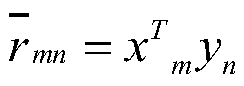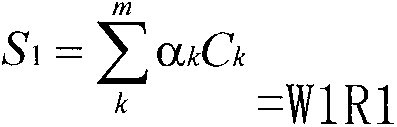Patents
Literature
59 results about "Trust factor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
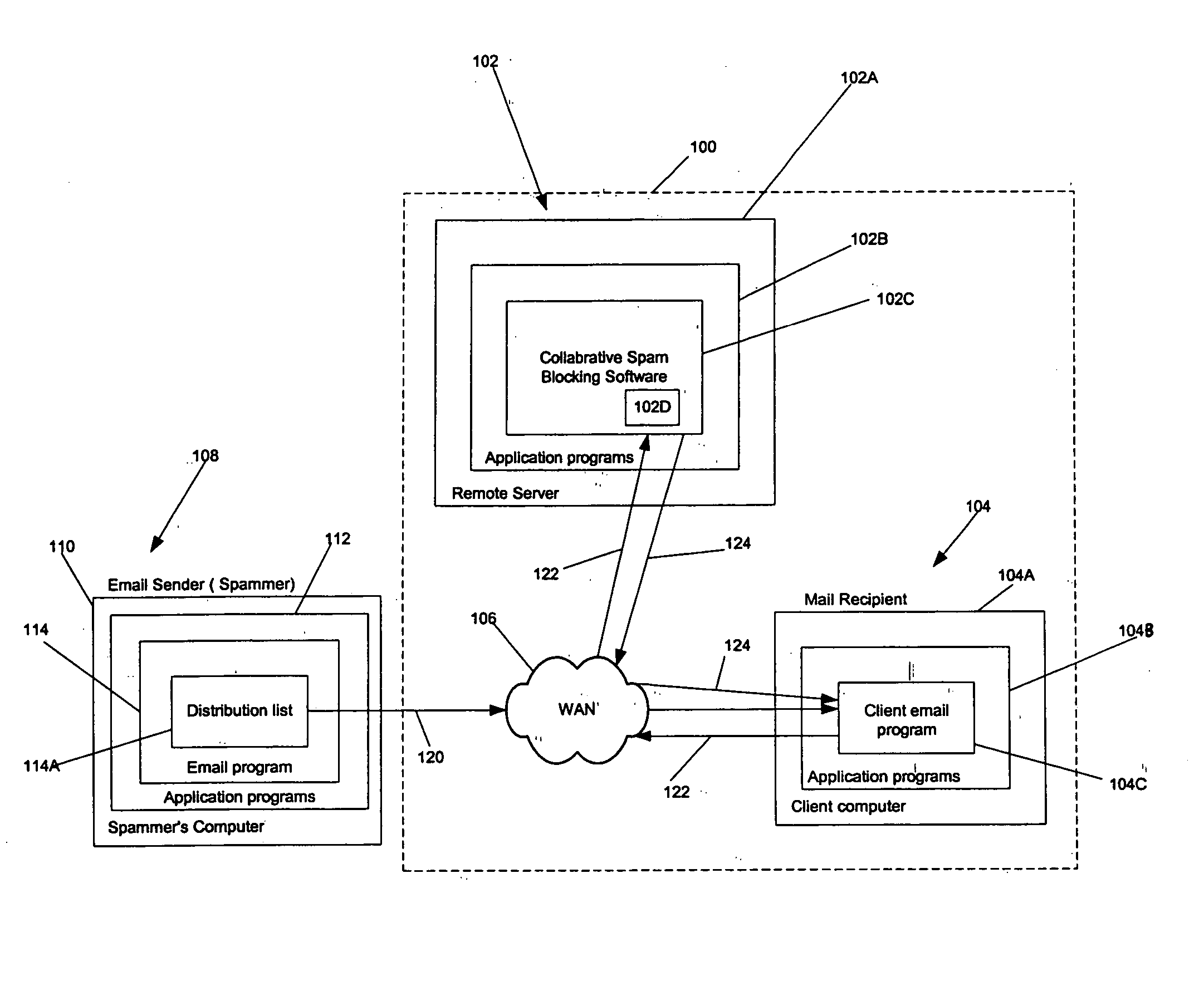
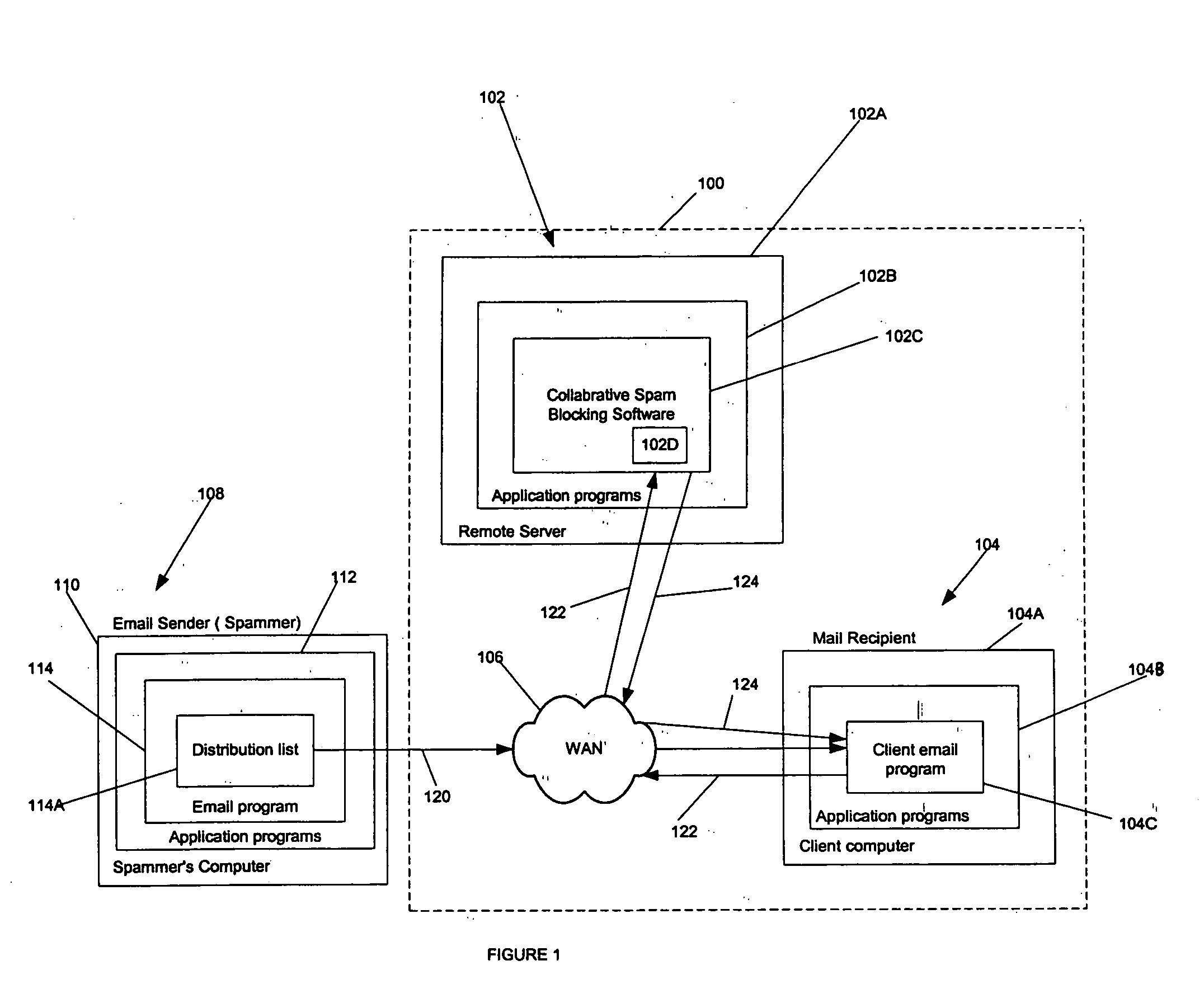
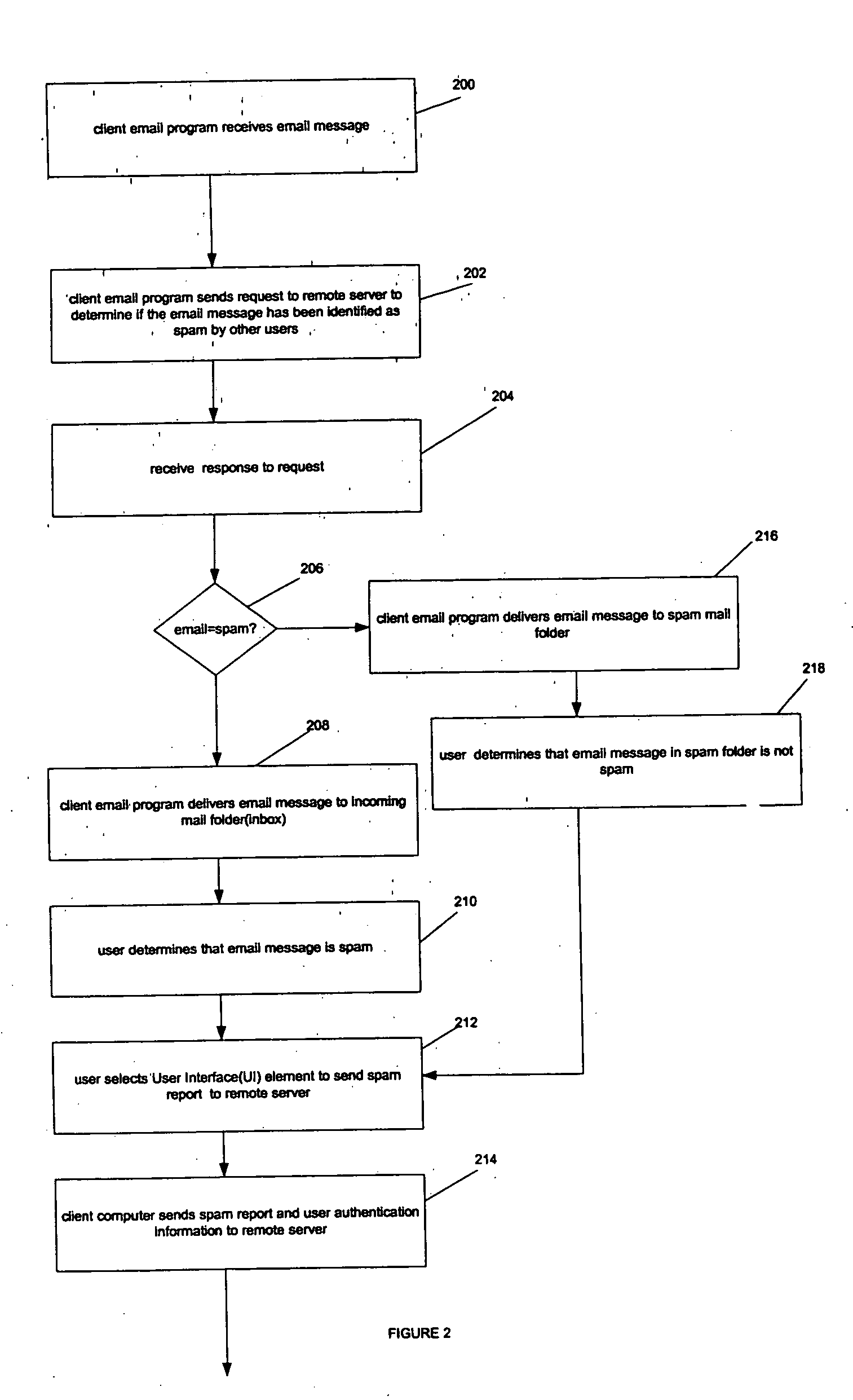
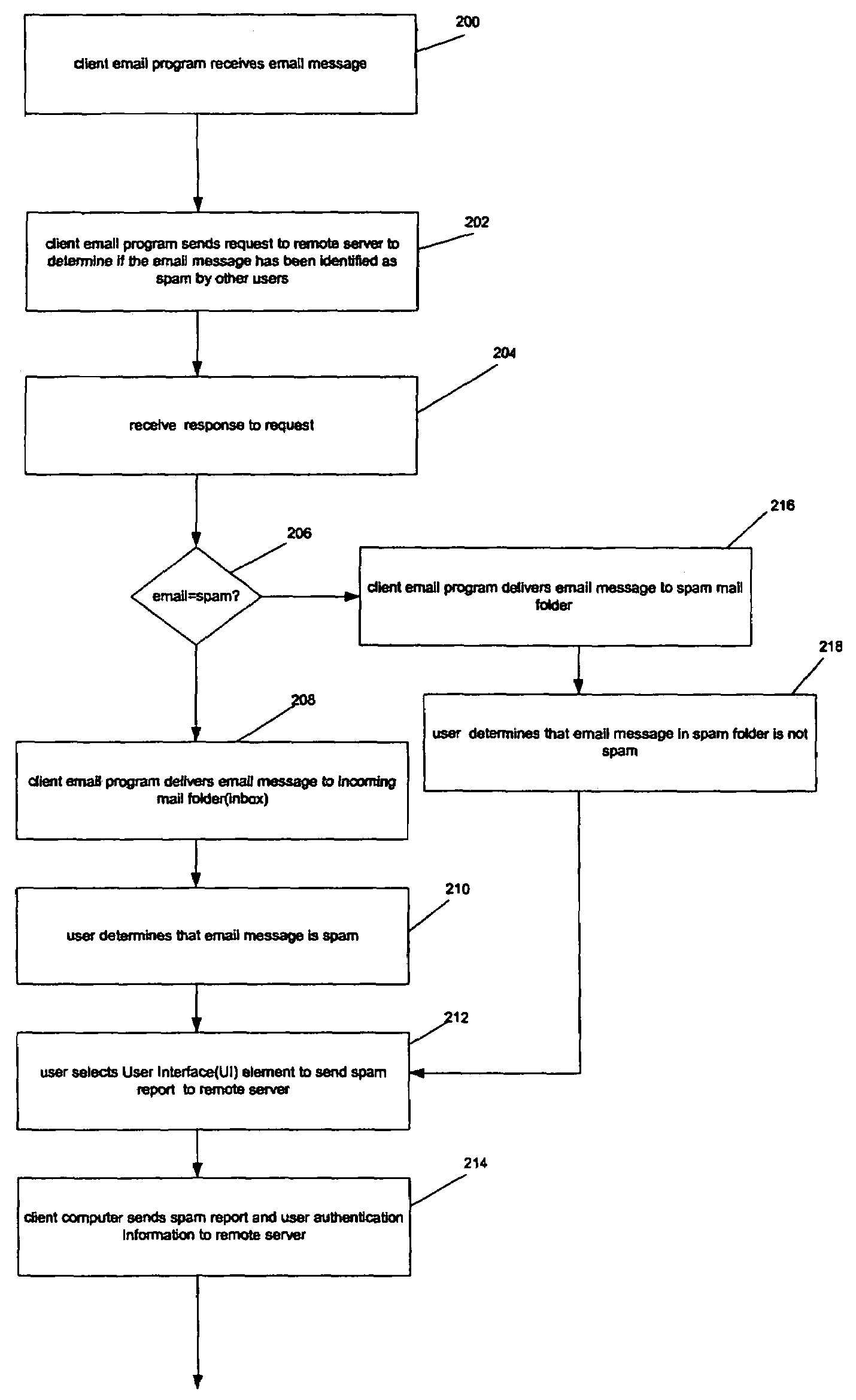
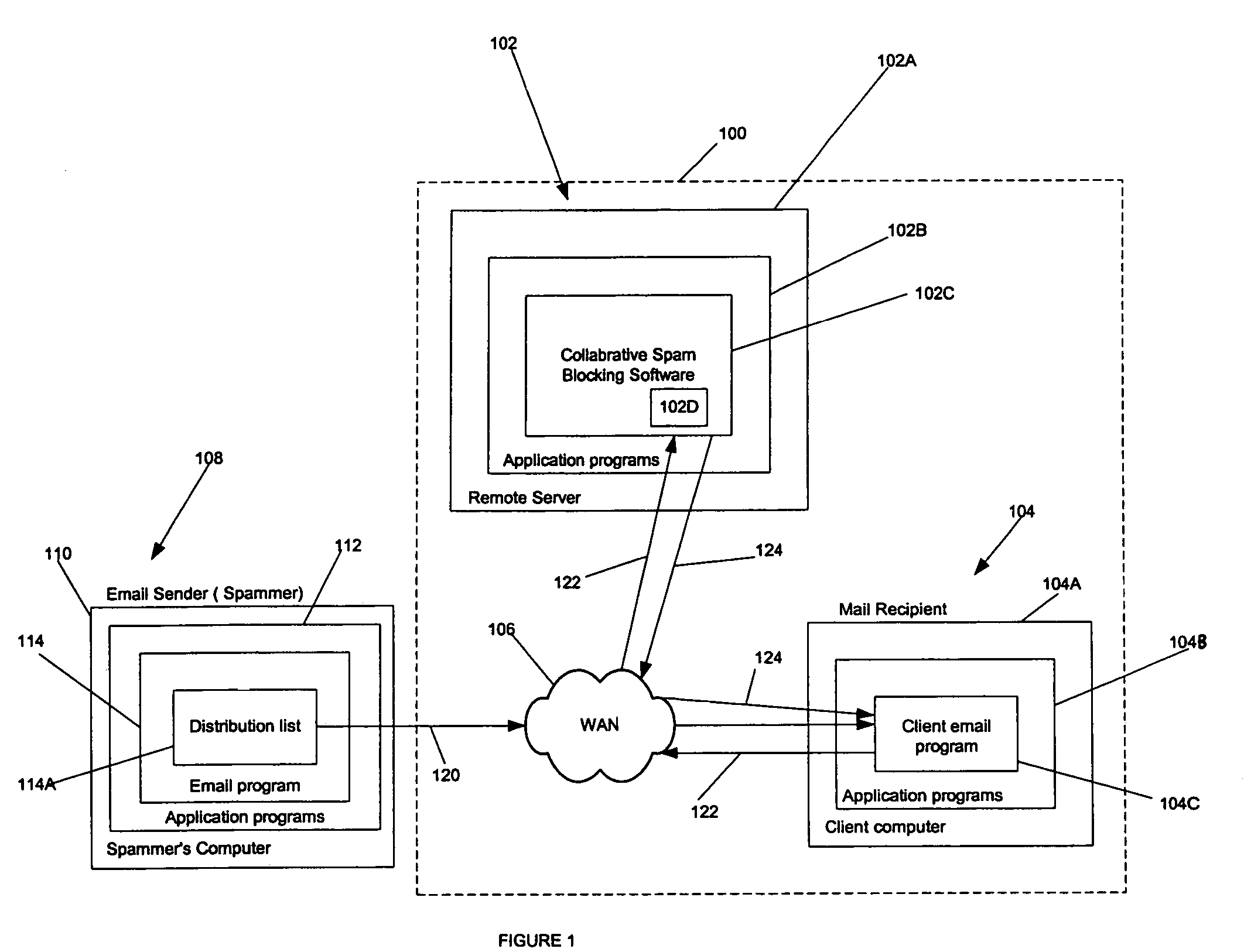
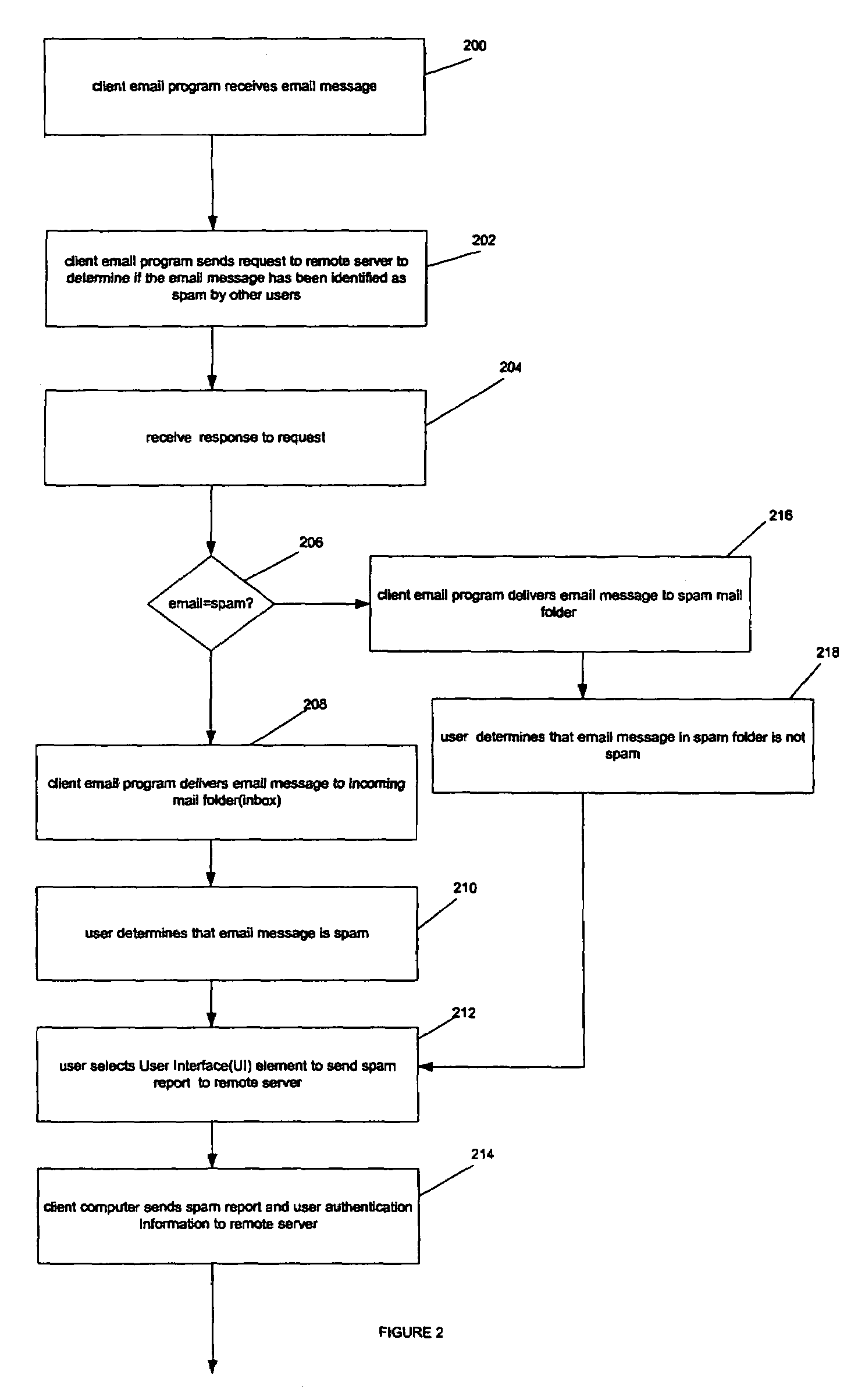
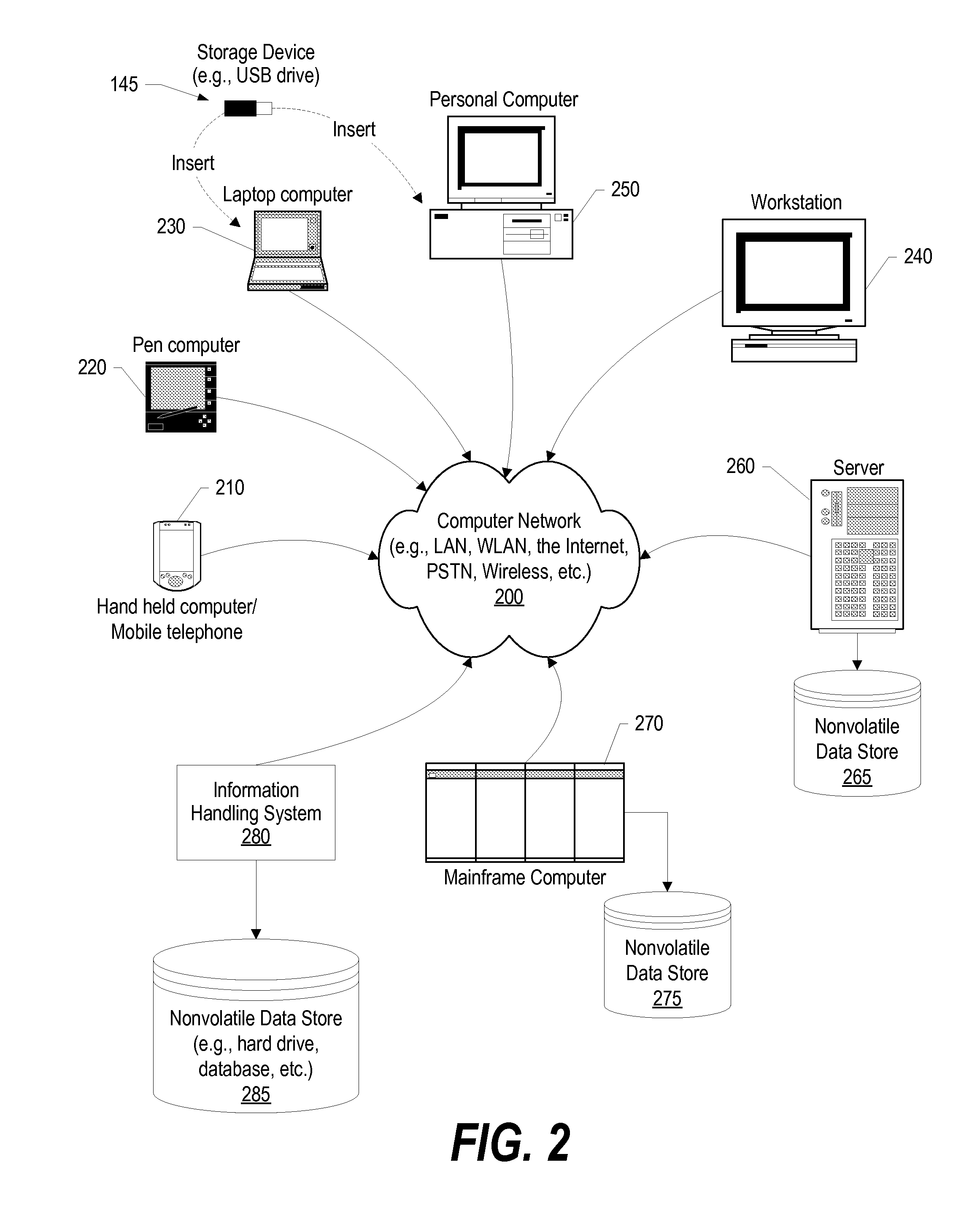
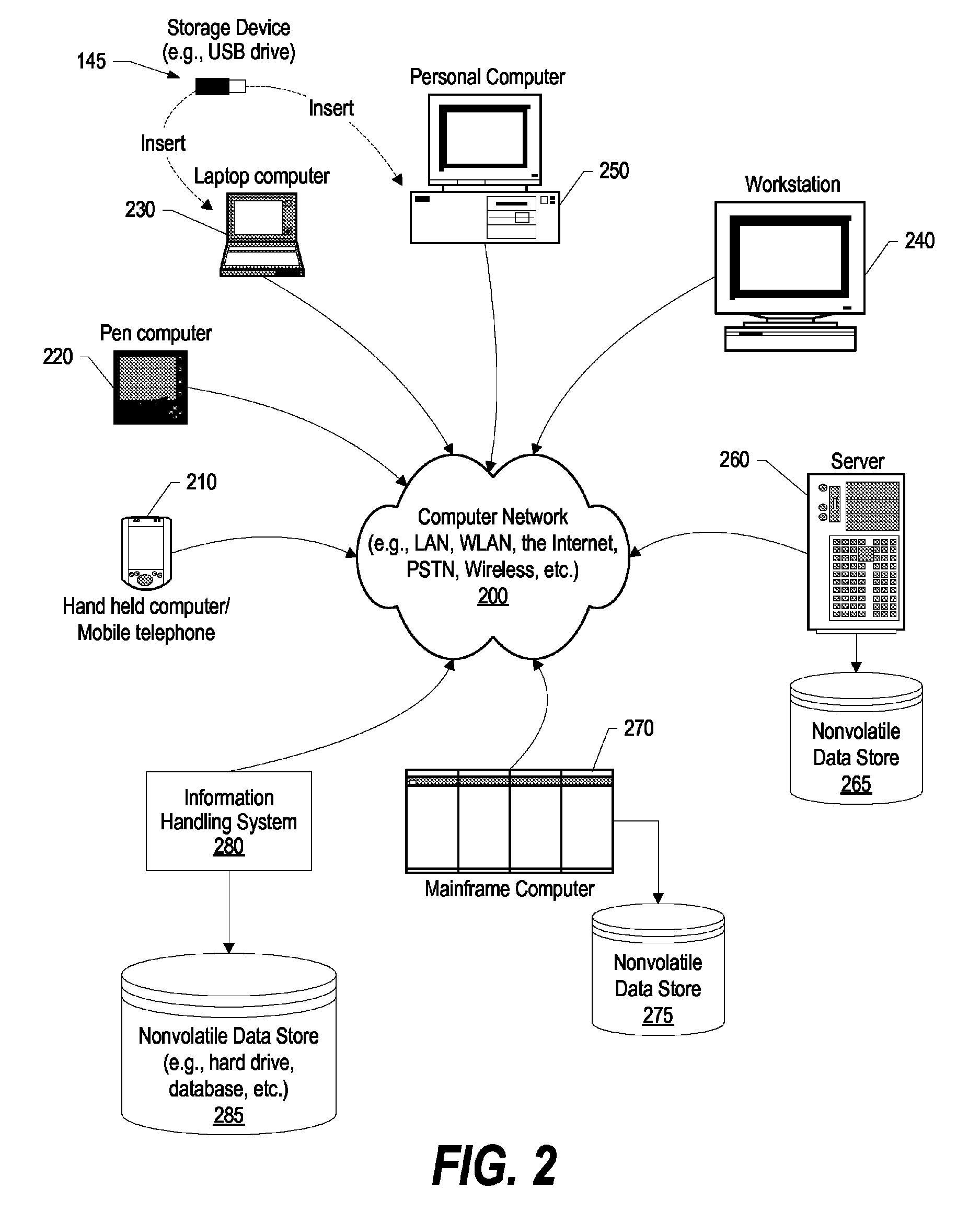
Method and apparatus to block spam based on spam reports from a community of users
ActiveUS20050114452A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust factor
In one embodiment, a method for operating a server is provided. The method comprises receiving a plurality of reports from a community of users, each report identifying an email message as spam or not spam; and determining if the email message is spam based on a number of the reports received from the community of users, and a trust factor associated with each user.
