Patents
Literature
43 results about "Simple Mail Transfer Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Simple Mail Transfer Protocol (SMTP) is a communication protocol for electronic mail transmission. As an Internet standard, SMTP was first defined in 1982 by RFC 821, and updated in 2008 by RFC 5321 to Extended SMTP additions, which is the protocol variety in widespread use today. Mail servers and other message transfer agents use SMTP to send and receive mail messages. Proprietary systems such as Microsoft Exchange and IBM Notes and webmail systems such as Outlook.com, Gmail and Yahoo! Mail may use non-standard protocols internally, but all use SMTP when sending to or receiving email from outside their own systems. SMTP servers commonly use the Transmission Control Protocol on port number 25.
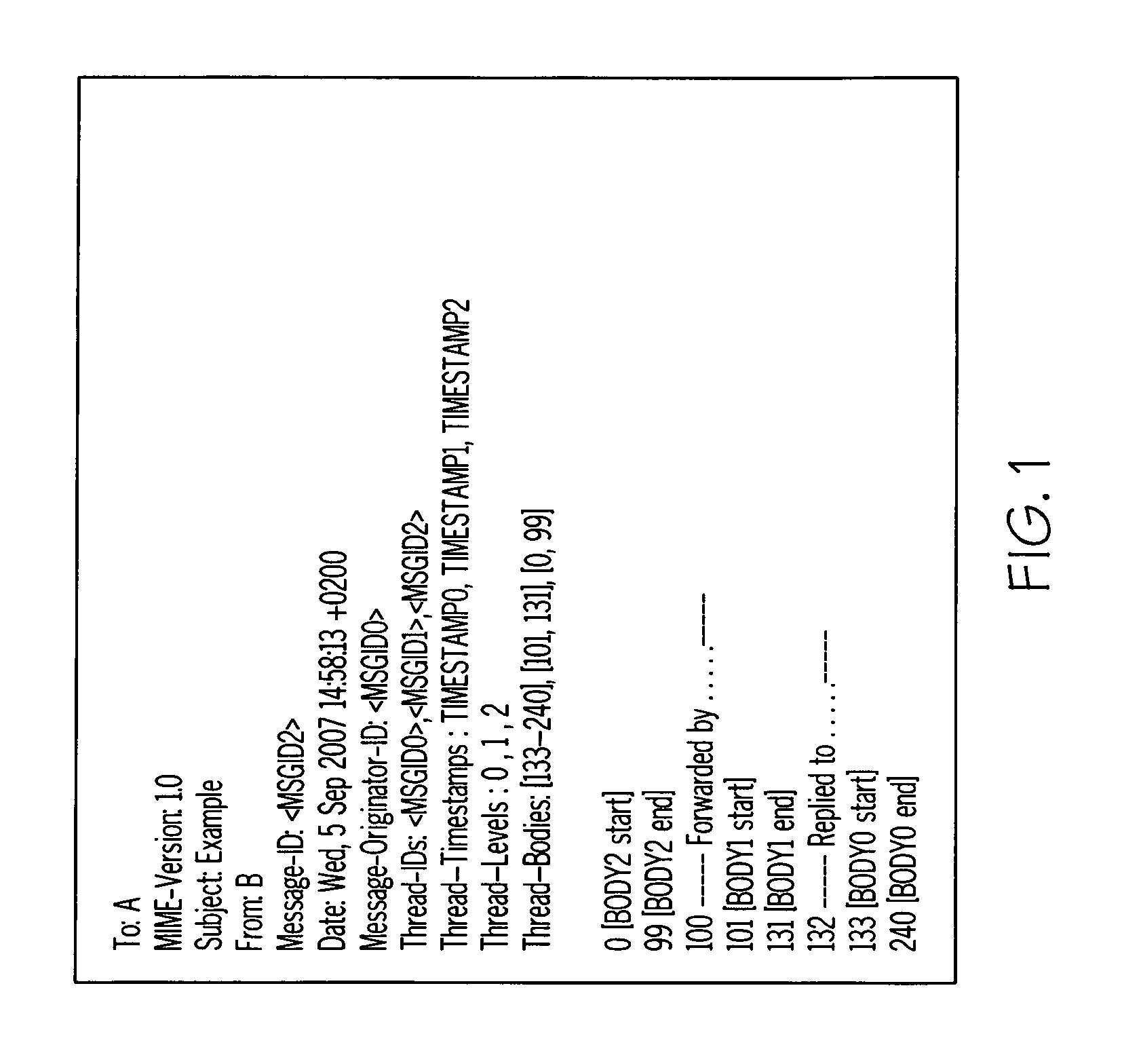
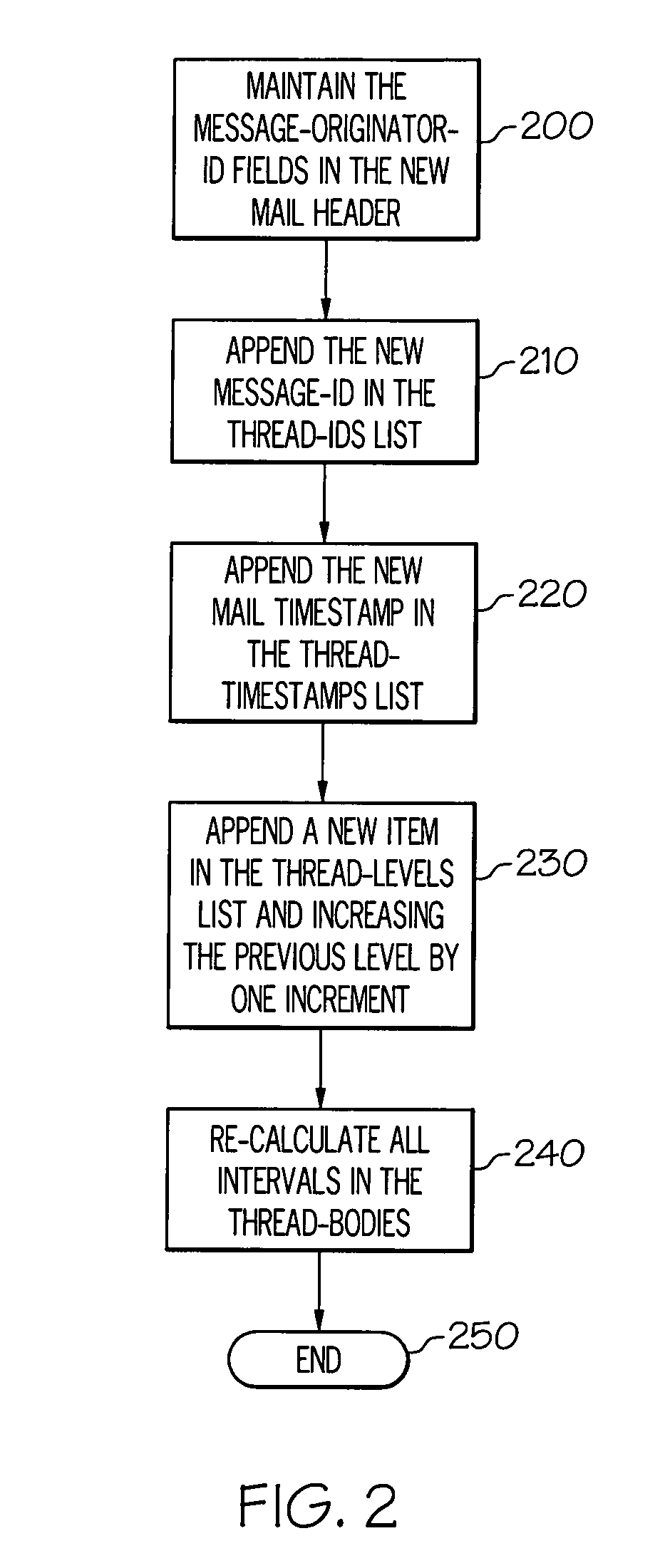
Thread based view and archive for simple mail transfer protocol (SMTP) clients devices and methods
InactiveUS7516186B1Data processing applicationsMultiple digital computer combinationsView basedTimestamp
A method for local archiving of e-mail messages in an e-mail client application according to various exemplary embodiments can include generating a mail thread including at least two e-mail messages transmitted and received between a message originator and at least one recipient; appending