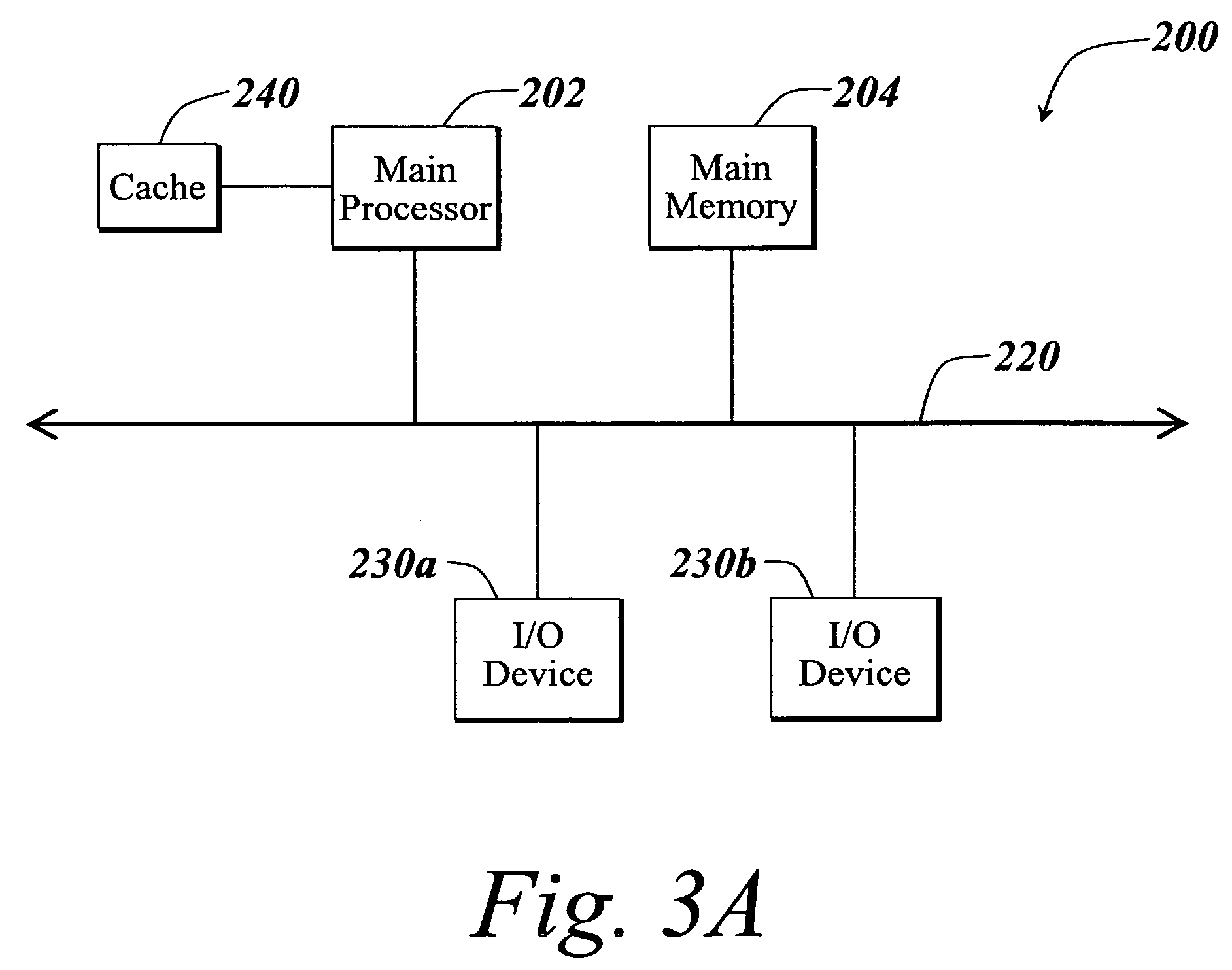
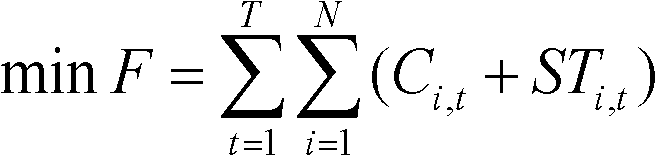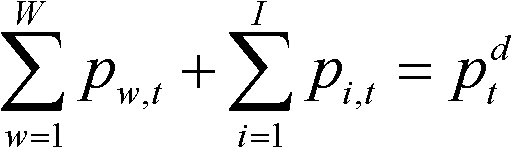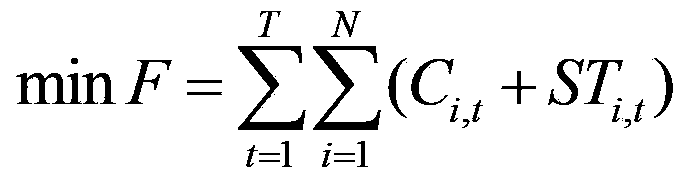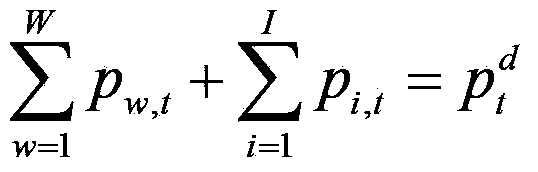Patents
Literature
152results about How to "Secure Access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
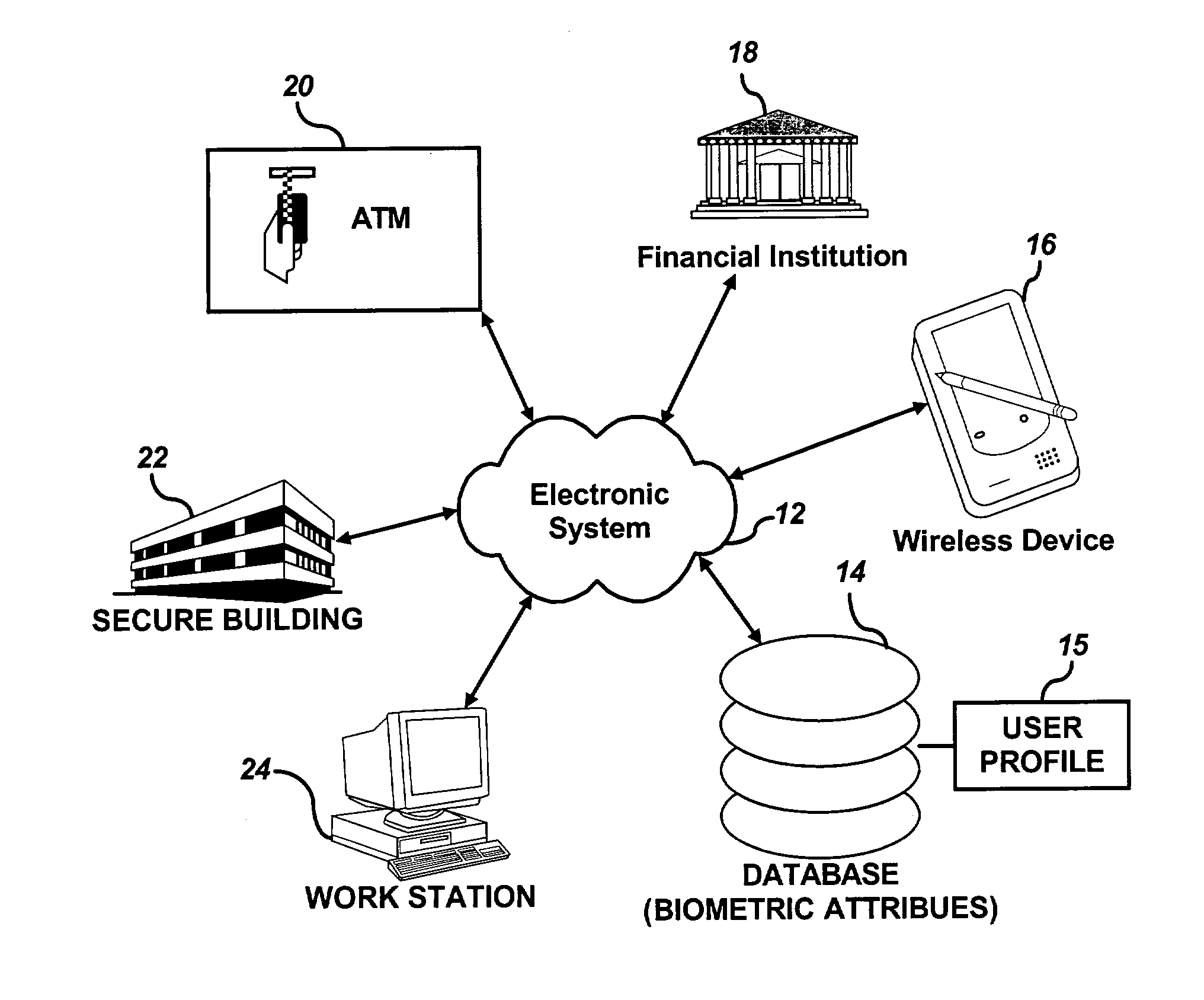
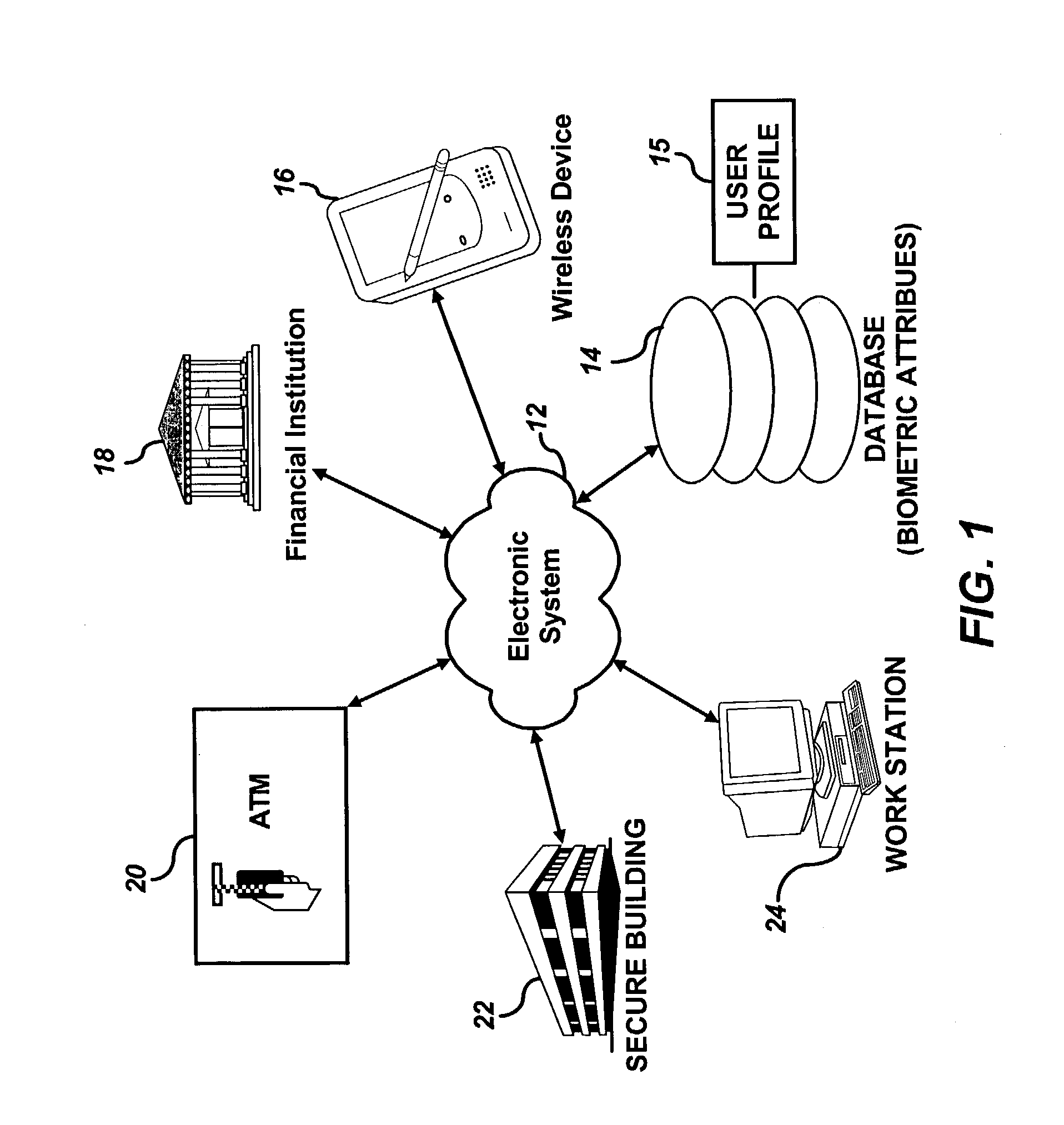
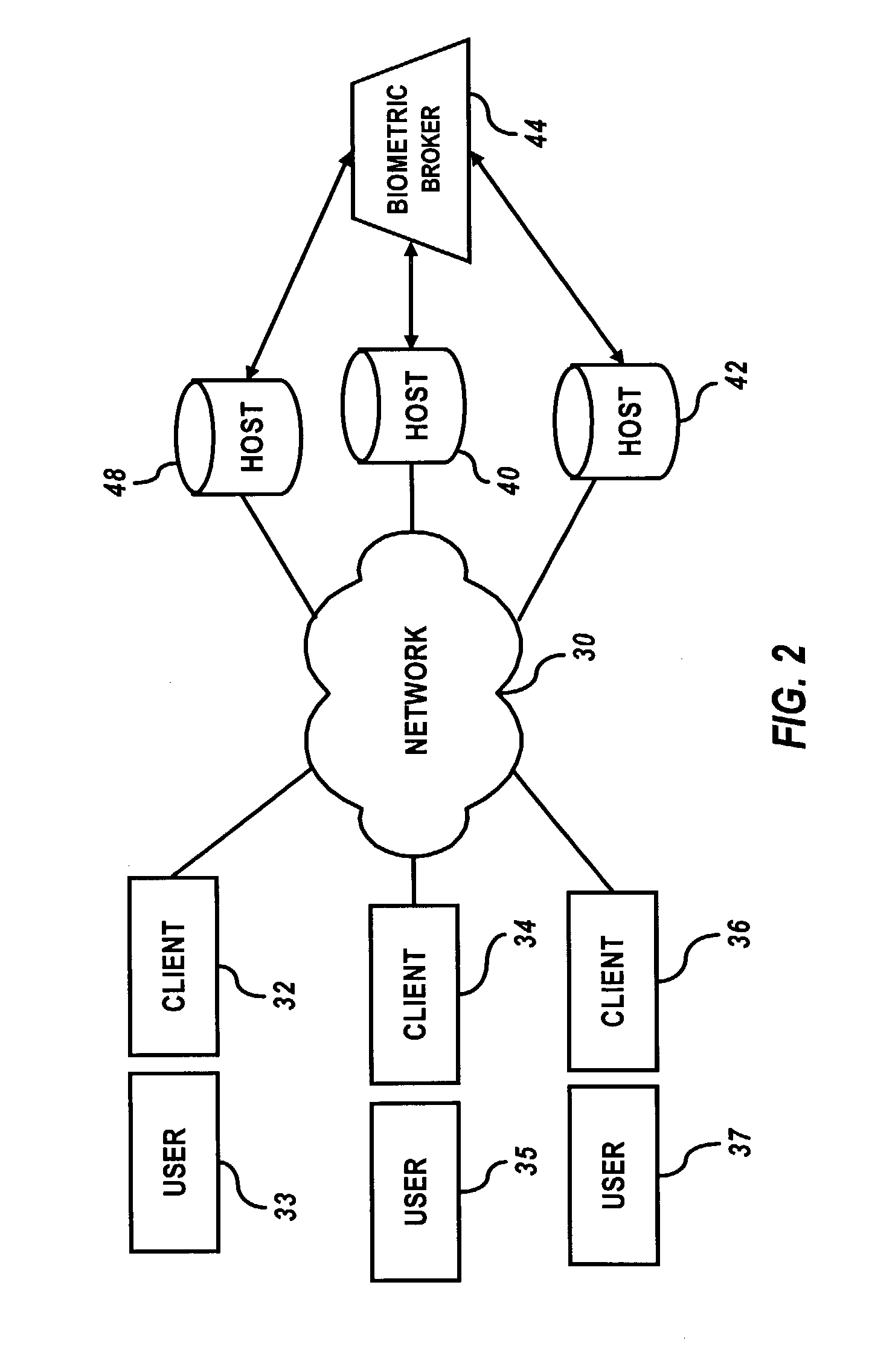
Random biometric authentication utilizing unique biometric signatures
InactiveUS20030163710A1Accurate authenticationSecure user accessDigital data processing detailsUser identity/authority verificationUser inputLayer thickness
A user can be challenged to provide at least one randomly selected biometric attribute. The randomly selected biometric attribute input by the user is automatically compared to a plurality of biometric attributes of the user contained in a user profile. The user can then be authenticated if the randomly selected biometric attribute input by the user matches at least one of the plurality of biometric attributes of the user contained in the user profile. Biometric attributes analyzed according to the methods and systems of the present invention, include, but are not limited to, for example, fingerprints, iris, retina, and / or tissue characteristics, such as skin morphology, skin layer thickness, collage density and orientation, tissue hydration, optical patent length differences, etc.
Owner:IP VENUE LLC
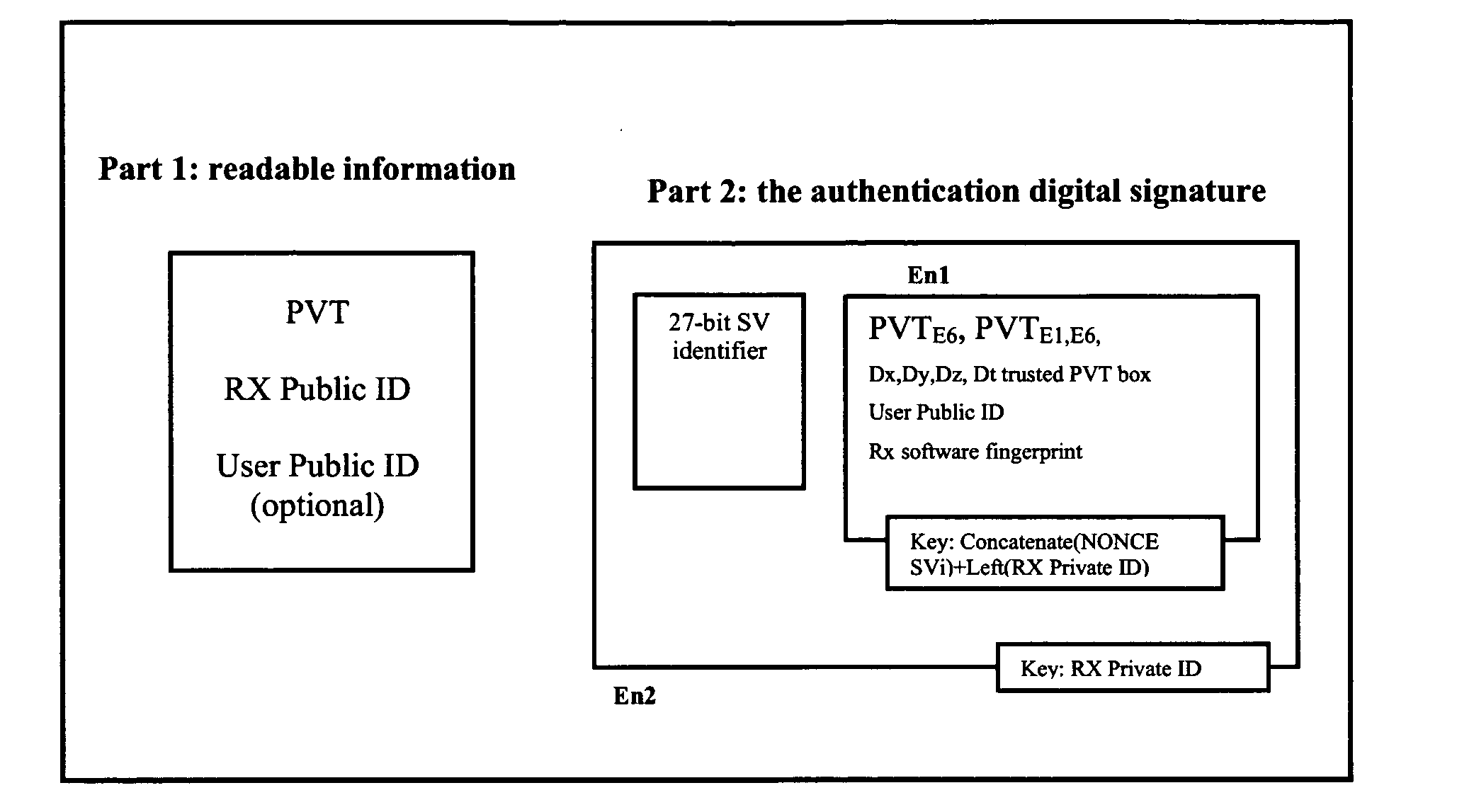
Method of providing an authenticable time-and-location indication
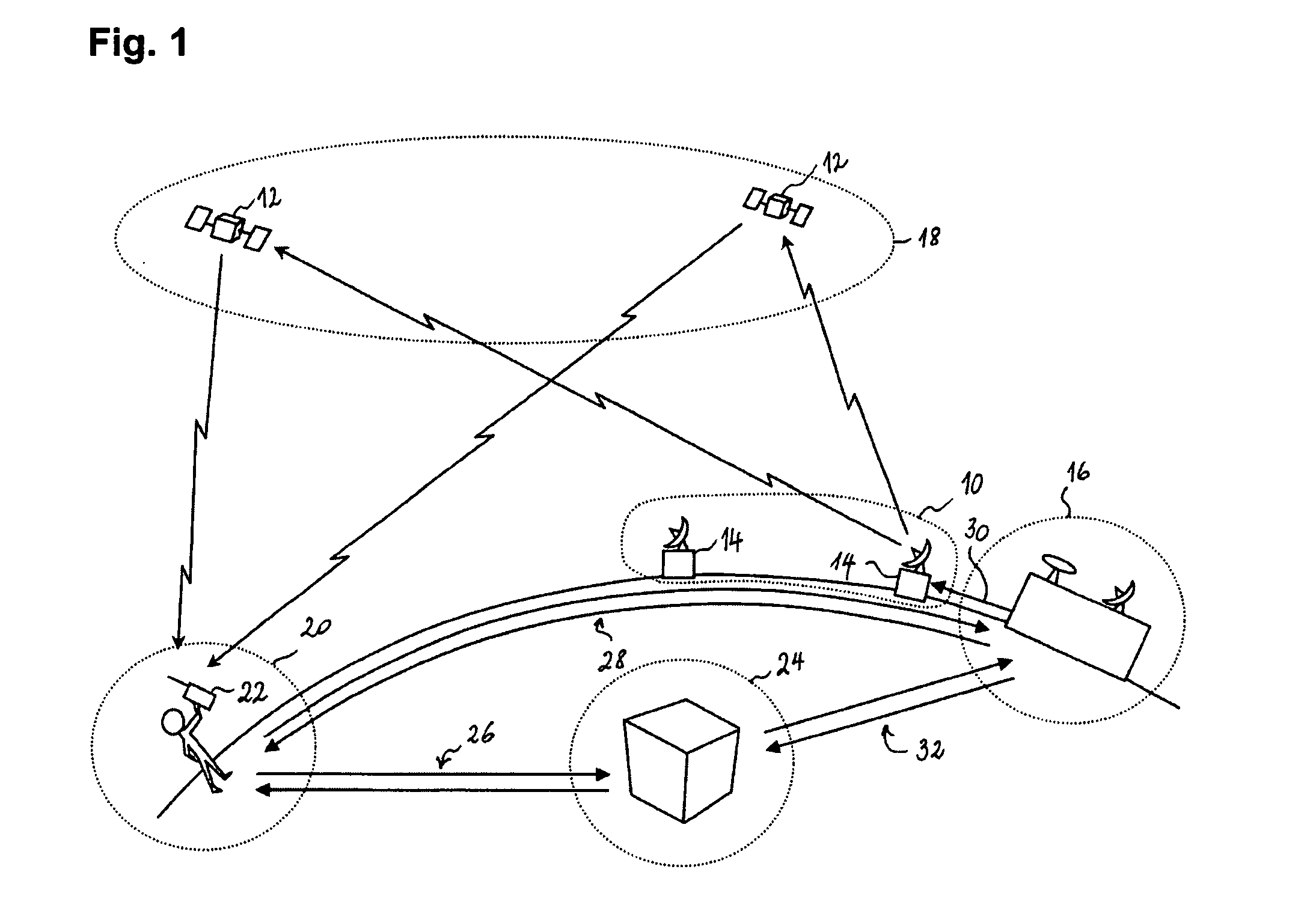
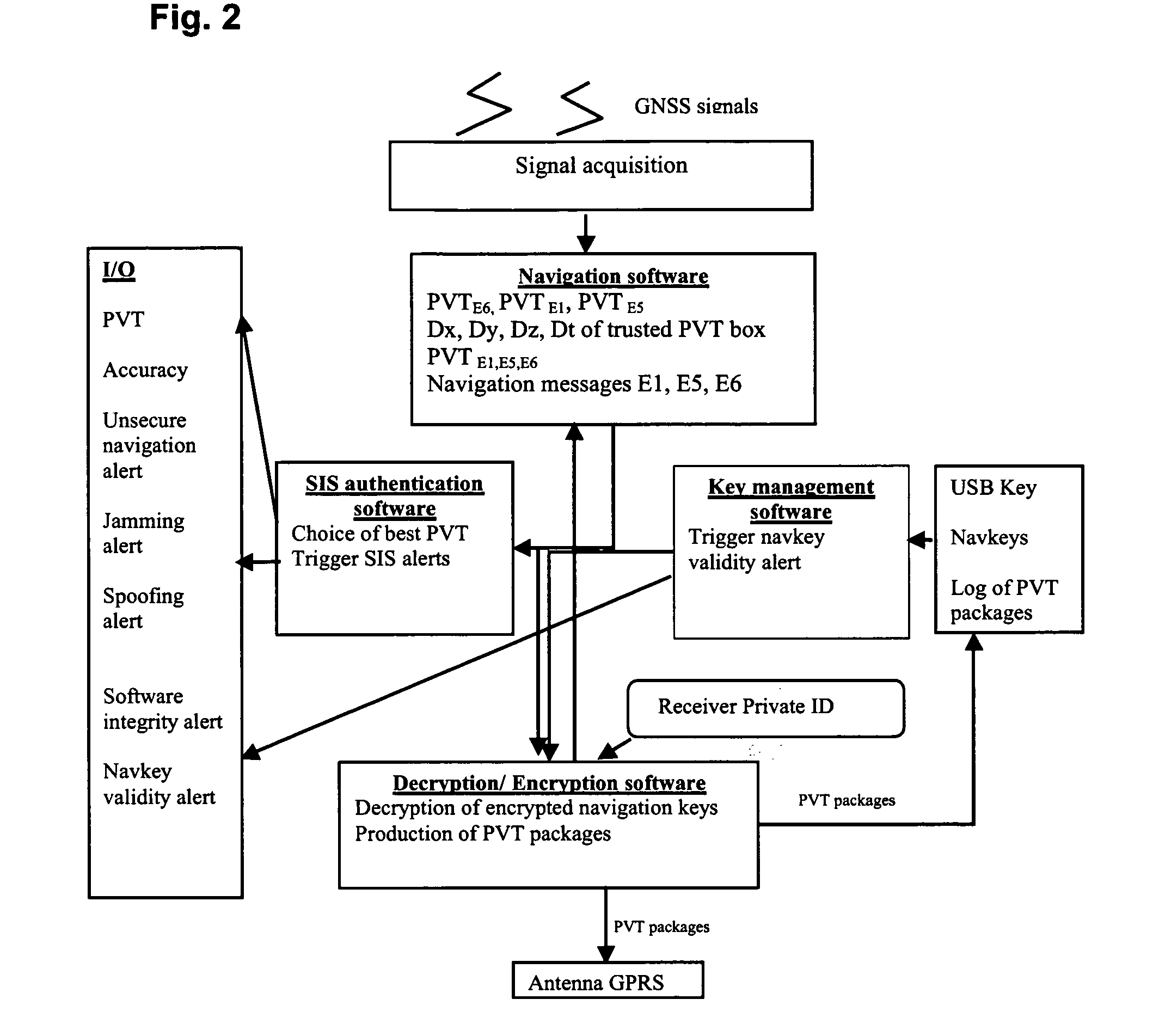
ActiveUS20130251150A1Secure accessAvoid receivingBeacon systems using radio wavesSecret communicationGeolocationEncryption
A method of providing an authenticable time-and-location indication using a radio-navigation signal receiver comprises receiving radio-navigation signals broadcast from a plurality of radio-navigation signal sources, at least some of the radio-navigation signals containing one or more cryptographic tokens protected by encryption, the cryptographic tokens being updated from time to time. The receiver retrieves, by decryption, the cryptographic tokens from the radio-navigation signals containing them. The receiver then determines positioning data, representing its geographical position and time, based on the radio-navigation signals received. The receiver generates a digital authentication code using a cryptographic function taking as inputs at least the positioning data and the retrieved cryptographic tokens, and produces a data package including a first part containing the positioning data and a second part containing the digital authentication code.
