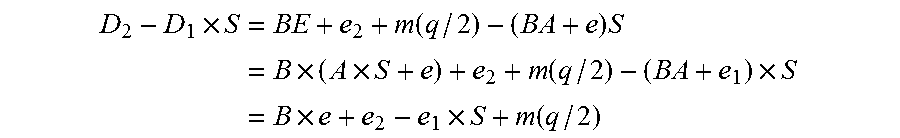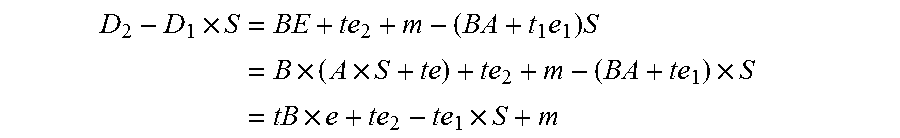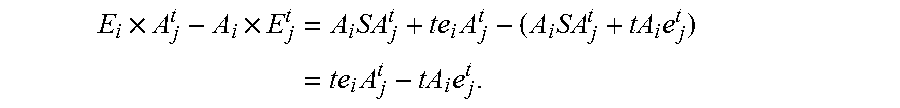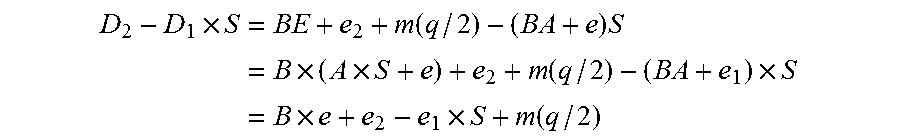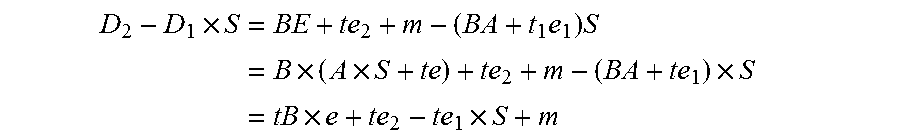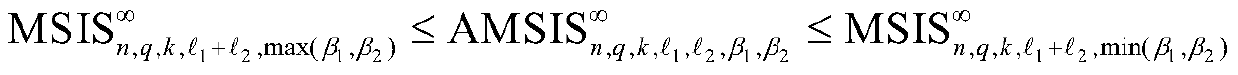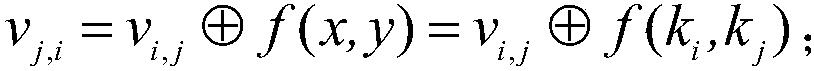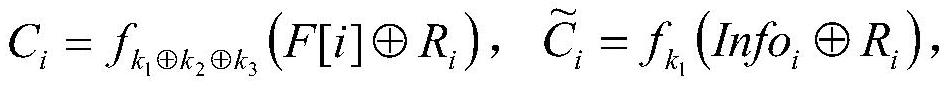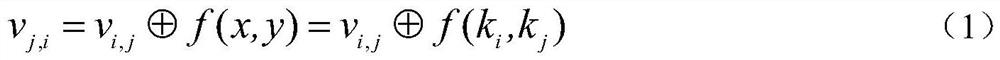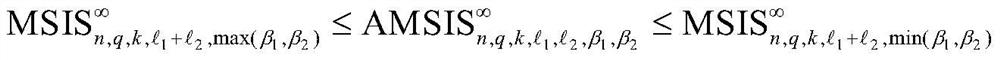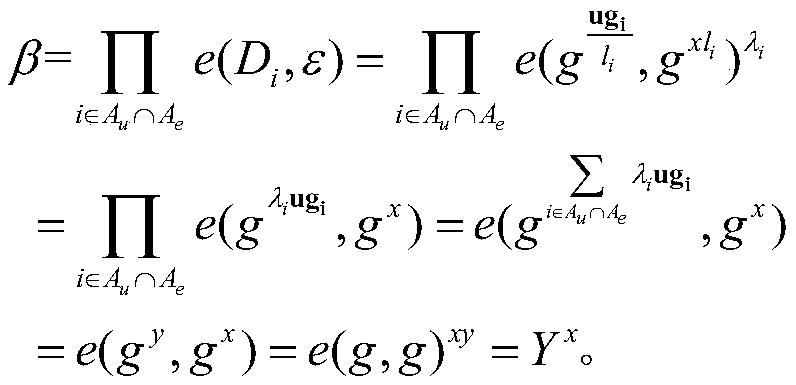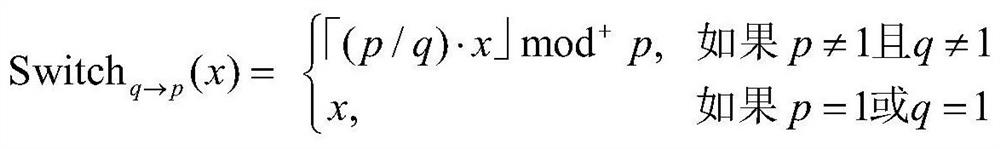Patents
Literature
37 results about "Provable security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Provable security refers to any type or level of security that can be proved. It is used in different ways by different fields. Usually, this refers to mathematical proofs, which are common in cryptography. In such a proof, the capabilities of the attacker are defined by an adversarial model (also referred to as attacker model): the aim of the proof is to show that the attacker must solve the underlying hard problem in order to break the security of the modelled system. Such a proof generally does not consider side-channel attacks or other implementation-specific attacks, because they are usually impossible to model without implementing the system (and thus, the proof only applies to this implementation).
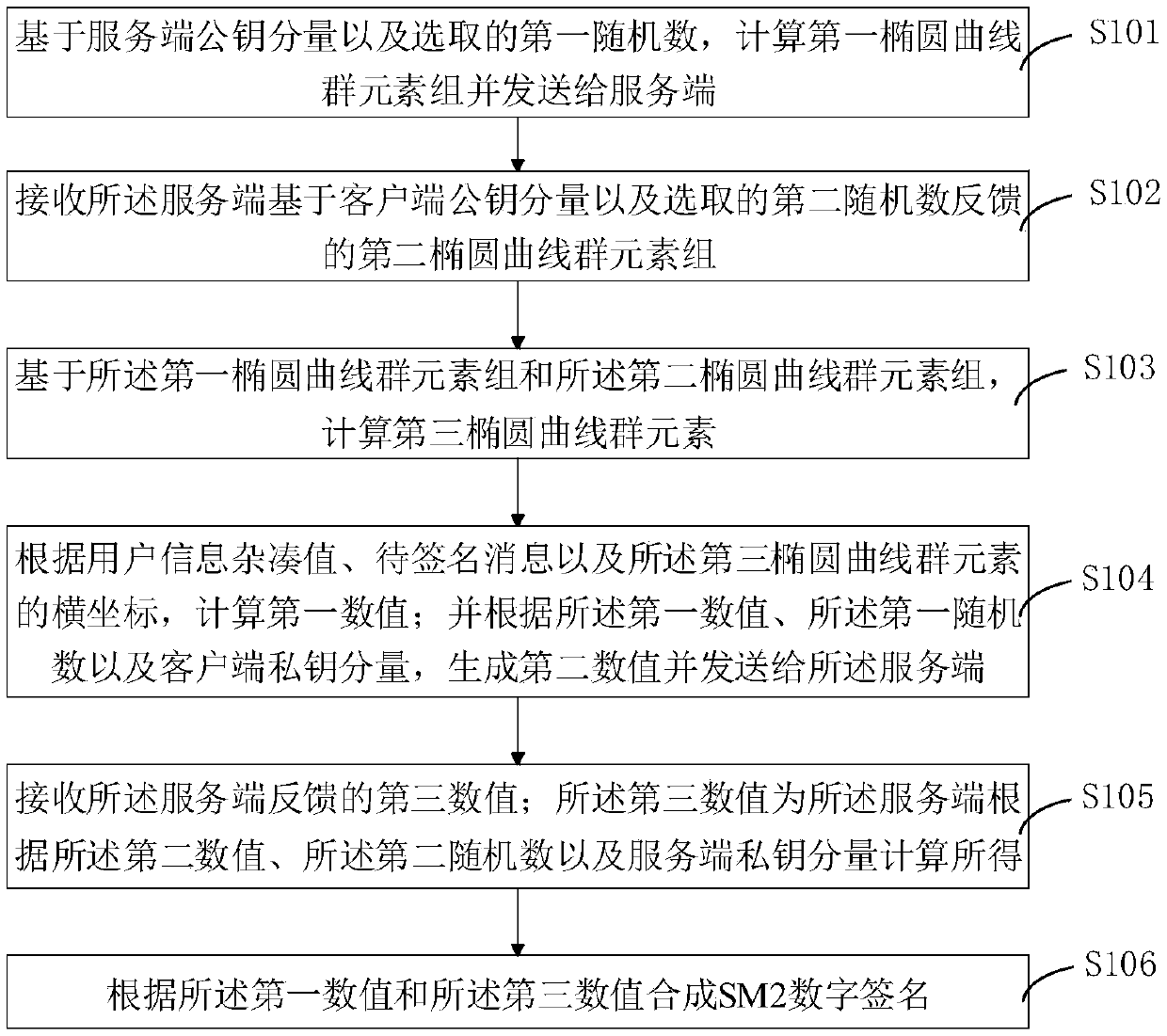
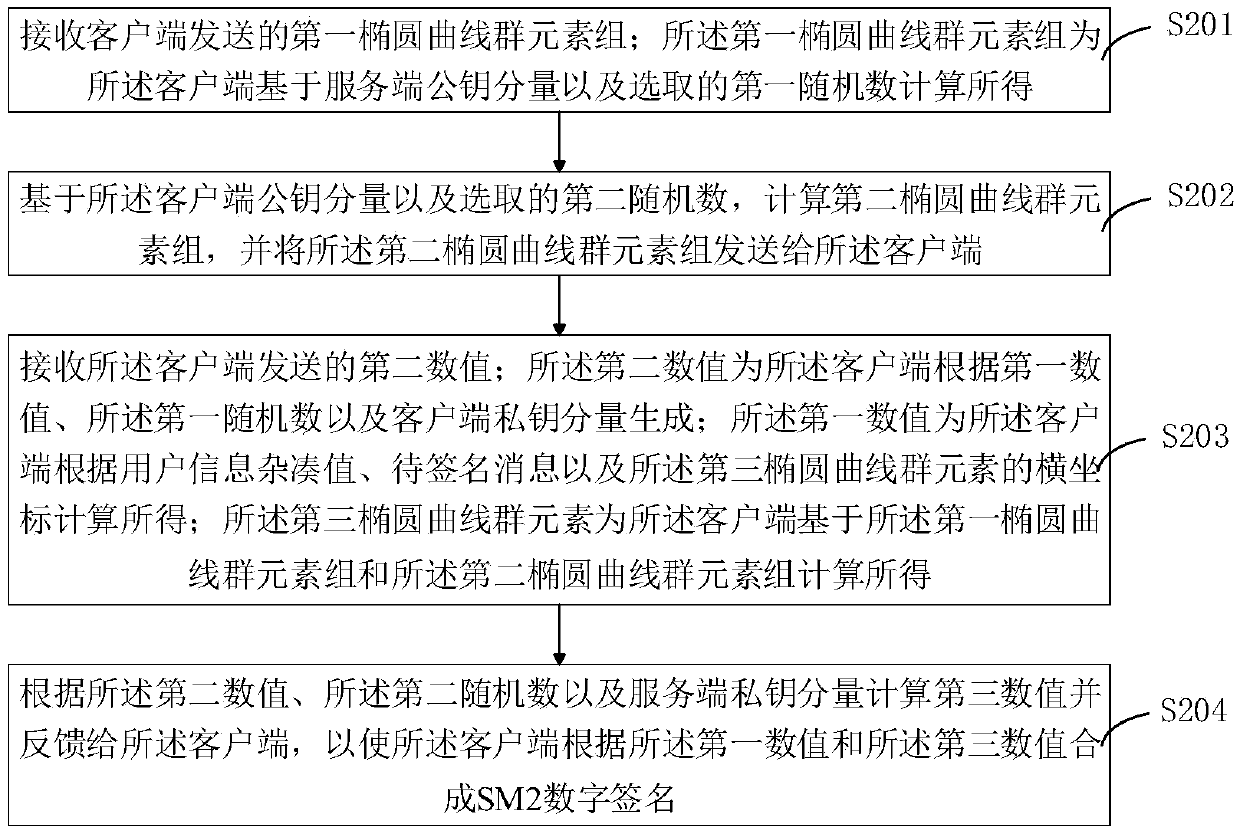
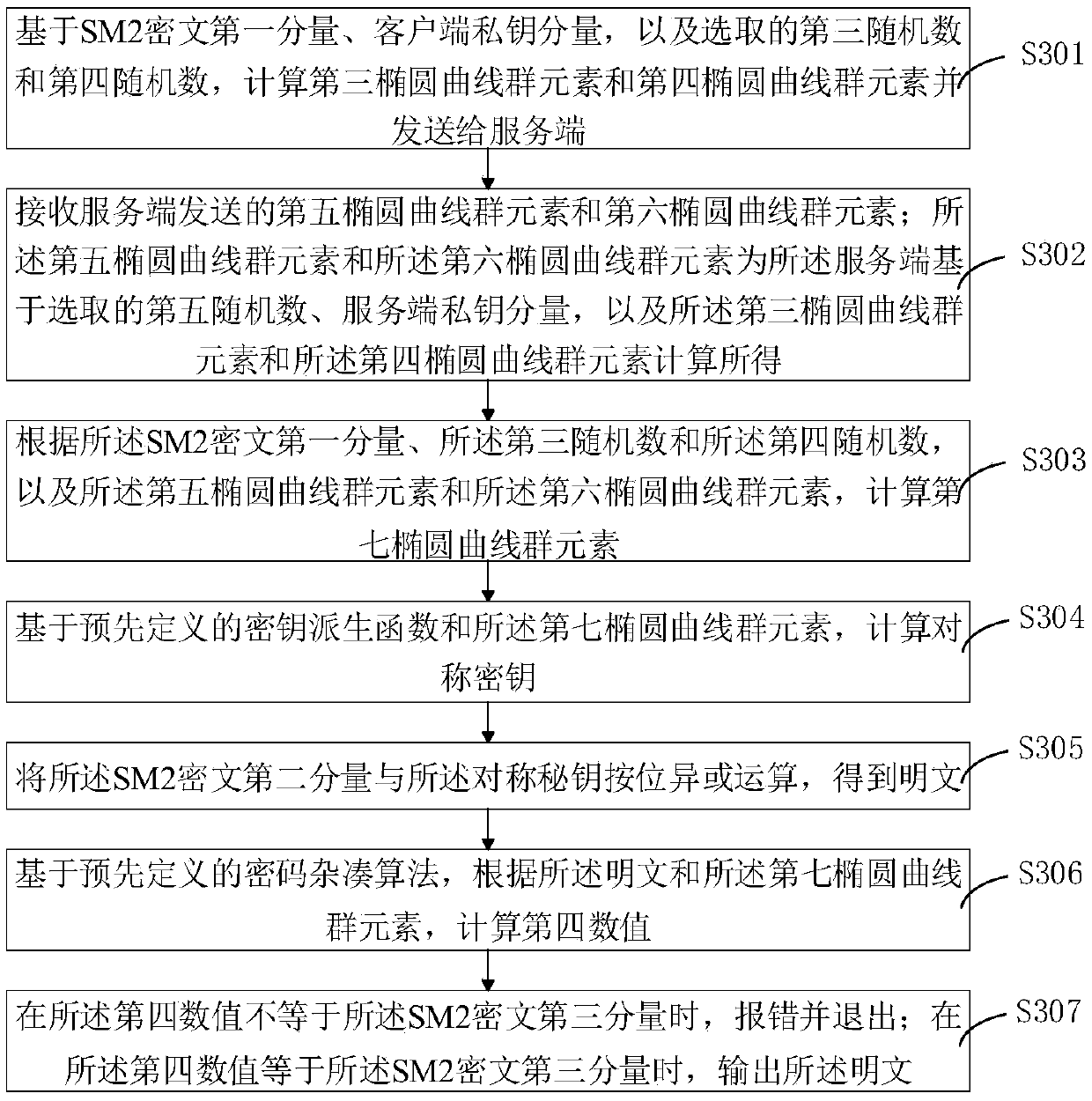
SM2 algorithm collaborative signature and decryption method, device and system
ActiveCN109672539APrivacy protectionProtect against malicious attacksUser identity/authority verificationDigital signatureUser privacy
The invention discloses a SM2 algorithm collaborative signature and decryption method, device and system. The collaborative signature method comprises the following steps: computing a first elliptic curve group element set and sending the a server-side to check; checking a second elliptic curve group element set fed back by the server-side, and computing a third elliptical curve group element based on the first elliptic curve group element set and the second elliptic curve group element set; computing a first numerical value according to a user information hash value, a to-be-signed message and an abscissa of the third elliptical curve group element; generating a second numerical value according to the first numerical value, the first random number and a client private key component, and sending the second numerical value to the server-side; receiving a third numerical value computed according to the second numerical value, the second random number and the server-side private key component; and synthesizing as a SM2 digital signature according to the first numerical value and the third numerical value. The method disclosed by the invention has features of verification input and provable security, more conforms to the actual application environment, and can protect the user privacy better.
