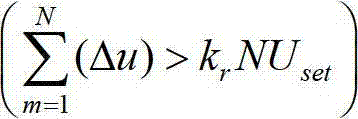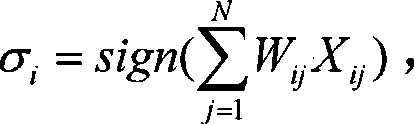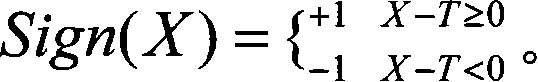Patents
Literature
209results about How to "Reduce computing requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
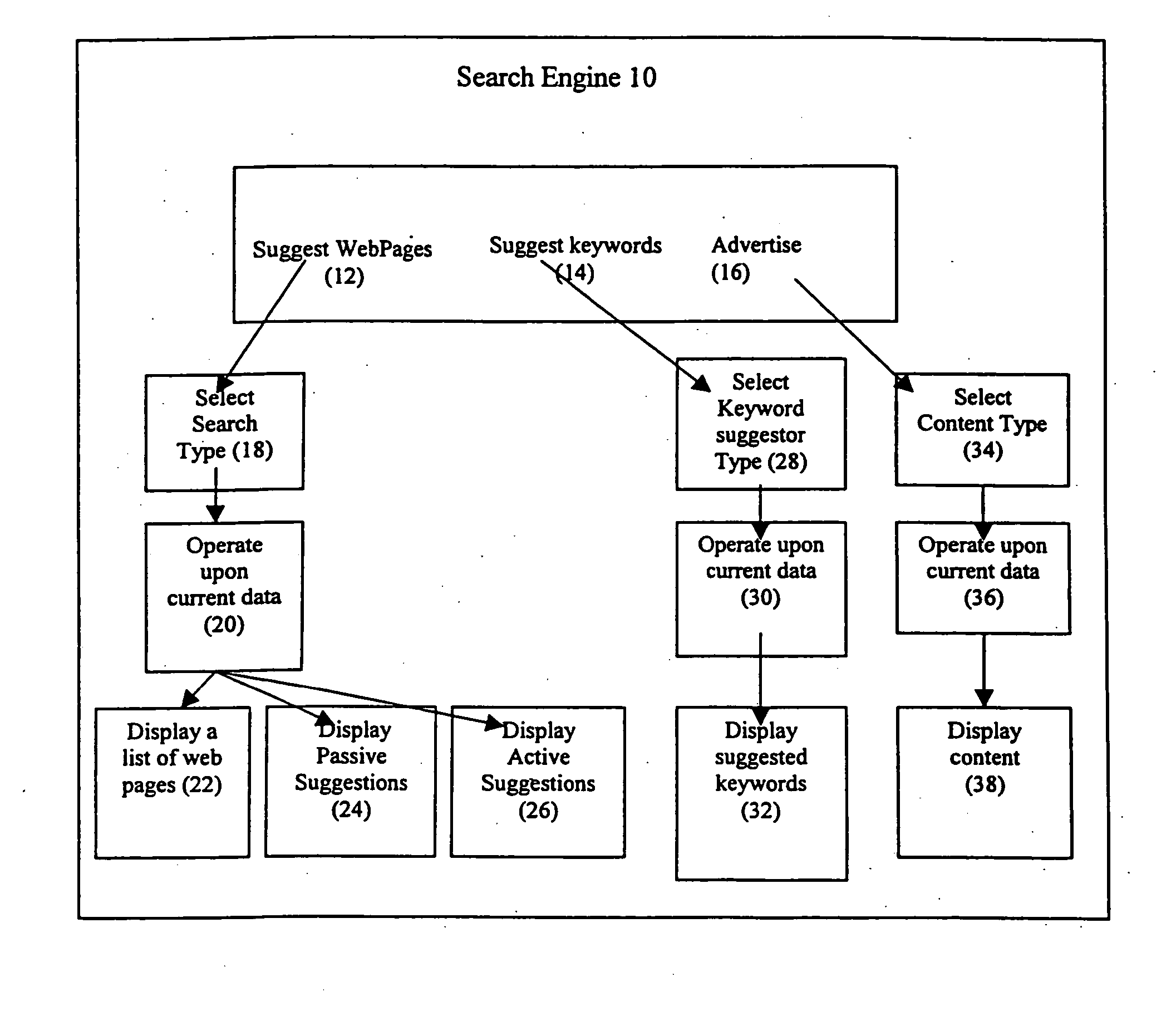
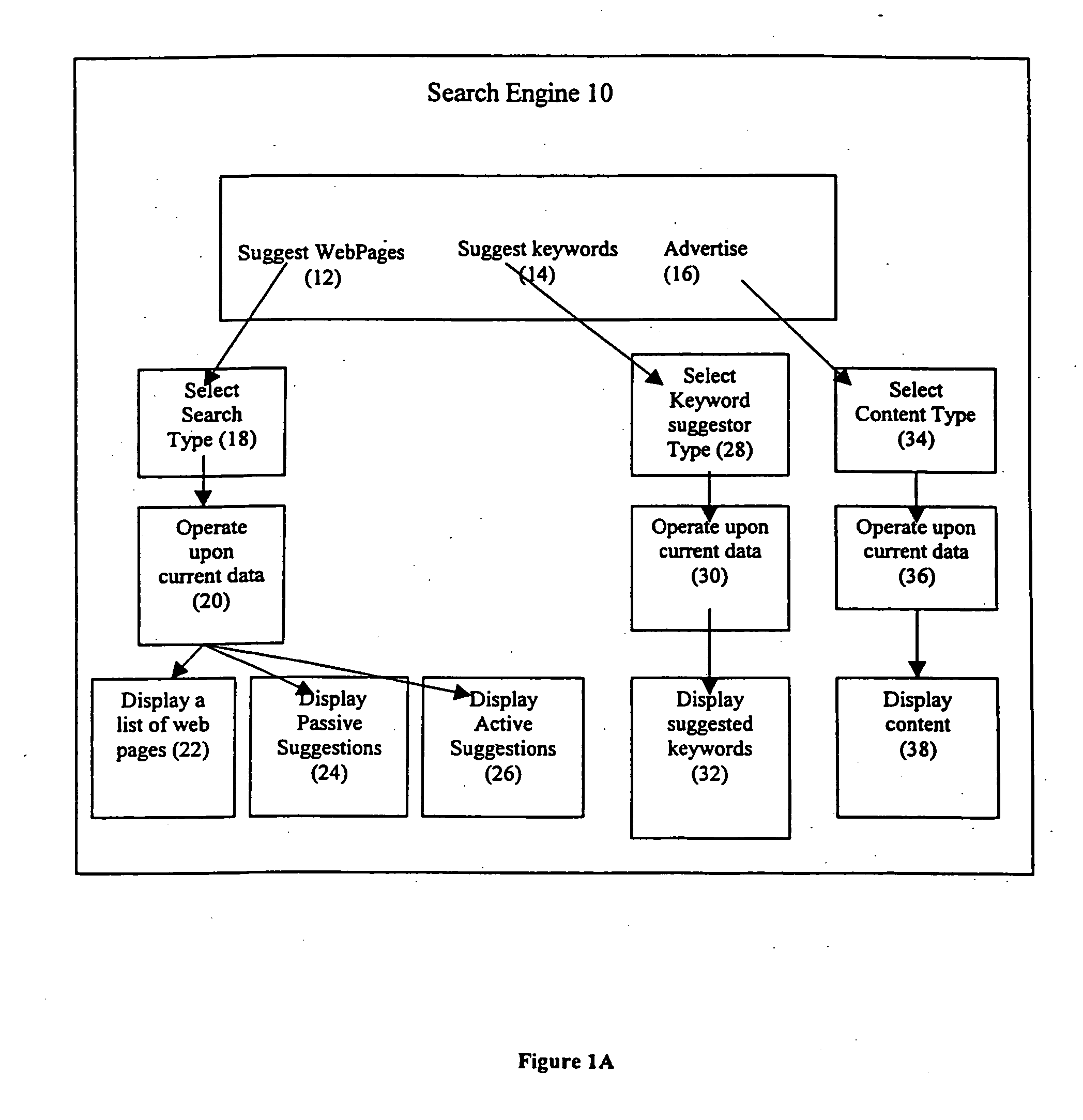
Search engine
InactiveUS20060100956A1Improve efficiencyImprove usabilityFinanceWeb data indexingWeb pageInternet search engines
The present invention provides for a method of updating an internet search engine database with the results of a user's selection of specific web page listings from the general web page listing provided to the user as a result of his initial keyword search entry. By updating the database with the selections of many different users, the database can be updated to prioritize those web listings that have been selected the most with respect to a given keyword, and thereby presenting first the most popular web page listings in a subsequent search using the same keyword search entry.
Owner:S L I SYST INC
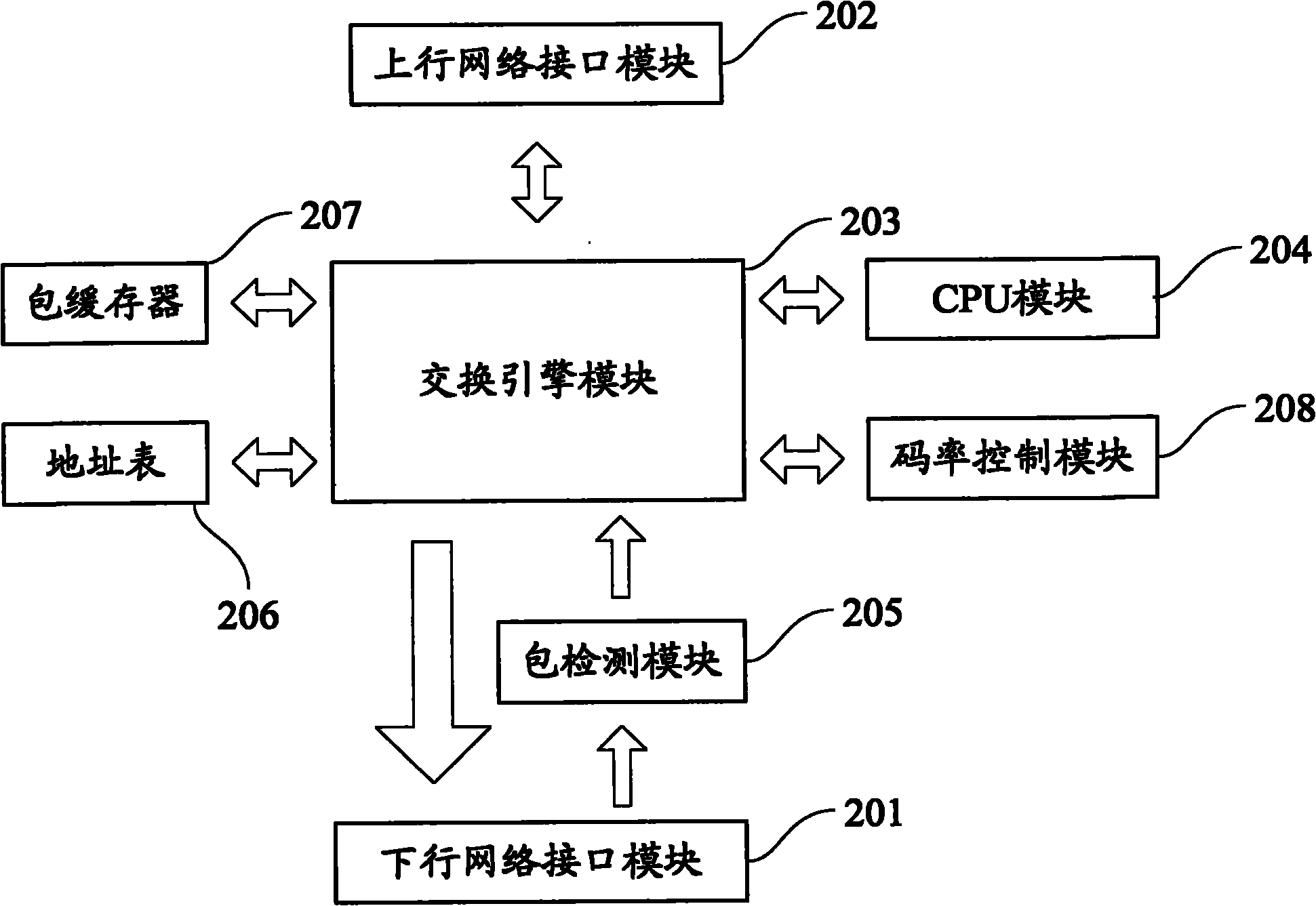
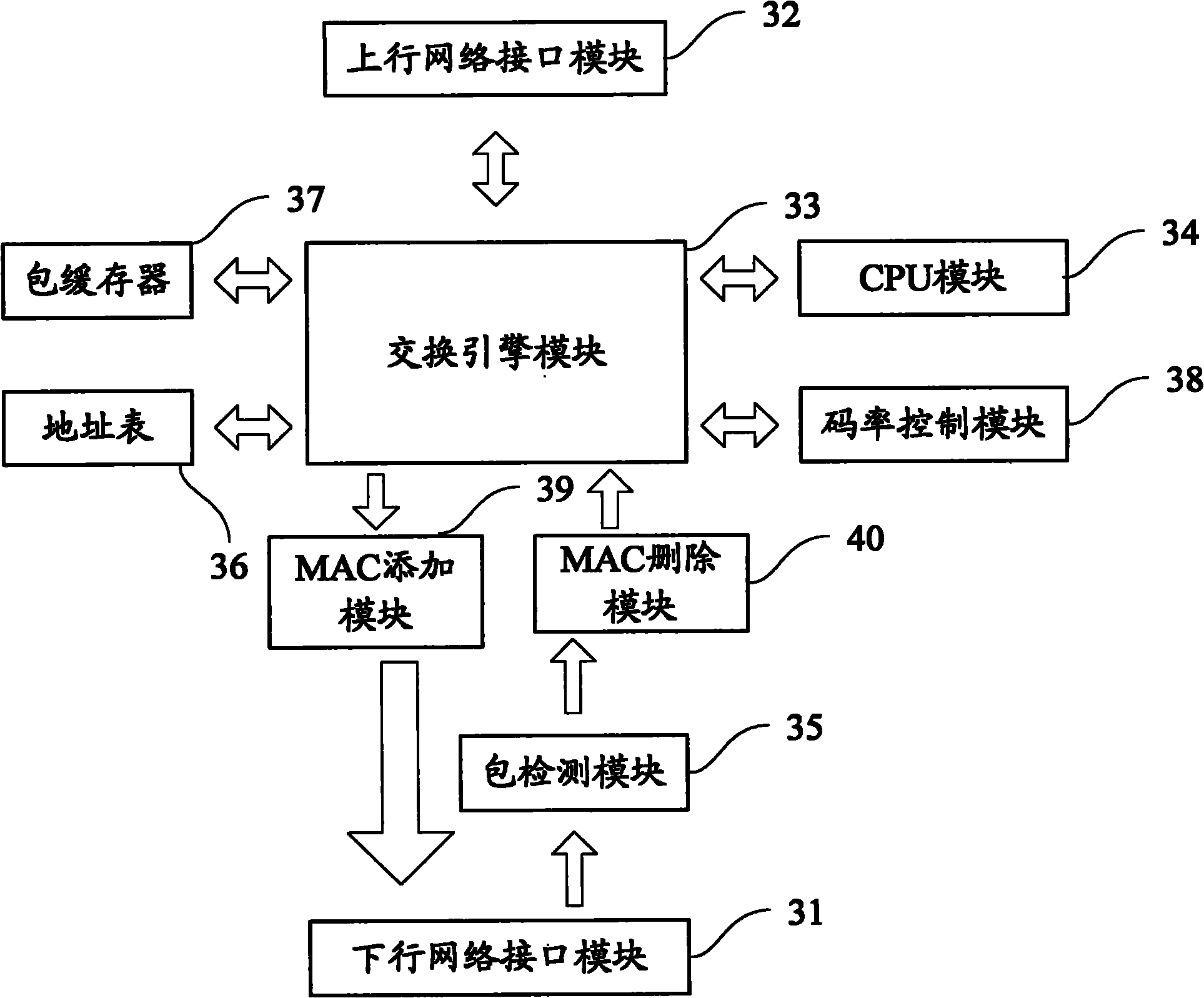
Communication method and communication system of novel network
ActiveCN101917492AAvoid delayMeet security needsSpecial service provision for substationTelecommunications linkCommunications system
The invention discloses a communication method of a novel network. The novel network is a network with a centralized control function and comprises a main control server and subordinate network equipment, and the subordinate network equipment comprises terminals. The method comprises the following steps that: the main control server configures downlink communication link for a current service; and the main control server sends the current service data packet sent by a source terminal to a target terminal according to the downlink communication link. Through the communication method and the communication system, the stability and smoothness of the transmission channel are ensured, the delay of multimedia services is prevented, the requirements for the state information security are met, the hardware resources are saved and the network transmission quality is guaranteed.
Owner:BEIJING QIANTANG NETWORK TECH
Site selection and transportation optimization method for super-large scale logistics distribution
ActiveCN103473612AReduce computing requirementsGreat innovationForecastingLogisticsDistractionCluster algorithm
The invention provides a site selection and transportation optimization method for super-large scale logistics distribution. The method comprises the steps of clustering, side selection planning and route planning, specially, the method comprises the steps that computing is carried out with a method combined by a from-bottom-to-top clustering method and a designating-based clustering algorithm; a given distribution center number is p, the best site selection scheme is computed with minimum total cost as a target; site selection schemes with different distribution center numbers are compared, administration cost is integrated, an ideal site selection scheme is selected; according to the requirements of distraction point numbers in each cluster and geographic information, the time requirement of distribution connecting of each distribution point and the traffic time requirement between points are computed; an ant colony algorithm is used, and the best distribution route is obtained by computing. According to the site selection and transportation optimization method for super-large scale logistics distribution, the problem that computing amount is large caused by the fact that distribution points are increased greatly is effectively solved, compared with existing site selection-route planning, computing expenditure is greatly lowered, and efficiency is obviously improved.
Owner:周伟华
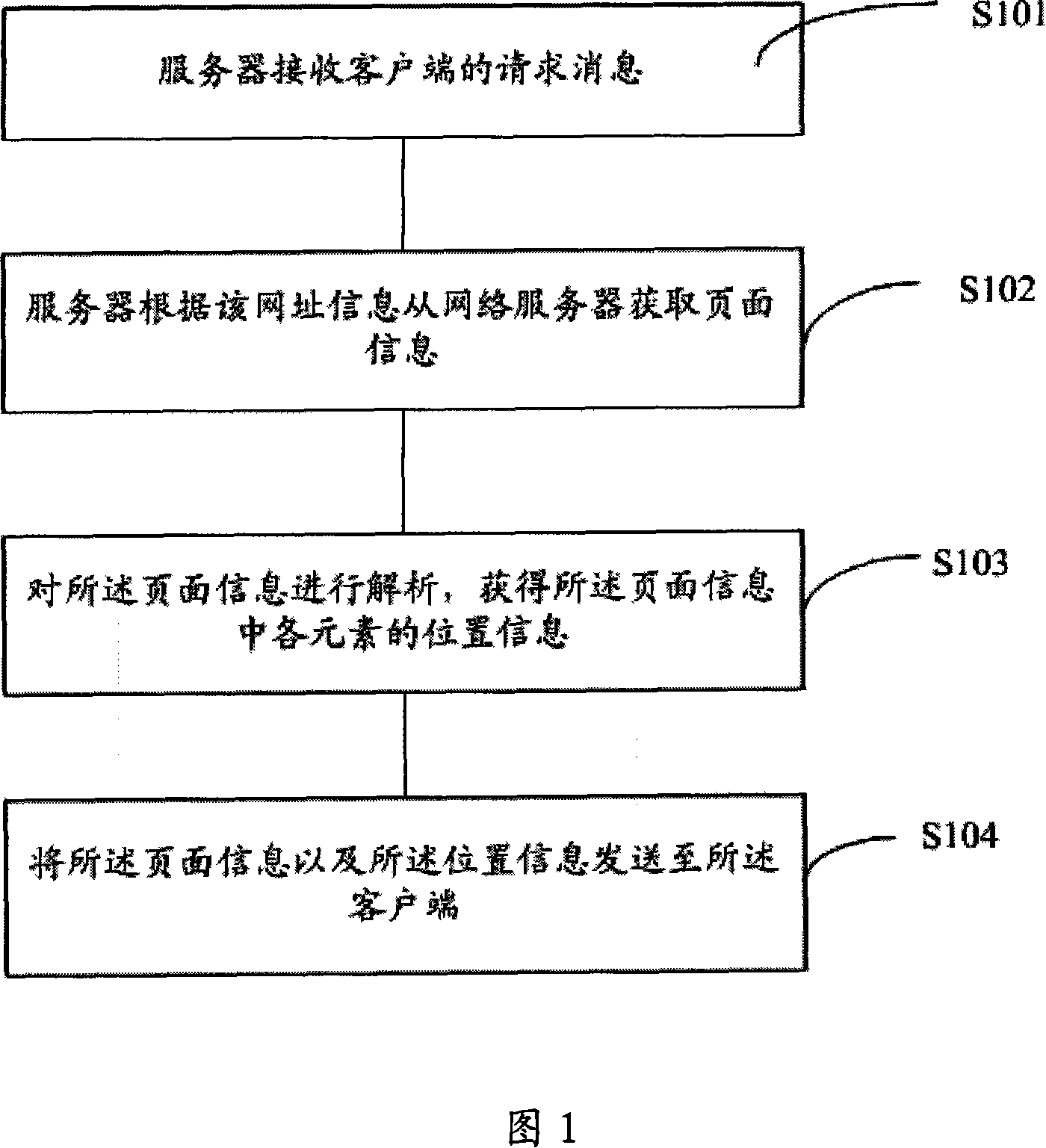
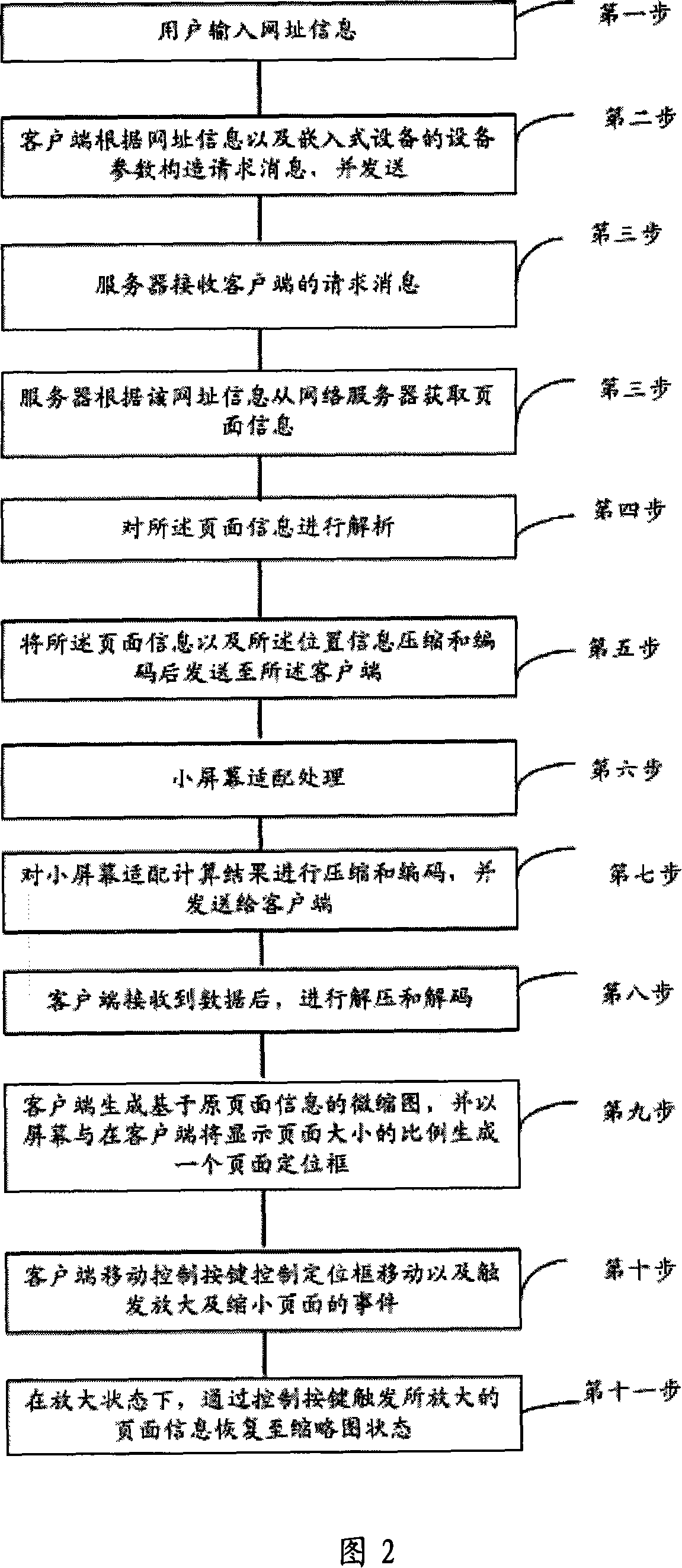
Method for browsing web of micro browser and micro browser
ActiveCN101202748AReduce computing requirementsIn line with the habitGeometric image transformationTransmissionClient-sideWeb page
The invention provides a method for browsing web pages by a micro browser. When the method is in use, a server terminal receives the request information from a client terminal; the request information carries network information and device attribute parameters; the invention gets the page information from a network server according to the network information; the page information is analyzed to get the position information of each element in the page information and the page information and the position information are transmitted to a client terminal. The invention also provides a corresponding micro browser. As the invention divides the browser into the server and the client terminal and the calculation process is finished by the server during the page typesetting, the calculation requirement on the client terminal is reduced; simultaneously, as the server calculates the position information of each element according to initial page design pattern during the page typesetting, the original design pattern is ensured when the client terminal displays the page information, thus according with a user custom and improving the experience of the user.
