Patents
Literature
439 results about "Validator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A validator is a computer program used to check the validity or syntactical correctness of a fragment of code or document. The term is commonly used in the context of validating HTML, CSS and XML documents or RSS feeds though it can be used for any defined format or language.
Computer system security service
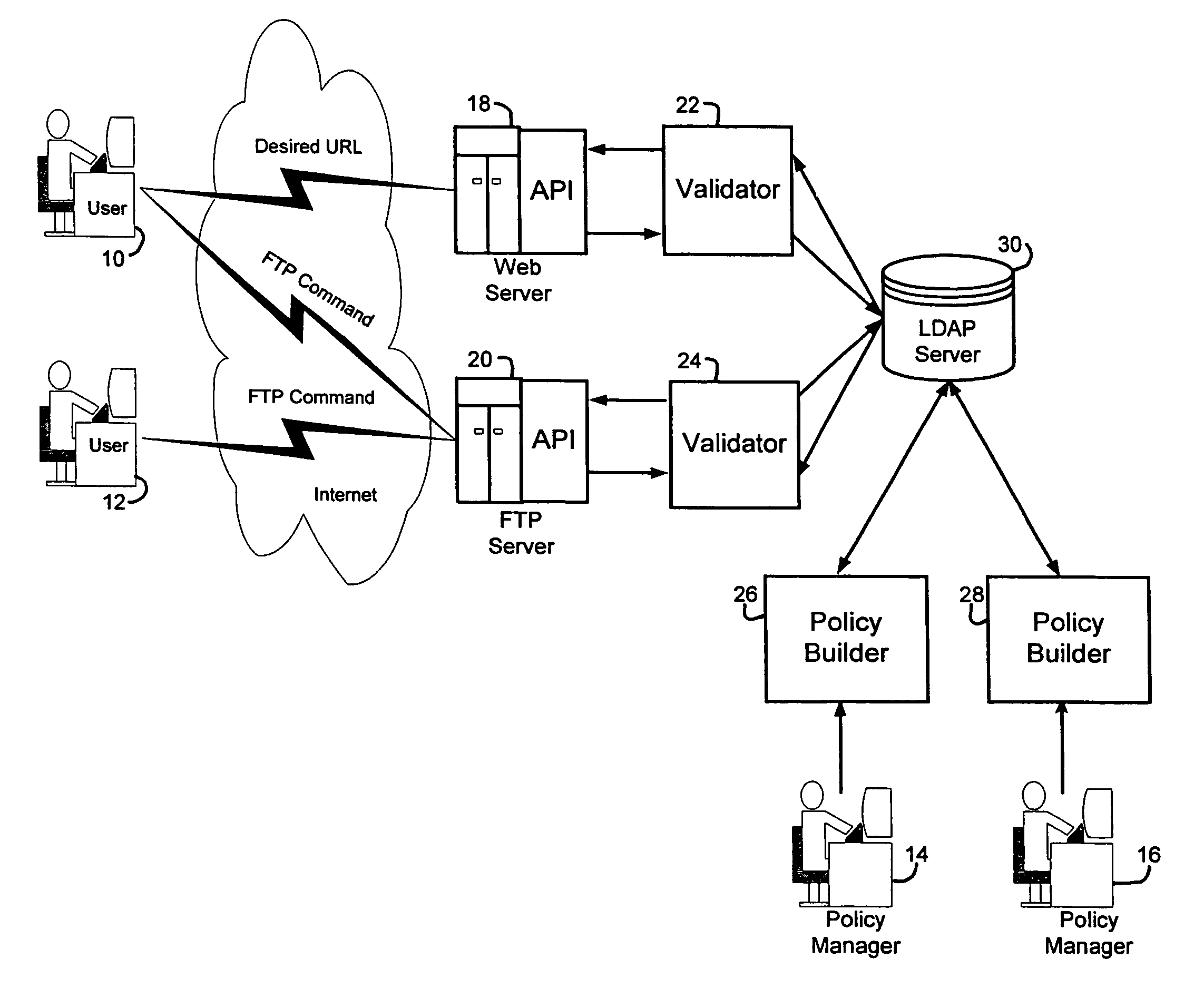
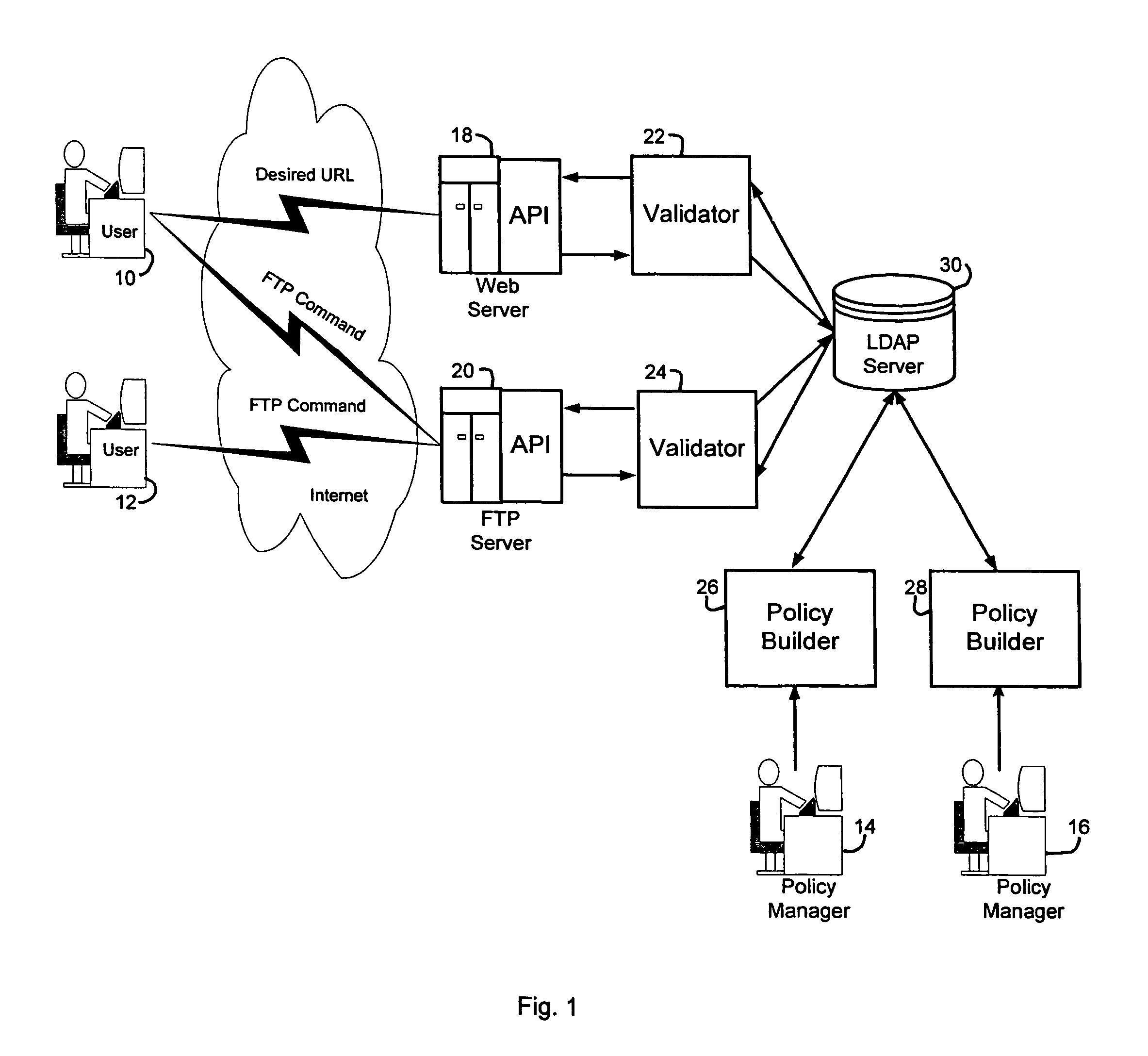
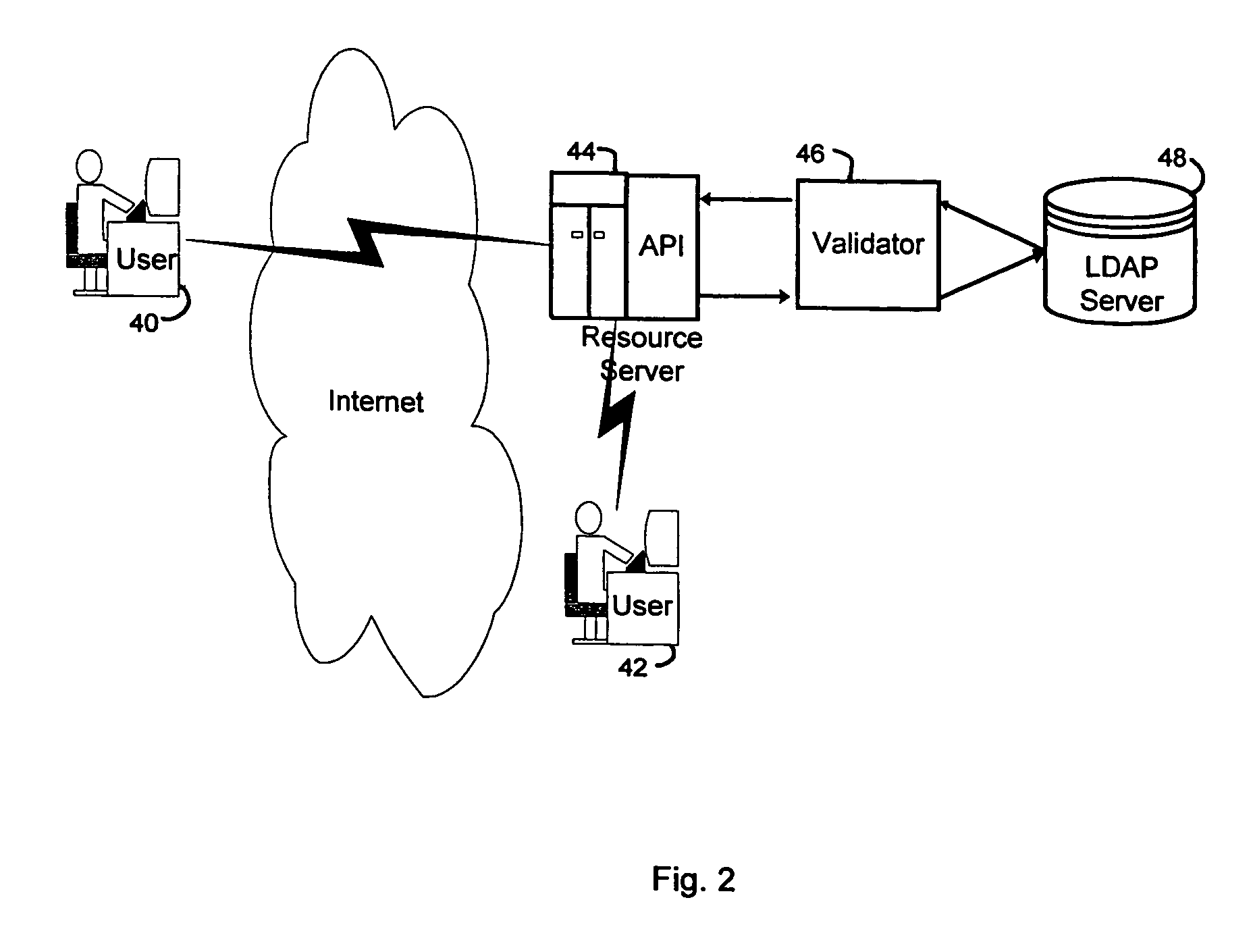
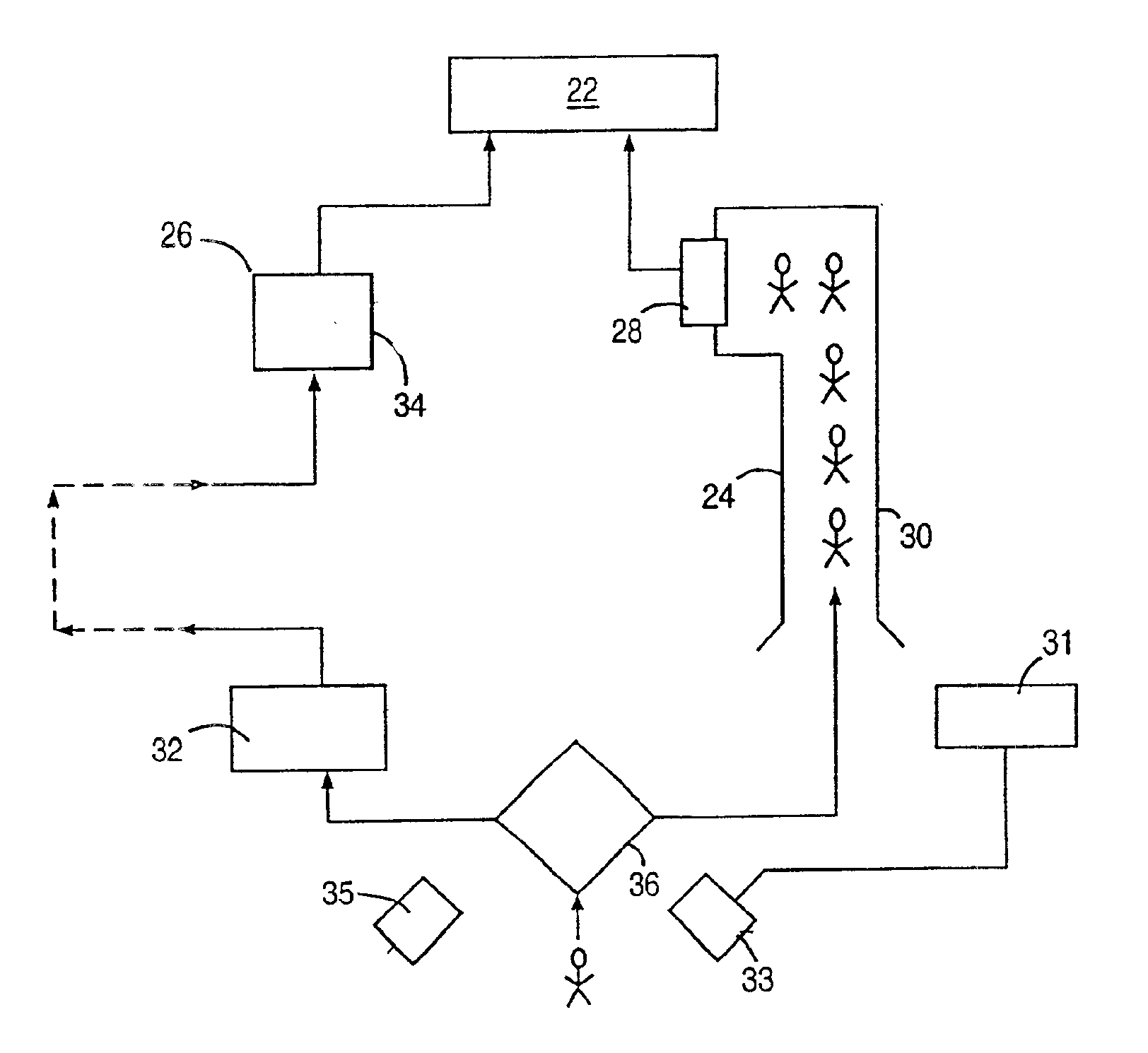
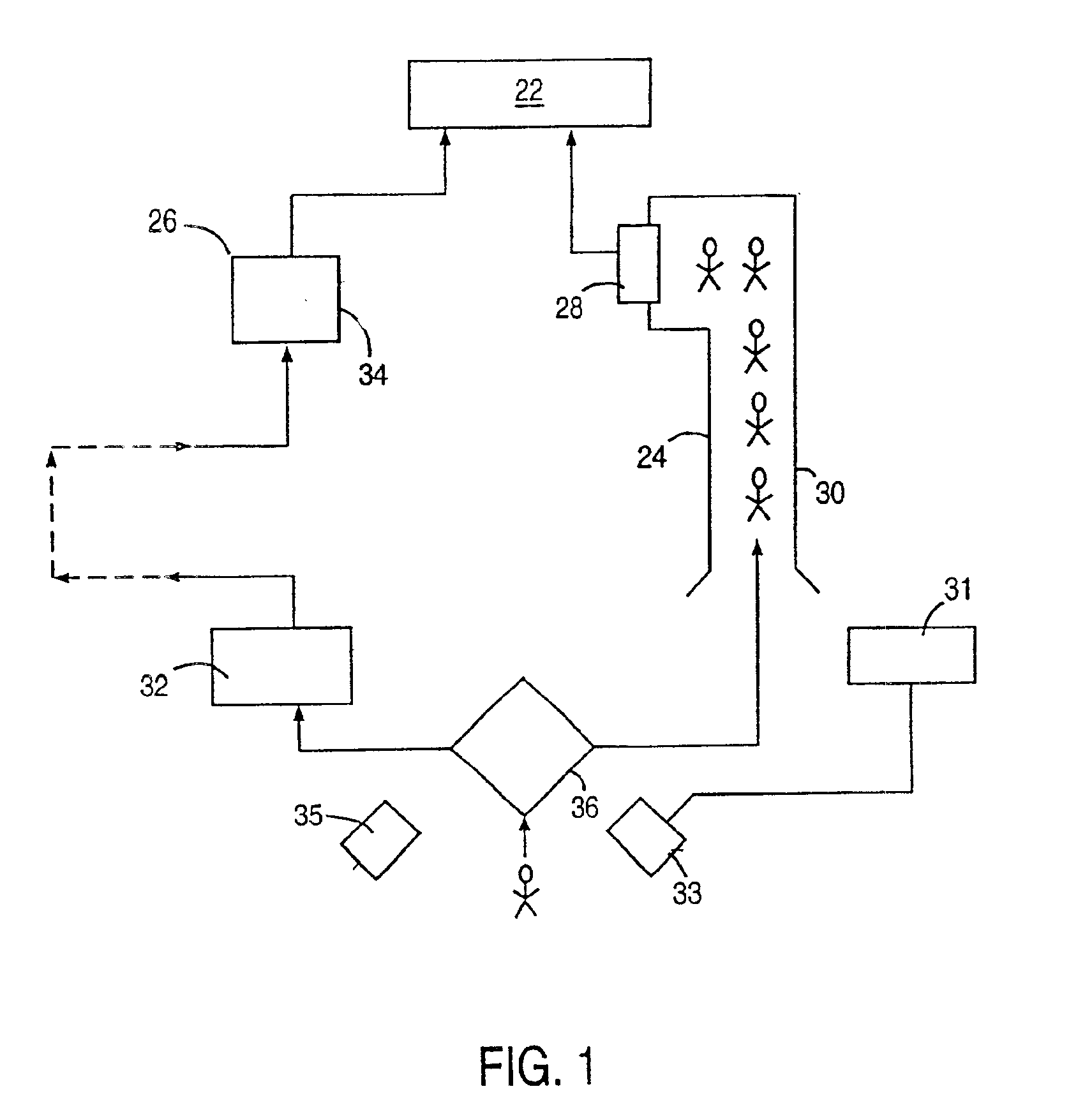
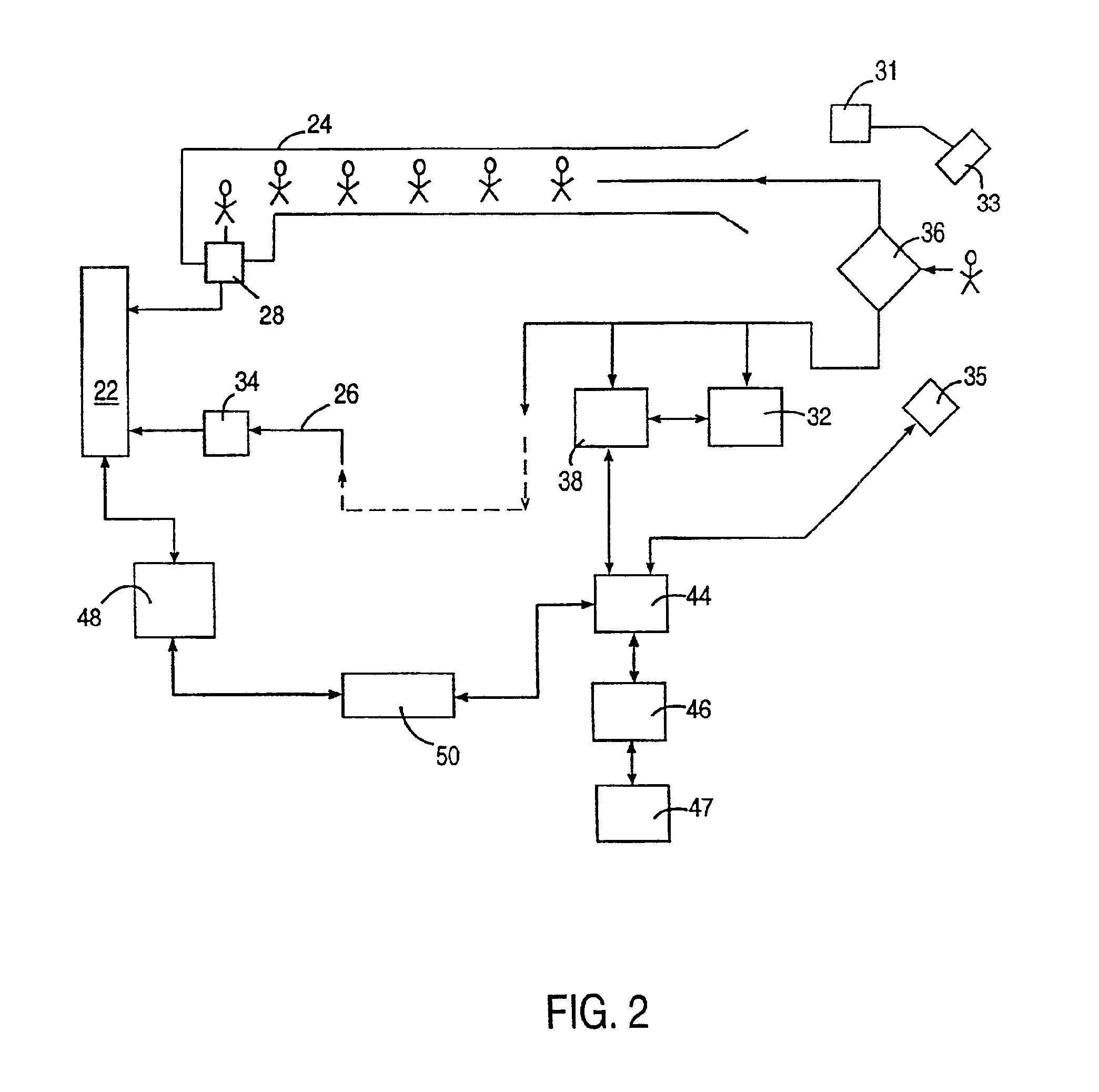
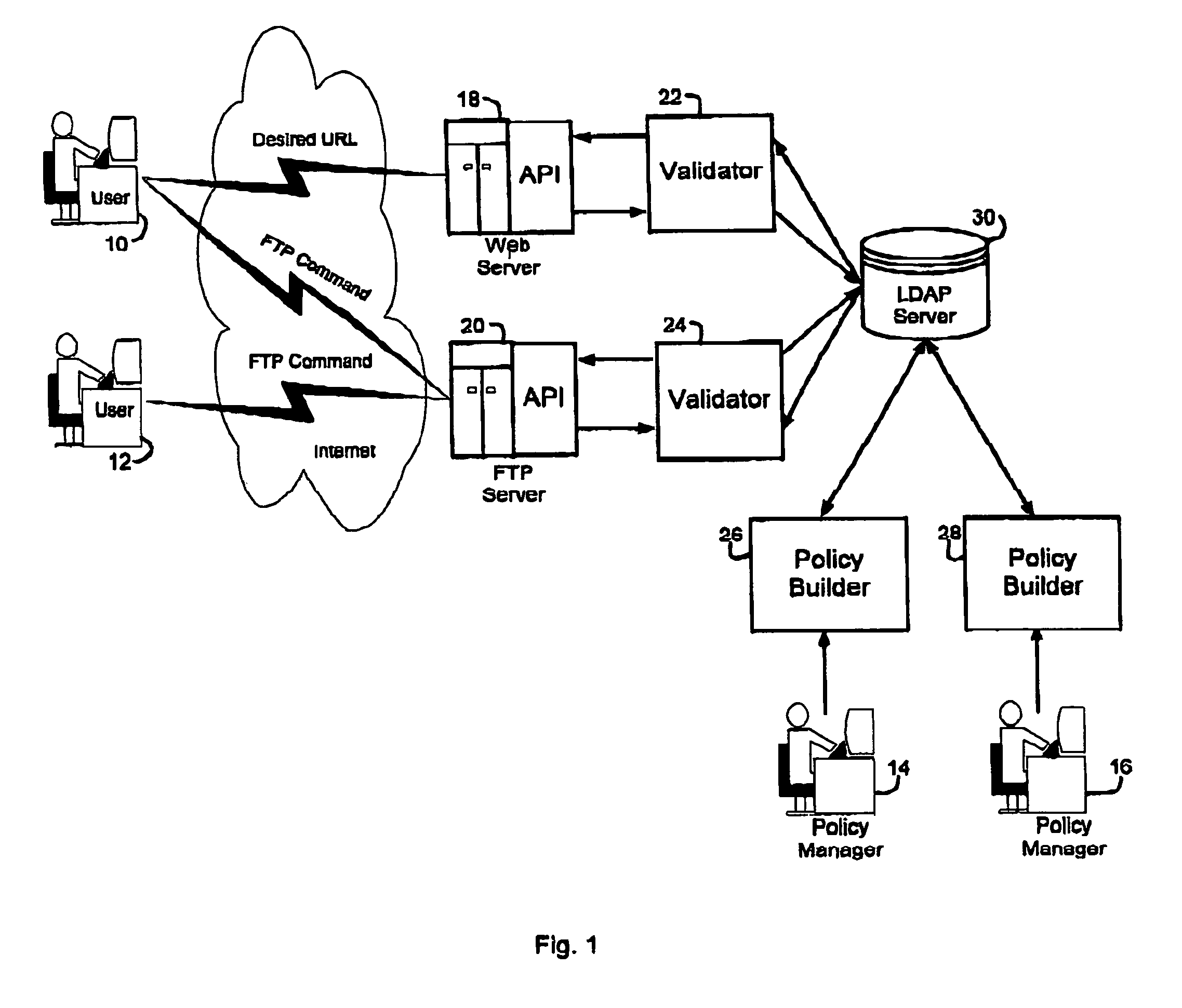
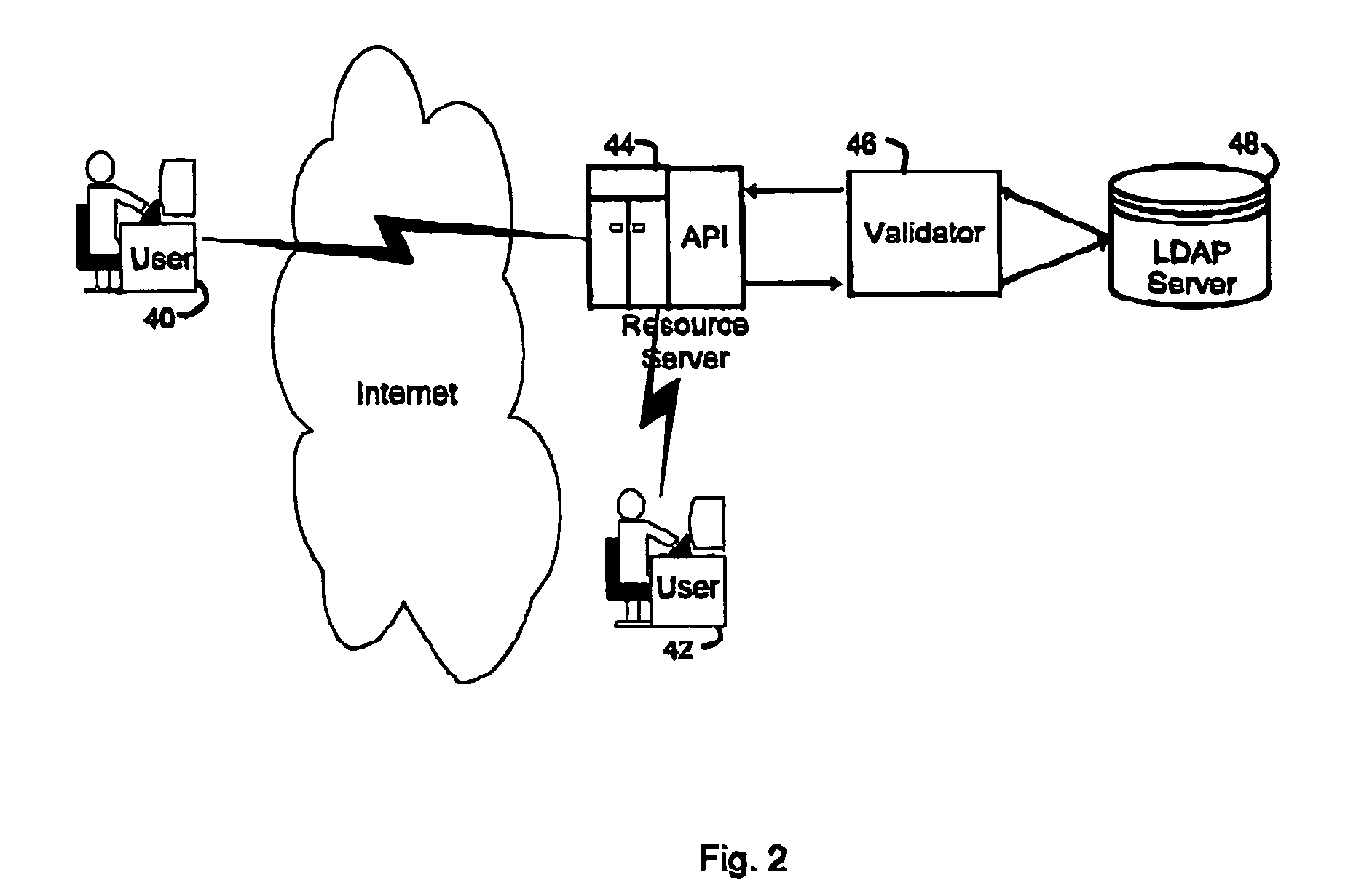
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
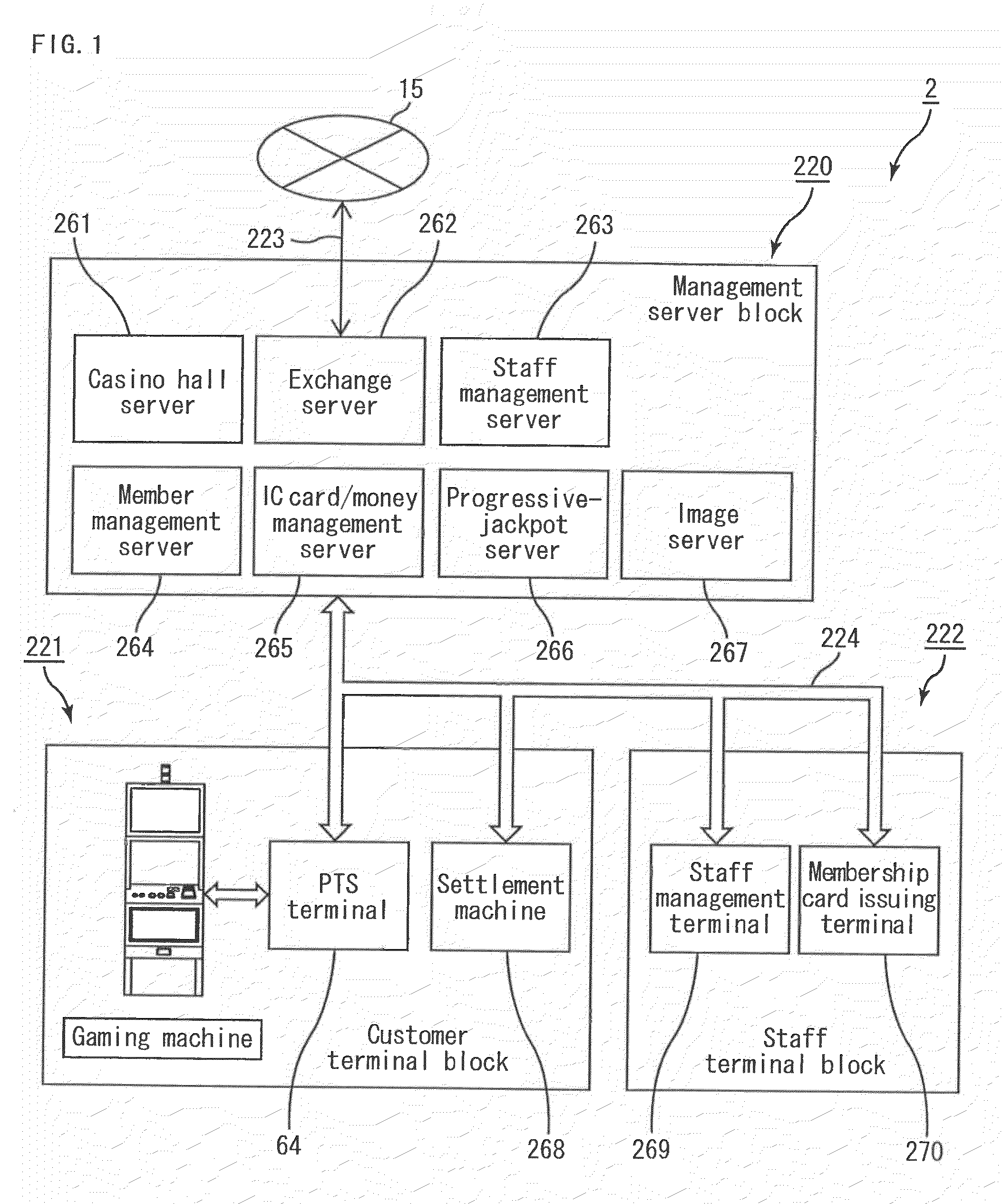
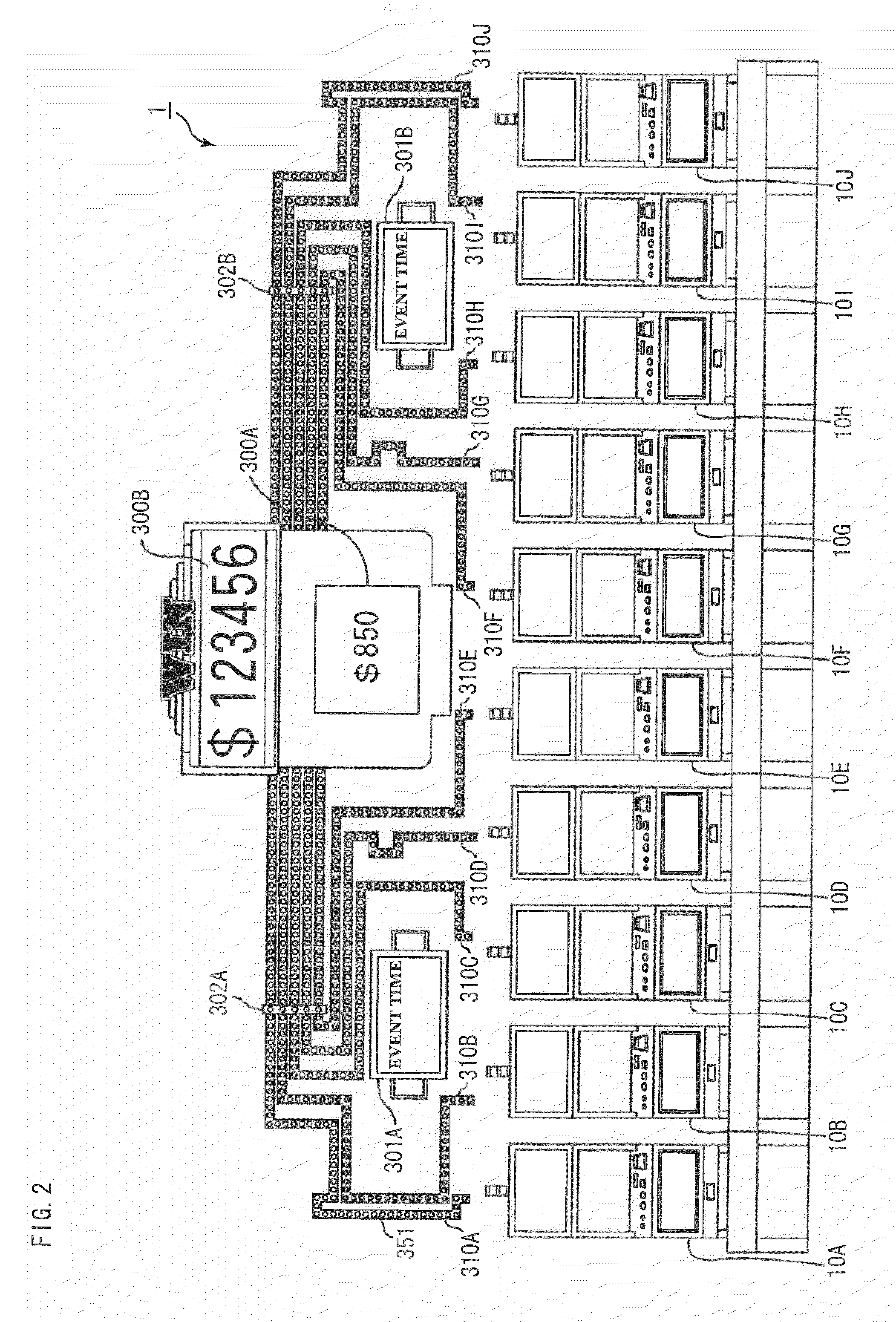
Currency value changing apparatus enabling player to play game using various currencies, gaming system where player can play game using various currencies, individual tracking apparatus, and individual tracking system
ActiveUS20100056260A1Reducing convenienceReduce the possibilityApparatus for meter-controlled dispensingCurrency conversionEngineeringGame play
The currency-value converter according to the present invention transmits amount-of-converted-currency data indicating the amount of basic currency identified based on the type of this currency, the amount of the currency and the exchange rate, to a controller installed in a gaming machine, when the type of currency accepted through a currency validator is not the basic currency. The exchange rate is a rate in which a correspondence relationship between an amount of the basic currency and an amount of another type of currency other than the basic currency is set for each type of currency other than the basic currency. Then, a game is played at the gaming machine based on the transmitted amount-of-converted currency.