Owner:深圳市电子商务安全证书管理有限公司
Cryptographic systems using pairing with errors
ActiveUS9246675B2Key distribution for secure communicationMultiple keys/algorithms usageKey exchangeID-based encryption
Using the same mathematical principle of paring with errors, which can be viewed as an extension of the idea of the LWE problem, this invention gives constructions of a new key exchanges system, a new key distribution system and a new identity-based encryption system. These new systems are efficient and have very strong security property including provable security and resistance to quantum computer attacks.
Owner:ALGO CONSULTING INC
New Cryptographic Systems Using Pairing with Errors
ActiveUS20150067336A1Key distribution for secure communicationMultiple keys/algorithms usageKey exchangeID-based encryption
Using the same mathematical principle of paring with errors, which can be viewed as an extension of the idea of the LWE problem, this invention gives constructions of a new key exchanges system, a new key distribution system and a new identity-based encryption system. These new systems are efficient and have very strong security property including provable security and resistance to quantum computer attacks.
Owner:ALGO CONSULTING INC
Authentication method of Ethernet passive optical network (EPON) system
InactiveCN101577620AOvercoming one-way authentication flawsGuaranteed source authenticityMultiplex system selection arrangementsKey distribution for secure communicationHash functionData integrity
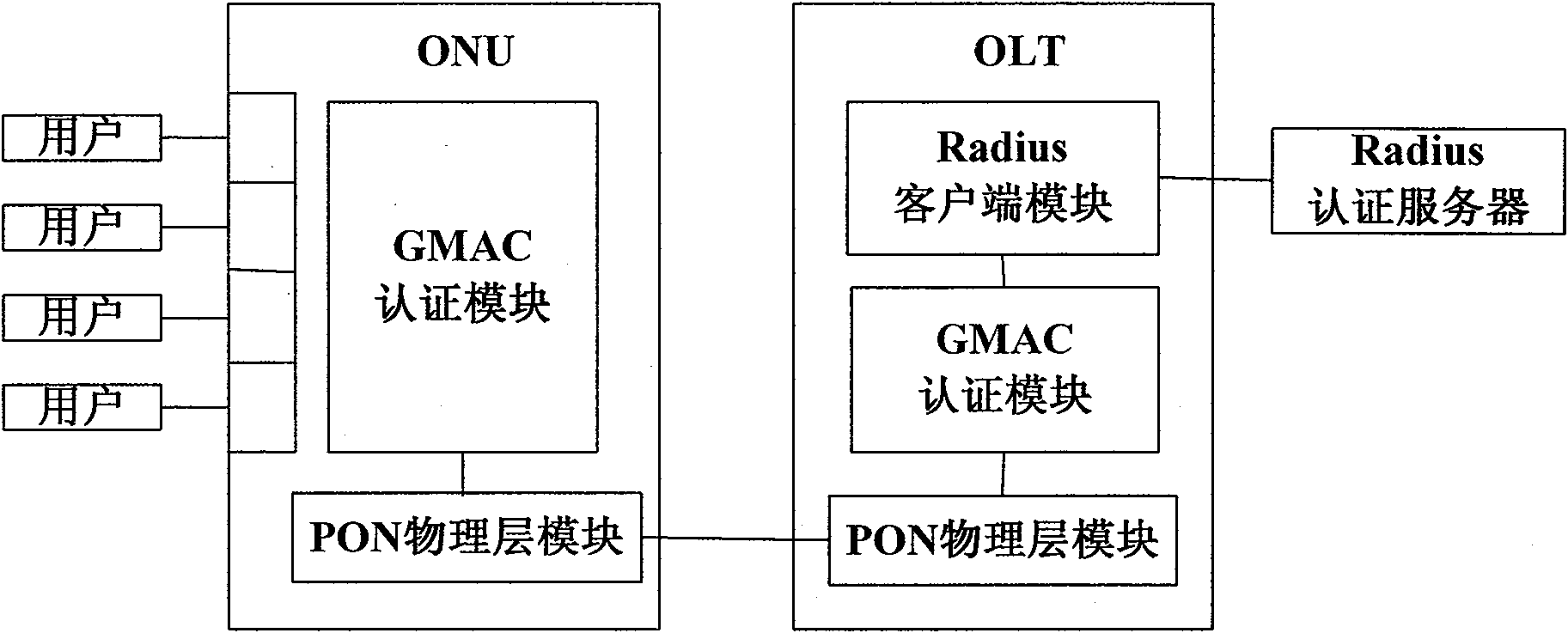
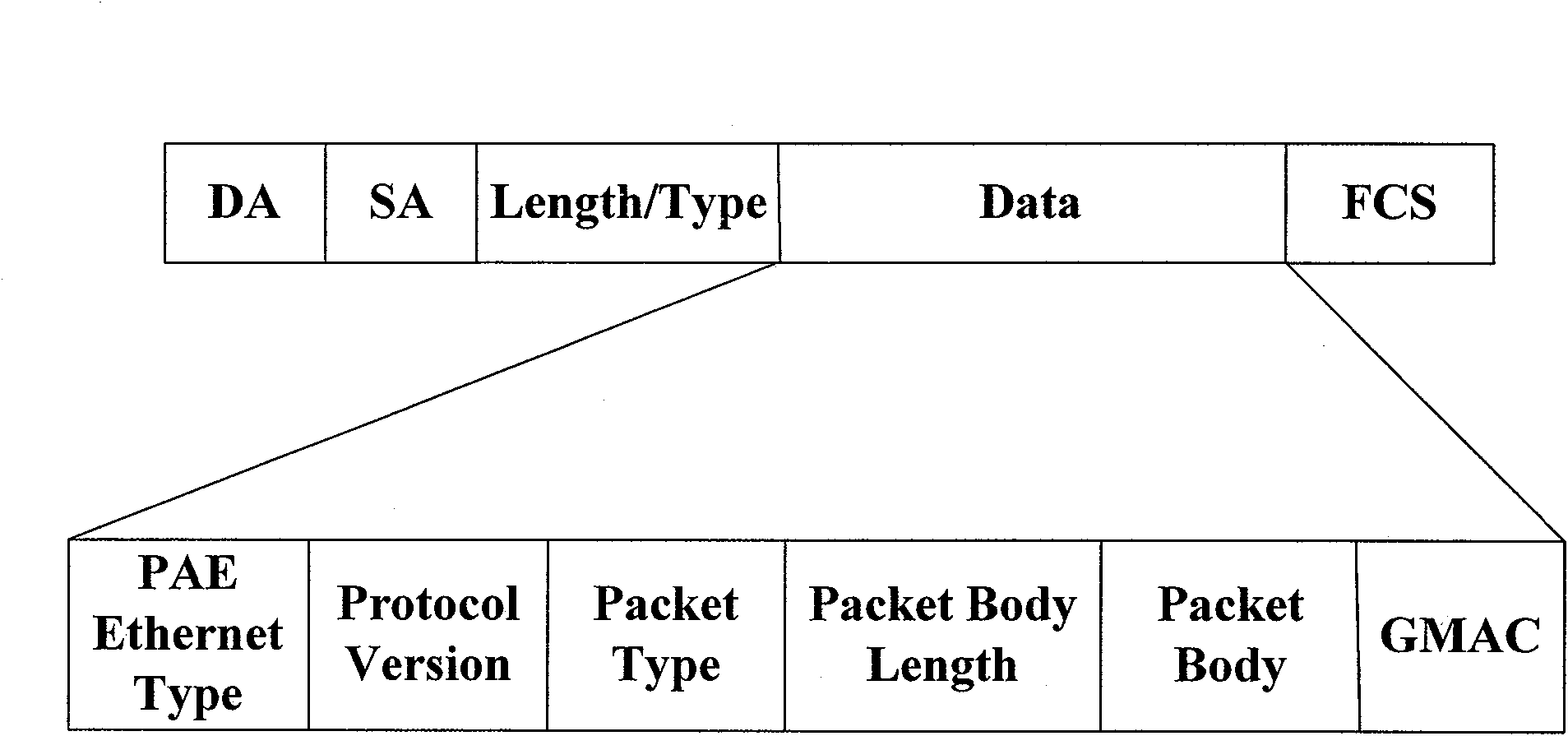
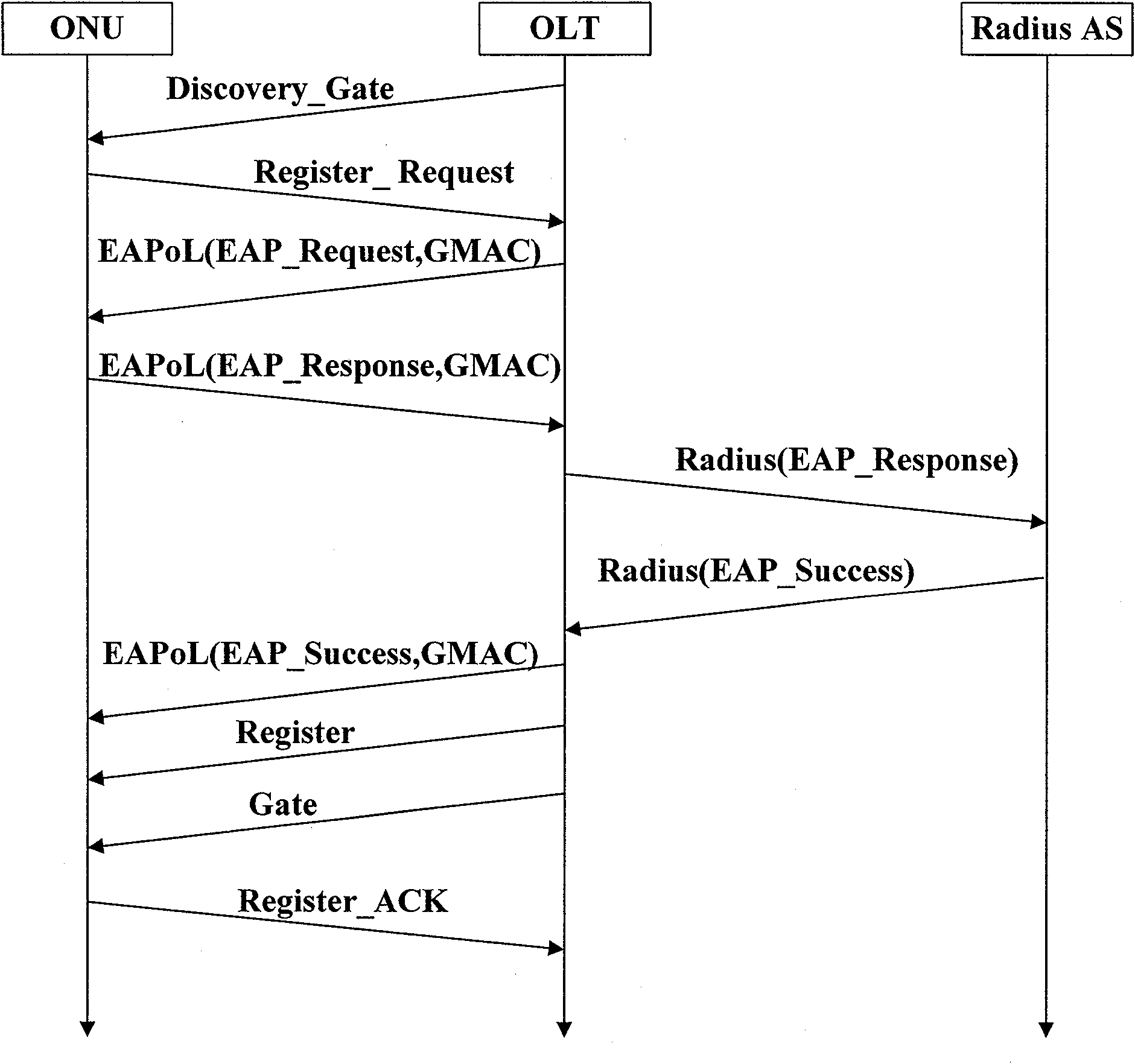
The invention provides an authentication method of an Ethernet passive optical network (EPON) system. By combining Galois field message authentication code (GMAC), the method realizes authentication process of the EPON system, can support ONU authentication and user authentication simultaneously, and designs a frame structure of the GMAC authentication of the EPON system and protocol process of the ONU authentication and the user authentication. The method can overcome the defect of one-way authentication existing in the EPON system authentication mode under the IEEE802.1X port access control mode, and effectively guarantee the source authenticity and data integrity of the authentication. GMAC has provable security, hash function structure thereof based on a binary Galois field multiplier is suitable for parallel and high-speed implementation of hardware and has increment authentication characteristic, thus leading the method to be capable of meeting the requirements of high-speed and effective identification authentication of the EPON system better and to have good security.
