Patents
Literature
95 results about "Trust score" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Trust Score™ is presented as a numerical value calculated and assigned to all users whether buying or selling. Points are awarded for completing tasks related to providing us with identifiable information. Each task is weighed in terms of it’s value as set by our algorithm.
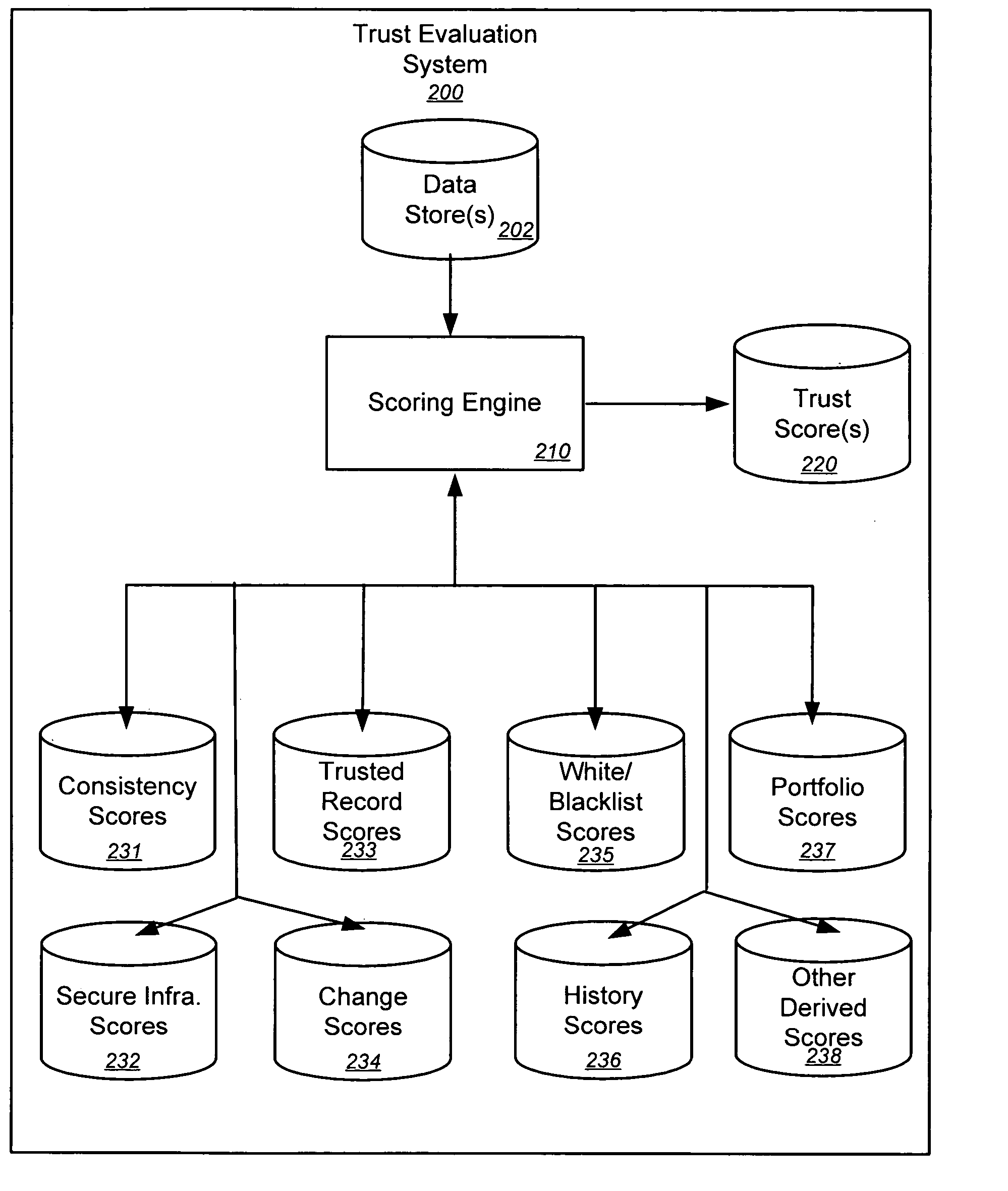
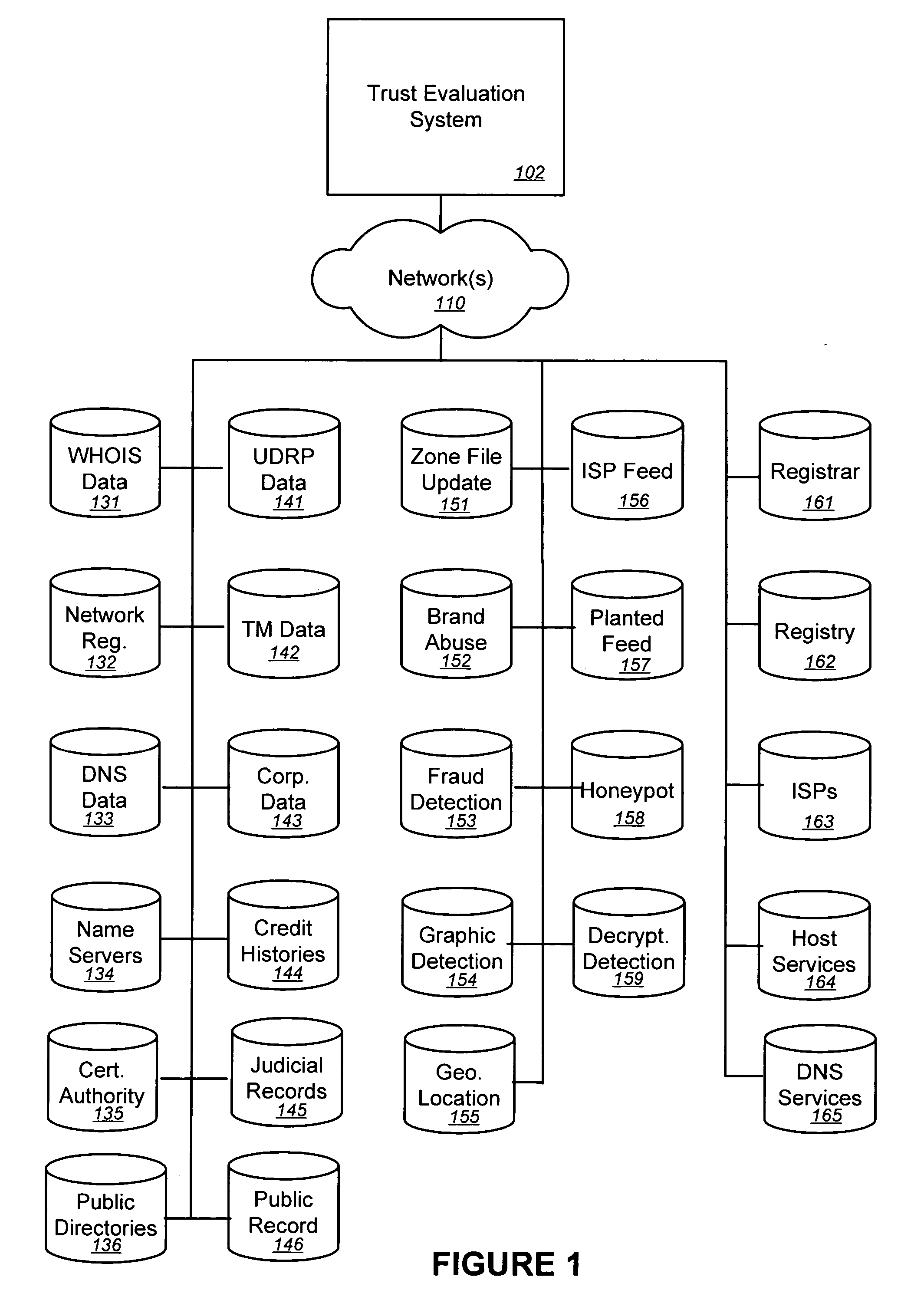
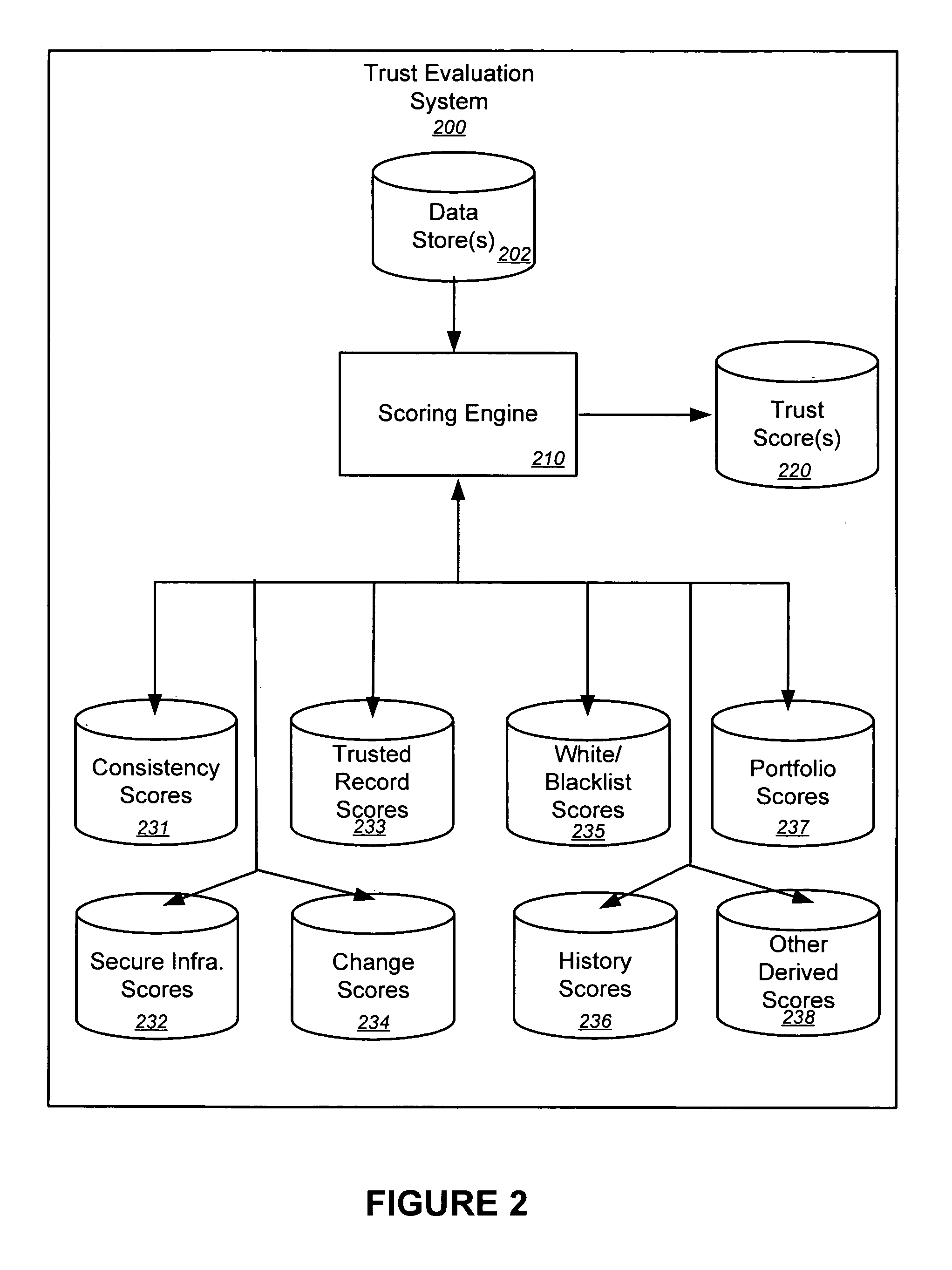
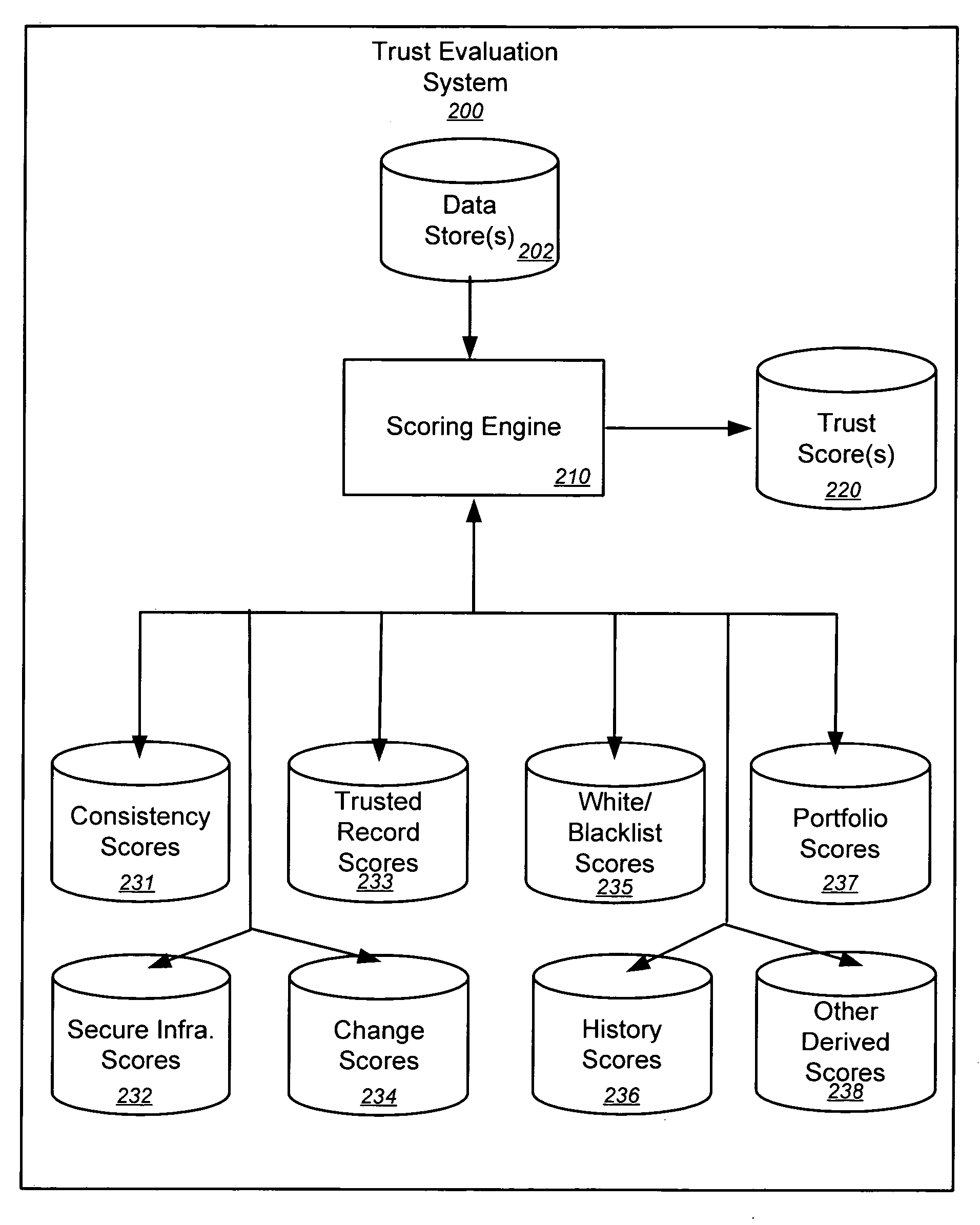
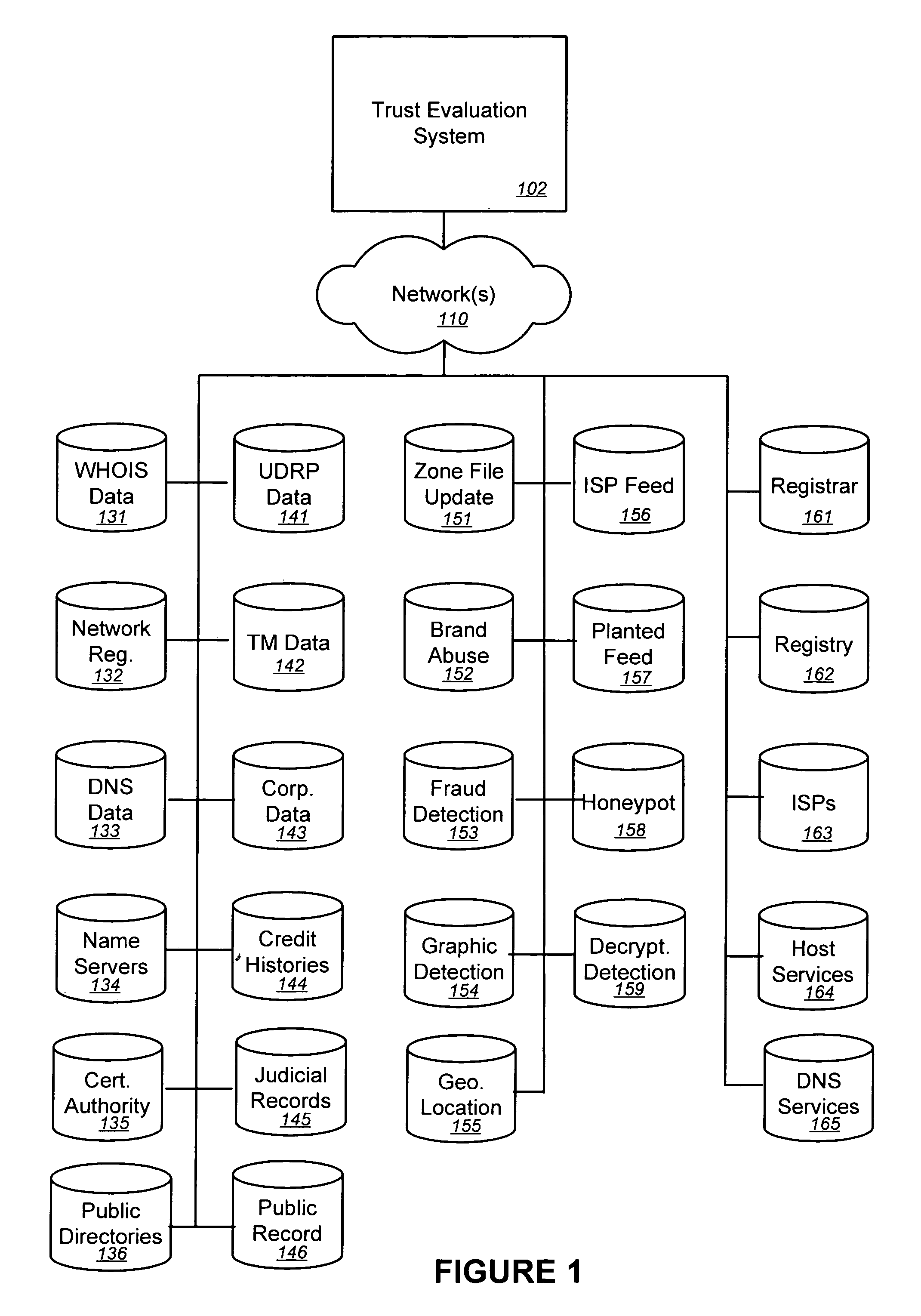
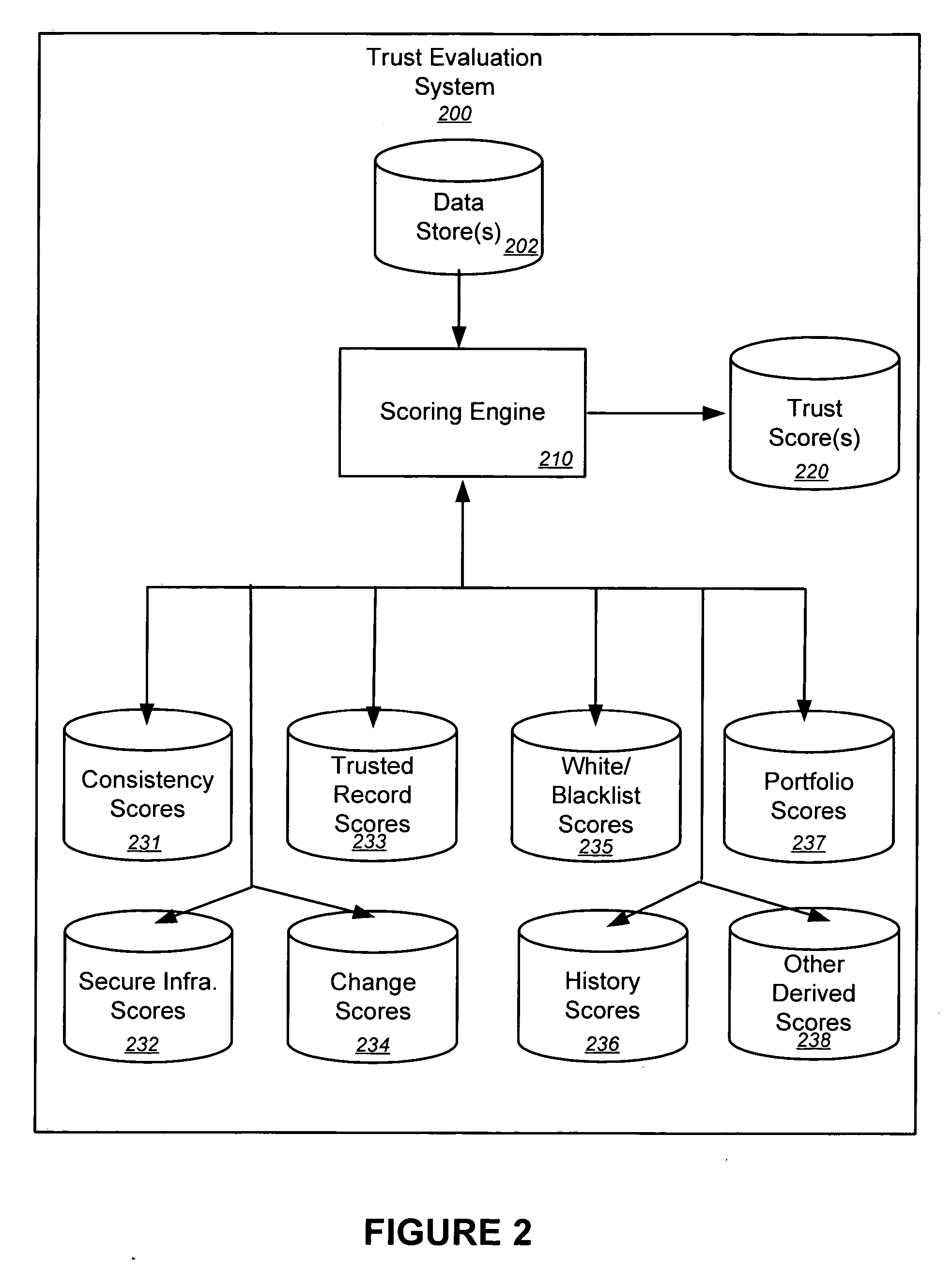
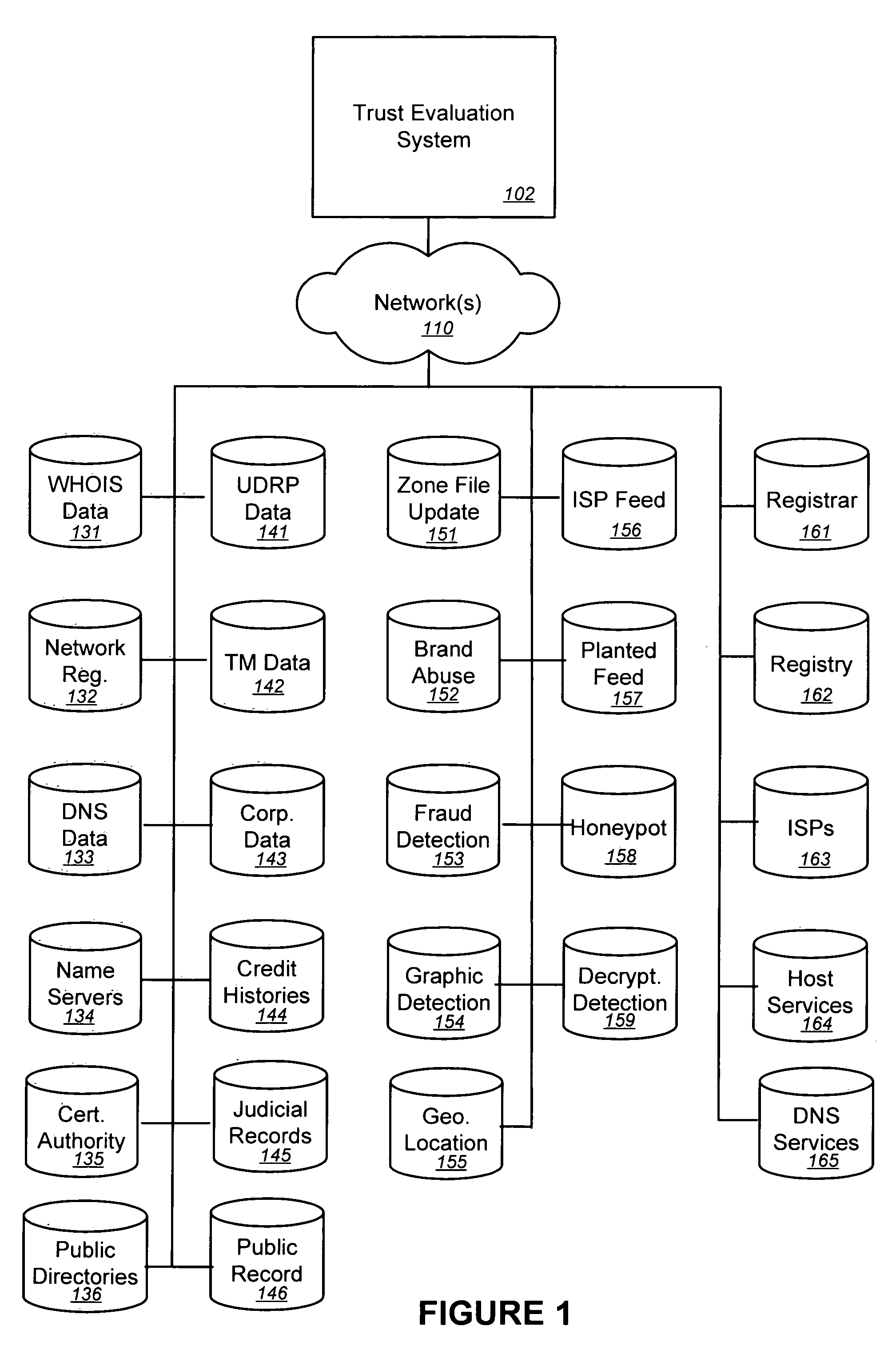
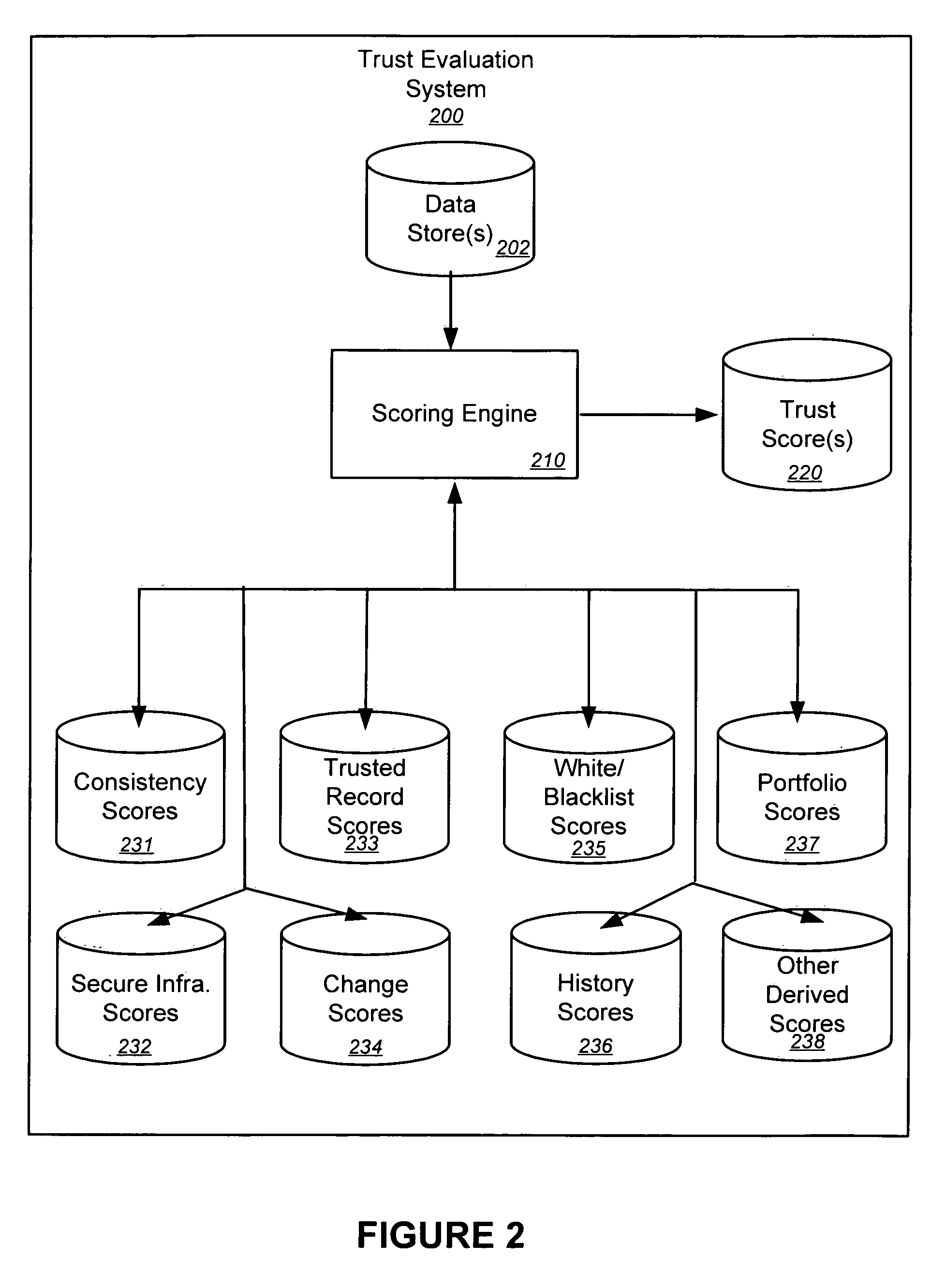
Trust evaluation systems and methods
InactiveUS20060212931A1Digital data processing detailsUser identity/authority verificationData storingEvaluation system
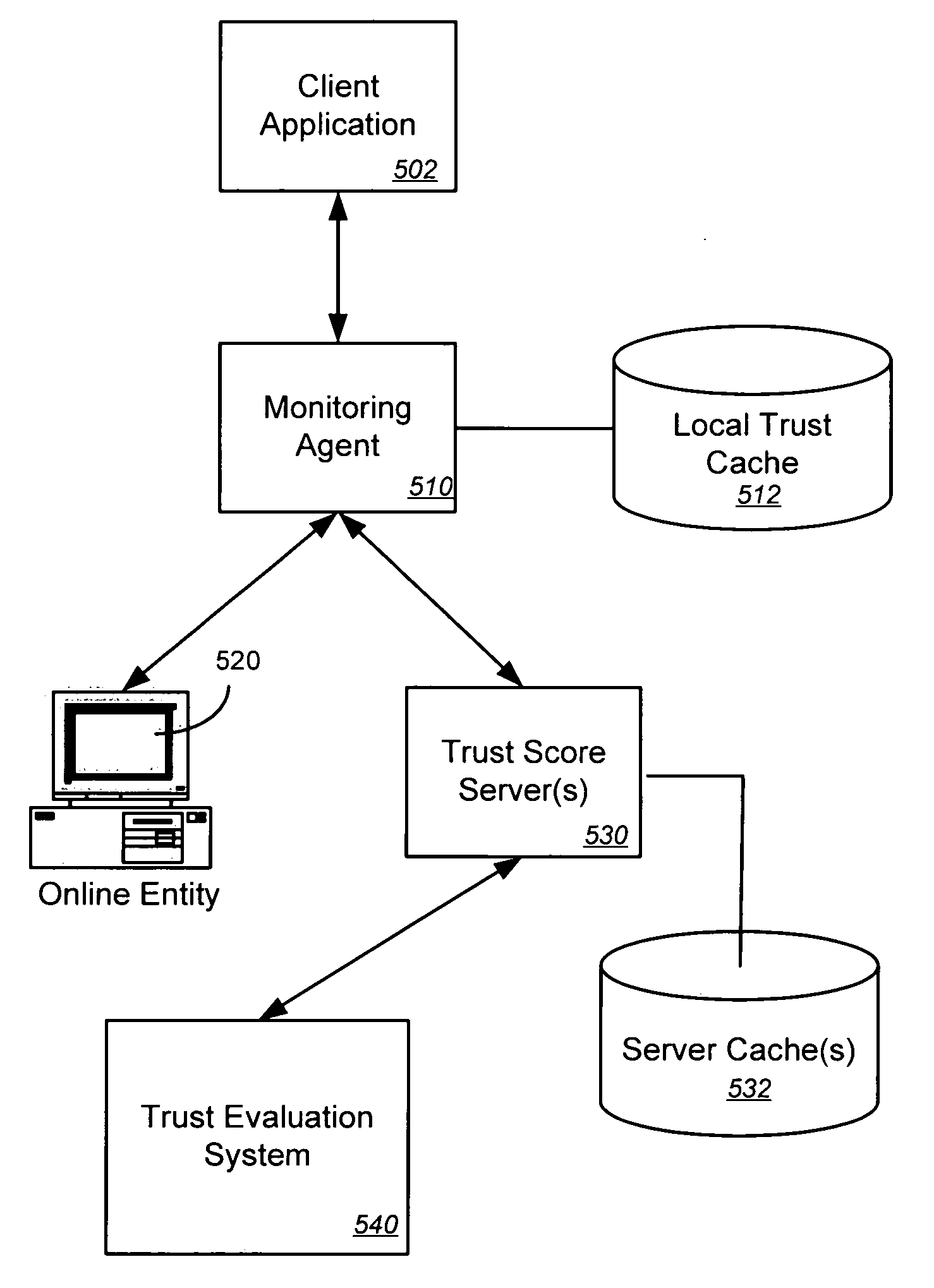
Embodiments of the present invention provide methods, systems, and software for implementing evaluating online entities and / or for providing a trust score for such entities. The trust score may provide an indication of the trustworthiness of the online entity. In some cases, data may be obtained from a variety of sources, and such data may be used to evaluate an online entity and / or to provide a score for the entity. In an aspect of the invention, a plurality of trust scores, each of which related to a behavioral characteristic and / or a category of activity, may be assigned to a particular entity. Such scores may be stored in one or more data stores and / or may be provided to others.
