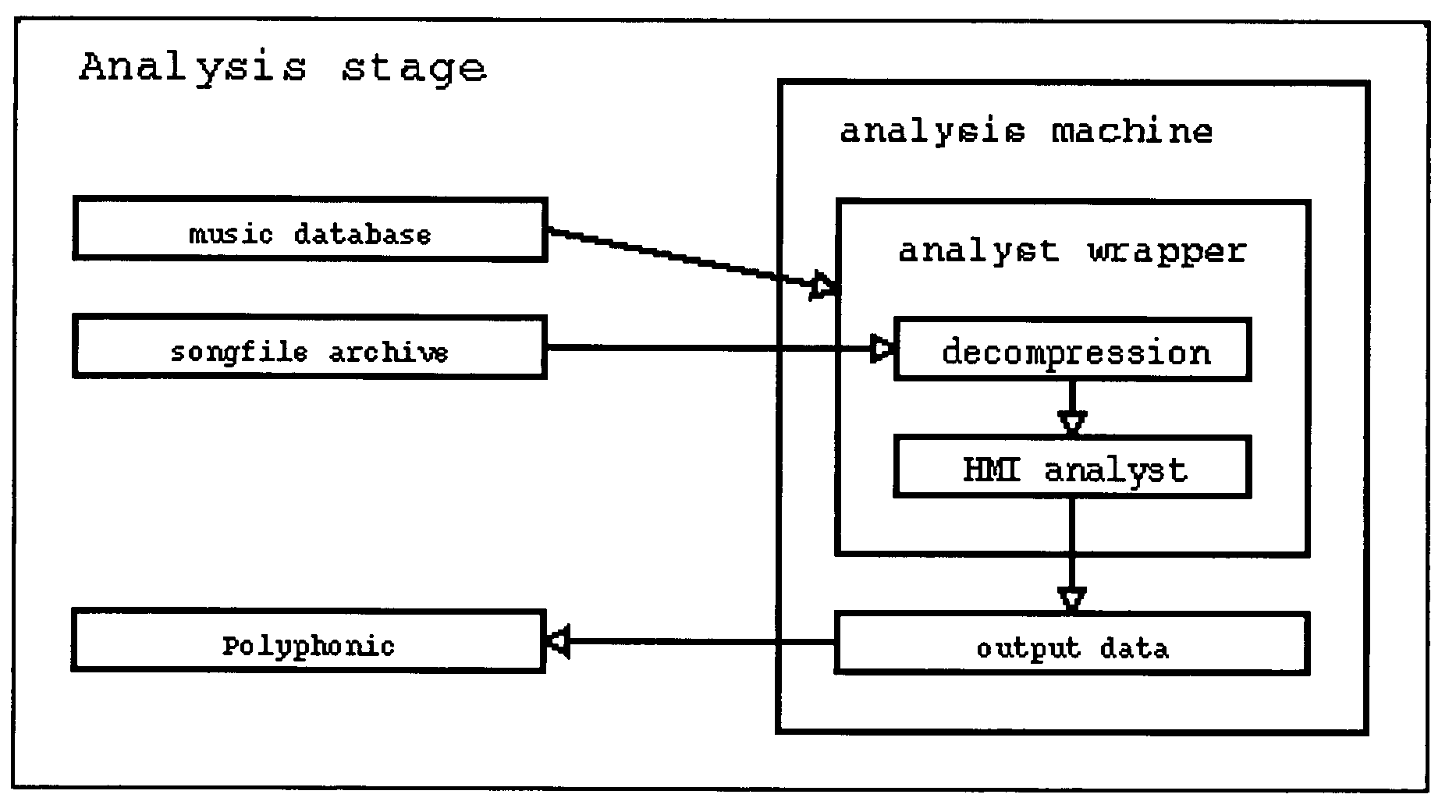
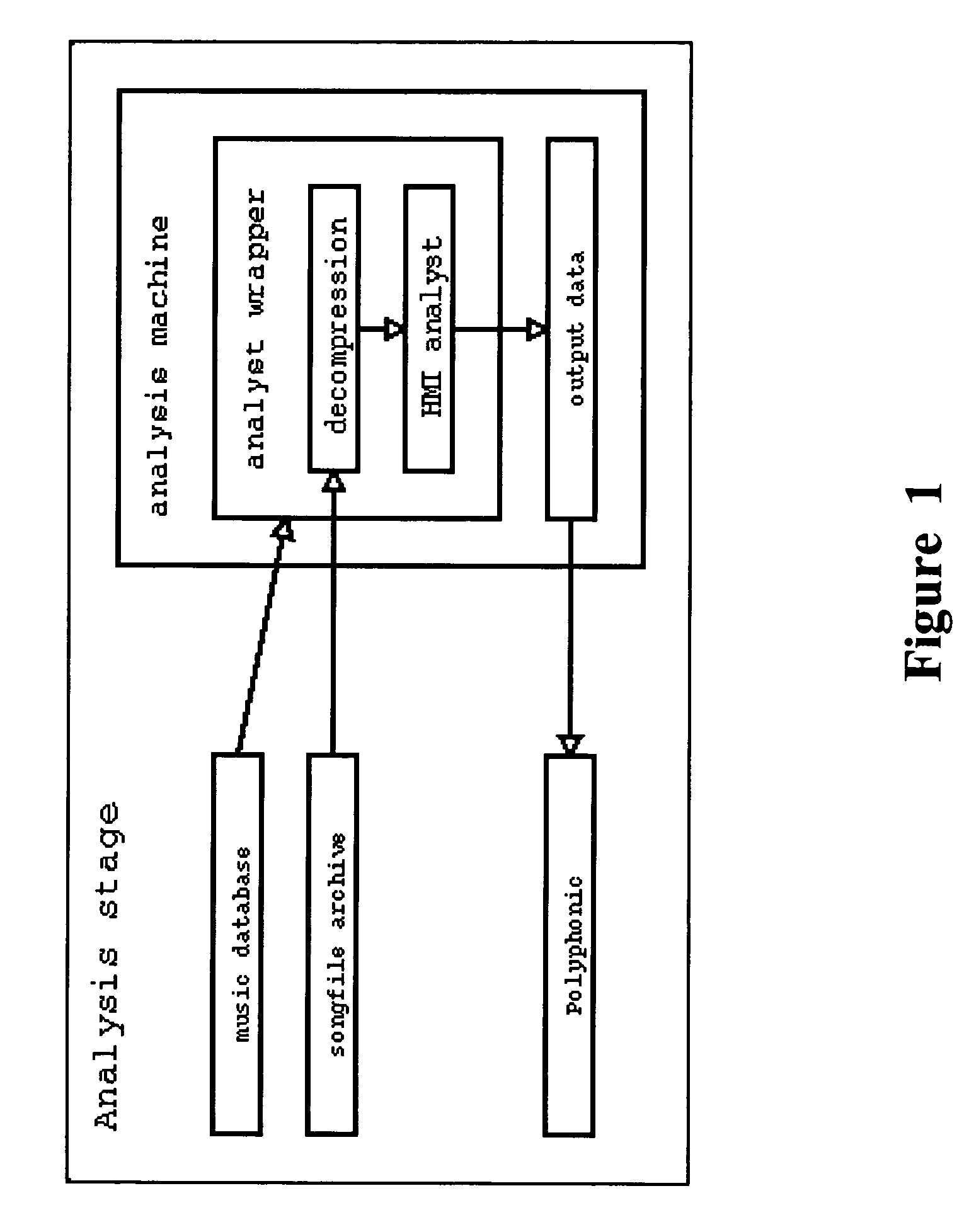
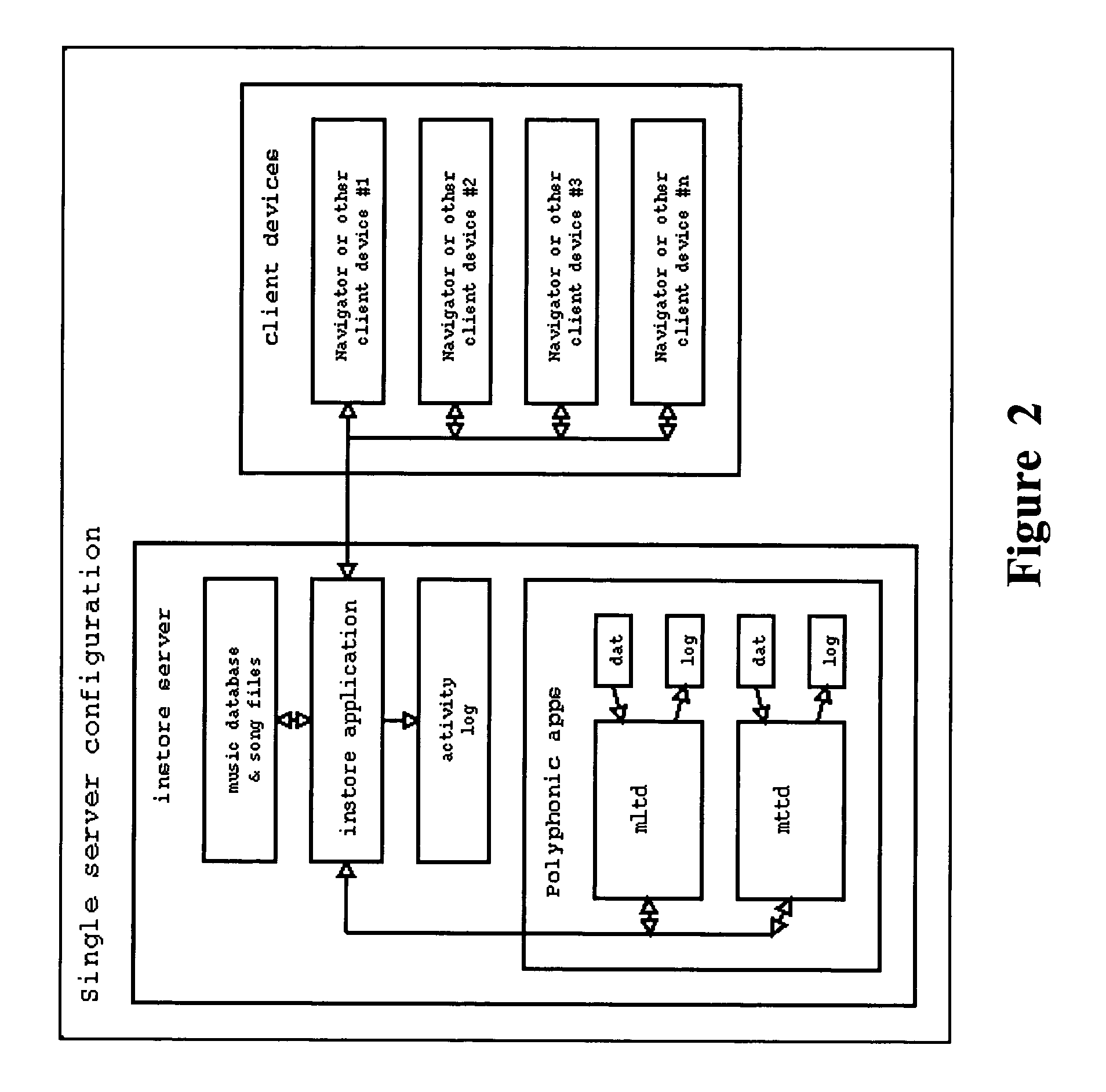
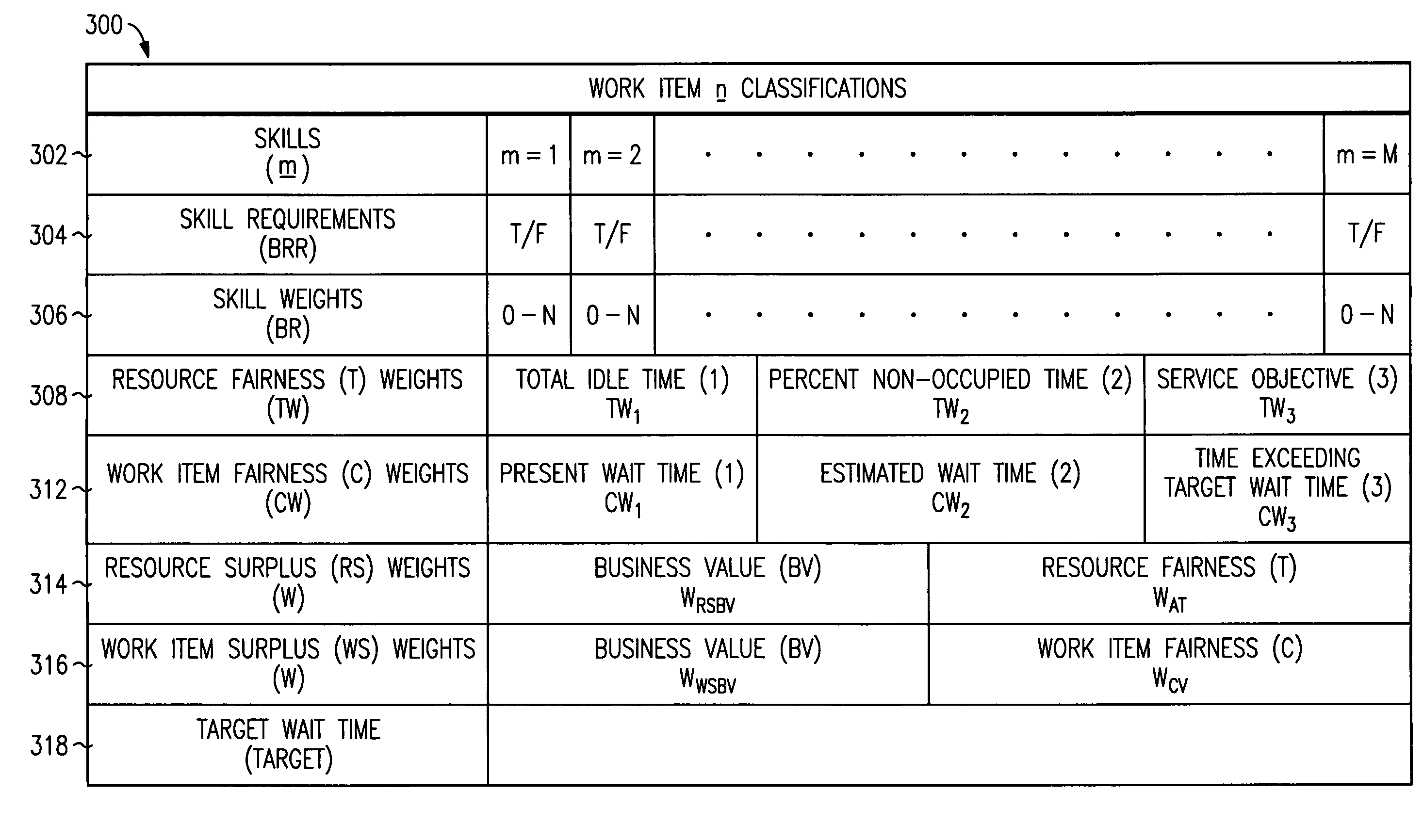
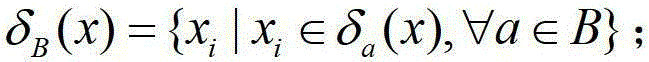Patents
Literature
386 results about "Business value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In management, business value is an informal term that includes all forms of value that determine the health and well-being of the firm in the long run. Business value expands concept of value of the firm beyond economic value (also known as economic profit, economic value added, and shareholder value) to include other forms of value such as employee value, customer value, supplier value, channel partner value, alliance partner value, managerial value, and societal value. Many of these forms of value are not directly measured in monetary terms.
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
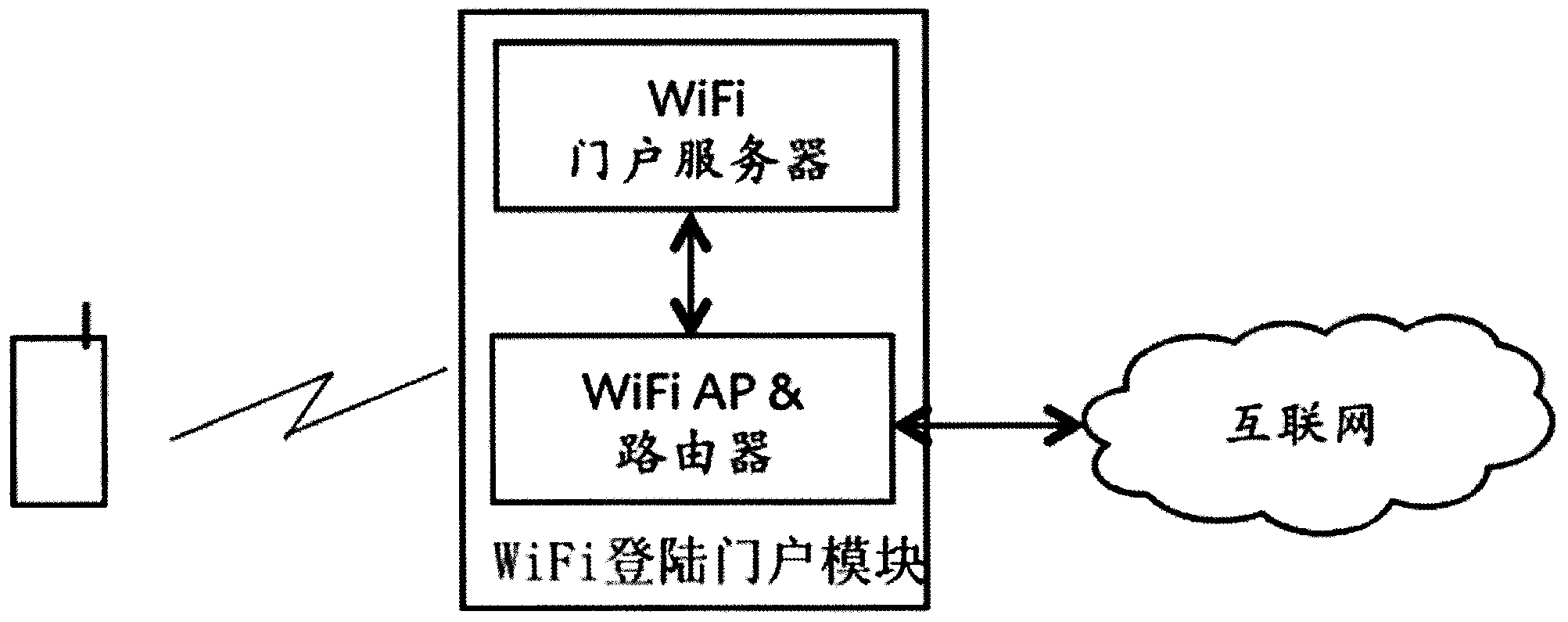
Information pushing system of WiFi (wireless fidelity) terminal and implementation method thereof
ActiveCN103402177AImprove experienceReal-time field precision marketingBroadcast service distributionMessaging/mailboxes/announcementsPersonalizationBehavioral analytics
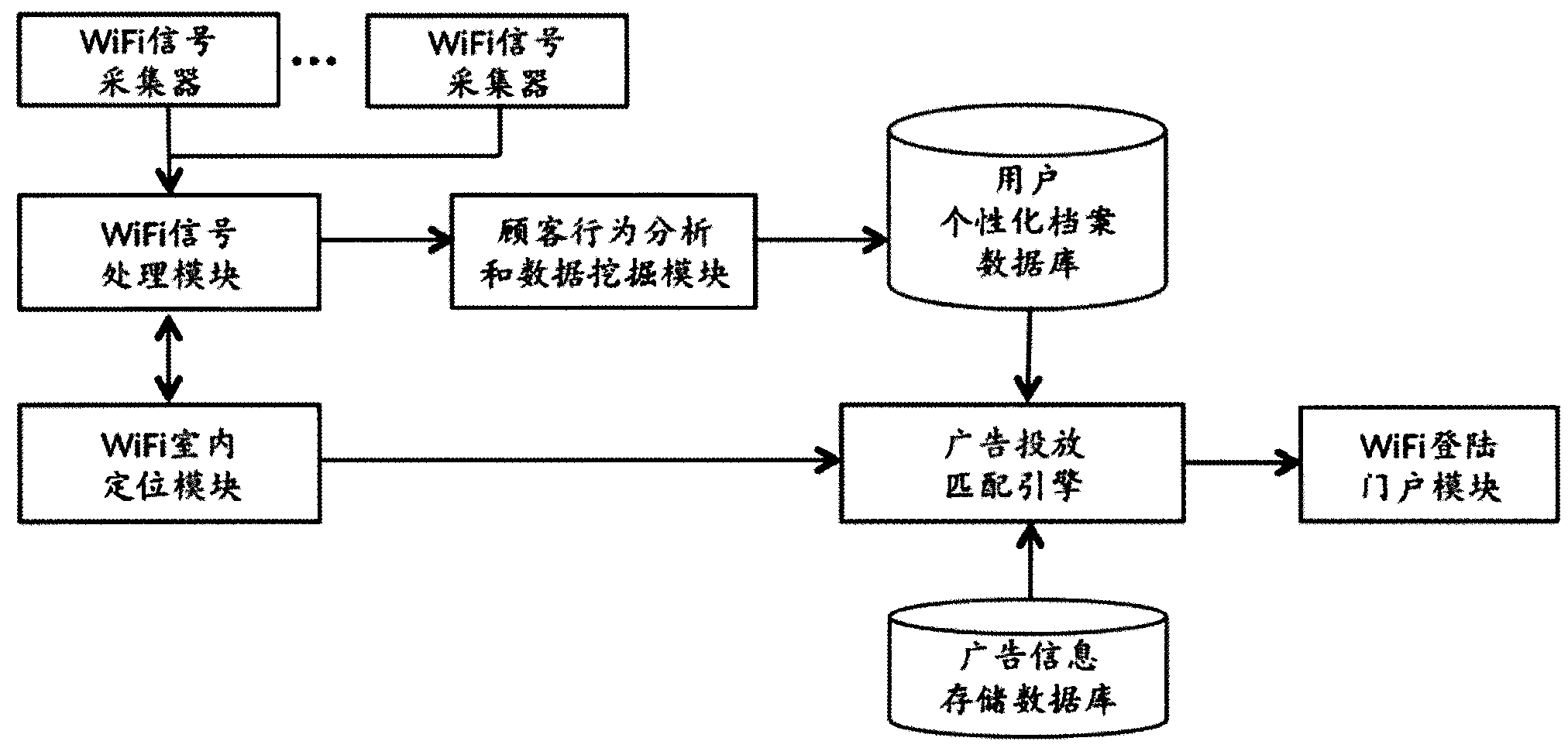
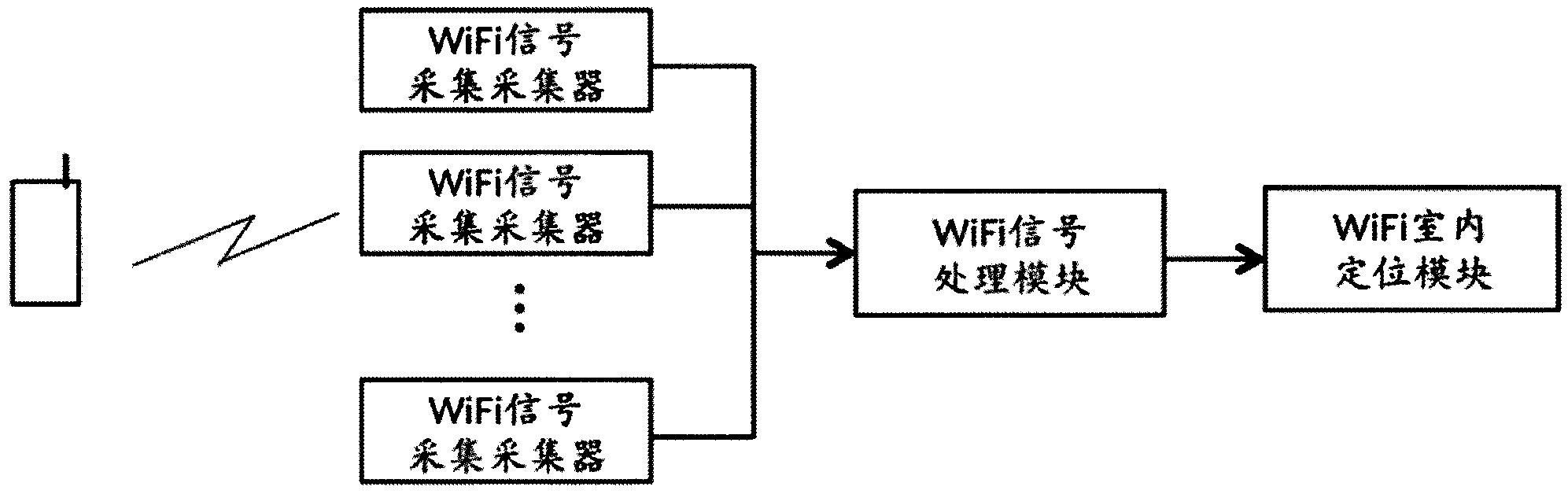
The invention discloses an information pushing system of a WiFi (wireless fidelity) terminal and an implementation method thereof. The system comprises a WiFi signal collector, a WiFi signal processing module, a WiFi indoor positioning module, a customer activity analyzing and data mining module, a user personality file database, an advertisement information storage database, an advertisement putting and matching engine and a WiFi logging portal module. The system is suitable for all terminals with the WiFi function, such as mobile phones, PADs (personal access device) and PCs (personal computer), and different software platforms, such as Andriod, wP, iOS, Windows, MAC OS and Linux, the WiFi terminals do not need any software modification and updating, and the applicable range is wide. The possible hobby of a consumer is judged through data analysis and mining, and the real-time and on-site precise marketing is realized for target users, so on one hand, the experience of the user consuming in business places is improved, and on the other hand, the commercial value of sellers and factories is improved.