Owner:BEIJING UNIV OF POSTS & TELECOMM
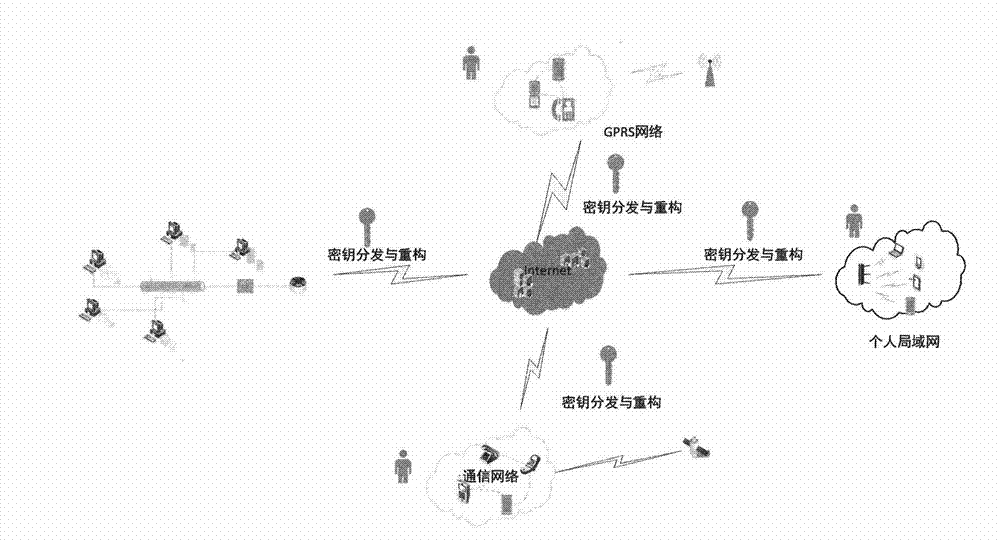
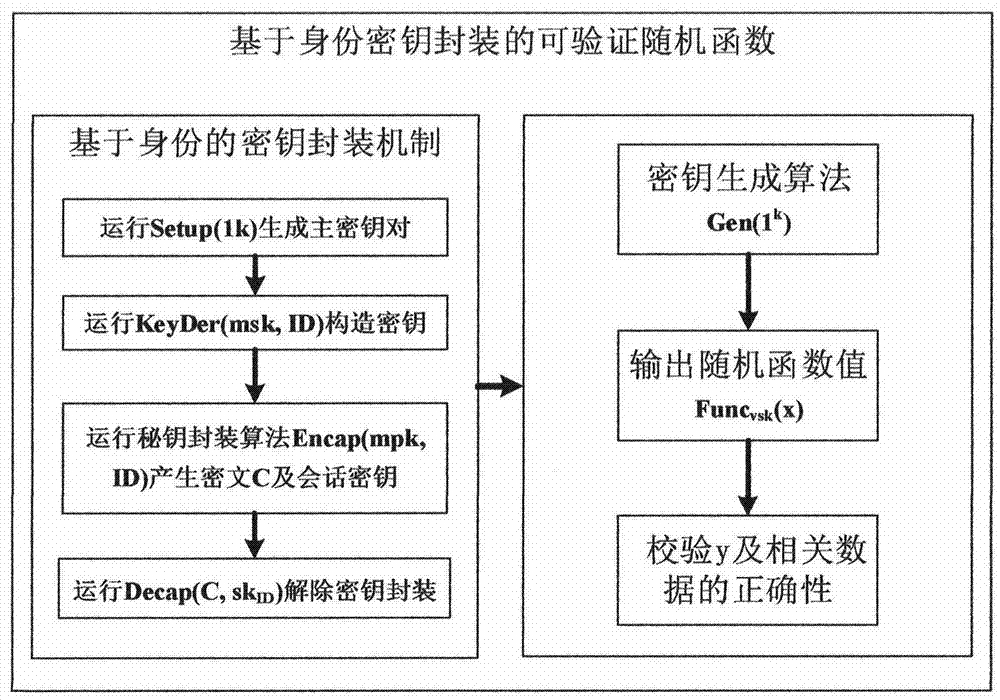
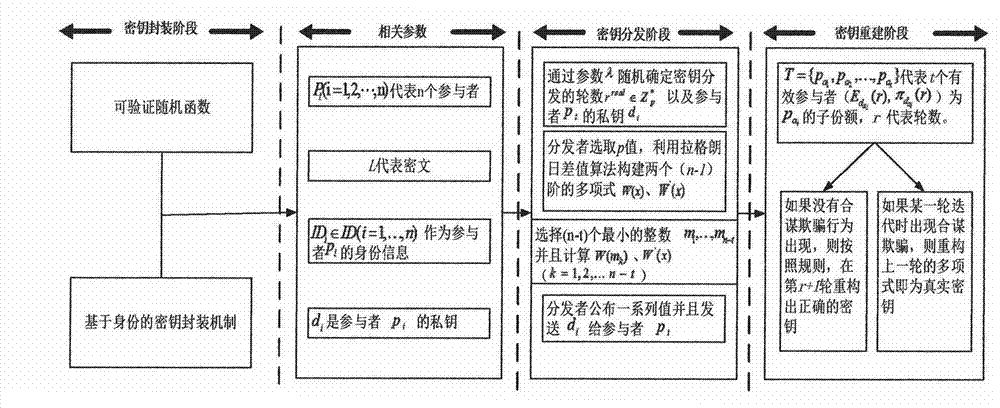
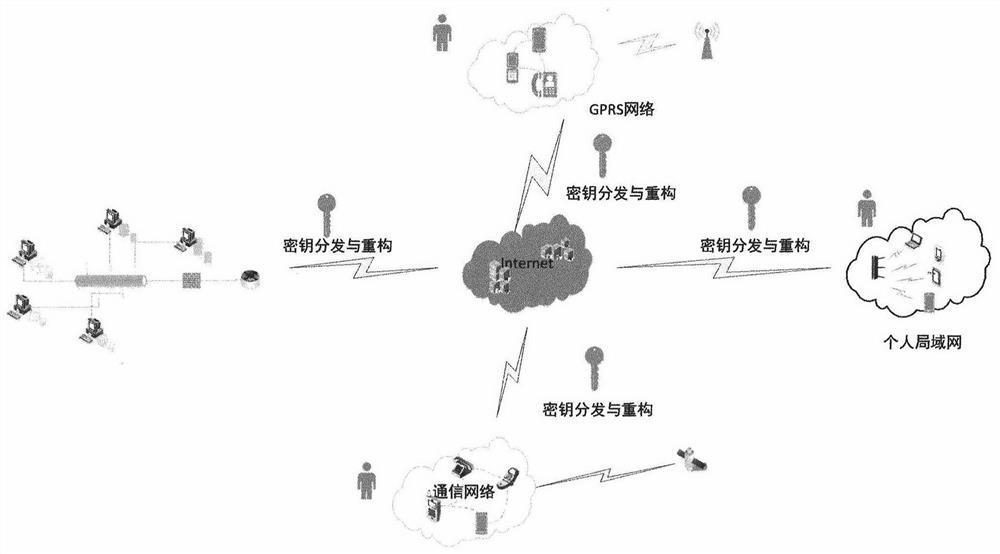
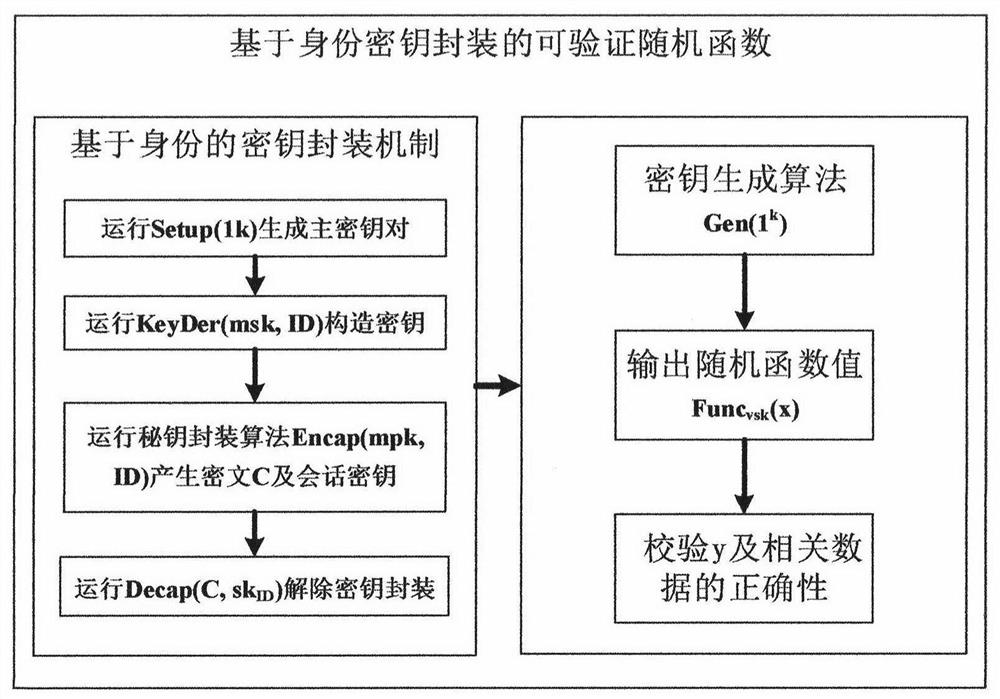
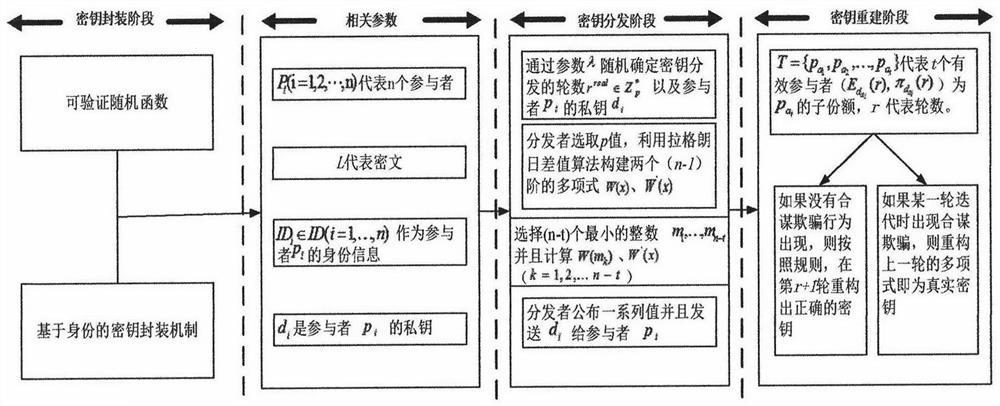
Key distribution and reconstruction method and device based on mobile internet
InactiveCN104754570AIncreased risk of deviating from agreementIncrease the number of expected execution roundsSecurity arrangementProvable securityReconstruction method
The invention provides a key distribution and reconstruction method based on the mobile internet. The method includes the steps of S1, constructing an identity-based key packaging model and a verifiable random function; S2, distributing keys; S3, reconstructing the keys. A calculable collusion-proof equilibrium method is designed, a protocol collusion-proof game-with-entropy model is constructed, and thus collusive attack of participants is prevented; a cryptographic protocol communication game model is constructed, and the defect that password protocols constructed in the broadcast communication network are unable to be implemented in the mobile internet is overcome; the key packaging mechanism applicable to the verifiable random function is studied, the rational key sharing protocol requiring no pubic key infrastructure is designed, and calculation fairness and delivery in the mobile internet is guaranteed; finally, the protocol is subjected to security analysis and proving through the theory of provable security.
Owner:HENAN NORMAL UNIV
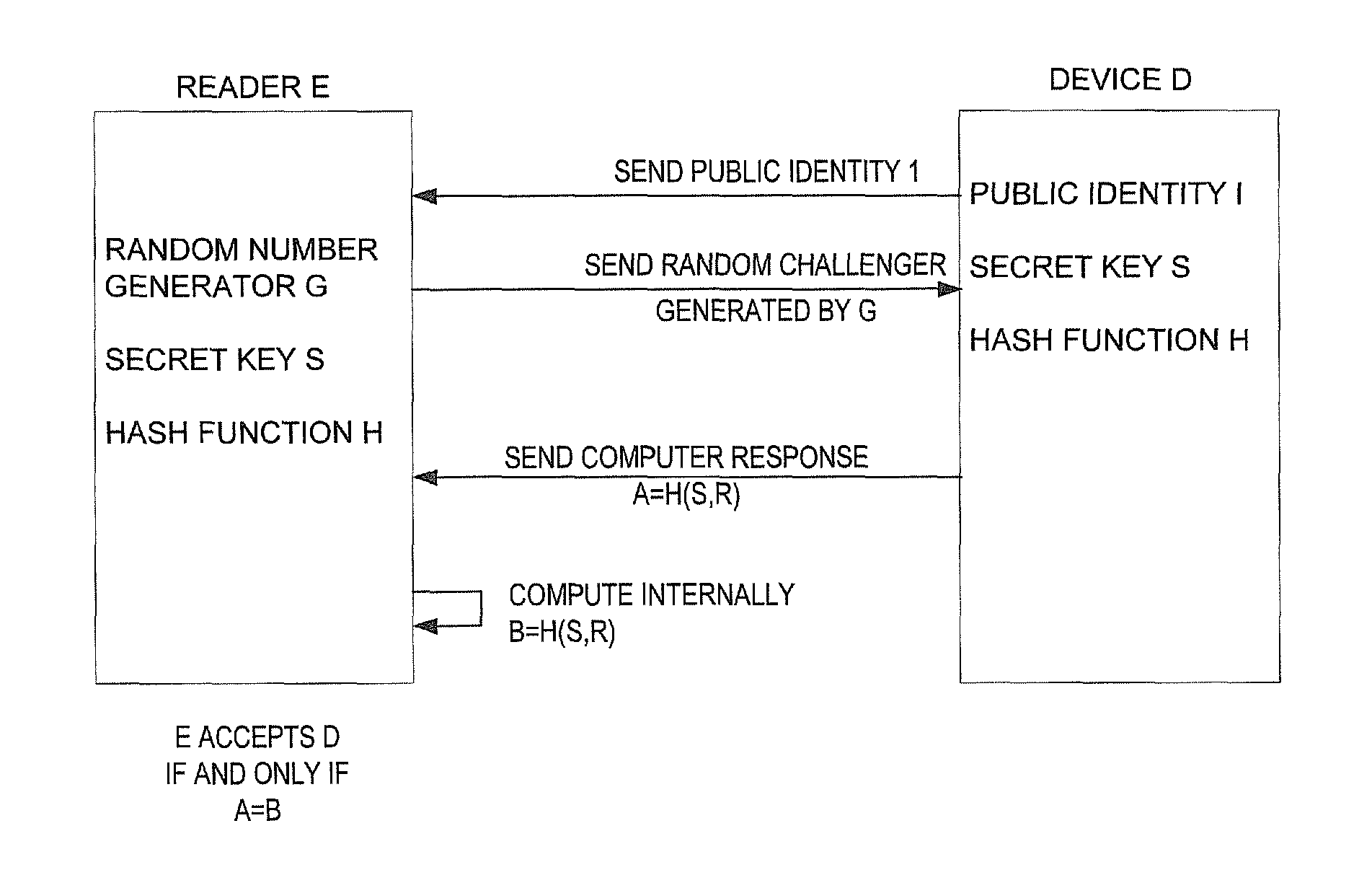
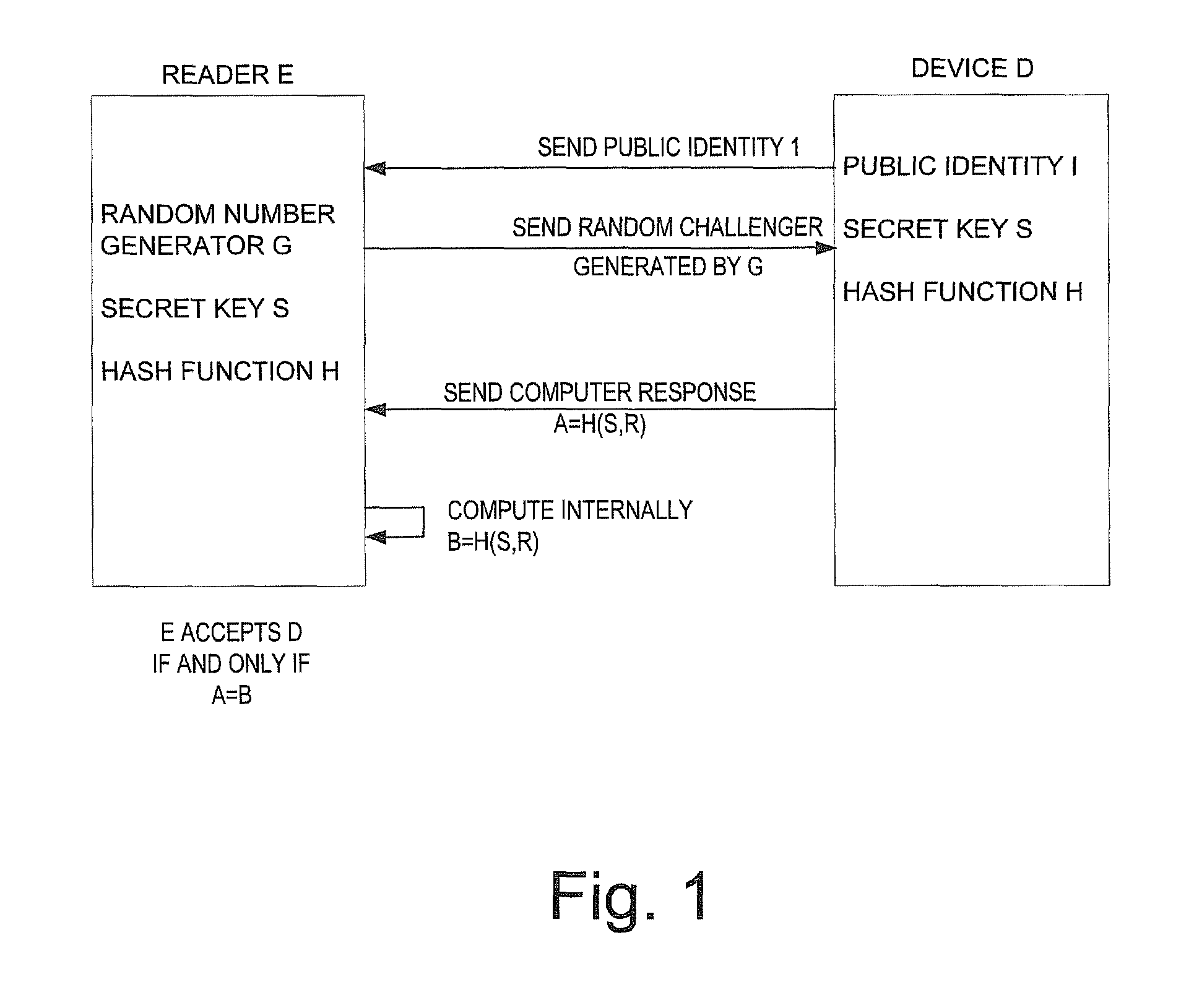
Method and apparatus for implementing a novel one-way hash function on highly constrained devices such as RFID tags
InactiveUS8291221B2Lot of storage on the RFID tag can be savedCompact representationUser identity/authority verificationSecret communicationComputer hardwareHash function
A method and apparatus for implementing a novel one-way hash function with provable security properties for authentication and non-authentication applications on highly constrained devices, with particular application to RFID tags.
Owner:YEDA RES & DEV CO LTD
Digital autograph method based on public key certificate on ellipse curve
InactiveCN1444167AFast securityFast operationUser identity/authority verificationCharacter and pattern recognitionDigital signatureProvable security
The present invention discloses a digital signature method on elliptic curve based on public key certificate. It is a digital signature method by proceeding from discrete logarithm problem on the elliptic curve and utilizing anti-collision miscellaneous function and public key certificate. It has the provable safety and quick operation speed. It can be extensively used in network communication, electronic business and bill, certificate and identity identification and information anti-false technology.
Owner:ZHEJIANG UNIV
Digital signature method based on lattices
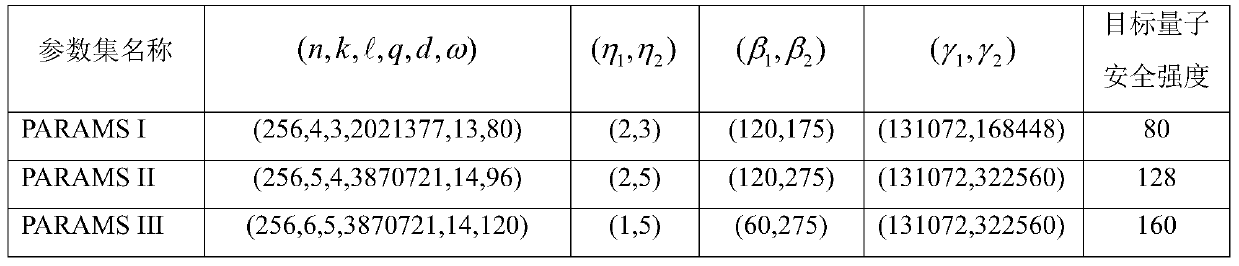
ActiveCN110138549AResist attackImprove securityKey distribution for secure communicationUser identity/authority verificationDigital signatureProvable security
The invention relates to a digital signature method based on lattices, and aims to design an efficient anti-quantum security digital signature method based on the mathematical difficulty problem on the lattices. Specifically, the invention firstly provides a kind of asymmetric modular small integer solution (AMSIS) mathematical difficulty problems, and also provides variations and generalization of the kind of mathematical difficulty problems. The present invention is based on the asymmetric deformation of an AMSIS mathematical difficulty problem and a model band error learning (MLWE) mathematical difficulty problem, provides the digital signature method based on lattices, which has the characteristics and advantages of high security, provable security, quantum computer attack resistance,short public and private key and signature length, high calculation efficiency, flexible parameter selection and the like.