Owner:ALIBABA (CHINA) CO LTD
High voltage direct current power transmission line protection method based on voltage and current mutation direction
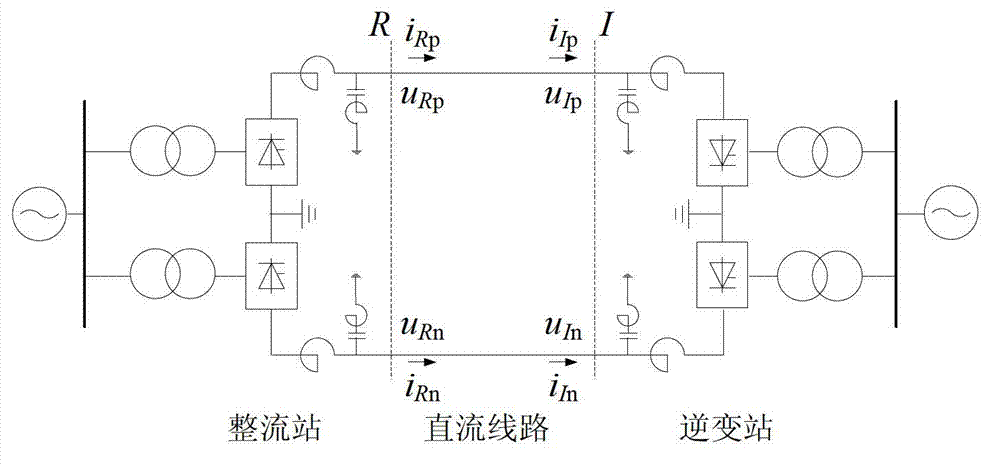
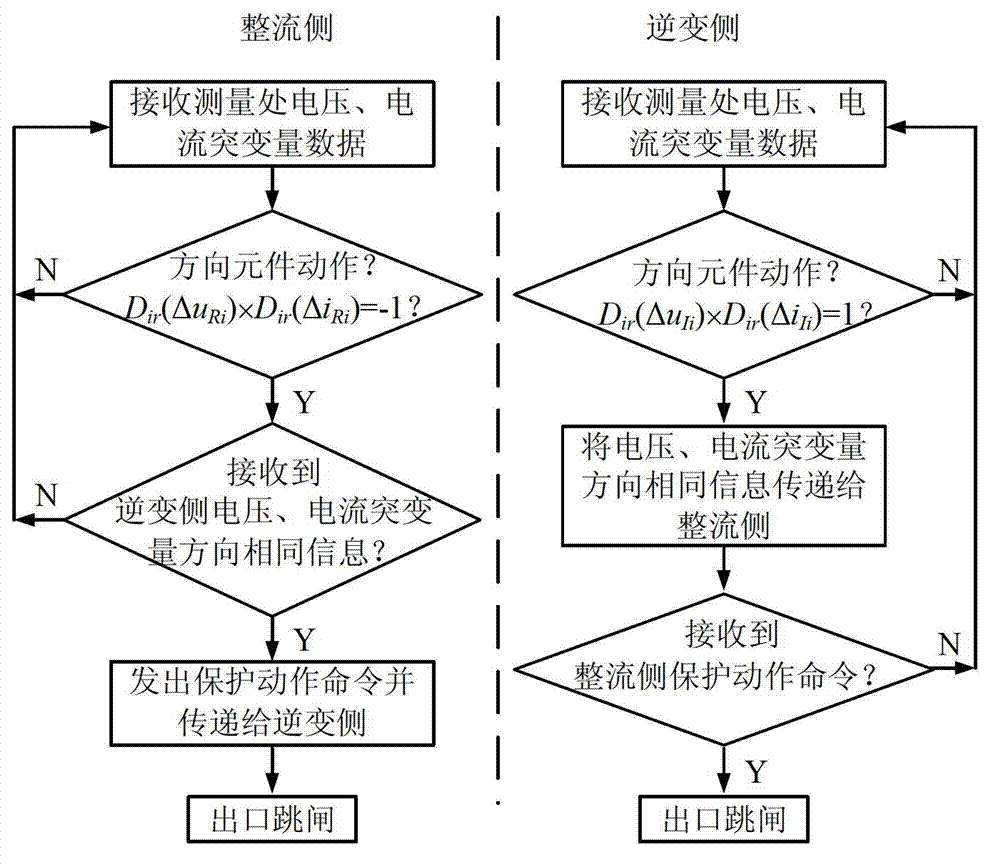
InactiveCN102820643AThe protection method is simple and clearReduce computing requirementsEmergency protective circuit arrangementsPower flowHigh-voltage direct current
The invention discloses a high voltage direct current power transmission line protection method based on a voltage and current mutation direction. The method comprises the following steps that when a fault exists in a line area, the directions of the voltage mutation quantity and the current mutation quantity at the protection measurement of a rectifying side are opposite, and the directions of the voltage mutation quantity and the current mutation quantity at an inverter side are the same; the feature is also applicable for anode lines and cathode lines; and faults at other areas do not satisfy the condition. Thus, the protection criterion of the high voltage direct current transmission line is structured and the protection method is disclosed. As the method provided by the invention is adopted in the protection of the direct current transmission line, actions can be performed fast and accurately when fault lightning, high impedance earthing faults and pole-pole faults exist in the line area; no error action is carried out under the situations of lightning disturbance, faults outside the line protection area and the like; the protection method is simple and clear; the requirement on communication channels is not high; the requirements on data calculating speed and sampling frequency are low; no synchronizing processing is required for sampled data; and various operation ways of a bipolar direct current power transmission system are applicable, and the practical value is high.
Owner:SHANDONG UNIV
Attribute-based searchable encrypted electronic medical record system and encryption method
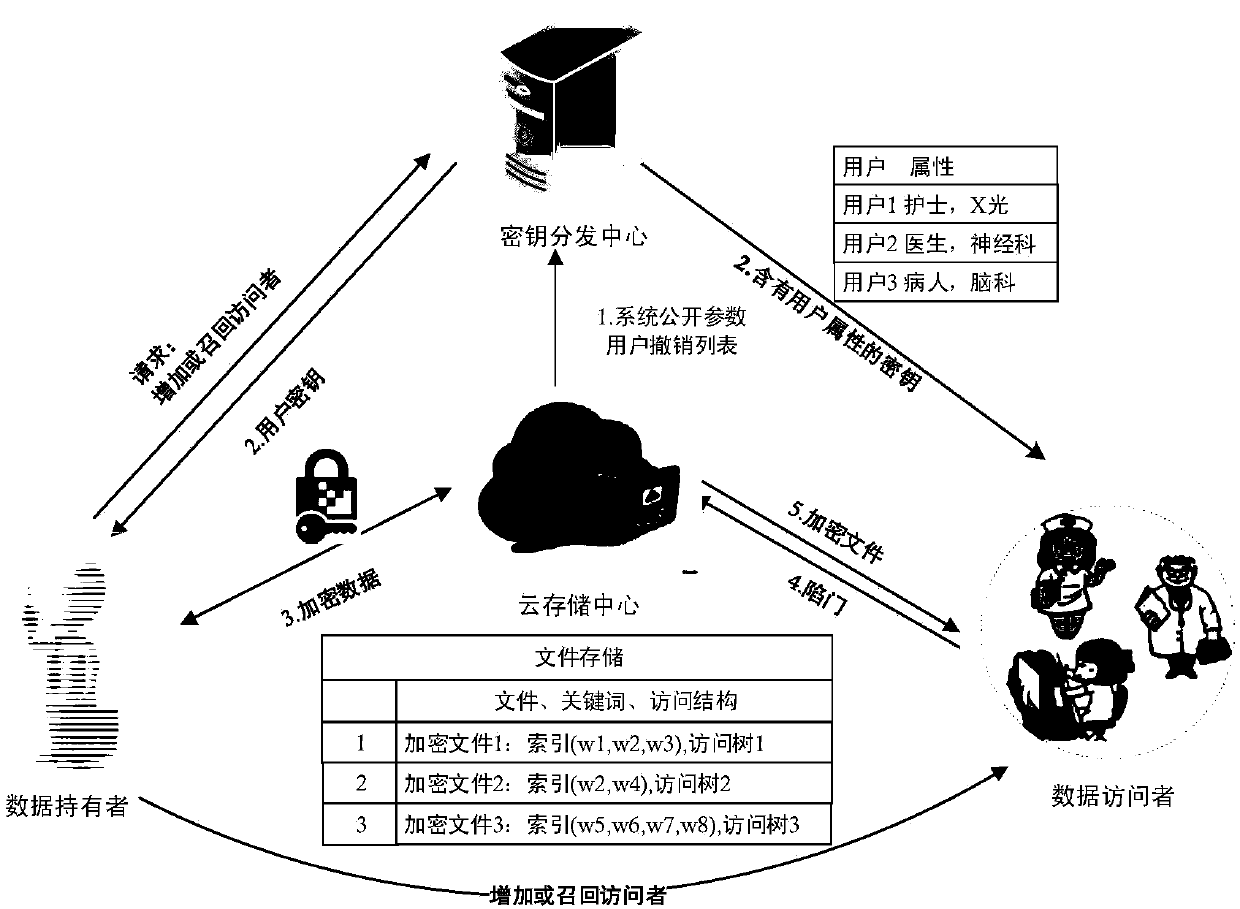
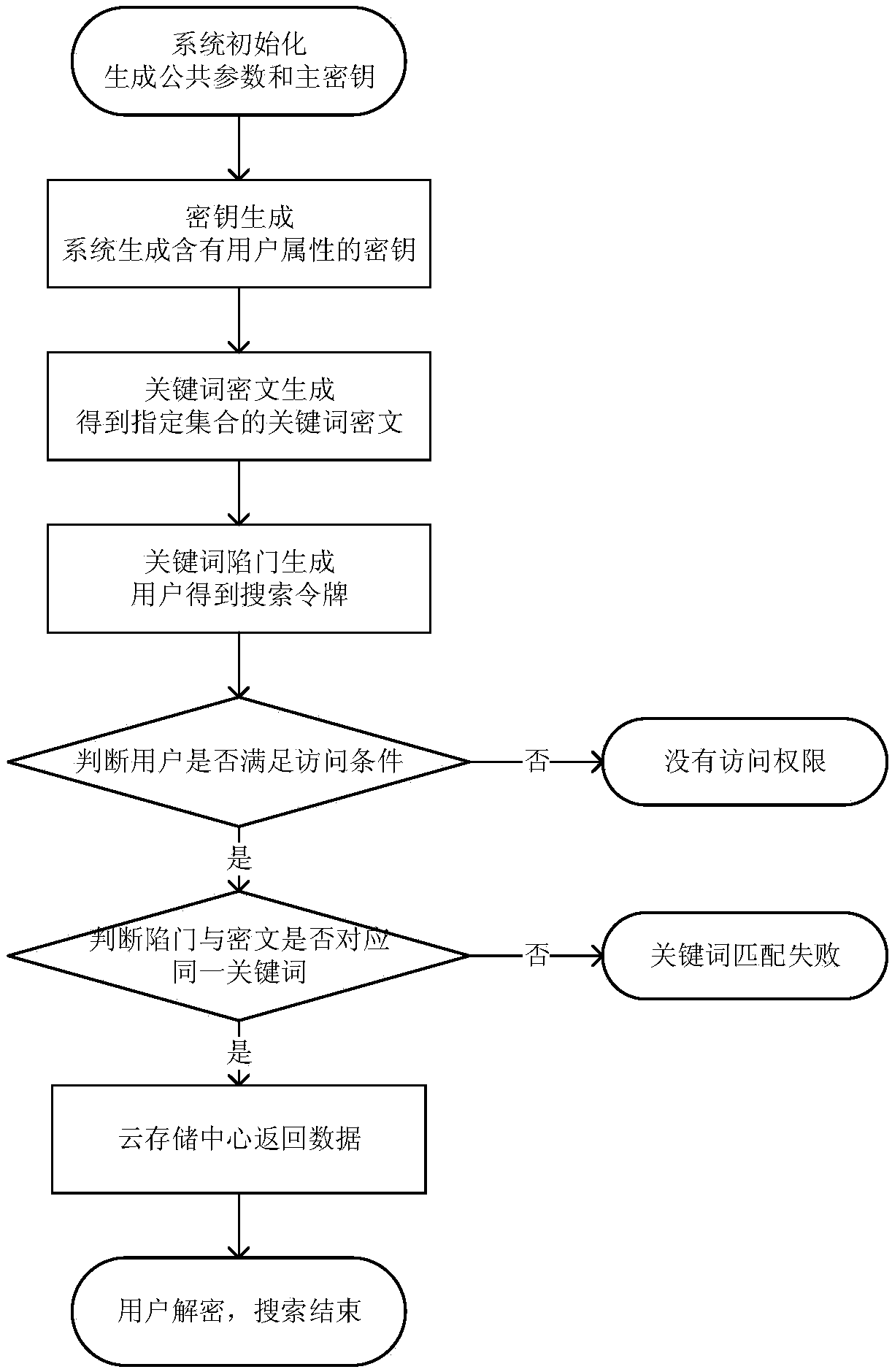
InactiveCN107634829AReduce computing requirementsReduce computational complexityKey distribution for secure communicationSpecial data processing applicationsMedical recordCiphertext
The invention discloses an attribute-based searchable encrypted electronic medical record system and an encryption method. The system comprises a key distribution center and a cloud storage center, wherein the key distribution center generates public parameters and a master key to initialize the system; the key distribution center generates and distributes keys containing user attributes to users;a data owner sets an access strategy before uploading medical record data, encrypts the data, and then uploads the data to the cloud storage center; a data visitor generates a trap door according tokeywords and the keys, and provides a query request to the cloud storage center; and after receiving the query request, the cloud storage center determines to return corresponding encrypted data to the data visitor according to the trap door and keyword ciphertexts. According to the scheme of the invention, the difficulty of key management in a multi-user environment can be reduced, data users canbe supported to accurately query the keywords of the ciphertexts, guessing attacks of the keywords can be resisted, and the leakage of privacy data can be effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
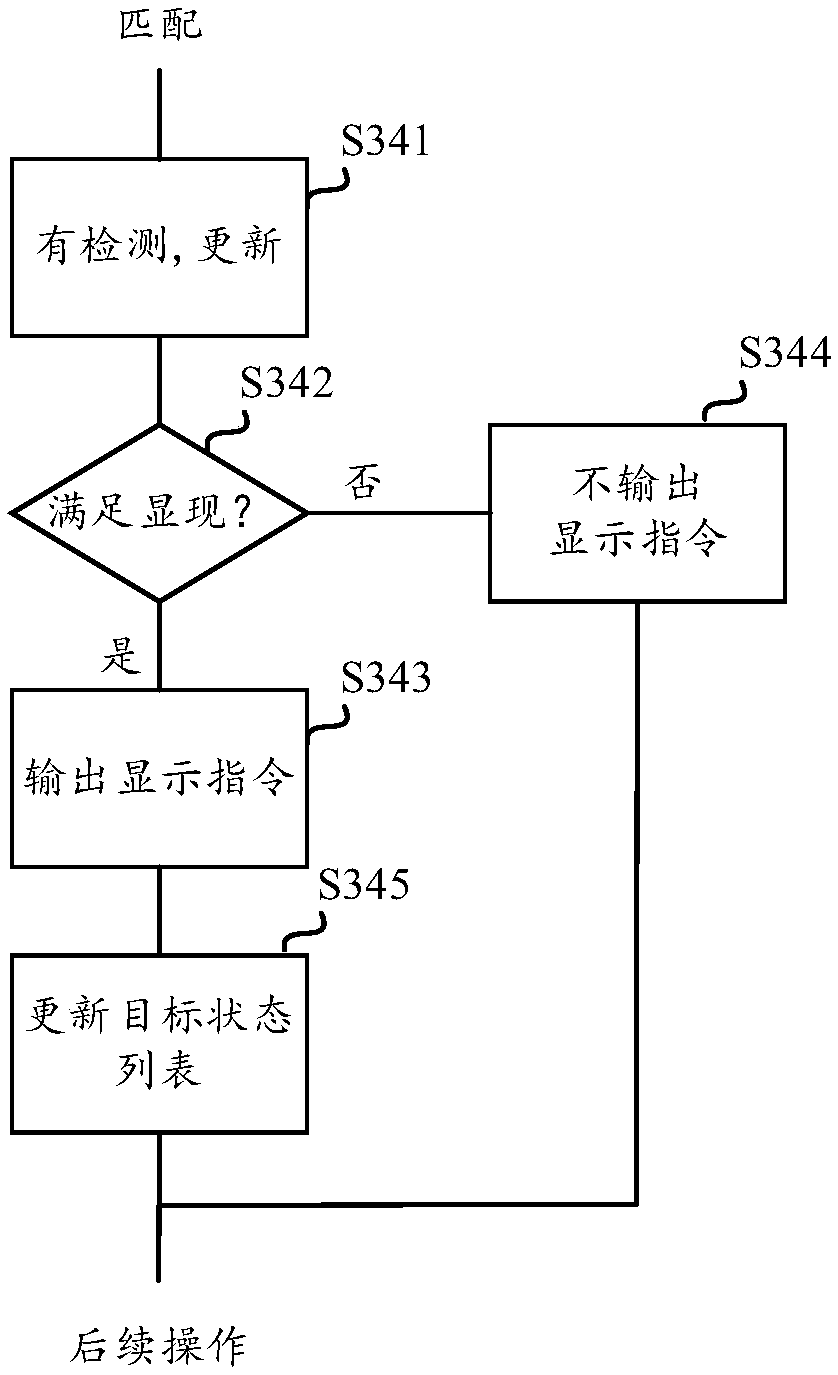
Multi-target tracking method and corresponding video analysis system
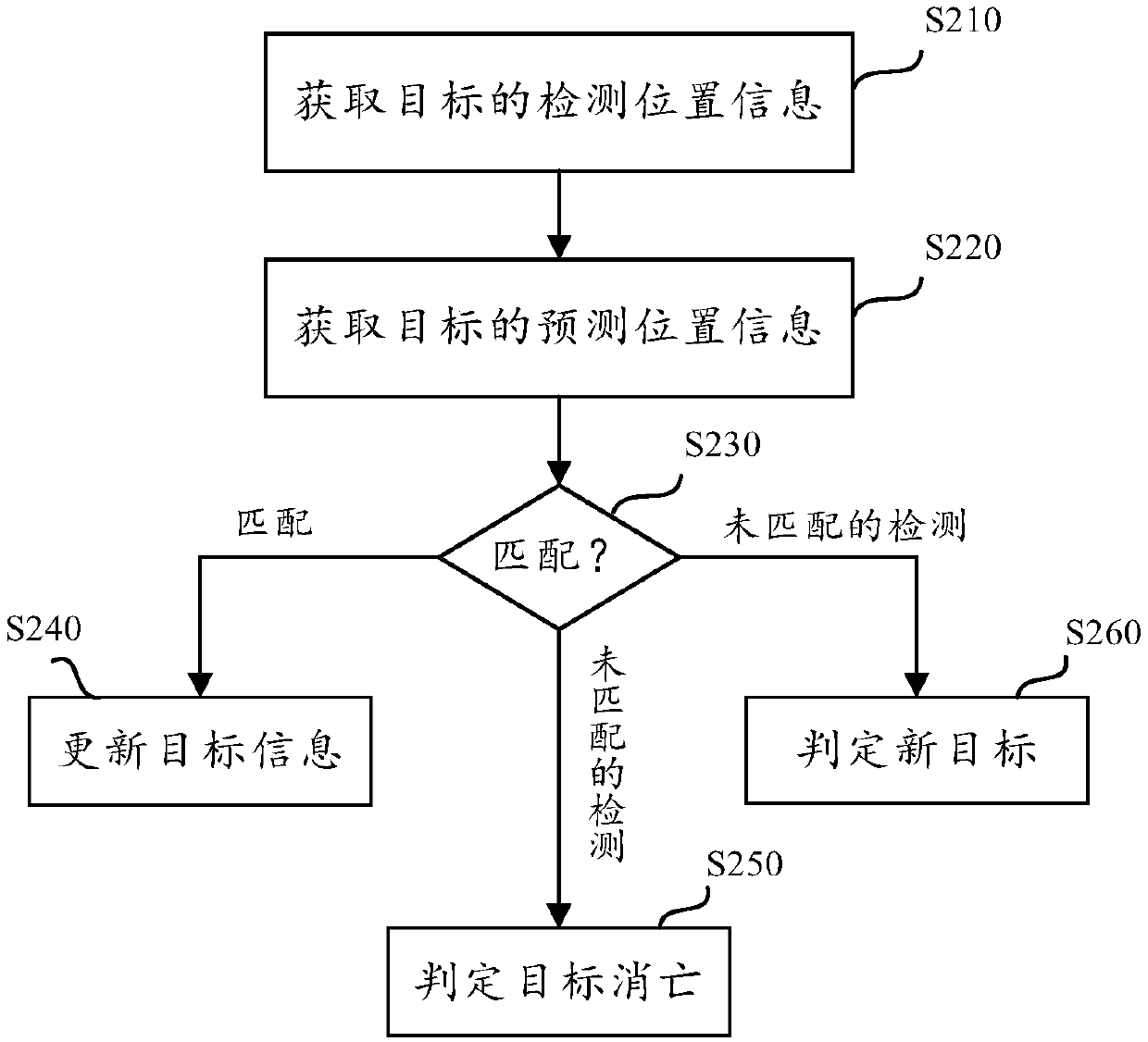
InactiveCN110751674AReduce computing requirementsGuaranteed Tracking AccuracyImage enhancementImage analysisPattern recognitionMulti target tracking
The invention discloses a multi-target tracking method and a corresponding video analysis system for implementing the scheme. The method comprises the following steps: acquiring detection position information of a target; obtaining predicted position information of the target; matching the obtained prediction position information with the detection position information; updating the state information of the target based on the detection position of the target under the condition that the detection position information of the target is judged to be matched with the prediction position information of the target; under the condition that it is judged that the prediction position of a certain target has no detection position matched with the prediction position, judging that the target is an extinction target; and judging that the target is a new target or a reappeared target under the condition of judging that the detection position of a certain target is not matched with the detection position of the target. Therefore, through reasonable allocation of the functional modules, high tracking precision requirements can be met while low-computing-power high-speed tracking is realized.
