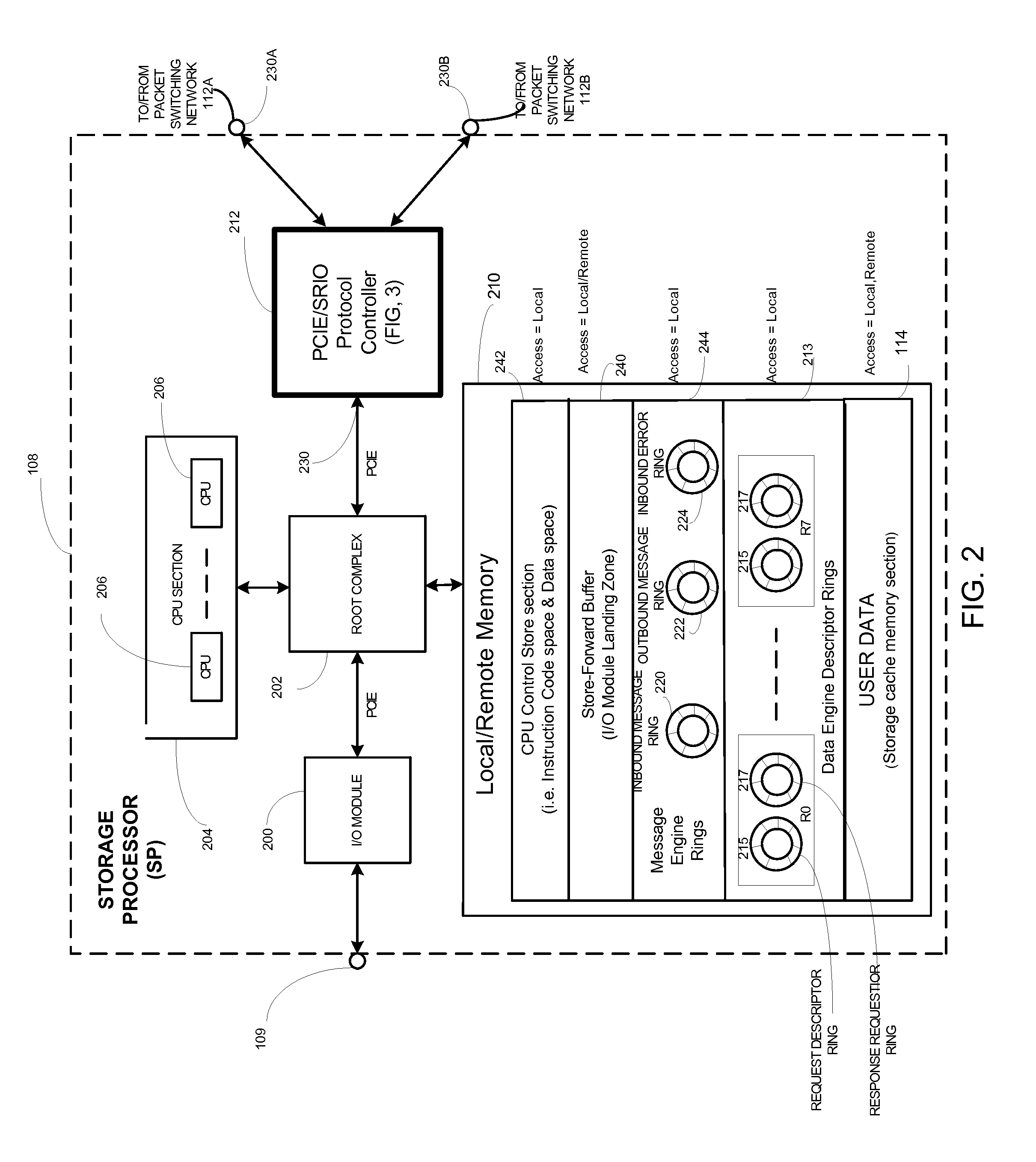
ActiveUS8090789B1Lower latencyImprove throughputMultiple digital computer combinationsTransmissionPaper data storageDistributed computing
A data storage system having protocol controller for converting packets between PCIE format used by a storage processor and Rapid IO format used by a packet switching network. The controller includes a PCIE end point for transferring atomic operation (DSA) requests, a data pipe section having a plurality of data pipes for passing user data; and a message engine section for passing messages among the plurality of storage processors. An acceleration path controller bypasses a DSA buffer in the absence of congestion on the network. Packets fed to the PCIE end point include an address portion having code indicating an atomic operation. An encoder converts the code from a PCIE format into the same atomic operation in SRIO format. Each one of a plurality of CPUs is adapted to perform a second DSA request during execution of a first DSA request.
Owner:EMC IP HLDG CO LLC
Storage capacity optimization in holographic storage media
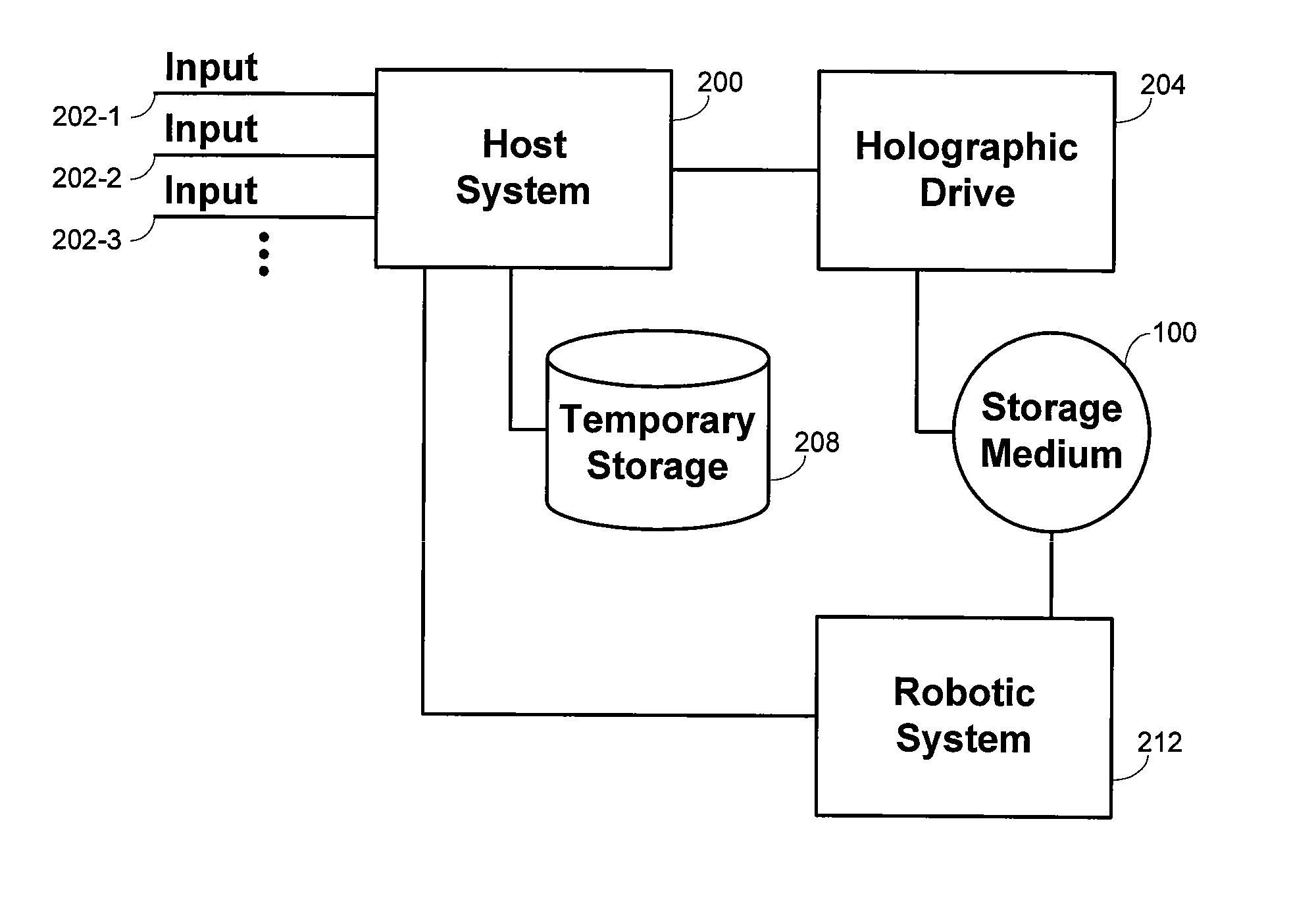
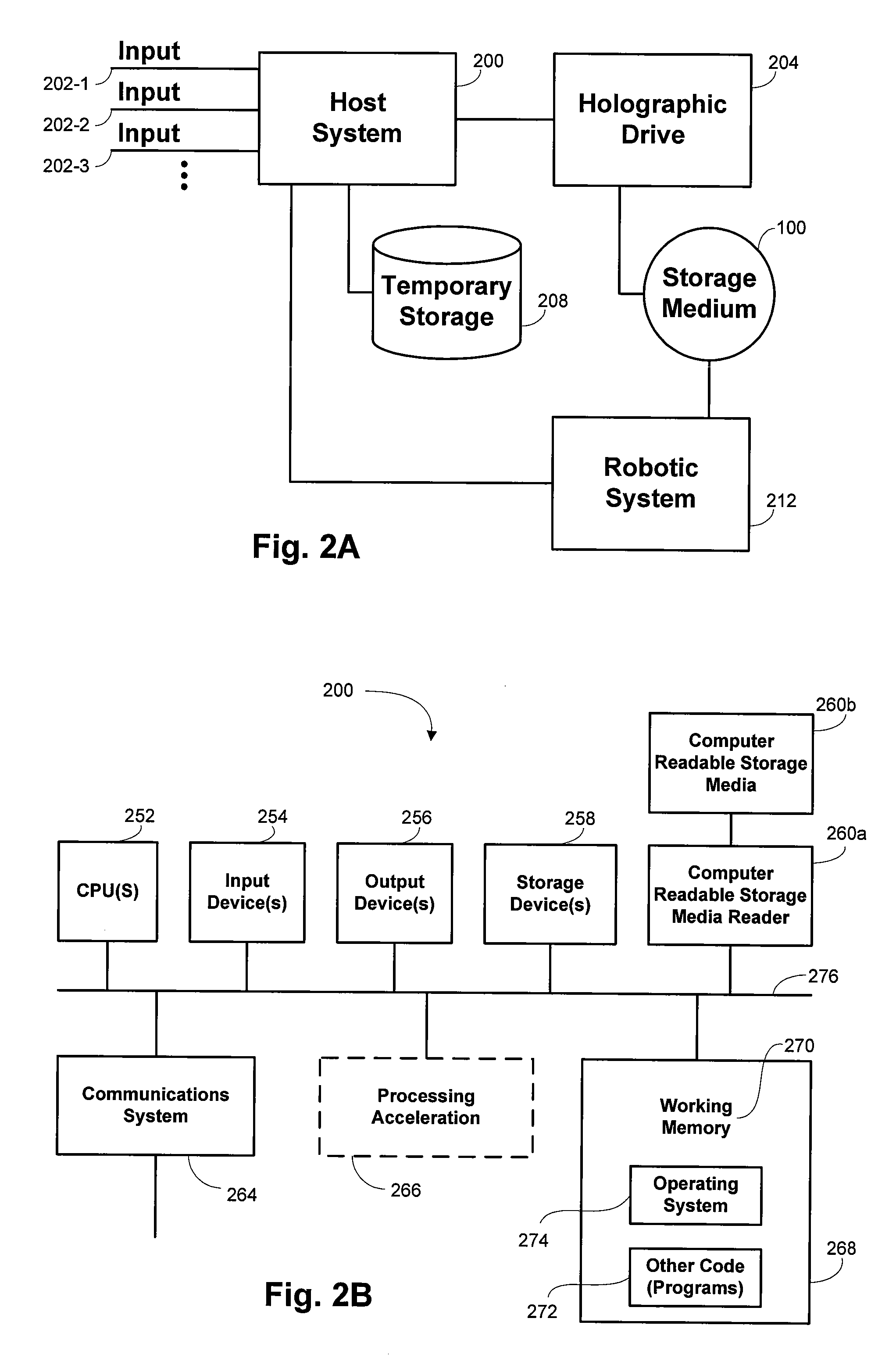
InactiveUS20080056042A1Avoid writingDigital storageDigital recording/reproducingPaper data storageHolographic storage
Methods and systems are provided for storing data holographically. Multiple distinct data packets are received. The data packets are stored on a temporary data storage. Data that includes the data packets are written holographically during a single write session to a photopolymer storage medium by optically interfering an optical data beam with an optical reference beam. The data are written physically to a data region on the photopolymer storage medium. A bleaching area of the photopolymer storage medium is exposed to a bleaching illumination to optically fix the bleaching area and prevent data from subsequently being written to the bleaching area. The bleaching area includes the data region.