Owner:MARKMONITOR
Implementing trust policies
InactiveUS20060212925A1Platform integrity maintainanceSpecial data processing applicationsInternet privacySality
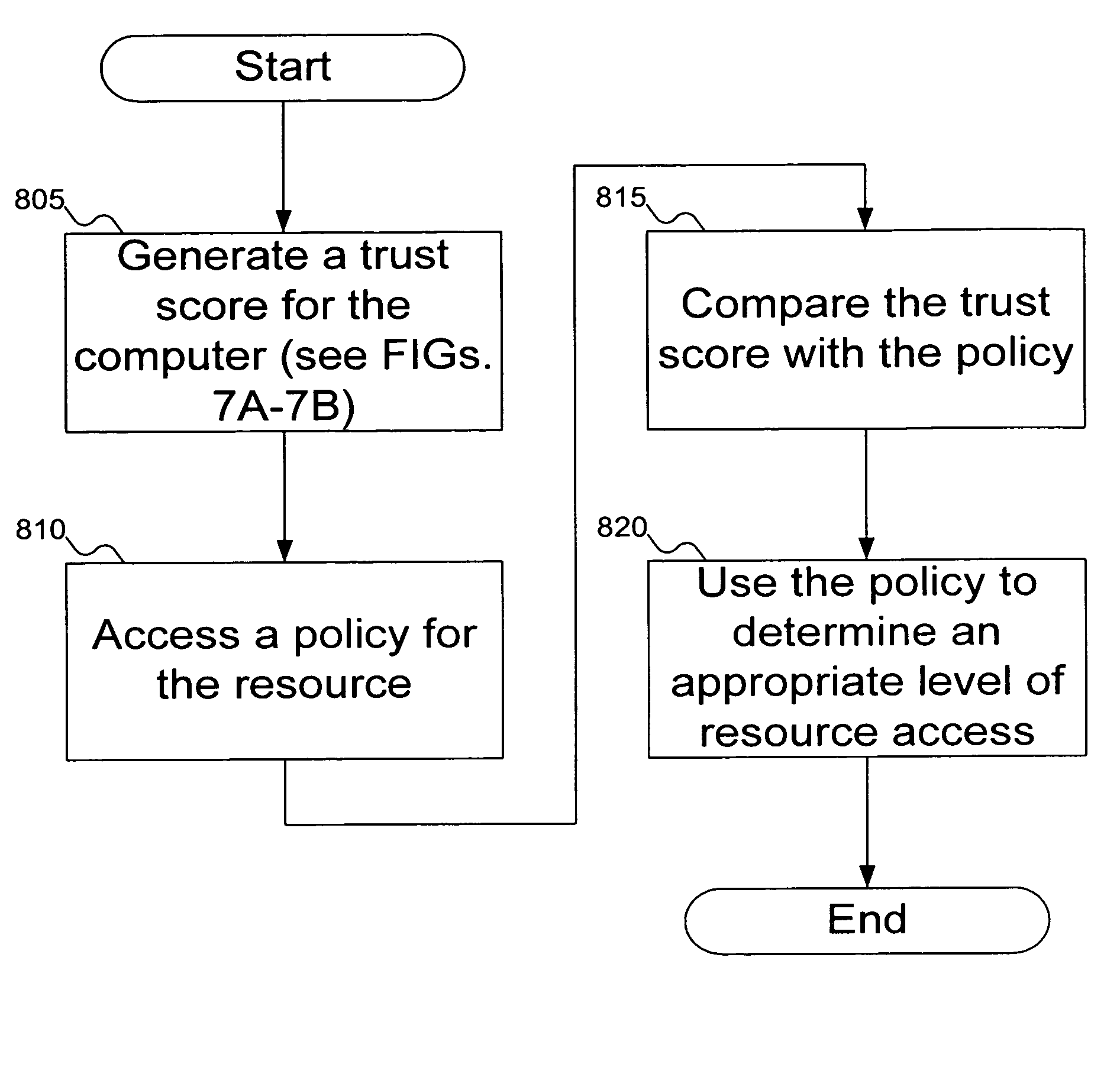
Embodiments of the present invention provide methods, systems, and software for implementing trust policies. Such policies may be implemented in a variety of ways, including at one or more border devices, client computers, etc. In accordance with various embodiments, a communication between a client computer (and / or application) and an online entity may be monitored and / or otherwise detected. The online entity may be identified, and / or one or more trust scores associated with the online entity may be obtained. Based on the trust scores, as well, perhaps as the nature of the communication, an action (such as allowing the communication, blocking the communication, quarantining the communication, warning a user, administrator, etc.) may be taken. In some cases, a trust policy may be consulted to determine what action should be taken with respect to a given communication.
Owner:MARKMONITOR
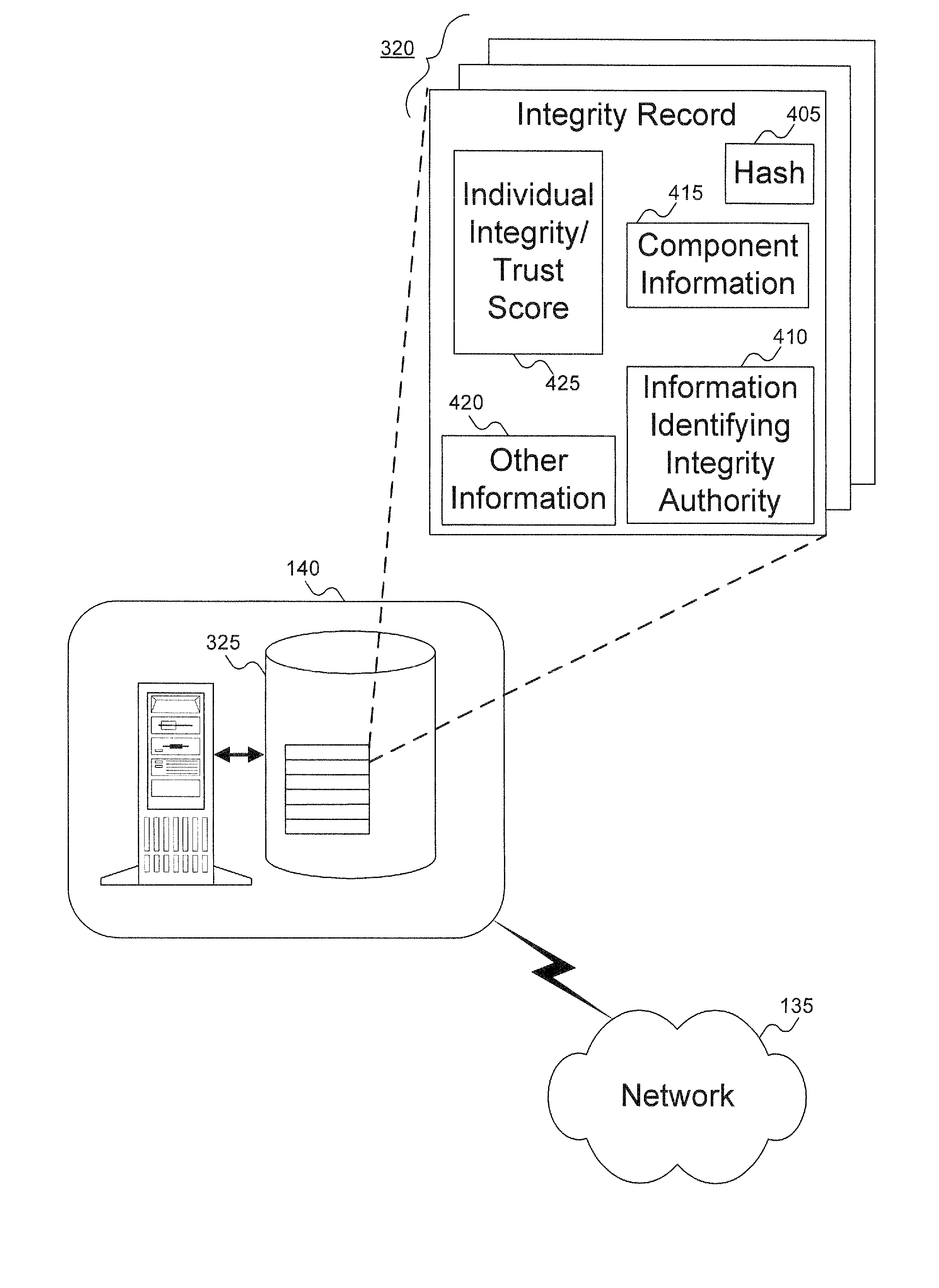
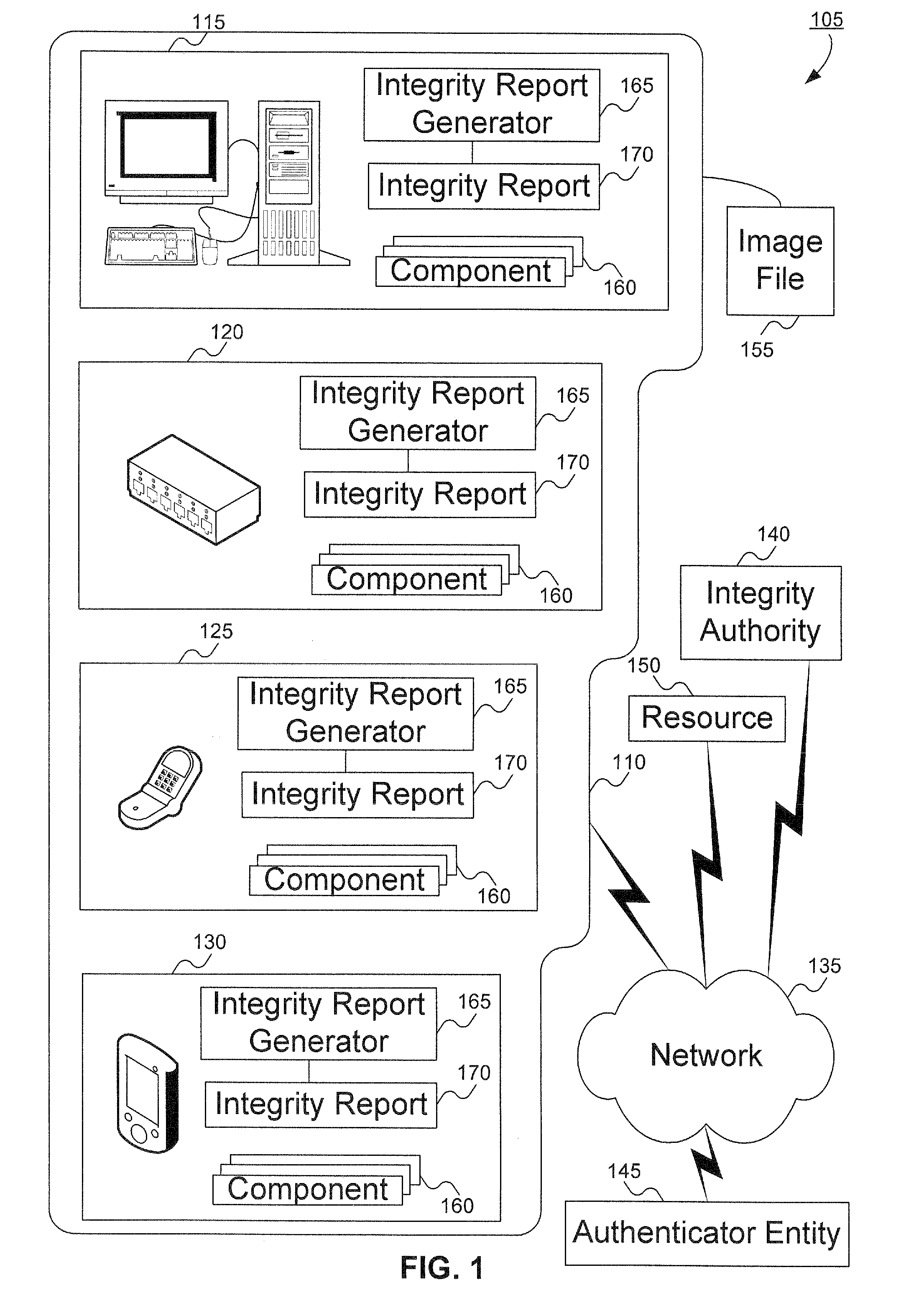
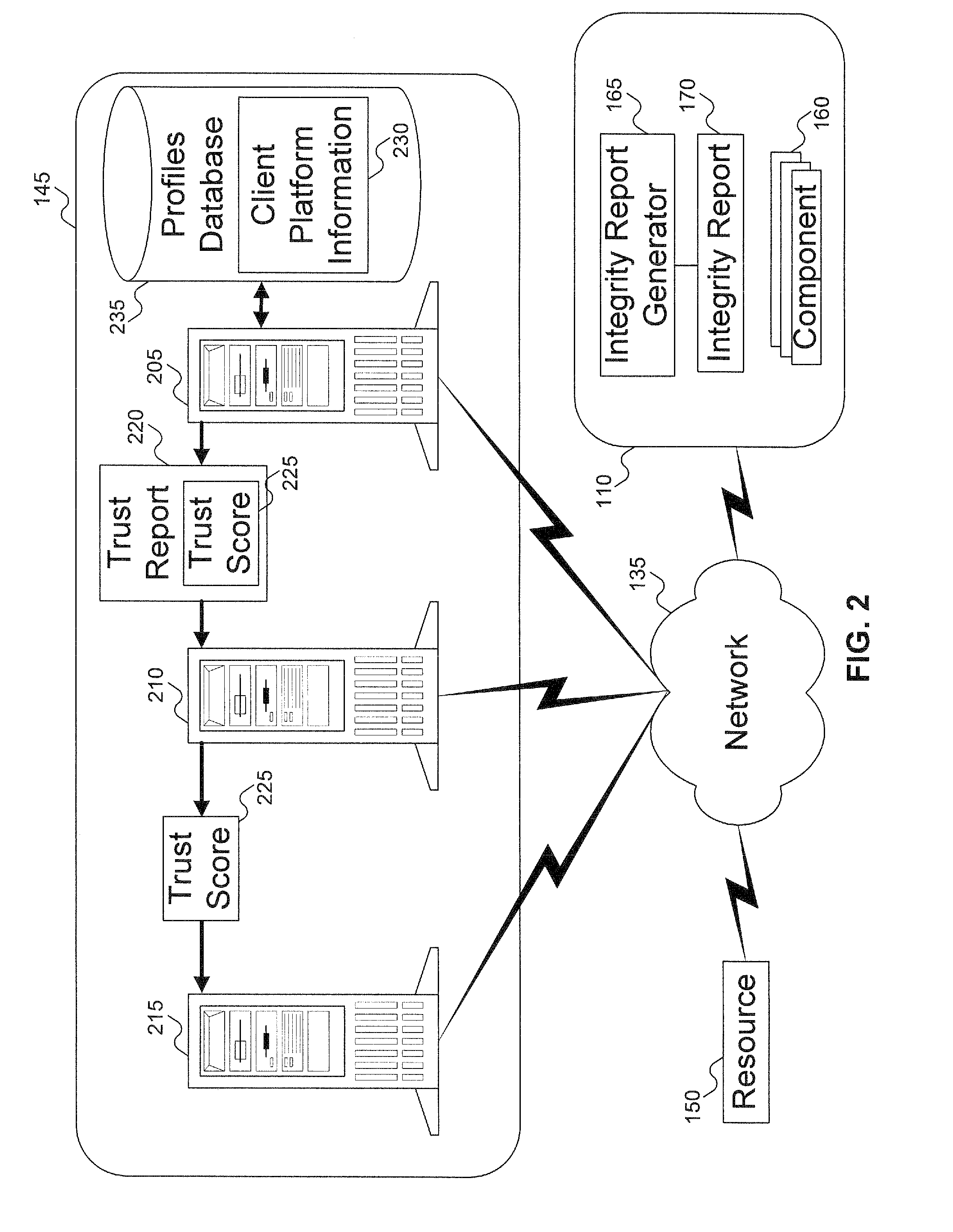
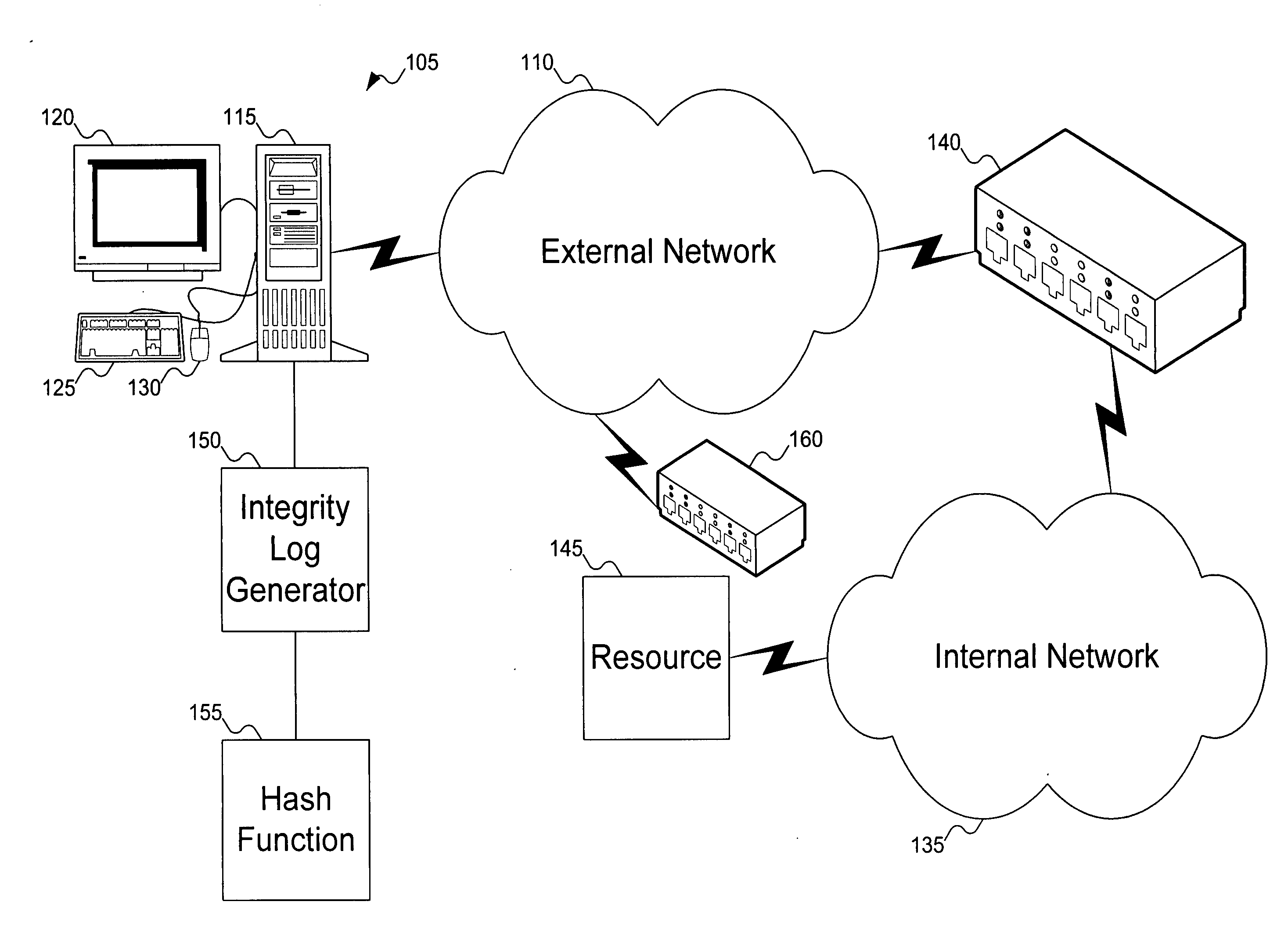
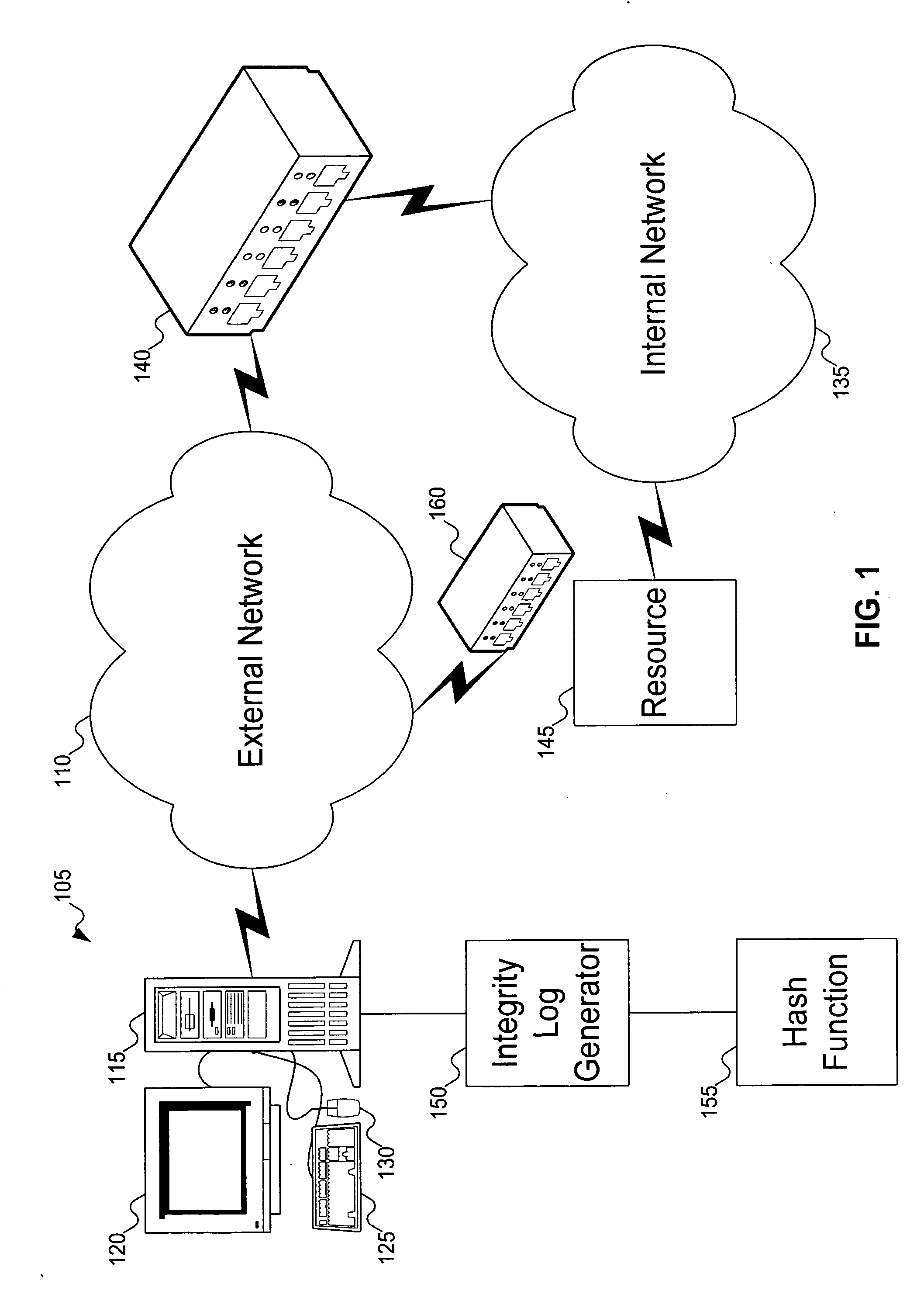
Method to verify the integrity of components on a trusted platform using integrity database services
InactiveUS20070143629A1Digital data processing detailsUser identity/authority verificationDatabase servicesClient-side
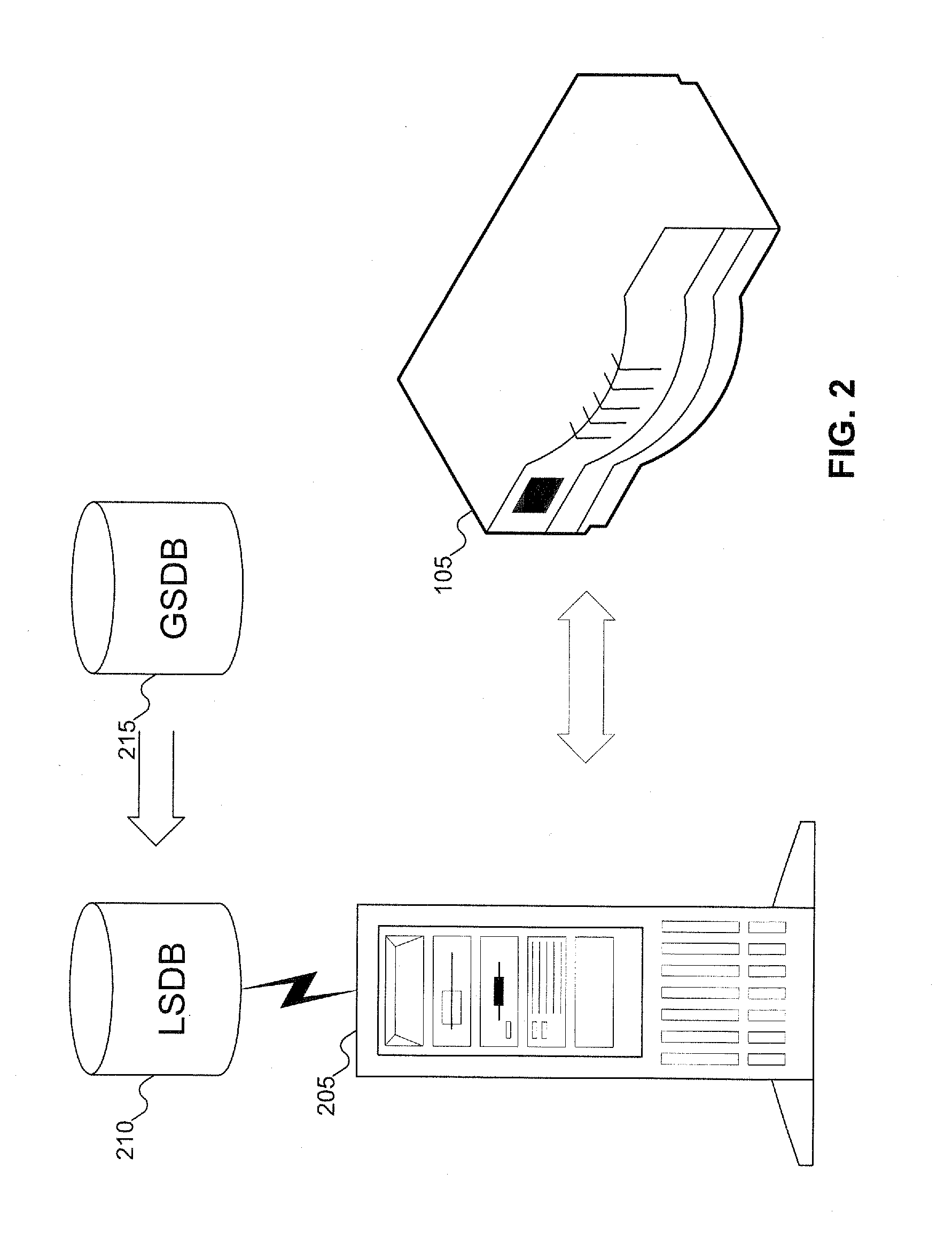
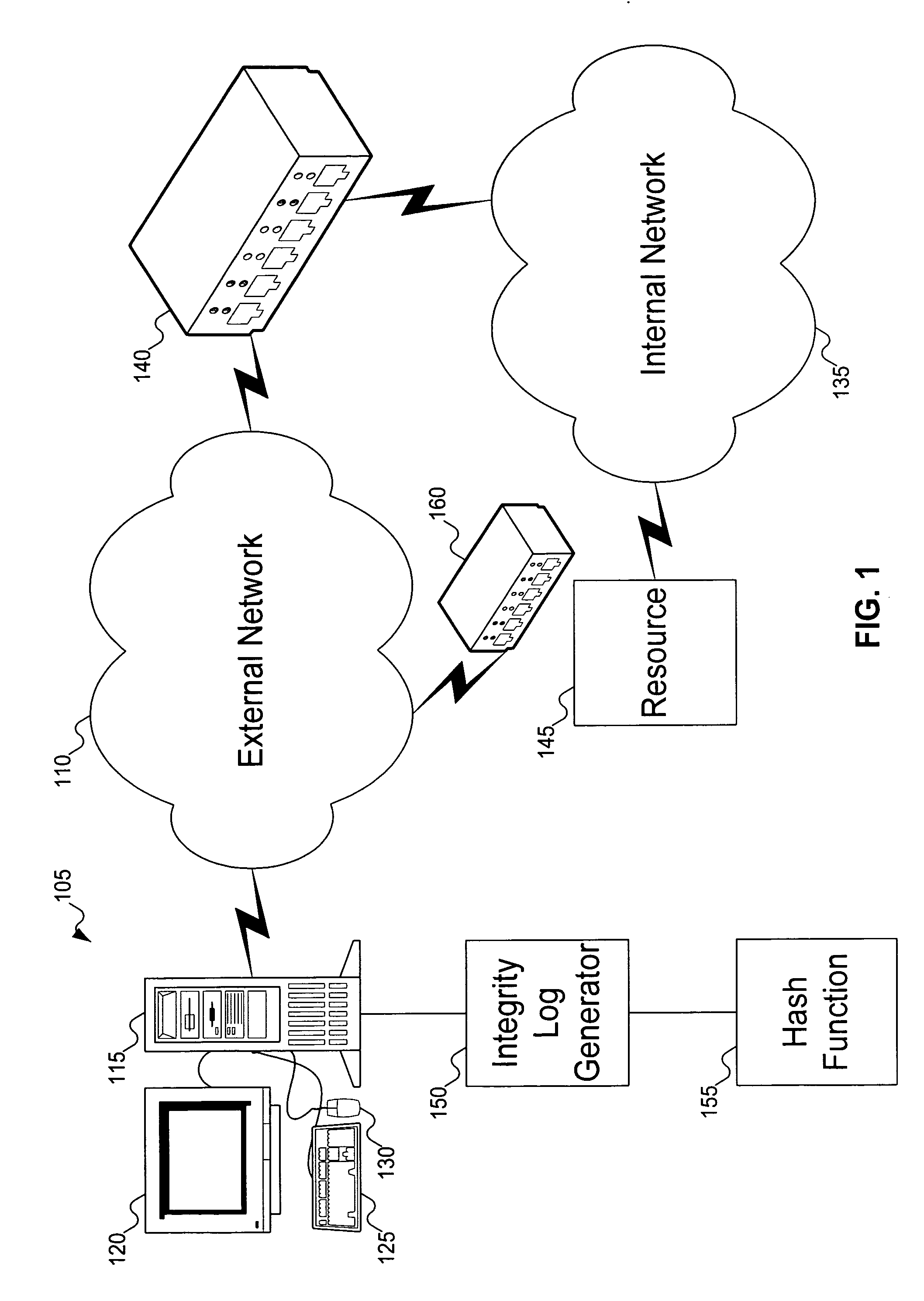
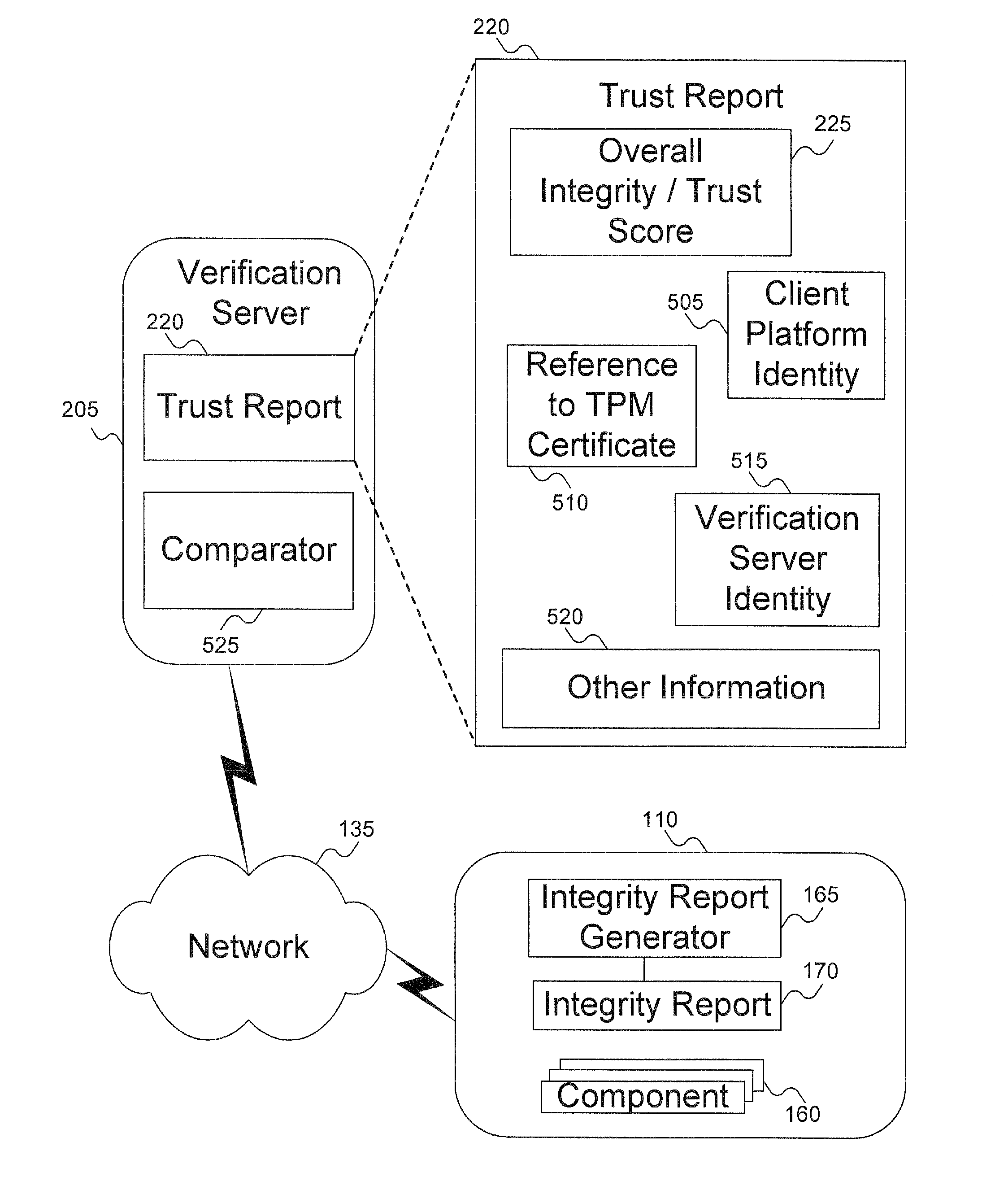
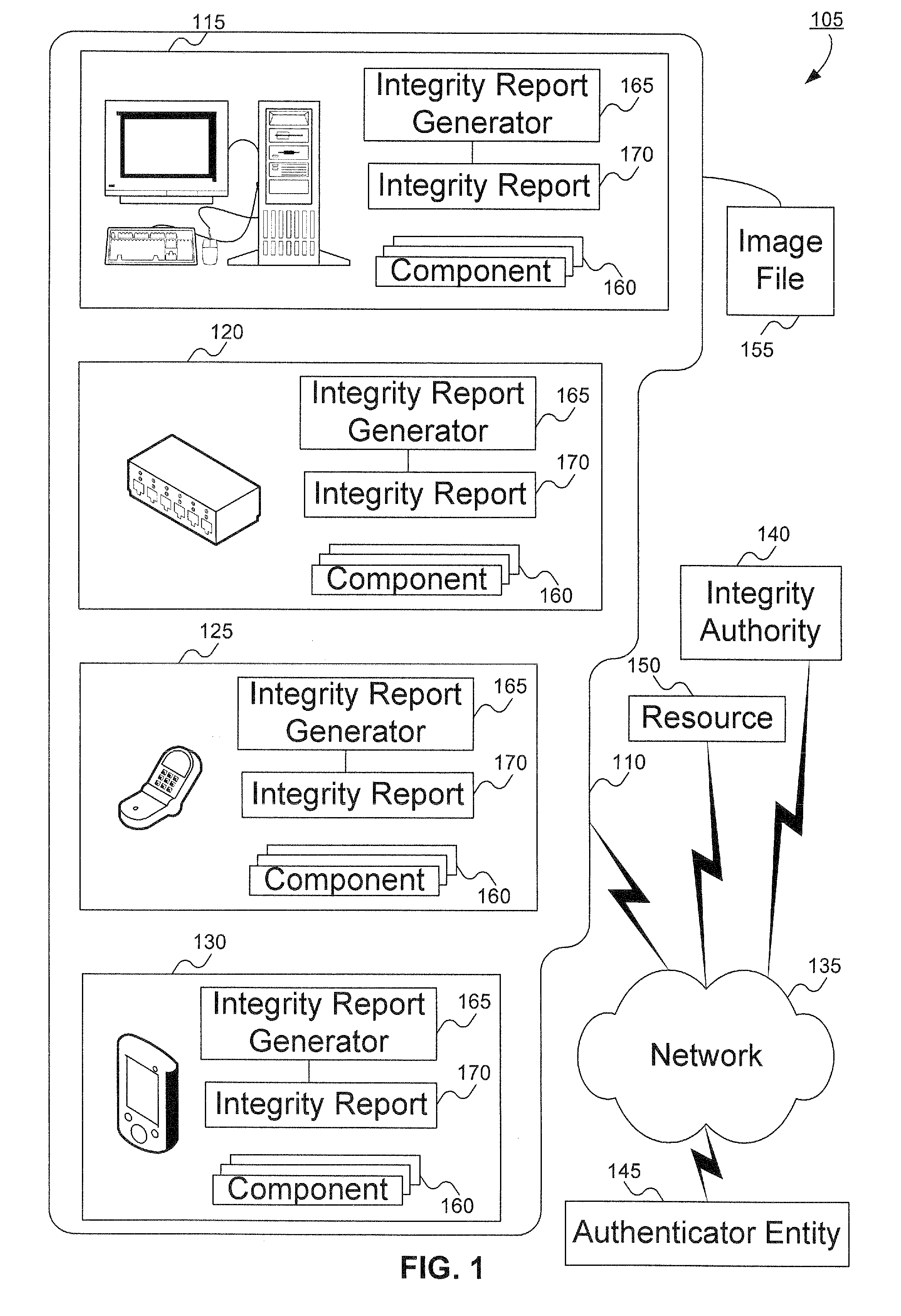
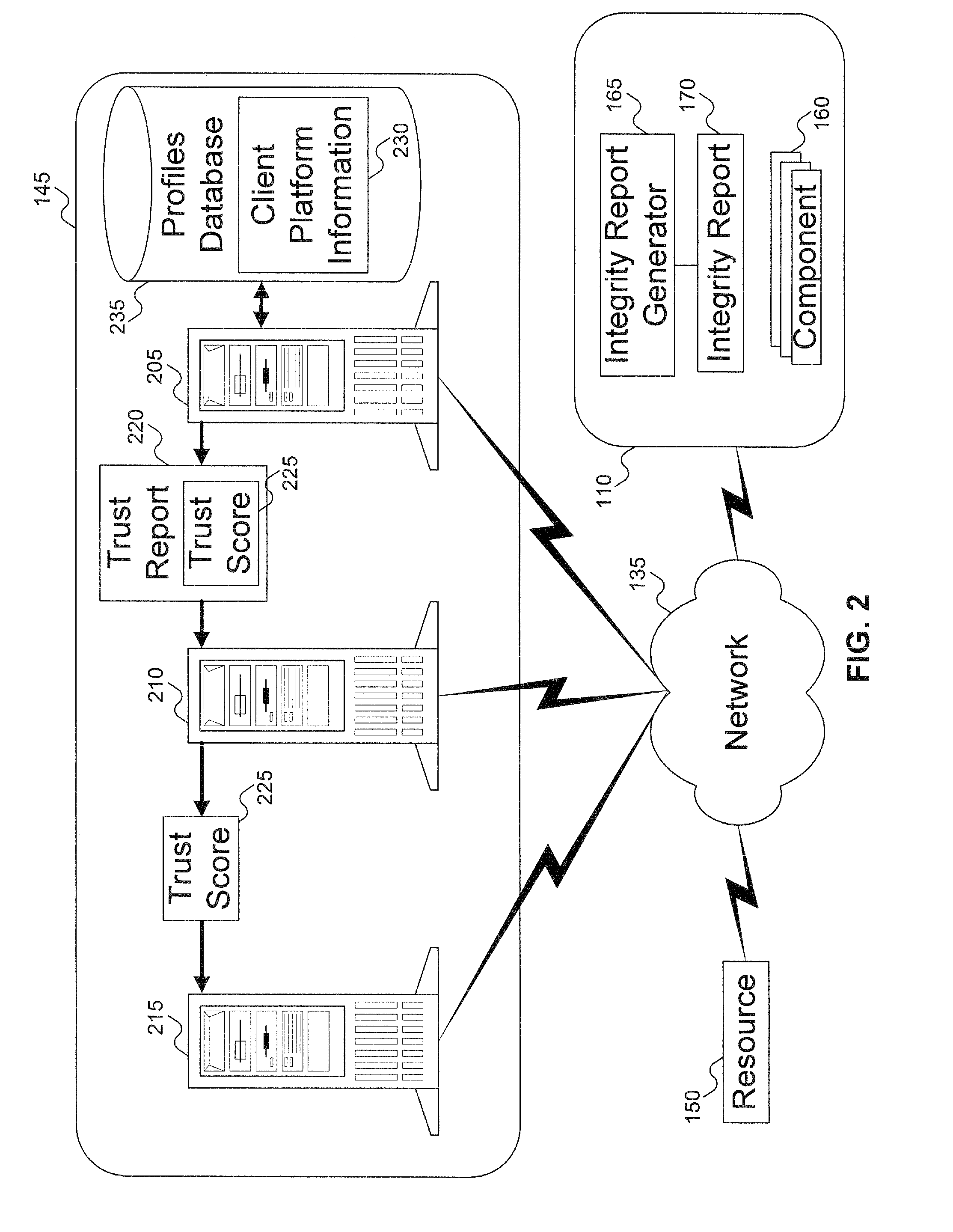
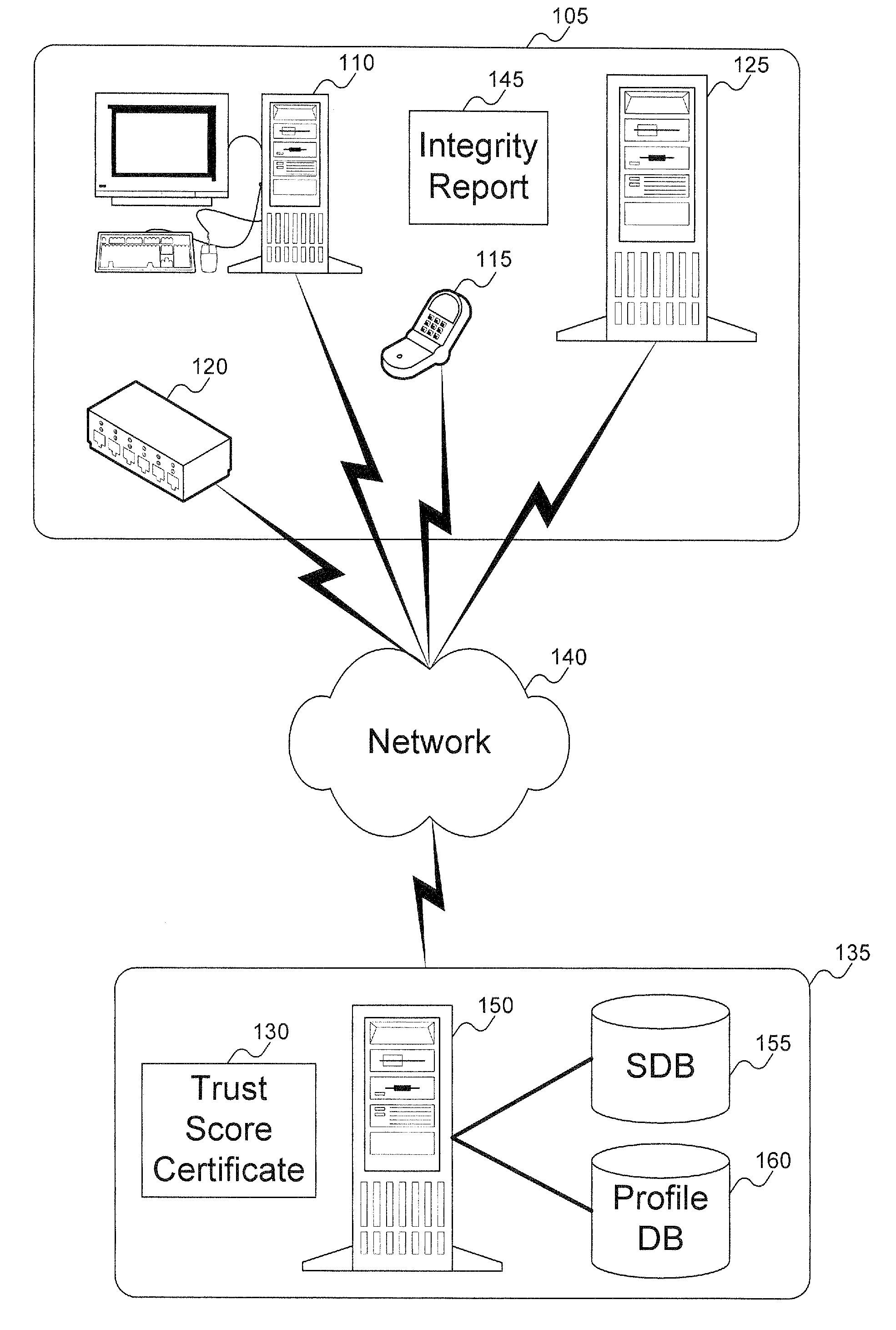
A client platform can be verified prior to being granted access to a resource or service on a network by validating individual hardware and software components of the client platform. Digests are generated for the components of the client platform. The digests can be collected into an integrity report. An authenticator entity receives the integrity report and compares the digests with digests stored in either a local signature database, a global signature database in an integrity authority, or both. Alternatively, the digests can be collected and stored on a portable digest-collector dongle. Once digests are either validated or invalidated, an overall integrity / trust score can be generated. She overall integrity / trust score can be used to determine whether the client platform should be granted access to the resource on the network using a policy.
Owner:SILICON VALLEY BANK +1
Consumer identity resolution based on transaction data
InactiveUS20140180826A1Complete banking machinesDiscounts/incentivesData processing systemTransaction data
