Patents
Literature
181 results about "Active storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
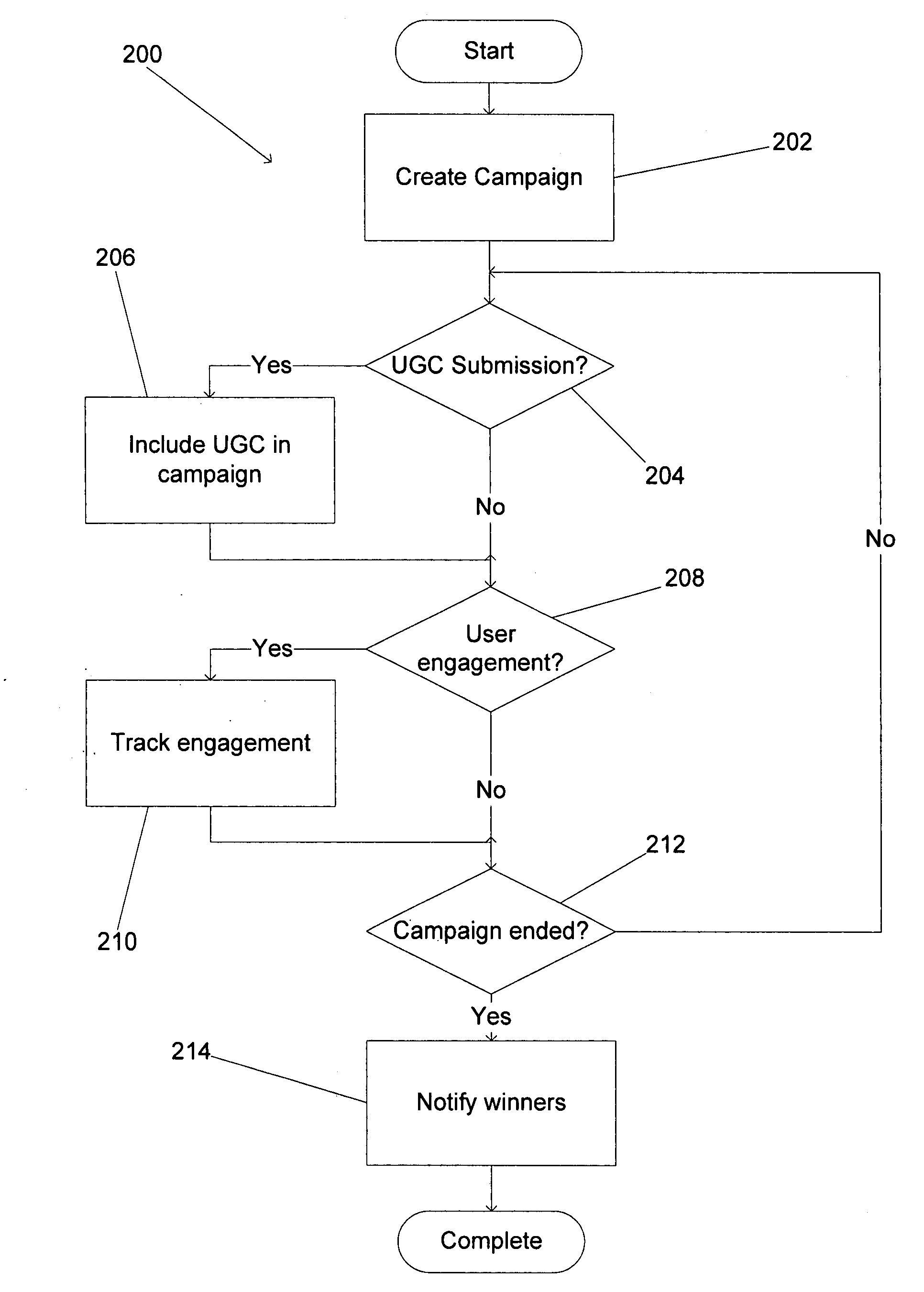
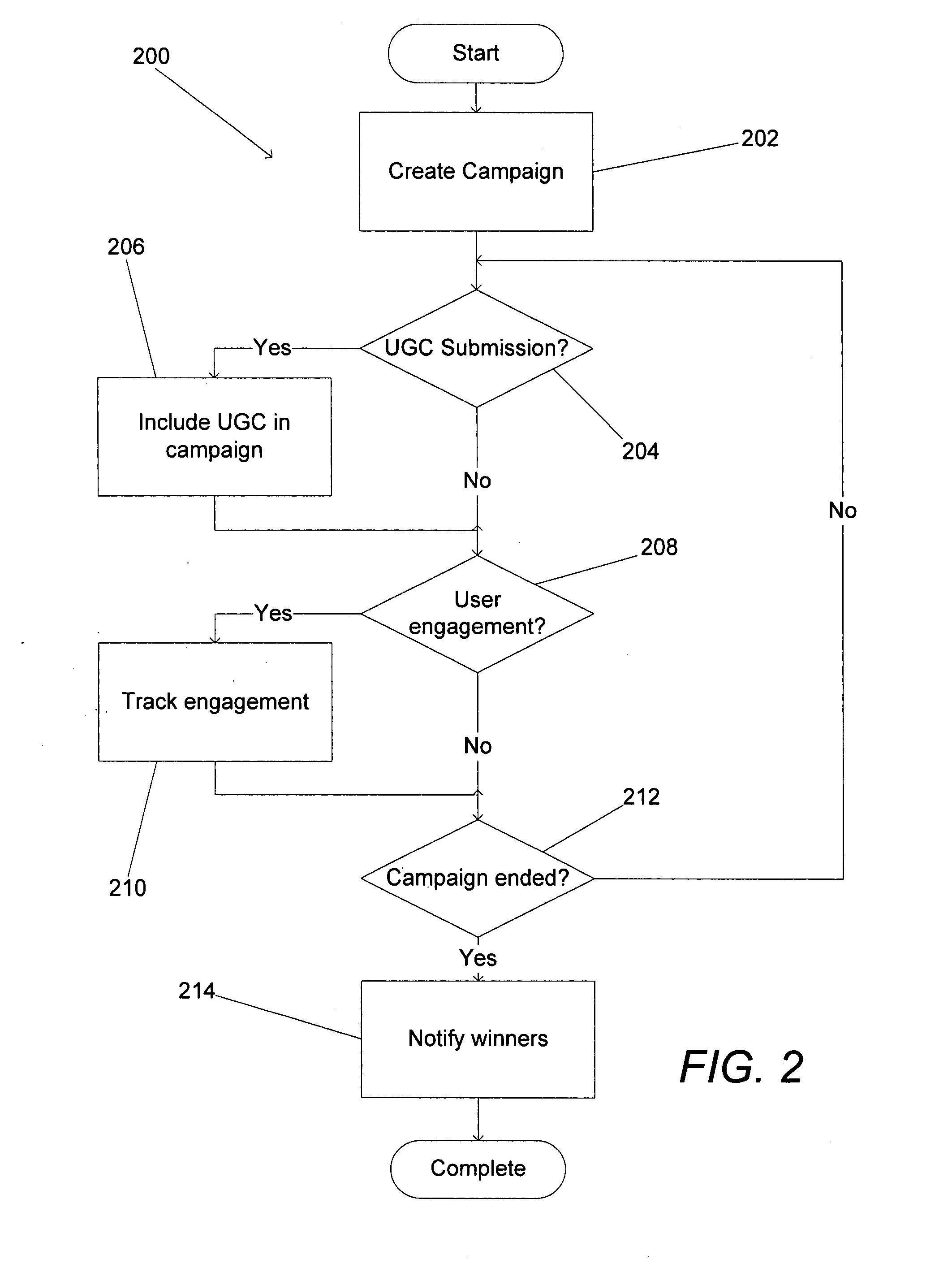
Online marketing platform
ActiveUS20080313011A1Market predictionsData acquisition and loggingUser deviceUser-generated content
Online marketing platforms are disclosed that harness user generated content to encourage the viral sharing and tracking of online marketing campaigns. One embodiment includes a campaign hosting system including a database connected to a network, a campaign creation device connected to the network and a plurality of user devices connected to the network. In addition, the campaign creation device is configured to provide campaign information to the campaign hosting system via the network, the campaign hosting system is configured to automatically create an online campaign that is customized according to the campaign information and to store the campaign as one of a plurality of online campaigns in the database, at least one of the user devices is configured to provide profile information to the campaign hosting system via the network, the campaign hosting system is configured to automatically create a user profile using the profile information and to store the user profile as one of a plurality of user profiles in the database, each user device is configured to engage with the online campaign by communicating with the campaign hosting system via the network and each user device is configured to access the user profile by communicating with the campaign hosting system via the network.
Owner:REPUTATION COM +1
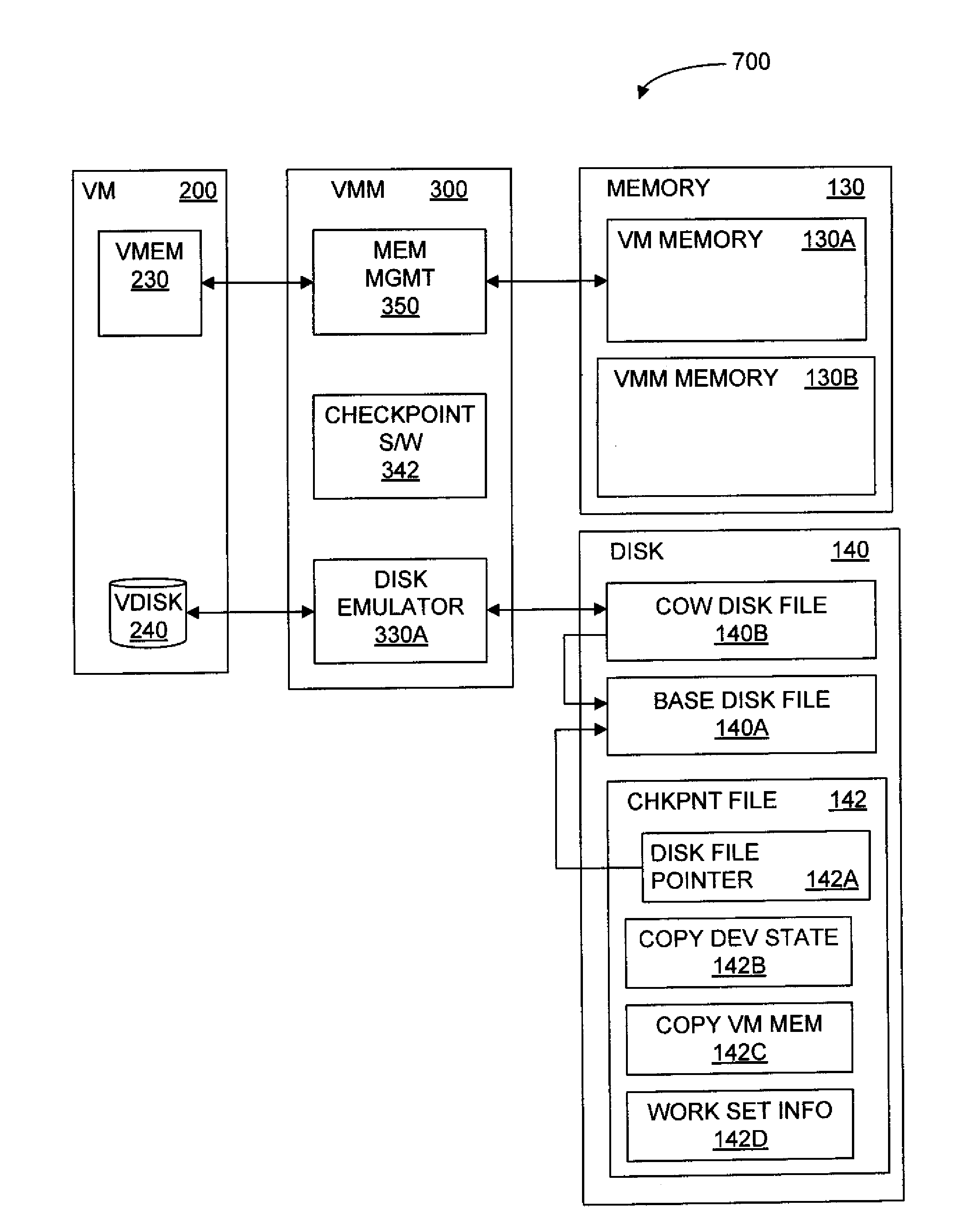
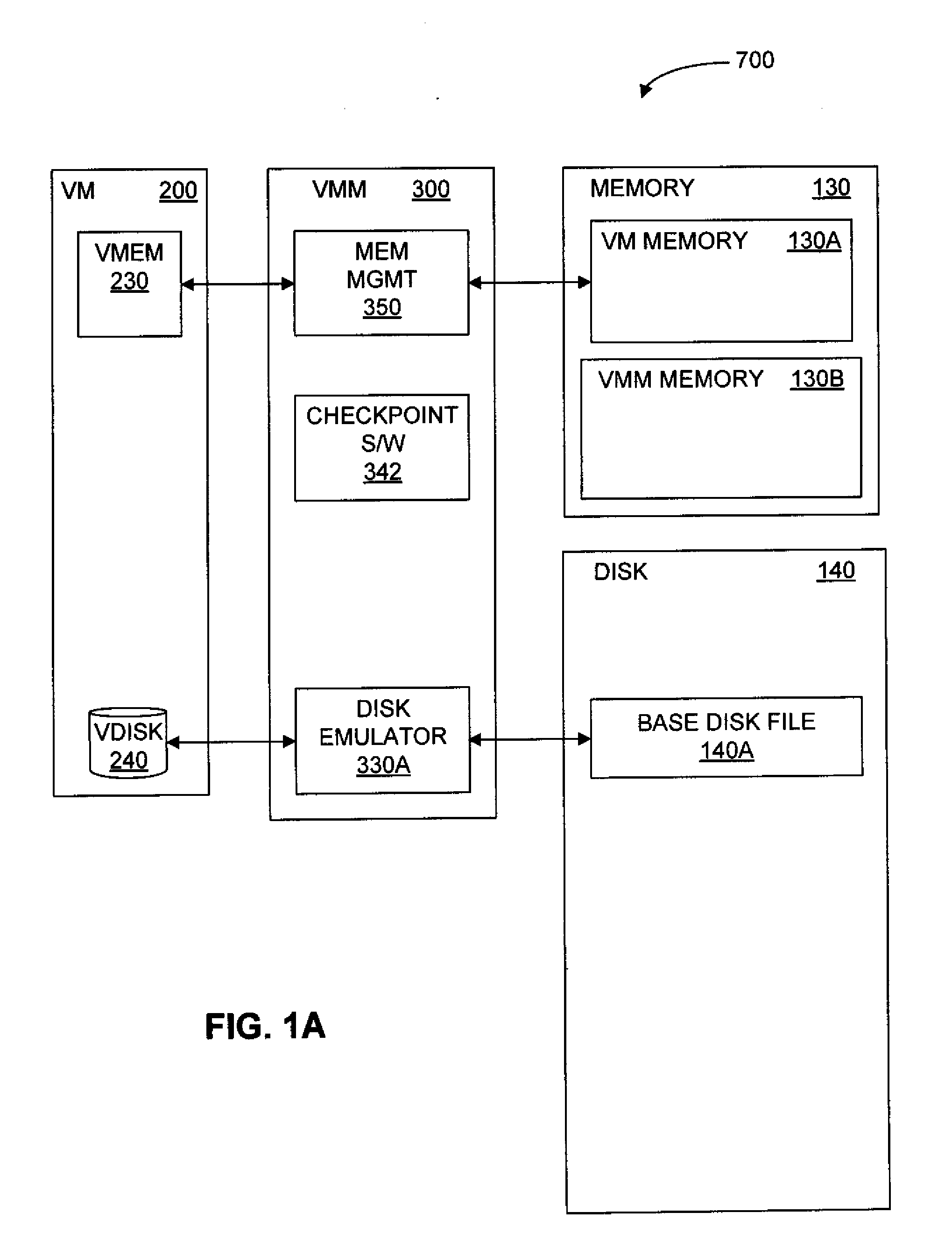
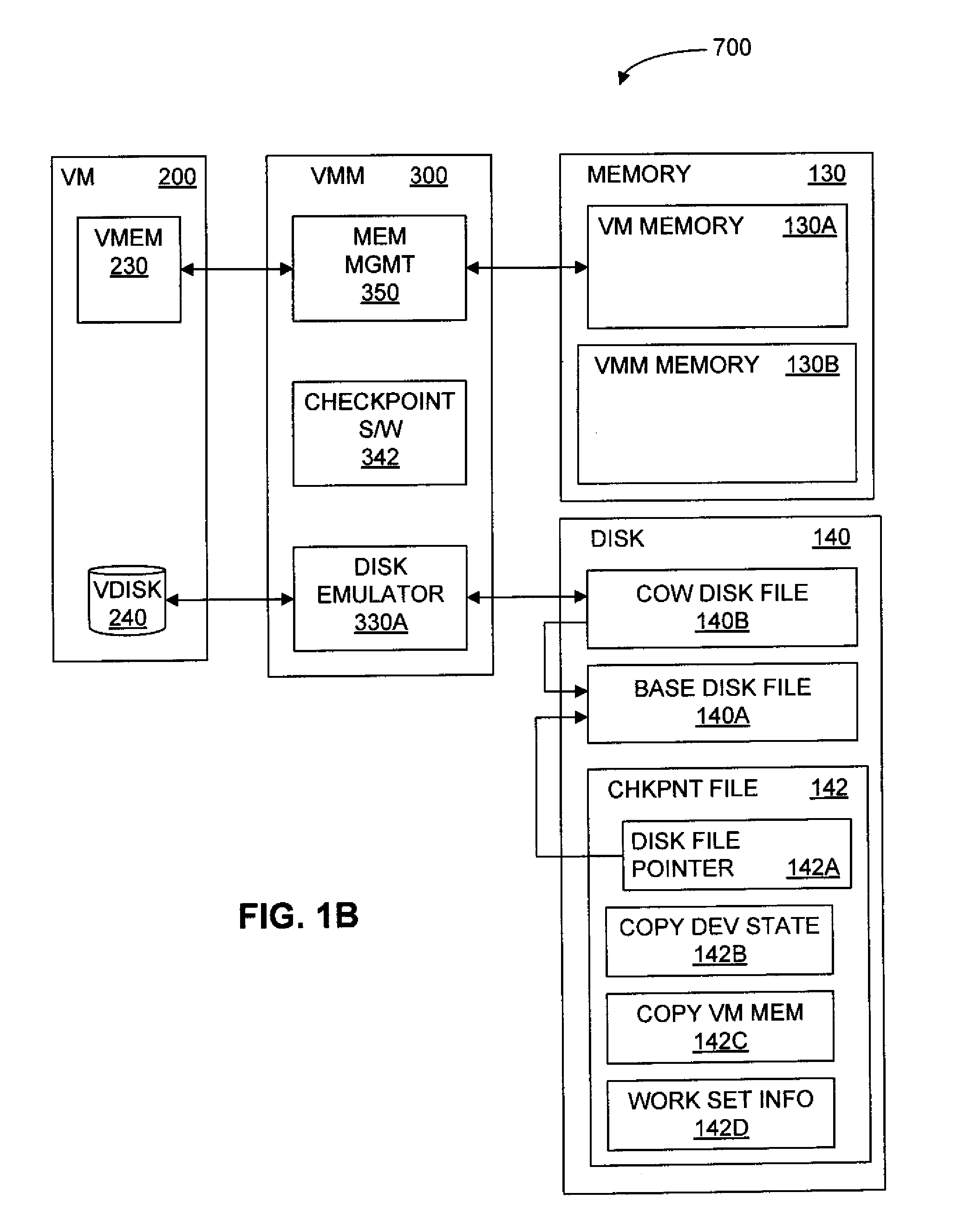
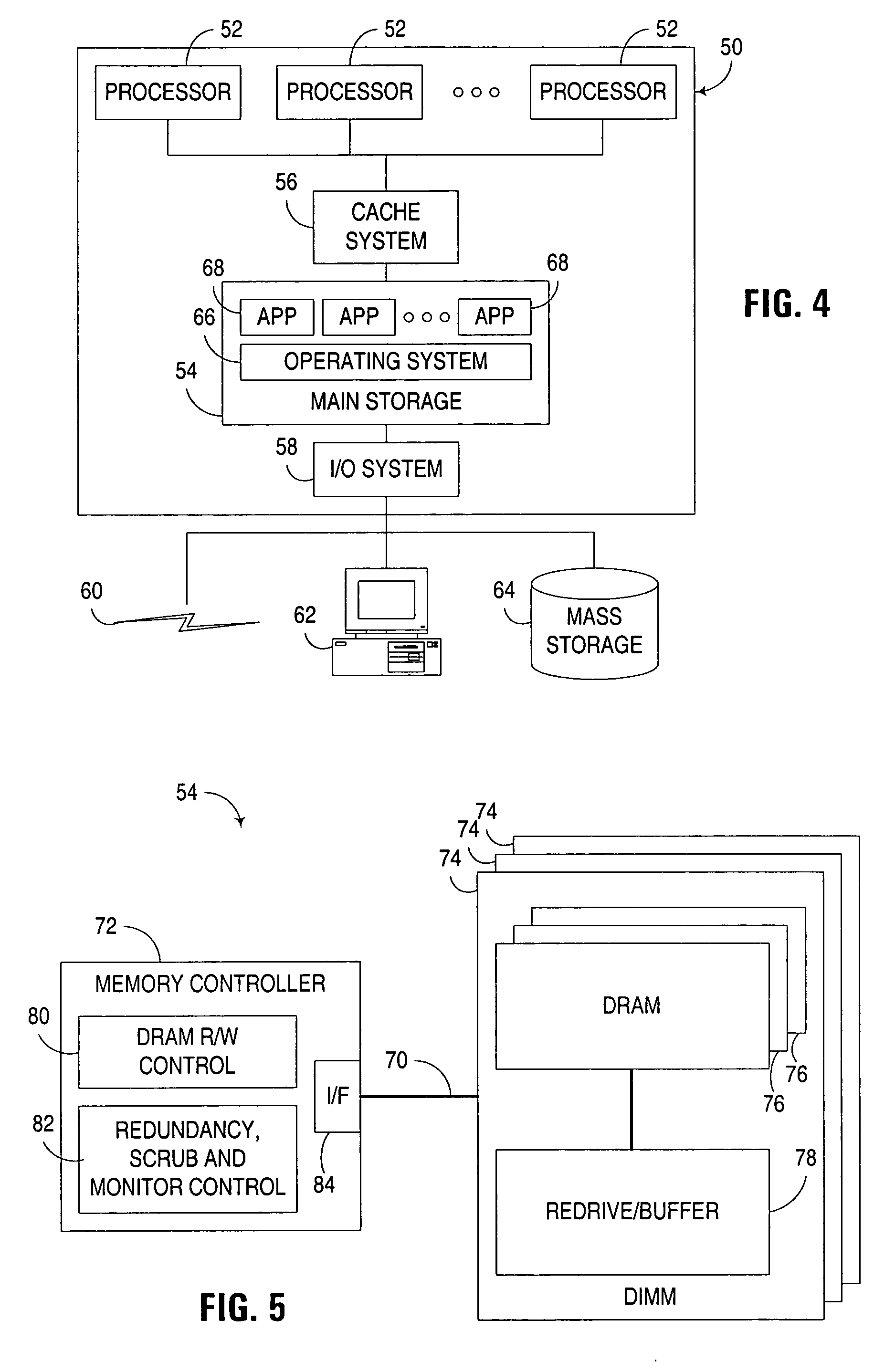
Saving and Restoring State Information for Virtualized Computer Systems
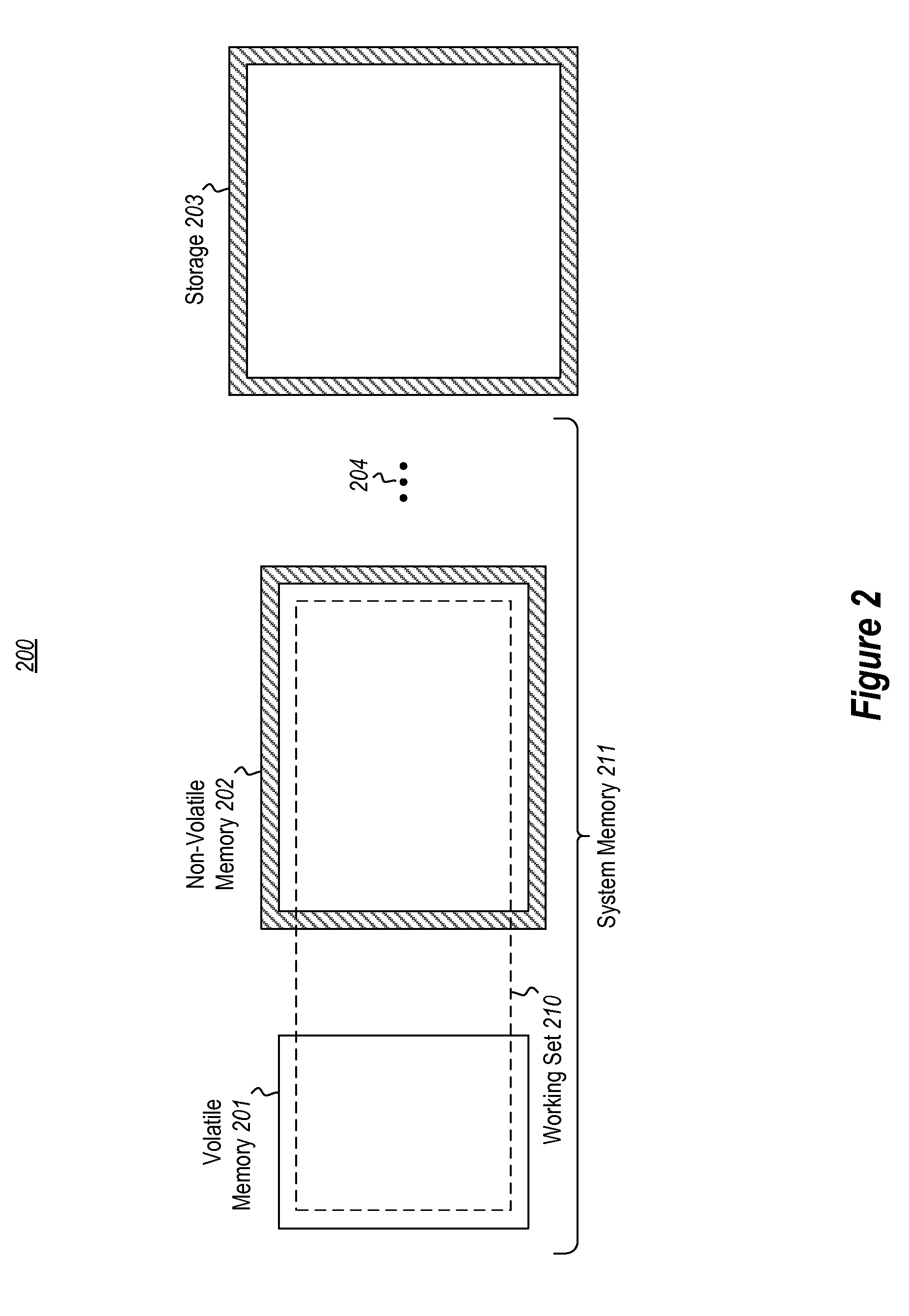
InactiveUS20100070678A1Error detection/correctionMemory adressing/allocation/relocationComputerized systemActive memory
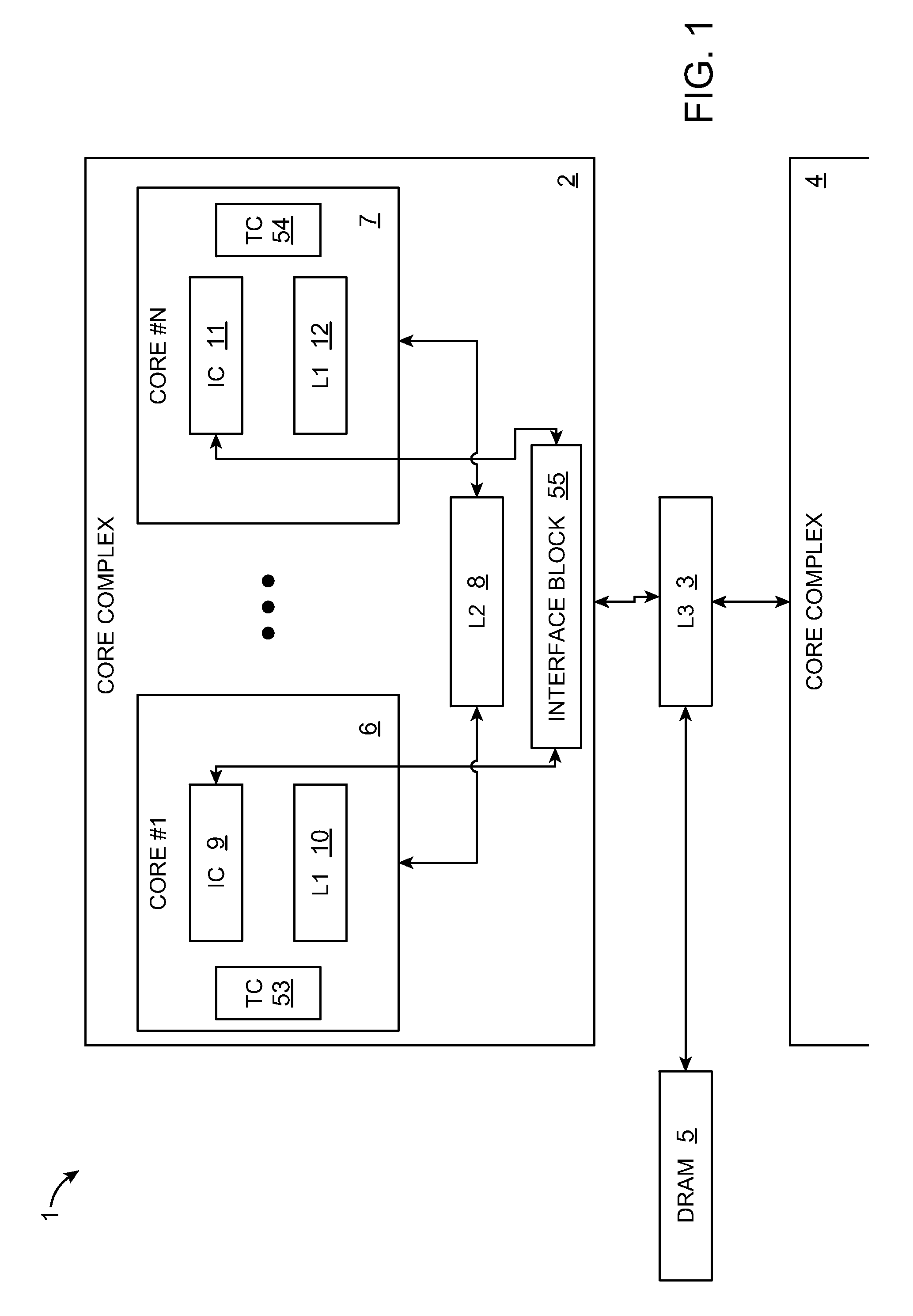
Prior to or while the state of a virtual machine (“VM”) is being saved, such as in connection with the suspension or checkpointing of a VM, a set of one or more “active” memory pages is identified, this set of active memory pages comprising memory pages that are in use within the VM before operation of the VM is suspended. This set of active memory pages may constitute a “working set” of memory pages. To restore the state of the VM and resume operation, in some embodiments, (a) access to persistent storage is restored to the VM, device state for the VM is restored, and one or more of the set of active memory pages are loaded into physical memory; (b) operation of the VM is resumed; and (c) additional memory pages from the saved state of the VM are loaded into memory after operation of the VM has resumed.
Owner:VMWARE INC
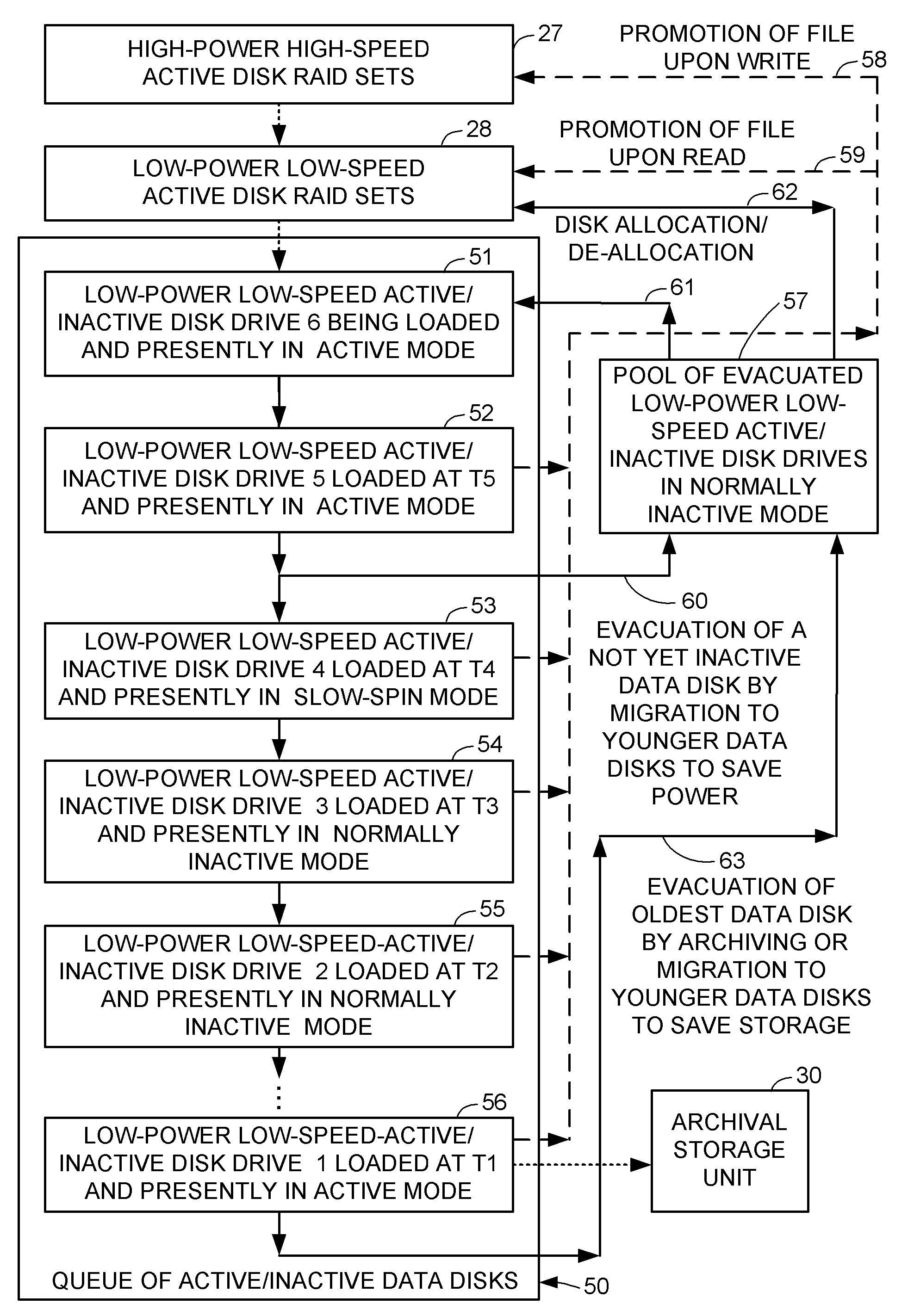
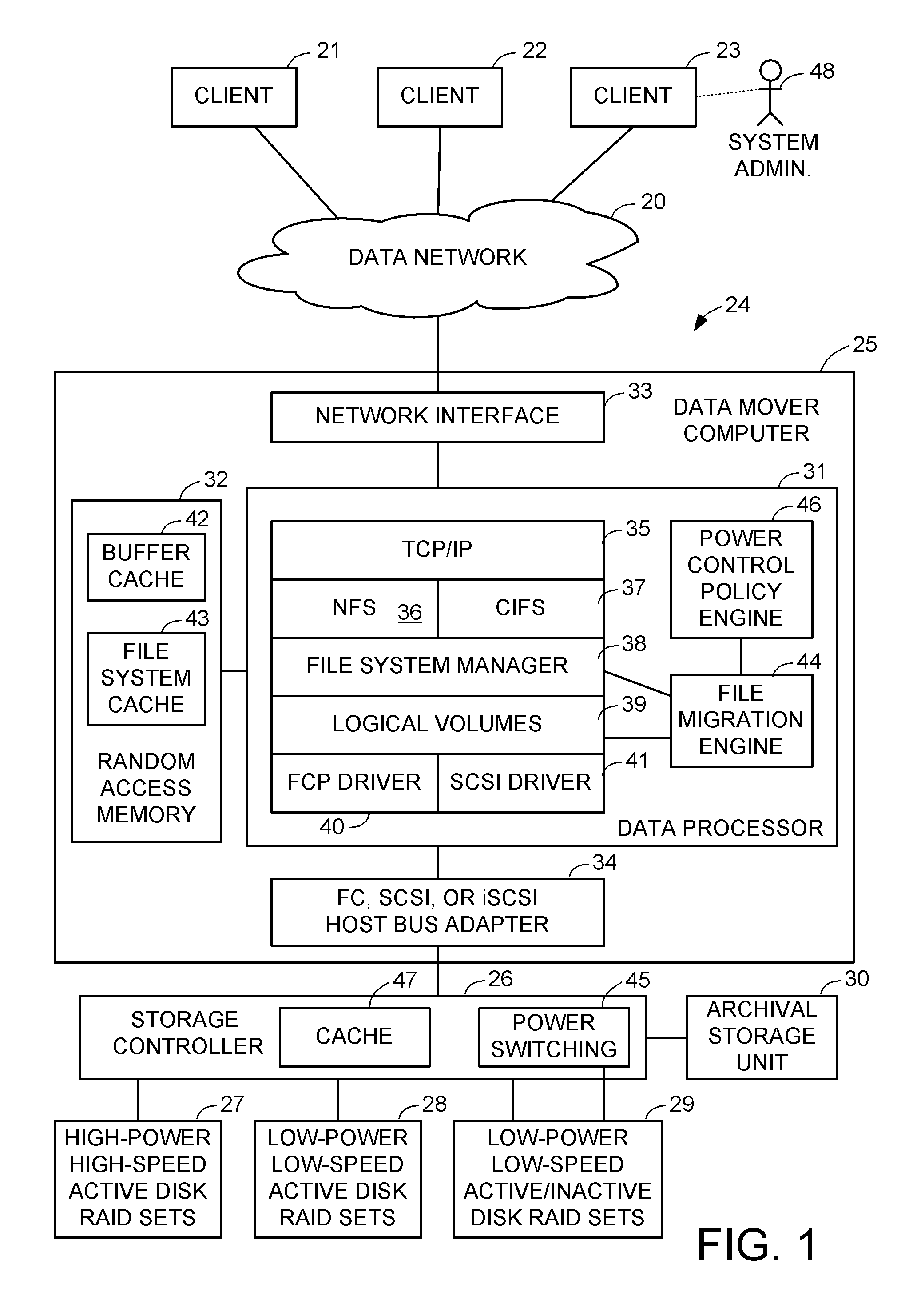
Intelligent file system based power management for shared storage that migrates groups of files based on inactivity threshold
A file server includes active storage containing frequently accessed files, and active / inactive disk drives for containing infrequently accessed files. Groups of the files having become inactive in the active storage are successively migrated to respective evacuated active / inactive disk drives so that each active / inactive disk drive is loaded with files having a similar probability of access when access to the active / inactive disk drive reaches an inactivity threshold for powering down the active / inactive disk drive. Storage of the active / inactive disk drives is reclaimed when an oldest group of the files is archived or when an active / inactive disk drive is evacuated by migrating files from the active / inactive disk drive to storage having been released in other disk drives by promotion of files for client access to the promoted files. Therefore, recovery of storage can be planned and scheduled in advance and performed efficiently in a background process.