Owner:SUN MICROSYSTEMS INC
Distributed data storage
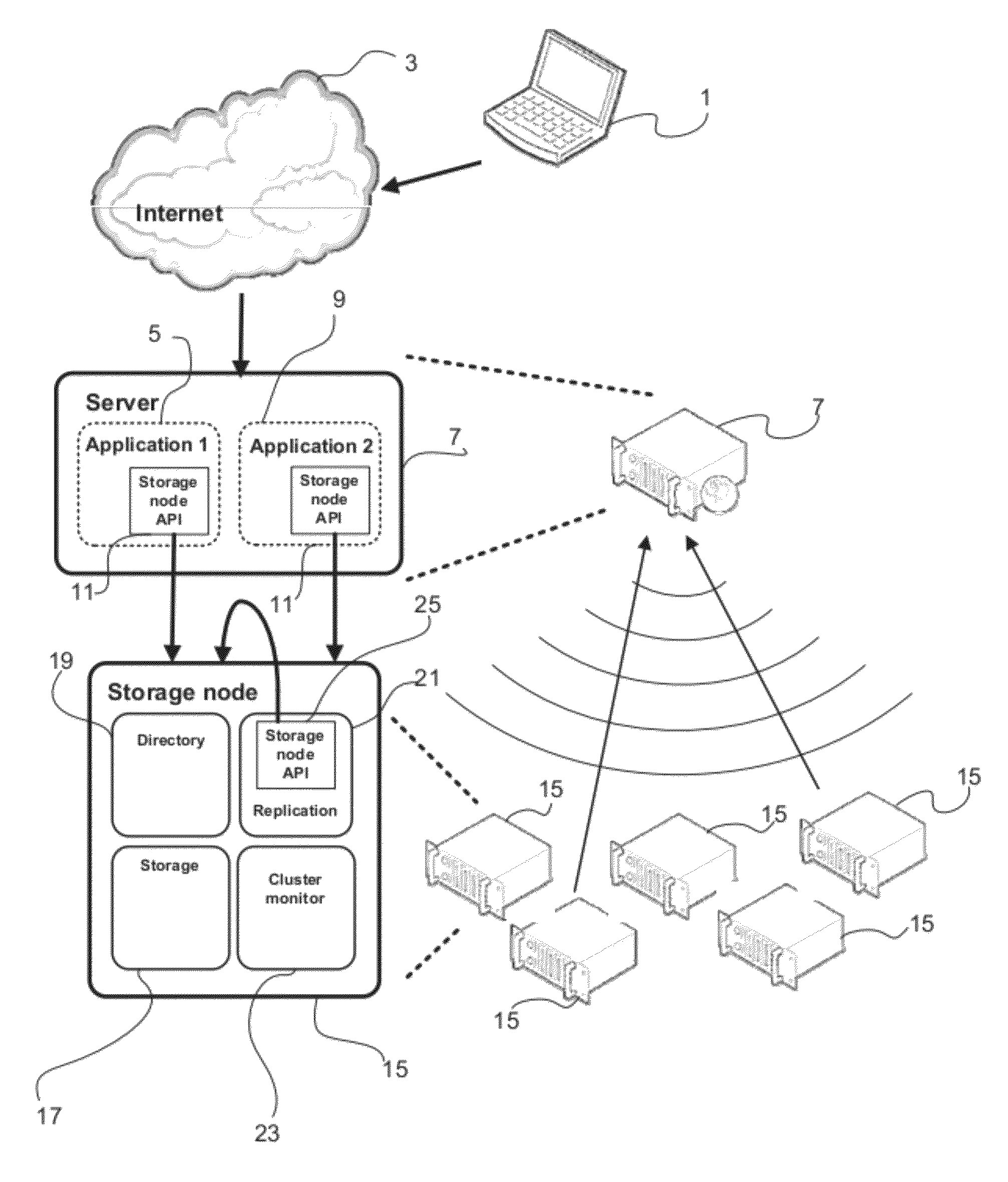
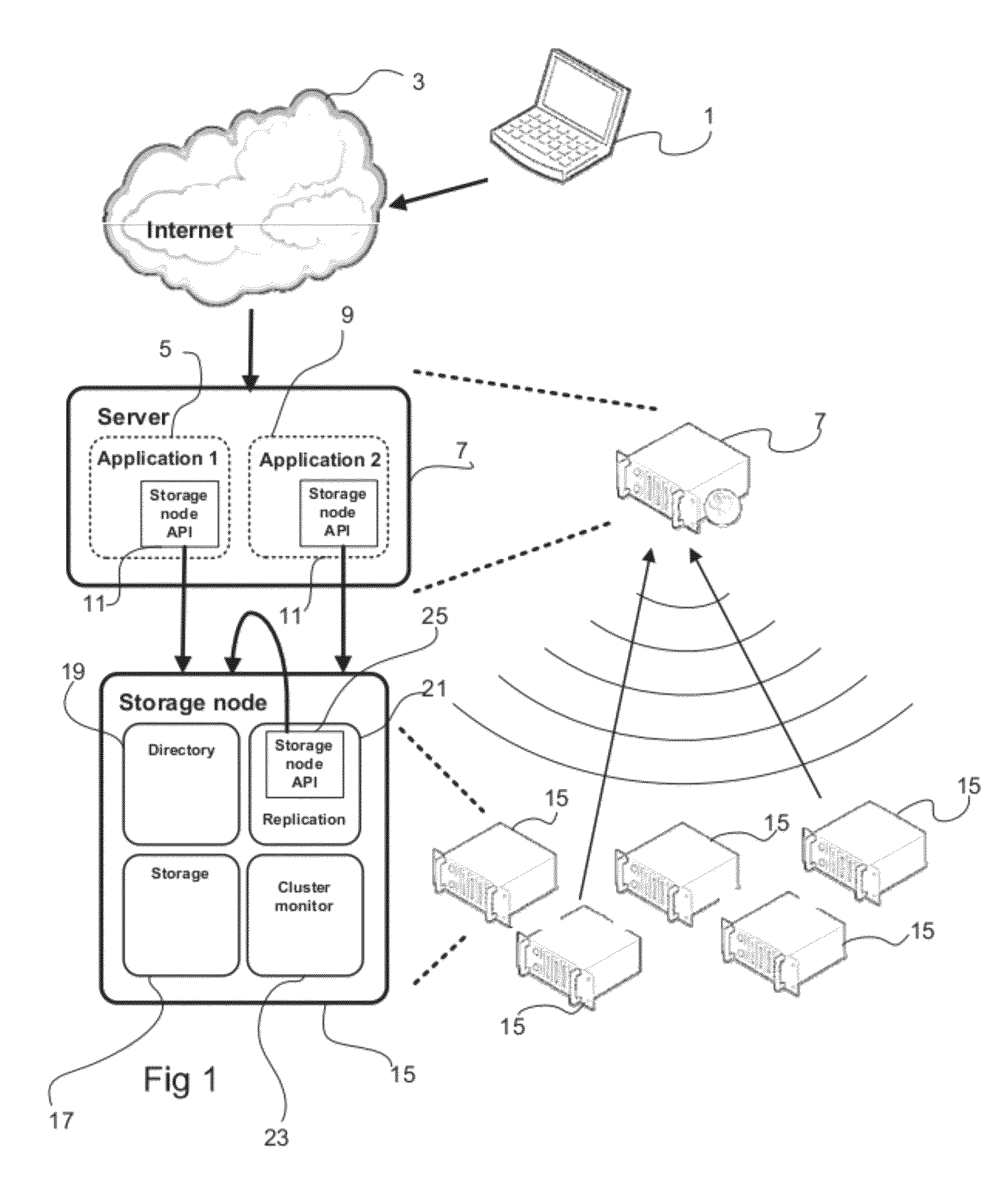
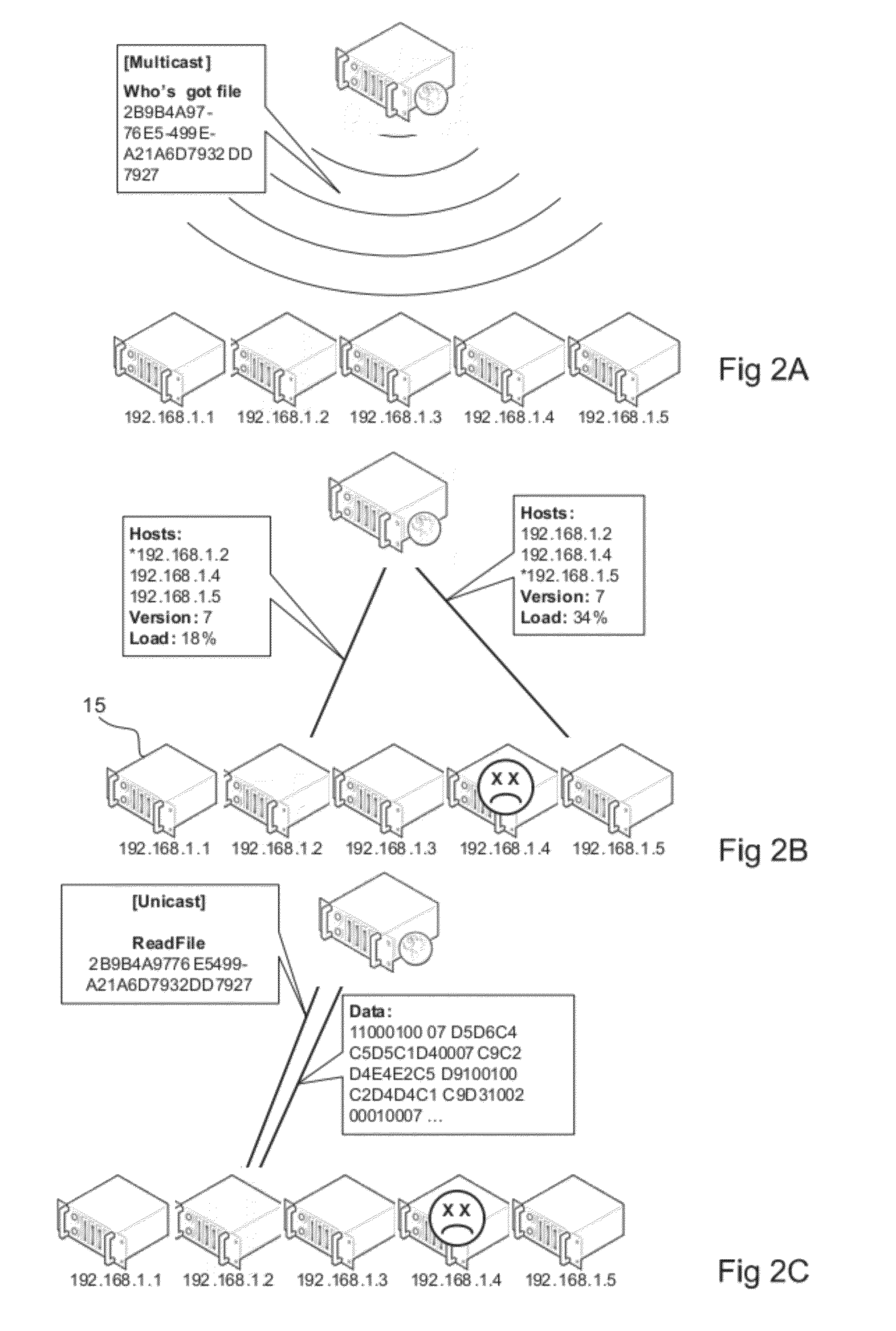
InactiveUS8850019B2Reduce maintenanceReduce riskSpecial service provision for substationError preventionPaper data storageDistributed data store
The present invention relates to a distributed data storage system comprising a plurality of storage nodes. Using unicast and multicast transmission, a server application may write data in the storage system. When writing data, at least two storage nodes are selected based in part on a randomized function, which ensures that data is sufficiently spread to provide efficient and reliable replication of data in case a storage node malfunctions.
