Patents
Literature
42238 results about "Computer equipment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
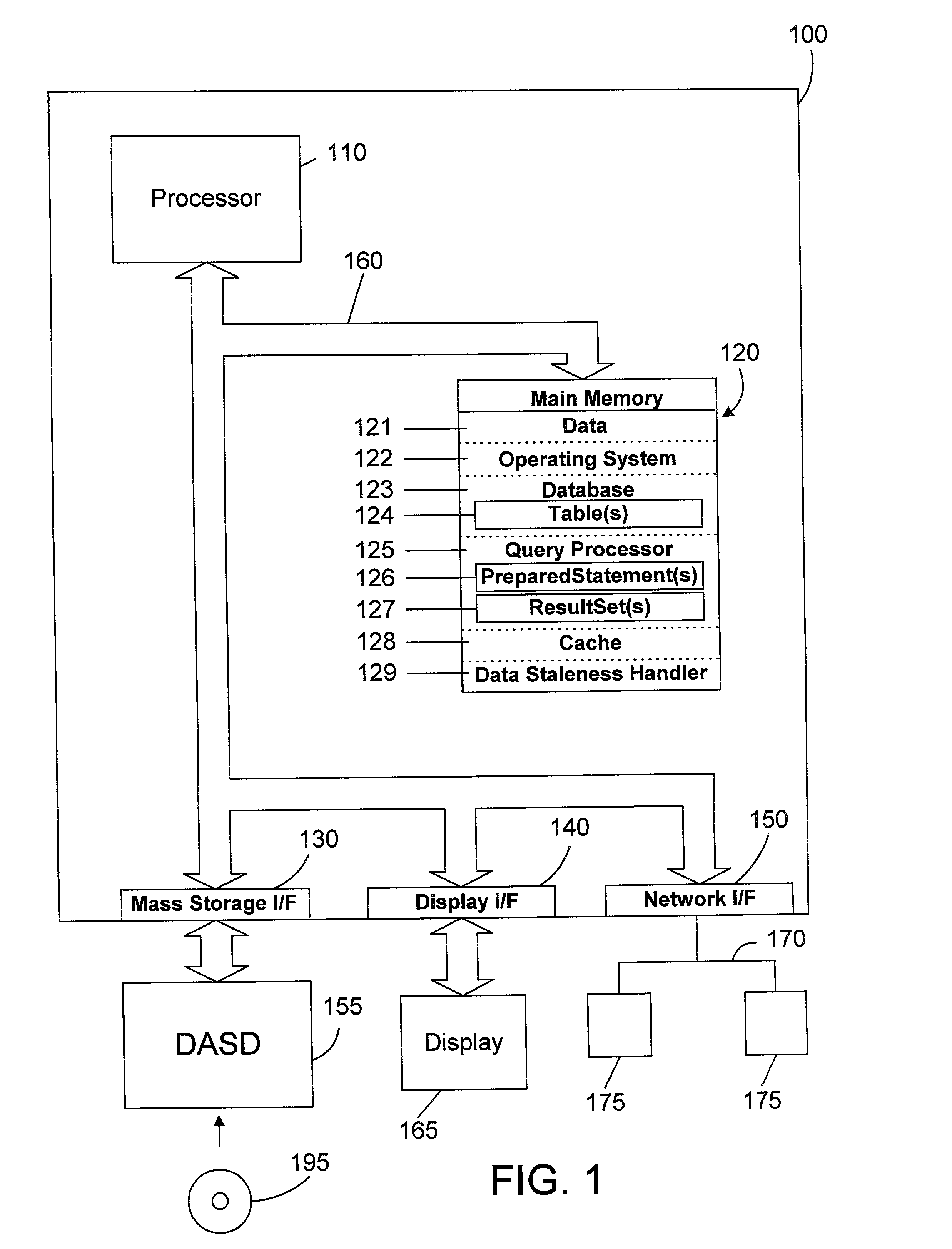
Your desktop or laptop computer is the cornerstone of your computer equipment; it includes internal components your computer requires to function and ports to attach peripherals that work in tandem with the computer. Computer equipment also includes peripherals that depend on a computer to operate properly.
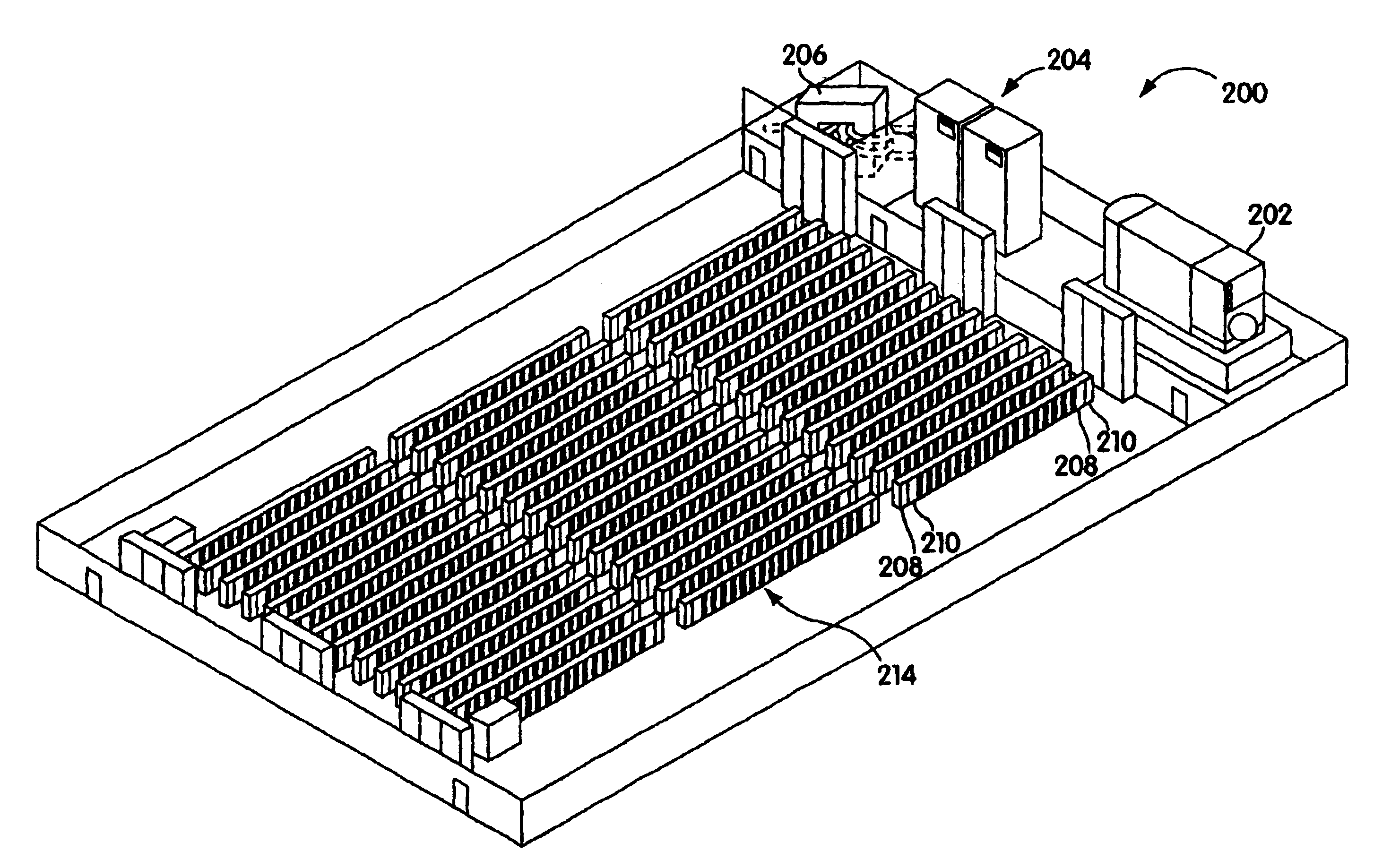
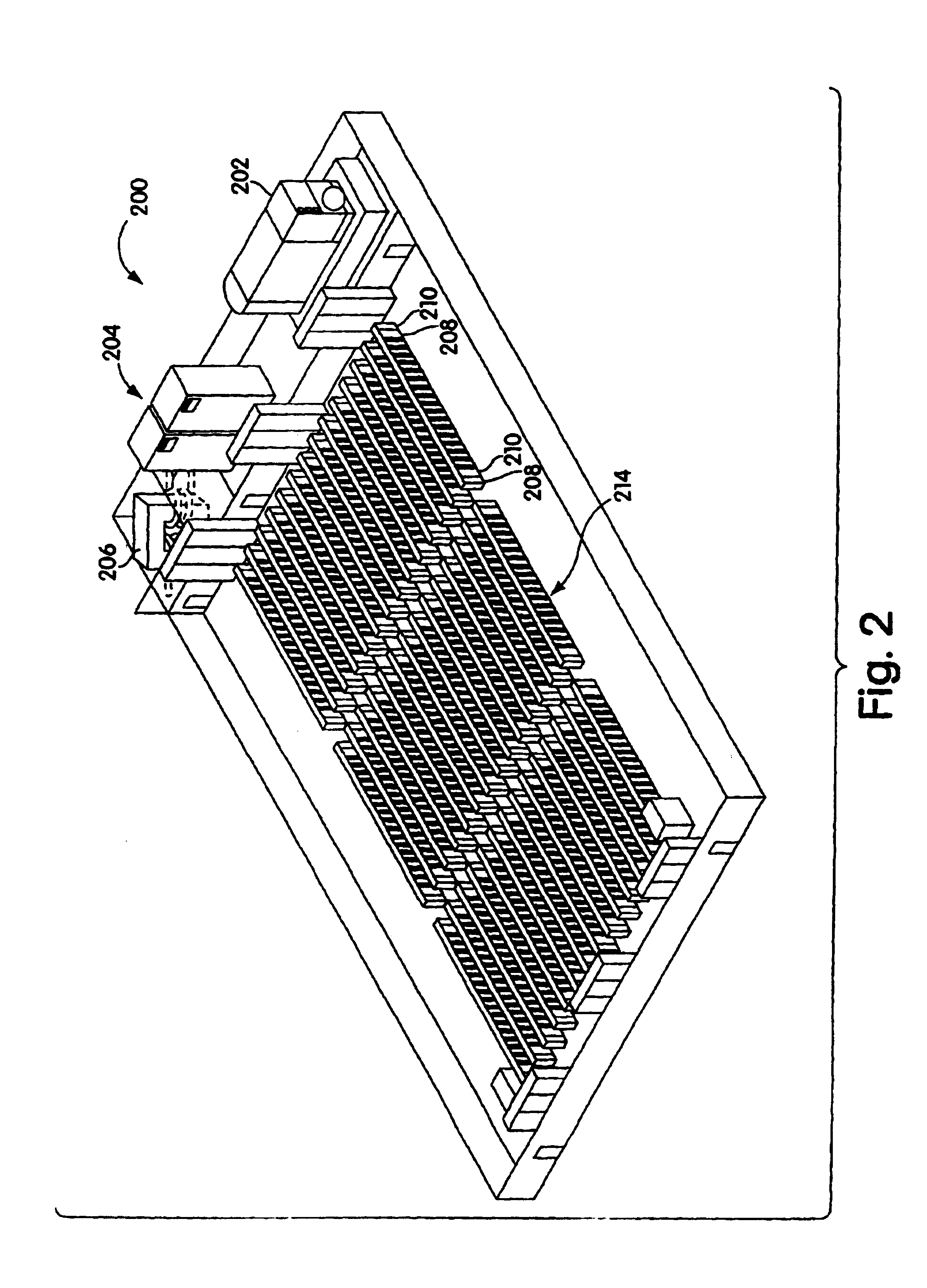
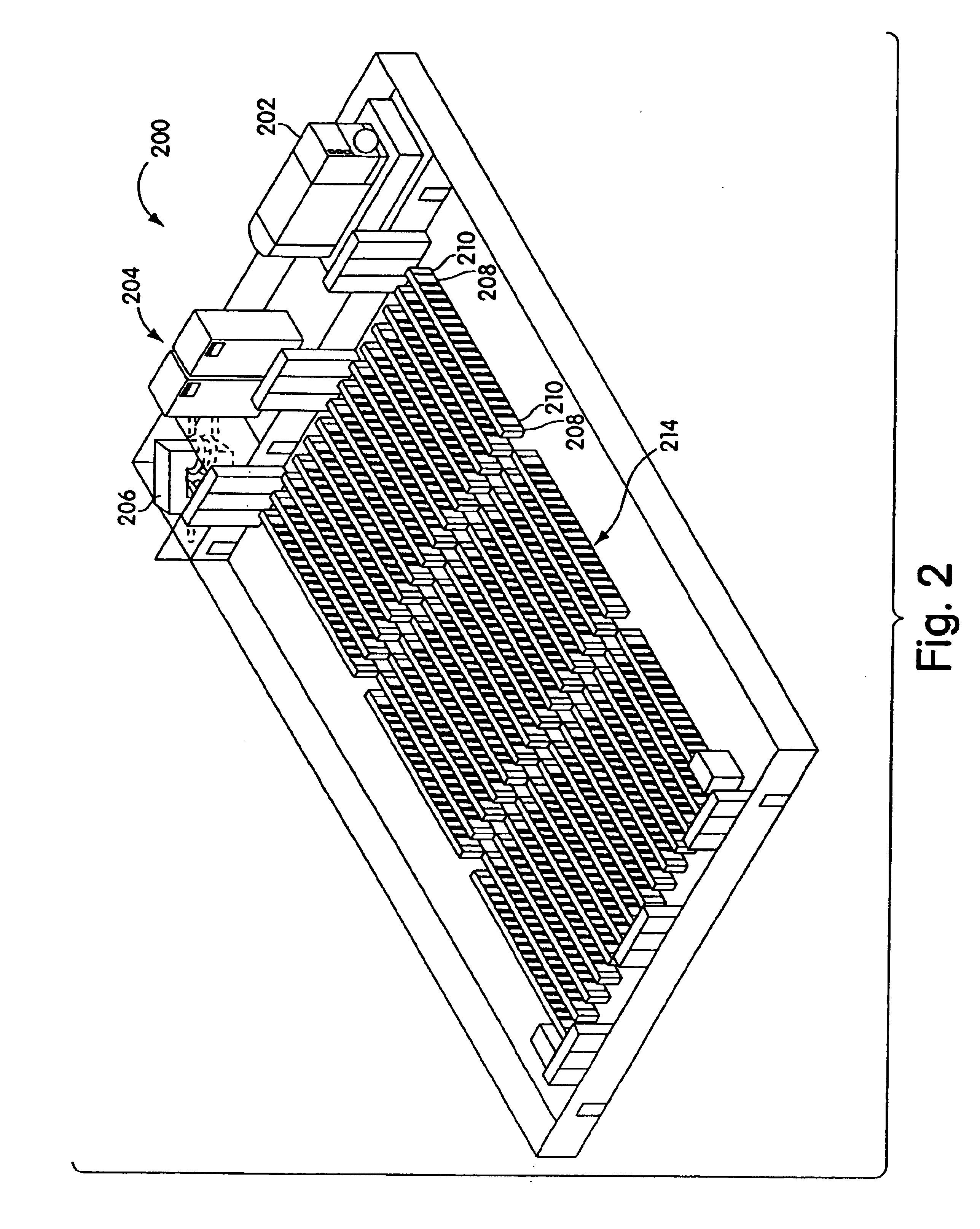
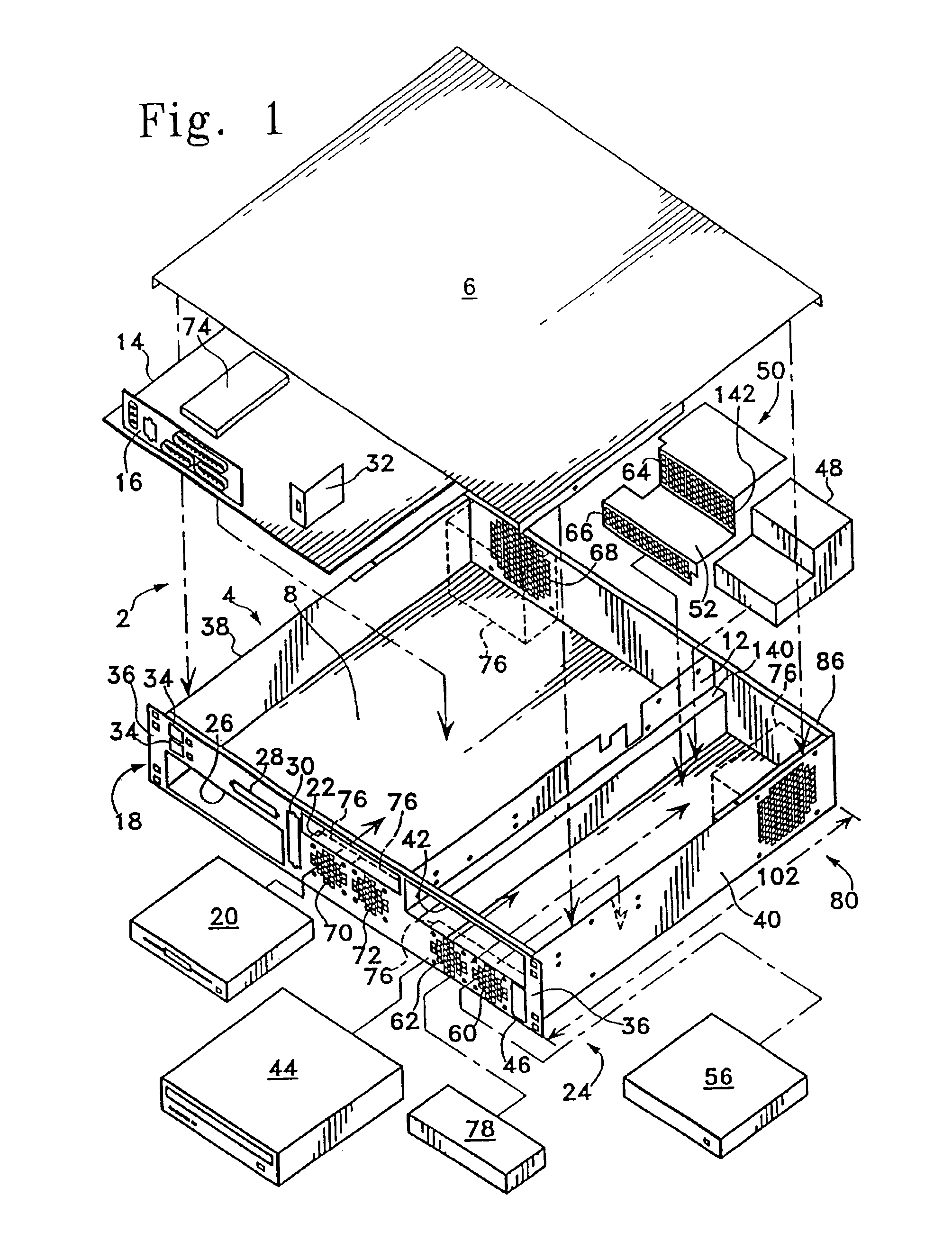
Adjustable scalable rack power system and method
Systems and method for installing computer equipment and power distribution equipment in facilities is provided. In one aspect, the present invention provides a power distribution rack, and uninterruptible power supply rack and a plurality of equipment racks. A plurality of power cables are run from the power distribution rack to each of the plurality of equipment racks using power cable tracks located on the roofs of the equipment racks.
Owner:AMERICA POWER CONVERSION CORP
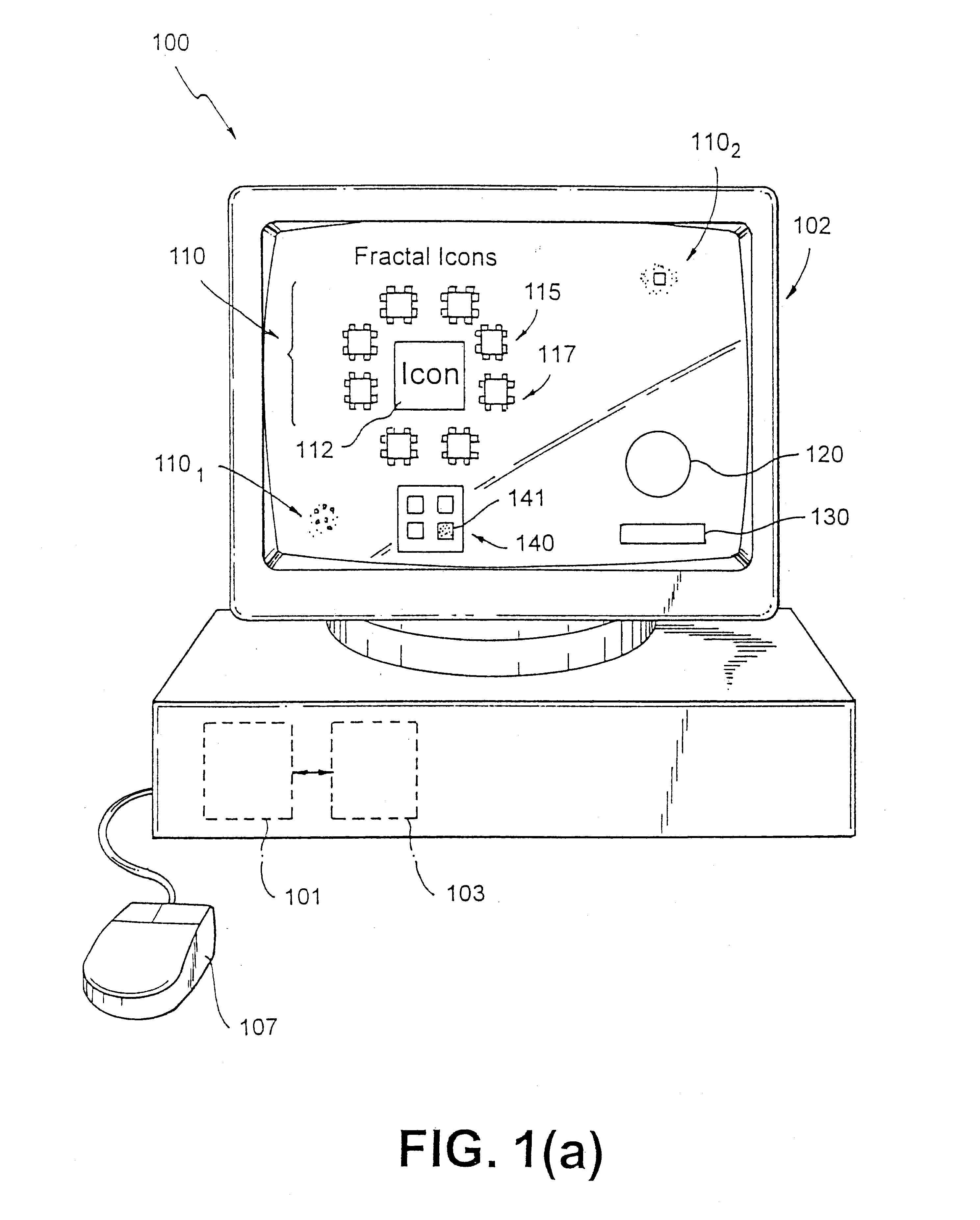
Information presentation system for a graphical user interface
InactiveUS6426761B1Easy to useImprove visibilityInput/output processes for data processingItem CollectionGraphics
Information presentation system comprises a computer device having a display terminal for providing a graphical user interface (GUI), capable of generating a cluster of items comprising graphical or textual elements for display thereof according to a fractal appearance. Each item in a cluster represents information having a degree of relatedness with information represented by other items in a cluster. A control mechanism is provided for controlling the spatial extent, nesting and arrangement of items within a cluster according to a specified criteria, which spatial extent and arrangement is controlled to provide optimal display and conserve screen display space on the display terminal. Users may manually enter a criteria for organizing and adjusting the spatial extent of a cluster in order to provide continuous display space on the computer display terminal. The invention may be implemented in text editors to provide a multiresolution annotation feature for portable and lap / palm-top computer devices having pen-based or keyboard based inputs.
Owner:IBM CORP
Method and system for controlling access, by an authentication server, to protected computer resources provided via an internet protocol network
InactiveUS7290288B2Mosaic printer telegraph systemDigital data processing detailsComputer resourcesThe Internet
A method and system for controlling access, by an authentication server, to protected computer resources provided via an Internet Protocol network that includes storing (i) a digital identification associated with at least one client computer device, and (ii) data associated with the protected computer resources in at least one database associated with the authentication server; authenticating, by the authentication server, the digital identification forwarded by at least one access server; authorizing, by the authentication server, the at least one client computer device to receive at least a portion of the protected computer resources requested by the at least one client computer device, based on the stored data associated with the requested protected computer resources; and permitting access, by the authentication server, to the at least the portion of the protected computer resources upon successfully authenticating the digital identification and upon successfully authorizing the at least once client computer device.
Owner:PRISM TECH
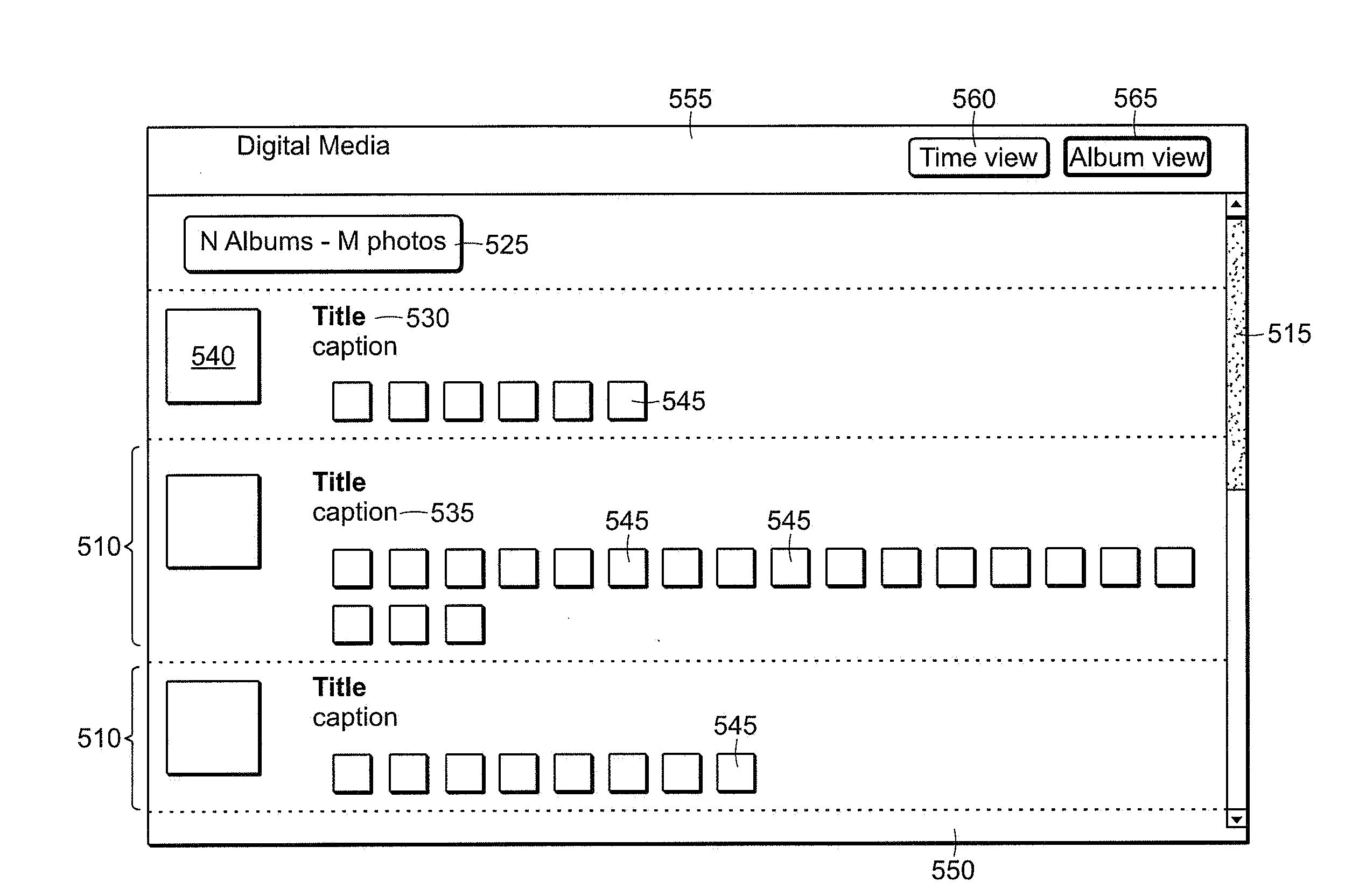
Method and apparatus for managing digital media content
ActiveUS20100174993A1Convenient and efficient accessMultimedia data browsing/visualisationMultiple digital computer combinationsGraphical user interfaceMediaFLO
Various aspects and embodiments are directed to a streamlined computer device and a graphical user interface that organizes interface elements into views of computer content for presentation to a user. Various views of digital media content permits users to easily and efficiently access various digital media content. Different views are used to provide an interface that is responsive to configurations of the device and responsive to activity being performed by the user. Aspects include permitting the user to maintain and manage digital media content libraries. According to some embodiments, the libraries comprise user digital media content and references digital media content. Functionality provided to a user can be tailored to the type of content displayed, accessed and / or managed. According to various aspects, methods and systems are provided for accessing and managing digital media libraries on a streamlined computing device with a plurality selectable I / O profiles. According to some embodiments, the methods may include displaying a GUI on a device, wherein the GUI comprises at least a plurality of views of digital media content, providing for transition between the plurality of views in response to selection of an I / O profile and in response to activation of a view selector component by a user, executing an association with the at least one of the plurality of visual representations with digital media content in response to selection, transitioning a display on the computing device to a view of the digital media content, and providing for display of user digital media content and referenced digital media content in the view of the digital media content.