Owner:江苏数原信息技术有限公司
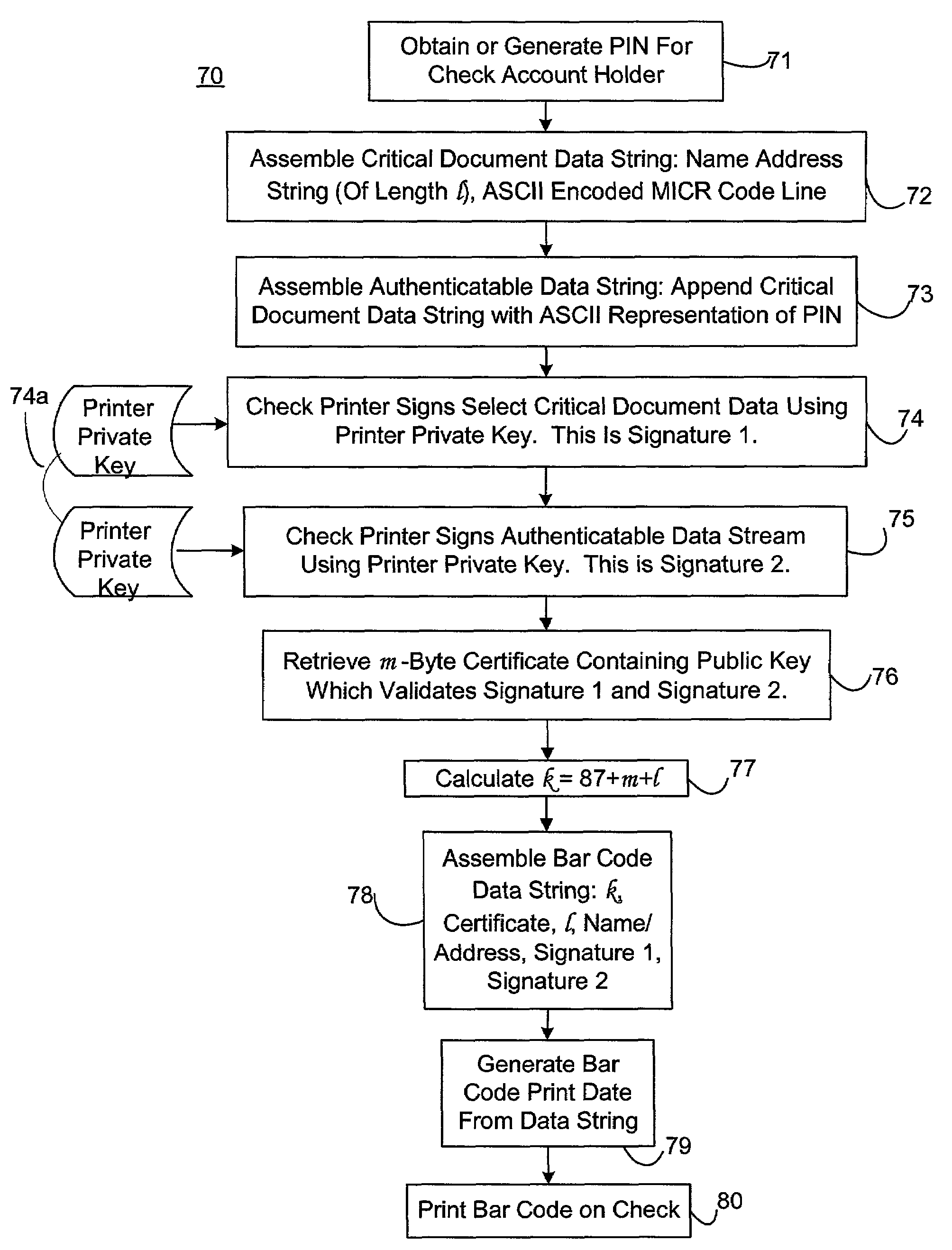
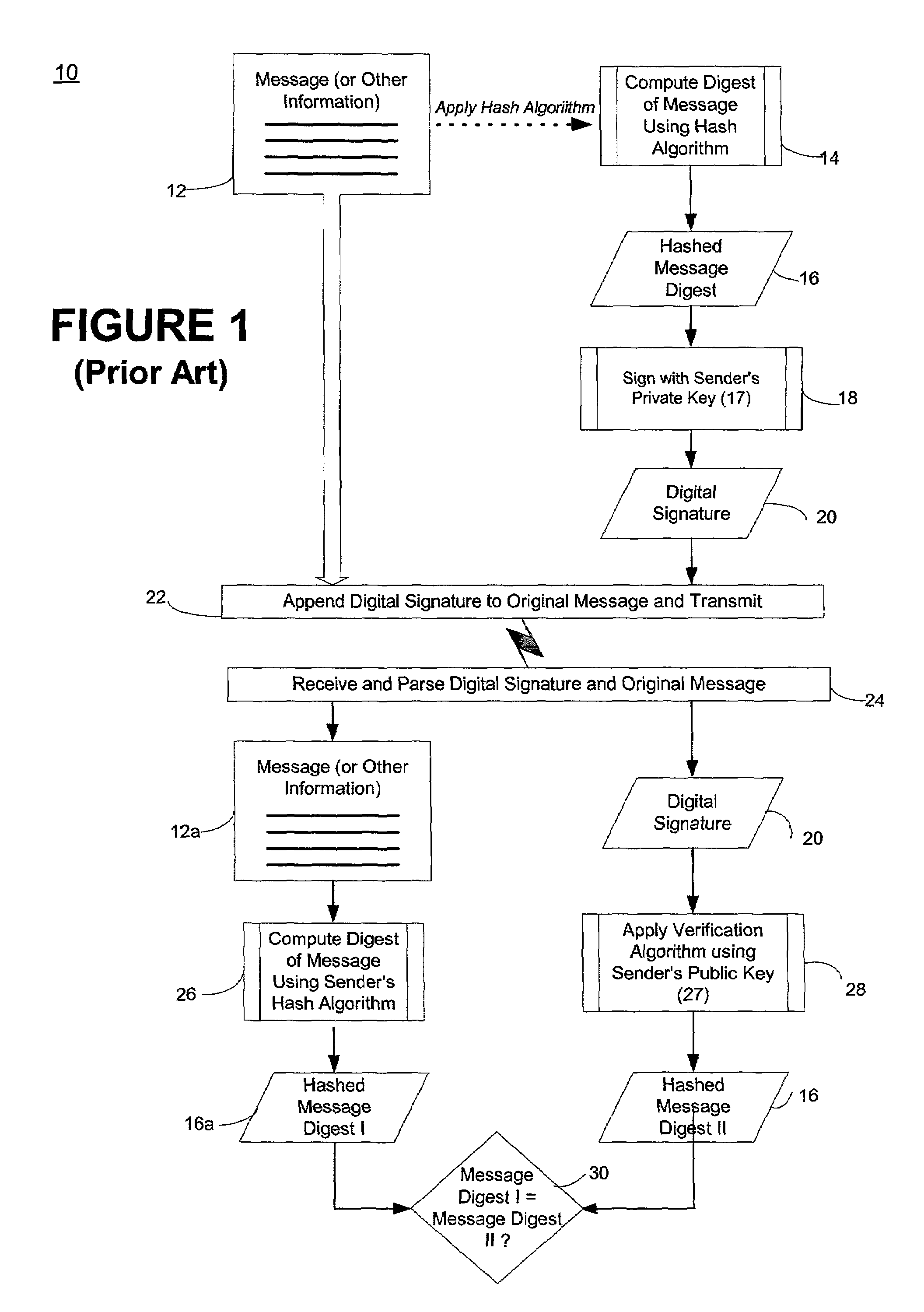
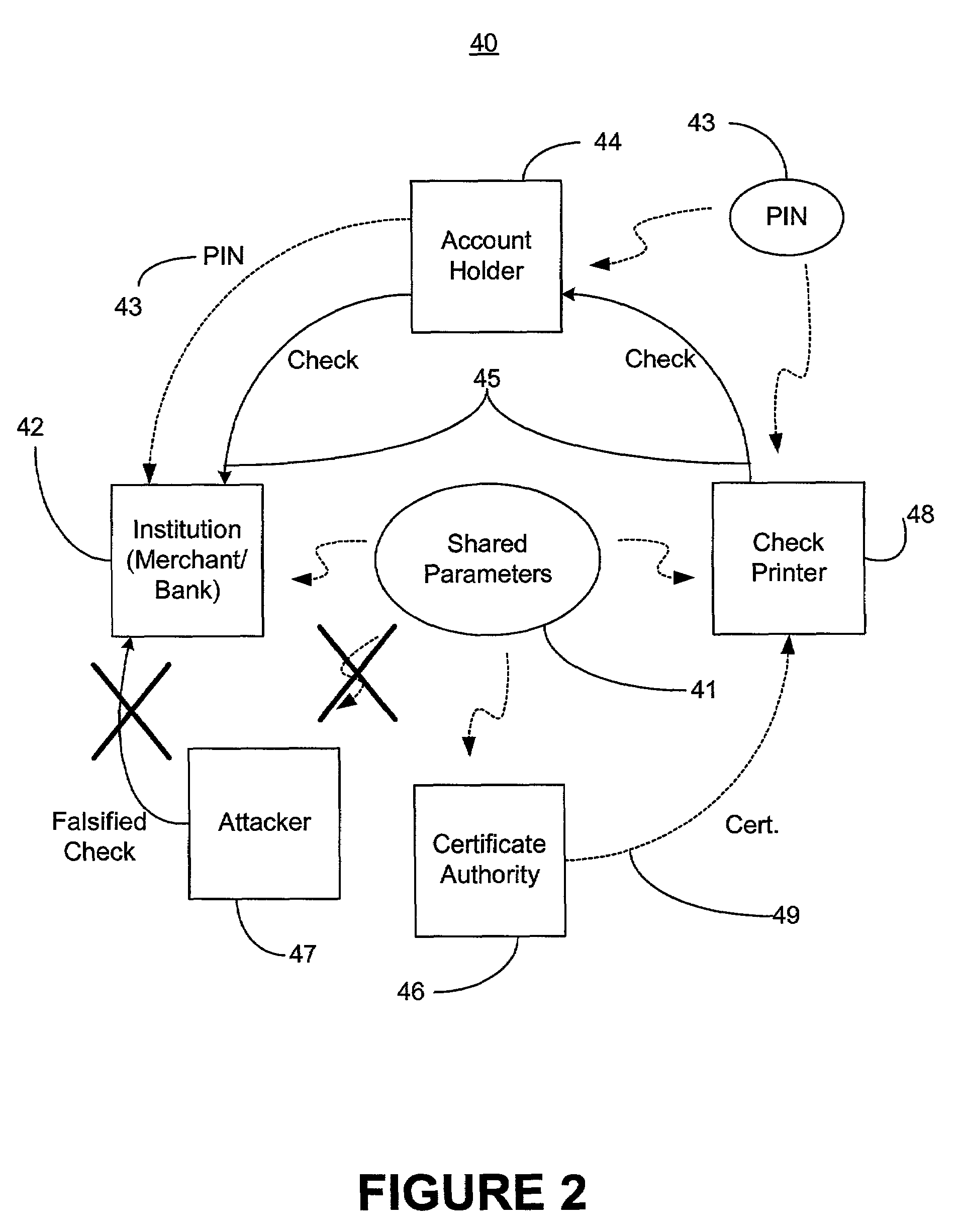
Self-authentication of value documents using digital signatures
ActiveUS7051206B1Low costImprove reliabilityKey distribution for secure communicationPaper-money testing devicesCredit cardPublic key certificate
An encryption-free technique for enabling the self-authentication of value documents (including personal and commercial checks) presented at a point of purchase or financial institution. Certain data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate issued from a trusted certificate authority. The signed data and public key certificate are stored on the value document, preferably in a two-dimensional bar code data format. In the case of certain personal value documents (such as checks, credit cards, passports, birth certificates, Social Security cards, etc.), a unique personal identification number (PIN) also may be included in the document data that is signed by a second digital signature. At a point of purchase, a merchant or teller can scan and read the data stored in the two-dimensional bar code and other magnetically recorded information, and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, if the personal value document contains the second digital signature, the document may be verified using a PIN-generating algorithm or other method that generates all permutations of PINs. The first digital signature alone may be used to authenticate selected data within the personal value document even when the PIN is not available. Similarly, in the case of a commercial value documents, authentication of pre-printed data may be based entirely upon only the first digital signature.
Owner:UNISYS CORP
Method and system for music recommendation
ActiveUS7081579B2Electrophonic musical instrumentsDigital data information retrievalBusiness valueRecommender system
An artificial intelligence song / music recommendation system and method is provided that allows music shoppers to discover new music. The system and method accomplish these tasks by analyzing a database of music in order to identify key similarities between different pieces of music, and then recommends pieces of music to a user depending upon their music preferences. An embodiment enables a user to evaluate a new song's similarity to songs already established as commercially valuable.
Owner:MUSIC INTELLIGENCE SOLUTIONS INC
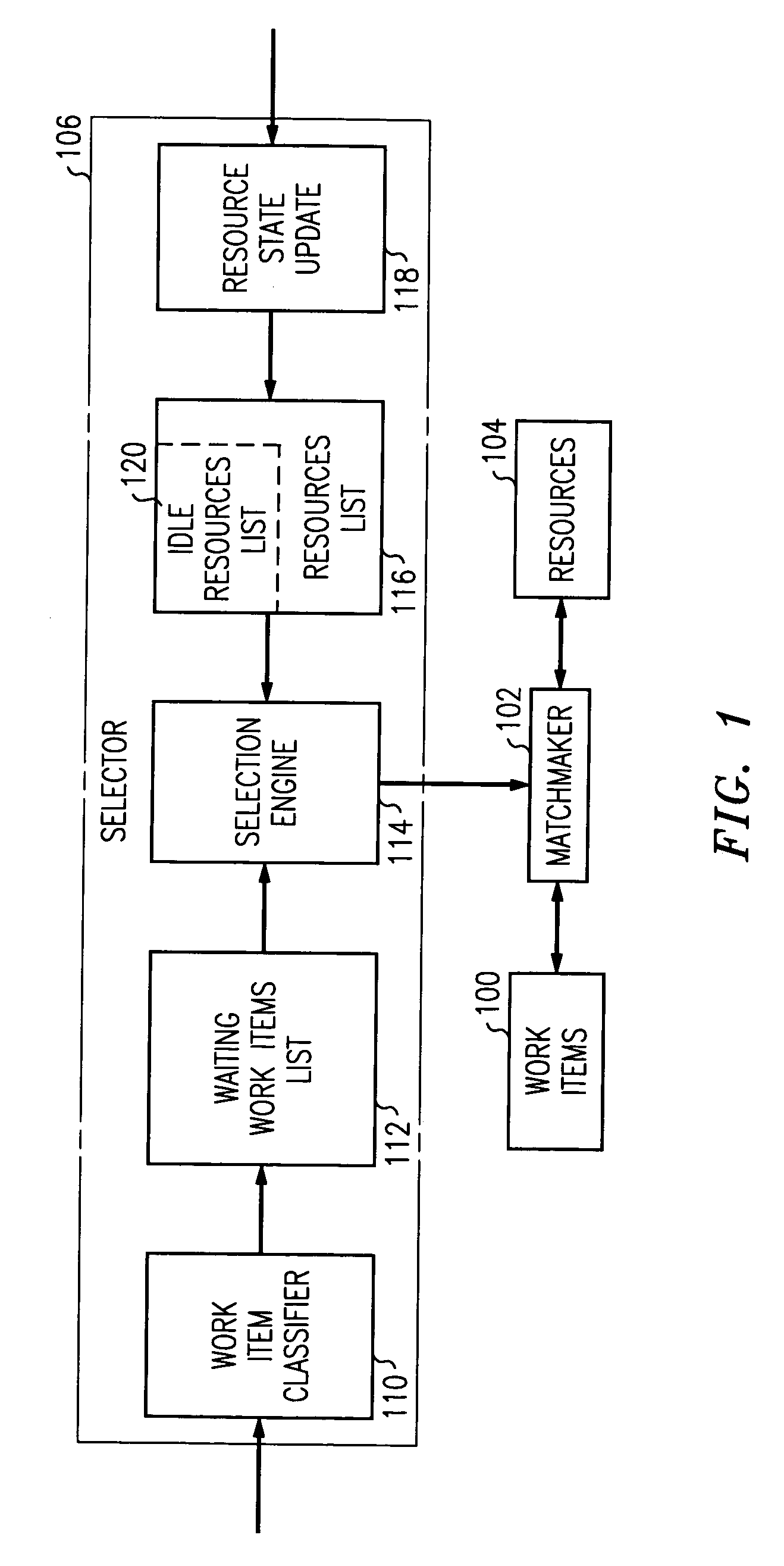
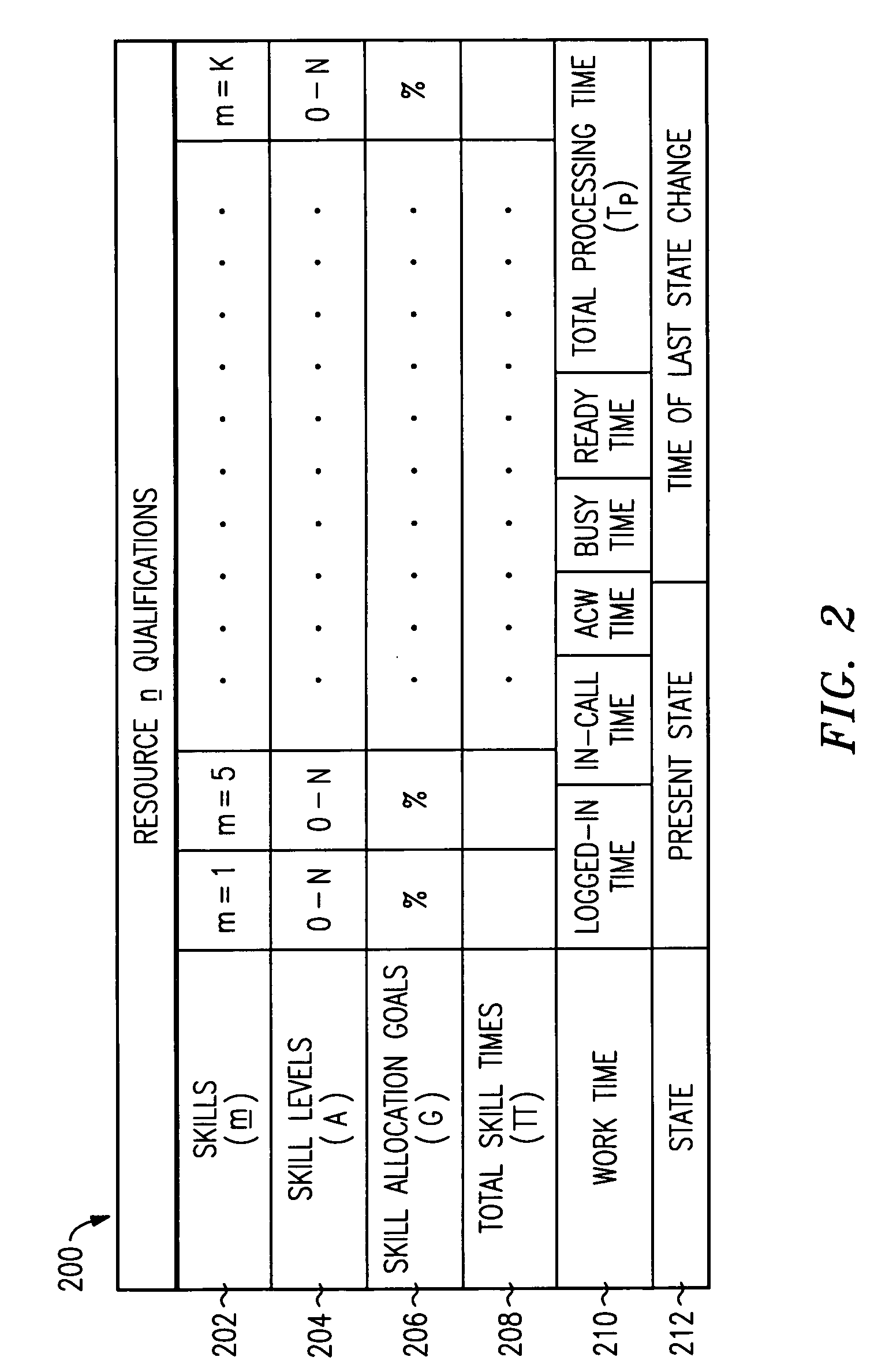
Arrangement for resource and work-item selection
InactiveUS7035808B1Optimize workflowImprove distributionSoftware engineeringDigital computer detailsSkill setsREMS Stakeholder
A workflow system (FIG. 1) employs a selection engine (114) that attempts to match work items (100) with resources (104) in such a way that it brings the most value to all of the stakeholders in the workflow. Under resource or work-item surplus conditions (FIG. 4 or 5), the selection engine determines either those available resources that possess skills needed by an available work item or those available work items that need skills possessed by an available resource, for each determined resource determines both a business value (RSBV) of having that resource service the work item and either a value (RTV) to that resource of servicing the work item or a value (WTV) to that work item of being serviced by the resource, and then selects the resource that has a best combined value of the business value and the value to the resource or work item.
Owner:AVAYA INC
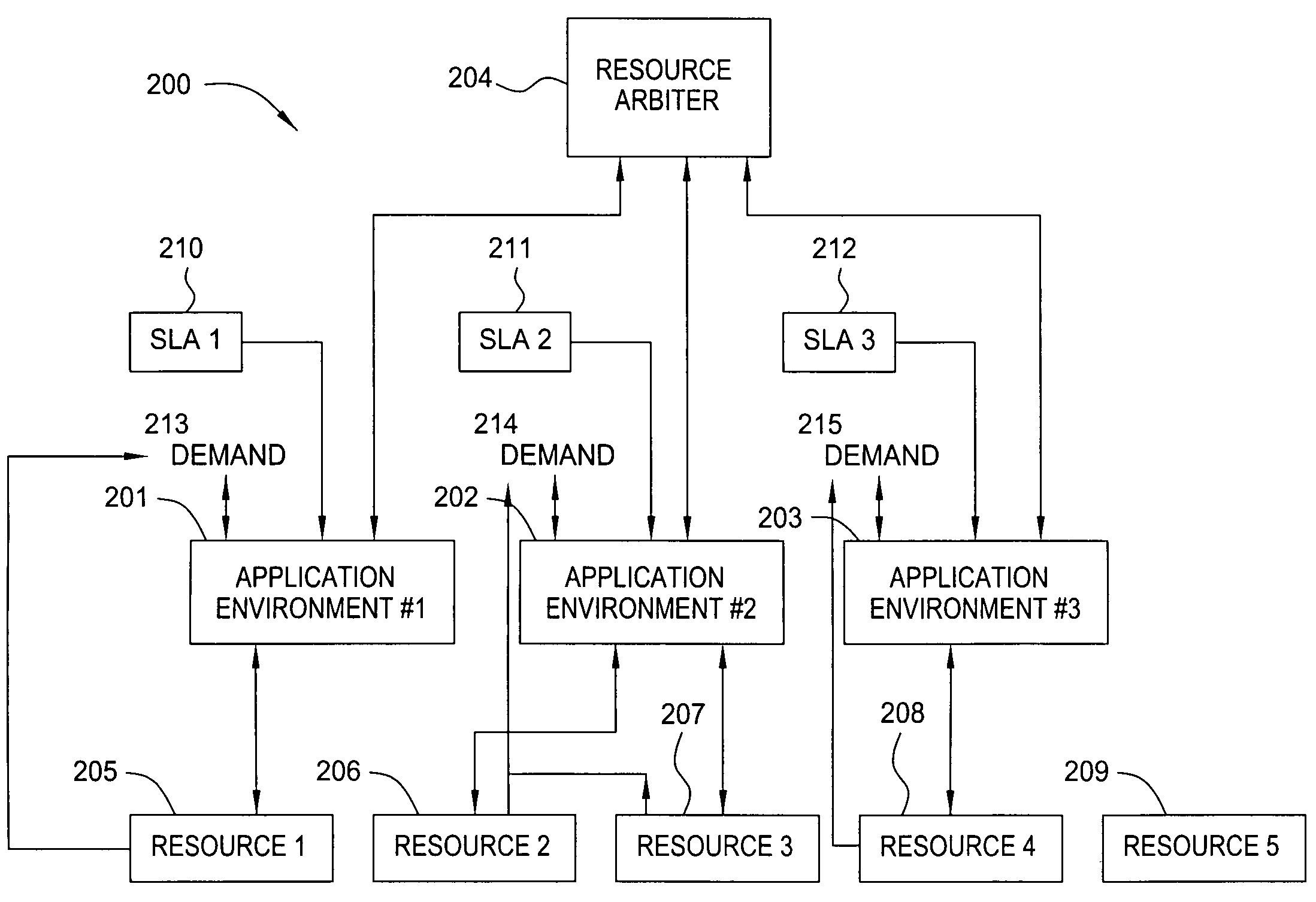
Method and apparatus for utility-based dynamic resource allocation in a distributed computing system
InactiveUS20050172291A1Quick decisionResource allocationMemory systemsDynamic resourceResource based
In one embodiment, the present invention is a method for allocation of finite computational resources amongst multiple entities, wherein the method is structured to optimize the business value of an enterprise providing computational services. One embodiment of the inventive method involves establishing, for each entity, a service level utility indicative of how much business value is obtained for a given level of computational system performance. The service-level utility for each entity is transformed into a corresponding resource-level utility indicative of how much business value may be obtained for a given set or amount of resources allocated to the entity. The resource-level utilities for each entity are aggregated, and new resource allocations are determined and executed based upon the resource-level utility information. The invention is thereby capable of making rapid allocation decisions, according to time-varying need or value of the resources by each of the entities.
Owner:IBM CORP
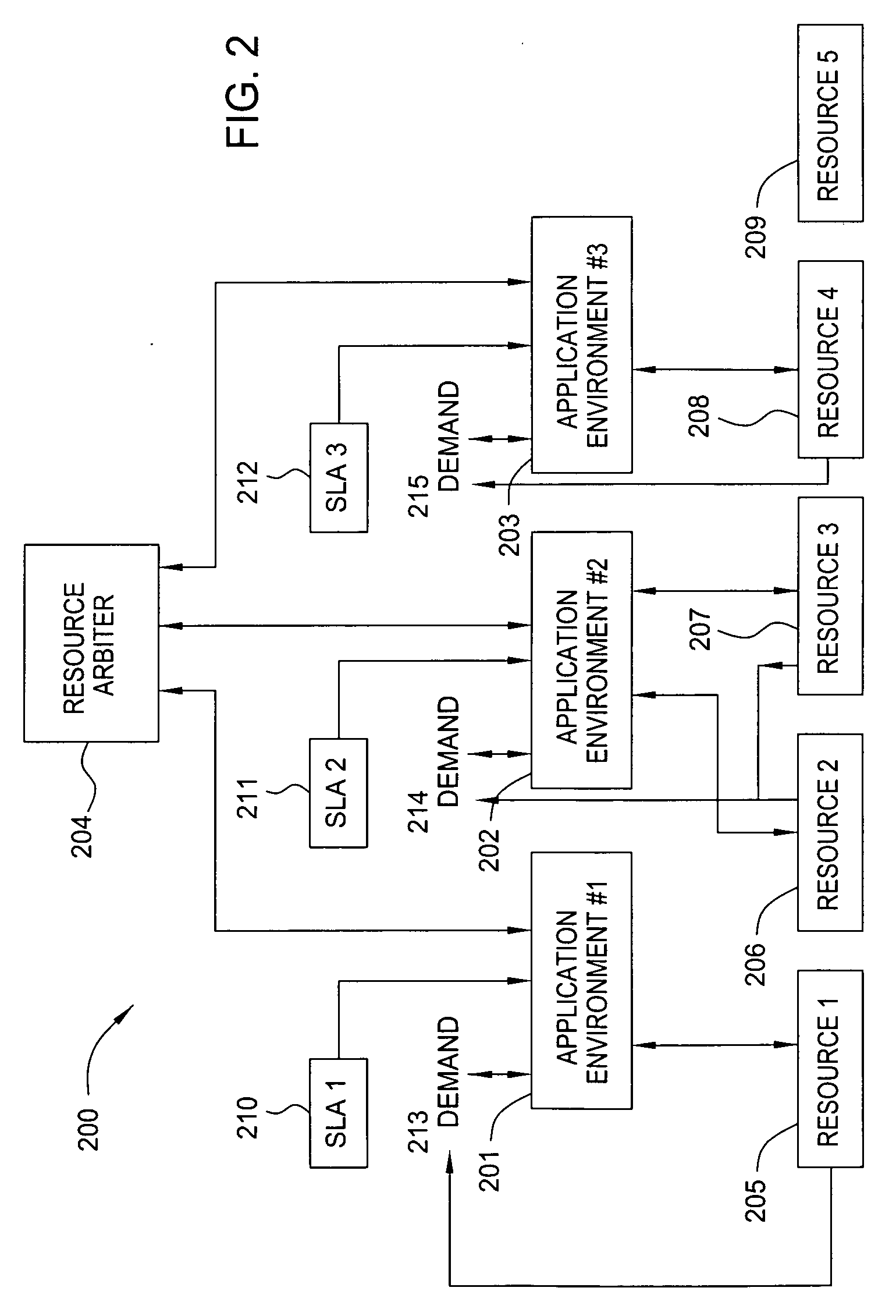
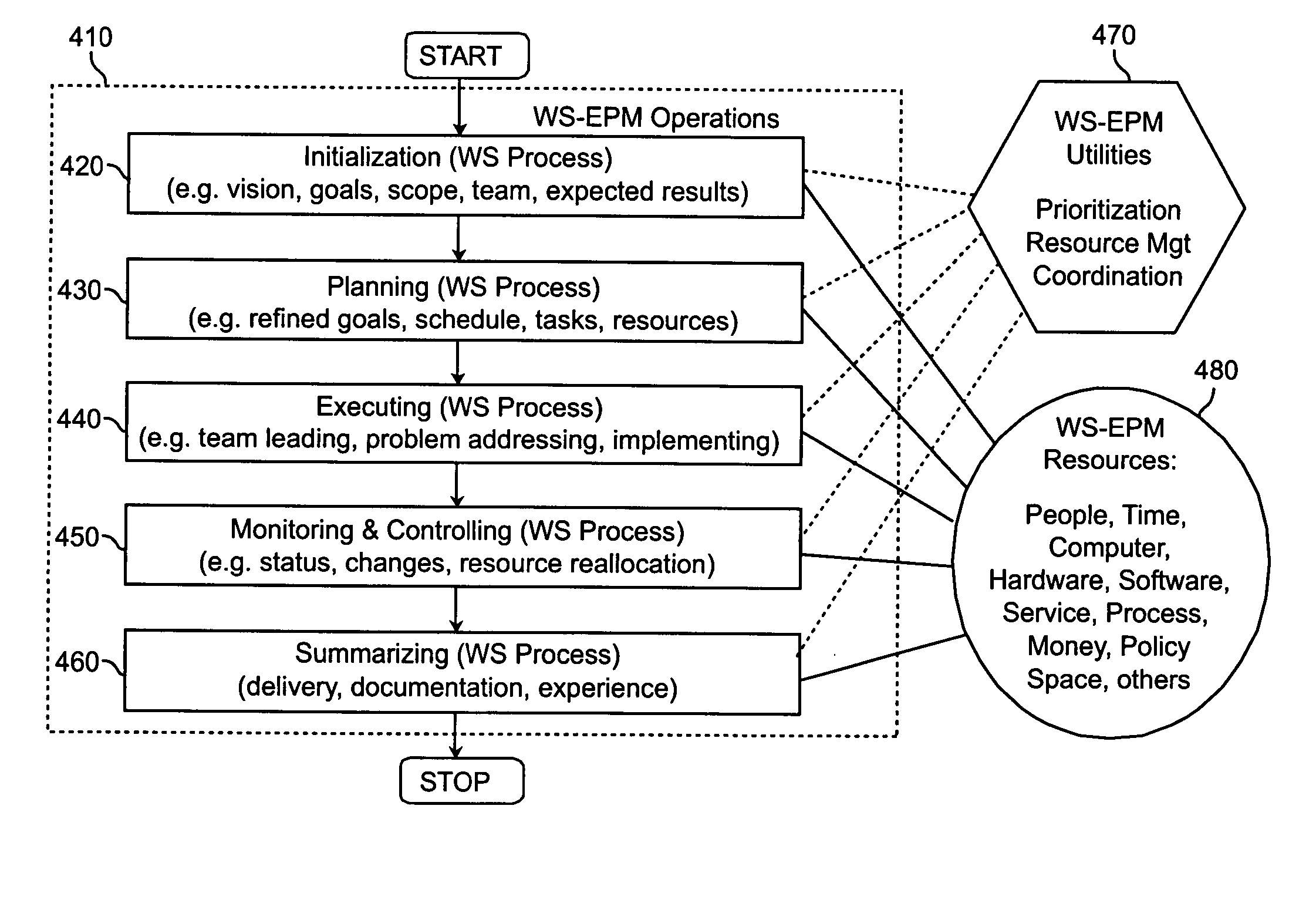
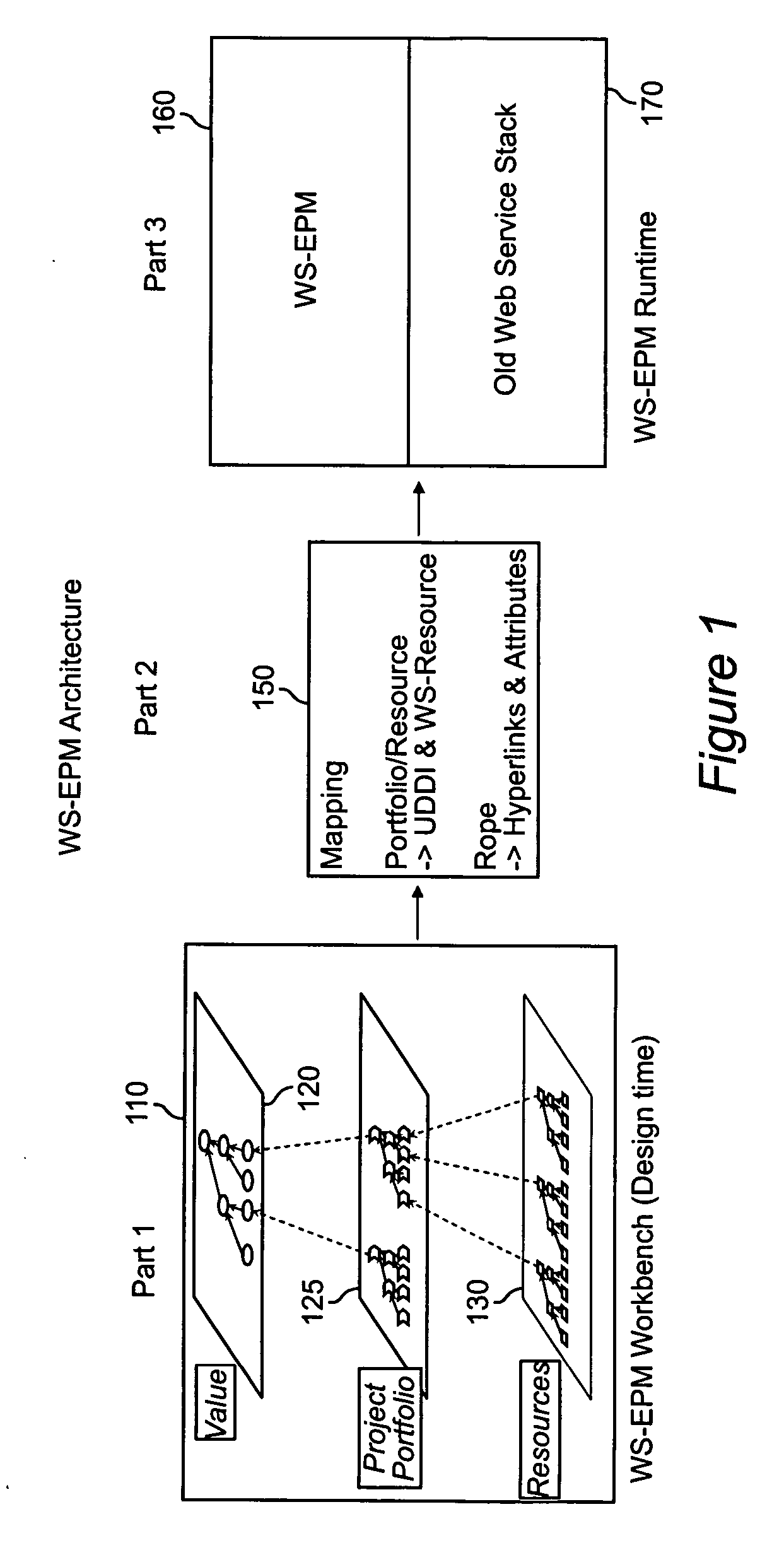
Method and apparatus for enabling enterprise project management with service oriented resource and using a process profiling framework
InactiveUS20070022404A1ResourcesSpecific program execution arrangementsService oriented enterpriseHyperlink
A service-oriented architecture for enterprise project management integrates business processes, human resources and project management within an enterprise or across the value chain network. A representation having direction and attributes is provided to show the dependencies between a business value layer and a project-portfolio layer, and between the project-portfolio layer and resources. The representation is mapped to a Web Services representation in UDDI, Web Services interfaces, and Web Services based business processes through rope hyper-linking.
