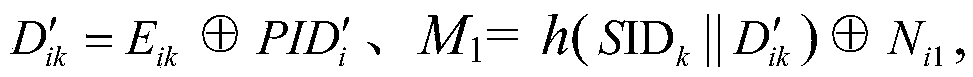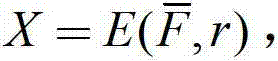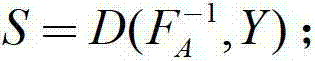Patents
Literature
476results about How to "Save computing power" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
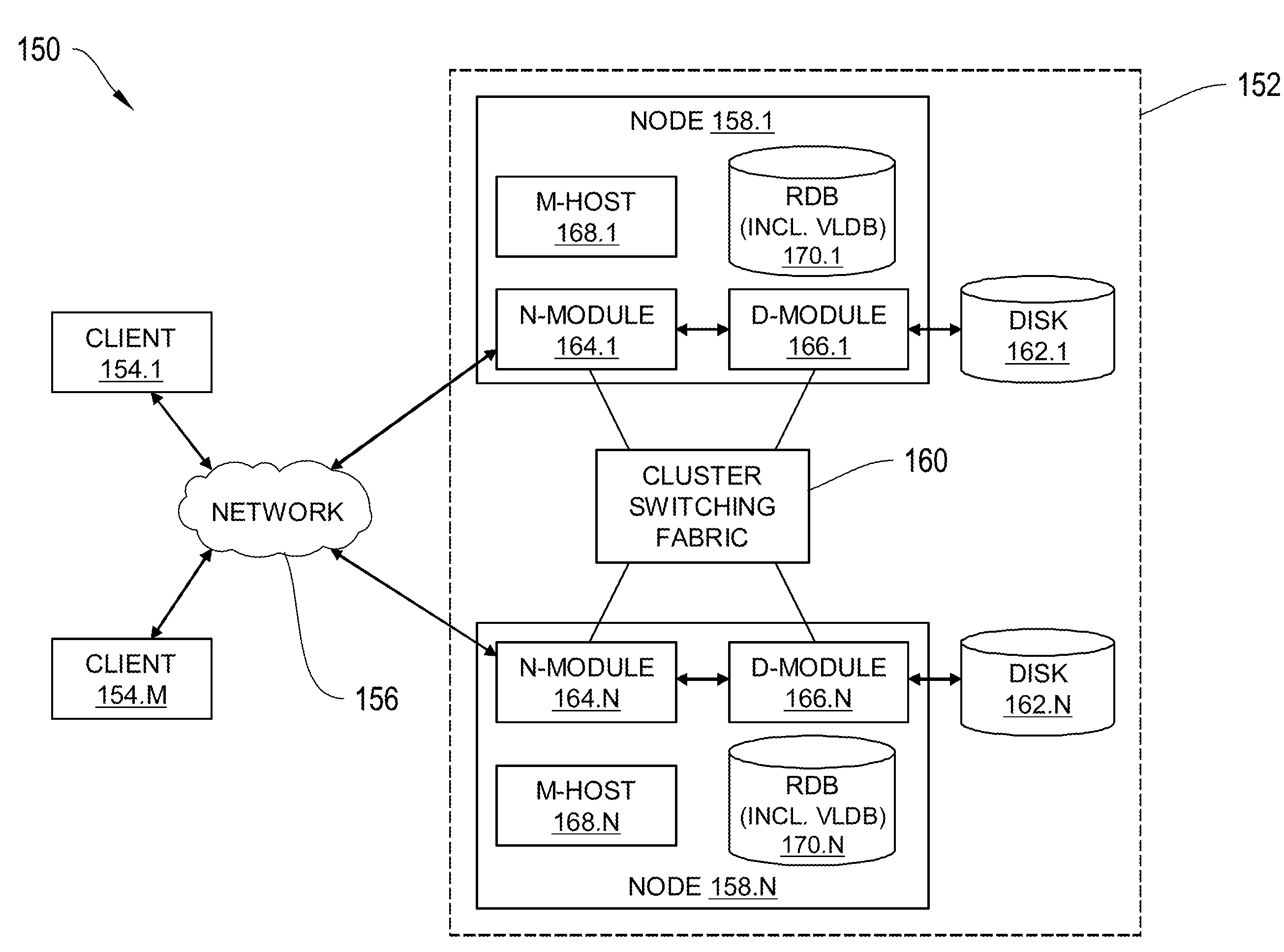
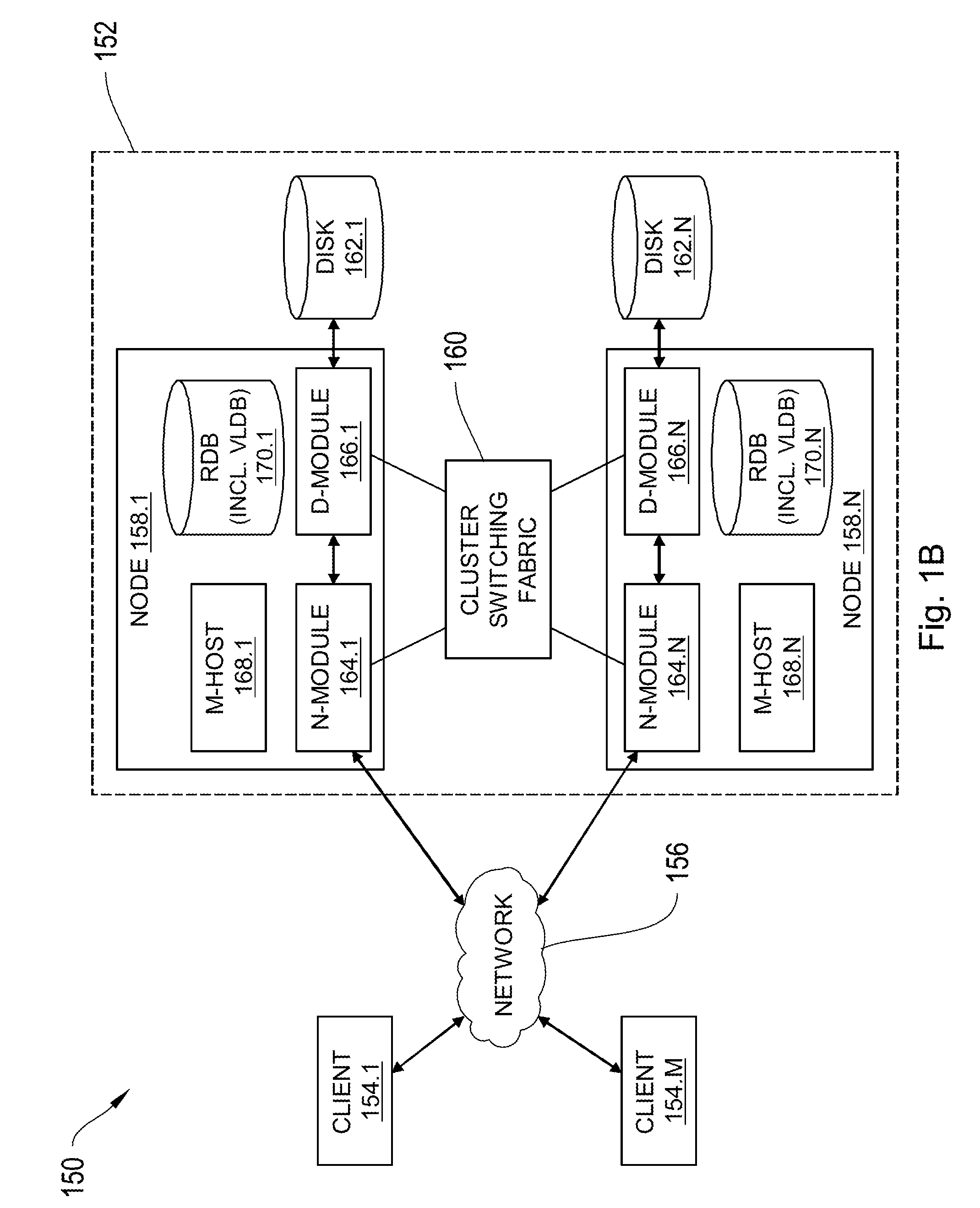
Systems and Methods for Tracking Block Ownership
InactiveUS20130262758A1Effective trackingSave computing powerMemory systemsInput/output processes for data processingInodeData structure
Systems and methods for, among other things, providing a storage system which allows for efficient tracking of in-use storage disk blocks using “sharing nodes”. Disk blocks are a result of low-level formatting, which breaks up the total storage capacity into a set number of blocks. High-level formatting of the disk creates the file system, and part of the file system may create metadata known as inodes, and associate an inode with each file, such that an inode tracks the disk blocks in use by that file, pointing from the file to a set of blocks. An S-node generator creates another type of metadata, complementary to an inode, known as an S-node data structure, such that an S-node data structure is associated with a block, and tracks the set of inodes using the block, pointing from the disk blocks to inodes.
Owner:NETWORK APPLIANCE INC
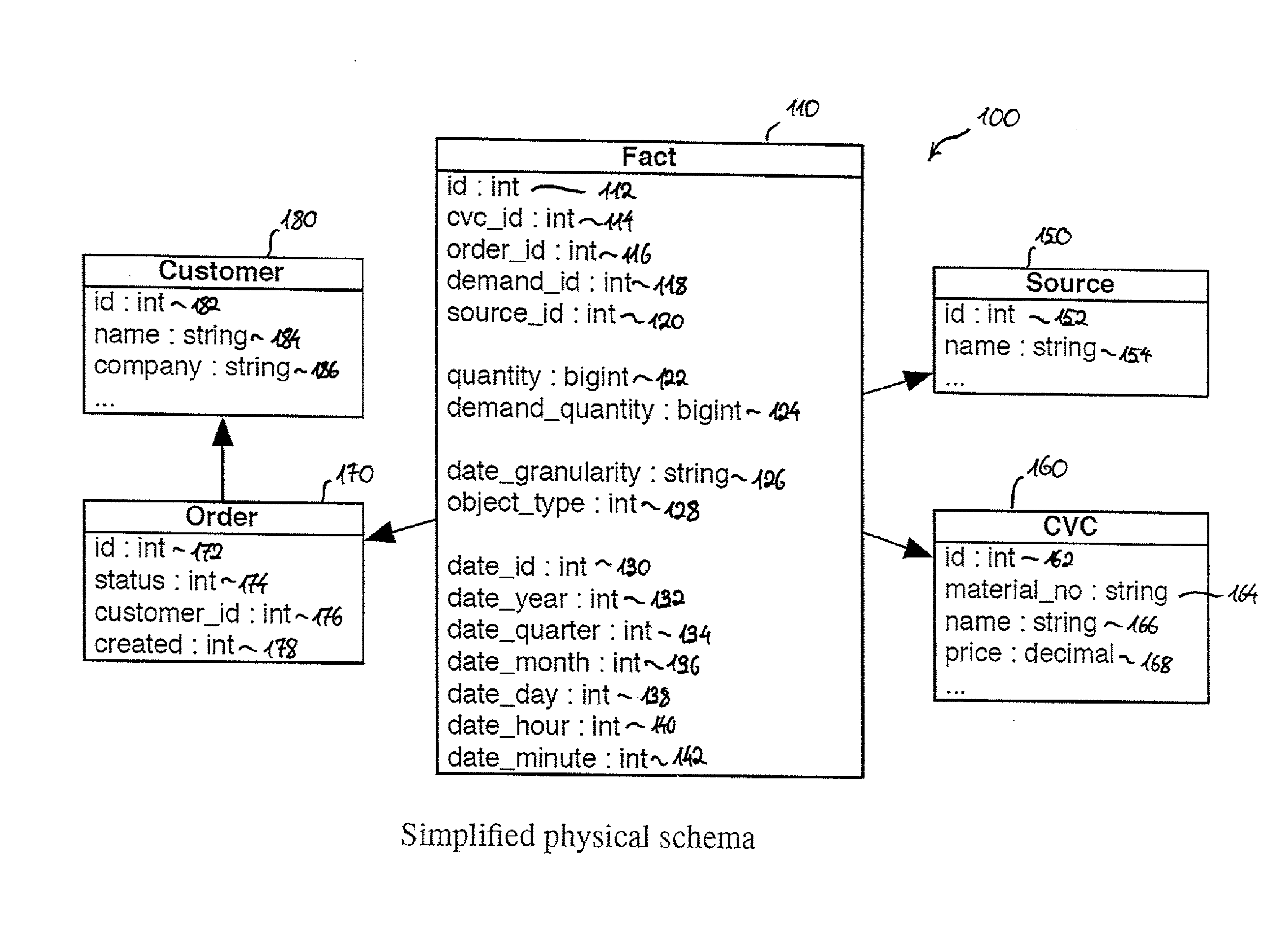
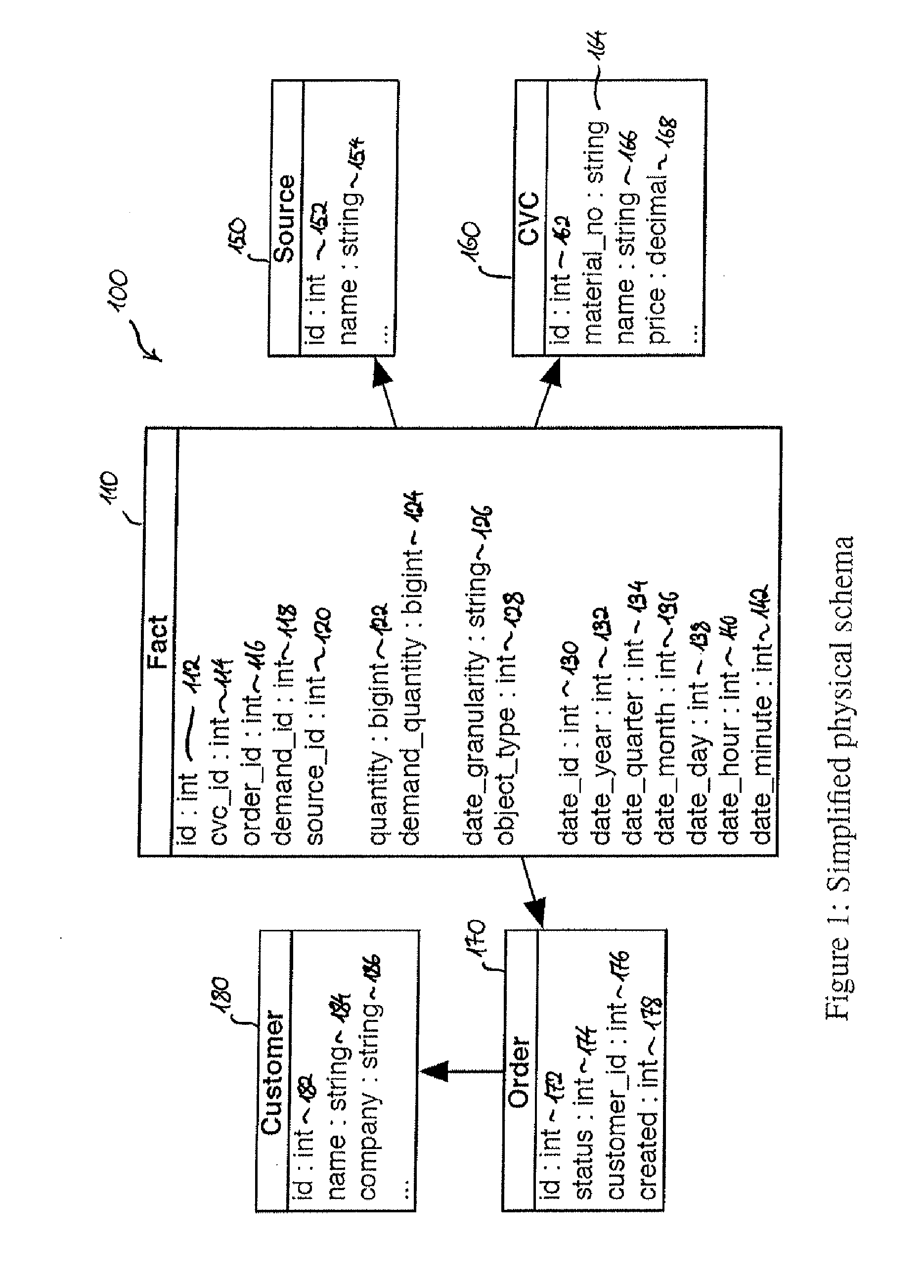
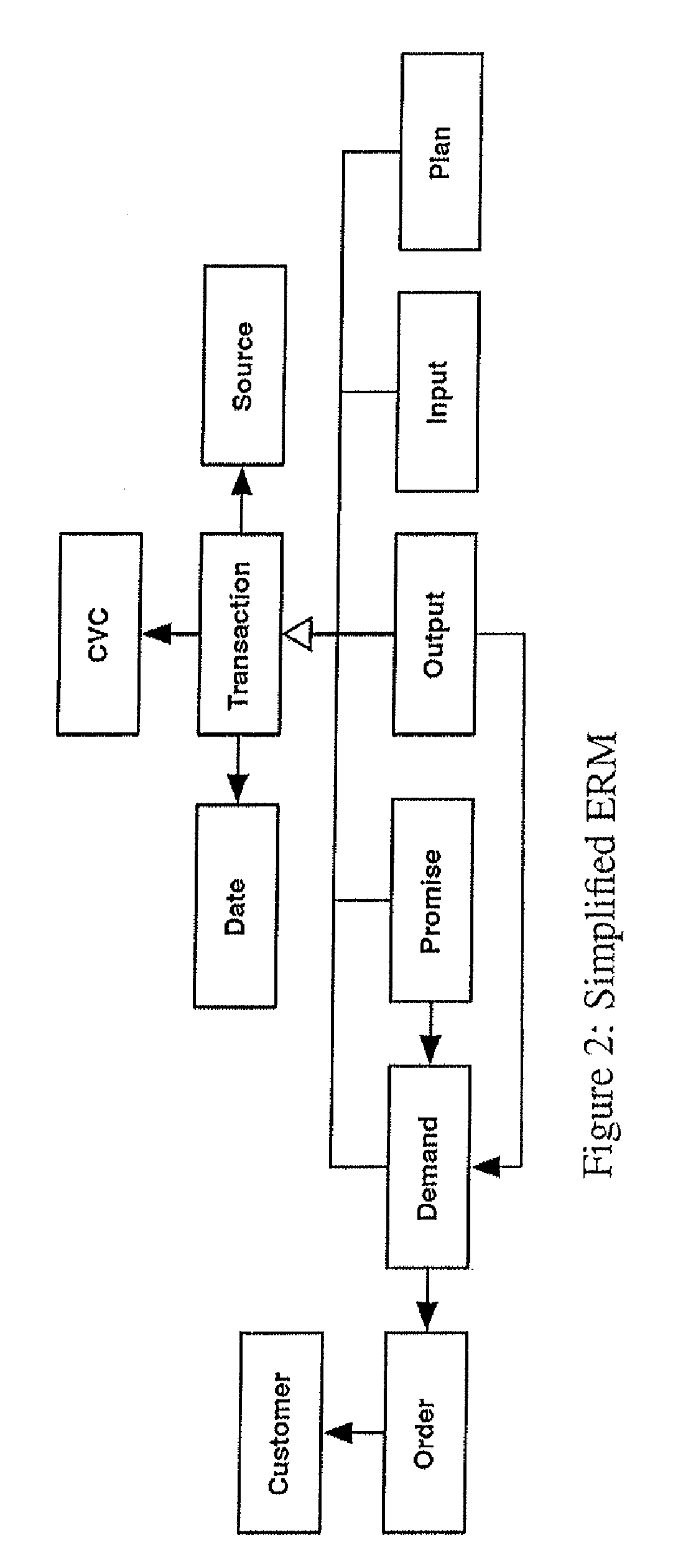
Available-To-Promise on an In-Memory Column Store
ActiveUS20120265728A1Improve performanceAffect performanceDigital data processing detailsMultiple digital computer combinationsEngineeringFact table
A system and method of determining an earliest delivery date for a demand on the basis of a fact table stored in a database, where the demand indicates both a desired date and a desired quantity for items from a stock, where a fact time series is comprised by and / or deducible from the fact table, and where the fact time series comprises fact tuples indicating both a fact date and a change in quantity of stock items that occurred on this fact date. The method includes generating an aggregated time series from the fact time series by defining and / or obtaining discrete time intervals, and generating, for at least one discrete time interval, an aggregated tuple indicating both its corresponding discrete time interval and the aggregated change in quantity of stock items that occurred in its corresponding discrete time interval.
Owner:HASSO PLATTNER INSTITUT FUR SOFTWARESYSTTECHN
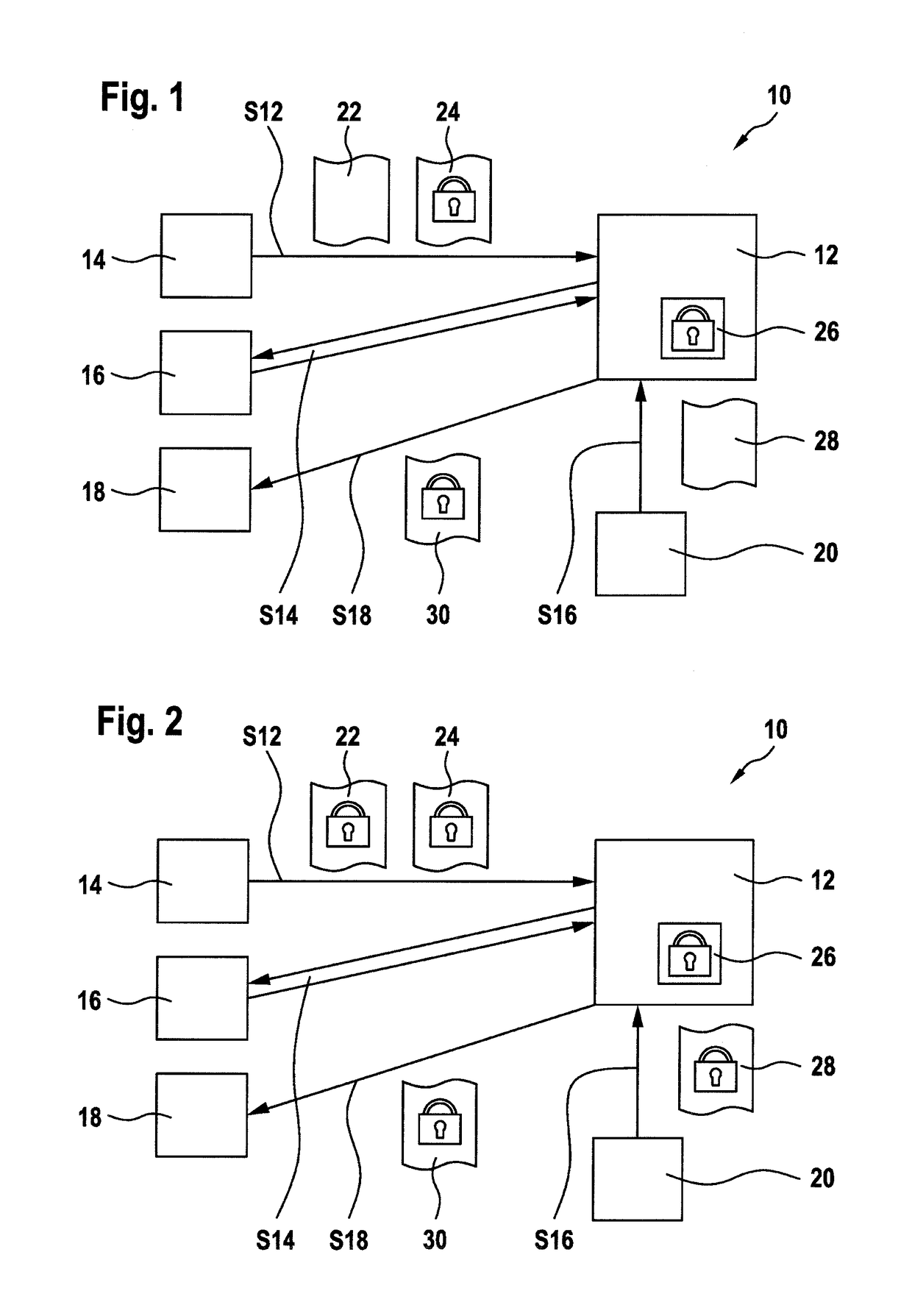
Machine learning based on homomorphic encryption
ActiveUS20180349740A1Minimize the differenceSave computing powerEncryption apparatus with shift registers/memoriesDigital computer detailsPlaintextLearning based
A method for evaluating data is based on a computational model, the computational model comprising model data, a training function and a prediction function. The method includes training the computational model by: receiving training data and training result data for training the computational model, and computing the model data from the training data and the training result data with the training function. The method includes predicting result data by: receiving field data for predicting result data; and computing the result data from the field data and the model data with the prediction function. The training data may be plaintext and the training result data may be encrypted with a homomorphic encryption algorithm, wherein the model data may be computed in encrypted form from the training data and the encrypted training result data with the training function. The field data may be plaintext, wherein the result data may be computed in encrypted form from the field data and the encrypted model data with the prediction function.
Owner:ABB (SCHWEIZ) AG
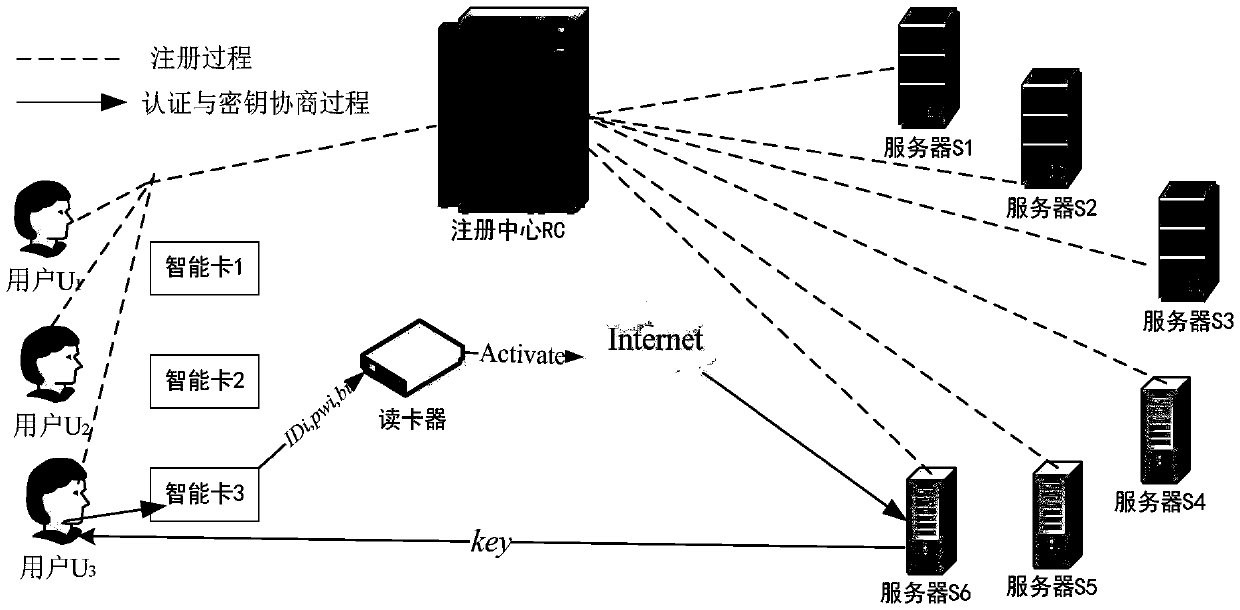
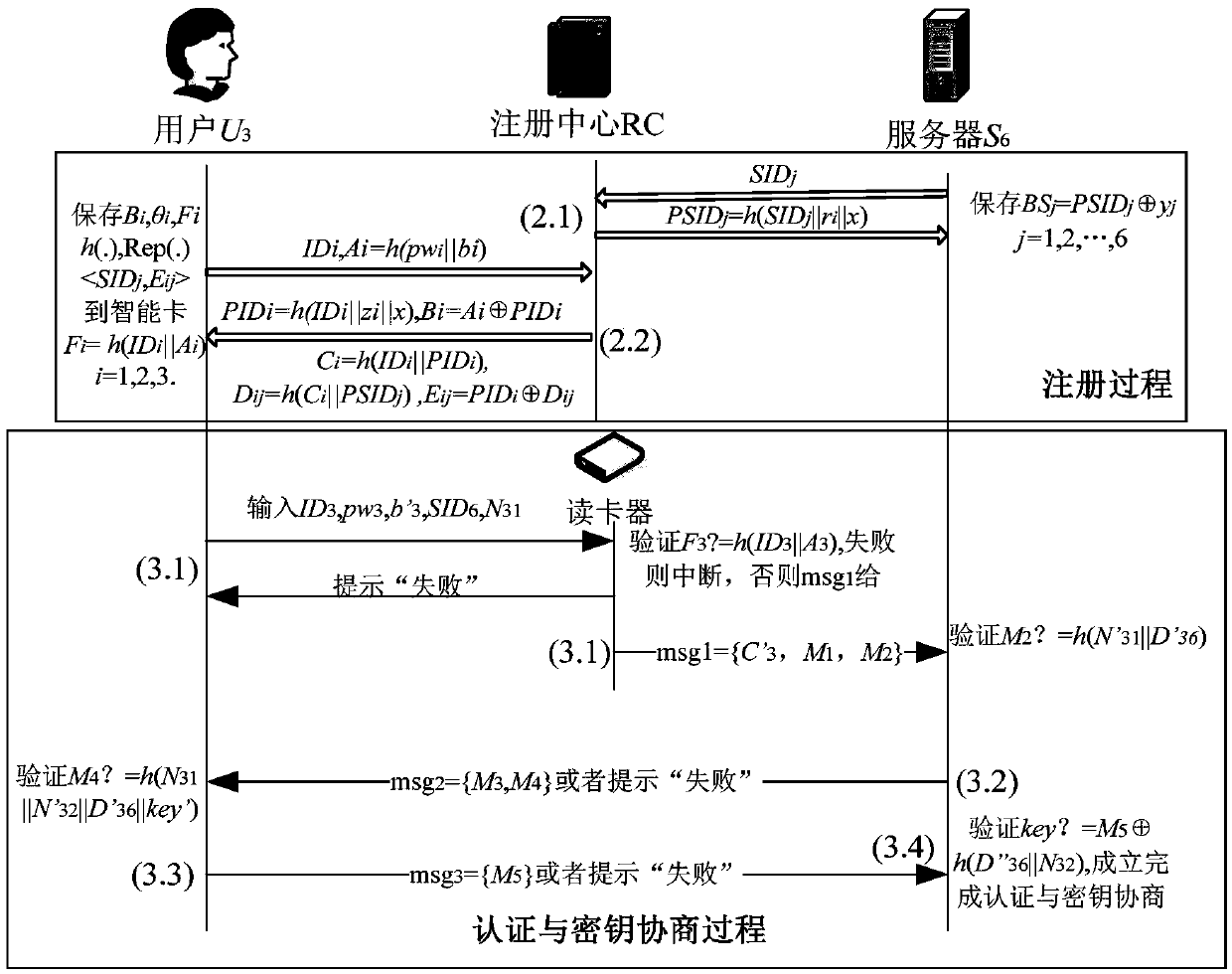
Lightweight anonymous authentication and key negotiation method in multi-server environment
The invention relates to a lightweight anonymous authentication and key negotiation method in a multi-server environment and belongs to the technical field of information safety. The method is characterized by achieving the anonymous authentication and key negotiation in the multi-server environment by means of the following three steps: (1) building a system and selecting system parameters; (2) registering in a registering center RC by a server and a user; (3) carrying out authentication and key negotiation by the user and a remote server so as to provide subsequent communication session keys. The lightweight anonymous authentication and key negotiation method is applicable to remote authentication of a mobile terminal and servers with low calculation capability, memory space and communication capability; the mobile terminal can log in any server registered by RC through a user name and a password; the server only can authenticate that the user is a valid user and cannot know the specific identity of the user, so that the privacy of the user is protected; the lightweight anonymous authentication and key negotiation method is excellent in expansibility; the two-party negotiation session keys are determined by random numbers Ni1 and Ni2 selected by authenticating for each time by two parties; the independence and the forward and backward security of the session keys are ensured.