Owner:北京信息科学技术研究院
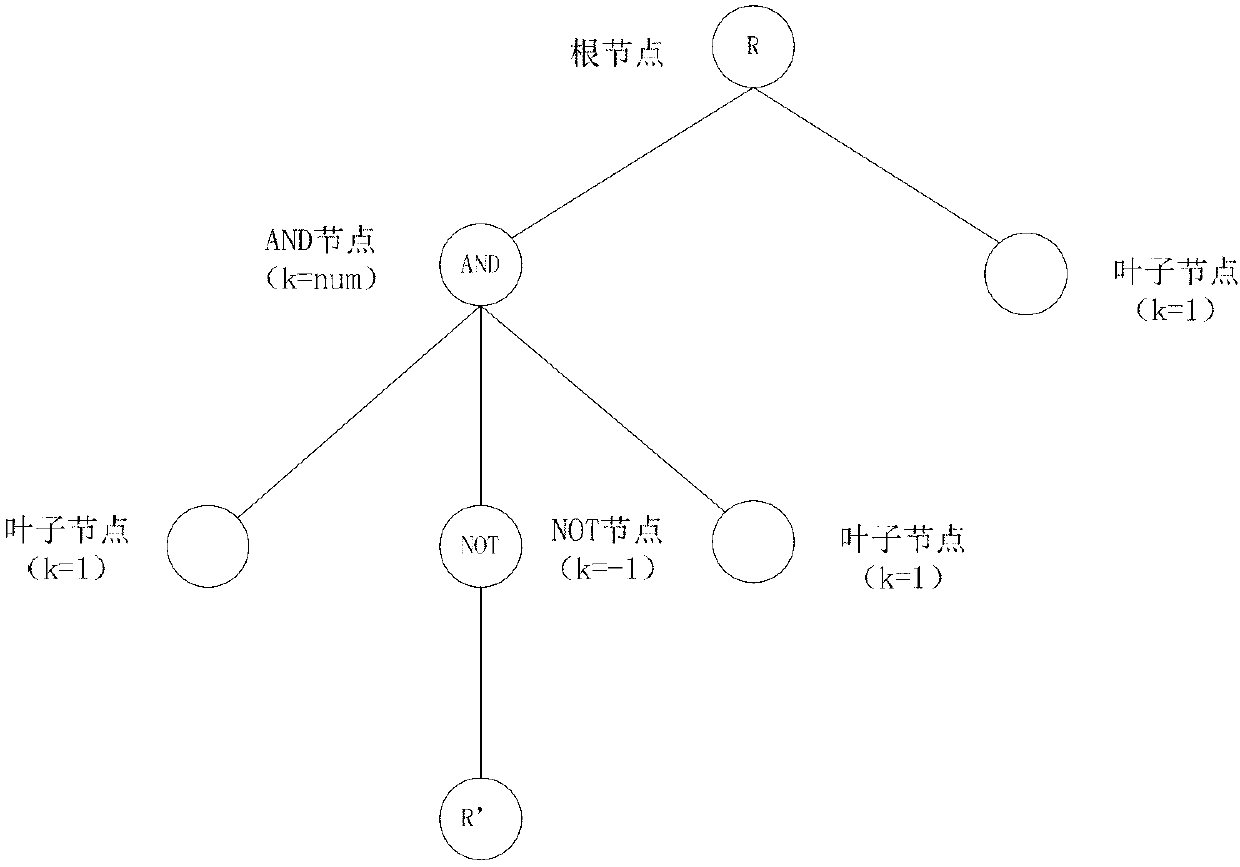
NOT operational character supported characteristic-based CP-ABE method having CCA security
The invention relates to a NOT operational character supported characteristic-based CP-ABE method having CCA security. An access control structure is an access control tree; a NOT node is added in the access control tree; and k is equal to -1. Meanwhile, according to regulation, a father node of the NOT node must be an ''AND'' node and only one intermediate node is hung under the NOT node; and thus the intermediate node is used as a root node to set a strategy tree and the strategy tree expresses a related strategy, set by an encryption party, of a NOT attribute. A high one-time signature technology is added to further enhance a security level of the method from a CPA security level to a CCA security level. Strategy expression based on an attribute encryption algorithm is enriched; security of the existing method is enhanced, thereby building the high access controlling capability; and moreover, the method has an encryption method with a provable security.
Owner:BEIHANG UNIV
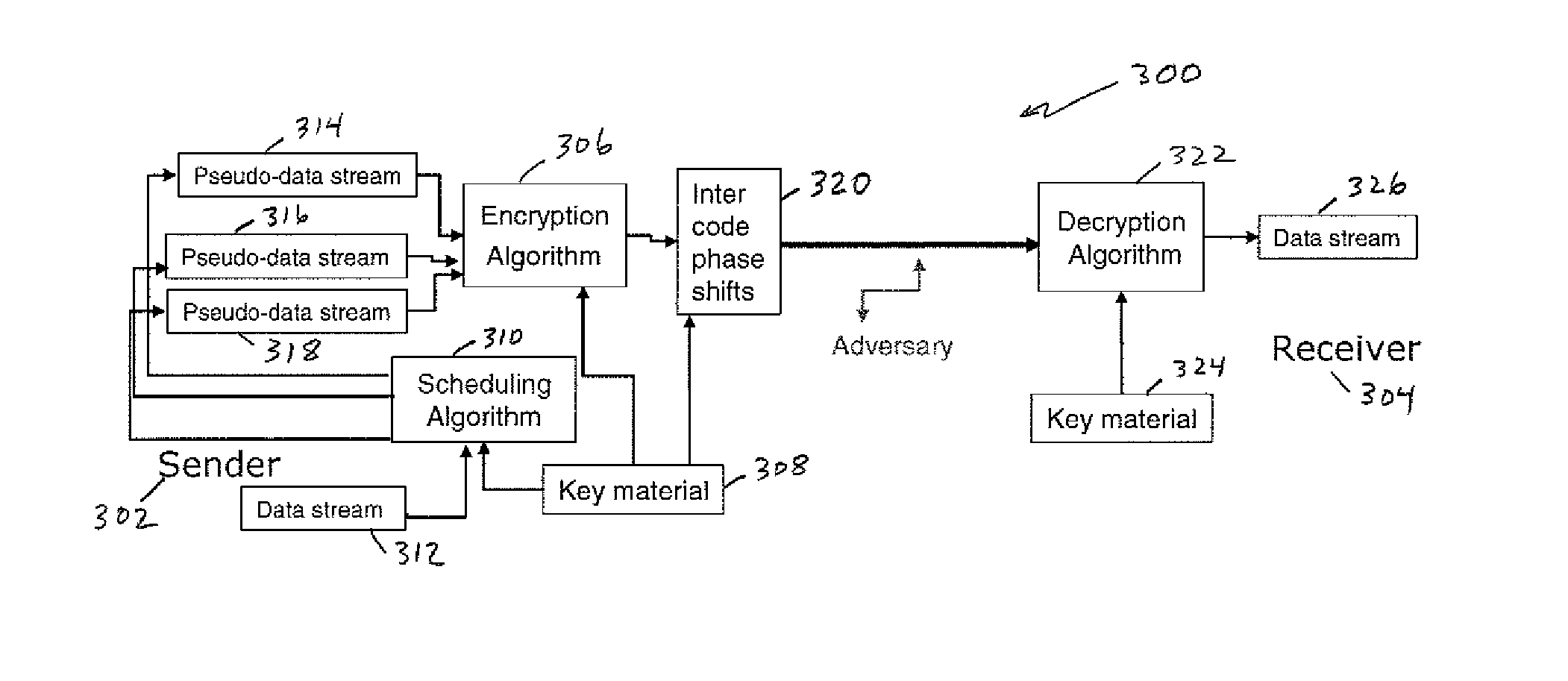
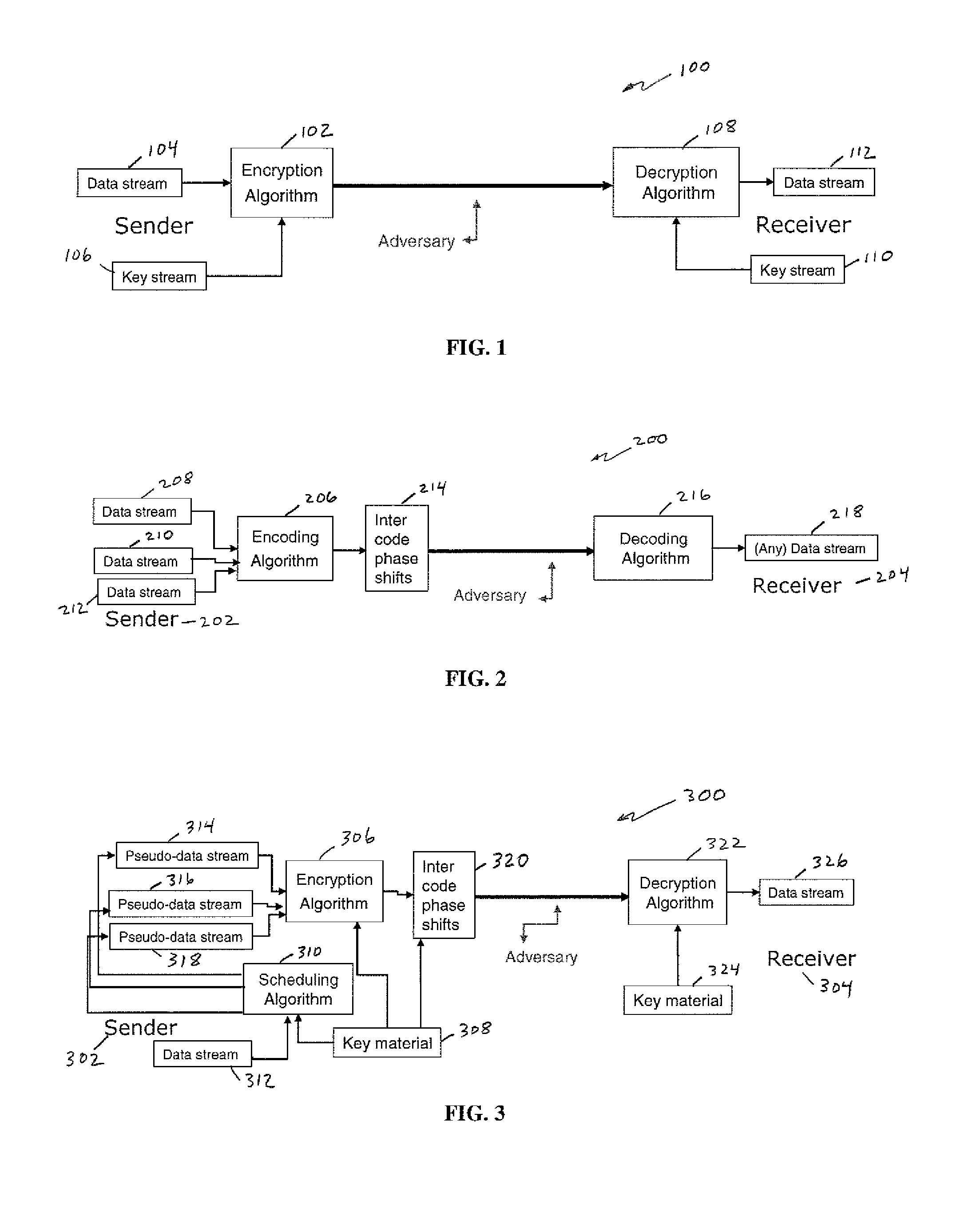
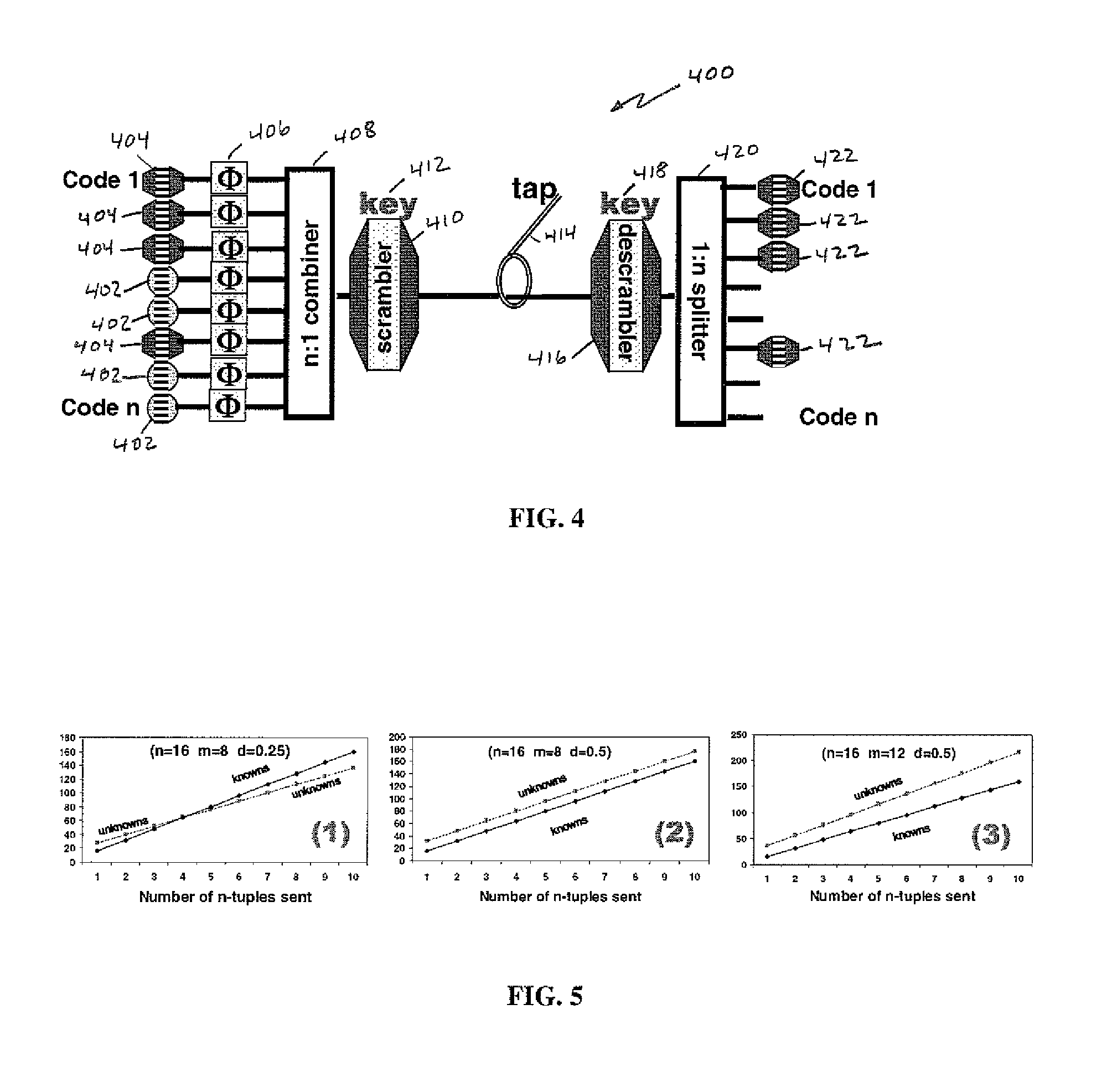
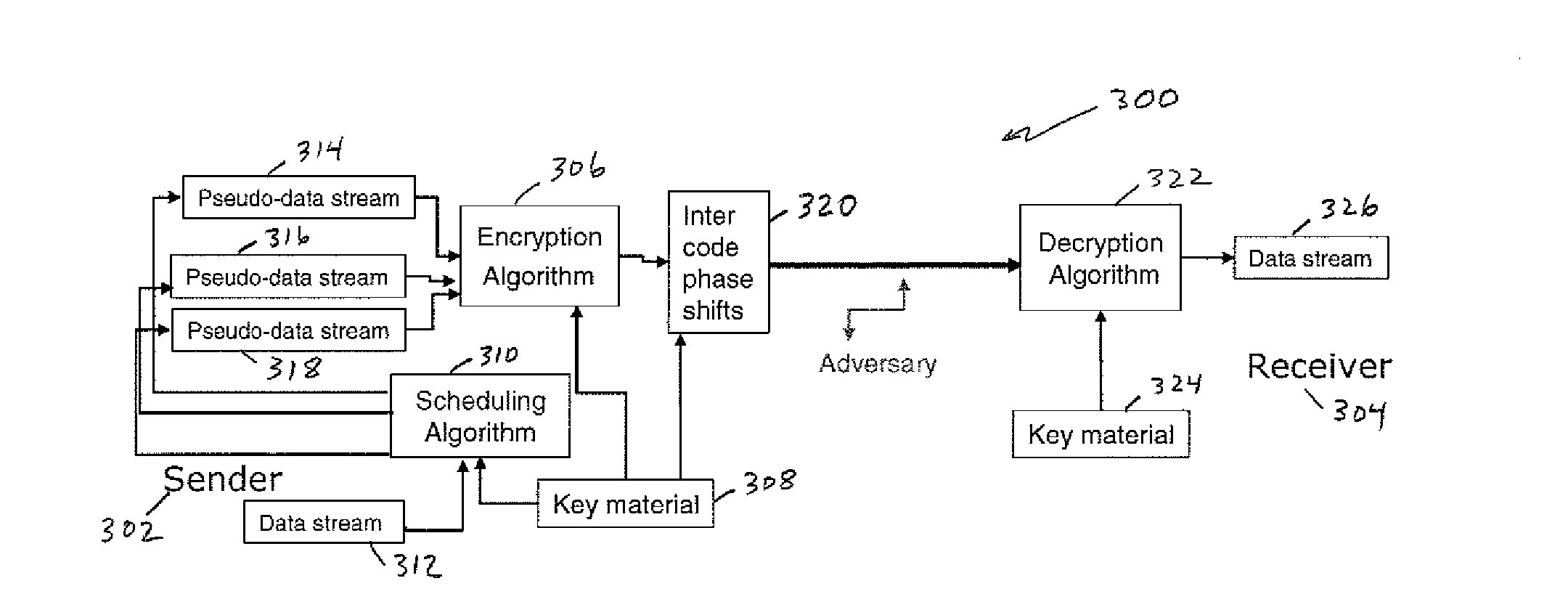
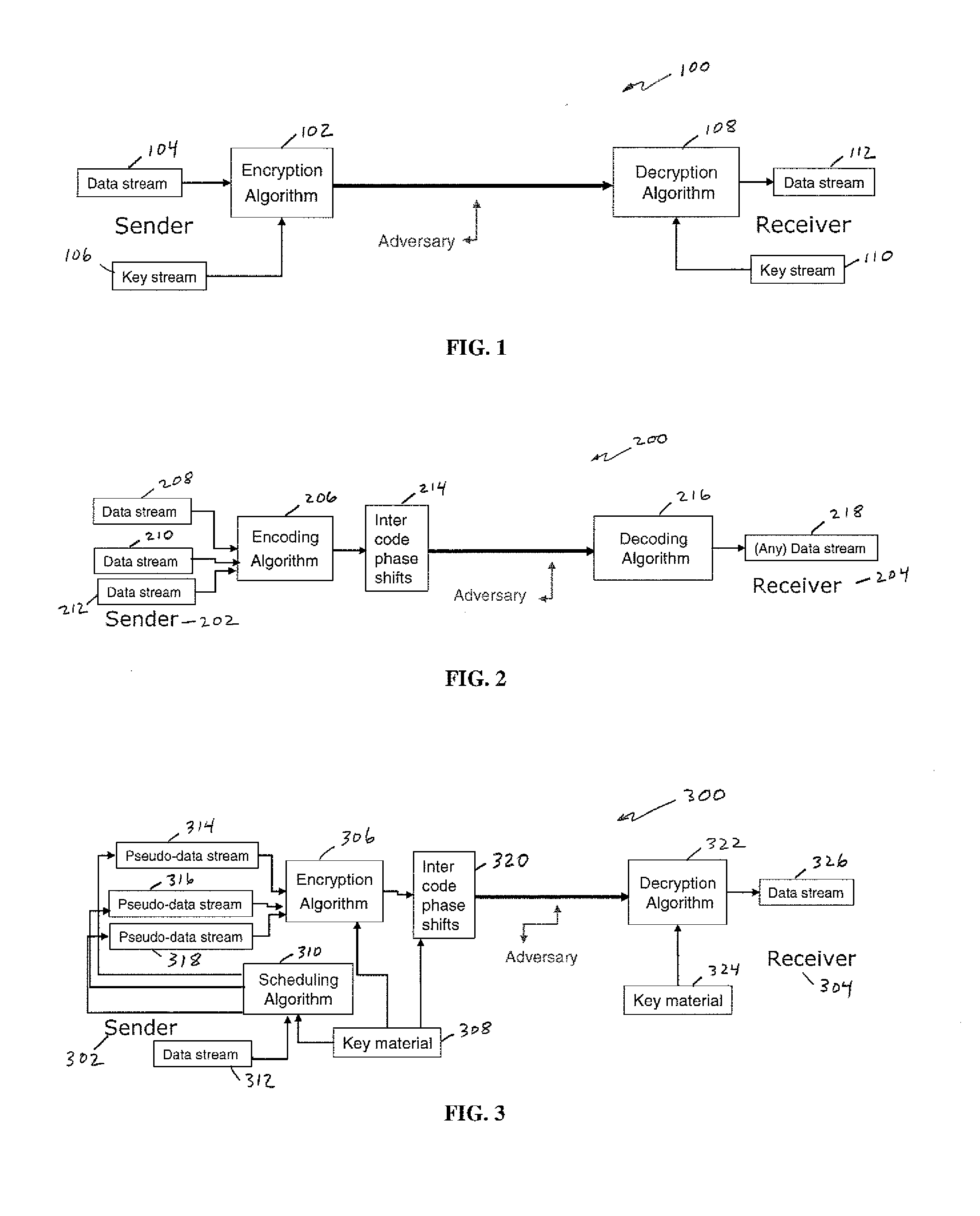
OCDM-based photonic encryption system with provable security
In an OCDM-based photonic encryption system by applying random noise on unused channels and varying the inter-code phases on realistic framing repetition, an OCDM-based encryption system with provable security guarantees results.