Owner:LITL
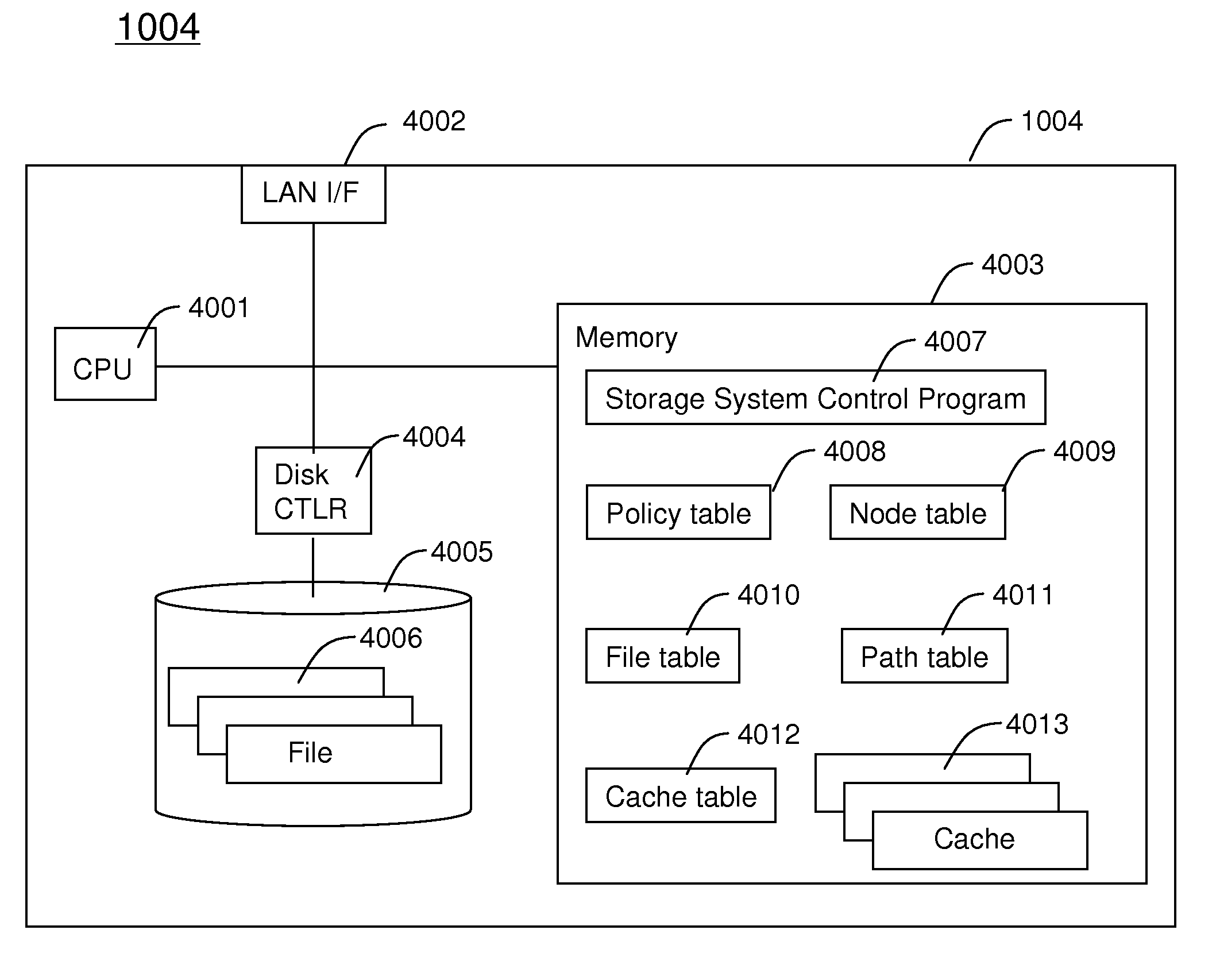
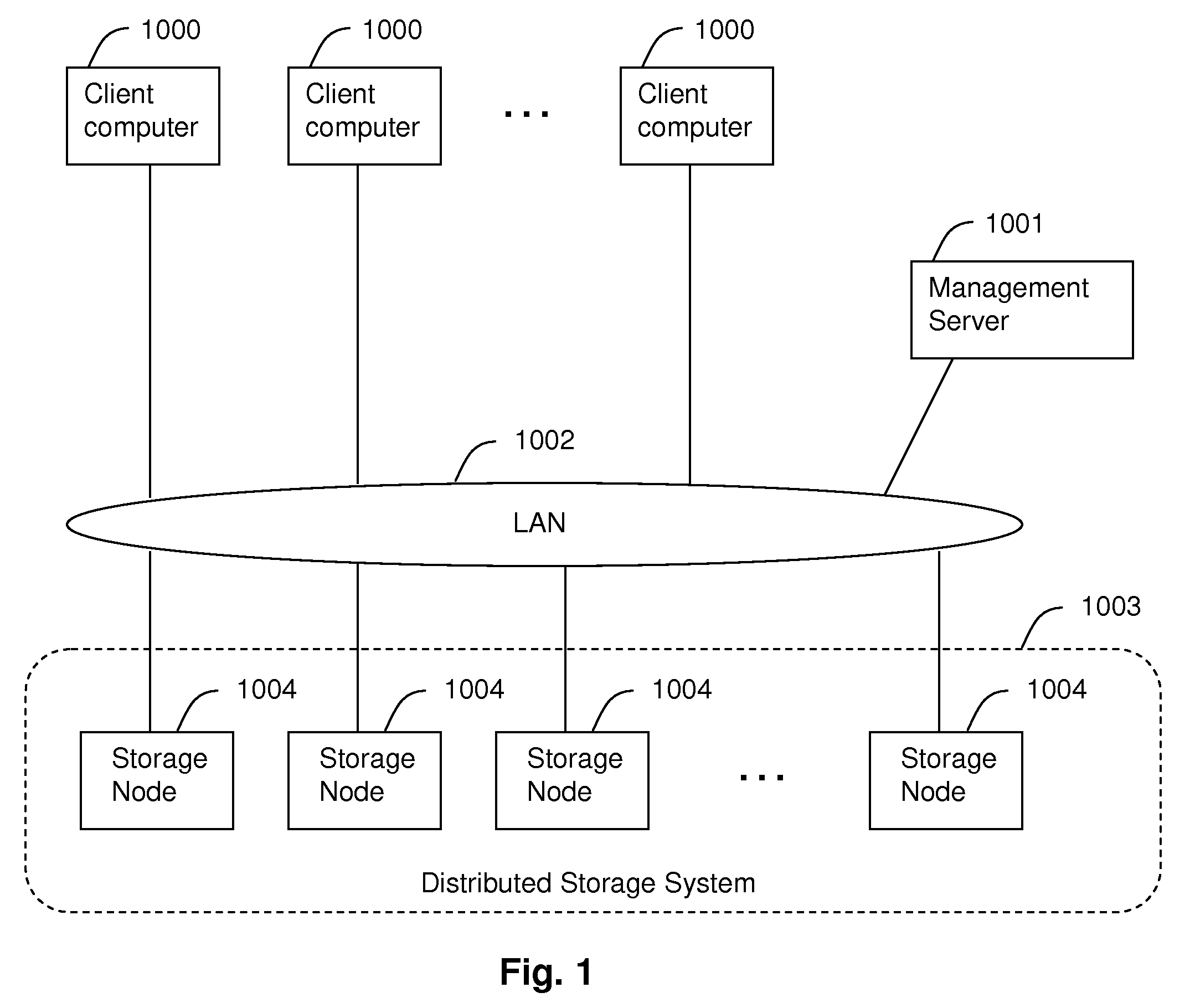
Method and apparatus for improving file access performance of distributed storage system
InactiveUS8086634B2Improve performanceReduce overheadDigital data information retrievalDigital data processing detailsNetwork connectivityDistributed memory systems
Embodiments of the invention provide methods and apparatus for improving the performance of file transfer to a client from a distributed storage system which provides single name space to clients. In one embodiment, a system for providing access to files in a distributed storage system comprises a plurality of storage nodes and at least one computer device connected via a network. Each storage node is configured, upon receiving a file access request for a file from one of the at least one computer device as a receiver storage node, to determine whether or not to inform the computer device making the file access request to redirect the file access request to an owner storage node of the file according to a preset policy. The preset policy defines conditions for whether to redirect the file access request based on at least one of file type or file size of the file.
Owner:HITACHI LTD
Methods and apparatus for implementing a virtualized computer system
InactiveUS20060074618A1Error detection/correctionAnalogue computers for electric apparatusVirtualizationVirtual computing
In one aspect, a method of creating a virtualized computer environment that represents a real world computer environment is provided. The real world computer environment comprises a plurality of components, the plurality of components comprising a plurality of computer devices and at least one network device that implements a network that interconnects the plurality of computer devices, the real world computer environment comprising at least one security facility that implements at least one security function in the real world computer environment. The method comprises acts of including in the virtualized computer environment a virtualized representation of at least one of the plurality of computer devices in the real world computer environment and implementing the at least one security function in the virtualized computer environment. In another aspect, a virtualized representation of the at least one network device is provided. In another aspect, software is executed in the virtual computer environment.
Owner:MICROSOFT TECH LICENSING LLC
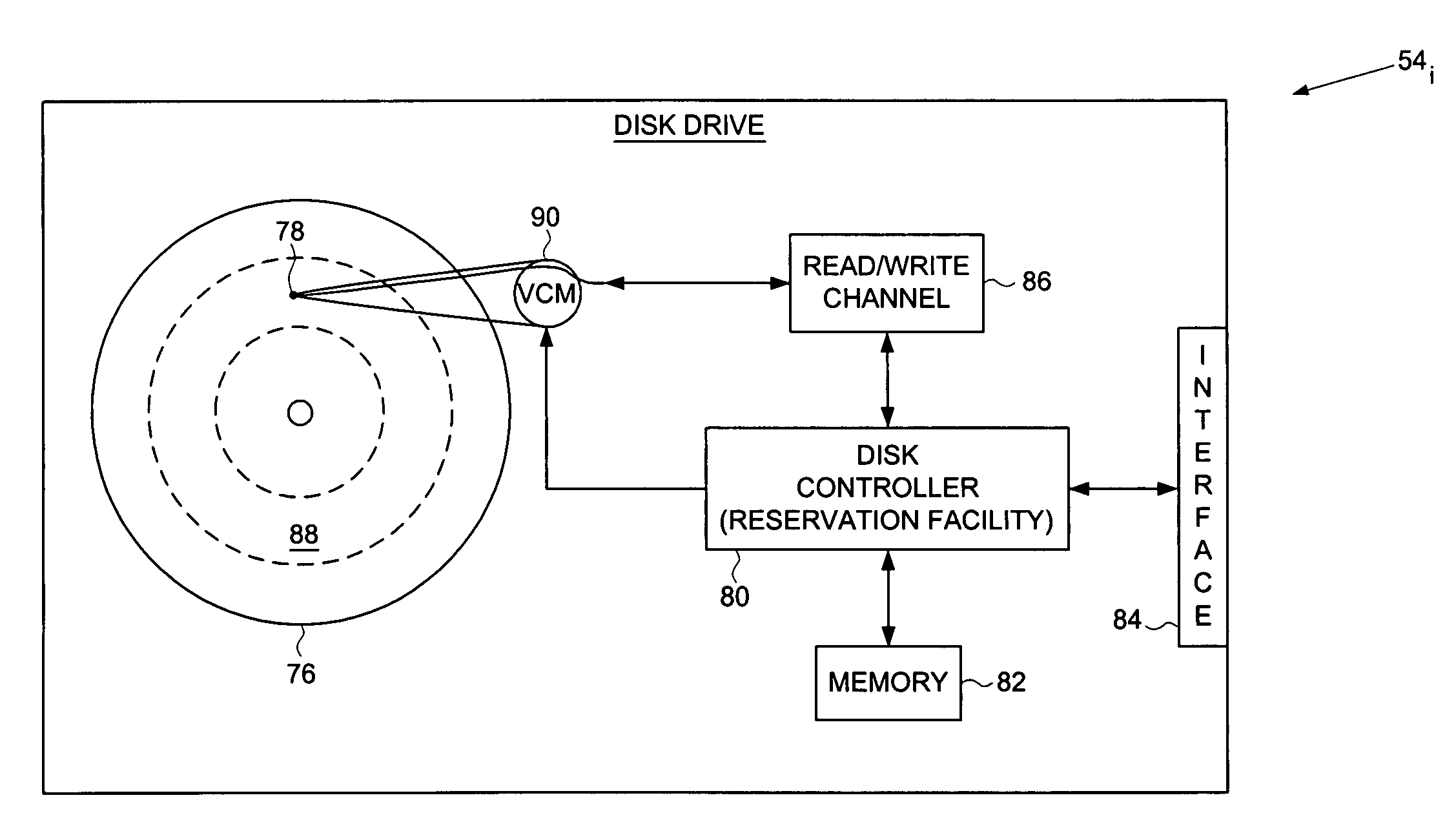
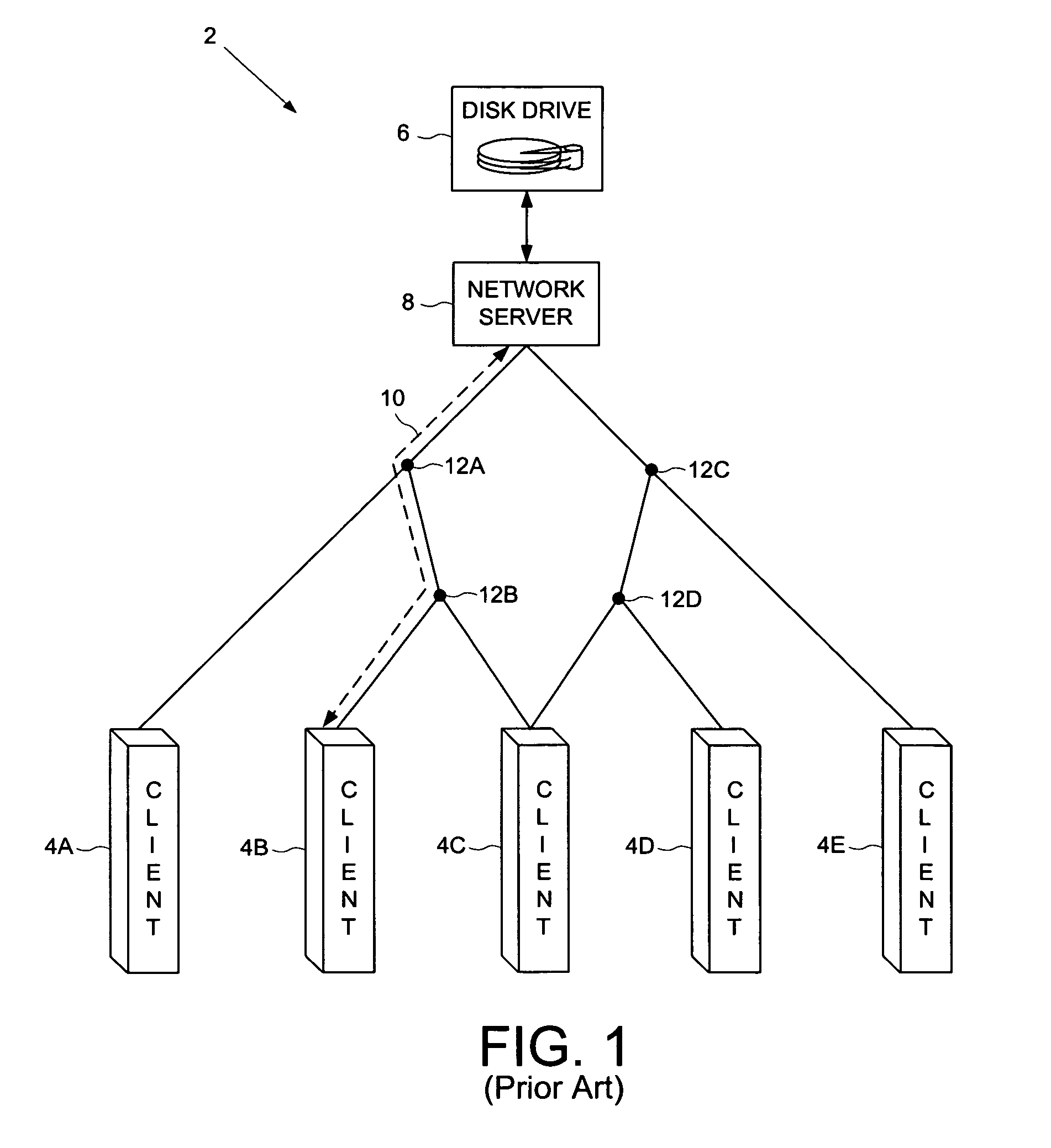
Resource reservation system in a computer network to support end-to-end quality-of-service constraints
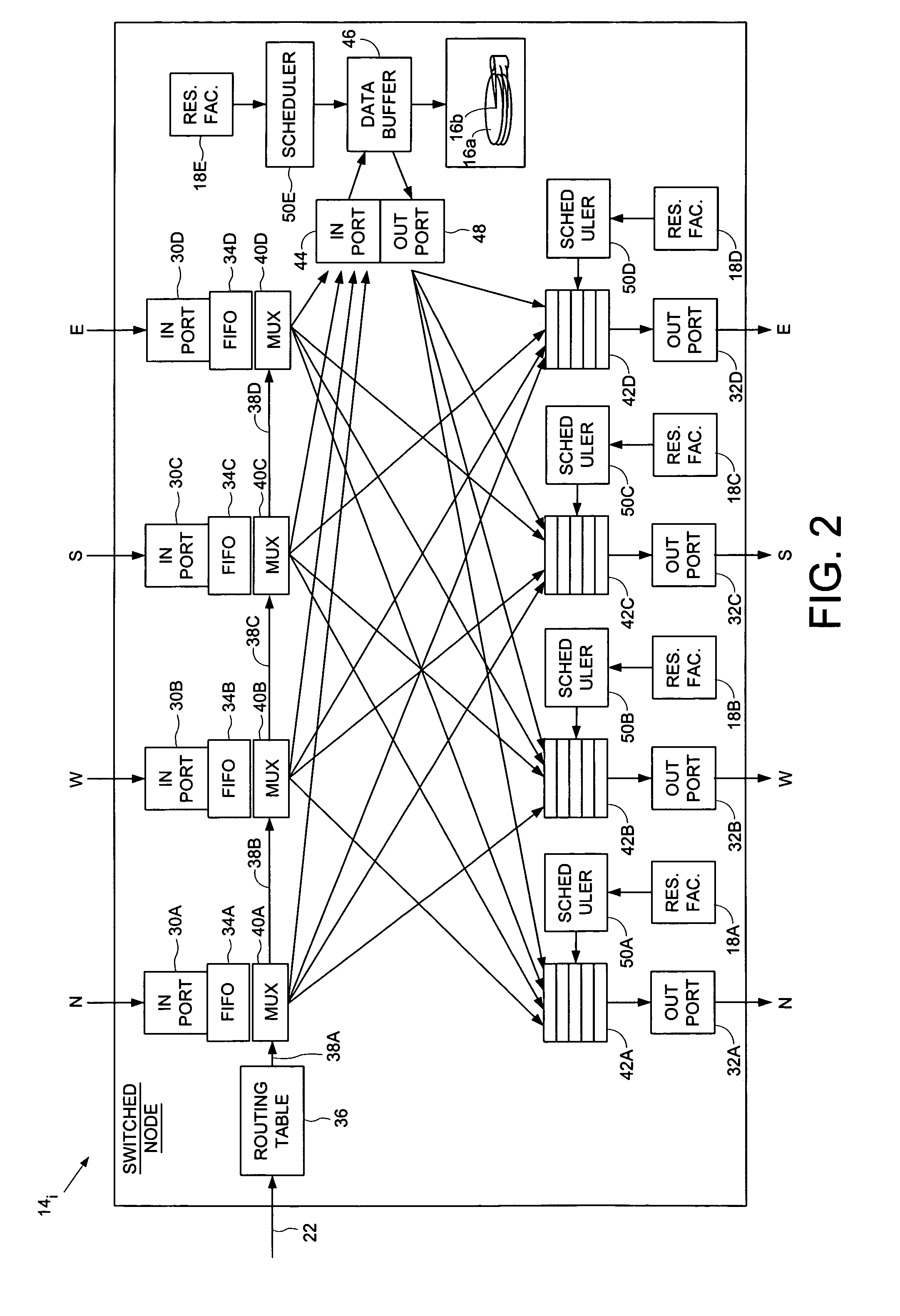
A computer network is disclosed comprising a plurality of interconnected computer devices including a plurality of disk drives for storing network data, each disk drive comprising a head and a disk. The computer network comprises a plurality of interconnected nodes, and a reservation facility for reserving resources within the disk drives and the nodes to support a predetermined Quality-of-Service constraint with respect to data transmitted between the disk drives through the nodes of the computer network. In one embodiment, a switched node is disclosed comprising switching circuitry having more than two bi-directional ports for simultaneously transmitting data in multiple dimensions through a computer network, a disk for storing data, a head actuated over the disk for writing data to and reading data from the disk, and a reservation facility for reserving resources associated with data read from the disk and written to the disk to support the predetermined Quality-of-Service constraint with respect to data transmitted through the computer network.
Owner:WESTERN DIGITAL TECH INC
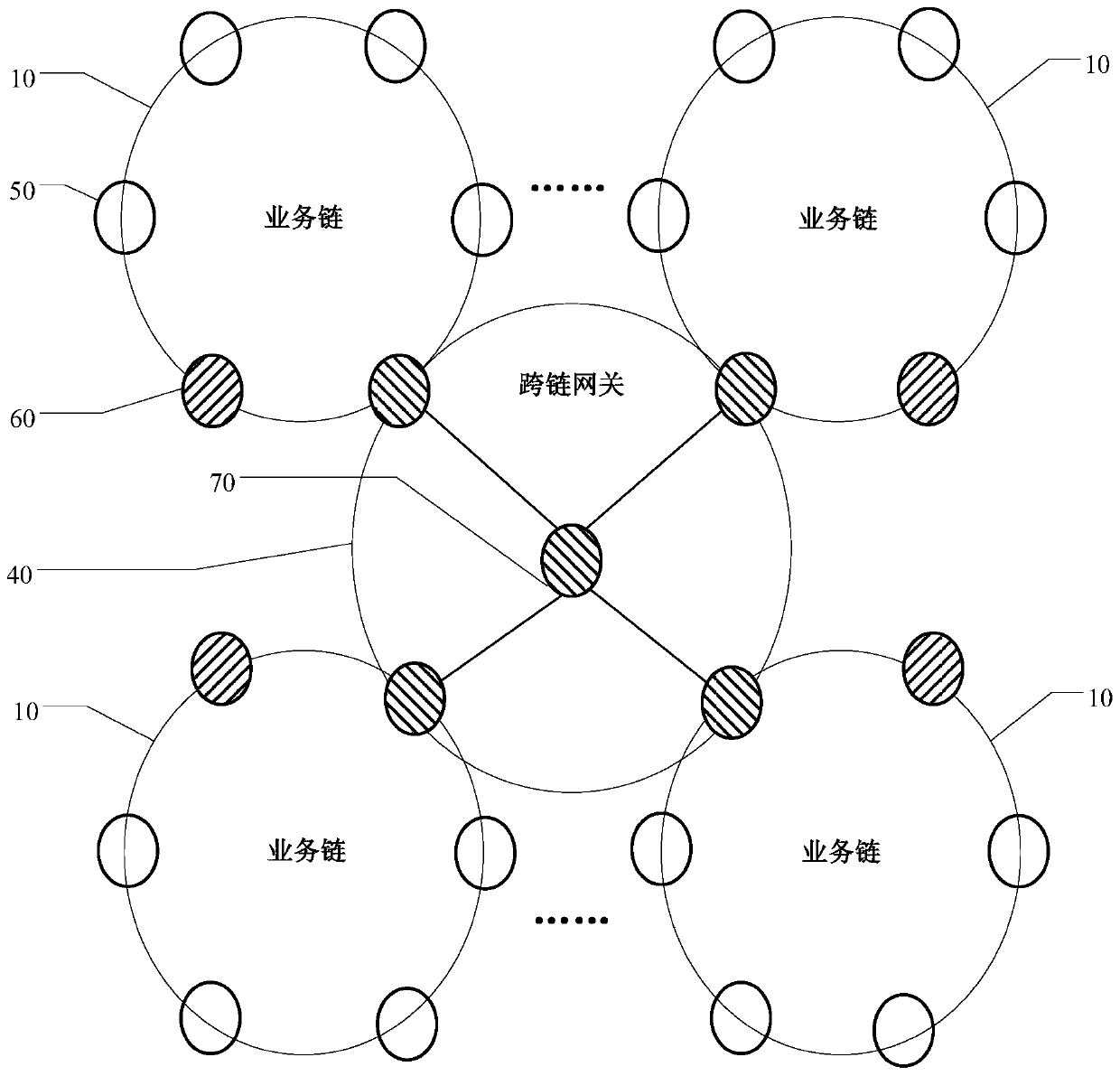
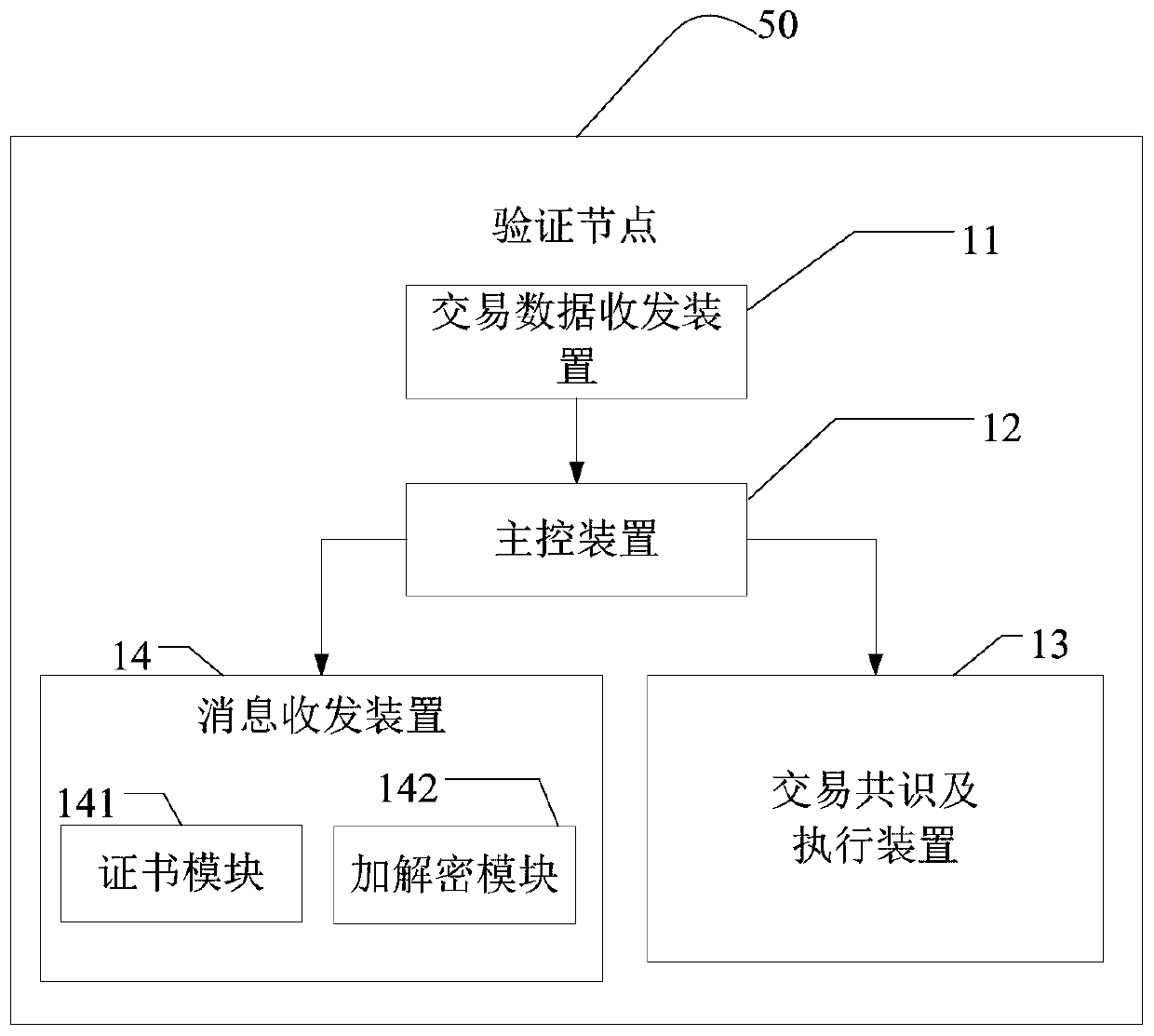
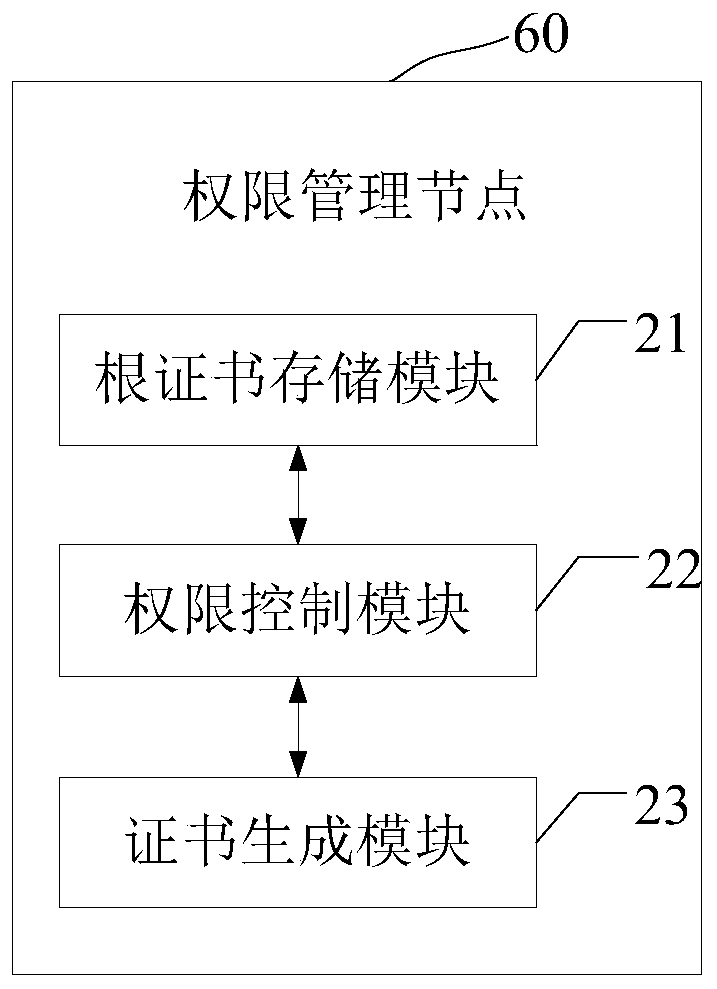
Blockchain-based cross-chain interconnection method, device and system
ActiveCN110266655AReach fusionSolve information silosFinanceUser identity/authority verificationInformation processingError processing
The invention provides a blockchain-based cross-chain interconnection method, a blockchain-based cross-chain interconnection system, computer equipment and a computer readable storage medium, and relates to the technical field of information processing. The system comprises a cross-chain gateway node and a plurality of service chains, each service chain comprises an authority management node, a gateway node and a plurality of verification nodes, and the gateway node in the plurality of service chains and the cross-chain gateway node form a cross-chain gateway; and the cross-chain gateway is used for realizing message format standardization and a cross-chain conversion protocol among the plurality of service chains so as to promote adaptation and forwarding of cross-chain messages, support error processing of request message timeout during cross-chain interconnection and finally realize mutual access and intercommunication of cross-chain data. Mutual access among the alliance chains of a plurality of different block chain technologies is achieved by introducing the bridging gateway chain, the problem of information island among a plurality of block chain systems is solved, and application and popularization of the block chain technology can be accelerated.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
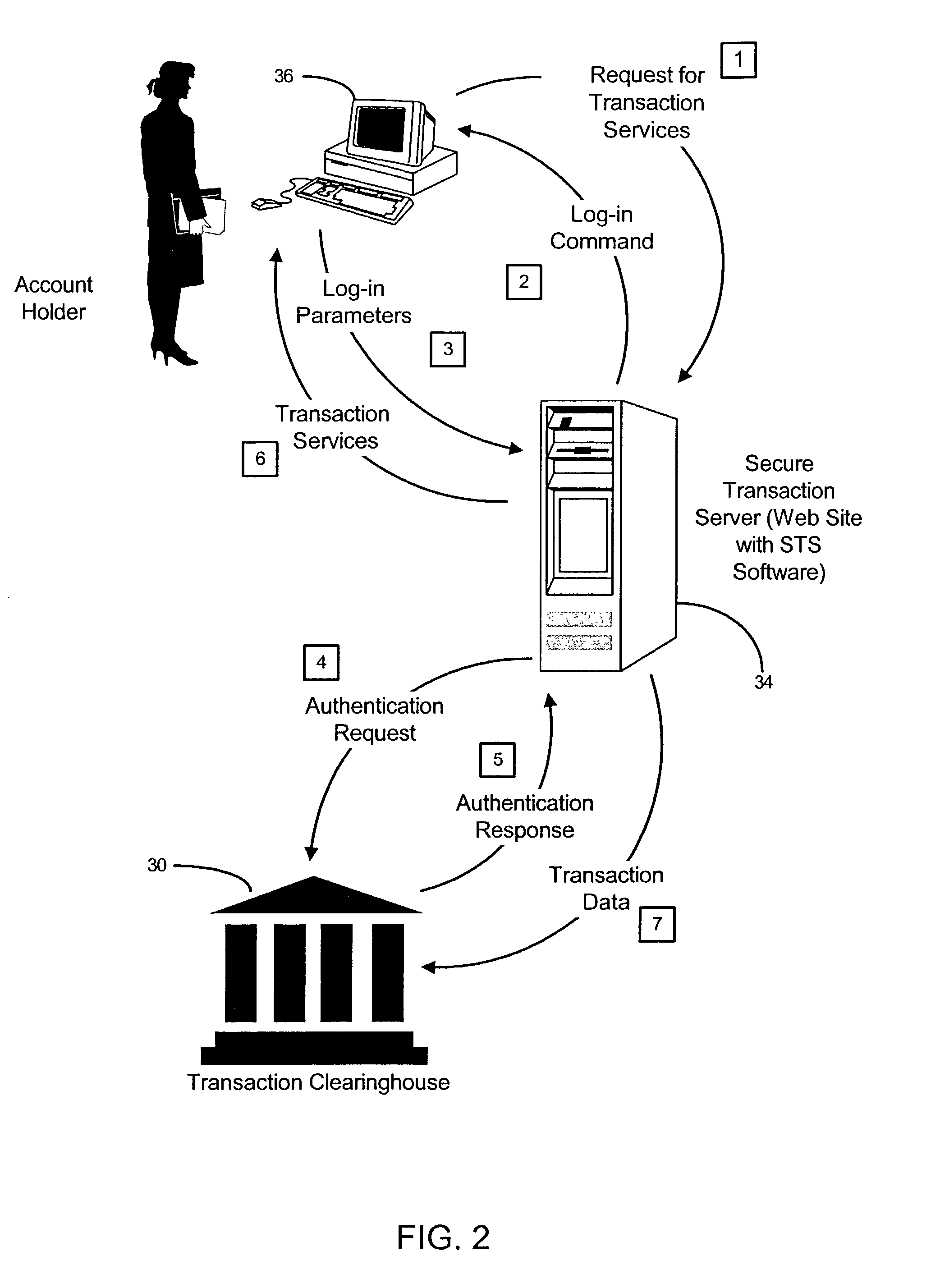
System and method for gathering, personalized rendering, and secure telephonic transmission of audio data
InactiveUS6529586B1Data processing applicationsAutomatic call-answering/message-recording/conversation-recordingPersonalizationThe Internet
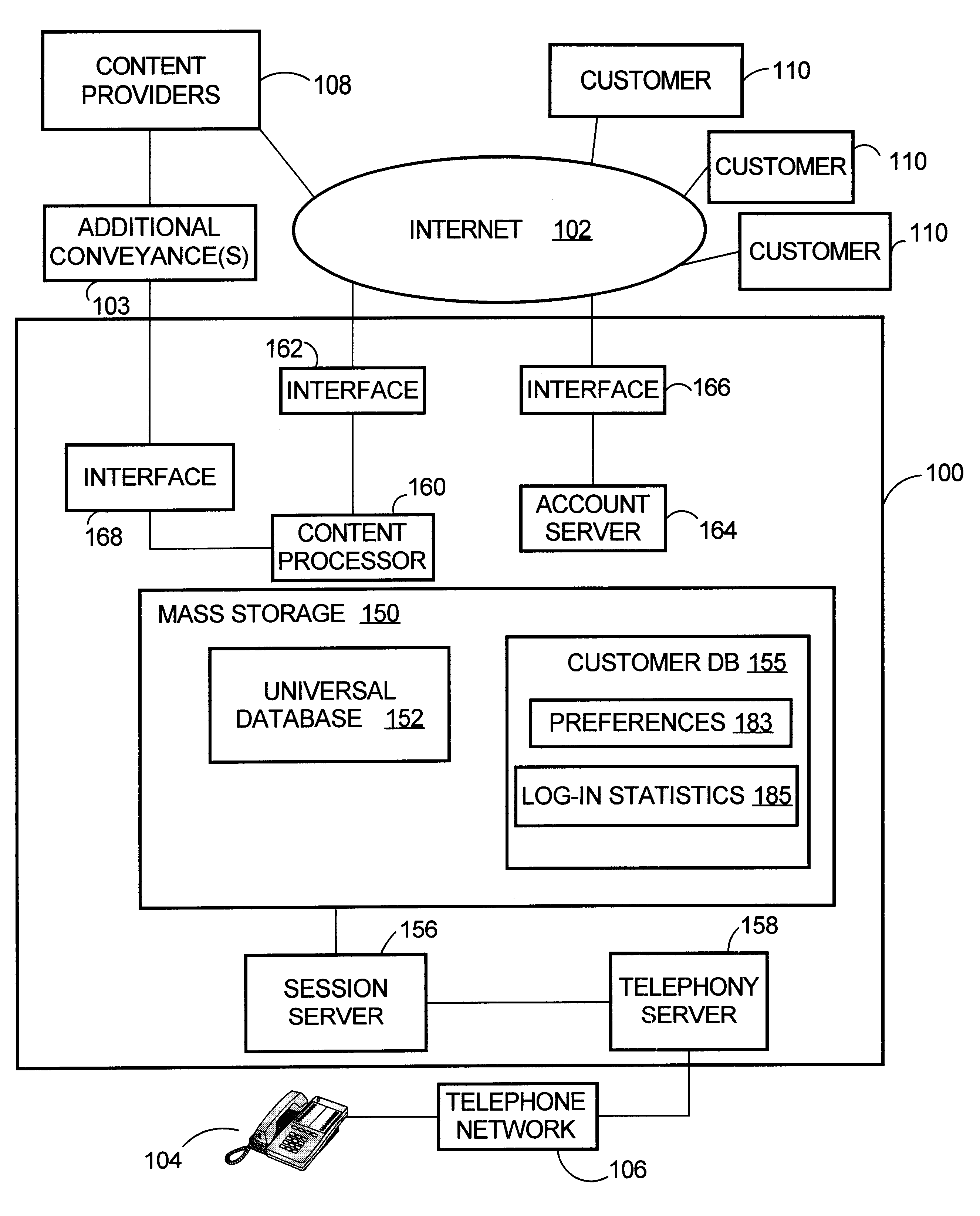
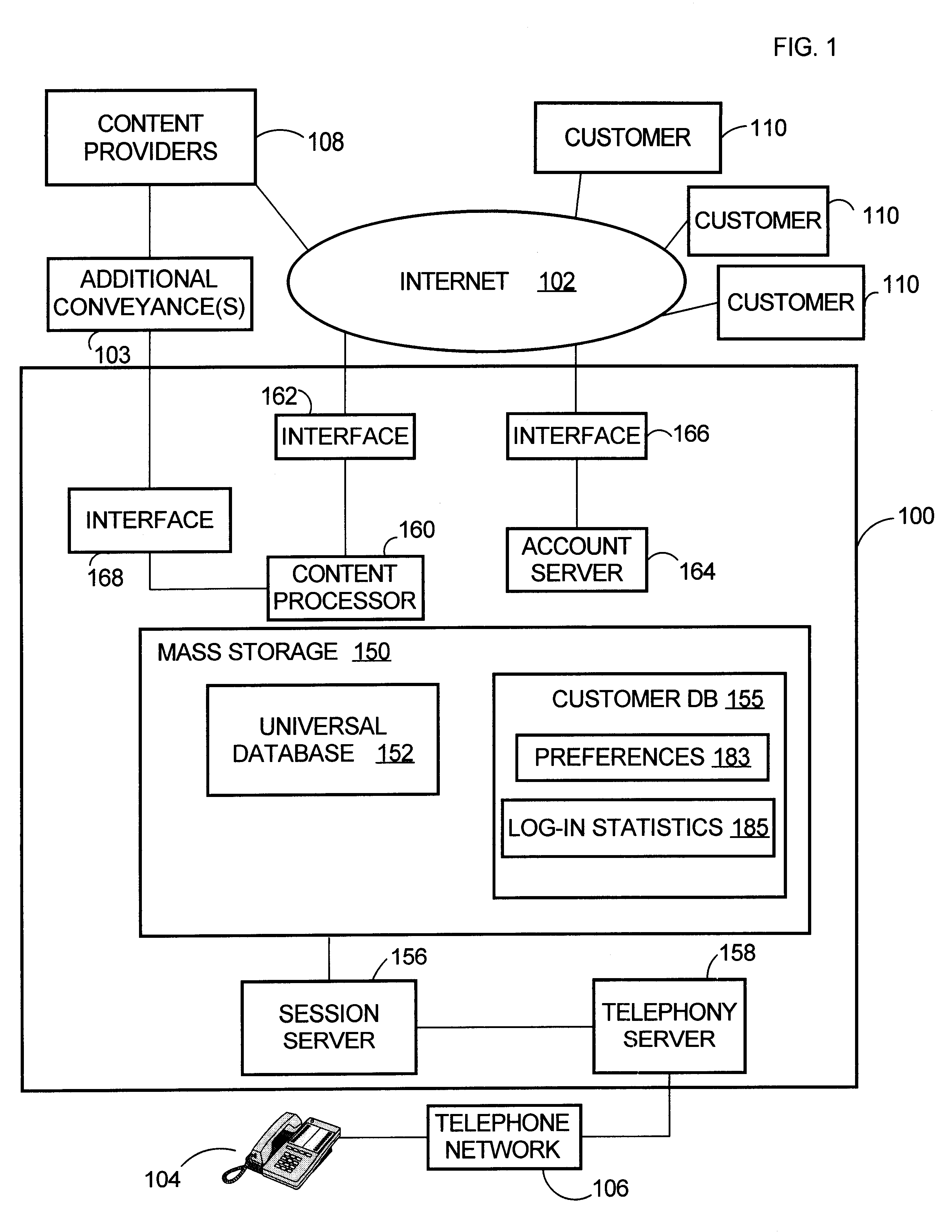
An audio information delivery system collects electronic data via Internet or other conveyance, and responsive to customer inquiries, selectively retrieves data from local stores in areas of interest to the inquiring customers, formats the data, and transmits the data in audio form to the customers via their telephones. Initially, an information delivery agency makes advance arrangements with remotely located content providers to repeatedly obtain information of prescribed character. Agency computers continually gather digitally stored audio and text information from the predefined content providers and assemble the gathered information into a universal database. Separately, the agency enrolls a number of individual customers, which includes obtaining each customer's preferences regarding information content and playback order. Responsive to a telephone call from a registered customer, agency's computers retrieve the caller's pre-stored preferences and proceed to identify information in the universal database that pertains to the caller's subject matter preferences. After preparing vocalizations of the text information, agency computer equipment audibly presents the audio information and vocalizations to the caller in predetermined order via the caller's telephone connection. This is achieved, for example, by using an intermediate telephone network such as a wireless carrier network.