Owner:UNIVERSAL ENTERTAINMENT CORP
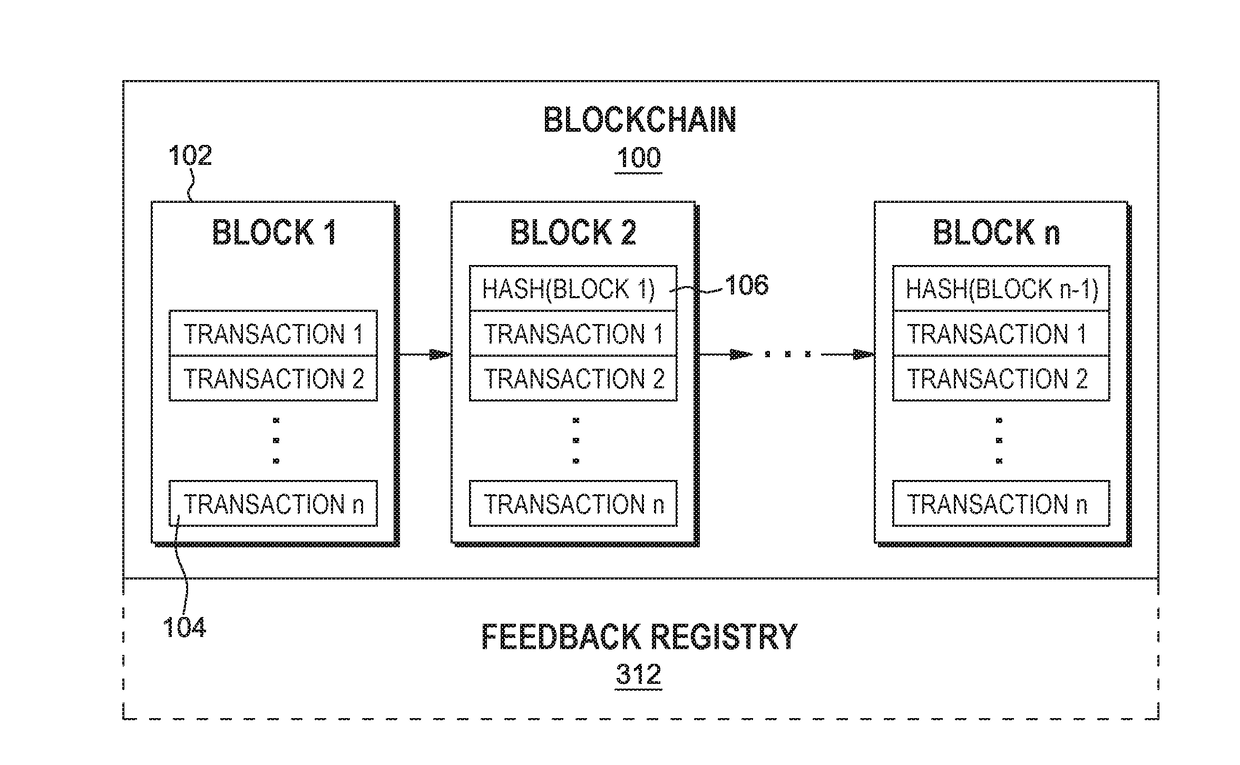
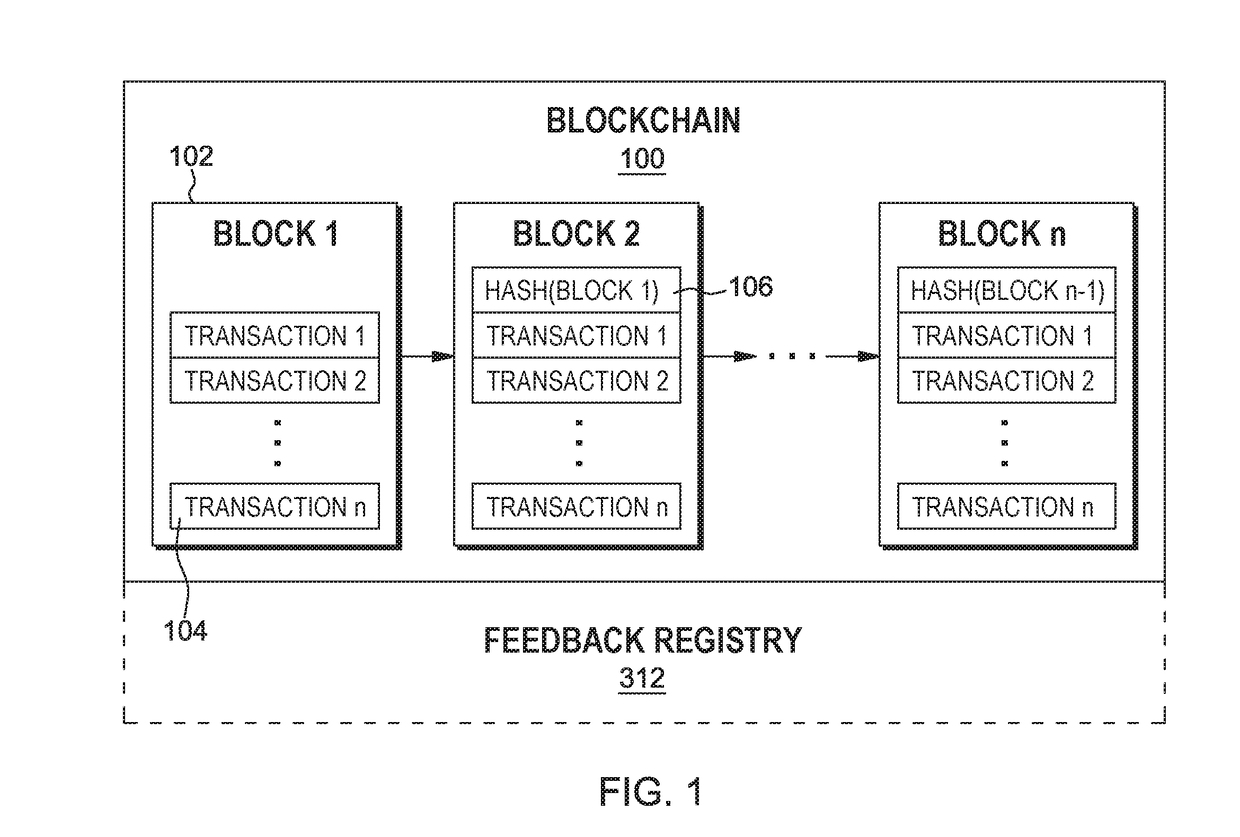
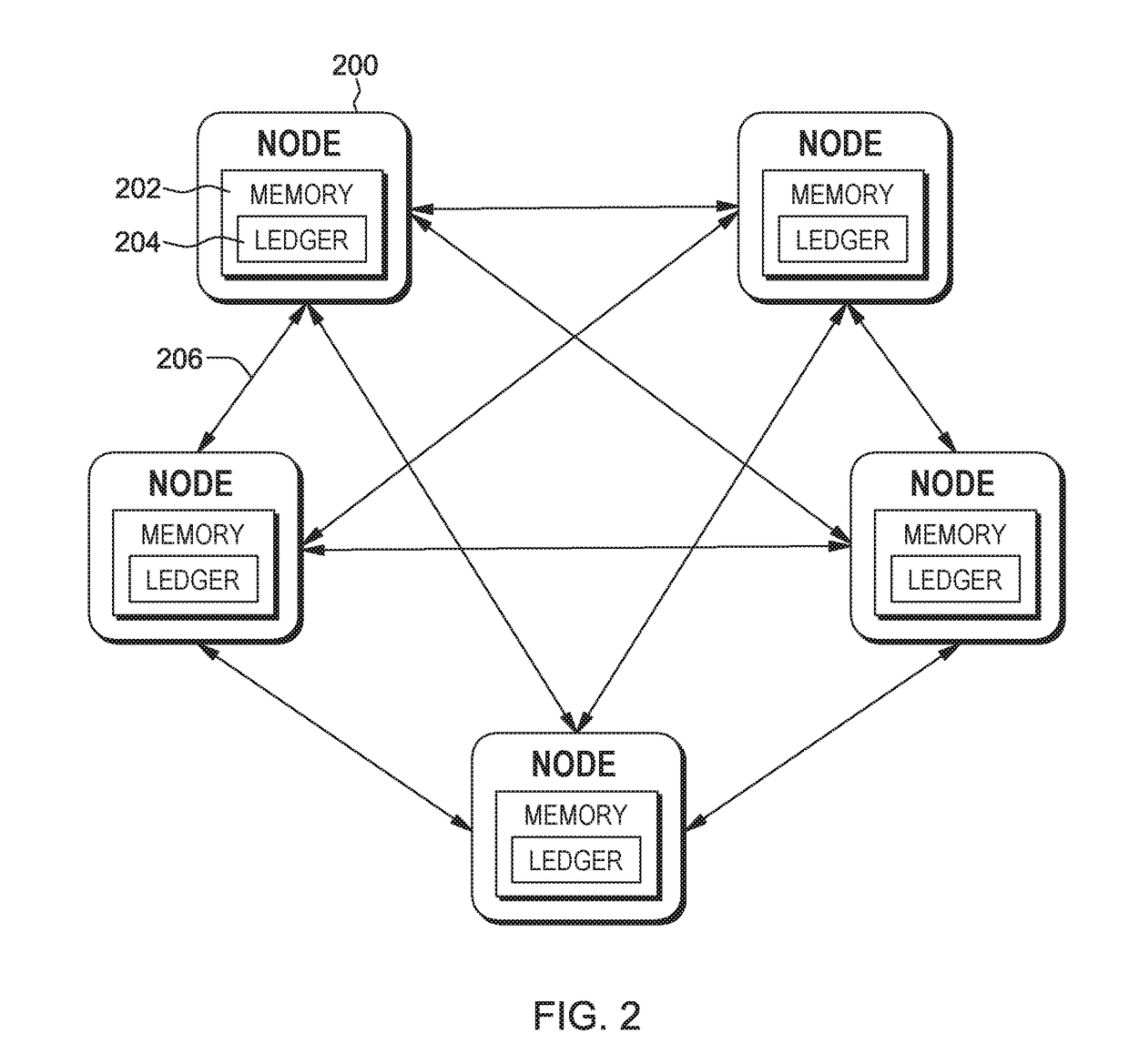
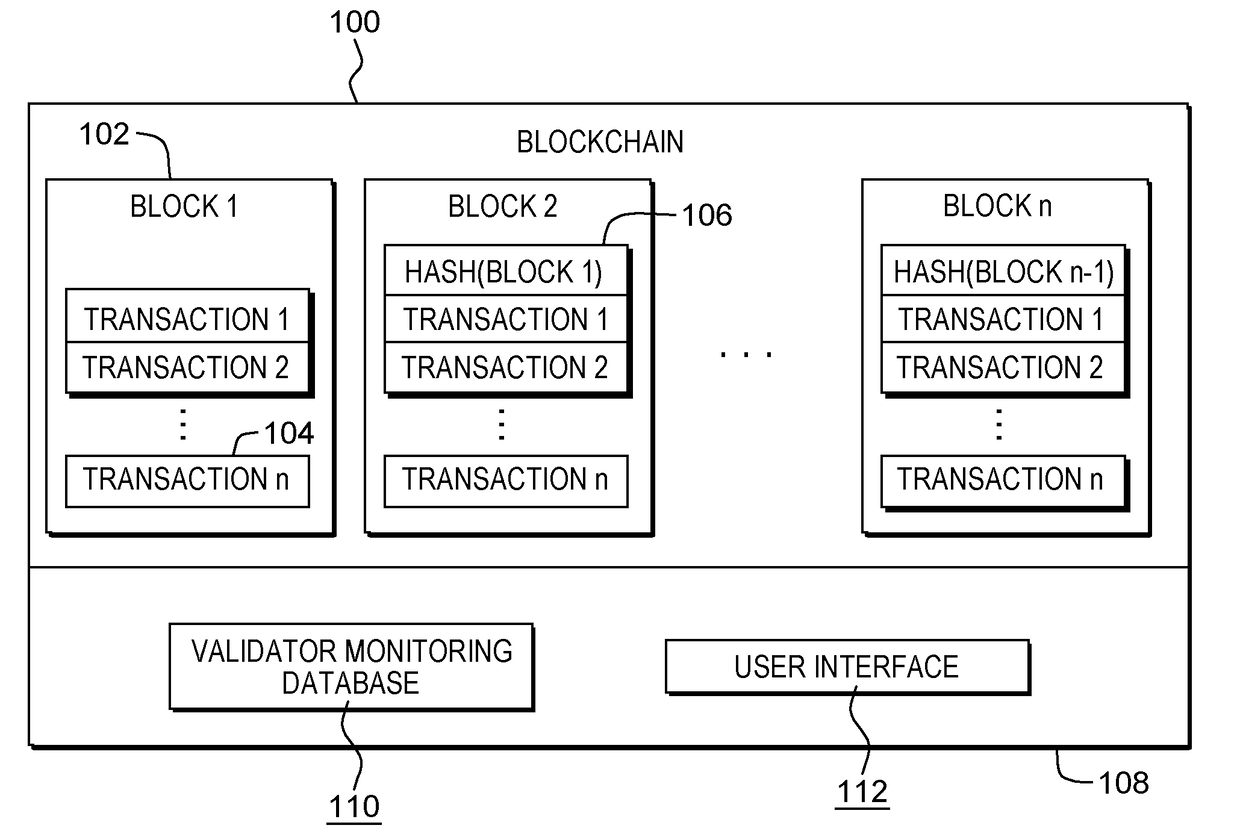
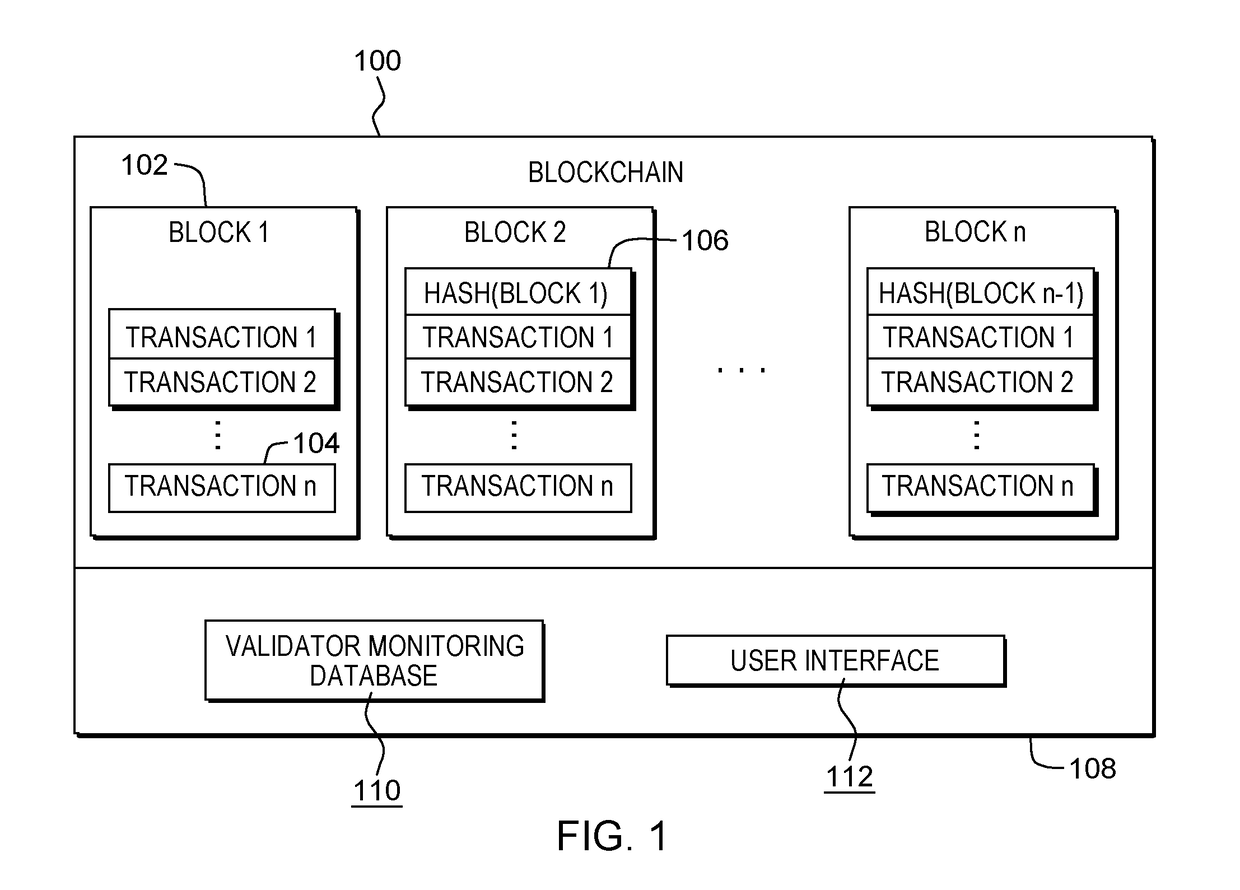
Establishing overlay trust consensus for blockchain trust validation system
ActiveUS20180101560A1Digital data information retrievalSpecial data processing applicationsVerification systemData mining
The system, method, and computer program product described herein provides a built-in feedback mechanism for a blockchain to sanction validator nodes that consistently “vote” in a manner that does not match the ultimate consensus. The method includes receiving a vote on whether to add a transaction to the blockchain, comparing the vote to a consensus decision on whether to add the transaction to the blockchain, determining based on the comparison that the vote does not match the consensus decision, in response to determining that the vote does not match the consensus decision, incrementing a value associated with the validator node in a feedback registry, determining that the value associated with the validator node is above a predetermined threshold value, and in response to determining that the value associated with the validator node is above the predetermined threshold, proposing a sanction of the validator node to the plurality of validator nodes.
Owner:IBM CORP
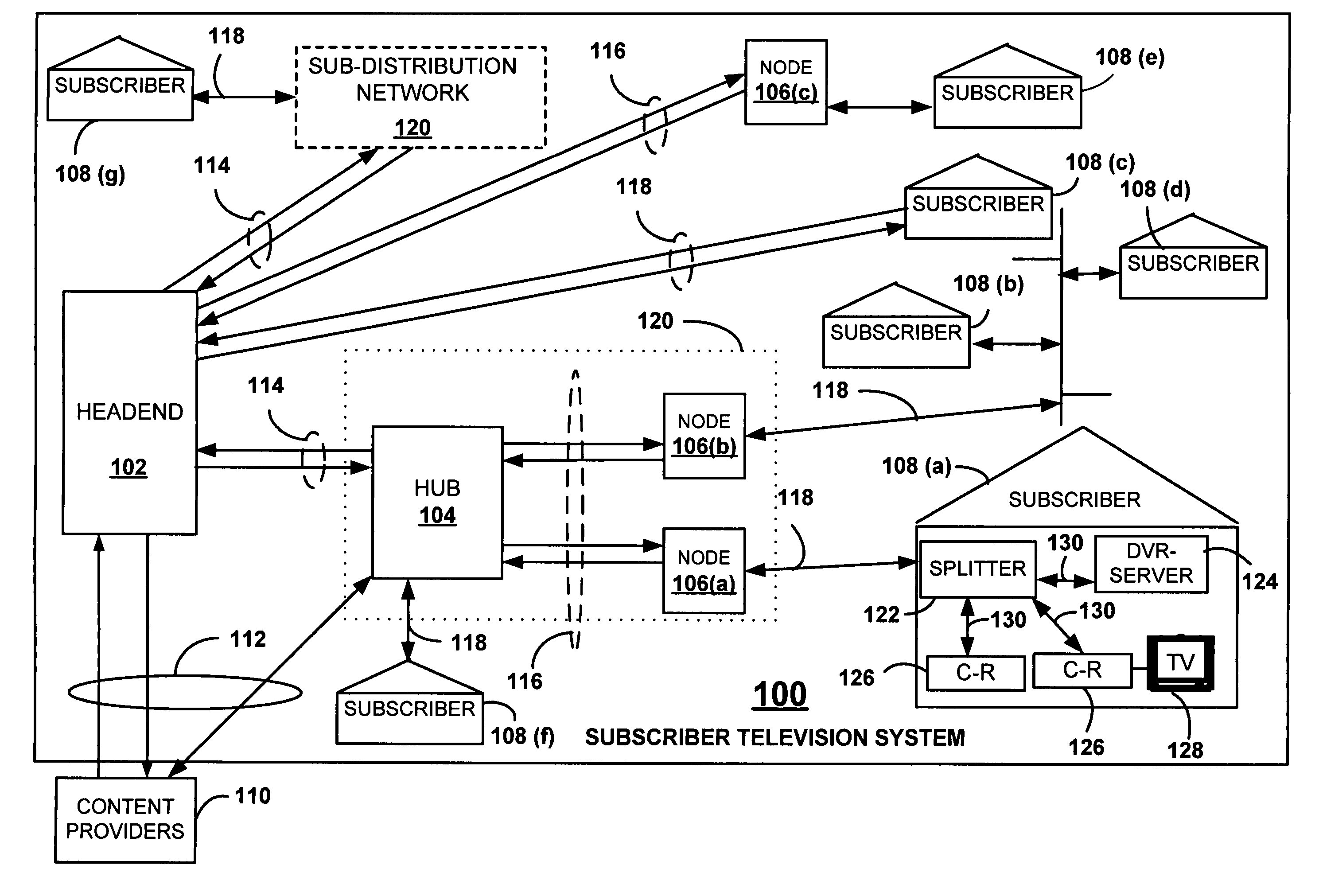
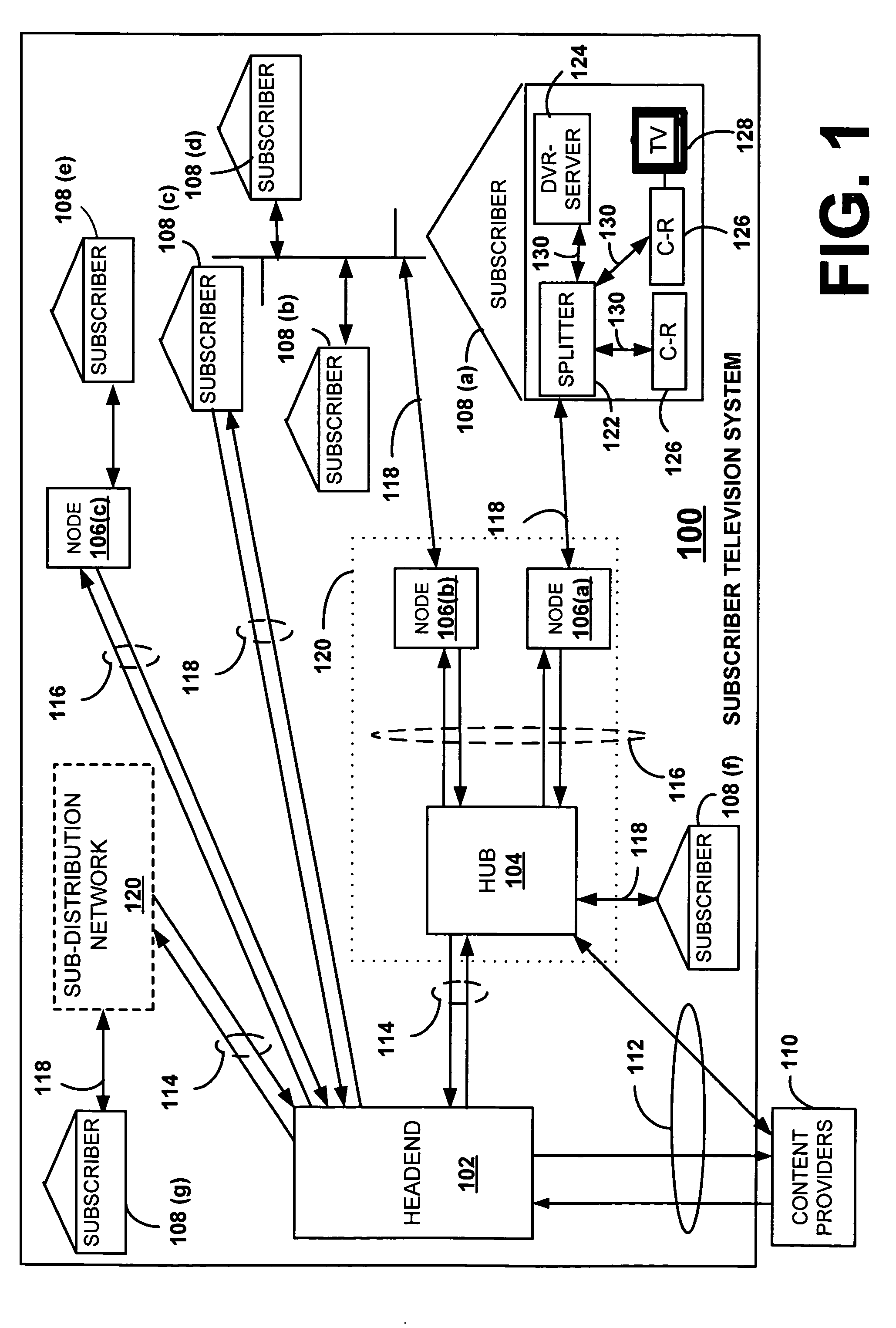
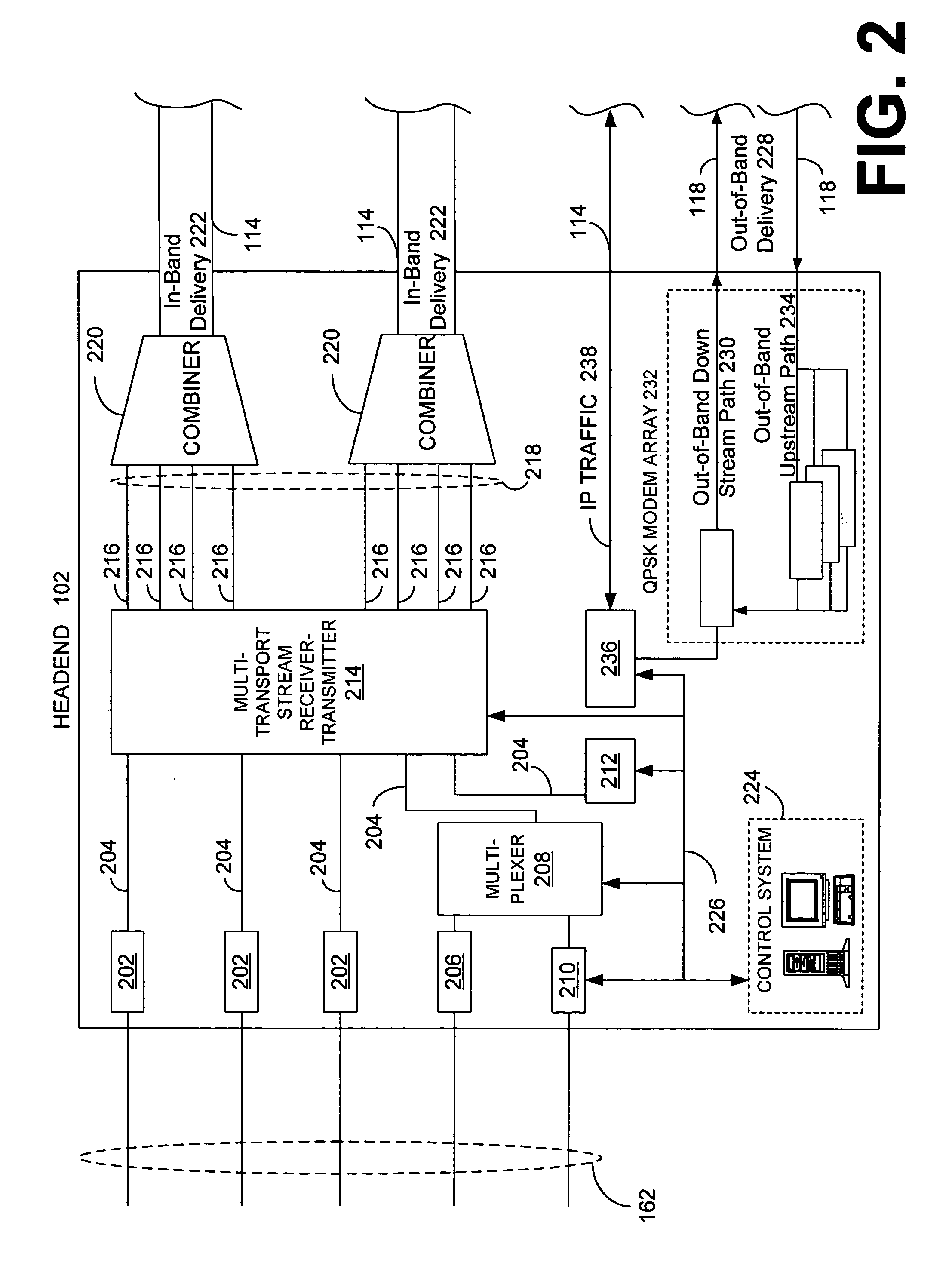
Validating client-receivers
InactiveUS20040237100A1Key distribution for secure communicationUser identity/authority verificationTelevision systemClient-side
In a subscriber television system having a headend, a server, and plurality of client-receivers, the server, which is remote from the headend, is adapted to receive a validation-message from one or more client-receivers. The validation-message includes content and an authentication-token. The server validates that the sender of the validation-message is a valid client-receiver of the subscriber television system using an authentication-token and a validator that is known to both the server and to at least one of the client-receivers.