Owner:TELCORDIA TECHNOLOGIES INC
Ocdm-based photonic encryption system with provable security
ActiveUS20100232608A1Reduced spectral efficiencyRobustness of securitySecret communicationProvable securityPhotonics
In an OCDM-based photonic encryption system by applying random noise on unused channels and varying the inter-code phases on realistic framing repetition, an OCDM-based encryption system with provable security guarantees results.
Owner:TELCORDIA TECHNOLOGIES INC
AES mask encryption method resisting high order power consumption analysis
ActiveCN107070633AResistance to Higher Order Differential Power AnalysisKey distribution for secure communicationEncryption apparatus with shift registers/memoriesLimited resourcesS-box
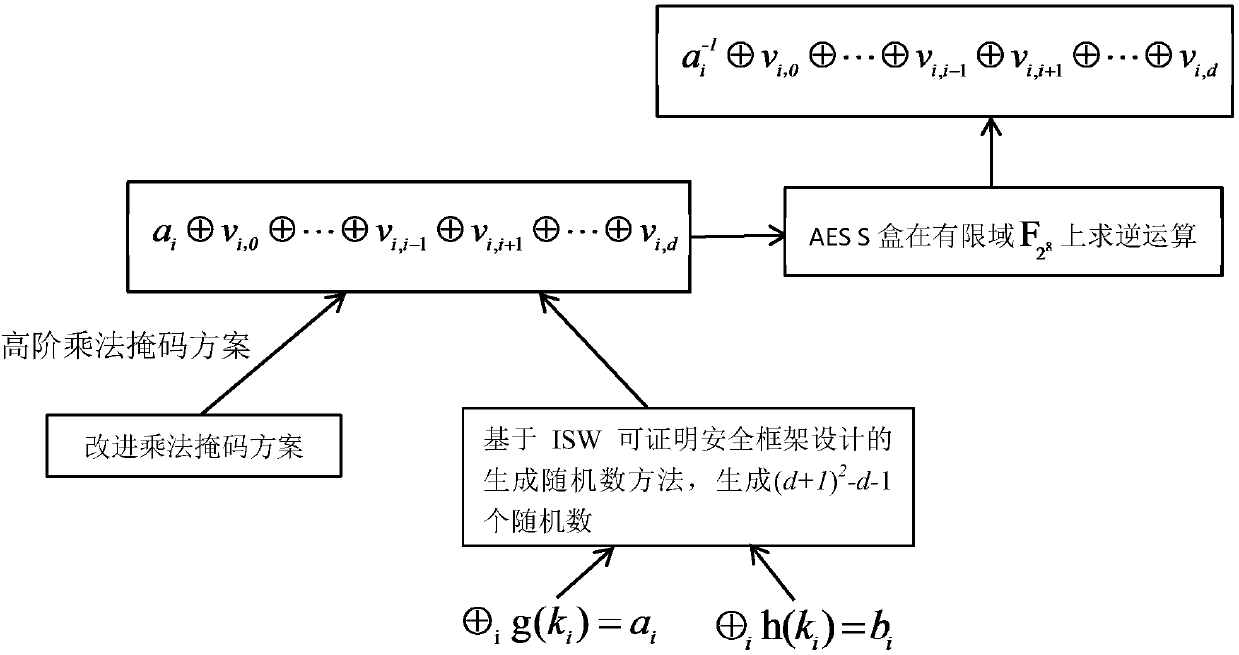
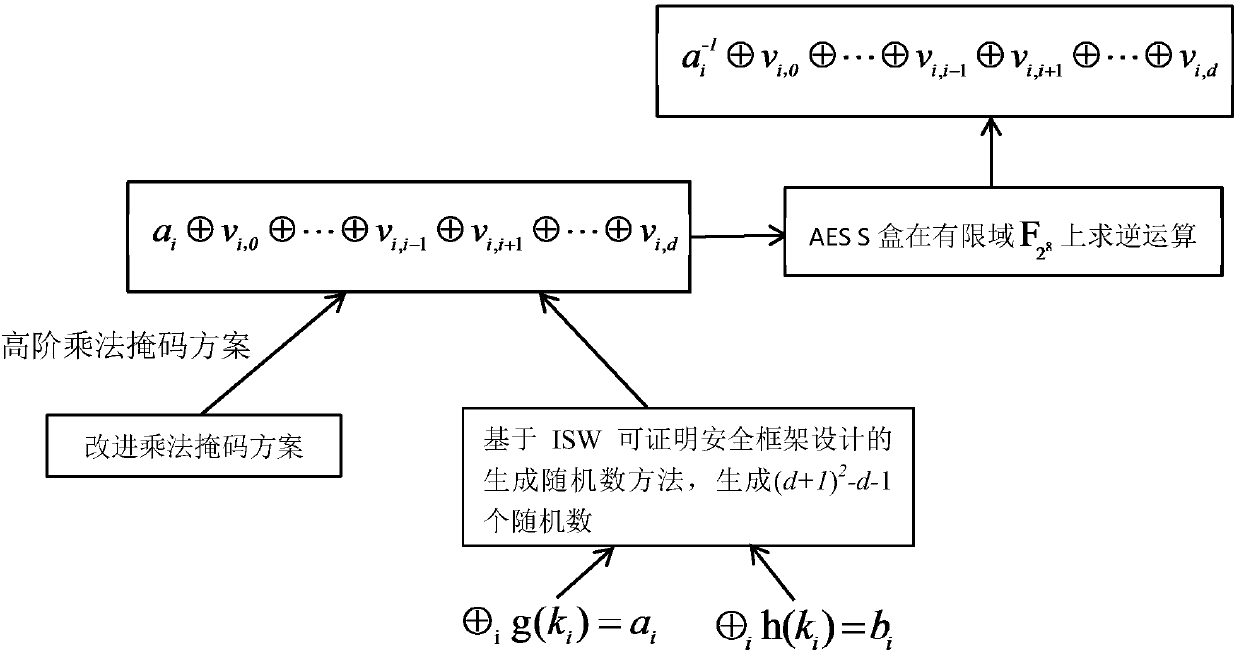
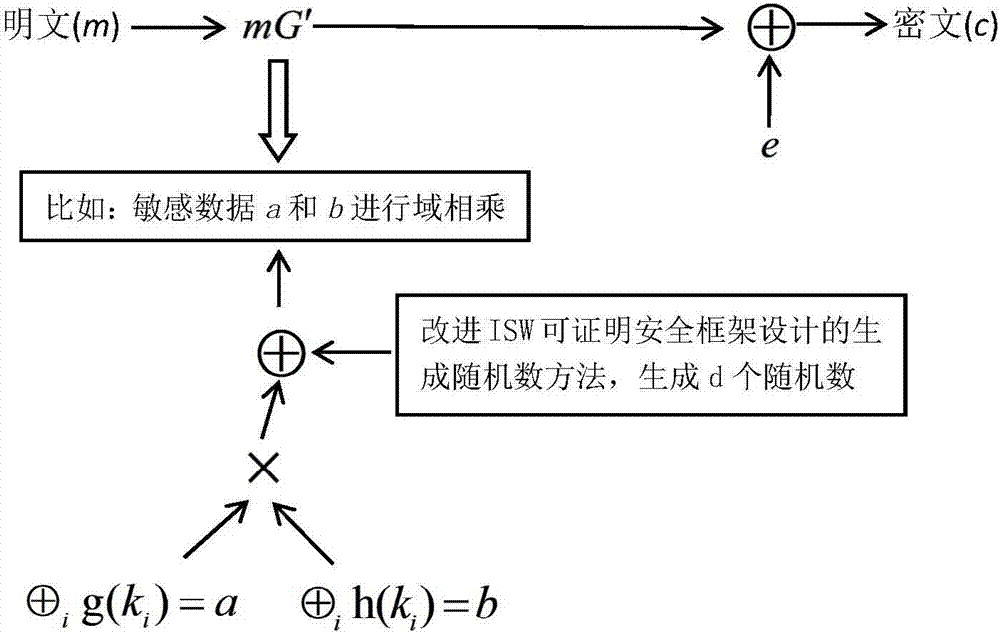
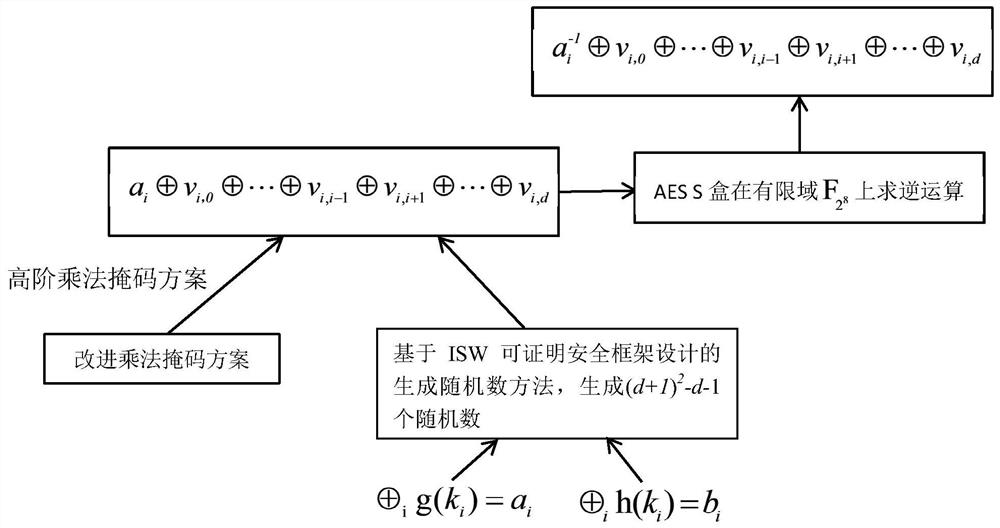
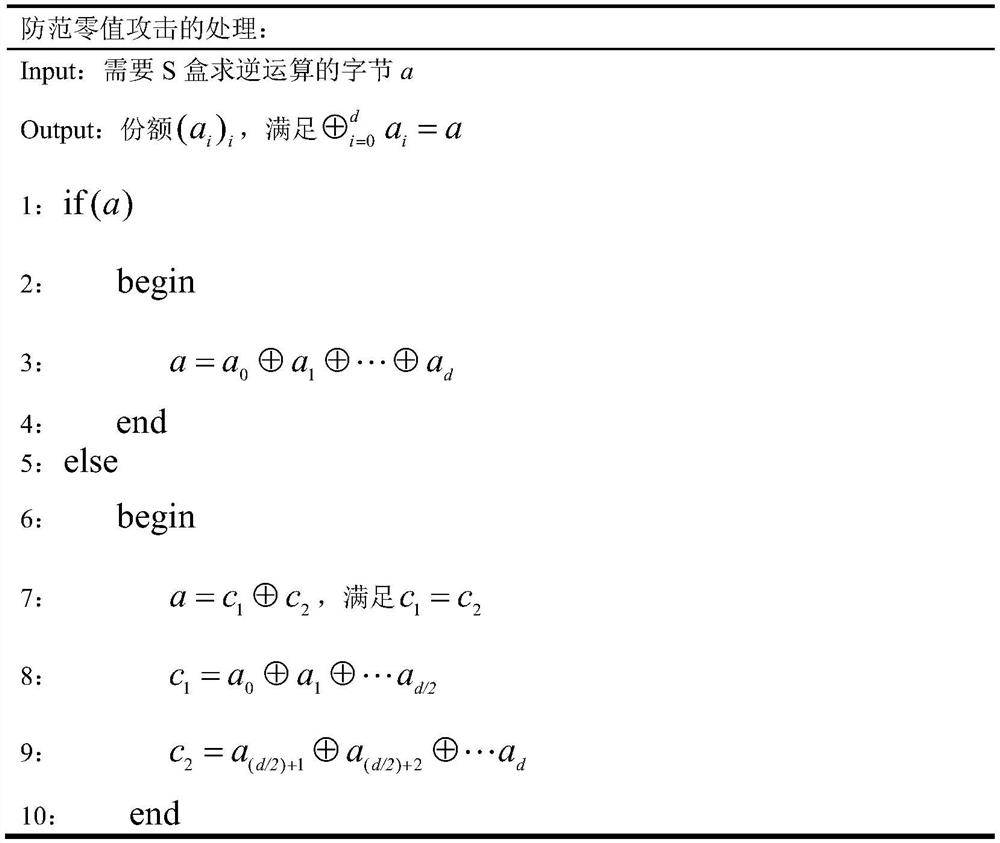
The present invention discloses an AES mask encryption method resisting high order power consumption analysis, that is, design of a mask protection solution resisting high order differential power consumption analysis, belonging to the technical field of information security. The present invention uses a mask technology design protection solution, so that the AES algorithm can resist high order differential power consumption analysis. The method mainly comprises the following steps of firstly, designing and generating a random number expression according to an Ishai-Sahai-Wagner provable security frame; and secondly, solving a security problem of zero attack in a one order multiplication mask solution provided by Akkar and used for protecting an AES password algorithm, designing a high order mask protection solution protecting the AES algorithm, and protecting, by using the random number generated in the first step, an S box non-linear operation with high energy consumption in protecting AES password algorithm. The AES password algorithm with high security and efficiency is more suited to an embedded environment with limited resources.