According to an embodiment, a data processing system for facilitating consumer identity resolution comprises: a first logic module adapted to receive at least two collections of consumer records from at least two different sources; a second logic module adapted to compute first trust scores for first data fields of the first collection and second trust scores for second data fields of the second collection; a third logic module adapted to generate a master collection of consumer records comprising at least one master consumer record that is correlated to a record from the first collection and a record from the second collection, the correlation being based on at least on the trust scores; and a fourth logic module adapted to receive a set of contextual transaction data. The data processing system is adapted to identify a consumer based on the contextual transaction data and the master collection of consumer records.
Owner:QUOTIENT TECH INC
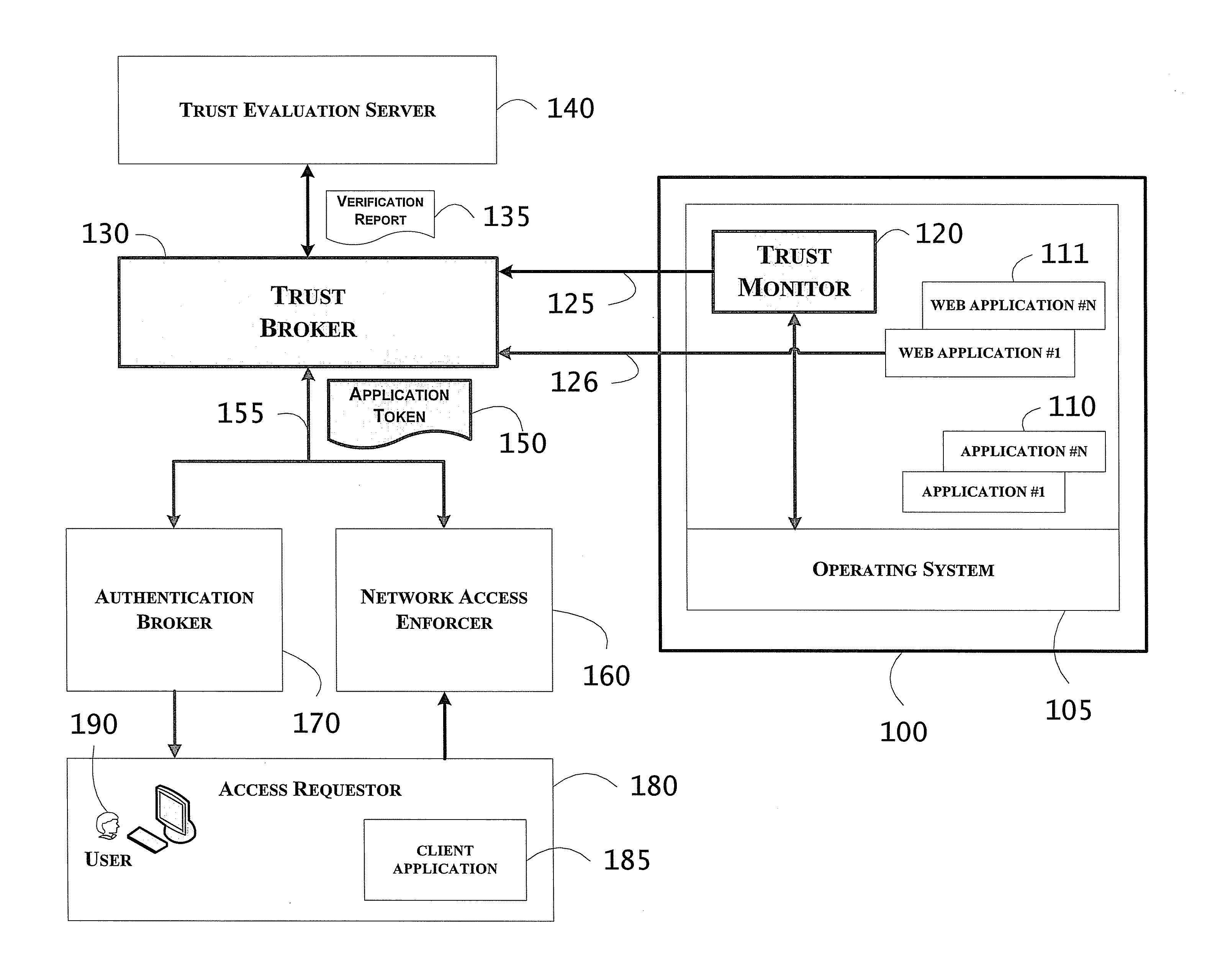
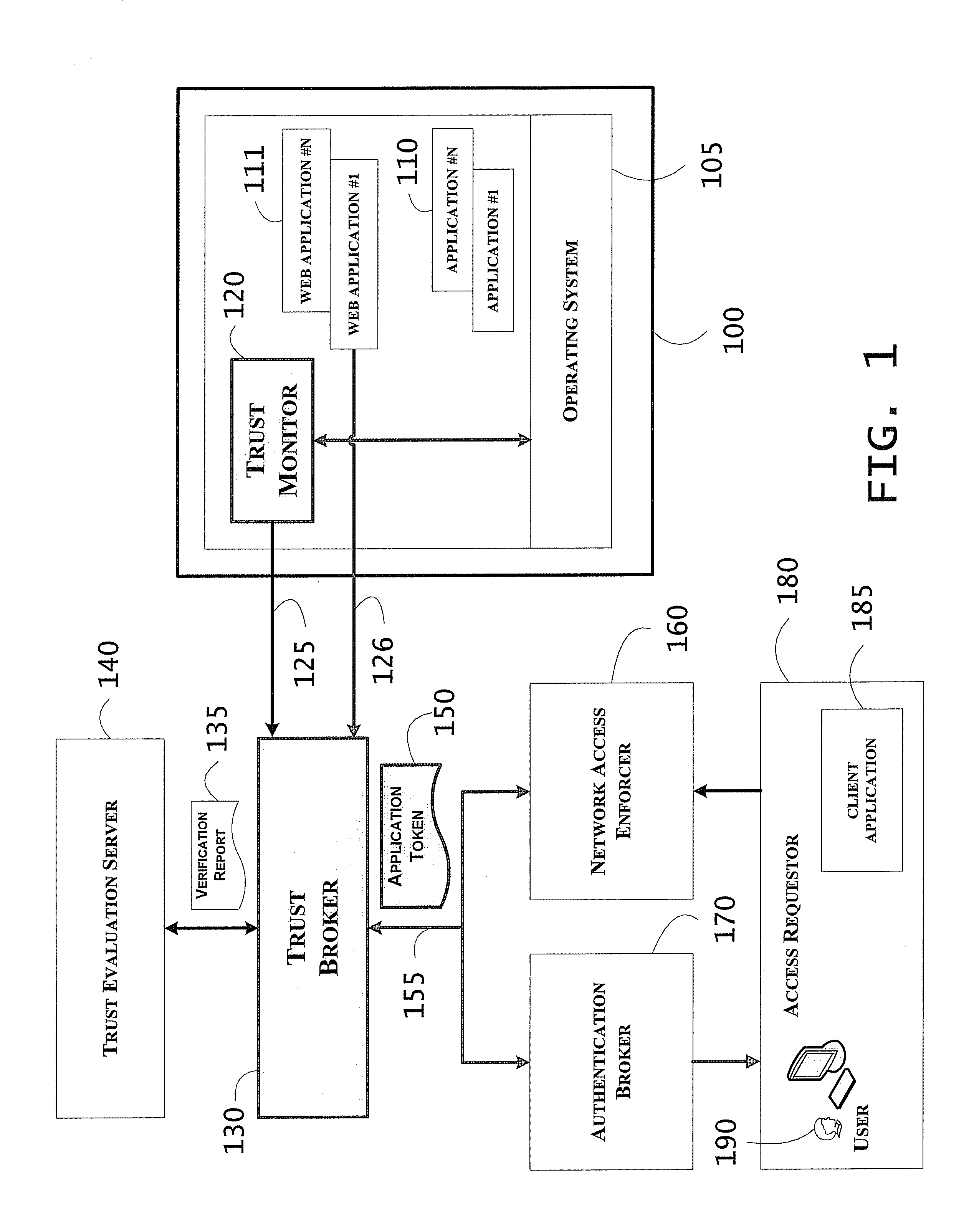
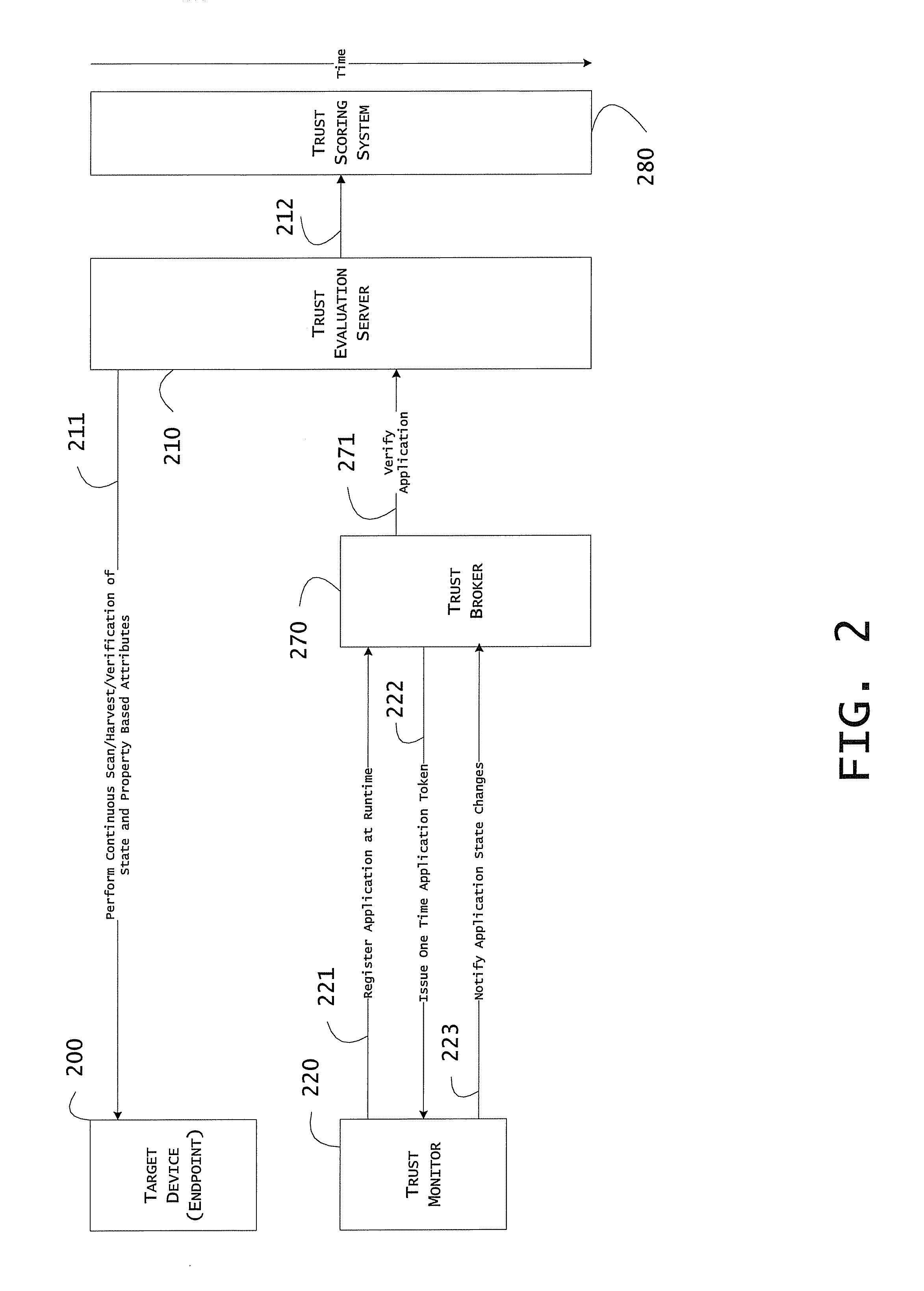
System including property-based weighted trust score application tokens for access control and related methods
InactiveUS20110179477A1Digital data processing detailsUser identity/authority verificationWeb applicationInternet privacy
A target device may have a target application and a web application thereon, and a trust broker may generate an application token having associated therewith a state attribute having at least one of a hash digest and a property value assertion, and weighted trust score. The application token may correspond to a level of trustworthiness, in near real time, of a running application instance of the target application. A trust monitor may monitor an execution state of the target application, and an authentication broker may authenticate a user to the web application and based upon a web services query for remote verification of the target application. A network access enforcer may control access of an authenticated user to the target application, and a trust evaluation server may interrogate the target application and generate a trust score.
Owner:KIP SIGN P1
Distribution of trust data
InactiveUS20060212930A1Digital data processing detailsUser identity/authority verificationInternet privacyClient-side
Embodiments of the present invention provide methods, systems, software for providing, distributing and / or using trust scores for online entities. In accordance with various embodiments, one or more trust score servers may be configured to provide trust scores, perhaps in response to a request (e.g., from another trust scores server, from a client, from a border device, etc.). In other embodiments, a computer (e.g., a border device, a client, etc.) may maintain a local cache of trust scores. In some cases, a computer may request a trust score for a particular online entity in response to receiving, detecting and / or attempting to transmit a communication with that online entity.
