Digital signature verification method and system
A technology of digital signature and verification method, applied in the direction of digital transmission system, transmission system, user identity/authority verification, etc., can solve the problems of low strength of file protection PIN code and easy cracking of digital signature, and improve the resistance to PIN code. The ability to guess attacks, the effect of simplifying complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
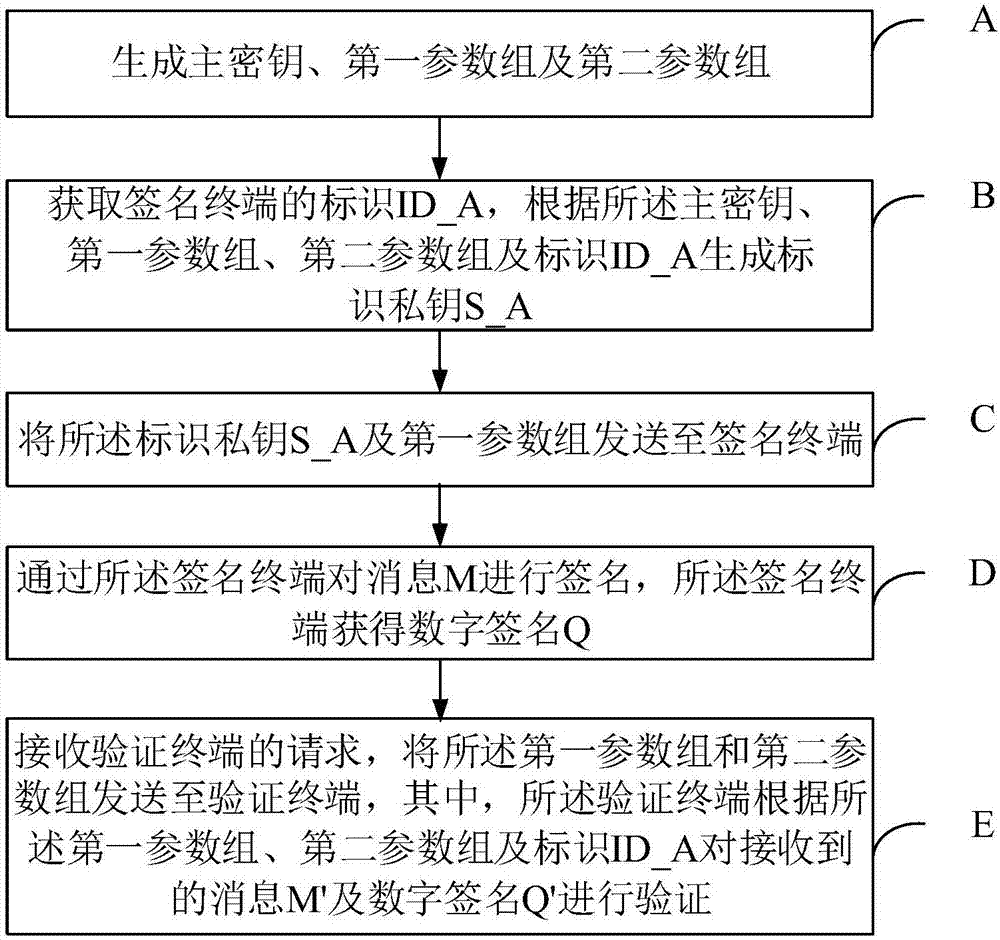
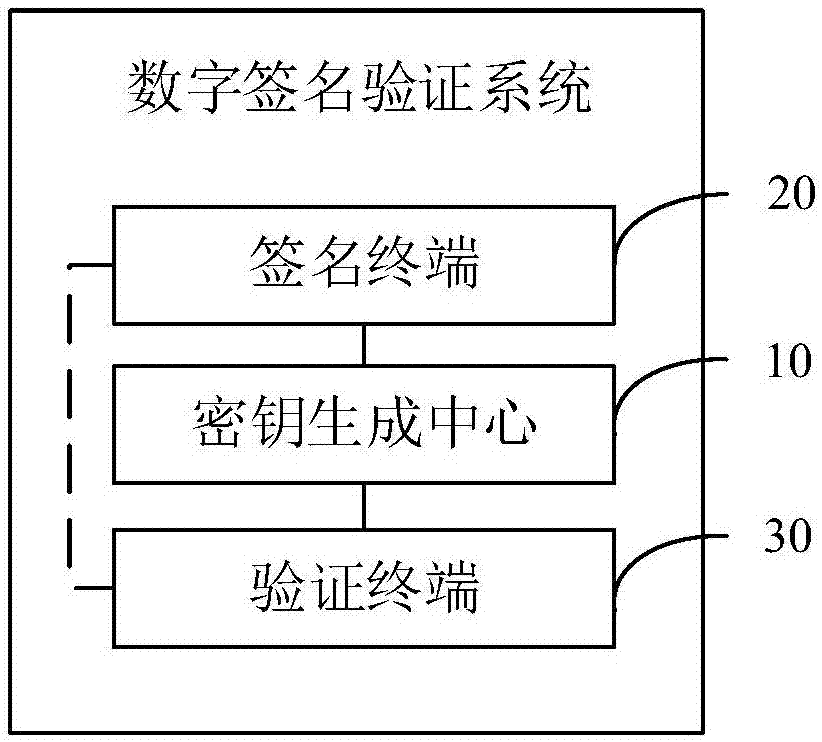
[0058] refer to figure 1 , the embodiment of the present invention proposes a digital signature verification method, comprising the following steps:
[0059] Step A: generating a master key, a first parameter set and a second parameter set;
[0060] Step B: Obtain the identification ID_A of the signing terminal, and generate the identification private key S_A according to the master key, the first parameter group, the second parameter group and the identification ID_A;
[0061] Step C: Send the identification private key S_A and the first parameter group to the signing terminal;
[0062] Step D: Sign the message M through the signing terminal, and the signing terminal obtains a digital signature Q;
[0063] Step E: Receive a request from the verification terminal, and send the first parameter group and the second p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com