Owner:COMPUVERDE
Removable storage device and authentication method
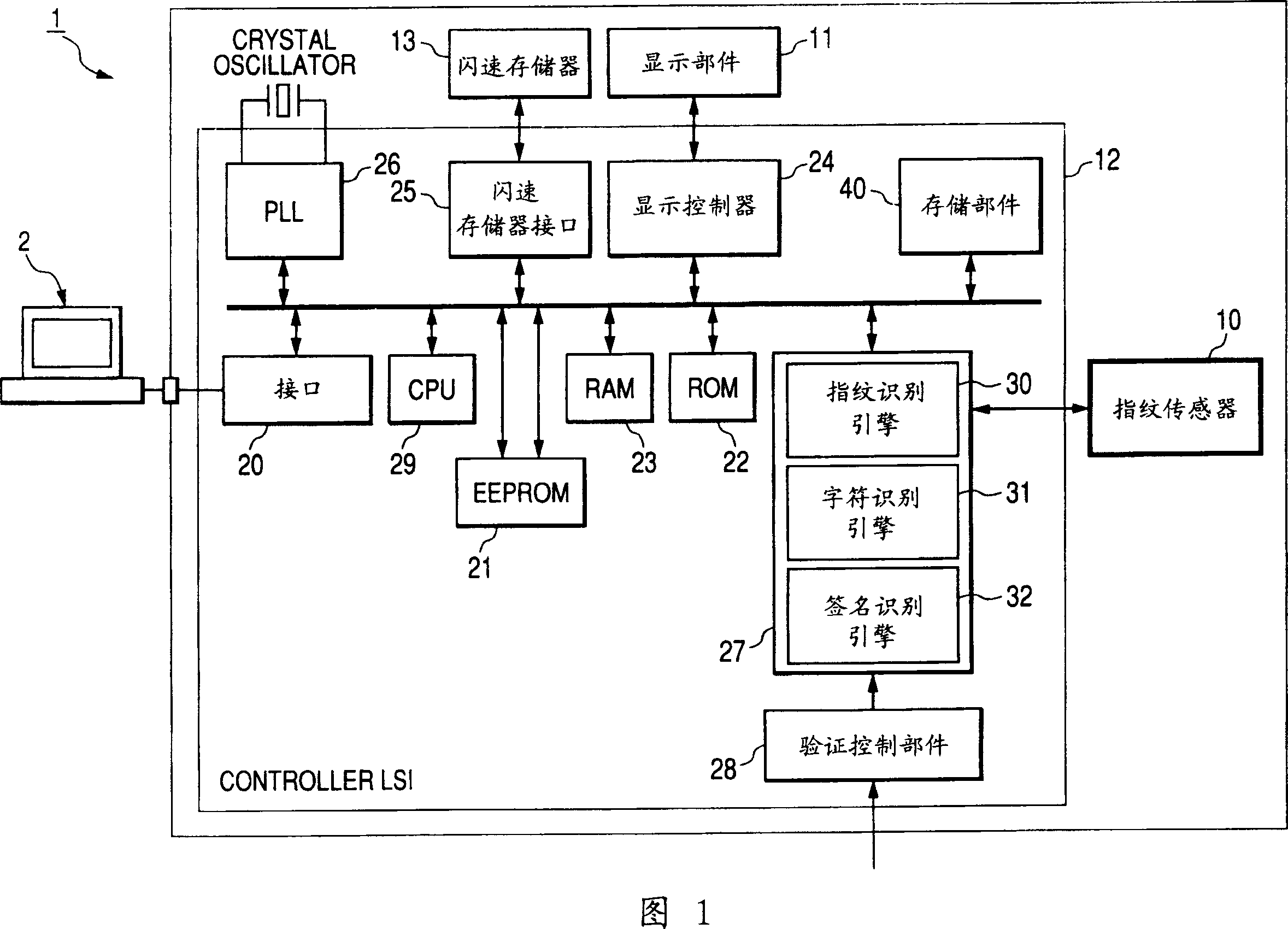
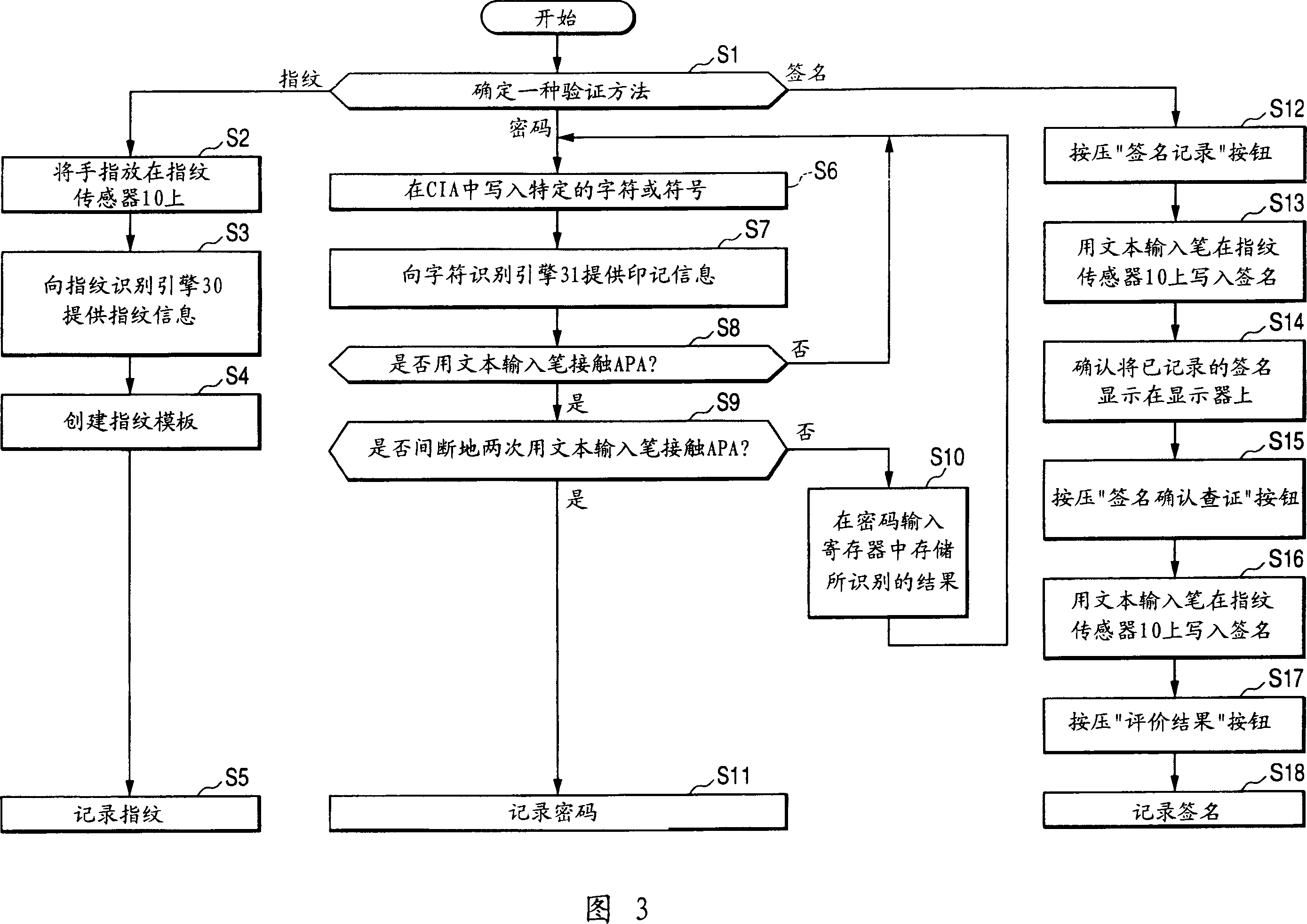
InactiveCN1996329AUnauthorized memory use protectionInternal/peripheral component protectionComputer hardwarePaper data storage
A removable storage device includes: an interface which is defined by a predetermined format and to which an external device is connectable; a data storage part in which data is stored and data is exchanged between the data storage part and the external device connected to the interface; a fingerprint reading sensor configured to read a fingerprint; authentication method selection unit for selecting an authentication method; first authentication means for verifying whether the fingerprint read by the fingerprint reading sensor is matched with a fingerprint registered beforehand by comparing them in accordance with the selection by the authentication method selection means; second authentication means for verifying whether character and symbol information extracted based on traces drawn on the fingerprint reading sensor is matched with registered character and symbol information registered beforehand by comparing them in accordance with the selection by the authentication method selection means; and determination means for determining whether to grant the external device access to the data storage part in accordance with an authentication result by the first authentication means or / and an authentication result by the second authentication means.
