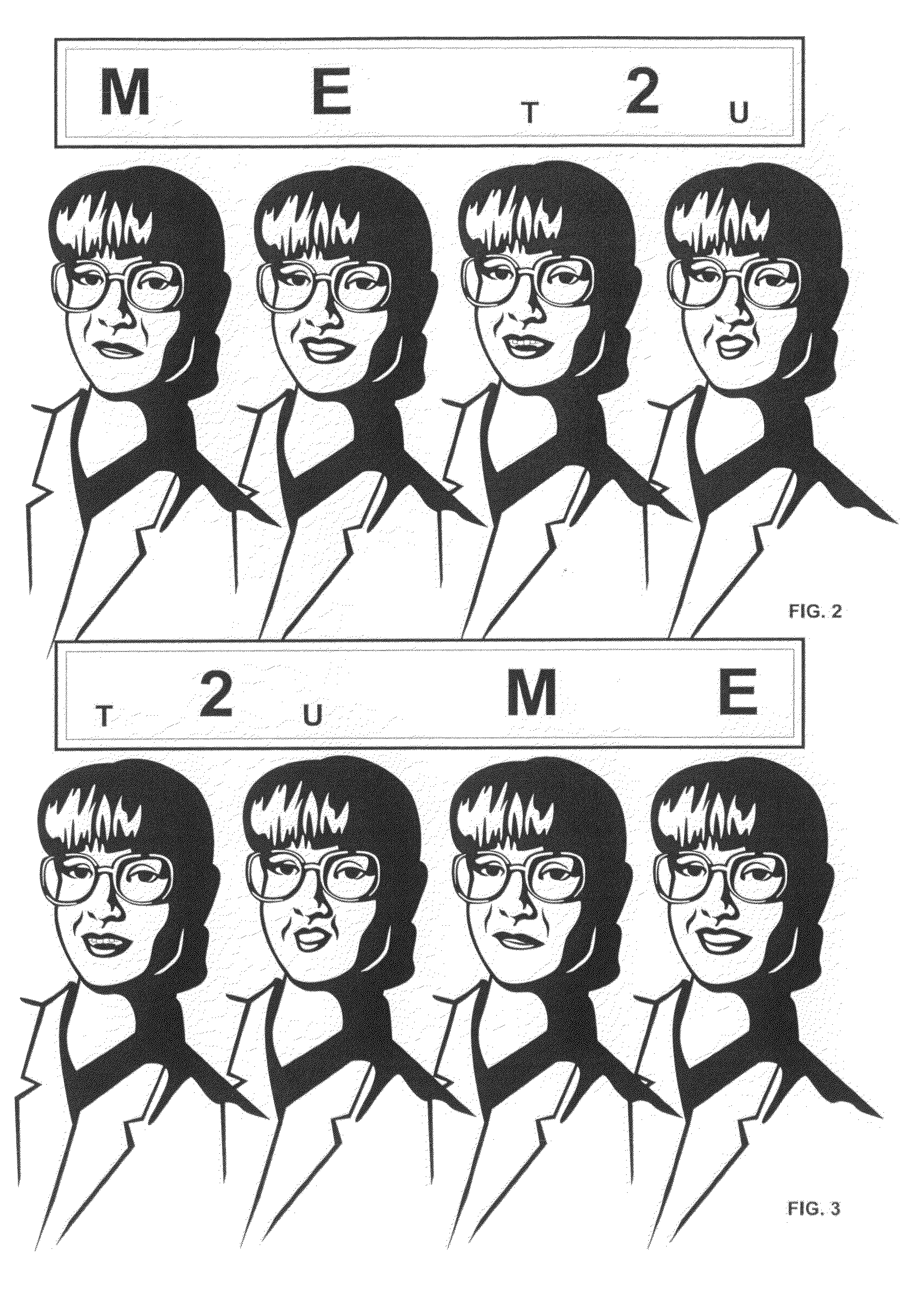Patents
Literature
170results about How to "Simplify the verification process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
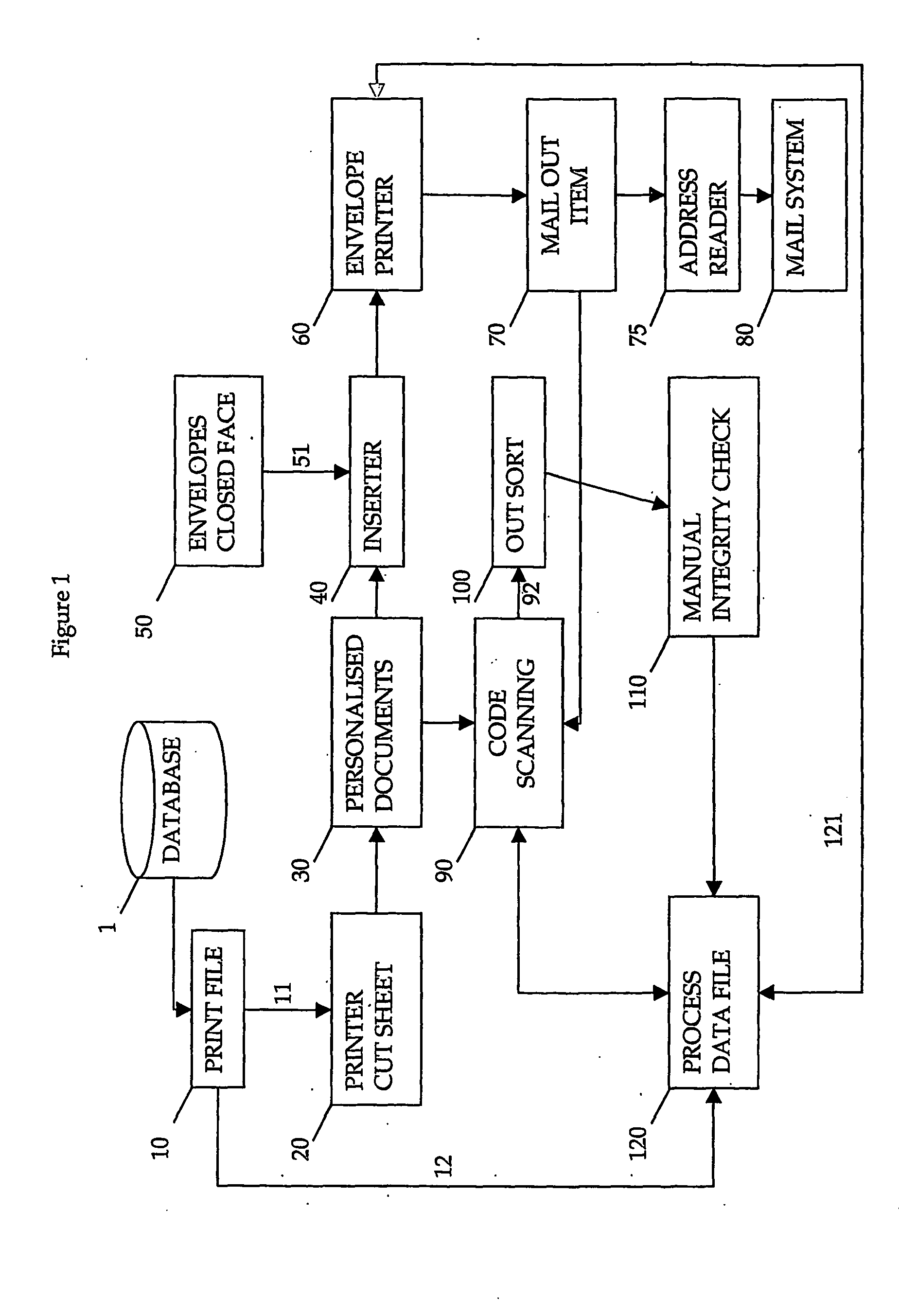
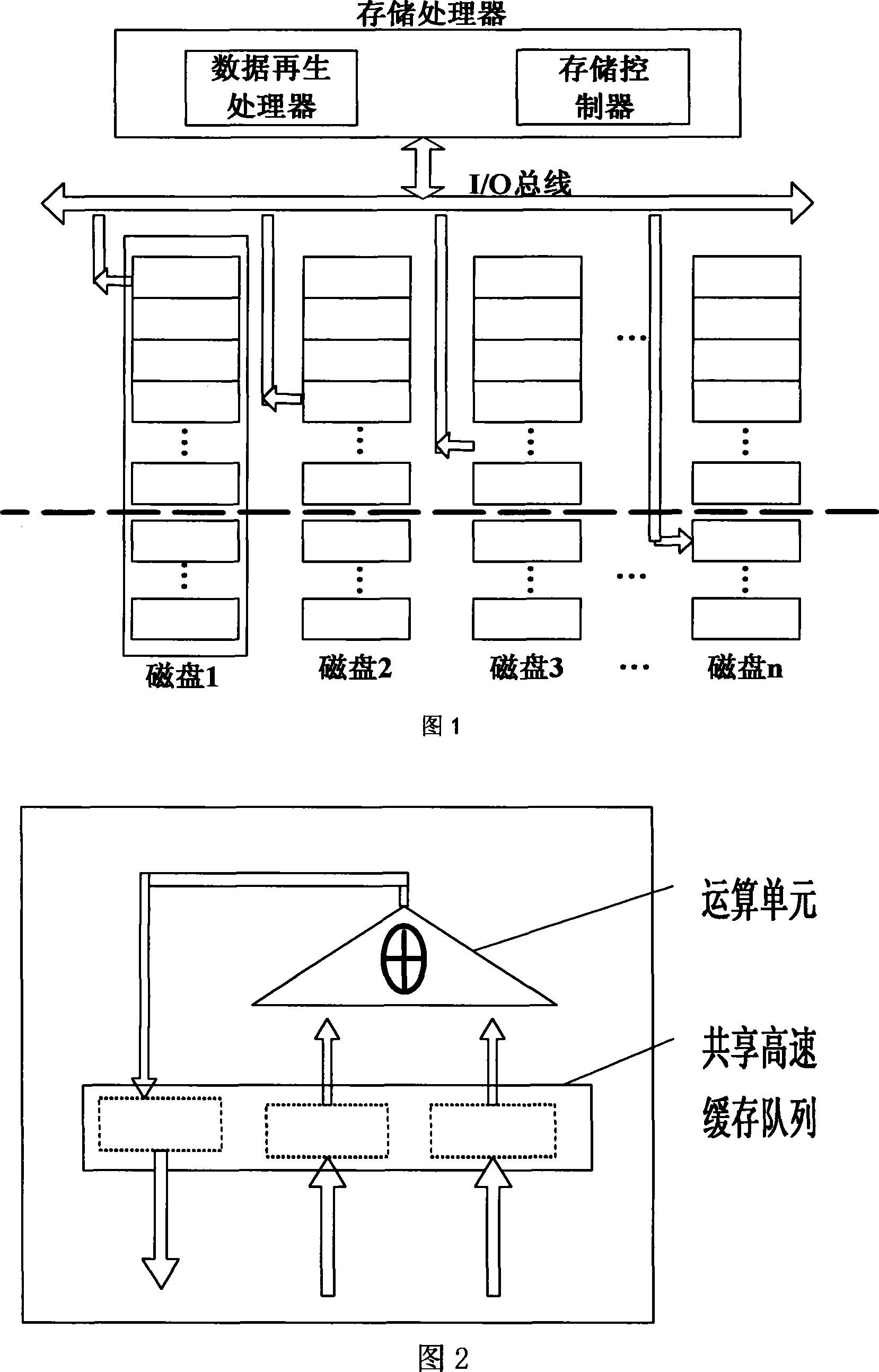
Method, device and system for communication through mobile communication network
ActiveCN102711105ASimplify the verification processImprove securityConnection managementSecurity arrangementRadio networksMobility management
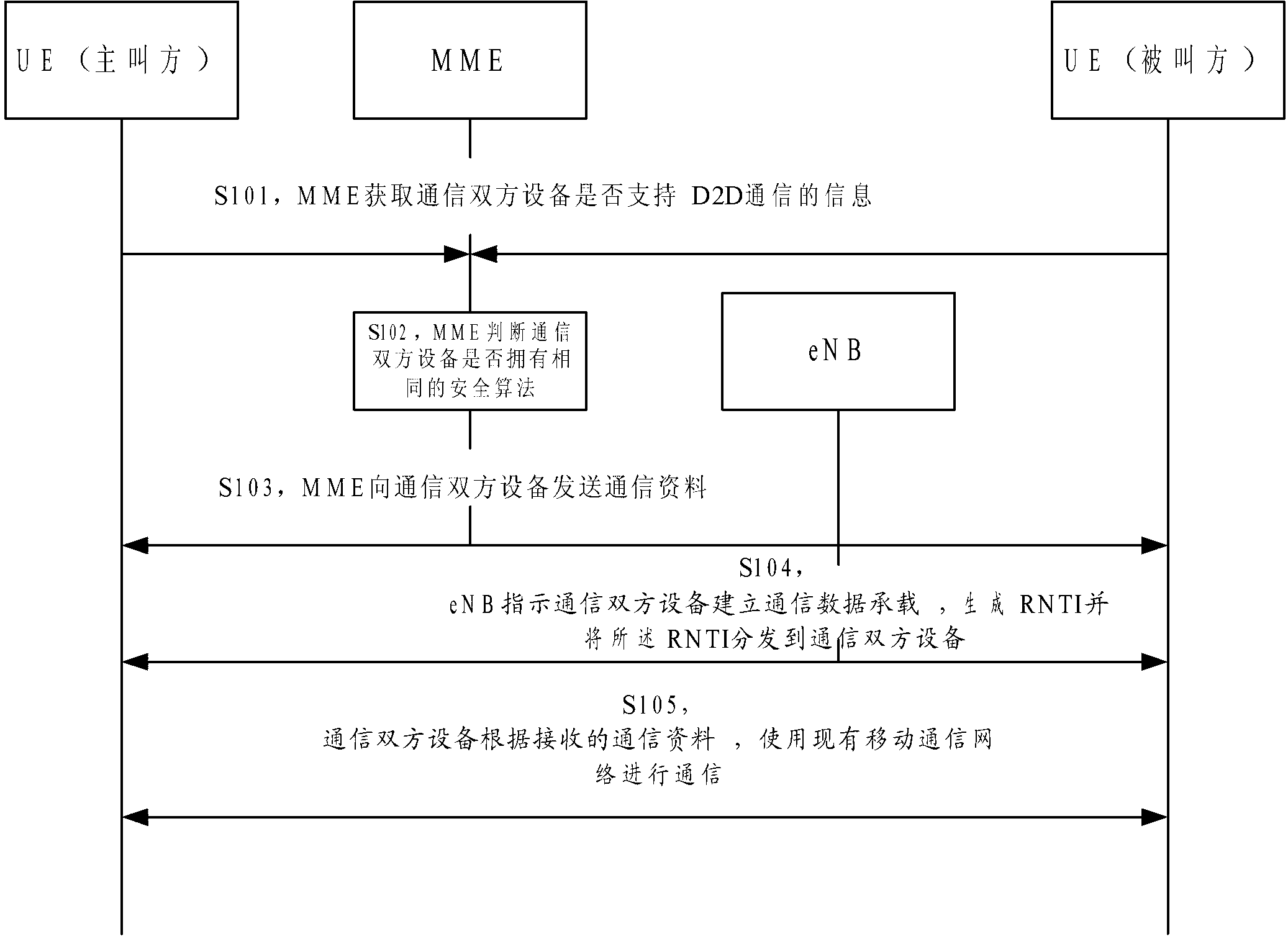
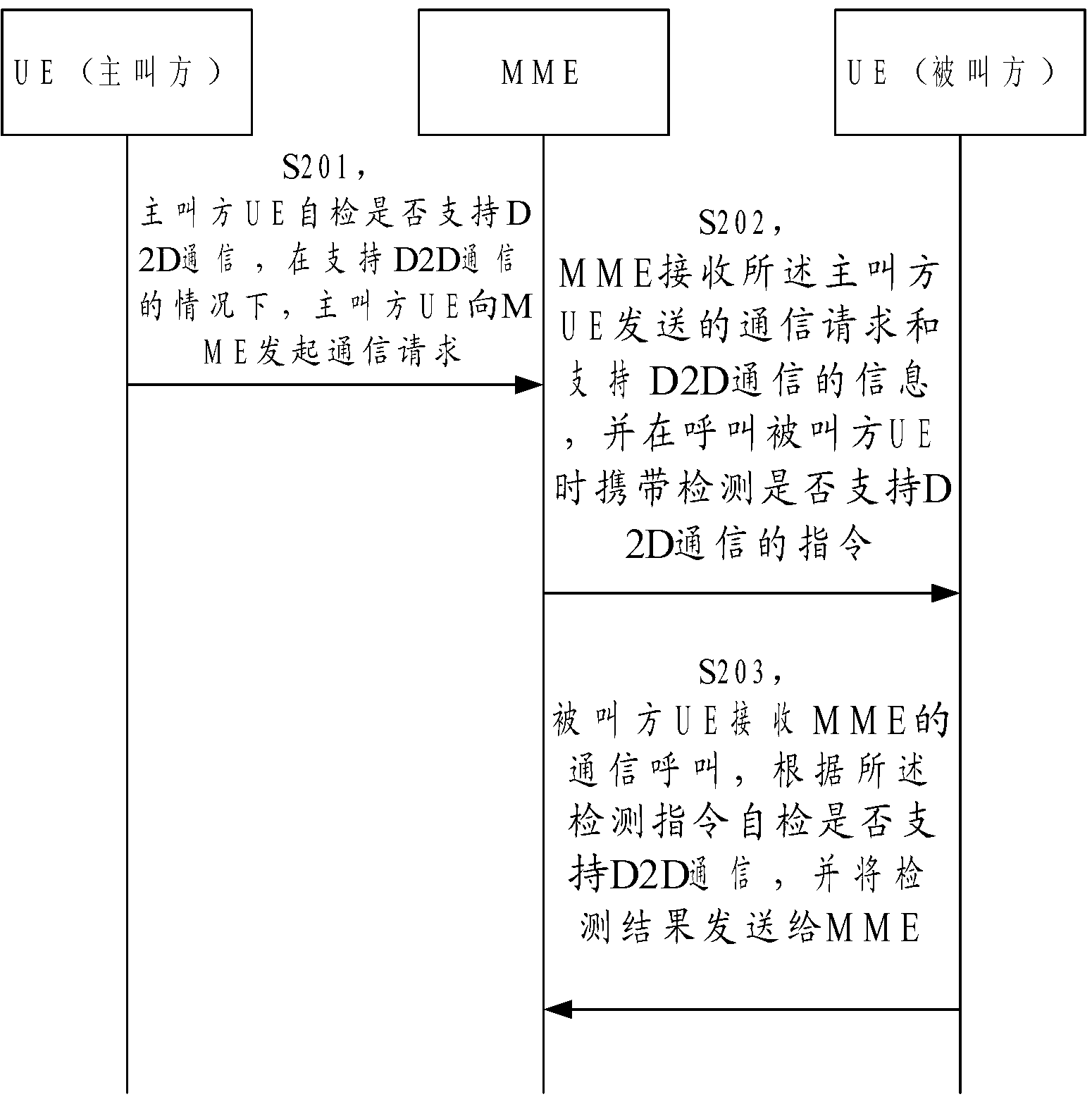
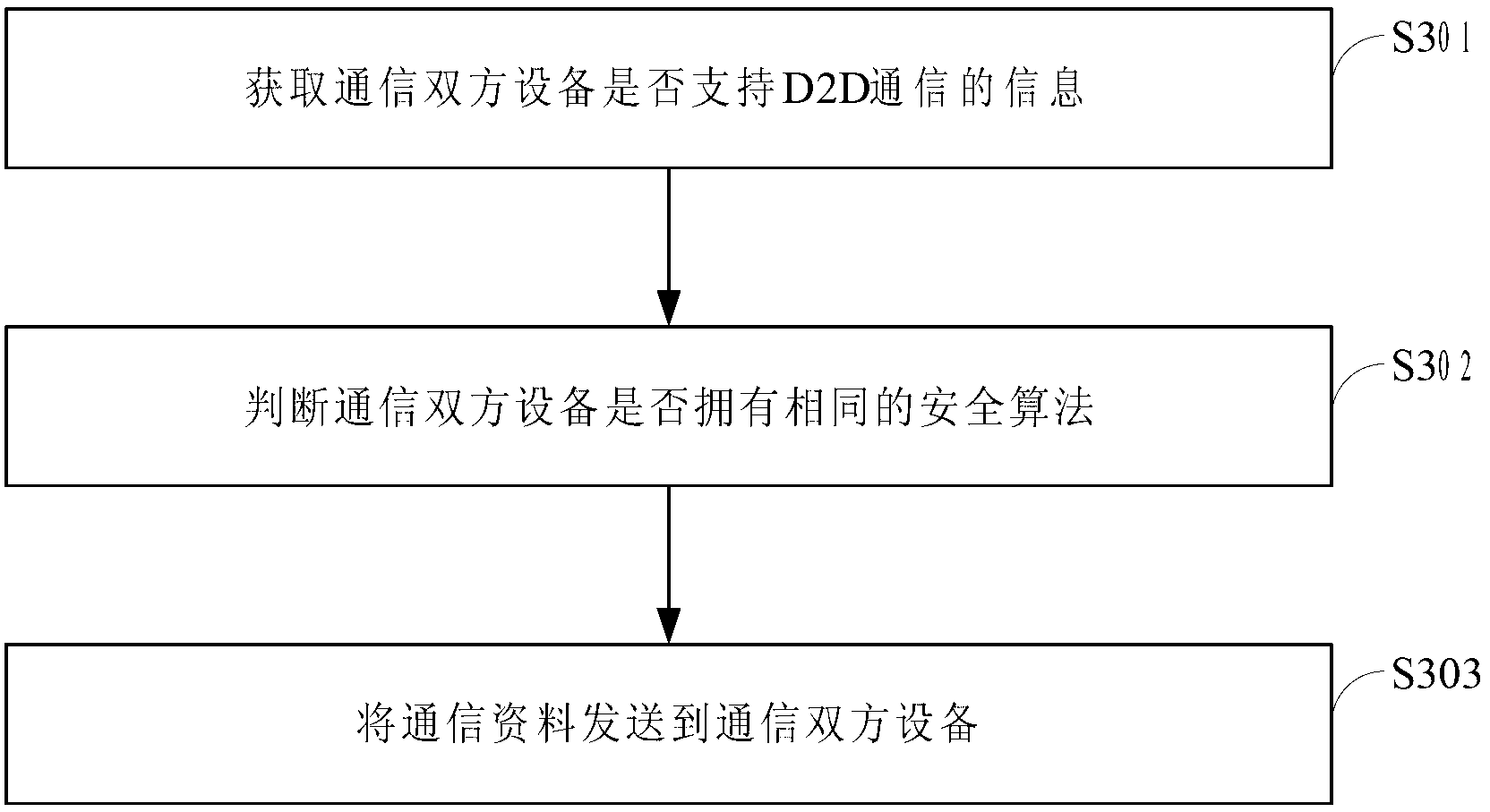
The invention is applied to the field of communication and provides a method for communication through a mobile communication network. The method comprises the following steps that mobility management entity (MME) sends communication materials to equipment of two communication parties; evolved Node B (eNB) indicates that the equipment of the two communication parties establishes communication data carriers, generates radio network temporary identity (RNTI), and distributes the RNTI to the equipment of the two communication parties; the equipment of the two communication parties performs communication according to received communication materials by using existing mobile communication network. By means of the embodiment of the method for communication through the mobile communication network, MME acquires information that whether UE (user equipment) can perform D2D (disk to disk) communication, then whether two communication parties can perform identical security algorithm is judged, security algorithm used by existing mobile communication is sent to the two communication parties, and the two communication parties are in communication through the security algorithm used by existing mobile communication technology, so that the mobile communication technology is applied in D2D communication aspect, and by means of the existing mobile communication technology, the verification process is simple, and security level is high.
