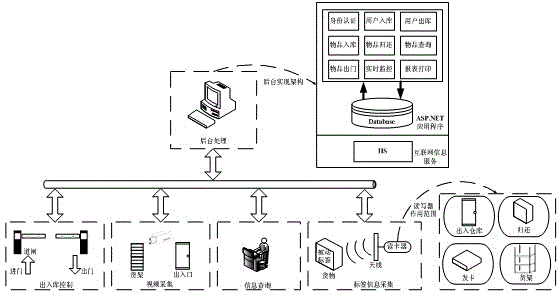
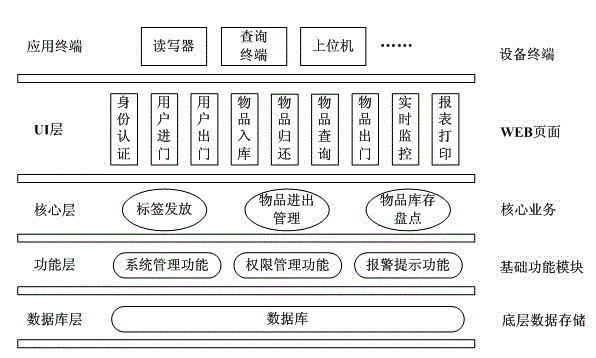
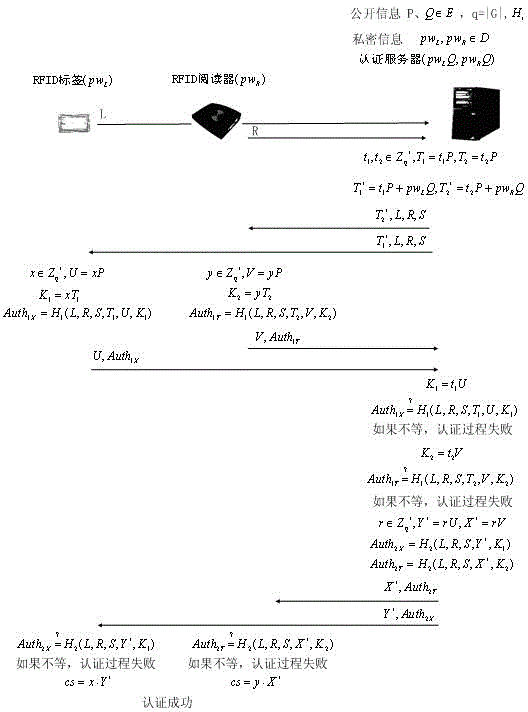
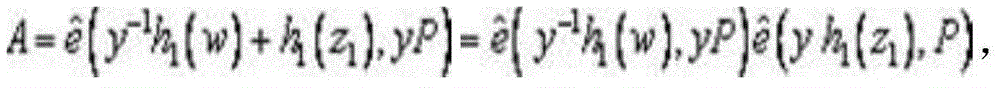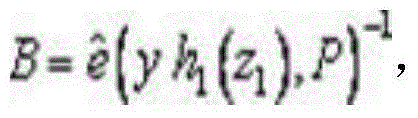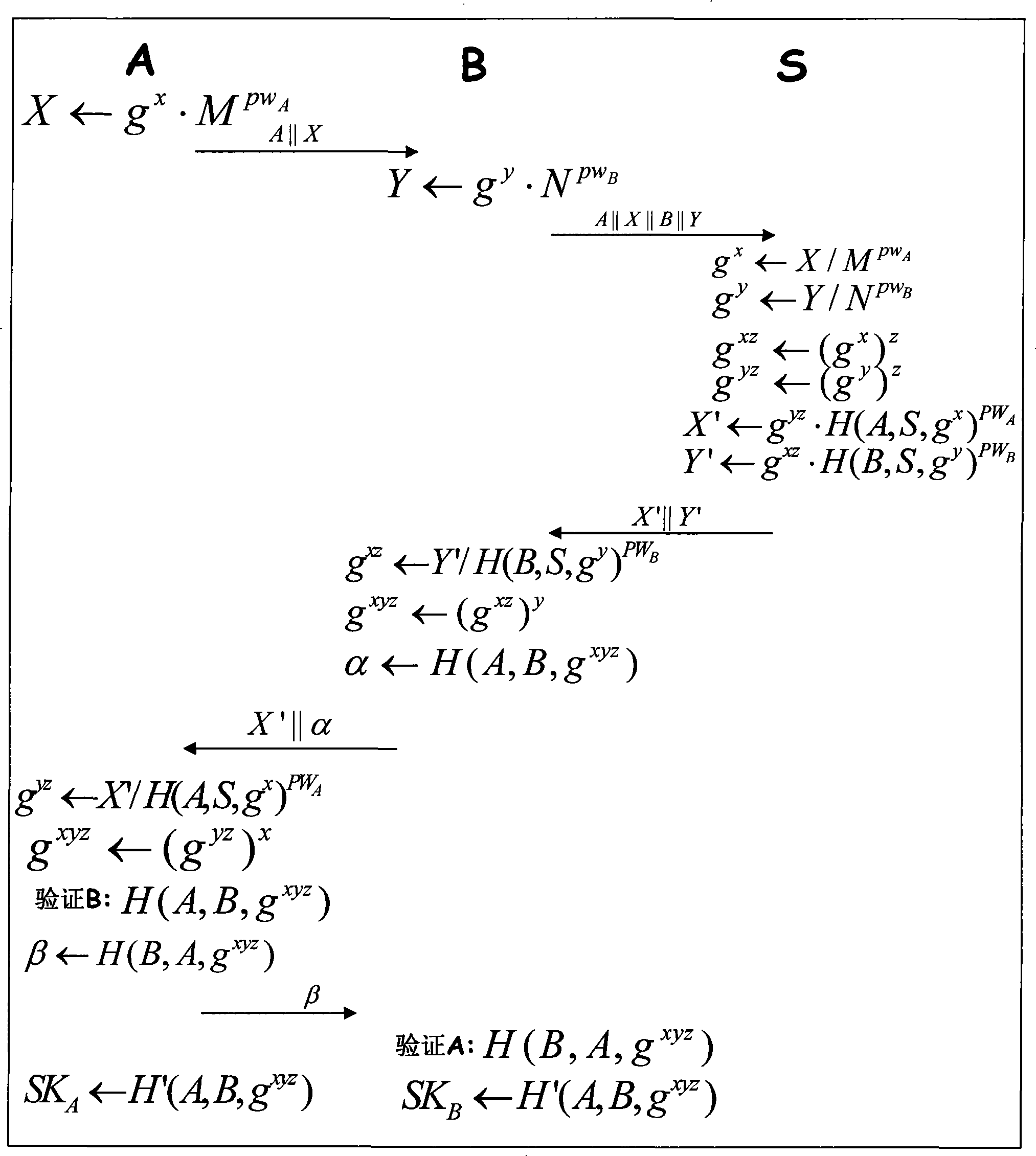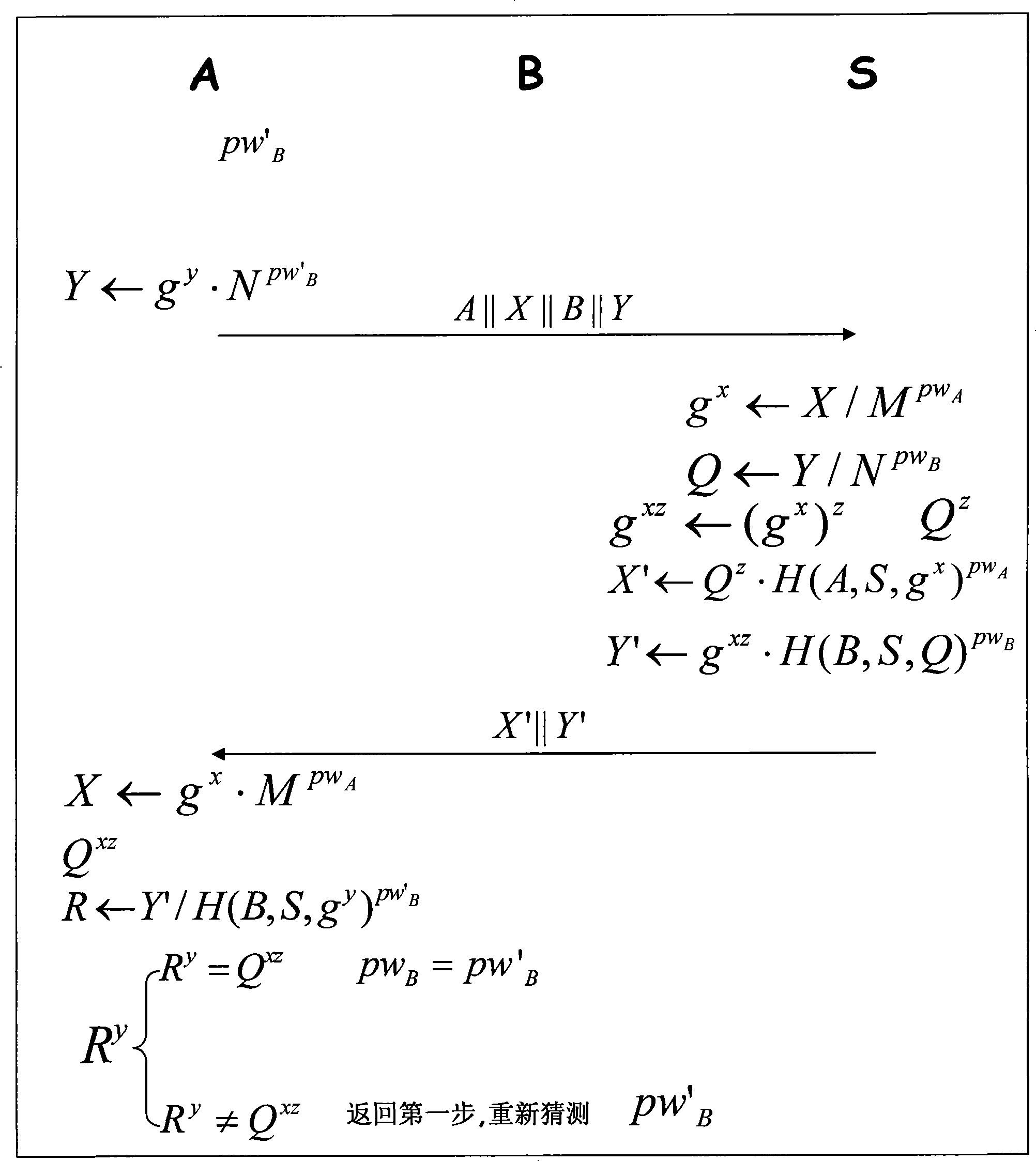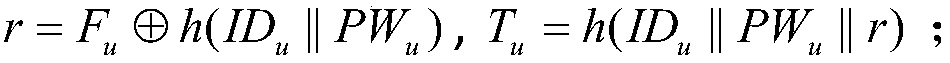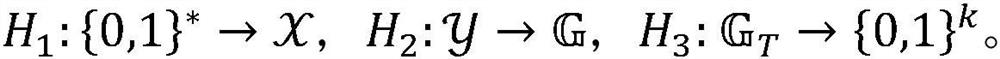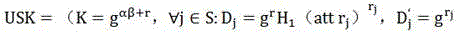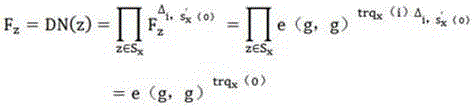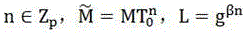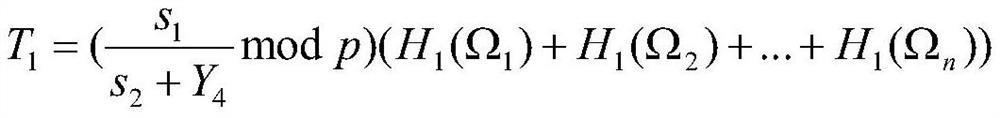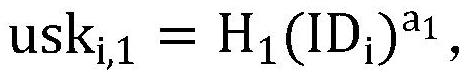Patents
Literature
67 results about "Guessing attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
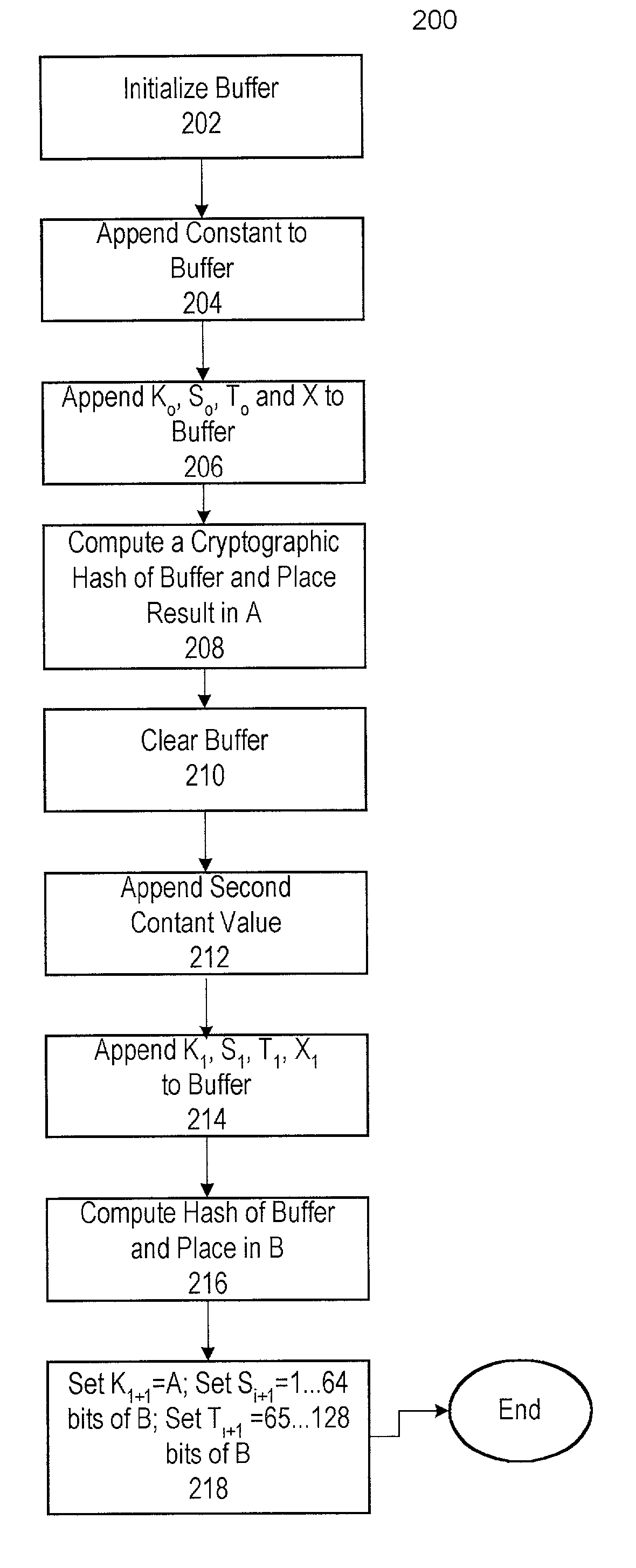
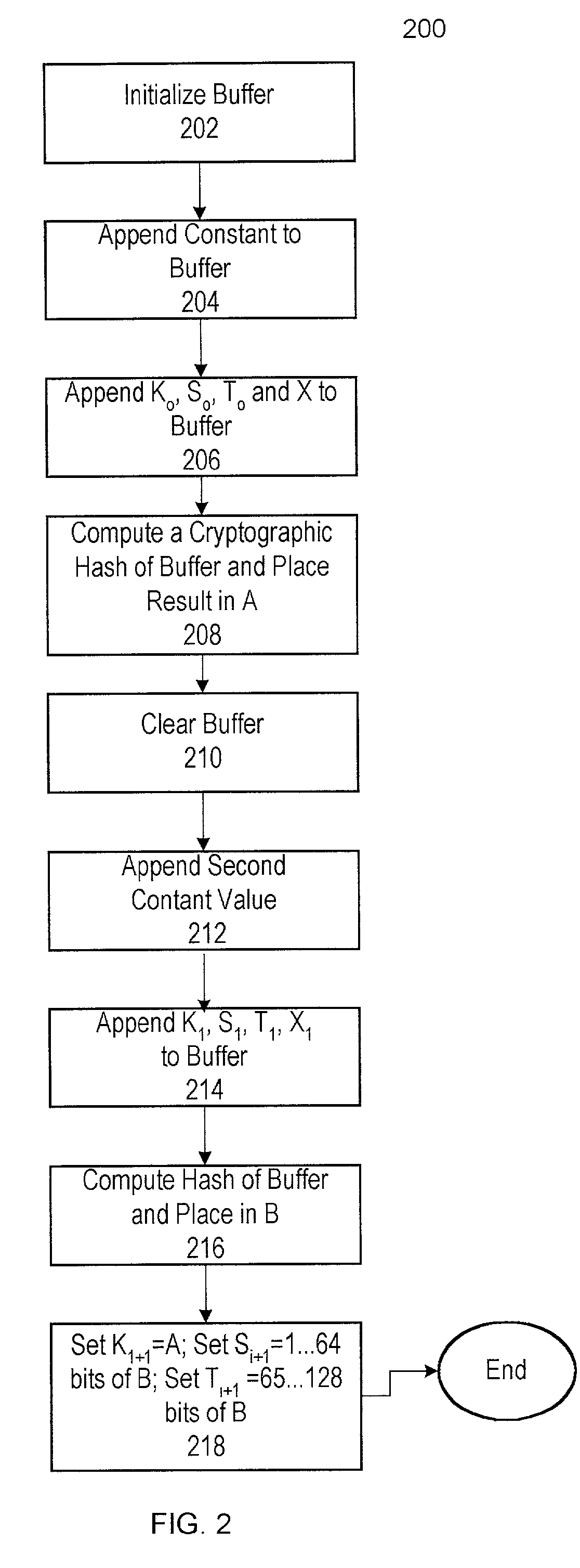
Method and apparatus for improved pseudo-random number generation
InactiveUS7007050B2Improve securityRandom number generatorsSecuring communicationSecure communicationMobile Telephone Service
A pseudo-random number generator (PRNG) for a cryptographic processing system is disclosed in which the PRNG is reseeded at each instance of input entropy and in which a standard timestamp variable used in determining random sequence outputs is replaced with a running counter. The method employed by the PRNG demonstrates increased resistance to iterative-guessing attacks and chosen-input attacks than those of previous technologies. The PRNG is suitable for use in, for example, a mobile telephone system for accomplishing secure communications.
