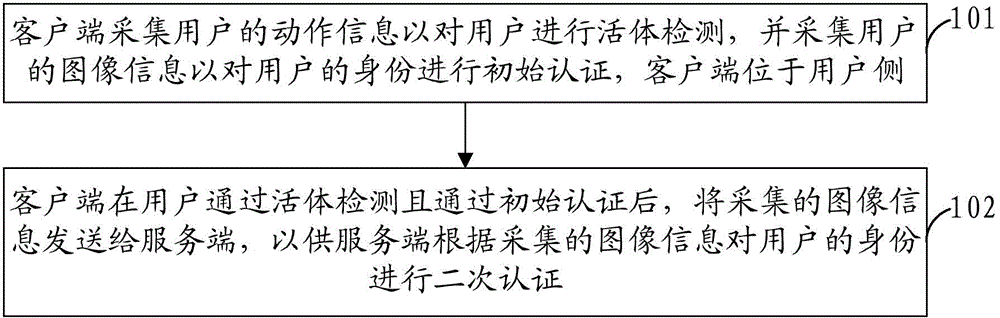
Patents
Literature
684results about How to "Improve authentication efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
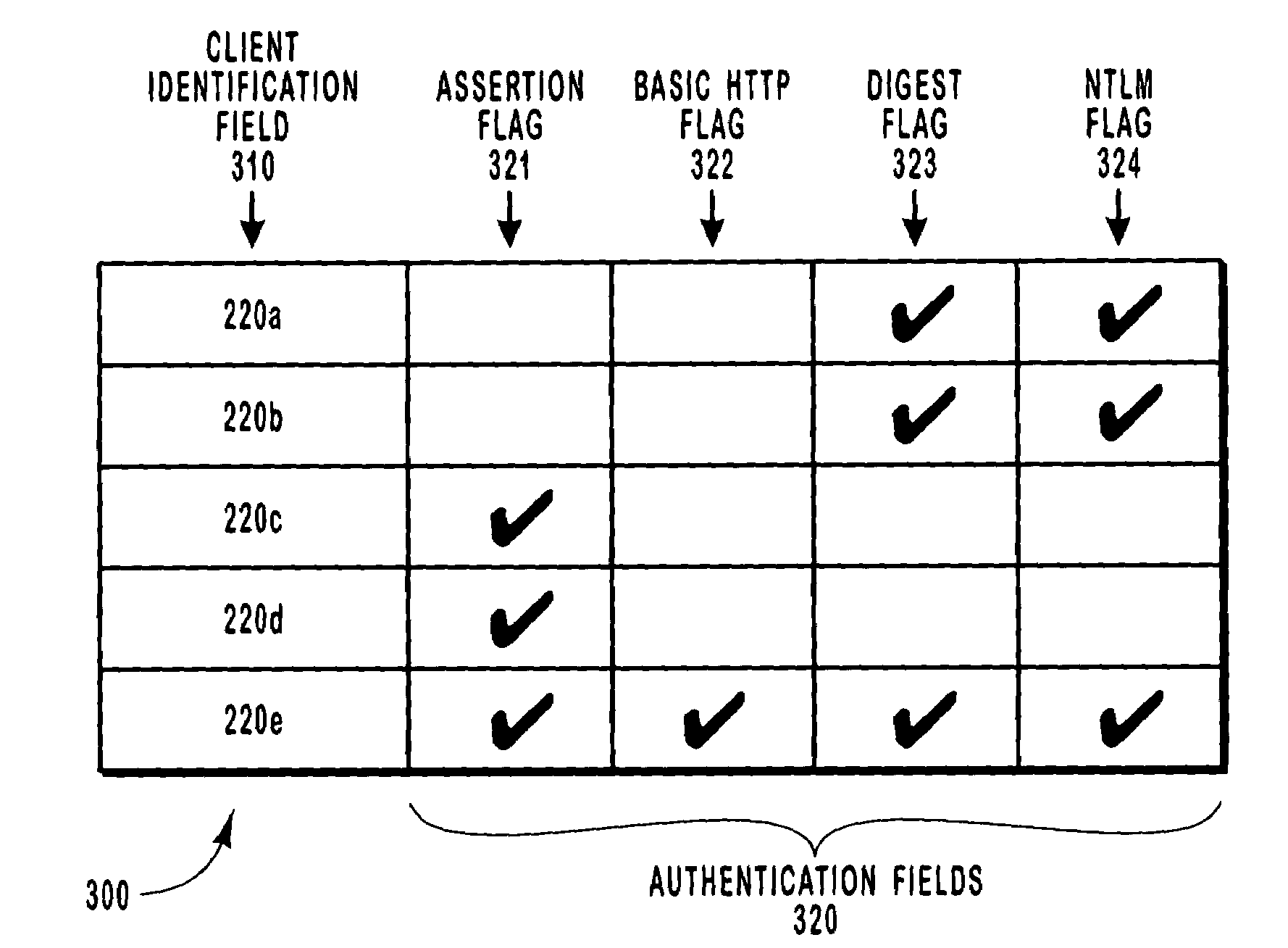
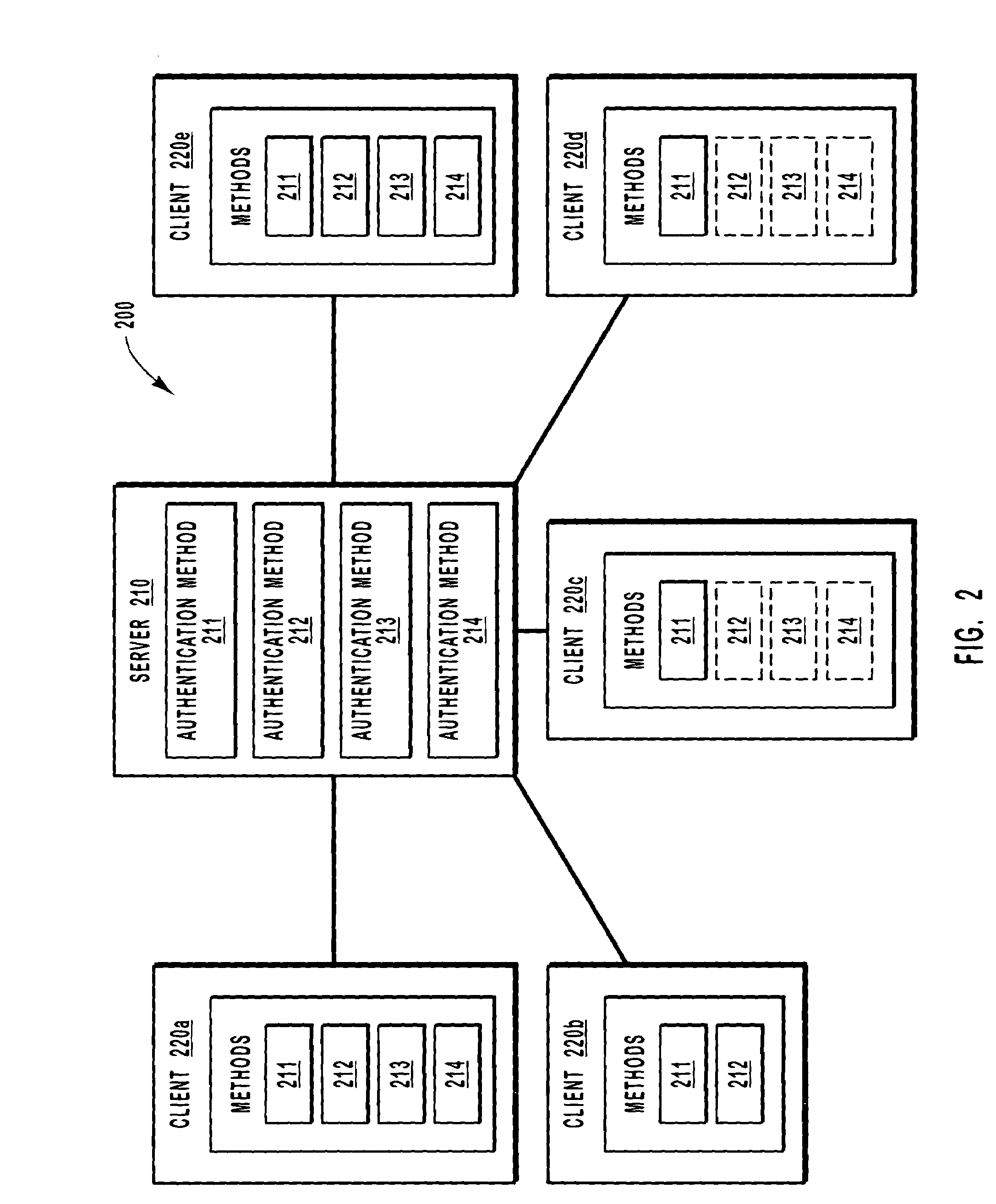
Methods and systems for selecting methodology for authenticating computer systems on a per computer system or per user basis
InactiveUS7444368B1Service degradationImprove authentication efficiencyRandom number generatorsUnauthorized memory use protectionComputerized systemClient-side
Method and systems are disclosed for enabling a computer system to generate a request that includes an instruction identifying the authentication method or methods to be used when authenticating a subset of the client computer systems or users network connected to a server computer system. The subset of client computer systems or users may include as little a single computer system or user. The request is then transmitted to the server computer system. When receiving subsequent requests for service from any of the subset of client computer systems or users, the server computer system will refer to the information in the instruction to determine which authentication methods are acceptable in authenticating the client computer system or user.
Owner:MICROSOFT TECH LICENSING LLC
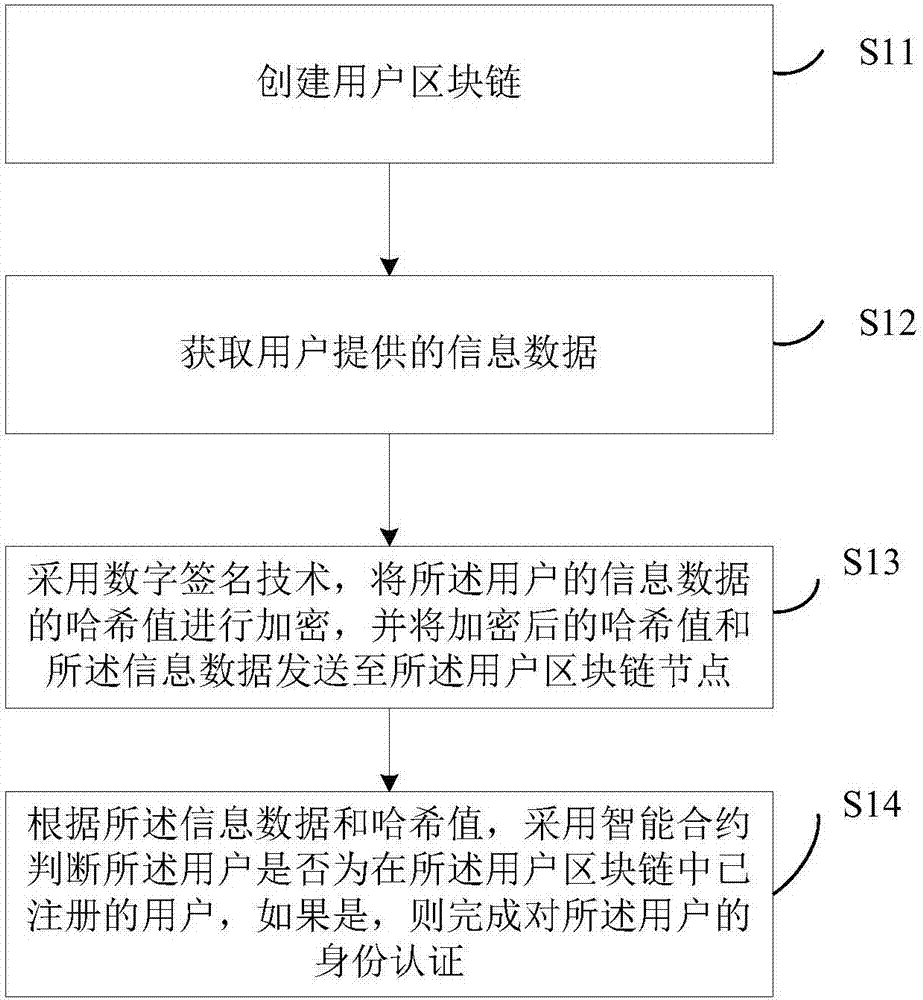
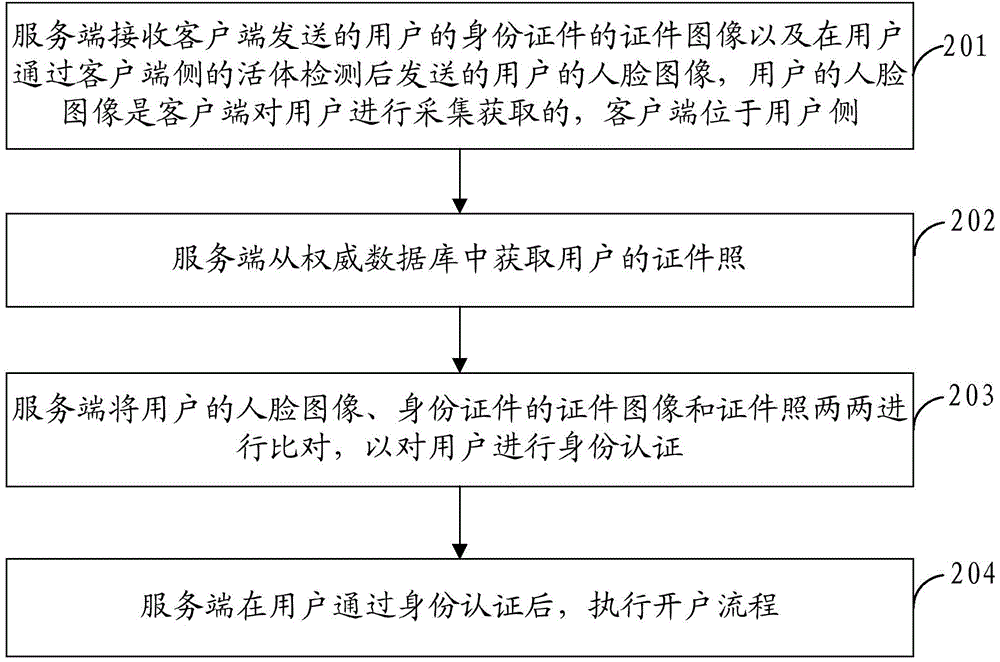
User authentication method and system
InactiveCN107257336AQuery speedQuick responseUser identity/authority verificationDigital data authenticationDigital signatureUser authentication
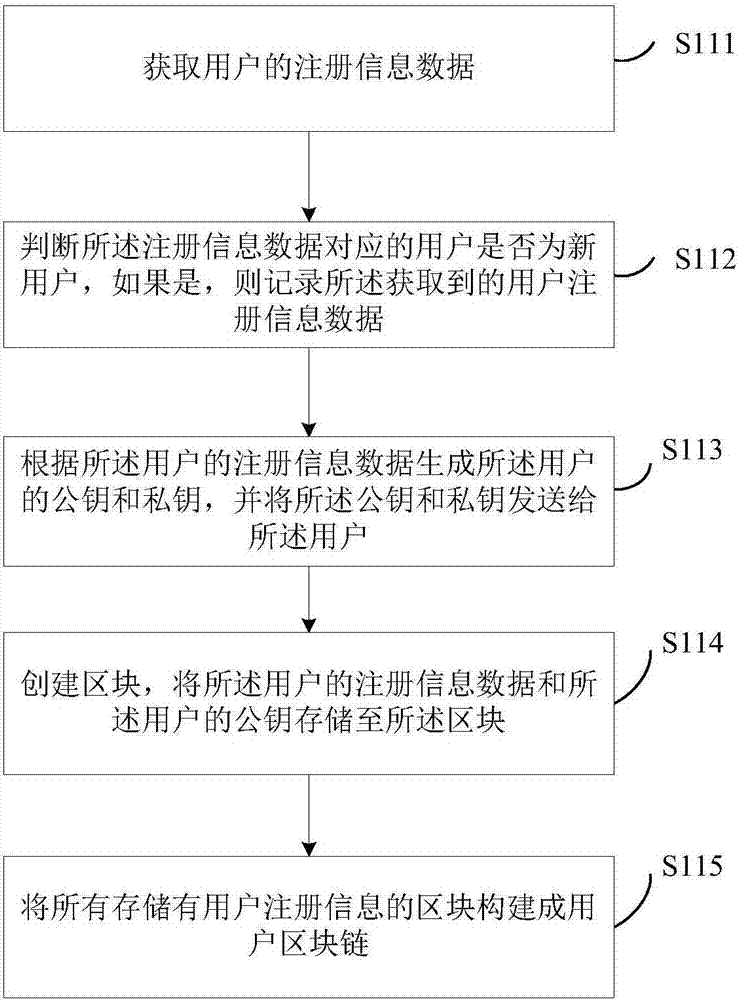
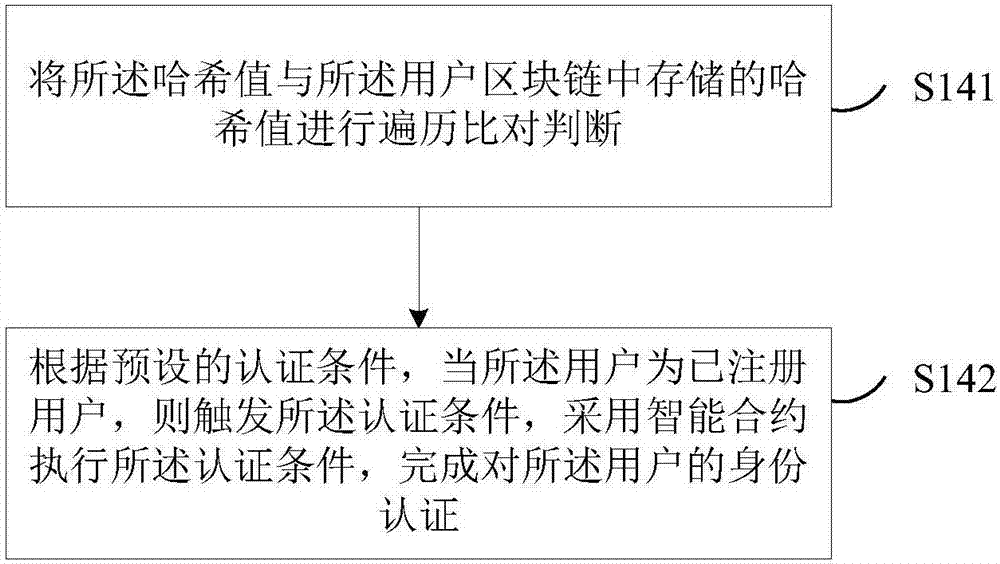
The invention discloses a user authentication method and system. The method comprises the steps of: creating a user block chain; obtaining information data provided by a user; encrypting the hash value of the information data of the user by adopting a digital signature technology, and sending the encrypted hash value and the information data to a user block chain node; and, according to the information data and the hash value, judging whether the user is a user registered in the user block chain or not, and if so, completing identity authentication of the user. By means of the user authentication method and system disclosed by the invention, the purpose of ensuring security of the user information and relatively high authentication efficiency can be achieved.
Owner:BEIJING HUITONG JINCAI INFORMATION TECH +2
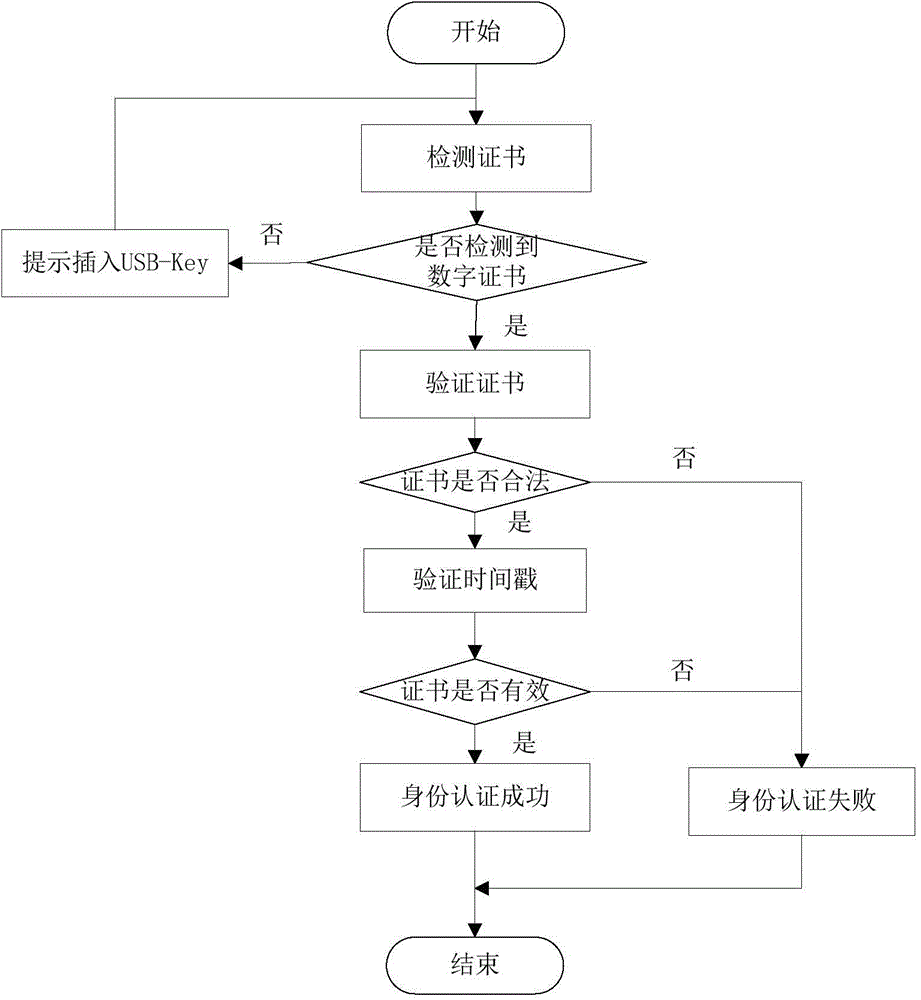
Device and method for identity authentication of person and identity card based on face recognition
InactiveCN106778607AImprove authentication efficiencyImprove accuracySpoof detectionFeature vectorValidation methods
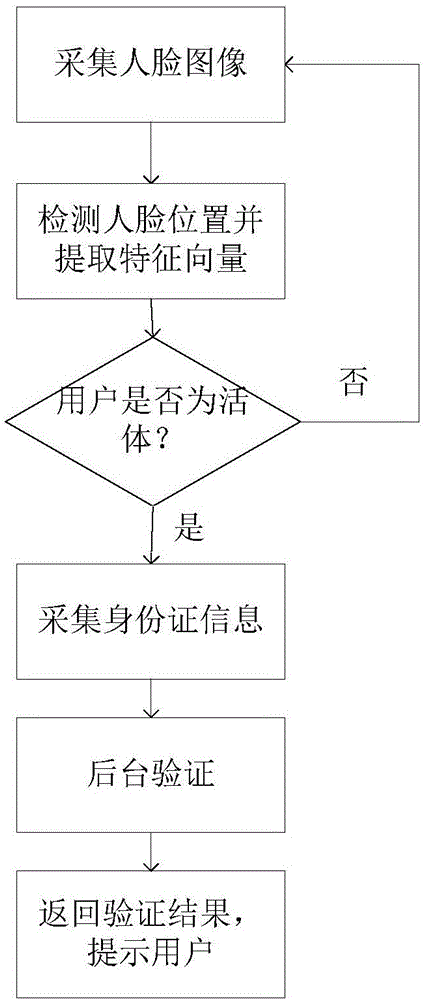
The invention discloses a method and device for identity authentication of a person and an identity card based on face recognition. The method for identity authentication of a person and an identity card based on face recognition comprises the following steps: collecting the face image; detecting the position of the face and extracting the feature vectors according to the face image; confirming whether the user is a live object or not, if not, returning and collecting the face image again; if so, collecting the identity card information; transmitting the extracted feature vectors and the identity card information to the background for authentication; returning the authentication results and prompting the user, which are performed by the background; if authentication is passed, updating the local and remote databases. According to the invention, the authentication efficiency of the ''witness the same'' is improved. The method for identity authentication of a person and an identity card based on face recognition is convenient for large-scale application in various occasions, and can solve the technical problems that the authentication is inaccurate caused by the slight change of the face due to the passage of time, the authentication to the person without carrying the identity card is difficult, and the like.