Owner:HUAWEI TECH CO LTD
Methods and systems for secure internet access and services
ActiveUS20150135282A1Improve security levelLower security levelDigital data processing detailsMultiple digital computer combinationsCable Internet accessInternet access
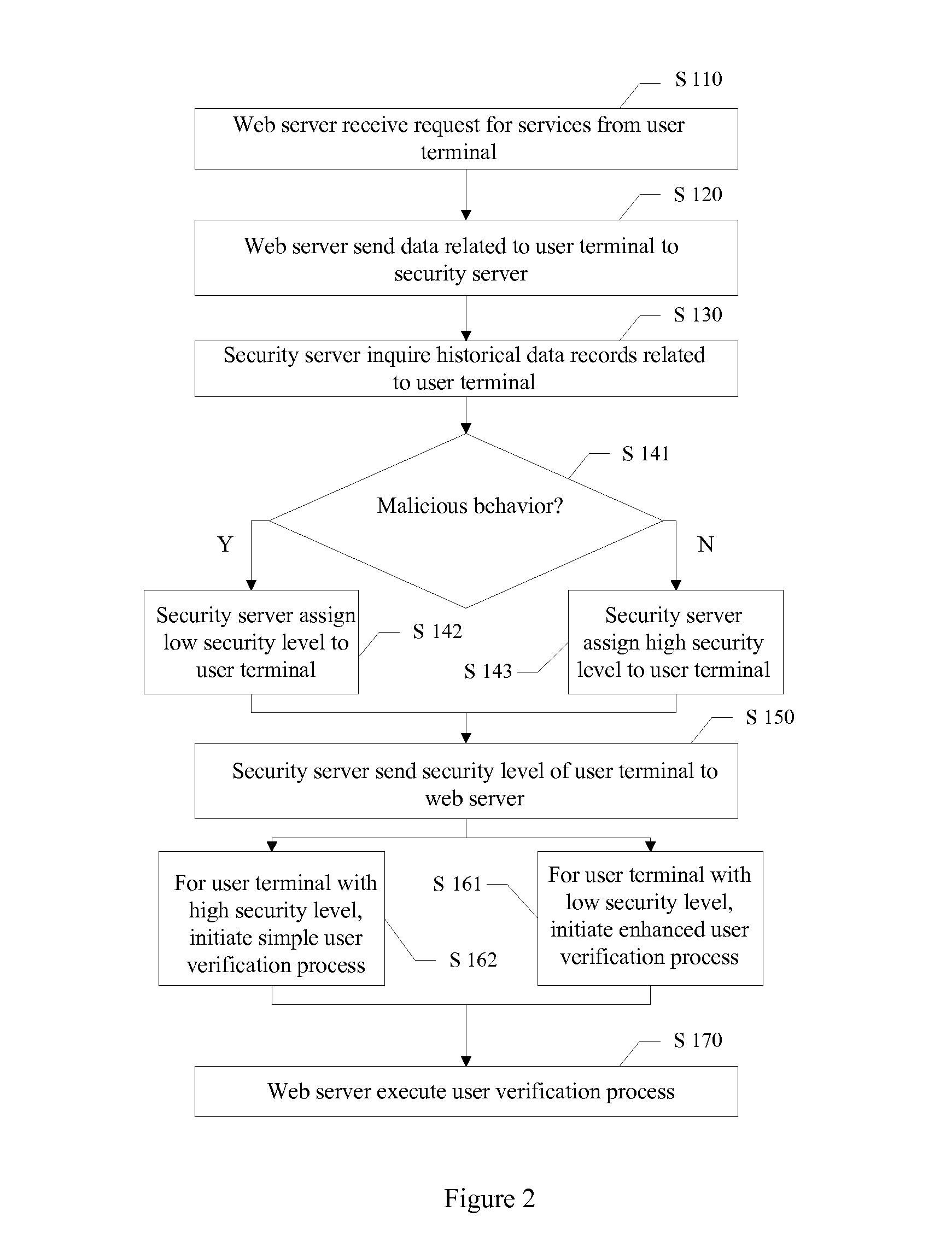
A method and system for providing secure internet access and services are disclosed. The method includes receiving a request for services from a user terminal, the request including user terminal data; sending the user terminal data to a security server; and receiving a security level of the user terminal from the security server. The security server determines the security level of the user terminal based on historical user data related to the user terminal. The method further includes initiating a verification process based on the security level of the user terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System and method for performing secure online transactions
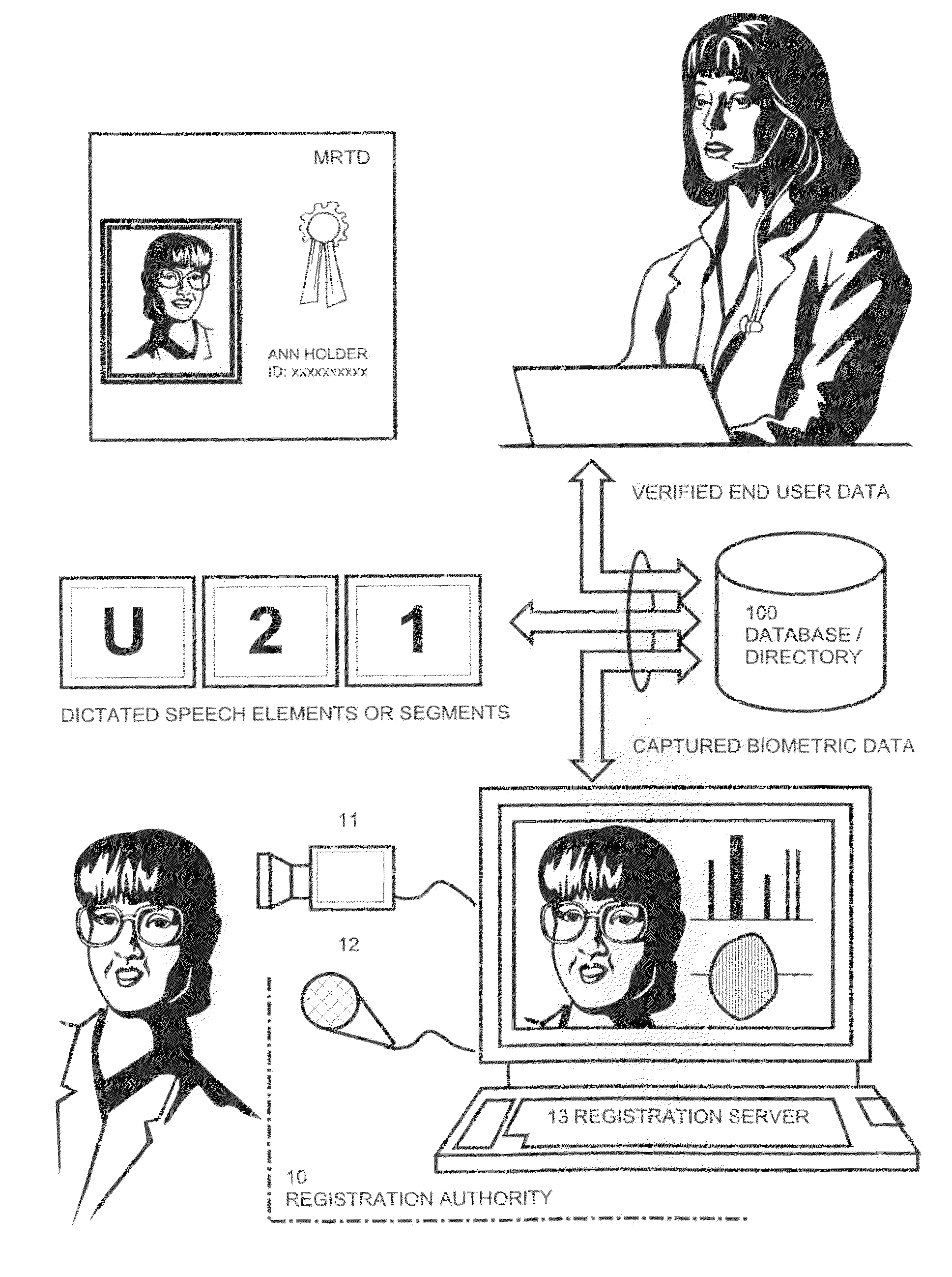
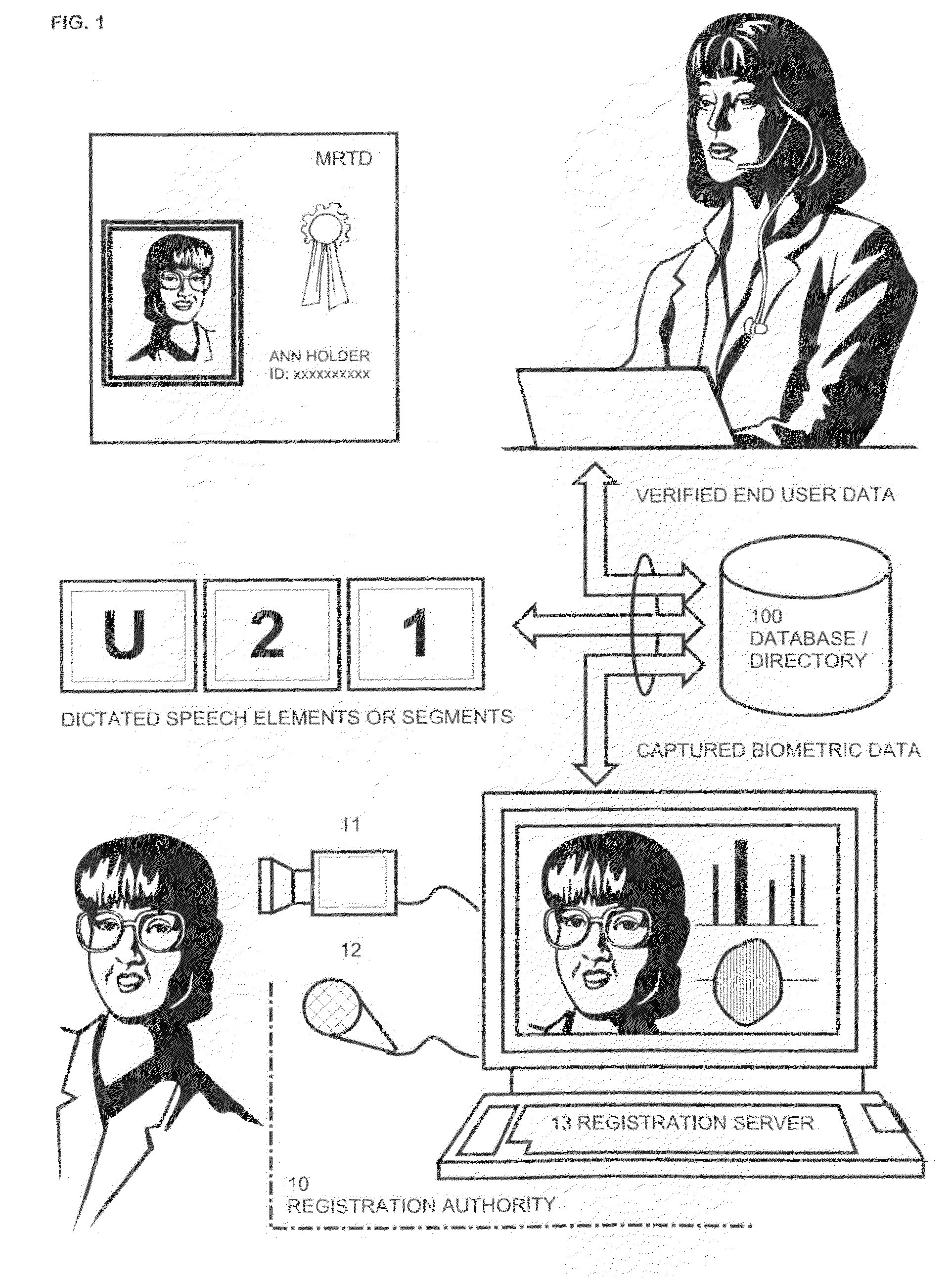
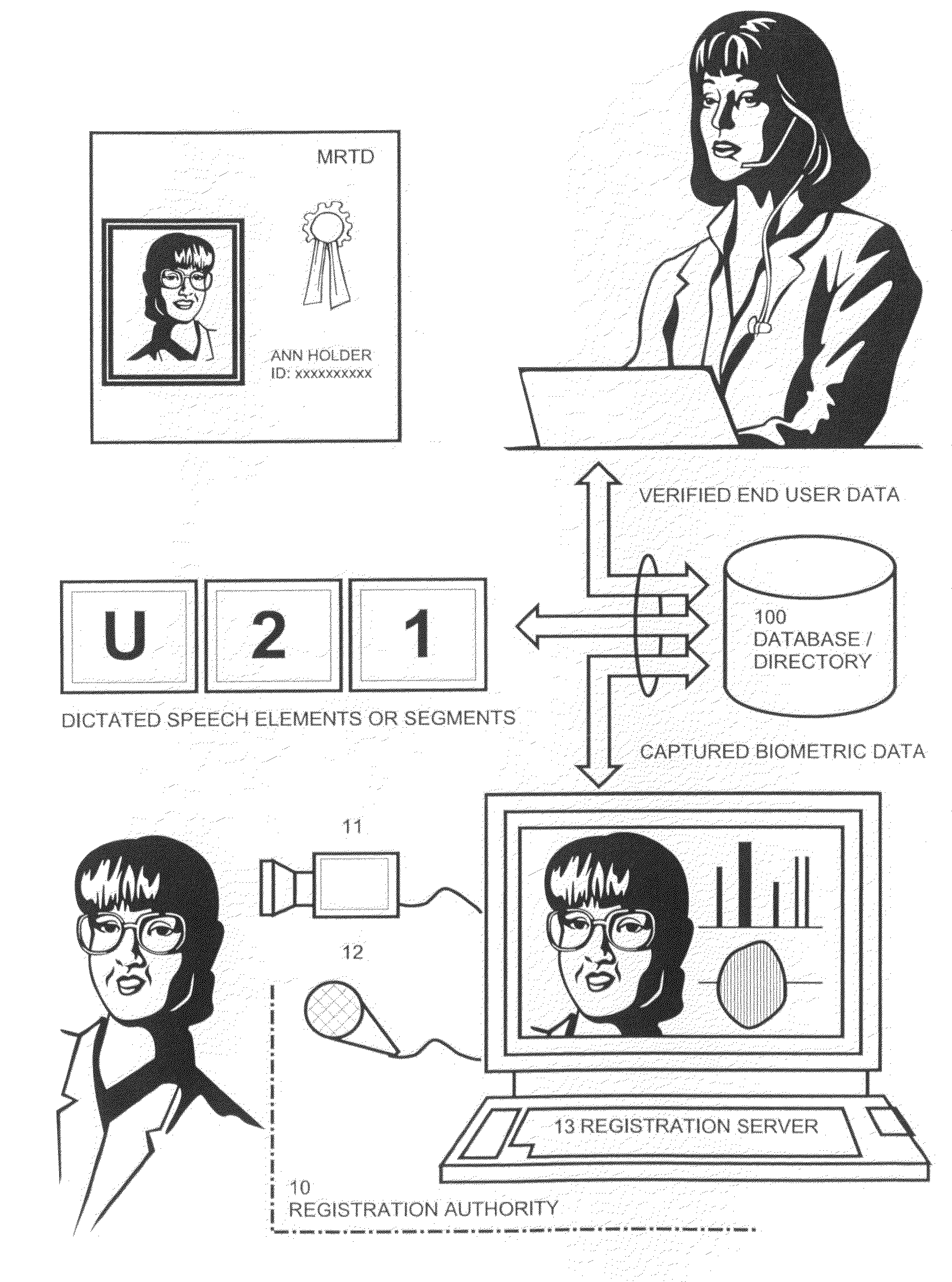
ActiveUS8370262B2Simplify the verification processImprove securityElectric signal transmission systemsDigital data processing detailsResponse processBiometric data
Owner:BLESSING
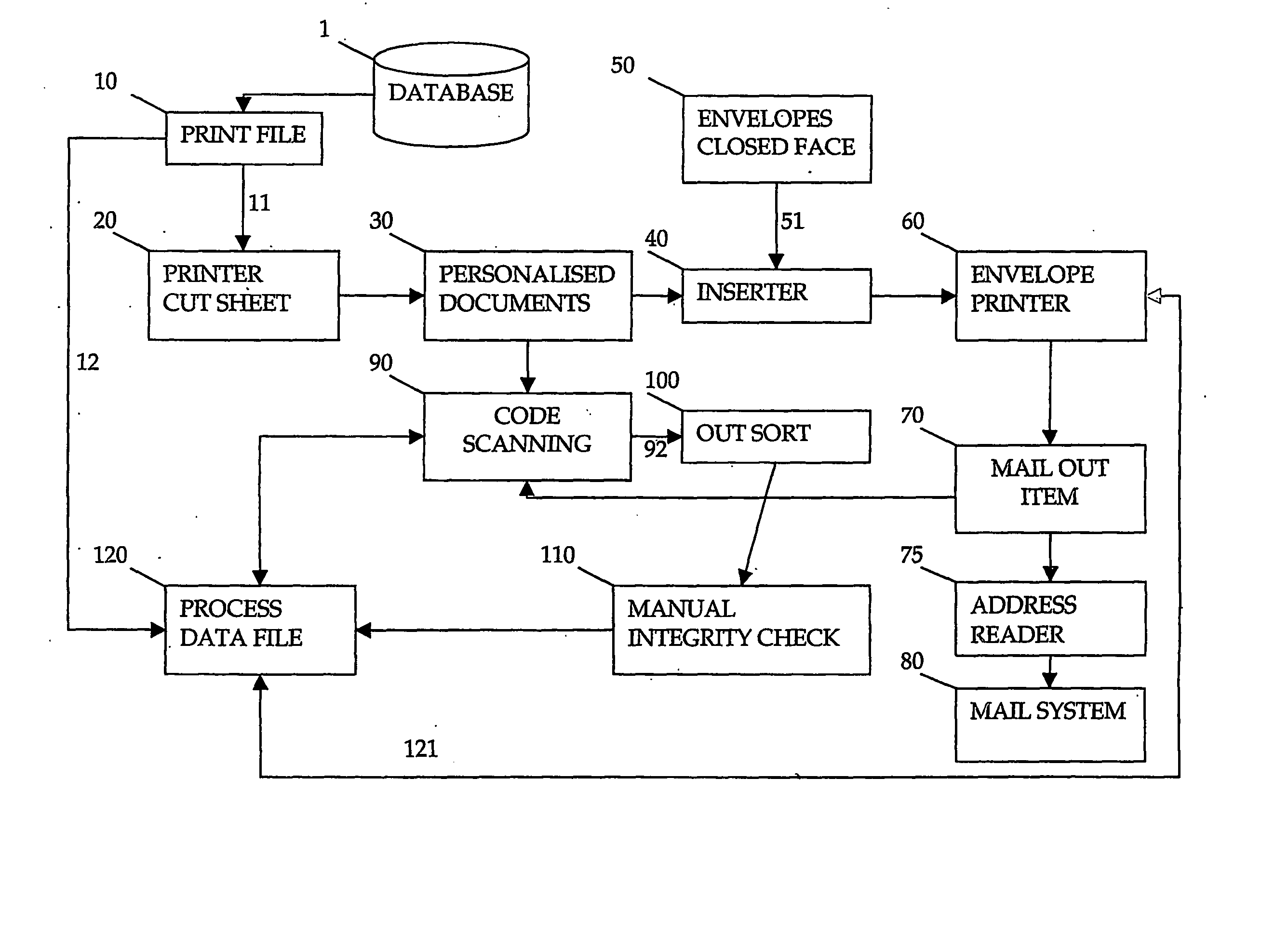
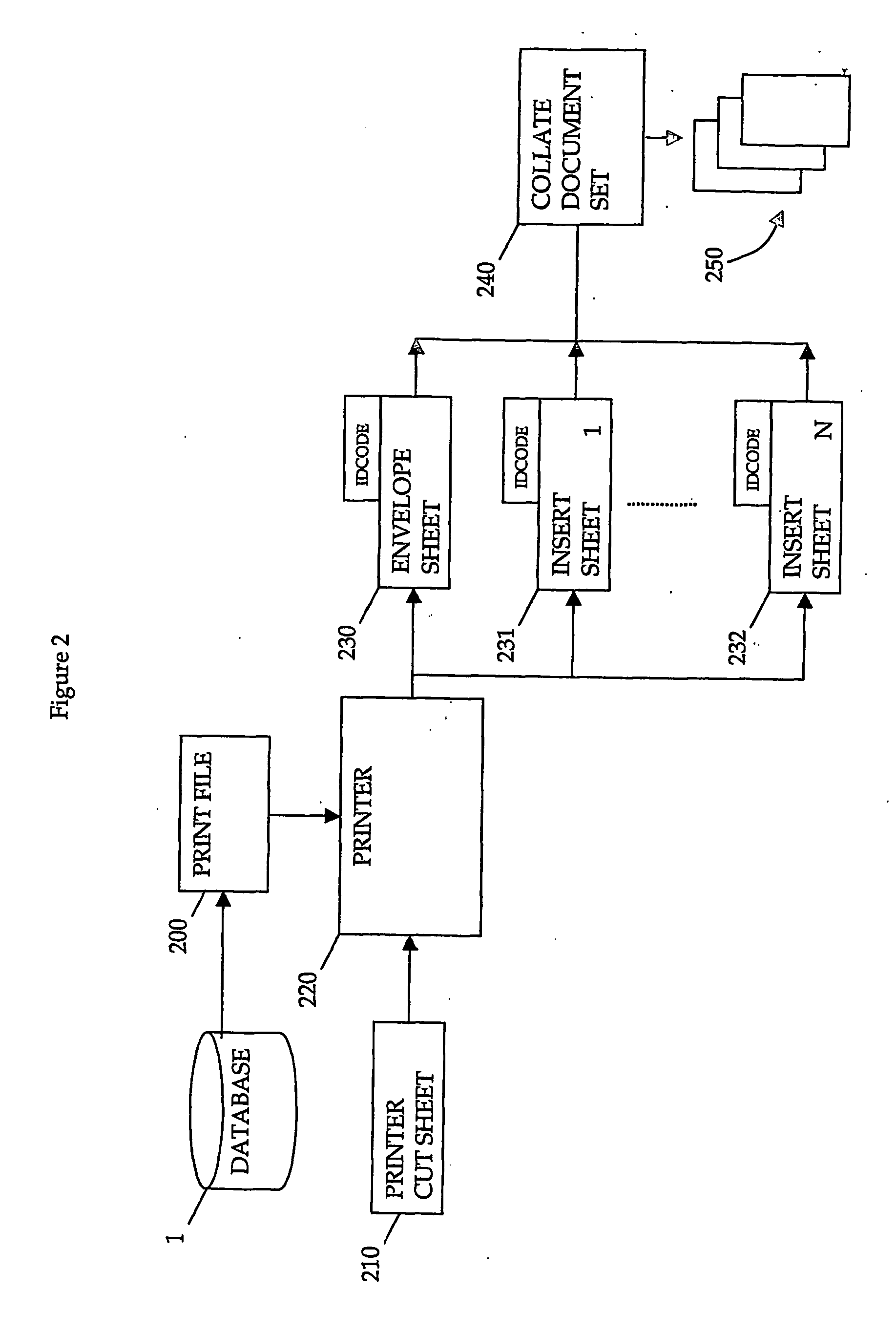
Method and apparatus for forming a document set
InactiveUS20060284360A1Reduce complexityReduces varietyOther printing matterBag making operationsEngineeringMechanical engineering
Owner:ENVELOPMENTS
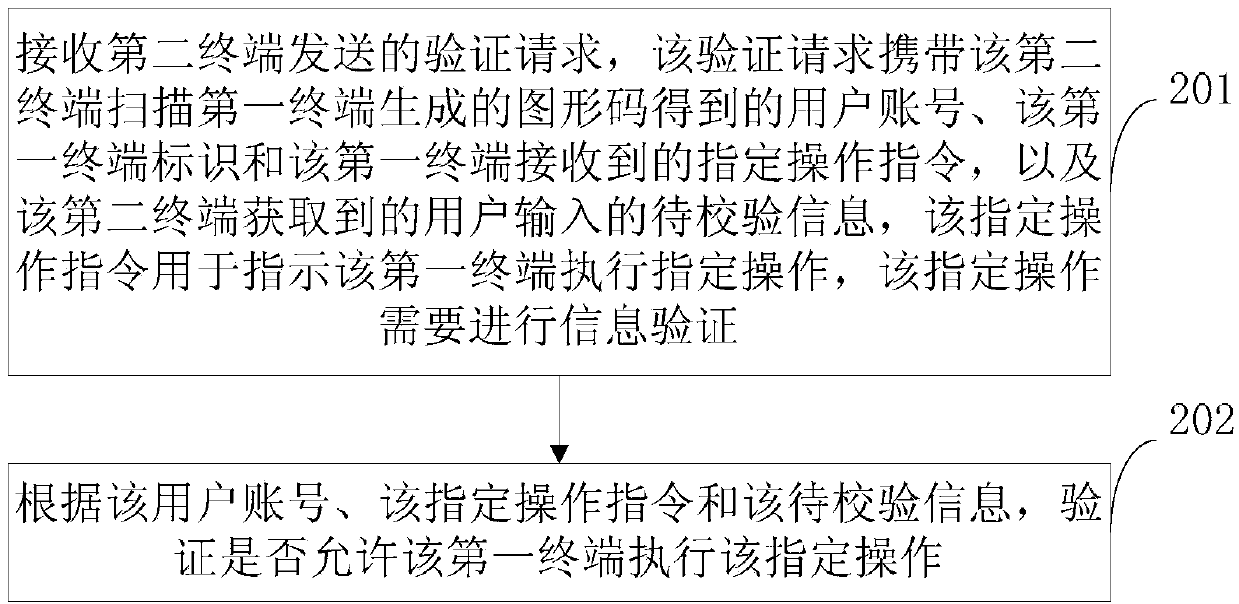
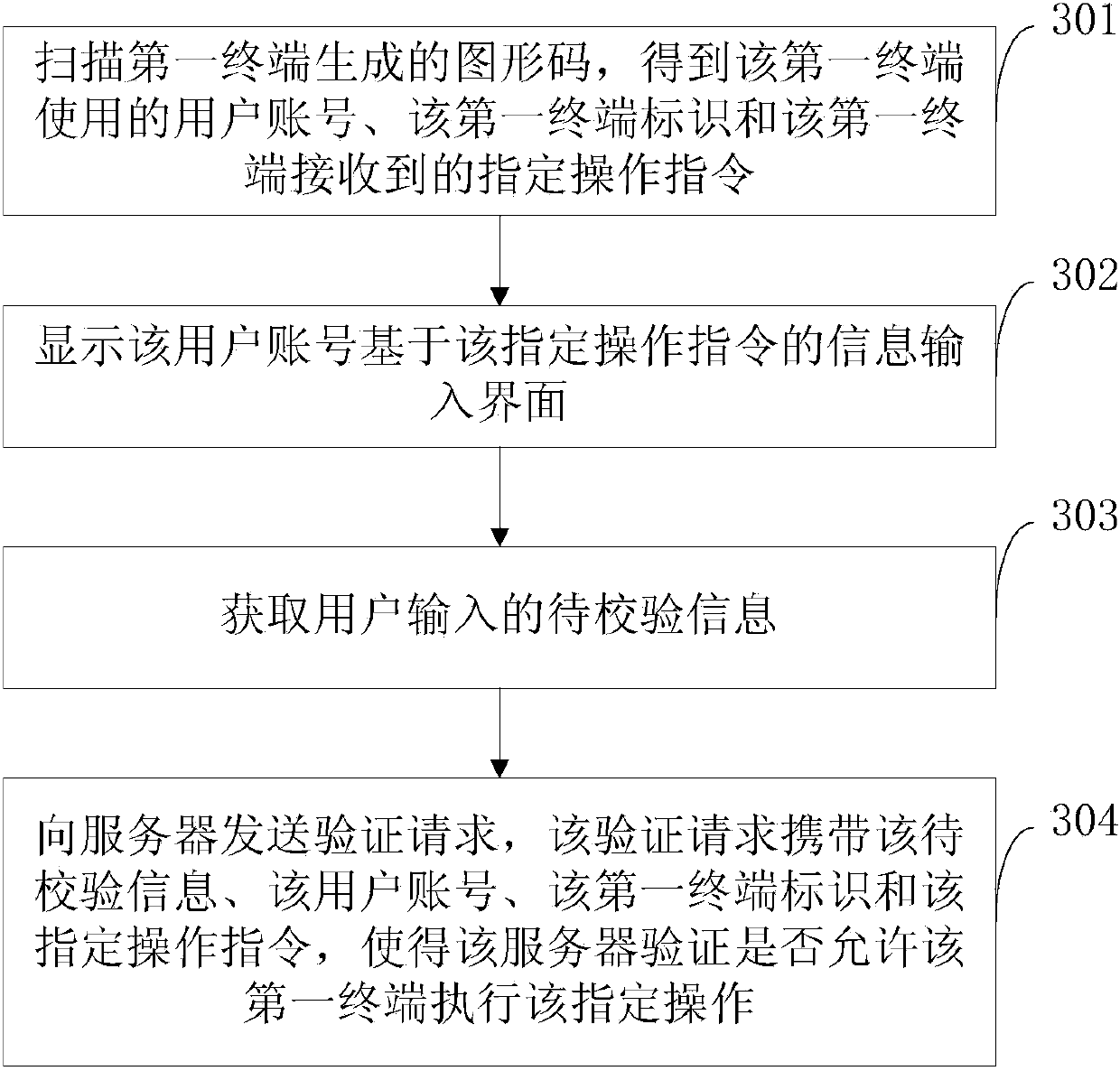
Information verifying method and device
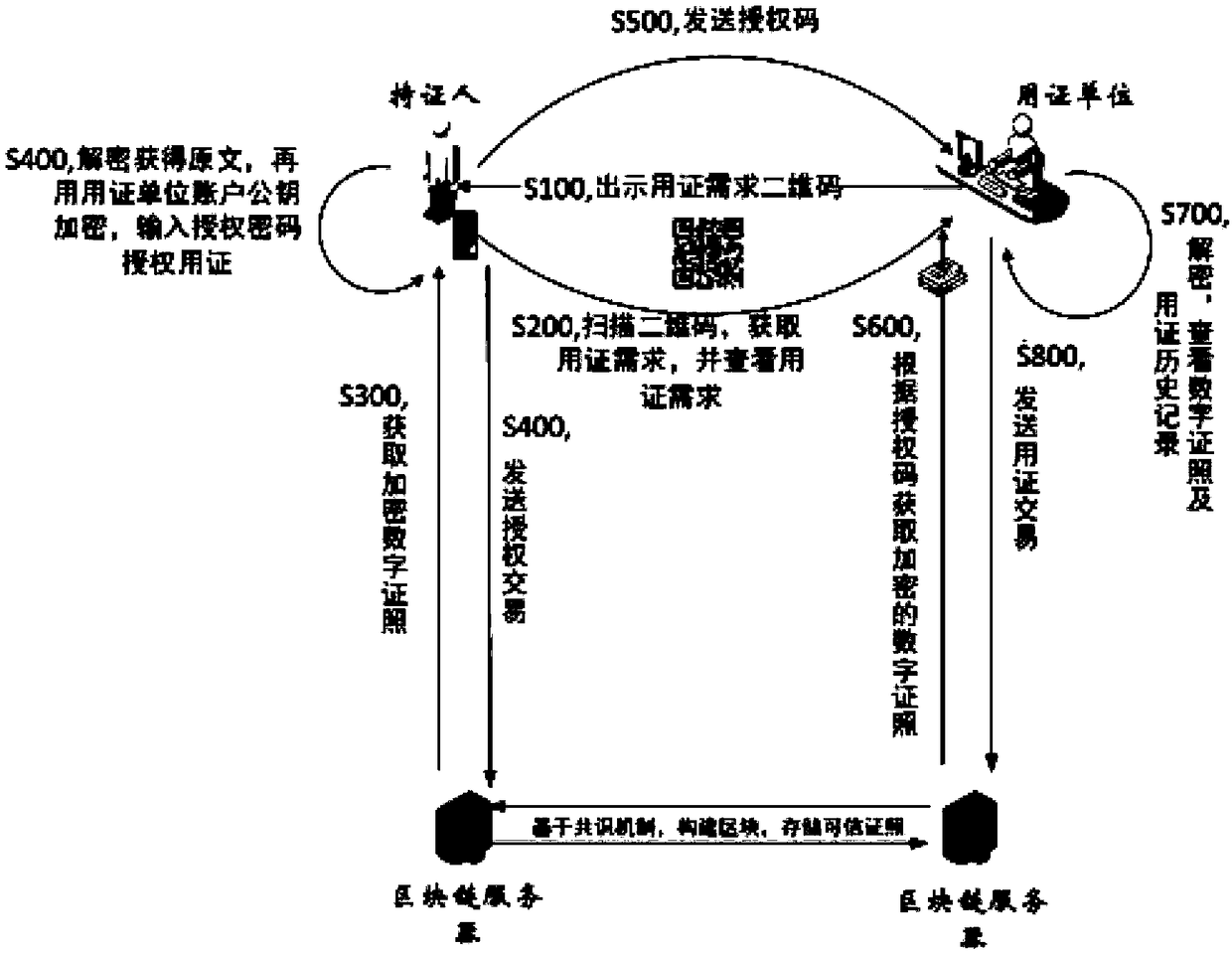
ActiveCN103634294AEasy inputSimplify the verification processUser identity/authority verificationInformation leakageGraphics
The invention relates to an information verifying method and an information verifying device, and belongs to the technical field of networks. The method comprises the steps that a first terminal receives specified operation instructions; according to the specified operation instructions, graphic codes are generated so that a second terminal displays an information input interface through scanning the graphic codes, in addition, information, input by users, to be checked is obtained, an verification request is sent to a server, and the server verifies whether a first terminal is allowed to execute the specified operation or not. The information verifying method and the information verifying device have the advantages that the input process of the information to be checked after the first terminal receives the specified operation instructions is transferred onto the second terminal, so the process for inputting the information to be checked is simpler and more convenient, the information verification process is simplified, the time for inputting the information to be checked is reduced, the information verification efficiency is improved, and in addition, a display screen of the second terminal is obviously smaller than that of the first terminal, the information leakage cannot be easily caused, and the safety is improved.