Owner:EMC IP HLDG CO LLC
Method and system for improving usable life of memory devices using vector processing
ActiveUS7139863B1Extended service lifeUseful life of flashMemory architecture accessing/allocationRead-only memoriesActivity levelActive data
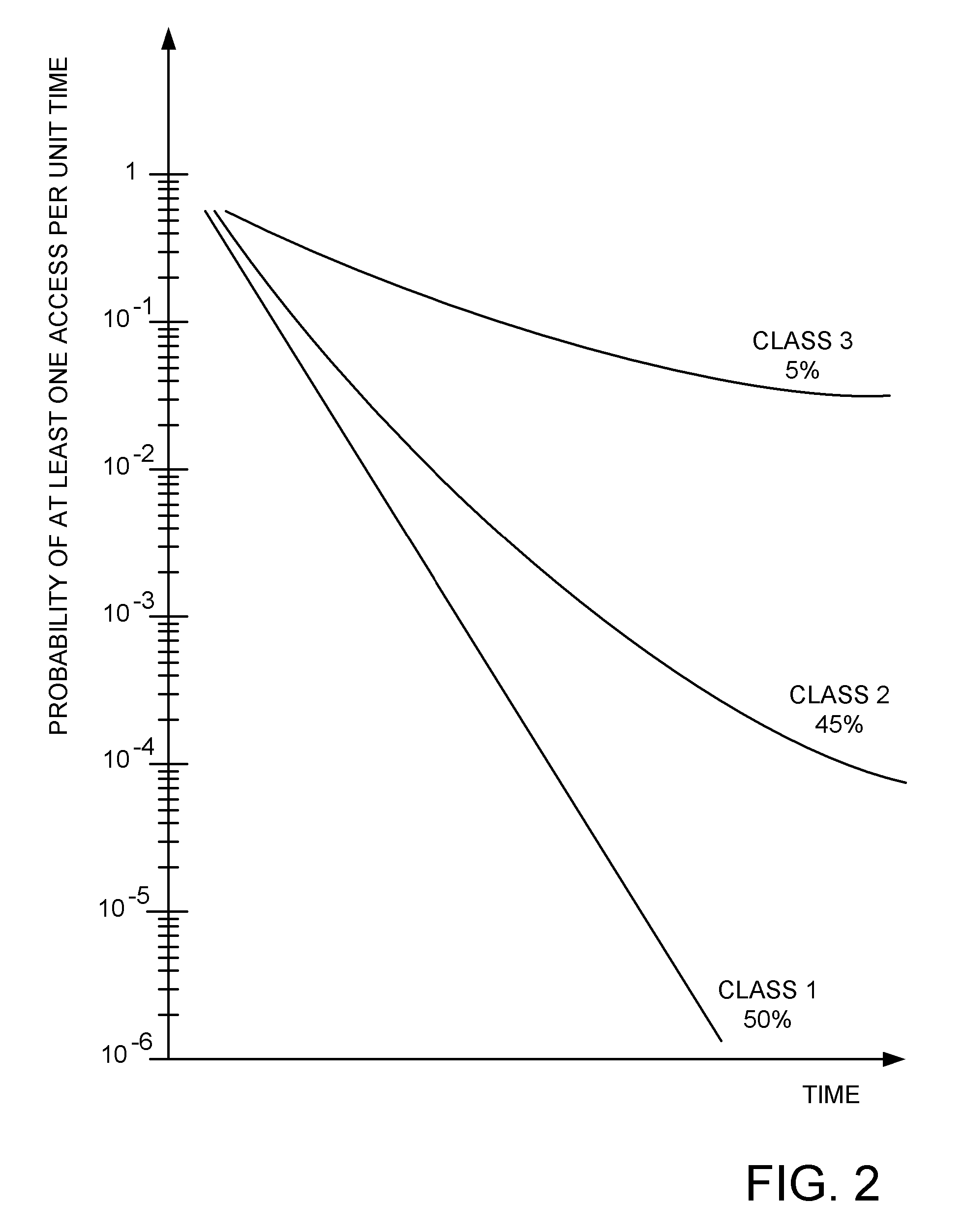
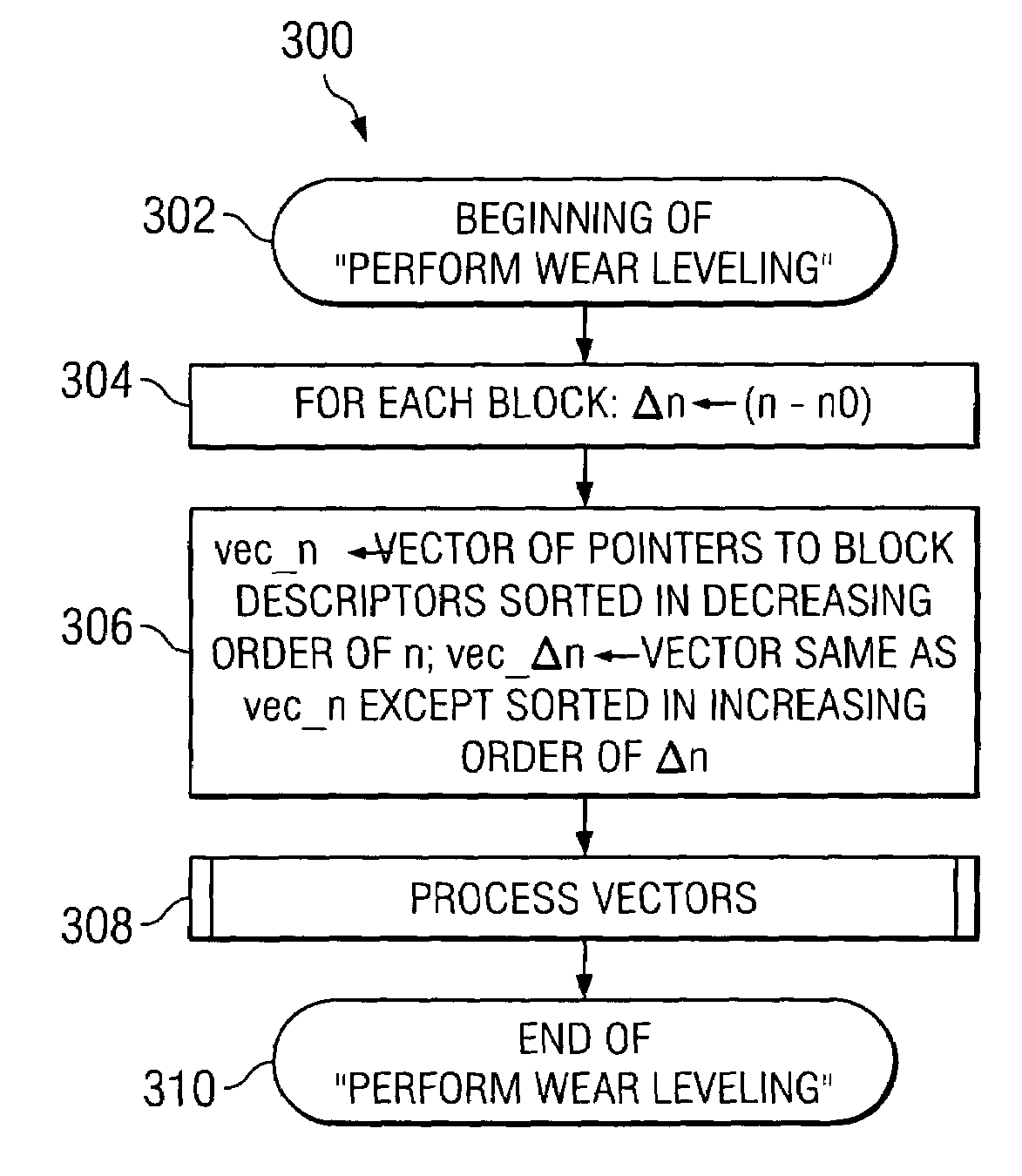
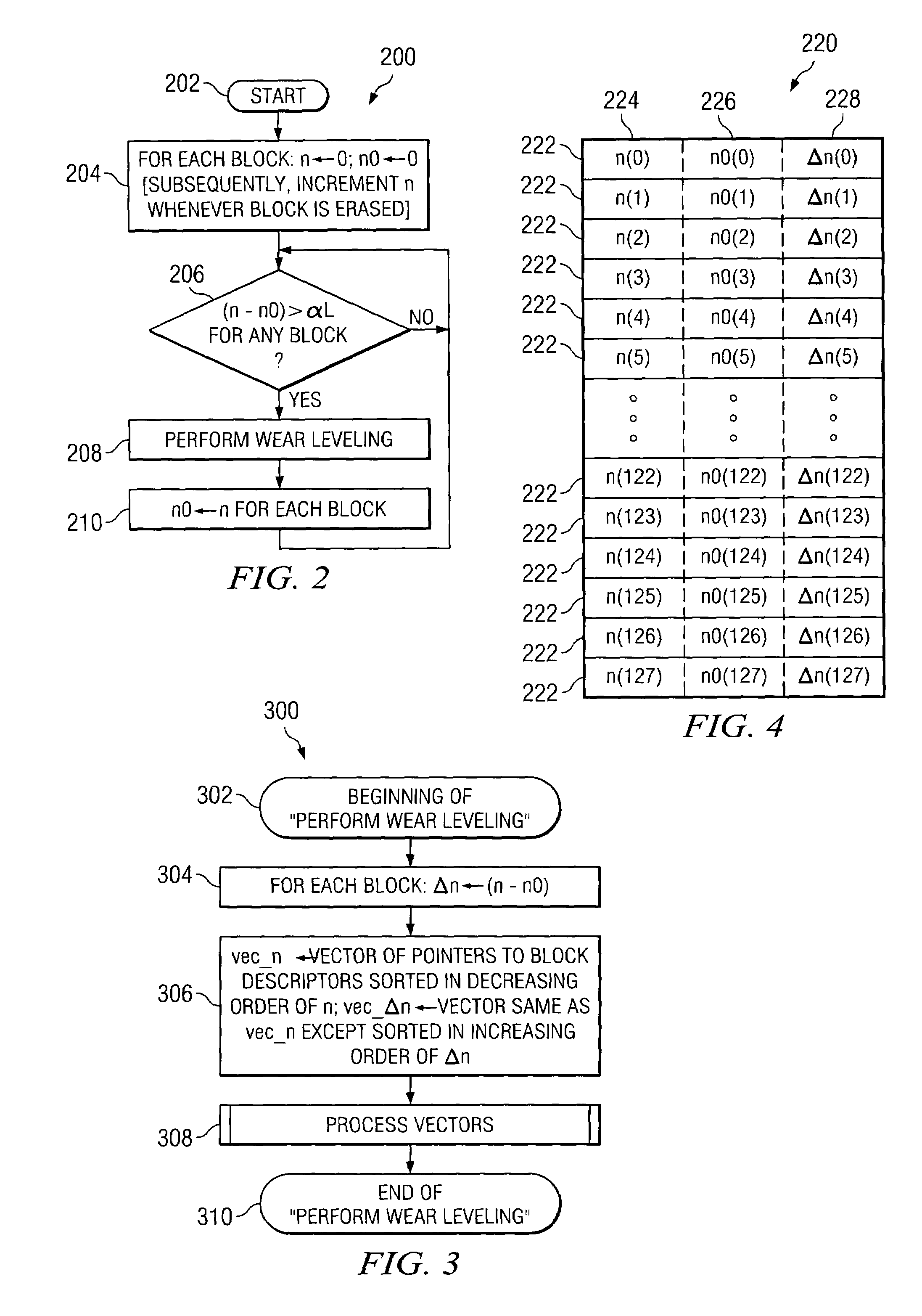
A method, system and apparatus for improving the useful life of non-volatile memory devices such as flash memory. The present wear-leveling technique advantageously improves the overall useful life of a flash memory device by strategically moving inactive data (data that has been infrequently modified in the recent past) to the memory blocks that have experienced the most wear since the device began operation and by strategically moving active data to the memory blocks that have experienced the least wear. In order to efficiently process and track data activity and block wear, vectors of block-descriptor pointers are maintained. One vector is sorted in decreasing order of overall block erase / write activity (block-wear indicator), whereas the other vector is sorted in increasing order of the number of times a block has been erased since the last wear-leveling event occurred (activity indicator for the data stored in the block). The activity levels of the data and the wear levels of the blocks are then easily compared and otherwise processed using pointers into these vectors to allow for more efficient processing than previous techniques used for wear leveling.
Owner:ORACLE INT CORP
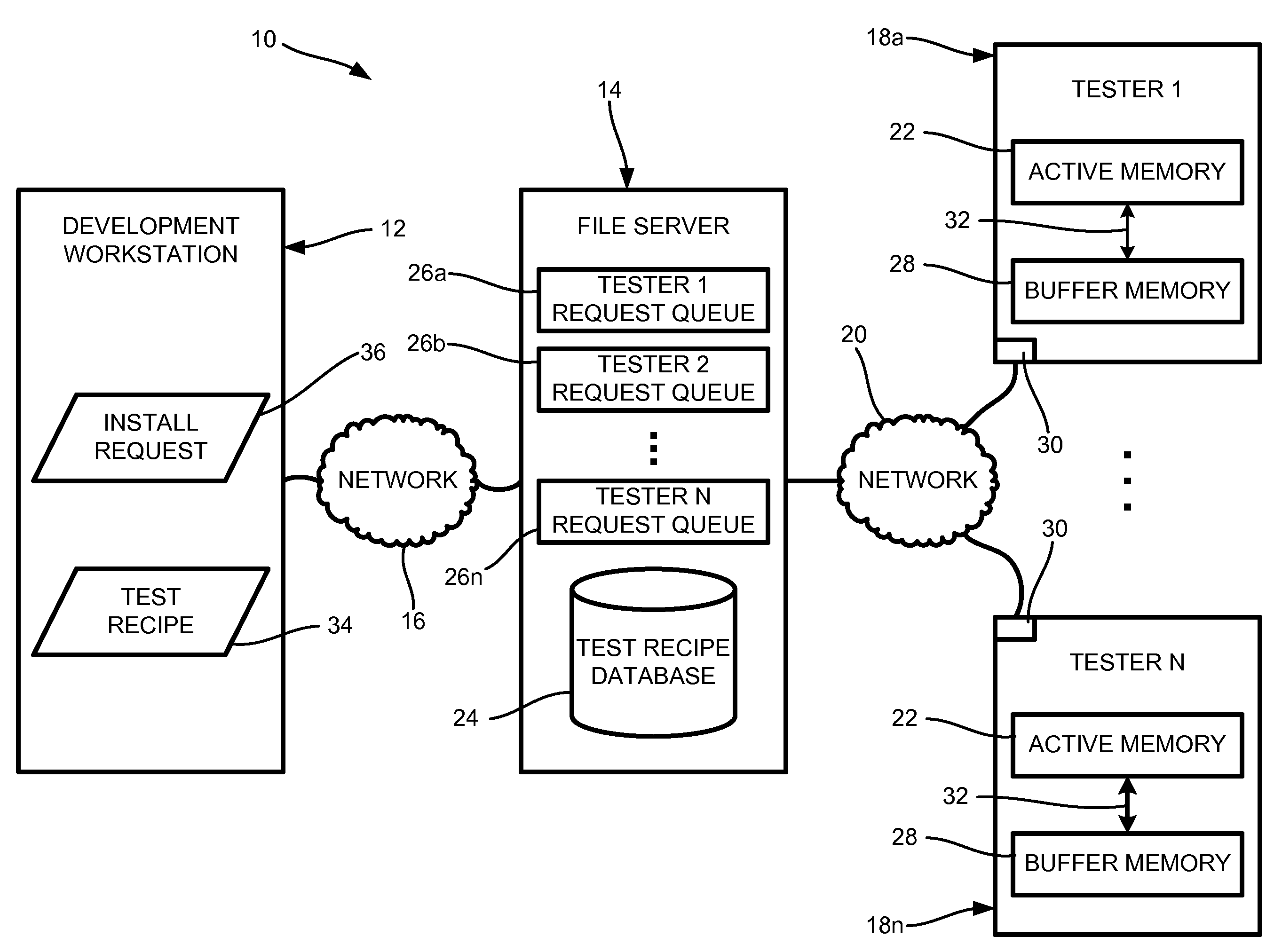
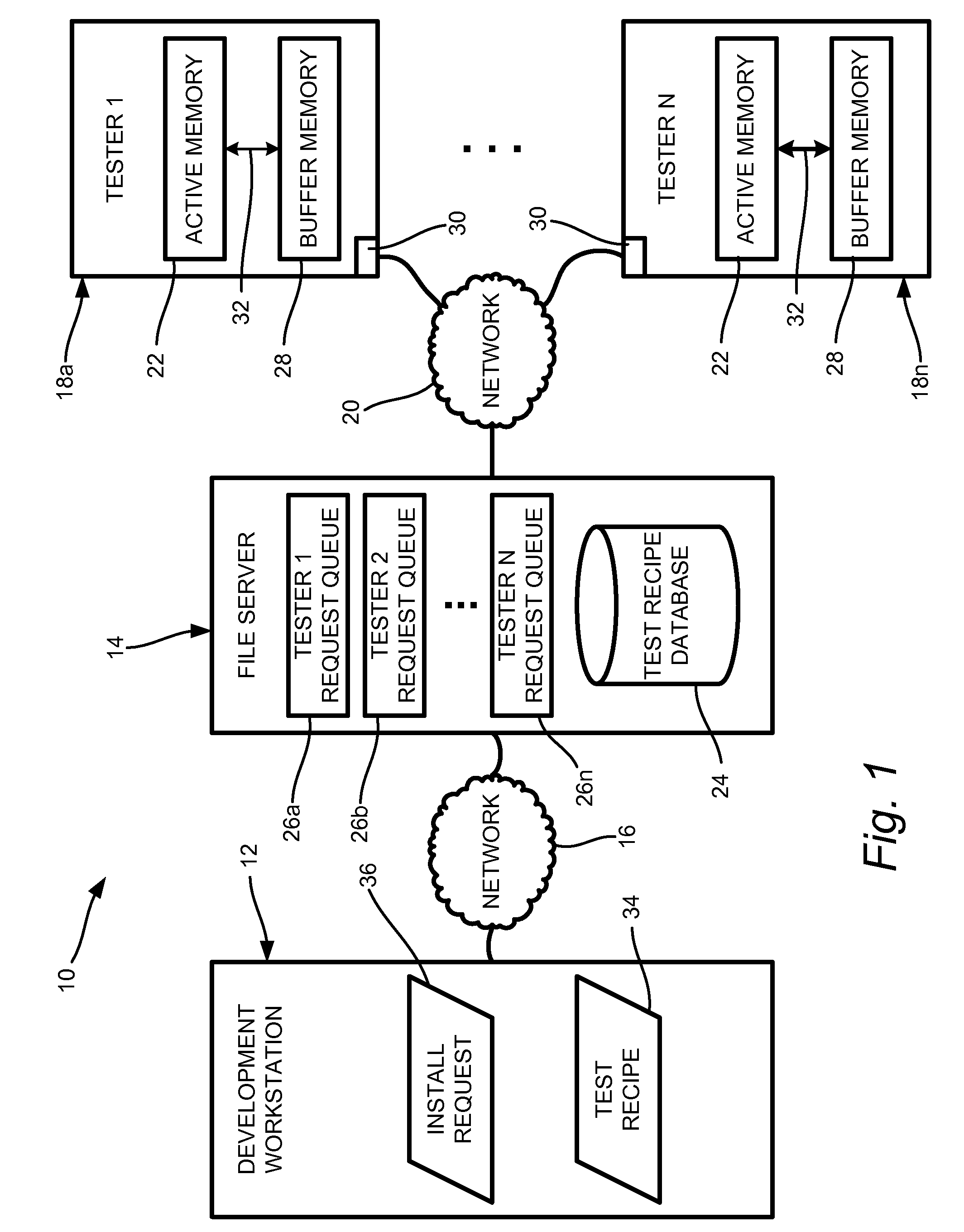
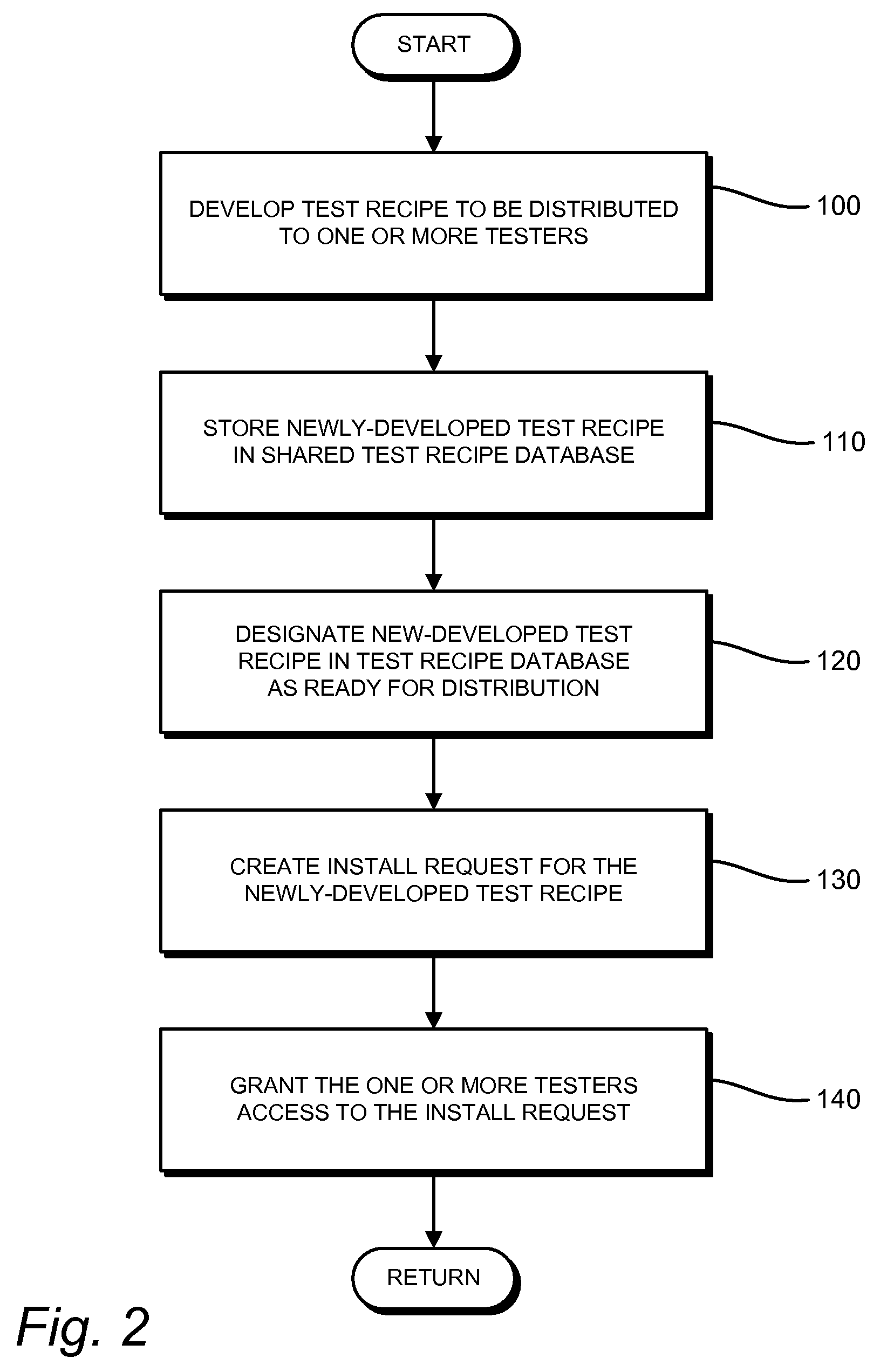
Test recipe distribution method and system
InactiveUS8452567B1Error detection/correctionSpecial data processing applicationsDistribution methodActive memory
Provided is a method and system for distributing a test recipe to a tester for conducting a test to determine if a device under test operates as designed. The method includes storing an active test recipe in an active memory in local communication with the tester, and initiating the test of the device under test to be performed by the tester according to a parameter included in the active test recipe stored in the active memory. A second parameter included in a second test recipe is received by the tester while conducting the test of the device under test according to the parameter included in the active test recipe. The method further includes storing the second parameter in a buffer memory in local communication with the active memory, and initiating a transfer of the second parameter from the buffer memory to the active memory. After initiation of the transfer of the second parameter to the active memory, a subsequent test to be performed by the tester according to the second parameter included in the second test recipe is initiated.
Owner:KEITHLEY INSTRUMENTS INC
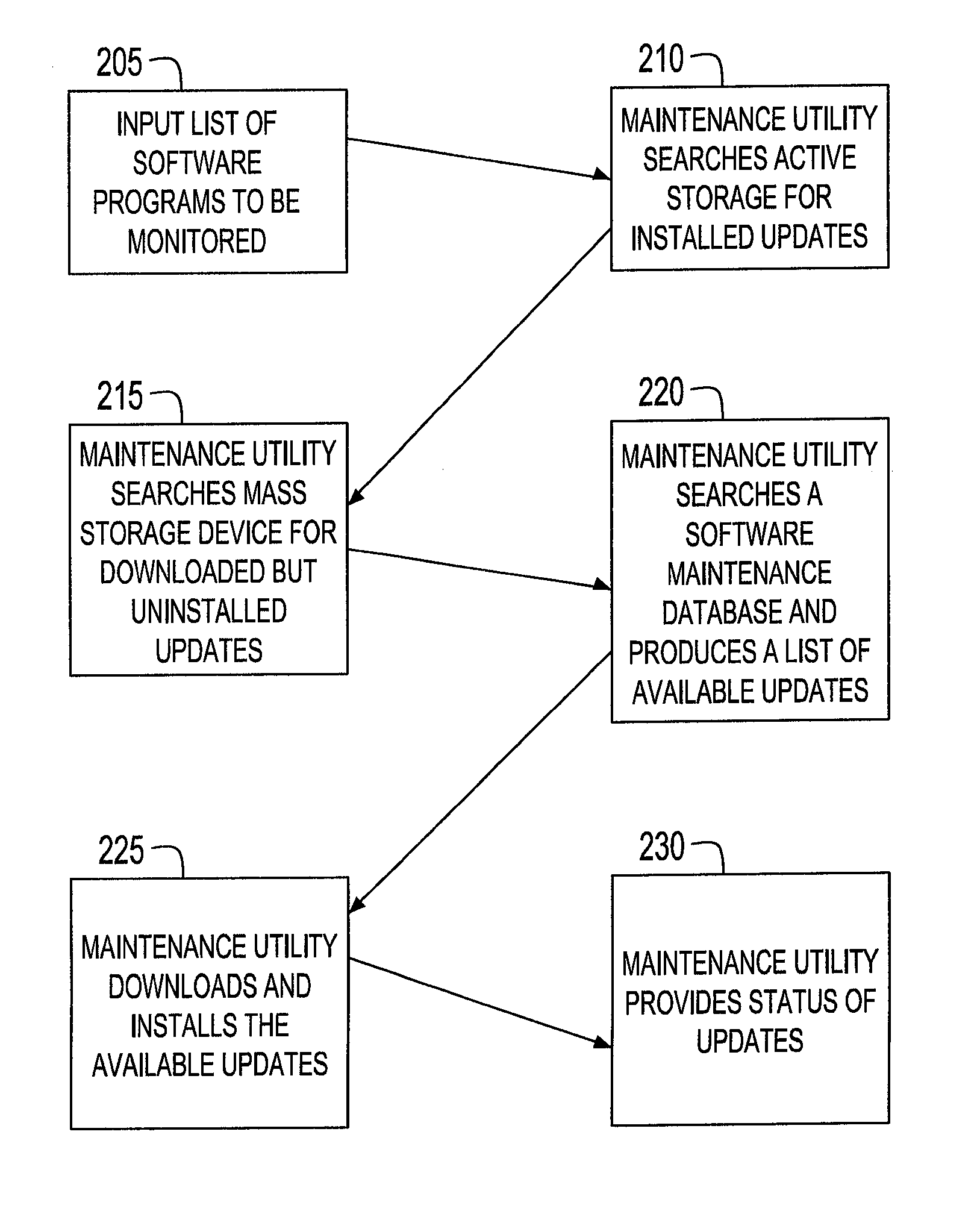
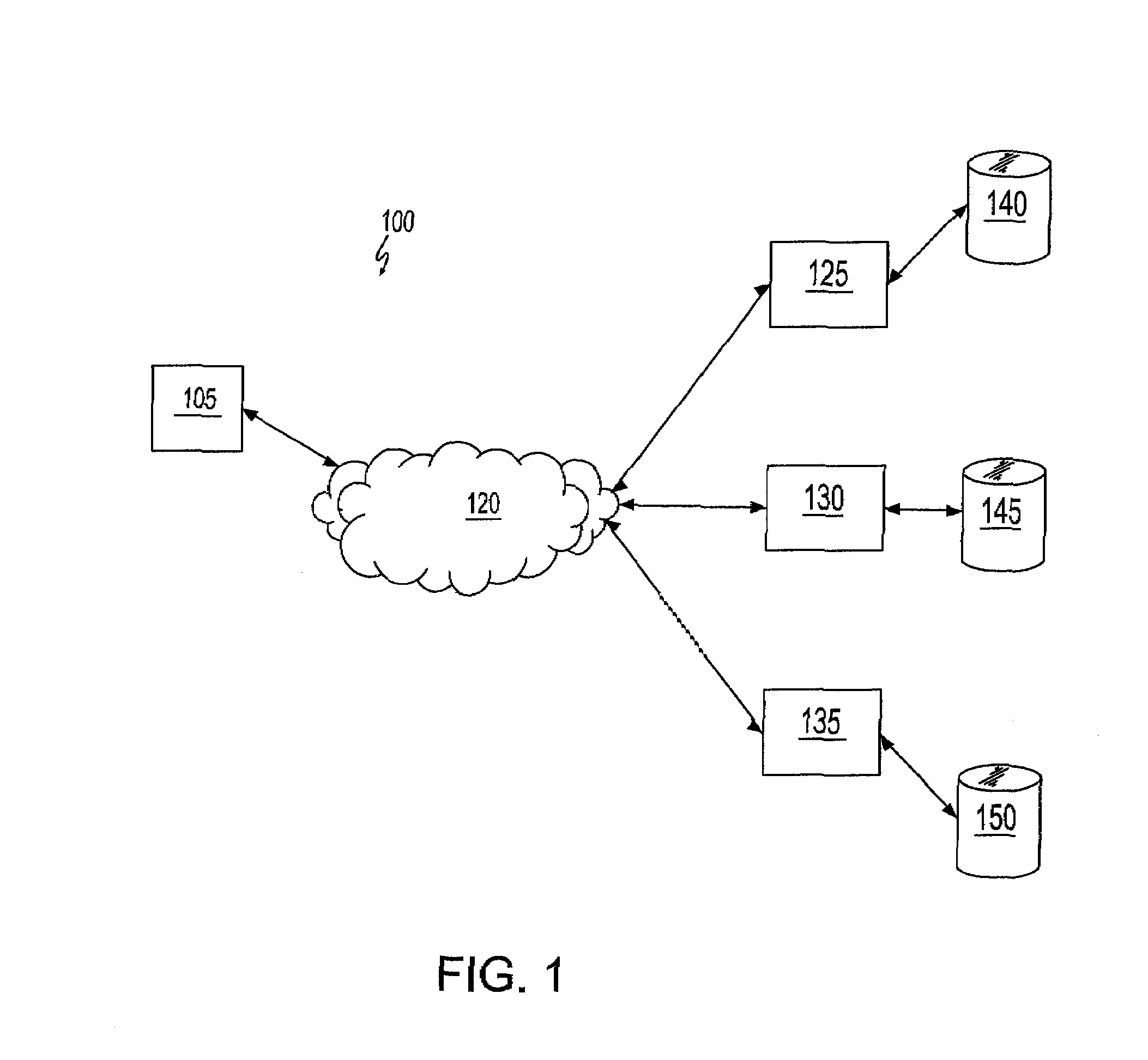
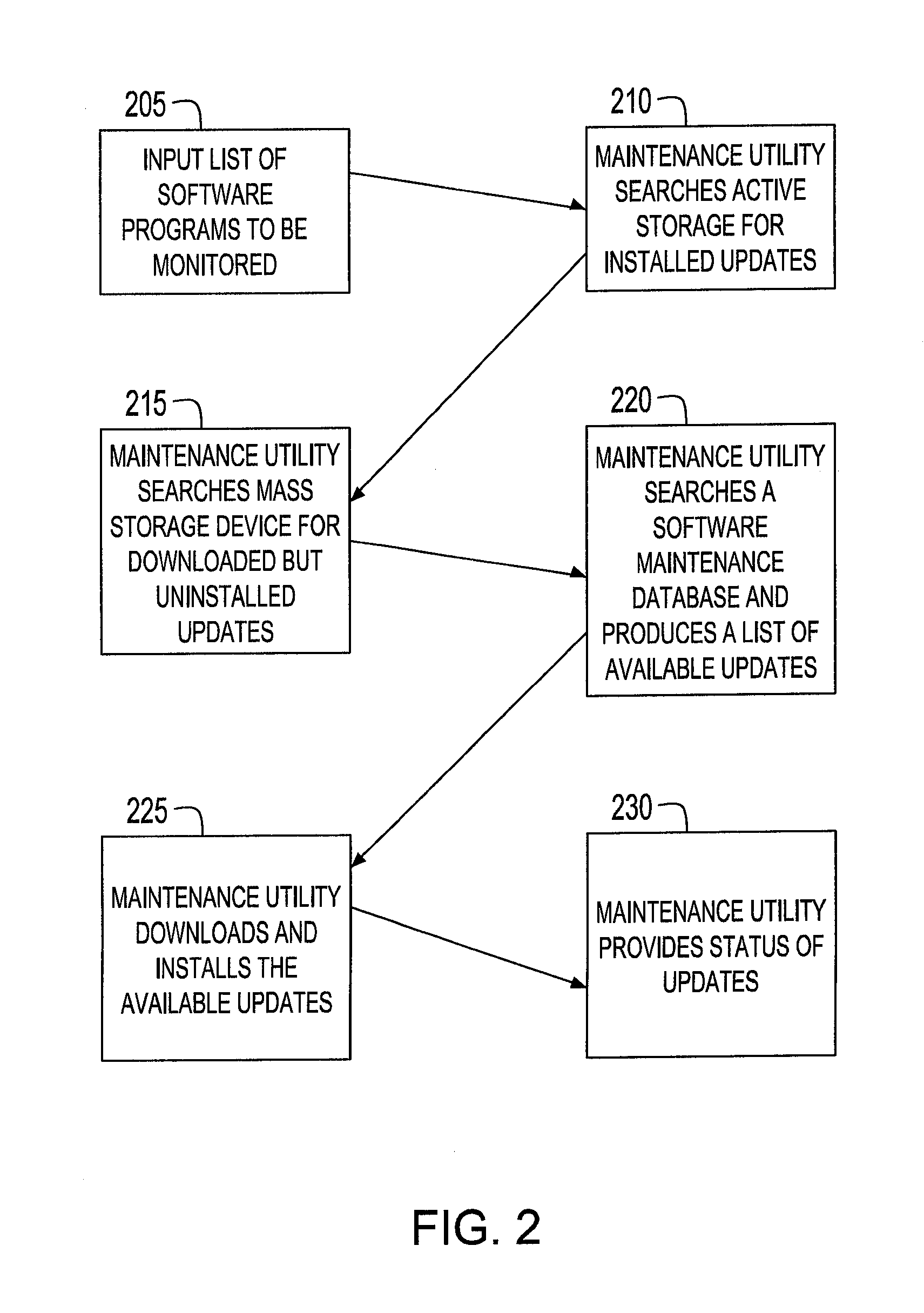
System and method for computer system maintenance
InactiveUS20070277167A1Specific program execution arrangementsMemory systemsComputerized systemSystem maintenance
A method of providing maintenance for a software program residing on a customer's computer system enables a customer to easily determine if there are any available updates for the software program, whether the available updates, if any, have been downloaded, which updates, if any, have been installed, and which installed updates, if any, have been activated. The method includes searching an active storage area on the customer's computer system while the software program is executing to determine the particular version of the software program. The method further includes searching a database of a software provider that provided the software program to determine if there is any update available for the software program, and if any update is available, downloading the update to the customer's computer system and installing the update.