Owner:XILINX TECH BEIJING LTD
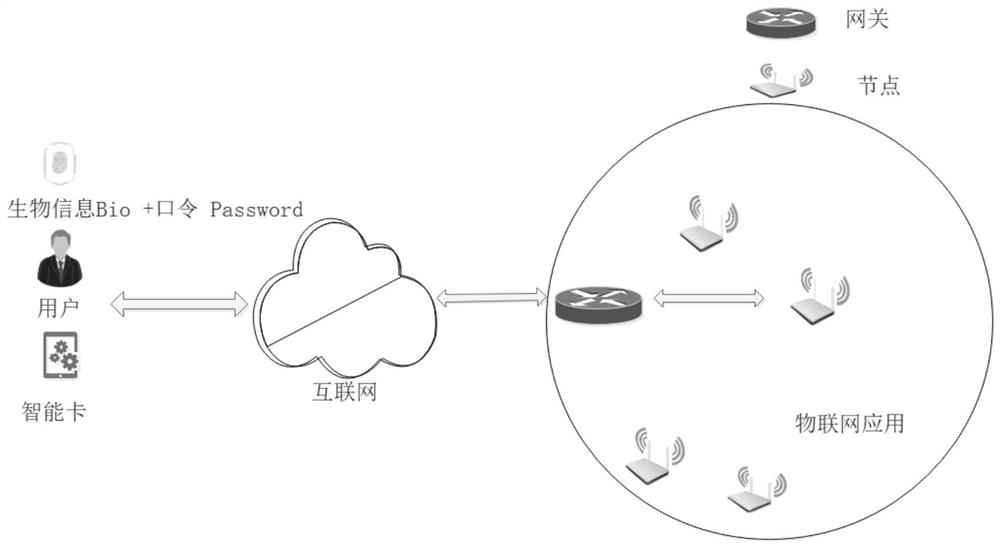
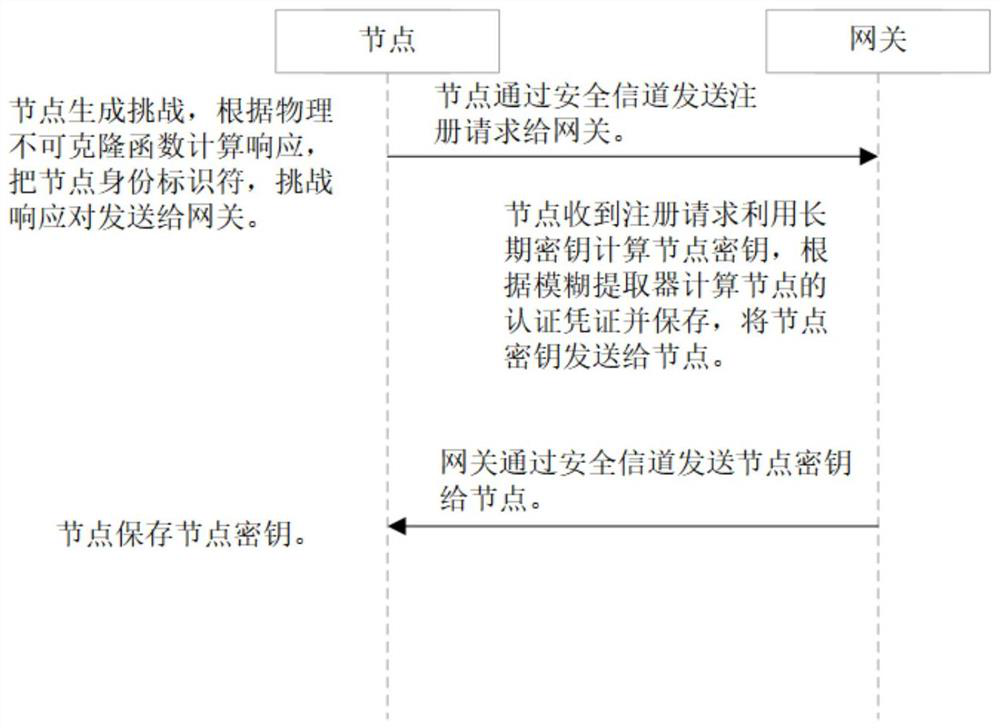
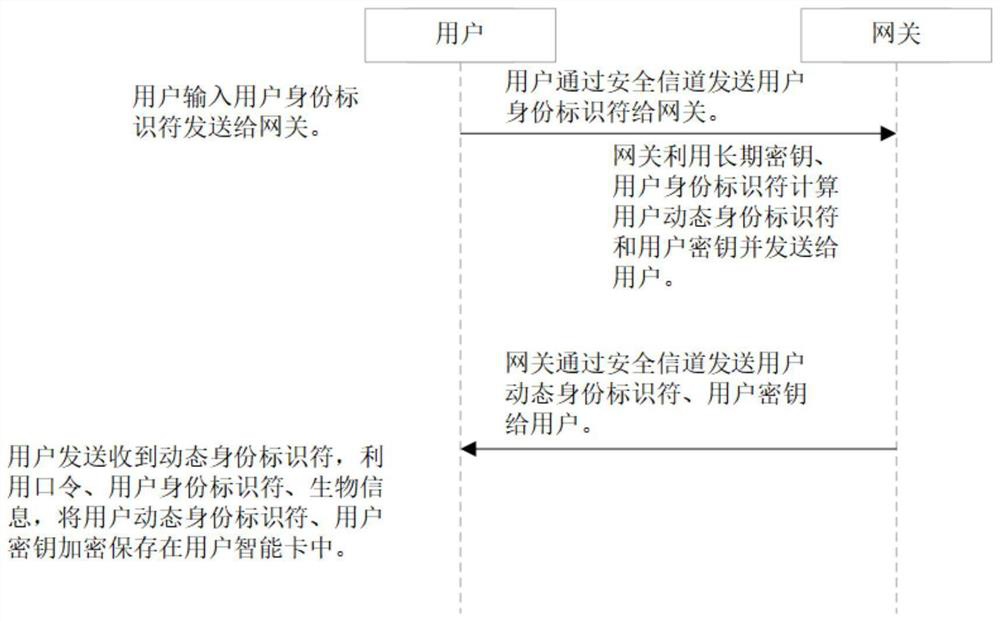
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
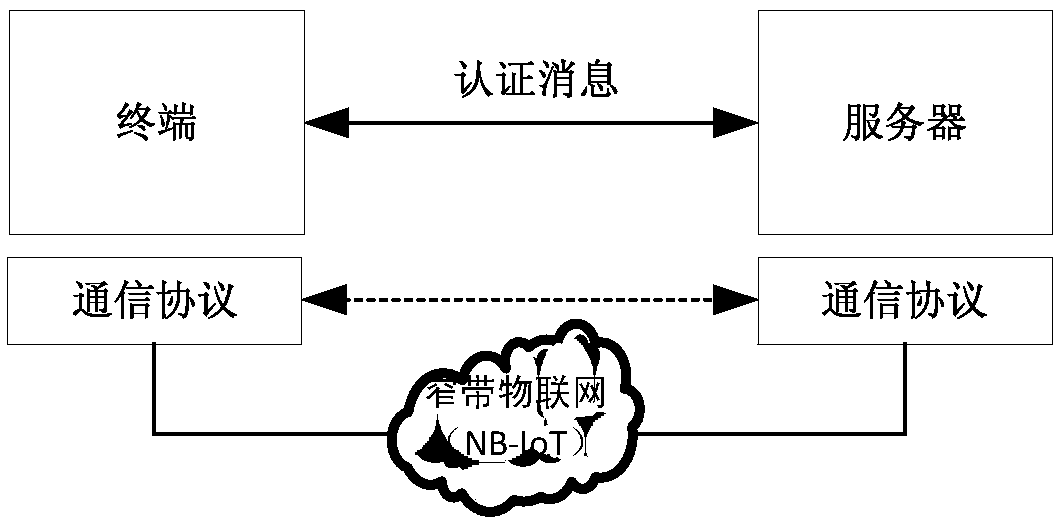
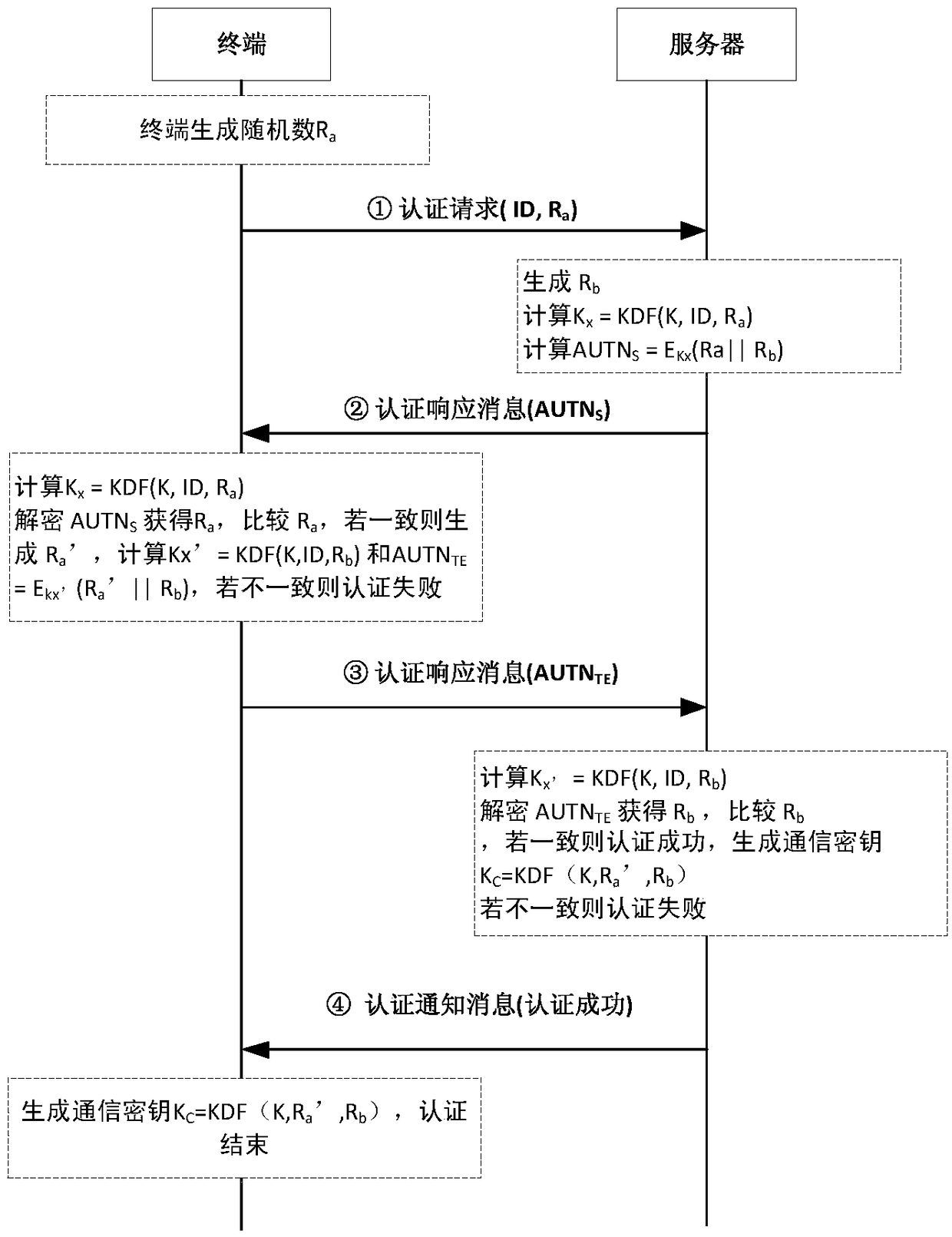
A lightweight secure authentication and key exchange method for narrowband Internet of things
ActiveCN108989318AAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeThe Internet
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
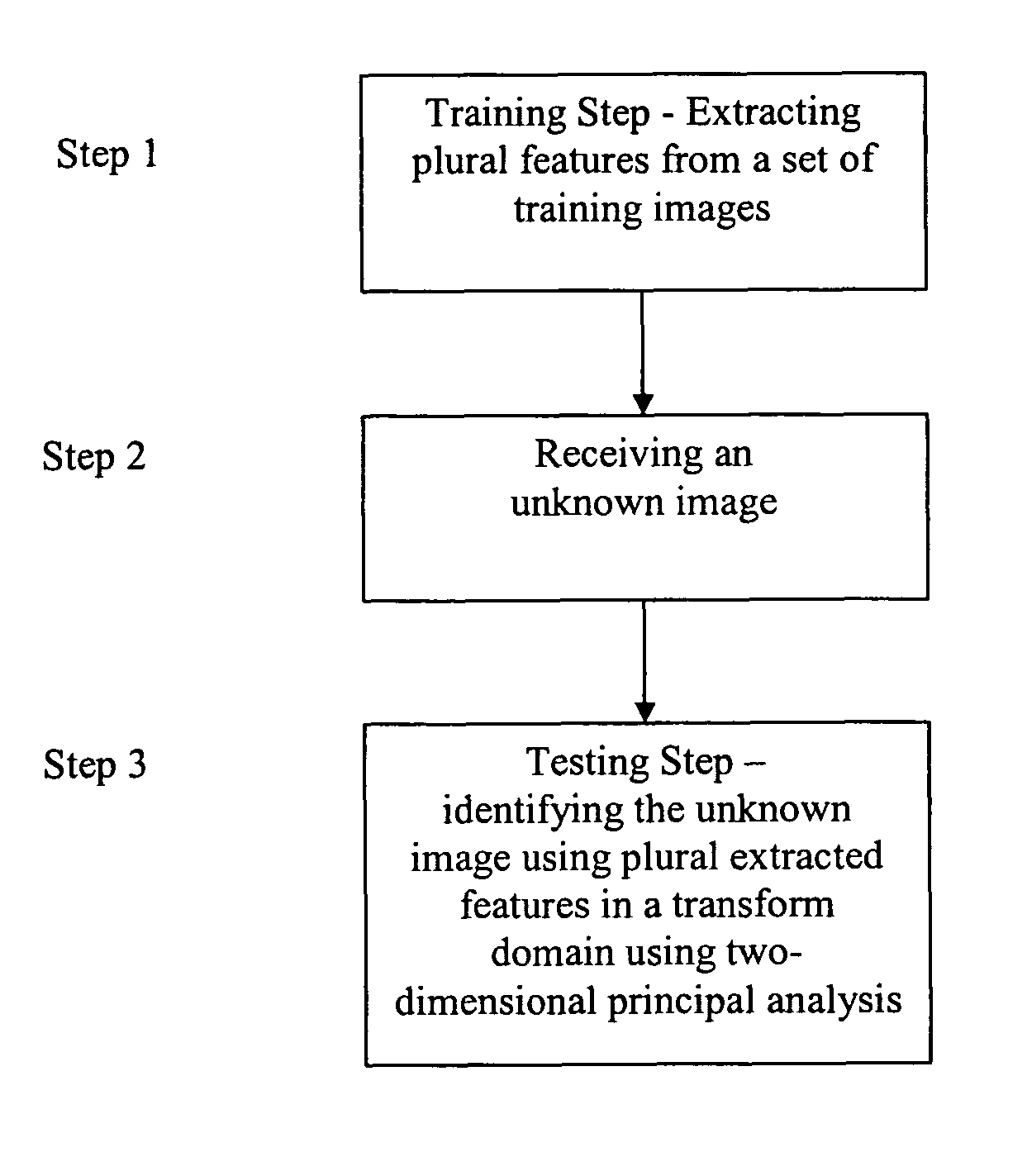
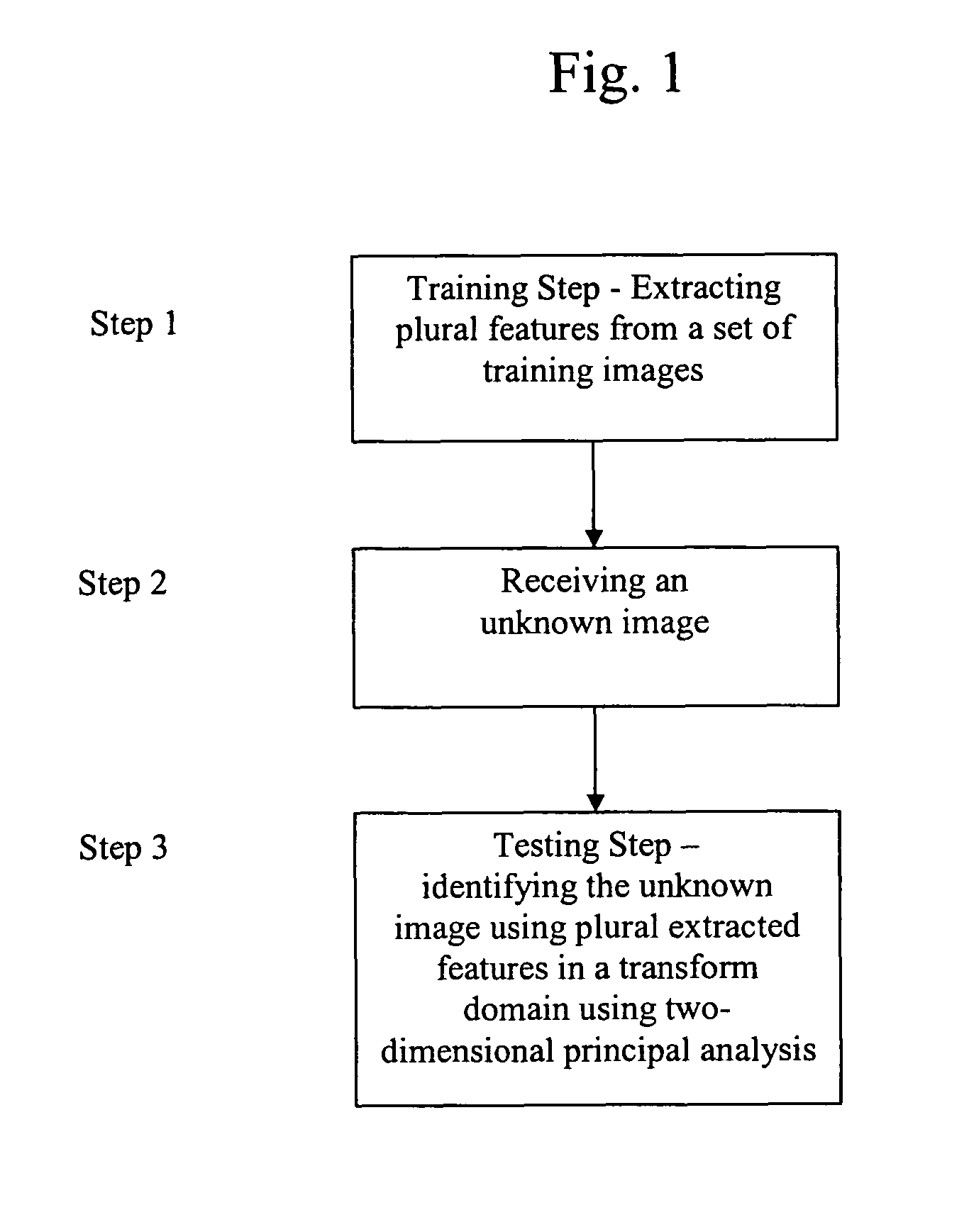
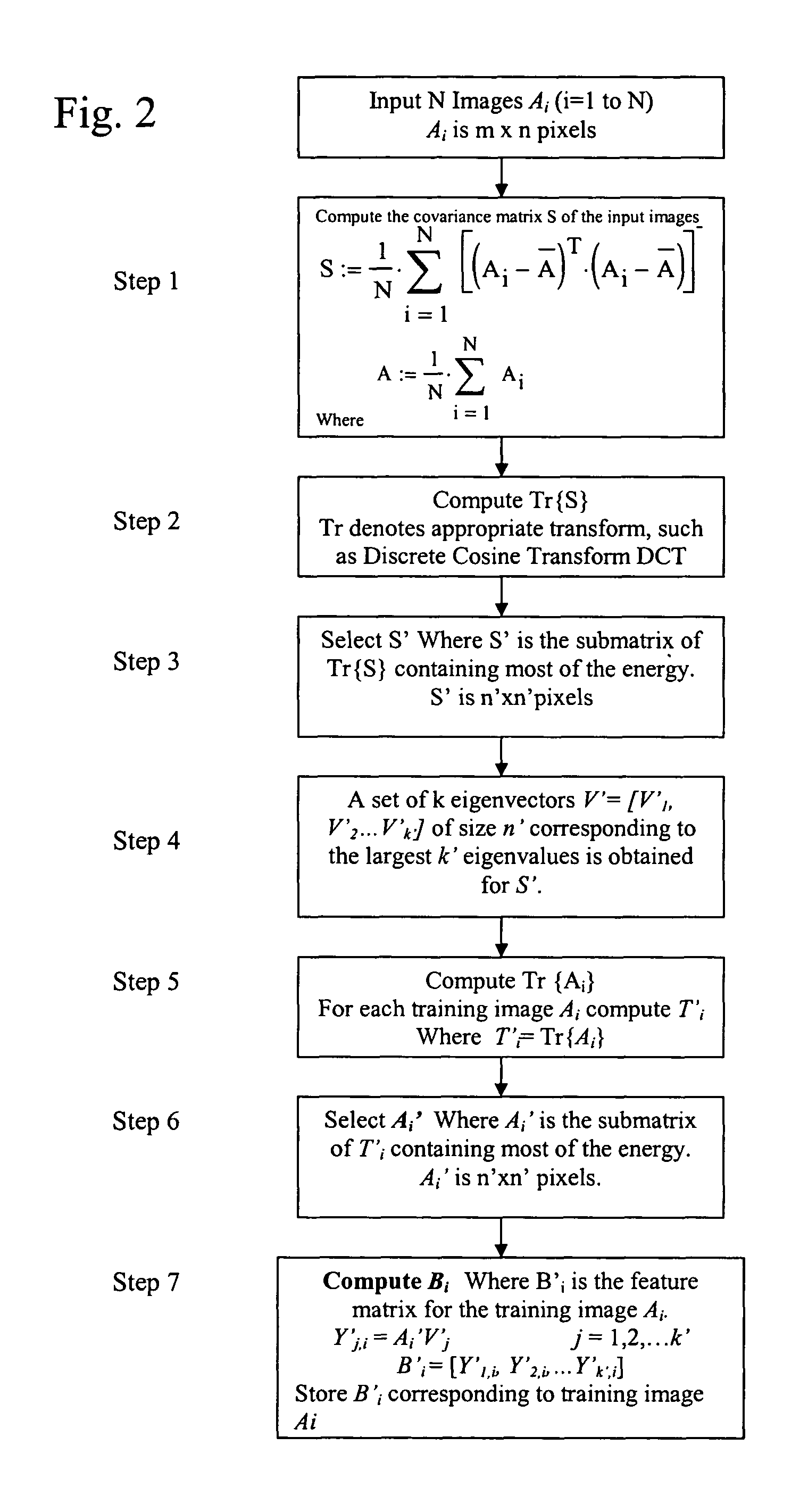
Recognition and classification based on principal component analysis in the transform domain
InactiveUS7724960B1Reduce storageReduce computing requirementsCharacter and pattern recognitionKernel principal component analysisComputation complexity
Methods, system apparatus and devices for classification and recognition that is based on principal component analysis and is implemented in the transform domain using the fast two-dimensional PCA to processes the signal in the transform domain. The signal is represented with a reduced number of coefficients, therefore reducing the storage requirements and computational complexity while yielding high recognition accuracy.