Owner:WSOU INVESTMENTS LLC
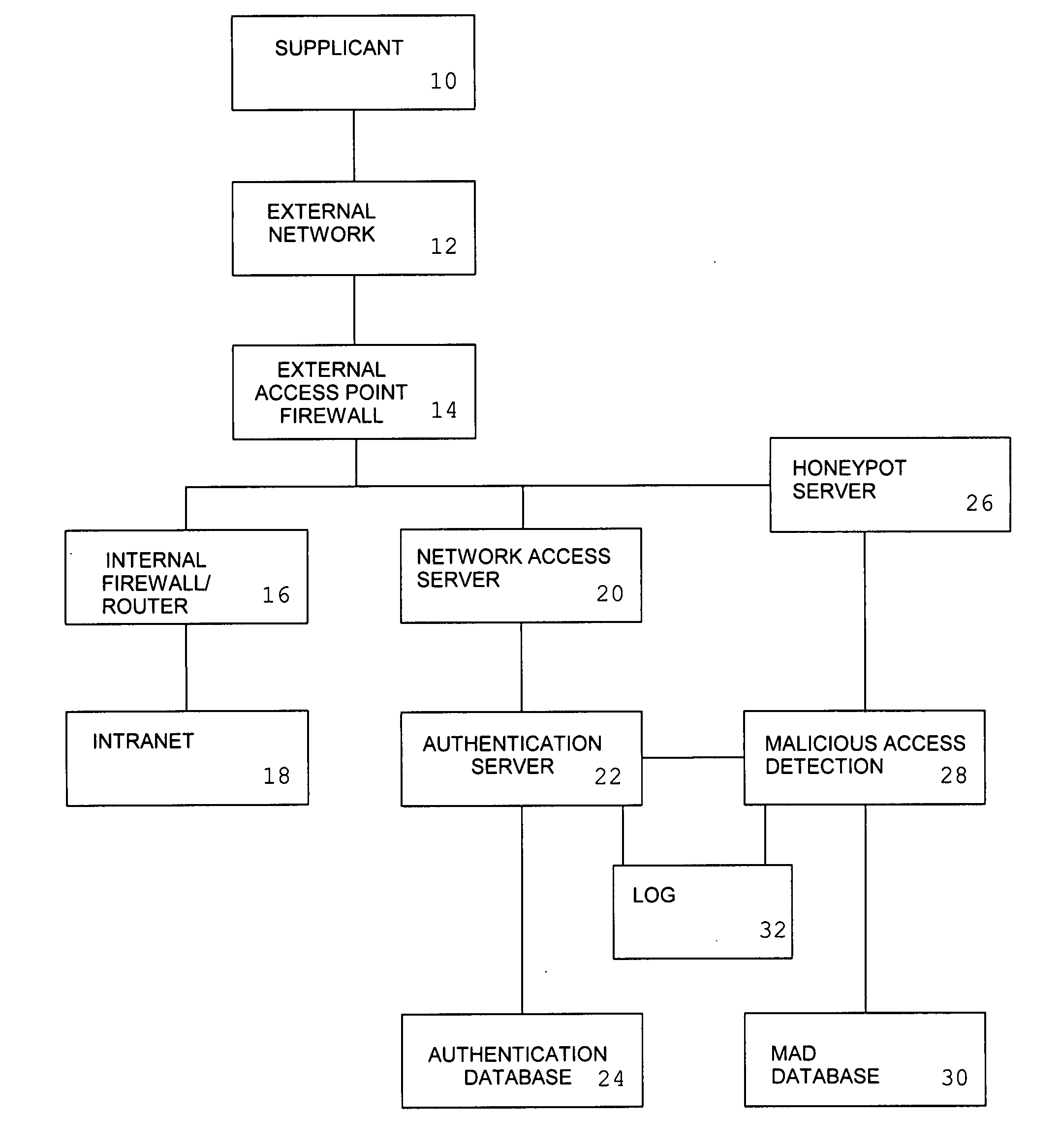
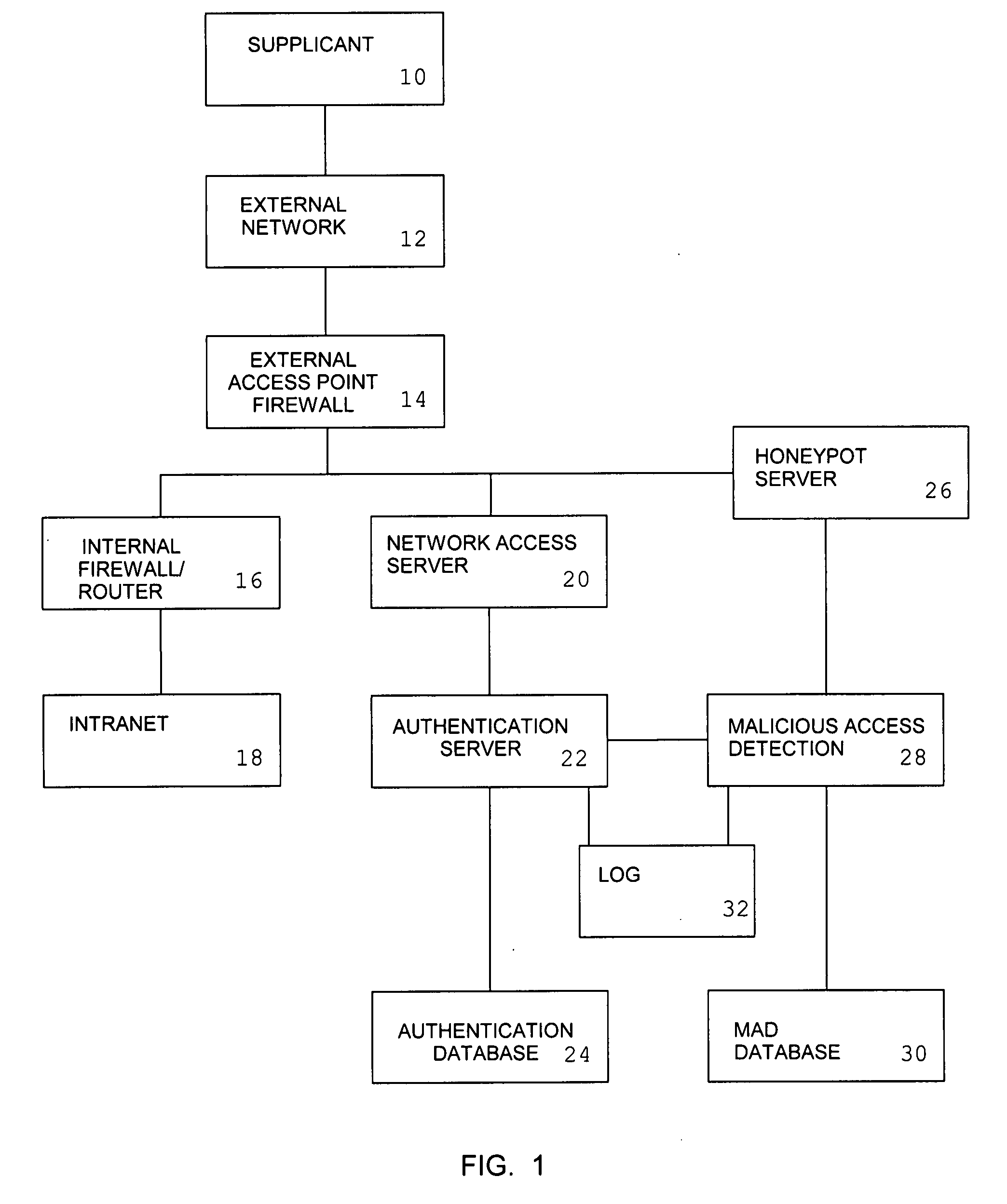
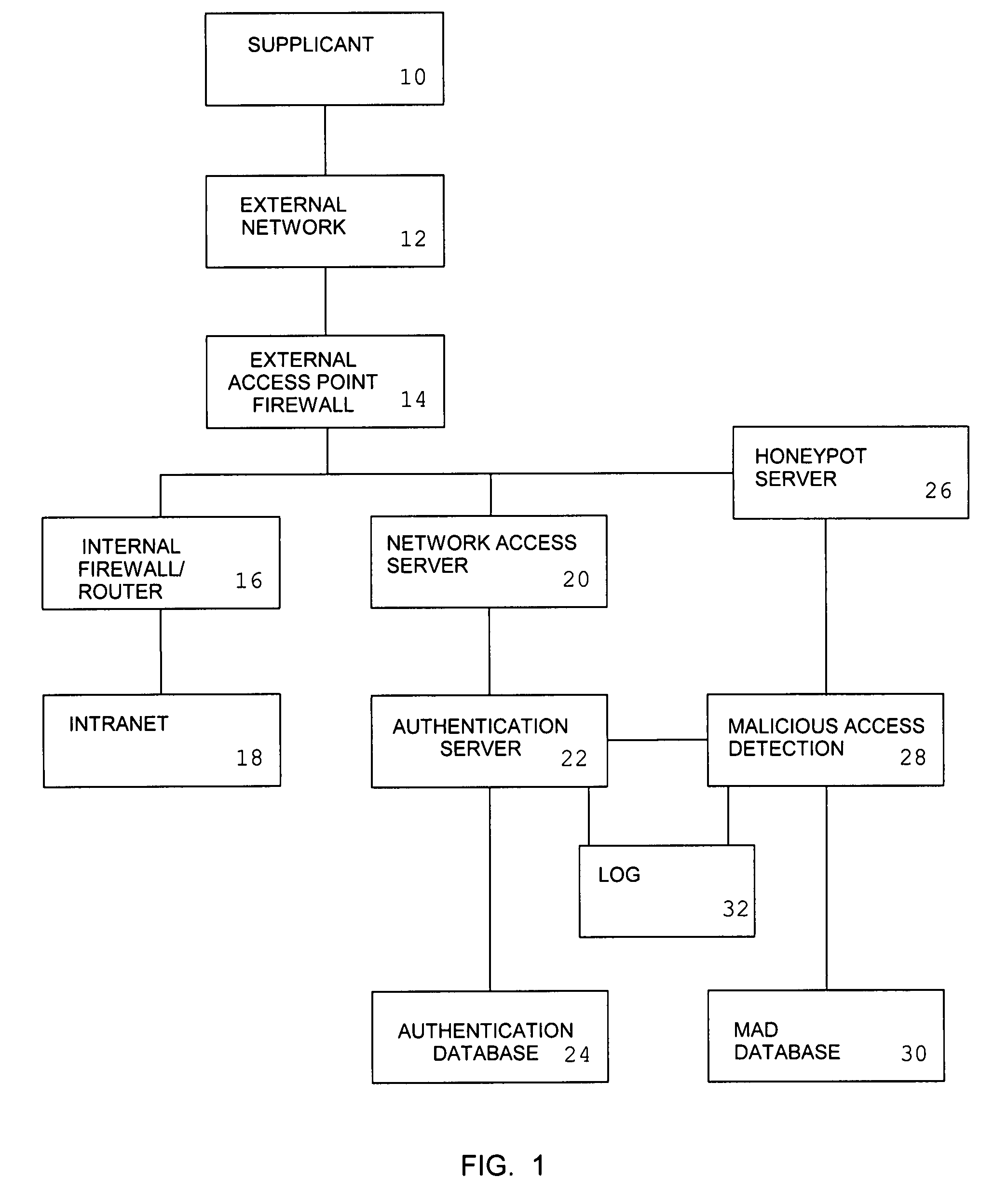
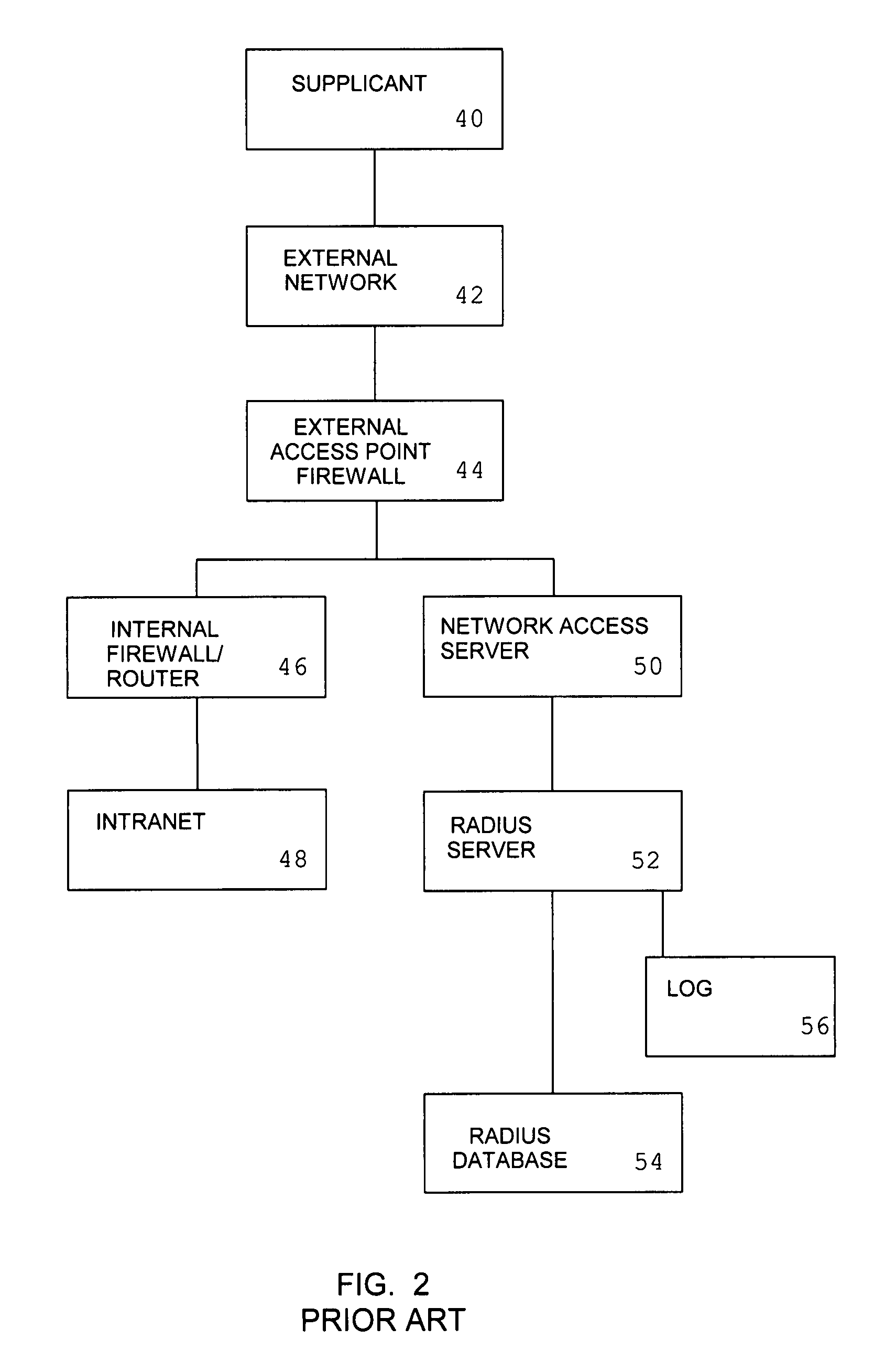
System and method for remote authentication security management
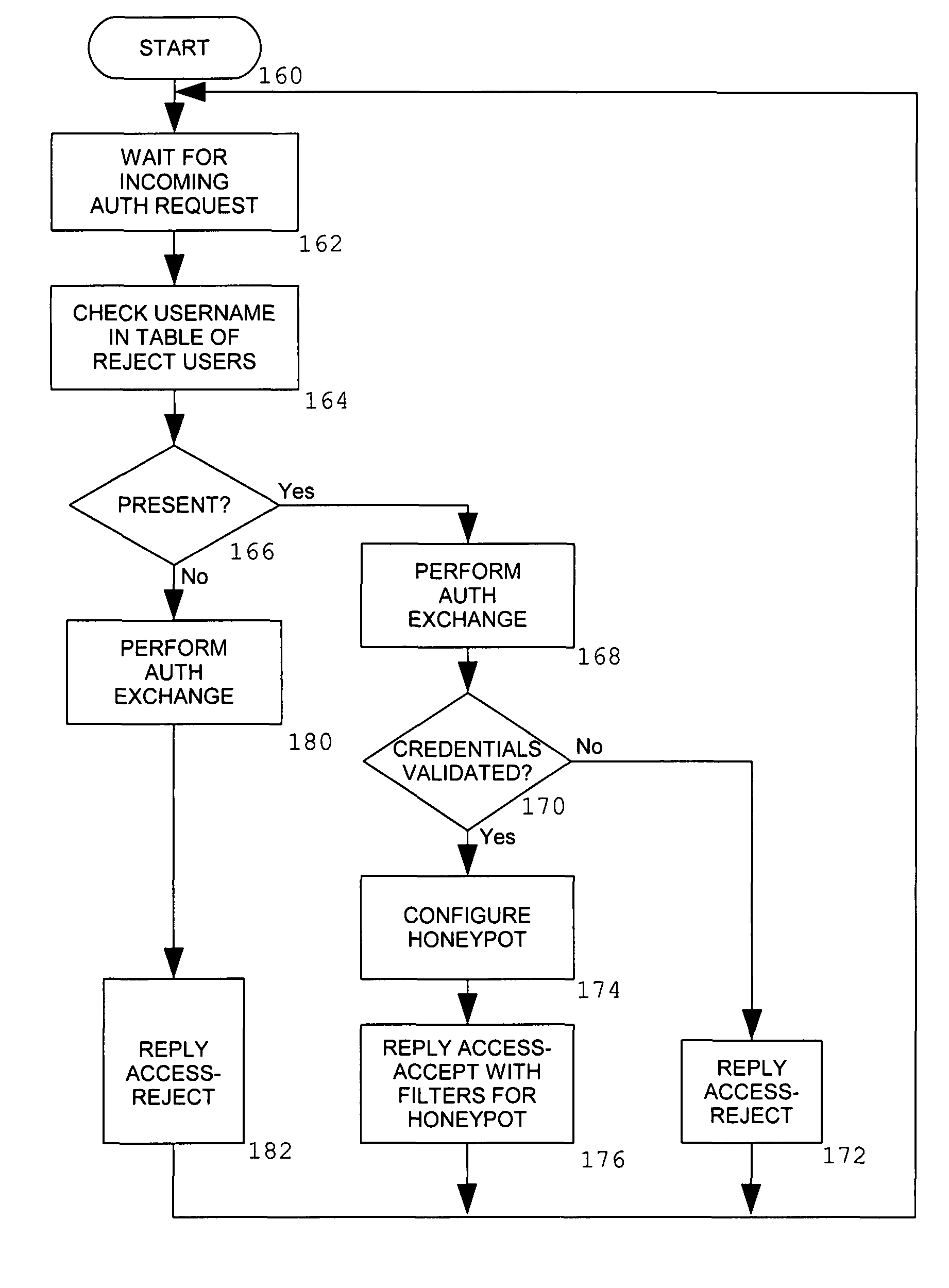
InactiveUS20080046989A1Reduce workloadReduce the possibilityMemory loss protectionDigital data processing detailsNetwork access serverInformation processing
An information processing system for remote access comprising a network access server and an authentication server is augmented with the ability to provide a simulated authentication process for authentication requests from attackers which do not correspond to authorized user names. Attackers whose requests form a password guessing attack for a user identity selected from a set of reject user names are redirected to a honeypot server.
Owner:INFORMED CONTROL
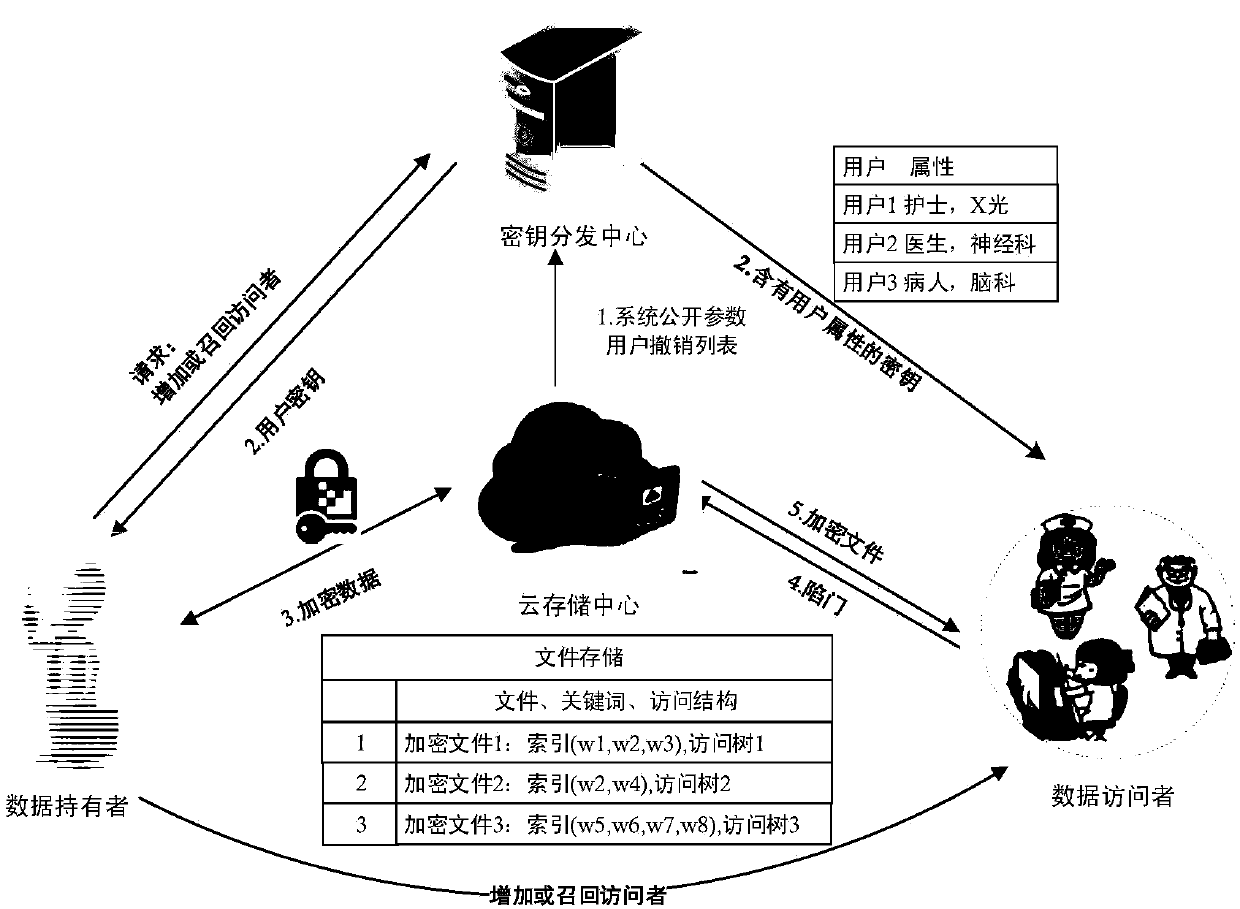
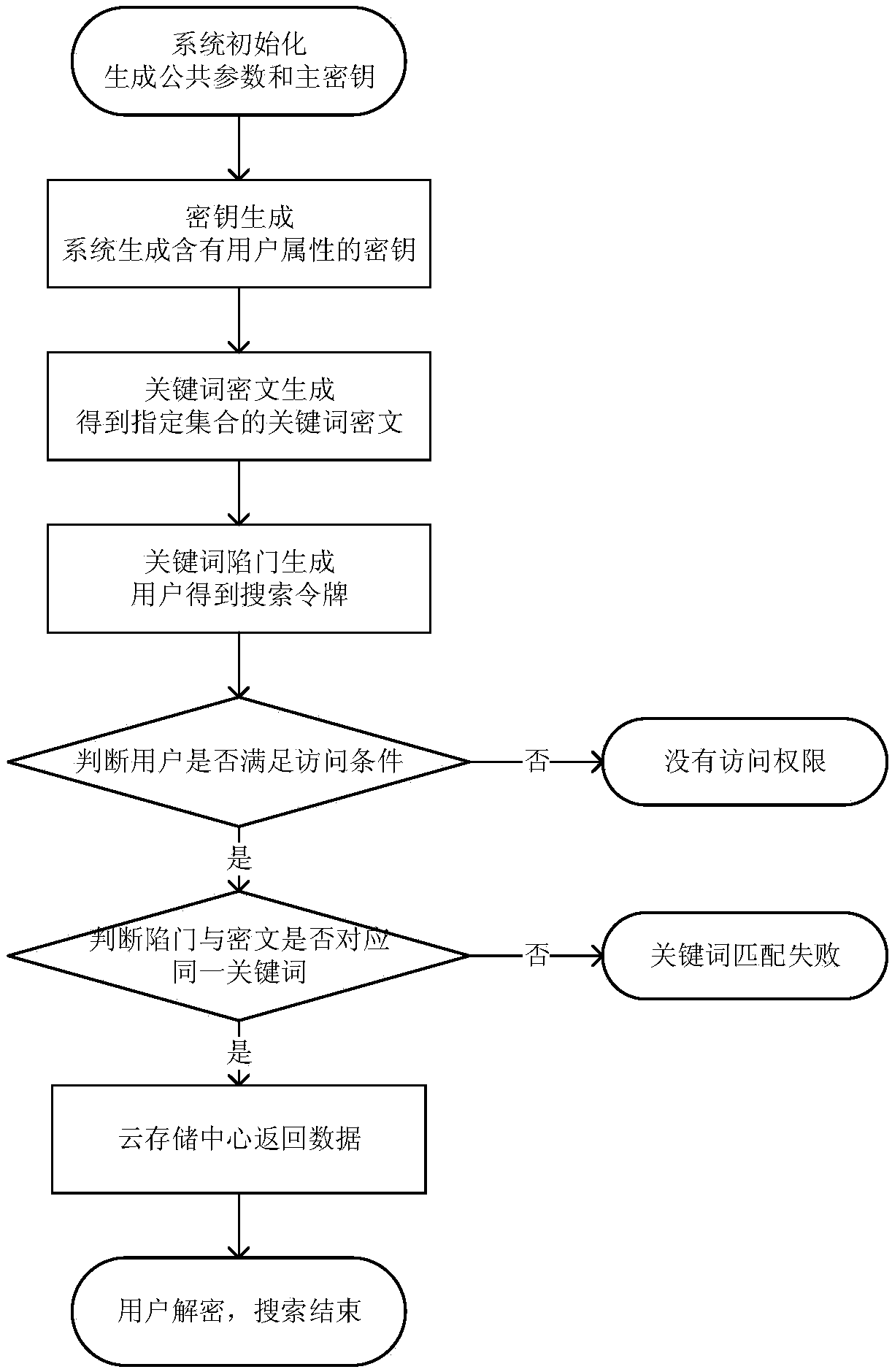
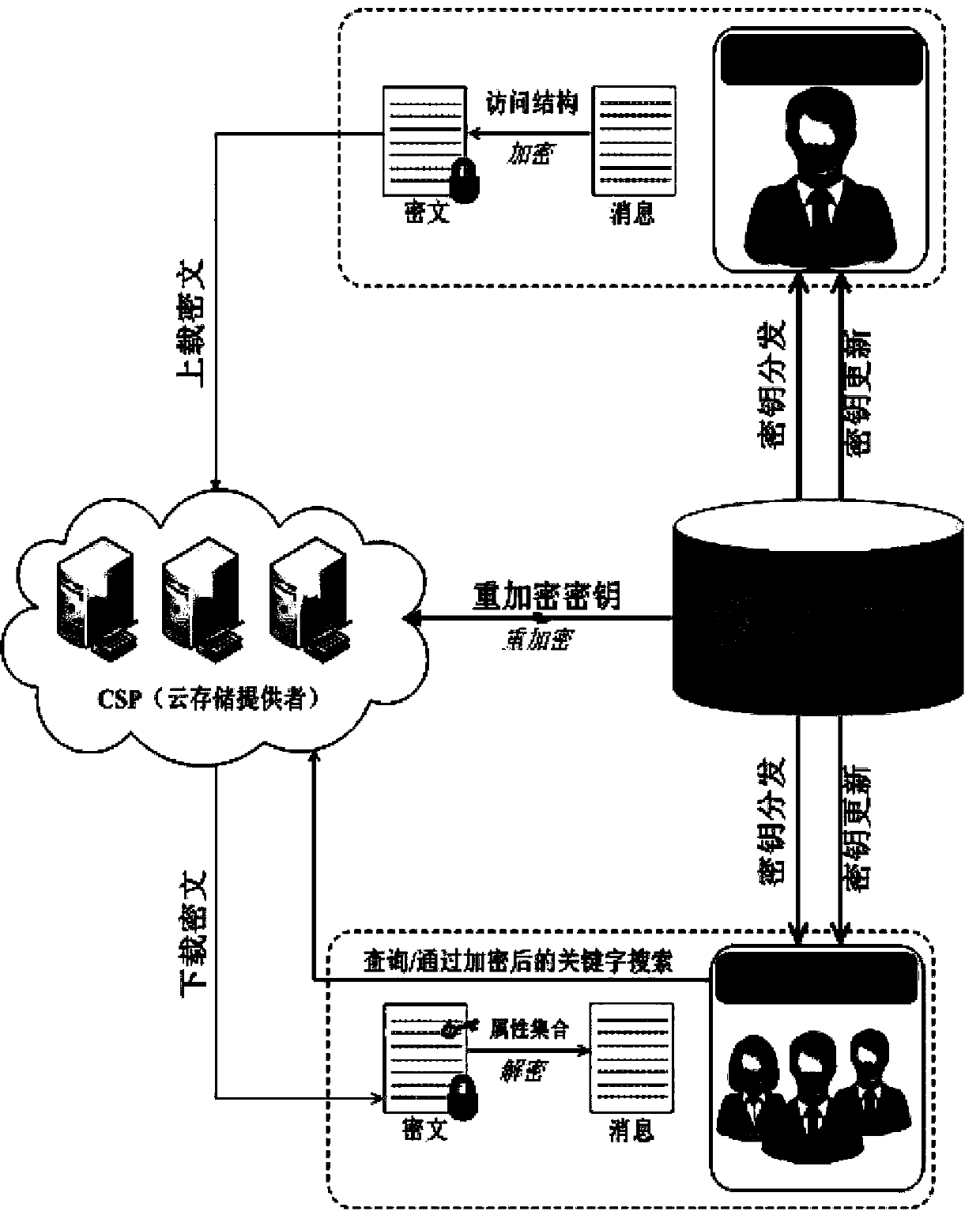
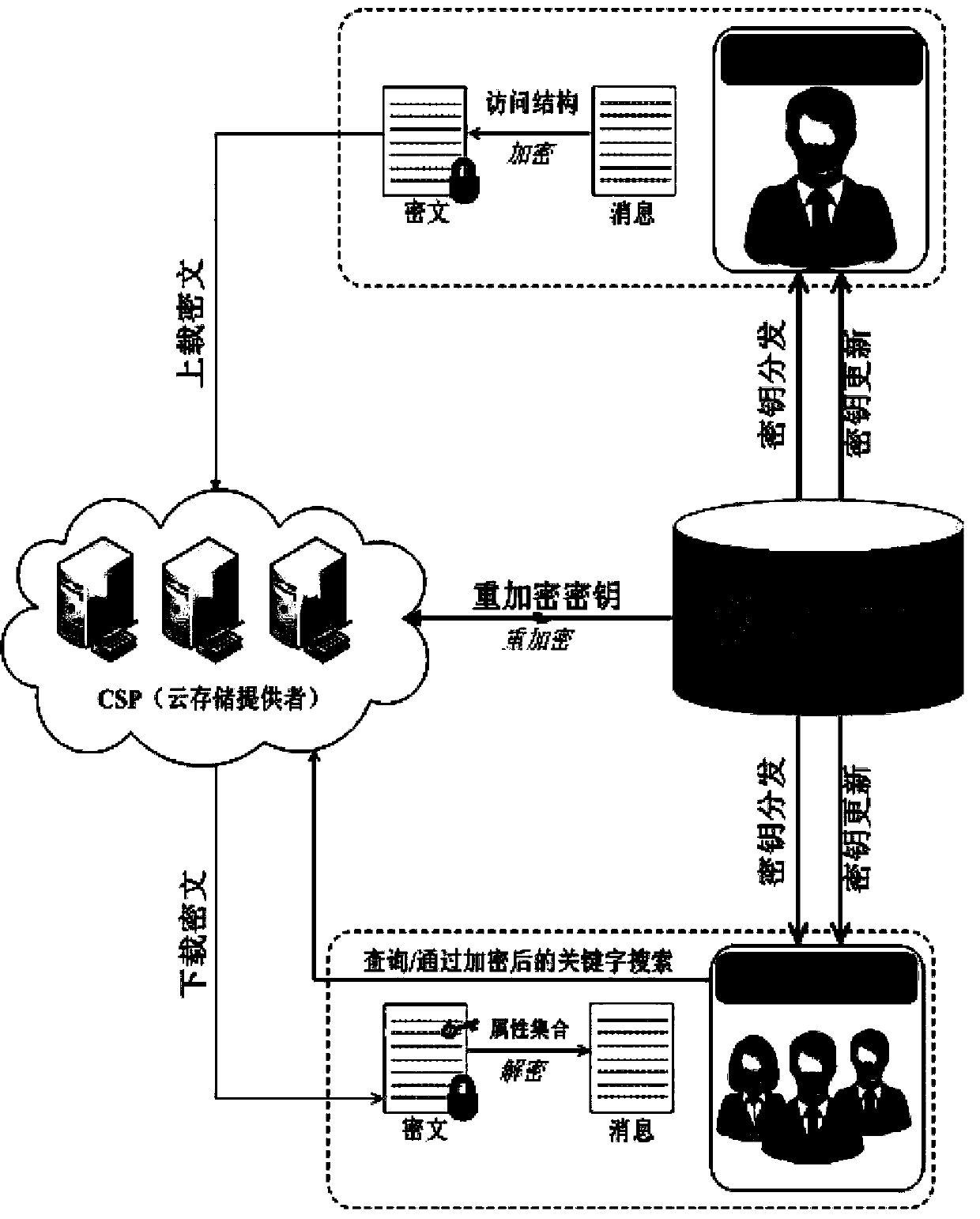
Attribute-based searchable encrypted electronic medical record system and encryption method
InactiveCN107634829AReduce computing requirementsReduce computational complexityKey distribution for secure communicationSpecial data processing applicationsMedical recordCiphertext
The invention discloses an attribute-based searchable encrypted electronic medical record system and an encryption method. The system comprises a key distribution center and a cloud storage center, wherein the key distribution center generates public parameters and a master key to initialize the system; the key distribution center generates and distributes keys containing user attributes to users;a data owner sets an access strategy before uploading medical record data, encrypts the data, and then uploads the data to the cloud storage center; a data visitor generates a trap door according tokeywords and the keys, and provides a query request to the cloud storage center; and after receiving the query request, the cloud storage center determines to return corresponding encrypted data to the data visitor according to the trap door and keyword ciphertexts. According to the scheme of the invention, the difficulty of key management in a multi-user environment can be reduced, data users canbe supported to accurately query the keywords of the ciphertexts, guessing attacks of the keywords can be resisted, and the leakage of privacy data can be effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