Owner:MARKMONITOR
Device reputation
ActiveUS20120233665A1Easily approvedLow trustDigital data processing detailsMultiple digital computer combinationsDevice typeUser device
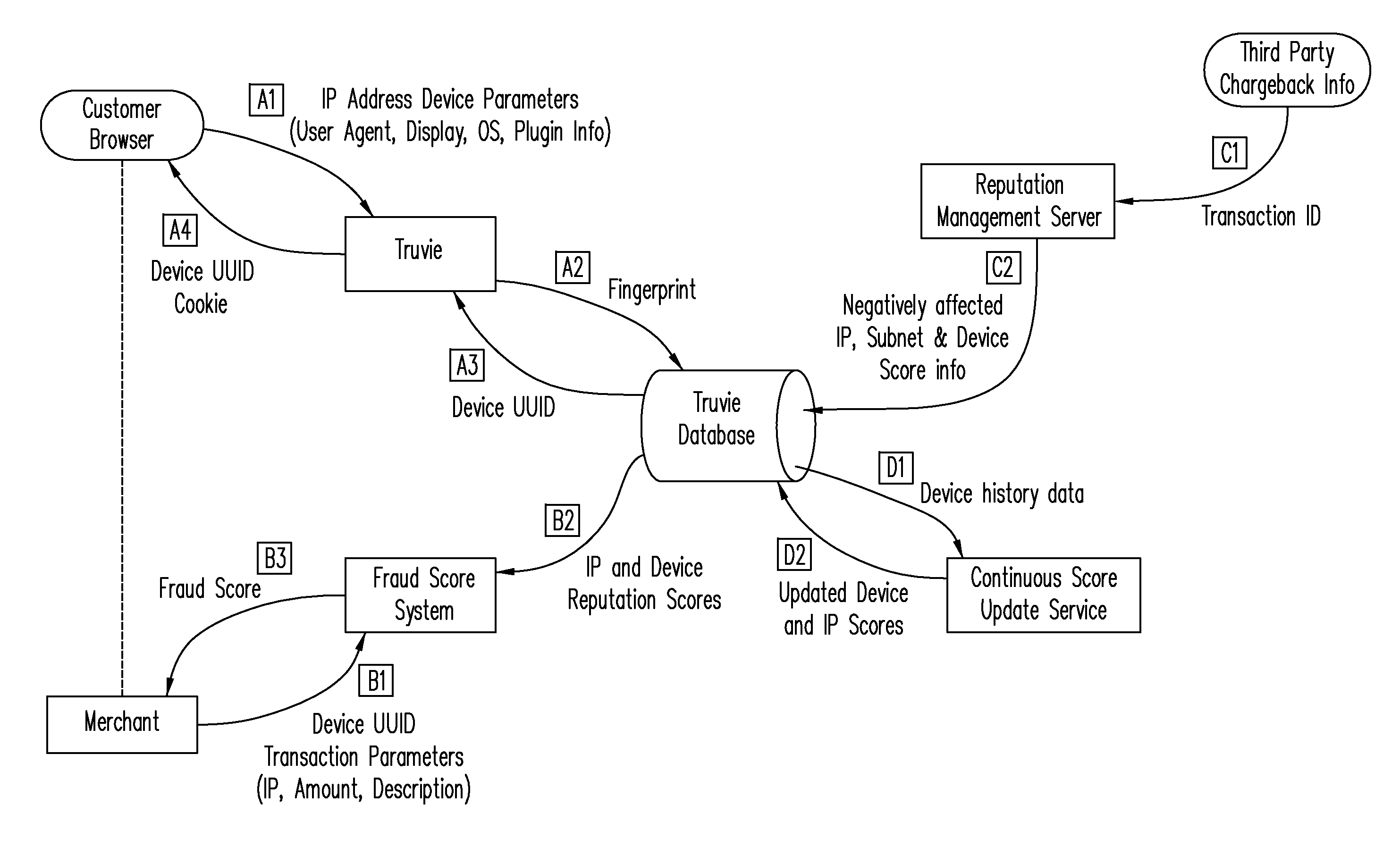
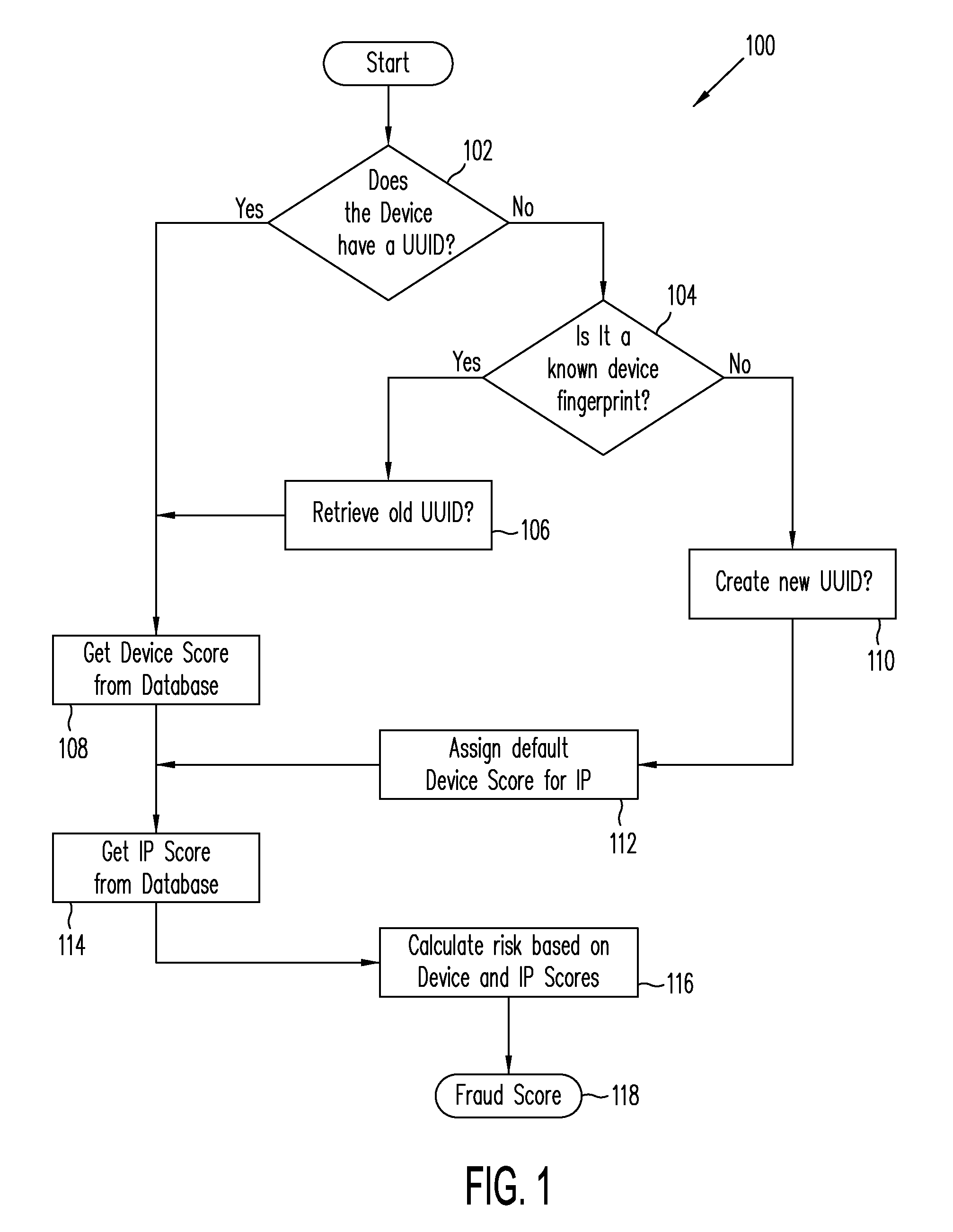
A user device is associated with a dynamic trust score that may be updated as needed, where the trust score and the updates are based on various activities and information associated with the mobile device. The trust score is based on both parameters of the device, such as device type, registered device location, device phone number, device ID, the last time the device has been accessed, etc. and activities the device engages in, such as amount of transactions, dollar amount of transactions, amount of denied requests, amount of approved requests, location of requests, etc. Based on a transaction request from the user device, the trust score and a network reputation score is used to determine an overall trust / fraud score associated with the transaction request.
Owner:PAYPAL INC
Trusted Eco-system Management System
A method comprising: providing a database comprising: a plurality of organizations; a plurality of members; and a plurality of questions; generating an assessment for each of the plurality of members from a subset of the plurality of questions; serving each assessment generated to each of the plurality of members; receiving a completed assessment comprising answers; recording in the database each member's completed assessment; generating a report for at least one of the plurality of organization's eco-system wherein the eco-system comprises members from the plurality of members and the report comprises a trust score for the eco-system.
Owner:EDGILE
Method and apparatus for providing multi-sensor multi-factor identity verification
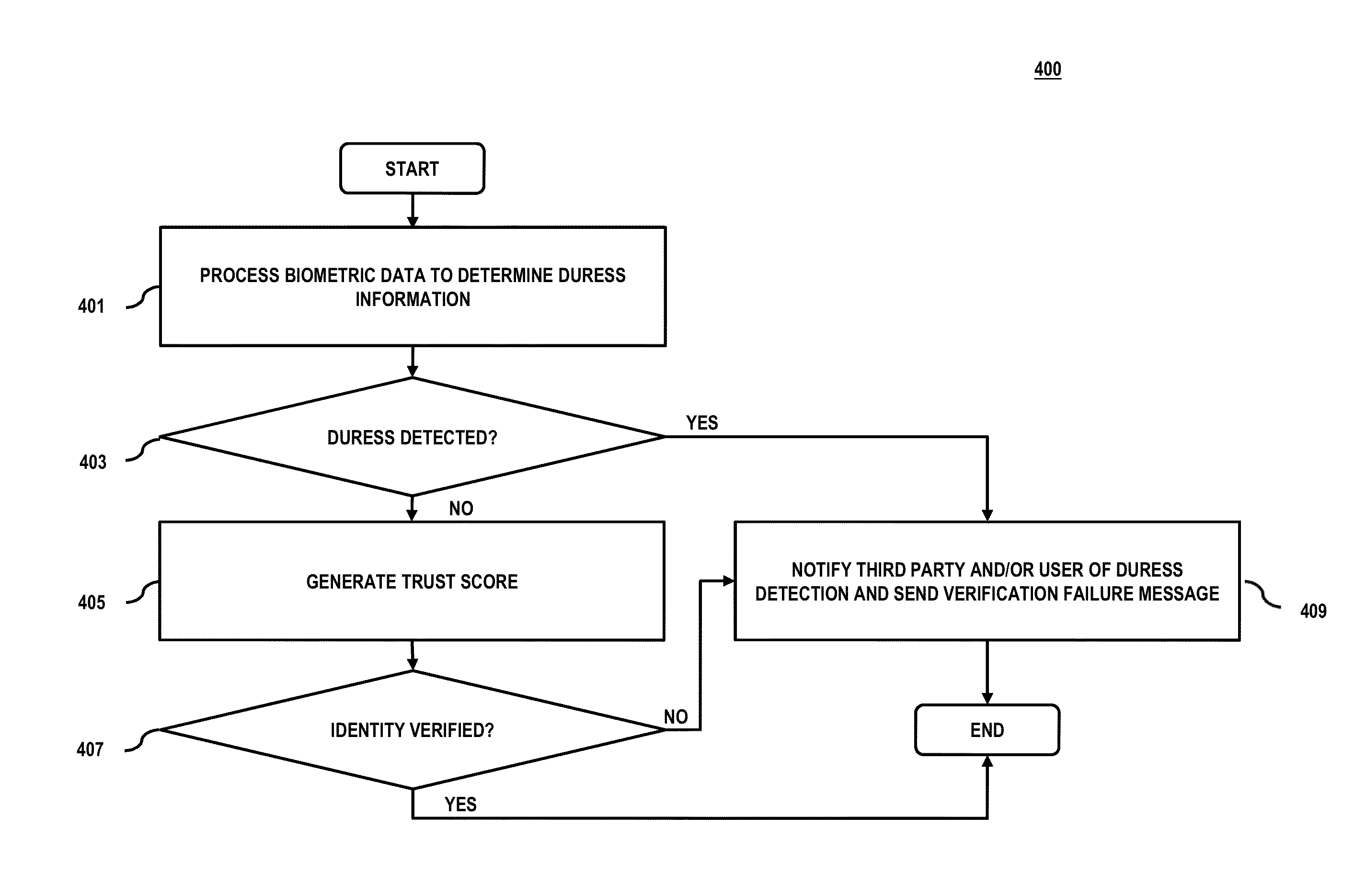
ActiveUS20140359722A1Digital data processing detailsMultiple digital computer combinationsMultiple contextBiometric data
An approach for multi-sensor multi-factor identity verification. An identity verification platform determines biometric data associated with a user from one or more sources. The one or more sources are associated with one or more respective network sessions. The platform generates one or more respective trust scores for the one or more sources, the one or more respective network sessions, or a combination thereof based on one or more contextual parameters associated with the user, the one or more sources, the one or more respective network sessions, or a combination thereof. Then the platform verifies an identity of the user based on the biometric data and the one or more respective trust scores.
Owner:VERIZON PATENT & LICENSING INC
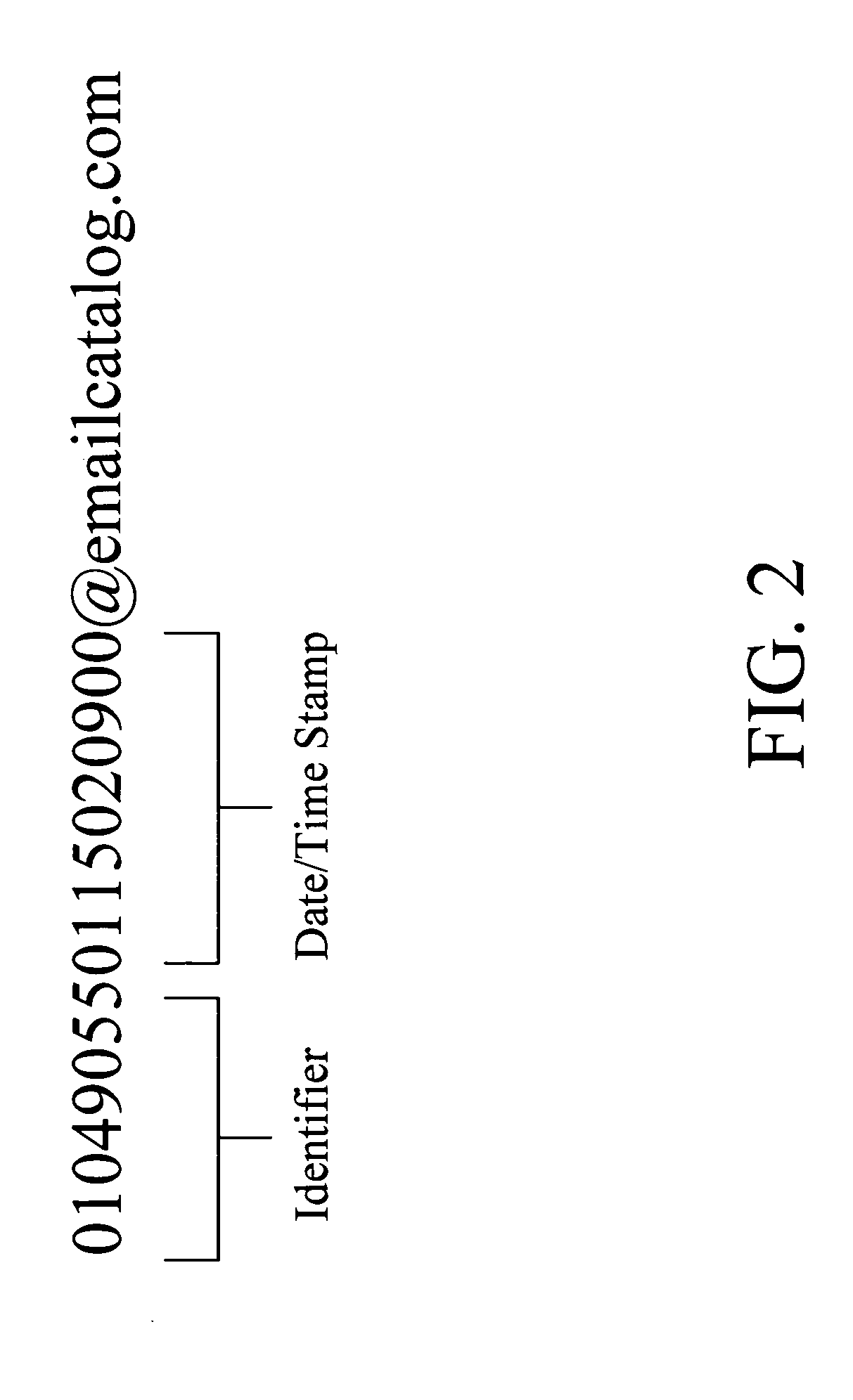
Dynamic online email catalog and trust relationship management system and method
InactiveUS20050204002A1Increase valueMultiple digital computer combinationsCommerceEmail marketingEmail address
A system is described for a Dynamic Online Email Catalog useful in providing a means to collect, categorize, arrange, store and display direct email marketing messages for the benefit of users by way of secure web access to assigned private user areas. The catalog further provides a means for ranking received email messages within specific product or service categories with priority placement given to those messages originating with product or service providers having the highest trust scores in which the score is a number representing an average time that a user's email address is active with a specific provider. Also described is a system and method for searching Internet records involving the receiving of a search request, prioritizing records according to trust score with those associated with product and service providers having the highest trust score receiving priority placement.
Owner:INLET IP HLDG
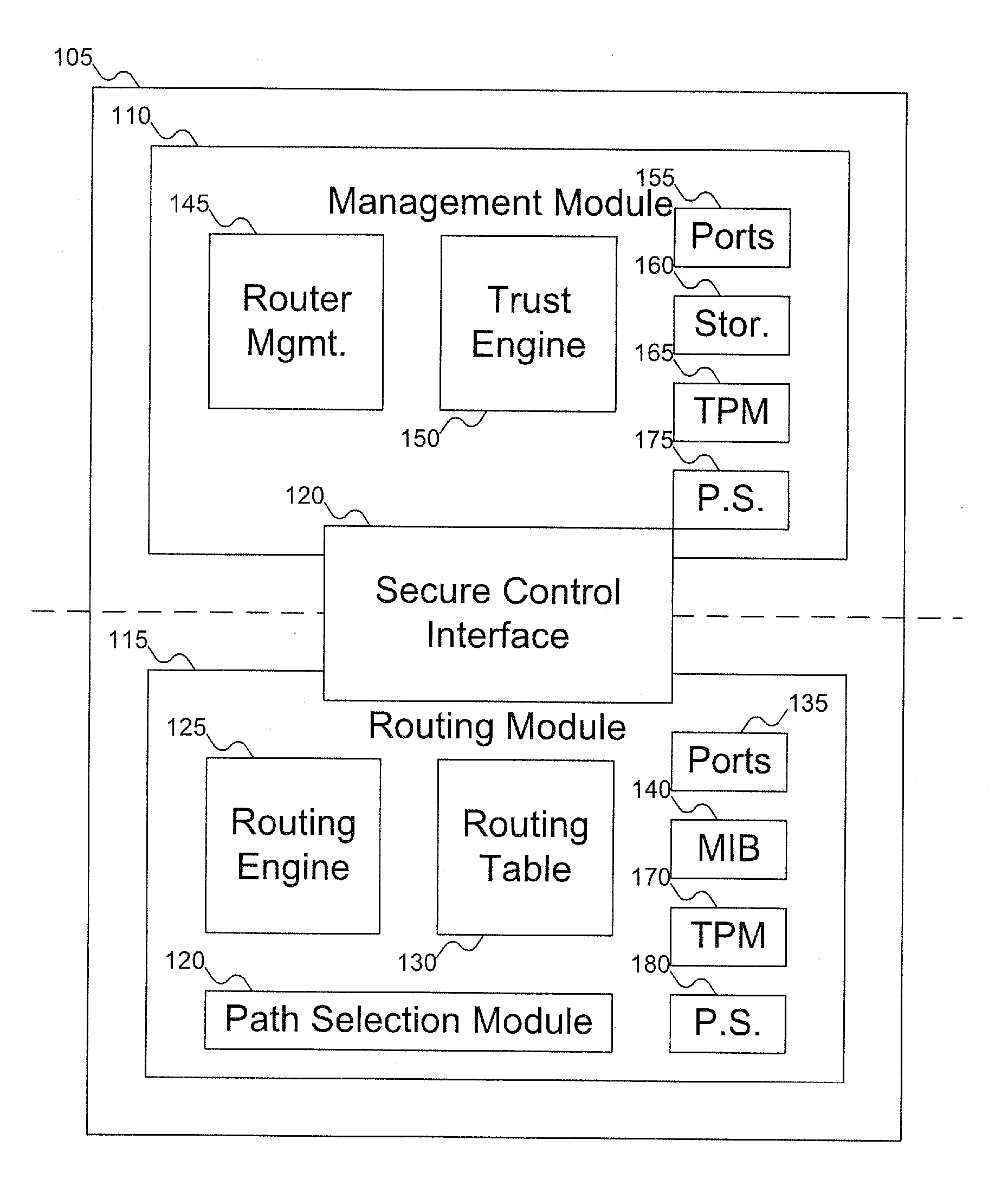
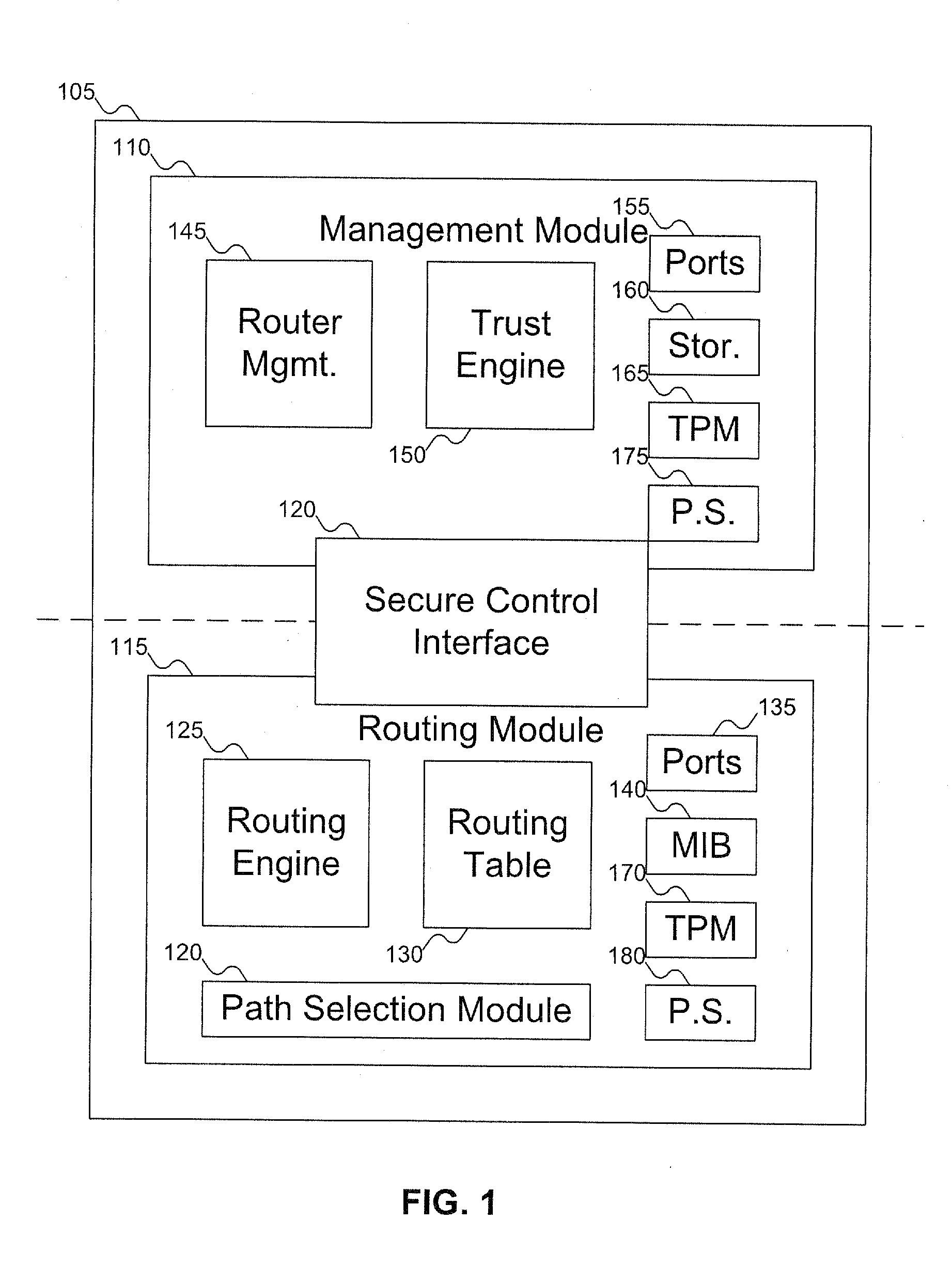
Method and apparatus to establish routes based on the trust scores of routers within an IP routing domain
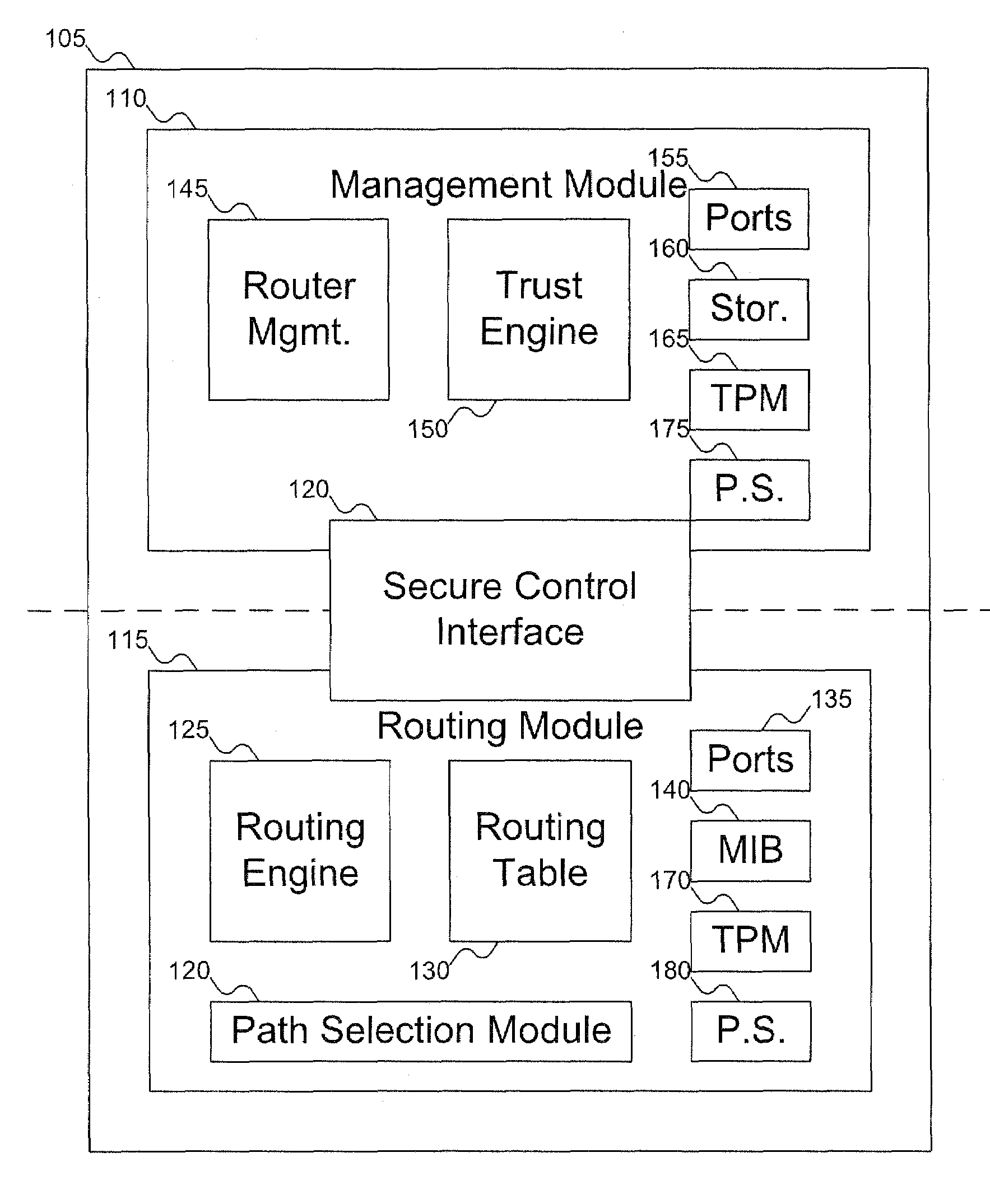
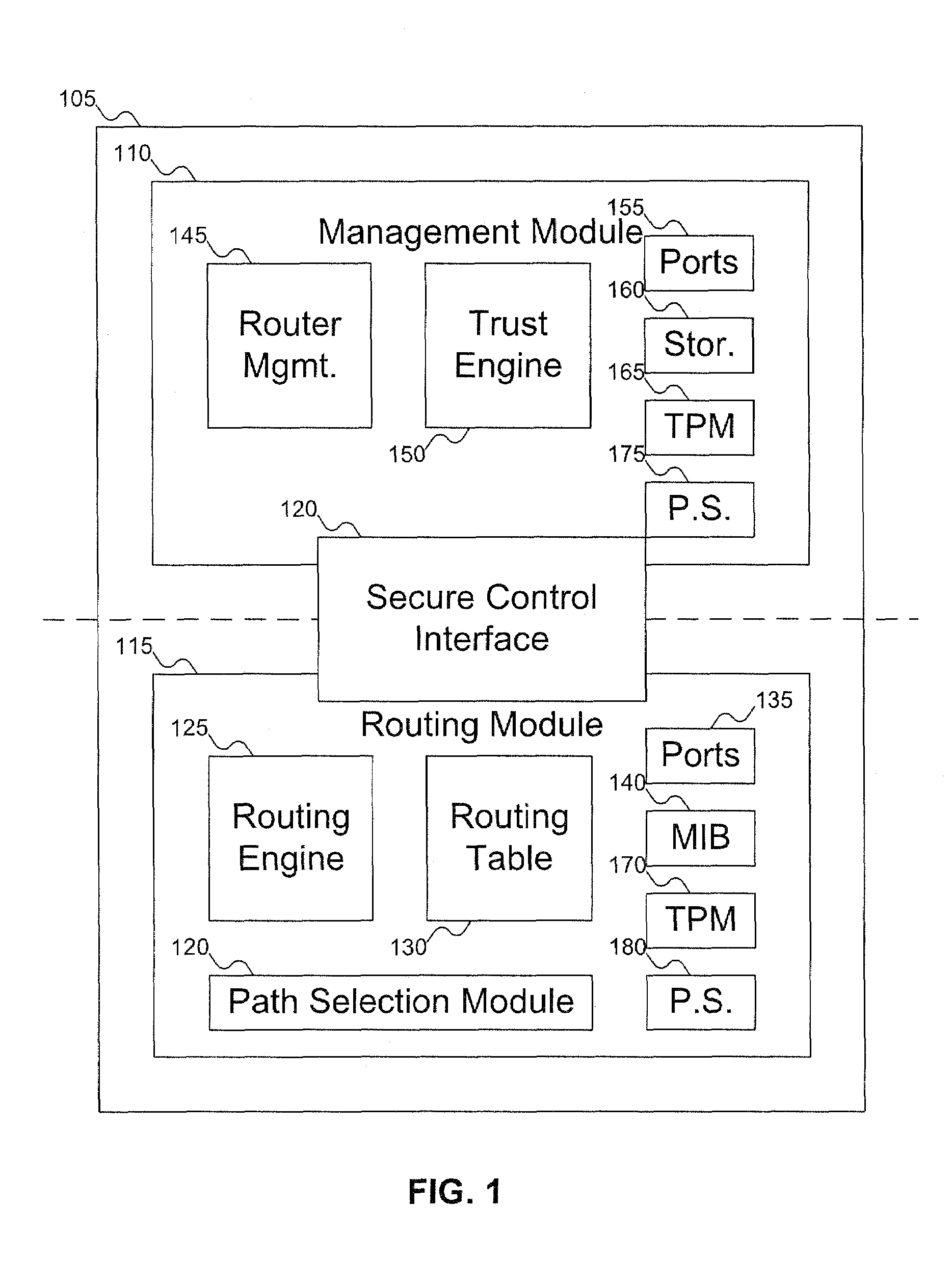
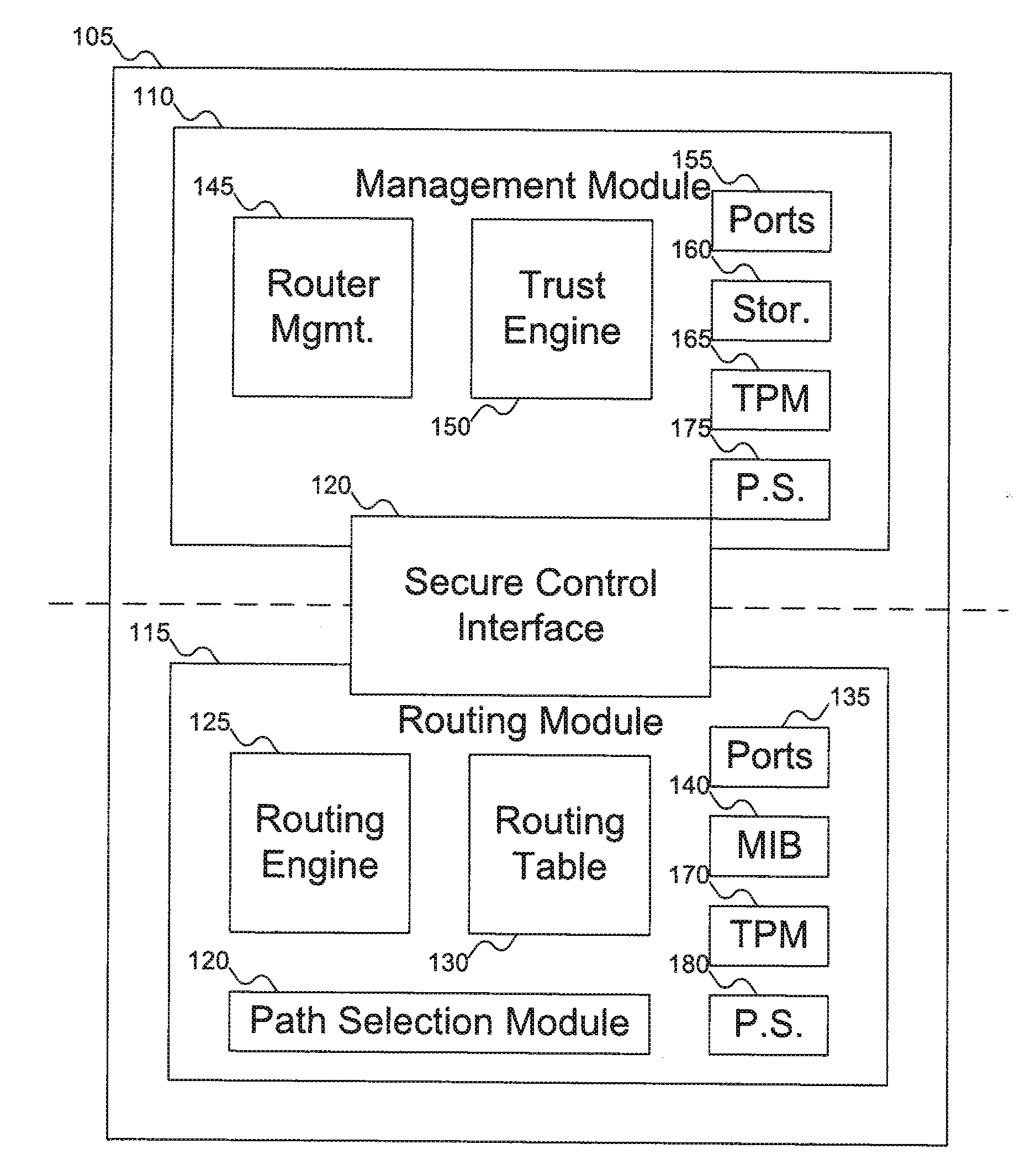
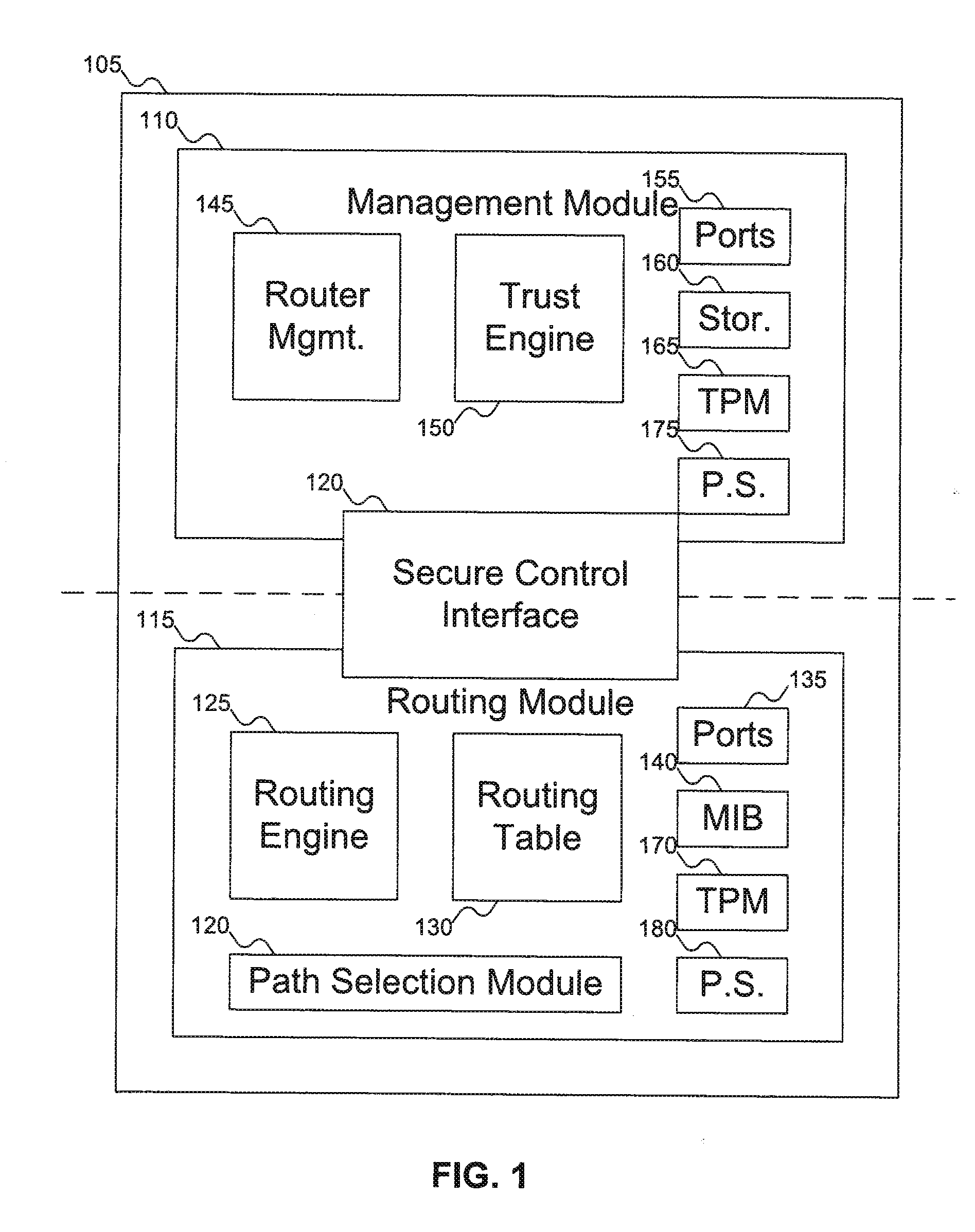
InactiveUS20070180495A1Digital data processing detailsUser identity/authority verificationComputer hardwareTrust score
A router includes a management module and a routing module. The routing module can be used to route data around a network. The management module can be used to manage the operation of the routing module, including generating an integrity report for the router, which can be used to generate a trust report for the router. The trust report can include an integrity / trust score for the router. The management module can control the routing module via a secure control interface.