Owner:日照市财金大数据有限公司
Secure lightweight McEliece public key mask encryption method
InactiveCN106911461ADefend against computing attacksReduce key sizeKey distribution for secure communicationCryptographic attack countermeasuresLimited resourcesSecret code
The present invention discloses a secure lightweight McEliece public key mask encryption method, and belongs to the technical field of information security. Design of the method is divided into two parts: constructing a Quasi-Dyadic MDPC code McEliece cipher code algorithm with a lightweight key and designing a mask protecting scheme that resists power-consumption analysis. According to the method of the present invention, a Quasi-Dyadic MDPC code is constructed and applied to a McEliece cipher code algorithm, so that the volume of a key is effectively reduced. According to the method of the present invention, mask technology is also used to design a protecting scheme, enabling the McEliece cipher code algorithm to resist power-consumption analysis. Meanwhile, the present invention solves the security problem that power consumption caused by using an ISW provable security framework core algorithm to generate a random number is prone to leak a share a and a share b simultaneously. The highly secure and highly efficient McEliece public key cipher code algorithm designed according to the method of the present invention is more applicable to an embedded environment with limited resources.
Owner:JIANGSU UNIV
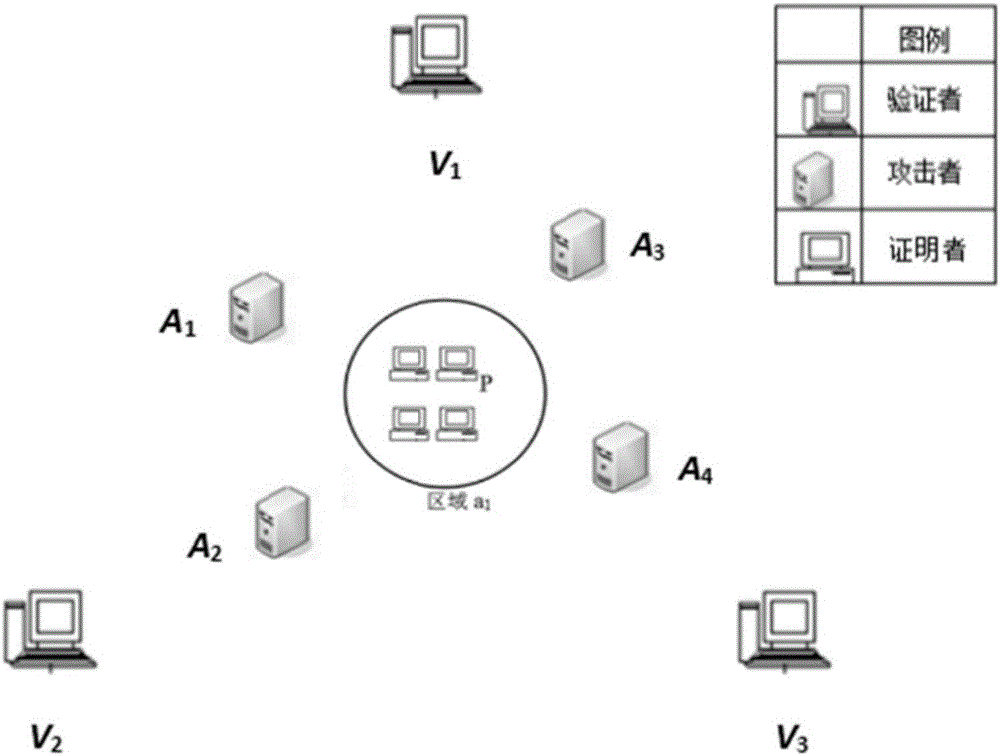
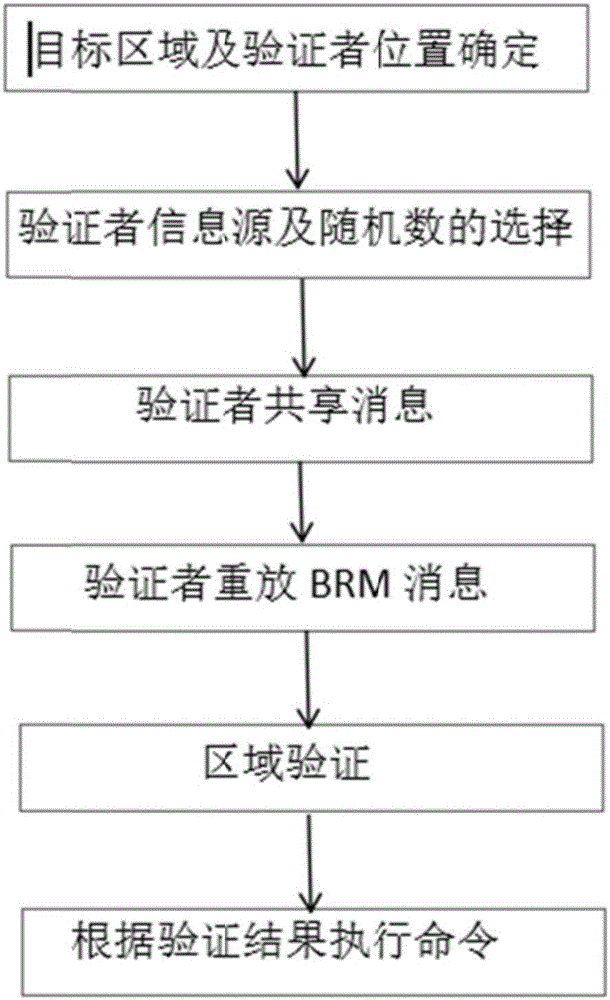
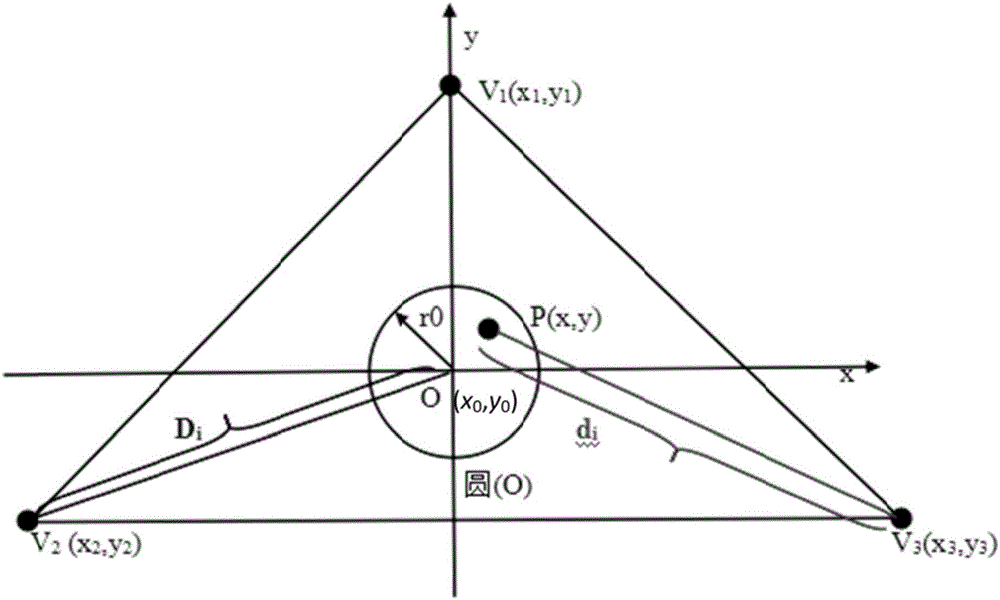
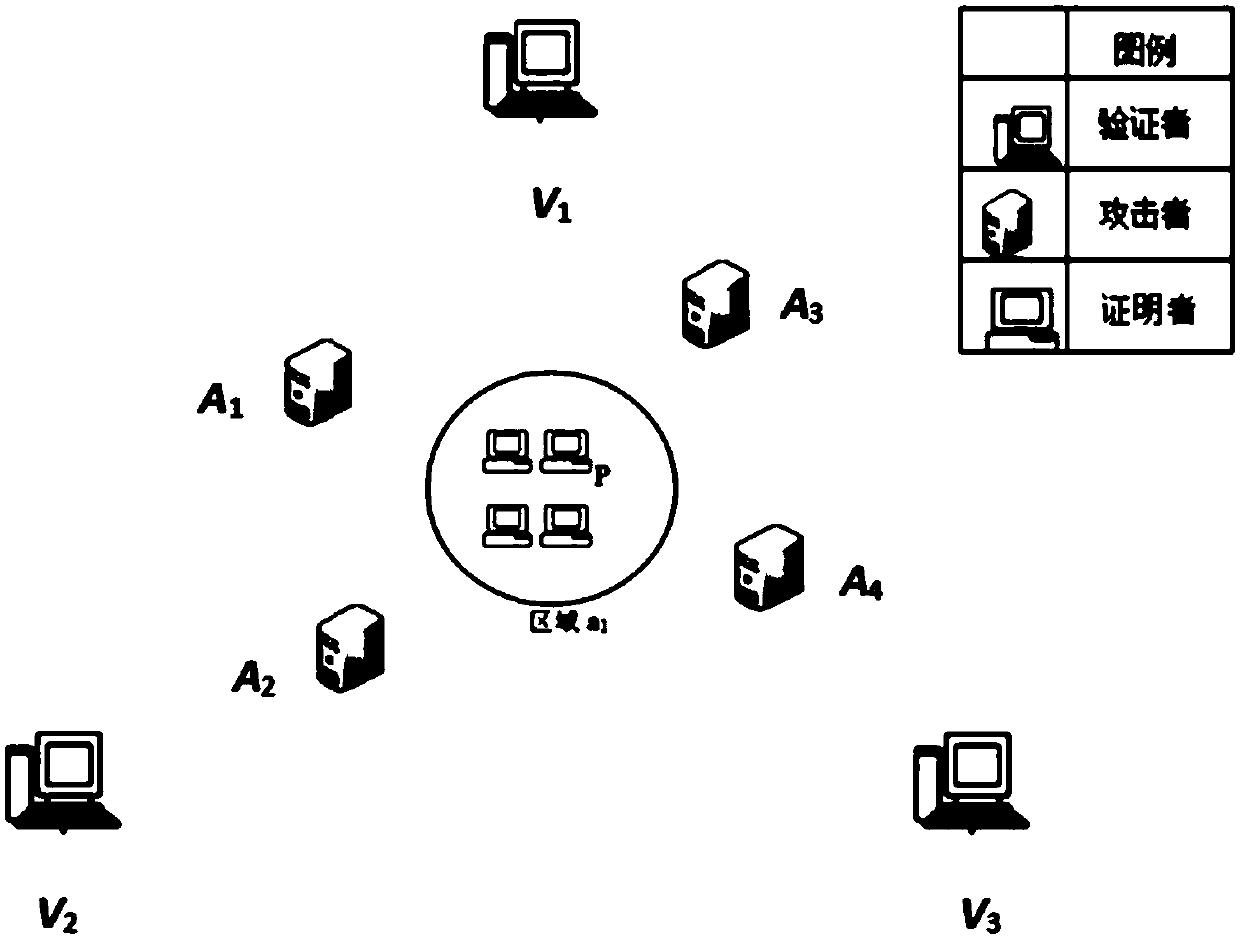
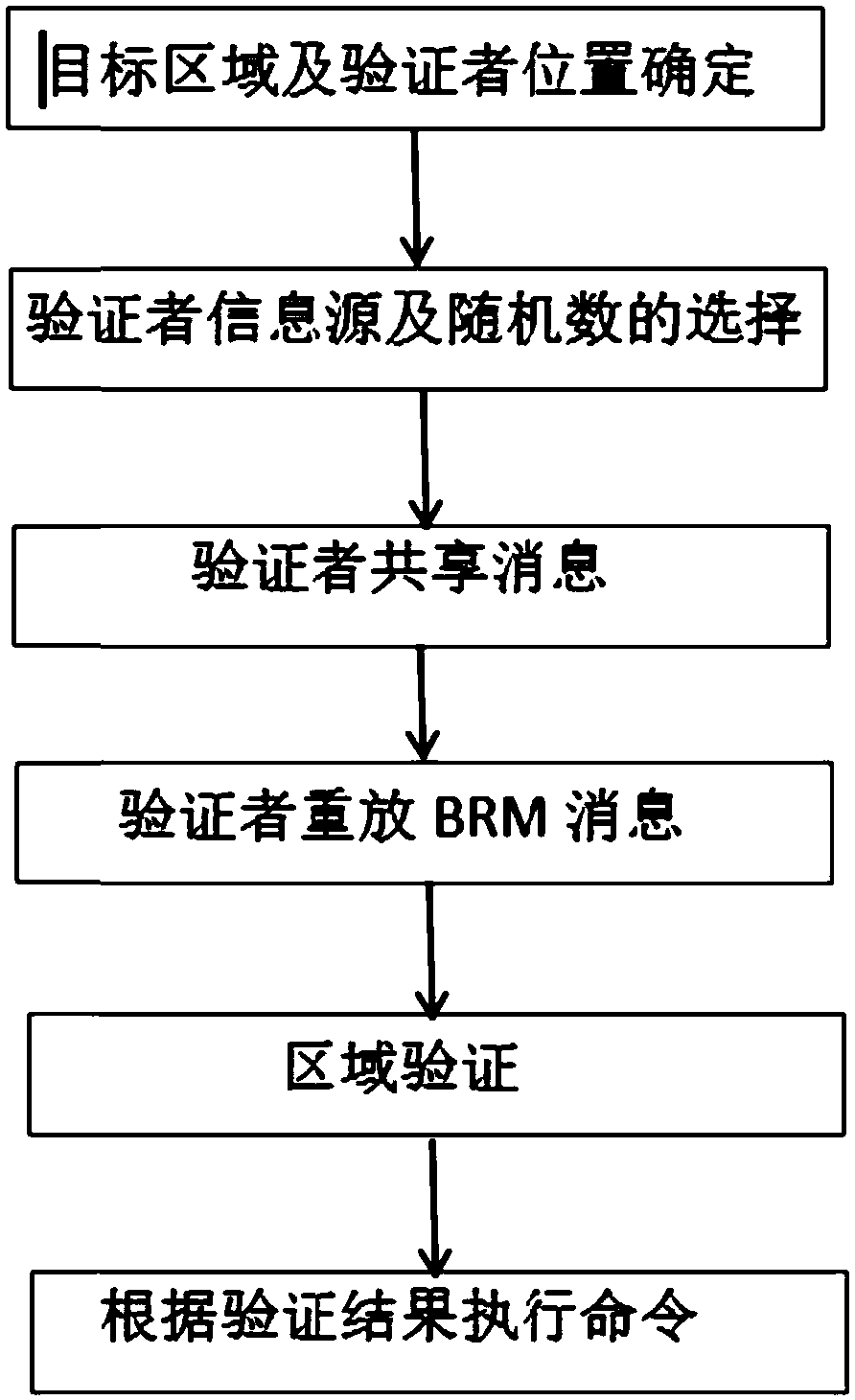
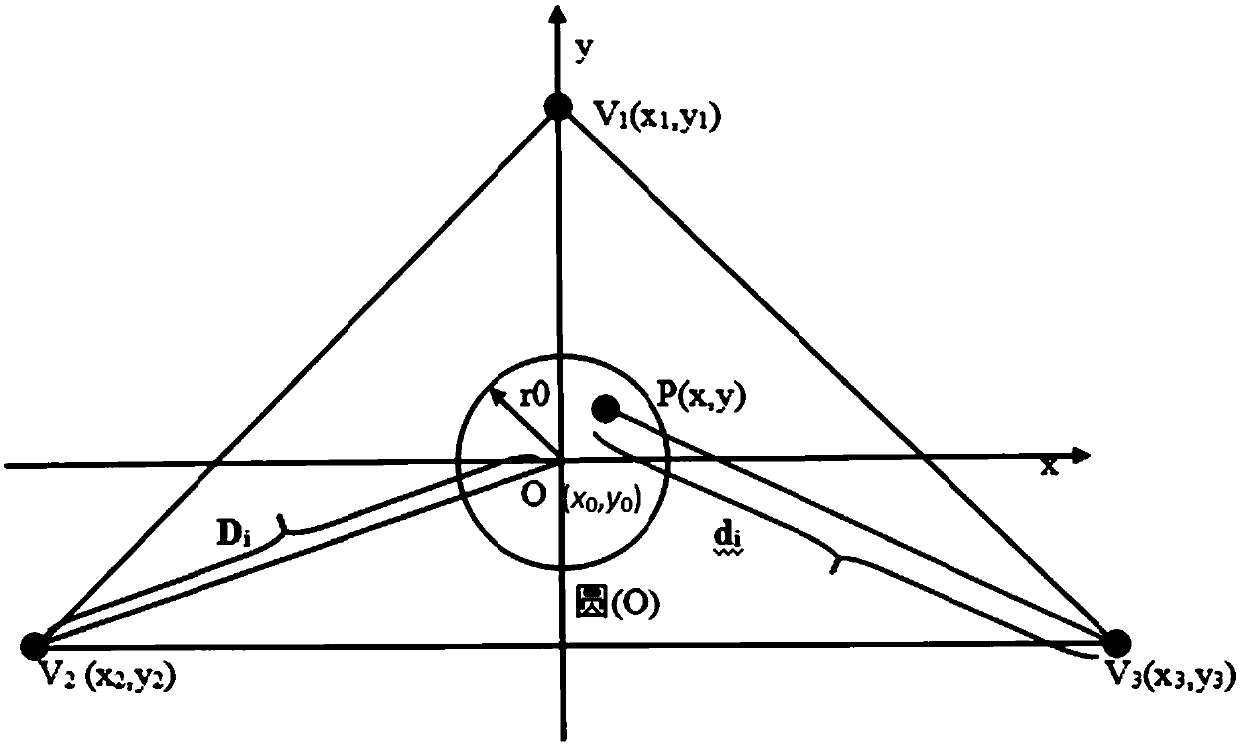
Equipment area provable security verification method with resistance to collusion attack
The invention discloses an equipment area provable security verification method with resistance to collusion attack and mainly solves the problem of absence of a security verification method with areas as credential information in existing position-based cryptography technologies. The implementation scheme of the method comprises steps as follows: a provable security verification model is built, and a prover is located in a target area; verifiers select information sources and random series and share information with one another, and the verifiers replay information in a broadcasting manner; a metric value is generated by the prover, and a verification value is calculated, and position information of the prover is broadcasted; the verifiers verify correctness of the verification value, whether the position information of the prover is accepted is judged, if the verification value passes the verification, the position information of the prover is broadcasted, otherwise, the verification value does not pass the verification, that is, the position claimed by the prover is not in the area, and the verification is finished. According to the method, any prover in the target area can effectively resist the collusion attack of multiple opponents after verification, and the security verification of the position of the prover is realized. The method can be used for verifying whether the equipment, namely, the prover, is located in the target area.