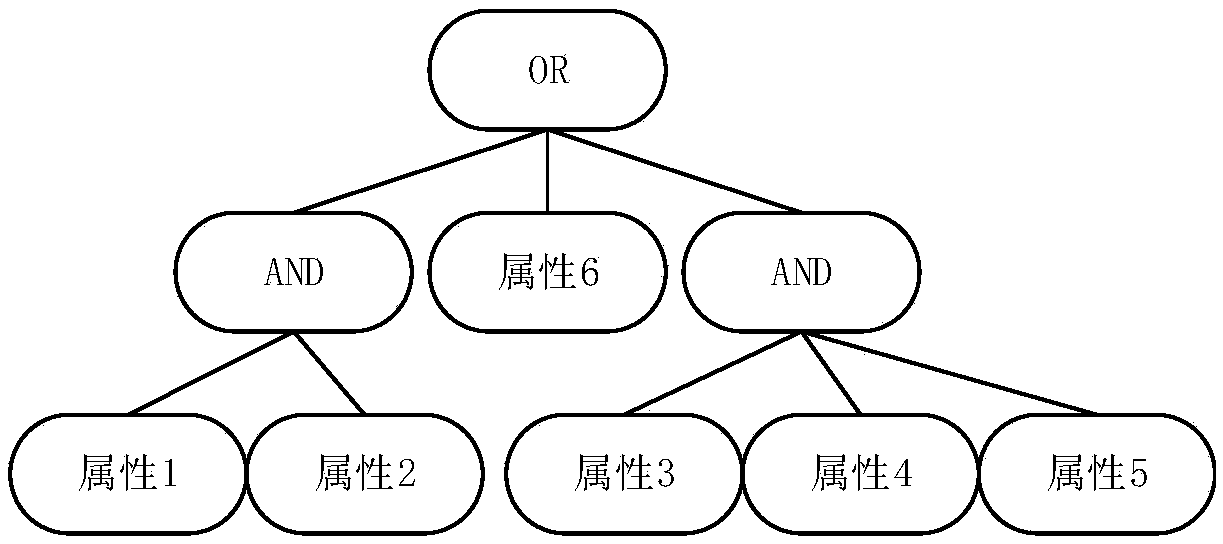
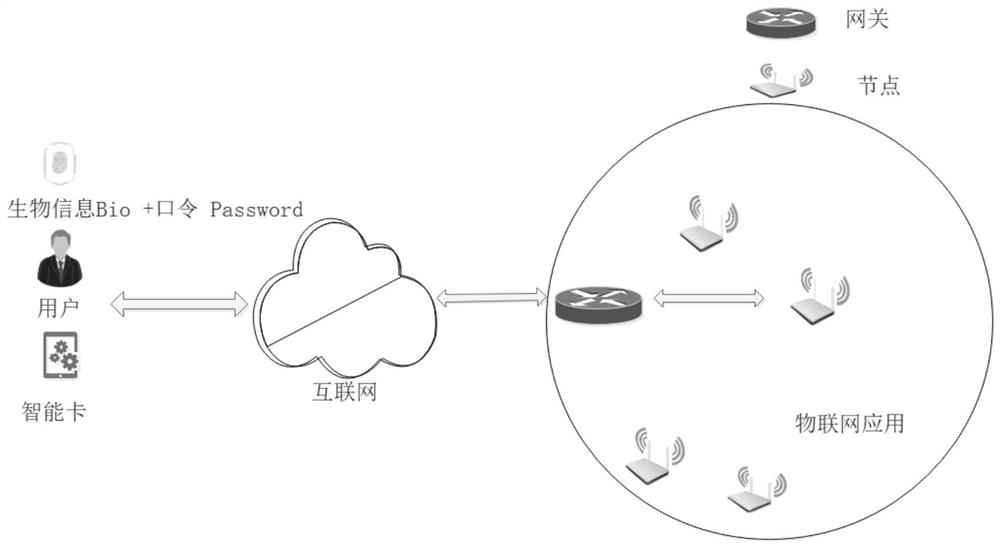
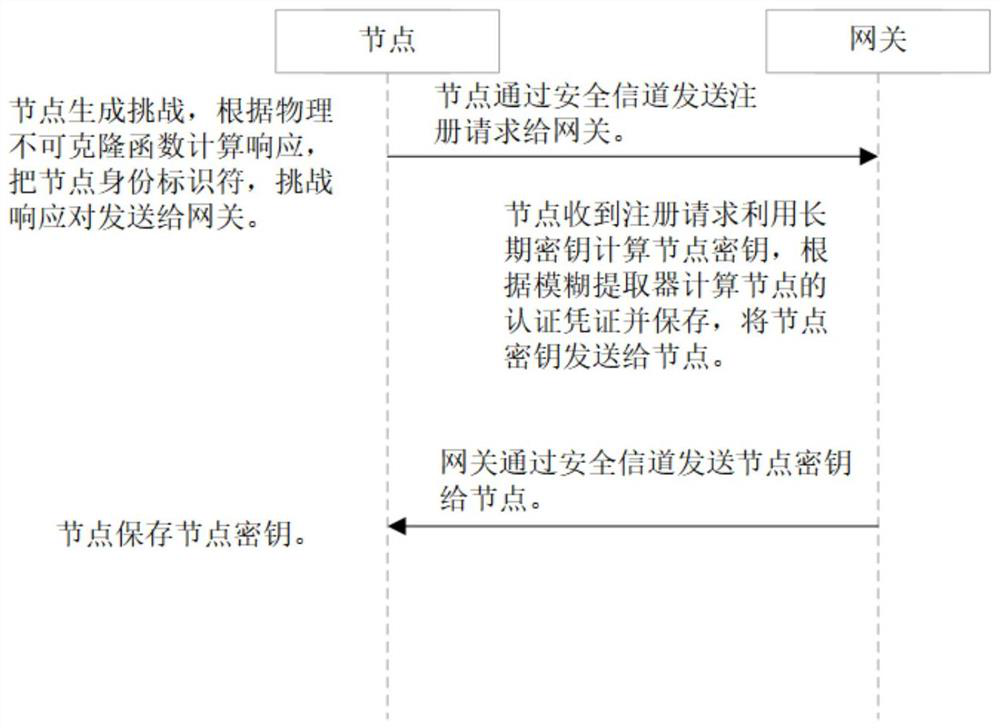
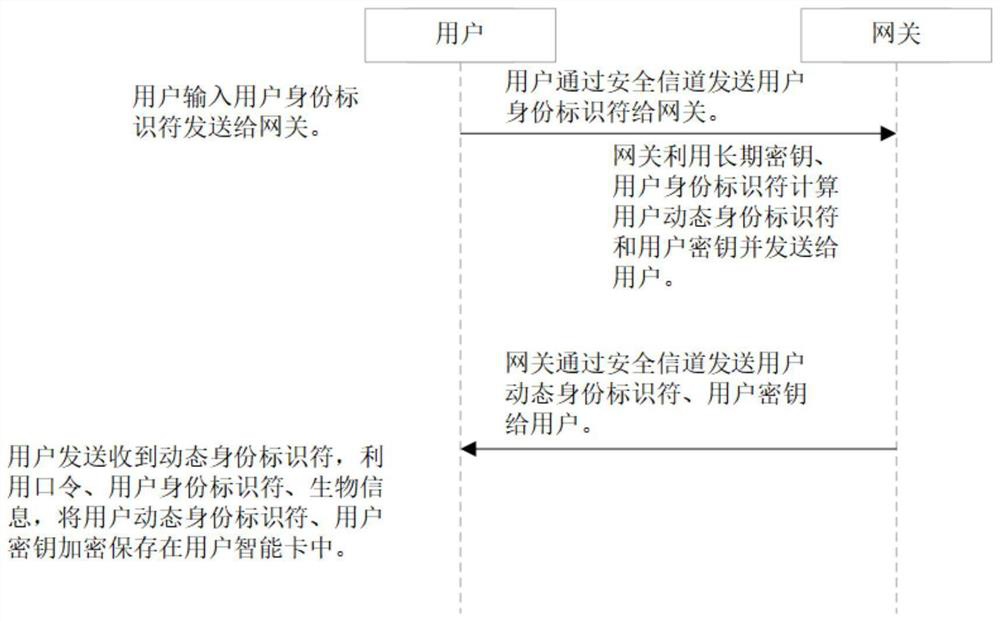
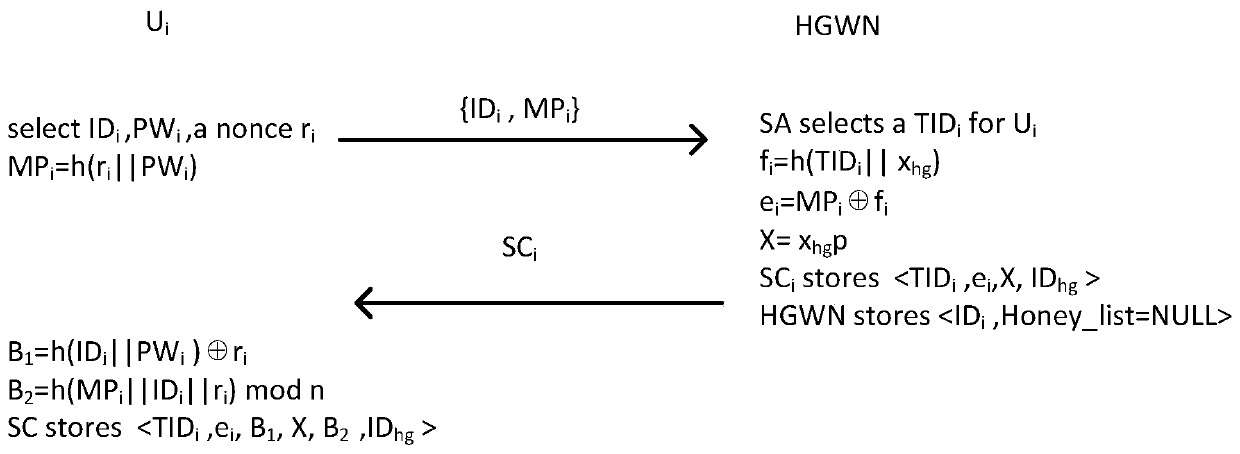
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
Retrieval system of encrypted data in secure cloud storage
PendingCN107734054APrevent Malicious BehaviorOffline KG attack preventionKey distribution for secure communicationDatabase queryingCloud storageDocumentation
The invention relates to a retrieval system of encrypted data in secure cloud storage. The retrieval system comprises a key generation center used for managing and distributing a public key / private key generated in the system; a cloud platform used for providing a data storage service to a data owner and responding to a search request of a user, that is, a data owner encrypts the data by utilizingthe public key and sends the encrypted data to the cloud platform for storage; and the user generates a query trap door and sends the query door to the cloud platform so as to search the encrypted data; and a calculation service provider for providing an online calculation service and interacting with the cloud platform to carry out calculation. The retrieval system of encrypted data in secure cloud storage supports multiple search and query modes; the system allows the user to search the encrypted documents from multiple data owners by utilizing one query trap door and supports flexible userauthorization and revocation mechanisms; and the system prevents offline keyword guessing attacks.
Owner:FUZHOU UNIV
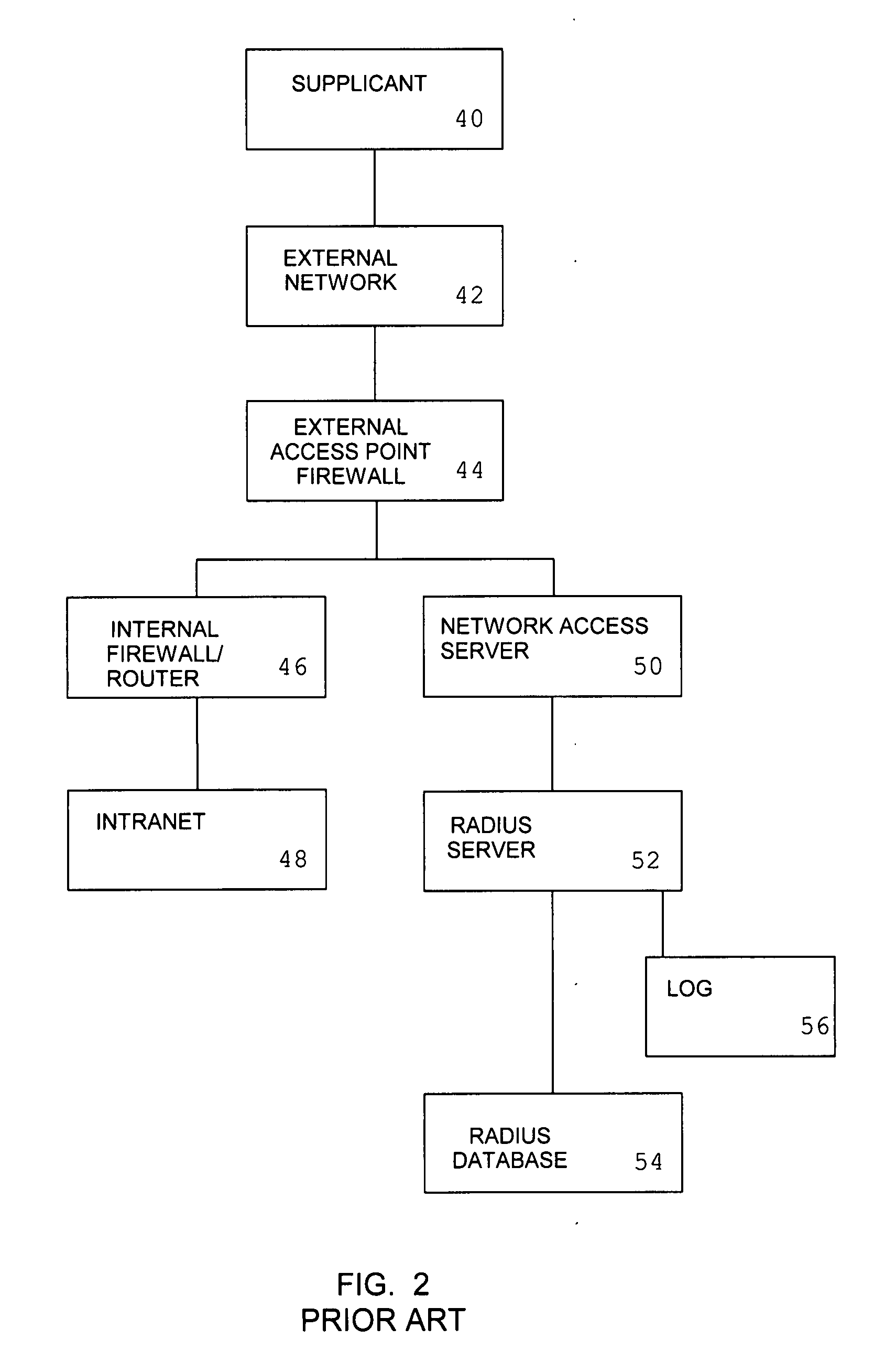
System and method for remote authentication security management
InactiveUS7934258B2Memory loss protectionDigital data processing detailsNetwork access serverInformation processing
An information processing system for remote access comprising a network access server and an authentication server is augmented with the ability to provide a simulated authentication process for authentication requests from attackers which do not correspond to authorized user names. Attackers whose requests form a password guessing attack for a user identity selected from a set of reject user names are redirected to a honeypot server.