Owner:EURON COMMUNITY EC
System and method for creating and tracking rich media communications
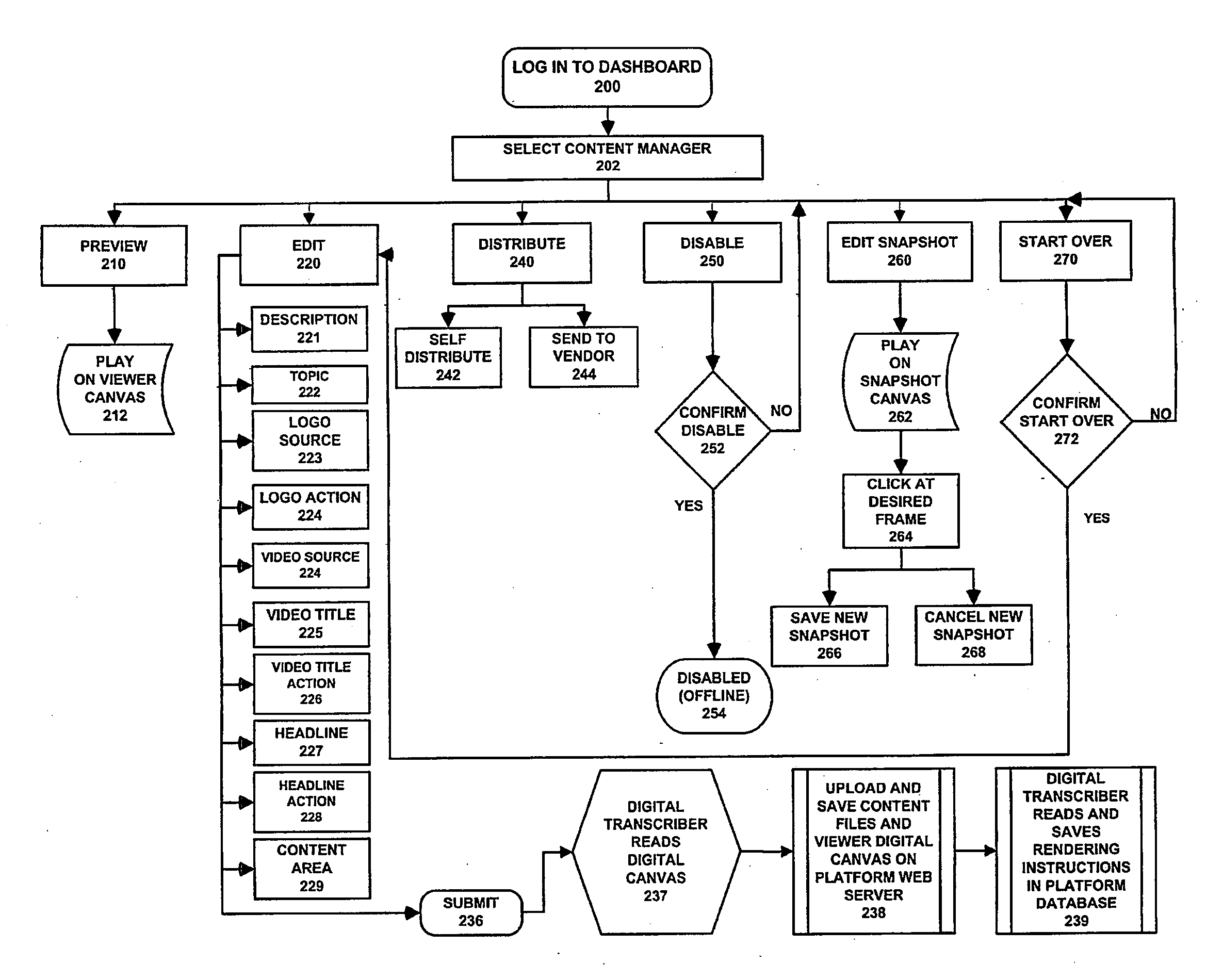
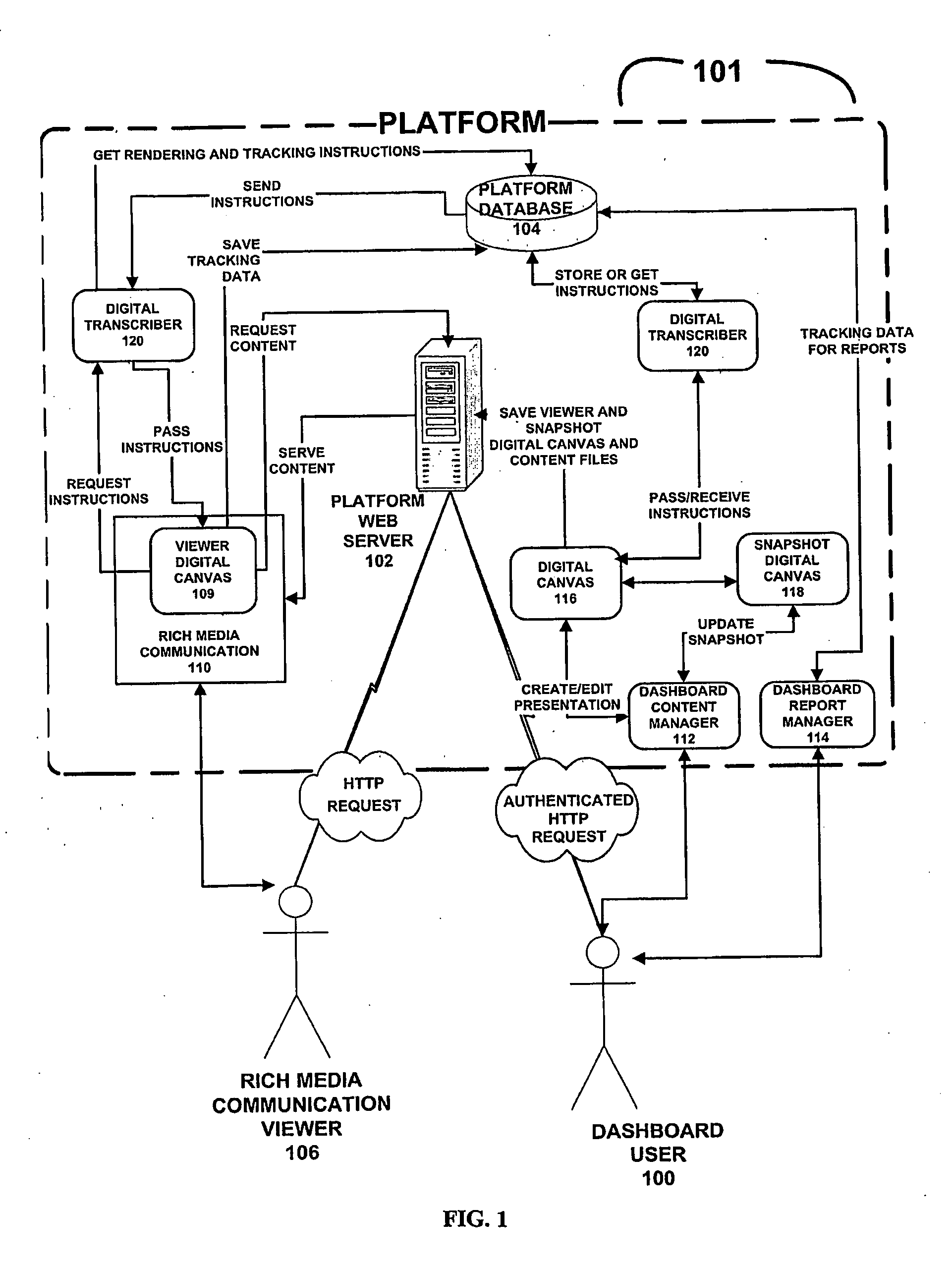
InactiveUS20090228572A1Preserving privacySecure accessDigital data information retrievalMultiple digital computer combinationsInteractive contentElectronic mail
The present invention includes a system, methods, and technology platform for instantly creating, delivering, updating, deploying, and inherently tracking one or more unique, multimedia rich, email and web-based communications campaigns or rich media presentations—all without any technical knowledge. Each rich media presentation created with the invention may consist of a unique, pre-defined collection of separately trackable interactive content elements which are programmatically collected, arranged and displayed as part of a complete audiovisual presentation. Upon distribution of such a presentation, tracking data from the viewer's interaction with the presentation may be retrieved.
Owner:FLIMP MEDIA
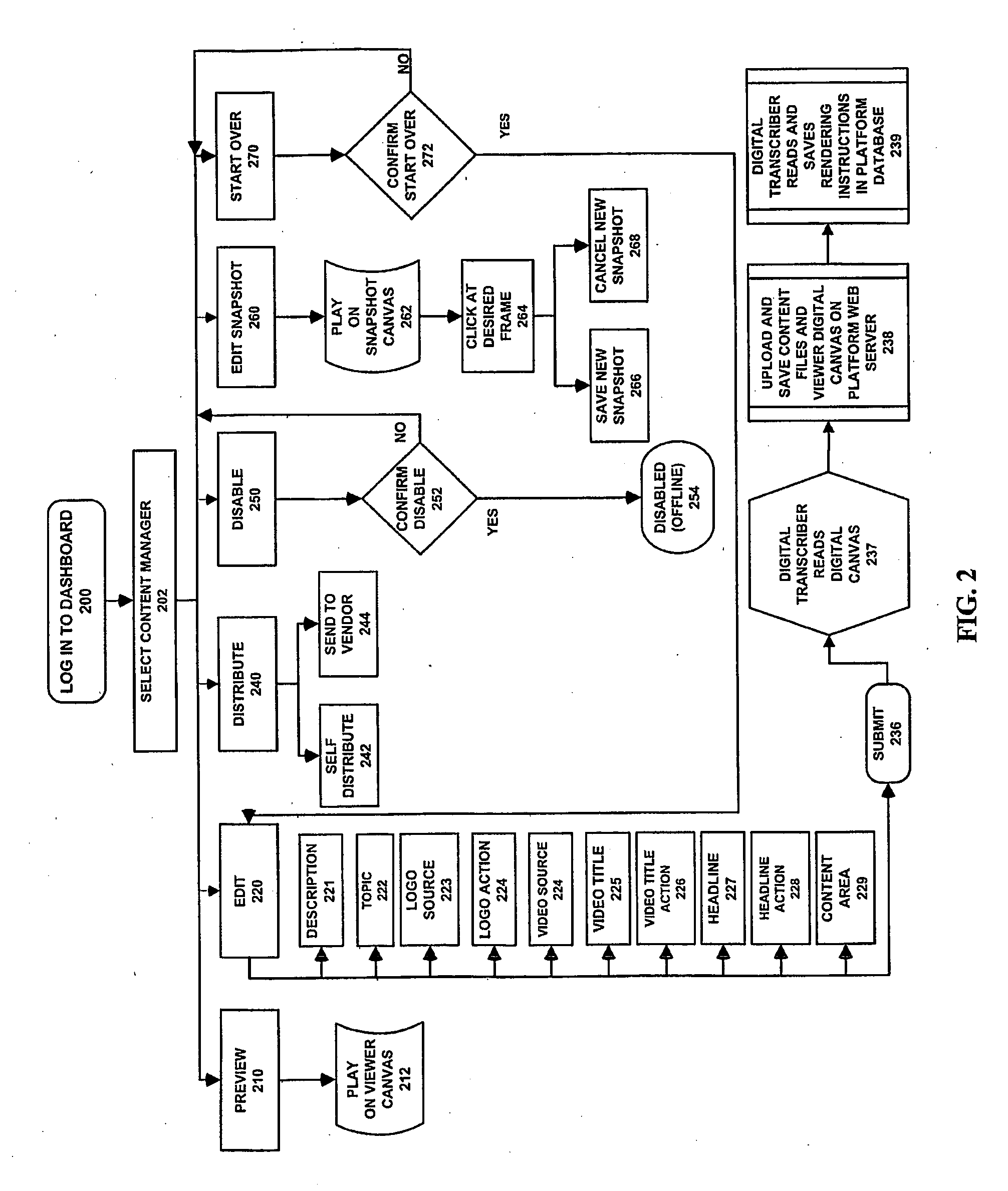
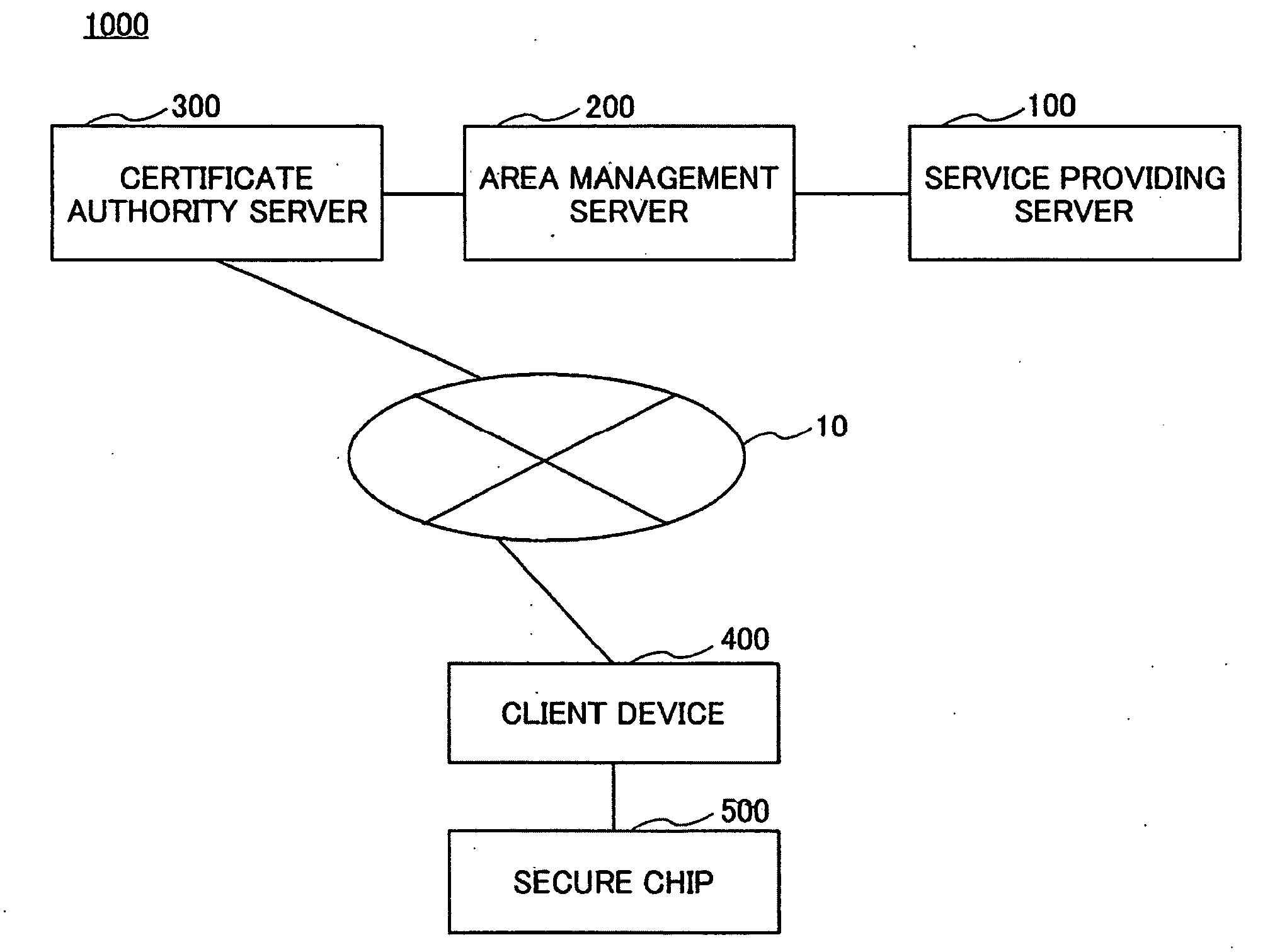
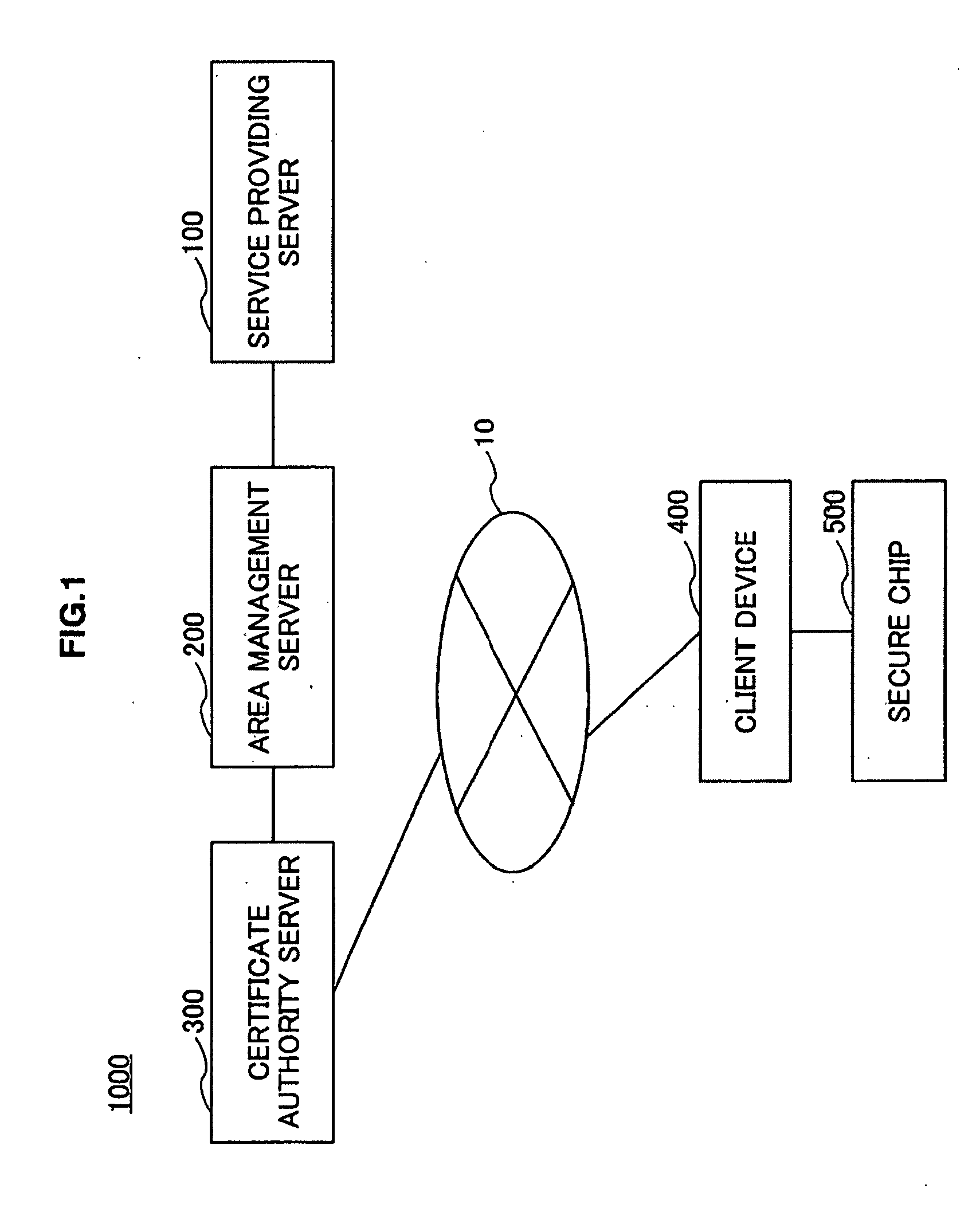
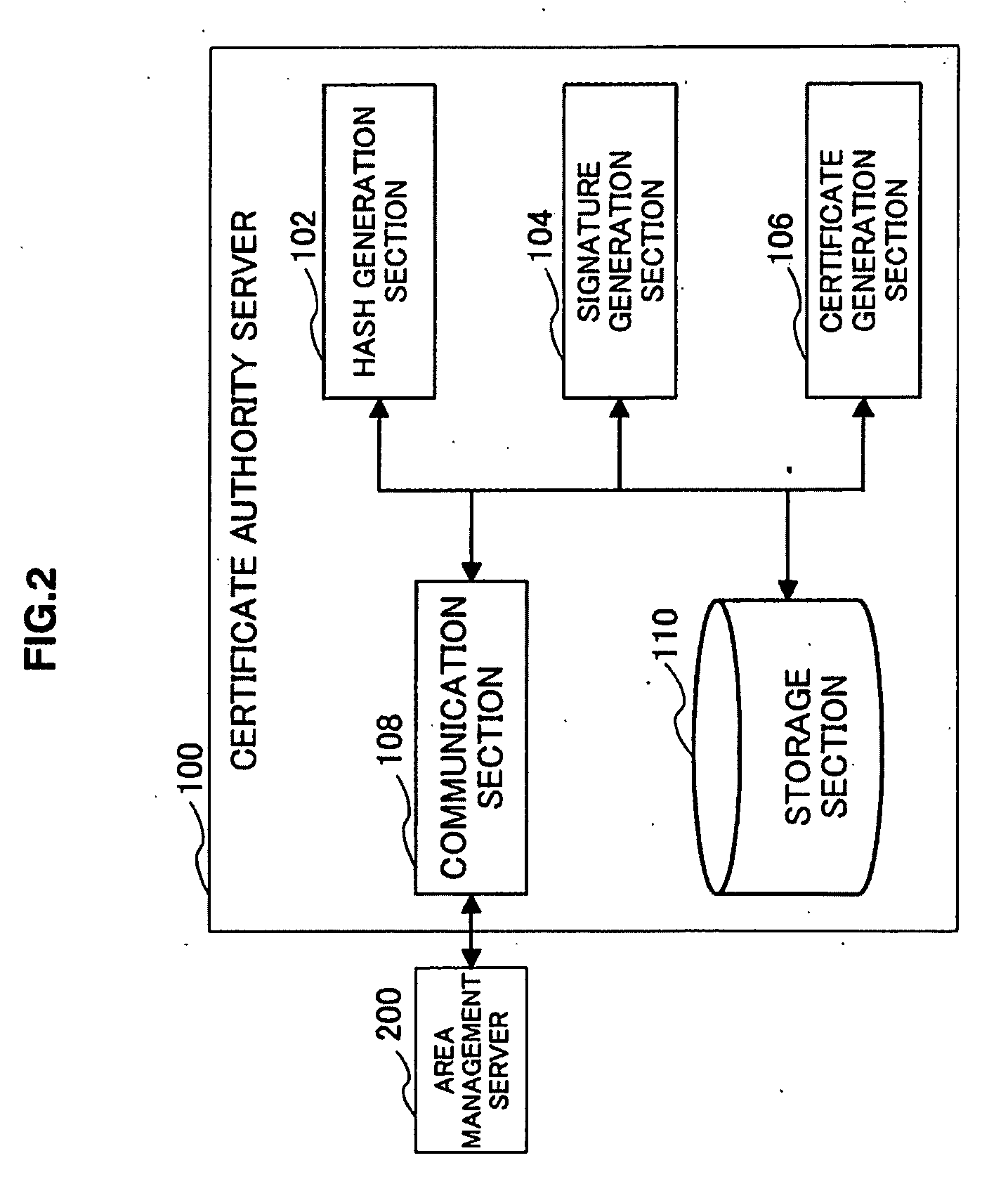
Service providing system, service providing server and information terminal device
InactiveUS20090217047A1Secure accessEasy accessUser identity/authority verificationUnauthorized memory use protectionClient-sideService provision
A service providing system is provided, which includes a client device capable of accessing a tamper-resistant secure memory, an area management server managing memory area of the secure memory and a service providing server providing service that uses the secure memory to the client device, and which improves the security at the time of sending an access control list provided by the area management server and an instruction set provided by the service providing server to the client device by using a digital signature and a certificate.
Owner:FELICA NETWORKS INC
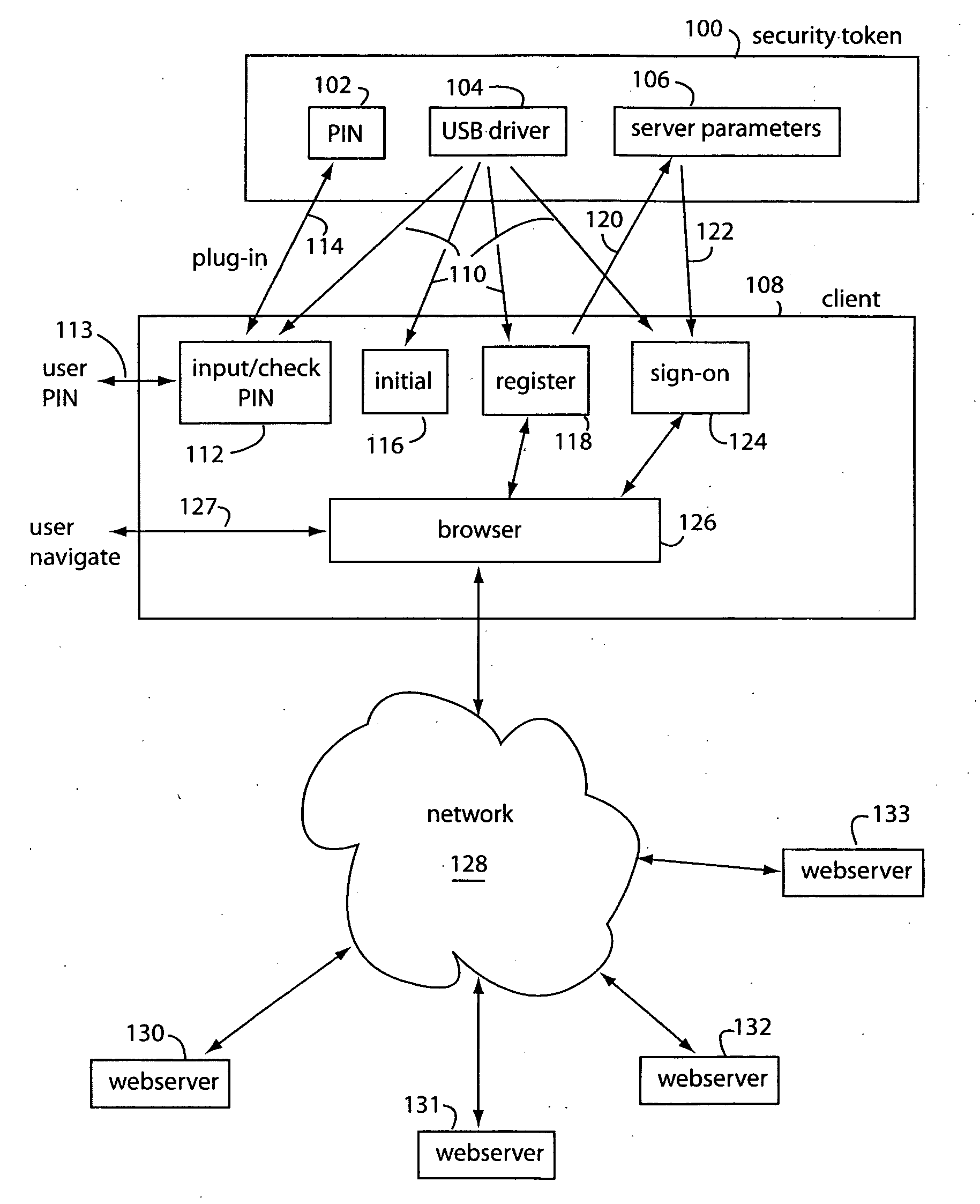
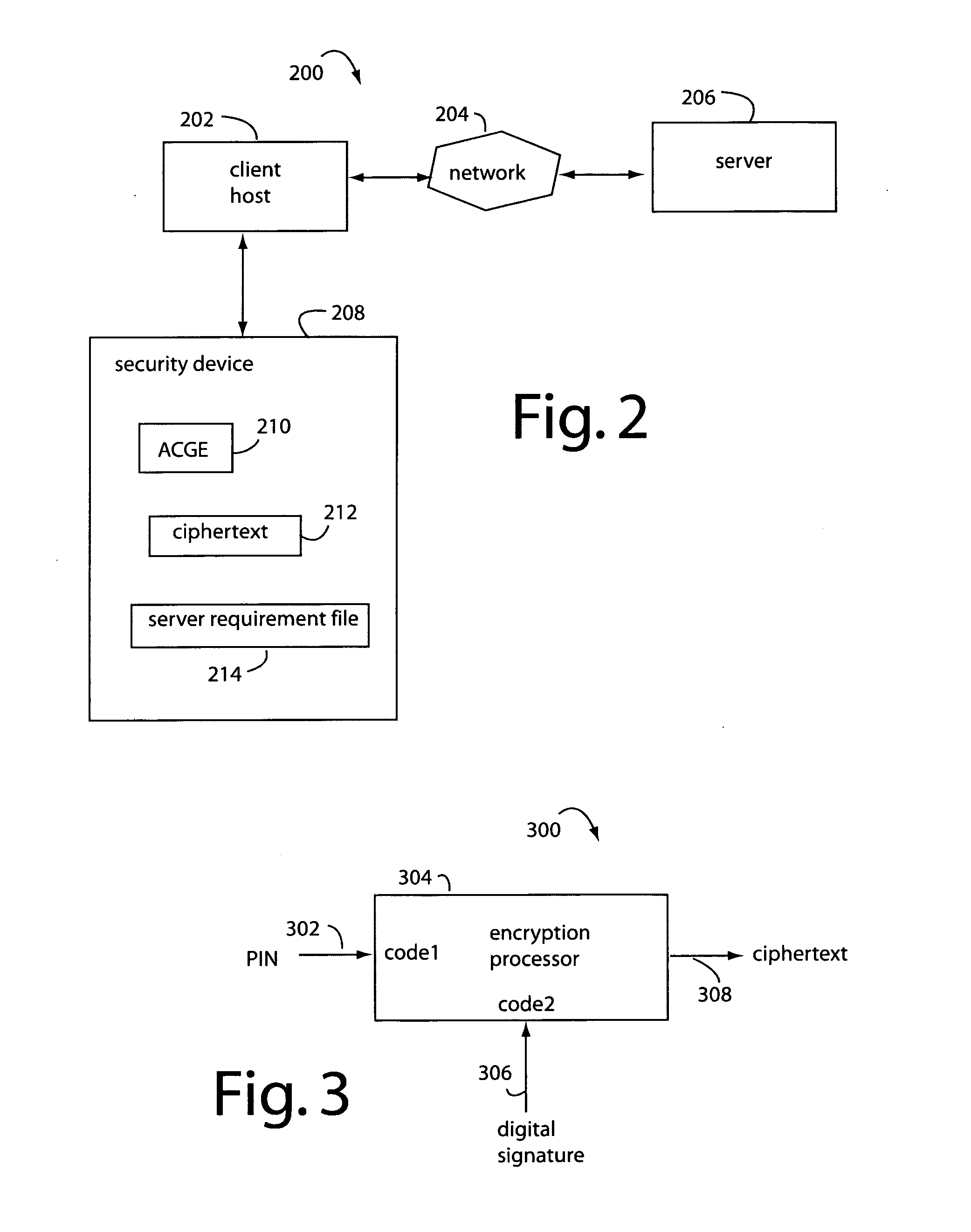
Security token
InactiveUS20080148057A1Secure user accessEasy loginUser identity/authority verificationDigital data authenticationPersonal identification numberPassword
A security method comprises initiating a security token with a particular user through a personal computer client by accepting a personal identification number (PIN) as a code1 input, wherein a user is expected to remember the PIN in later accesses of the servers. And, generating a master key as code2 which does not need to be remembered by the user. Then, encrypting the code2 with a symmetric key cipher, using the code1 input as an encryption key, and storing the ciphertext in the security token. Later, registering the user with a USER_ID at a server with a SERVER_ID, and a password. And, obtaining the PIN from the user as a code1 which is used as a decryption key to decrypt the ciphertext back to its original code2. And, computing the password from the USER_ID, SERVER_ID, and code2. Afterwards, logging-on the user with a USER_ID at a server with a SERVER_ID, and a password.