Owner:XIAOMI INC
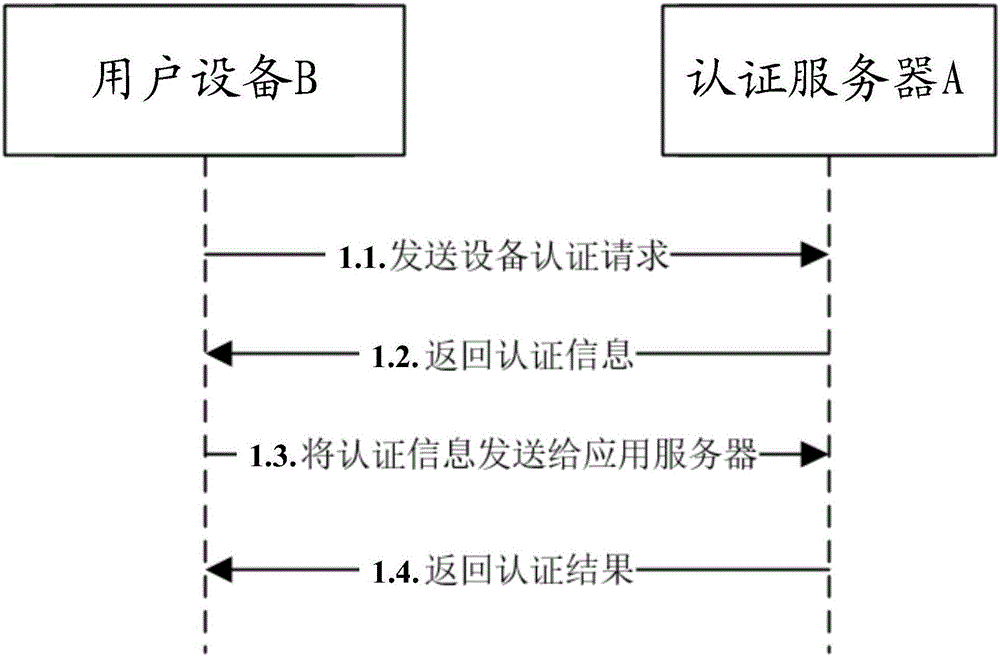
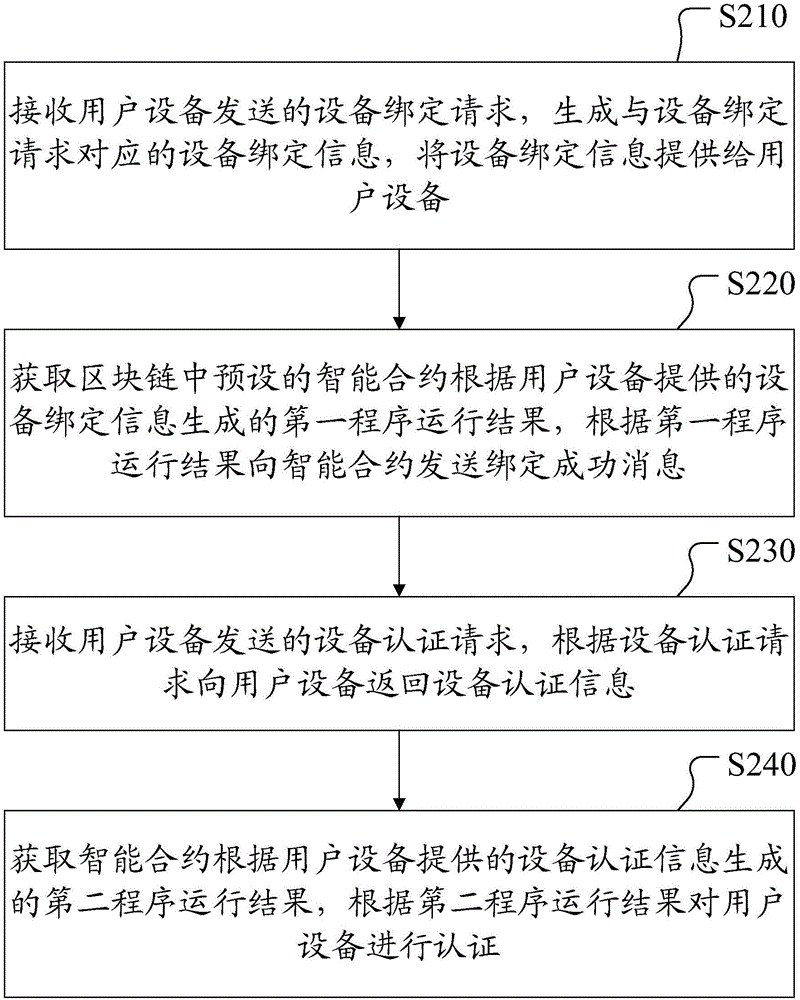
Block chain based equipment certification method, certification server and user equipment
ActiveCN106453415ASimplify the verification processImprove efficiencyTransmissionProtocol authorisationSmart contractSoftware engineering
The invention discloses a block chain based equipment certification method, a certification server and user equipment, and relates to the technical field of equipment certification. The method includes: receiving an equipment binding request sent by the user equipment, generating equipment binding information corresponding to the equipment binding request, and providing the equipment binding information to the user equipment; acquiring a first process running result generated by a smart contract, and sending a binding success message to the smart contract according to the first process running result; receiving an equipment certification request sent by the user equipment, and returning equipment certification information to the user equipment according to the equipment certification request; acquiring a second process running result generated by the smart contract, and performing certification on the user equipment according to the second process running result. Therefore, the block chain smart contract is used for saving the equipment binding information to make the equipment information not tampered, and the problems in the prior art are solved.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
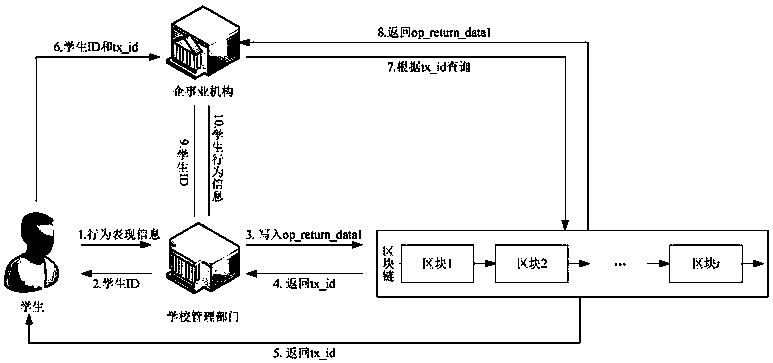
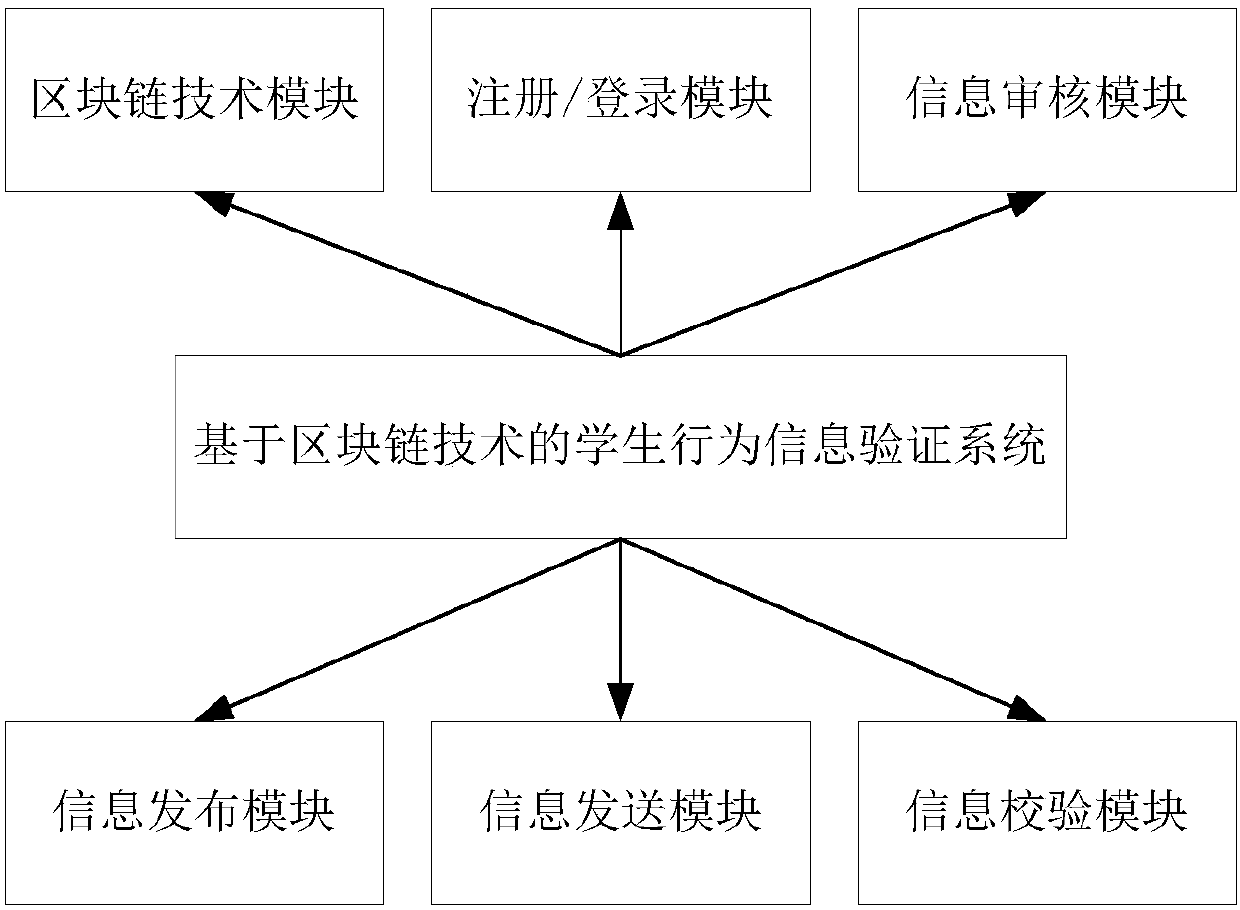
Student behavior information verification system based on blockchain technology
InactiveCN107832907AImprove reliabilityReduce human resource consumptionEncryption apparatus with shift registers/memoriesResourcesTamper resistanceInformation support
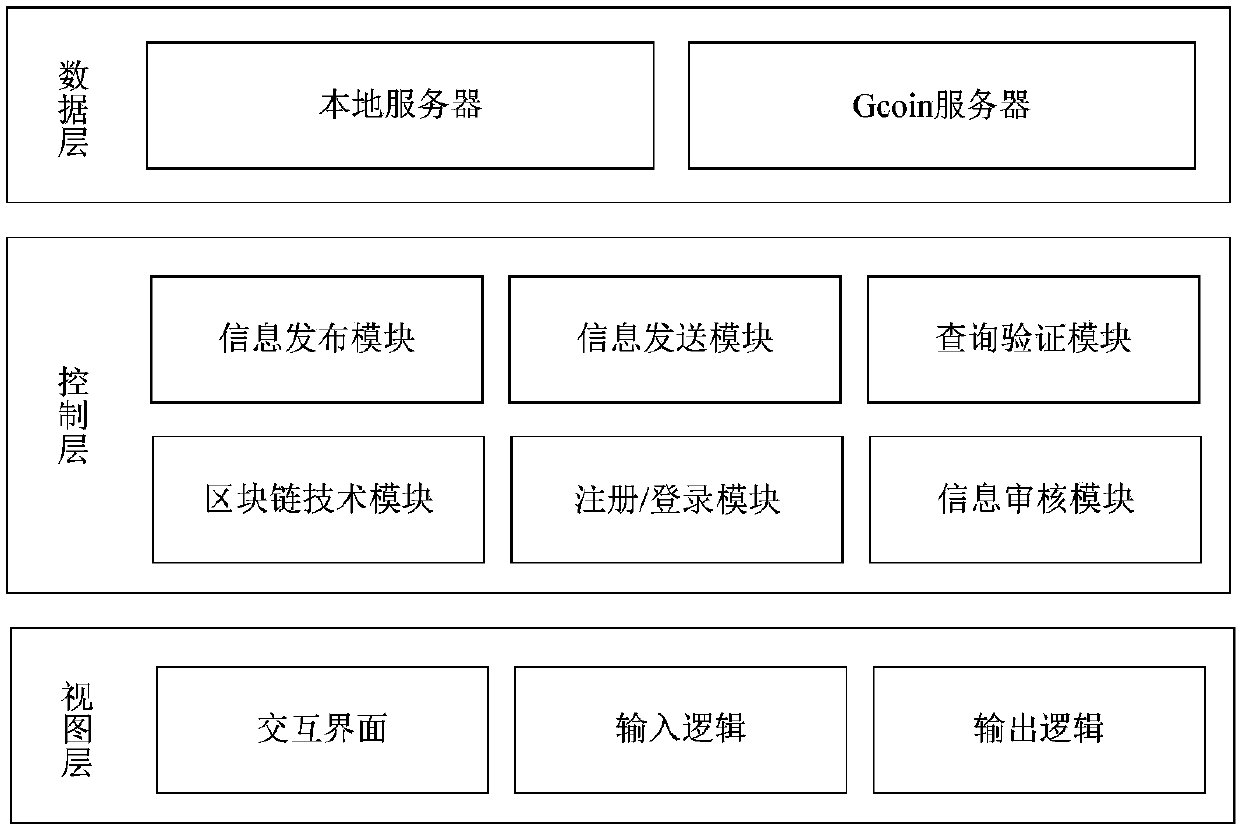
The invention discloses a student behavior information verification system based on a blockchain technology. The characteristics of distributed structure, automatic trust establishment, tamper-proofing, anti-counterfeiting, traceability and the like are used to solve the problems of high information verification cost, low efficiency, insecure security and the like, which are caused by damage or loss of student behavior information supporting materials. The system consists of a blockchain technology module, a registration / login module, an information release module, an information audit module,an information sending module and a query verification module. A relatively complete student behavior information chain is formed, and a unified interface service is provided for external parties. Onthe basis of ensuring the validity and reliability of student behavior information verification, the system greatly improves the work efficiency of tedious self-certification and verification of students, school management departments, enterprises, institutions and the like, and reduces the human resource cost of student behavior information maintenance.
Owner:CENTRAL UNIVERSITY OF FINANCE AND ECONOMICS
Method and apparatus for providing multiple data class differentiation with priorities using a single scheduling structure
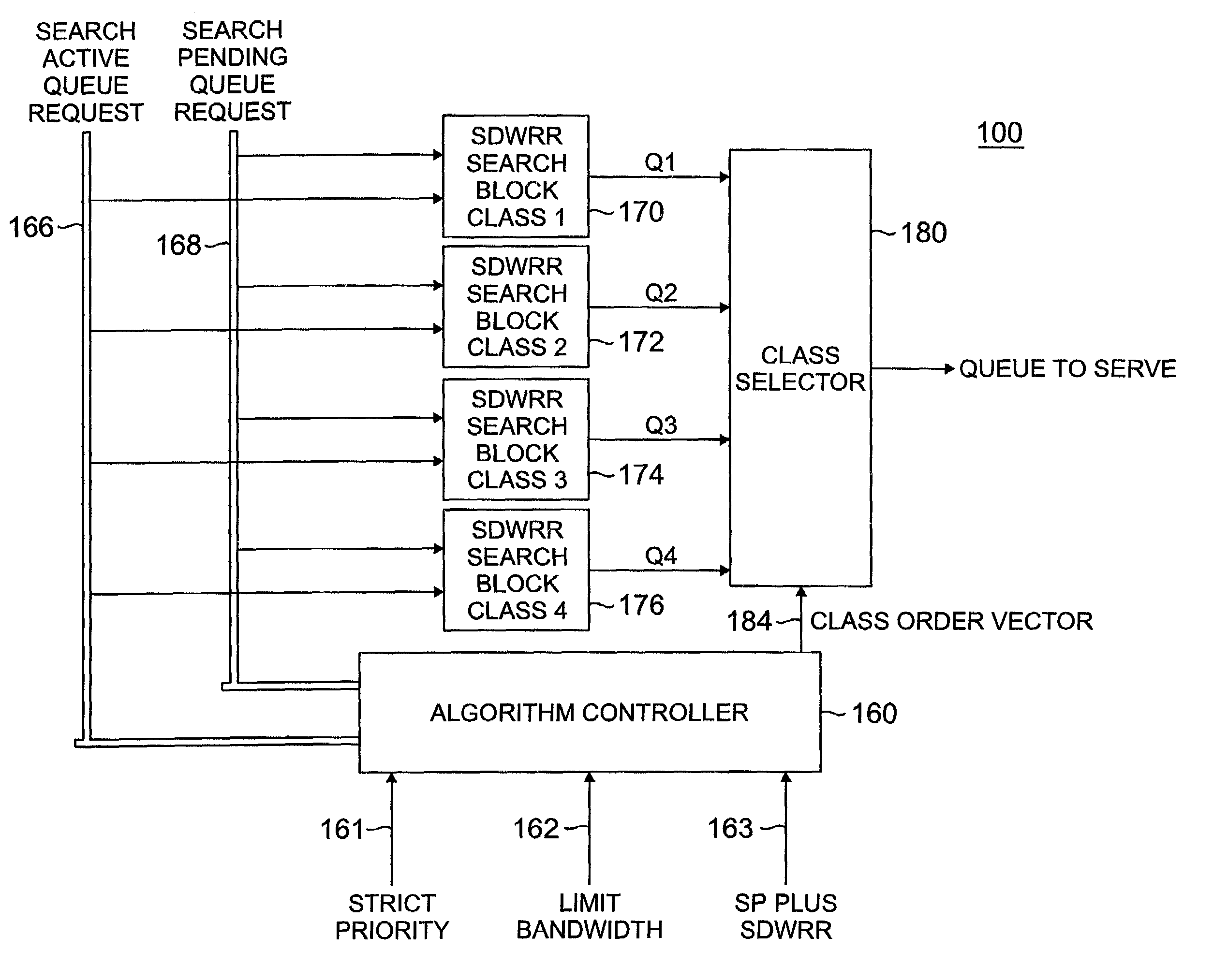
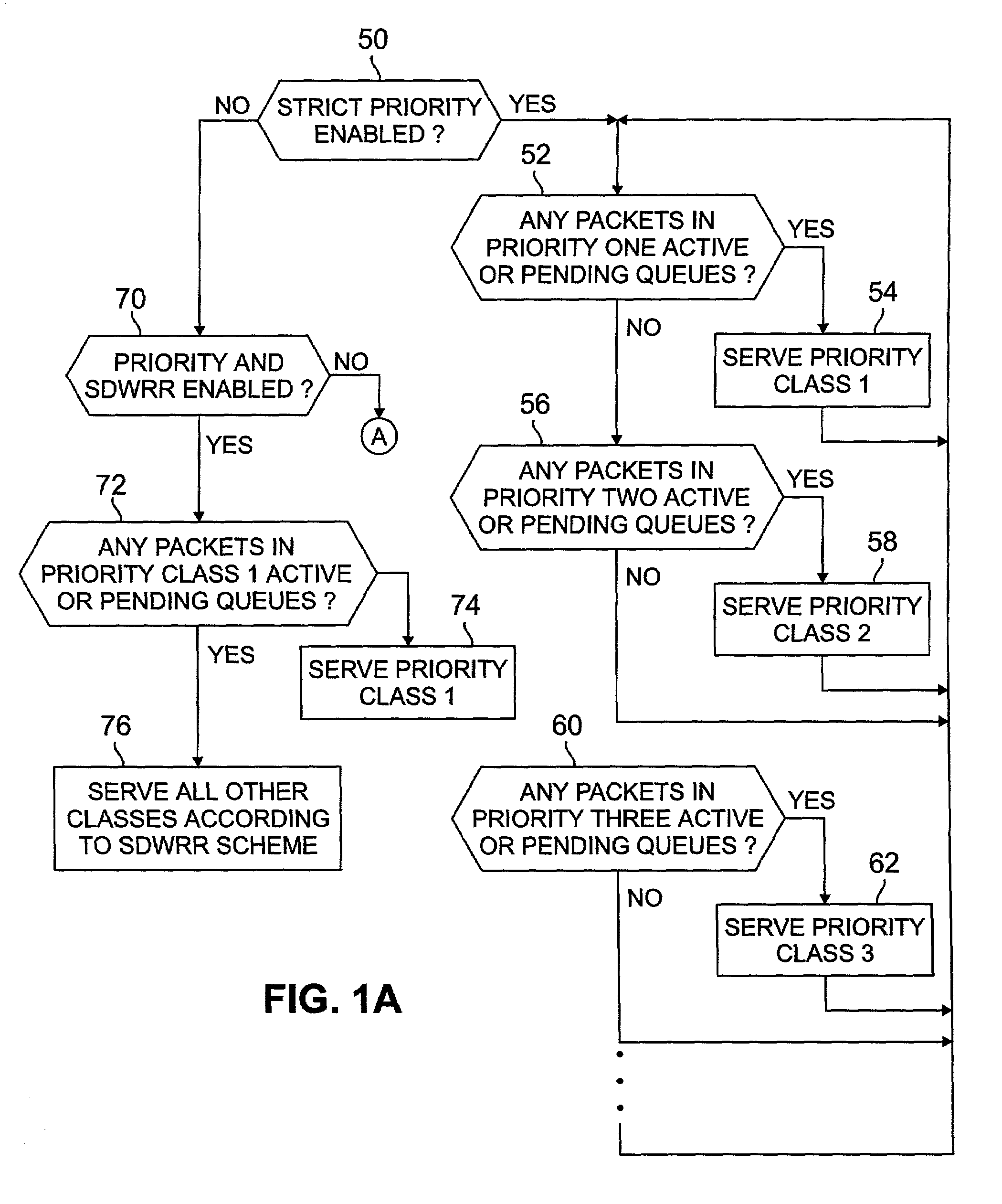
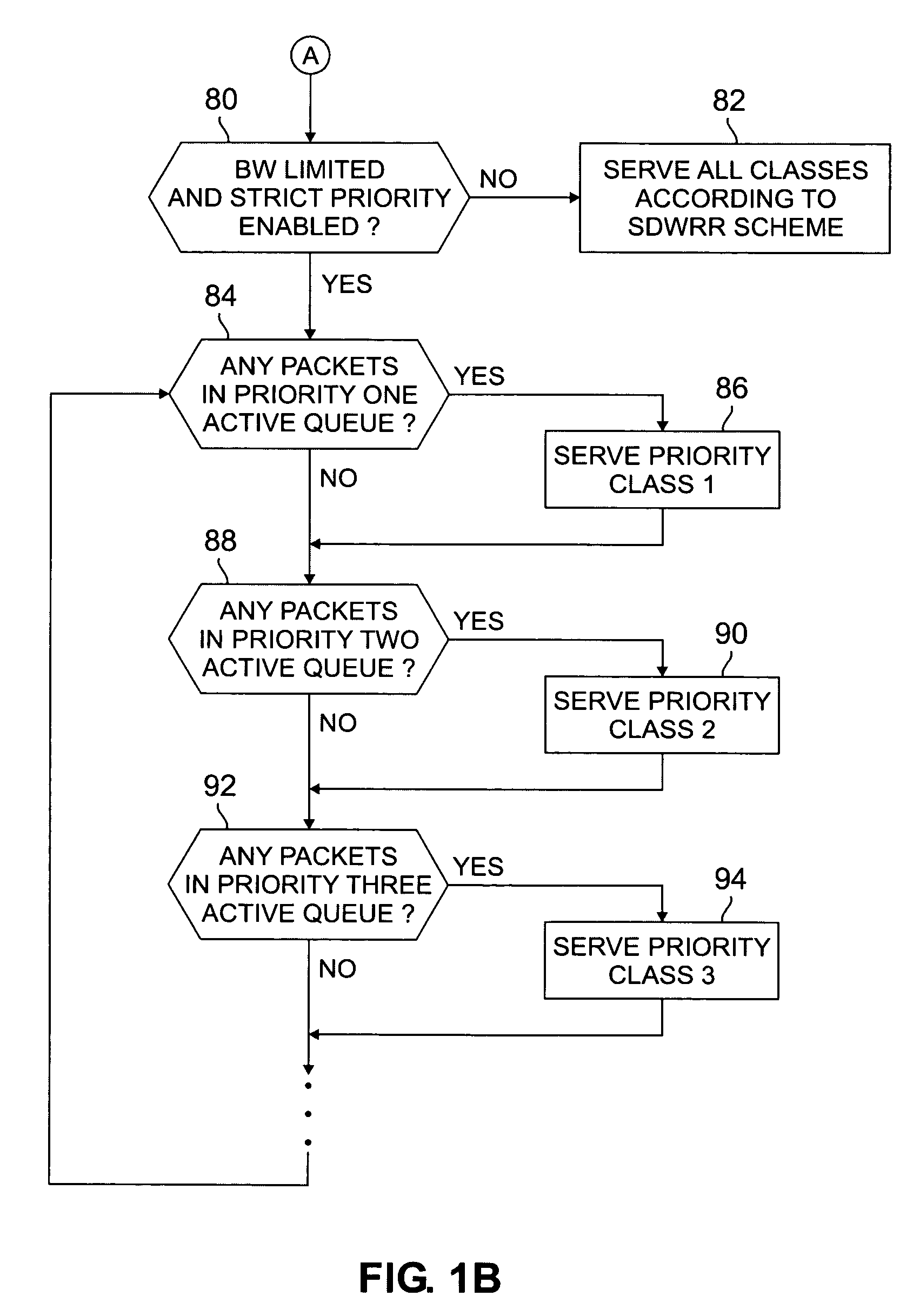
InactiveUS7159219B2Reduced space requirementsSimplifies design verification processError preventionTransmission systemsData classDistributed computing
A scheduler for shared network resources implementing a plurality of user selectable data scheduling schemes within a single hardware device. The schemes include strict priority, priority for one class plus smooth deficit weighted round robin for the other classes, bandwidth limited strict priority and smooth deficit weighted round robin for all user classes. The network operator selects one of the four schemes by enabling or disabling certain bits in the hardware device.
Owner:INTEL CORP
System and method for performing secure online transactions
ActiveUS20090138405A1Not presentSimplify the verification processElectric signal transmission systemsDigital data processing detailsService providerService provision
The system and method performing secure online-transactions based on challenge / response procedures executed by a terminal of at least one customer and by a terminal of a service provider, such as a bank, which terminals are connected to a network, preferably the Internet. The inventive method including:capturing biometric elements, such as audio and video samples or related biometric data, from the customer during an enrolment procedure and storing the biometric elements in a database, which is accessible by the service provider's terminalexecuting synchronised challenge procedures for each transaction in order to produce identical challenges based on current transaction data;capturing biometric data from the customer's response to the challenge with the customer's terminal;delivering transaction data together with the biometric data of the customer's response to the service provider's terminal;retrieving and assembling biometric elements according to the challenge in order to assemble response in the service provider's terminal; andcomparing the biometric data of customer's response with the data of the assembled response and performing the requested transaction in the event that the data of the responses match.