Owner:CISCO TECH INC
Flexible loyalty points programs
InactiveUS20080051193A1Credit registering devices actuationPayment protocolsLoyalty programData file
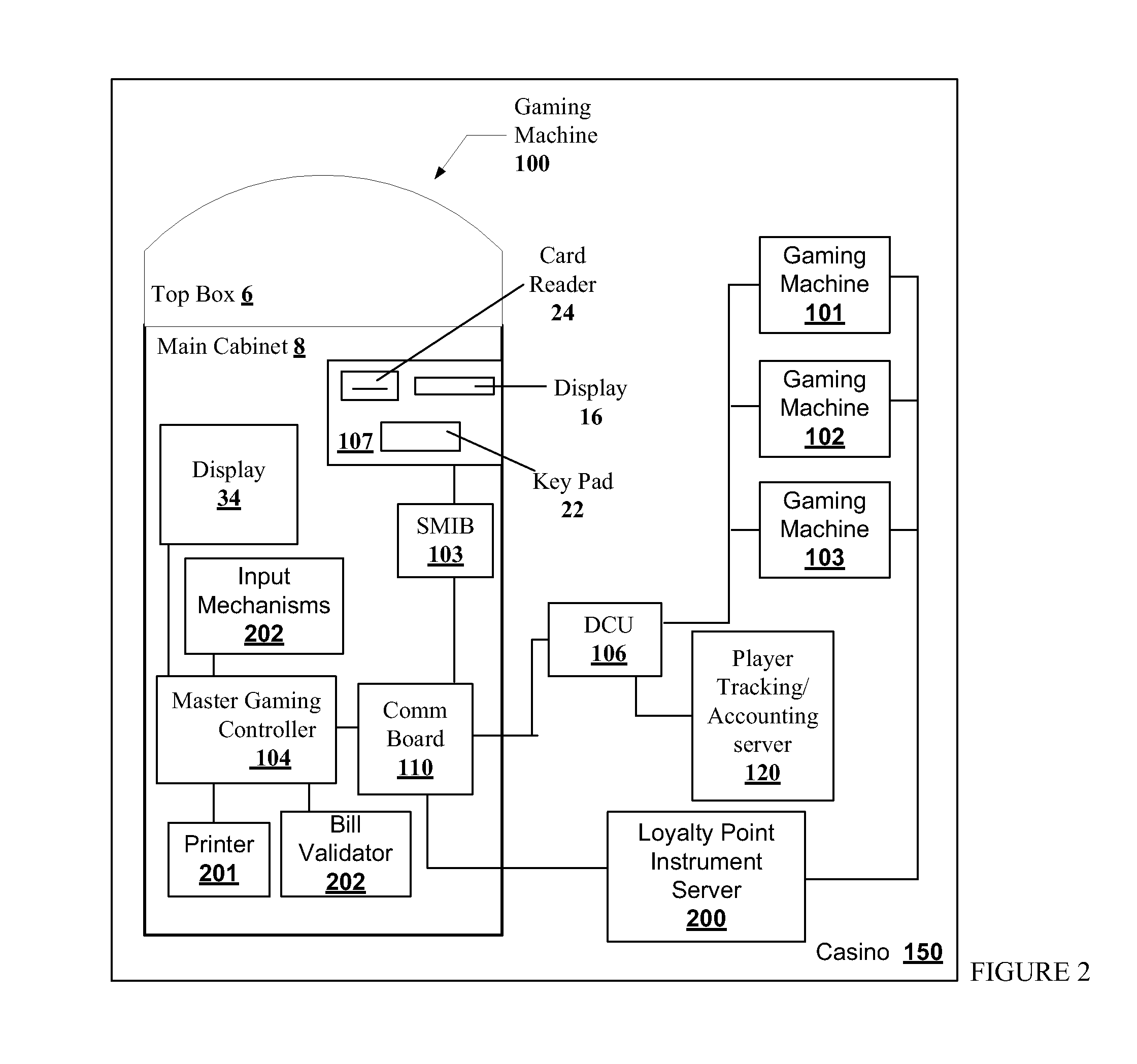
A disclosed a gaming machine includes an input mechanism with a non-physical contact data interface. The non-physical contact data interface may be capable of reading loyalty program data from a loyalty program instrument without contact between the loyalty program instrument and the non-physical contact data interface. The input mechanism with the non-physical contact data interface may be one of a bill validator, a bar-code reader and a Radio Frequency Identification (RFID) tag reader. The loyalty program instrument may be a substrate including at least one of a 1-D bar-code printed on the substrate, a 2-D bar-code printed on the substrate, a symbol printed on the substrate, alpha-numeric character printed on the substrate, a RFID tag embedded in the substrate, a RFID tag printed on the substrate and combinations thereof. The loyalty program instrument may be used to store an index to a record in a database or a portable data file.
Owner:IGT
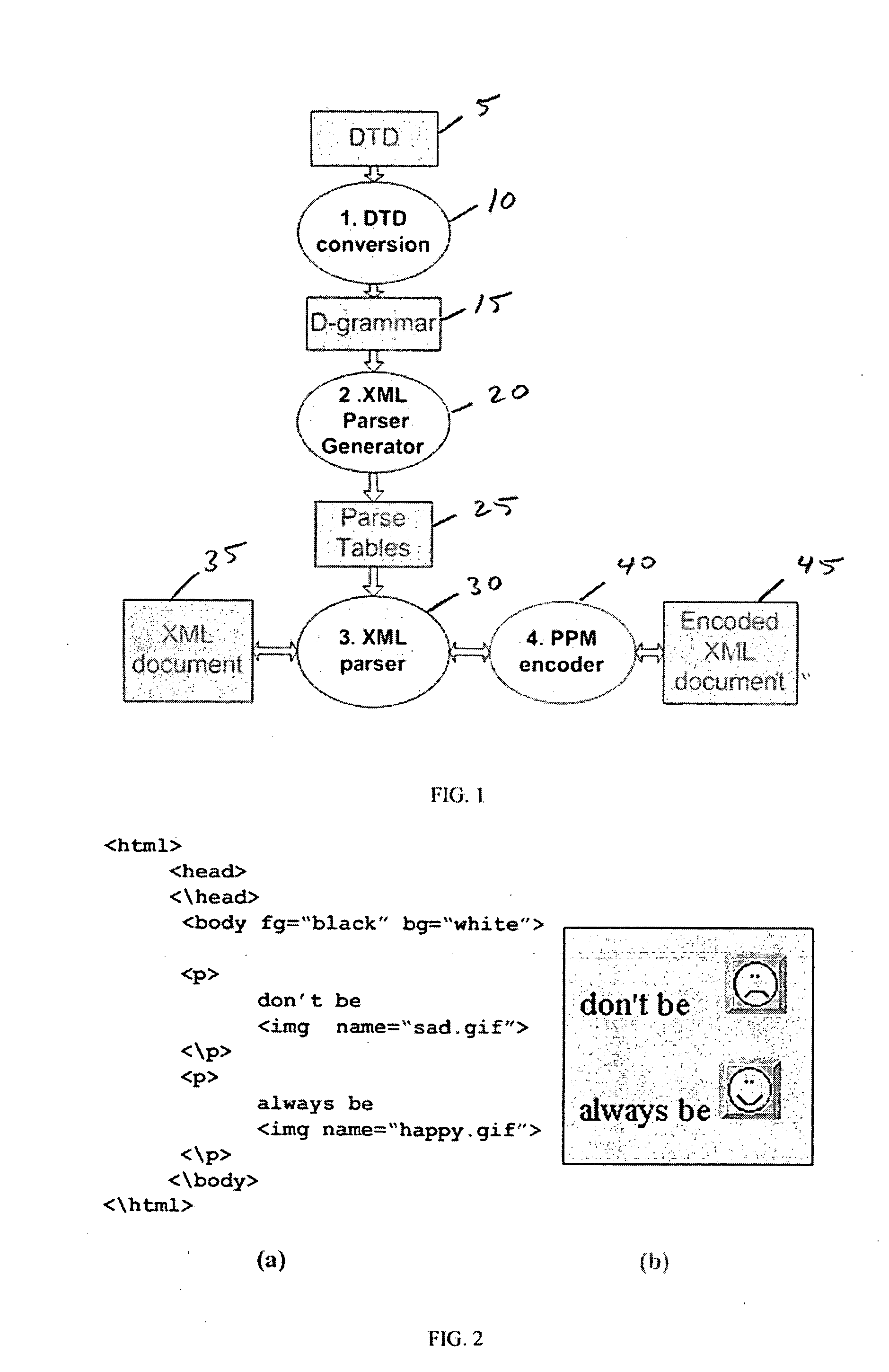
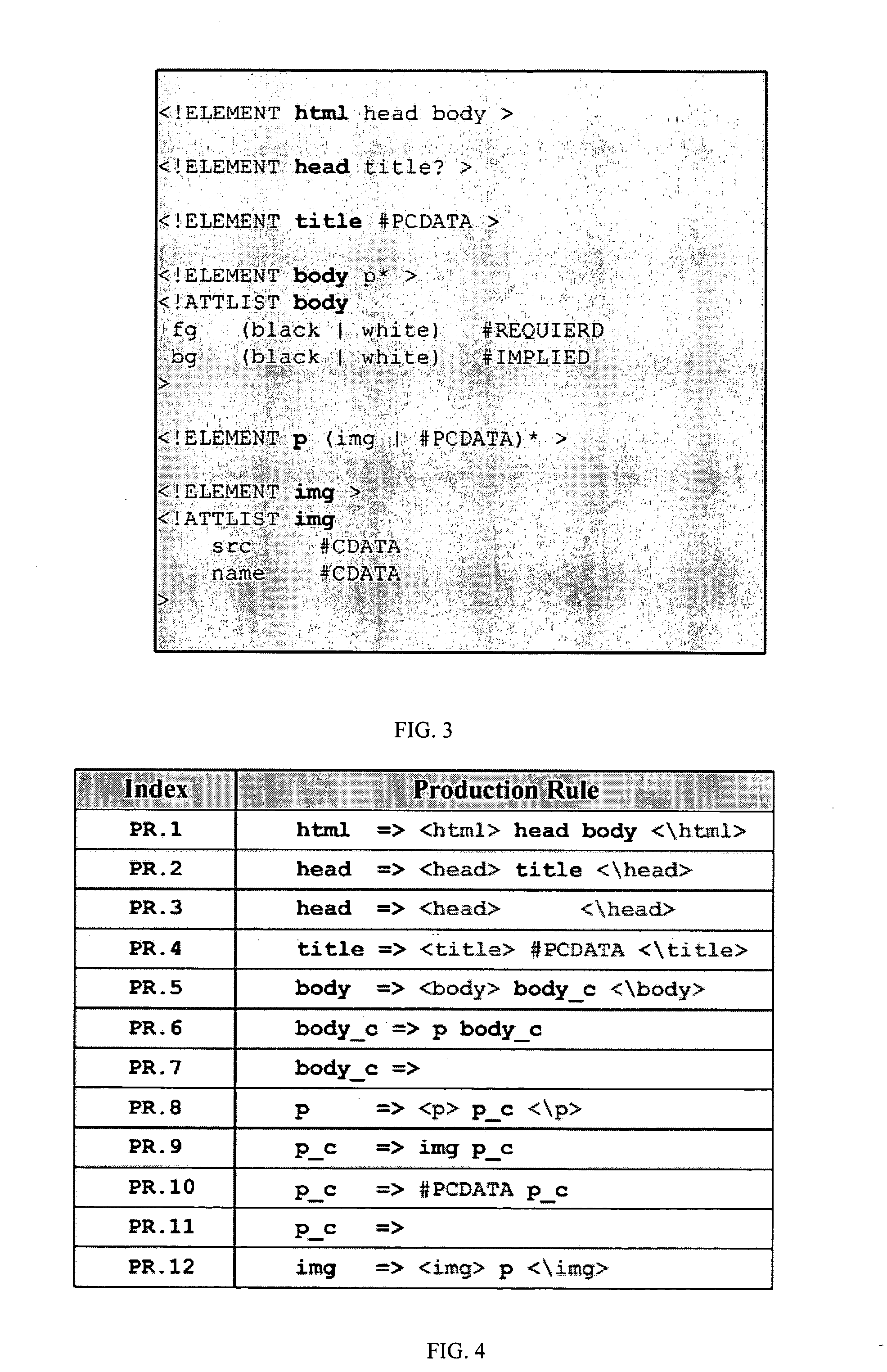
XML parser
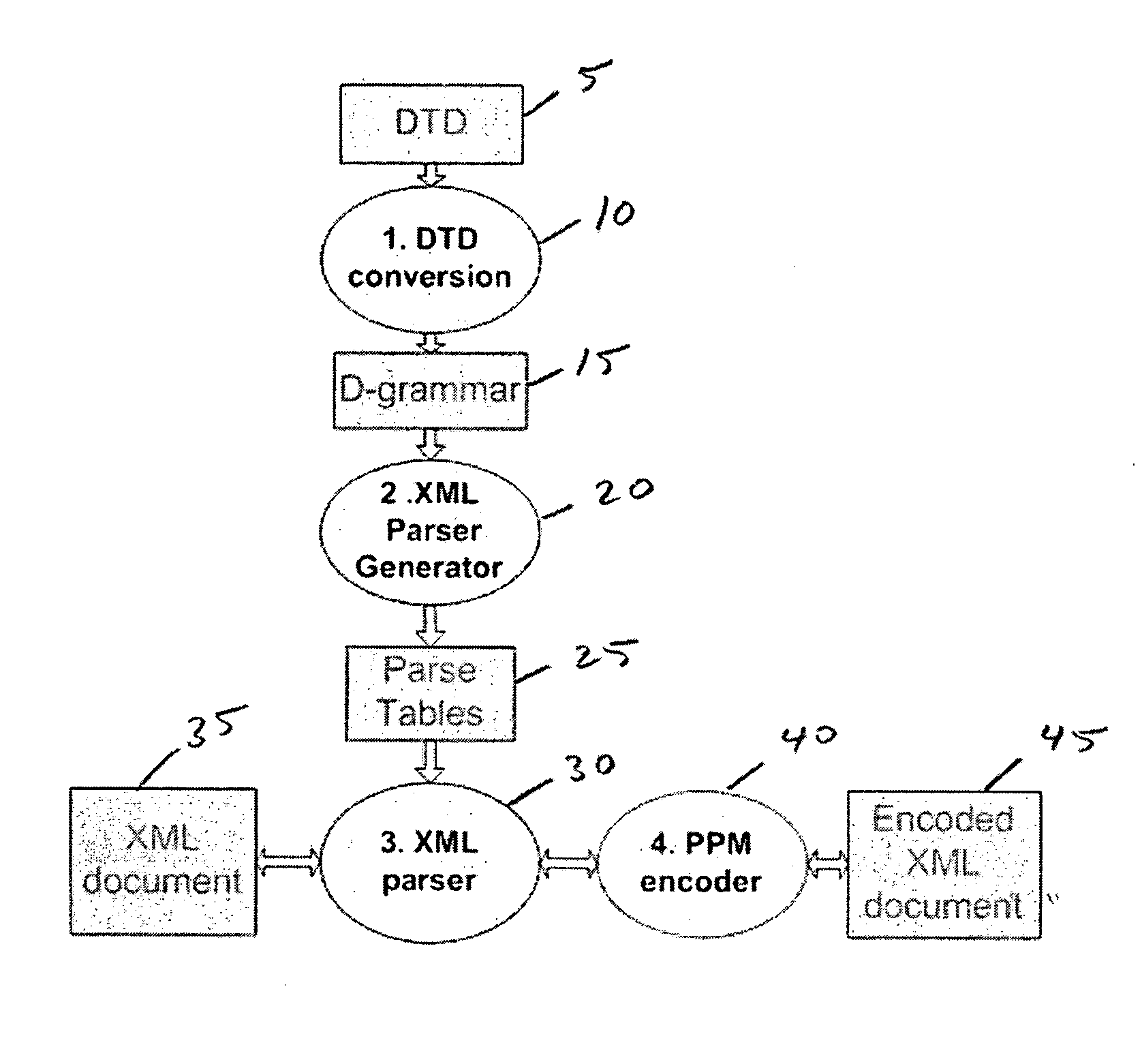
InactiveUS20060117307A1Easy to compressFacilitates top down parsingNatural language data processingProgram controlDocument type declarationMultiple context
A method of generating a parser of a source code file that references a syntactic dictionary, a method of compressing the file, and apparatuses that use the methods. The syntactic dictionary is converted into a corresponding plurality of expressions, of a context-free grammar, that are a grammar of the source code. The parser is constructed from the expressions. The source code is compressed using the parser. Preferably, the grammar of the source code file is a D-grammar and the expressions are regular expressions. Preferably, the parser is a deterministic pushdown transducer. An important case of the present invention is that in which the source code is XML code and the syntactic dictionary is the document type declaration of the XML code. Apparatuses that use a parser of the present invention include compressors, decompressors, validators, converters, editors, network devices and end-user / hand-held devices.
Owner:RAMOT AT TEL AVIV UNIV LTD
System and method to dynamically setup a private sub-blockchain based on agility of transaction processing
ActiveUS20180121909A1Encryption apparatus with shift registers/memoriesCryptography processingTransaction processing systemValidator
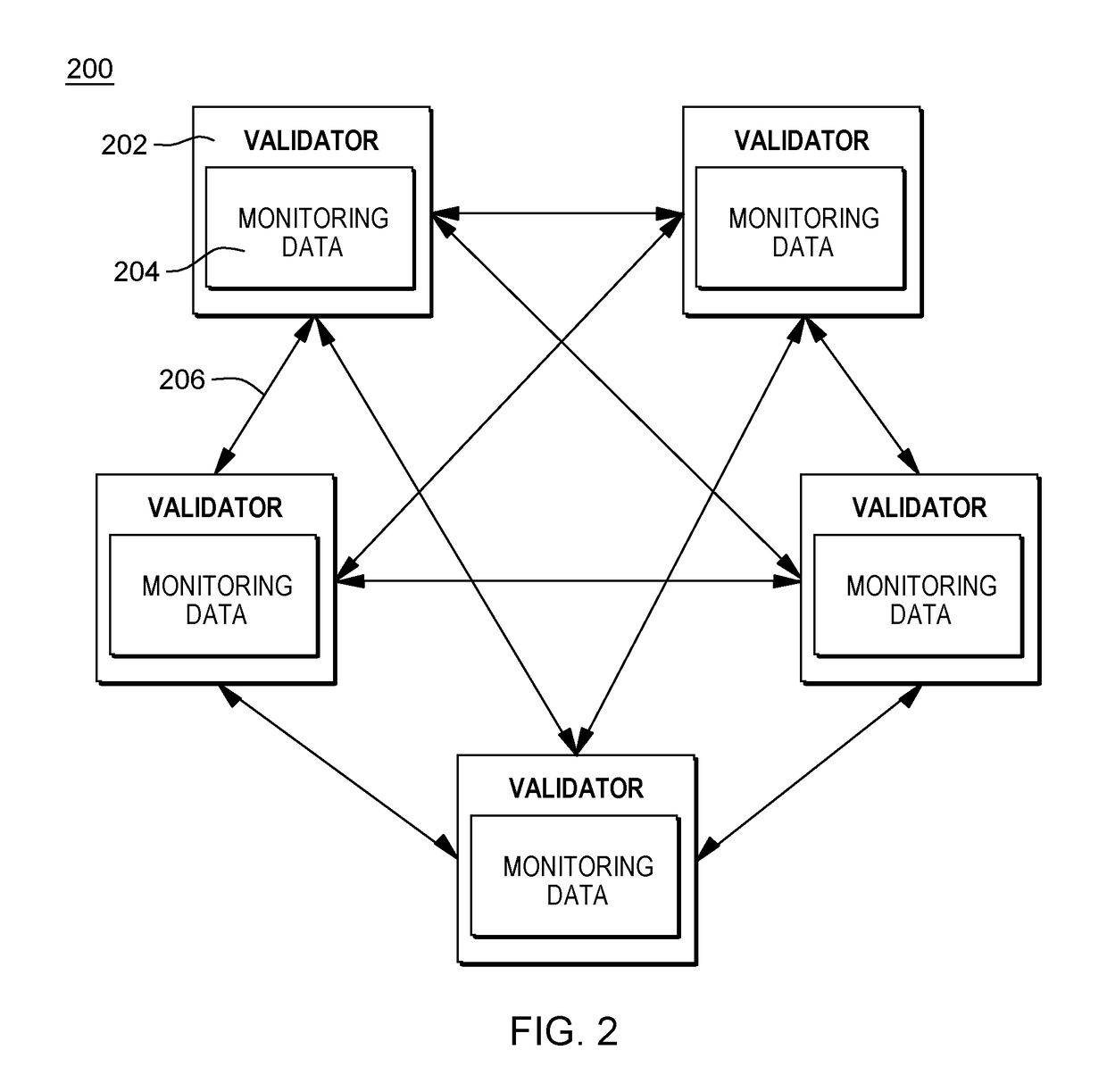
The creation of a private sub-blockchain from a main blockchain is disclosed including receiving a request including a trust requirement and an agility requirement, receiving monitoring data from at least one of a plurality of validator nodes of the main blockchain, the monitoring data generated by monitoring the execution of transactions and the exchange of consensus messages by one or more of the plurality of validator nodes, determining a minimum number of validator nodes required to meet the trust requirement, identifying a subset of the plurality of validator nodes of the main blockchain that meets the agility requirement based on the received monitoring data, the subset containing at least the determined minimum number of validator nodes required to meet the trust requirement, and creating a private sub-blockchain of the main blockchain, the private sub-blockchain including the identified subset of the plurality of validator nodes of the main blockchain.
Owner:IBM CORP
File system level integrity verification and validation
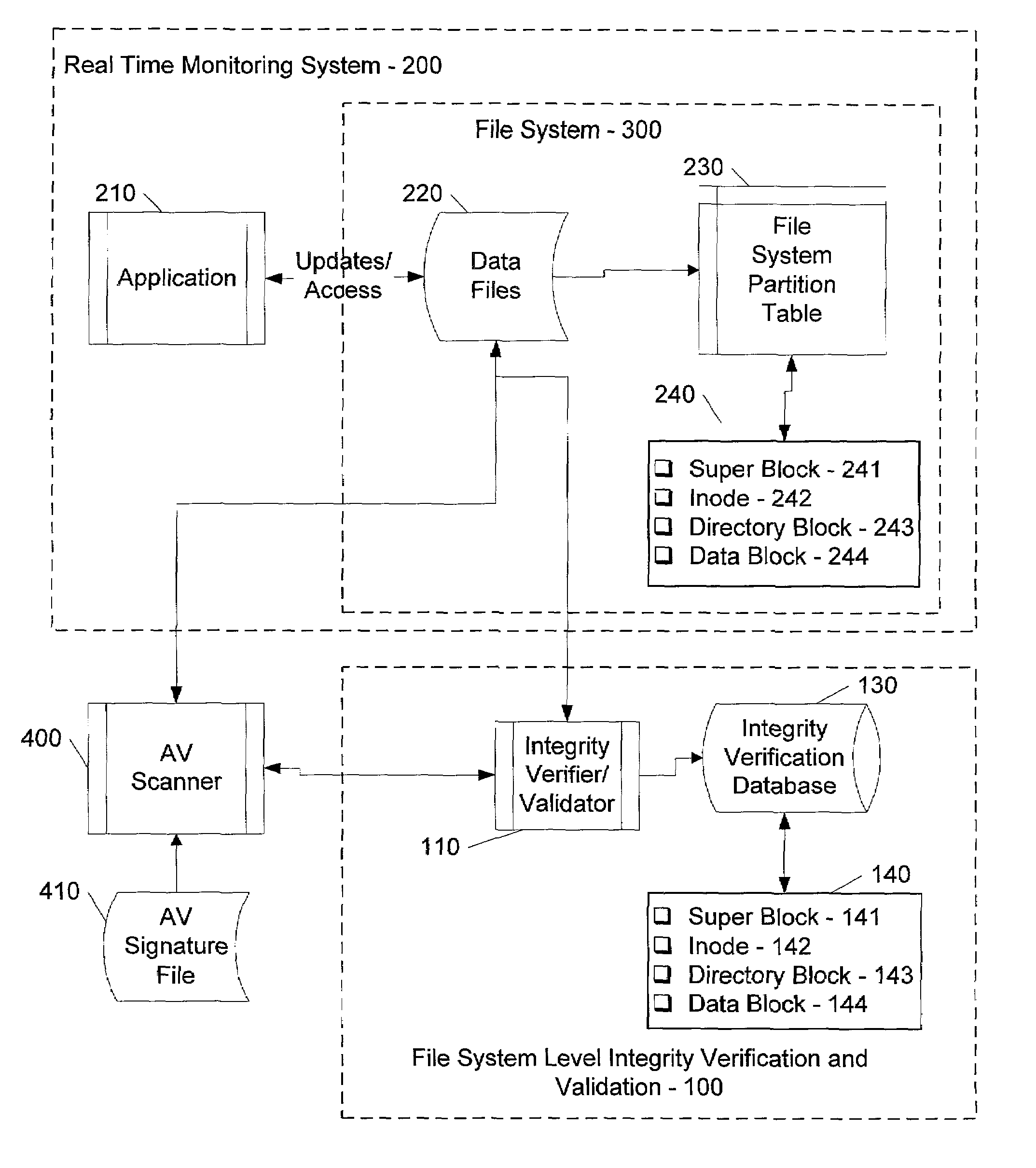
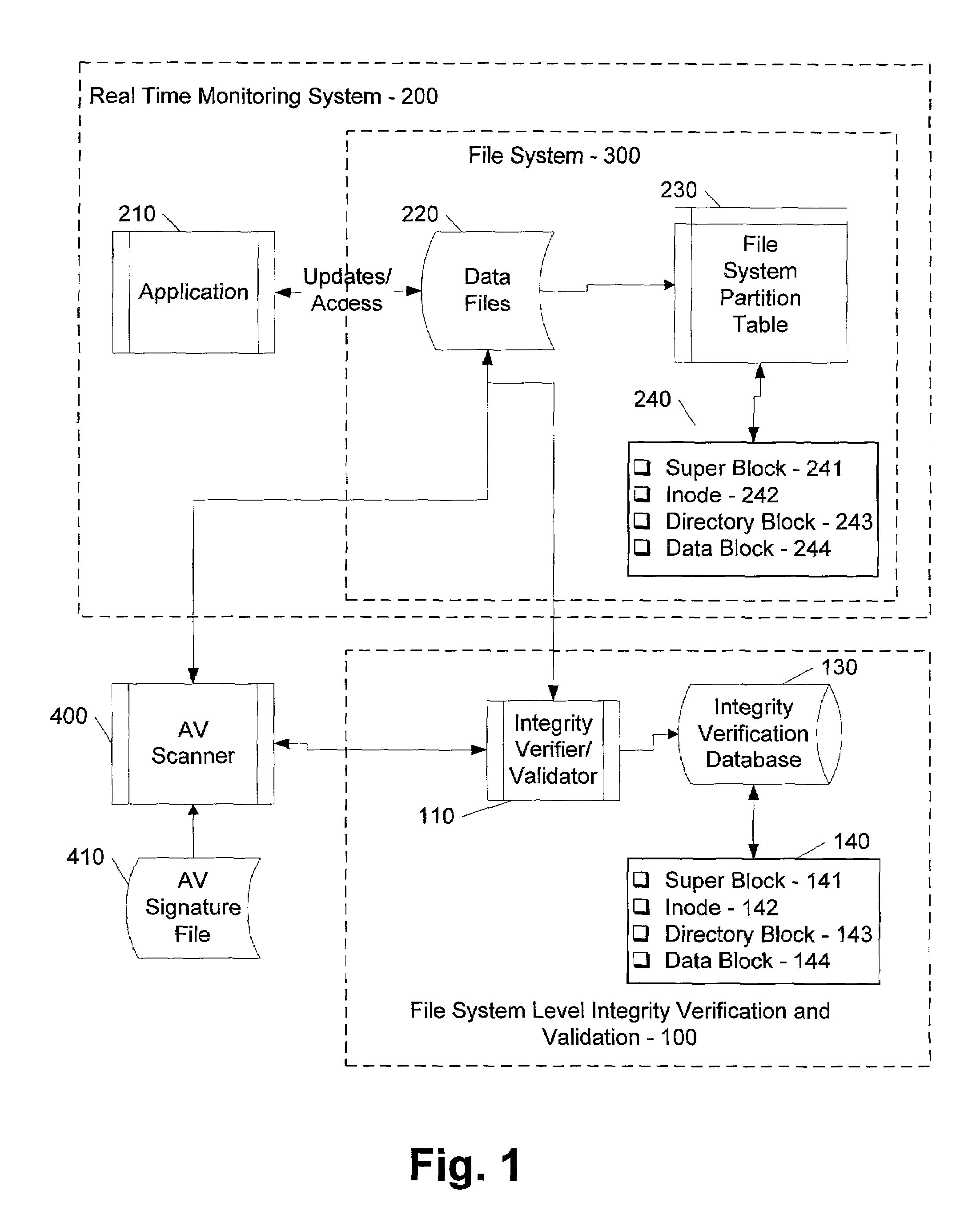
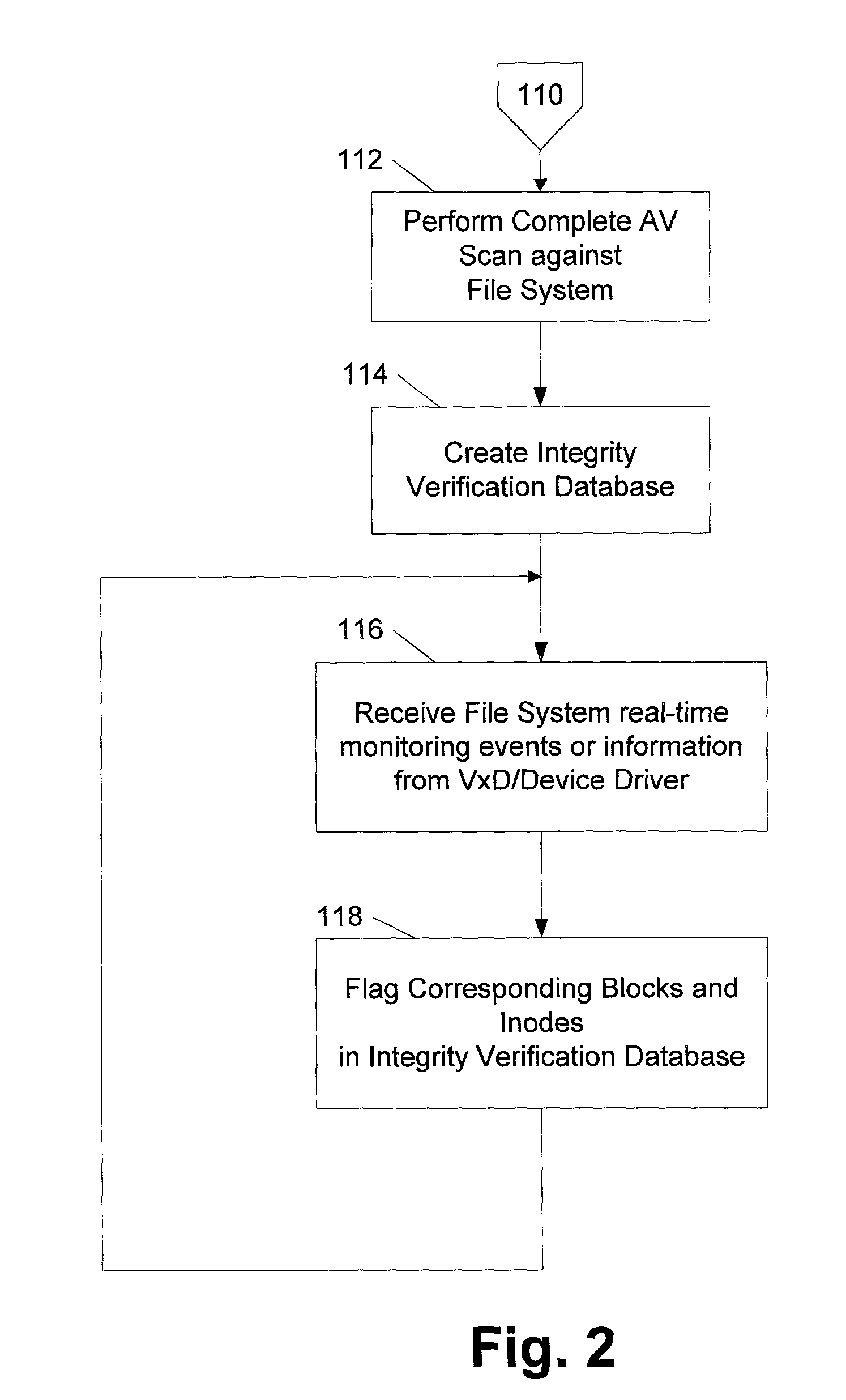
ActiveUS7069594B1Preventing rescanningGood level of efficiencyMemory loss protectionError detection/correctionAnti virusInode
An integrity verifier and validator is provided in which an initial anti-virus scan is performed against an entire file system to verify the integrity of the file system and create a corresponding file system level integrity verification database of known scanned regions of the file system. The database contains a copy of the file system's partition table referencing the range of occupied inodes and directory blocks. When new or updated content is written to the file system the integrity of the corresponding occupied inodes and directory blocks is no longer assured, and the integrity verifier flags them on the database for rescanning. Subsequent attempts to rescan any portion of the file system triggers the integrity validator to scan the database to validate whether that portion of the file system falls within any of the occupied inodes or directory blocks that have been flagged for rescanning. If they are not flagged, then rescanning of that portion of the file system is unnecessary as the integrity of at least that portion is assured. However, if they are flagged, then the anti-virus software rescans that portion of the file system for the presence of viruses.