Owner:ORACLE INT CORP
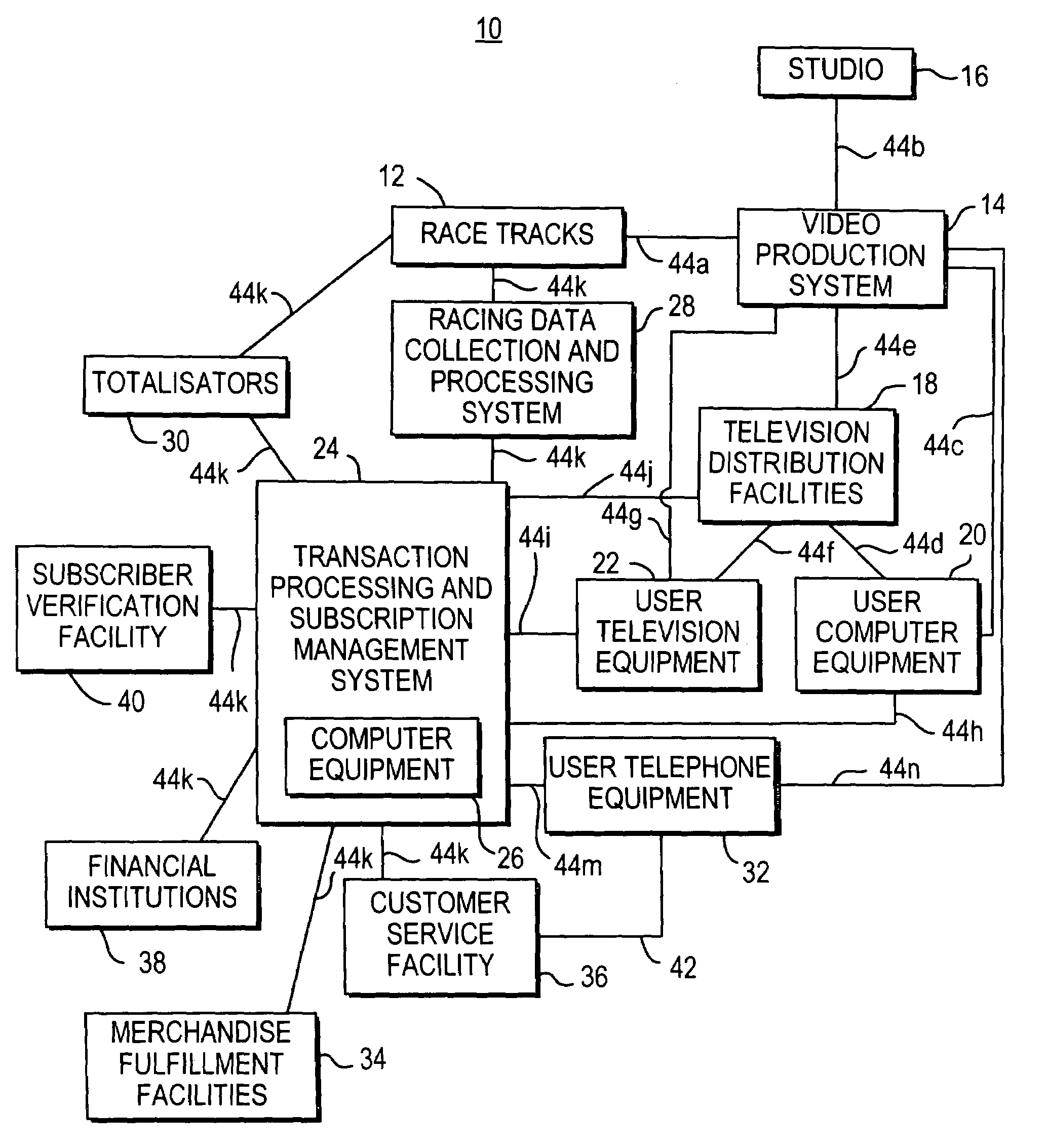
Cellular telephone interactive wagering system
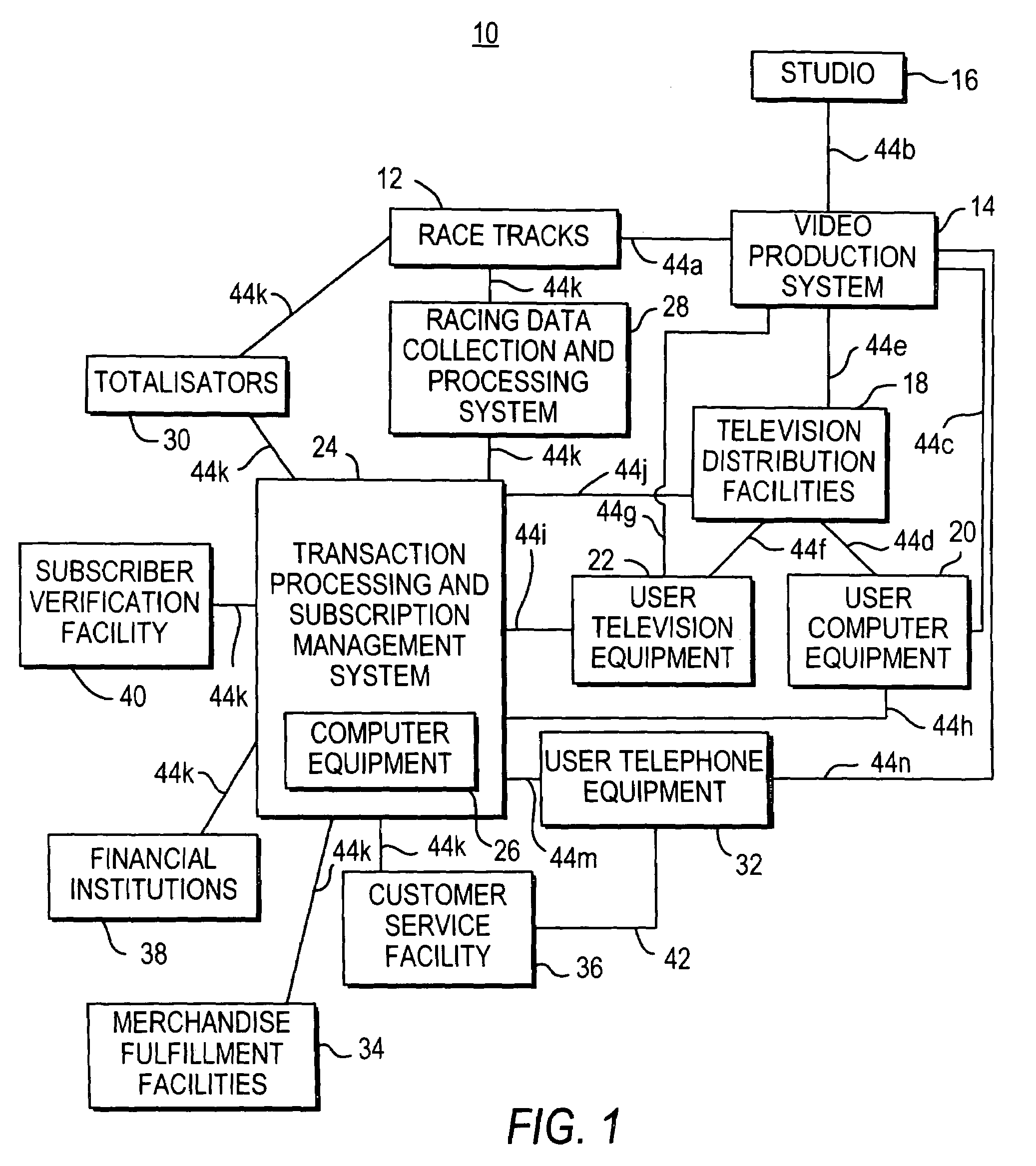
InactiveUS7379886B1Easy to set upReservationsRecombinant DNA-technologyTelevision equipmentTransaction processing system
Systems and processes for interactive wagering are provided. A cellular telephone or handheld computing device may be used to access an interactive wagering service. Television equipment and computer equipment may be used to access the service. A user may view information on wagers such as current odds and other racing data for horses or other runners on the cellular telephone or other device. The user may create a corresponding off-track wager with the cellular telephone or other device that may be sent to a transaction processing and subscription management system. The transaction processing and subscription management system may handle the wager transaction and adjust the user's account balance.
Owner:ODS PROPERTIES
Allocating funds for payment of transactional account statements
InactiveUS20050075975A1Affording financial disciplineFinanceBilling/invoicingSet-asideComputer science
Systems and methods for providing electronic management of transactional accounts. A computer device is used to provide financial resource allocation and accountability among various groups of accounts, including source accounts and transactional accounts. When a user employs a transactional account to make a purchase, the amount of the purchase is electronically set aside, frozen or otherwise held from a source account and preserved until a payment is required for the transactional account at the close of a billing period. Accordingly, when a payment for the transactional account is required, funds are available for full payment of all purchases made during the billing cycle, thereby affording financial discipline to the user.
Owner:IN2M CORP
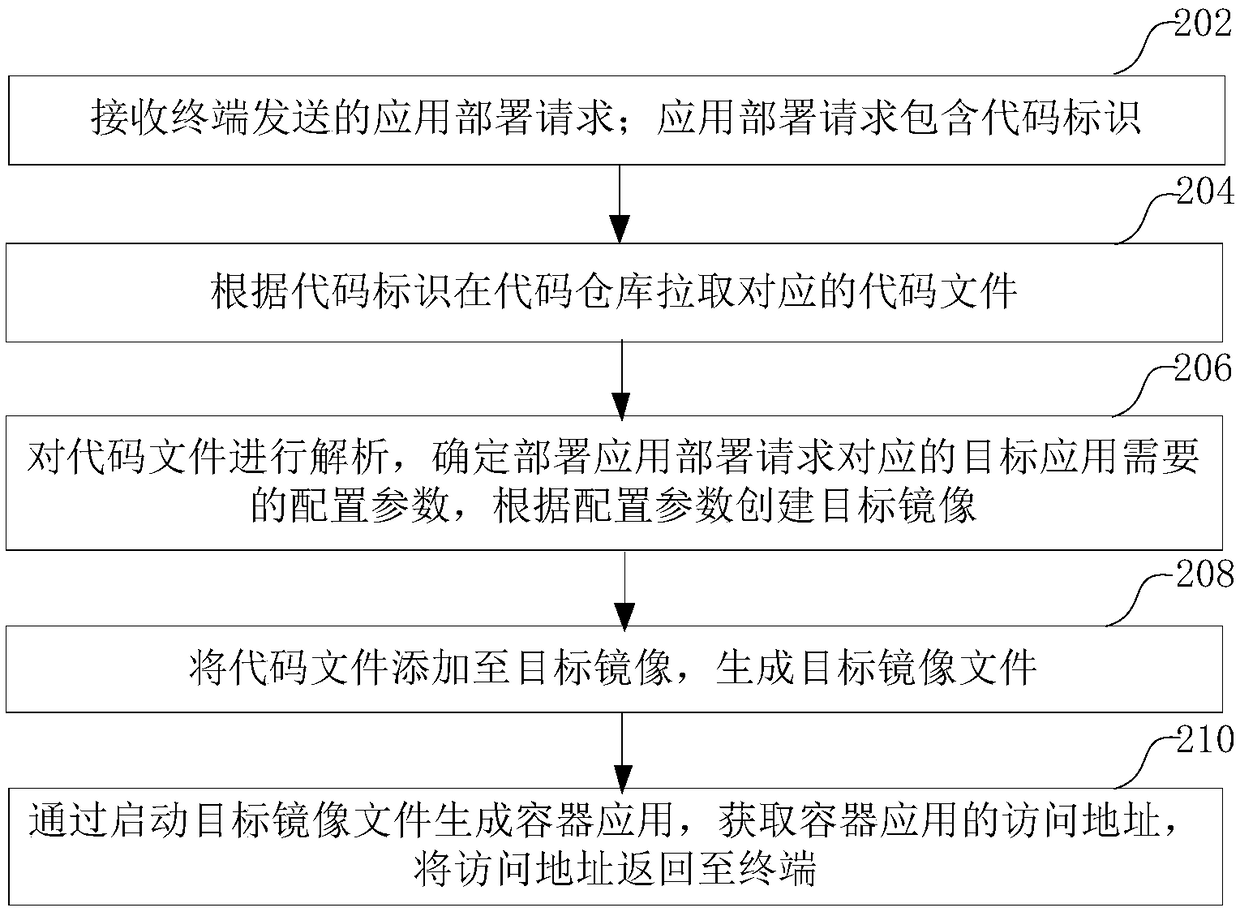
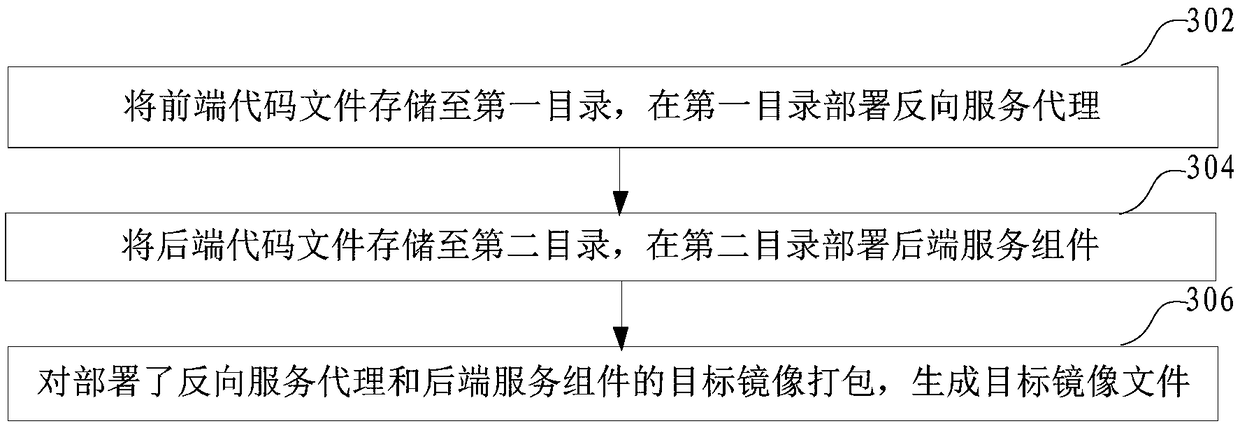
Container application deployment method and device, computer equipment and storage medium
ActiveCN108958927AReduce configuration operationsLower application thresholdResource allocationEnergy efficient computingComputer terminalMirror image
The application relates to a container application deployment method and device, computer equipment and a storage medium. The method includes the following steps: receiving an application deployment request sent by a terminal, wherein the application deployment request includes a code identifier; pulling a corresponding code file in a code repository according to the code identifier; parsing the code file, determining configuration parameters required to deploy a target application corresponding to the application deployment request, and creating a target mirror image according to the configuration parameters; adding the code file to the target mirror image to generate a target mirror image file; and starting the target mirror image file to generate a container application, acquiring an access address of the container application, and returning the access address to the terminal. By adopting the method, the deployment threshold of the container application can be lowered, and the deployment efficiency of the container application can be improved.
Owner:KANG JIAN INFORMATION TECH (SHENZHEN) CO LTD
Distributive storage controller and method
ActiveUS20040049700A1Safe storageReduce risk of leakageInput/output to record carriersDigital data processing detailsHard disc driveControl store
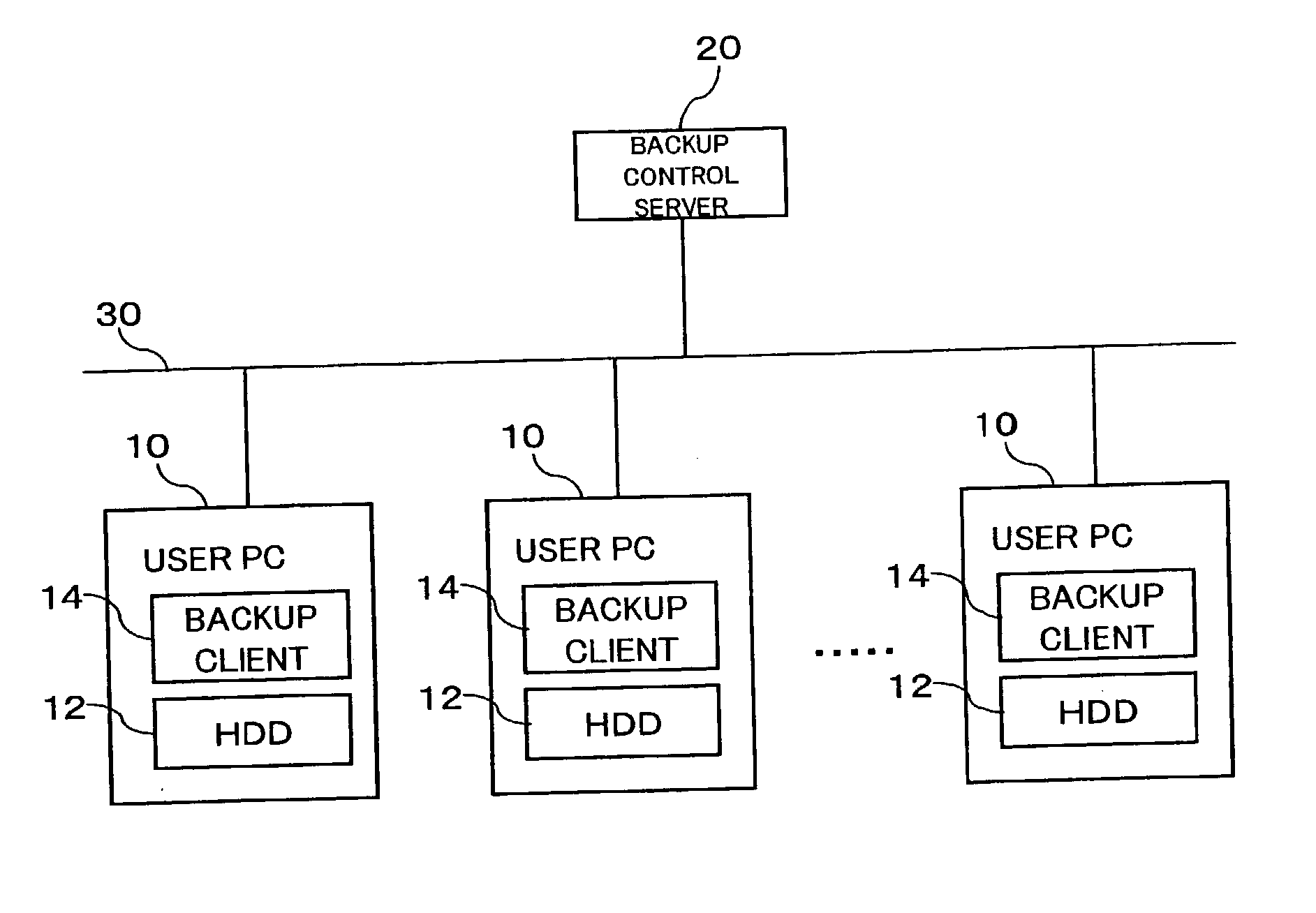
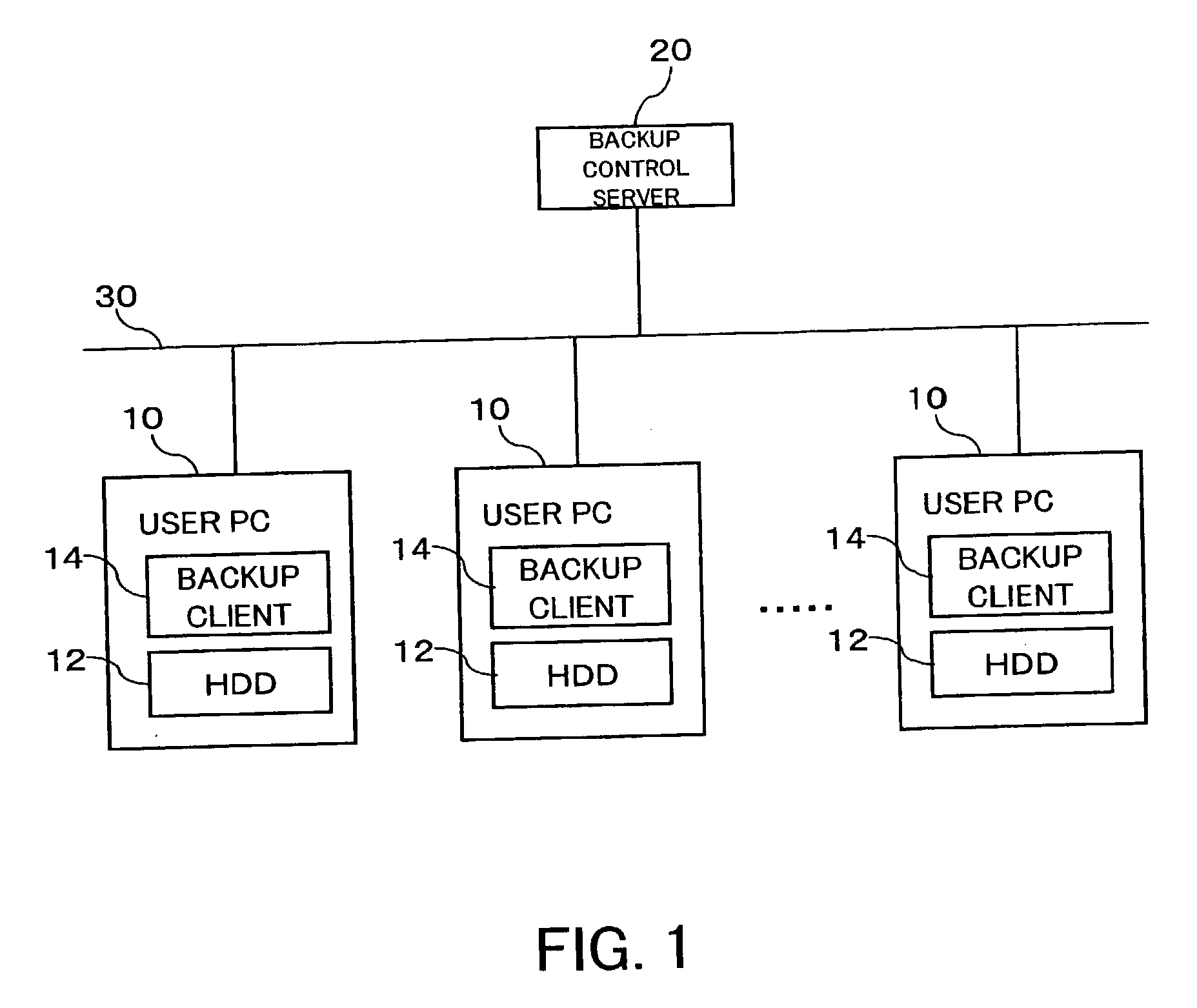
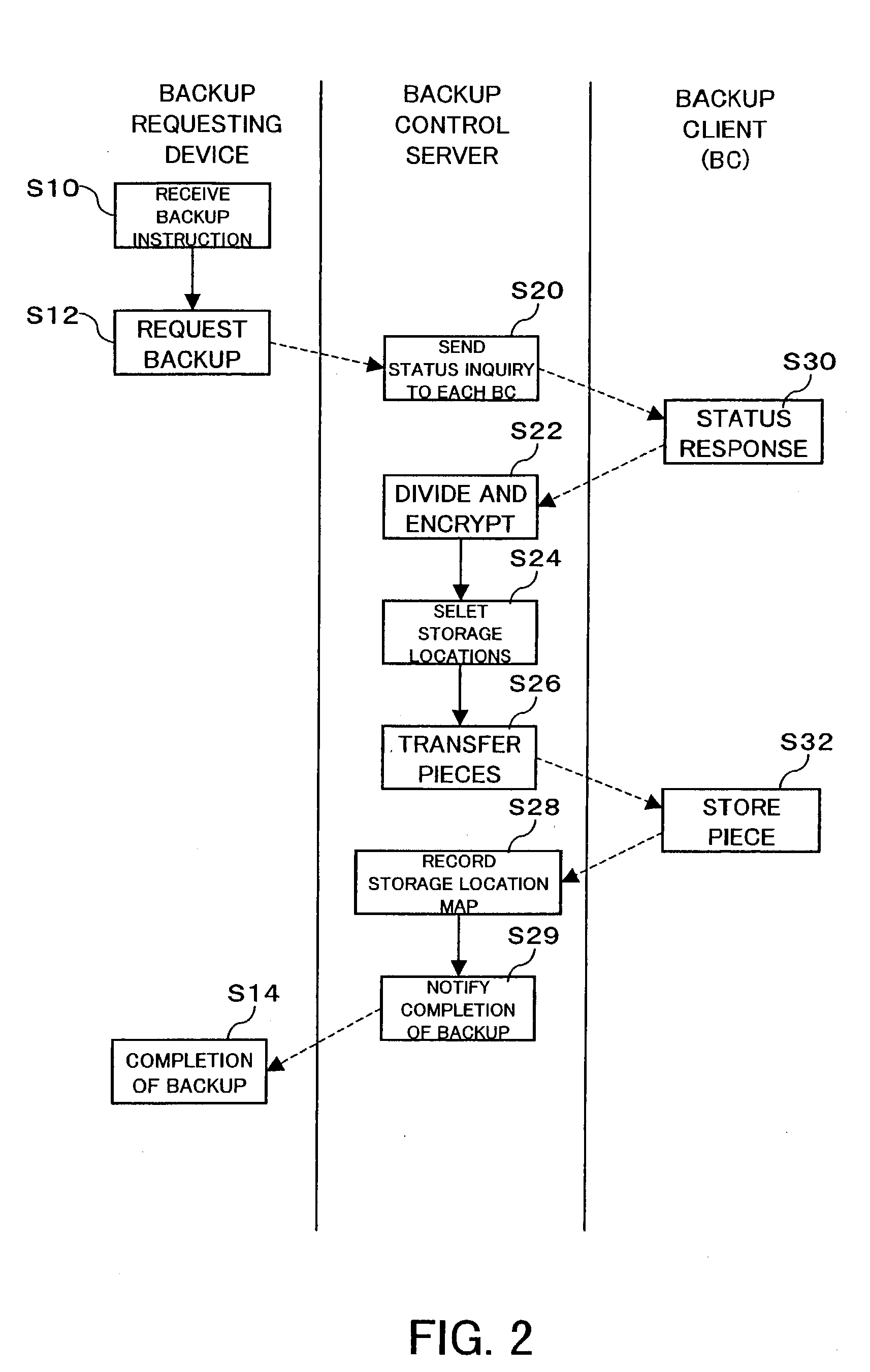
An inexpensive data storage technique utilizing available capacity in individual computer devices connected to a network is provided. When a backup client (BC) (14) of a user PC receives a backup instruction for a file from a user, the backup client (14) requests backup to a backup control server (20). The backup control server (20) divides and encrypts the file to be backed up into a plurality of encrypted pieces, transfers the encrypted pieces to user PCs (10), and stores the encrypted piece in the HDDs (12) of the user PCs (10). When the destributively backed up file is to be extracted, the user PC 10 obtains each encrypted piece from the user PCs 10 on which they are stored, and combines and decrypts the encrypted pieces to restore the original file.