Owner:BLESSING
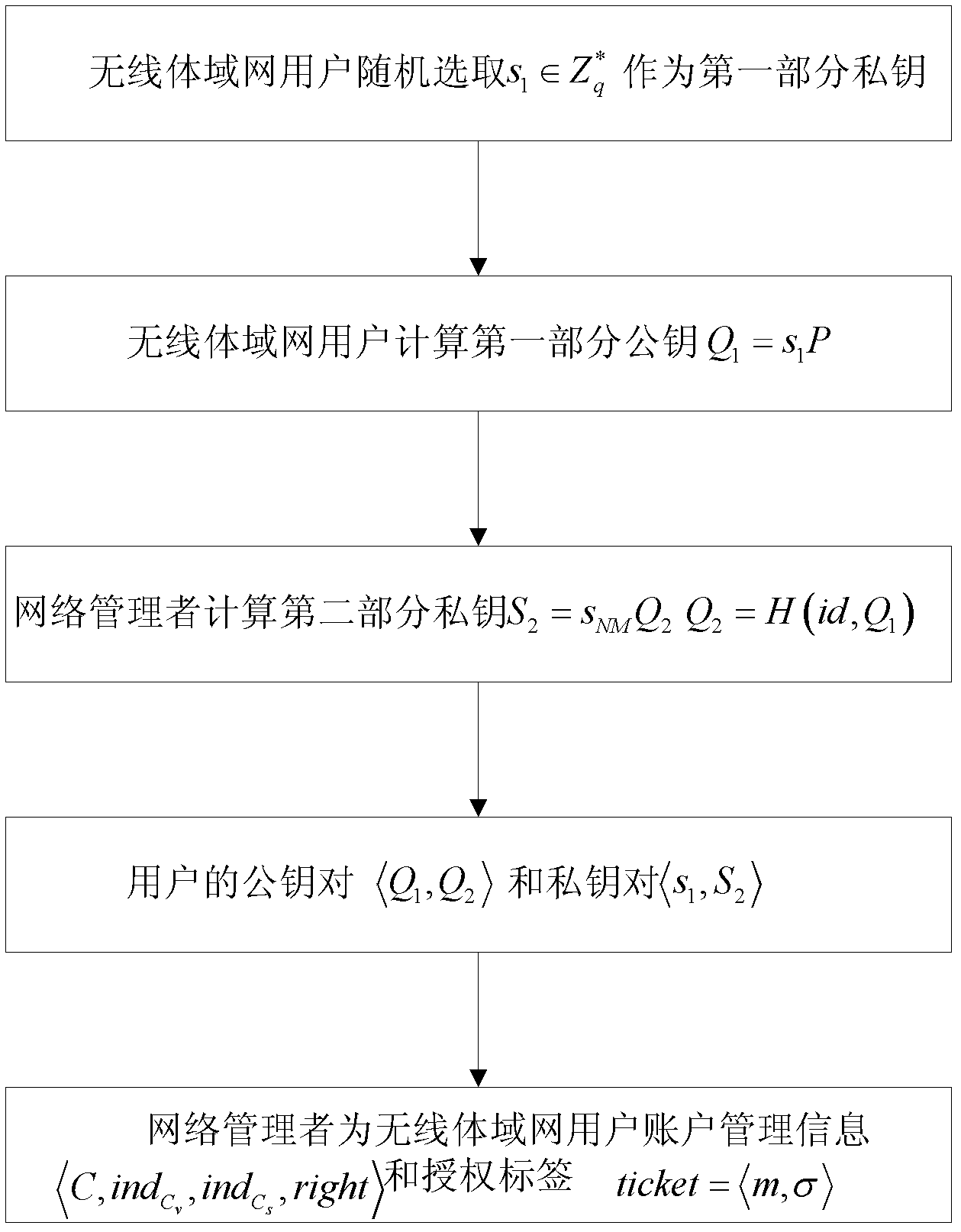
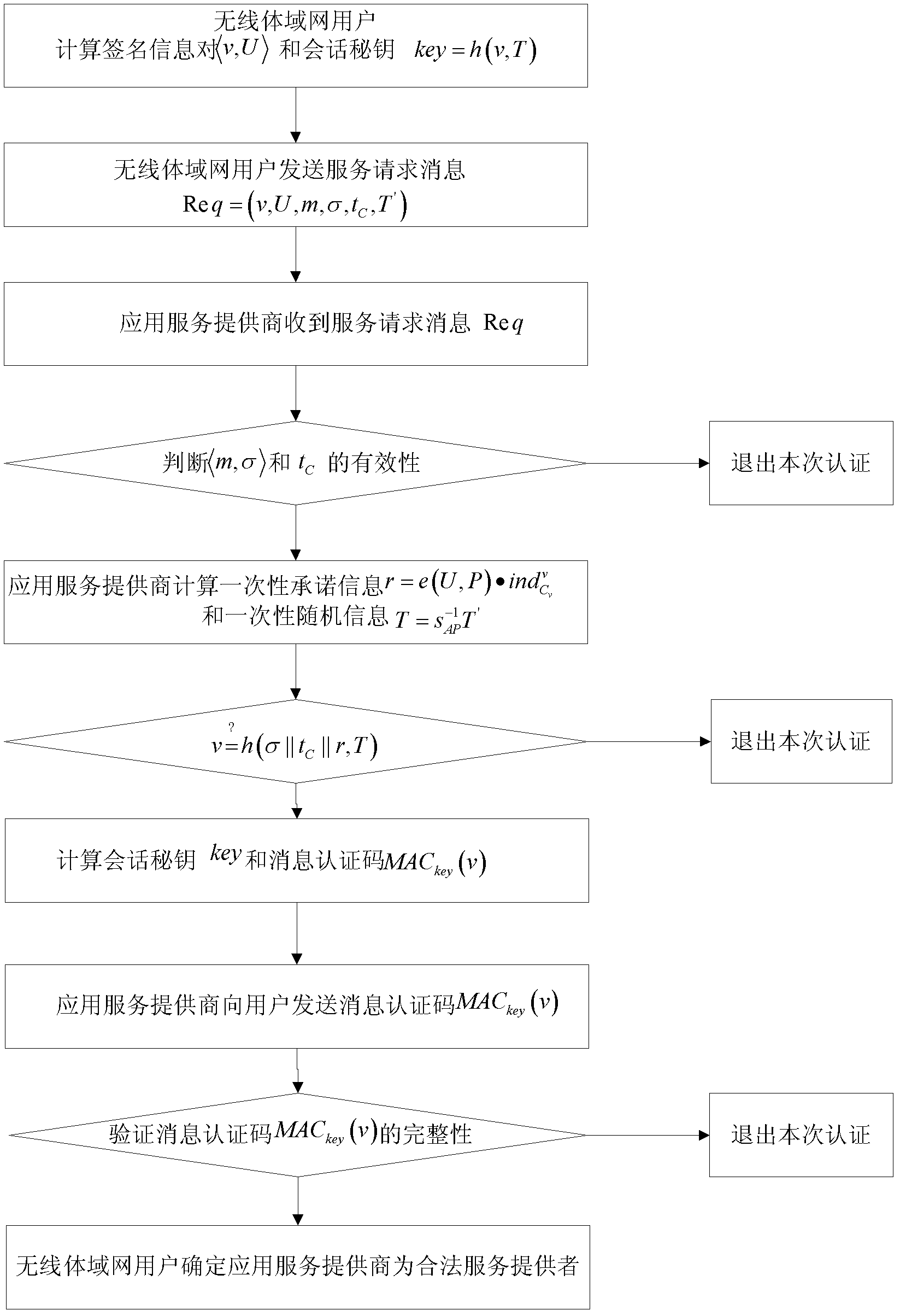
Certificate-free remote anonymous authentication method for wireless body area network
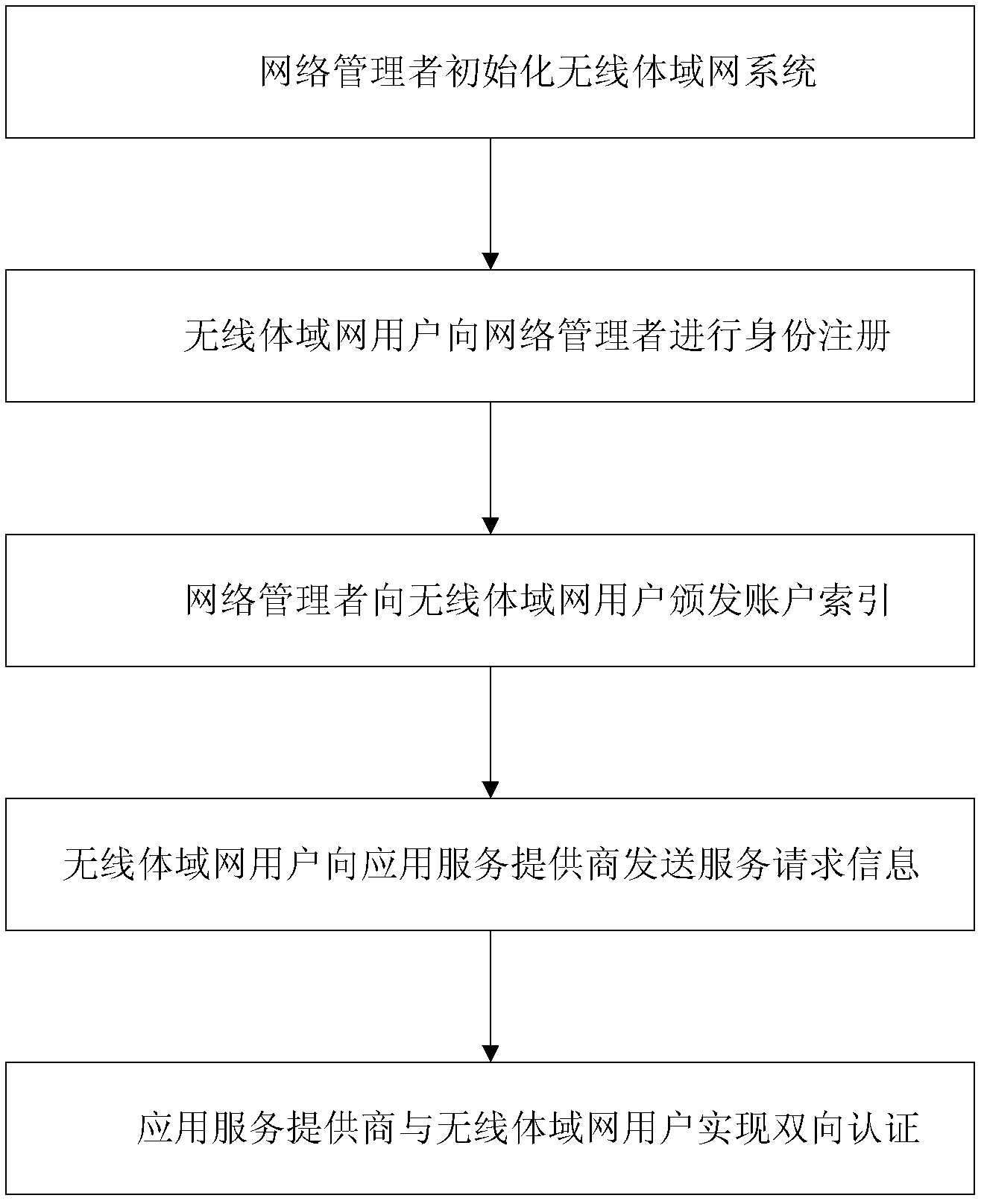
InactiveCN102624530AGood anonymityImprove securityPublic key for secure communicationUser identity/authority verificationComputation complexityBody area network
The invention discloses a certificate-free anonymous authentication method for a wireless body area network, which mainly solves the anonymity problem of wireless body area network remote authentication, and mainly comprises the steps as follows: 1) a network manager initializes a whole wireless body area network system; 2) a wireless body area network user carries out identity register from the network manager; 3) the network manager issues an account index to the wireless body area network user; 4) the wireless body area network user uses the account index to disguisedly send a service request to the network manager; and 5) bidirectional authentication between an application service provider and the wireless body area network user is achieved. According to the invention, a certificate is not required, the defect of no key escrow is avoided, the security performance is high, the degree of complexity of calculation is low, and the method can be used for remote medical treatment monitoring and on other application occasions.
Owner:XIDIAN UNIV
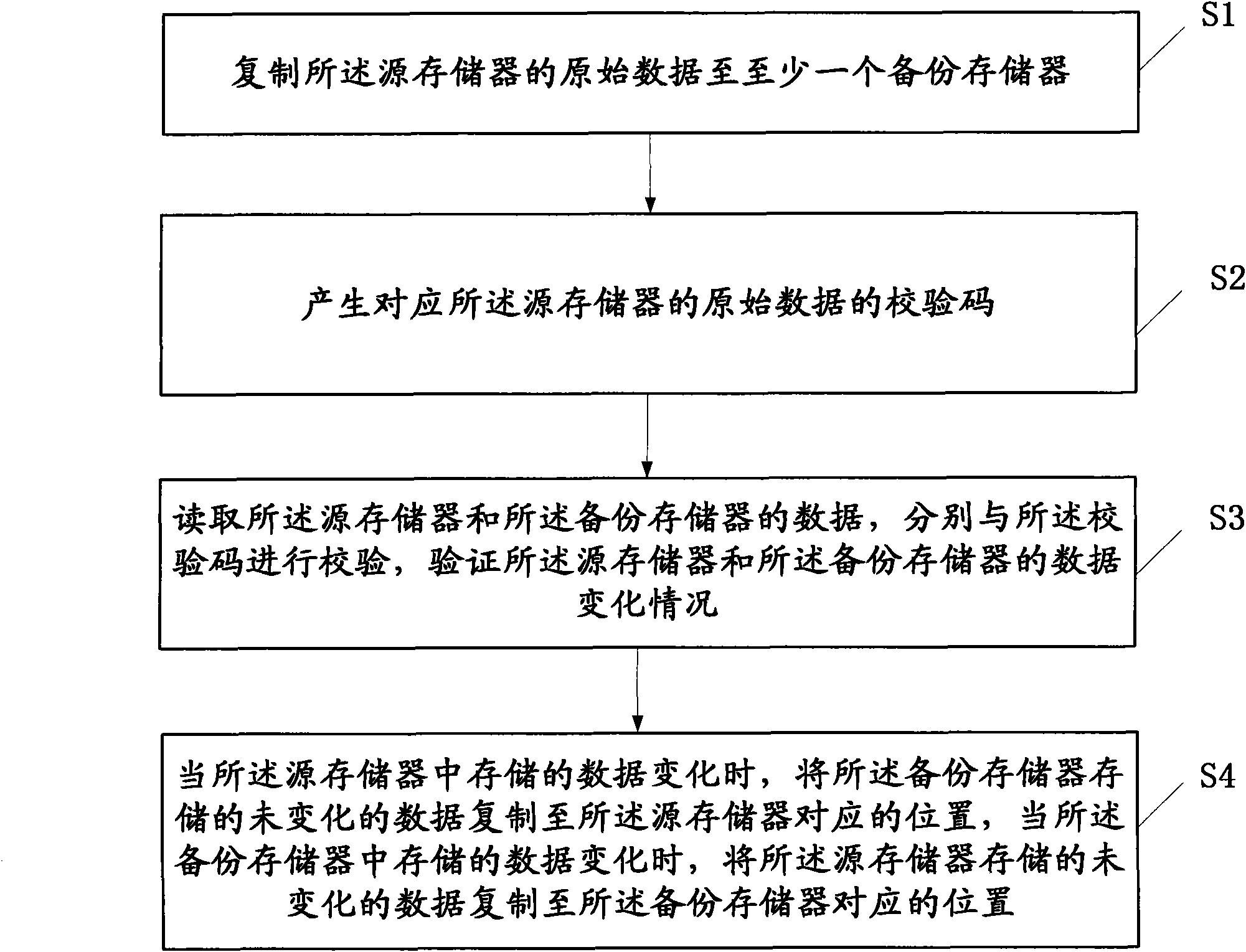
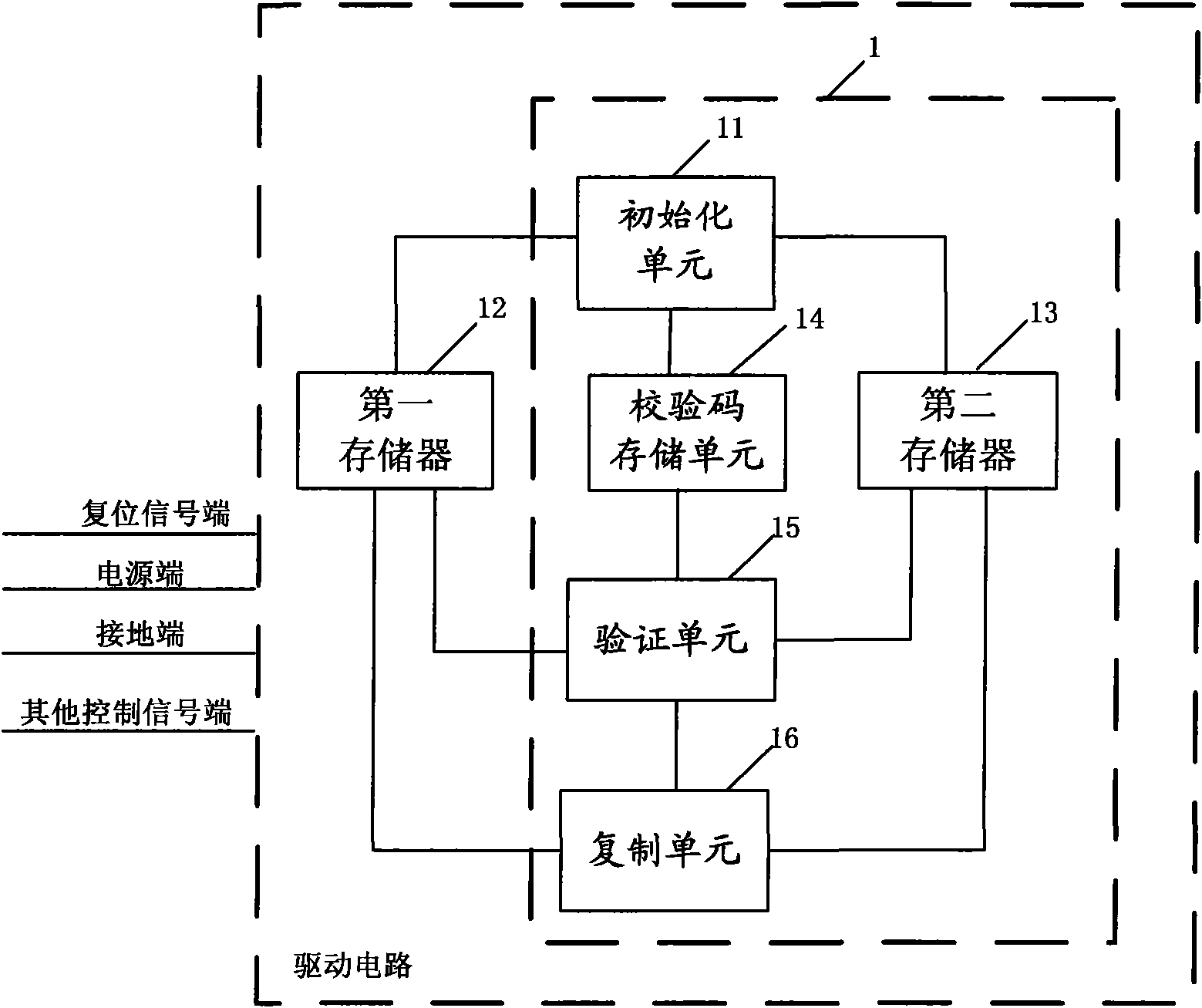
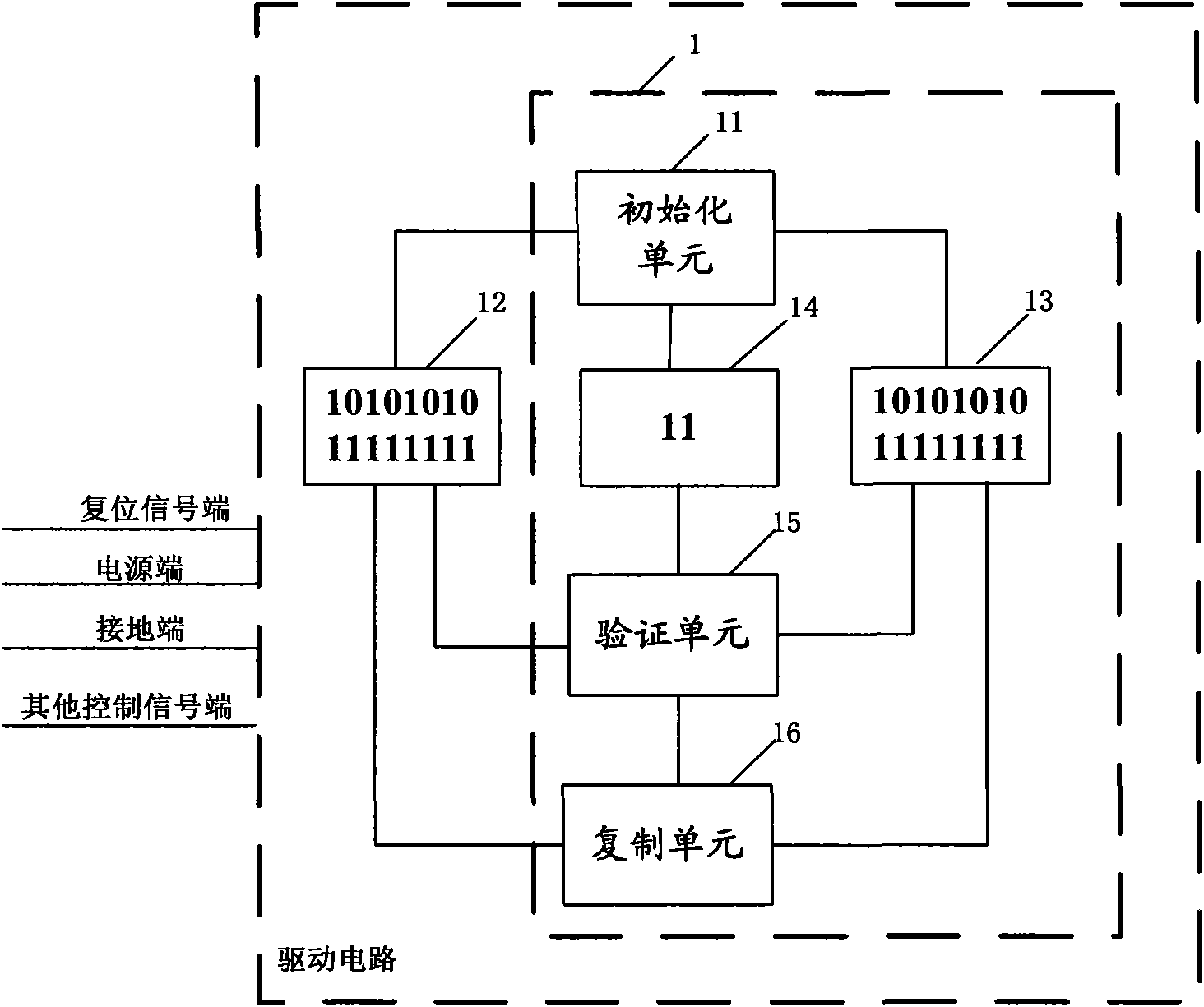
Method and device for maintaining data of drive circuit
ActiveCN102103834AAchieve data recoverySimplify the verification processCathode-ray tube indicatorsElectrostatic dischargeOperating system
The invention provides a method and device for maintaining data of a drive circuit. The drive circuit comprises a source memory for storing original data. The method comprises the following steps: duplicating the original data in the source memory to at least one backup memory; generating check codes corresponding to the original data in the source memory; periodically reading the data in the source memory and the data the backup memories and checking the data respectively with the check codes to verify whether the data in the source memory and the data in the backup memories change; and whenthe data stored in the source memory changes, duplicating the unchanged data stored in the backup memories to the corresponding positions of the source memory, and when the data stored in the backup memories change, duplicating the unchanged data stored in the source memory to the corresponding positions of the backup memories. According to the technical scheme adopted by the invention, the problem that destroying of the information in the memories caused by ESD (electrostatic discharge) leads to failure of the circuit to work normally can be effectively solved.
Owner:SHANGHAI TIANMA MICRO ELECTRONICS CO LTD
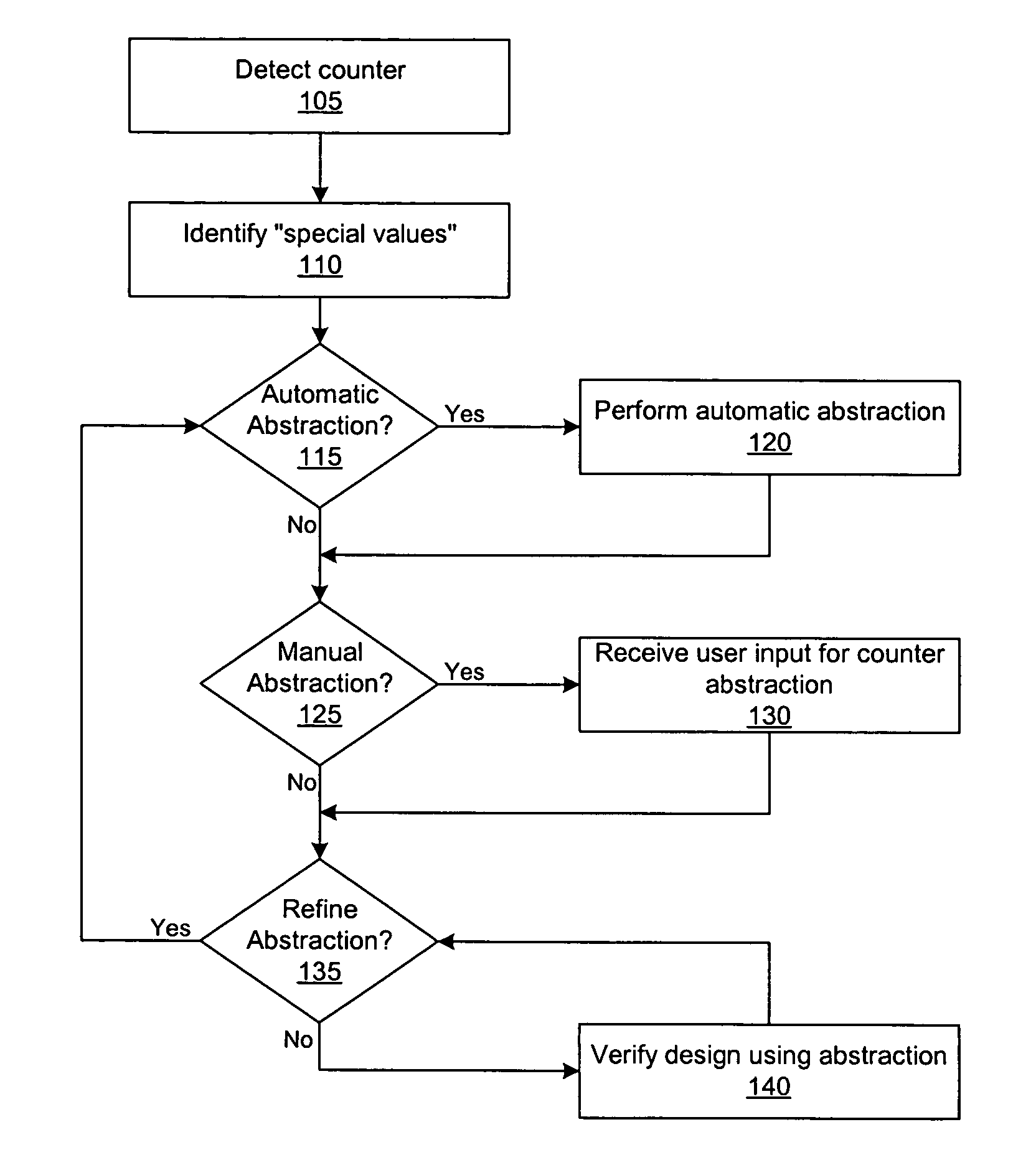
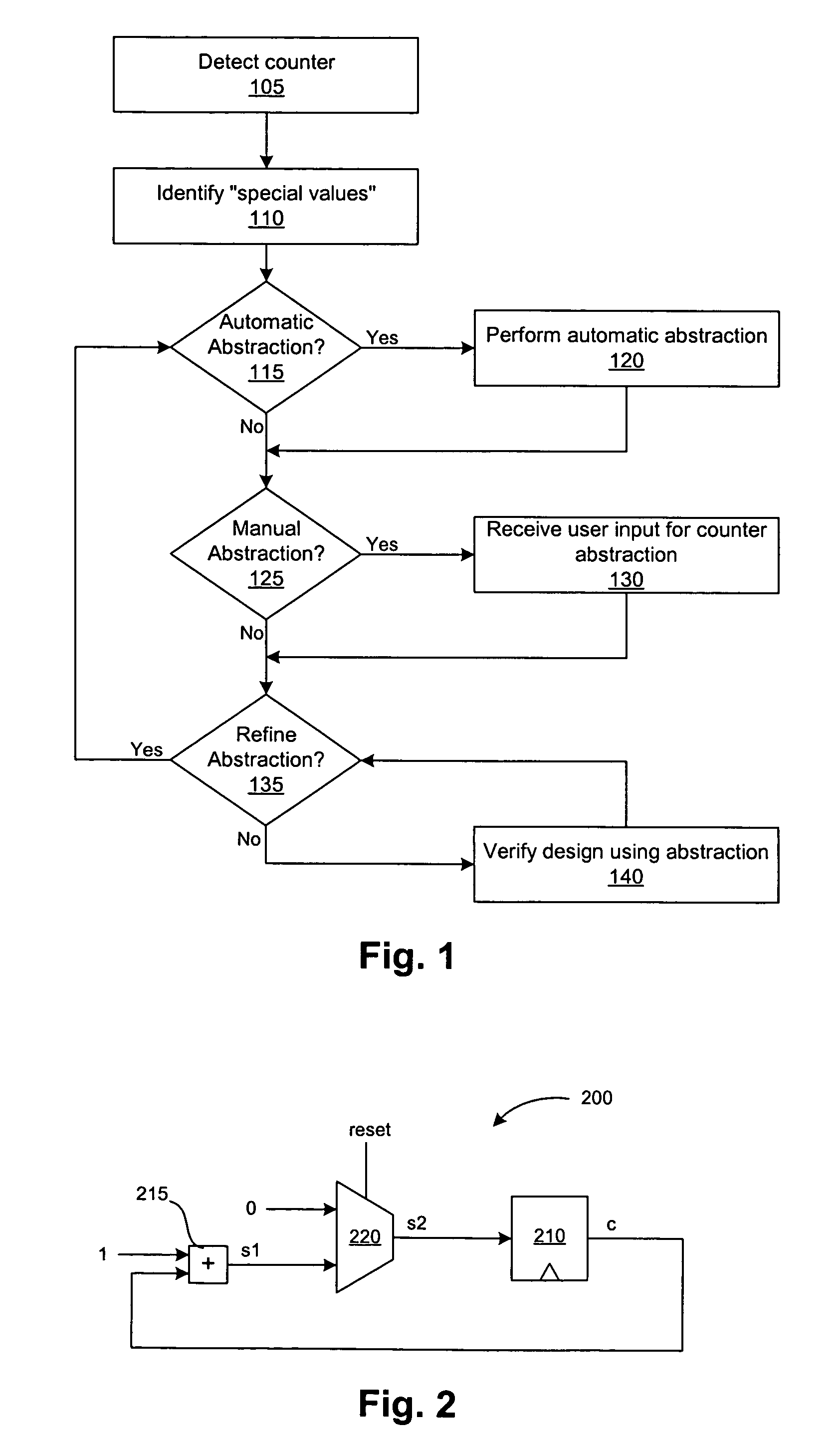
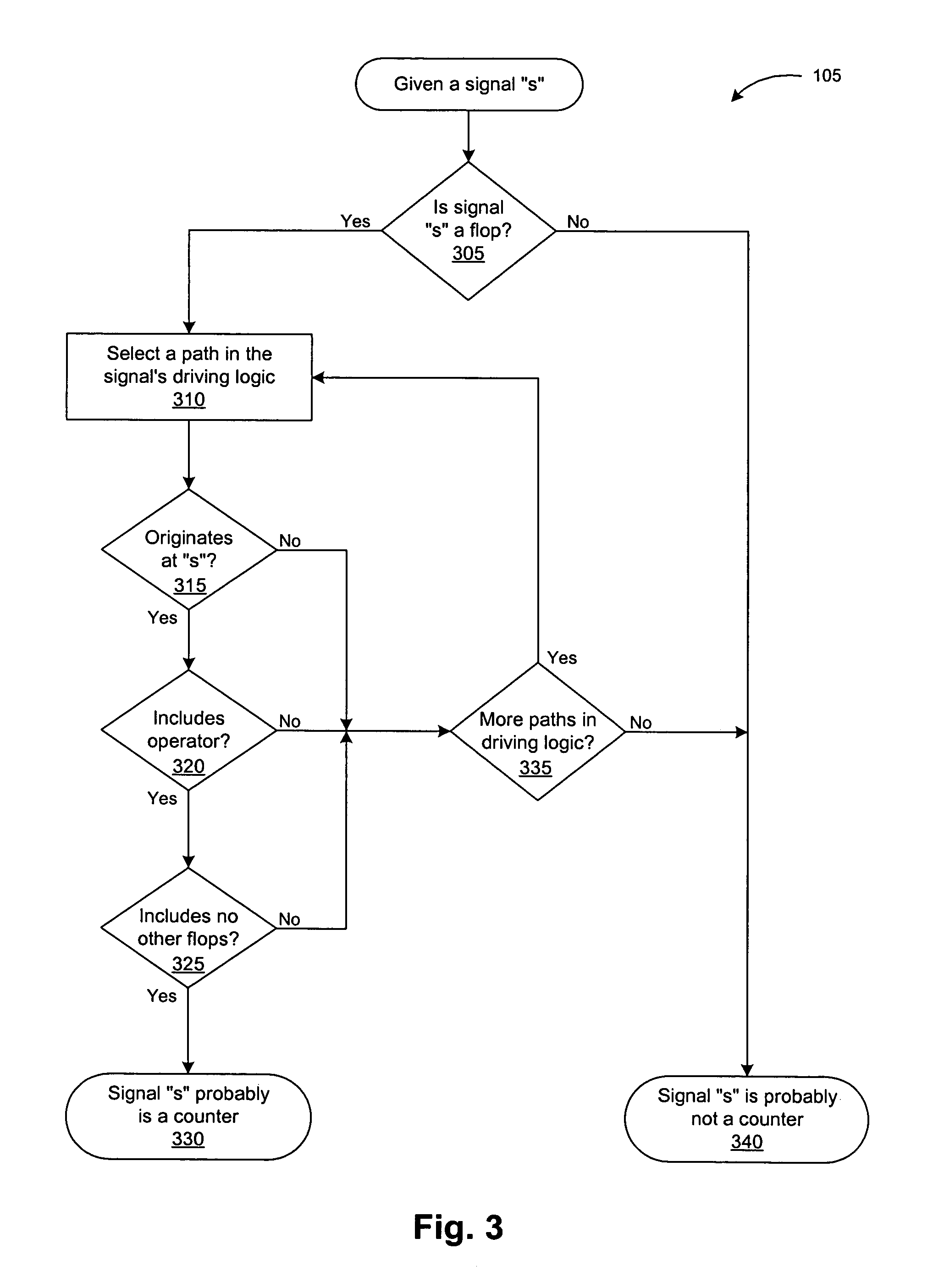
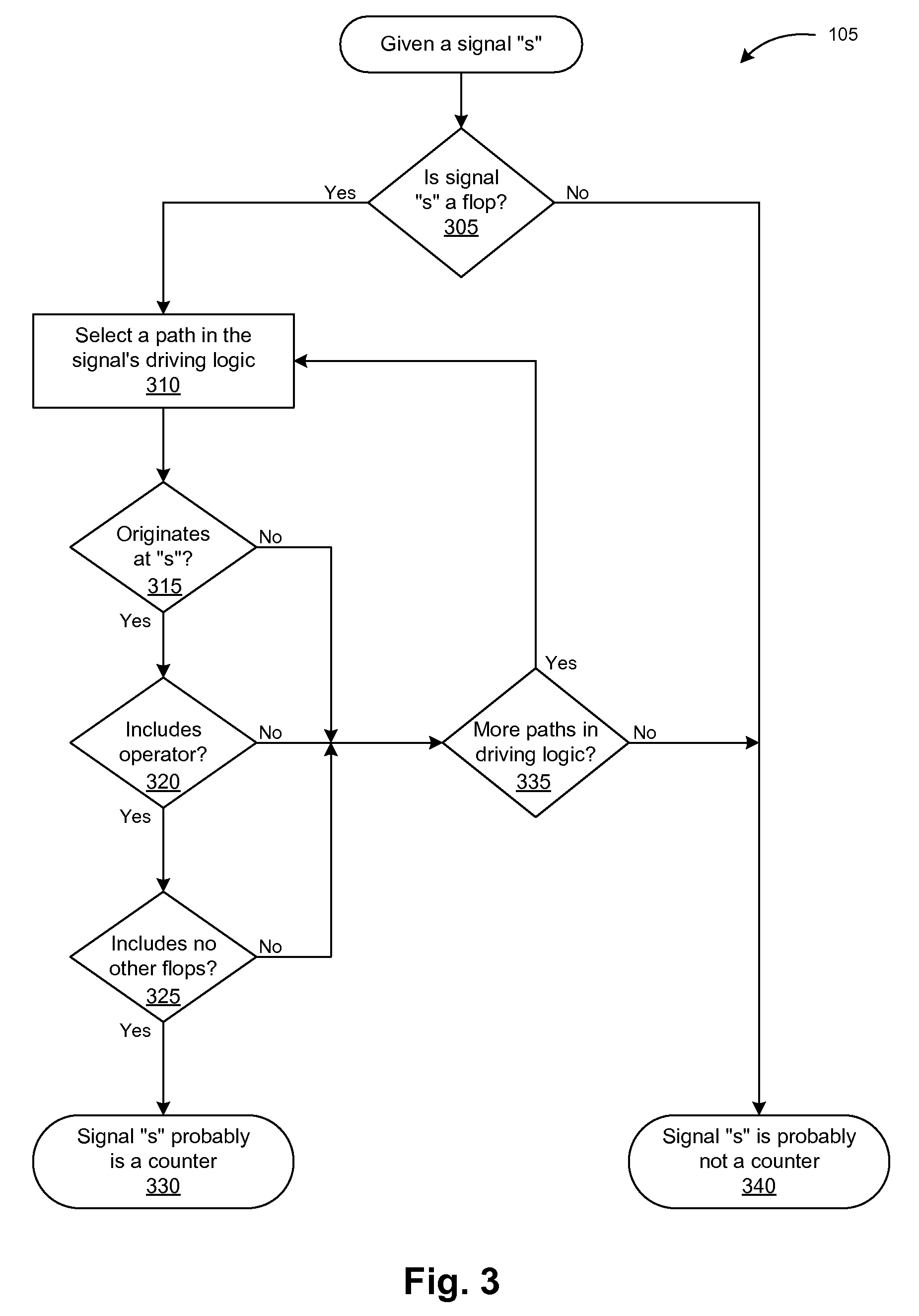
Managing formal verification complexity of designs with counters
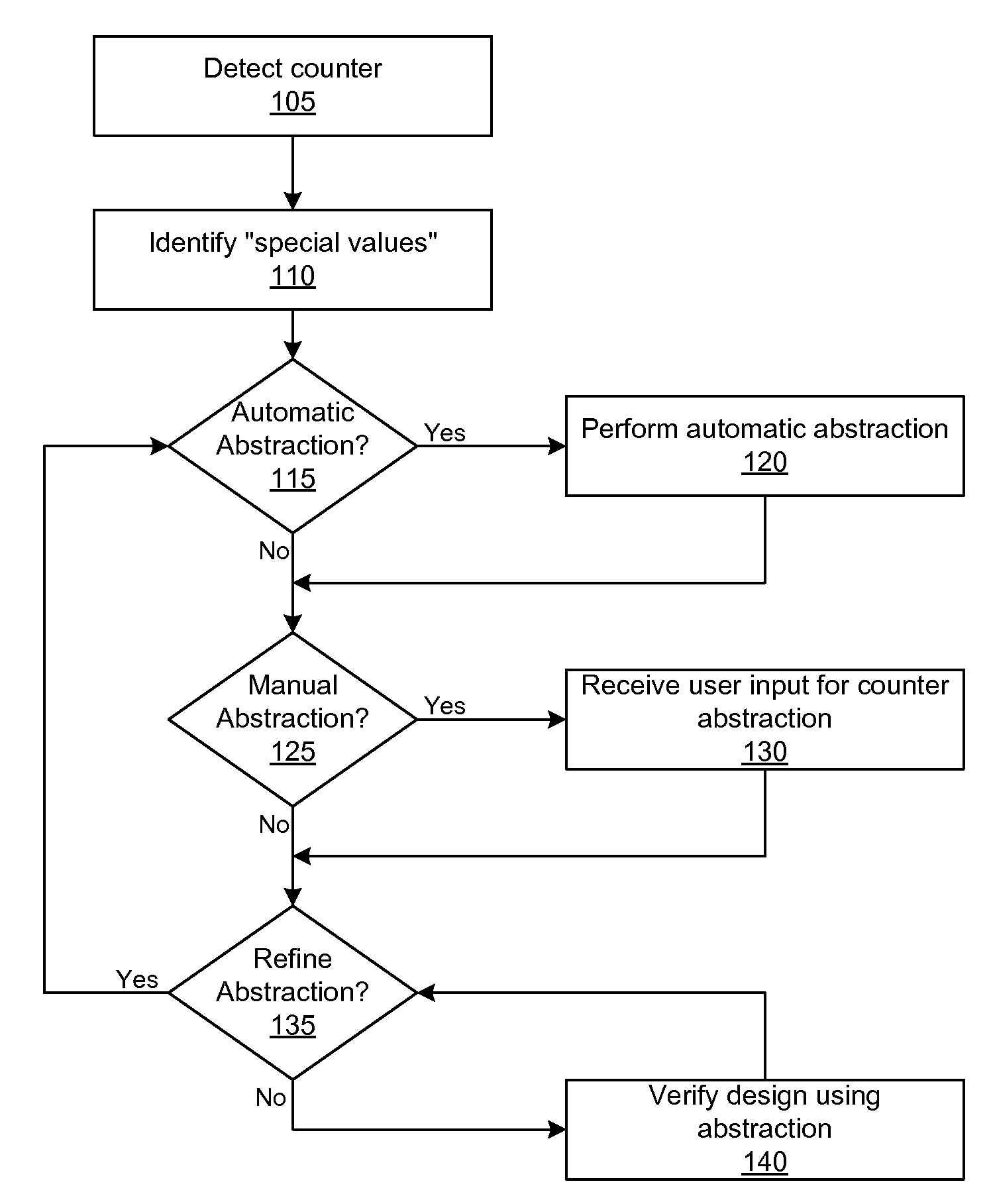
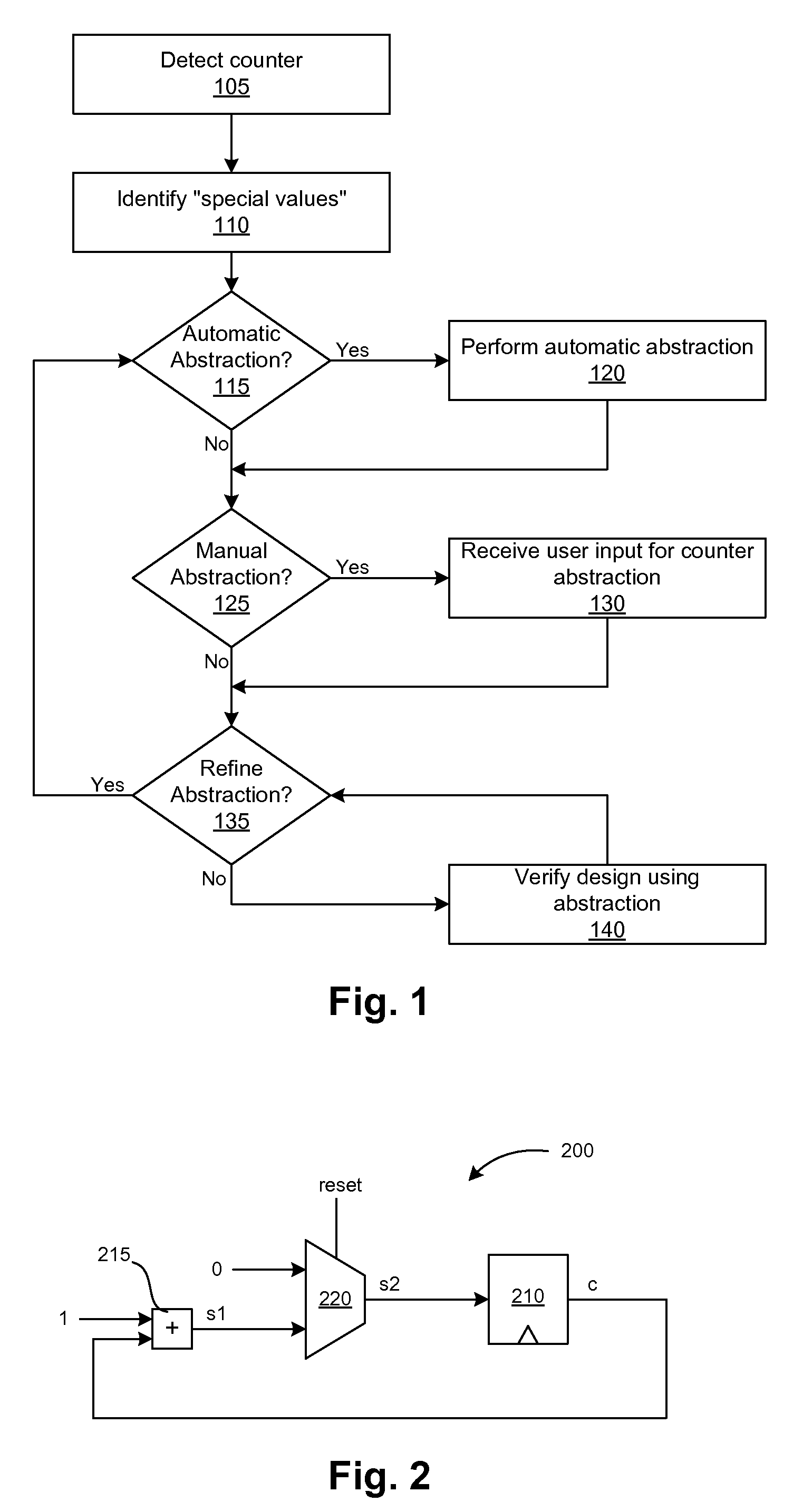
ActiveUS7418678B1Eliminate redundancyCounter intuitiveCAD circuit designSoftware simulation/interpretation/emulationComputer architectureCircuit design
A counter abstraction tool generates an abstraction model for one or more counters in a circuit design for use with a formal verification system. The tool detects the presence of a counter in a circuit design, identifies one or more special values for the counter, and creates an abstraction for the counter. The tool can automatically perform the abstraction, guide a user in configuring the appropriate abstraction for the counter, or perform a combination of automatic and manual abstraction. The tool may further accommodate related counters.