Owner:IBM CORP
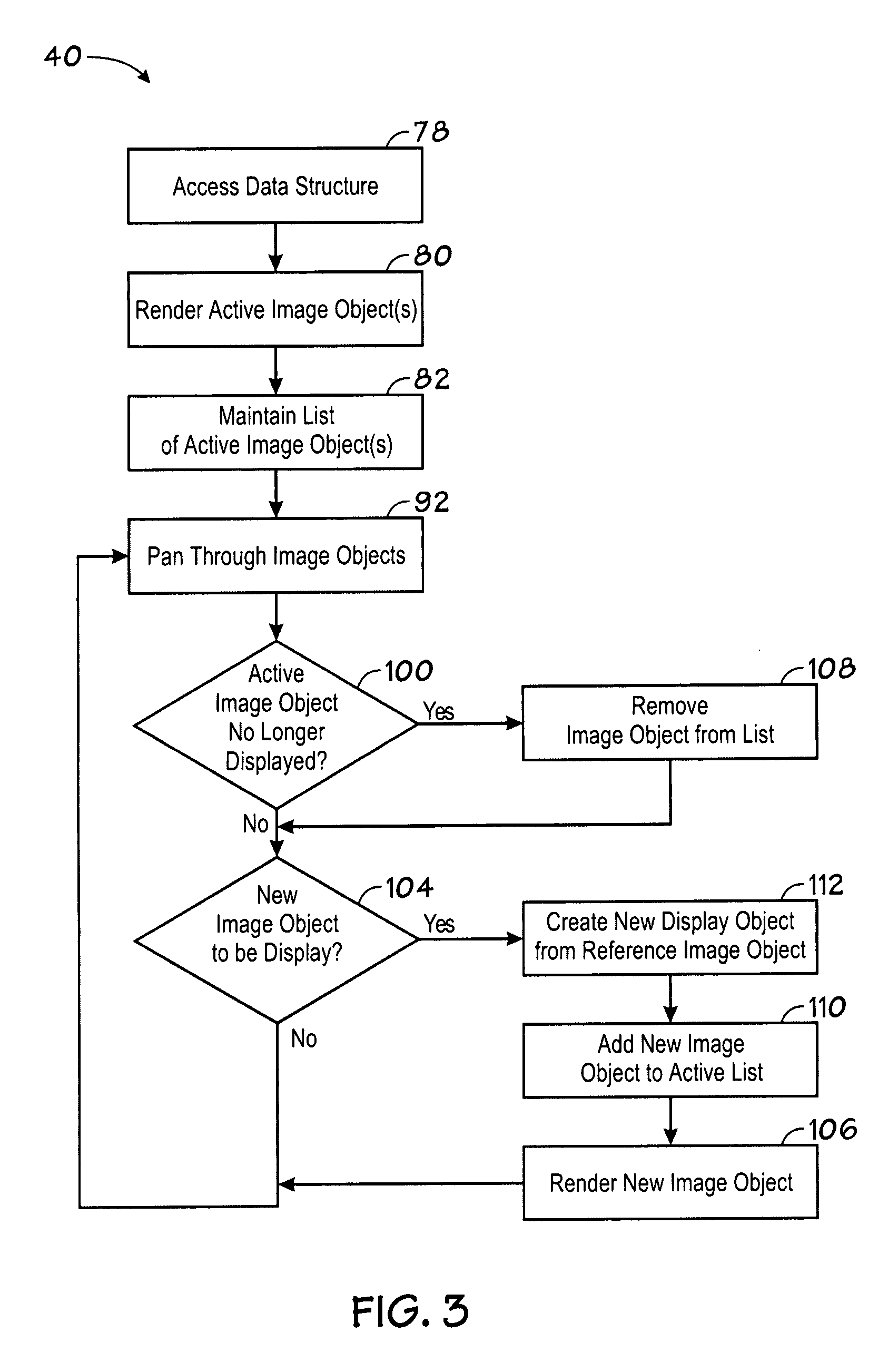
Low memory rendering of graphical objects
InactiveUS20090064045A1Low memory usageImprove performanceInput/output processes for data processingArray data structureData store
A method for displaying graphical objects is provided. In one embodiment, the method includes accessing a data structure including a plurality of sequential data objects and the location of associated graphical data stored in a non-volatile storage device. Further, the method may include rendering a first graphical object associated with a first data object of the data structure in a viewport of a device, including loading the graphical data for the first data object from the non-volatile storage into an active memory. The method may also include rendering a second graphical object in the viewport based on the location of the second data object with respect to the first data object within the data structure. In one embodiment, graphical data for data objects is loaded into the active memory on an as-needed basis. Various devices, machine-readable media, and other methods for displaying graphical objects are also provided.
Owner:APPLE INC
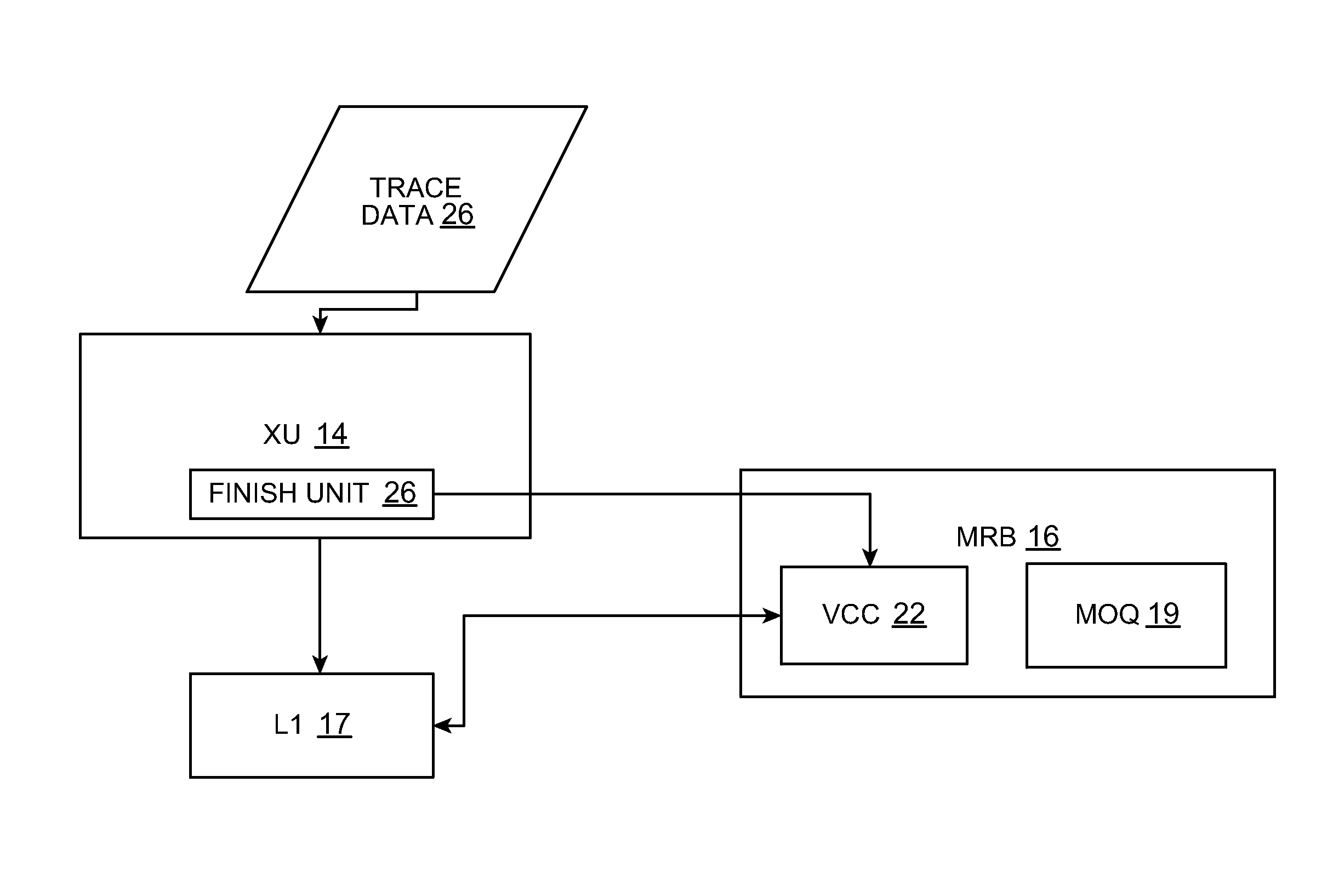
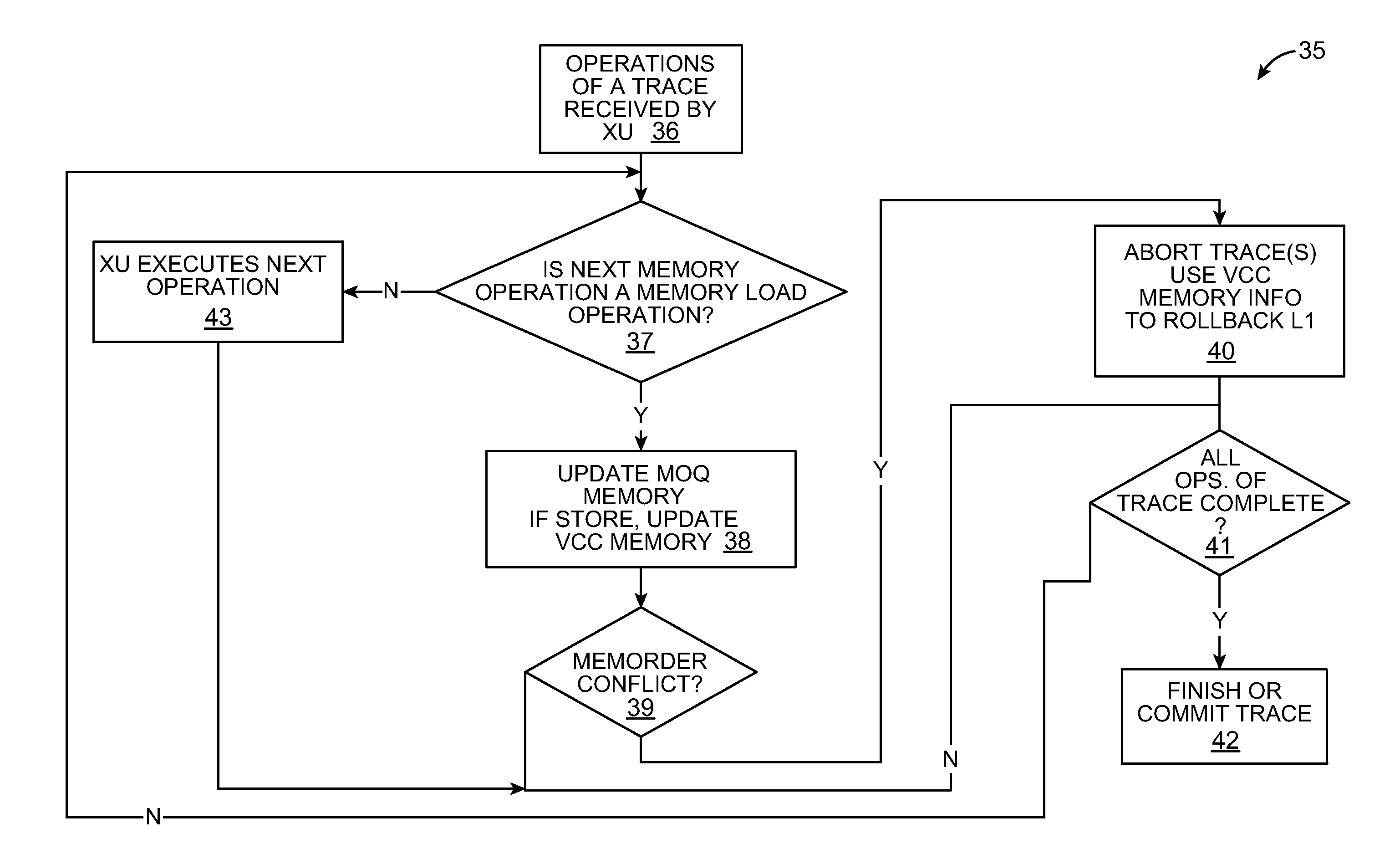
Data cache rollbacks for failed speculative traces with memory operations
This invention includes a circuit for tracking memory operations with trace-based execution. Each trace includes a sequence of operations that includes zero or more of the memory operations. The memory operations being executed form a set of active memory operations that have a predefined program order among them and corresponding ordering constraints. At least some of the active memory operations access the memory in an execution order that is different from the program order. Checkpoint entries are associated with each trace. Each entry refers to a checkpoint location. Memory operation ordering entries correspond to each one of the active memory operations. Violations of the ordering constraints result in overwriting the checkpoint locations associated with the selected trace as well as the checkpoint locations associated with traces that are younger than the selected trace.
Owner:SUN MICROSYSTEMS INC
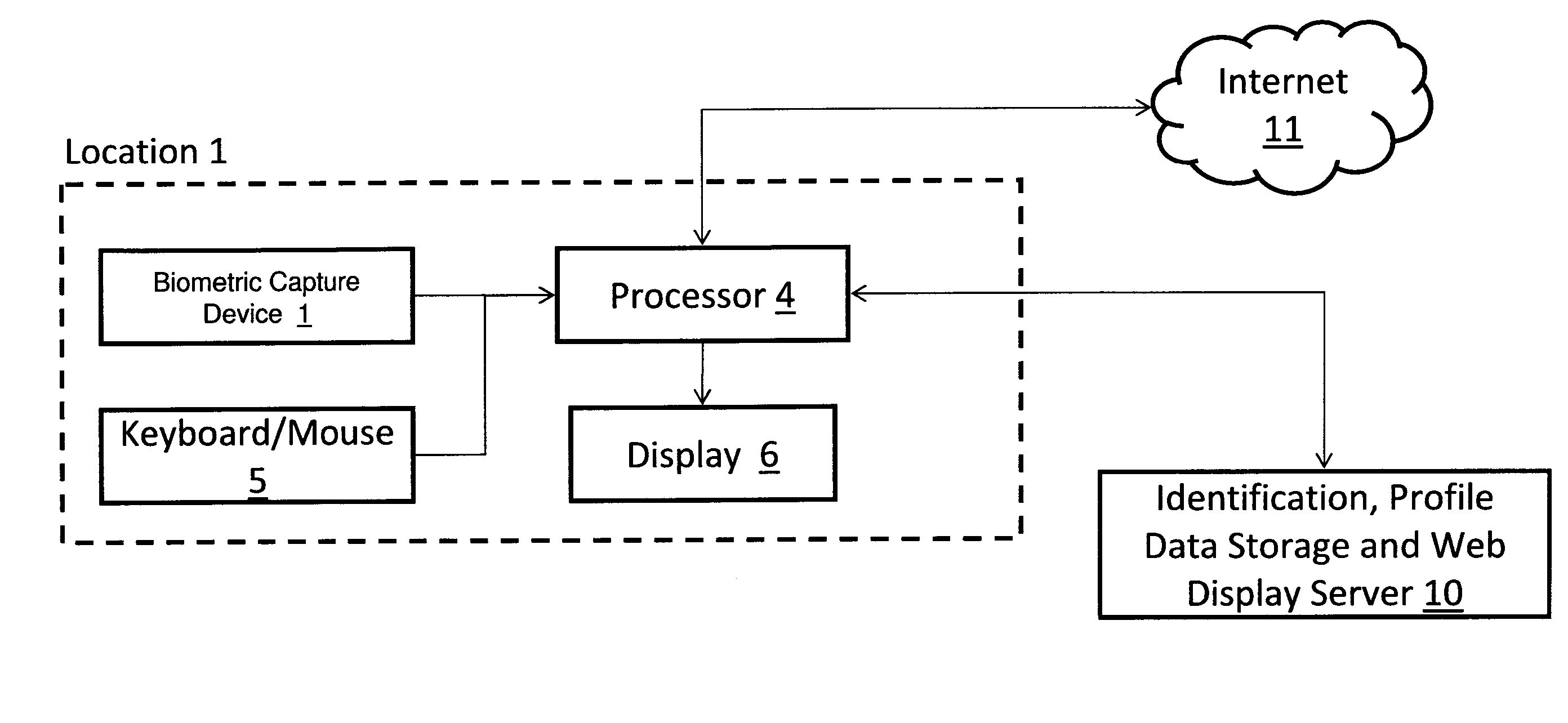
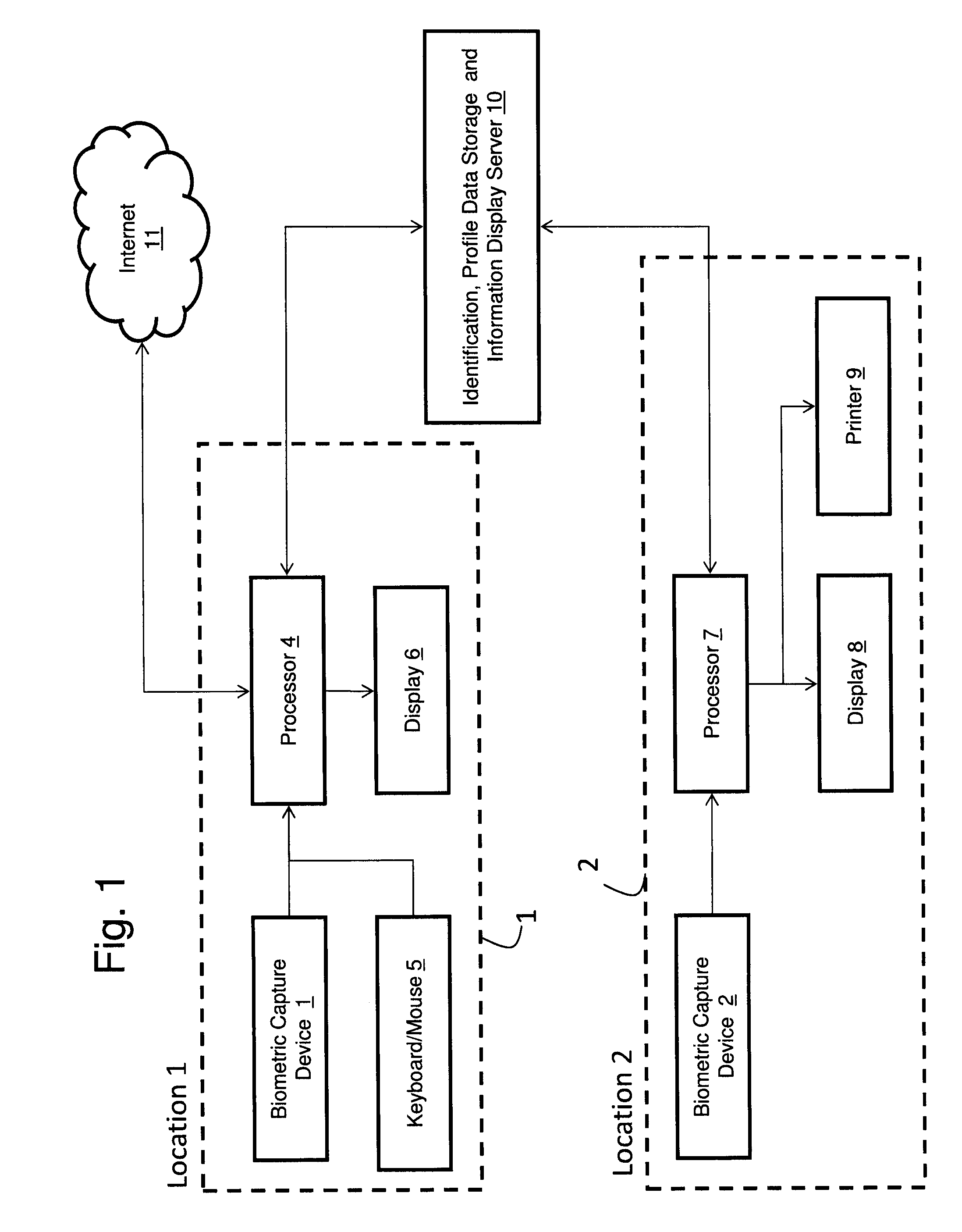
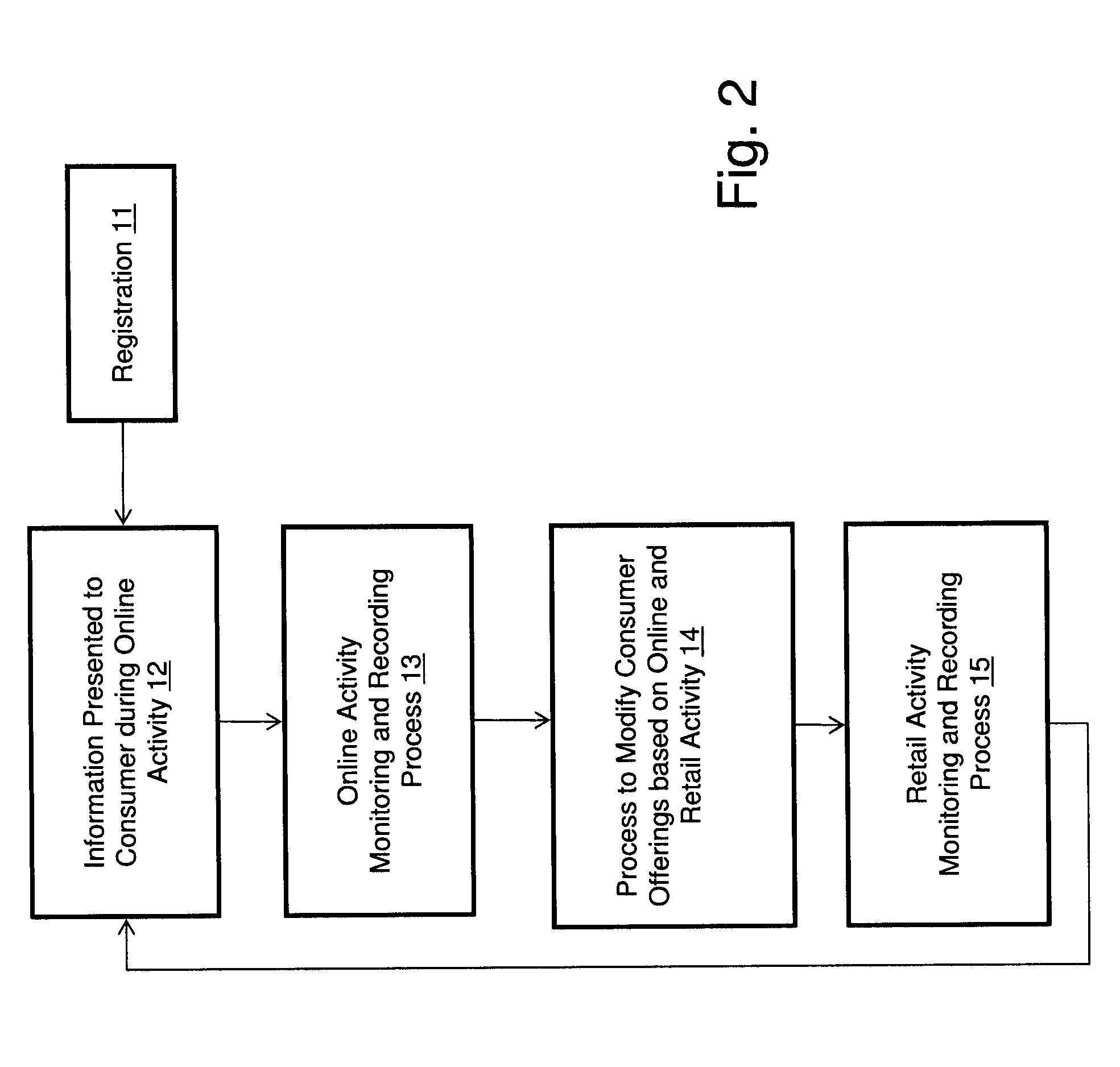
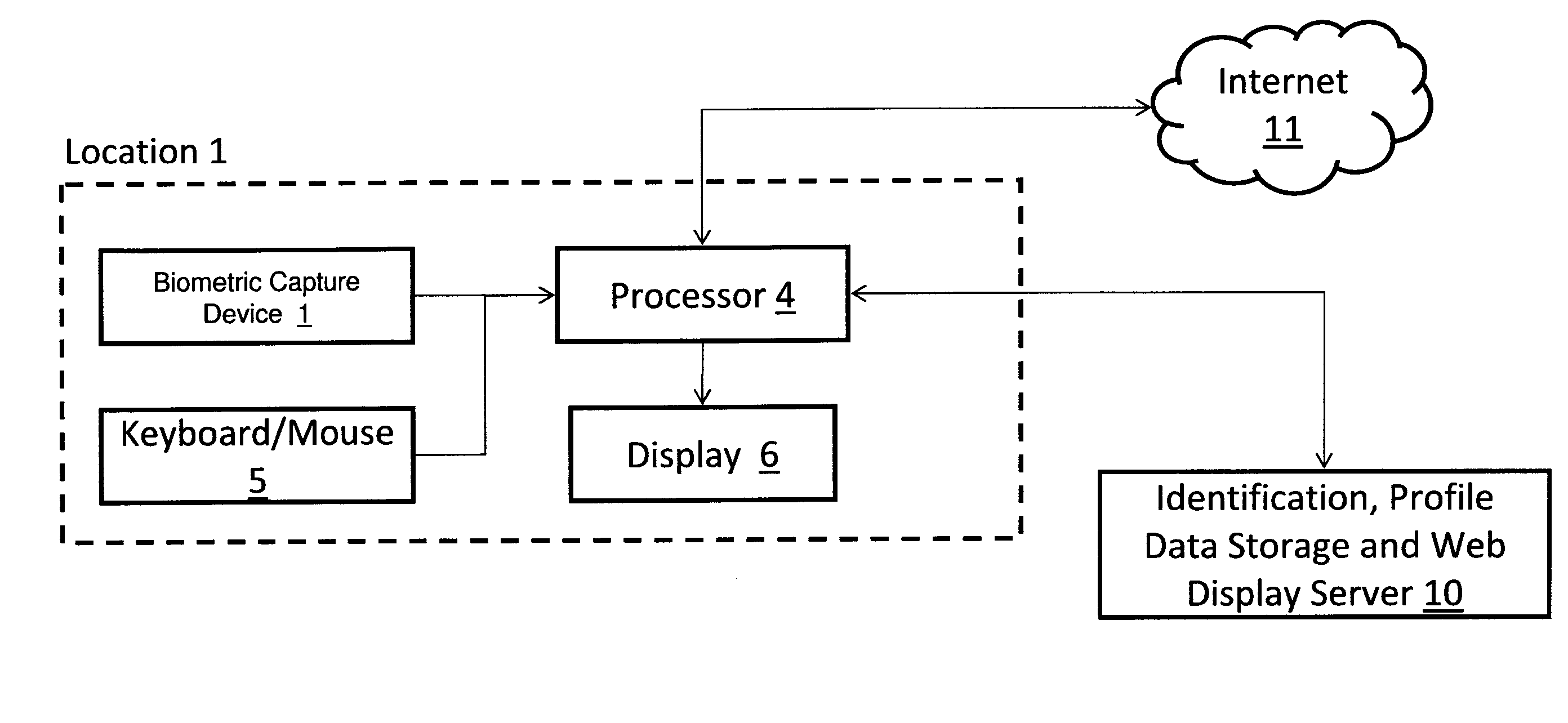
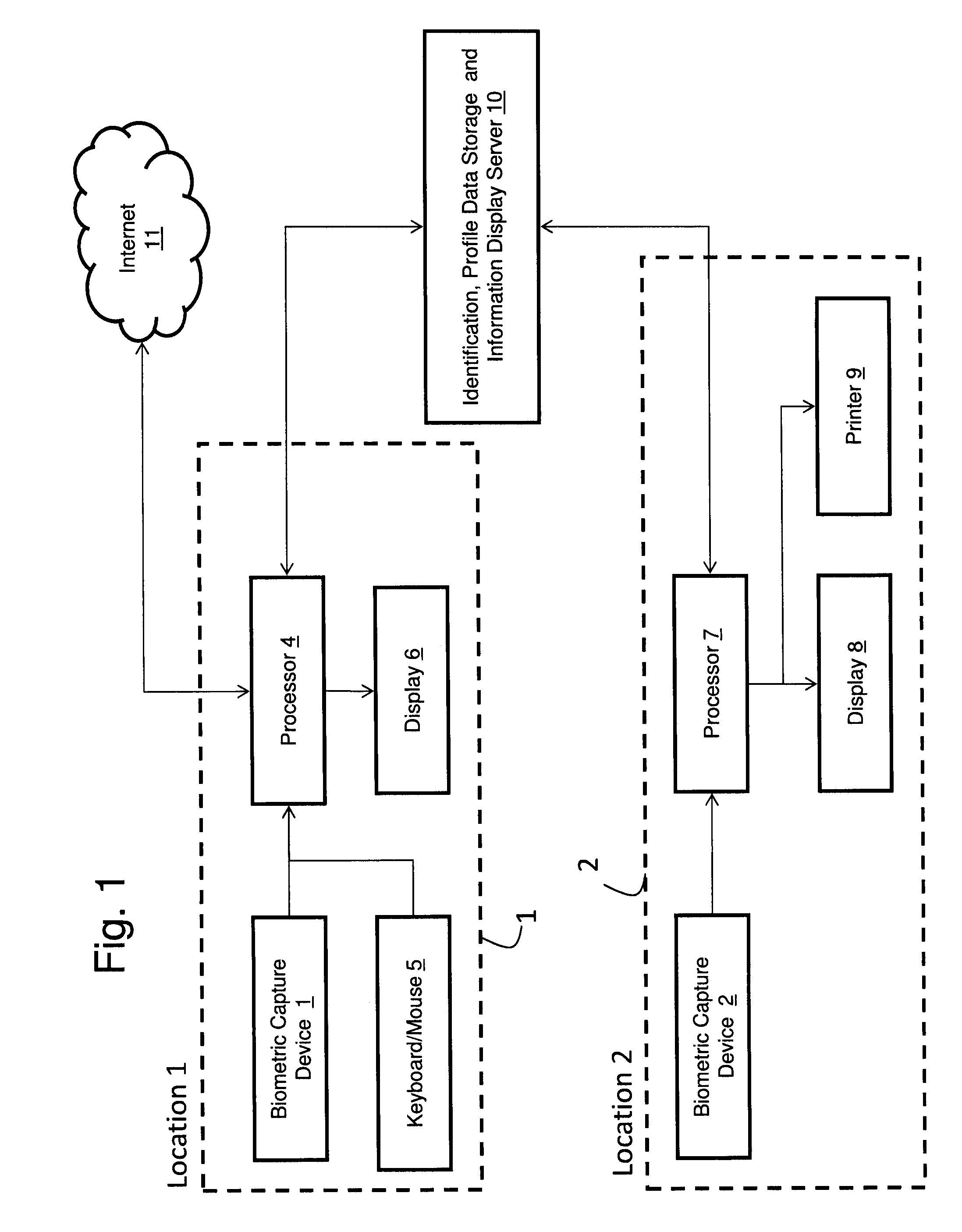
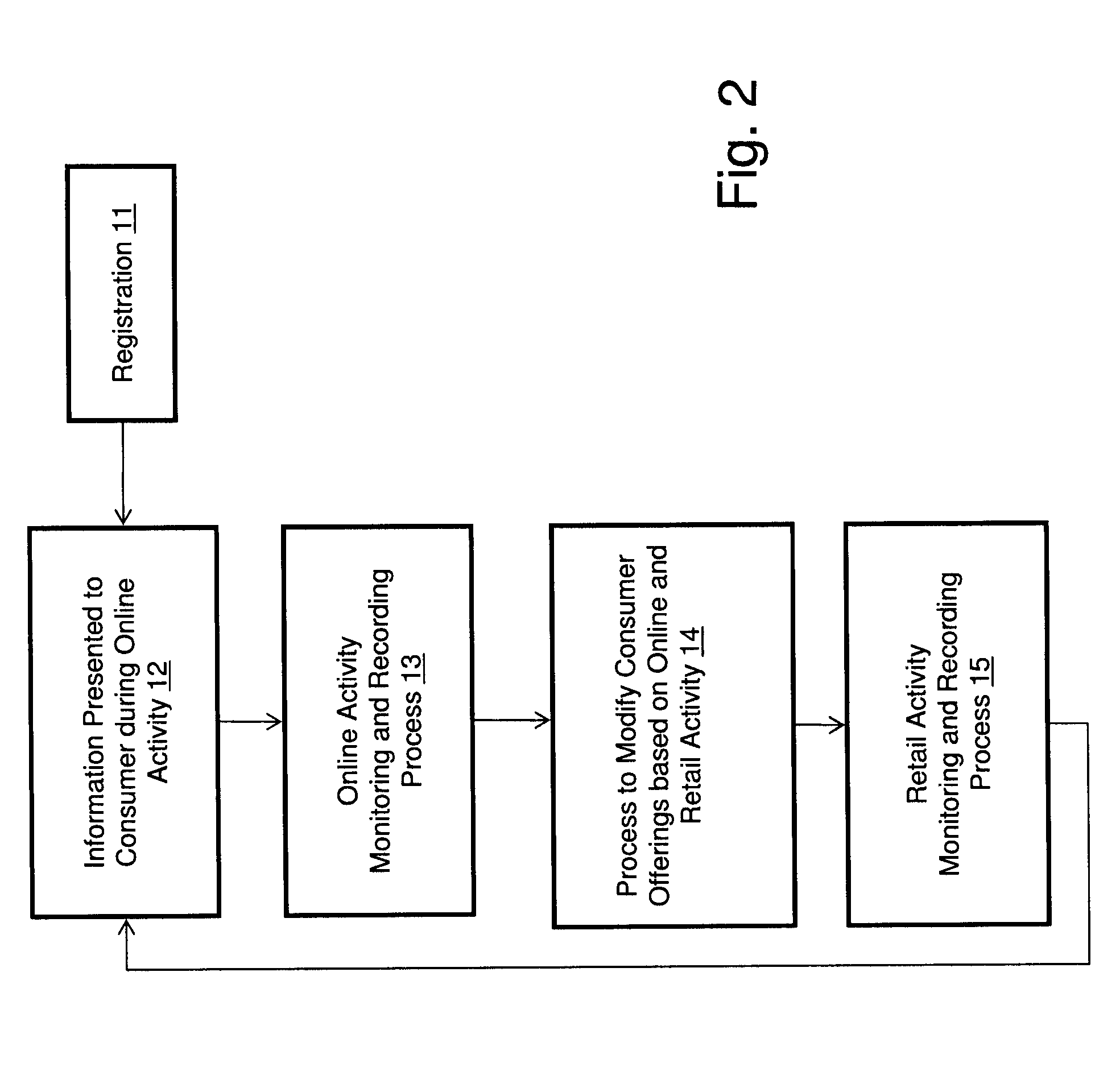
Measuring Effectiveness of Advertisements and Linking Certain Consumer Activities Including Purchases to Other Activities of the Consumer
InactiveUS20110119111A1Improve efficiencyEfficient preparationMarket predictionsDatabase indexUnique identifier
A method for linking online computer activity with non-online consumer activity by creating a unique identifier for each consumer; storing online and non-online consumer activity in a database indexed by the unique identifier; and modifying online or non-online consumer offerings based on processing the stored online and non-online consumer activity.
