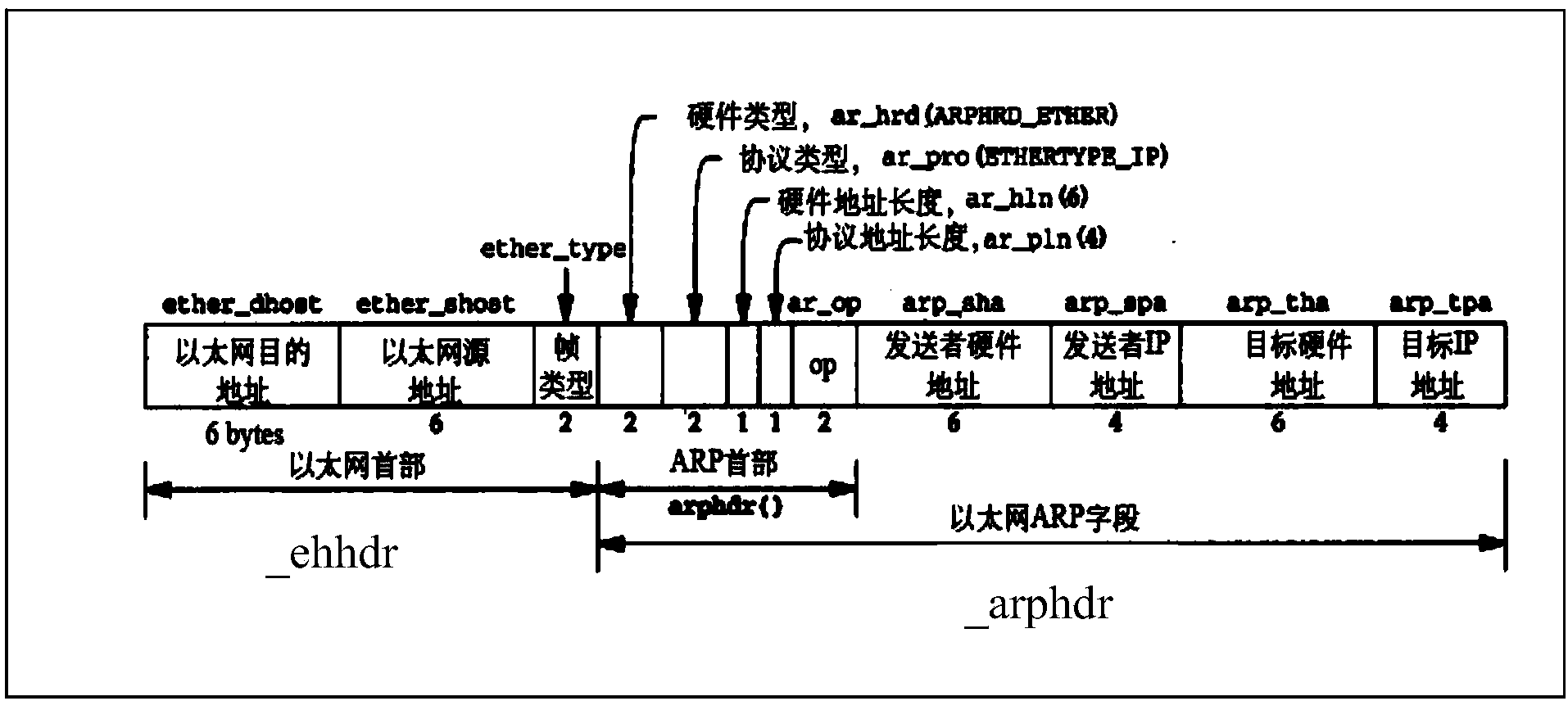
Patents
Literature
2363results about How to "Reduce risk of leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
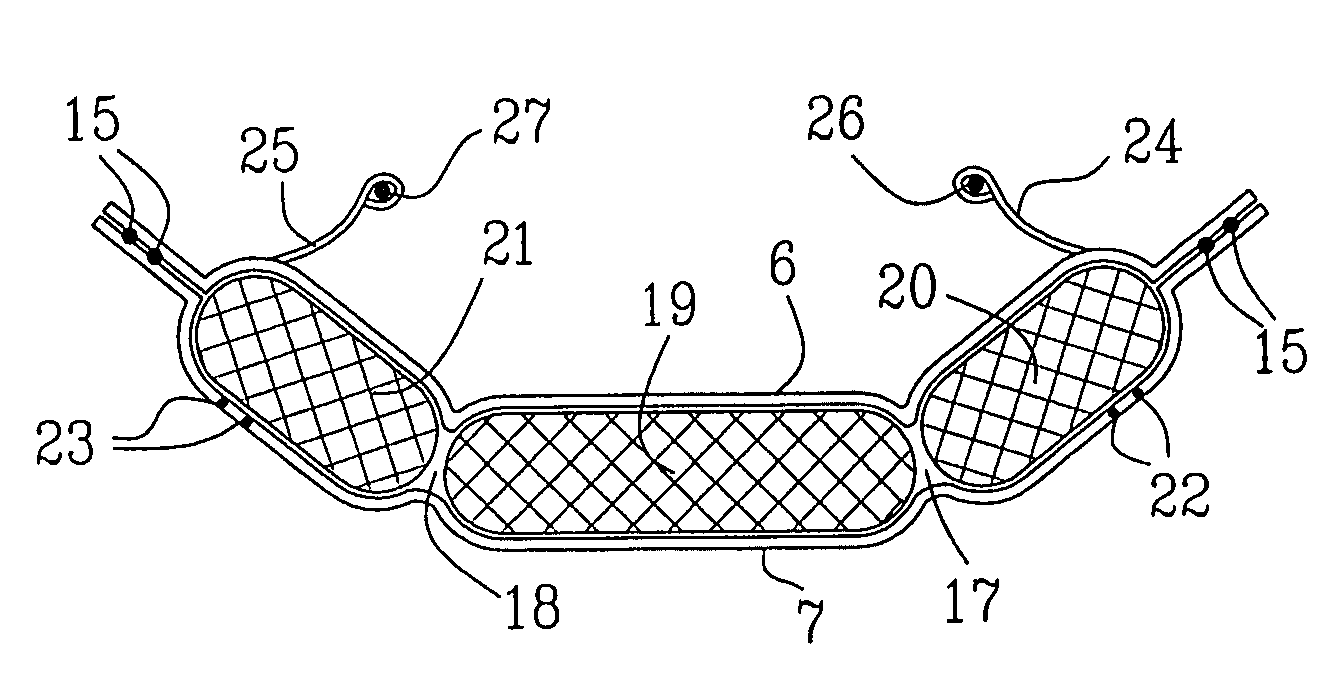
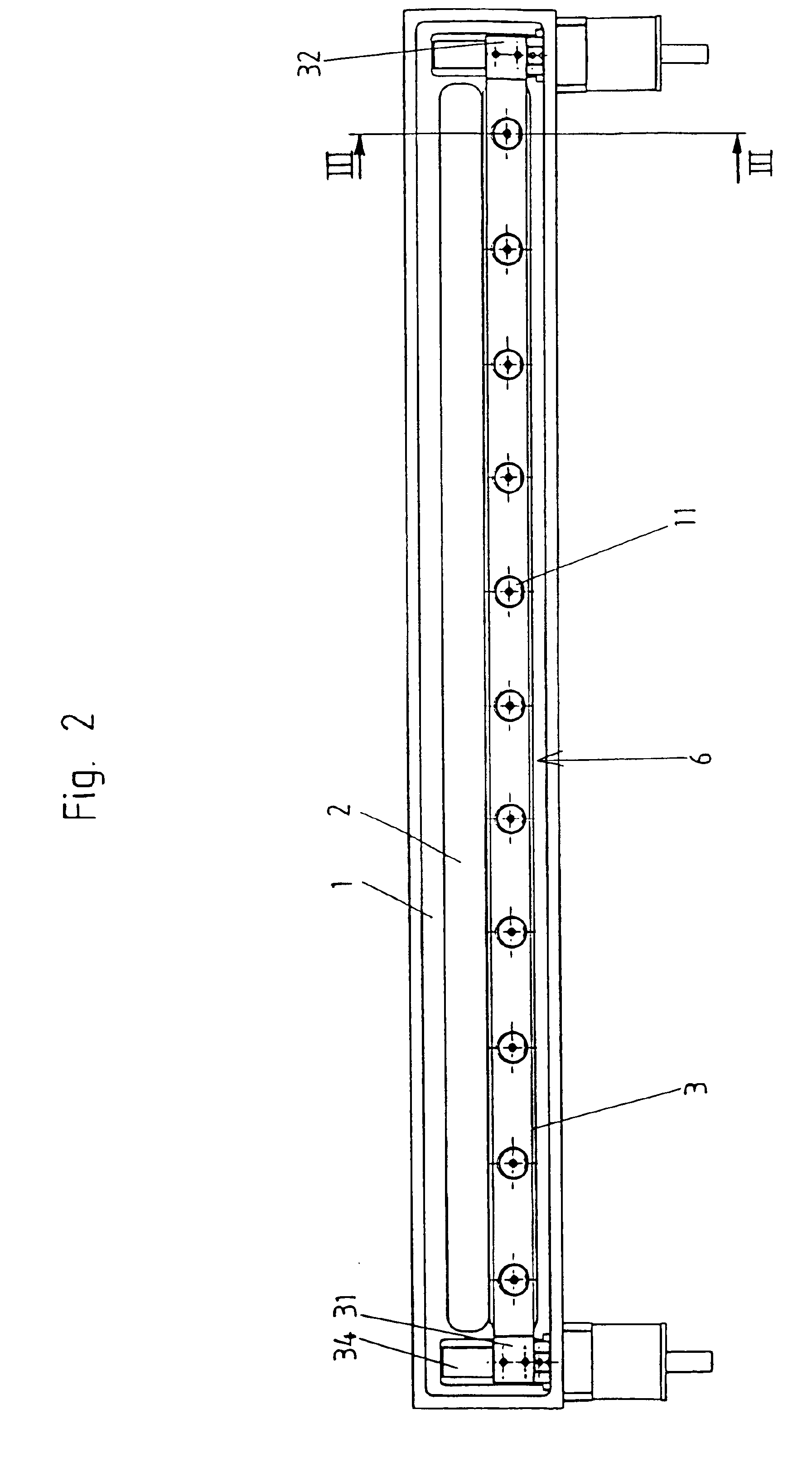
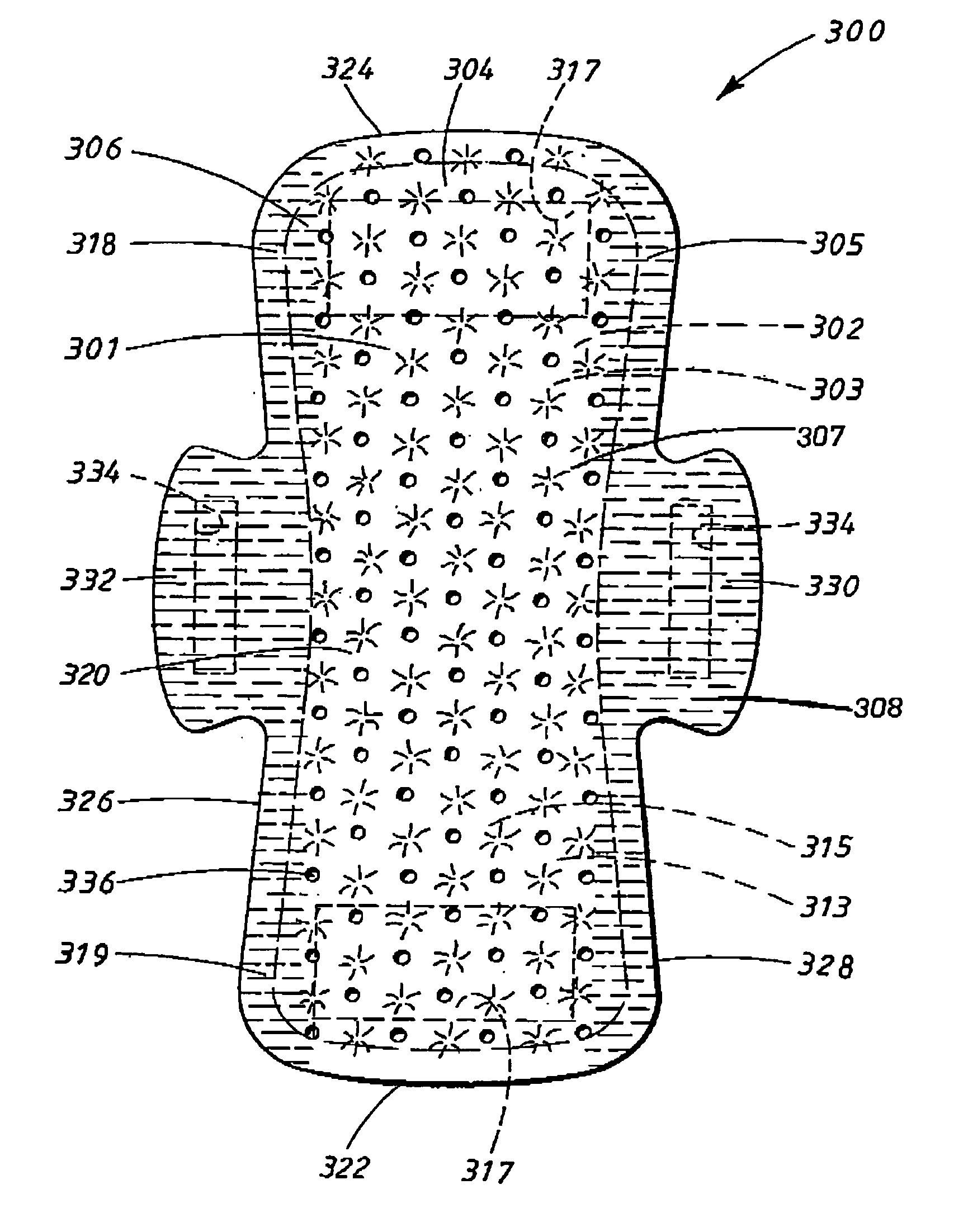
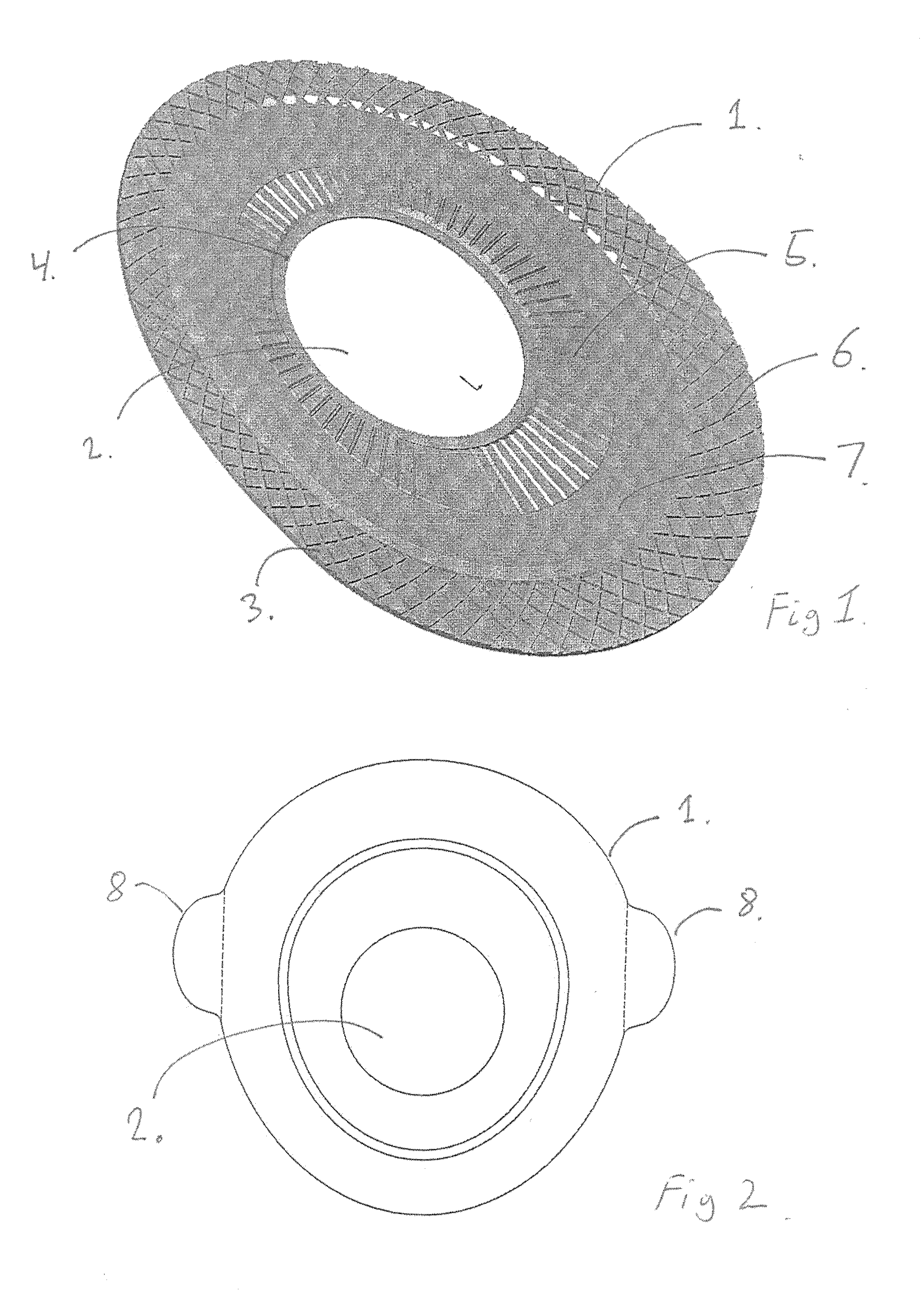
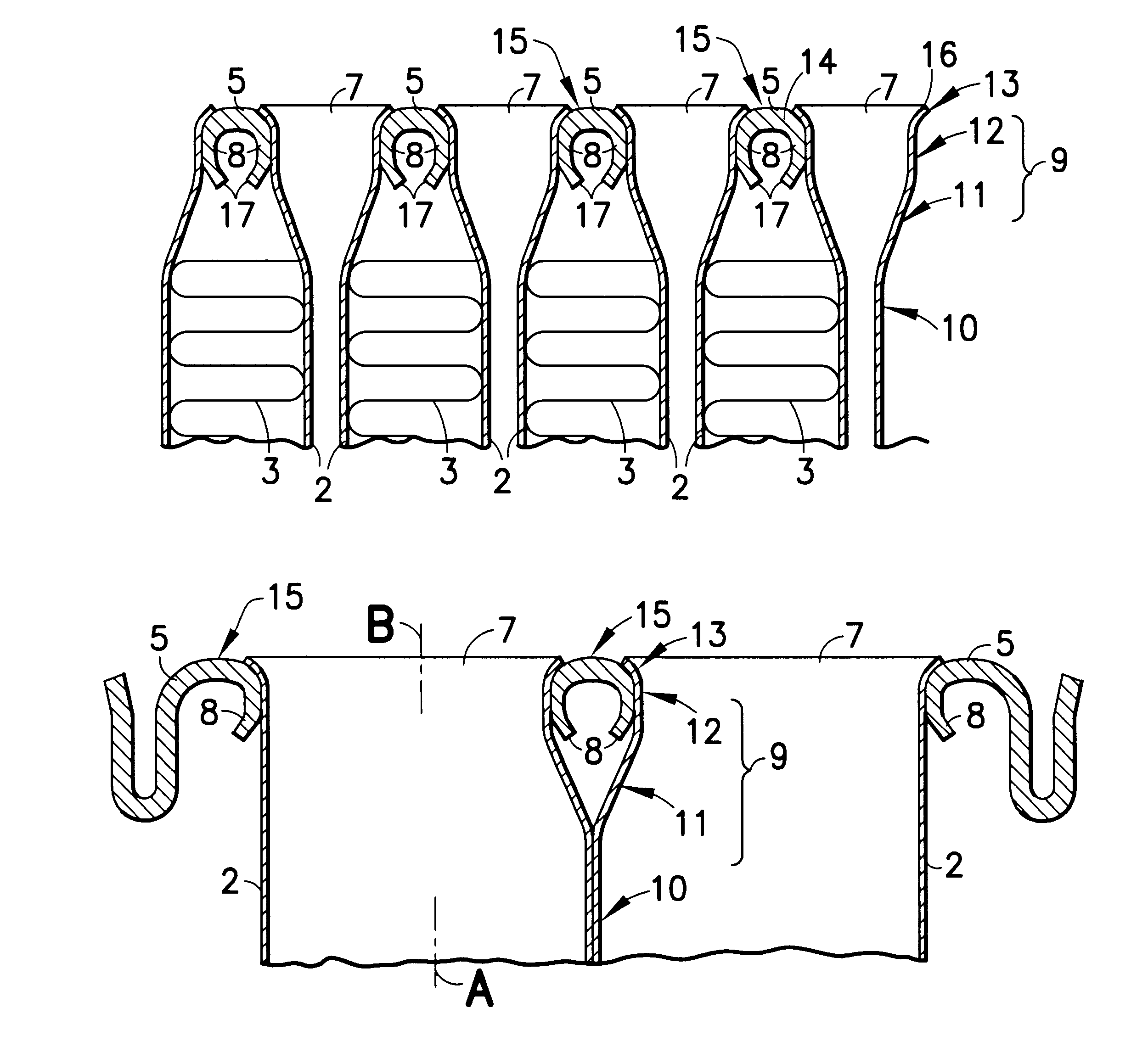
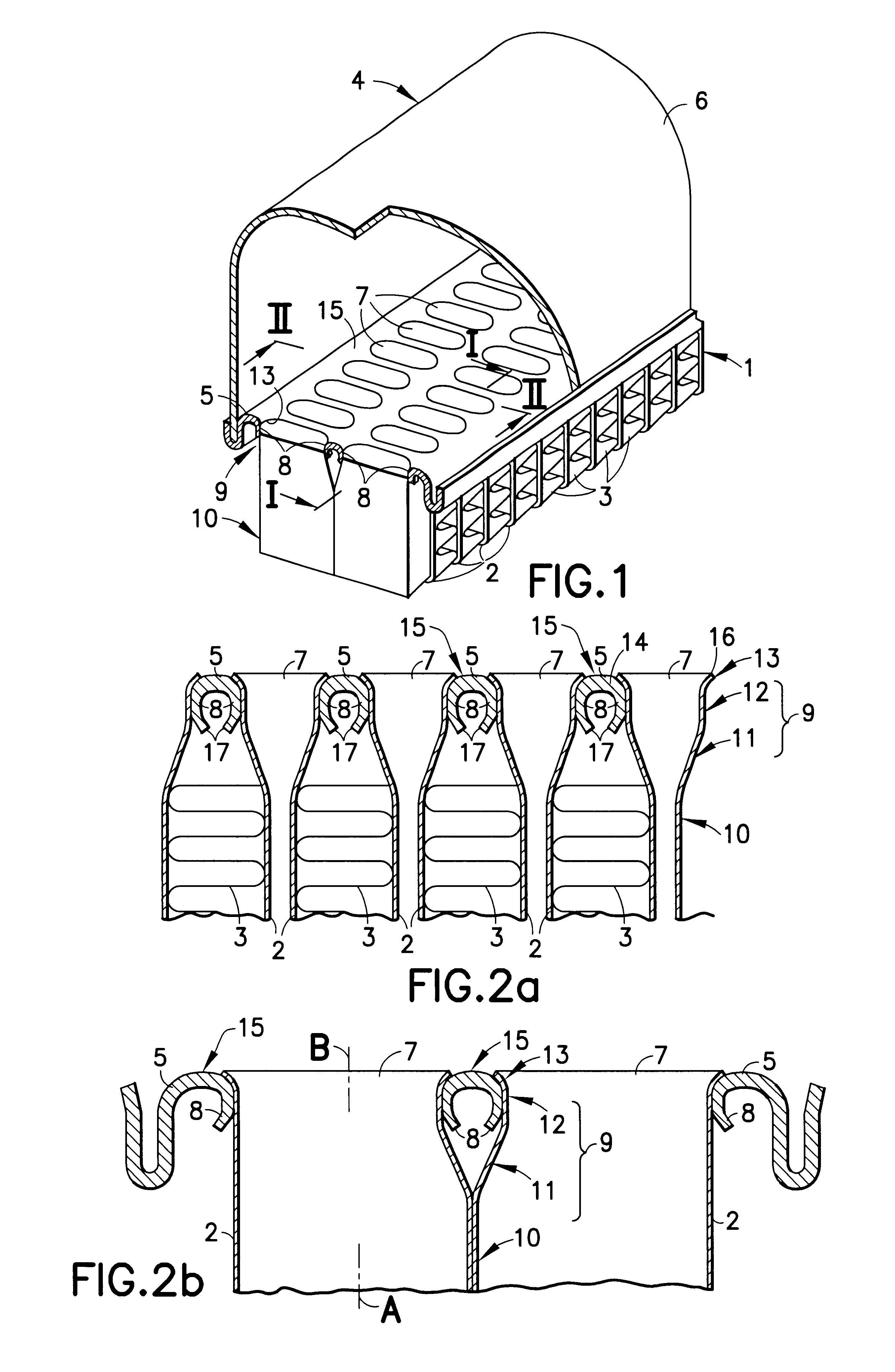
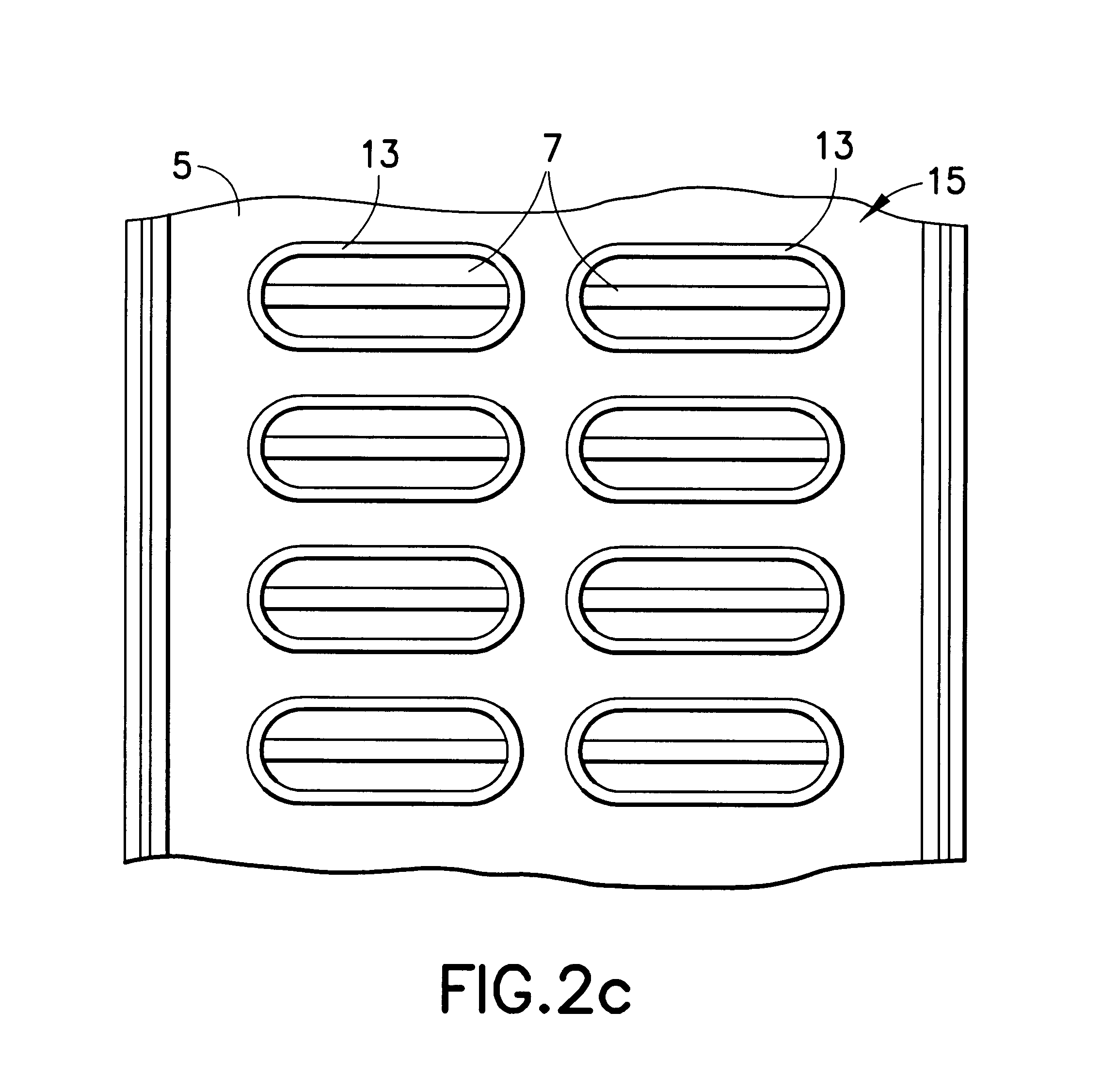
Absorbent article
InactiveUS20070244455A1Increased fit and comfortNarrow widthSanitary towelsBaby linensMechanical engineeringCrotch
An absorbent core in an absorbent article is provided with at least two folding guides extending in a substantially longitudinal direction in the crotch region and dividing at least a part of the crotch region of the absorbent core in a central portion and two lateral portions as seen in a transverse direction. At least two stretchable crotch elastic members are arranged in the crotch portion of the article and are attached to the absorbent core and / or to the inner or outer cover. At least a substantial portion of the crotch elastic members are positioned laterally outside the respective folding guide so as to cause said two lateral portions of the absorbent core to be raised along said folding guides with respect to the central portion.