Owner:JASPER DESIGN AUTOMATION
Method and apparatus for morphological modeling of complex systems to predict performance
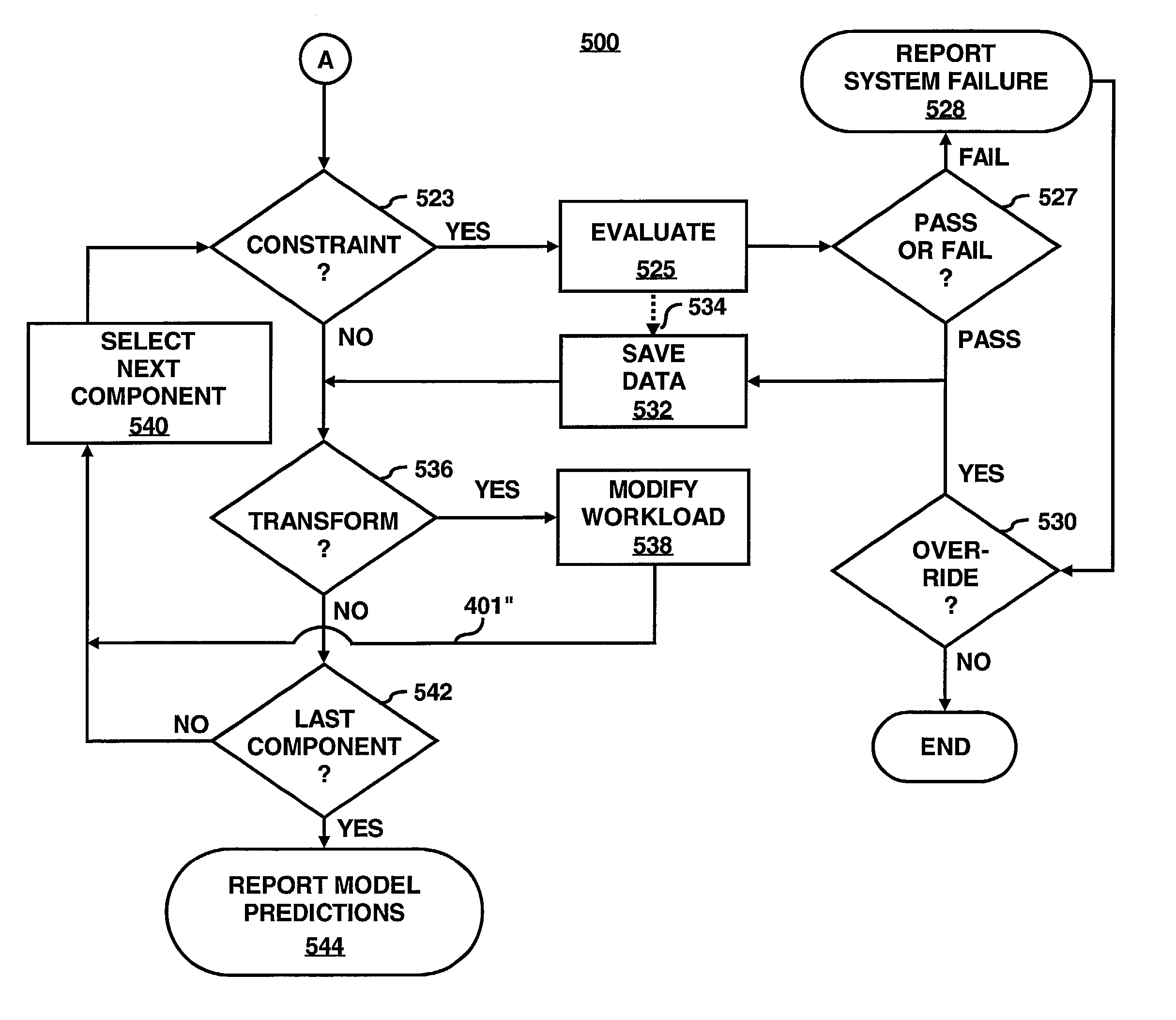
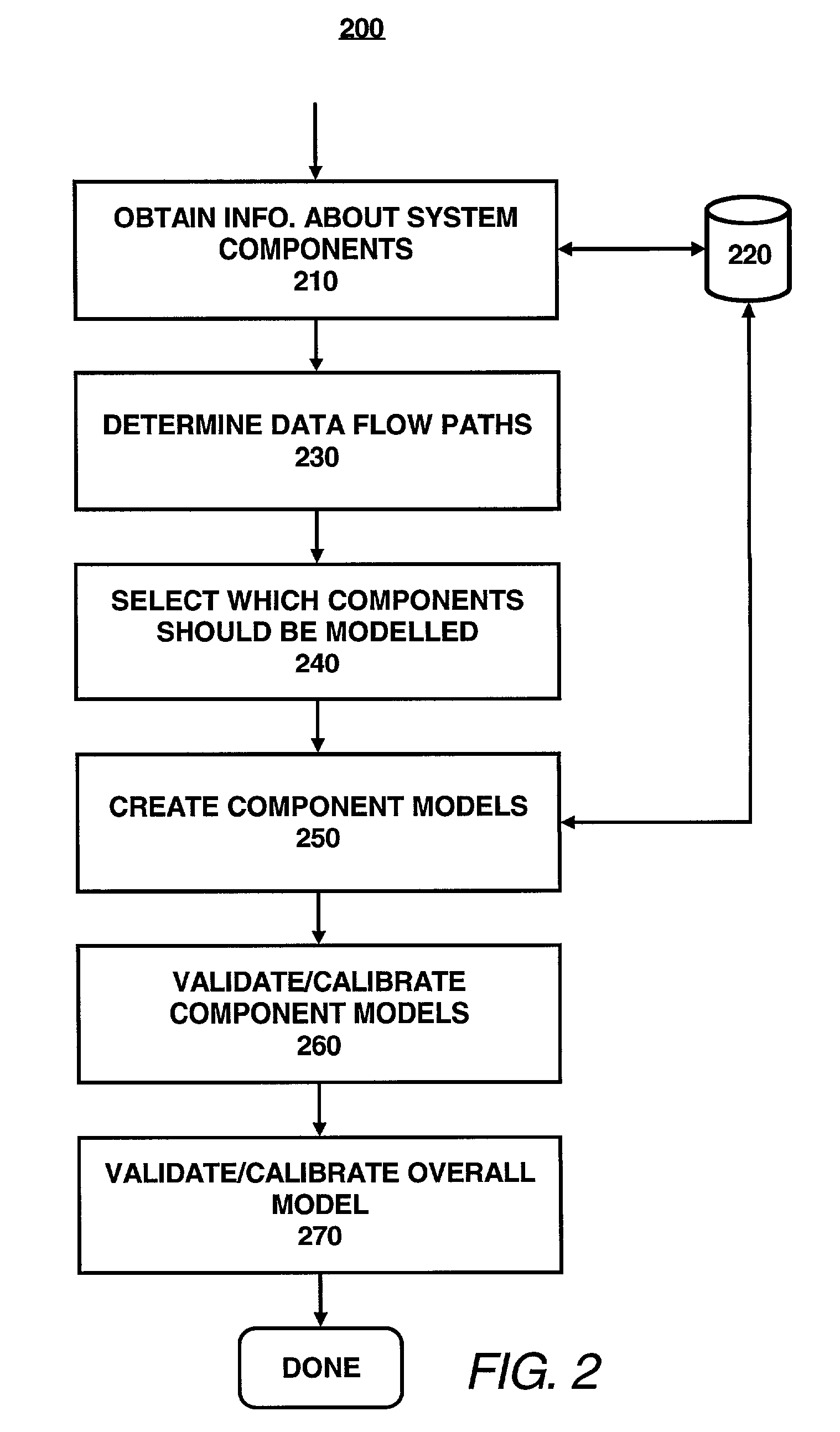
InactiveUS7050956B2Reduce complexityEasy modelingHardware monitoringSpecific program execution arrangementsMethod evaluationWorkload
A method predicts performance of a system that includes a plurality of interconnected components defining at least one data flow path. The method references a workload specification for the system. The method models the system using one or more component models. Each component model represents selected one or more of the components. Each component model is arranged in like relationship to the data flow path as the selected one or more of the components represented by the component model. Each component model is (a) a constraint upon the workload specification input to that component model or (b) a transformer of the workload specification input to that component model so as to result in one or more output workload specifications that are input workload specifications to subsequent component models along the data flow path or (c) both a constraint and a transformer. At least one of the component models is a constraint. At least some of the component models along the data flow path operate on the workload specification. In one preferred form, operating on the workload specification involves arranging the component models in a hierarchy corresponding to the data flow path; using the specified workload specification as input to the topmost component model in the hierarchy; and applying one or more of the component models to its input workload specification, starting with the topmost component model and then component models at progressively lower levels in the hierarchy. Output workload specification at one level is input workload specification at the next lower level. If the component model comprises a constraint, the method evaluates whether the input workload specification satisfies or violates the constraint. If the component model comprises a workload specification transform, the method modifies the input workload specification so as to produce one or more output workload specifications.
Owner:HEWLETT PACKARD DEV CO LP
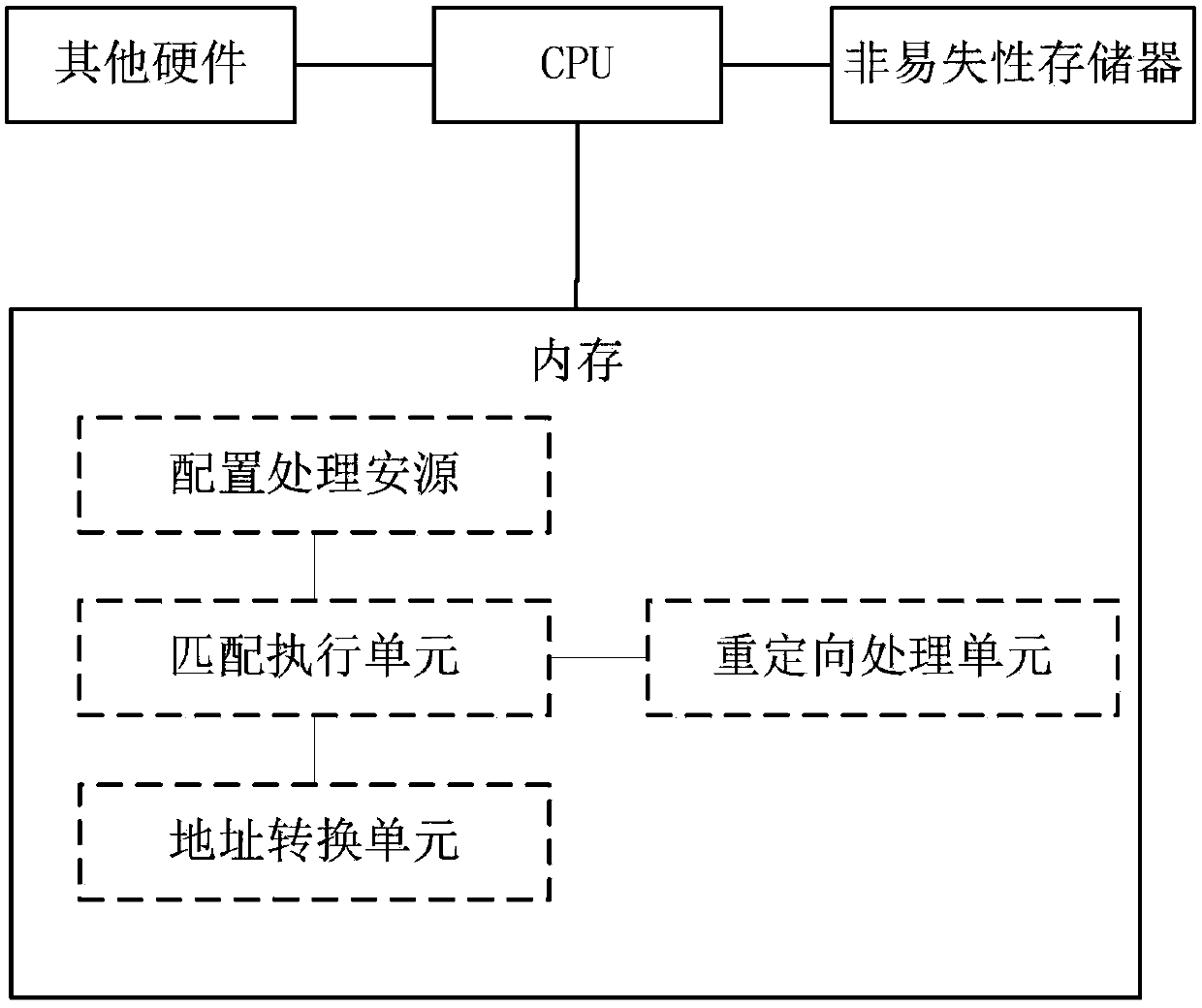
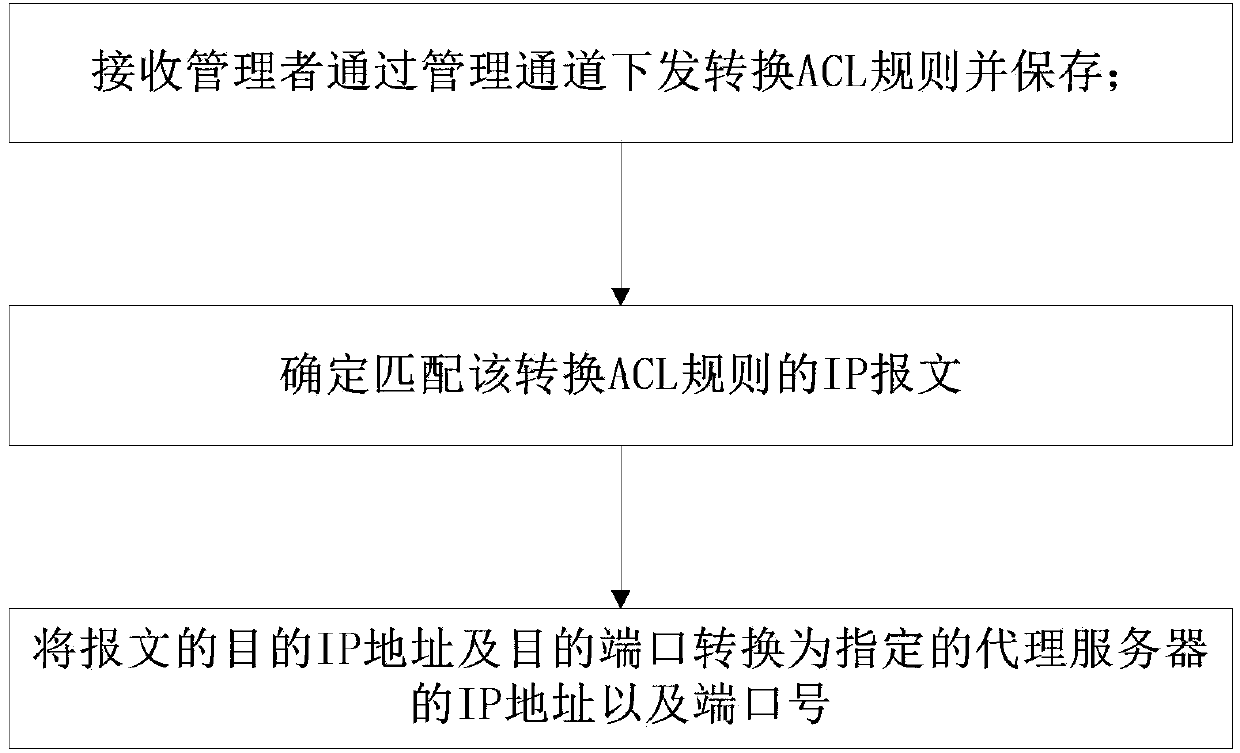
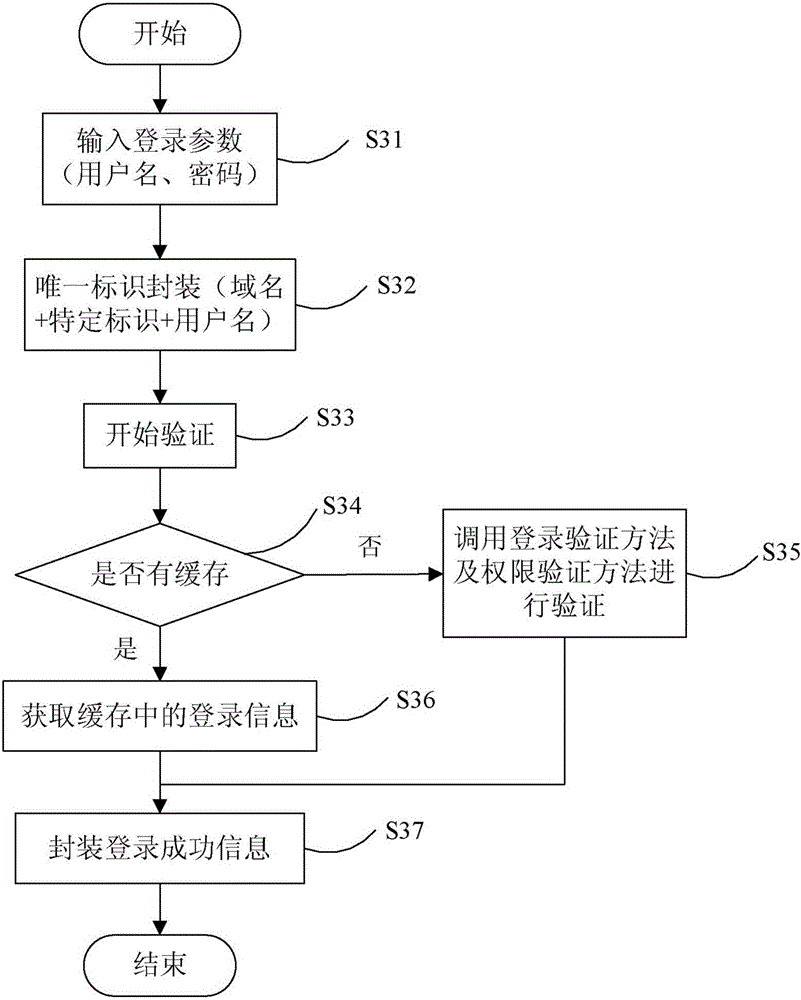
Terminal service method and apparatus
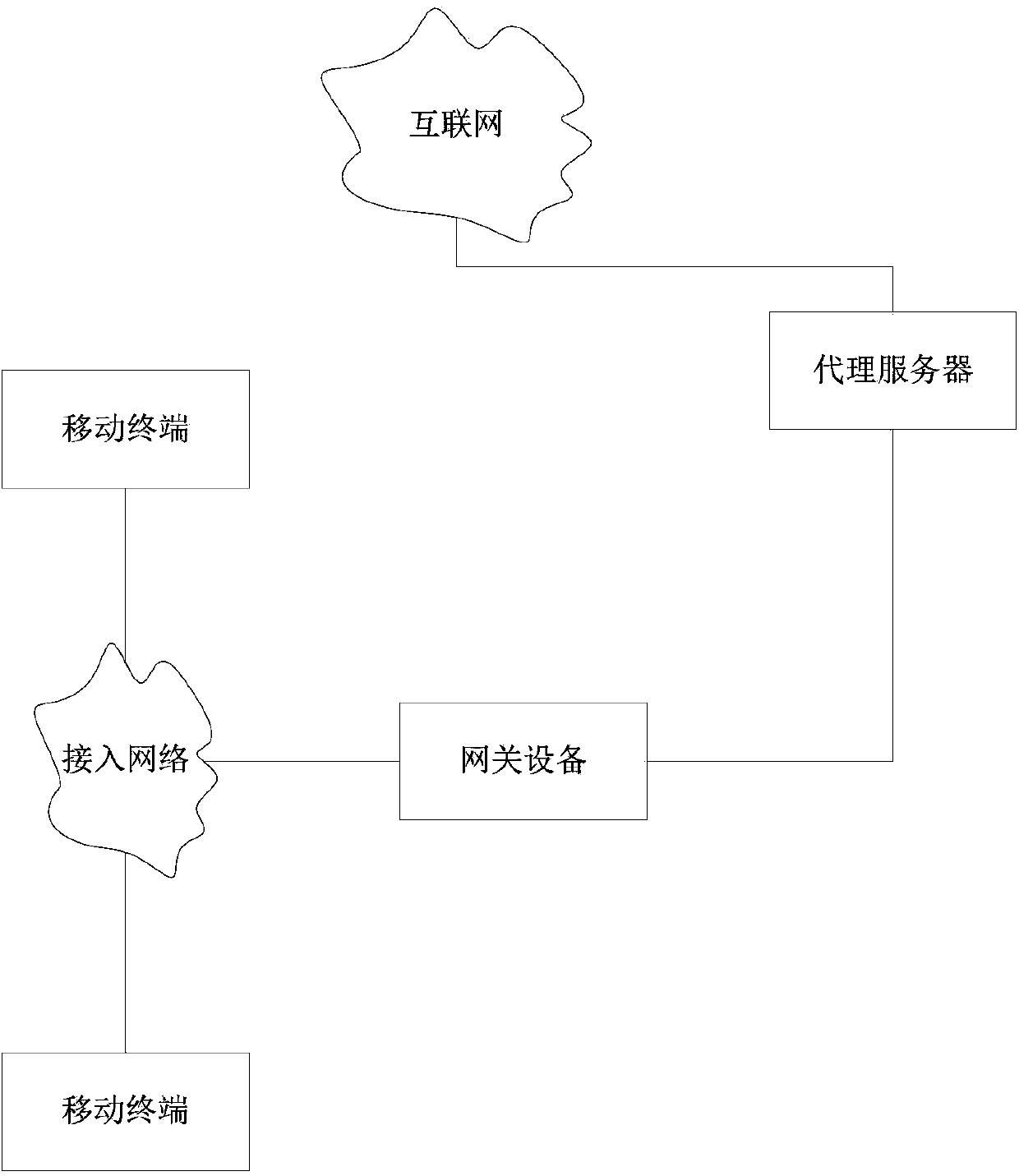
ActiveCN103475746ASimplify workSimplify the verification processTransmissionIp addressComputer terminal
The invention provides a terminal service method and device which are applied to network equipment arranged between a mobile terminal and an agent server. The method comprises the following steps: step A, receiving and storing a conversion ACL rule assigned by an administrator through a management channel, wherein the conversion ACL rule is used for filtering out an IP message which is specified by the administer and has a target IP address belonging to a specified network segment; step B, checking whether the IP message matches the conversion ACL rule, if so, skipping to step C for processing; and step C, correspondingly converting the target IP address and the destination port of the IP message into the IP address of a specified agent server and a specified port, and sending the modified IP message to the agent server. Compared to the prior art, by using the terminal service method and device, the work assigned by the NAT configuration of the administrator is greatly simplified, and the checking and inspection work of the administer in maintaining the NAT configuration can also be substantially simplified.