e-mail identification data into a header of the at least two e-mail messages when transmitted. The method may also include archiving related e-mail messages within the mail thread in an e-mail client application, comprising: searching for the related e-mail messages by identifying each e-mail message having a same message originator field; and merging non-redundant segments of each e-mail message into a single message document hierarchically by response level and timestamp. The method may further include displaying, on a display screen, the single message document according to a conversational view based upon a perspective of the response level of a user within the mail thread.
Owner:IBM CORP
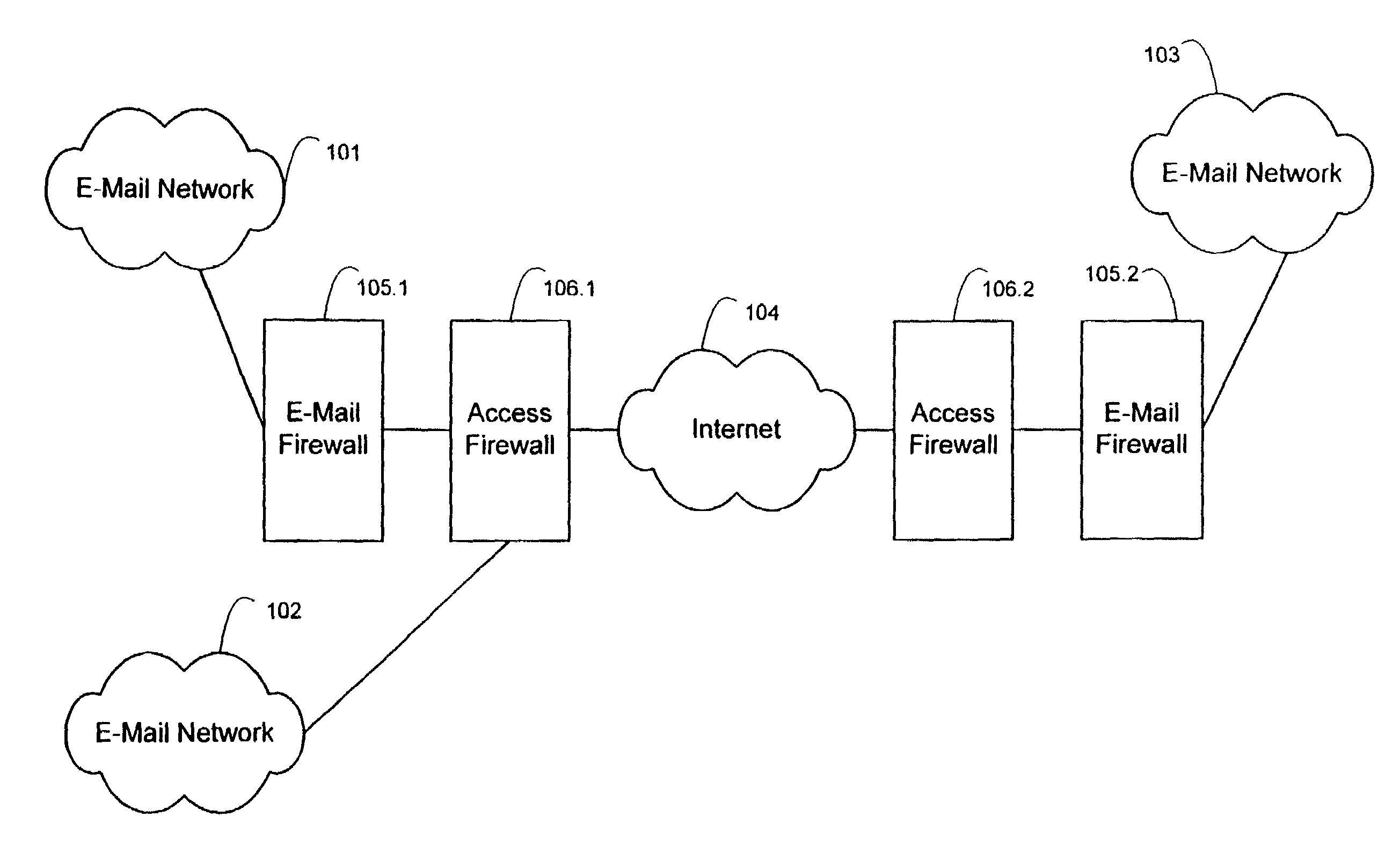
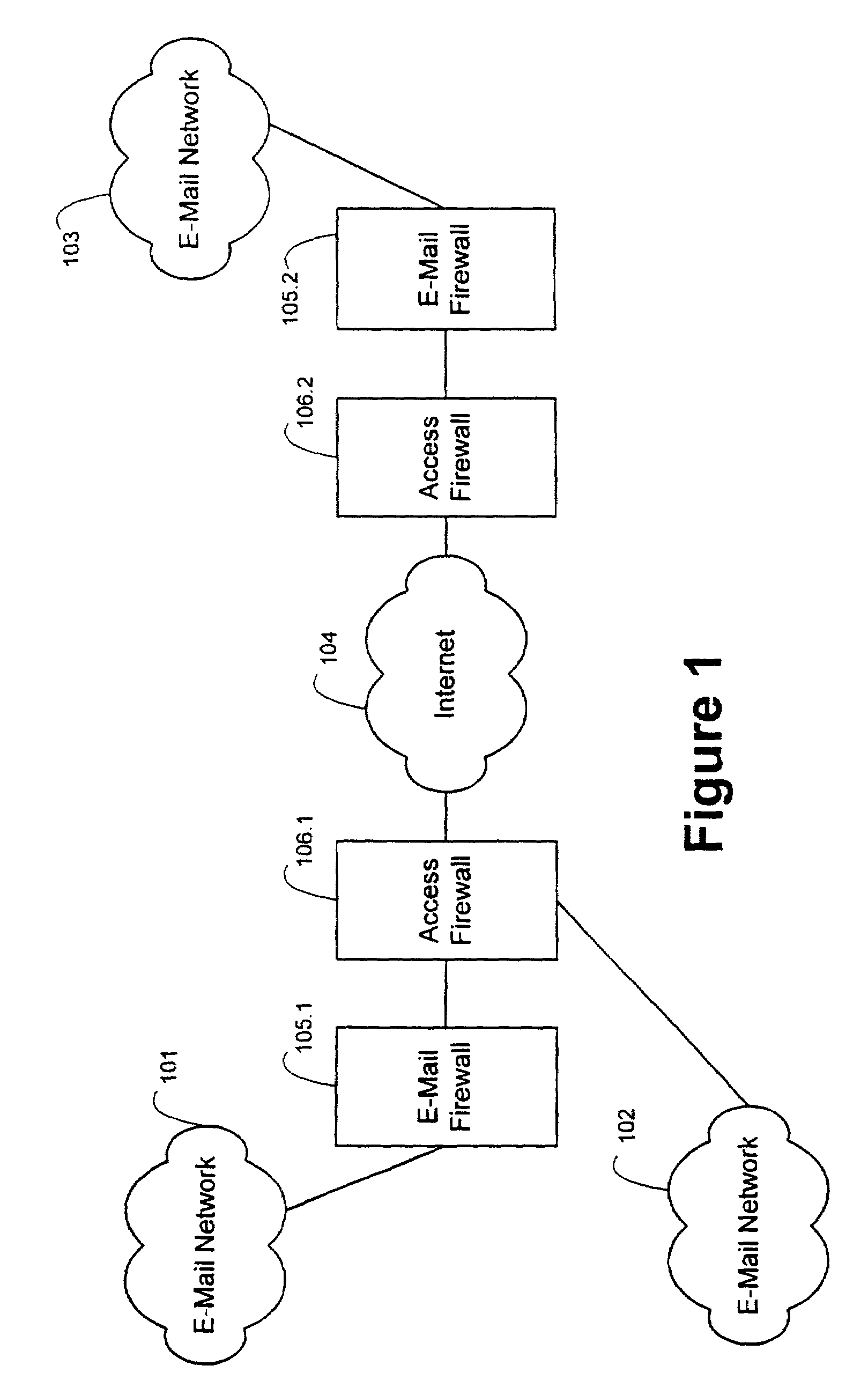
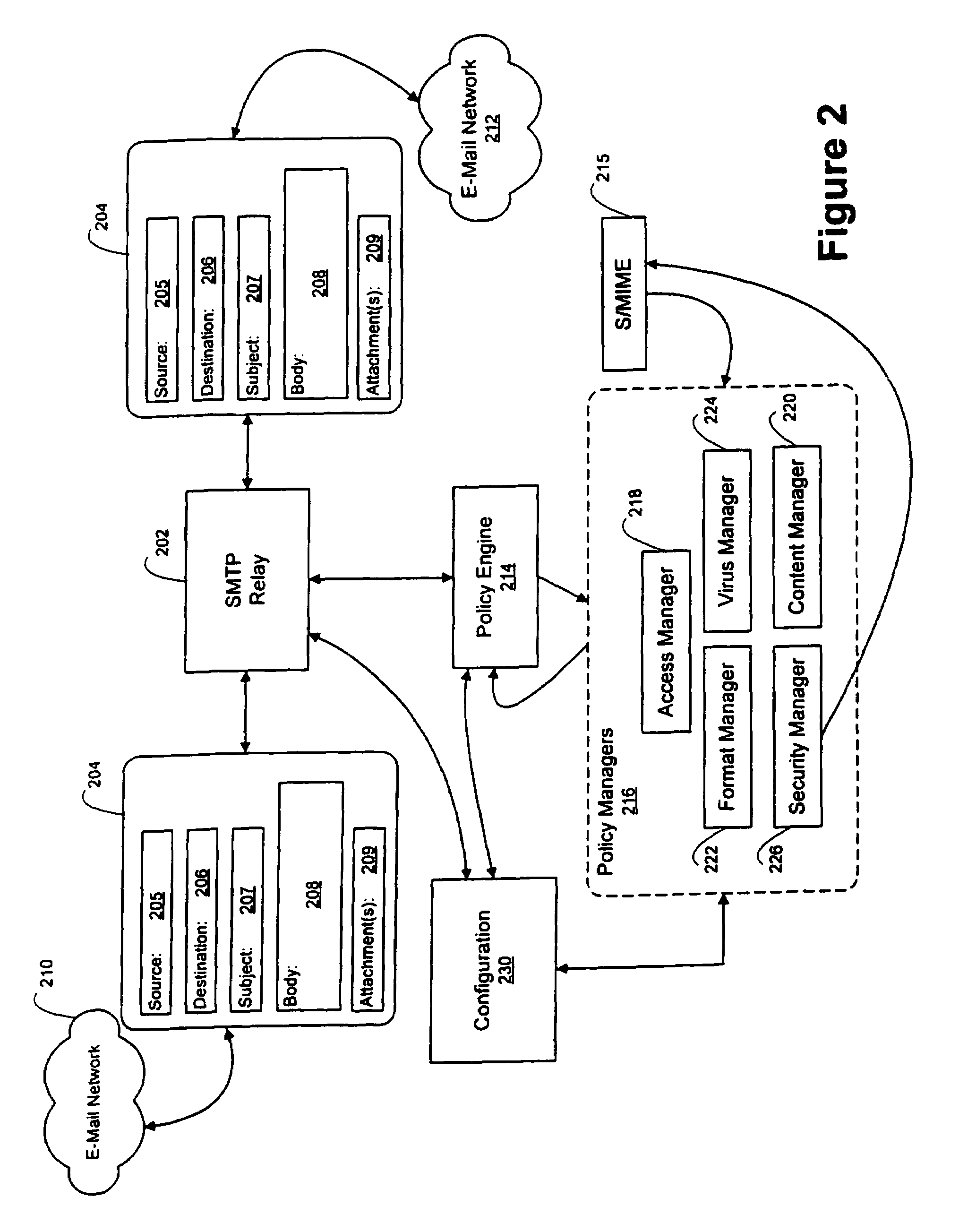
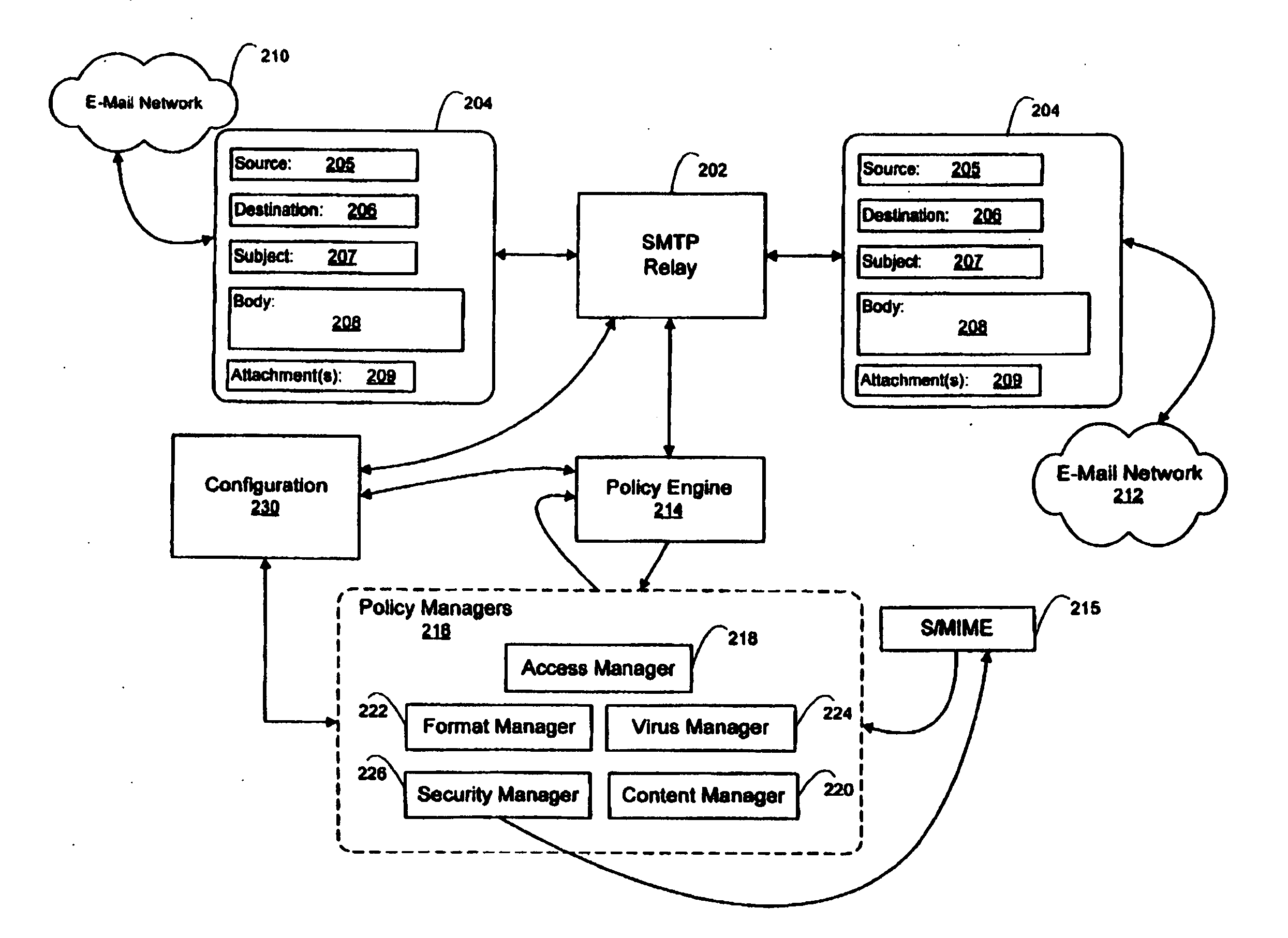
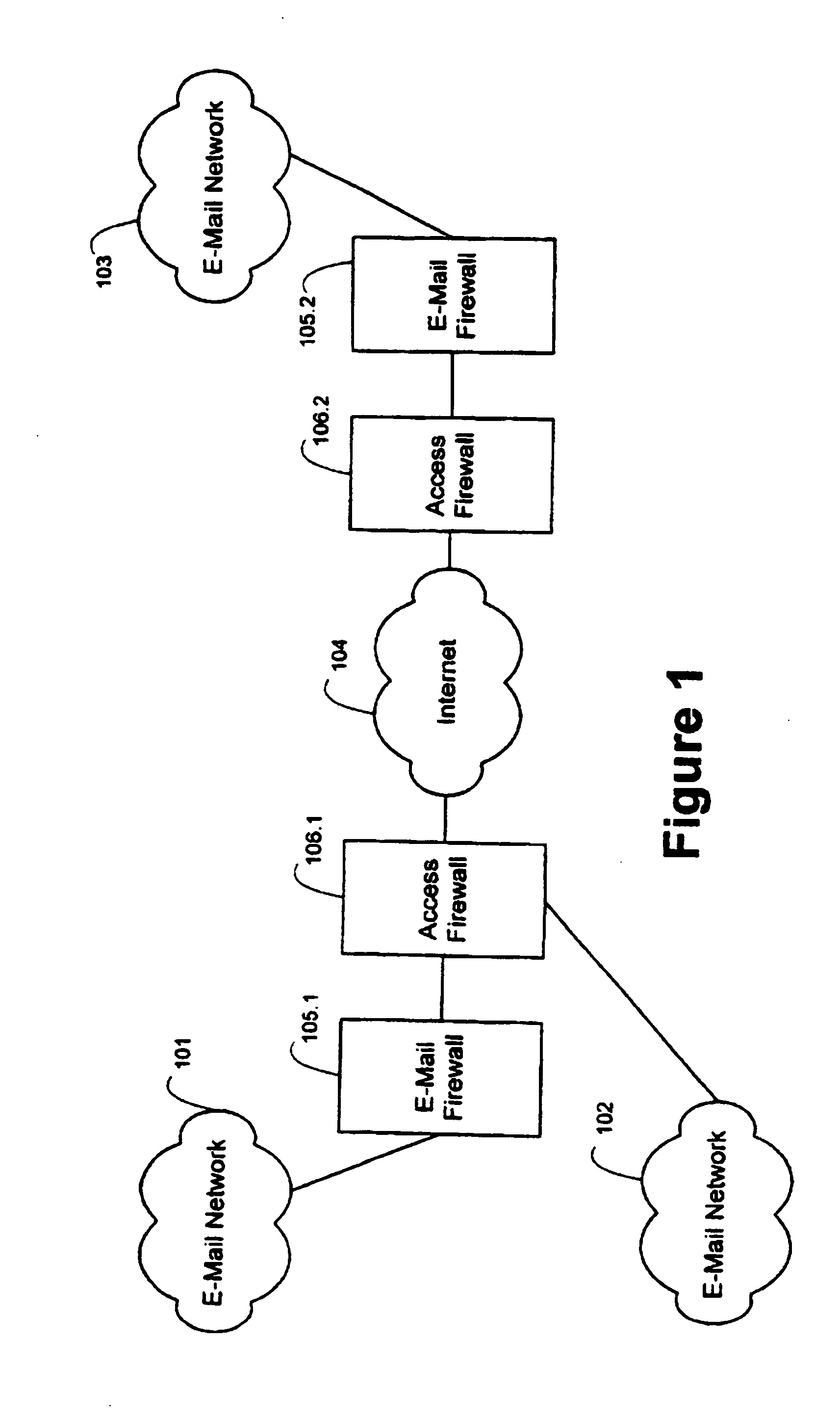
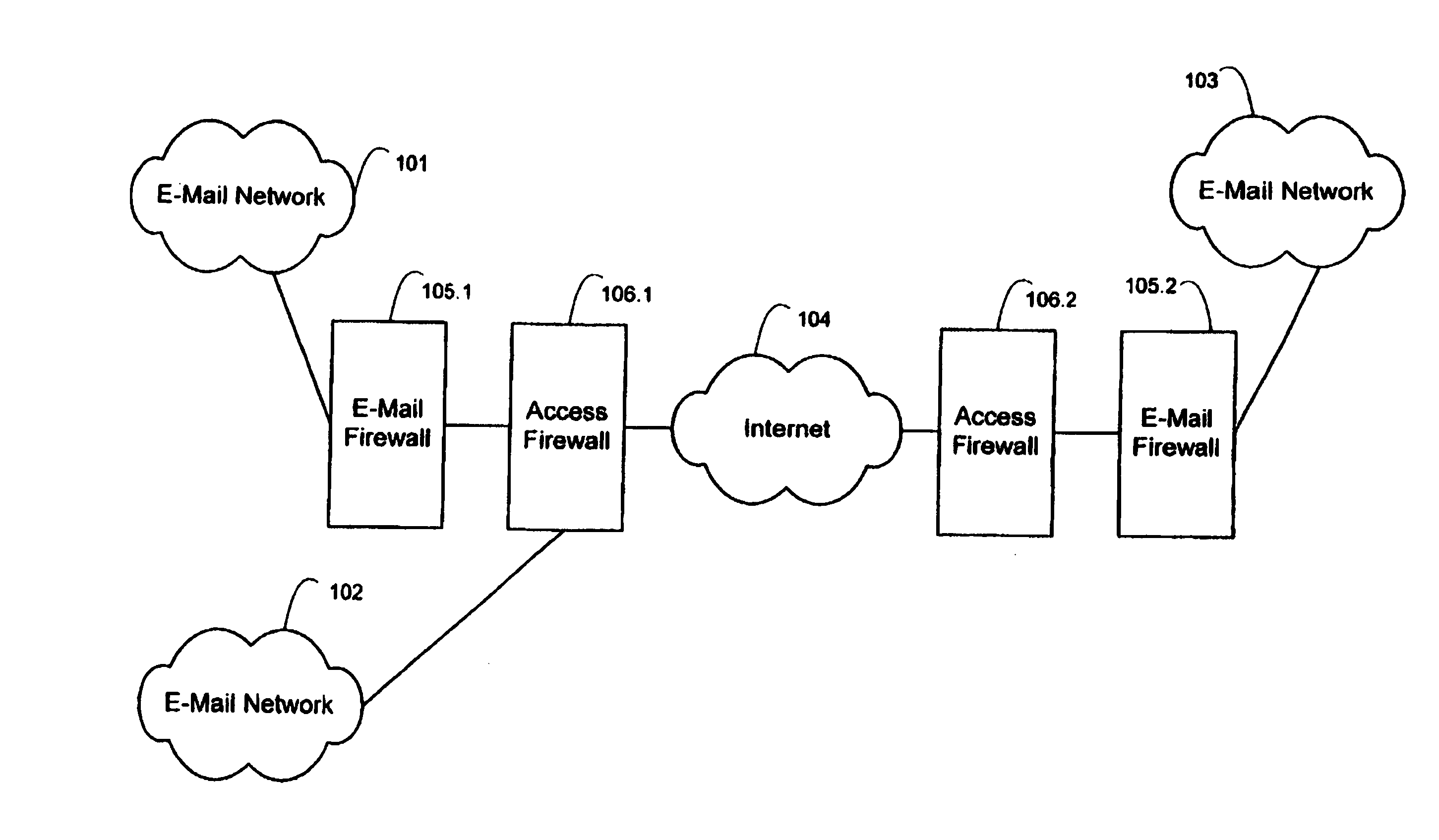
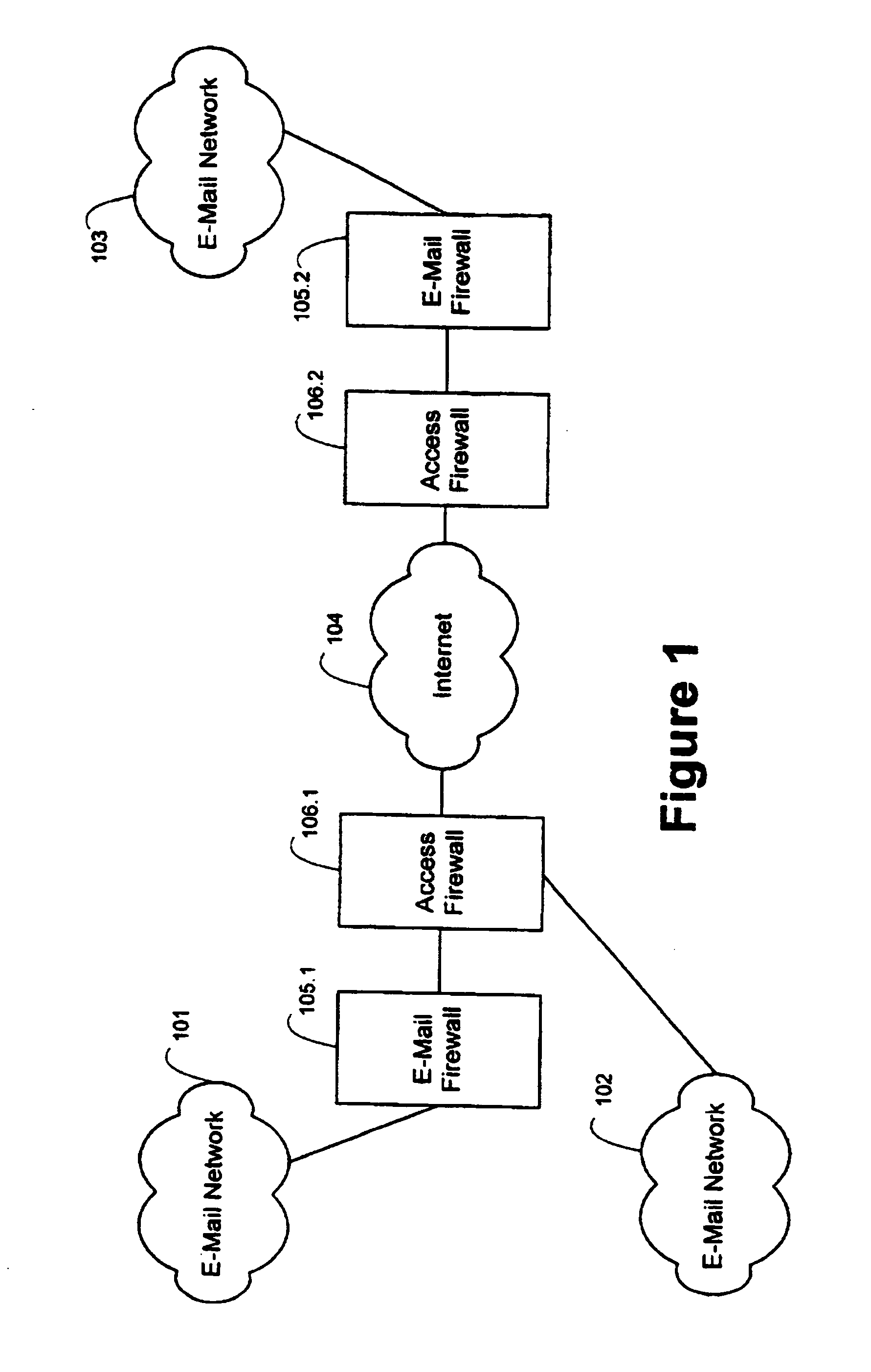
E-mail firewall with stored key encryption/decryption
InactiveUS7162738B2Easy to controlKey distribution for secure communicationMemory loss protectionVirusContent management
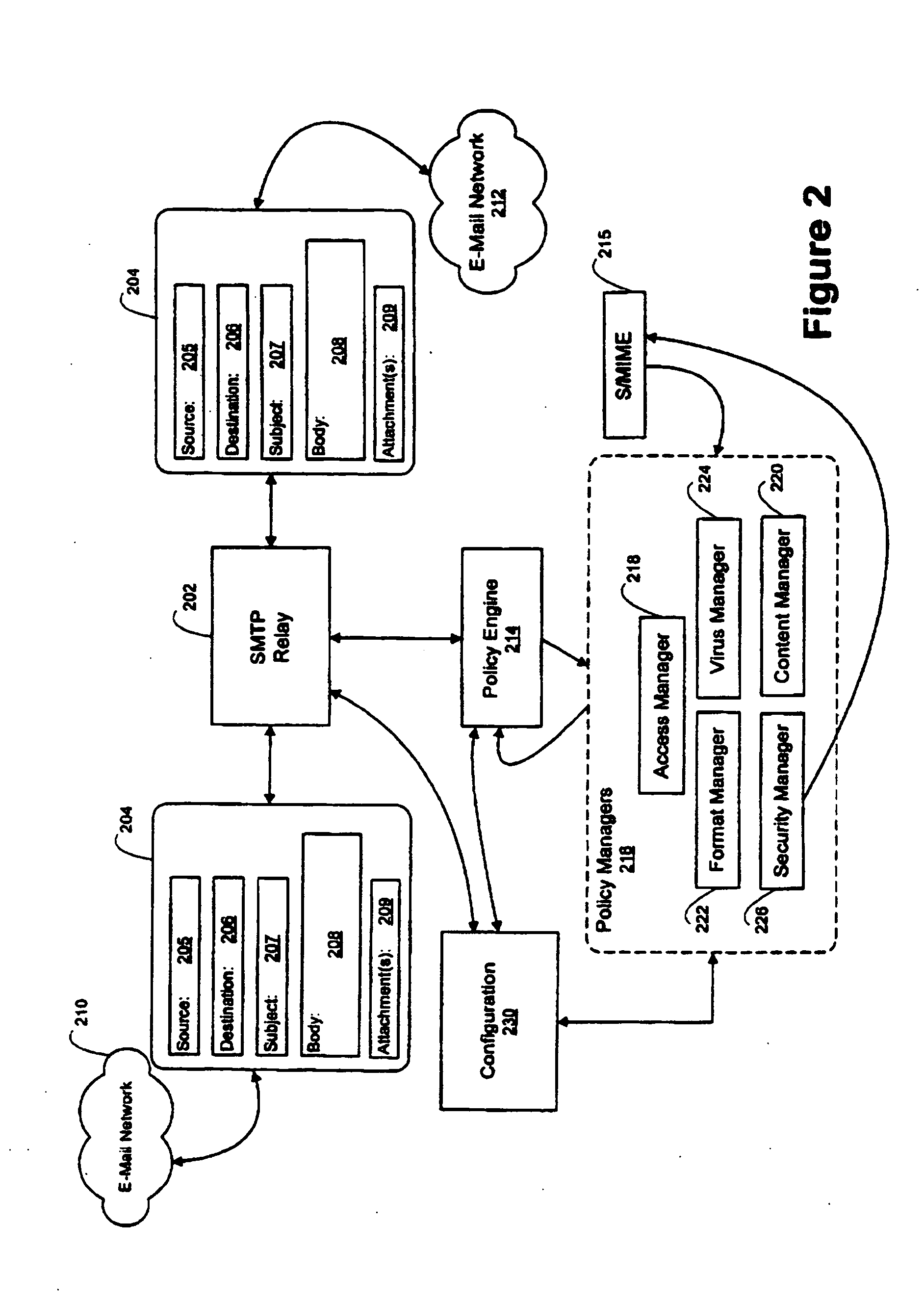
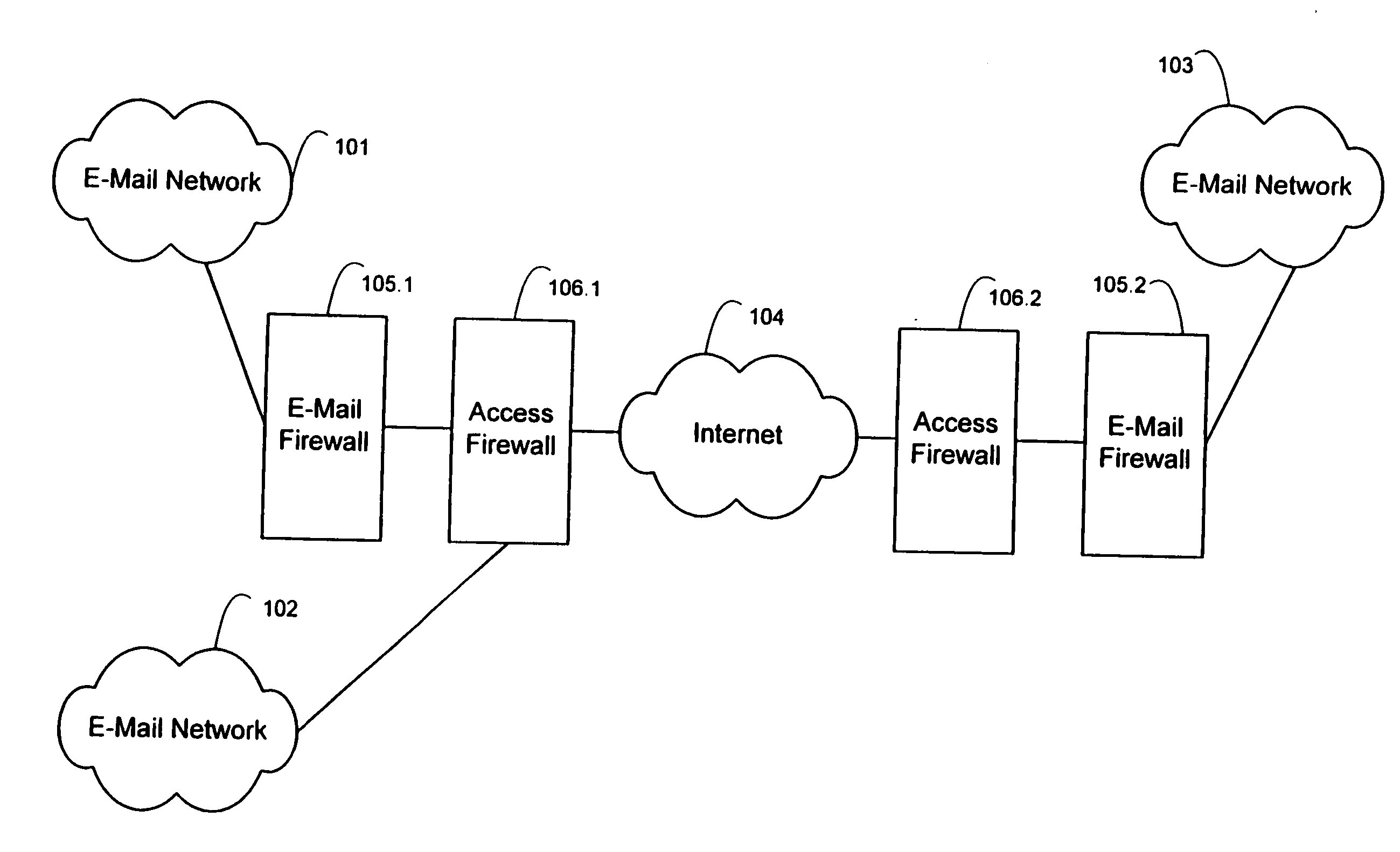
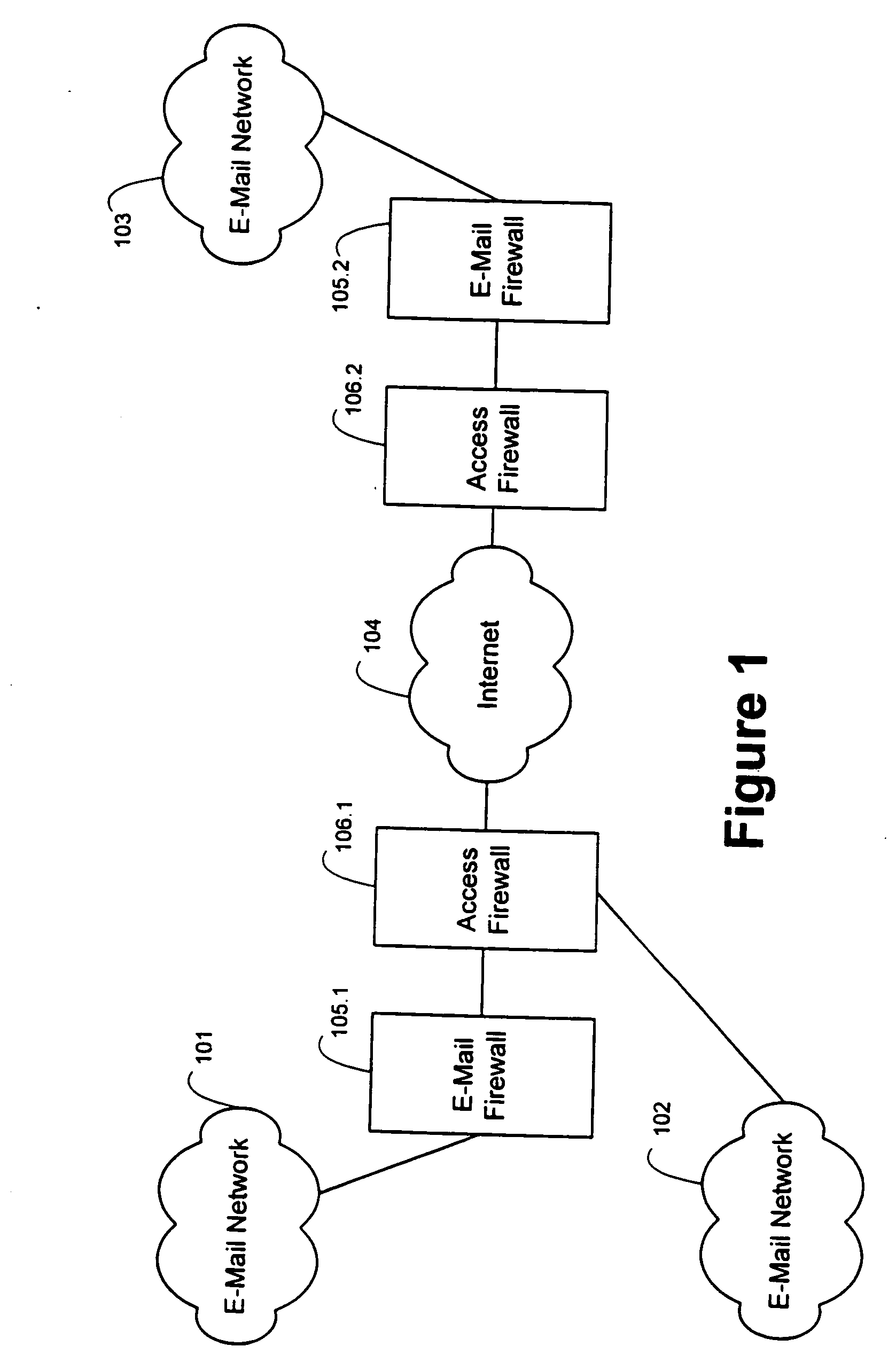
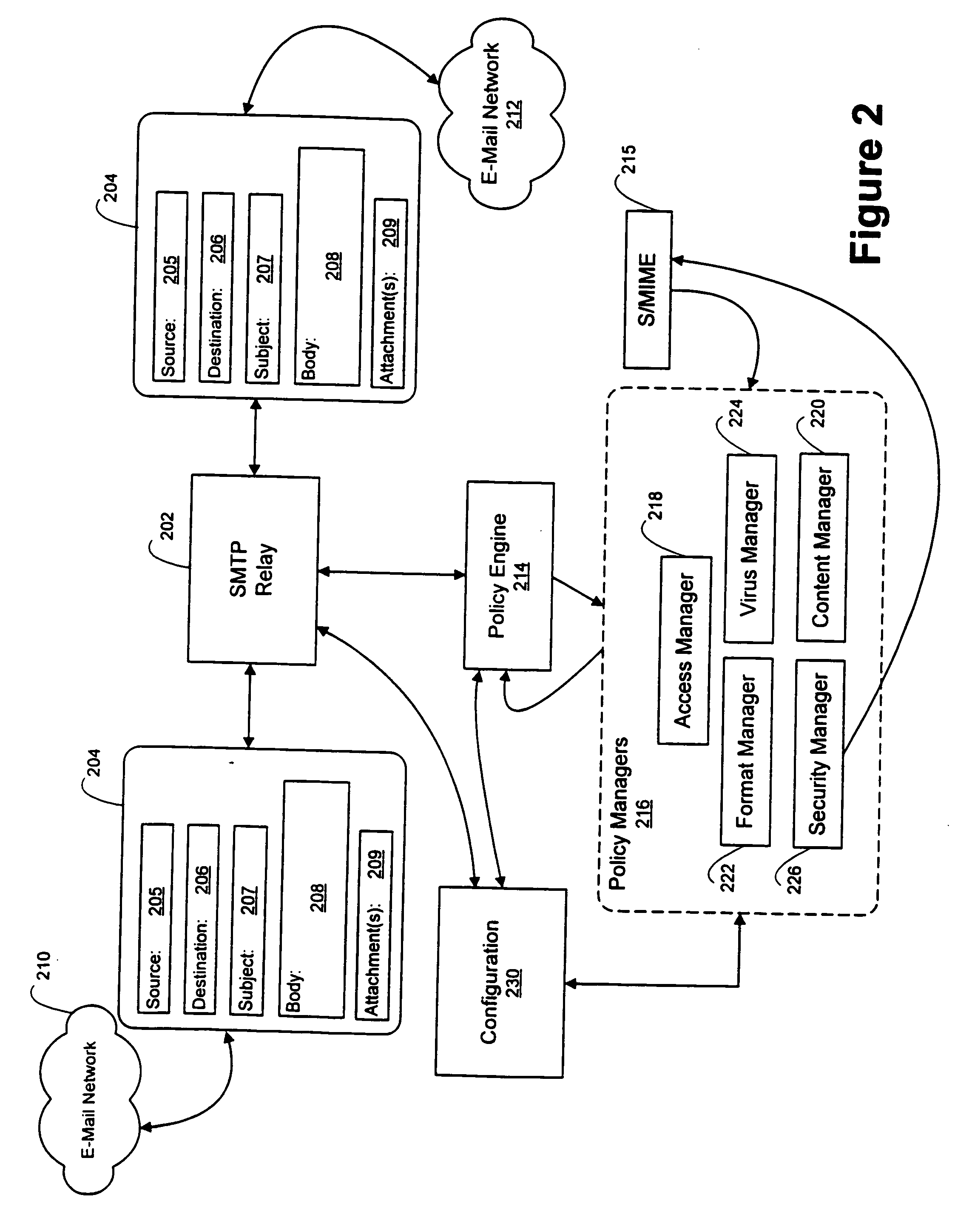
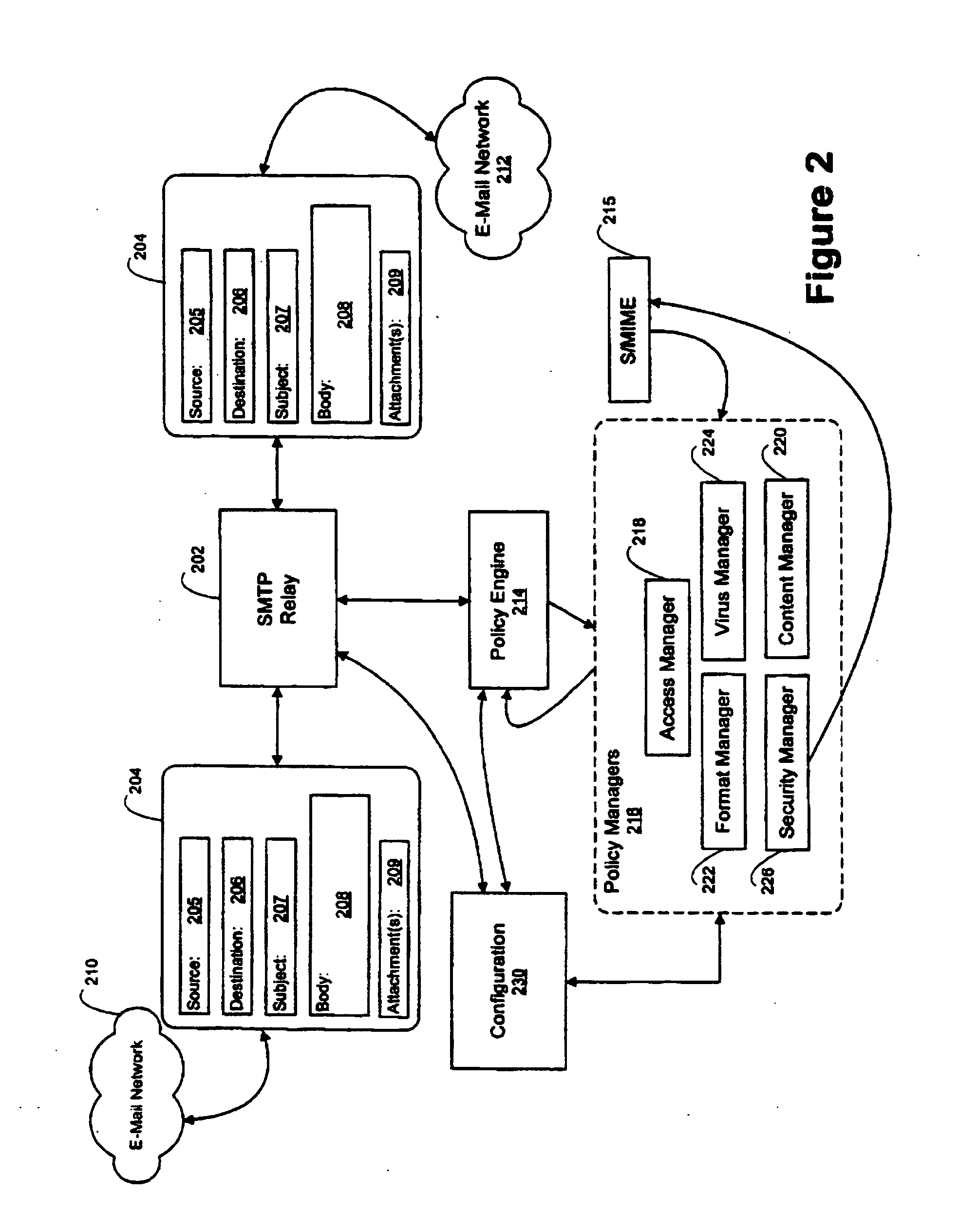
An e-mail firewall (105) applies policies to e-mail messages (204) between a first site and a plurality of second sites in accordance with a plurality of administrator selectable policies (216). The firewall comprises a simple mail transfer protocol (SMTP) relay (202) for causing the e-mail messages (204) to be transmitted between the first site and selected ones of the second sites. A plurality of policy managers (216) enforce administrator selectable policies. The policies, such as encryption and decryption policies, comprise at least a first source / destination policy (218), at least a first content policy (202) and at least a first virus policy (224). The policies are characterized by a plurality of administrator selectable criteria (310), a plurality of administrator selectable exceptions (312) to the criteria and a plurality of administrator selectable actions (314, 316, 322) associated with the criteria and exceptions. The policy managers comprise an access manager (218) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the source / destination policy (218). The policy managers (216) further comprise a content manager (220) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the content policy (220), and a virus manager (224) for restriction transmission of e-mail messages (204) between the first site and the second sites in accordance with the virus policy (224).
