Website secure access realization method and apparatus
A website access and security access technology, applied in the network field, can solve the problems of not being able to add dynamically and the degree of automation is not high, and achieve the effect of ensuring safe access, improving flexibility and automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
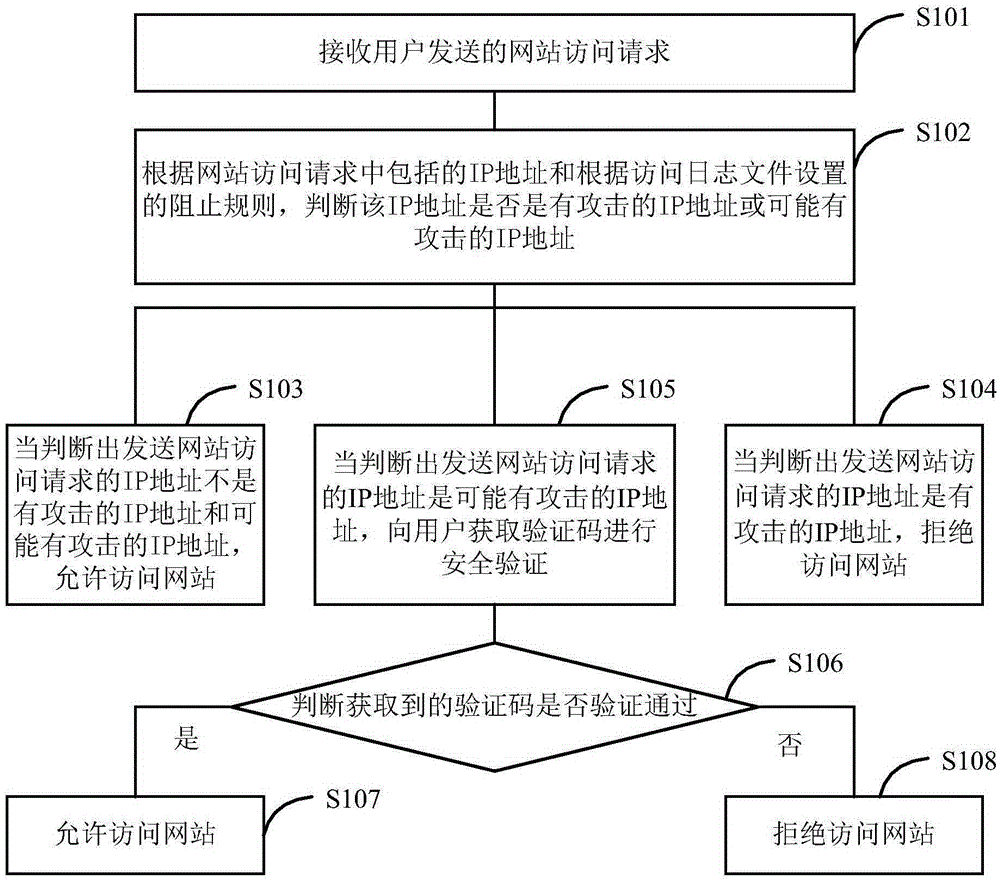
[0051] Embodiment 1 of the present invention provides a method for implementing secure website access, the process of which is as follows figure 1 shown, including the following steps:
[0052] Step S101: Receive a website access request sent by a user.
[0053]When a user wants to visit a website, a website access request will be sent, and the website access request at least includes the IP address information of the user who sent the request.
[0054] Step S102: According to the IP address included in the website access request and the blocking rules set according to the access log file, it is judged whether the IP address is an attacking IP address.
[0055] Wherein, the blocking rule is a blocking rule set for IP addresses with attacks and IP addresses with possible attacks according to the access log files. Access log files can be obtained in real time or periodically, and the blocking rules can be updated when attacking IP addresses and possible attacking IP addresses ...