Owner:UNIV OF CENT FLORIDA RES FOUND INC
Drilling histogram compilation method based on field documentation data and automatic cartographic generalization
ActiveCN104915521AEnsure electronic unified storageEasy to storeSpecial data processing applicationsDocumentation procedureWell logging
The invention discloses a drilling histogram compilation method based on field documentation data and automatic cartographic generalization. The drilling histogram compilation method comprises the following technical modules independently used for pre-processing and storing original field data according to the rules of geological documentation and histogram drawing, combining with expertise and well logging explanation result data to carry out knowledge innervation and the cartographic generalization on the histogram, automatically classifying and archiving a comprehensive result, putting the comprehensive result into storage and carrying out user-defined printing and outputting on a result map. When a comprehensive drilling histogram is drawn through the technical system, the integral generation of the histogram can be realized, a working principle that original documentation data supports map frame generation and expert knowledge leads a final achievement can be embodied, contradiction that originally collected data is artificially tampered and industry knowledge innervation can not be carried out is avoided, the workflows of the comparison of geological documentation data and well logging data and the regulation of stratum (rock stratum) boundary line regulation can be simplified, the compilation efficiency of the drilling histogram can be greatly improved, and the drawing of the histogram can be more normative.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Dynamic password safe login method
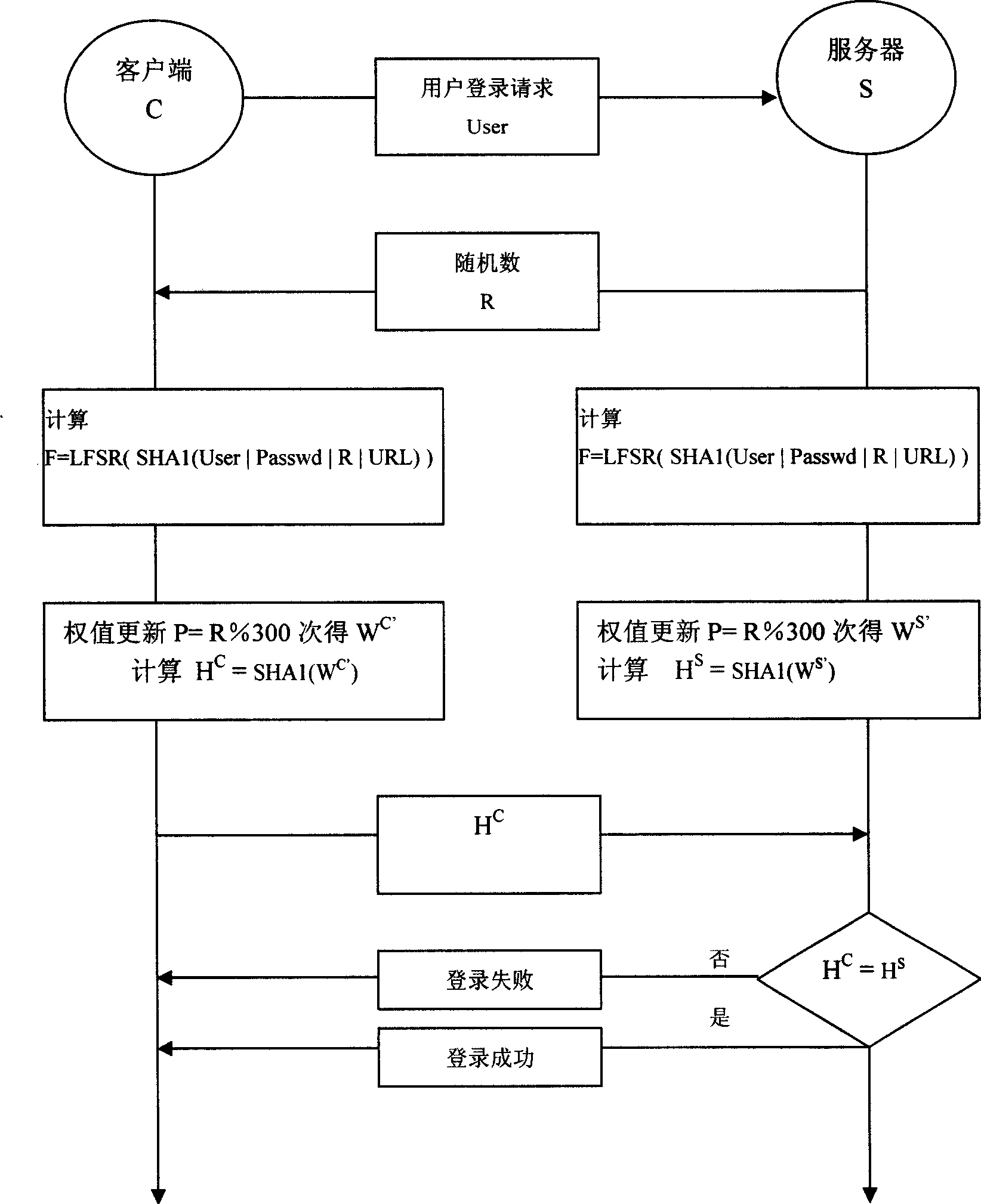
InactiveCN101459516AInnovative ideasGreat innovationUser identity/authority verificationPhysical realisationPasswordMapping algorithm
A dynamic password security login method is provided, which sets that a client and a server have weight synchronous models with the same parameters, and comprises the following steps: initiating a login request by the client, and sending a user name to the server, generating a random number by the server and returning to the client, obtaining that M=user 'Passwd' R, H=SHA1(M), F=LFSR (H) by respective calculations of the client and the server, obtaining the same weight WC=WS according to the mapping algorithm of a random number sequence F, leading the weight synchronous model to study P=%n order by the client according to the random number, wherein R is the random number, n is a preset value, sending the weight vector WC after updating P orders to the server after Hash algorithm SHA1(WC), and leading the weight synchronous model to study P orders by the server to obtain the weight vector WS after updating P orders, and calculating the Hash value SHA1 (WS) thereof, wherein the identification is success if the SHA1 (SC)=SHA1(WS), or is false. The dynamic password security login method has simple use, highly-effective security and low cost.
Owner:ZHEJIANG UNIV OF TECH
Lightweight target identification method and device based on rotating rectangular frame
ActiveCN108960230AFew parametersReduce complexityCharacter and pattern recognitionState of artAlgorithm
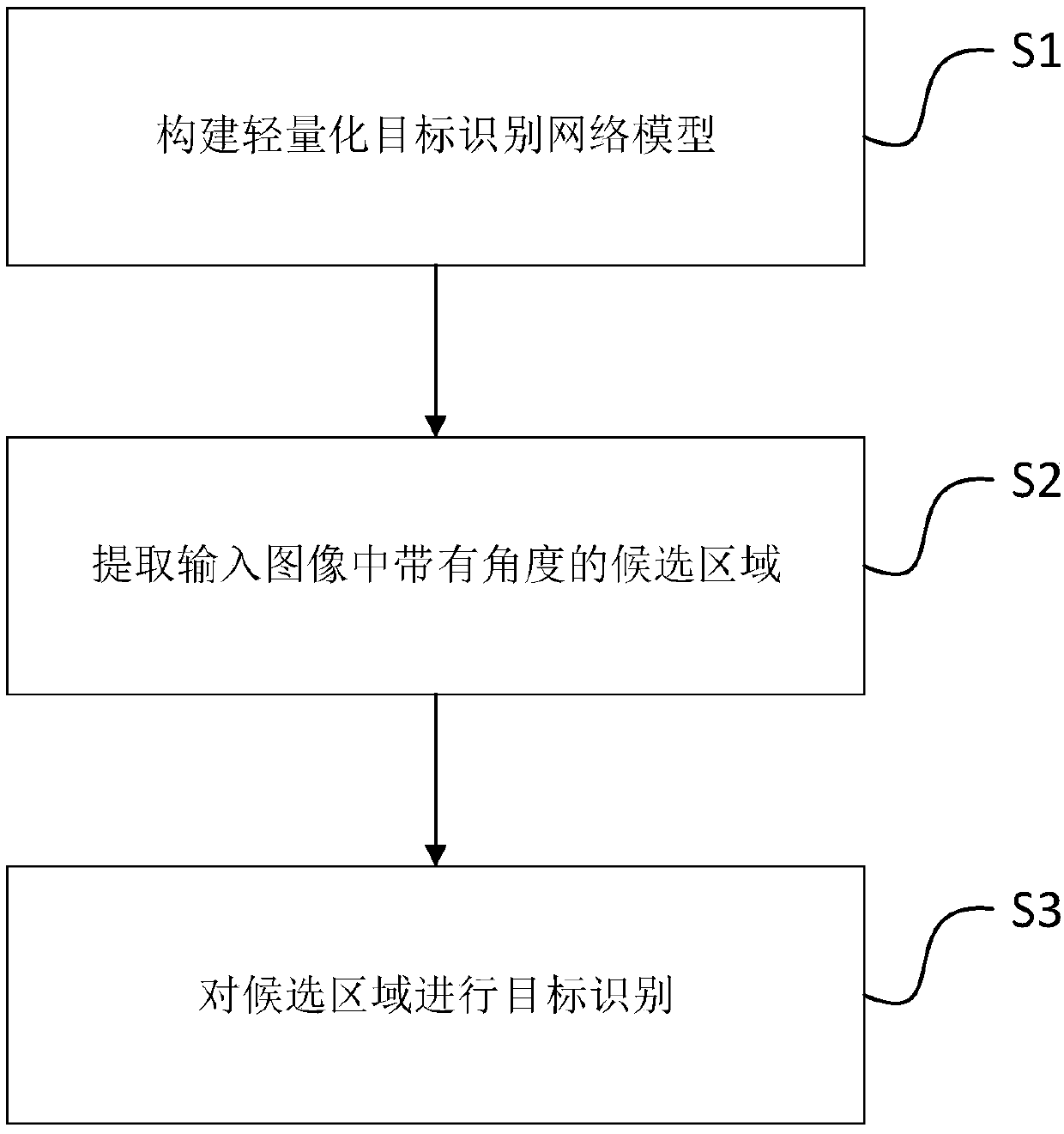
The invention belongs to the image analysis technology field and especially provides a lightweight target identification method and device based on a rotating area. In the prior art, the complexity ofa target identification algorithm is high and multiple angle targets are difficult to identify. In the invention, the above problems are solved. The invention provides a lightweight target identification method based on a rotating rectangular frame. The method comprises the following steps of based on a target identification network model constructed in advance, carrying out target identificationon an input image; and acquiring the target type of the input image. The target identification network model is constructed based on a convolutional neural network and comprises a target extraction module and a target identification module. In the invention, through merging and compressing the existing convolutional neural networks, network parameters are reduced and the complexity of the algorithm is decreased.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Laser line scanning 3D detection method and system based on scanning galvanometer and event camera
ActiveCN109458928ASimple algorithmSmall amount of calculationUsing optical meansGalvanometerLaser scanning
The invention belongs to the field of 3D detection and measurement, and particularly relates to a laser line scanning 3D detection method and system based on a scanning galvanometer and an event camera. The method comprises the following steps: the laser line is reflected to an object to be detected by the scanning galvanometer, so that laser line scanning is achieved; the event camera is adoptedto collect laser line signal information reflected from the object to be measured, and pixel points with changed brightness on the object to be measured and corresponding time points are stored and output; the position coordinate of the space point of the object to be detected scanned by the laser line at the moment is calculated through the relative position between the scanning galvanometer andthe event camera, the pixel point output in the step 2 and the scanning galvanometer rotation angle corresponding to the moment point corresponding to the pixel point; the steps are repeated to complete all space point coordinates of the object to be measured so as to obtain 3D point cloud data of the object to be measured, thereby solving the limitations of frame rate, resolution and illuminationresistance in the current 3D scheme.
Owner:XI AN ZHISENSOR TECH CO LTD
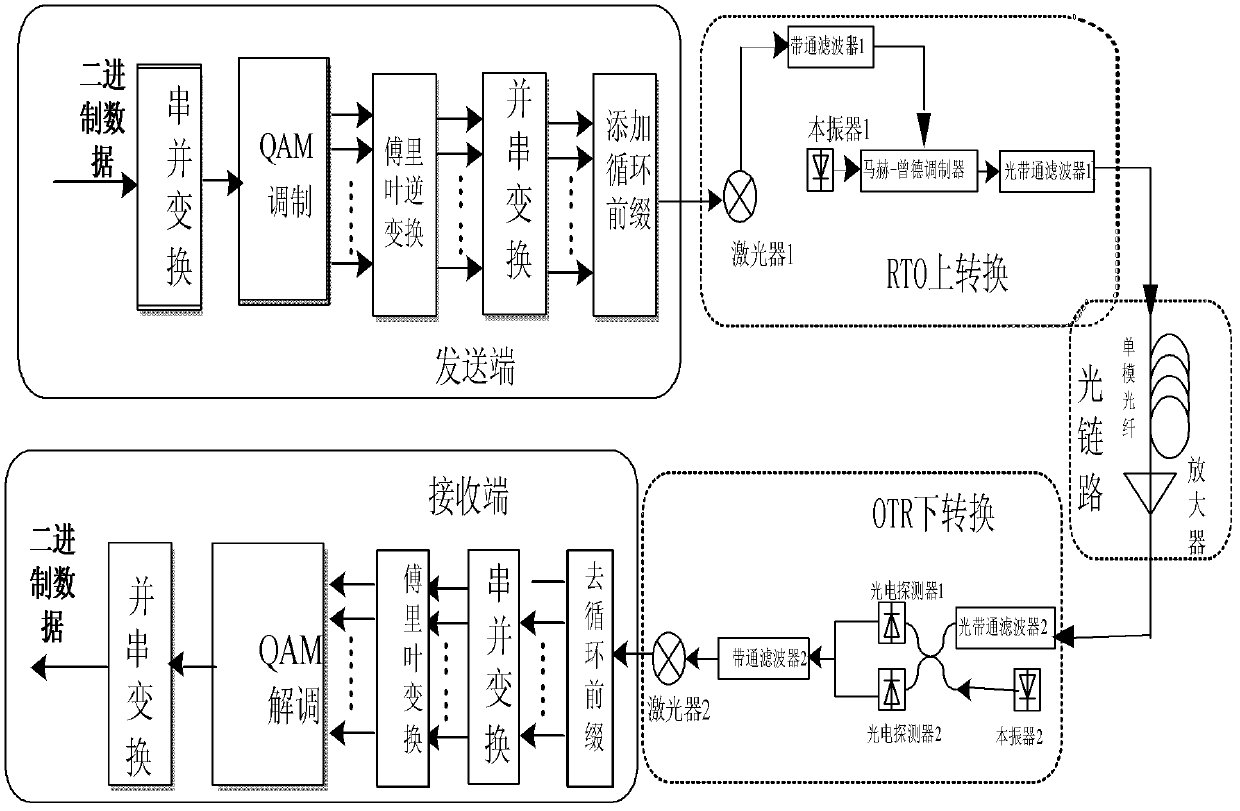
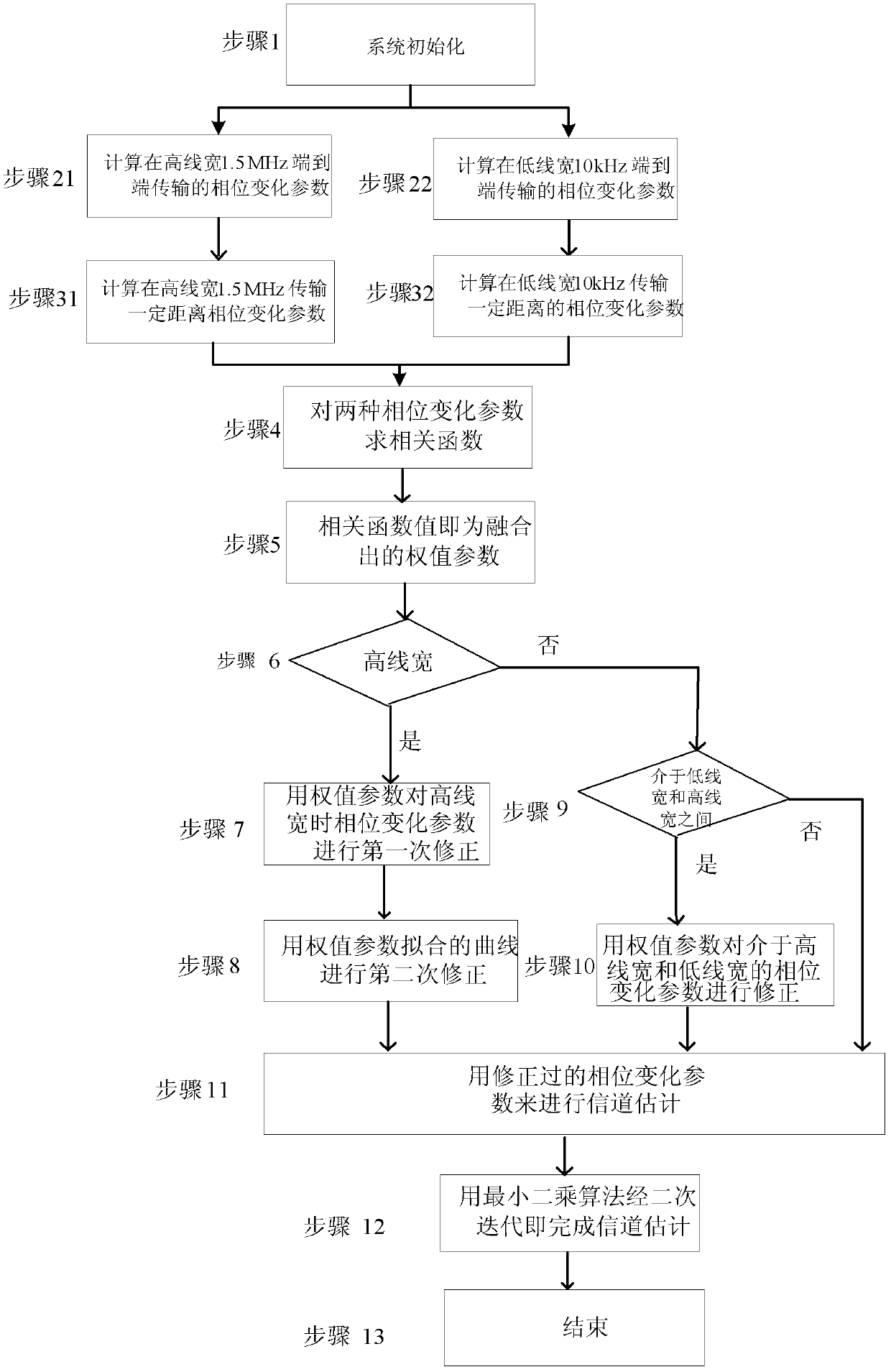
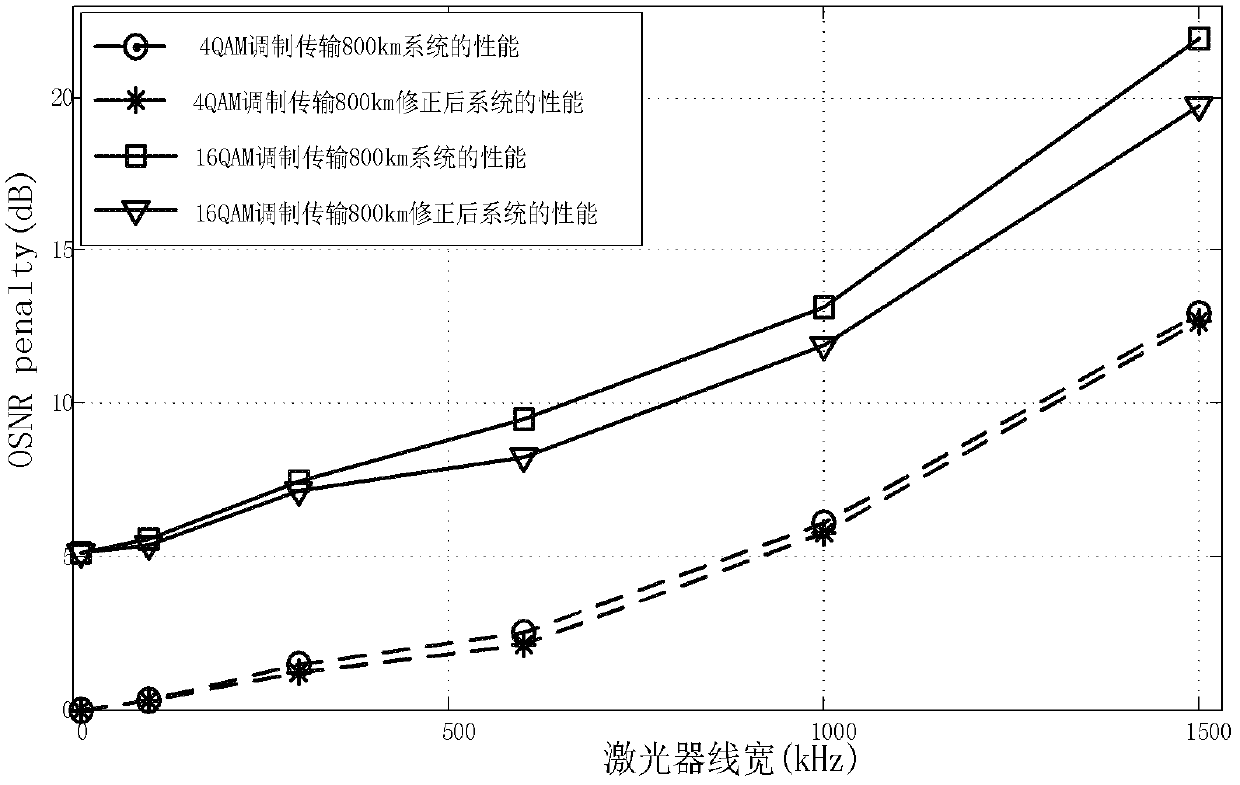
Channel Estimation Method under Phase Noise Compensation in Coherent Optical Orthogonal Frequency Division Multiplexing System
InactiveCN102281249AImprove performanceImprove system performanceMulti-frequency code systemsTransmitter/receiver shaping networksFiber-optic communicationPhysics
The invention relates to a channel estimation method under phase noise compensation in a coherent optical OFDM system, which belongs to the technical field of optical fiber communication and signal processing. The method includes: aiming at different linewidths of the laser, calculating the sum of the phase change parameters of the laser in the high linewidth and low linewidth transmission distance L, and the phase change parameter between the high linewidth and the low linewidth is, using The formula calculates the weight parameters of fusion. The phase change parameters between high line width and low line width and high line width are weighted and corrected respectively, and the phase change parameters of high line width can be corrected a second time according to the curve fitted by multiple weights . The least squares algorithm is selected, and the second iteration completes the estimation of the entire channel. Compared with other algorithms, the present invention can flexibly switch between high and low line widths of the laser, and achieve adaptive compensation of phase noise under different line widths by adjusting the weight coefficients, while significantly improving the high line width. wide system performance.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