Owner:INFORMED CONTROL
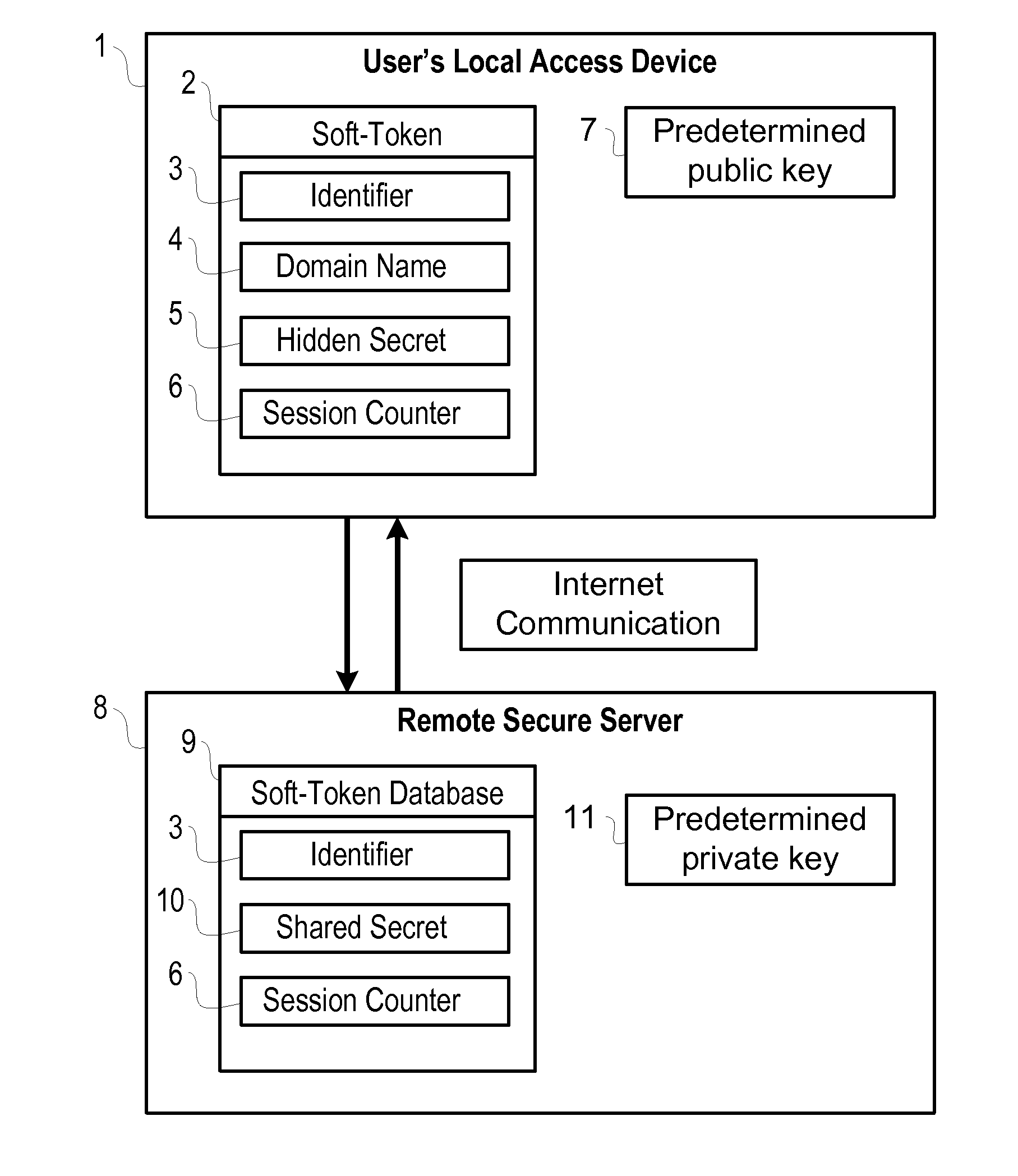
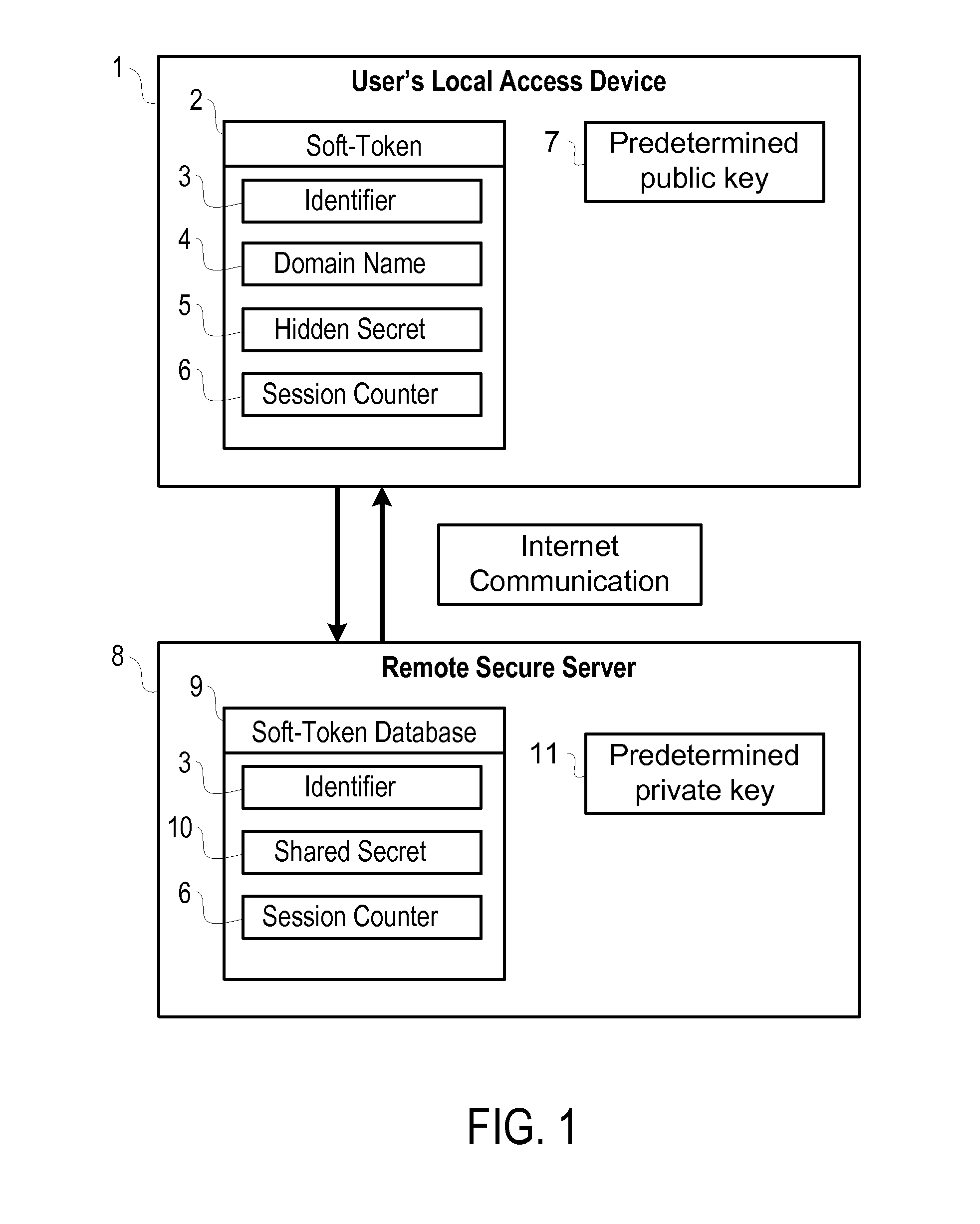
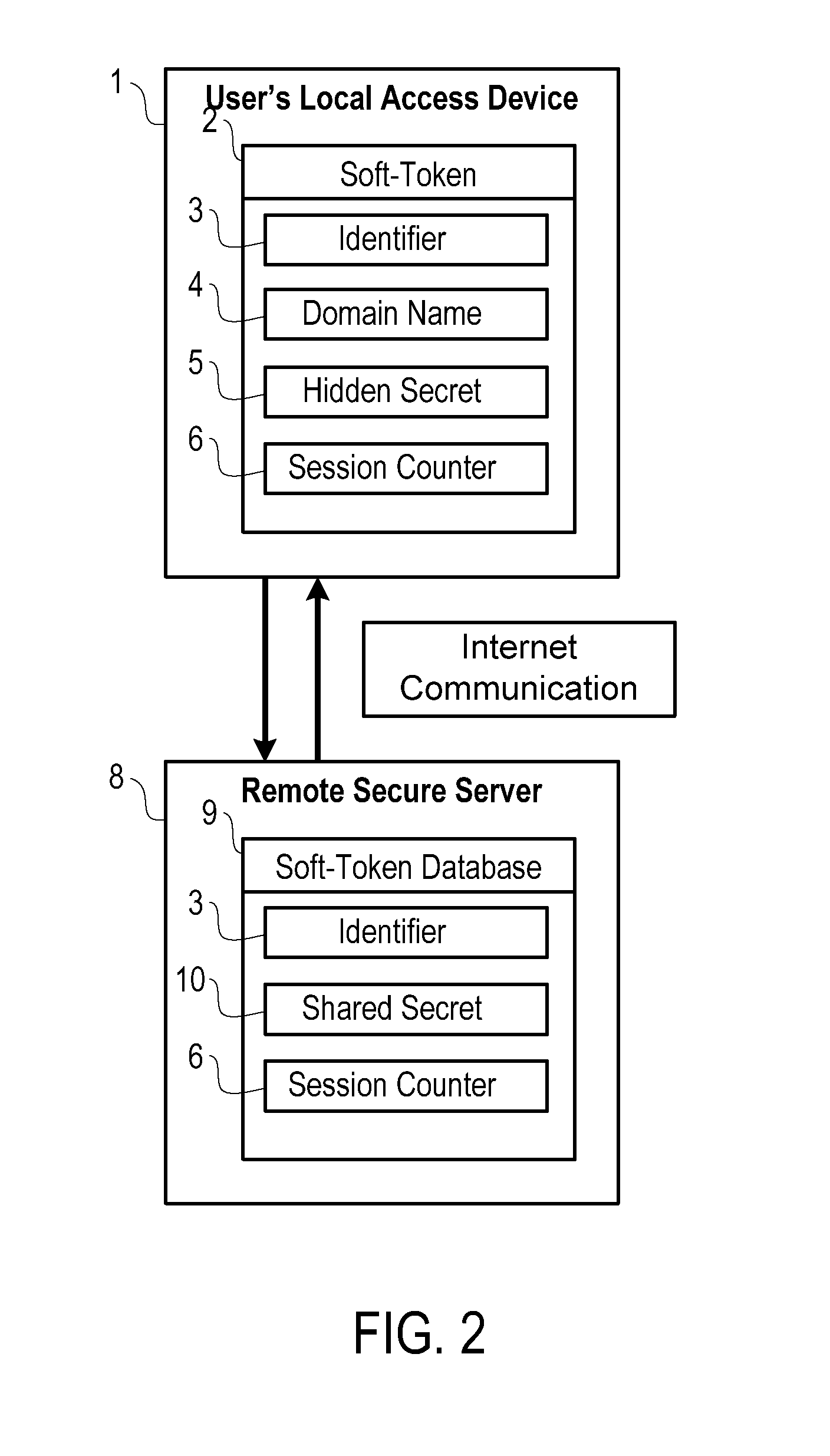
Soft-Token Authentication System
ActiveUS20130097427A1User identity/authority verificationComputer security arrangementsInternet privacyAuthentication system
A system for authenticating a user and his local device to a secured remote service with symmetrical keys, which utilizes a PIN from the user and a unique random value from the local device in such a way that prevents the remote service from ever learning the user's PIN, or a hash of that PIN. The system also provides mutual authentication, verifying to the user and local device that the correct remote service is being used. At the same time, the system protects against PIN guessing attacks by requiring communication with the said remote service in order to verify if the correct PIN is known. Also, the system works in such a way as to change the random value stored on the user's local device after each authentication session.
Owner:CYBRSECURITY CORP
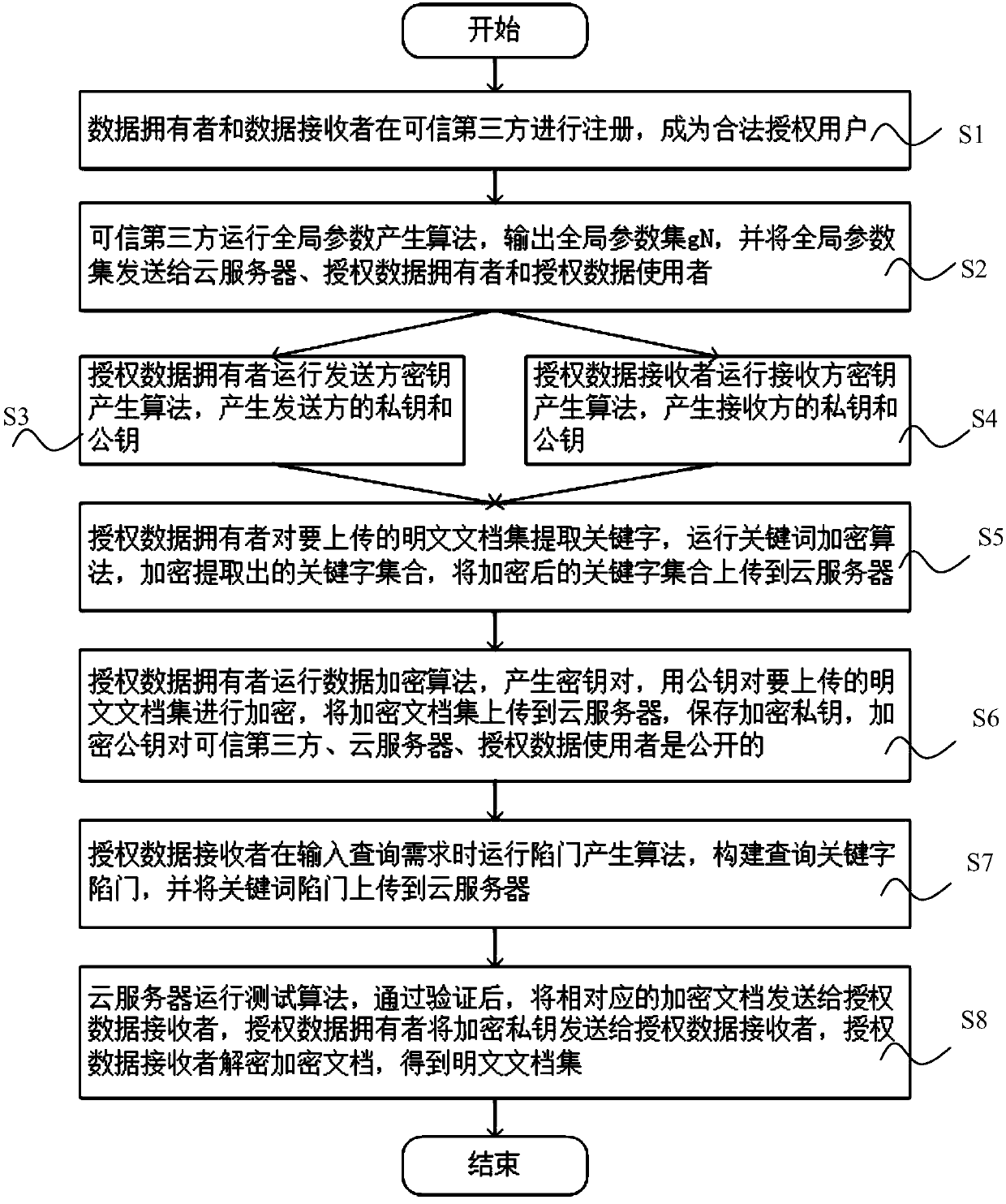
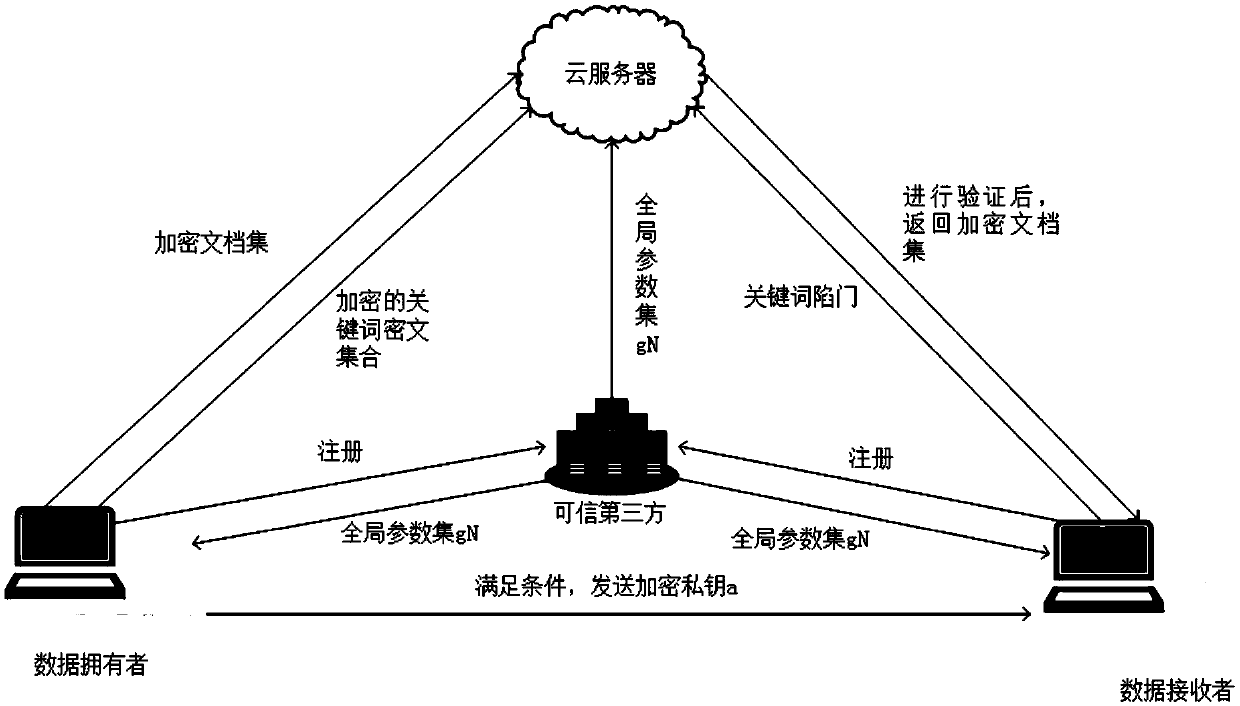
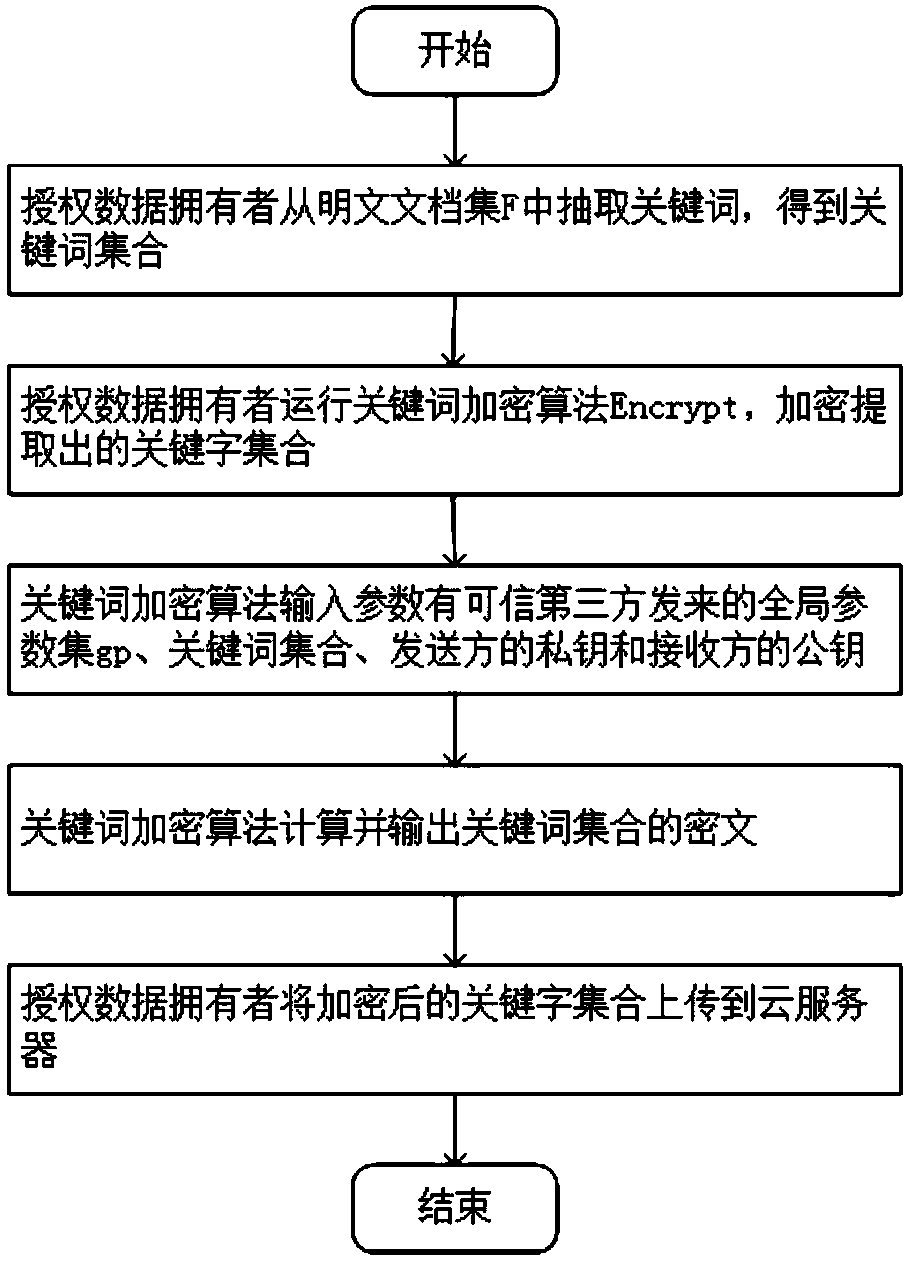
A public key encryption method supporting multi-keyword search against keyword guess attack
InactiveCN109086615AUnforgeableOvercoming the Problem of Guessing AttacksDigital data protectionTransmissionThird partyCiphertext
The invention discloses a public key encryption method for supporting multi-keyword search to resist the attack of keyword guess. The method comprises the following steps: a data owner and a data receiver are registered as a legal authorized user in a trusted third party; the trusted third party runs the global parameter generation algorithm, outputs the global parameter set and sends it to the cloud server, the authorized data owner and the authorized data receiver. The data owner receives the global parameter set and sends the encrypted document set and the keyword ciphertext to the cloud server. The data receiver receives the global parameter set, constructs the keyword trap according to the query sentence, and sends the keyword trap to the cloud server. The cloud server receives the global parameter set, encrypts the ciphertext document, the keyword ciphertext and the keyword trap, and returns the satisfied ciphertext document to the authorized data recipient by running the test algorithm verification. The invention effectively solves the problem of keyword guess attack, realizes keyword search, and has obvious advantages in computational efficiency and communication cost.