Owner:XIDIAN UNIV
Identity method based on public key certificate
InactiveCN1449154AFast operationUser identity/authority verificationProvable securityDiscrete logarithm
The invention relates to an identity verification method based on shared key certificates. It is a method of varying identity based on discrete logarithms with collision resist different functions and shared certificate. It is safe with a fast calculation speed, which has been proved. It can be used in identity verification so as to control storage, electric business, bills, certificates and the identity verification of information transmitters in communication
Owner:ZHEJIANG UNIV
Key exchanging method based on public key certificate
InactiveCN1449153AFast operationMultiple keys/algorithms usageUser identity/authority verificationKey exchangeDigital signature
The invention relates to a method of changing secret keys based on shared key certificates. It is a method of shared certificate and digital signature based on discrete logarithms in large prime number area and Diffie-Hellman secret key changing agreement, and with collision resist different functions. It is safe with a fast calculation speed, which has been proved.
Owner:ZHEJIANG UNIV
Hybrid secure communication method for key data quantum encryption
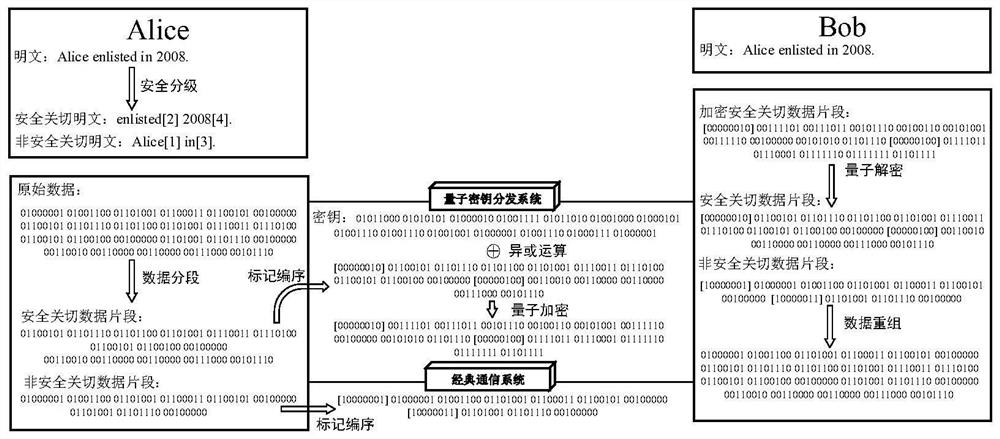
PendingCN114172636AAvoid occupyingIncrease speedKey distribution for secure communicationSecure communicationData stream
The invention discloses a hybrid secure communication method and system for key data quantum encryption and a storage medium, and the method comprises the steps: segmenting data in a communication service data stream according to different security levels through data analysis and discrimination or manual recognition and calibration; a quantum secret communication system in a'one-time pad 'working mode is used for transmitting data fragments calibrated as'security switching', a common communication system is used for transmitting other data fragments, and original communication service data flow is restored through fragment recombination. The hybrid secure communication method is compatible with other various technical schemes for improving the quantum secure communication rate from a physical layer, the rate pressure faced by the physical layer can be partially shared by an application layer, and meaningless calling of non-switching data on quantum keys is avoided through communication service data stream preprocessing. The maximum utilization of the quantum secure communication bandwidth is realized on the premise that key data has mathematically provable security, and an important support can be provided for a practical quantum secure communication network.
Owner:军事科学院系统工程研究院网络信息研究所
Authentication key negotiation method and system against continuous leakage
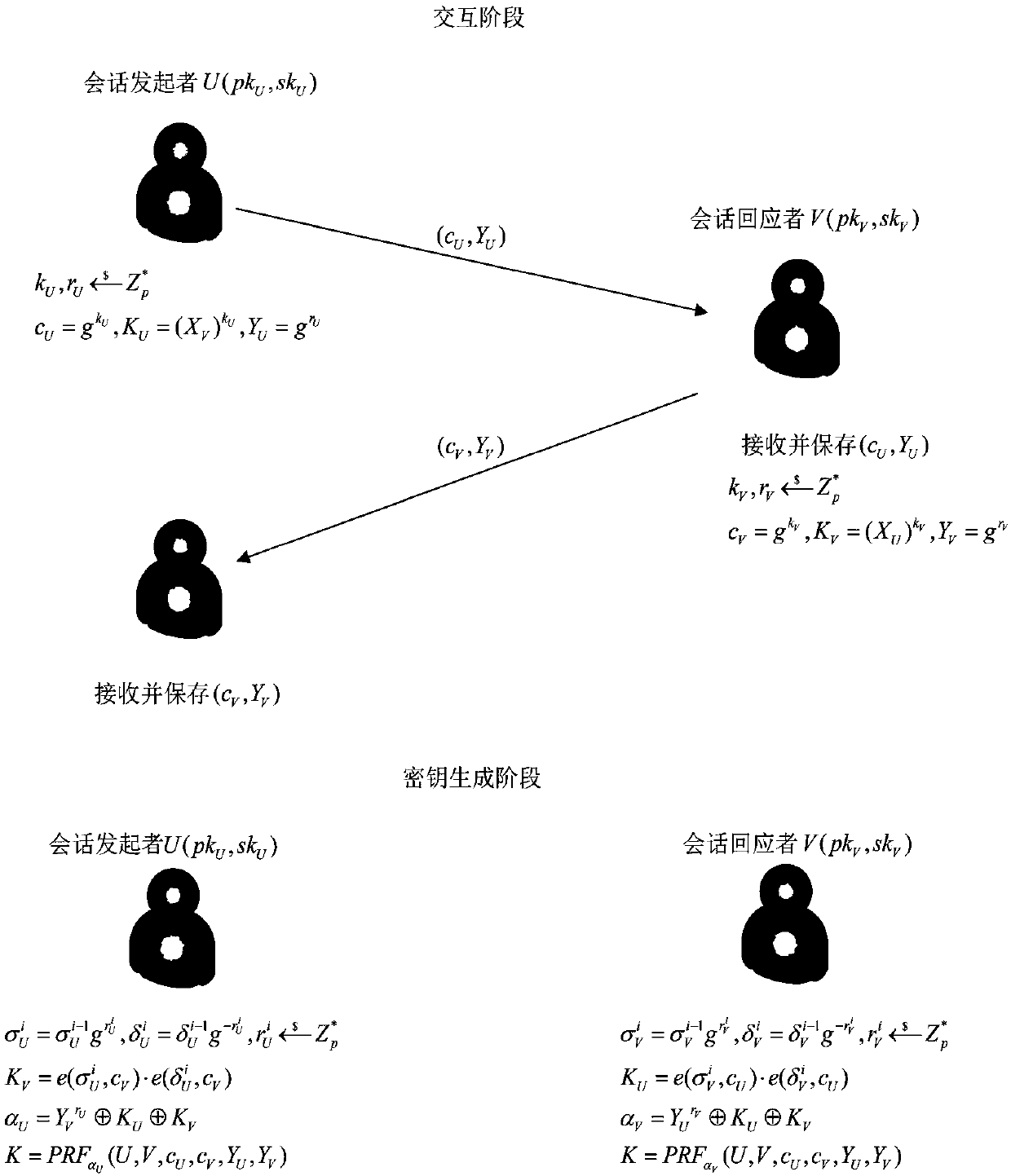
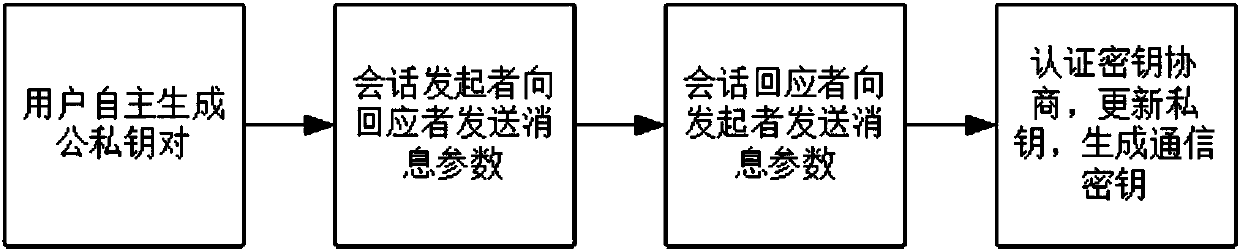
InactiveCN108599948ANo support requiredImprove securityKey distribution for secure communicationPublic key for secure communicationSecure communicationProvable security
The invention discloses an authentication key negotiation method and system against continuous leakage. The system is composed of two users, respectively a session initiator and a responder; and eachuser has a pair of public and private keys. The method in the invention first performs system initialization and then performs a first interaction, and the session initiator sends a message parameterto the responder; then a second interaction is carried out, and the session responder responds to the initiator with the message parameter; finally, the session initiator and the responder authenticate key negotiation, update own private keys and generate a common communication key. The authentication key negotiation method and system against continuous leakage in the invention are particularly suitable for the secure communication of both parties, are high in security as having achieved cryptographically provable security, and is high in practicability as being able to execute safely and stably still in a continuous leakage environment; and in combination with an elliptic curve and bilinear pairing technology, a session key authentication negotiation protocol against continuous leakage isproposed, and the scheme efficiency is high.
Owner:HUBEI UNIV OF TECH
Encryption key exchange method based on public key centificate on elliptic curve
The exchange method is based on discrete-logarithm issue and Diffie-Hellman cipher key exchange protocol on the elliptical curve and assisted with anti-impact odds and ends function, session key exchange method of public key certificate and digital signature. The method is good at security which can be certified and it has quick operation speed.
Owner:ZHEJIANG UNIV
Key exchanging method based on public key certificate
InactiveCN1192542CFast operationMultiple keys/algorithms usageUser identity/authority verificationKey exchangeDigital signature
The invention relates to a method of changing secret keys based on shared key certificates. It is a method of shared certificate and digital signature based on discrete logarithms in large prime number area and Diffie-Hellman secret key changing agreement, and with collision resist different functions. It is safe with a fast calculation speed, which has been proved.
Owner:ZHEJIANG UNIV
A leak-resistant group user authentication key agreement method and system
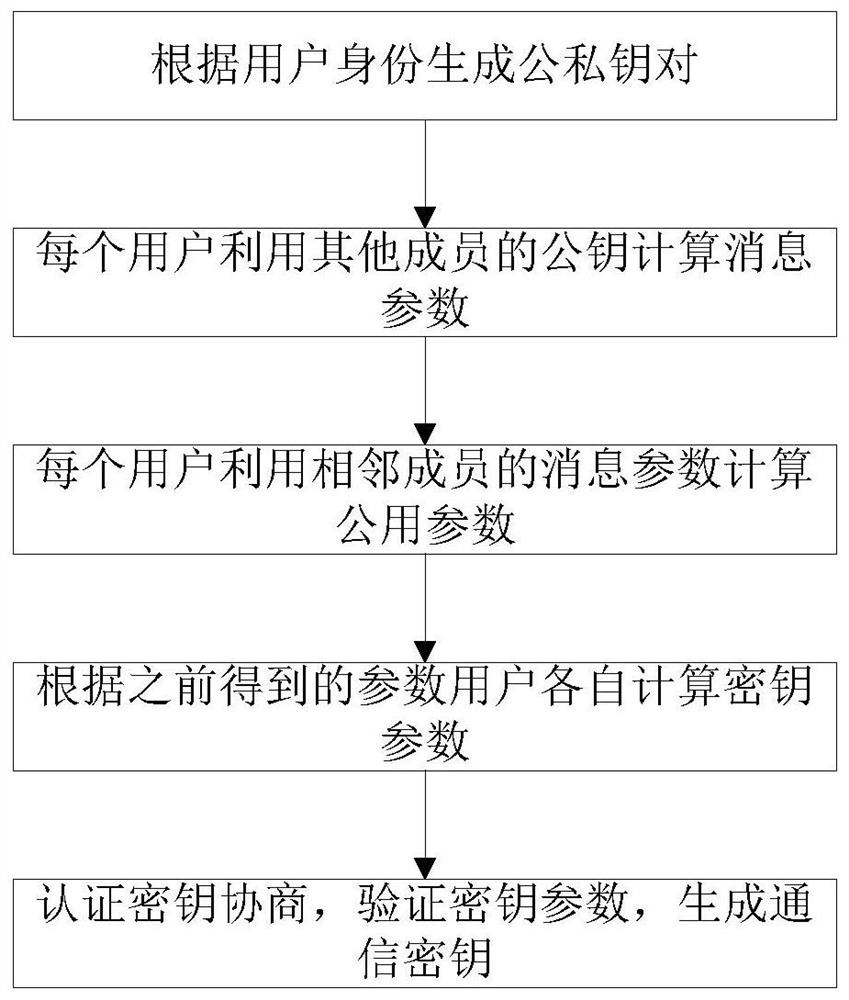
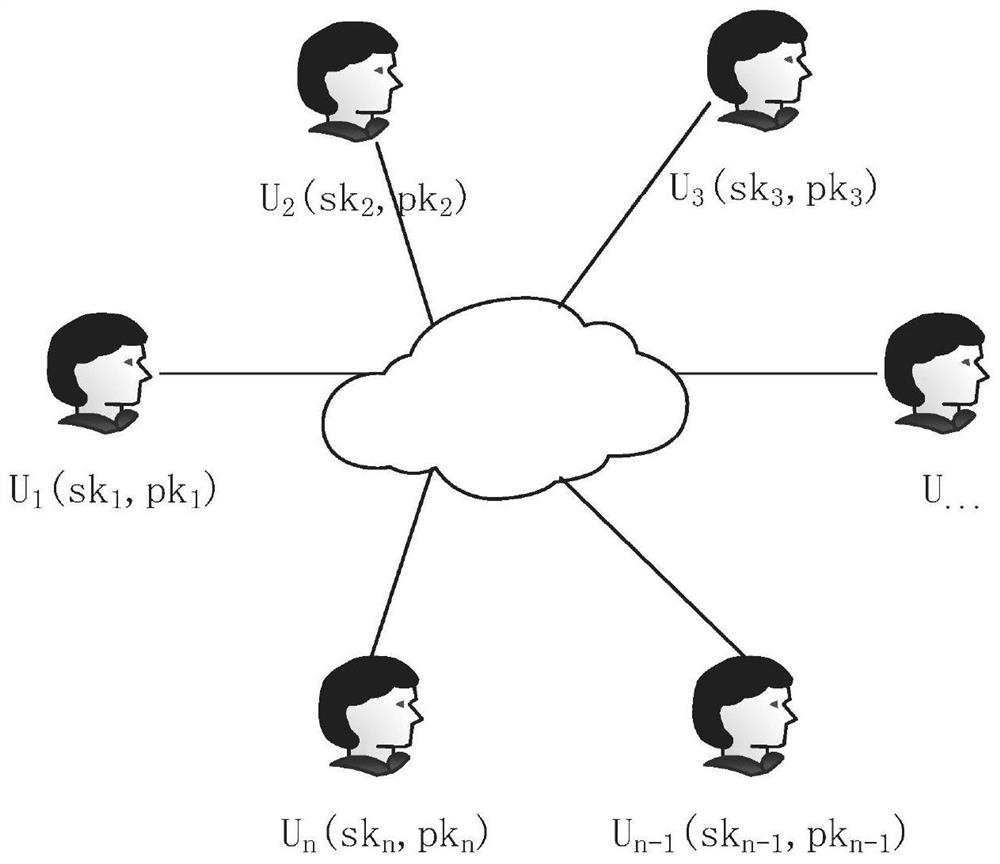
ActiveCN108667606BImprove securitySafe and Stable ExecutionKey distribution for secure communicationPlaintextAttack
The invention discloses an anti-leakage group user authentication key negotiation method and system. The anti-leakage group user authentication key negotiation system is a group composed of n user members; each user has a pair of private and public keys; and the key has a public key encryption algorithm which can meet adaptive selection of plaintext afterward leakage attack security and specifically comprises a key generation algorithm, an encryption algorithm and a decryption algorithm. The method comprises five parts, including, system initialization, first interaction for generation of message parameters, second interaction for generation of public parameters, third interaction for generation of key parameters, and authentication key negotiation for verification of the key parameters and generation of a system communication key. The anti-leakage group user authentication key negotiation method and system have reached to the provable safety in cryptology, are high in safety, can be still implemented safely and stably in a leakage environment and have very high practicability; by combining with a public key encryption algorithm, an anti-leakage group authentication key negotiationprotocol is provided, and a scheme efficiency is increased.