Owner:NEW H3C TECH CO LTD
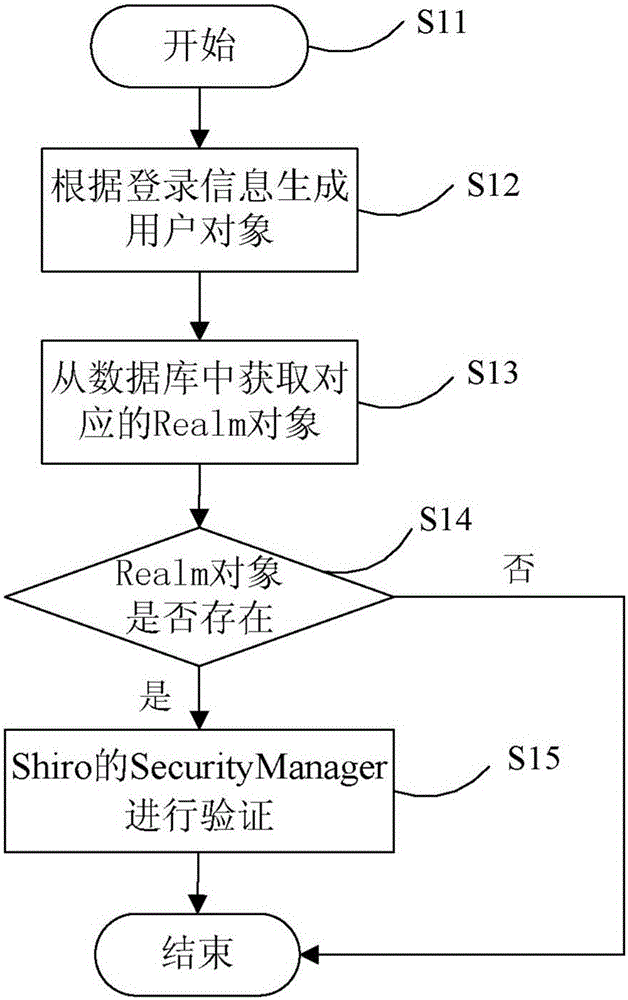
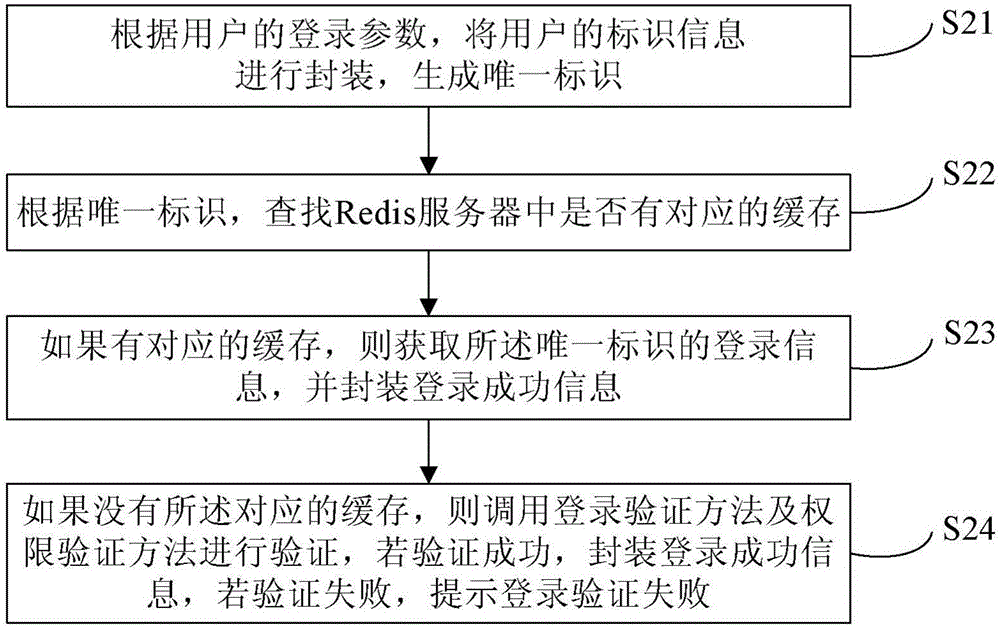
Shiro authentication method based on Redis storage
ActiveCN106487744AEasy to operateImprove efficiencyTransmissionHigh level techniquesExpiration TimeValidation methods
The invention provides a Shiro authentication method based on Redis storage. Through placing a session into an Redis for caching, the memory consumption can be reduced to solve the problem of memory overflow; and as an expiration time algorithm is introduced to automatically eliminate a cache, the efficiency and the hit rate of the cache are improved, thereby guaranteeing data to be stored efficiently and reliably. The method comprises the steps of carrying out encapsulation on identification information of a user according to login parameters of the user to generate a unique identifier; according to the unique identifier, finding whether the corresponding cache exists in an Redis server; if the corresponding cache exists, obtaining login information of the unique identifier and encapsulating login successful information; and if the corresponding cache does not exist, calling a login authentication method and an authority authentication method for authentication, if the authentication is passed, encapsulating the login successful information, and if the authentication is failed, prompting the login authentication is failed.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
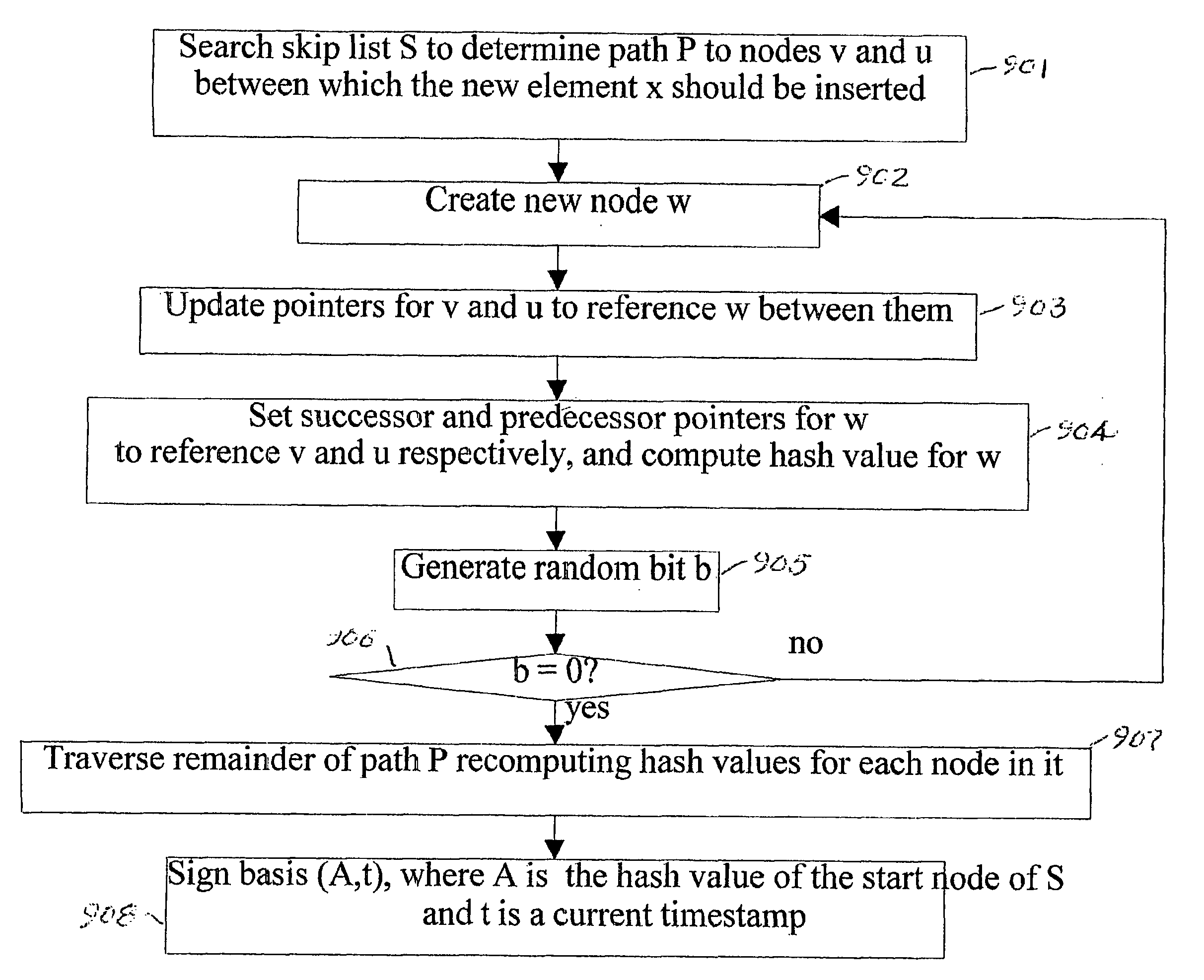
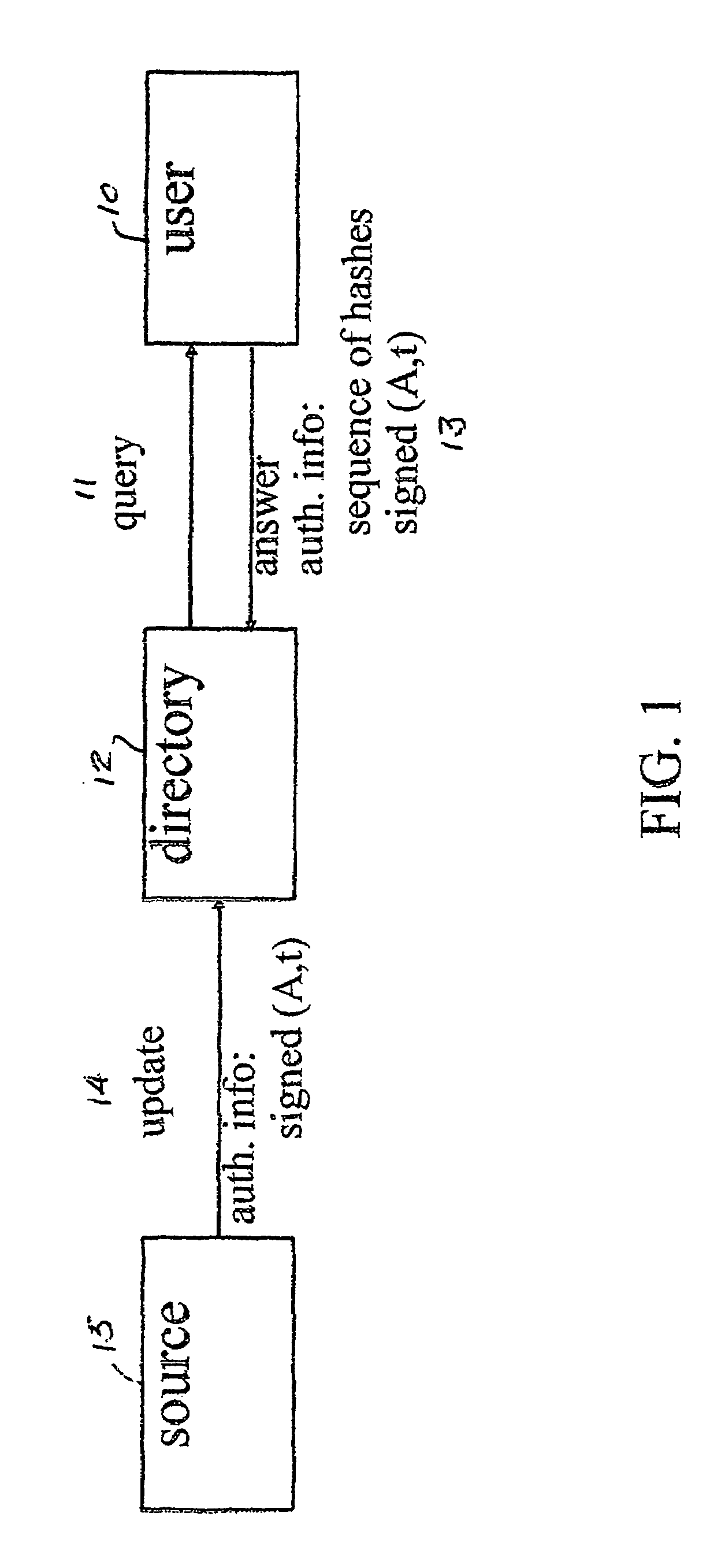
Efficient authenticated dictionaries with skip lists and commutative hashing
ActiveUS7257711B2Practical to maintainSimple calculationData processing applicationsUser identity/authority verificationSkip listCryptographic hash function
An efficient and practical method for dynamically maintaining an authenticated dictionary uses a skip list data structure and communicative hash functions to provide a dictionary database (201) that stores information objects so that any individual object can be authenticated as belonging or not belonging to the dictionary. The authentication consists of a short sequence of vales that begin with an element and a sequence of values that, when hashed in order using a cryptographic associative hash function, create the same value as the hashed digest of the entire dictionary. Rather than hashing up a dynamic 2-3 tree, hashes are created in a skip list. Validation of the result of the authenticating step is provided if the hash of the short sequence matches a signed hash of the entire skip list.
Owner:BROWN UNIVERSITY +1
Method of speech sound used as secret key to achieve data resource cloud storage management
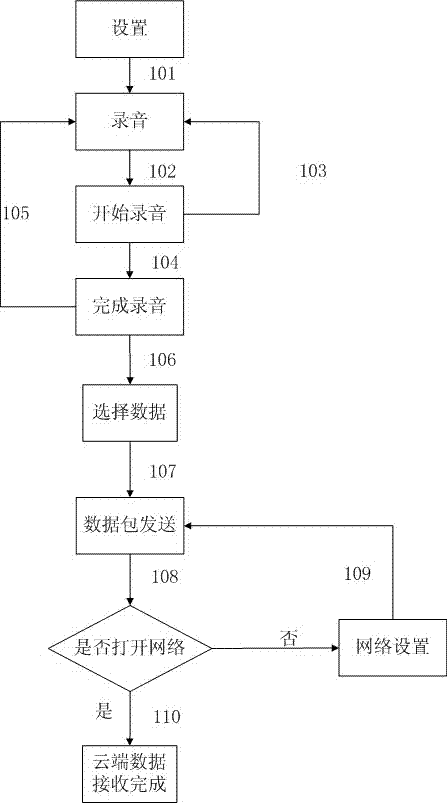
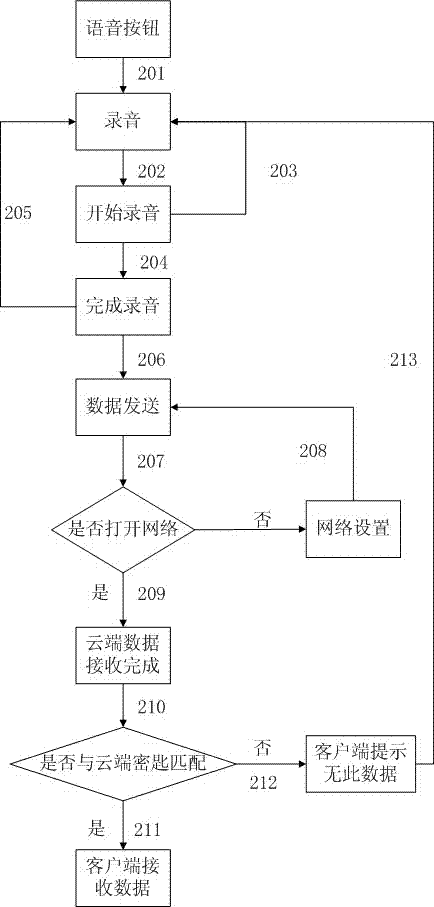
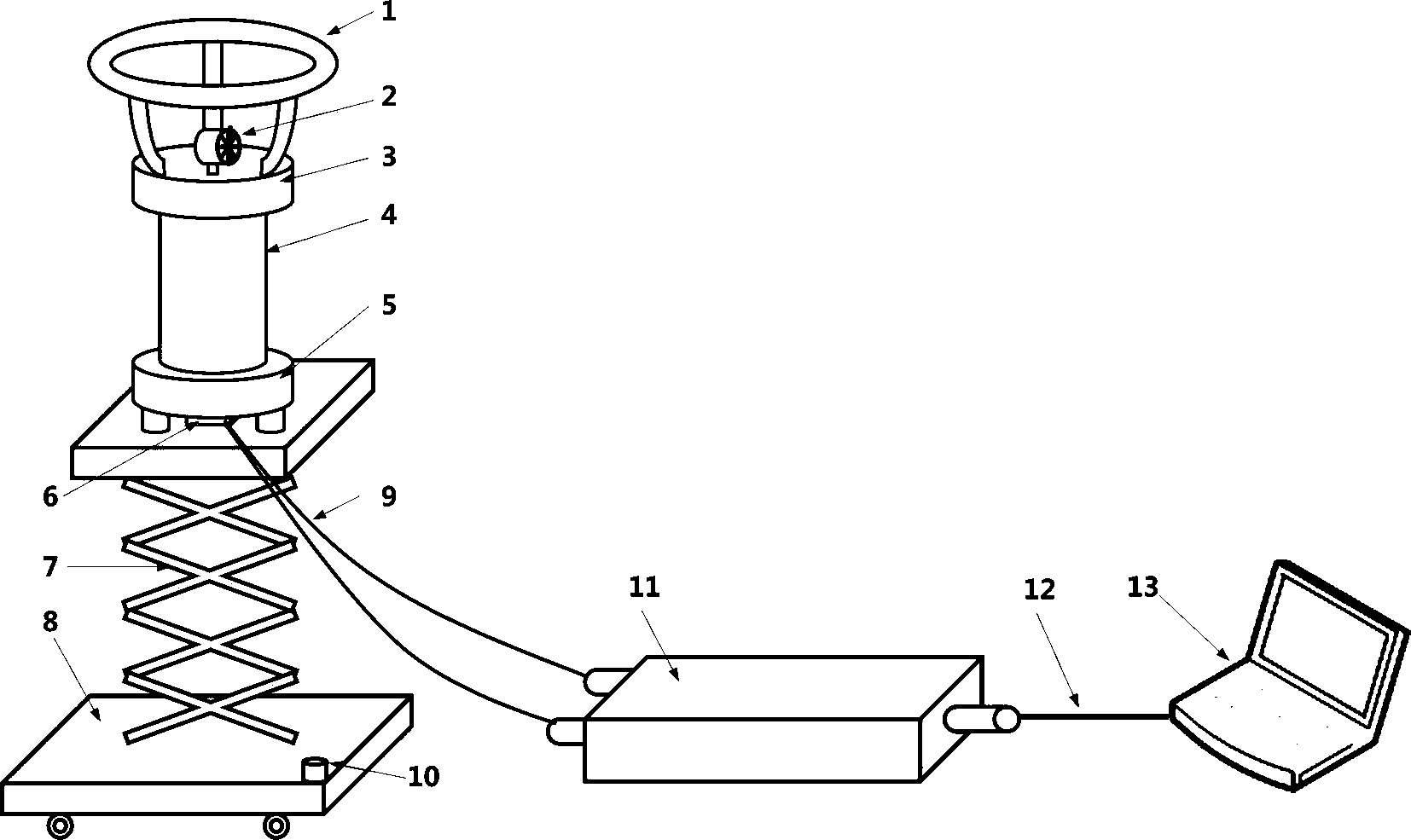
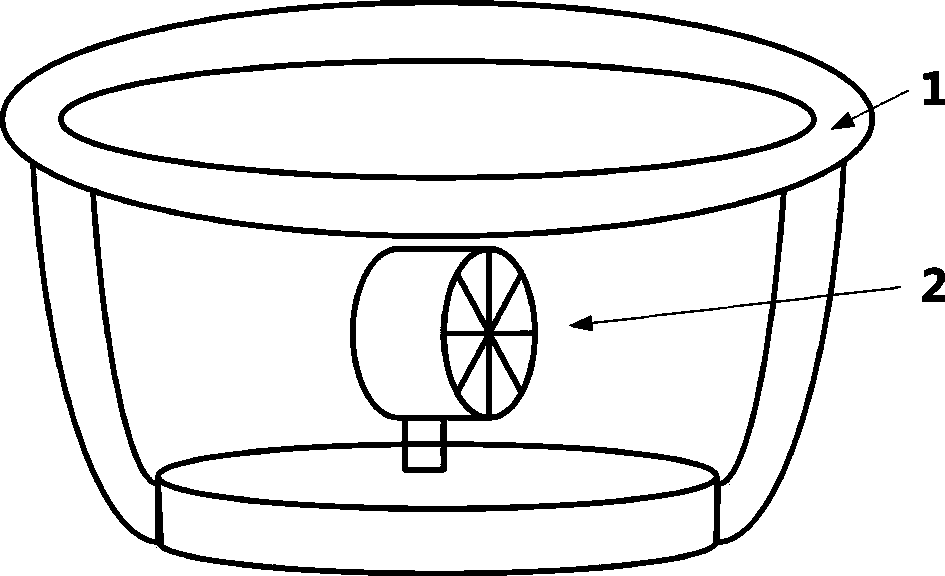
InactiveCN103118002ASolve data security issuesSimple experienceSpeech recognitionTransmissionEnvironmental noiseComputer hardware
The invention discloses a method of speech sound used as a secret key to achieve data resource cloud storage management. The method of speech sound used as a secret key to achieve the data resource cloud storage management is characterized in that after users complete recording under a recording interface, recording files can be encrypted and compressed, and then the recording files can be sent to a cloud server. The cloud server can be used for doing voice frequency analysis for the received records and the whole stored records and extracting sound features. The influence caused by environmental noise, information channel and speakers can be reduced as soon as possible. The analyzed speech sound information features are matched with backup speech sound information features. After the matching is succeeded, data resources backup by the speech sound secret key of a cloud storage server is returned to a corresponding client side. The client side can be used for receiving the backup data resources. When the matching is failed, error messages can be returned, and then the client side can be used for reminding users. A speech recognition technology can be used for resolving the safe problems of user registration, code management and the like. The user experience can be improved. A cloud server storage technology is used for reducing to occupy individual equipment resource occupying and overcoming the shortcomings of data loss and the like.
Owner:北京飞漫软件技术有限公司
Voltage transformer online verifying system based on SF6 parallel-plate capacitor
ActiveCN104375112ASimplify the verification processShorten the calibration cycleElectrical measurementsShielded cableCapacitance
The invention provides a voltage transformer online verifying system based on an SF6 parallel-plate capacitor. The system comprises a primary voltage sensing unit, a digitalization collecting unit, an optical signal processing unit and an intelligent processing unit. The system is characterized in that the primary voltage sensing unit adopts the SF6 parallel-plate capacitor as a voltage sensing unit and obtains primary voltage signals by detecting currents in capacitance; the primary voltage sensing unit is connected or disconnected with a primary wire through a lifting platform, so that online obtaining of high-voltage signals is achieved; output of the primary voltage sensing unit is connected with the digitalization collecting unit through a shield cable; output of the digitalization collecting unit is digital quantity optical signals transmitted to the intelligent processing unit of the lower-voltage side through the optical signal processing unit. The SF6 parallel-plate capacitor is adopted as a standard mutual inductor, so that online obtaining of the high-voltage signals is achieved. Along with increase of voltage classes, the size and the weight are not increased much, and the system is light due to gas insulation and suitable for a transformer substation site.