Owner:SHANGHAI MARITIME UNIVERSITY
Two-factor authentication key agreement protocol suitable for multi-gateway wireless sensor network
ActiveCN110234111AResistance to replay attacksResistance to insider attacksSecurity arrangementKey-agreement protocolPassword
The invention provides a double-factor authentication key agreement protocol suitable for a multi-gateway wireless sensor network. The protocol is divided into five stages: an initialization stage, aregistration stage, a login stage, an authentication stage and a key change stage. Fuzzy verification and honeywords methods are adopted in the user authentication part, so that the united password identity guessing attack based on the stolen intelligent card is effectively resisted. In the scheme, key negotiation is based on discrete elliptic curve encryption and can resist sensor capture attacks, so that the forward security of the protocol is ensured.
Owner:BEIHANG UNIV
Fuzzy keyword public key searchable encryption scheme achieving unrecognizable trap door
The invention discloses a fuzzy keyword public key searchable encryption scheme achieving an unrecognizable trap door. According to the scheme, the public key of a server is used for encrypting keywords and data files and an external attacker cannot acquire any information if not having the secret key of the server, thereby being incapable of using a safety channel for transmission. The scheme also achieves unrecognizable trap door such that the external attacker cannot attack the trap door by using keyword guessing attack. The scheme not only supports accurate keyword searchable encryption, but also supports search when input keywords have any spelling mistake or inconsistent formats, thereby greatly improving system availability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for generating three parts cipher key negotiation
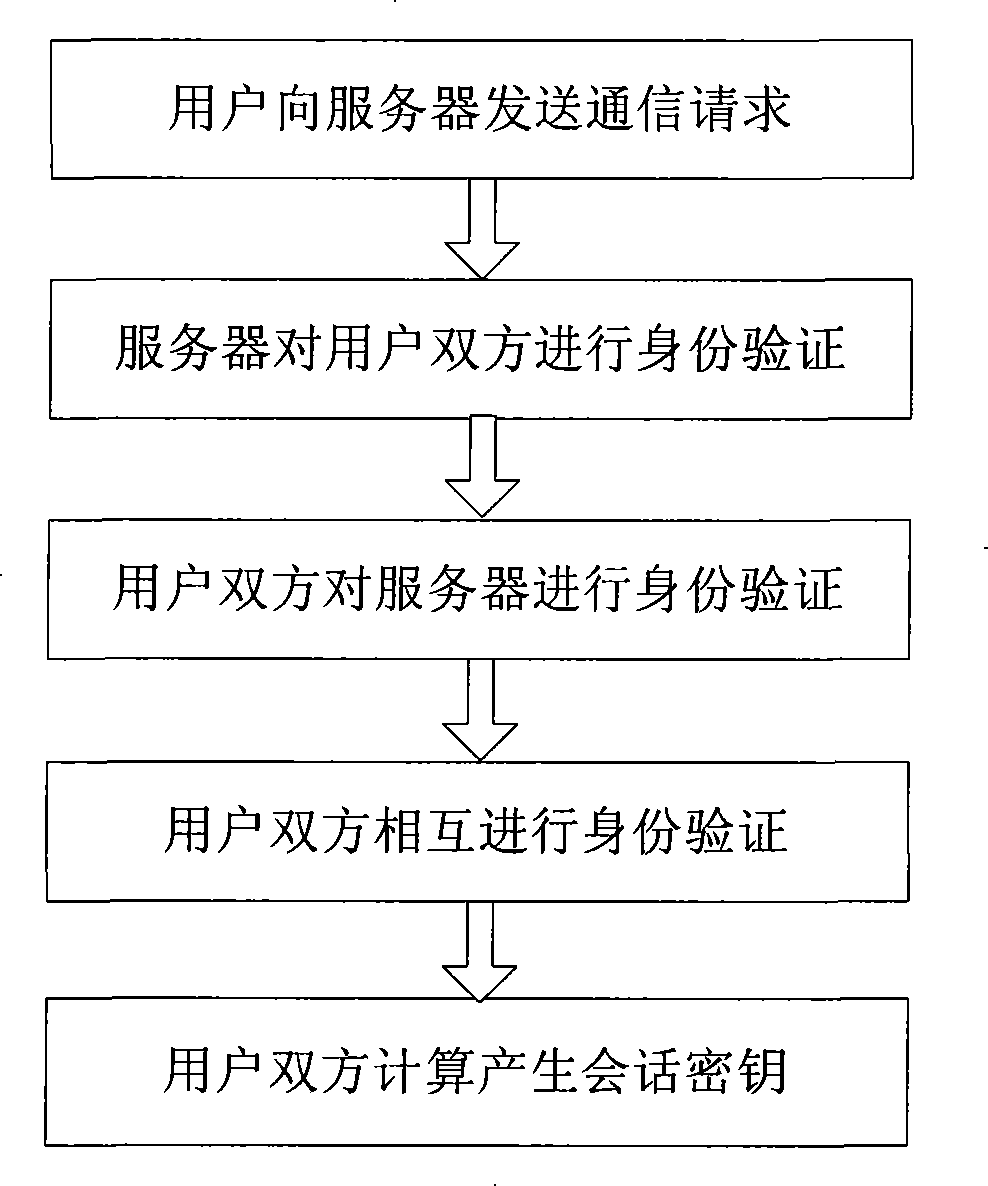
InactiveCN101252577AKey distribution for secure communicationUser identity/authority verificationKey exchangeHash function
The invention belongs to the communication technical field, relating to the safety problem of network communication, in particular to the three party key exchange protocol, namely, 3PAKE protocol focusing on password authentication of a network structure. Basing on the CDH assumption and using the difficulty of discrete logarithm and the unilateralism of hash function, the invention includes three key steps that firstly, the certifications of the two users asking for communication are certified by the server; secondly, the certification of the server is verified by the two users asking for communication; thirdly, certifications of the two users asking for communication are mutually verified. The invention overcomes the vulnerabilities of masquerading attack for the starter, masquerading attack from the responder, the attack from the middleman and the on-line password guess attack all existed in the S-3PAKE protocol; has the capacities of resisting frequent attack, the attack from the middleman, the masquerading attack from the starter, the masquerading attack from the responder, the off-line guess attack and the replay attack; has forward security and known key security; and also has the characteristic of perfectly resisting on-line guess attack.
Owner:天津启云科技有限公司
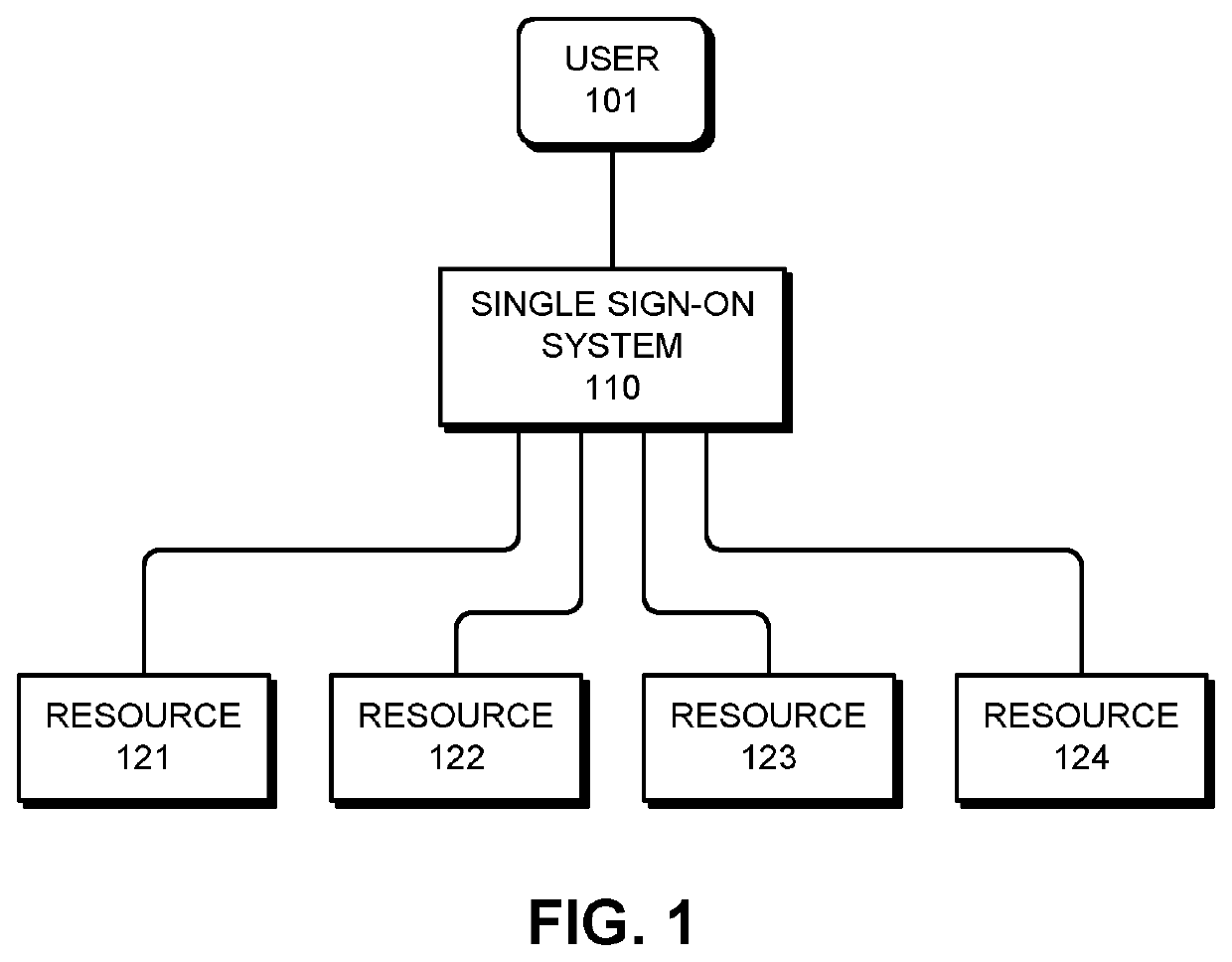
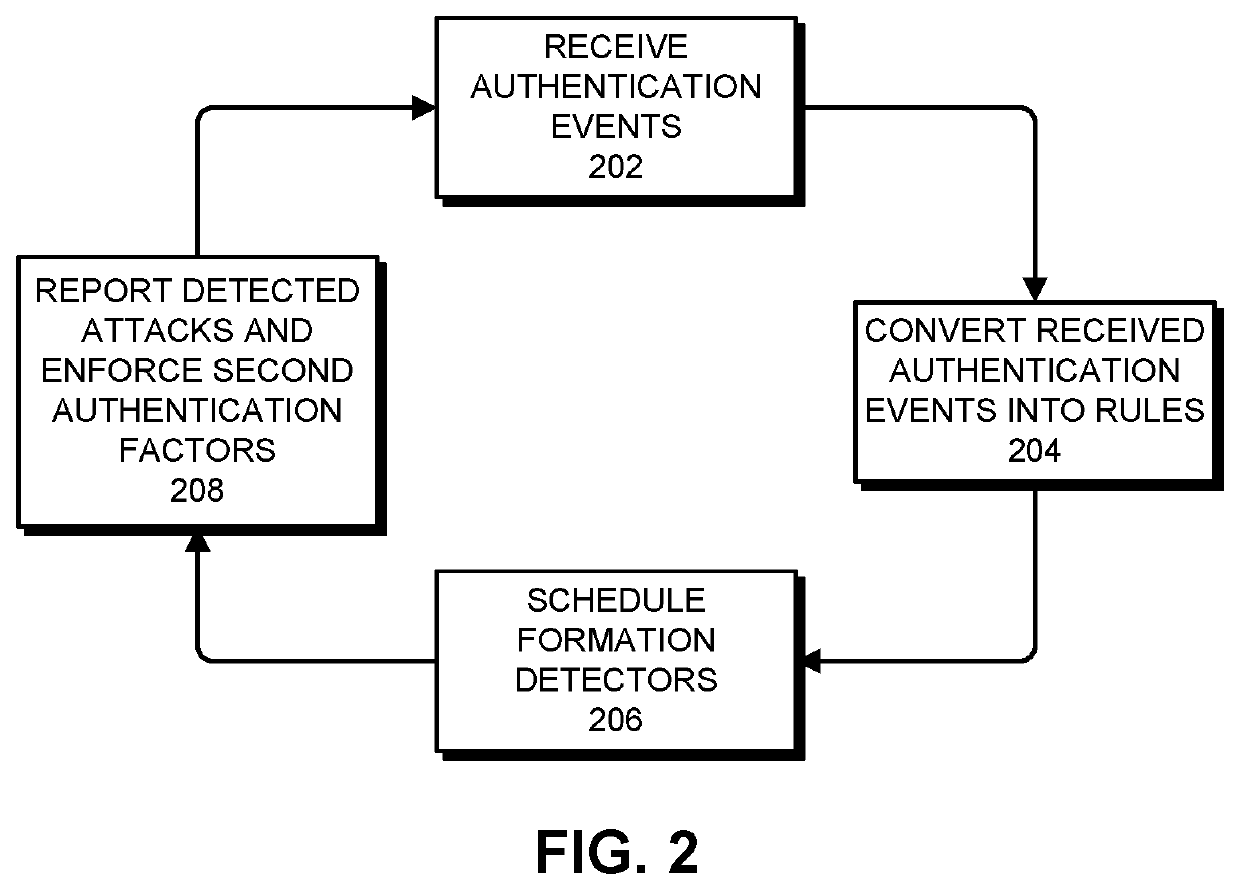
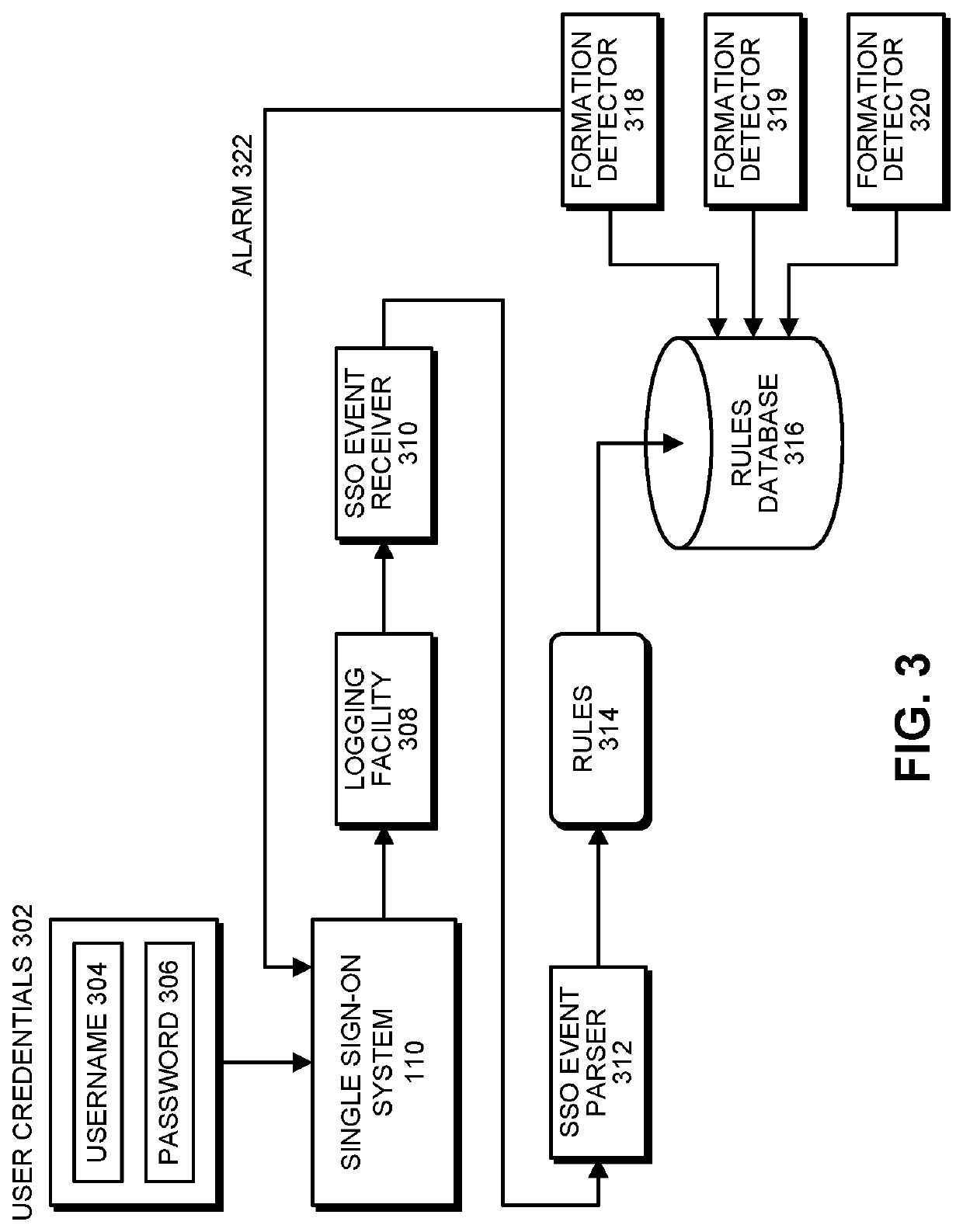
System and method for protecting online resources against guided username guessing attacks
ActiveUS20190384897A1Authentication is convenientDigital data authenticationTransmissionResource identifierGuessing attack
The system receives a stream of authentication events, which are associated with authentication events. Next, the system attempts to detect a formation of authentication events, wherein a formation comprises a time window of authentication events that satisfy a formation criterion, which is based on one or more of: a username for the authentication attempt, an Internet Protocol (IP) address from which the authentication attempt originated, and a resource identifier for a computing resource that the authentication attempt was directed to. If a formation is detected, the system determines a number of valid usernames in the formation. If the number of valid usernames is one or less, the system computes a username similarity score for authentication events in the formation, which is a function of a string distance between usernames in the formation. If the username similarity score exceeds a threshold value, the system reports a potential username guessing attack.
Owner:ORACLE INT CORP
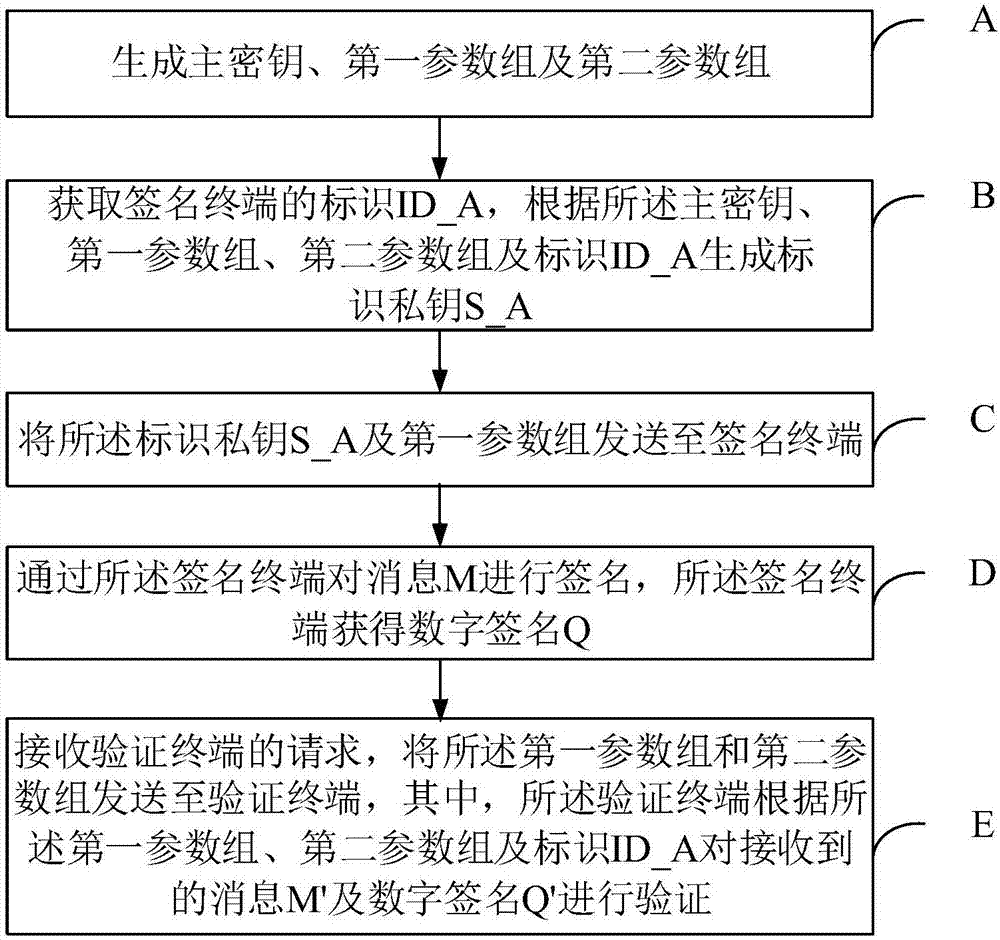
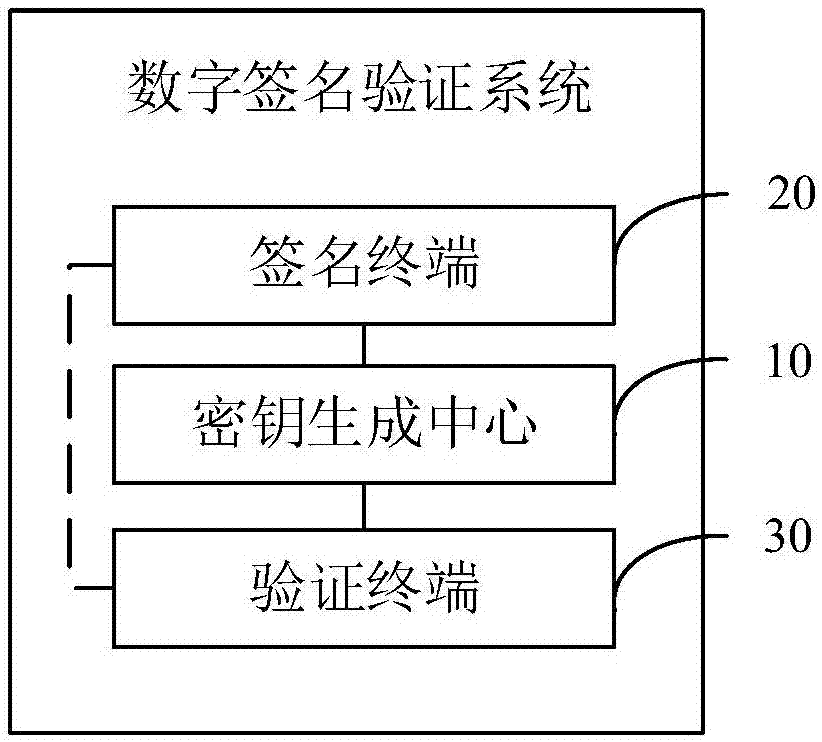
Digital signature verification method and system
ActiveCN106899413ASimplify complexityImproved ability to guess attacksKey distribution for secure communicationUser identity/authority verificationThird partySystems management
The invention provides a digital signature verification method and system. The user identity is used as the public key of the user, the private key is calculated by the trusted third party using the identity private key generation method, and the user does not need to apply for and exchange the certificate, thus greatly simplifying the complexity of cryptographic system management. The generated identity private key is protected using the PIN code and system features at the signature terminal. The signature terminal signatures information using the protected identity private key and a part of identity cryptographic system parameters, so that the digital signature function is achieved, and the ability to resist the PIN code guessing attack is effectively improved.