Owner:BEIJING GZT NETWORK TECH
Biometrics-based device for detecting indentity of people and identification
InactiveCN101669824AReduce work intensityReduce error ratePerson identificationCharacter and pattern recognitionFace detectionProcess module
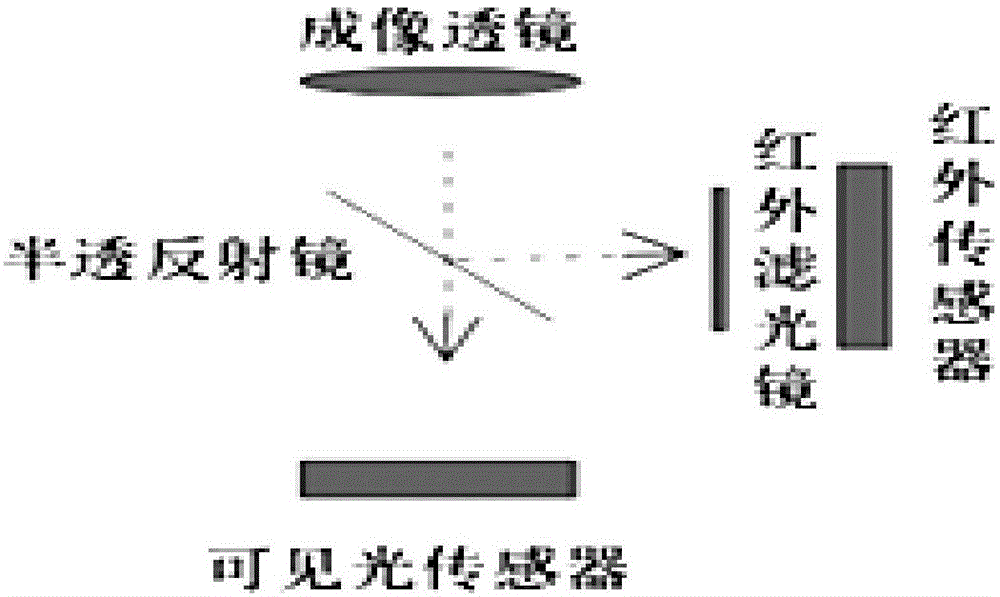
The invention discloses a biometrics-based device for detecting identity of people and identification, which comprises an omni-directional vision sensor used for acquiring the facial image of an ID card holder, an ID card reader used for reading the photograph information in a bulit-in chip of the second-generation ID card and a microprocessor used for comparing whether the facial photograph imagestored in the built-in chip of the second-genration ID card and the facial images acquired by the omni-directional vision sensor are consistent or not, wherein the microprocessor comprises a data module used for reading photograph image in the ID card, a first facial detecting module, a first facial feature extraction module, a panoramicpicture reading module, a second facial detecting module, animage expanding module, a second facial feature extraction module, an identity detecting module for the biological feature of people and the ID card and a decision-layer voting and processing module.The device adopts biometrics identification technology, can greatly improve the efficiency for validating the ID card, and reduce the working strength and error rate of office personnels.
Owner:ZHEJIANG UNIV OF TECH
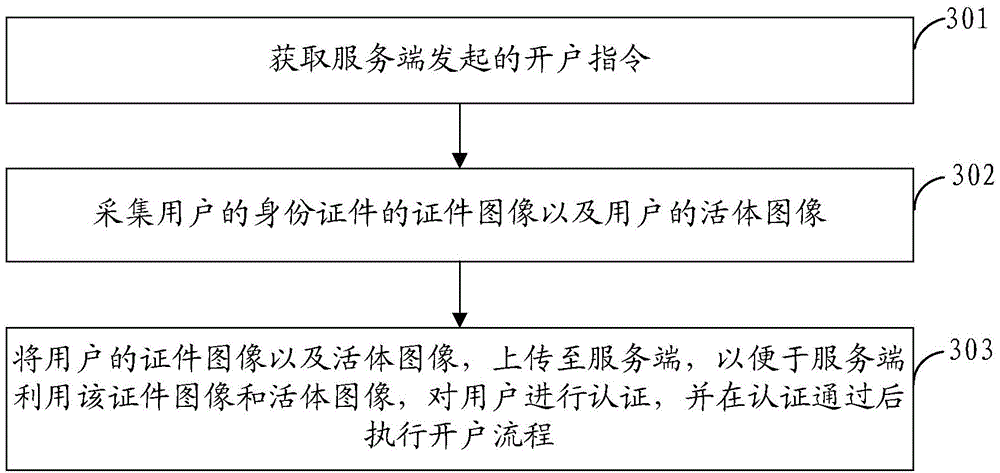
Method for authenticating identities, method for opening accounts, devices and systems
InactiveCN105989263AEnsure safetyPrevent Phishing AttacksDigital data authenticationComputer scienceAuthentication
The invention provides a method for authenticating identities, a method for opening accounts, devices and systems. The method for authenticating the identities includes acquiring action information of users by the aid of a client to carry out bioassay on the users and acquiring image information of the users to initially authenticate the identities of the users; transmitting the acquired image information to a server by the client after the users pass the bioassay and the identities of the users are initially authenticated, and secondarily authenticating the identities of the users by the aid of the server according the acquired image information. The client is positioned on a user side. The methods, the devices and the systems have the advantages that the identity authentication efficiency can be improved, and the implementation cost can be reduced.
Owner:ADVANCED NEW TECH CO LTD
Mobile ad hoc authentication method, network and system
InactiveCN101192928AImprove efficiencyMake the most of processing resourcesEnergy efficient ICTUser identity/authority verificationNetwork structureMobile ad hoc network
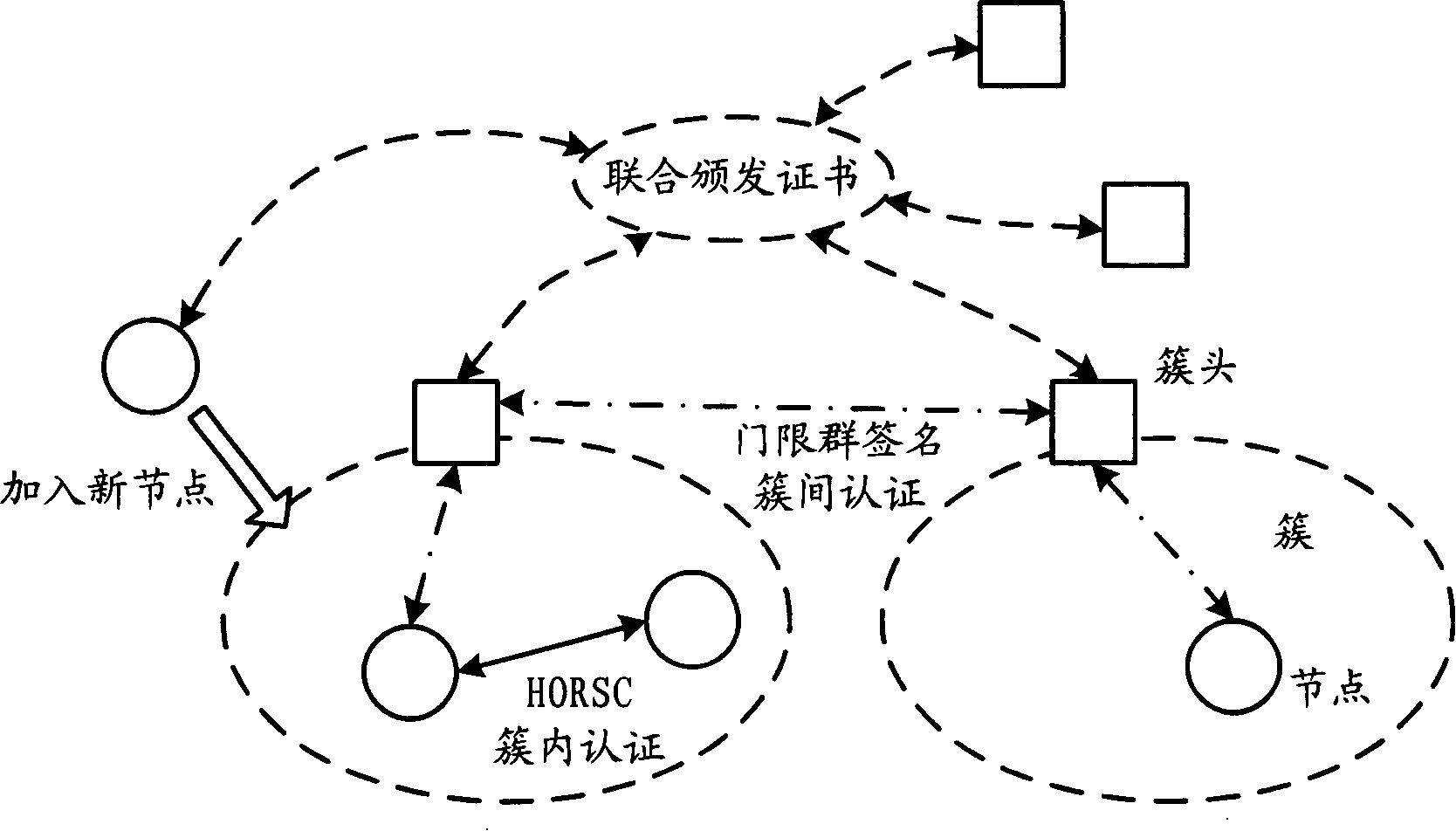
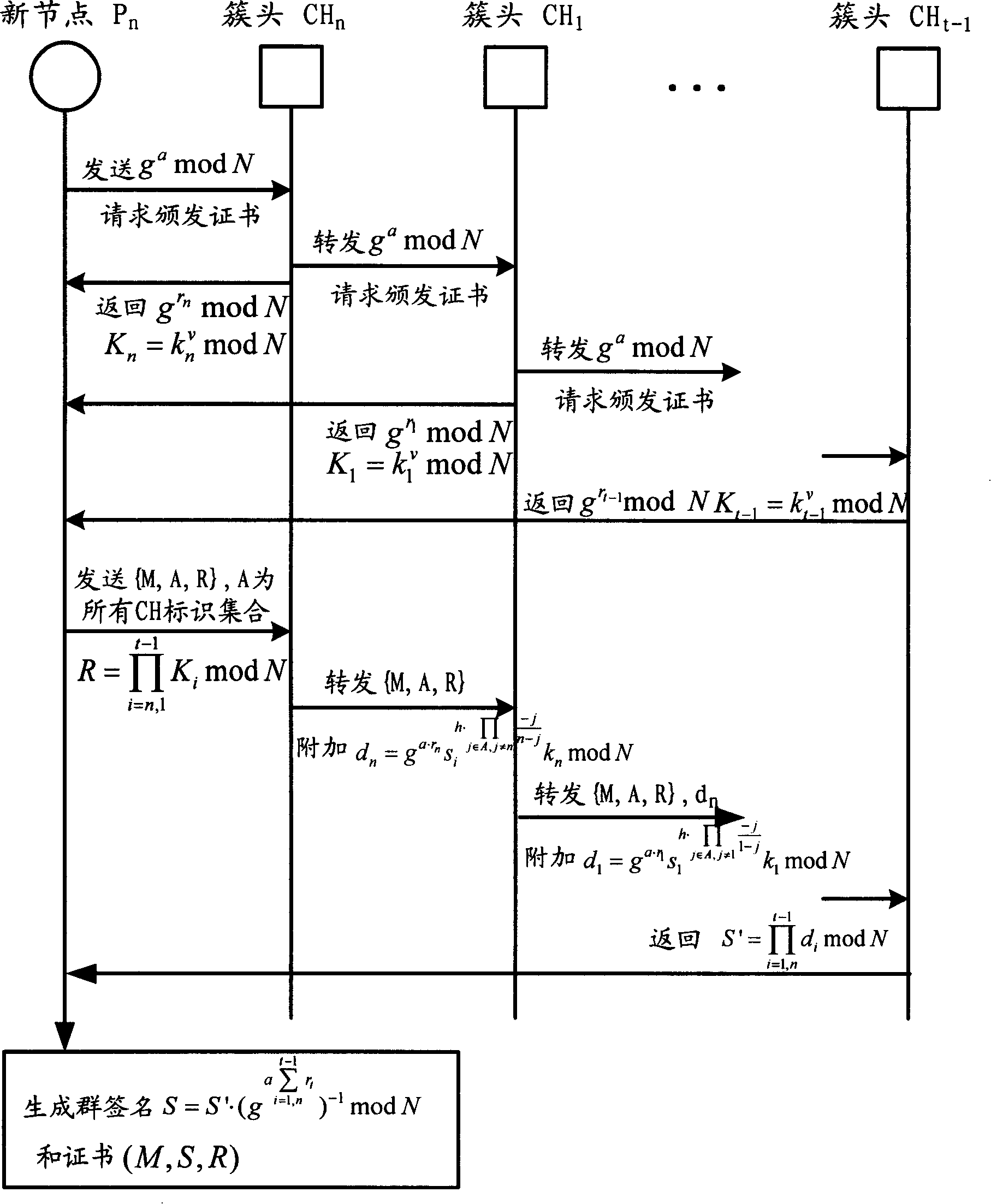
The invention relates to the communication field and discloses an authentication method, a network and a system of mobile ad hoc network, which ensures the realization of layer distribution type authentication scheme of cluster mobile ad hoc network; and the requirement on computer processed resources is rational, which can be realized in practical application environment. The invention adopts a group network structure of cluster mobile ad hoc network and advocates layer distribution identity authentication scheme; and the inter-cluster communication used an improved new threshold group signature protocol which improves the original threshold group signature method based on GQ and decreases power index calculation times, improves calculation parallelism and reduces the requirement on processed resources; at the time of initialization, a certificate and a sub key are issued by the system uniformly; cluster heads which have enough numbers of sub keys can jointly recover system keys, thereby carrying out the group signature to issue certificates to new added nodes and using multi-leap serial communication for realizing united group signature.
Owner:HUAWEI TECH CO LTD +1
Authentication method and system for wireless local area network terminal
InactiveCN102196434AImprove authentication efficiencyNetwork topologiesSecurity arrangementPasswordSecret code
The invention discloses an authentication method for a wireless local area network terminal, which comprises the following steps of: receiving a user login authentication information-carried Internet access request message sent by a terminal, by network-side equipment, wherein user login authentication information is generated and transmitted to a terminal to be stored by the network-side equipment when the previous login of the terminal is successful, and comprises user information and an authentication-free period; applying the user information in the received user login authentication information to authenticate the terminal when the network-side equipment judges that the terminal is just within the authentication-free period according to the authentication-free period in the received user login authentication information; and the network-side equipment sends a successful authentication message to the terminal after the authentication is successful. When the authentication method and system are adopted, the problem of low authentication efficiency caused by needing a user to repeatedly input a user name and a password in the authentication process of a wireless local area network in the prior art is solved.
Owner:CHINA MOBILE COMM GRP CO LTD
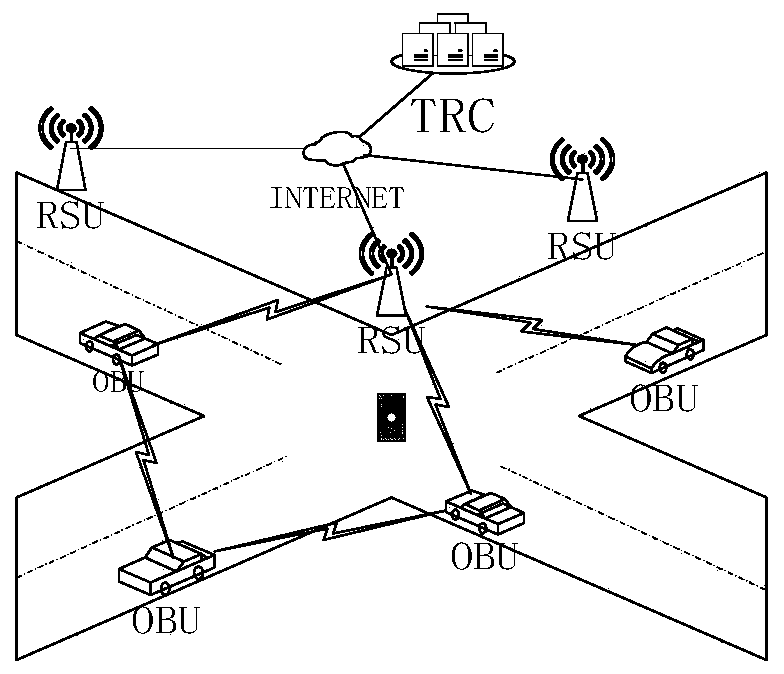
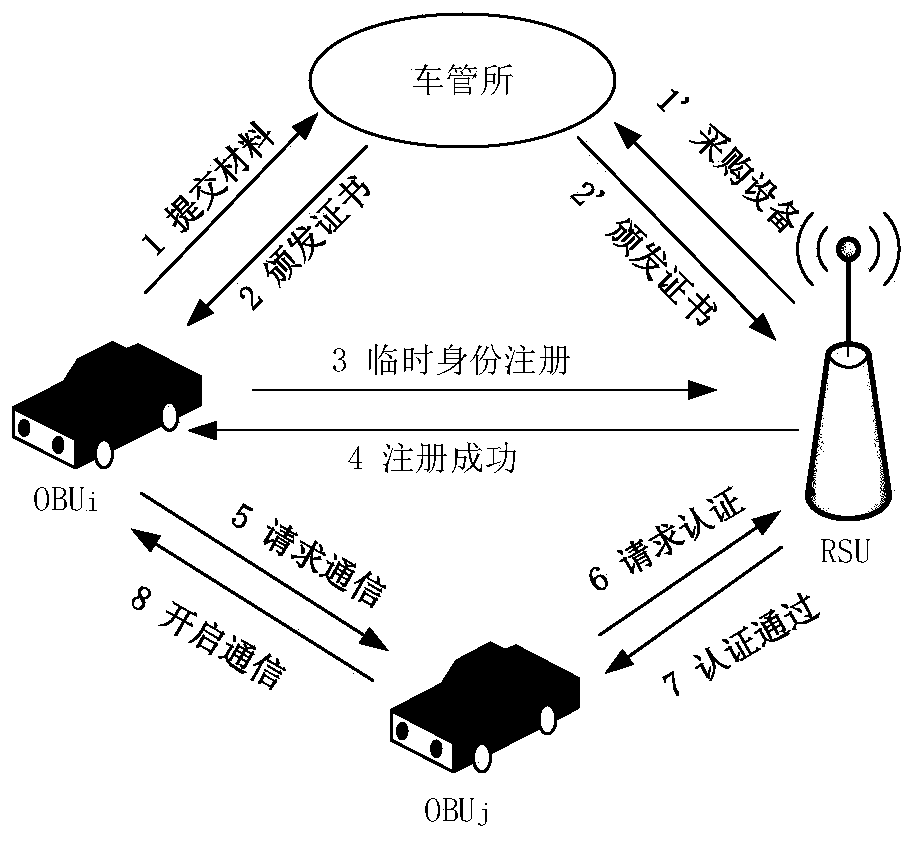
Car networking authentication and key agreement method based on certificateless aggregation signature
ActiveCN108471351ATroubleshoot hosting issuesEliminate administrative overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRandom parametersComputer science
The invention discloses a car networking authentication and key agreement method based on certificateless aggregation signature. The method mainly comprises the following steps: A, establishing a key:a public-private key pair of a vehicle is bound to a real identity, and even if the temporary identity changes, the vehicle public-private key pair is not updated; B, registration and authorization:a random number for vehicle application and the real identity of the vehicle are stored in a constructed temporary identity index database; C, authentication and key negotiation: by introducing a random parameter, the vehicle reconstructs a secret pre-signature issued by a registration tracking center for the vehicle temporary identity in the authorization issuance stage, and a roadside facility (RSU) aggregates and forwards the signature information of the vehicle; and the method has conditional anonymity, can resist temporary private key compromise attacks and is high in security, high in authentication efficiency and low in system overhead.