Owner:深圳市迅威恒达信息技术有限公司
Programming of an extended path for an autonomous mobile unit for the subsequent traversing of path sections that are temporarily blocked
InactiveUS7251548B2Save computing powerSave memory spaceAutomatic obstacle detectionInstruments for road network navigationReal-time computing
Owner:SIEMENS AG
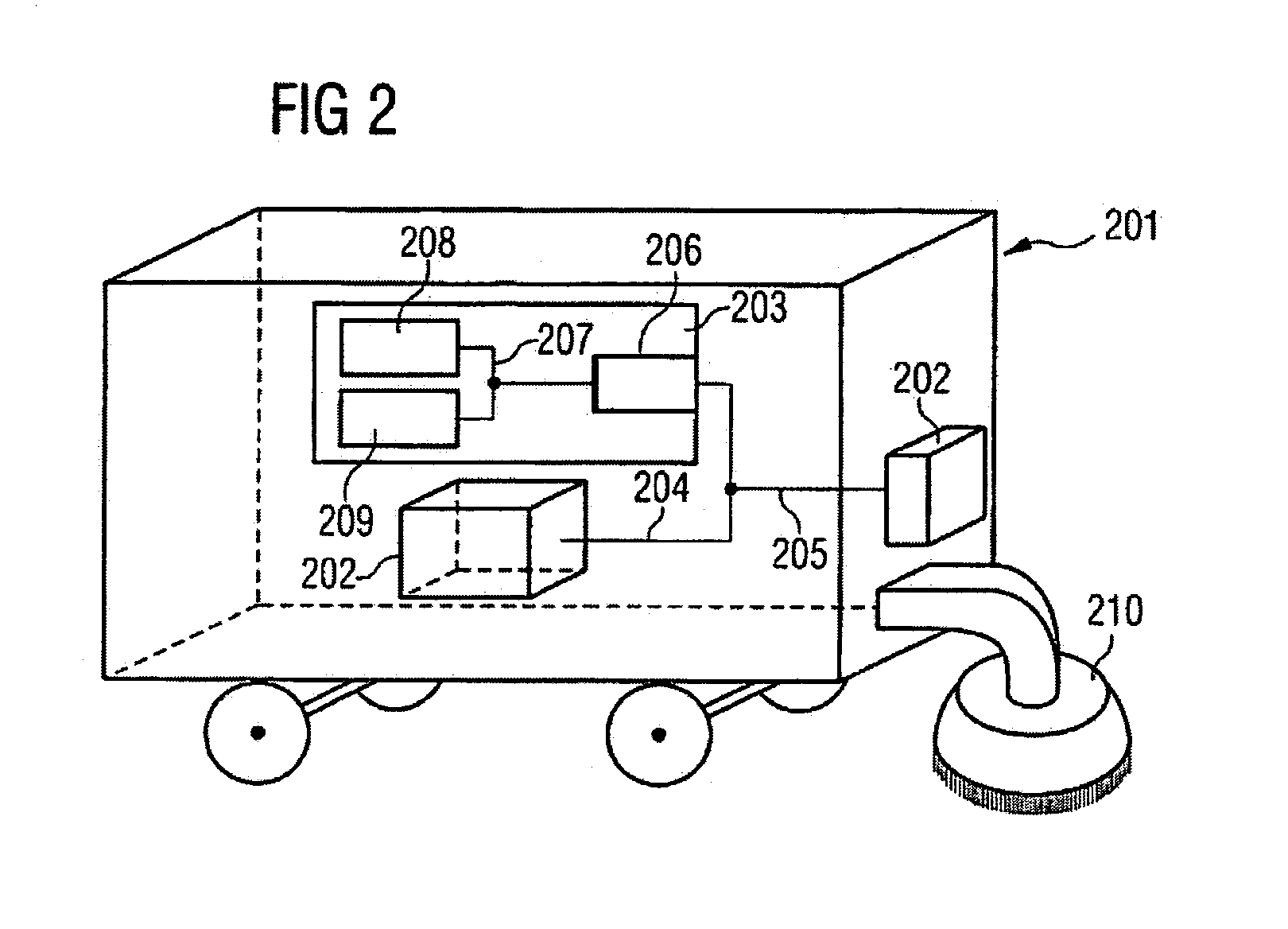
Method and computer program product for lighting a computer graphics image and a computer
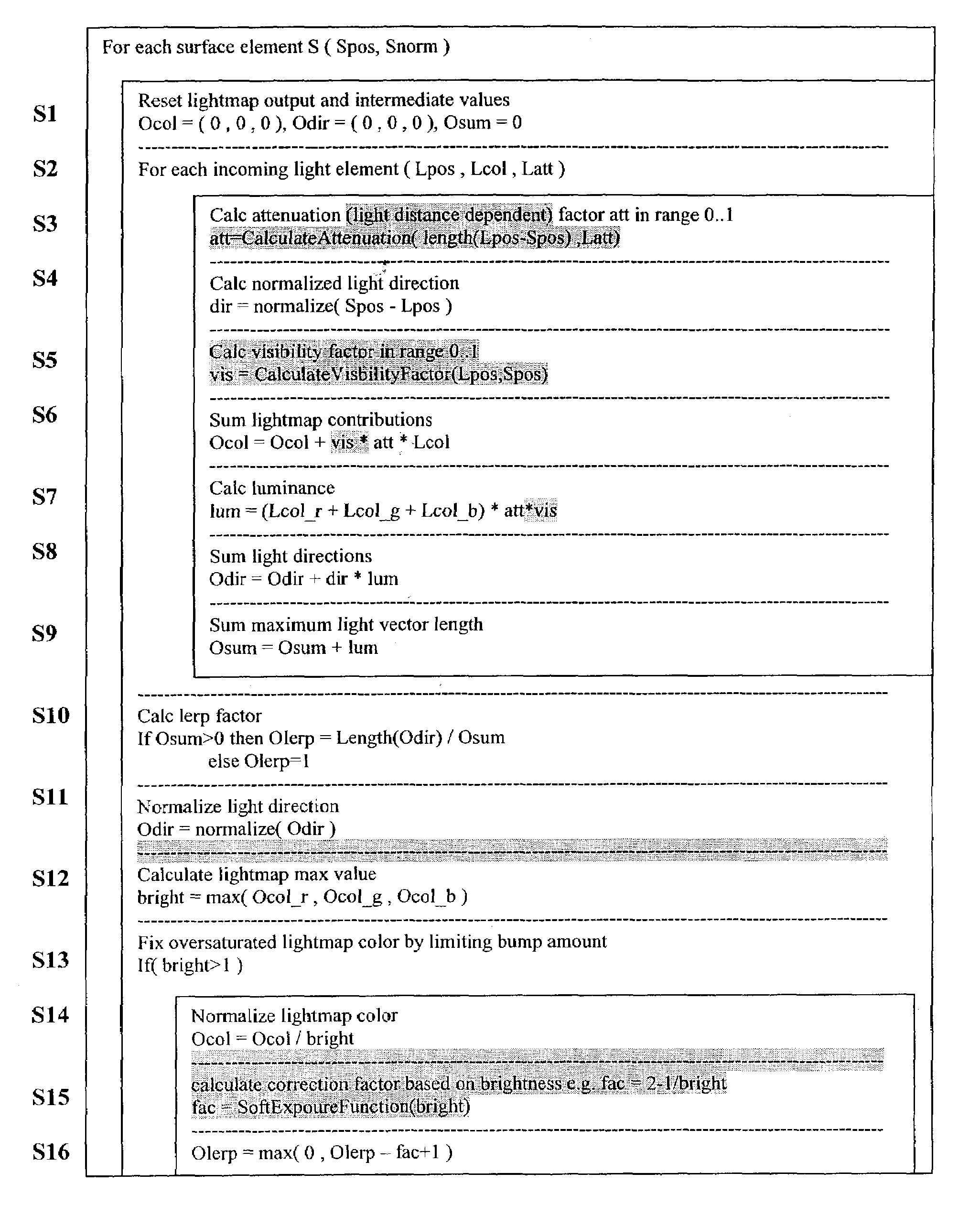
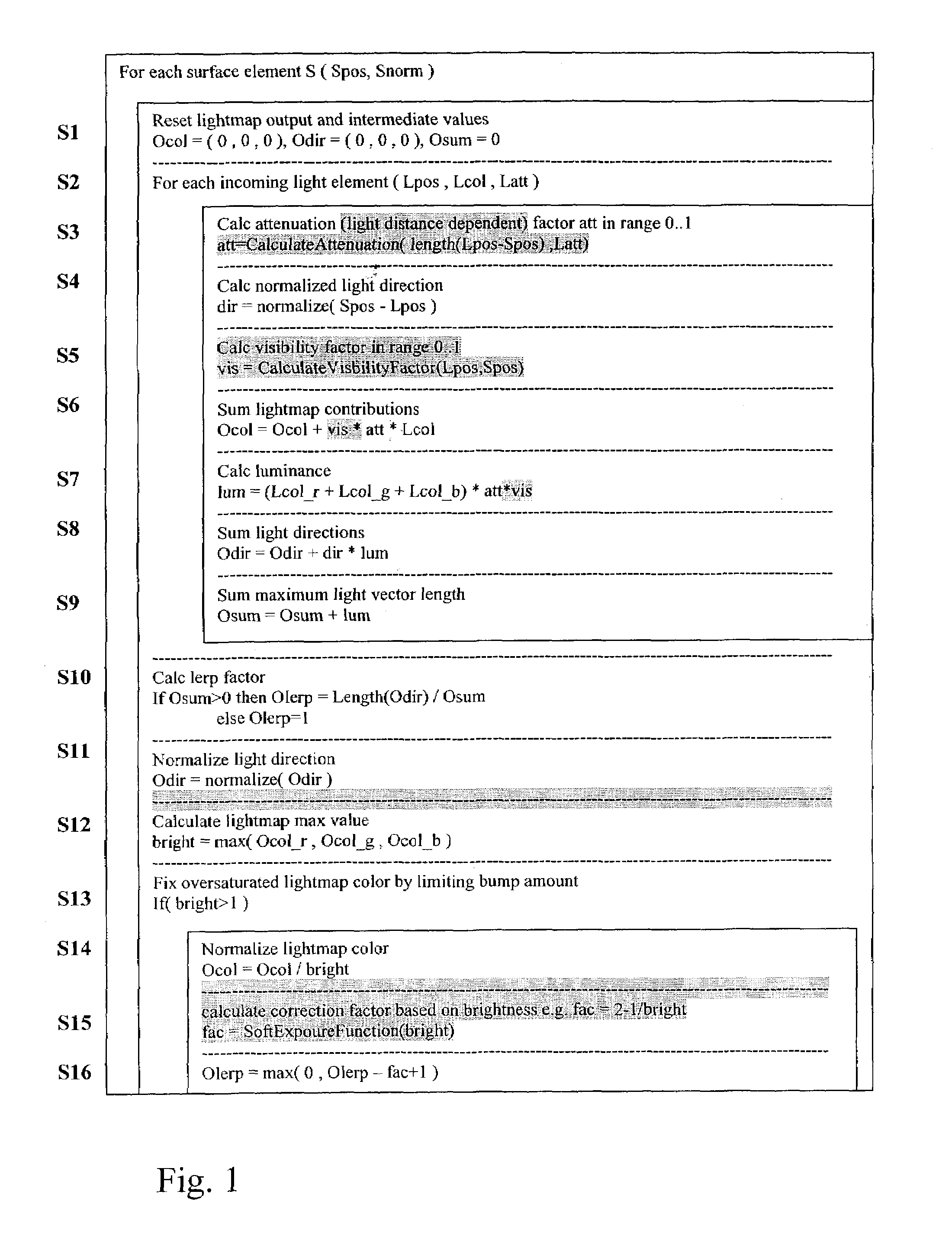
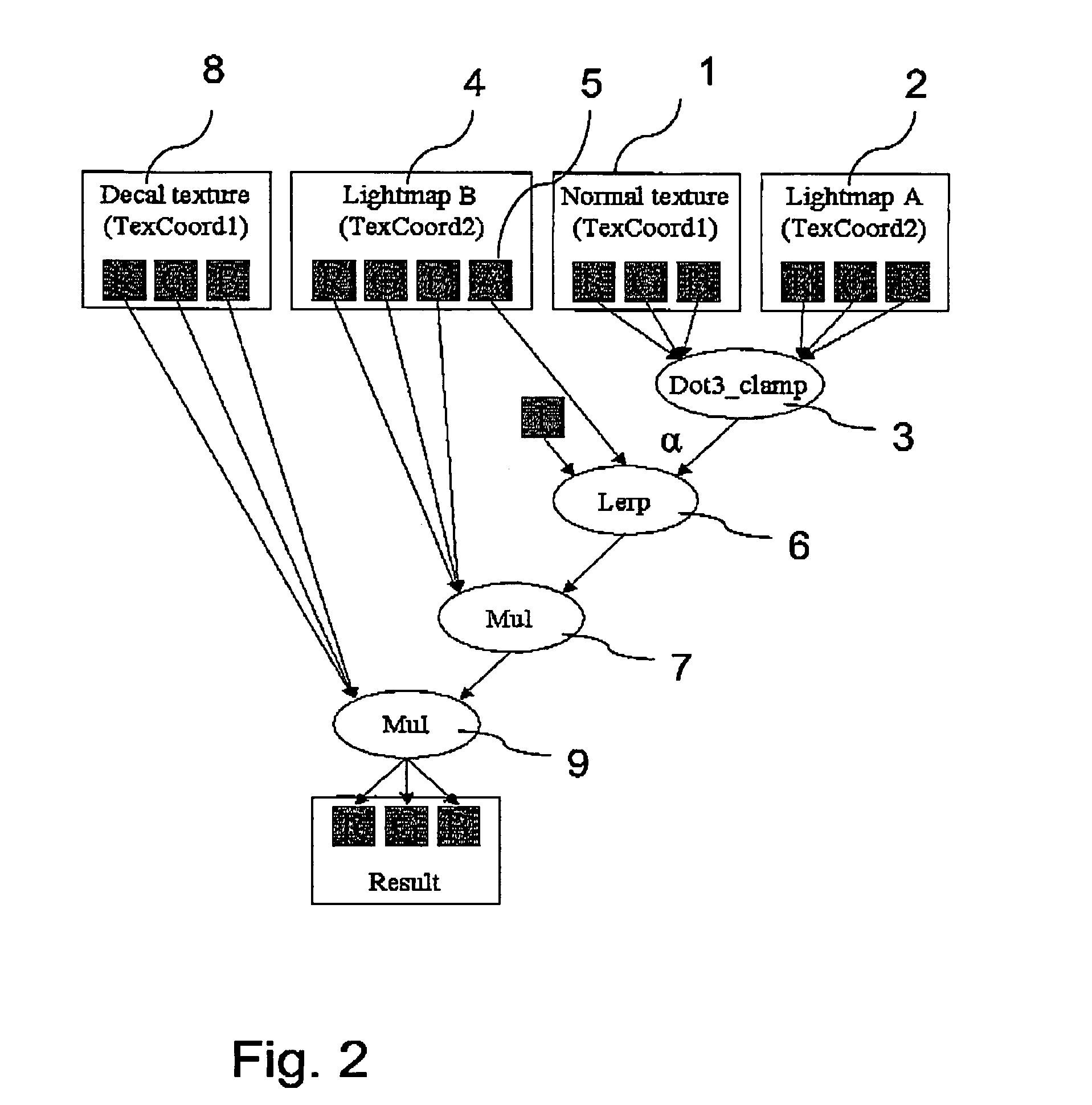
The invention relates to a method to and a computer program product for lighting a computer graphics image to be rendered. It is assumed that a plurality of light sources illuminate one or more objects of the scene to be rendered thus causing a complex lighting situation. For reducing the complexity of the lighting situation and saving computing time the lighting condition is pre-calculated by approximating at least two and preferably all light sources by a single fictitious light source in a pre-calculating step. In the step of pre-calculating, there is computed an approximated light direction for at least two selected ones of the light sources and an approximated light color for the selected light sources by weighting color contributions thereof. The step of pre-calculating is performed for selected areas of a surface of objects present in the scene and results in coefficients that are stored, for these selected areas, in a lightmap or in vertices representing the object surface. The coefficients are retrieved by subsequent method steps for rendering the computer graphics image using the approximated light condition. The invention applies not only to diffuse lighting but is, with a minor modification, also of use for calculating specular lighting.
Owner:CRYTEK IP HLDG
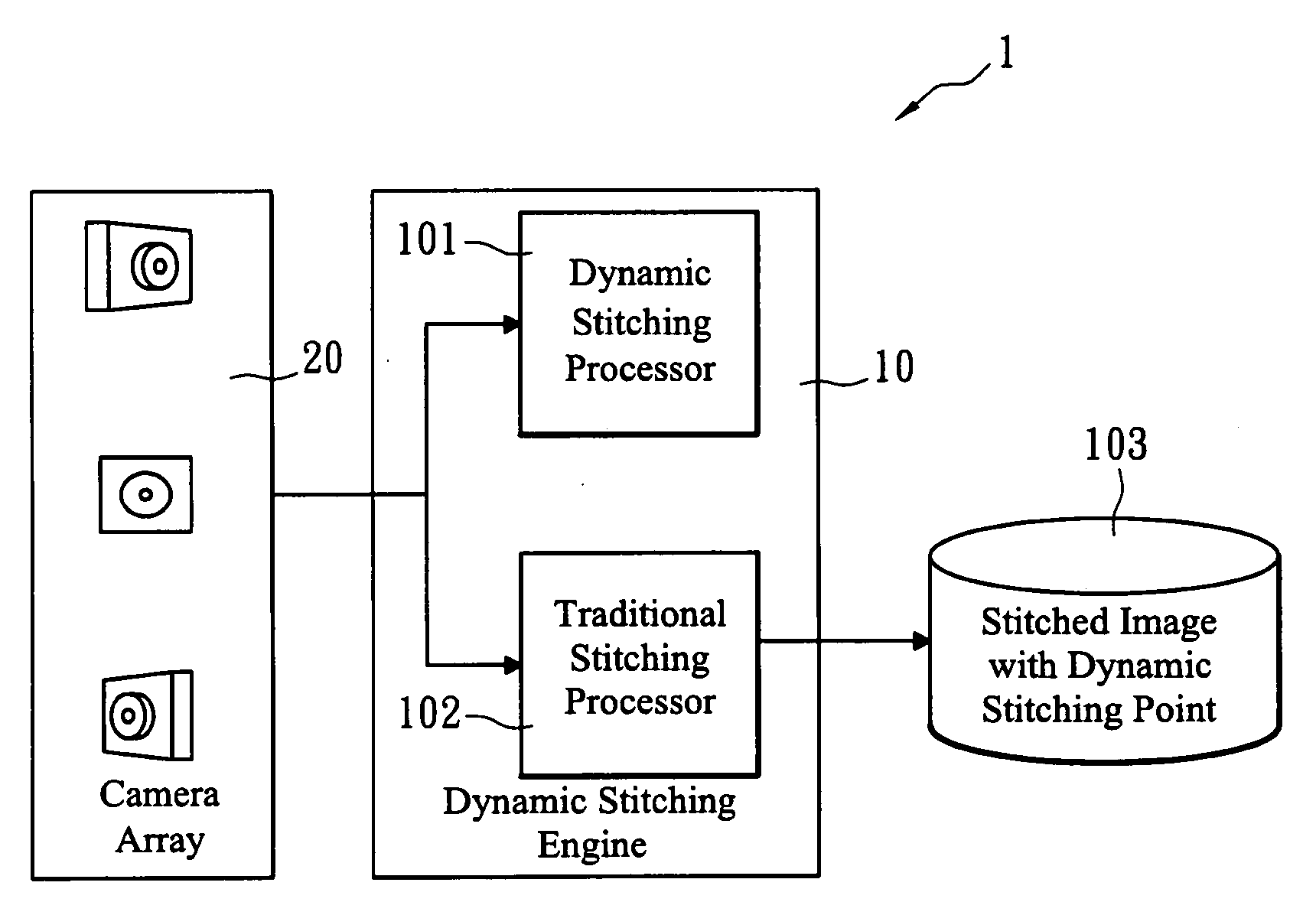
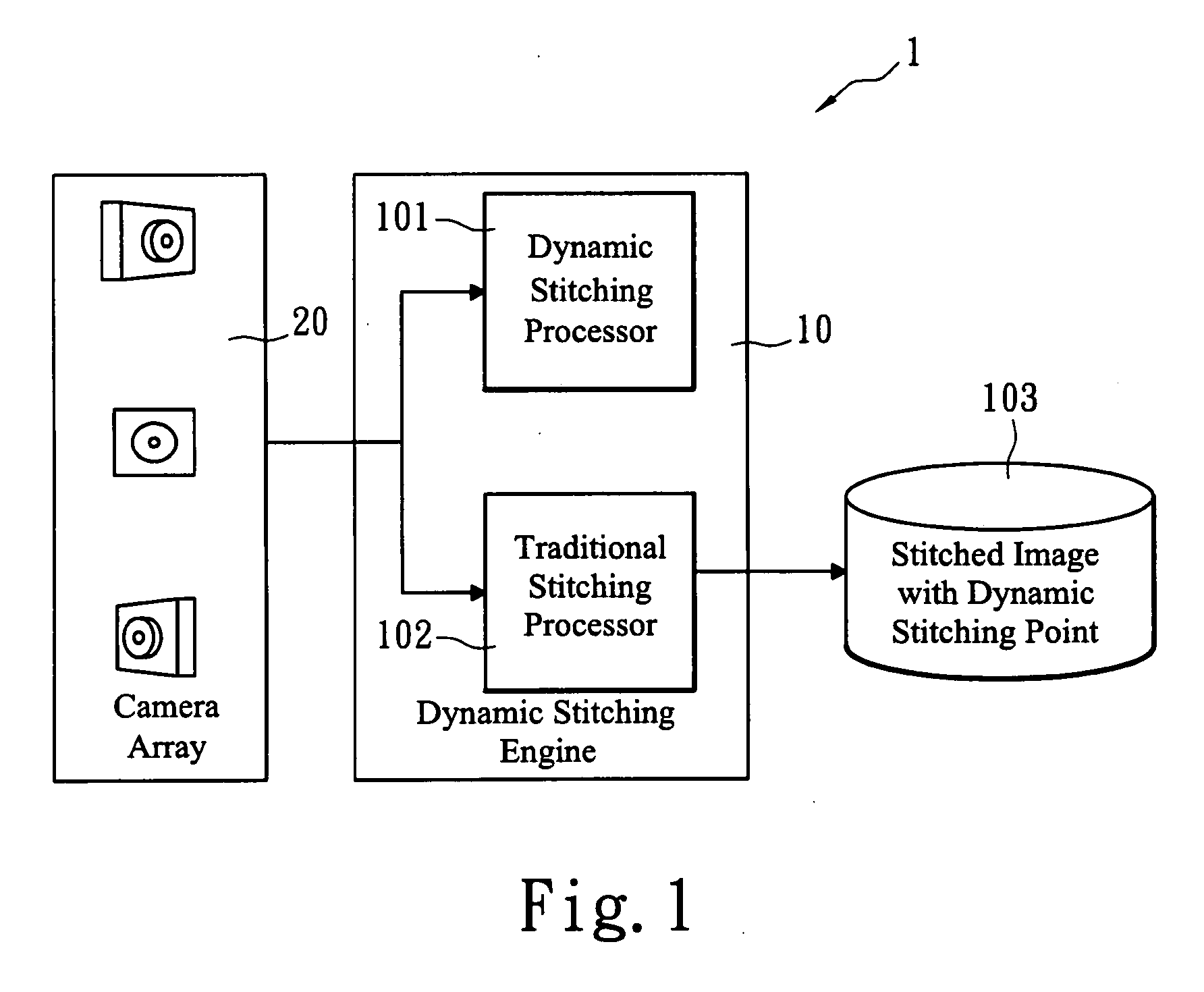
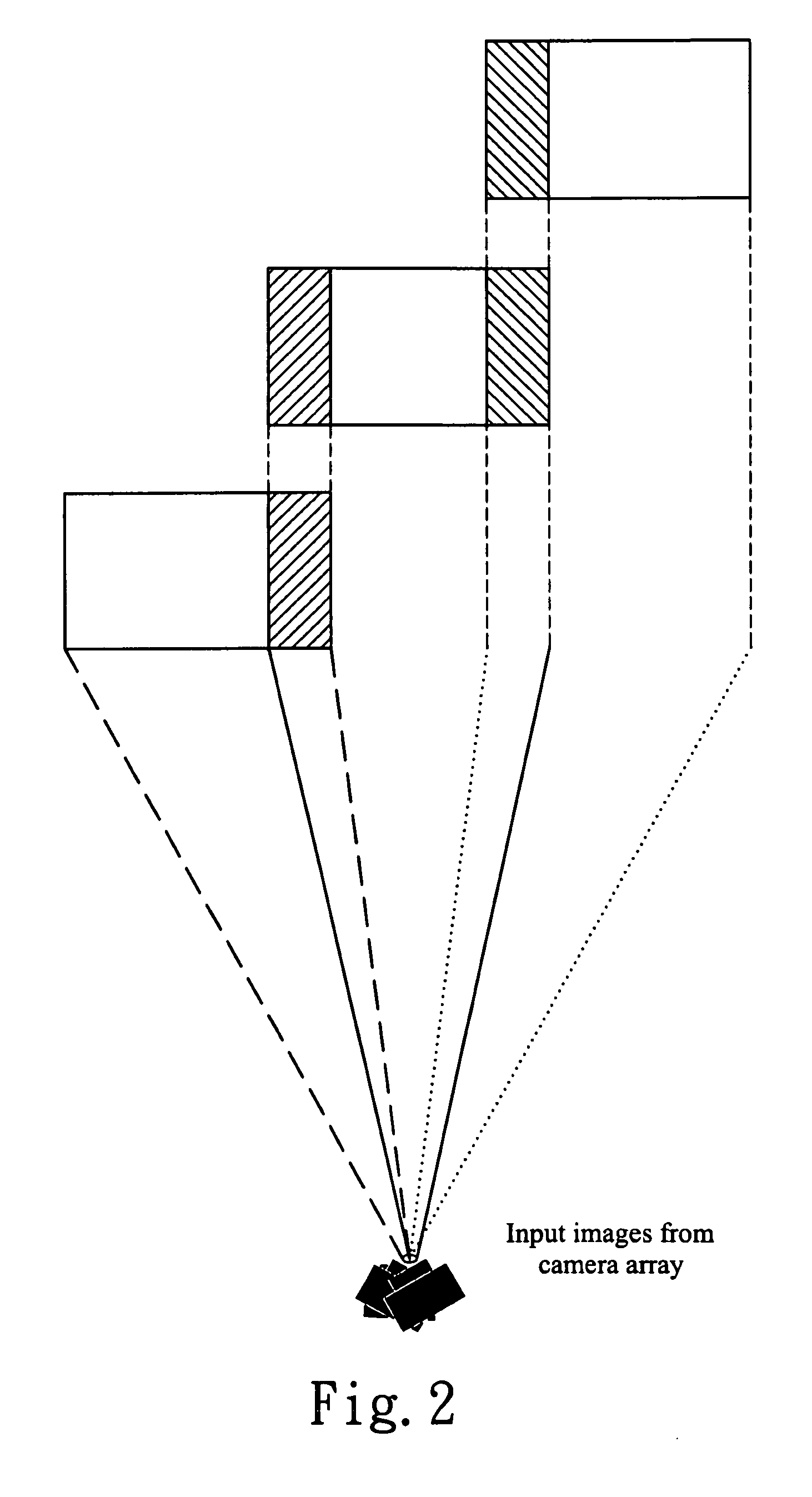
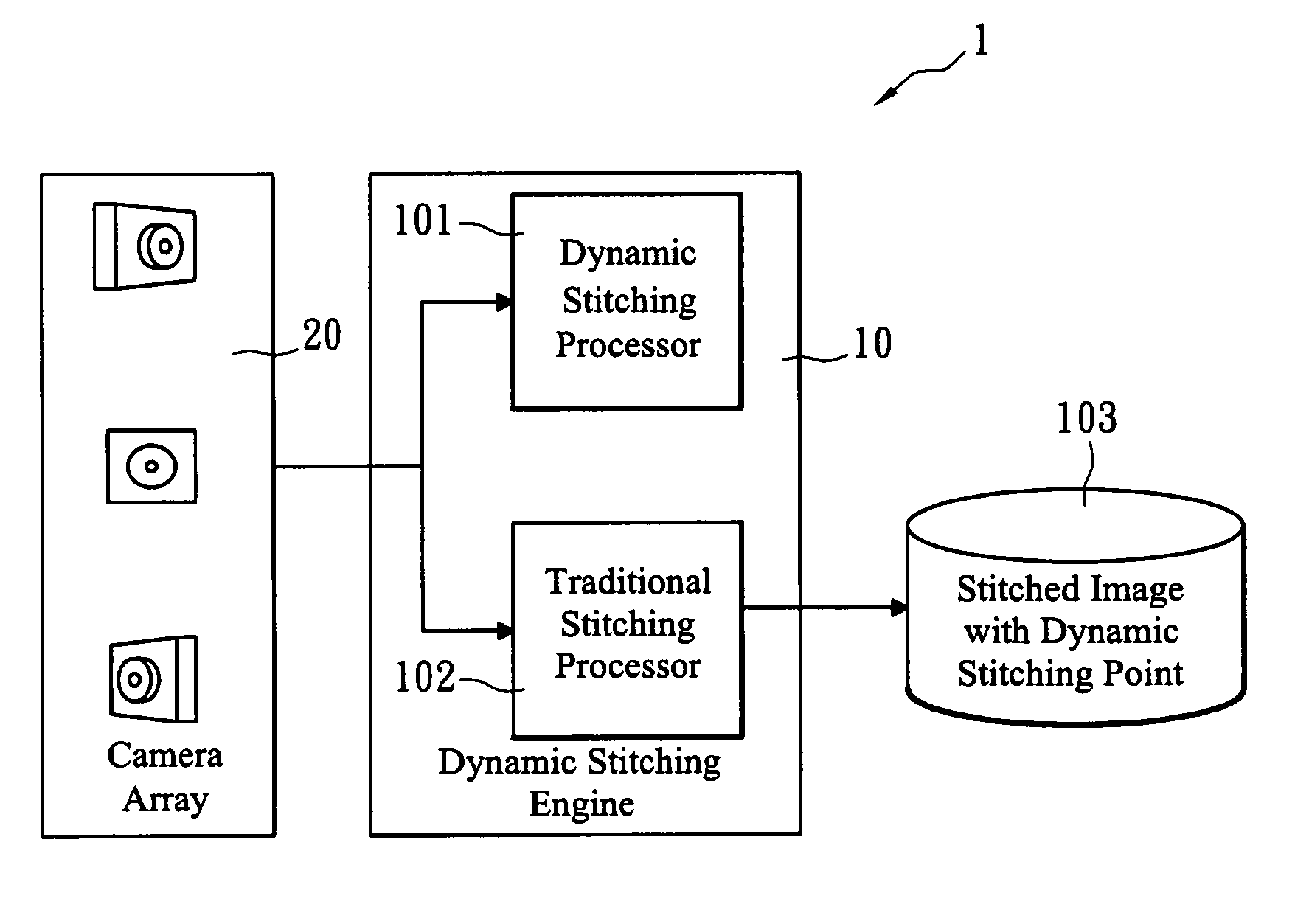
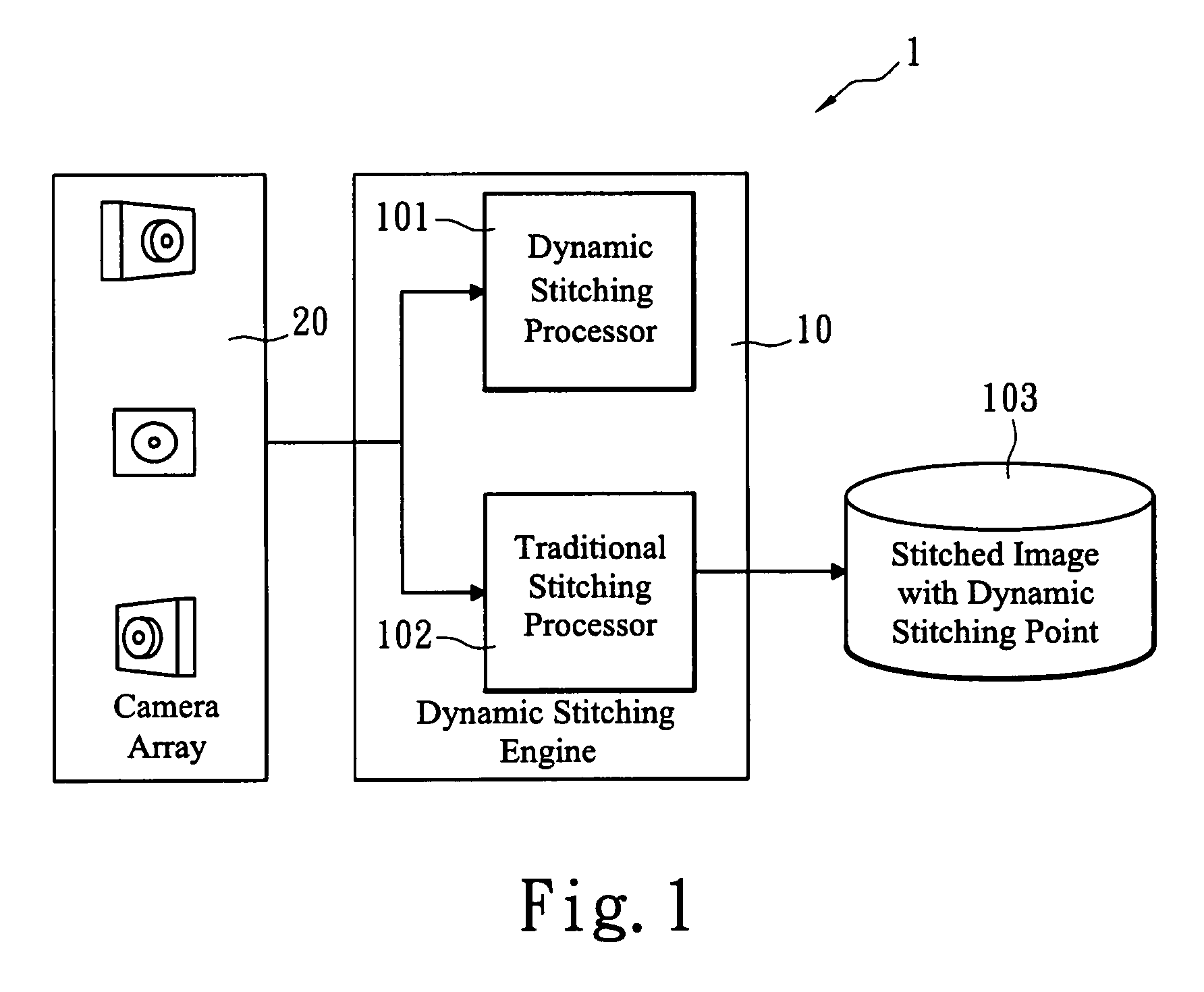