Owner:IBM CORP
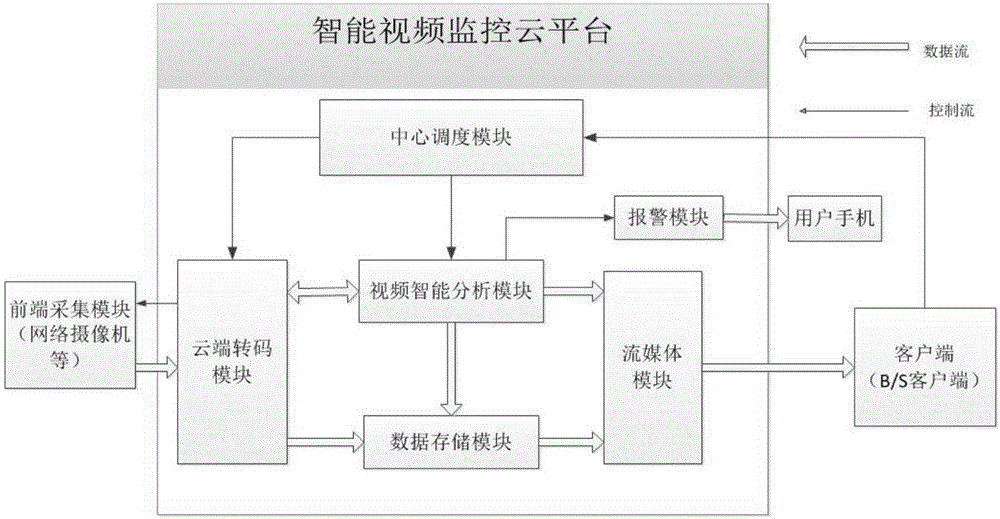
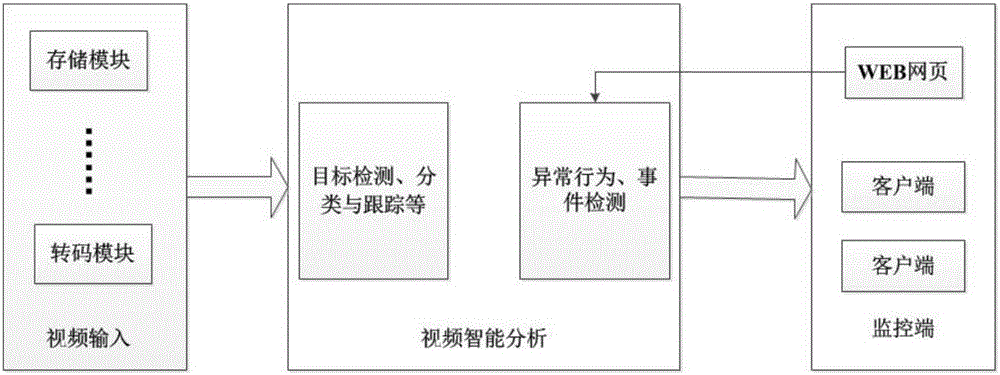
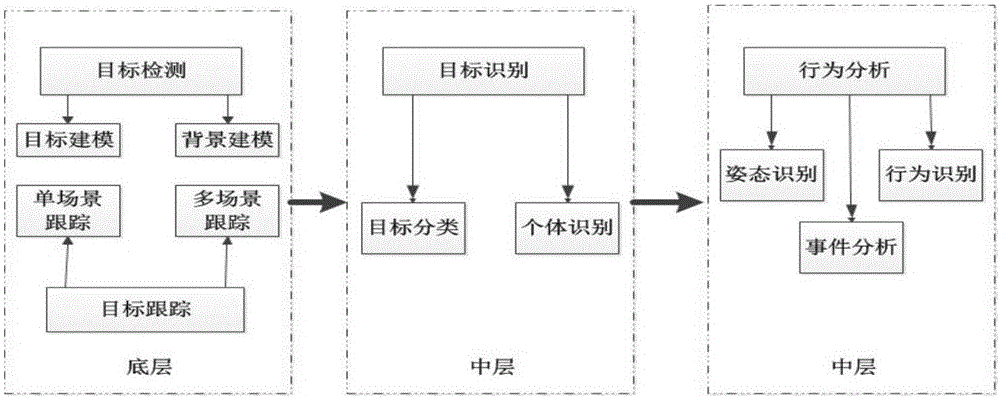
Smart video monitoring system based on cloud platform
InactiveCN106375721AImprove bindingQuality improvementClosed circuit television systemsTransmissionVideo monitoringTranscoding
The invention relates to a smart video monitoring system based on a cloud platform, and belongs to the technical field of remote smart monitoring. The system is characterized in that a video monitoring cloud platform is developed on a server cluster established on the basis of a Hadoop cloud computing platform, and video data acquired by front-end equipment are transmitted to a server in a stream way; through adoption of a massive distributed cloud computing technology, real-time tracking, processing, analysis and outputting of video streams are realized; and a service is provided externally, so that a terminal user can perform checking and calling conveniently. In the system, the characteristics of distributed high-concurrence access storage, high availability, rapid response, easiness in management and maintenance and the like are integrated. Video acquisition, video encoding and transcoding, video data storage, a streaming media distributed server and a client are all distributed on a physical host node in an access network. Compared with a conventional video monitoring system, the smart video monitoring system has the advantages that video real-time processing and transcoding efficiency and video data storage capacity are increased greatly; the requirement of people on the video monitoring system in a big data era is met; and a relatively large commercial value is achieved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
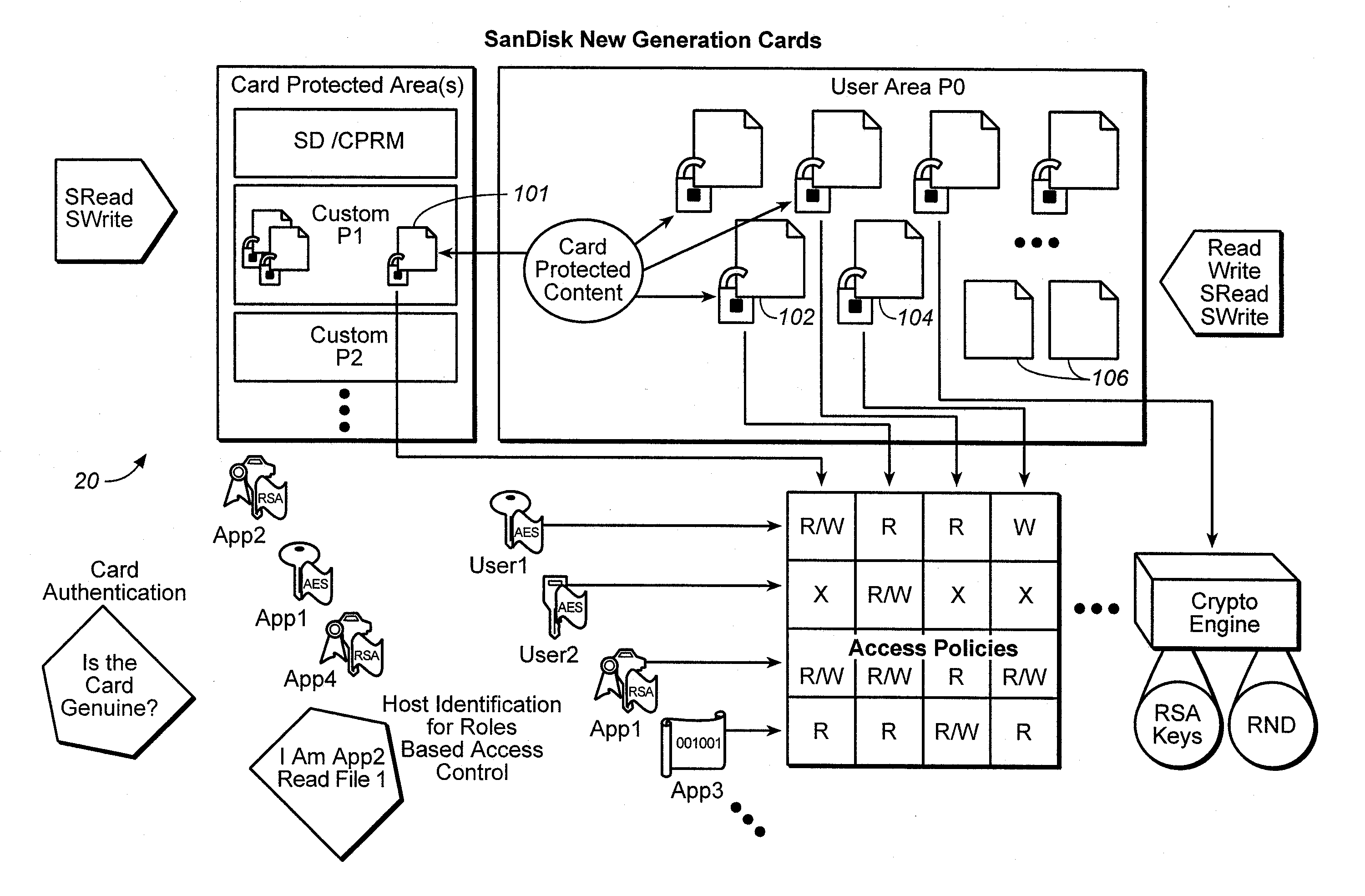
Control structure for versatile content control
InactiveUS20060242151A1Easy to optimizeImprove versatilityProgram/content distribution protectionSpecial data processing applicationsComputer networkMultiple applications
A tree structure stored in the storage medium provides control over what an entity can do even after gaining access. Each of the nodes of the tree specifies permissions by an entity who has gained entry through such node of the tree. Some trees have different levels, where the permission or permissions at a node of the tree has a predetermined relationship to permission or permissions at another node at a higher or lower or the same level in the same tree. By requiring entities to comply with the permissions so specified at each of the nodes, the tree feature of this application allows a content owner to control which entities can take action, and which actions each of the entities can take, irrespective of whether the tree has different levels. To enhance the commercial value that can be provided by the mobile storage medium, it is desirable for mobile storage devices to be capable of supporting more than one application simultaneously. When two or more applications are accessing the mobile storage device at the same time, it can be important to be able to separate the operations of the two or more applications so that they do not interfere with one another in a phenomena referred to herein as crosstalk. Two or more preferably hierarchical trees control access to the memory. Each tree comprises nodes at different levels for controlling access to data by a corresponding set of entities where a node of each tree specifies permission or permissions of the corresponding entity or entities for accessing memory data. The permission or permissions at a node of each of the trees has a predetermined relationship to permission or permissions at another node at a higher or lower level in the same tree. Preferably, there is no crosstalk between at least two of the trees.
Owner:SANDISK TECH LLC
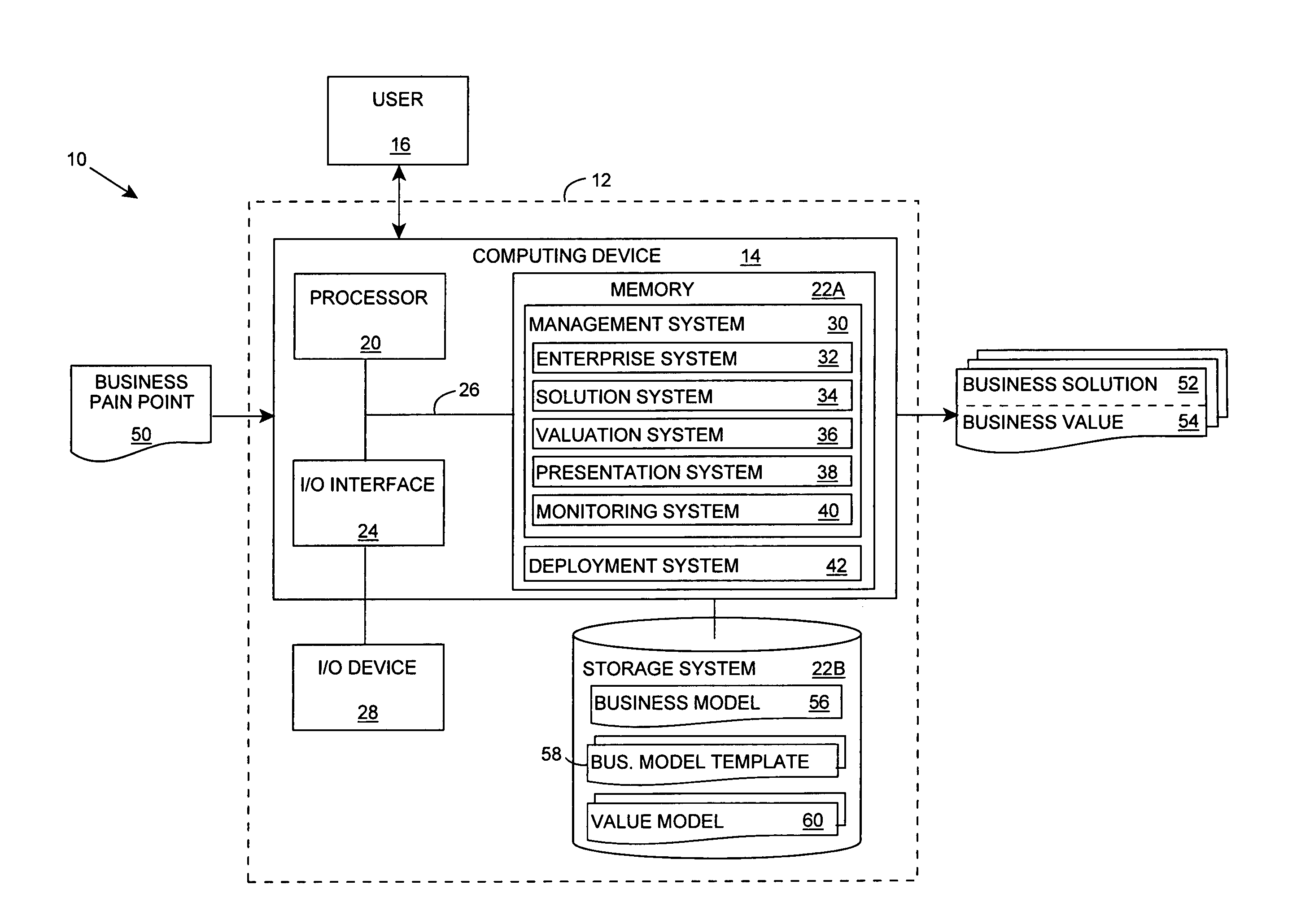
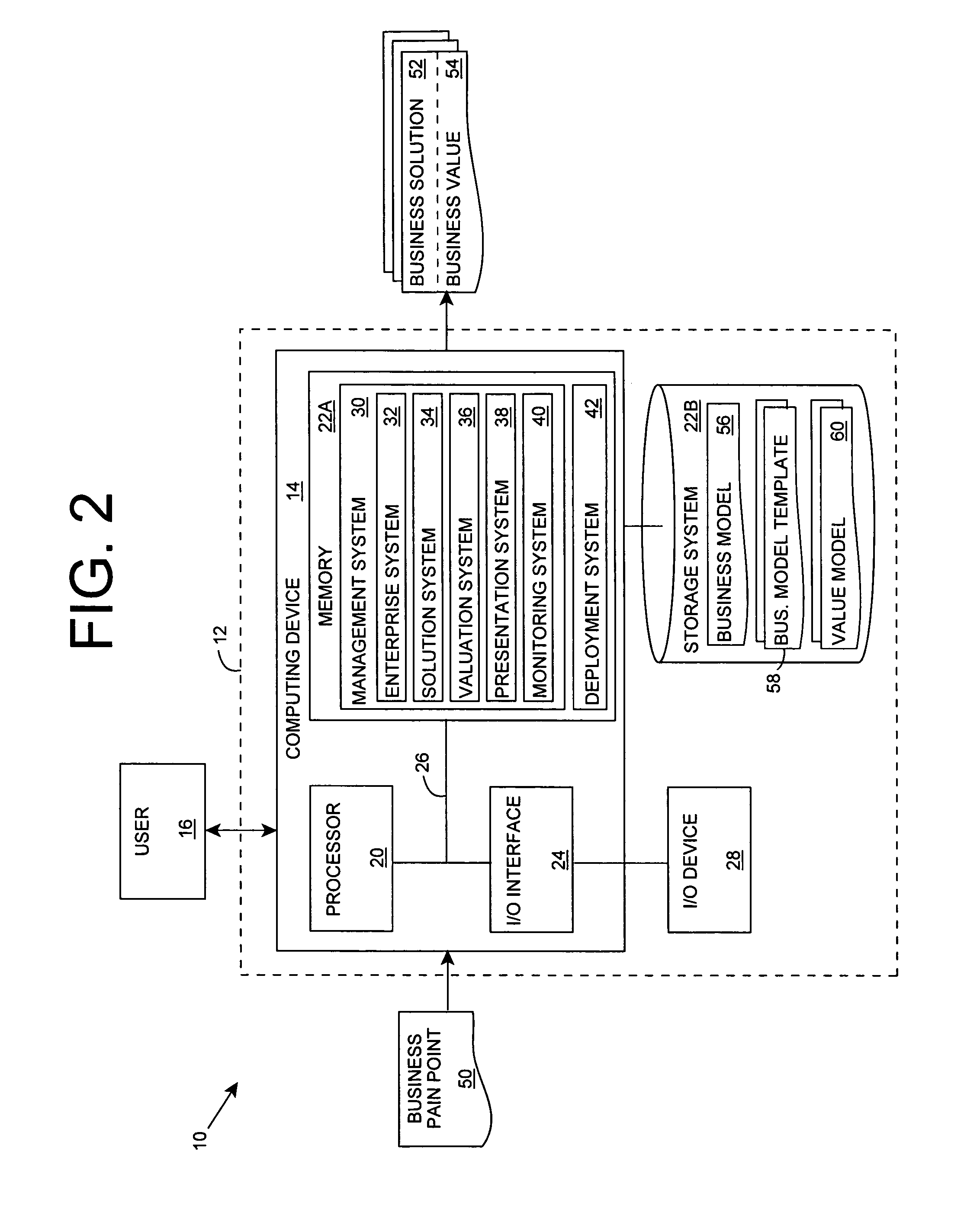
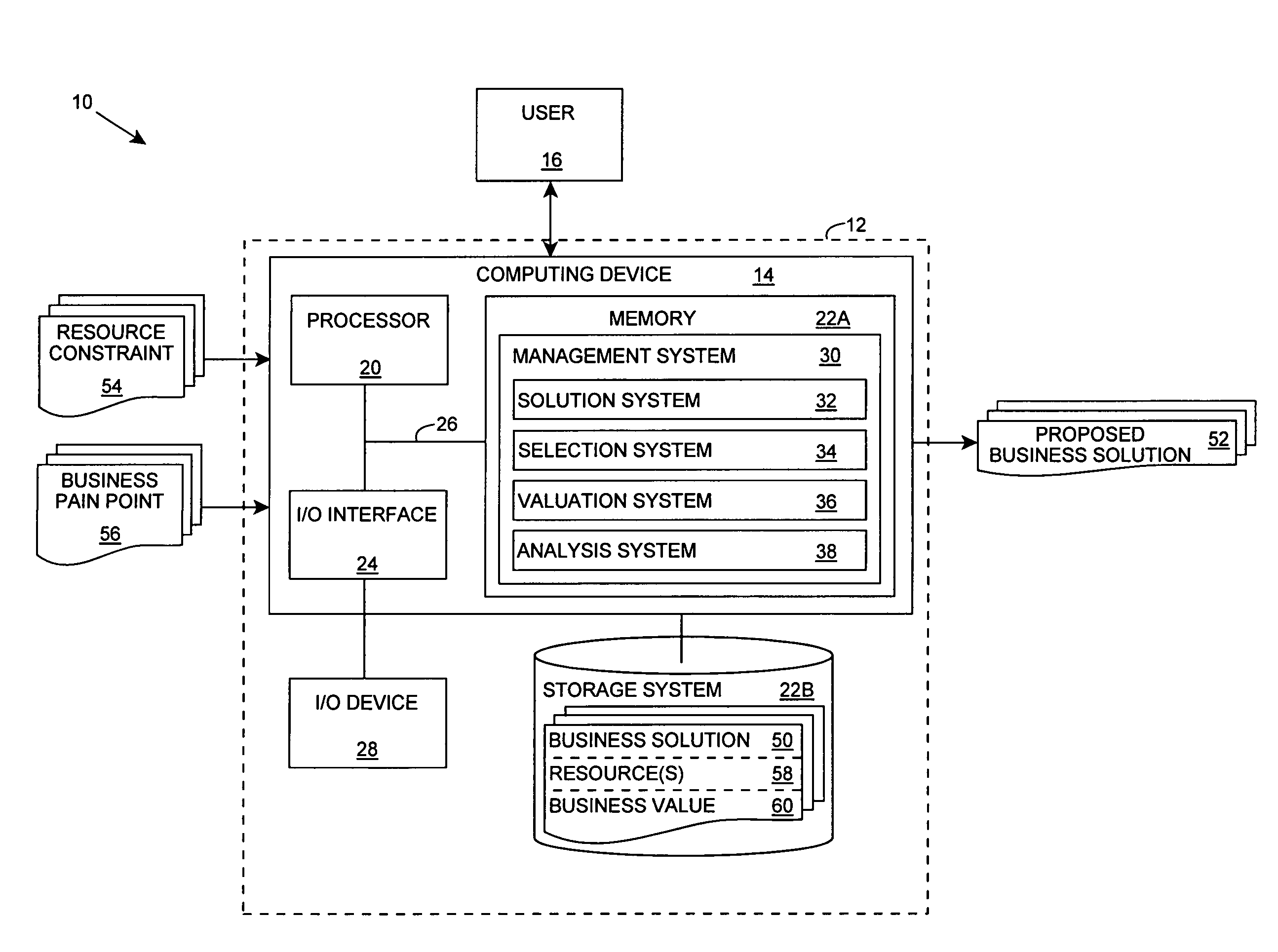
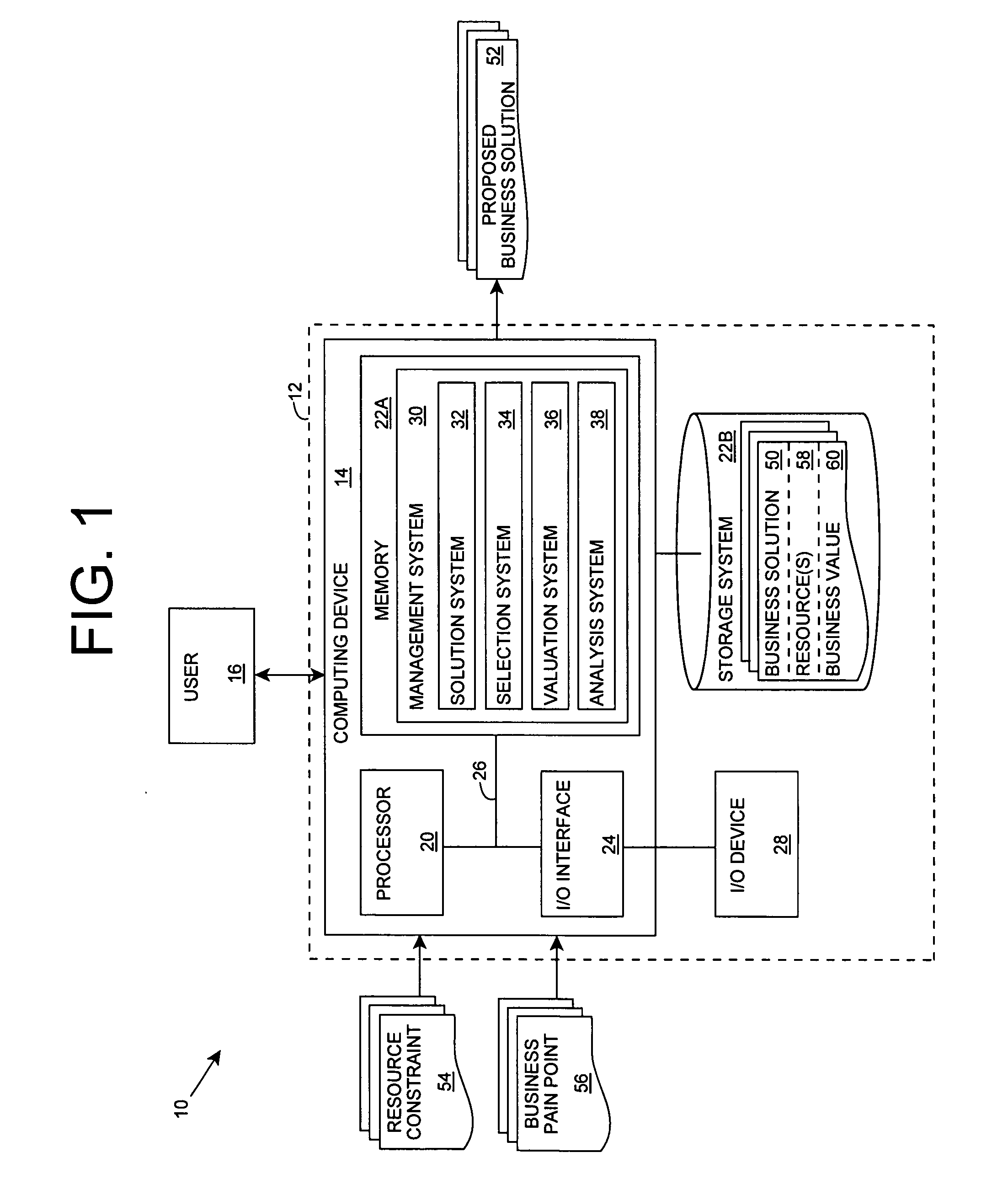
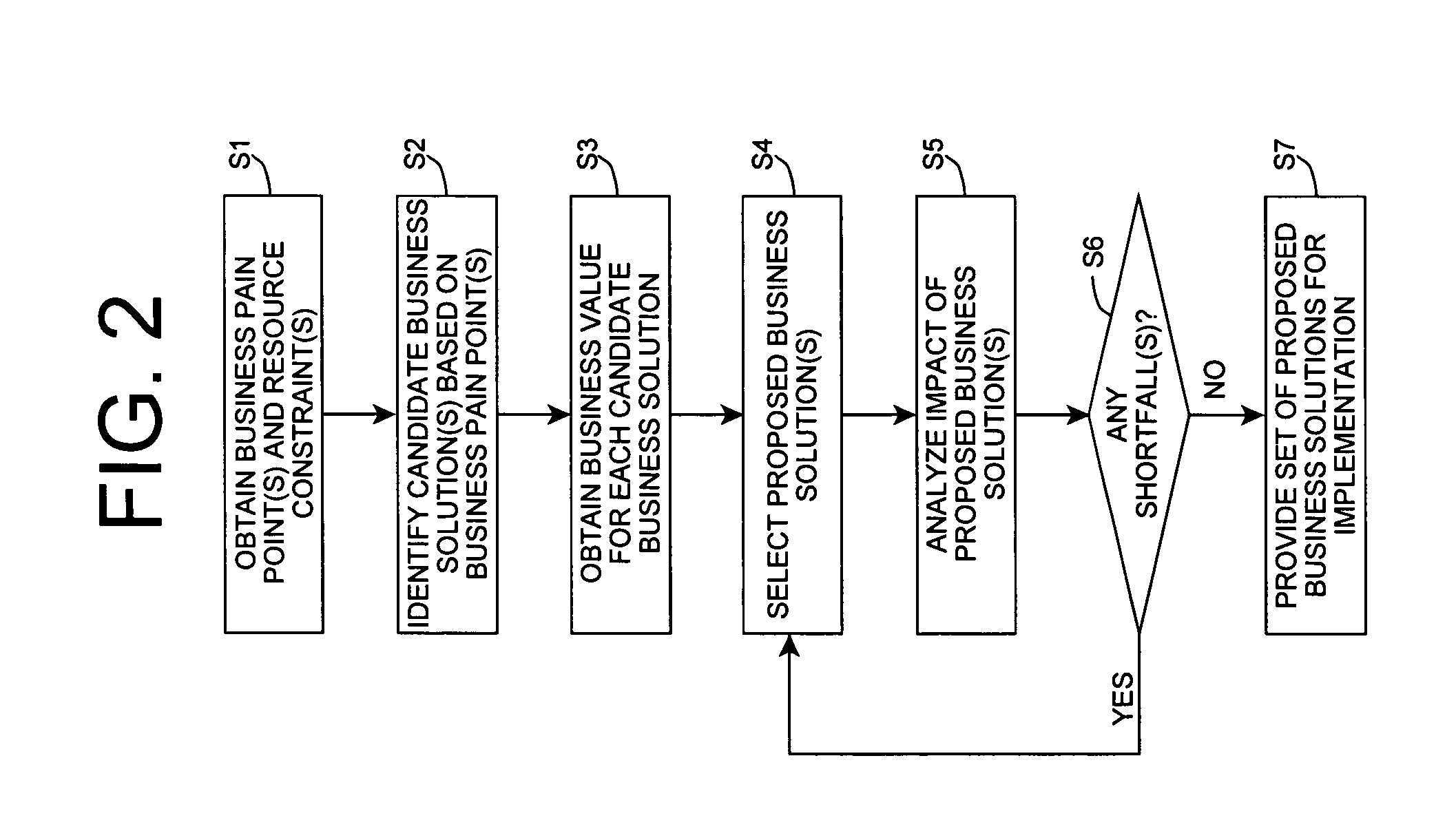
Business solution evaluation
InactiveUS20070038501A1Reduce designEasy to solveData processing applicationsSpecial service for subscribersBusiness value
An improved solution for managing a set of business solutions is provided. Each business solution includes one or more modifications to one or more business concerns for a target enterprise. A value model that comprises a value for each of the business concerns is used to determine a business value that is anticipated to be provided by each business solution. The business solutions can then be prioritized based on their business value. As a result, the invention enables business solutions to be compared based on their anticipated business value, rather than their features / functionality.