Owner:PROOFPOINT INC
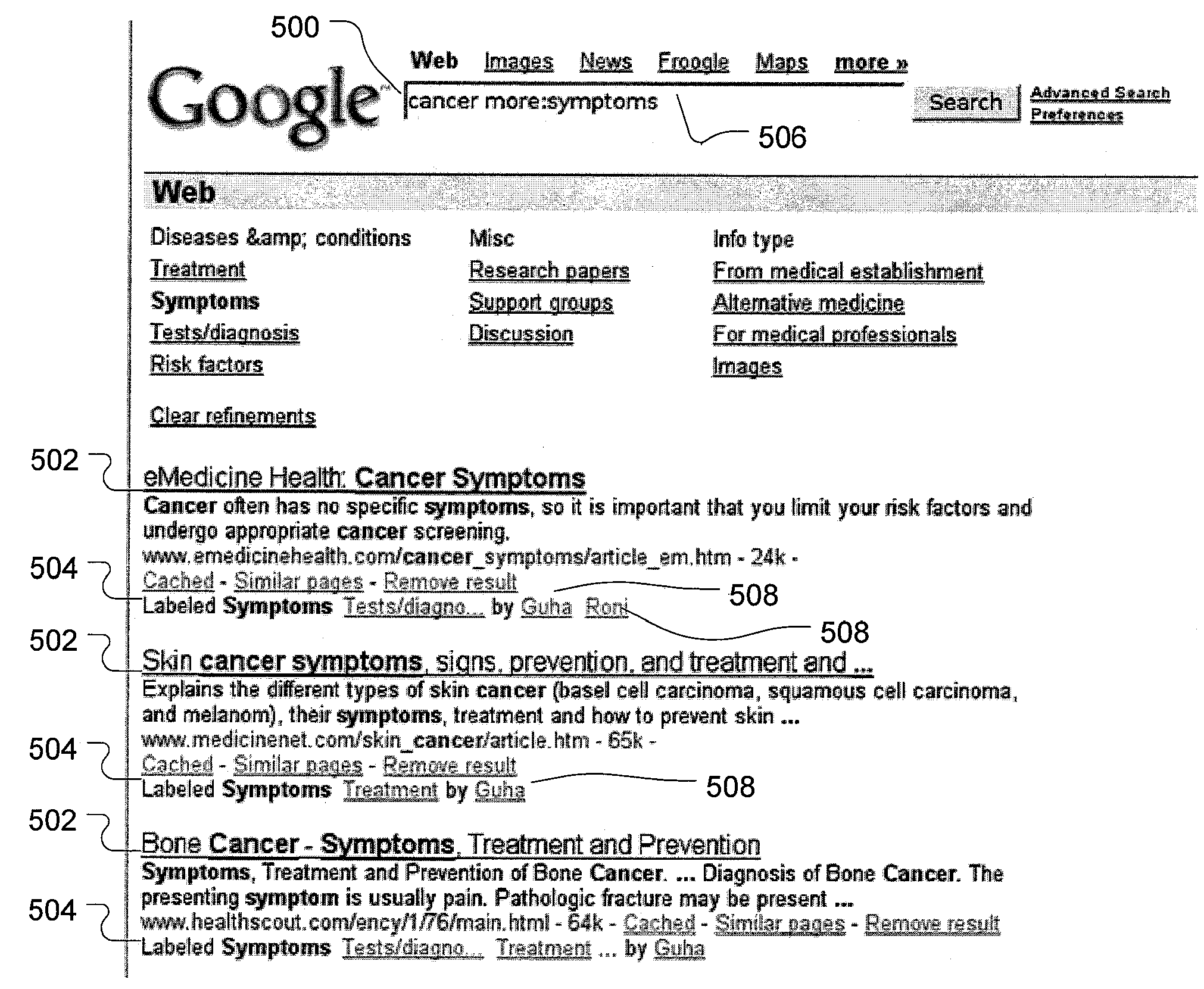
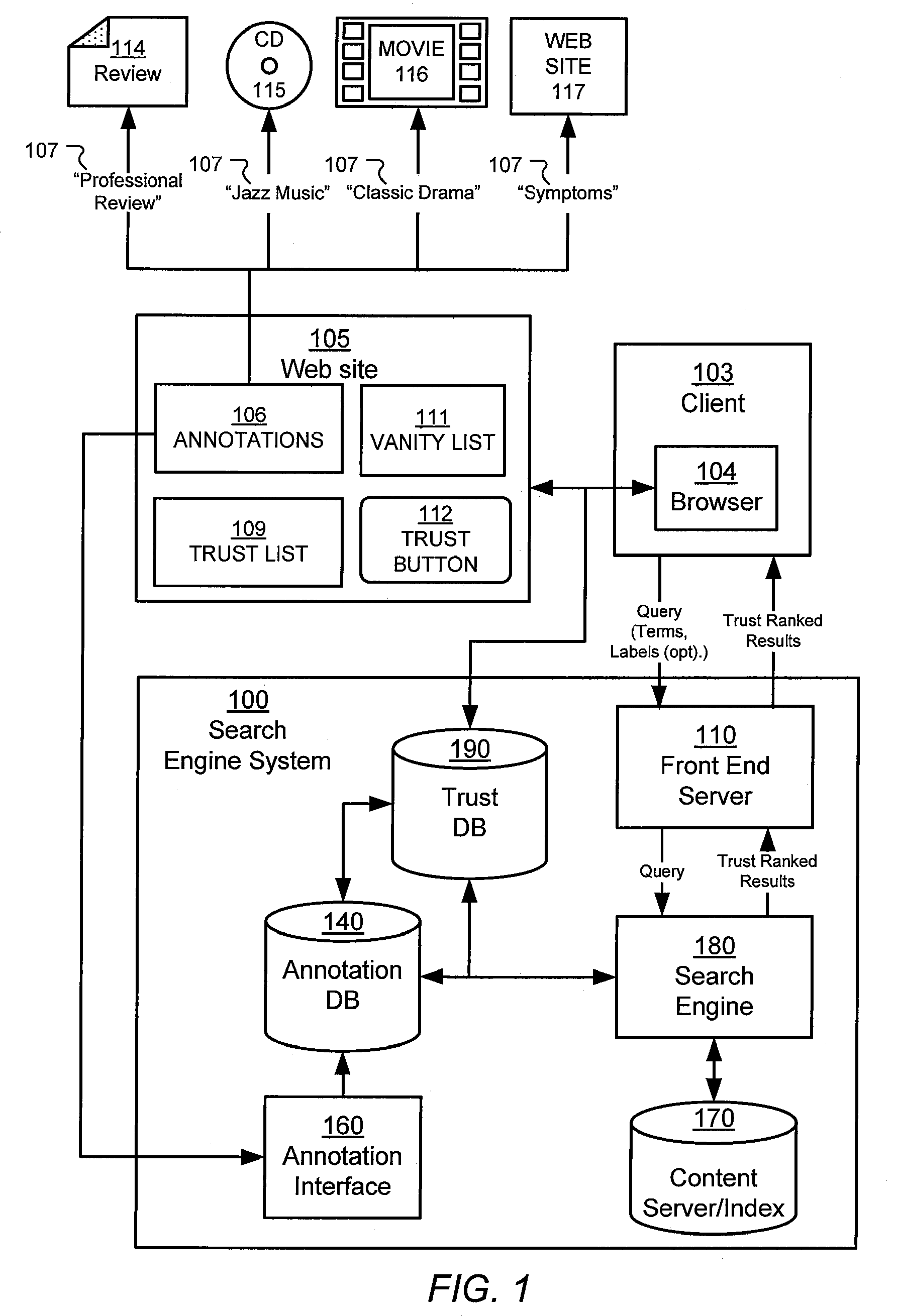
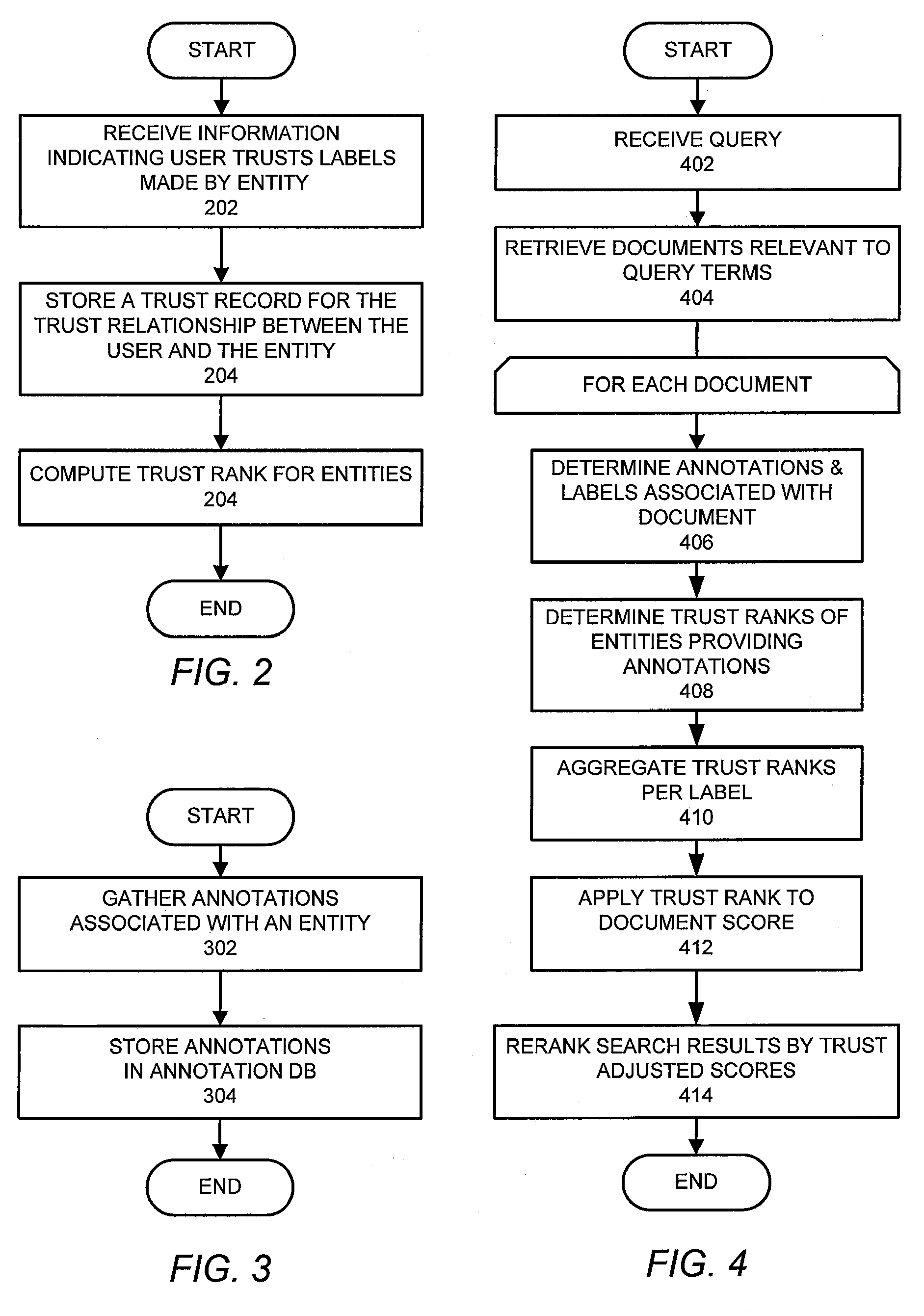
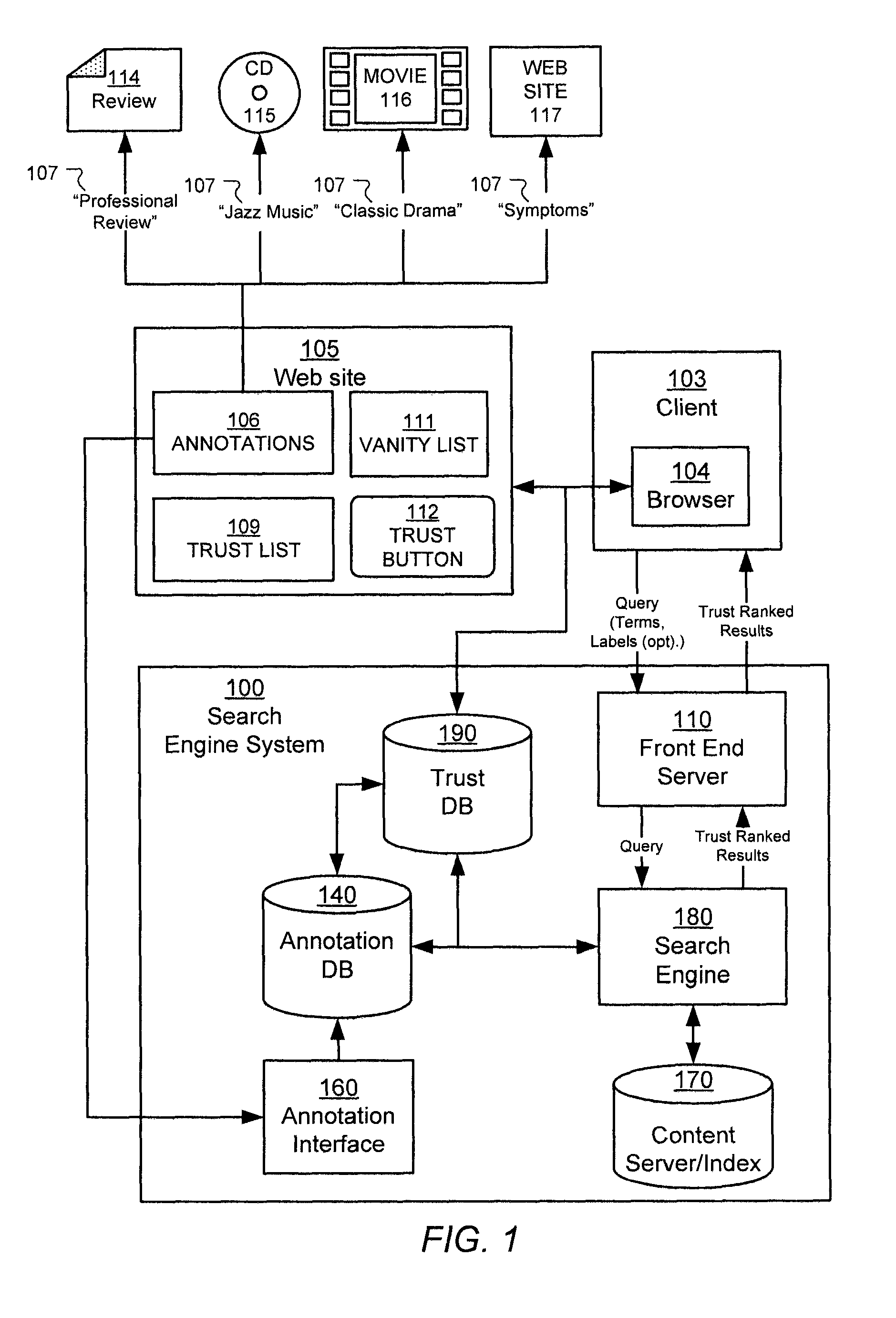
Search result ranking based on trust
A search engine system provides search results that are ranked according to a measure of the trust associated with entities that have provided labels for the documents in the search results. A search engine receives a query and selects documents relevant to the query. The search engine also determines labels associated with selected documents, and the trust ranks of the entities that provided the labels. The trust ranks are used to determine trust factors for the respective documents. The trust factors are used to adjust information retrieval scores of the documents. The search results are then ranked based on the adjusted information retrieval scores.
Owner:GOOGLE LLC
Method and apparatus to block spam based on spam reports from a community of users
ActiveUS7373385B2Digital data processing detailsUser identity/authority verificationInternet privacyTrust factor
In one embodiment, a method for operating a server is provided. The method comprises receiving a plurality of reports from a community of users, each report identifying an email message as spam or not spam; and determining if the email message is spam based on a number of the reports received from the community of users, and a trust factor associated with each user.