Advanced dynamic stitching method for multi-lens camera system
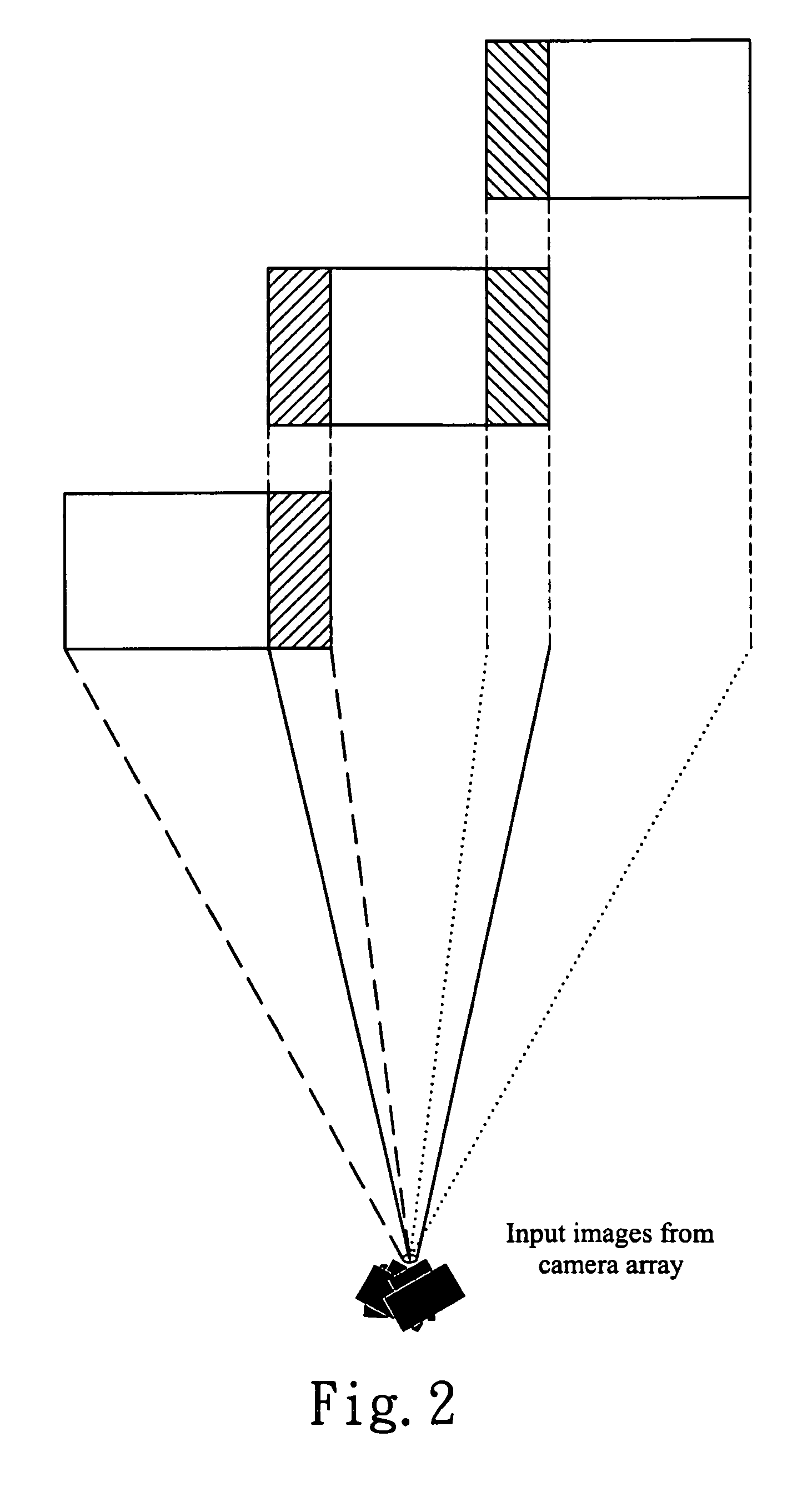
InactiveUS20090051778A1Quick searchSuppresses parallax phenomenonTelevision system detailsClosed circuit television systemsParallaxComputer science
An advanced dynamic stitching method for multi-lens camera system is disclosed. This invention aims to address the parallax phenomenon which exists in a multi-lens camera system. Stitching points vary with the object distance. In a video stitching system, a fast search engine to update the stitching points dynamically is needed. This invention provides an advanced method to reduce the high computation power required for the traditional block matching method of finding stitching points. As a result, the stitching points can be adjusted dynamically with the method of this invention.
Owner:SONY TAIWAN
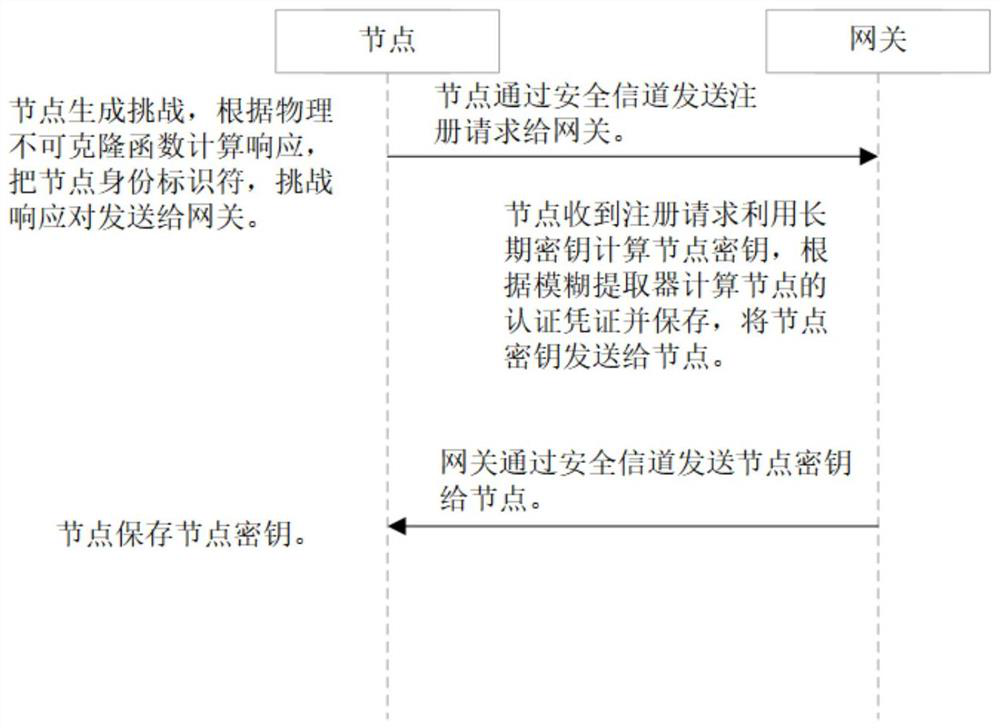
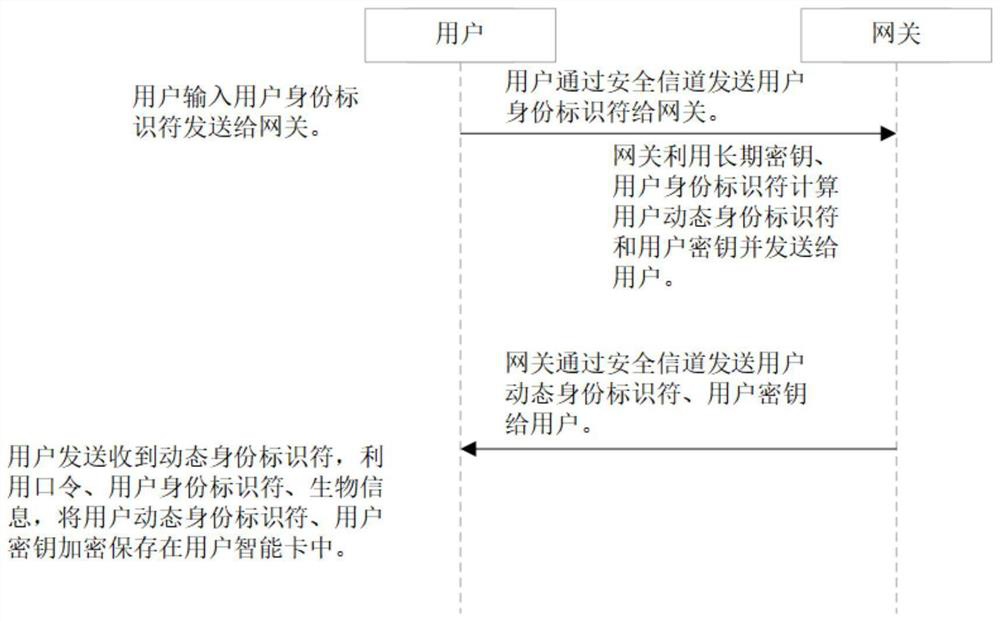
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
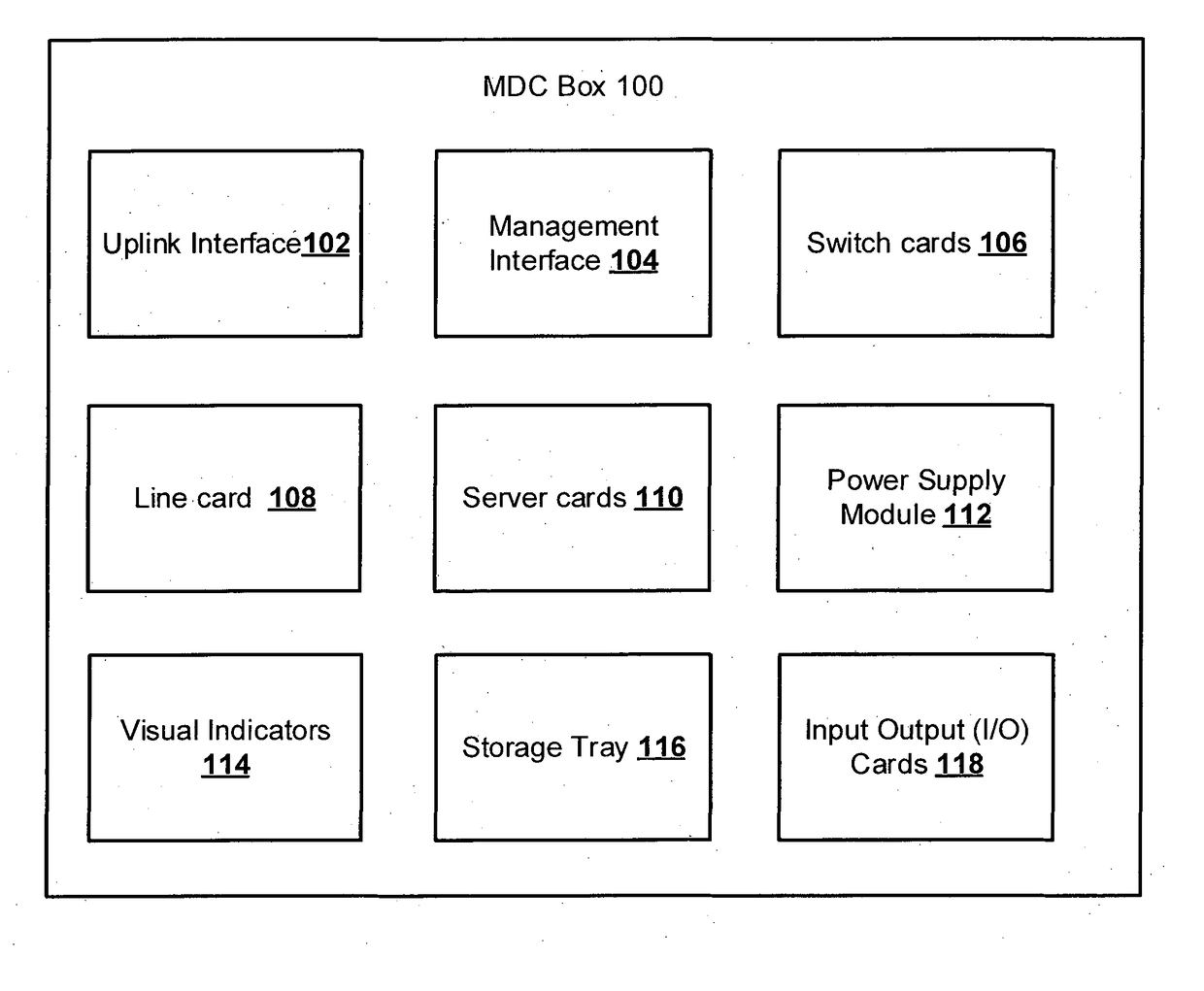
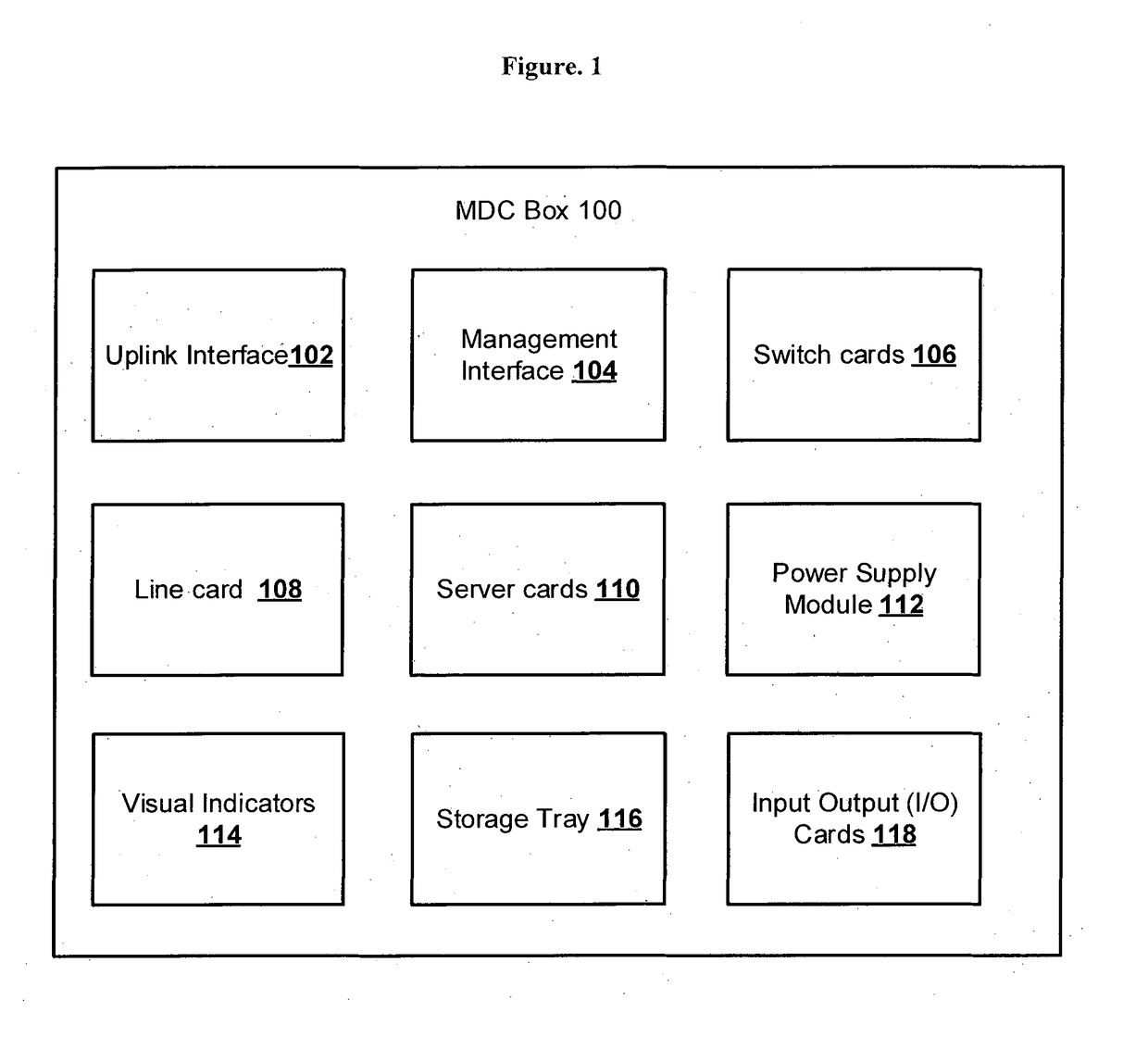
Micro data center (MDC) in a box system and method thereof
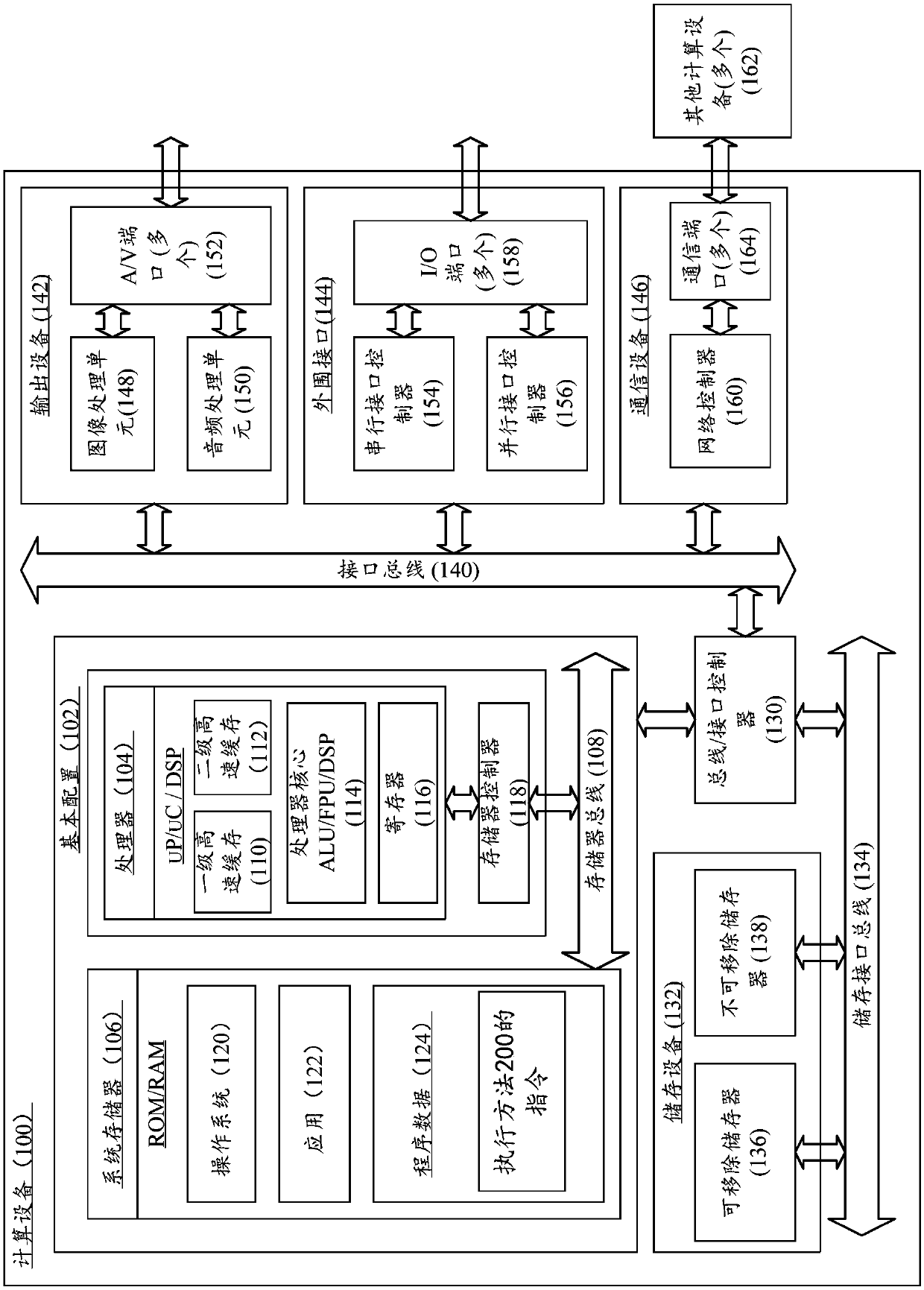
InactiveUS20180213669A1Data and faster and efficientlyEfficient and fast processingServersPower supply for data processingBox modelData center
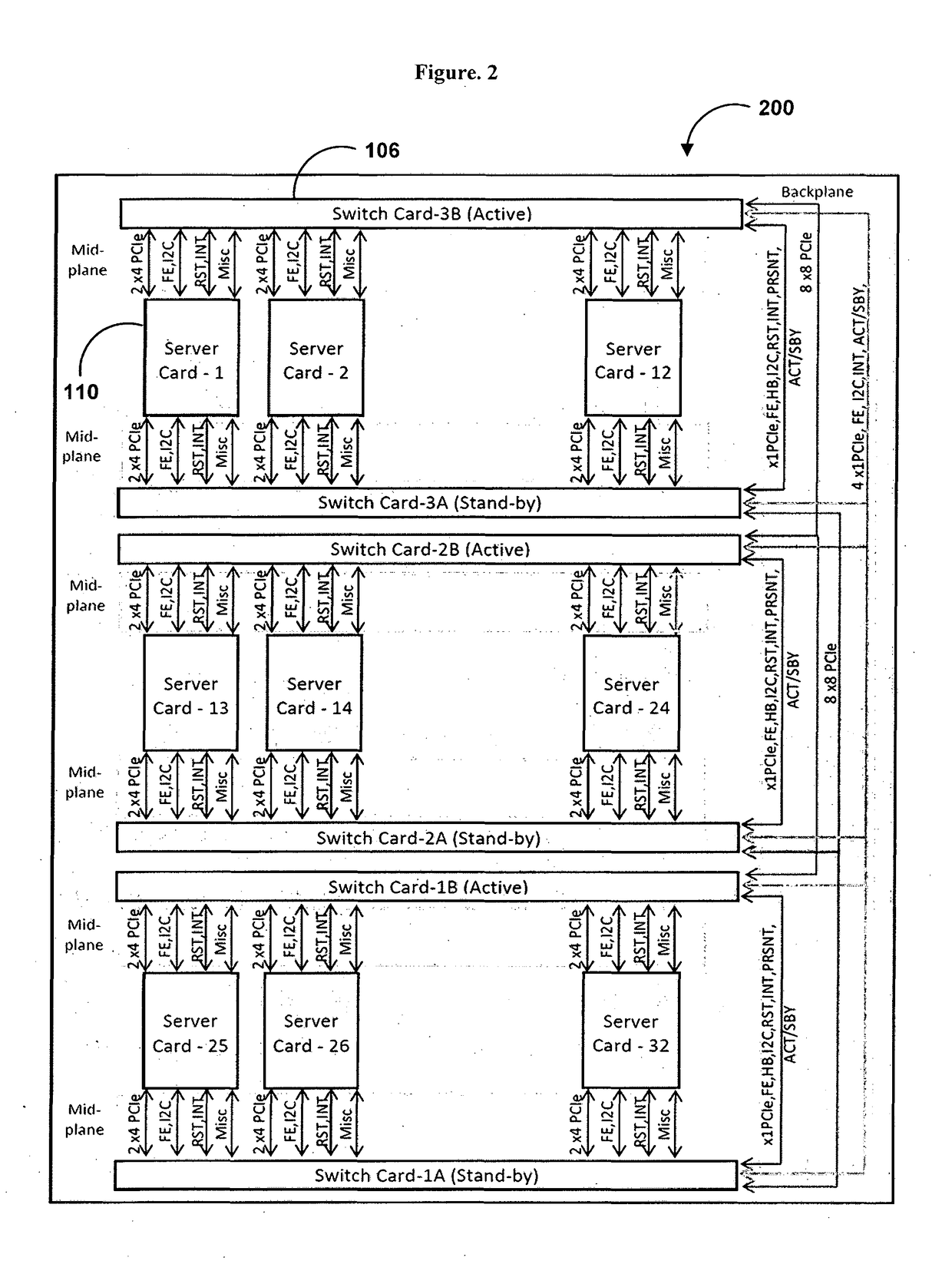
The various embodiments of the present invention disclose a Micro Data Center (MDC) system, wherein the system comprising a rack mountable box (100) housing, one or more uplink interfaces (102), one or more management interfaces (104), one or more switch cards (106), one or more line cards (108), one or more server cards (110), a power supply module (112), one or more visual indicators (114), a storage tray (116), and one or more Input-Output (I / O) cards (118), wherein the MDC system is a reconfigurable data center in a box model, where the one or more components of the MDC system are interoperably connected through on a peripheral component interconnect express (PCIe) Express MDC Super compute Fabric.