Owner:SHENZHEN OLYM INFORMATION SECURITY TECHOLOGY CO LTD
A security authentication method based on smart home
ActiveCN109088735ARealize intelligent security authenticationEnsure safetyKey distribution for secure communicationUser identity/authority verificationHome environmentPassword
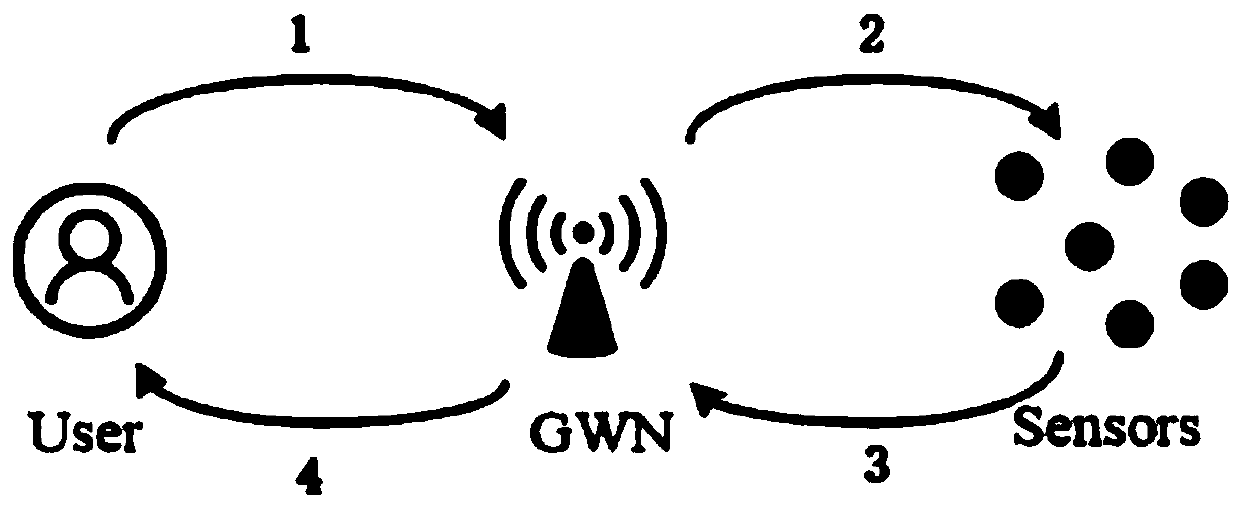
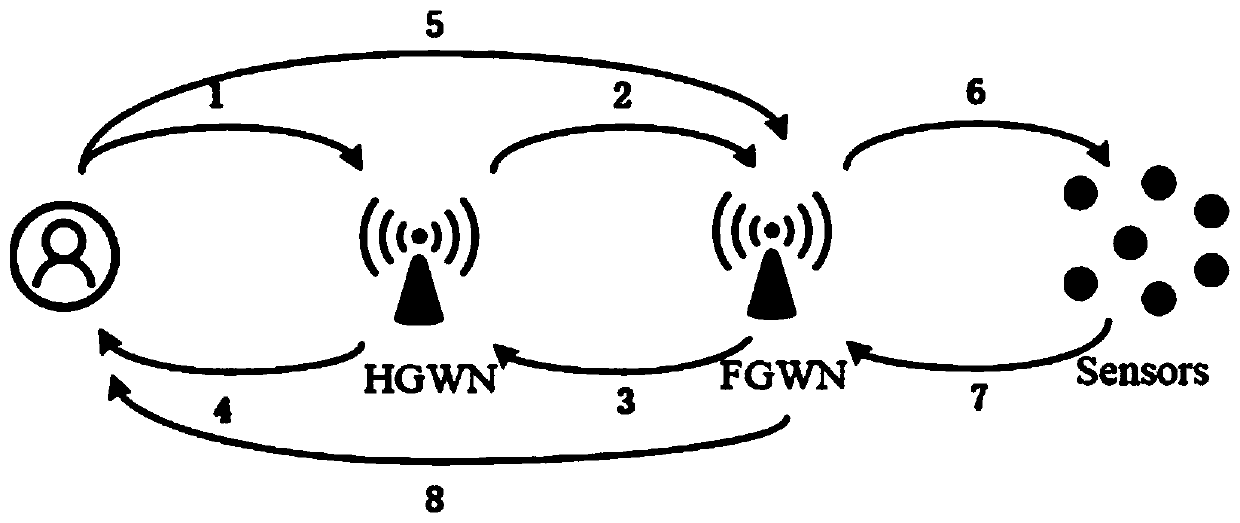
The invention discloses a safety authentication method based on intelligent home. The invention comprises the following steps: step 1, a user registers and authenticates at a home gateway; step 2, theuser registers and authenticates at a home gateway. 2, the home gateway sends a message to the intelligent terminal; 3, authenticating the intelligent terminal and forming a session secret key replyphase; 4, the home gateway replies to the user stage; 5, a session secret key is formed between the user and the intelligent terminal. The invention provides a new M2M mode, which is based on the usermobile terminal to transmit information through the home gateway to control the intelligent home terminal, so as to realize the intelligent safety authentication of the home environment, and ensure the message transmission and the data safety in the intelligent home. The invention can provide security attributes such as user anonymity, mutual authentication, session key security, perfect forwardsecurity and the like, and can also resist offline password guessing attack and camouflage attack. And the performance comparison shows that the proposed mechanism has high efficiency.
Owner:HANGZHOU NORMAL UNIVERSITY
Radio frequency identification system safety certification and key agreement method
InactiveCN103560881AEasy transferNo impact on securityUser identity/authority verificationSensing record carriersPrivacy protectionAuthentication server
The invention discloses a radio frequency identification system safety certification and key agreement method. According to the radio frequency identification system safety certification and key agreement method, transmission of public values of the two communication parties is simplified, the public values are transmitted through a certification server, influences on the safety performance are avoided, and therefore even through the server is broken into, it is certain that following certification can not be passed. In the certification process, three-round communication and seven-step operation are required to be executed to generate a session key, and compared with same-class methods, the radio frequency identification system safety certification and key agreement method has the advantage that efficiency is greatly improved. The radio frequency identification system safety certification and key agreement method has the advantages of being safe, low in storage cost and communication cost, novel, easy to implement and the like. By means of the radio frequency identification system safety certification and key agreement method, server leakage attack, midwayer attack, off-line guessing attack and not-detectable on-line guessing attack can be effectively defended, meanwhile, a bidirectional certification session key with high safety performance and forward safety performance are provided, and the radio frequency identification system safety certification and key agreement method is quite suitable for RFID application systems which must provide privacy protection.
Owner:NANJING UNIV OF POSTS & TELECOMM
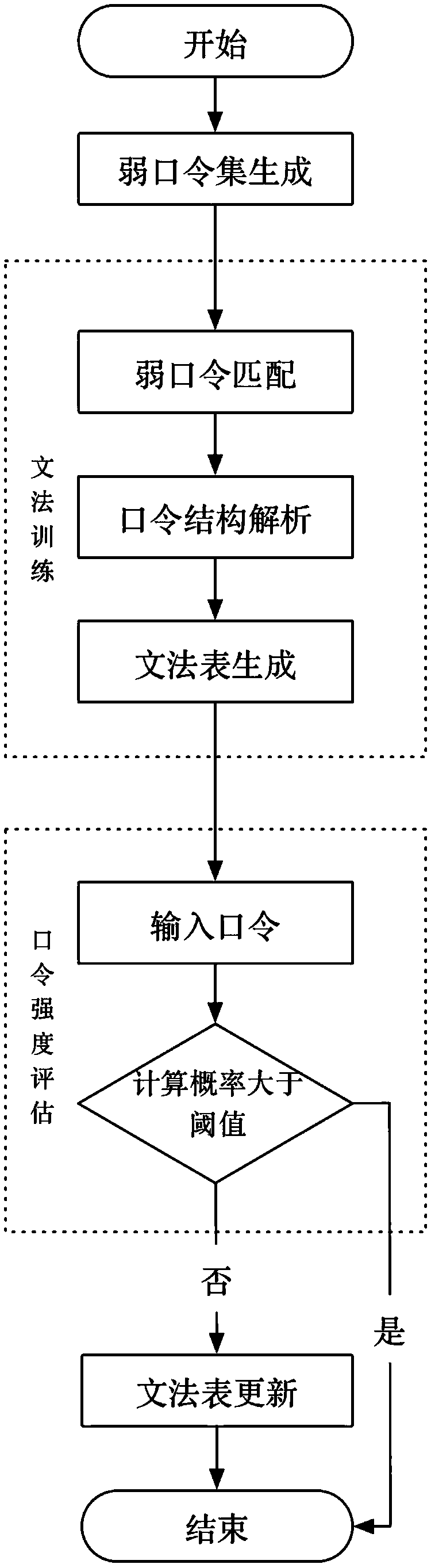
Group-based password intensity assessment method
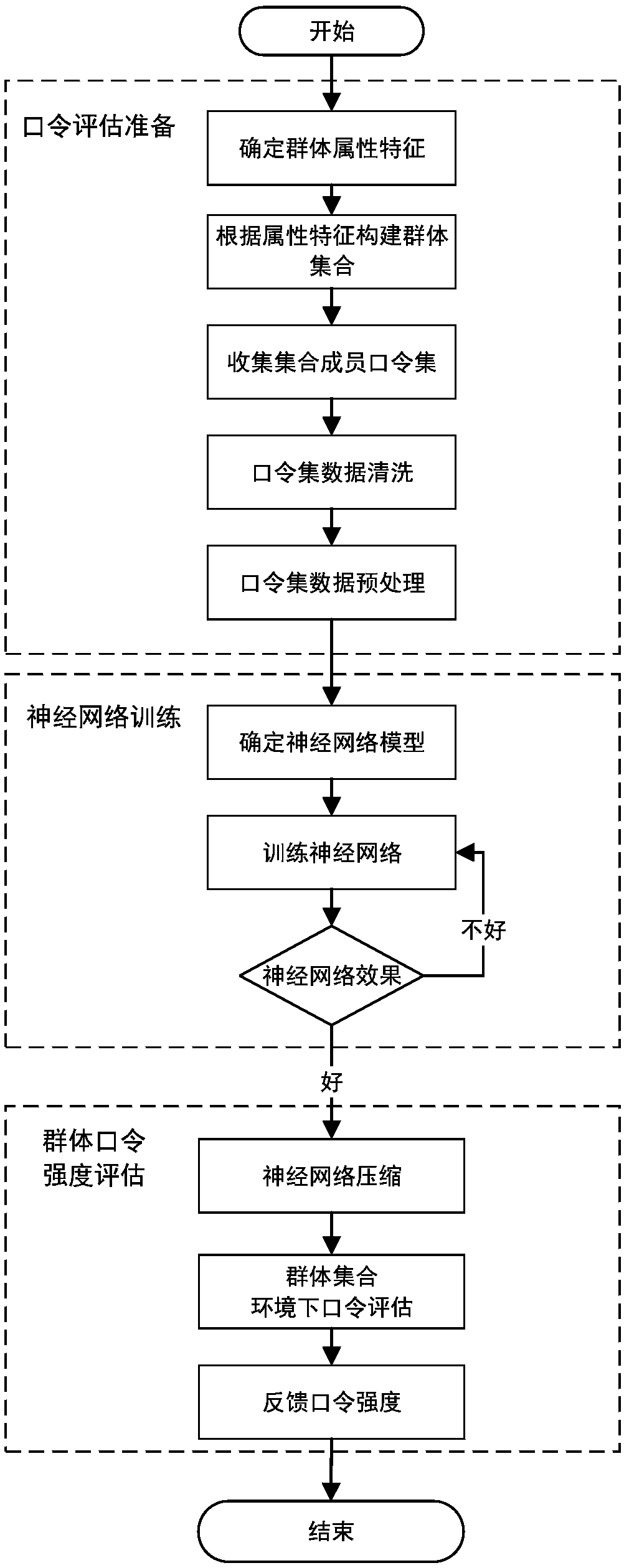
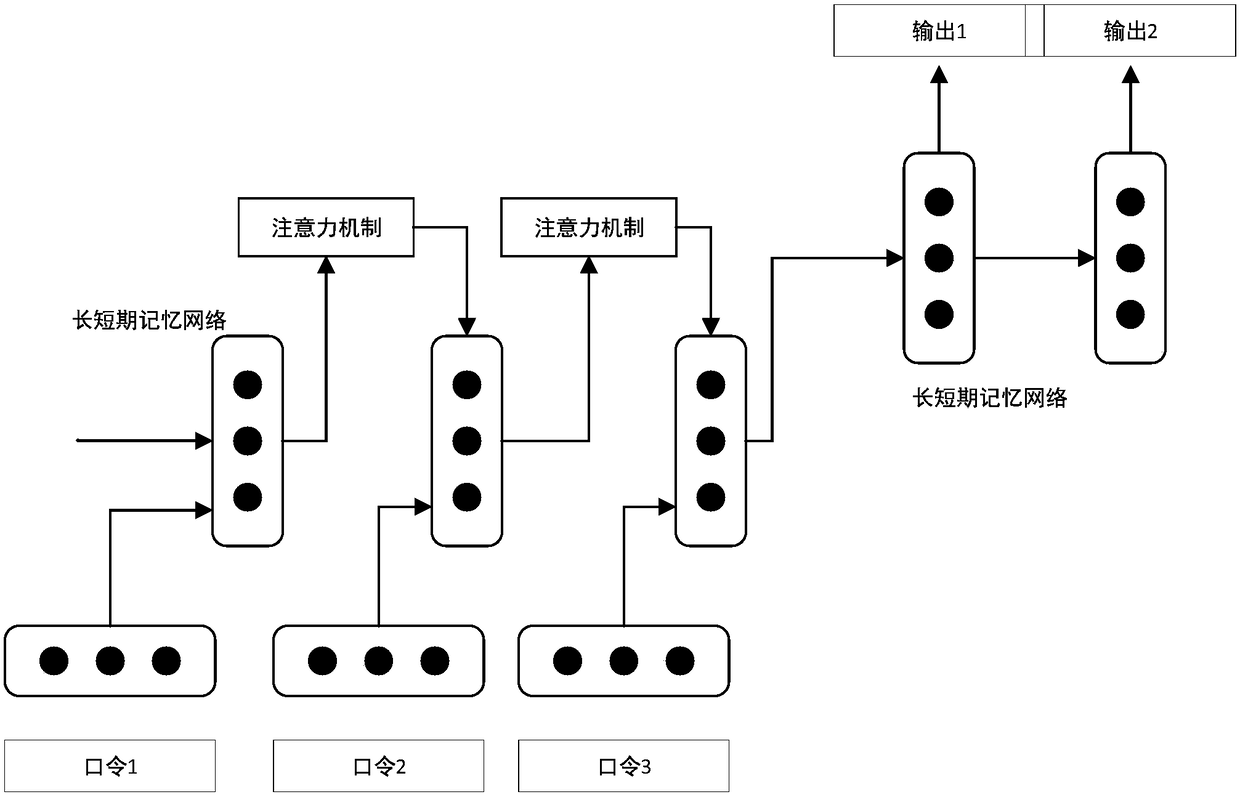
InactiveCN108509790AImprove securityImprove accuracyDigital data authenticationNeural architecturesNerve networkPassword
The invention discloses a group-based password intensity assessment method. The method comprises the steps of password assessment preparation, neural network training and group password intensity assessment, wherein the password assessment preparation step comprises the sub-steps of determining group attribute features, constructing a group set according to the attribute features, collecting a password set, cleaning password set data, and finishing password set data preprocessing; the neural network training step comprises the sub-steps of determining a neural network model, and collecting preprocessing results to train a neural network; and the group password intensity assessment step comprises the sub-steps of inputting a password to the trained neural network, and assessing the intensity of the password in a trained group. The intensity of the password in the group is assessed by utilizing the neural network; the neural network is compressed to achieve the plug and play effect; thepassword intensity is timely fed back; a weak password of the group is eliminated to a certain extent; the capability of resisting password guessing attacks by the password is enhanced; and the password security is improved.
Owner:EAST CHINA NORMAL UNIV
Keyword searchable delay encryption method and system
PendingCN112861153AHigh costMeet the requirements of real-world scenariosDigital data protectionSpecial data processing applicationsInternet privacyCiphertext
The invention relates to a keyword searchable delayed encryption method and system. The method at least comprises the steps of generating a searchable ciphertext Cw and / or a file ciphertext for a keyword w of at least one to-be-uploaded file in a delayed encryption mode based on a public key PK, and uploading the searchable ciphertext Cw and / or the file ciphertext to a cloud server; at least one retrieval trap door Tw generated for the keyword w to be retrieved based on the private key SK is sent to a cloud server, the cloud server retrieves all the searchable ciphertexts Cw based on the retrieval trap door Tw to obtain the corresponding searchable ciphertexts Cw, and corresponding file ciphertexts are determined based on the searchable ciphertexts Cw obtained through retrieval and fed back to a receiving end. According to the method, the generation time of the searchable ciphertext is delayed, and the keyword guessing attack difficulty of an attacker is increased, so that the keyword guessing attack between the cloud server and the sending end and between the cloud server and the receiving end is realized in a scene without a secure channel, a specified trusted server, a priori keyword space and strict user authentication. The searchable public key encryption has the characteristic of resisting keyword guessing attack.
Owner:HUAZHONG UNIV OF SCI & TECH
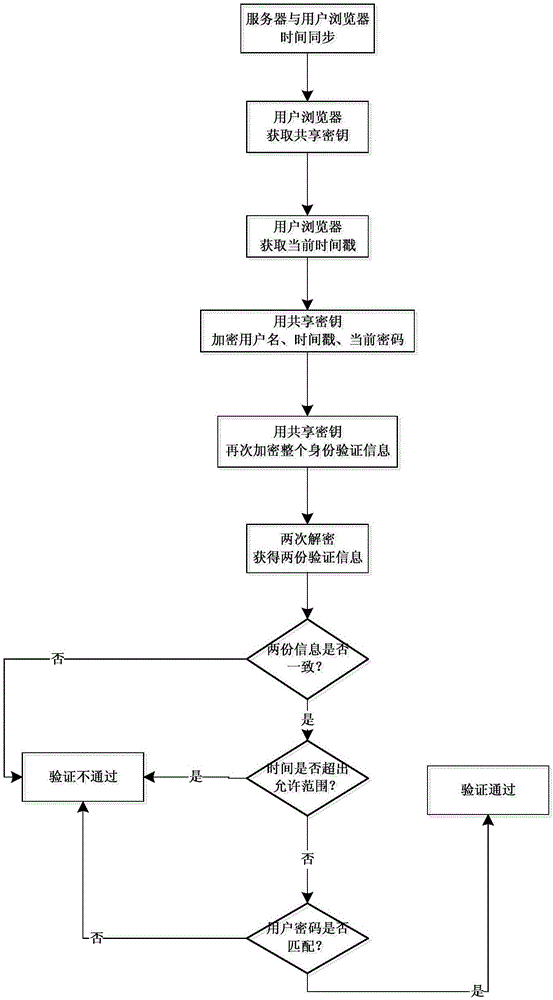
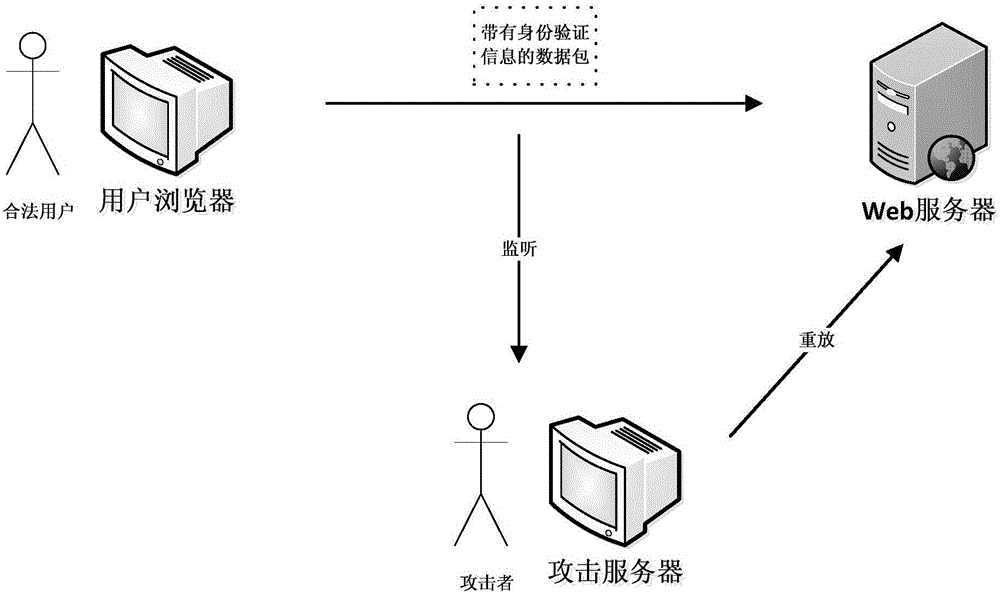
Identity verification method for resisting password-guessing replay attack
InactiveCN106534196AAvoid the problem of password crackingAchieve the effect of anti-password guessing replay attackTransmissionTimestampWeb application
The invention relates to the technical field of identity authentication, in particular to an identity verification method for resisting a password-guessing replay attack. The identity verification method related by the invention comprises the following steps: first of all, carrying out time synchronization on a server and a user browser which needs identity verification; then obtaining a shared key by the user browser via an https mechanism; obtaining a current timestamp; carrying out encryption on a usename and the timestamp together with a password by employing the shared key by the user browser; then encrypting whole identity verification information with the shared key again; then carrying out two times of decryption by a server side to obtain two pieces of identity verification information; then making a comparison respectively, and if the two pieces of the identity verification information are completely consistent, comparing the timestamp with a current time; and at last, verifying whether a usename and password combination in the information is consistent with the usename and password combination stored in a system, and if yes, executing the verification is passed. According to the identity verification method related by the invention, the identity verification via the password-guessing attack is avoided; and the identity verification method can be used in the identity verification of a Web application.
