PUF-based three-factor anonymous user authentication protocol method in Internet of Things
A user authentication, Internet of Things technology, applied in the field of Internet of Things and Internet of Things security, can solve the problems of inappropriate Internet of Things environment, large amount of calculation, inability to resist offline password guessing attacks, physical cloning attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
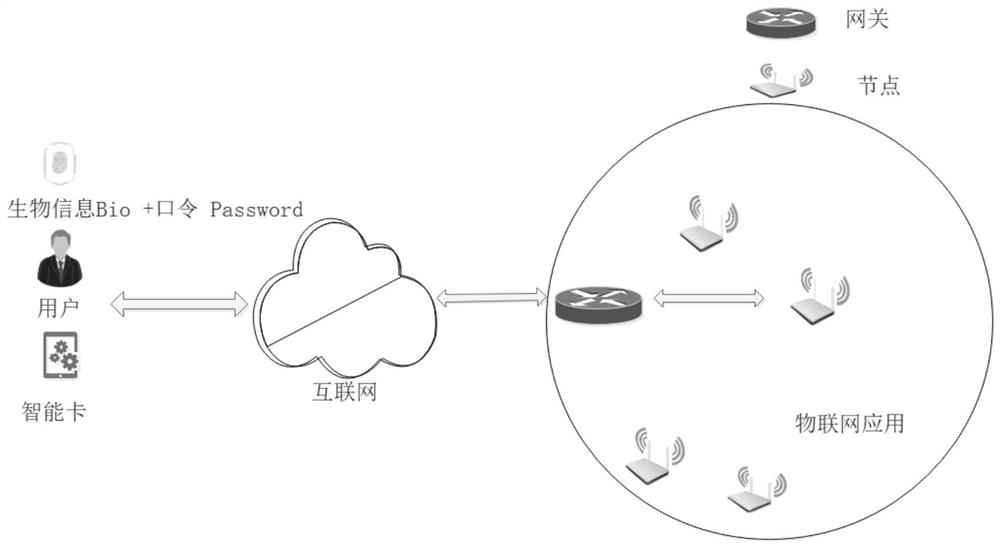
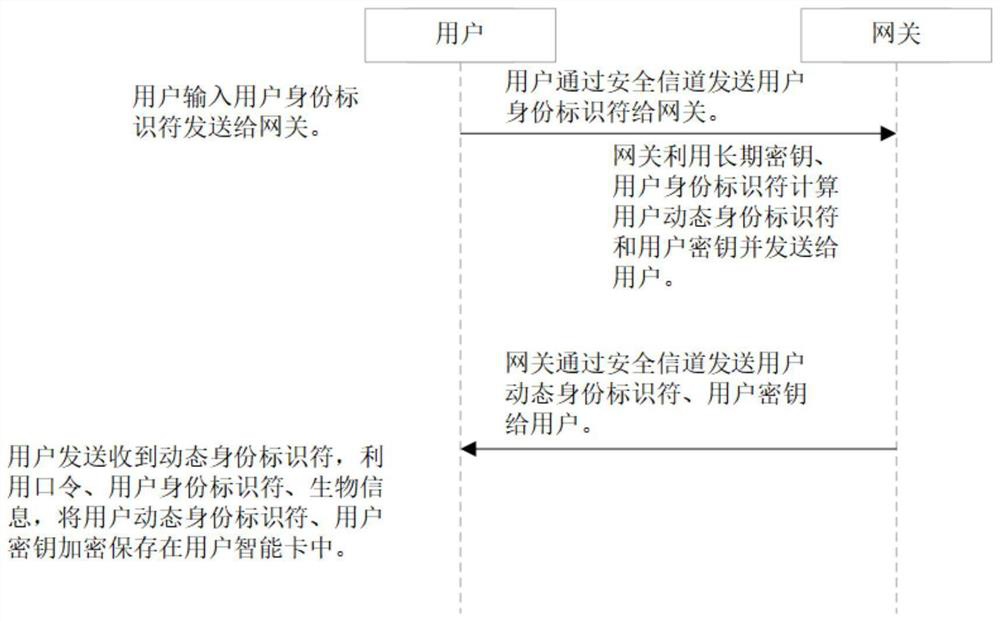
[0043] The Internet of Things is based on the Internet of Computers to form a world where everything is connected to help people make better decisions. In the existing IoT environment, the data collected by nodes is often private and sensitive. Users remotely access sensitive data collected by IoT nodes through the Internet, and the Internet is in a public channel, so how to ensure data security during communication is very important. Authentication and key agreement protocol is an important mechanism to ensure the security of communication between users and nodes. Such as figure 1 The communication architecture diagram of the Internet of Things application is shown. The Internet of Things is based on the computer Internet. Various devices use near-field communication technology, wireless data communication and other technologies to form an Internet of Things system covering everything in the world. It has passed the certification With the key agreement protocol, users, gate...