Owner:湖北宜电电气有限公司
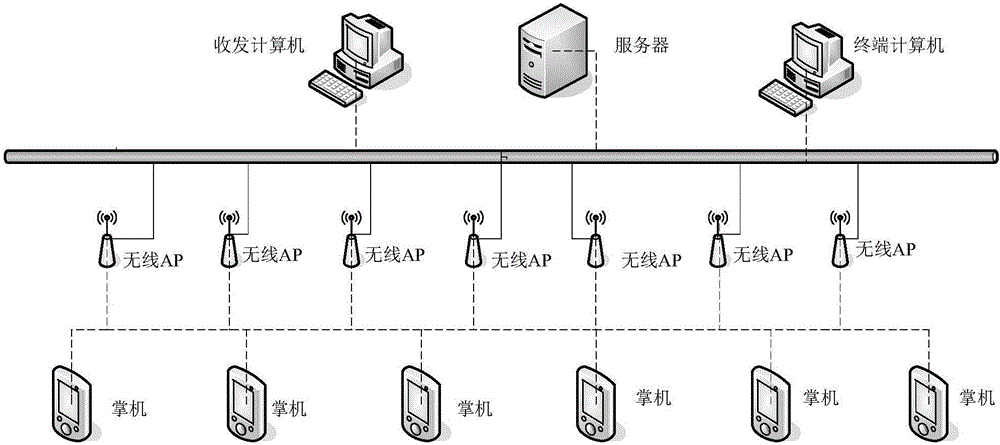
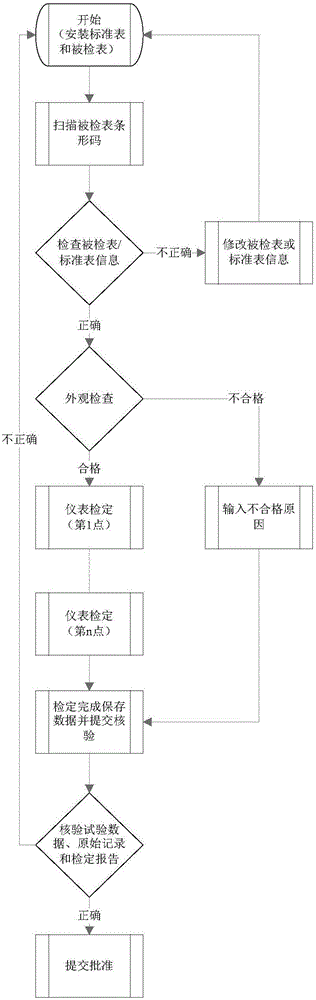
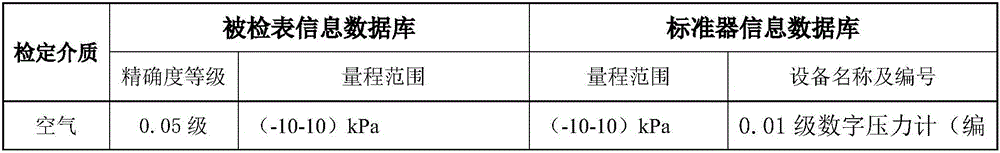
Thermal meter verification management system and method based on WLAN (wireless local area network)
ActiveCN106767991ASimplify the verification processReduce wasteCo-operative working arrangementsBarcodeAlarm management
The invention discloses a thermal meter verification management system and method based on a WLAN (wireless local area network). The method comprises the steps as follows: acquiring a unique bar code of a verified thermal meter to call meter information for storage, acquiring key words according to the acquired meter information, matching standard information, an original record and a verification report format, producing corresponding standard values to calculate various error indexes of the meter, generating verification conclusions, and completing management of each verification site. An artificial intelligence based verification management system is constructed by use of the WLAN and wireless equipment, meter verification automation, automatic alarming in case of verification overtime, meter out-of-tolerance alarming management and other functions are realized, the meter verification process is greatly simplified, and the thermal meter verification management system and method have the characteristics that the working efficiency is improved, the labor intensity is reduced and misoperation is reduced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
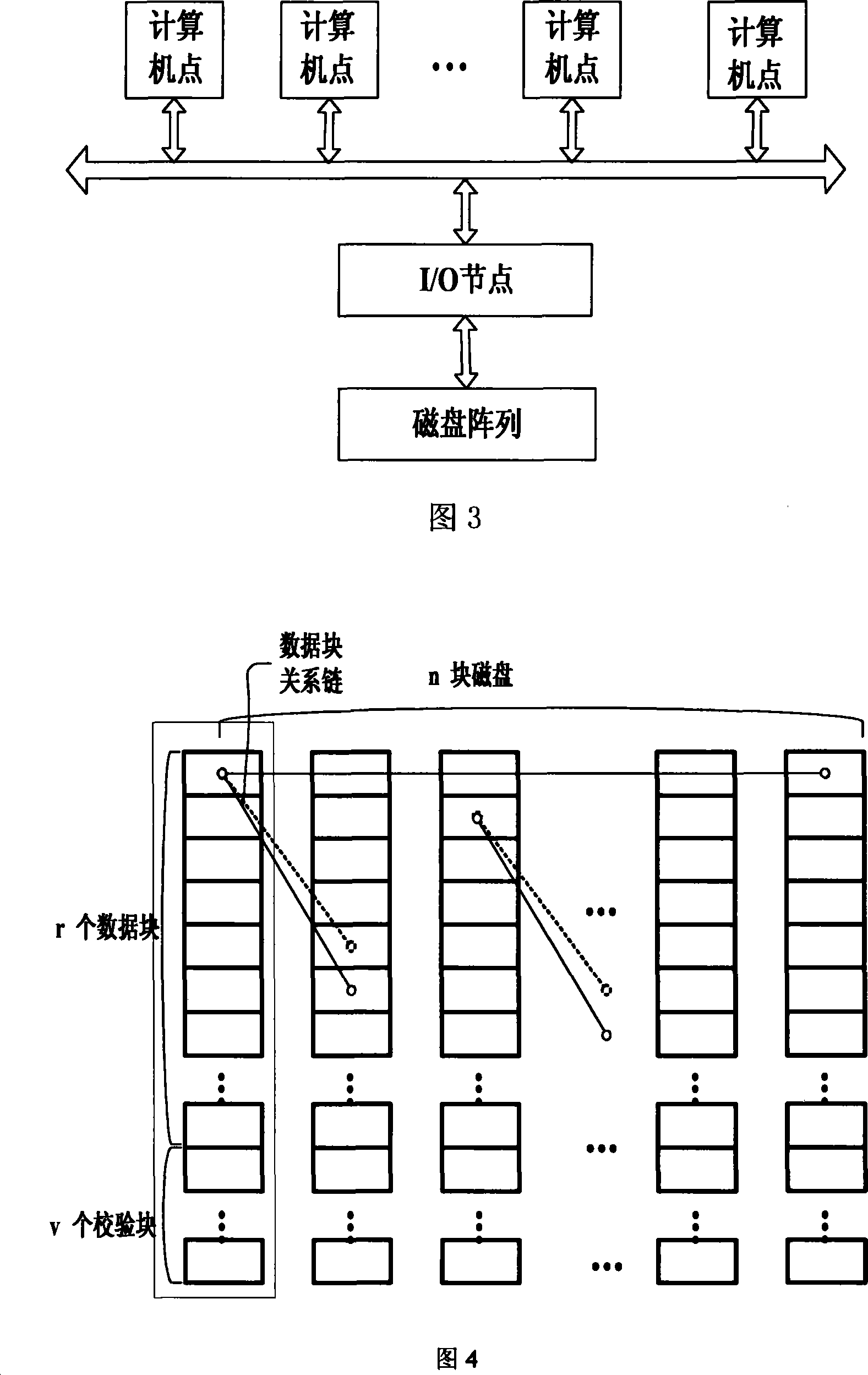
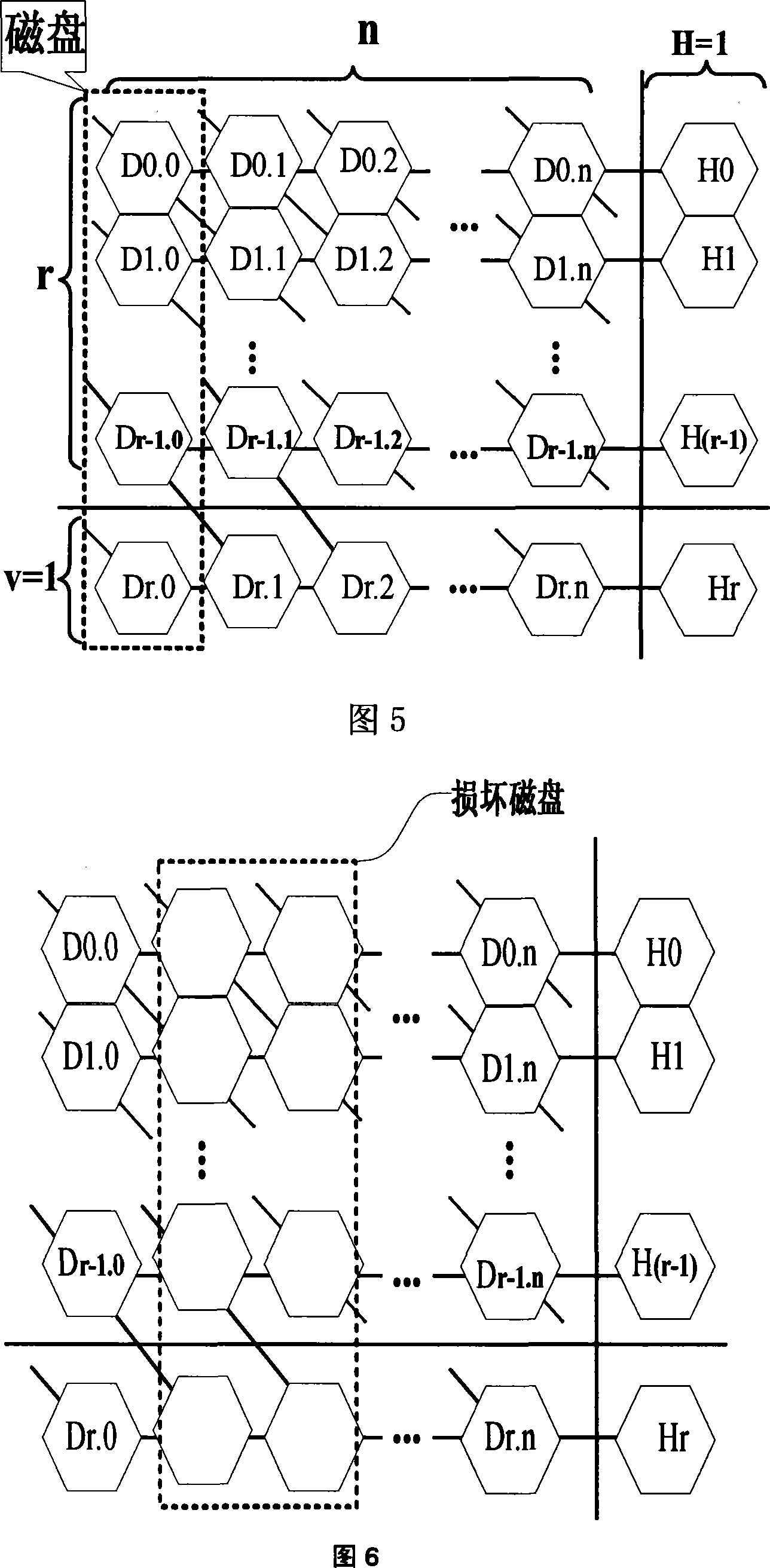
Method for cluster system data fault tolerance
InactiveCN101251812ASimplify the rebuild processSimplify the verification processRedundant data error correctionFault toleranceOriginal data
The invention relates to a data fault tolerance method applicable for a cluster system; when check data is constructed and generated, a data block is transferred to a data reproduction processor from the data stored in a disk driver of a storage unit array; through an exclusive OR operation, the check data is generated and written out to a corresponding check data block, or the data in the data block and the data in the check data block are operated and written out to a corresponding data block. When the data is lost caused by the physical damage of the disk or other causes, the data in the undamaged data block of a connecting relation chain is read to a data regeneration manager and operated to generate lost data; therefore, the reproduced and lost data is written to corresponding data block of a corresponding backup disk or an original data storage data block position, thereby realizing the regeneration and reconstruction of the lost data. Through implementing the invention, the data in a damaged disk of a disk array is restored and reconstructed in time; further the lost data in a single disk or a plurality of disks are reproduced or regenerated in the disk array.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
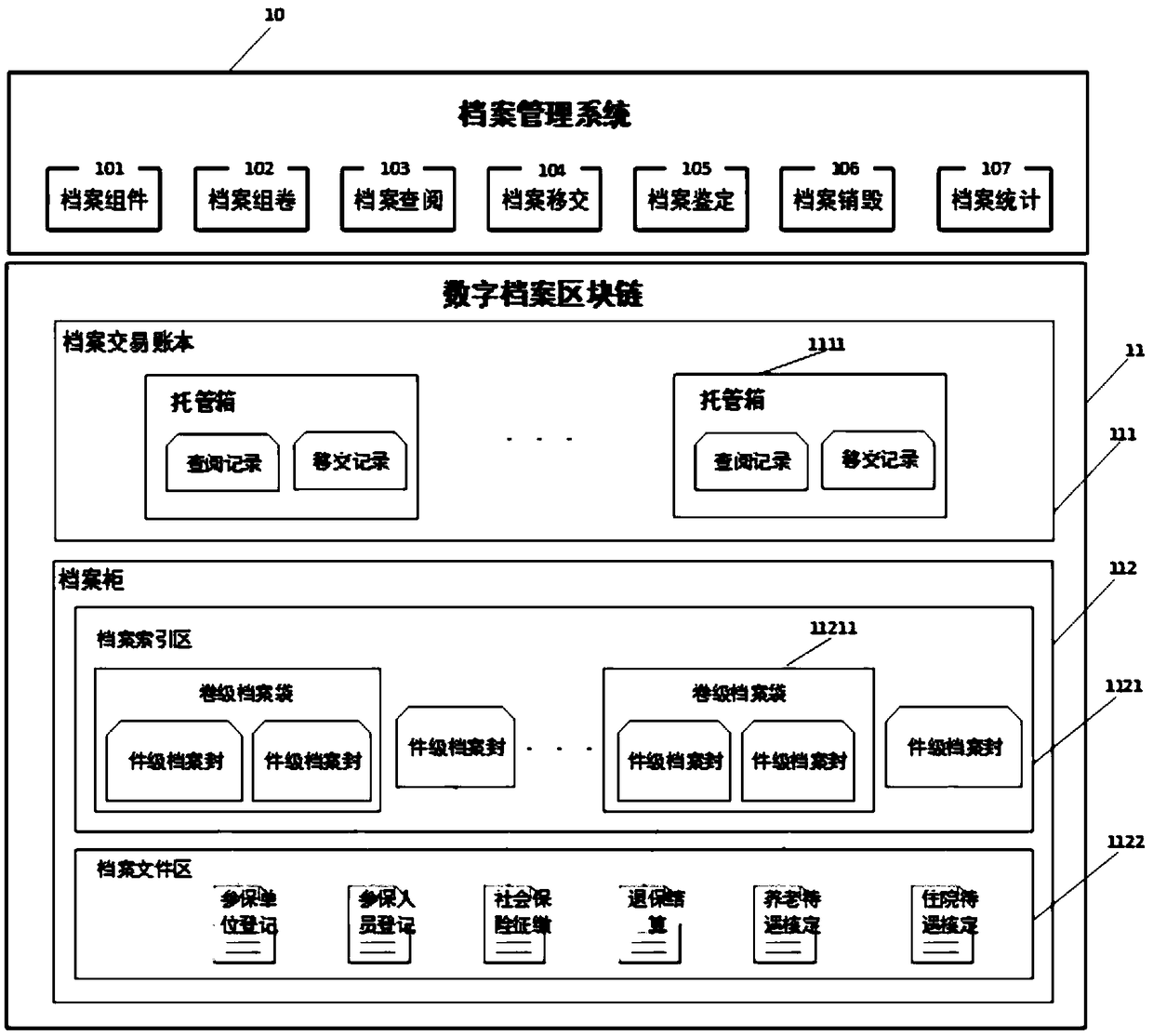
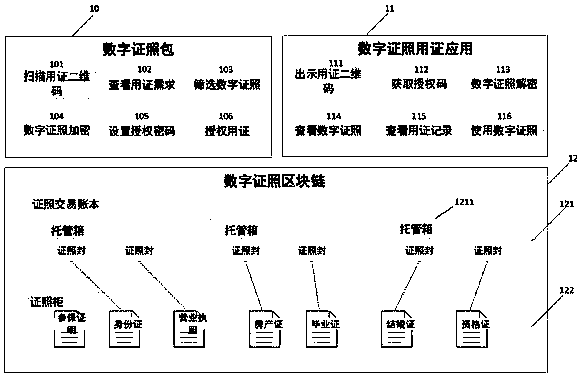
Digital archive system based on blockchain
ActiveCN108763463ASimplify the verification processReduce audit costsDigital data protectionSpecial data processing applicationsBlockchainAuthorization
The invention provides a digital archive system based on a blockchain. The digital archive system includes an archive management system and a digital archive blockchain. The archive management systemincludes modules of archive piece forming, archive volume forming, archive viewing, archive handover, archive identification, archive destruction and archive counting. The digital archive blockchain includes an archive transaction account book and an archive cabinet. According to the digital archive system, authorization passwords are set, blockchain encryption technology is utilized, entire-network maintenance is carried out, thus tampering cannot occur, security, authenticity and credibility of digital archives are guaranteed, phenomena of usurping, illegal accessing and the like of the archives are eliminated, a traditional archive verification process is simplified, auditing costs are reduced, low-cost use of the archives is realized, and at the same time, losses caused by archive tampering and forging on units are also avoided. Archive management service behaviors at any time can be queried, and viewing and handover records cannot be tampered with, and can be traced. Identity confirmation and qualification authentication are realized, digital economy development and new-old kinetic energy conversion are facilitated, trust costs are reduced, and social system running efficiencyis improved.
Owner:DAREWAY SOFTWARE
Electric vehicle traction motor design parameter verification method
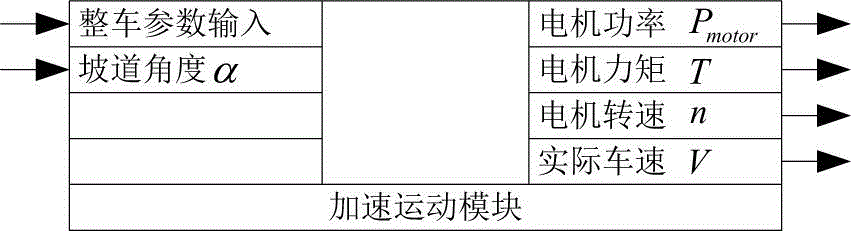
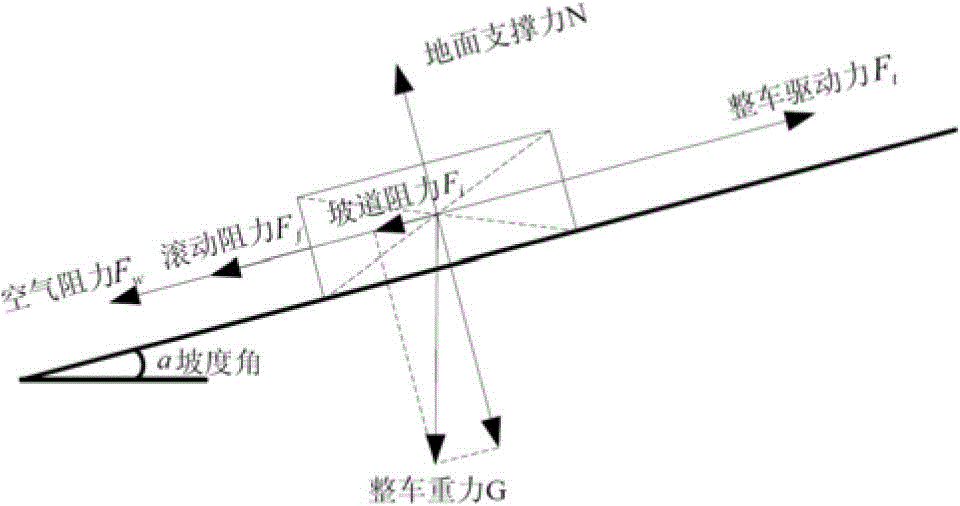
ActiveCN105811670ASimplify the verification processElectric machinesManufacturing dynamo-electric machinesElectric machineComputer module
The invention relates to the electric vehicle power assembly design field, to be specific, relates to an electric vehicle traction motor design parameter verification method. The electric vehicle traction motor design parameter verification method comprises (1) arrangement of a uniform motion calculation module and an accelerated motion calculation module; (2) arrangement of a highest speed calculation module, a common speed calculation module, and a maximum gradient calculation module; and arrangement of an accelerated motion condition calculation module; (3) arrangement of a verification module; (4) selection of verification values according to a maximum principle. The electric vehicle traction motor design parameter verification method has advantages of simple process, comprehensive verification, and reasonable result.
Owner:SHANGHAI DAJUN TECH
Feature code verification platform system and feature code verification method
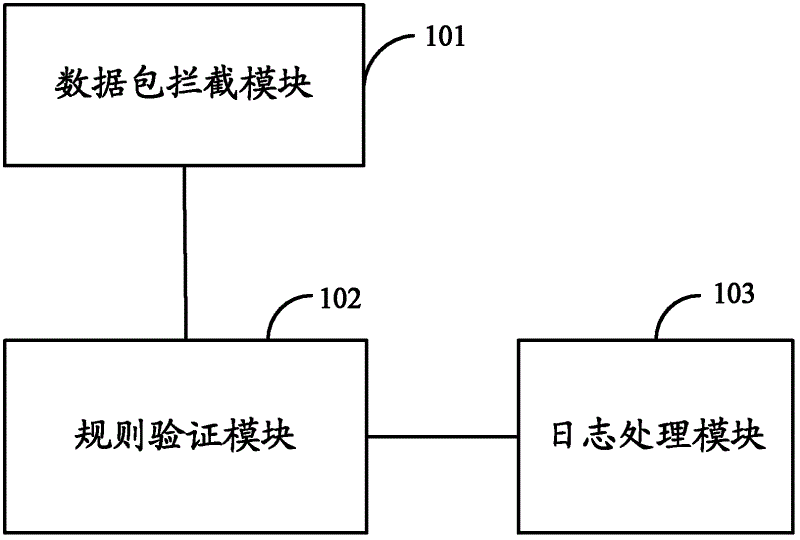
ActiveCN102624721ASimplify the verification processImprove verification efficiencyData switching networksValidation methodsNetwork packet
The embodiment of the invention provides a feature code verification platform system and a feature code verification method. The feature code verification platform system comprises a packet interception module, a rule verification module and a log processing module; the packet interception module is used for intercepting the communication packets of various applications and / or each protocol layer in a test host; the rule verification module is used for executing operations set by a set verification policy on the packets of the applications and / or the protocol layers to be monitored by using a feature code in the intercepted packets according to the verification policy and generating logs corresponding to the operations; and the log processing module is used for respectively processing and outputting the log corresponding to each operation in order to determine whether the feature code to be tested is valid. The invention solves the problem that the efficiency of conventional feature code verification is low.
Owner:神州绿盟成都科技有限公司
Payment system, payment method and information checking method
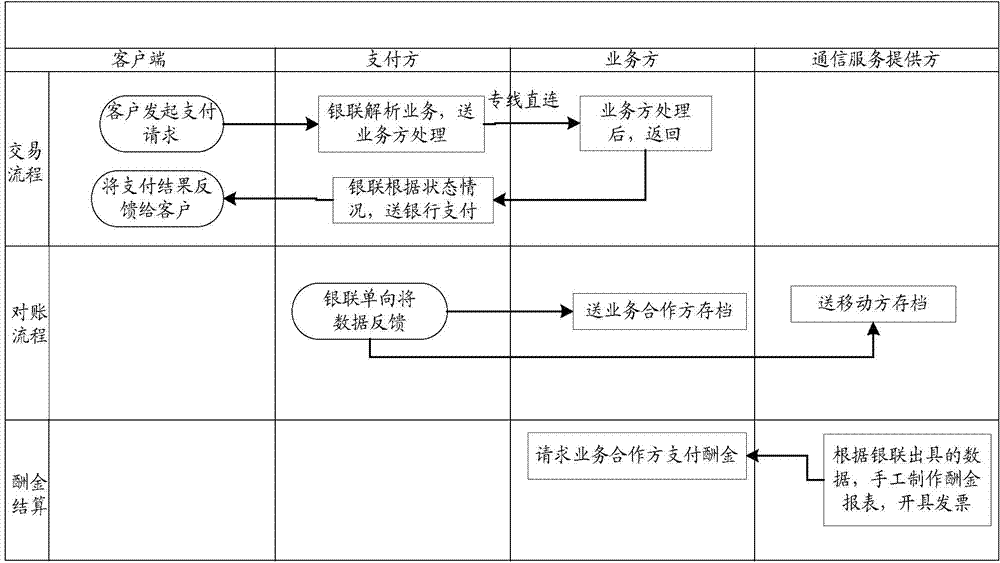
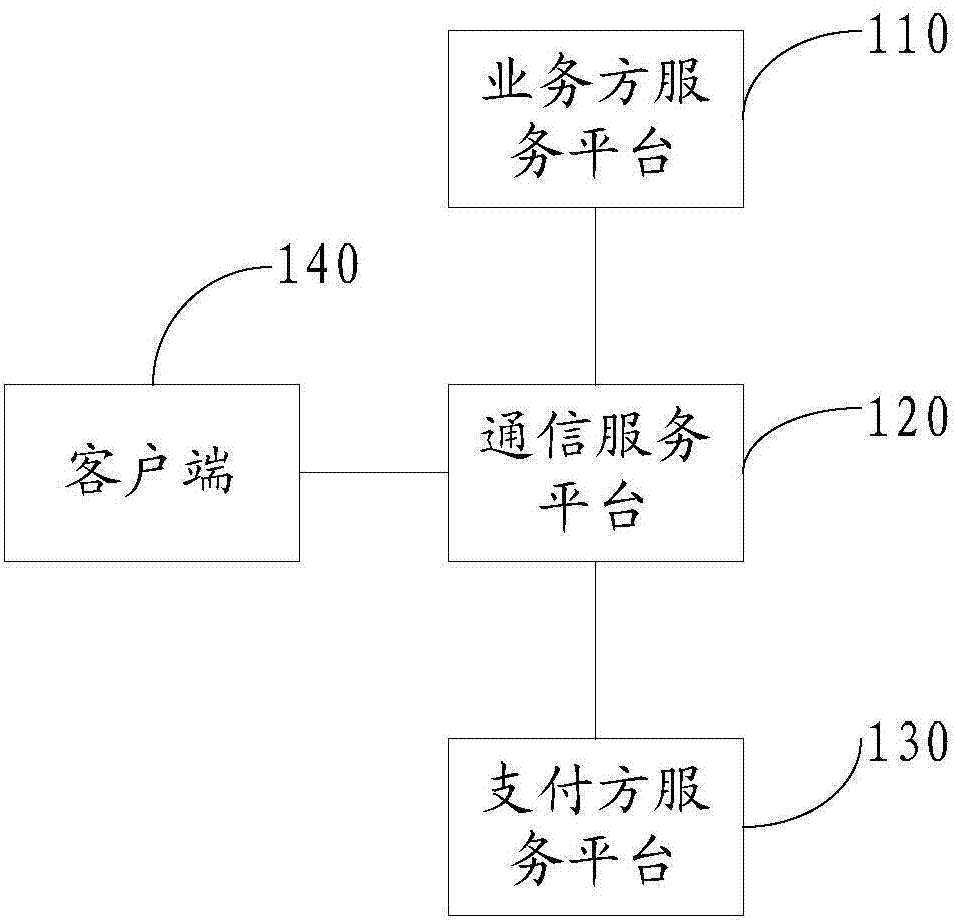
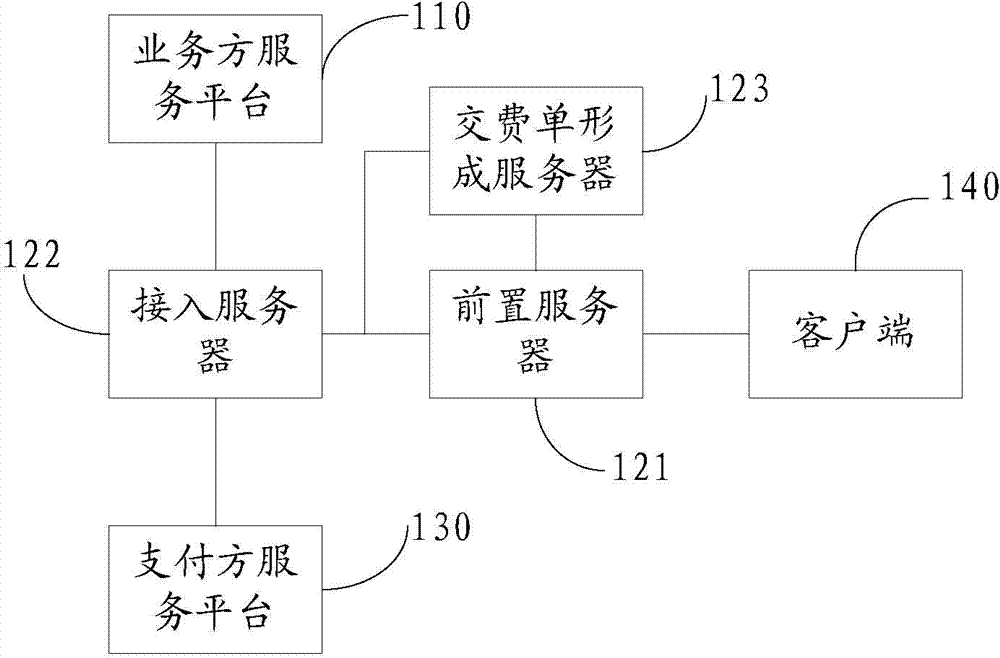
ActiveCN104766202AIncrease controlTimely processingProtocol authorisationPayment systemCommunications server
The invention discloses a payment system, a payment method, and an information checking method. The system comprises a payment-side service platform, a business-side service platform, and a communication service platform of a communication server. The communication service platform is connected with the payment-side service platform and the business-side service platform. The communication service platform is used for receiving a payment request of a client and judging whether to form a fee information list corresponding to the payment request and including payment information; if a fee information list is formed, the communication service platform sends a payment instruction to the payment-side service platform according to the fee information list; and if a fee information list is not formed, the communication service platform acquires payment information from the business-side service platform, forms a fee information list, and sends a payment instruction to the payment-side service platform according to the fee information list after the fee information list is formed. The payment-side service platform is used for receiving the payment instruction and carrying out payment according to the payment instruction. The business-side service platform is used for providing payment information for the communication service platform.
Owner:ZUNYI BRANCH OF CHINA MOBILE GRP GUIZHOU COMPANY
Managing formal verification complexity of designs with multiple related counters
ActiveUS7647572B1Eliminate redundancyCounter intuitiveCAD circuit designSoftware simulation/interpretation/emulationComputer architectureCircuit design
A counter abstraction tool generates an abstraction model for one or more counters in a circuit design for use with a formal verification system. The tool detects the presence of a counter in a circuit design, identifies one or more special values for the counter, and creates an abstraction for the counter. The tool can automatically perform the abstraction, guide a user in configuring the appropriate abstraction for the counter, or perform a combination of automatic and manual abstraction. The tool may further accommodate related counters.