Owner:SCA HYGIENE PROD AB
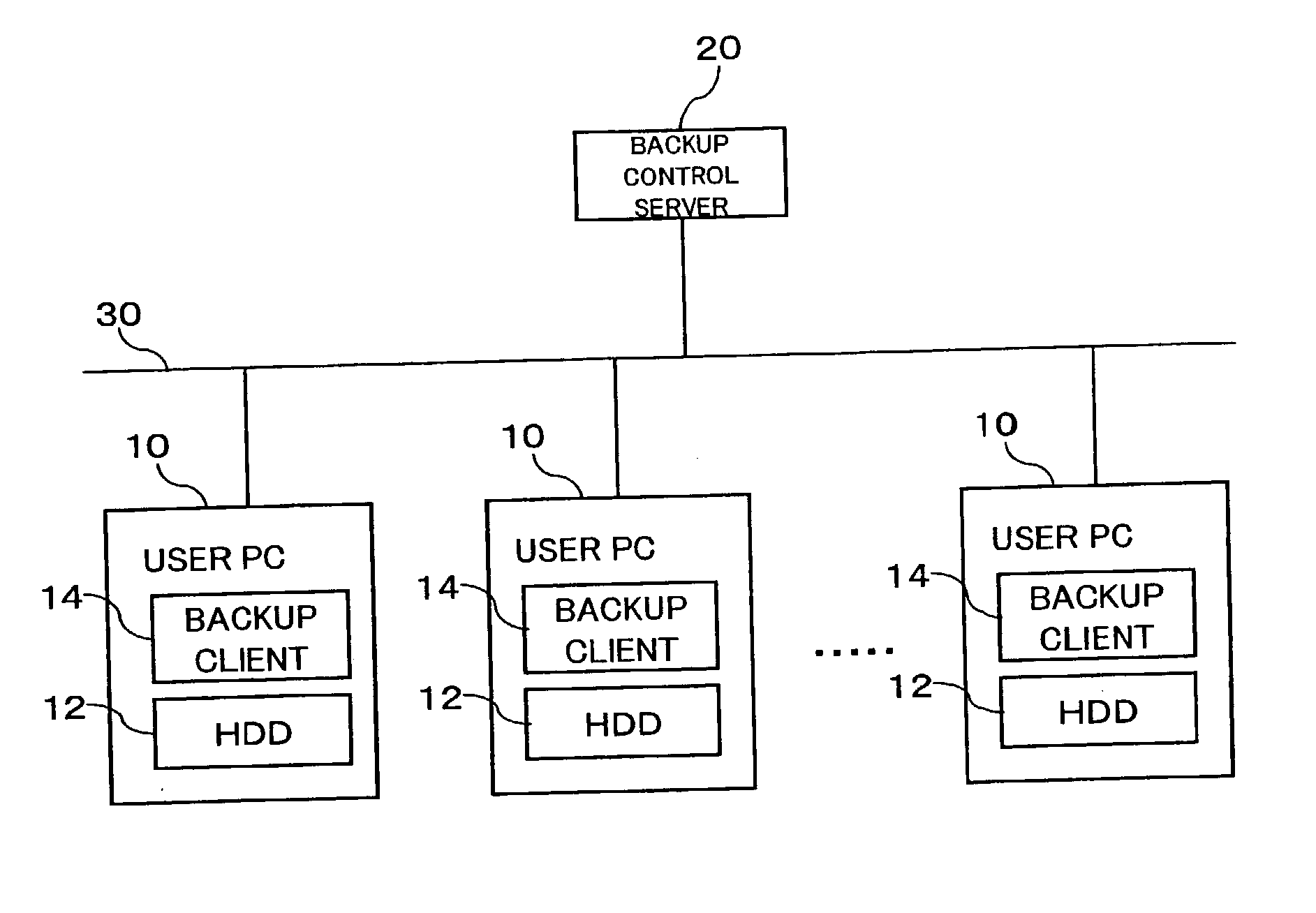
Distributive storage controller and method
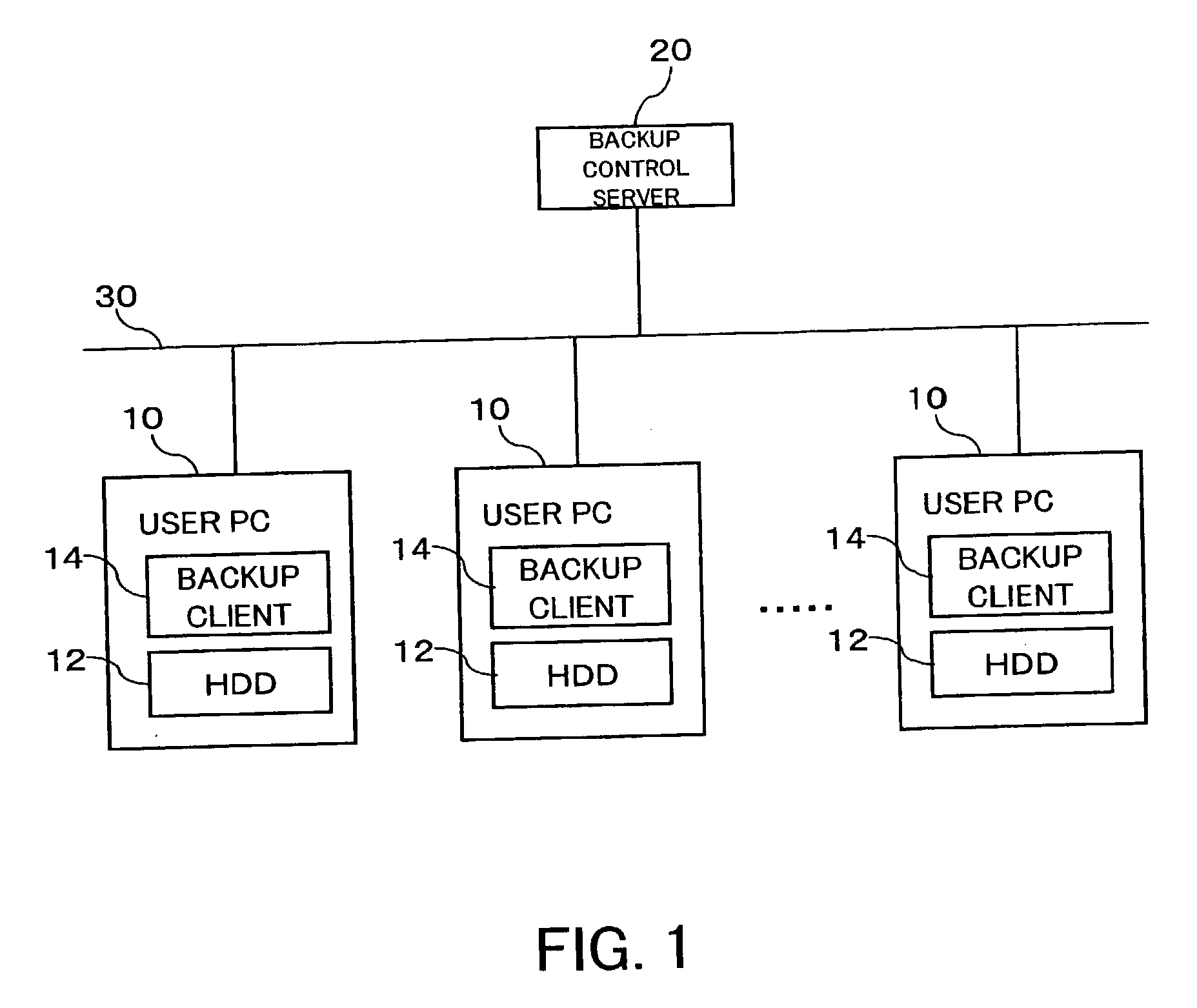
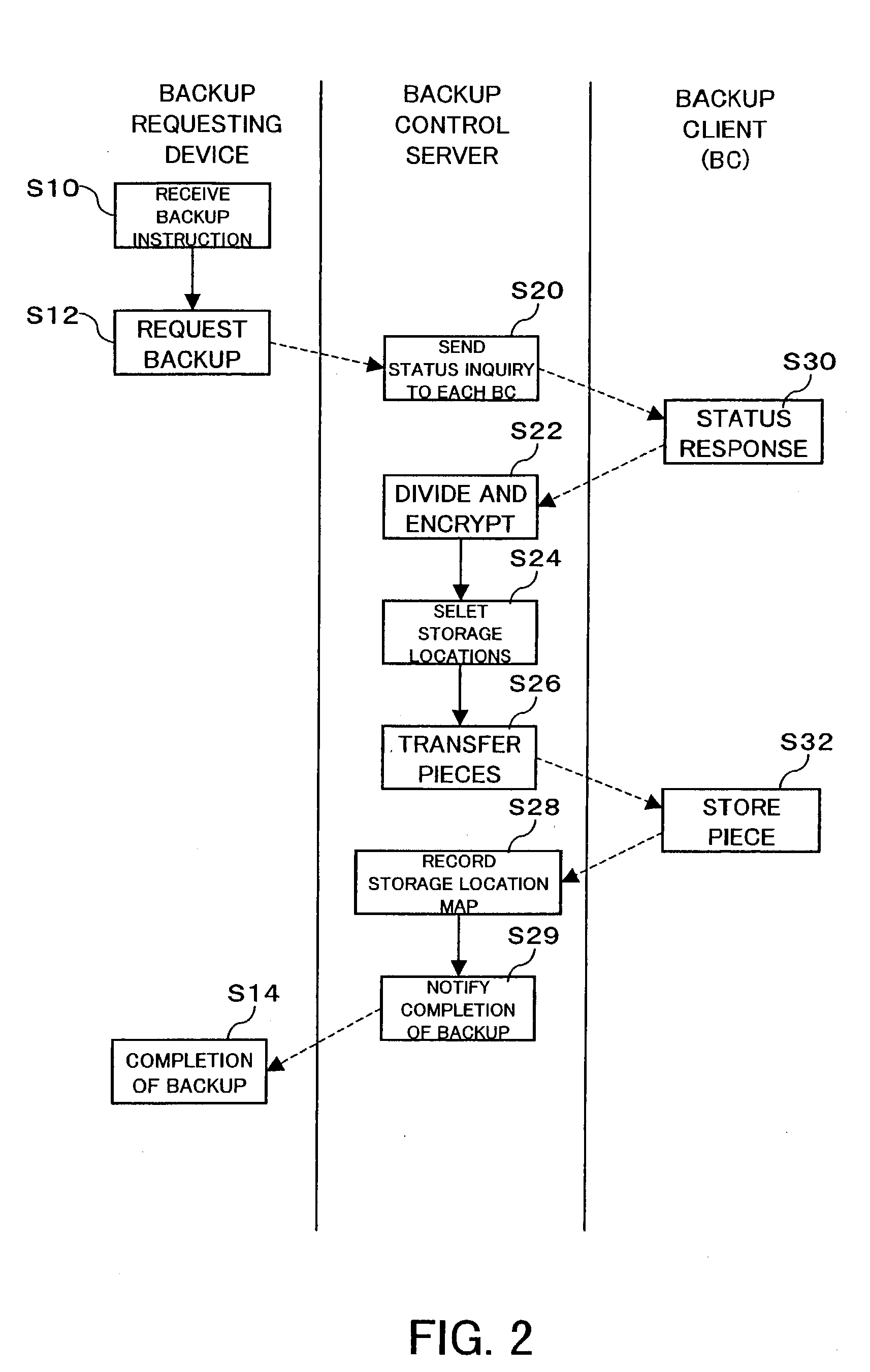
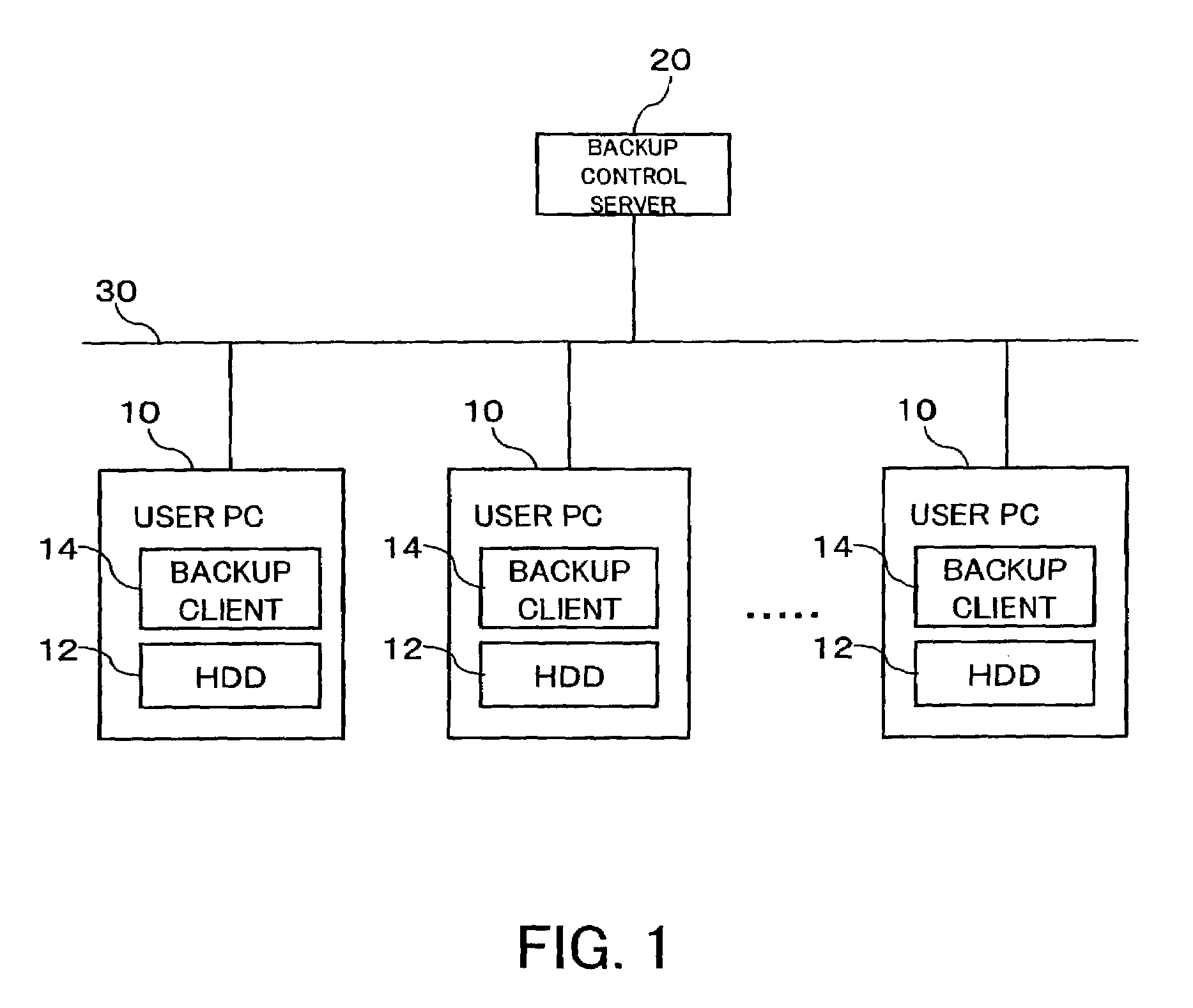
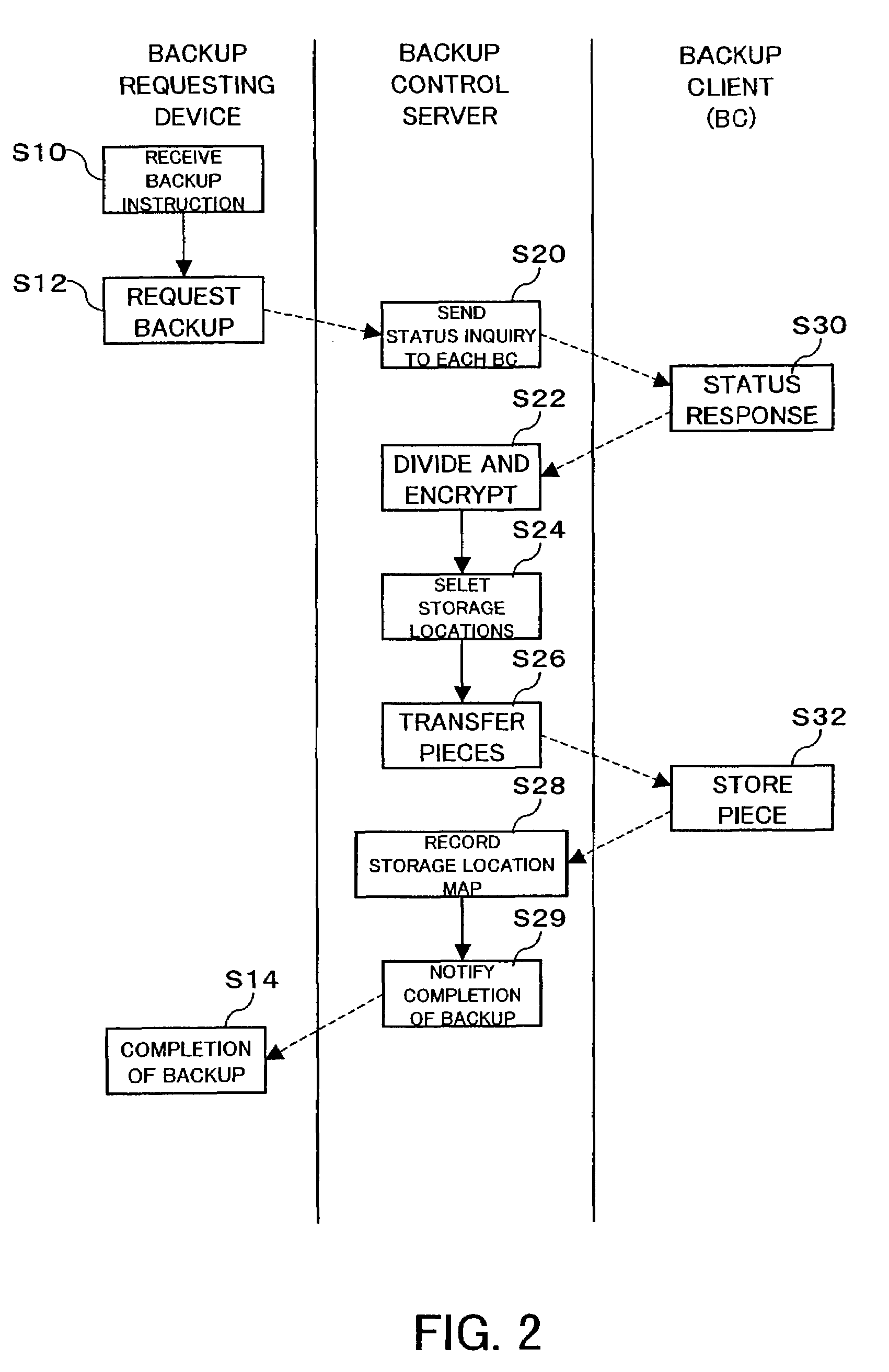
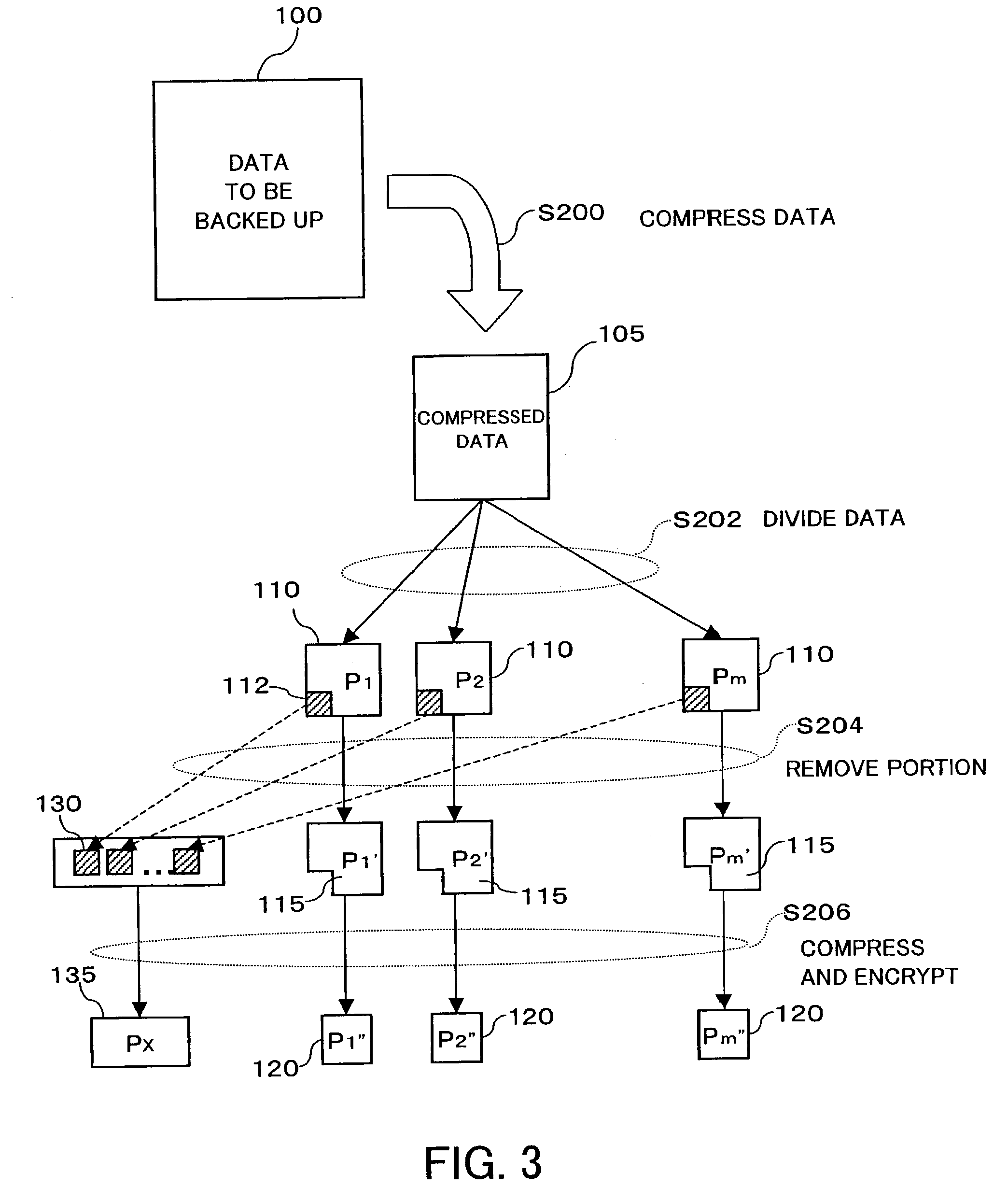
ActiveUS20040049700A1Safe storageReduce risk of leakageInput/output to record carriersDigital data processing detailsHard disc driveControl store
An inexpensive data storage technique utilizing available capacity in individual computer devices connected to a network is provided. When a backup client (BC) (14) of a user PC receives a backup instruction for a file from a user, the backup client (14) requests backup to a backup control server (20). The backup control server (20) divides and encrypts the file to be backed up into a plurality of encrypted pieces, transfers the encrypted pieces to user PCs (10), and stores the encrypted piece in the HDDs (12) of the user PCs (10). When the destributively backed up file is to be extracted, the user PC 10 obtains each encrypted piece from the user PCs 10 on which they are stored, and combines and decrypts the encrypted pieces to restore the original file.
Owner:FUJIFILM BUSINESS INNOVATION CORP
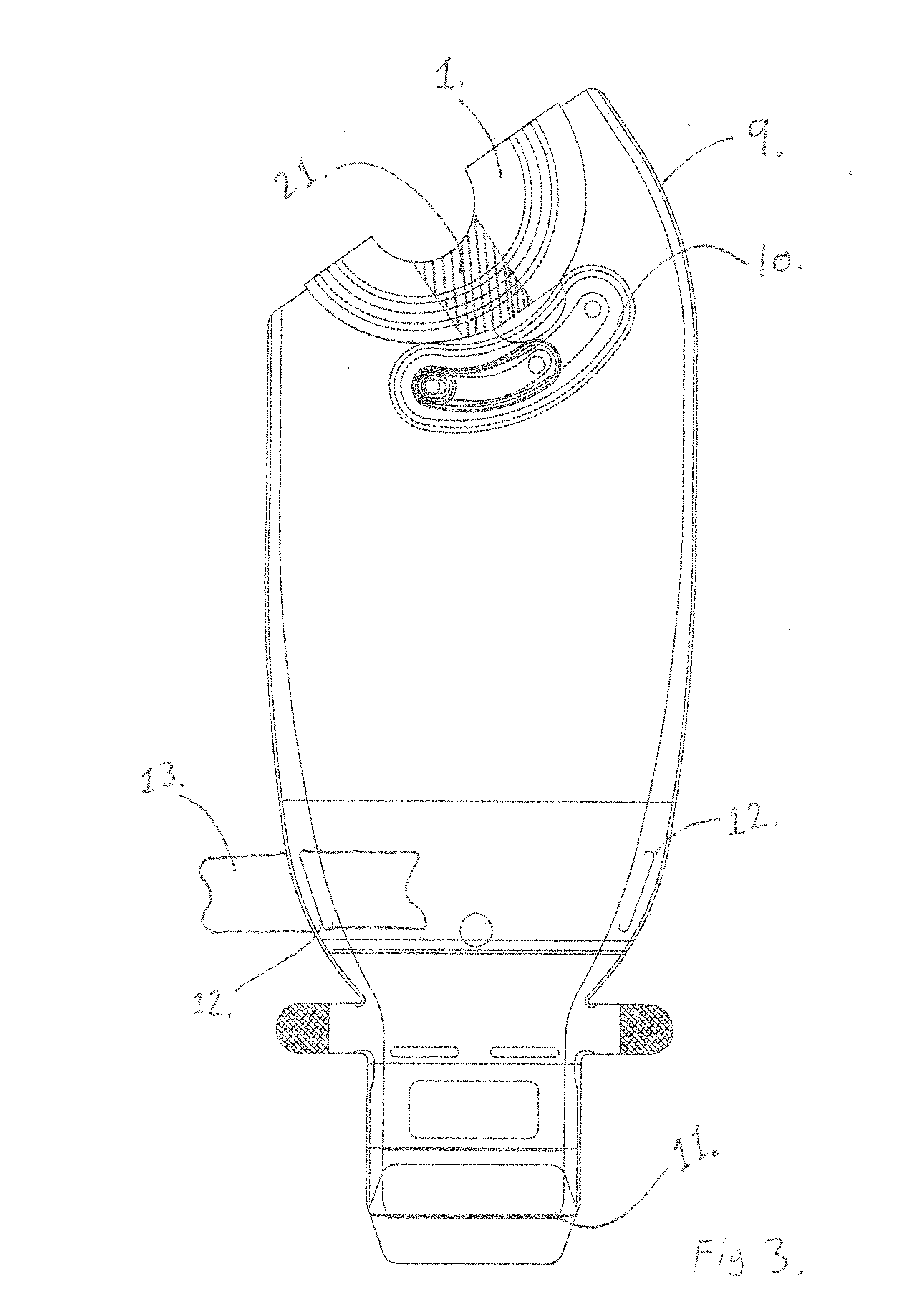
Closure device for vacuum closure of at least one opening in a wall
InactiveUS6899316B2Easy maintenanceReduce risk of leakagePillowsOperating means/releasing devices for valvesMechanical engineeringPiston cylinder
A closure device for a vacuum closure of at least one opening in a wall having a valve place, at least one piston-cylinder unit, at least one carrier unit, at least one cylinder bore hole, at least two sealing rings, and a line. The valve plate is associated with an opening and is displaceable between an open position in which it releases the opening, a position in which it covers the opening but is raised from the wall and a closed position in which it covers the opening and contacts the wall. The at least one piston-cylinder unit serves to displace the valve to the different positions and includes a pneumatically actuated piston. At least one carrier unit is connected to a piston rod which serves to displace the valve to the different positions.