Owner:IBM CORP
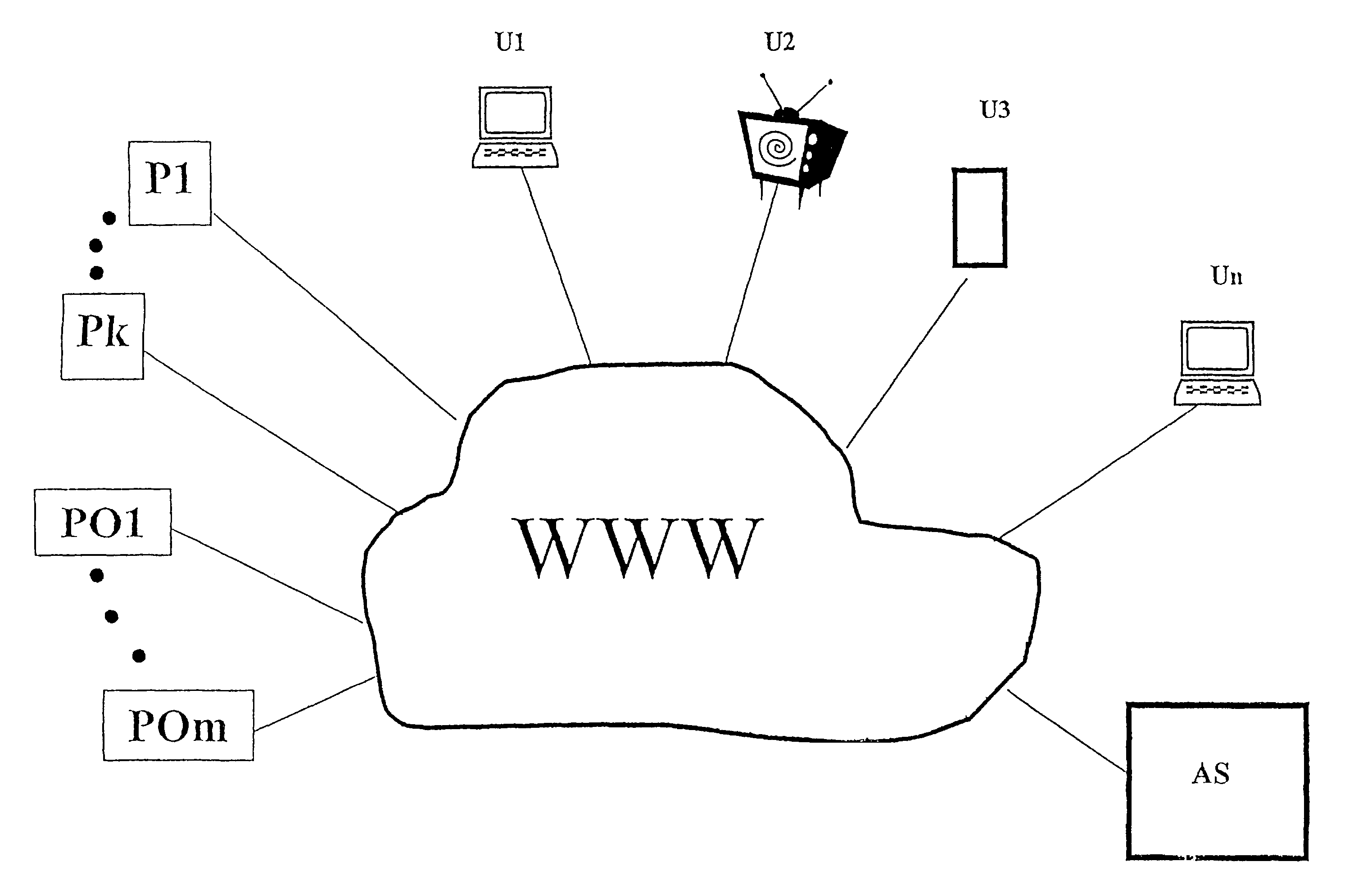
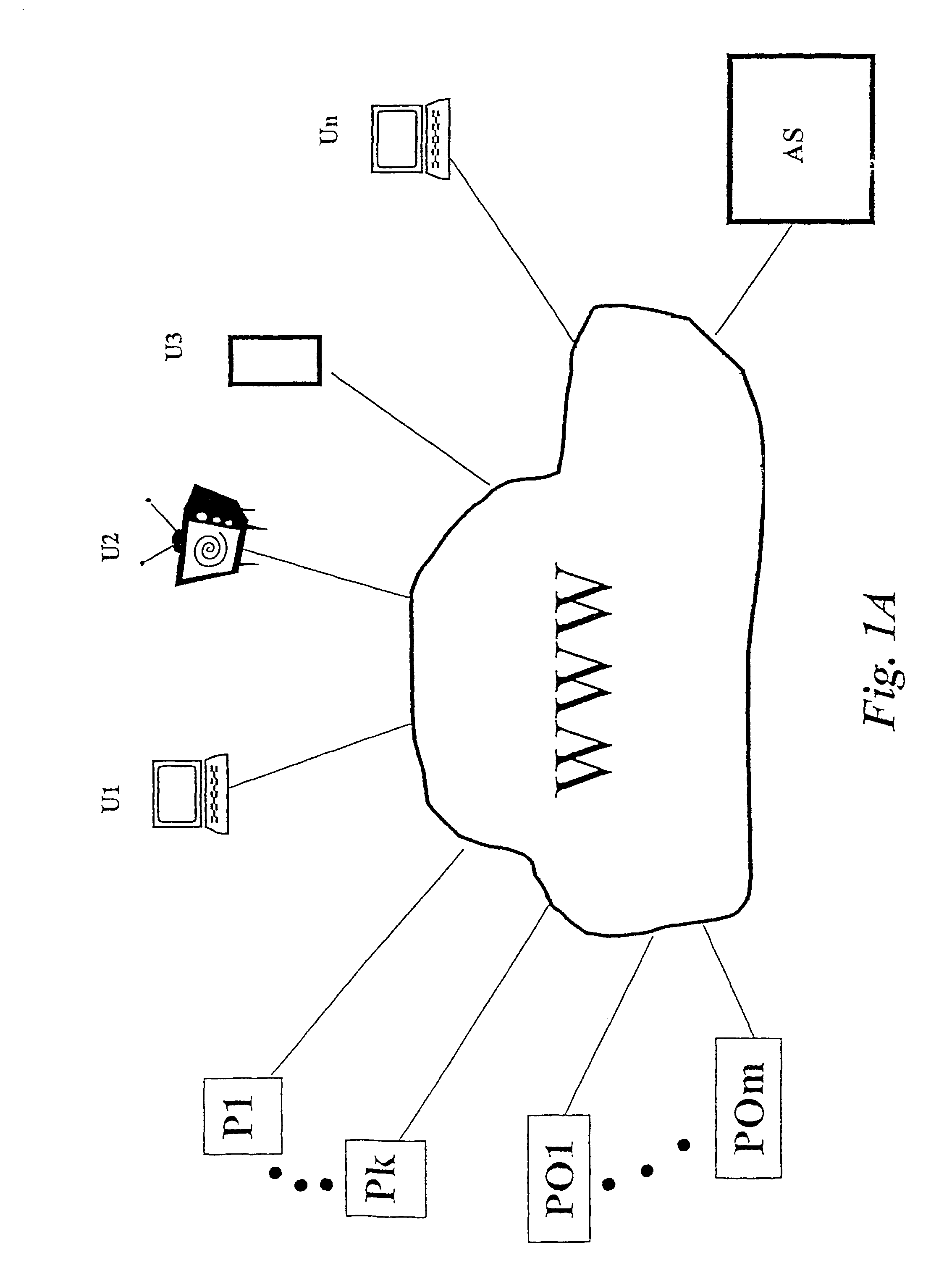
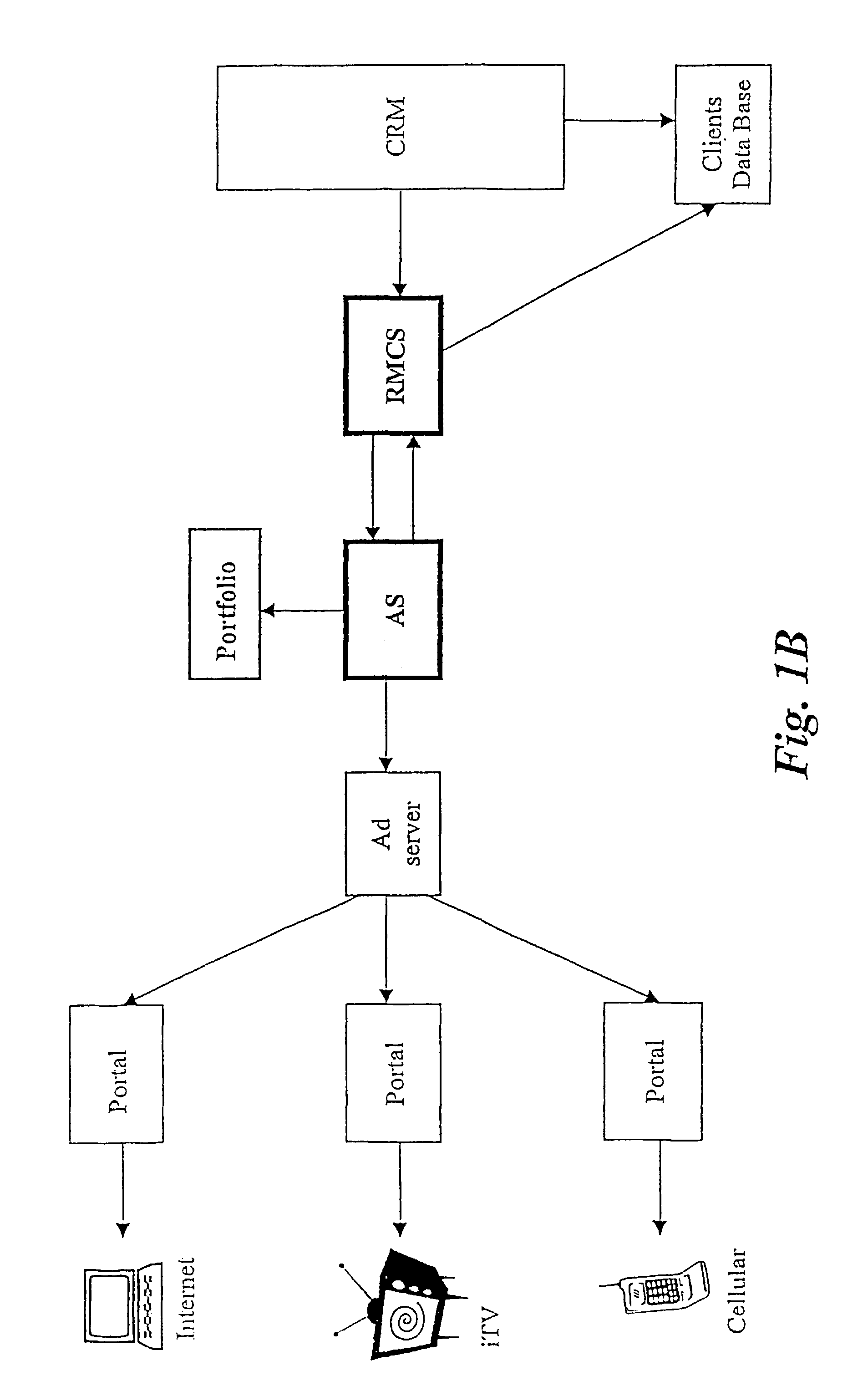
User-driven data network communication system and method
A system is disclosed for messaging over a data network, such as the Internet and interactive TV, which allows every registered user to generate and update one or more user portfolio(s) containing information relative to Providers and / or individuals of which the user is willing to view their messages. The messages are displayed inside the space of the webpage where usually banners are shown. The system may provide benefits to the user upon displaying messages with commercial value to him. The disclosed messaging system allows an easy and effective communication path between providers and users any time publicly or privately in the banner area of a web site, which does not occupy additional space on the user's browser, and does not require the user to load another application besides his browser.
Owner:CONVERSANT
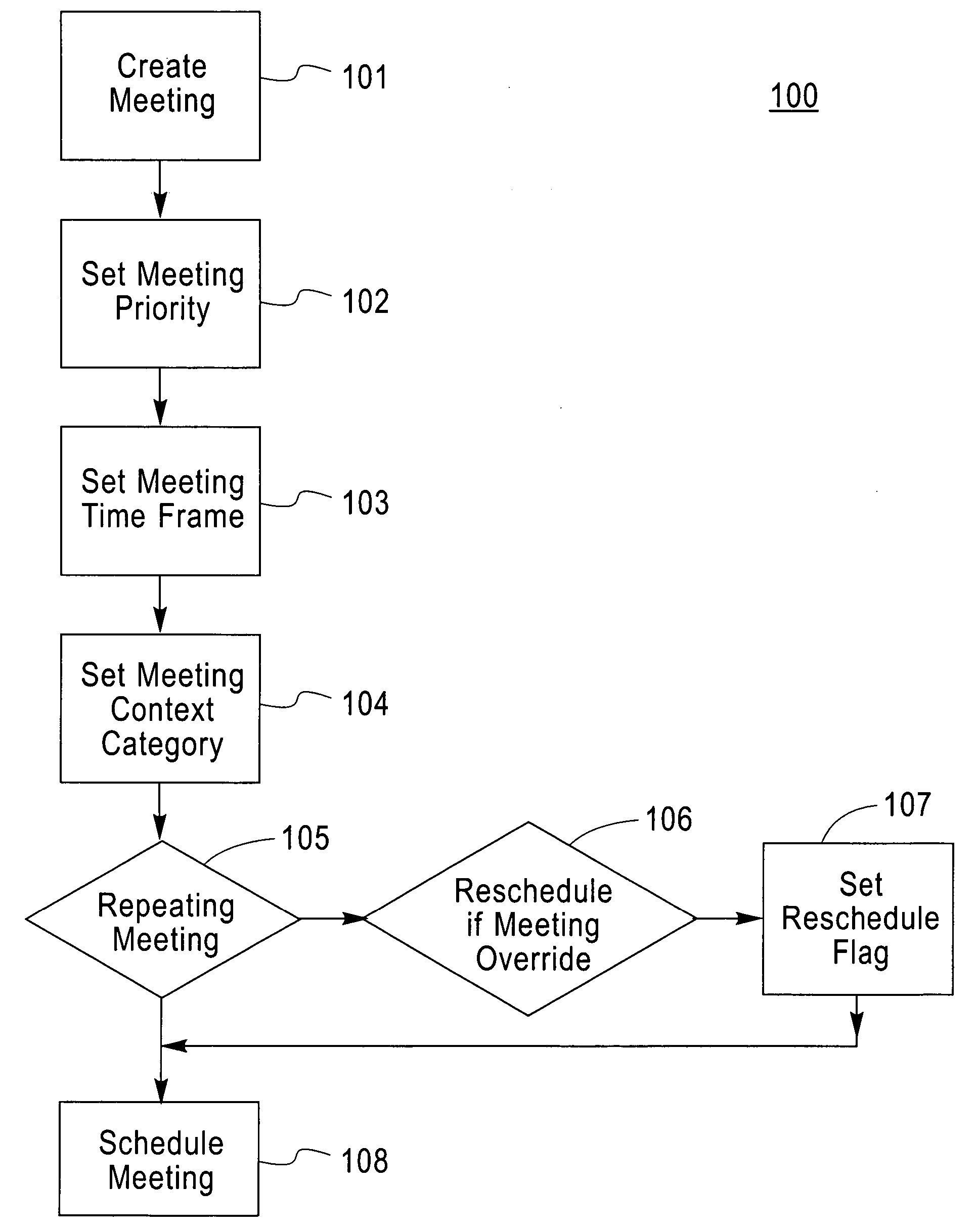
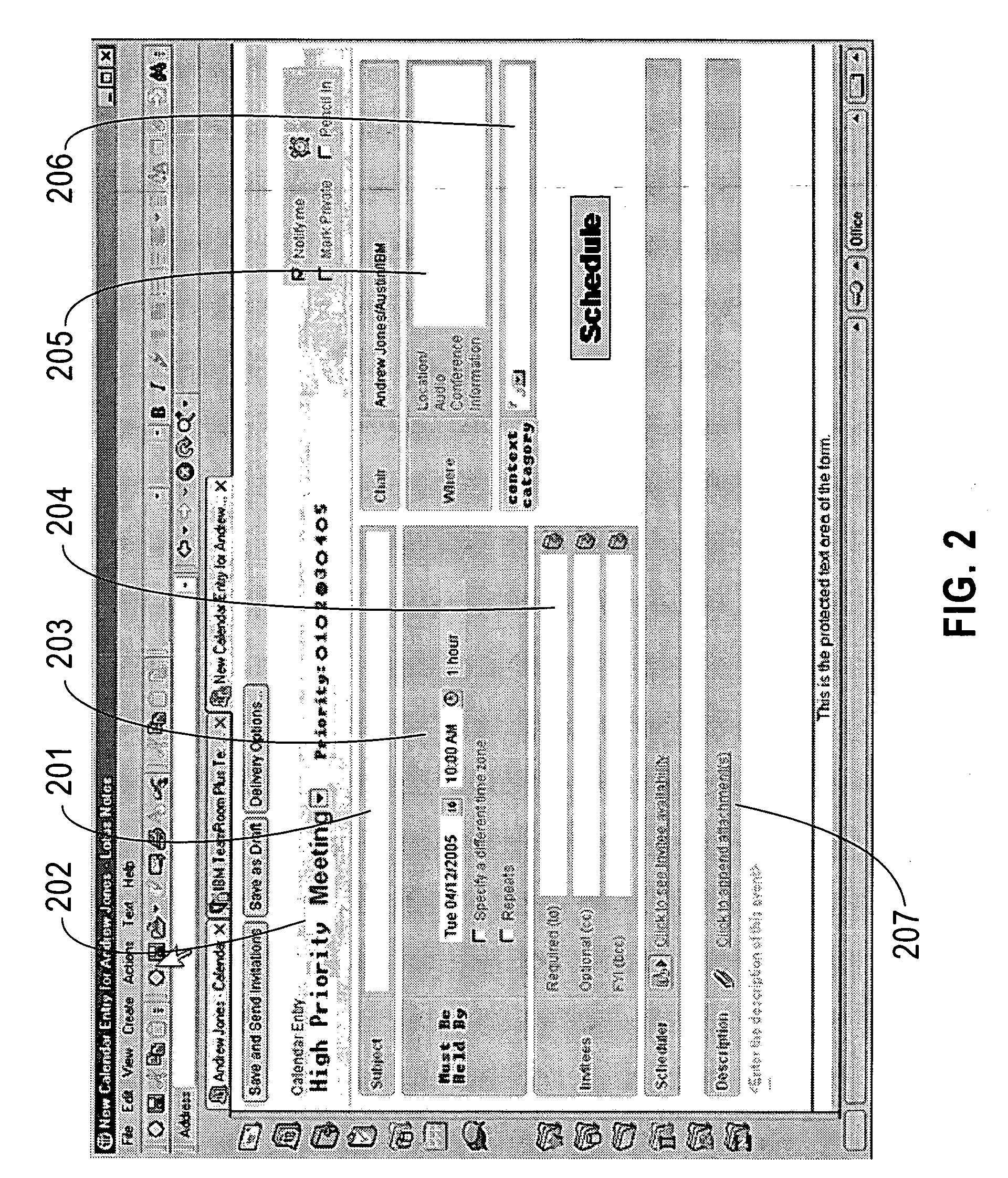
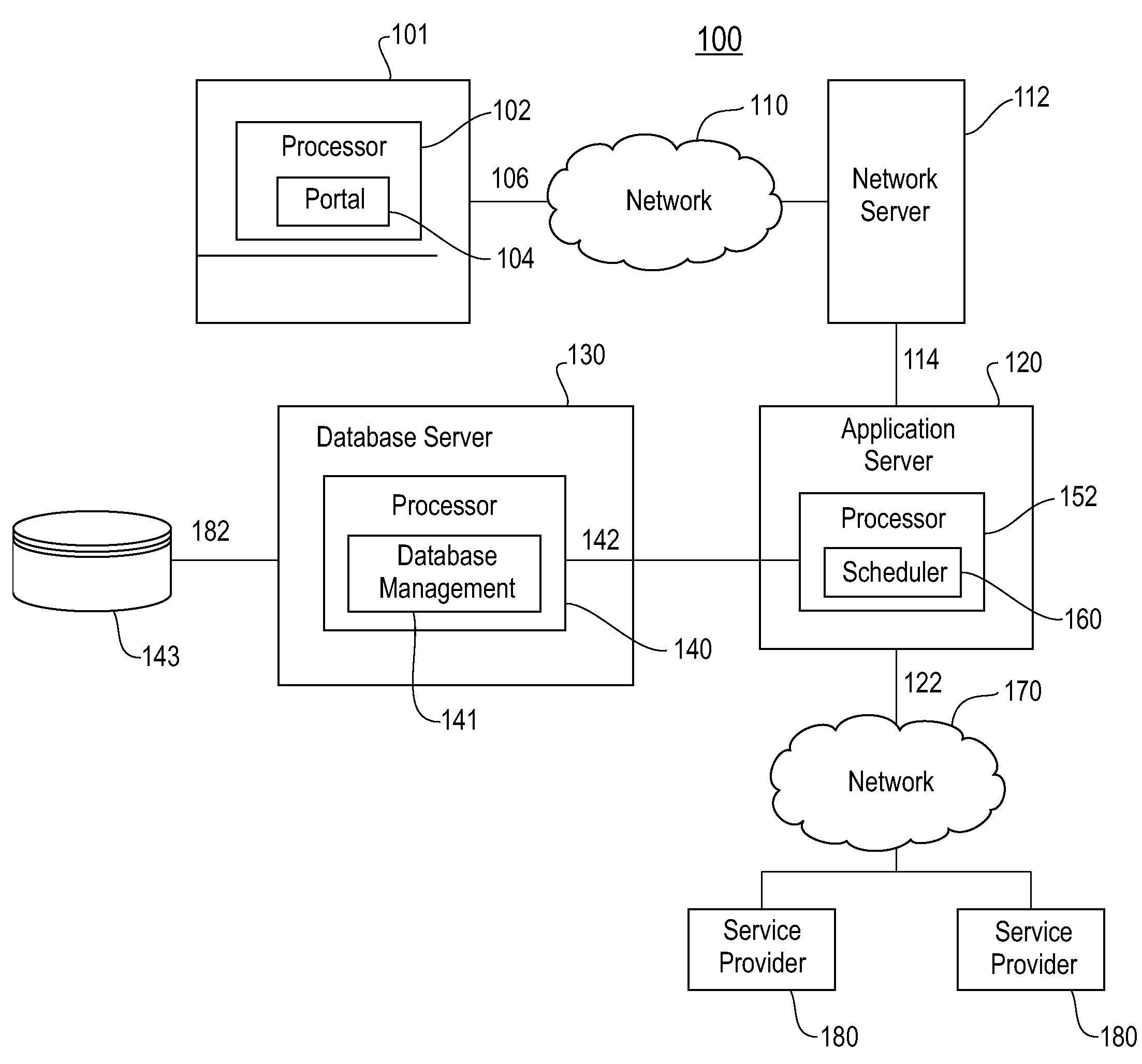
Method and structure for overriding calendar entries based on context and business value
InactiveUS20070005409A1Reduce effortShorten the timeMultiprogramming arrangementsContext basedBusiness value
A method and structure for automatically scheduling a meeting in an electronic calendar system. Calendars of all participants invited to a meeting being scheduled are accessed. Each participant's calendar is checked whether that participant is available for the meeting, in accordance with a priority of the meeting. The meeting is scheduled on each participant's calendar if all said participants are available.
Owner:IBM CORP
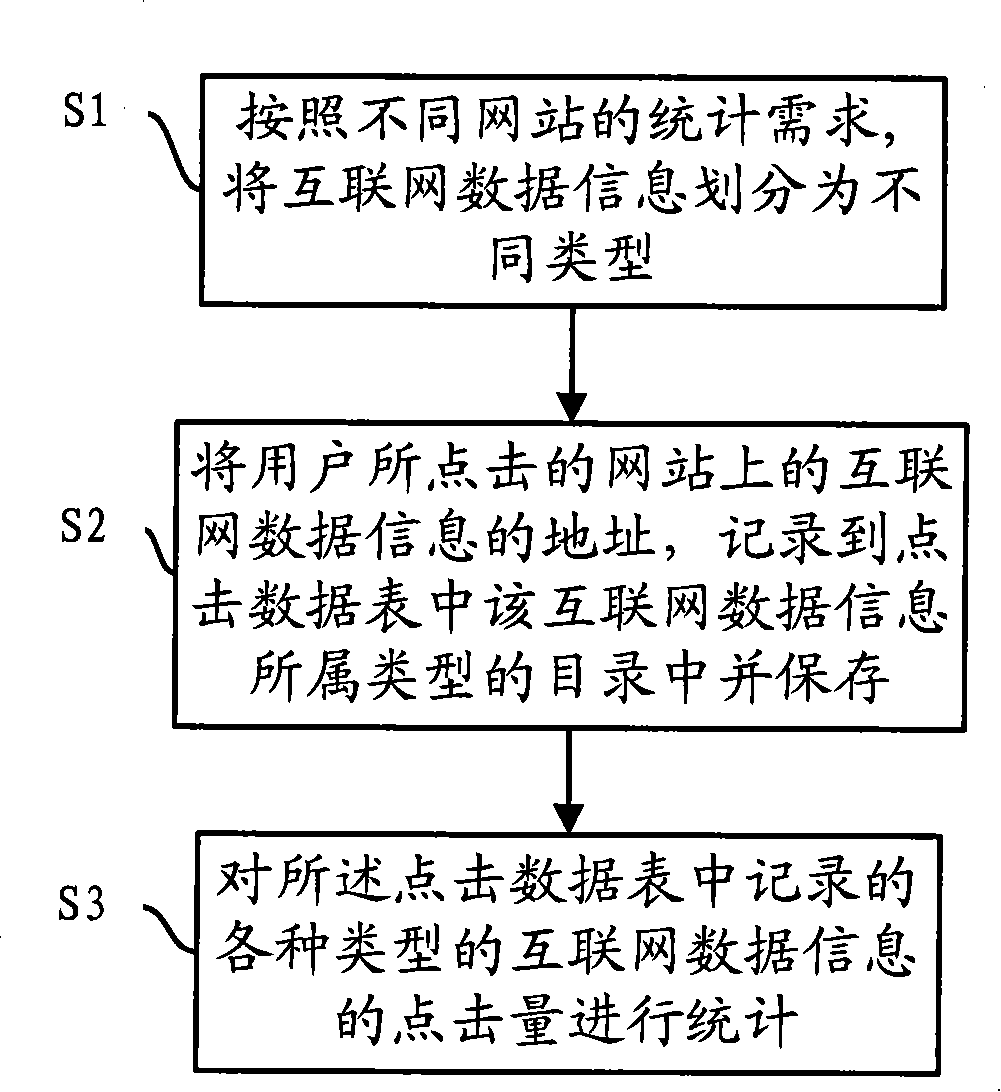
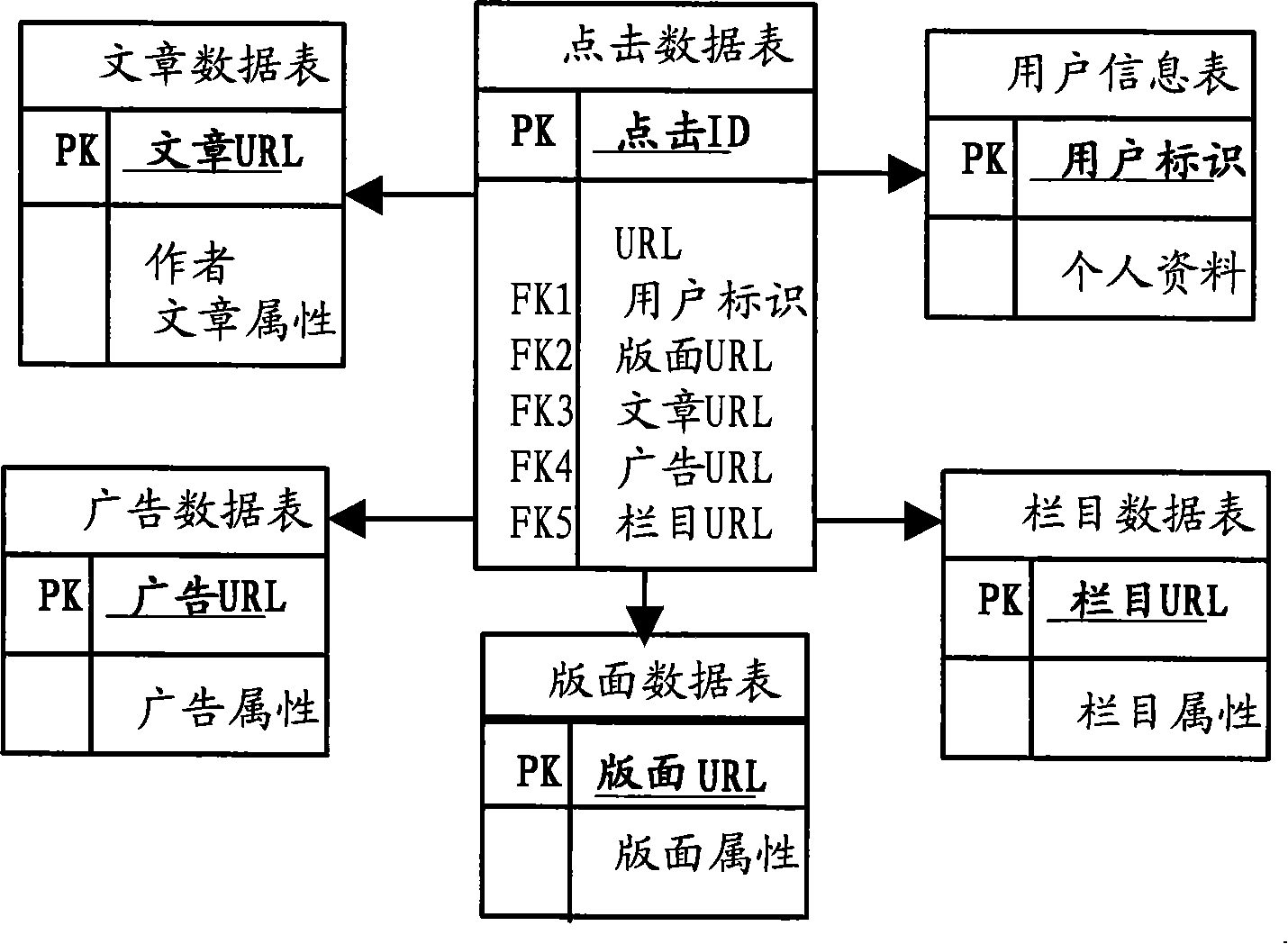
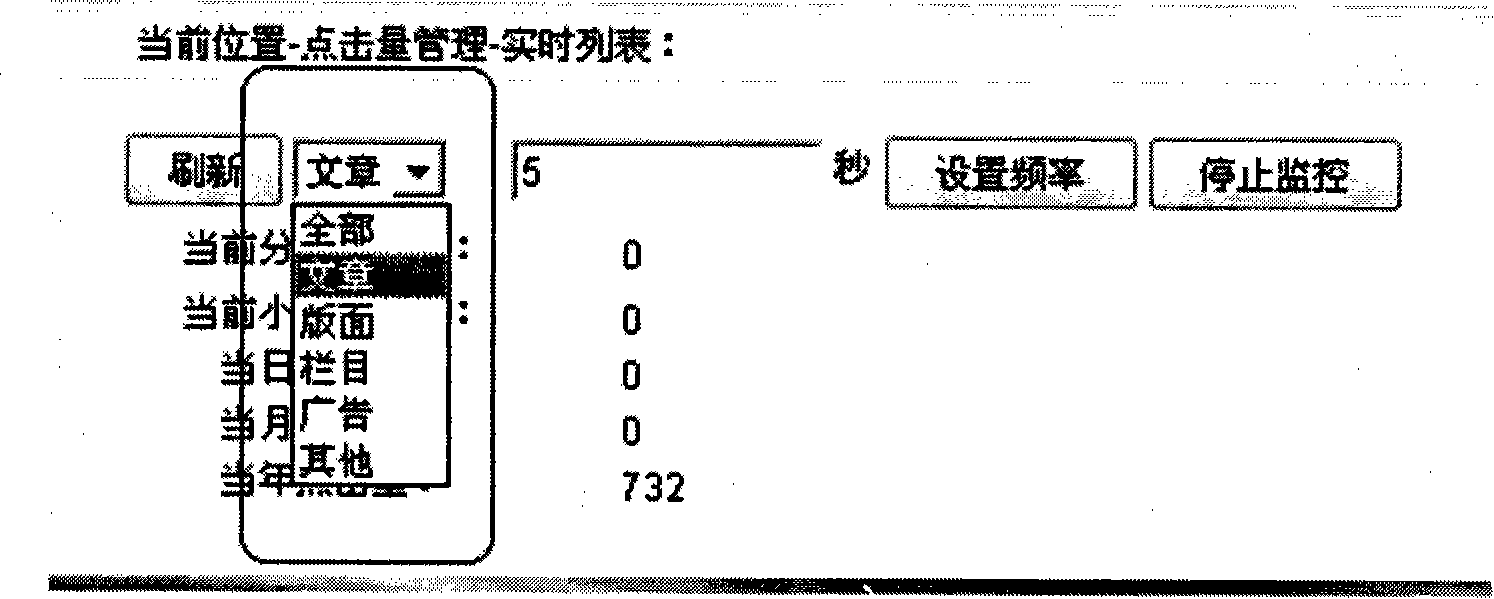
Statistical method and device of internet data information clicking rates
InactiveCN101159592AReduce the burden onData switching networksSpecial data processing applicationsGranularityData information
The invention discloses a statistical method and a device of internet data information click volume, relating to the field of statistics of computer internet data information. The invention aims to solve the problems that the prior click volume statistical tool can not meet the requirements for the website operators and advertisers. The statistical method of internet data information click volume comprises: dividing the internet data information into different types according to the statistical requirements for different websites; recording the address of the internet data information clicked by the user on the website in the directory of the type that the internet data information belongs to in the click data list; and counting the click volume of different types of internet data information stored in the click data list. The statistical device of internet data information click volume comprises a classification module, a record module, a storage module and a statistical module. The invention realizes the multi-granularity statistics of website elements and has good commercial value.