Owner:OHANAE
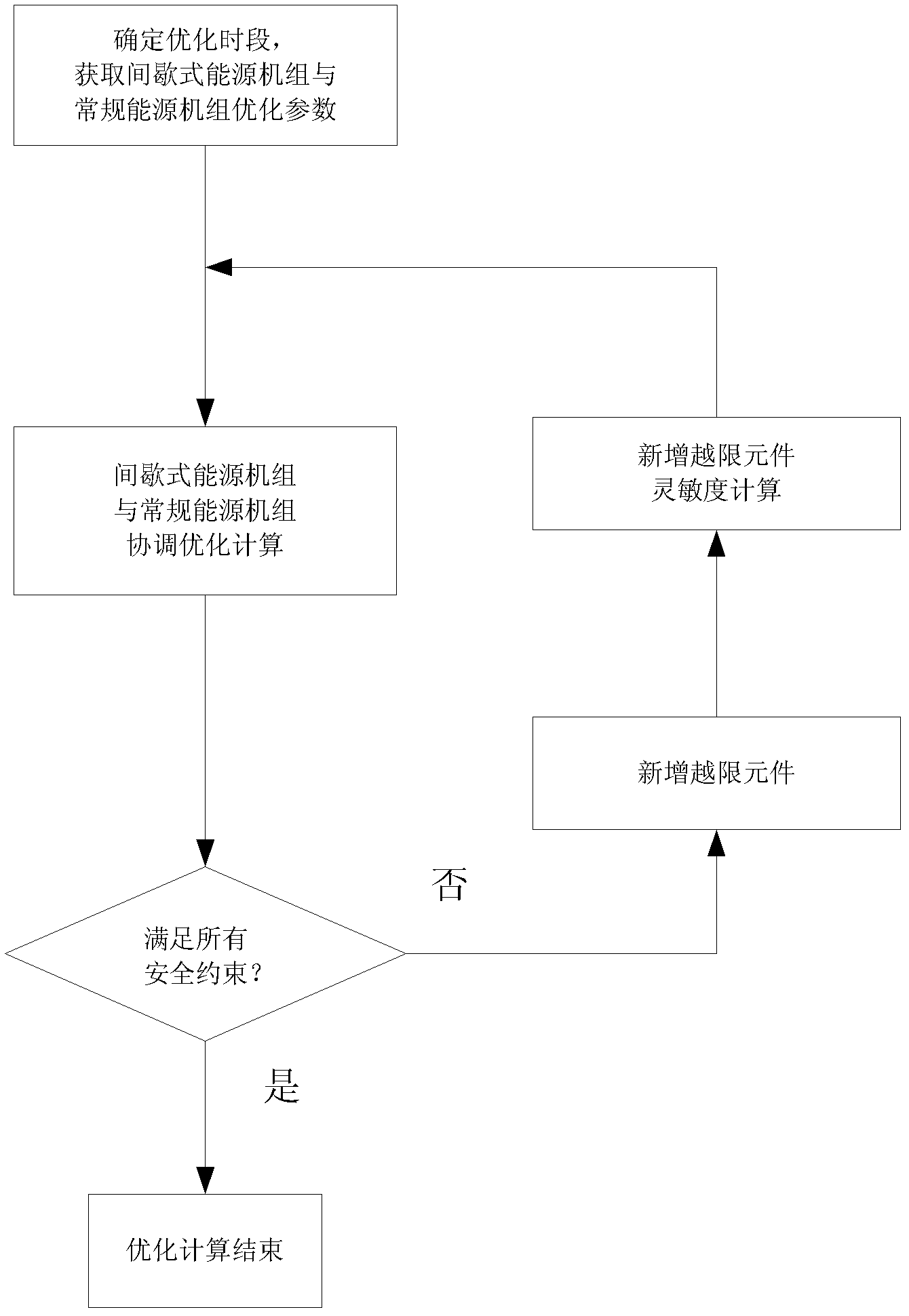
Generation plan optimizing method in intermittent energy and conventional energy coordinated dispatching mode
InactiveCN102496968ACoordinated scheduling implementationGuaranteed enforceabilitySingle network parallel feeding arrangementsElectricityPower system scheduling
The invention discloses a generation plan optimizing method in an intermittent energy and conventional energy coordinated dispatching mode, belonging to the technical field of power system dispatching automation. To minimize the generation cost of the system, the coordinated dispatching of an intermittent energy unit and a conventional energy unit is comprehensively considered, and various constraint conditions are taken into consideration to optimize the generation plan of a computing group, thereby ensuring the safe access of intermittent energy such as wind power and the like, and being favorable for improving the intelligence level and decision making ability of the generation dispatching after the access of the intermittent energy. Meanwhile, the method has the characteristics of low computing strength and strong adaptability, and is more suitable for the popularization and application of the dispatching mechanisms with relatively high wind power access power in our country.
Owner:NARI TECH CO LTD +1
Method and system for operating database
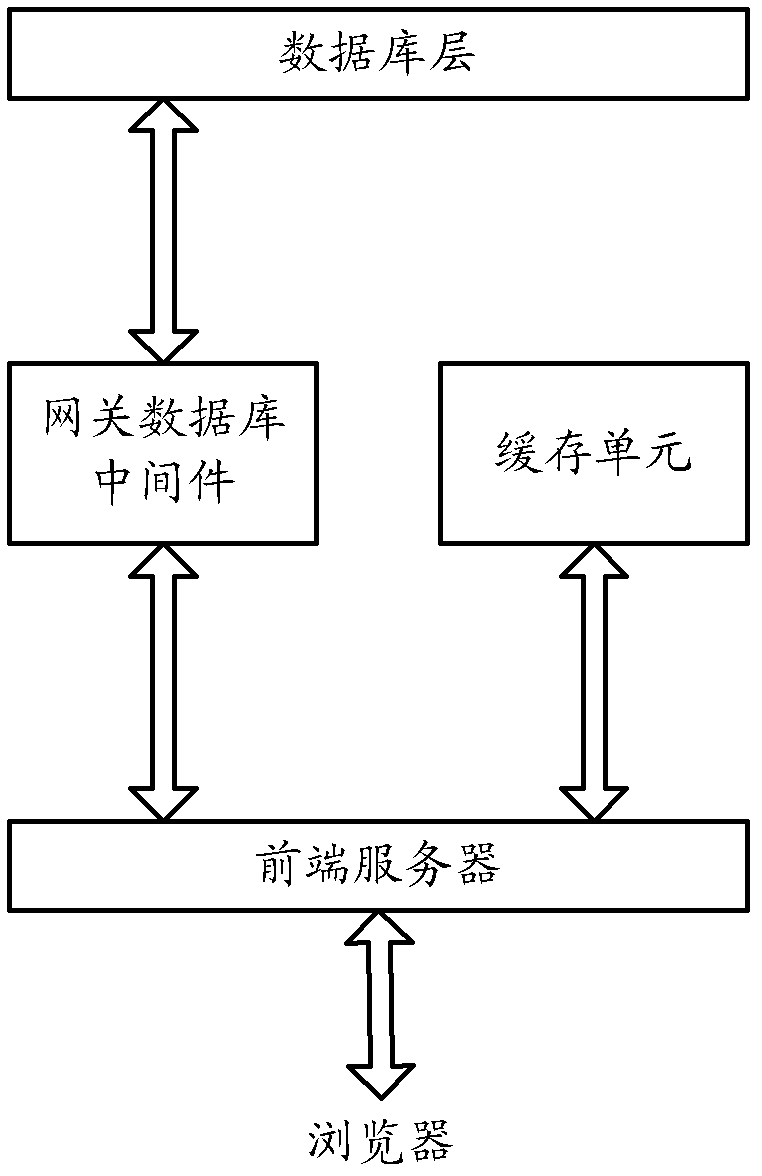
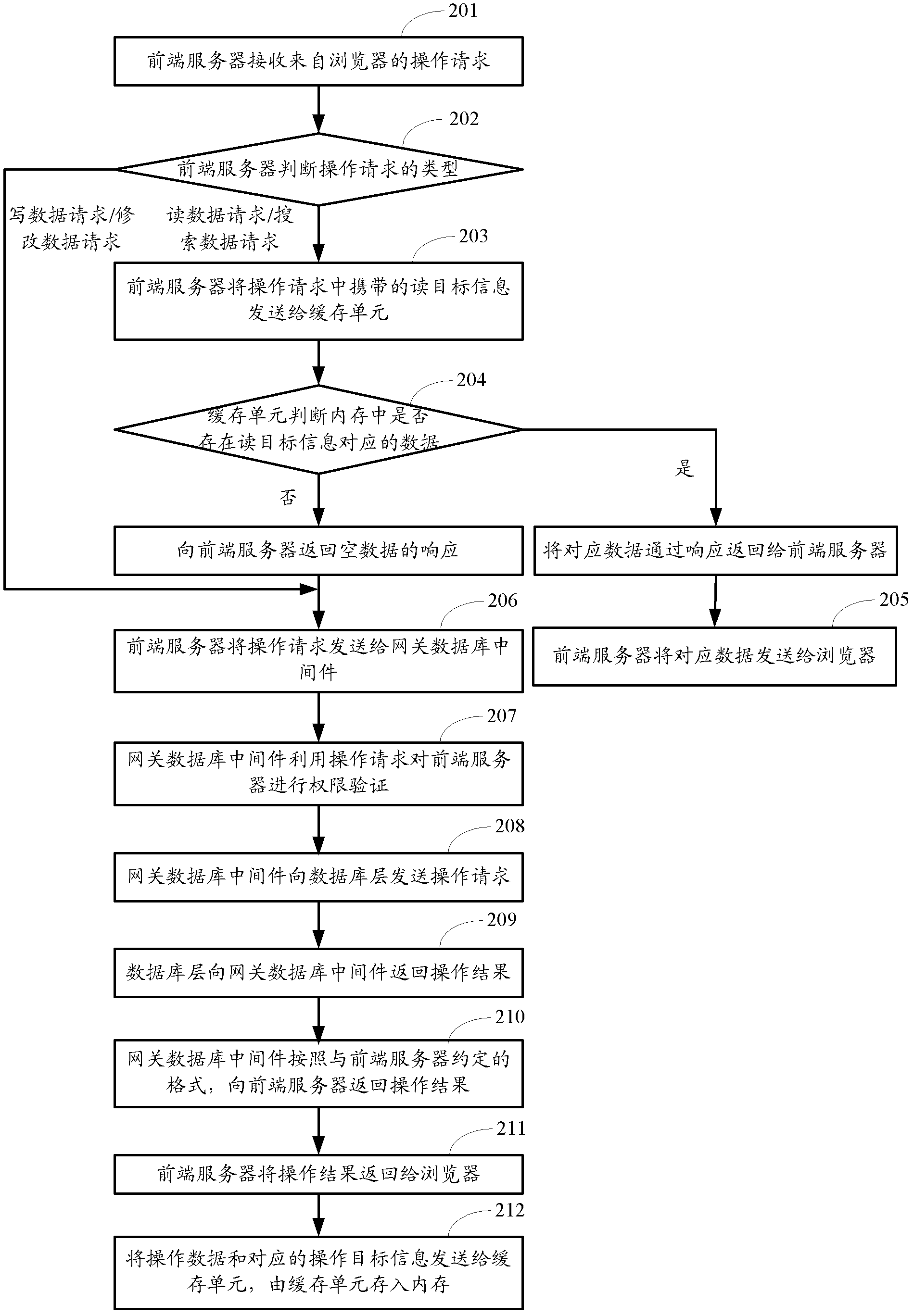
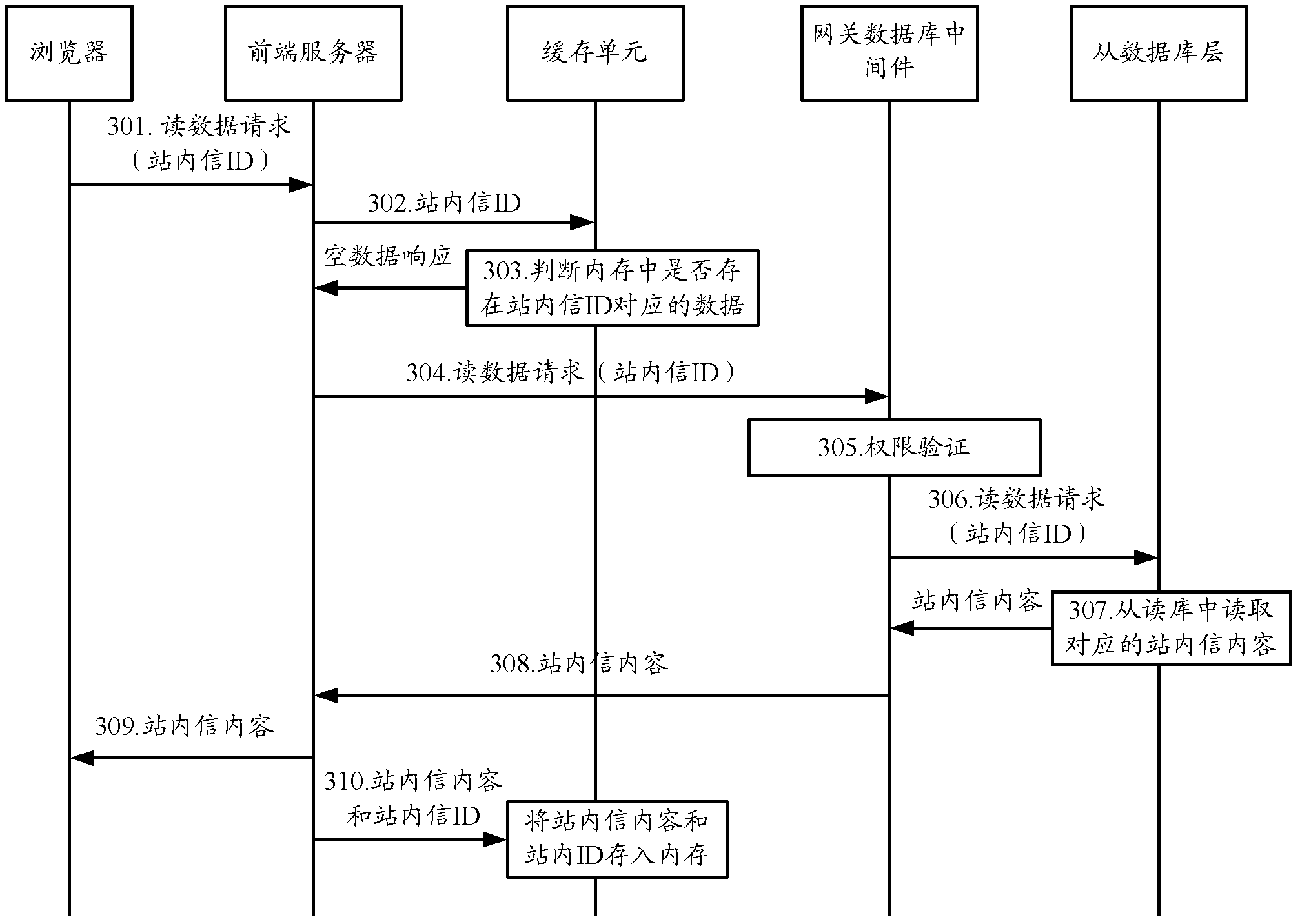
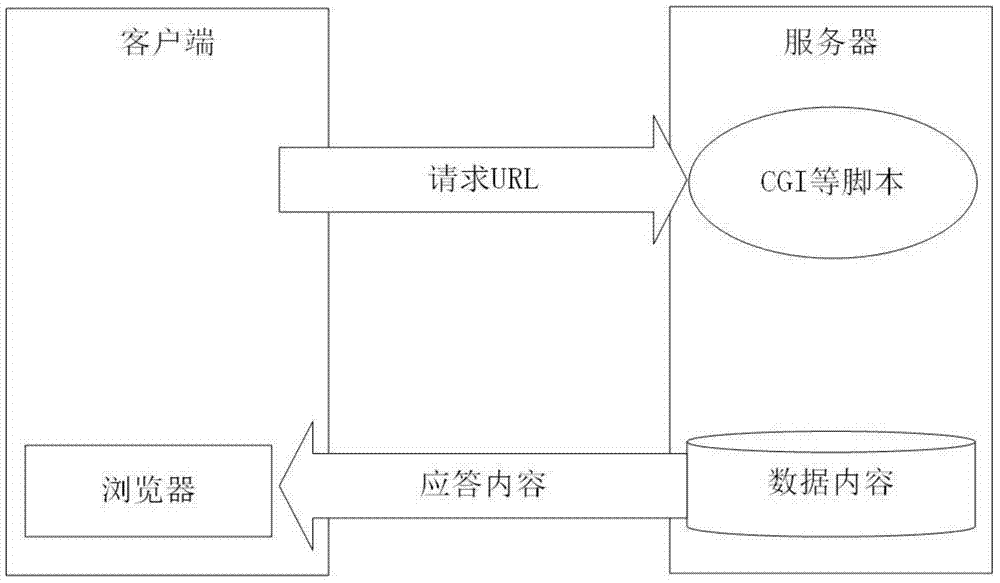
ActiveCN102426594AAvoid direct manipulationSecure AccessSpecial data processing applicationsMiddlewareData library
The invention provides a method and system for operating a database. The method comprises the following steps of: sending an operation request from a browser to a gateway database middleware by a front-end server; sending the operation request to a database layer by the gateway database middleware after the front-end server passes the right certification; operating the database by the database layer according to operating target information in the operation request and returning back an operating result to the gateway database middleware; and sending the operating result to the front-end server by the gateway database middleware according to a format appointed with the front-end server. According to the method, the gateway database middleware is used for separating the operation to the database from the front-end server and is used as an operating interface between the front-end server and the database, and the right control is realized on the gateway database middleware, thereby efficiently ensuring the access safety of the database and being beneficial to the upgrading and expanding of a project.
Owner:沈文策
Method and Systems for Placing Physical Boundaries on Information Access/Storage, Transmission and Computation of Mobile Devices
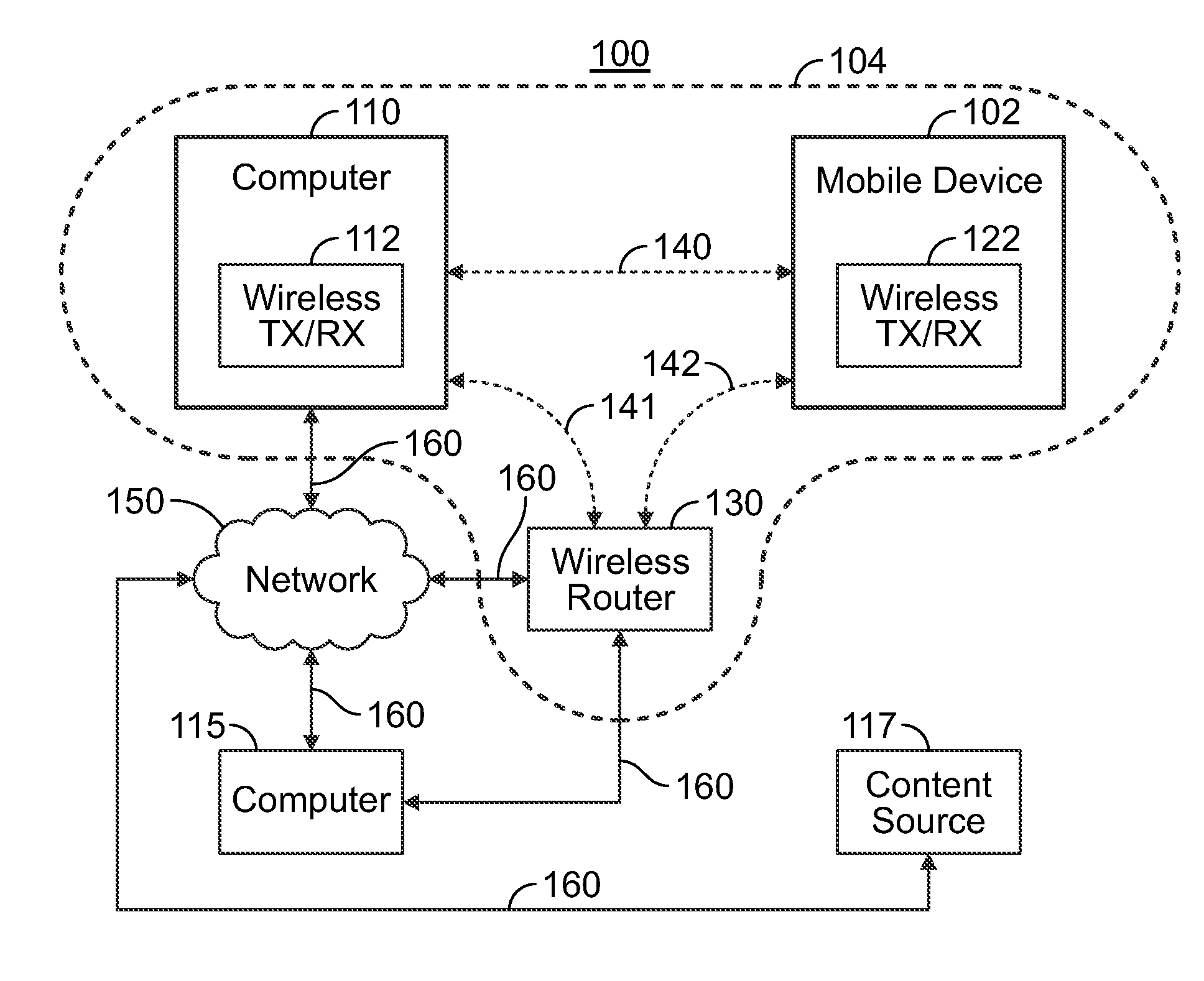
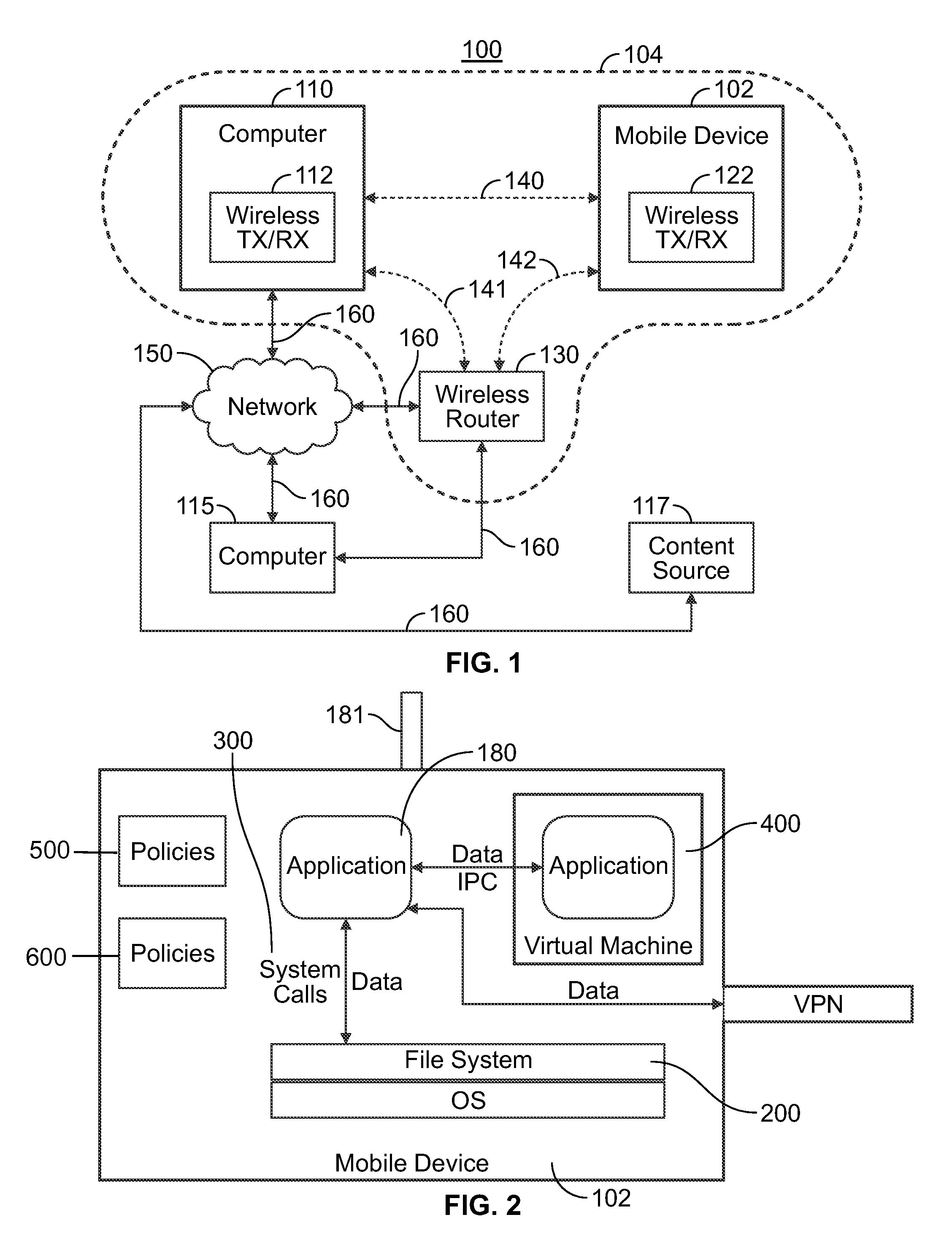
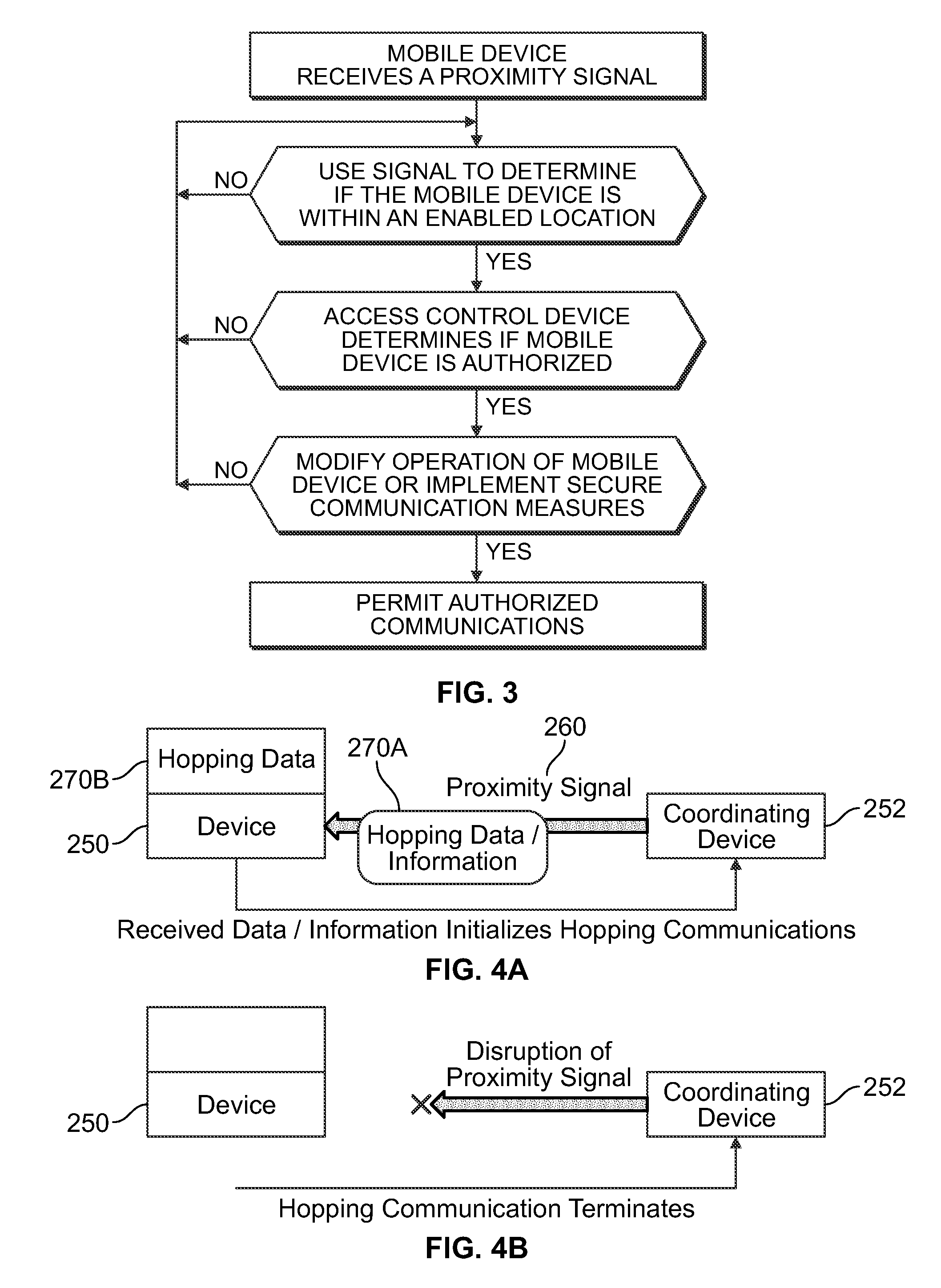
InactiveUS20160112871A1Prevent being durably storedEasy accessDigital data processing detailsMultiple digital computer combinationsComputer networkUnique identifier
A system and method for restricting access to information using short range wireless communications, the system is provided. The system and method include a short range wireless network serving a predetermined enabled location. The network is configured to provide authentication data to a computing device. The authentication data specific may be specific to an enabled location and may further include a unique identifier. The network is configured to receive from authentication data from the computing device. The network is further configured to verify the authentication data received from the computing device and, upon verification, the network permits communication between the computing device and the network for the enabled location.