Owner:VAT HLDG AG
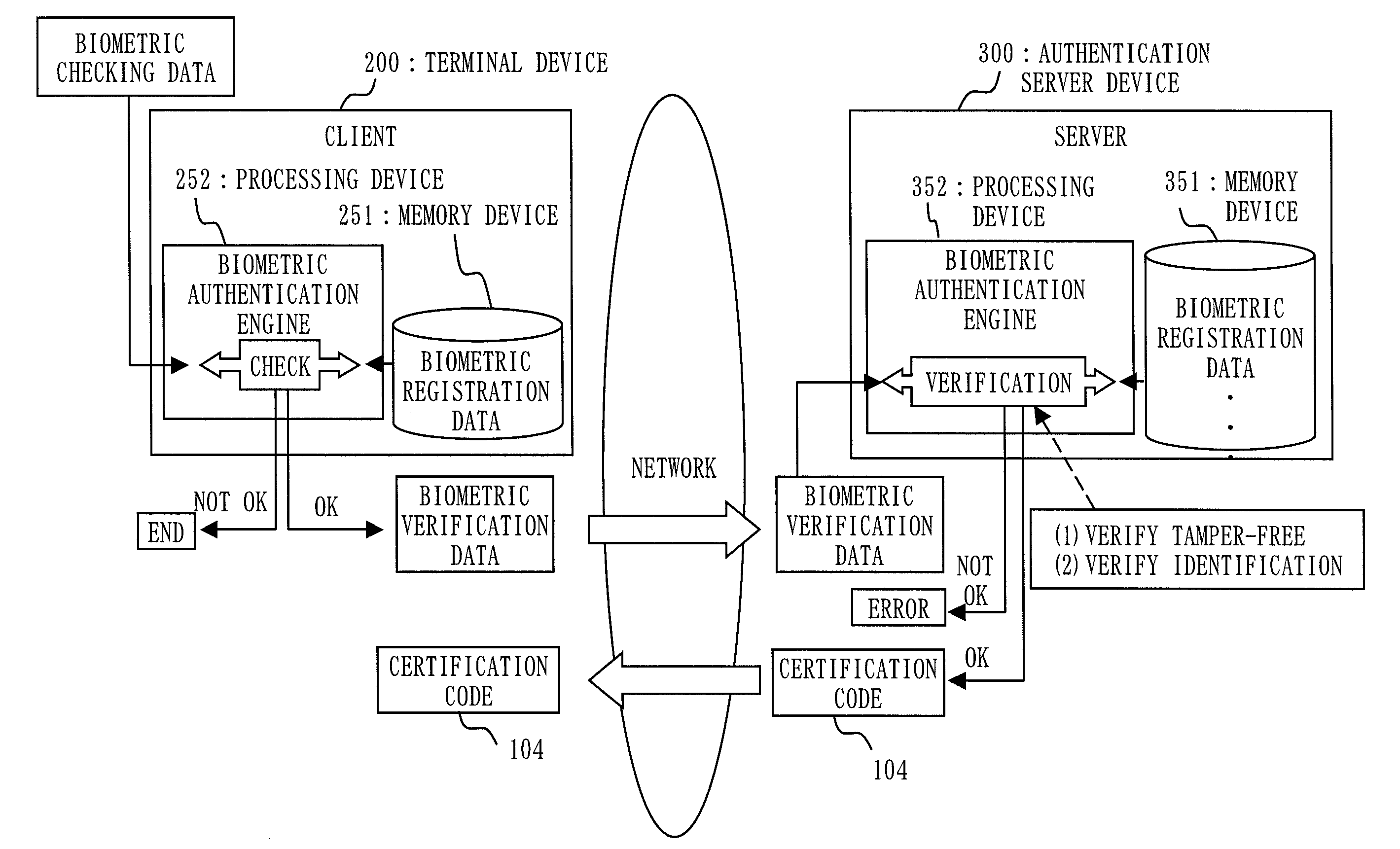
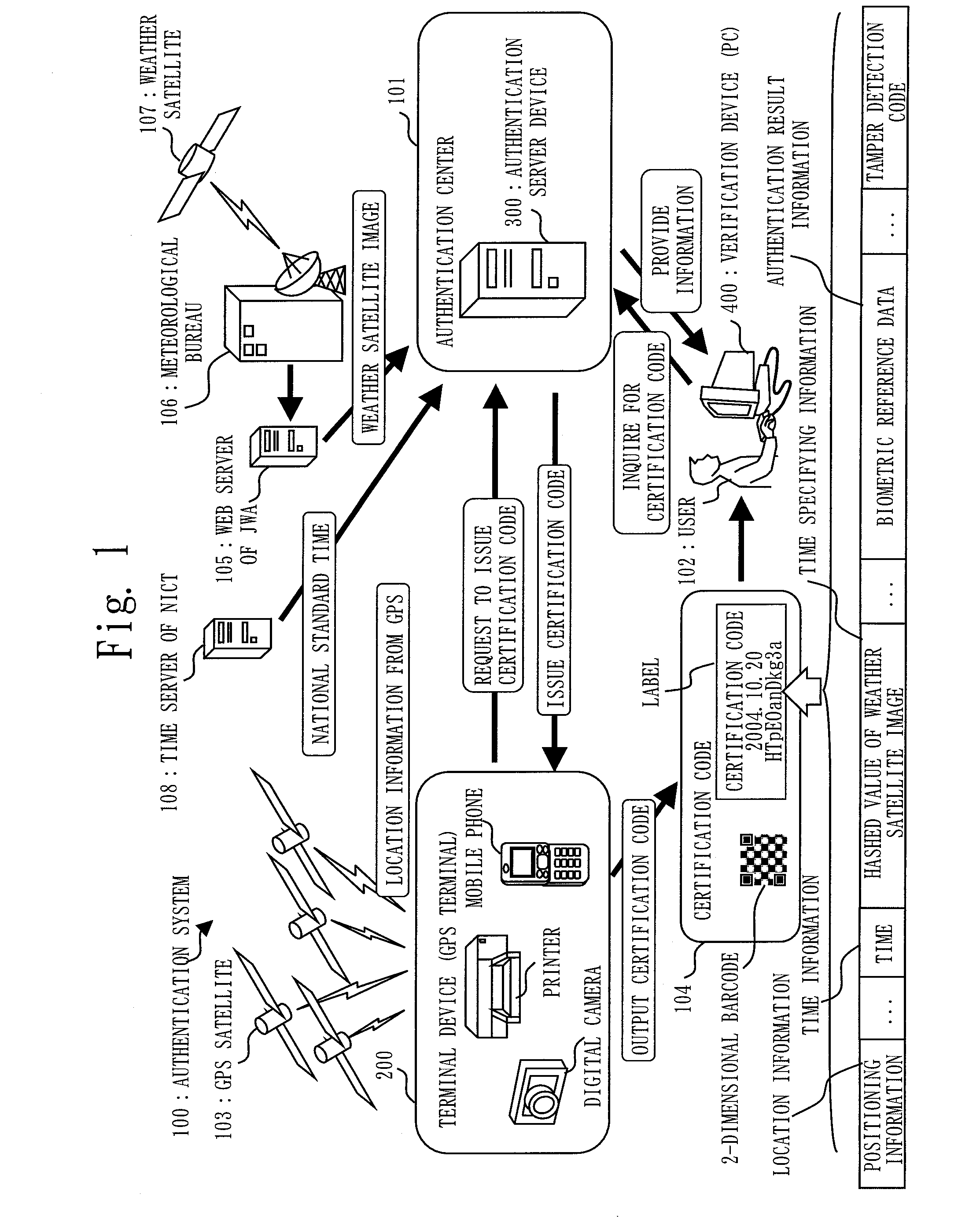
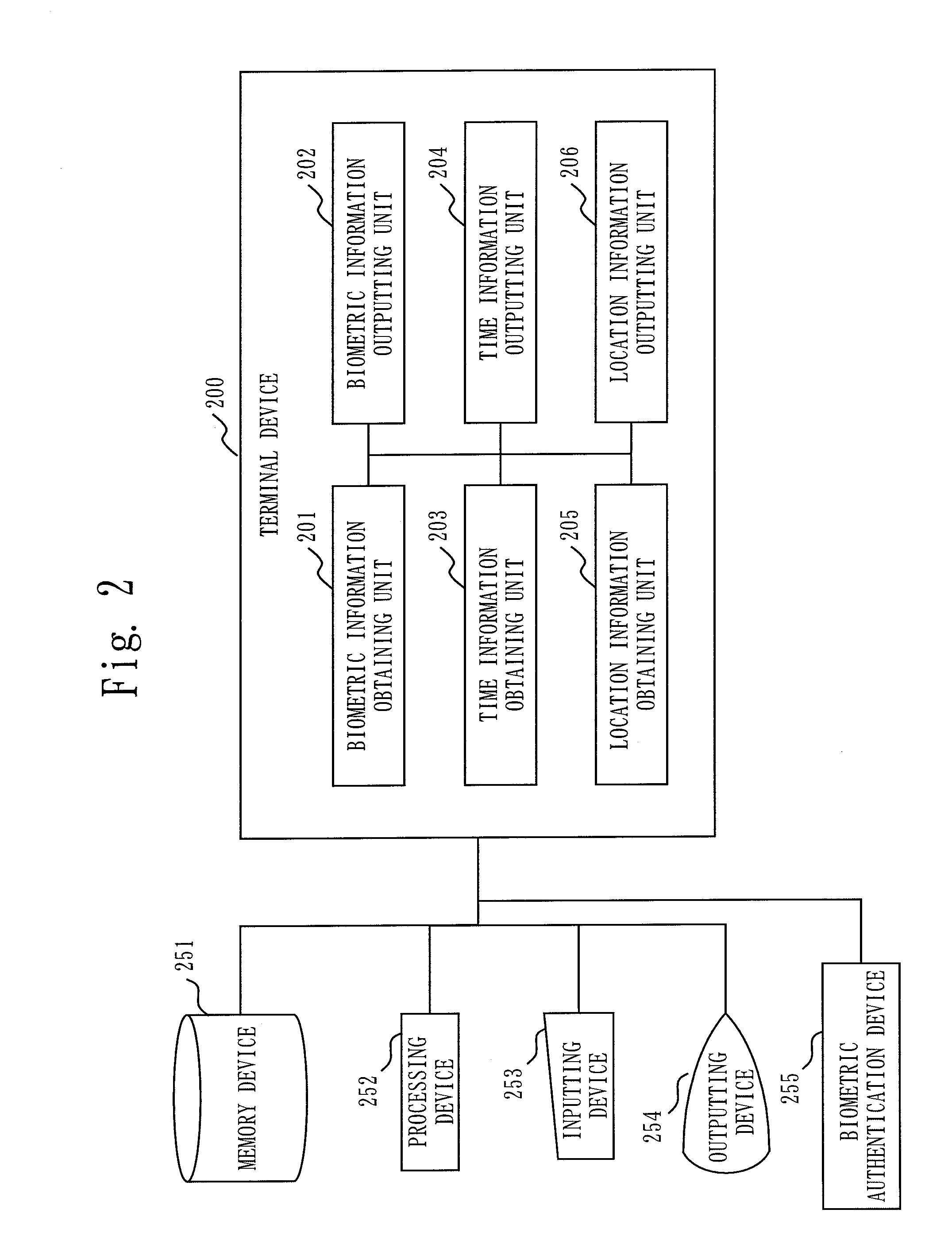
Authenticating server device, terminal device, authenticating system and authenticating method
InactiveUS20100223663A1Reduce the possibilityReduce risk of leakageDigital data processing detailsUser identity/authority verificationSatelliteIntegrated circuit
It is an object to identify, for example, a subject who generates a certain event in addition to certifying a time and / or a location of the event. A terminal device 200 sends positioning information and a time from a GPS satellite 103 and biometric information of a user to an authentication server device 300 to request for issuance of a certification code 104. The authentication server device 300 carries out biometric authentication of the user by comparing the biometric information received from the terminal device 200 with reference data of the user which is maintained beforehand. When the biometric authentication succeeds, the authentication server device 300 generates the certification code 104 by combining the reference data, the time, a hashed value of a weather satellite image, and the positioning information used for the biometric authentication. The terminal device 200 receives the certification code 104 from the authentication server device 300 and uses the certification code 104 received by outputting to a label, a photo, an IC (integrated circuit) tag, etc.
Owner:MITSUBISHI ELECTRIC CORP
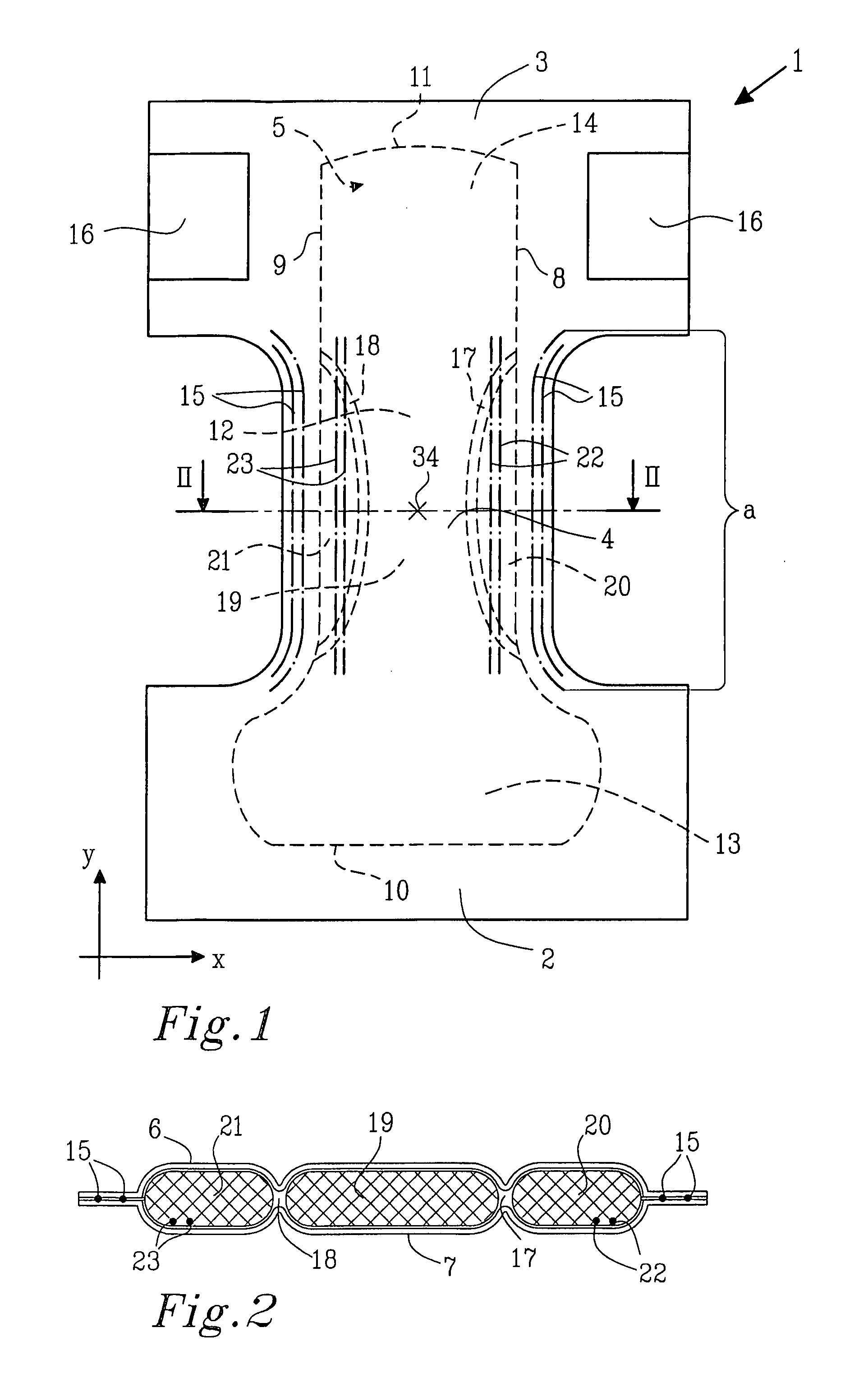
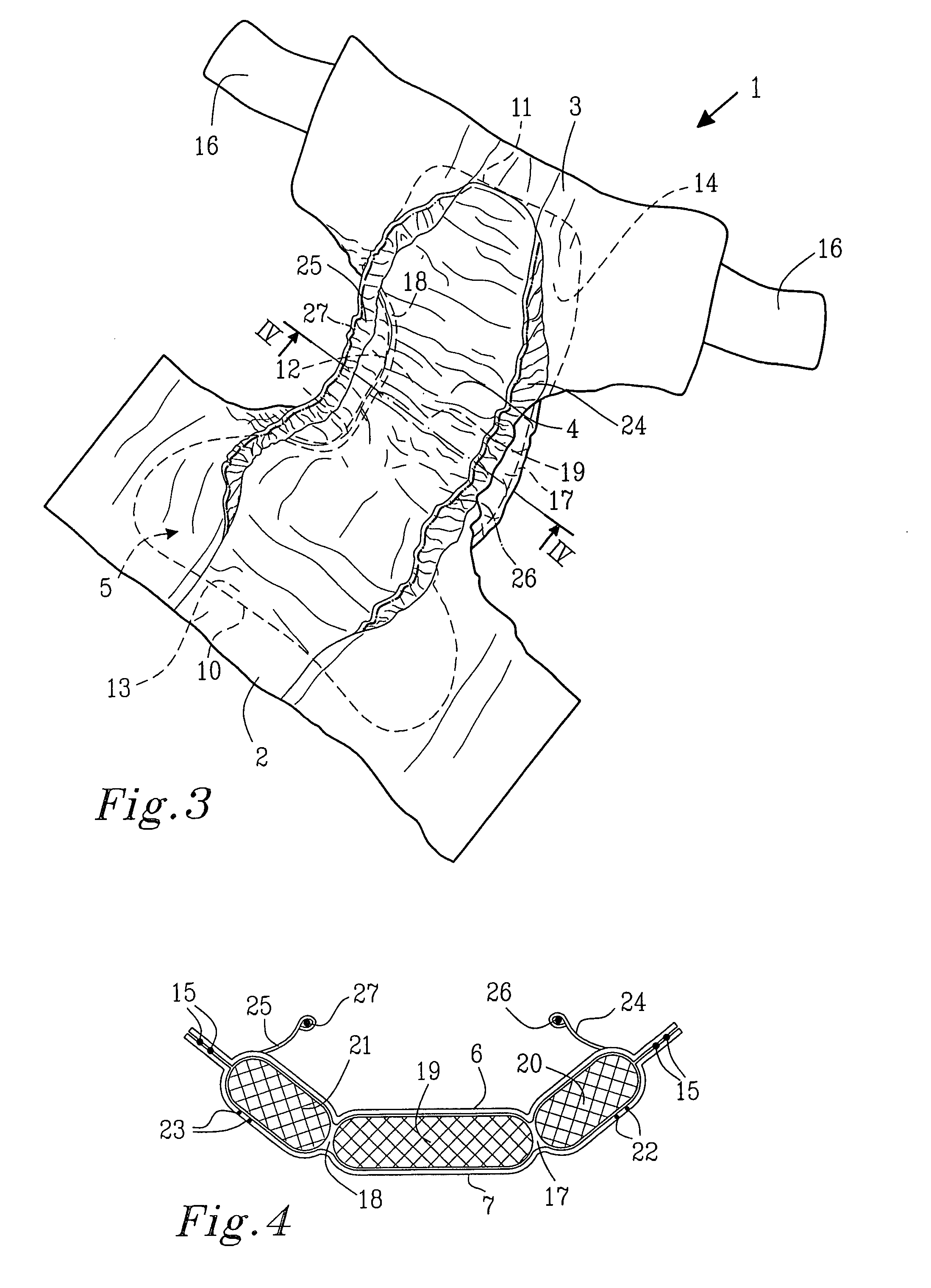
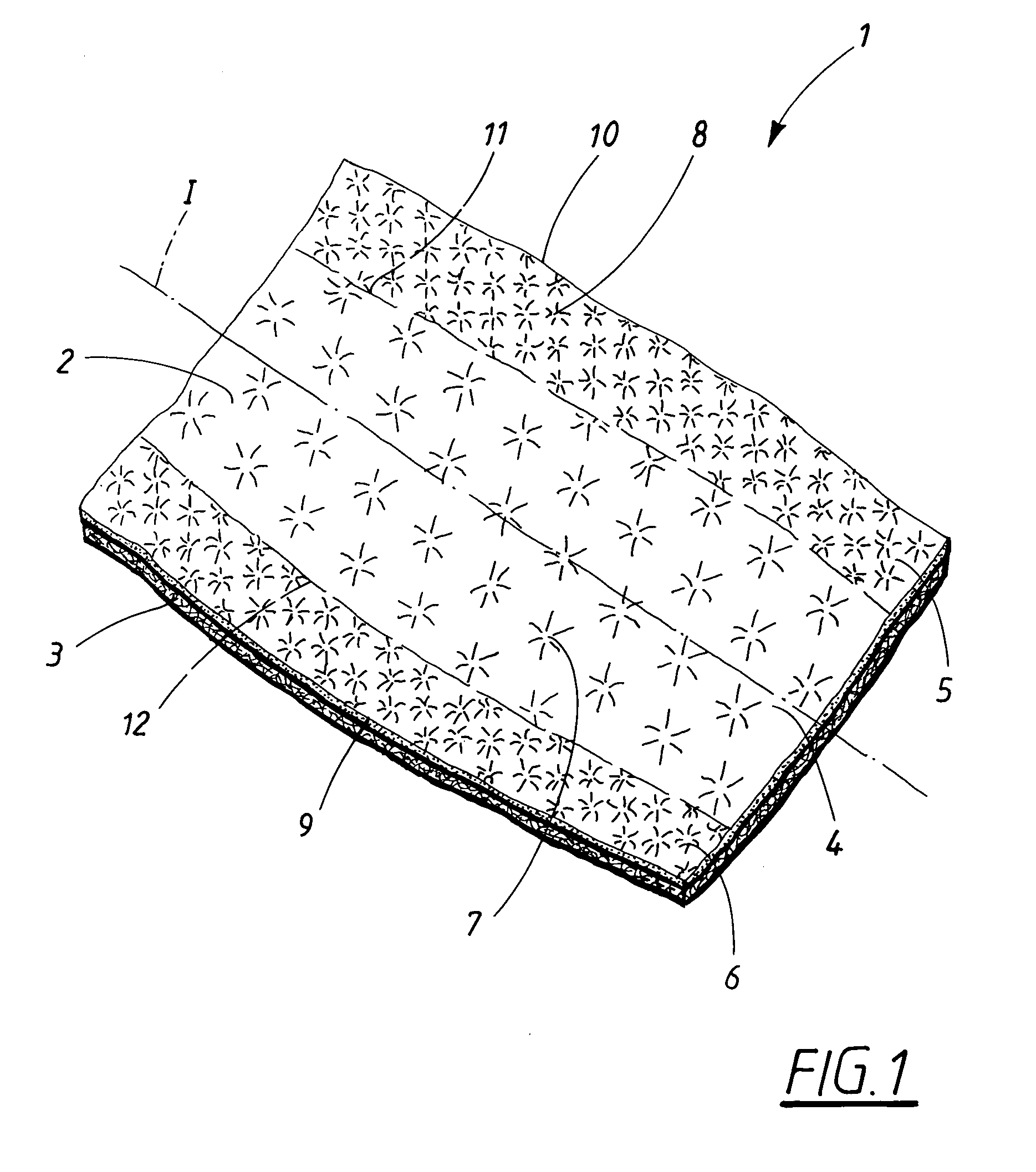
Material laminate for use as a covering sheet in an absorbent article
InactiveUS6916969B1Reduce risk of leakageReduce riskLayered productsBaby linensFiberThermoplastic materials
The invention relates to a material laminate for use as a covering sheet on absorbent articles such as sanitary napkins, incontinence protectors, diapers, pant diapers, or the like. The material laminate comprises a first, fluid pervious fibrous material layer and a second fluid pervious porous material layer, wherein at least one of the two material layers comprises thermoplastic material and wherein the two material layers are mutually connected by means of the covering material laminate exhibiting bond sites within which the thermoplastic material has been caused to at least partially soften or melt and thereby bond the two material layers together. In the planar extension, the material laminate exhibits two side portions extending in the length direction and having an extension in the width direction from a respective longitudinal side edge and a distance in towards the longitudinal central axis of the material laminate and a central portion positioned between the side portions in the planar extension of the material laminate, wherein the first material layer and the second material layer in the central portion of the material laminate are intermittently bonded together with a first bond pattern and that the first material layer and the second material layer in the two side portions of the material laminate are intermittently bonded together with a second bond pattern wherein the percentage bonded area in relation to the total area in the two side portions is greater then the percentage bonded area in relation to the total area in the central portion. The invention further pertains to an absorbent article comprising the material laminate.