Owner:PROOFPOINT INC
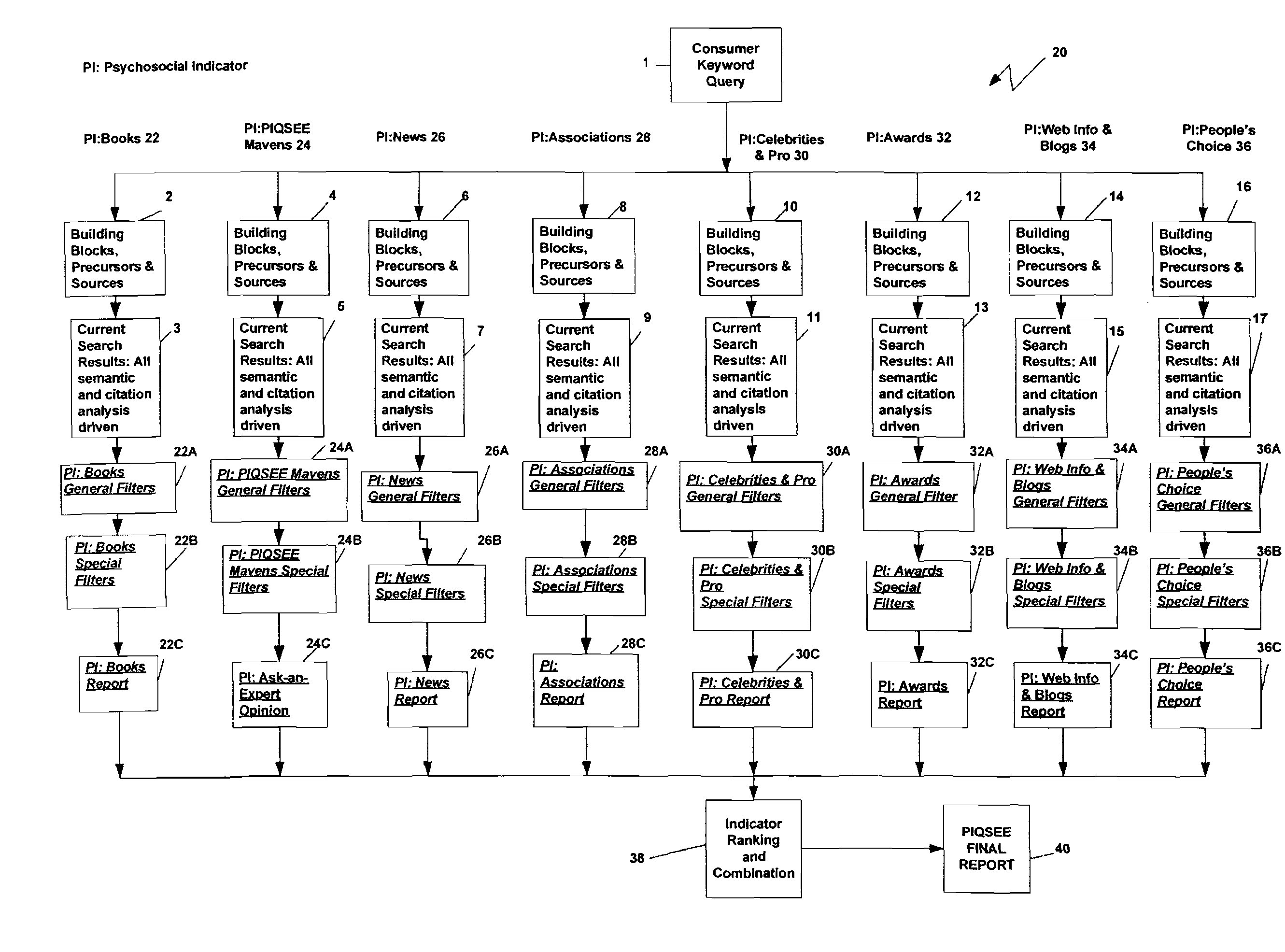
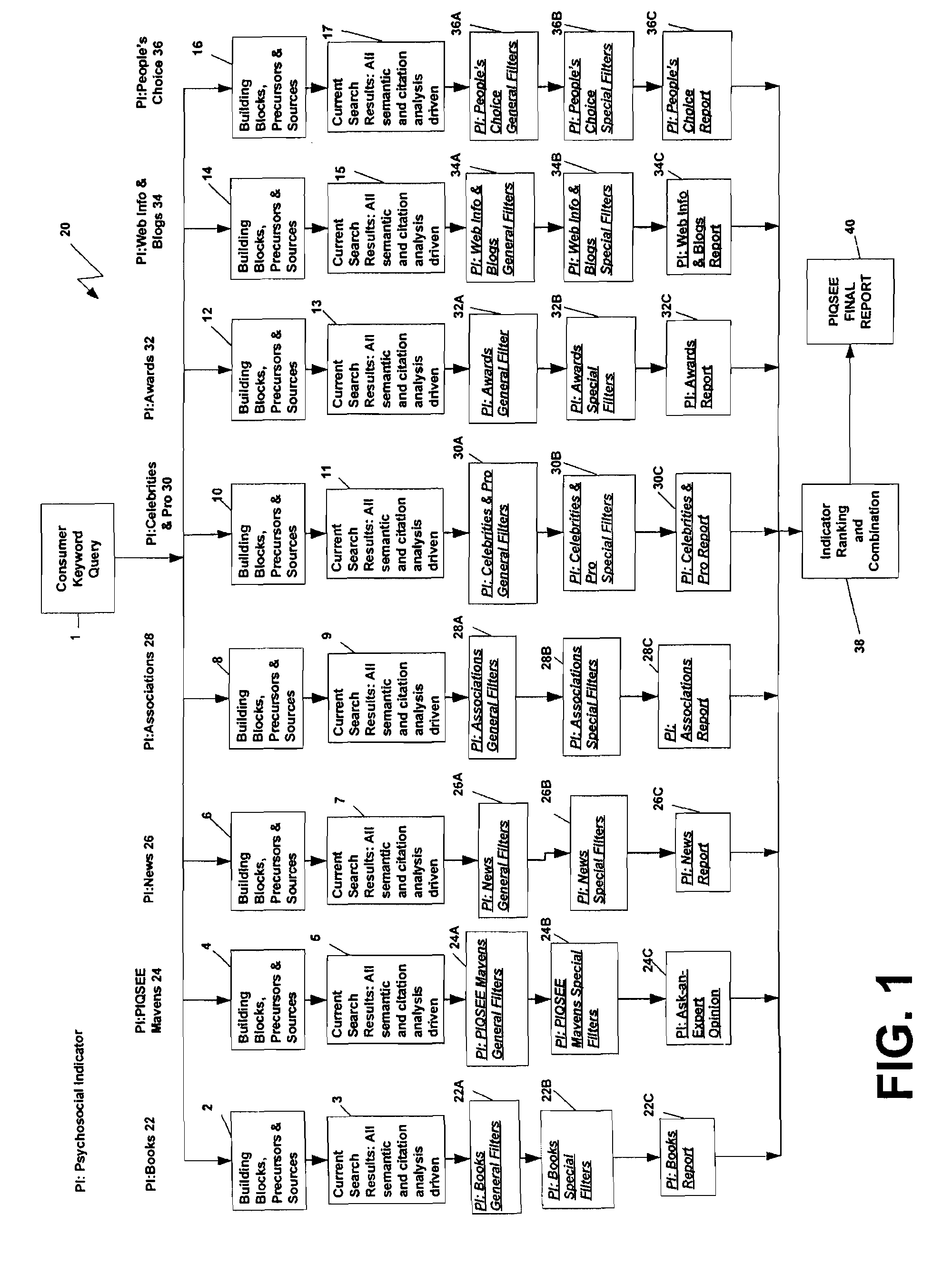
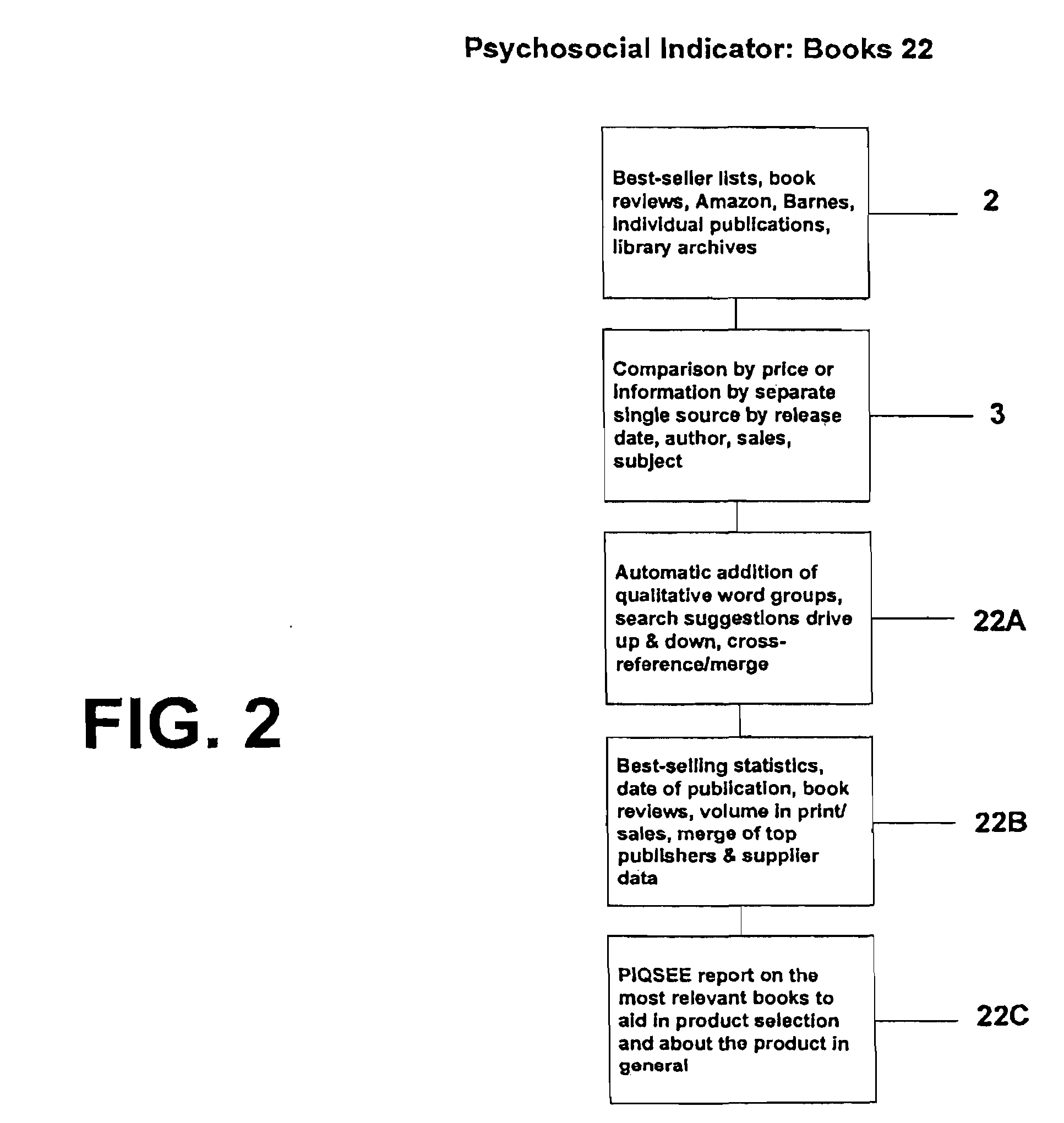
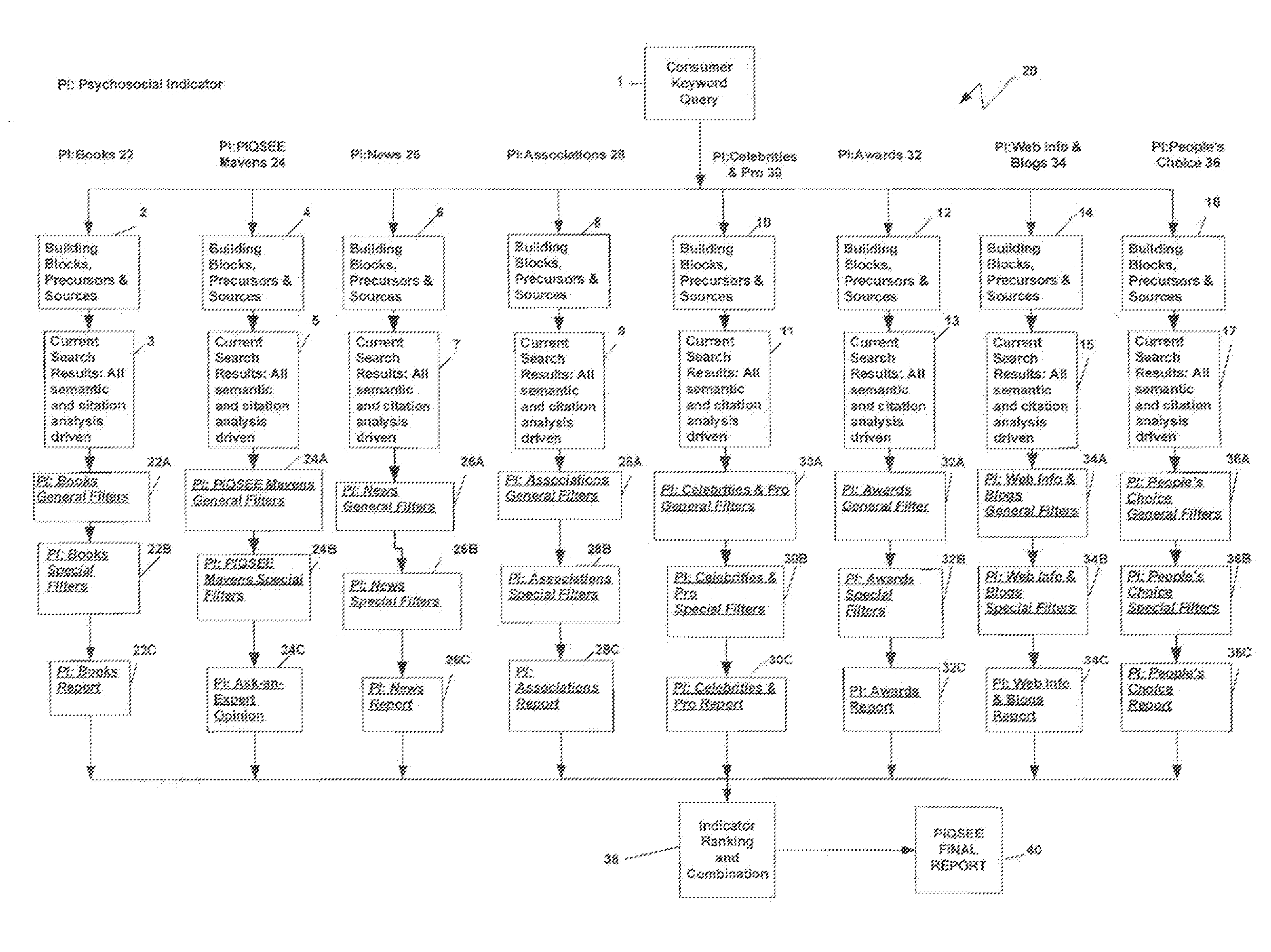
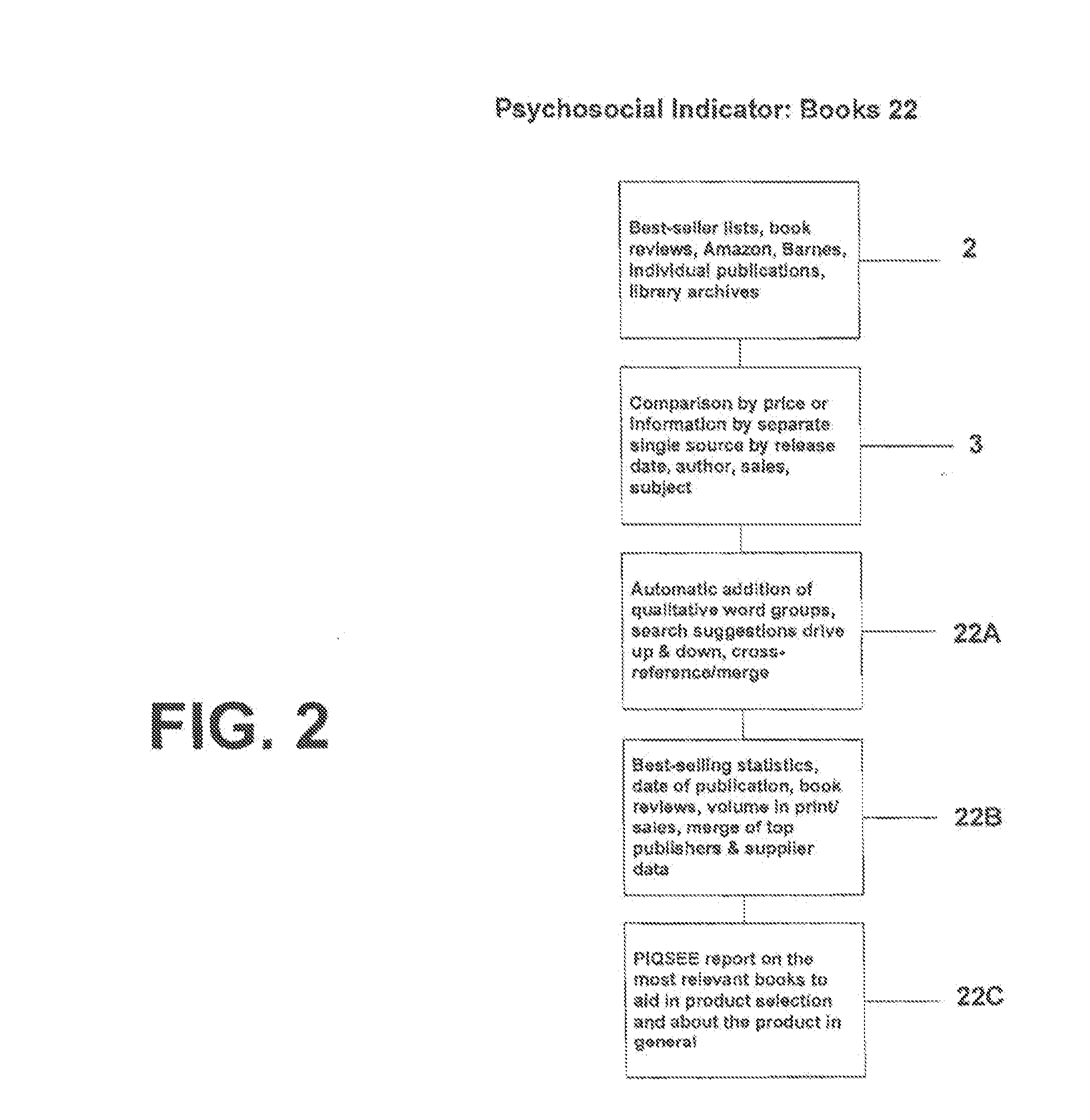
Qualitative search engine based on factors of consumer trust specification
InactiveUS20090037412A1Digital data processing detailsRelational databasesTrust factorQualitative property
A method of providing a search engine for use on global computer networks which identifies and merges categories of information that reflect, influence and imitate intelligent choice by concurrently searching one or more of eight factors of consumer trust: books, experts, news and articles, associations, celebrities and pro choice, awards, web information and blogs and people's choice. The results from the search of these selected consumer trust factors are then combined to generate a final report.
Owner:BARD KRISTINA BUTVYDAS +1
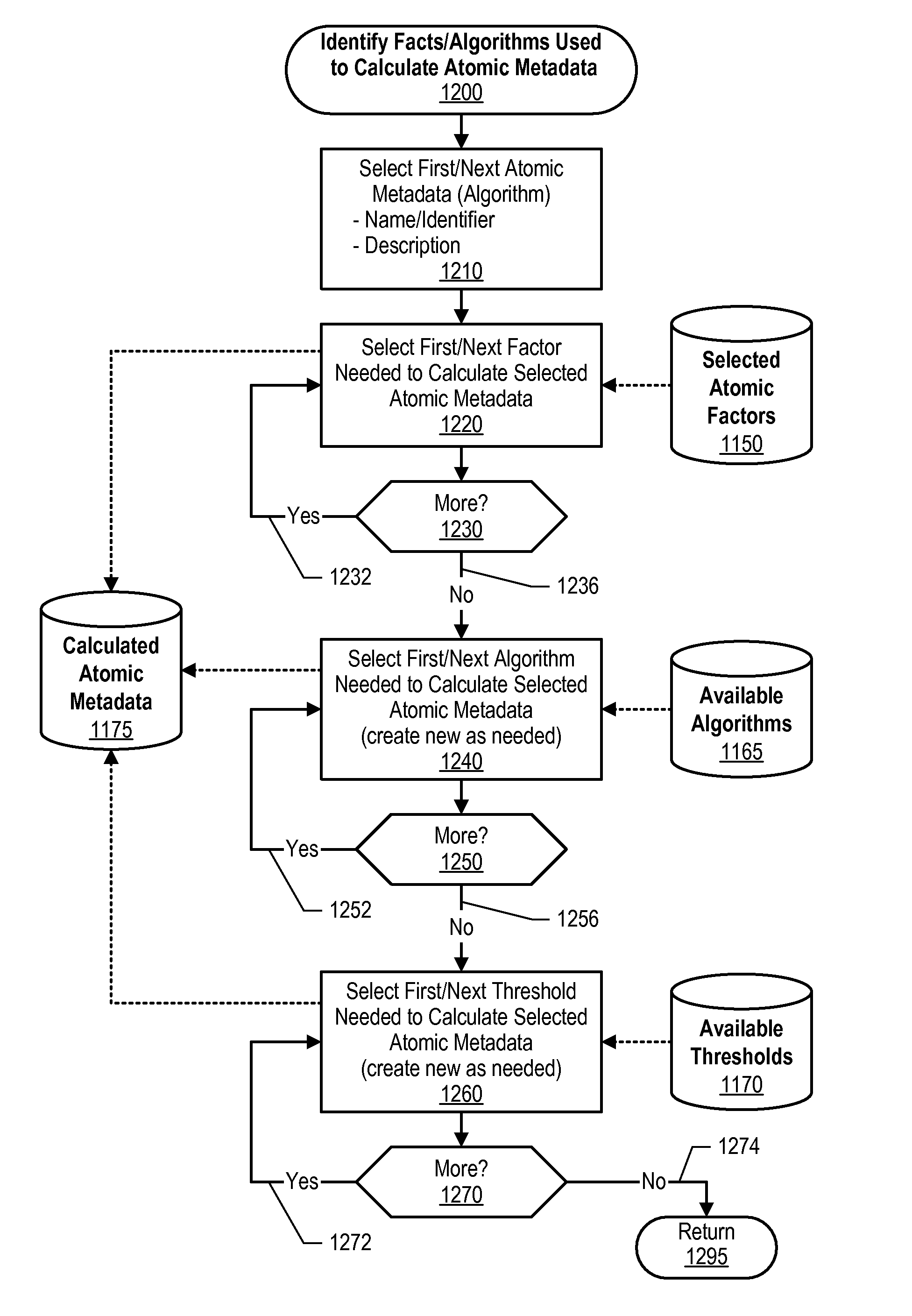
Configurable trust context assignable to facts and associated trust metadata
An approach is provided for selecting a trust factor from trust factors that are included in a trust index repository. A trust metaphor is associated with the selected trust factor. The trust metaphor includes various context values. Range values are received and the trust metaphor, context values, and range values are associated with the selected trust factor. A request is received from a data consumer, the request corresponding to a trust factor metadata score that is associated with the selected trust factor. The trust factor metadata score is retrieved and matched with the range values. The matching results in one of the context values being selected based on the retrieved trust factor metadata score. The selected context value is then provided to the data consumer.
Owner:IBM CORP
Sensor network trust evaluation method based on node behaviors and D-S evidence theory
InactiveCN101835158AImprove adaptabilityFully reflect the degree of contributionNetwork topologiesSecurity arrangementTrust factorFuzzy classification
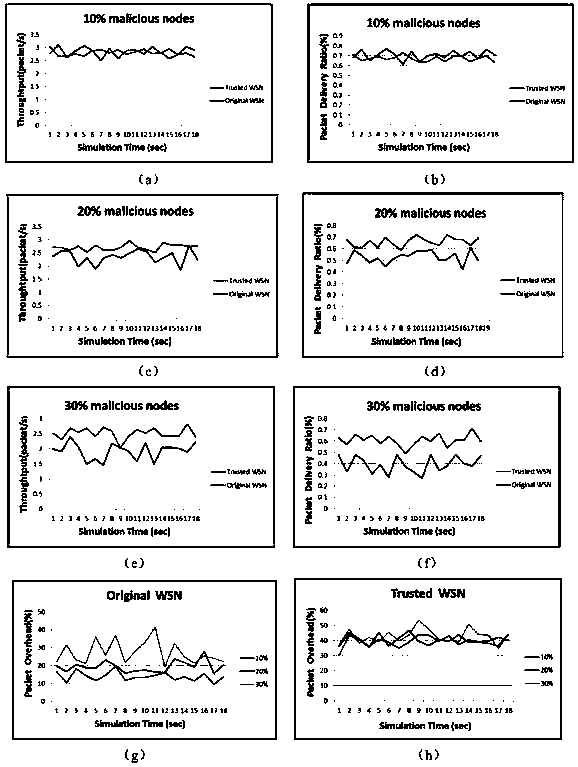
The invention discloses a sensor network trust evaluation method based on node behaviors and a D-S evidence theory, comprising the following five steps: 1) designing various trust factor strategies for nodes in a wireless sensor network; 2) setting trust factor weights according to network application scenes and simultaneously calculating the node behavior coefficient mu to obtain the direct trust value and multiple indirect trust value of an evaluated object; 3) calculating a fuzzy subset membership function for each trust value by utilizing the concepts of membership and linguistic variables of a fuzzy set theory, performing fuzzy classification on the various the trust values to form the basic confidence function of the D-S evidence theory; 4) calculating the evidence difference of thedirect trust value and the indirect trust values of the evaluated node and altering the weights of the indirect trust values; and 5) adopting the Dempster synthesis rule to obtain the comprehensive trust value of the evaluated node and a final basic confidence designated value according to the altered trust weights. The invention solves the problem of difficult identification of malicious nodes in a network and ensures the safety of network data transmission.