Owner:蓝马舱行智能科技(上海)有限公司
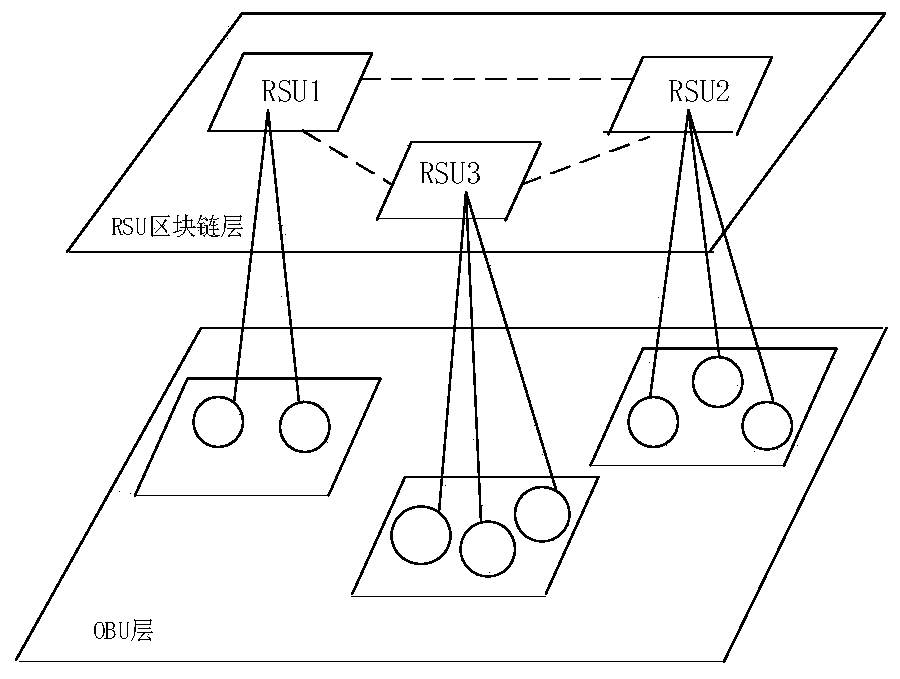
Motorcade establishment and management method and system based on block chain and PKI authentication mechanism
ActiveCN109687976ASolve authentication problemsTroubleshoot account management issuesKey distribution for secure communicationParticular environment based servicesSecure communicationThe Internet
The invention belongs to the technical field of safety communication between motorcades in Internet of Vehicles, and discloses a motorcade establishment and management method and system based on a block chain and a PKI authentication mechanism. The method is mainly divided into two parts of motorcade establishment and group key agreement and update; the motorcade establishment part comprises the following main processes of member registration, member identity authentication and group head aggregate signature; and the group key agreement and update part comprises the following main processes ofgroup key agreement and group key update for dynamic joining and exiting of a vehicle. According to the method and the system, the block chain is combined with the PKI authentication mechanism, a problem of identity authentication of the vehicle, a server and an RSU in the Internet of Vehicles is solved; the motorcade establishment is completed based on an elliptic curve, a bilinear pairing technology and an aggregate signature; and the group key agreement and update can be realized based on a DDH difficulty problem, the forward and backward safety is achieved, and the safety of member communication in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
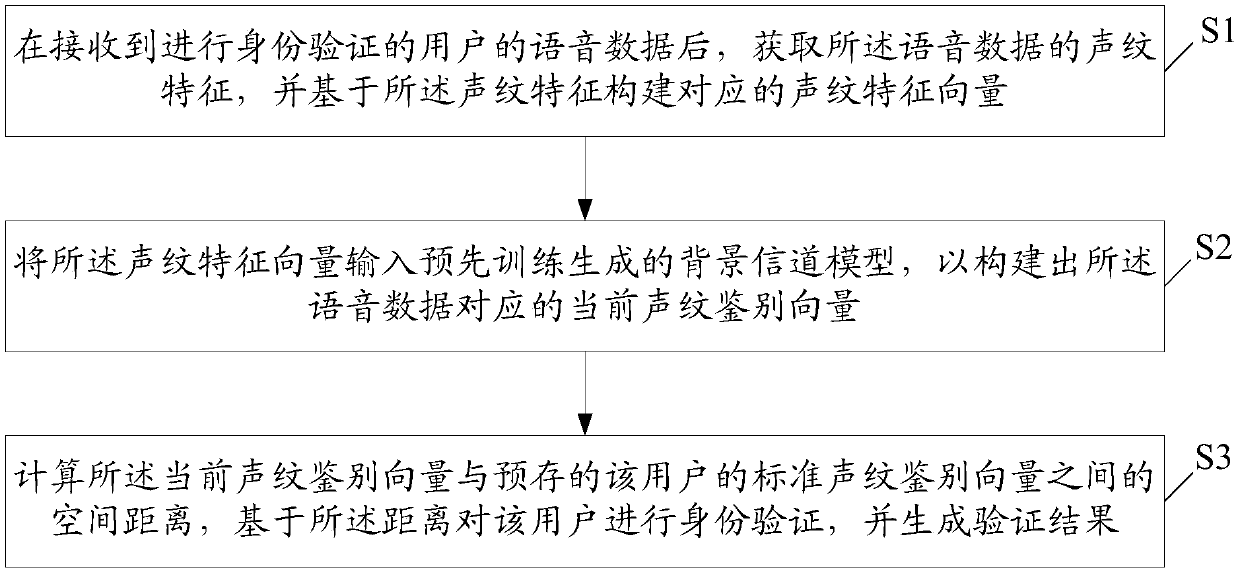
Identity verification method and system based on voiceprint recognition
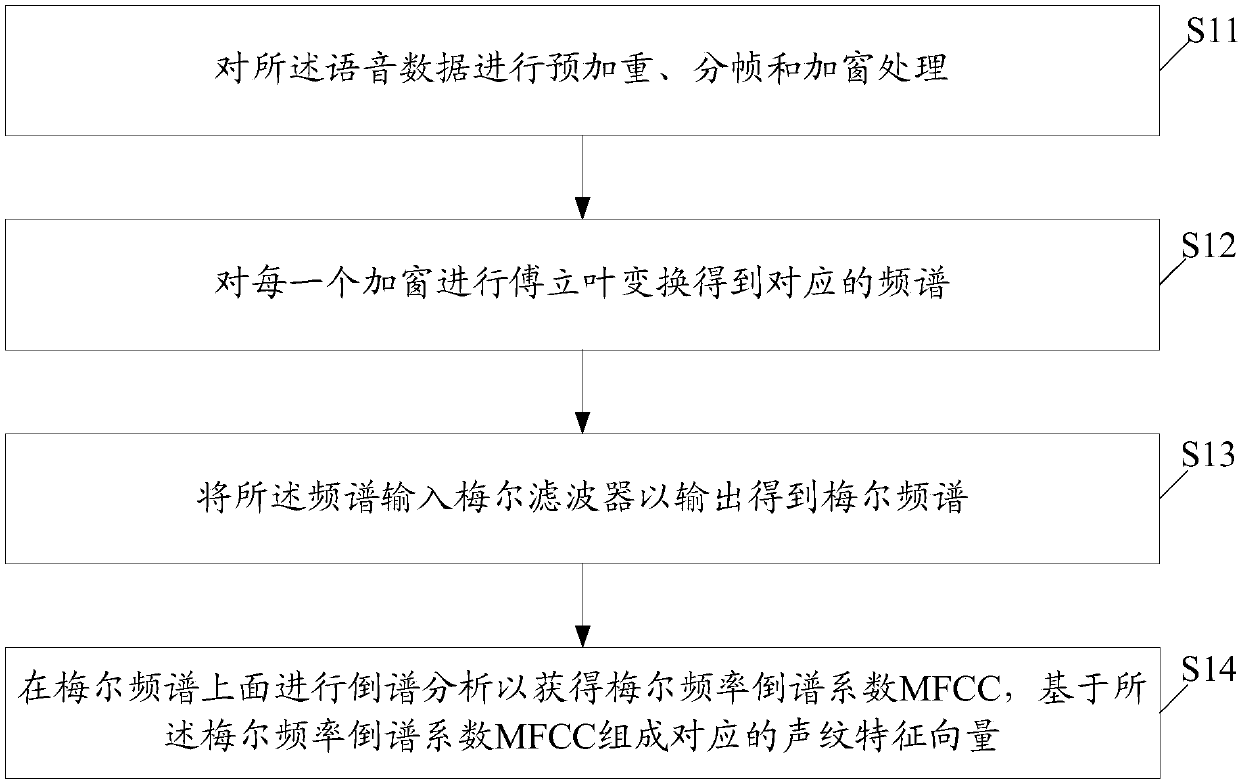
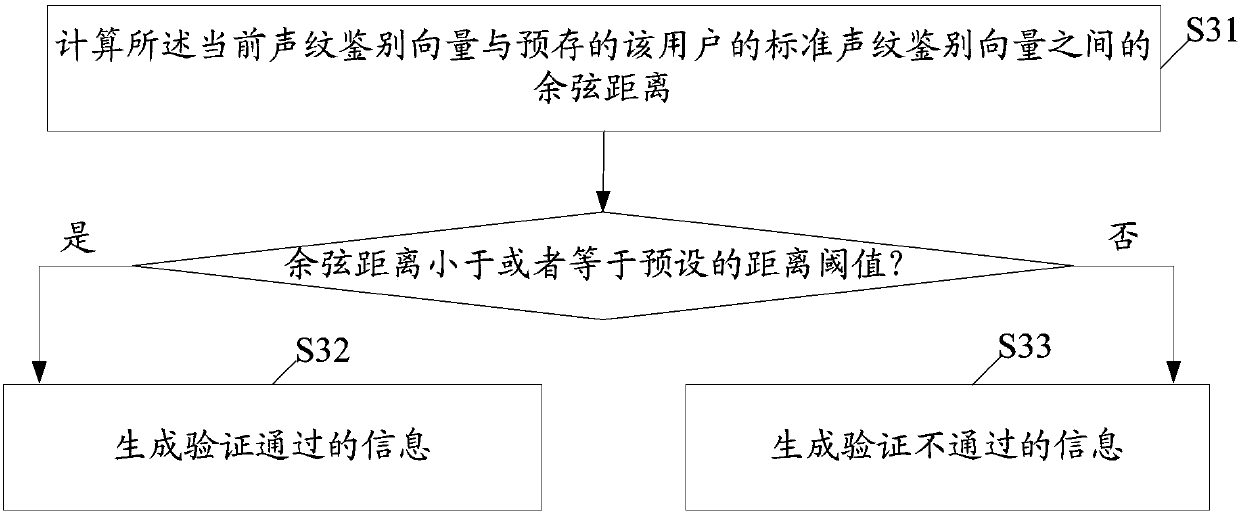
InactiveCN107068154APreserve voiceprint featuresAccurately describe the characteristics of the background voiceprintSpeech recognitionTransmissionFeature vectorUser authentication
The invention relates to an identity verification method and system based on voiceprint recognition, and the method comprises the steps: obtaining the voiceprint features of voice data after the voice data of a user, the identity of who will be identified, is received, and constructing a corresponding voiceprint feature vector based on the voiceprint features; inputting the voiceprint feature vector into a pre-trained generated background channel model, so as to construct a current voiceprint discrimination vector corresponding to the voice data; calculating the spatial distance between the current voiceprint discrimination vector and a pre-stored standard voiceprint discriminating vector of the user, carrying out the verification of the identity of the user based on the distance, and generating a verification result. The method can improve the accuracy and efficiency of identity verification of the user.
Owner:PING AN TECH (SHENZHEN) CO LTD
VANET access authentication method adopting identity-based short group signatures
InactiveCN107071774ARelieve pressureReduce waiting timeUser identity/authority verificationSecurity arrangementProtocol for Carrying Authentication for Network AccessRevocation
The invention provides a VANET anonymous access authentication method adopting identity-based short group signatures. The method comprises the following steps: each valid on-board unit obtains a private key, a signature public key, an initial pseudonym, and an initial trust value issued by a third-party trusted authority; each valid roadside unit obtains a signature private key, a signature public key, a group private key, and a group public key issued by the third-party trusted authority; two-way access authentication is carried out between each on-board unit and the corresponding roadside unit upon first access to a VANET by each on-board unit; one certain on-board unit signs a message and sends the signed message through broadcasting, and the on-board unit receiving the message authorizes a signature; a real identity of each on-board unit is calculated when the on-board unit is a malicious node or the real identity needs to be revealed; and the VANET carries out identification and revocation on the malicious nodes. The method provided by the invention has the advantages that an identity-based short group signature scheme is applied in the process of mobile communication among vehicle nodes of the VANET protocol, so that the identity-based short group signatures can be used to effectively protect the privacy of the vehicle nodes; and the malicious nodes can be efficiently and accurately identified and revoked through an evaluation mechanism, so that high scheme security can be effectively ensured.
Owner:郭明一
Block chain based equipment certification method, certification server and user equipment
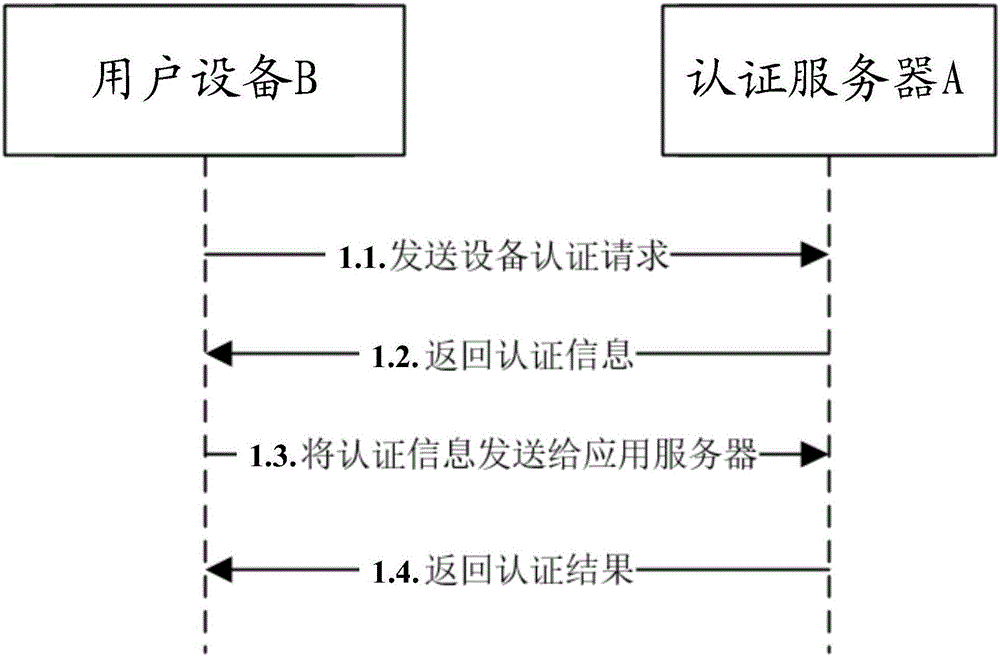
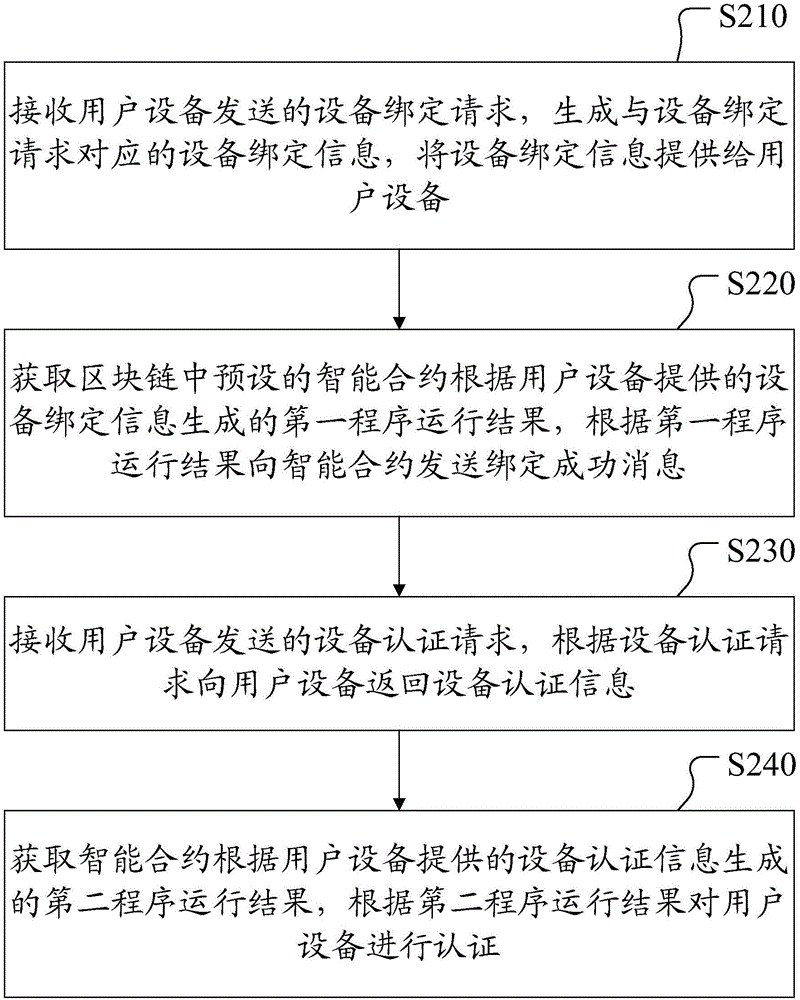
ActiveCN106453415ASimplify the verification processImprove efficiencyTransmissionProtocol authorisationSmart contractSoftware engineering
The invention discloses a block chain based equipment certification method, a certification server and user equipment, and relates to the technical field of equipment certification. The method includes: receiving an equipment binding request sent by the user equipment, generating equipment binding information corresponding to the equipment binding request, and providing the equipment binding information to the user equipment; acquiring a first process running result generated by a smart contract, and sending a binding success message to the smart contract according to the first process running result; receiving an equipment certification request sent by the user equipment, and returning equipment certification information to the user equipment according to the equipment certification request; acquiring a second process running result generated by the smart contract, and performing certification on the user equipment according to the second process running result. Therefore, the block chain smart contract is used for saving the equipment binding information to make the equipment information not tampered, and the problems in the prior art are solved.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
CAN bus authentication method and system based on broadcasting
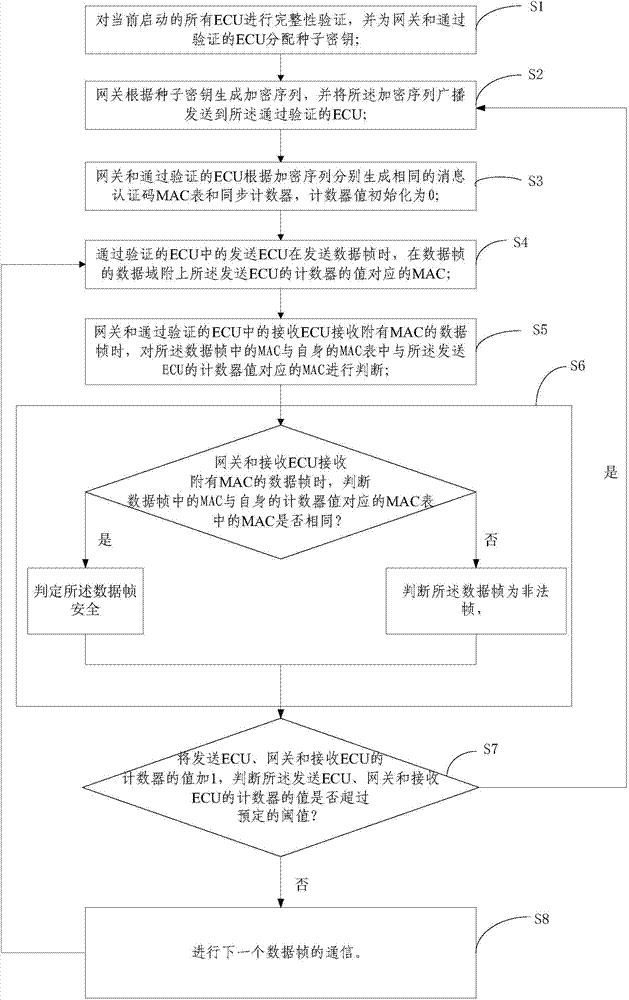
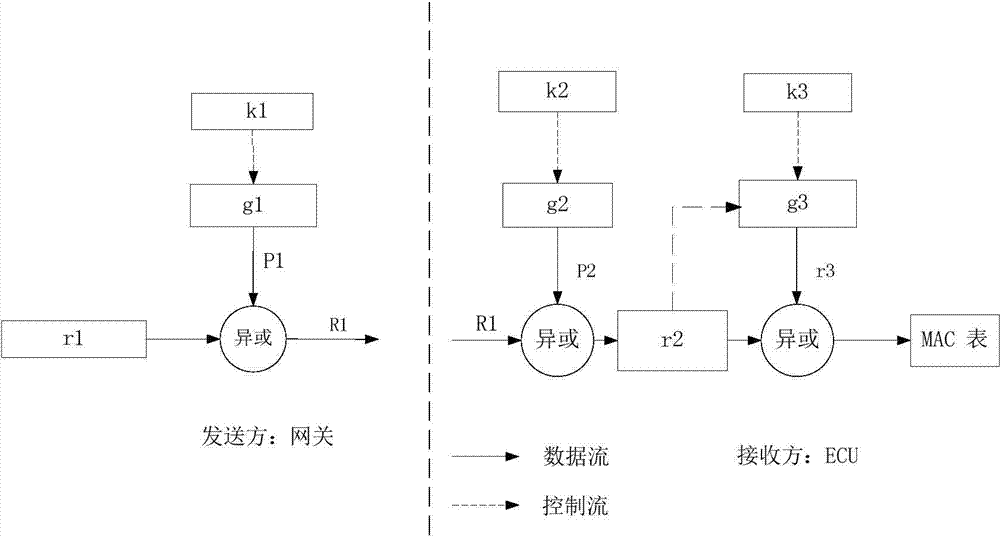
ActiveCN104767618AAvoid attackEffective judgmentUser identity/authority verificationBus networksComputer hardwareData field
The invention relates to a CAN bus authentication method and system based on broadcasting. The method includes the steps that completeness verification is conducted on all ECUs, seed secret keys are distributed for a gateway and the ECUs passing the verification; the gateway generates an encryption sequence, and the encryption sequence is sent to the ECUs passing the verification through broadcasting; the gateway and the ECUs passing the verification generate identical message authentication code (MAC) tables and identical synchronous counters, wherein the initial value of the counters is zero; the sending ECU attaches the MAC corresponding to the value of the counter of the sending ECU to the data field of a sending data frame; the gateway and the receiving ECU judge whether the MAC in the data field is identical with the MAC in the MAC tables corresponding to the counters of the gateway and the receiving ECU or not; if yes, the data frame is judged to be safe, and if not, the data frame is judged to be the illegal frame; the values of the counters of the sending ECU, the gateway and the receiving ECU are added by one, and whether the values of the counters of the sending ECU, the gateway and the receiving ECU exceed the preset threshold value or not is judged; if yes, an MAC table is generated again; if not, the next frame of communication is conducted, and communication of a next data frame is conducted. According to the CAN bus authentication method and system, due to the fact that a message authentication code is added to the data frames in communication, the attack on the CAN bus can be defended.