Owner:SONY CORP
Unified voltage generation method with improved power efficiency
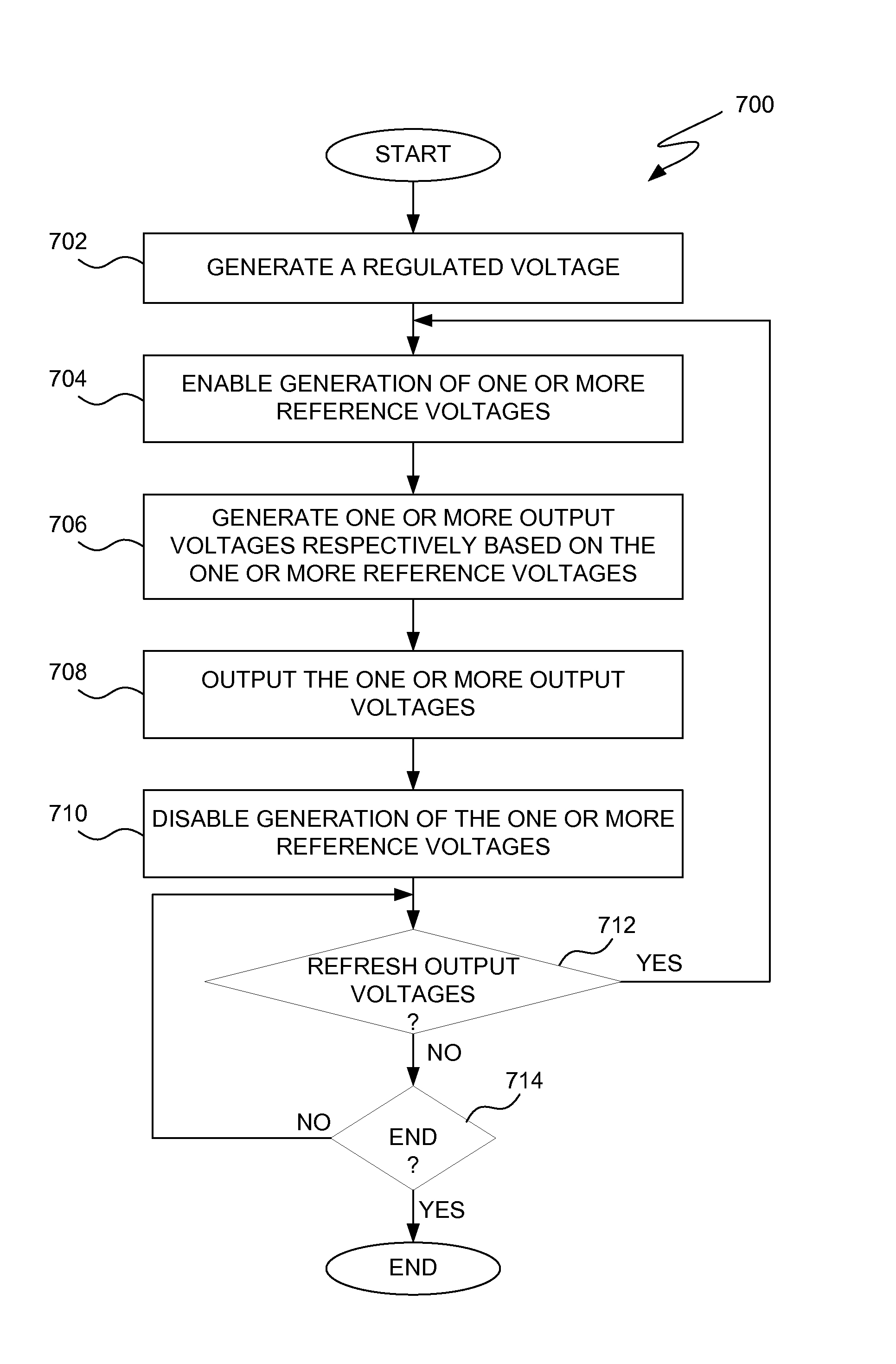
ActiveUS7440342B2Reduce power consumptionImprove power efficiencyDc-dc conversionDigital storagePaper data storageEngineering
Unified voltage generation techniques for efficiently generating a plurality of operational voltages for use within an electronic device, such as a memory system (e.g., memory product) providing data storage, are disclosed. A voltage generation circuit can generate a regulated base output voltage. The voltage generation circuit can include one or more voltage output circuits that produce different operational voltages from the regulated base output voltage. According to one aspect of the invention, the voltage output circuits can be disabled when the different operational voltages are at their appropriate voltage potentials, thereby reducing power consumption by the voltage output circuits. The voltage generation circuit is therefore able to operate with improved power efficiency.
Owner:SANDISK TECH LLC
Method and system for parallel file operation in distributed data storage system with mixed types of storage media
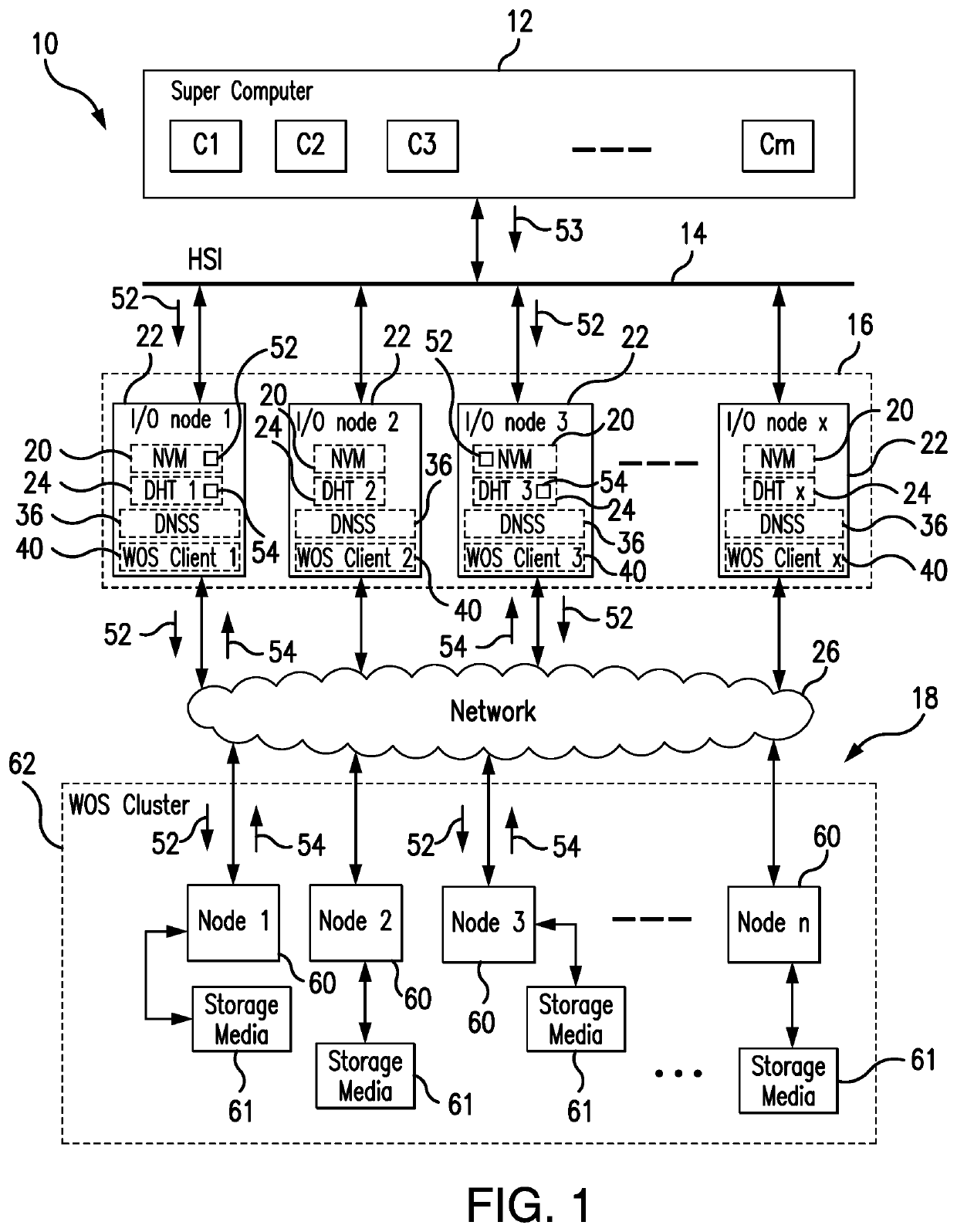
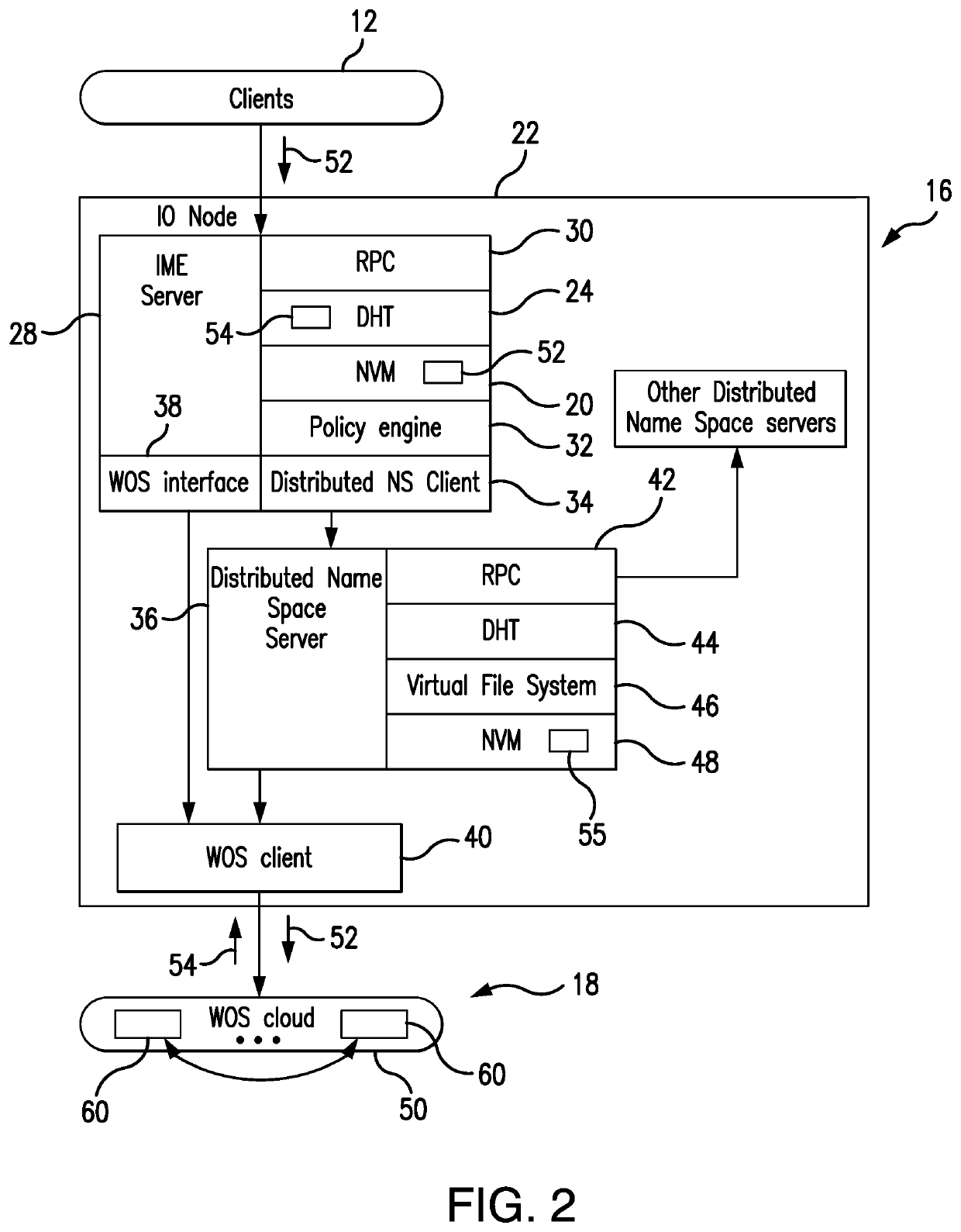
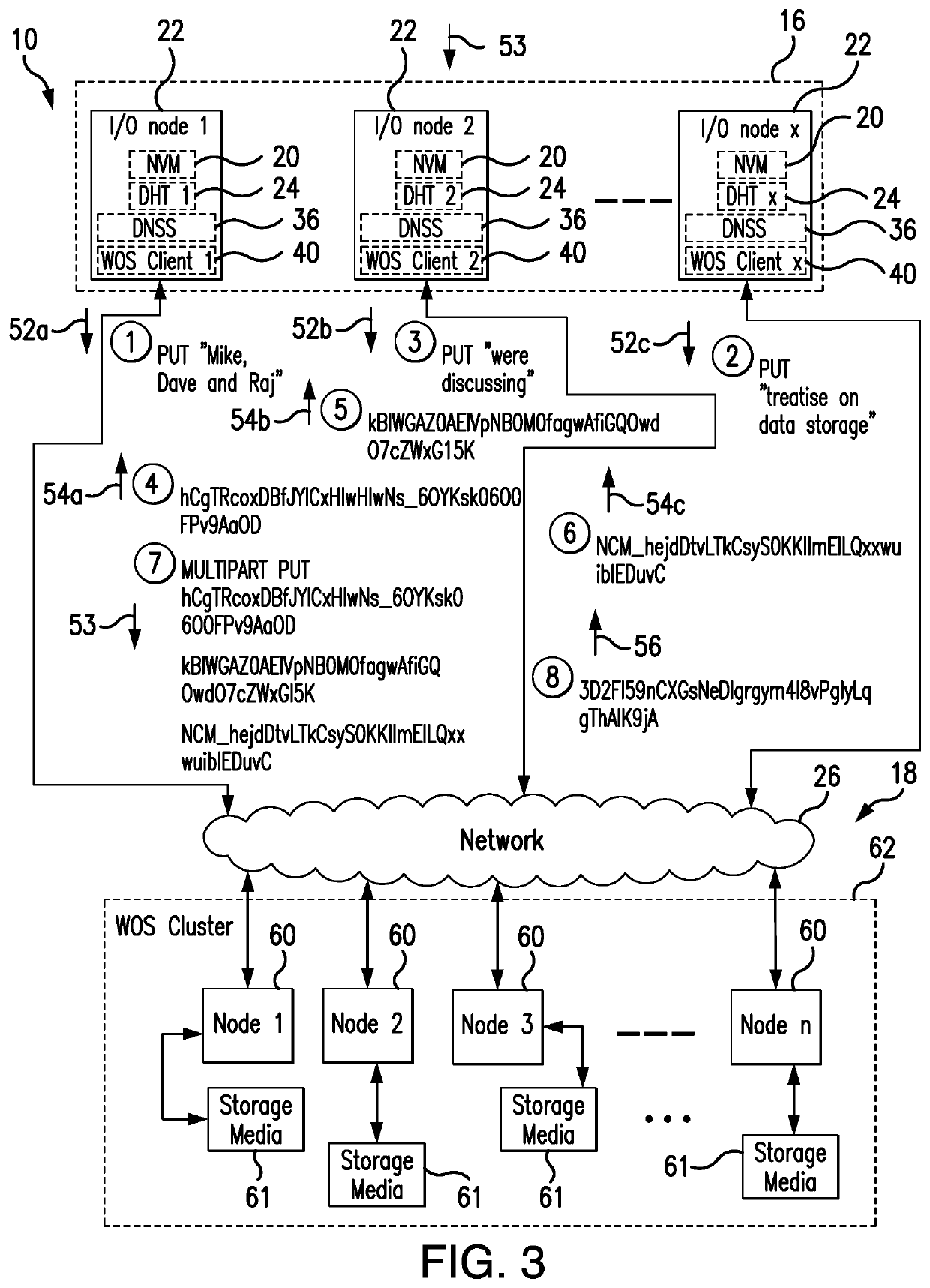
ActiveUS10503693B1Write efficientlyLower latencyDigital data processing detailsFile access structuresPaper data storageData set
The present invention is directed to a distributed data migration and storage system and method configured for fully parallel writing and retrieval of data objects to (and from) the Web Object Scaler (WOS) object storage system with highly efficient accessibility and using a simplified set of filing commands. The data objects migrate between data generating entities and the WOS object