Owner:FUJIFILM BUSINESS INNOVATION CORP
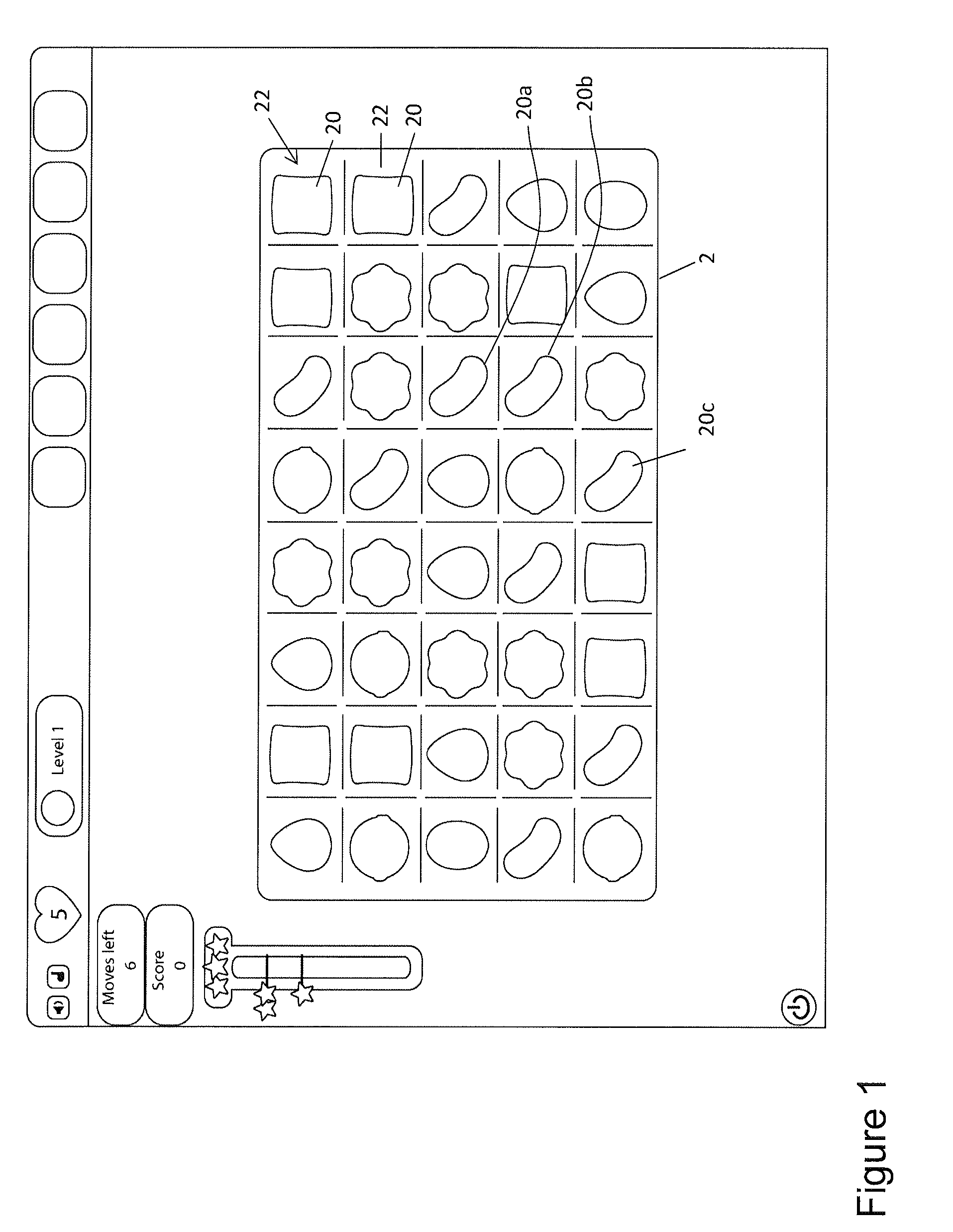
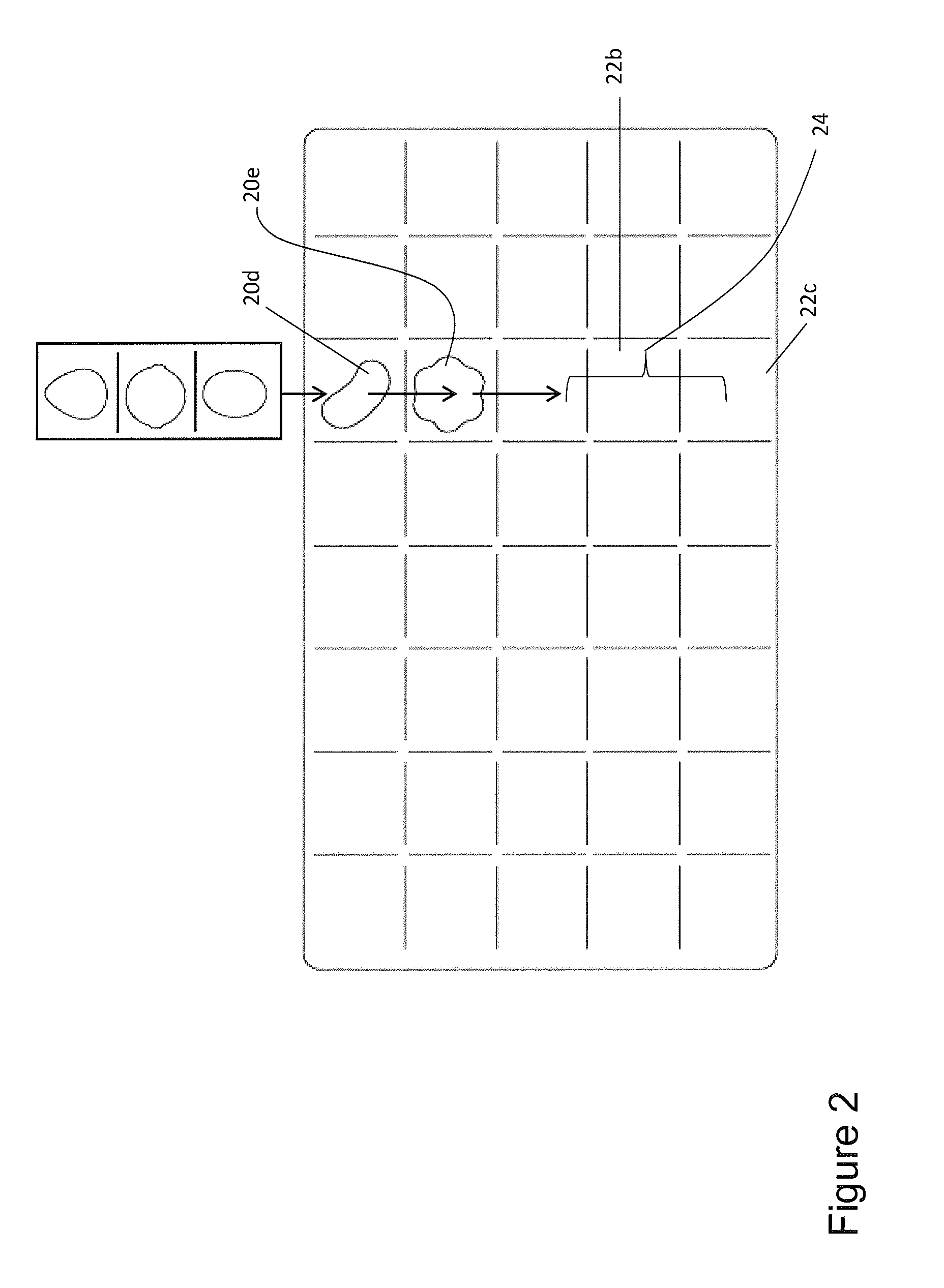
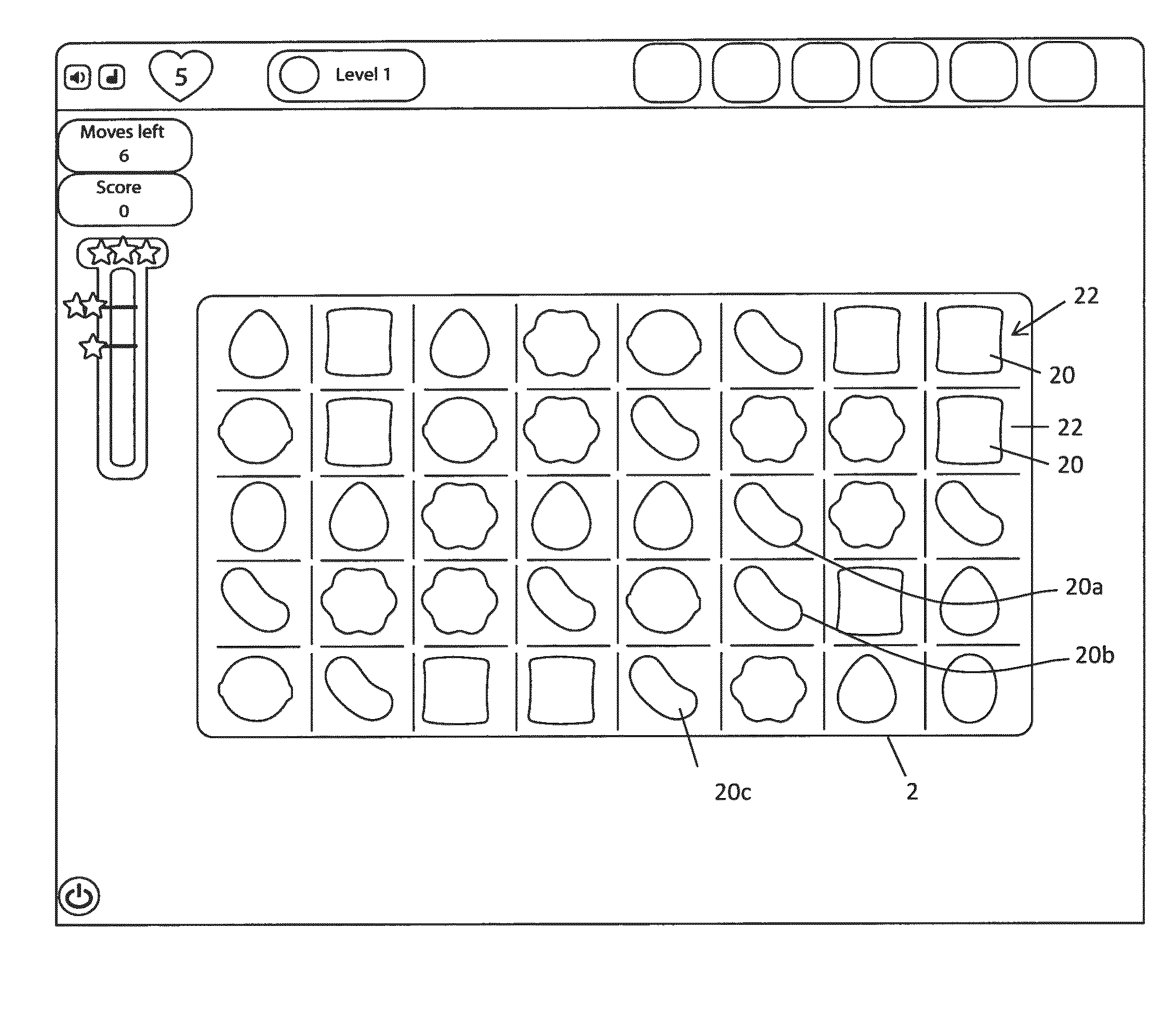
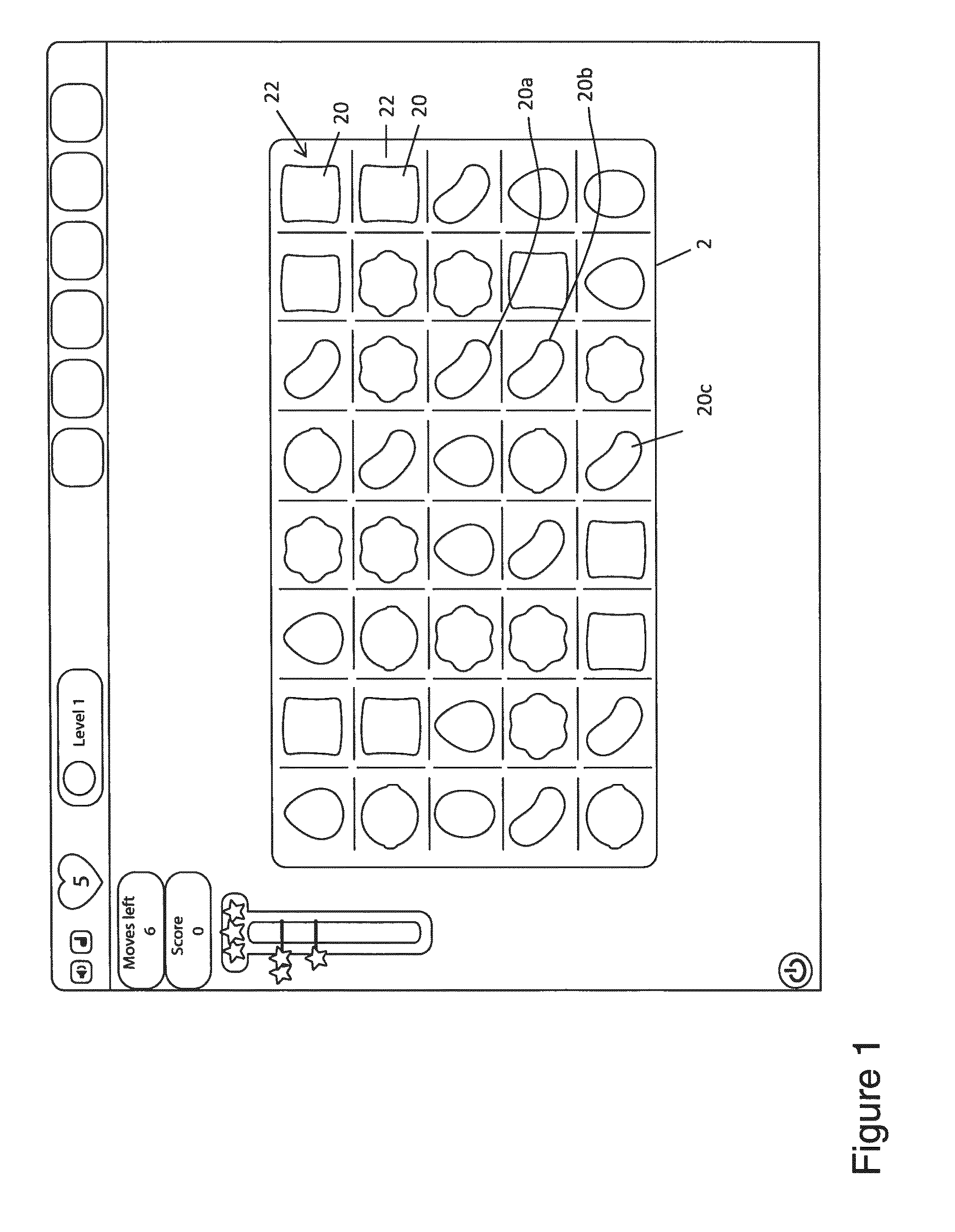
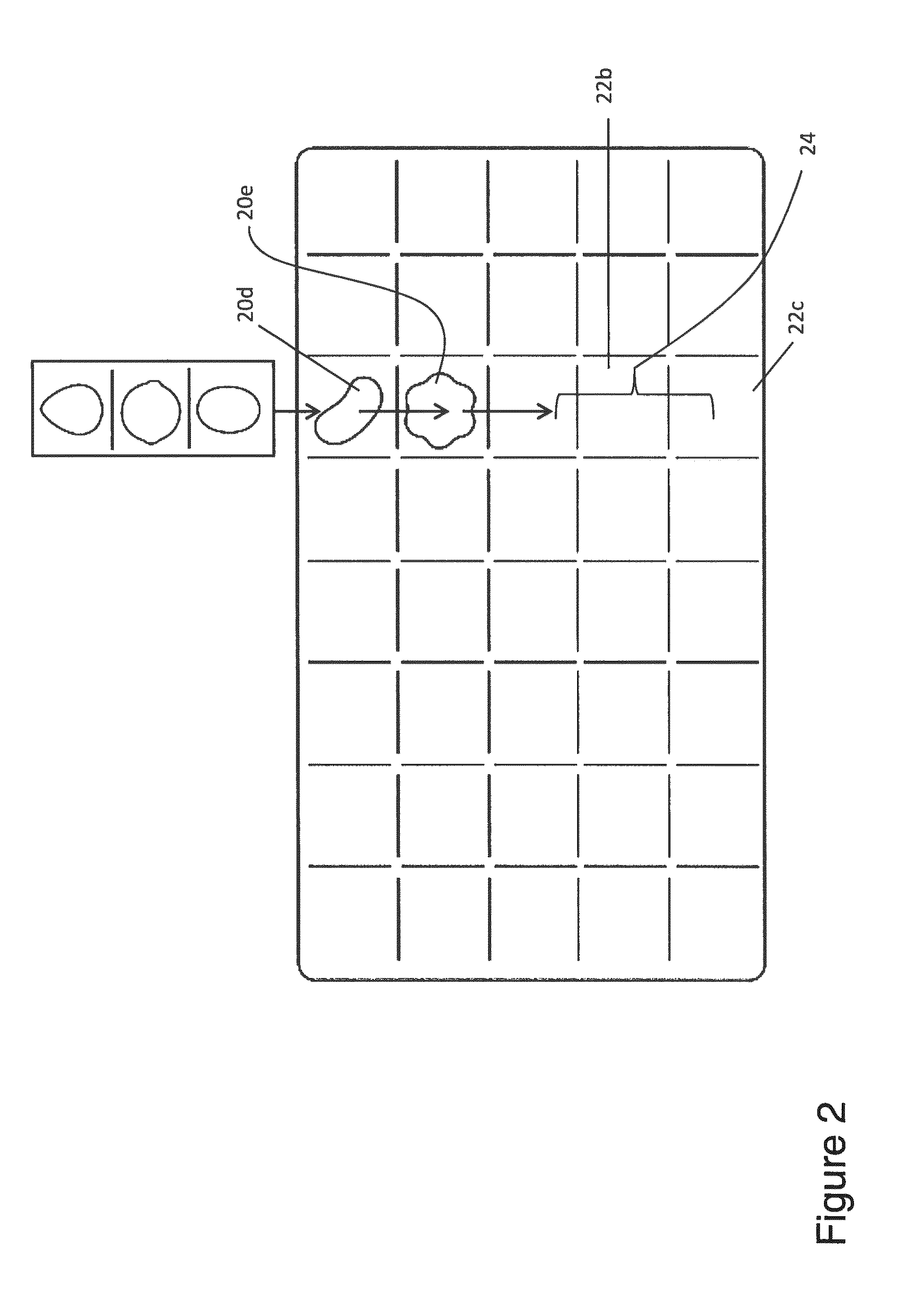
Controlling a user interface of a computer device
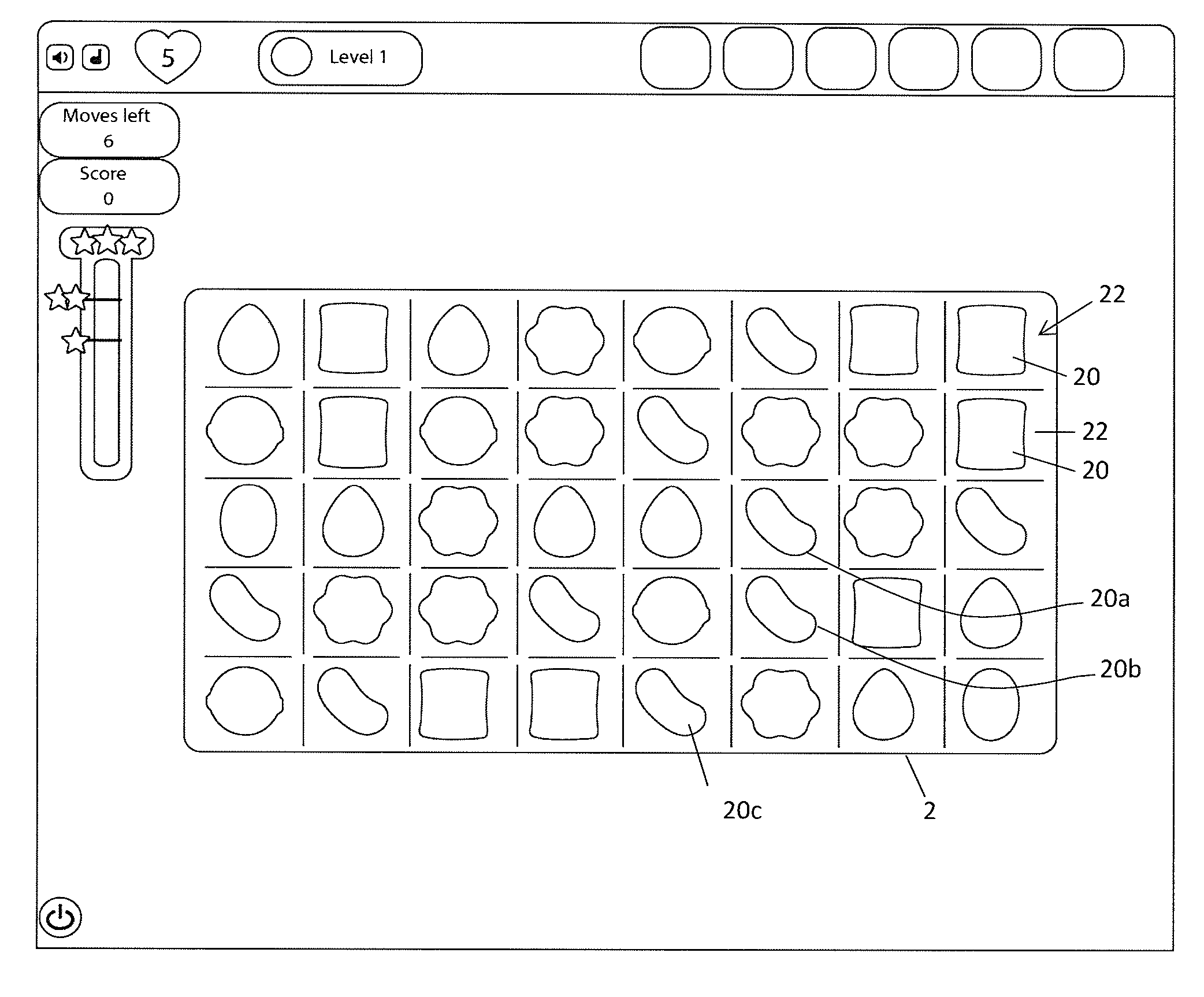
A computer device has user interface configured to display user actuatable game elements and to detect user input when a user engages with a game element; and a processor configured to receive a detected user input and on detecting a match game condition to control the user interface to remove at least three game elements from the display and to provide on the user interface replacement user actuatable game elements, wherein the manner of providing each replacement game element has a graphical representation governed by a tile associated with each game element, wherein each tile has a selectable physics which controls at least one of (i) the direction in which it moves to replenish a vacancy left by the removed user game elements; and (ii) the speed at which it moves to replenish the vacancy.