False-inversion preventing control structure for anti-clamping system of vehicle window
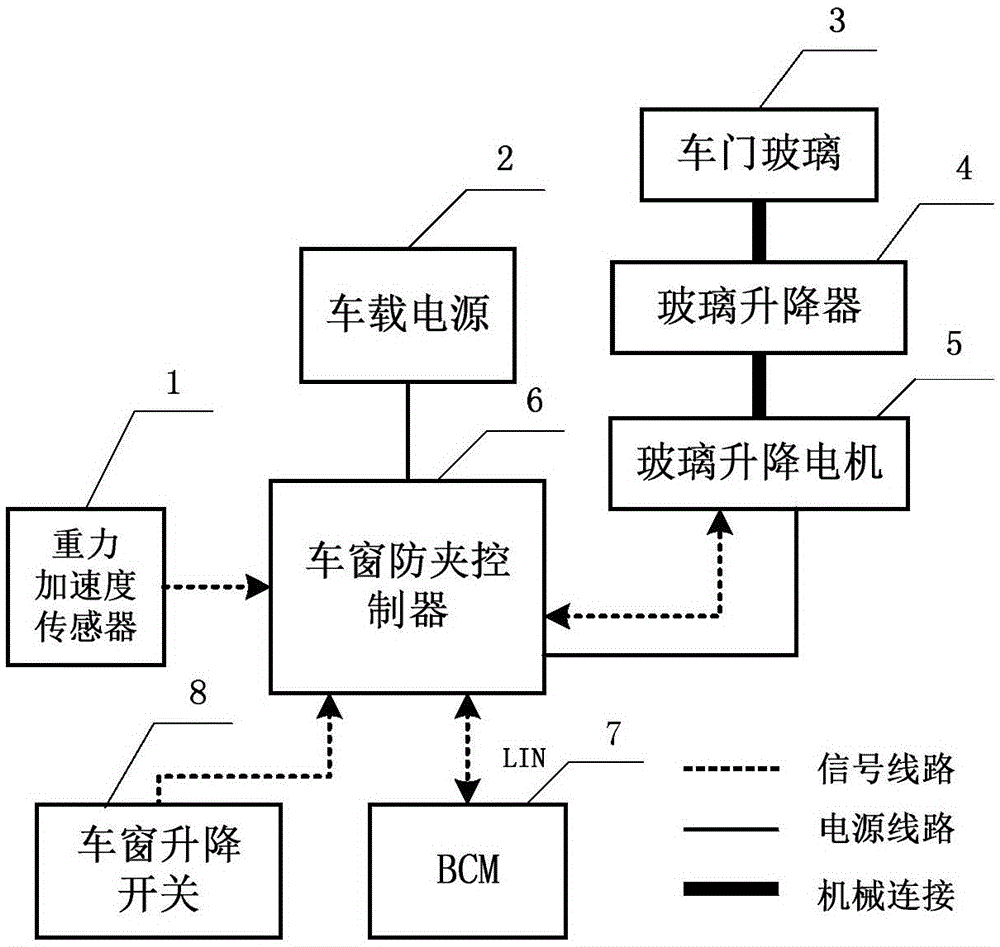
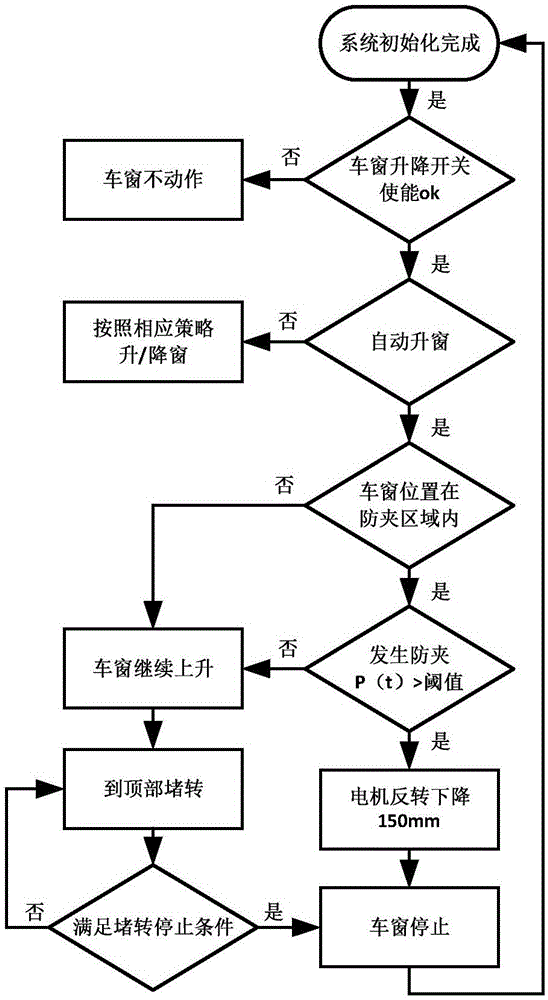
ActiveCN105064844AEliminate false reversalsImprove user experiencePower-operated mechanismCar doorElectric energy
The invention discloses a false-inversion preventing control structure for an anti-clamping system of a vehicle window. The false-inversion preventing control structure is characterized by comprising a vehicle-window anti-clamping controller, wherein the vehicle-window anti-clamping controller periodically acquires values of a gravity acceleration sensor, input signals of a vehicle-window lifting switch, and door-lock or control signals of a BCM; after the vehicle-window anti-clamping controller performs synthetic judgment, the electric energy of a vehicle-mounted power supply is input to a glass lifting motor by controlling a relay to be closed, the motor rotates and outputs torque, and a glass lifter is driven through a worm wheel and a worm, so that the glass on a vehicle door is driven to ascend or descend. Through the adoption of the structure disclosed by the invention, the change of gravitational acceleration of a vehicle in the perpendicular direction during running is directly detected, so that the false inversion generated by road surface factors is eliminated, and the using experience of users is improved; the demand of a system for the calculating amount of the controller is reduced; the disturbance resisting capability of the system is improved; and the reliability is improved.
Owner:CHERY AUTOMOBILE CO LTD
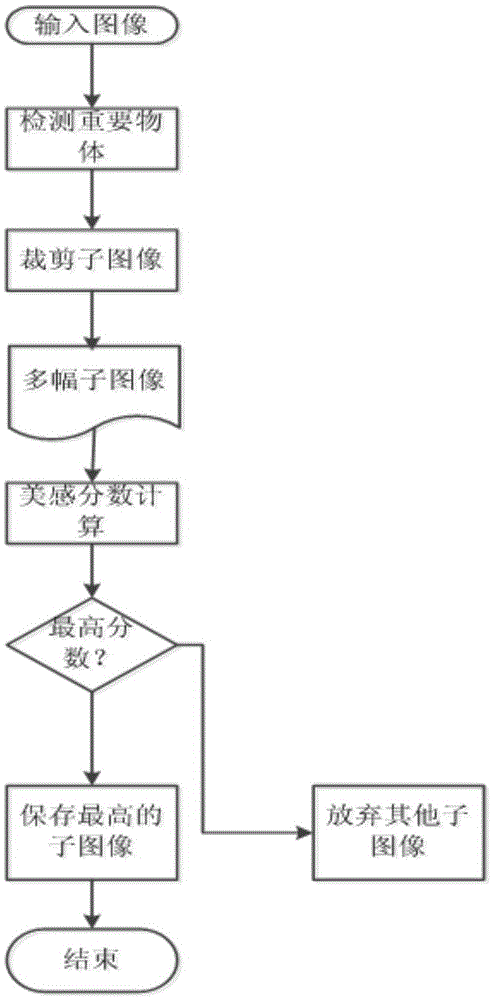
Content-based image aesthetic quality improvement method
InactiveCN105528757AImage aesthetic quality is simpleEasy to implementGeometric image transformationPattern recognitionDermabrasion
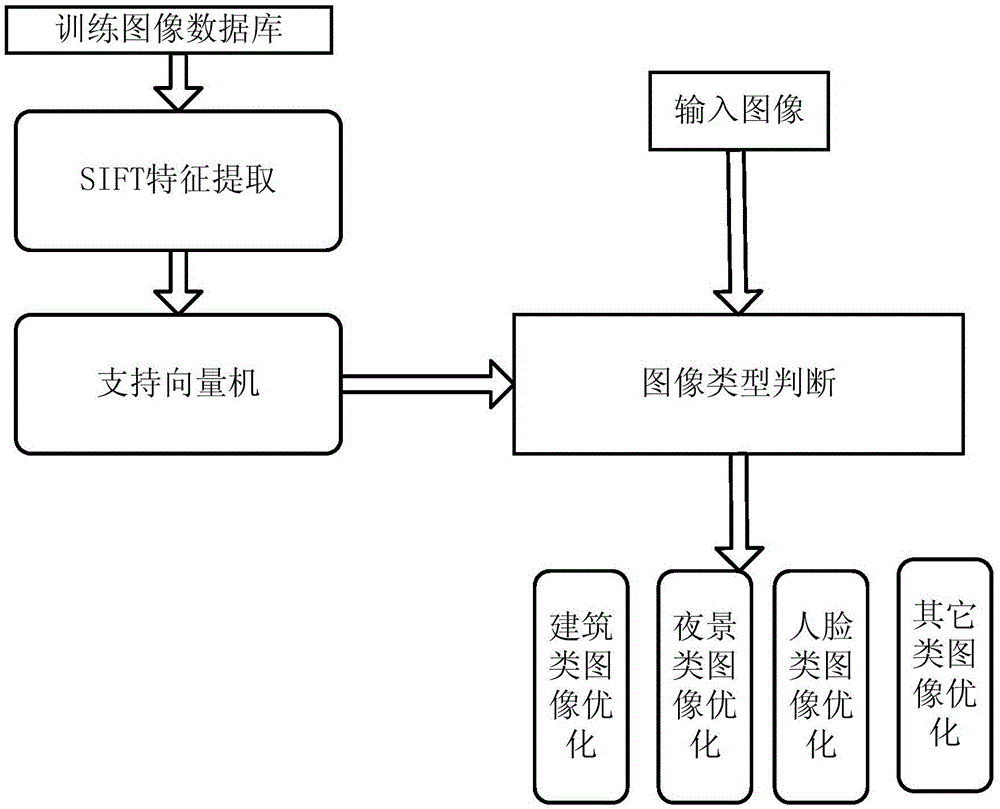
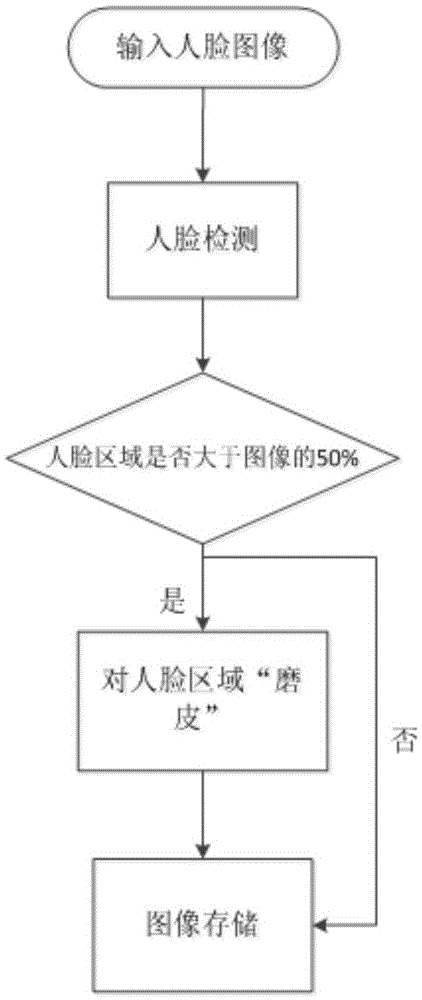
The present invention discloses a content-based image aesthetic quality improvement method. According to a pre-trained category classifier, images with the need of adjustment are subjected to the image classification of four categories, and the images are face category images, building category images, night scene category images and other types of images. For the four categories of images, the corresponding image aesthetic quality improvement is carried out. The face category images are subjected to face dermabrasion processing. The building category images are subjected to horizontal and vertical plane adjustment processing. The night scene category images are subjected to removing dynamic flur processing. The other types of images are subjected to image adjustment composition processing through image cropping. According to the method, the image aesthetic quality improvement is subjected to adaptive adjustment according to the image content, the algorithm realization is simple, and the method is easily adapted to a mobile terminal with weak computing ability to realize.
Owner:SOUTH CHINA UNIV OF TECH
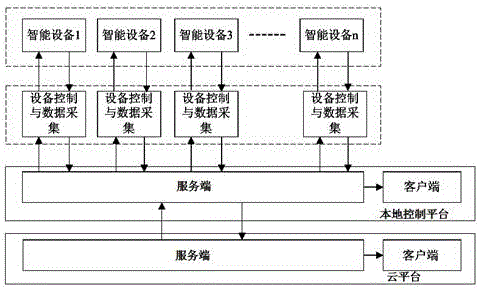
Service-oriented industrial production control and monitoring method and system
ActiveCN106774240ARealize hierarchical monitoringImprove learning effectElectric testing/monitoringResourcesInformation sharingClient-side
The invention discloses a service-oriented industrial production control and monitoring method and system. The system is mainly formed by intelligent devices, an intelligent device control and acquisition module, local control platform servers, local control platform clients, a cloud platform server, and a cloud platform client. Services provided by different production server providers are combined and planned by high-efficiency production process planning, local control platforms and a cloud platform perform graded monitoring and information sharing on the intelligent devices, each local control platform dynamically updates fault determination conditions to the cloud platform, the cloud platform performs synchronization with the local control platforms regularly, the learning ability and the online upgrading ability of the intelligent devices can be improved, the fault detection ability and the fault early warning ability of the intelligent devices are improved, the system represents combination of intelligent production, intelligent factories, and intelligent business, the production management is more efficient, and the system is an important composition of intelligent manufacture.
Owner:SOUTH CHINA UNIV OF TECH
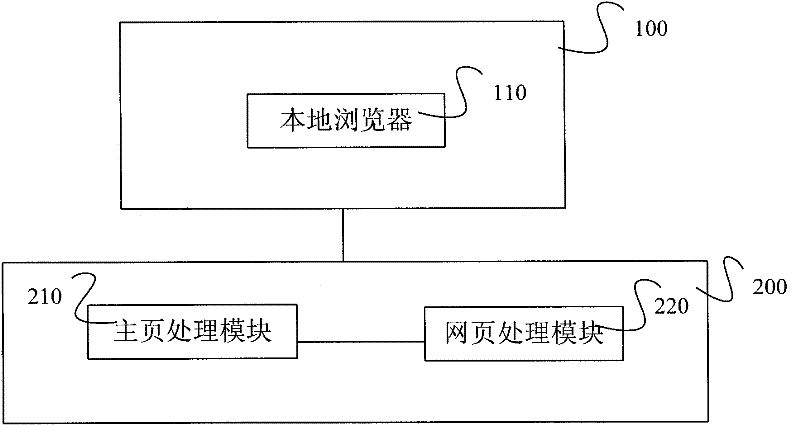
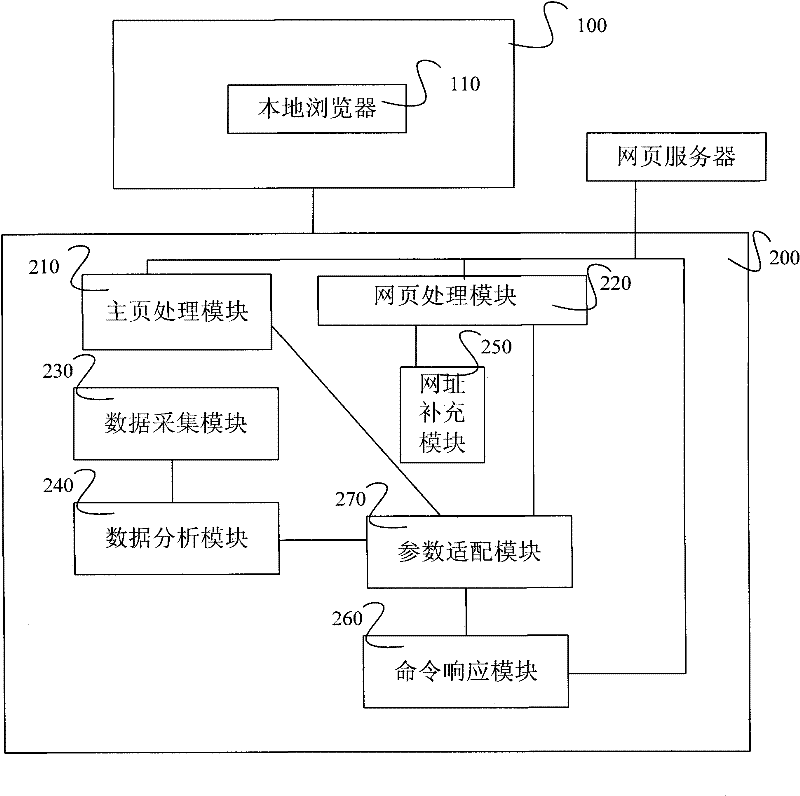
Implementation method and system thereof for intelligent browser of mobile terminal
ActiveCN102163196AReduce computing requirementsMeet the corresponding parameter requirementsSubstation equipmentEnergy efficient computingComputer terminalWeb page
The invention relates to an implementation method and a system thereof for an intelligent browser of a mobile terminal. The method comprises the following steps that: step 1, the mobile terminal obtains an intelligent browser homepage from an intelligent browsing system, wherein the intelligent browser homepage comprises a functional region and a page region; step 2, after obtaining the intelligent browser homepage, the mobile terminal transmits a webpage obtaining request to the intelligent browsing system through the intelligent browser homepage while being needed to browse the webpage; step 3, the intelligent browsing system receives the webpage obtaining request of the mobile terminal, obtains the webpage requested by the mobile terminal, embeds the obtained webpage requested by the mobile terminal into the page region of the intelligent browser homepage and transmits the intelligent browser homepage embedded with the webpage to the mobile terminal; step 4, a mobile terminal localbrowser receives the intelligent browser homepage, and parses and represents the intelligent browser homepage. The implementation method and the system thereof for the intelligent browser of the mobile terminal can migrate the capability of the terminal to a network side through a web edition browser, so that operation requirements on the terminal are reduced, and power consumption is also reduced.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
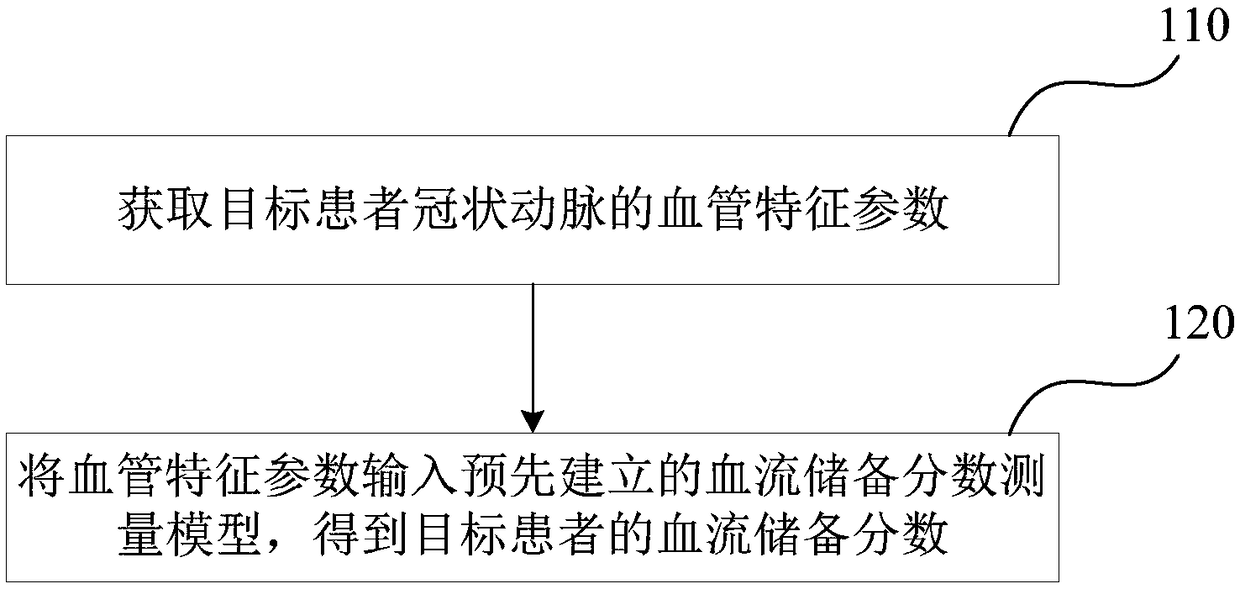
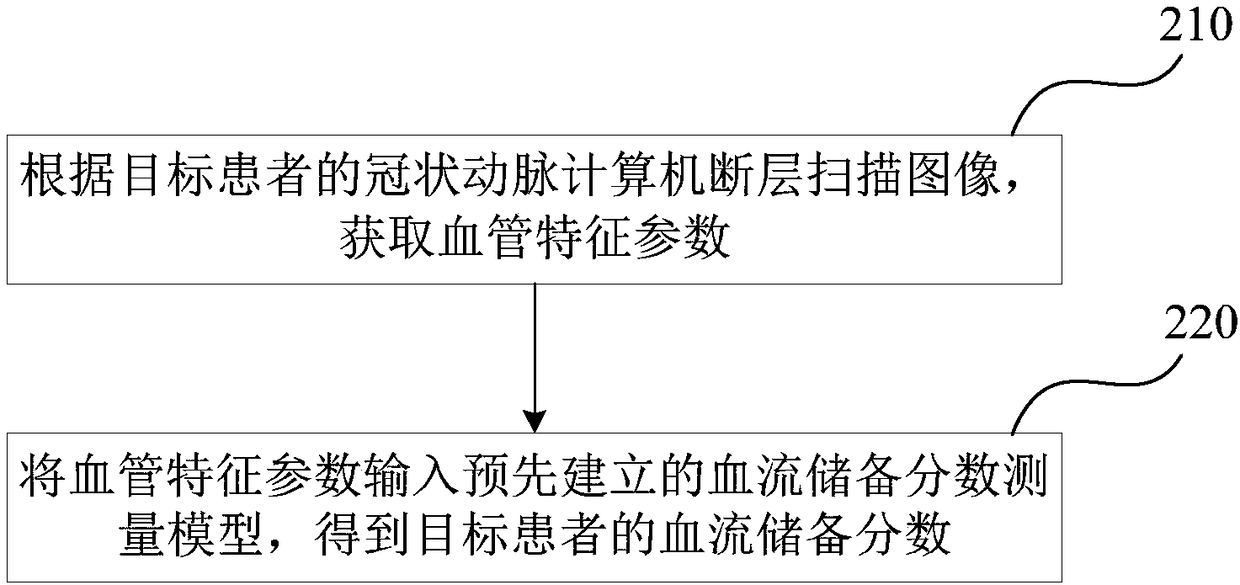
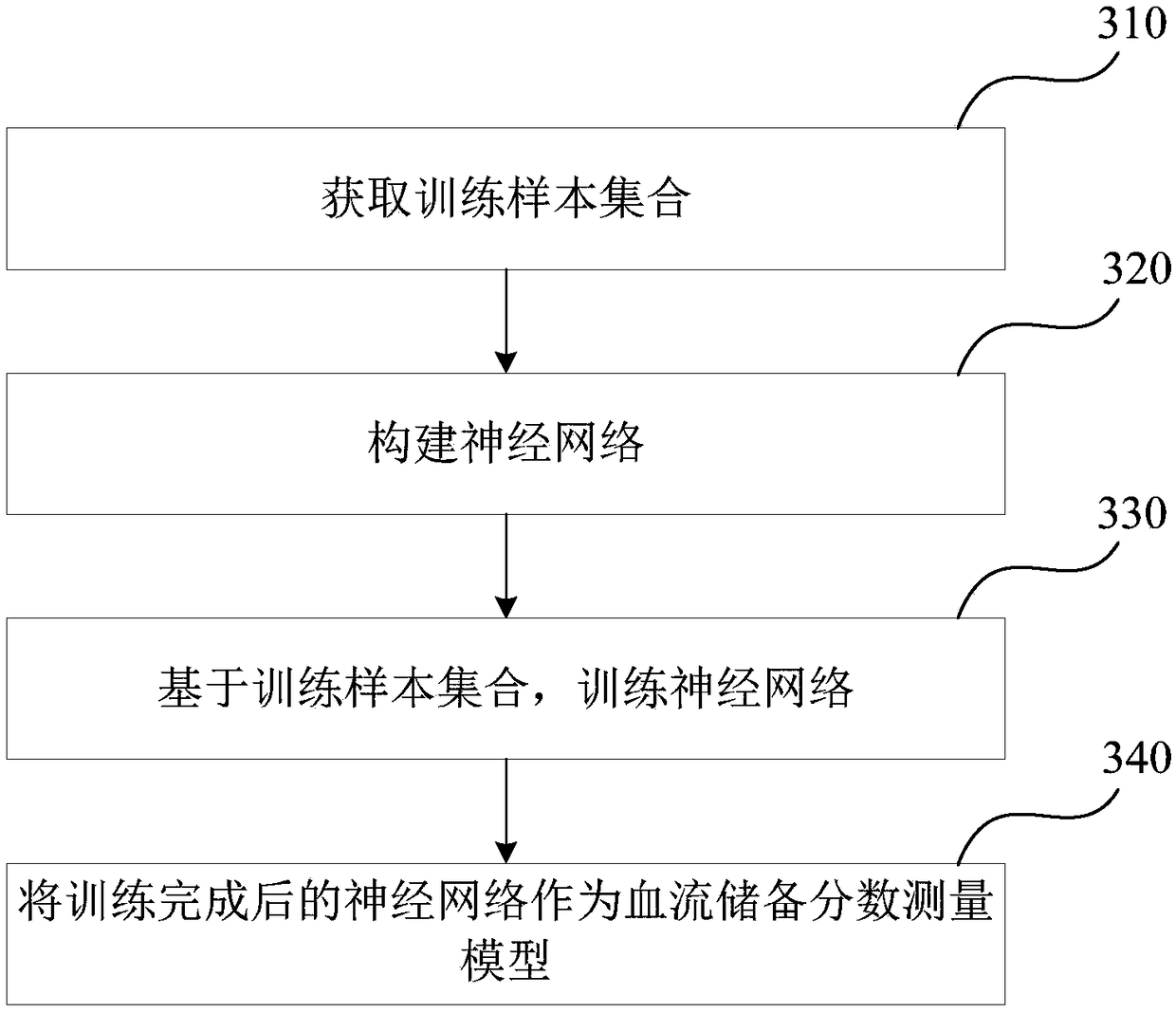
Method and device for measuring fractional flow reserve
ActiveCN108451540ANo need to useQuick measurementComputerised tomographsTomographyCoronary arteriesRadiology
The invention discloses a method and a device for measuring fractional flow reserve. The method comprises: obtaining a blood vessel characteristic parameter of a target patient's coronary artery, wherein the blood vessel characteristic parameter includes a blood vessel cross section radius of a set position and a stenotic characteristic parameter of a stenotic area of the coronary artery; inputting the blood vessel characteristic parameter into a pre-established fractional flow reserve measurement model, to obtain the fractional flow reserve of a target patient. The method and the device solveproblems that time consumption for measuring the fractional flow reserve and requirement for equipment calculation are high, and the method and the device can measure the fractional flow reserve efficiently and accurately in real time.