storage through an intermediate Burst Buffer tier (supported by the Infinite Memory Engine) without the utilization of a serial process substantially simultaneously through parallel channels. The metadata for each object is captured with appropriate pointers for efficient finding of the object in the WOS storage system. The WOS nodes return the stored objects' ID (OIDs) corresponding to the objects storage address which are used for the object access.
Owner:DATADIRECT NETWORKS
Test paper data storage method, device and electronic device
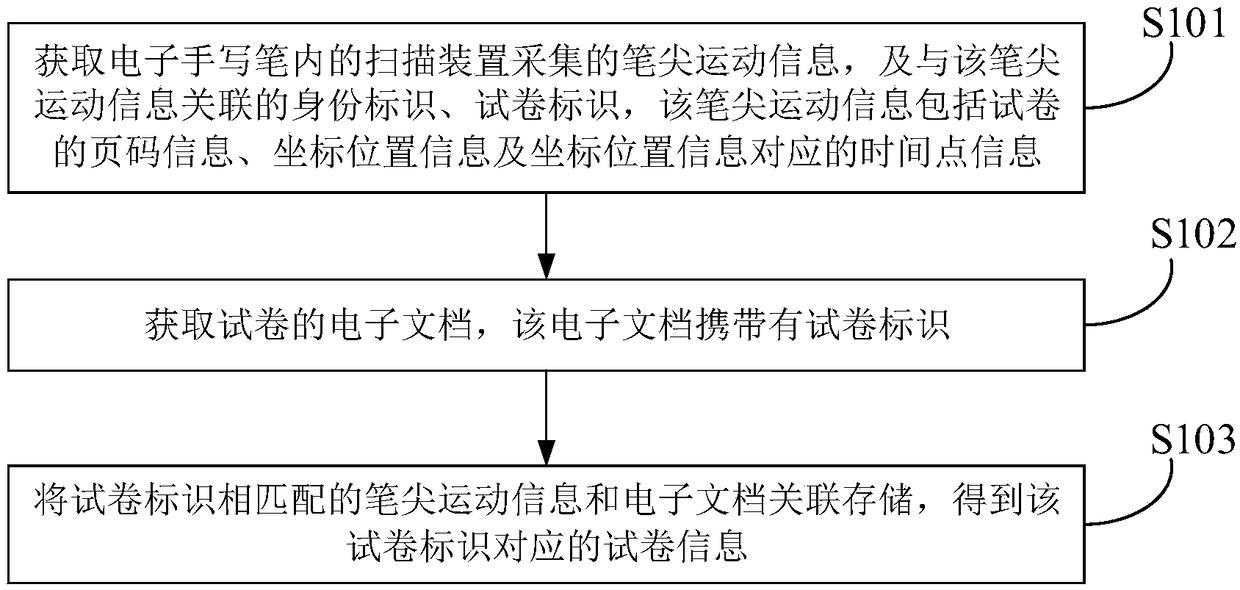
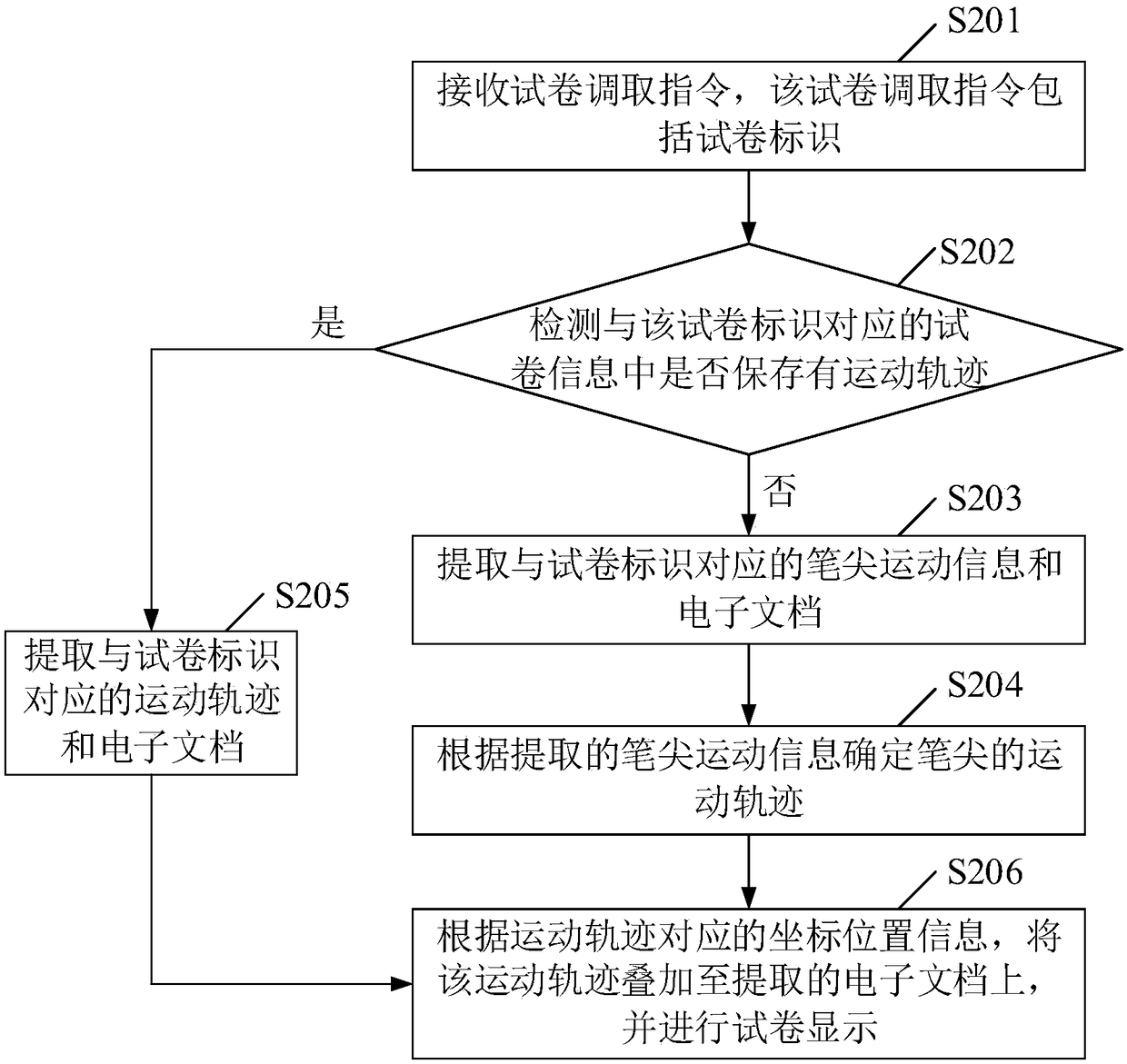
InactiveCN109086336AEasy extractionEasy to analyzeData processing applicationsDigital ink recognitionElectronic documentPaper data storage
A test paper data storage method, device and electronic device is provided, The invention relates to the technical field of teaching management, wherein, the method comprises the following steps: obtaining the pen tip motion information collected by a scanning device in an electronic handwriting pen, and an identity mark associated with the pen tip motion information, and a test paper mark, wherein the pen tip motion information comprises page number information, coordinate position information and time point information corresponding to the coordinate position information of the test paper; obtaining an electronic document of an examination paper, the electronic document carrying an identification of the examination paper; the corresponding test paper information being obtained by storingthe pen tip motion information matched with the test paper identification and the electronic document in association. Compared with the prior art, the scheme can store the electronic document, the answer information and the marking information electronically