Owner:JASPER DESIGN AUTOMATION
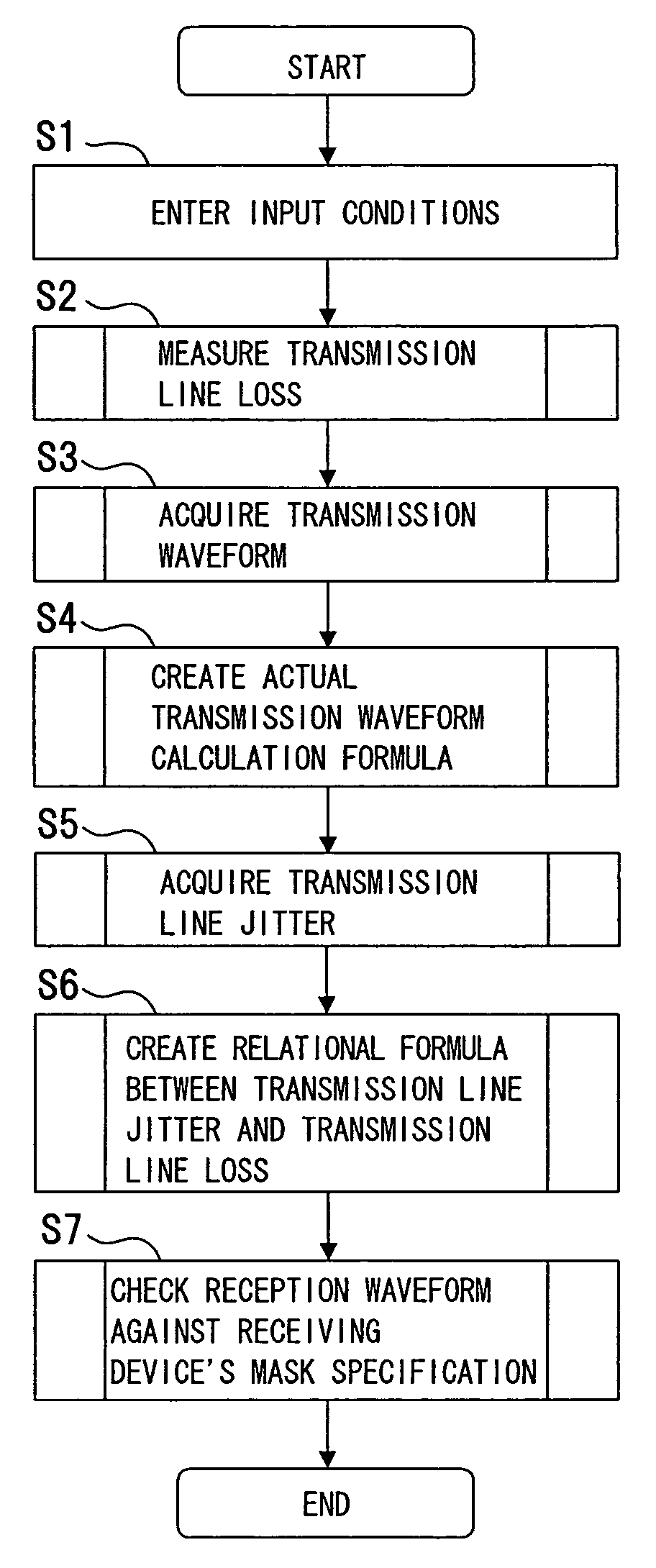
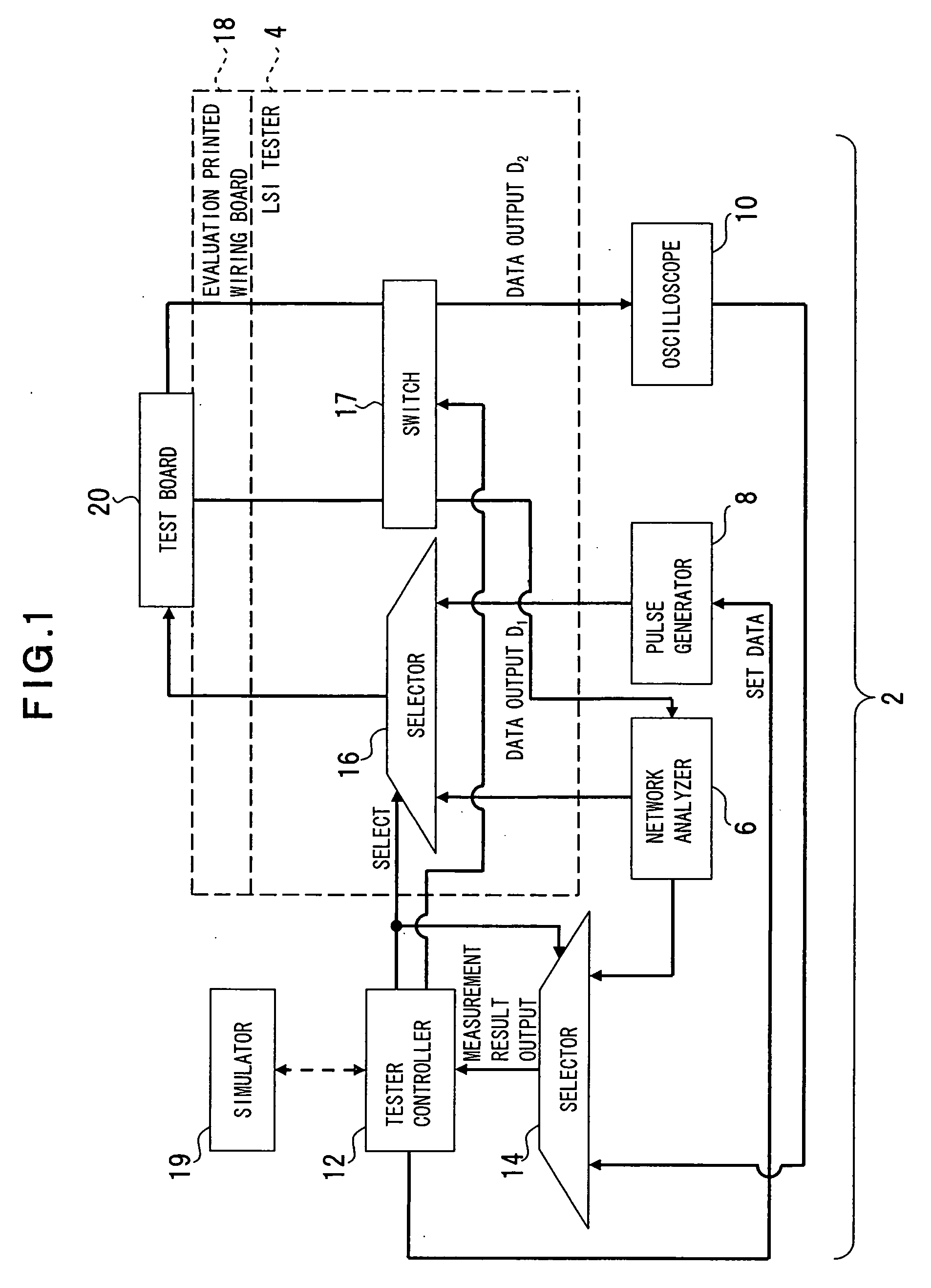
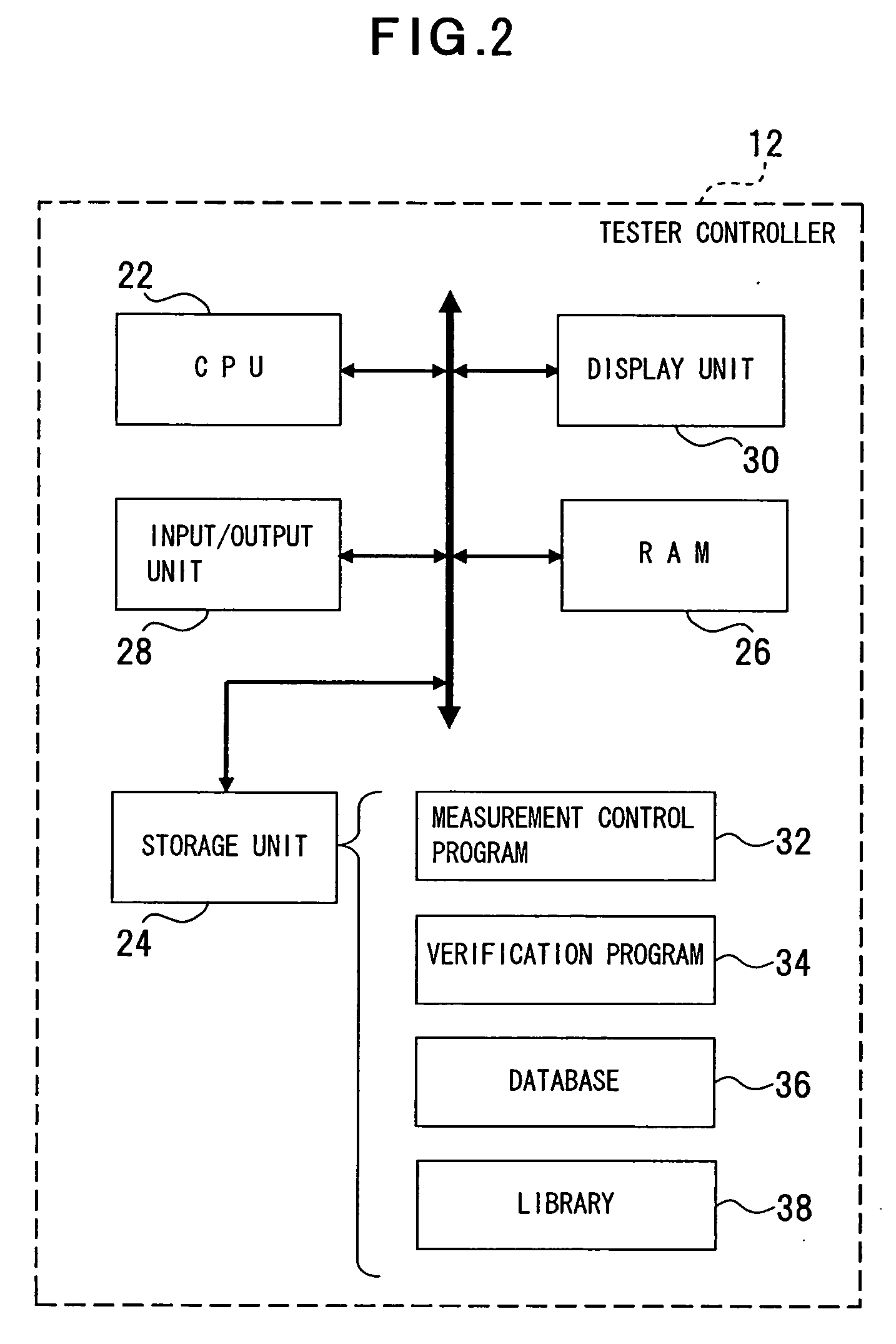
Apparatus, method and program for verification of transmission margin
InactiveUS20060062234A1Simplify the verification processReduce in quantityData switching by path configurationPulse characteristics measurementsLeading edgeEngineering
The present invention relates to verification of a transmission margin of various transmission lines transmitting a signal such as a high-speed digital signal and ensures improved verification accuracy. A transmission margin verification apparatus according to the present invention is configured with a measurement unit (e.g., LSI tester 4, network analyzer 6, pulse generator 8, oscilloscope 10) operable to measure a transmission loss and a leading edge waveform of pseudo transmission lines (e.g., transmission lines 56, 62, 66) corresponding to a target device 44 to be verified, and a calculation unit (tester controller 12) operable to reference the transmission line loss and the leading edge waveform measured by the measurement unit, calculate a transmission waveform of the target device, and associate the transmission waveform with a mask of the target device to calculate a transmission margin of the target device.
Owner:FUJITSU LTD
Write message prospect processing method and device facing board-level high-speed bus
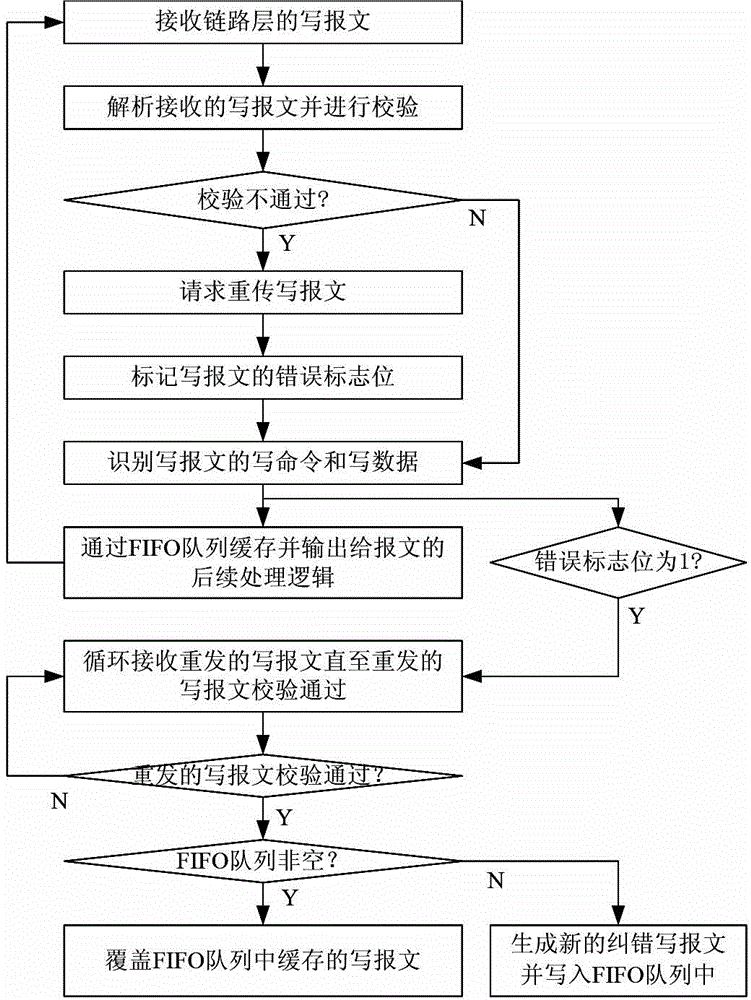
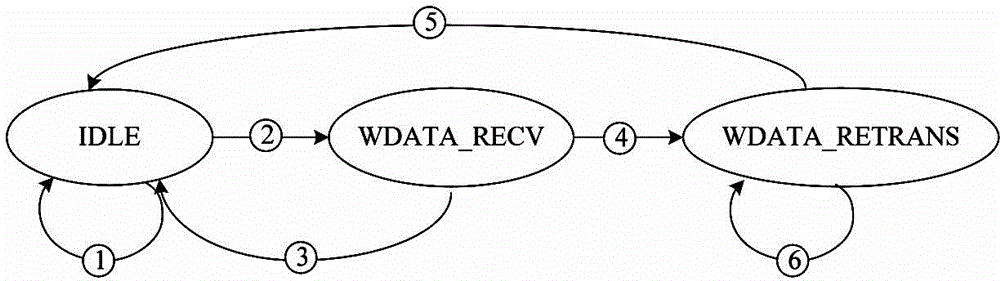
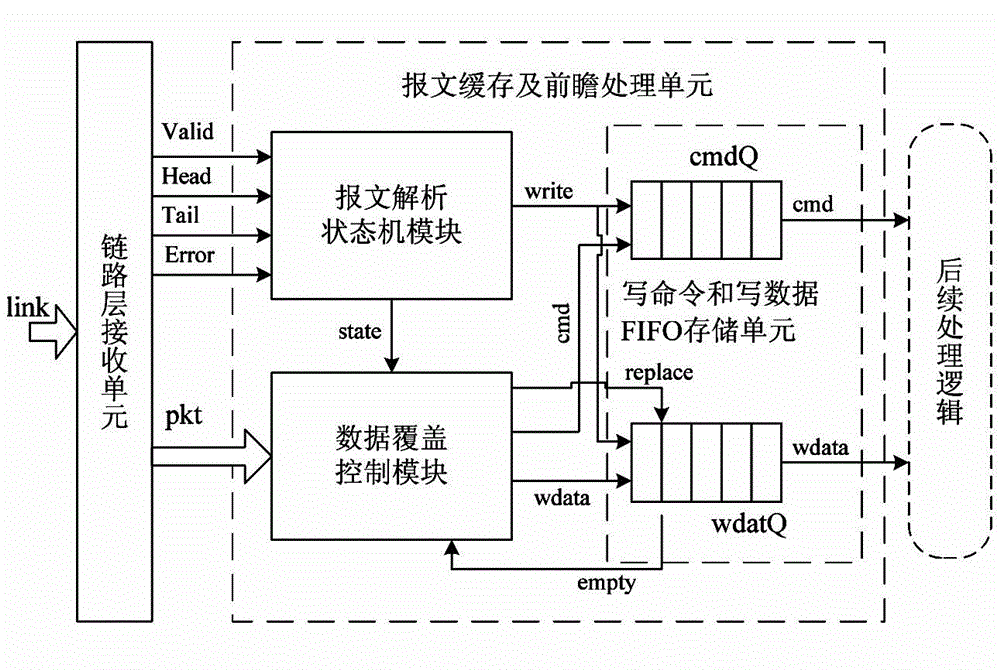
ActiveCN104866454AReduce processing latencyImprove performanceElectric digital data processingComputer hardwareWriting messages
The invention discloses a write message prospect processing method and device facing a board-level high-speed bus. The method comprises the following steps: receiving a write message of a link layer; carrying out checking; setting error flag bits; requesting retransmission when the checking result shows that the message is unqualified; identifying the write command and the write data of the write message; caching the write command and the write data through an FIFO queue; outputting the write command and the write data to follow-up message processing logic; detecting the error flag bits of the write message; receiving retransmitted write messages when any error flag bit exists till no error flag bit exists; covering the cached write message if the FIFO queue is not empty; generating a new error correction write message if the FIFO queue is empty, and writing the new error correction write message into the FIFO queue. The device comprises a link layer receiving unit and a message cache and prospect processing unit which are related in the method. The method and device have the advantages that the performance of a storage system can be improved; distinguishing of types of write requests and write data in follow-up processing and cancellation of inaccurate write requests and data are voided; the logic design and verification in follow-up processing are simplified.
Owner:NAT UNIV OF DEFENSE TECH
Digital certificate authorization using device based on block chain and use method thereof
InactiveCN108763942ASave work costsSimplify the verification processDigital data protectionDigital data authenticationBlockchainAuthorization
The invention provides a digital certificate authorization using device based on a block chain and a use method thereof. The digital certificate authorization using device based on the block chain comprises: a digital certificate package module which is used for management and use of the license by the licensee; a digital certificate application module which is used for a certificate unit to manage and use the certificate of the licensee; a digital certificate block chain module which is used for storing certificate information. According to the invention, by setting the authorization passwordand using the block chain encryption technology, whole network maintenance and anti-tampering, the digital certificate is guaranteed to be safe, authentic and trustworthy.
Owner:DAREWAY SOFTWARE
Multi-application platform access method, device and system
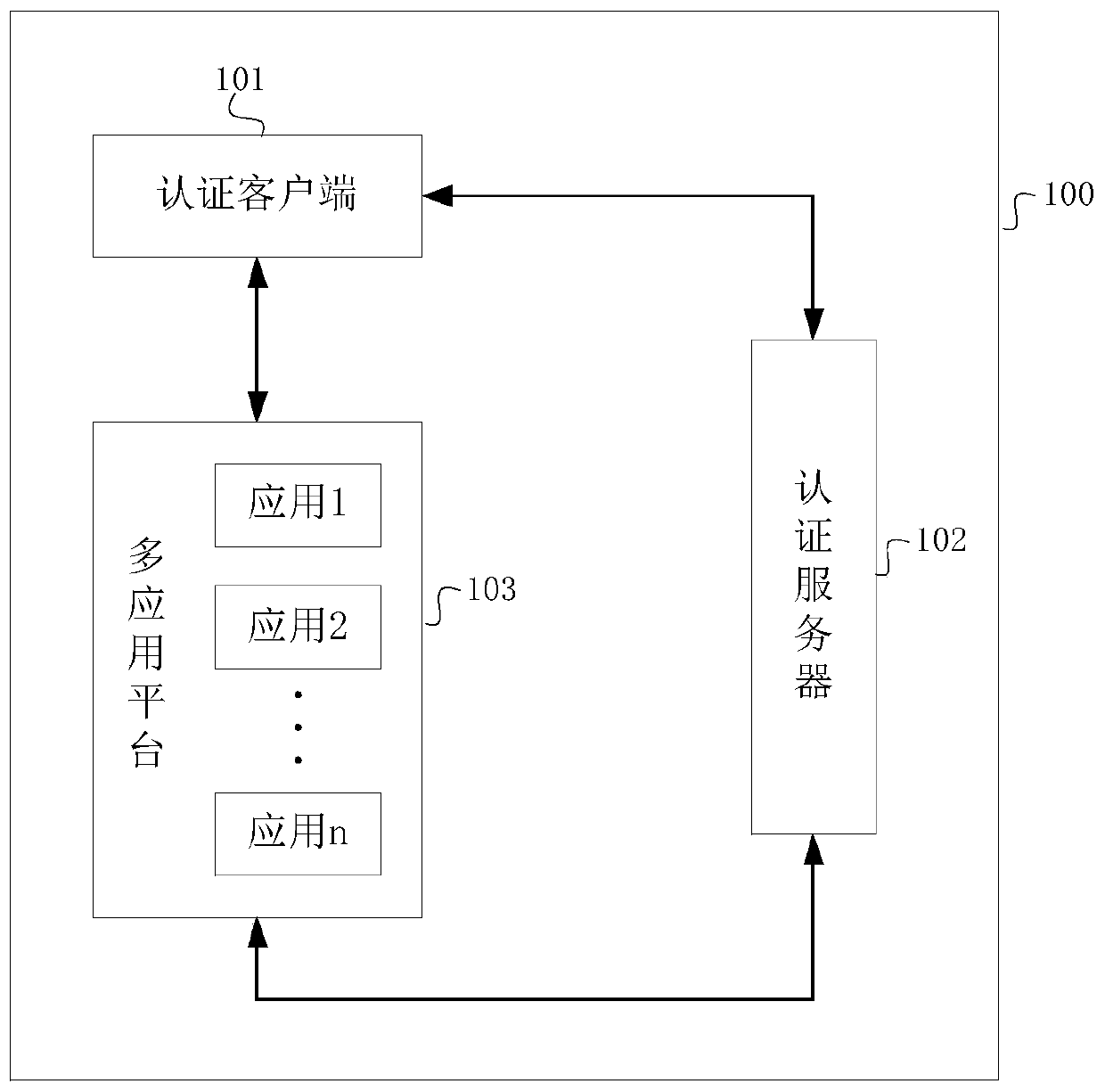
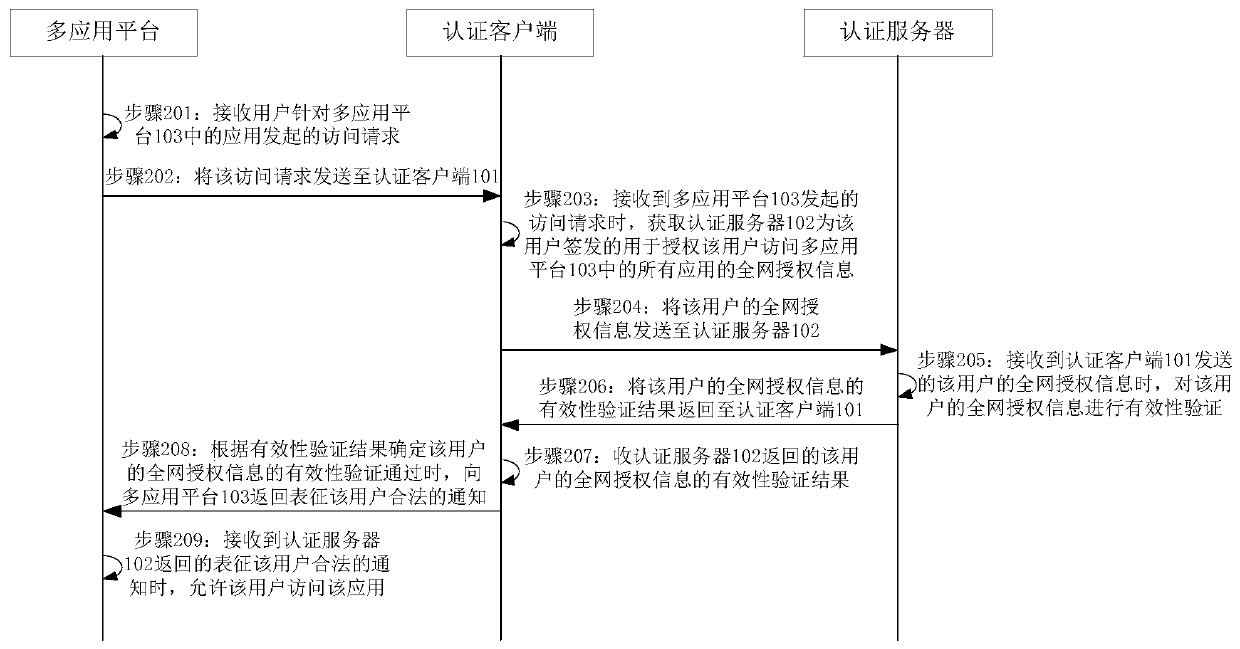
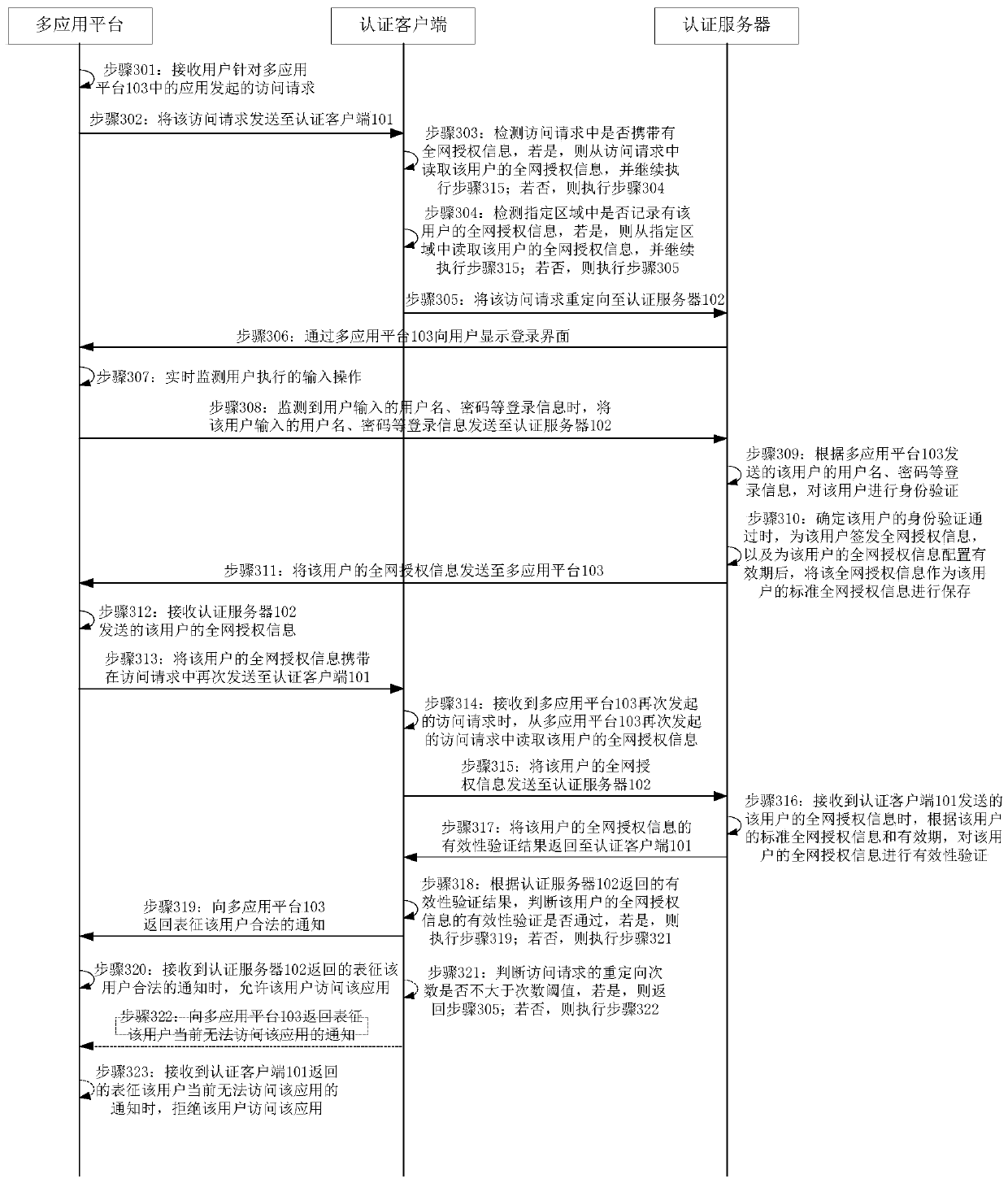
InactiveCN110247907ASecure AccessSimplify the verification processTransmissionAuthentication serverComputer security
The invention discloses a multi-application platform access method, a multi-application platform access device and a multi-application platform access system, which are applied to the technical field of computers and are used for solving the problems of complicated verification process and low access efficiency of the existing multi-application platform access method. Specifically, the method comprises the steps of receiving an access request initiated by a user for applications in a multi-application platform, and obtaining whole network authorization information which corresponds to the user and is used for authorizing the user to access all applications in the multi-application platform, carrying out validity verification on the whole network authorization information of the user through the authentication server, and allowing the user to access the application when the validity verification of the whole network authorization information of the user is determined to be passed. Therefore, the whole network authorization information is configured for the user through the authentication server, so that the user only needs to perform validity verification on the whole network authorization information of the user when accessing the application in the multi-application platform, thereby simplifying the verification process and improving the application access efficiency while ensuring the access security of the multi-application platform.
Owner:DEEPBLUE TECH (SHANGHAI) CO LTD
Electronic ticket verification system
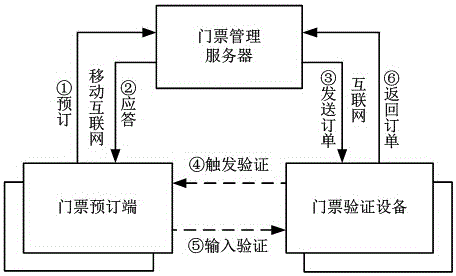
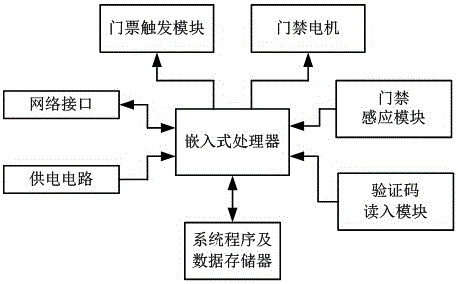
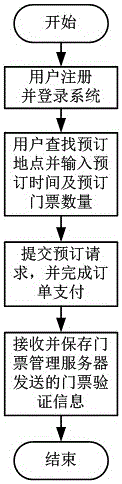
PendingCN106530412ASimplify the verification processShorten the timeTicket-issuing apparatusReservationsComputer architectureHuman power
The invention provides an electronic ticket verification system, which comprises a ticket management server, a ticket verification device, a ticket reservation end, and a door access device. The ticket management server and the ticket verification device are connected through the internet. The ticket management server is connected with the ticket reservation end through the mobile internet or the wireless internet. The ticket verification device controls the on / off state of the door access device. The ticket verification operation of the entire system comprises the steps of (1) reservation; (2) responding; (3) order sending; (4) triggering the verification; (5) inputting and verifying; (6) returning to the order process. According to the technical scheme of the invention, the electronic ticket verification system saves the time of a user spent in finding an electronic ticket and simplifies the ticket verification process. At the same time, more tickets can be verified within the same period of time. Moreover, no other workers participate in the entire ticket verification process, so that the labor cost is greatly saved.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com