Owner:WHITE CHRISTOPHER JULES
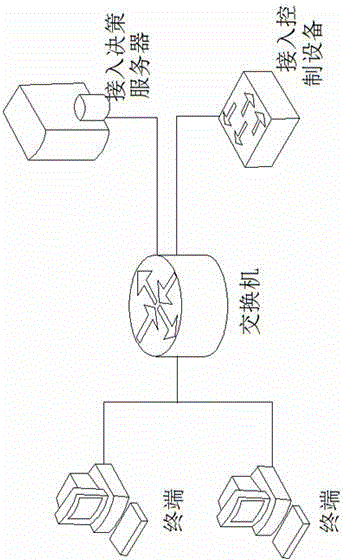
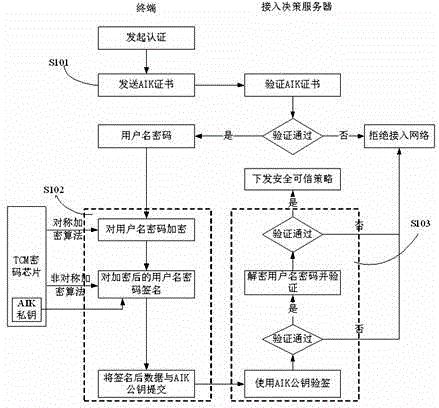
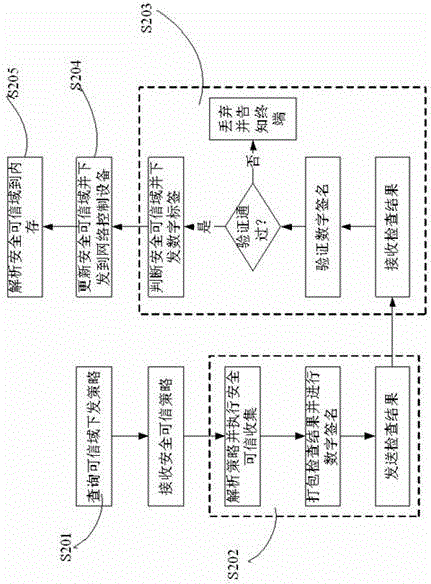
Trusted network access and access control system and method
ActiveCN104618396AImplement access controlImplement network access controlUser identity/authority verificationNetwork access serverNetwork Access Protection
The invention discloses a trusted network access and access control system. The control system comprises a network access requester, a network access decision-maker and a network access controller. When the network access requester accesses to the network, platform identity authentication is carried out, and secure and trusted states of the requester are detected; the secure and trusted states are sent to the network access decision-maker, and the decision-maker judges the secure and trust level of the requester and gives a network access decision; the network access decision is sent to the network access controller, and the controller limits the requested network access. The invention further discloses a trusted network access and access control method. The control system carries out the platform identity authentication on the basis of TCM and ensures the network access control while avoids identity forging. Network areas are divided on the basis of a digital label technology and dynamically updated, network self-adaption is realized, and the access security of different logical areas is ensured. Secure and trusted strategies are configured, and combined with the TCM cryptographic algorithm, so that the security and credibility of the platform state of the requester are ensured.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Information security control system
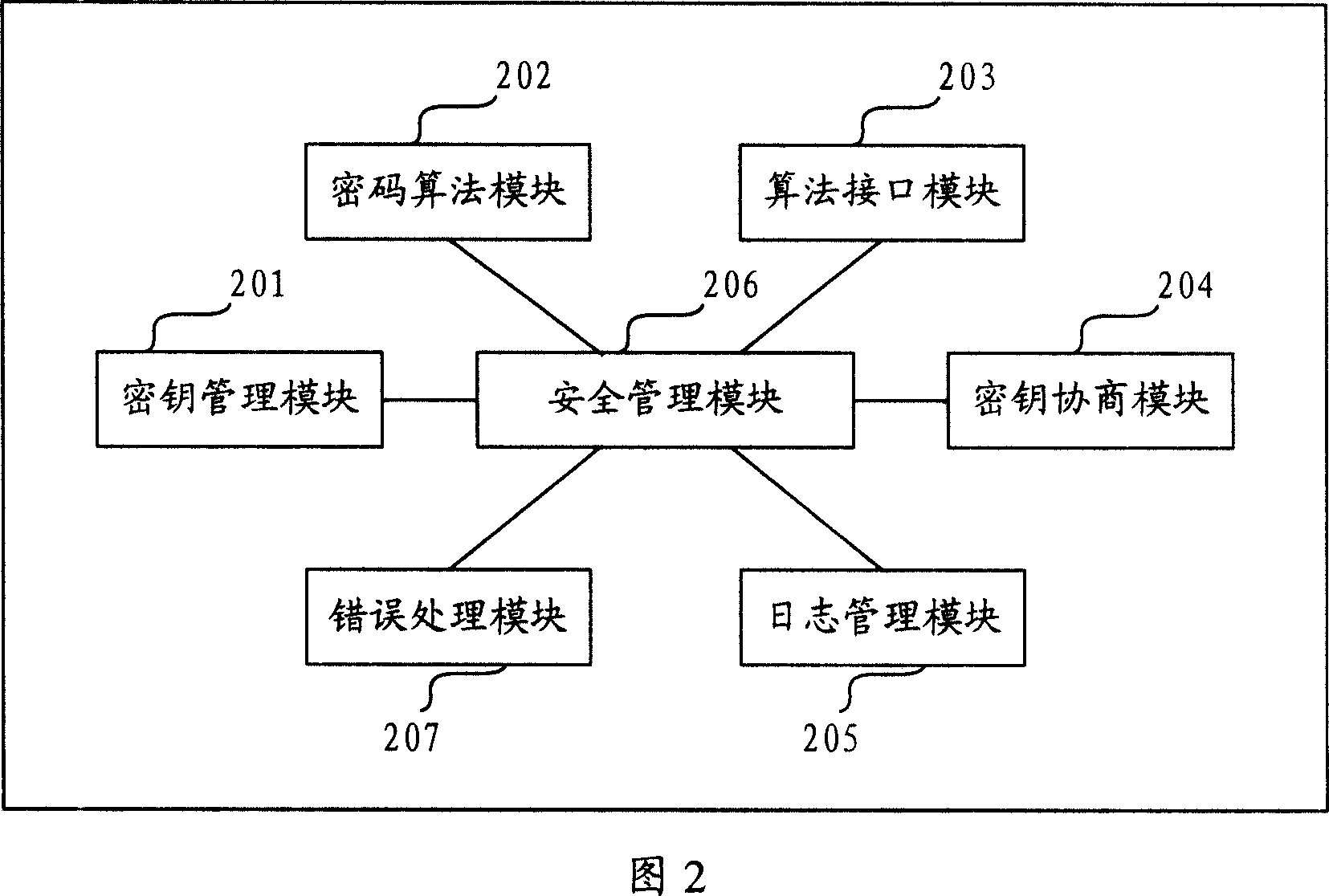
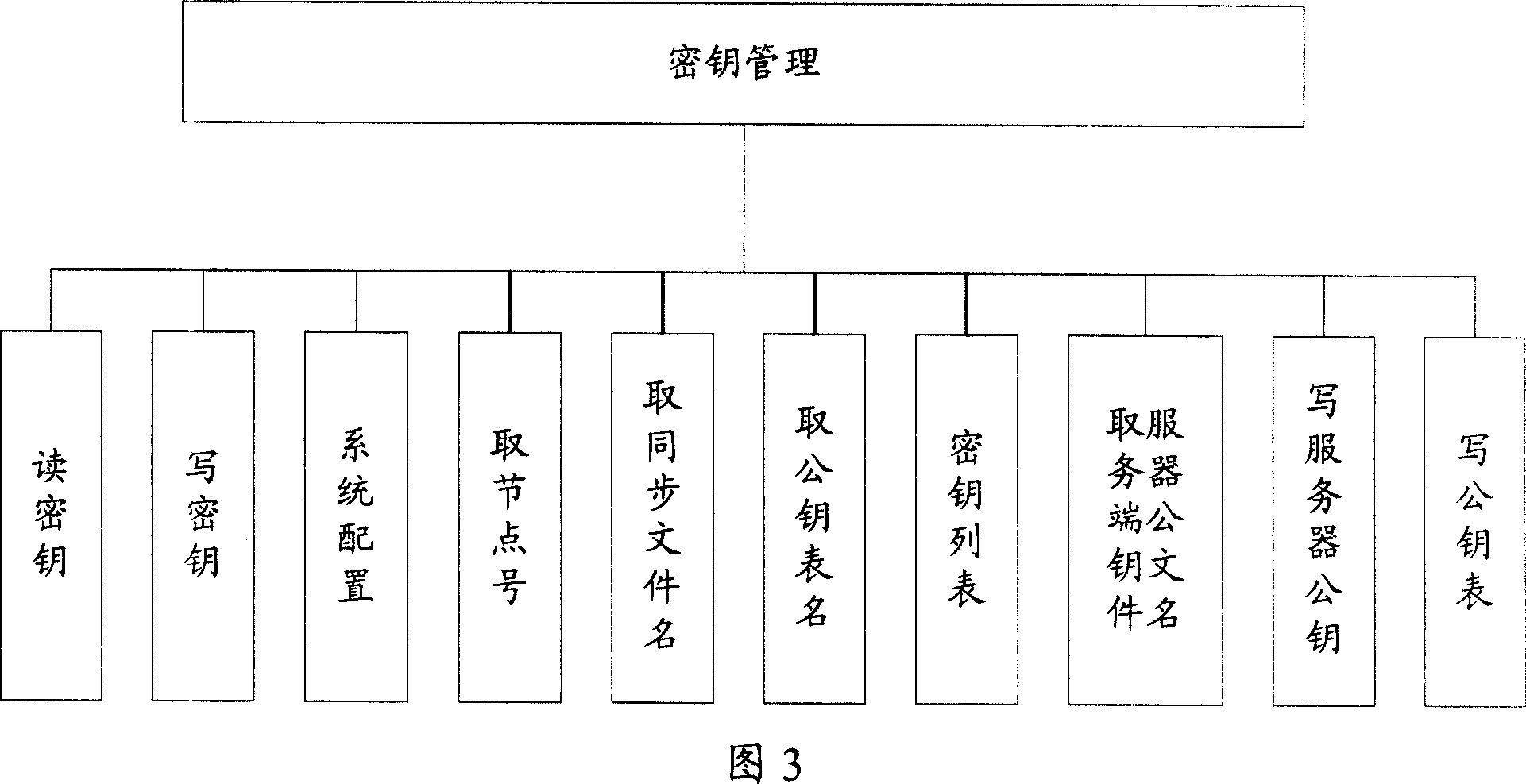
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
Methods and apparatus for secure online access on a client device
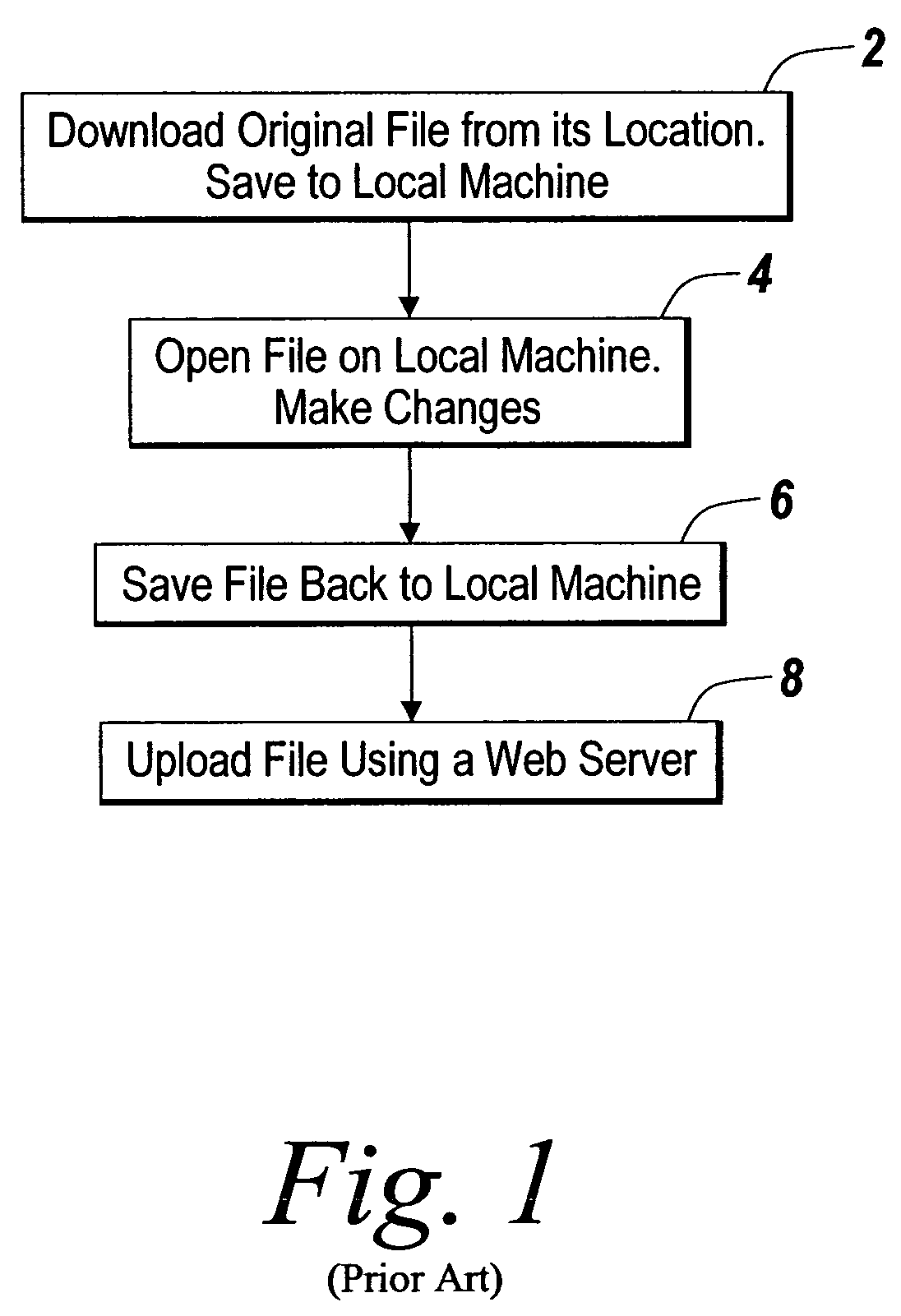
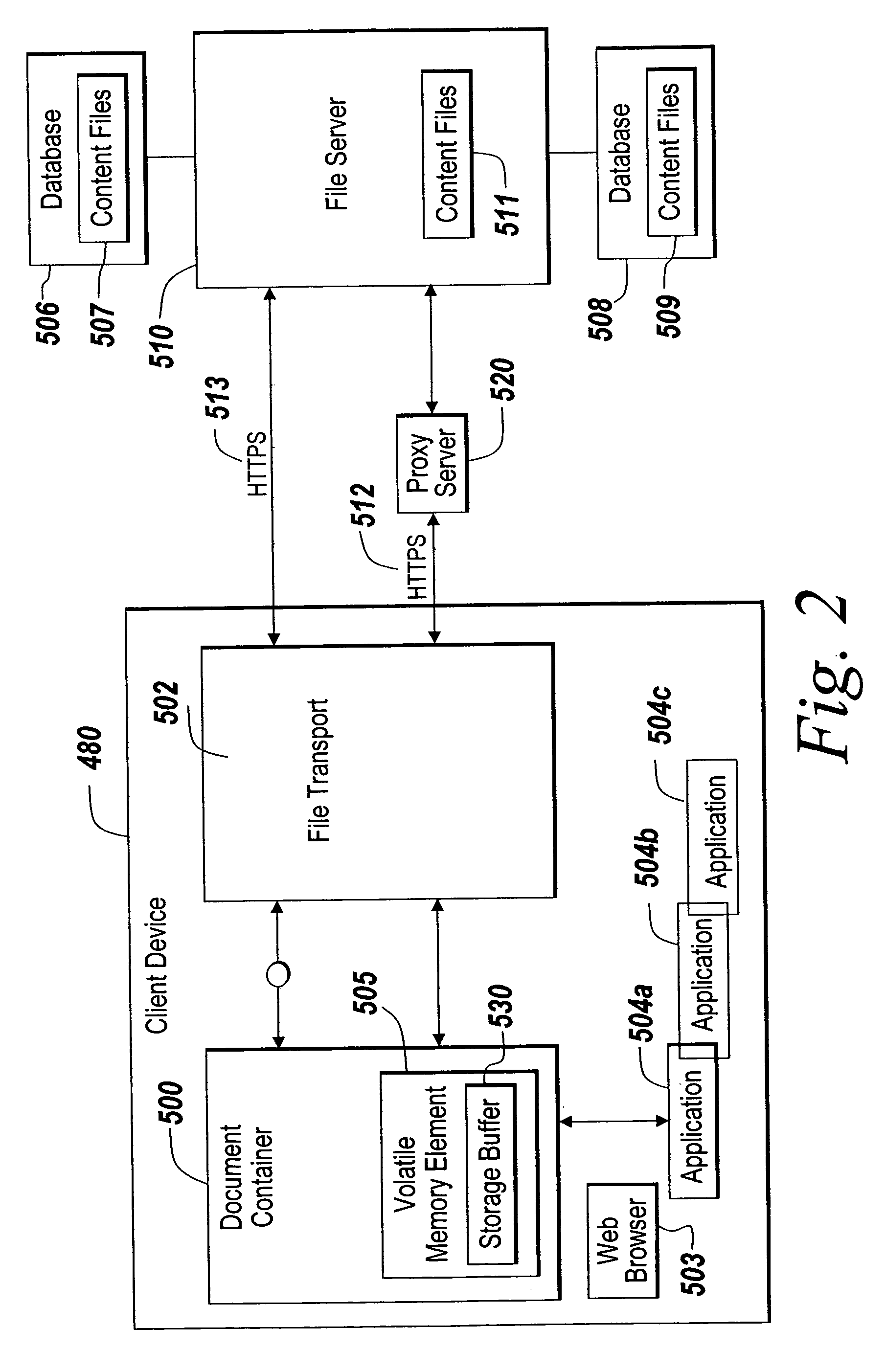
ActiveUS7797724B2Prevent unwanted disclosure of confidential informationManipulation is limitedComputer security arrangementsTransmissionClient-sideSecurity question
A method of securely accessing at a client device content from a server without using the non-volatile memory of the client device is disclosed. The bypassing of non-volatile memory lessens the security risk of unauthorized viewing of the server originated content. An transport mechanism is initiated on a client device and creates a document container. Downloaded documents from a server are mapped into the document container and saved within the document container in volatile memory. Substitute menus are generated within the container to replace application menus. User documents are saved directly to the originating server via the substitute menus. The downloaded copies in volatile memory automatically delete when the document container is destroyed thereby reducing security concerns of unauthorized viewing of the content at the client device.
Owner:CITRIX SYST INC
Method for realizing safe access of terminal of internet of thing
ActiveCN102065430ARealize managementSecure AccessNetwork topologiesSecurity arrangementThe InternetComputer terminal
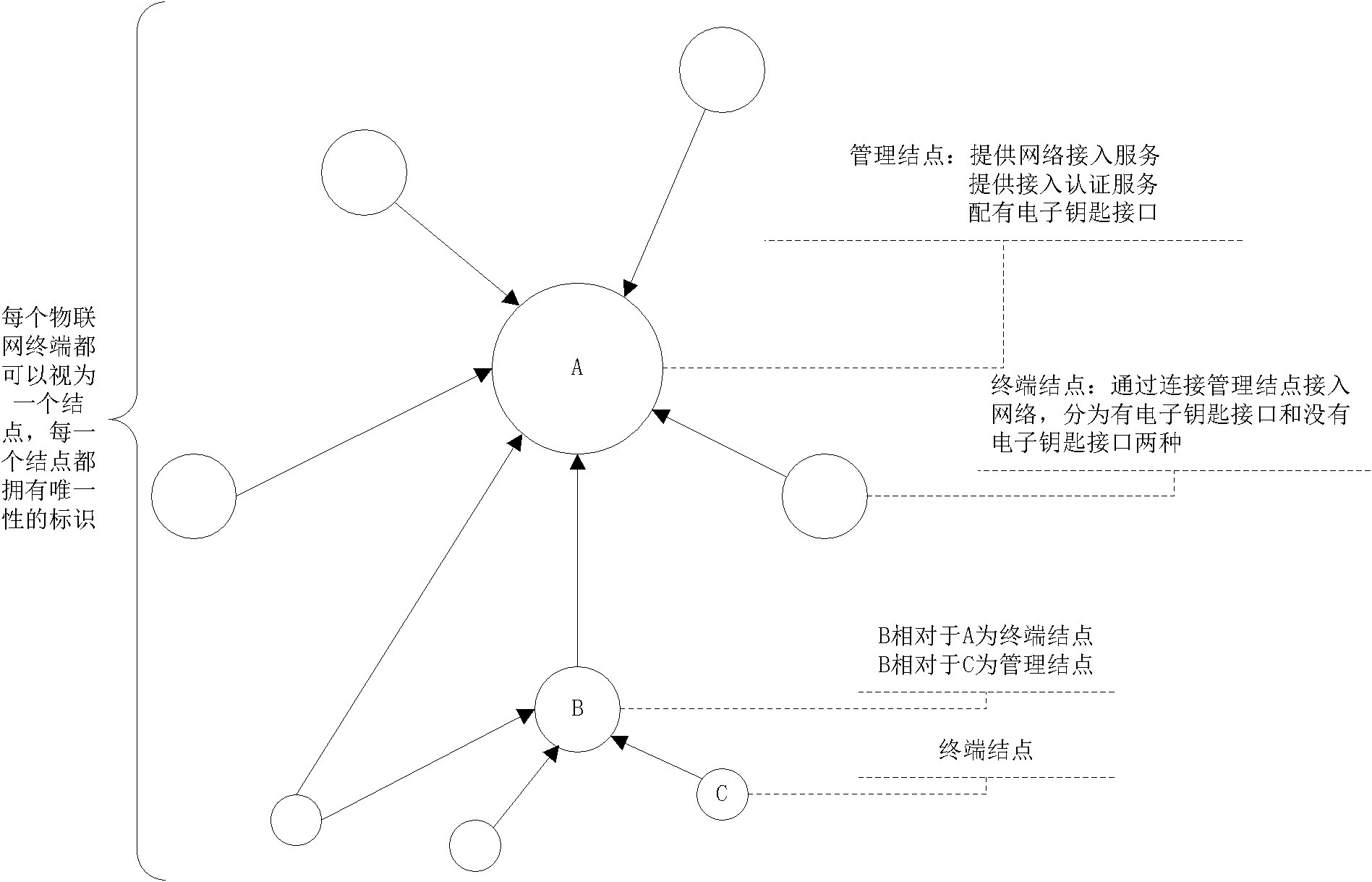
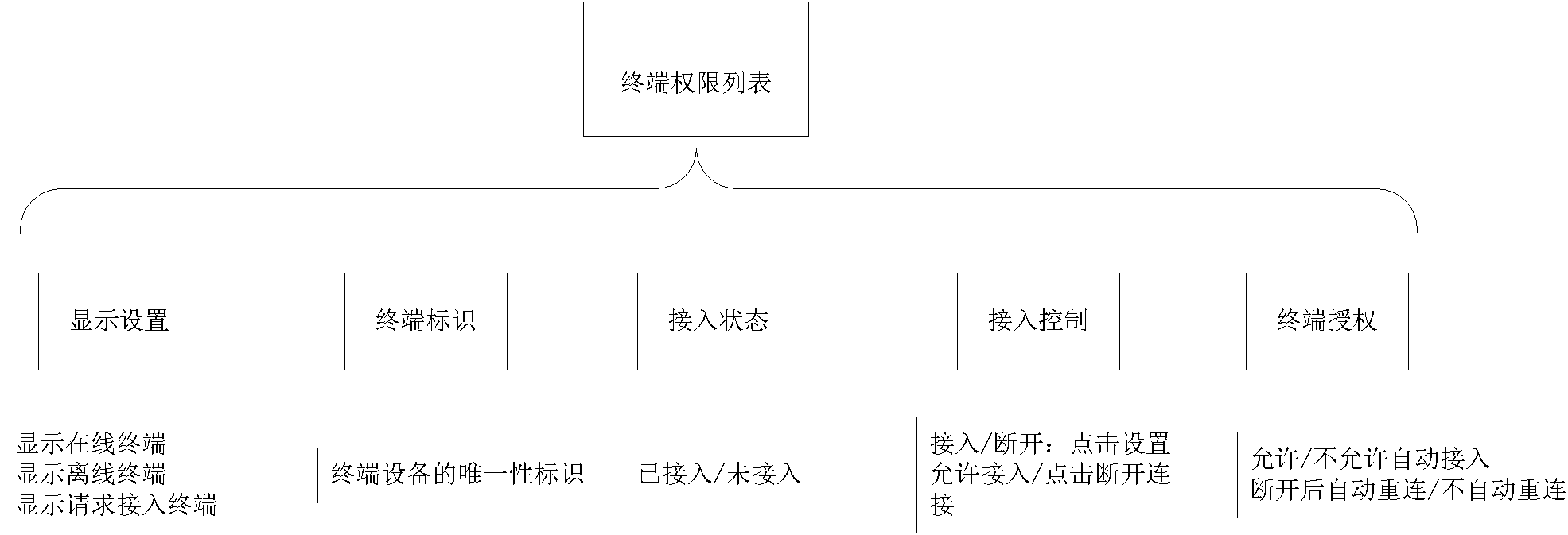
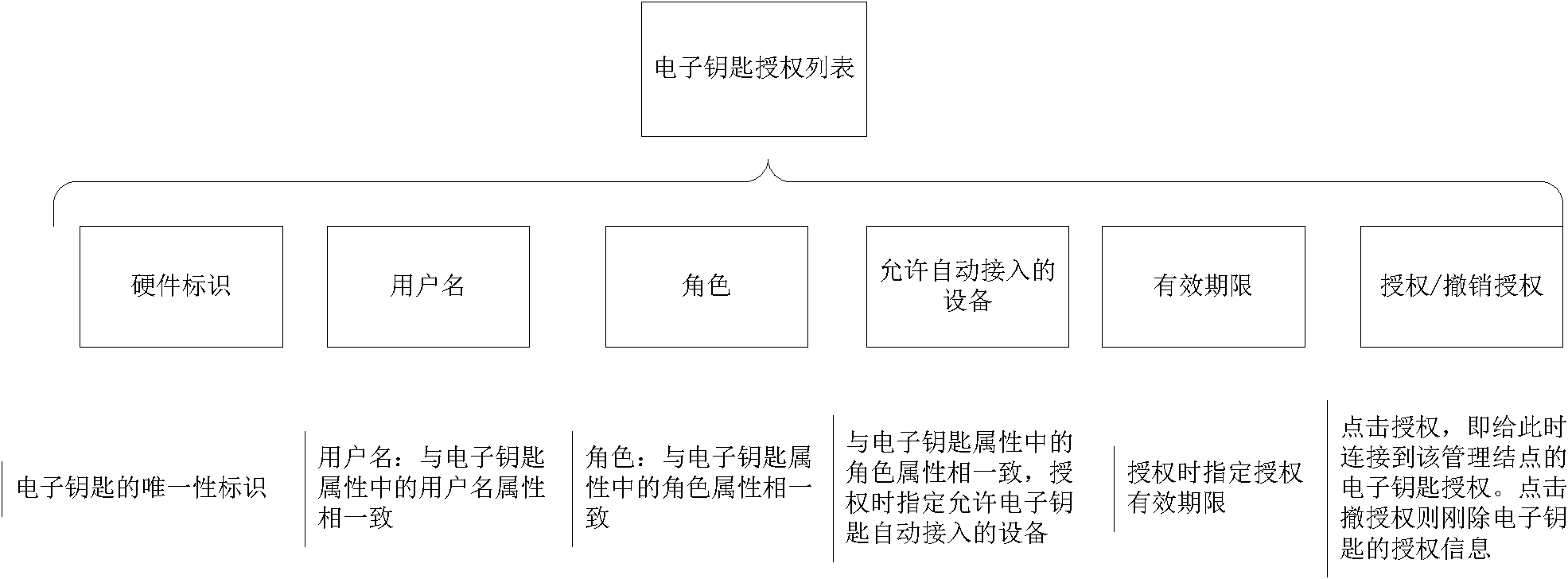
The invention discloses a method for realizing safe access of a terminal of internet of thing, which comprises the steps of: storing an authorization message in an electronic key, and using the authorization message as an identity identification, wherein the authorization message is used as a private key signature by an authorized management node and stored in the authorized management node; writing the authorization message into the electronic key in an electronic key authorization list of the management node; when no terminal node connected with the electronic key applies to accessing the internet, searching a terminal authorization list by the management node to judge whether the access of the terminal node is allowed; and when the terminal node connected with the electronic key applies to accessing the internet, firstly executing the operation without the electronic key by the management node, and if the terminal is failed to access, searching the electronic key authorization listto judge whether the access of the terminal node is allowed. According to the method realizing the safe access of the terminal of the internet of thing, disclosed in the invention, the problem of safe access of the terminal can be effectively solved, a great amount of terminals of the internet of thing can be effectively managed, and the rapid automatic access of the terminals of the internet of thing can be realized.
Owner:无锡鼎驰信息科技有限公司
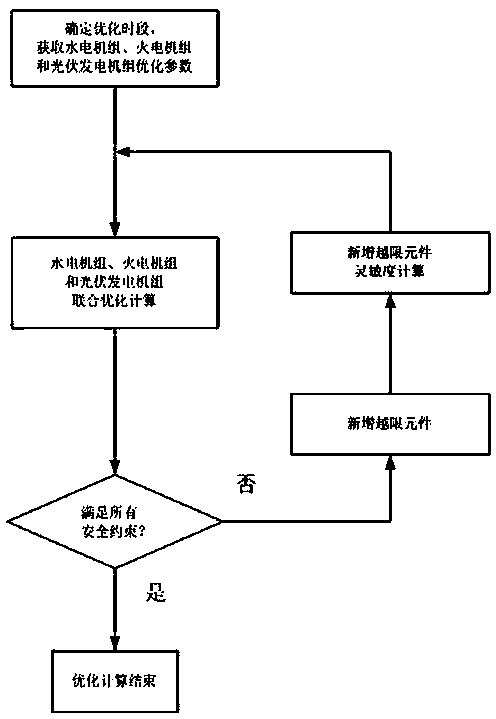
Water, fire and light combined optimization power generation scheduling optimization method considering security constraints
InactiveCN103414206AGuaranteed enforceabilitySecure AccessSingle network parallel feeding arrangementsResourcesNew energyPower system scheduling
The invention belongs to the technical field of electric power system dispatching automation and relates to a water, fire and light combined optimization power generation scheduling optimization method considering security constraints. According to the water, fire and light combined optimization power generation scheduling optimization method, the objective of the method is to realize minimum power generation cost of a system; comprehensive considerations are given to coordinated scheduling of hydroelectric, thermal power and photovoltaic power generator sets; all kinds of constraint conditions are considered, such that optimal computation is performed power generation scheduling of the generator sets; safe access of new energy such as photovoltaic power generation power can be ensured; the improvement of intelligent level and decision making ability of power generation scheduling after the access of the new energy can be facilitated; and through interactive iteration solution of two sub-problems of optimization calculation and safety correction, the power generation scheduling of the hydroelectric, thermal power and photovoltaic power generator sets, which satisfy a requirement for network safety, can be obtained, and therefore, the performability of the power generation scheduling can be ensured. The water, fire and light combined optimization power generation scheduling optimization method considering security constraints of the invention is advantageous in low calculation strength and strong adaptability, and is more suitable for being popularized and applied to scheduling mechanisms of which photovoltaic power generation power access power is larger in China.