Owner:ESSITY HYGIENE & HEALTH AB
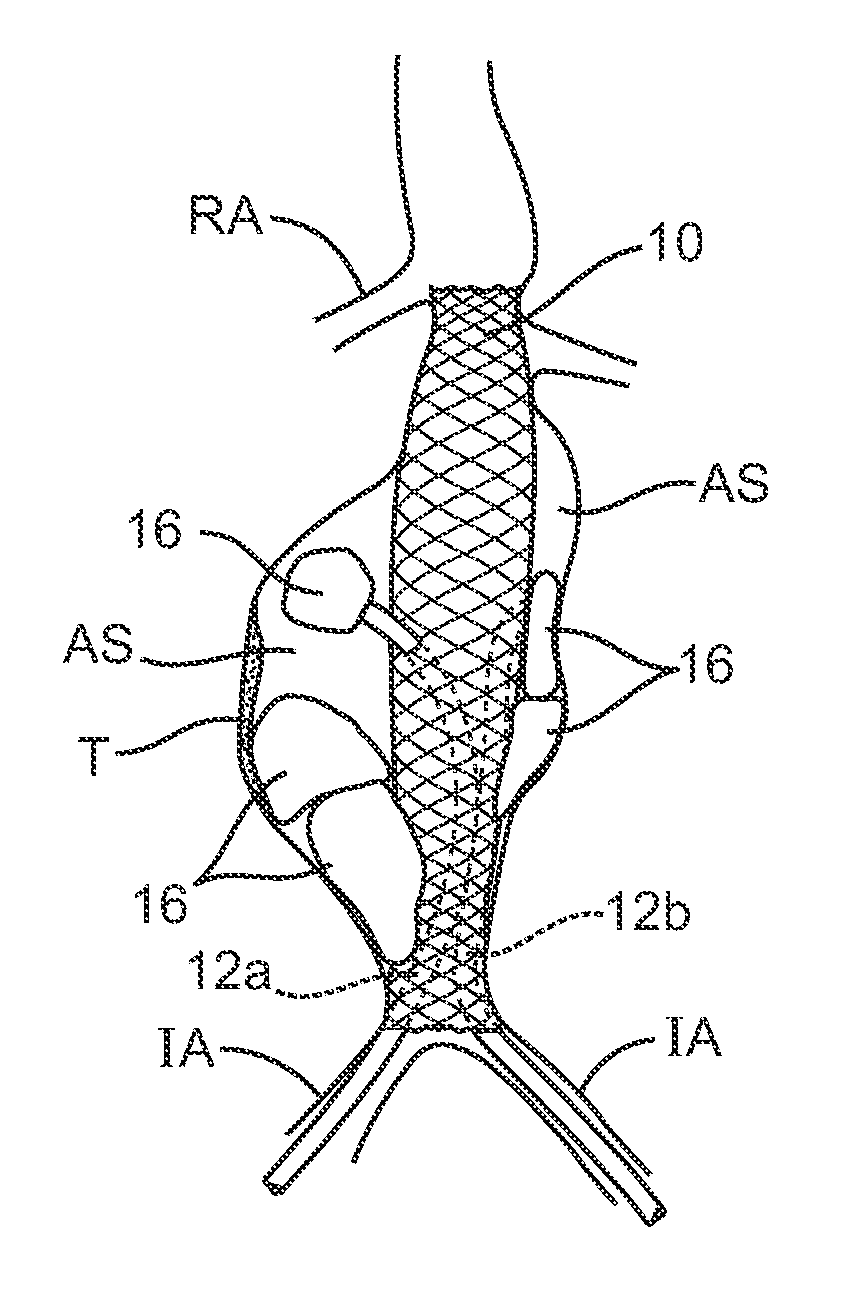
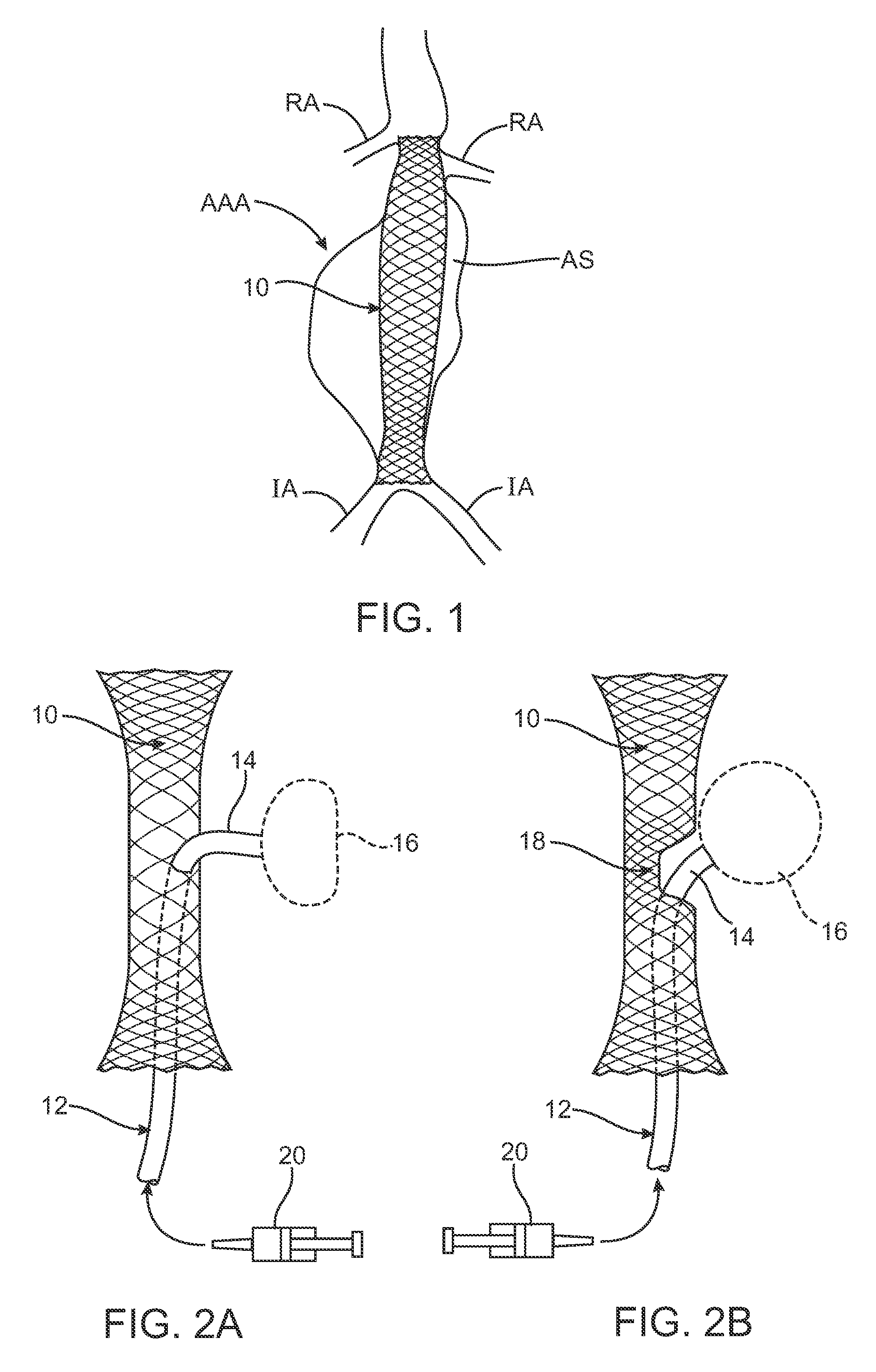
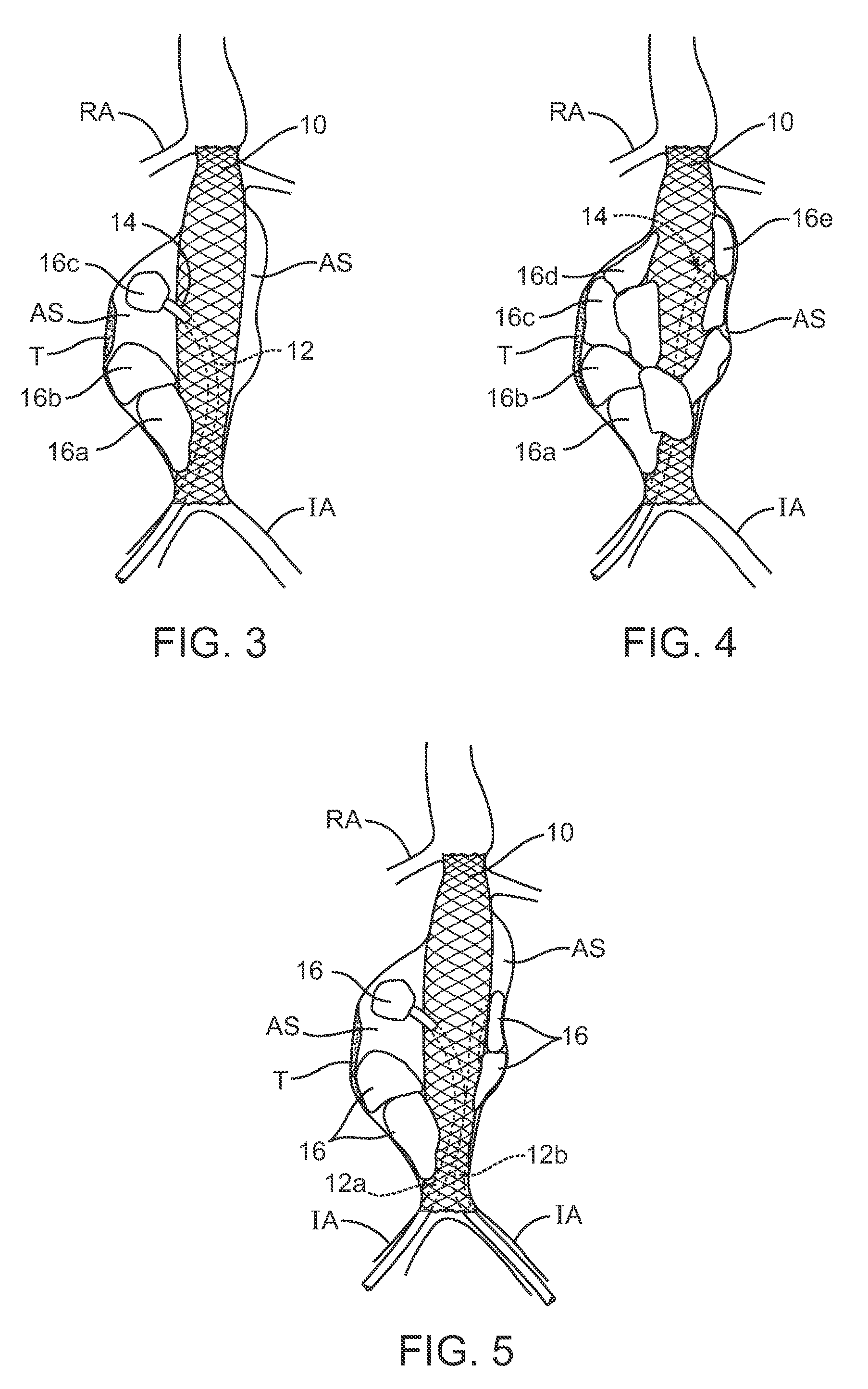
Methods and systems for aneurysm treatment using filling structures
InactiveUS20070150041A1Prevent leakageInhibit migrationStentsOcculdersAneurysm treatmentIliac Aneurysm
Aneurysms are treated by placing a scaffold across an aneurysmal sac to provide a blood flow lumen therethrough. An aneurysmal space surrounding the scaffold is filled with one or more expandable structures which are simultaneously or sequentially expanded to fill the aneurysmal space and reduce the risk of endoluminal leaks and scaffold migration. The expandable structures are typically inflatable and delivered by delivery catheter, optionally with an inflation tube or structure attached to the expandable structure.
Owner:ENDOLOGIX LLC
Collecting bag
InactiveUS6814720B2Easy to disassembleReduce risk of leakageHeating/cooling contact switchesNon-surgical orthopedic devicesStomaEngineering
A flange for a medical collecting bag having an aperture allowing bodily fluids or exudates to enter the bag. The flange has an inner rim delimiting the aperture therein, and a central area encircling the aperture, which area has a predetermined weakening line pattern. The force needed for removing the bag flange from the skin or a body side member is smaller than the force needed for breaking the weakening lines which enables a simple gradual enlargement of the aperture of an ostomy device for adaptation of the aperture to the size of the stoma or for adaptation of the aperture to the size of a wound, as well as a complete removal of the bag flange when substituting the bag.
Owner:COLOPLAST AS
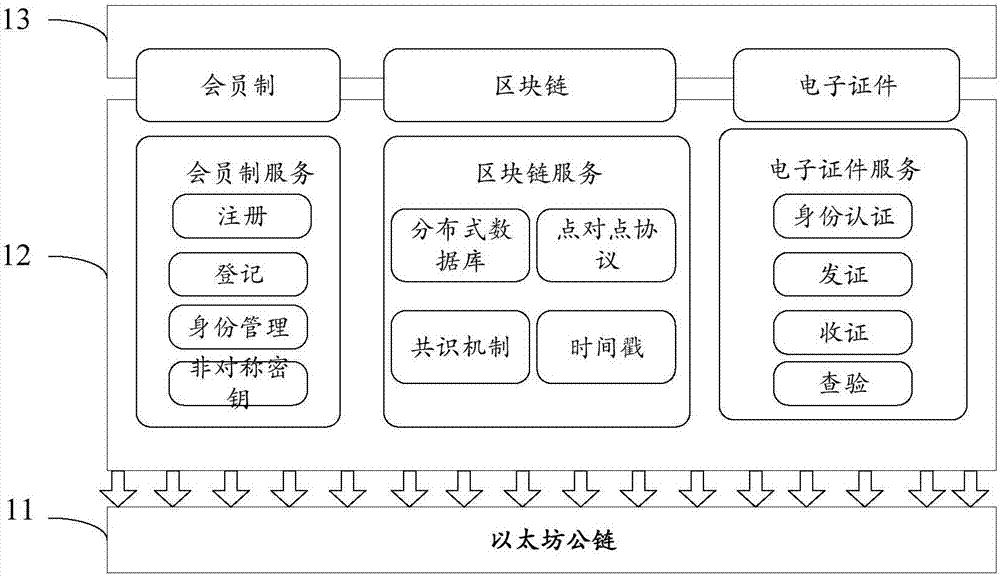
Electronic certificate management method and related equipment
ActiveCN107231351ARealize distributed managementImprove storage reliabilityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesChain networkInformation security
The invention discloses an electronic certificate management method and related equipment. The method comprises the steps as follows: the electronic equipment processes an electronic certificate in response to a received processing command; an encrypted processing record is broadcasted into a block chain network, thus allowing a node of the block chain network to store the encrypted processing record into a block chain of the block chain network. According to the scheme of the method provided by the invention, distributed management of the electronic certificate is achieved, storage reliability of the electronic certificate is improved, the risk of tampering or leaking certificate information is reduced, and information security and credibility of the electronic certificate are effectively ensured.
Owner:YGSOFT INC
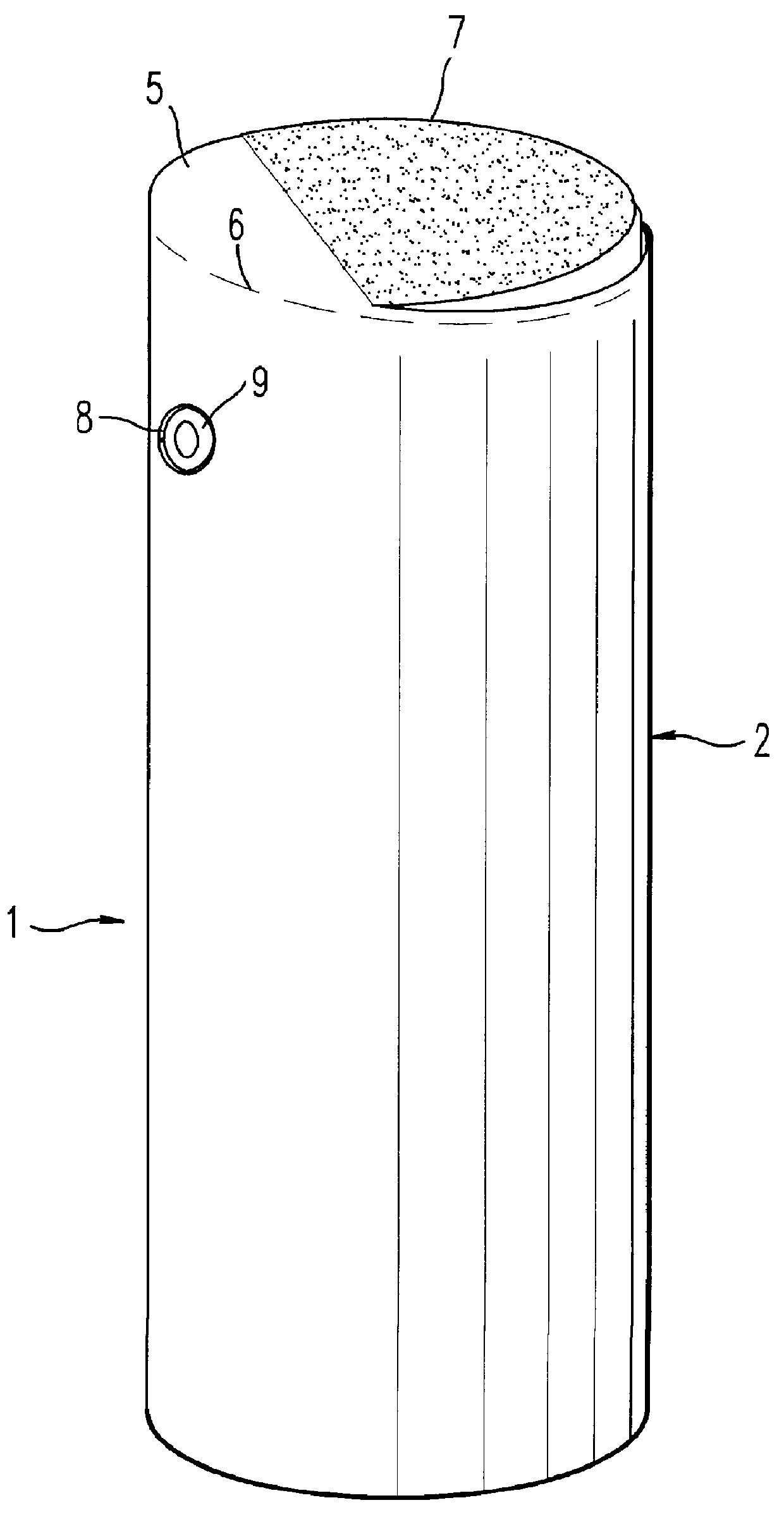
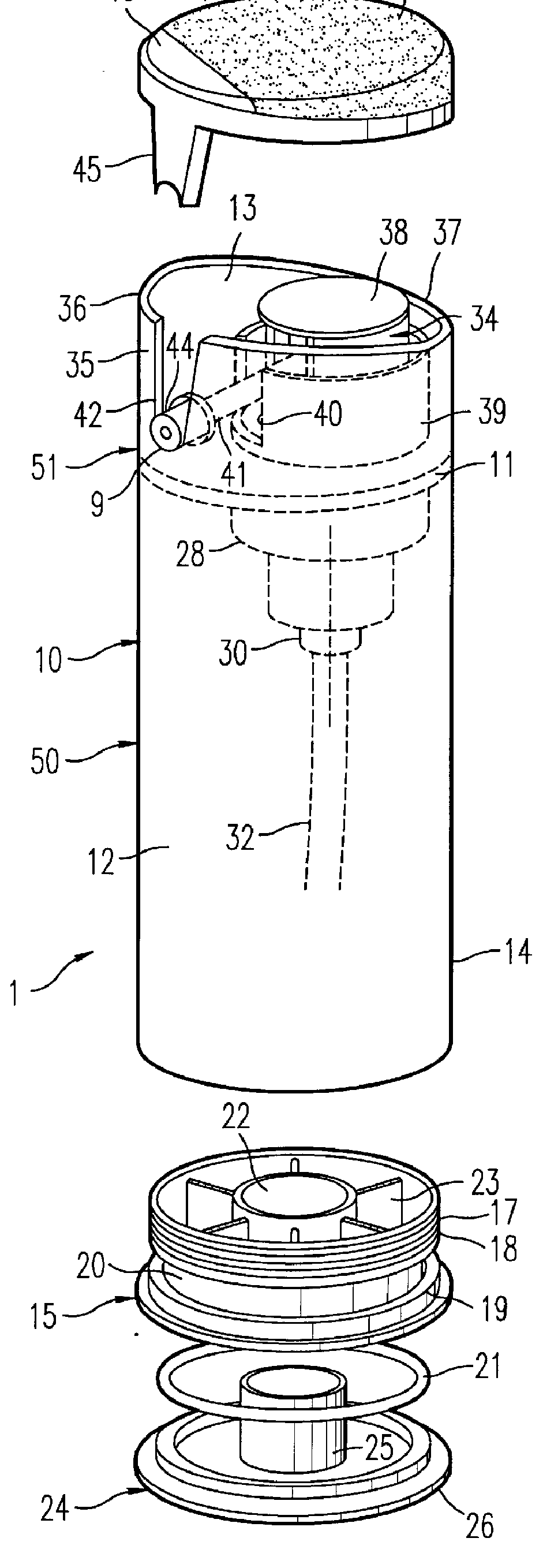
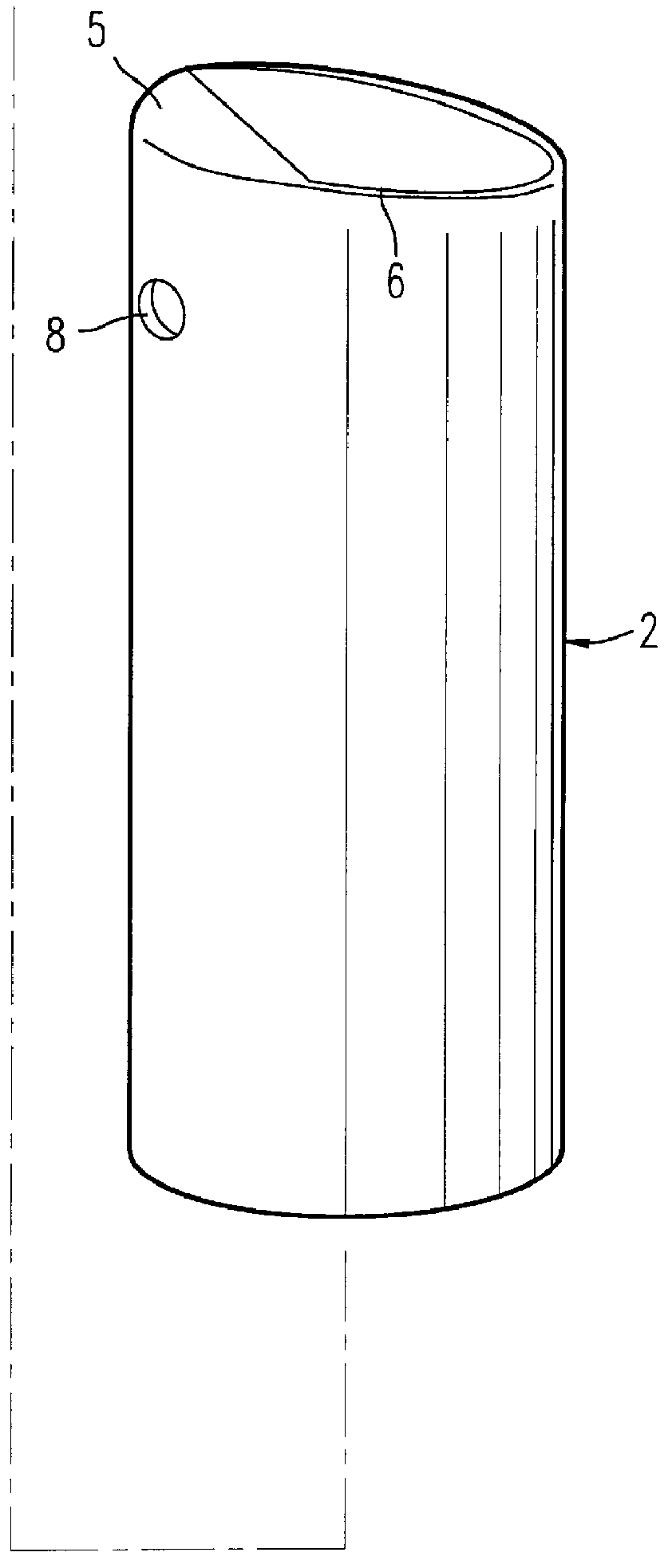
Pump-type packaging unit for a liquid or semi-liquid product
InactiveUS6089410AImprove aestheticsSimple and economic to obtain industriallyLarge containersLiquid transferring devicesLiquid productBiomedical engineering
A unit (1) for packaging and dispensing a liquid or semi-liquid product includes a body (10) with an axis X, forming a reservoir (12) for the liquid or semi-liquid product, the reservoir (12) being surmounted by a pump (30) actuable by an actuating element (34). The product emerges through at least one opening arranged in an outlet element (9) connected to the pump (30) by a conduit (41) forming a flexible connection. The outlet element (9) is held substantially immovably in position on a fixed portion (51) of the body (10) surmounting the reservoir (12), the actuating element (34) being independently mounted relative to the fixed portion (51) of the body (10).
Owner:LOREAL SA
Faecal management device
ActiveUS20100168693A1Efficient use ofOperational securityNon-surgical orthopedic devicesBodily discharge devicesButtocksPerianal skin
A faecal management device suitable for attachment directly to the perianal skin between the buttocks of the wearer. The device utilises an optimised adhesive wafer in order to securely attach the device to the skin of the wearer so that the device is maintained in position for the entire period of wear, including circumstances or periods of wear during which the wearer is active, i.e. not bedridden. In addition the faecal management device of the present invention has the ability for easy application of the device.