Owner:KOCHUKUNJU PRASAD LALATHUPUTHANPURA
Vehicle driving redundancy control system and method
InactiveCN110737192AAvoid crashing out of controlReduce loadSafety arrangmentsCar drivingControl system
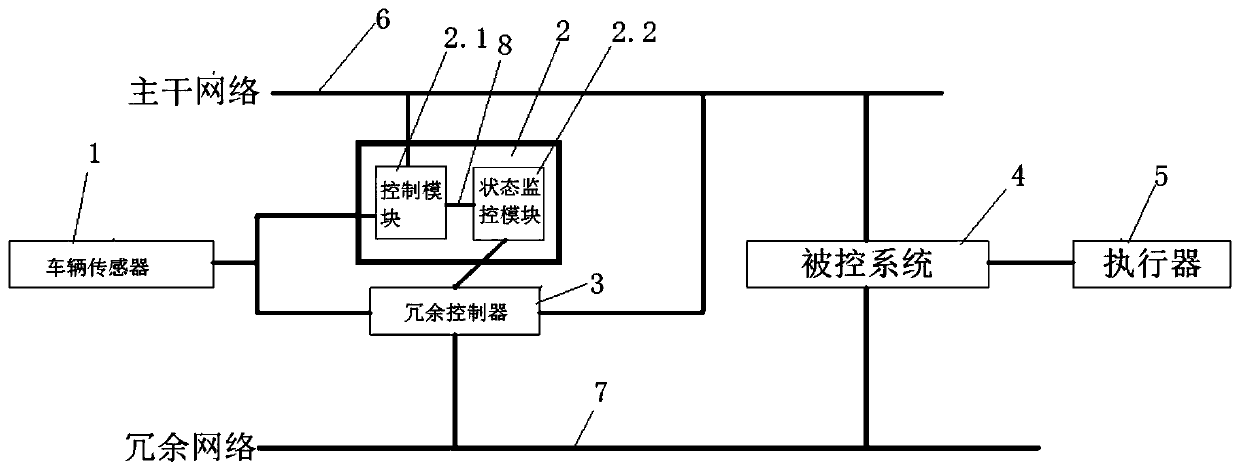
The invention discloses a vehicle driving redundancy control system which comprises a vehicle sensor, a controller, a redundancy controller, a controlled system, an actuator, a trunk network and a redundant network; the controller comprises a control module and a state monitoring module; the control module is used for receiving sensing signals of the vehicle sensor uninterruptedly, generating a corresponding vehicle control instruction according to the sensing signals and sending the vehicle control instruction to the controlled system through a trunk network; the controlled system operates the actuator to execute a corresponding vehicle control action according to the vehicle control instruction; and the state monitoring module is used for detecting whether the control module has a fault.According to the invention, the integrity and the communication reliability of the control system can be guaranteed more effectively while the cost of the controller is guaranteed.
Owner:DONGFENG COMML VEHICLE CO LTD
Method for object tracking
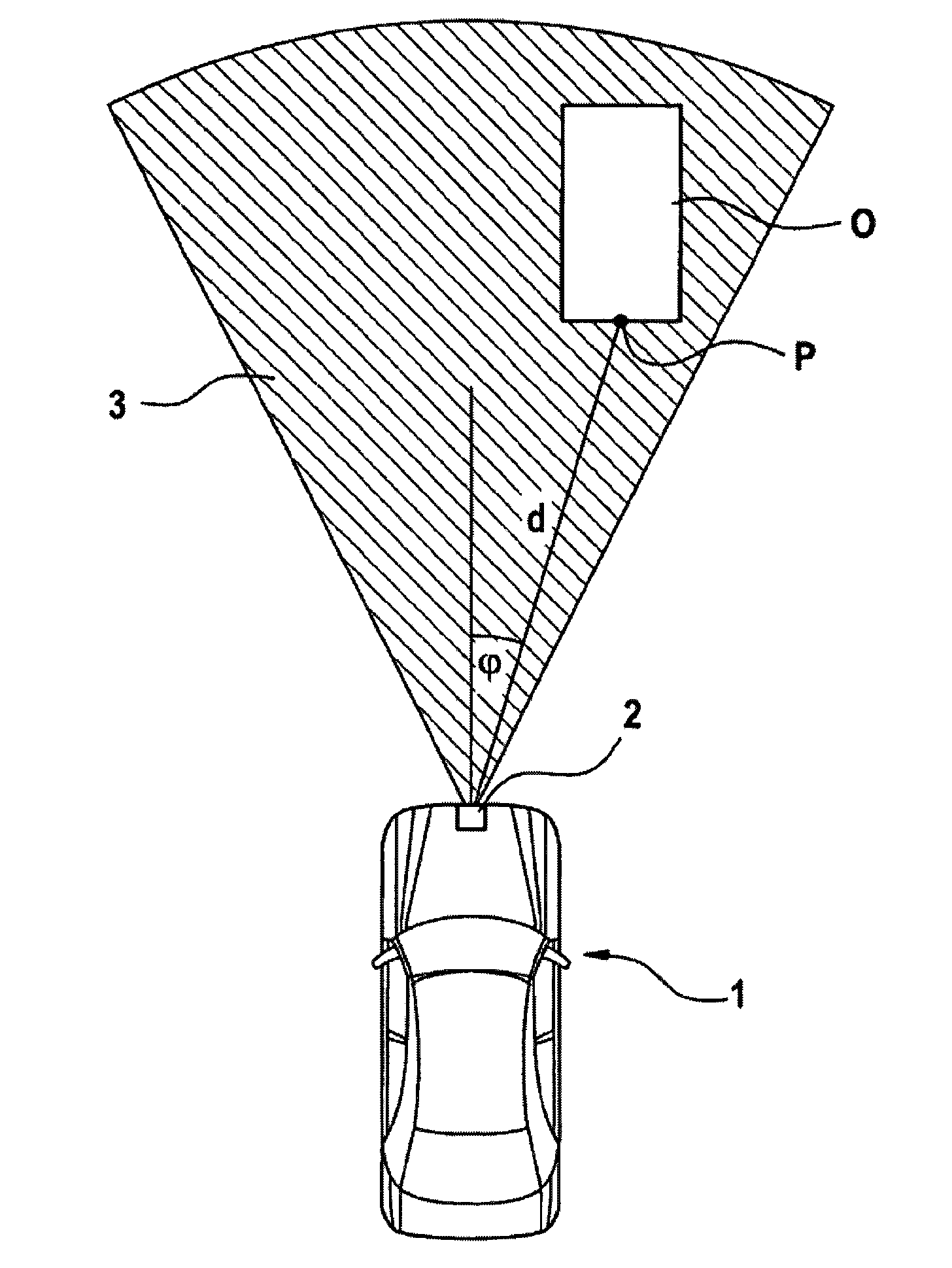
ActiveUS20090080701A1Reduce effortSave computing powerTelevision system detailsImage analysisMobile objectPedestrian
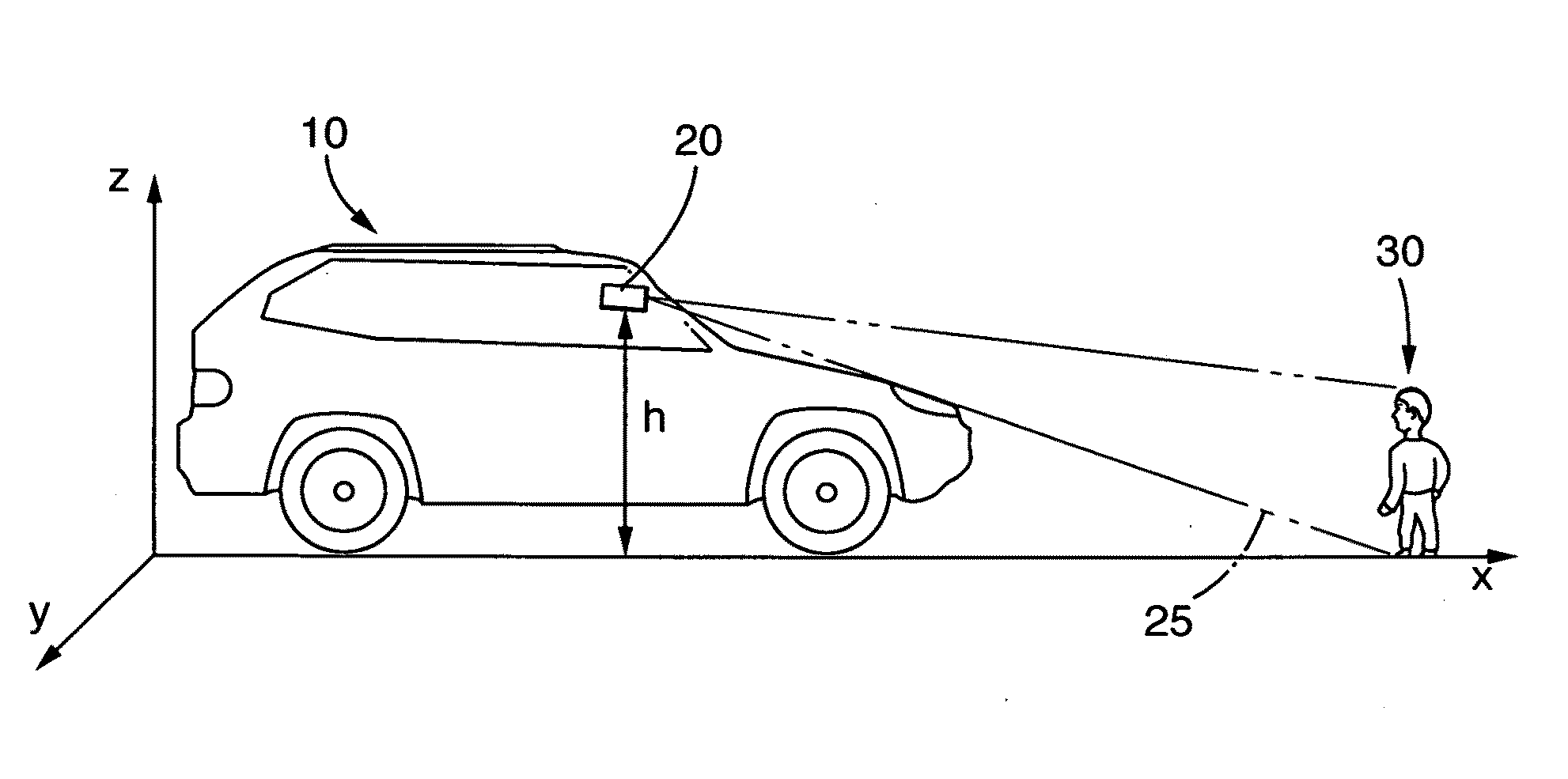
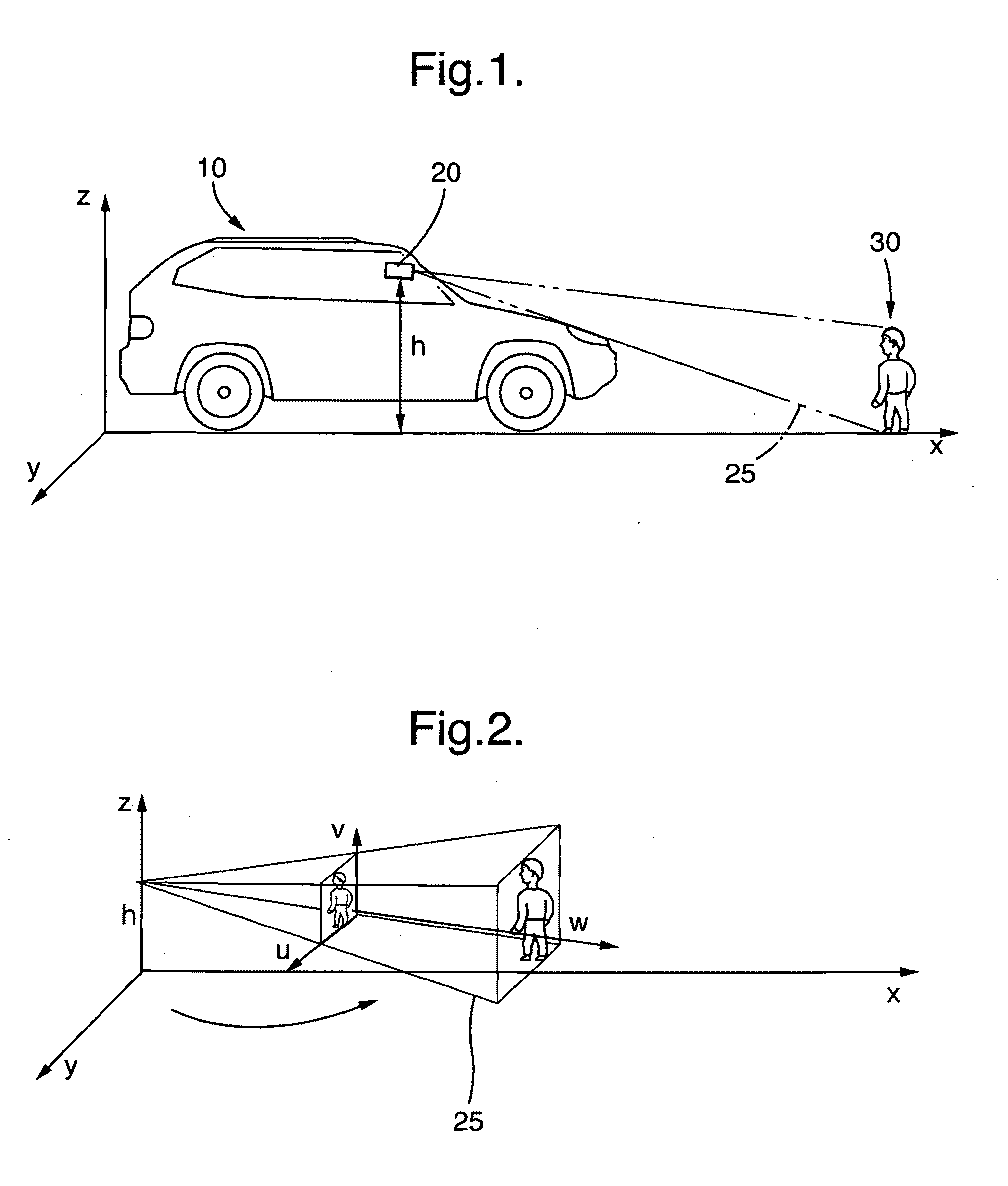
The present invention relates to a method for the recognition and tracking of a moving object, in particular of a pedestrian, from a motor vehicle, at which a camera device is arranged. An image of the environment including picture elements is taken in the range of view of the camera device (20) by means of the camera device at regular time intervals and those picture elements are identified with the help of an image processing system which correspond to moving objects to be tracked. A picture element is extracted for each of these objects which represents a projection in image coordinates of that spatial point at which the object contacts a road plane The movement of the corresponding spatial point in the road plane is tracked by means of a state estimator which uses an at least four-dimensional state vector whose components are a position of the spatial point in the road plane and an associated speed in the road plane, wherein the tracking of the movement by the state estimator includes the steps that a prediction is generated for the state vector, this prediction is converted into image coordinates via suitable projection equations, an error to be expected for this prediction is calculated in image coordinates by means of a covariance matrix, and this prediction is compared with the picture element extracted in a later image and is updated.