Owner:BEIHANG UNIV
Apparatus, system, and method for determining and implementing estimate reliability
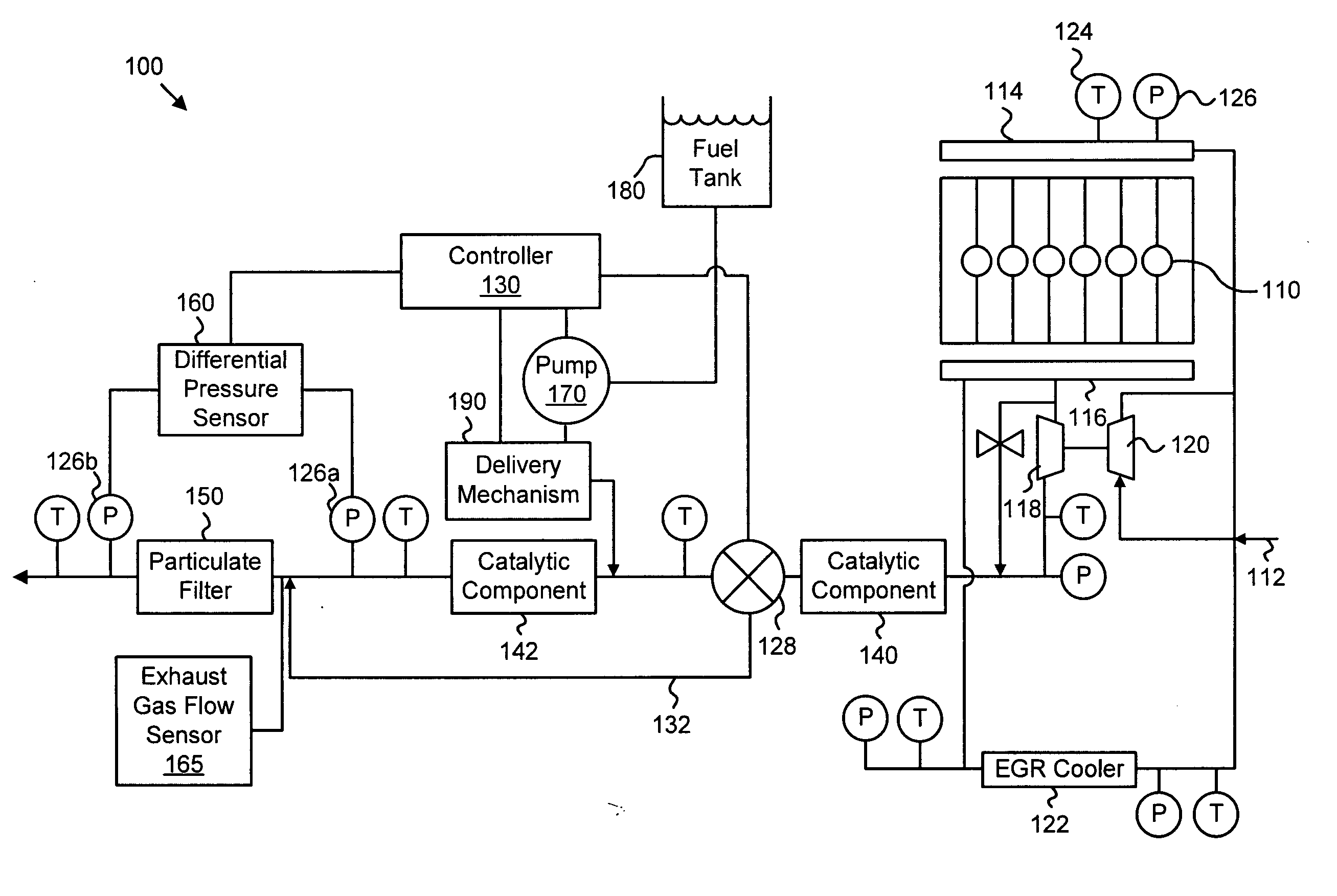
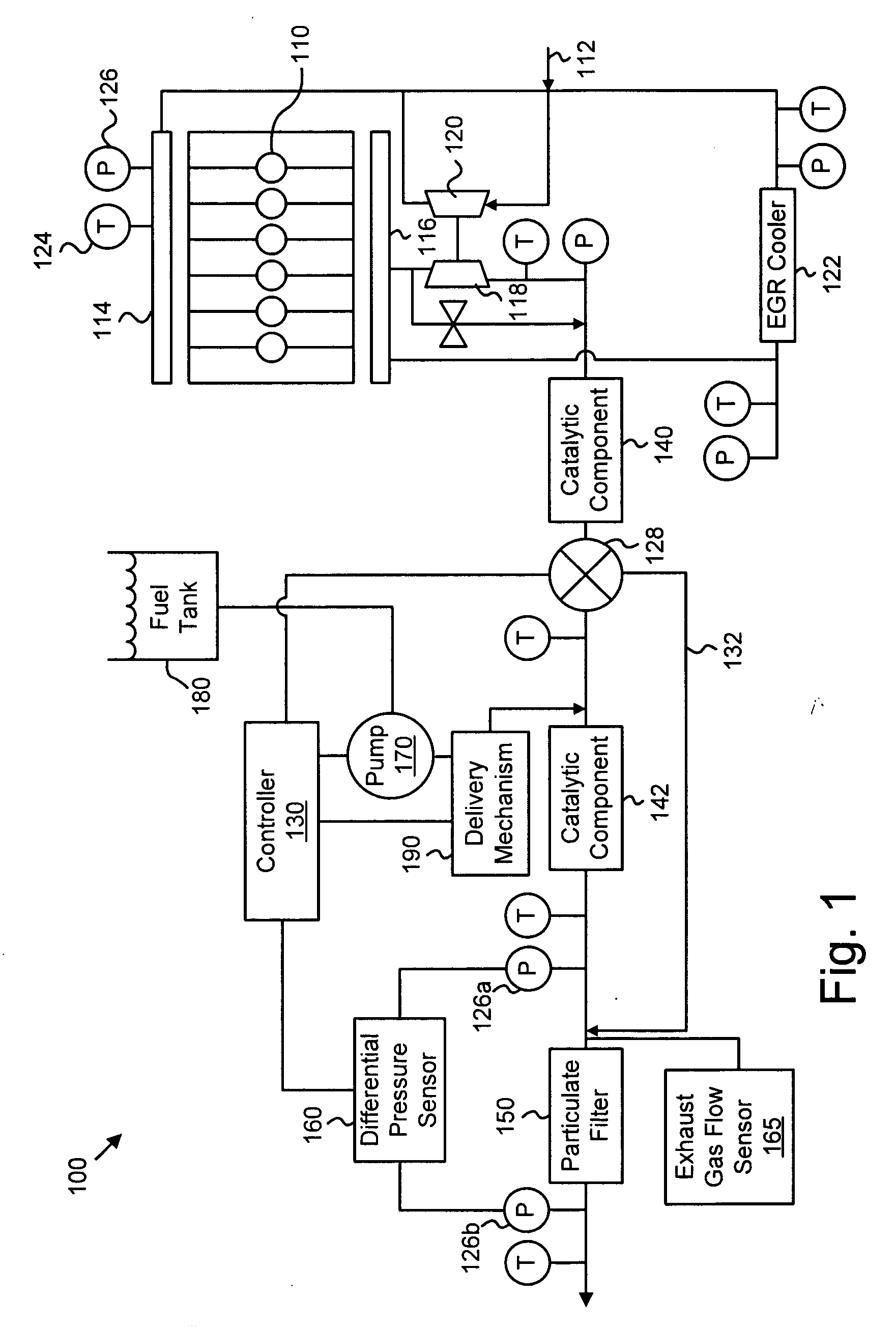
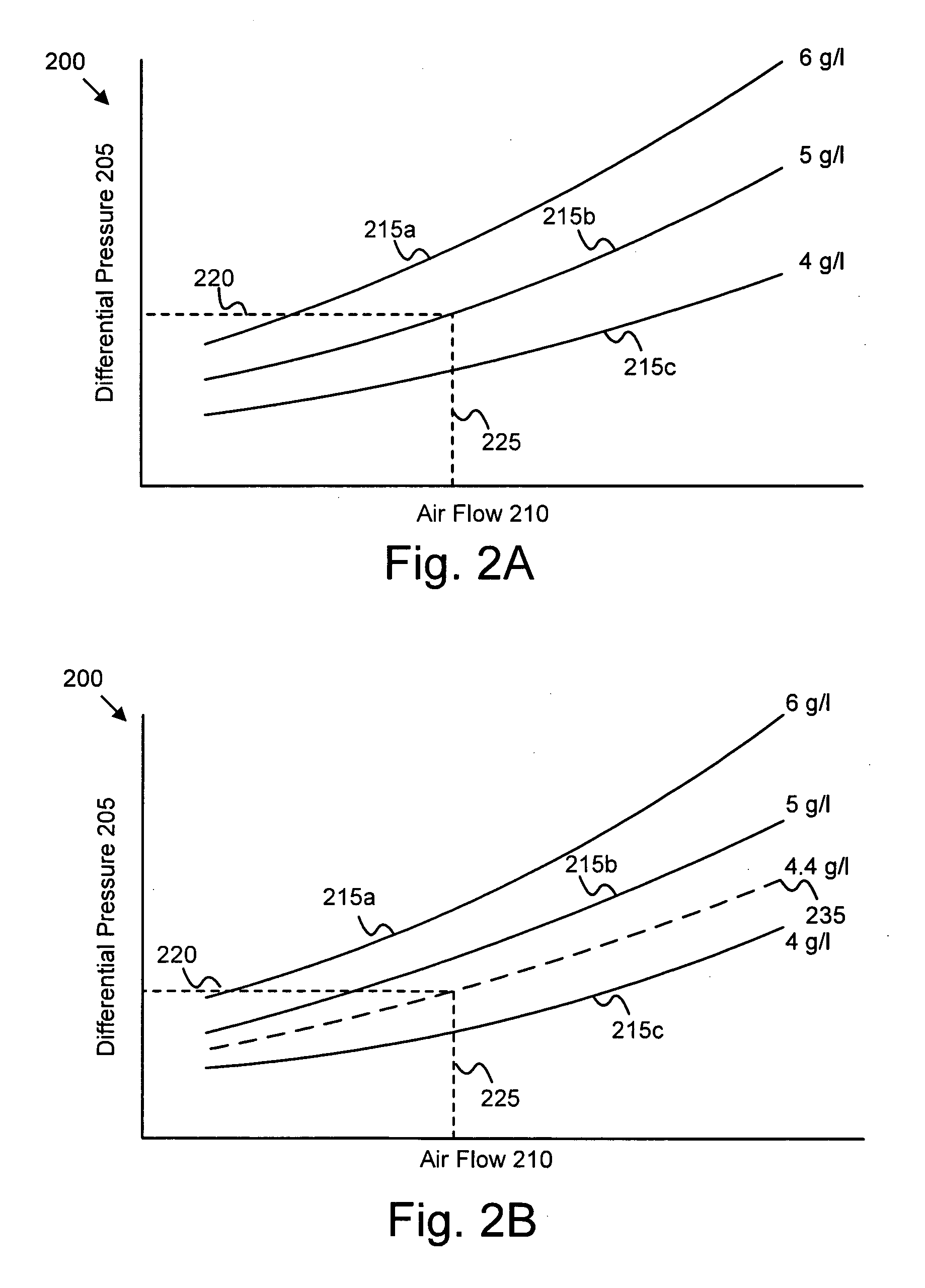
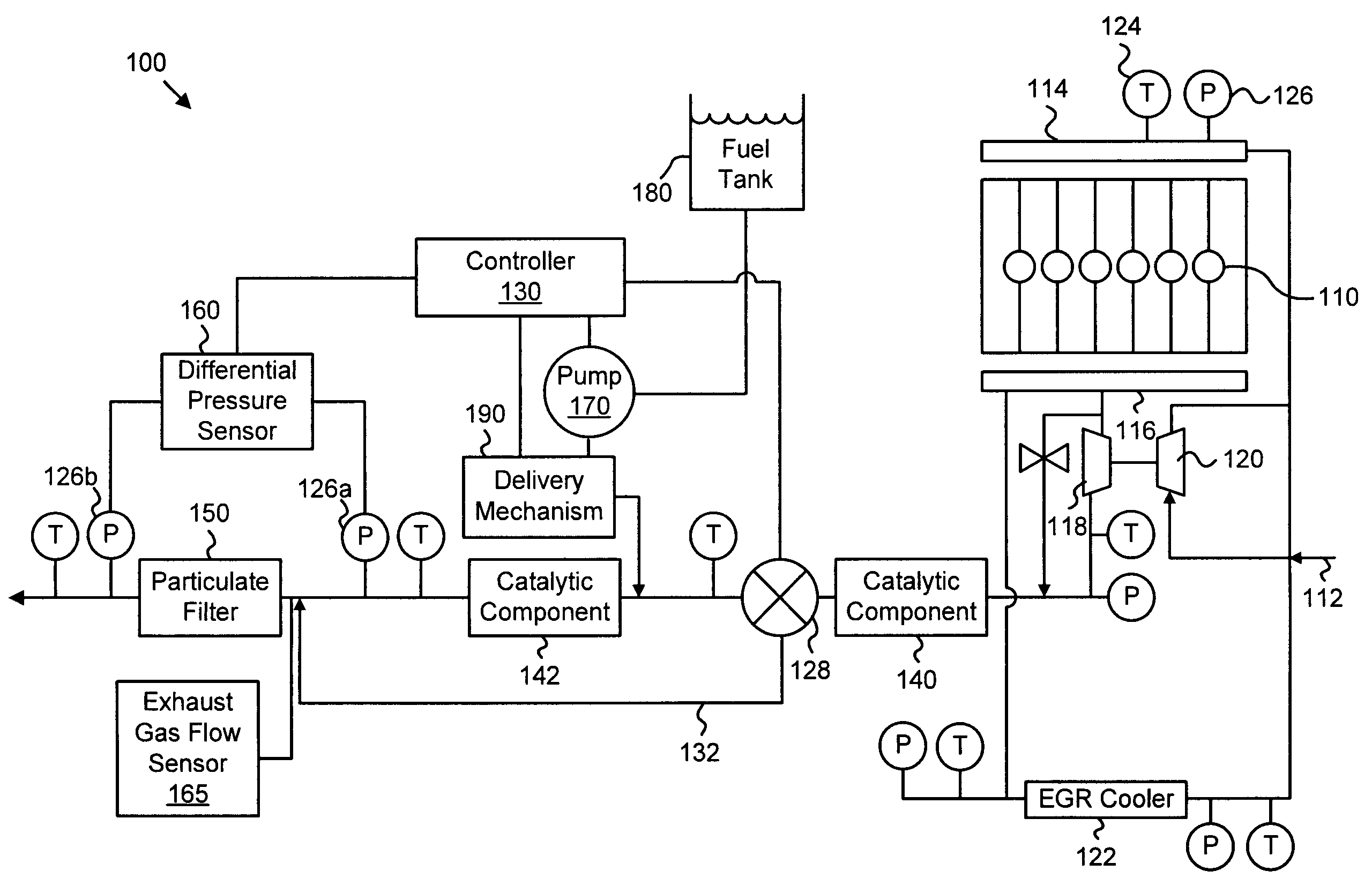
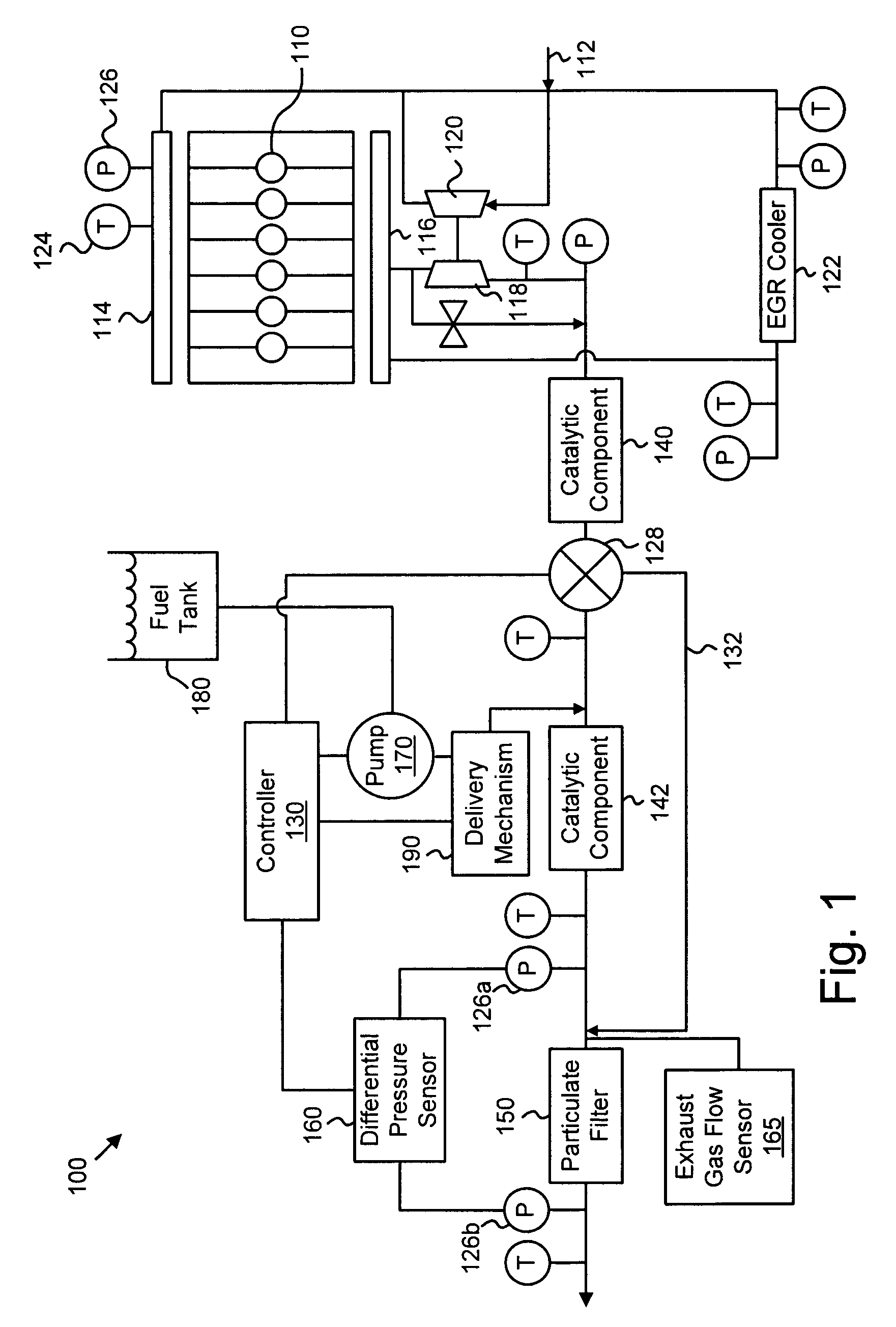
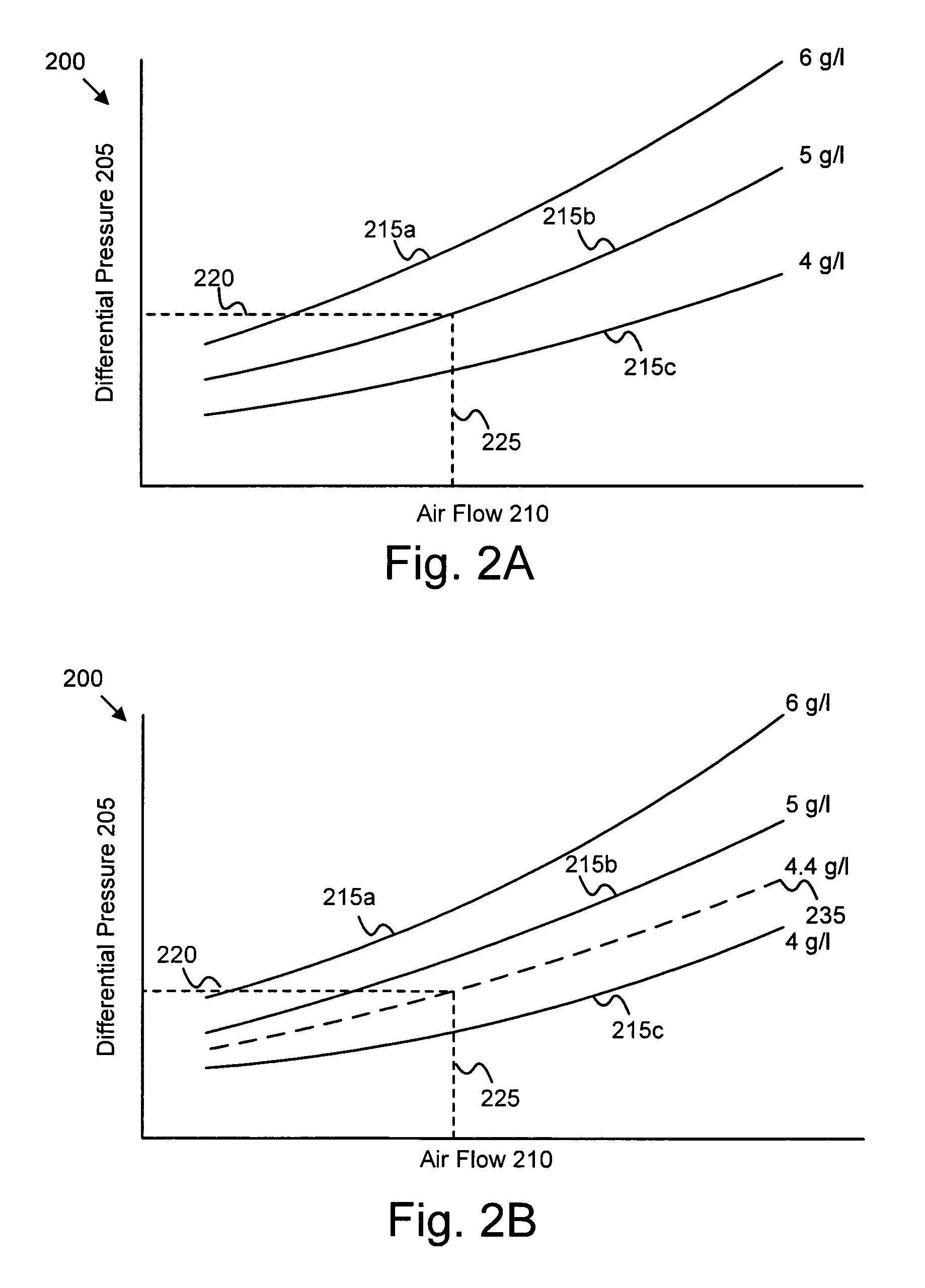
ActiveUS20070056272A1Overcomes shortcomingNon-fuel substance addition to fuelInternal combustion piston enginesLow-pass filterTrust factor
An apparatus, system, and method are disclosed for determining the reliability of an estimate such as particulate accumulation on a diesel particulate filter, weighing the estimate according to a function of its reliability, weighing a prediction of particulate accumulation on the filter according to a function of the estimate's reliability, and combining the weighted estimate and weighted prediction to determine a combined particulate load estimate. The degree of reliability can be expressed as a trust factor, and a function of the trust factor can be used in a low-pass filter of the estimate. The trust factor value depends on filter air flow and particulate distribution in one embodiment. Regeneration of the particulate filter may be initiated depending on the value of the combined particulate load estimate.
Owner:CUMMINS INC
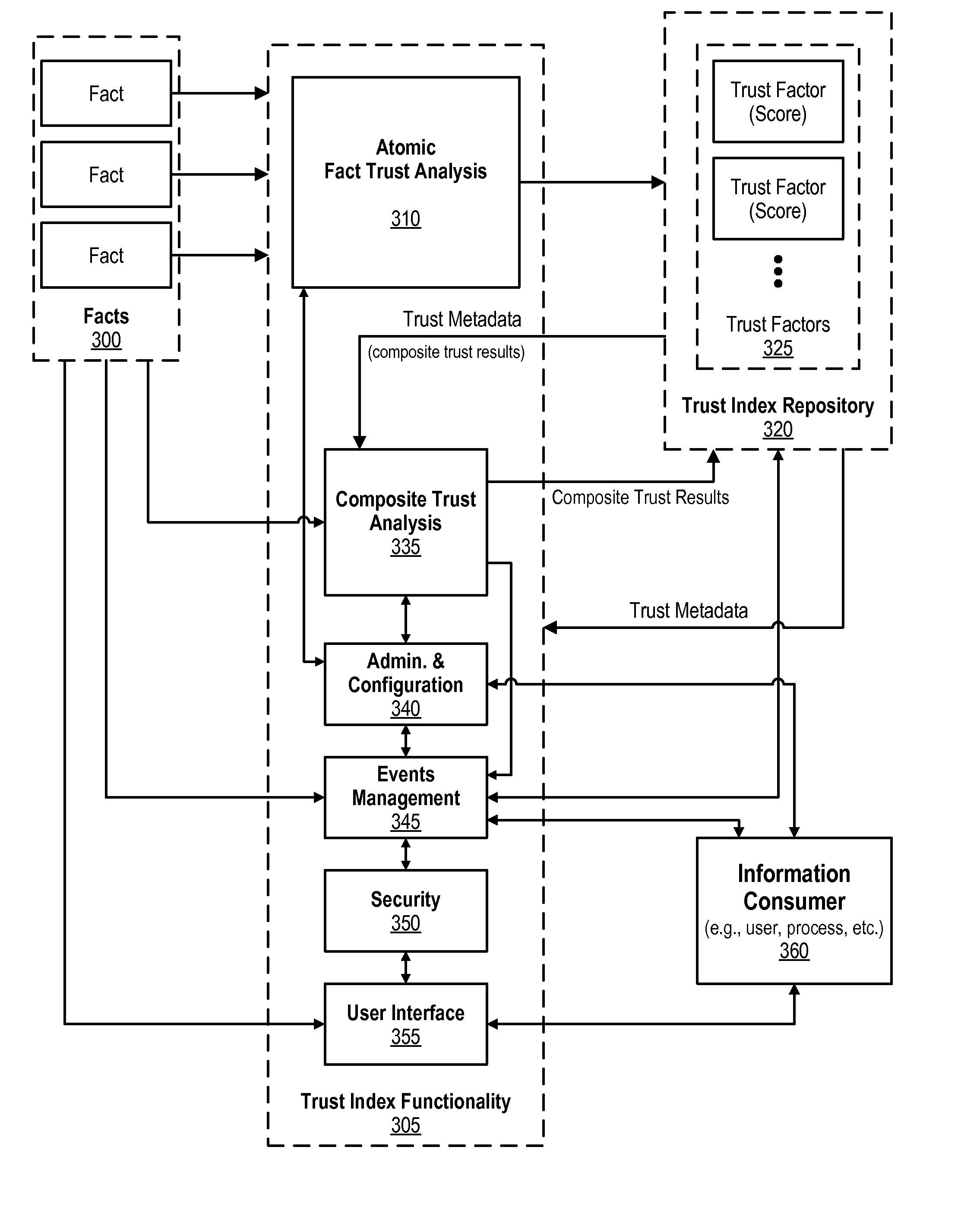
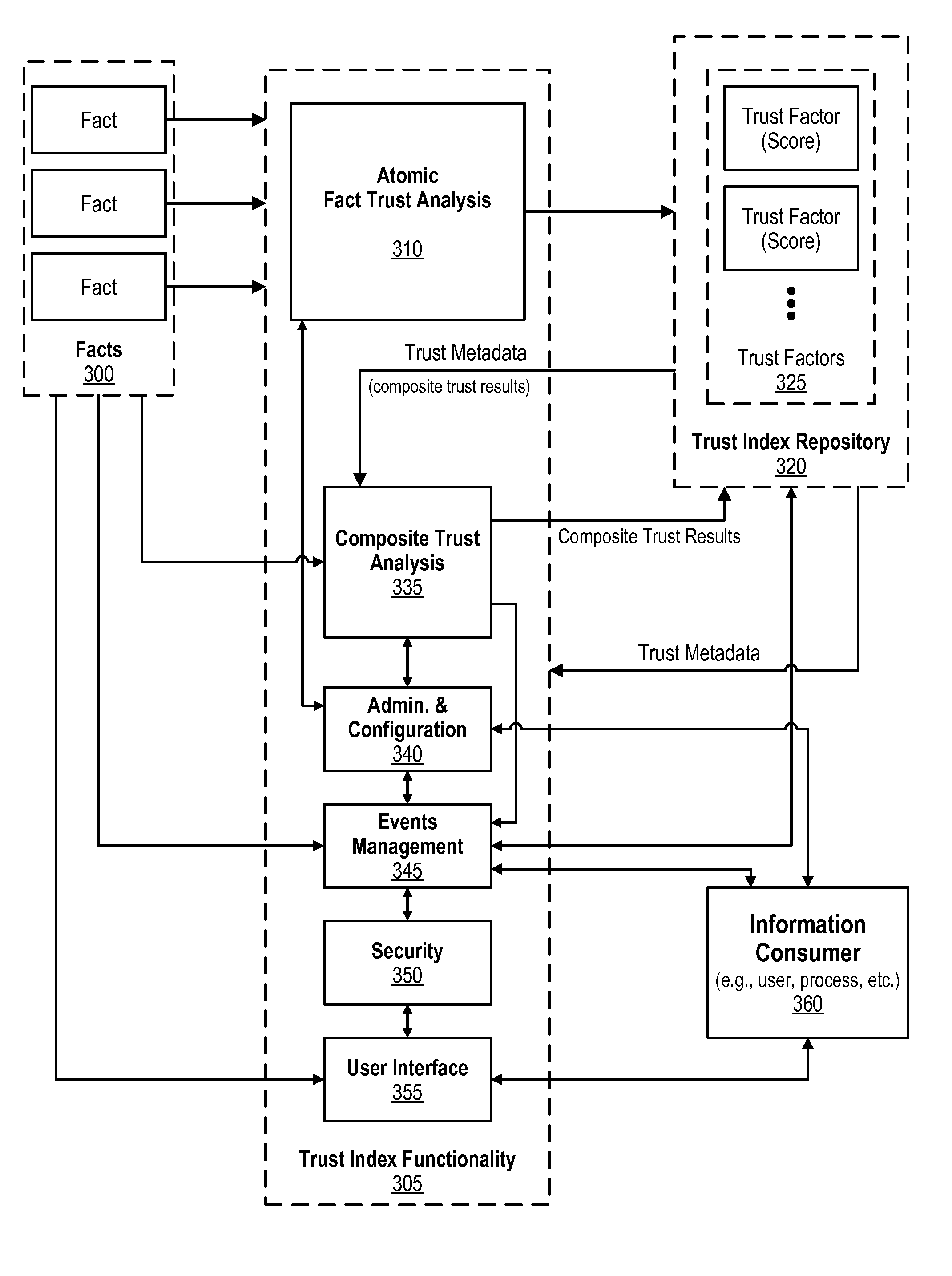
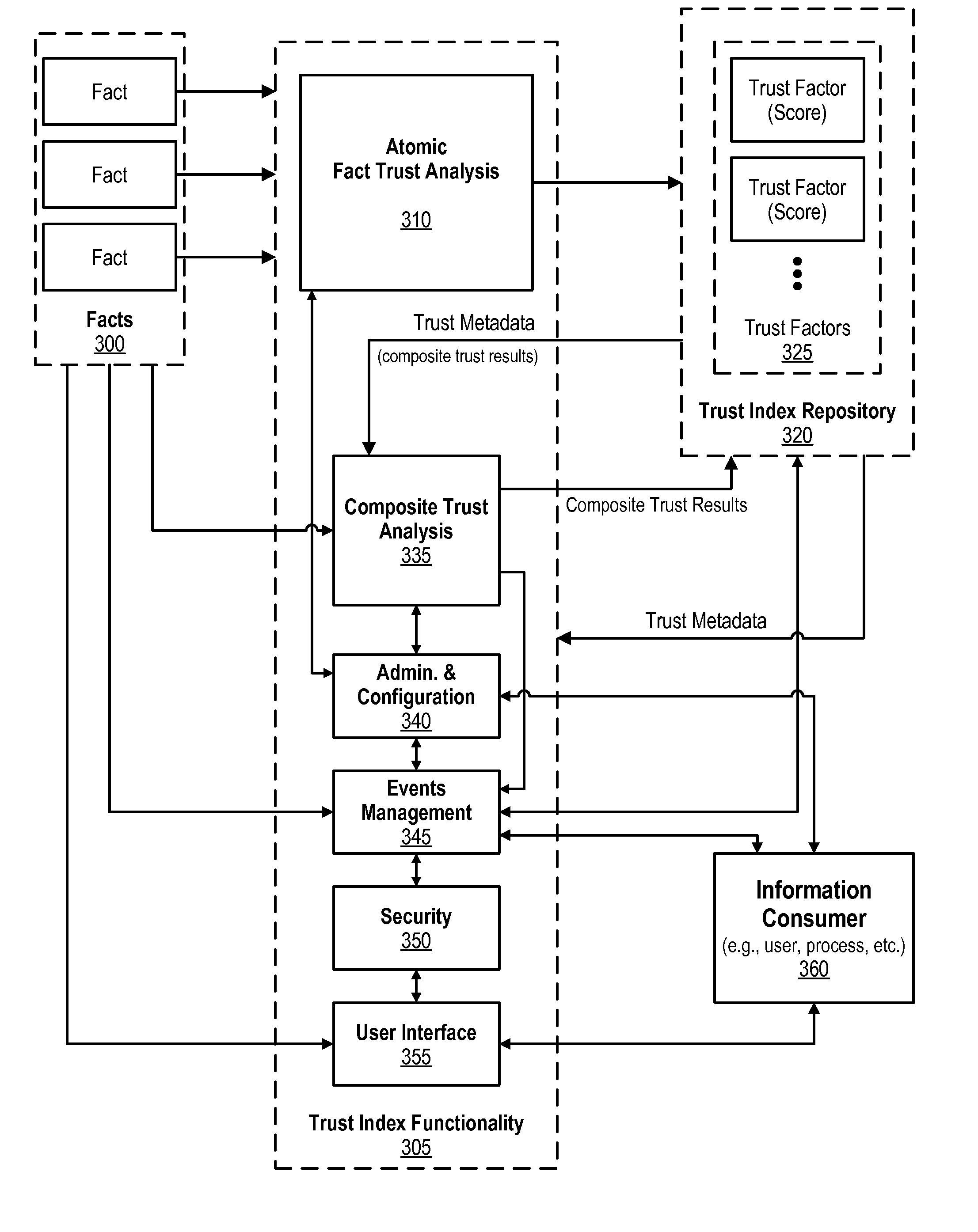
Trust Index Framework for Providing Data and Associated Trust Metadata
InactiveUS20100106558A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust factor
An approach is provided in which facts are received and then one or more atomic fact trust analyses are performed on the facts. The atomic fact trust analyses result in various atomic trust factor scores. Composite trust analysis is performed using the atomic trust factor scores. The composite trust analyses result in composite trust factor scores. The atomic trust factor scores and the composite trust factor scores are stored in a trust index repository that is managed by a trust index framework. A request is then received for trusted data, the request being from an information consumer. The trust index framework then retrieves one of the composite trust factor scores from the trust index repository, with the retrieved composite trust factor score corresponding to the trusted data request, and this the retrieved composite trust factor score is provided to the information consumer.