and form a complete electronic archive, and can view the electronic document, the answer information and the marking information separatelyin the later period, which is suitable for long-term storage and can realize quick retrieval, and is convenient for data extraction and analysis in the later period.
Owner:深圳闳宸科技有限公司
Paper indexing system based on block chain technology
InactiveCN111651462AImprove indexing speedAvoid regulationDatabase updatingDatabase distribution/replicationPaper data storageData Origin
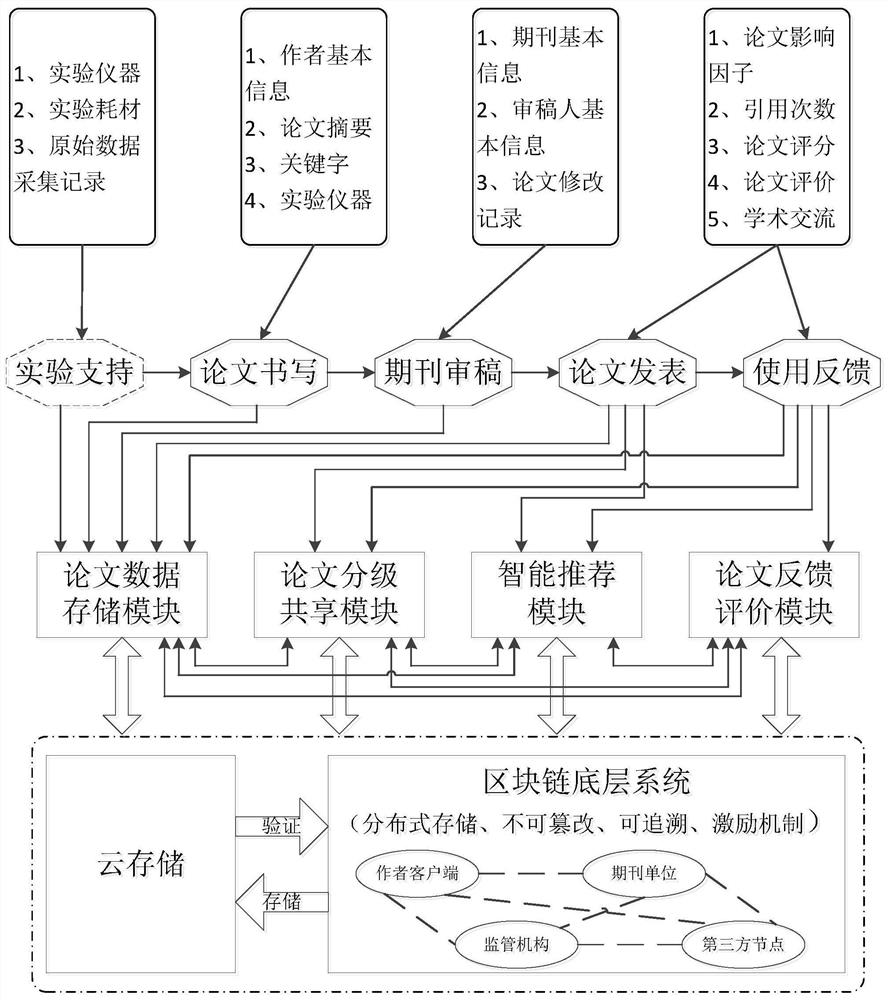
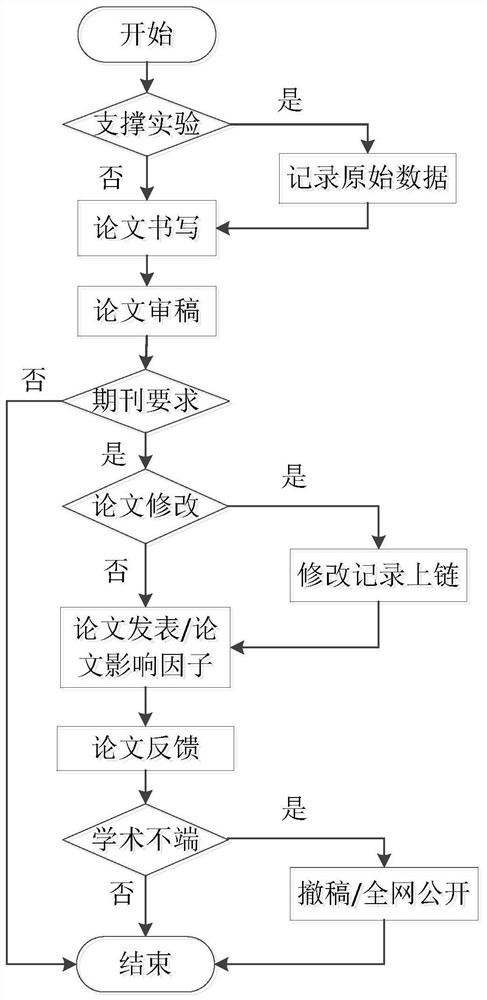
The invention discloses a paper indexing system based on a block chain technology. According to the system, an information distributed storage, non-tampering, traceable and excitable blockchain platform is used as a bottom architecture, and the blockchain platform of the system is connected with four functional modules, including a paper data storage module, a paper hierarchical sharing module, anintelligent recommendation module and a paper feedback evaluation module; wherein data sources of the paper data storage module comprise authors, periodicals, manuscript reviewers and referers, and the paper data storage module is used for storing full-process information of each piece of paper from writing, submitting, manuscript reviewing, publishing, referencing and feeding back; the method has the advantages that the blockchain technology is utilized, the full life cycle of writing, submitting, reviewing, publishing, quoting and feeding back of each paper can be public and transparent, paper experiment data are public, transparent, credible and traceable, academic achievement counterfeiting can be effectively avoided, the paper index speed can be increased, and paper can be effectively supervised.