Owner:COLOPLAST AS
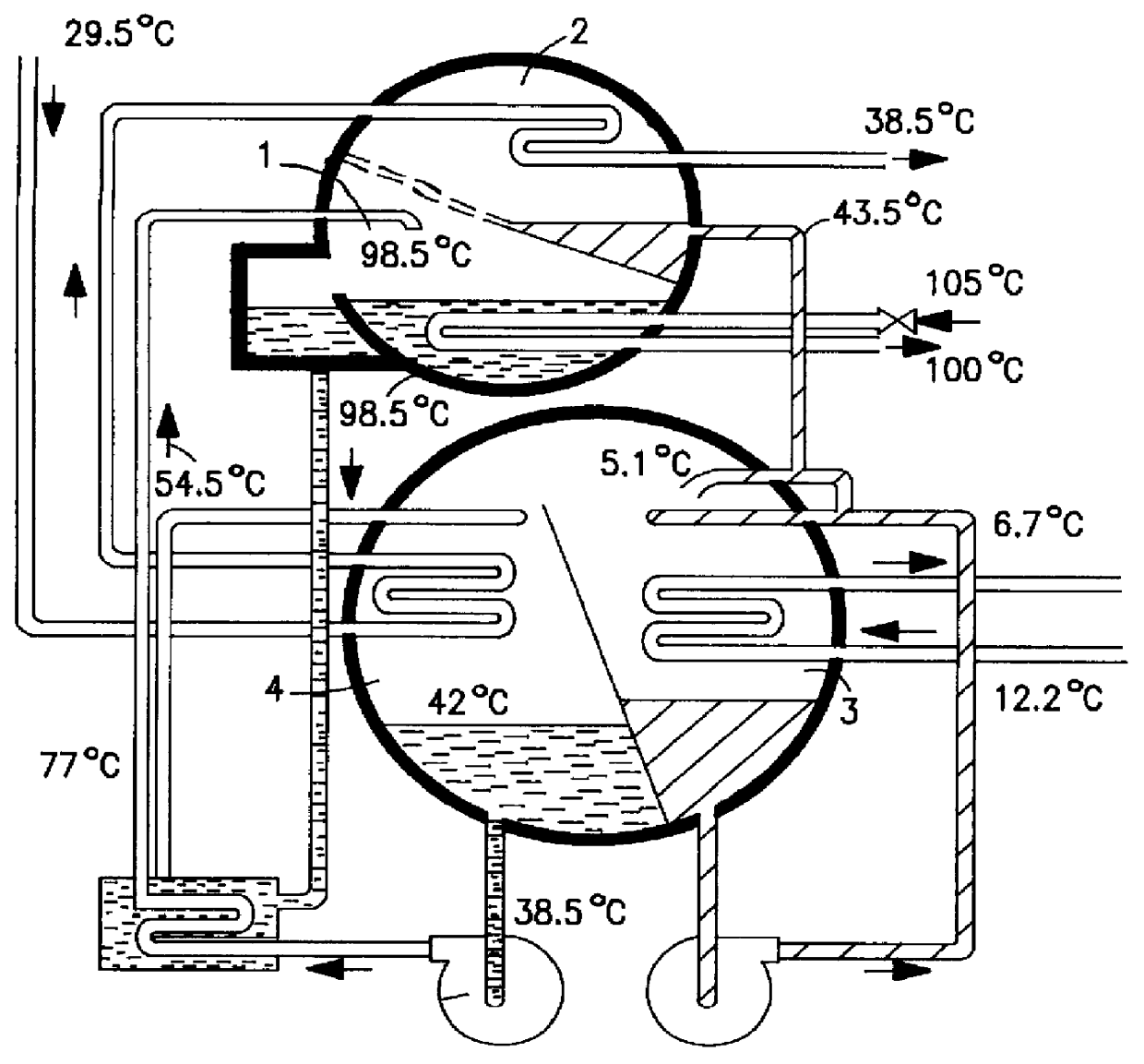
Arrangement for transferring heating and cooling power
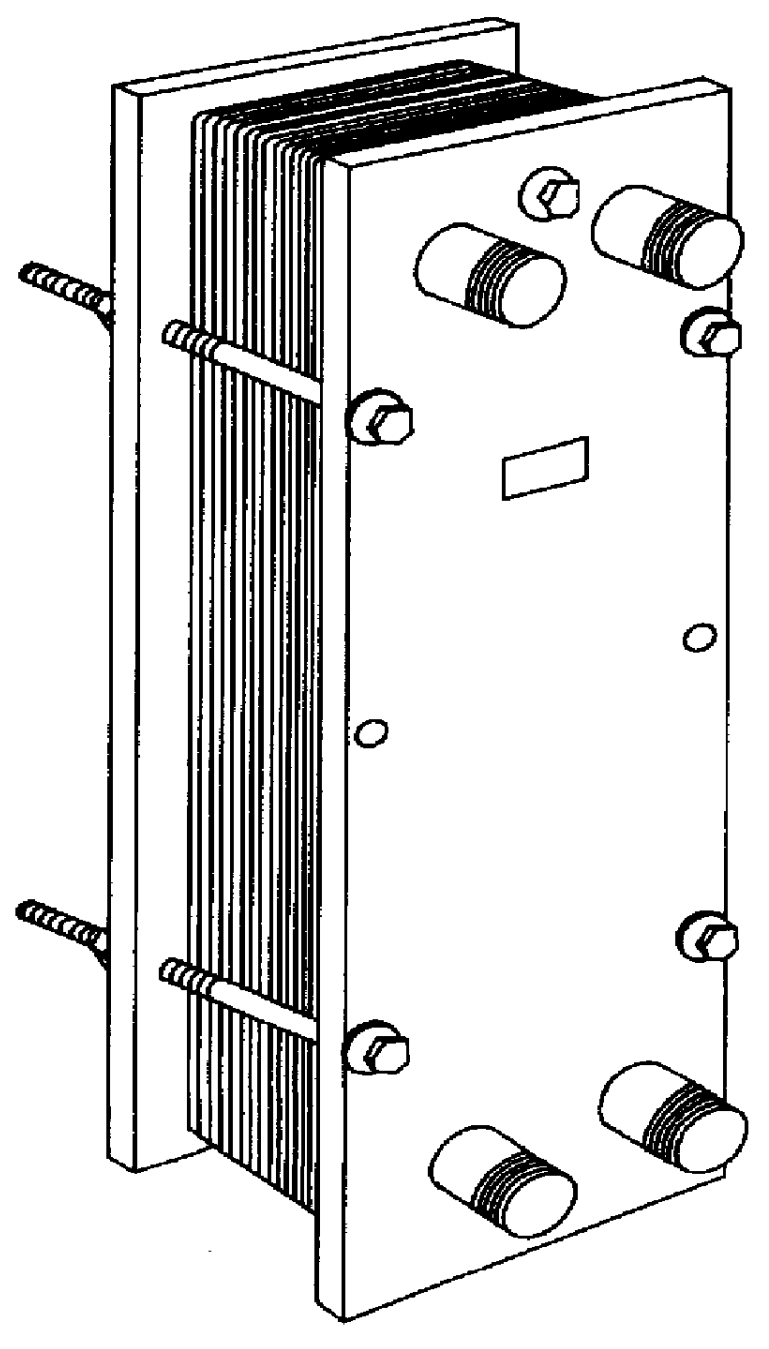
InactiveUS6158238ALow flow resistanceReduce distanceEnergy efficient heating/coolingClimate change adaptationPlate heat exchangerEngineering
PCT No. PCT / FI97 / 00515 Sec. 371 Date Mar. 31, 1999 Sec. 102(e) Date Mar. 31, 1999 PCT Filed Sep. 3, 1997 PCT Pub. No. WO98 / 10233 PCT Pub. Date Mar. 12, 1998An apparatus for transferring heating and cooling power by means of two heat transfer media, wherein at least one of the heating media is arranged to be evaporated or condensed. To reduce the need for space, the apparatus includes a shell (3) inside which at least one plate heat exchanger (1,2) is arranged loosely, flow slots (19) of the heat exchanger being arranged to be completely or mainly open towards the shell (3) in such a manner that the evaporating or condensing heat transfer medium can flow to the plate heat exchanger or from the plate heat exchanger from different sides of the plate heat exchanger on the whole length of that slot (19) which is open.
Owner:ABB POWER +1
Adsorbing pathogen-inactivating compounds with porous particles immobilized in a matrix
InactiveUS20060093999A1Reduce riskEnhance abilityBioreactor/fermenter combinationsBiological substance pretreatmentsPathogenMatrix method
Methods and devices are provided for reducing the concentration of low molecular weight compounds in a biological composition containing cells while substantially maintaining a desired biological activity of the biological composition. The device comprises highly porous adsorbent particles, and the adsorbent particles are immobilized by an inert matrix. The matrix containing the particles is contained in a housing, and the particles range in diameter from about 100 μm to about 1500 μm. The device can be used to adsorb and remove a pathogen-inactivating compounds from a biological composition such as a blood product.
Owner:CERUS CORP
Perfusion system
InactiveUS6287273B1Prolonged and increased therapeutic effectReduce risk of leakageStentsBalloon catheterBlood streamPerfusion fluid
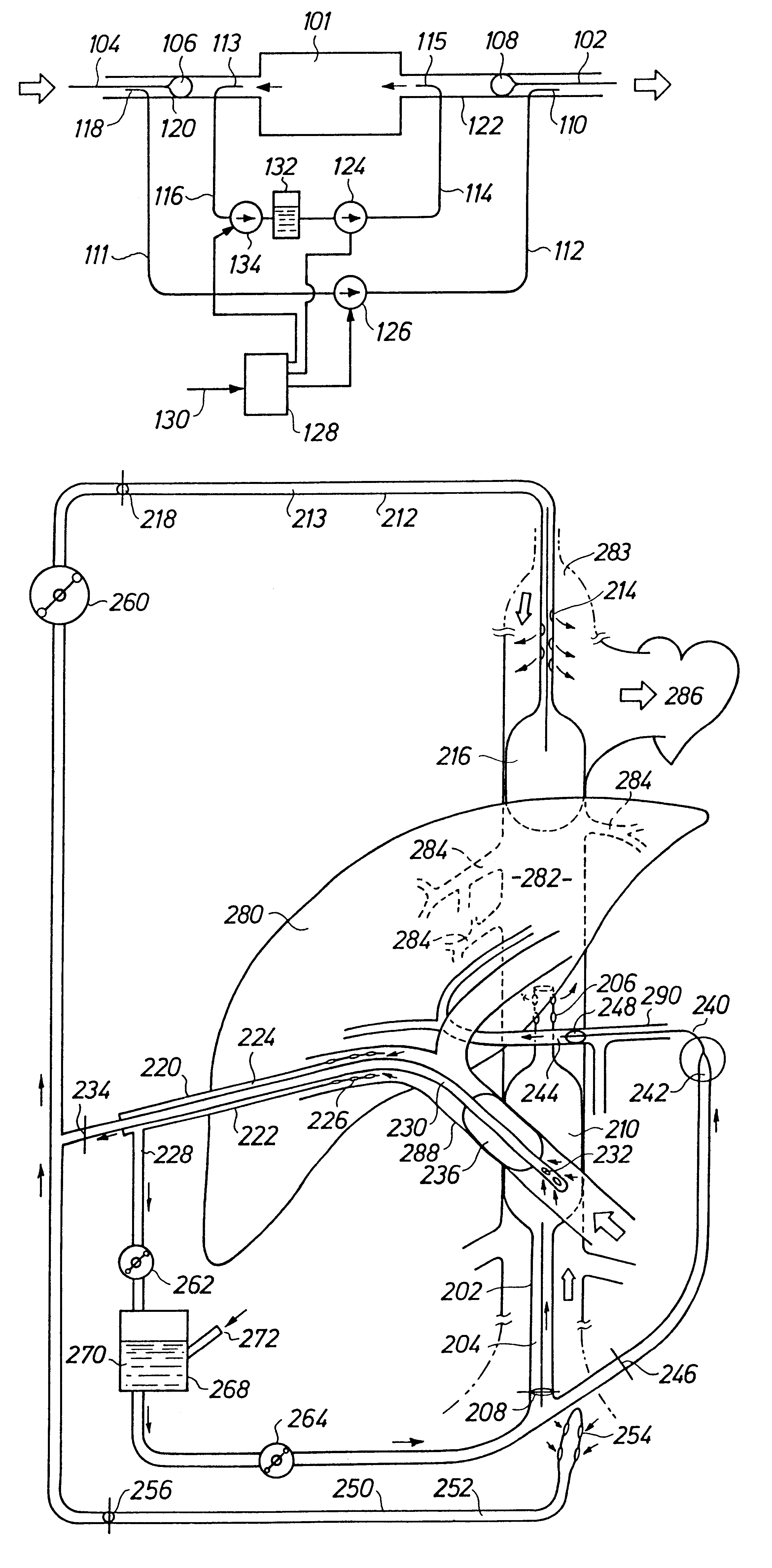
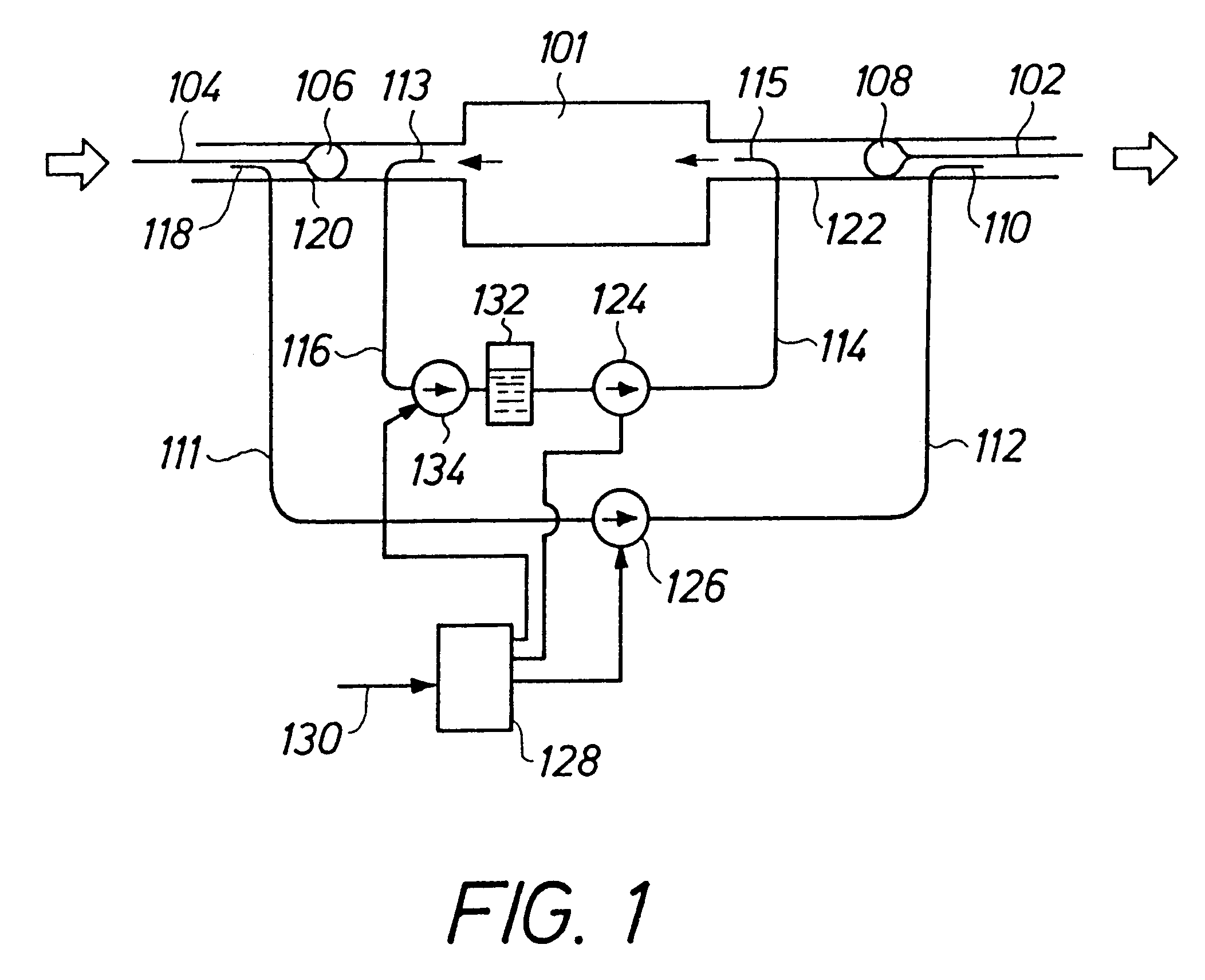
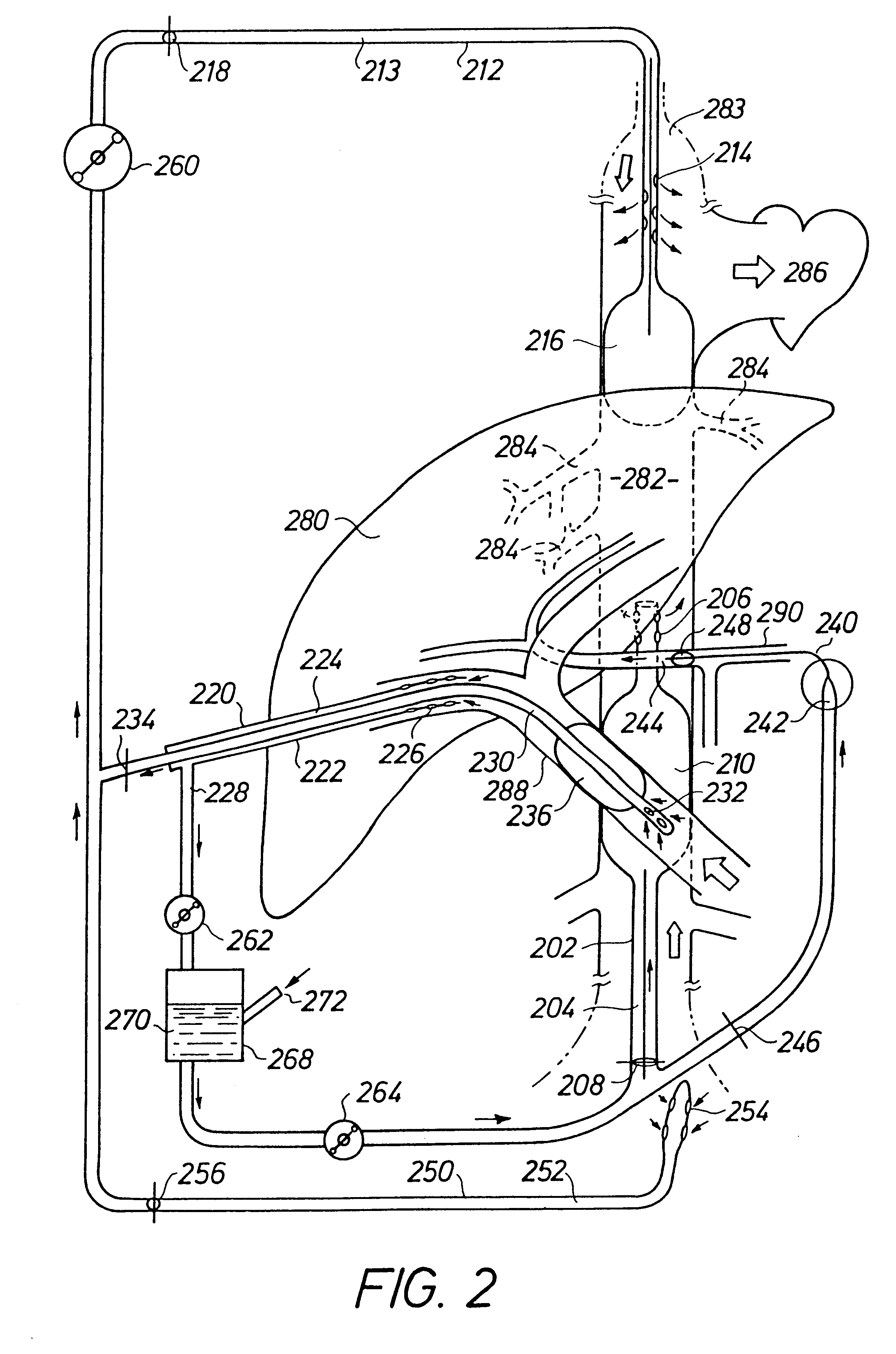
A perfusion system for non-surgically isolating and perfusing an organ, particularly the liver (101), in a patient, and including; by-pass cathether apparatus having inlet and outlet lumens (111, 112) introducible into the blood vessels of the organ percutaneously and devised so as to by-pass the blood flow past the organ in a by-pass circuit; perfusion catheter apparatus having inlet and outlet lumens (114, 116) introducible into the blood vessels percutaneously and being devised so as to lead the flow of perfusion fluid in a perfusion circuit through the organ; occlusive seals (106, 108) for isolating the organ from the systemic blood flow; pump apparatus including a by-pass pump (261), a perfusion fluid pump (124) and a suction pump (134) for establishing a negative relative pressure at the perfusion outlet from the organ; and control apparatus (128) coupled to the pumps (124, 126, 134) so as to control the operation thereof such that the outflow of fluid from the organ exceeds the inflow of fluid into the organ in the perfusion circuit due to a net volume contribution of blood from the systemic circulation entering the isolated organ.
Owner:ARGMED +1
Removing compounds from blood products with porous particles immobilized in a matrix
InactiveUS7037642B2Reduce concentrationMaintain biological activityImmobilised enzymesOther blood circulation devicesWhole blood productSorbent
Methods and devices are provided for reducing the concentration of low molecular weight compounds in a biological composition containing cells while substantially maintaining a desired biological activity of the biological composition. The device comprises highly porous adsorbent particles, and the adsorbent particles are immobilized by an inert matrix.
Owner:CERUS CORP
Distributive storage controller and method
ActiveUS7337331B2Inexpensively storing dataSafe storageInput/output to record carriersDigital data processing detailsControl storeClient-side
An inexpensive data storage technique utilizing available capacity in individual computer devices connected to a network is provided. When a backup client (BC) (14) of a user PC receives a backup instruction for a file from a user, the backup client (14) requests backup to a backup control server (20). The backup control server (20) divides and encrypts the file to be backed up into a plurality of encrypted pieces, transfers the encrypted pieces to user PCs (10), and stores the encrypted piece in the HDDs (12) of the user PCs (10). When the destributively backed up file is to be extracted, the user PC 10 obtains each encrypted piece from the user PCs 10 on which they are stored, and combines and decrypts the encrypted pieces to restore the original file.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Faecal management device
ActiveUS8277427B2Efficient use ofOperational securityNon-surgical orthopedic devicesBodily discharge devicesButtocksPerianal skin
A fecal management device suitable for attachment directly to the perianal skin between the buttocks of the wearer. The device utilizes an optimised adhesive wafer in order to securely attach the device to the skin of the wearer so that the device is maintained in position for the entire period of wear, including circumstances or periods of wear during which the wearer is active, i.e. not bedridden. In addition the fecal management device of the present invention has the ability for easy application of the device.
Owner:COLOPLAST AS
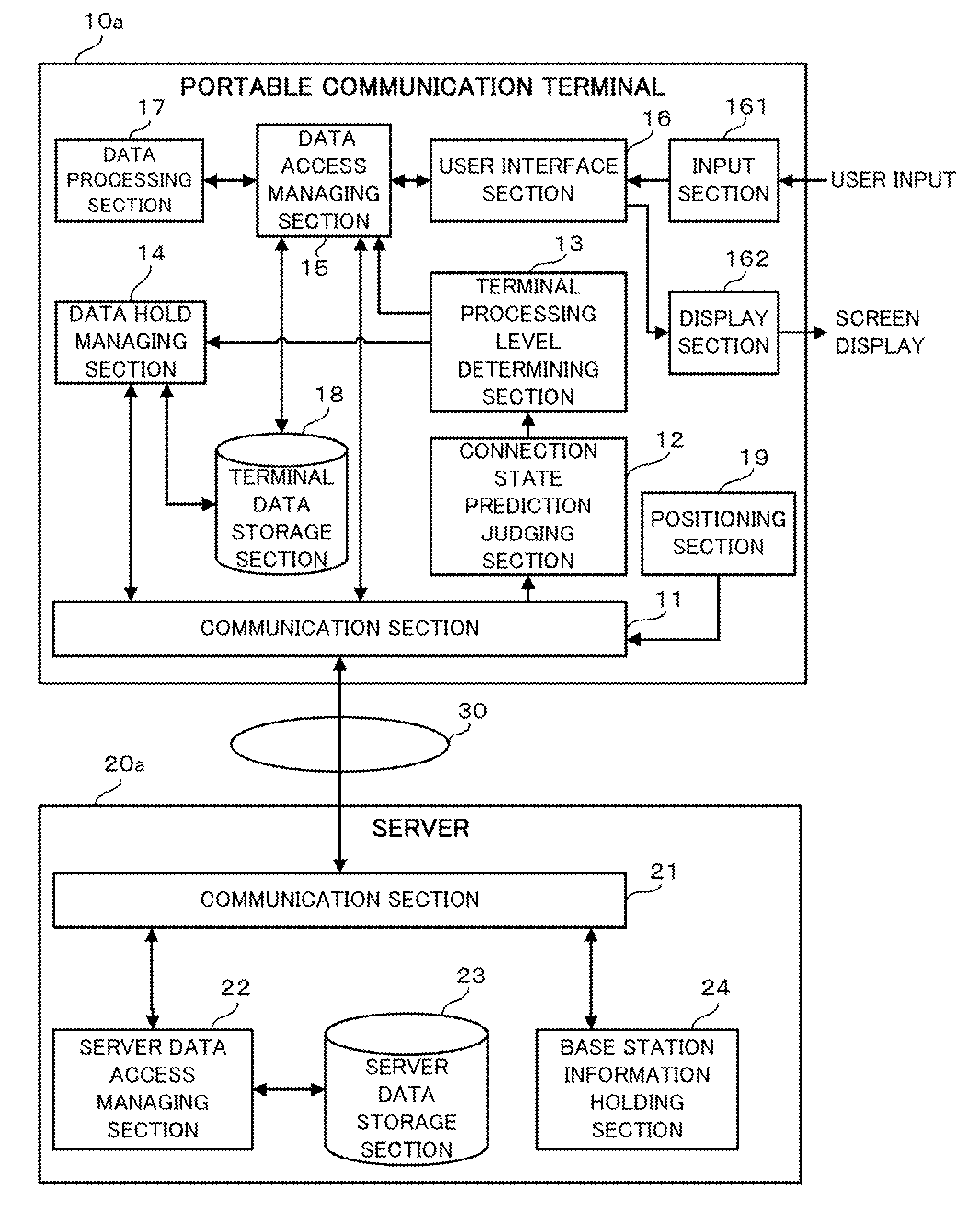
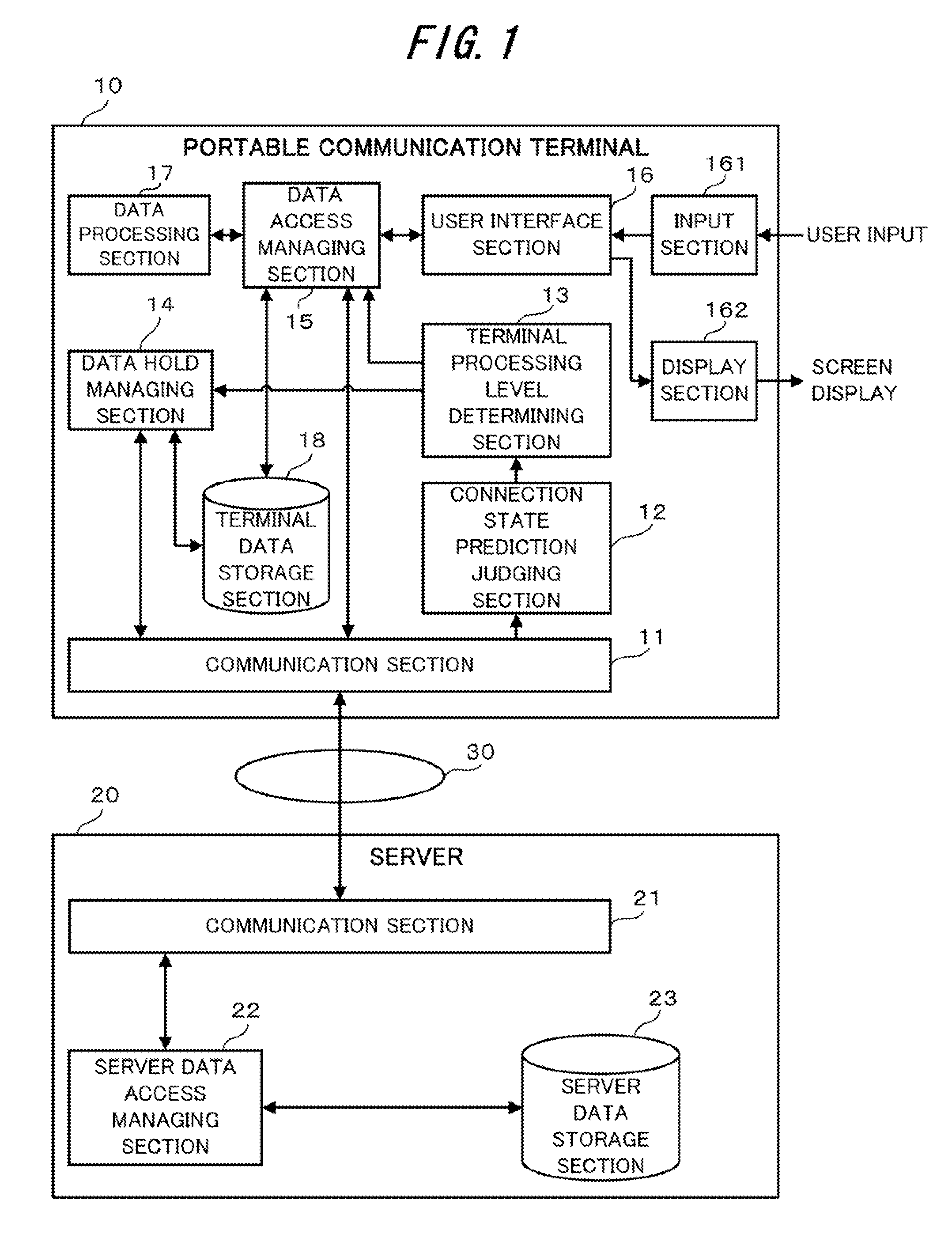
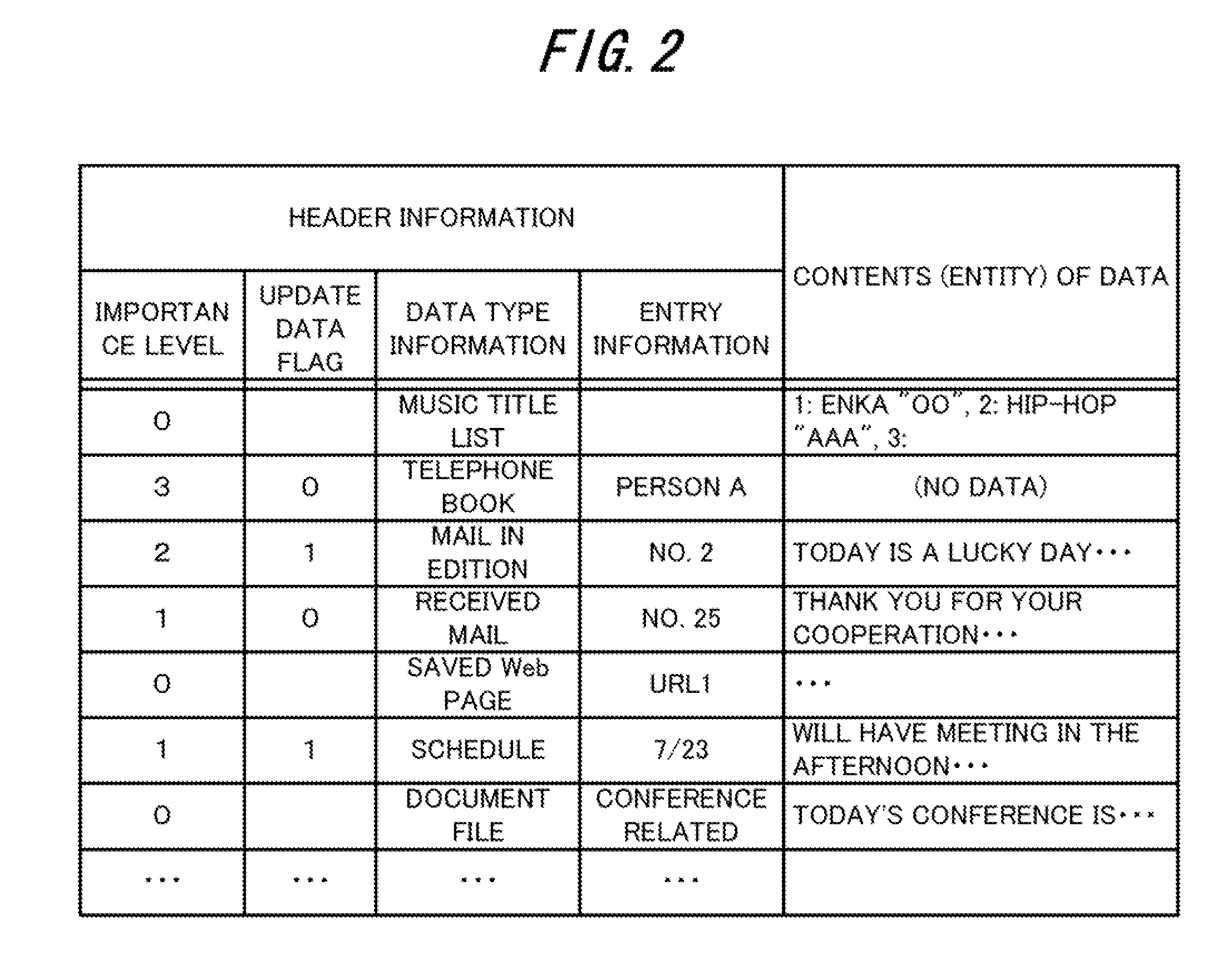
Data processing method for portable communication terminal and portable communication terminal
InactiveUS20100197282A1Reduce risk of leakageSecure convenienceUnauthorised/fraudulent call preventionSpecial service for subscribersState predictionData access
A terminal data storage section (18) of a portable communication terminal (10) stores the importance level of each piece of stored data. A connection state prediction judging section (12) predicts a change in the communication state of the connection to a server (20). A terminal processing level determining section (13) determines the terminal processing level of data based on the prediction result. When a data access becomes necessary, a data access managing section (15) determines whether a data access destination is the portable communication terminal (10) itself or the server (20) based on the importance level of the data and the then terminal processing level. When the terminal processing level is changed, a data hold managing section (14) deletes the data whose importance level is changed to an importance level which inhibits the data from being held at the changed terminal processing level from the terminal data storage section (18).
