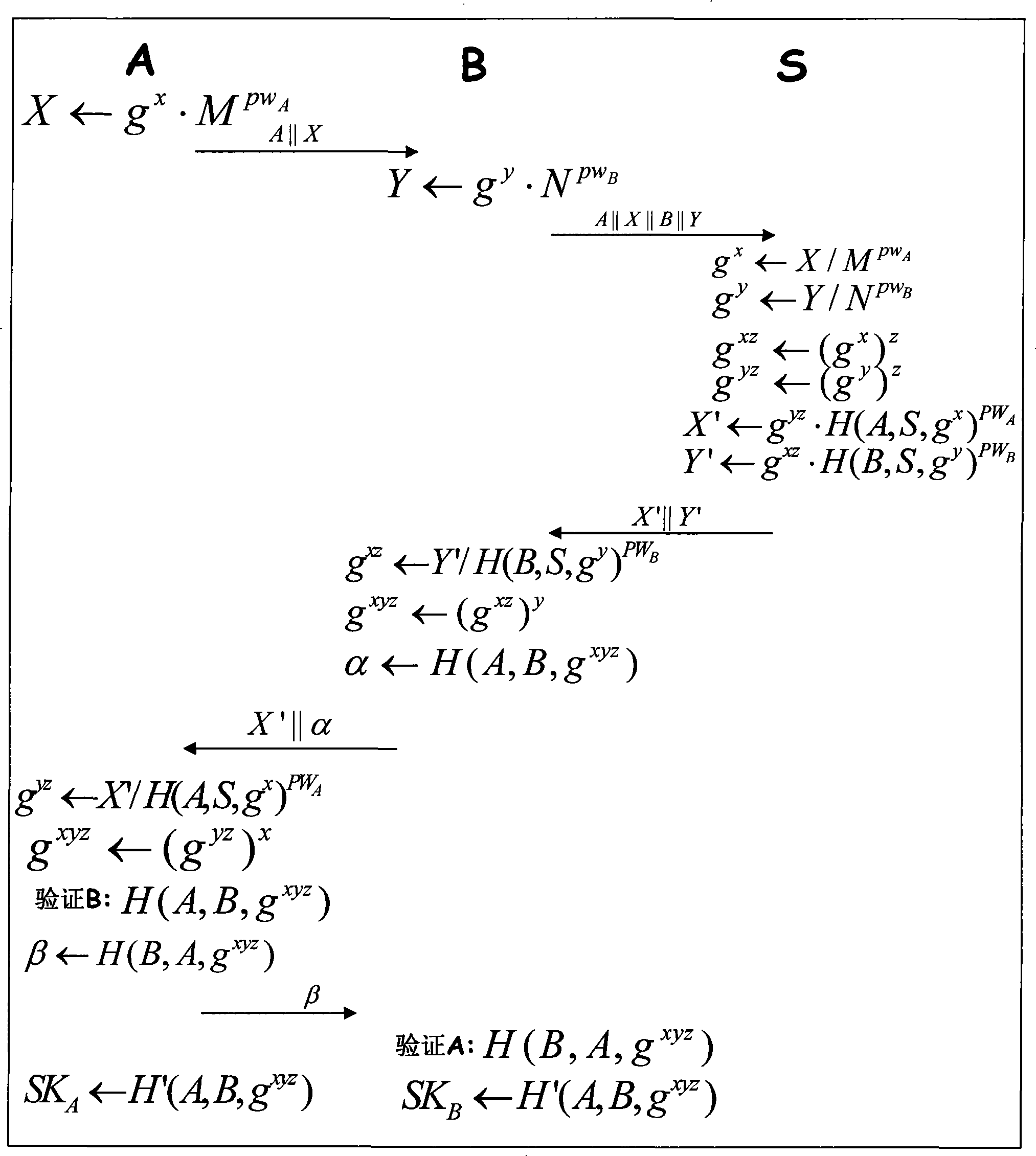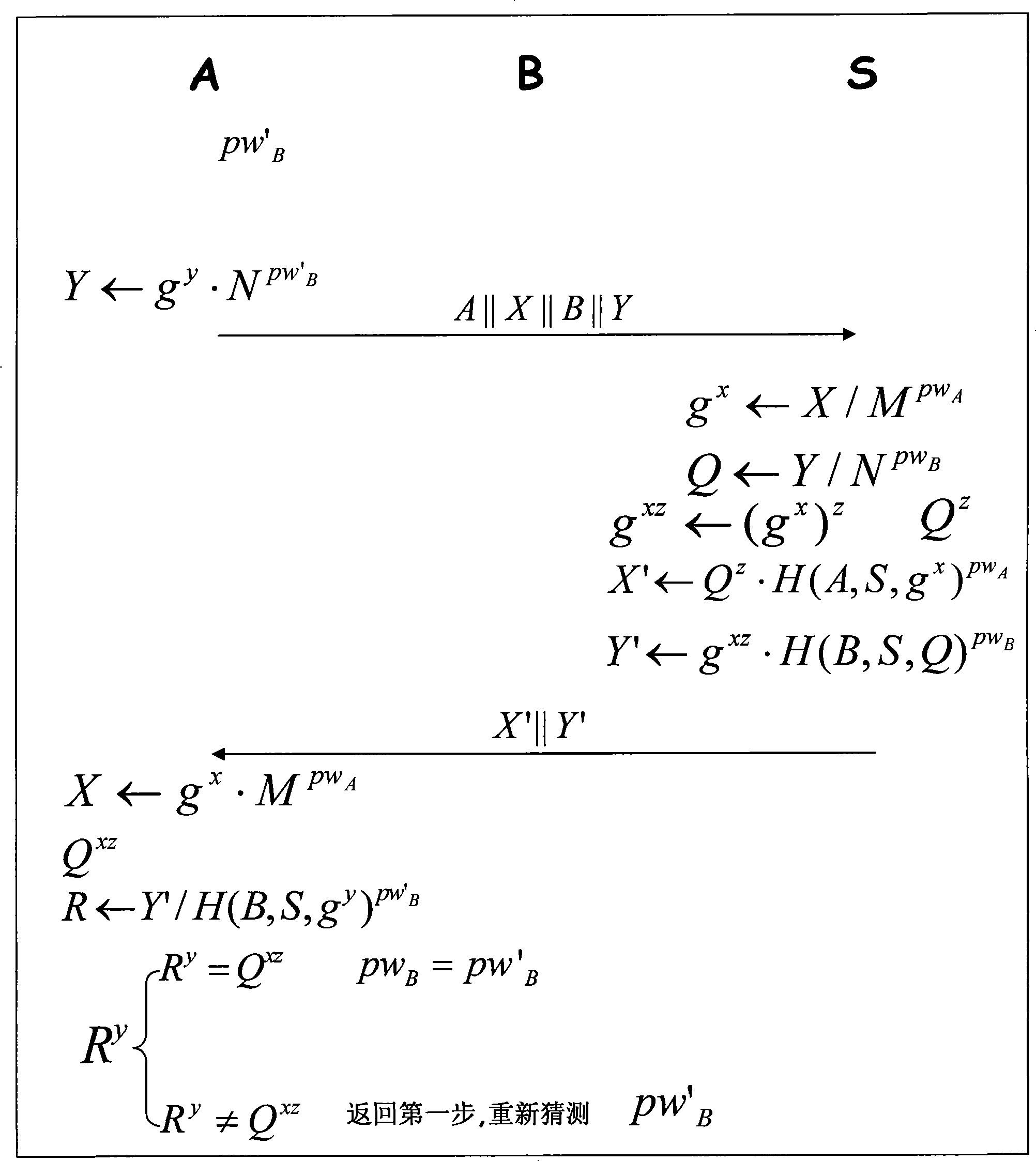Method for generating three parts cipher key negotiation
A technology of key negotiation and generation method, applied in the field of communication, which can solve the problems such as the inability to verify the communication parties, the inability to resist man-in-the-middle attacks, and the inability to directly confirm the identity of the other party.
Inactive Publication Date: 2008-08-27
天津启云科技有限公司
View PDF0 Cites 12 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In 2005, Wen et al. proposed a three-party key encryption protocol (3PAKE protocol) based on password authentication using Weil pairs, and pointed out that their protocol has provable security. However, Nam et al. found that 3PAKE The protocol is not immune to man-in-the-middle attacks
[0004] In 2006, Lu et al. proposed a method based on the CDH assumption (that is, using the intractable assumption of discrete logarithms that g x with g y , can not find g xy ) S-3PAKE protocol, the design idea of this protocol is to assume that two users (user A and user B) are trying to negotiate a session key, but before the key negotiation, there is no shared information between them , so neither party in the communication can directly verify the identity of the other party, which means that neither party can directly confirm whether the identity of the other party is true. Authenticating the identity of the other party, then user A will mistakenly think that he is communicating with user B. Obviously, this communication is not safe