Owner:IBM CORP
Search result ranking based on trust
A search engine system provides search results that are ranked according to a measure of the trust associated with entities that have provided labels for the documents in the search results. A search engine receives a query and selects documents relevant to the query. The search engine also determines labels associated with selected documents, and the trust ranks of the entities that provided the labels. The trust ranks are used to determine trust factors for the respective documents. The trust factors are used to adjust information retrieval scores of the documents. The search results are then ranked based on the adjusted information retrieval scores.
Owner:GOOGLE LLC
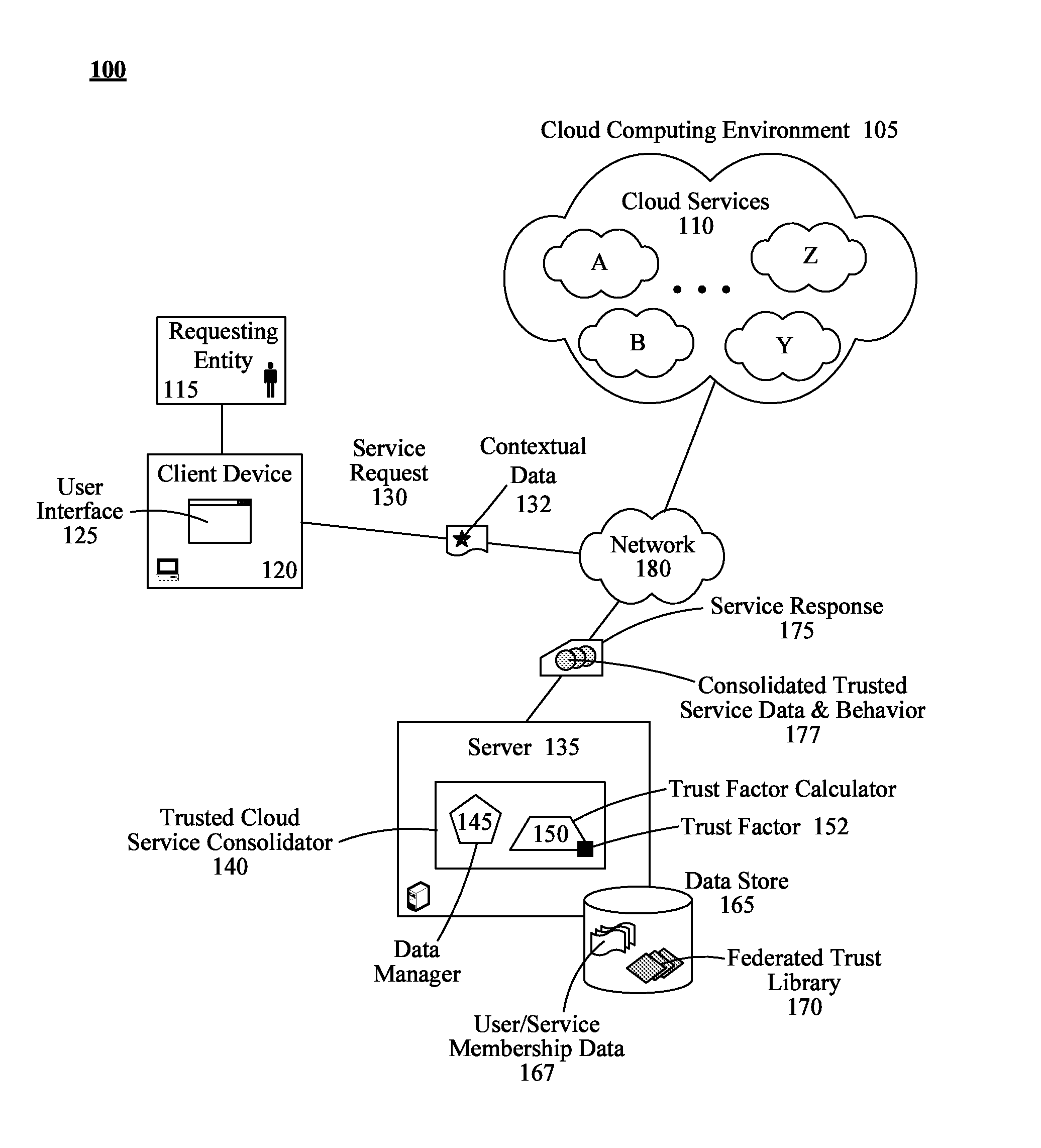
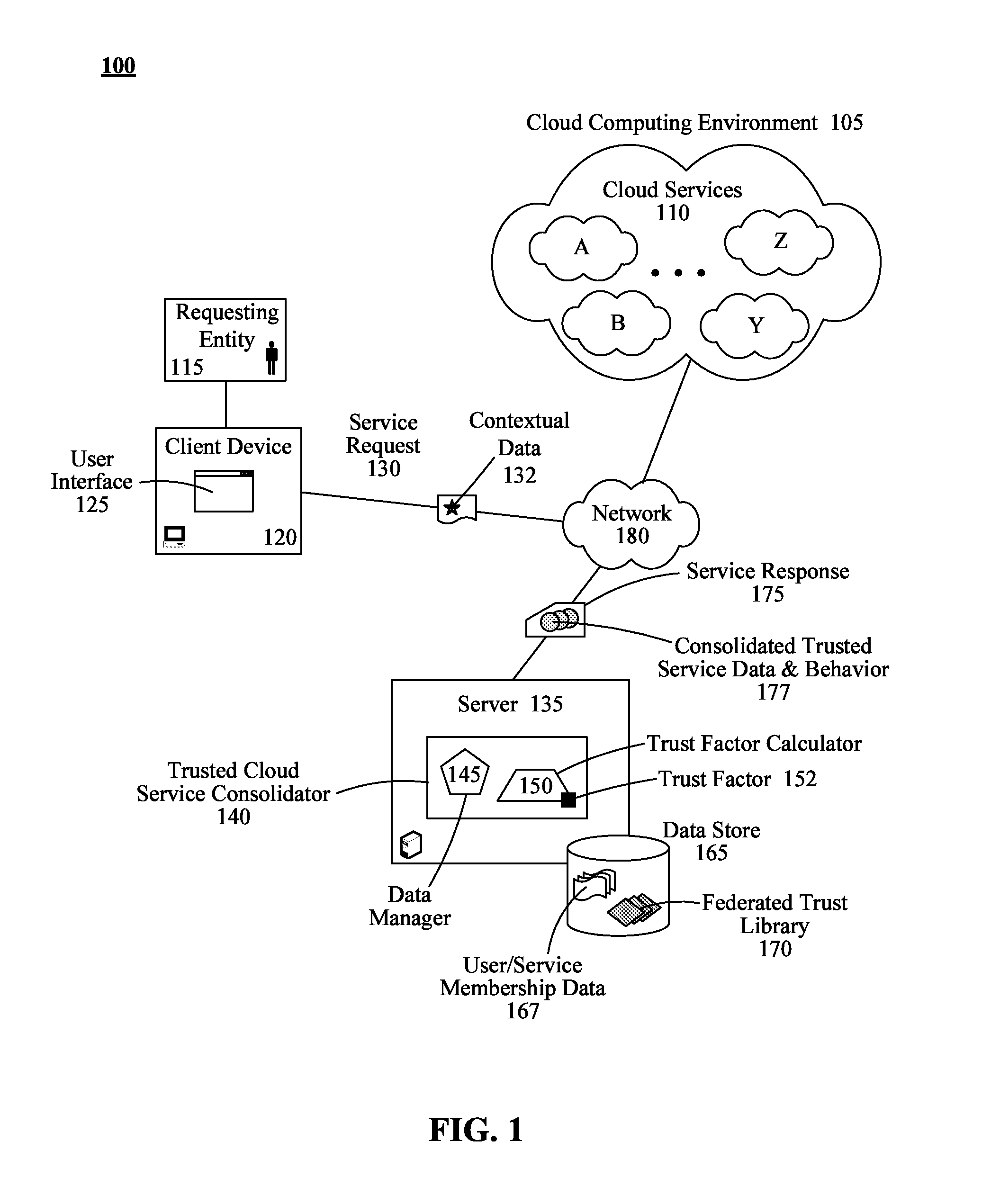
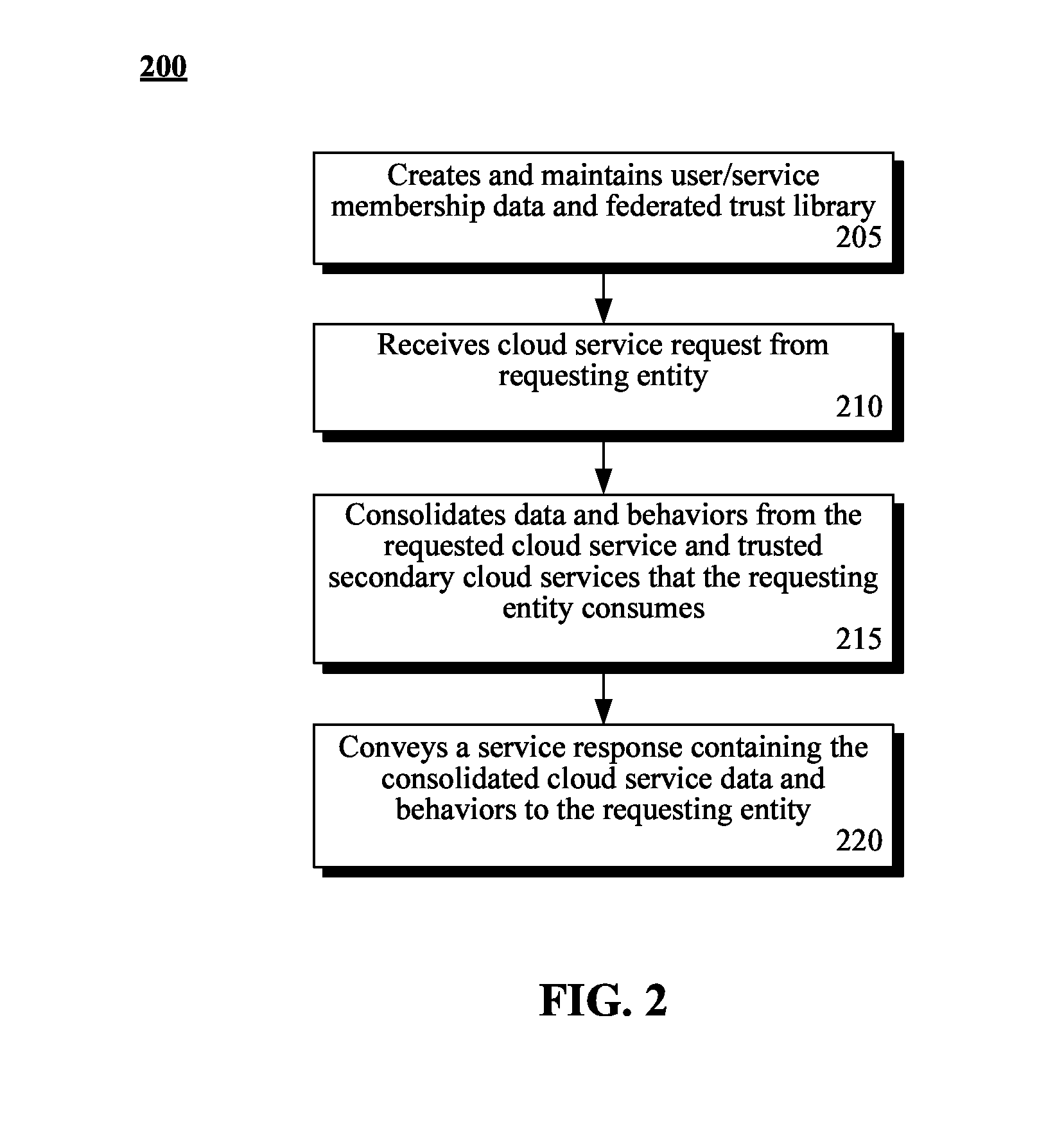
Consolidating disparate cloud service data and behavior based on trust relationships between cloud services
A method for consolidating cloud service data and behaviors can begin with the compilation of user / service membership data that associates requesting entities with subscribed cloud services by a trusted cloud service consolidator. A federated trust library housing inter-service trust information for the cloud services contained in the user / service membership data can be created. In response to a service request from a requesting entity, trusted secondary cloud services can be identified for the requesting entity. Identification of the trusted secondary cloud services can be based upon trust factors synthesized from data contained in the federated trust library. Data satisfying the service request and associated behaviors from each trusted secondary cloud service can then be consolidated into a unified data structure. A behavior can be an executable action supported by a trusted secondary cloud service. The unified data structure can be conveyed to the requesting entity in a service response.
Owner:IBM CORP
Clustered wireless sensor network cluster head election model based on evolutionary game mechanism
InactiveCN106488393ASave energyOptimize computing overheadNetwork topologiesWireless commuication servicesTrust factorWireless sensor networking
The invention relates to a clustered wireless sensor network cluster head election model based on an evolutionary game trust mechanism. The cluster head election model comprises three system models, namely, a wireless sensor network model, a JDL (Joint Director of Laboratories) model, and an evolutionary game model. According to the clustered wireless sensor network cluster head election model based on an evolutionary game trust mechanism provided by the invention, an improved JDL model and an evolutionary game algorithm are adopted, the dynamic characteristic of network communication and the time-effectiveness of trust are fully considered, an optimal cluster head is elected on the premise of considering trust factors such as communication, energy and data, and moreover, the computation overhead is optimized, and the energy of nodes is saved.
Owner:TIANJIN UNIV
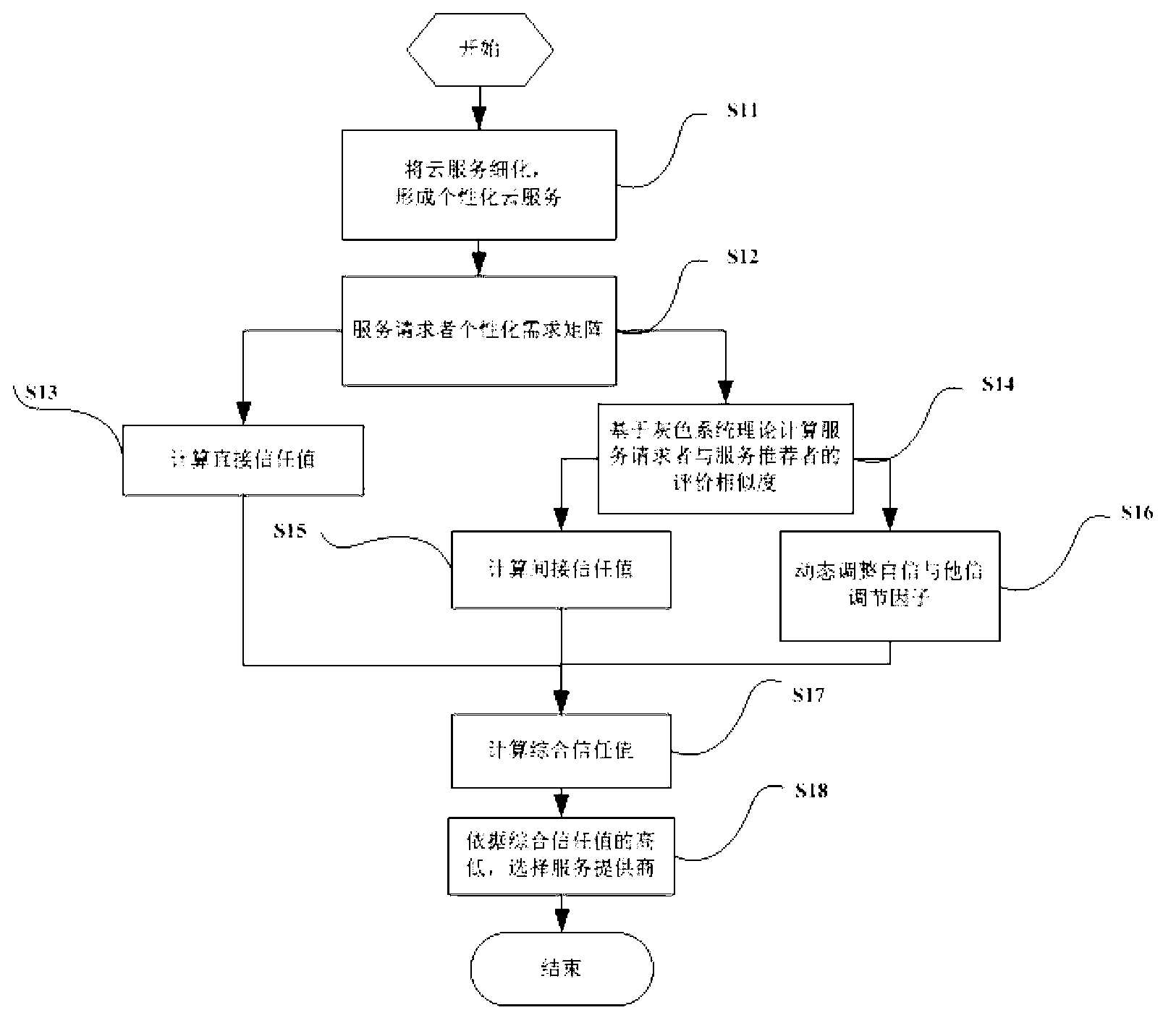
Dynamic trust model establishing system
ActiveCN103237023AMeet individual needsQuantitative precisionTransmissionPersonalizationInternet privacy
The invention discloses a dynamic trust model establishing system. By detailing cloud services and utilizing service attributes with finer grit as study subjects, direct trust value and indirect trust value of a service requester for a service provider are calculated, self-confident factors and trust factors are dynamically adjusted by evaluation similarity to obtain comprehensive trust value finally. The comprehensive trust value is used as indication value of trust relation between the service requester and the service provider, and the purpose of quantifying the trust relation of the service requester and the service provider completely and accurately is achieved. The service requester quantifies the trust relations of different service providers, the service provider with high comprehensive trust value can be conveniently selected according to practical application, and requirement of the service requester for personalization is met to the greatest extent.
Owner:成都尧它大数据有限公司
Trust Event Notification and Actions Based on Thresholds and Associated Trust Metadata Scores
ActiveUS20100107244A1Memory loss protectionDigital data processing detailsInternet privacyTrust factor
An approach is provided for selecting one or more trust factors from trust factors included in a trust index repository. Thresholds are identified corresponding to one or more of the selected trust factors. Actions are identified to perform when the selected trust factors reach the corresponding threshold values. The identified thresholds, identified actions, and selected trust factors are stored in a data store. The selected trust factors are monitored by comparing one or more trust metadata scores with the stored identified thresholds. The stored identified actions that correspond to the selected trust factors are performed when one or more of the trust metadata scores reach the identified thresholds. At least one of the actions includes an event notification that is provided to a trust data consumer.
Owner:DAEDALUS BLUE LLC
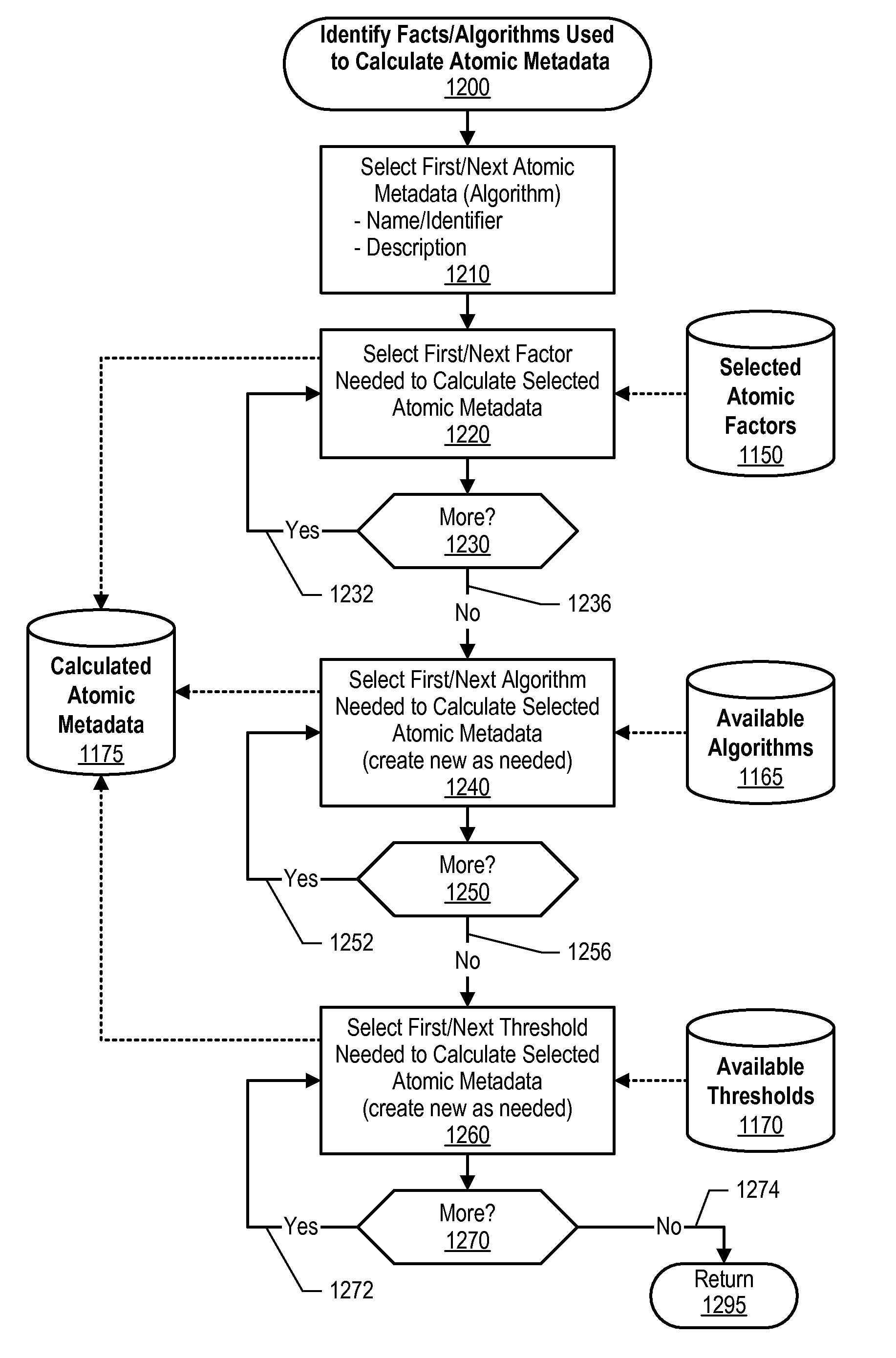
Generating Composite Trust Value Scores Based on Assignable Priorities, Atomic Metadata Values and Associated Composite Trust Value Scores
An approach is provided in which atomic trust scores are computed using a atomic trust factors that are applied to a plurality of metadata. A first set of composite trust scores are computed using some of the atomic trust scores. The composite trust scores are computed using a first set of algorithms. Some of the algorithms use a factor weighting value as input to the algorithm. A second plurality of composite trust scores is computed using some of the composite trust scores that were included in the first set of scores as input. A fact and one of the second set of composite trust scores are presented to a user. The presented composite trust score provides a trustworthiness value that corresponds to the presented fact.
Owner:IBM CORP
Trust event notification and actions based on thresholds and associated trust metadata scores
An approach is provided for selecting one or more trust factors from trust factors included in a trust index repository. Thresholds are identified corresponding to one or more of the selected trust factors. Actions are identified to perform when the selected trust factors reach the corresponding threshold values. The identified thresholds, identified actions, and selected trust factors are stored in a data store. The selected trust factors are monitored by comparing one or more trust metadata scores with the stored identified thresholds. The stored identified actions that correspond to the selected trust factors are performed when one or more of the trust metadata scores reach the identified thresholds. At least one of the actions includes an event notification that is provided to a trust data consumer.
Owner:DAEDALUS BLUE LLC
Apparatus, system, and method for determining and implementing estimate reliability
ActiveUS7484357B2Internal combustion piston enginesNon-fuel substance addition to fuelLow-pass filterTrust factor
An apparatus, system, and method are disclosed for determining the reliability of an estimate such as particulate accumulation on a diesel particulate filter, weighing the estimate according to a function of its reliability, weighing a prediction of particulate accumulation on the filter according to a function of the estimate's reliability, and combining the weighted estimate and weighted prediction to determine a combined particulate load estimate. The degree of reliability can be expressed as a trust factor, and a function of the trust factor can be used in a low-pass filter of the estimate. The trust factor value depends on filter air flow and particulate distribution in one embodiment. Regeneration of the particulate filter may be initiated depending on the value of the combined particulate load estimate.