Owner:NEW FOUNDER HLDG DEV LLC +2
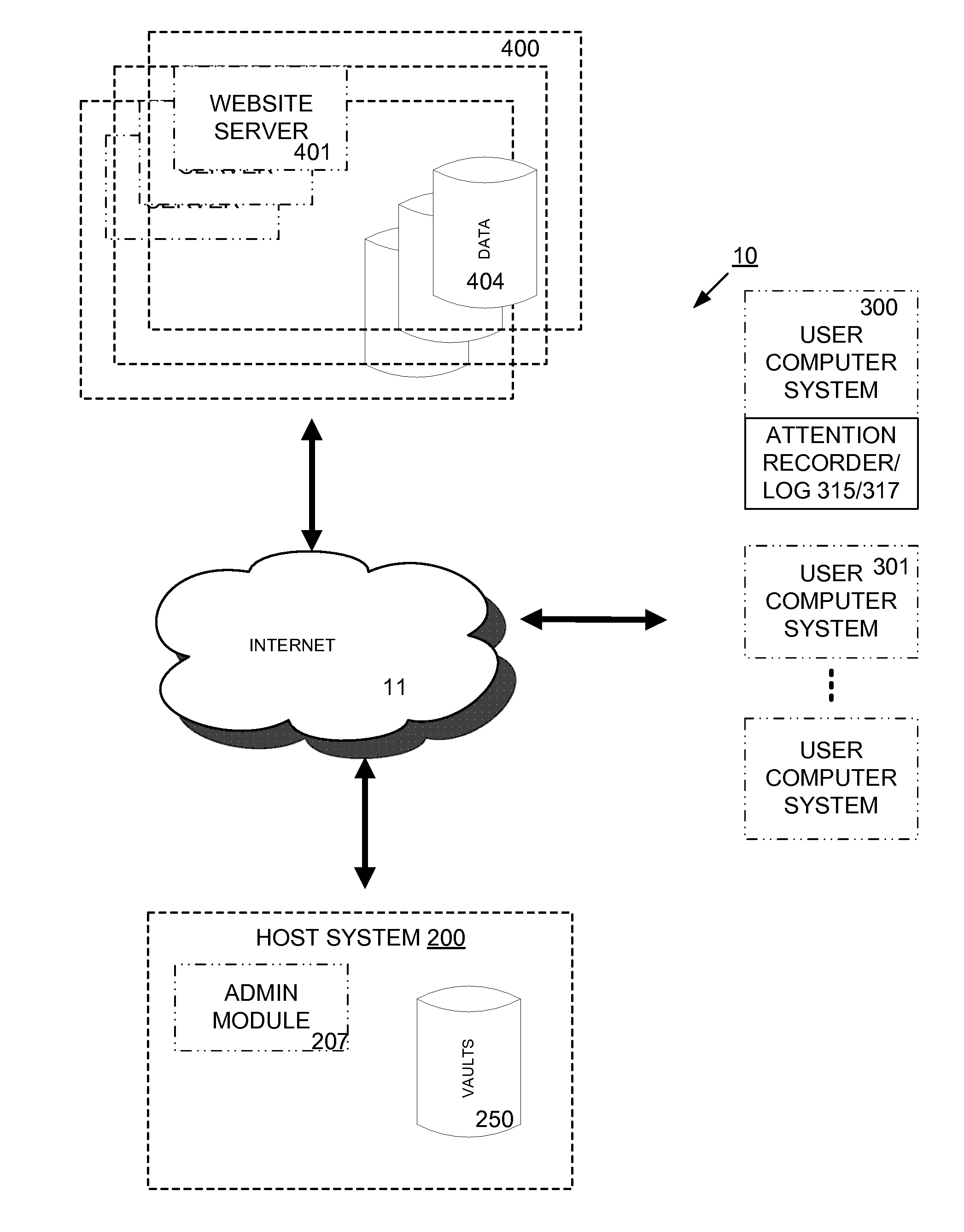
Methods and Systems for Storing, Processing and Managing User Click-Stream Data
InactiveUS20100169802A1Input/output for user-computer interactionDigital data processing detailsWeb siteStreaming data
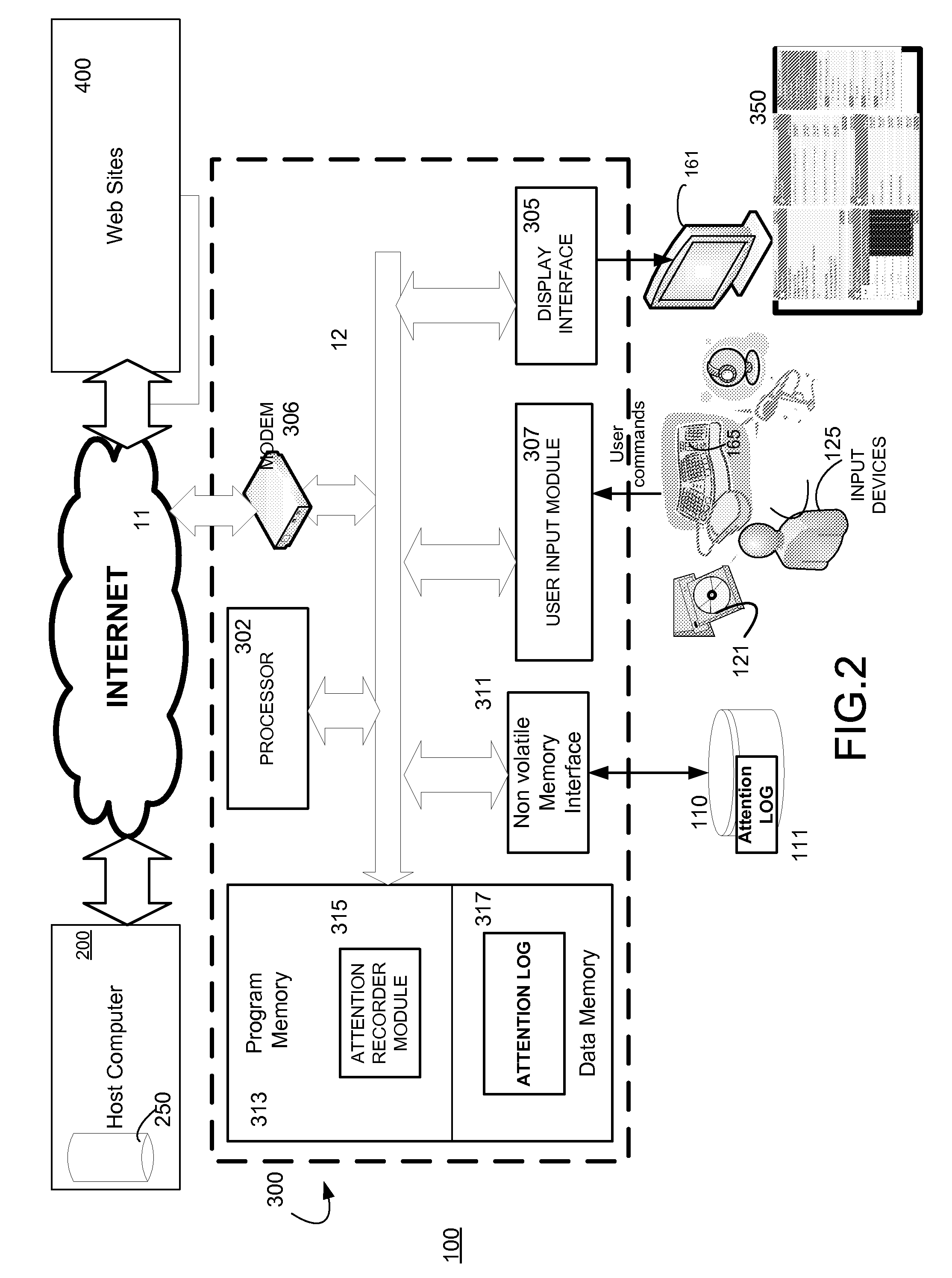
Methods and systems for enabling users to capture, store, and analyze attention data, particularly Internet website click-stream data. Captured, stored attention data may be used by the individual, or, through permissions, the data may be made available to other private and commercial users. The invention thus enables users to recognize both personal and potential commercial value from an electronic record of their attention. The invention includes not only the basic capture and store of attention data, but also the ability to process attention data in a variety of different manners.
Owner:SOCIAL MEDIA NETWORKS
Screen audience rating counting and content recommendation system and method based on two-way set top box
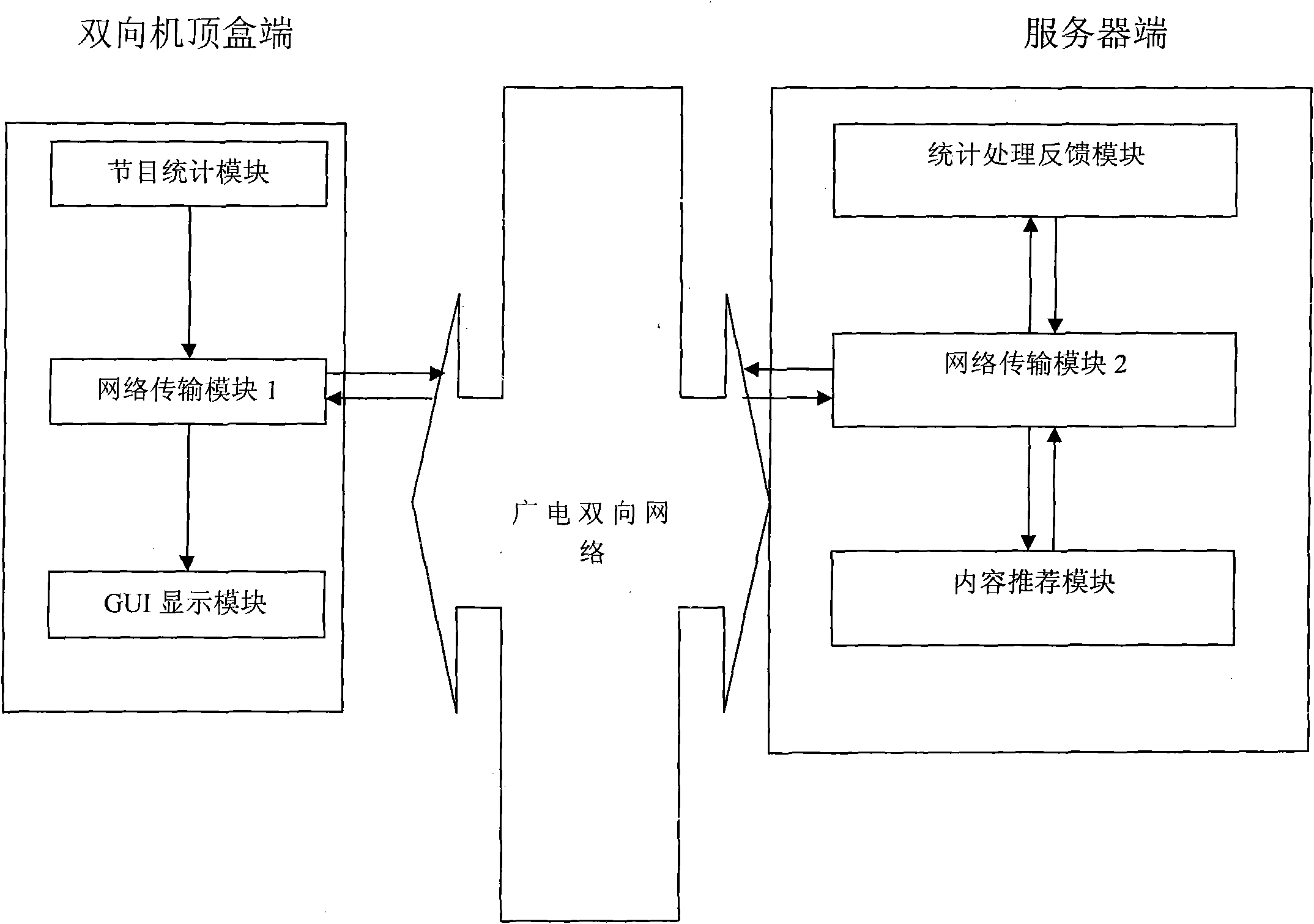
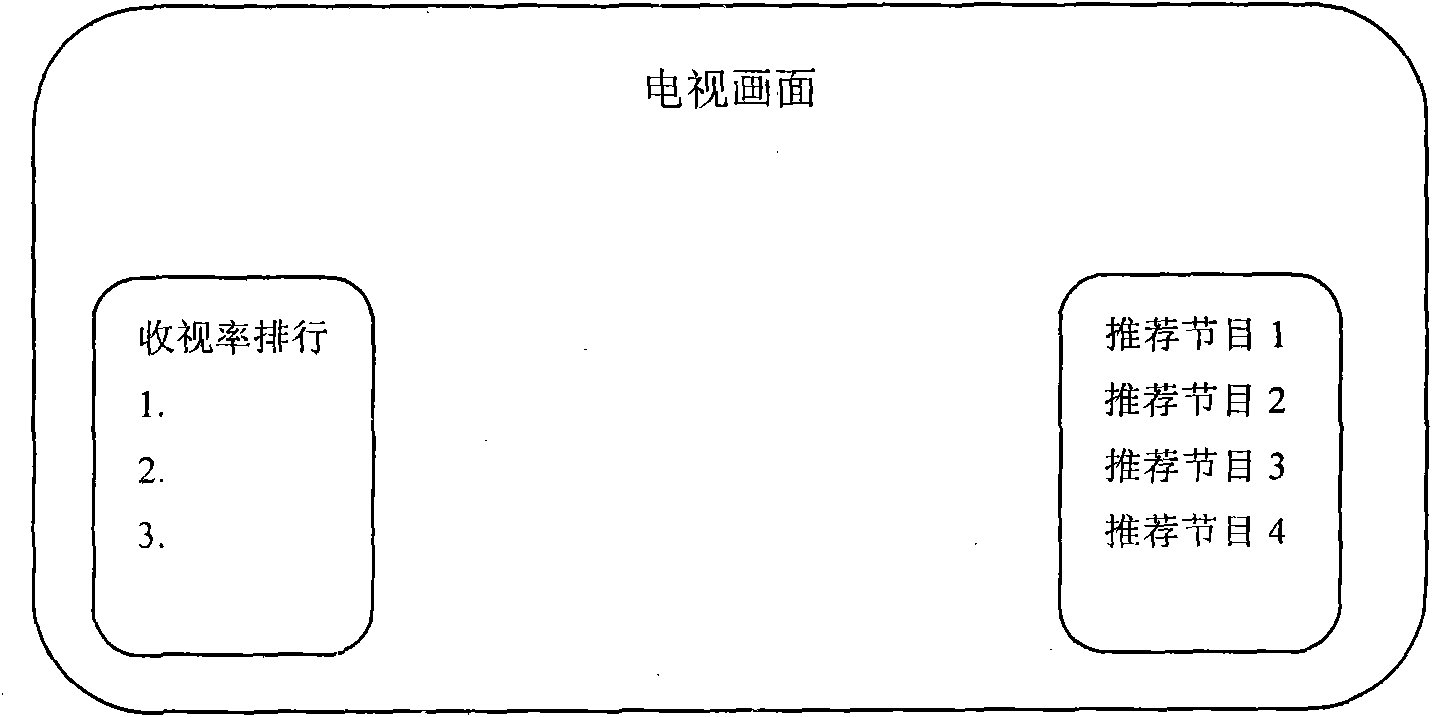
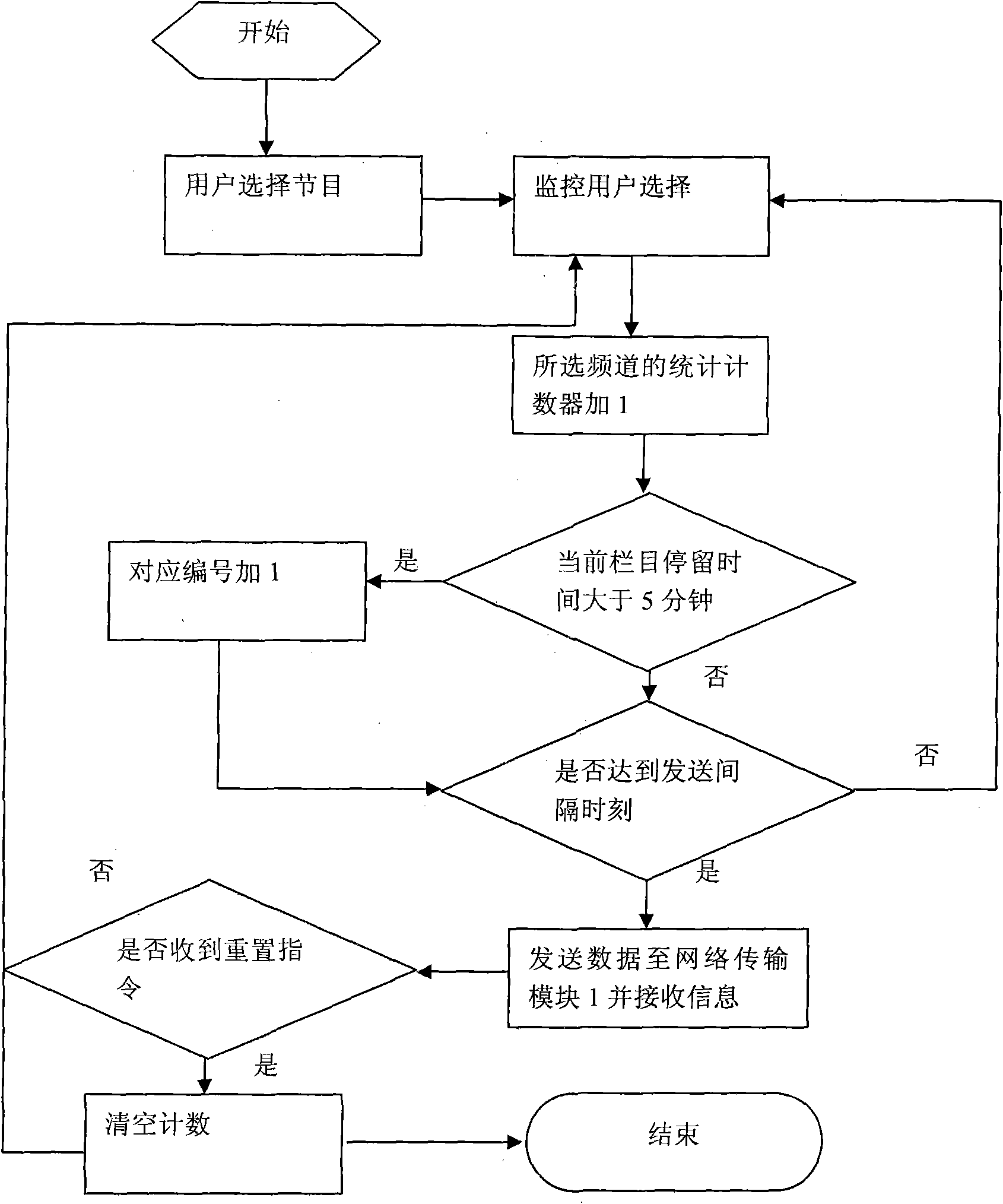
InactiveCN101835027AAccurately monitor playbackAccurately understand the selectionTelevision system detailsColor television detailsRelevant informationBusiness value
The invention discloses screen audience rating counting and content recommendation system and method based on a two-way set top box, belonging to the technical field of the application of digital TV set top boxes. In the method, a counting module is provided in digital TV program playing by utilizing the communication function of the two-way set top box and used for carrying out accumulative counting on programs and uploading a result to a central server; and the counting can be emptied according to required server ends. The audience rating of each program can be learnt by utilizing counted information server ends, and the related program recommendation can be provided for users by a video recommendation system according to user information for viewing programs and displayed on a set top box control interface in a menu manner. The system can provide accurate audience rating real-time counting for users and merchants as well as related information for the users, thereby greatly benefiting to the merchants and the users and having strong commercial values.
Owner:新兴县万马有线电视网络有限公司
Quality of service aware scheduling for composite web service workflows
A method of assigning web service requests to service providers includes searching for an optimal assignment from all possible assignments using a genetic algorithm (GA) that represents possible assignments as chromosomes, and converging towards an assignment of web service request to service providers that maximizes overall business value for all workflows to the service providers. An adaptive mutation scheme is used to introduce mutation into populations of chromosomes. The mutation scheme includes a mutation rate that increases when chromosomes under evaluation fail to improve its workload against the metric over a certain number of generations.
Owner:IBM CORP
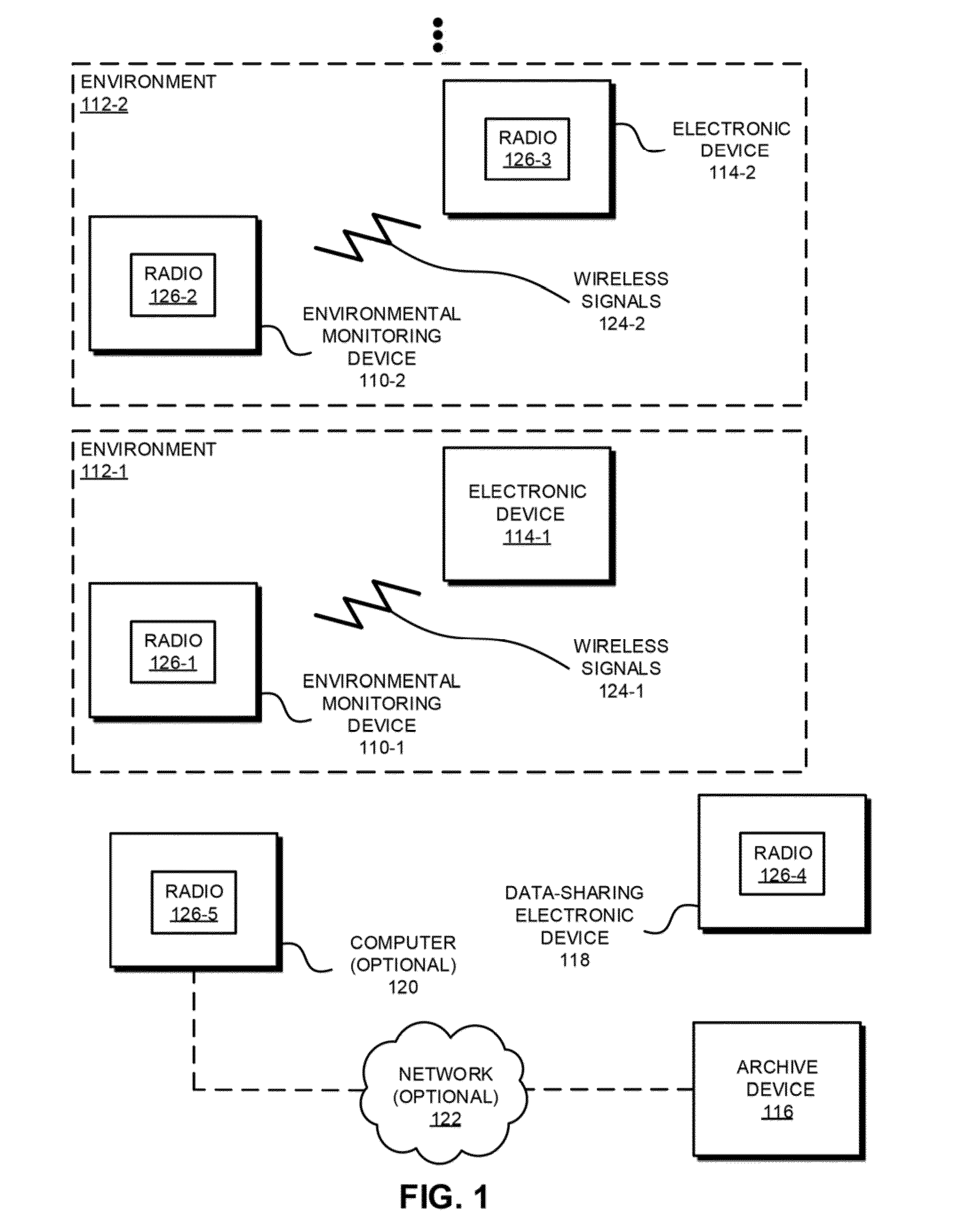
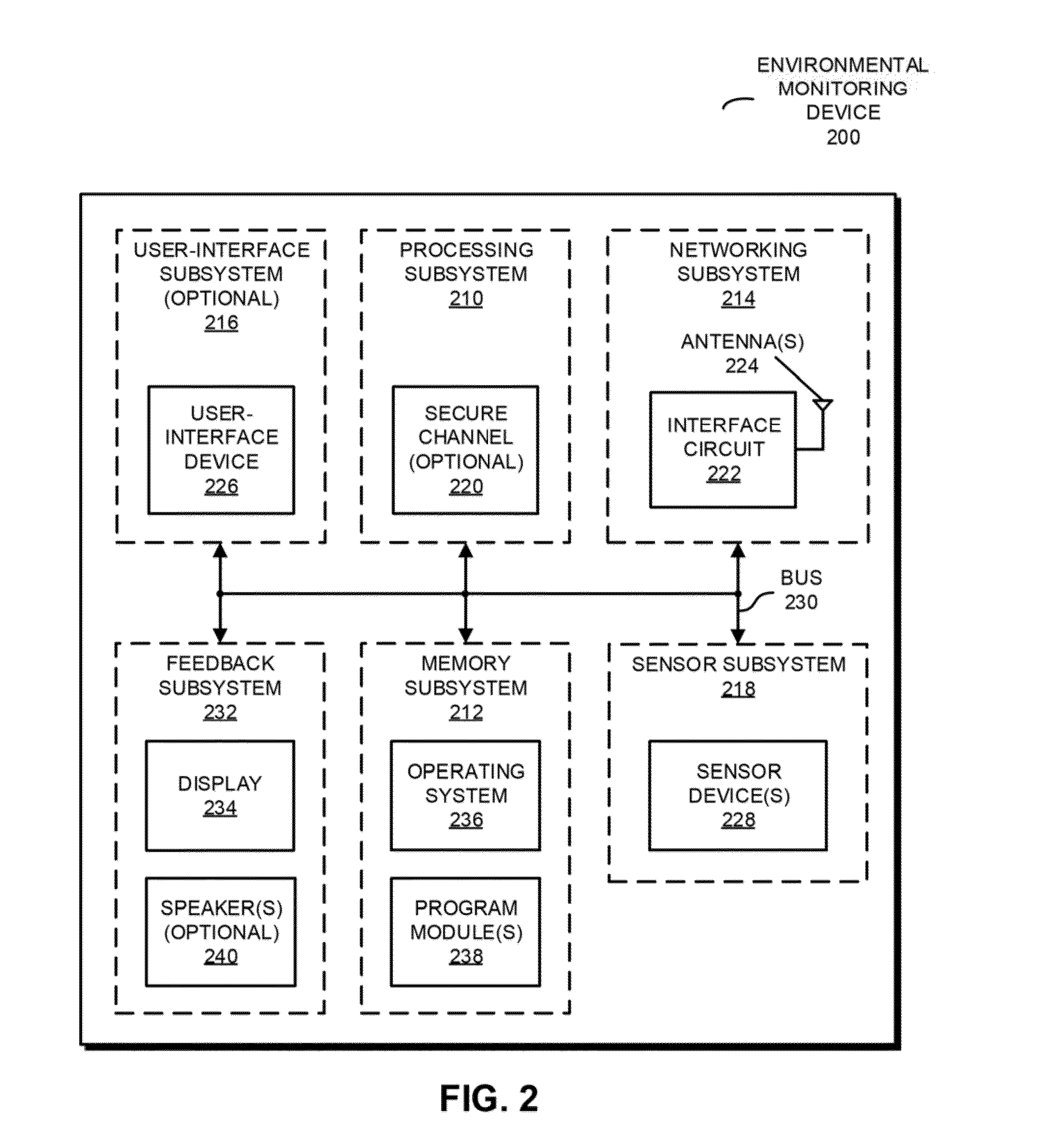
Environmental monitoring device
An electronic device that determines a risk metric for a physical object associated with an environment is described. This electronic device receives sensor data from a set of electronic devices (which may or may not include the electronic device) that are located in separate, neighboring or proximate environments. The sensor data represents environmental conditions in these environments. By analyzing and comparing the sensor data the electronic device assesses the environmental condition and determines the risk metric for at least one of the environments (such as a risk metric for a power failure). Furthermore, the risk metric may be used to calculate a financial value, such as a commercial value or an insurance premium of the physical object associated with at least the one environment. Note that the physical object may be included in at least the one environment or at least the one environment may include the physical object.