Owner:TUMBLEWEED COMM CORP
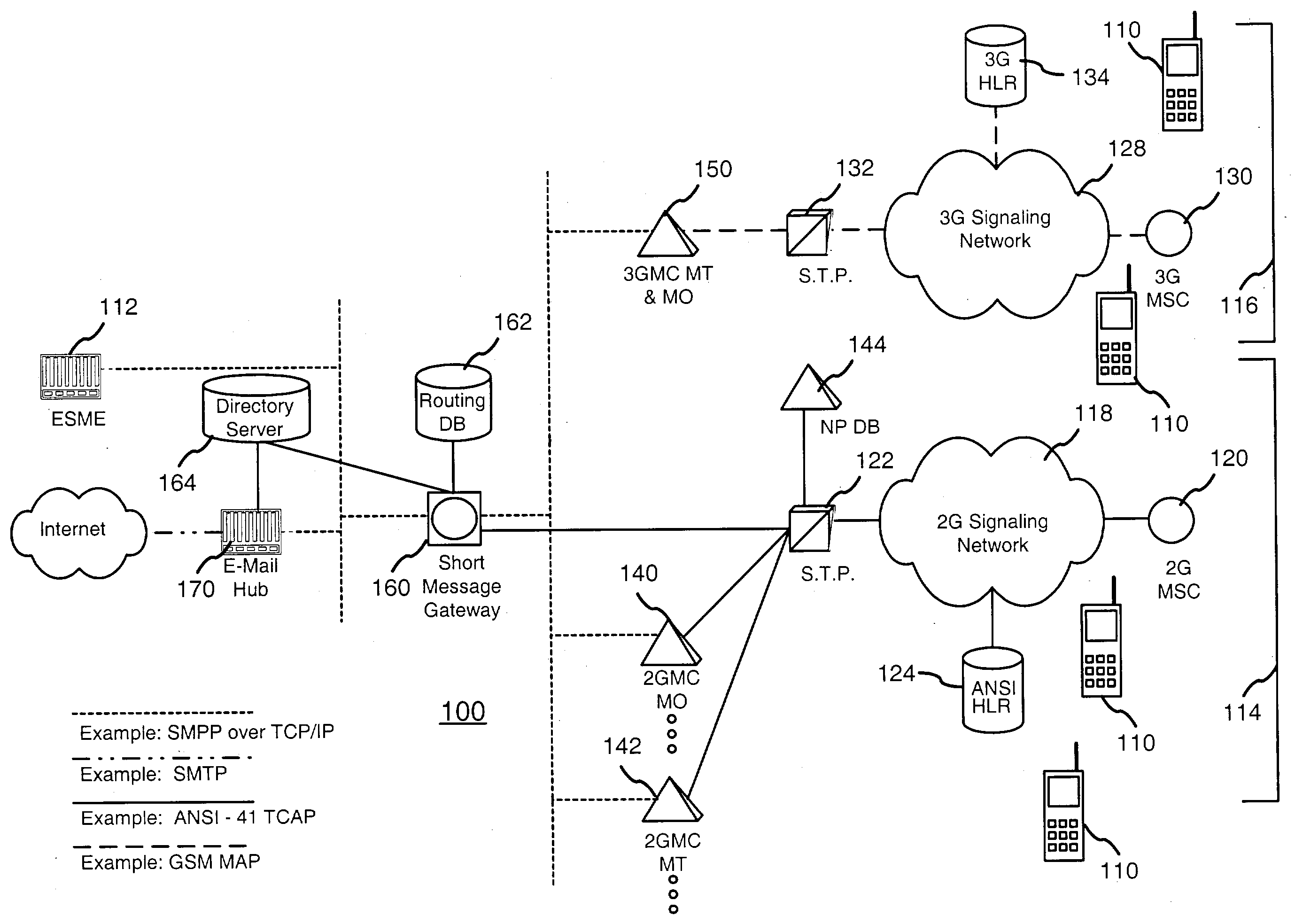
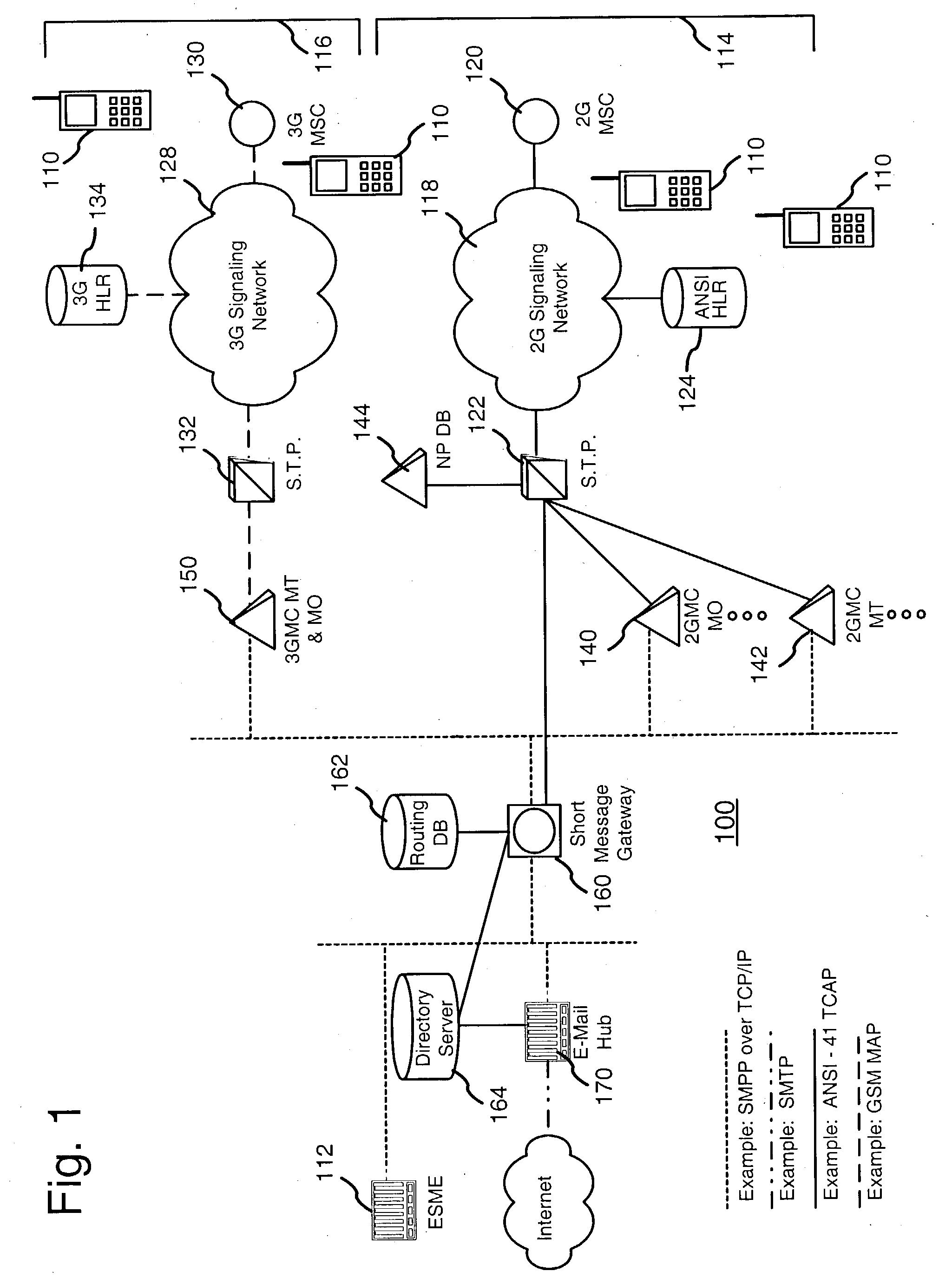
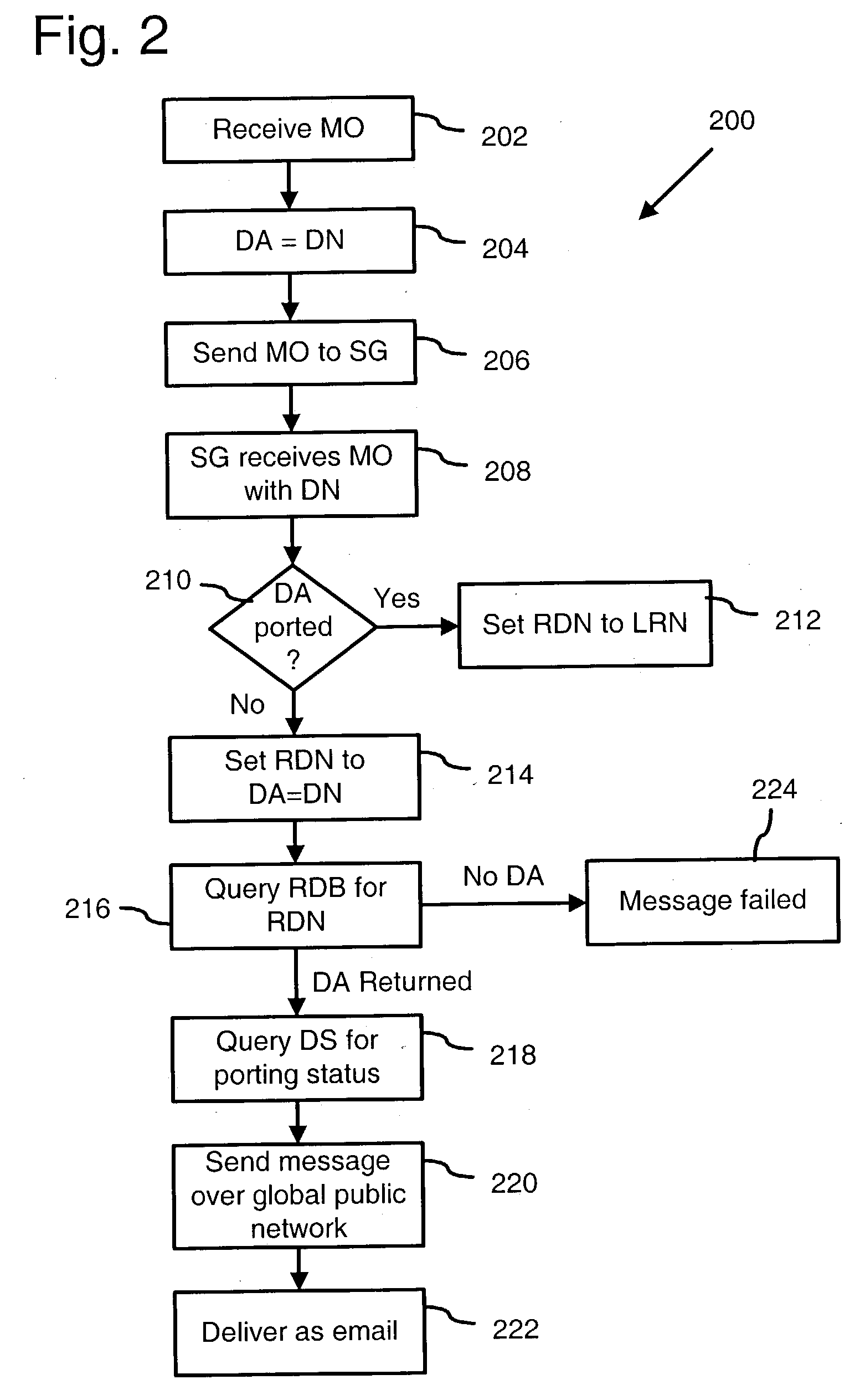
Inter-carrier short text message delivery
InactiveUS20040142707A1Facilitate transmissionRadio/inductive link selection arrangementsWireless commuication servicesShort Message Peer-to-PeerShort Message Service
A method is provided for routing mobile telephone short text messages between different mobile telephone messaging networks, including mobile telephone messaging networks operated by a single carrier (i.e., intra-carrier messaging) or by different carriers (i.e., inter-carrier messaging). The method includes receiving a short text message at a mobile telephone short message gateway operated by a first mobile telephone carrier, the short text message having a destination directory number (DN). The short message gateway determines that the destination directory number (DN) is associated with one of two or more mobile telephone networks. The two or more mobile telephone networks may be operated by the first mobile telephone carrier alone or by the first mobile telephone carrier and another carrier. The short text message is then routed to the appropriate mobile telephone network based upon its destination directory number (DN). In a particular implementation, the short text message is a Short Message Service (SMS) message, and the short message gateway is a Short Message Peer to Peer (SMPP) gateway. The routing of the SMS includes reformatting it to include a Simple Mail Transfer Protocol (SMTP) address of an SMPP gateway of the mobile telephone messaging network to which the SMS message is directed. The SMS message is then sent as an SMTP message over the Internet.
Owner:AT&T WIRELESS SERVICES
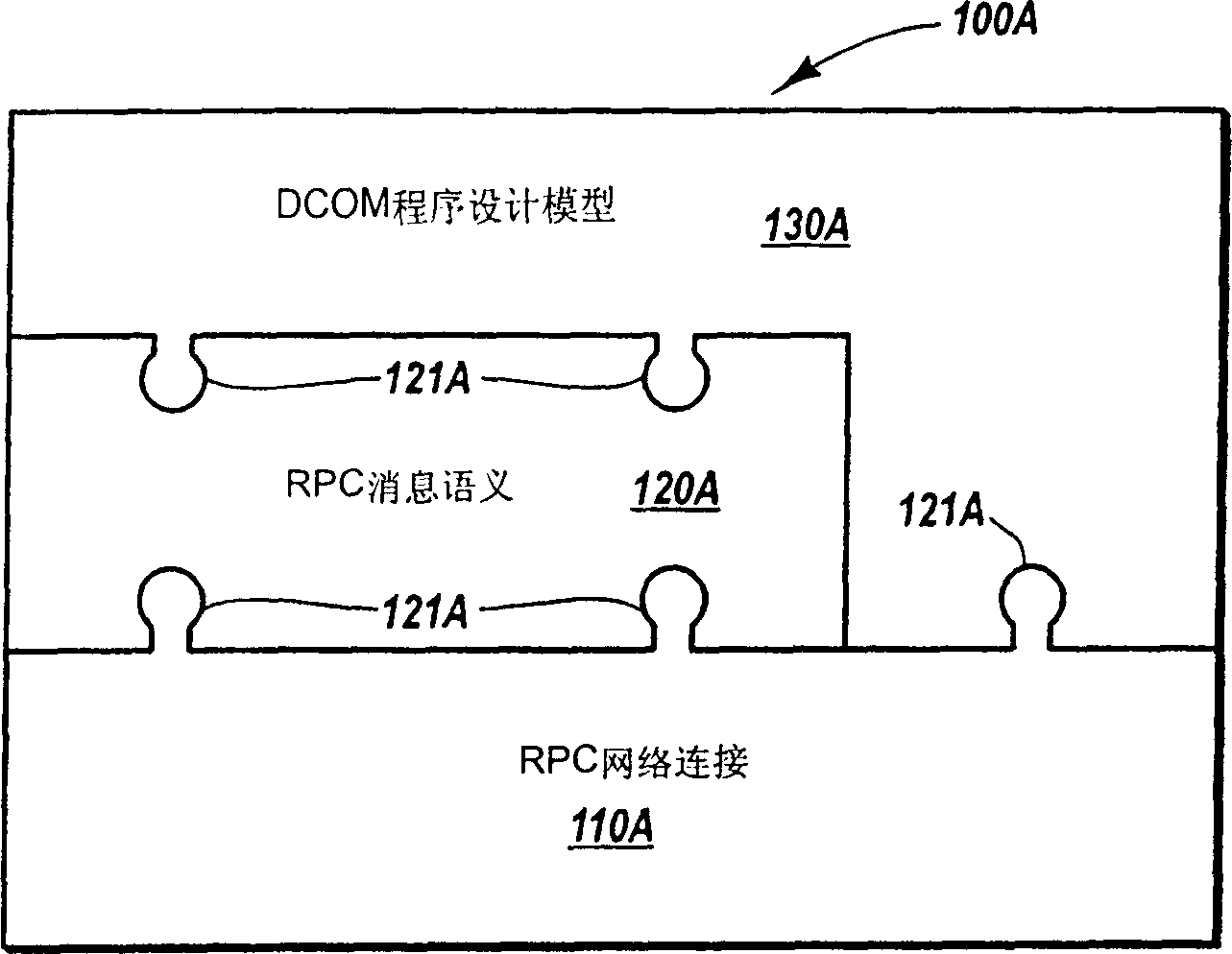
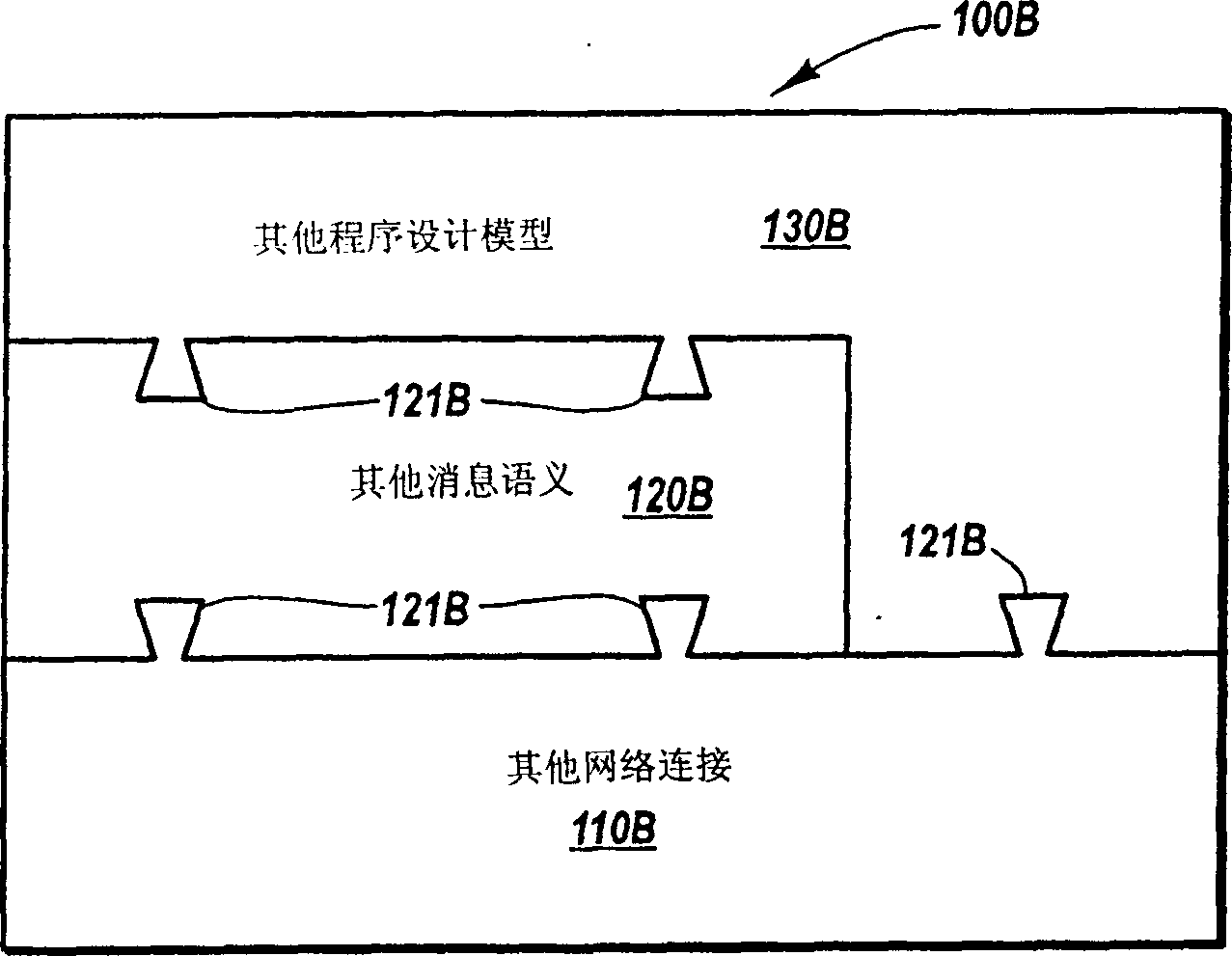
Transmitting and receiving messages through a customizable communication channel and programming model
InactiveUS7200676B2Filing/rasping devicesMultiprogramming arrangementsComputer hardwareMessage passing
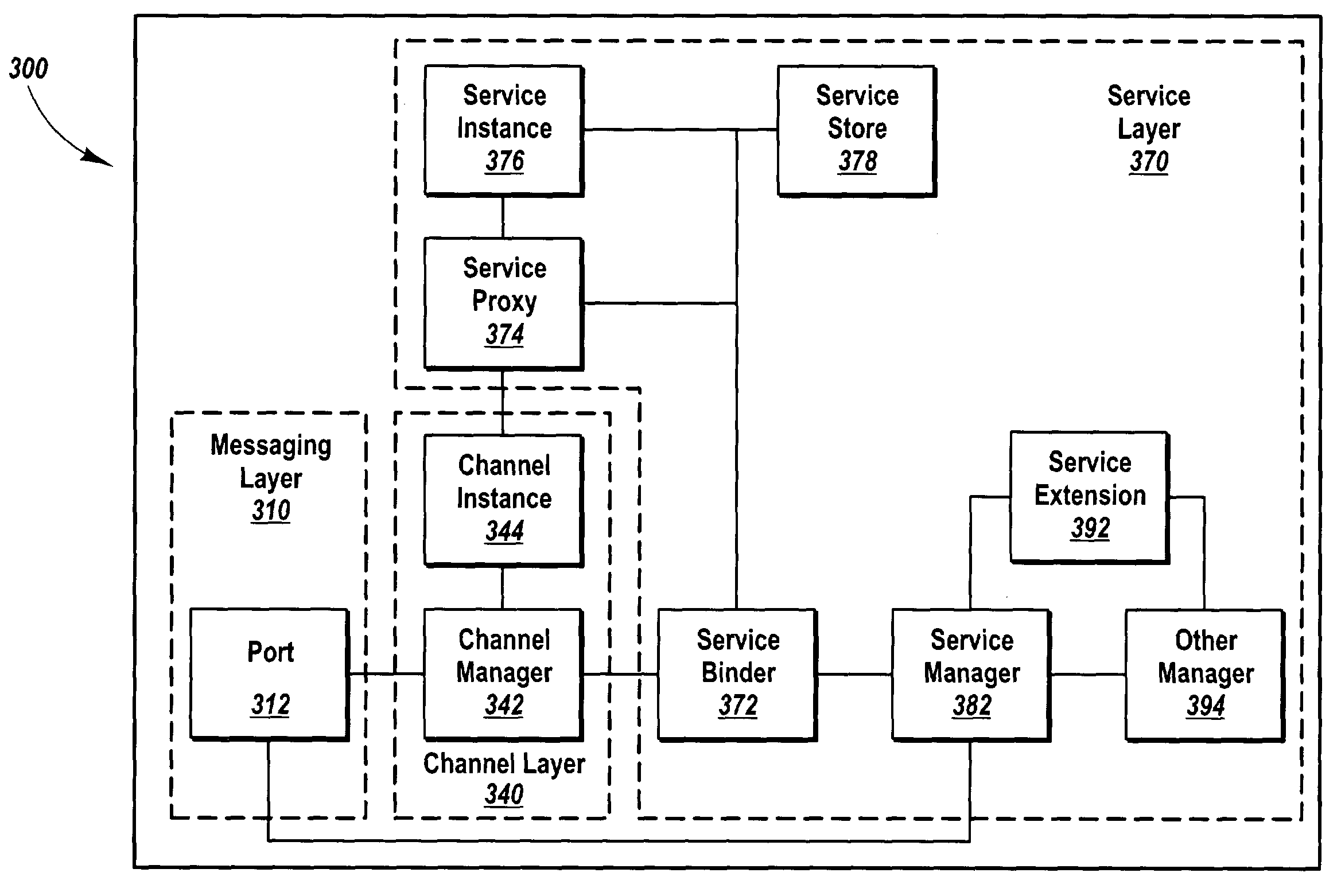
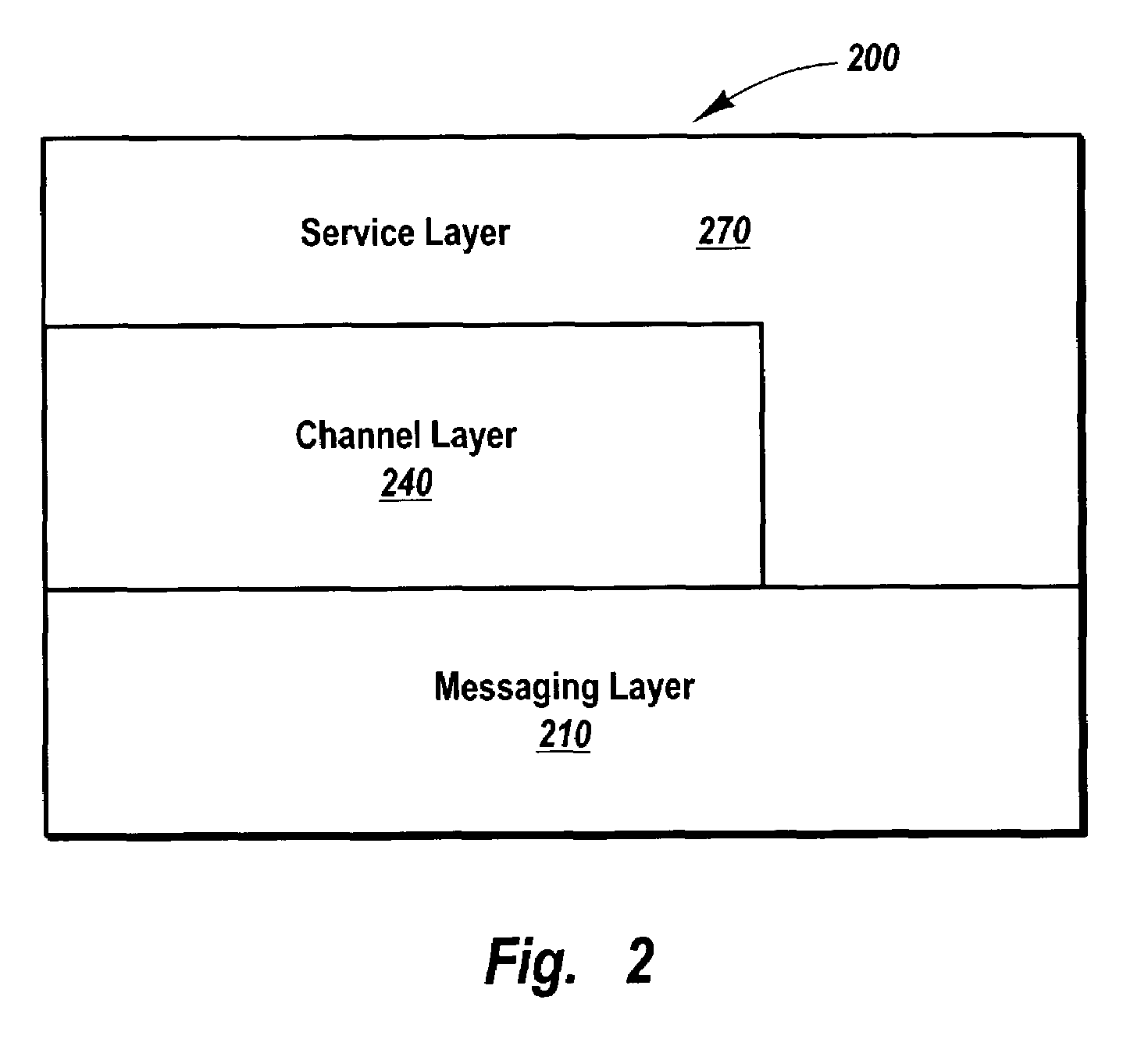
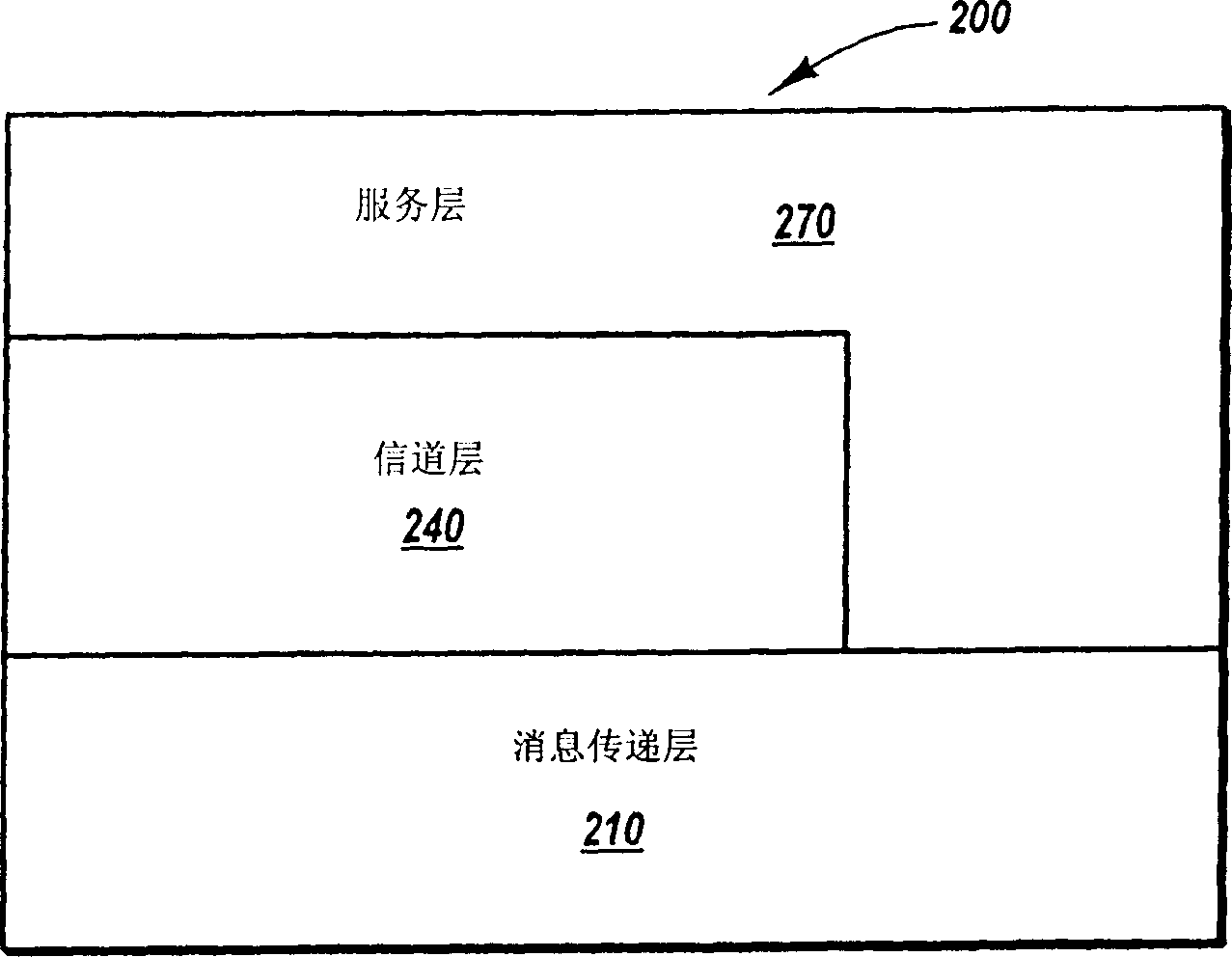