Owner:KIP SIGN P1 +1
Method to control access between network endpoints based on trust scores calculated from information system component analysis
InactiveUS7272719B2Digital data processing detailsUser identity/authority verificationComputerized systemData mining
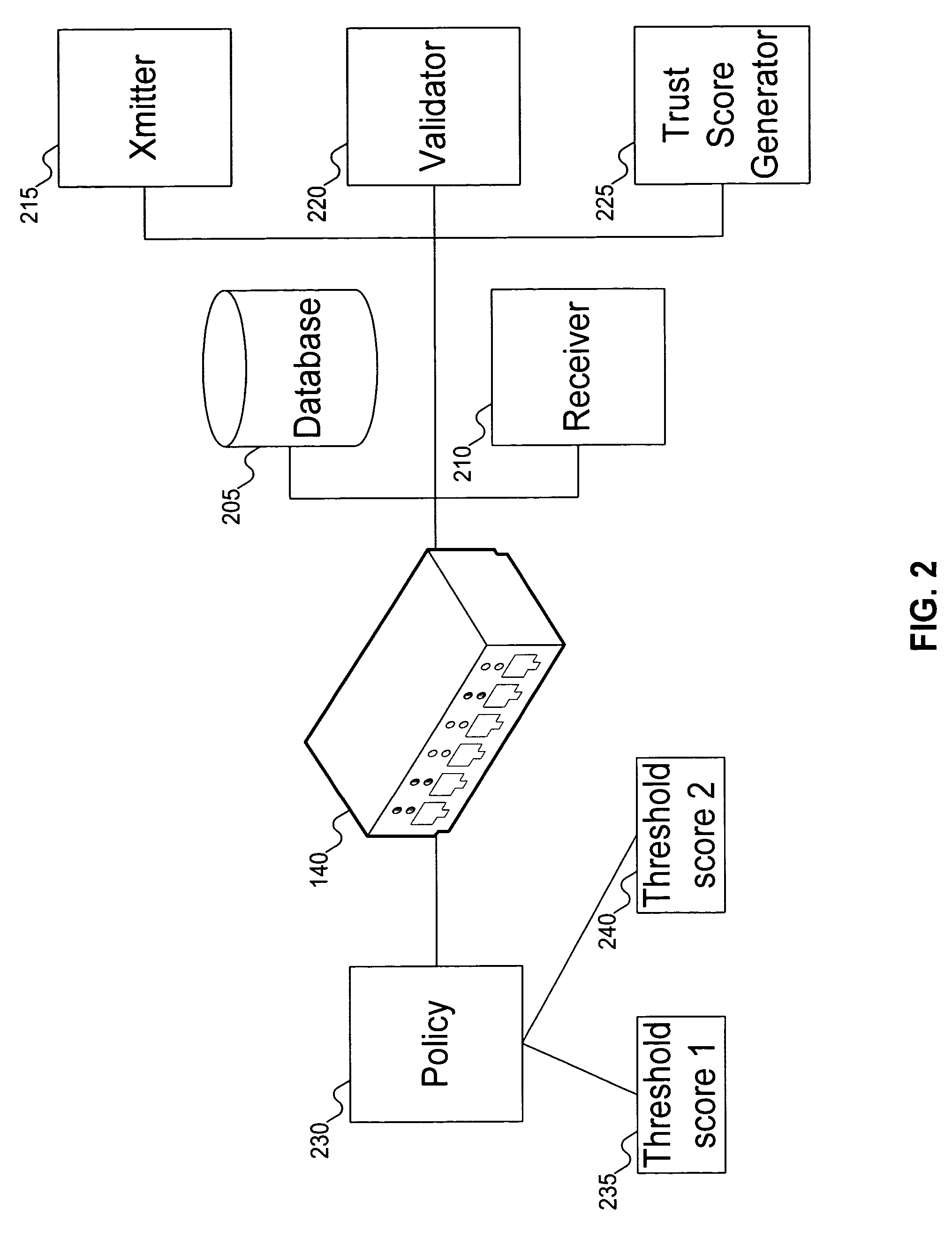
Signatures are generated for modules in a computer system. The signatures can be assembled into an integrity log. The signatures are compared with signatures in a database in an integrity validator. Once signatures are either validated or invalidated, a trust score can be generated. The trust score can then be used to determine whether the computer system should be granted access to a resource using a policy.
Owner:SILICON VALLEY BANK +1
Method to verify the integrity of components on a trusted platform using integrity database services
InactiveUS8266676B2Digital data processing detailsUser identity/authority verificationDatabase servicesTrust score
A client platform can be verified prior to being granted access to a resource or service on a network by validating individual hardware and software components of the client platform. Digests are generated for the components of the client platform. The digests can be collected into an integrity report. An authenticator entity receives the integrity report and compares the digests with digests stored in either a local signature database, a global signature database in an integrity authority, or both. Alternatively, the digests can be collected and stored on a portable digest-collector dongle. Once digests are either validated or invalidated, an overall integrity / trust score can be generated. She overall integrity / trust score can be used to determine whether the client platform should be granted access to the resource on the network using a policy.
Owner:SILICON VALLEY BANK +1
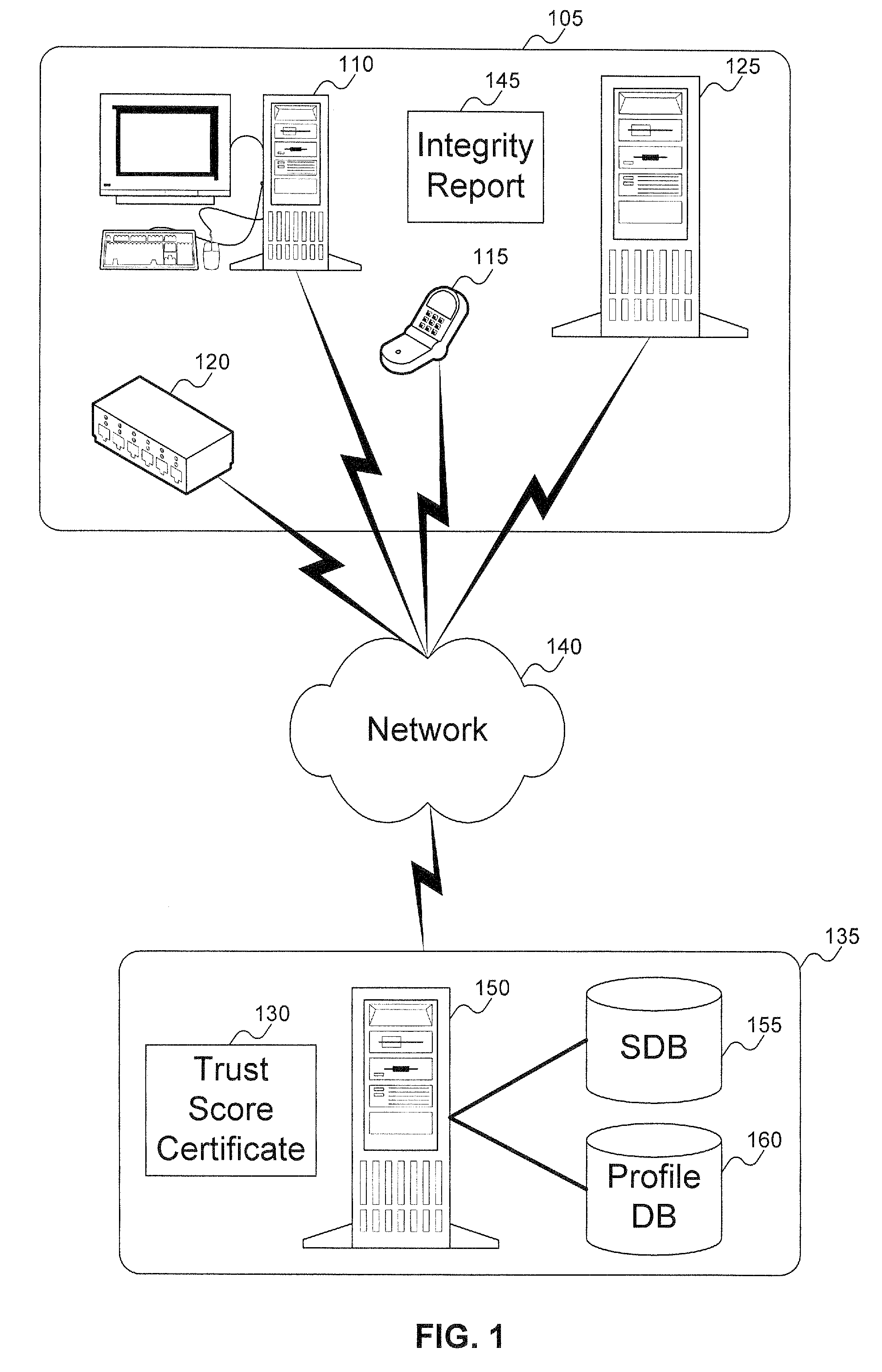
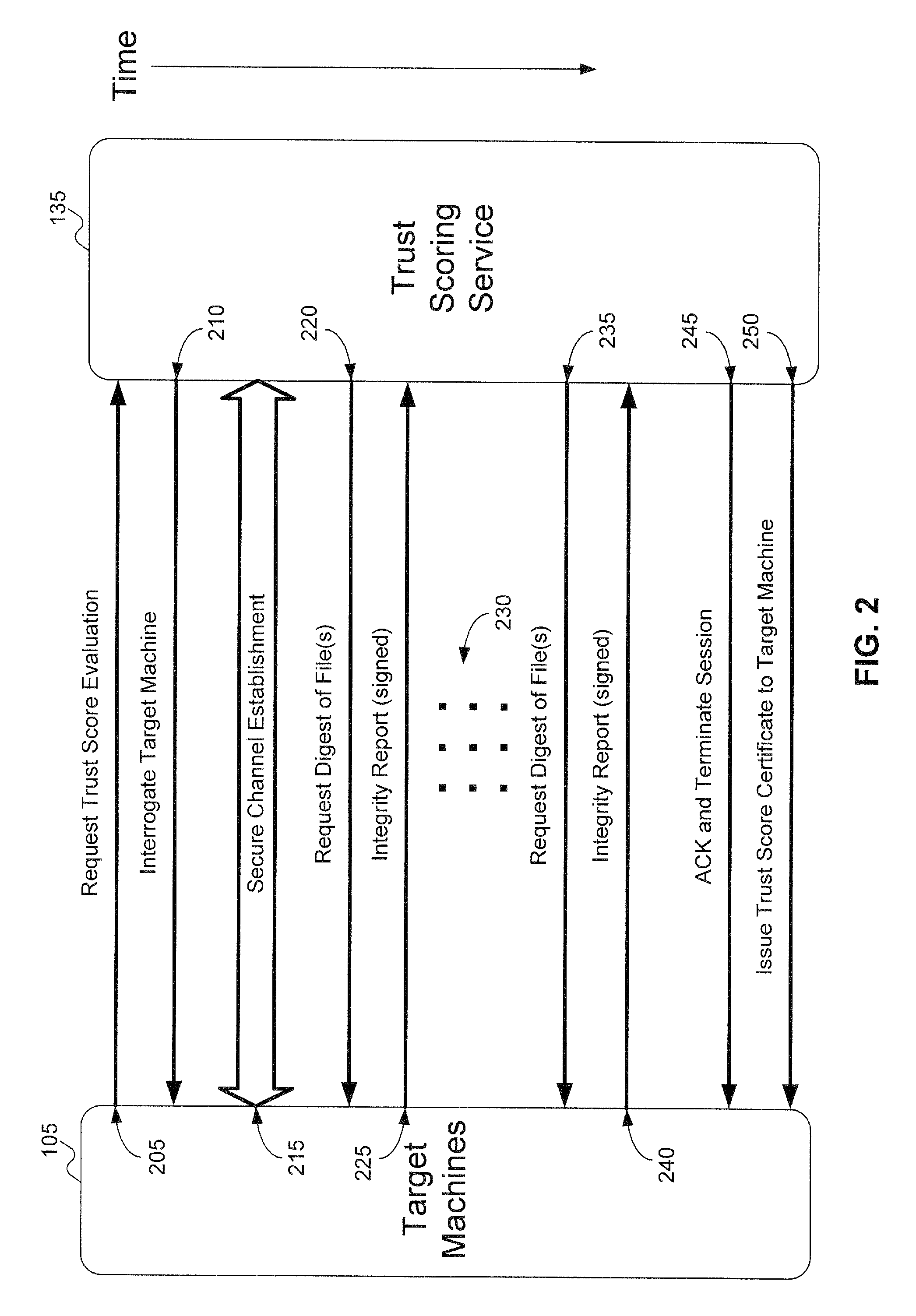
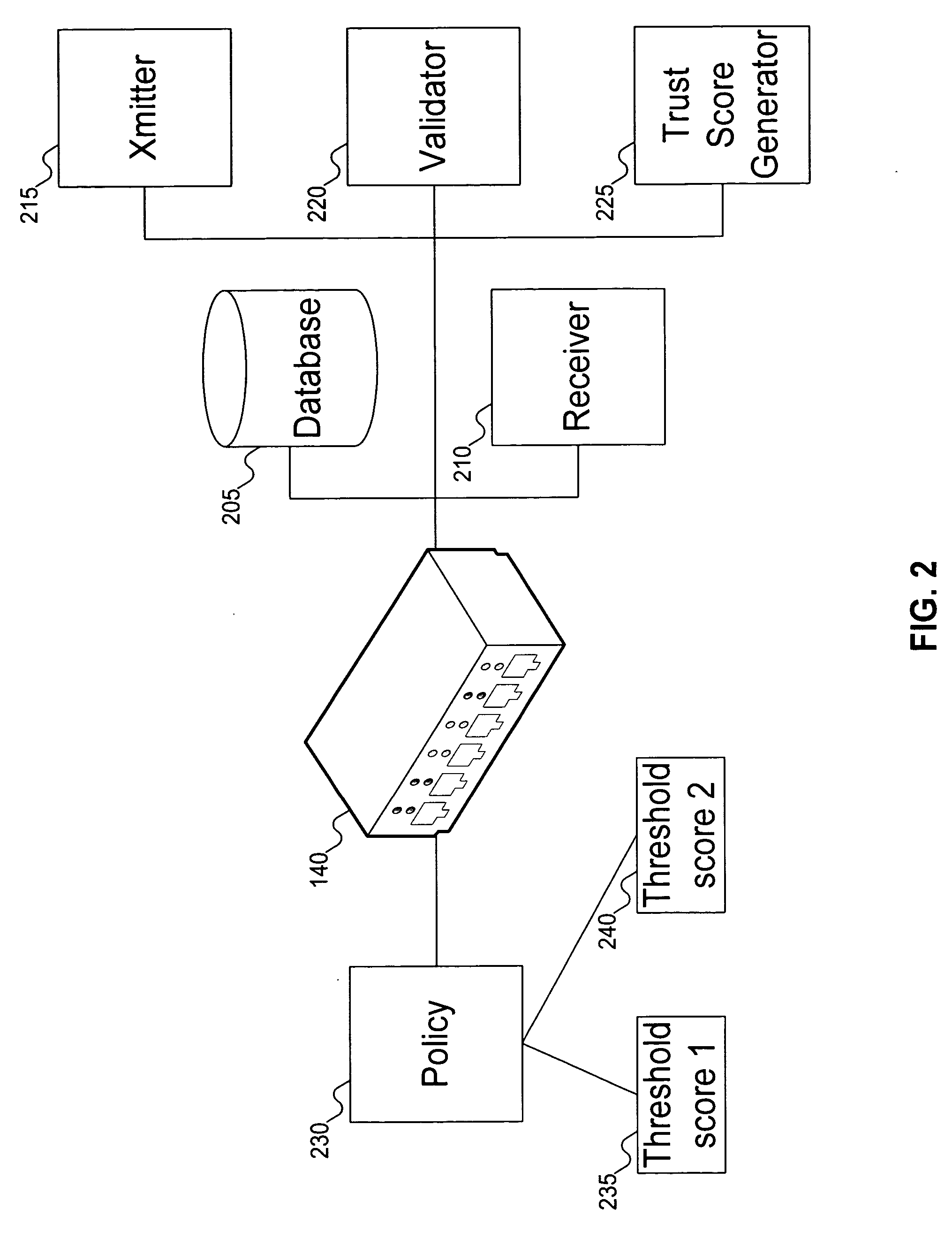
Method and system to issue trust score certificates for networked devices using a trust scoring service
InactiveUS8327131B1Digital data processing detailsUser identity/authority verificationWeb serviceHome page
A target machine can be verified prior to being granted access to a resource on a network by interrogating and analyzing digests of various elements of the target machine. The digests can be collected into an integrity report and provided to a Trust Scoring Service. The Trust Scoring Service receives the integrity report and compares the digests with signatures stored in a signature database. A trust score certificate can then be issued to the target machine. The Trust Scoring Service can include a Score Evaluation Server which can interact with a Kerberos Authentication Server and a Ticket Granting Server to embed a trust score within a Kerberos Ticket to enforce a richer set of access policies. The integrity of a web server can be verified and a Trust Score Certificate Logo can be displayed on a corresponding home page of a merchant. By clicking on the Trust Score Certificate Logo, a user can verify the integrity of the merchant's web servers prior to completing a transaction with the merchant.