Owner:LEEO
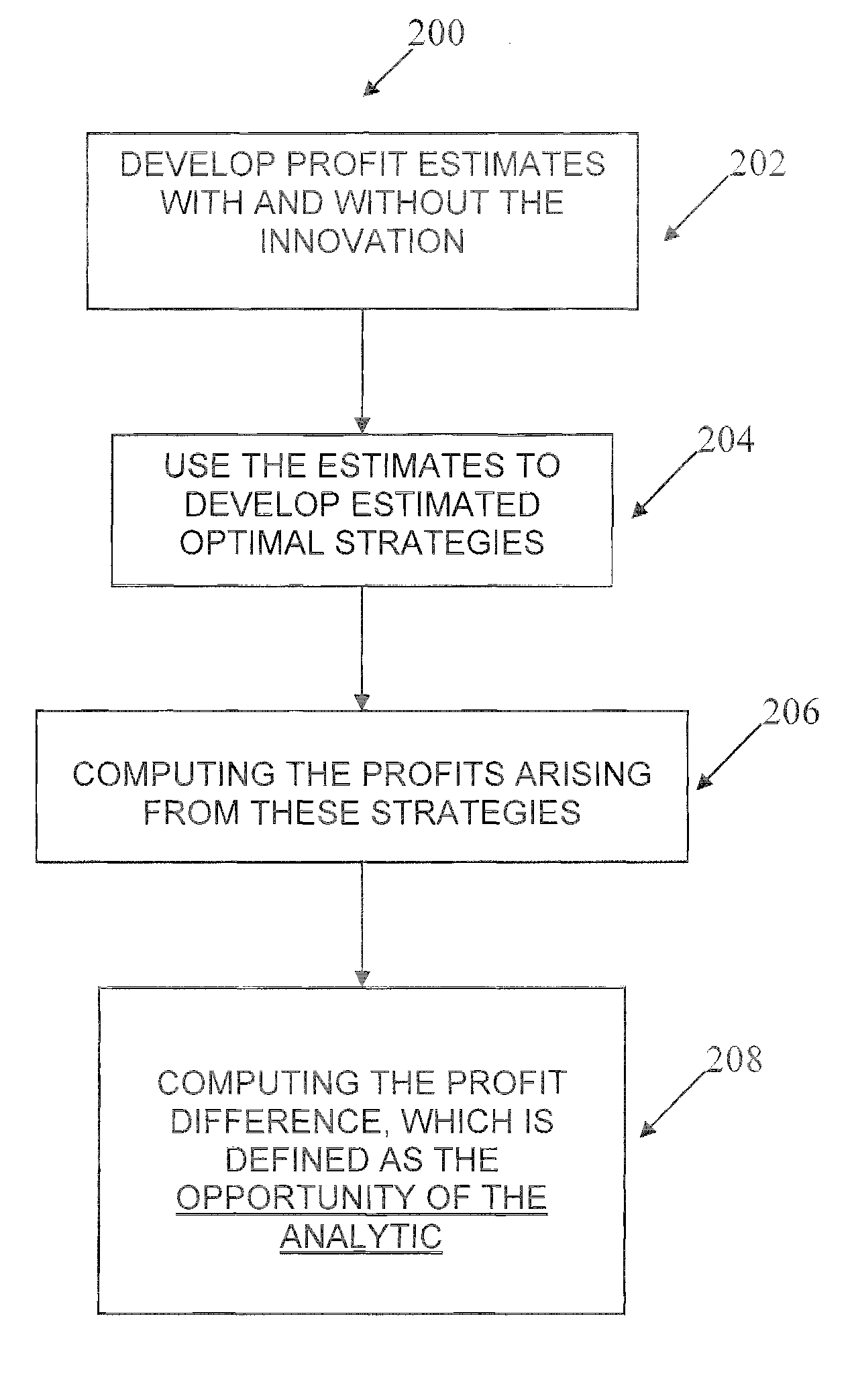
Apparatus and method for simulating an analytic value chain
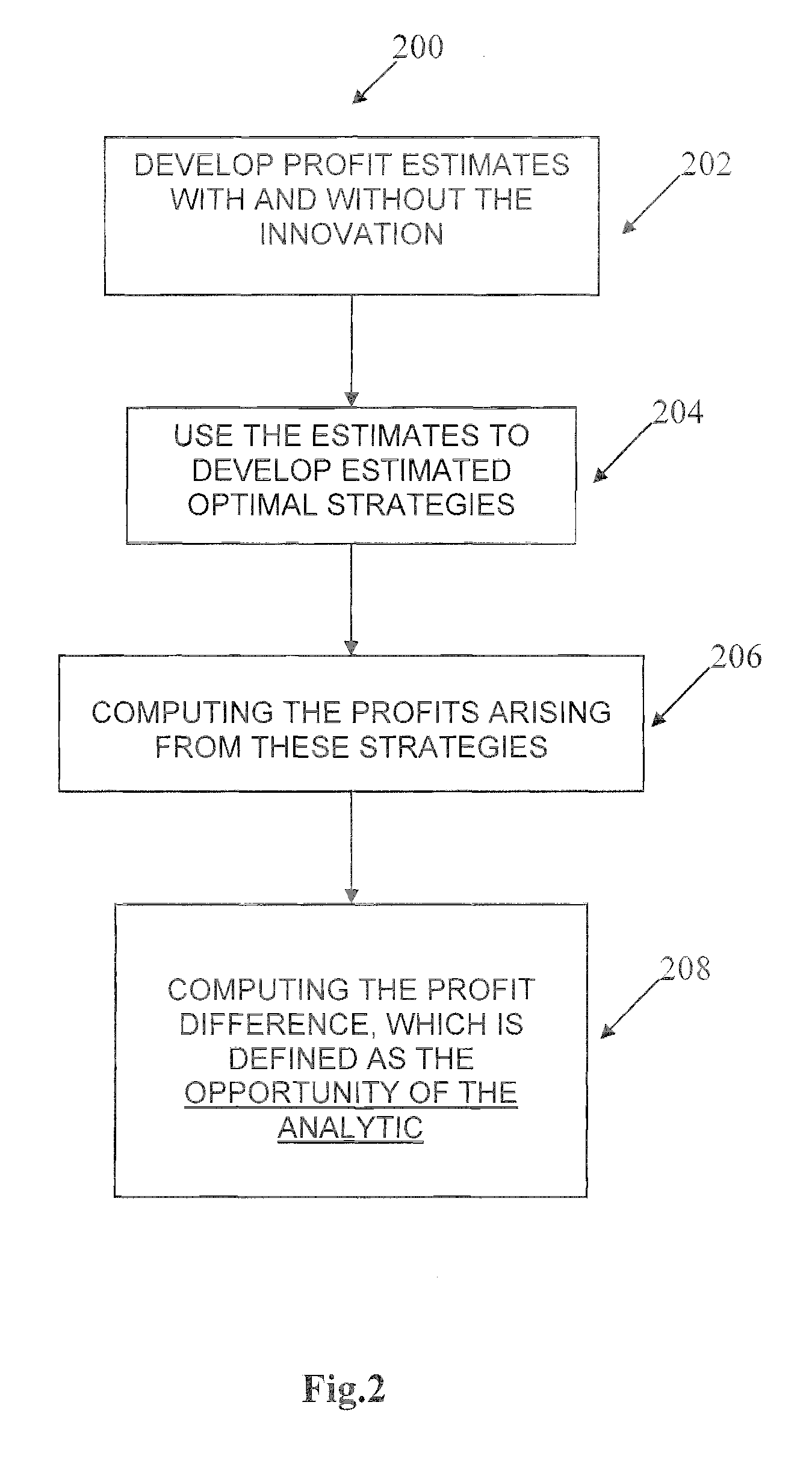
A computer-implemented simulator models the entire analytic value chain so that data generation, model fitting and strategy optimization are an integral part of the simulation. Data collection efforts, data mining algorithms, predictive modeling technologies and strategy development methodologies define the analytic value chain of a business operation: data→models→strategies→profit. Inputs to the simulator include consumer data and potential actions to be taken regarding a consumer or account. The invention maps what is known about a consumer or an account and the potential actions that the business can take on that consumer or account to potential future financial performance. After iteratively performing simulations using varying inputs, modeling the effect of the innovation on a profit model, the simulator outputs a prediction of the commercial value of an analytic innovation.
Owner:FAIR ISAAC & CO INC
Electronic commerce platform online to offline (O2O) business model
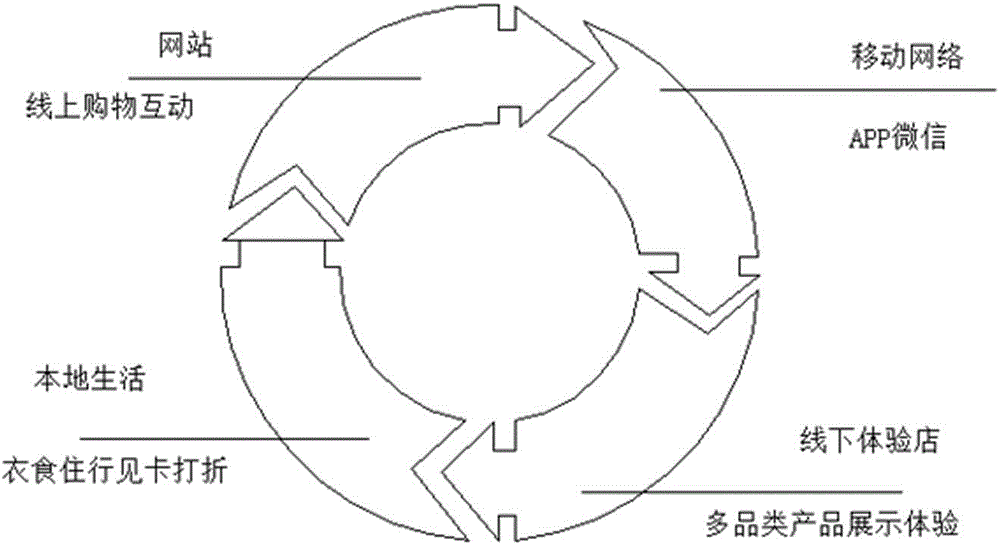
The invention discloses an electronic commerce platform online to offline (O2O) business model and relates to a business mode. According to the electronic commerce platform O2O business model, an internet website and a mobile terminal form an electronic commerce online trading platform, an experience store and a localized commercial tenant form an offline trading terminal, data sharing and collecting of the functions of the online trading platform and the offline trading terminal are achieved through the software development technique, all-network seamlessly connection can be achieved, trading can be completed anytime anywhere, member information can be guided in rapidly, and shopping and consumption can be achieved. By means of the electronic commerce platform O2O business model, the barrier of an electronic commerce traditional online platform and an offline retail trading platform is removed, each other's advantages can be complemented, multi-channel showing and selling of merchants' commodities are promoted, the brand influence is improved, more customers in different shopping channels are attracted, multiaspect interaction experience of users is improved, and brand-new commercial value is achieved.
Owner:HONGHUI SHANGHAI INFORMATION TECH SERVICECO
Wireless field intensity breath detecting method and device and breath detector
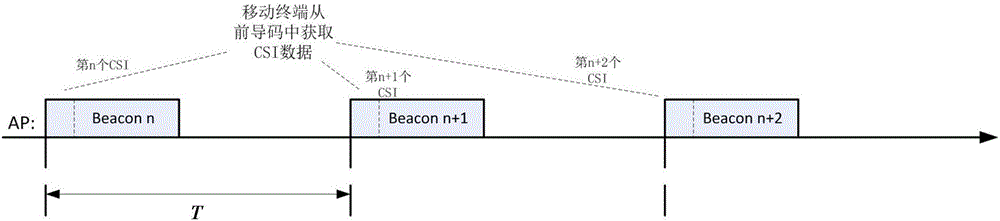
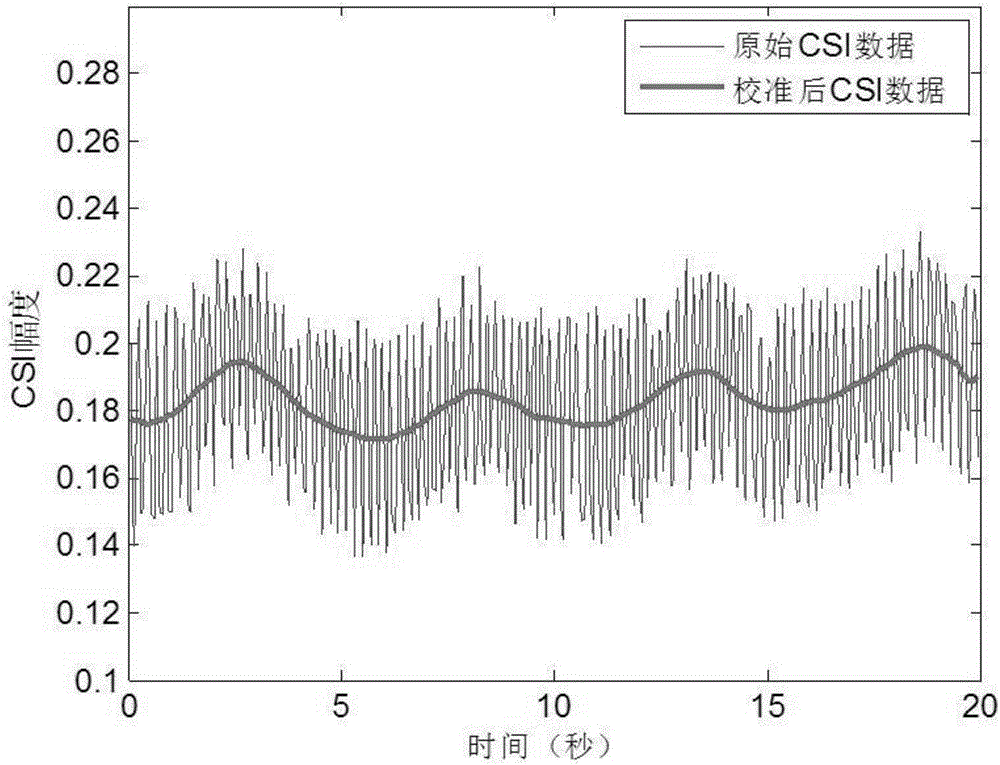
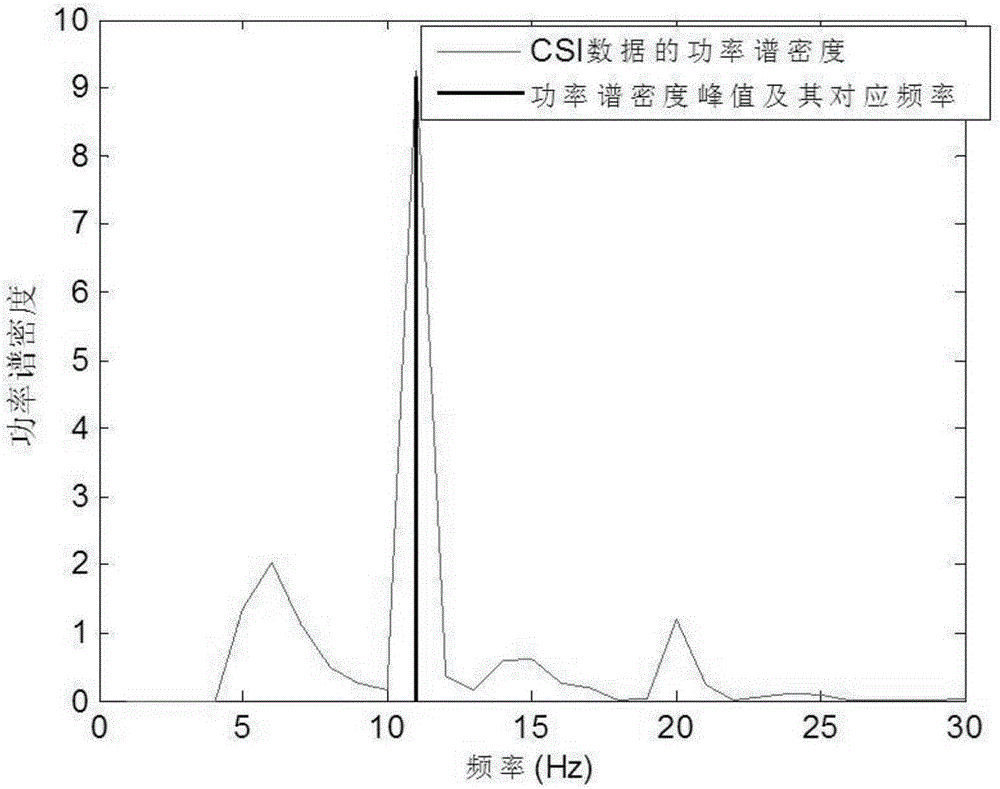
The invention provides a wireless field intensity breath detecting method and device and a breath detector. Channel state information CSI is extracted from existing 802.11WiFi wireless signals and is utilized for acquiring the weak changes, caused by breath during sleep of people, of the wireless signals, and therefore the aim of tracking and detecting the human body breath condition is achieved. By means of a CSI extracting step, a data correction step and a breath rate detecting step, an existing 802.11a / g / n WiFi network and a mobile terminal are utilized, no professional wearable sensor is needed, the wireless field intensity breath detector is customized, besides, the device can be installed in a mobile terminal of a user as software, and detection can be achieved by upgrading existing wearable equipment. Therefore, the device can be popularized to home environments in a large scale, serves as an applied product for people to carry out long-term human body health monitoring every day and has very high application and business value.
Owner:SHENZHEN UNIV
Business solution management
InactiveUS20070129981A1Value maximizationFinanceMultiprogramming arrangementsComputer scienceBusiness value
A method, system, and program product for managing one or more business solutions is provided. One or more candidate business solutions, each of which has a corresponding set of resource requirements and a corresponding business value that is based on a risk and an expected return are used to generate a set of proposed business solutions that maximizes a total value while remaining within a set of resource constraints. In this manner, business decisions regarding particular business solutions to implement can be made with an understanding as to relative risk and / or a total value that will be provided to a business entity.
Owner:IBM CORP
Allocation of Application Licenses within Cloud or Infrastructure
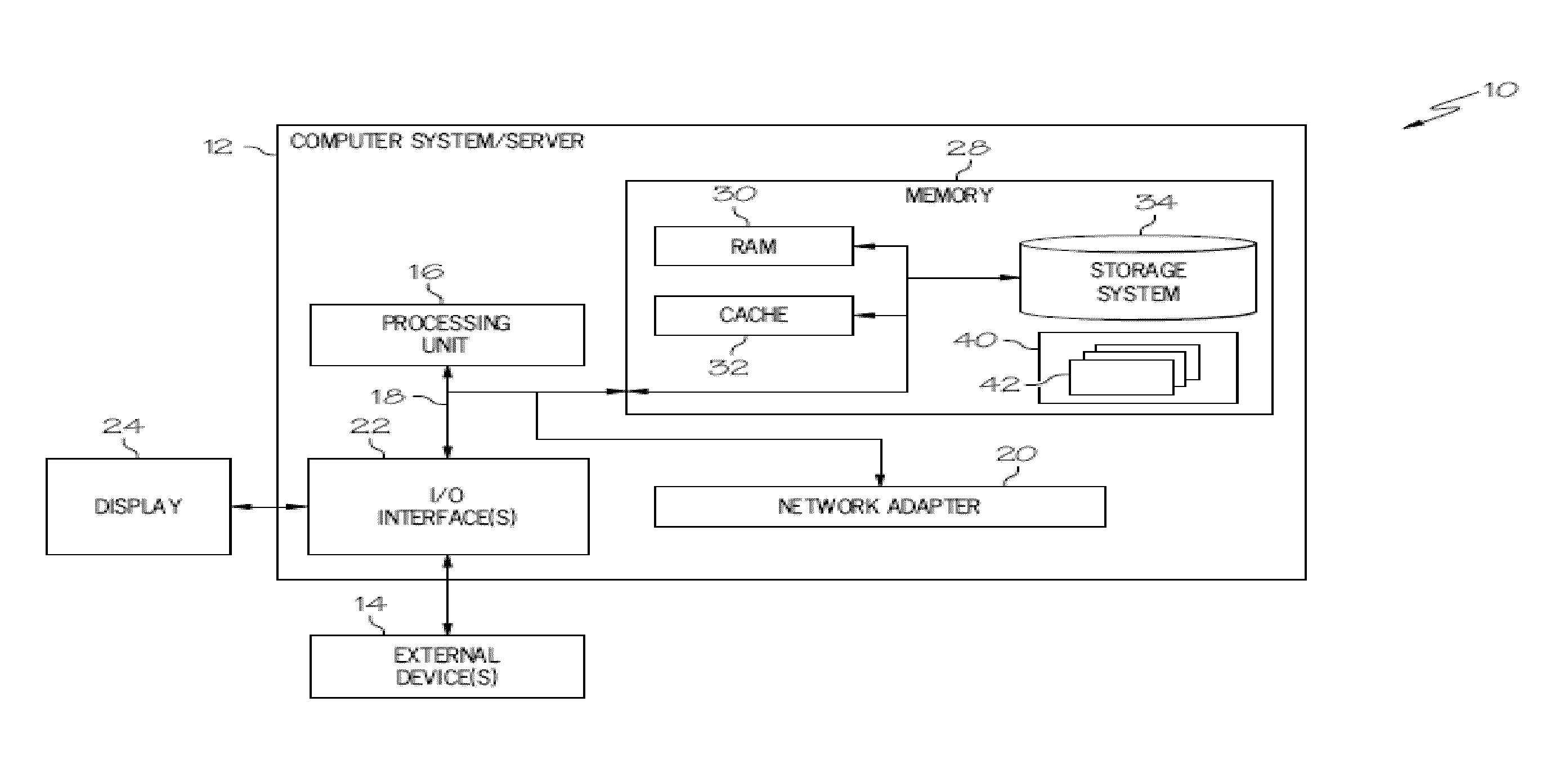
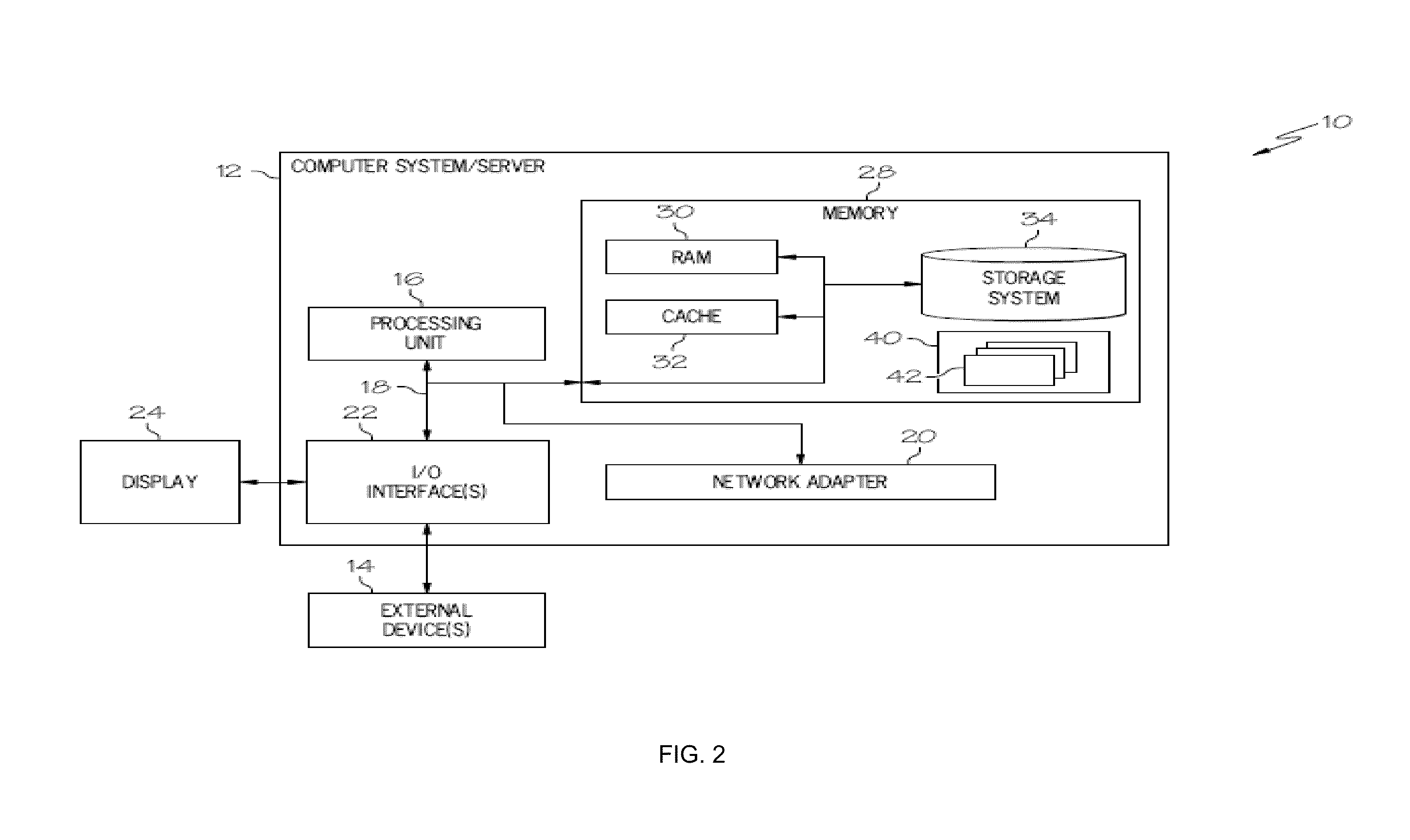
ActiveUS20130262250A1Digital computer detailsBuying/selling/leasing transactionsComputerized systemApplication software
A method for allocation of application licenses includes establishing a computing environment comprising a licensed application or service accessed by at least two users, each user having an associated computer system; establishing an ordered list of users for a licensed application or service, in which users have a predefined priority based on a business value or function; establishing at least one user attribute comprising whether a user's virtual machine will be archived and saved for later resumption if the user's license is at least one of suspended, removed, or reallocated; and establishing at least one disqualification threshold for at least one user.
Owner:IBM CORP
Hadoop-based fast neighborhood rough set attribute reduction method
ActiveCN103336790AReduce outputImprove analysis efficiencySpecial data processing applicationsTime complexityLarge scale data
The invention discloses a Hadoop-based fast neighborhood rough set attribute reduction method. The method comprises the following steps: a, establishing a distributed platform based on the Hadoop; b, defining a neighborhood rough set; c, generating a candidate set; d, calculating the importance of each attribute; e, selecting the attribute with the largest importance and adding the attribute into the candidate set; f, judging whether a stop condition is met or not; g, storing conditions selected by characteristics. The method is based on the Hadoop distributed platform to analyze the parallelization of a parallel data mining algorithm so as to realize the parallelization of a neighborhood rough set attribute reduction algorithm; the time complexity of the parallelized attribute reduction is greatly lowered, the output of an intermediate result in the performing intermediate process is greatly reduced, and the analysis efficiency of large-scale data is improved, so that numerous and varied mass data are converted into available data with information and business values, thereby completing mining and analysis optimizing of data.