Owner:KING COM
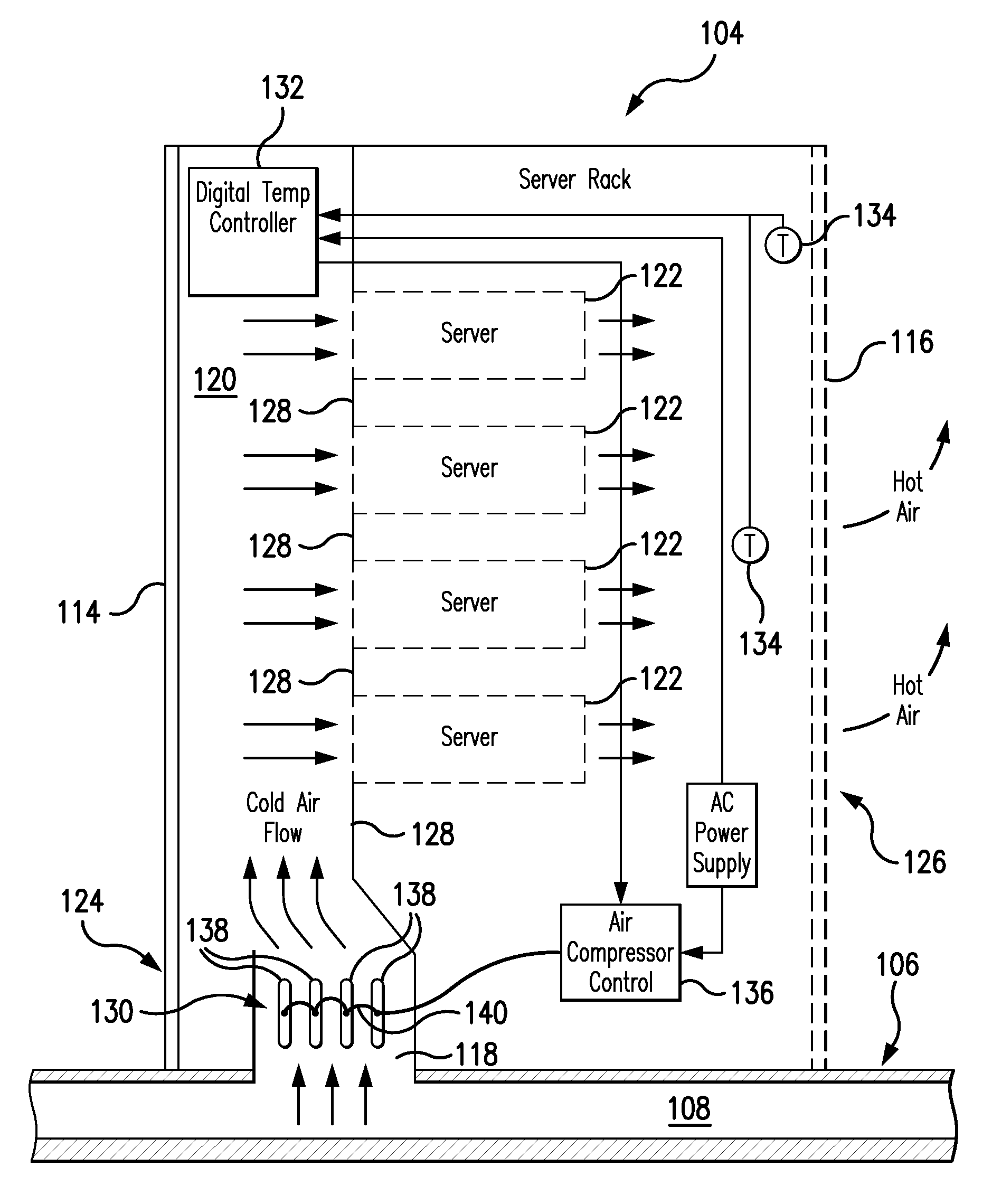
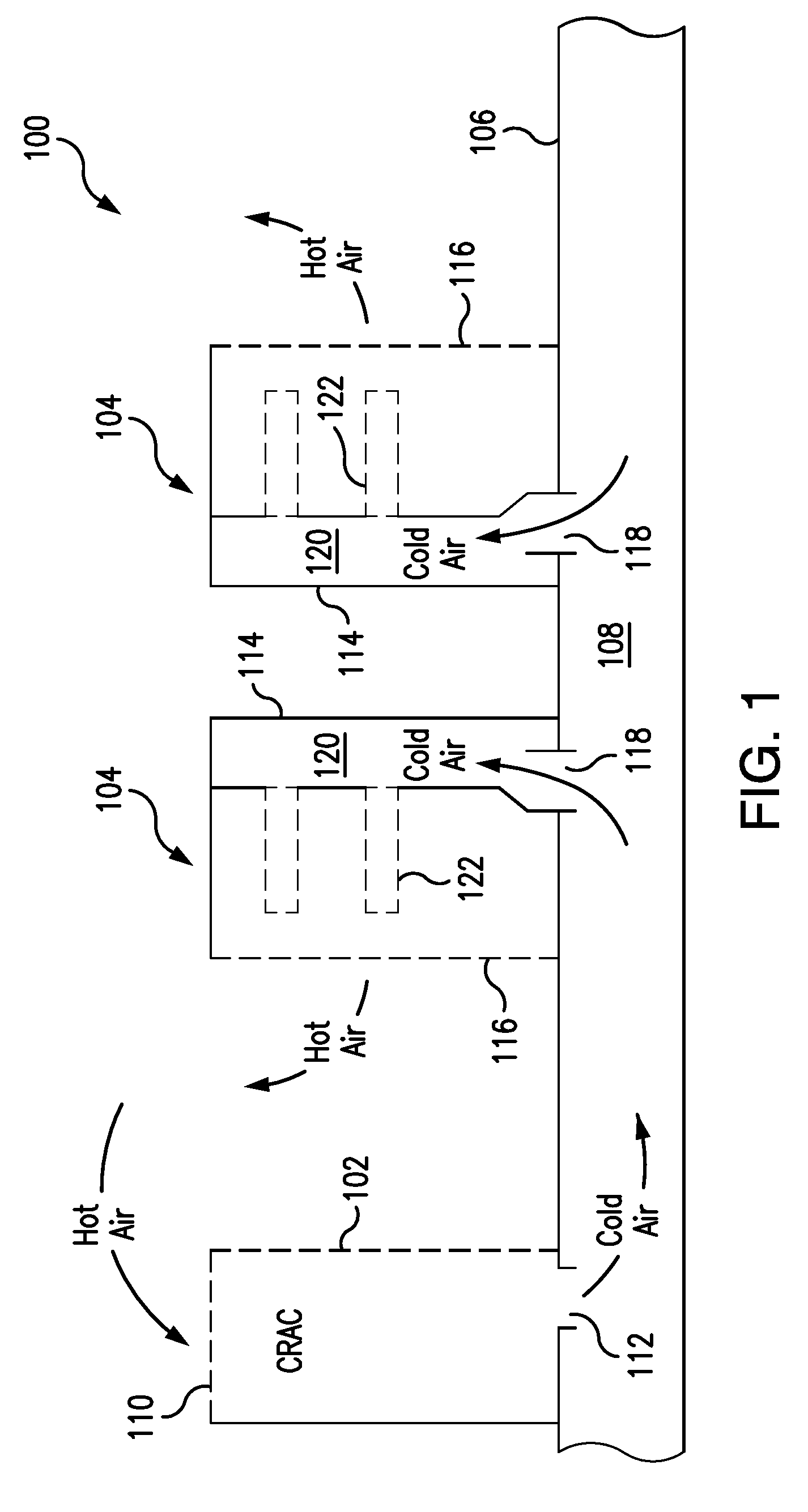
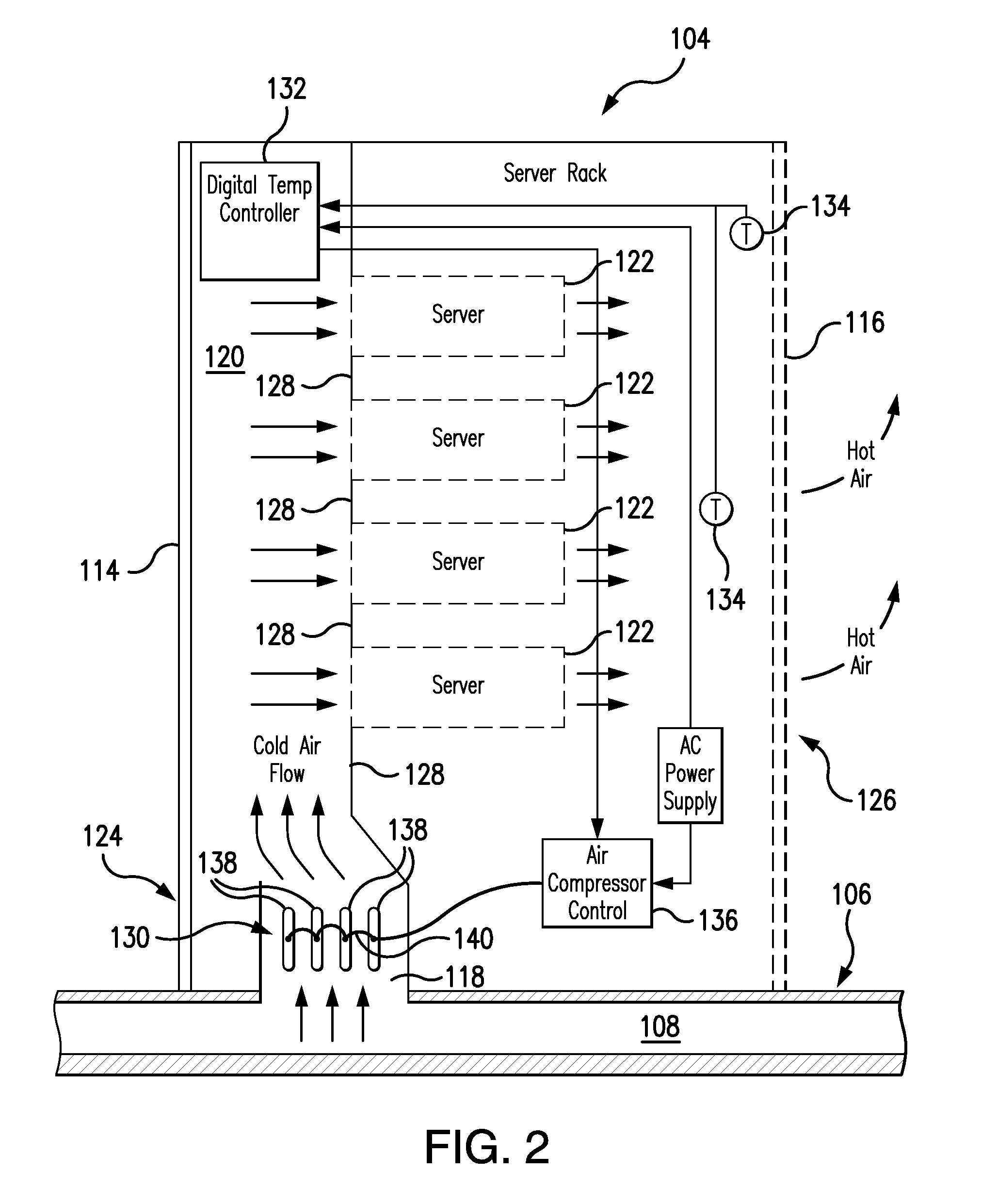
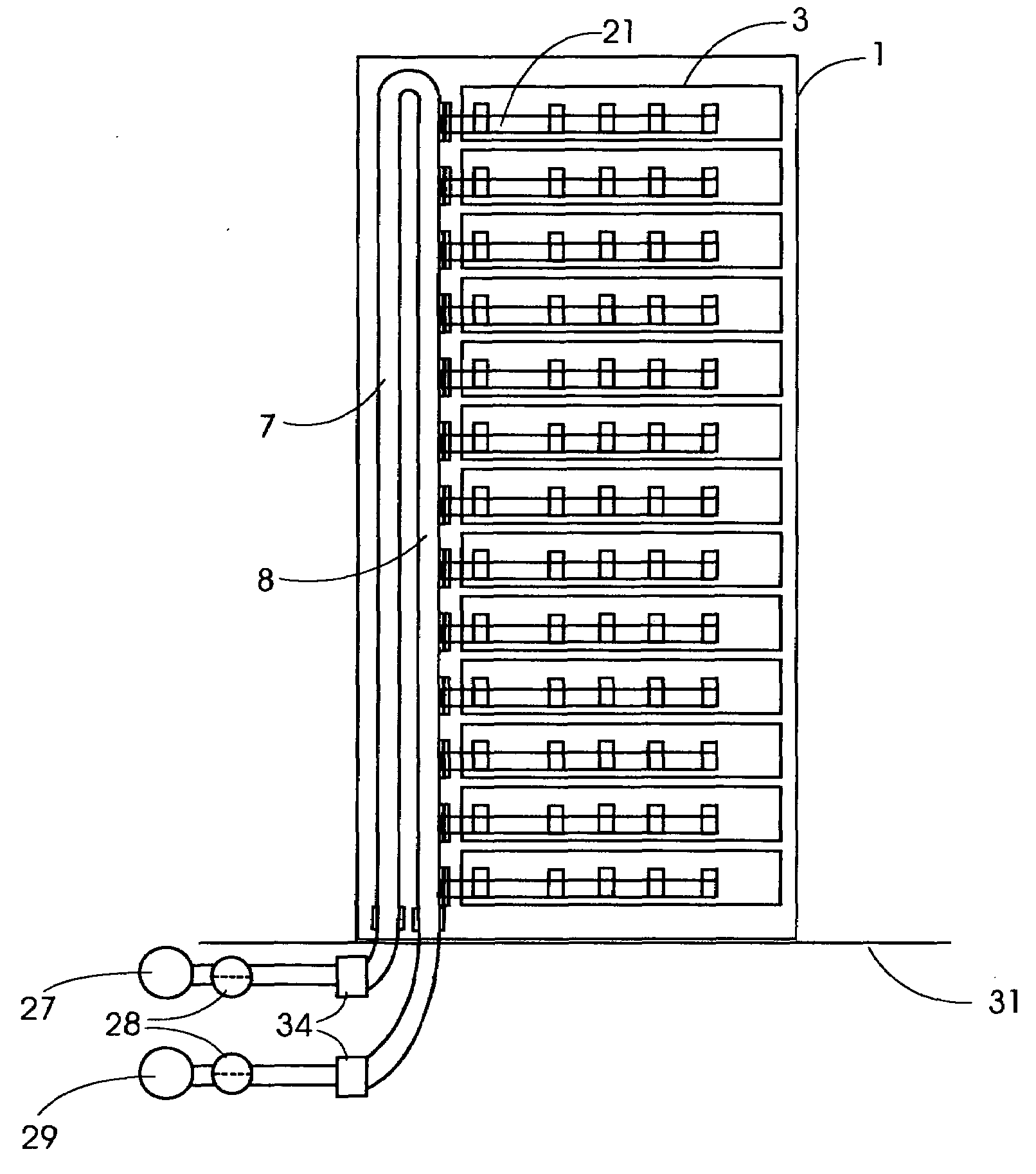
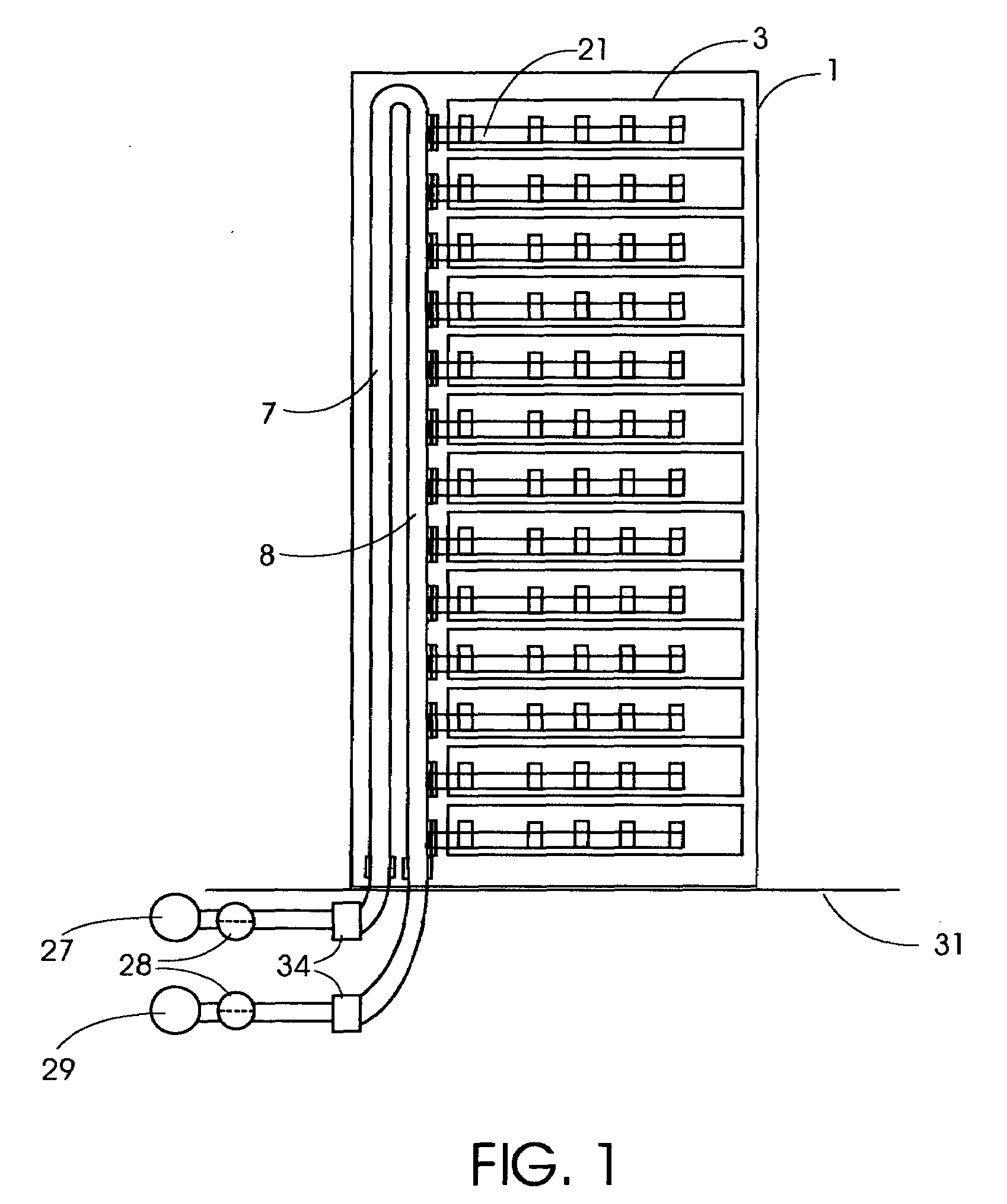
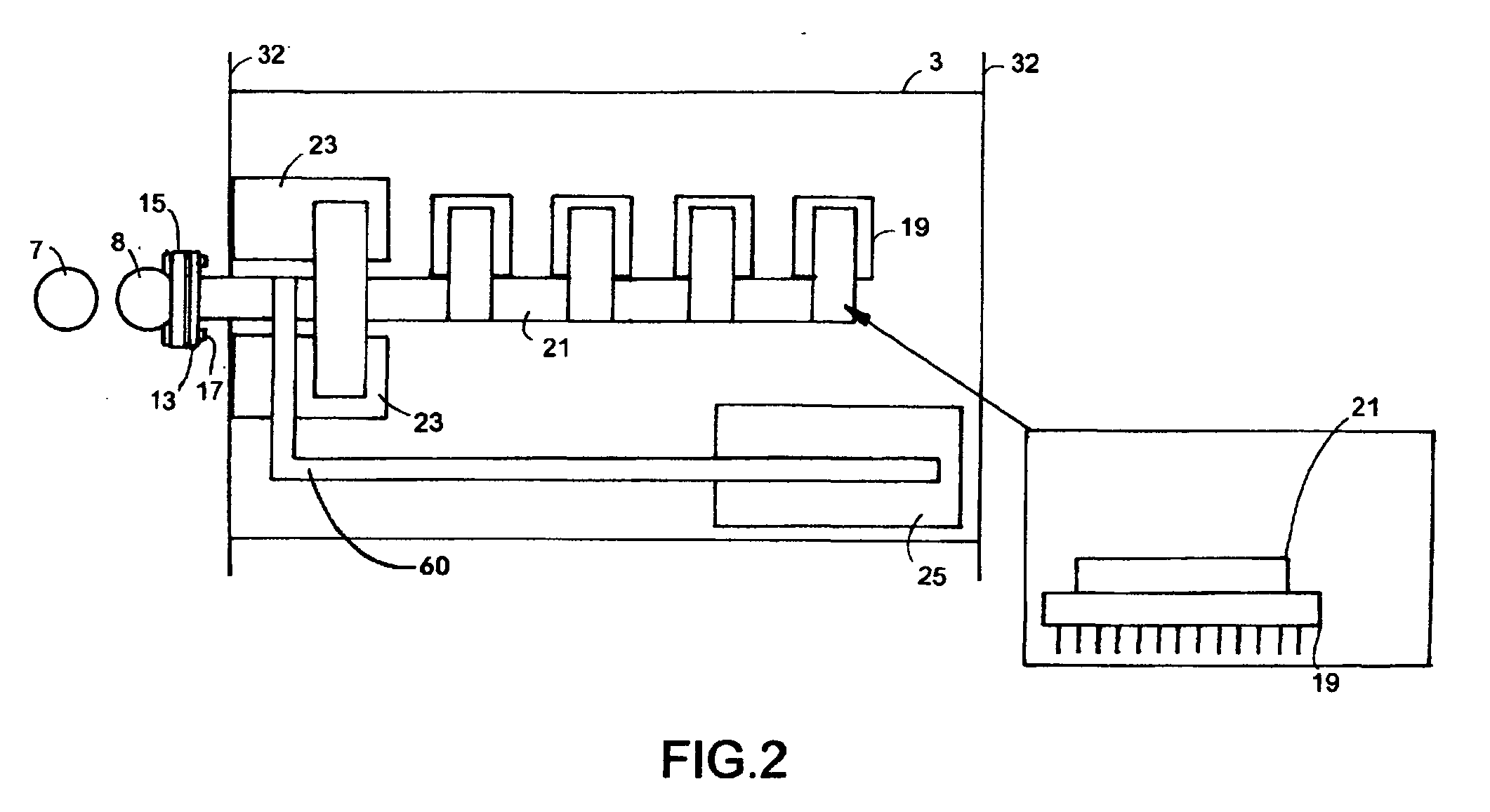
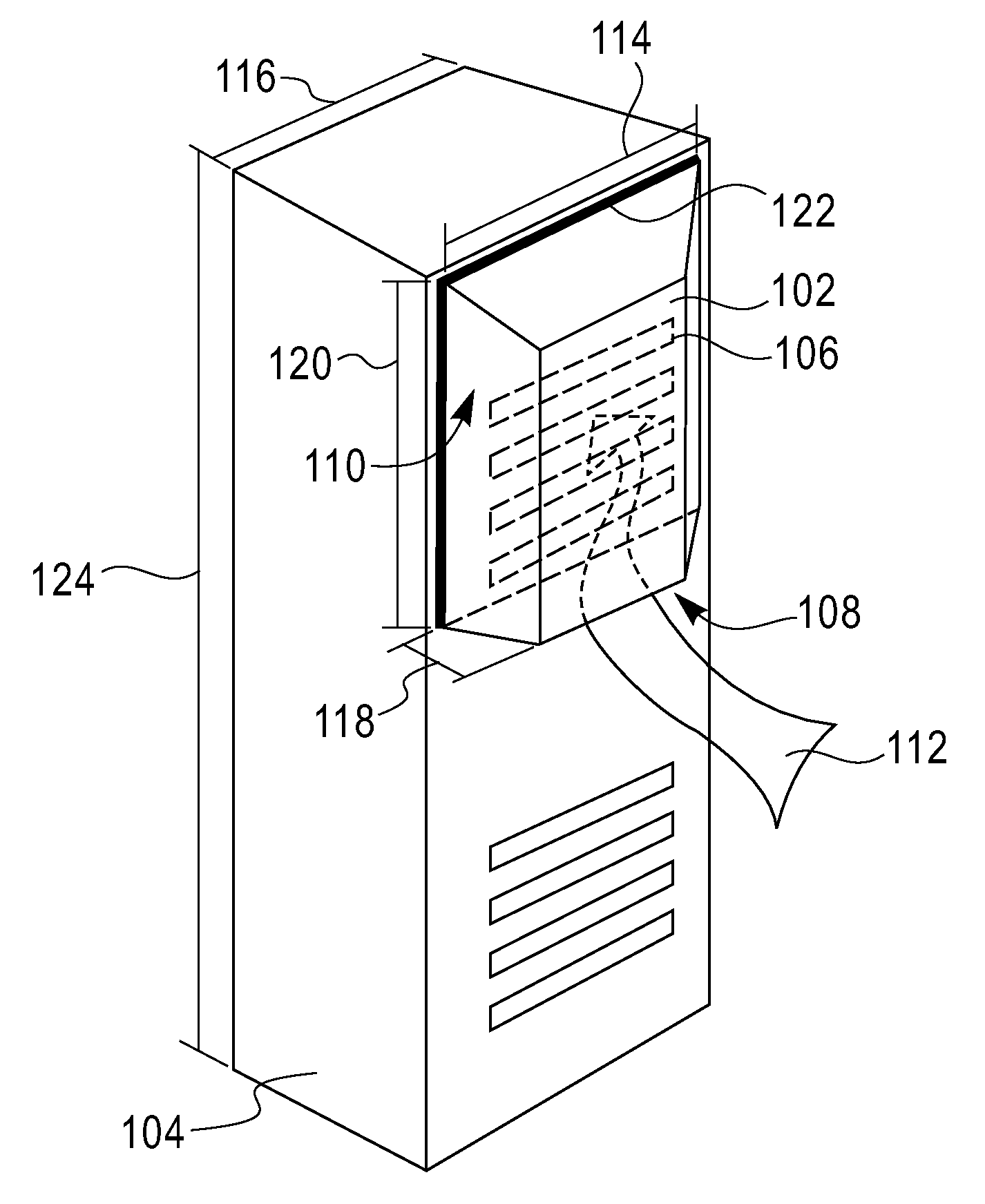
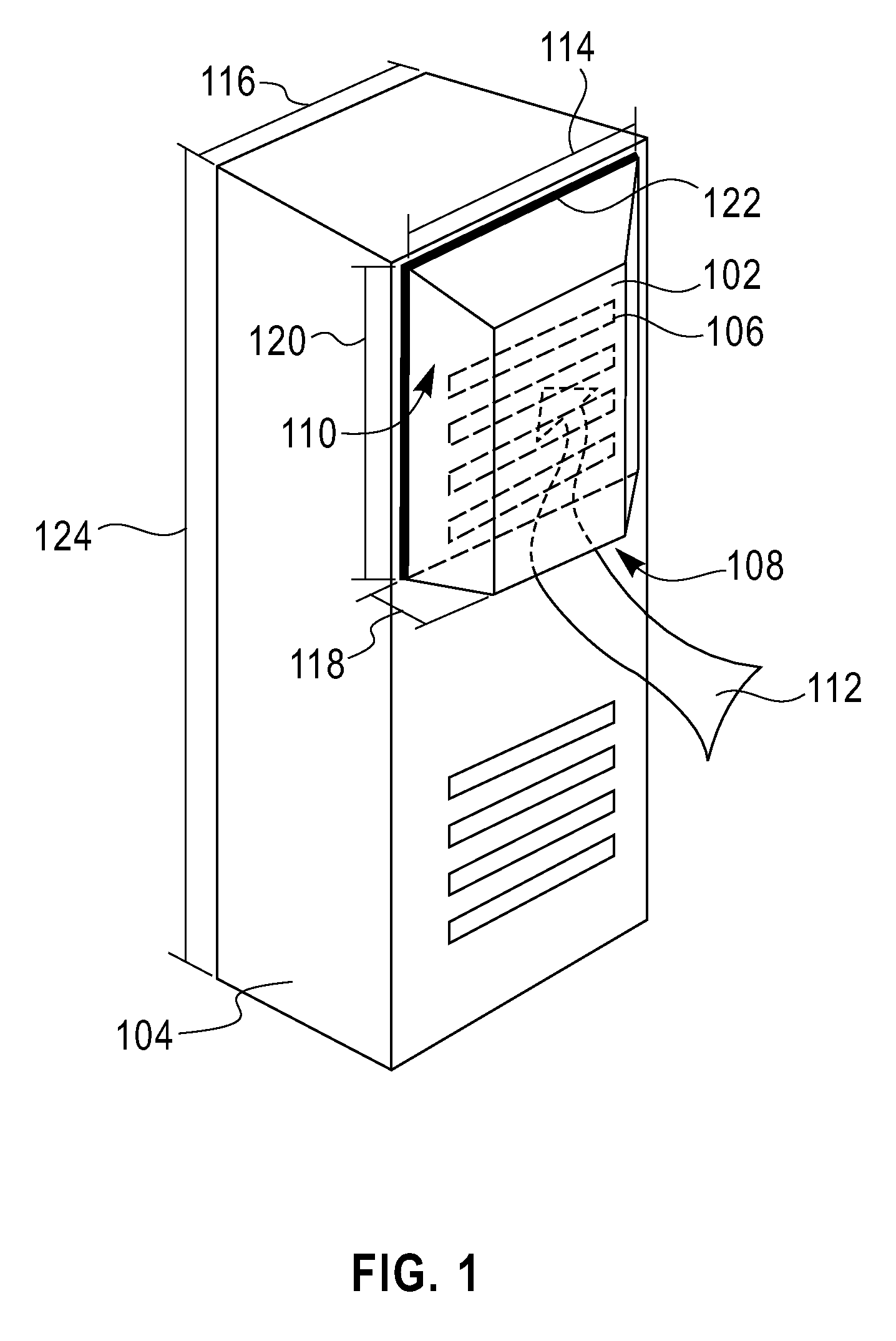
Cooling System for a Computer Server Cabinet in a Data Center
InactiveUS20100317278A1Space heating and ventilation safety systemsDomestic cooling apparatusCold airData center
A system for cooling computer equipment in a data center. The system includes a raised floor defining a pressurized under-floor plenum; a computer room air conditioning unit disposed on the raised floor and having a hot air inlet and a cold air outlet, wherein the cold air outlet is in fluid communication with pressurized under-floor plenum; and a server cabinet housing server equipment and including a pressurized vertical plenum in fluid communication with under-floor plenum via an inlet duct. The server cabinet is configured to receive a cold air stream from the under-floor plenum via the inlet duct into the vertical plenum and draw the cold air across the server equipment to provide cooling without the use of external fans. The system may also include an inflatable airfoil damper assembly disposed within the inlet duct and configured to provide failsafe variable airflow to the vertical plenum within the server cabinet.
Owner:BLACKROCK
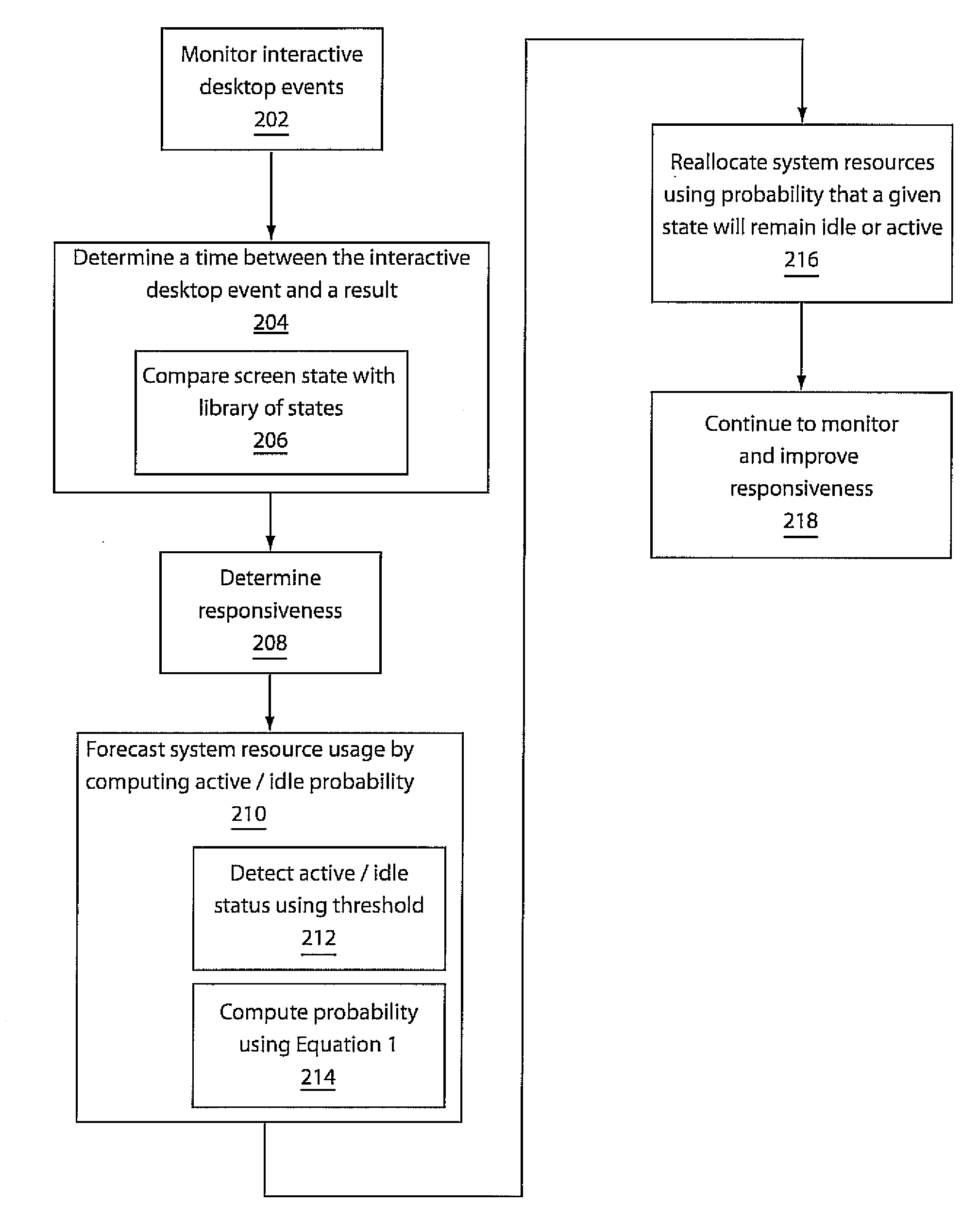
System and method for efficient allocation of resources in virtualized desktop environments
ActiveUS20100306163A1Improve responsivenessPower network operation systems integrationError detection/correctionVirtualizationOperating system
A system and method for managing responsiveness of virtual desktops using passive monitoring includes monitoring interactive desktop events for a computer device and measuring a time between the interactive desktop event and a result of the interactive desktop event. Based on the time, desktop responsiveness is evaluated. System resources are reallocated to improve the responsiveness.
Owner:IBM CORP
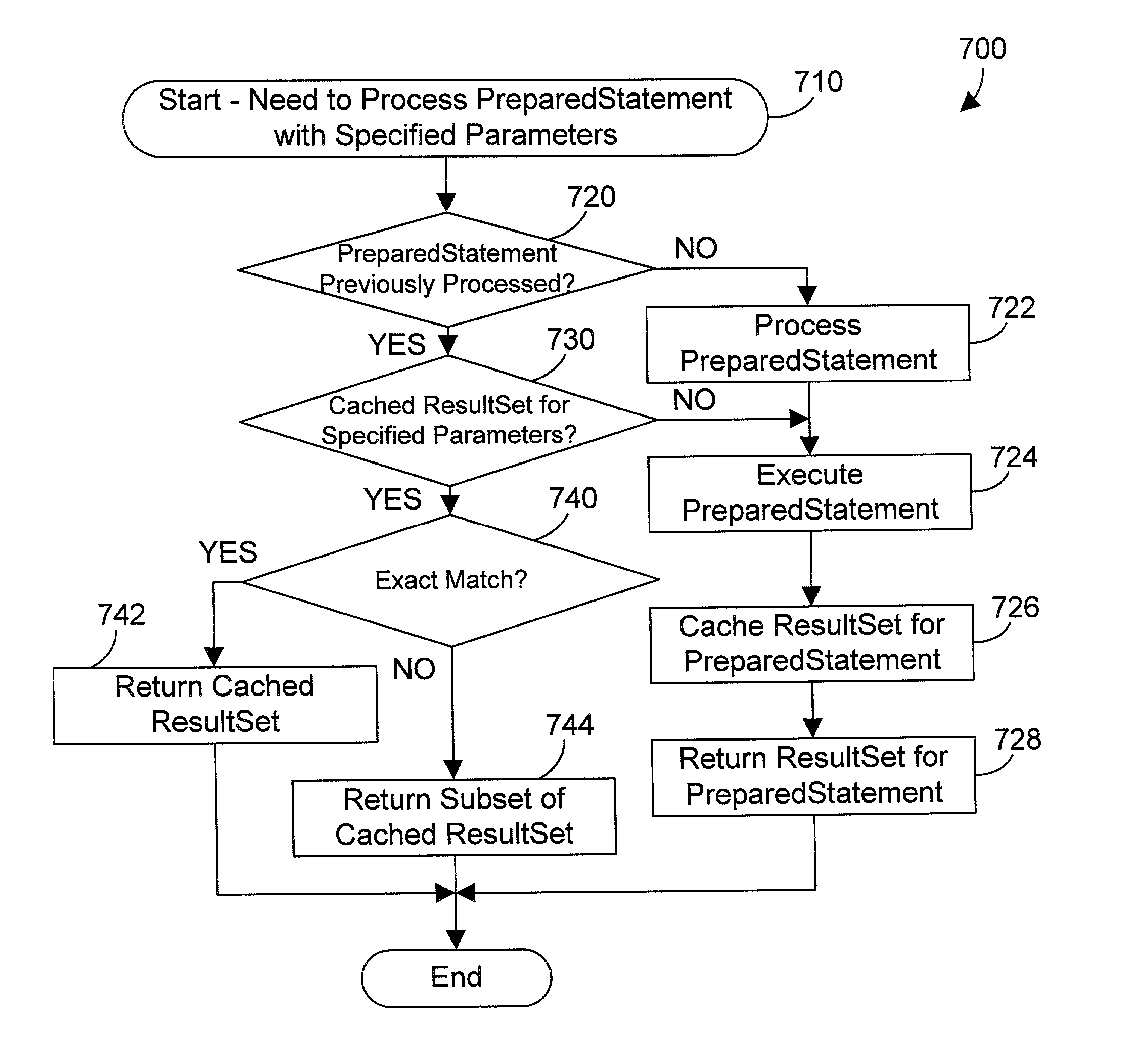
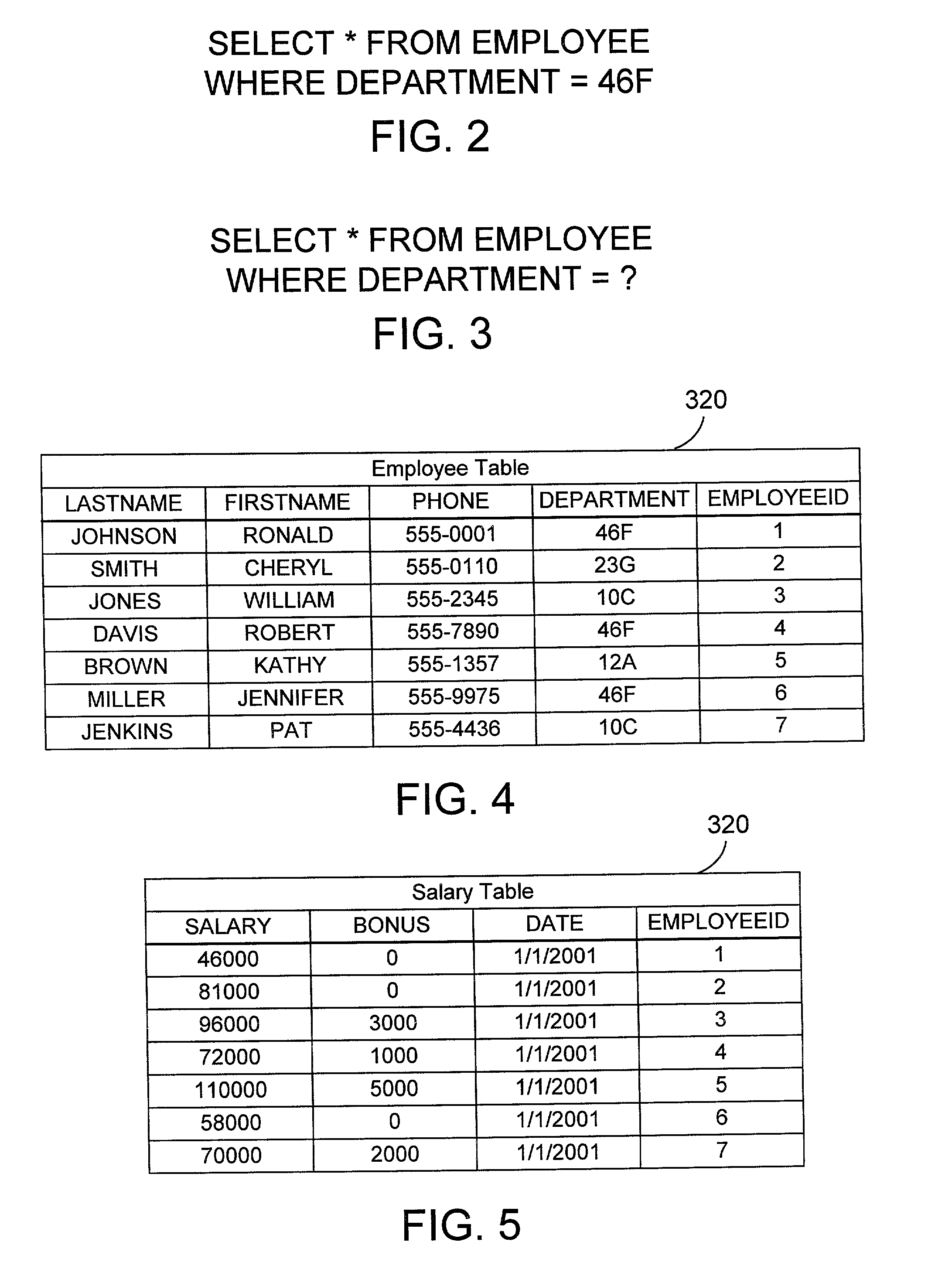
Computer apparatus and method for caching results of a database query
InactiveUS7089228B2Data processing applicationsDigital data information retrievalDatabase queryParallel computing
A query processor caches data retrieved from executing prepared statements, and uses the cached data for subsequent accesses to the data, if certain conditions for using the cached data are met. The preferred embodiments also include a data staleness handler that takes care of issues that arise from data that may have changed in the database but is not reflected in the cache. One way to handle data staleness in the cache is to specifically enable or disable caching in a query. If caching is disabled, the query processor will access the data in the database. Another way to handle data staleness in the cache is to provide a timer that causes the cache to be invalidated when the timer times out. Yet another way to handle data staleness in the cache is to provide specified conditions that must be met for caching to occur, such as time or date limitations. Still another way to handle data staleness in the cache is to provide an update trigger for the data in the database that corresponds to the cached data. When the data in the database is updated, the update trigger fires, causing the cache to be invalidated. Note that invalidating the cache could also be followed by automatically updating the cache. By caching the results of processing a prepared statement, other queries that use the same prepared statement may be able to access data in the cache instead of going to the database.