Owner:KIP SIGN P1
Scoring Persons and Files for Trust in Digital Communication
ActiveUS20100169265A1Multiple digital computer combinationsFuzzy logic based systemsTrusted authorityInternet privacy
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
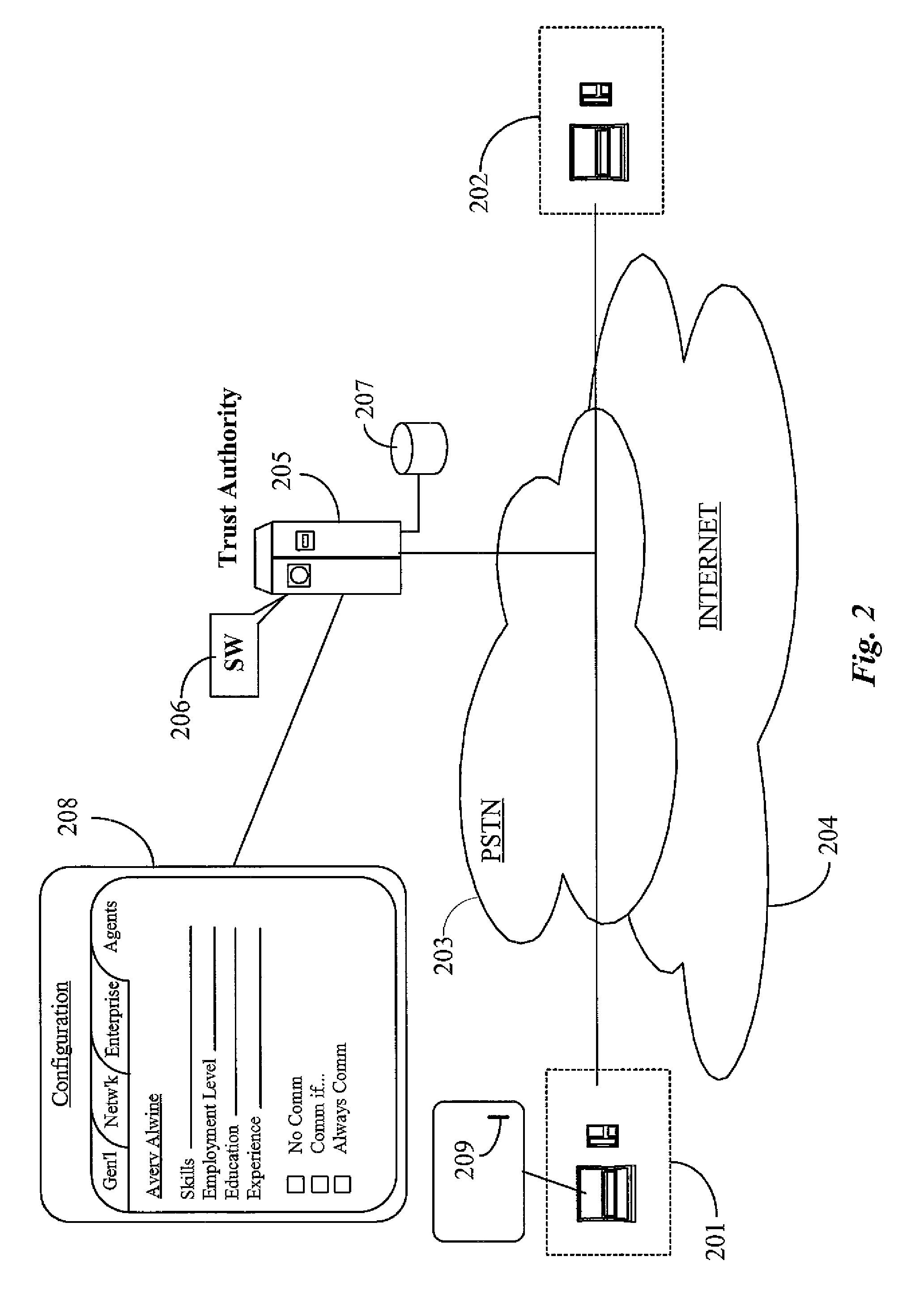
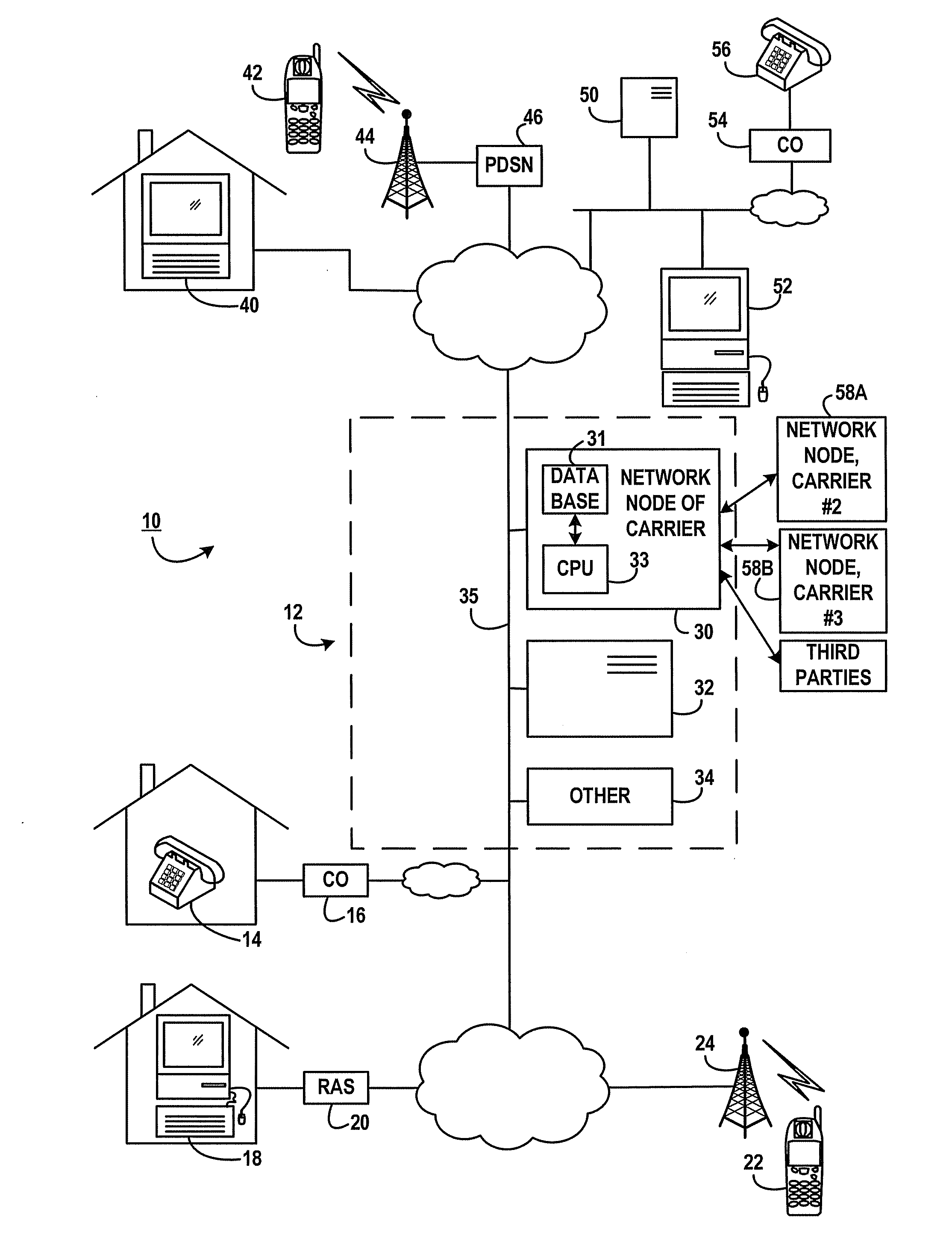
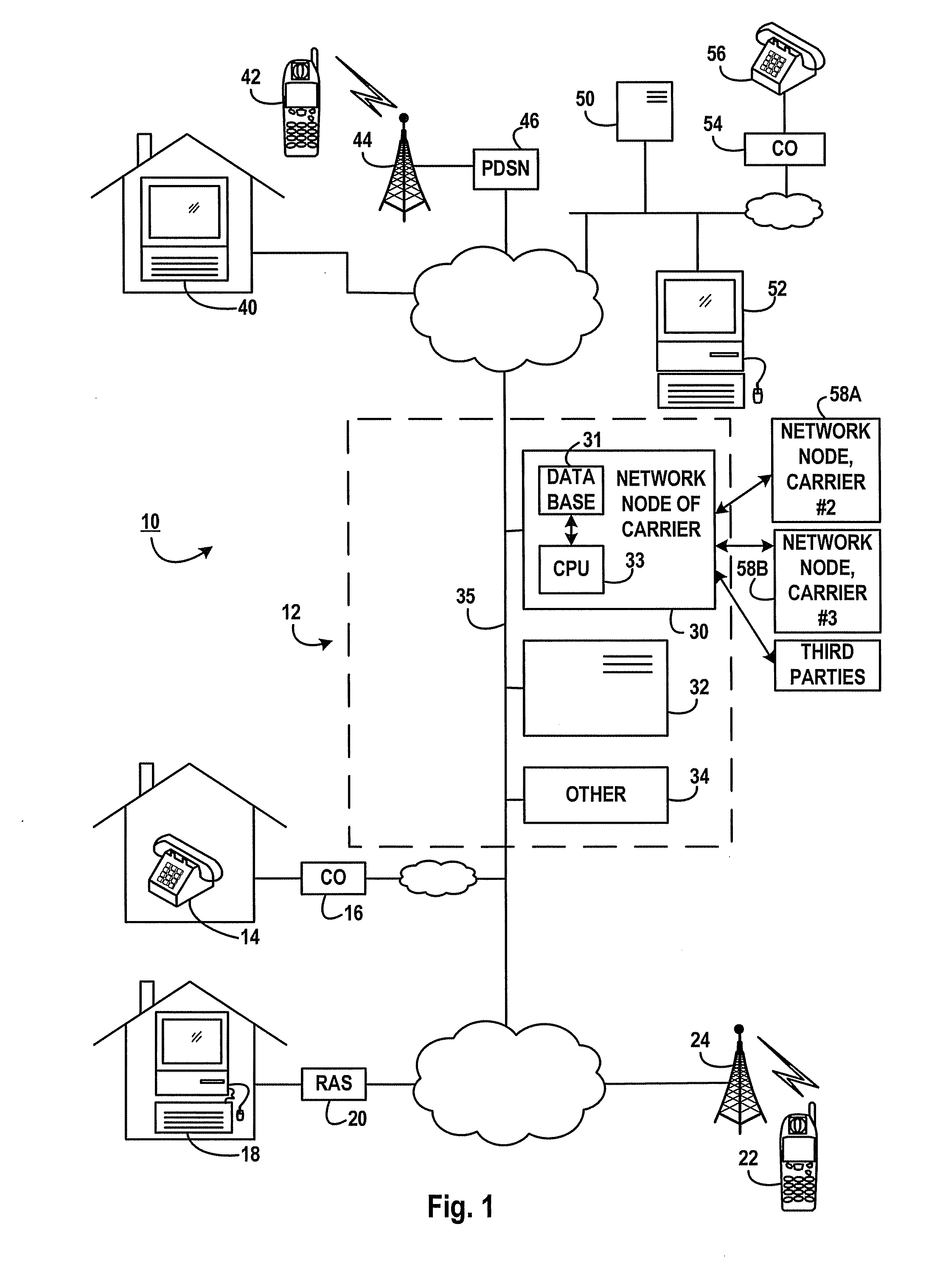
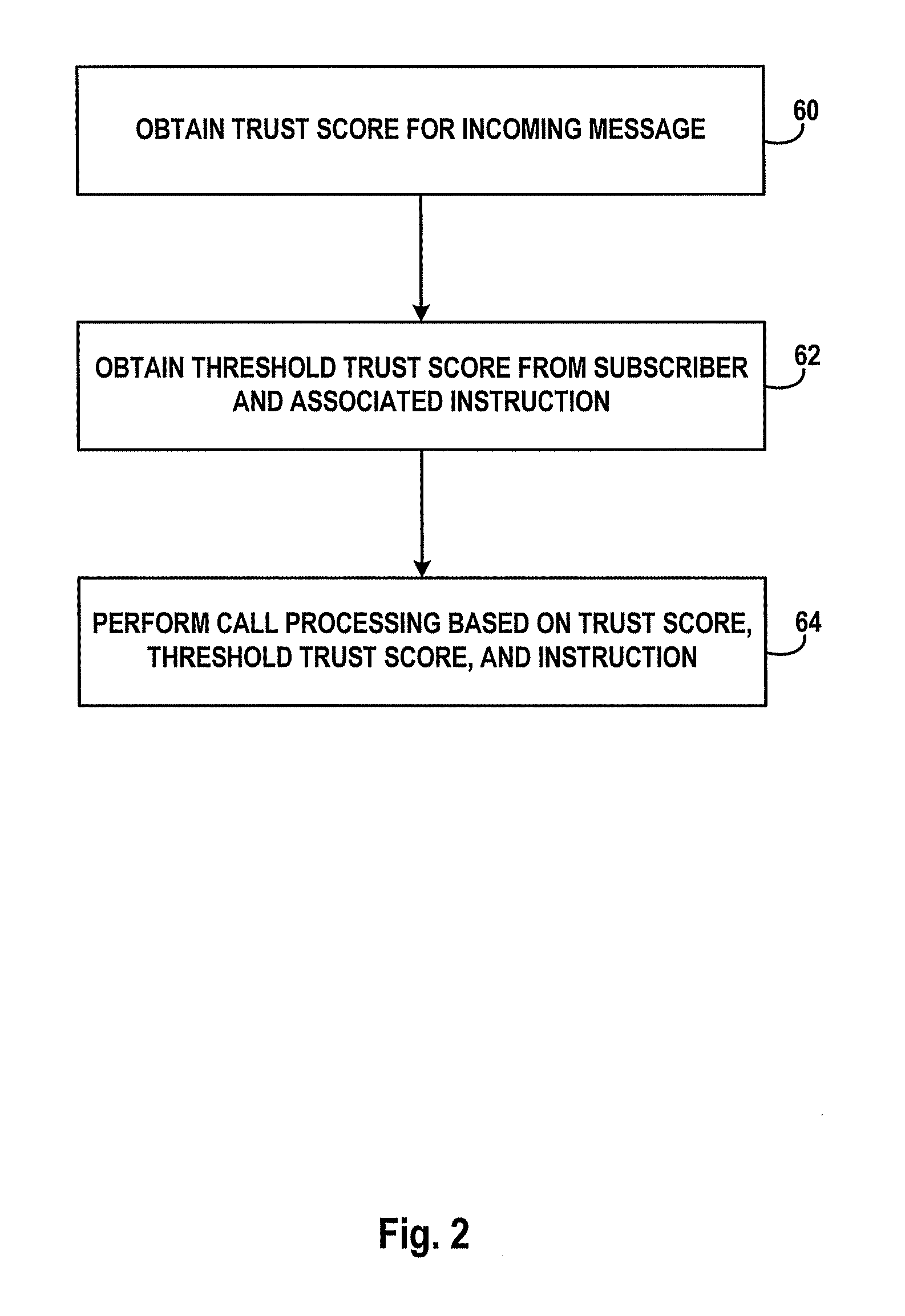
Call processing using trust scores based on messaging patterns of message source
Messaging patterns for a plurality of subscribers are obtained and analyzed to determine a “trust score” that is an indication of the likelihood that a given message for a particular subscriber is of interest, as opposed to unwanted, e.g., spam or telemarketing phone calls. Subscribers establish or set trust score thresholds and call processing actions to take based on the thresholds and the trust score for a given incoming communication. For example, if a subscriber establishes a processing action of “block call” for calls with a “low” threshold trust score, and an incoming message (email, SMS, instant message, or phone call) has a trust score of “low” or “very low”, the message is blocked. Conversely, if the trust score for the message is “high” and the user has specified to pass through “high” trust score messages, the message is passed through. Various algorithms can be used compute trust scores based on messaging patterns.
Owner:SPRINT SPECTRUM LLC
Dynamic pairing system for securing a trusted communication channel
ActiveUS20110313925A1Shorten the time to marketIncrease propensityFinancePayment architectureTotal riskInternet privacy
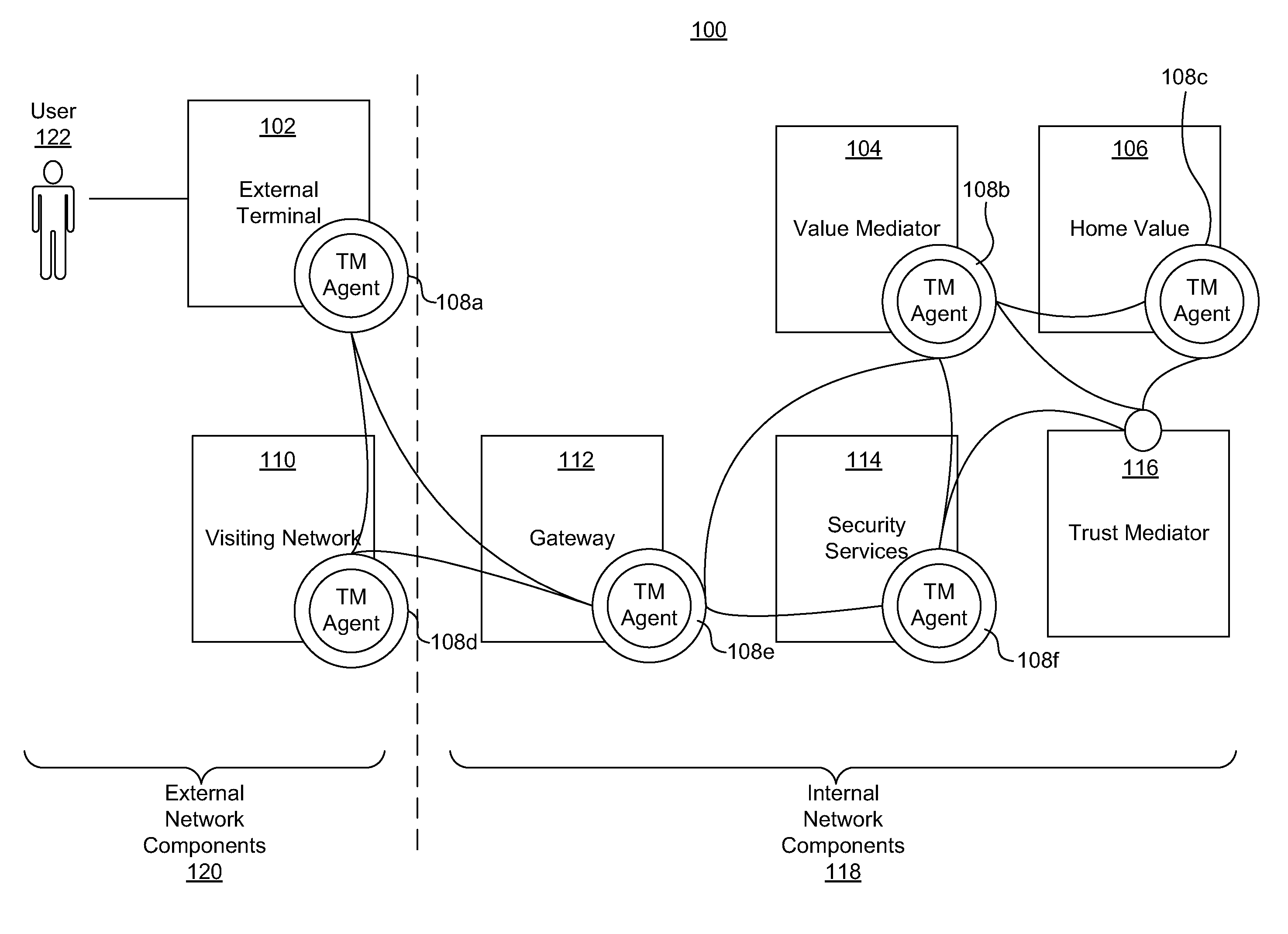
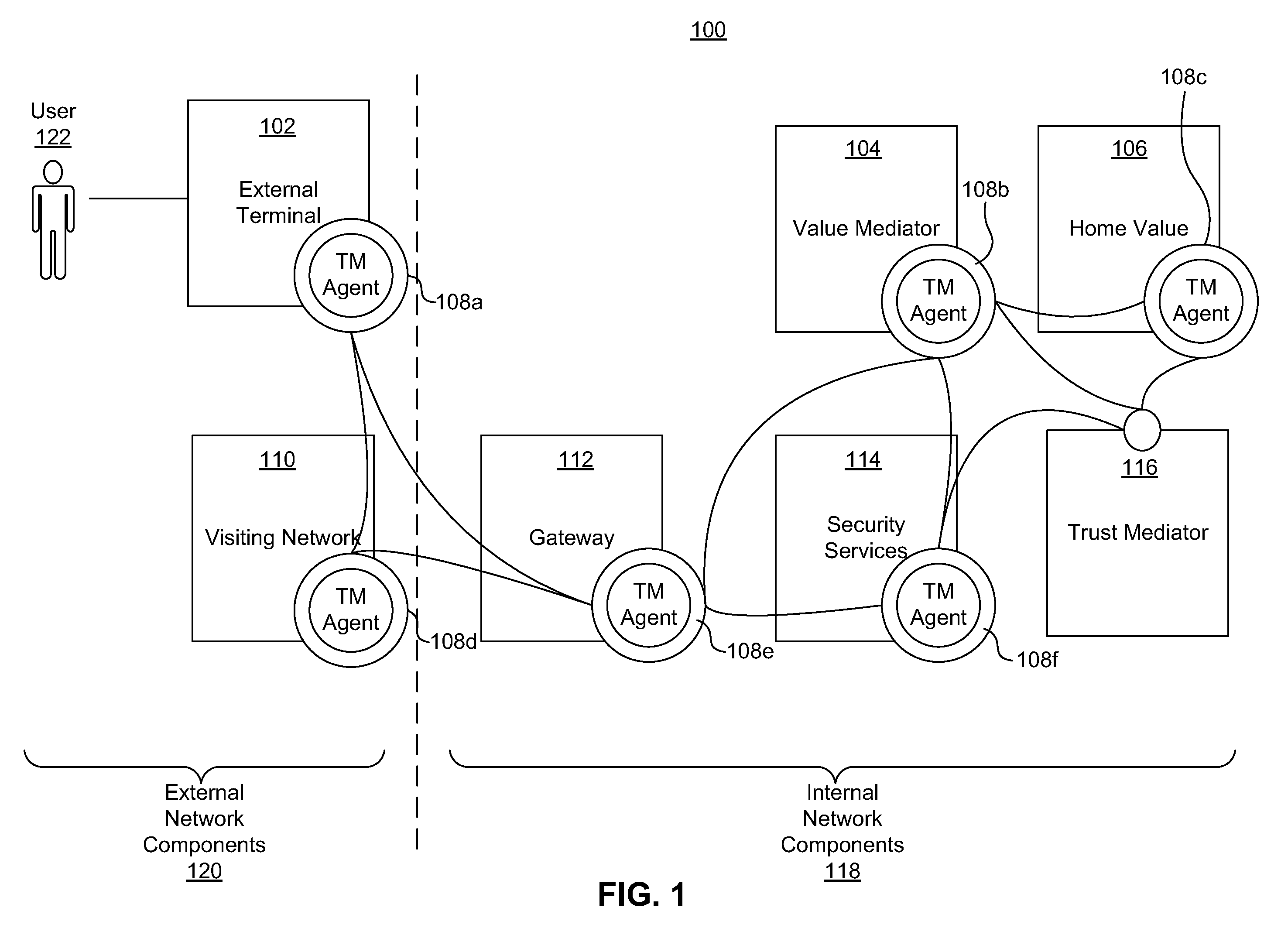
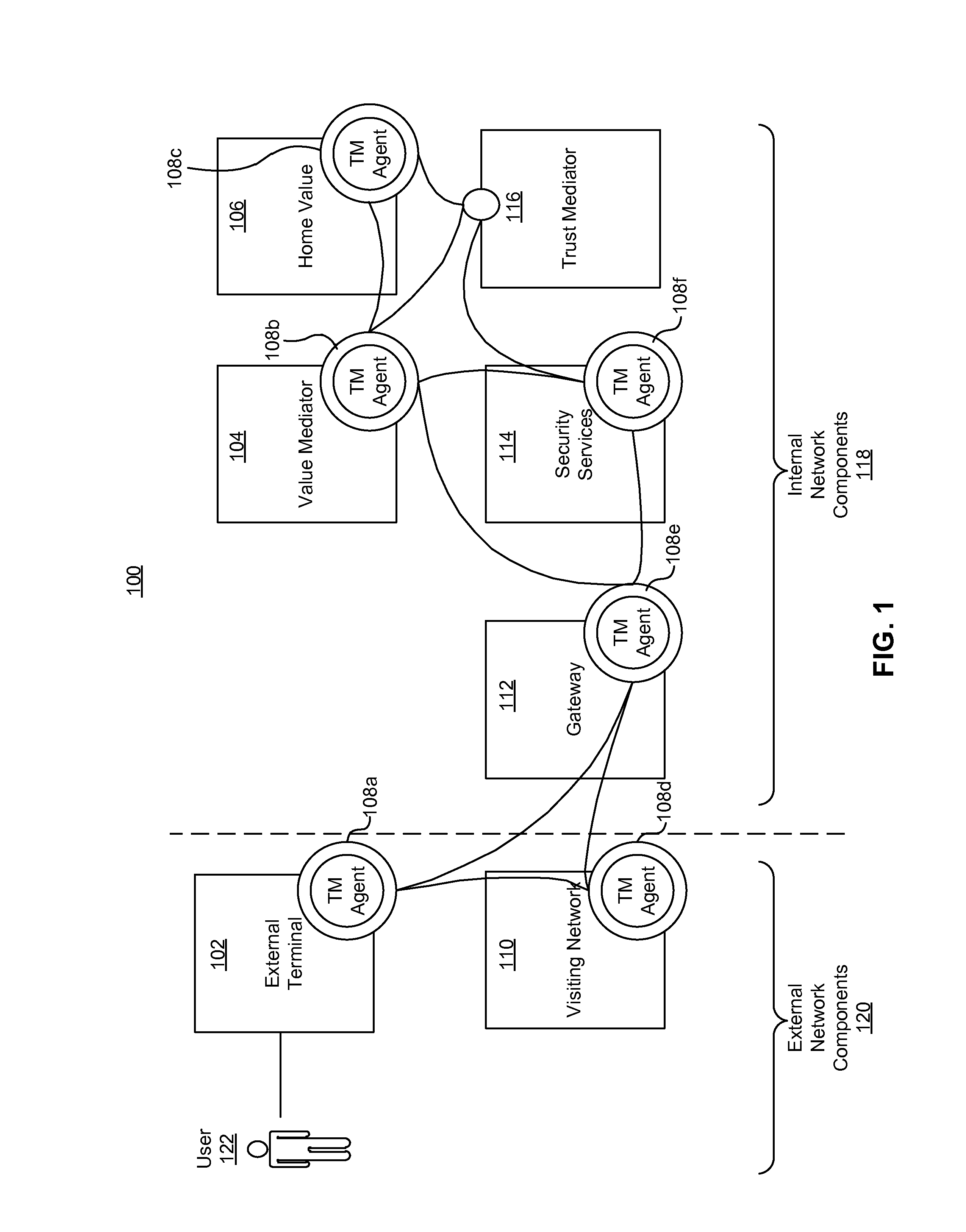
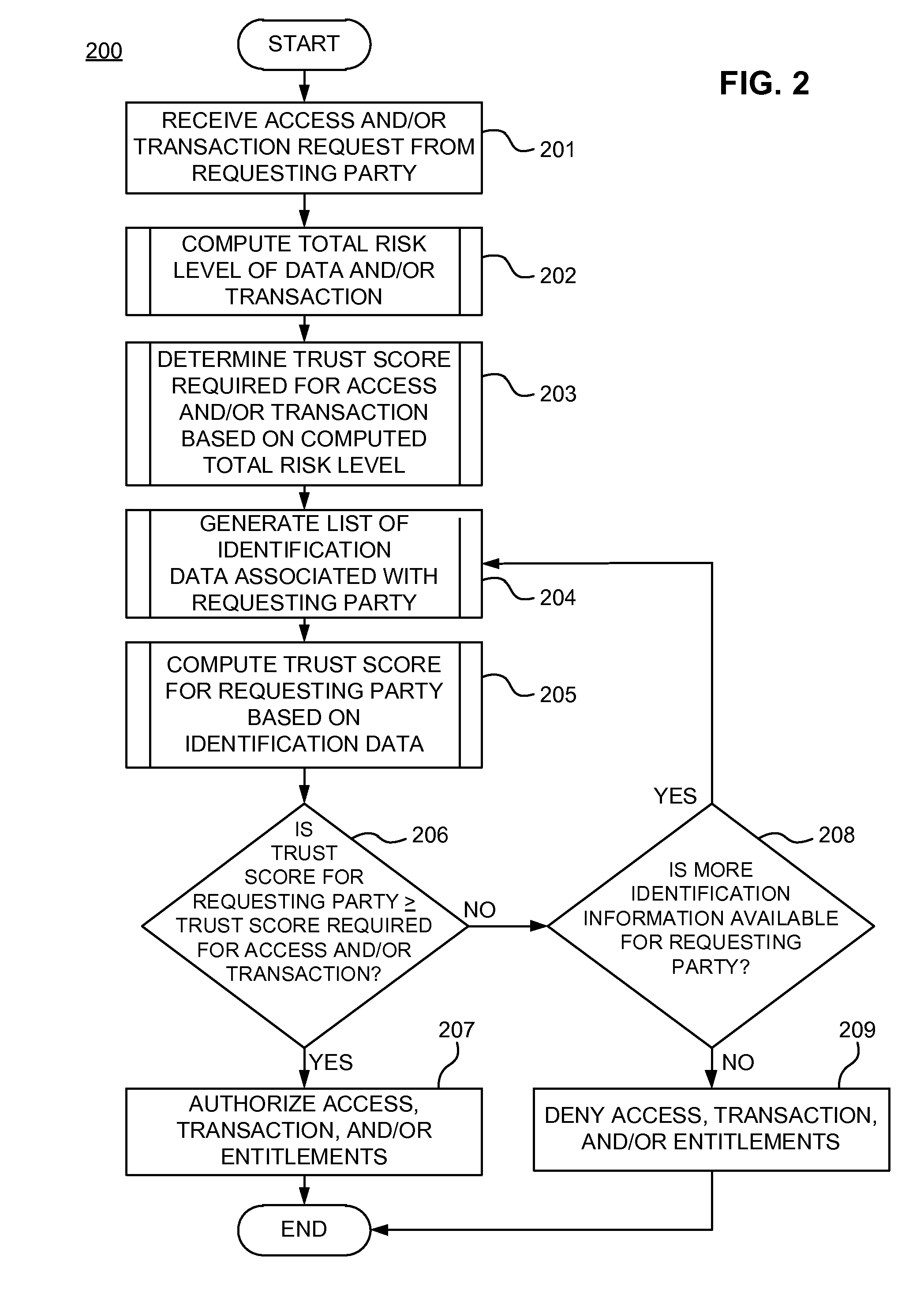
A system for securing a trusted communications channel for a mobile financial transaction is provided by receiving, from a user via an external terminal, a request for an access control entitlement to complete a financial transaction. A total risk level associated with the financial transaction is computed. A required trust score is determined based on the total risk level. User identification data associated with the user is received from one or more data sources. The user identification data is validated. A user trust score associated with the user is computed based on the validated identification data. The user trust score is compared to the required trust score. The access control entitlement is transmitted to the user via the external terminal if the user trust score is greater than or equal to the required trust score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Method and apparatus to establish routes based on the trust scores of routers within an IP routing domain
InactiveUS7733804B2Digital data processing detailsData switching by path configurationComputer hardwareTrust score
A router includes a management module and a routing module. The routing module can be used to route data around a network. The management module can be used to manage the operation of the routing module, including generating an integrity report for the router, which can be used to generate a trust report for the router. The trust report can include an integrity / trust score for the router. The management module can control the routing module via a secure control interface.
Owner:KIP SIGN P1 +1
Method and apparatus to establish routes based on the trust scores of routers within an IP routing domain
InactiveUS20100218236A1Digital data processing detailsComputer security arrangementsComputer hardwareComputer module
A router includes a management module and a routing module. The routing module can be used to route data around a network. The management module can be used to manage the operation of the routing module, including generating an integrity report for the router, which can be used to generate a trust report for the router. The trust report can include an integrity / trust score for the router. The management module can control the routing module via a secure control interface.
Owner:KIP SIGN P1
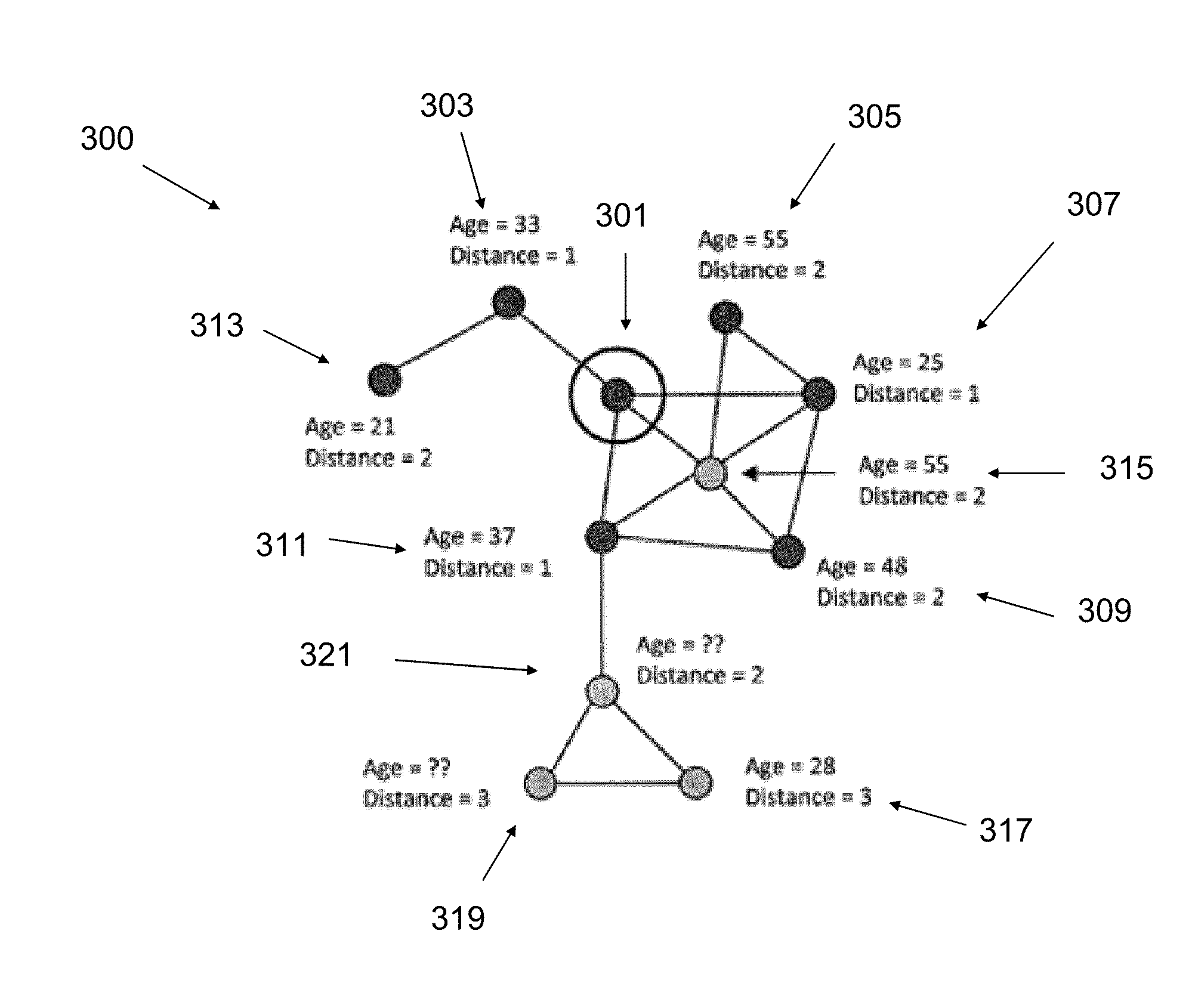
Social network risk analysis
An enhanced social network module associated with an entity may create a social network for an individual, group, and / or organization. The module may then use the social network to determine risk associated with insuring a member of the social network. The determined risk may be used to calculate a rate for insuring the member. Additional features of the module may allow for the calculation of a group rate for insuring all members of the social network, the calculation of various centrality measures for each member of the social network, the calculation of a trust score for any given member, and the ability to poll members of the social network to determine various characteristics of any given member.