Owner:HUZHOU TEACHERS COLLEGE
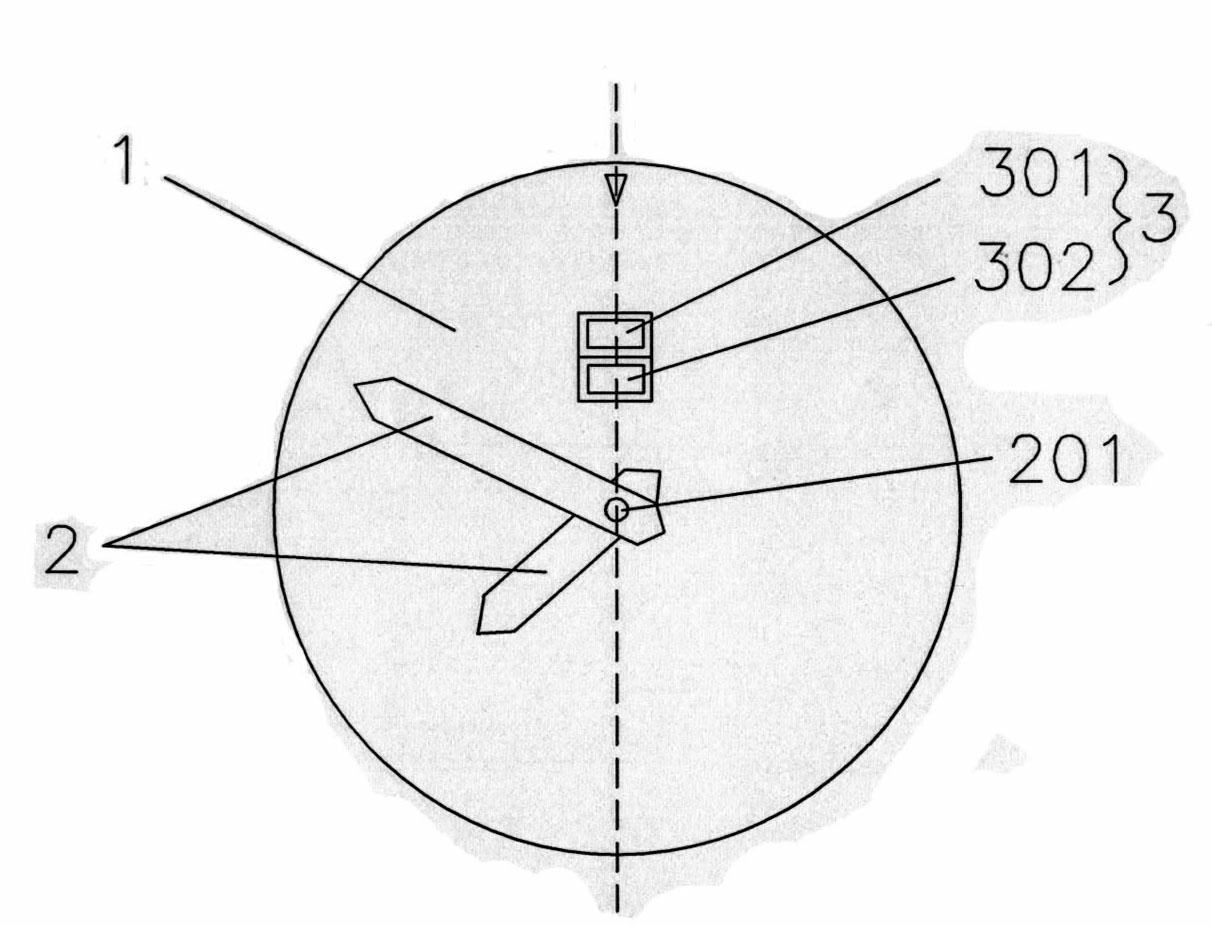
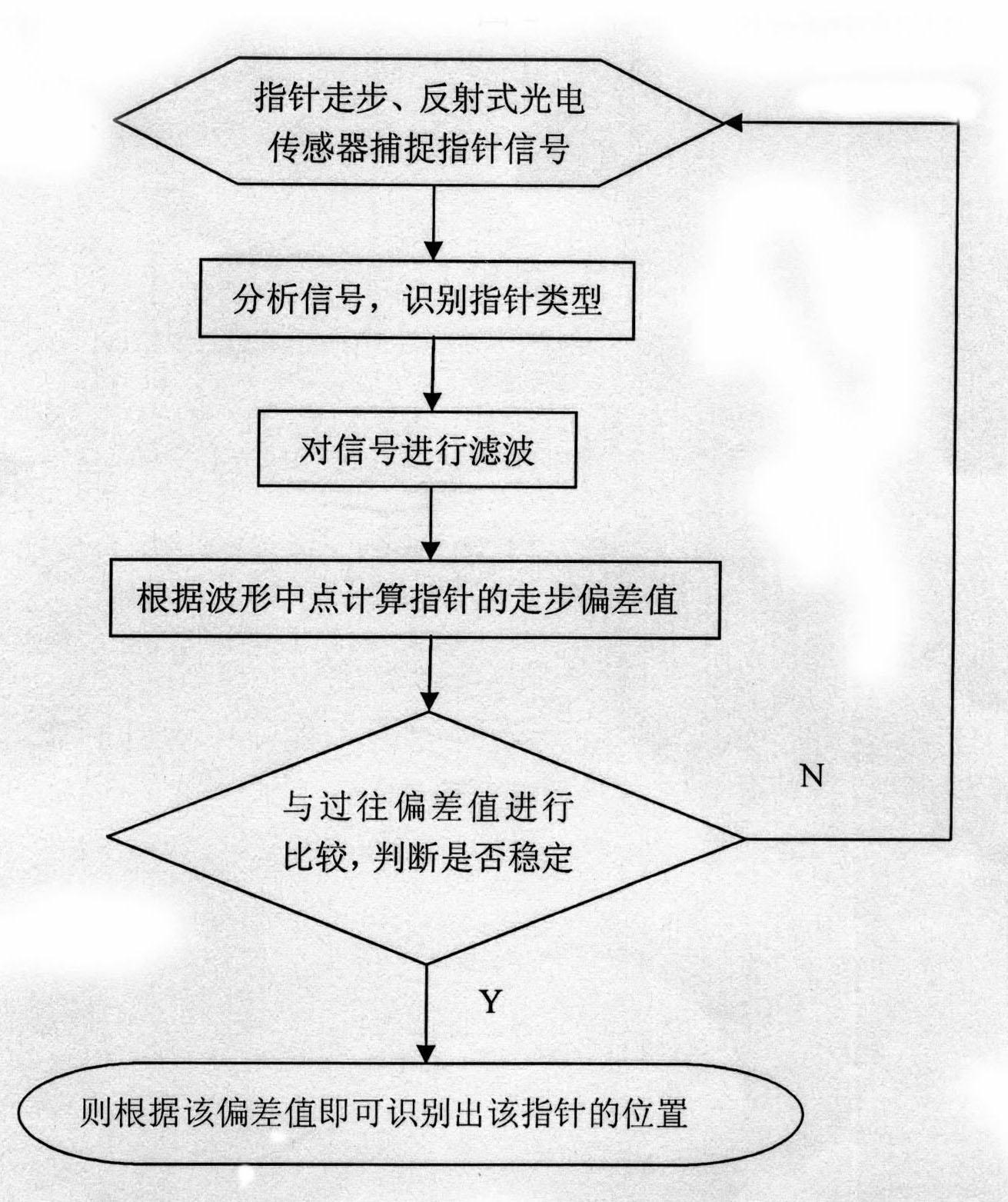
A pointer positioning mechanism of a watch, its positioning method, and pointer zeroing and pointer correction methods
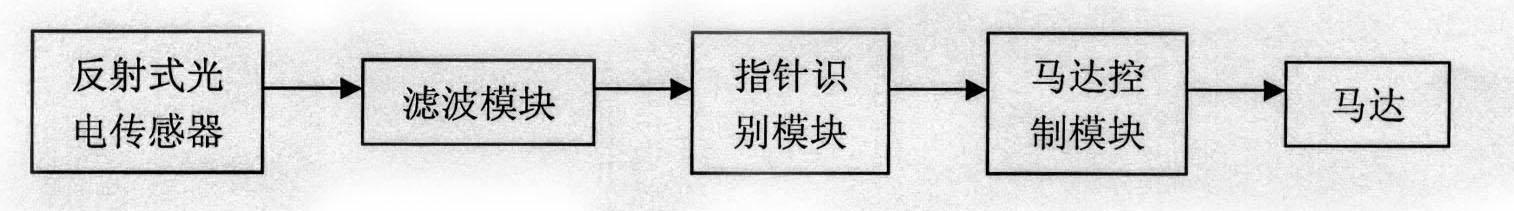
ActiveCN102289191ASmall sizeOvercome the defect of small installation spaceElectric windingSetting time indicationAutocorrectionSignal-to-noise ratio (imaging)
The invention discloses a mechanism for positioning pointers of a watch and methods for positioning, resetting and calibrating the pointers and belongs to the technical field of the watch. The invention is technically characterized in that: an ordinary reflecting photoelectric sensor is arranged on the front surface of a movement of the watch and used for capturing pointer signals which are generated during the sweeping of the pointers; a microprocessor processes the pointer signals; a filtering module of the microprocessor performs correlation filtering on the pointer signals to improve the signal to noise ratio of the pointer signals; a pointer identification module performs statistic analysis and characteristic analysis on the pointer signals to determine the position of each pointer; and a motor control module controls the pointers to move according to the position of each pointer, so that the pointers can be automatically calibrated and reset. In the scheme, an ordinary process installation requirement is only required without designing of a special detection component, so that a technology for automatically calibrating the pointers of the watch can be popularized and applied on a large scale, the cost of products can be greatly reduced, and the invention has an important technical significance and a business value.
Owner:东莞丝丽雅电子科技有限公司
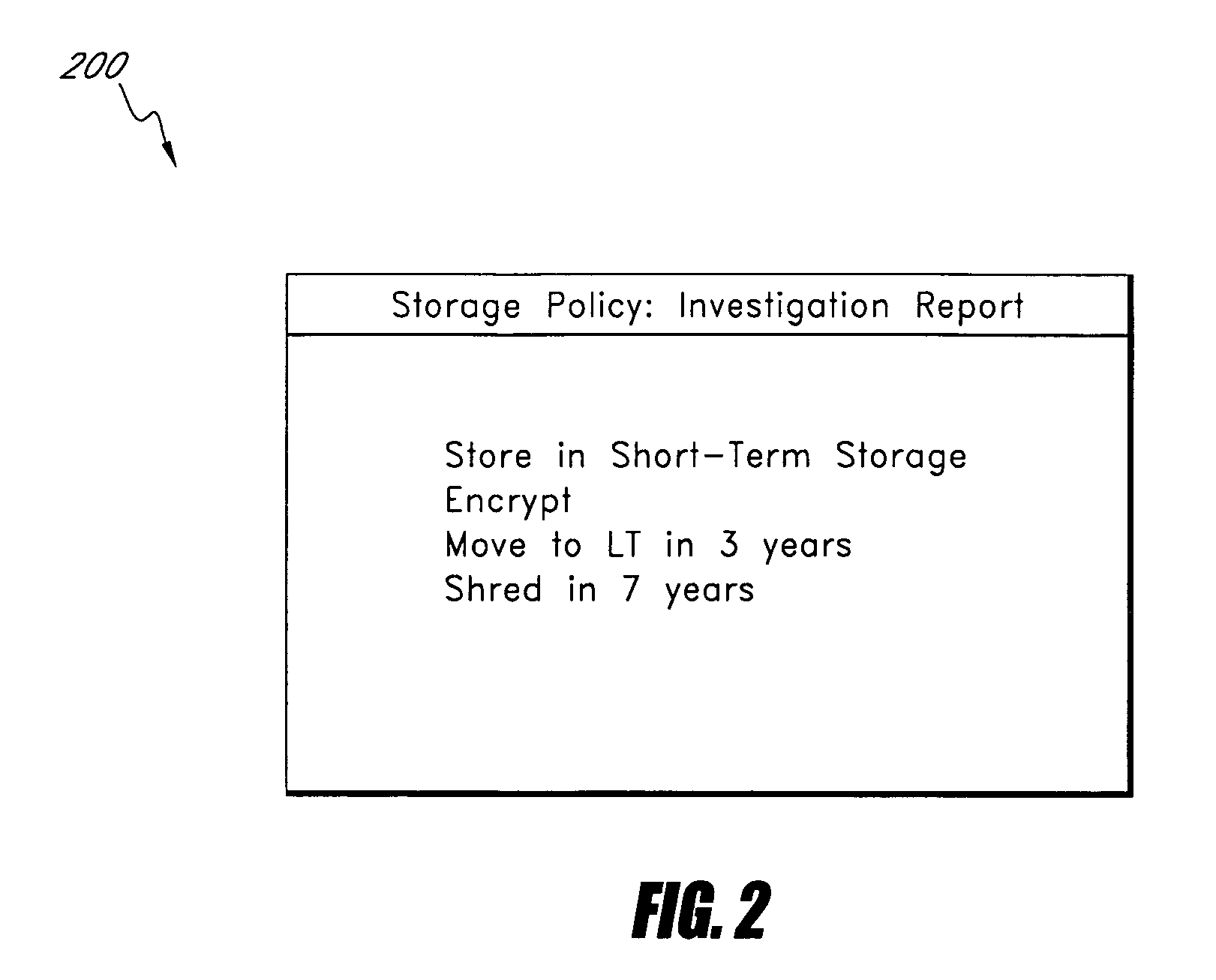
Method for Developing Enterprise Information Life Cycle Management Polices and Solutions
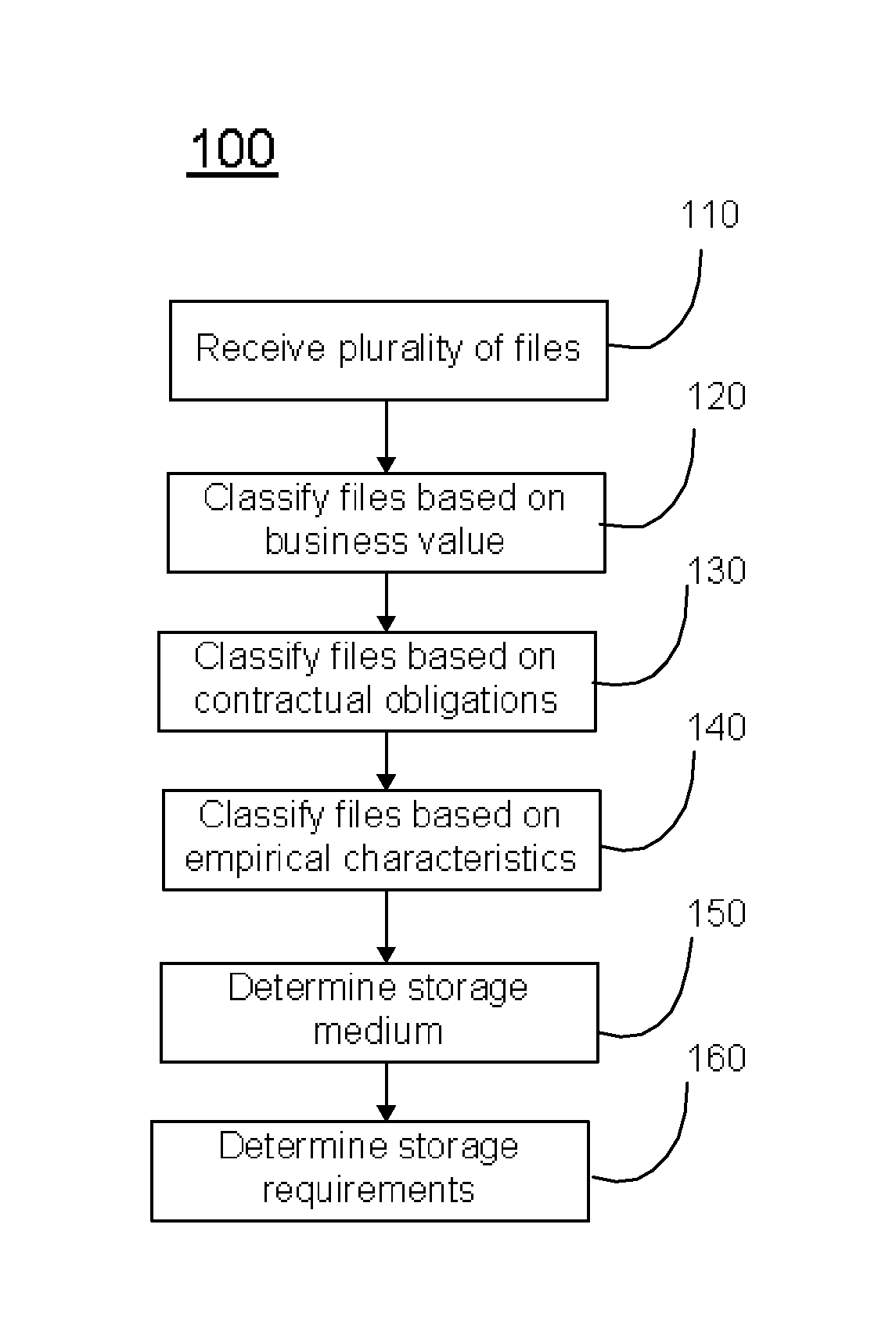
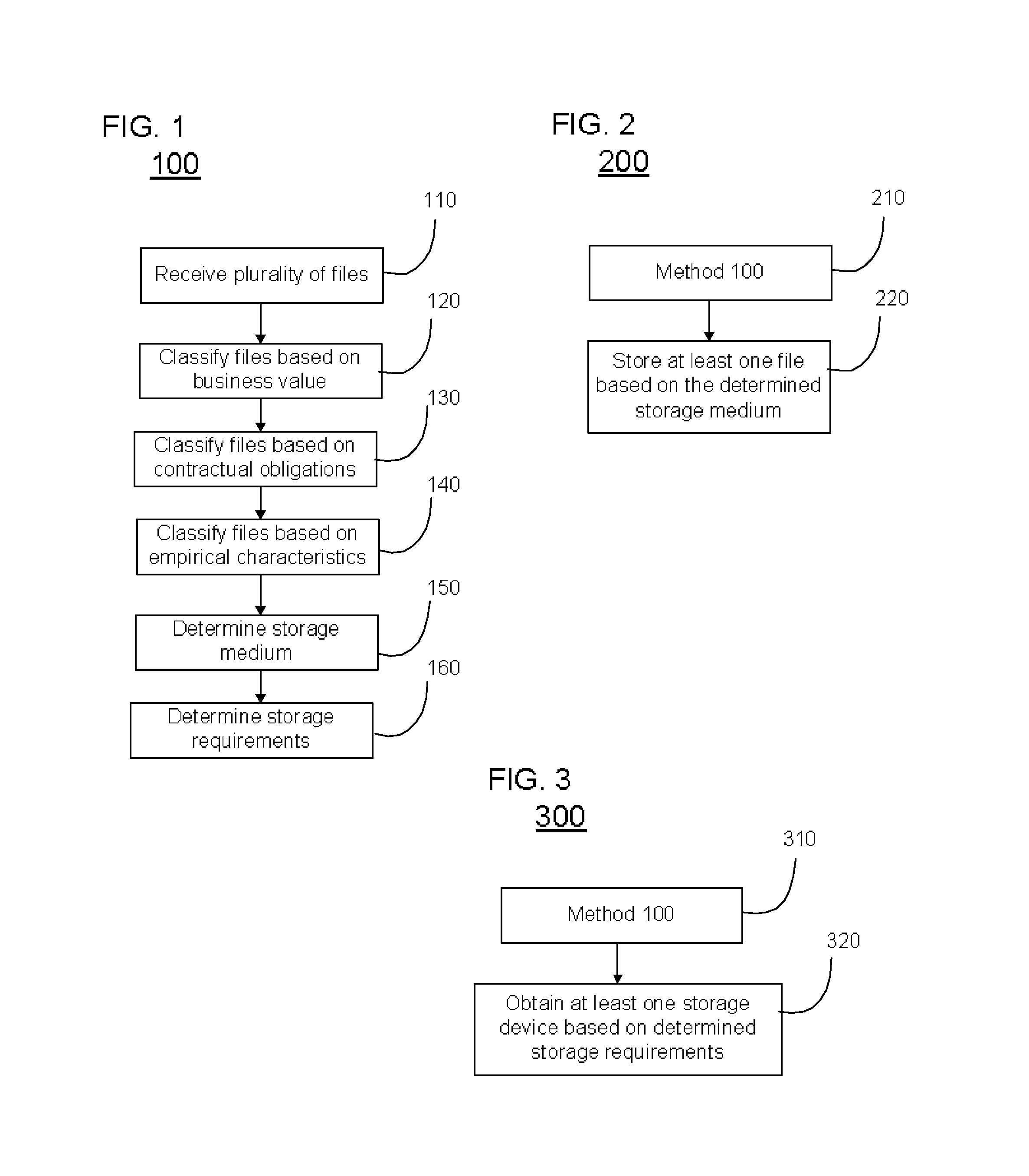
A method for determining storage requirements includes receiving a plurality of files to be stored, classifying the plurality of files based on business value, classifying the plurality of files based on contractual obligations, classifying the plurality of files based on empirical characteristics, and determining a storage medium based on the classified business value, classified contractual obligation, and classified empirical characteristics. The method further includes determining storage requirements based on the determined storage mediums.
Owner:IBM CORP
Methods and systems for evaluating technology assets
A technology maturity evaluation (TME) computer device is provided for evaluating a technology asset of an entity is provided. The TME computer device includes a memory device for storing data including a plurality of business value questions and a plurality of technical maturity questions, and a processor in communication with the memory device. The TME computer device is programmed to receive an asset identifier identifying an asset selected for evaluation and to electronically display business value questions and technical maturity questions for the selected asset, wherein each question is designated for a response by a subject matter expert. The TME computer device is further programmed to receive response data from each of the subject matter experts and calculate a business value score and a technical maturity score for the selected asset based on the response data.
Owner:MASTERCARD INT INC
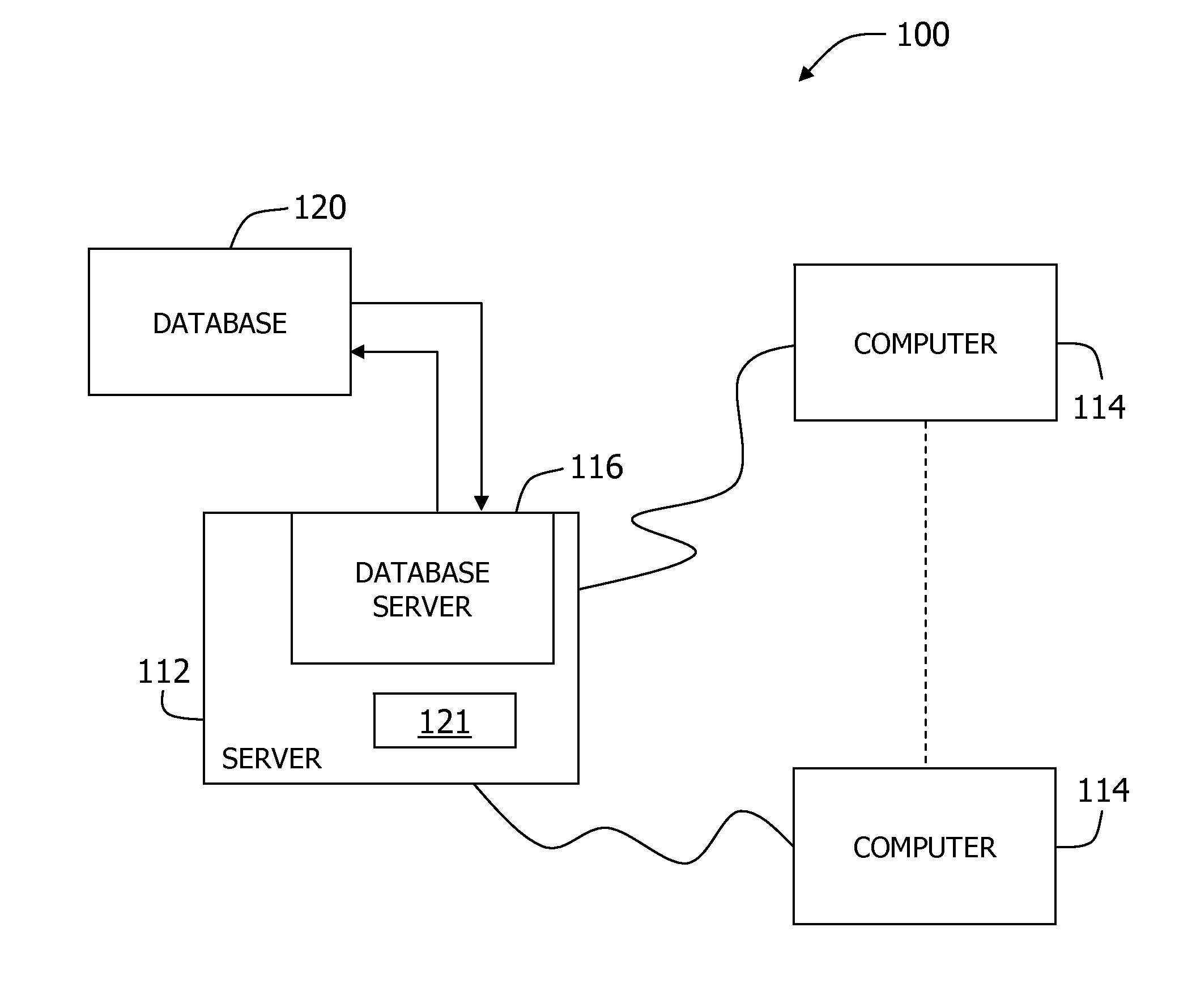
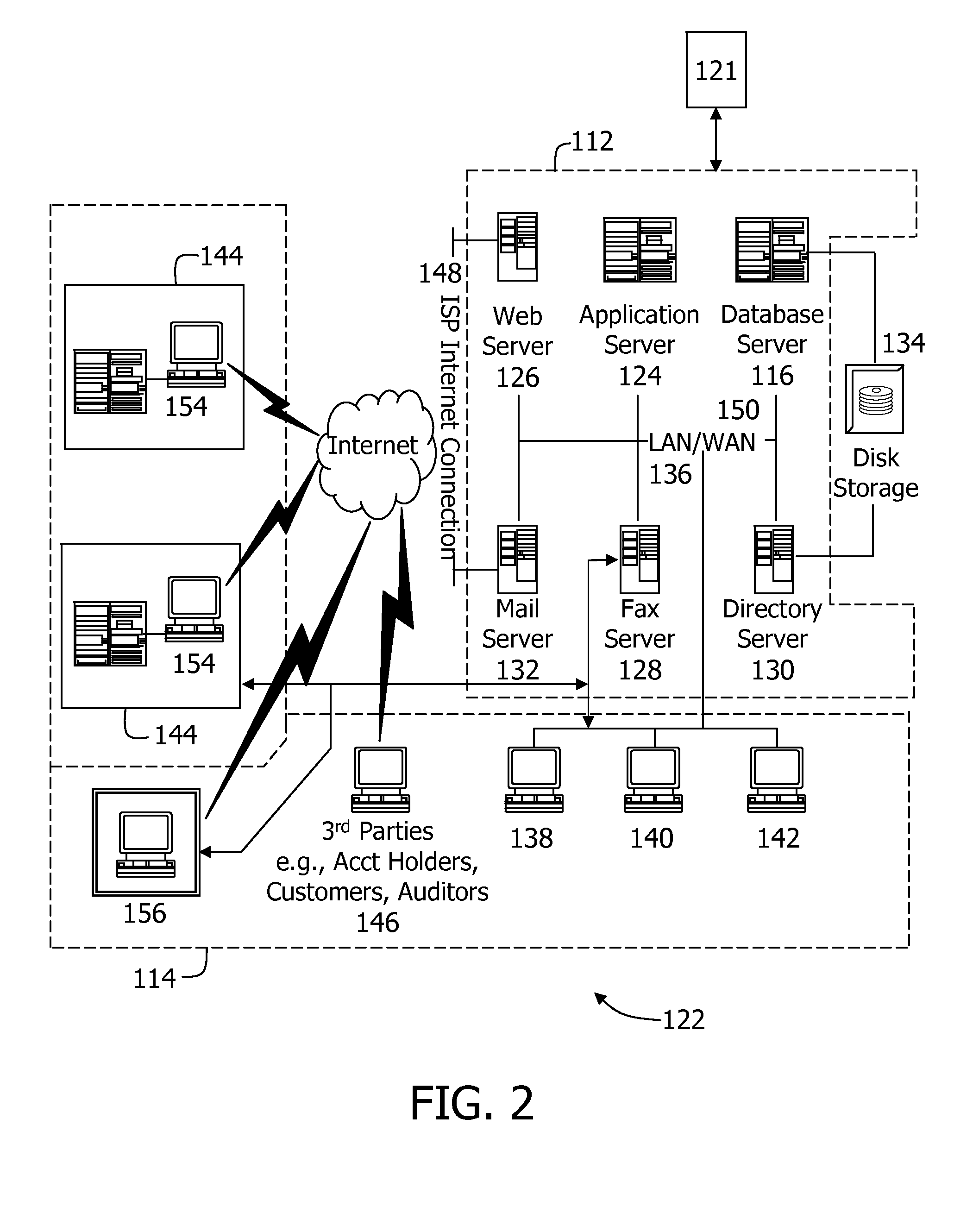
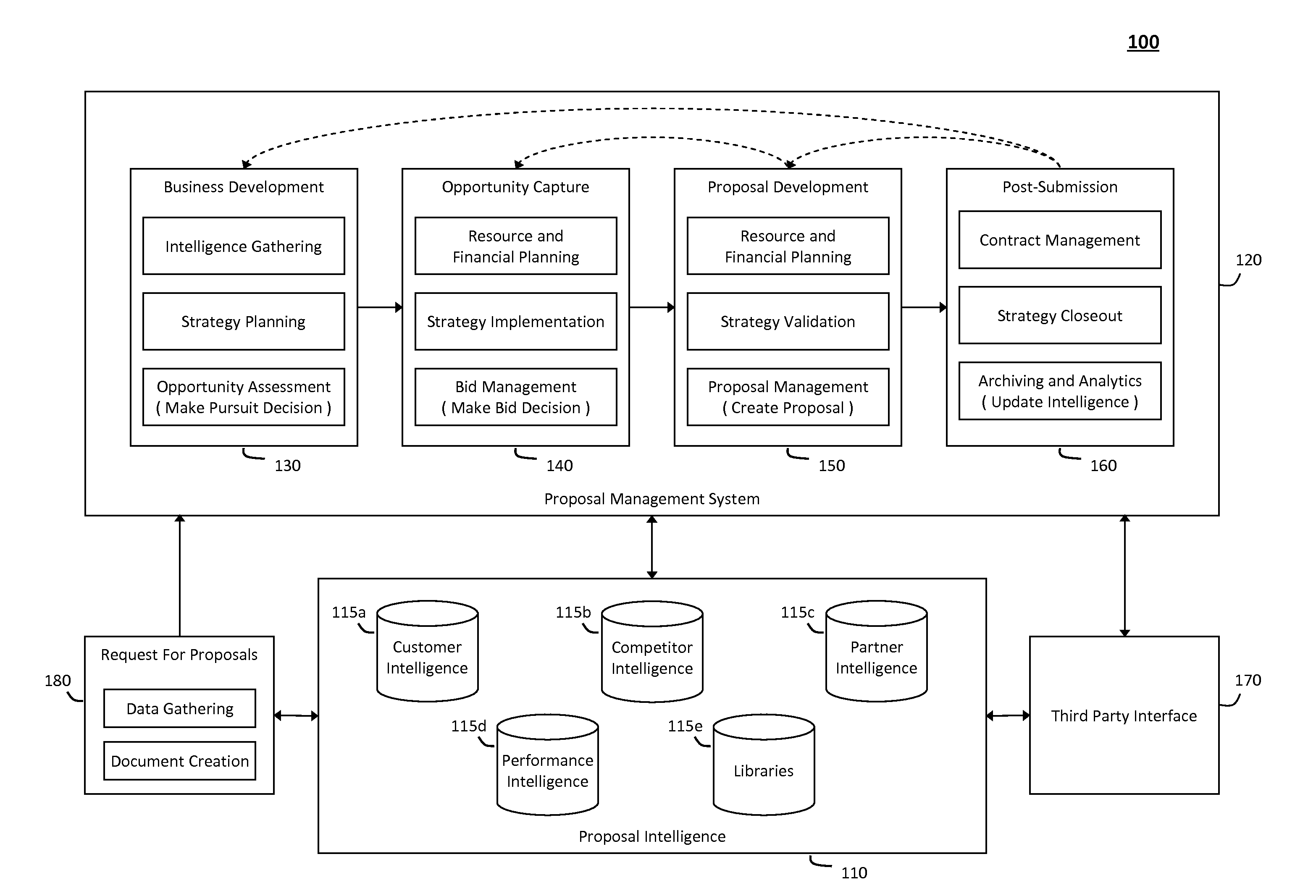
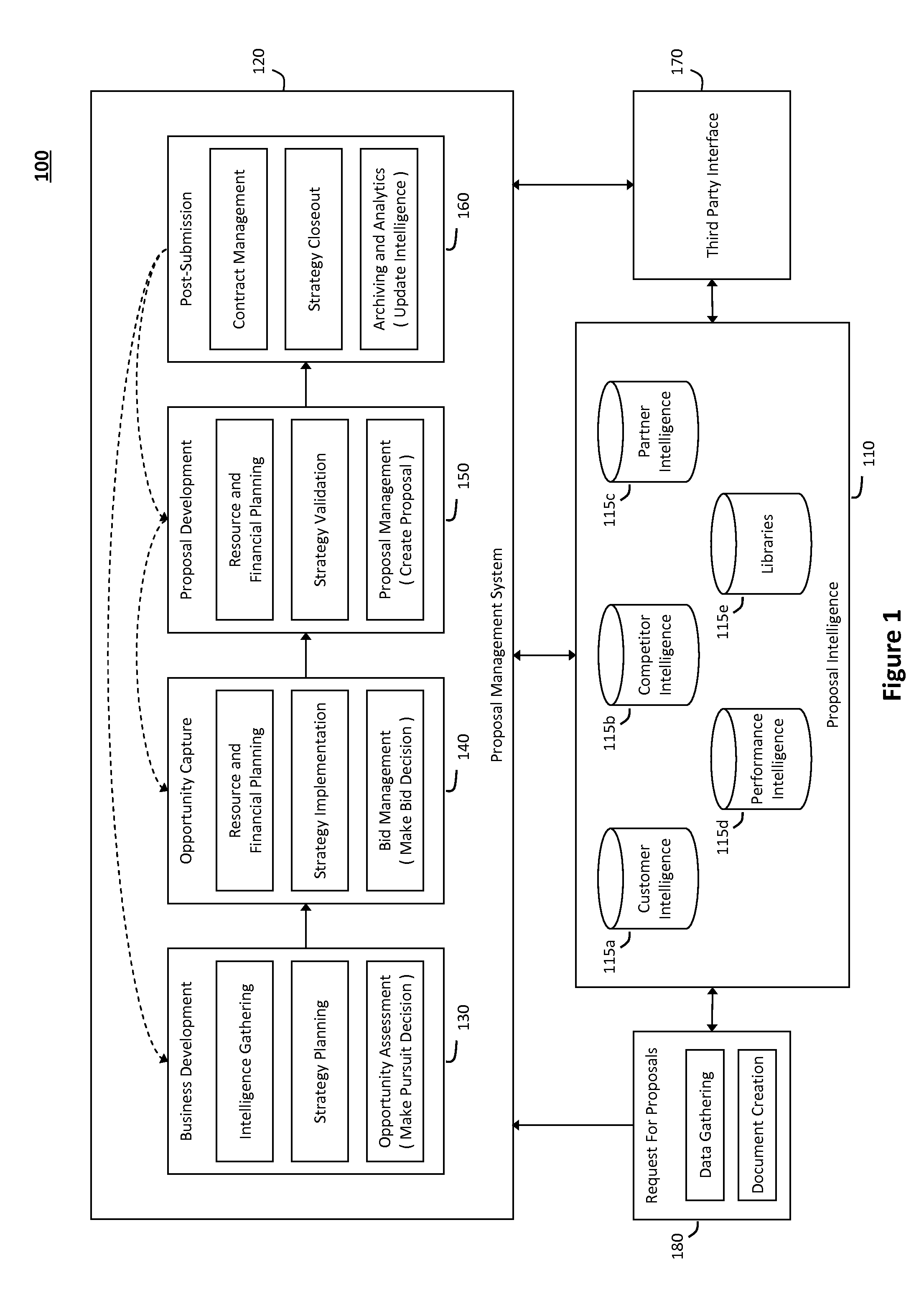
System and method for managing a proposal lifecycle
The system and method described herein may integrate an enterprise proposal management system with various enterprise systems, applications, data sources, and other resources to provide a comprehensive solution to manage and coordinate a proposal lifecycle and data associated therewith. In particular, the system and method described herein may integrate and use business information stored in various data sources to execute repeatable and effective strategies to manage business development and proposal efforts, reduce the time that proposal authors spend to search, retrieve, and use content from past proposals to create proposals likely to win new business, coordinate collaboration across organizational teams involved in managing proposal, reliably track capture and proposal pipelines, and preserve documents, data, and other information relevant to the proposal lifecycle, thereby providing real business value in day-to-day proposal management operations.