Methods, systems, and computer program products for abstracting processing layers within a messaging infrastructure so that changes or enhancements can be made to the infrastructure while retaining existing functionality. Message transport implementations are abstracted within a message layer, allowing other layers within the infrastructure to interact with messages in a more structured fashion, largely independent of message transport. Transport examples include named pipes, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), etc. A channel layer above the message layer abstracts message exchange implementations, allowing other layers within the infrastructure to send and receive messages in a more structured fashion, largely independent of the message exchange semantics of a specific implementation. Message exchange examples include datagrams, dialogs, monologs, queues, and the like. Above the channel layer and message layer, a service layer abstracts the binding implementations that bind message exchange implementations to user code implementations.
Owner:MICROSOFT TECH LICENSING LLC
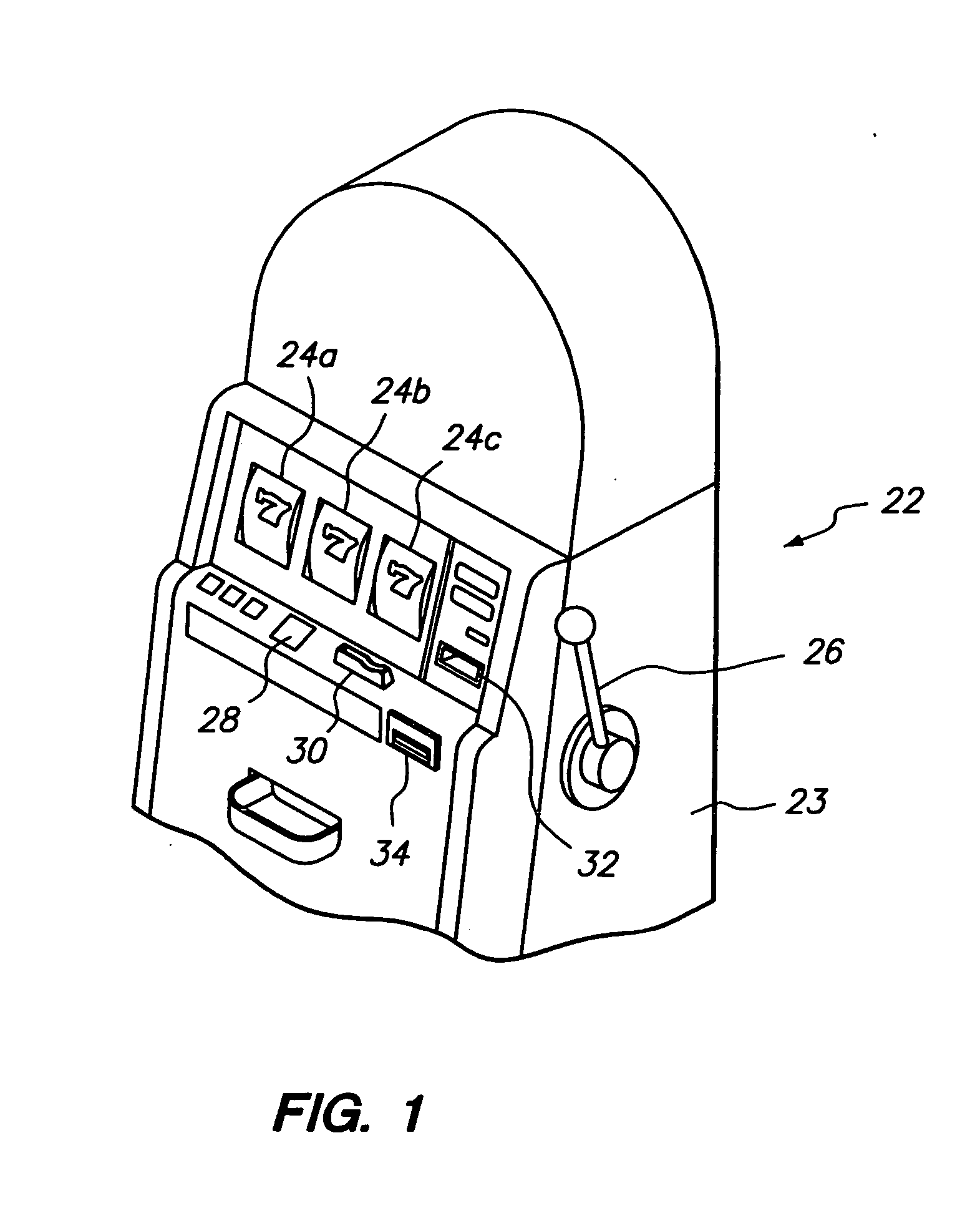
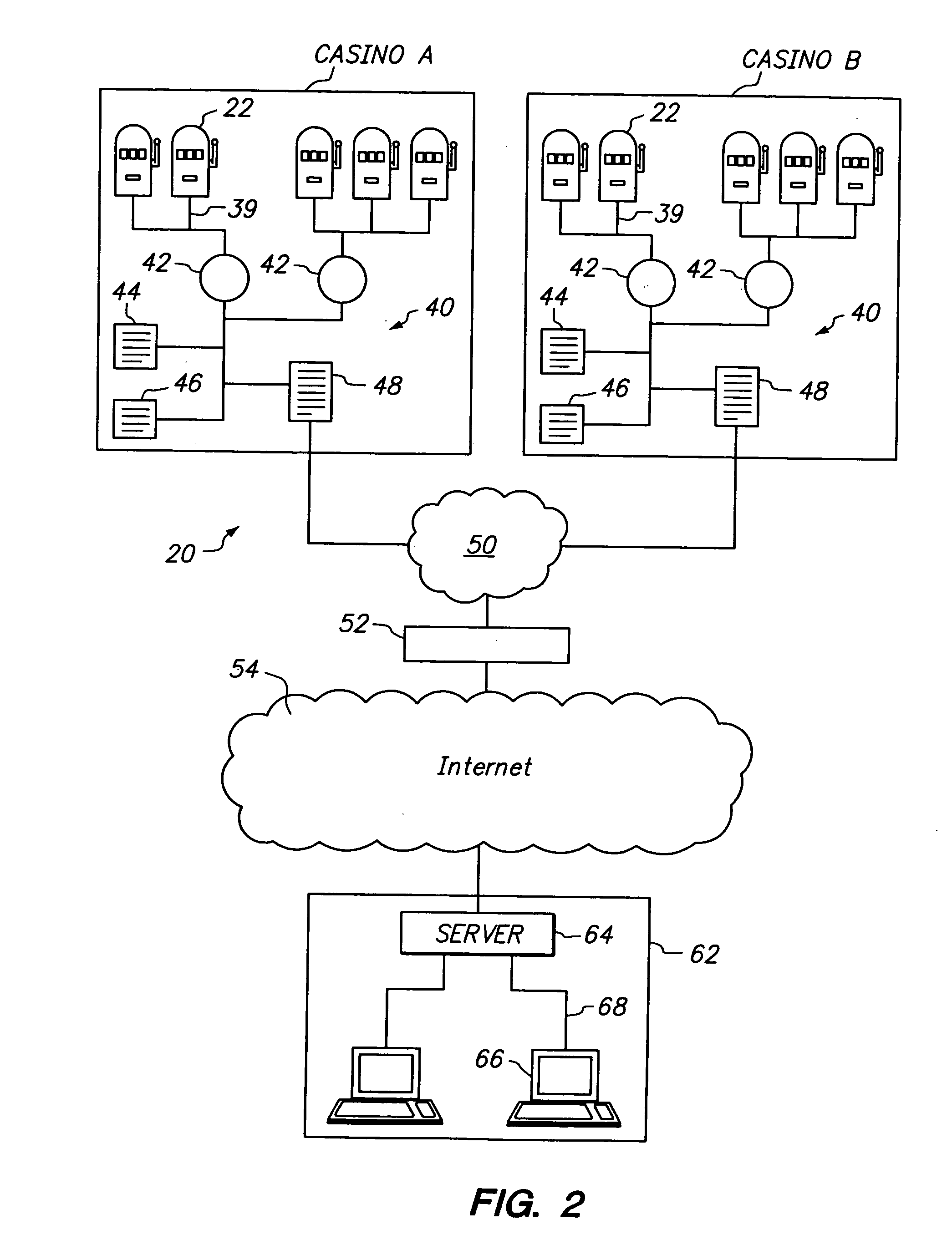
Method and apparatus for supporting wide area gaming network
InactiveUS20050090313A1Monitoring usingApparatus for meter-controlled dispensingVideo gamesComputer hardwareWide area
A method of monitoring and providing support to a gaming device that includes monitoring the gaming device to determine an occurrence of an event, generating a message regarding the event, encoding the message, transmitting the message to a remote location over a communication link, receiving the message at the remote location, decoding the message, analyzing the message, and initiating a response to the message. In one embodiment, the event comprises an error or fault and the message regarding the event is transmitted using the simple mail transfer protocol (SMTP). Embodiments of the invention comprise apparatus forming a part of a gaming network or system including gaming devices such as gaming machines. In one embodiment, the apparatus comprises servers associated with a remote service center and message data storage.