Owner:SHENZHEN INST OF ADVANCED TECH
System, method and apparatus for searching geographic area using prioritized spatial order
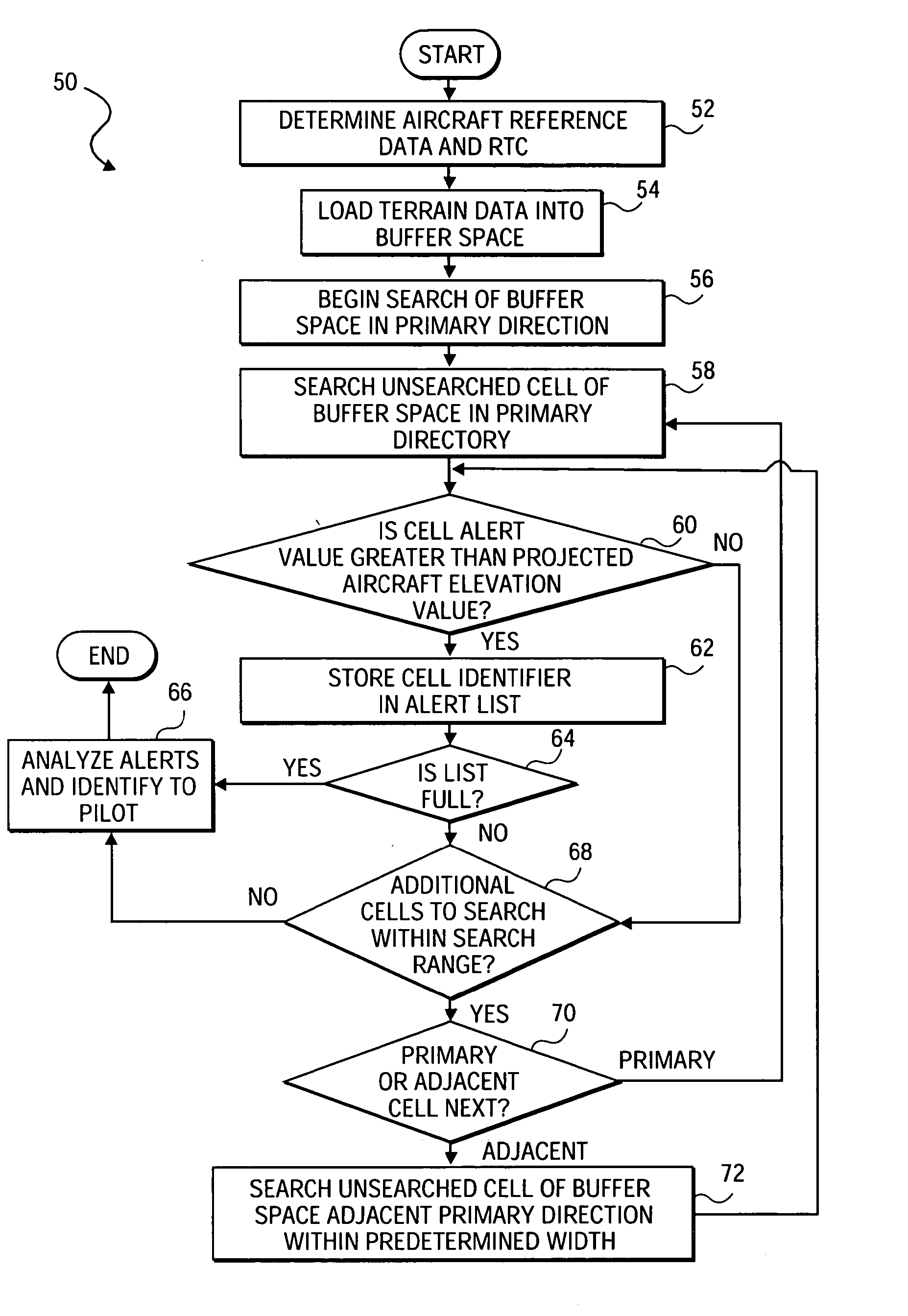
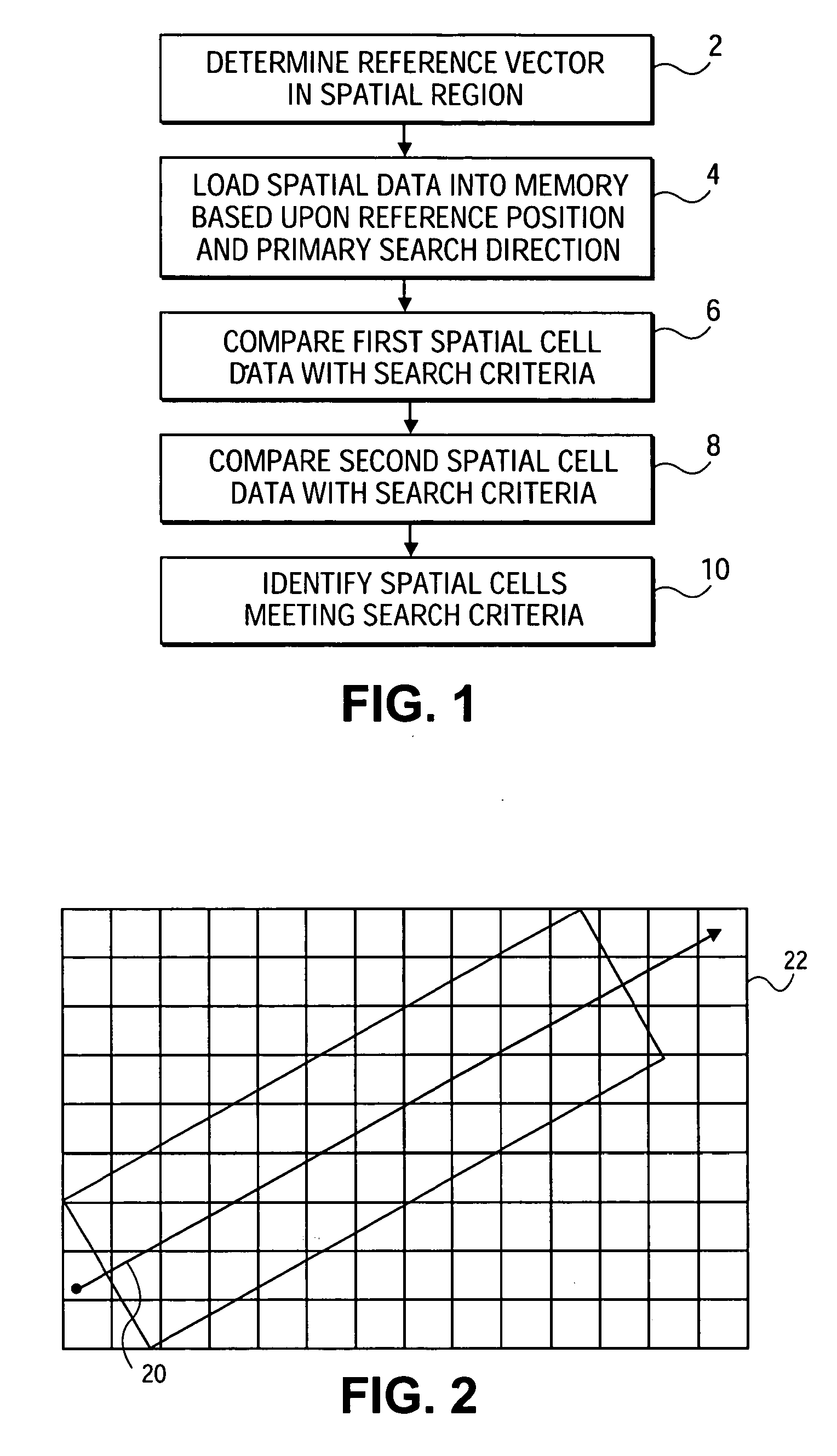
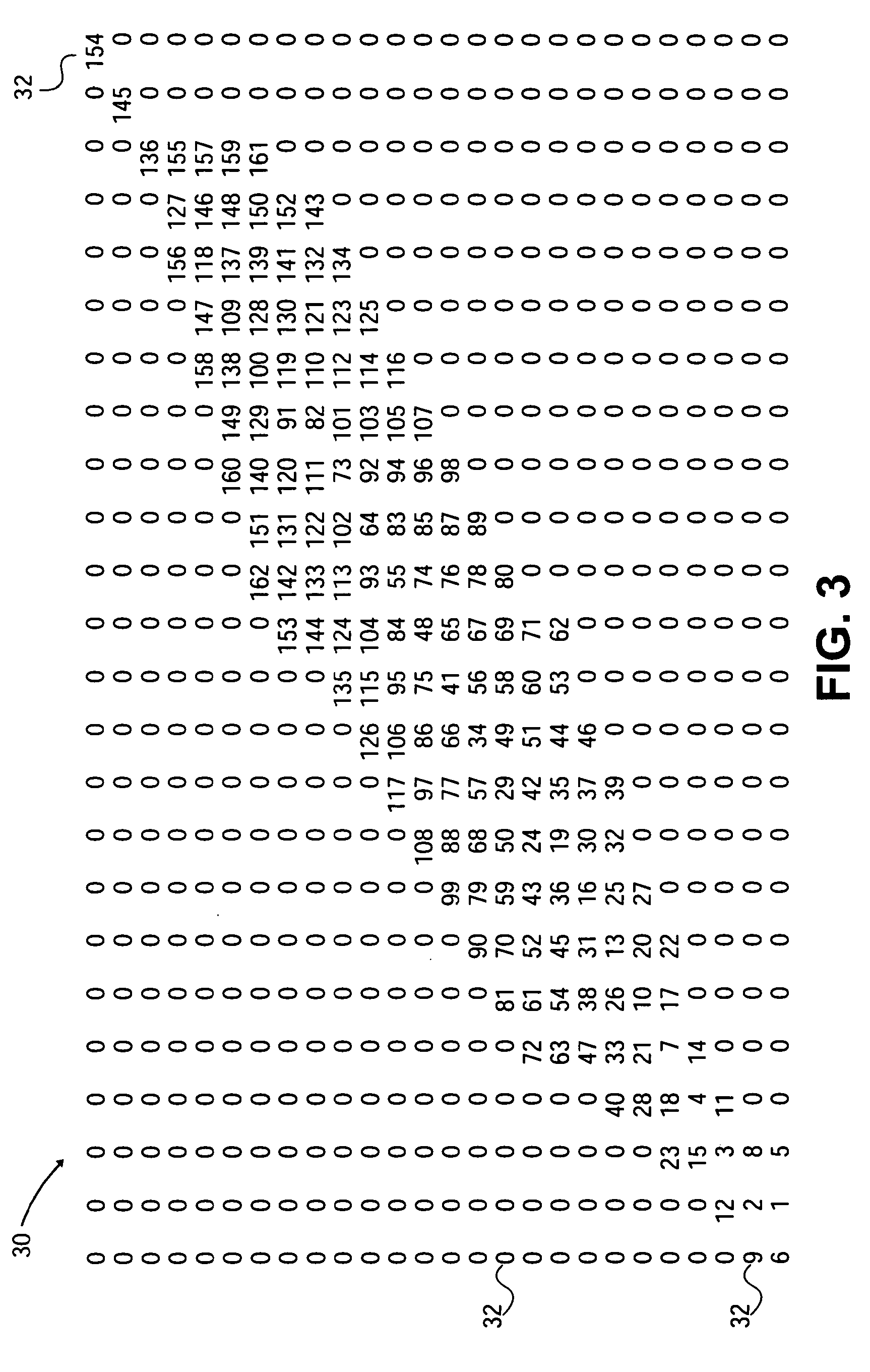
InactiveUS20080103691A1Reduce processReduce computing requirementsInstruments for road network navigationRoad vehicles traffic controlData bufferGeographic area
A spatial data search method, system and apparatus for identifying particular data of significance around a reference vector through the spatial data. The method involves determining a reference vector within a spatial region for which spatial data exists, loading a portion of the spatial data including the data around the reference vector into a memory buffer, and searching the spatial data in a prioritized order. The method, system and apparatus have particular utility in searching geographic data for a terrain awareness and warning system (“TAWS”) and display in an aircraft. Embodiments of the present invention provide advantages over existing sequential and radial search methods, significantly reducing the processing and calculations required and providing faster alerts to pilots.
Owner:GARMIN INT
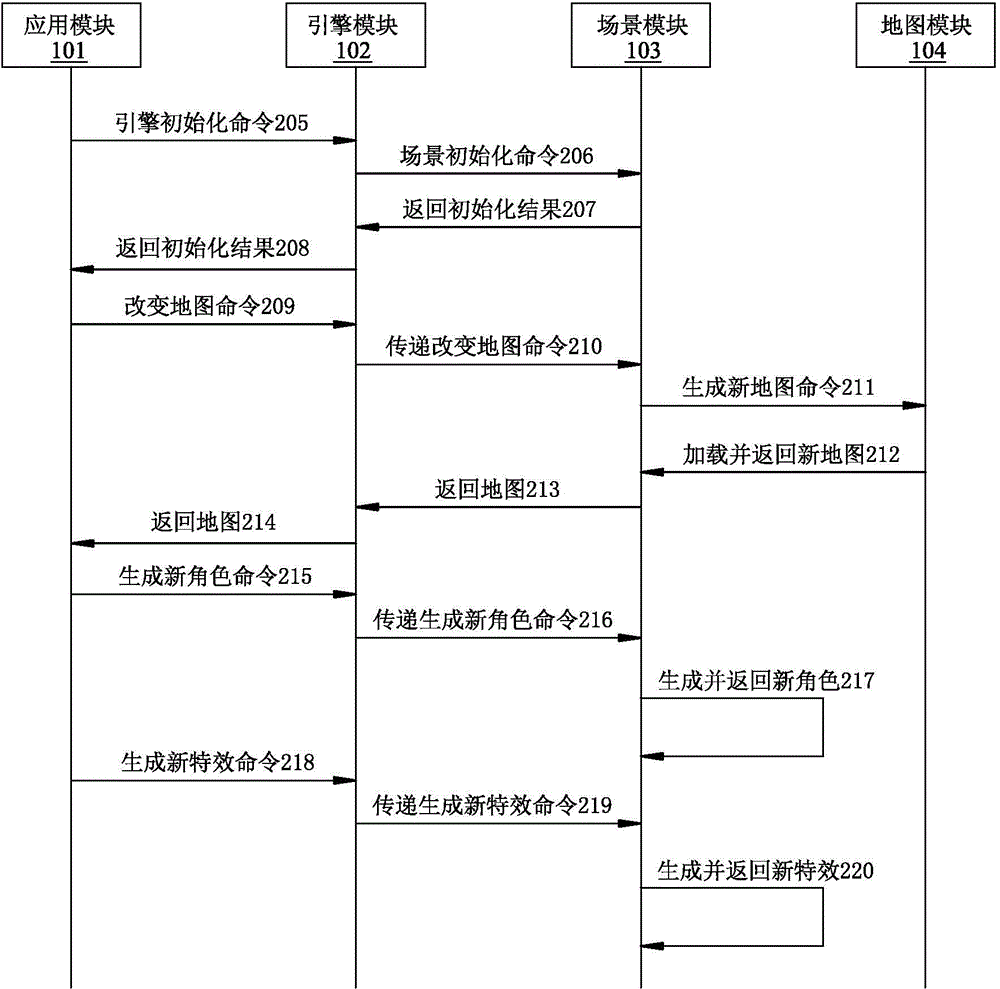
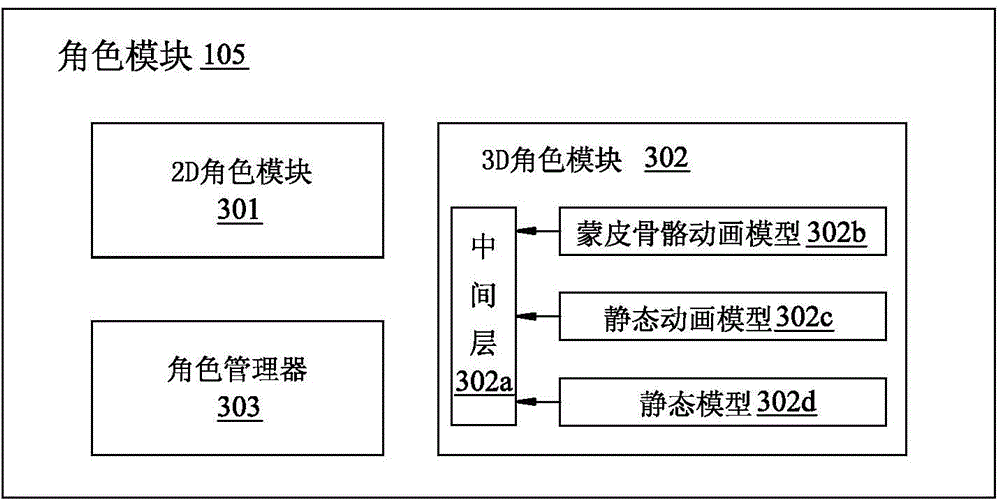
Game engine system and call method for exploiting 2D scene and 3D role
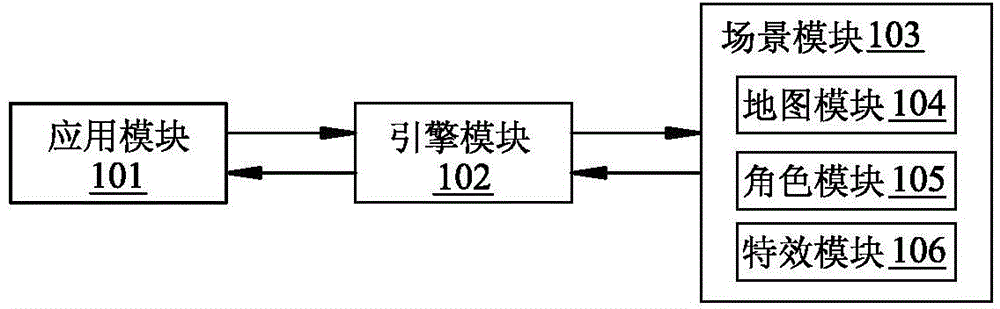
ActiveCN104958900AReduce computing requirementsStrong development functionAnimationVideo gamesSimulationComputer module
The invention provides a call method for a game engine system and the game engine system for exploiting a 2D scene and a 3D role. The game engine system comprises an application module, an engine module and a scene module. The call method comprises the steps that 1 initialization is conducted on the engine module through the application module; 2 the application module sends an order of changing a map to the engine module, the scene module sends an order of generating the new map to call a map module, and the 2D-scene map is loaded and is returned to the scene module; 3 the application module sends an order of generating a new role to the engine module, and the scene module calls a role module to generate a new 2D or 3D role and return the new 2D or 3D role to the scene module according to the order of generating the new role; 4 the application module sends an order of generating a new special effect, and the scene module calls a special-effect module to generate a new 2D or 3D special effect and return the new 2D or 3D special effect to the scene module according to the order of generating the new special effect.