Owner:LENOVO INNOVATIONS LTD HONG KONG
Absorbing pathogen-inactivating compounds with porous particles immobilized in a matrix
InactiveUS6951713B2Reduce risk of leakageReduce decreaseImmobilised enzymesOther blood circulation devicesWhole blood productSorbent
Methods and devices are provided for reducing the concentration of low molecular weight compounds in a biological composition, while substantially maintaining a desired biological activity of the biological composition. The device comprises highly porous adsorbent particles, and the adsorbent particles are immobilized by an inert matrix. The matrix containing the particles is contained in a housing, and the particles range in diameter from about 1 μm to about 200 μm. The matrix can be fibrous, and the particles can have a surface area greater than 750 m2 / g and a pore diameter between about 25 and 800 Å. The device can be used to adsorb and remove a pathogen-inactivating compound that is a nucleic acid-binding compound such as psoralen, an acridine derivative or a dye from a biological composition such as a blood product.
Owner:CERUS CORP
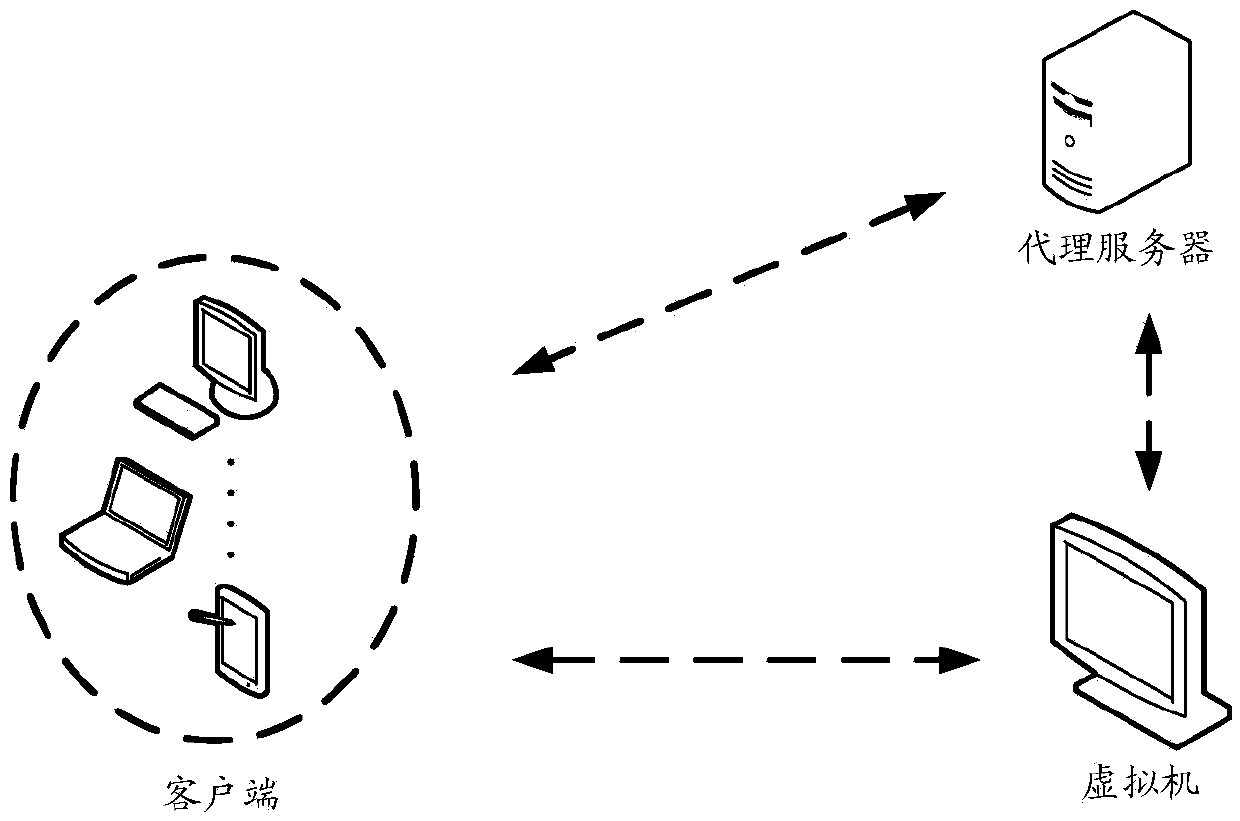
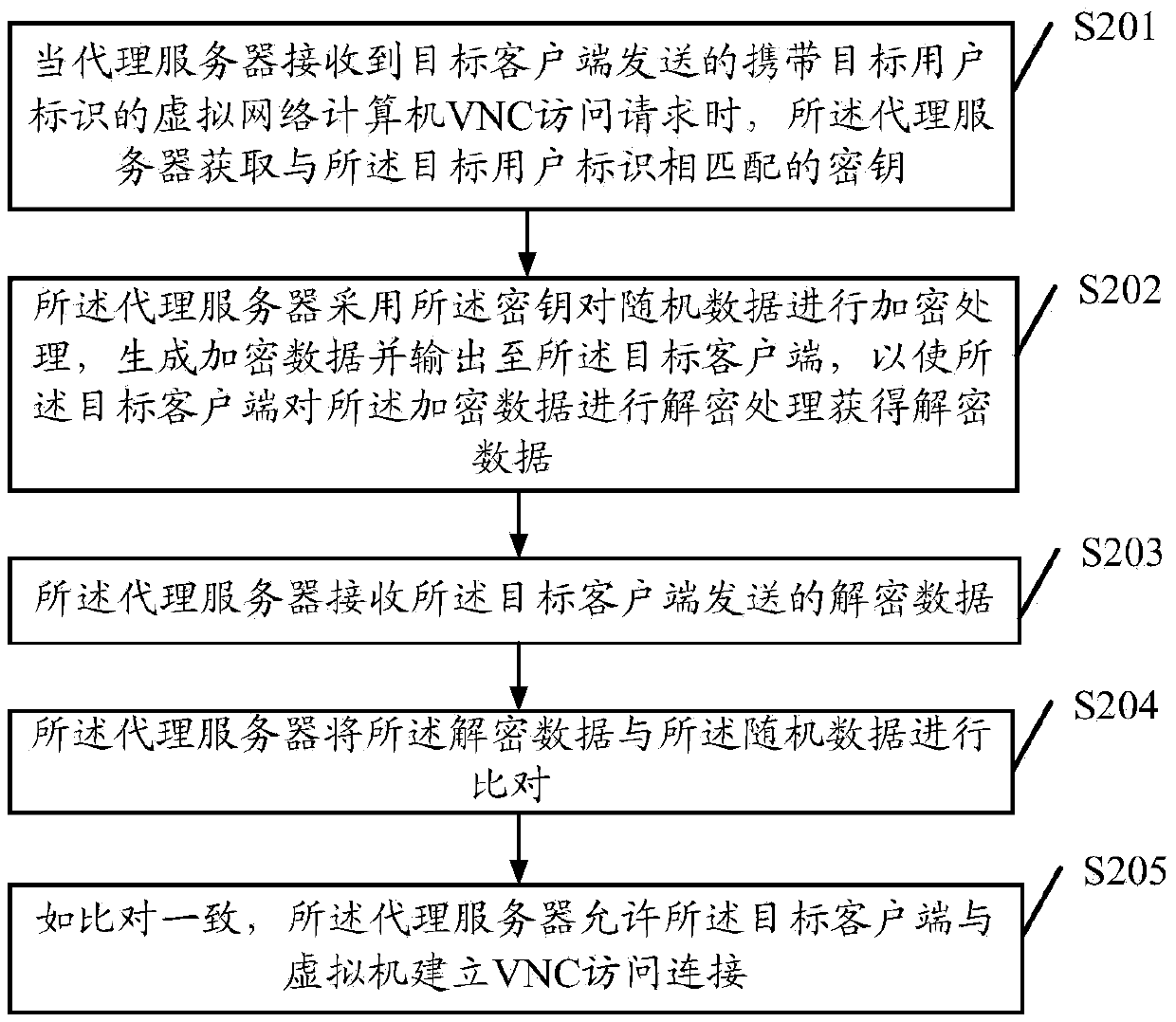
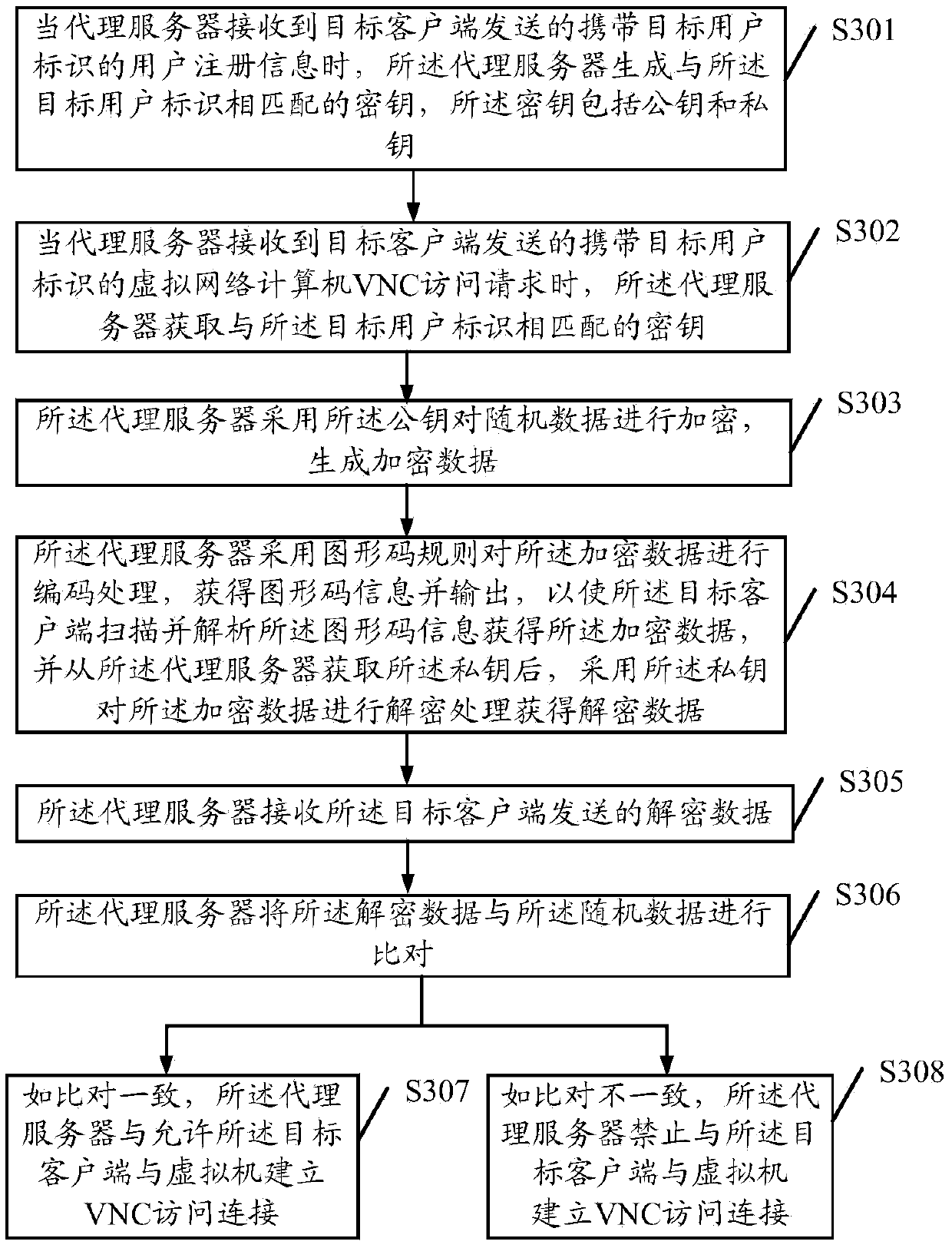
Remote access method, agent server and client end
The embodiments of the invention disclose a remote access method, an agent server and a client end, wherein the method comprises the steps that: when the agent server receives a virtual network computer VNC access request carrying a target user identifier; and sent by a target client end, the agent server obtains a secret key matched with the target user identifier; the secret key is utilized for carrying out encryption processing on random data, and encrypted data is generated and output to the target client end so as to enable the target client end to carry out decryption processing on the encrypted data and obtain decrypted data; the encrypted data sent by the target client end is received; the encrypted data is compared with the random data; and if the encrypted data is consistent with the random data, the target client end is allowed to establish a VNC access connection with a virtual machine. According to the embodiments of the invention, invalid VNC access caused by information leakage is voided, the information leakage risk is reduced, and the safety of the VNC access is improved.
Owner:HUAWEI TECH CO LTD
Collecting bag
InactiveUS20030060786A1Easy to disassembleReduce risk of leakageHeating/cooling contact switchesNon-surgical orthopedic devicesStomaEngineering
A flange for a medical collecting bag having an aperture allowing bodily fluids or exudates to enter the bag, wherein the flange has an inner rim delimiting the aperture therein, and wherein the flange has a central area encircling the aperture which area has a predetermined weakening line pattern wherein the force needed for removing the bag flange from the skin or a body side member is smaller than the force needed for breaking the weakening lines enables a simple gradual enlargement of the aperture of an ostomy device for adaptation of the aperture to the size of the stoma or for adaptation of the aperture to the size of a wound and a complete removal of the bag flange when substituting the bag.
Owner:COLOPLAST AS
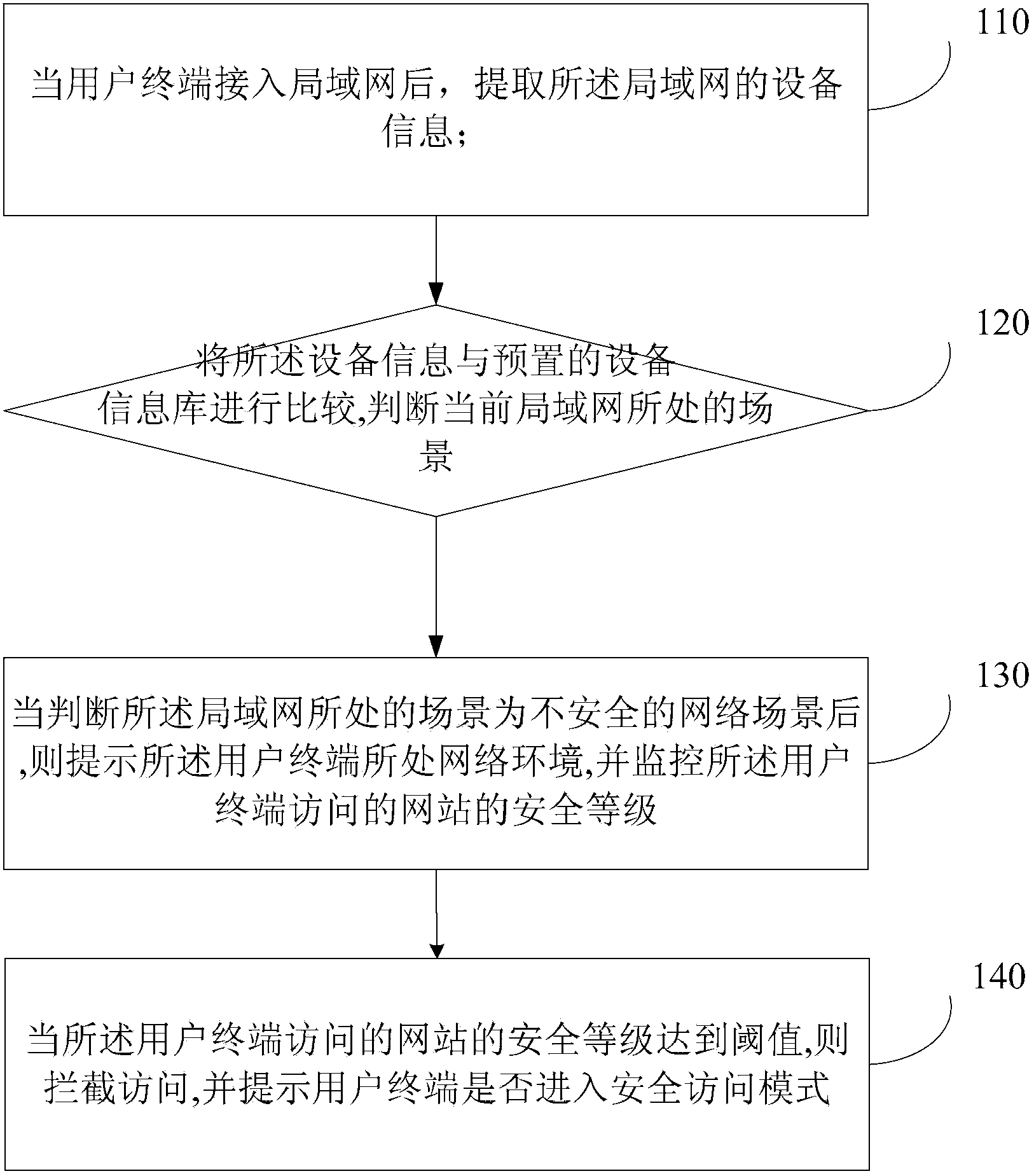
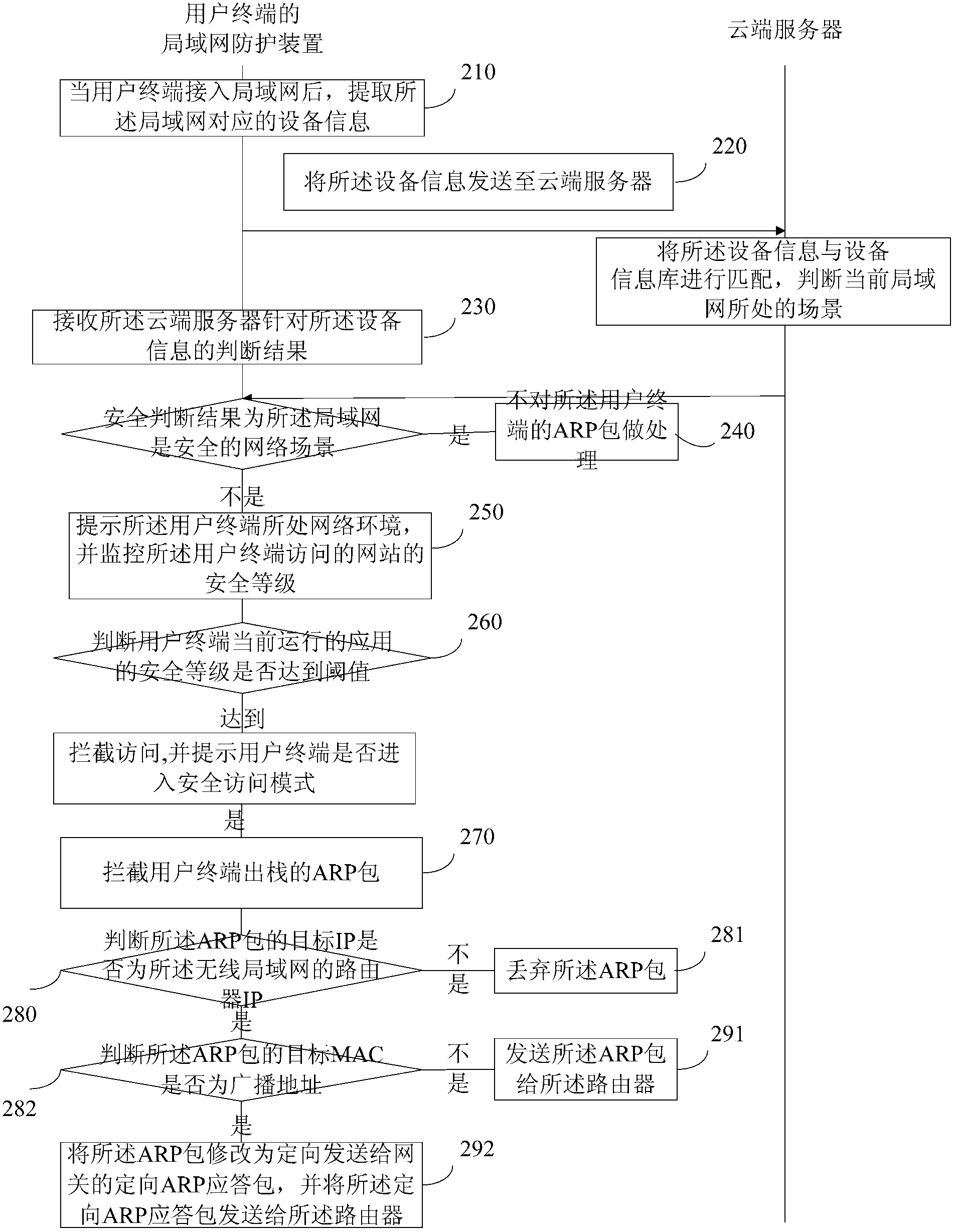
User network access scenario-based protection method and device
ActiveCN103368941ASolve the problem of exposure to other terminals in the LANFix security issuesTransmissionSecurity arrangementScenario basedWeb environment
The invention discloses a user network access scenario-based protection method and device and relates to the field of computer safety. The method comprises the following steps of extracting a device identification which corresponds to a local area network after a user terminal is accessed to the local area network; comparing the device identification with a preset device identification library to judge a scenario in which the current local area network is located; prompting a network environment in which the user terminal is located after the scenario in which the local area network is located is judged to be an unsafe scenario, and monitoring the safety level of the network accessed by the user terminal; and intercepting access when the safety level of the network accessed by the user terminal reaches a threshold value, and promoting whether the user terminal enters a safety access mode. The method and the device disclosed by the invention have the beneficial effects that the risk that the information of the user terminal leaks is lowered, and the safety of the information of the user terminal is enhanced.