Owner:TSINGHUA UNIV
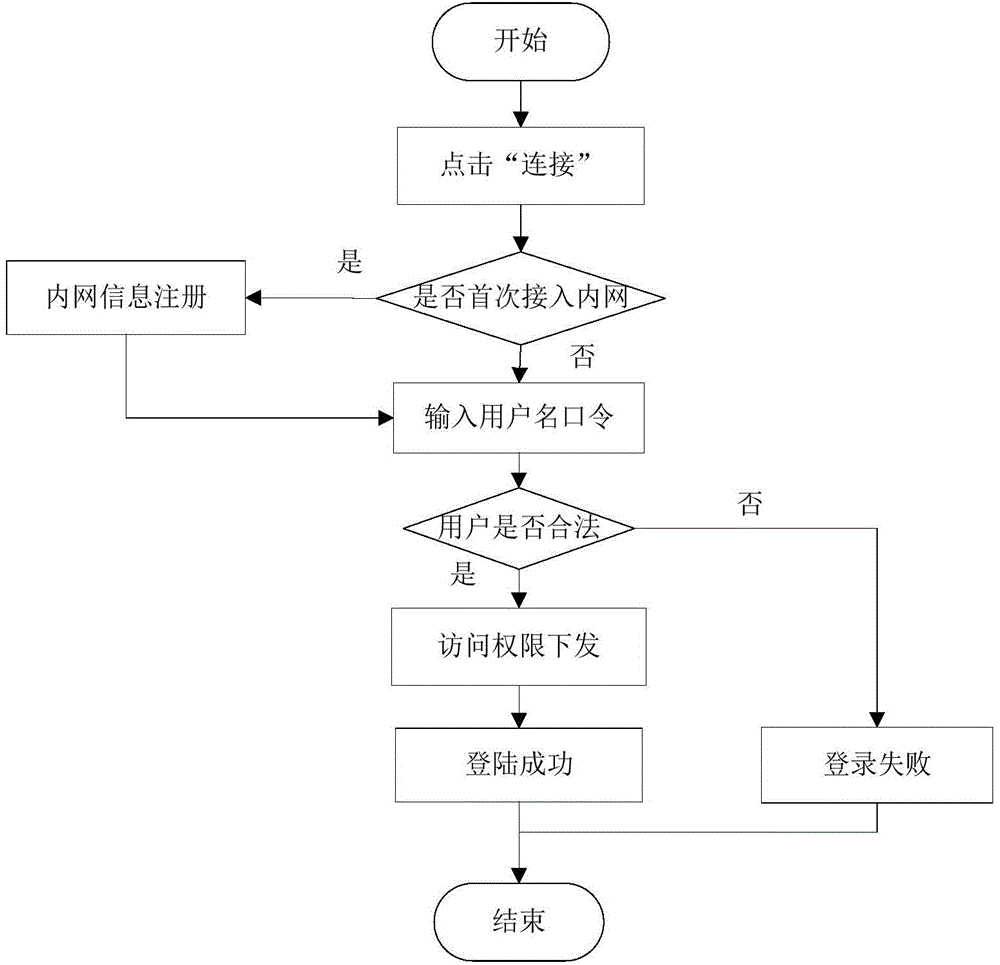
Secure access control system and method for network terminal nodes
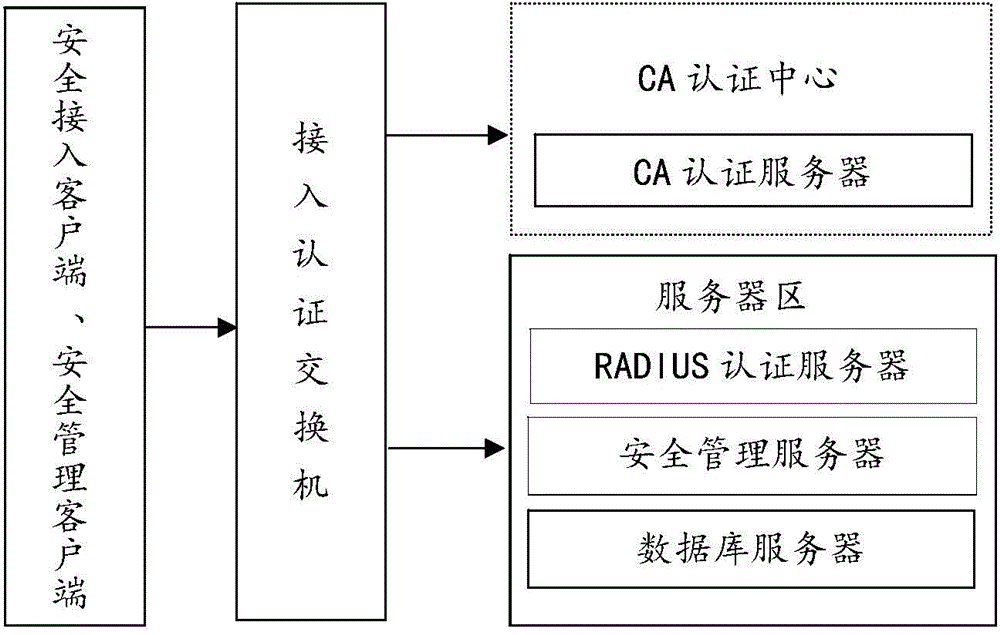
InactiveCN104796261AReal-time monitoring of identity informationReal-time monitoring of the access verification processUser identity/authority verificationNetwork terminationPrivate network
The invention discloses a secure access control system and method for network terminal nodes. A C / S (client / server) architecture is provided between a secure access client and a CA (certificate authority) authentication server, and another C / S architecture is provided between the secure access client and an RADIUS (remote authentication dial-in user service) authentication server; the two C / S architectures are used for user identity authentication and terminal access authentication, respectively. A B / S (browser / server) architecture is provided between a security management client and a security management server and is used mainly for registering and checking user information, setting network access group permissions and controlling and monitoring secure access in real time. The secure access control system and method has the advantages that the access terminals can be subjected to trusted identity authentication, trusted access authentication, terminal proxy authentication, network access permission control and network access state real-time monitoring; a trusted terminal access control system based on identity authentication is achieved and is stable and reliable and is high in authentication efficiency, violations such as NAT (network address translation) and proxy services can be detected and warned accurately, network states of terminal users are monitored and controlled through a web management interface, and the needs of private networks for safety management can be fully met.
Owner:CHANGAN UNIV
Efficient anonymous identity authentication method in Internet of Vehicles environment
ActiveCN111372248AImprove authentication efficiencyEnhanced anonymityPublic key for secure communicationParticular environment based servicesInternet privacyAttack
The invention provides an efficient anonymous identity authentication method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to the technical scheme, the method comprises the following steps of vehicle offline registration, online registration and rapid identity authentication. The method has the beneficial effects that a temporary identity certificate Token mechanism is set, so that the authentication efficiency is improved while the vehicle anonymous two-way communication is realized; a block chain distributed account book mode is utilized, so that data traceability and tamper resistance are guaranteed, and the problems of relatively low identity authentication efficiency, easiness in attack and the like caused by traditional PKI authentication centralization of the Internet of Vehicles are solved; the combination of the blockchain PBFT consensus mechanism and the smart contract greatly reduces the authenticationtime delay of the traditional method.
Owner:NANTONG UNIVERSITY
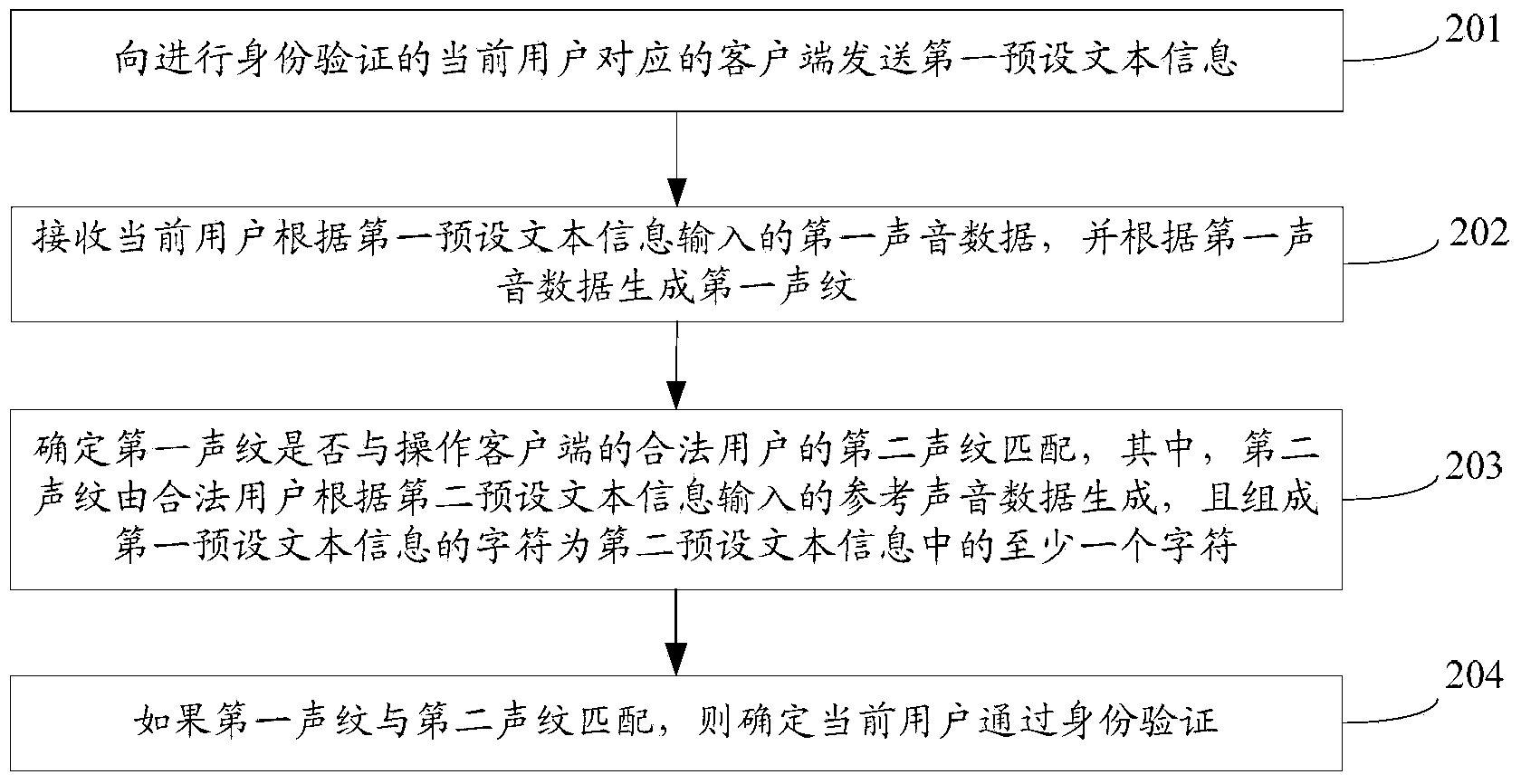
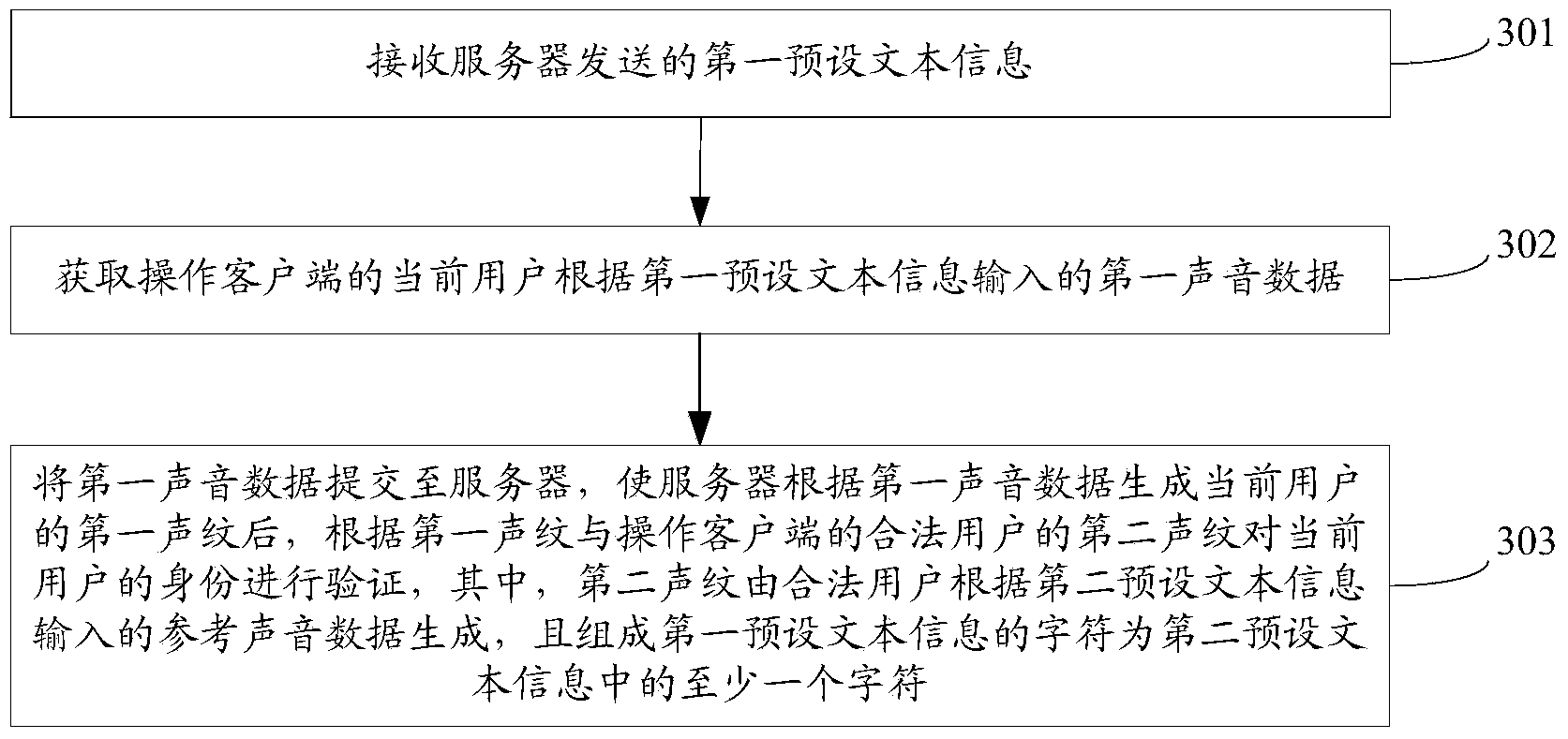
Identity verifying method, server, client side and system
ActiveCN104168270AReduce configuration requirementsImprove authentication efficiencyUser identity/authority verificationTelecommunicationsDependability
The invention discloses an identity verifying method, a server, a client side and a system. The method comprises the steps that a first preset text message is sent to the client side corresponding to a current user; first sound data input by the current user according to the first preset text message are received; a first vocal print is generated according to the first sound data; whether the first vocal print is matched with a second vocal print of a legal user or not is determined, wherein the second vocal print is generated according to reference sound data input by the legal user according to a second preset text message, and one of characters composing the first preset text message is at least one of characters in the second preset text message; if the first vocal print is matched with the second vocal print of the legal user, it is determined that the current user passes the identity verification. The identity verification is achieved by matching the first vocal print of the current user with the second vocal print of the legal user, the configuration requirement for the terminal where the client side is located is low, accordingly, the application range is wide, the identity verification is not affected by the environment where the client side is located, the identity verification is more reliable, and the identity verifying efficiency can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
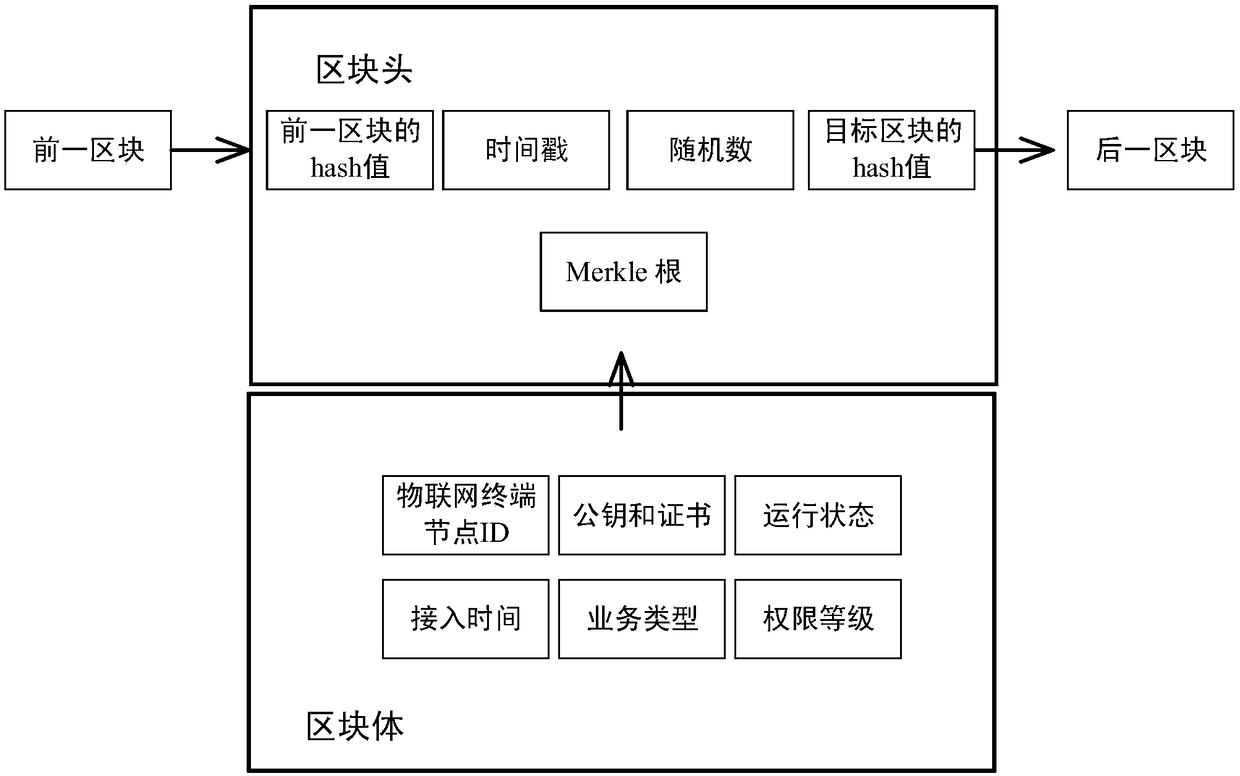
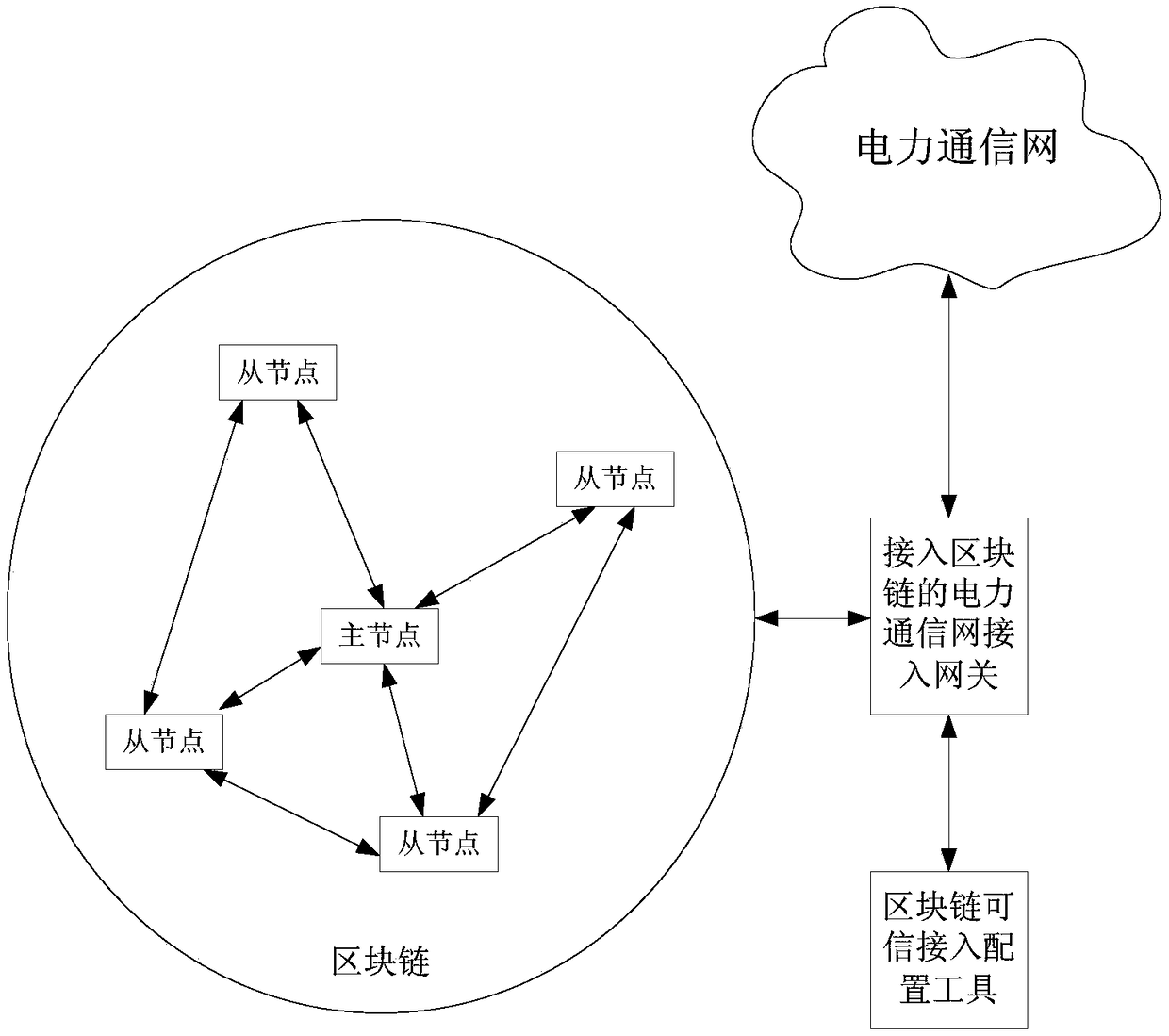
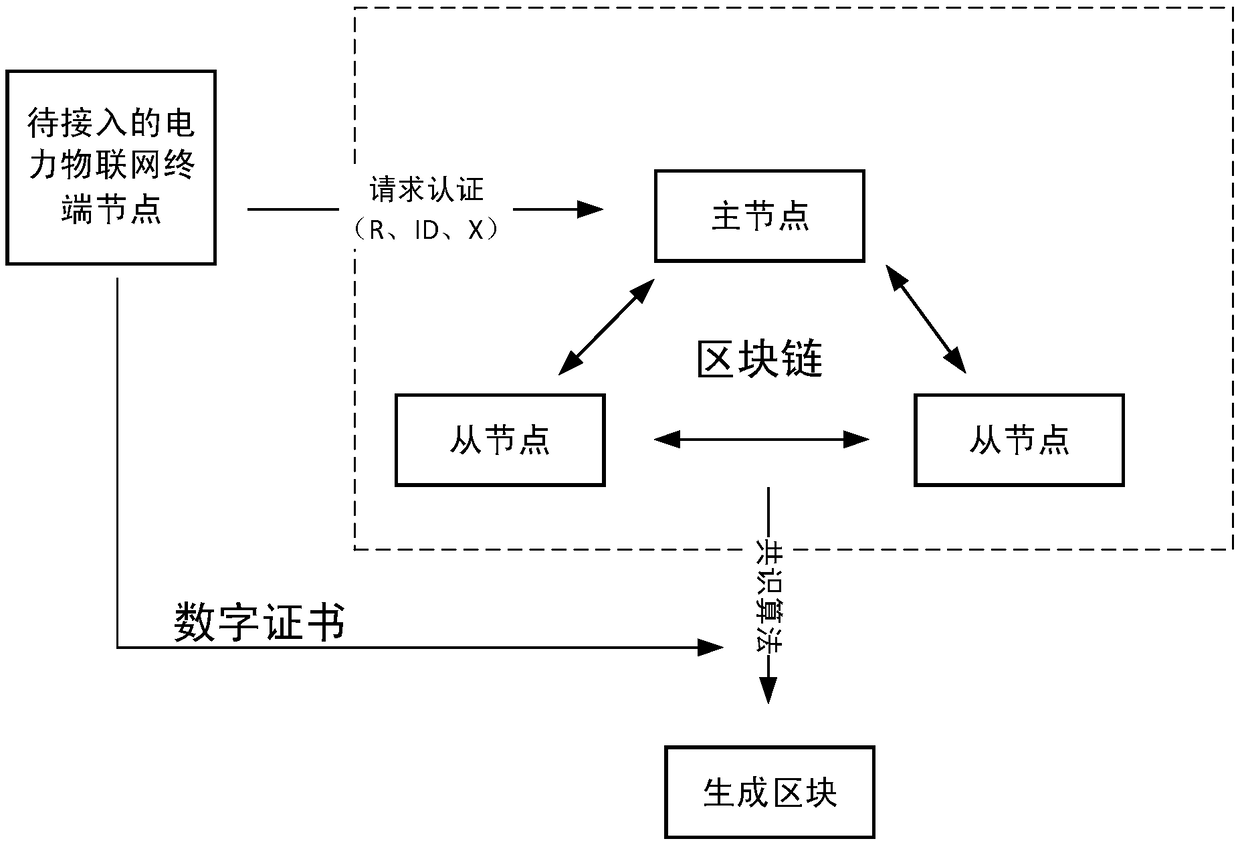
Block chain-based method for accessing power Internet of Things terminal
InactiveCN109495516AReduce communication pressureReduce computing pressureKey distribution for secure communicationUser identity/authority verificationAccess methodCiphertext
The invention provides a Block chain-based method for accessing a power Internet of Things terminal, comprising the steps of: connecting a to-be-accessed power Internet of Things terminal to a masternode, and initiating an authentication request; the master node responding to the authentication request, and randomly selecting nodes that meet the condition of a threshold number from the block chain to form an authentication group; encrypting a public key G and an identity ID of the to-be-accessed power Internet of Things terminal by using a private key to obtain a digital signature ciphertextX, and sending the identity ID, a terminal public value R and the digital signature ciphertext X to the master node; the master node encapsulating and sending the authentication request information toa member node of the authentication group; the authentication group running PBFT consensus algorithm, and obtaining an authentication result by performing distributed authentication through two-two exchanging of the authentication information between the nodes of the authentication group; generating a new block in the block chain, and returning confirmation information to the to-be-accessed powerInternet of Things terminal; and the power Internet of Things terminal returning encrypted confirmation information to an access gateway. The block chain-based power Internet of Things terminal access method can improve the security and efficiency of authentication.