Owner:MCAFEE LLC
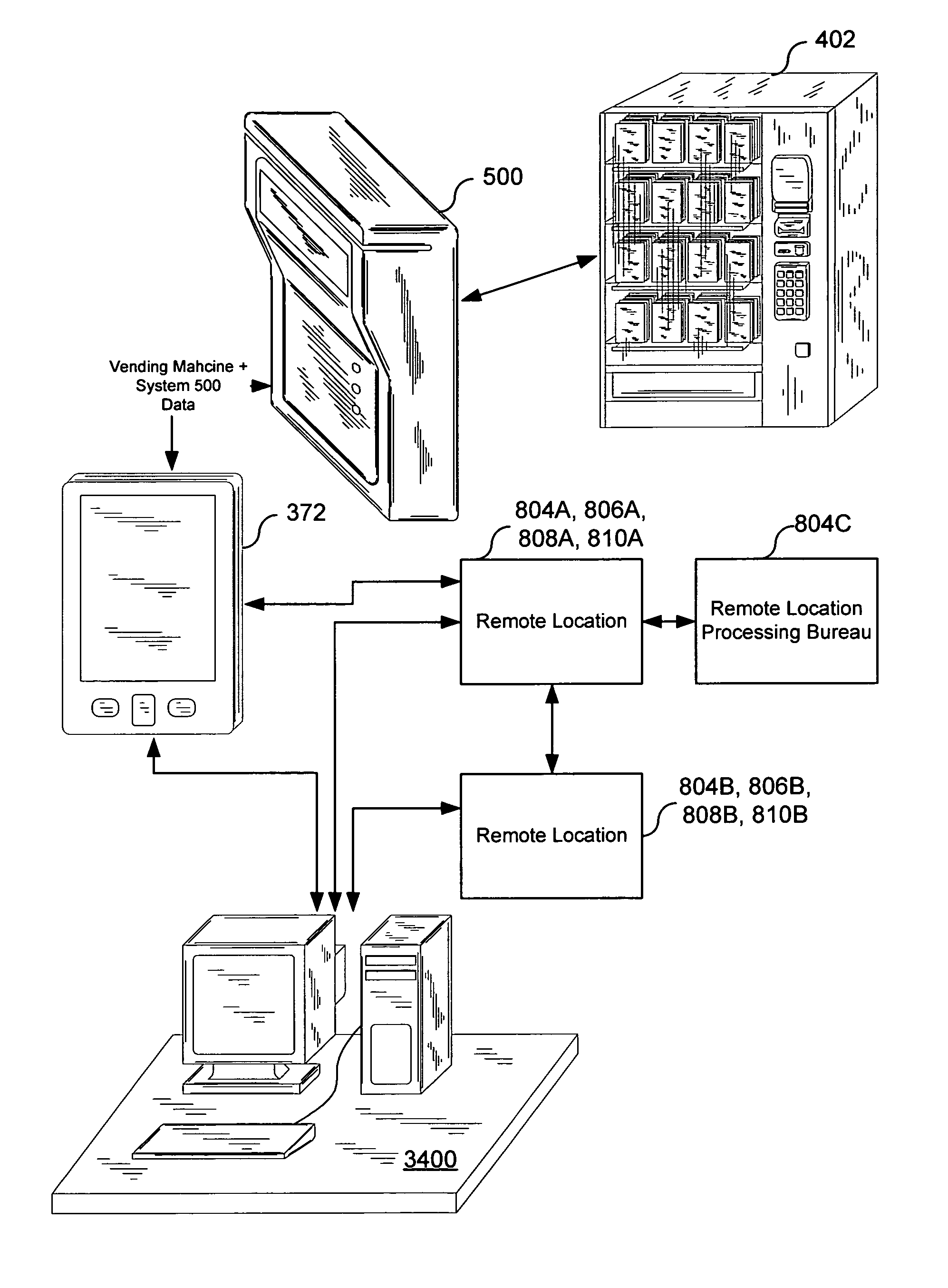
Cashless vending system with tethered payment interface
InactiveUS7464867B1International currency conversion processing fees are minimizedSensing record carriersBuying/selling/leasing transactionsCredit cardEngineering
Owner:CANTALOUPE INC
Flexible loyalty points programs
A gaming machine comprising a non-physical contact data interface is described. The non-physical contact data interface may be capable of reading loyalty program data from a loyalty program instrument without contact between the loyalty program instrument and the non-physical contact data interface. The non-physical contact data interface may be one of a bill validator, a bar-code reader and a Radio Frequency Identification (RFID) tag reader. The loyalty program instrument may be a substrate including at least one of a 1-D bar-code printed on the substrate, a 2-D bar-code printed on the substrate, a symbol printed on the substrate, alpha-numeric character printed on the substrate, a RFID tag embedded in the substrate, a RFID tag printed on the substrate and combinations thereof. The loyalty program instrument may be used to store an index to a record in a database or a portable data file.
Owner:IGT
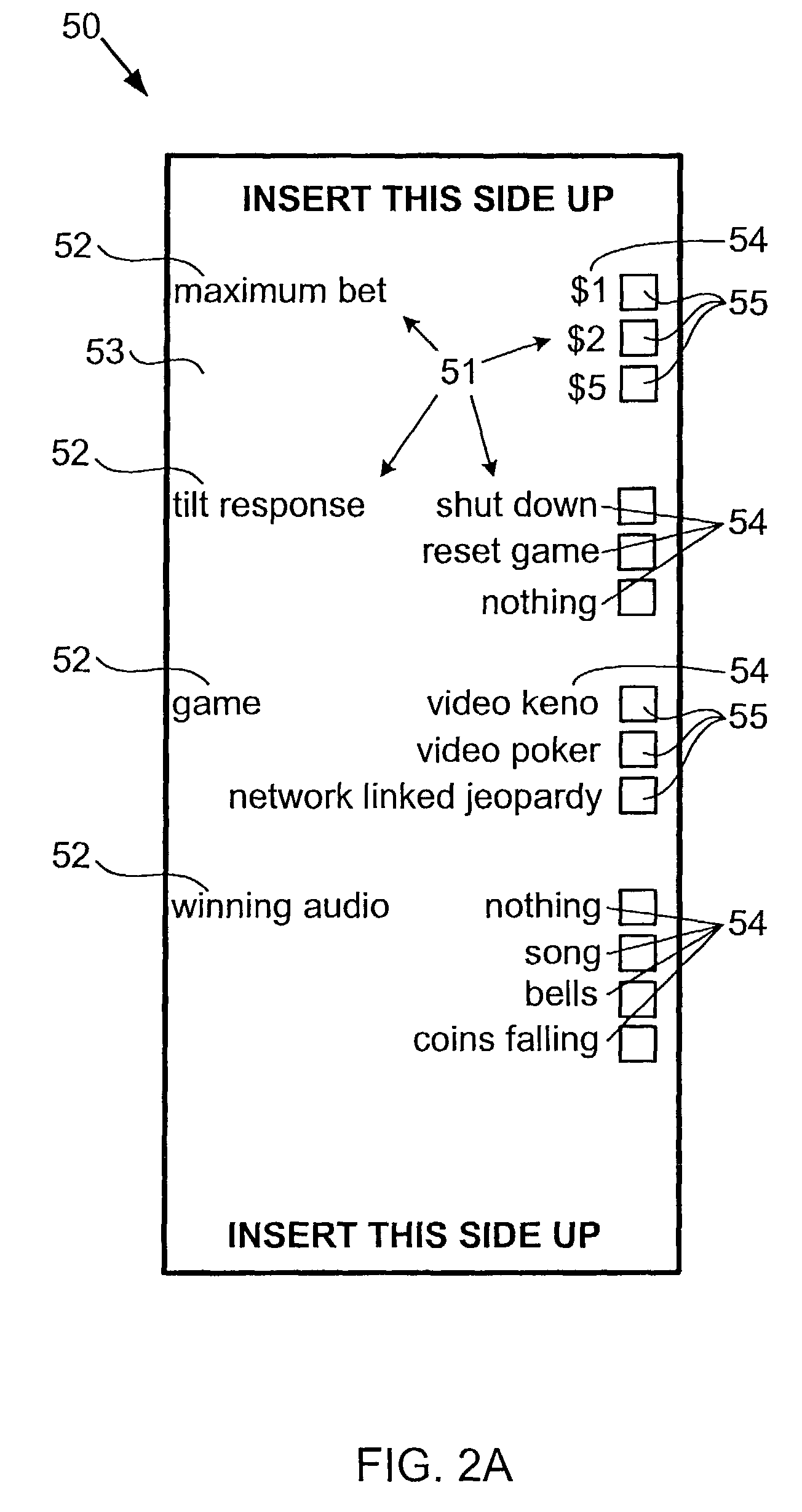
Scan based configuration control in a gaming environment
InactiveUS7909699B2Increase heightImprove configurationApparatus for meter-controlled dispensingVideo gamesComputer hardwarePaper based
This invention provides automated systems and methods for configuring and reconfiguring gaming machines and games playable on a gaming machine. The automated systems and methods employ a complementary gaming machine configuration device, such as a paper-based ticket, and interface operably associated with a gaming machine, such as a note acceptor or bill validator that receives and reads the paper-based ticket. The gaming machine configuration device stores game parameter configuration information in the form of configuration indicia. The indicia may contain the content required to effect configuration directly or may do so indirectly by containing a reference to a location where a set of configuration parameters have been stored. This location may reside within the gaming machine or external to it, but accessible via. a communications link. The interface reads the indicia from the configuration device, and provides a signal to a processor responsible for managing the gaming machine. The processor has access to software or memory that stores associations between the configuration indicia and configuration and reconfiguration commands for the parameters. The processor and software are then designed or configured to convert the signal provided by the interface to commands that act on appropriate mechanisms of the gaming machine to configure or reconfigure the games and / or gaming machine components responsible for expression of the affected game parameters.
Owner:IGT
Dual cash box note and ticket validator
A bill acceptor system for accepting bills, vouchers, scrip, tickets and / or currency into an electronic gaming machine or alternative type of customer service device. The system includes a validator assembly capable of identifying acceptable notes and discriminating between currency and non-currency notes. The system also includes a transport assembly for transporting notes from the validator to a dual section cash box. The dual section cash box is configured to receive and hold notes received from the bill acceptor in different compartments.
Owner:JCM AMERICAN CORP
Method and apparatus for managing attraction admission
The invention is a method and system for managing admission to an attraction. In one or more embodiments, the system comprises a first queue by which customers may access the attraction by waiting in line and a second queue by which customers may access the attraction in a manner which avoids the first queue. The system includes a first validator for validating an entitlement of a customer to receive an assigned time in the future for accessing the attraction via the second queue, a media distributor for distributing a media to an entitled customer, the media including the assigned time at which the entitled customer is entitled to access the attraction in the future, and a second validator for validating the entitled customer access to the attraction at the time provided on the media. In accordance with a method of the invention, a customer may access an attraction in a manner which avoids standing in a first waiting line by verifying entitlement to utilize a second queue, obtaining a pass entitling the customer to access the attraction at a future time, and returning to the attraction at the future time and gaining access with the pass. In this method, the customer may leave the vicinity of the attraction between when the pass is issued and the future time at which the customer is entitled to access to the attraction.
Owner:DISNEY ENTERPRISES INC
Computer system security service
InactiveUS7757271B2Digital data processing detailsComputer security arrangementsAccess networkGraphics
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Dual cash box note and ticket validator
InactiveUS6889849B2Orderly and efficient stacking of the notesPaper-money testing devicesCoin-freed apparatus detailsEngineeringVoucher
Owner:JCM AMERICAN CORP
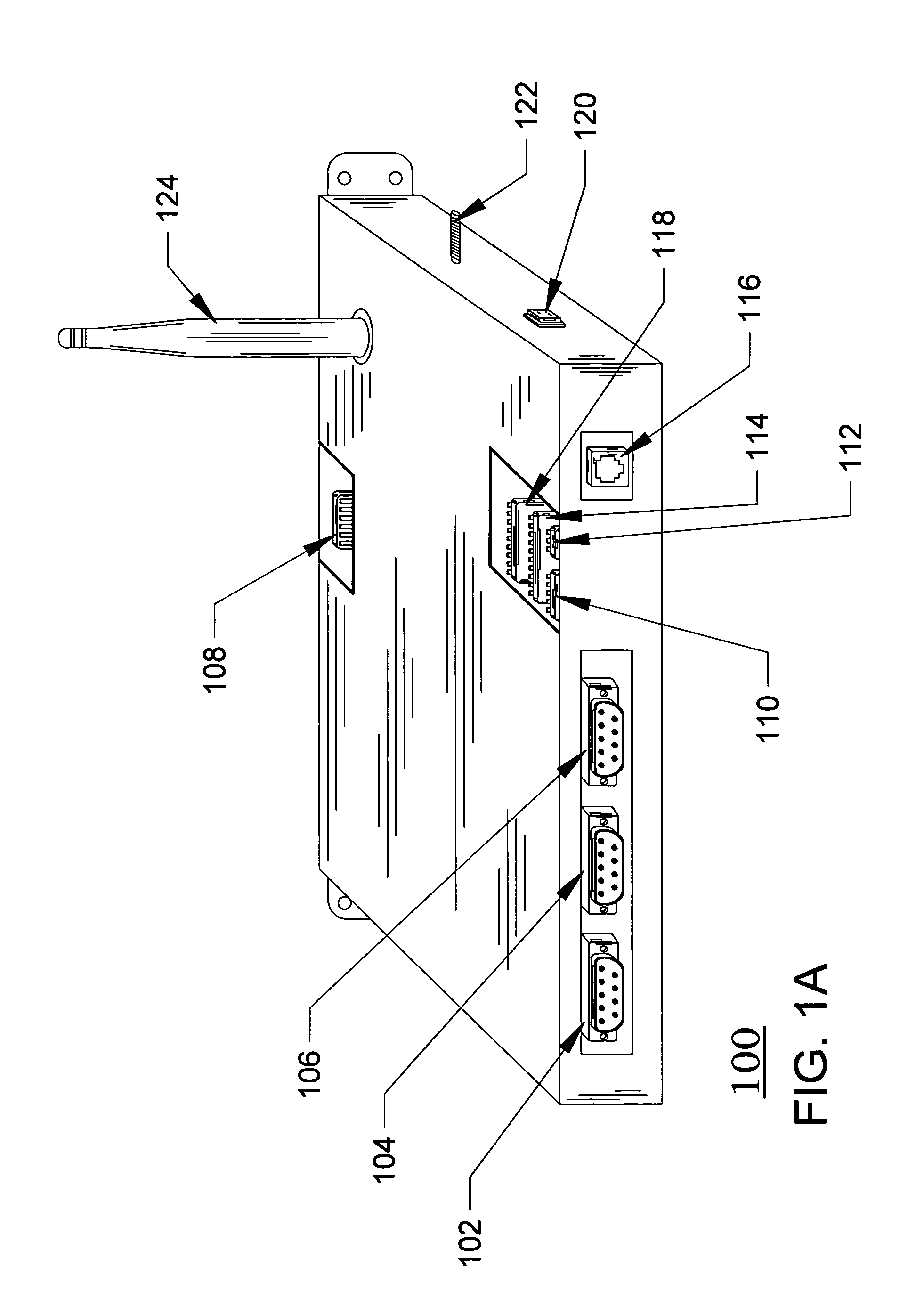
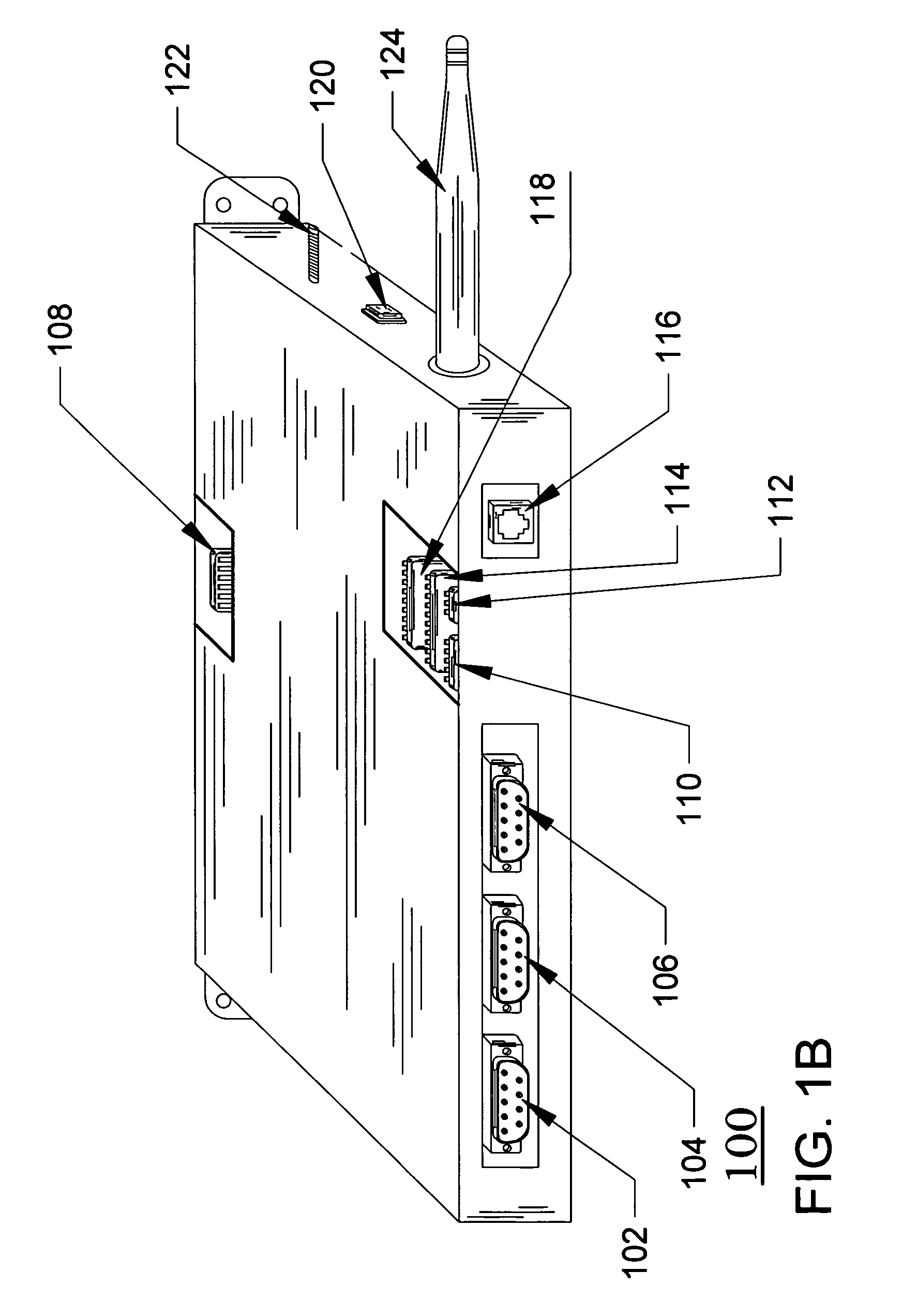
Standard peripheral communication
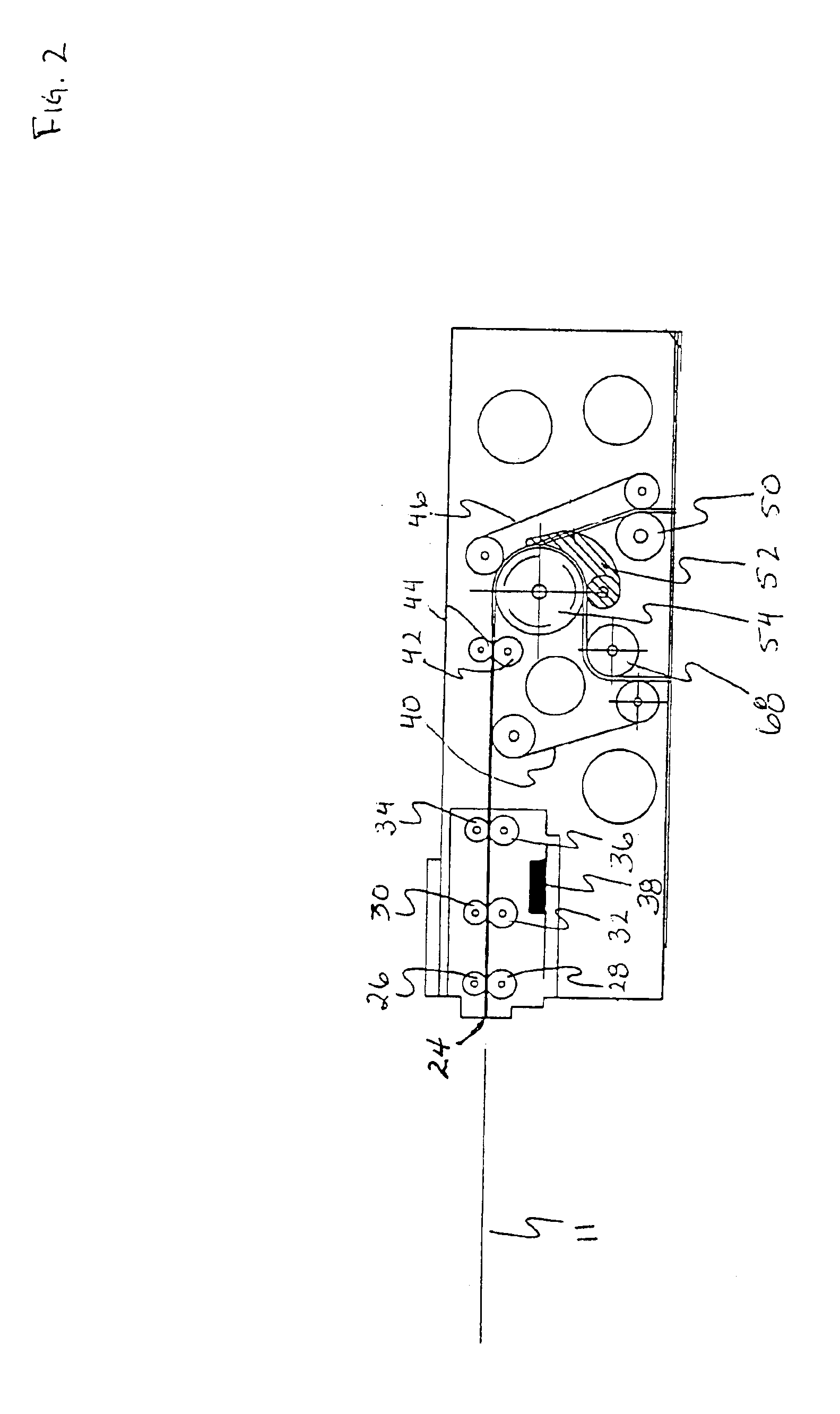
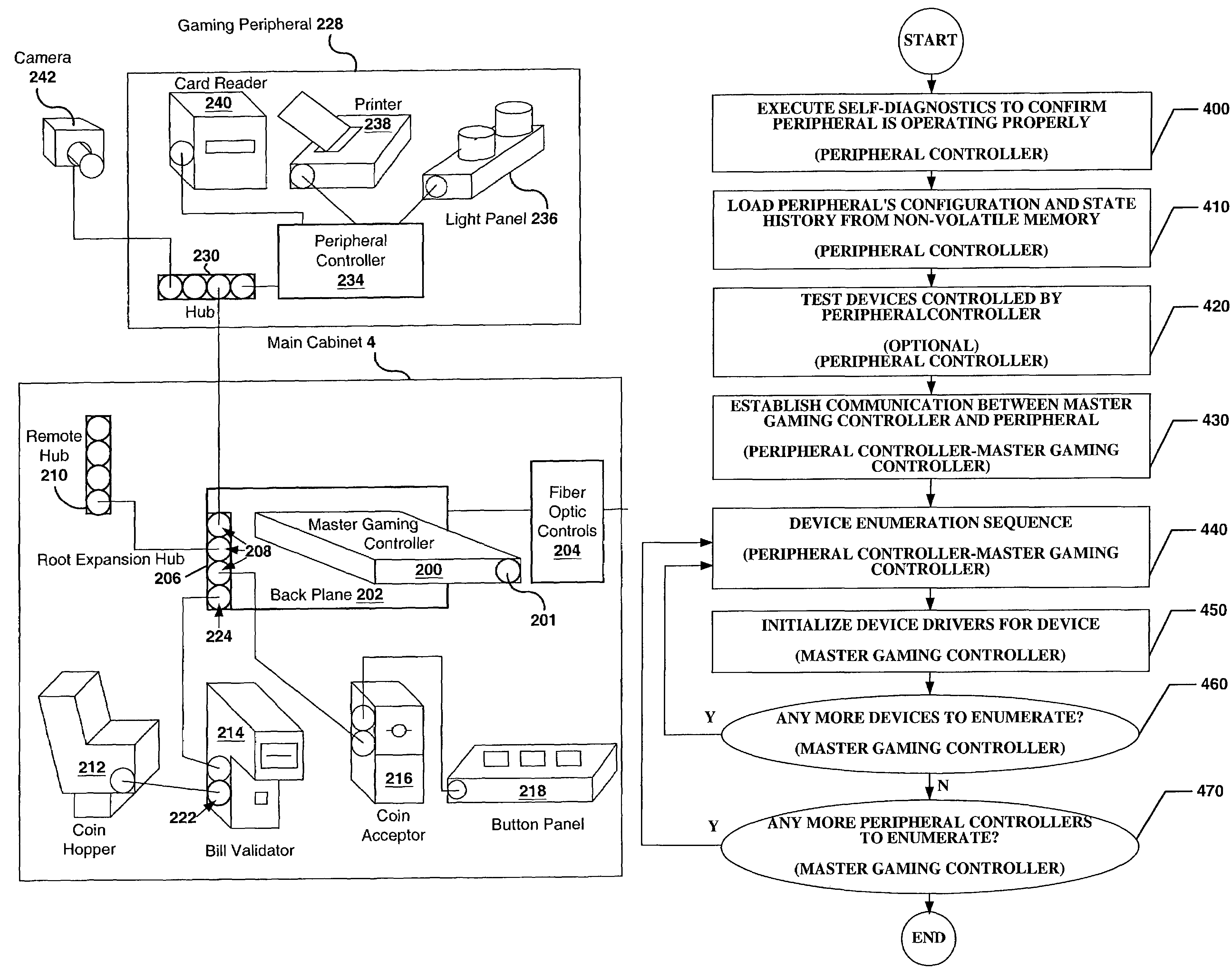
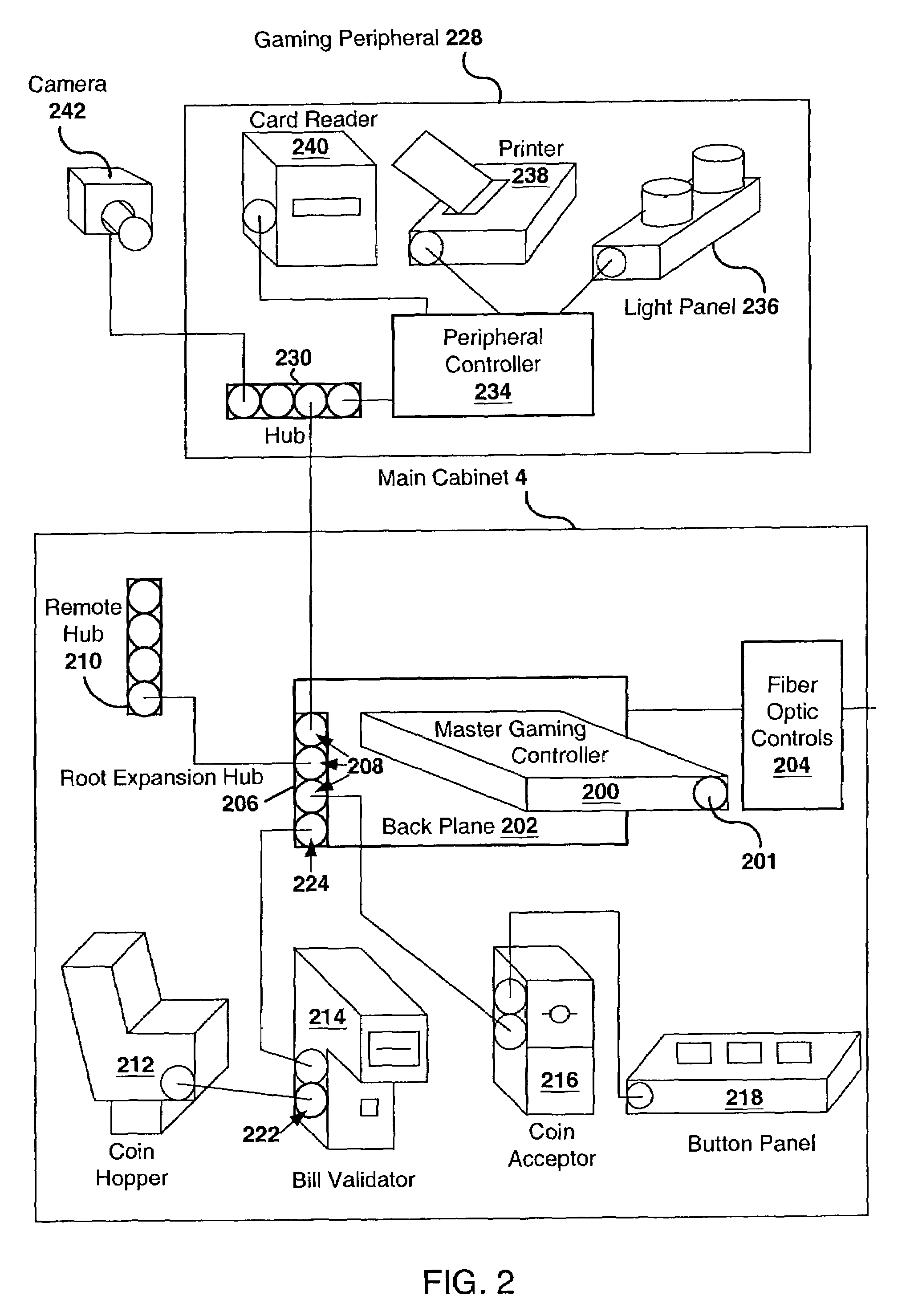
InactiveUS7351147B2Improve securityApparatus for meter-controlled dispensingVideo gamesSpecific functionUSB
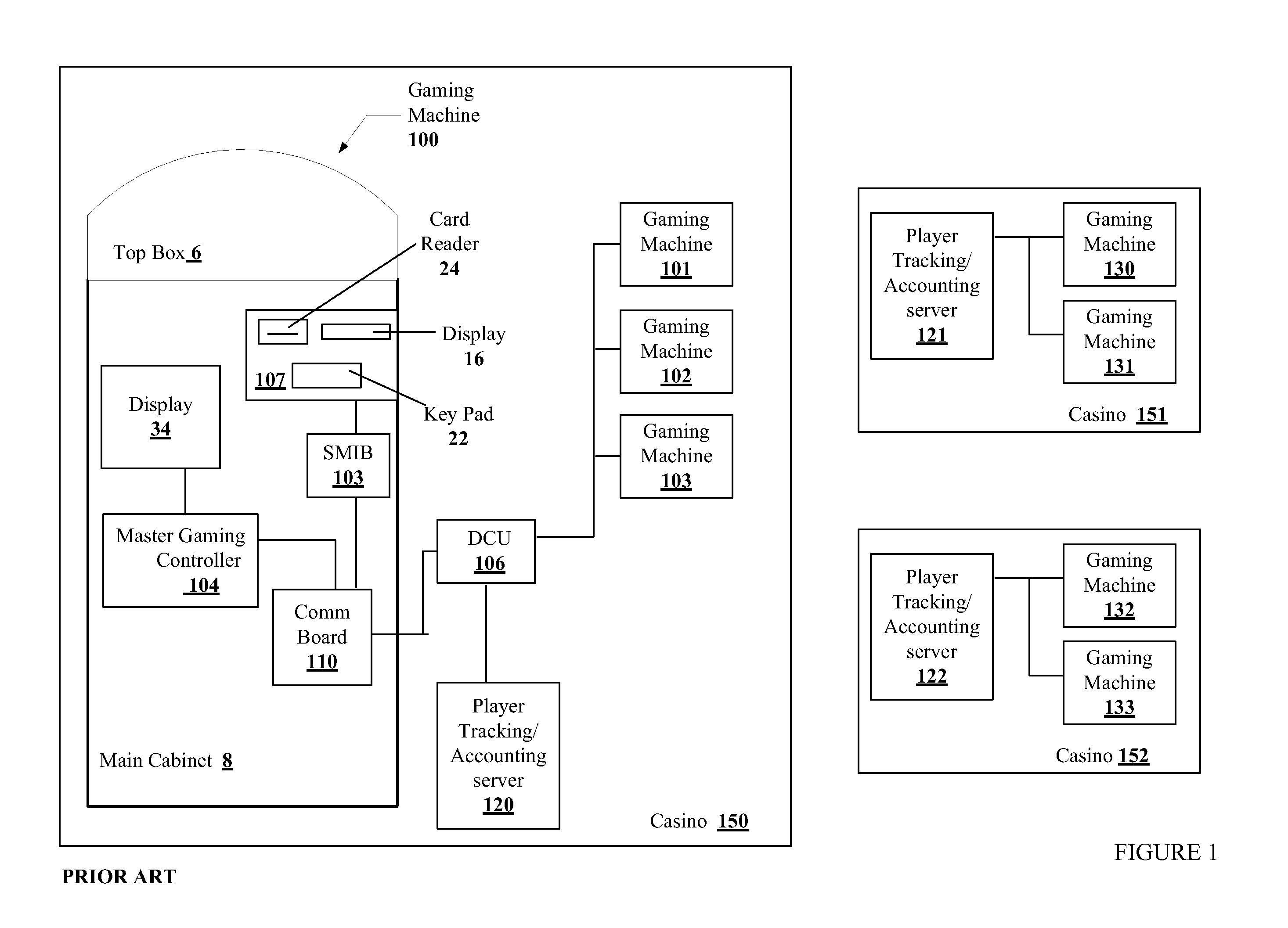
A disclosed gaming machine has a plurality of “gaming peripherals,” each communicating with a master gaming controller via a standard peripheral interface such as the USB (Universal Serial Bus). Further, the gaming peripherals employ a standard peripheral controller and one or more specialized “peripheral devices” (e.g., the actual lights, bill validators, ticket printers, etc. that perform the specific functions of the gaming peripherals). Much of the hardware associated with the peripheral controller is identical from one gaming peripheral to the next. Only a portion of the peripheral controller hardware is specific to the different types of gaming peripherals.