Owner:BEIJING QIHOO TECH CO LTD
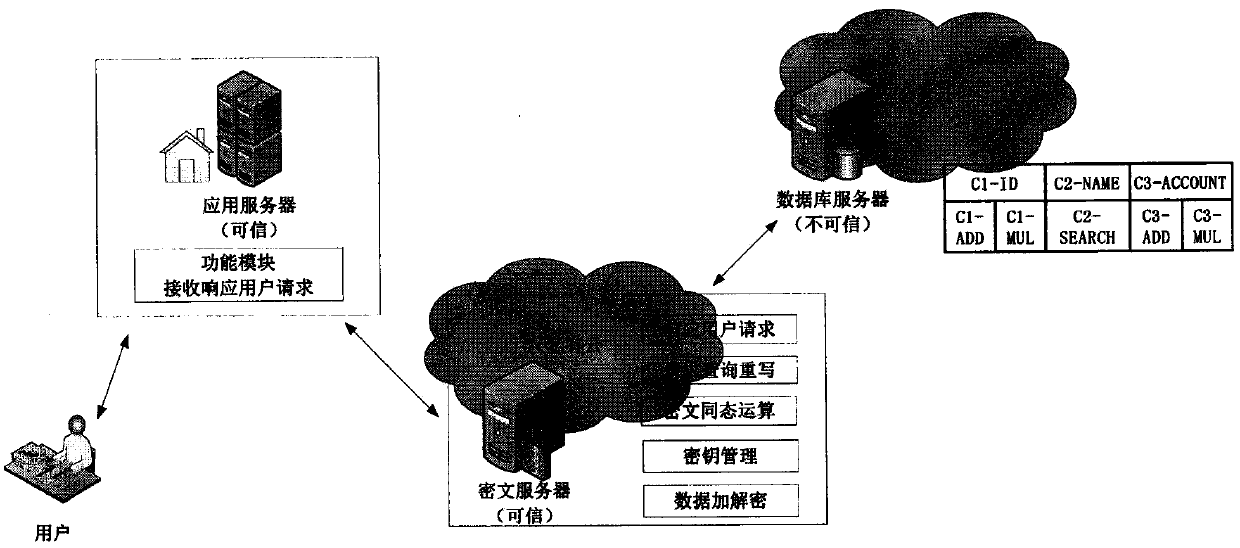
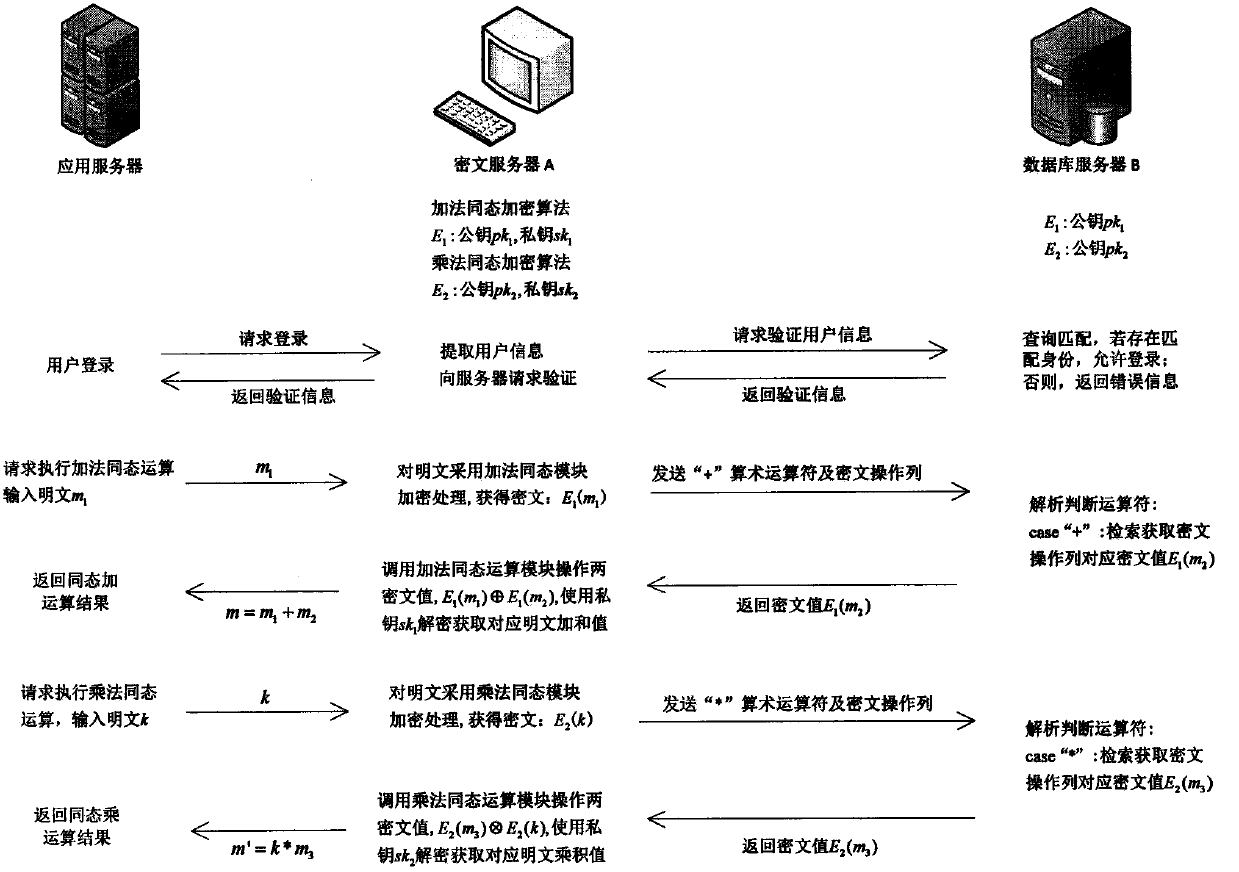
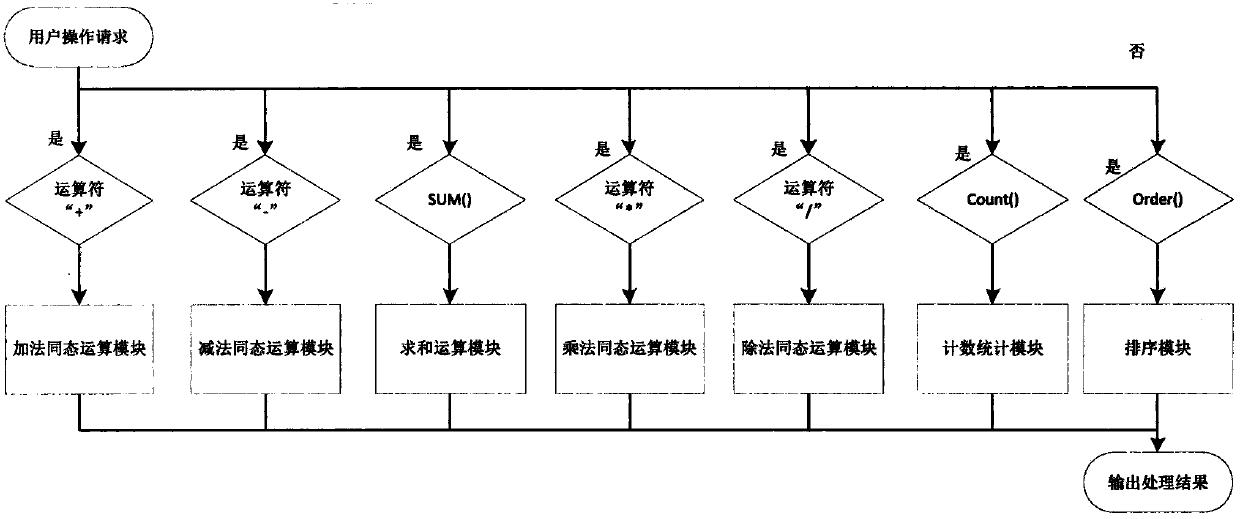
Quasi-fully homomorphic ciphertext data operation method and system
InactiveCN107592195AAvoid insecuritySolving inefficienciesSecuring communicationThird partyCiphertext
The present invention discloses a quasi-fully homomorphic ciphertext data operation method and system and belongs to the ciphertext database and network data privacy protection technical field. The fully homomorphic cipher operation-based hybrid cloud platform architecture is provided, existing database configurations are not needed to be drastically modified, and therefore, a construction mode issimple; a ciphertext server is defined to support homomorphic calculation, query interception rewriting, data encryption and decryption, key management and other functions, is deployed at the privatecloud platform of a local data center and can establish a connection between the local data center and a third-party public cloud platform; a classified field extension mode is adopted, field extension is performed on numerical value data and character type data; by means of mode innovation, quasi-fully homomorphic ciphertext conventional arithmetic calculation is performed on the numerical valuedata through a functional demand-based cipher service strategy; query / operation is directly performed on ciphertext data; and therefore, the processing efficiency of the data and the security of thestorage and retrieval of the data can be improved.
Owner:BEIJING ELECTRONICS SCI & TECH INST
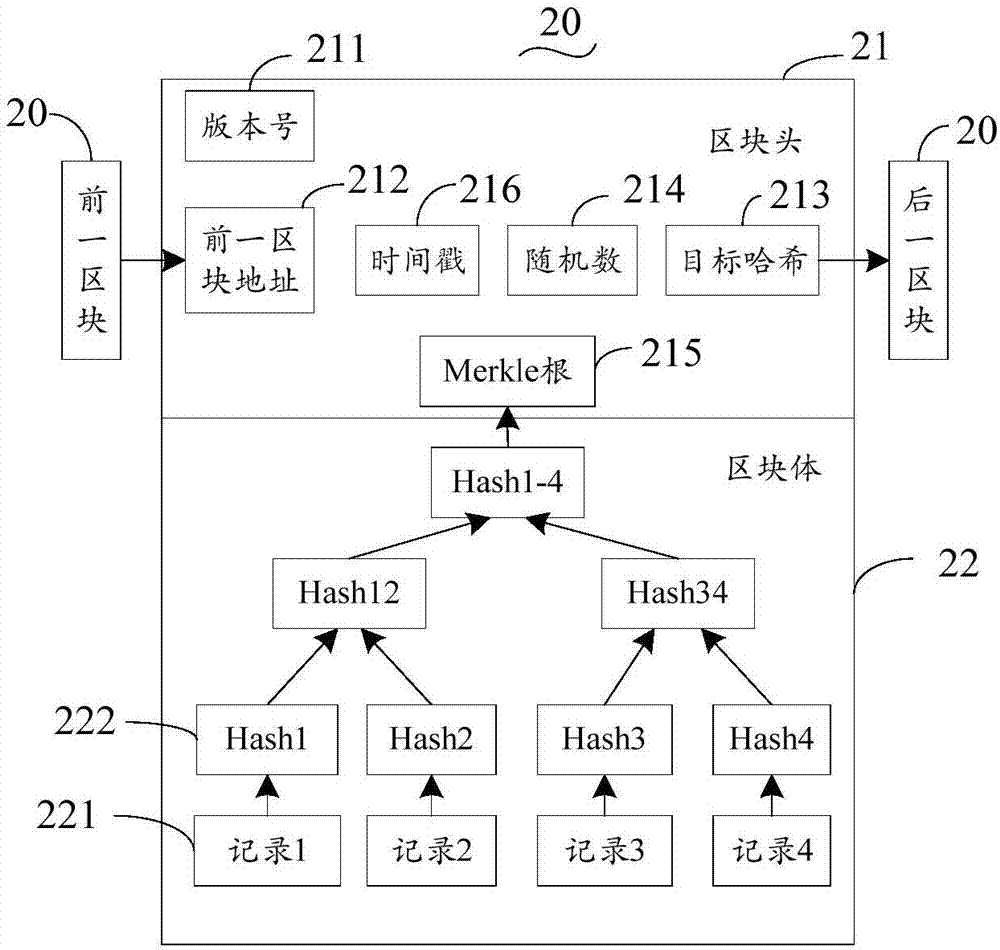
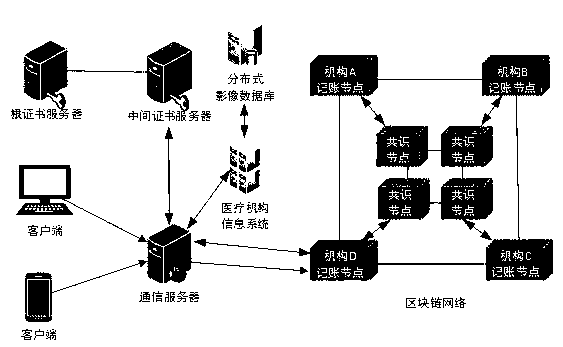
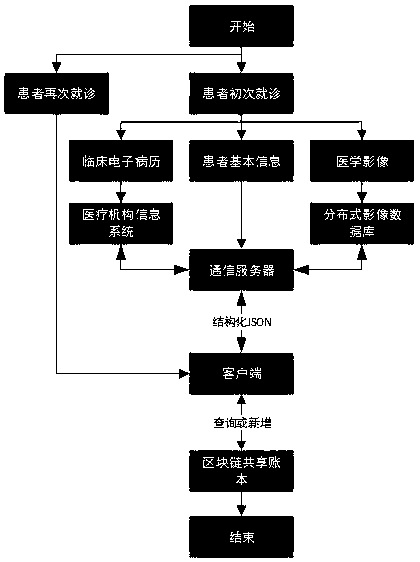
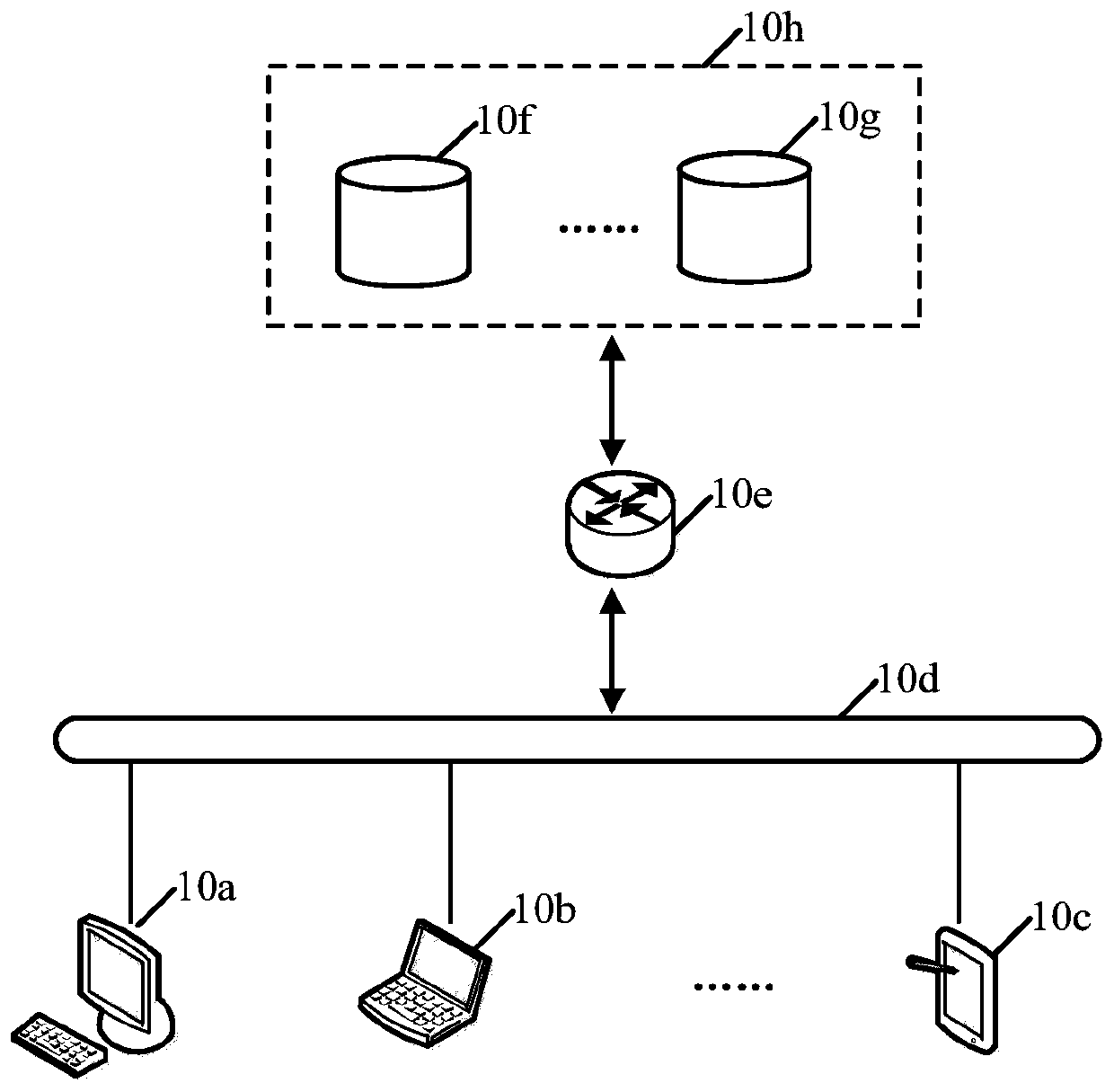
Medical data platform based on block chain technology
InactiveCN109243548AIsolation damageReduce risk of leakageDigital data information retrievalPublic key for secure communicationData synchronizationData platform
The invention discloses a medical data platform based on the block chain technology. The medical data platform comprises a terminal, a server module, a data storage module and a block chain network. The terminal exchanges data with the data storage module and the block chain network through the server module. The server module comprises a communication server, an intermediate certificate server and a root certificate server and is used for processing data interaction between the modules and allocating certificates to the block chain network nodes. The data storage module comprises a medical information system and a distributed image database and is used for data storage. The block chain network comprises multiple institutional accounting nodes and multiple consensus nodes. The accounting nodes perform mutual data synchronization. The medical data platform based on the block chain technology has the advantages that the existing medical information is stored in the block chain shared account book so that all the medical institutions can share the medical information related to the patients, and the privacy protection function of the medical data can be realized by using the encryption algorithm and thus sharing of the medical data can be facilitated and the security of the sensitive information can also be protected.
Owner:GUANGDONG UNIV OF TECH
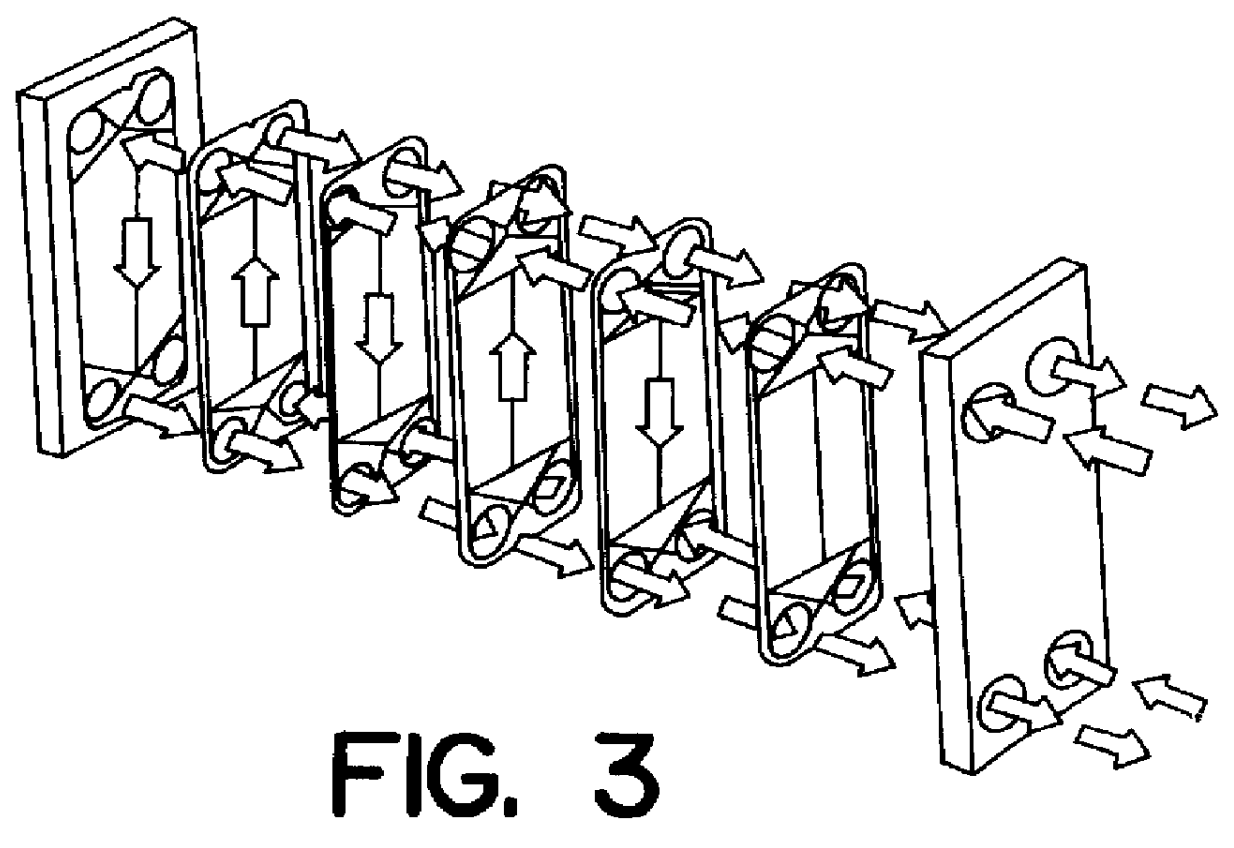
Heat exchanger and method of producing the same
InactiveUS6263570B1Reduce riskIncrease quantityStationary conduit assembliesBranching pipesEngineeringMechanical engineering
A heat exchanger for vehicles comprises firstly a heat-exchanger assembly consisting of flat liquid-conveying tubes and surface-enlarging means, secondly an inlet tank, and thirdly an outlet tank. The inlet tank and the outlet tank have a connection plate with a number of connection holes for the tubes. At each hole, the plate has a projecting connecting sleeve element. Each tube has at its ends a widened main portion which is accommodated on said connecting sleeve element. A rounded transitional area is formed between the connection plate and each connecting sleeve element, and the main portion is inserted in the conecting sleeve element and is applied with its outside against the inside of the connecting sleeve element. Each tube has at its ends an end portion which is widened in relation to the main portion, merges with the main portion and is applied against the transitional area. In a method of producing such a heat exchanger, the widened end area of the tubes are inserted in the connecting sleeve elements and are widened further in such a manner that each tube end is applied against the transitional area between the plate and the respective connecting sleeve element.