Owner:NARI TECH CO LTD
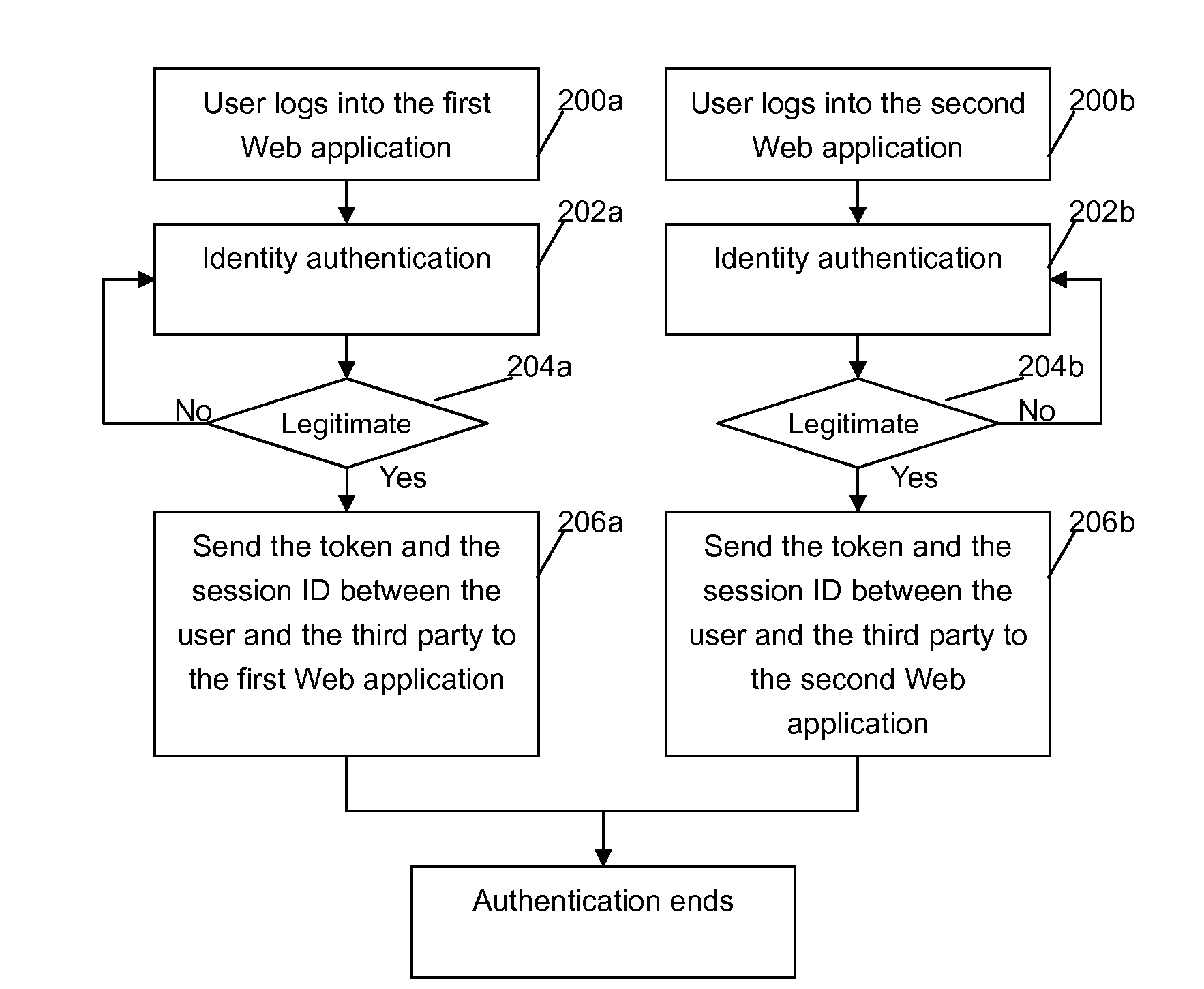
Method and apparatus for providing identity management for users in a web environment
ActiveUS20100024005A1Secure accessAvoid transmissionDigital data processing detailsMultiple digital computer combinationsWeb environmentApplication software
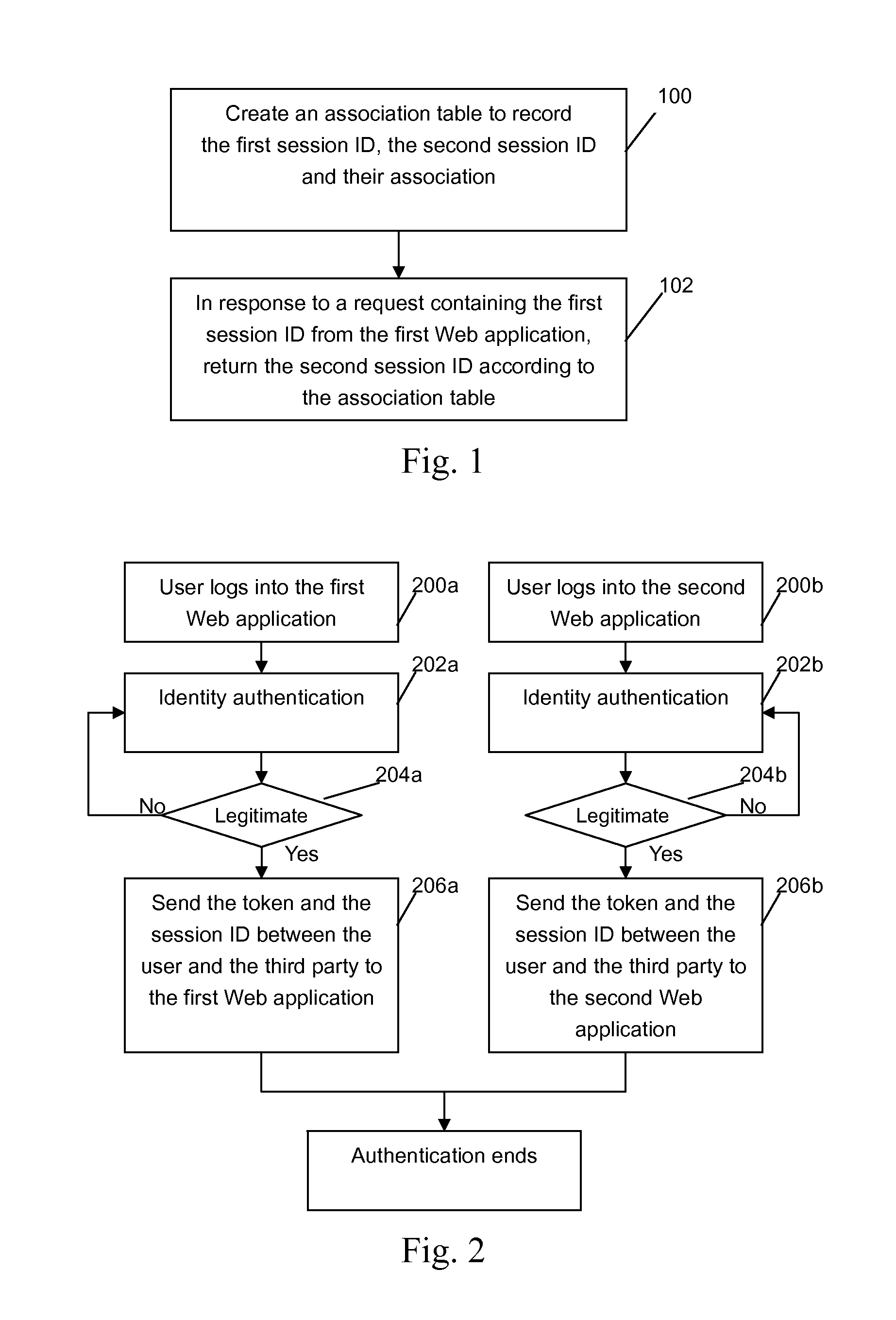
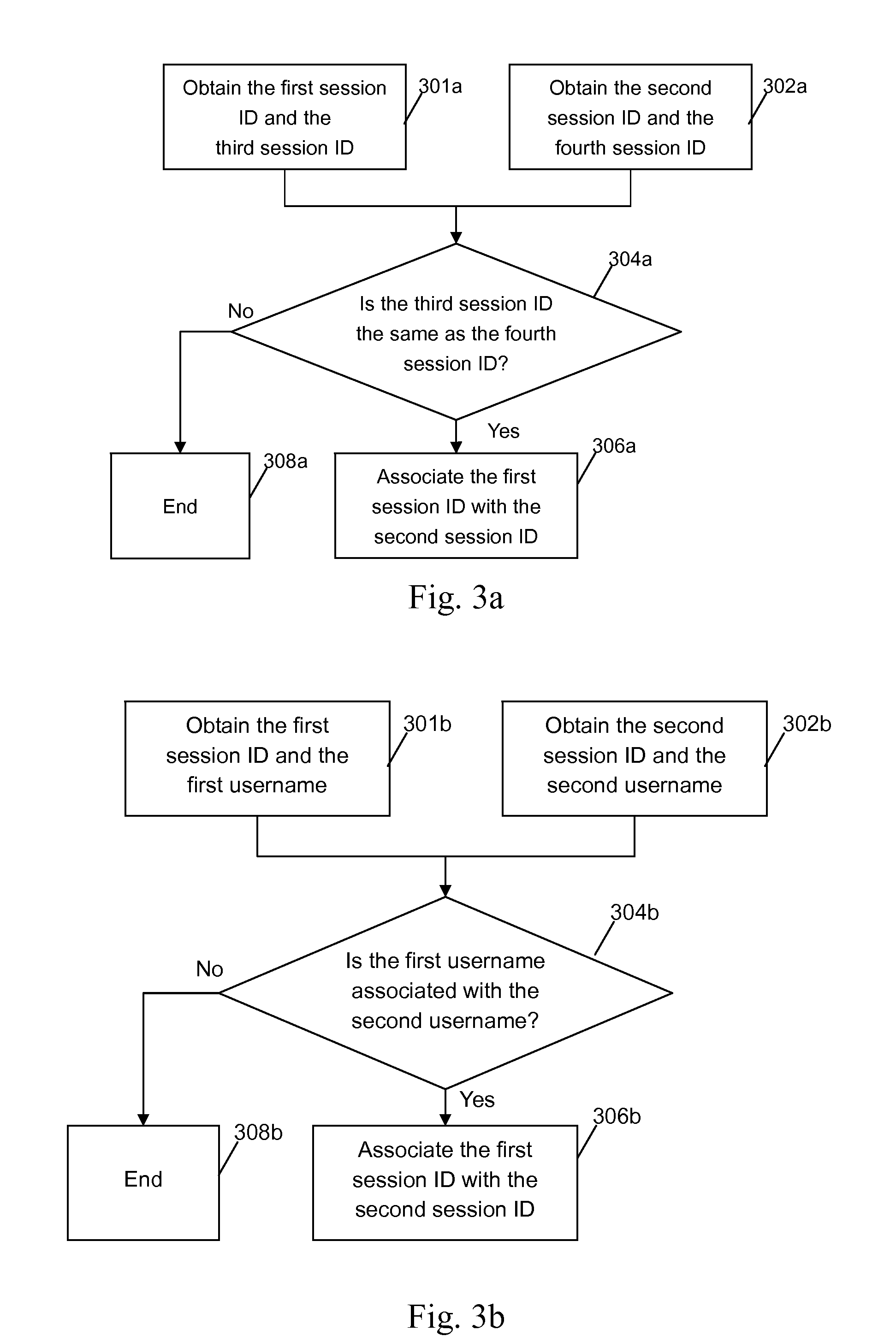
An identity management method, apparatus, and computer readable article of manufacture tangibly embodying computer readable instructions for executing the identity management method. The method includes: creating an association table to record a first session ID between the user and the first Web application, a second session ID between the user and the second Web application, and an association of the IDs; sending a session ID request containing the first session ID by the first Web application to a return module; receiving the session ID request and searching by the return module for the associated second session ID in the association table according to the first session ID; and returning the second session ID to the first Web application, thereby providing identity management for a user in a Web environment in which a first Web application accesses a second Web application on behalf of the user.
Owner:AIRBNB
Communication method base on dual-network redundant universal network model
ActiveCN101378334AReliable transmissionSecure AccessAutomatic systemsError preventionNetwork connectionDual network
The invention relates to a communication method based on a dual network redundancy general network model, which comprises the steps of: constructing a redundant network; constructing redundant equipment; broadcasting data; transmitting the data; and managing a node module. Compared with the prior art, the invention provides an extremely abstract general network model, thereby separating a logic application layer and a network communication layer and ensuring the reliable data transmission by the redundant network by using the serial-number repeated packet filtering technology; a minimal path for transmitting the data is dynamically calculated according to the network connection relationship among all the network nodes, thus realizing the arbitrary point-to-point communication among all the modules; the master / backup roles of the node are switched in real time according to the master / backup states of the node in the system, thus realizing the automatic conversion of the sending and receiving of the data; illegal connection is actively rejected according to the configuration of the system nodes, thus ensuring the safe access of the whole system.
Owner:CASCO SIGNAL
Method and device for having access to webpage safely and downloading data through intelligent terminal
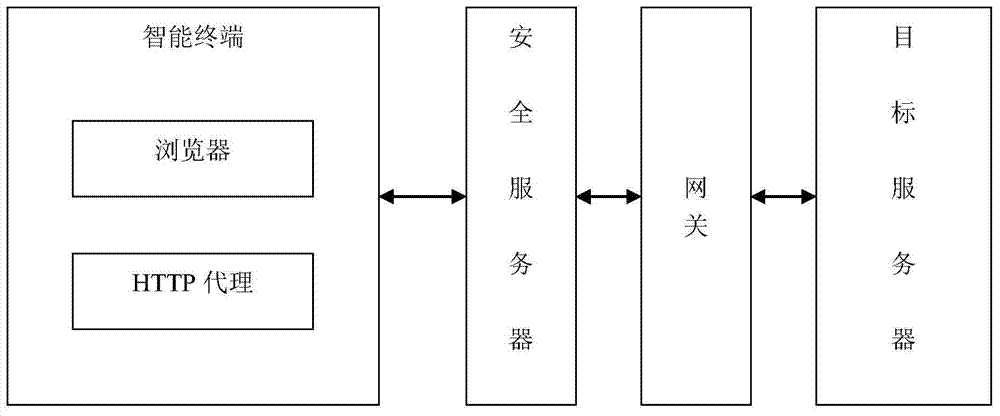
InactiveCN103763308AAvoid security issuesSolve Internet security problemsTransmissionClient-sideProxy server
The invention discloses a method and device for having access to a webpage safely through an intelligent terminal. The system comprises the intelligent terminal and a browser located on the intelligent terminal, wherein the intelligent terminal is connected with a security server, and the security server and a target server are connected with a gateway. The method includes the steps that the intelligent terminal starts local monitoring service, and an HTTP proxy server of the browser is set as a local address; the browser receives an access request, and the access request is forwarded to a local designated port by means of the HTTP proxy server; after the intelligent terminal monitors and receives the access request of the browser, identity authentication is started; after authentication, request data are forwarded to the security server after being encrypted; after the security server decrypts the data, the data are sent to the target server; the security server receives response data, decrypts the response data and forwards the response data to a client; the client receives the response data, decrypts the response data and feeds back the response data to the browser.
Owner:北京明朝万达科技股份有限公司
Method for technically controlling secure access to embedded system memory
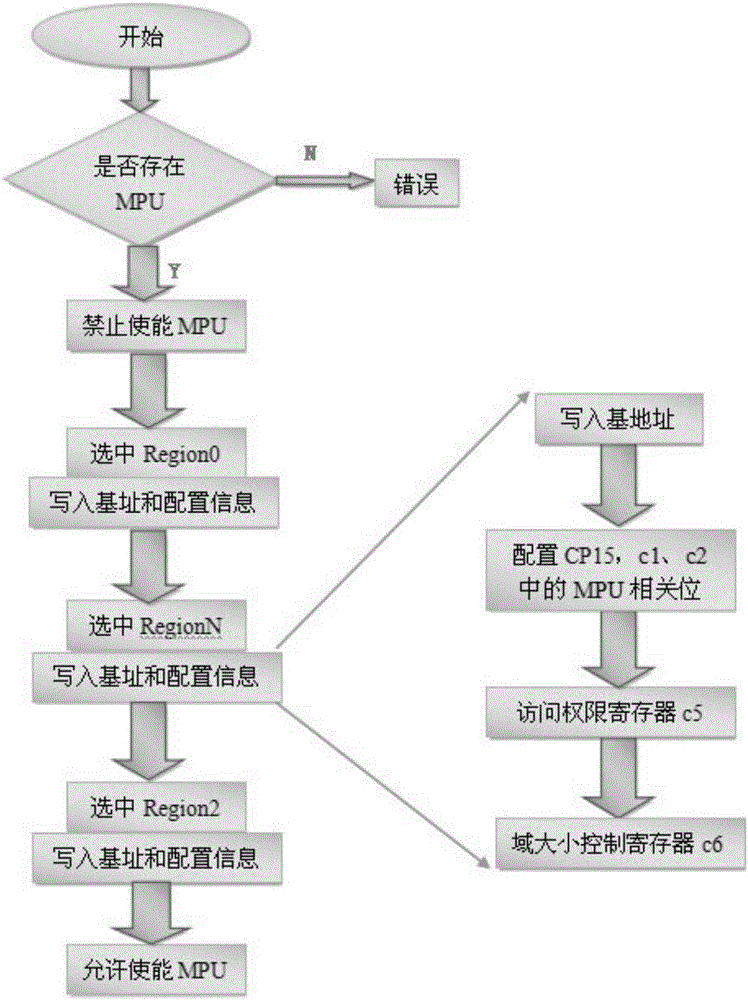
ActiveCN105787360ARealize dynamic switchingEnsure legitimate accessInternal/peripheral component protectionPlatform integrity maintainanceWrite bufferOperational system
The invention discloses a method for technically controlling secure access to an embedded system memory. The method includes the following steps of initially designing a system of a memory secure access mechanism, wherein an MPU memory protection unit is introduced, domain attributes of different grades are distributed, and an access attribute and a system initiating progress are set; secondly, designing the secure access to the memory for switching of embedded operation system process context, wherein a domain control module is set, the system process context is set, and switching of the system process content is achieved in the domain control module. The illegal access of all address space resources are detected and limited through a processor MPU hardware mechanism, the boundary control and context switching of any task of the embedded real-time multi-task operation system for accessing resources of other tasks is achieved, distributing and designing of cache, writing buffer and MPU attributes of different storage spaces in the system are achieved, and the control over secure access to all background domains in the memory is ensured.
Owner:HANGZHOU BYTE INFORMATION TECH CO LTD
Method and system for implementing safety access public network of network terminal as well as special network access controller thereof
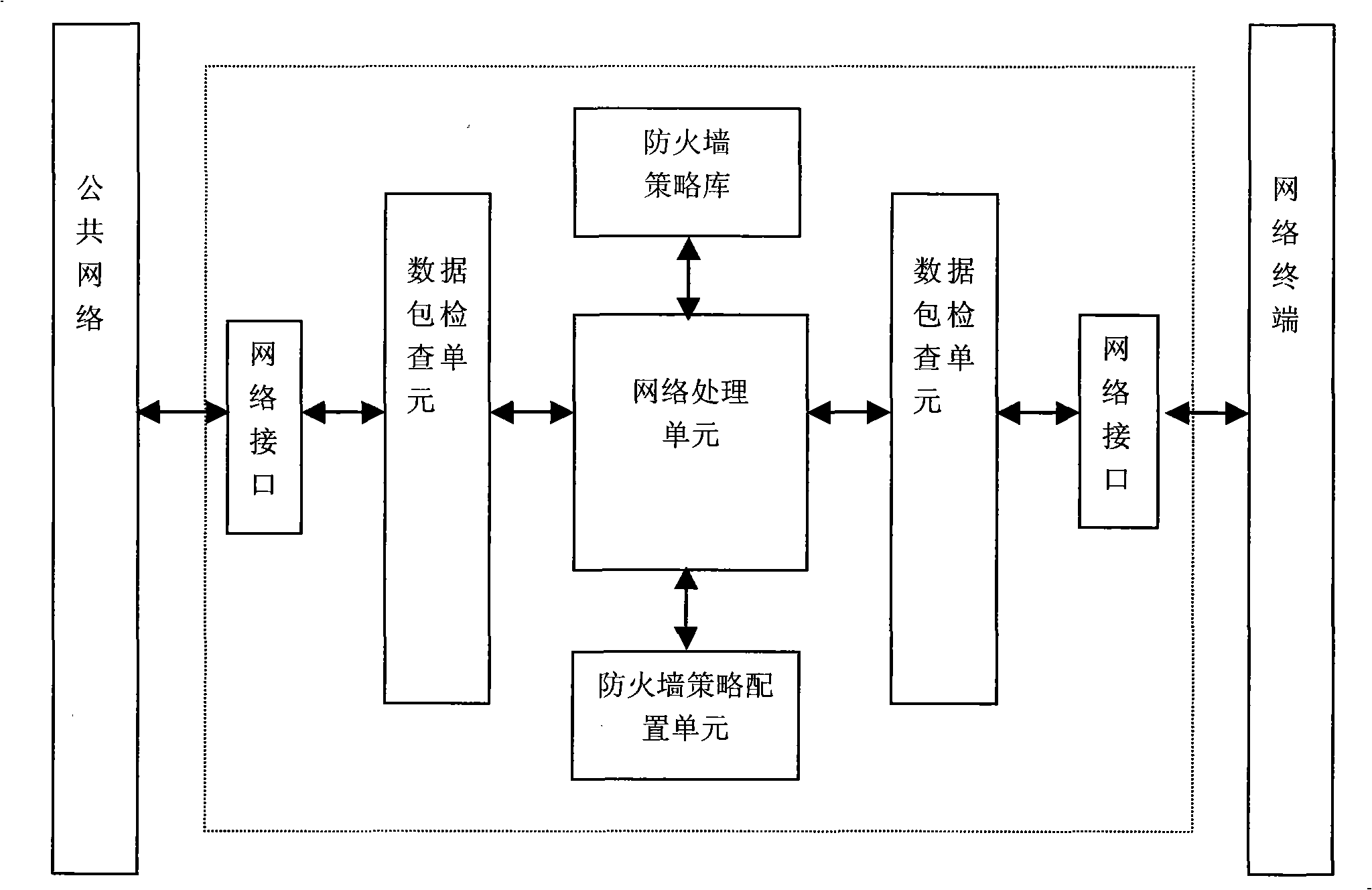
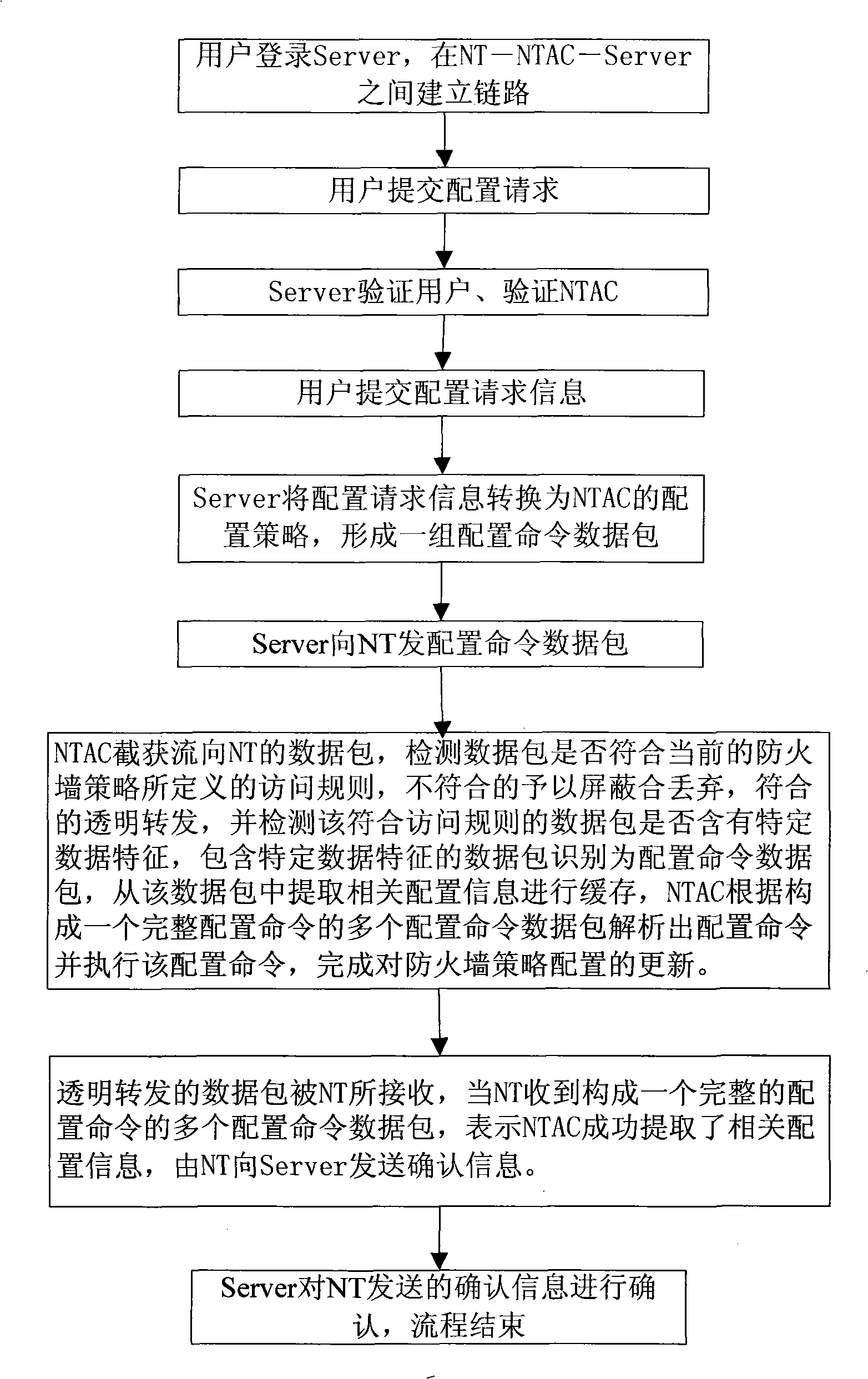
ActiveCN101355415ASecure AccessEasy to useNetwork connectionsSecuring communicationNetwork terminationNetwork packet
The invention discloses a method for realizing that a network terminal can safely access a public network. The method comprises the following steps: a network access controller is connected in series between the network terminal and the public network; when a firewall strategy database is required to be configured, a user on a network terminal submits configuration request information; the network access control server generates a group of corresponding configuration command data packet which is transmitted to the network terminal according to the configuration request information; the group of configuration command data packet is captured by the network access control server which is connected in series on the link so as to analyze and execute the corresponding configuration command and complete the update to the configuration of firewall policy; and the user on the network terminal access the public network under the security protection of the firewall policy configured by the network access control server. The invention also discloses a system for realizing that the network terminal can safely access the public network and the network access control server. The method, the system and the network access control server not only can ensure that the network terminal can safely access the public network, but also can be convenient for a user to use.
Owner:苏州凌犀物联网技术有限公司
Standby volume analytical method under coordinating dispatch mode of batch-type energy and conventional energy
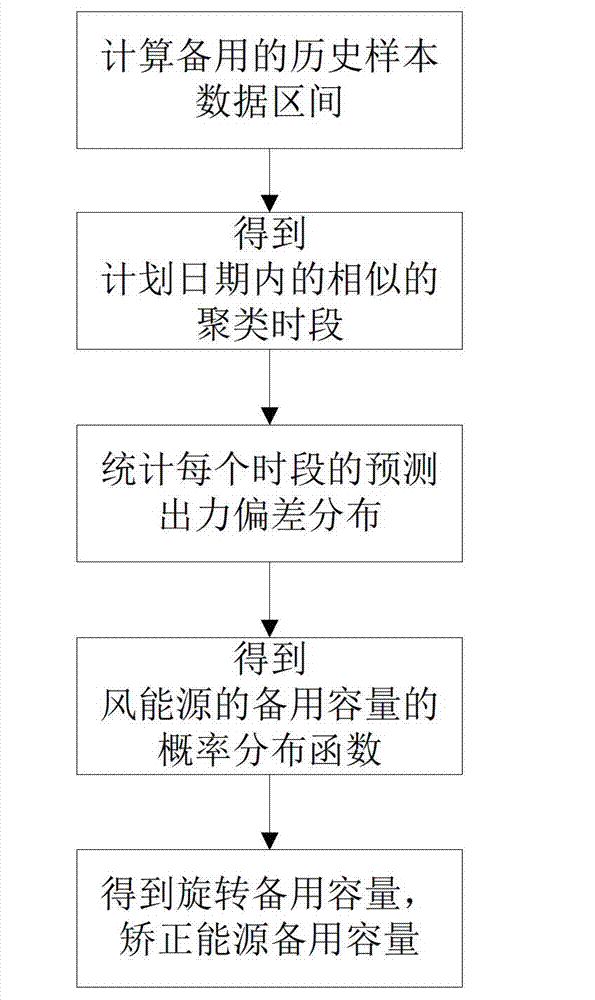
ActiveCN102810860AGuaranteed enforceabilityEnsure safetySingle network parallel feeding arrangementsWind energy generationElectricityNormal density
The invention discloses a standby volume analytical method under a coordinating dispatch mode of batch-type energy and conventional energy. The method comprises the following five steps of calculating a standby past sample data region, obtaining similar cluster time intervals in a planed date, carrying out statics on a forecast output power deviation distribution of each time interval, obtaining a probability density function of the standby volume of wind energy, and calculating a rotation standby volume of a system under the coordinating dispatch mode of the batch-type energy and the conventional energy. With the adoption of the analytical method, according to a consideration of the coordinating dispatch of assembling units of the batch-type energy and the conventional energy, statics and analysis on data of past wind-power operation are carried out to form the current requirement on the rotation standby volume, safety guarantee is provided for the coordinating dispatch of the batch-type energy and the conventional energy, a reasonable standby volume is provided, and the realization of economical requirement on operation of a power system is facilitated. The method has the characteristics of low calculation intensity and strong adaptability, and is more suitable for popularization and application of connecting with dispatch mechanisms with larger power of wind power.