Owner:IGT
Smart card device and method used for transmitting and receiving secure e-mails
ActiveUS7178724B2Overcome disadvantagesComputer security arrangementsData switching networksIp addressSmart card
A system and method for transmitting and receiving secure e-mails is disclosed. A smart card device stores both private and public keys for an encryption algorithm. The smart card device is preferably a USB smart card device and interfaces a host having a client e-mail program. E-mails are transferred to and / or from the client e-mail program and e-mail server via the smart card while decrypting and encrypting any transmitted and / or received e-mails within the smart card device. The smart card device stores an IP address for an e-mail server. A Simple Mail Transfer Protocol outgoing parameter is set from the client e-mail program to an IP address for the smart card device.
Owner:STMICROELECTRONICS SRL
Media System
Streaming media is provided over a network using a non-streaming-specific transfer protocol, in which a media stream is stored on a server as multiple individual media files, and a playlist is provided indicating which media files are required for output of a specific part of the media stream; wherein multiple different playlists are provided to respective different media streaming clients, in response to requests relating to corresponding different parts of the media stream. A user interface is provided on the client device, in which an interactive media event is displayed including streaming media, and secondary media content.
Owner:SKY CP LTD
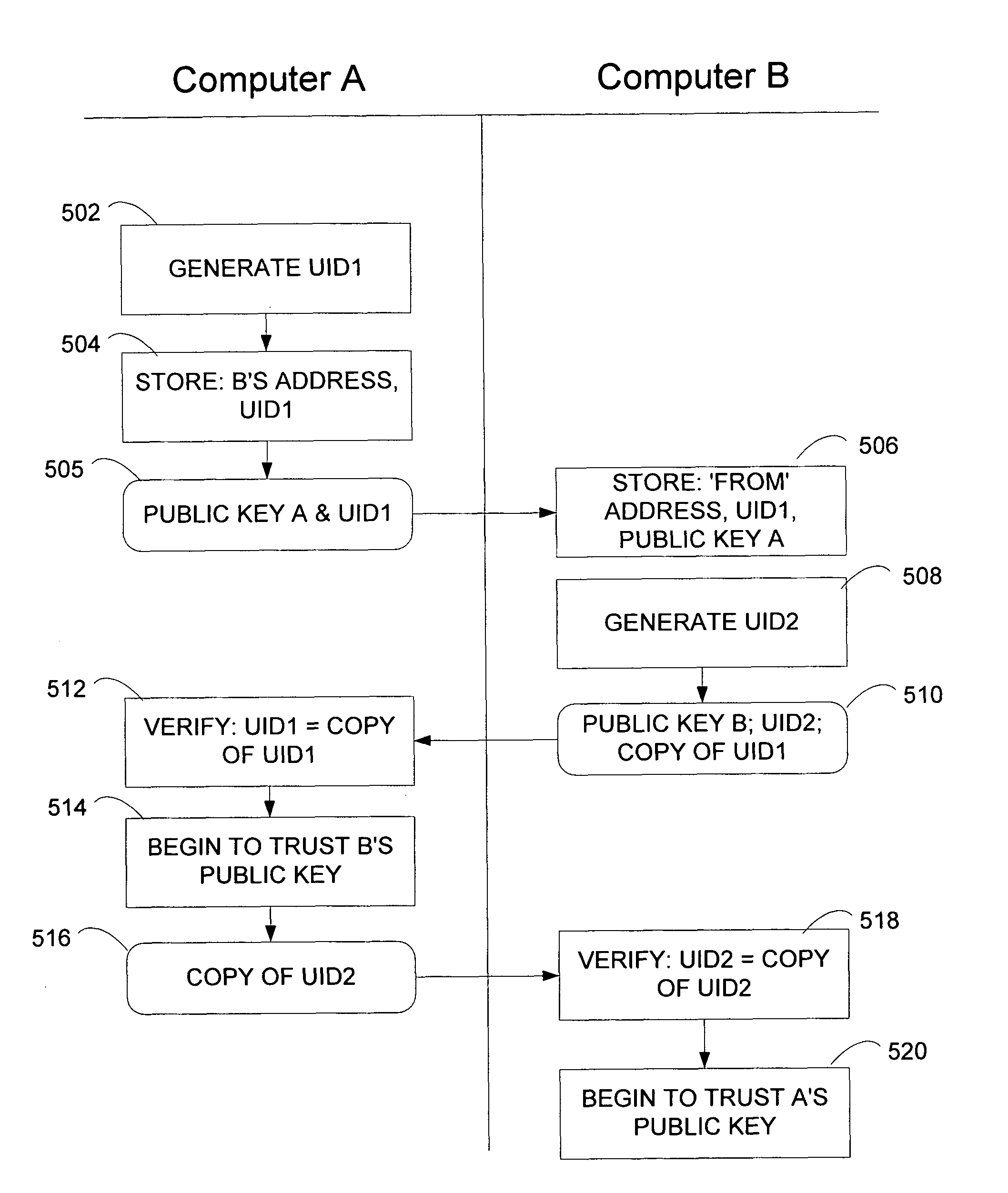
Authenticated exchange of public information using electronic mail
InactiveUS7721093B2Key distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessDigital object
Methods and systems are provided for using an existing email transfer protocol, such as SMTP, to exchange digital objects in an authenticated manner. The provided methods and systems solve the bootstrapping problem of computer identities for P2P communication by authenticating the exchange of public information. If the electronic mail protocols are strong, in that sending an email message to a given address results in the message reaching that address with a high degree of confidence, then the exchange of public information performed in accordance with embodiments of the invention is confidently authenticated.
Owner:MICROSOFT TECH LICENSING LLC
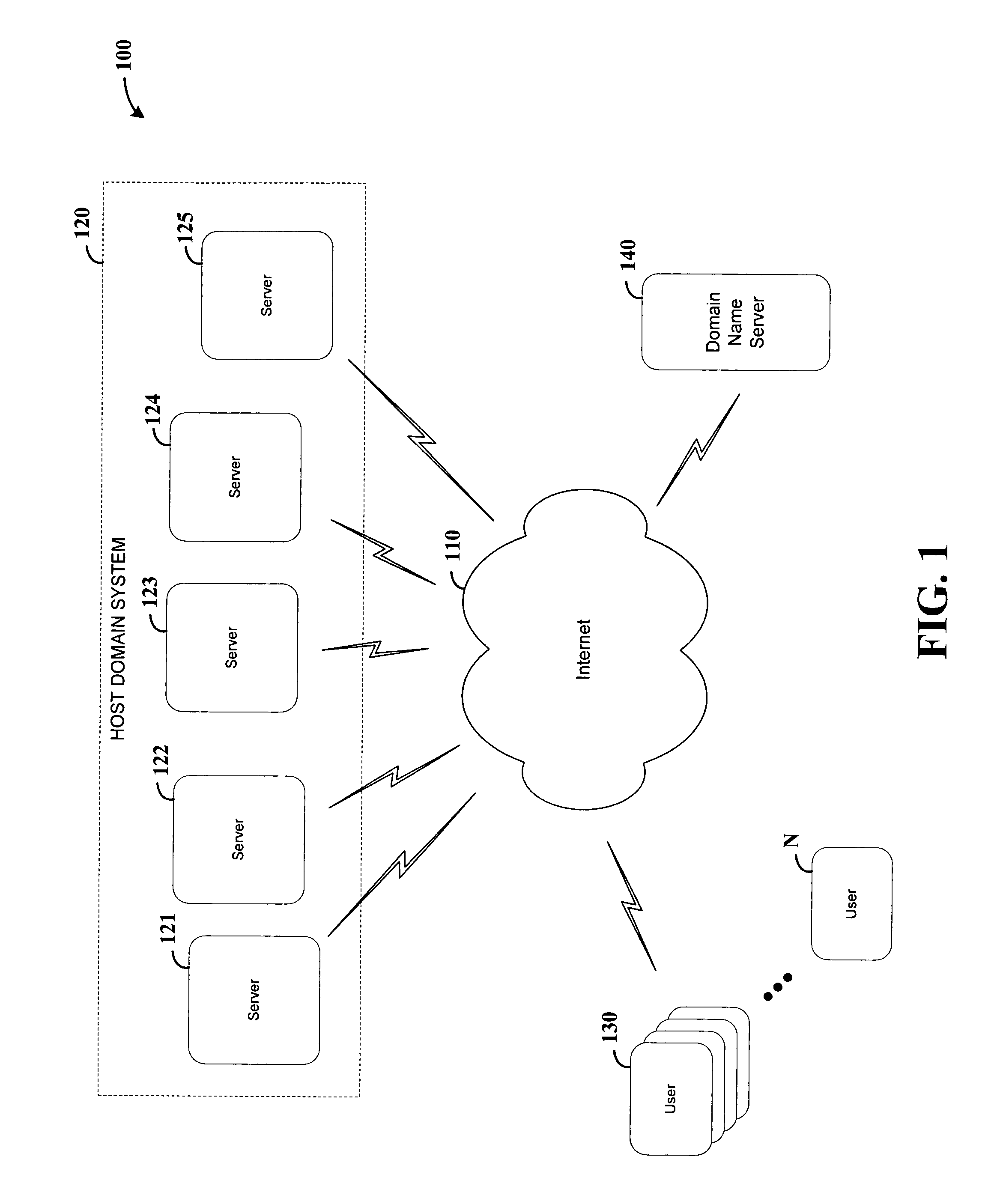
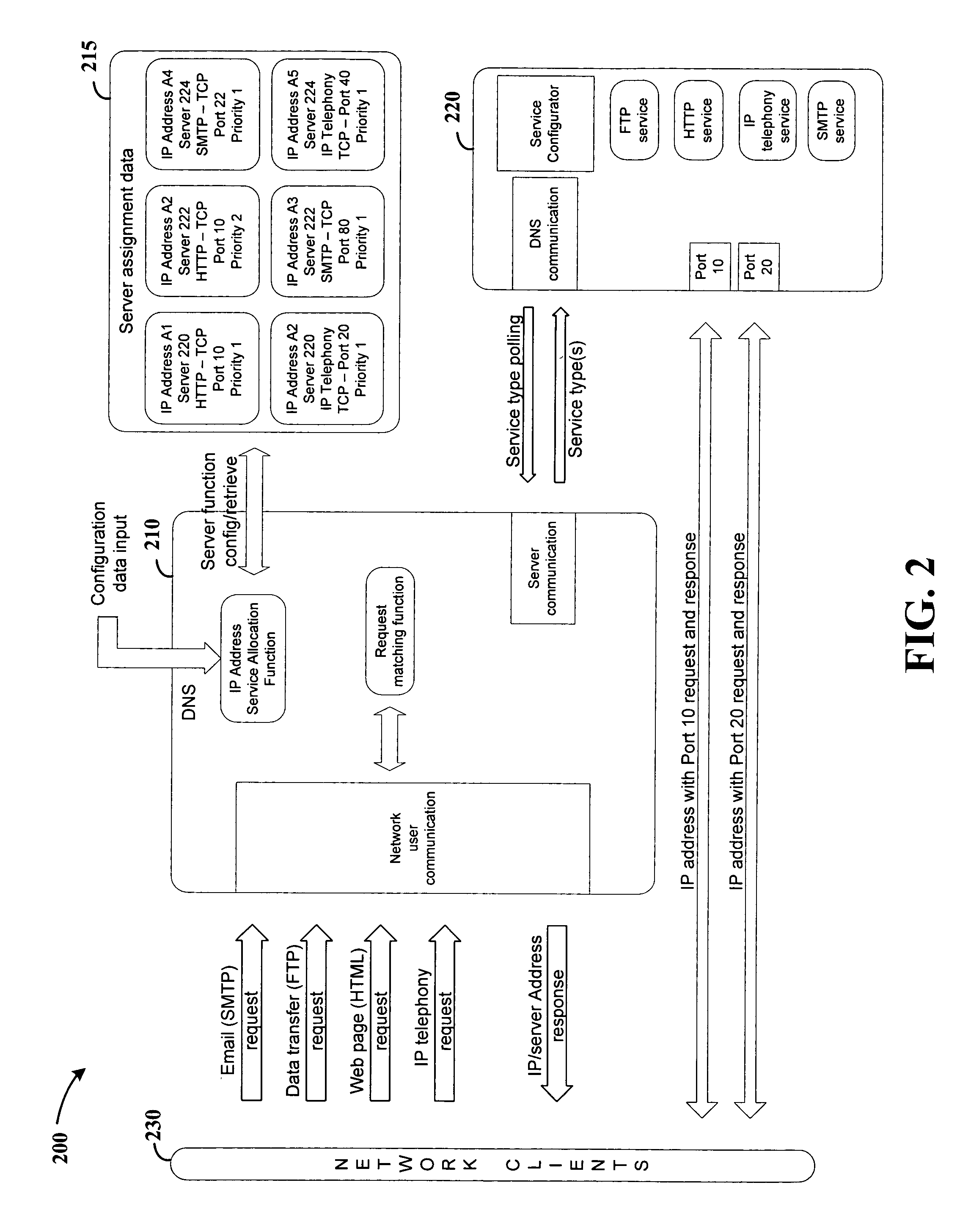
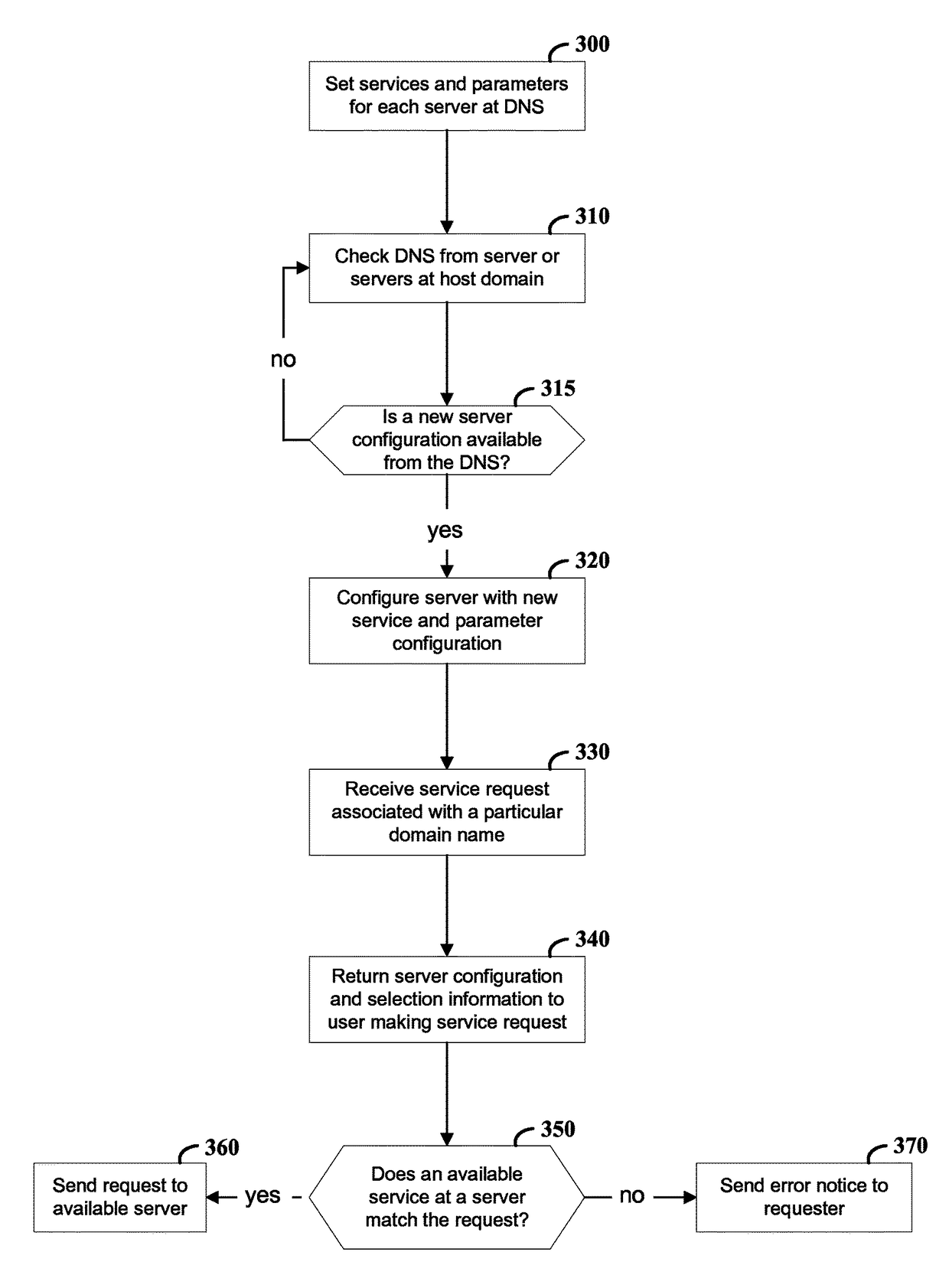
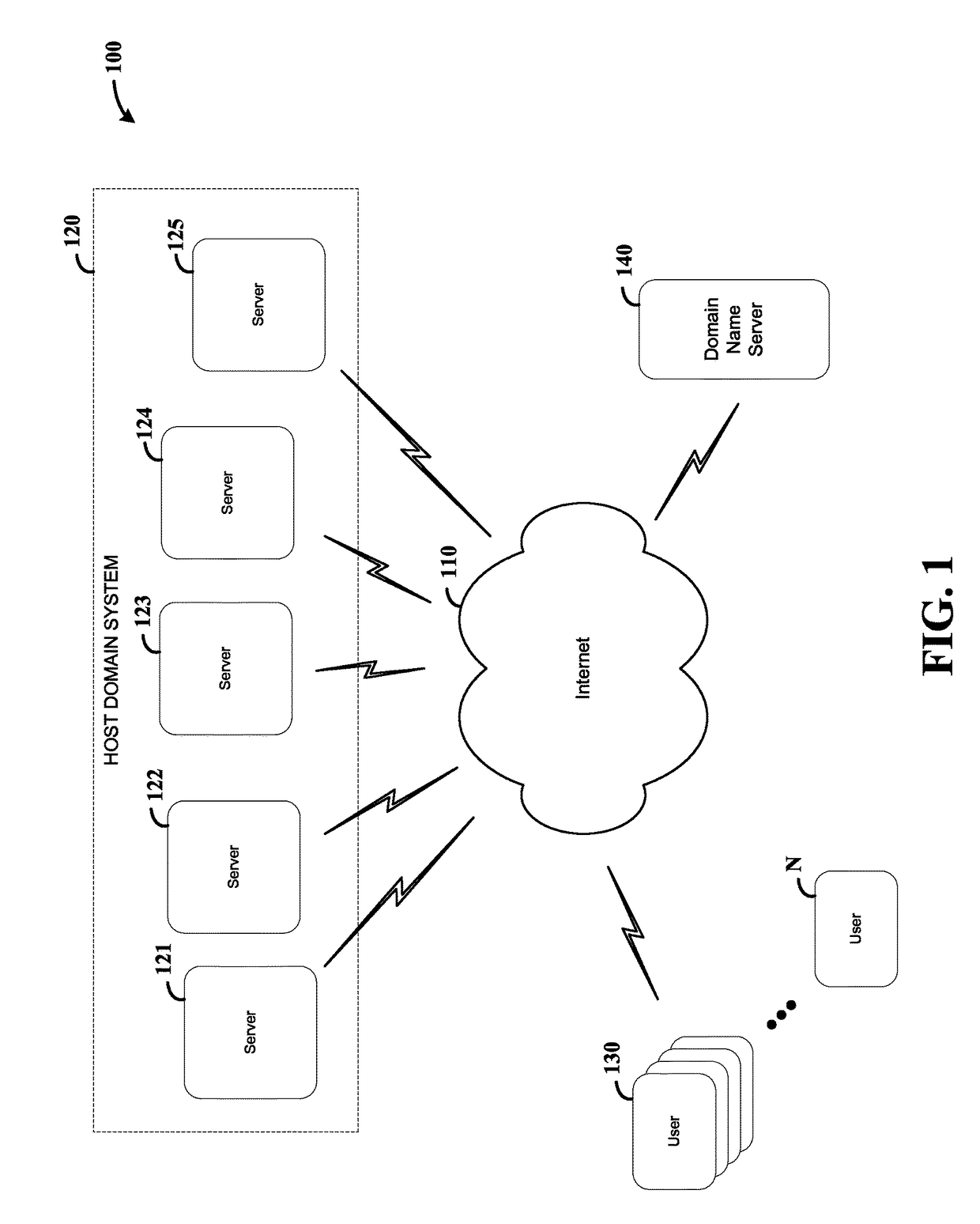
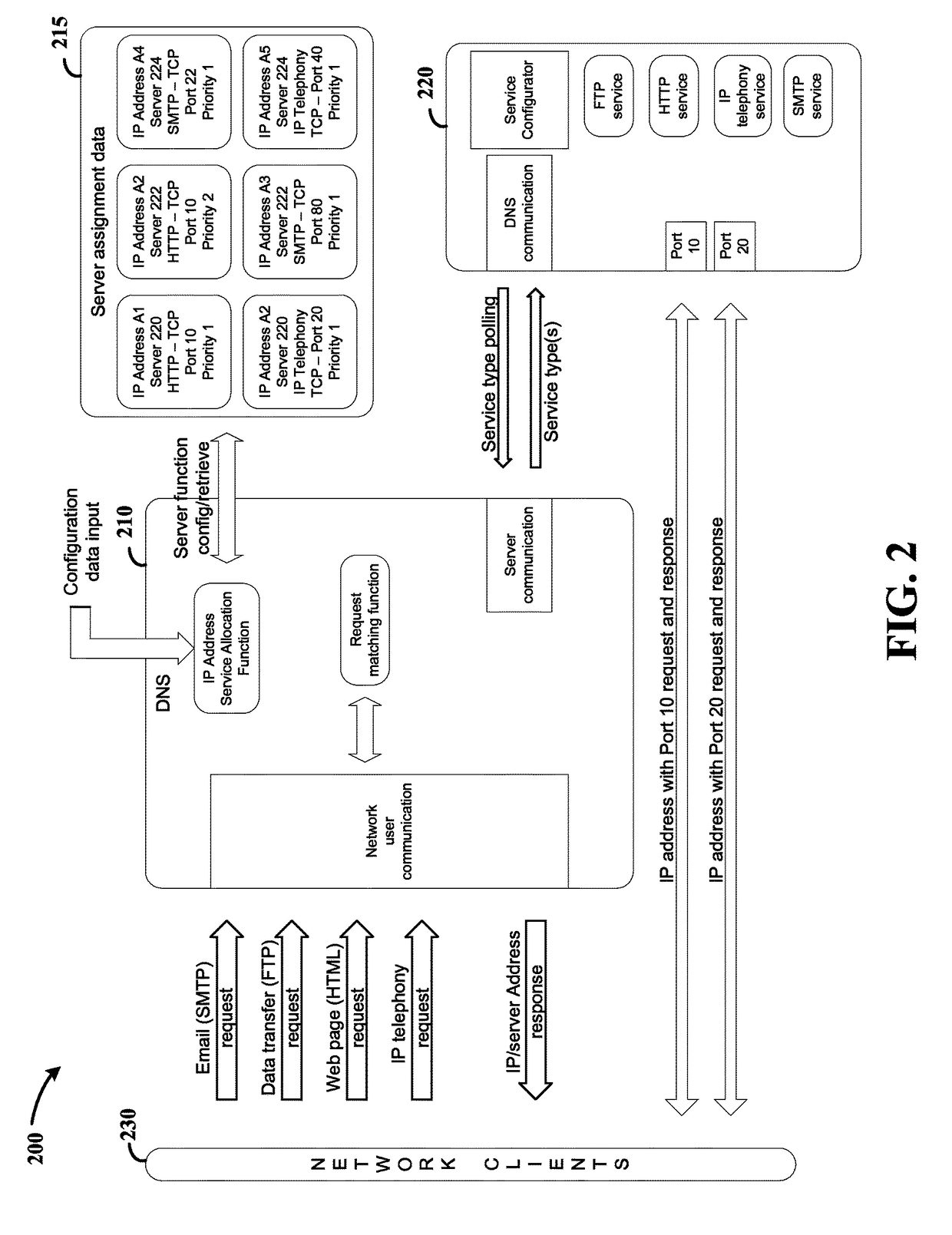
Server-based service configuration system and approach
Network service providers are managed using a server-side configuration approach. According to an example embodiment of the present invention, a host network location includes two or more servers that automatically reconfigure their services in response to controller service settings corresponding to each server. Each server reads configuration information provided at a controller such as a domain name server (DNS), and in response, starts a network-based service corresponding to the configuration information. For instance, each of the two or more servers may be adapted to provide mail service via simple mail transfer protocol (SMTP) and web service via hyper text transfer protocol (HTTP). In this regard, when a DNS associates a first one of the servers with HTTP services and a second one of the servers with SMTP services, each server reconfigures its services accordingly, e.g., at a selected configuration time after startup or in response to an initiating event.