Owner:WALEO ENGINE COOLING
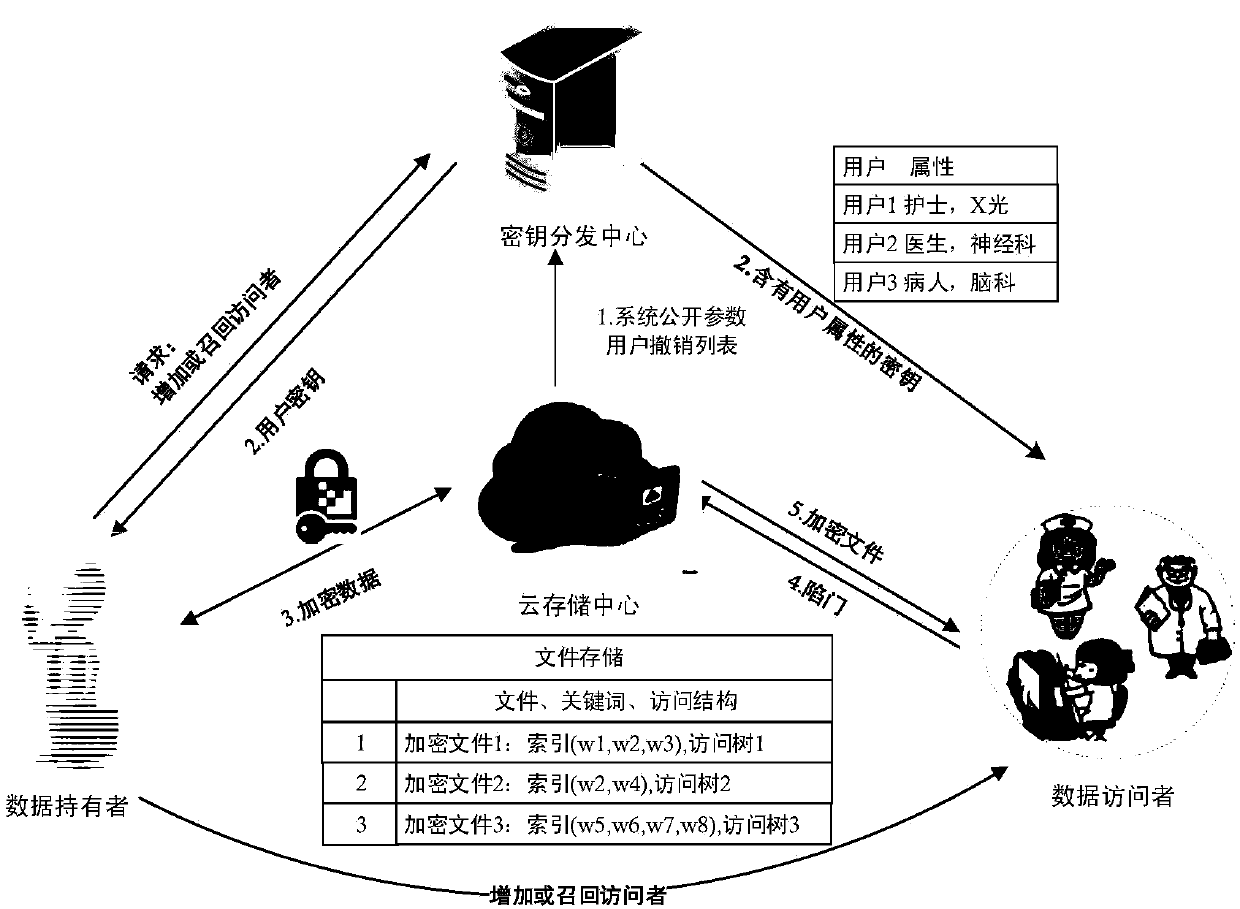
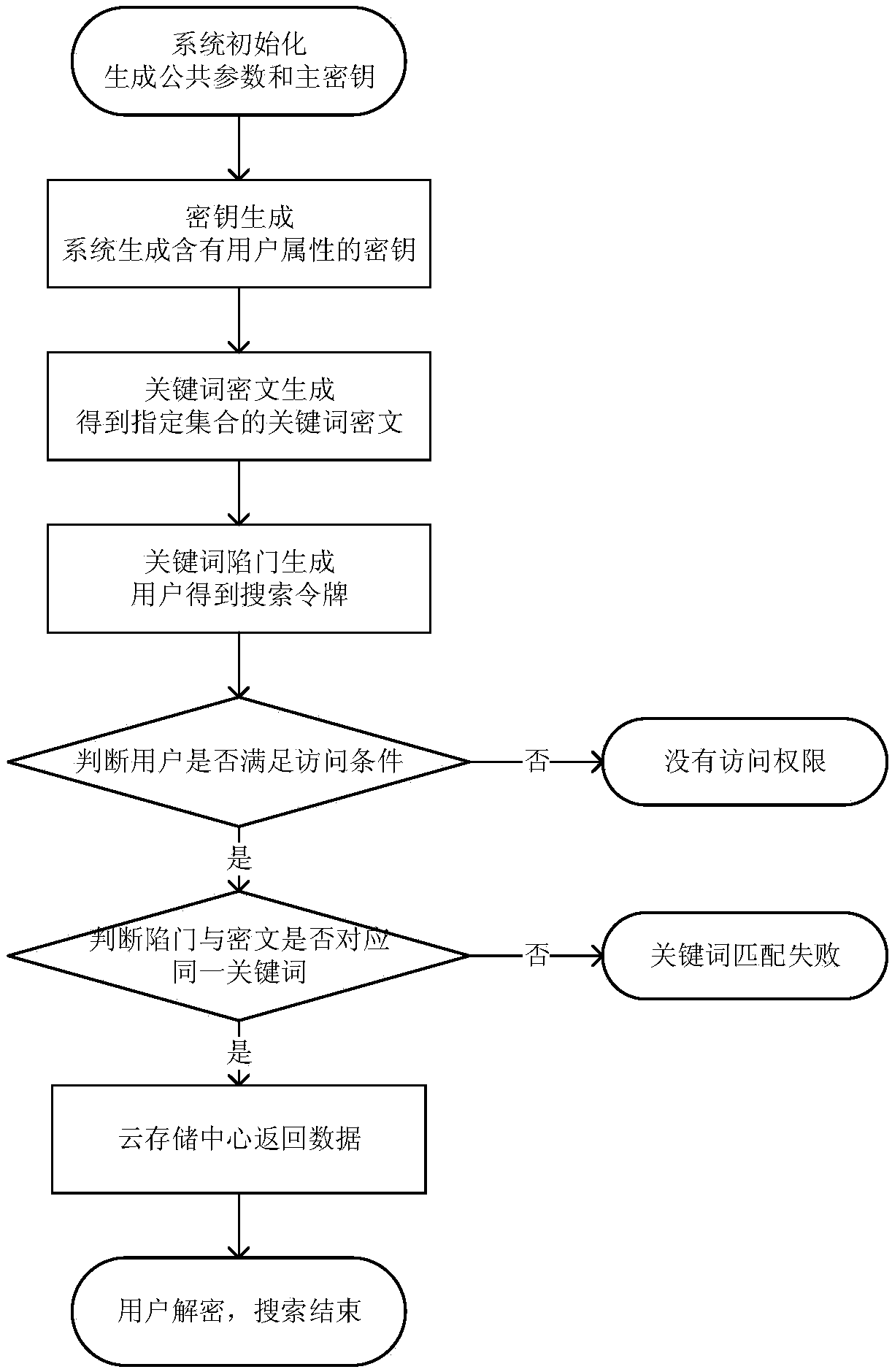
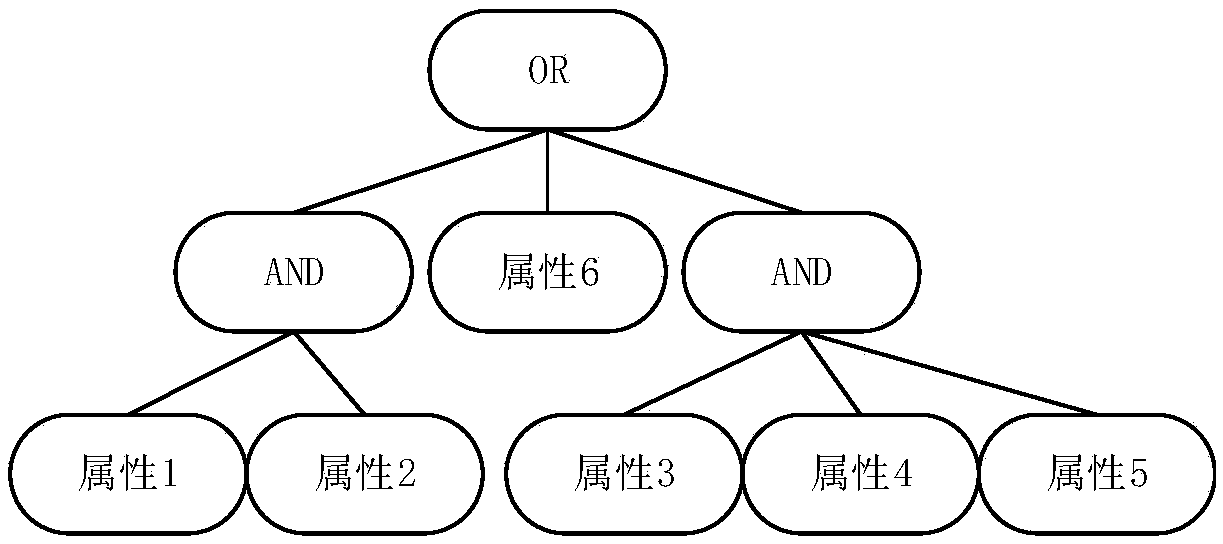
Attribute-based searchable encrypted electronic medical record system and encryption method
InactiveCN107634829AReduce computing requirementsReduce computational complexityKey distribution for secure communicationSpecial data processing applicationsMedical recordCiphertext
The invention discloses an attribute-based searchable encrypted electronic medical record system and an encryption method. The system comprises a key distribution center and a cloud storage center, wherein the key distribution center generates public parameters and a master key to initialize the system; the key distribution center generates and distributes keys containing user attributes to users;a data owner sets an access strategy before uploading medical record data, encrypts the data, and then uploads the data to the cloud storage center; a data visitor generates a trap door according tokeywords and the keys, and provides a query request to the cloud storage center; and after receiving the query request, the cloud storage center determines to return corresponding encrypted data to the data visitor according to the trap door and keyword ciphertexts. According to the scheme of the invention, the difficulty of key management in a multi-user environment can be reduced, data users canbe supported to accurately query the keywords of the ciphertexts, guessing attacks of the keywords can be resisted, and the leakage of privacy data can be effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
Pet waterer and feeder
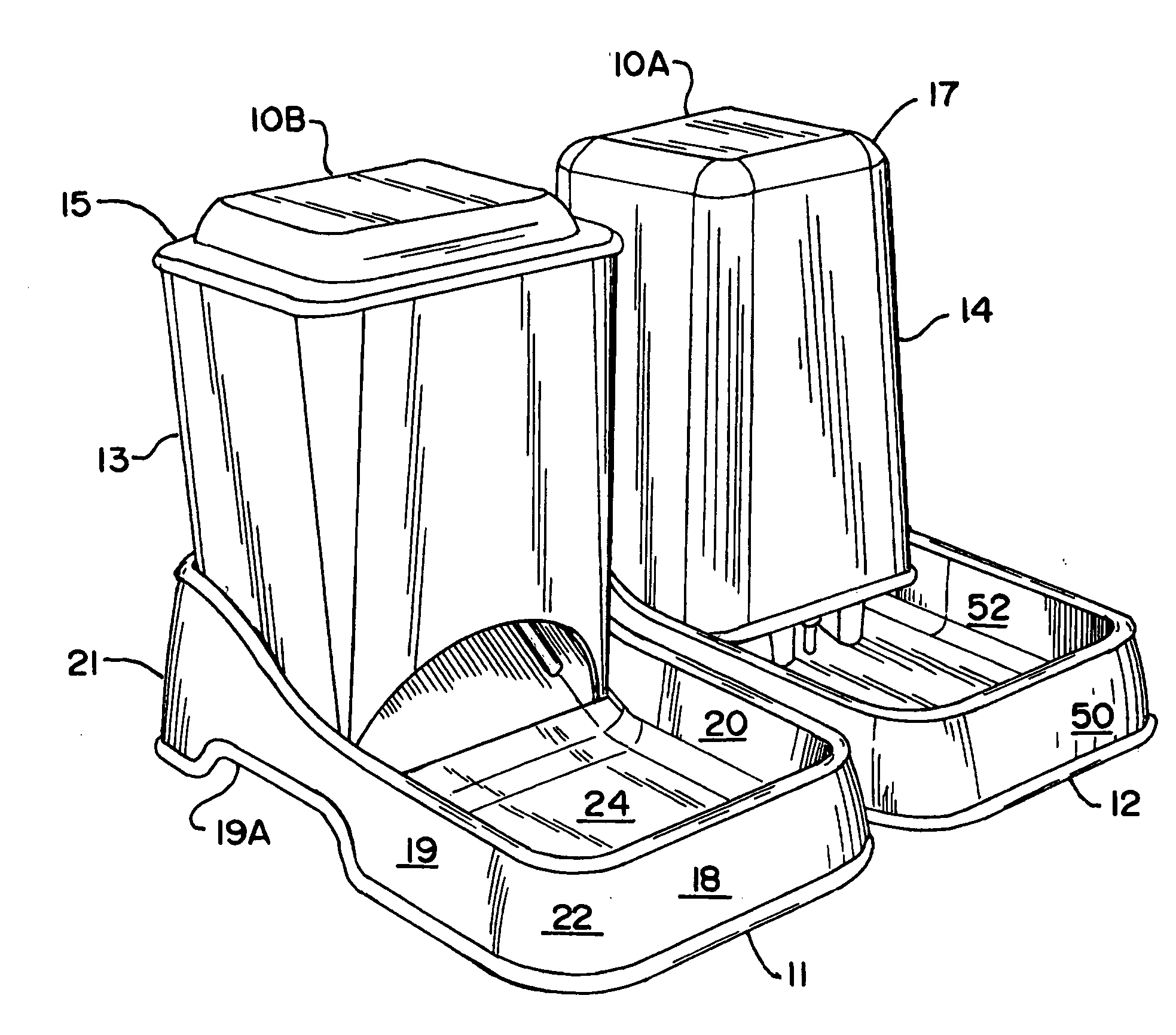
InactiveUS20060196433A1Reduce cloggingImproved dispensing of foodAnimal watering devicesAnimal feeding devicesBiomedical engineeringFodder
Owner:VAN NESS PLASTIC MOLDING
Integrated water-cooled power battery box
PendingCN108039434AMeet the intensityFulfil requirementsBattery isolationSecondary cellsPower batteryMechanical property
The invention relates to the technical field of electric cars, in particular to an integrated water-cooled power battery box. The integrated water-cooled power battery box provided by the invention comprises a box cover, a box body and a temperature regulating power system, wherein the box body is made of an aluminum alloy material and is manufactured by an extrusion moulding technology; a circulating flow passage is formed in the wall of the box body; a circulating loop for a temperature regulating medium to flow circularly is arranged inside the wall of the box body; and the temperature regulating power system can drive the temperature regulating medium to circularly flow in the circulating loop. In such a way, a water cooling board and a battery box are designed in an integrated manner,a hollow aluminum alloy section is adopted to achieve lightweight design, mechanical properties such as strength and rigidity are met, the integrated water-cooled power battery box is simpler in structure, better in technical performance and smaller in occupied space, and the comprehensive cost can be reduced; the heat-dissipating, cooling and temperature-raising and heating functions can be achieved by using one set of temperature regulating power system, the integrated water-cooled power battery box is simpler in structure, more convenient and fast to use and smaller in occupied space, themanufacturing cost and the using cost can be reduced, and the heat-dissipating efficiency and the heating efficiency can be improved.
Owner:BEIJING PRIDE NEW ENERGY BATTERY
Block chain private key generation method and device
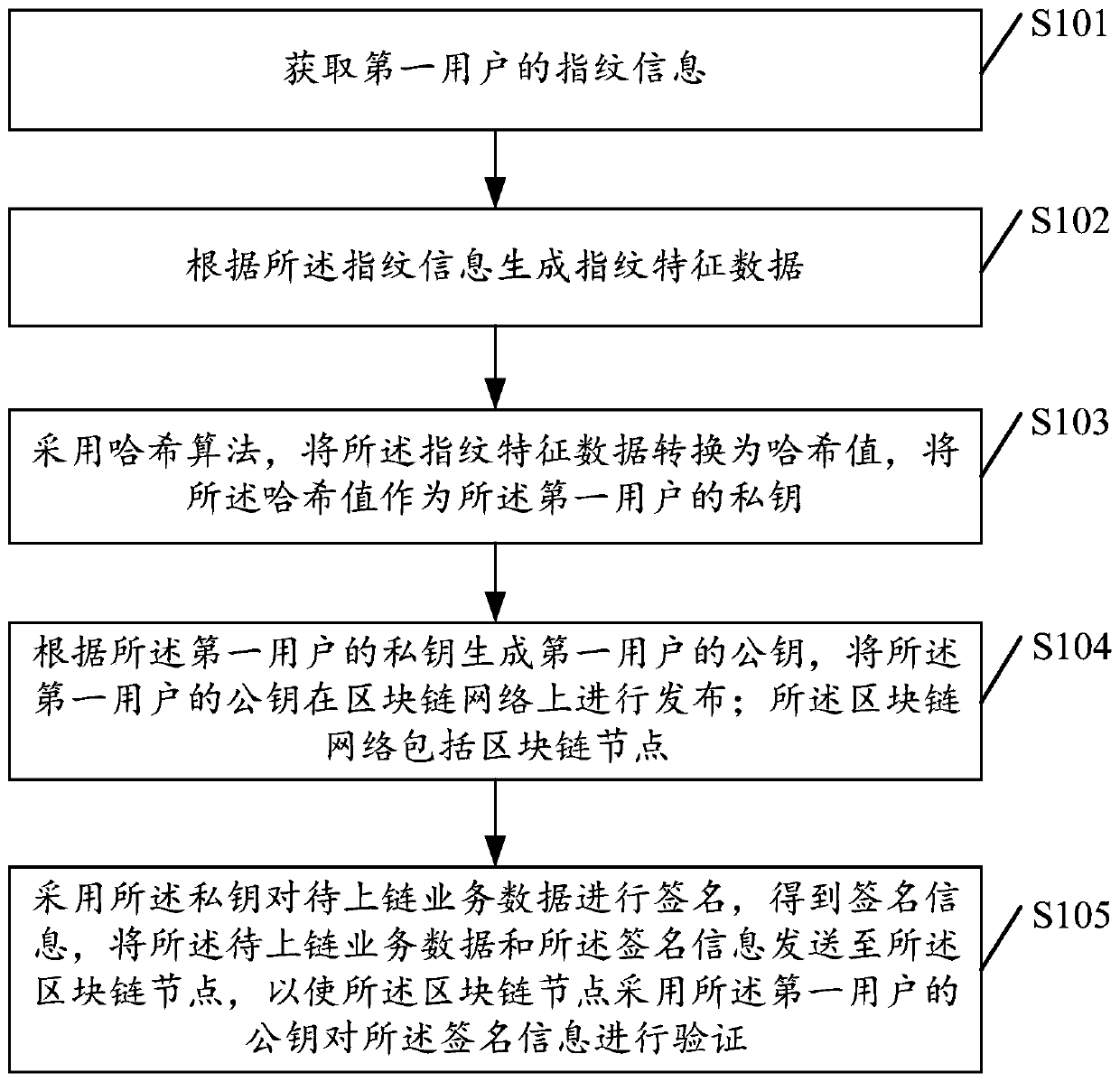
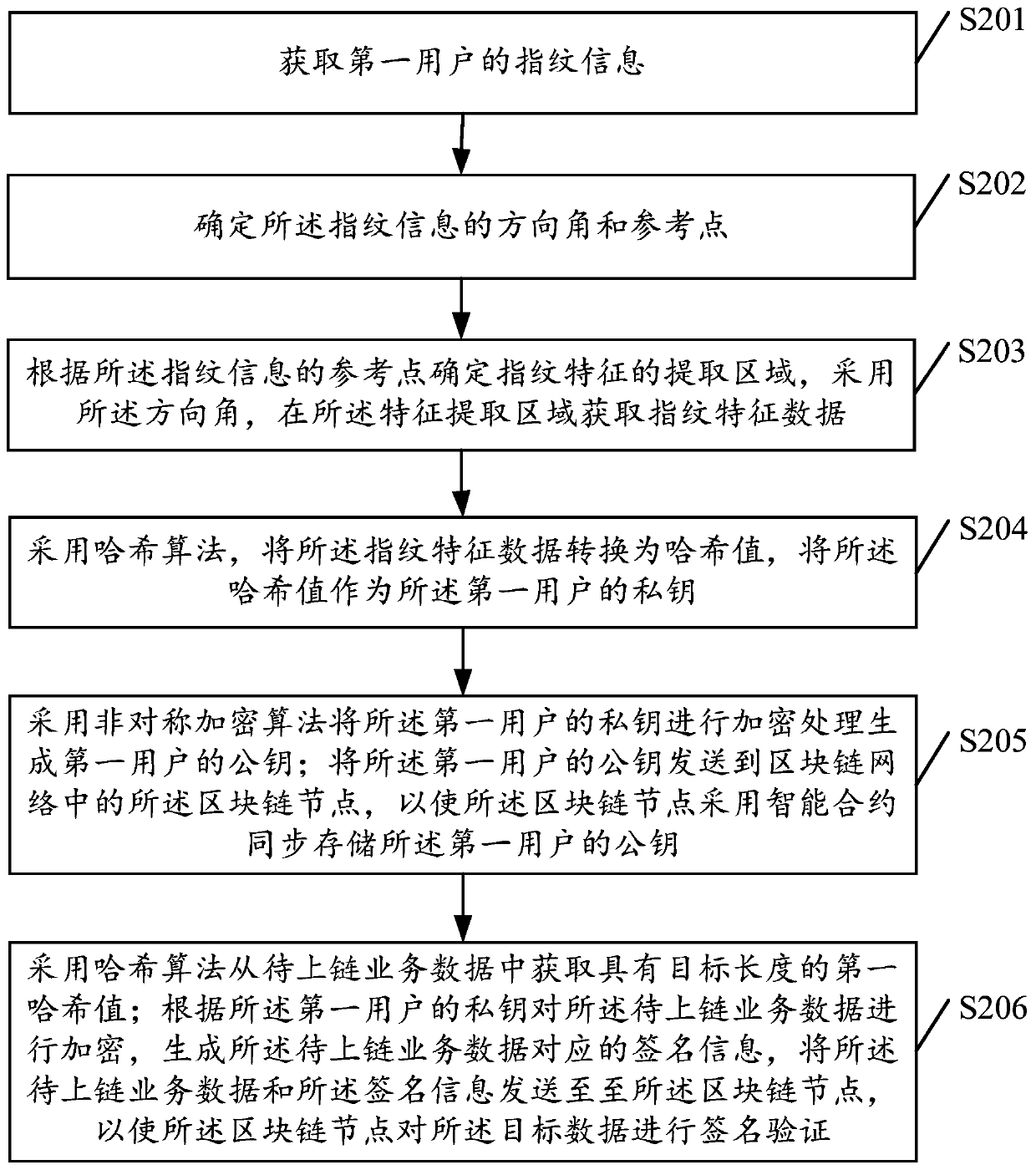
ActiveCN110601853AReduce risk of leakageImprove securityUser identity/authority verificationFeature dataChain network
The embodiment of the invention discloses a blockchain private key generation method and device. The method comprises the following steps: obtaining fingerprint information of a first user; generatingfingerprint feature data according to the fingerprint information; converting the fingerprint feature data into a hash value by adopting a hash algorithm, and taking the hash value as a private key of the first user; generating a public key of the first user according to the private key of the first user, and publishing the public key of the first user on a blockchain network, wherein the block chain network comprises block chain nodes; and signing to-be-uploaded service data by adopting the private key to obtain signature information, and sending the to-be-uploaded service data and the signature information to the blockchain node, so as to enable the blockchain node to verify the signature information by adopting the public key of the first user. By adopting the method and the device, the risk of information leakage can be reduced, and the data security is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Key generation method, encrypted data analyzing method, devices and key managing center
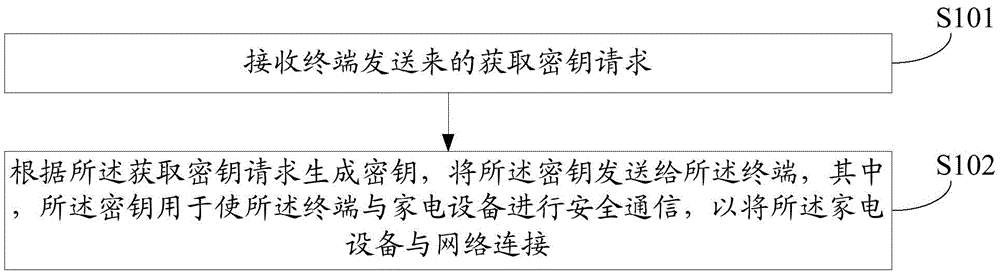
ActiveCN105577680AReduce risk of leakageImprove securityKey distribution for secure communicationUser identity/authority verificationSecure communicationComputer terminal
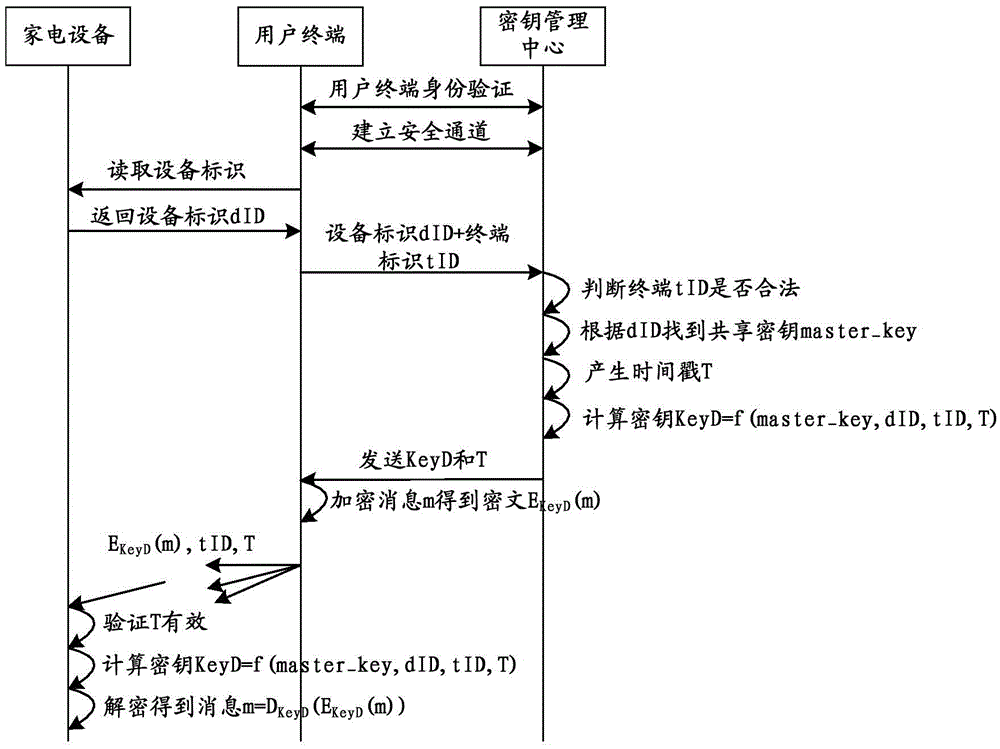
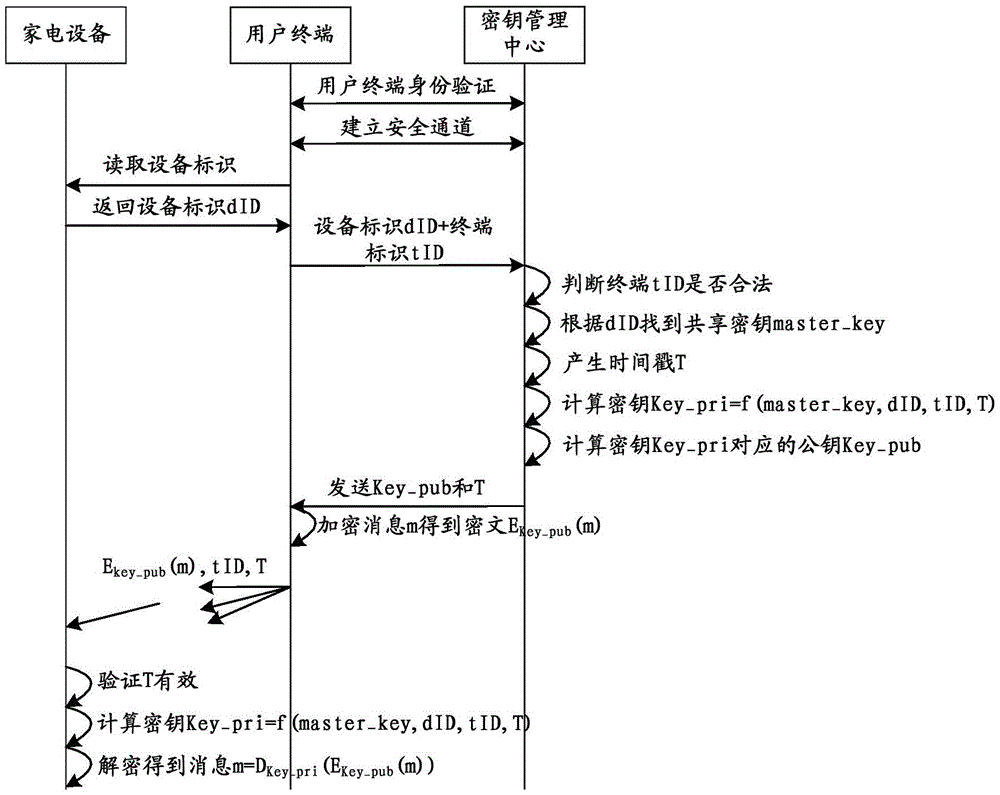
The invention discloses a key generation method, an encrypted data analyzing method, devices and a key managing center. According to the methods, the devices and the center of the invention, the key managing center receives a key obtaining request sent by a terminal; a key is generated according to the key obtaining request; the key is sent to the terminal; therefore, the terminal carries out secure communication with household appliances through the key; the household appliances are connected to a network; the key leakage risk is greatly reduced; and the problem in the prior art that the networking security of the configured household appliances is low is effectively solved.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
Method for obtaining root key and server
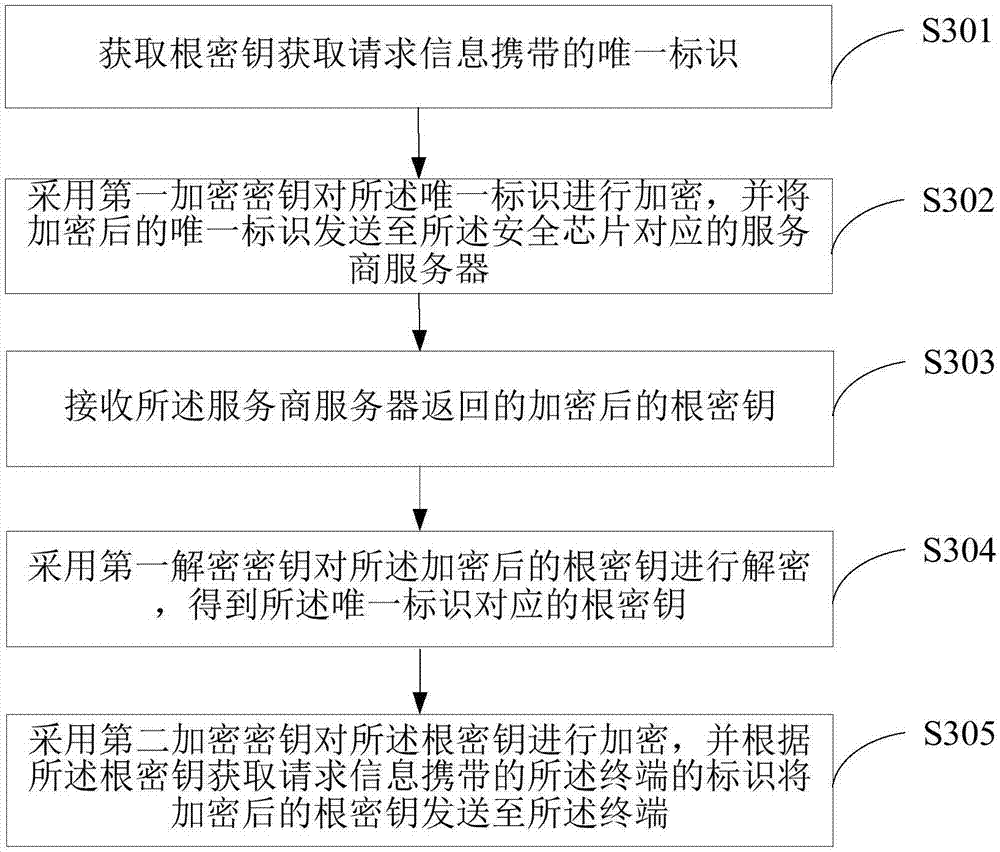
InactiveCN107276756AReduce risk of leakageImprove transmission securityKey distribution for secure communicationSecurity arrangementTransfer procedureUnique identifier
The embodiment of the invention discloses a method for obtaining a root key and a server. The method comprises the steps of obtaining a unique identifier of a security chip carried by root key obtaining request information, wherein the root key obtaining request information is sent by a terminal; encrypting the unique identifier through adoption of a first encryption key and sending the encrypted unique identifier to a service provider server corresponding to the security chip; receiving the encrypted root key returned by the service provider server; decrypting the encrypted root key through adoption of a first decryption key, thereby obtaining the root key corresponding to the unique identifier; encrypting the root key through adoption of a second encryption key and sending the encrypted root key to the terminal according to an identifier of the terminal carried by the root key obtaining request information; and decrypting the encrypted root key by the terminal through adoption of a second decryption key, thereby obtaining the root key. According to the embodiment of the invention, the risk of leaking the root key in a transmission process can be effectively reduced, the transmission security of the root key is improved, and the security of the information in the terminal is improved.
Owner:SHENZHEN GIONEE COMM EQUIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com