Owner:IGT
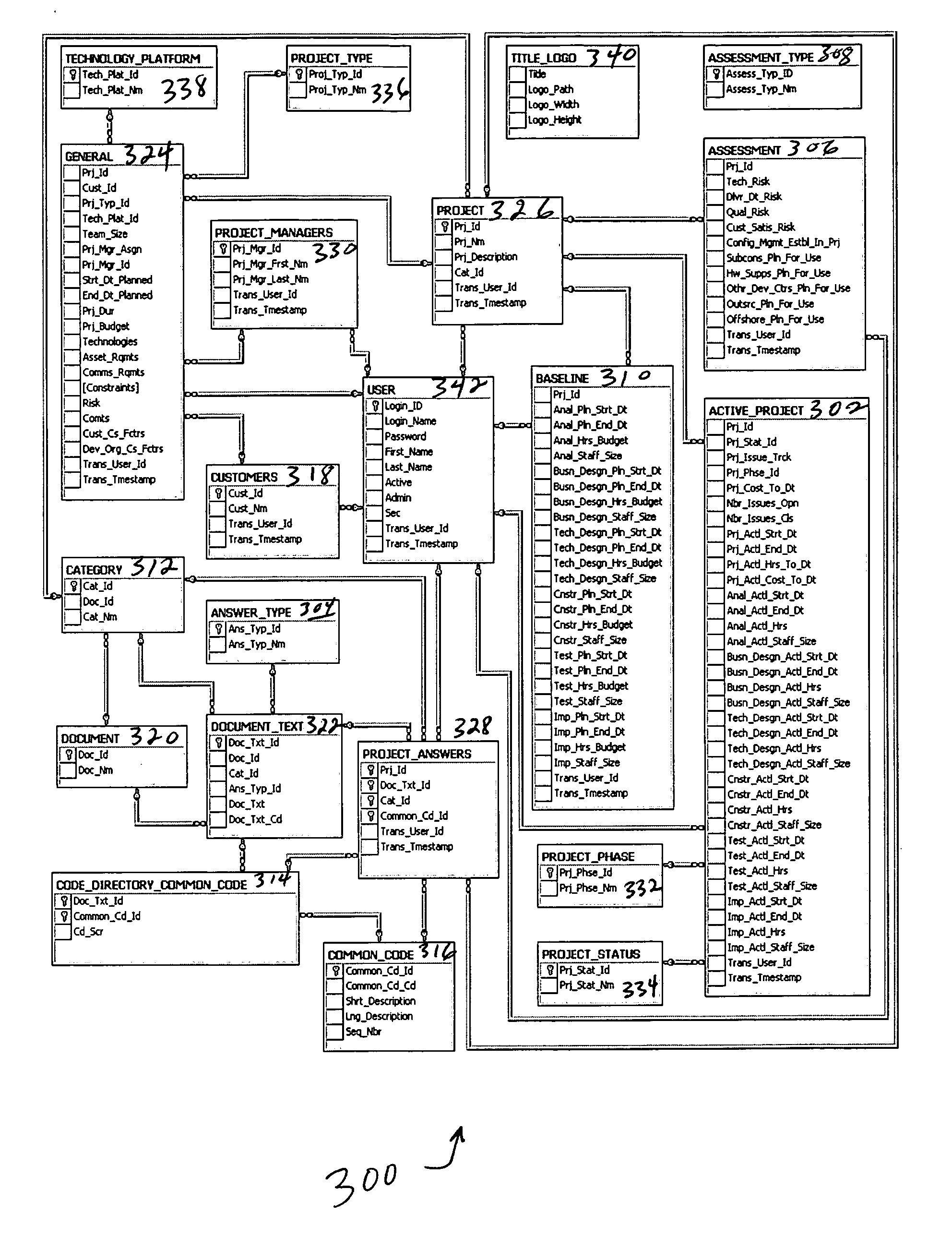
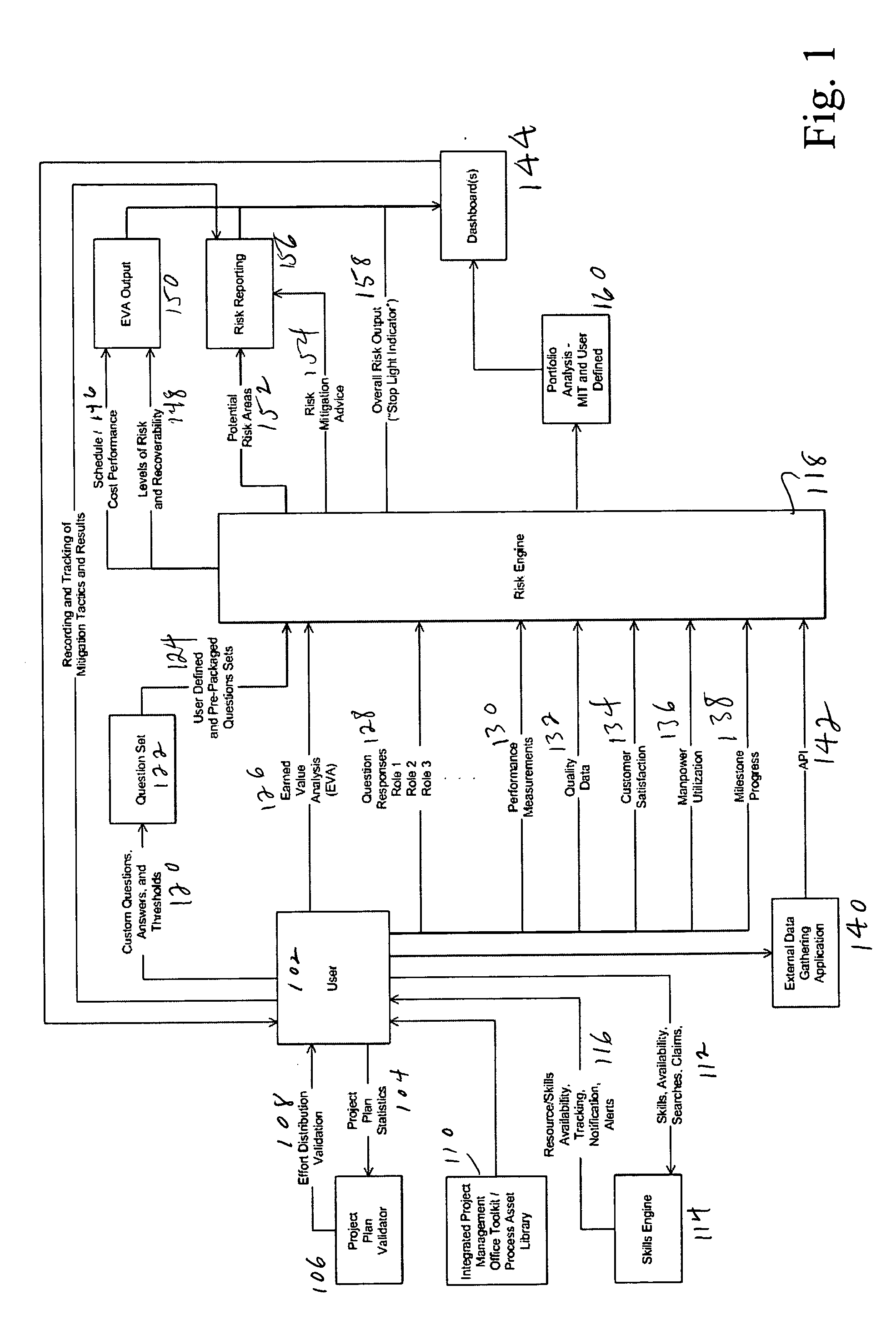
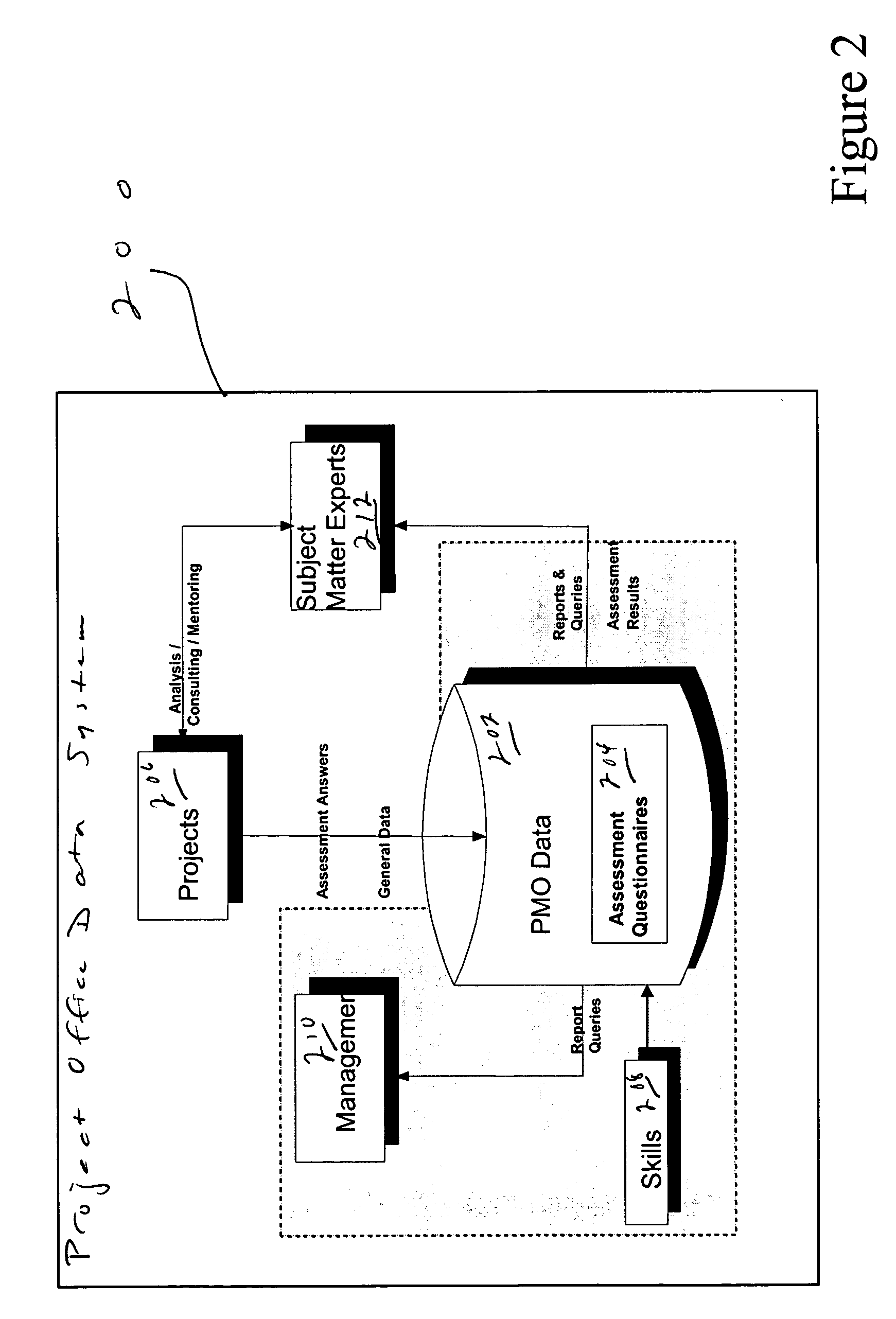
System and method for an automated project office and automatic risk assessment and reporting
ActiveUS20060173762A1Avoid lost organizational productivityImprove abilitiesFinanceResourcesRisk levelRisk identification
In the automation of project risk identification, various qualitative and quantitative measures are combined to report a project's risk level, areas, and mitigation in an automatic and objective manner. The software package includes a risk assessment and report framework and a risk engine, a portfolio analysis, a project plan validator, an integrated project management office toolkit and process asset library, and an integrated skills tracking, locating and availability module with a skills engine.
Owner:COMP AID INC
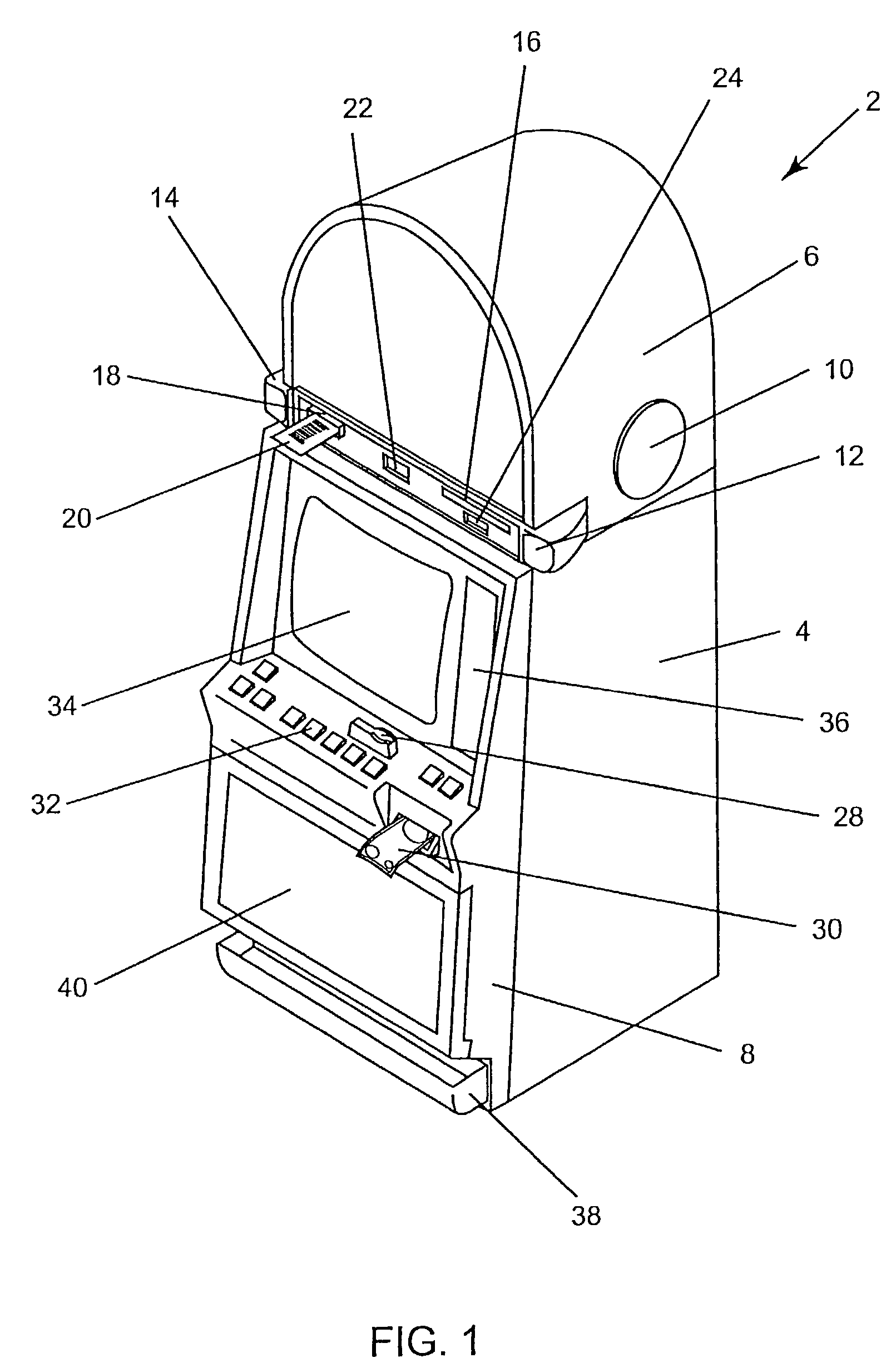
Gaming machine having components located in a bumper recess
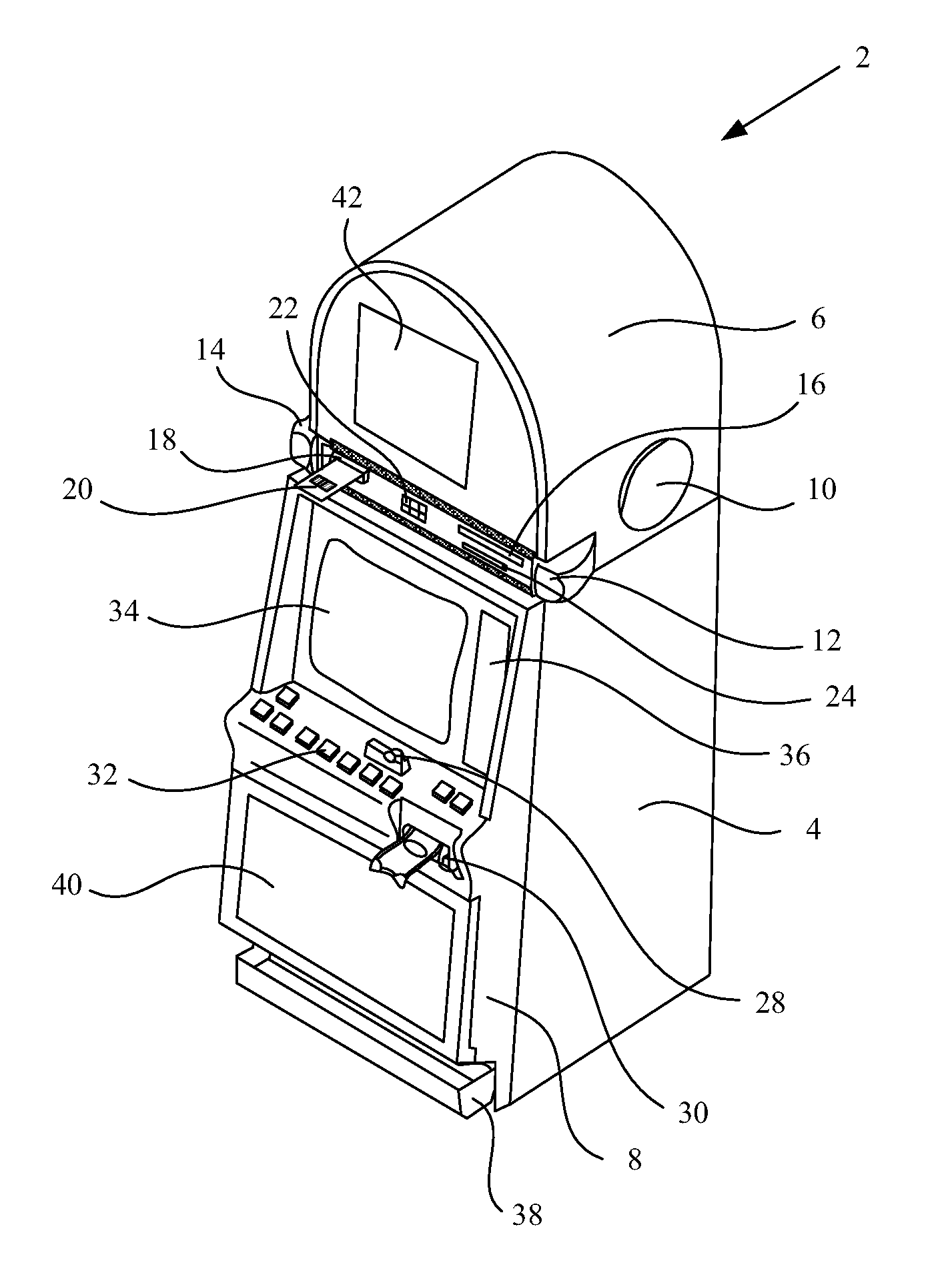
A gaming machine includes a bumper which is preferably positioned at the front-most portion of a play area of the gaming machine. The bumper defines a recessed area. Gaming machine components such as player input devices including a keypad, buttons, and / or card reader slot, or other components such as a ticket printer slot and / or bill validator slot, are located at or in the recessed portion of the bumper of the gaming machine.