Owner:乐道互动(北京)软件技术有限公司
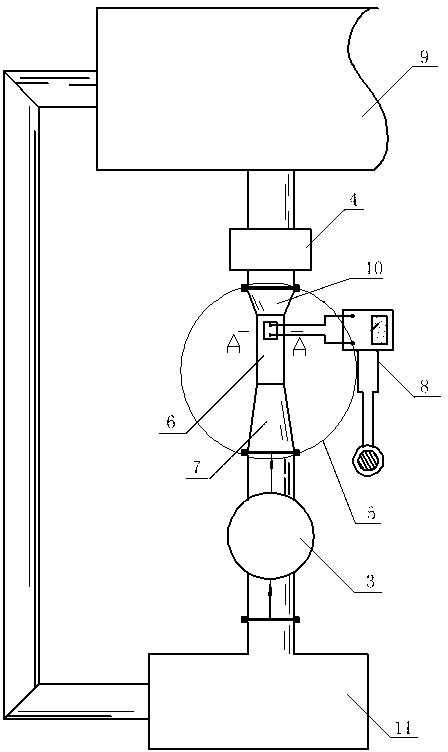
Device and method for detecting drilling fluid return flow
The invention discloses a device and a method for detecting drilling fluid return flow. The device comprises one or more flow measuring short sections (5) arranged between a drilling fluid return port (3) of a shaft and a vibration screen (4); the flow measuring short sections comprise a rectangular-cross-section overflow section (6) and a horn mouth buffer section at two ends of the rectangular-cross-section overflow section (6); a fluid level sensor (1) is installed on the top of the rectangular-cross-section overflow section (6); a flow speed sensor (2) is installed inside the internal fluid in the rectangular-cross-section overflow section (6); and the fluid level sensor (1) and the flow speed sensor (2) are respectively connected with a calculation and display alarming unit (8) electrically. With the adoption of the device and method for detecting the drilling fluid return flow, the problems that an existing mud return flow measuring device is not high in precision, delayed in reaction, larger in error especially when the flow is smaller and the like are solved; the measuring section adopts a rectangular cross section that the fluid level and the height are in linear change; the requirements of flow detecting equipment on the calculation means are reduced; and the device and method for detecting drilling fluid return flow is high in measurement precision and good in timeliness.
Owner:SOUTHWEST PETROLEUM UNIV
System and method for detecting product shape integrity based on asynchronous time domain vision sensor
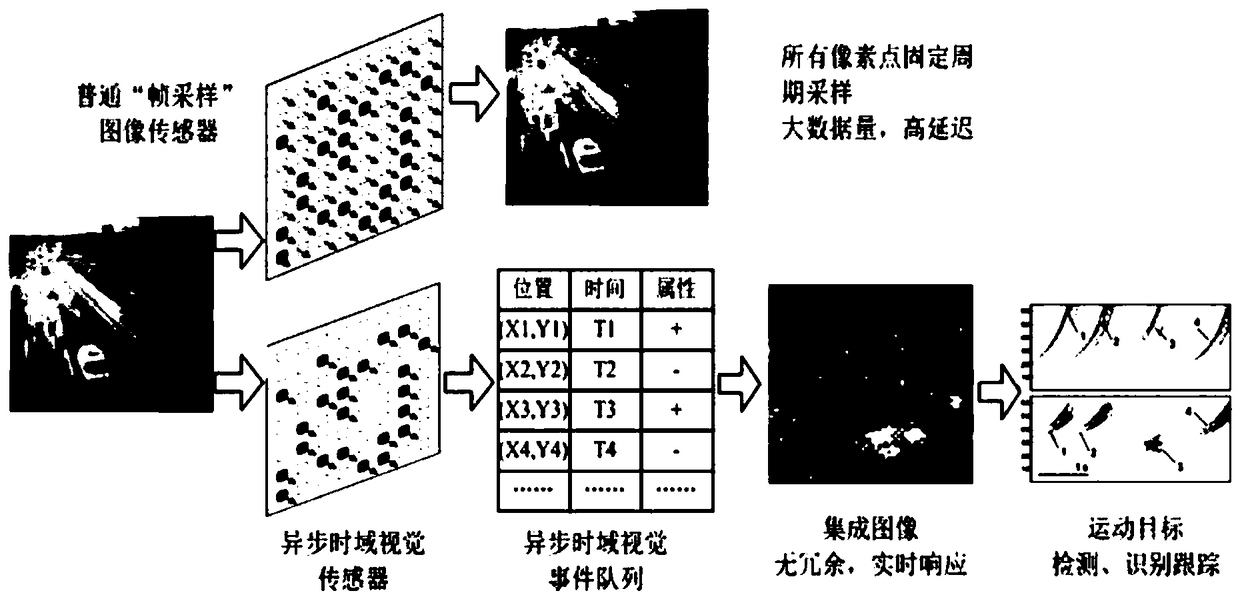
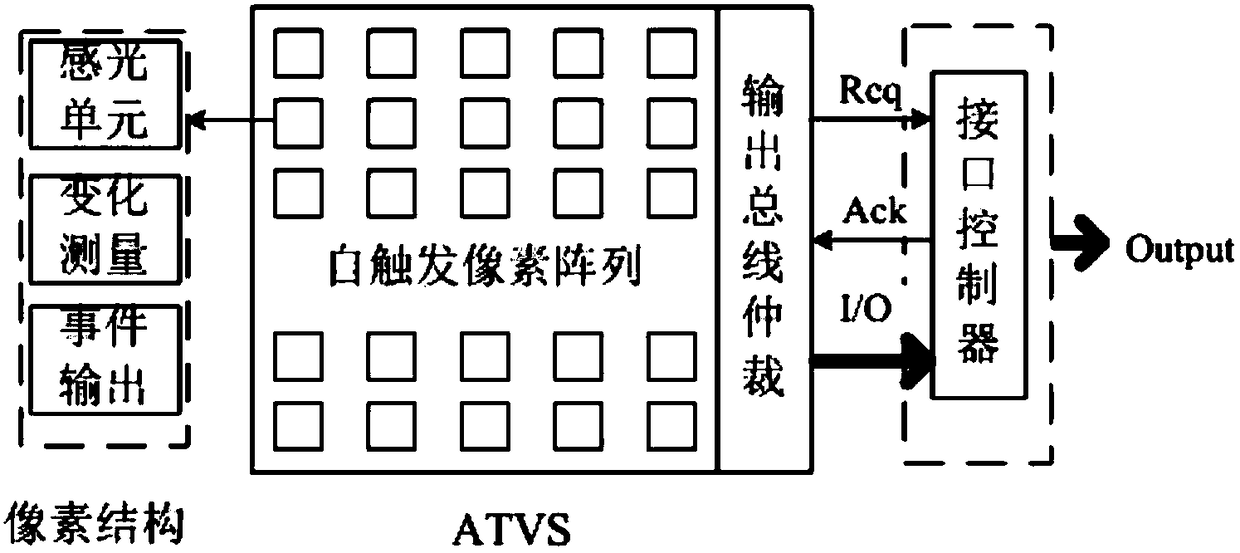
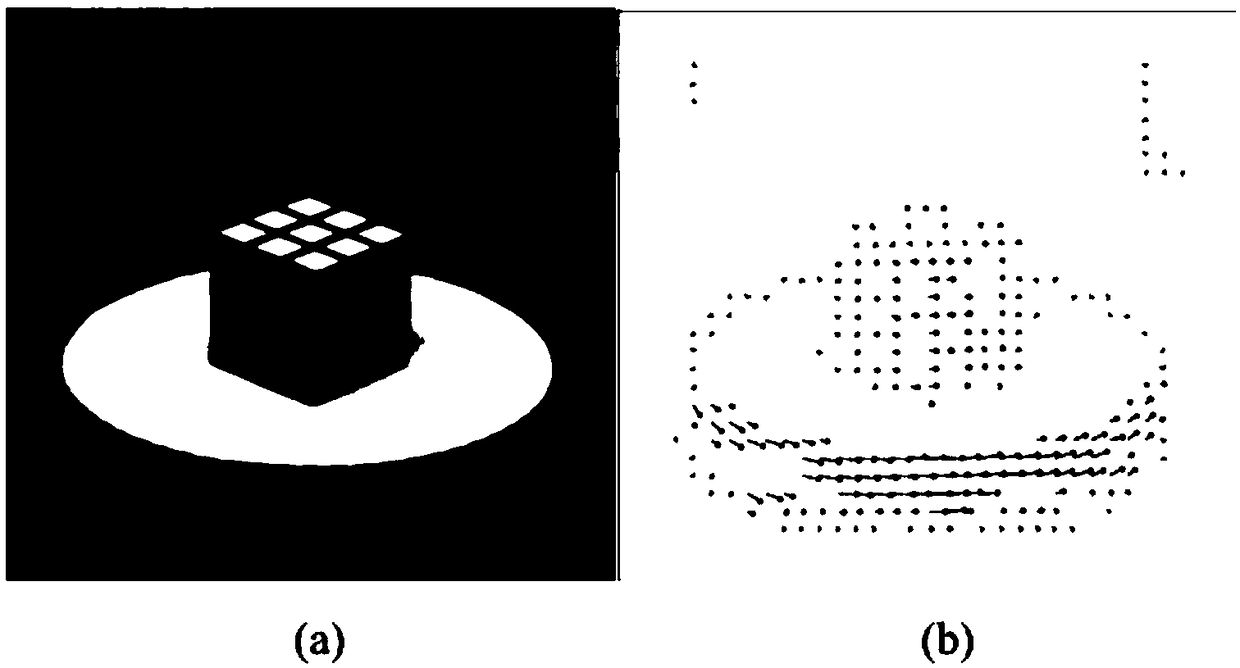
InactiveCN105203045AReduce computing requirementsReduce storage requirementsUsing optical meansTime domainTemporal vision
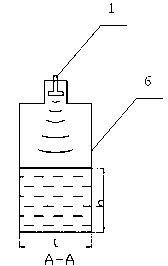
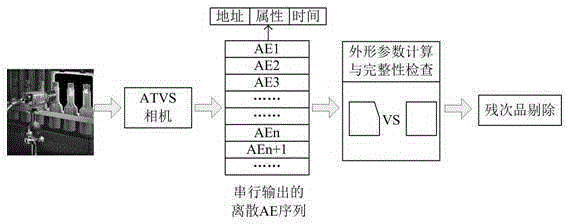
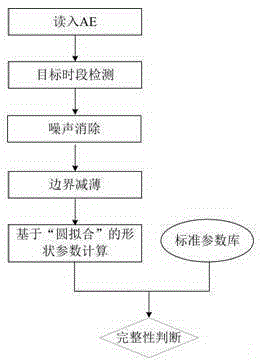
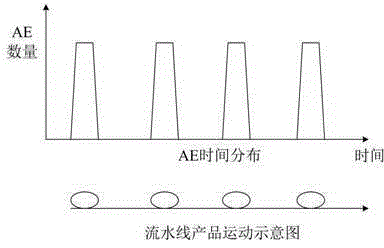
The invention discloses a system and a method for detecting the product shape integrity based on an asynchronous time domain vision sensor. The method comprises an algorithm for checking the integrity of an overall structure of the system and the product shape. The overall structure of the system comprises a camera adopting a time domain vision sensor and a processing portion containing a caching and calculating unit. A software algorithm takes activity events outputted by a TVS (temporal vision sensor) as input, and AE (activity event) sets with the address and the time being discrete represent actual products moving on an assembly line. Shape parameters of each moving object are calculated according to address distribution conditions of each AE set, and checking for the product shape integrity is realized through comparing the parameters reflecting the product shape with shape parameters of an integral product. Compared with an existing system, the system disclosed by the invention has significant performance and cost advantages and has wide application prospects.
Owner:TIANJIN NORMAL UNIVERSITY
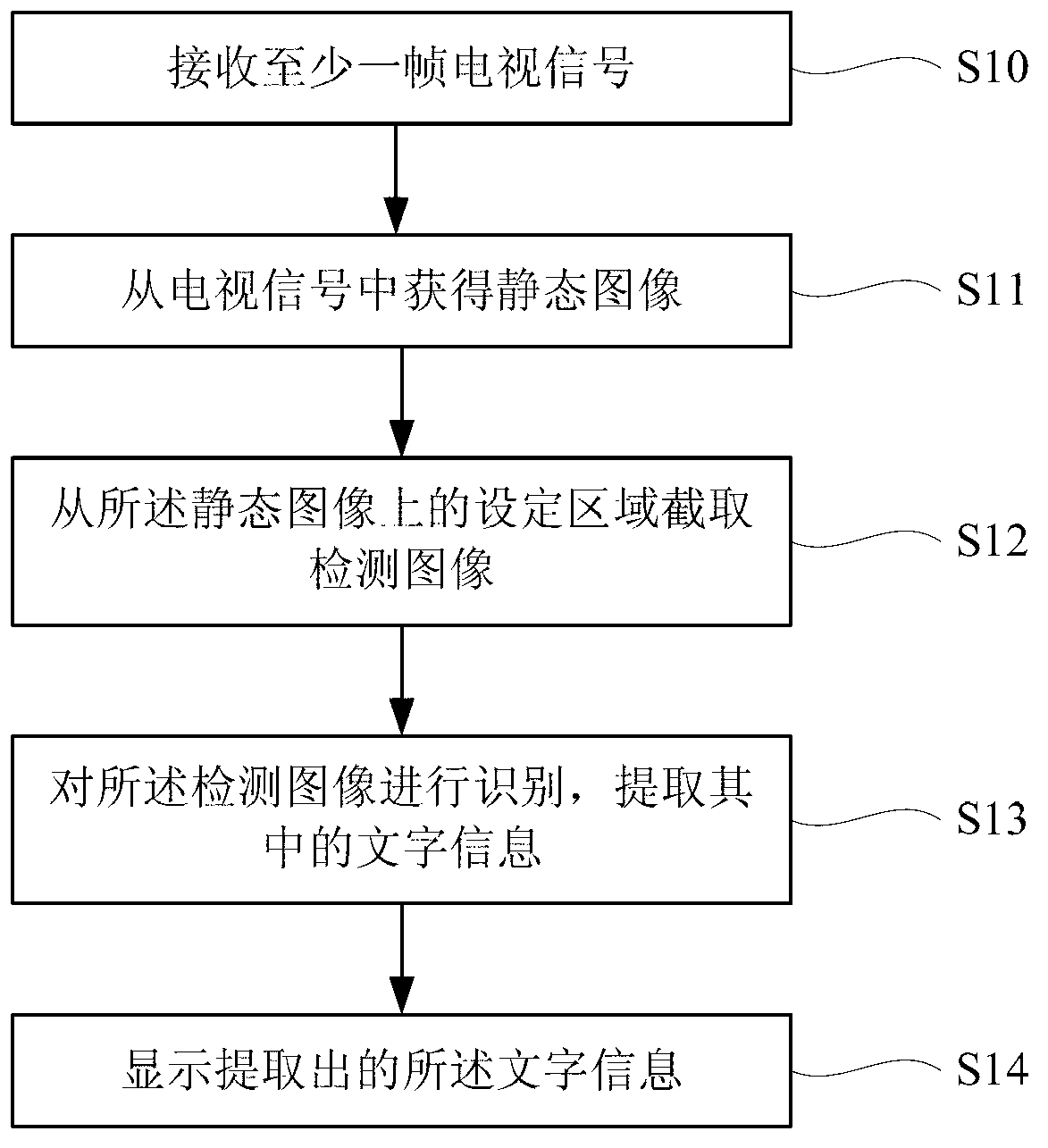
Method for extracting and displaying text messages from television signal and television
ActiveCN102802074AEasy extractionReduce computing requirementsCharacter and pattern recognitionSelective content distributionTelevision setVIT signals
The invention discloses a method for extracting and displaying text messages from a television signal and a television. The method comprises the steps of: receiving at least one frame of television signal; obtaining a static image from the television signal; intercepting a detection image from a set region on the static image, wherein the set region covers the text messages on the static image; identifying the detection image, extracting the text messages; and displaying the extracted text messages. According to the invention, specially aiming at the characteristics of the text messages on a television image, through intercepting a part on the static image, including texts, the detection image with a smaller detection region is formed; therefore, compared with the prior art, the method has the advantages of reducing operation requirements, and increasing identification efficiency; and according to the particularity of the television signal, through comparing two frames of images, an image background can be removed, and the text messages can be conveniently extracted.