Owner:JIANGSU ELECTRIC POWER CO
Communication method, device and system based on combined public key cryptography system
InactiveCN103825733AReduce the number of interactionsImprove authentication efficiencyKey distribution for secure communicationPublic key for secure communicationKey generation centerComputer security
The invention provides a communication method, device and system based on a combined public key cryptography system. The method includes the steps of obtaining a private key of a first node from a secret key generating center through the first node, obtaining identification of a second node according to an adjacent node identification list, calculating a public key of the second node according to the identification of the second node, calculating a shared secret key parameter of the first node according to the secret key of the first node and the public key of the second node, then, calculating a shared secret key of the first node according to the shared secret key parameter of the first node, generating a first secret key verification code corresponding to the shared secret key of the first node, sending shared secret key verification information with the first secret key verification code to the second node, and receiving shared secret key response information from the second node. The calculation steps can be completed offline, the number of times of interaction between the nodes is lowered, and therefore when the first node starts verification, verification can be completed in a quite short period of time, and verification efficiency is improved.
Owner:HUAWEI TECH CO LTD
Network real-name system implementing method
InactiveCN101136750AImprove authentication efficiencyImprove security levelUser identity/authority verificationApplication serverWeb authentication
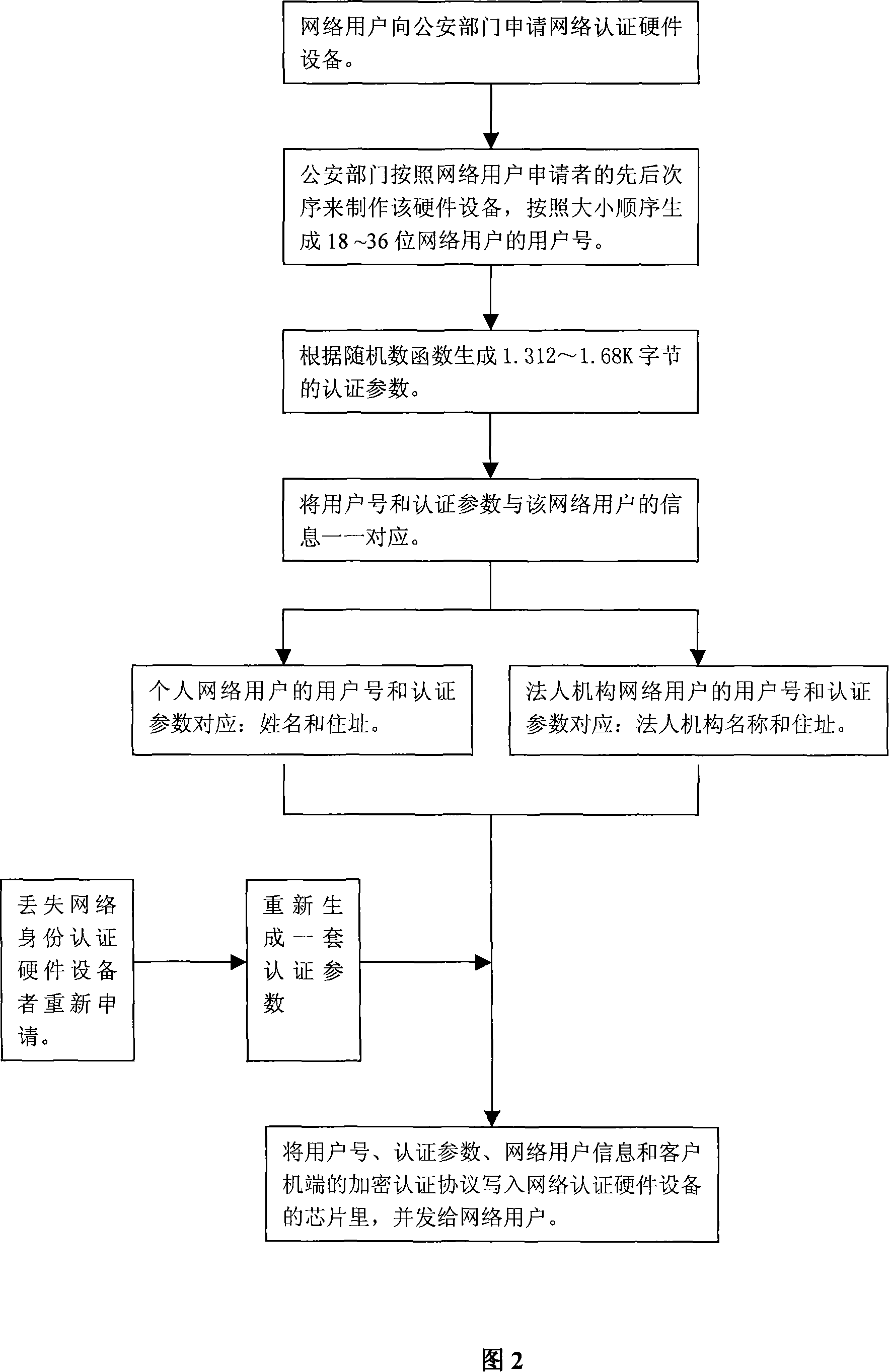
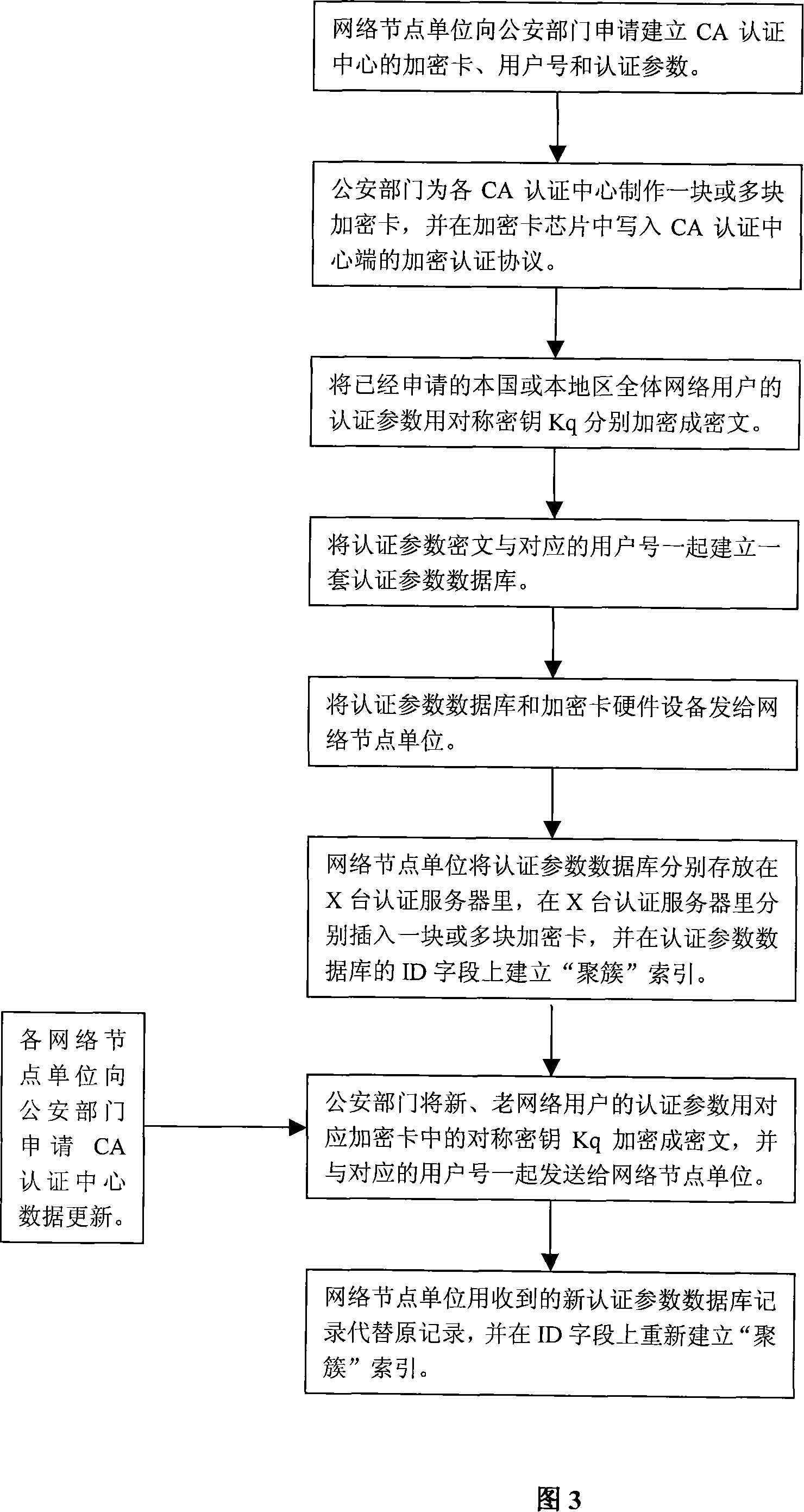
The implement method for real name system establishes center of authentication (CA) respectively for network nodes i.e. WEB server as unit. The method connects WEB server with CA and network resources or application servers (AS) in series mode. Identifiers and authentication parameters of overall network users in homeland or local area are stored in AS of CA in advance. Protocol of cryptographic authentication based on algorithm of symmetric cryptography and technique of combined symmetric cryptographic key are built in hardware chips at two ends of client and CA. all CAs in each network node can provide authentication of network ID for overall network users in homeland or local area. Each network user holds hardware device for network authentication. Through authentication of CA in each network node, resources or application server in each network node logs on network. Thus, the method implements management on networks in homeland or local government through real name system.
Owner:BEIJING JINAOBO DIGITAL INFORMATION TECH
Network access verifying method, system and apparatus
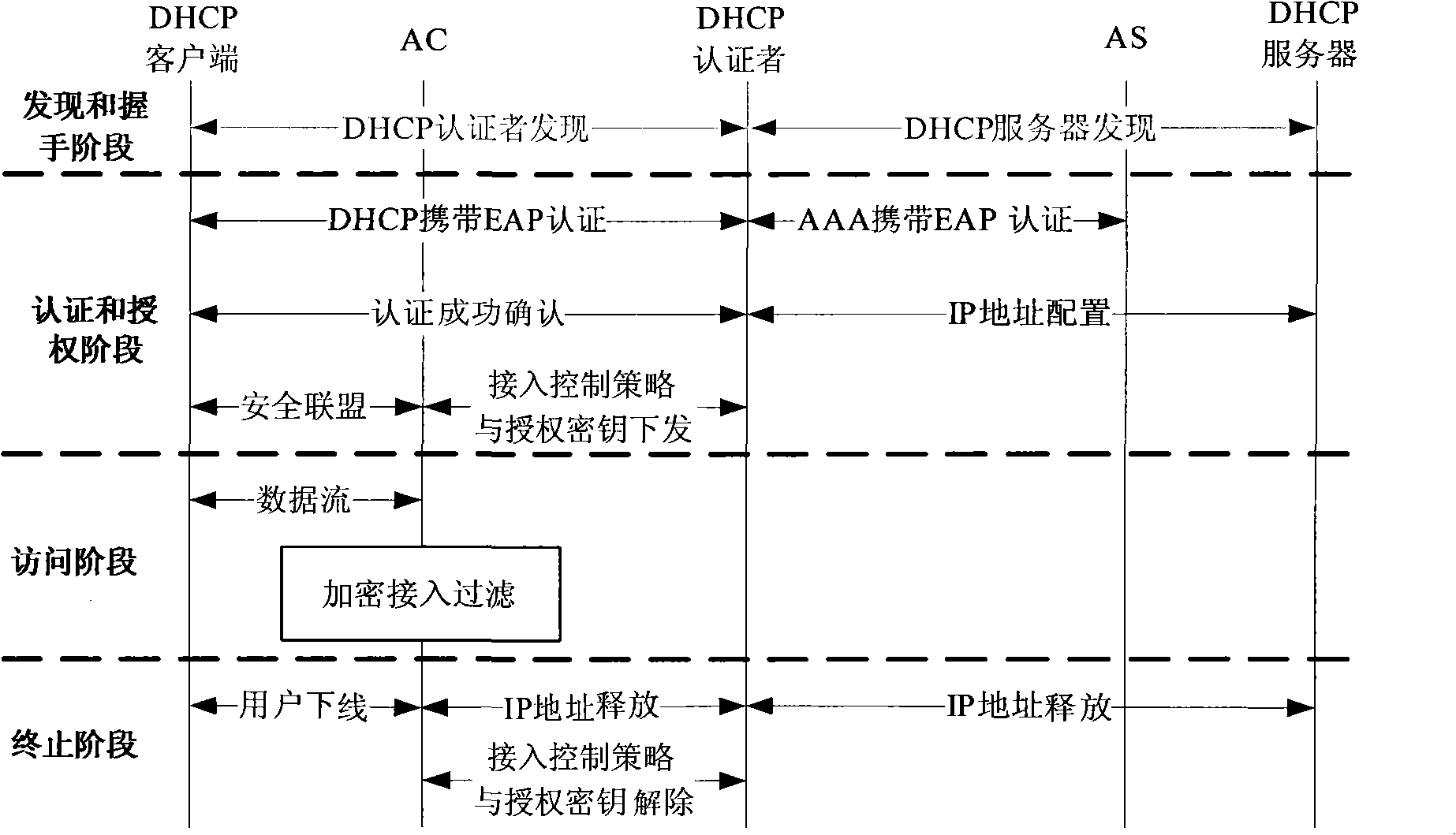
InactiveCN101340287ARealize monitoringEnsure safetyUser identity/authority verificationData switching networksComputer configurationNetwork addressing
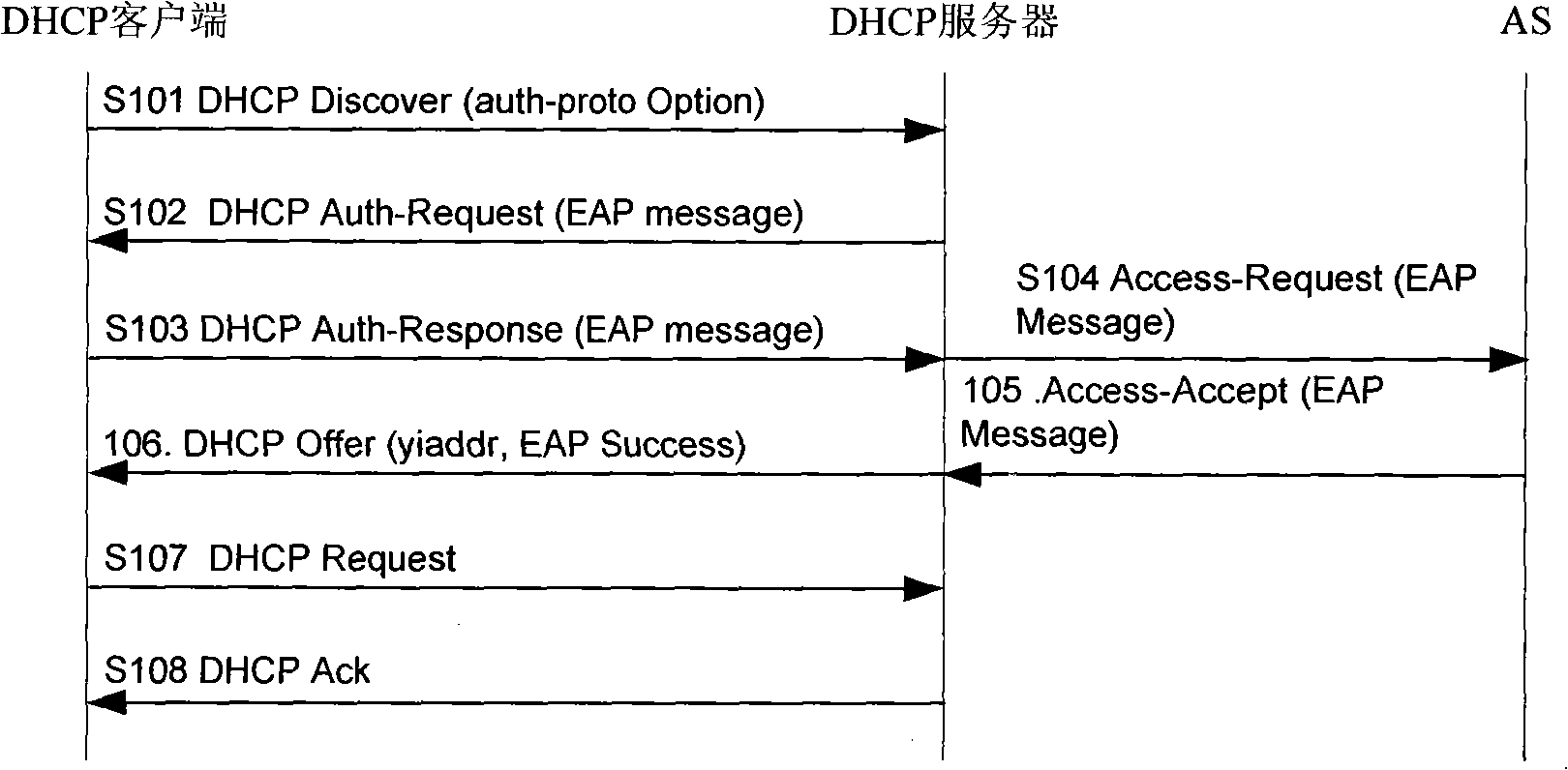
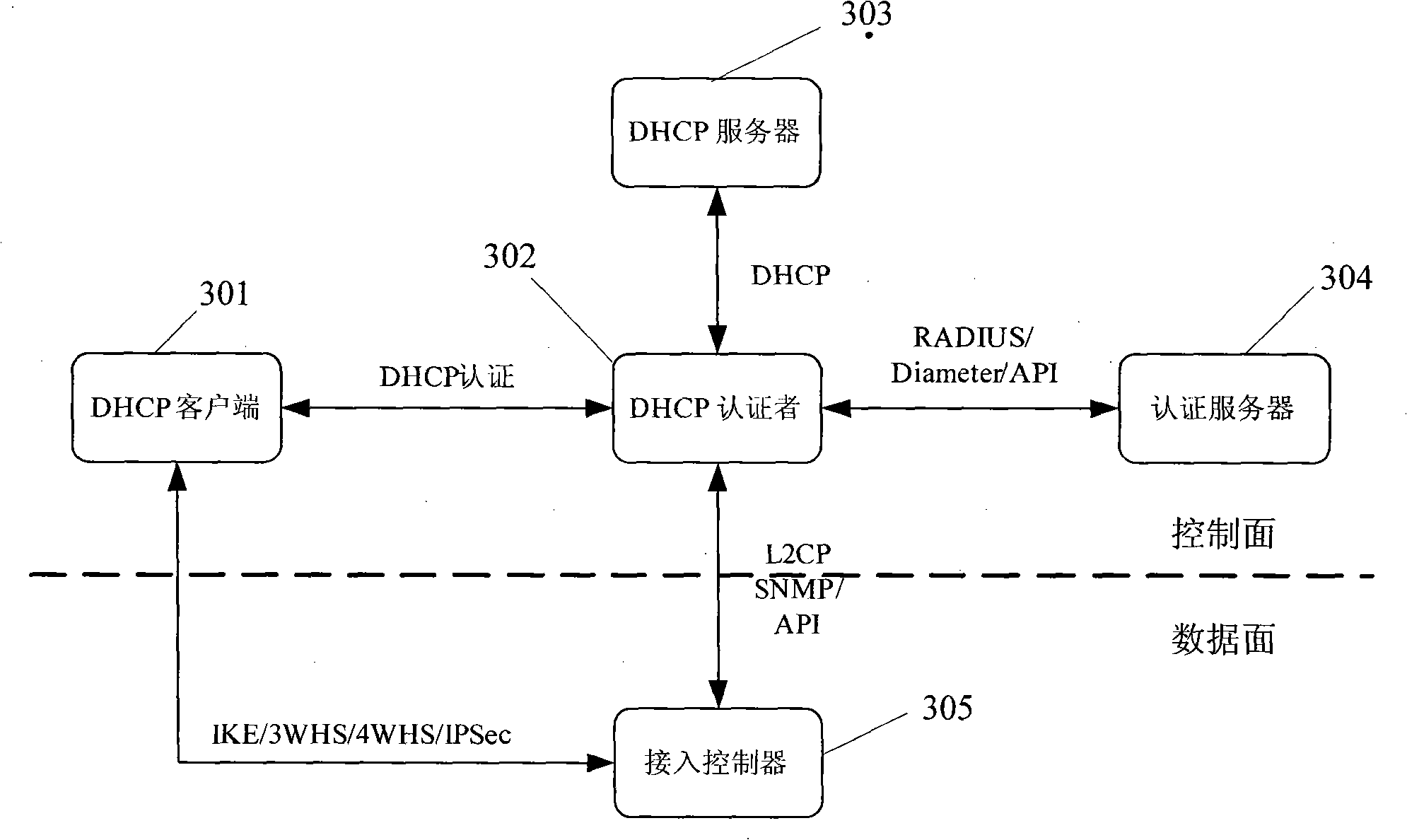
The invention discloses an authentication method for network access and includes the following steps: access authenticator receives discovery message which is sent by a client terminal of a dynamic host computer configuration protocol and provides a first configuration information of a first network address used in the authentication process for the client terminal of the dynamic host computer configuration protocol in a way that the authenticator interact information with a server of the dynamic host computer configuration protocol; the client terminal of the dynamic host computer configuration protocol is authenticated according to the first configuration information and the interactive information of the authentication server; after the authentication is successfully finished, the server of the dynamic host computer configuration protocol provides a second configuration information of a second network address used in the conversation process for the client terminal of the dynamic host computer configuration protocol. The method also discloses a network access system, an access authentication device and an access controller. The implementation of the embodiment of the invention realizes the stability of the authentication process.