Owner:COLE KEPRO INT
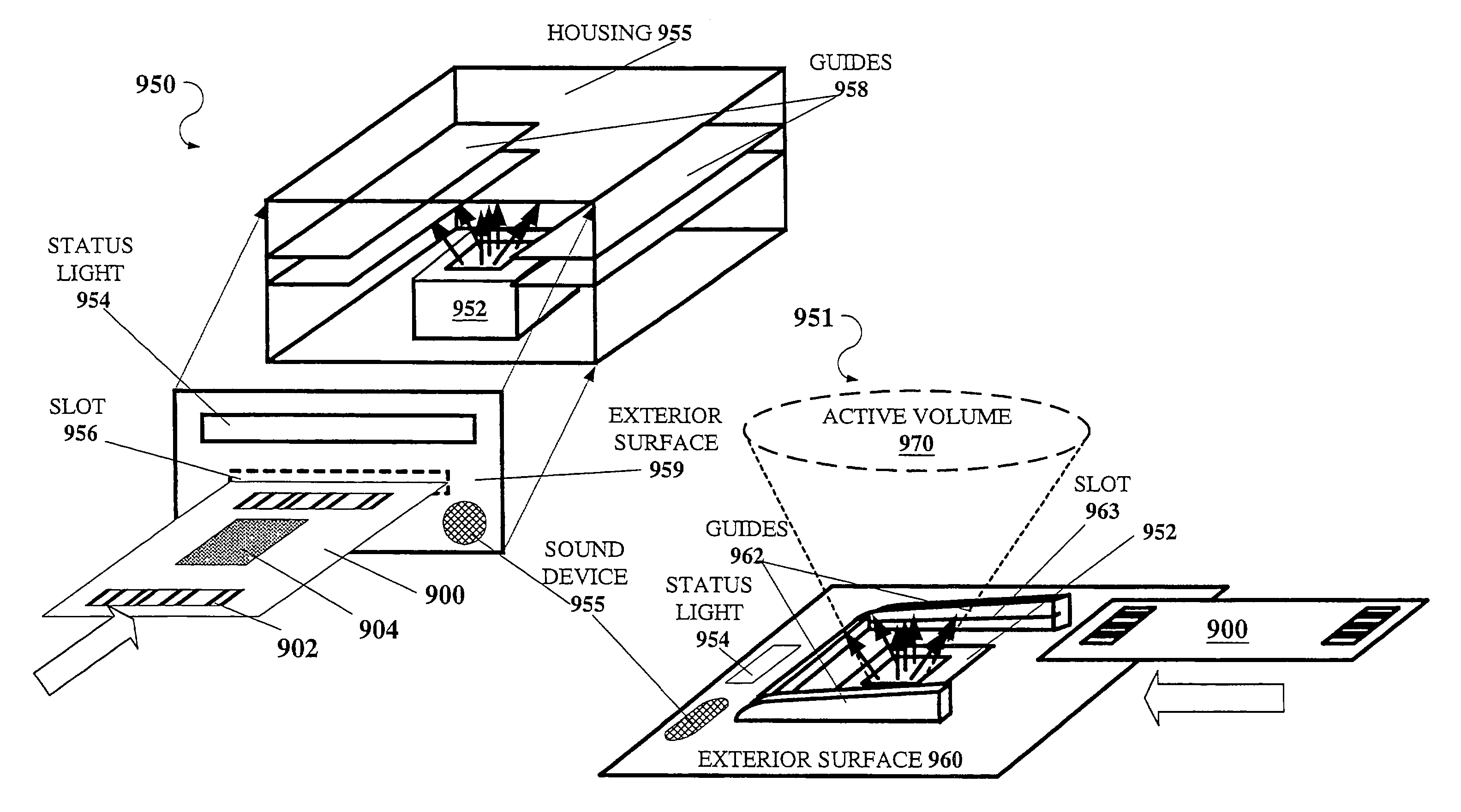
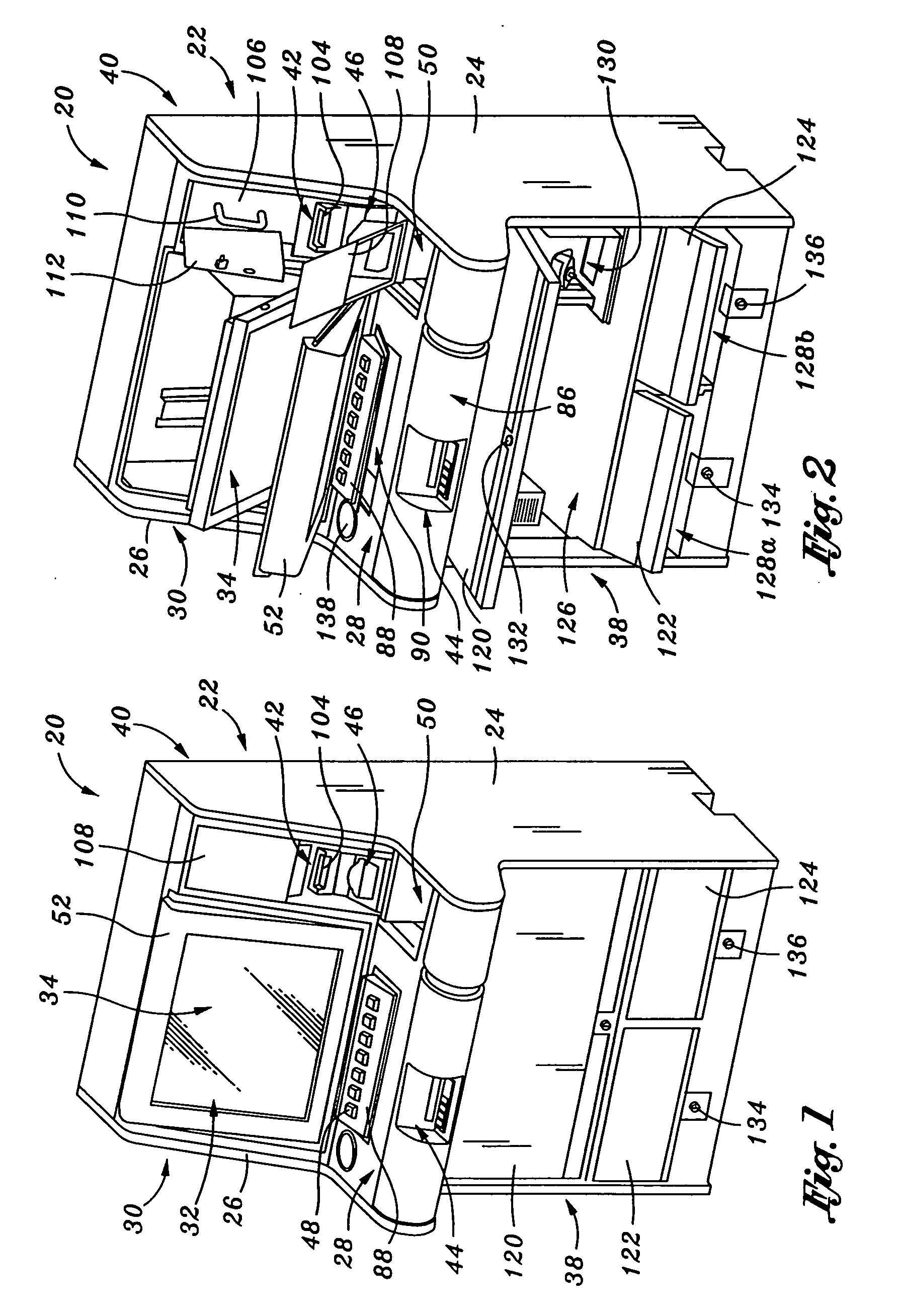
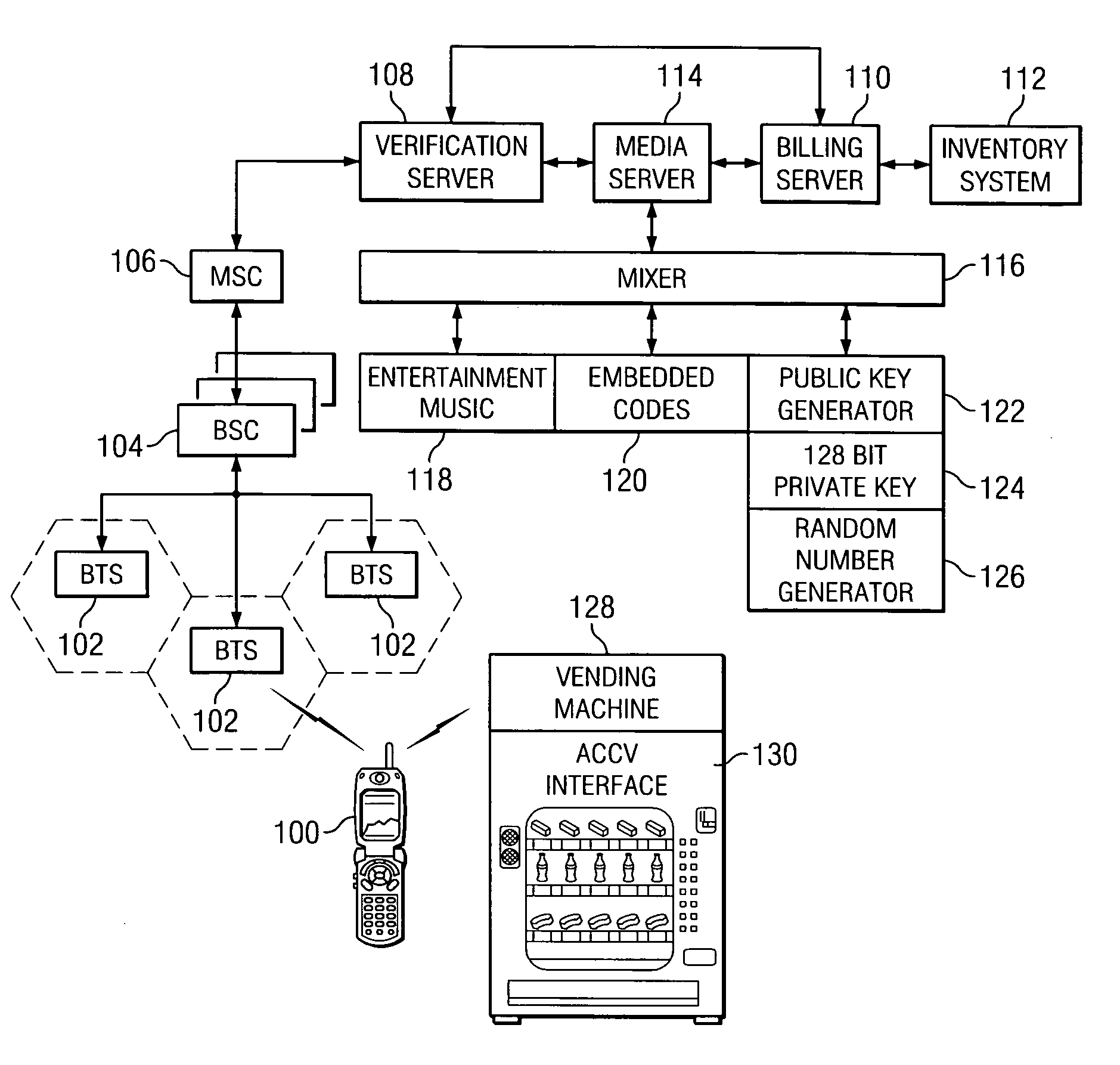
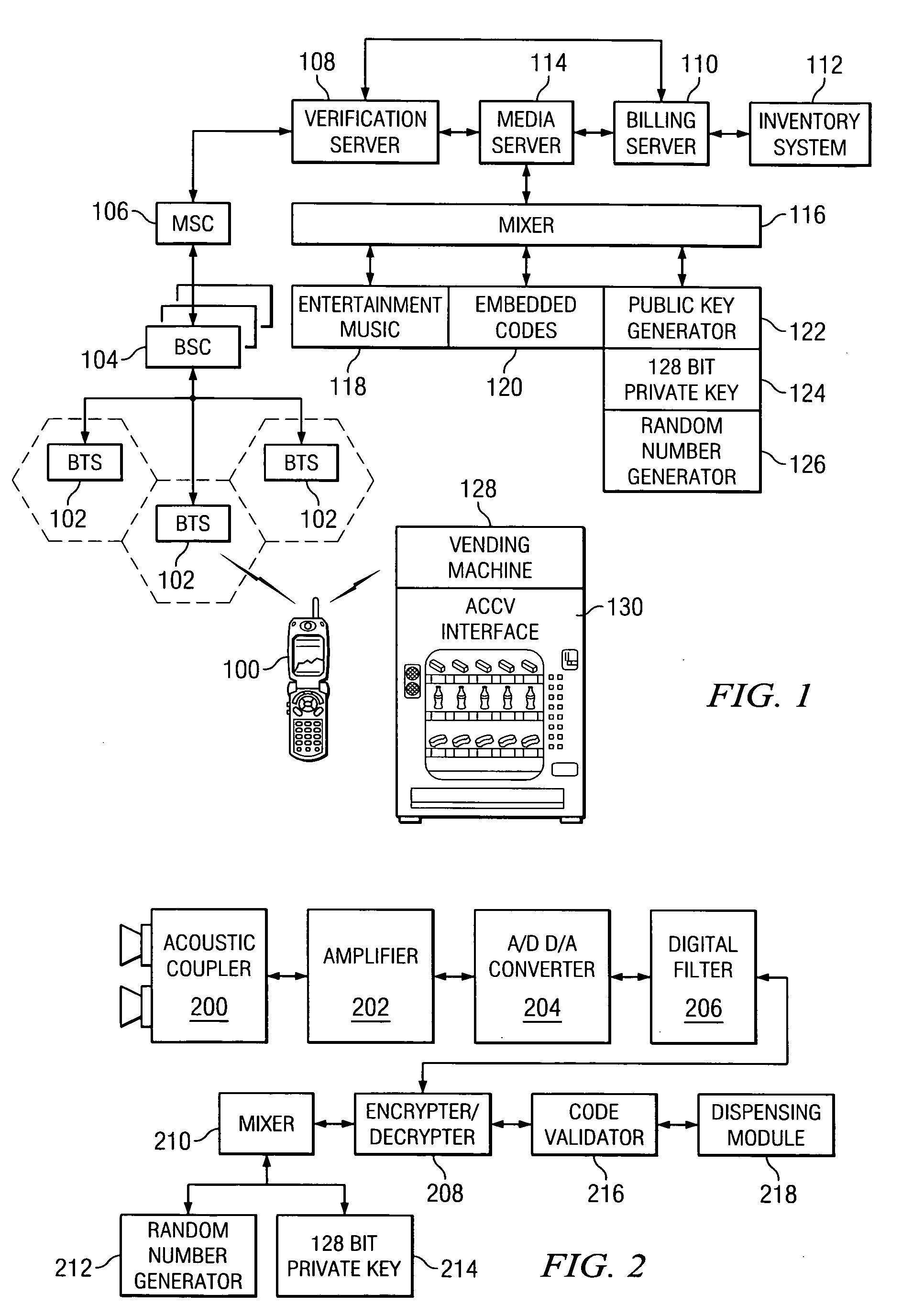
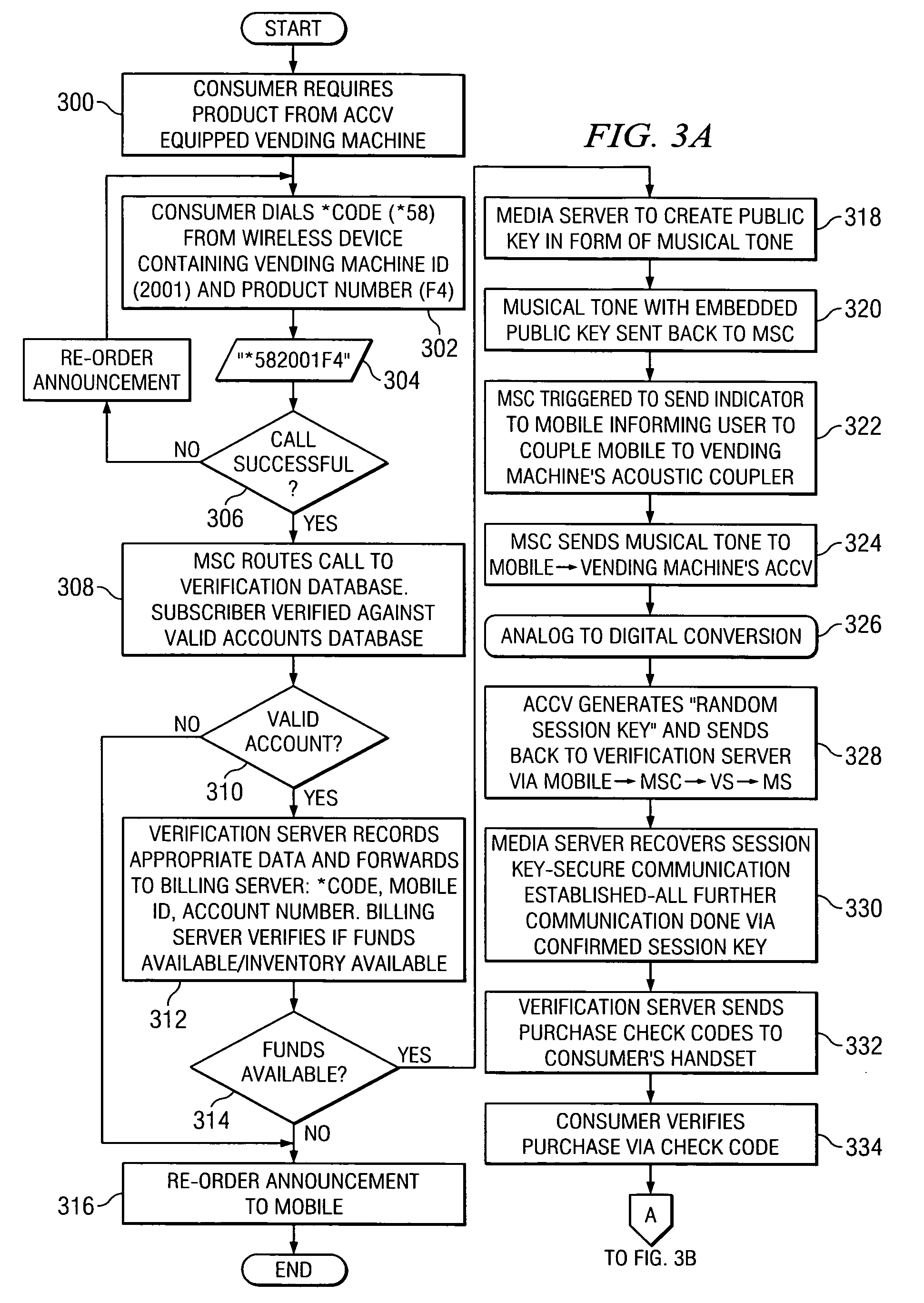
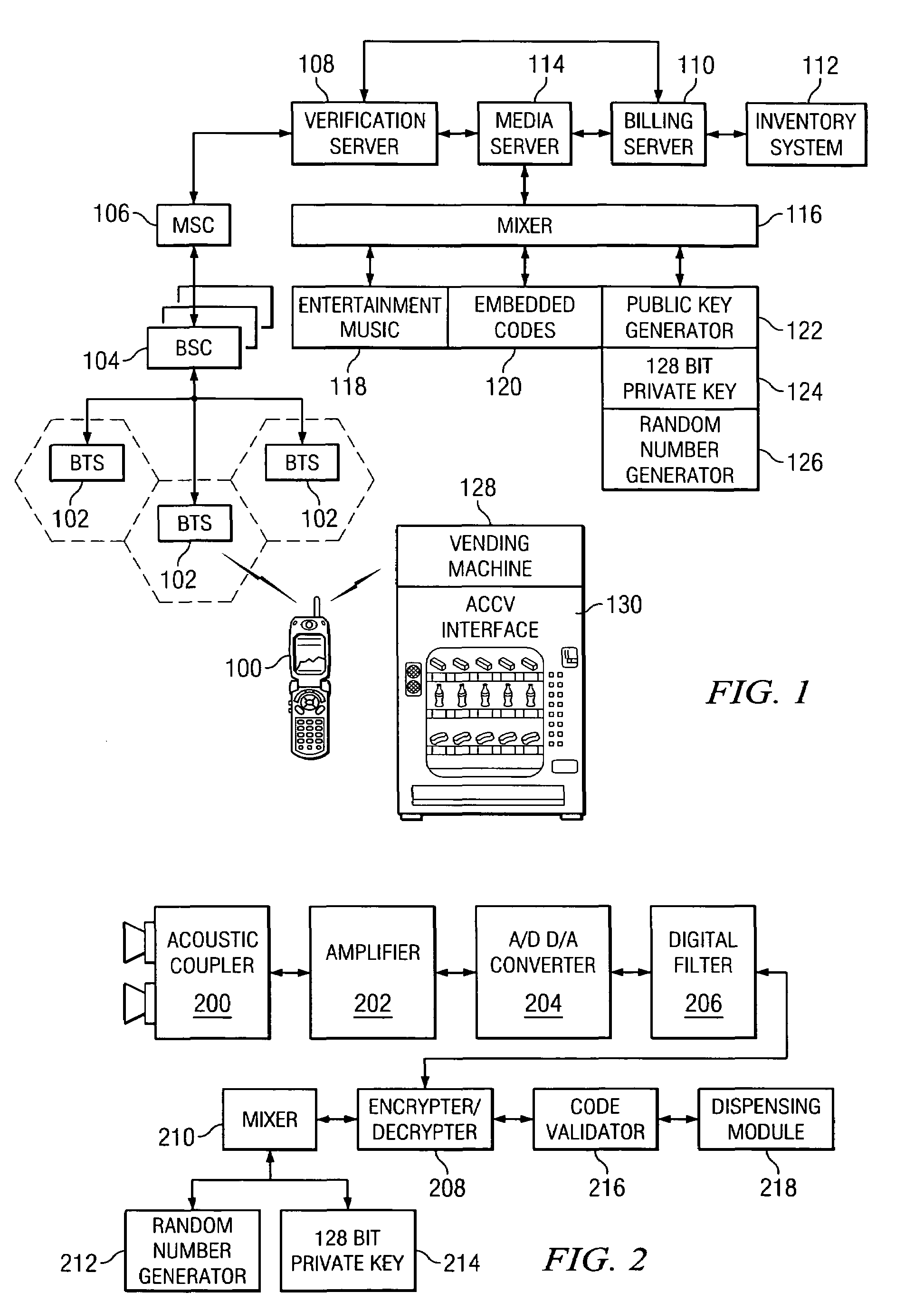
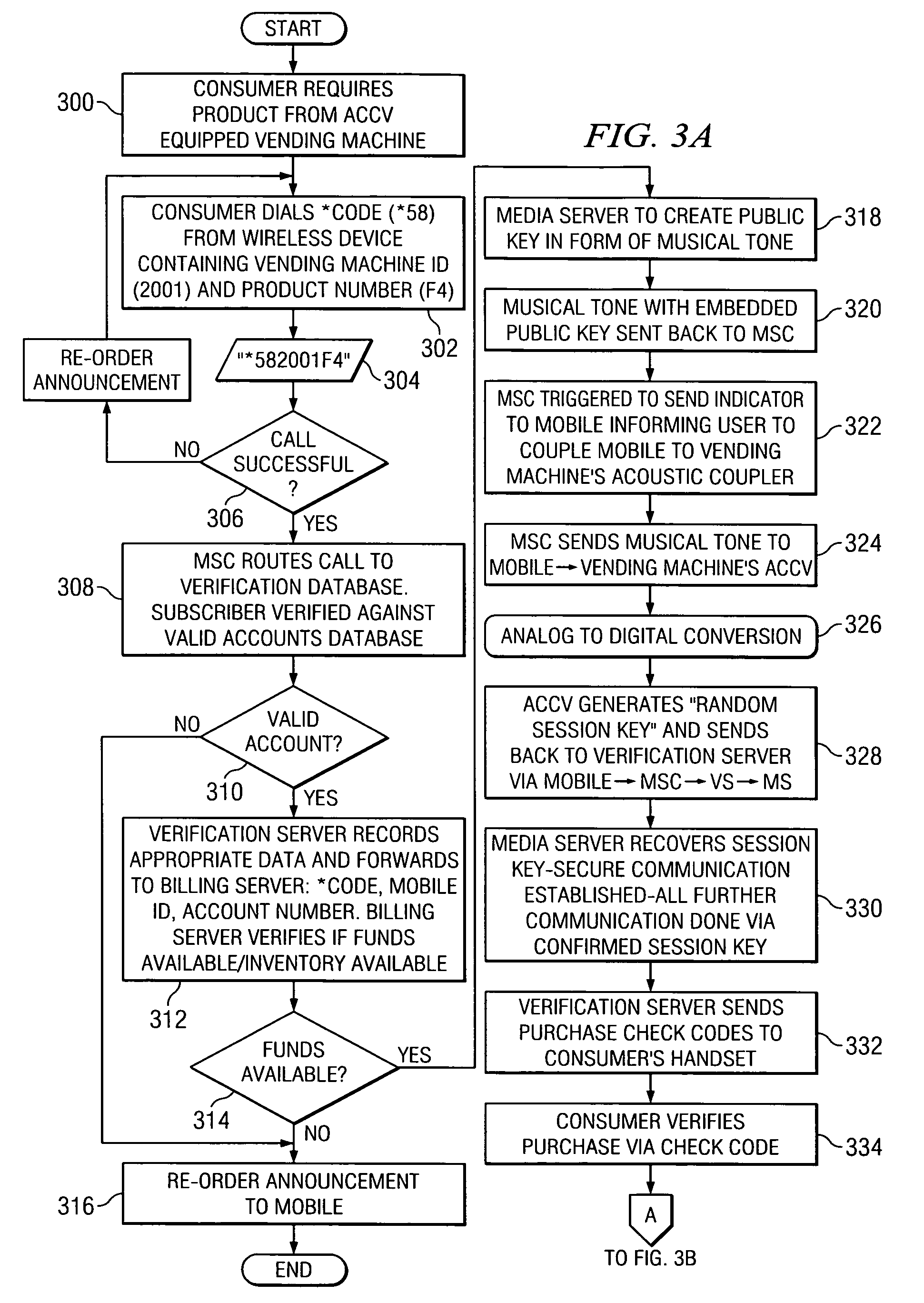
Coinless vending system, method, and computer readable medium using an audio code collector and validator
InactiveUS20070063027A1Coin-freed apparatus detailsSpecial service for subscribersMobile deviceValidator
A system, method, and computer readable medium, wherein a vending machine comprising an audio code collector and a code validator is adapted to receive audio tones from a mobile device, and wherein the audio tones include authentication codes and dispense codes to control dispensing of product from the vending machine.
Owner:ALCATEL LUCENT SAS
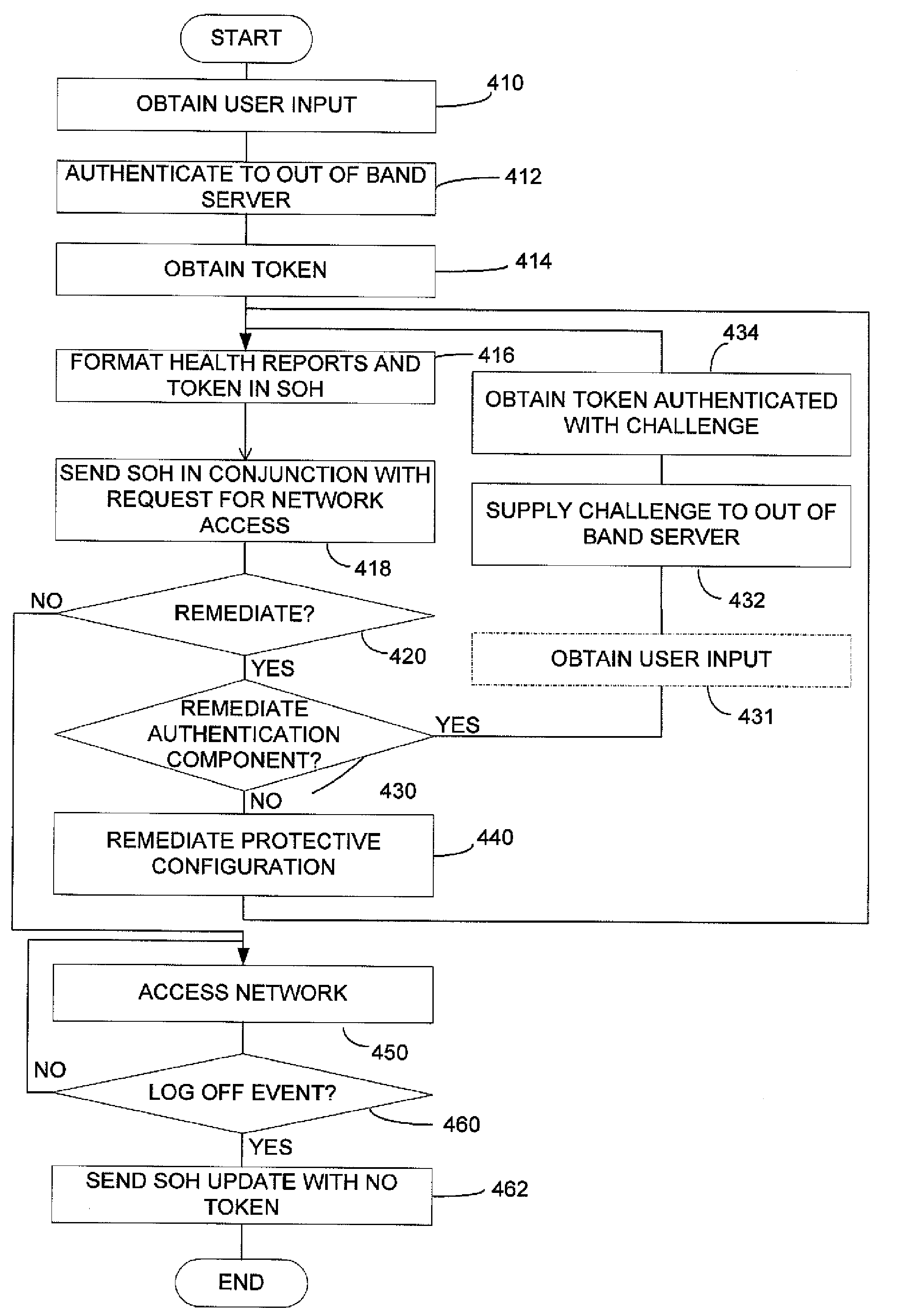
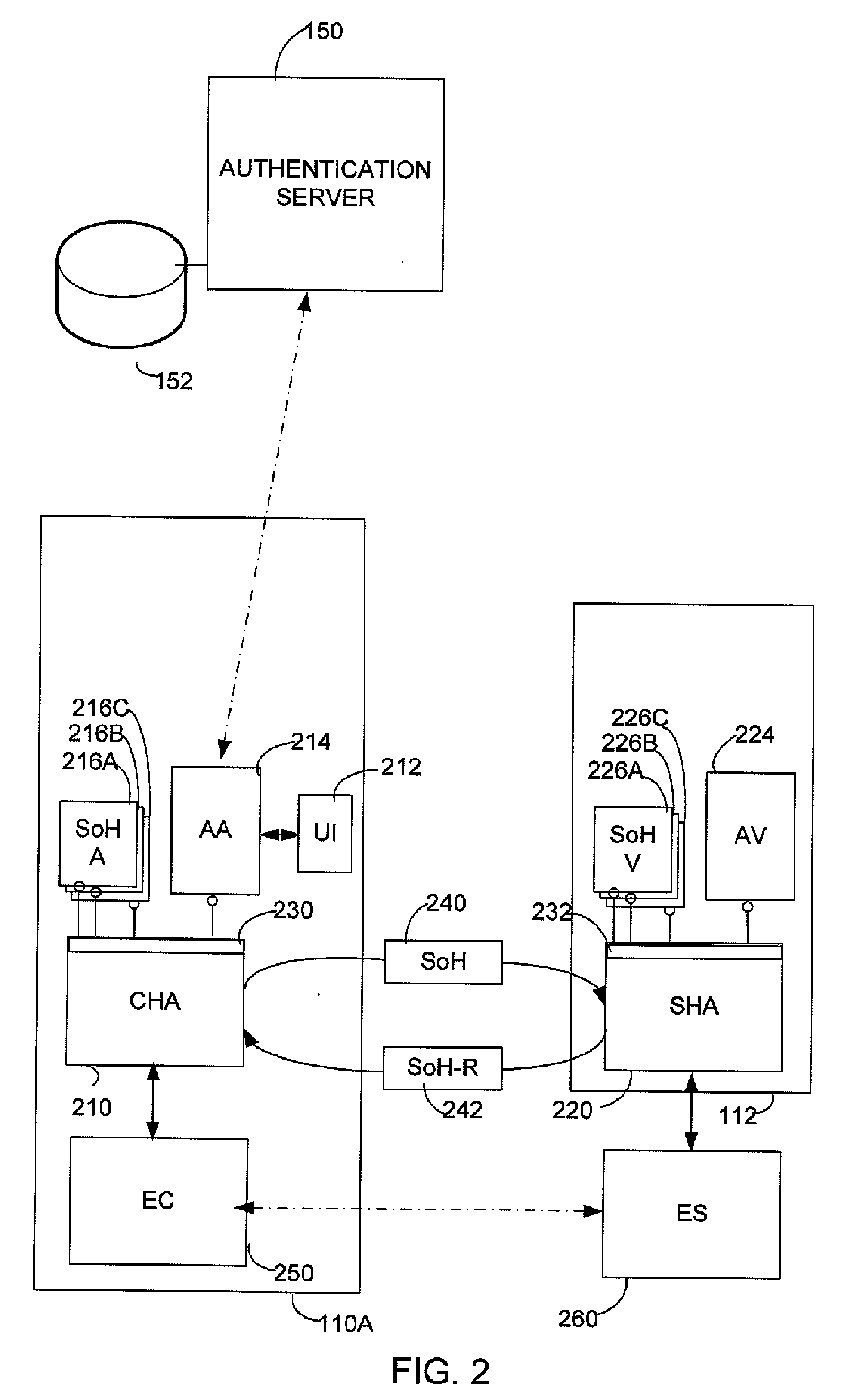
Authentication in a network using client health enforcement framework
ActiveUS20100115578A1Optimize networkEasy to mergeDigital data processing detailsUser identity/authority verificationClient-sideComputer science
A network with authentication implemented using a client health enforcement framework. The framework is adapted to receive plug-ins on clients that generate health information. Corresponding plug-ins on a server validate that health information. Based on the results of validation, the server may instruct the client to remediate or may authorize an underlying access enforcement mechanism to allow access. A client plug-in that generates authentication information formatted as a statement of health may be incorporated into such a framework. Similarly, on the server, a validator to determine, based on the authentication information, whether the client should be granted network access can be incorporated into the framework. Authentication can be simply applied or modified by changing the plug-ins, while relying on the framework to interface with an enforcement mechanism. Functions of the health enforcement framework can be leveraged to provide authentication-based functionality, such as revoking authorized access after a period of user inactivity or in response to a user command.