Owner:EYELOCK
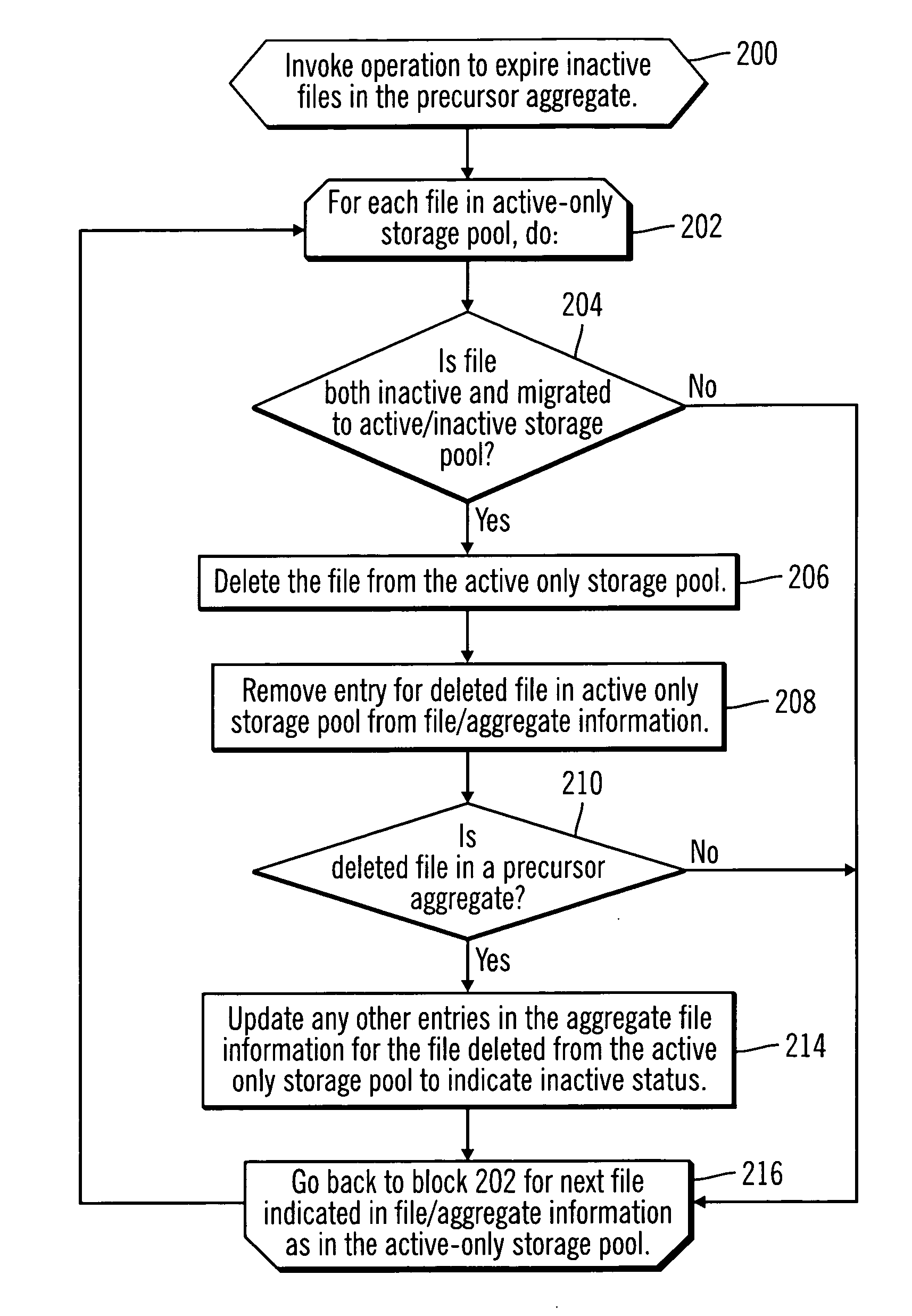
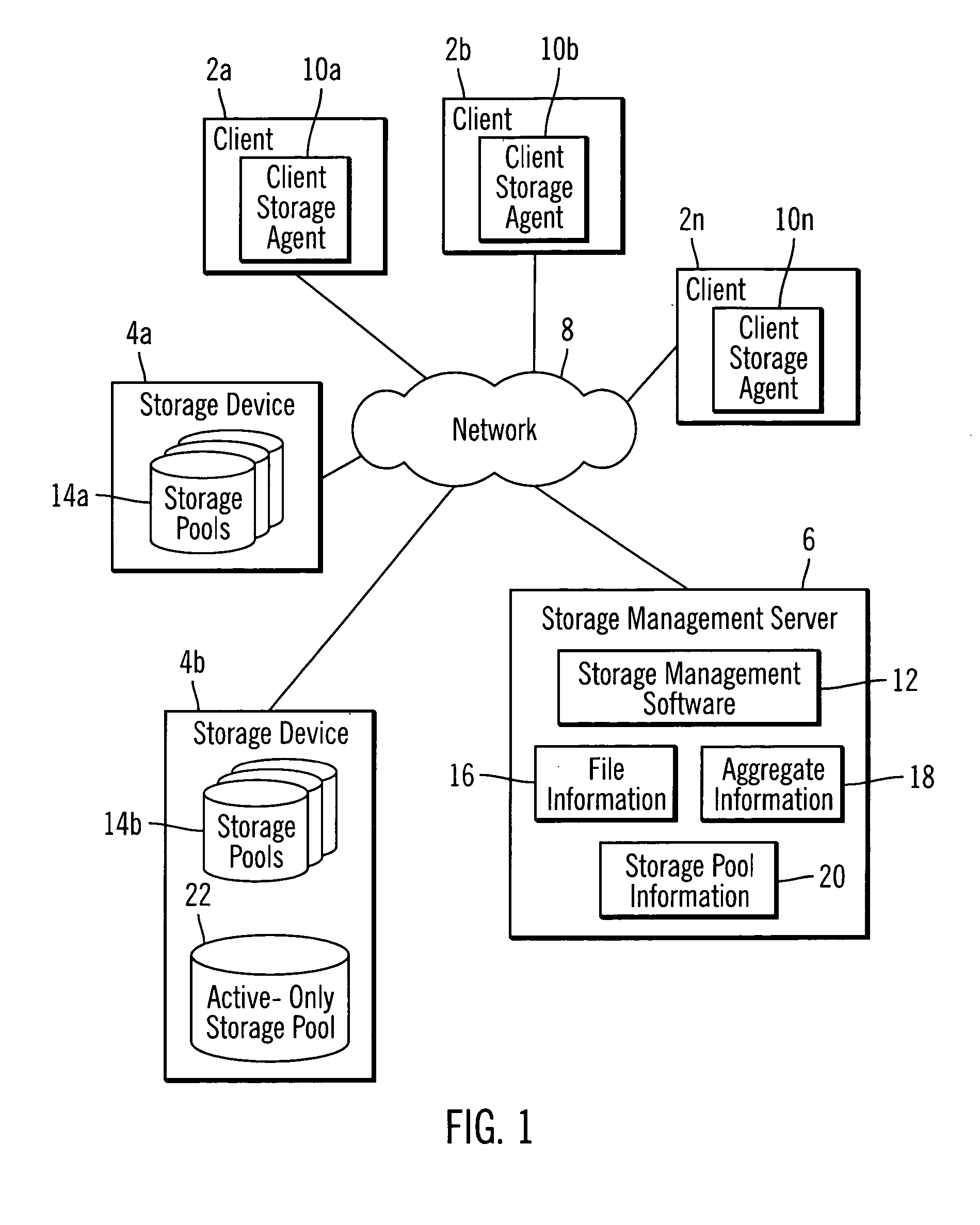
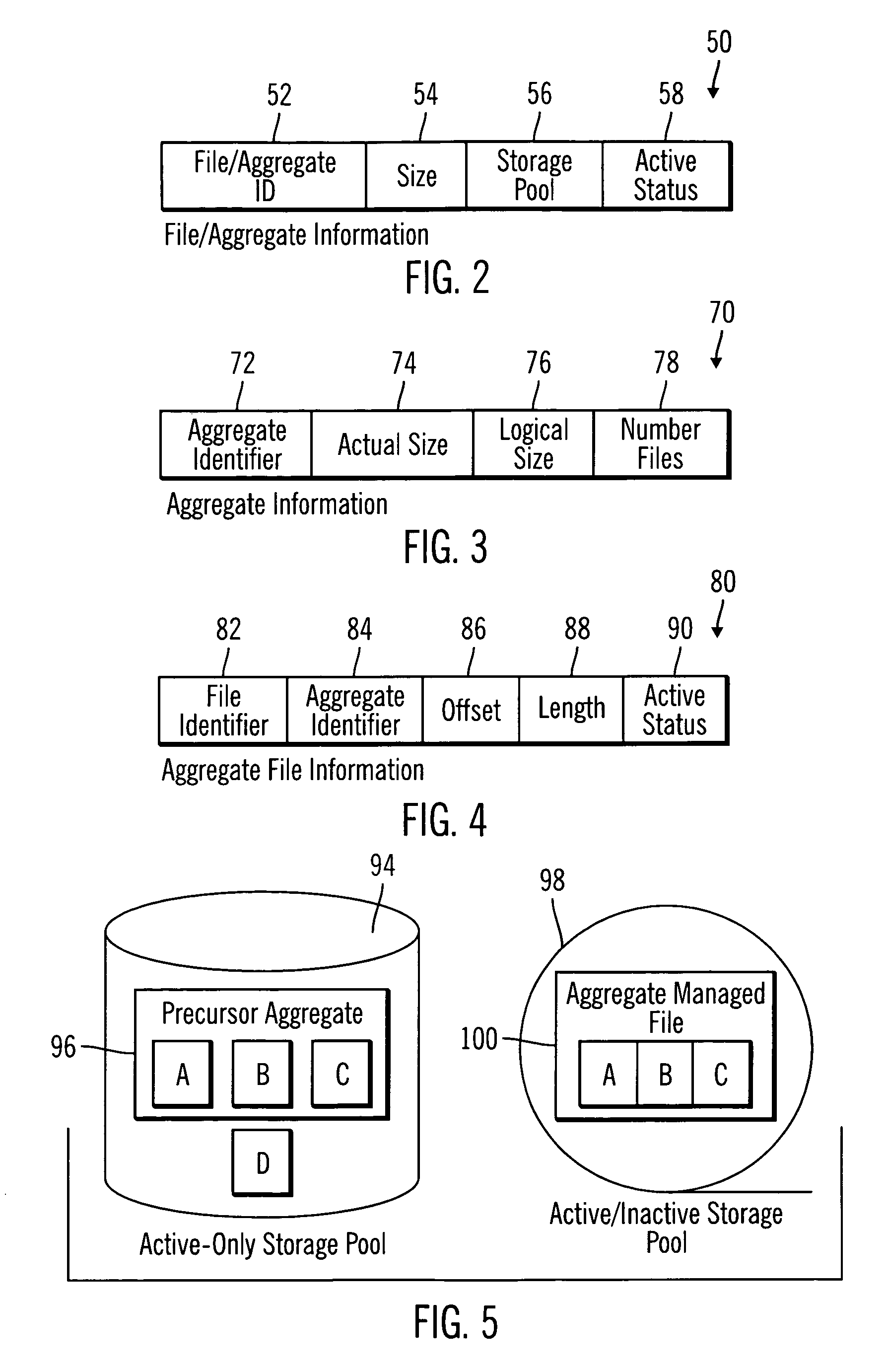
Maintaining an aggregate including active files in a storage pool in a random access medium
InactiveUS20070043787A1Data processing applicationsSpecial data processing applicationsActive storageStorage pool
Provided are a method, system, and program for maintaining an aggregate including active files in a storage pool in a random access medium. An active-only storage pool is configured in a random access device. The active-only storage pool is intended to include only active files and not inactive versions of files. A plurality of files in the active-only storage pool are associated with a precursor aggregate in the active-only storage pool. One file associated with the precursor aggregate in the active only storage pool is deactivated to produce an inactive version of the deactivated file. The precursor aggregate is associated with the inactive version of the file in response to the deactivation. A determination is made of the inactive version of at least one file in the precursor aggregate. The determined inactive version of the at least one file is deleted from the active only storage pool.
Owner:IBM CORP
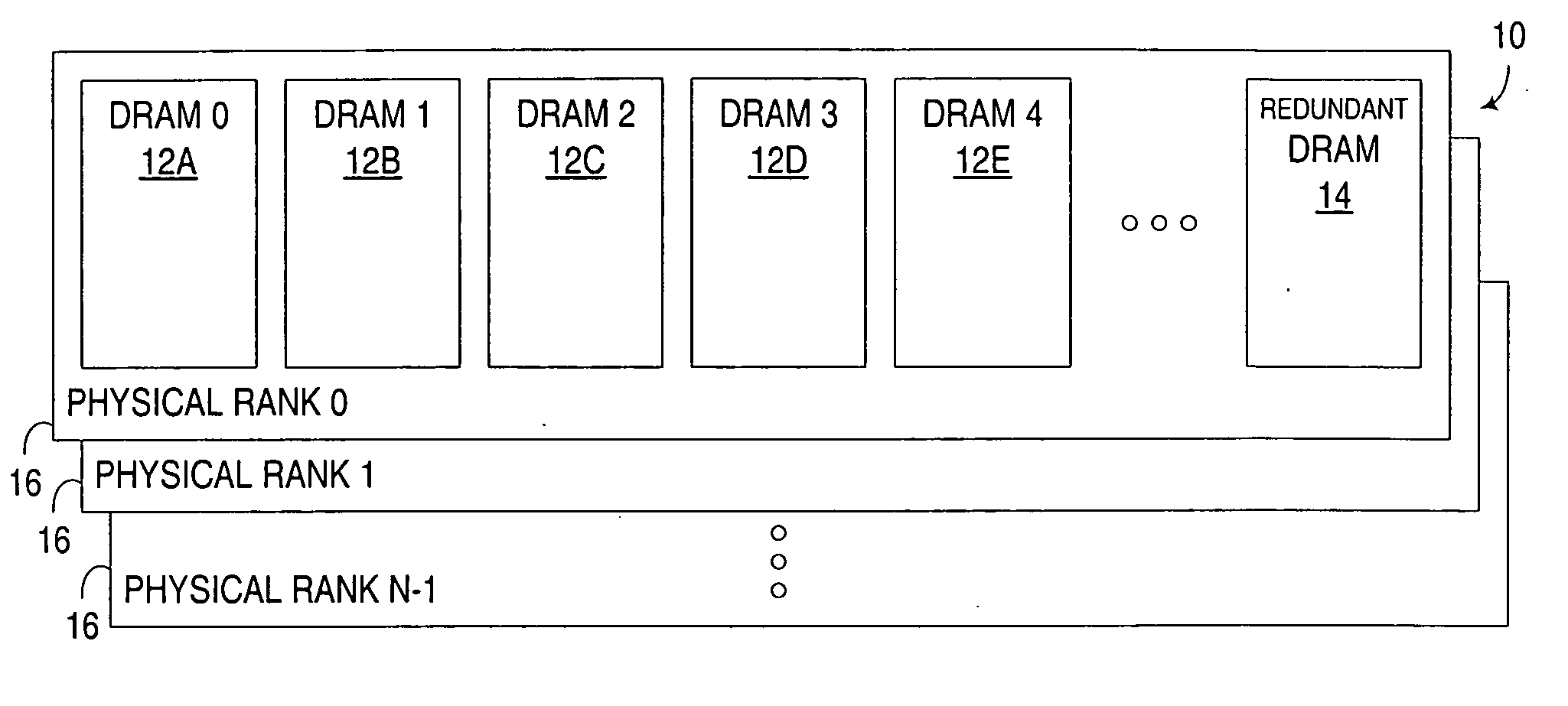
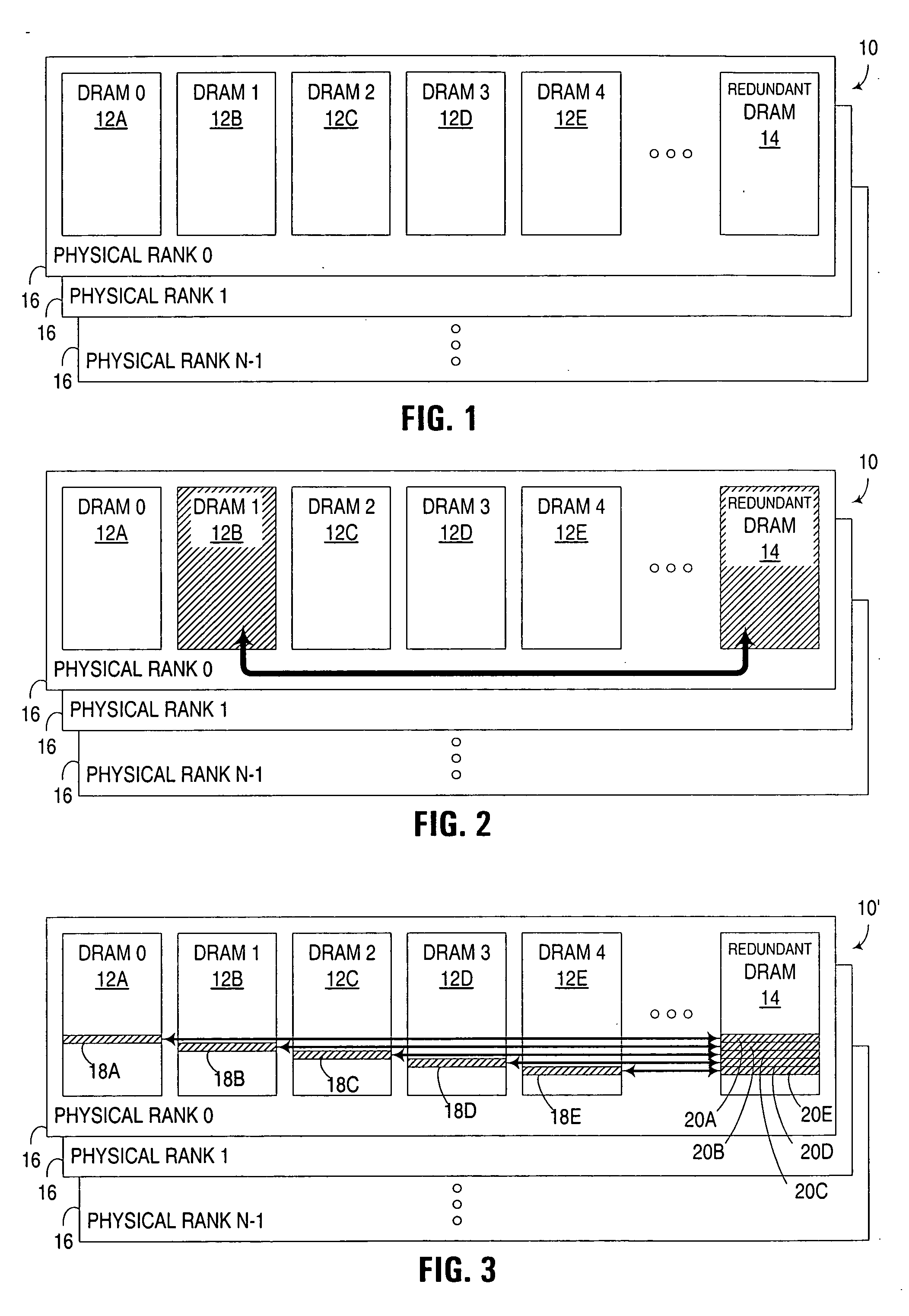
Monitoring of solid state memory devices in active memory system utilizing redundant devices
ActiveUS20060129899A1Facilitate active monitoringError detection/correctionStatic storageMemory addressActive monitoring
Redundant capacity in a memory system is utilized to facilitate active monitoring of solid state memory devices in the memory system. All or part of the data stored in an active solid state memory device, and used in an active data processing system, may be copied to at least one redundant memory device, e.g., by transitioning a memory address range that was allocated to the active memory device to the redundant memory device. By doing so, memory access requests for the memory address range, which would normally be directed to the active memory device, may instead be directed to the redundant memory device, thus enabling the active memory device to be tested (e.g., via writing and reading test data patterns to the active memory device) without interrupting system access to that memory address range.
Owner:IBM CORP
Measuring Effectiveness of Advertisements and Linking Certain Consumer Activities Including Purchases to Other Activities of the Consumer
InactiveUS20120239458A9Improve efficiencyEfficiently identify an individualMarket predictionsDatabase indexUnique identifier
A method for linking online computer activity with non-online consumer activity by creating a unique identifier for each consumer; storing online and non-online consumer activity in a database indexed by the unique identifier; and modifying online or non-online consumer offerings based on processing the stored online and non-online consumer activity.
Owner:EYELOCK
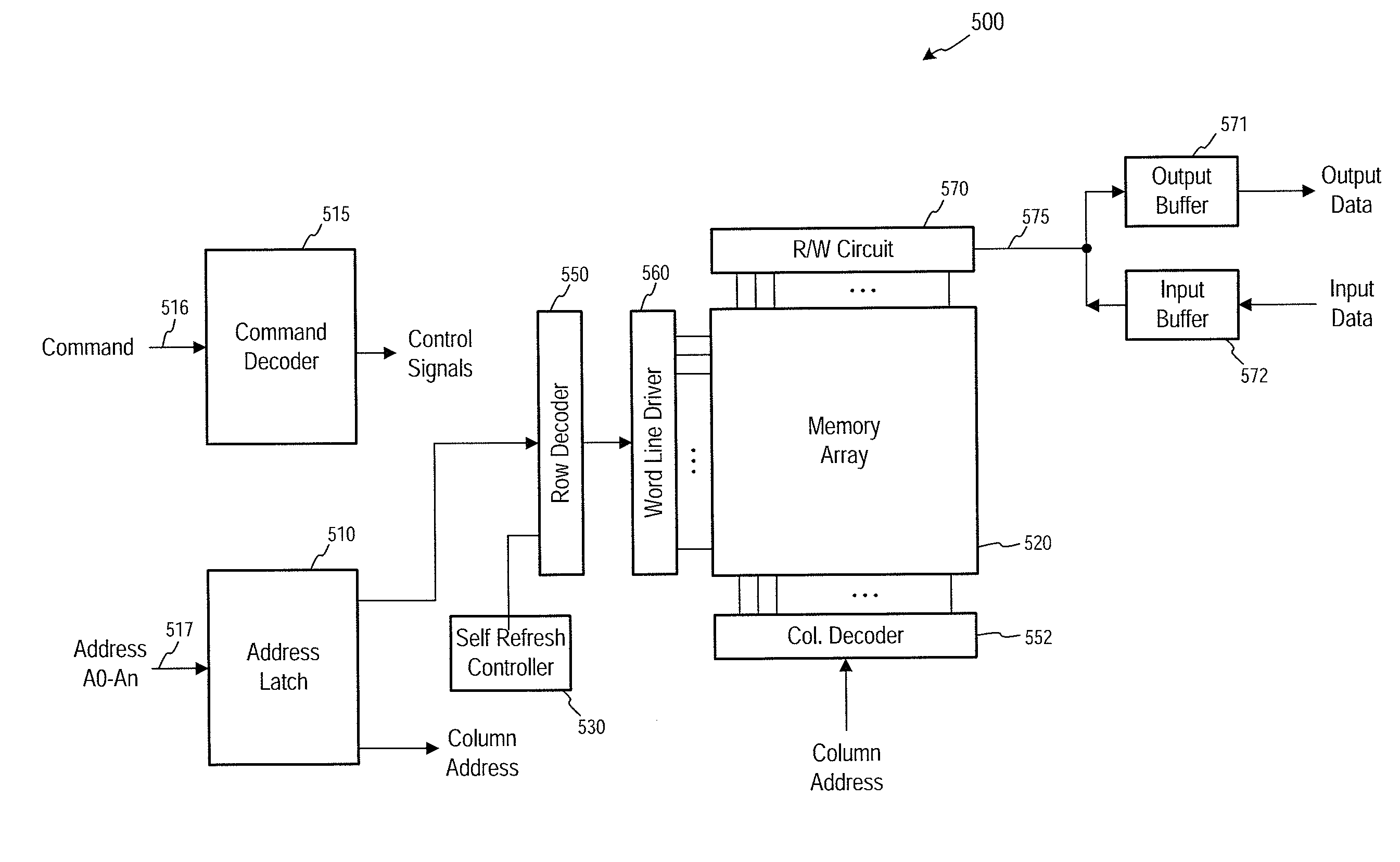
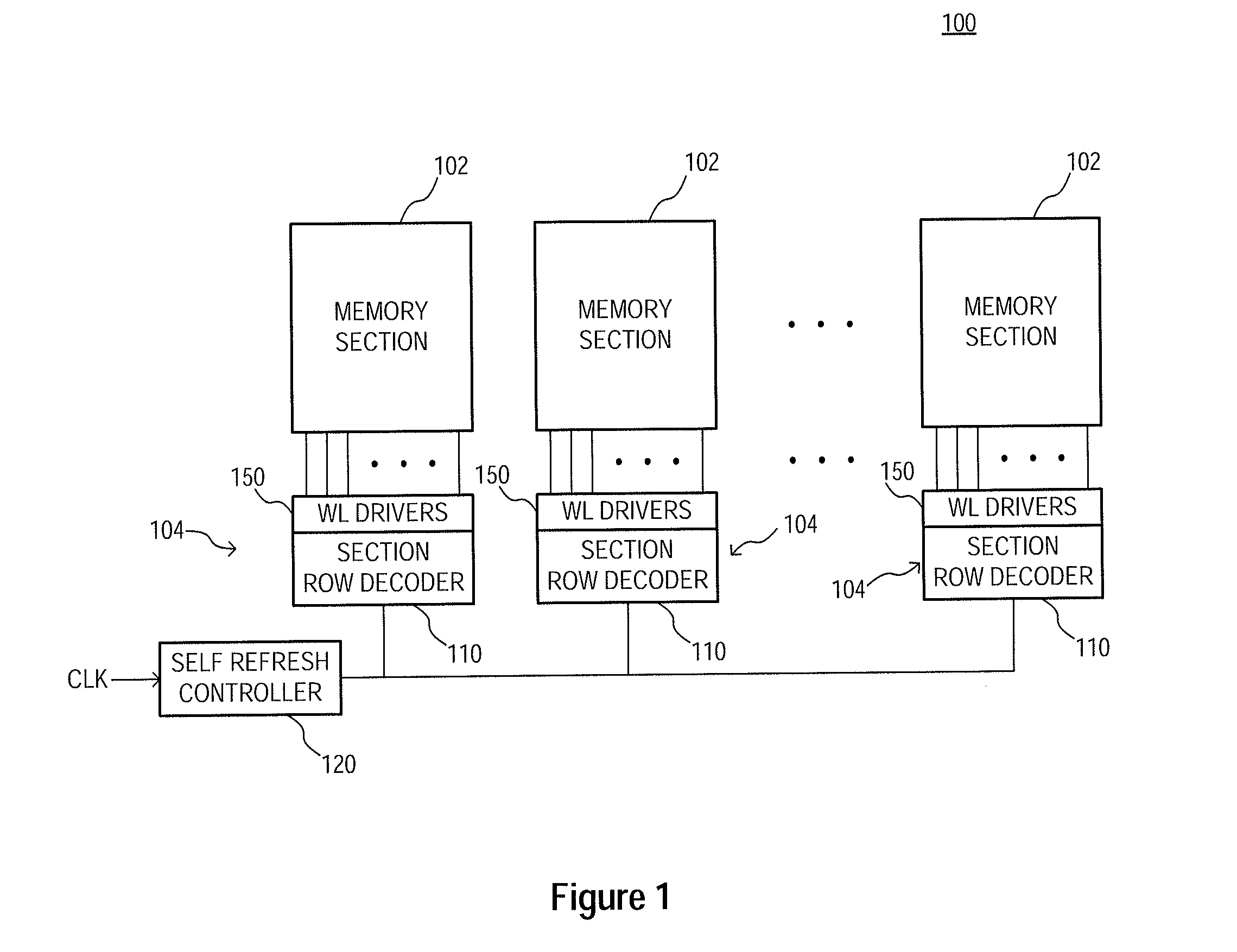
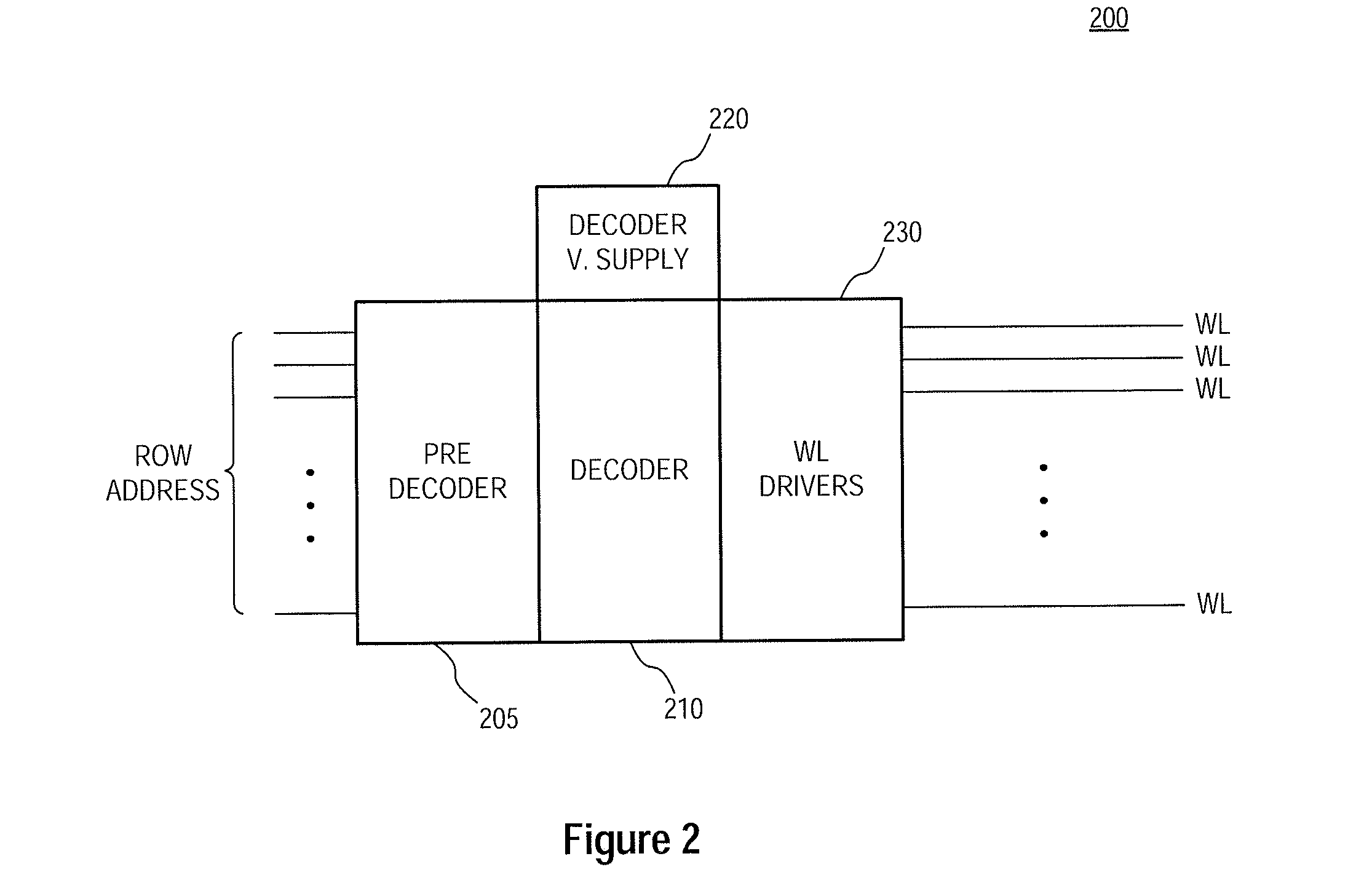
Memory refresh methods, memory section control circuits, and apparatuses
Apparatuses, memory section control circuits, and methods of refreshing memory are disclosed. An example apparatus includes a plurality of memory sections and a plurality of memory section control circuits. Each memory section control circuit is coupled to a respective one of the plurality of memory sections and includes a plurality of access line drivers, each of which includes a plurality of transistors having common coupled gates. During an operation of the apparatus a first voltage is provided to the commonly coupled gates of the transistors of at least some of the access line drivers of the memory section control circuit coupled to an active memory section and a second voltage is provided to the commonly coupled gates of the transistors of the access line drivers of the memory section control circuit coupled to an inactive memory section control circuit, wherein the first voltage is greater than the second voltage.