Owner:INT BUSINESS MASCH CORP
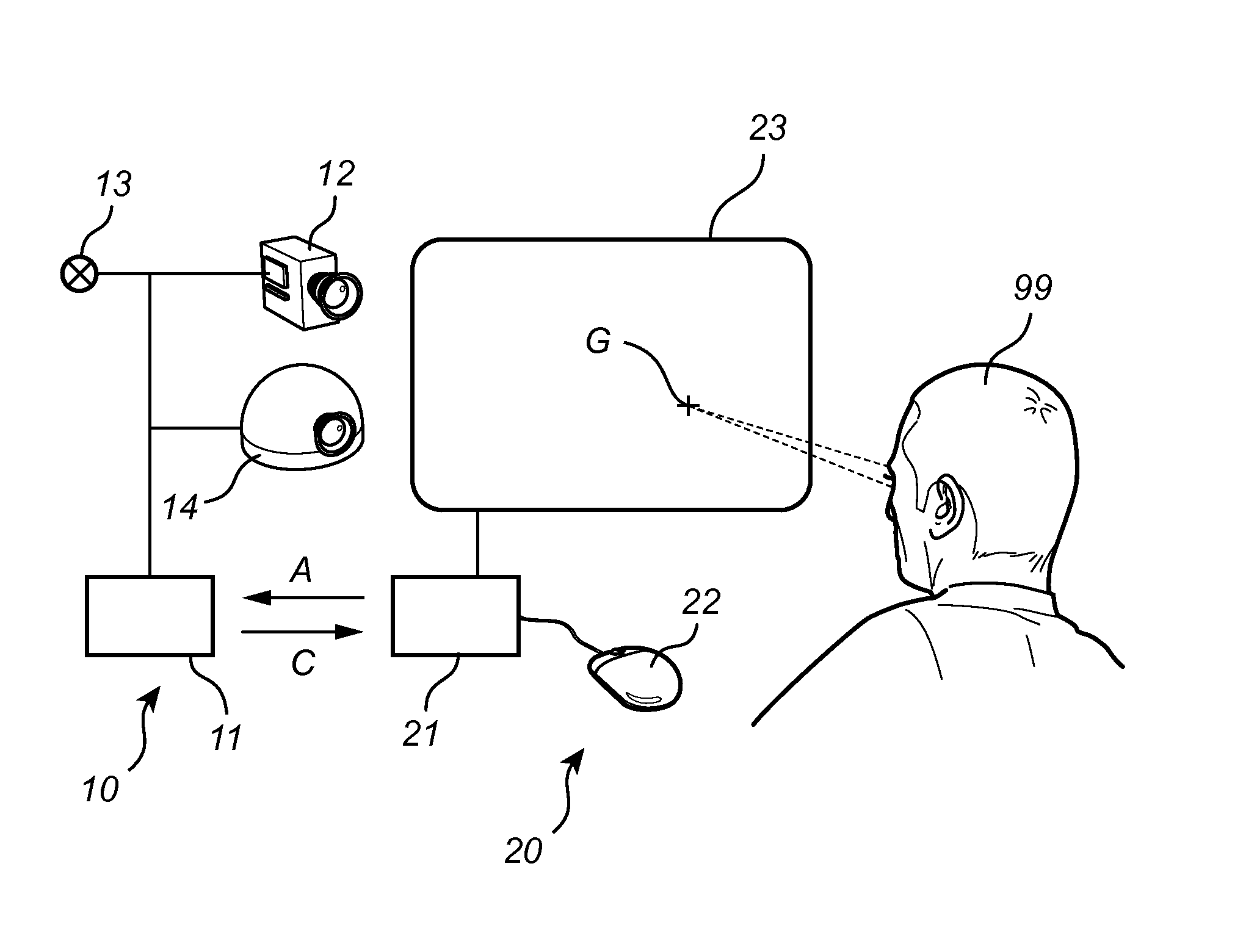
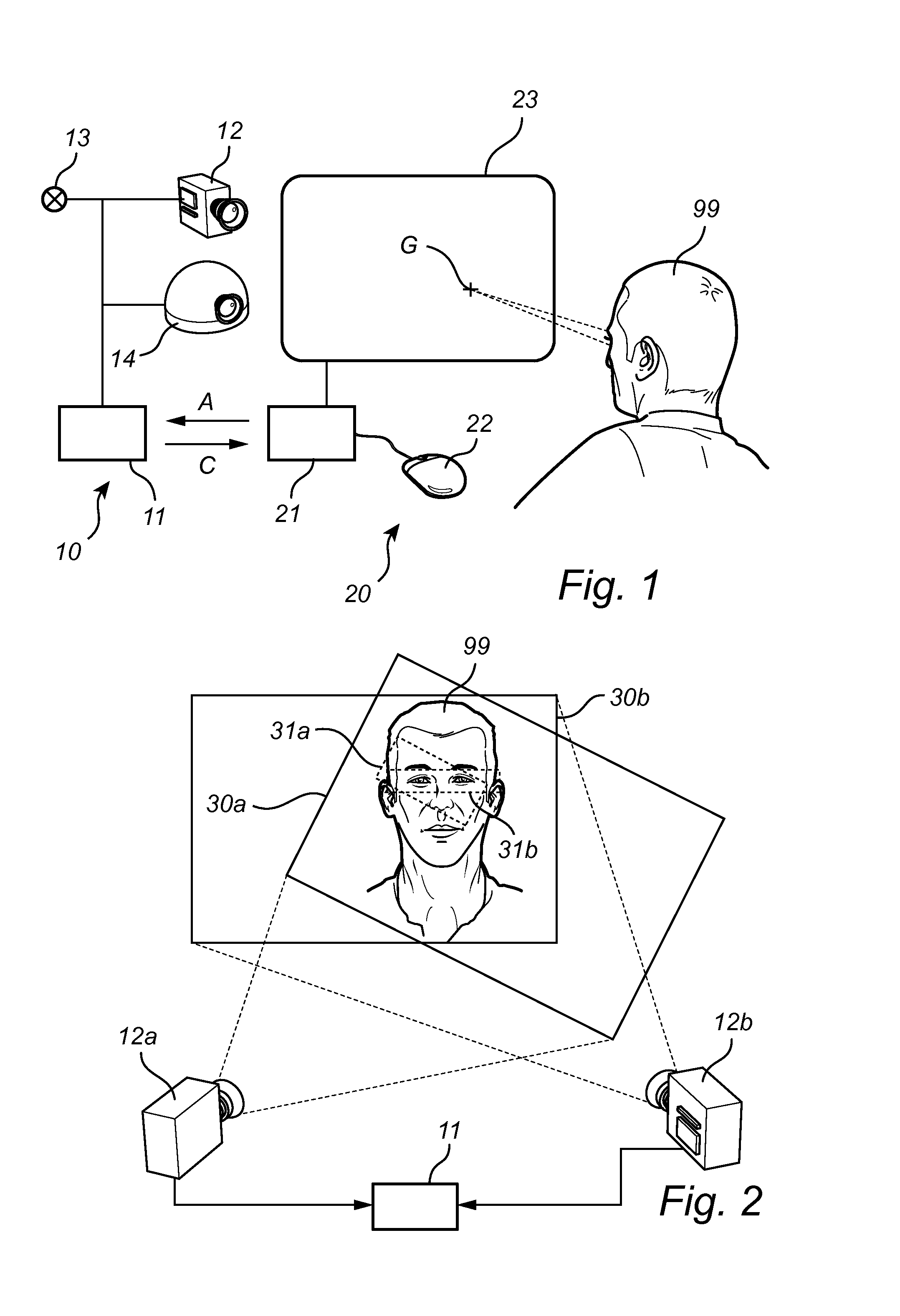
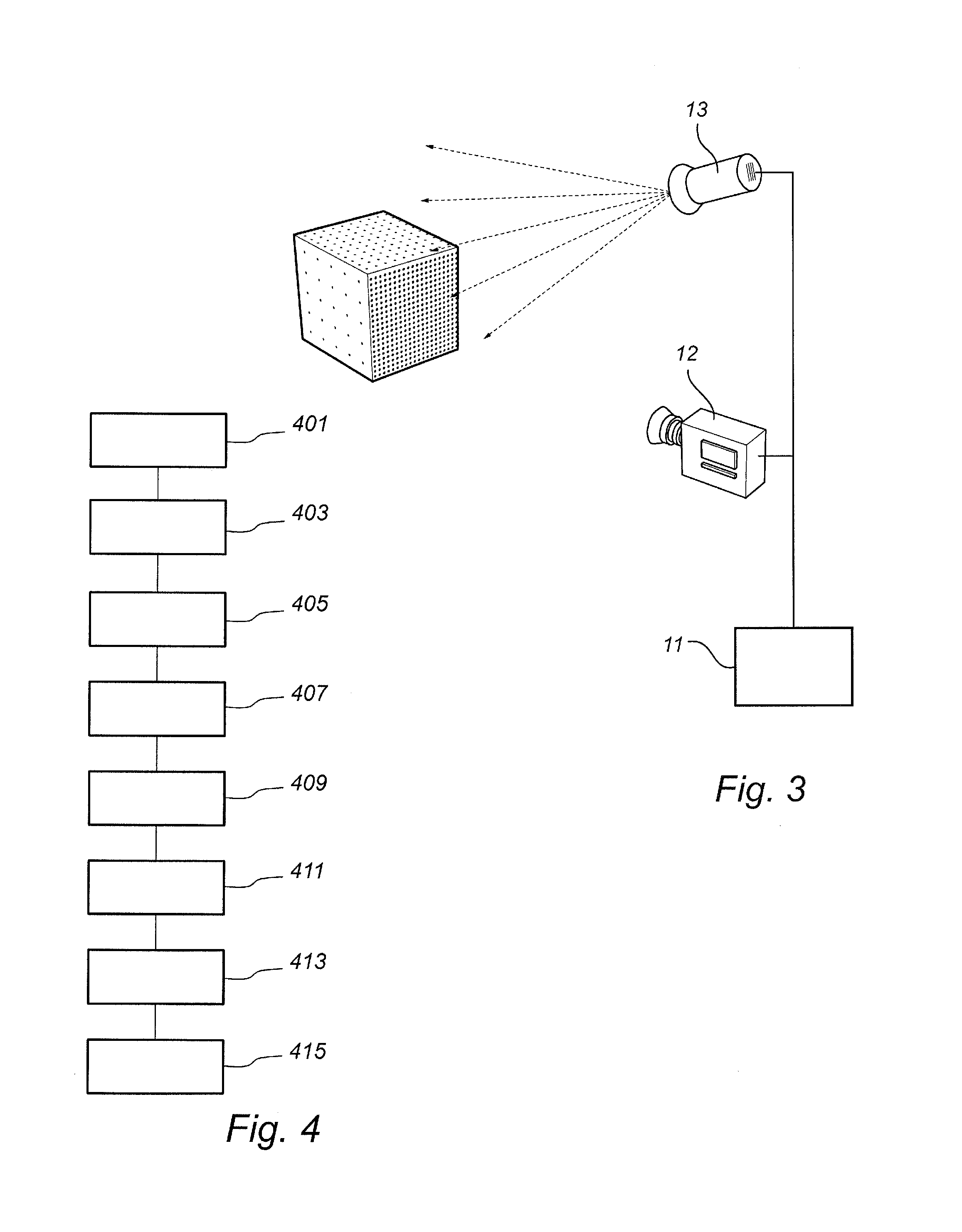
Fast wake-up in a gaze tracking system
ActiveUS20140043227A1Lower latencyReduced dynamicsInput/output for user-computer interactionDigital data processing detailsPower modeControl signal
A gaze tracking system, leaving a low power mode in response to an activation signal, captures an initial burst of eye pictures in short time by restricting the image area of a sensor, with the purpose of enabling an increased frame rate. Subsequent eye pictures are captured at normal frame rate. The first gaze point value is computed memorylessly based on the initial burst of eye pictures and no additional imagery, while subsequent values may be computed recursively by taking into account previous gaze point values or information from previous eye pictures. The restriction of the image area may be guided by a preliminary overview picture captured using the same or a different sensor. From the gaze point values, the system may derive a control signal to be supplied to a computer device with a visual display.
Owner:TOBII TECH AB
Toolless mounting system and method for an adjustable scalable rack power system
Systems and method for installing computer equipment and power distribution equipment in facilities is provided. In one aspect, the present invention provides a power distribution rack, and uninterruptible power supply rack and a plurality of equipment racks. A plurality of power cables are run from the power distribution rack to each of the plurality of equipment racks using power cable tracks located on the roofs of the equipment racks. A plurality of data cables run between the plurality of equipment racks using data cable tracks located on the roofs of the equipment racks. The power cable tracks and data cable tracks are designed to be installed on the roofs of the equipment racks without the need for tools.
Owner:AMERICA POWER CONVERSION CORP
High efficiency heat removal system for rack mounted computer equipment
InactiveUS20090262495A1Minimize energy usageEfficient transportDomestic cooling apparatusDigital data processing detailsHeat conductingEngineering
An efficient method of heat removal from rack mounted computer equipment, network gear and other electronic equipment, consisting of solid heat conducting components in direct contact with the heat generating sources. In particular, this invention is primarily focused on the ability to efficiently and effectively cool computer equipment in standard computer rack cabinets.This invention utilizes a design that retains the general existing form factor of the rack mounted computer equipment, but uses direct contact heat transfer to a metal heat transfer conduit (Copper, Aluminum or other metal or efficient heat conducting material) contained within the computer equipment chassis. Furthermore, it is thermally coupled to an external rack mounted solid-to-fluid heat exchanger as an efficient method of heat transfer and removal. This is much more efficient than air as heat transfer medium which it the common method of heat removal from existing standardized rack mounted computer equipment.This invention covers the design of the heat transfer components within the chassis of rack mounted computer server and the heat transfer system components external to the server within rack enclosure, as well as the external cooling system components necessary to connect to existing fluid based heat transfer and removal systems and processes.
Owner:NEUDORFER JULIUS
Controlling a user interface of a computer device
ActiveUS20140235338A1Increase engagementOptimal control methodApparatus for meter-controlled dispensingVideo gamesGraphicsUser input
A computer device has user interface configured to display user actuatable game elements and to detect user input when a user engages with a game element; and a processor configured to receive a detected user input and on detecting a match game condition to control the user interface to remove at least three game elements from the display and to provide on the user interface replacement user actuatable game elements, wherein the manner of providing each replacement game element has a graphical representation governed by a tile associated with each game element, wherein each tile has a selectable physics which controls at least one of (i) the direction in which it moves to replenish a vacancy left by the removed user game elements; and (ii) the speed at which it moves to replenish the vacancy.
Owner:KING COM
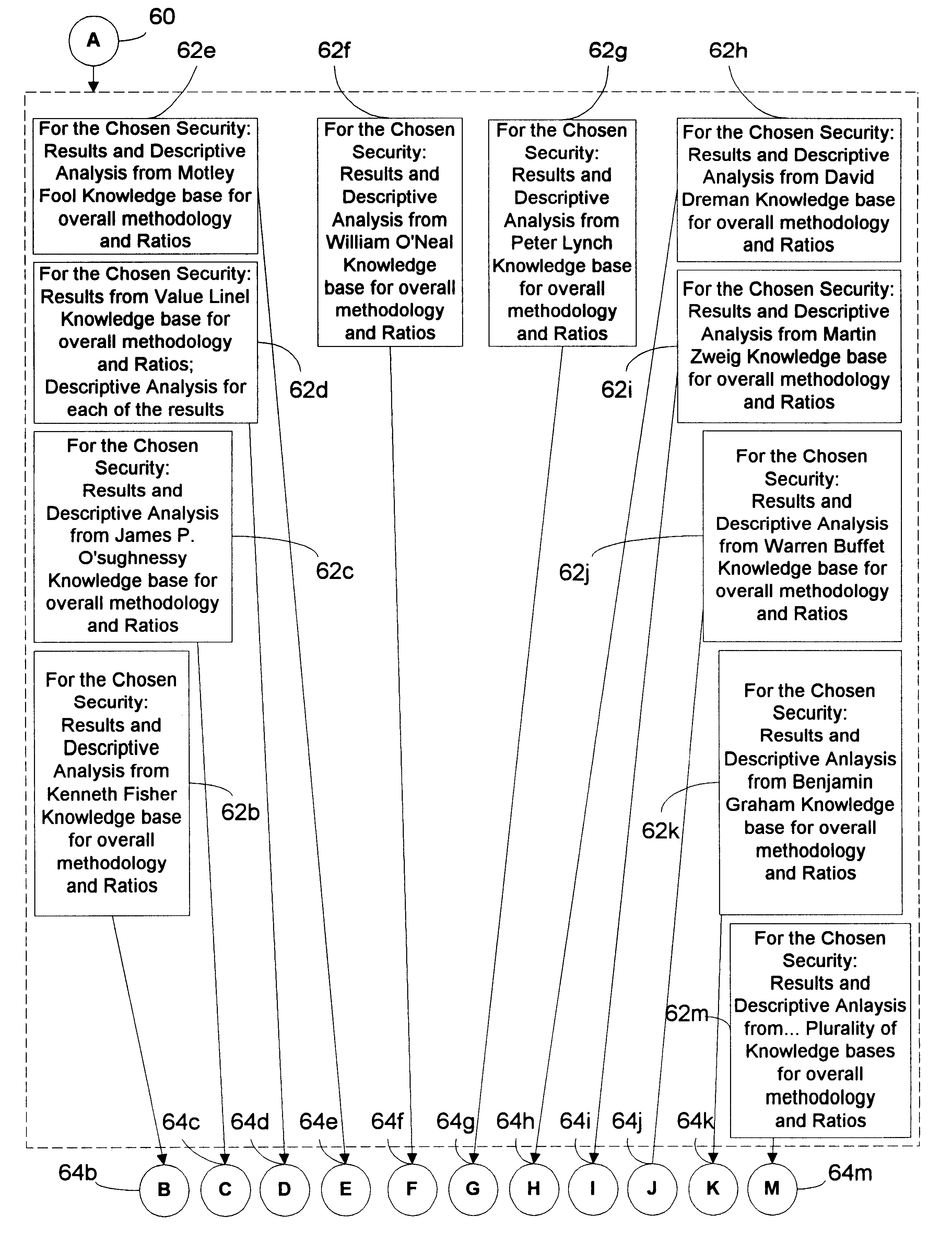
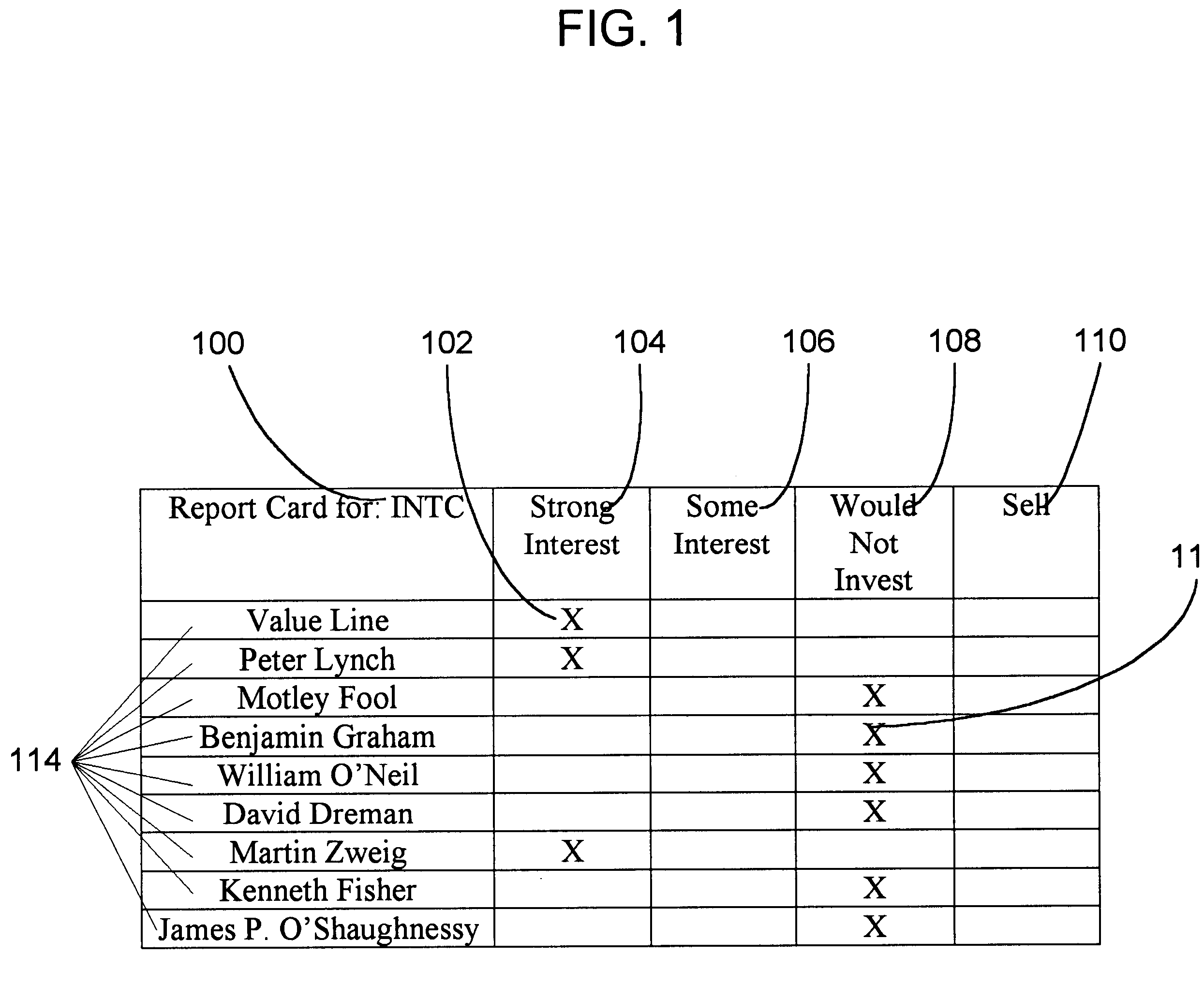
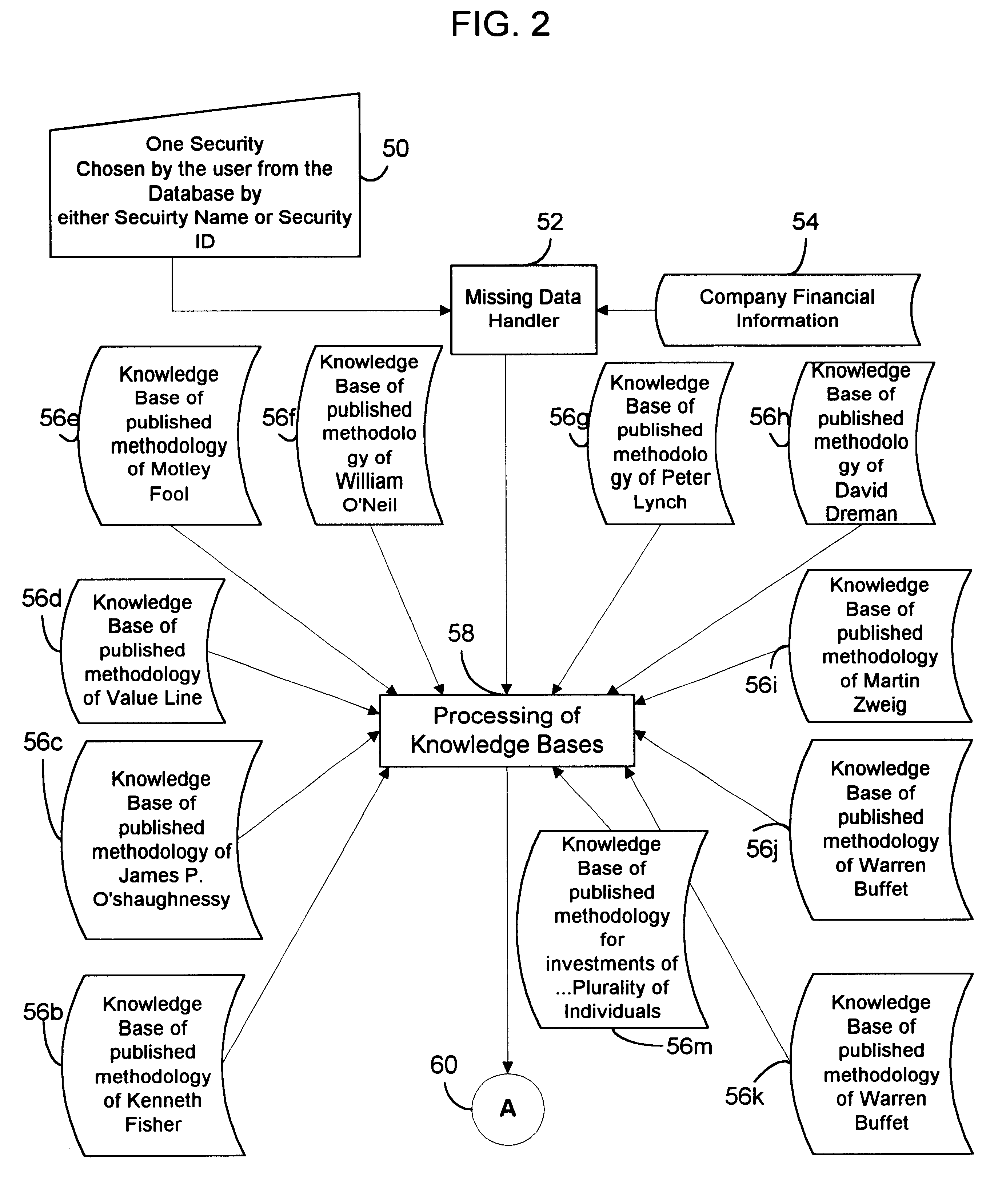
Computer based device to report the results of codified methodologies of financial advisors applied to a single security or element
The invention utilizes computer apparatus to automatically generate a display or report containing the result for a plurality of investment advisor methodologies (FIG. 2) for one specific security at a time (FIG. 18a). The user is not required to input any more information than the security identification because the information required for the calculations is readily available in the data storage means (FIG. 3, box 54). In addition to the result, a descriptive analysis (FIG. 7) can be provided which illustrates the reasoning (FIG. 7, box 144) of the particular advisor (FIG. 7, box 140) in support of the result (FIG. 7, box 146). Also a report can be provided for individual ratios (FIG. 8) applied to one specific security (FIG. 8, box 166) at a time for a plurality of investment advisor methodologies (FIG. 8, box 168). Another type of display or report the system could generate is an analysis by a plurality of advisors (FIG. 26, box 262), of a particular element selected from a list of elements (FIG. 23), within a related subject matter.