Owner:8X8 INC
E-mail firewall with stored key encryption/decryption
InactiveUS20070245416A1Easy to controlMultiple keys/algorithms usageData taking preventionInternet privacyTrunking
An e-mail firewall (105) applies policies to e-mail messages (204) between a first 5 site and a plurality of second sites in accordance with a plurality of administrator selectable policies (216). The firewall comprises a simple mail transfer protocol (SMTP) relay (202) for causing the e-mail messages (204) to be transmitted between the first site and selected ones of the second sites. A plurality of policy managers (216) enforce—administrator selectable policies. The policies, such as encryption and decryption policies, comprise at least a first source / destination policy (218), at least a first content policy (202) and at least a first virus policy (224). The policies are characterized by a plurality of administrator selectable criteria (310), a plurality of administrator selectable exceptions (312) to the criteria and a plurality of administrator selectable actions (314, 316, 322) associated with the criteria and exceptions. The policy managers comprise an access manager (218) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the source / destination policy (218). The policy managers (216) further comprise a content manager (220) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the content policy (220), and a virus manager (224) for restriction transmission of e-mail messages (204) between the first site and the second sites in accordance with the virus policy (224).
Owner:AXWAY
Bot-Network Detection Based on Simple Mail Transfer Protocol (SMTP) Characteristics of E-Mail Senders Within IP Address Aggregates
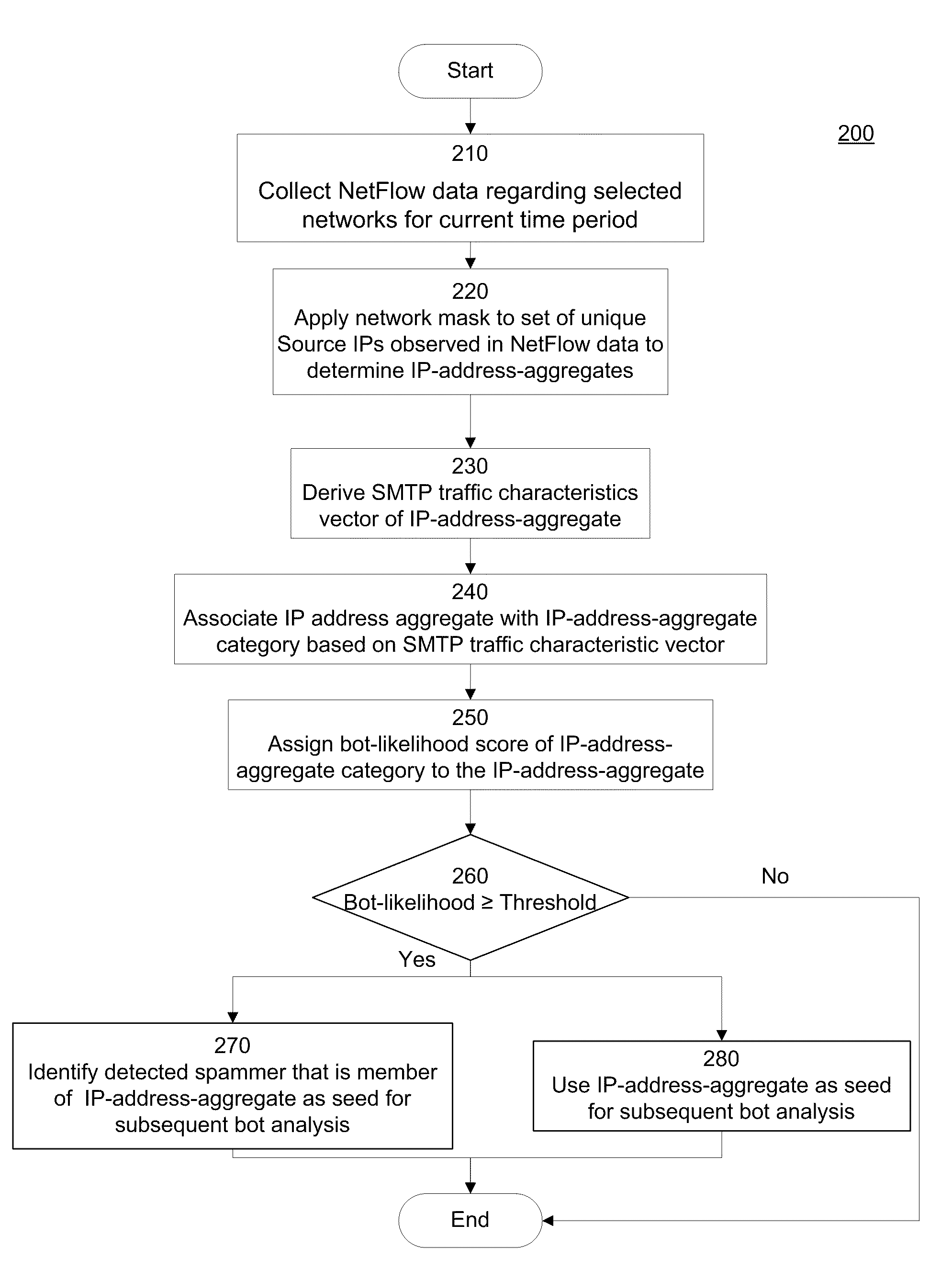
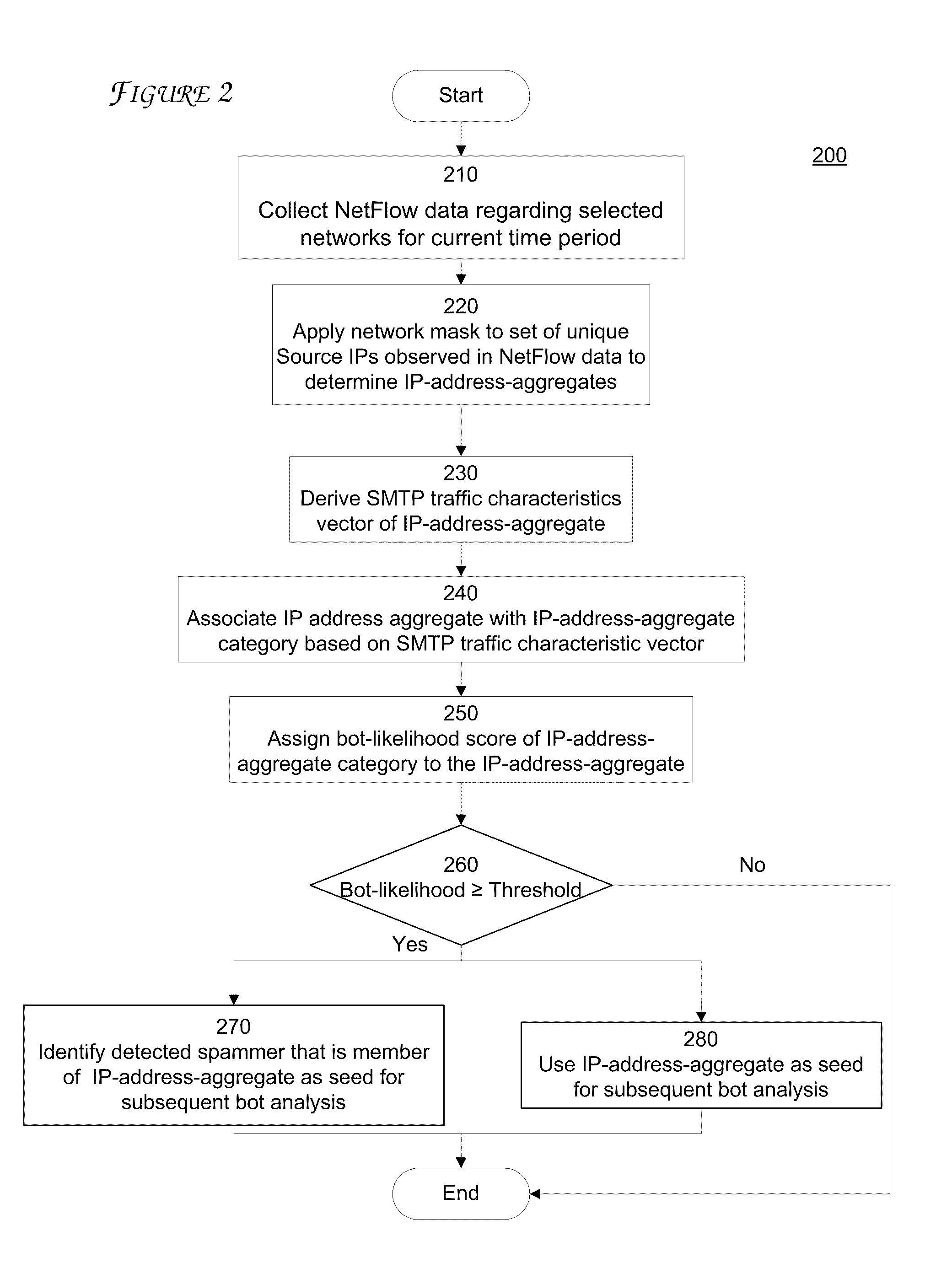
ActiveUS20110252472A1Memory loss protectionError detection/correctionTraffic characteristicIp address
A method and system for determining whether an IP address is part of a bot-network are provided. The IP-address-aggregate associated with the IP address of an e-mail sender is determined. The IP-address-aggregate is associated with an IP-address-aggregate-category based on the current SMTP traffic characteristics of the IP-address-aggregate and the known SMTP traffic characteristics of an IP-address-aggregate-category. A bot-likelihood score of the IP-address-aggregate-category is then associated with IP-address-aggregate. IP-address-aggregate-categories can be established based on historical SMTP traffic characteristics of the IP-address-aggregates. The IP-address-aggregates are grouped based on SMTP characteristics, and the IP-address-aggregate-categories are defined based on a selection of IP-address-aggregates with similar SMTP traffic characteristics that are diagnostic of spam bots vs. non-botnet-controllers spammers. Bot likelihood scores are determined for the resulting IP-address-aggregate-categories based on historically known bot IP addresses.