Owner:MICRON TECH INC
Methods, Architecture, and Apparatus for Implementing Machine Intelligence and Hierarchical Memory Systems
ActiveUS20080201286A1Accurate identificationMathematical modelsDigital computer detailsPattern sequenceAlgorithm
Sophisticated memory systems and intelligent machines may be constructed by creating an active memory system with a hierarchical architecture. Specifically, a system may comprise a plurality of individual cortical processing units arranged into a hierarchical structure. Each individual cortical processing unit receives a sequence of patterns as input. Each cortical processing unit processes the received input sequence of patterns using a memory containing previously encountered sequences with structure and outputs another pattern. As several input sequences are processed by a cortical processing unit, it will therefore generate a sequence of patterns on its output. The sequence of patterns on its output may be passed as an input to one or more cortical processing units in next higher layer of the hierarchy. A lowest layer of cortical processing units may receive sensory input from the outside world. The sensory input also comprises a sequence of patterns.
Owner:NUMENTA INC
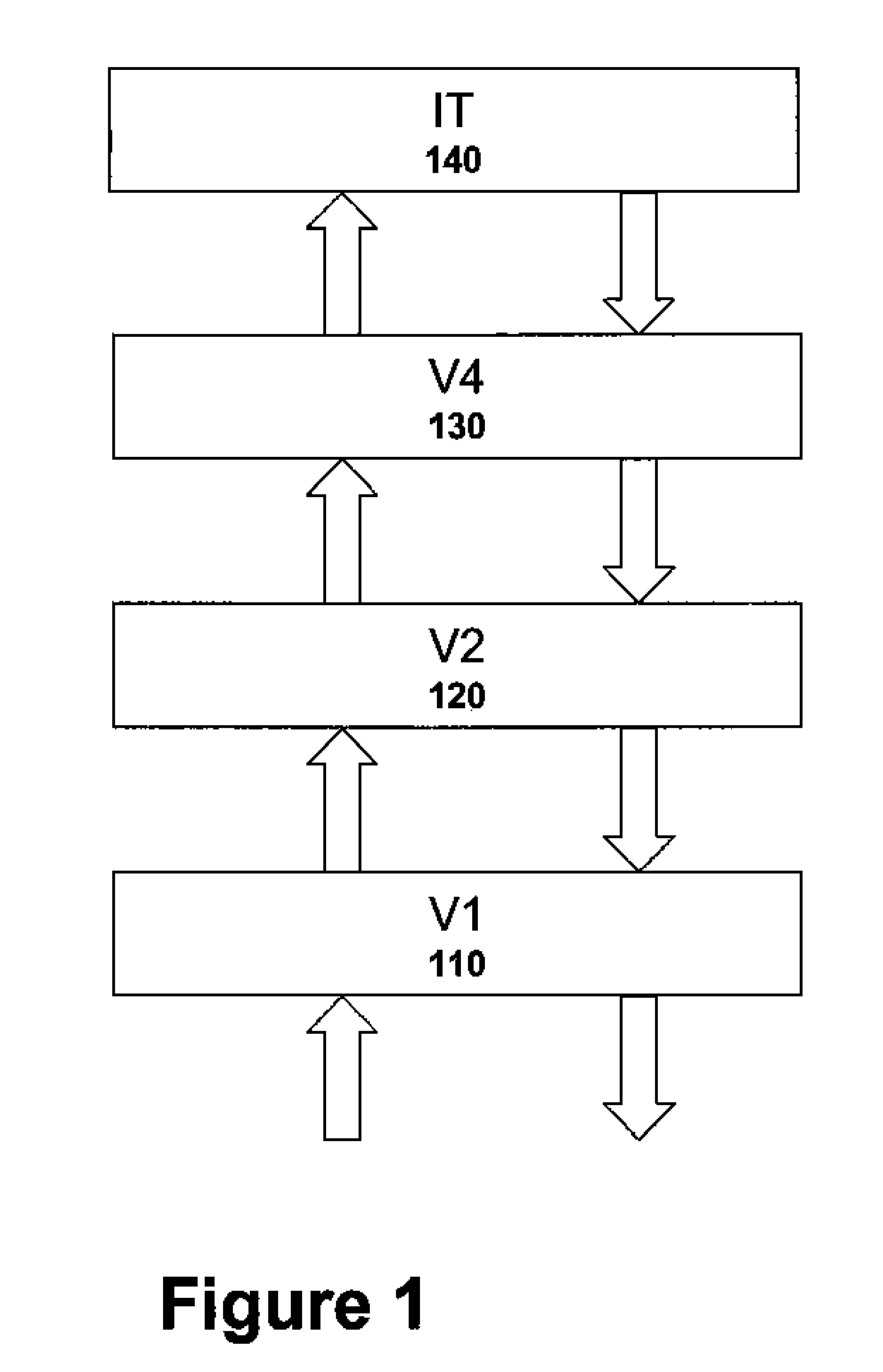
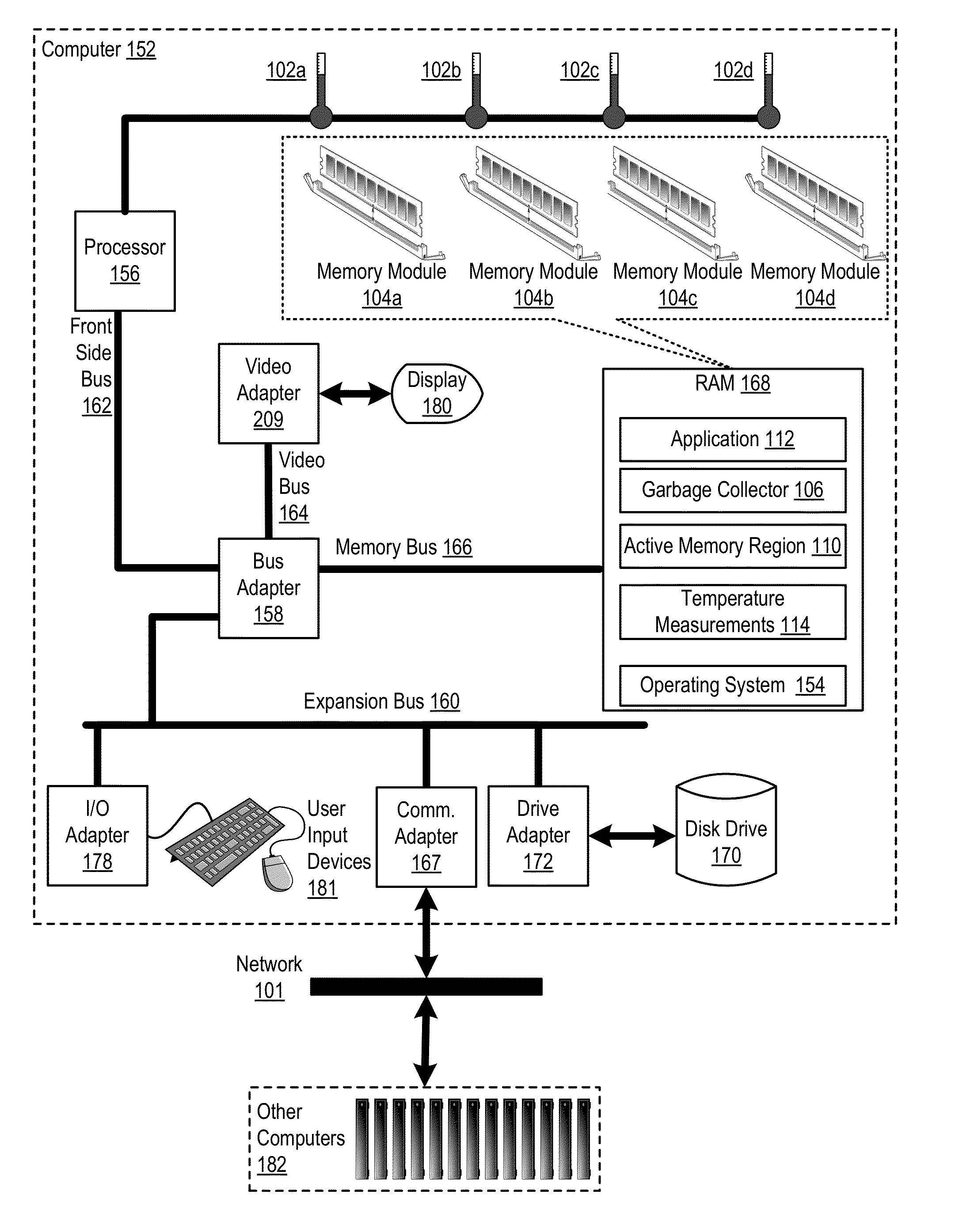
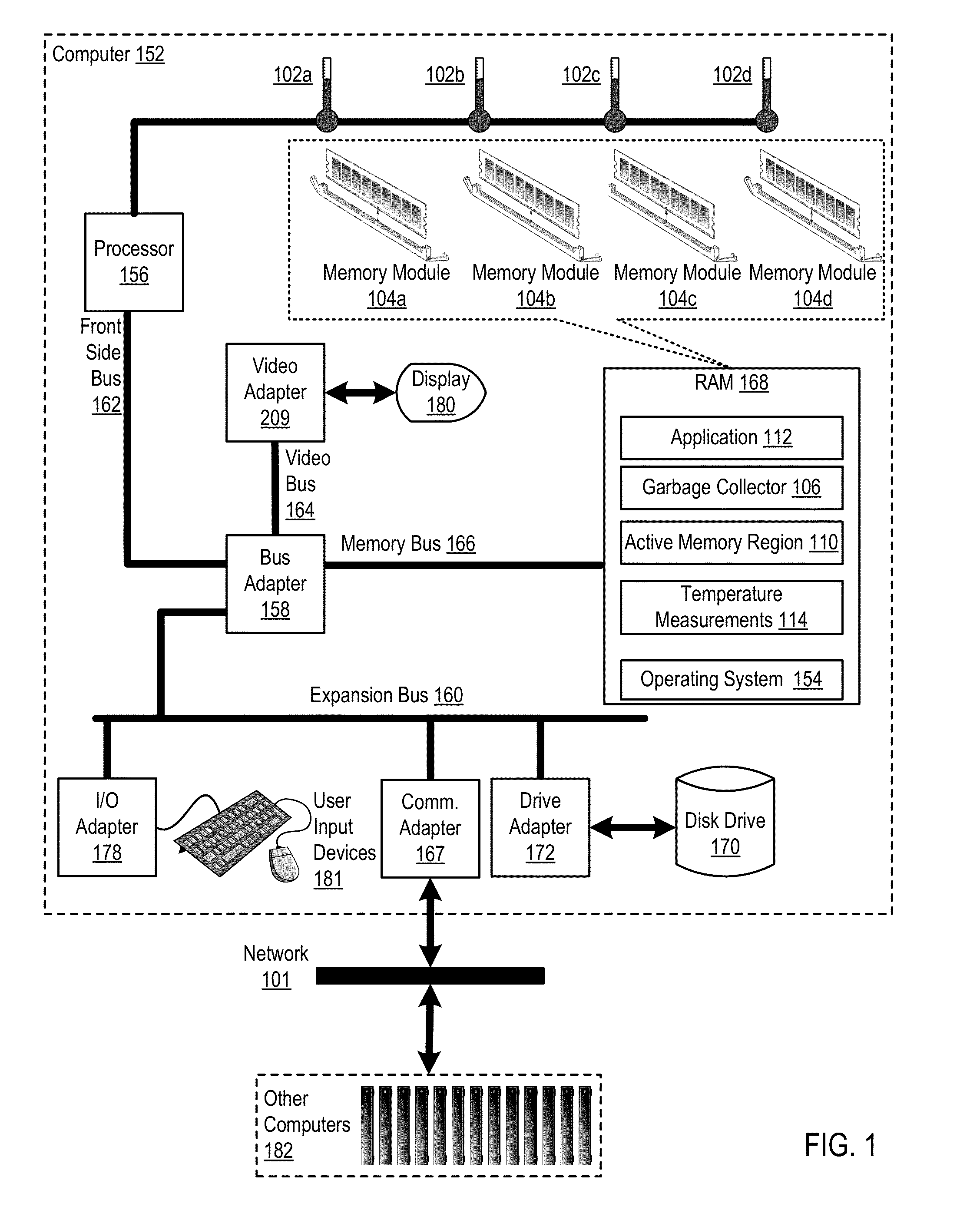
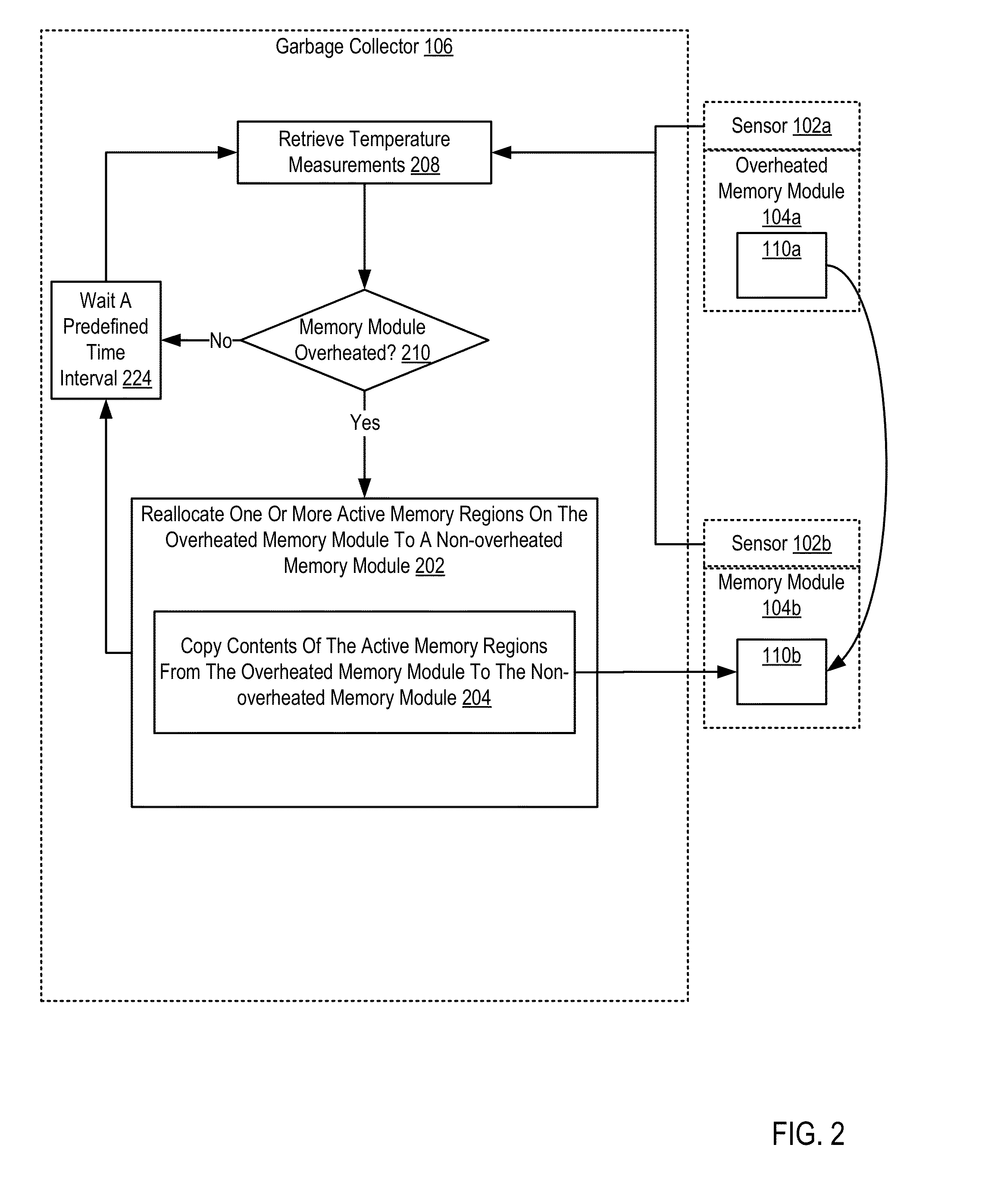
Administering Thermal Distribution Among Memory Modules Of A Computing System
InactiveUS20130067136A1Energy efficient ICTMemory adressing/allocation/relocationWaste collectionParallel computing
A computing system includes a number of memory modules and temperature sensors. Each temperature sensor measures a temperature of a memory module. In such a computing system a garbage collector during garbage collection, determines whether a temperature measurement of a temperature sensor indicates that a memory module is overheated and, if a temperature measurement of a temperature sensor indicates a memory module is overheated, the garbage collector reallocates one or more active memory regions on the overheated memory module to a non-overheated memory module. Reallocating the active memory regions includes copying contents of the active memory regions from the overheated memory module to the non-overheated memory module.
Owner:IBM CORP
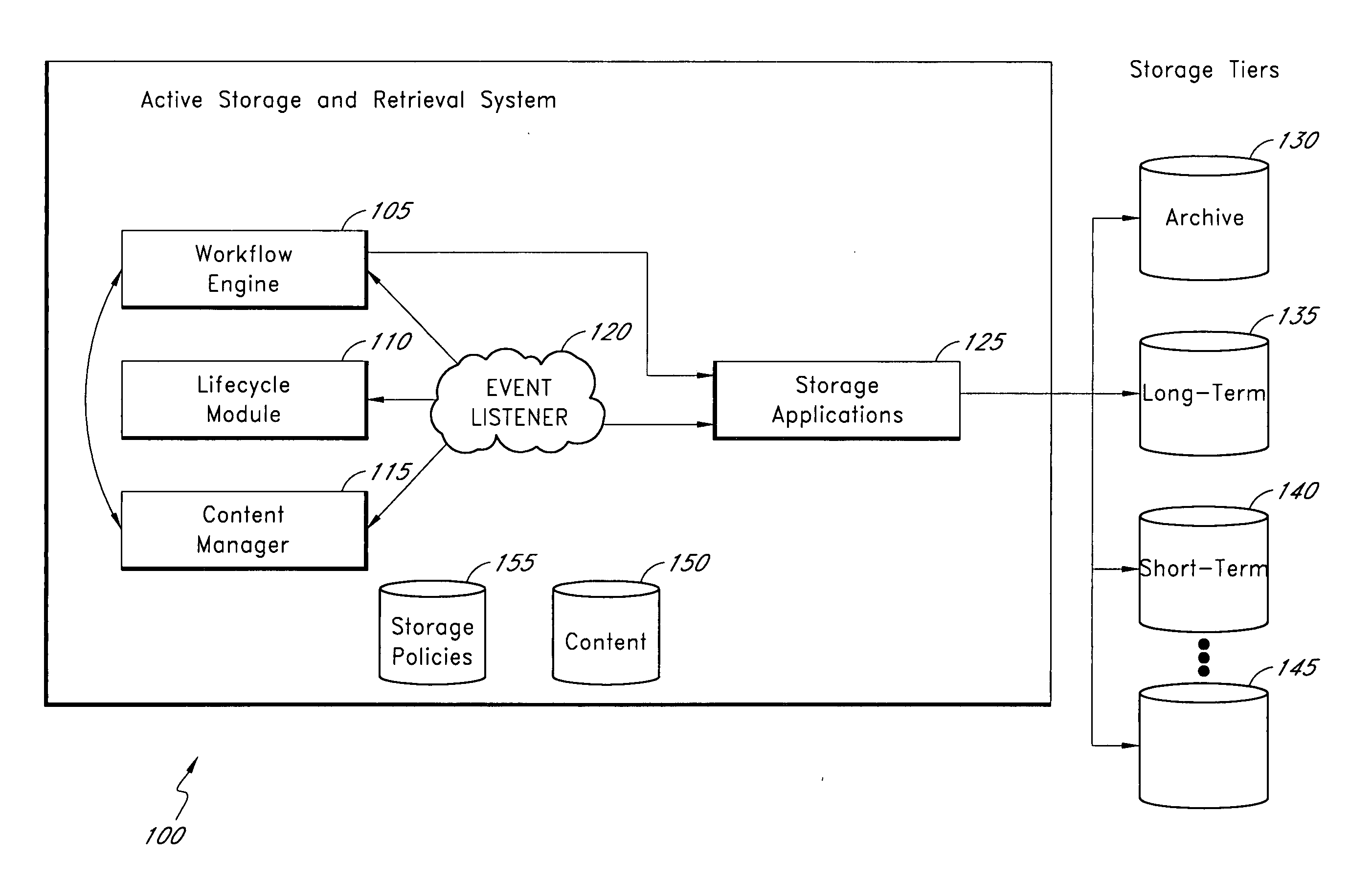
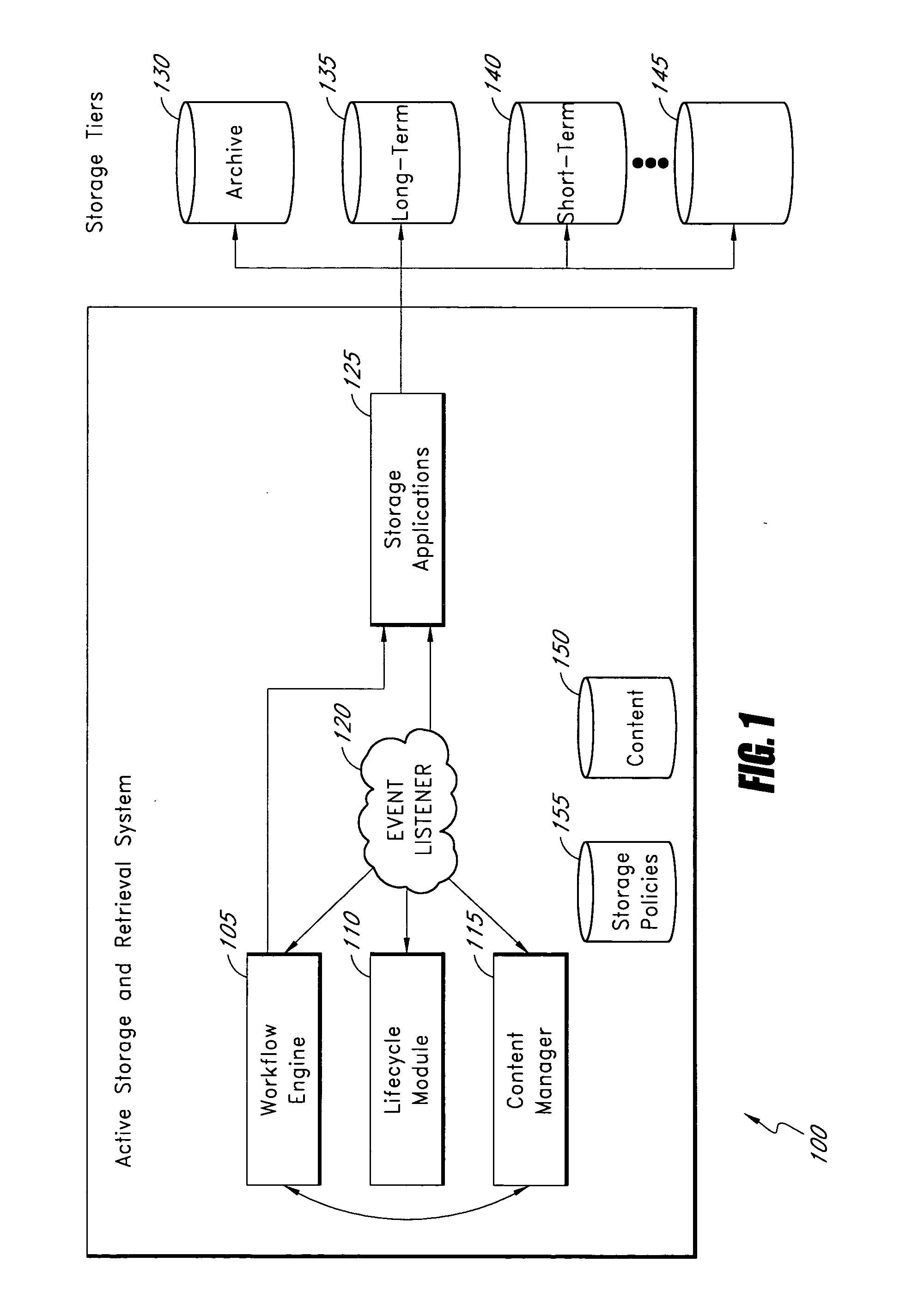
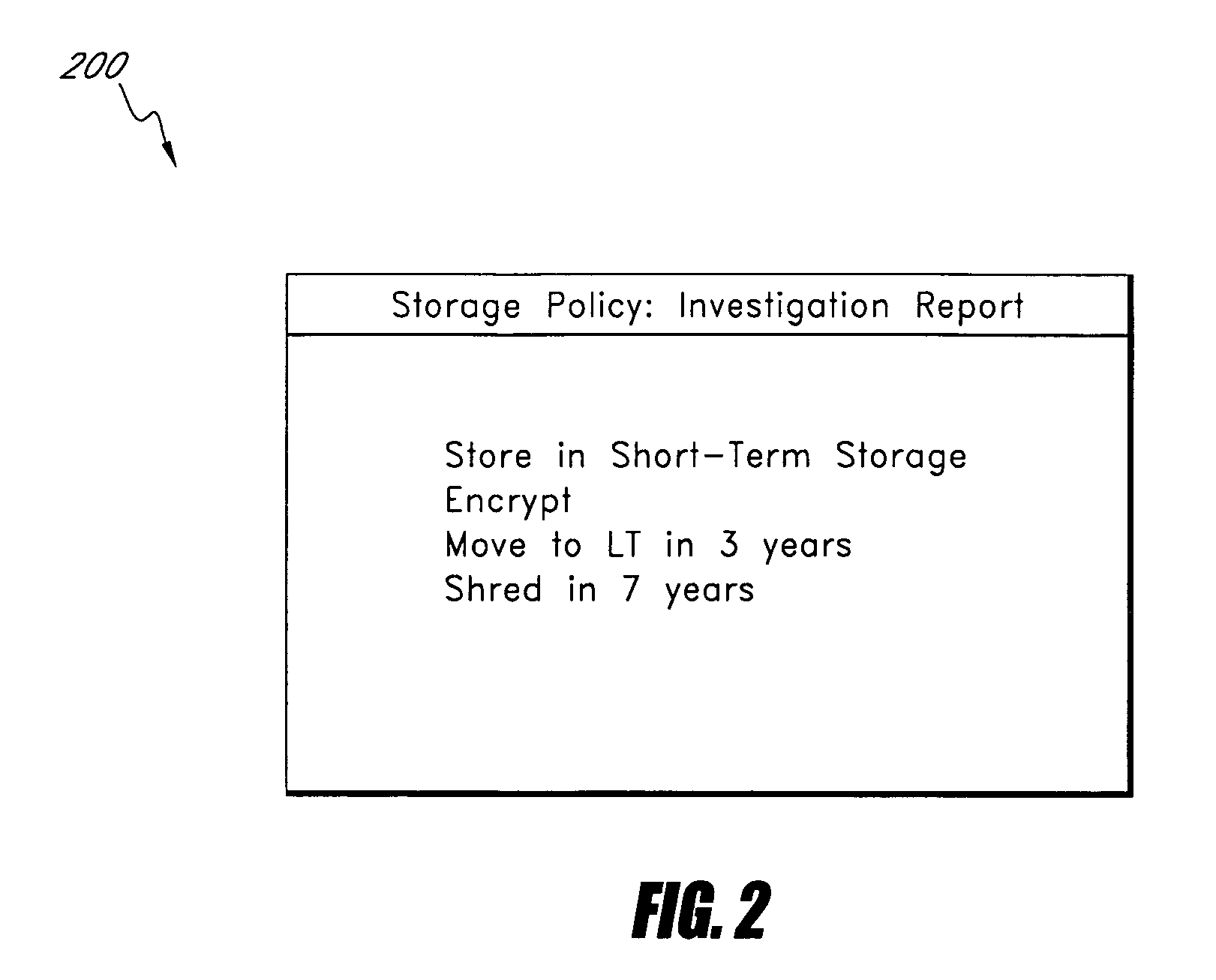
Active storage and retrieval systems and methods
InactiveUS20070271306A1Accurately reflectDigital data information retrievalDigital data processing detailsStorage managementActive storage
A data storage management system comprises a workflow engine, a lifecycle module, and a storage application. The workflow engine is configured to manage a plurality of defined business processes and to execute at least one process step associated with at least one data item. The lifecycle module is configured to detect a change in lifecycle of the at least one data item. The storage application is configured to perform at least one storage action on the data item as a result of the data item reaching a step in a business process, the data item having a change in lifecycle, the data item having a change in metadata, or an event occurring to the data item. Application layer information about data derived from operation of the system allows the system to make more accurate determinations of business value of data and to determine appropriate storage actions to perform on data.
Owner:LINKEDIN
Efficient method of data transfer between register files and memories
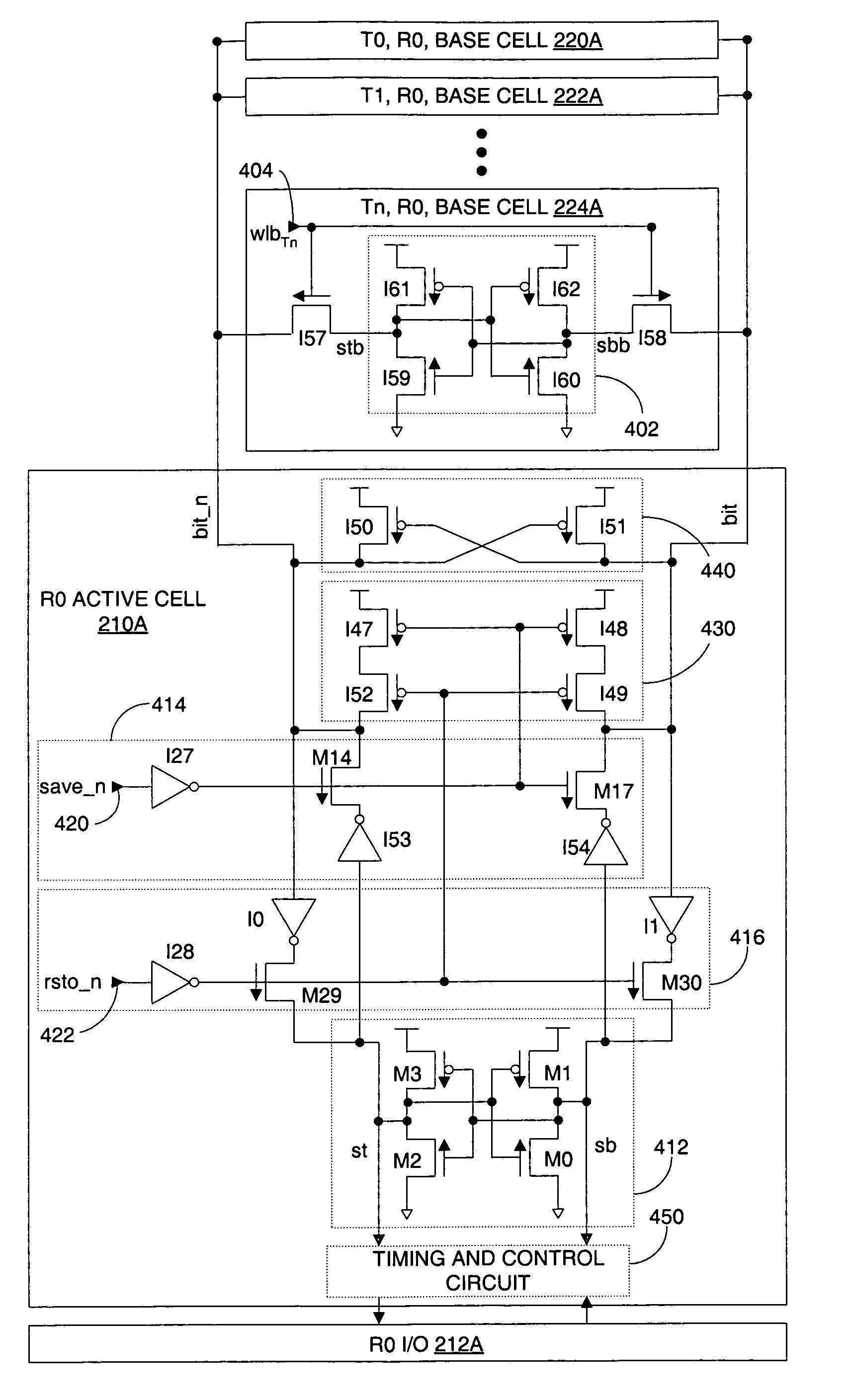
A memory system includes an active storage circuit and at least one base storage circuit. The at least one base storage circuit is coupled to the active storage circuit though at least one pass gate, at least one driver and a bit line. The at least one pass gate and the at least one driver have a device size substantially similar to a device size of each one of the devices in the active storage circuit and the at least one base storage circuit. A method of swapping data between two storage circuits is also described.
Owner:ORACLE INT CORP
Trace based rollback of a speculatively updated cache
This invention includes a circuit for tracking memory operations with trace-based execution. Each trace includes a sequence of operations that includes zero or more of the memory operations. Traces execute atomically and become eligible for commitment after all the operations in the trace have executed. The memory operations being executed form a set of active memory operations that have a predefined program order among them and corresponding ordering constraints. At least some of the active memory operations access the memory in an execution order that is different from the program order. Checkpoint entries are associated with each trace. Each entry refers to a checkpoint location. Memory operation ordering entries correspond to each one of the active memory operations. Rollback requests result in overwriting the checkpoint locations associated with the selected trace as well as the checkpoint locations associated with traces that are younger than the selected trace.