Owner:HUBEI UNIV OF TECH
Device area provable security verification method against collusion attack
The invention discloses an equipment area provable security verification method with resistance to collusion attack and mainly solves the problem of absence of a security verification method with areas as credential information in existing position-based cryptography technologies. The implementation scheme of the method comprises steps as follows: a provable security verification model is built, and a prover is located in a target area; verifiers select information sources and random series and share information with one another, and the verifiers replay information in a broadcasting manner; a metric value is generated by the prover, and a verification value is calculated, and position information of the prover is broadcasted; the verifiers verify correctness of the verification value, whether the position information of the prover is accepted is judged, if the verification value passes the verification, the position information of the prover is broadcasted, otherwise, the verification value does not pass the verification, that is, the position claimed by the prover is not in the area, and the verification is finished. According to the method, any prover in the target area can effectively resist the collusion attack of multiple opponents after verification, and the security verification of the position of the prover is realized. The method can be used for verifying whether the equipment, namely, the prover, is located in the target area.
Owner:XIDIAN UNIV
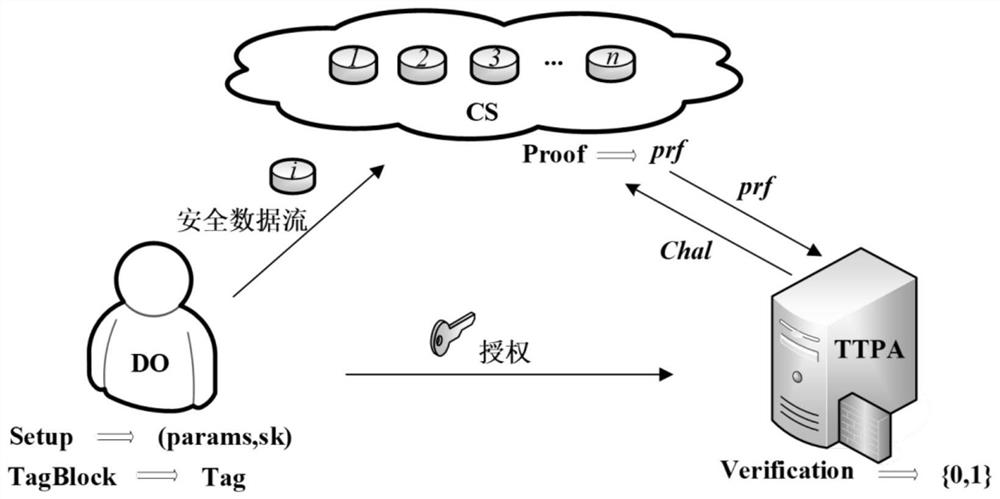
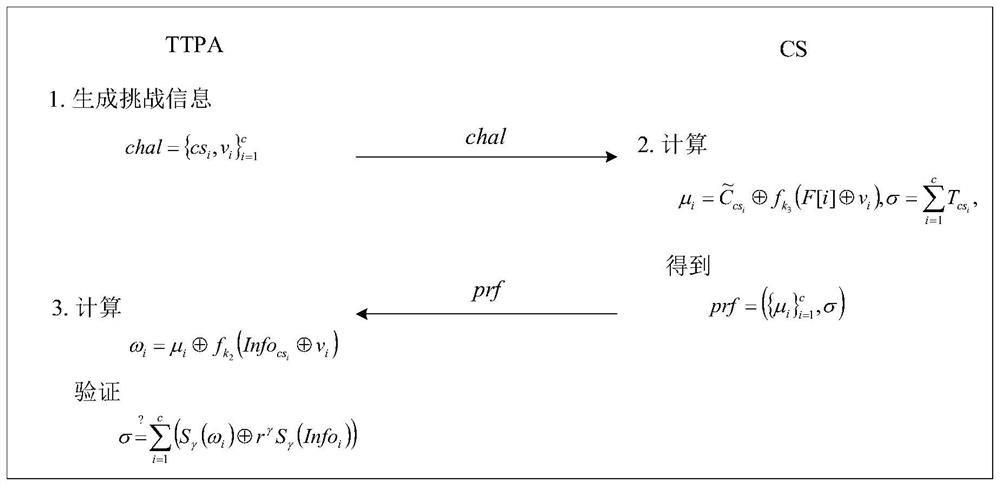
An Efficient and Safe Outsourcing Big Data Auditing Method in Cloud Environment
ActiveCN109145650BLow computational costLess computational costDigital data protectionTransmissionThird partyData integrity
The invention discloses an efficient and safe outsourced big data auditing method in a cloud environment. Based on algebraic signatures and XOR homomorphic functions, by adopting algebraic signature technology, the invention has lower calculation overhead and communication costs compared with the prior art. In addition, the present invention introduces TTPA, a trusted third-party auditor, to implement big data integrity verification through TTPA, effectively reducing the computing overhead of data owners. The security proof shows that the proposed scheme is provably secure under the security model. The performance analysis shows that, compared with the existing schemes, the present invention has less calculation overhead for the server, and effectively reduces the calculation, storage and communication costs of the verifier during the verification process.
Owner:JINAN UNIVERSITY
An AES Mask Encryption Method Against High-Order Power Analysis
ActiveCN107070633BResistance to Higher Order Differential Power AnalysisKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPower analysisAttack
Owner:日照市财金大数据有限公司
A method and device for key distribution and reconstruction based on mobile Internet
InactiveCN104754570BIncreased risk of deviating from agreementIncrease the number of expected execution roundsKey distribution for secure communicationUser identity/authority verificationComputer networkAttack
The present invention provides a key distribution and reconstruction method based on the mobile Internet, which includes the following steps: S1, constructing an identity-based key encapsulation model and a verifiable random function; S2, distributing the key; S3, The key is reconstructed. Design a computable anti-collusion equilibrium method, construct an anti-collusion entropy game model of the protocol, and prevent participants from colluding to attack; construct a communication game model of a cryptographic protocol, and make up for the defect that the cryptographic protocol constructed under the broadcast communication network cannot be implemented in the mobile Internet environment ; study the key encapsulation mechanism suitable for verifiable random functions, design a rational key sharing protocol without public key infrastructure, and ensure the fairness and delivery of computing in the mobile Internet environment; finally, use the provable security theory to analyze the protocol Conduct security analysis and proof.
Owner:HENAN NORMAL UNIV
A Lattice-Based Digital Signature Method
ActiveCN110138549BResist attackImprove securityKey distribution for secure communicationUser identity/authority verificationAlgorithmDigital signature
The invention relates to a lattice-based digital signature method, aiming at designing an efficient anti-quantum safe digital signature method based on the mathematical difficulty problem on the lattice. Specifically, the present invention first proposes a class of asymmetric modular small integer solution (AMSIS) mathematically difficult problems, and also provides variants and generalizations of this type of mathematically difficult problems. Through the asymmetric deformation based on the AMSIS mathematical difficulty problem and the modular error learning (MLWE) mathematical difficulty problem, the present invention proposes a digital signature method on a lattice, which has high security, provable security, resistance to quantum computer attacks, and public-private key It has the characteristics and advantages of short signature length, high calculation efficiency, and flexible parameter selection.
Owner:北京信息科学技术研究院
Convertible proxy signcryption method with provable security
InactiveCN105071942AGuaranteed confidentialityMultiple keys/algorithms usageUser identity/authority verificationConfidentialitySigncryption
The invention relates to a convertible proxy signcryption method with provable security of cloud security control and is used for protecting privacies of users. The method mainly comprises the generation of proxy signing keys, signing, message recovery and signature verification, signature conversion and the like; the main difference between the general proxy signcryption scheme is as follows: the public keys, the proxy certificates and parameters of an original signer and a proxy signer cannot be transmitted as public parameters, and also need to be recovered as the message. The convertible proxy signcryption method with provable security provided by the invention can guarantee the confidentiality of the identities of the original signer and the proxy signer, so as to be applied to an authentication protocol of cloud computing.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
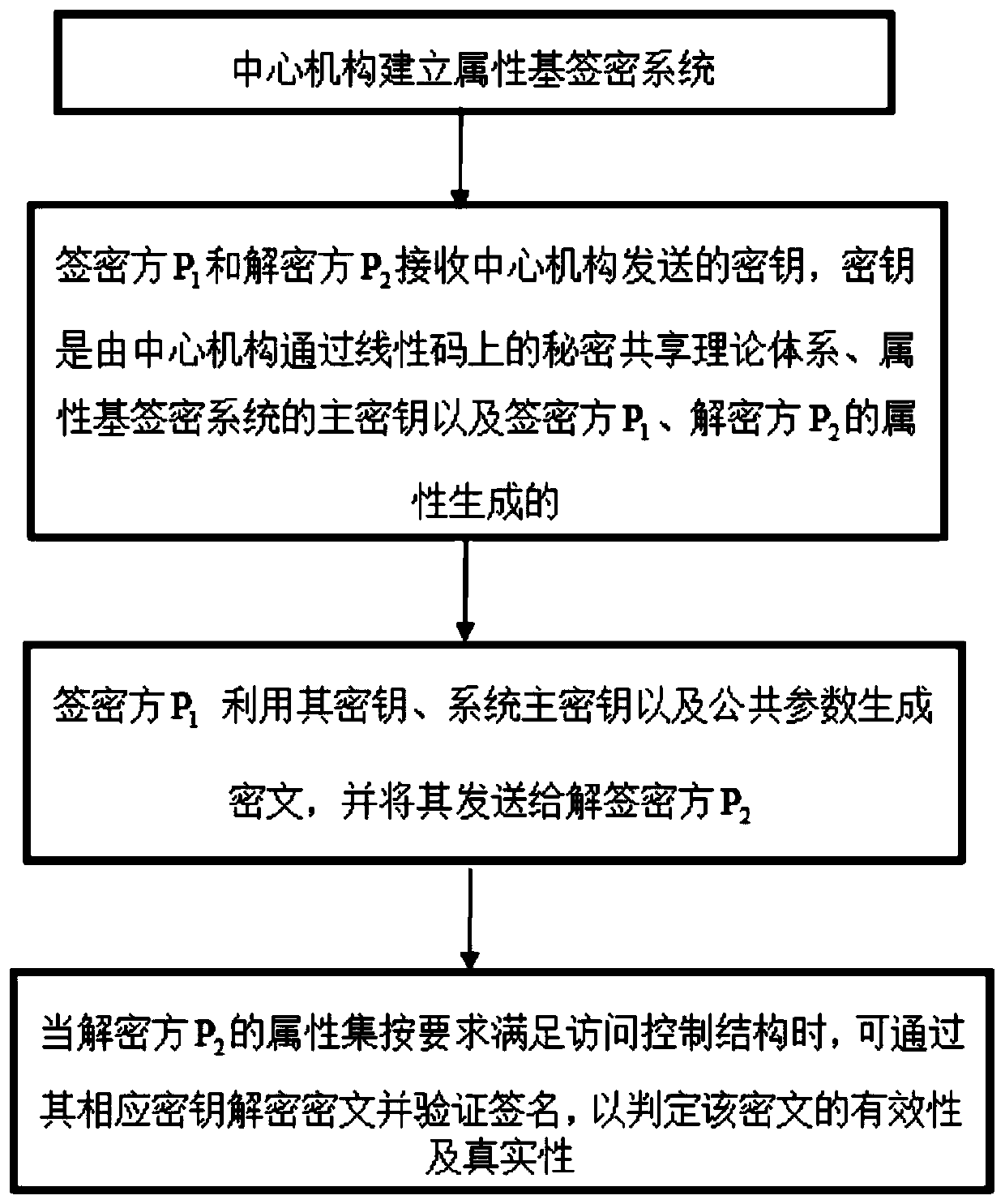
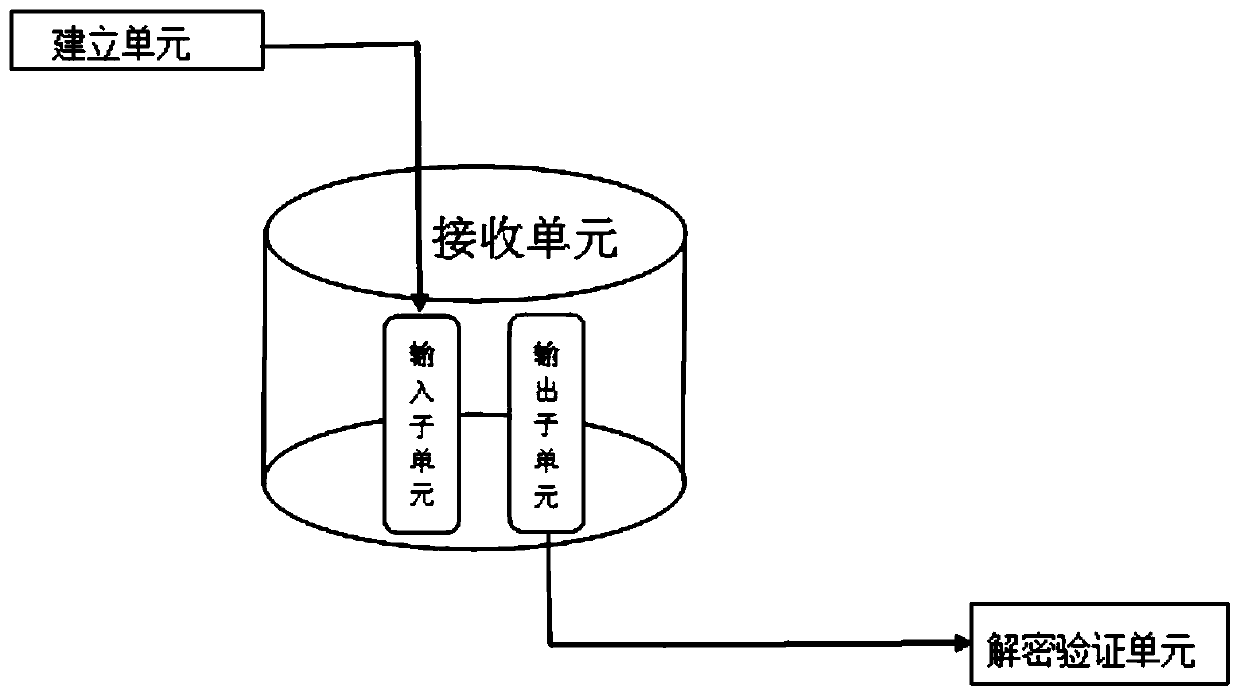
A Provably Secure Attribute-Based Signcryption Method Under Standard Model
ActiveCN107104802BGuaranteed confidentialityImprove integrityKey distribution for secure communicationPublic key for secure communicationCiphertextConfidentiality
Owner:SHAANXI NORMAL UNIV
Identity method based on public key certificate
InactiveCN1192546CFast operationUser identity/authority verificationProvable securityDiscrete logarithm
The invention relates to an identity verification method based on shared key certificates. It is a method of varying identity based on discrete logarithms with collision resist different functions and shared certificate. It is safe with a fast calculation speed, which has been proved. It can be used in identity verification so as to control storage, electric business, bills, certificates and the identity verification of information transmitters in communication
Owner:ZHEJIANG UNIV
A Lattice-Based Public Key Encryption Method
ActiveCN110138752BResist attackShorten the lengthKey distribution for secure communicationAlgorithmCiphertext
The invention discloses a lattice-based public key encryption method. The present invention first proposes a class of AMLWE mathematical difficulty problems, and also provides variants and generalized definitions of this type of mathematical difficulty problems. Based on the AMLWE mathematical difficulty problem, the present invention proposes a lattice-selected plaintext-safe public key encryption method. Based on the encryption method, the present invention also provides a key encapsulation mechanism for selecting ciphertext security and a public key encryption method for selecting ciphertext security. The public key encryption method and key encapsulation mechanism designed by the present invention have the characteristics and advantages of provable security, resistance to quantum computer attacks, short length of public key and ciphertext, high calculation efficiency, and flexible parameter selection. Using a general transformation method, the present invention also provides a (authenticated) key exchange protocol.
Owner:北京信息科学技术研究院
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com