Attack defense method and device
A technology of attack characteristics and access traffic, applied in the field of data communication, can solve the problems of inability to achieve the effect of protection, attack, and inability to intercept attack traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
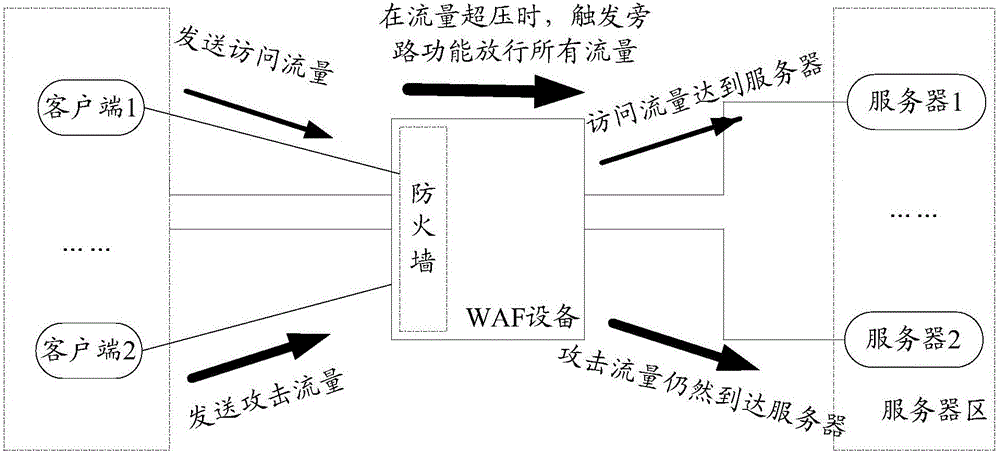
[0016] Usually, a web application firewall is used to detect user traffic (ie, access traffic) accessing a website server, thereby intercepting attack traffic attacking the website server. However, the WAF device needs to consume device performance by detecting whether the access traffic matches the attack characteristics; if the access traffic reaches a certain amount, the WAF device will enter the traffic overpressure state, which will trigger the bypass function to release all traffic, resulting in the inability to intercept the attack traffic .
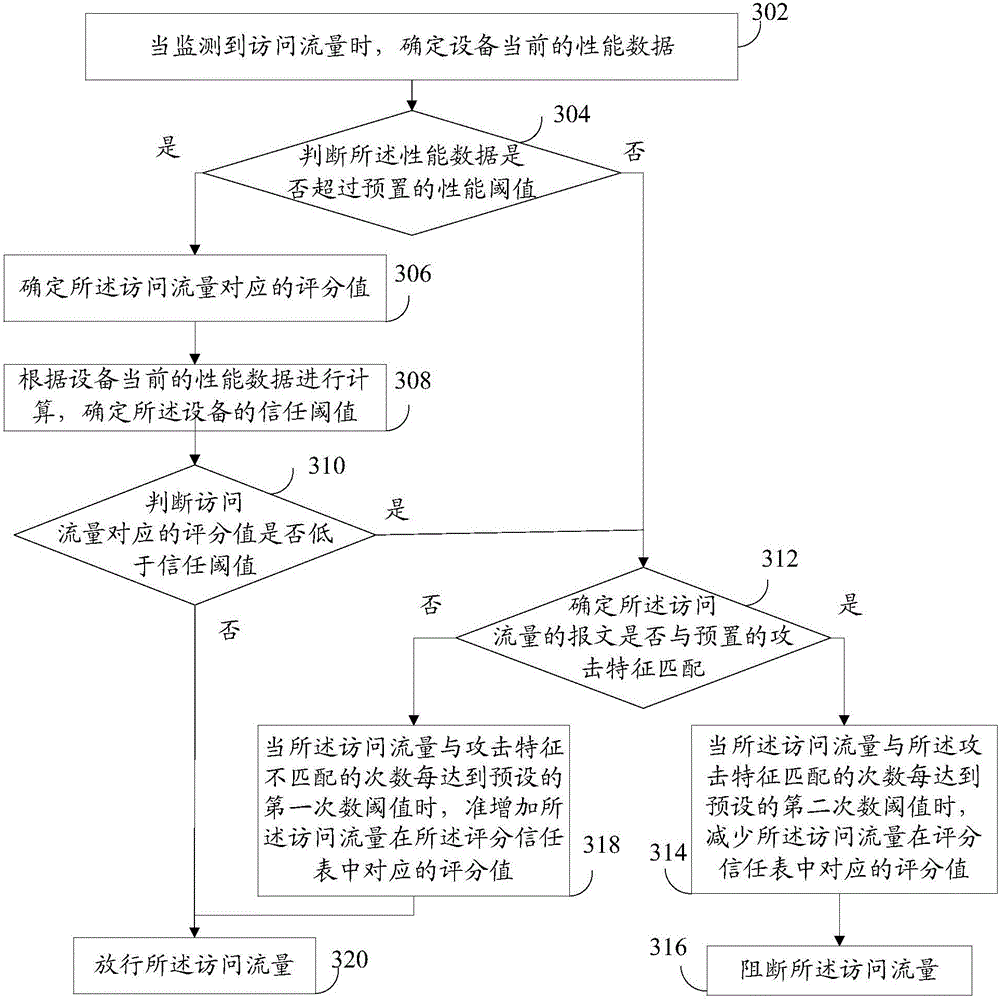
[0017] One of the core concepts of the embodiment of the present application is that the WAF device triggers the trust scoring function in the traffic overp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com