Owner:CUMMINS INC
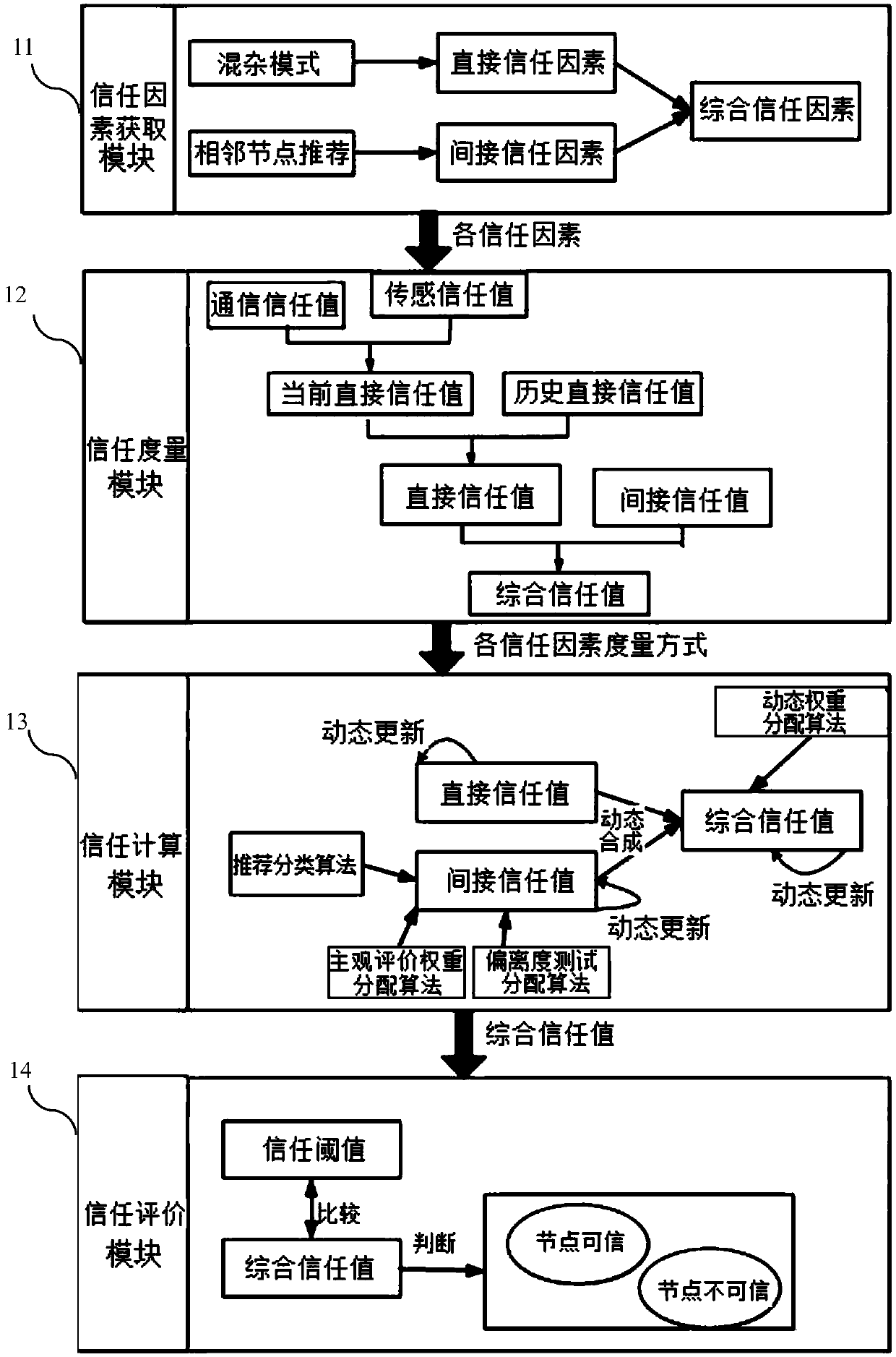
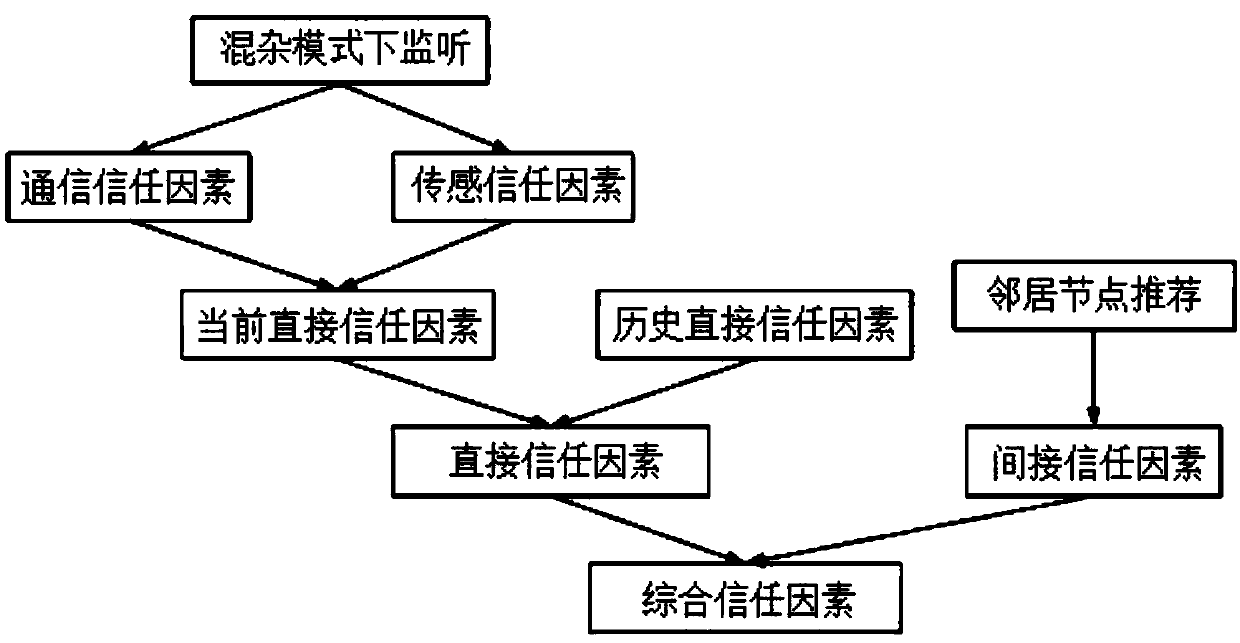
Multi-factor-based dynamic trust evaluation system and method for wireless sensor network
The invention discloses a multi-factor-based dynamic trust evaluation system and method for a wireless sensor network. The system is characterized by comprising a trust factor obtaining module (11), atrust measurement module (12), a trust calculation module (13) and a trust evaluation module (14). The method comprises the steps of: (1), obtaining various trust factors, which possibly influence anode trust value; (2), defining the measurement modes of the various trust factors; (3), realizing each trust calculation; and (4), judging whether a target node is trustable or not by comparing the comprehensive trust value of the target node obtained in a trust calculation process with a trust threshold value. Compared with the prior art, the multi-factor-based dynamic trust evaluation system and method for the wireless sensor network have the active advantages that: because a behaviour when a node transmits sensor data is comprehensively considered, the behaviour of the node can be monitored more comprehensively; the fact that an untrusted node in a network is effectively processed in time can be ensured; in addition, the trust value of the node is measured in a manner of integrating direct trust with indirect trust; and thus, the evaluation result deviation problem of the node is solved.
Owner:TIANJIN UNIV
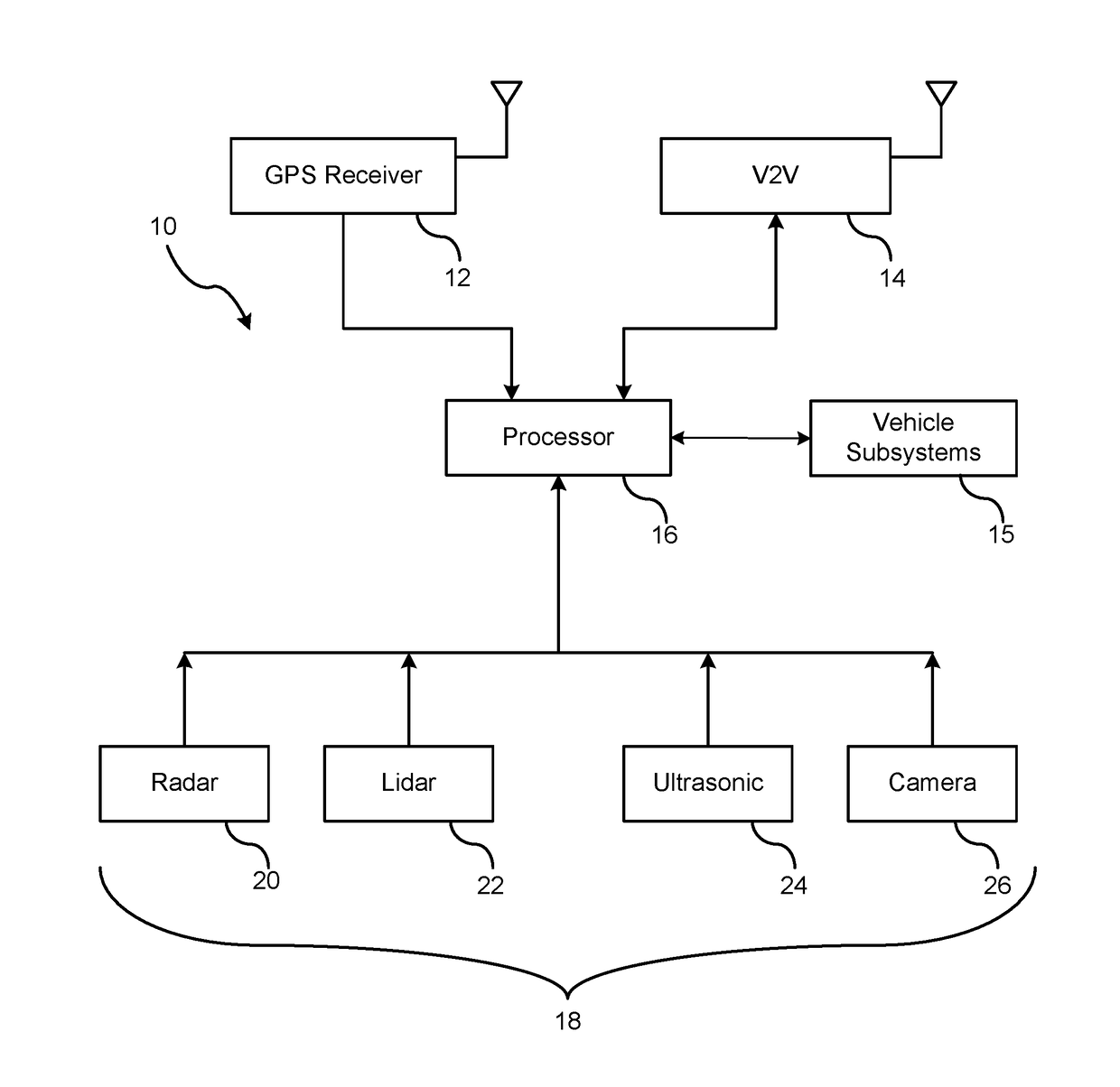
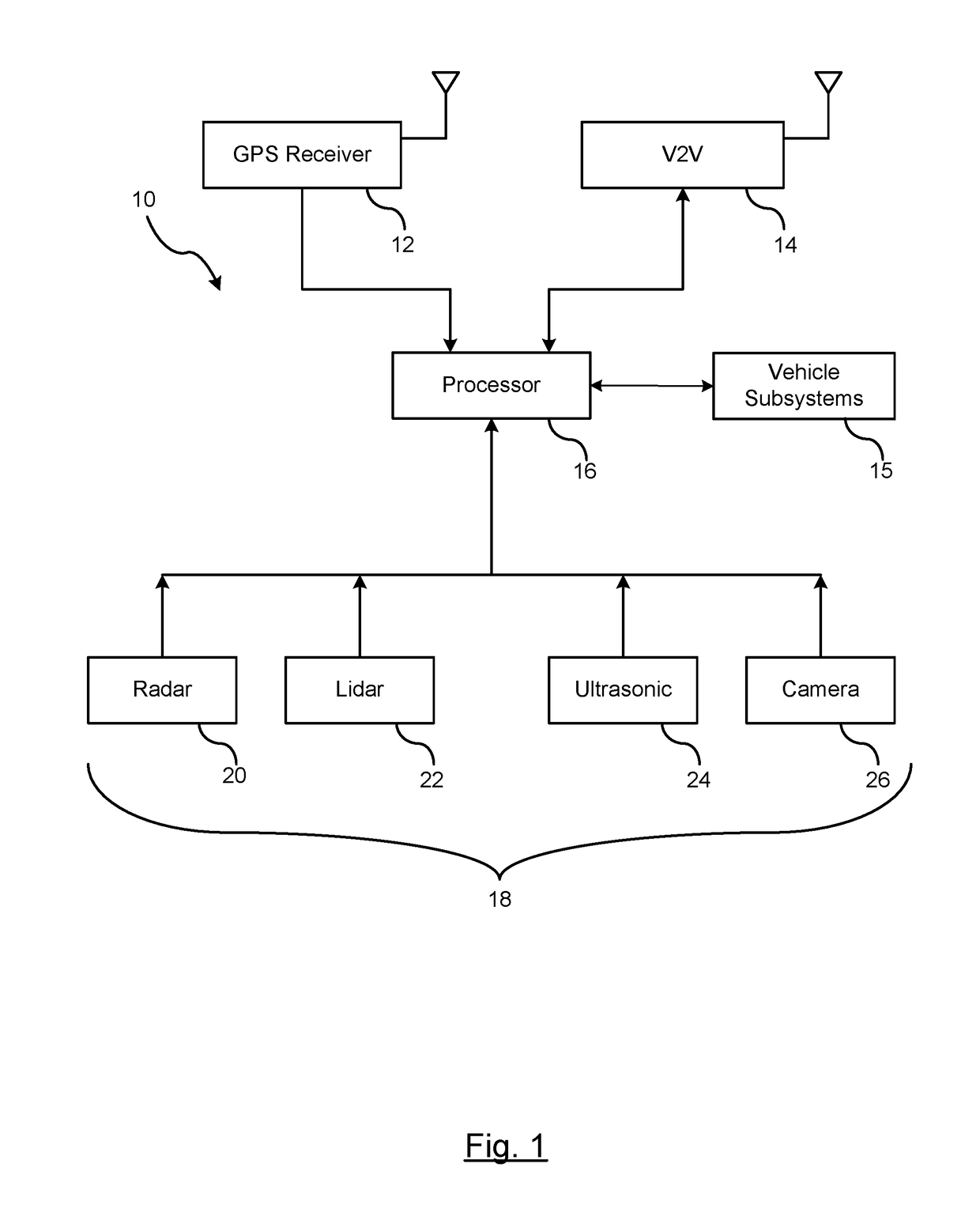
V2V Collaborative Relative Positioning System
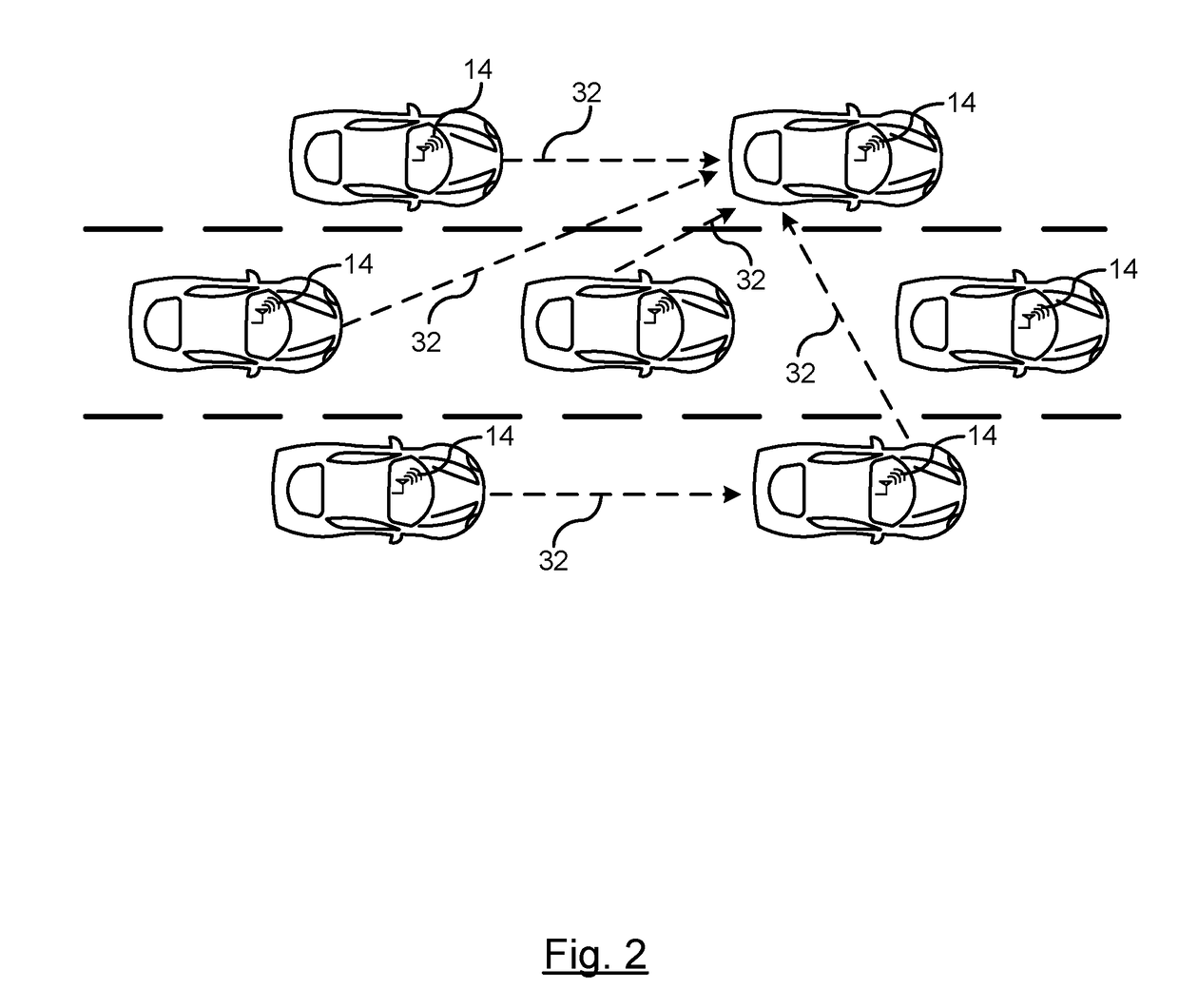
ActiveUS20180203130A1ConfidencePosition fixationBroadcast service distributionTrust factorPositioning system
A method is provided of enhancing GPS data of a host vehicle within a cluster. V2V messages within the cluster are exchanged. A respective vehicle having a highest GPS trust factor is identified utilizing GPS data within the V2V messages. The GPS data of the host vehicle is adjusted as a function of GPS position of the identified vehicle and relative position data between the host vehicle and the identified vehicle.
Owner:FORD GLOBAL TECH LLC
Monitoring for fraudulent or harmful behavior in applications being installed on user devices
Software applications to be installed on user devices are monitored. Authenticity of the applications is evaluated using a plurality of inputs to provide a result. The plurality of inputs may include trust factors. The trust factors may be used to generate a security evaluation. In response to the result, an action is performed such as providing a notification to a developer of a fraudulent version of an application or providing a security assessment for an application.
Owner:LOOKOUT MOBILE SECURITY
Generating composite trust value scores, and atomic metadata values and associated composite trust value scores using a plurality of algorithms
An approach is provided in which atomic trust scores are computed using a atomic trust factors that are applied to a plurality of metadata. A first set of composite trust scores are computed using some of the atomic trust scores. The composite trust scores are computed using a first set of algorithms. Some of the algorithms use a factor weighting value as input to the algorithm. A second plurality of composite trust scores is computed using some of the composite trust scores that were included in the first set of scores as input. A fact and one of the second set of composite trust scores are presented to a user. The presented composite trust score provides a trustworthiness value that corresponds to the presented fact.
Owner:INT BUSINESS MASCH CORP
A CF recommendation method fusing matrix decomposition and user project information mining
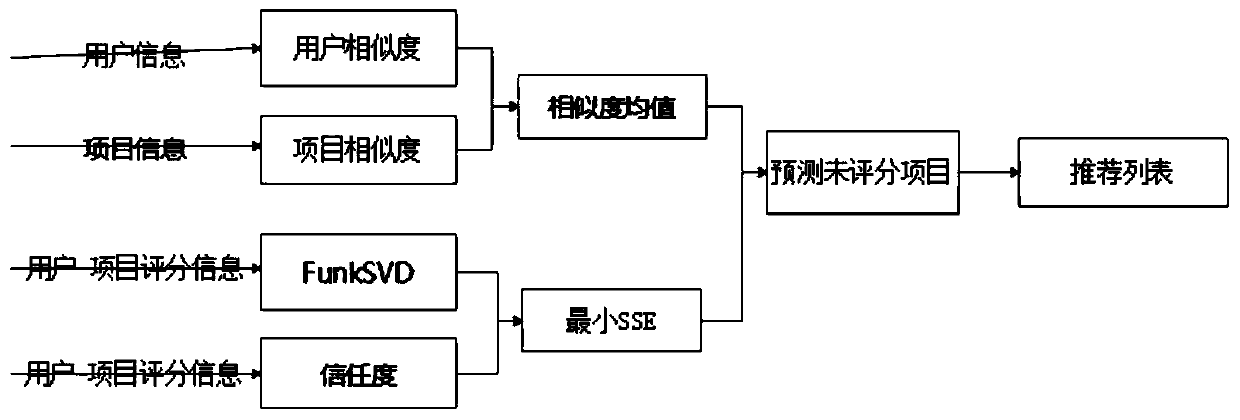
ActiveCN109740064AOvercome data sparsityOvercome cold startDigital data information retrievalSpecial data processing applicationsMatrix decompositionProject type
The invention provides a CF (collaborative filtering) recommendation method fusing matrix decomposition and user project information mining. The CF recommendation method comprises the following steps:reading historical score data and project type data information of a user on an article; based on the FunkSVD model, optimizing and decomposing the user score matrix, and adding a similarity factor to calculate and generate a user score prediction matrix; calculating optimal similarity by optimizing CF users and project information occupying different proportions, predicting user scores, and generating Top-N recommendation lists. The method has the advantages that (1) the user scoring matrix is optimized and decomposed based on the FunkSVD model, and the trust factor is added to predict the user scoring matrix, so that the problem of low prediction accuracy caused by data sparseness of a traditional matrix decomposition model is relieved; (2) similarity is calculated based on the user information and the project information, and the problem of cold start caused by excessive dependence on historical data in a traditional recommendation algorithm is solved; and (3) a trust degree relationship between users is introduced, so that the recommendation precision and interpretability of a traditional CF recommendation algorithm are improved.