Owner:I3SOLUTIONS
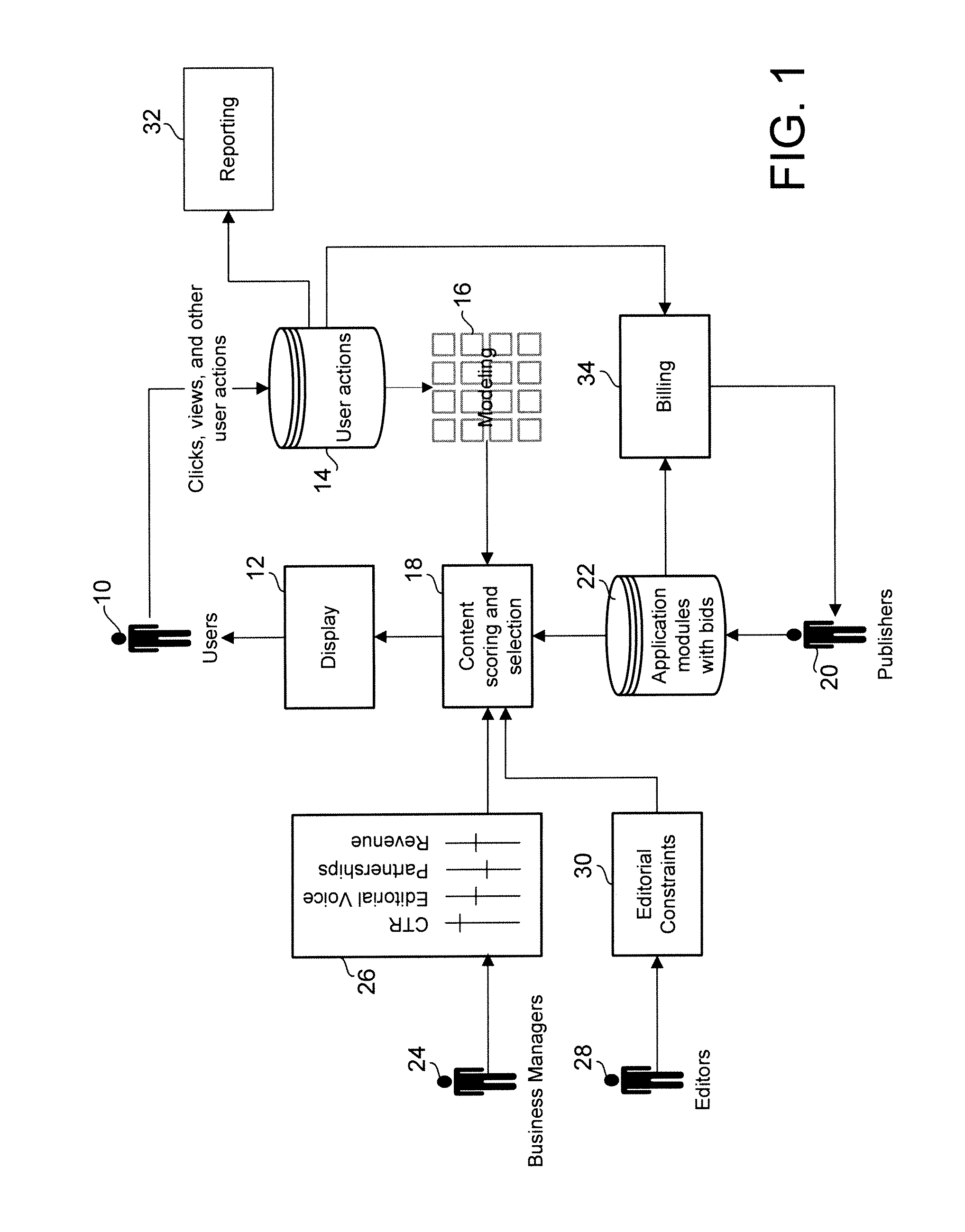
Bidded marketplace for applications
ActiveUS20110202821A1MarketingSpecial data processing applicationsGraphicsHuman–computer interaction
Methods and systems for presenting application modules on a graphical display page are provided. In accordance with one embodiment, content to be displayed on a graphical display page is determined. Then, content features which describe the content that is to be displayed on the graphical display page, and user features which describe characteristics of users are determined. For each application in the plurality of application modules, the probability that specific users will select the application module when displayed on the graphical display page with the determined content is determined based on the content features and the user features. For each application module in the plurality of application modules, an overall score is determined based on the determined probability that the user will select the application module and a commercial value to be paid by a publisher of the application module when it is selected. The recommended application modules are determined to be those application modules in the plurality of application modules which have the highest overall score and which satisfy a set of constraints. Representations of the recommended application modules are displayed on the graphical display page.
Owner:GOOGLE LLC
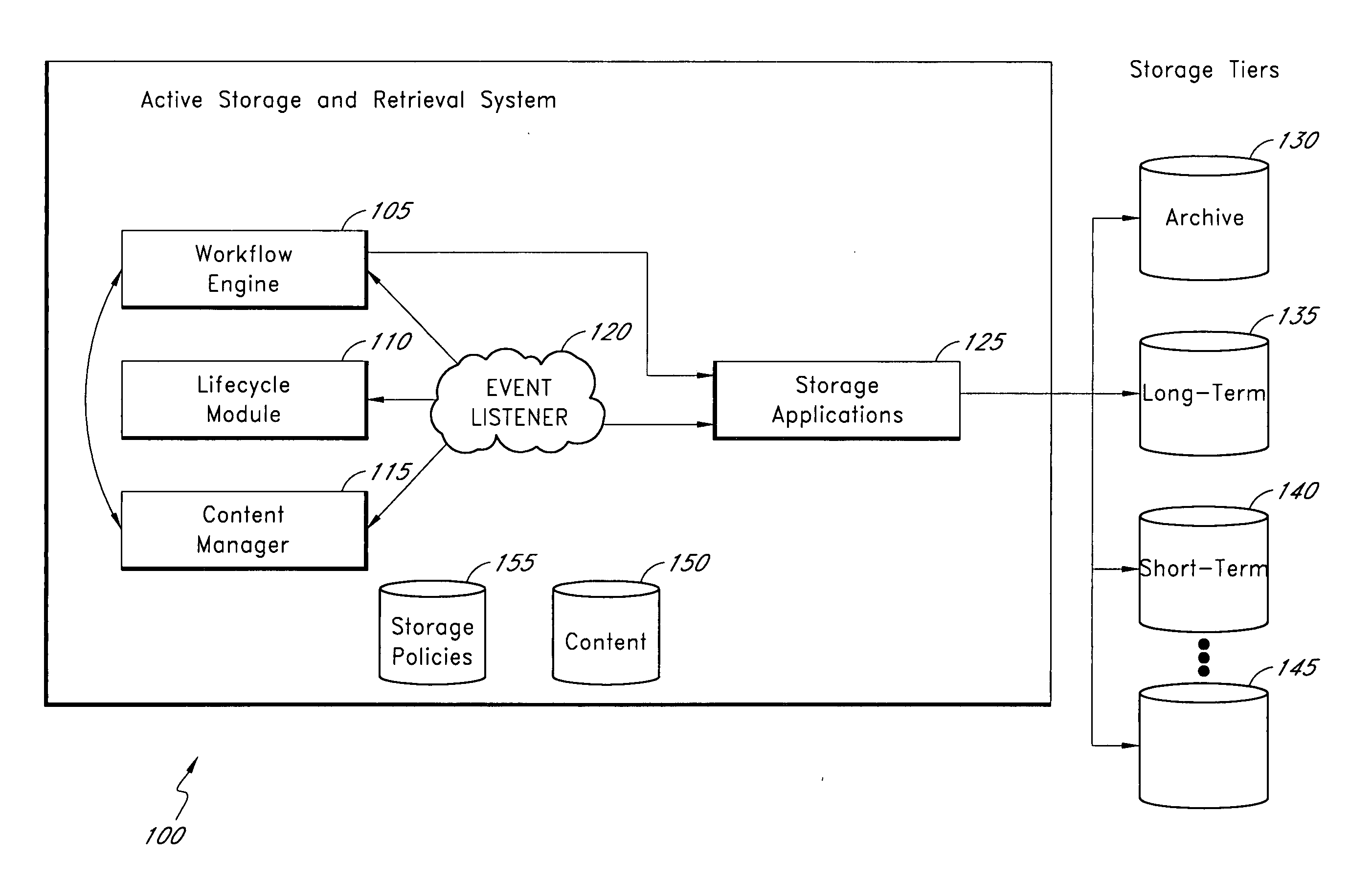
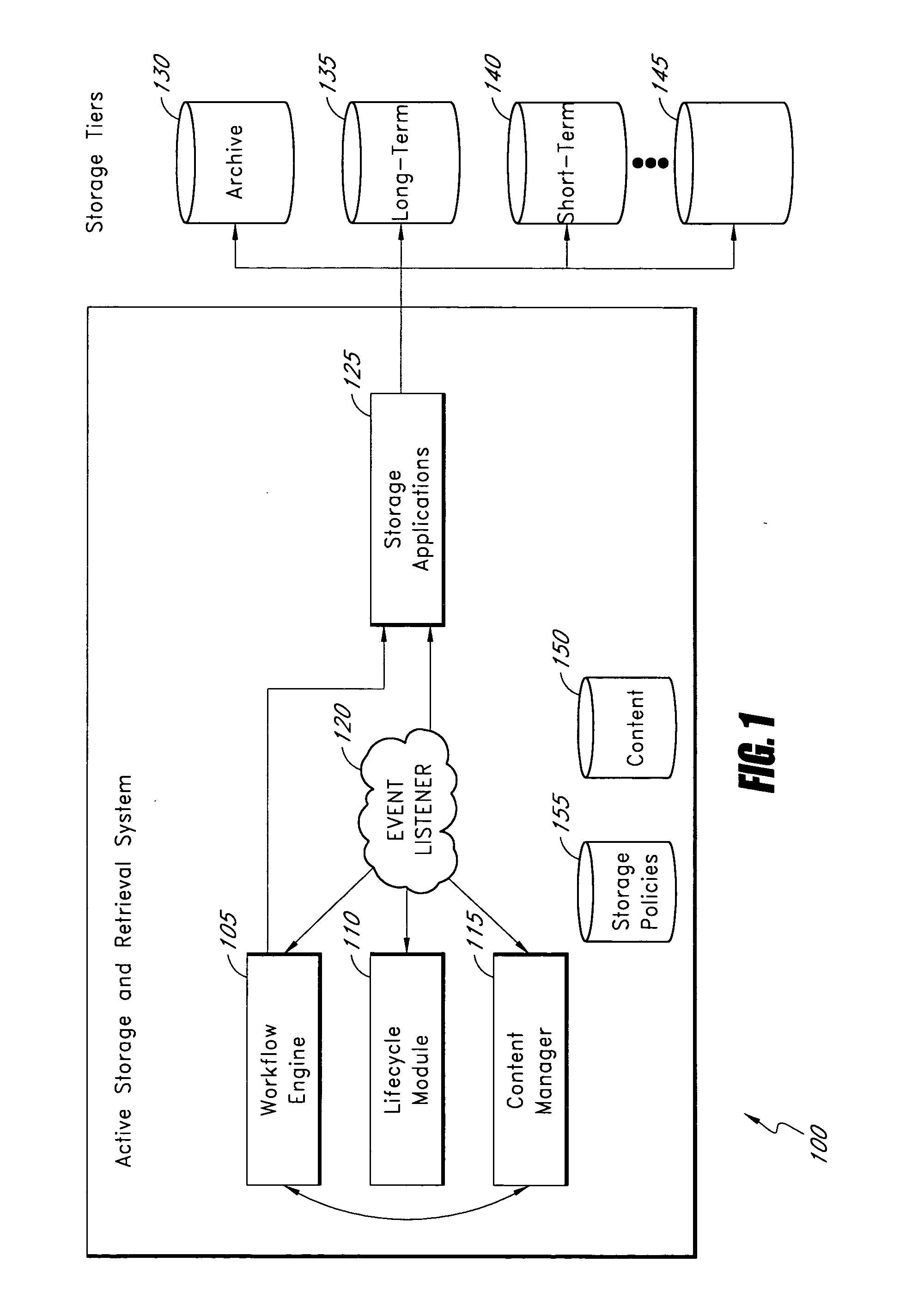
Active storage and retrieval systems and methods
InactiveUS20070271306A1Accurately reflectDigital data information retrievalDigital data processing detailsStorage managementActive storage
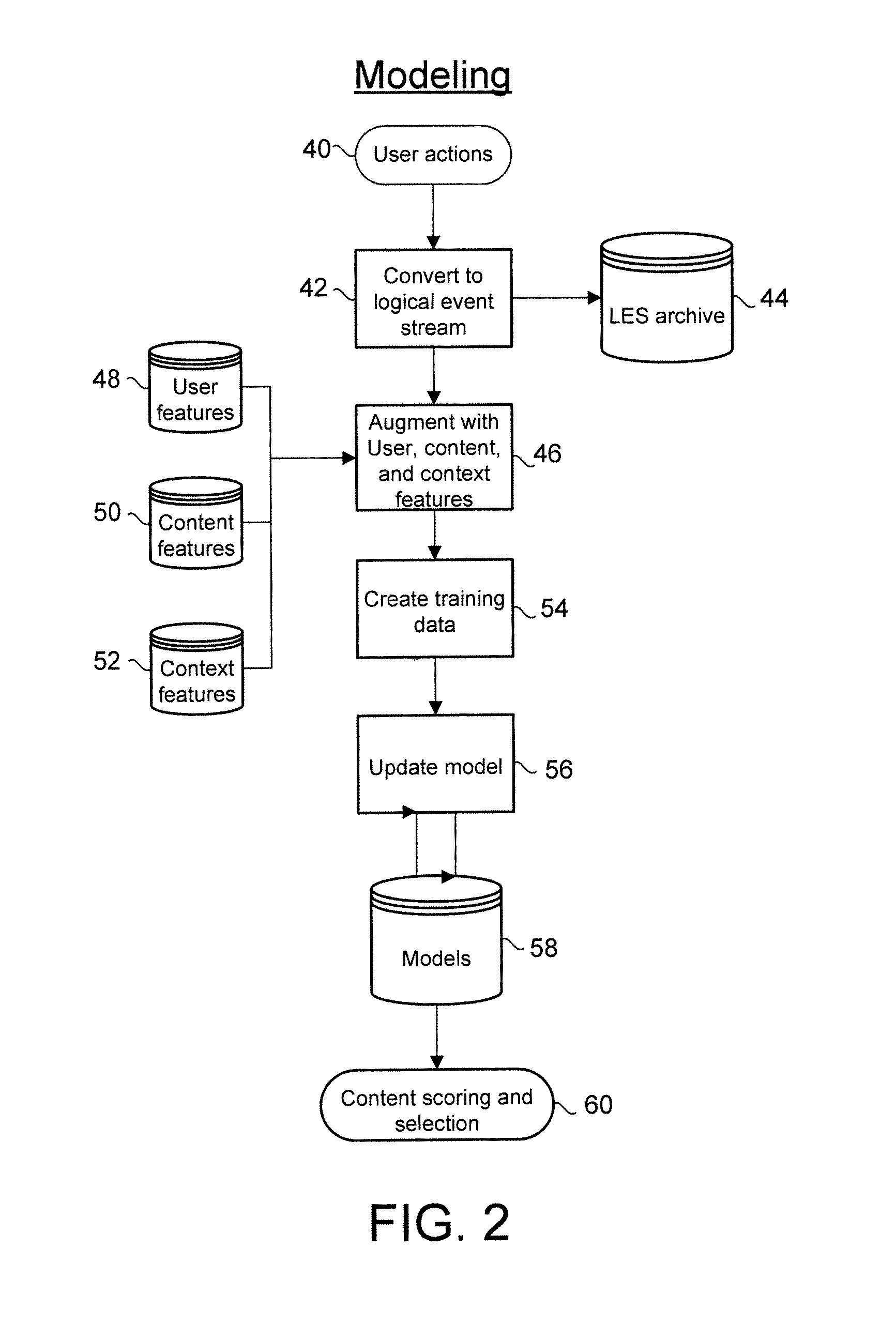
A data storage management system comprises a workflow engine, a lifecycle module, and a storage application. The workflow engine is configured to manage a plurality of defined business processes and to execute at least one process step associated with at least one data item. The lifecycle module is configured to detect a change in lifecycle of the at least one data item. The storage application is configured to perform at least one storage action on the data item as a result of the data item reaching a step in a business process, the data item having a change in lifecycle, the data item having a change in metadata, or an event occurring to the data item. Application layer information about data derived from operation of the system allows the system to make more accurate determinations of business value of data and to determine appropriate storage actions to perform on data.
Owner:LINKEDIN
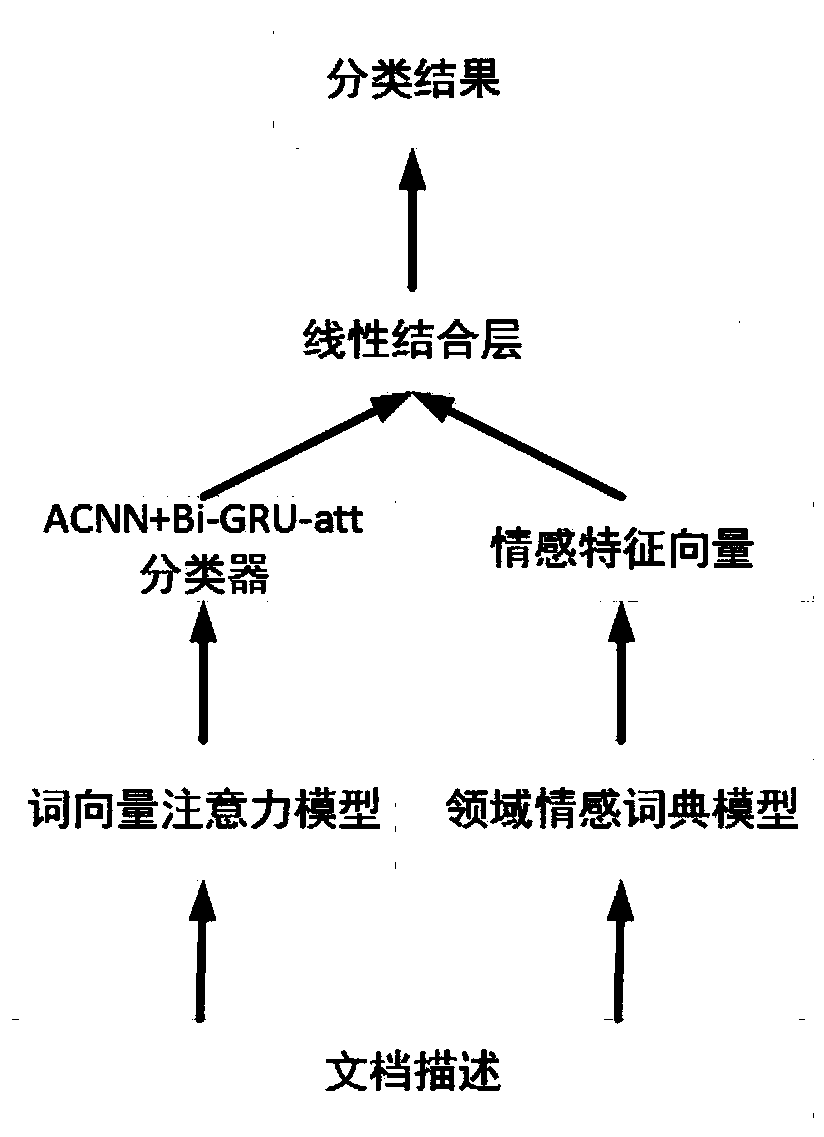
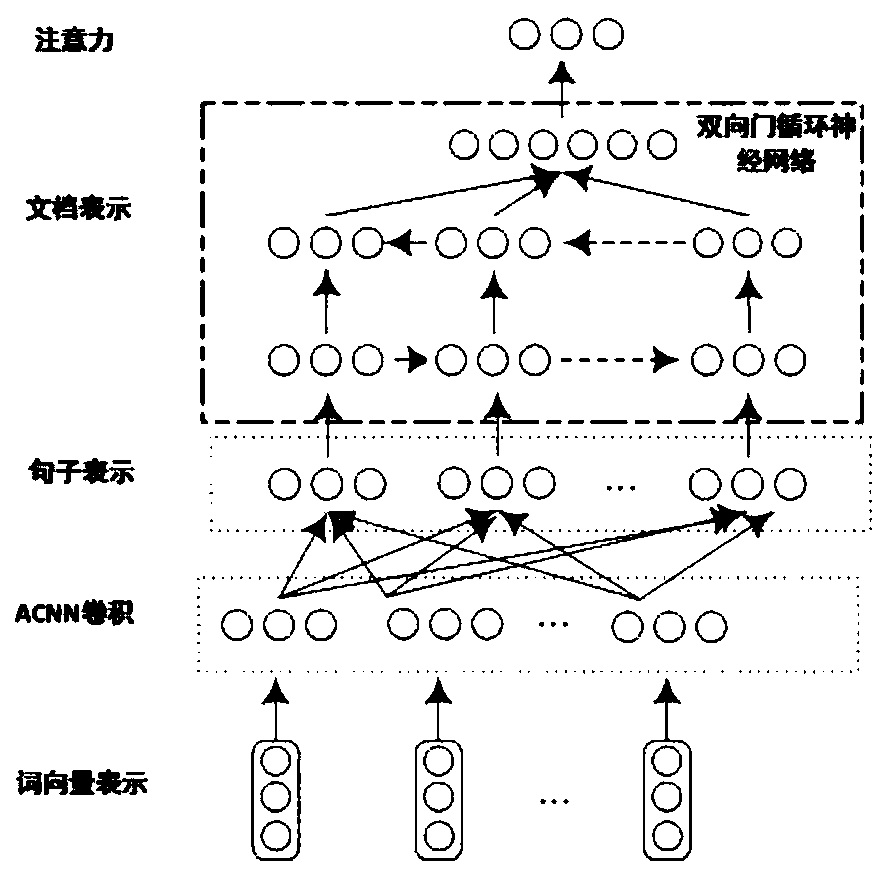
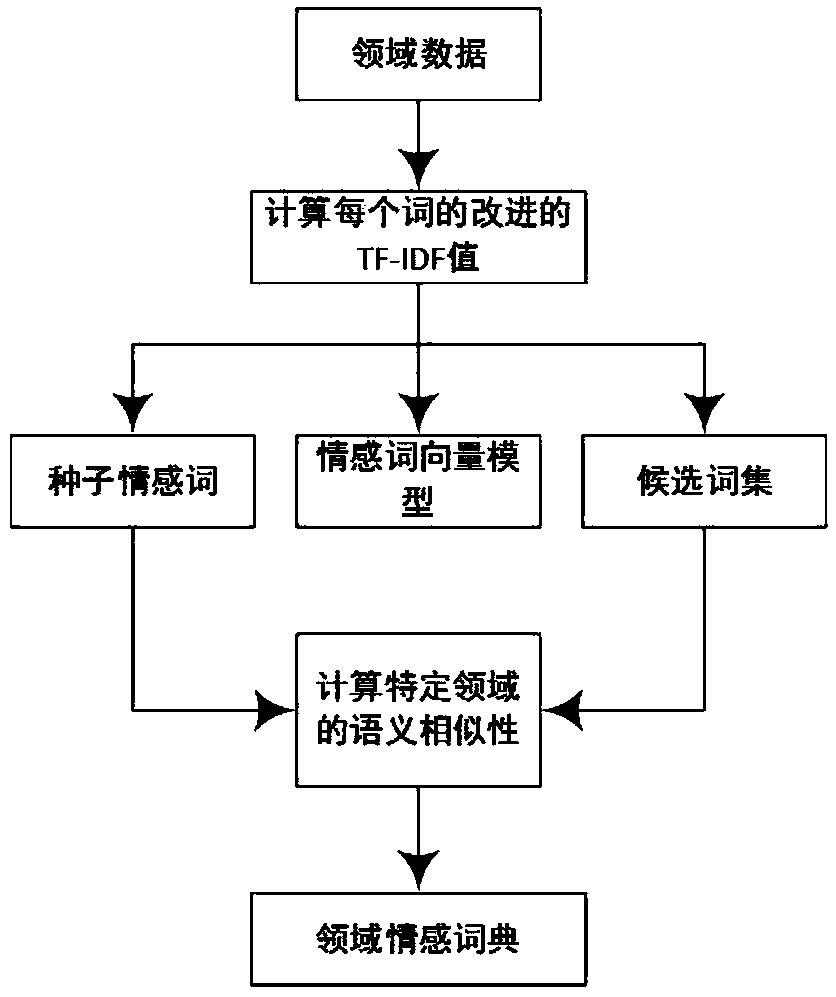
Document-level sentiment analysis method based on specific domain sentiment words
ActiveCN108804417AMake up for the lack of domain specific wordsVersatilitySemantic analysisCharacter and pattern recognitionData setAlgorithm
The invention provides a document-level sentiment analysis method based on specific domain sentiment words. The method is implemented by the following steps of collecting a document data set, traininga set of prototype words by using a Skip-gram word vector model to obtain a word vector corresponding to each prototype word, recombining the word vectors by utilizing an attention mechanism, and capturing a relation between non-continuous words in the word vectors; synthesizing the words and sentences by using an asymmetric convolutional neural network and a bidirectional gate recurrent neural network based on the attention mechanism respectively, thereby forming document vector characteristics; generating sentiment eigenvectors by utilizing a domain sentiment dictionary of the Skip-gram word vector model; and finally, combining the document vector characteristics and the sentiment eigenvectors by utilizing a linear combination layer to form document characteristics beneficial to document classification. The sentiment analysis is widely applied to the product analysis, the commodity recommendation, the stock price trend prediction and the like; and the method provided by the invention can accurately and efficiently carry out sentiment analysis on documents, and has great commercial values.
Owner:SHANDONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com