Owner:SUN MICROSYSTEMS INC
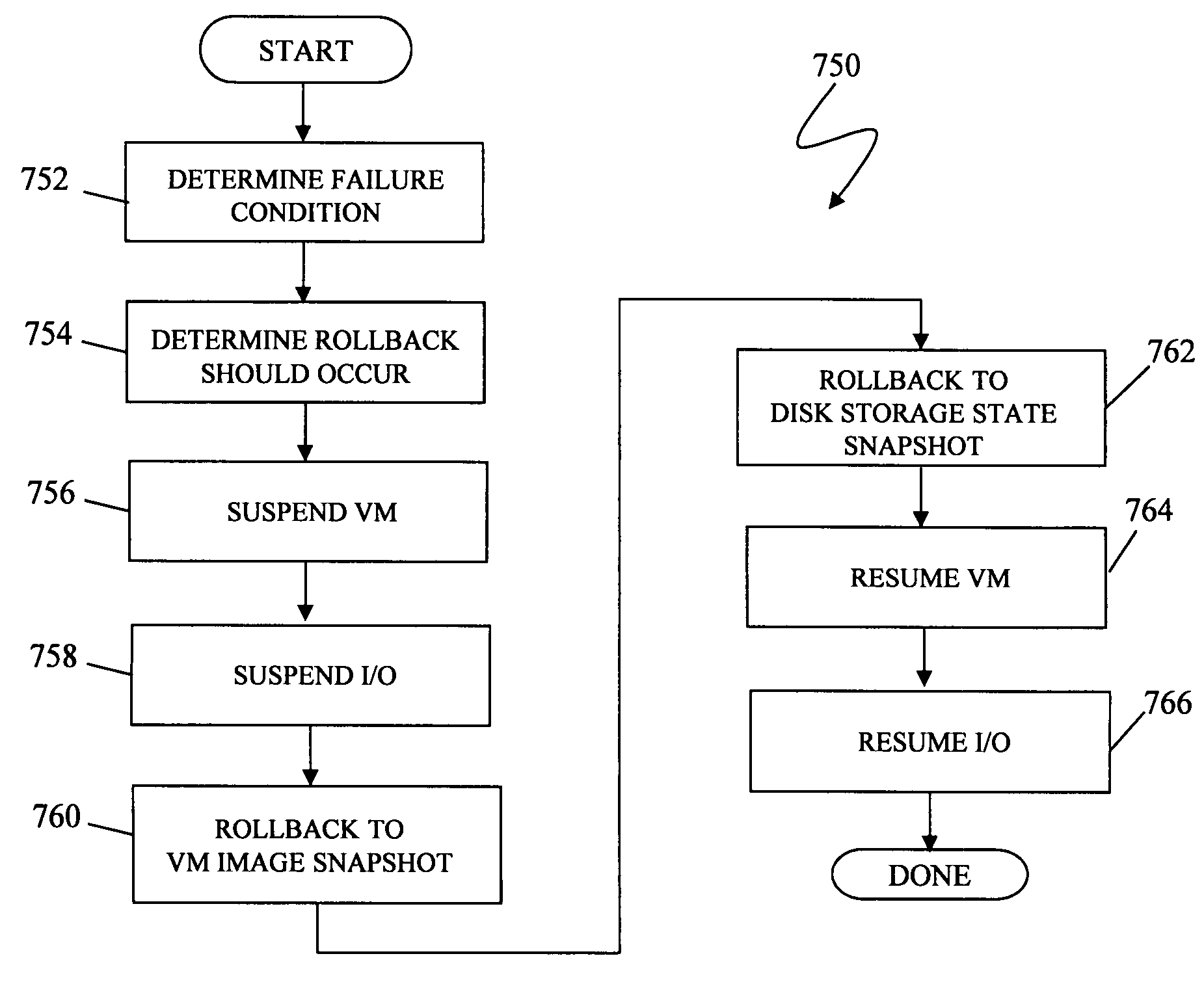
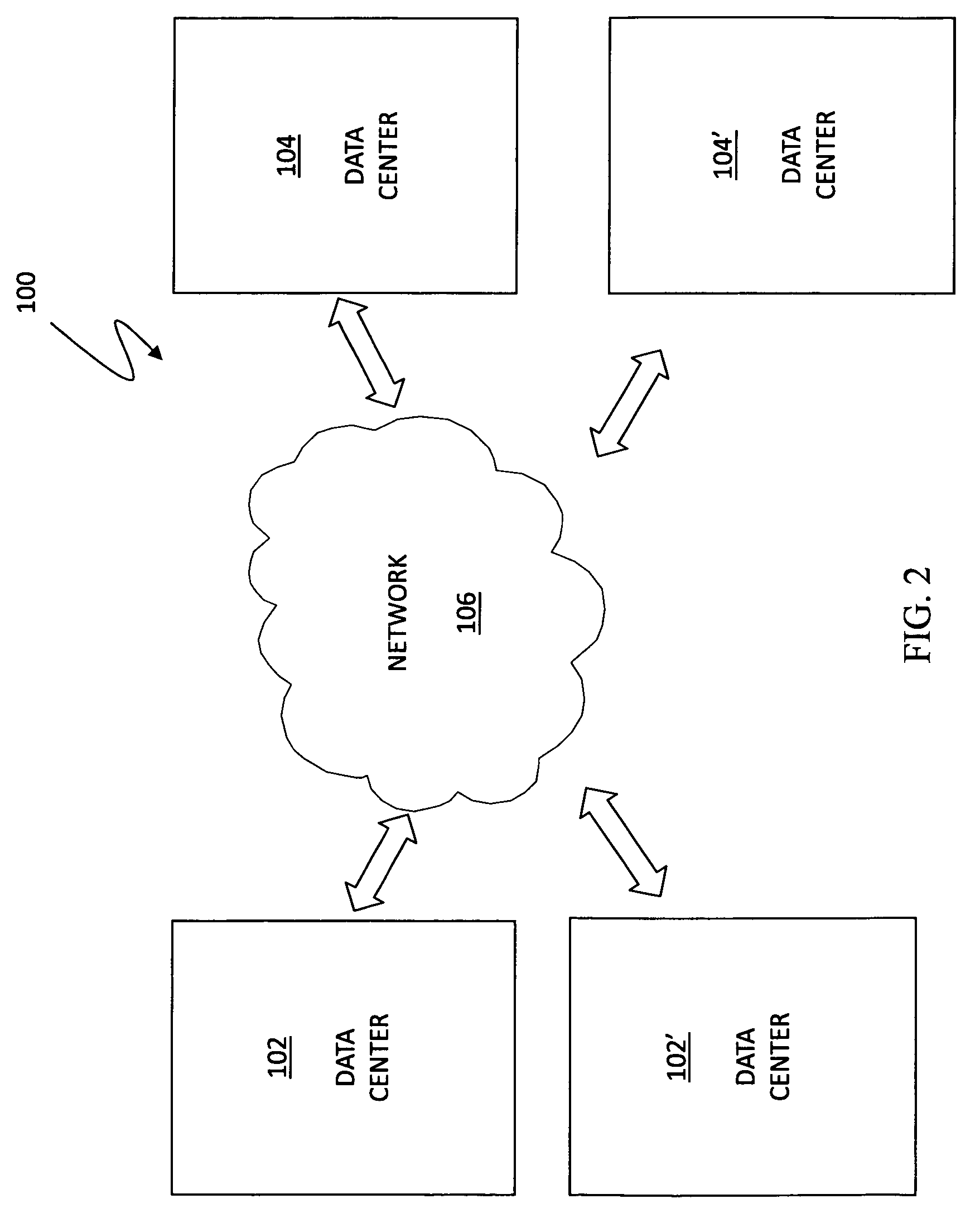
Active/active storage and virtual machine mobility over asynchronous distances
ActiveUS8667490B1Resource allocationSoftware simulation/interpretation/emulationActive storageActive systems
A system for providing mobility of a virtual machine between a first site and a second site of an active / active system is disclosed. For a virtual machine operating on the first site, it may be determined that the second site is a destination site between the first site and the second site. While the virtual machine is operating on the first site, storage data may be transferred from the first site to the second site. Operation of the virtual machine may be suspended on the first site. Operation of the virtual machine may be resumed on the second site. In the event of link failure between the first site and the second site, operation of the virtual machine may be maintained on the second site.
Owner:EMC IP HLDG CO LLC
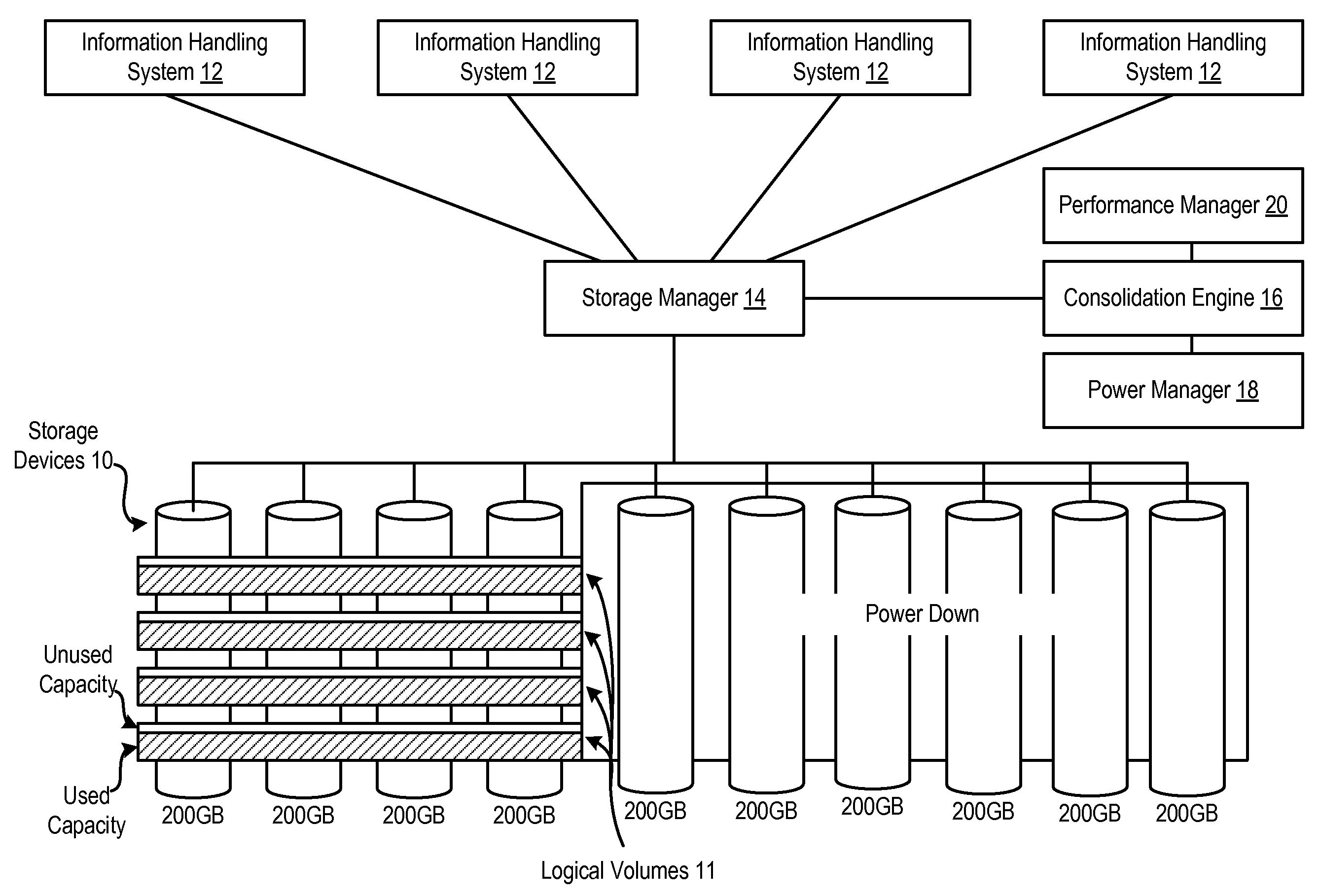
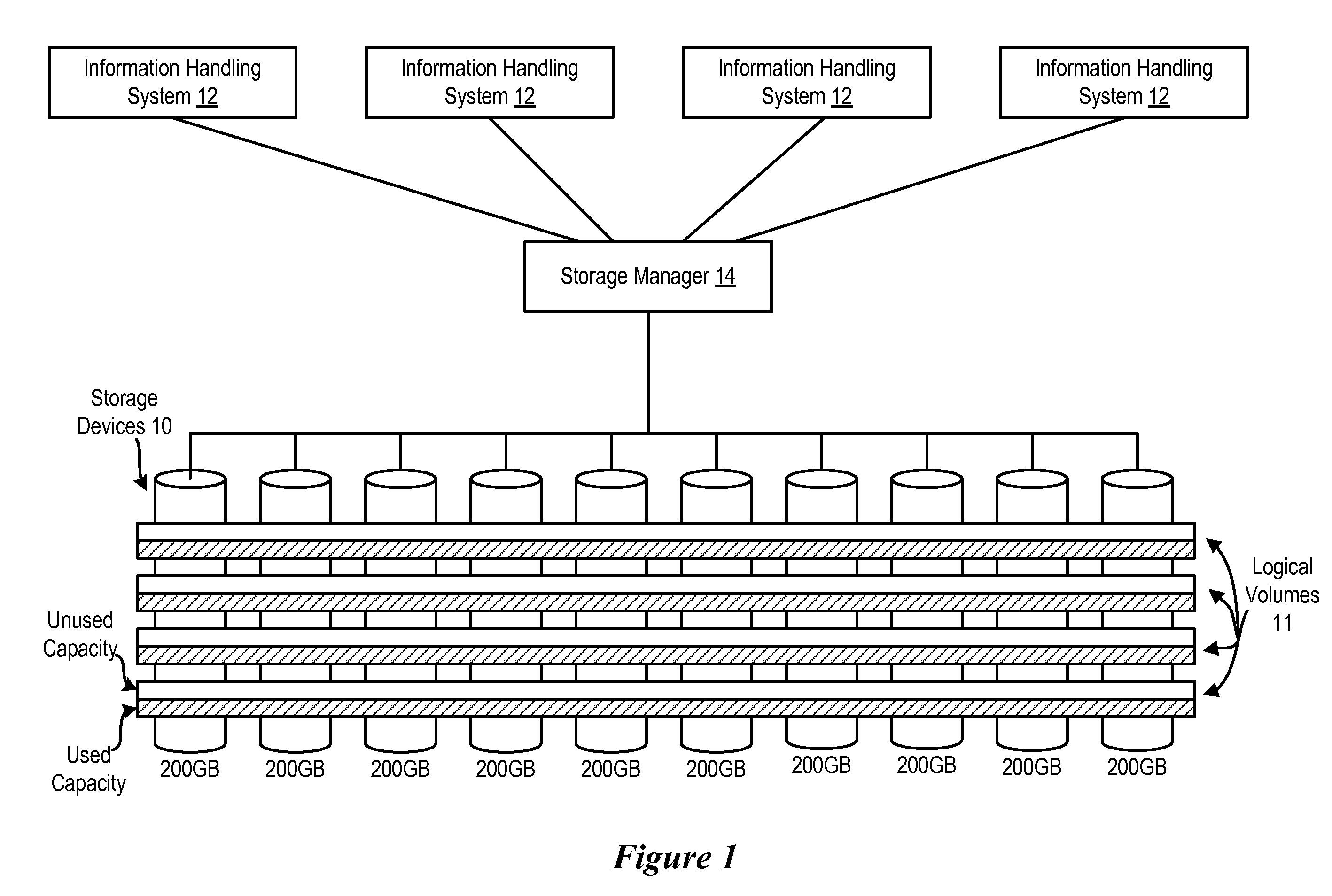
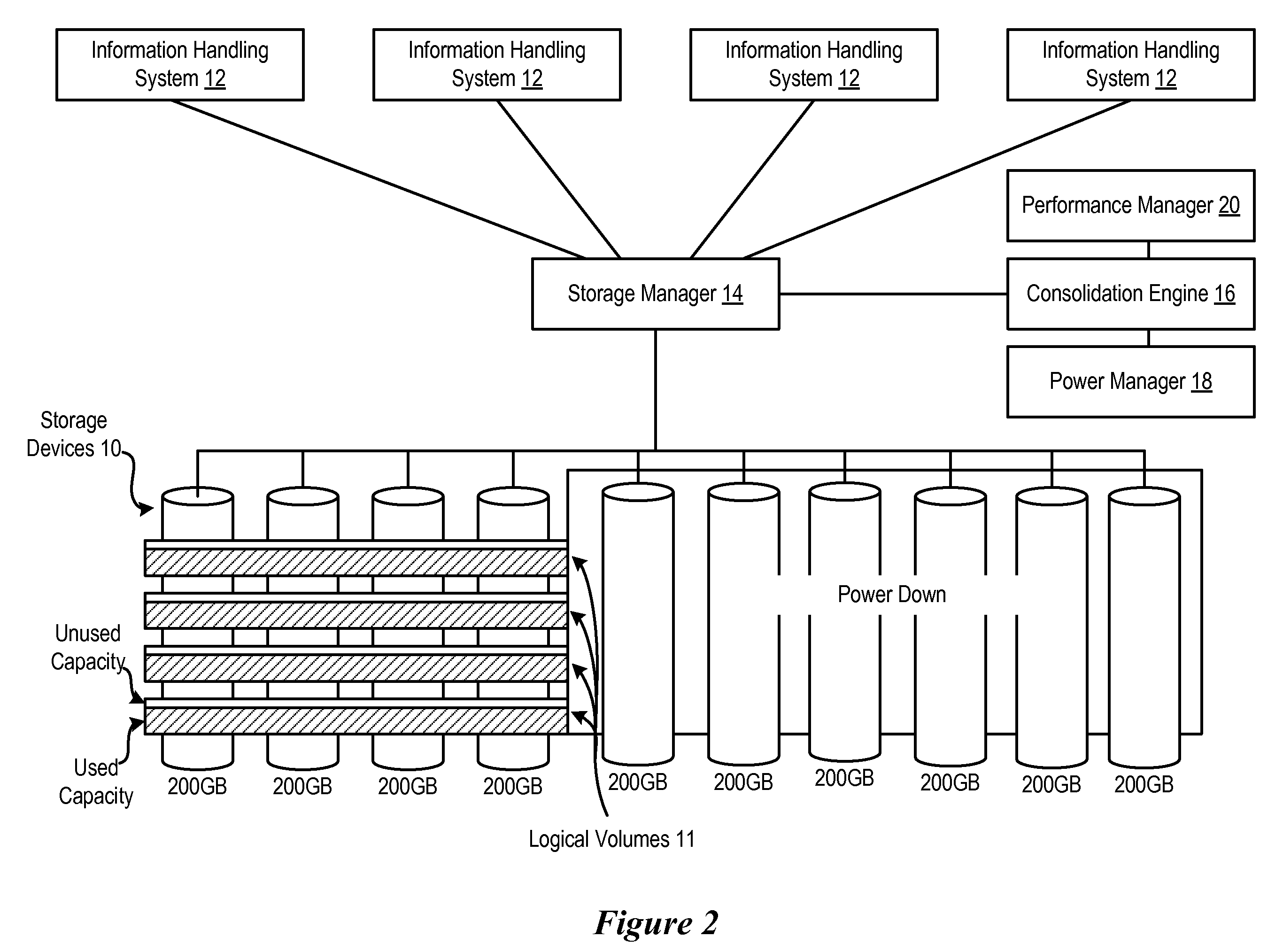
System and Method for Managing Storage Device Capacity Usage
ActiveUS20090049320A1Reduce in quantityReduce power consumptionEnergy efficient ICTPower supply for data processingActive storageHandling system
Information handling system storage devices are managed to reduce power consumption by consolidating stored information to less than all of plural storage devices and powering down the storage devices that are no longer storing information. If a predetermined buffer of unused capacity is detected at the storage devices, then a powered down storage device is powered up to store additional information. The storage devices are consolidated to maintain desired performance parameters, such as by monitoring I / O performance for information stored on active storage devices.
Owner:DELL PROD LP
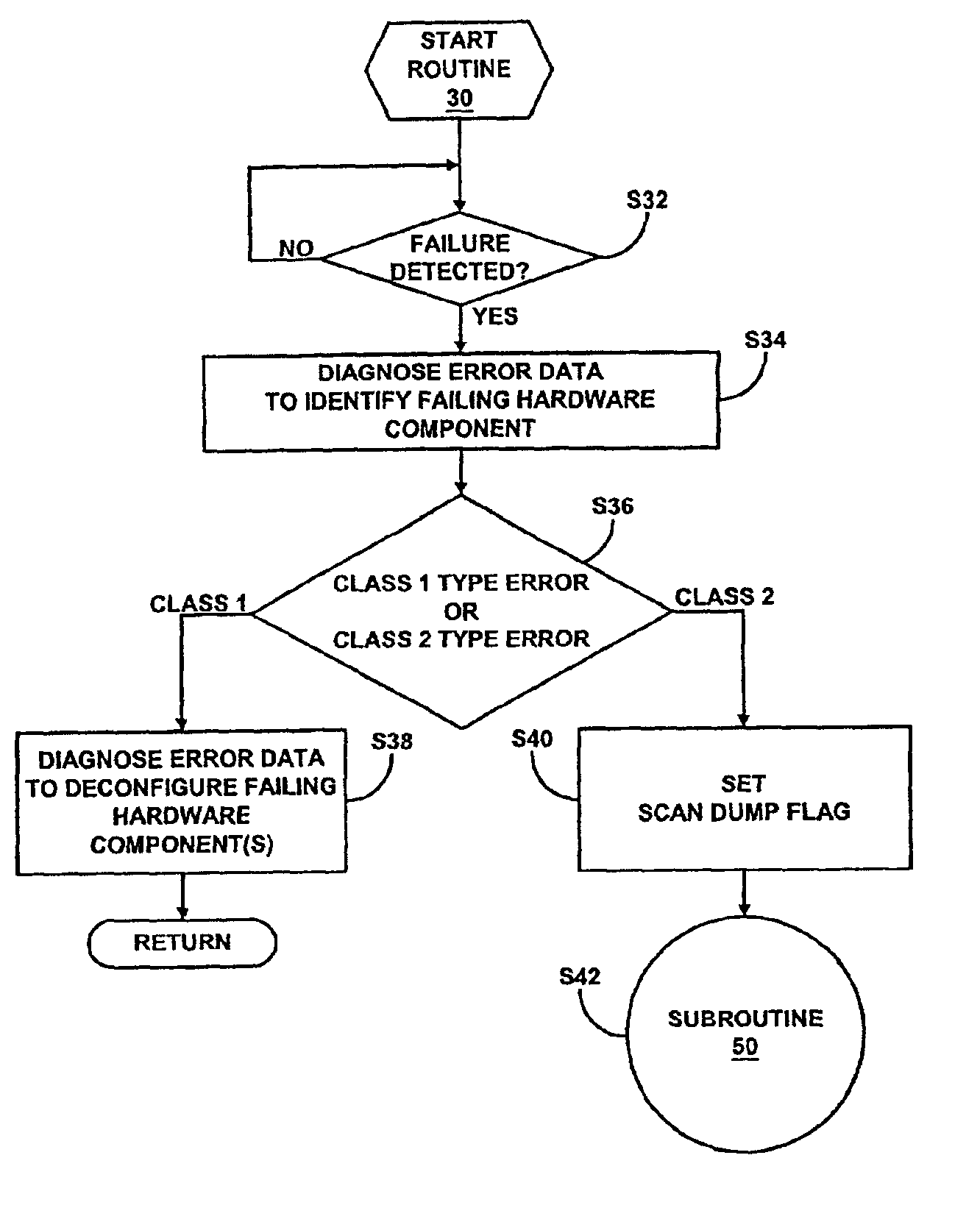
Conditional hardware scan dump data capture
A computer for implementing a method for conditionally capturing hardware scan dump data to minimize the reboot recovery time employs a service processor operable to detect a failure of another hardware component of the computer. Upon detection, the service processor will conditionally capture hardware scan dump data. The first condition for capturing hardware scan dump data is the service processor being activated into an active storing mode of operation labeled “Always”. The second condition for capturing hardware scan dump data is the service processor being activated to a reactive storing mode of operation labeled “As Needed” and the error causing the operational failure being a type of error where hardware scan dump data is needed or desired by a system engineer in correcting the operational failure. By conditionally capturing hardware scan dump data, the amount of data being processed over multiple failures of the computer is minimized.
Owner:IBM CORP
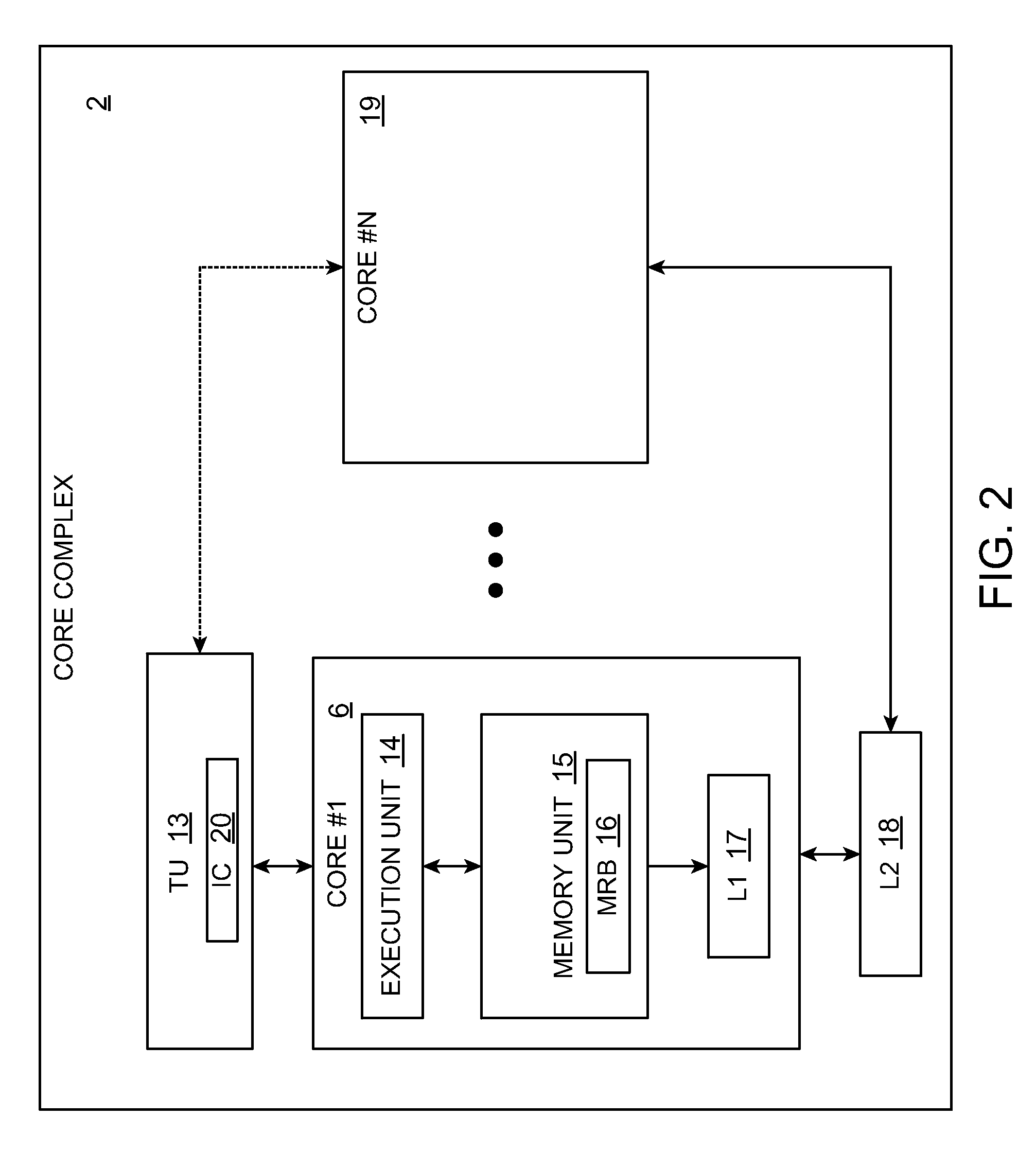
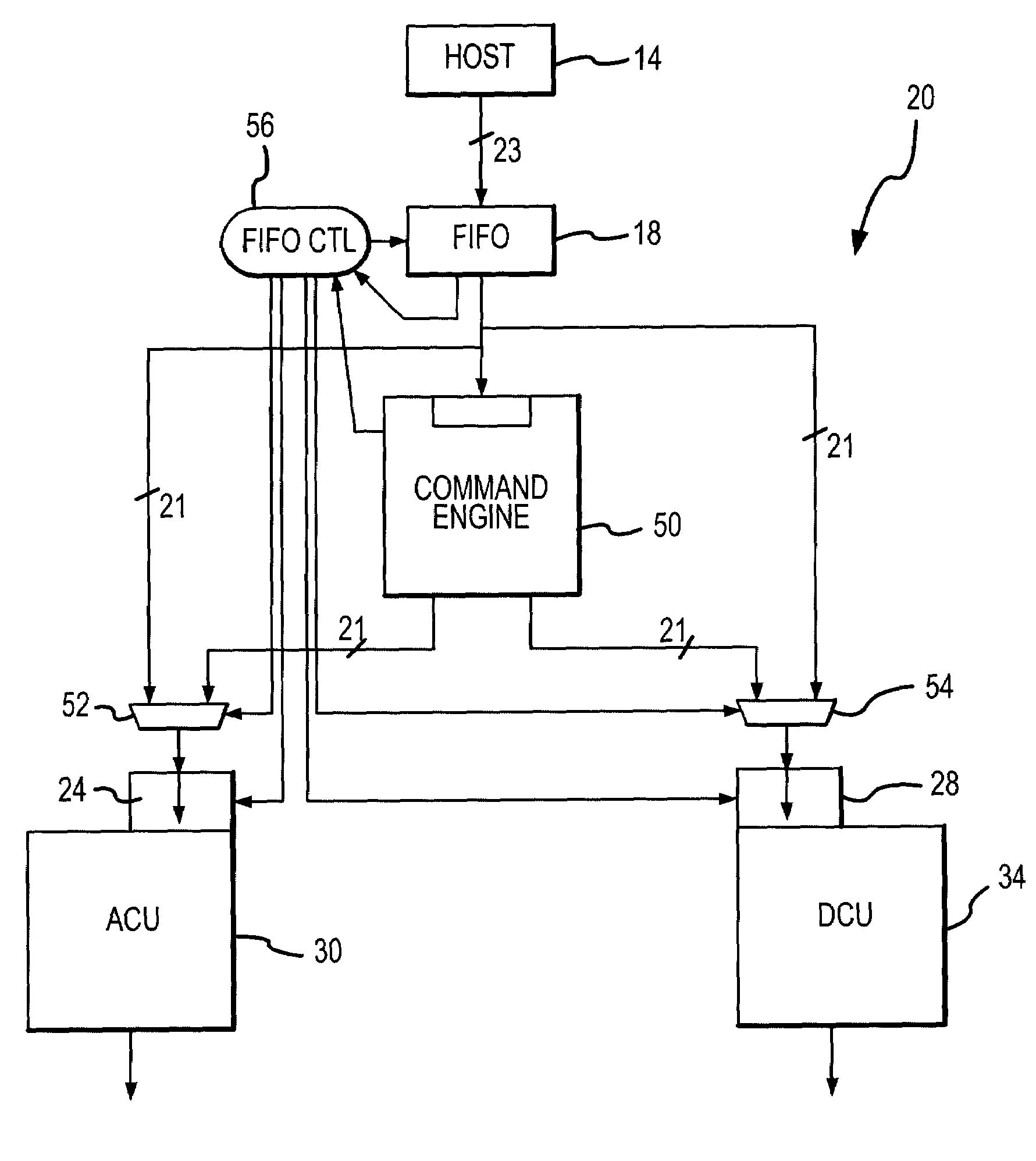
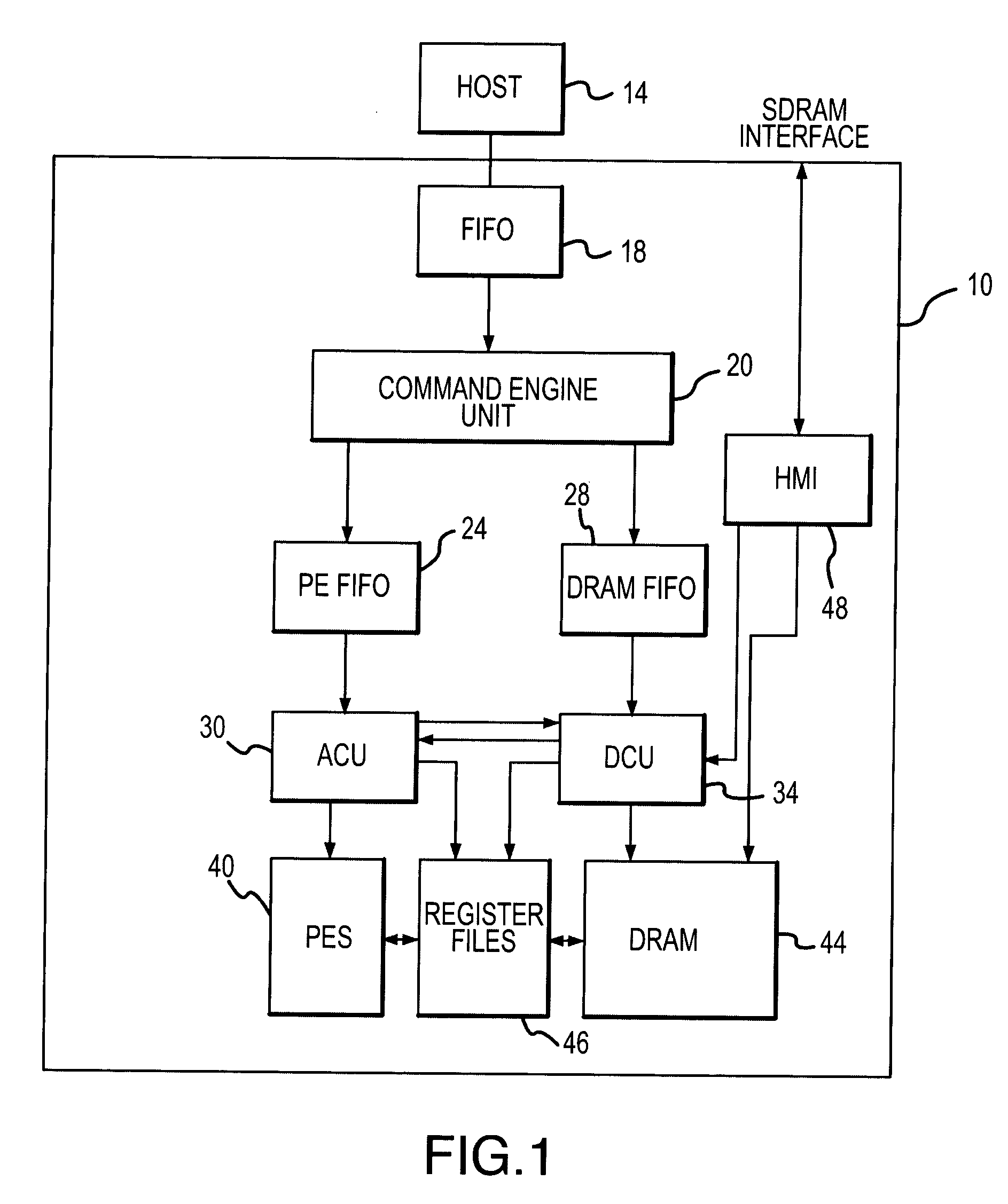
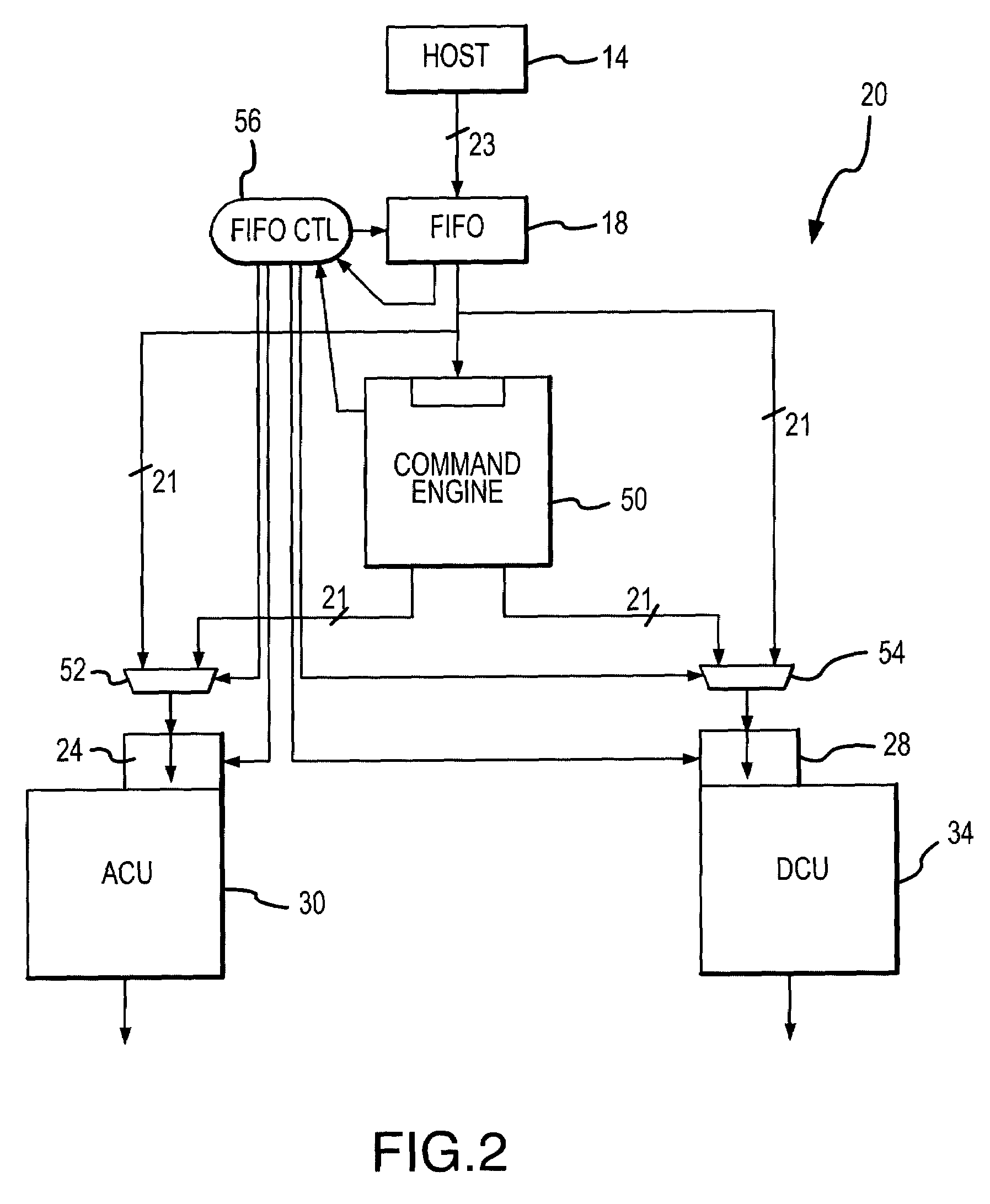
Active memory command engine and method
ActiveUS7181593B2Program controlArchitecture with single central processing unitInstruction memoryMemory address
A command engine for an active memory receives high level tasks from a host and generates corresponding sets of either DCU commands to a DRAM control unit or ACU commands to a processing array control unit. The DCU commands include memory addresses, which are also generated by the command engine, and the ACU command include instruction memory addresses corresponding to an address in an array control unit where processing array instructions are stored.