Owner:ALLSTATE INSURANCE
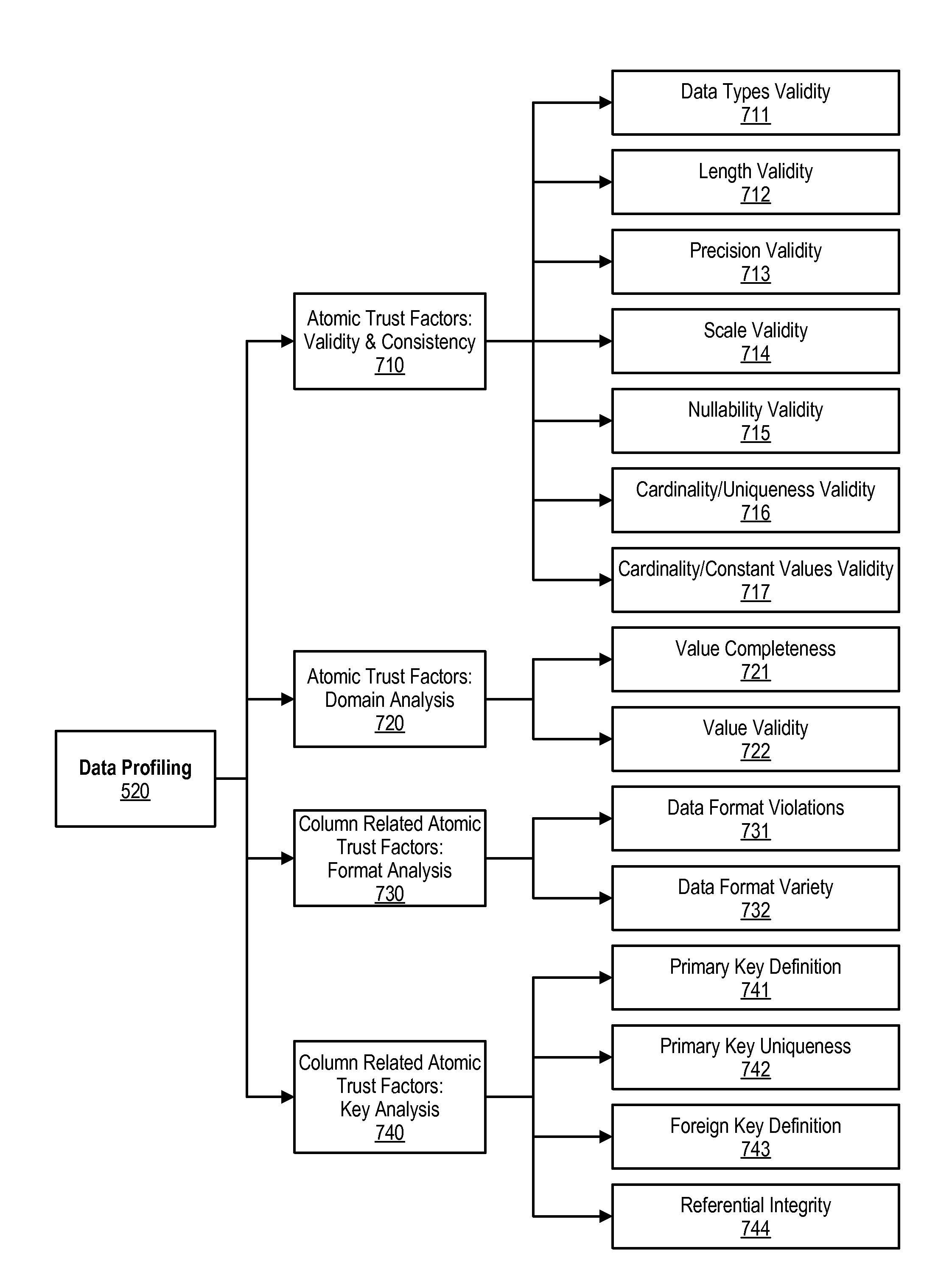
Generating Composite Trust Value Scores Based on Assignable Priorities, Atomic Metadata Values and Associated Composite Trust Value Scores
An approach is provided in which atomic trust scores are computed using a atomic trust factors that are applied to a plurality of metadata. A first set of composite trust scores are computed using some of the atomic trust scores. The composite trust scores are computed using a first set of algorithms. Some of the algorithms use a factor weighting value as input to the algorithm. A second plurality of composite trust scores is computed using some of the composite trust scores that were included in the first set of scores as input. A fact and one of the second set of composite trust scores are presented to a user. The presented composite trust score provides a trustworthiness value that corresponds to the presented fact.
Owner:IBM CORP
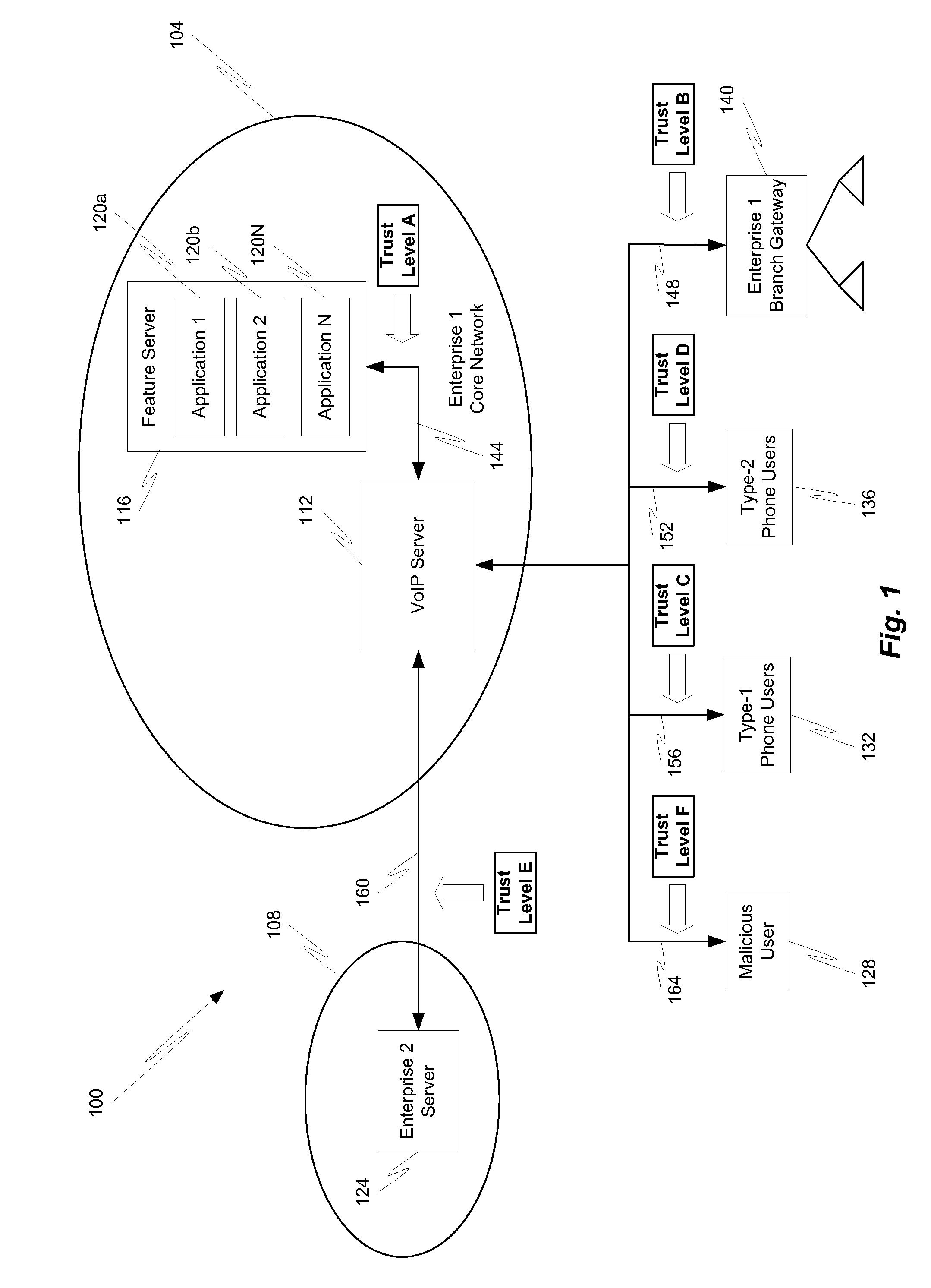
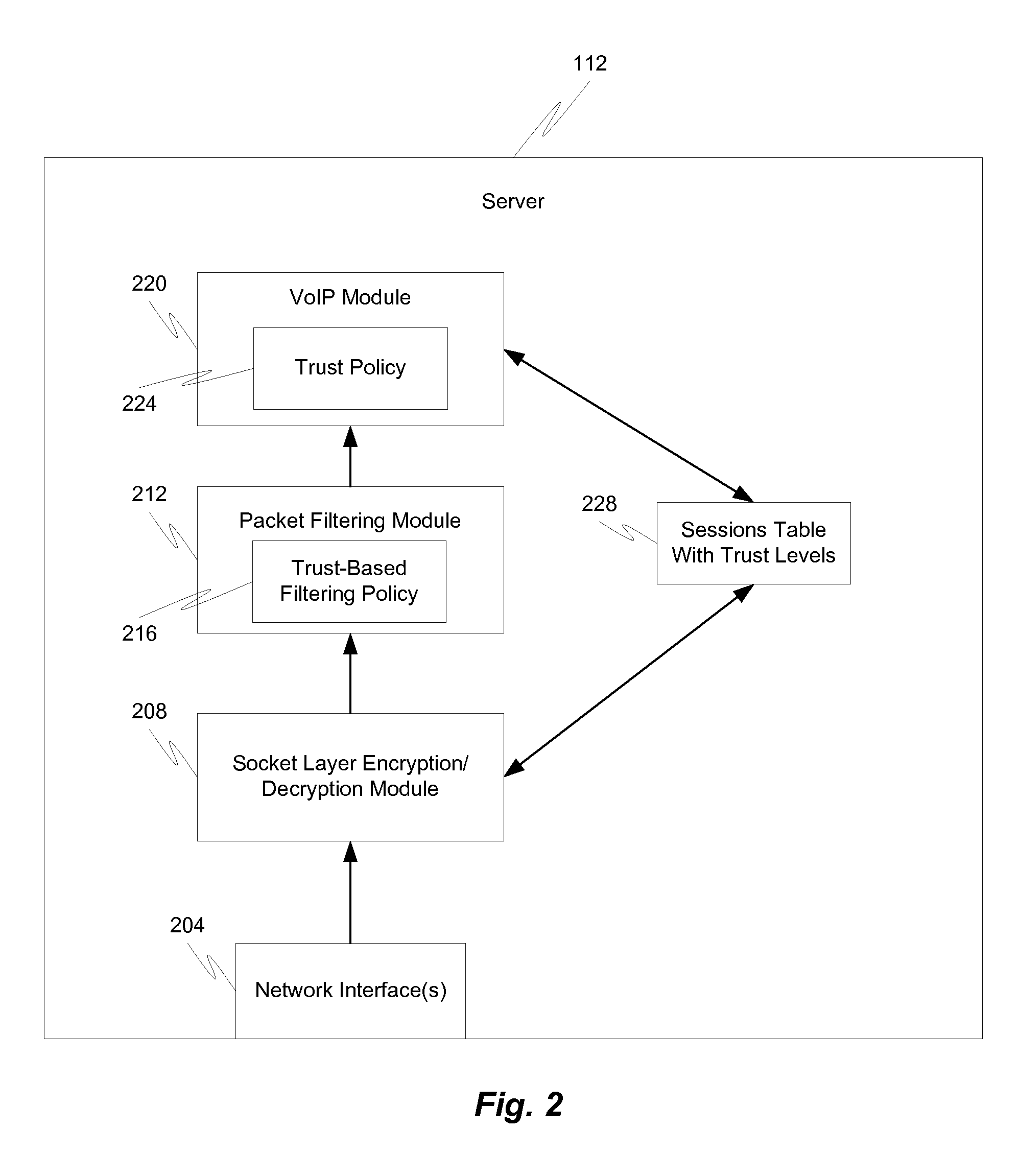
Trust based application filtering
ActiveUS20110072508A1Easy to implementGood flexibilityMultiple digital computer combinationsProgram controlComputer networkFiltering rules
Methods, devices, and systems are provided for filtering packets and other communication messages or portions thereof. Particularly, mechanisms are provided for efficiently determining and applying a set of trust-based filtering rules. Trust scores may be assigned to various connections and packets received on a particular connection may have filtering rules applied thereto in accordance with the trust score of the connection.
Owner:AVAYA INC
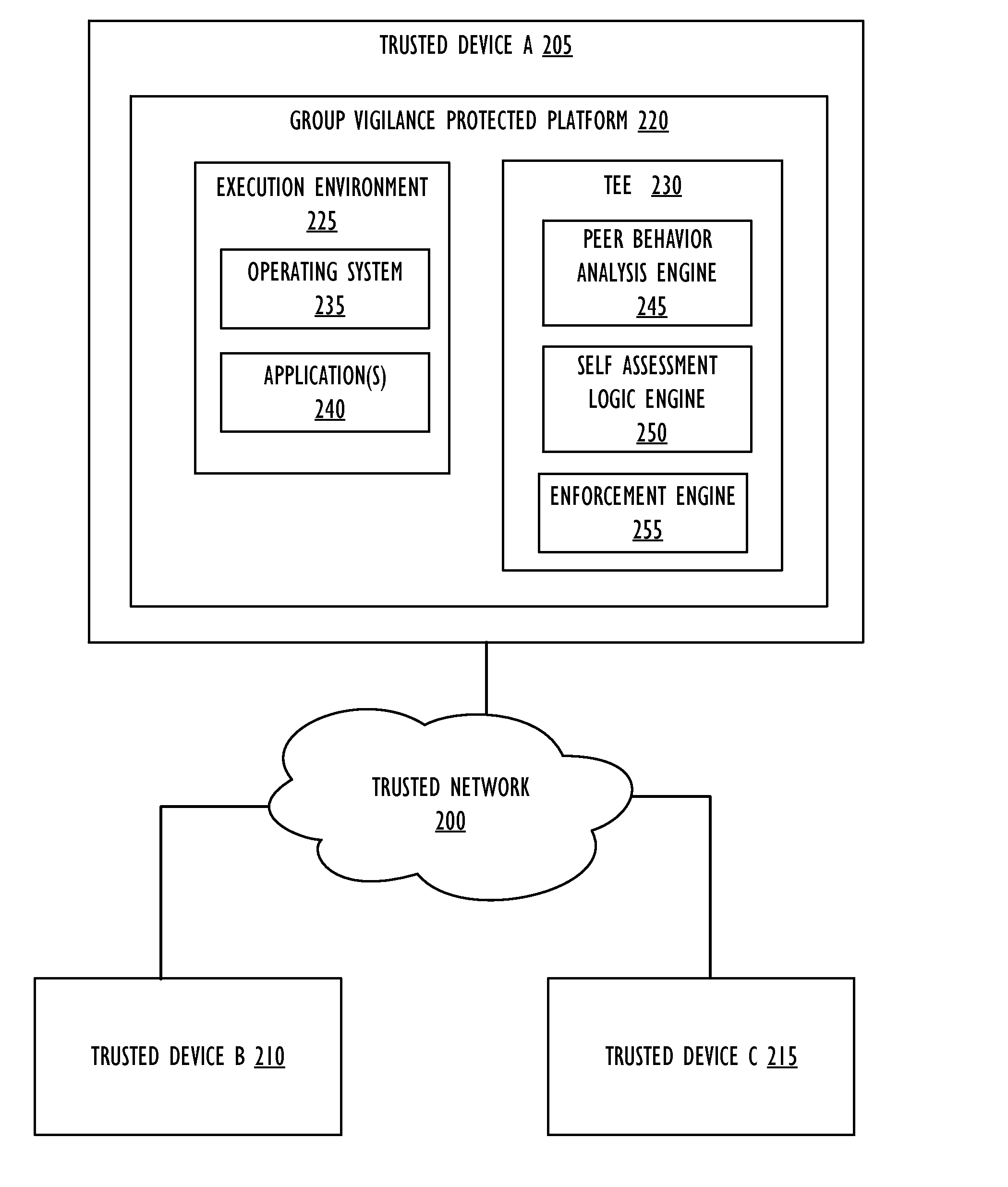
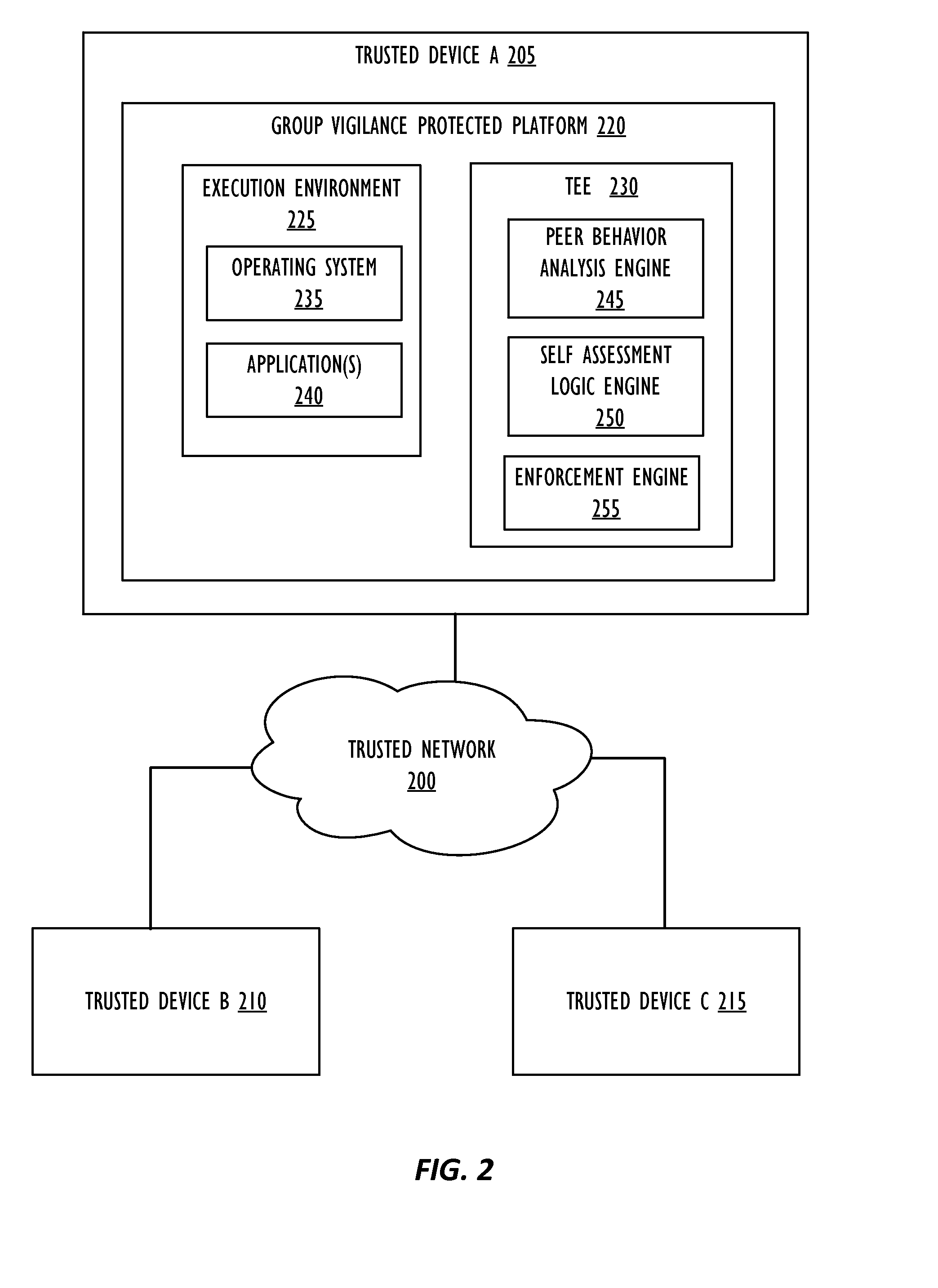
Peer-to-Peer Group Vigilance
ActiveUS20160381079A1Digital data processing detailsAnalogue secracy/subscription systemsTrust scorePeer-to-peer
Providing peer-to-peer network security includes collecting, by a local trusted network device, local trust data related to behavior of the local trusted network device, receiving, by one or more remote trusted network devices, additional trust data for the local trusted network device, calculating a combined trust score for the local trusted network device based on the local trust data and additional trust data, and modifying activity of the local trusted network device based on the combined trust score.
Owner:MCAFEE LLC
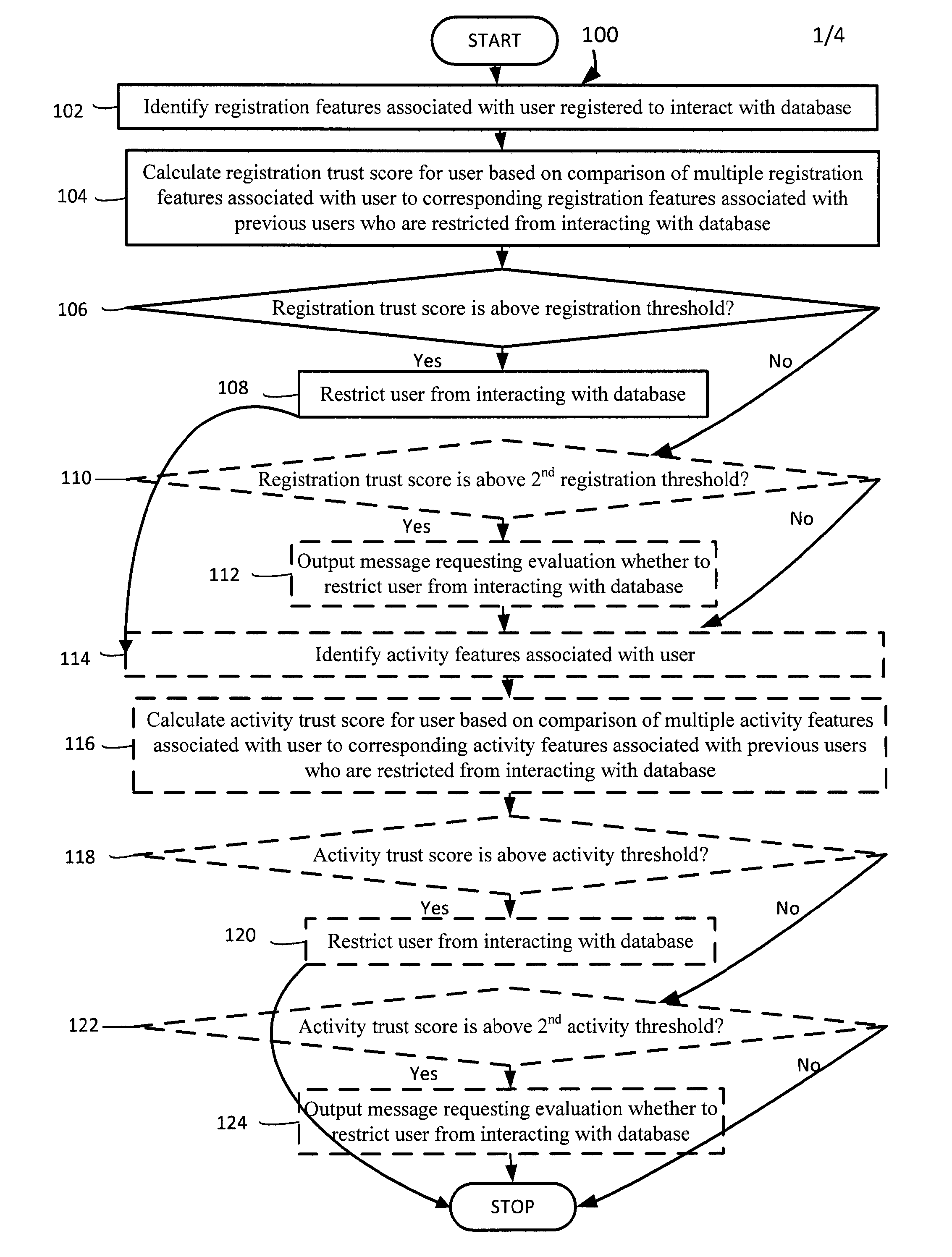
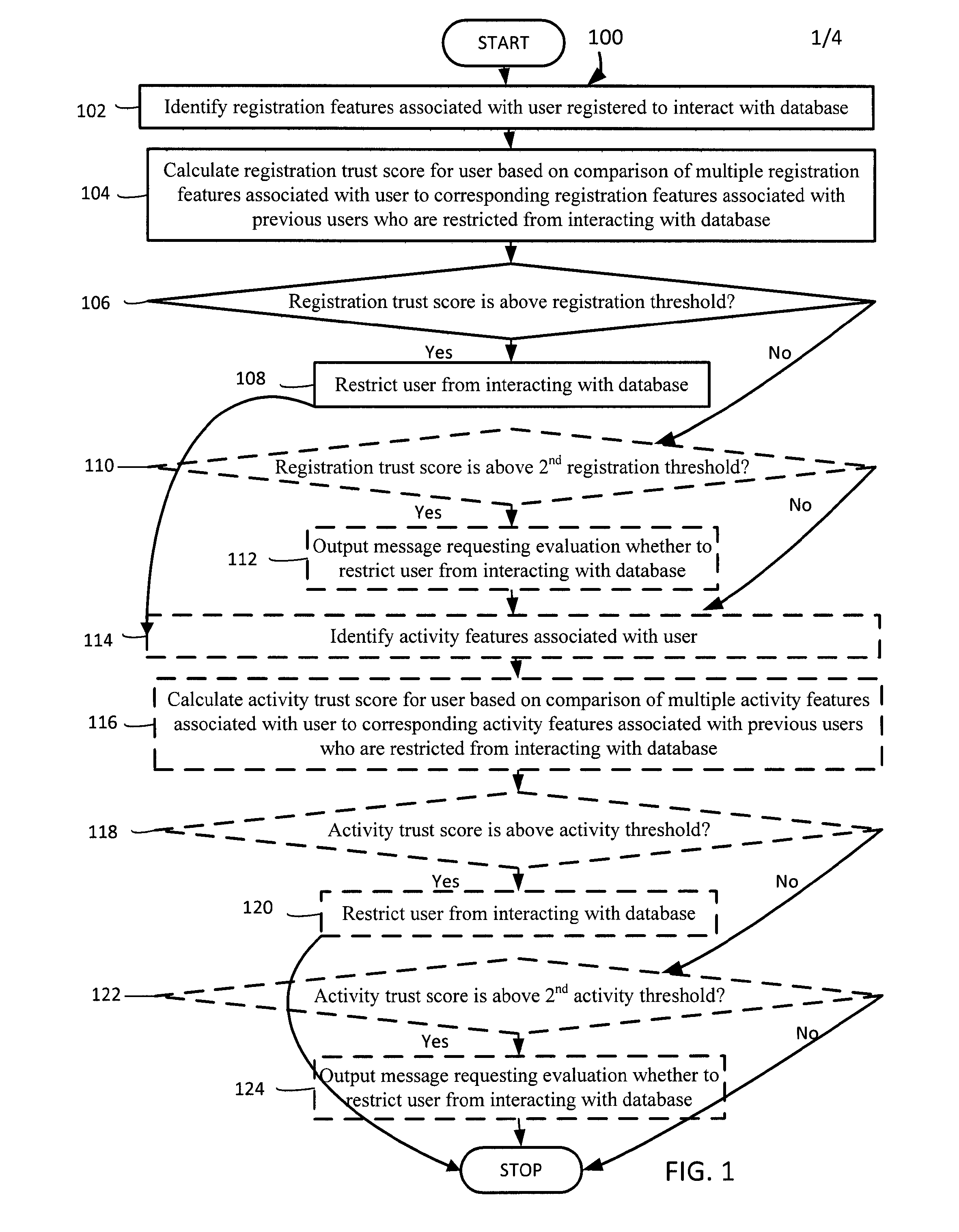
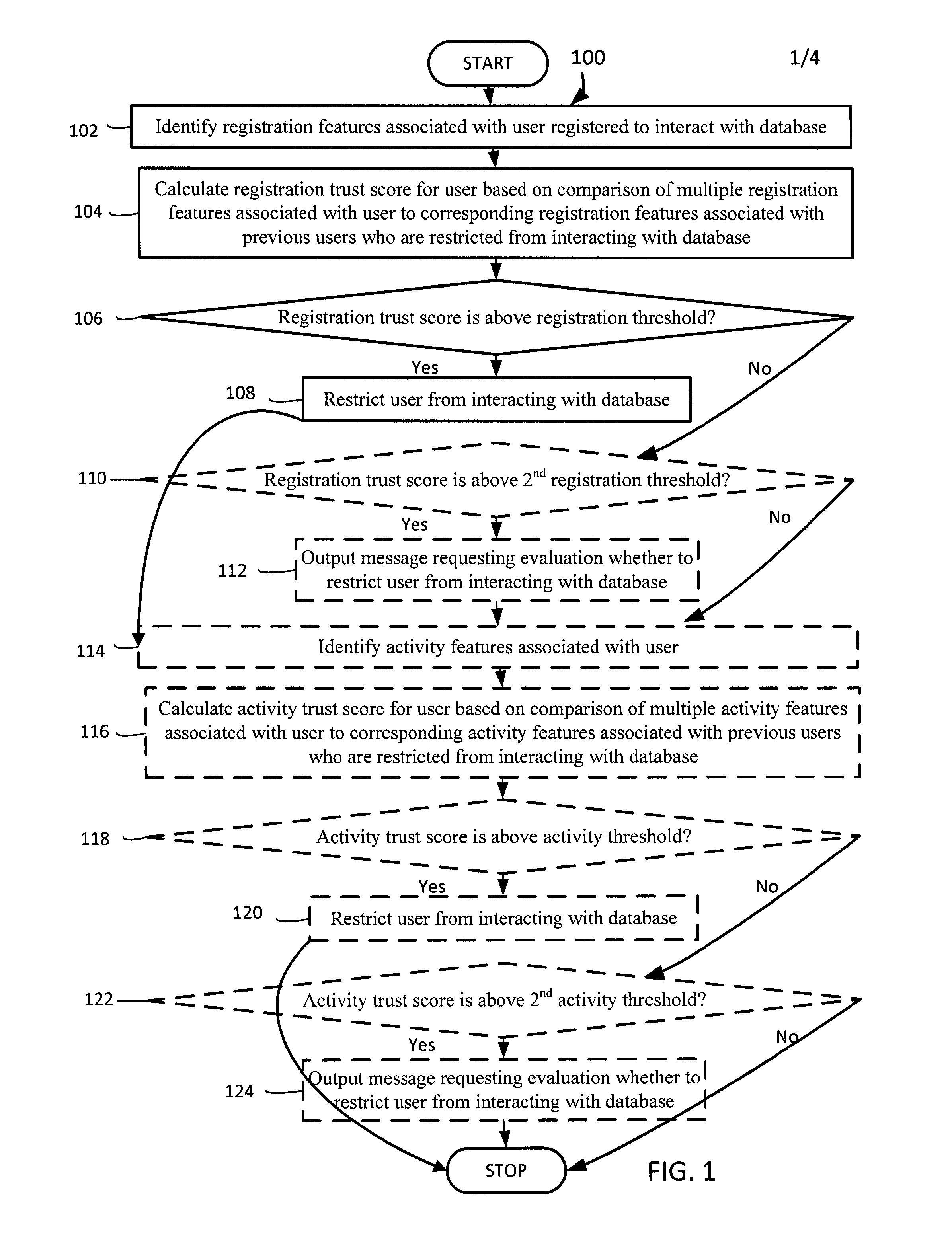
User trust scores based on registration features
InactiveUS20160140355A1Not addressDigital data processing detailsDigital data protectionSystem identificationTrust score
User trust scores based on registration features is described. A system identifies registration features associated with a user registered to interact with a database. The system calculates a registration trust score for the user based on a comparison of multiple registration features associated with the user to corresponding registration features associated with previous users who are restricted from interacting with the database and / or corresponding registration features associated with previous users who are enabled to interact with the database. The system restricts the user from interacting with the database if the registration trust score is above a registration threshold.