Owner:MICROSOFT TECH LICENSING LLC
System and method of providing credentials in a network
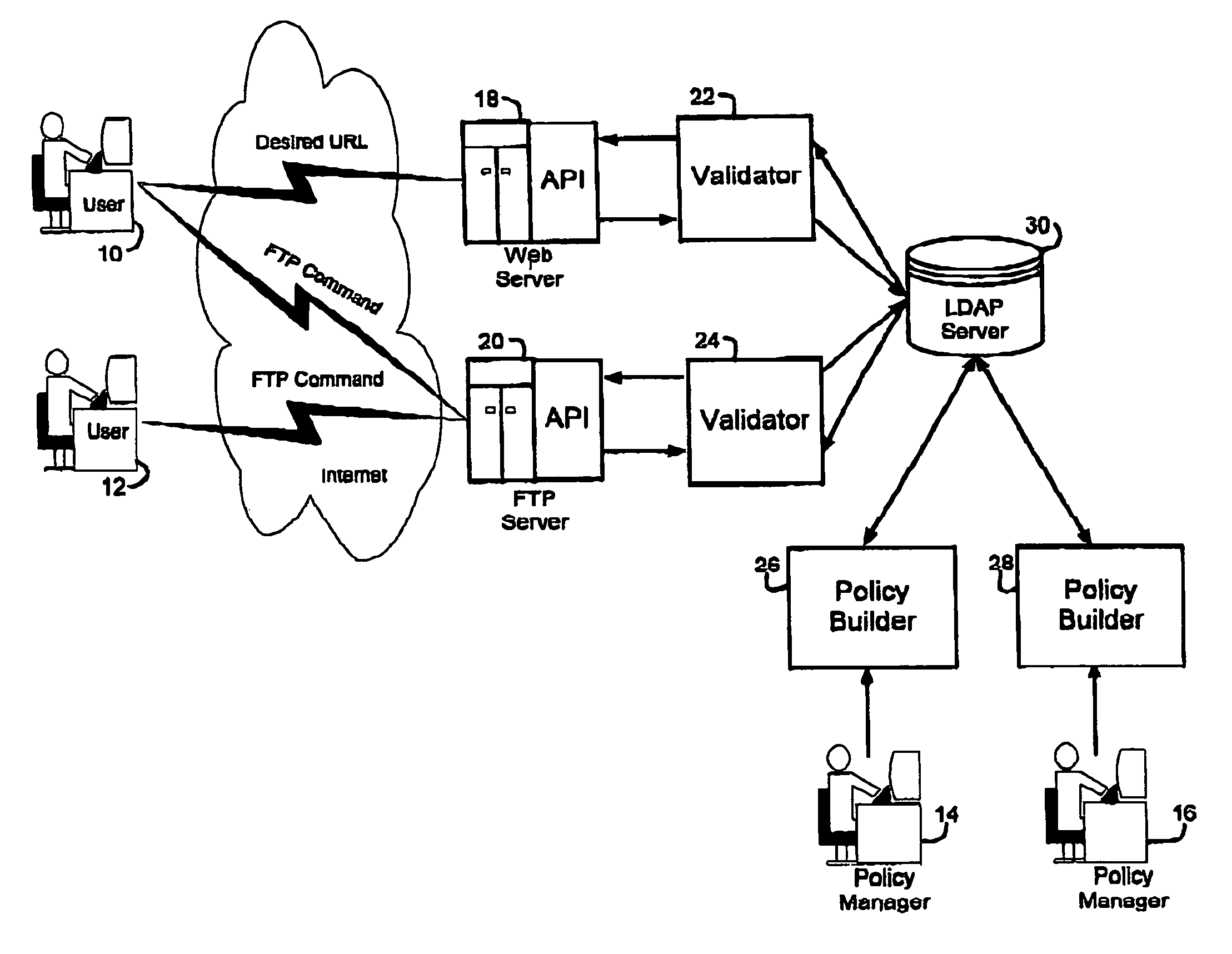
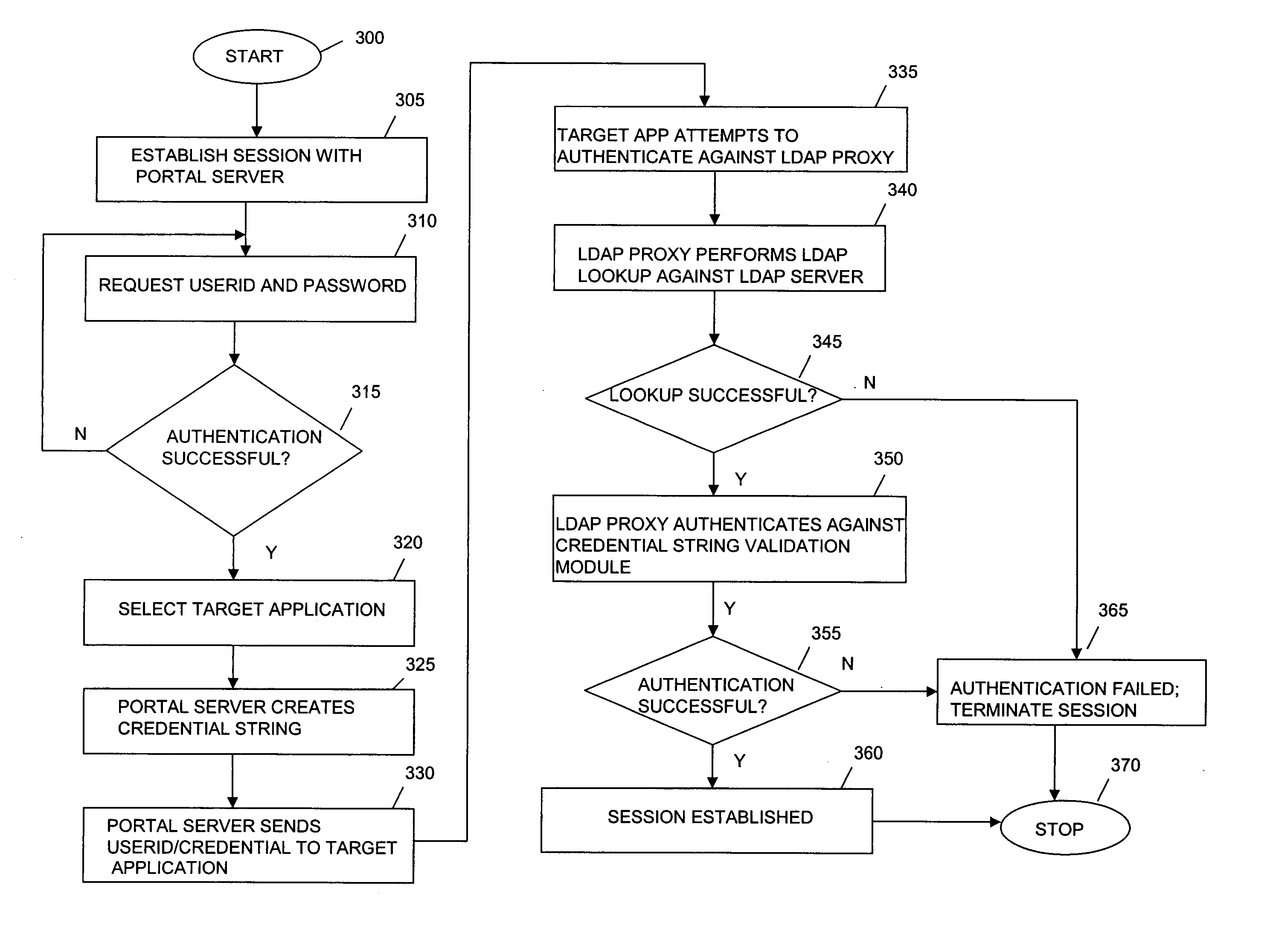
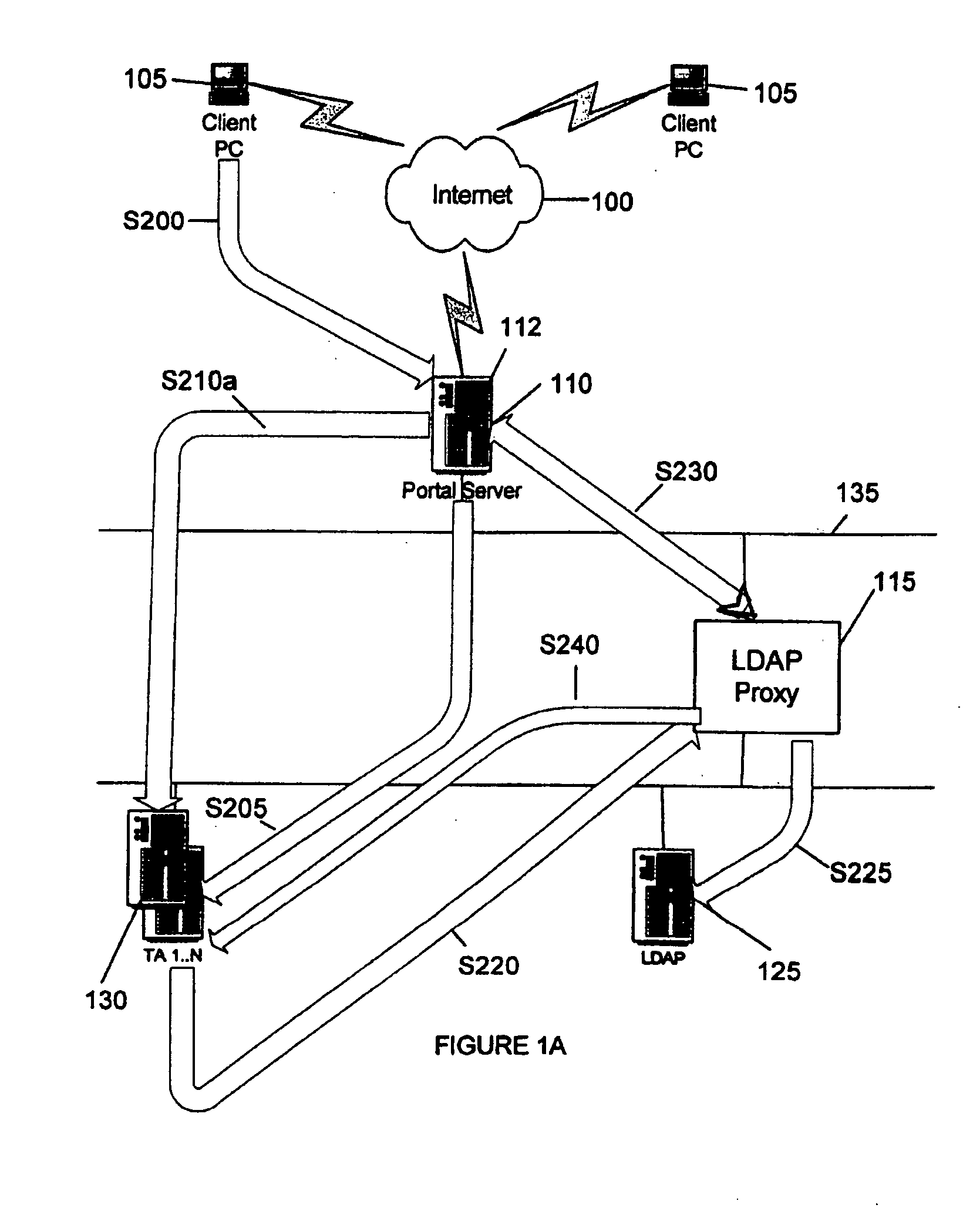
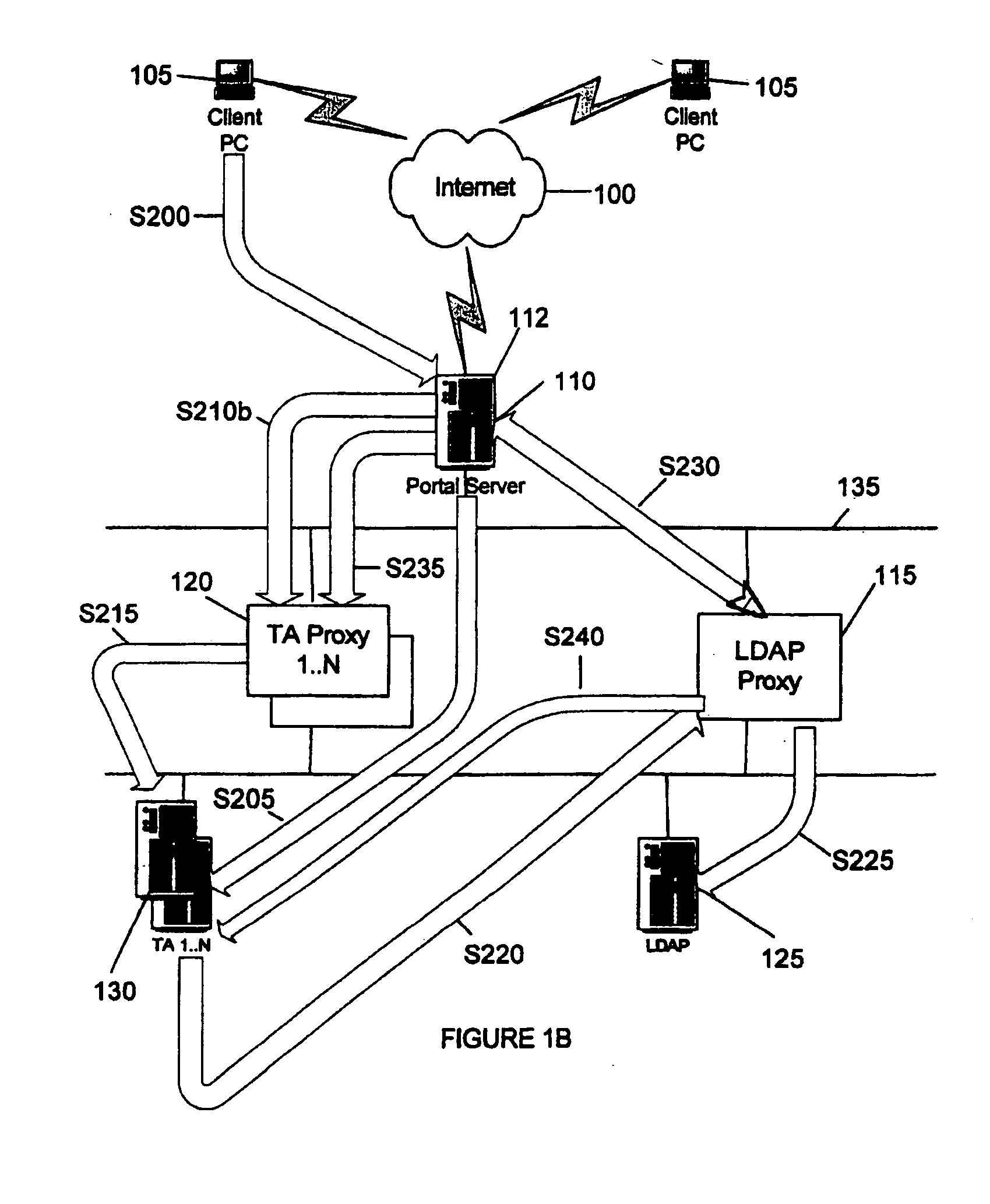
InactiveUS20050198501A1Digital data processing detailsUser identity/authority verificationPasswordValidator
A method and system is provided to provide single sign on (SSO) functionality in a network that avoids storing a user's credentials in persistent storage. A session may be initiated with a portal which sends a session ID derivative as a credential string instead of a user's password to a target application. When the target application attempts to authenticate the user, by sending a request to a LDAP directory, the request is intercepted by a LDAP proxy that instead validates the UserID with the LDAP directory and the password is validated by a credential validator component which verifies with the portal that the credential string presented as the user password has been produced from the active session ID. In an embodiment, the credential string validator validates each short-living credential only once and upon detecting a second validation request for the same string, initiates a security breech process. A target application proxy may also be employed to terminate all sessions with the UserID when duplicate session requests occur.
Owner:IBM CORP
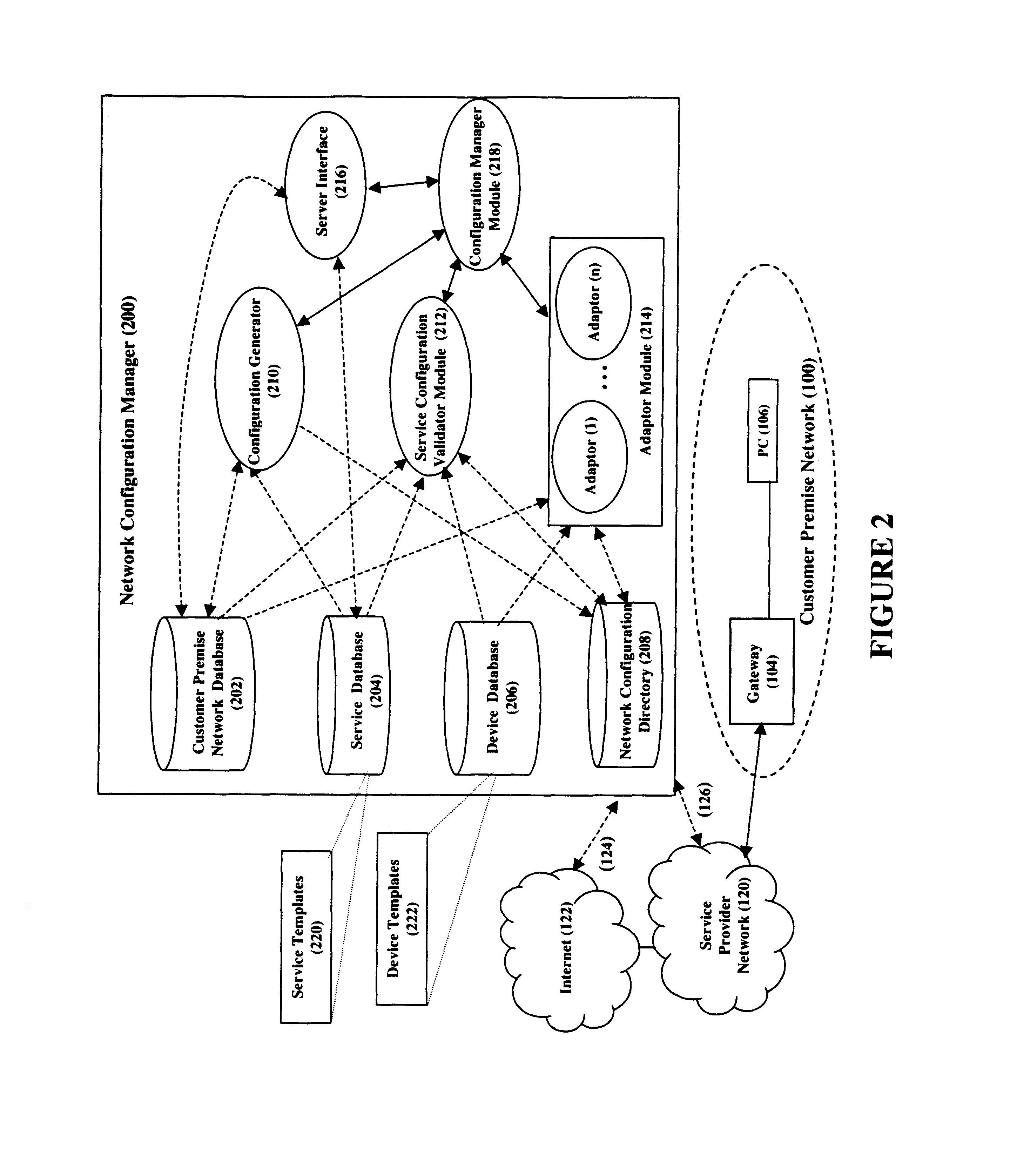
Template based configuration and validation of a network for enabling a requested service to be compatible with the previously enabled services
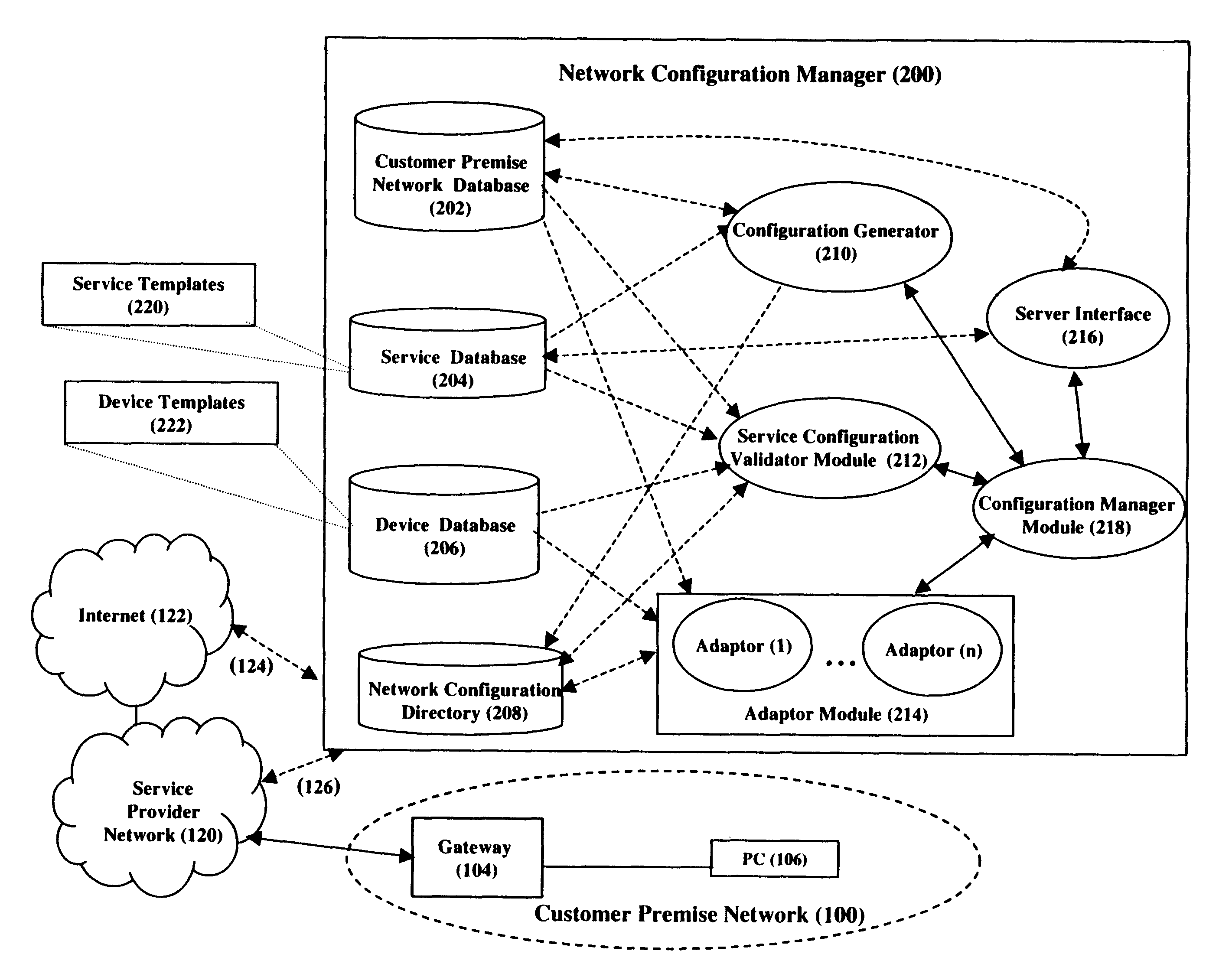
InactiveUS6766364B2Time-division multiplexMultiple digital computer combinationsTemplate basedClient-side
Customer premise network configuration to enable a new service within the network is provided by a network configuration manager. The network configuration manager is either manually or automatically invoked upon a new service being used in the network. The configuration manager obtains a service template for the service, which template provides generic end-to-end requirements for enabling the service. A configuration generator generates vendor-neutral device-configuration settings from the service template. A service configuration validator module then validates the service. Finally, an adaptor module translates the vendor-neutral device-configuration settings to vendor specific configuration settings corresponding to the devices in the network and configures the devices.
Owner:CITRIX SYST INC
Method and system for web integrity validator
ActiveUS20150256556A1Avoid detectionMemory loss protectionError detection/correctionClient-sideValidator
A computer-implemented method and system for the validation of a true browsing user on a website is disclosed. The invention allows for the collection of data regarding the evolving threat landscape created by online attackers. The system and method fingerprint user behavior to detect differences between a local user, a remote / foreign user, and an automated script. The system then covertly transmits that information back to a financial institution client without giving online attackers the opportunity to notice such transmittal. Certain embodiments of the invention also correspond with the browsing user to validate their identity. The claimed system and method proactively reveal attackers and attack ploys, additionally enabling institutions and security consultants to adapt to attacks in an automated fashion.
Owner:HUMAN SECURITY INC
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082327A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
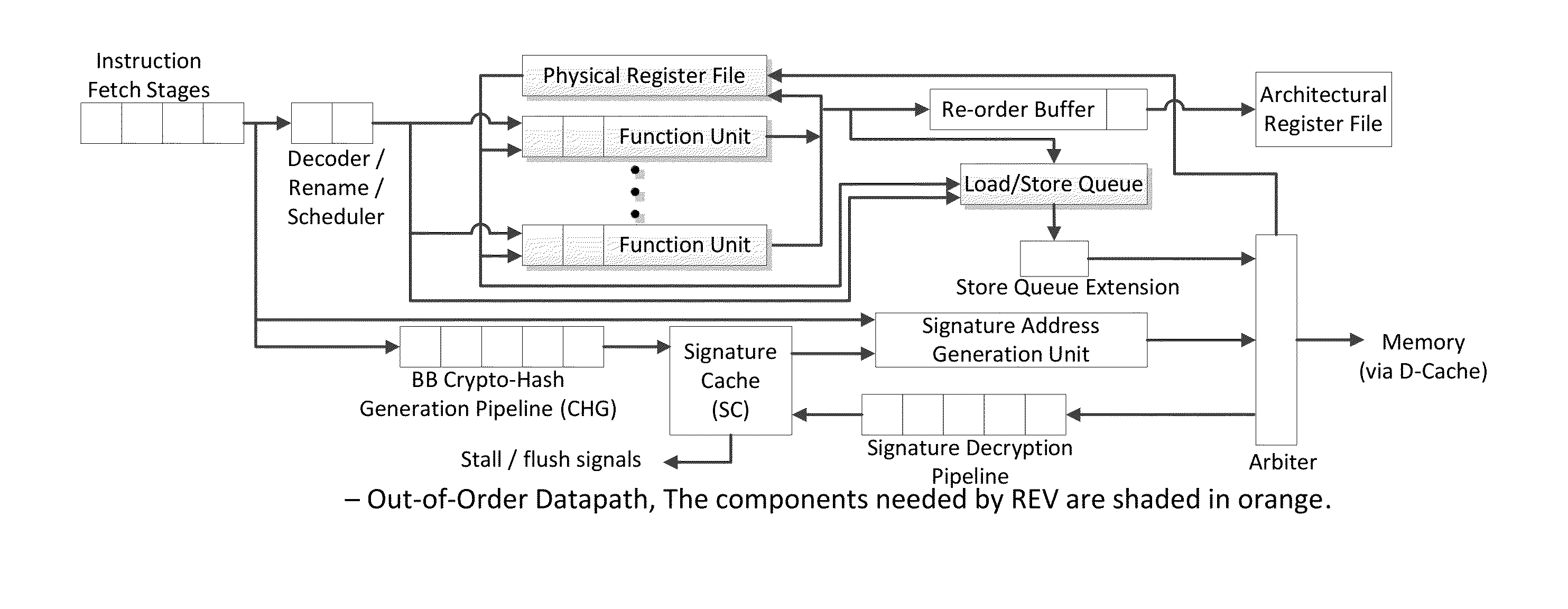
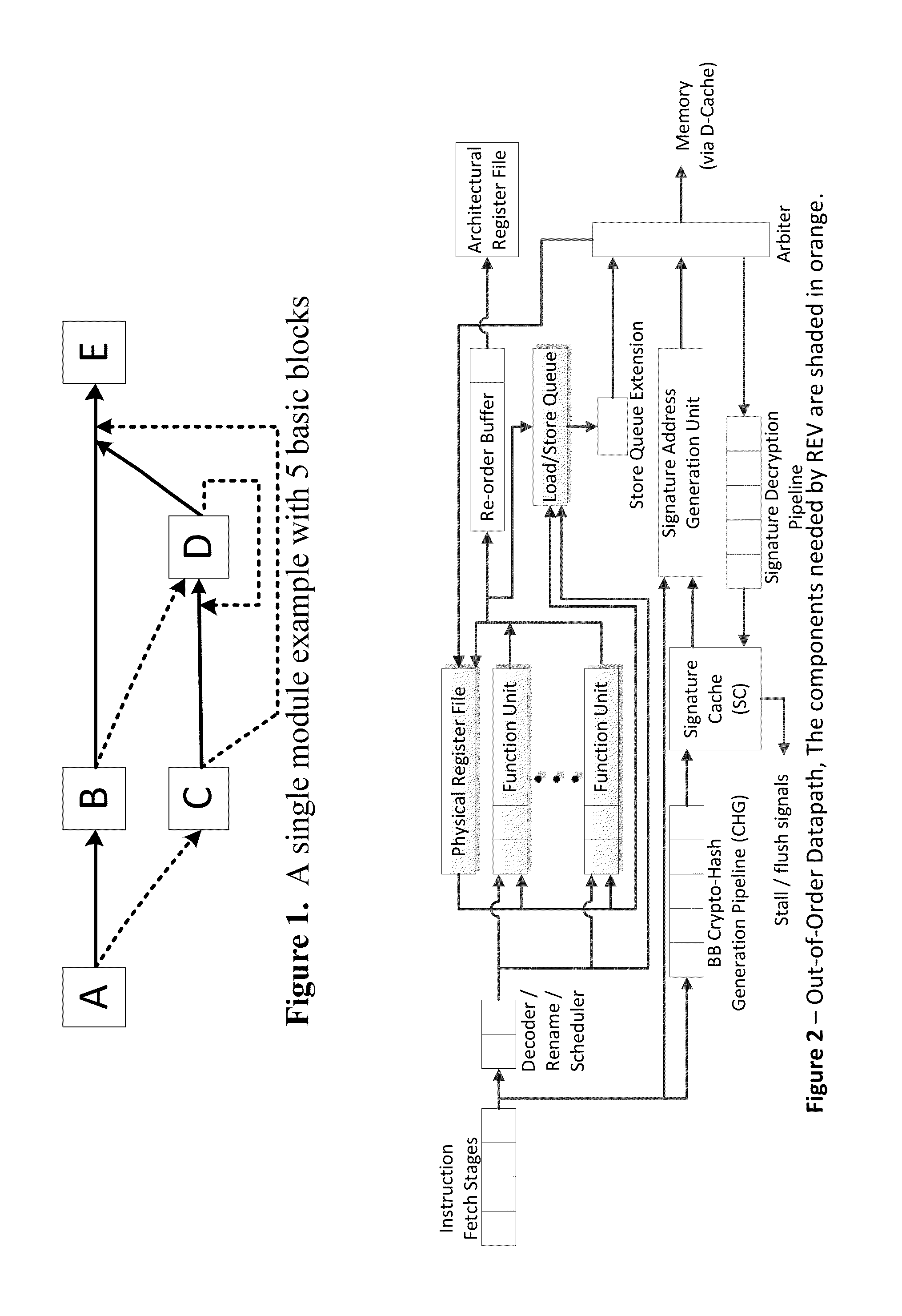
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Verification engine for user authentication
InactiveUS8032927B2Less intrusiveMore flexibleDigital data processing detailsUser identity/authority verificationWeb siteThird party
Owner:MATTHEWS INT CORP
Method to control access between network endpoints based on trust scores calculated from information system component analysis
InactiveUS7272719B2Digital data processing detailsUser identity/authority verificationComputerized systemData mining
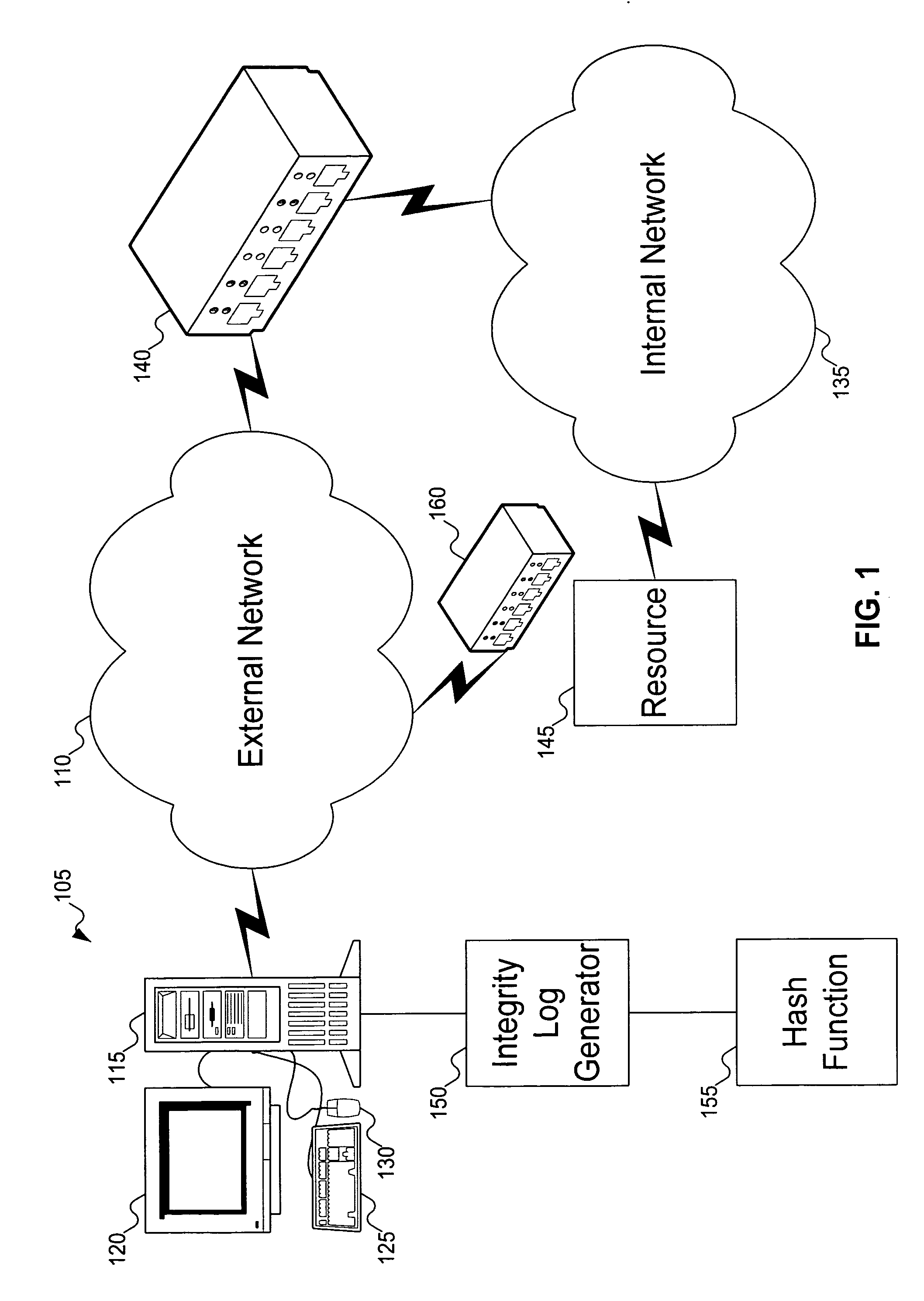
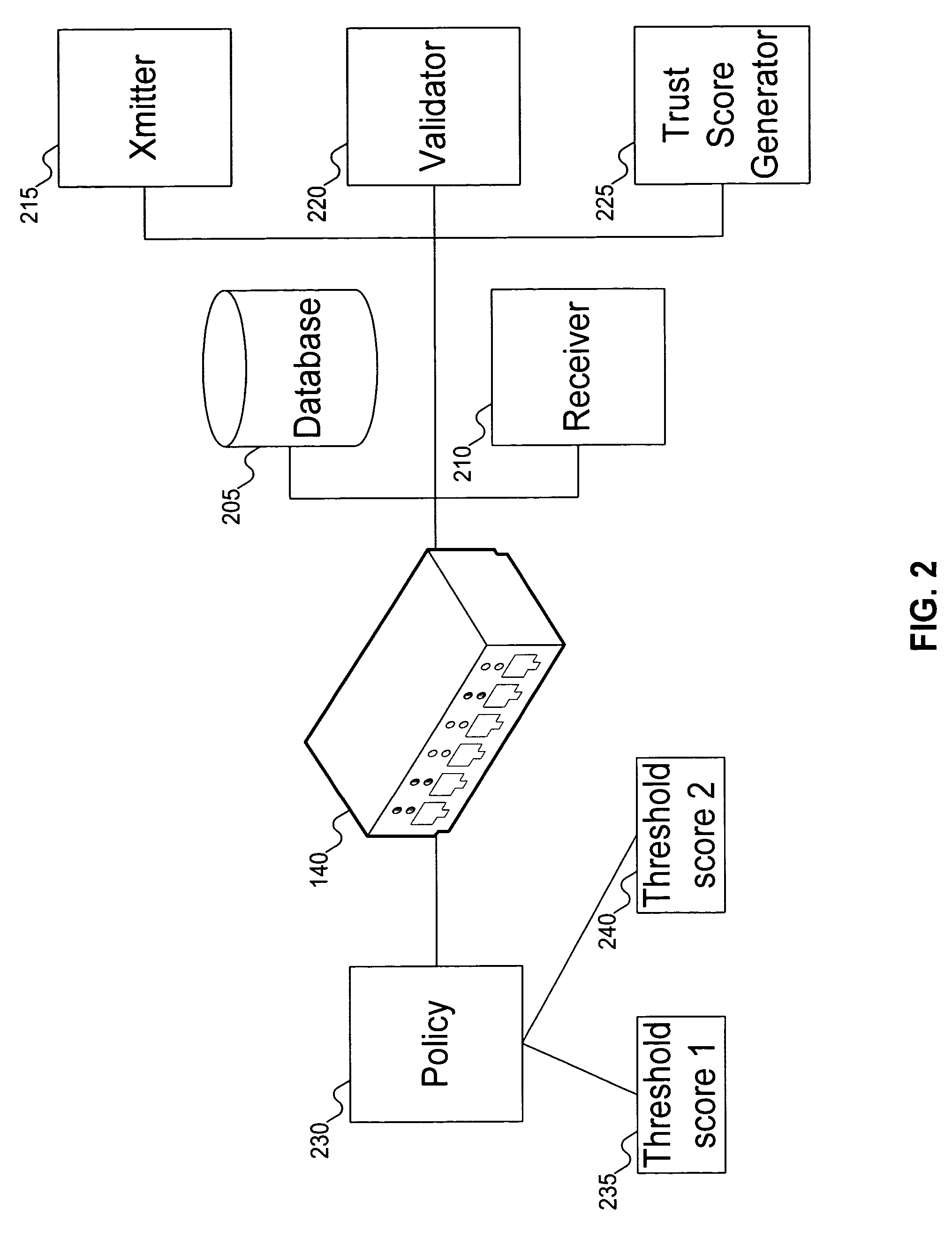
Signatures are generated for modules in a computer system. The signatures can be assembled into an integrity log. The signatures are compared with signatures in a database in an integrity validator. Once signatures are either validated or invalidated, a trust score can be generated. The trust score can then be used to determine whether the computer system should be granted access to a resource using a policy.