Embodiment 2
[0062] The three-factor anonymous user authentication protocol method based on PUF in the Internet of Things is the same as that in Embodiment 1, and the cryptographically secure Hash function h( ) function described in step (1) of the present invention is either a SHA series algorithm or a national secret SM3 algorithm. The cryptographic security Hash function h( ) function is the SHA series algorithm, and the output length is 256 or 521 bits; when the cryptographic security Hash function h( ) function is the national secret SM3 algorithm, the output length is 256 bits; the SHA series algorithm Released by the American Institute of Standards and Technology, it is the most widely used Hash function with high security. National Secret SM3 is released by the State Cryptography Administration of China. Its security and efficiency are comparable to SHA-256. SHA series algorithms or National Secret SM3 The algorithm is used for the generation and verification of message authenticati...
Embodiment 3
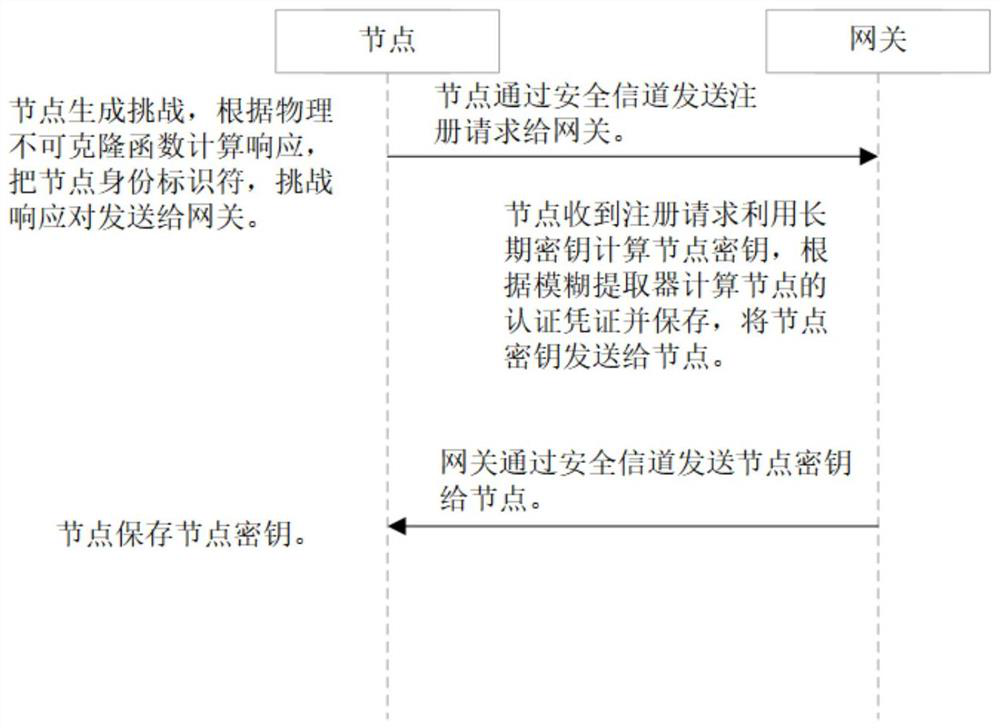
[0064] The three-factor anonymous user authentication protocol method based on PUF in the Internet of Things is the same as embodiment 1-2, and the physical unclonable function PUF described in step (2.1) of the present invention has the following properties: 1) For the same node with PUF that has not been tampered with , input the same challenge C, will output the same response R; 2) For different PUF nodes, input the same challenge C, will output different responses R, PUF makes the node unclonable and tamper-proof, any tampering will make PUF becomes a brand-new PUF', once the node is cloned or tampered with, it will not be successfully authenticated. During the registration process, the gateway saves the authentication credentials of the node equipped with PUF. During the authentication process, the gateway verifies the PUF output of the node according to the saved authentication credentials. Once the node is attacked by physical cloning, the PUF of the node becomes The ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com