Owner:MICRON TECH INC
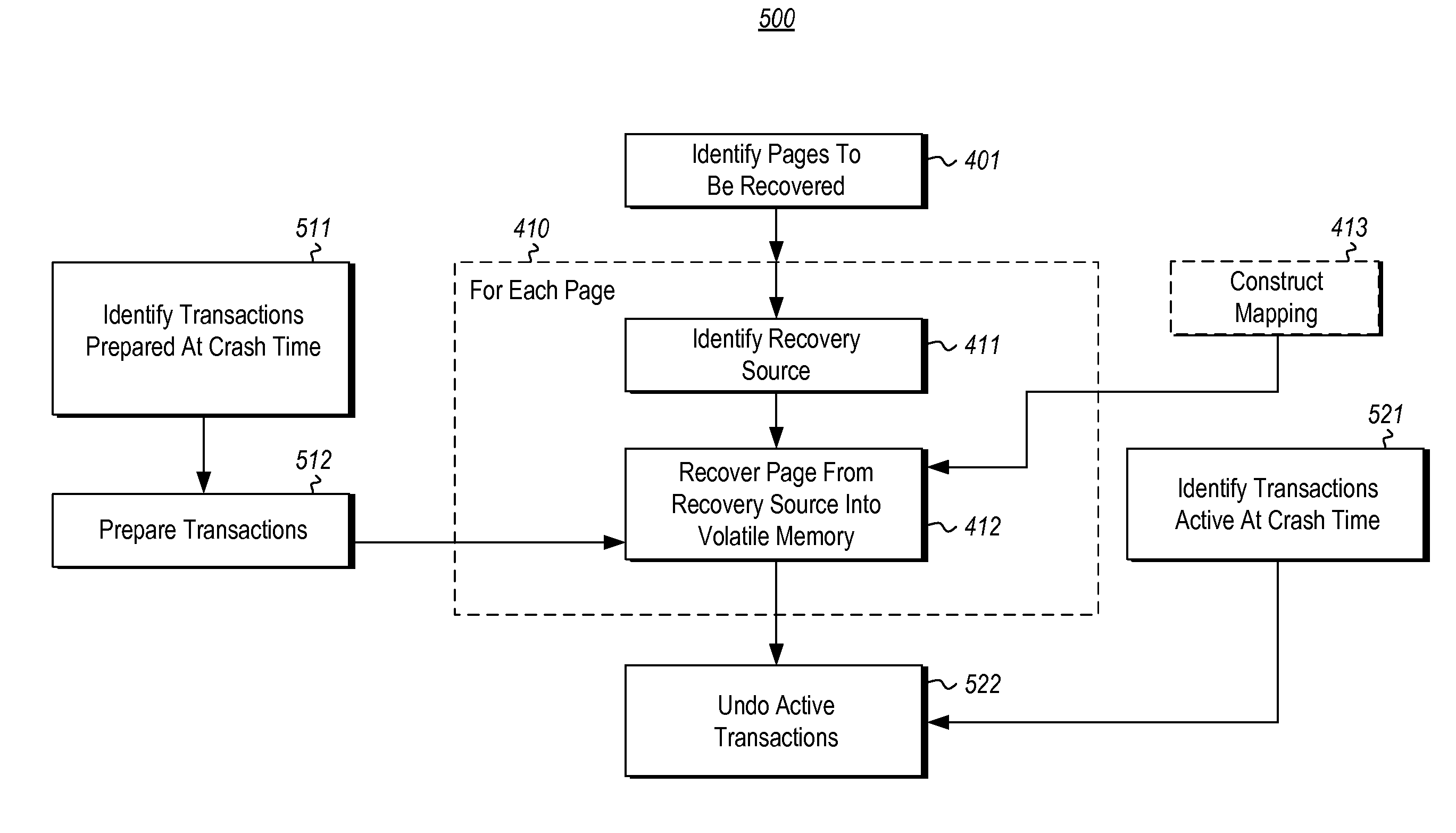
Crash recovery using non-volatile memory
ActiveUS20150121126A1Access speedShorten recovery timeNon-redundant fault processingRedundant operation error correctionActive memoryComputing systems
Crash recovery of a computing system in the context in which the computing system includes a volatile memory which has contents lost due to the crash, an intermediate non-volatile memory that (together with the volatile memory) contributes to the active memory of the computing system, and non-volatile storage. The recovery occurs by identifying pages that were in the volatile memory at the time of the crash. For each of these pages, the recovery determines whether to recover the page into the volatile memory from either the intermediate non-volatile memory or the storage, and then performs the recovery. In embodiments in which access speeds for the intermediate non-volatile memory may be much faster than for the storage, and in which much of the pages to be recovered are recovered from the intermediate non-volatile memory, the recovery time may be reduced.
Owner:MICROSOFT TECH LICENSING LLC
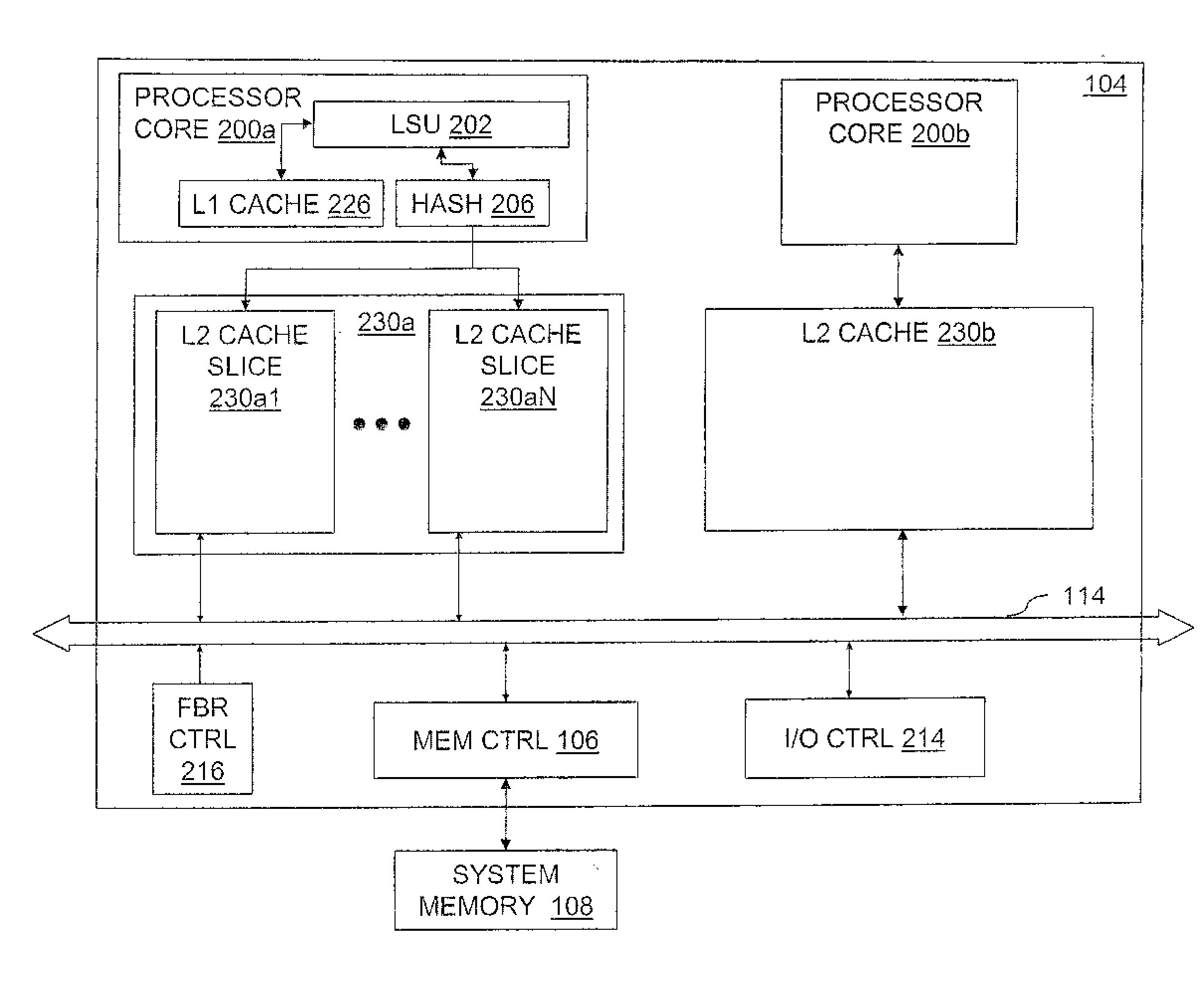
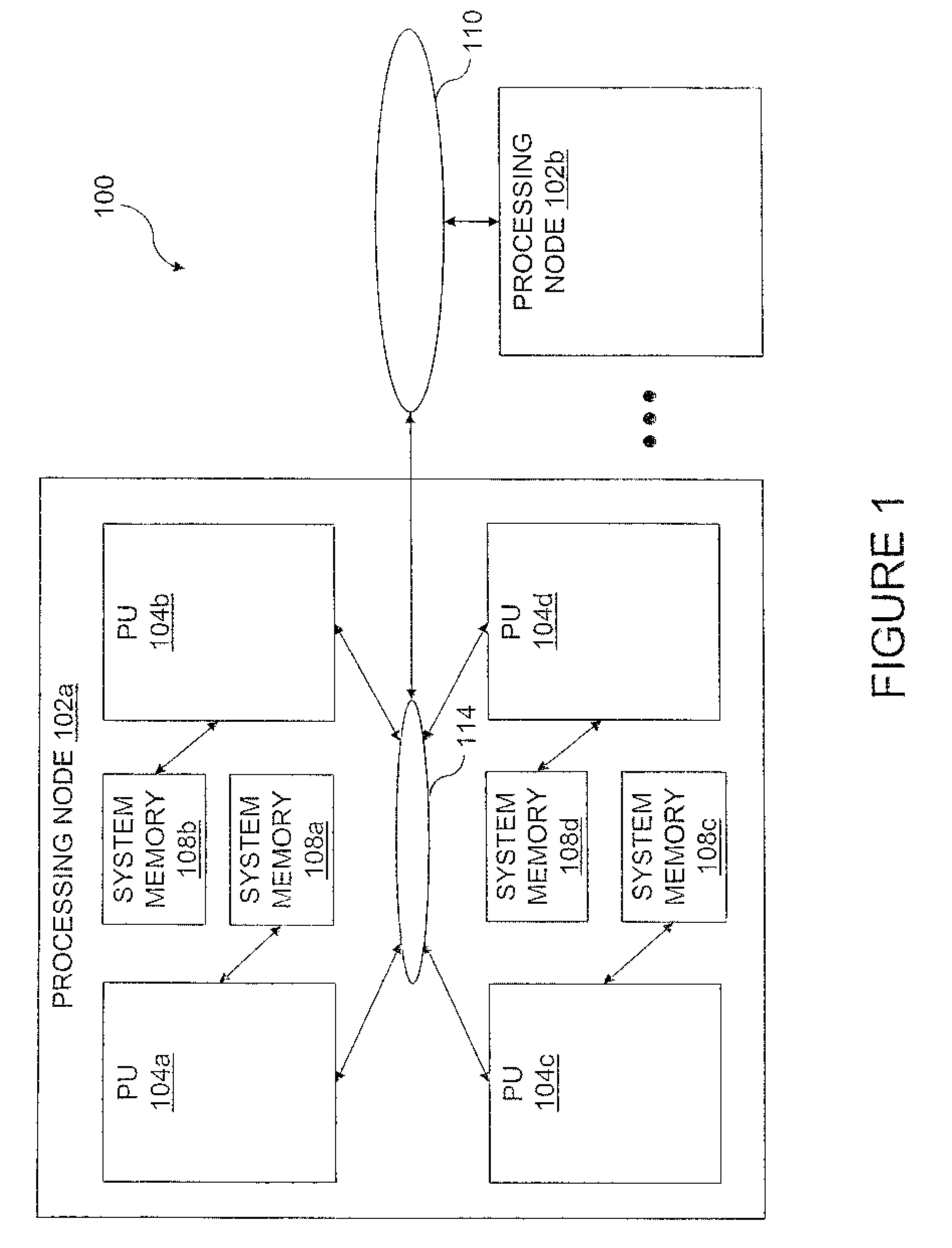
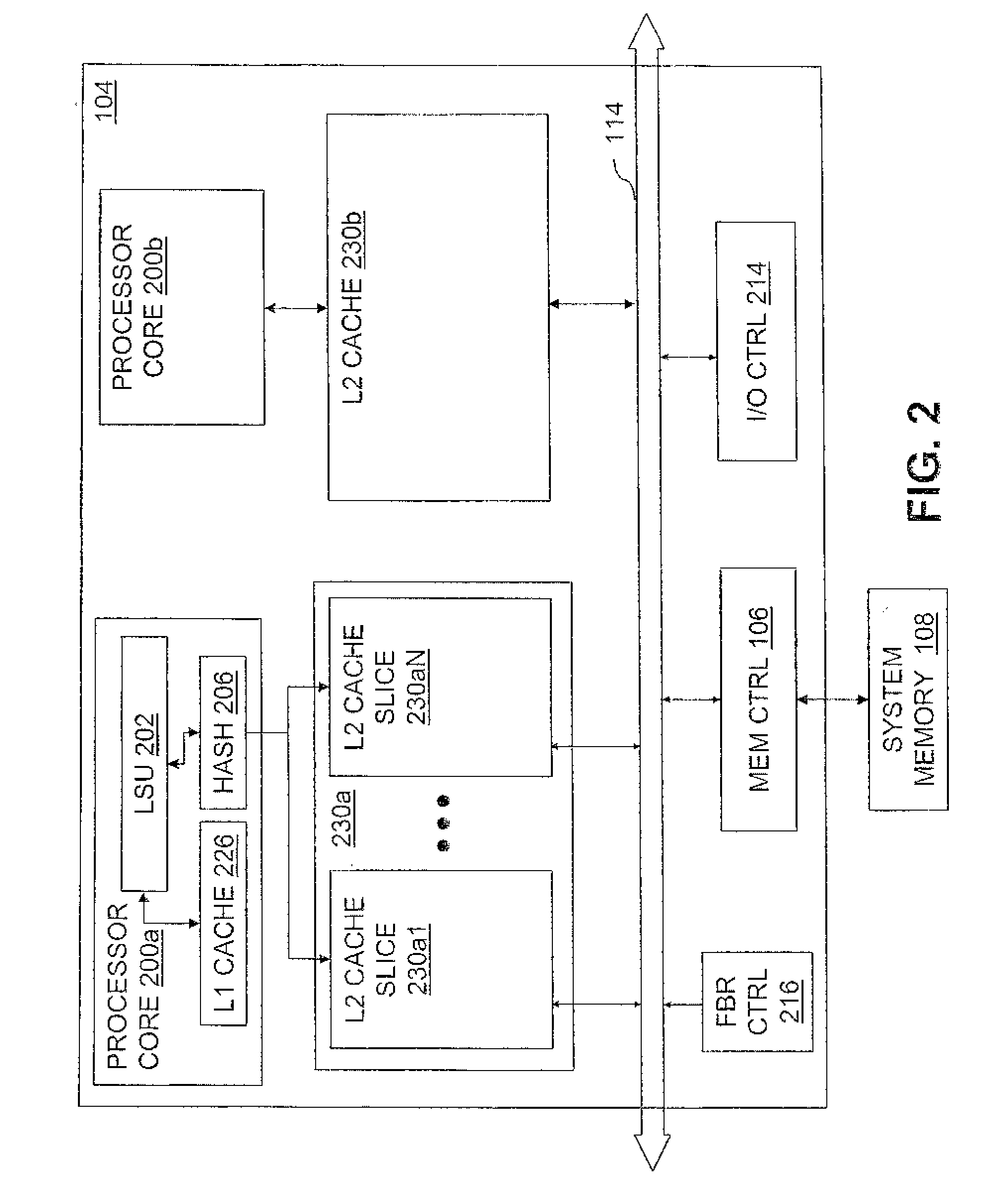
Data Processing System, Processor and Method of Data Processing in which Local Memory Access Requests are Serviced on a Fixed Schedule
InactiveUS20080016278A1Memory systemsMicro-instruction address formationData processing systemFixed time schedules
A processing unit includes a local processor core and a cache memory coupled to the local processor core. The cache memory includes a data array, a directory of contents of the data array. The cache memory further includes one or more state machines that service a first set of memory access requests, an arbiter that directs servicing of a second set of memory access requests by reference to the data array and the directory on a fixed schedule, address collision logic that protects memory access requests in the second set by detecting and signaling address conflicts between active memory access requests in the second set and subsequent memory access requests, and dispatch logic coupled to the address collision logic. The dispatch logic dispatches memory access requests in the first set to the one or more state machines for servicing and signals the arbiter to direct servicing of memory access requests in the second set according to the fixed schedule.
Owner:IBM CORP
Fieldbus upgradable apparatus and method
InactiveUS20070234339A1Avoid disturbanceFunction increaseData processing applicationsSoftware engineeringOperational systemEntry point
Owner:INVENSYS
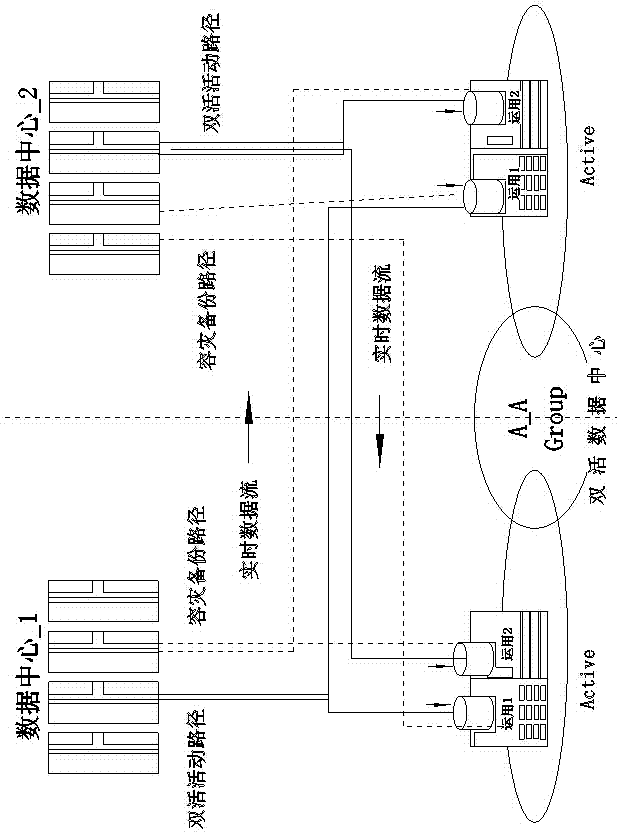
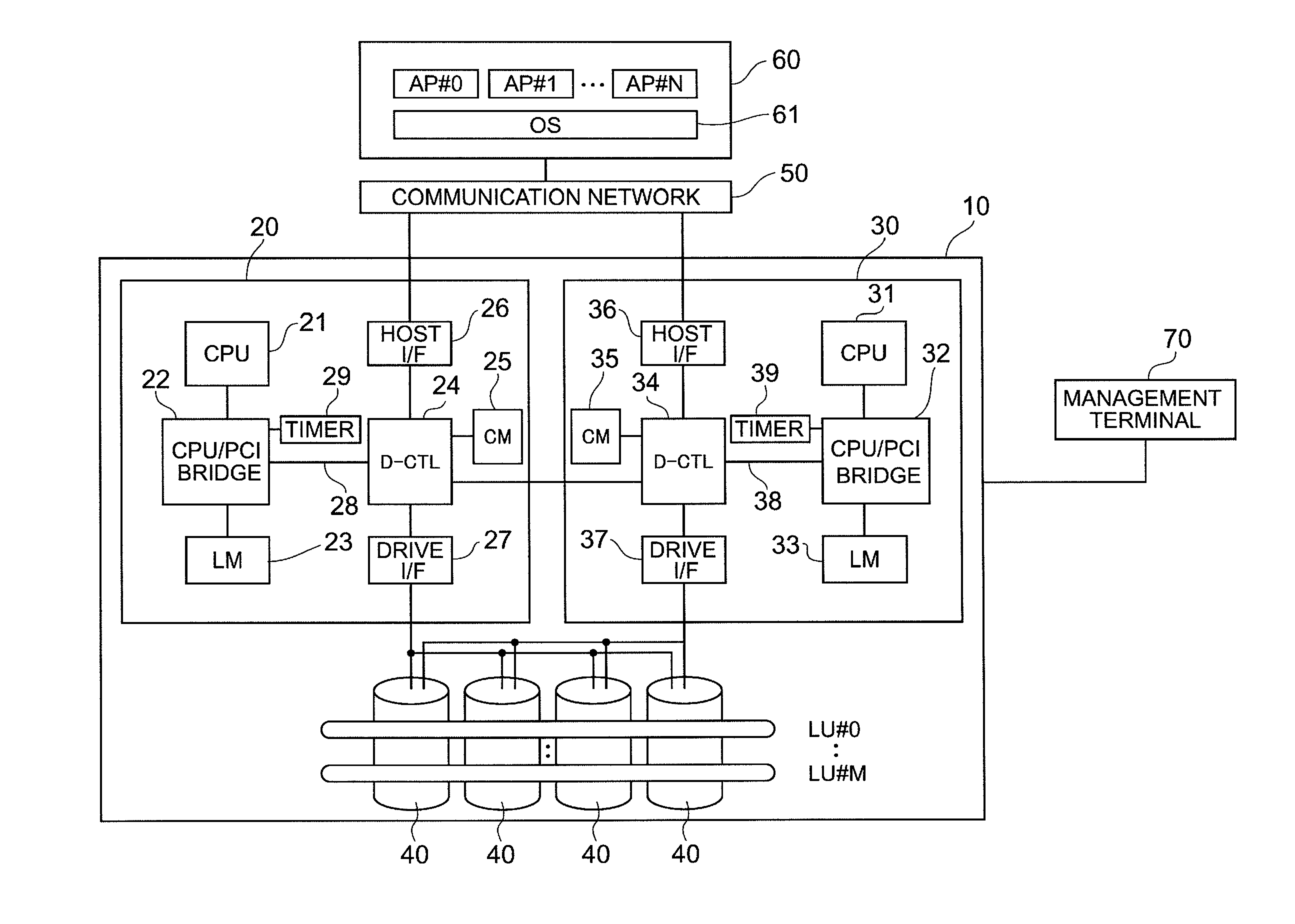
Dual-active storage system design method based on dual-active logical volumes
InactiveCN104331254ADoes not affect normal useAccess will not affectInput/output to record carriersRedundant hardware error correctionComputer architectureSystems design
The invention provides a dual-active storage system design method based on dual-active logical volumes, which belongs to the fields of dual-active designs for storage system data, mirroring technology and disaster recovery and backup. By establishing the dual-active relation between logical volumes in two sets of storage systems, the two logic volumes provide the same access mechanism for the upper layer, so that the data of two data centers are the same in real time and the failure of any set of storage system does not affect the usage of the data centers at two places. Dual-active data access is realized, the risk of disaster recovery systems is decreased, service downtime is prevented, and the capability of a comprehensive solution is enhanced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
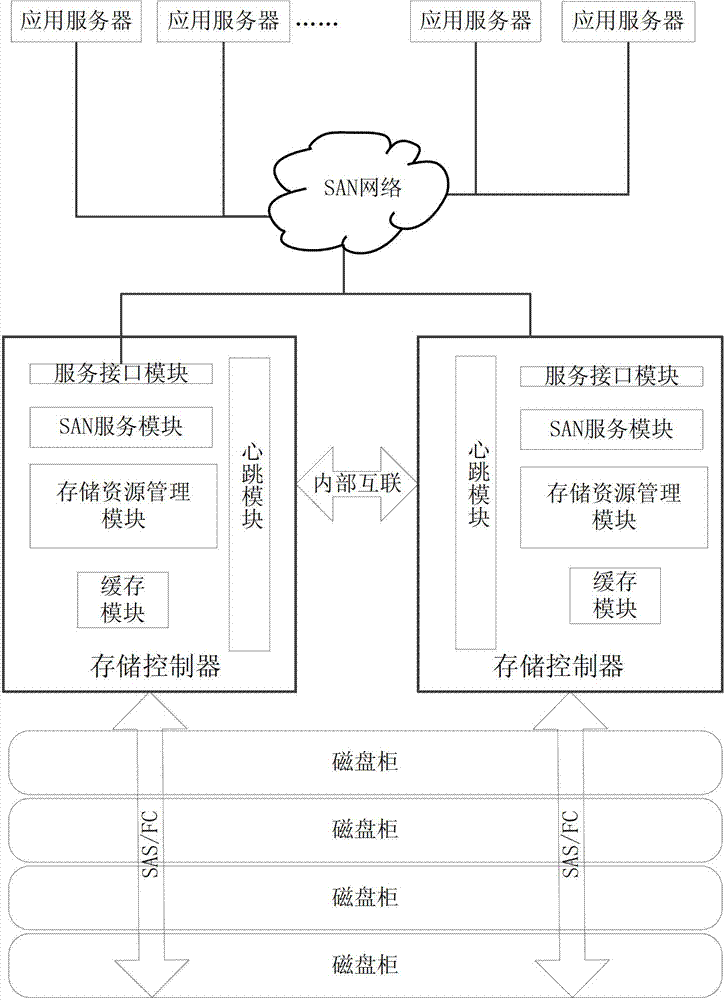
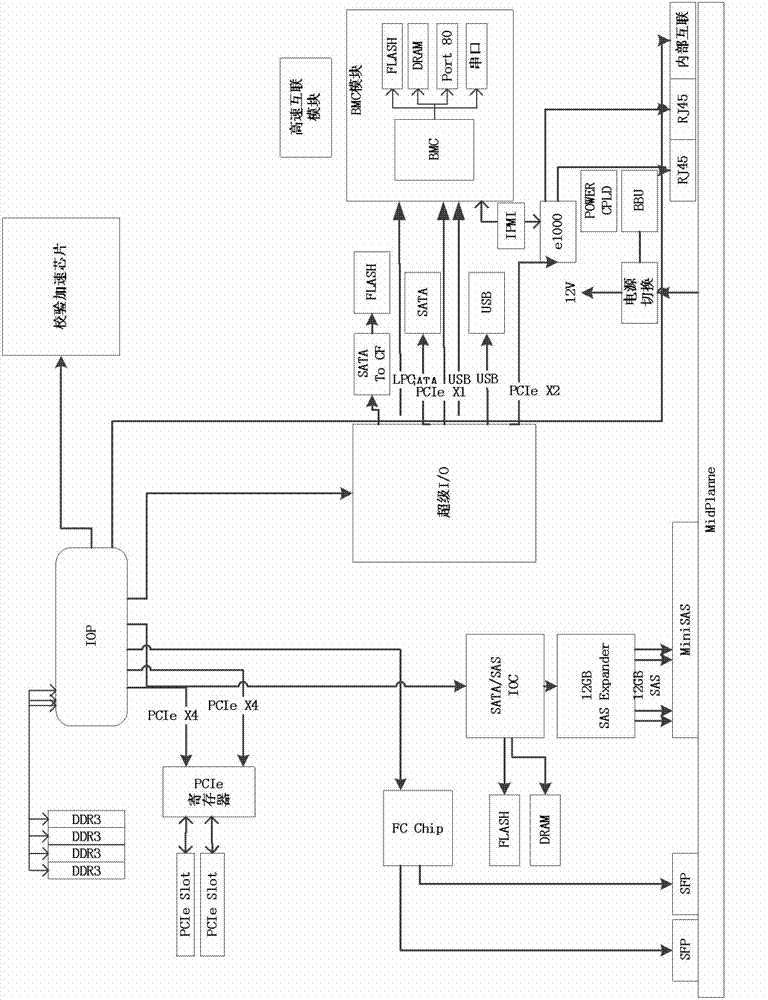
Double-control double-active storage control system and method
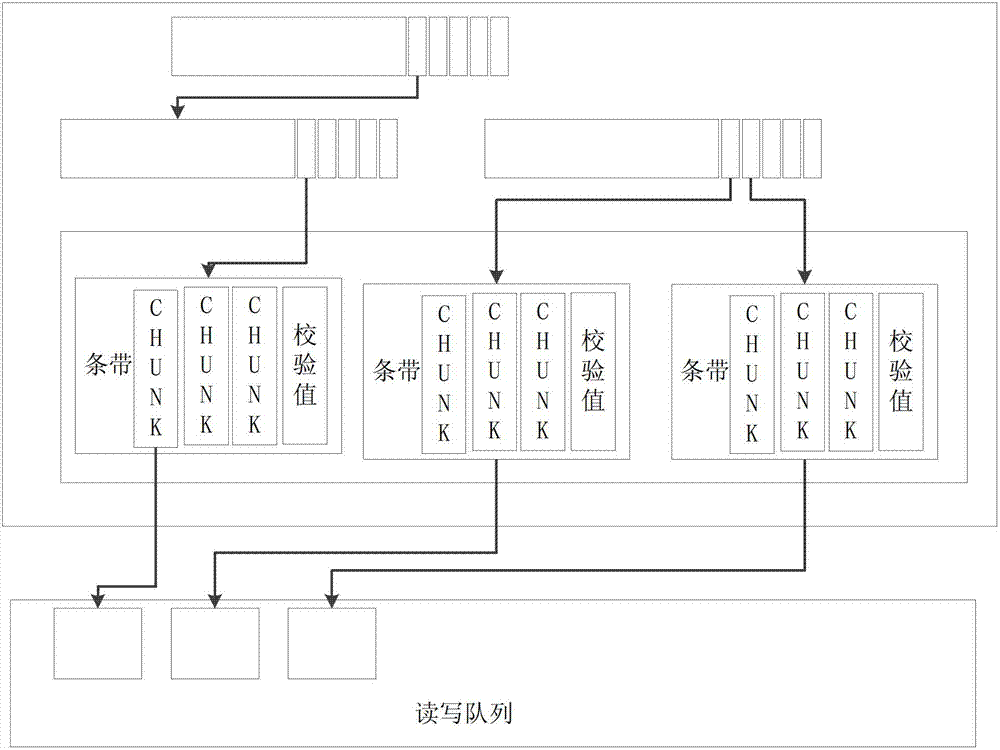
InactiveCN103092786ARealize simultaneous reading and writingIncrease profitElectric digital data processingApplication serverGranularity
The invention discloses a double-control double-active storage control system and a method. The double-control double-active storage control system comprises two storage controllers and further comprises a magnetic disk cabinet which is connected with the two storage controllers, wherein each storage controller comprises a storage resource management module and a cache module. The storage controllers receive requests of an application server, and flash corresponding caching data in the cache modules to the magnetic disk cabinet with a magnetic disk array stripe as a unit, or read data in the magnetic disk cabinet to the cache modules with the stripe as the unit. Occupied magnetic disk cabinet resources are released after completion of flashing or reading. According to the double-control double-active storage control system and the method, due to the fact that the storage resource management granularity is refined, simultaneous reading and writing of the two controllers are achieved from a macroscopic view. Transmission buses and computing resources are fully utilized, and the storage performance is improved. Furthermore, due to the fact that a novel storage resource management mode is adopted, the use ratio of bus resources of the double controllers and the computing resources is improved, the storage performance and volume are improved, and the switching time of storage system breakdown is lowered.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Storage system and method for changing configuration of cache memory for storage system
InactiveUS20120011326A1Minimize impactChange the configuration of a cache memoryMemory architecture accessing/allocationMemory adressing/allocation/relocationEvent triggerActive storage
The configuration of a cache memory can be changed while minimizing the influence over input-output performance with a host system on the active storage system.A data transfer control unit transfers data via a cache memory by a write-after method; and as triggered by an event where an amount of input to and output from an object area in the cache memory falls below a certain value, the data transfer control unit switches from the write-after method to a write-through method and then transfers data via the cache memory. Subsequently, as triggered by an event where there is no longer any input to and output from the object area in the cache memory, a processor changes the configuration of the cache memory relating to the object area.