Owner:HUAWEI TECH CO LTD
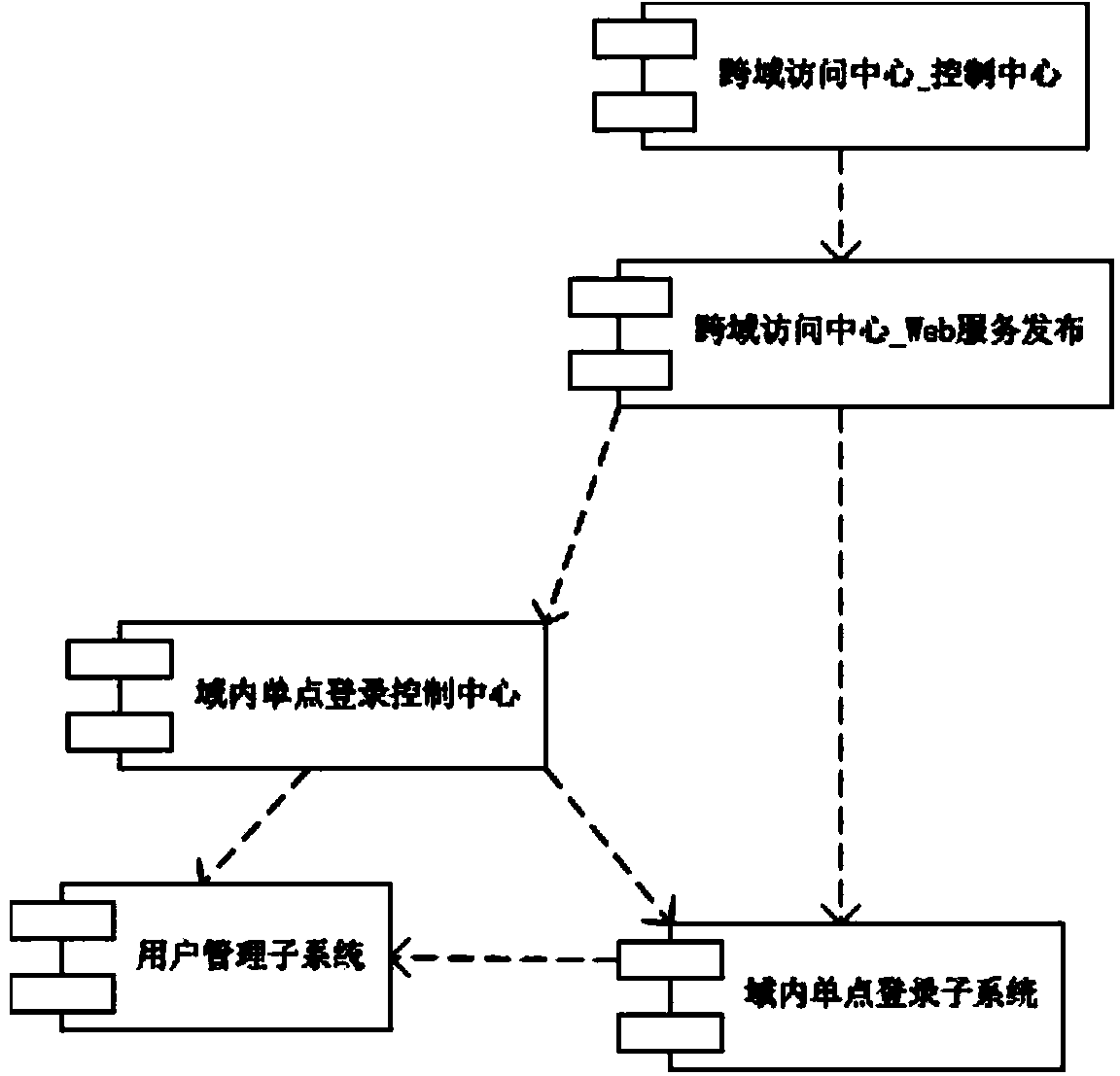
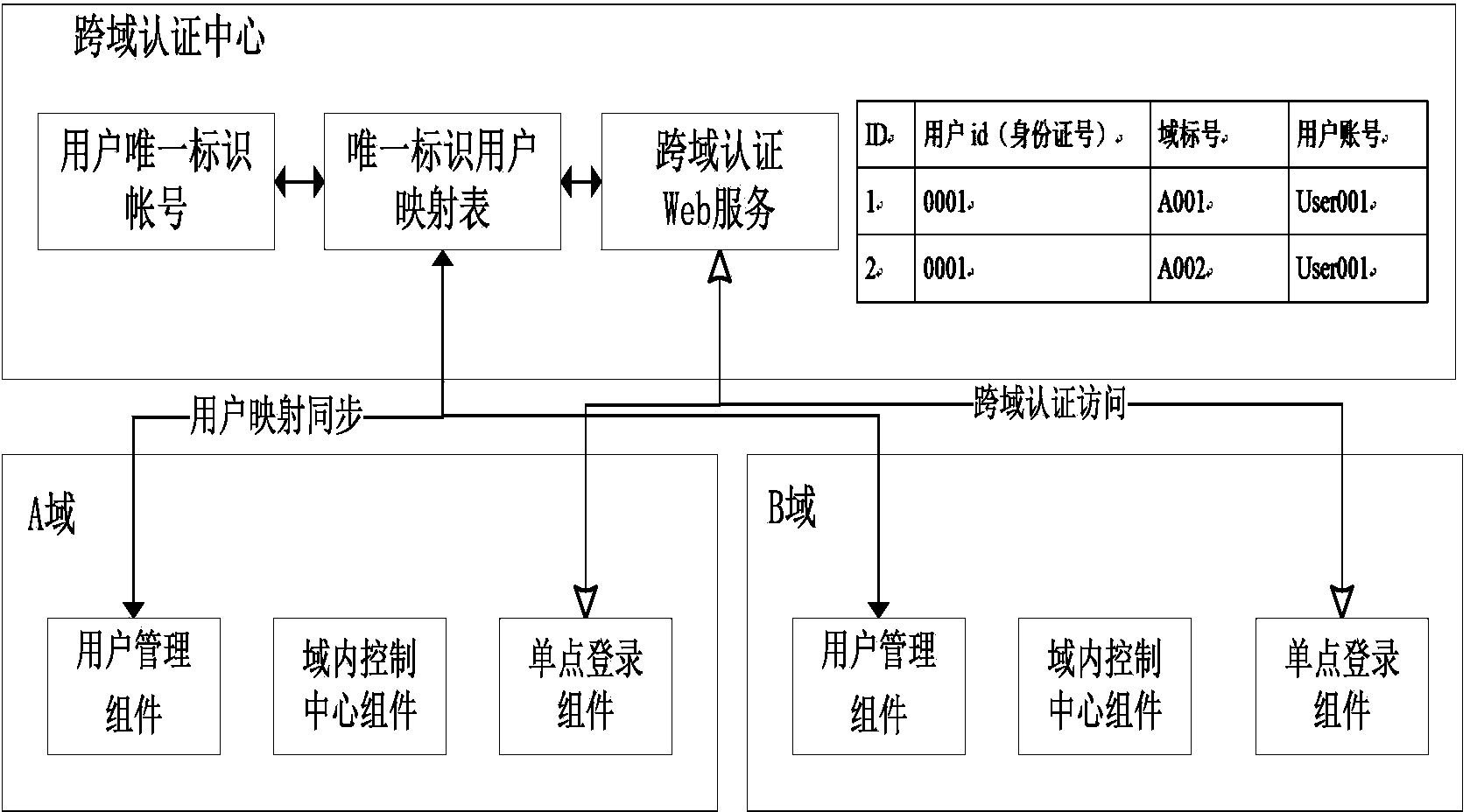
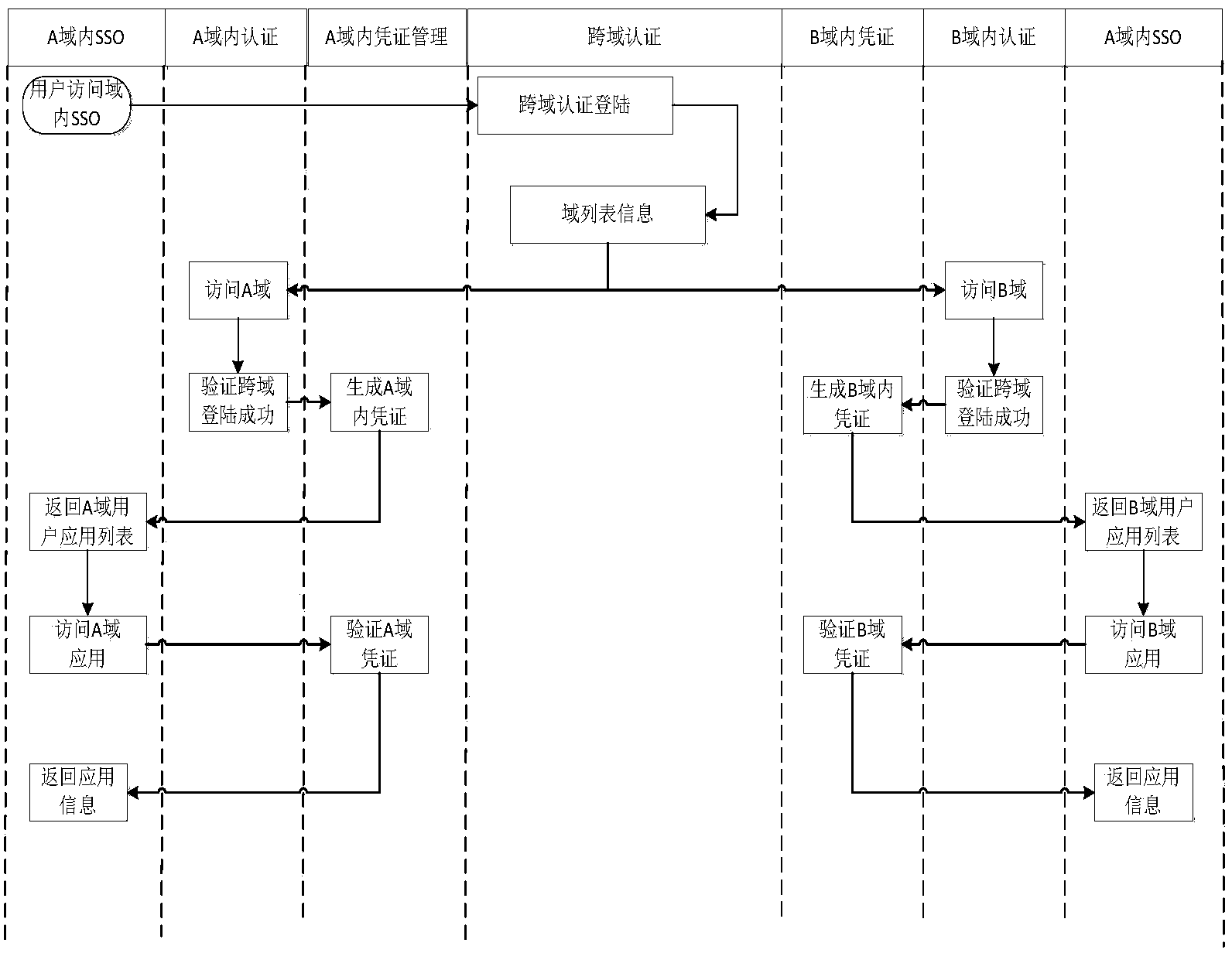
Cross-domain single point login system and method based on SAML
The invention discloses a cross-domain single point login system and method based on the SAML. The cross-domain single point login system comprises a cross-domain access center module, an inside-domain single point login sub-system module, a user management sub-system module and an inside-domain single point login control center module, wherein the cross-domain access center module comprises a cross-domain user data mapping synchronizing module, a multi-stage domain ID generating module and a multi-stage domain access authentication interface module. According to the cross-domain single point login system, the inside-domain authentication of multi-stage domains is improved to the unified cross-domain authentication among the multi-stage domains by establishing a cross-domain access center, inlets of the multi-stage domains are integrated by integrating unified authentication sources, the cross-domain single point login system becomes more efficient, the time for having access to the multi-stage domains is saved for users, and the authentication efficiency is improved.
Owner:XIAN FUTURE INT INFORMATION CO LTD +1
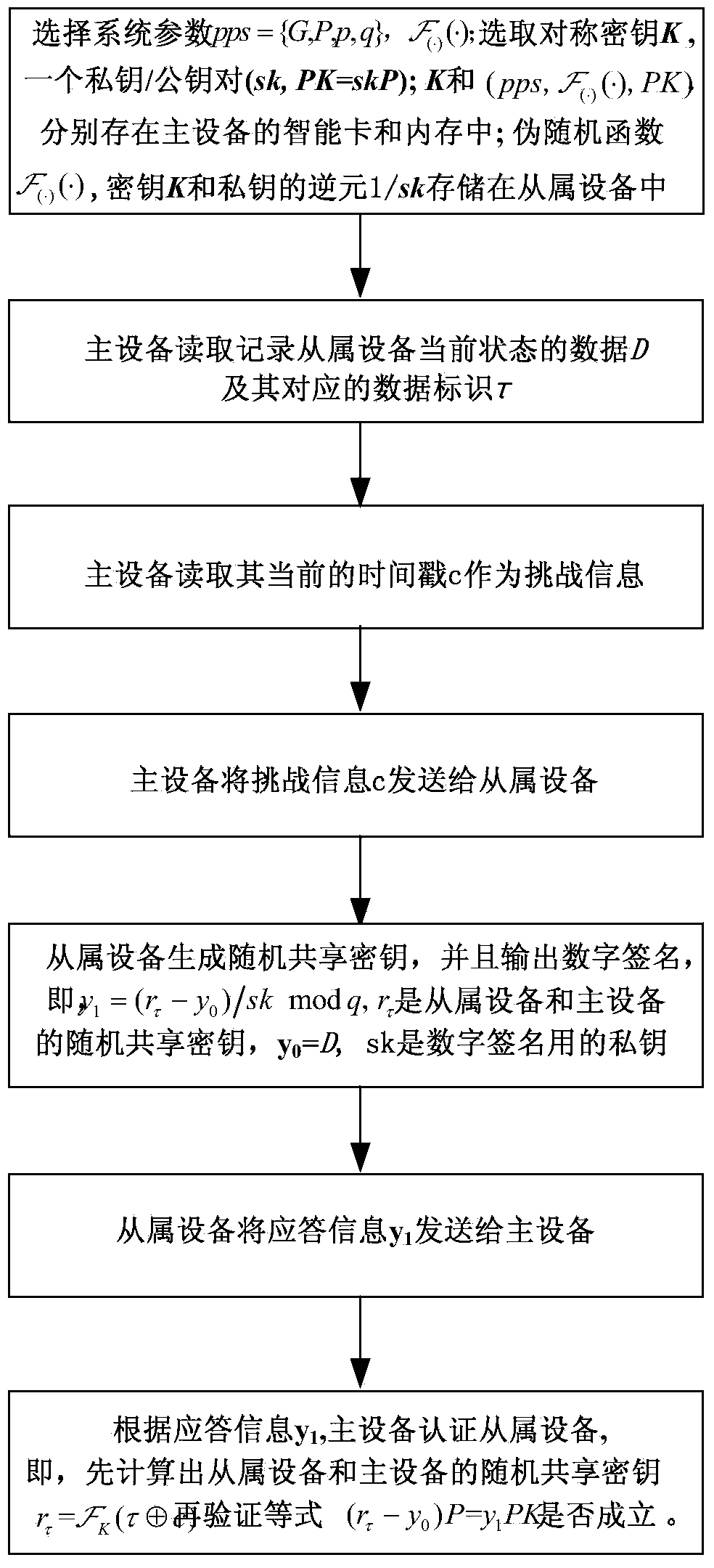
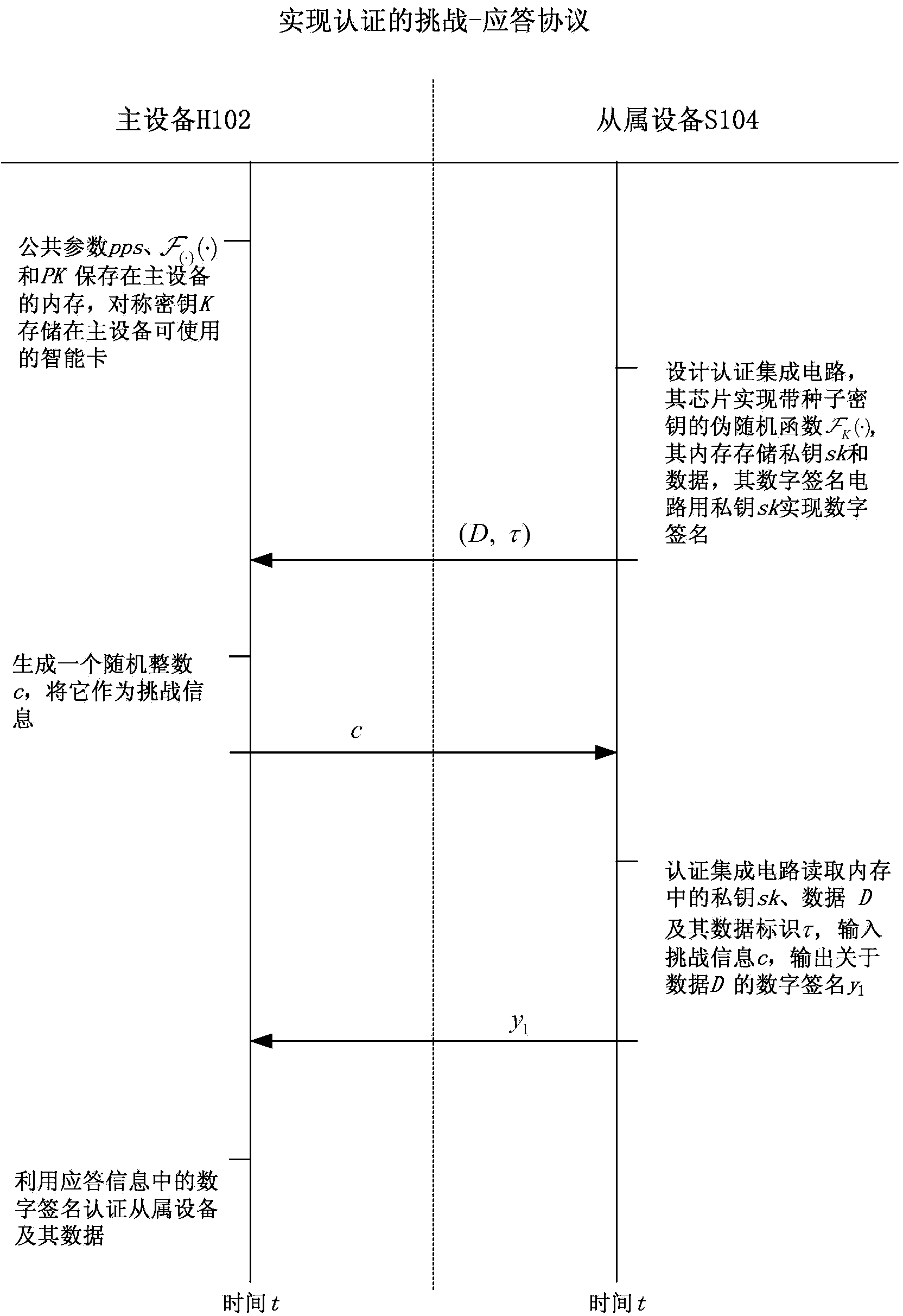
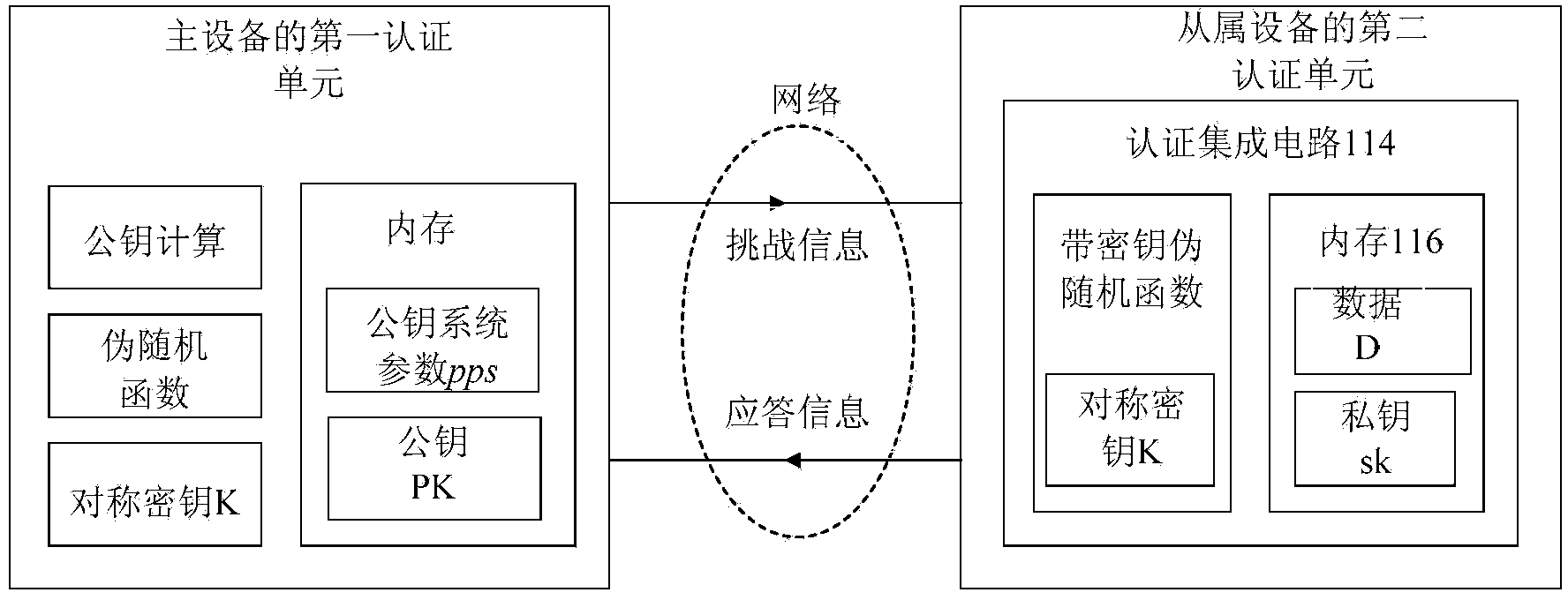
Slave device authentication method and system for master device
InactiveCN104393999AProtect Confidential InformationReduce usageKey distribution for secure communicationUser identity/authority verificationDigital signatureEngineering
The invention discloses a slave device authentication method and system for a master device. The authentication method comprises the following steps: a common parameter, a symmetric key, a pseudo-random function, and a public key / private key between the master device and a slave device are generated, and the master device reads and records the data of the current state of the slave device and then sends challenge information to the slave device; the slave device outputs a random shared key corresponding to the challenge information and a data identifier by virtue of the pseudo-random function with a seed key, and then generates a digital signature corresponding to the read data according to the private key and the random shared key; after receiving response information containing the digital signature, the master device recovers the corresponding random shared key by virtue of the symmetric key and the pseudo-random function first and then authenticates the effectiveness of the response information in combination with the public key and the digital signature. The method can authenticate a plurality of slave devices at the same time and has the advantages of high computational efficiency and low communication cost.