Owner:BEIJING UNIV OF CHEM TECH +1
Ranking information providers
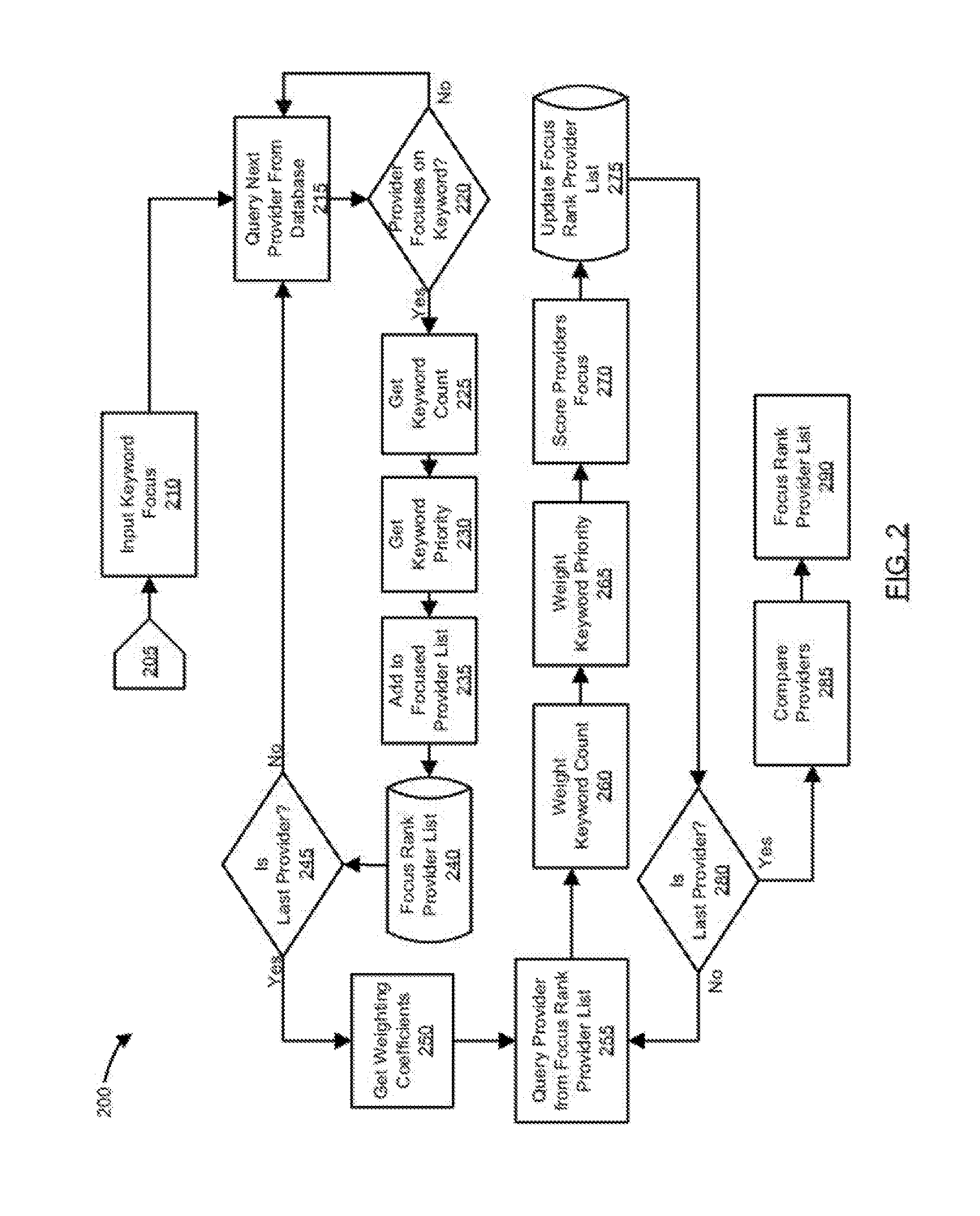
PendingUS20160283952A1Digital data information retrievalSpecial data processing applicationsFull text searchPersonalization
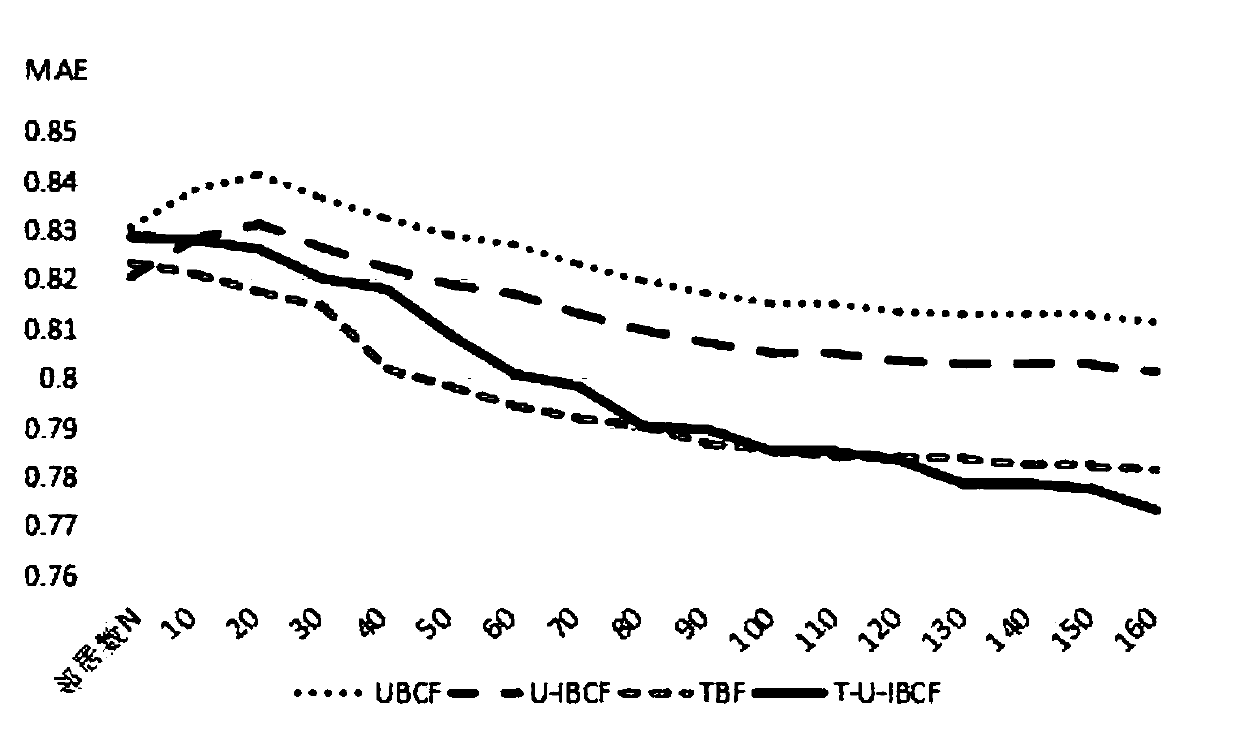
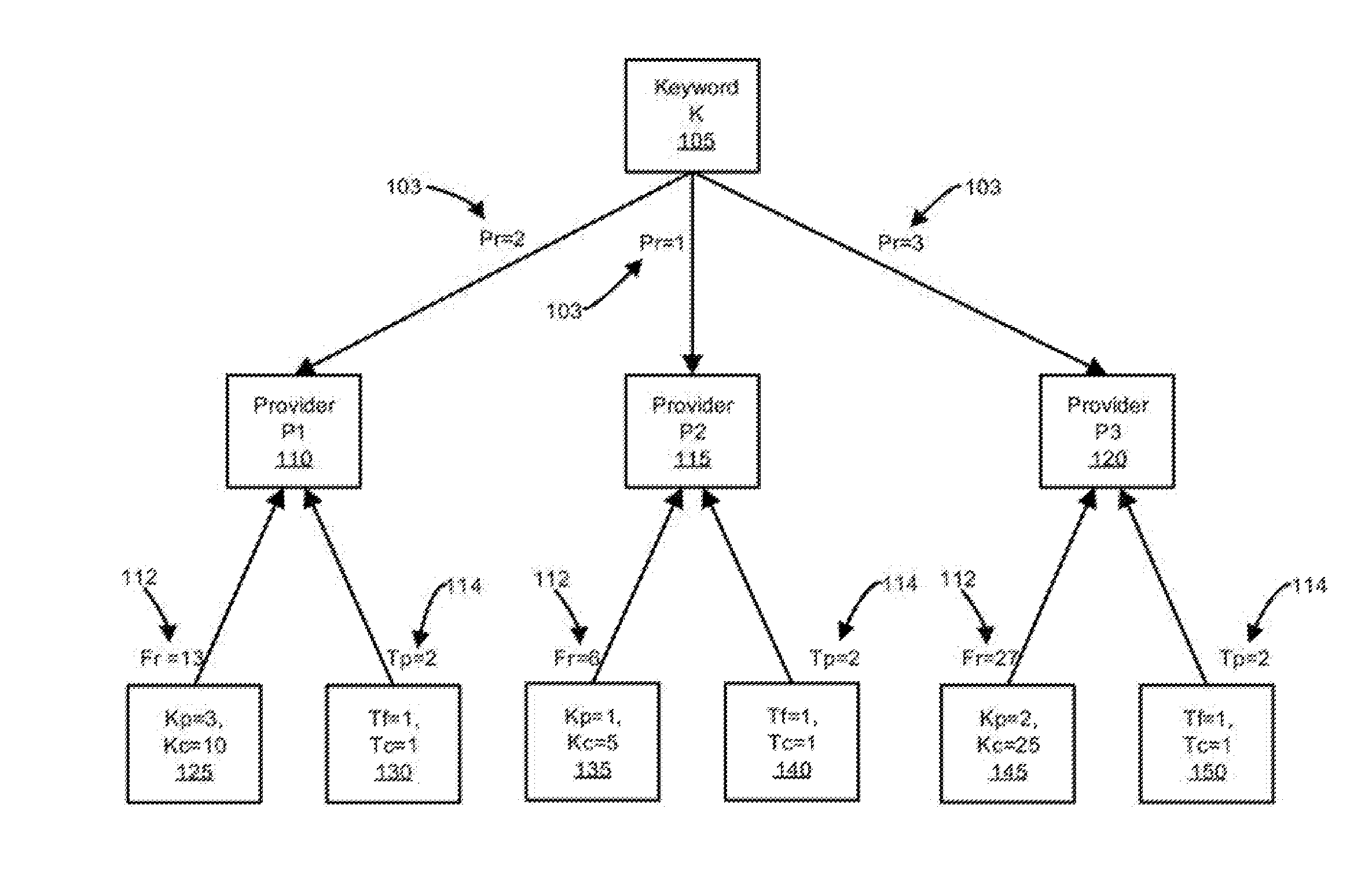
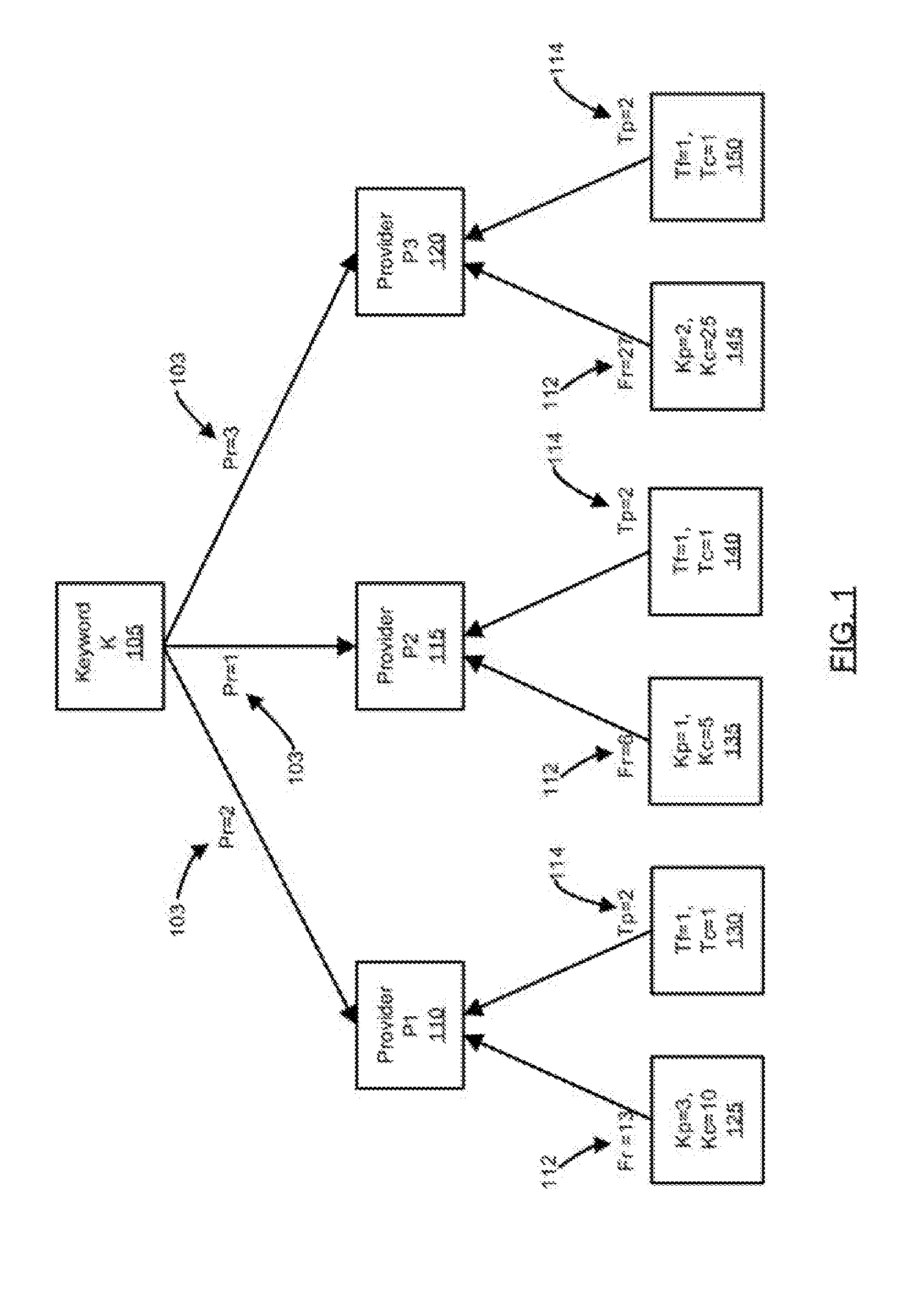
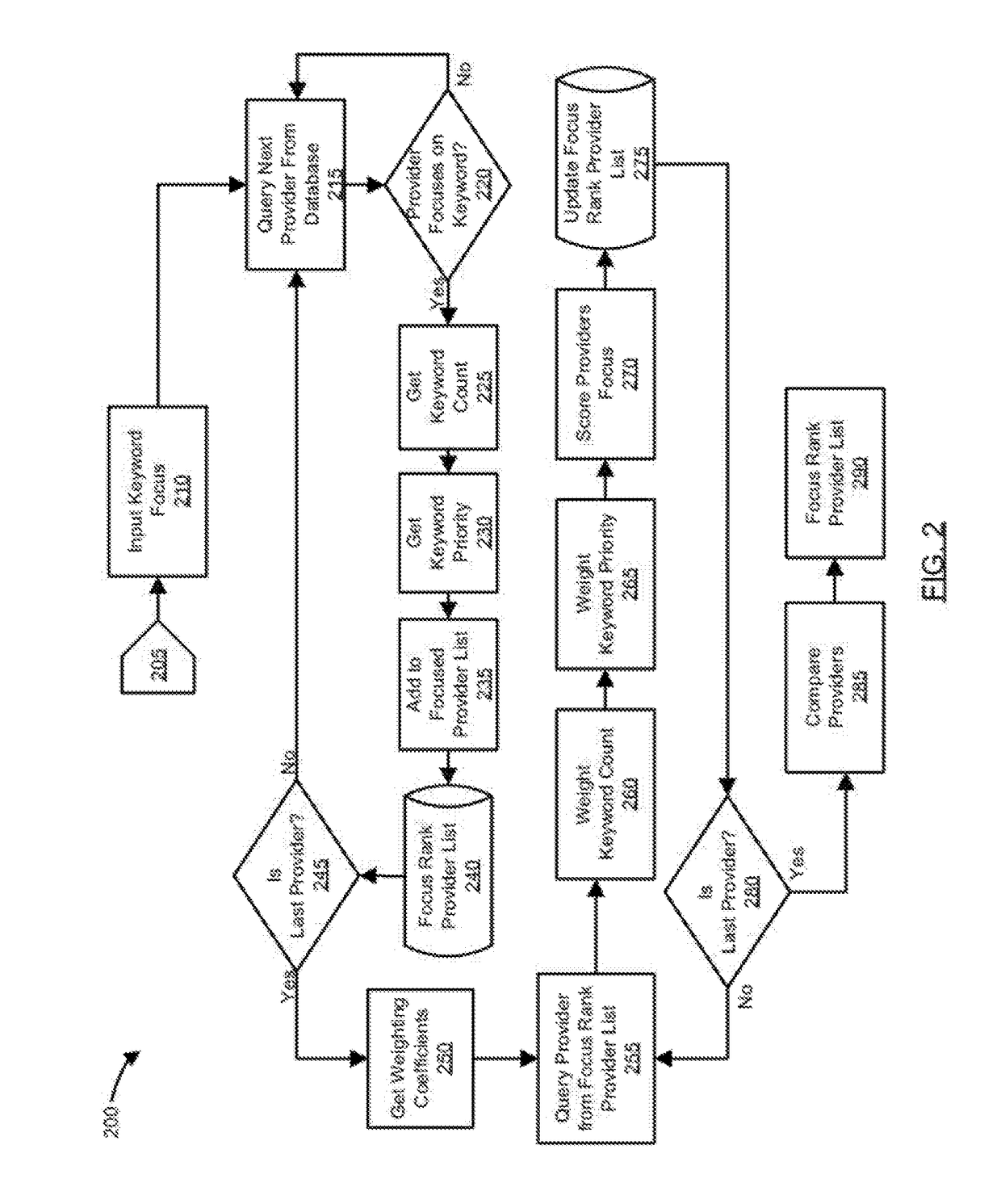
A system and method for ranking providers is provided. The method may include ranking information providers based on their focus and trust in specific keyword contexts. The focus trust rank assigned to a specific information provider may be calculated from their focus for a given keyword that is the subject of an information search. A provider's focus trust rank may additionally or alternatively be calculated based on one or more of the total keyword count set by the provider, the number of consumers who trust the provider, matching trust factors, or a measure of a maturity of the provider in a system using the method for ranking and, thus, filtering providers. Consumers may optionally be provided with the ability to apply their personalized list of focused and trusted providers to transform the results of a full text search such that their trusted providers always rank to the top and optionally can trust providers which are returned in the search.
Owner:AGINGO
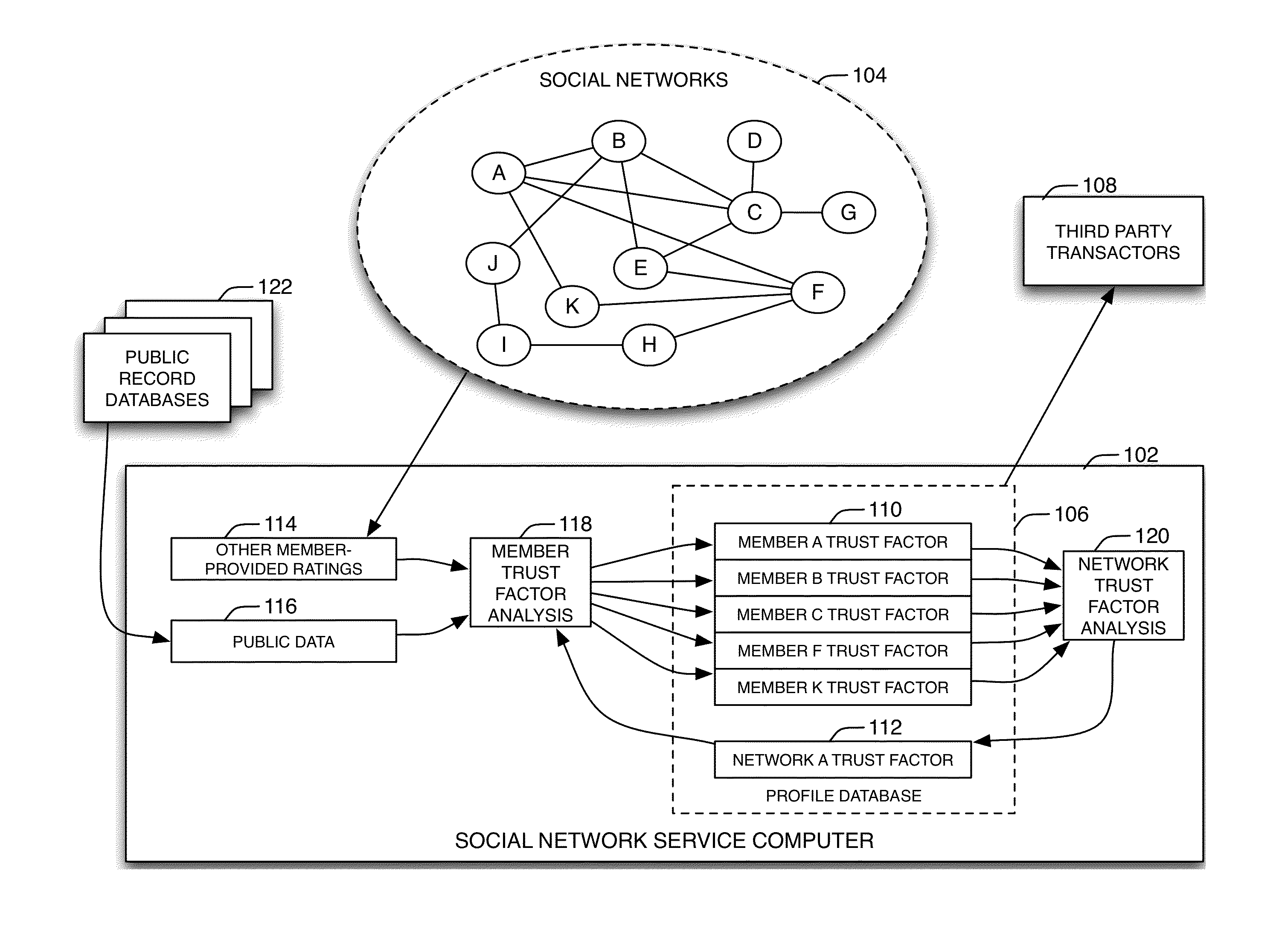
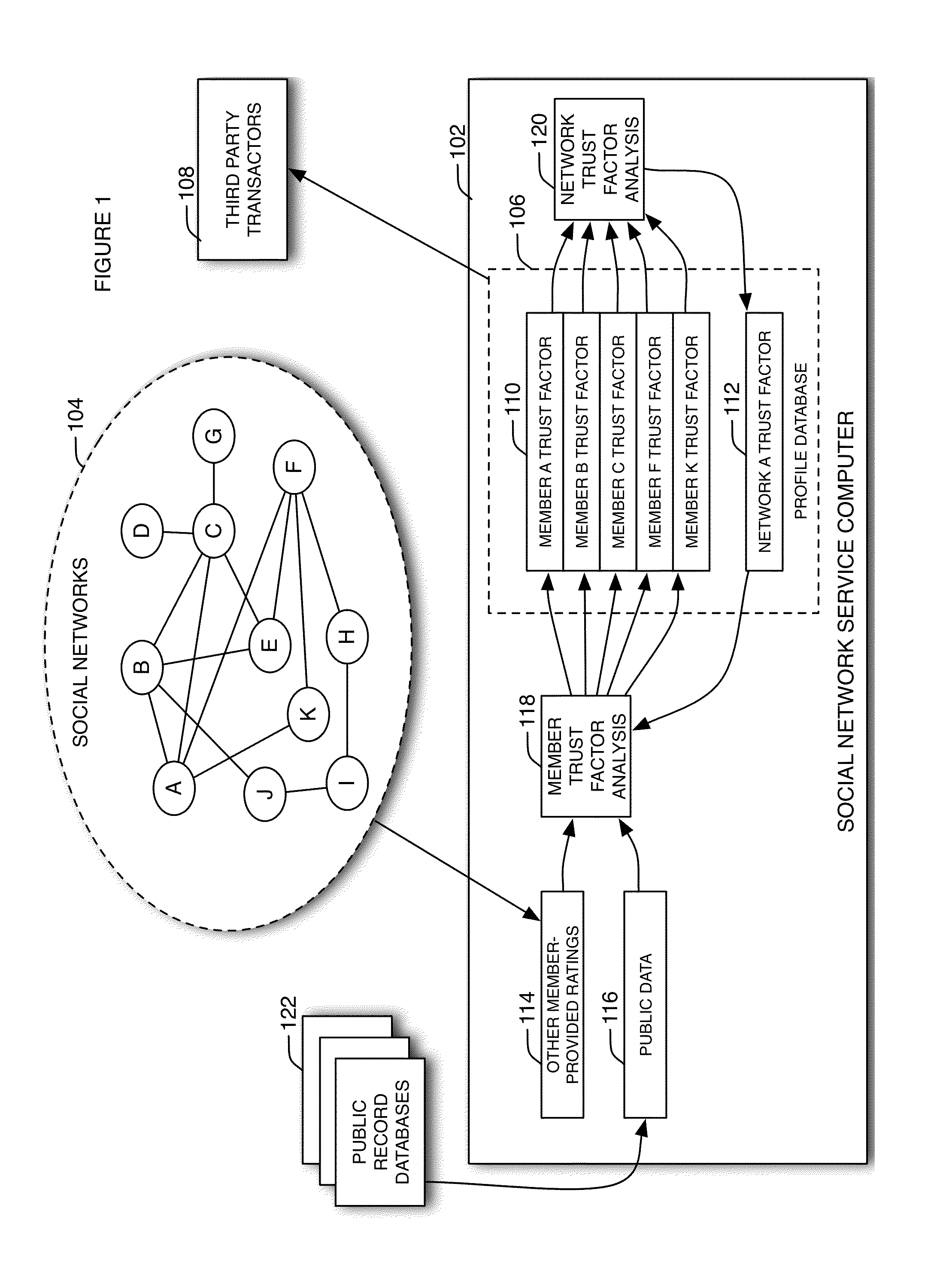
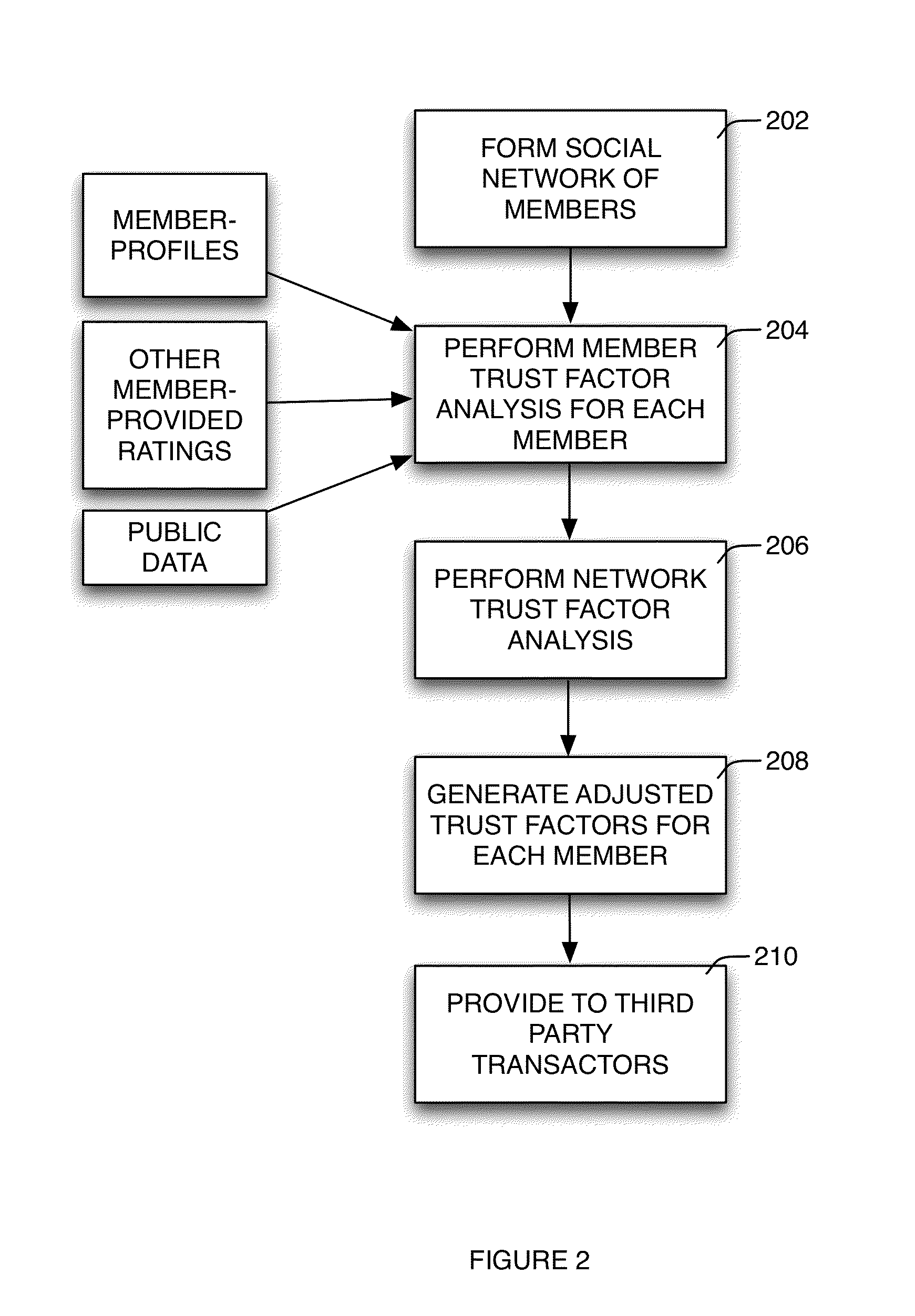
Method and system for providing trust analysis for members of a social network
A computer-implemented method of providing a trust analysis comprising forming, using a social network server computer, a social network comprising a plurality of members, each of said members registering with said social network server computer and providing a member profile, each of said member profiles comprising information associated with said member; performing with the social network server computer a member trust factor analysis to generate a member trust factor for each of the plurality of members; performing with the social network server computer a network trust factor analysis of the member trust factors to generate a network trust factor for the social network; and for each of the plurality of members, generating with the social network server computer an adjusted member trust factor by adjusting the member trust factor by the network trust factor.
Owner:SIGNATURE SYST
Configurable Trust Context Assignable to Facts and Associated Trust Metadata
An approach is provided for selecting a trust factor from trust factors that are included in a trust index repository. A trust metaphor is associated with the selected trust factor. The trust metaphor includes various context values. Range values are received and the trust metaphor, context values, and range values are associated with the selected trust factor. A request is received from a data consumer, the request corresponding to a trust factor metadata score that is associated with the selected trust factor. The trust factor metadata score is retrieved and matched with the range values. The matching results in one of the context values being selected based on the retrieved trust factor metadata score. The selected context value is then provided to the data consumer.
Owner:IBM CORP
Collaborative filtering method for user interest harmony similarity
InactiveCN110399549AAccurate recommendationRecommendation list for recommendation accuracyDigital data information retrievalSpecial data processing applicationsTrust factorRating matrix
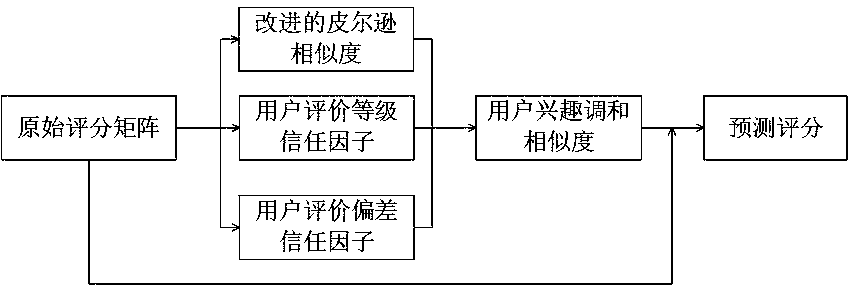
The invention relates to a collaborative filtering method for user interest harmony similarity. The method comprises the following steps: decomposing an original scoring matrix; introducing a time-based user interest degree weight function into a Pearson similarity function; and combining with the user evaluation grade trust factor and the user evaluation deviation trust factor to obtain user interest harmony similarity, obtaining a recommendation result by utilizing the original scoring matrix and the user interest harmony similarity, and recommending items meeting requirements to the user. According to the method provided by the invention, the recommendation precision can be remarkably improved compared with a traditional probability matrix decomposition method under the condition that the user scoring data is sparse, and the interested articles can be recommended according to the user in different time periods.