Owner:SALESFORCE COM INC
Method to control access between network endpoints based on trust scores calculated from information system component analysis
InactiveUS20060117184A1Digital data processing detailsUser identity/authority verificationData miningTrust score
Signatures are generated for modules in a computer system. The signatures can be assembled into an integrity log. The signatures are compared with signatures in a database in an integrity validator. Once signatures are either validated or invalidated, a trust score can be generated. The trust score can then be used to determine whether the computer system should be granted access to a resource using a policy.
Owner:SILICON VALLEY BANK +1
Dynamic pairing system for securing a trusted communication channel
ActiveUS20140379581A1Shorten the time to marketIncrease propensityFinanceProtocol authorisationRisk levelComputer network
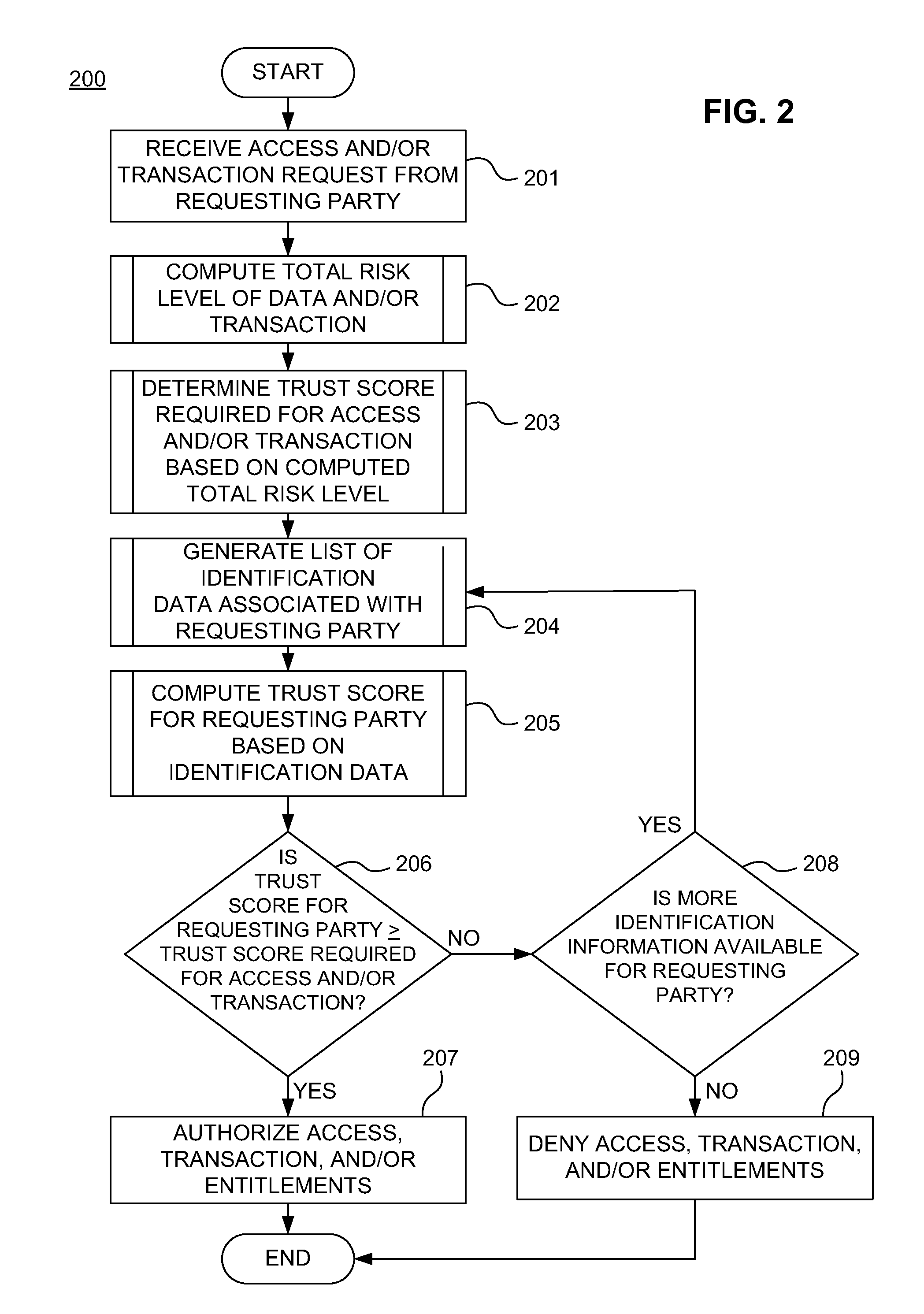
A system, method, and computer-readable medium for securing a mobile financial transaction are provided. A table matches each one of a plurality of transaction risk levels to a corresponding one of a plurality of required user trust scores, correspondingly. A financial transaction risk level associated with a financial transaction is computed. A user trust score associated with the user is computed based on user identification data associated with the user. The financial transaction risk level is matched to a corresponding one of the plurality of transaction risk levels stored in the table. The one of the plurality of required trust scores that corresponds to the corresponding one of the plurality of transaction risk levels stored in the table is identified. If the user trust score is greater than or equal to the identified one of the plurality of required trust scores, then the financial transaction is authorized.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
Trust modeling
ActiveUS9154491B1Data processing applicationsDigital data processing detailsInternet privacyTrust level
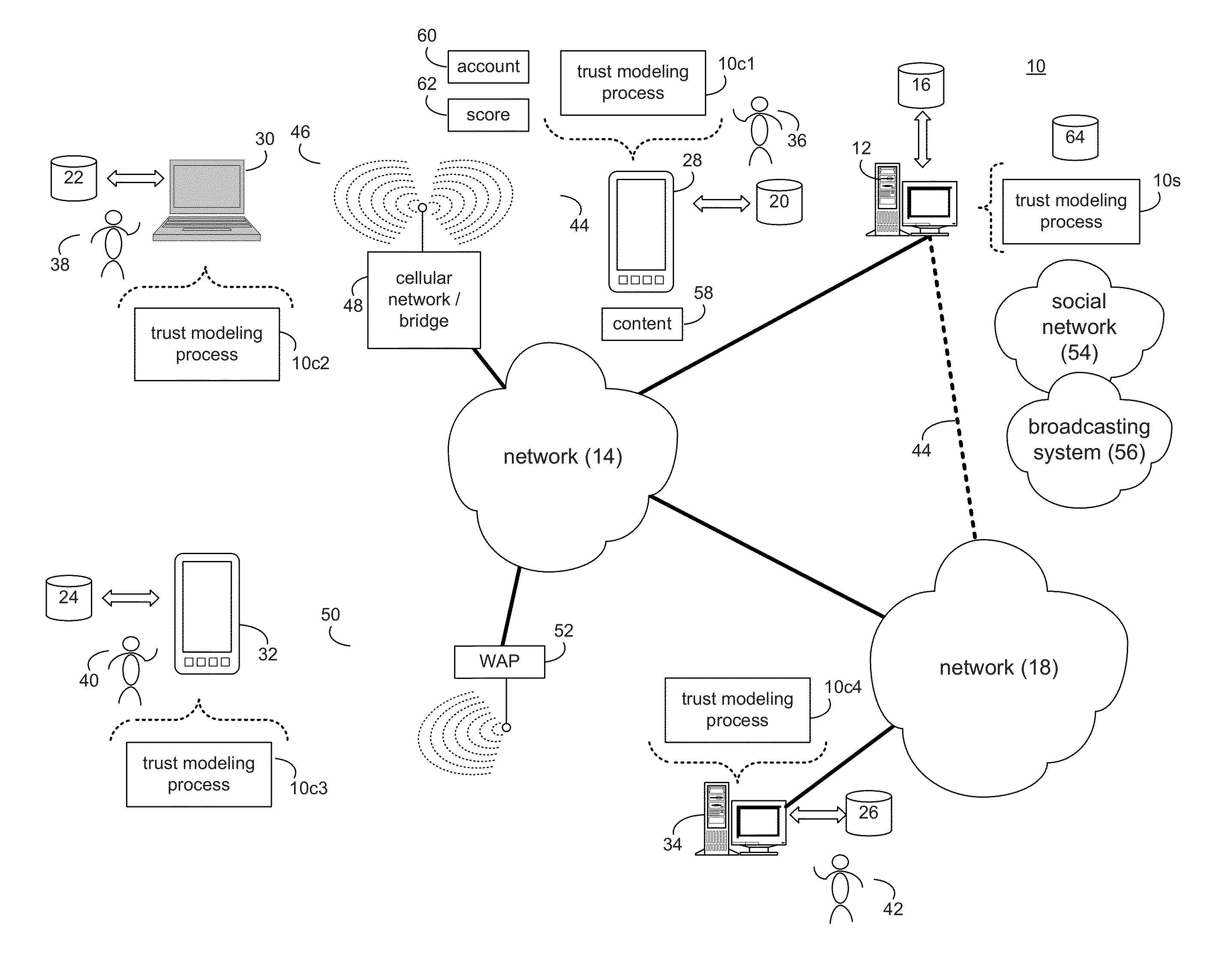
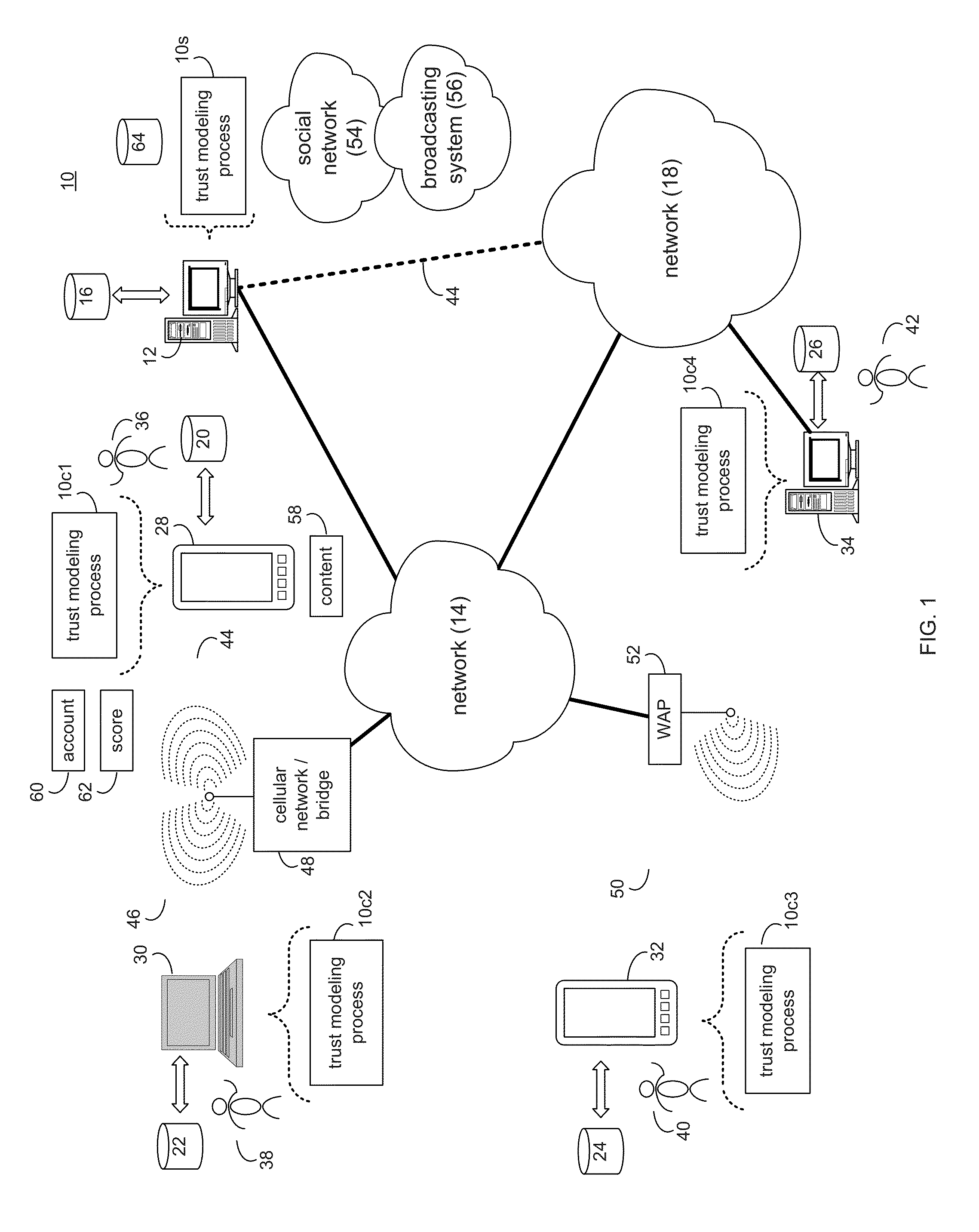
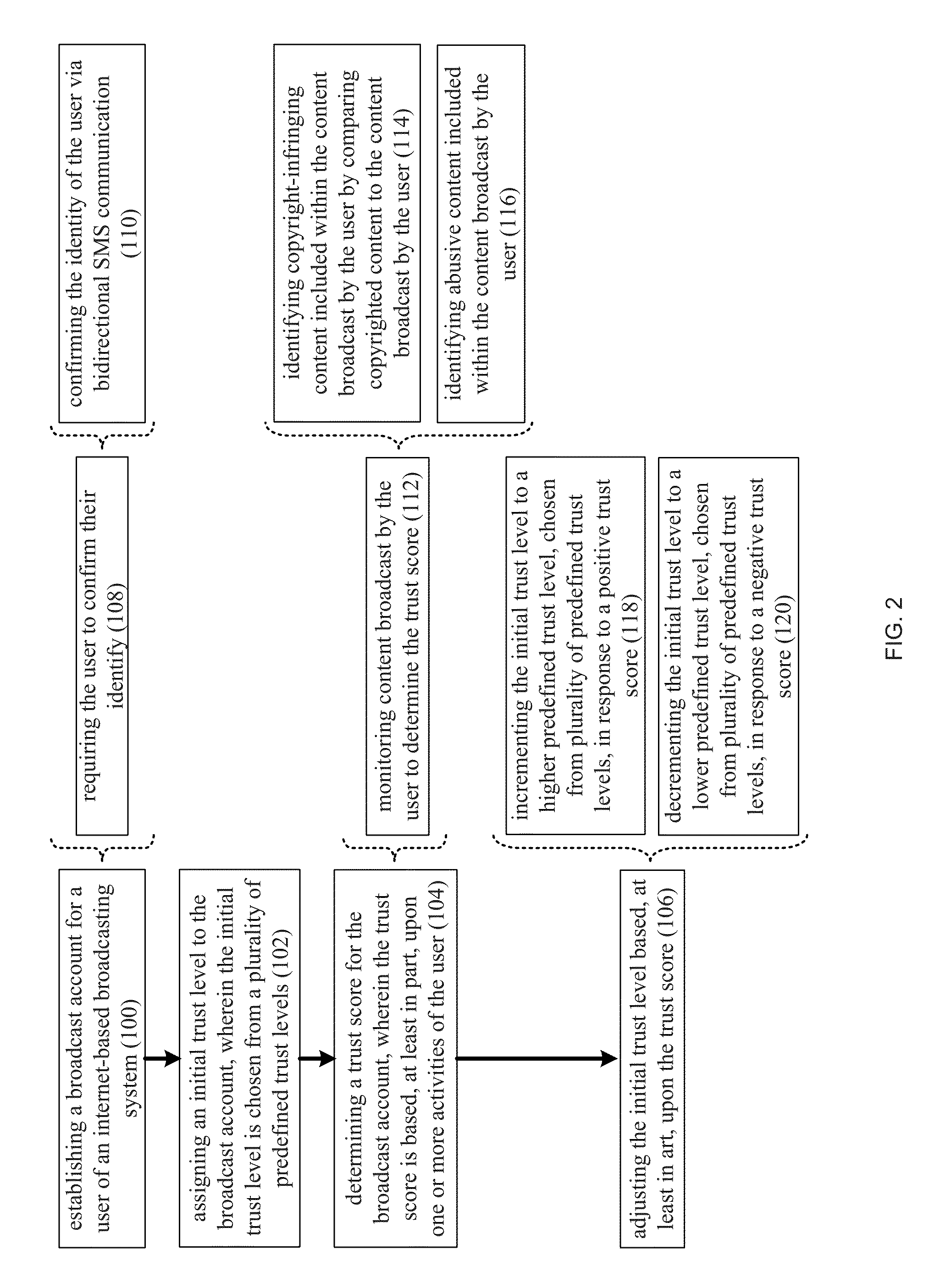
A method and computing system for establishing a broadcast account for a user of an internet-based broadcasting system. An initial trust level is assigned to the broadcast account. The initial trust level is chosen from a plurality of predefined trust levels. A trust score is determined for the broadcast account. The trust score is based, at least in part, upon one or more activities of the user. The initial trust level is adjusted based, at least in art, upon the trust score.
Owner:GOOGLE LLC
Calculating trust scores based on social graph statistics
ActiveUS9264329B2Network traffic/resource managementMultiple digital computer combinationsSocial graphTrust score
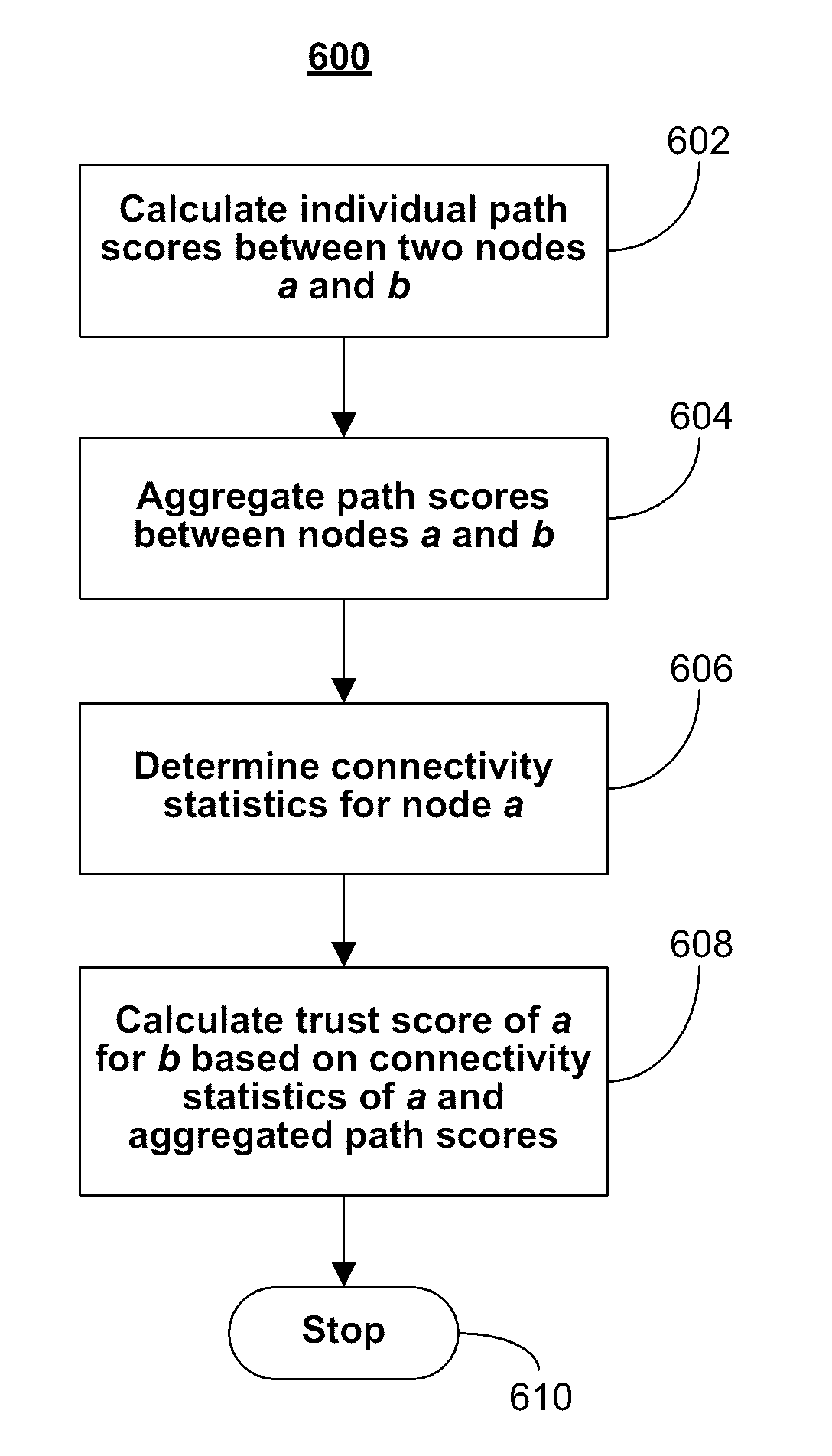
Systems and methods for calculating trust scores (trustworthiness) based on social graph statistics are described herein. The trust scores (trustworthiness) may be determined within or between individuals, groups, and / or entities represented by nodes in a social graph or other network. Social graph analytics may be used to determine connectivity statistics for each node in the social graph or network. The trust score may then be calculated by analyzing a number of paths connecting nodes in the network and the connectivity statistics associated with the nodes of the network. This trust score may then be used to make prospective real-world decisions, such as a request for credit or initiating a transaction.
Owner:WWW TRUSTSCI COM INC
Location based trusted computing nodes in a cloud computing architecture
ActiveUS20170155662A1Increase the scope of applicationExpand the scope ofSatellite radio beaconingCoding/ciphering apparatusTrusted ComputingProcessing element
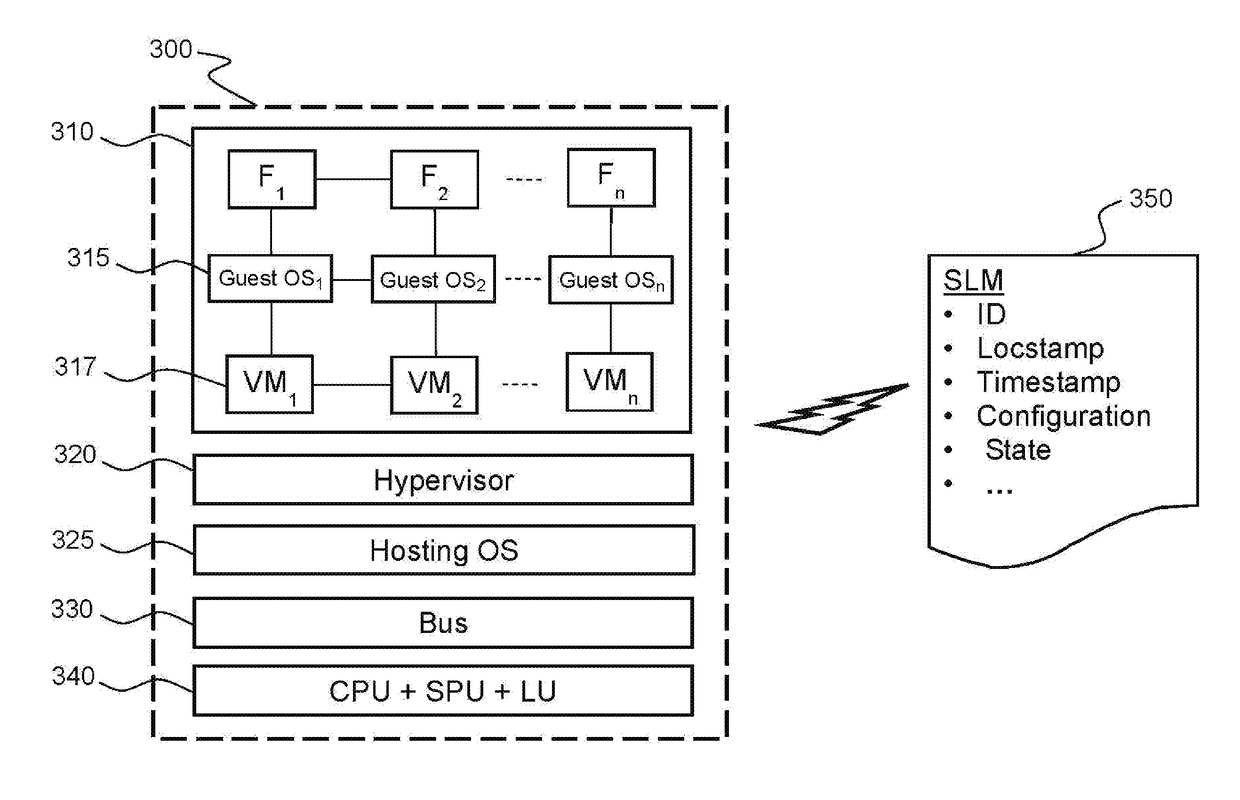
The invention discloses trusted computing nodes (TCNs) configured to control their location and migration of applications run on virtual machines resident thereon. The invention allows a controlled use of cloud computing resources and virtual network functions by sensitive applications. This is achieved by embedding a secure processing unit (SPU) and a localization unit (LU) in the TCNs. The LU acquires GNSS signals and the TCN generates a secure location message comprising a secure ID and a locstamp of the TCN. A TCN Registry may be created by an operator of a collection of TCNs as a database of trust scores of the trusted computing nodes which will be used to control the allocation of tasks to said TCNs based, at least in part; on the trust scores. The trust scores may also be used directly by the other TCNs to allocate the tasks which they have control on.
Owner:CENT NAT DE LA RECHERCHE SCI
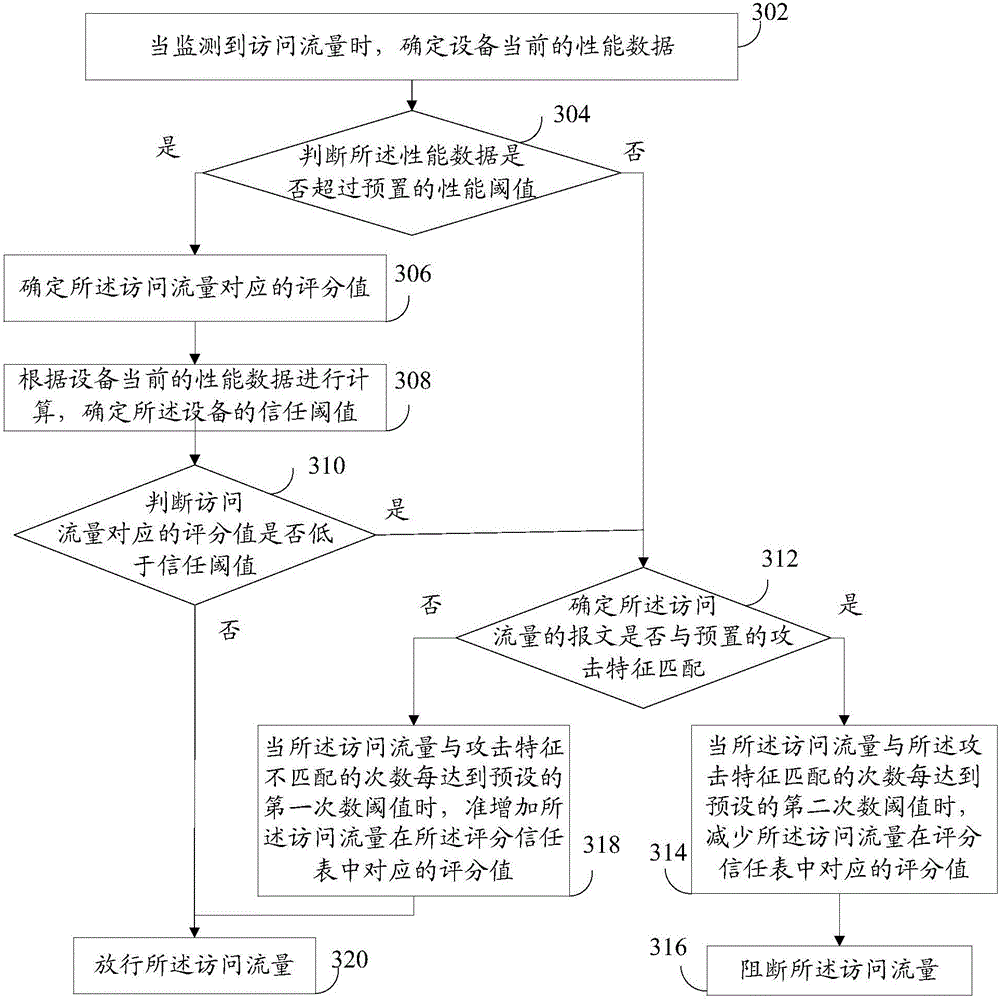
Attack defense method and device
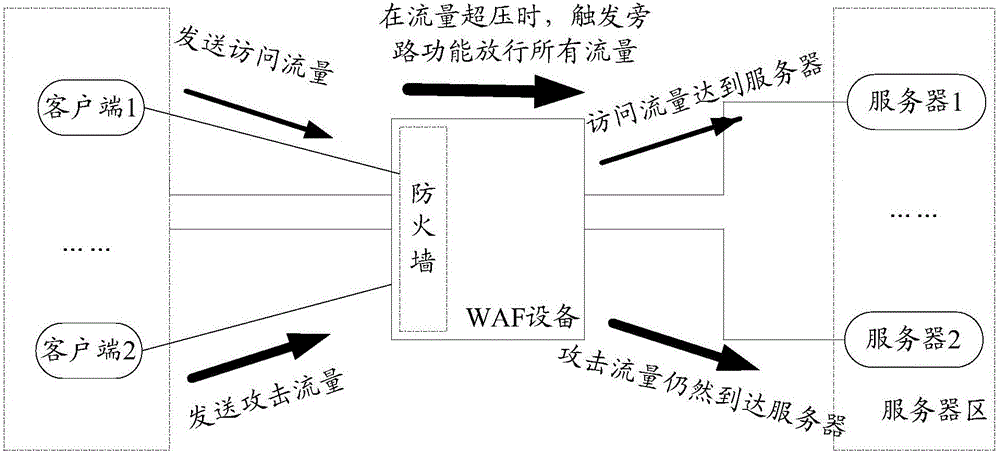
The embodiment of the invention provides an attack defense method and device, and the method comprises the steps: when access flow is monitored, the performance state of equipment is determined; when the performance state is a target state, a score value corresponding to the access flow is determined; calculation is performed according to the present performance data, and a trust threshold value of the equipment is determined; when the score value is lower than the trust threshold value, whether the access flow matches with a preset attack characteristic is determined; and when the access flow matches with the attack characteristic, the access flow is cut. According to the embodiment, a trust score function of WAF equipment is triggered under a flow excess pressure state, whether the score value corresponding to the access flow is lower than the trust threshold value is judged to determine if the access flow needs to be subjected to a deep attack detection, so that attack flow can be detected and intercepted, safety of web server can be ensured, which means, the protecting effect is reached.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com