Owner:HISENSE
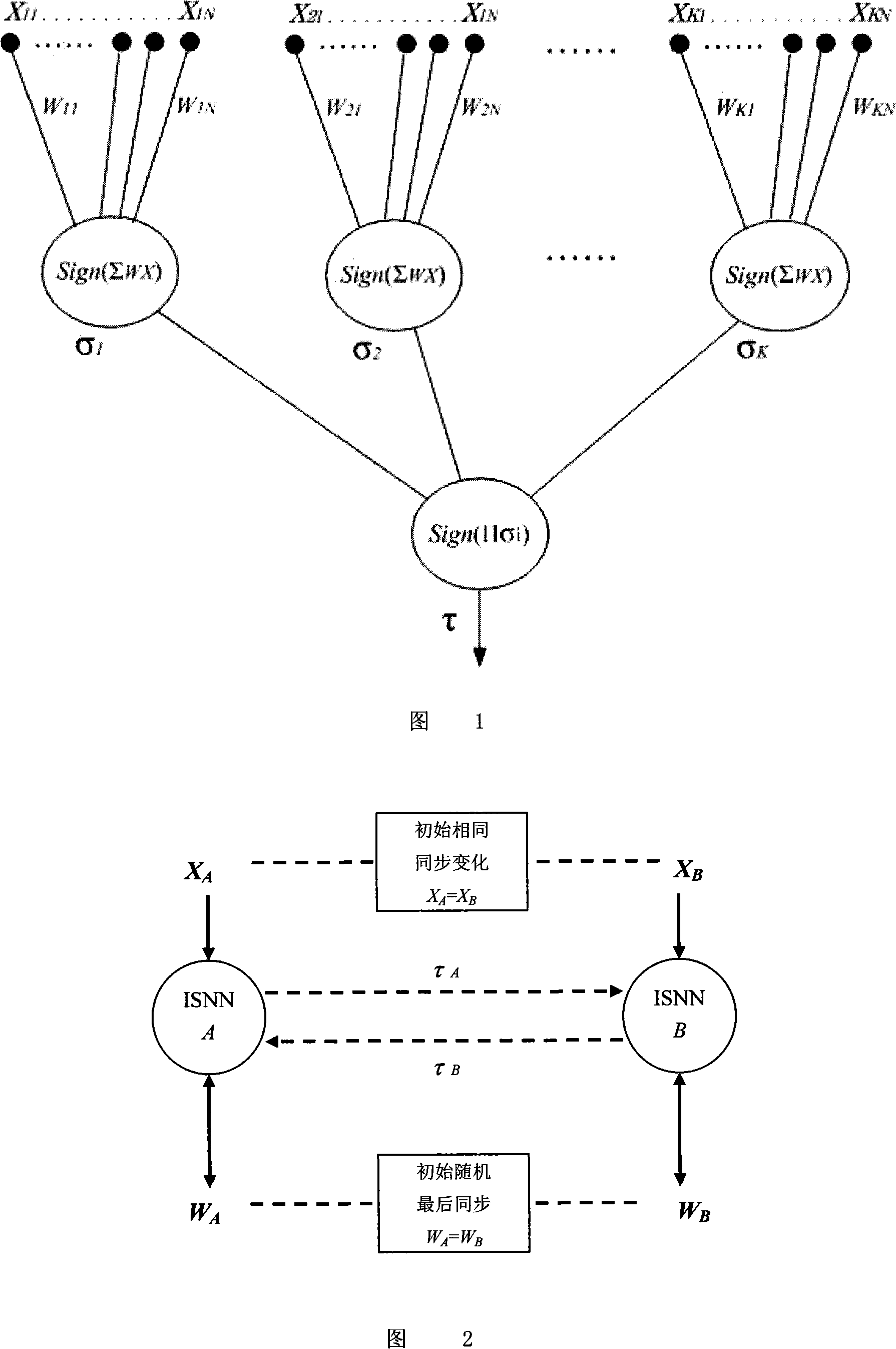
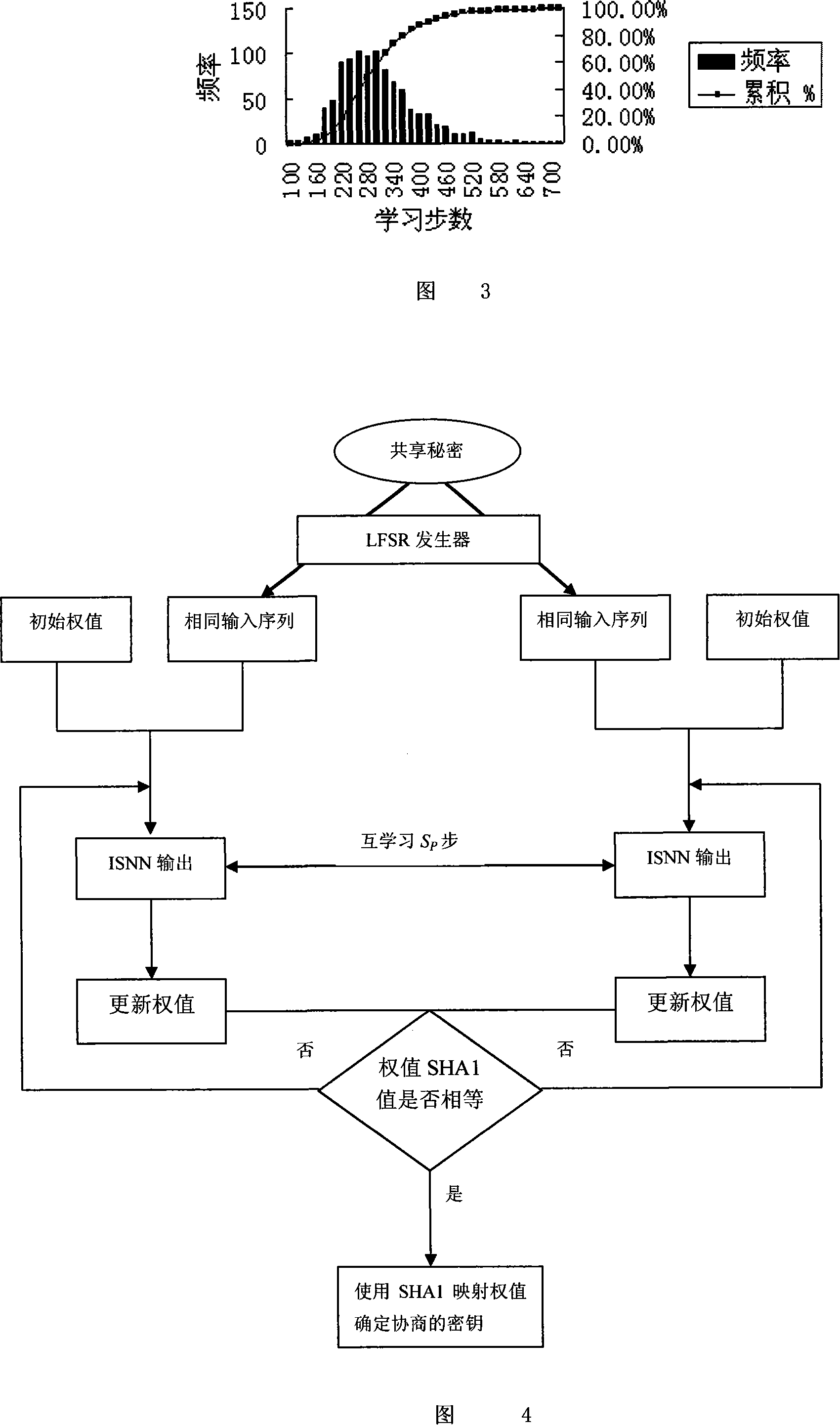
Neural network weight synchronization based lightweight key negotiation method
InactiveCN101141248AReduce computing requirementsFast executionKey distribution for secure communicationPublic key for secure communicationNerve networkOperand
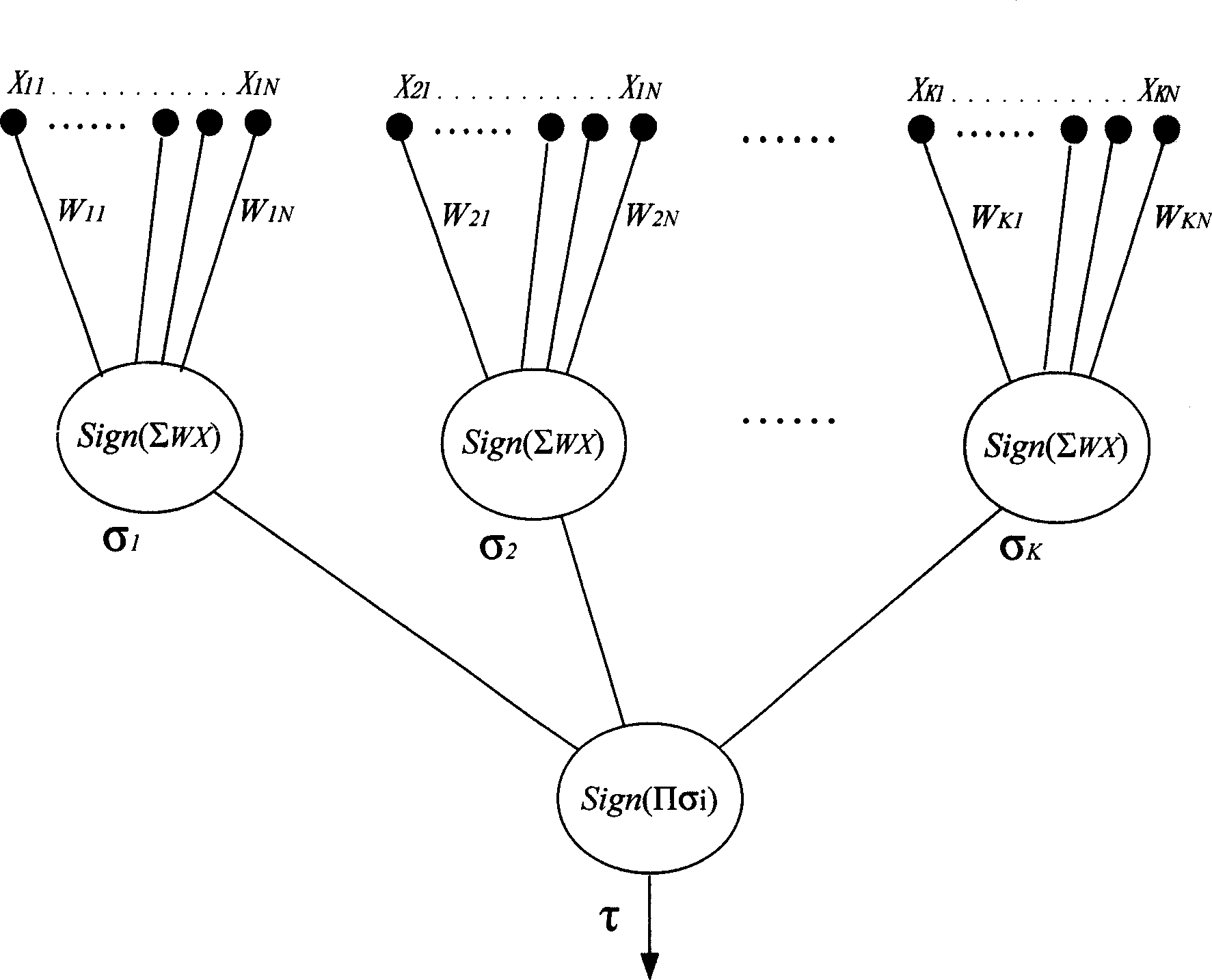
A neural network weight value synchronization-based lightweight key consultation method of which two neural networks with the same input perceptions are interacted, namely, the continuous renew of the weight value vector output, so as to realize the weight value of two neural networks. Based on the traditional random number generator LFSR and Hash algorithm SHA 1, the perception neural network is discretized and extended to the multilayered model, while the synchronic property of weight value is unchanged. Thus, the synchronic weight value can be mapped to the conversation key, which means the key coordination and renew can be applied. The utility model provides a synchronic lightweight key coordination method which is based on the neural network weight value and suitable to flush-type environment. Such method is provided with low operand and low computing resource requirement.
Owner:ZHEJIANG UNIV OF TECH
Multi-frequency emission beam formation method and application
InactiveCN105259557AImprove real-time performanceReduce hardware complexityElectromagnetic wave reradiationSonarBeam direction
The invention discloses a multi-frequency emission beam formation method. The method includes: (1) the beam direction of an emission array of a crossed array is divided into a plurality of sectors, a series of sector sonar beam signals of different frequencies are emitted in sequence in each sector, and the sector sonar beam signals with each frequency point to a beam direction in the corresponding sector; and (2) after the sector sonar beam signals with all the frequencies in each sector are emitted, sonar echo signals are received by employing a reception array in the crossed array, frequency information corresponding to all the sector sonar beam signals in each sector is extracted via discrete Fourier transform, beam formation calculation is performed in frequency domains corresponding to the frequency information, and a beam intensity result is obtained. According to the method, the emission time of the crossed array can be reduced, the beam performance similar to a two-dimensional plane reception array is obtained, and the complexity of an underwater real-time three-dimensional acoustic imaging system is reduced. The invention also discloses the application of the method in the reconstruction of three-dimensional acoustic images.
Owner:ZHEJIANG UNIV
A Harris corner detection method for asynchronous time domain vision sensor is presented
PendingCN109509213AReduce data redundancyImprove real-time performanceImage enhancementImage analysisEvent streamVision sensor
The invention discloses a corner detection method based on a novel photoelectric imaging device-an asynchronous time domain vision sensor, and provides a concrete implementation step. This new imagingdevice is only sensitive to the light intensity change in the shooting scene, so its output visual information has the characteristics of real-time, very low redundancy and small amount of data. Compared with the traditional frame sampling imaging, the computation and storage requirements are greatly reduced, so it is more suitable for high-speed vision applications. The core idea of the invention is firstly to construct a continuously changing velocity surface by using the asynchronous event stream output from the visual sensor, and then to realize the event-driven corner detection on the velocity surface by using the Harris corner detection principle.
Owner:TIANJIN NORMAL UNIVERSITY
Fast detection method for spatial dynamic point target under moving platform
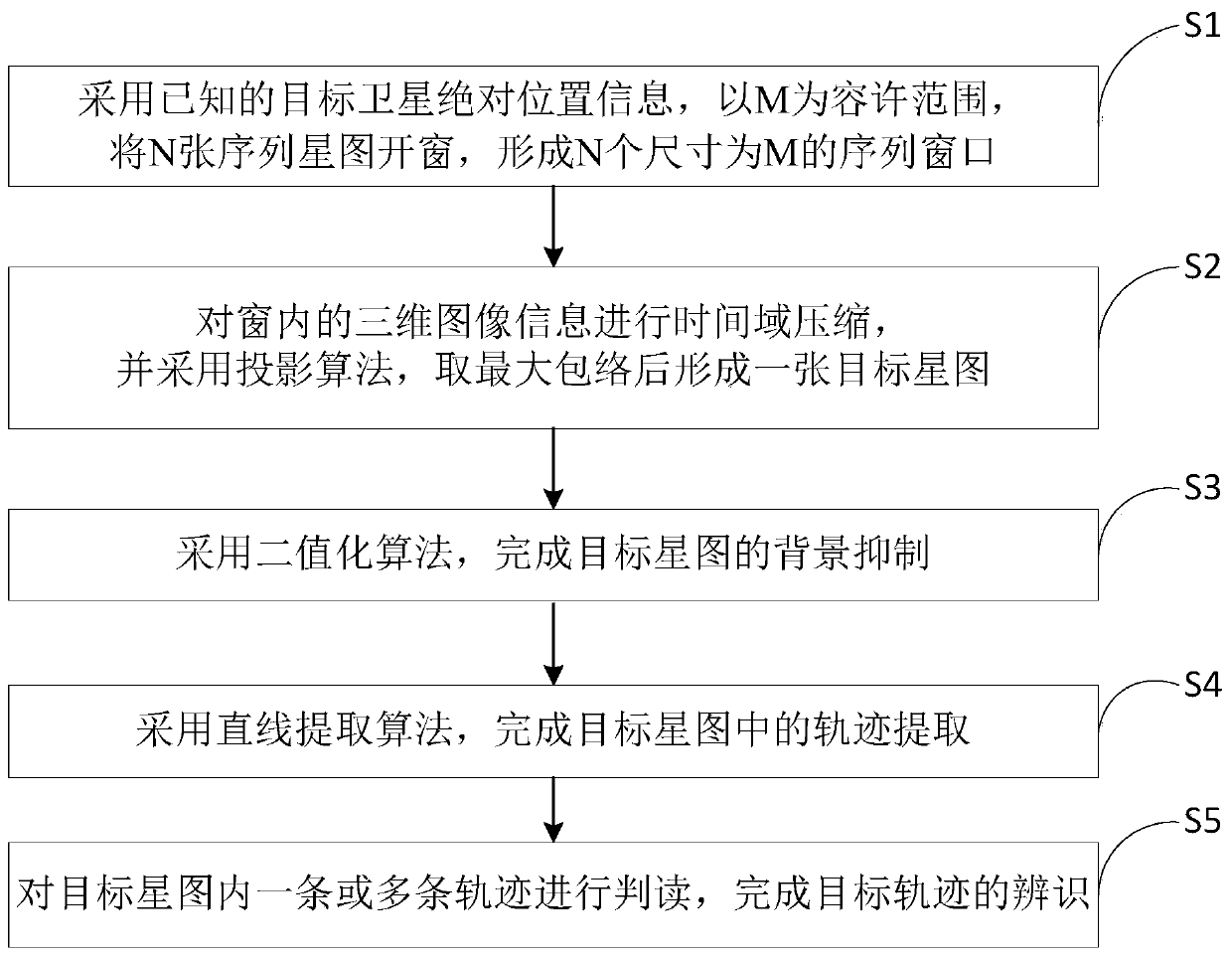
ActiveCN109708627AReduce computationReduce dependenceInstruments for comonautical navigationNavigation by astronomical meansTime domainProjection algorithms
The invention discloses a fast detection method for a spatial dynamic point target under a moving platform. The method comprises steps that the known target satellite absolute position information isutilized, M is taken as the allowable range, and N sequence star maps are opened to form N sequence windows with the size M; S2, time domain compression is performed on the three-dimensional image information in the windows, the projection algorithm is utilized, after taking the maximum envelope, a target star map is formed; S3, the binarization algorithm is utilized to complete background suppression of the target star map; S4, the linear extraction algorithm is utilized to complete trajectory extraction in the target star map; and S5, one or more trajectories in the target star map are interpreted to complete identification of the target trajectory. The method is advantaged in that a problem of fast detection of the spatial dynamic point target when a space camera is in the dynamic environment is solved, the application background of spatial dynamic point target detection is greatly improved, and the detection speed is improved.
Owner:SHANGHAI AEROSPACE CONTROL TECH INST
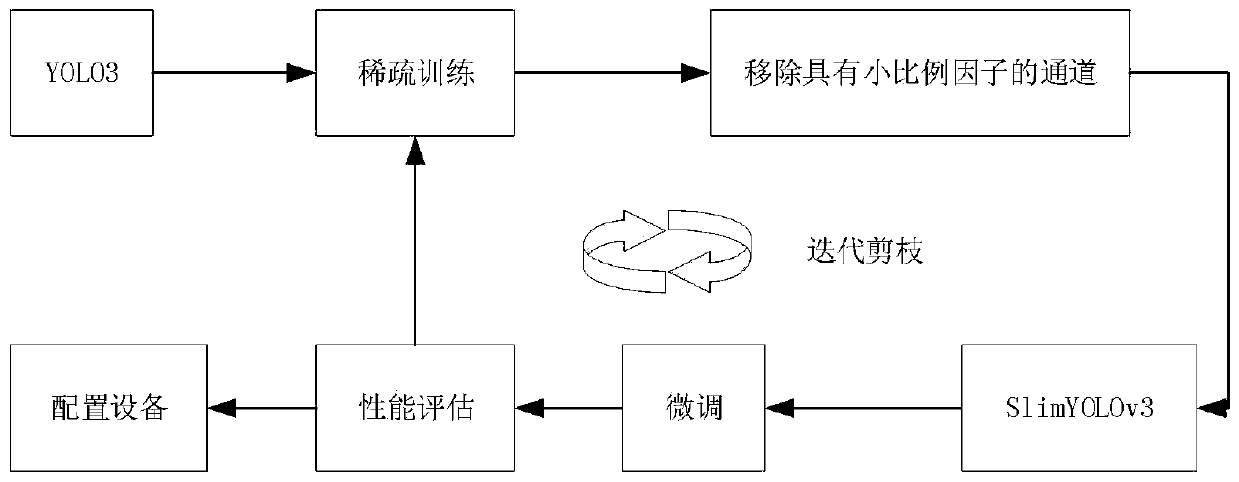
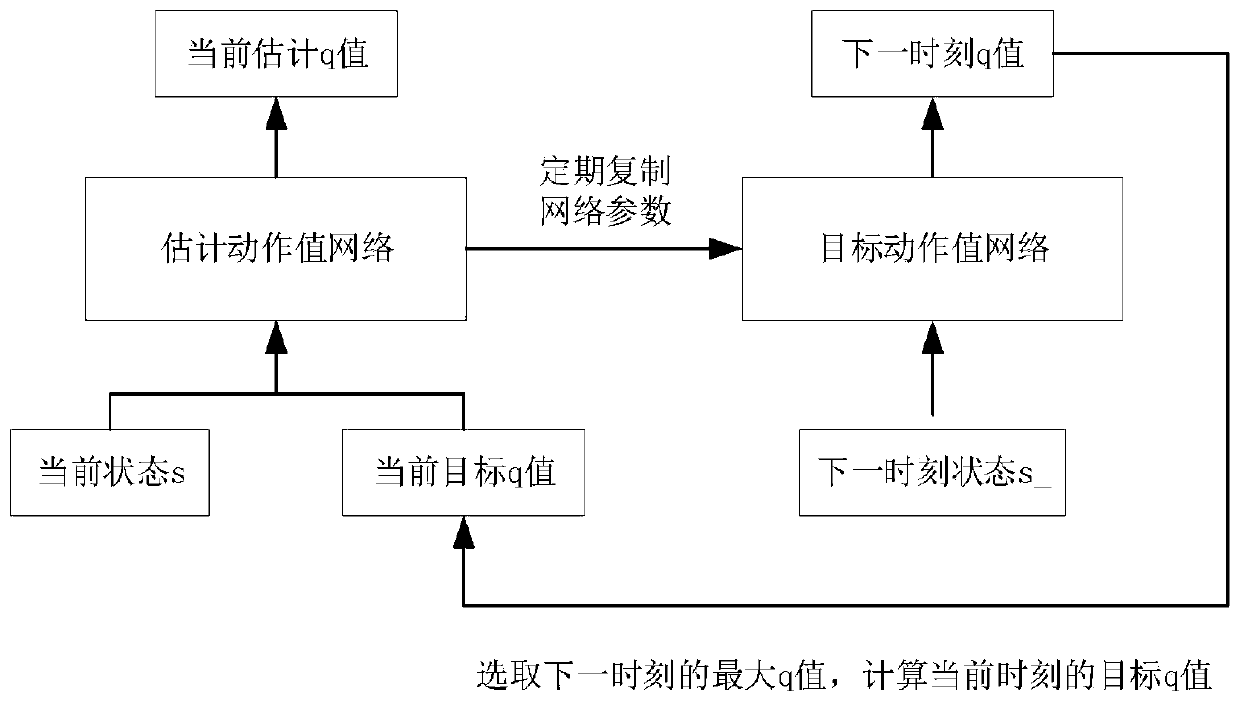
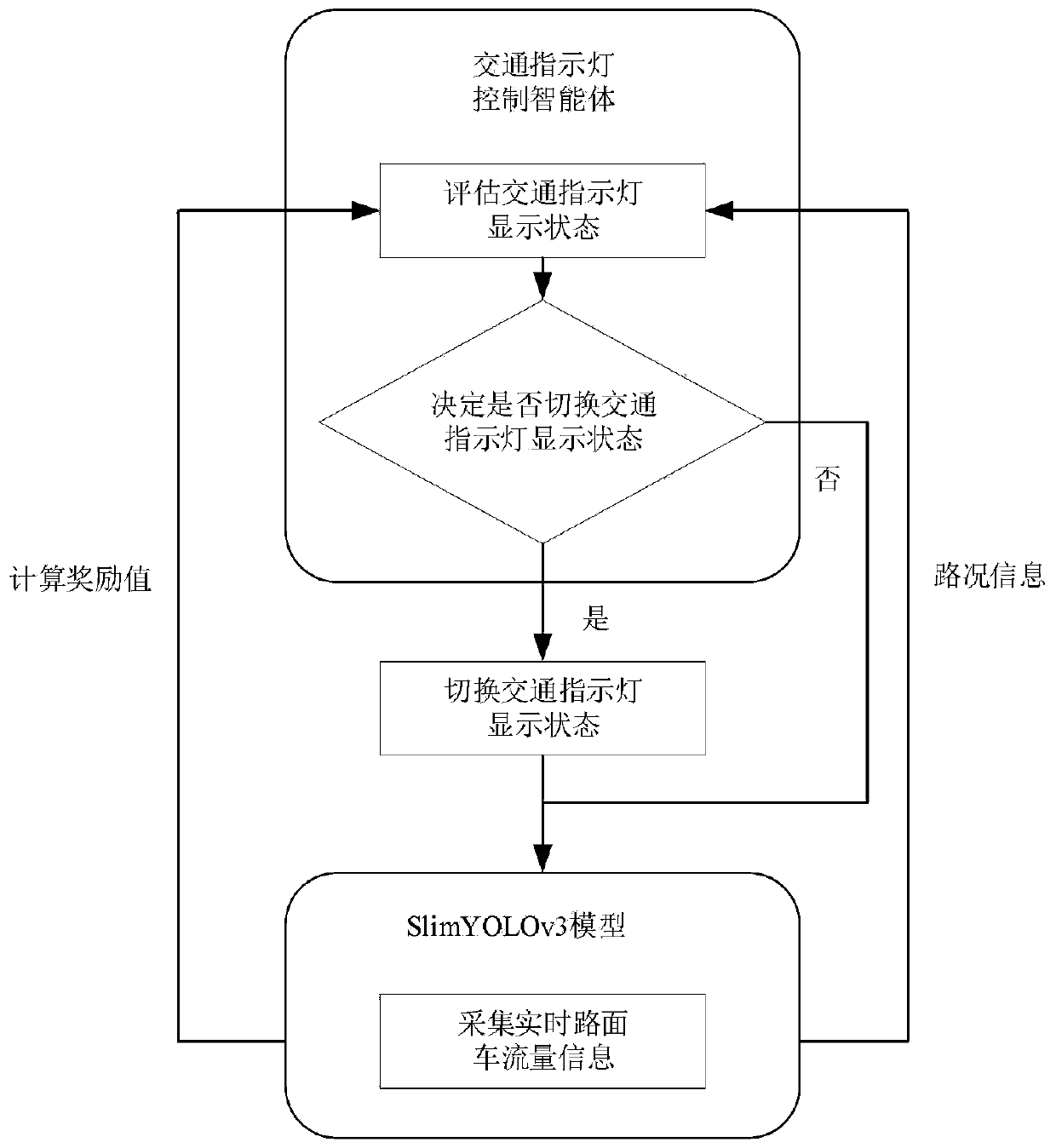
Idle traffic light intelligent control method based on reinforcement learning
InactiveCN110930734AReduce training parametersReduce computing requirementsControlling traffic signalsGreedy algorithmSimulation
The invention relates to an idle traffic light control method based on reinforcement learning, and the method comprises the following steps of employing a SlimYOLOv3 model to sense an environment, analyzing a scene, recognizing all vehicle types of targets in the scene, and positioning the positions of the targets through defining a bounding box around each target; adopting a DQN-based reinforcement learning method to train a traffic light control intelligent agent, a) defining an action space, enabling the traffic lights to randomly select actions according to probabilities, and adopting a greedy algorithm to randomly select the actions according to the probabilities; b) defining a state space, wherein the road surface state observed at any moment is the number of vehicles in different intervals in each direction, and an observation state value is a six-dimensional vector; c) defining a reward function, wherein the penalty weights of the three interval road sections are respectively defined as the specification, and the reward value is the sum of the penalty weights of the road sections; and d) learning a strategy enabling the reward value to be the highest by adopting the DQN-based reinforcement learning method to obtain the traffic light control intelligent agent with high performance.
Owner:TIANJIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com