Owner:NARI TECH CO LTD +1
Data processing apparatus and access control method therefor
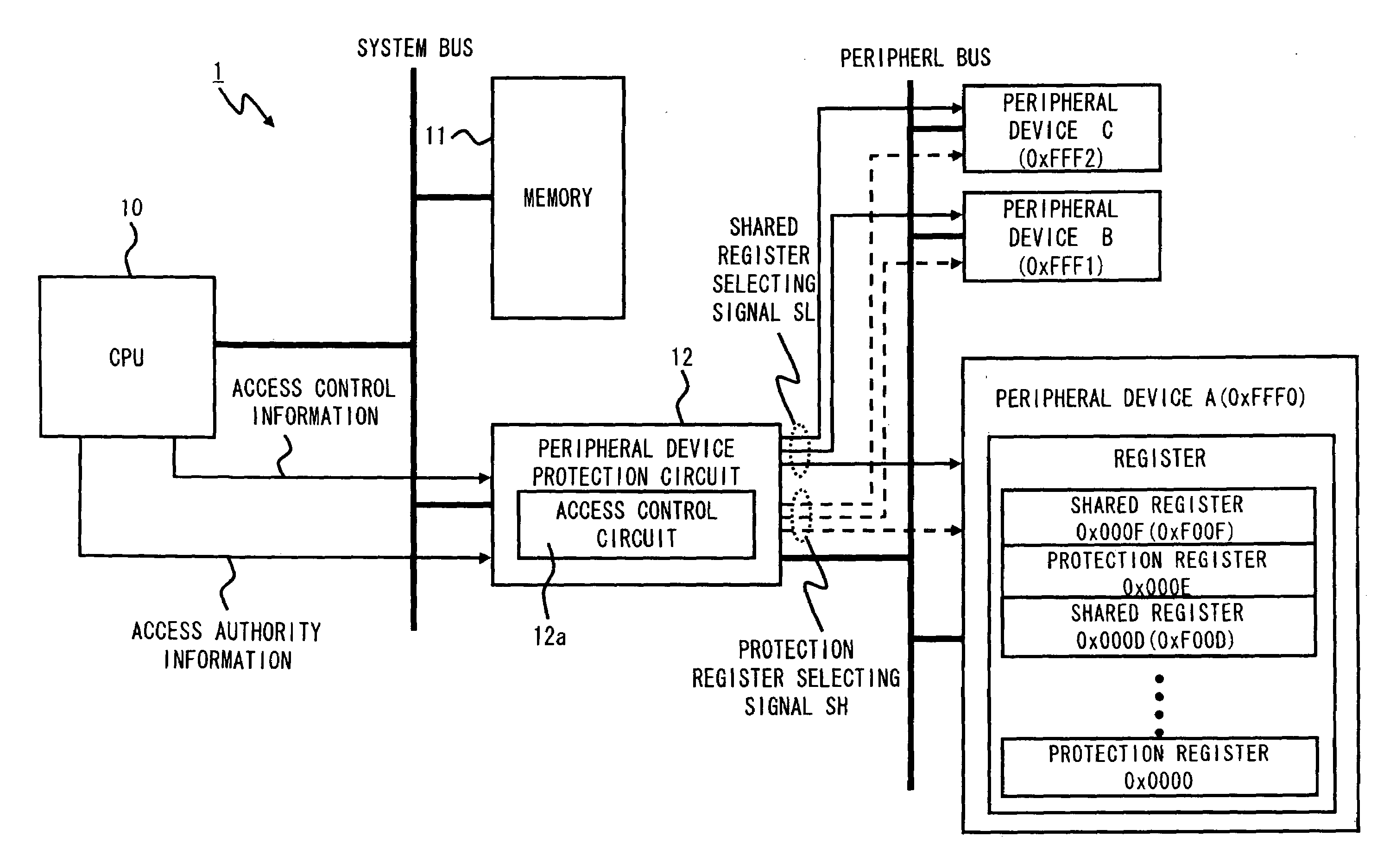
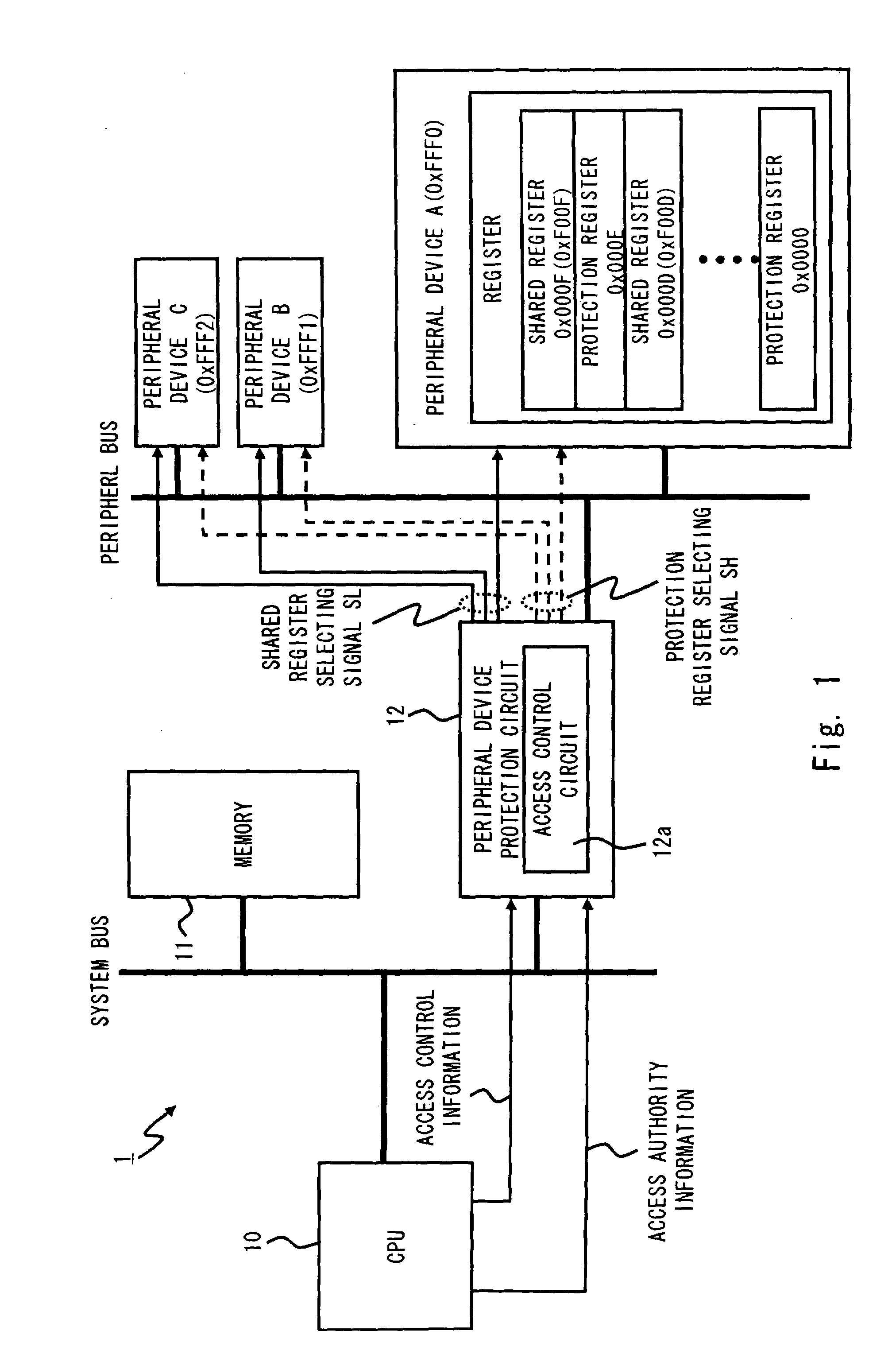
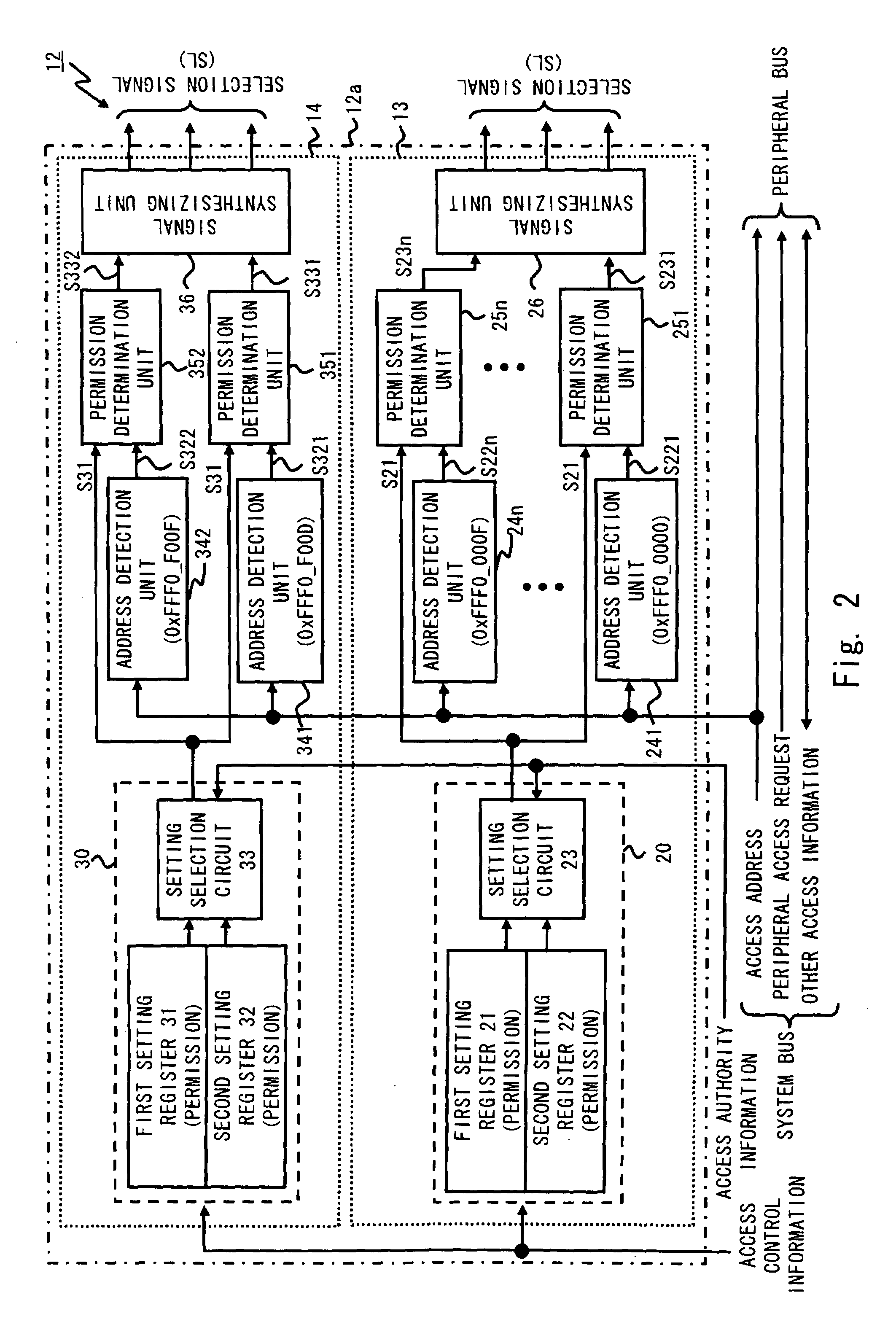
InactiveUS20090271861A1High speed accessEnsure reliabilityDigital data processing detailsUnauthorized memory use protectionProcessor registerPerformed Procedure
A data processing apparatus according to the present invention includes: peripheral devices each including a plurality of registers each storing a preset value or data; a processing unit to output access authority information indicative of a first access authority level or a second access authority level, which is an access authority level lower than the first access authority level, according to a program to be executed, and to output an access address to specify a specific register; and a peripheral device protection circuit connected to the processing unit and receiving the access authority information and the access address so as to control access of the processing unit to the peripheral devices. The peripheral device protection circuit controls whether to permit the access to the specific register specified by the access address, based on the access authority level indicated by the access authority information.
Owner:RENESAS ELECTRONICS CORP
Tamper-proof license camera system and method
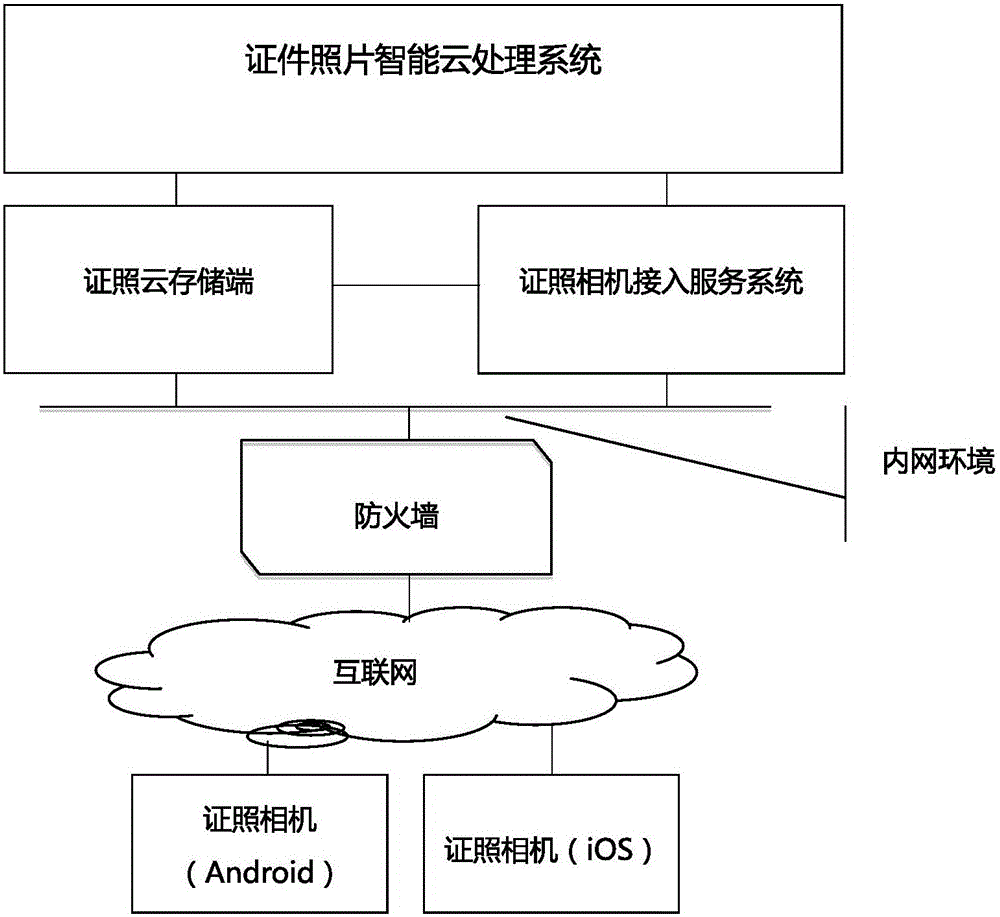
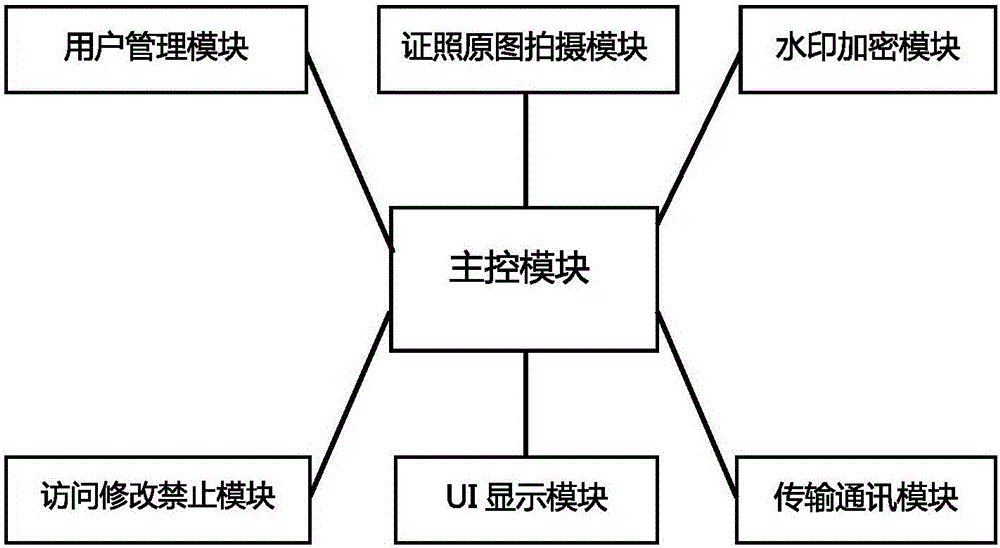
ActiveCN105141842APrevent tamperingEnsure information securityTelevision system detailsColor television detailsTamper resistanceAccess modification
The invention discloses a tamper-proof license camera system and method. The tamper-proof license camera system comprises a license camera, a license camera access server and a license cloud storage, wherein the license camera comprises a license original picture shooting module, an access modification prohibition module, a watermark encryption module and a transmission communication module. The tamper-proof license picture shooting method comprises the following steps: shooting license original pictures by the license camera; in the process of shooting and generating the license original pictures, prohibiting users or other software to access the original picture data, and prohibiting users or other software to modify the license original picture data; writing the shot license original pictures into a fragile watermark and encrypting the shot license original pictures; performing compression and secondary encryption on the pictures after being performed watermark encryption, and transmitting the pictures to an independent storage space of a license cloud storage end for conservation. The tamper-proof license camera system and method provided by the invention can guarantee the authenticity and timeliness of pictures in the processes from imaging to generating standard license pictures, submitting and transmitting, prevent pictures from being tampered, and can very conveniently and easily acquire the license pictures.
Owner:GUANGZHOU XINGFU NETWORK TECH
Network system for secure communication
ActiveUS20180375870A1Communication securityEnable secure communicationKey distribution for secure communicationUser identity/authority verificationSecure communicationNetworked system
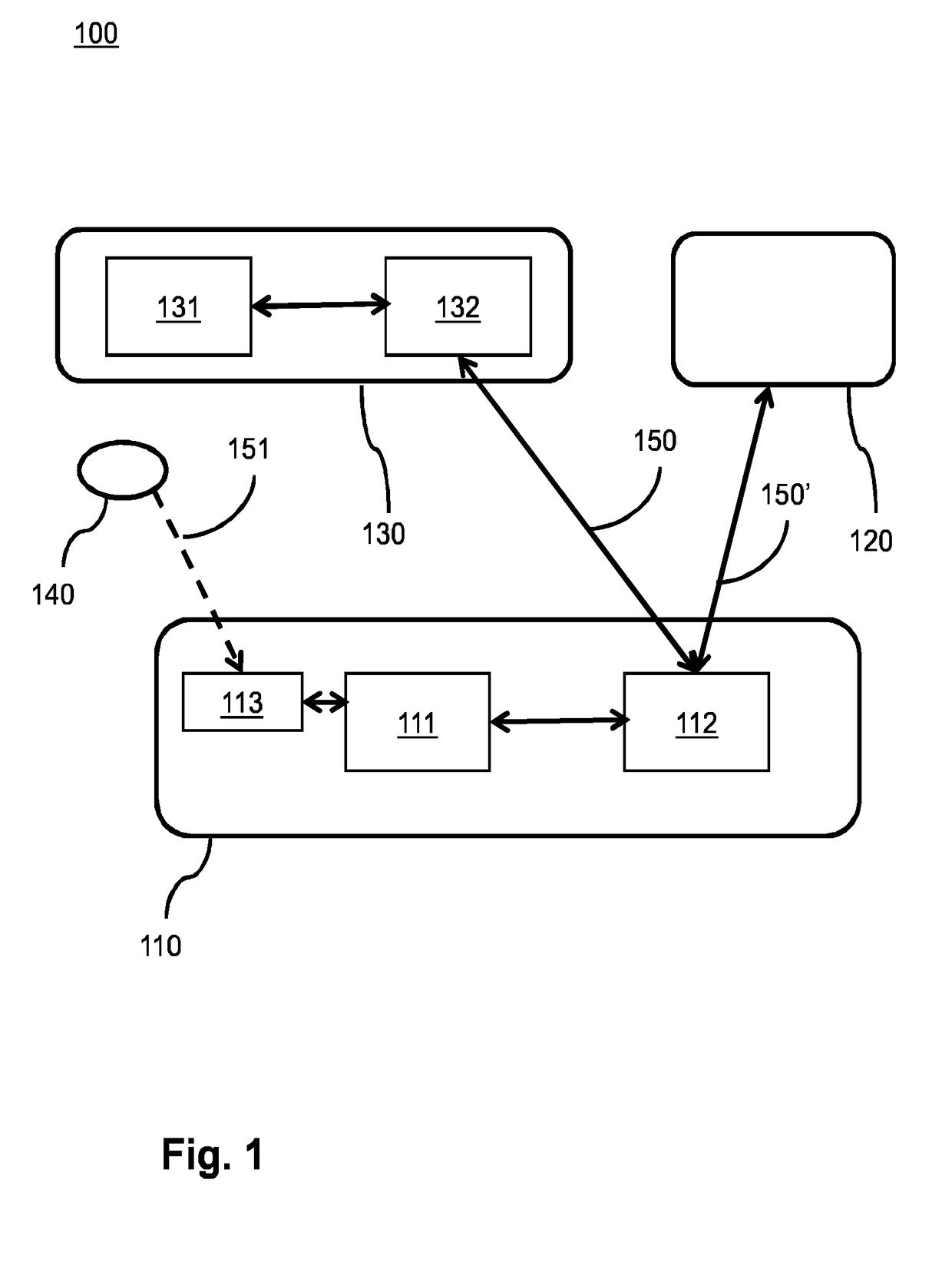
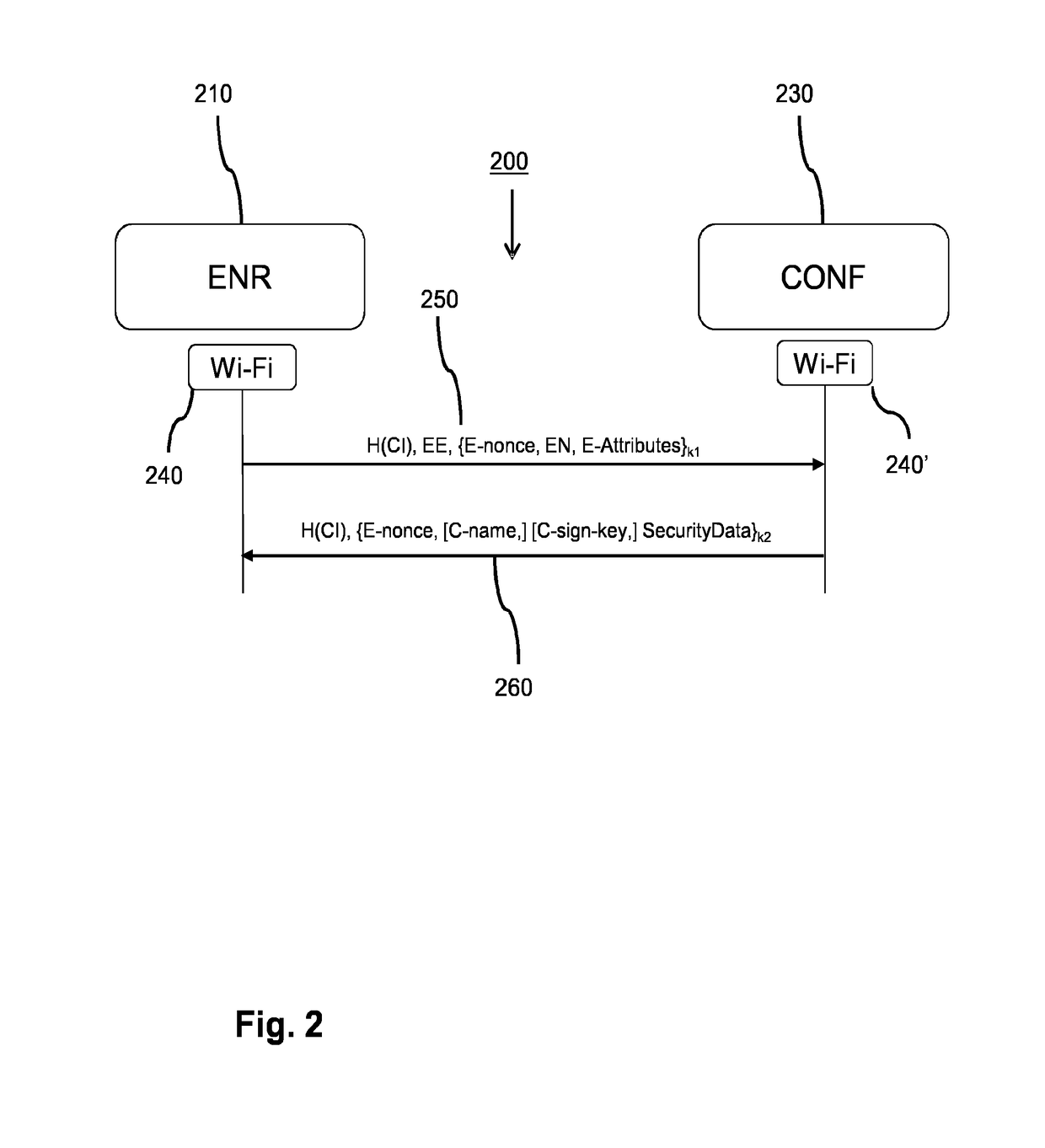
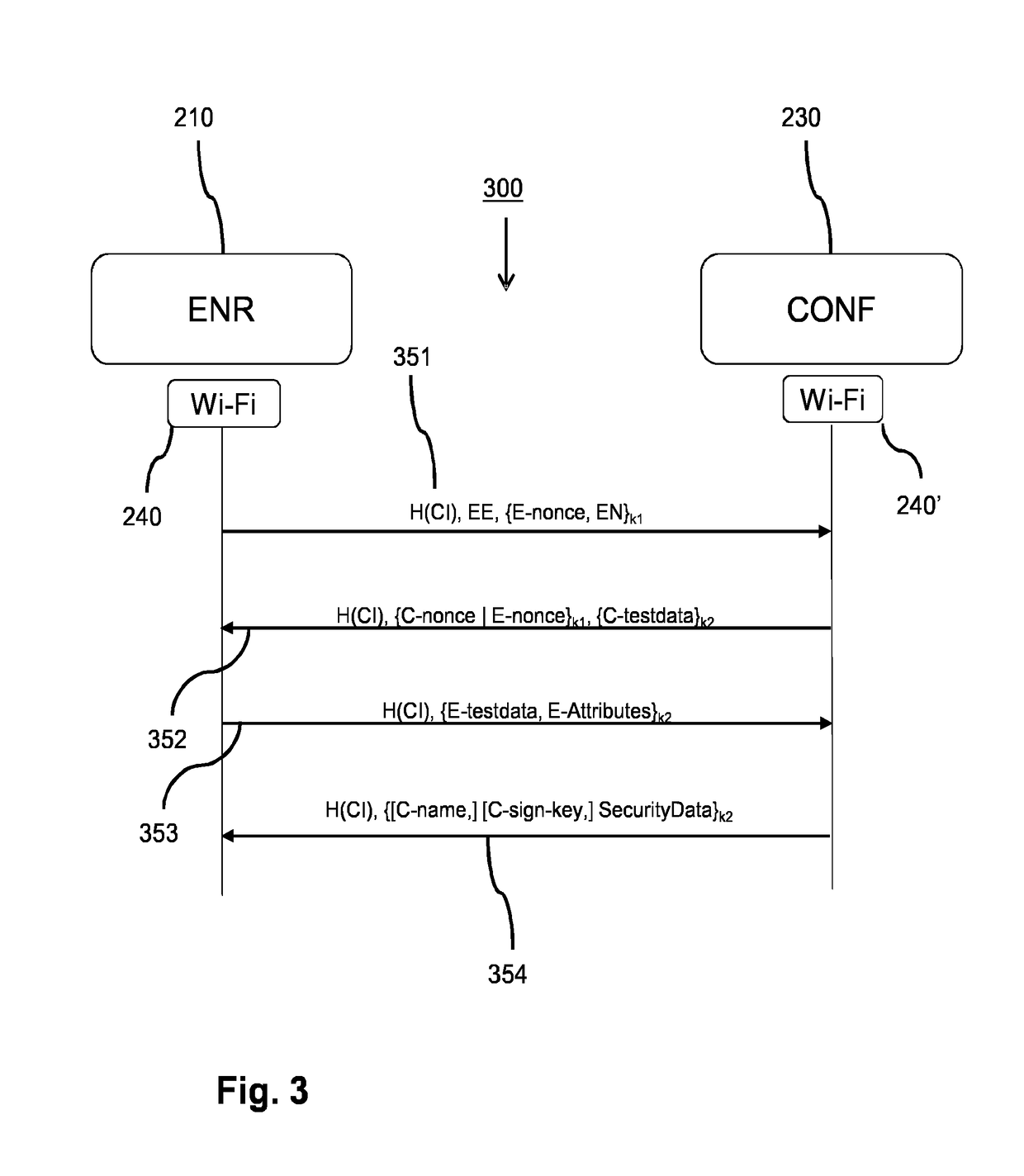
In a network system (100) for wireless communication an enrollee (110) accesses the network via a configurator (130). The enrollee acquires a data pattern (140) that represents a network public key via an out-of-band channel by a sensor (113). The enrollee derives a first shared key based on the network public key and the first enrollee private key, and encodes a second enrollee public key using the first shared key, and generates a network access request. The configurator also derives the first shared key, and verifies whether the encoded second enrollee public key was encoded by the first shared key, and, if so, generates security data and cryptographically protects data using a second shared key, and generates a network access message. The enrollee processor also derives the second shared key and verifies whether the data was cryptographically protected and, if so, engages the secure communication based on the second enrollee private key and the security data.
Owner:KONINKLJIJKE PHILIPS NV
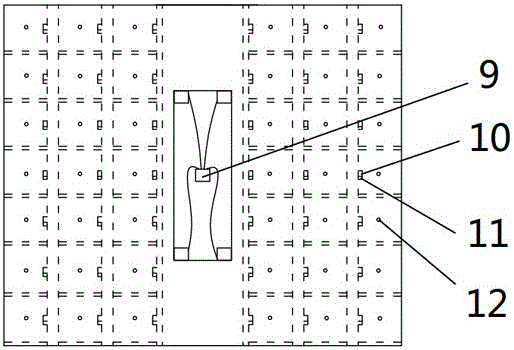
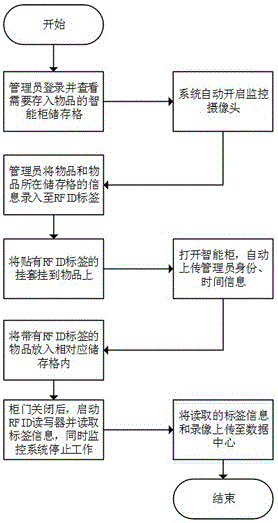
Dangerous chemical storage cabinet
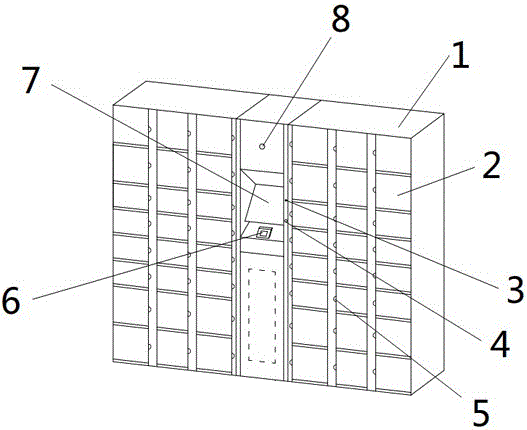
InactiveCN106774562ASecure AccessSafeguard storageIndividual entry/exit registersSimultaneous control of multiple variablesVideo monitoringChemical storage
The invention relates to a dangerous chemical storage cabinet. The dangerous chemical storage cabinet comprises a cabinet body, wherein the cabinet body comprises a plurality of storage cells, a door is mounted on each storage cell, an electronic lock connected with a main control device is arranged between each door and the corresponding storage cell, the main control device is provided with an identity authentication device, an information acquisition device, an input-output device, a video monitoring device, an alarm device and a wireless data transmission device, the main control device is connected with a remote server; and a temperature sensor, a humidity sensor, a smoke detector, a dehumidifying machine core and a cooler are arranged in each storage cell of the cabinet body. According to the dangerous chemical storage cabinet provided by the invention, a storage environment for dangerous chemicals in the cabinet can be monitored in real time and adjusted automatically; the storage information of the dangerous chemicals and the condition of entering and exiting the cabinet body of the dangerous chemicals are read in real time; the problems that information management cannot implemented in time and is not perfect, and the safety supervision is not in place during manual operation are solved, supervision level and working efficiency are effectively improved, and the storage and access security of the dangerous chemicals is guaranteed.