Owner:YANTAI UNIV
Computer protection against malware affection
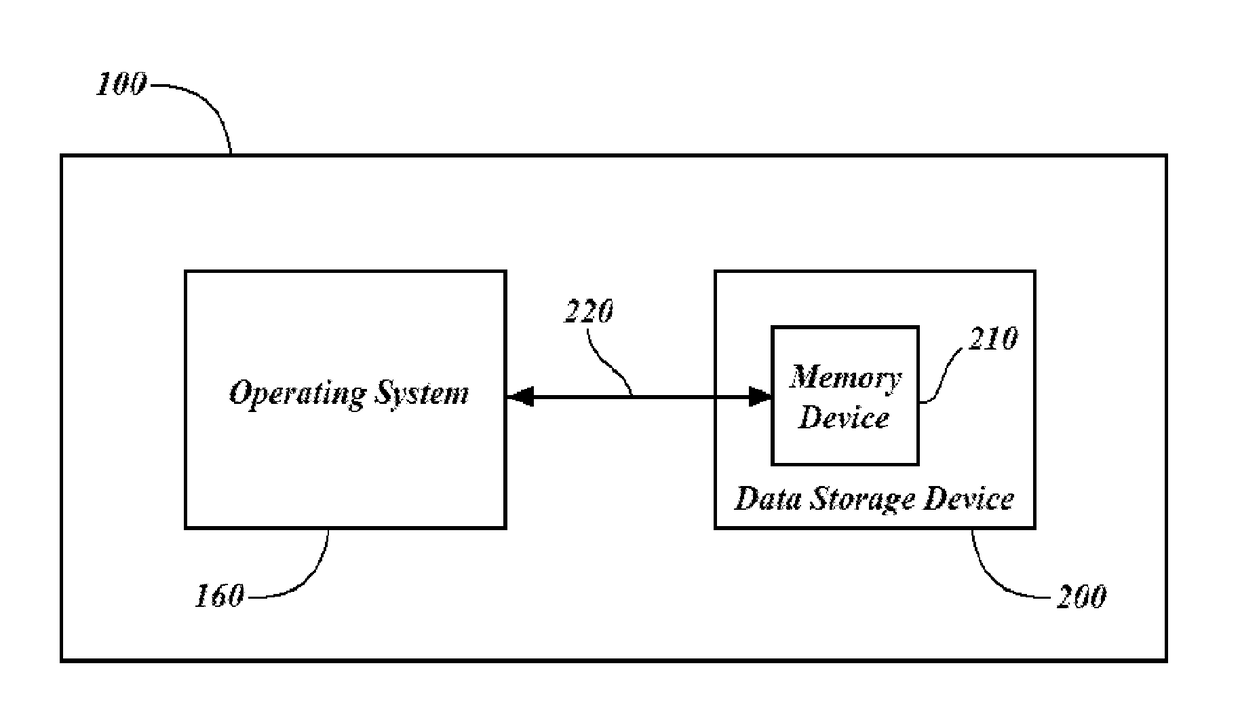
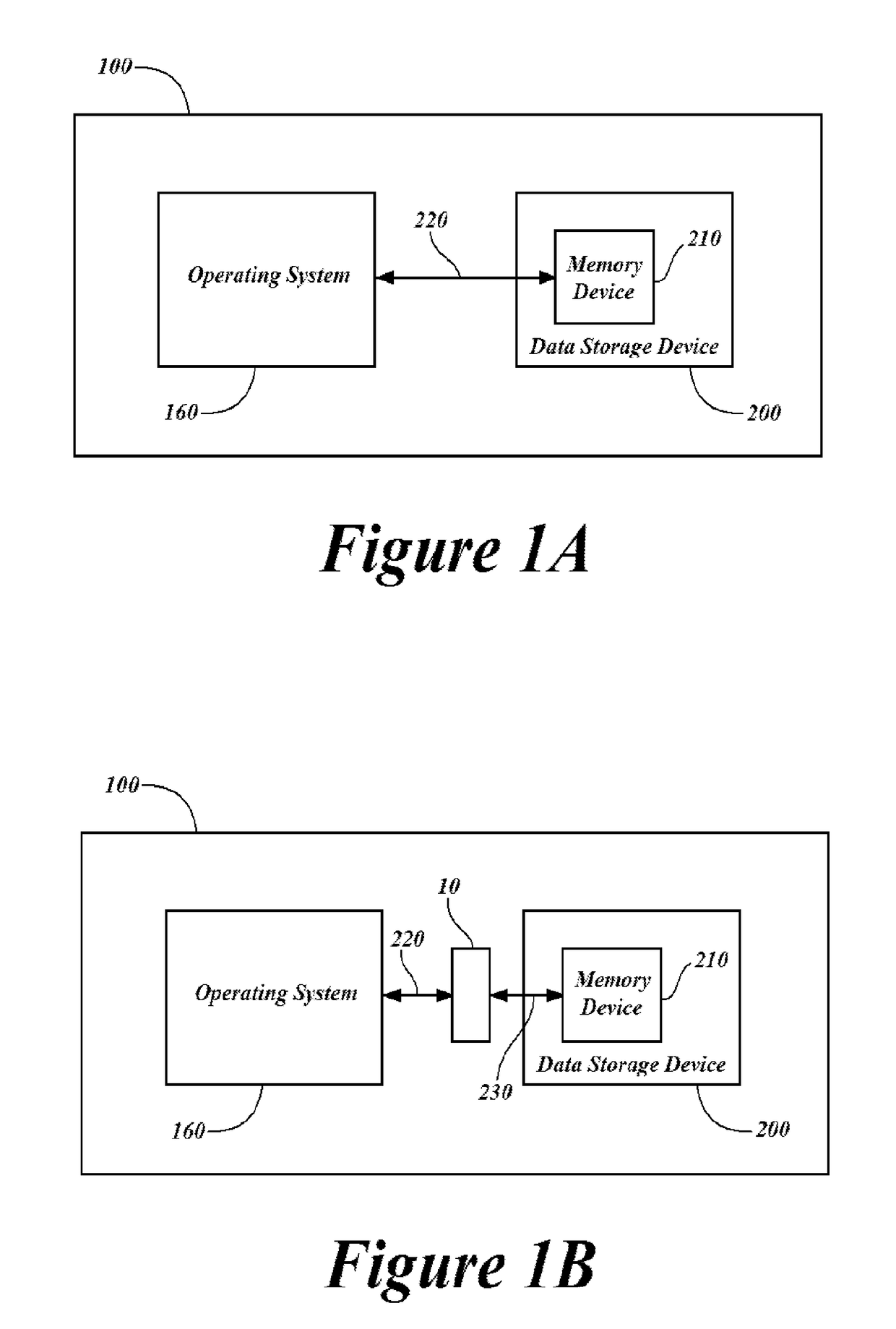
ActiveUS9129111B2Memory loss protectionError detection/correctionPaper data storageOperational system
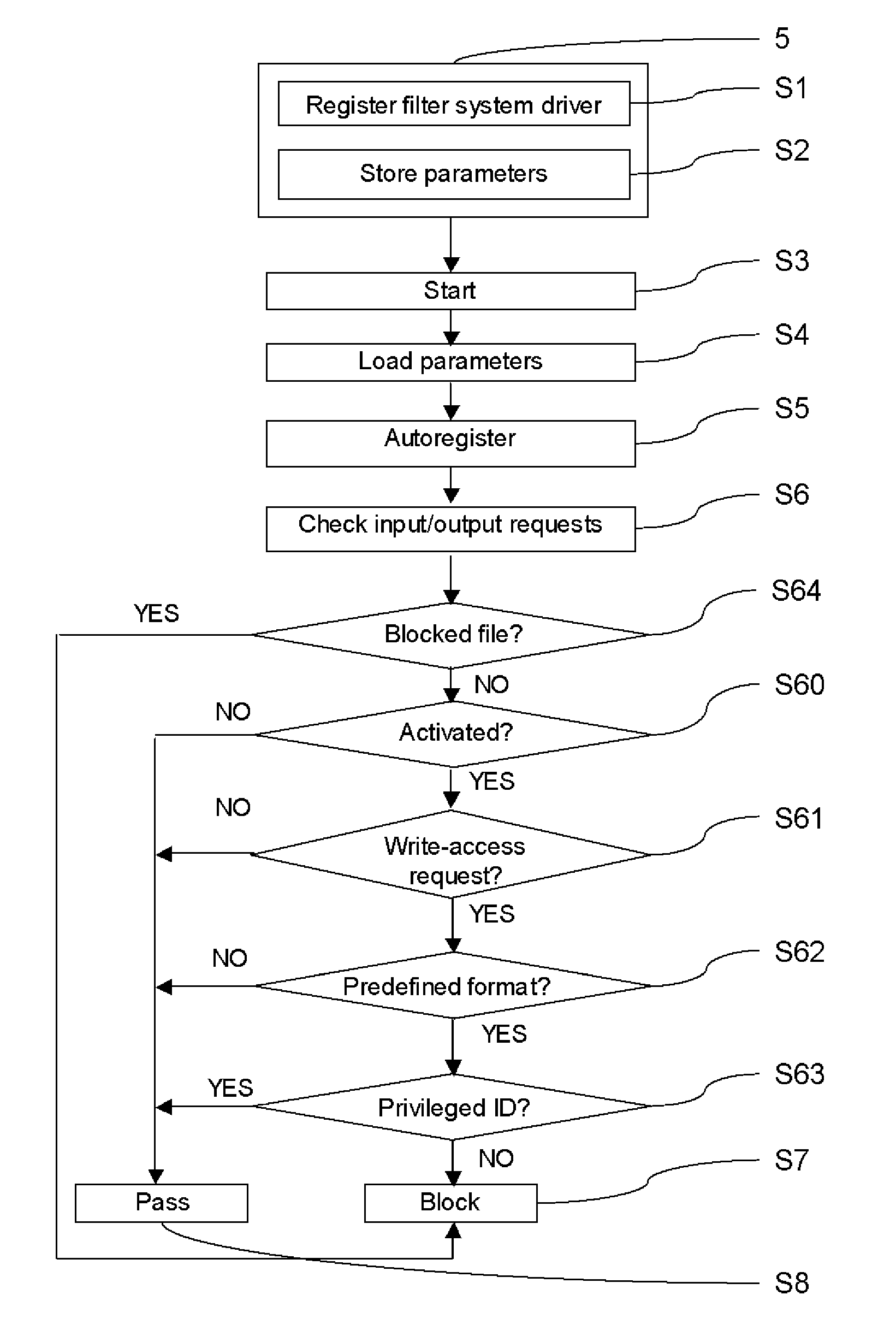
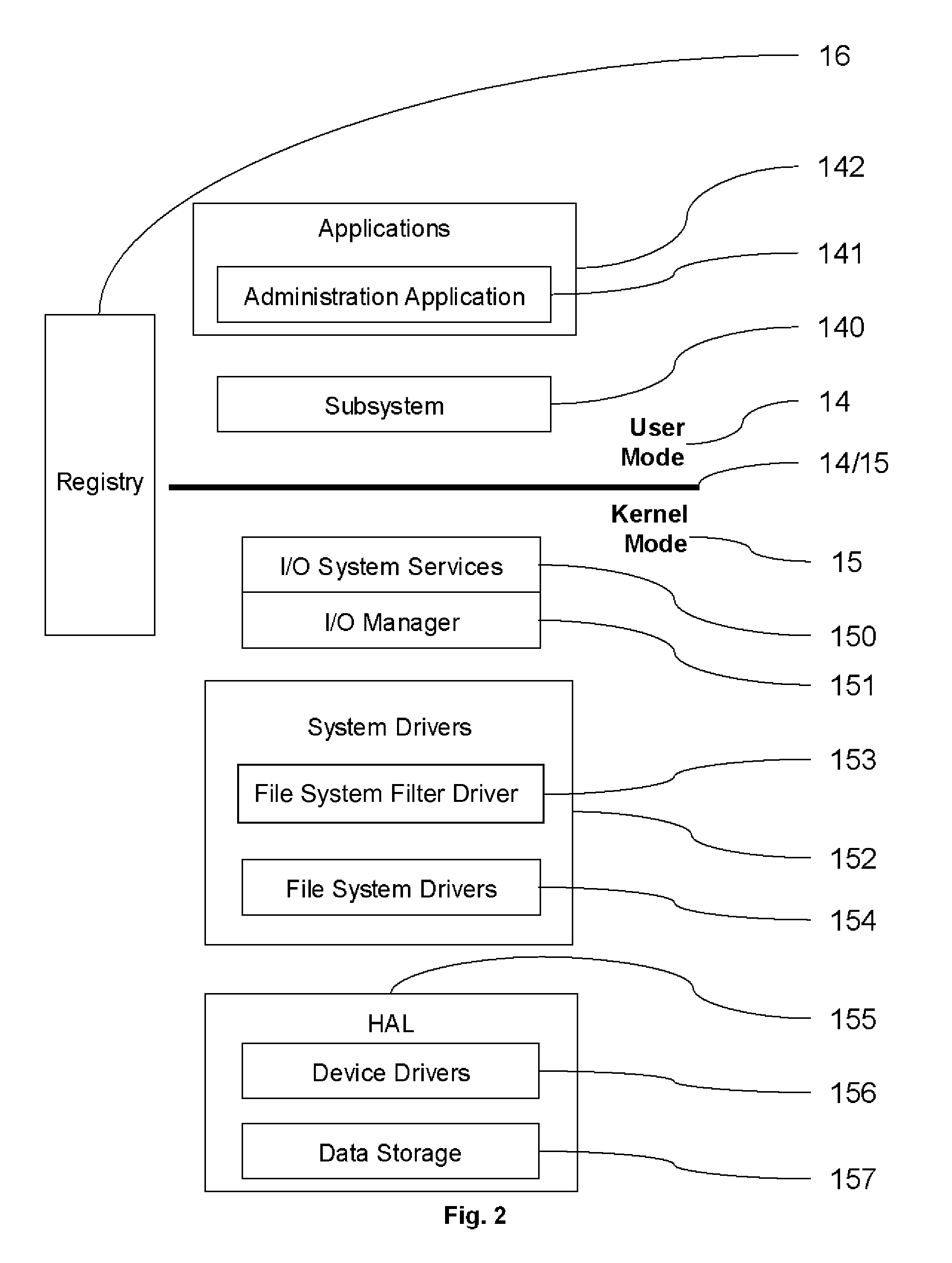
A method is provided of protecting a computer against malware affection. The computer has a data storage and an operating system for managing the data storage. The method comprises providing a filter module in the operating system which operates to detect an attempt to store data in the data storage, to determine a data format of the data to be stored in the data storage, and to prevent storage of the data if the data format is determined to relate to a predefined type. The filter module may be provided as a file system filter driver in a kernel of the operating system. The filter module may be arranged to operate between an input / output manager of the operating system and a driver associated with the data storage. The input / output manager and driver associated with the data storage may form part of the kernel of the operating system.