Therefore, we believe that the S-3PAKE protocol cannot effectively resist online password guessing attacks when the attacker itself is a legitimate user with an authentication password with the server
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
[0071] The technical solution of the present invention has been described in detail in the content of the present invention. The description will not be repeated here, but it should be noted that: for user and server identity information and user passwords of different complexity (number of digits) and the use of a finite cyclic group G with different parameters g, p, the present invention can have many implementation.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
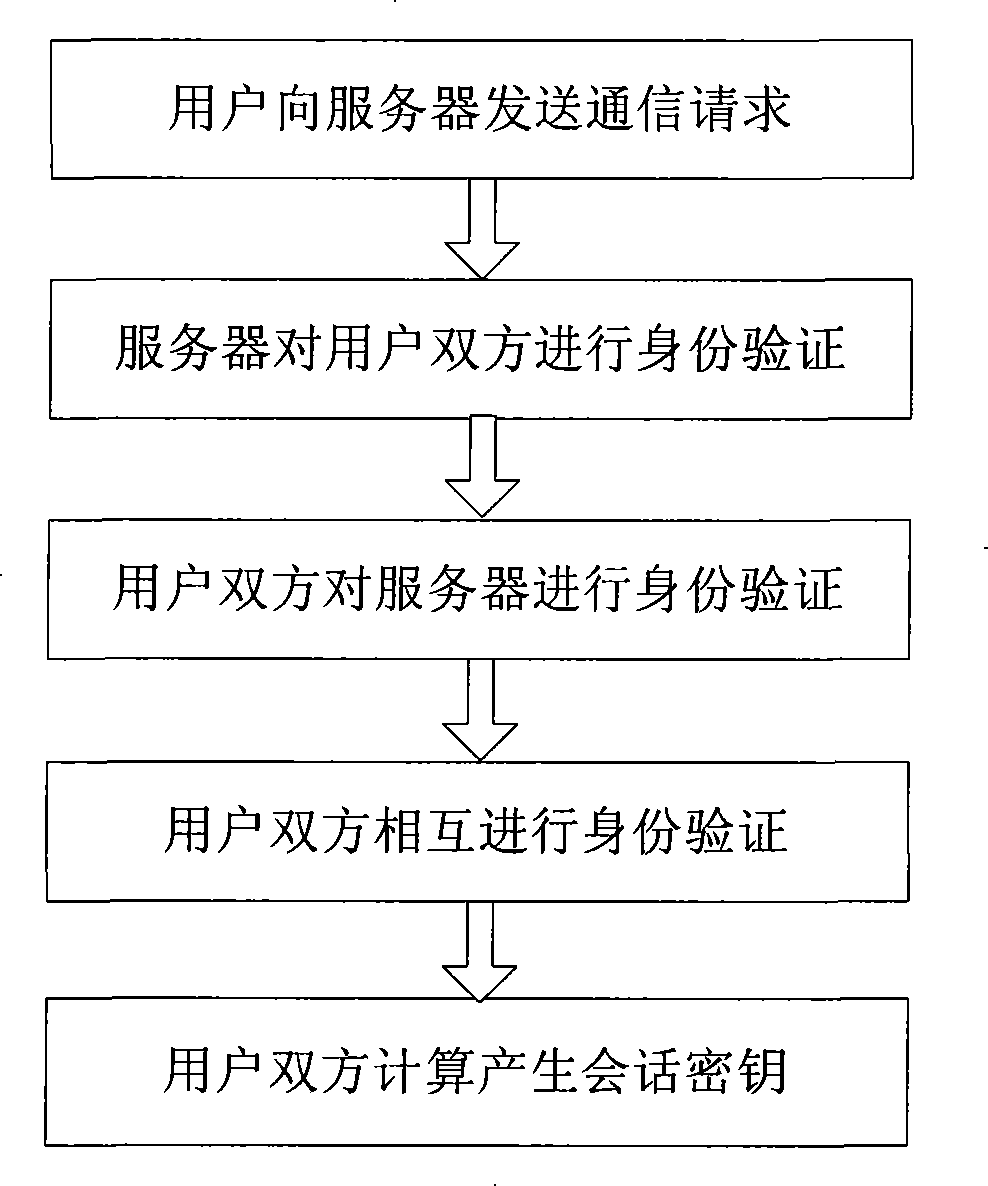
The invention belongs to the communication technical field, relating to the safety problem of network communication, in particular to the three party key exchange protocol, namely, 3PAKE protocol focusing on password authentication of a network structure. Basing on the CDH assumption and using the difficulty of discrete logarithm and the unilateralism of hash function, the invention includes three key steps that firstly, the certifications of the two users asking for communication are certified by the server; secondly, the certification of the server is verified by the two users asking for communication; thirdly, certifications of the two users asking for communication are mutually verified. The invention overcomes the vulnerabilities of masquerading attack for the starter, masquerading attack from the responder, the attack from the middleman and the on-line password guess attack all existed in the S-3PAKE protocol; has the capacities of resisting frequent attack, the attack from the middleman, the masquerading attack from the starter, the masquerading attack from the responder, the off-line guess attack and the replay attack; has forward security and known key security; and also has the characteristic of perfectly resisting on-line guess attack.
Description
technical field [0001] The invention belongs to the technical field of communication, relates to the security problem of network communication, and particularly relates to a three-party key exchange protocol (3PAKE protocol) based on password authentication of a "user-server-user" network structure. Background technique [0002] With the continuous development of computer network technology and the wide application of network, more and more attention has been paid to the security issues in network communication. In the field of secure communication, the key agreement protocol is one of the important cryptographic mechanisms. The key agreement protocol is a protocol for two entities to negotiate a communication key on a public network. The final result of the agreement is that both parties can confirm that only the other party can have the negotiated communication key, and other third parties cannot obtain the communication key. [0003] In 2004, Lee et al. proposed two thre...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06H04L9/08H04L9/32
Inventor 许春香罗淑丹张敏
Owner 天津启云科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com