Owner:ZHEJIANG UNIV OF TECH
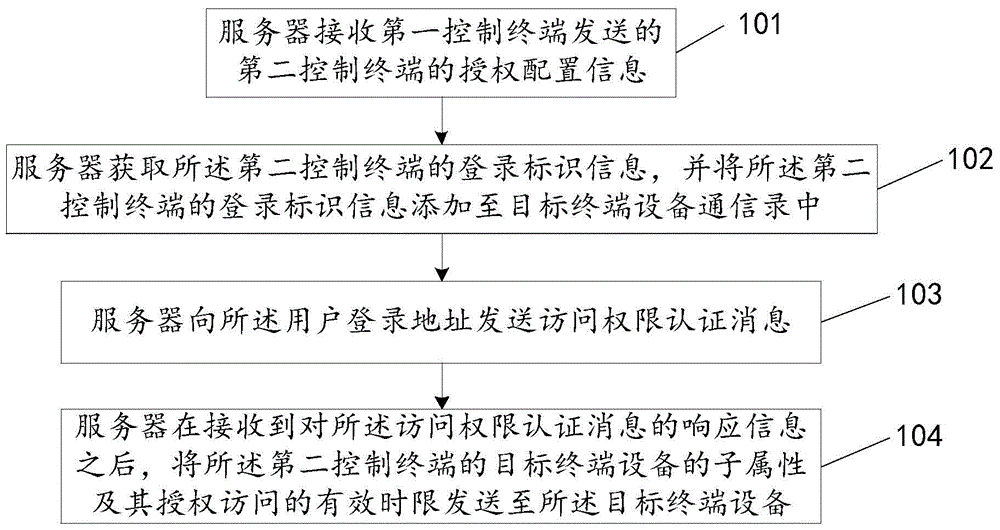
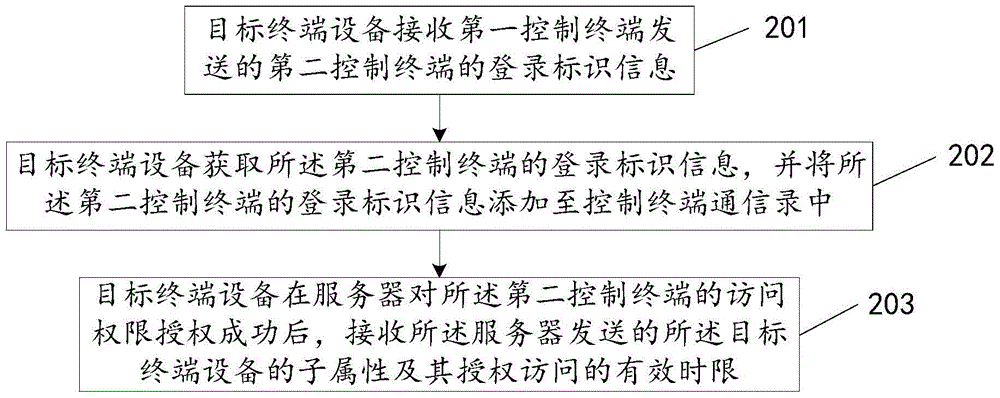
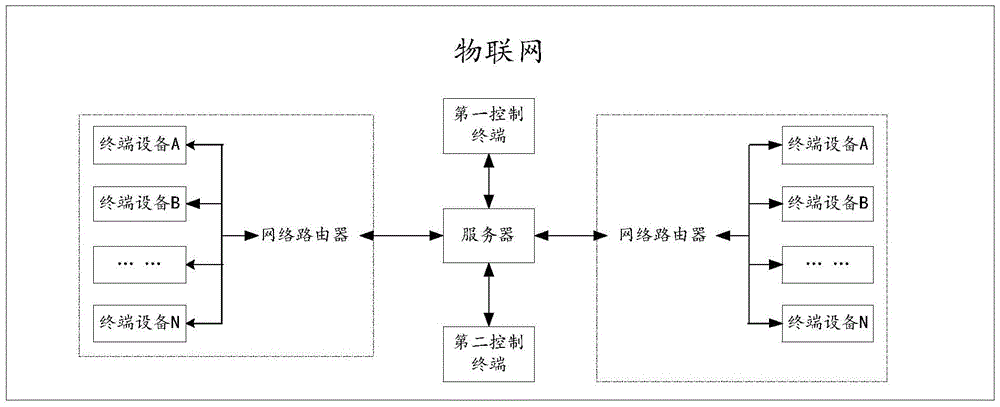
Access authorization method and system of terminal device, server, and object terminal device
The invention is mainly applied to a process of access authorization of a terminal device in the Internet of things, relates to the technical field of a terminal, and discloses an access authorization method and system of a terminal device, a server, and an object terminal device, for the main purpose of ensuring access security of a terminal device in Internet of things. The method provided by the technical scheme comprises the following steps: a server receiving authorization configuration information of a second control terminal, sent by a first control terminal; obtaining registration identification information of the second control terminal, and adding the registration identification information of the second control terminal into an address book of an object terminal device, wherein the address book of the object terminal device is used for limiting terminal devices having access authority of control terminals; sending access an authority authentication message to a user registration address; and after response information of the access authority authentication message is received, sending sub-attributes of the object terminal device of the second control terminal and its effective time limit of access authorization to the object terminal device.
Owner:向三名
Method and system for changing data transfer bus
ActiveCN101789171AFlexible configurationEasy to upgradeElectric signal transmission systemsBus networksInformation processingLossless compression
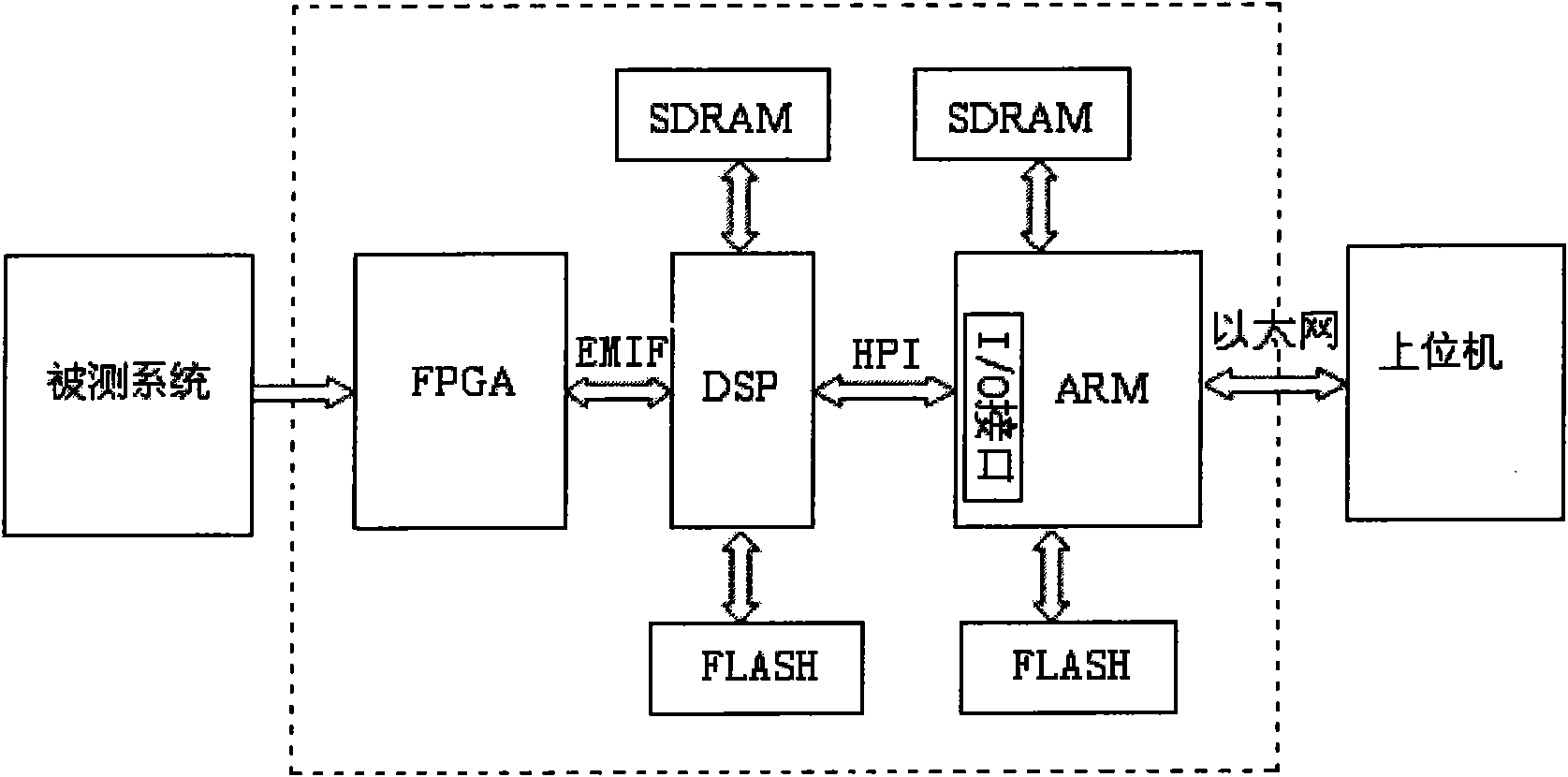
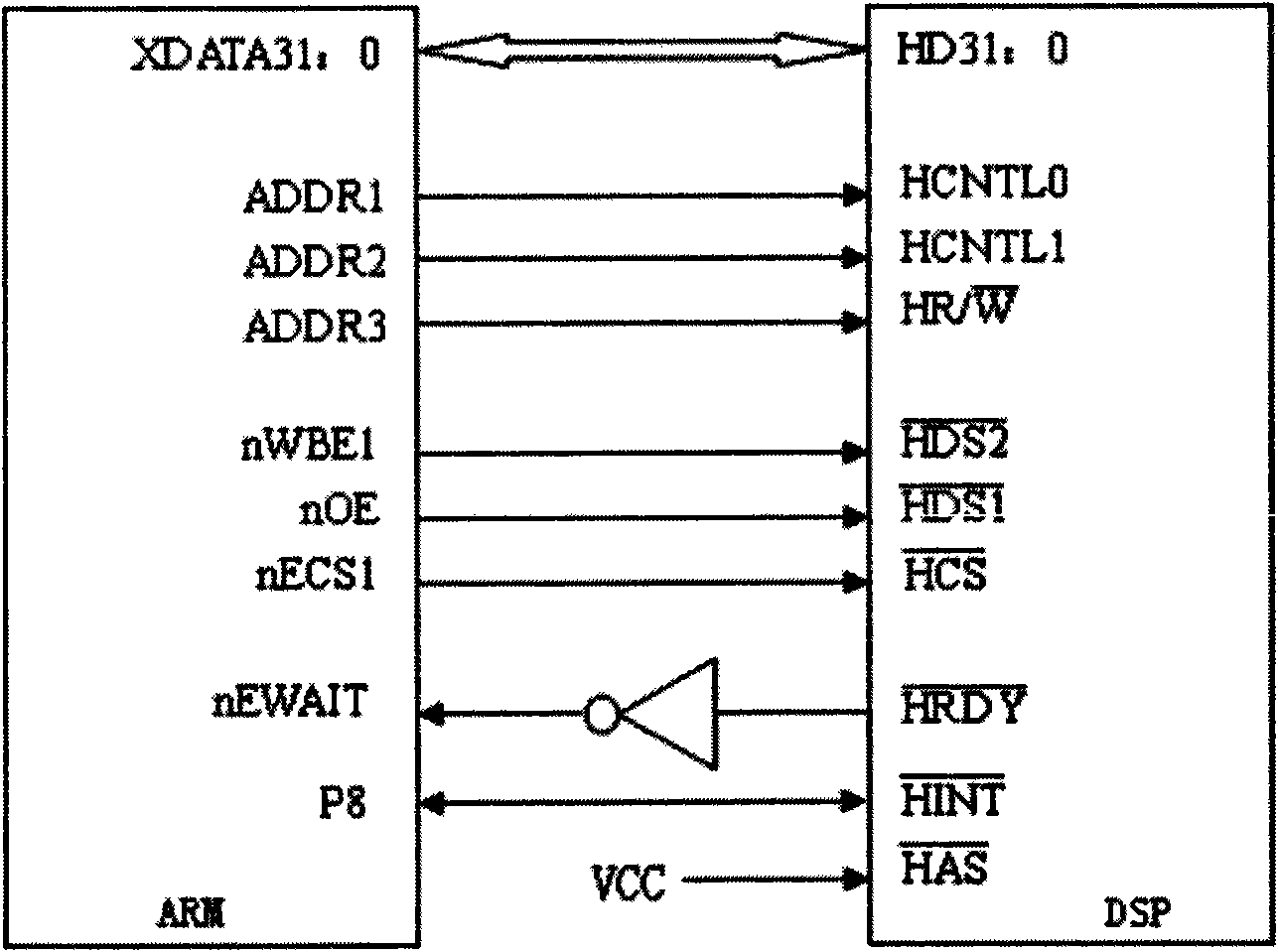
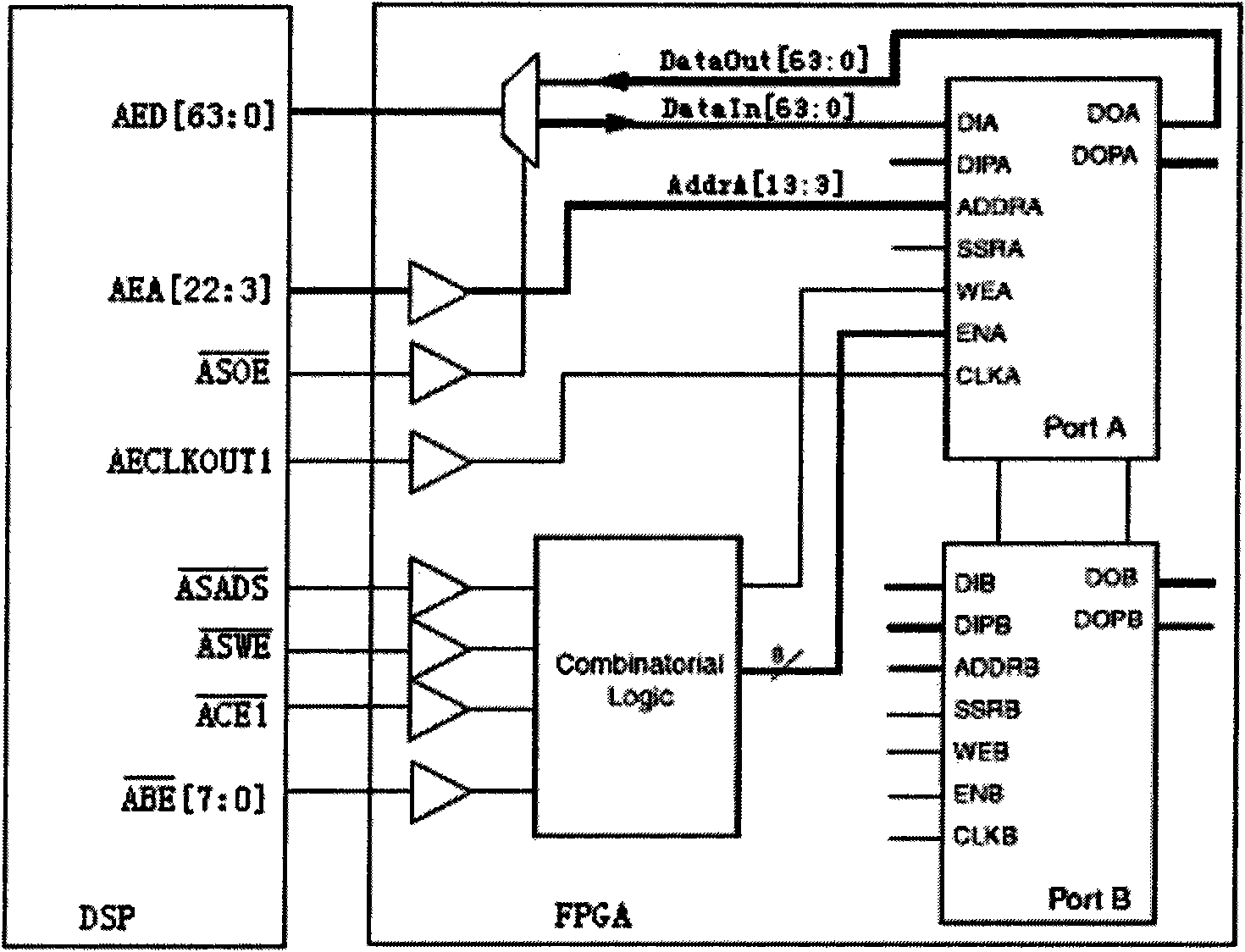
The invention discloses a method for changing a data transfer bus, which comprises the following steps: receiving telemetry parallel data (sub)frame by (sub)frame, and converting the parallel data into serial data; carrying out the lossless compression on the serial data; transferring the compressed data to an upper computer via Ethernet; and demodulating, recording and storing various physical variables by the upper computer according to the data transfer protocol and the data telemetry protocol of the product. Accordingly, a tester can complete the remote setting of working conditions and the task of information query interaction by the upper computer. An information processing platform system has a structure of FPGA (field programmable gate array), DSP (digital signal processor) and ARM (advanced reduced instruction set computer machine), wherein the FPGA completes the task of converting the parallel data to the serial data; the DSP reads the data processed by the FPGA and completes the task of the lossless compression of the data; and the ARM reads the coded data from the DSP and achieves the real-time communication with the upper computer via the Ethernet. The invention not only solves the problem of signal distortion, but also meets the requirement for the real-time performance of information transfer; and meanwhile, the system serves the functions of the gateway and embedded Web, thereby guaranteeing the safe access of the system to the Ethernet.
Owner:凯迈(洛阳)电子有限公司
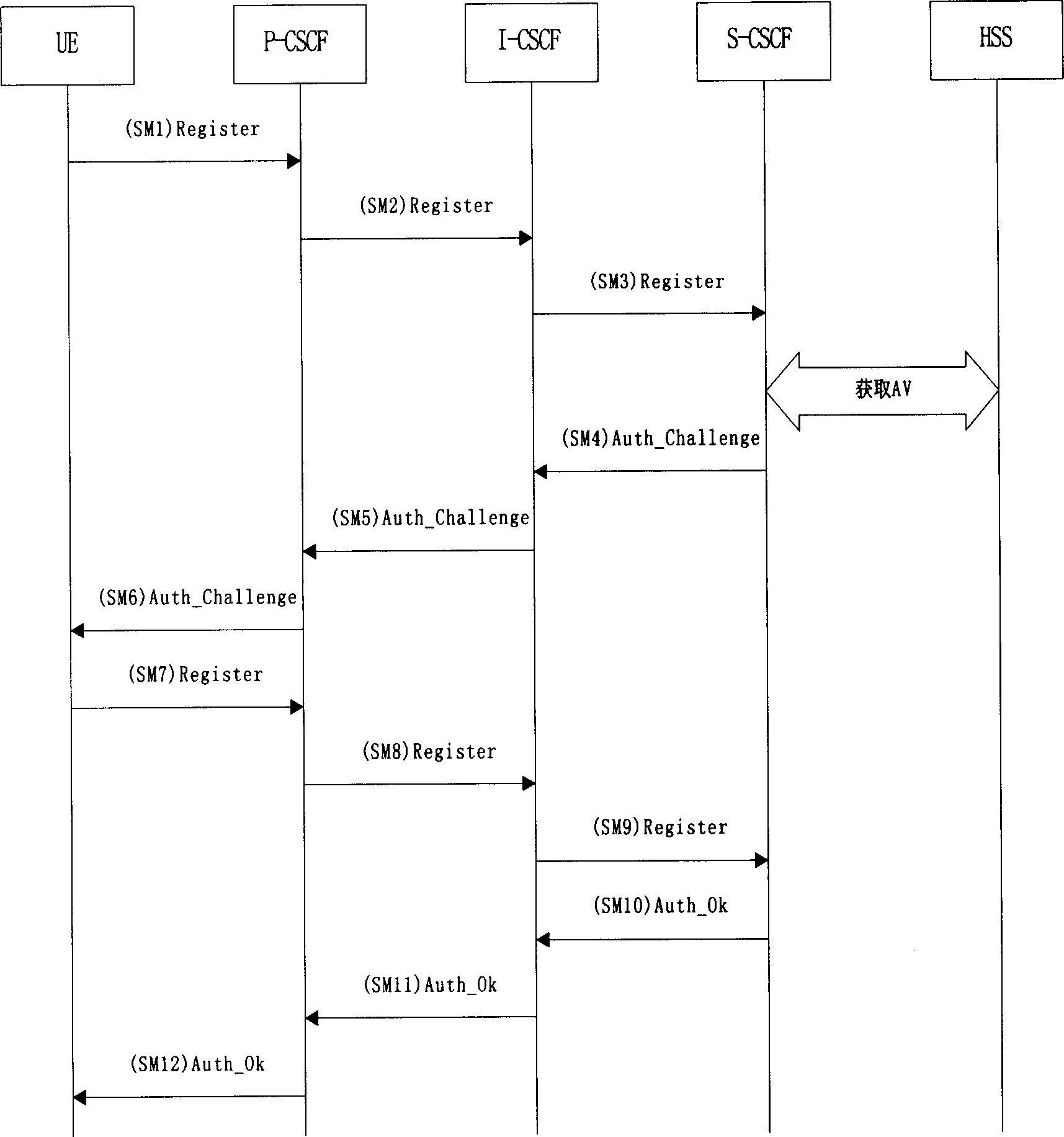
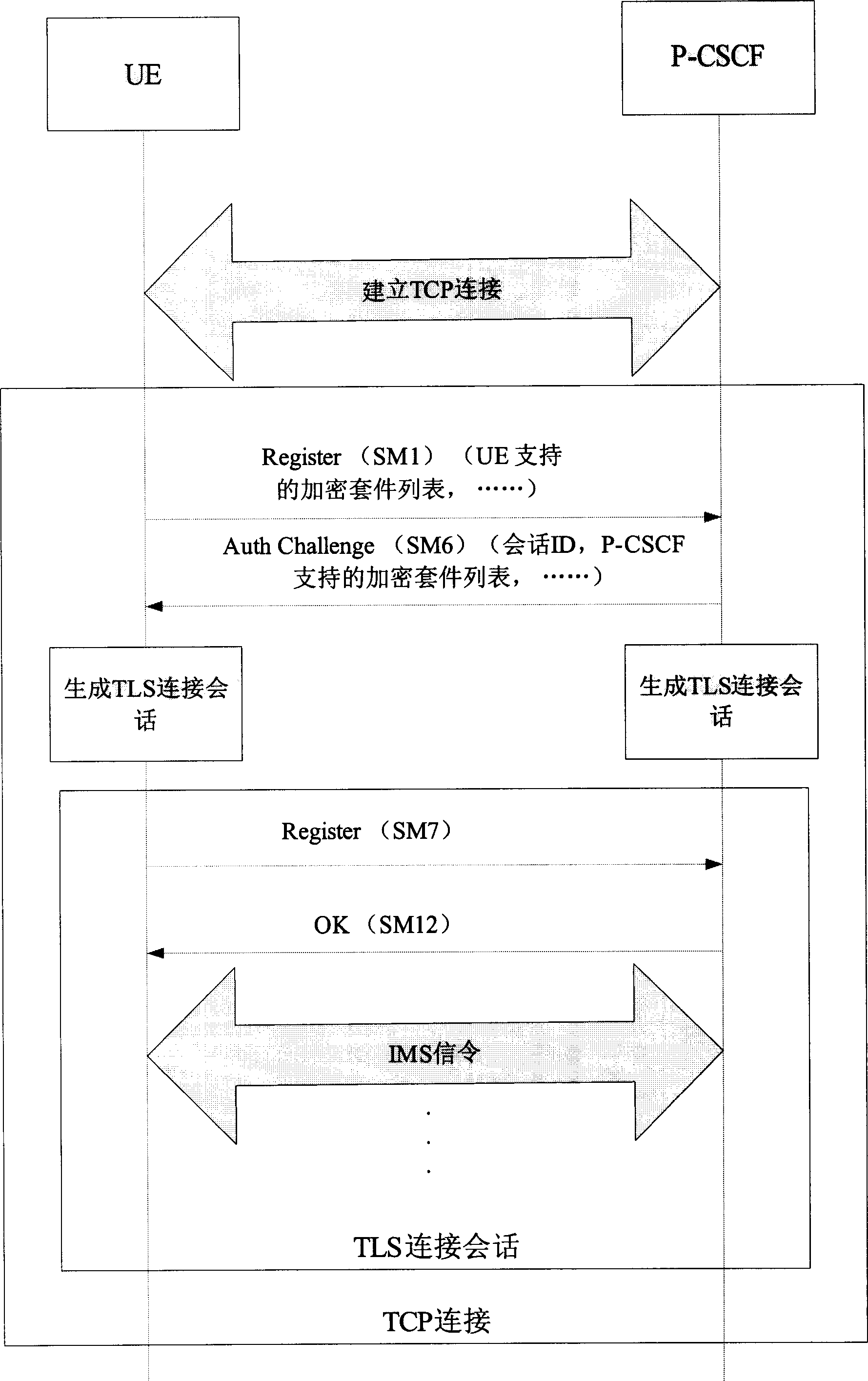
Method for protecting access security of IP multimedia subsystem based on TLS
ActiveCN1697368ASimple processOvercoming weak two-way authentication problemsData switching by path configurationSecuring communicationProtocol for Carrying Authentication for Network AccessMan-in-the-middle attack
In registration process through UE, using IMS AKA protocol to negotiate with P -CSCF, the method discloses uses TLS connect session in TCP connection. Then, the TLS connect session guarantees transmission security of IMS signaling between UE and P -CSCF. Features are: simple implementing procedure, being able to protect access safety of IMS. Comparing with prior art, the invention overcomes issue of weak bi-directional authentication so that attacker is not able to implement intermediator attack.
Owner:ZTE CORP
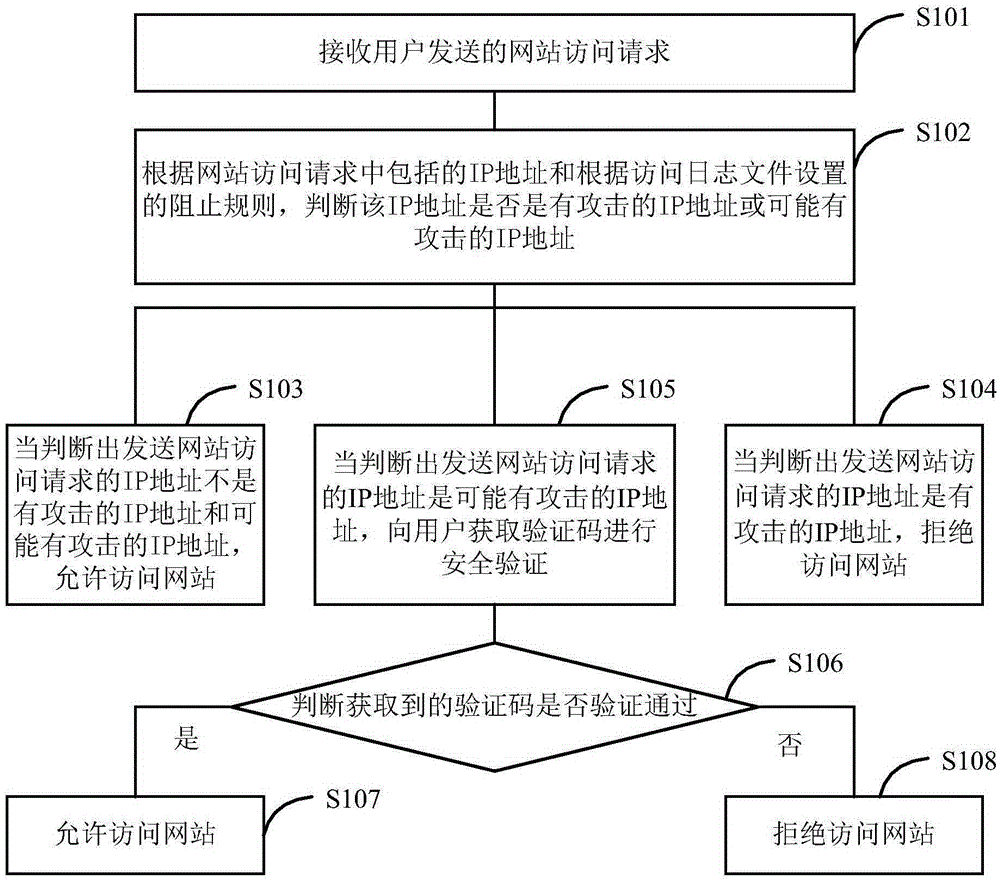
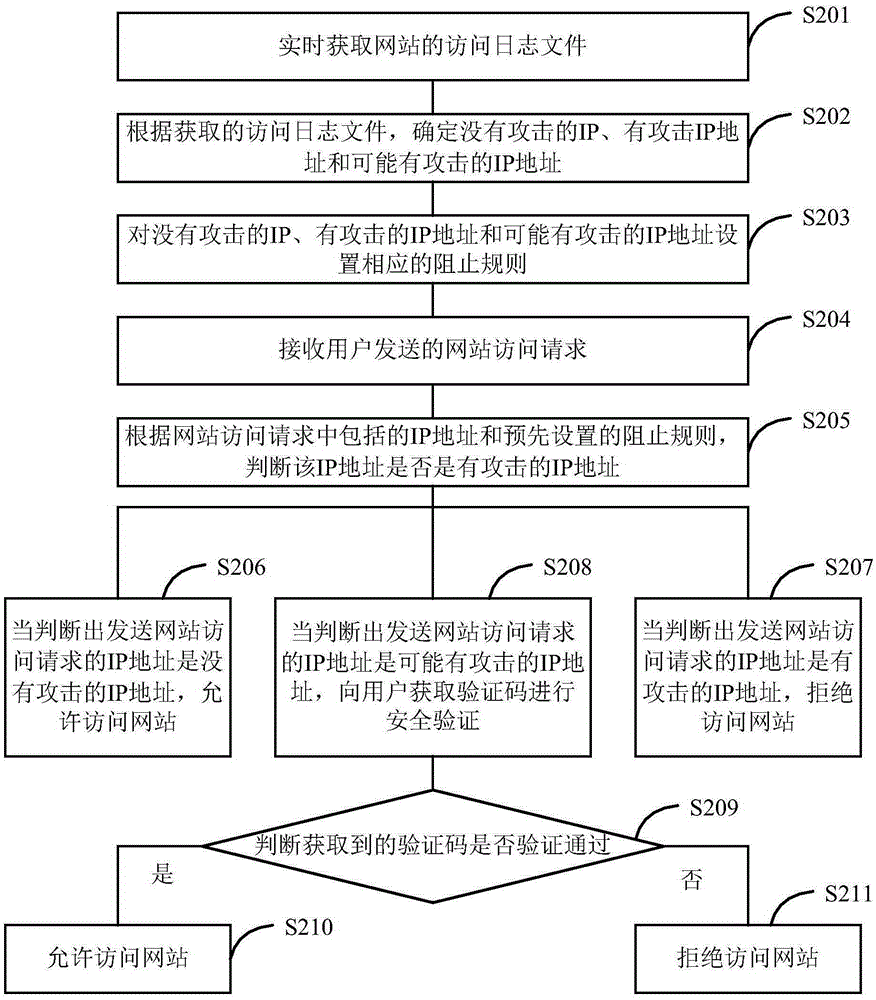
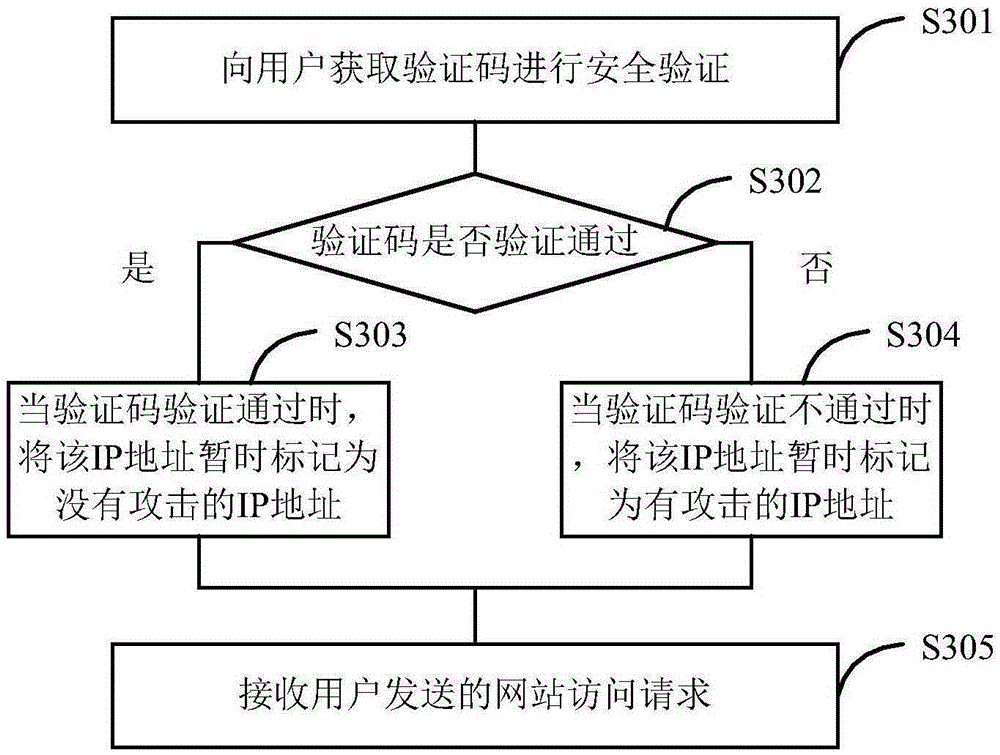
Website secure access realization method and apparatus
The embodiments of the invention provide a website secure access realization method and apparatus. The method comprises the following steps: receiving a website access request sent by a user; according to an IP address included in the request and according to prevention rules set by an access log file, determining whether the IP address is an attacking IP address or a possible attacking IP address; when it is determined that the IP address is neither an attacking IP address nor a possible attacking IP address, allowing access to a website; when it is determined that the IP address is an attacking IP address, rejecting the access to the website; when it is determined that the IP address is a possible attacking IP address, obtaining a verification code from a user for security verification, and in case of successful verification, allowing the access to the website; and in case of verification failure, rejecting the access to the website. The method provided by the invention can dynamically adjust access restriction rules according to a dynamical access log, realizes dynamic adjustment of network security access, and accordingly improves the flexibility and the automation degree of arrangement of network security access rules.