Embodiment 2
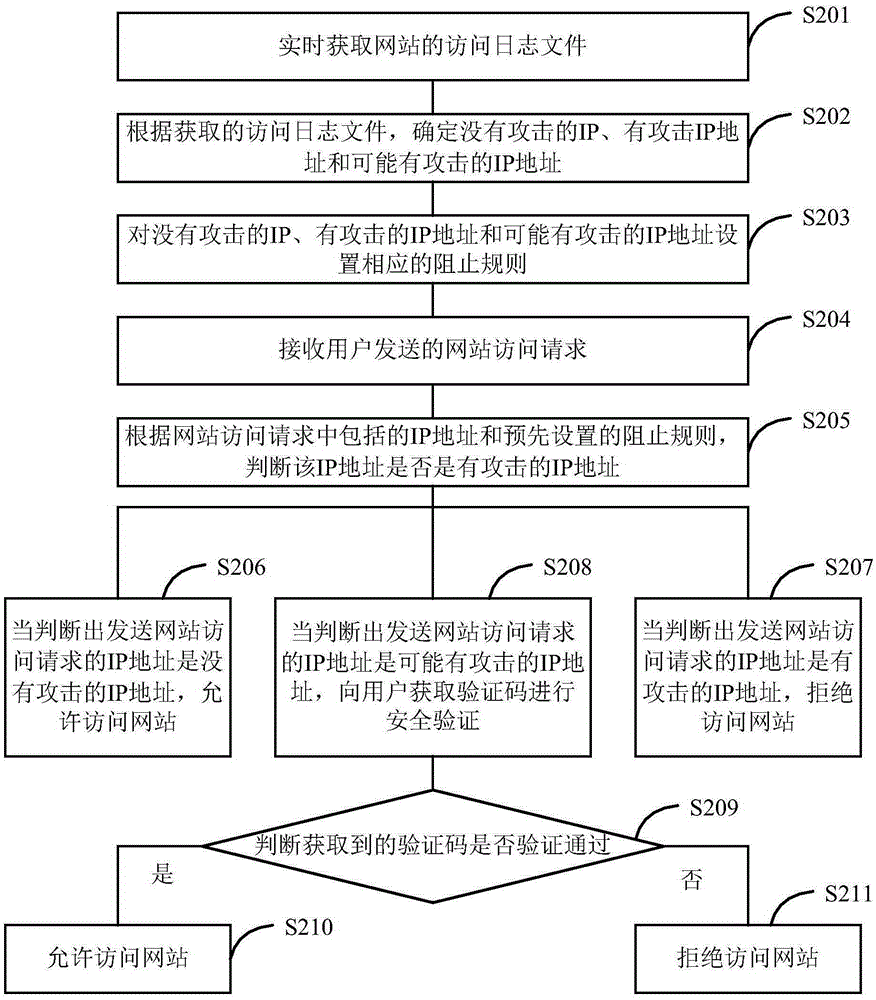
[0071] Embodiment 2 of the present invention provides a method for implementing secure website access. Before the access security verification described in Embodiment 1, it also includes the process of setting blocking rules. The method flow of this embodiment is as follows figure 2 shown, including the following steps:
[0072] Step S201: Obtain the access log files of the website in real time or periodically.
[0073] The Nginx system pushes the access log files to the kafka queue of the storm system in real time through the flume system, so as to obtain the access log files of the website in real time. You can also set the acquisition period to periodically acquire access log files.
[0074] Among them, Flume is a highly available, highly reliable, and distributed massive log collection, aggregation, and transmission system. Flume supports customizing various data senders in the log system to collect data; at the same time, Flume provides Ability to perform simple proces...
Embodiment 3
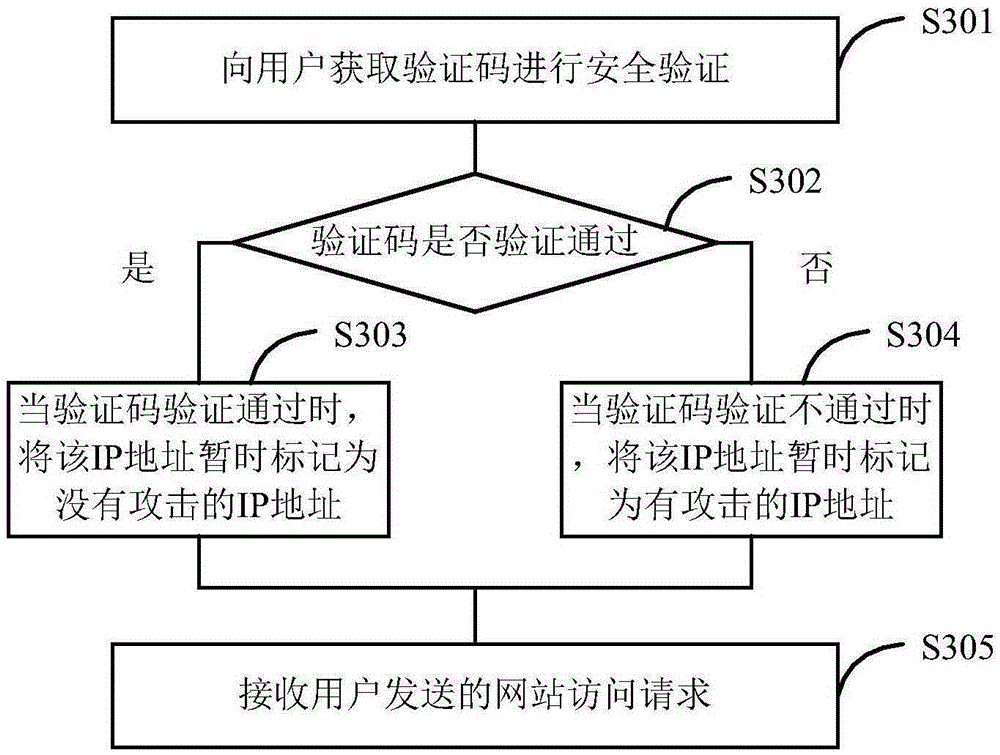
[0097] Embodiment 3 of the present invention provides a method for implementing secure website access. On the basis of the methods in Embodiment 1 and Embodiment 2, some blocking rule setting operations are added after inputting the verification code for IP addresses that are judged to be likely to be attacked. , its process is as follows image 3 shown, including the following steps:
[0098] Step S301: Obtain a verification code from the user for security verification.
[0099] For the IP address that may be attacked, at this time, it can be reverse-proxyed to a verification code webpage, allowing the user to enter the verification code through the client. If a verification code is entered, security verification is performed after obtaining the verification code.
[0100] Step S302: Whether the verification code is verified or not.
[0101] When the verification code is verified, step S303 is executed; when the verification code is not verified, step S304 is executed.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com