Owner:ROTHWELL WILLIAM GRANT
Reducing error correction latency in a data storage system having lossy storage media
InactiveUS20160103733A1Number of bit errorIncrease contributionRead-only memoriesRedundant data error correctionPaper data storageComputer hardware
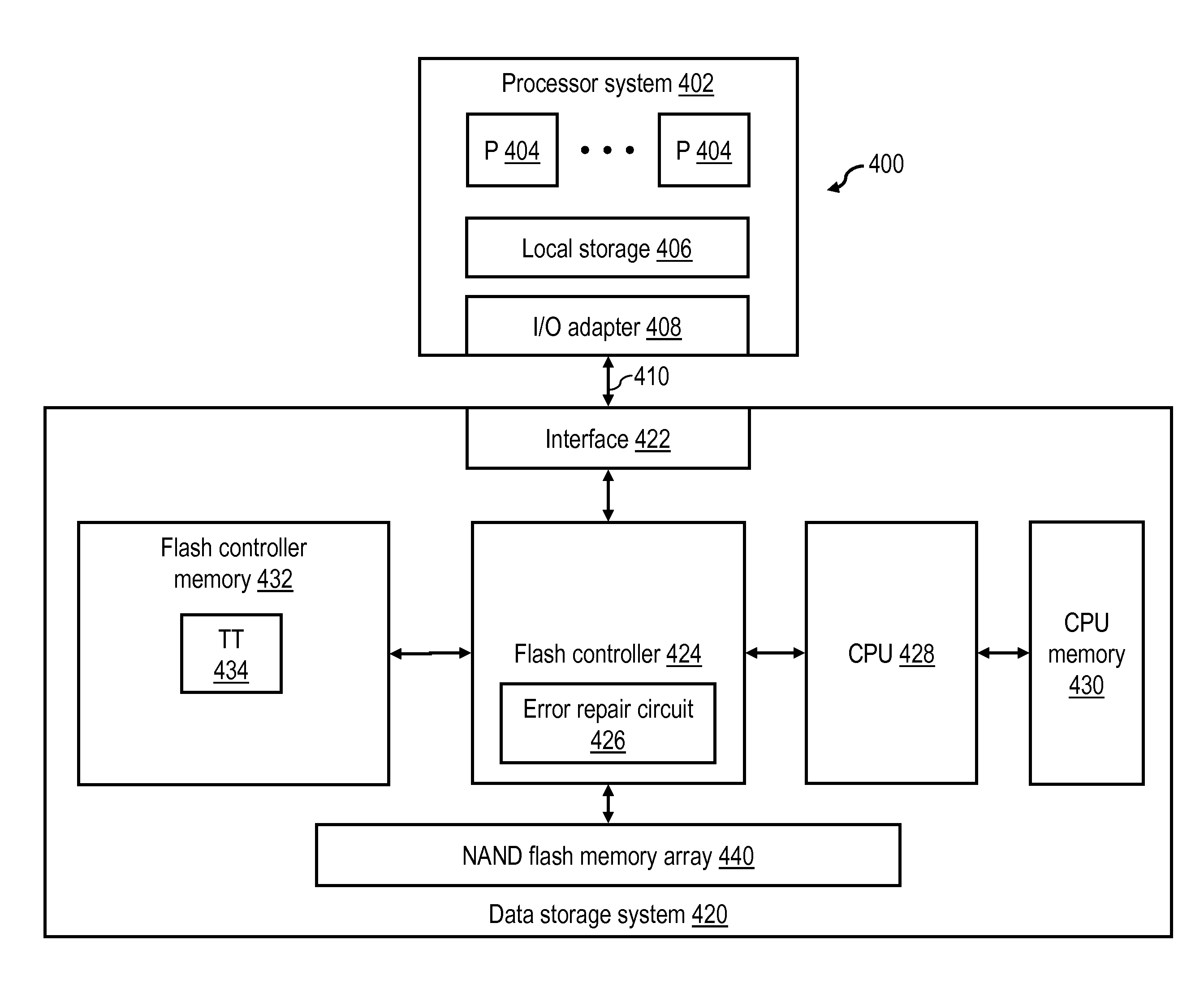
In at least one embodiment, a read operation in a data storage system having lossy storage media includes fetching target data of the read operation from a lossy storage device into a buffer, transferring the target data from the buffer to an external controller external to the lossy storage device via a communication bus, performing error location processing on the target data during the transferring of the target data, communicating error location information regarding at least one error location to error repair logic via the communication bus, the error repair logic repairing the at least one error in the target data using the error location information, and the external controller causing the target data as repaired to be transmitted toward a destination. By deserializing the suboperations comprising the read operation, read latency can be reduced.
Owner:IBM CORP
Data protection in data storage system
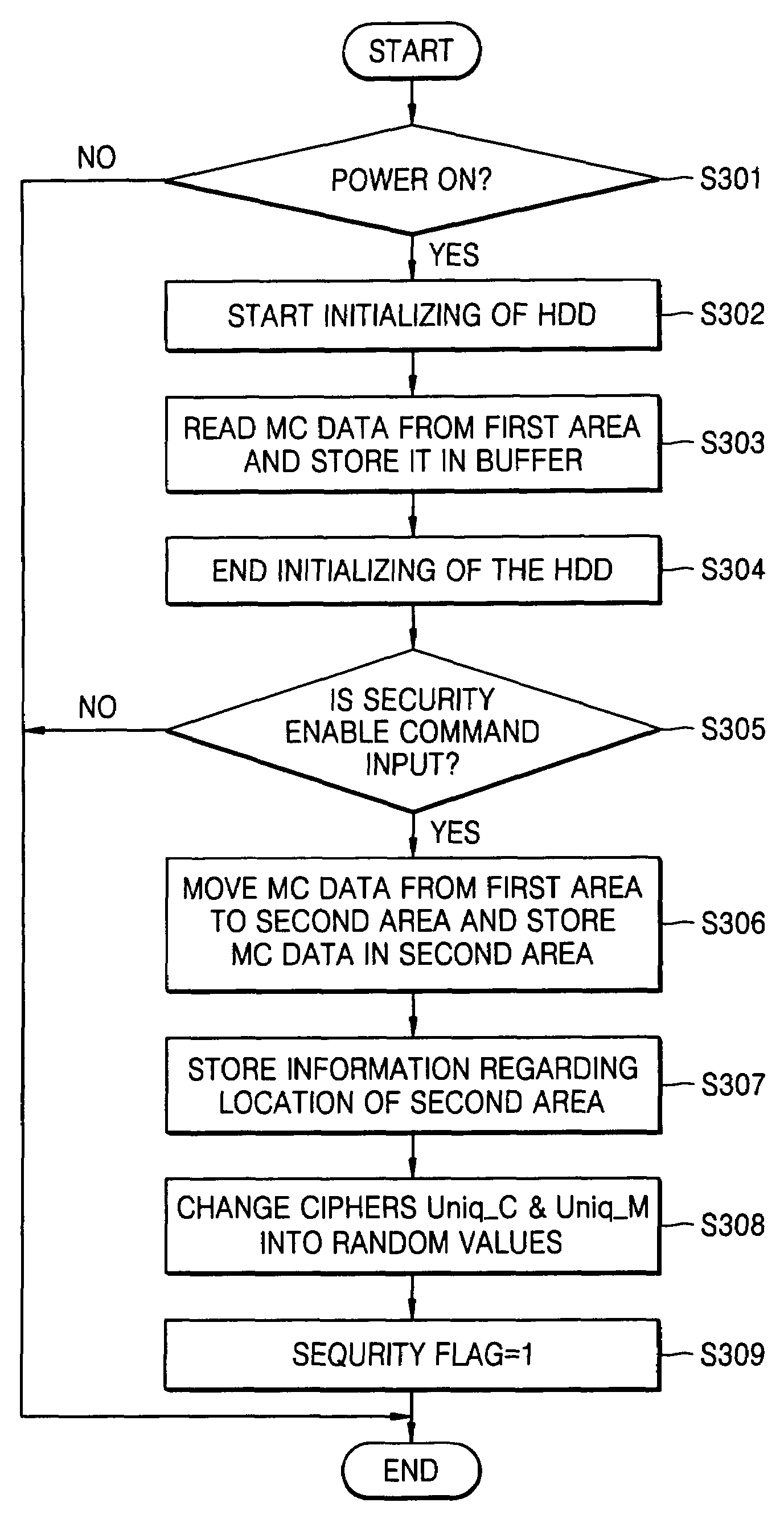
For protecting data within a data storage system, such as a hard disk drive, security enable mode is entered. In that mode, initialization data is moved from a first area of a disk to a second area of the disk with a location of the second area being randomly generated. The initialization data is then erased from the first area. Also, a first cipher for firmware and a second cipher for a disk are both changed into a randomly generated value. Later, access to the initialization data from the second area is granted in the security enable mode if the first and second ciphers are the same.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com