Owner:新浪技术(中国)有限公司
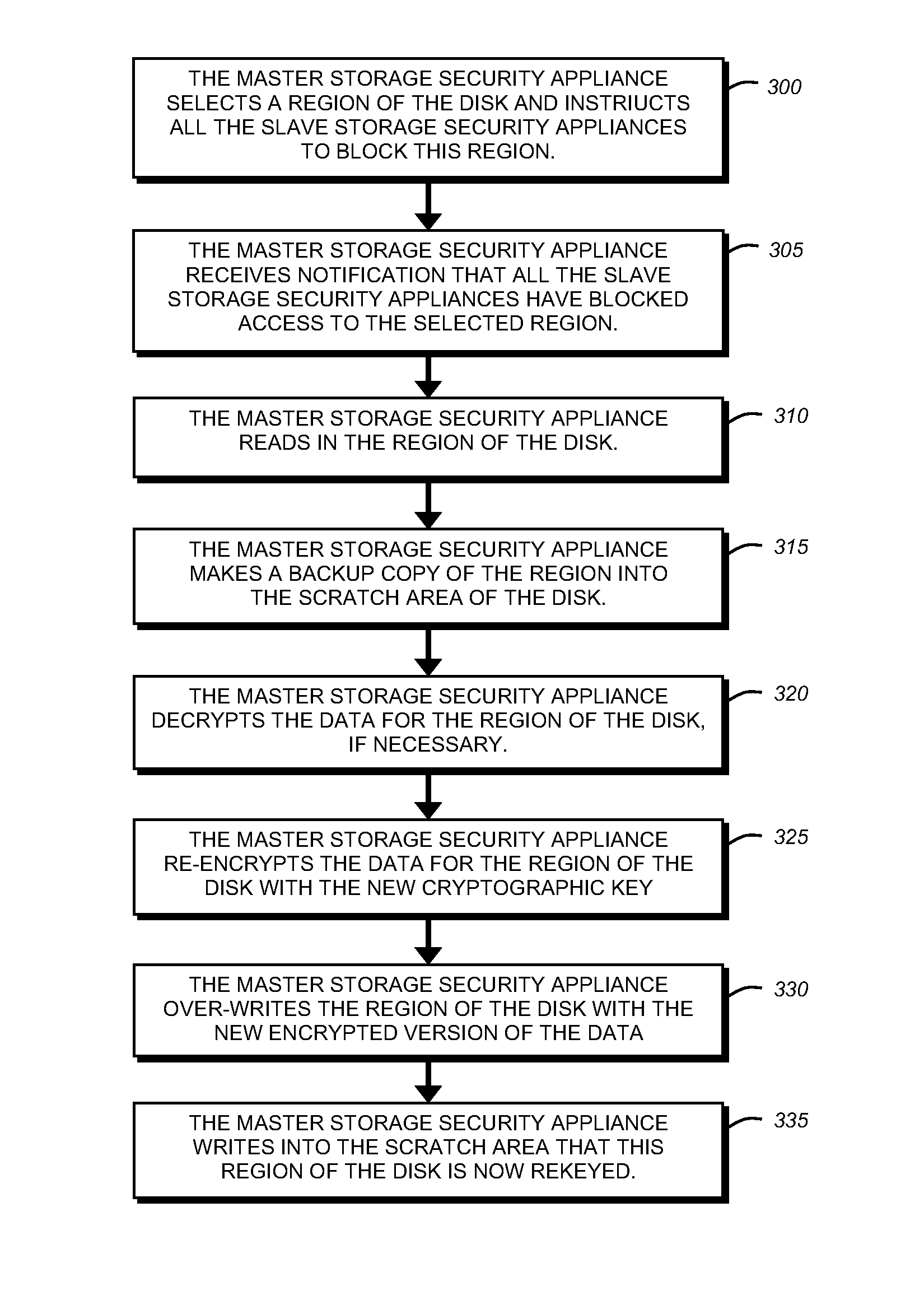
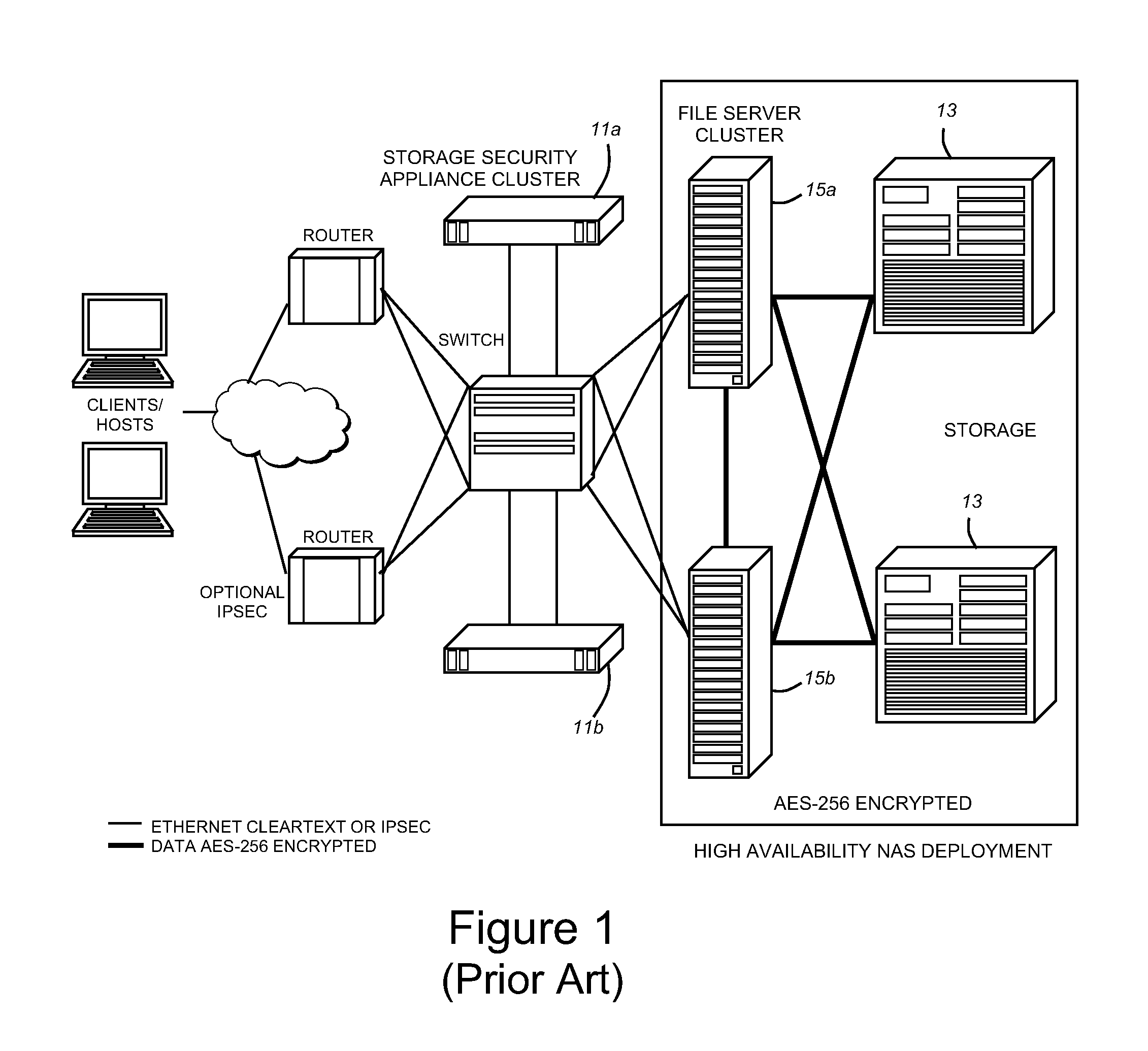
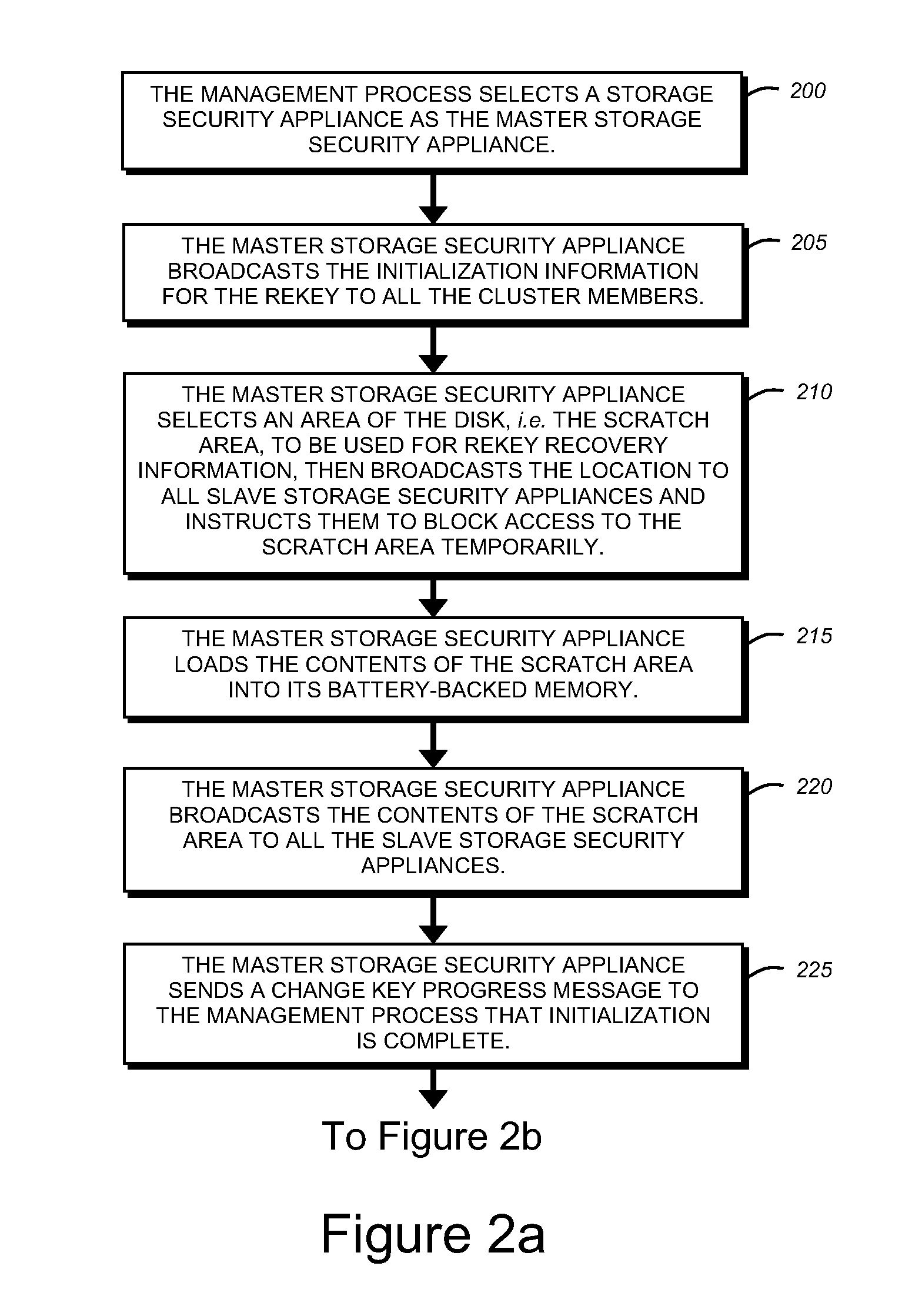
Background encryption of disks in a large cluster
ActiveUS8171307B1Secure accessDigital data processing detailsUnauthorized memory use protectionStorage securityEncryption
The invention provides for rekeying a large cluster of storage security appliances which allows more than two of the storage security appliances to proxy a single storage medium while encrypting the storage medium in a manner that is transparent to any attached server. The invention provides a method for synchronizing encryption of the disk among a large cluster of storage security appliances, while allowing all of the storage security appliances involved to access the storage device being rekeyed in a secure fashion.
Owner:NETWORK APPLIANCE INC
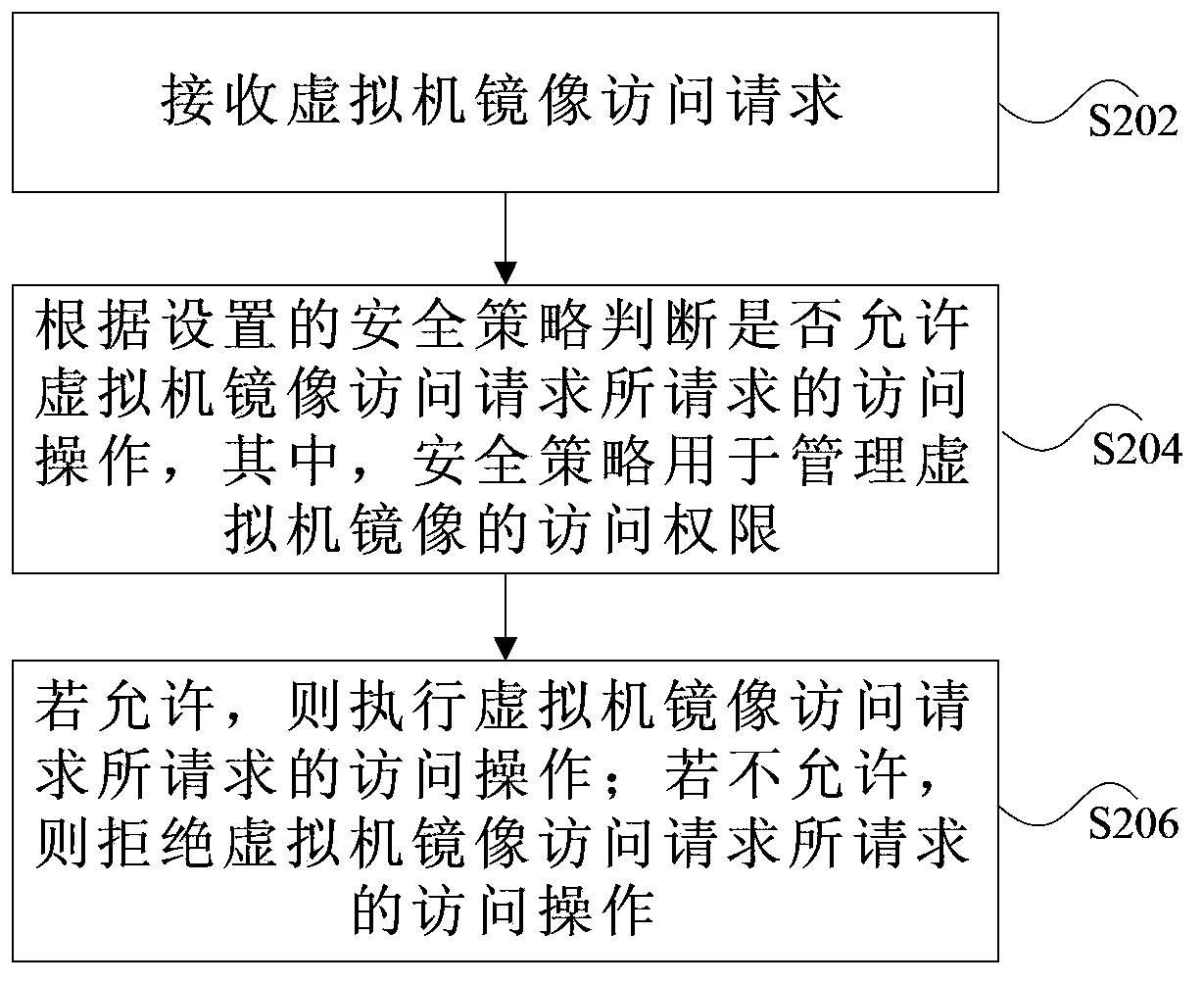
Safety control method and device for virtual machine mirror images
InactiveCN103457974ASecure AccessGuaranteed legalityTransmissionSoftware simulation/interpretation/emulationSecurity policyVirtual machine
The invention discloses a safety control method and device for virtual machine mirror images. The method comprises the steps that in a virtual machine system, a safety strategy is preset and is used for protecting the safety of the virtual machine images in the whole life period; in the operation period and in the rest period of the virtual machine mirror images, an access control mechanism is adopted so as to prevent theft and modification conducted on the virtual machine mirror images; before the virtual machine images start, safety inspection is adopted to prevent mis-configuration and cheat to the preset virtual machine mirror images. The safety control method and device for the virtual machine mirror images solve the problem that potential safety hazards exist when the virtual machine mirror images are accessed, and ensures the access safety of a virtual machine mirror images.
Owner:ZTE CORP
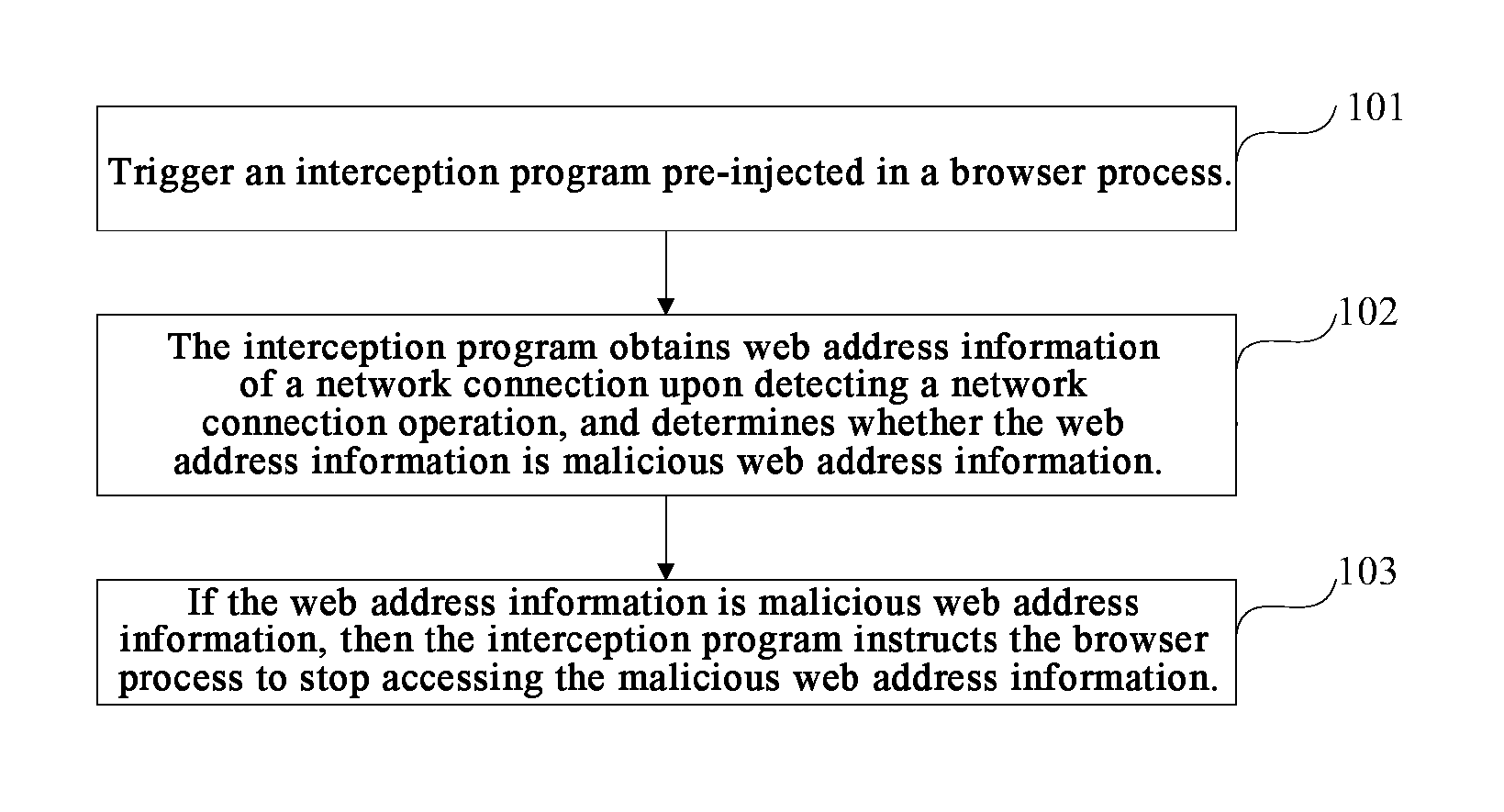
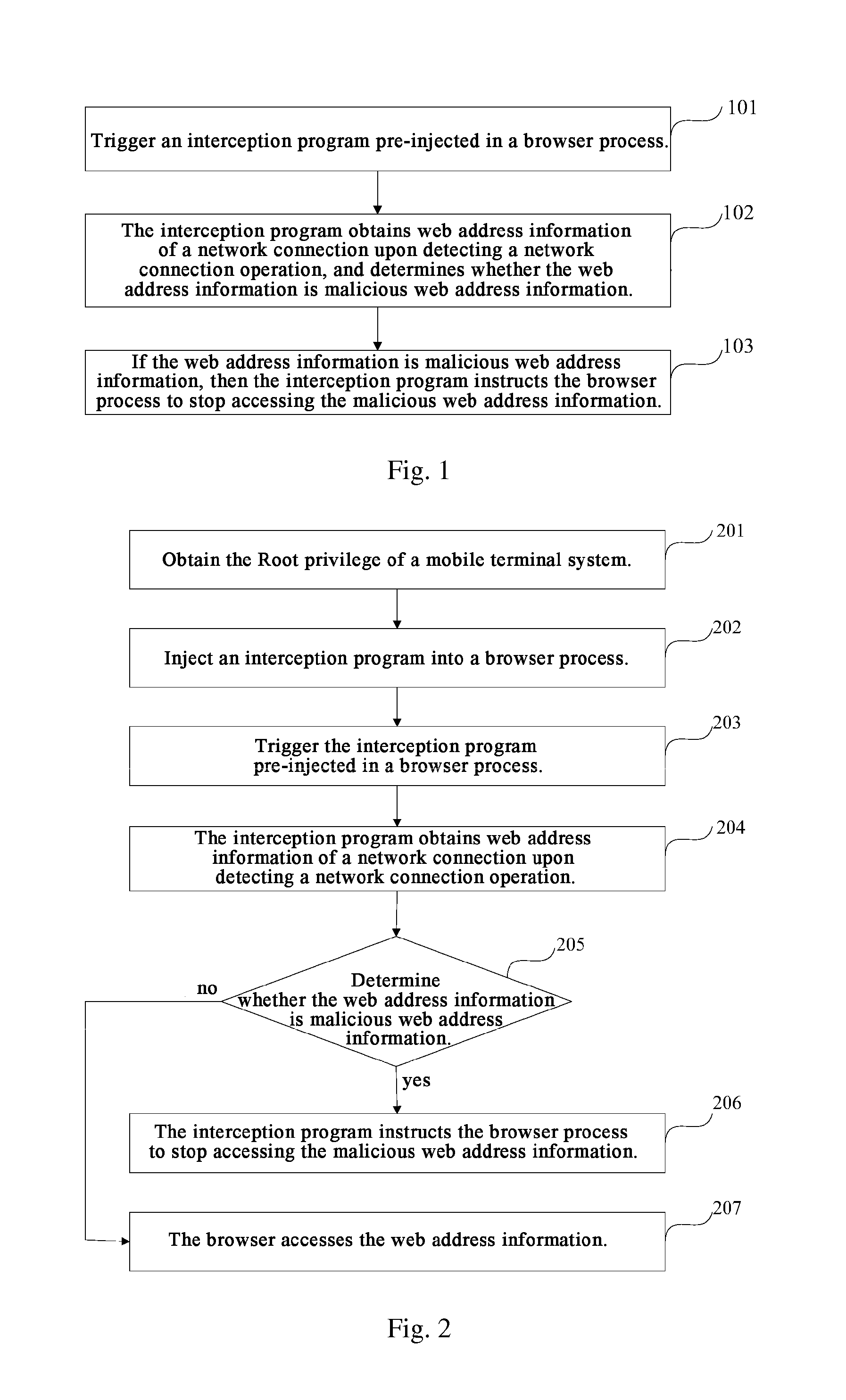
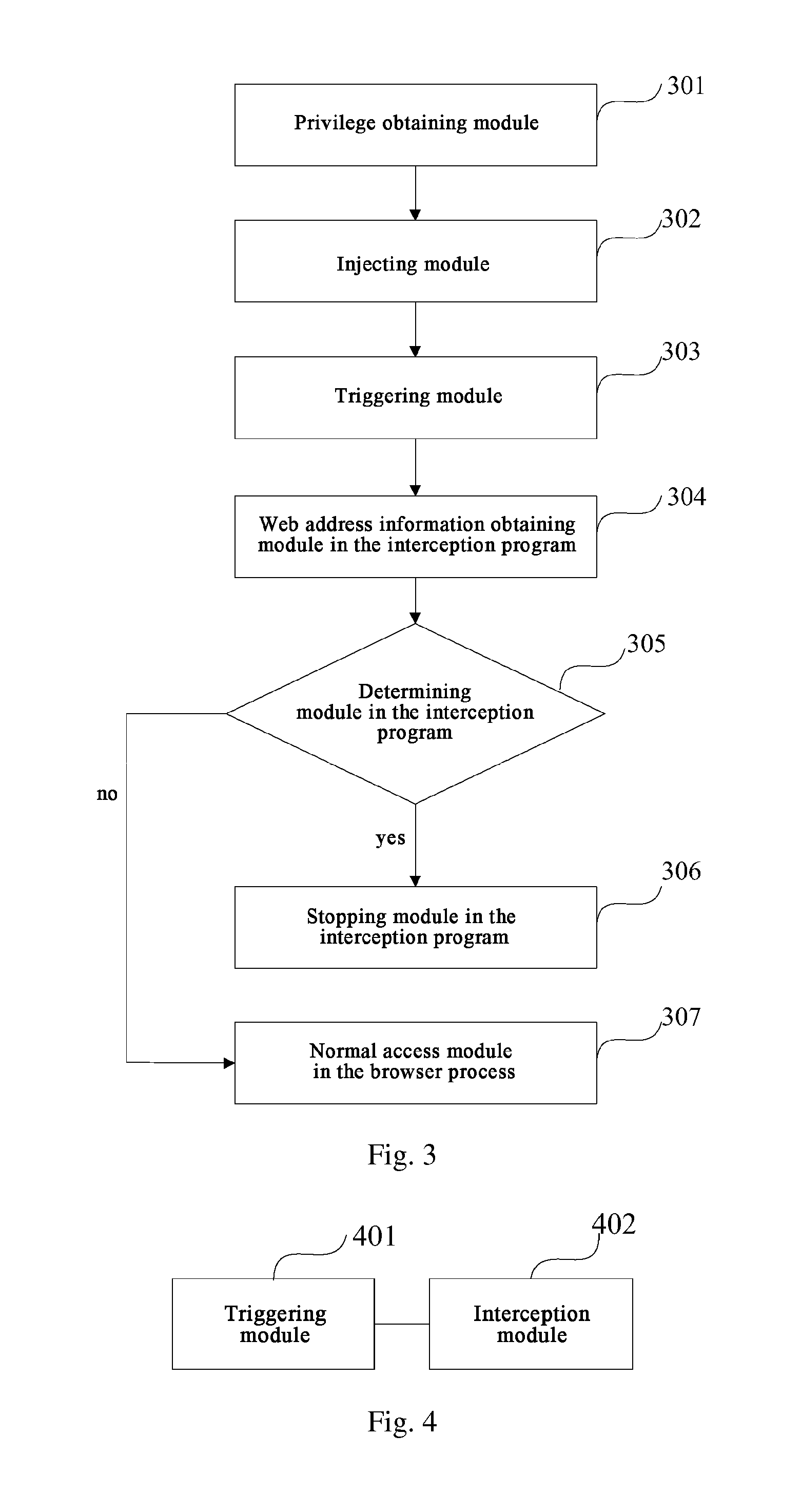
Method, Device And System For Intercepting Web Address
ActiveUS20150381645A1Secure network accessSecure AccessMemory loss protectionError detection/correctionNetwork connectionUniform resource locator
Disclosed are a method, device and system for intercepting a web address. The method comprises: triggering an interception program pre-injected in a browser process; the interception program obtaining web address information of a network connection upon detecting a network connection operation, and determining whether the web address information is malicious web address information; and if the web address information is malicious web address information, the interception program instructing the browser process to stop accessing the malicious web address information. The present disclosure can interrupt a connection of a malicious URL in time.
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com