Owner:JINAN UNIVERSITY
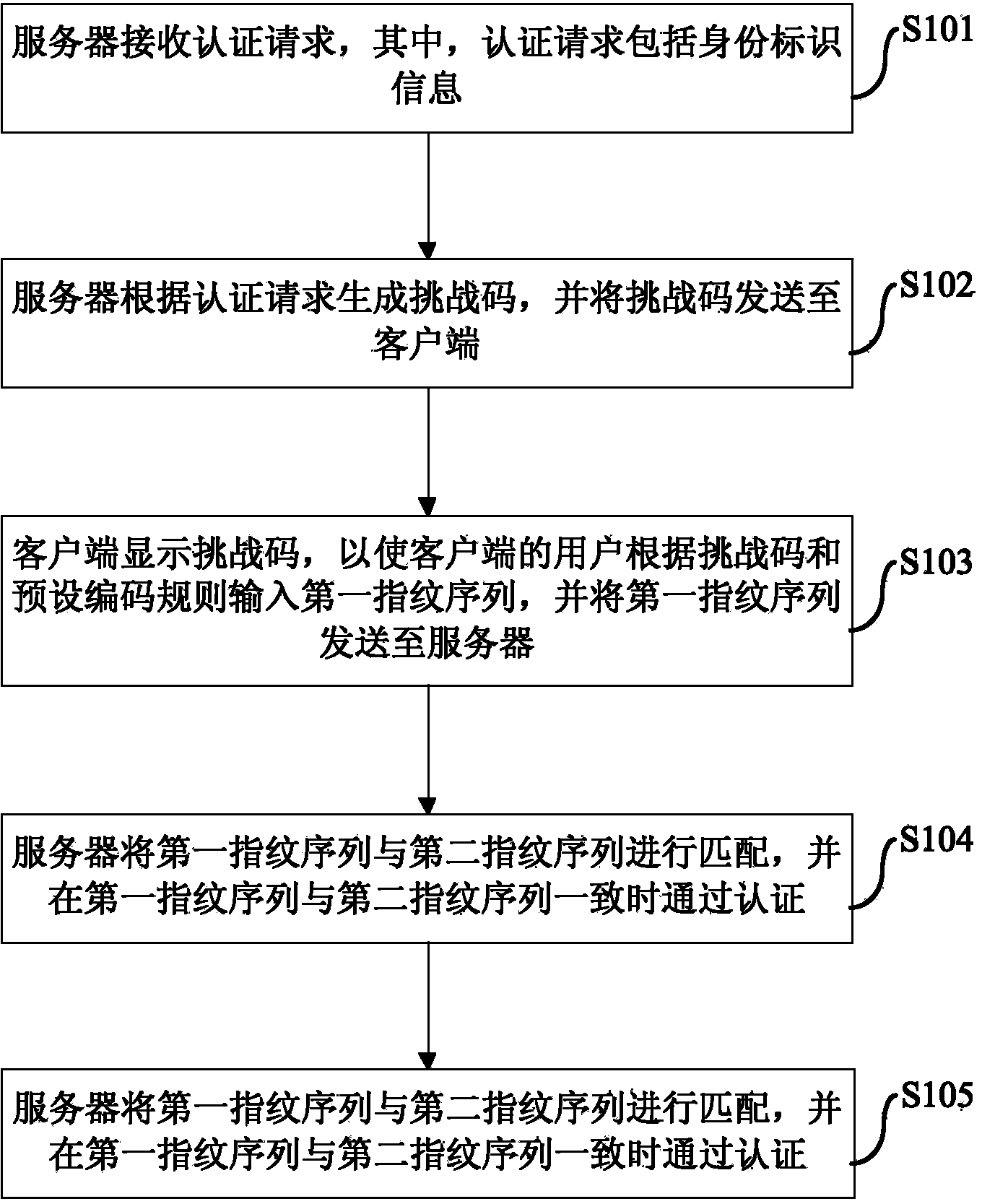
Authentication method and system based on fingerprints
InactiveCN103595719AImprove experienceImprove securityUser identity/authority verificationDigital data authenticationPasswordUser authentication
The invention provides an authentication method and system based on fingerprints. The authentication method includes the steps that a server receives an authentication request, wherein the authentication request comprises identity information; the server generates challenge codes according to the authentication request and sends the challenge codes to a client side; the client side displays the challenge codes, and then a user of the client side inputs a first fingerprint sequence according to the challenge codes and a preset coding rule and sends the first fingerprint sequence to the server; the server acquires a corresponding prestored fingerprint set and a coding rule corresponding to the prestored fingerprint set according to the identity information and generates a second fingerprint sequence according to the challenge codes, the fingerprint set and the coding rule; the server matches the first fingerprint sequence with the second fingerprint sequence, and authentication is achieved when the first fingerprint sequence is matched with the second fingerprint sequence. According to the method based on the fingerprints, user authentication efficiency can be improved, the risk that the password of the user is stolen or cracked is reduced, and safety of the identity information of the user is improved.
Owner:TSINGHUA UNIV
Message authentication method based on semi-trusted management center in vehicle networking
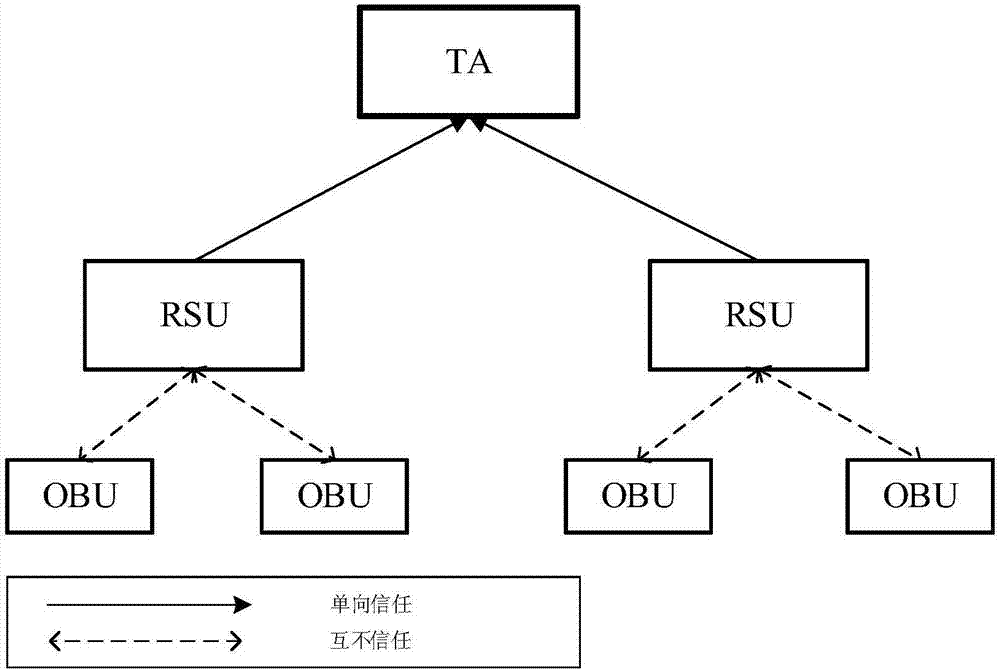
ActiveCN109067525AIdentity privacy leakIn line with realityKey distribution for secure communicationPublic key for secure communicationIn vehicleKey distribution
The invention discloses a message authentication method based on a semi-trusted management center in the vehicle networking. The user communicates with RSU and other vehicles arranged on both sides ofthe road through OBU, and extracts, analyzes and effectively utilizes the message, so that the vehicle runs more safely, and the user can obtain more efficient service at the same time. The inventionis based on the environment of a semi-trusted management center, more realistic, at the same time the vehicle's pseudonym is generated by the vehicle, RSU and STA together, RSU and STA trace the identity of the vehicle jointly, A single party cannot obtain the true identity of the vehicle, thus the safety is improved.The invention adopts the self-healing key distribution method to exclude the revoked vehicles from the group, so that the vehicles do not need to store and query the revoked list, the storage space, the resources are calculated and the searching time are reduced, and the efficiency of the message authentication is improved.
Owner:ANHUI UNIVERSITY
Authentication method and system based on block chain
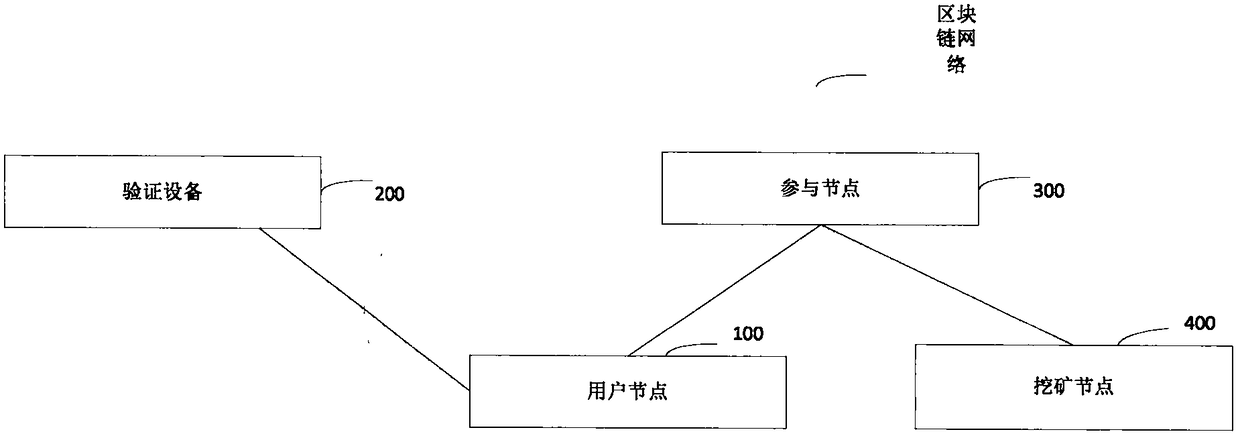
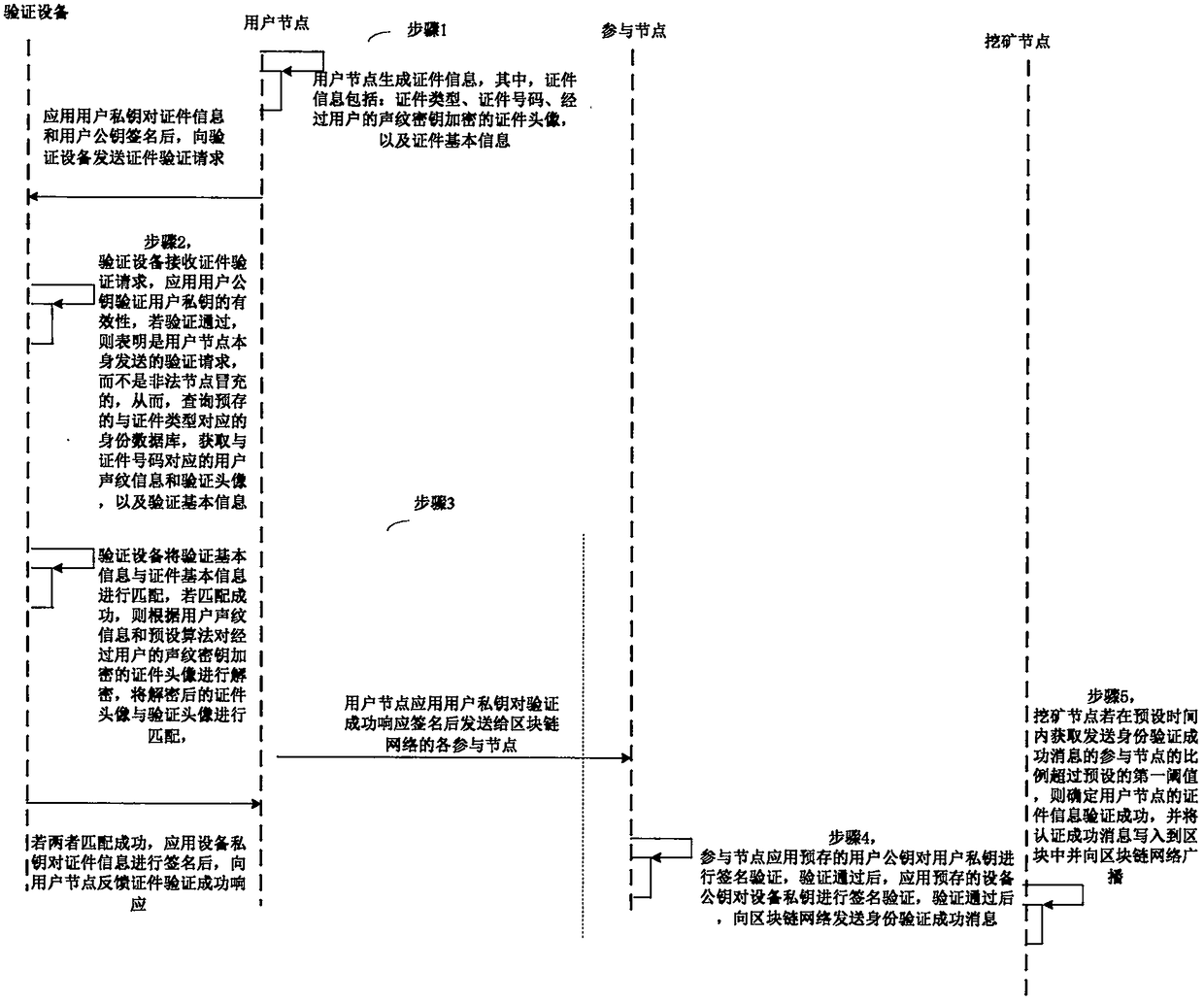
ActiveCN109359691ARealize online certificationLower Authentication RestrictionsMetadata audio data retrievalDigital data protectionChain networkAuthentication
The invention provides an authentication method and system based on a block chain. The method comprises the following steps: a user node generates credential information and basic credential information; after signing, the user node sends a credential verification request to a verification device; The verification device verifies the validity of the signature, and if the verification passes, the user voice print information and the verification head image, as well as the verification basic information; The authentication device matches the authentication basic information with the certificatebasic information, If the matching is successful, the certificate image encrypted by the user's voiceprint key is decrypted according to the user's voiceprint information and a preset algorithm, so that each participating node determines whether the user node has successfully verified the certificate information, and if the matching is successful, the authentication success message is written intoa block and broadcast to a block chain network. Thus, the online authentication of the certificate information is realized, the authentication limitation is reduced, and the authentication efficiencyand security are improved on the basis of guaranteeing the authentication reliability.
Owner:全链通有限公司
Distributed cloud authentication system based on random instruction, apparatus and method thereof
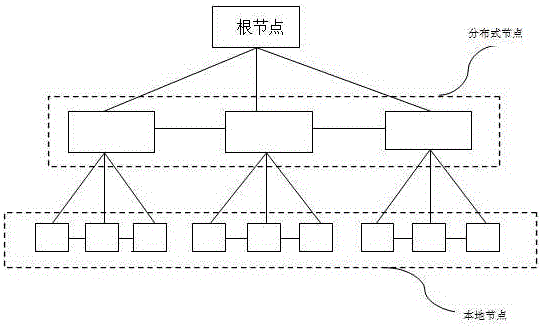
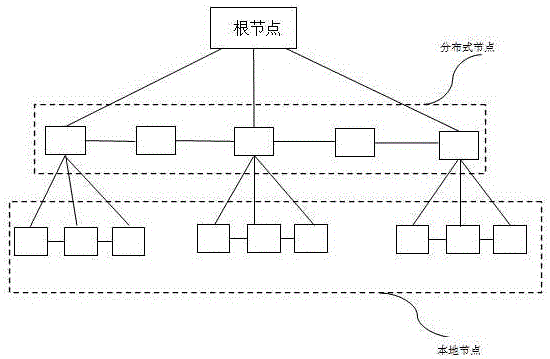
InactiveCN105915542AReduce occupancyRun fastTransmissionAuthentication systemAuthentication information
A distributed cloud authentication system based on a random instruction comprises a terminal, a root node, a distributed node and a local node. The system is characterized in that the root node does not authenticate authentication information sent by a terminal, a random instruction distributed node carries out authentication and sends the authentication information to the distributed node; the distributed node sends an authentication result to the root node; and the root node determines the result sent by the distributed node according to a preset threshold and sends a determination result to the terminal. Further, a process that the root node determines the result sent by the distributed node according to a preset threshold comprises the following steps that the root node carries out determination according to an assigned authenticated distributed node number; if the authenticated distributed node number is greater than a half of an assigned distributed node number, authentication is performed continuously; and if the authenticated distributed node number is less than a half of the assigned distributed node number, the authentication is terminated.
Owner:惠众商务顾问(北京)有限公司
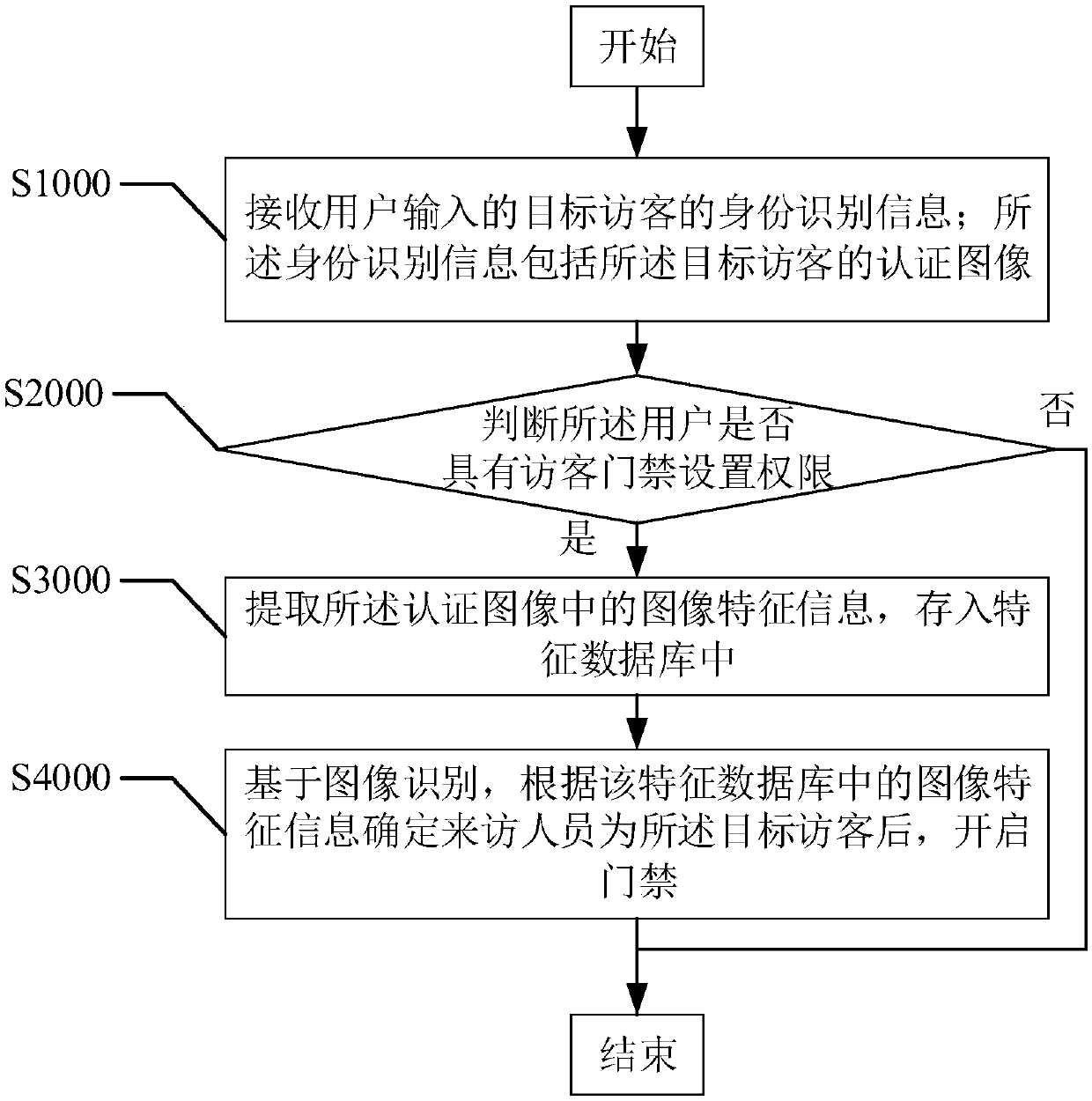
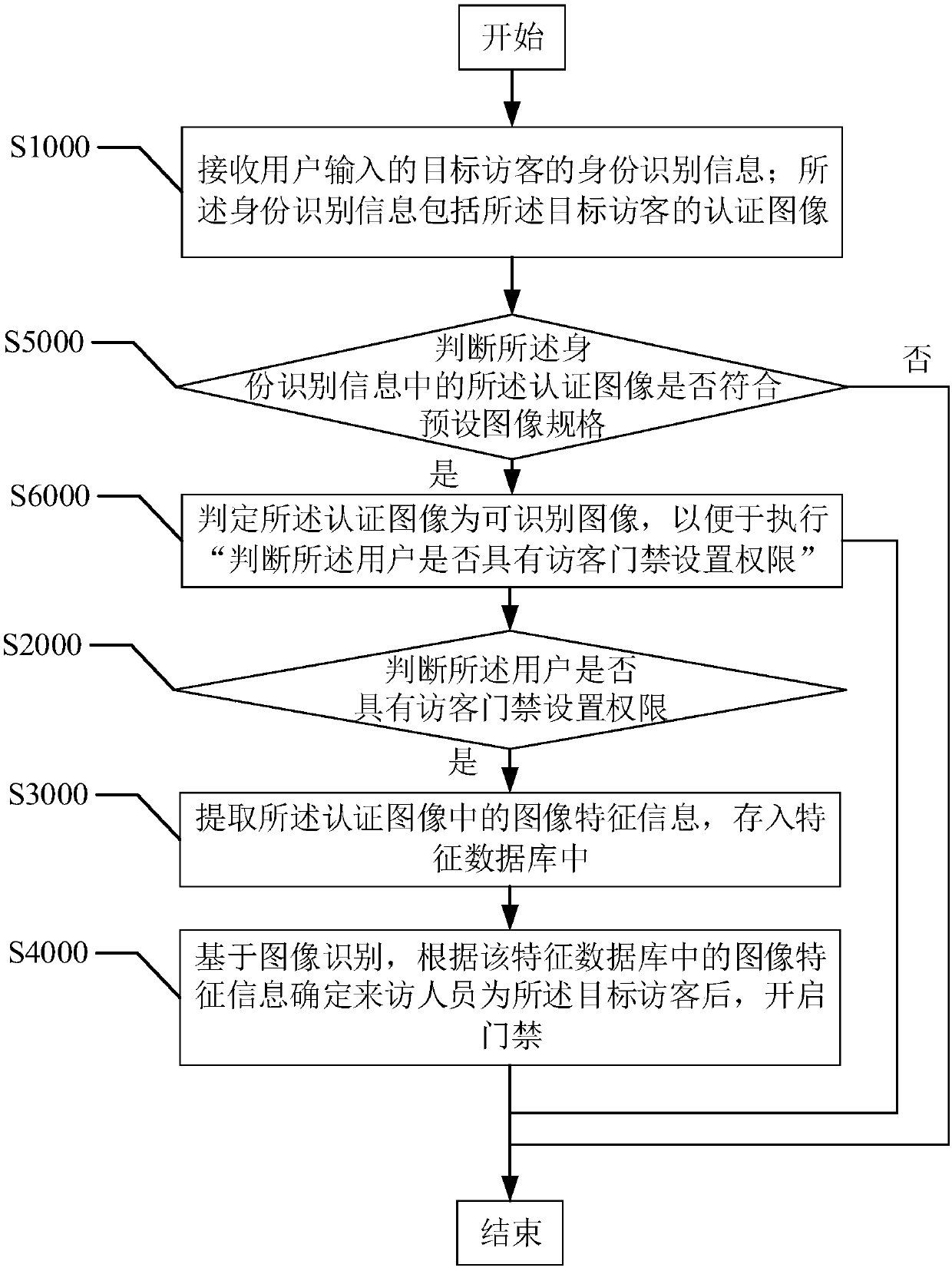
Method and device for controlling visitor access control system based on image recognition
InactiveCN109598831AImprove authentication efficiencyImprove management efficiencyBiometric pattern recognitionIndividual entry/exit registersManagement efficiencyBluetooth
The invention provides a method and device for controlling a visitor access control system based on image recognition, wherein the method comprises the following steps: receiving identity identification information of a target visitor input by a user; determining whether the user has a permission for setting a visitor access control; if so, extracting image feature information in an authenticationimage, and storing the information in a feature database; and opening the access control after determining, based on the image recognition, that the visitor is the target visitor according to the image feature information in the feature database. The method realizes that the information of the target visitor is pre-recorded by the user, whether the visitor is the target visitor is determined by the image recognition technology according to the pre-recorded image feature information when the target visitor comes and will pass the access control, and authentication without using a password, Bluetooth, or a visitor's mobile phone is realized by opening the access control after the determination, thereby avoiding the cumbersome steps of manually inputting a password and pulling out the terminal, improving the authentication and management efficiency of the access control, and improving the user experience.