Owner:APTIV TECH LTD
Method and device for compressing image
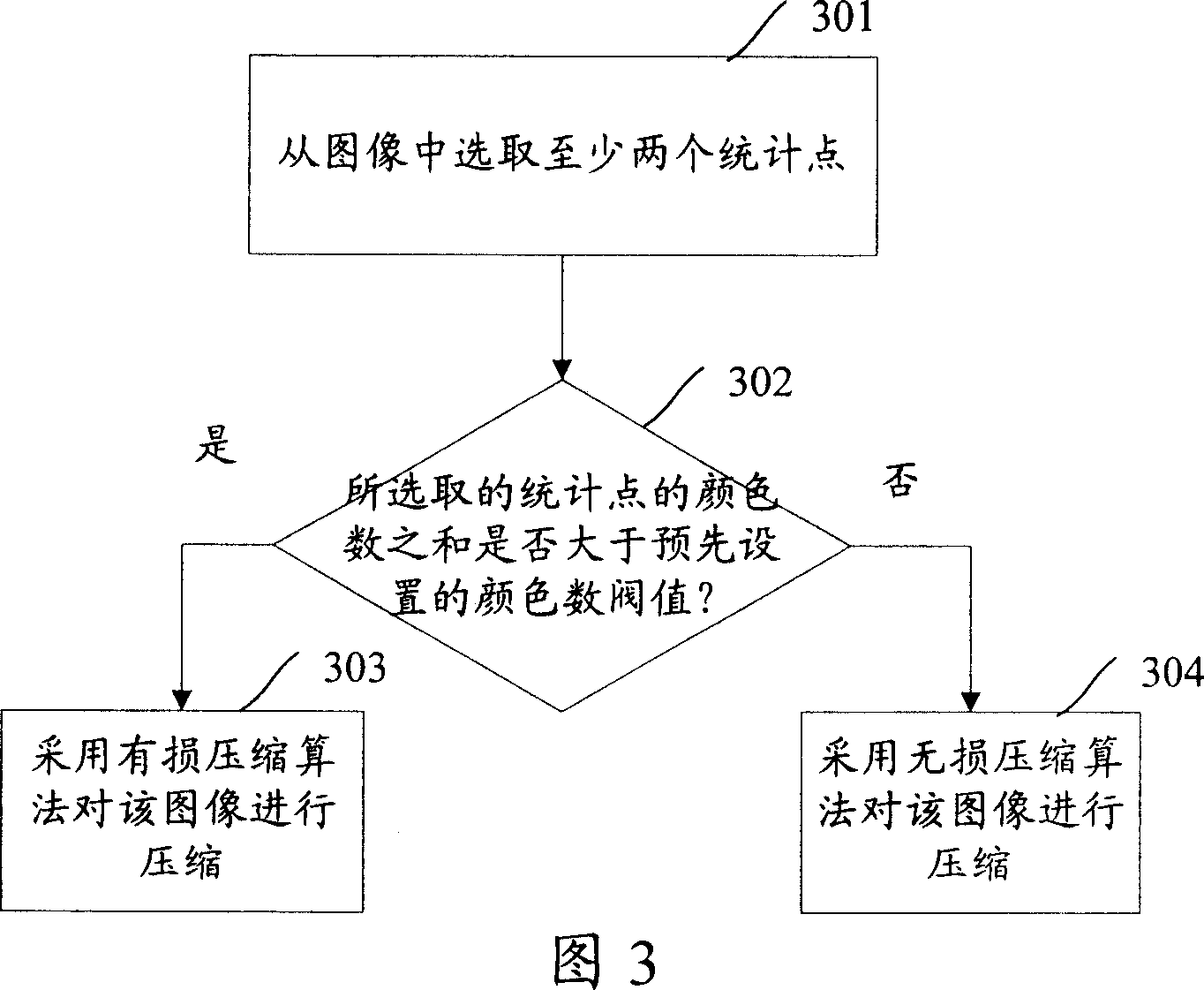
ActiveCN101075348AImprove processing efficiencySave computing powerImage codingCompression deviceImage type
A method for compressing image includes selecting at least two statistic points from image, judging whether color number sum of two selected statistic points is greater than preset color number threshold or not and applying destructive compression algorithm to carry out compression on image if it is or otherwise applying nondestructive compression algorithm to carry out compression on image. The compression device used for realizing said method is also disclosed.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Certificateless multi-receiver signcryption method with multivariate-based cryptosystem
InactiveCN102811125APrivacy protectionImprove securityPublic key for secure communicationUser identity/authority verificationCiphertextConfidentiality
The invention discloses a certificateless multi-receiver signcryption method with a multivariate-based cryptosystem. The certificateless multi-receiver signcryption method is used for solving the technical problem of poor security of an existing certificateless signcryption method. The technical scheme includes that the method includes: firstly, using a key generation center to generate system parameters, and selecting a secure multivariable encryption algorithm to generate keys; and enabling a user U to obtain system private keys of the key generation center and generate the private keys to user keys prior to that a user Alice with the identity IDA sends signcryption messages to a user group L={ID1, ID2,...,IDt}, and accepting or refusing ciphertext sigma by means of un-signcryption. By the aid of the multivariate-based cryptosystem, high security of anti-quantum computation is achieved, and the certificateless multi-receiver signcryption method is still high in security facing attack of a quantum computer. Compared with the background art, the certificateless multi-receiver signcryption method is small in computation and high in security, has the advantages of completeness, confidentiality, unforgeability, forward security, backward security, receiver privacy protection and the like and is capable of resisting existing known attack.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Vehicle access system
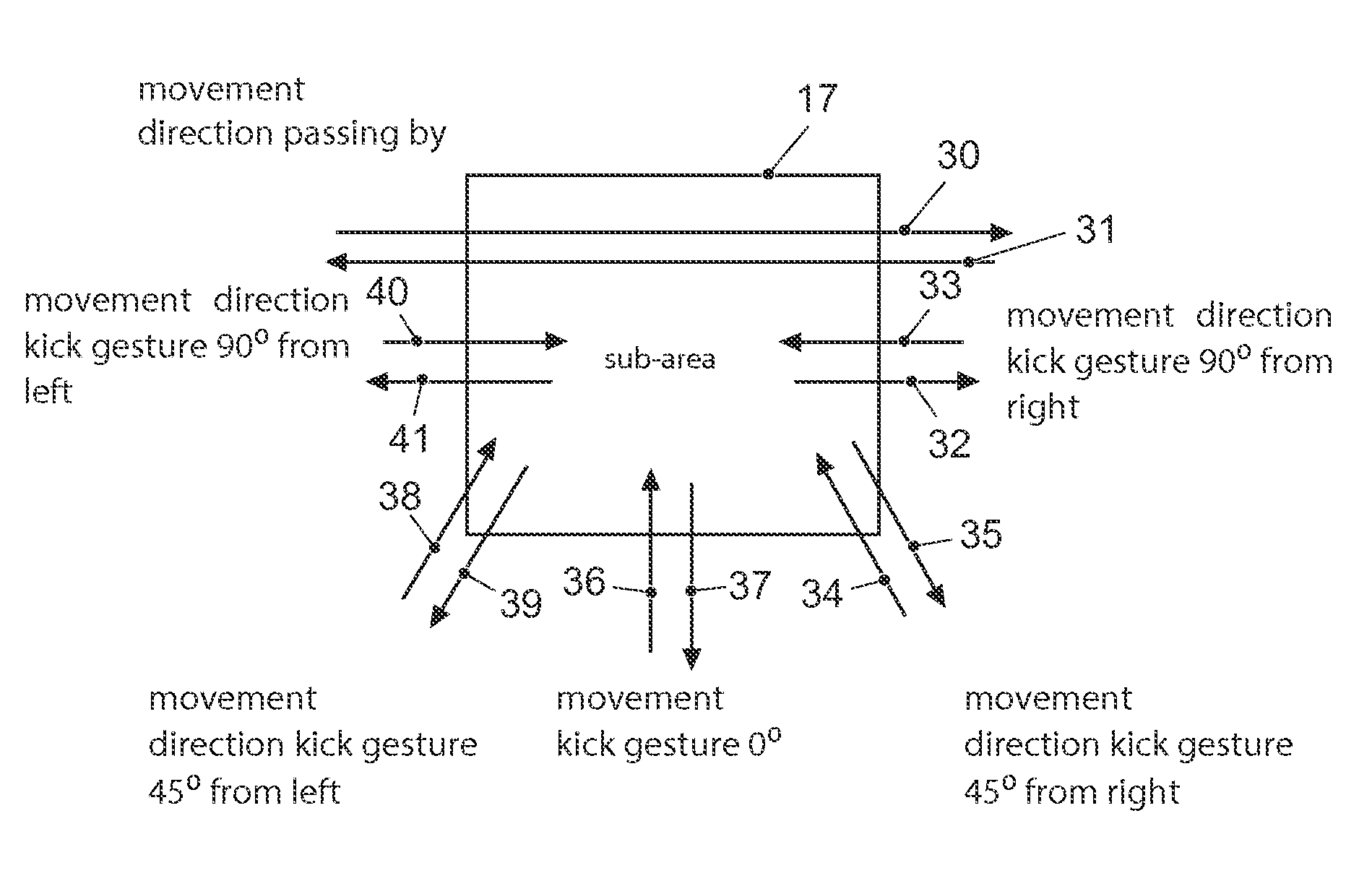
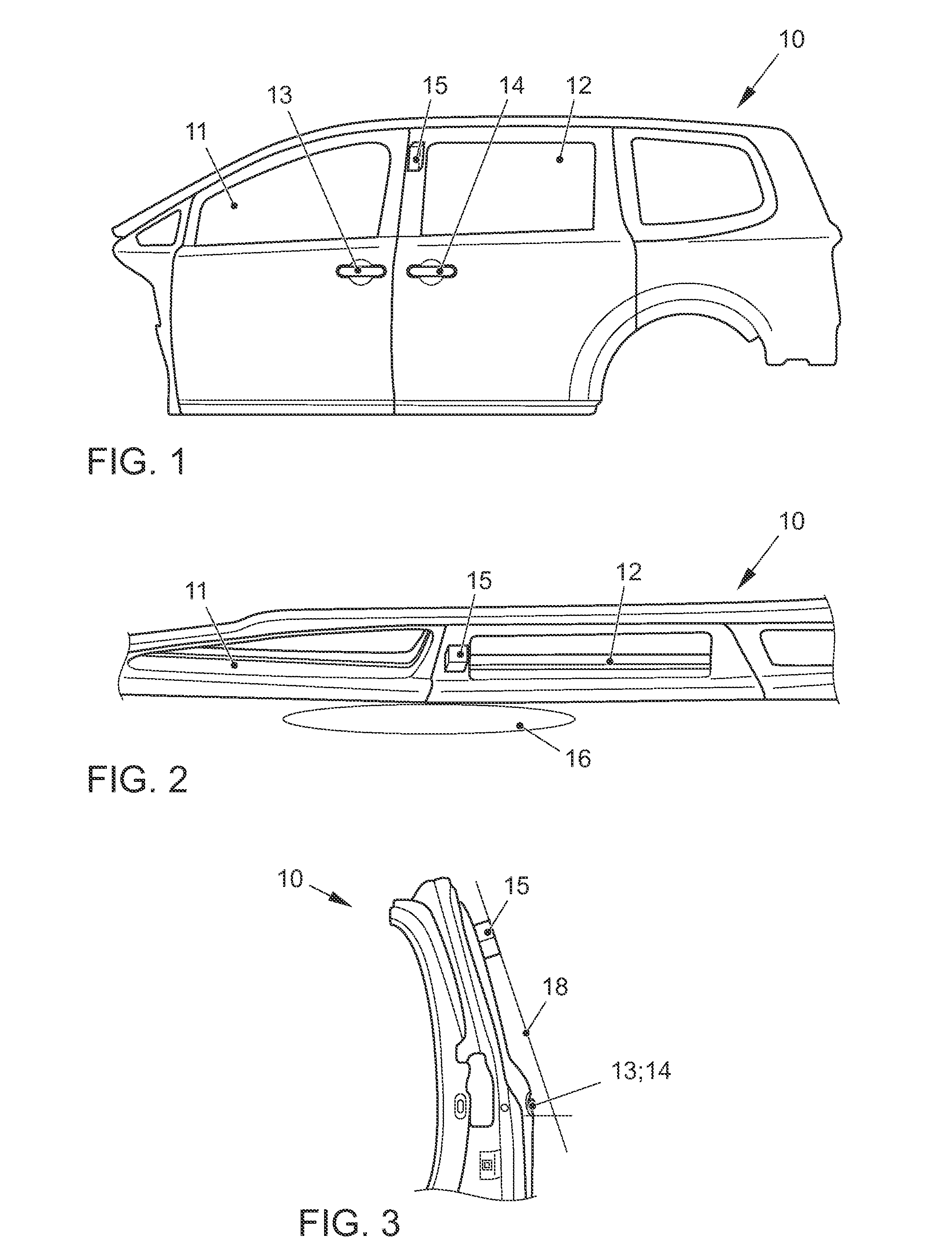
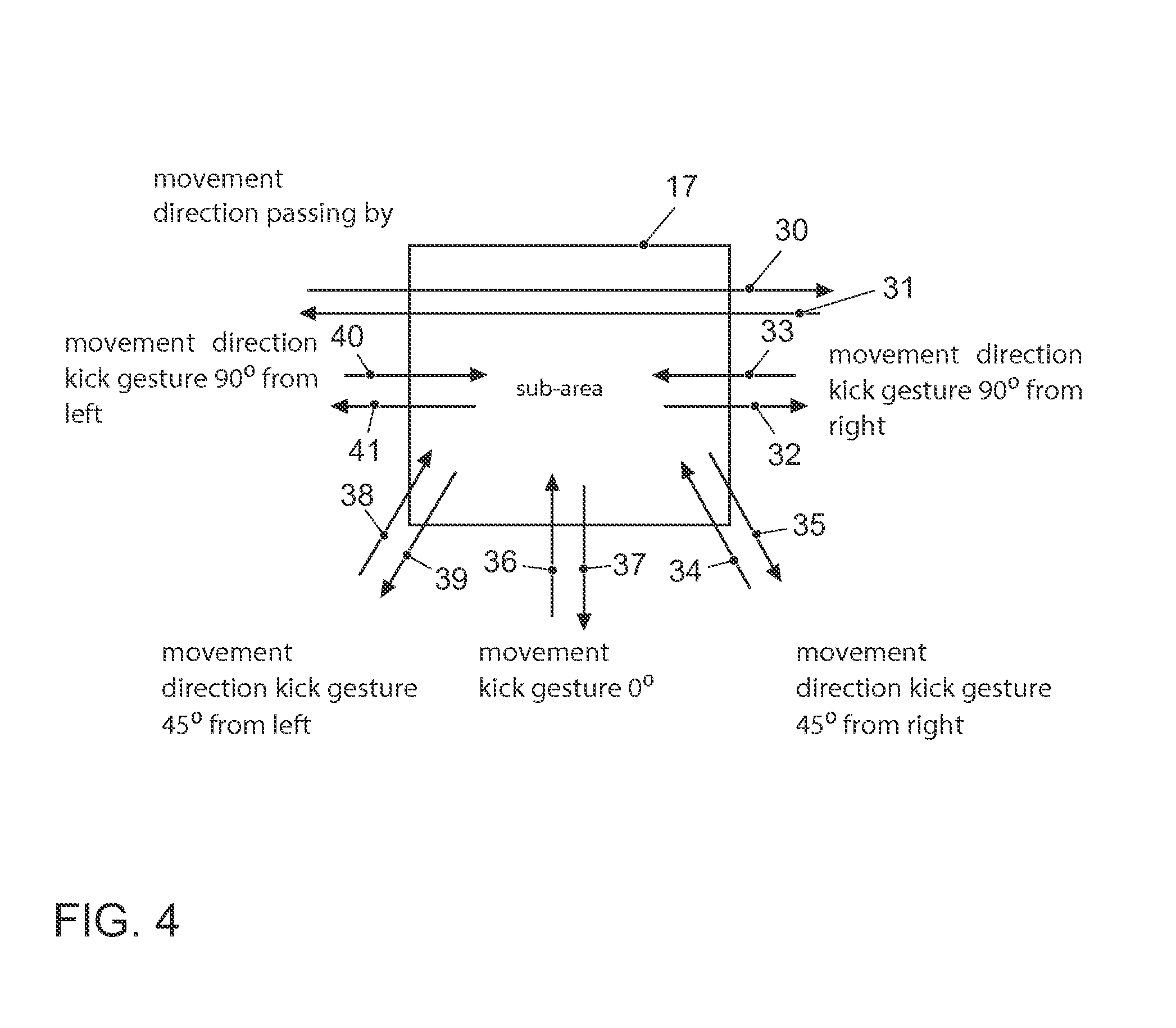
ActiveUS20160096509A1Simple and fast and reliable identificationIncrease energy levelInput/output for user-computer interactionTelevision system detailsEmbedded system
A method for an access system for a vehicle includes the steps of recording a first optical information in a specific area surrounding the vehicle and detecting an object approaching the vehicle as a function of the recorded first optical information. As a function of detecting the approaching object, a second optical information in the surrounding area is recorded, and gesture information of the object is identified as a function of the second optical information. A locking device or door opening device of the access system is triggered as a function of gesture information.
Owner:VOLKSWAGEN AG
Advanced dynamic stitching method for multi-lens camera system
InactiveUS8004557B2Quick searchSuppresses parallax phenomenonTelevision system detailsClosed circuit television systemsParallaxMatch method
An advanced dynamic stitching method for multi-lens camera system is disclosed. This invention aims to address the parallax phenomenon which exists in a multi-lens camera system. Stitching points vary with the object distance. In a video stitching system, a fast search engine to update the stitching points dynamically is needed. This invention provides an advanced method to reduce the high computation power required for the traditional block matching method of finding stitching points. As a result, the stitching points can be adjusted dynamically with the method of this invention.
Owner:SONY TAIWAN
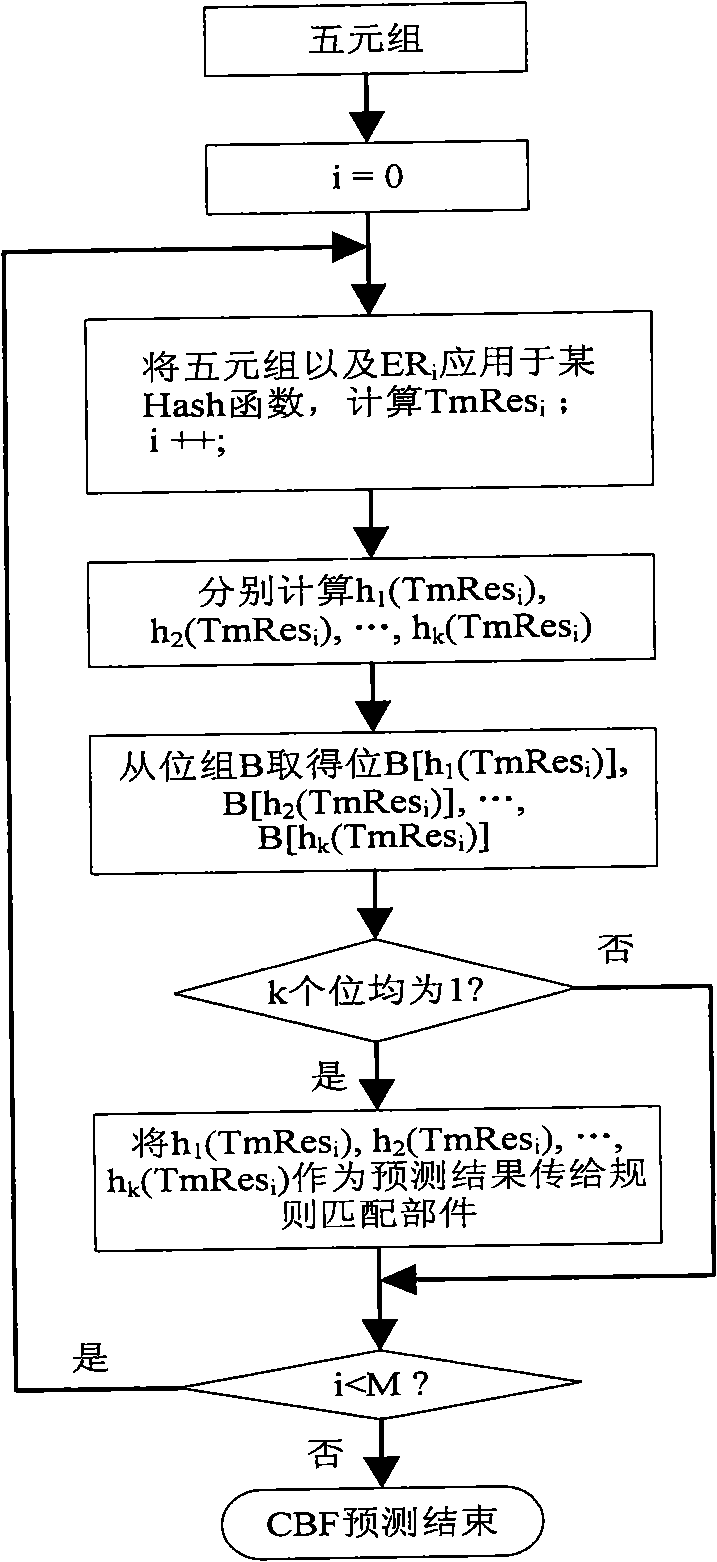
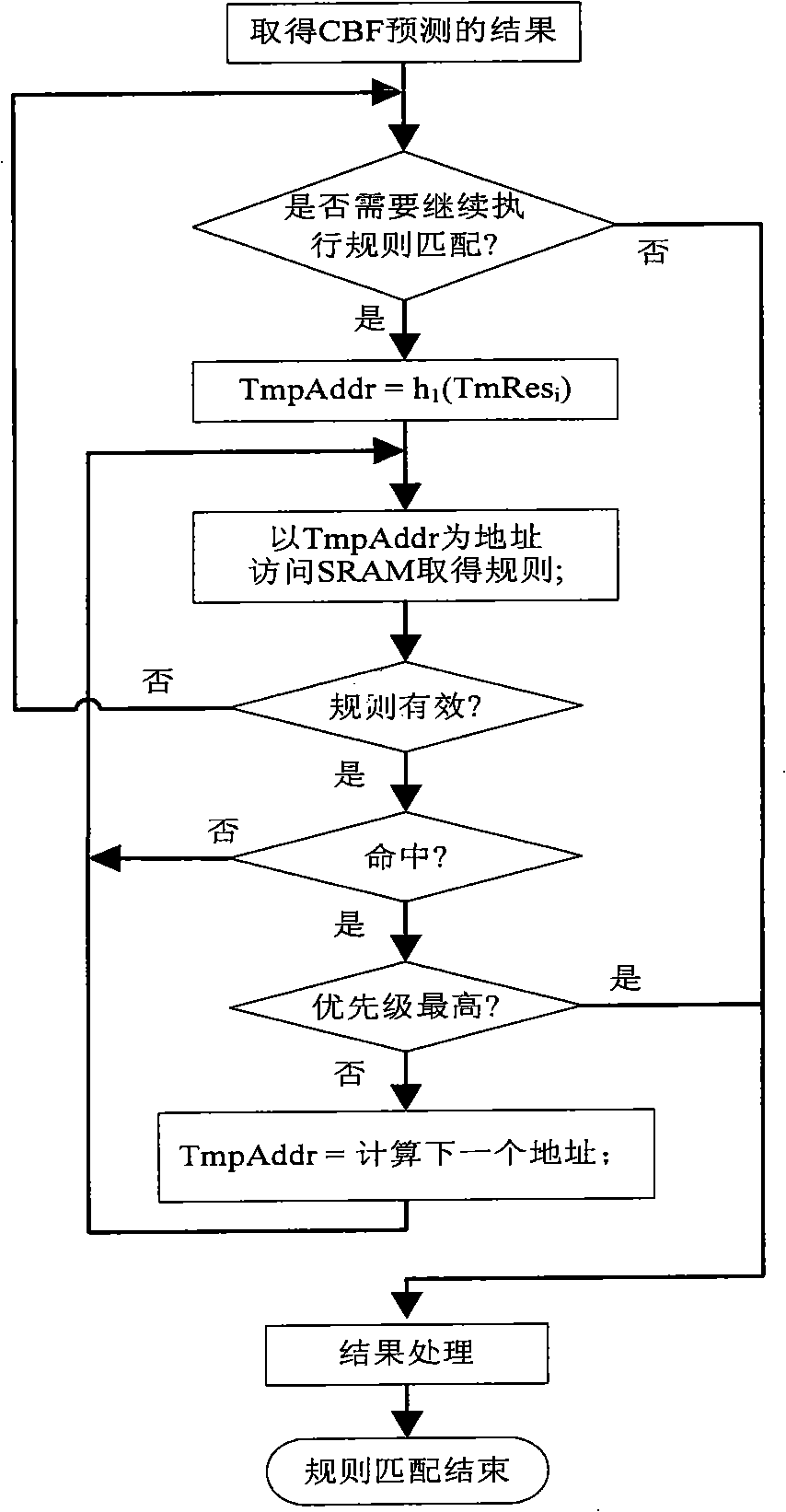
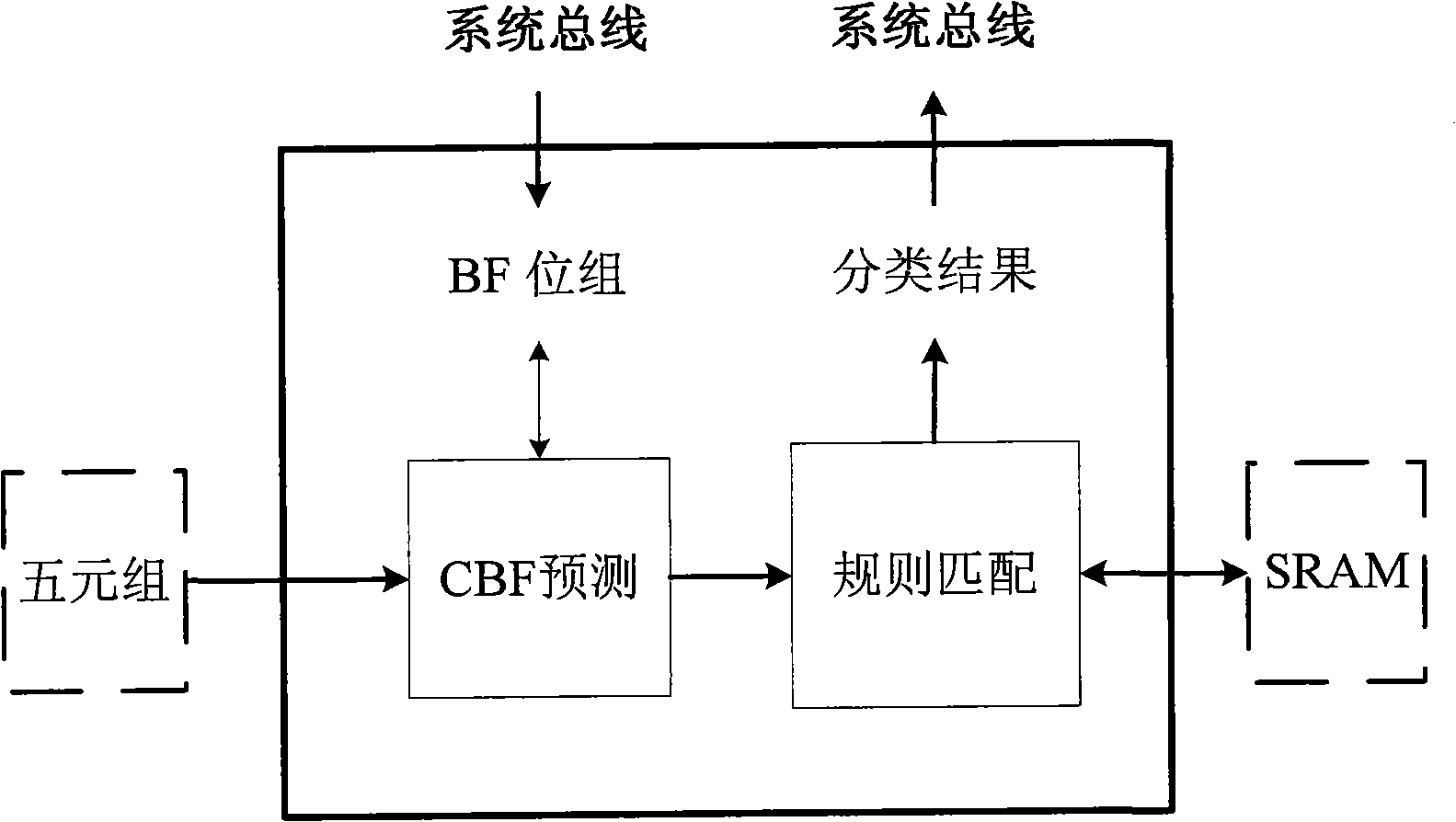
IP packet classification method and apparatus
The invention proposes a packet-classification method and the implementation device based on the Bloom Filter, including a Counting Bloom Filter forecasting module used for executing the forecast based on the Counting Bloom Filter towards the 5-tuple of the received and extracted IP packet of the network device and acquiring the forecast result and a rule matching module used for matching the forecast result with the rule table organized into a Hash table and determining the rule applied on the IP packet. The SRAM storage rule can be adopted to support the large rule set with the size of more than 100K and the real-time updating of the rule set; besides, the packet-classification method and the implementation device based on the Bloom Filter have extensibility and reduce the average storage accessing time to less than once and process the IP packet flow with the speed of 10Gbps or even higher speed through line-speed processing under certain conditions.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Data aggregation method based on compressed sensing in wireless sensor network
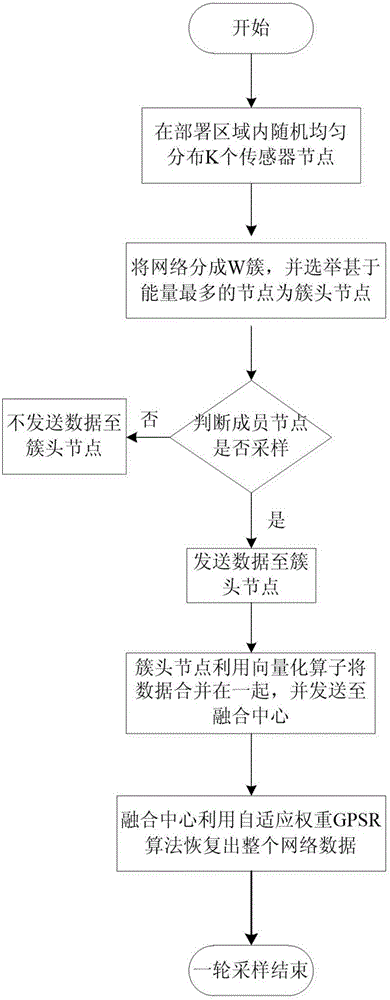
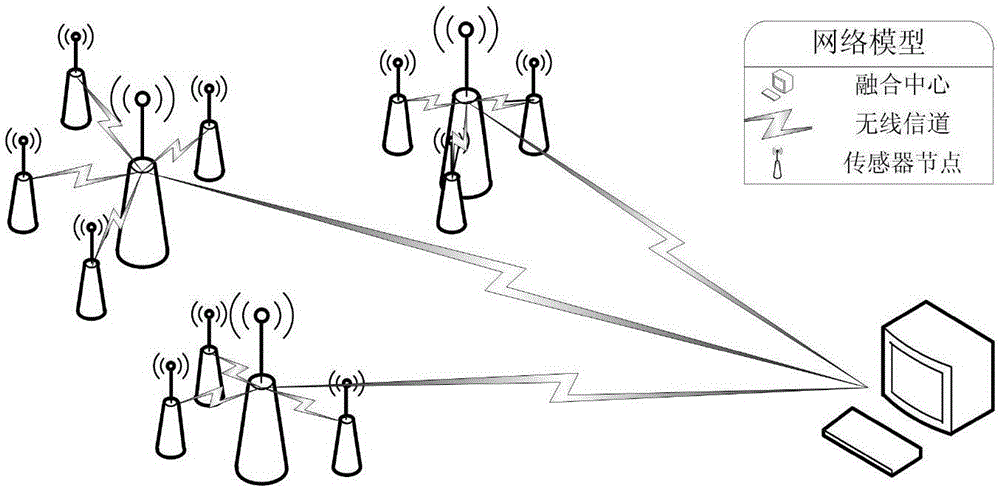
ActiveCN106792435ALimit lifetimeExtend your lifeParticular environment based servicesNetwork topologiesFusion centerPattern recognition
The invention discloses a data aggregation method based on compressed sensing in a wireless sensor network. The method includes: uniform clustering of the sensor network is performed, a node with the most residual energy is selected as a cluster head node, member nodes independently select whether to participate in sampling with the probability ptx, and the cluster head node always participate in sampling; then sampling nodes obtain original signals f and obtain sparse representations x thereof through transform of sparse transform bases, x are projected in a measuring matrix phi, sparse measuring signals y are obtained and sent to the cluster head node, and the cluster head node merges the collected measuring signals to a signal Y by employing vectorization operators and sends the signal Y to a fusion center; and finally the fusion center performs reconstruction on the signals one by one by employing an adaptive weight GPSR algorithm and recovers the sparse representations X thereof. According to the method, the characteristics of noise-containing signals, large data bulk, and high timeliness requirement of the wireless sensor network are completely achieved, the adaptive weight GPSR algorithm does not need to know the signal sparsity in advance, and all high-dimensional signals can be accurately reconstructed in a short period.
Owner:XIDIAN UNIV
Method for object tracking
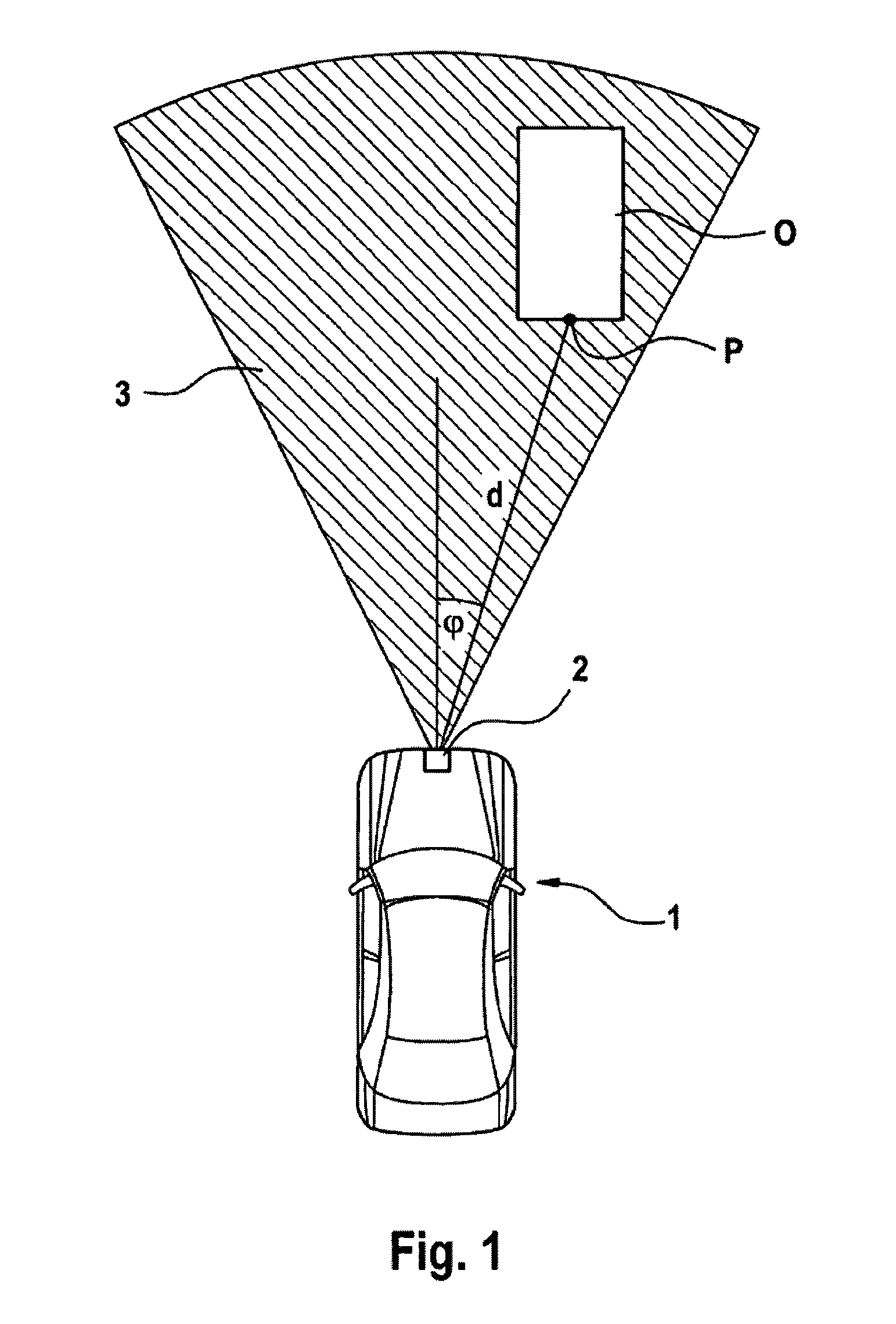
ActiveUS8055020B2Reduce effortSave computing powerTelevision system detailsImage analysisImaging processingField of view
The present invention relates to a method for the recognition and tracking of a moving object, in particular of a pedestrian, from a motor vehicle, at which a camera device is arranged. An image of the environment including picture elements is taken in the range of view of the camera device (20) by means of the camera device at regular time intervals and those picture elements are identified with the help of an image processing system which correspond to moving objects to be tracked. A picture element is extracted for each of these objects which represents a projection in image coordinates of that spatial point at which the object contacts a road plane The movement of the corresponding spatial point in the road plane is tracked by means of a state estimator which uses an at least four-dimensional state vector whose components are a position of the spatial point in the road plane and an associated speed in the road plane, wherein the tracking of the movement by the state estimator includes the steps that a prediction is generated for the state vector, this prediction is converted into image coordinates via suitable projection equations, an error to be expected for this prediction is calculated in image coordinates by means of a covariance matrix, and this prediction is compared with the picture element extracted in a later image and is updated.