Owner:HENAN POLYTECHNIC UNIV
Qualitative Search Engine Based On Factors Of Consumer Trust Specification
InactiveUS20110252015A1Digital data processing detailsRelational databasesTrust factorQualitative property
A method of providing a search engine for use on global computer networks which identifies and merges categories of information that reflect, influence and imitate intelligent choice by concurrently searching one or more of eight factors of consumer trust: books, experts, news and articles, associations, celebrities and pro choice, awards, web information and blogs and people's choice. The results from the search of these selected consumer trust factors are then combined to generate a final report.
Owner:BARD KRISTINA BUTVYDAS +1
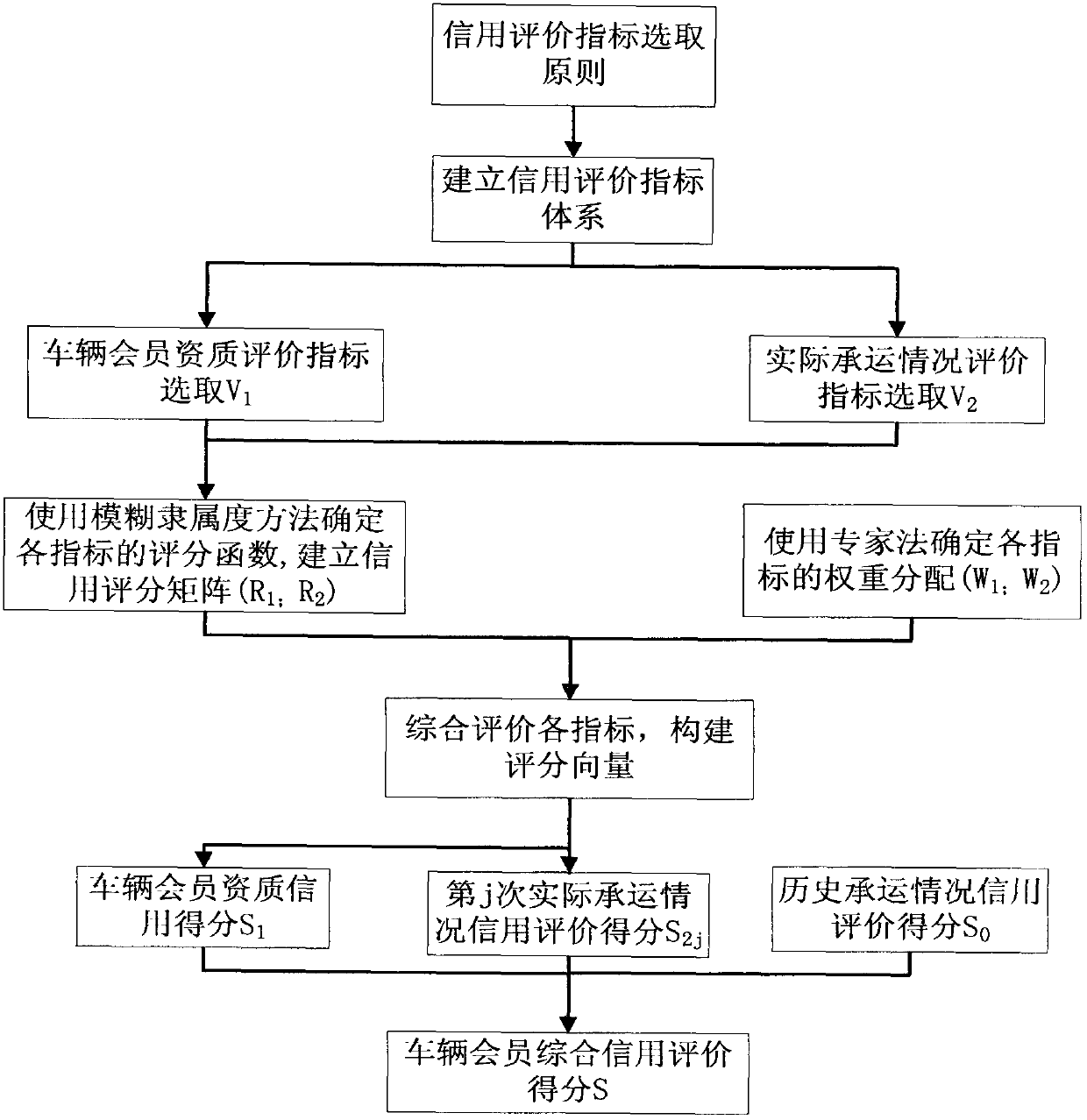
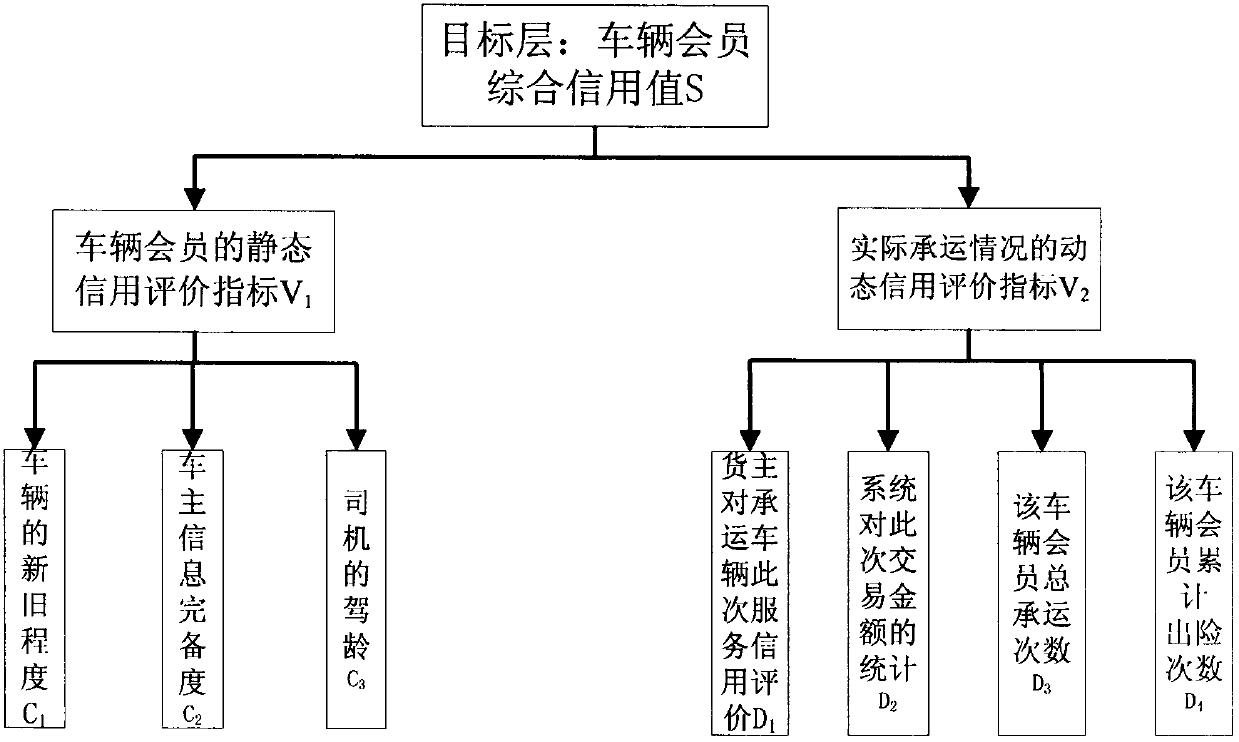
Vehicle member credit evaluation method
The invention relates to a vehicle member credit evaluation method. Accumulated credit evaluation data extracted after transaction behavior completion by a transaction party is used as an evaluation basis and a plurality of trust factors that influence the trust relationship measure and include vehicle owner service satisfaction degree evaluation by a cargo owner after transaction completion, the number of times of vehicle carrying, the benefit amount created for the system by the vehicle, and accident occurrence frequency during vehicle carrying and the like can be considered comprehensively; and then a multi-factor weighted average method and fuzzy comprehensive evaluation method-based credit evaluation model and an evaluation method are put forward. According to the invention, various factors are considered comprehensively and an evaluation method is brought forward by using the algorithm. Problems of multiple factor existence, fuzziness, and subjective judgment and the like during the transaction process can be well solved; and the defects of imperfection and non-concise property of the existing evaluation system on the network can be overcome. Therefore, the cargo owner can know comprehensive credit information of a to-be-selected vehicle clearly and visually and thus makes a decision rapidly and reasonably, thereby improving the operation efficiency and the service quality of the whole system as well as scientificity of transaction selection.
Owner:中储南京智慧物流科技有限公司
System for transparent authentication across installed applications
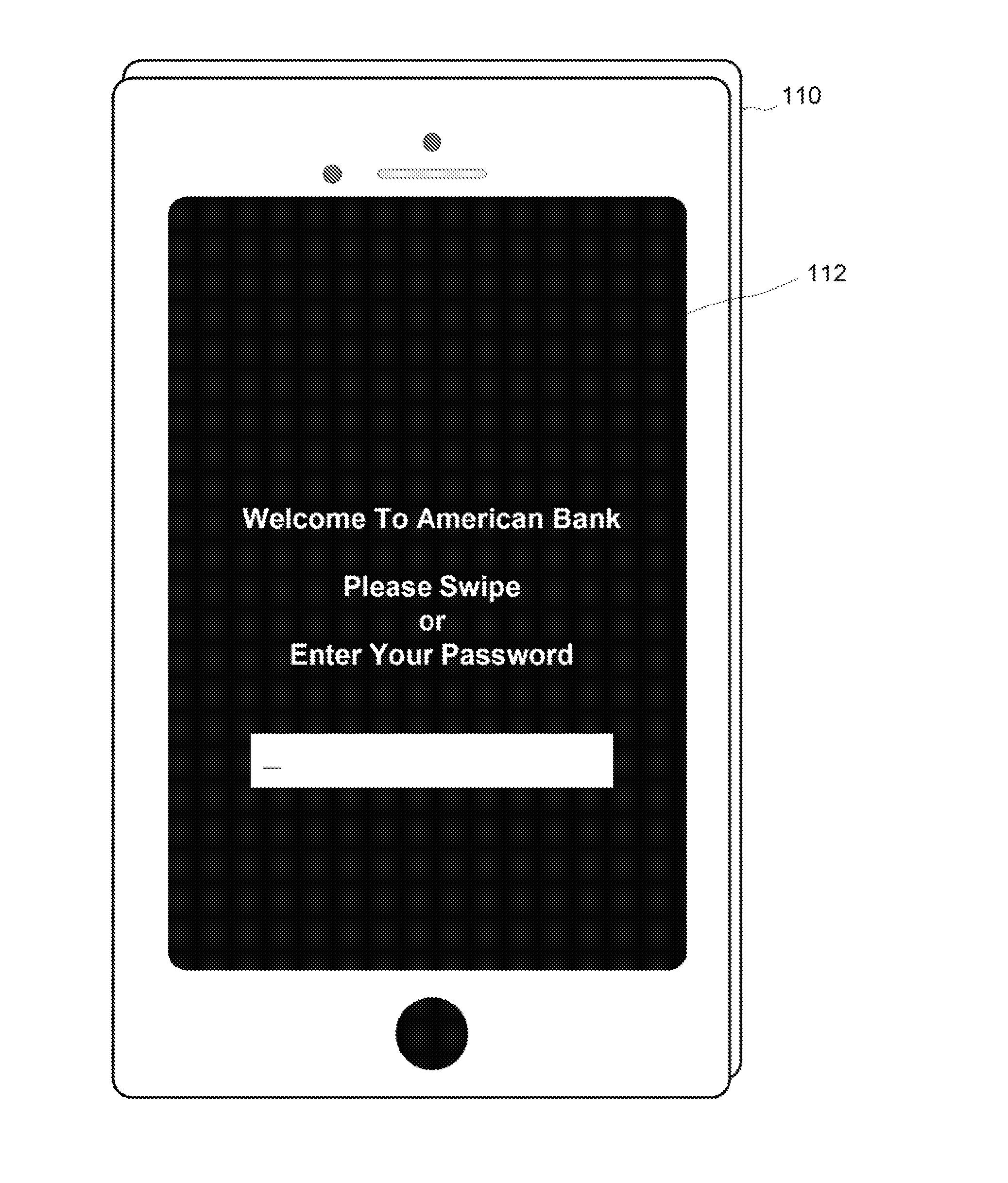
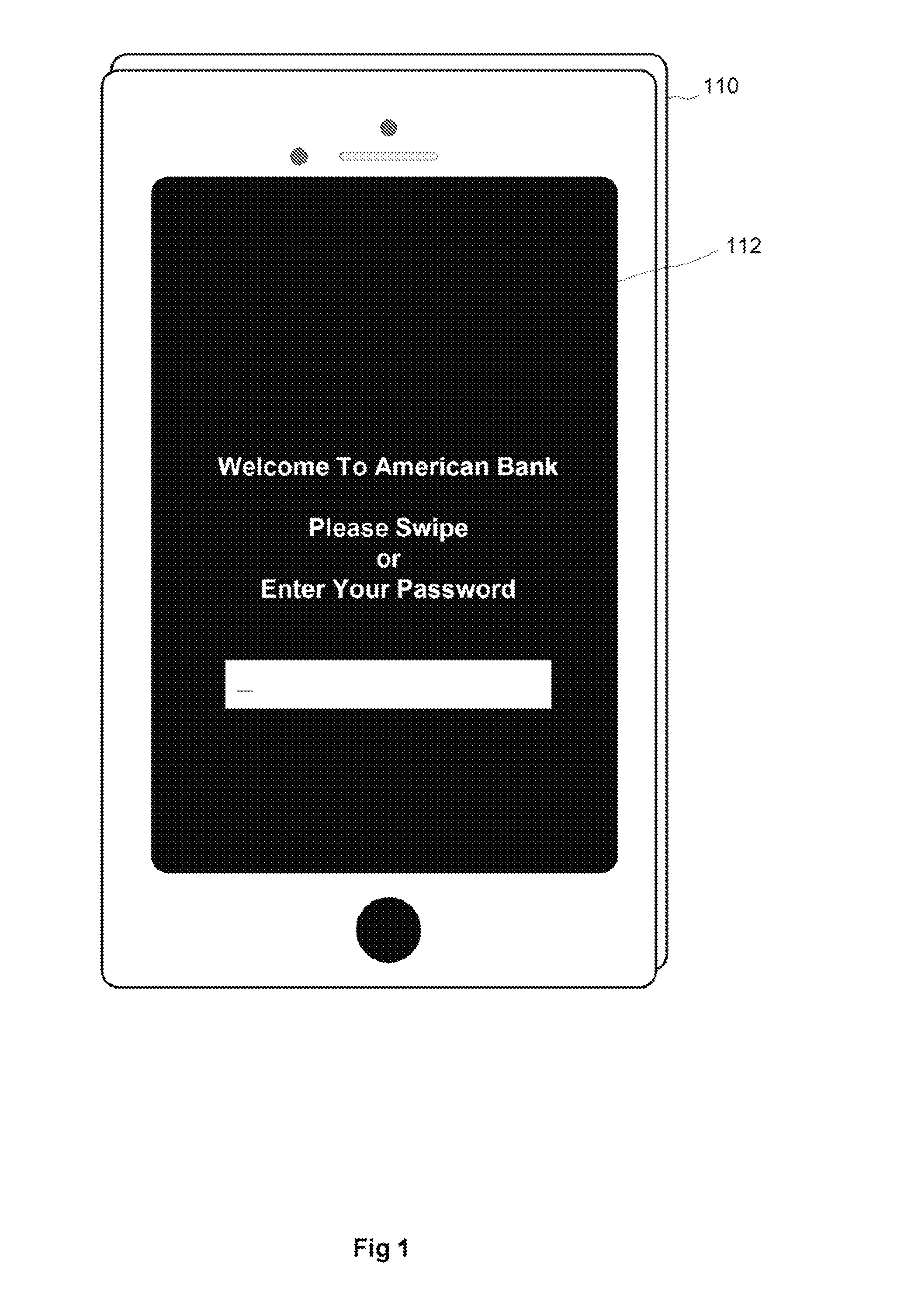
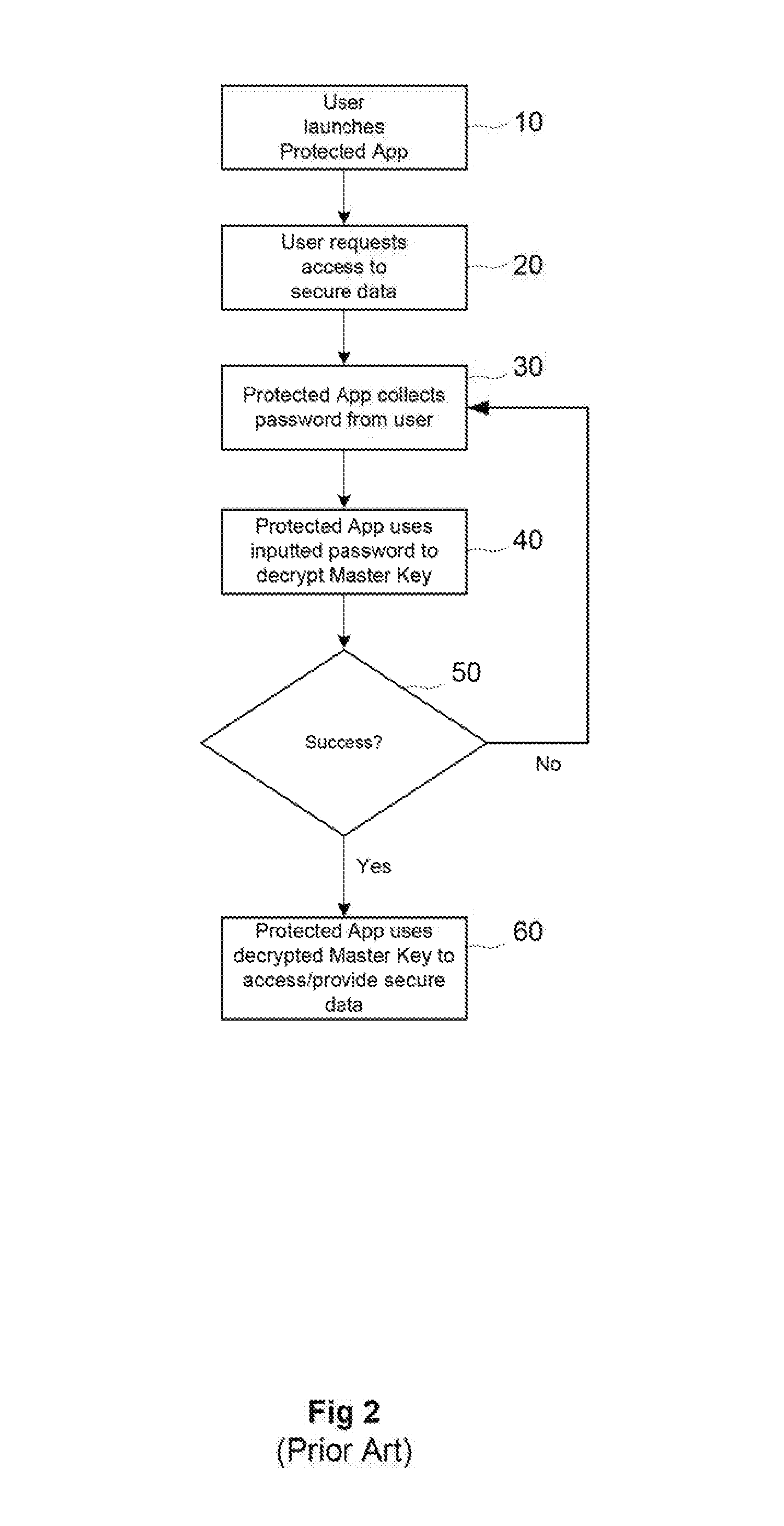
InactiveUS20170041145A1Not easily manipulatedEasy to useKey distribution for secure communicationMultiple keys/algorithms usagePasswordTrust factor
A system for authenticating mobile device users transparently is disclosed. This invention improves on the existing flaws by deriving encryption keys from environmental condition data when the user and device are trusted. The keys are then cryptographically hashed and compared with repository hashed data to determine if the conditions match a prior set of conditions. If a match is found and trust factors are sufficient, the system uses the condition data to decrypt a master key that allows access to secure data in the same manner as would a user-provided password. The security system cannot be bypassed if the device is stolen, as an attacker would have to replicate the exact environment and behavioral attributes employed and learned from the user without any knowledge as to the factors that constitute them because the factors are not maintained by the system.
Owner:TRUSTED MOBILE LLC D B A SENTEGRITY
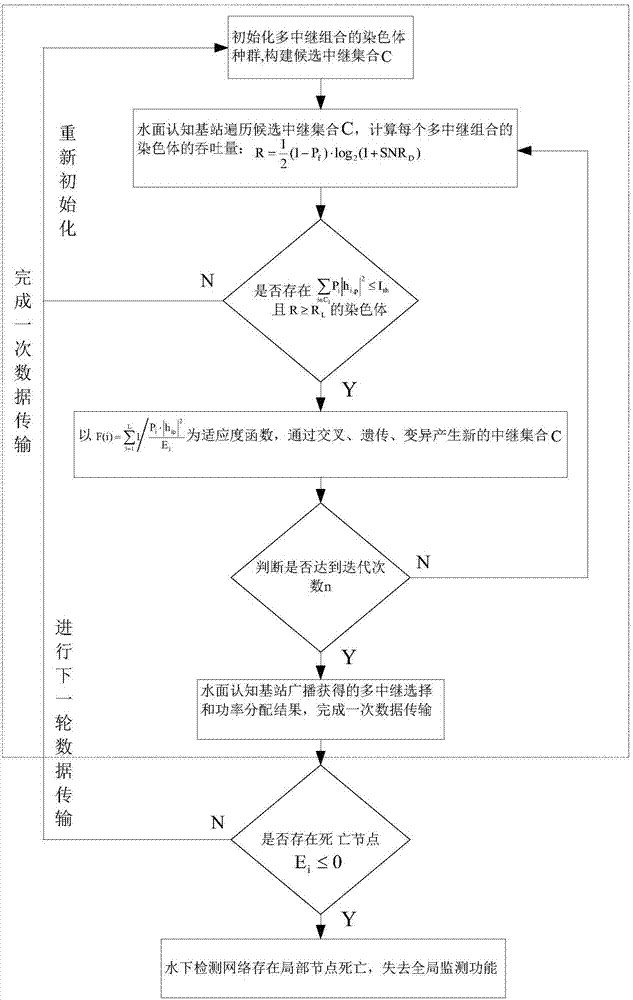
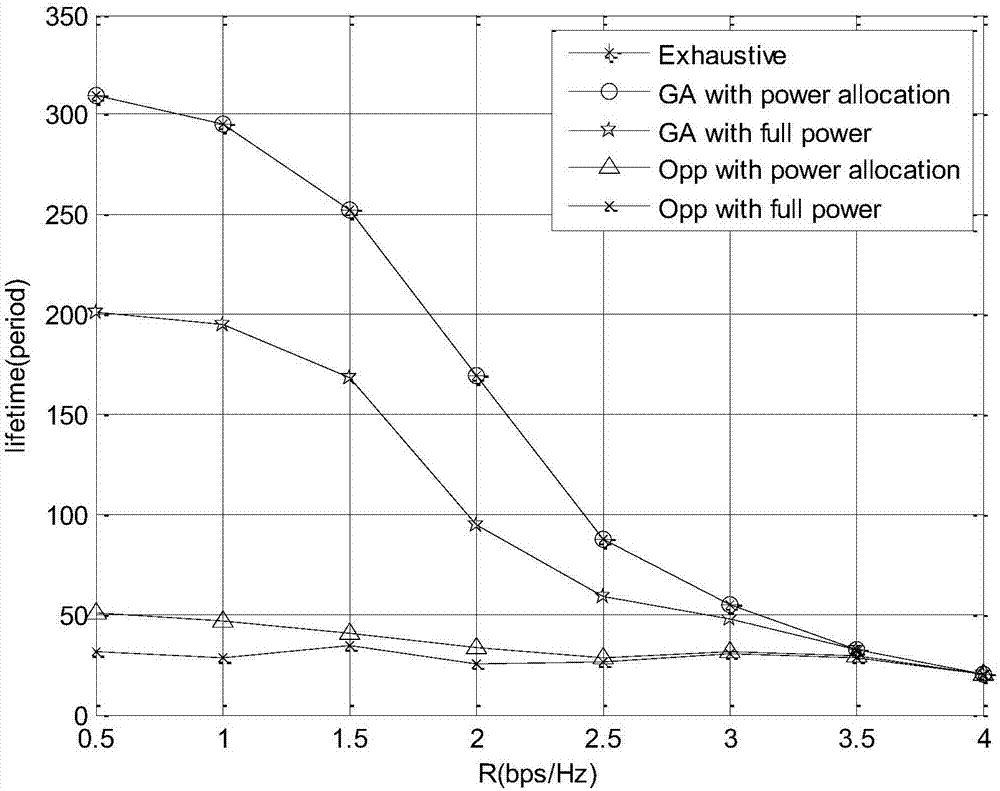
Multi-relay cooperative cognitive underwater acoustic system relay selection and power optimization method
ActiveCN106953678AImprove multi-relay perception efficiencyAlleviate resource constraintsPower managementRadio transmissionFrequency spectrumTelecommunications
The invention discloses a multi-relay cooperative cognitive underwater acoustic system relay selection and power optimization method, which is characterized in that a relay trust factor is built to evaluate the relay performing in allusion to conditions of spectrum resource shortage, channel fading and severe time delay in underwater acoustic communication by adopting a relay trust factor proportion weighted cooperative sensing method and a DF forwarding protocol based underwater acoustic multi-relay selection and power optimization method, relays participate in cooperative sensing in a mode of proportion weighting, and the sensing accuracy is effectively improved. Meanwhile, network interference limitations and residual energy are brought into a utility function in a multi-relay cooperative network, relay selection and power optimization are performed based on a genetic algorithm from the perspectives of power optimization and residual energy consumption, and the network is enabled to be more balanced in energy consumption.
Owner:YANSHAN UNIV
Ranking information providers
InactiveUS20170323019A1Well formedDigital data information retrievalSpecial data processing applicationsPersonalizationFull text search
A system and method for ranking providers is provided. The method may include ranking information providers based on their focus and trust in specific keyword contexts. The focus trust rank assigned to a specific information provider may be calculated from their focus for a given keyword that is the subject of an information search. A provider's focus trust rank may additionally or alternatively be calculated based on one or more of the total keyword count set by the provider, the number of consumers who trust the provider, matching trust factors, or a measure of a maturity of the provider in a system using the method for ranking and, thus, filtering providers. Consumers may optionally be provided with the ability to apply their personalized list of focused and trusted providers to transform the results of a full text search such that their trusted providers always rank to the top and optionally can trust providers which are returned in the search.
Owner:AGINGO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com