Owner:G CLOUD TECH
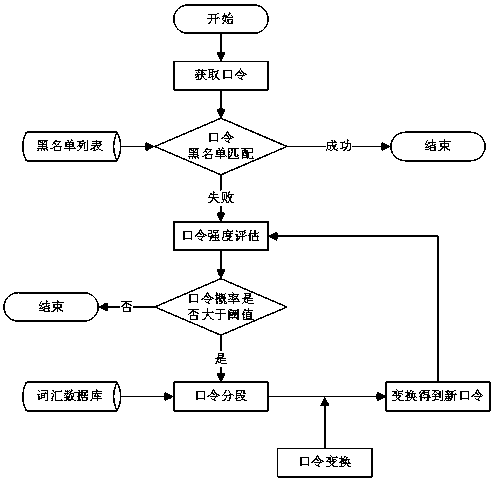
Semantic transformation-based password enhancing method
InactiveCN108763918AEnhanced ability to resist password guessing attacksImprove securityDigital data authenticationTransformation algorithmPassword
The invention discloses a semantic transformation-based password enhancing method. The method comprises the following steps of: command blacklist matching: matching a password submitted by a user withan existing password blacklist; password strength assessment: assessing the strength of the password through comparing a generation probability for calculating user passwords with a set probability threshold value; password segmentation: segmenting the password into a plurality of fragments after carrying out semantic analysis on weak password; and password semantic transformation and enhancement: transforming the password fragments through a predefined transformation algorithm to ensure that the enhanced password and the original password has certain similarity. According to the method, theusers are fundamentally enabled to use fewer weak passwords through using a blacklist technology, and algorithms such as password strength assessment and semantic analysis and segmentation are used, so that the password availability is ensured, the password strength is improved, the guessing attack defensing ability of the passwords is strengthened and the password safety is improved.
Owner:EAST CHINA NORMAL UNIV
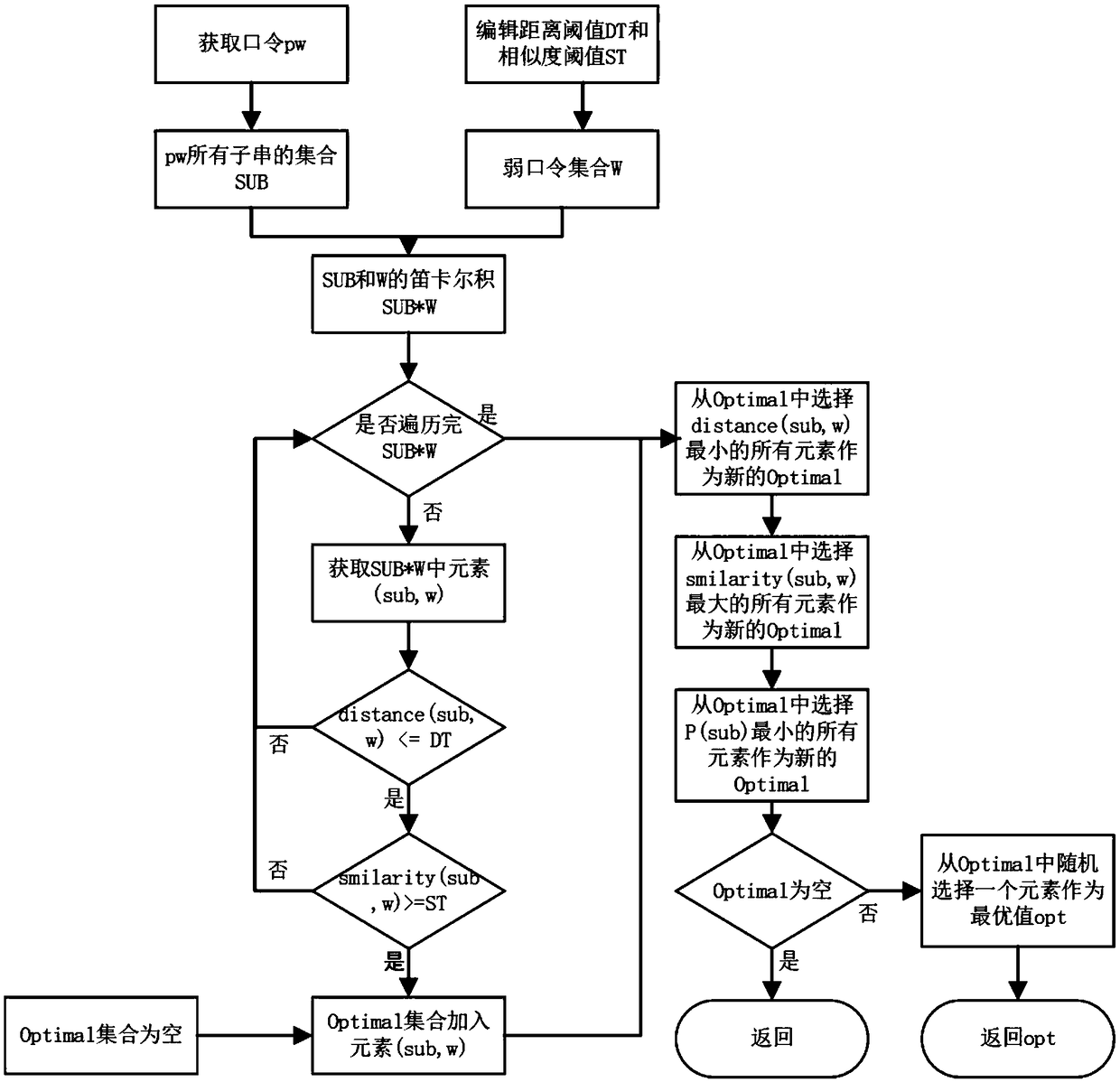
Password strength evaluation method based on weak password deduction
ActiveCN108647511AEnhanced capabilities for guessing attacksHigh precisionDigital data authenticationPasswordFrequency of occurrence
The invention discloses a password strength evaluation method based on weak password deduction, and the method comprises the following steps: 1) generation of a weak password set: selecting highly ranked passwords as the weak password set from a password sample according to a mode of a descending order of frequency of occurrence; 2) grammar training: parsing passwords in a training set based on the weak password set, and generating a probability context-free grammar table with a weak password tag; 3) password strength evaluation: inputting the password, calculating probability of the passwordaccording to the grammar table generated through the grammar training, wherein the higher a probability value is, the lower the password strength is; 4) updating of the grammar table: according to theinput password, dynamically adjusting distribution probability of the probability context-free grammar with the weak password tag. In the method provided by the invention, the password similar as thepassword in the weak password set is deduced through the existing probability context-free grammar, the method inherits efficiency and robustness of the conventional password strength evaluation method and simultaneously can eliminate potential weak passwords, enhance password-guessing attack resistance ability of the passwords and improve security of users.
Owner:EAST CHINA NORMAL UNIV
Searchable attribute-based encryption method for resisting keyword guessing attack
ActiveCN111147508AResistant to Guessing AttacksImplement access controlKey distribution for secure communicationSpecial data processing applicationsAccess structureCiphertext
The invention relates to a searchable attribute-based encryption method for resisting keyword guessing attack. A cloud storage provider (CSP) is responsible for storing data and providing keyword retrieval for legal users in a system. The authorization center is responsible for initialization of the system, generation of a secret key and updating operation of a ciphertext and the secret key. And the data owner is responsible for uploading ciphertext data of a specified access structure. The data user obtains the private key or the updated private key from the authorization center; a ciphertextis downloaded from a cloud storage provider (CSP), the ciphertext is successfully decrypted only when an attribute list of the ciphertext is matched with an access structure embedded in the ciphertext, and after a receiver decrypts the ciphertext, a data user can submit encrypted keywords to the cloud storage provider to retrieve the ciphertext. According to the method, fine-grained access control and ciphertext retrieval in a cloud environment can be realized, and keyword guessing attacks can be resisted.
Owner:FUJIAN NORMAL UNIV
Keyword search algorithm based on attribute encryption in cloud computing
InactiveCN106612270AEnsure safetyGood against collusionKey distribution for secure communicationPublic key for secure communicationAttribute-based encryptionOnline and offline
The invention puts forward a keyword search algorithm based on attribute encryption in cloud computing. First, a user chooses a trusted search server in order to minimize keyword guessing attack from the search server. A secure channel is needed only when the user is receiving a search server public key and a user private key. For data transmitted in an insecure channel, even if a malicious user intercepts the information, the user cannot recover any information through online and offline keyword guessing attack. Moreover, the scheme of the method supports flexible multi-user access control and search proof generation by users, and is applicable to a cloud environment.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
Privacy-protected identity-based encryption method and system with keyword search
InactiveCN111786790AEliminate burdensome certificate management problemsNo secure channelPublic key for secure communicationUser identity/authority verificationCiphertextPrivacy protection
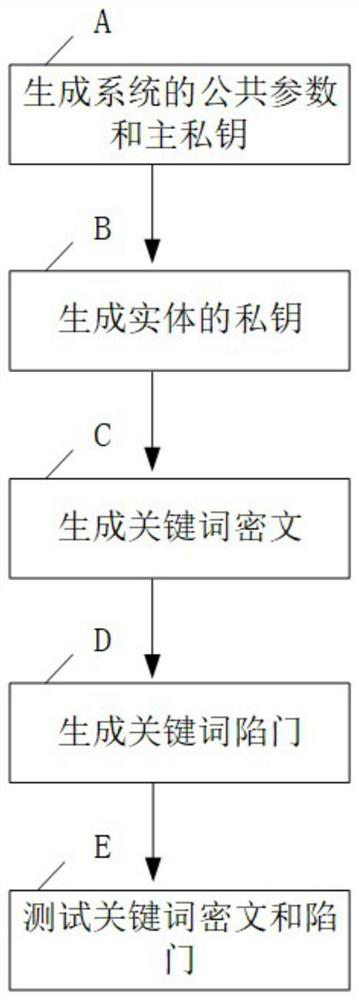
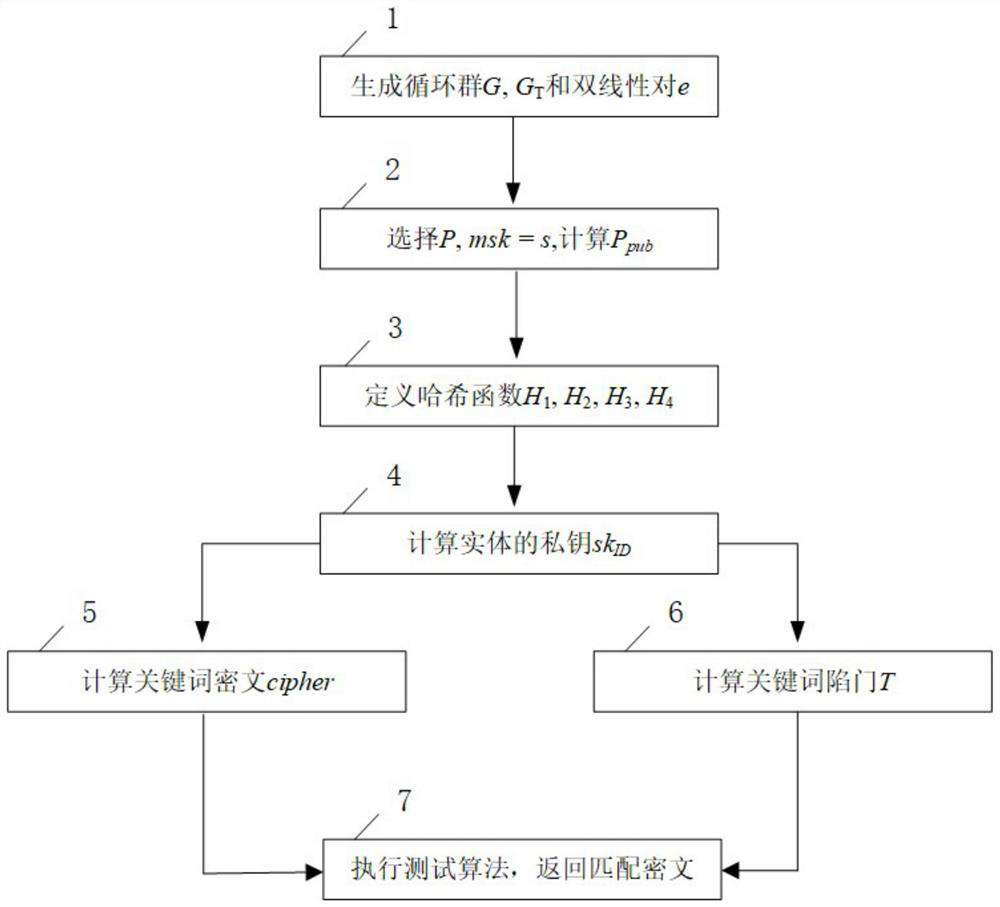
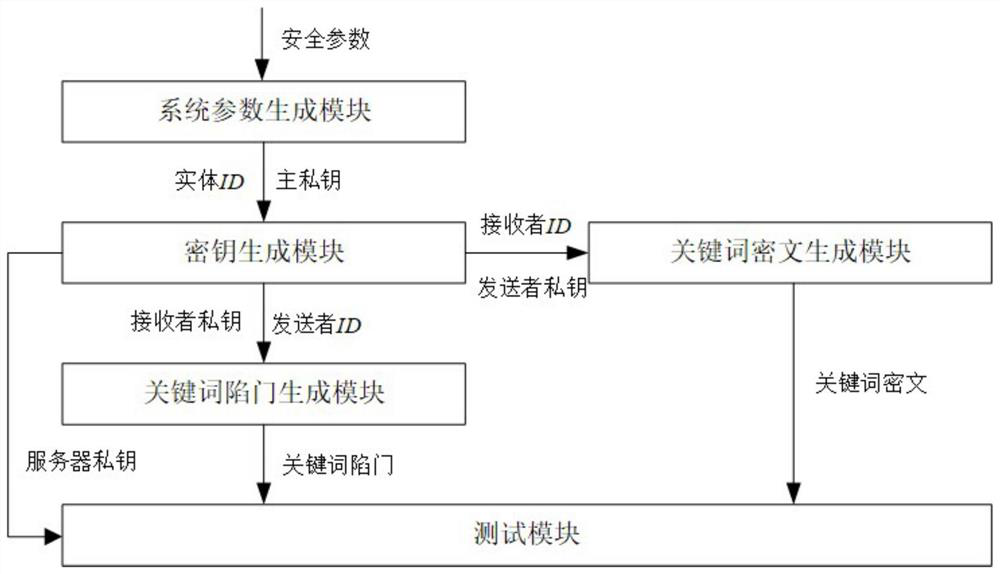
The invention discloses a privacy-protected identity-based encryption method with keyword search. The method comprises the steps of generating public parameters and a main private key of a system, generating a private key of an entity, generating a keyword ciphertext, generating a keyword trap door and testing. The invention also discloses a privacyprotected identity-based encryption system with keyword search. The system comprises a system parameter generation module, a key generation module, a keyword ciphertext generation module, a keyword trap door generation module and a test module. According to the technical scheme, a ciphertext search function for privacy protection is provided, keyword guessing attacks based on an identity encryption method for existing keyword search can be effectively resisted, and the purpose of protecting user privacy is achieved.
Owner:HOHAI UNIV
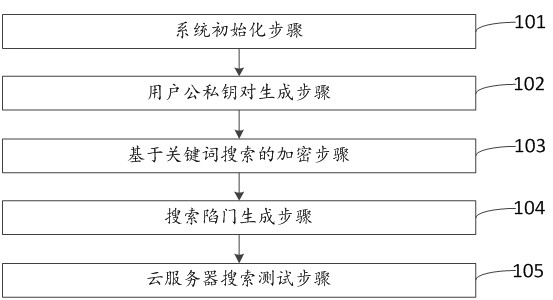
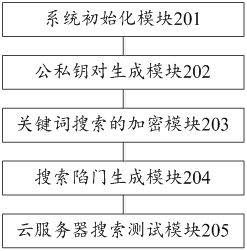
Lightweight searchable encryption method and device based on elliptic curve
ActiveCN112560075AEnable secure sharingGuaranteed confidentialityDigital data protectionComputations using residue arithmeticOriginal dataCloud data
The invention provides a lightweight searchable encryption method and device based on an elliptic curve. The method comprises the following steps: a system initialization step; a user public and private key pair generation step; an encryption step based on keyword search; encrypting the original data file by using a universal public key encryption technology; a search trap door generating step; and a cloud server search testing step. According to the keyword guessing attack resistant lightweight searchable encryption method, an elliptic curve cryptographic algorithm is utilized, and the requirements on calculation and storage expenditure are relatively low, so that the keyword guessing attack resistant lightweight searchable encryption method has a lightweight characteristic, can be widelyapplied to various mobile intelligent terminal platforms with limited hardware resources, and has a keyword guessing resistance characteristic; therefore, the server cannot guess the keywords queriedby the user, and the information security of the cloud data is effectively guaranteed.
Owner:SOUTHWEST PETROLEUM UNIV
Connection keyword authentication searchable encryption method based on national cryptographic algorithm
ActiveCN111930881AKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The invention relates to a connection keyword authentication searchable encryption method based on a national cryptographic algorithm. The method comprises the following steps of: (1) initializing analgorithm; (2) generating a public and private key pair; (3) generating an encryption key through key negotiation; (4) encrypting a document; (5) generating a security index; (6) sending a security list to a cloud server; (7) generating a search token; (8) generating search results; (9) comparing the results; (10) circulating; (11) feeding back the search results; and (12) obtaining a plaintext result. Connection keyword search is supported, it is ensured that a security index can only be generated by a data sender, and keyword guessing attacks of the cloud server are resisted. It is ensured that the token is only matched with the security index sent by the data sender, the ciphertext of the data sender is obtained, the method does not involve bilinear pairing operation with large calculation expenditure when the keyword index is generated, and only one-time bilinear pairing operation is needed when the search token is generated.