Owner:REESE JOHN P
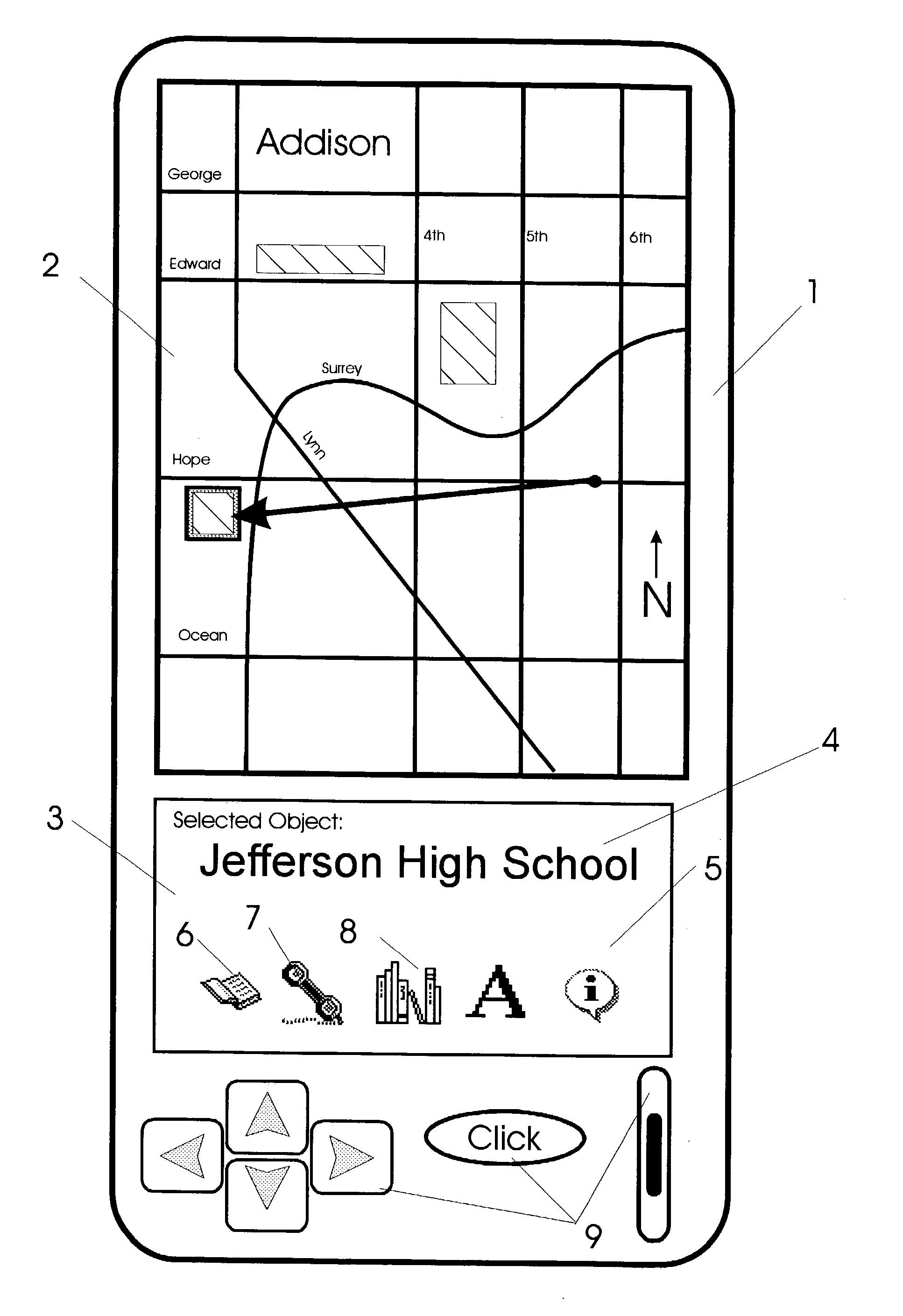
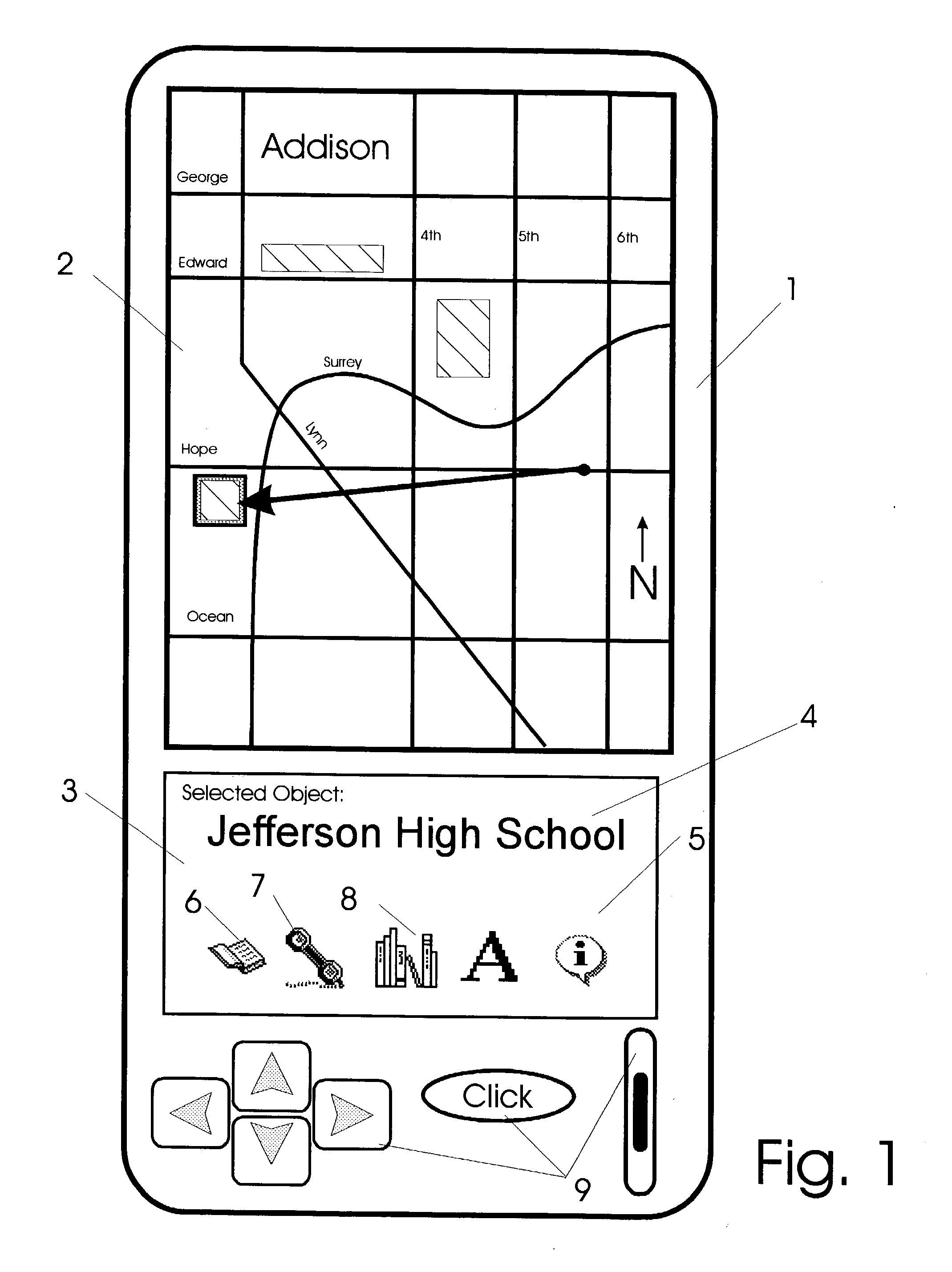
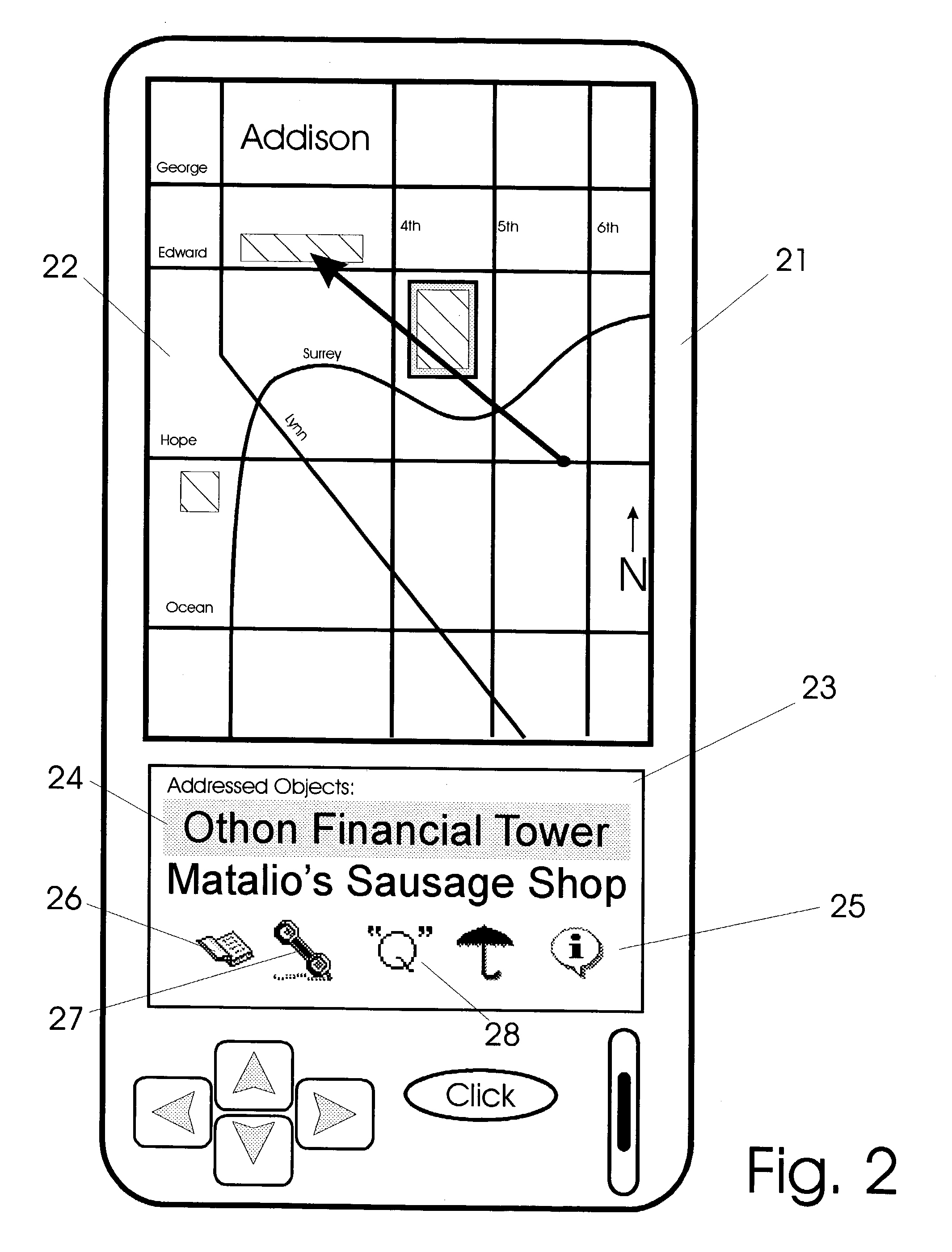
Apparatus and methods for interfacing with remote addressing systems
InactiveUS20030184594A1Navigational calculation instrumentsCathode-ray tube indicatorsForm and functionComputer device
Devices for remotely addressing objects via pointing action are provided with graphical user interfaces. In response to an object being addressed, a computer device and software provide graphical user interfaces which relates to objects being addressed. As different types of objects are addressed, user interfaces provided change in form and function to agree with the type of category of object being addressed at that instant. Devices have position and attitude determining facility in communication with a computer having prerecorded data. The data includes information relating to object types and corresponding graphical user interfaces.
Owner:ELLENBY JOHN +3
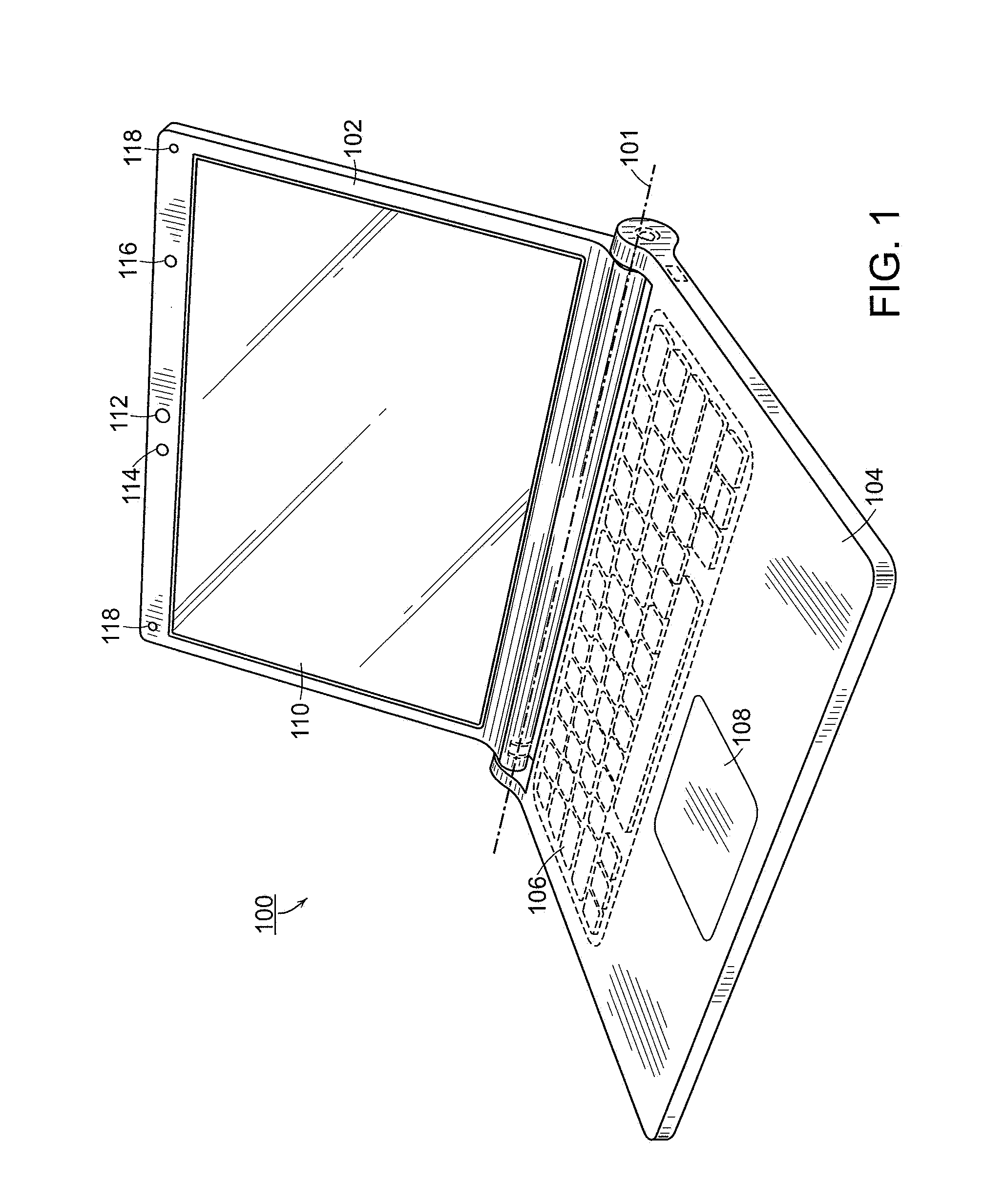
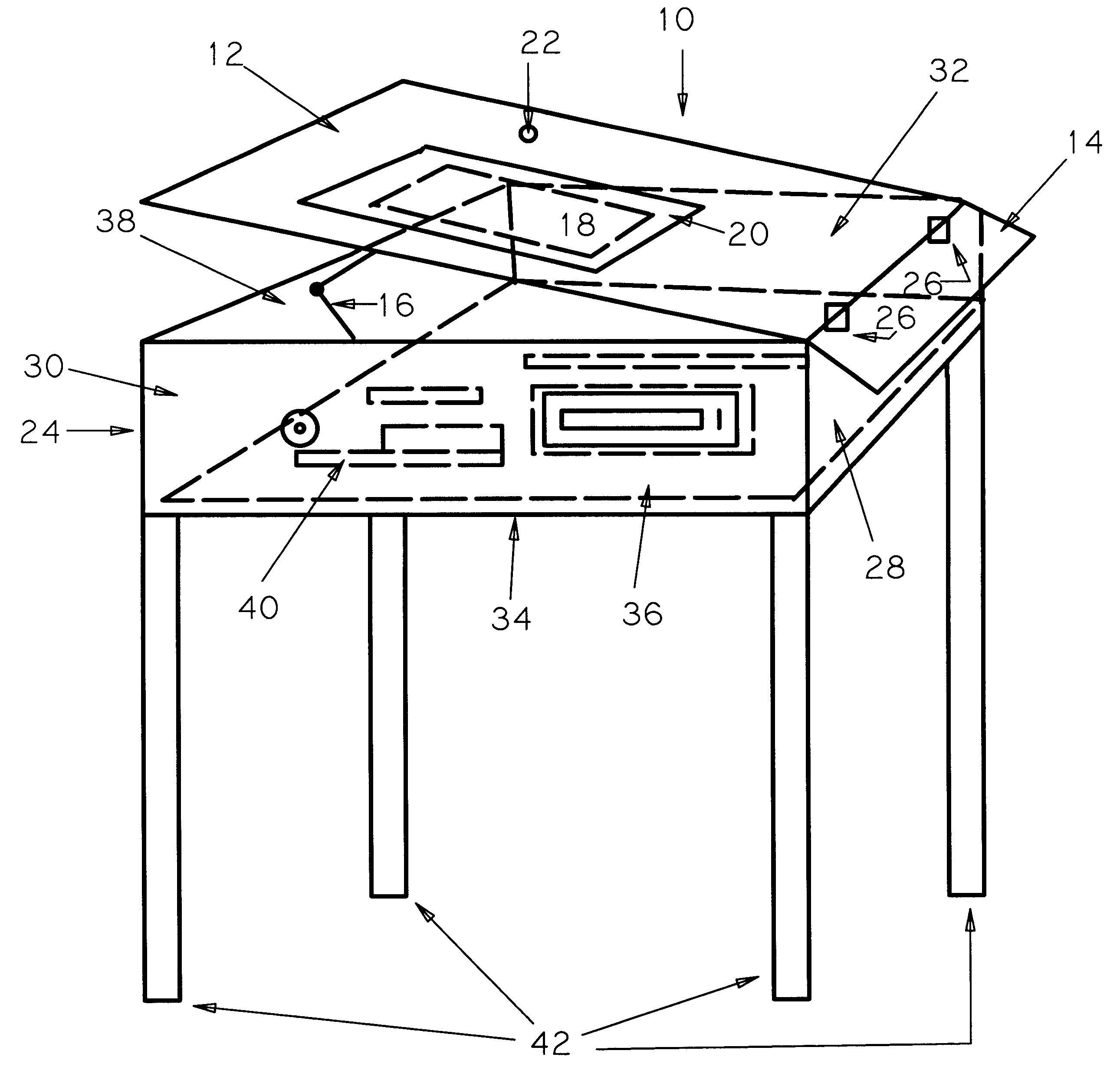
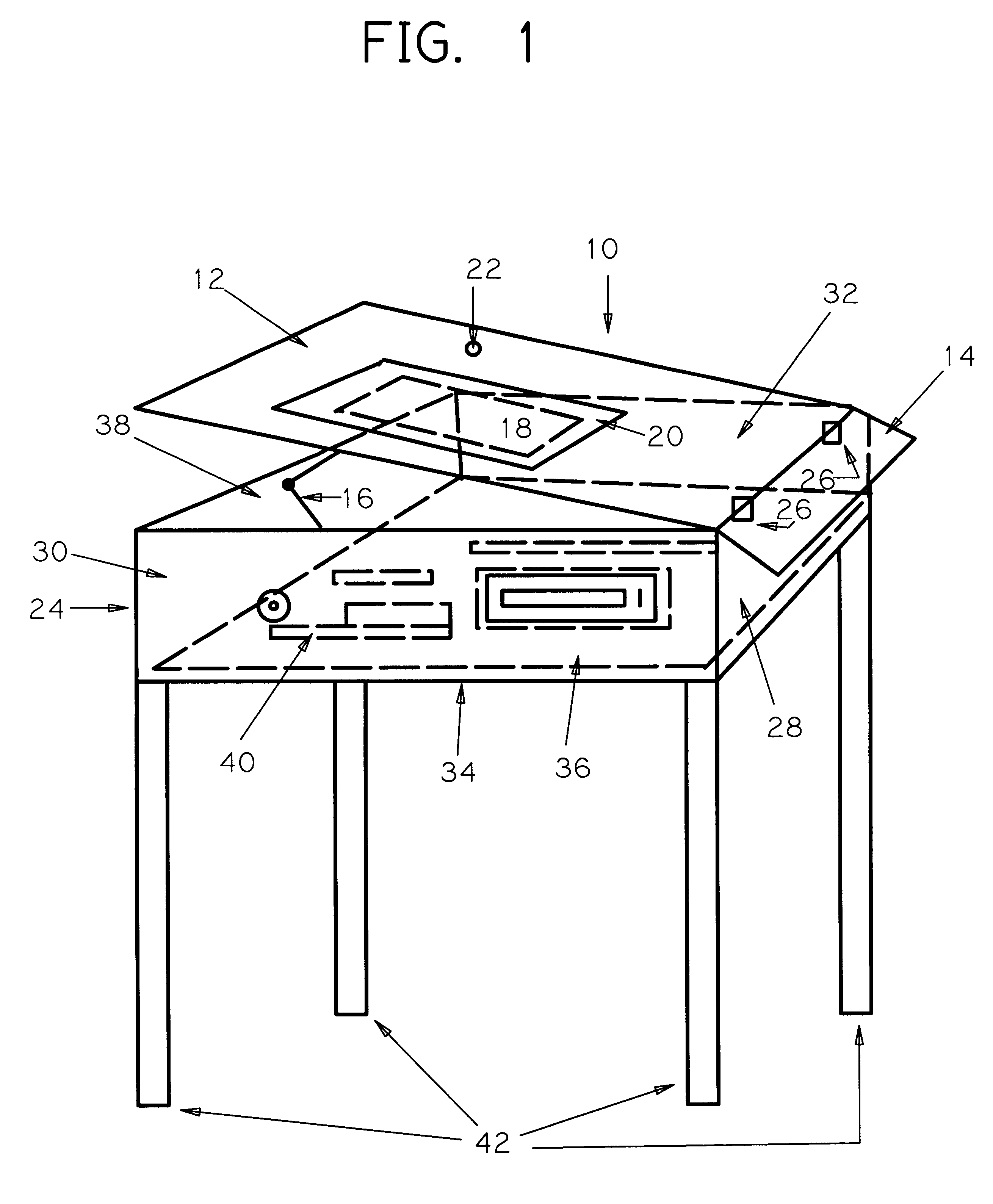
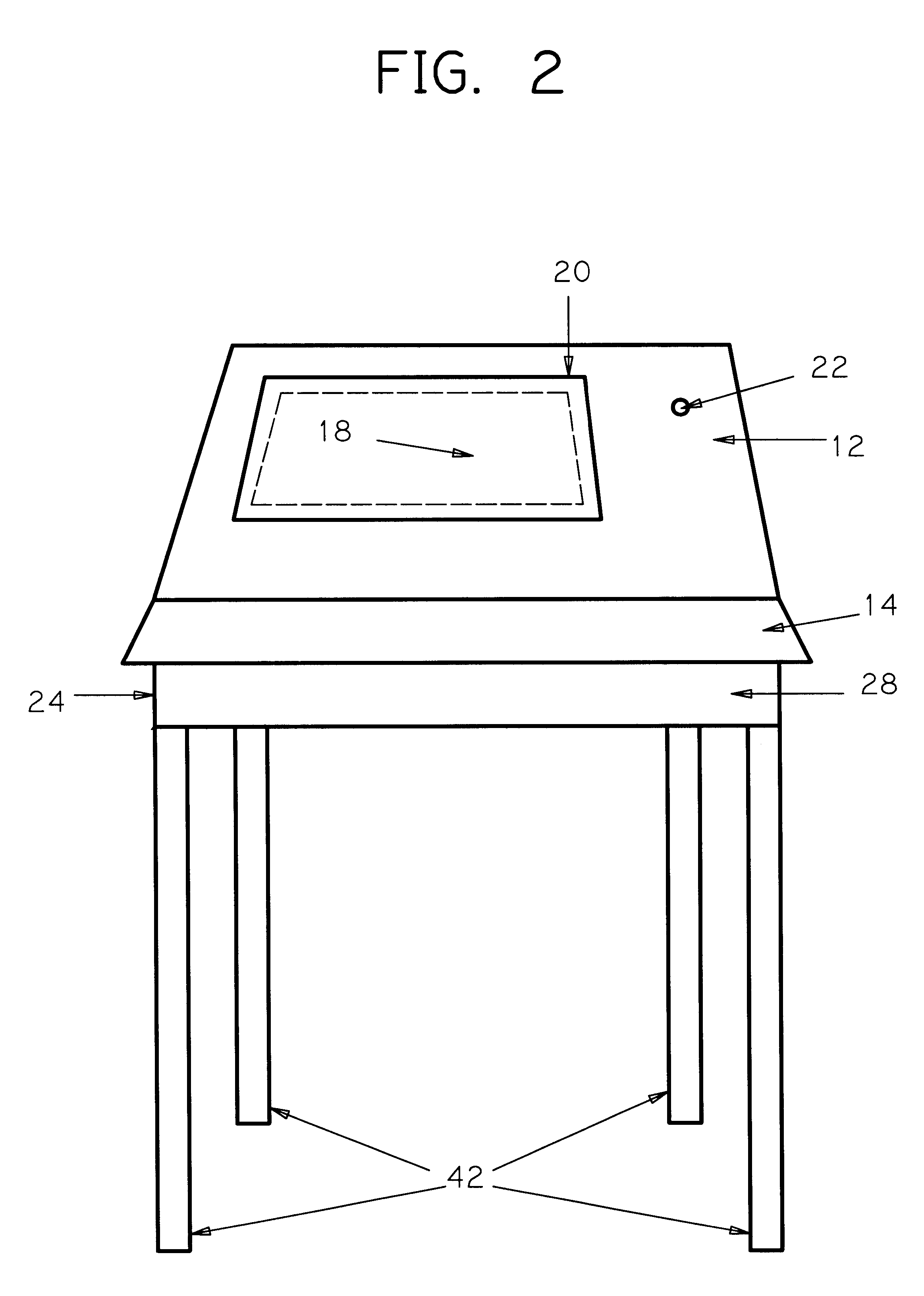
Computer in a desk
A school, home or commercial desk that can be used for traditional tasks and yet provides readily available access to computer equipment. The computer in a desk (10) is comprised of a desk body (24) that houses the internal components of a standard computer; a desk top (12) that houses the flat panel screen (18) beneath a view panel (20) that is mounted flush with the surface of the desk top (12); a keyboard tray (14) that holds the standard computer keyboard; and a support system of four adjustable legs (42). The desk top (12), keyboard tray (14), and legs (42) are all adjustble to suit the users specific ergonomic needs. The desk body (24) consists of a front panel (28), back panel (30), right side panel (32),and left side panel (34), bottom panel (36), and top panel (38) that give the computer in a desk (10) its shape, support and access to available, installed computer components. Furthermore, the computer in a desk (10) can be used for traditional and computer related tasks regardless of the user adjusted.
