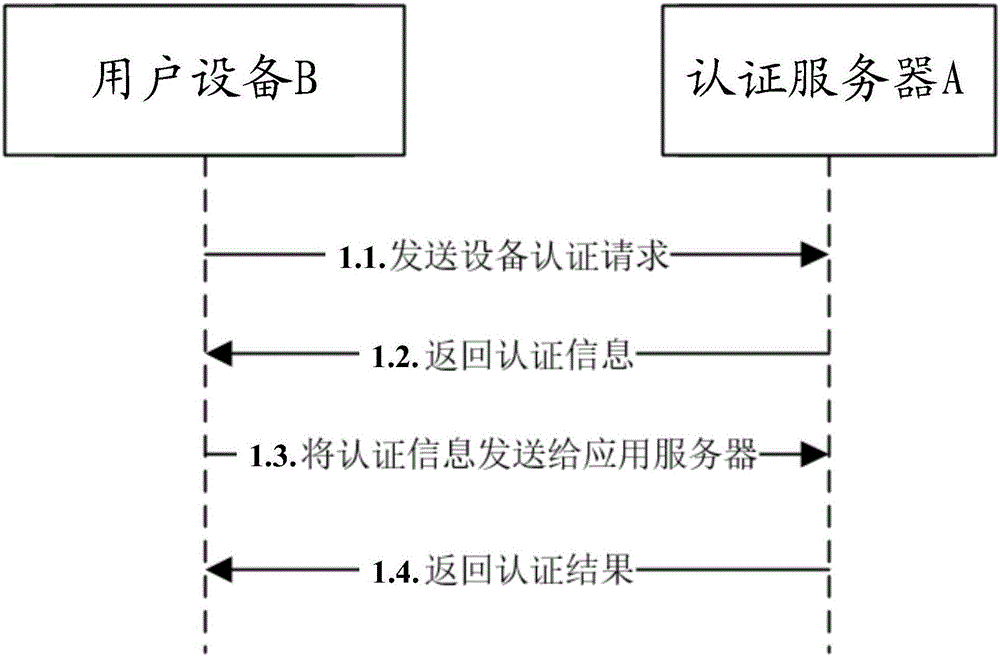
Block chain based equipment certification method, certification server and user equipment
An authentication server and device authentication technology, applied in the direction of instruments, data processing applications, payment systems, etc., can solve problems such as attacks, third-party hijacking of authentication information, and inability to guarantee the uniqueness of user equipment, so as to improve efficiency and simplify the verification process. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
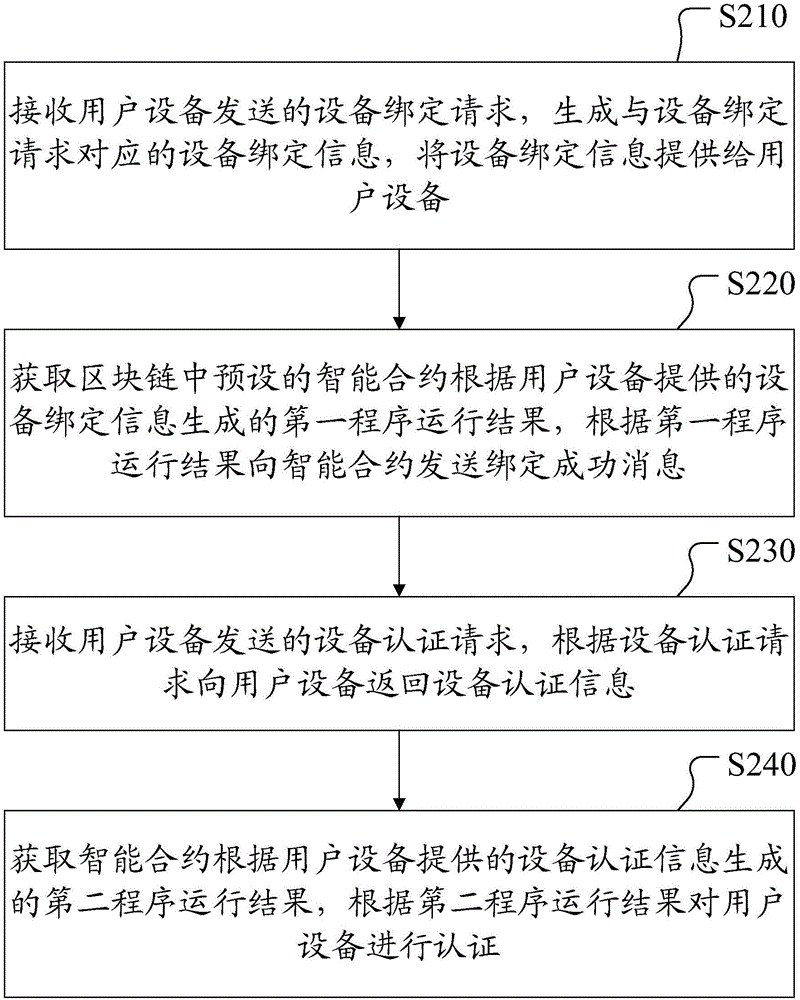
[0024] figure 2 It is a flow chart of a blockchain-based device authentication method provided in Embodiment 1 of this application. Such as figure 2 As shown, the method includes:
[0025] Step S210: Receive a device binding request sent by the user equipment, generate device binding information corresponding to the device binding request, and provide the device binding information to the user equipment.
[0026] In the embodiment of the present invention, in order to ensure the uniqueness of the user equipment that initiates the authentication request, before performing the authentication operation, the binding information of the user equipment needs to be stored in the smart contract of the block chain. Therefore, it is necessary to generate corresponding and unique device binding information for the device binding request sent by the user equipment, and return the device binding information to the user equipment, so that the user equipment can send the device binding in...
Embodiment 2
[0037] image 3 It is a flow chart of a blockchain-based device authentication method provided in Embodiment 2 of the present application, and the execution body of the method is preferably an authentication server. Such as image 3 As shown, the method includes:
[0038] Step S310: Set up the smart contract, and broadcast the smart contract to the blockchain.
[0039] Specifically, the preset smart contract is broadcast to the blockchain network in the form of blockchain transactions, and after verification by most nodes, the smart contract reaches a consensus on the blockchain network, and then the smart contract can run on the blockchain network. Among them, the structure of the above smart contract is divided into three parts, namely the smart contract blockchain account address, data part and program part, and the program part of the smart contract can realize three functions, one is to write data to the data part , which is used to perform data writing operations on ...
Embodiment 3
[0052] Figure 4 It is a flow chart of a blockchain-based device authentication method provided in Embodiment 3 of the present application, Figure 4 The execution subject of the shown method may be a user equipment. Such as Figure 4 As shown, the method includes:
[0053] Step S410: Send a device binding request to the authentication server, and receive device binding information returned by the authentication server according to the device binding request.
[0054] In this embodiment, in order to ensure the uniqueness of the user equipment that initiates the authentication request, before performing the authentication operation, it is necessary to perform a binding operation on the user equipment, and store the binding information of the user equipment in the smart contract of the block chain . Therefore, after the user equipment sends a binding request to the authentication server, the authentication server needs to generate corresponding and unique device binding info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com