Owner:APTIV TECH LTD
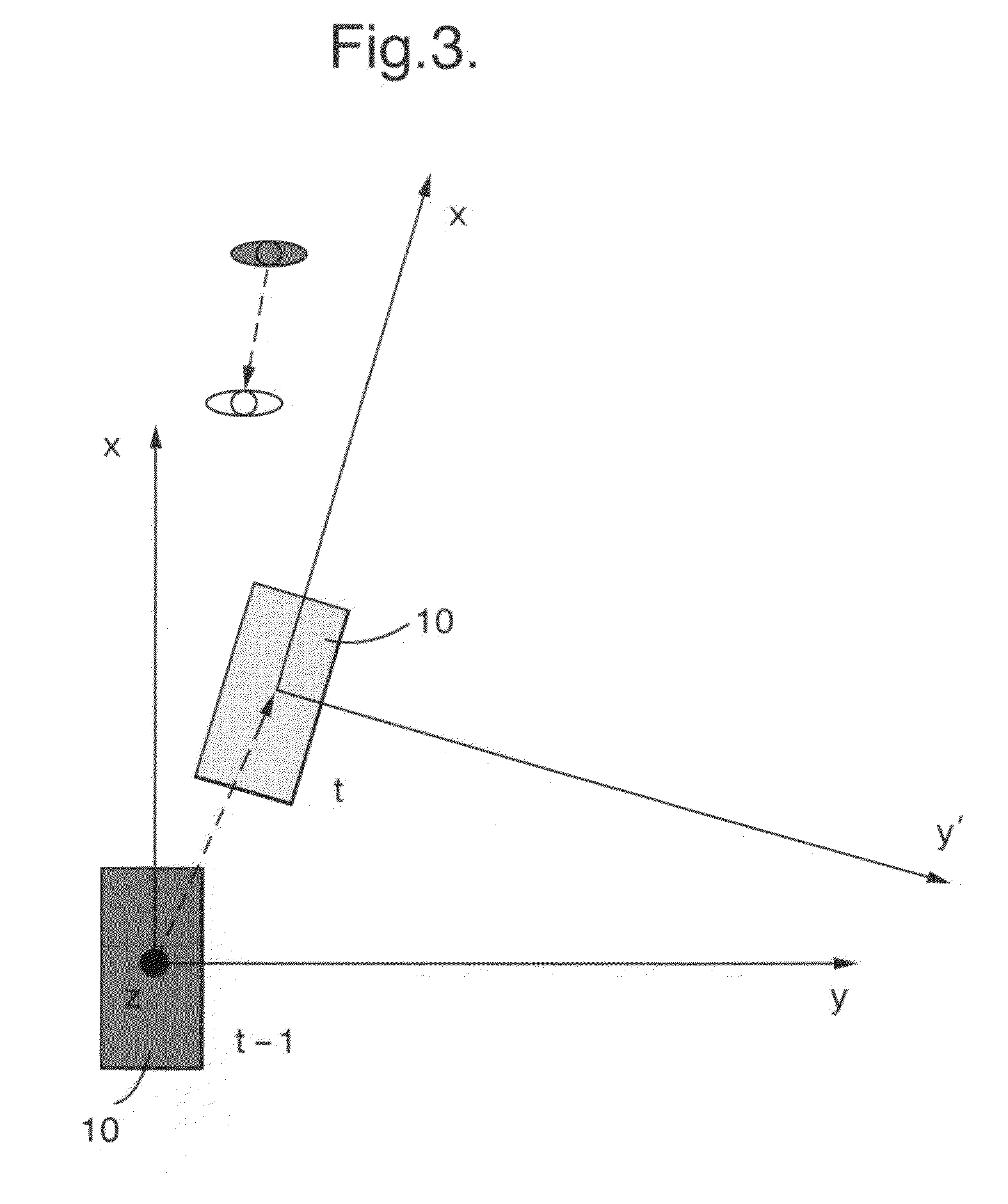
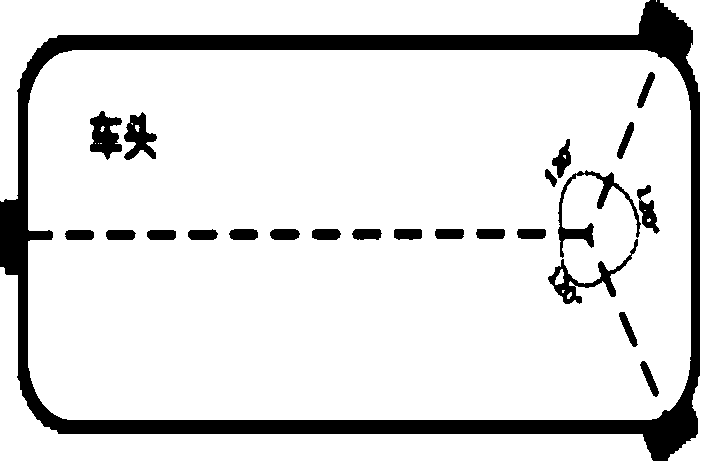
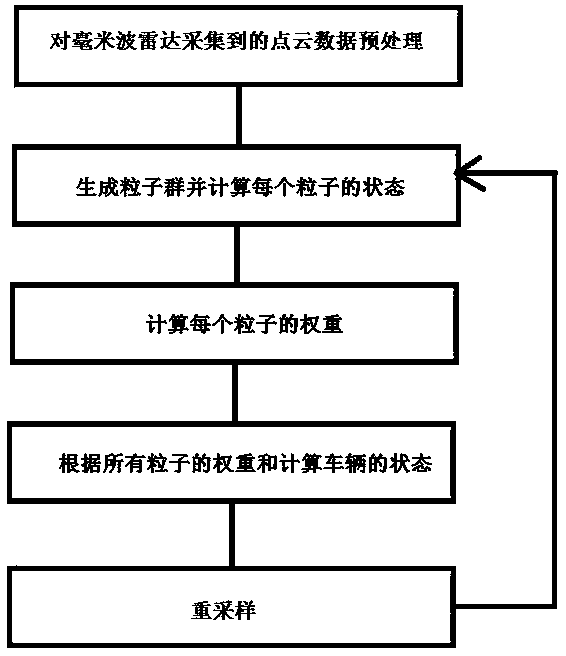
Automatic driving vehicle positioning method based on millimeter wave radar
ActiveCN110888125AObvious price advantageSave computing powerSatellite radio beaconingRadio wave reradiation/reflectionData matchingPoint cloud
The invention discloses an automatic driving vehicle positioning method based on millimeter wave radar, which is mainly used for realizing vehicle lane level positioning based on vehicle information fed back by sensors such as millimeter wave radar, GPS and the like in combination with an improved particle filtering algorithm. According to the method, the linear velocity and the angular velocity of a vehicle in a vehicle ODOM are inputted into a prediction model of a filtering algorithm, point cloud data preprocessed by a millimeter-wave radar and a constructed occupied grid map are subjectedto data matching and a new particle weight is calculated. In addition, in order to improve the robustness of the positioning algorithm, the traditional algorithm is improved, and positioning results and corresponding confidence coefficients are calculated according to different weight sums of particles; and in the resampling stage, part of new particles calculated according to GPS position information are added into the particle swarm. The cost of the whole positioning system is effectively reduced while the vehicle positioning precision is ensured and the popularization of the automatic driving technology is facilitated.
Owner:AUTOCORE INTELLIGENT TECH NANJING CO LTD
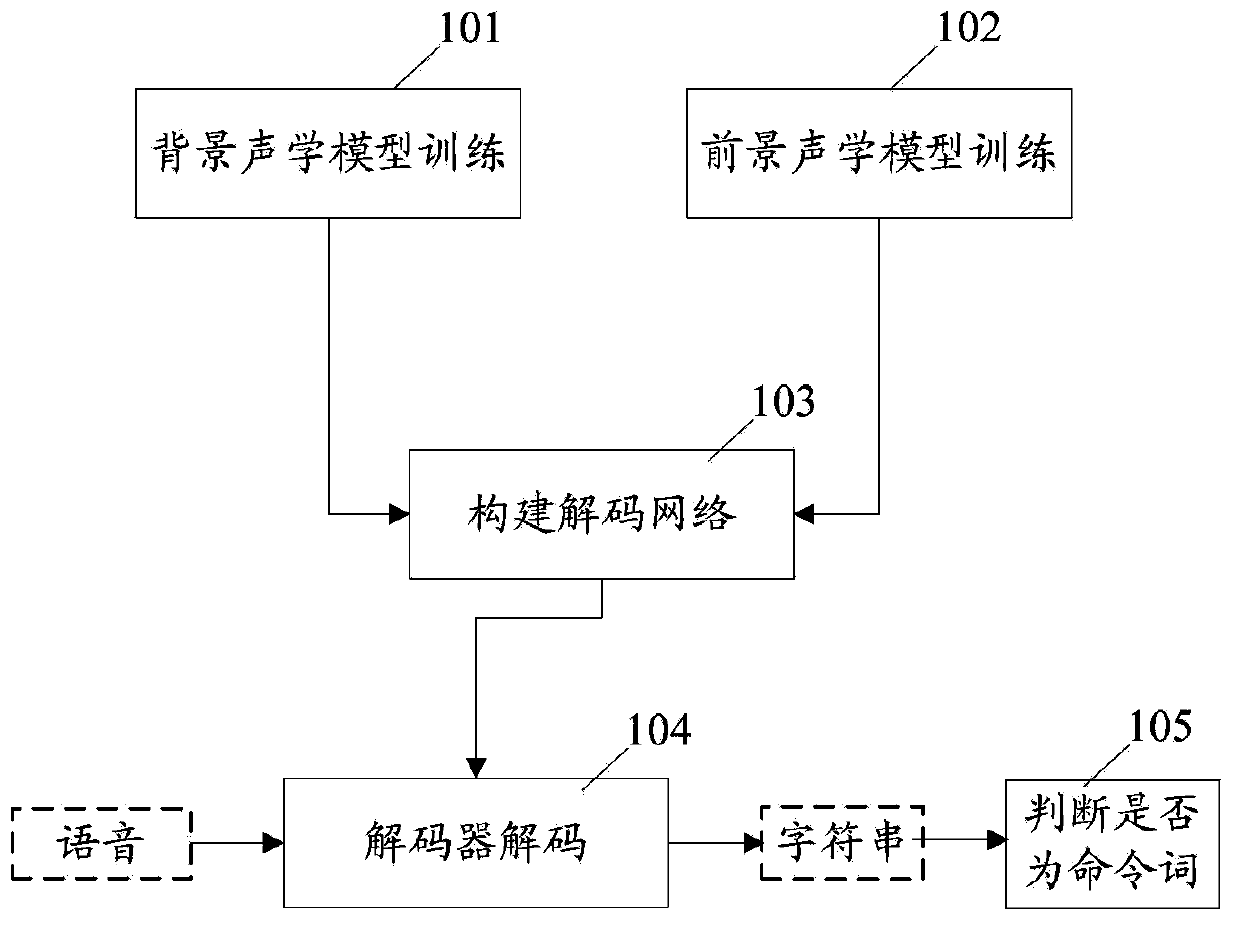
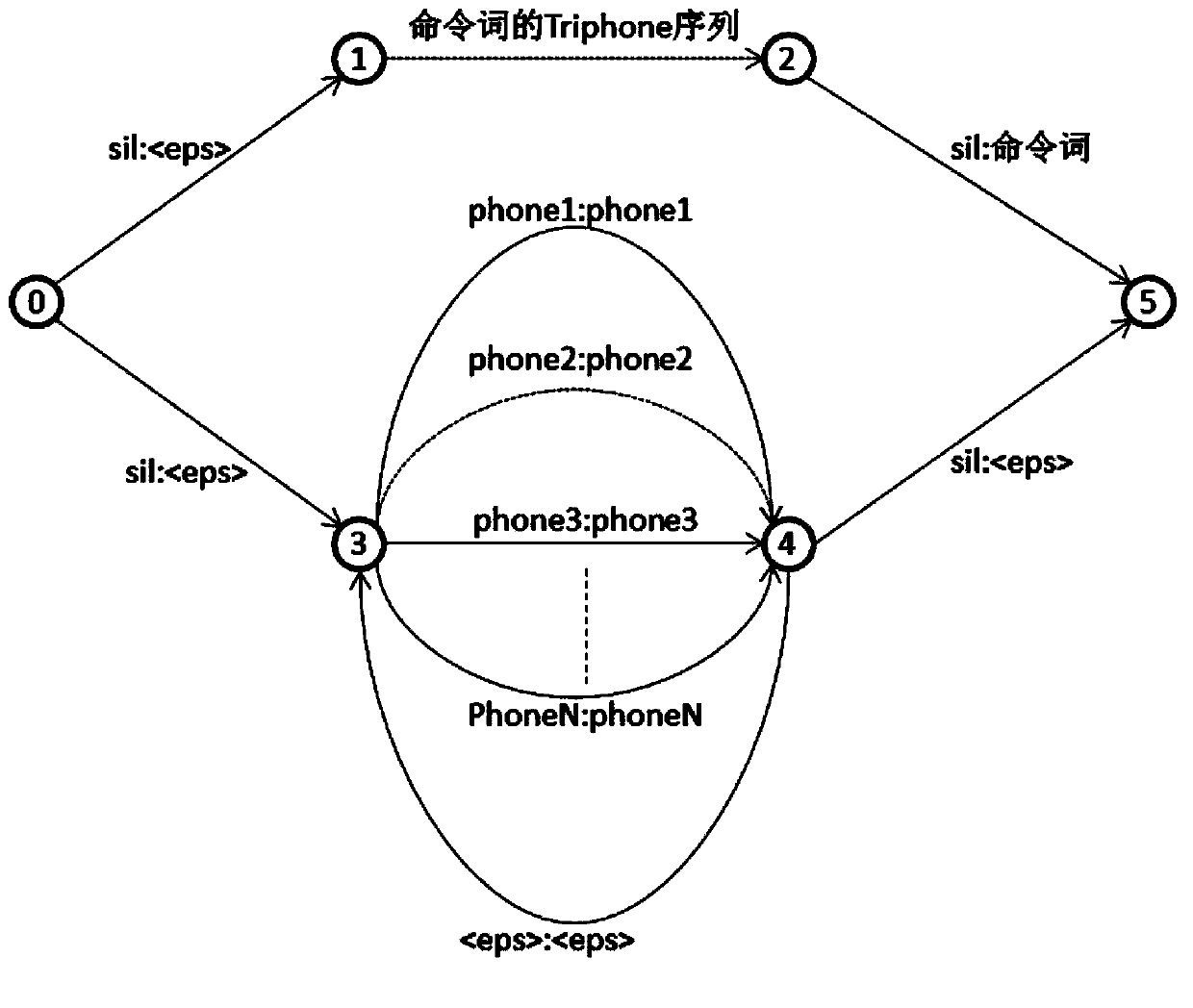
Method and system for recognizing voice commands
ActiveCN103971685AImprove recognition accuracySave computing powerSpeech recognitionAcoustic modelSpeech sound
A method of recognizing speech commands includes generating a background acoustic model for a sound using a first sound sample, the background acoustic model characterized by a first precision metric. A foreground acoustic model is generated for the sound using a second sound sample, the foreground acoustic model characterized by a second precision metric. A third sound sample is received and decoded by assigning a weight to the third sound sample corresponding to a probability that the sound sample originated in a foreground using the foreground acoustic model and the background acoustic model. The method further includes determining if the weight meets predefined criteria for assigning the third sound sample to the foreground and, when the weight meets the predefined criteria, interpreting the third sound sample as a portion of a speech command. Otherwise, recognition of the third sound sample as a portion of a speech command is forgone.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
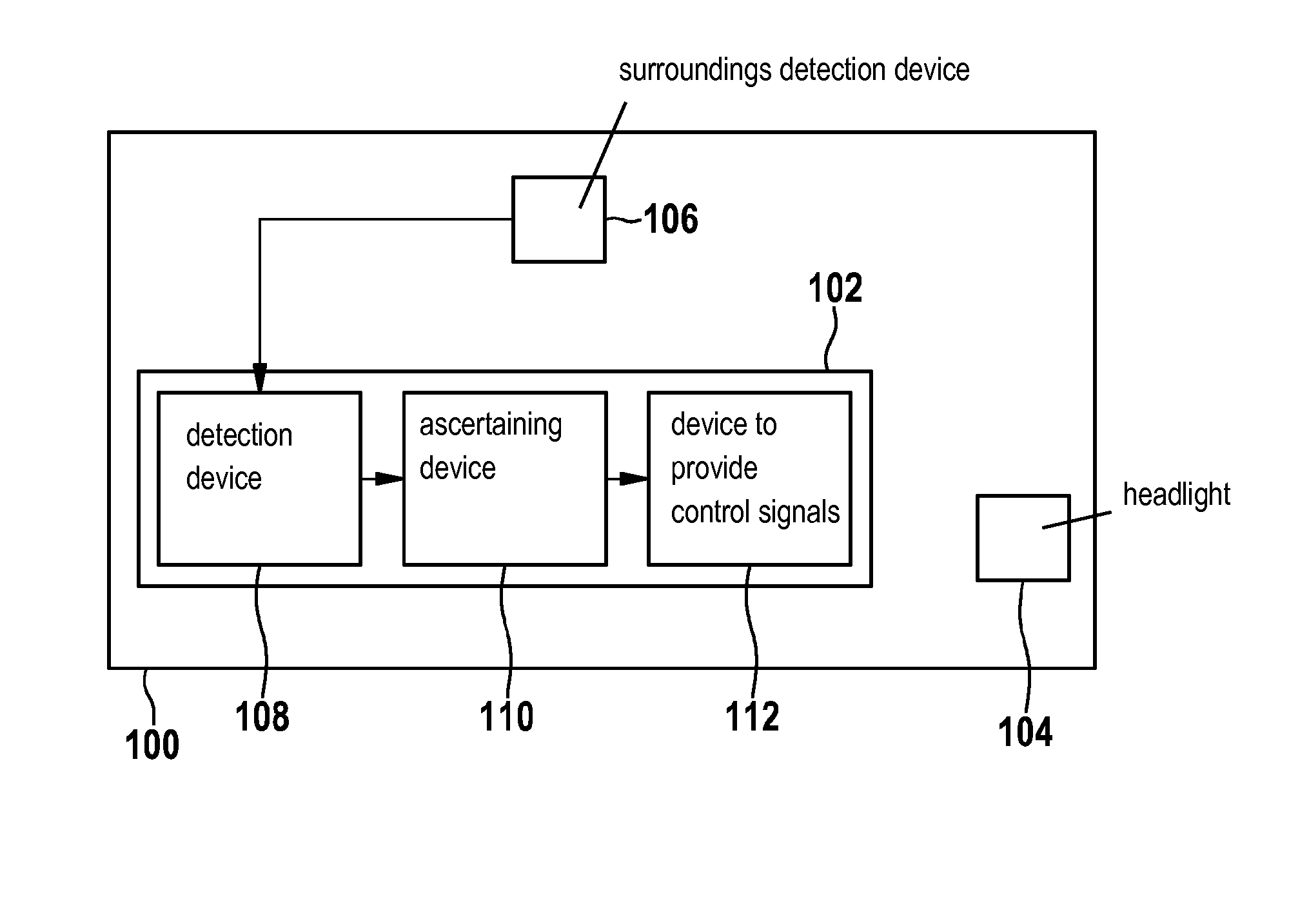
Method and control unit for adapting an upper headlight beam boundary of a light cone
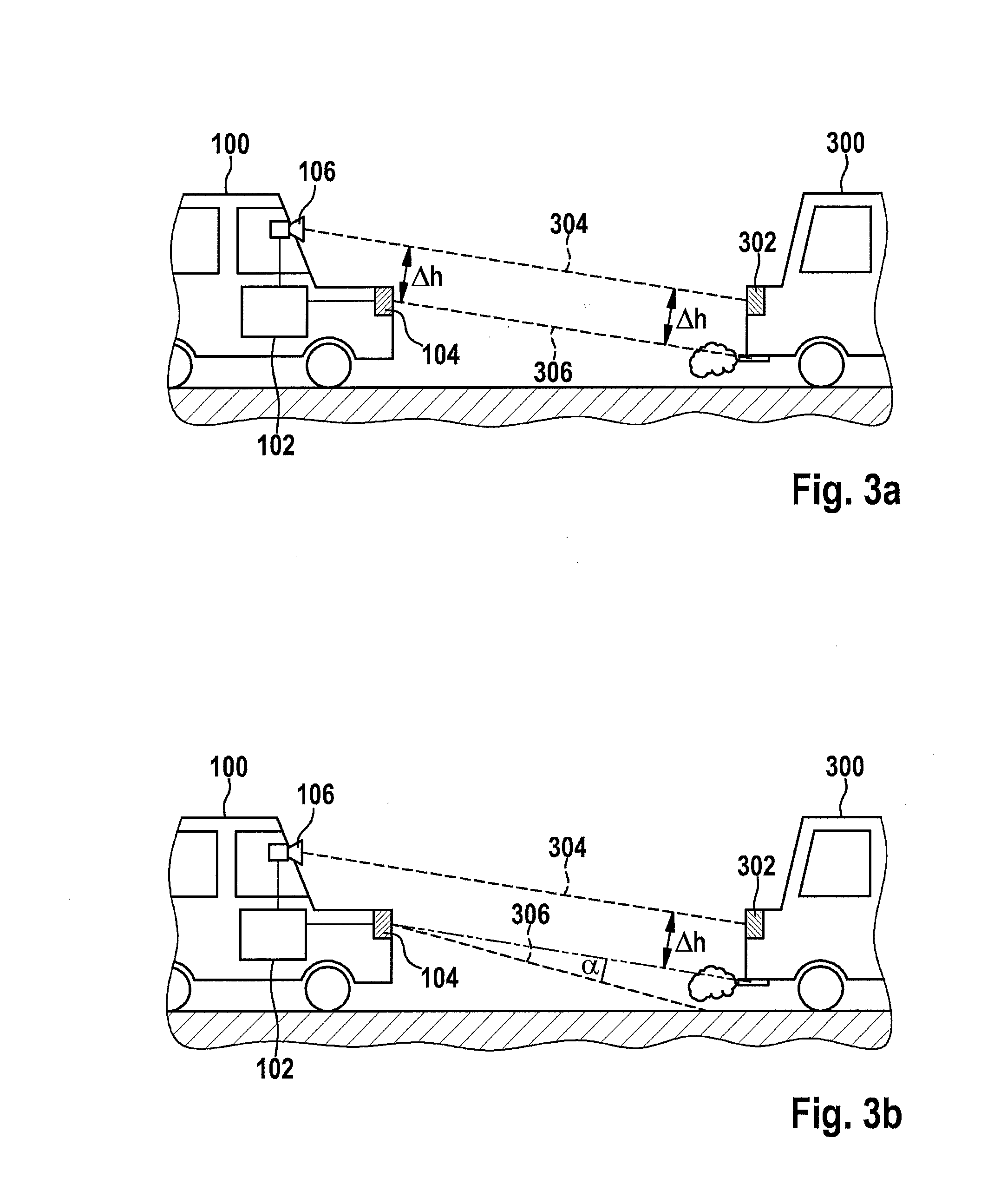
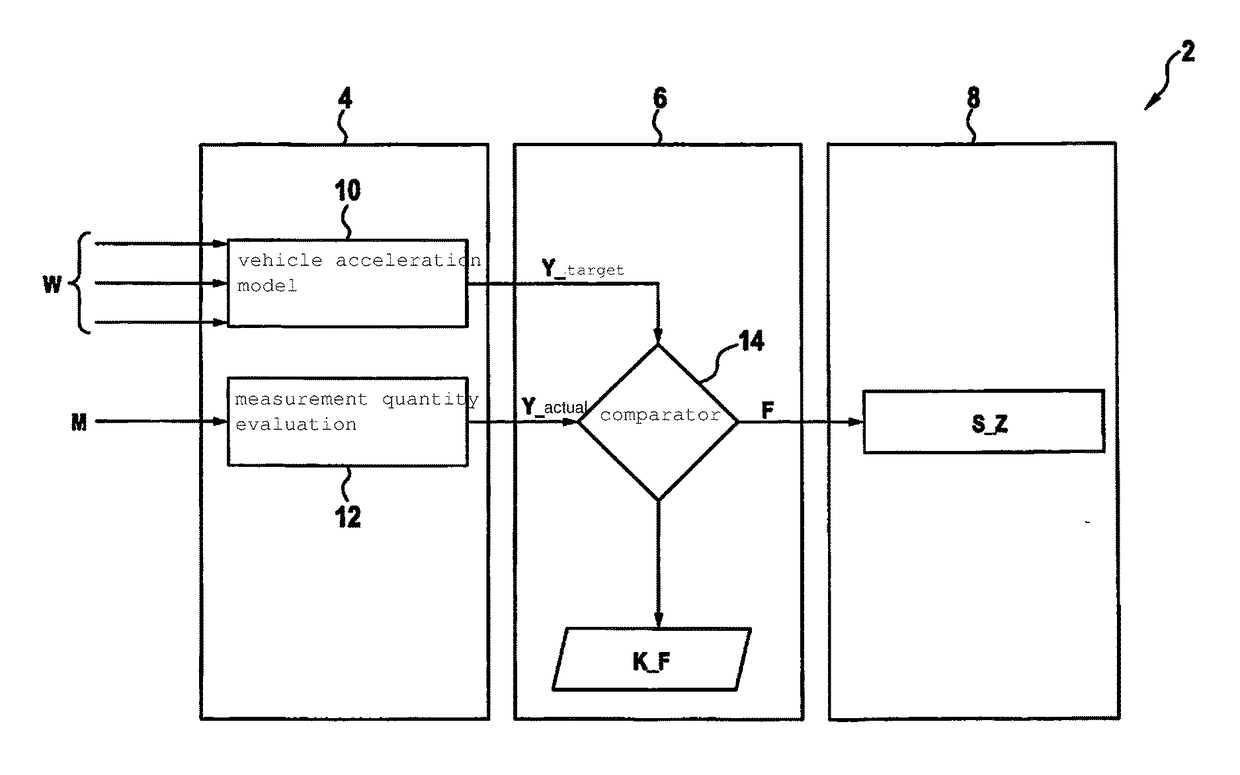
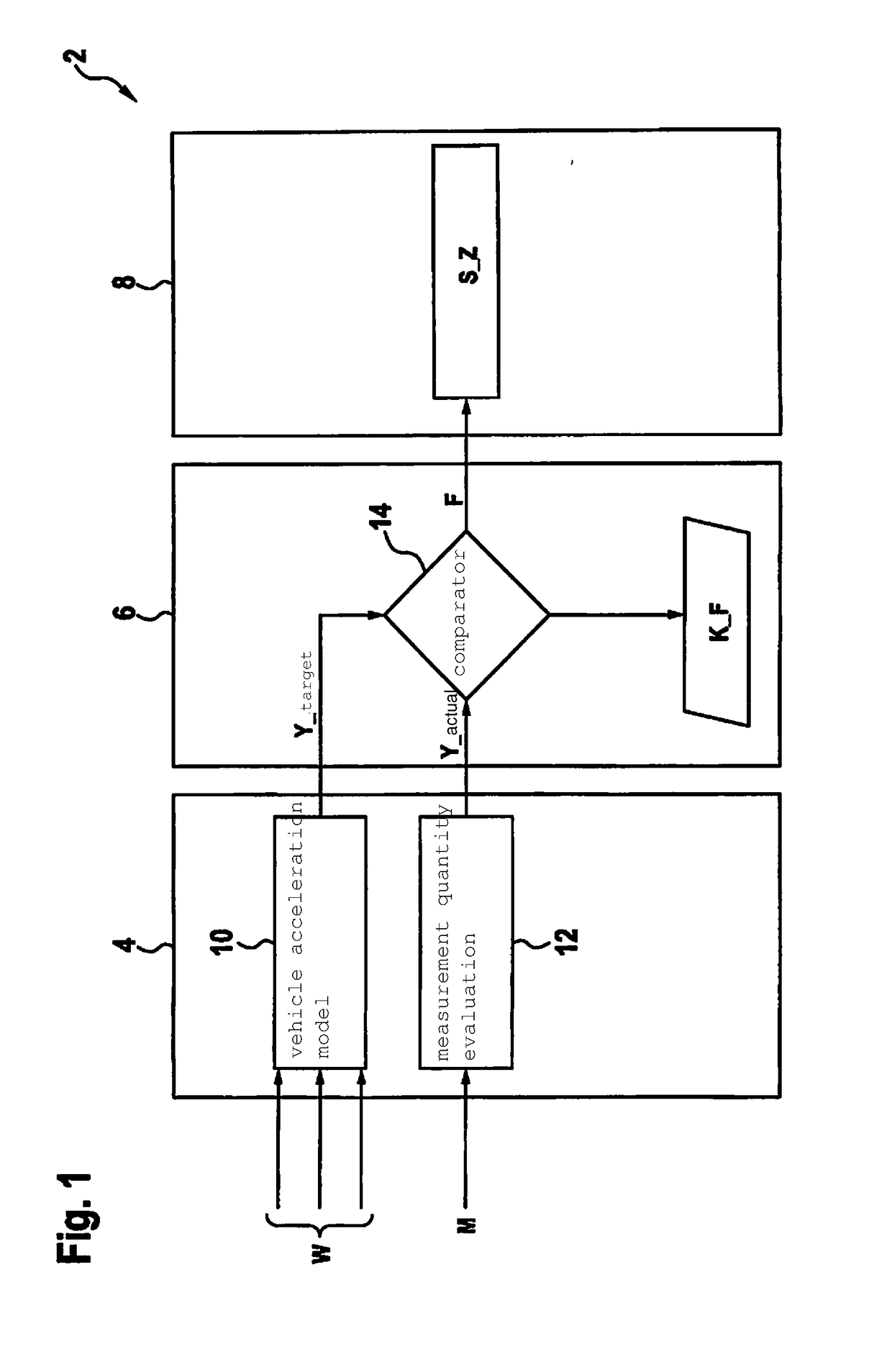
ActiveUS20150051797A1Increase probabilitySafety value may also become smallVehicle headlampsDigital data processing detailsControl signalRoll rate
A method for adapting an upper headlight beam boundary of a light cone of at least one headlight of a vehicle. The method includes detecting a time curve of a pitch rate of the vehicle or a value that is dependent on the pitch rate and / or of a roll rate of the vehicle or a value that is dependent on the roll rate. The method also includes ascertaining an envelope curve and / or an amplitude of the time curve and / or an average value of the time curve. The method also includes providing a control signal for adapting the upper headlight beam boundary of the headlight beam.