Owner:BEIJING QDING INTERCONNECTION TECHNOLOGY CO LTD
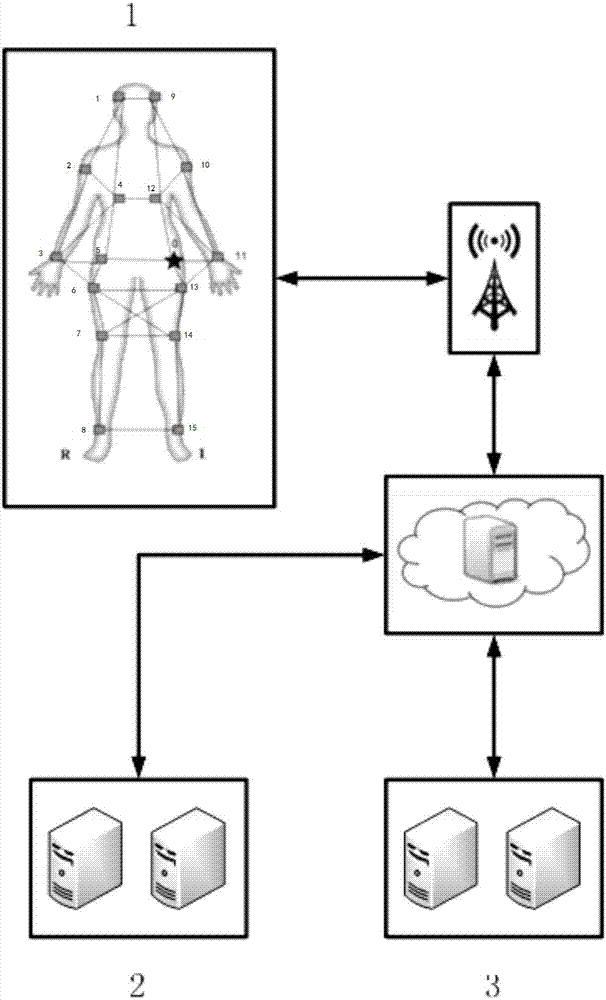
Medical big data processing method based on body area network and cloud computing
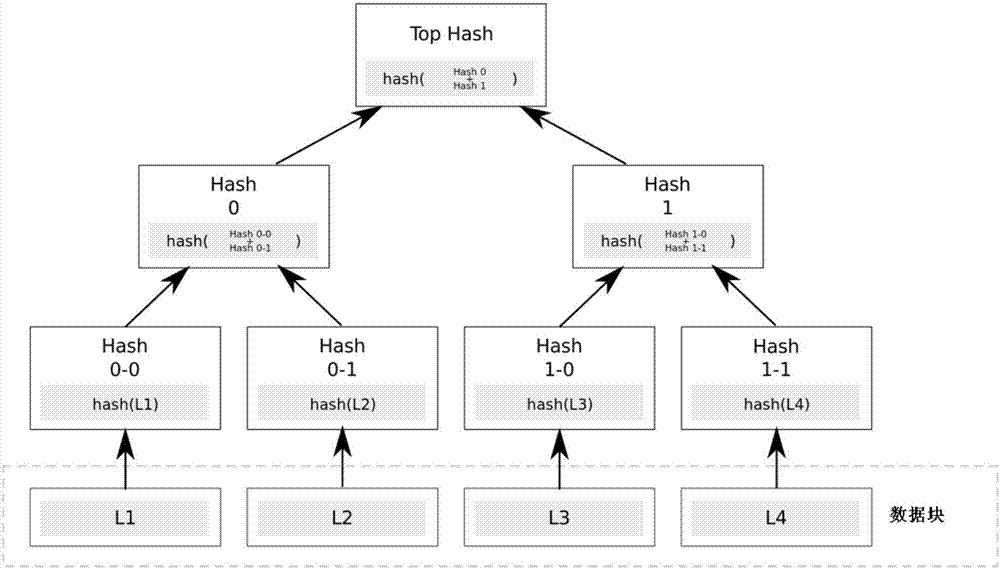
ActiveCN107040510AEnsure safetyReduce transmissionInput/output to record carriersTransmission systemsReal time analysisDiffie–Hellman key exchange
The invention discloses a medical big data processing method based on a body area network and cloud computing. The method comprises the steps that a physiological sensor senses user physiological data, generates a symmetric key for encryption of data through utilization of an APTEEN protocol and a Diffie-Hellman key exchange protocol, signs the data through utilization of a Merkle tree and transmits the processed data to a mobile device; the mobile device decrypts the data uploaded by the physiological sensor, verifies a user identity and completeness of the transmission data and sends verified user data to a cloud server for data storage and data analysis; and the cloud server stores a data analysis result and sends the data analysis result to the mobile device. According to the method, the medical data is stored and protected through adoption of a transmission encryption technology, so the problem that the privacy of a patient is leaked is effectively solved; and the data is transmitted to the cloud server in real time through a wireless network, redundancy eliminated storage and real-time decision analysis problems for the real-time transmission data are solved through utilization of a big data technology, and the security protection and real-time analysis of the medical big data are realized.
Owner:HUAQIAO UNIVERSITY
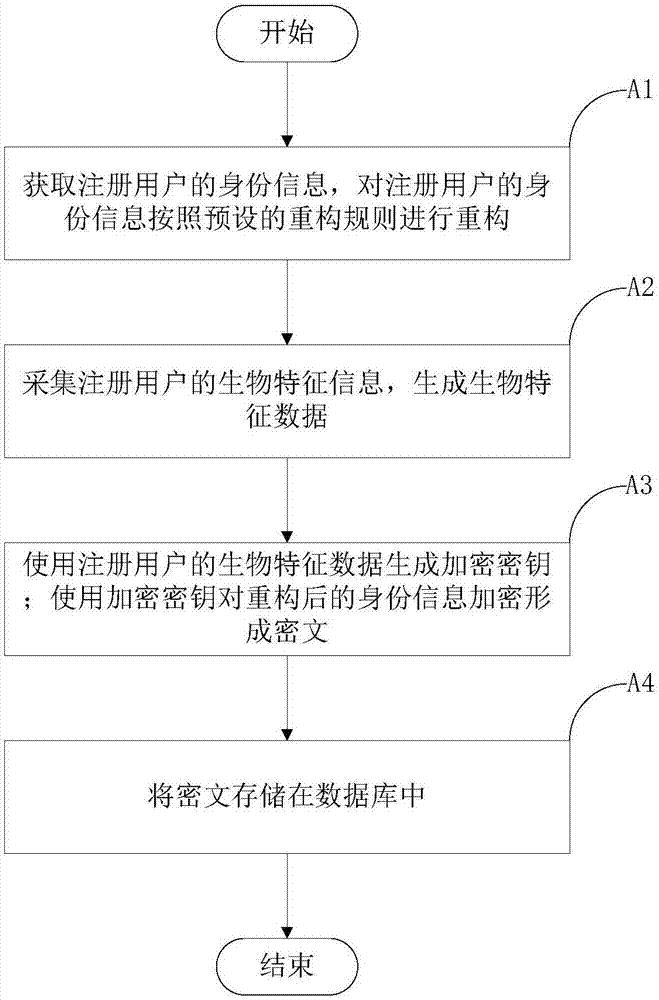
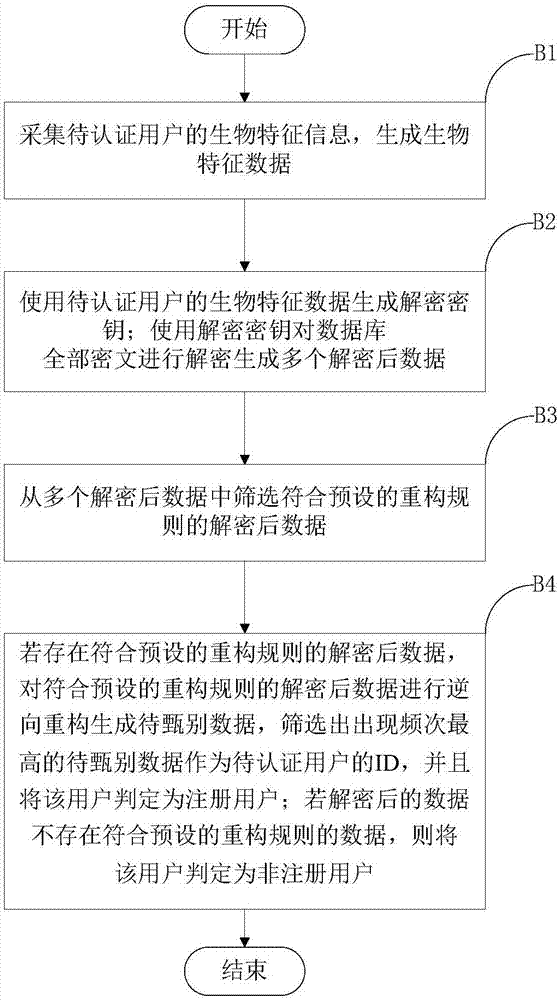
Identity authentication method and system based on biological characteristics and memory medium
ActiveCN107332659AImprove securityWill not cause lossKey distribution for secure communicationBiometric dataCiphertext
The invention discloses an identity authentication method based on biological characteristics and relates to the technical field of biological characteristic data processing. The method comprises the steps of obtaining and reconstructing identity information of a registered user; collecting biological characteristic information of the registered user and generating biological characteristic data; through adoption of a preset key generation method, generating an encryption key through utilization of the biological characteristic data of the registered user; encrypting the reconstructed identity information through utilization of the encryption key, thereby generating a ciphertext; collecting the biological characteristic information of a to-be-authenticated user and generating the biological characteristic data; generating a decryption key through utilization of the biological characteristic data of the to-be-authenticated user; decrypting the ciphertext through utilization of the decryption key and generating a plurality of pieces of decrypted data; and screening the decrypted data consistent with a reconstruction rule, carrying out reverse reconstruction to generate to-be-identified data, screening the to-be-identified data with the highest occurrence frequency as the identity information of the to-be-authenticated user, and judging the user as the registered user. The invention also discloses another identity authentication method based on the biological characteristics.
Owner:武汉真元生物数据有限公司
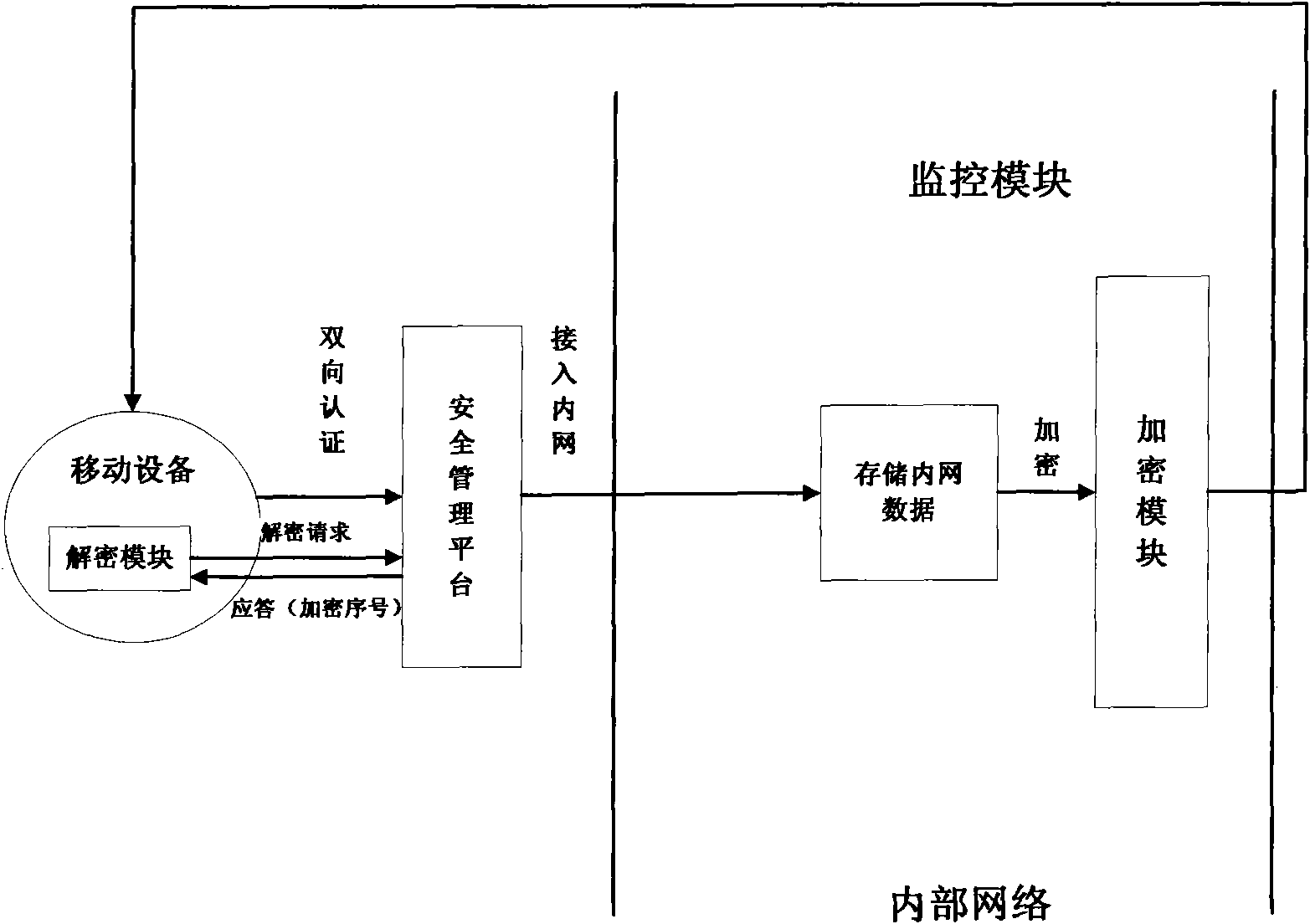
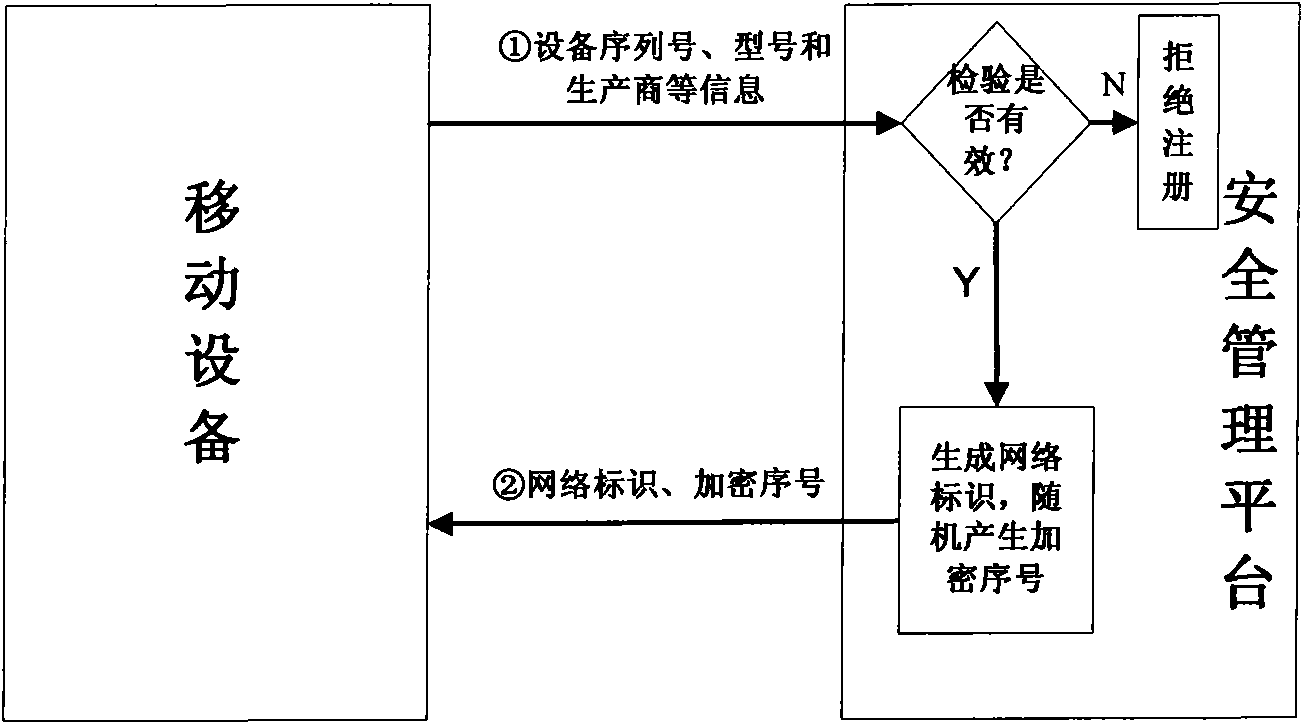
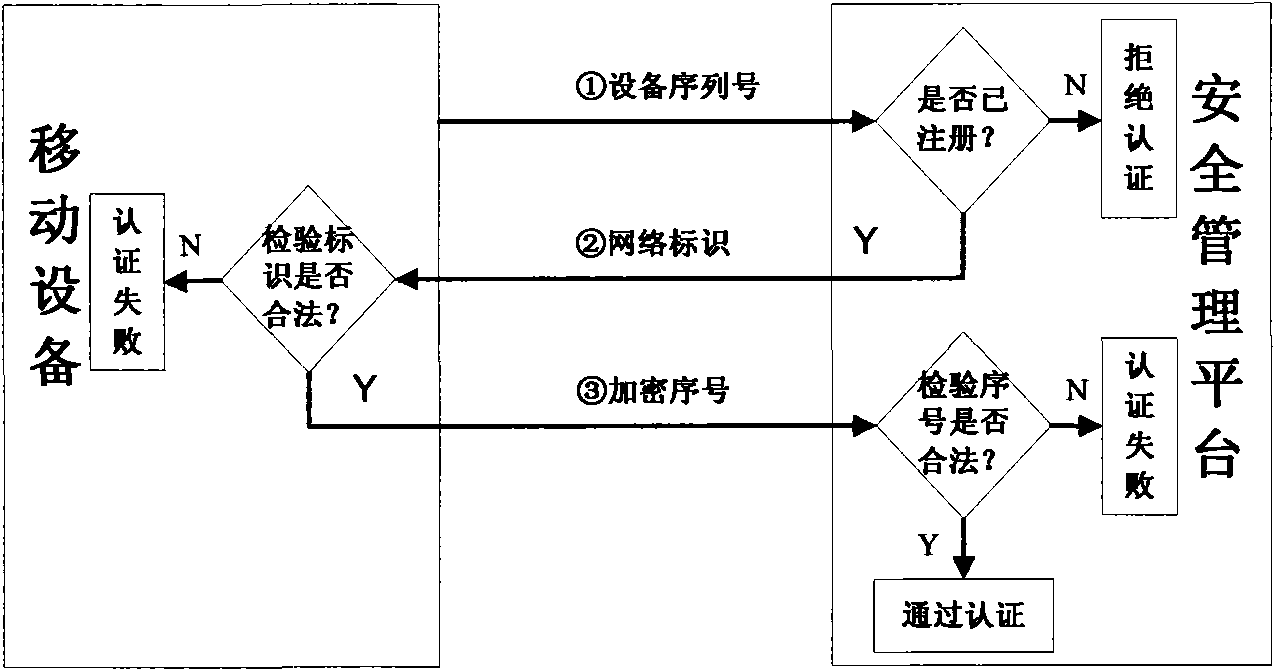
Realization system and method for safely visiting and storing intranet data by mobile equipment
InactiveCN101800738AAchieve authenticationDefend against impersonation attacksUser identity/authority verificationData switching by path configurationConfidentialityMobile device
The invention discloses a realization system and a method for safely visiting and storing intranet data by mobile equipment. The method comprises the following steps: judging whether the mobile equipment is registered or not by a security management platform; carrying out mutual authentication on the registered mobile equipment; allowing the accession to the intranet after the authentication success; rejecting the accession to the intranet of unregistered mobile equipment and authentication failed mobile equipment; invoking an encryption module when a monitoring module discovers that the mobile equipment is about to store the intranet data in the intranet into the mobile equipment per se; selecting corresponding encryption methods by the encryption module under the monitoring of the monitoring module according to the confidentiality levels of the intranet data for encrypting the intranet data to be stored into the mobile equipment; and inquiring whether the encryption data is confidentiality data or not by a decryption module to the monitoring module in the intranet when the encryption data stored in the mobile equipment needs to be decrypted, and then, selecting corresponding methods for decrypting the encryption data. The invention implements different encryption and decryption methods according to different confidentiality levels, improves the encryption and decryption efficiency and data confidentiality, integrally utilizes the mutual authentication method and the encryption and decryption method, and improves the security of the intranet data.
Owner:JINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com