Owner:HITACHI LTD
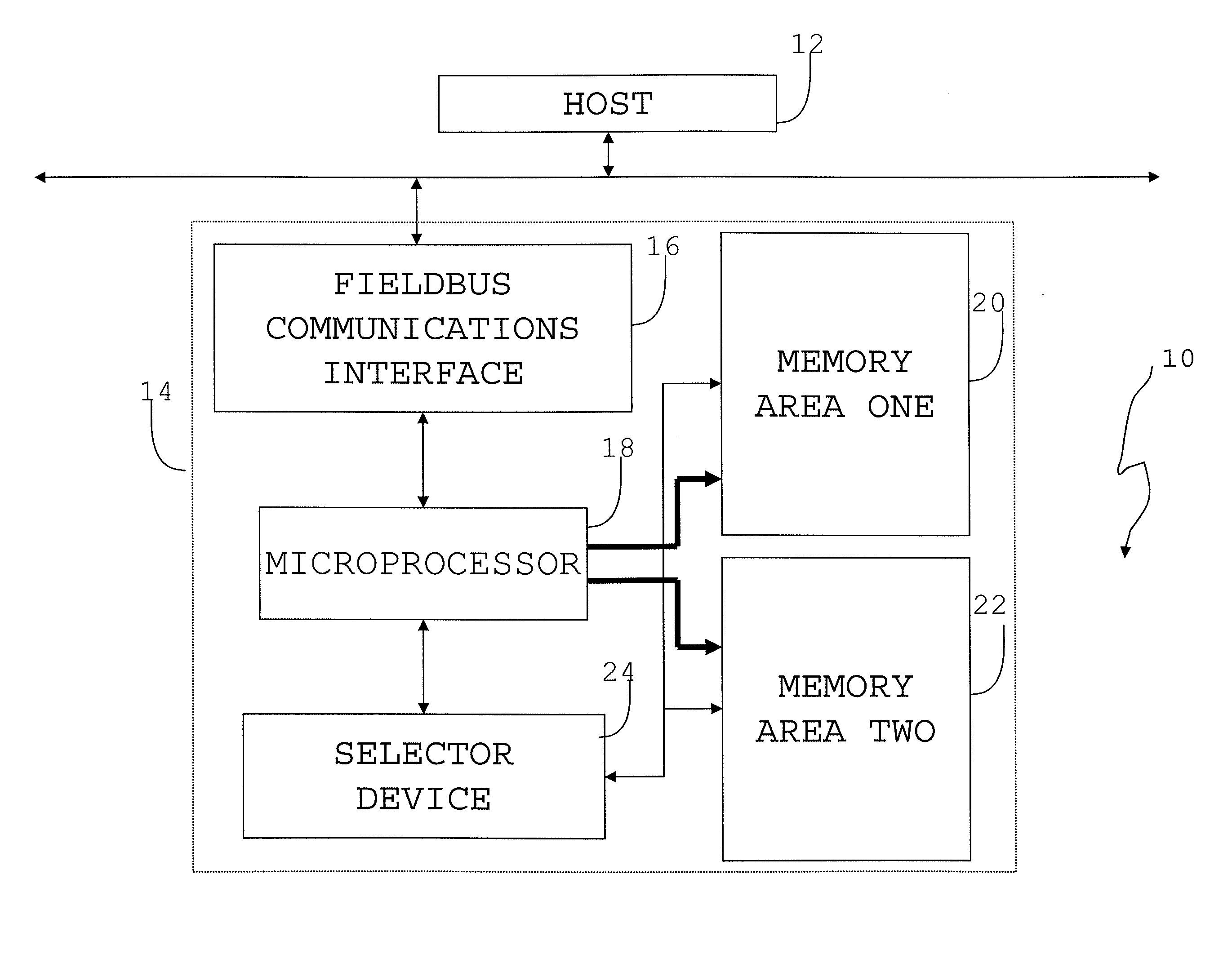
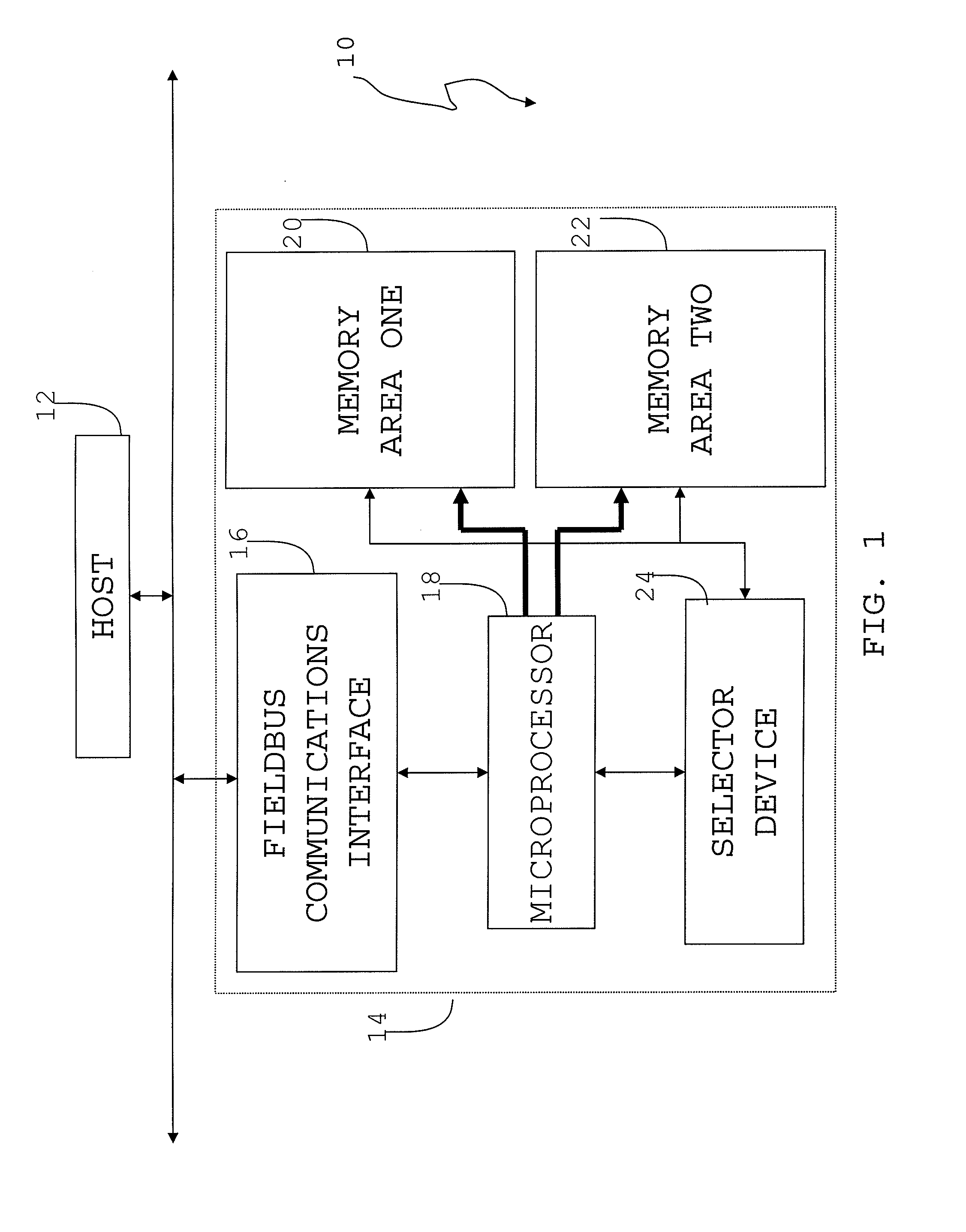
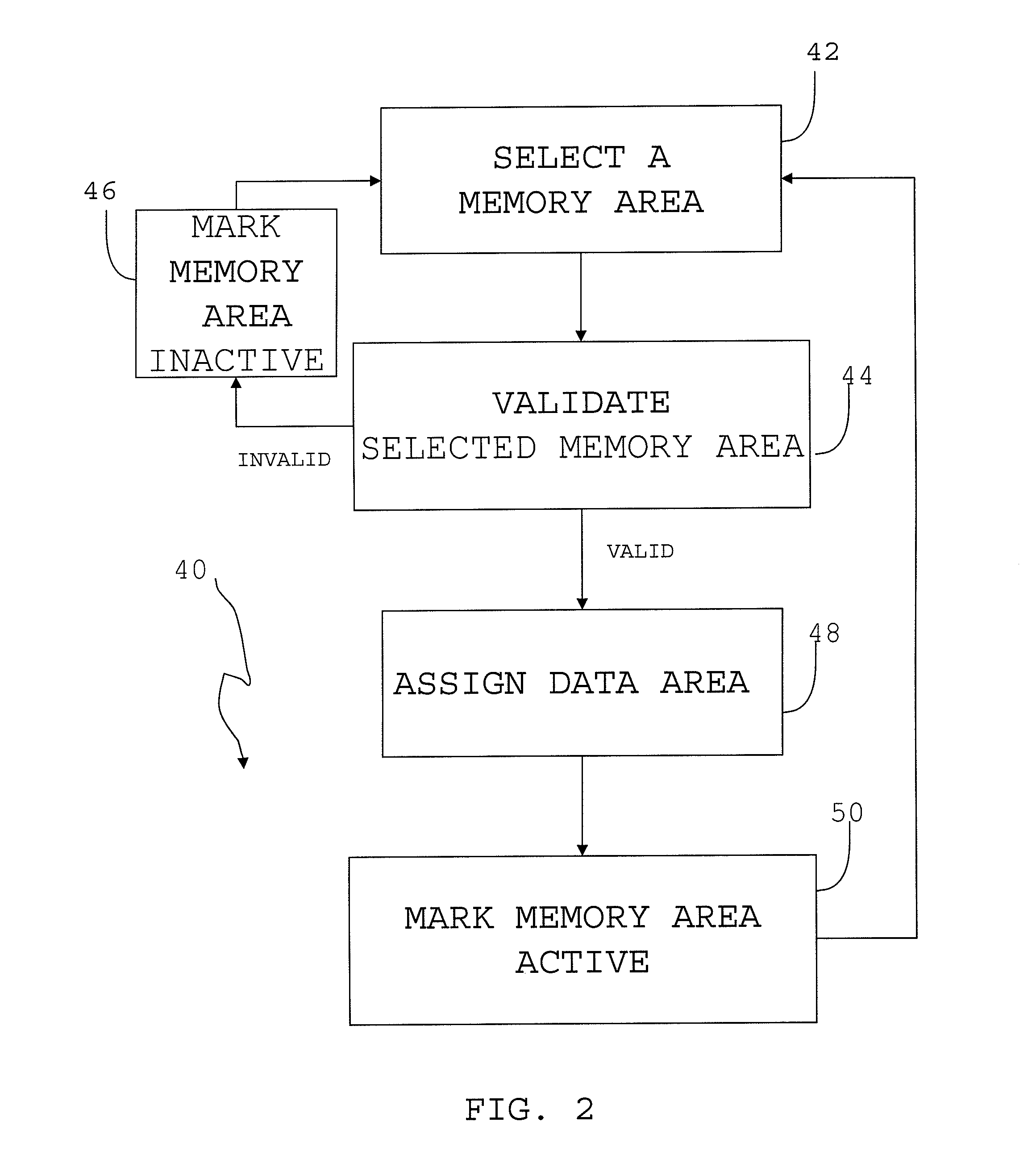
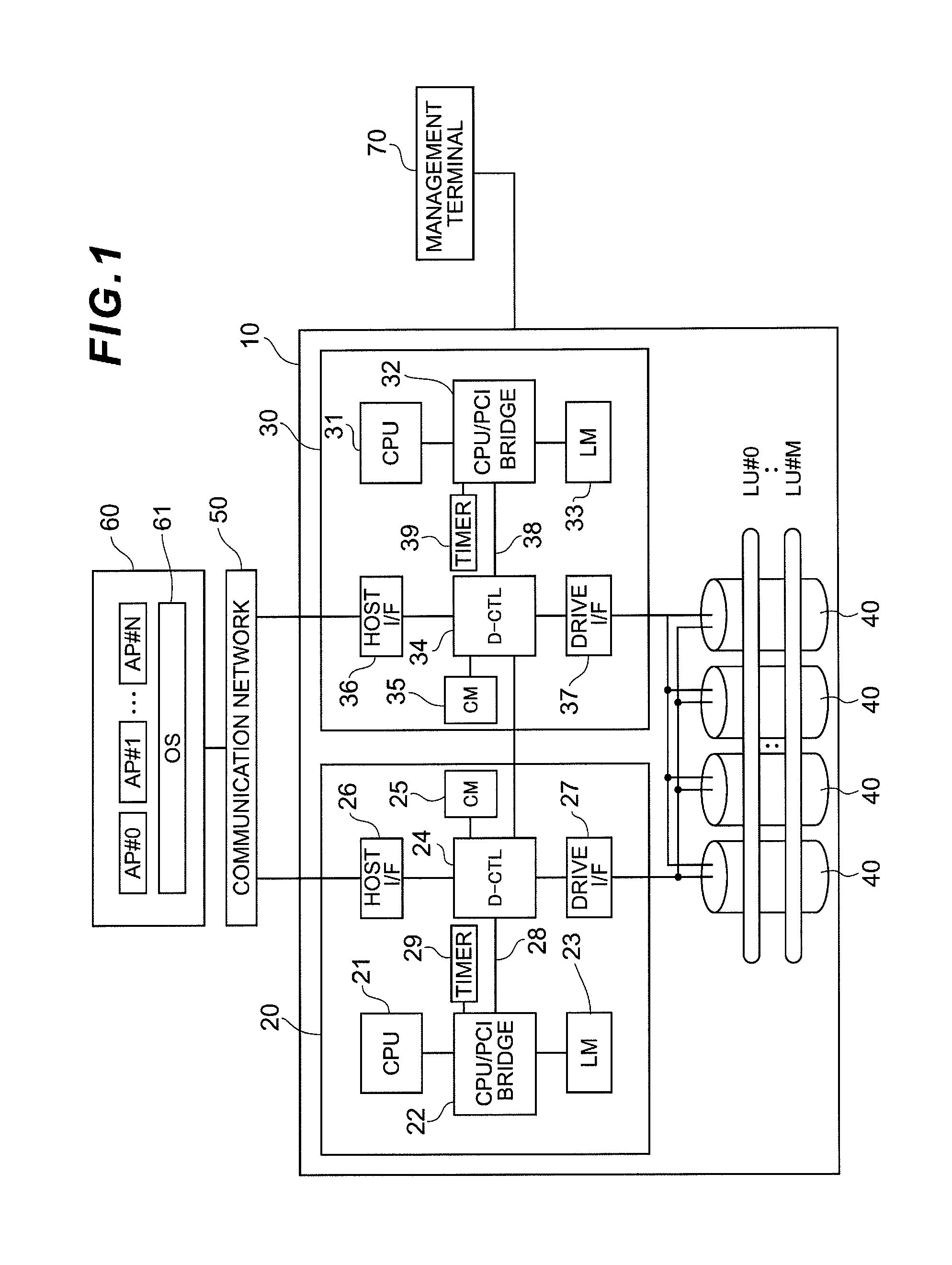
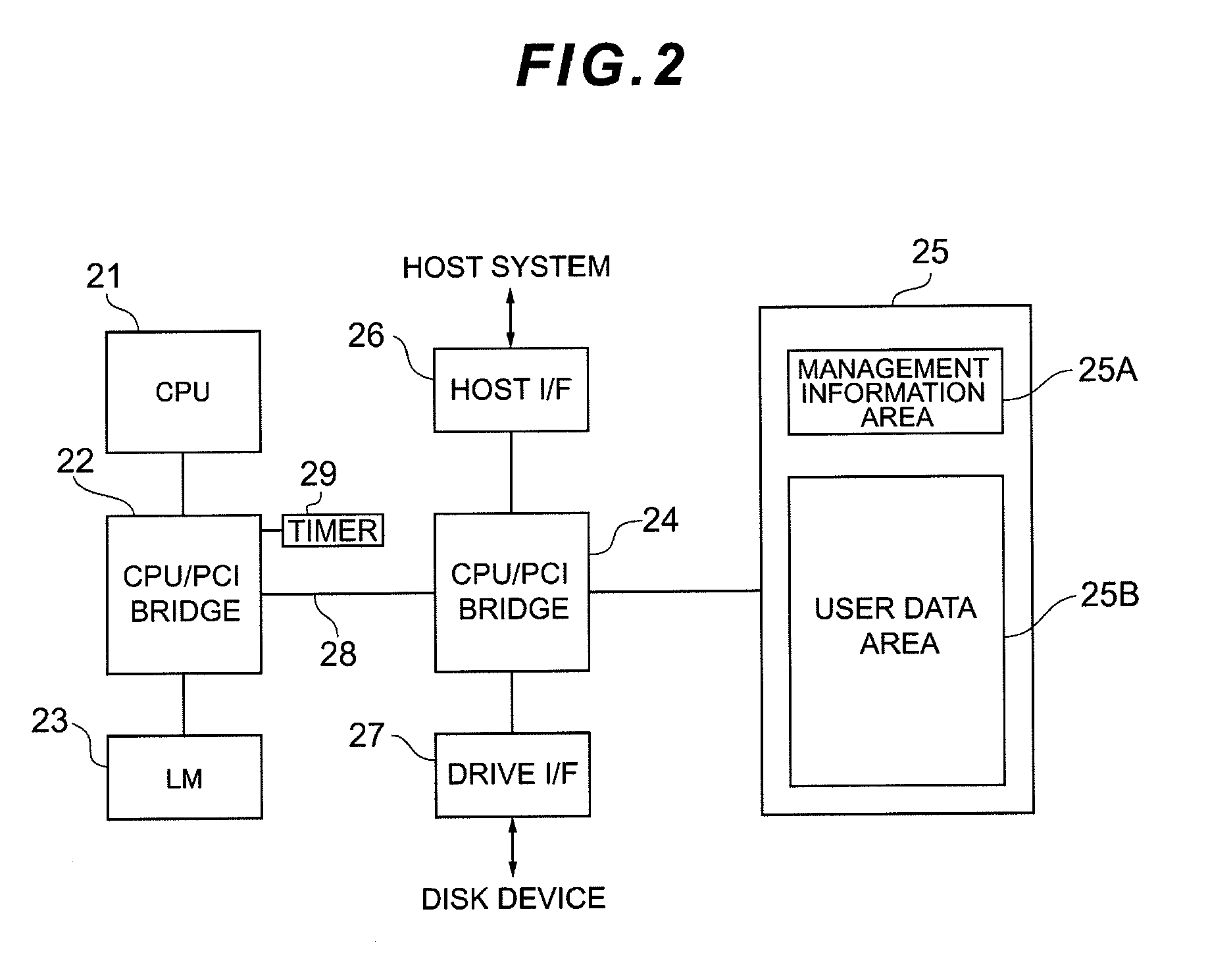
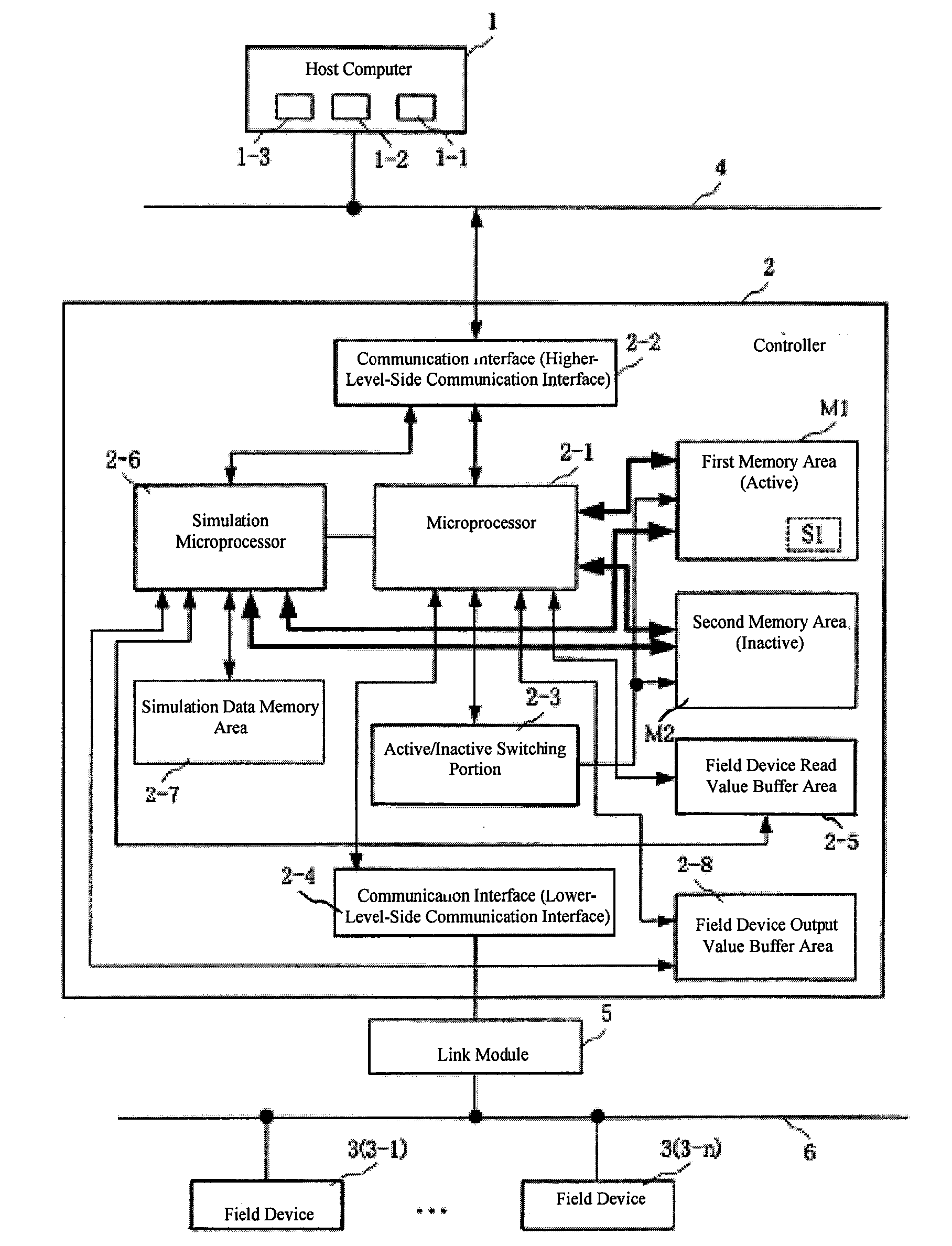
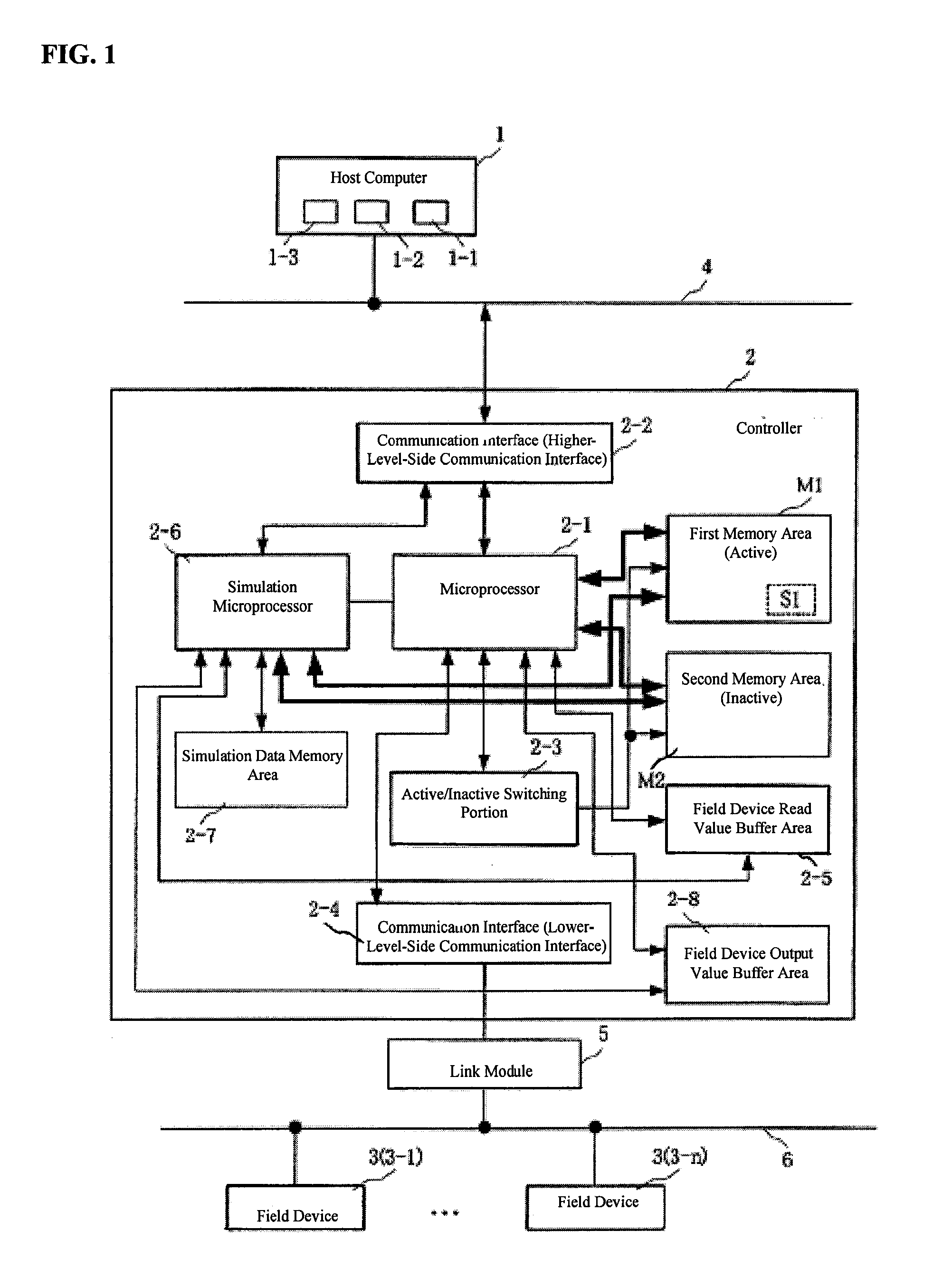
Field bus system
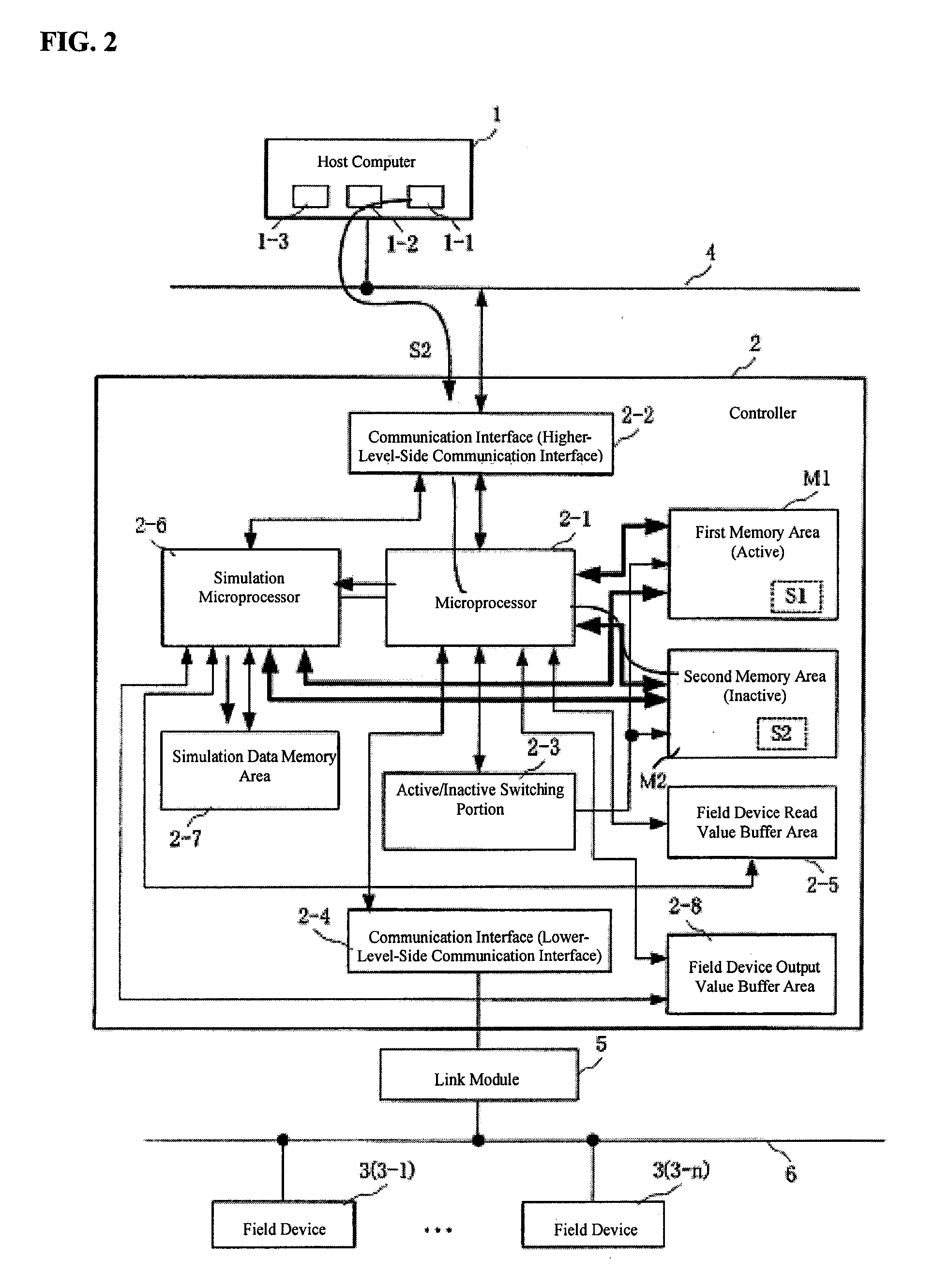
A controller is provided with a first memory area and a second memory area, where a pre-update software is stored with the first memory area as the active area and an updated software is downloaded with the second memory area as an inactive memory area. A microprocessor for simulations performs a simulation of the control of the operation of a Held device using the updated software that has been downloaded. The execution status of the simulation can be monitored using a host computer. If the evaluation result of the state of execution of the simulation by an operator is “Pass,” then an activate command is sent to the controller. As a result, the active / inactive are switched in the controller.
Owner:YAMATAKE HONEYWELL CO LTD
On demand storage group management with recapture
InactiveUS20110072230A1Memory systemsInput/output processes for data processingLower limitActive storage
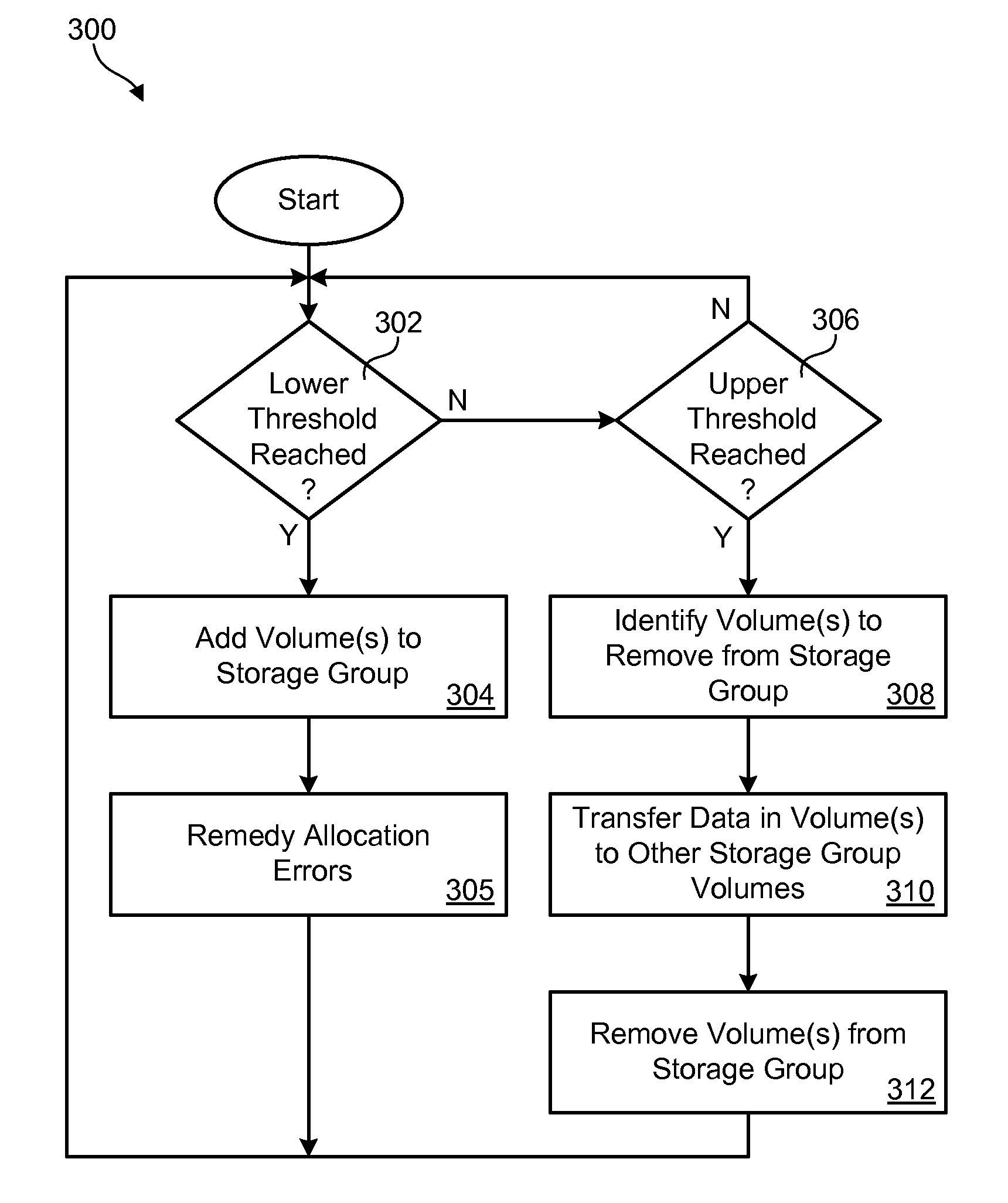
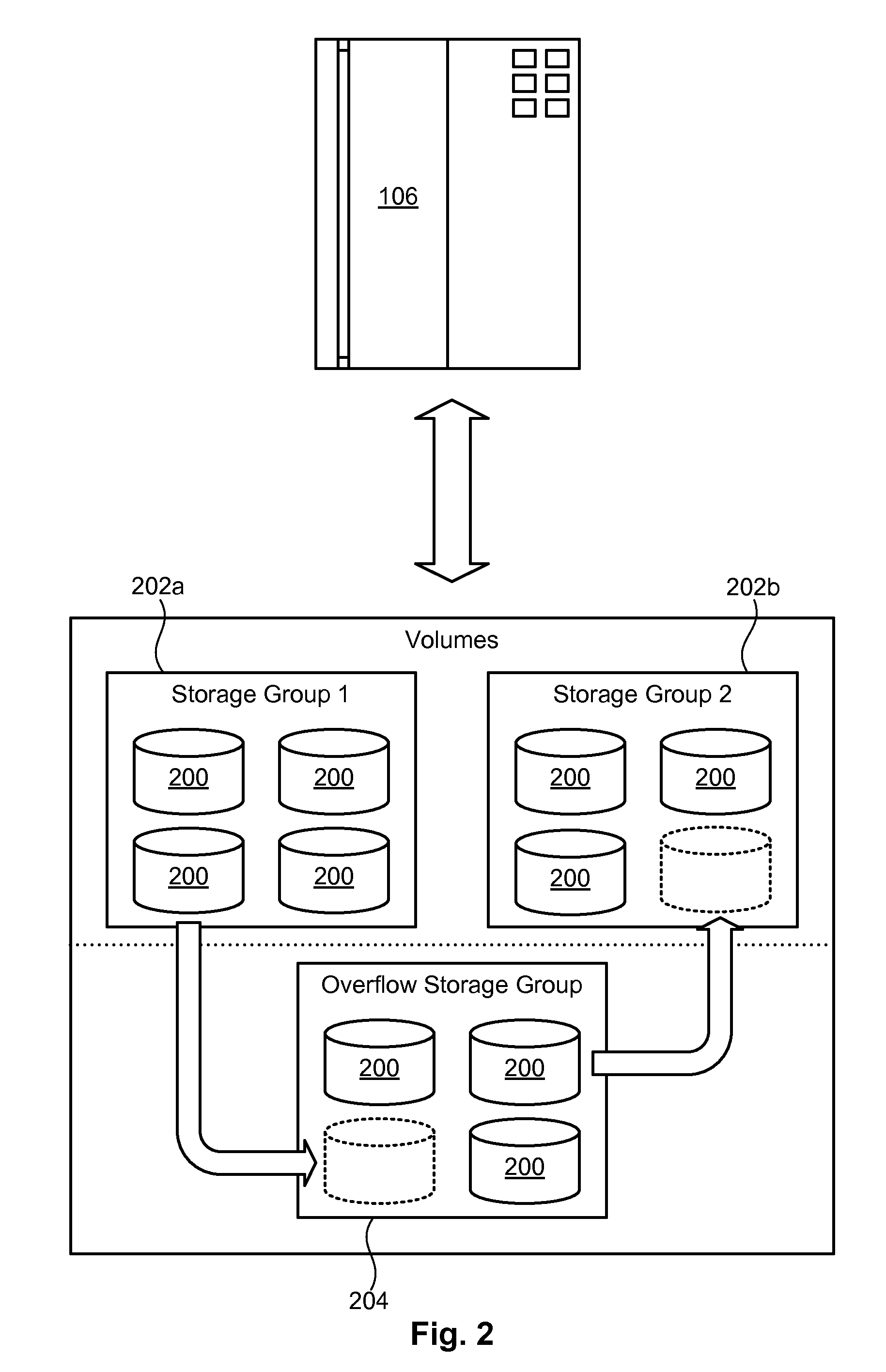
A method to dynamically adjust the amount of free space in a storage group is disclosed herein. In certain embodiments, such a method may include monitoring the amount of free space in an active storage group. The method may further include maintaining an overflow storage group containing unused volumes. When the free space in the active storage group falls below a lower threshold value, the method may automatically move a volume from the overflow storage group to the active storage group. Conversely, when the free space in the active storage group exceeds an upper threshold value, the method may automatically transfer data from a volume in the active storage group to other volumes in the active storage group, and move the volume from the active storage group to the overflow storage group. A corresponding computer program product and apparatus are also disclosed herein.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com