Owner:ROBERT BOSCH GMBH
Method and device for the prediction and adaptation of movement trajectories of motor vehicles
ActiveUS9081387B2Rapid responseAvoid collisionBraking element arrangementsSteering linkagesEngineeringMotor vehicle crash
A method and a device are for prediction and adaptation of movement trajectories of a vehicle for assisting the driver and / or for preventing or reducing the severity of a collision. Situatively required movement trajectories for assisting the driver or collision avoidance are determined using an environment sensor system. Physically possible movement trajectories are determined from characteristic properties of the driving dynamics of the vehicle and from the coefficient of friction between the tires and the road up to a maximum coefficient of friction. An intersection between the above two sets of trajectories is determined, and only trajectories that are included in this intersection are taken into account for the prediction and adaptation of movement trajectories for the driving assistance or collision avoidance function.
Owner:CONTINENTAL TEVES AG & CO OHG
A target tracking method and computing device
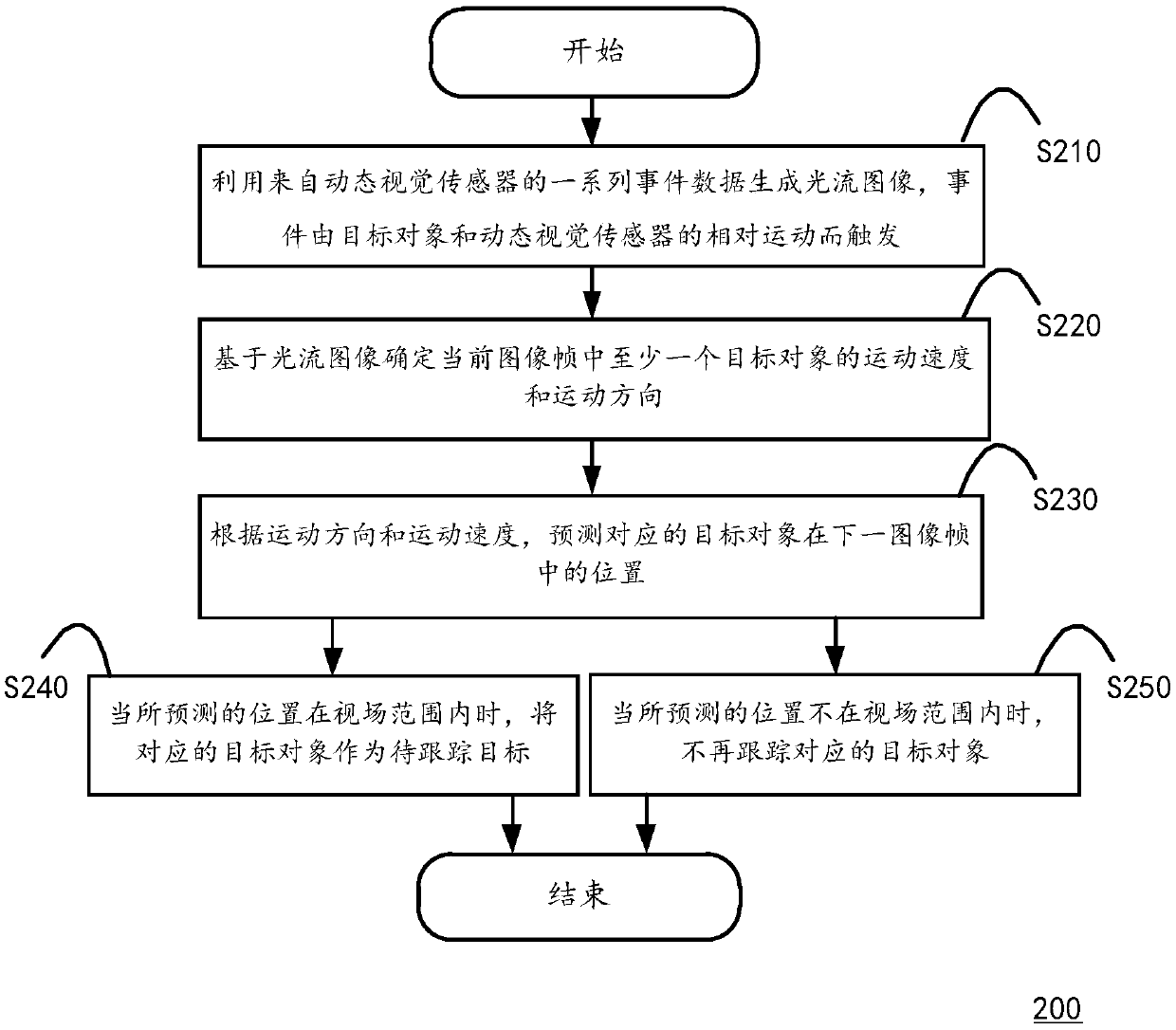
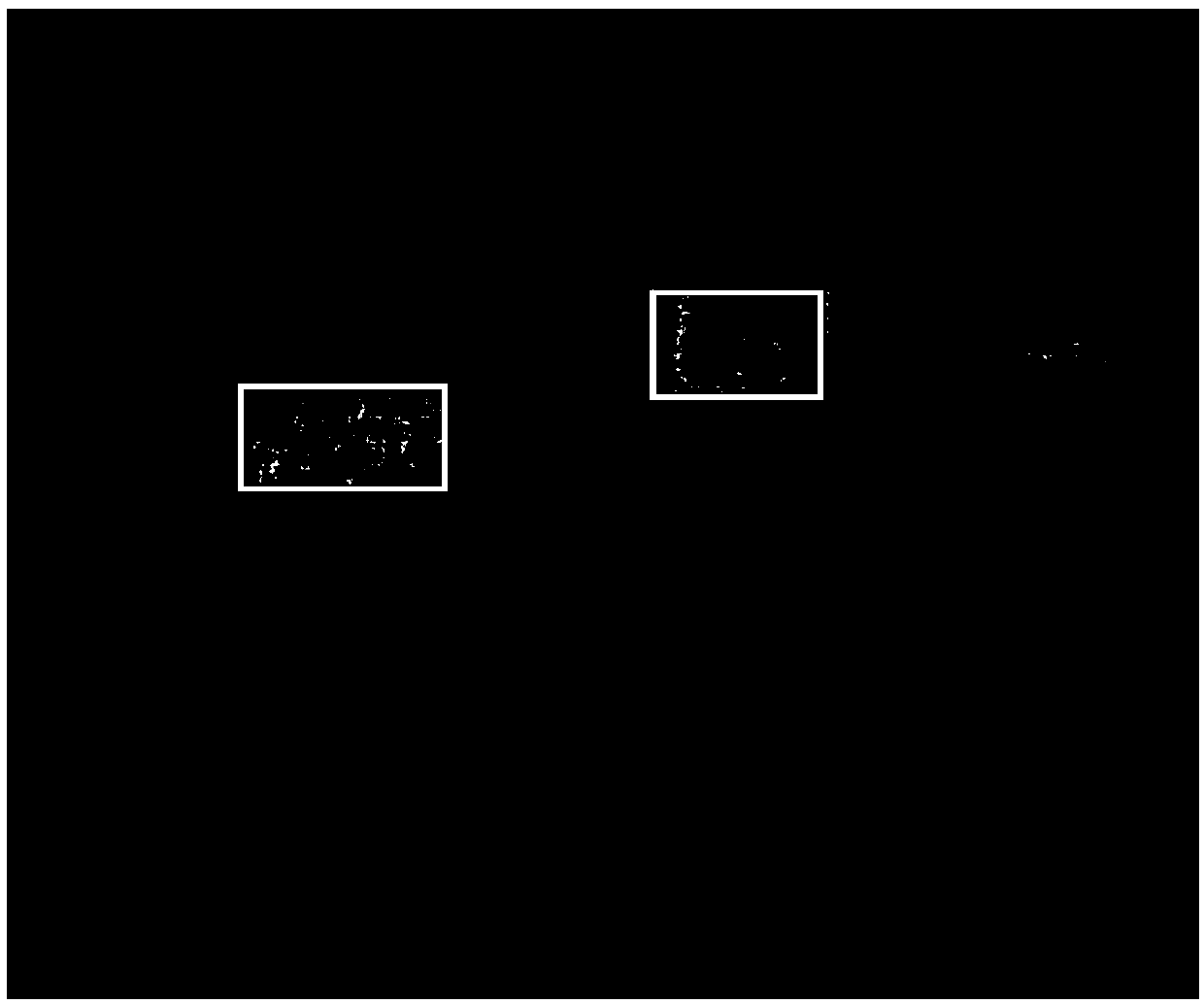
ActiveCN109544590AGuaranteed accuracySave computing powerImage enhancementImage analysisOptical flowMotion direction
The invention discloses a target tracking method suitable for execution in a computing device, which includes that steps of generating an optical flow image by using a series of event data from a dynamic vision sensor, the event being triggered by a relative motion of the target object and the dynamic vision sensor; Determining a motion speed and a motion direction of at least one target object ina current image frame based on an optical flow image; Predicting the position of the corresponding target object in the next image frame according to the motion direction and the motion speed; And when the predicted position is within the field of view, taking the corresponding target object as the target to be tracked. The invention also discloses a corresponding computing device.
Owner:OMNIVISION SENSOR SOLUTION (SHANGHAI) CO LTD
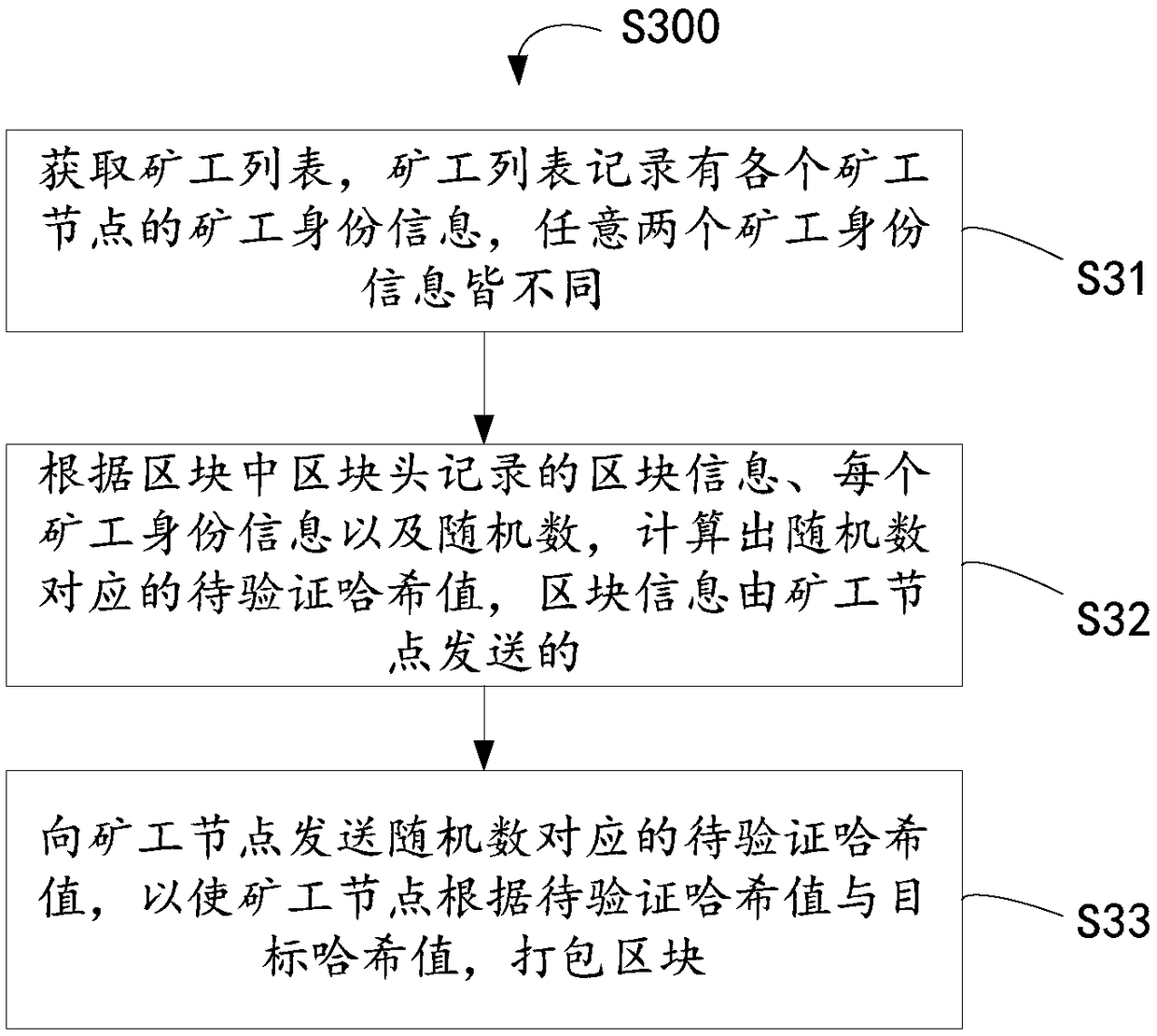
Distributed mining method, mining machine and block chain system
The invention relates to the technical field of block chains, in particular to a distributed mining method, a mining machine and a block chain system. The method comprises the following steps: a listof miners is obtained; The hash value to be verified corresponding to the random number is calculated according to the block information recorded in the block head, the identity information of each miner and the random number, and the block information is sent by the miner node; The hash value to be verified corresponding to the random number is sent to the miner node, so that the miner node packsthe block according to the hash value to be verified and the target hash value. On the one hand, because the proxy node completes the calculation of the hash value to be verified which requires highcomputational force, the hash value to be verify is sent to the miner node for consensus verification, the miner node can select a digger with low computational force to complete the dig work, and therefore, the digger node can satisfy the equipment with low computational force to participate in the digging work, and the universality is improved, so that the digging work becomes fairer. On the other hand, save energy consumption can be relatively saved.
Owner:SHENZHEN FIIIPAY CO LTD
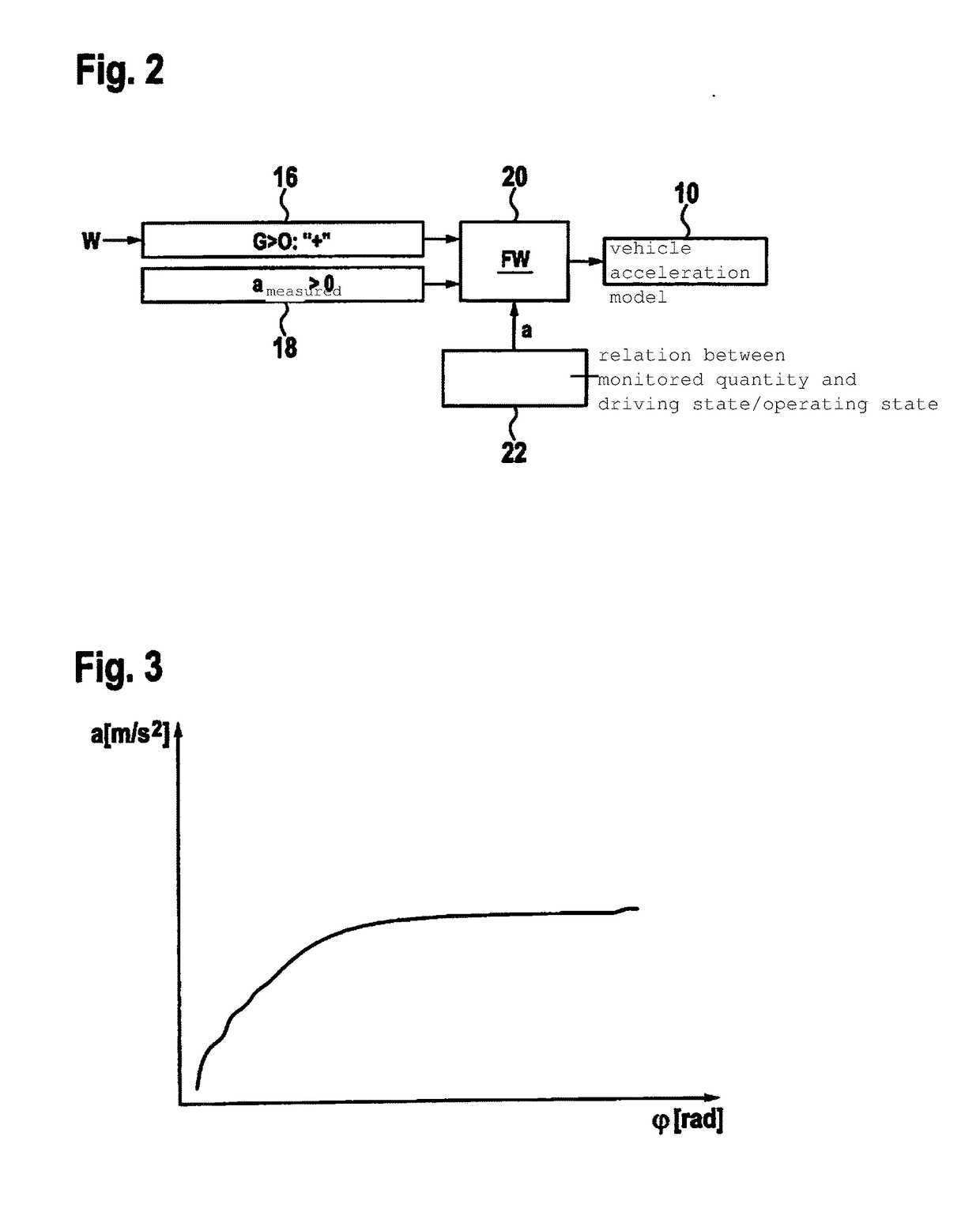
Method for monitoring a drive-by-wire system of a motor vehicle
ActiveUS20180009444A1Easy to adaptEasy to parameterizeRegistering/indicating working of vehiclesTesting/monitoring control systemsDrive by wireEngineering
A method for monitoring a drive-by-wire system of a motor vehicle, including: temporally offset reading in of at least two input values of an input quantity of an operating element of the motor vehicle; ascertaining a change over time or rate of change over time of the input quantity from the at least two read-in input values; determination of a monitored quantity for the motor vehicle operation from the change over time or rate of change over time; selection of a monitoring function on the basis of the monitored quantity; monitoring of the monitored quantity for the ascertained motor vehicle operation by the monitoring function.
Owner:ROBERT BOSCH GMBH
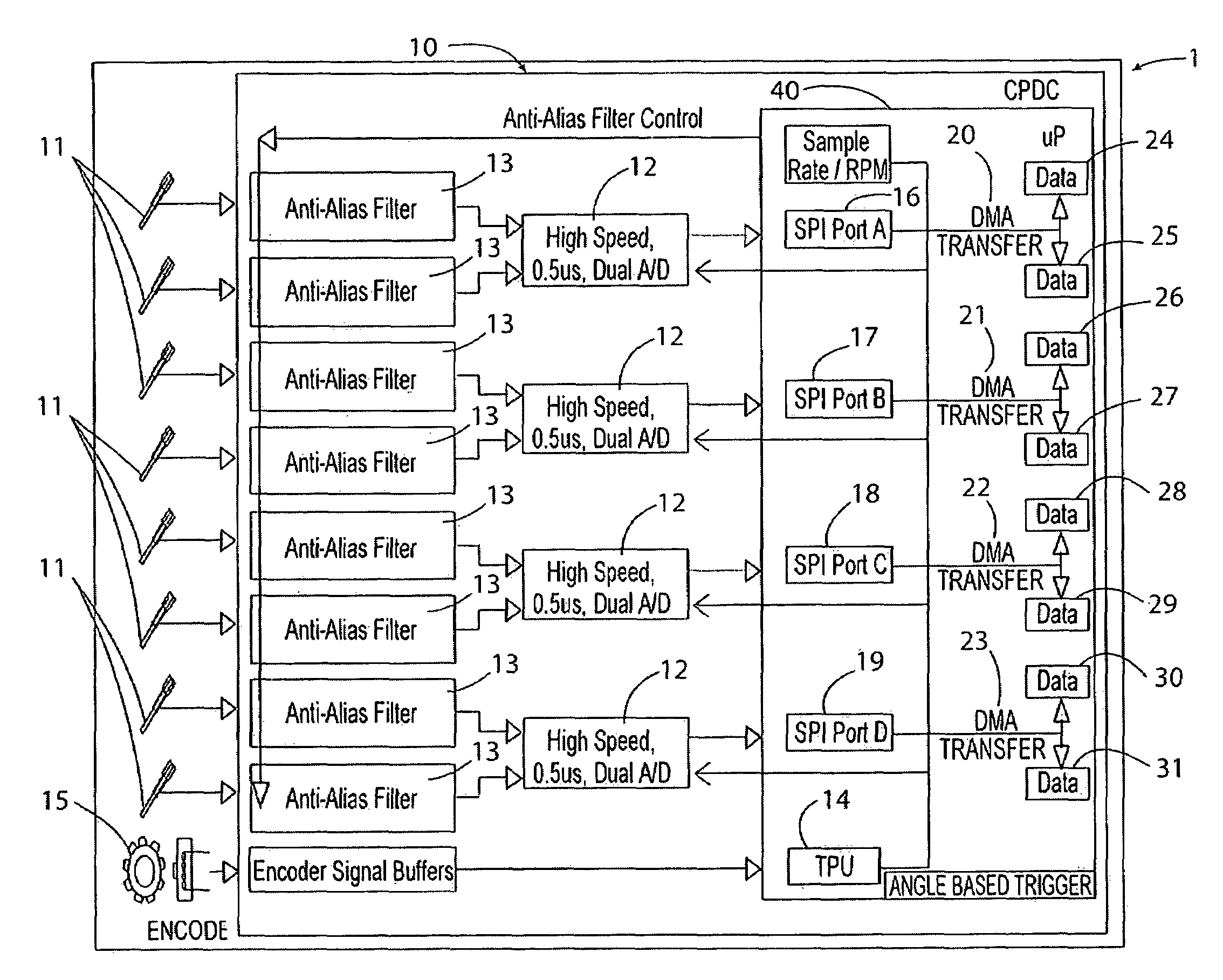
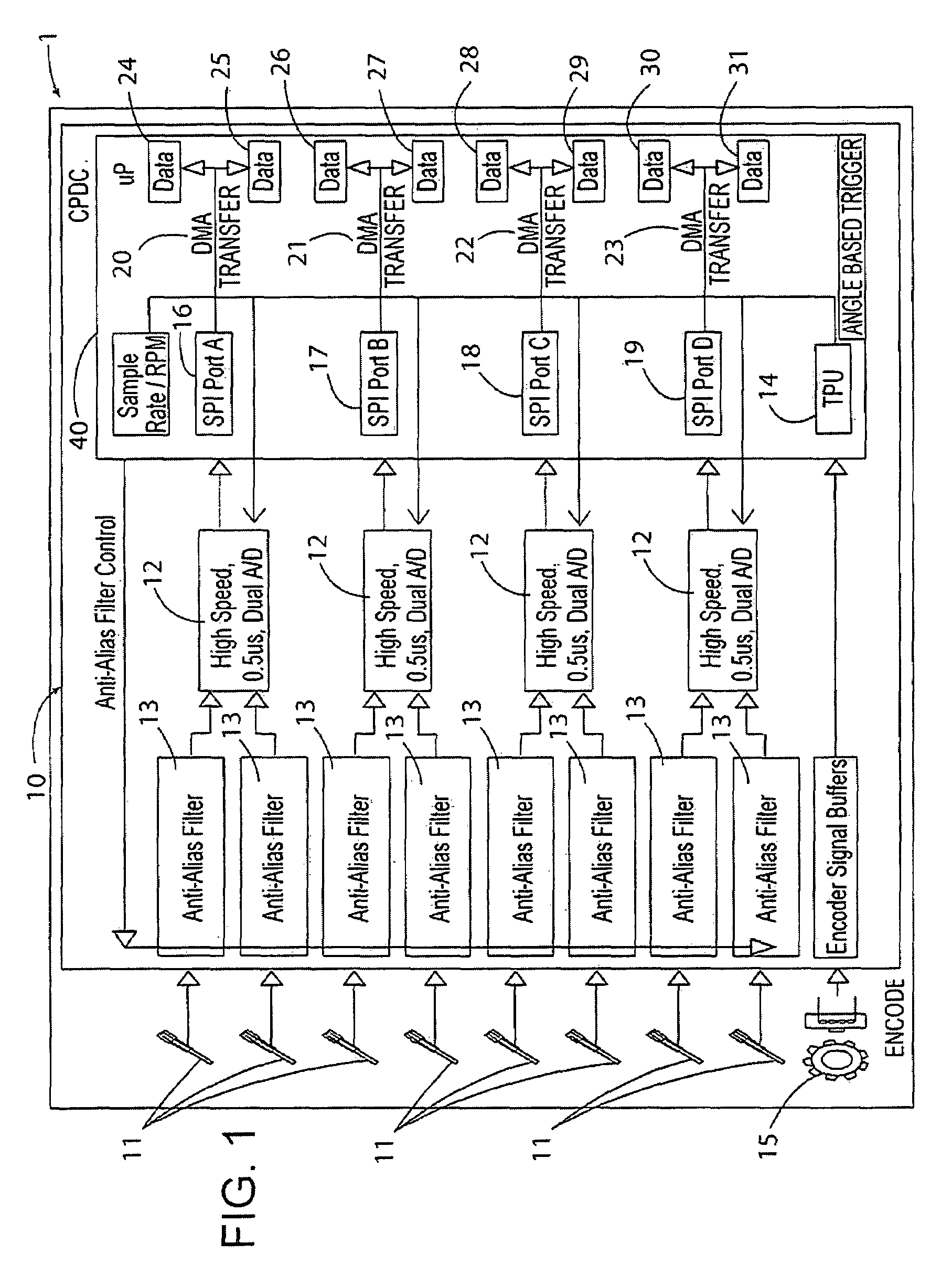
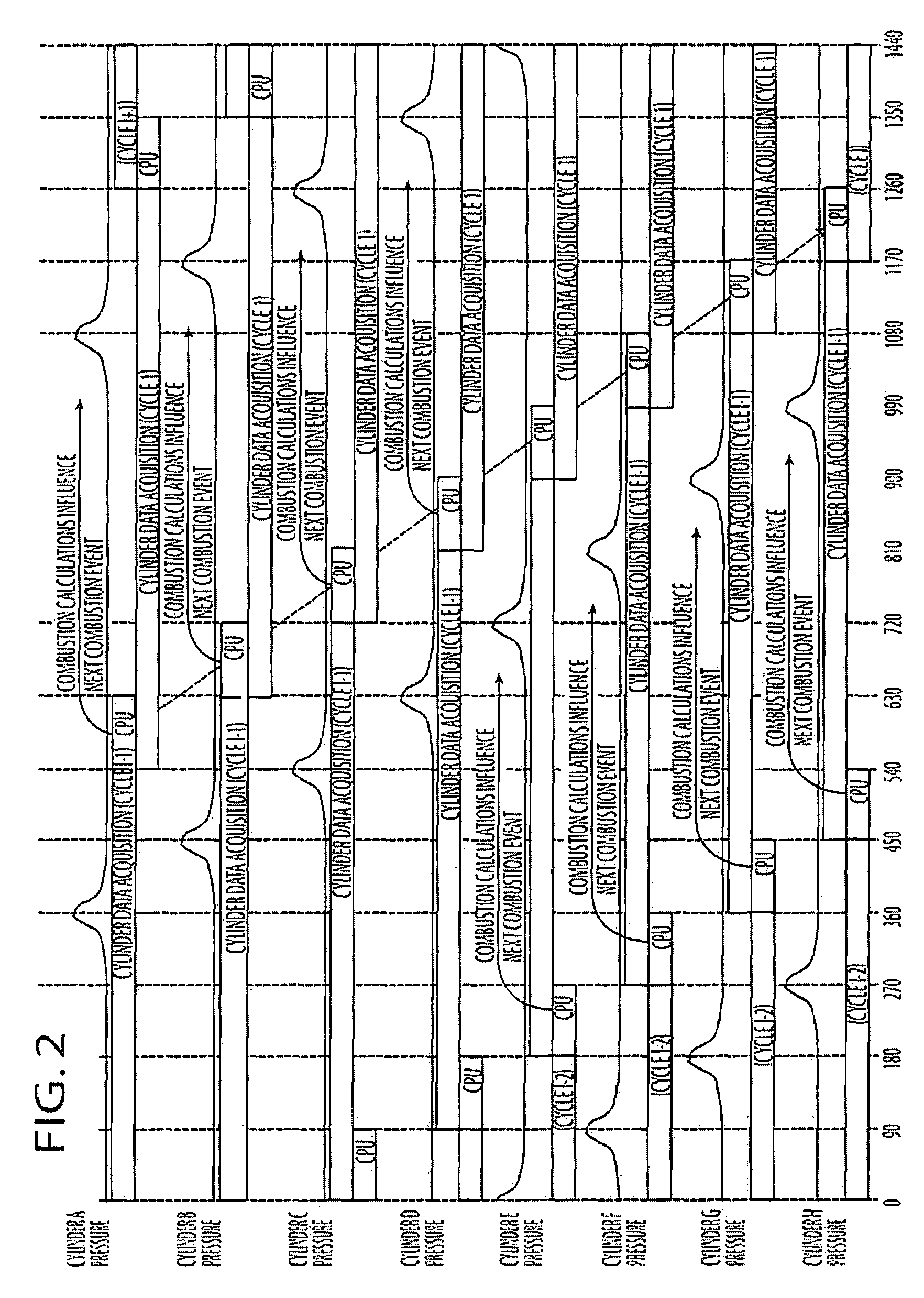
Cylinder-pressure-based electronic engine controller and method
ActiveUS7606655B2Save computing powerReduce amountAnalogue computers for vehiclesElectrical controlControl systemData acquisition
Owner:DELPHI TECH IP LTD
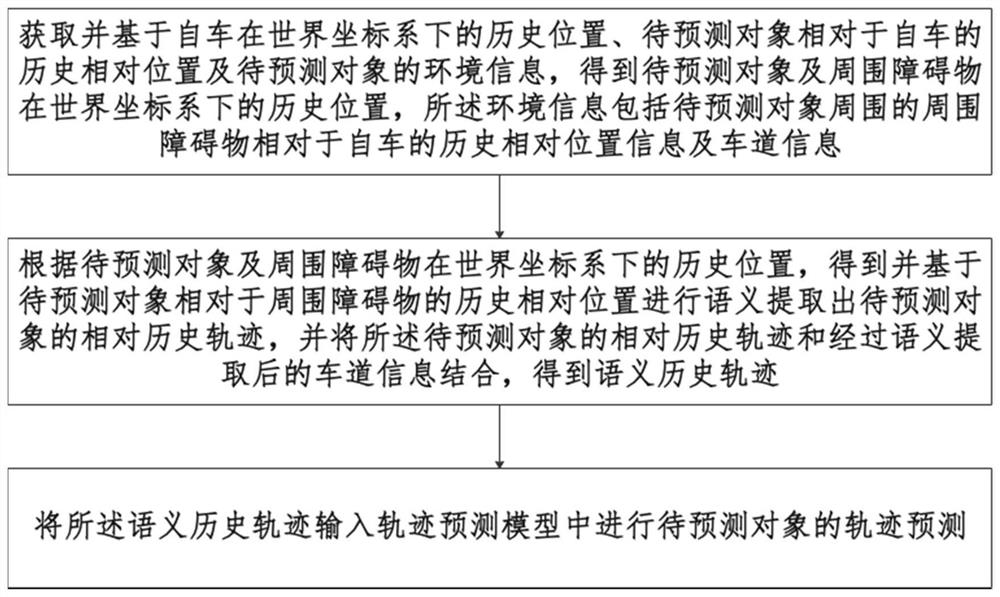
Trajectory prediction system and method, electronic equipment and readable storage medium
PendingCN112651557AAccurate Prediction AccuracySave computing powerForecastingNeural architecturesObject basedEngineering
The invention provides a trajectory prediction system and method, electronic equipment and a readable storage medium, and the method comprises the steps: obtaining the historical position of an automatic vehicle in a world coordinate system, the historical relative position of a to-be-predicted object relative to the automatic vehicle, and the environment information of the to-be-predicted object, based on the historical position of the automatic vehicle in the world coordinate system, the historical relative position of the to-be-predicted object relative to the automatic vehicle and the environment information of the to-be-predicted object, obtaining the historical positions of the to-be-predicted object and surrounding obstacles in the world coordinate system; according to the historical positions of the to-be-predicted object and the surrounding obstacles in the world coordinate system, obtaining and semantically extracting the relative historical trajectory of the to-be-predicted object based on the historical relative positions of the to-be-predicted object relative to the surrounding obstacles, and combining the relative historical trajectory with the lane information subjected to semantic extraction to obtain a semantic historical trajectory; and inputting the semantic historical trajectory into the trajectory prediction model to perform trajectory prediction of the to-be-predicted object. According to the method, the unmanned driving computing power is greatly improved, the computing consumption in the unmanned driving operation is minimized, the prediction precision can be ensured, and the engineering requirements are better met.