Owner:JYRINGI CRAIG
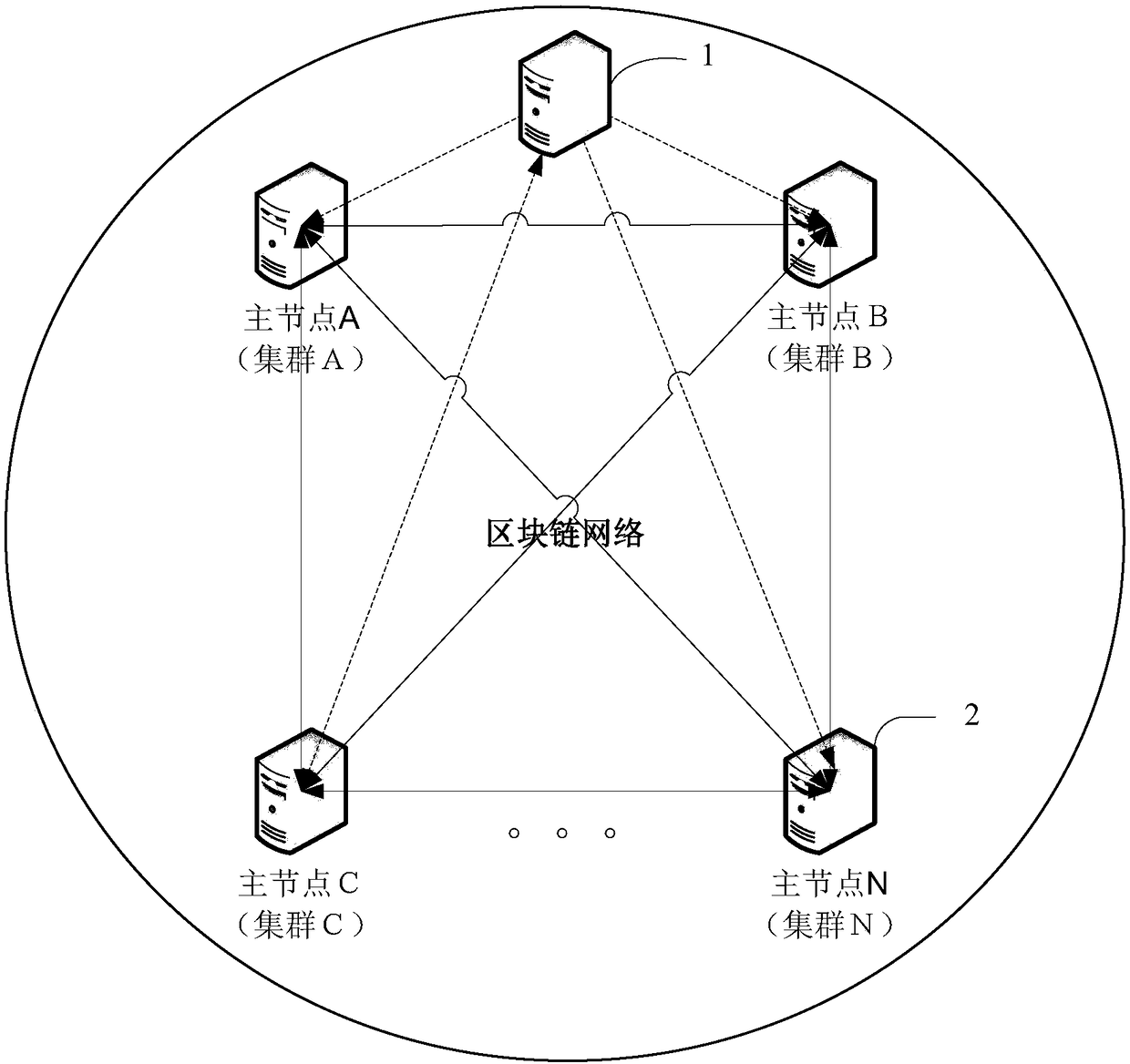
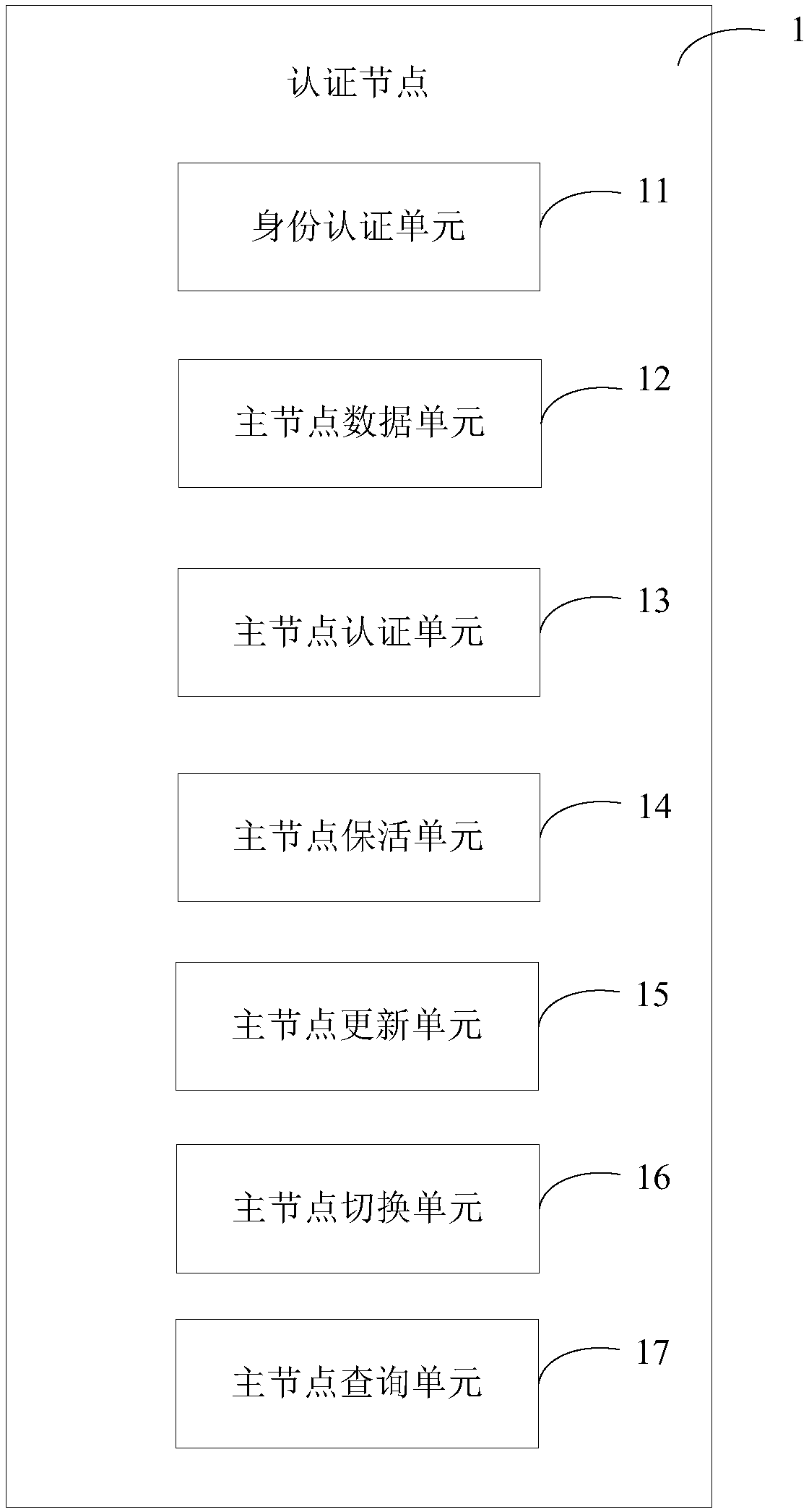
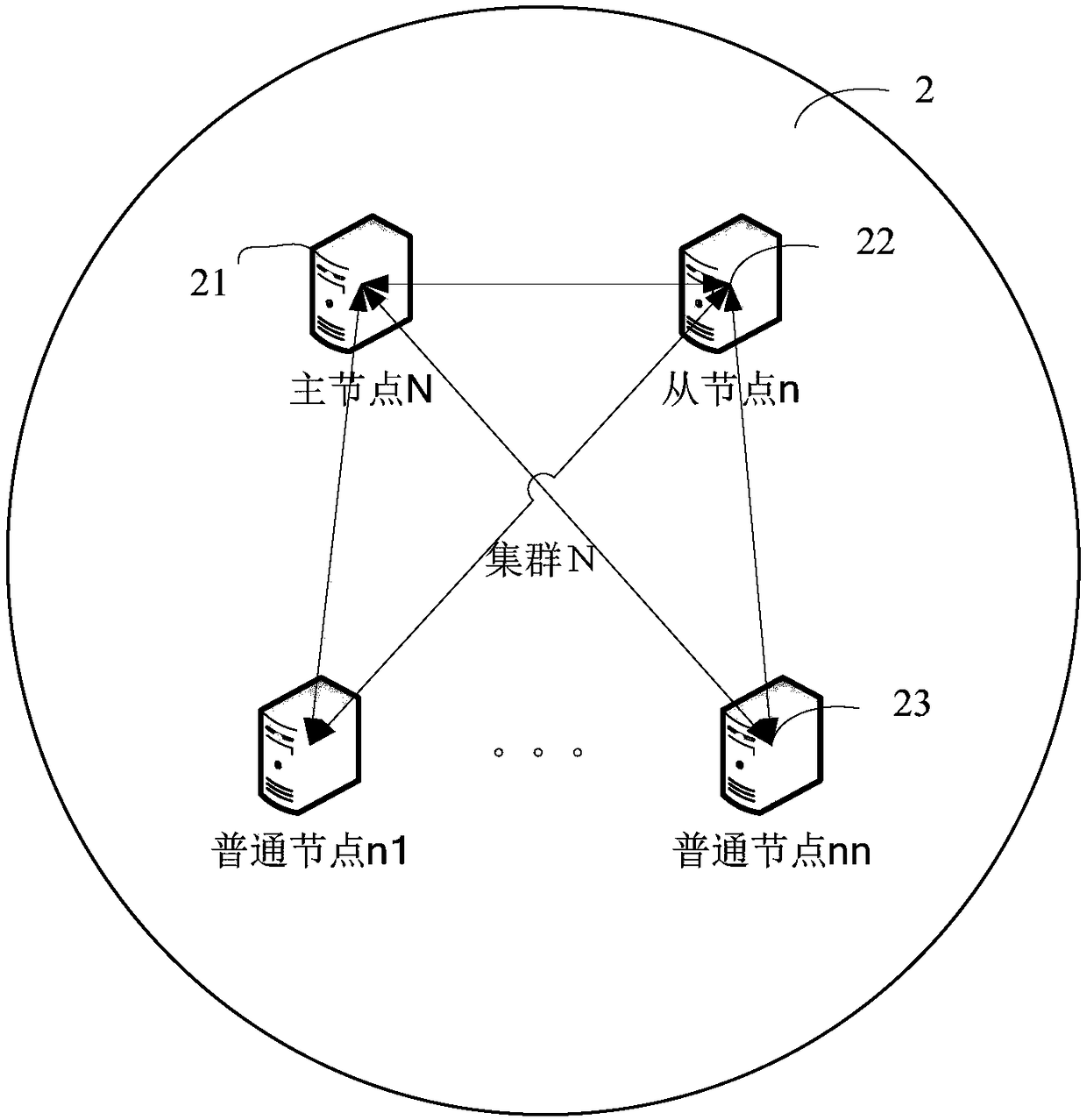
Block chain multi-activity high-availability system, computer equipment and method
ActiveCN108134706AImprove reliabilityMeet high availability requirementsData switching networksHigh availabilityChain network
The invention provides a block chain multi-activity high-availability system, a method, computer equipment and a computer readable storage medium, and relates to the technical field of block chains. The system comprises an authentication node and a plurality of block chain nodes, wherein each block chain node is a cluster; a main node in the cluster participates in a block chain; a block chain network is formed by a plurality of clusters; the communication between the block chains is completed by the main node; after the block chains reach the consensus, the main node in each cluster synchronously updates the block chain data to a slave node and a common node; when a main node of a fault cluster in the cluster fails or is has a consensus error, master-slave election is carried out througha master-slave election rule, the slave node is switched to serve as the main node to provide a block chain service, and the authentication node informs other clusters except the fault cluster to update the main node information of the fault cluster. According to the block chain multi-activity high-availability system, the computer equipment and the method, the reliability of the whole block chainis greatly improved, and the requirement for high availability of a bank for 7*24 hours is met.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA +1
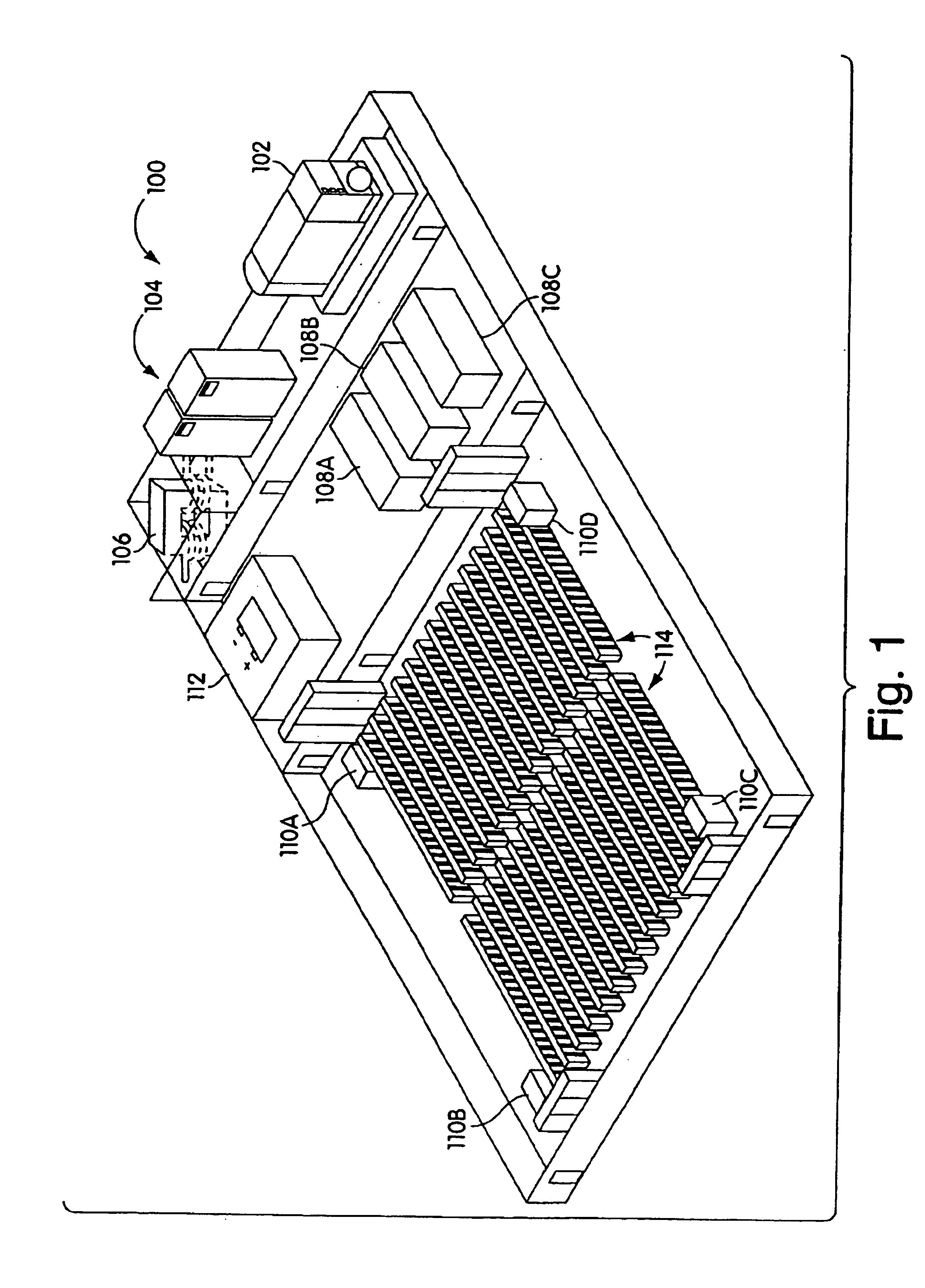
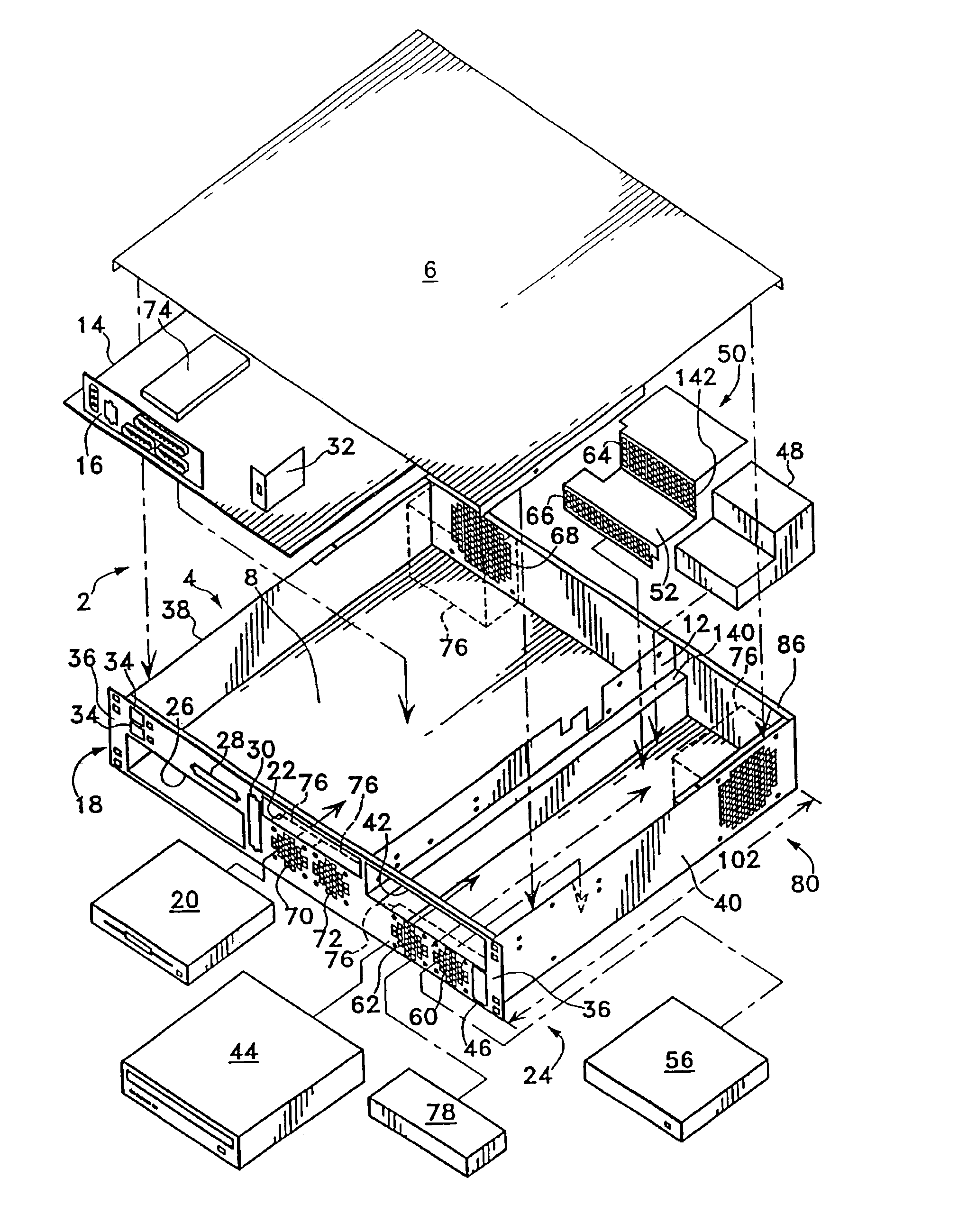
High density computer equipment storage systems
InactiveUS6850408B1Maximization of overall densityHigh densityServersFurniture partsHigh densityEngineering
A computer is provided having a main board with I / O connectors mounted thereon, and a chassis including a front panel providing access to the I / O connectors and to all components requiring intermittent access provided for the computer.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
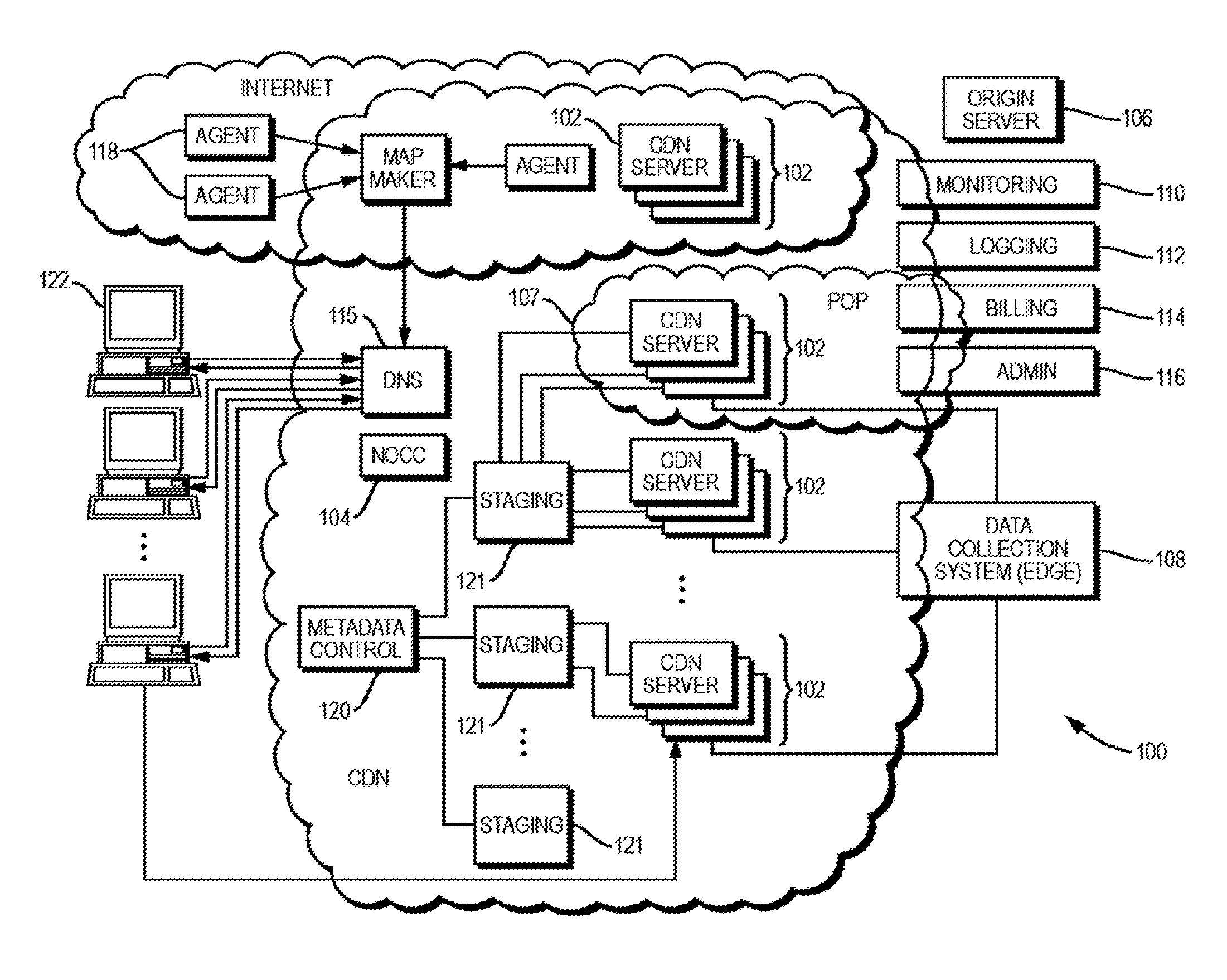
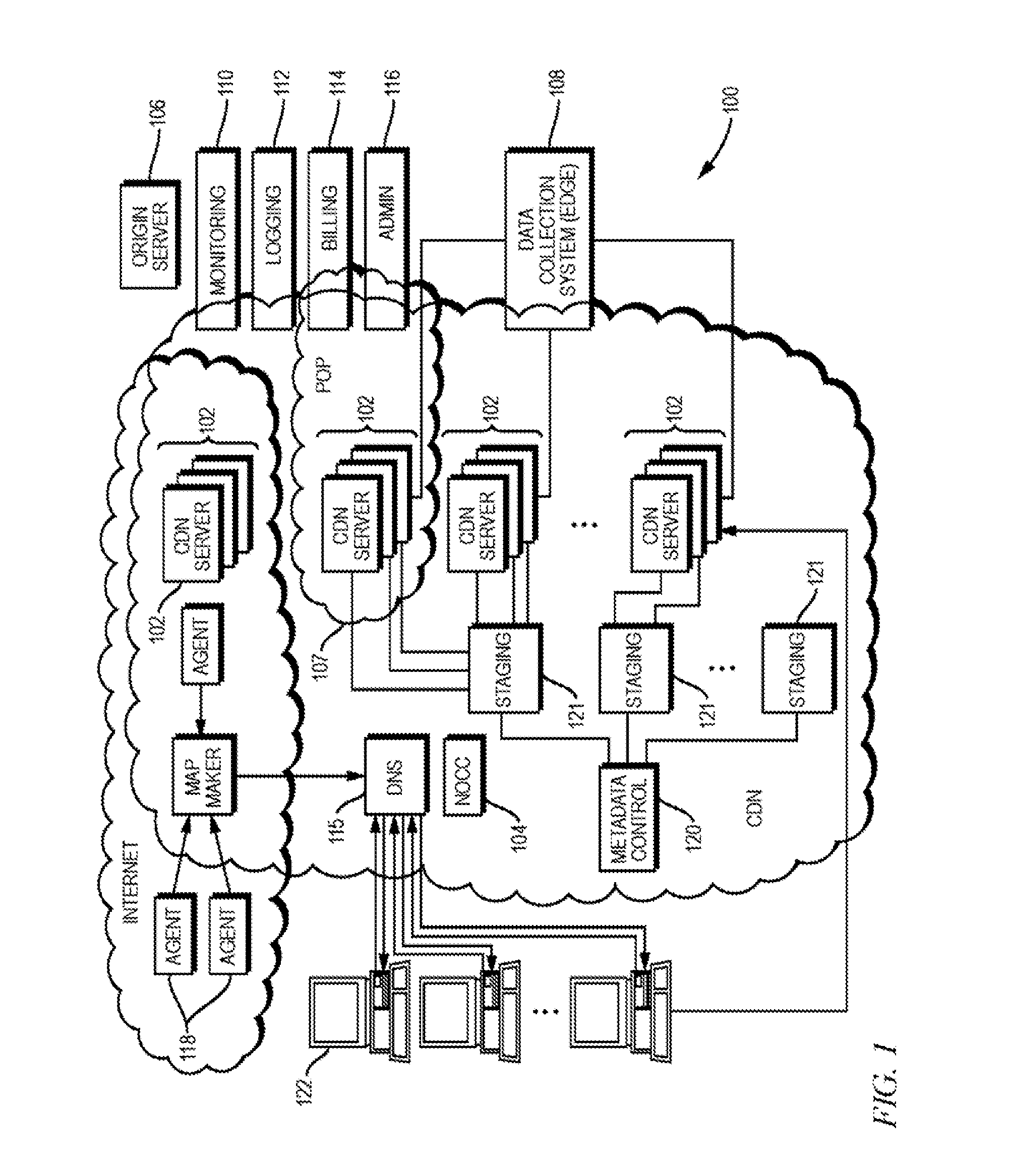
Dynamically populated manifests and manifest-based prefetching
Described herein are, among other things, systems and methods for generating and using manifests in delivering web content, and for using such manifests for prefetching. Manual and automated generation of manifests are disclosed. Such manifests preferably have placeholders or variables that can be populated at the time of the client request, based on data known from the request and other contextual information. Preferably though without limitation an intermediary device such as a proxy server, which may be part of content delivery network (CDN), performs the function of populating the manifest given a client request for a page. An intermediary or other computer device with a populated manifest can utilize that completed manifest to make anticipatory forward requests to an origin to obtain web resources specified on the manifest, before receiving the client's requests for them. In this way, many kinds of content may be prefetched based on the manifest.
Owner:AKAMAI TECH INC
Abnormal flow detection method and device, computer equipment and storage medium
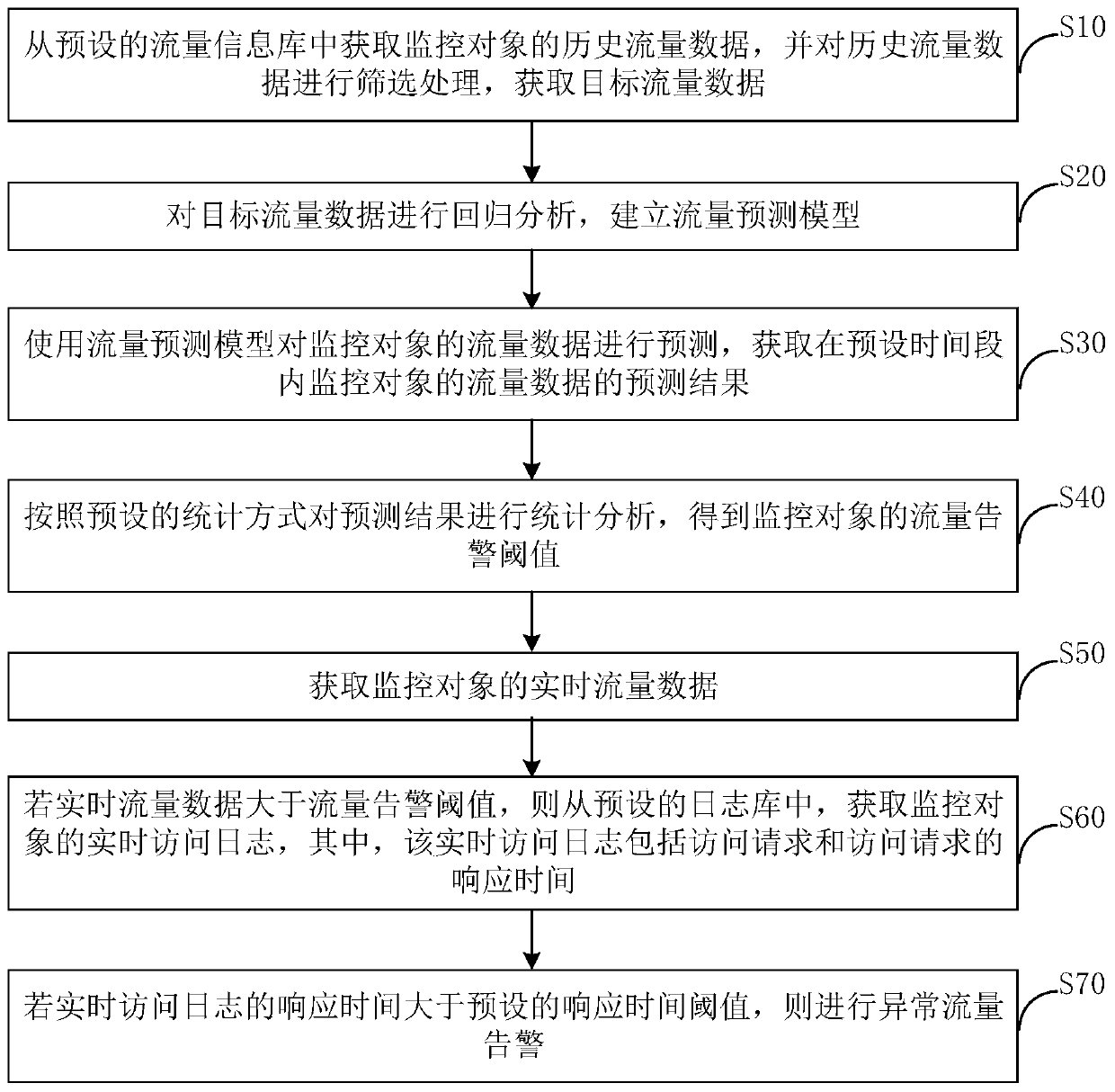
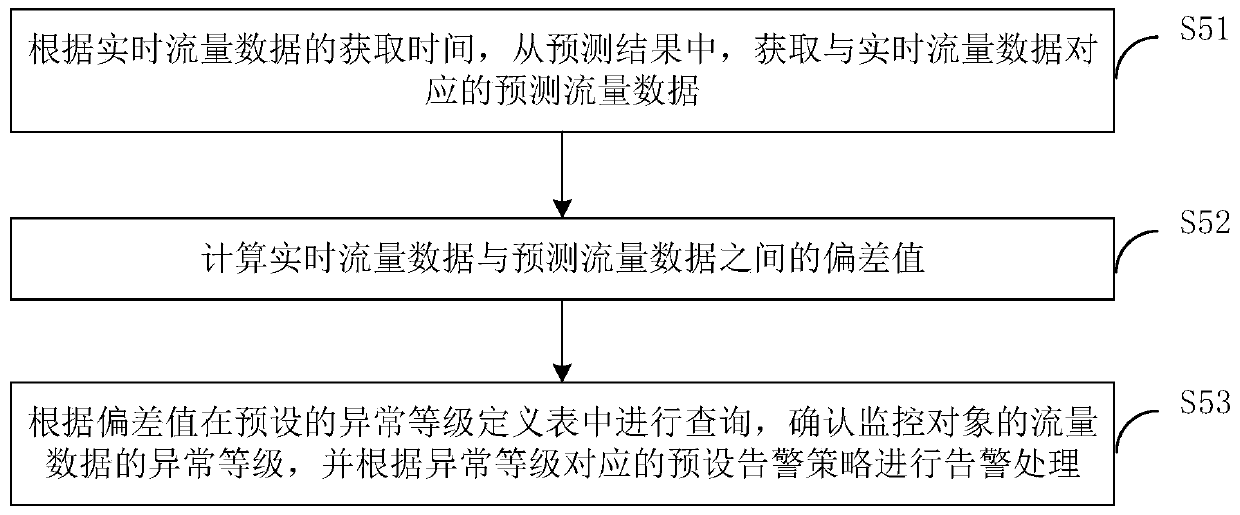
PendingCN110086649AImprove accuracyEliminate false alarmsData switching networksHigh level techniquesTraffic predictionTime segment
The invention discloses an abnormal flow detection method and device, computer equipment and a storage medium. The method comprises the following steps of: screening the historical flow data of the monitoring object; obtaining target traffic data, carrying out regression analysis on the target traffic data; establishing a flow prediction model, predicting the flow data of the monitored object by using the flow prediction model; obtaining a prediction result of the flow data of the monitoring object in a preset time period, carrying out statistical analysis is on a prediction result according to a preset statistical mode; obtaining a traffic alarm threshold value of the monitored object, further obtaining a real-time access log of the monitored object when the real-time traffic data of themonitored object is greater than the traffic alarm threshold value, and performing abnormal traffic alarm if the response time of the real-time access log is greater than the response time threshold value. According to the embodiment of the invention, the accuracy of the alarm threshold can be improved, judgment is carried out by combining the response time of the service, and thus the accuracy ofabnormal flow detection is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Techniques for Data Center Cooling
Techniques for cooling in a data center are provided. In one aspect a computer equipment rack is provided comprising one or more air inlets; one or more exhaust outlets, and one or more of: an air inlet duct mounted to the computer equipment rack surrounding at least a portion of the air inlets, the air inlet duct having a lateral dimension that approximates a lateral dimension of the computer equipment rack and a length that is less than a length of the computer equipment rack, and an air exhaust duct mounted to the computer equipment rack surrounding at least a portion of the exhaust outlets, the air exhaust duct having a lateral dimension that approximates the lateral dimension of the computer equipment rack and a length that is less than the length of the computer equipment rack.
Owner:GLOBALFOUNDRIES US INC
Scribble matching
InactiveUS6018591ASave powerImprove performanceCharacter and pattern recognitionAlgorithmElastic matching
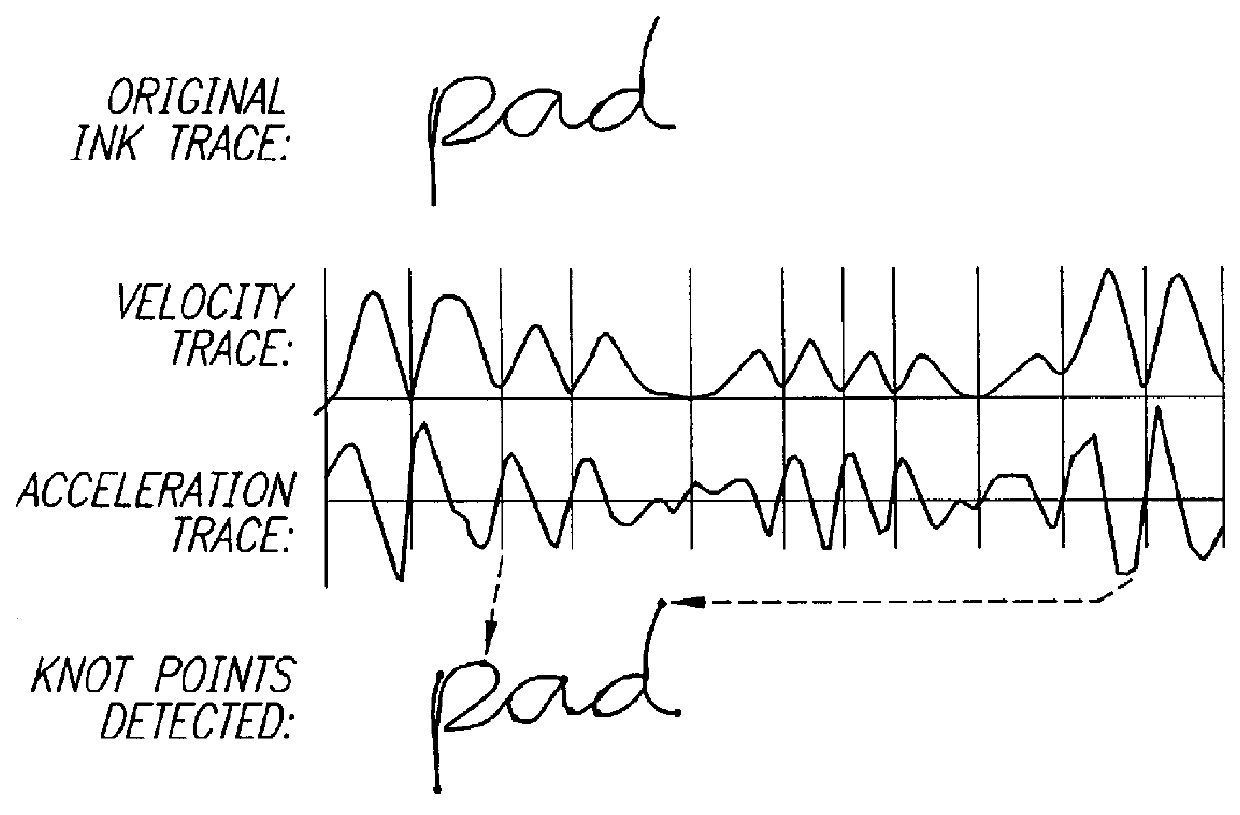
The present invention relates to scribble matching methods, ie. methods for searching samples of electronic ink without having first to translate the ink into ASCII text. The methods of the present invention find application in pen-based computer devices. The invention entails the identification and encoding of velocity minima in the input scribble. Three scribble matching algorithms are described-a syntactic matcher, a word matcher and an elastic matcher. The syntactic matcher encodes the input scribble according to the shape of the scribble in the region of the velocity minima. The word matcher encodes the input scribble according to the heights of the velocity minima from a reference line, using a continuous height encoding scheme. The elastic matcher encodes the input scribble according to a classification of the velocity minima and intermediate points. The use of velocity minima in the encoding of scribble input provides a stable set of points and leads to improved performance in comparison with known scribble matching methods.
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com