Owner:SILICON VALLEY BANK +1
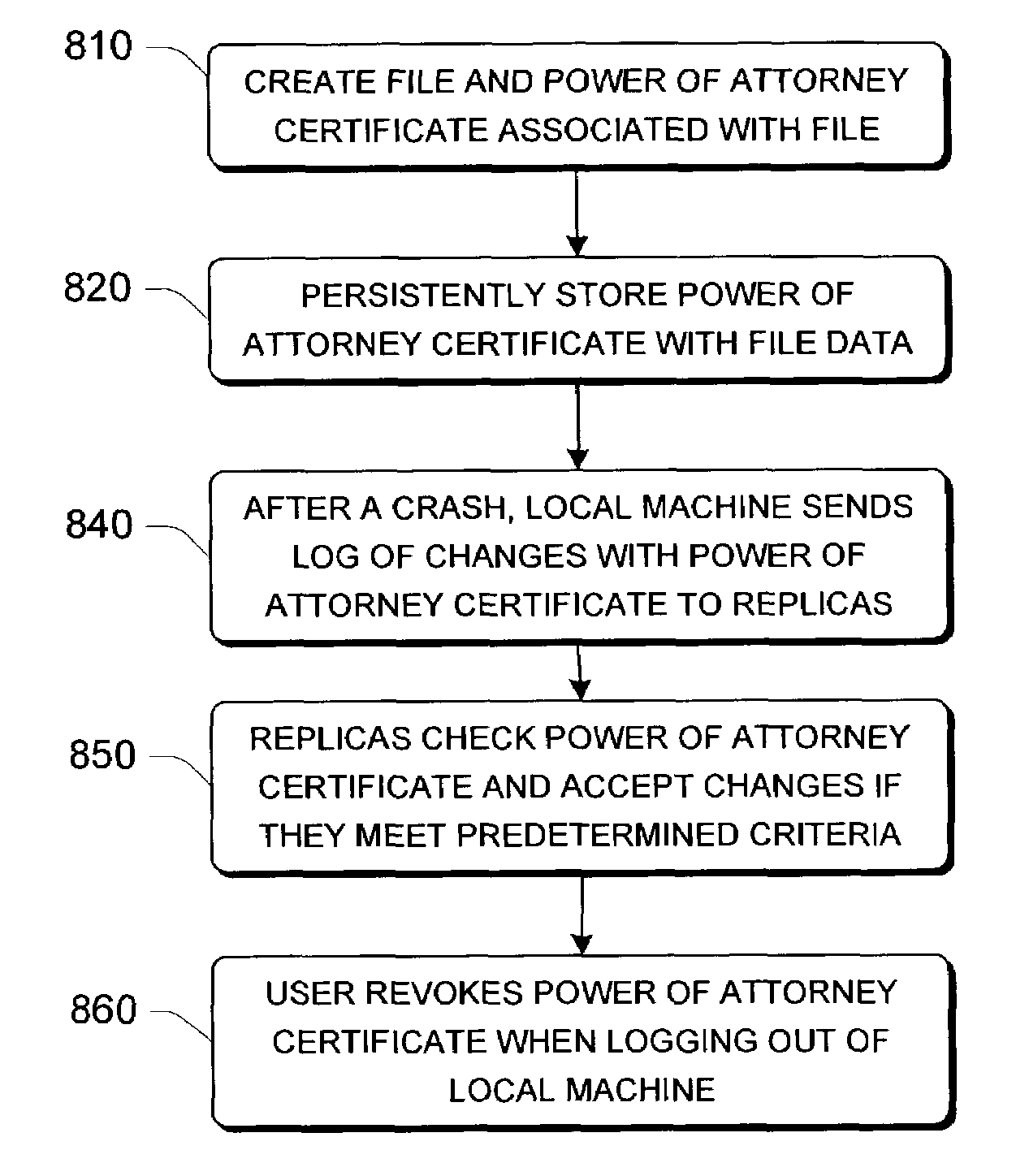
Secure recovery in a serverless distributed file system
InactiveUS7428751B2Avoid selectionDigital data processing detailsUser identity/authority verificationSecret shareDistributed File System
Systems and methods for secure file writes after a catastrophic event are allowed over an unauthenticated channel in a serverless distributed file system if an authenticator accompanies the secure file writes. The authenticator can be a power-of-attorney certificate with time limitations, a vector of message authenticated code, or a single message authenticator with secured with a secret shared among members of the serverless distributed file system. The serverless distributed file system includes at least 3f+1 participating computer members, with f representing a number of faults tolerable by the system. The group requires at least one authenticator for file creation and file uploads. Any changes to files stored among the members can be made over an unauthenticated channel if the file changes are secured by the authenticator and the group is able to verify the authenticator.
Owner:MICROSOFT TECH LICENSING LLC
Coinless vending system, method, and computer readable medium using an audio code collector and validator
InactiveUS7721958B2Coin-freed apparatus detailsSpecial service for subscribersMobile deviceValidator
A system, method, and computer readable medium, wherein a vending machine comprising an audio code collector and a code validator is adapted to receive audio tones from a mobile device, and wherein the audio tones include authentication codes and dispense codes to control dispensing of product from the vending machine.
Owner:ALCATEL LUCENT SAS
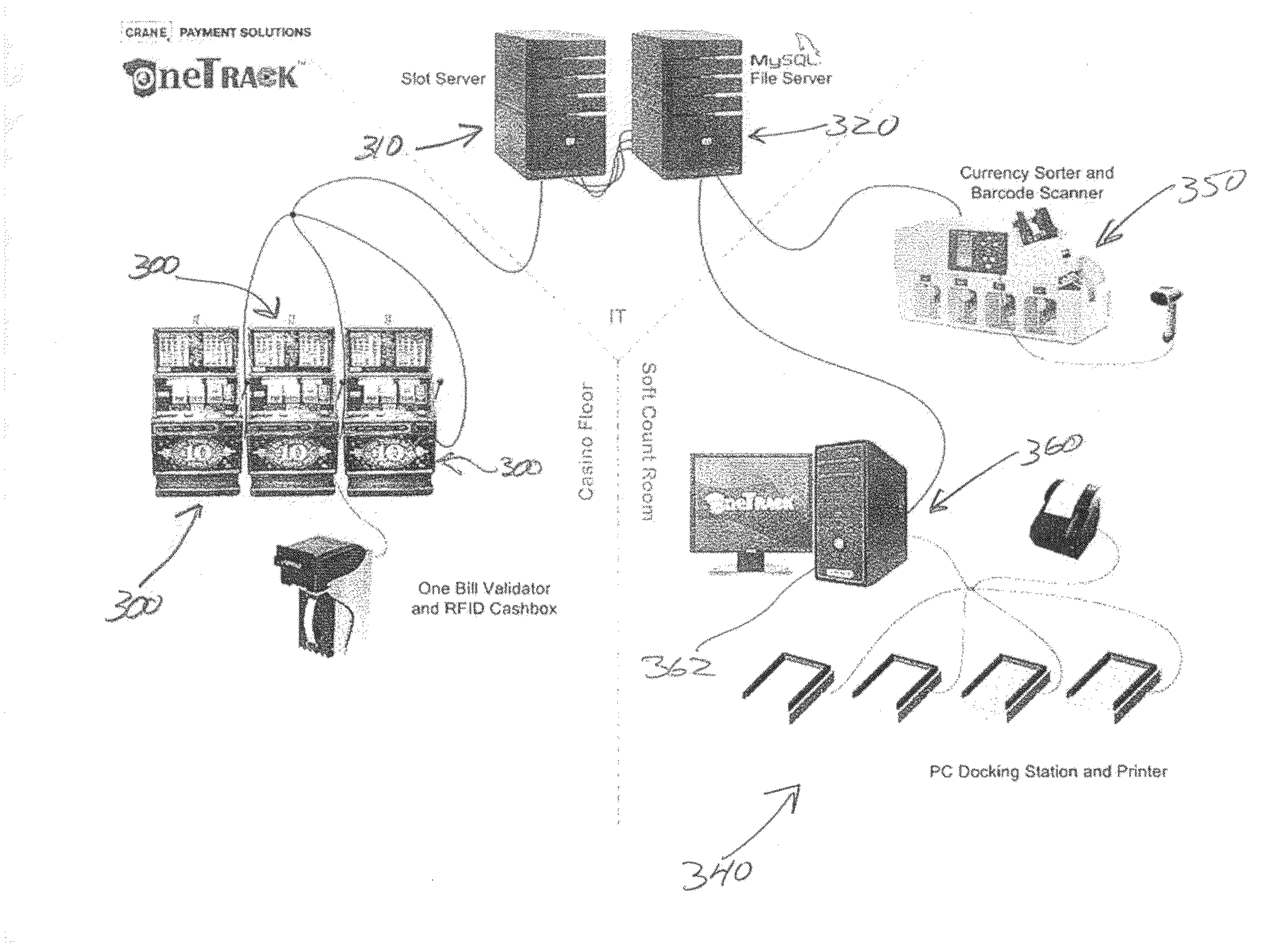
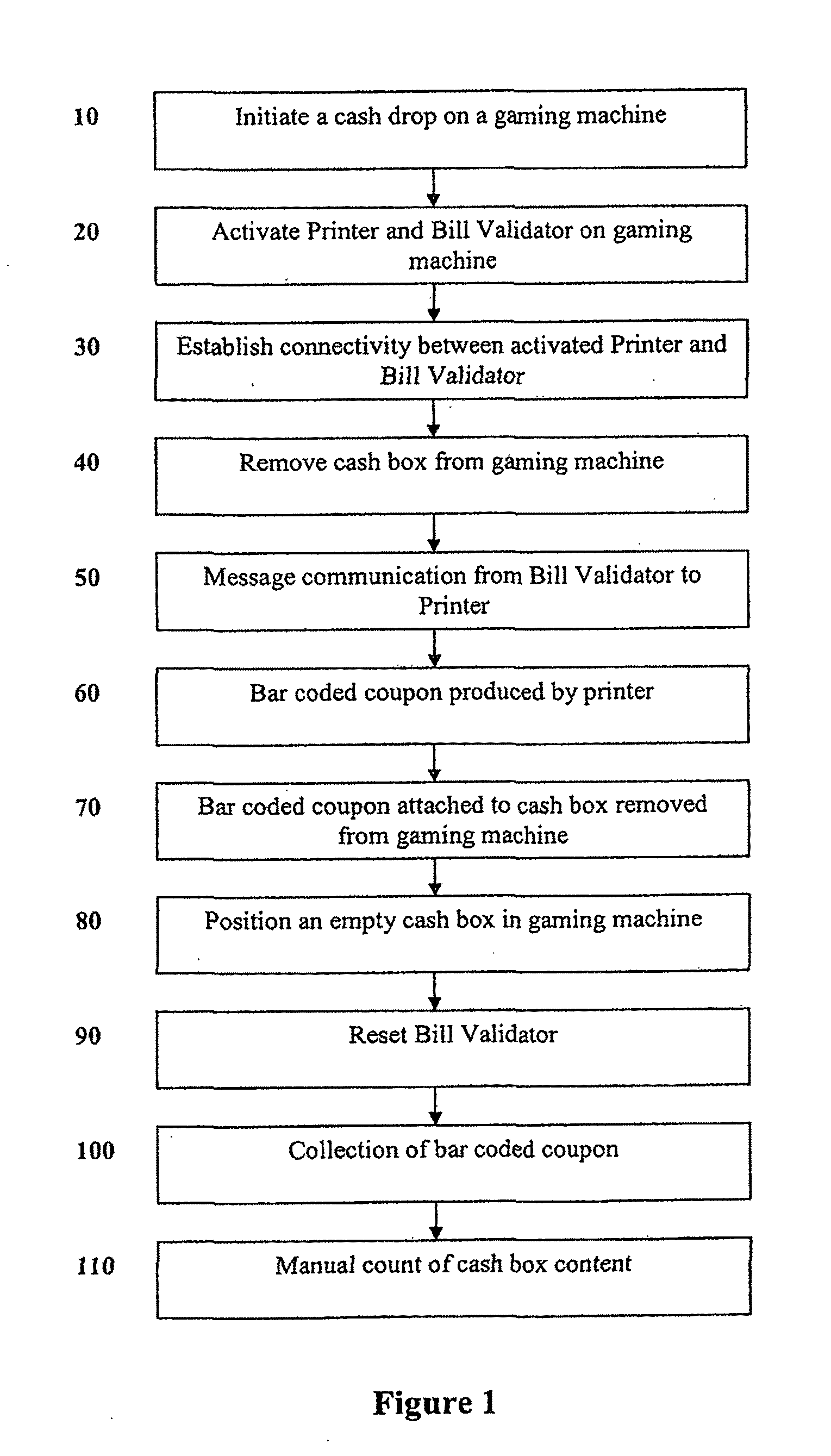
Cashbox coupon for a gaming machine
ActiveUS20100323789A1Improve security featuresCoin/currency accepting devicesPayment architectureInterconnectionValidator
The present invention provides a method for an additional security feature on a gaming machine regarding the content of a cashbox positioned within the gaming machine through the printing of a coupon. The method involves transferring information from a bill validator to a printer all within a gaming machine wherein the transfer of the information is achieved by a serial port connection between the bill validator and the printer.The present invention also provides a system for an additional security feature to a gaming machine through the printing of a coupon containing information relating to the content of a cashbox positioned within the gaming machine. The coupon is produced by information retrieved from the bill validator. The transfer of the information from the bill validator to the printer is achieved through a serial port interconnection between the bill validator and the printer.
Owner:CRANE CANADA
RFID encoder and verifier
ActiveUS7114654B2Easy to migrateDigitally marking record carriersTransmission systemsComputer hardwareData stream
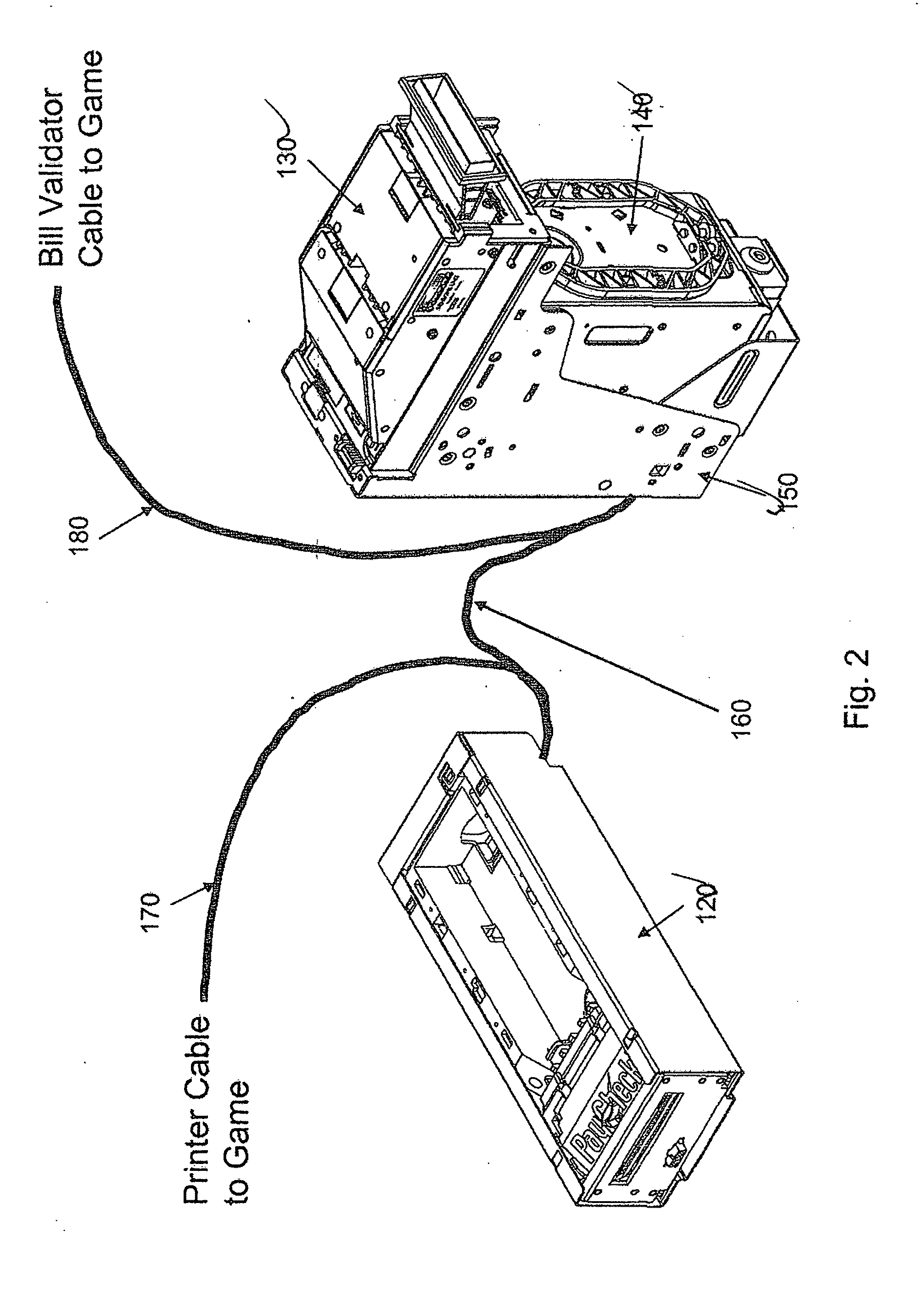
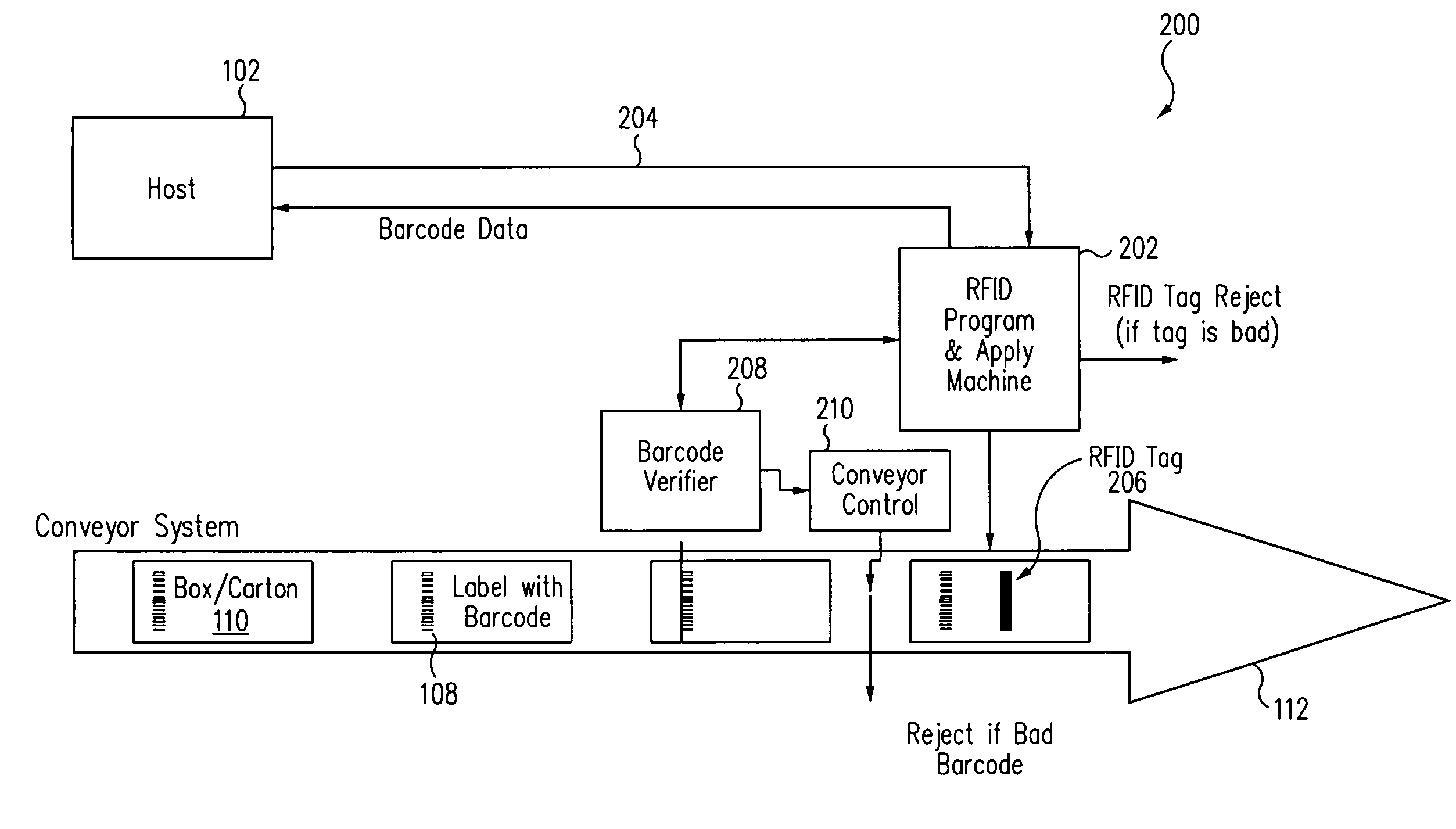
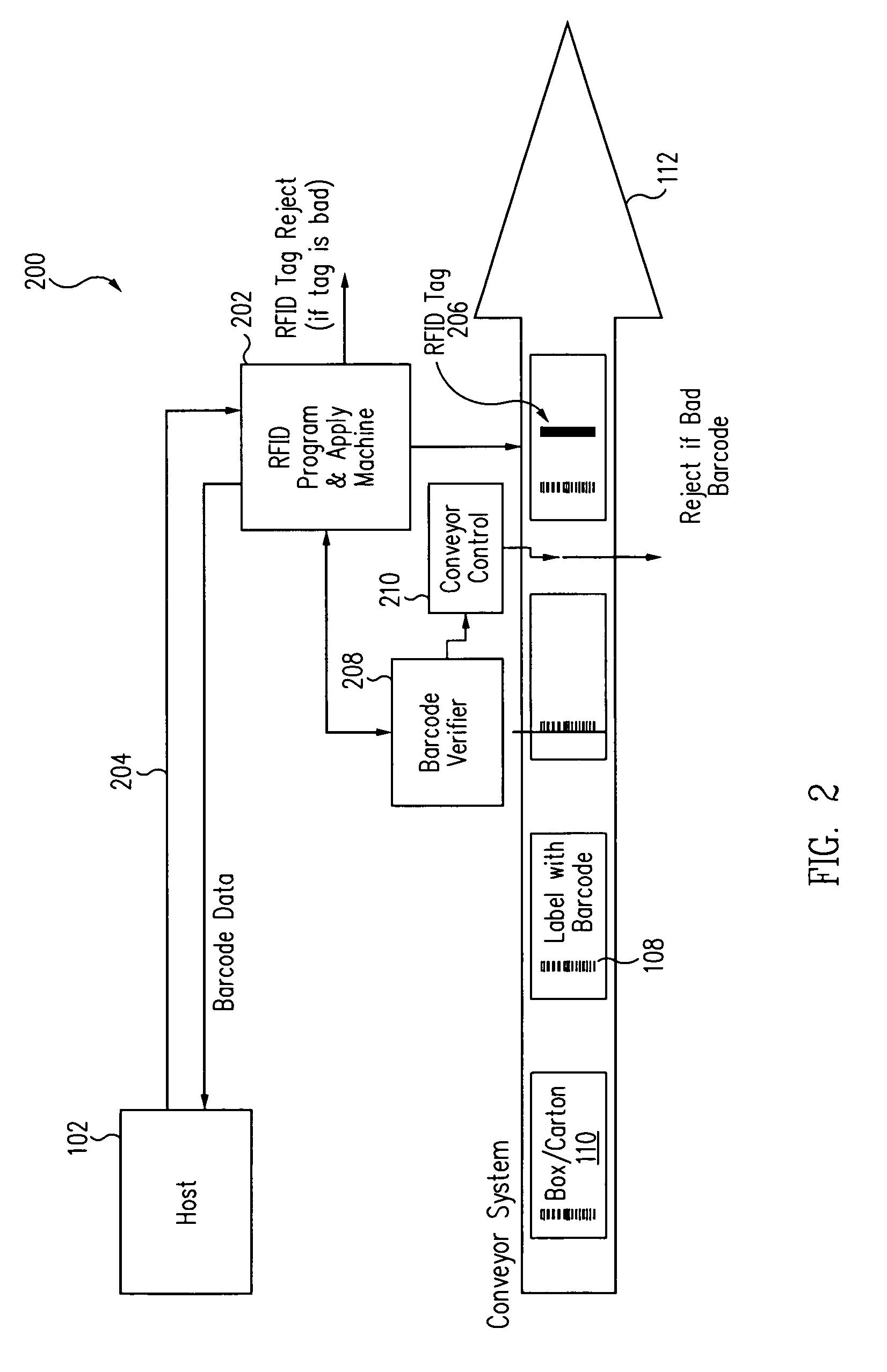
An RFID encoder is used in conjunction with a barcode print and apply system. The RFID encoder utilizes information obtained from a data stream from a host computer, from a corresponding barcode label, or other source to program an RFID label. The programmed label can then be applied with an integrated applicator or an external applicator. The RFID encoder can also verify that an RFID tag or label has been properly encoded and has the same content as the corresponding barcode label. The RFID can further verify that the barcode has been properly printed. If both barcode and RFID tag contain the correct data, both types of labels are attached to a package, enabling the package to be read optically and with radio frequency signals.
Owner:TSC AUTO TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com