Owner:NANJING UNIV OF SCI & TECH
Lightweight password guessing dictionary generation method and device based on variational auto-encoder
PendingCN113051873AReduce training timeGuaranteed timelinessNatural language data processingDigital data authenticationAlgorithmPassword
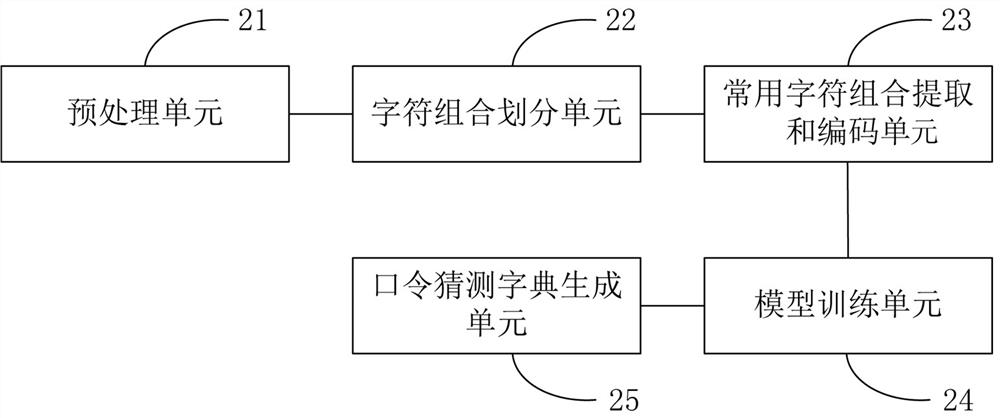
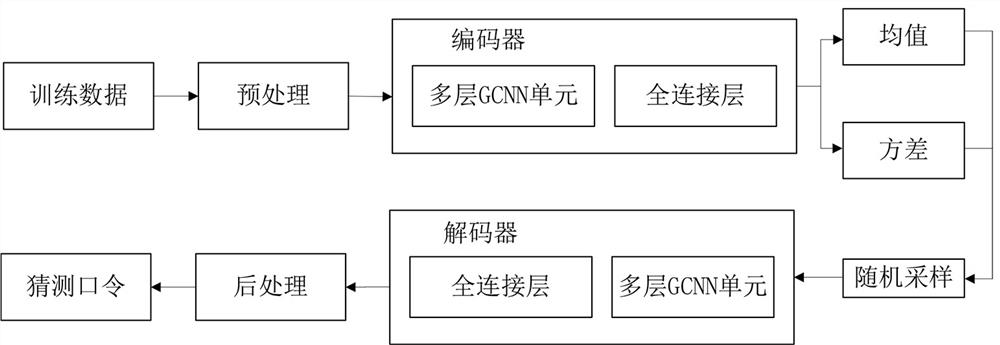
The invention belongs to the technical field of network security, and particularly relates to a lightweight password guessing dictionary generation method and device based on a variational auto-encoder, and the method comprises the steps: carrying out the preprocessing of passwords in a training set according to a preset condition, and obtaining a password set in a unified format; dividing the password set according to the structure to obtain password fragments, and segmenting each password fragment into character combinations by using an n-gram method; screening out a common character combination according to preset parameters, and then coding the password in a vector form; initializing a variational auto-encoder model, and training the variational auto-encoder model by using the vector form password until a loss function value does not decrease any more; and generating guess passwords by using the trained variational auto-encoder model, and performing descending order arrangement according to the occurrence frequency of the generated passwords to obtain a password guess dictionary. According to the method, the model training time and the generation time of the password guessing dictionary are greatly shortened, the success rate of password guessing is improved, and the timeliness of dictionary guessing attacks is ensured.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Password enhanced and updatable blind key management method in cloud storage
ActiveCN113098681ASingle point of failure attack avoidancePrevent impersonation attacksKey distribution for secure communicationUser identity/authority verificationKey serverCiphertext
The invention discloses a password enhanced and updatable blind key management method in cloud storage, and belongs to the technical field of communication. According to the invention, a group of authentication servers are introduced, before interaction between the user and the key server, identity authentication is carried out on the user and the authentication servers through passwords, and meanwhile, the authentication times of the user in one period are limited, so that pretending attack and password guessing attack of an enemy are prevented. According to the invention, the collusion between the honest but curious cloud server and the key server is resisted, and by introducing a group of authentication servers, the collusion between the key server and the cloud server cannot recover the ciphertext message of the user. According to the invention, a plurality of key servers are introduced, so that the single-point failure attack of one key server is avoided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A Multi-Keyword Searchable Public Key Encryption Method
ActiveCN108599937BSimple calculationMeet search needsKey distribution for secure communicationPublic key for secure communicationThird partyCiphertext
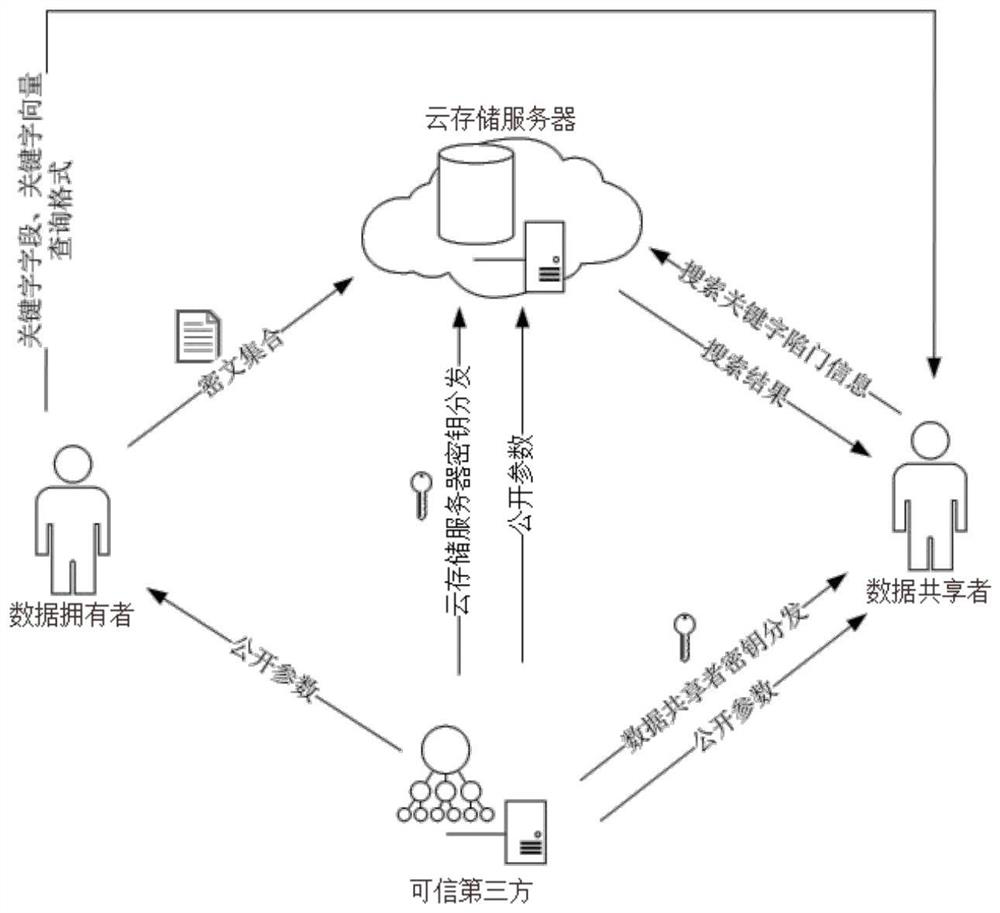
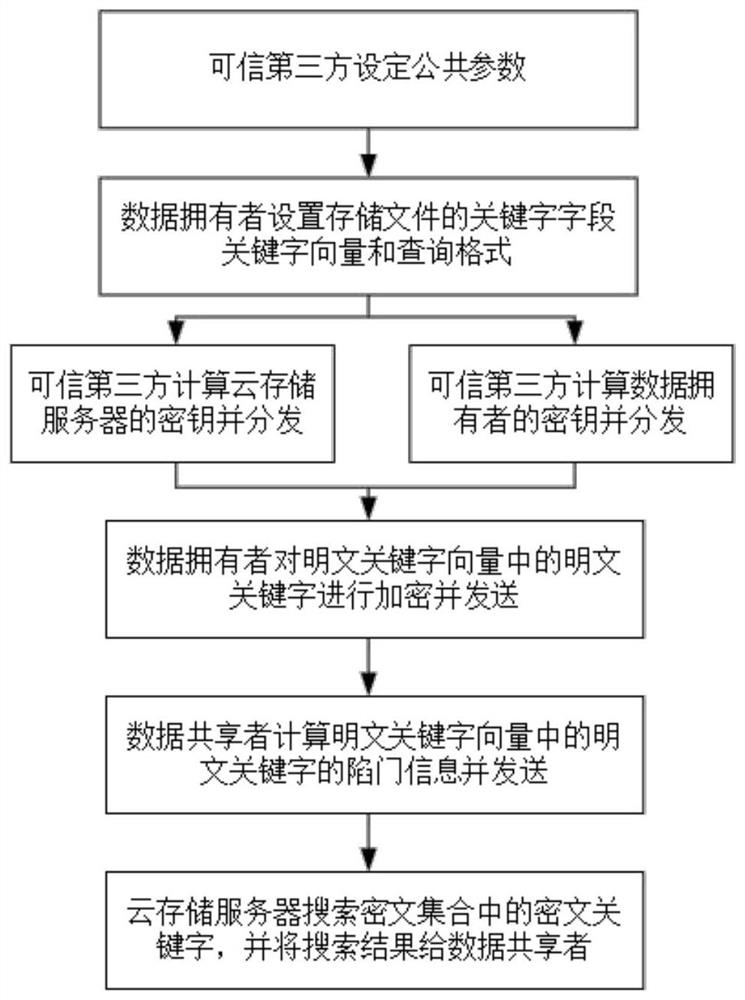
The invention provides a public key encryption method supporting the searching of multiple keywords, used for solving the technical problem that the existing public key encryption method capable of searching multiple keywords is complex in ciphertext keyword computing process. The method comprises the implementation steps as follows: 1, a credible third party sets a public parameter; 2, a data owner sets a keyword field, a keyword vector and a query format of a storage file; 3, a credible third party computes keys of a cloud storage server and a data sharer; 4, the data owner encrypts the plaintext keyword in a plaintext keyword vector and sends the same; 5, the data sharer computes trap door information of the plaintext keyword in the plaintext keyword vector and sends the same; and 6, the cloud storage server searches the ciphertext keyword in a ciphertext set, and sends the searched ciphertext keyword to the data sharer. According to the invention, the ciphertext information and trap door information of the keyword can be transmitted under the public channel, and the keyword speculation attack can be resisted.
Owner:XIDIAN UNIV
Wireless sensor network authentication method and system, and electronic equipment
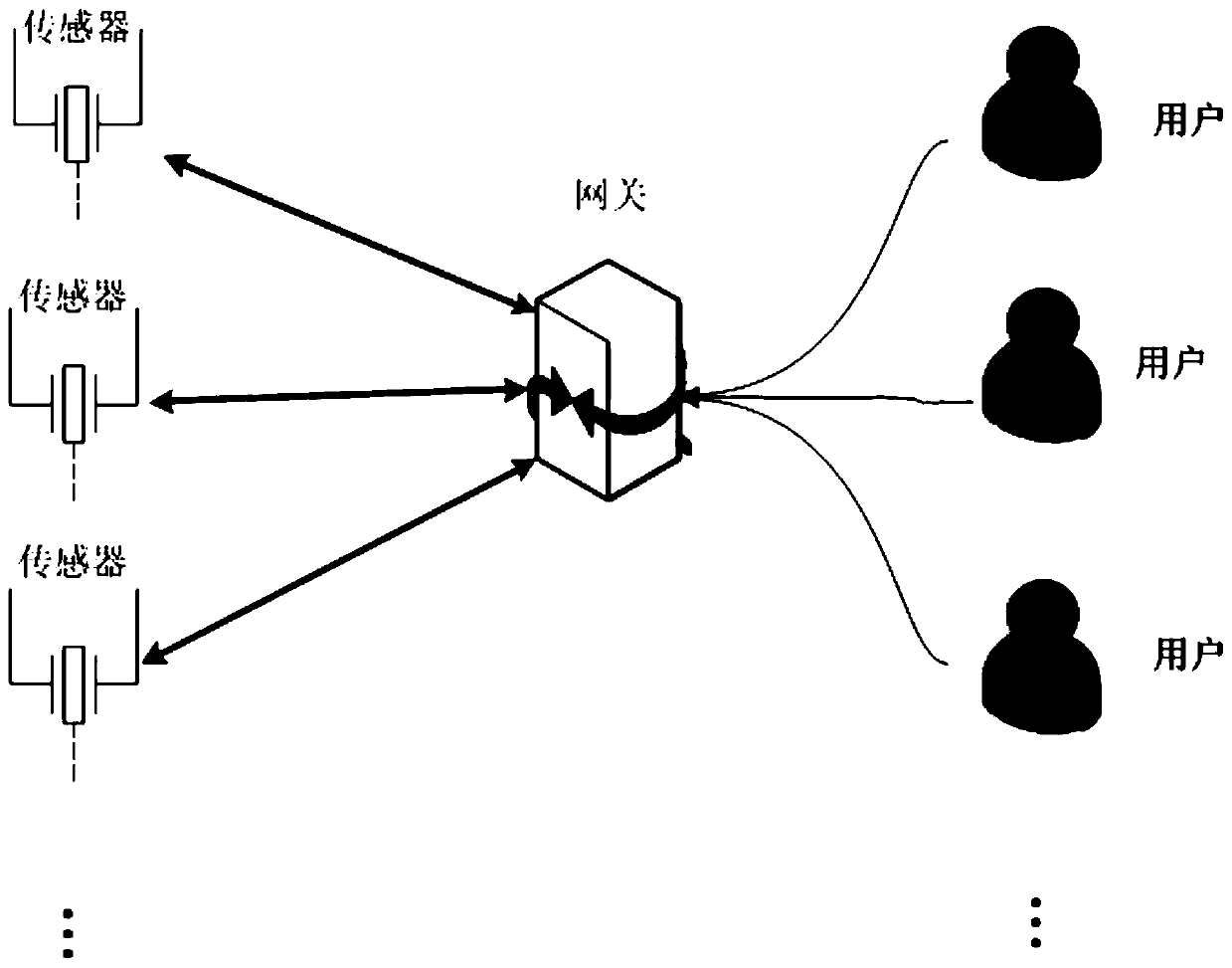
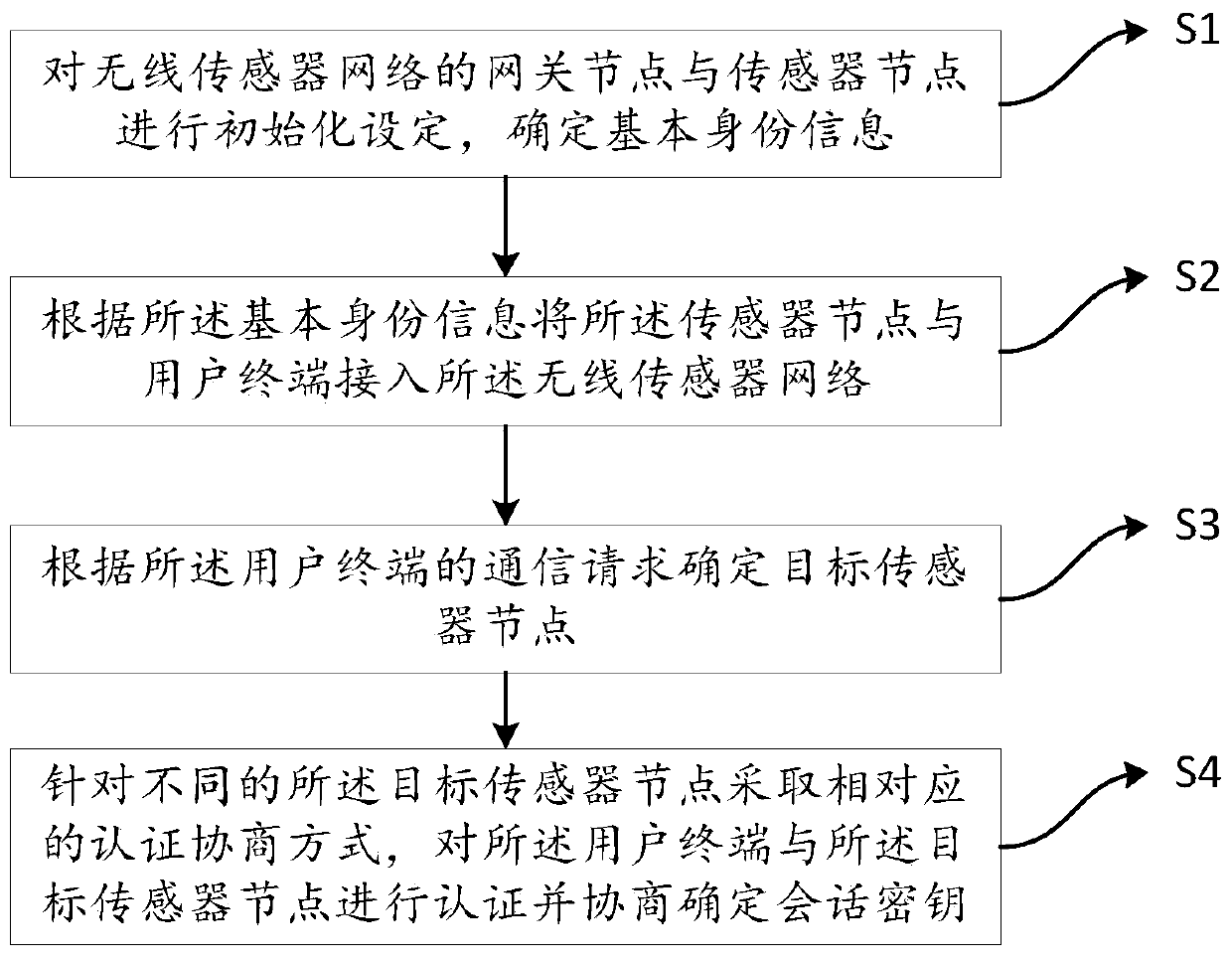
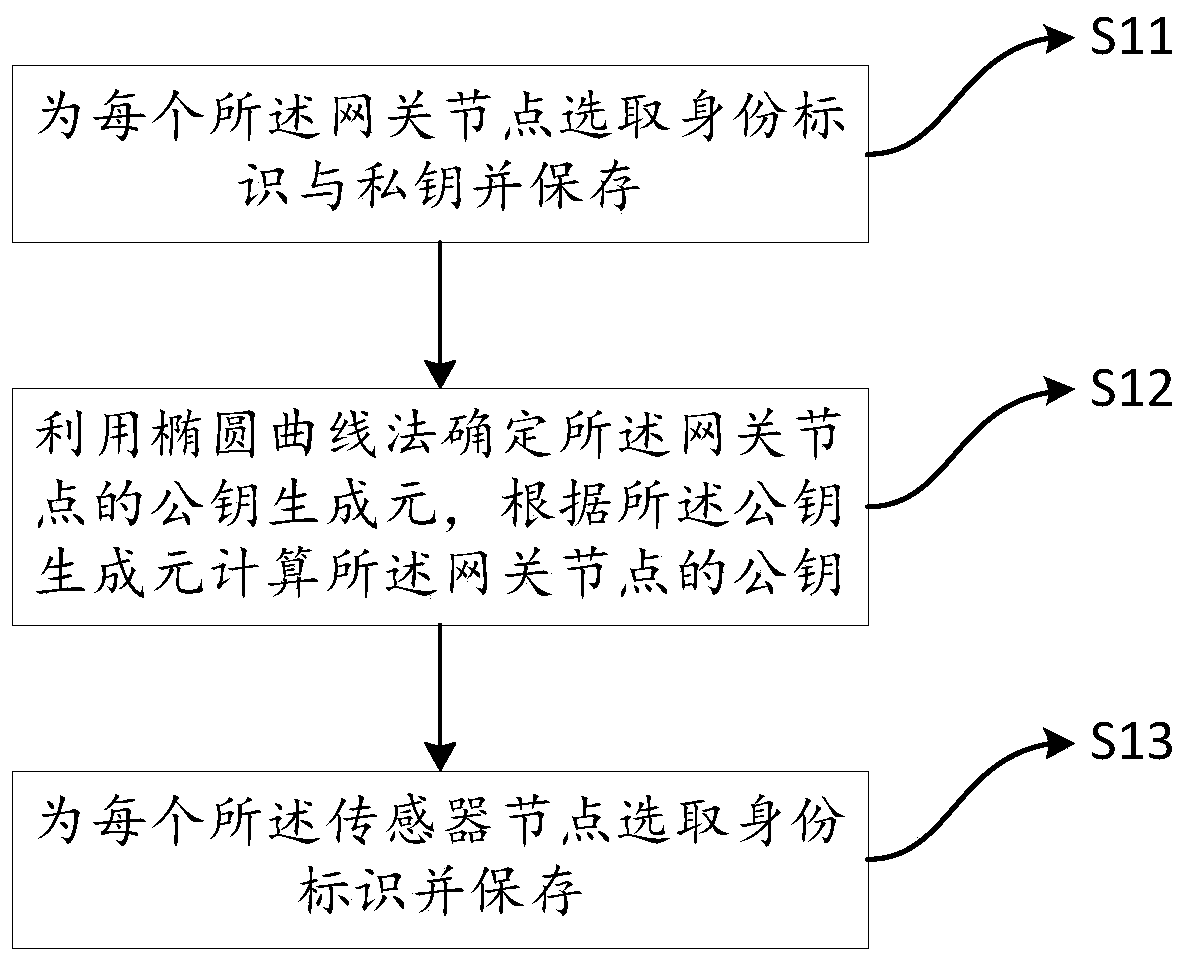
ActiveCN110933675AAchieve securityAchieve forward securityNetwork topologiesSecurity arrangementPasswordWireless sensor networking
The invention discloses a wireless sensor network authentication method and a system, and electronic equipment, and aims to solve the problems that off-line password guessing attacks cannot be resisted and forward security cannot be ensured. The method comprises the following steps: carrying out initialization setting on a gateway node and a sensor node of the wireless sensor network by utilizingan elliptic curve modular multiplication, and determining basic identity information; accessing the wireless sensor network by the sensor node and a user terminal according to the basic identity information; determining a target sensor node according to the communication request of the user terminal; and adopting corresponding authentication negotiation modes for different target sensor nodes, andauthenticating and negotiating the user terminal and the target sensor nodes to determine a session key. The system and the electronic equipment are used for executing the wireless sensor network authentication method.
Owner:BEIJING QIANXIN TECH
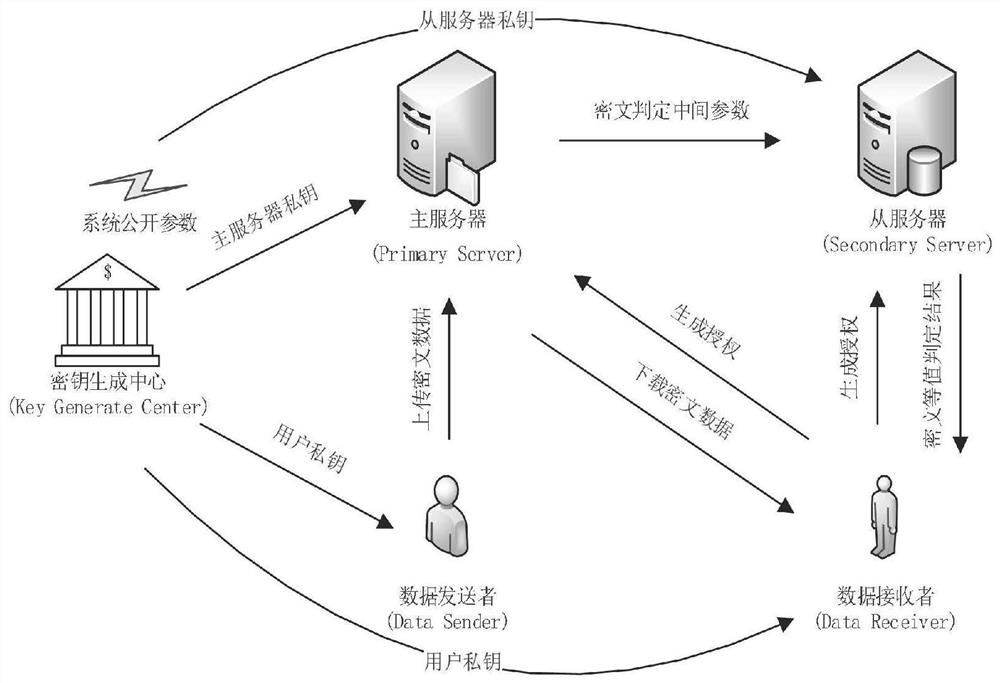
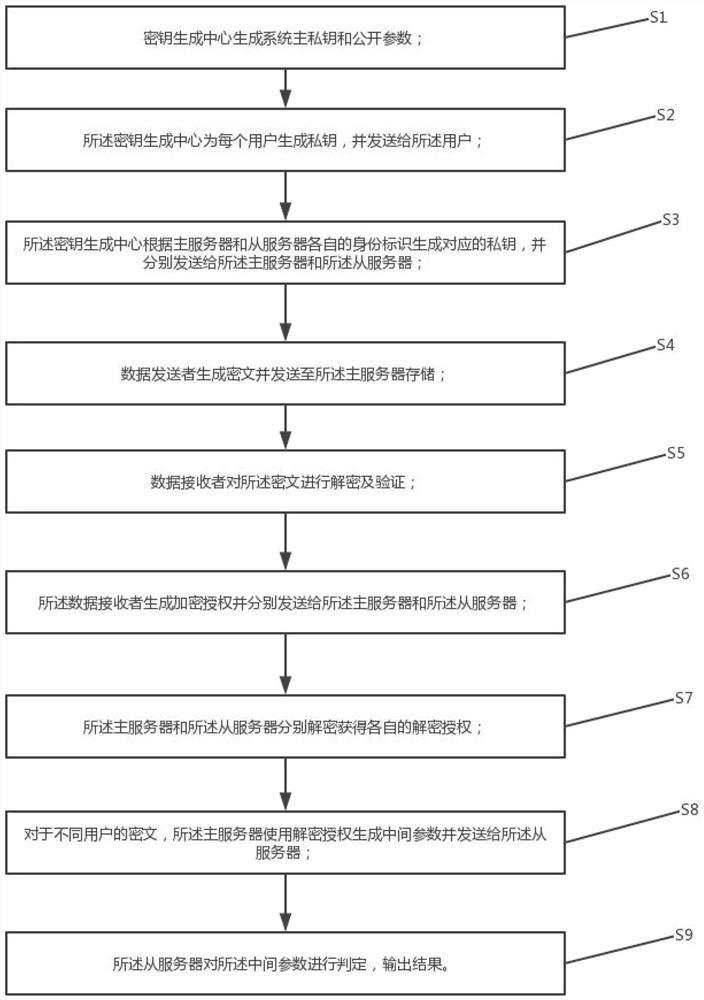
Identity-based dual-server authorization ciphertext equivalence judgment method
PendingCN113779593AResistant to Guessing AttacksAddress administrative burdenDigital data protectionCiphertextTheoretical computer science
The invention discloses an identity-based double-server authorization ciphertext equivalence judgment method, which takes a unique identity identifier of a user as a public key, stores user data and executes ciphertext equivalence judgment in a non-conspired double-server mode, and can effectively resist single-server keyword guessing attack. Before the double servers are not authorized, the double servers do not have the right to execute any operation on the outsourcing ciphertext of the user. After the authorization generated by the user is obtained, the master server and the slave server can only execute the ciphertext equivalence judgment process in succession, that is, the master server generates intermediate parameters for ciphertext judgment, and the slave server completes ciphertext equivalence judgment according to the intermediate parameters and returns a final judgment result to the user. The problems that an existing related public key encryption method faces public key certificate management burden, and a related method based on a single server model is difficult to resist keyword guessing attacks are solved.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com