Owner:际络科技(上海)有限公司
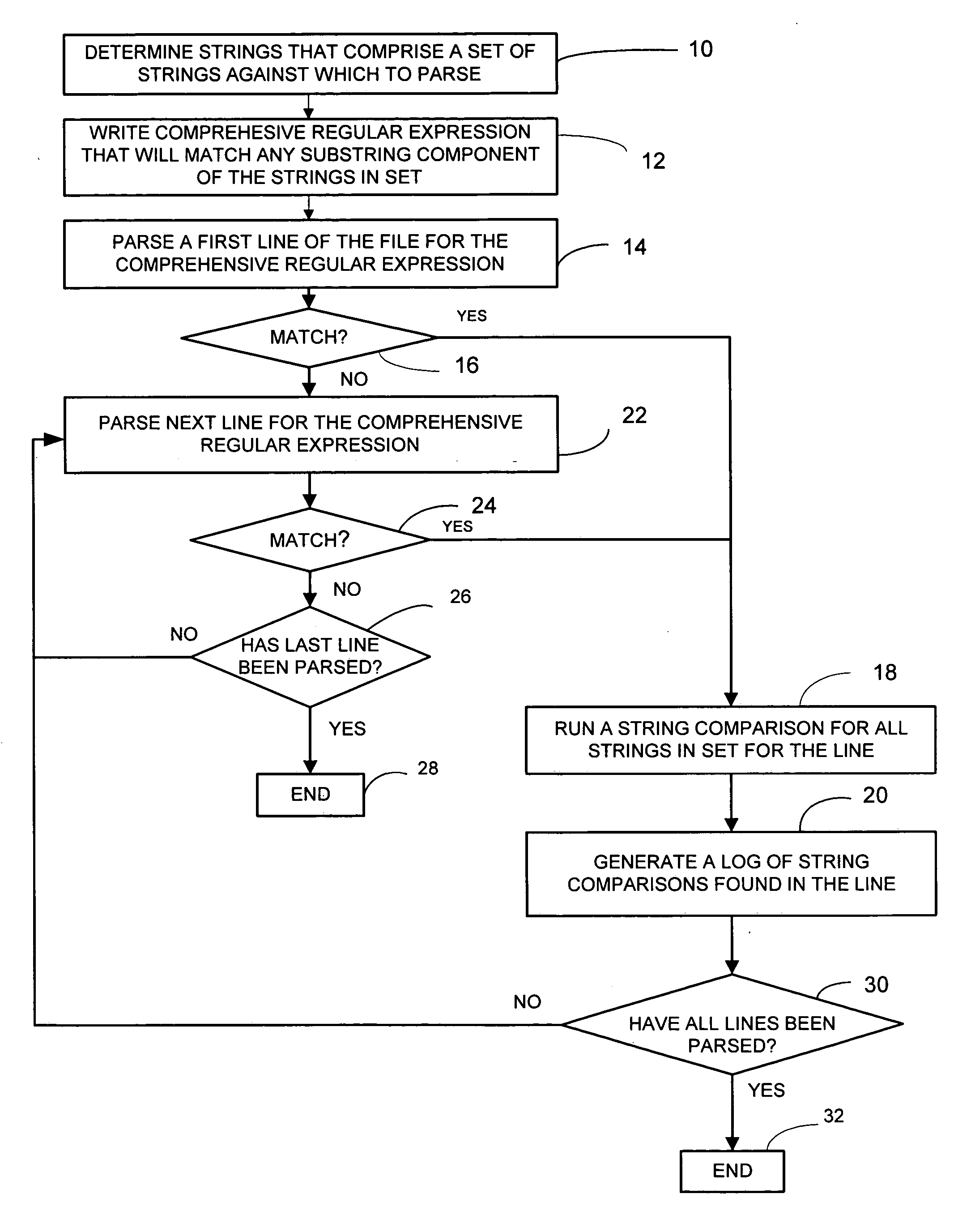
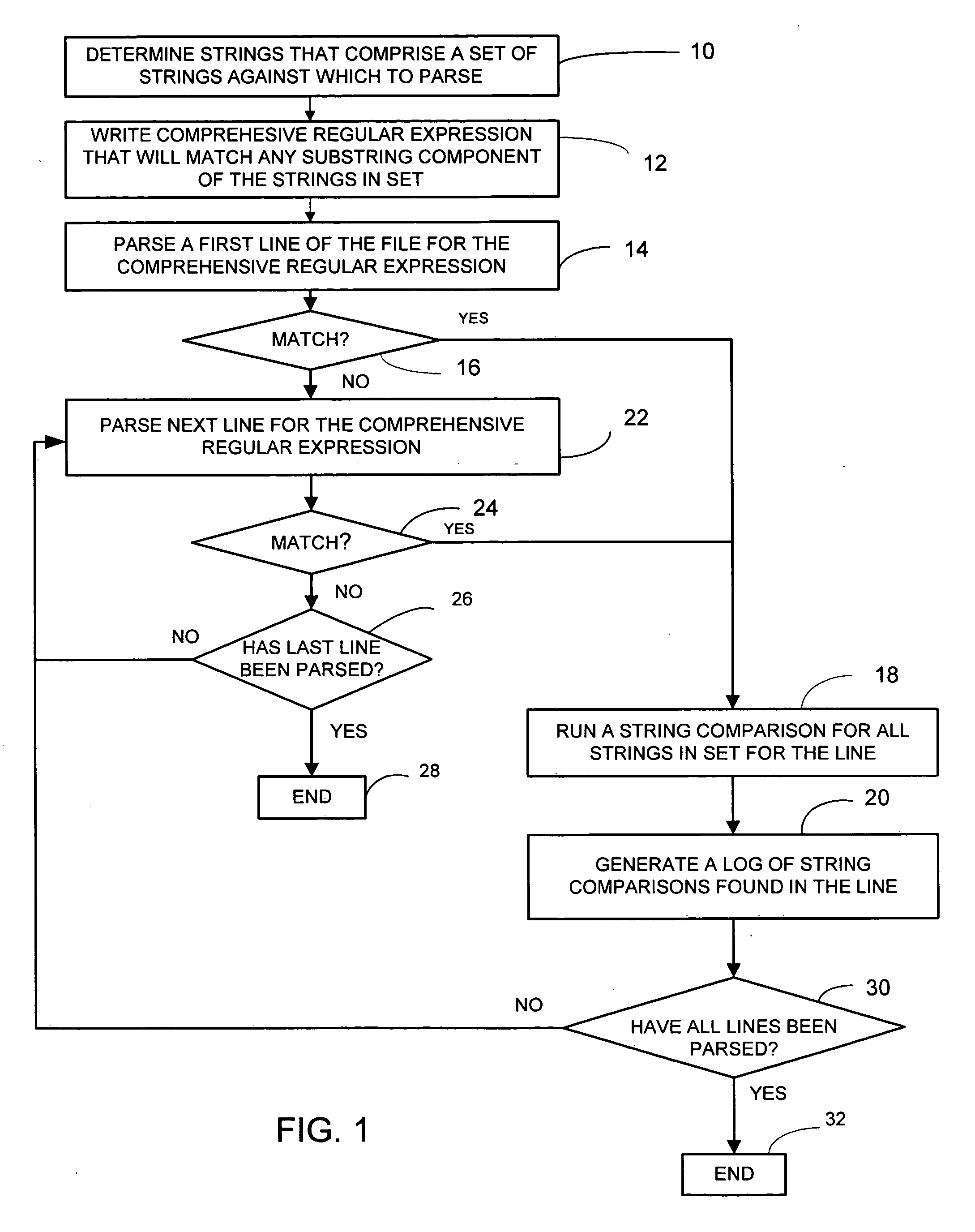
Method of efficiently parsing a file for a plurality of strings
InactiveUS20060265357A1Save computing powerImprove parsing speedEnergy efficient ICTDigital data information retrievalMainframe computerRegular expression
A preferred embodiment of the method of the present invention parses a large computer file for a selected set of target strings in a manner whereby computing power is conserved and parsing speed is increased. The method parses for the selected set of target strings by initially writing a comprehensive regular expression that will return a match if any component of the target strings in the set are present in a line of the computer file. If a regular expression match is made in a line, string comparisons for all of the strings in the set of target strings are run for the line. The preferred embodiment preferably generates a log of all positive string comparisons that are made in the file.
Owner:HEWLETT PACKARD DEV CO LP
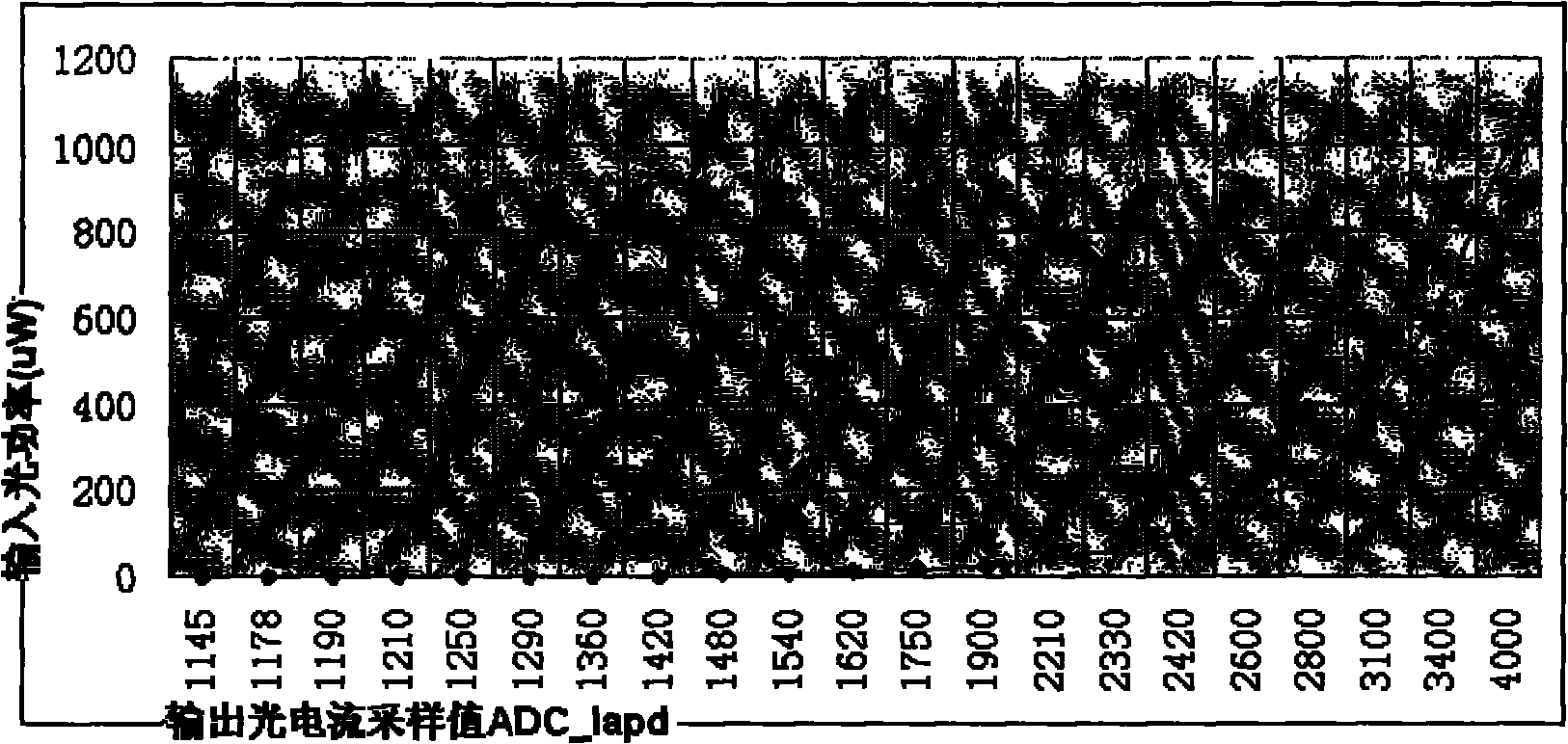
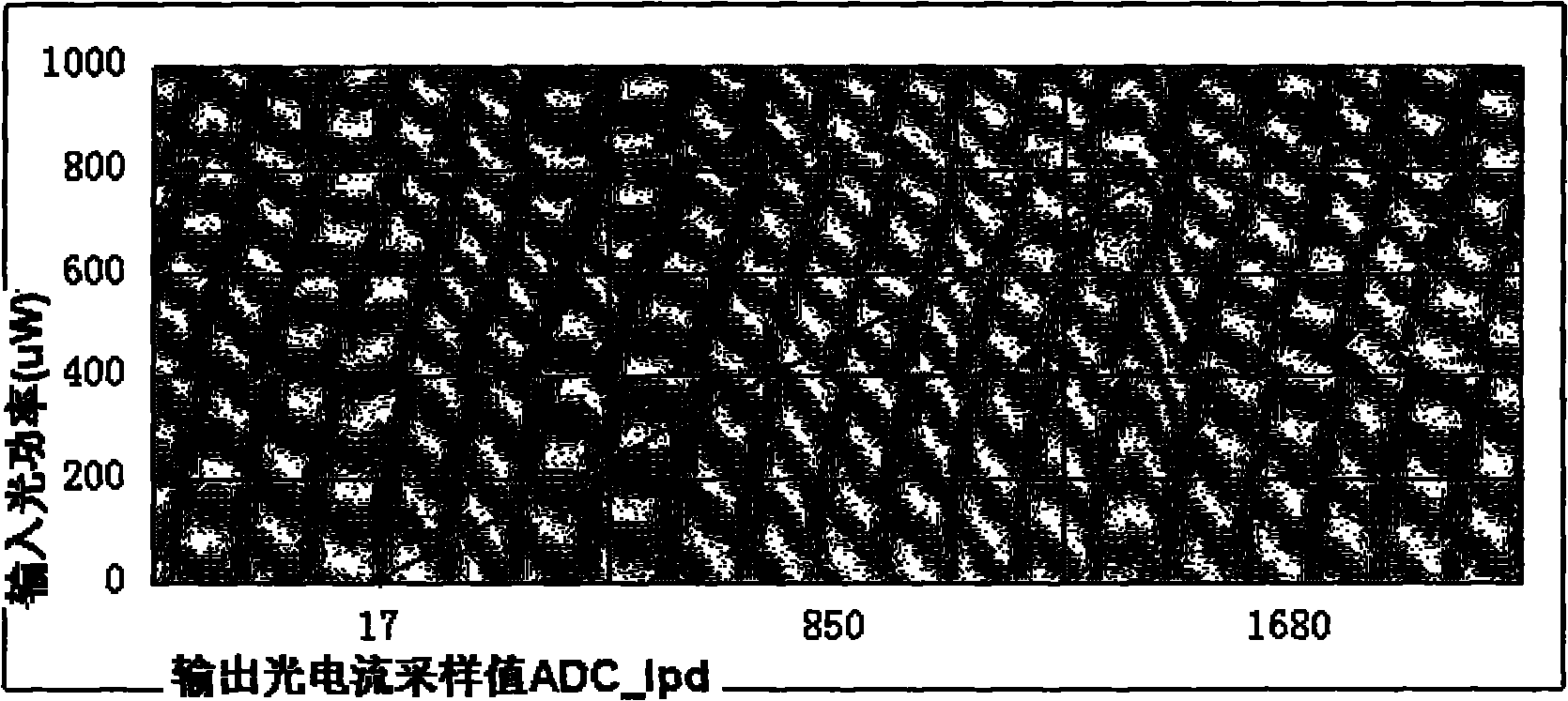
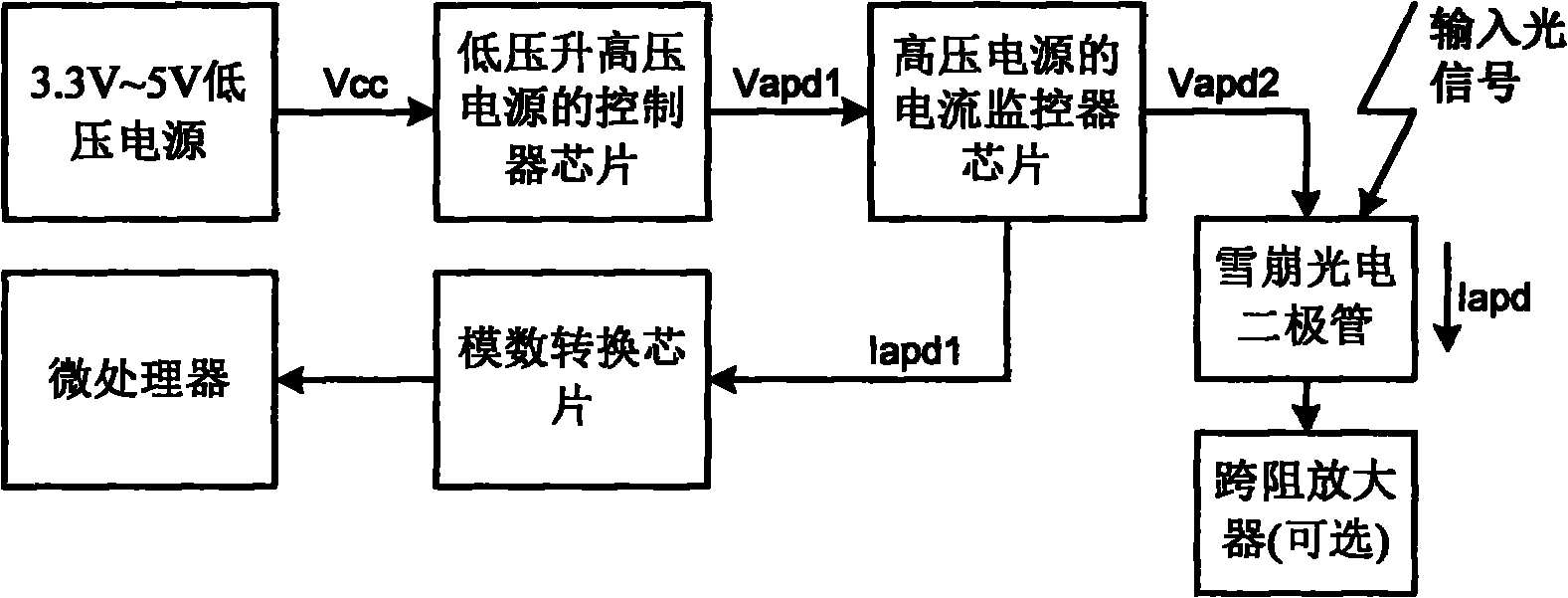
Method and device for monitoring input optical power of avalanche photoelectric diode
InactiveCN101871813ALow costComputing skills are not requiredPhotometry using electric radiation detectorsMeasurement using digital techniquesOptical powerOptical receivers
The invention discloses a method and a device for monitoring the input optical power of an avalanche photoelectric diode, and provides a novel ROSA; a planar optical waveguide splitter splits a received input optical signal into two circuits, wherein one circuit of light with high optical power is distributed to the traditional avalanche photoelectric diode of an optical receiver and is applied to an original optical receiver, and the other circuit of light with low optical power is distributed to a linear photoelectric diode for improving the monitoring precision to the input optical power. The technical scheme can reduce the cost and the complicacy of a monitoring system to the input optical power of the traditional avalanche photoelectric diode in the optical receiver, and improve the monitoring precision to the input optical power.
Owner:CHENGDU SUPERXON COMM TECH CO LTD
Application method of hybrid continuous information analysis technology in medicine
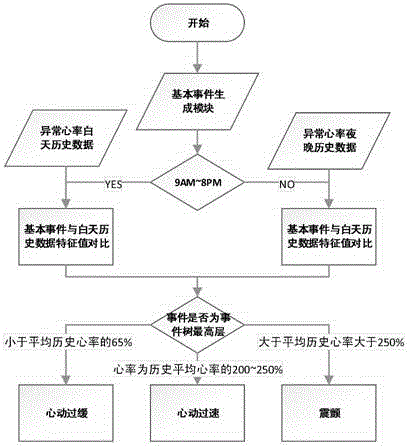
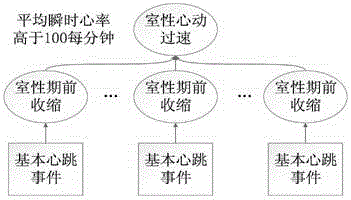
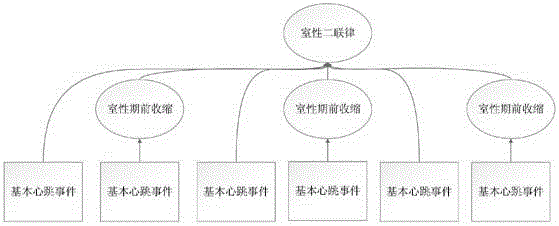
ActiveCN106037720ARelieve pressurePattern matching precision and personalizationDiagnostic recording/measuringSensorsInformation analysisContinuous analysis
The invention discloses an application method of a hybrid continuous information analysis technology in medicine. The method comprises the following steps: acquiring an electrocardiogram signal from electrocardiogram equipment by virtue of an electrocardiogram signal acquisition module in an electrocardiogram hybrid continuous analysis system; then pre-processing the electrocardiogram signal by virtue of an electrocardiogram detection module; extracting signal characteristics from the processed signal by virtue of an electrocardiogram detection method, and forming a plurality of basic heart rate events which are analyzed by a composite event processing heart rate identification module; comparing the basic heart rate events with information in a patient historical database module by virtue of the composite event processing heart rate identification module through a hybrid continuous analysis module therein, so that abnormal heart rate events are identified out; transmitting an abnormal heart rate alarm and pre-diagnosis information to a pre-diagnosis output module in the case of serious abnormal heart rate events; and transmitting alarm and help information to patient's doctors and / or family members by virtue of the pre-diagnosis output module.
Owner:GUIZHOU UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com