Authentication method of Ethernet passive optical network (EPON) system
A passive optical network and authentication method technology, applied in the field of Ethernet passive optical network system authentication, to achieve the effects of preventing replay attacks, preventing tampering, and achieving good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
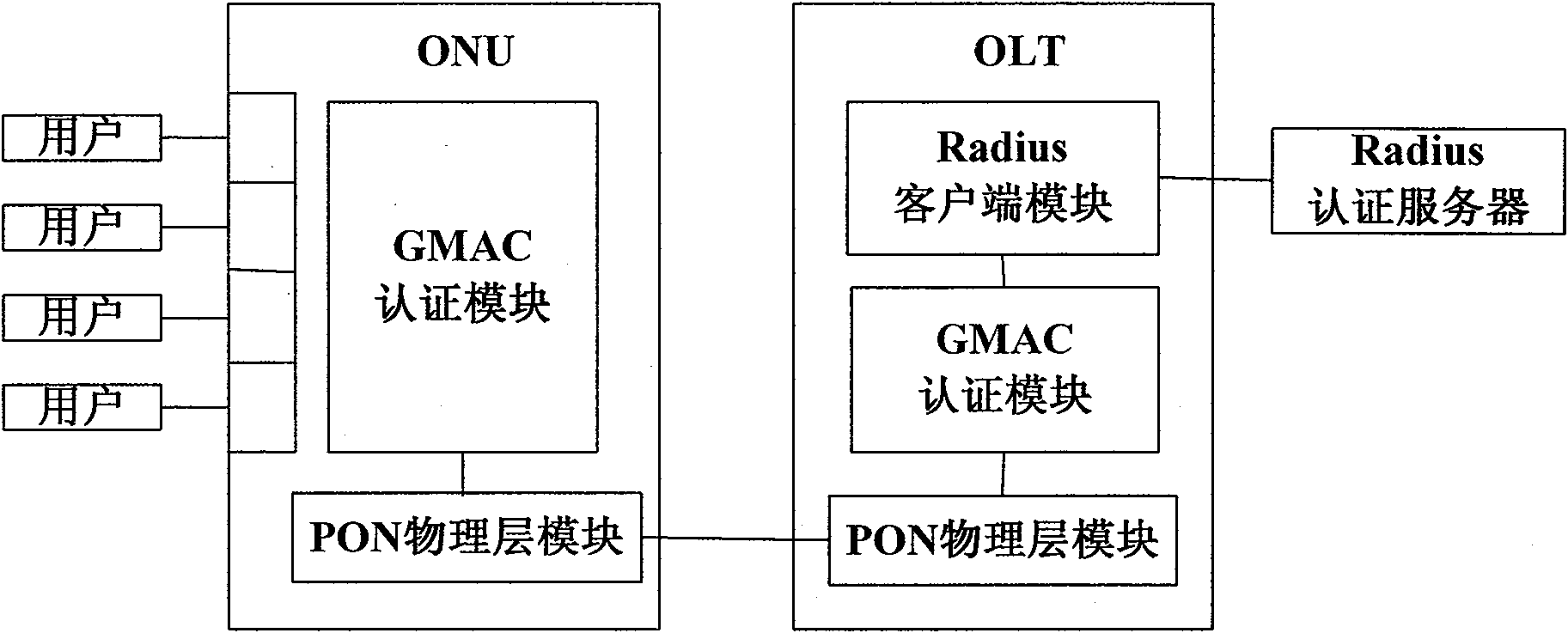
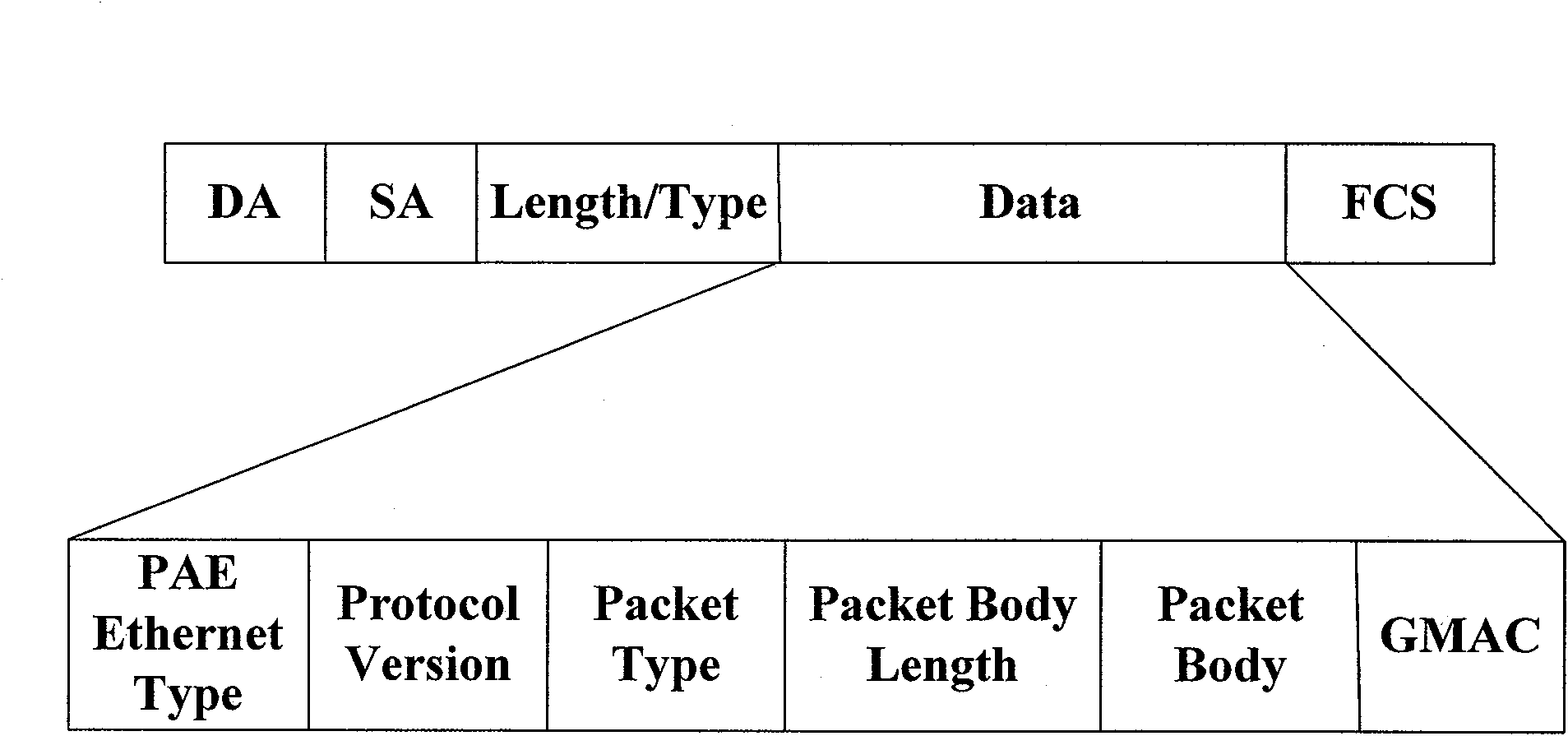
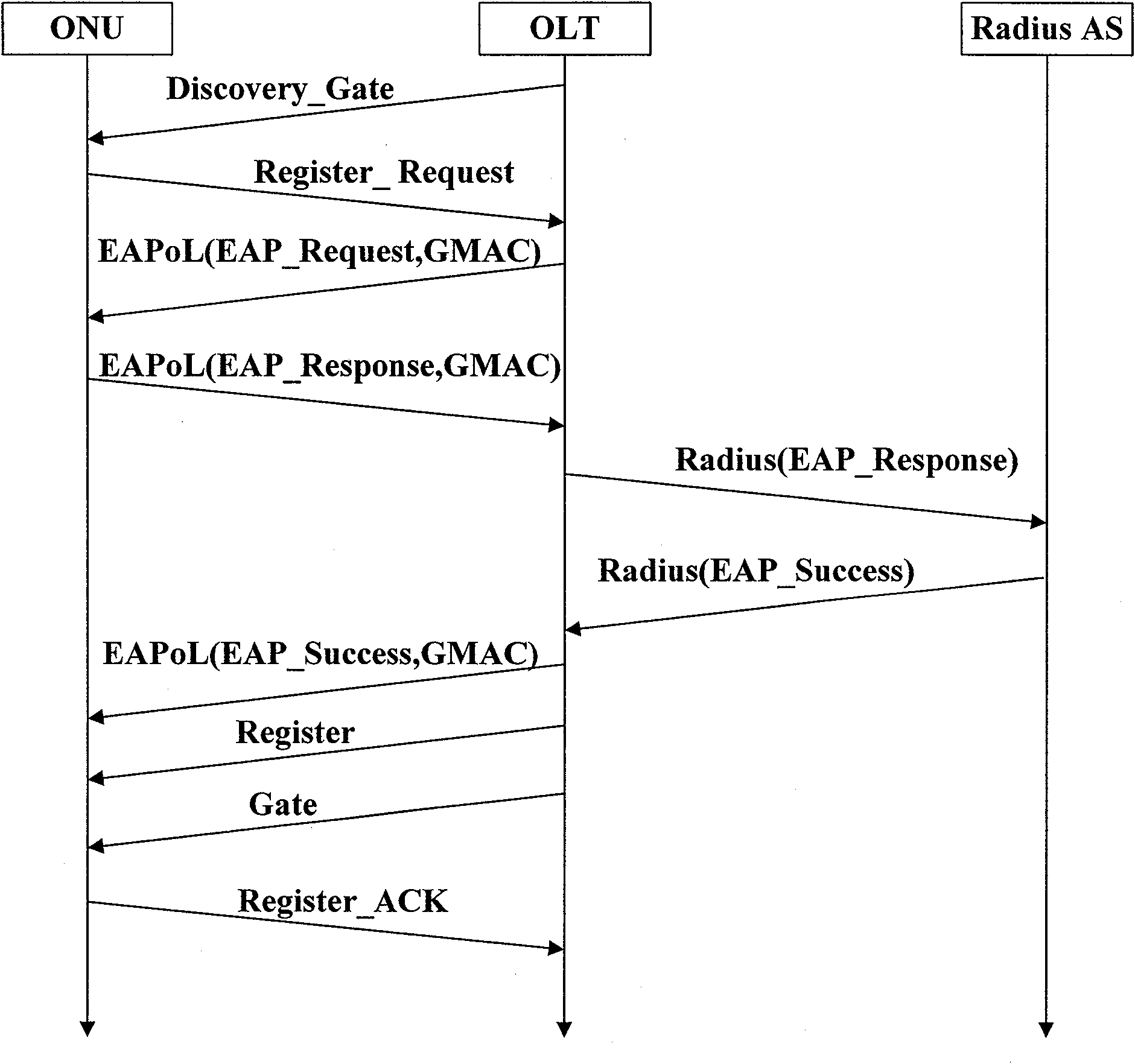
[0037] The present invention realizes the authentication process of the EPON system in combination with Galois domain message authentication code (GMAC), can support ONU authentication and user authentication at the same time, and designs the frame structure of EPON system GMAC authentication, and the protocol flow of ONU authentication and user authentication , can overcome the one-way authentication defect existing in the EPON system authentication mode under the IEEE 802.1x port access control mode, and effectively guarantee the source authenticity and data integrity of the authentication. The whole authentication process involves four parts: user, ONU, OLT and Radius authentication server. In the implementation process of ONU authentication and user authentication, they respectively assume the roles of applicant, authenticator, and authentication server to ensure that legitimate ONUs and authorized users access EPON system. Among them, the authentication module with GMAC f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com