Owner:AT&T INTPROP I L P
E-mail firewall with stored key encryption/decryption
InactiveUS20070005983A1Easy to controlMultiple keys/algorithms usageData taking preventionContent managementDistributed computing
An e-mail firewall (105) applies policies to e-mail messages (204) between a first 5 site and a plurality of second sites in accordance with a plurality of administrator selectable policies (216). The firewall comprises a simple mail transfer protocol (SMTP) relay (202) for causing the e-mail messages (204) to be transmitted between the first site and selected ones of the second sites. A plurality of policy managers (216) enforce-administrator selectable policies. The policies, such as encryption and decryption policies, comprise at least a first source / destination policy (218), at least a first content policy (202) and at least a first virus policy (224). The policies are characterized by a plurality of administrator selectable criteria (310), a plurality of administrator selectable exceptions (312) to the criteria and a plurality of administrator selectable actions (314, 316, 322) associated with the criteria and exceptions. The policy managers comprise an access manager (218) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the source / destination policy (218). The policy managers (216) further comprise a content manager (220) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the content policy (220), and a virus manager (224) for restriction transmission of e-mail messages (204) between the first site and the second sites in accordance with the virus policy (224).
Owner:AXWAY
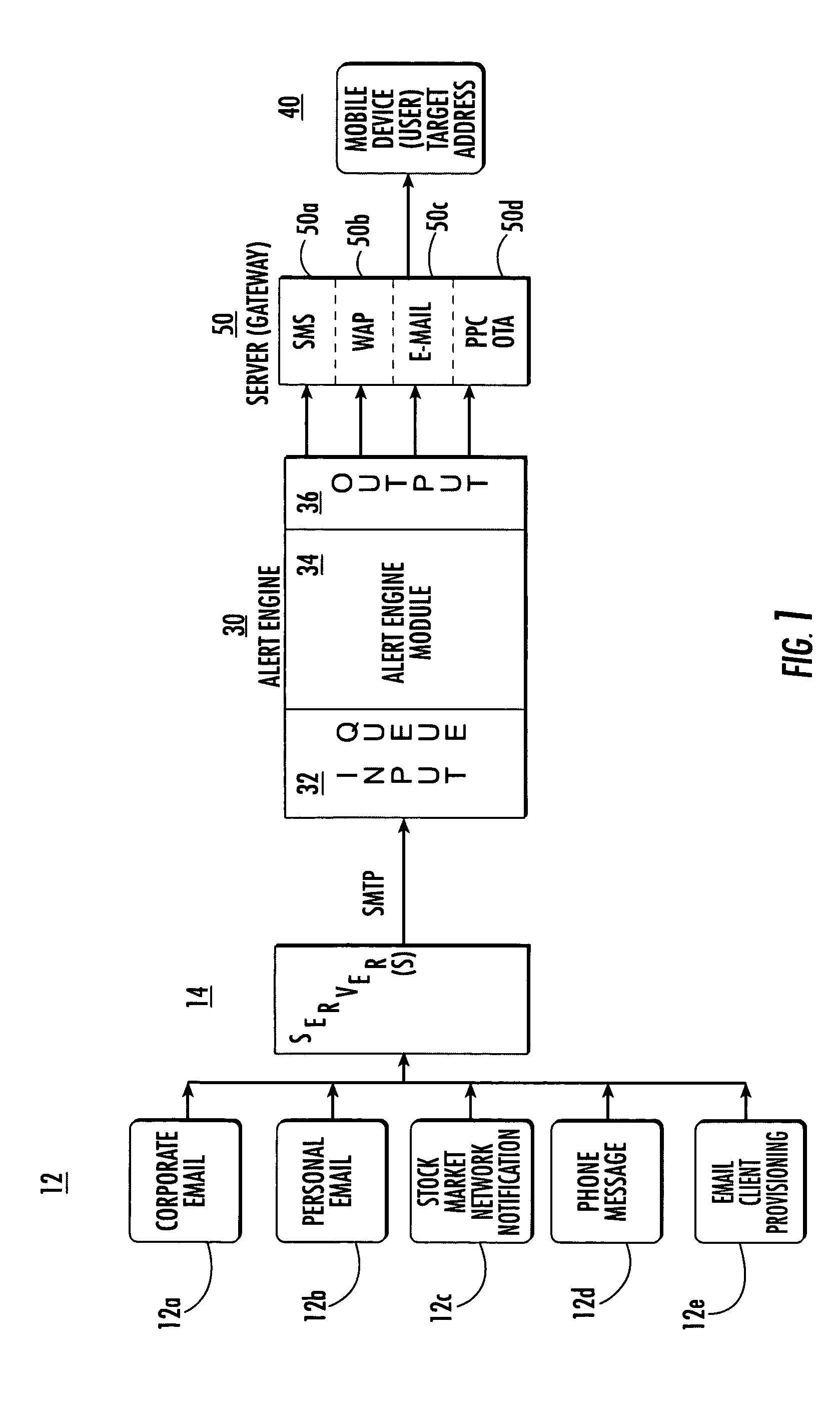
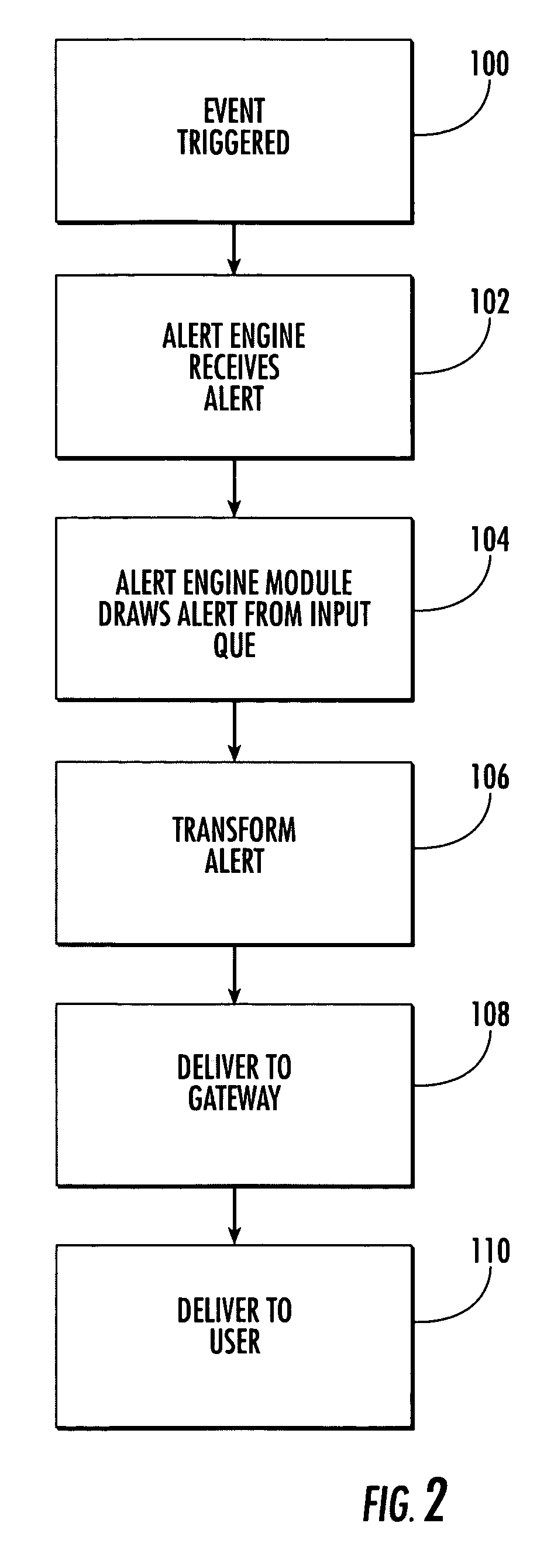
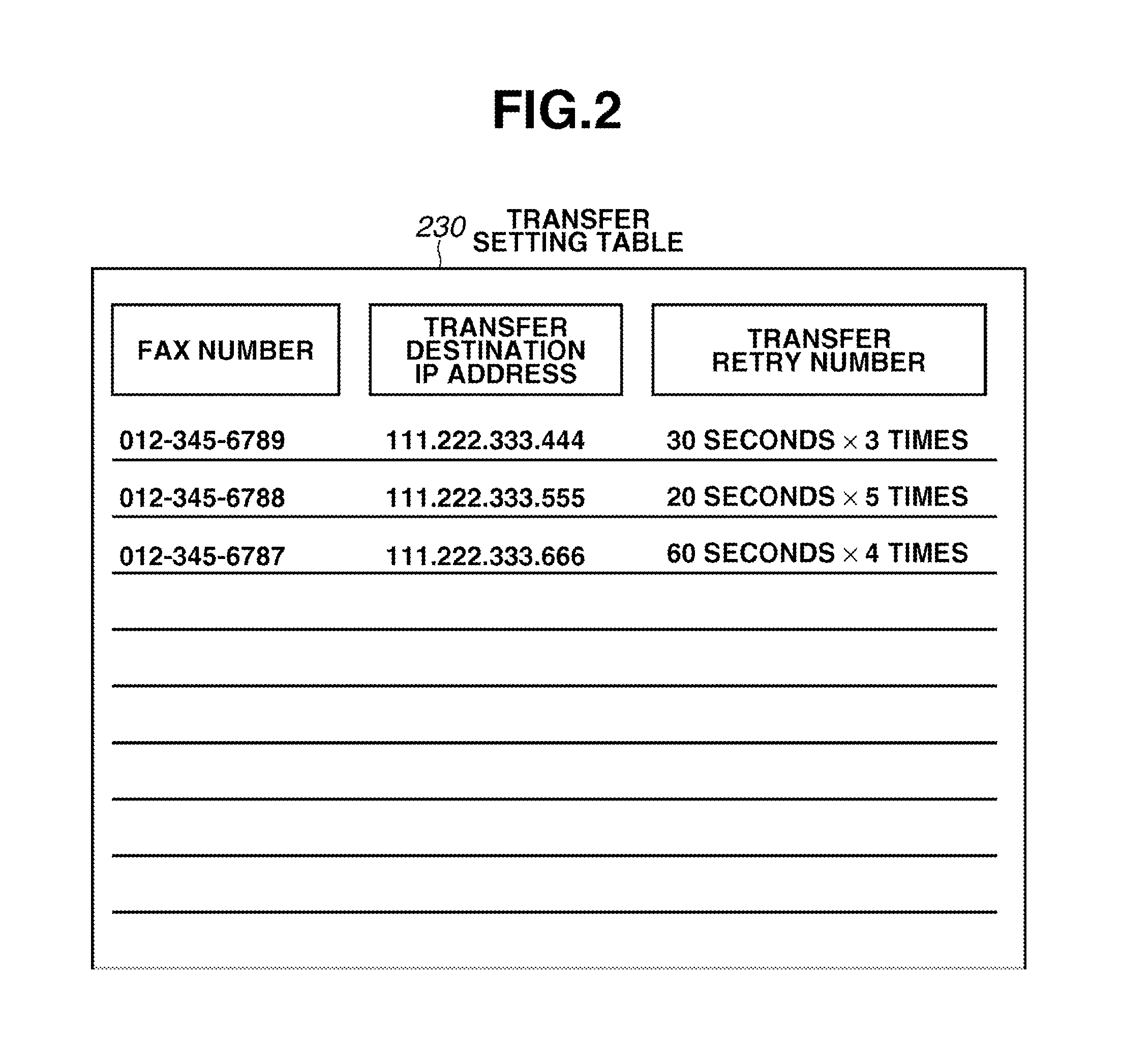
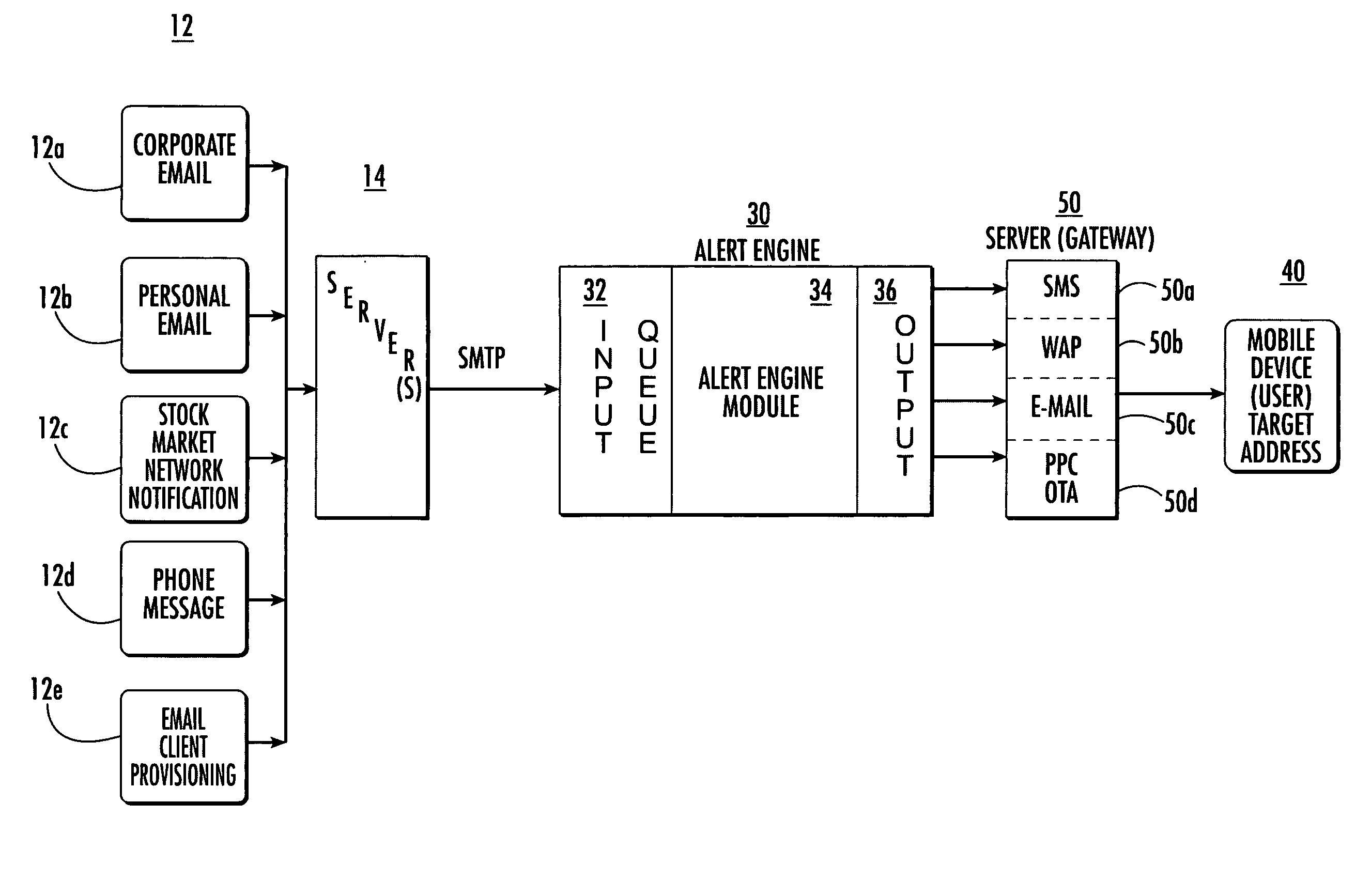
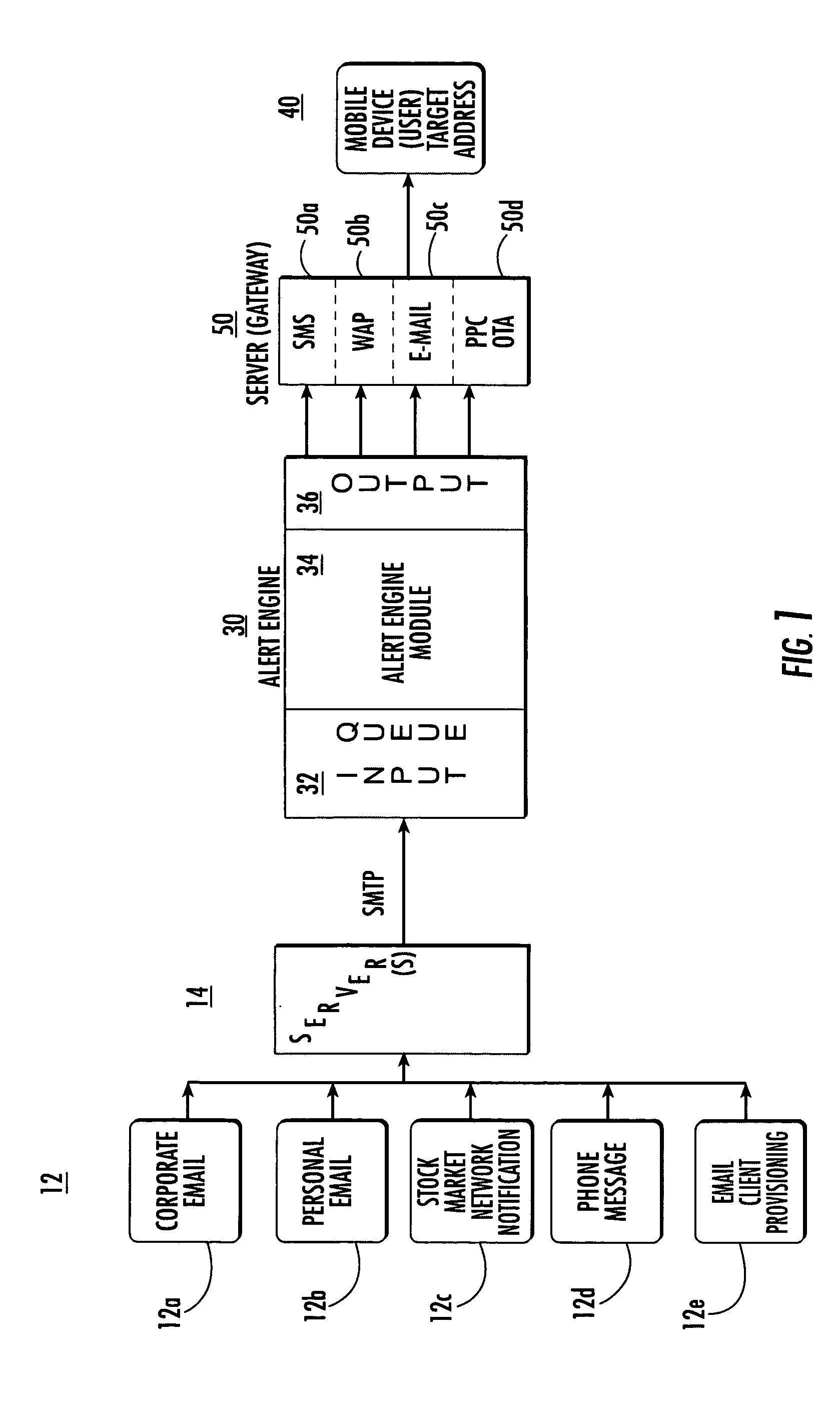
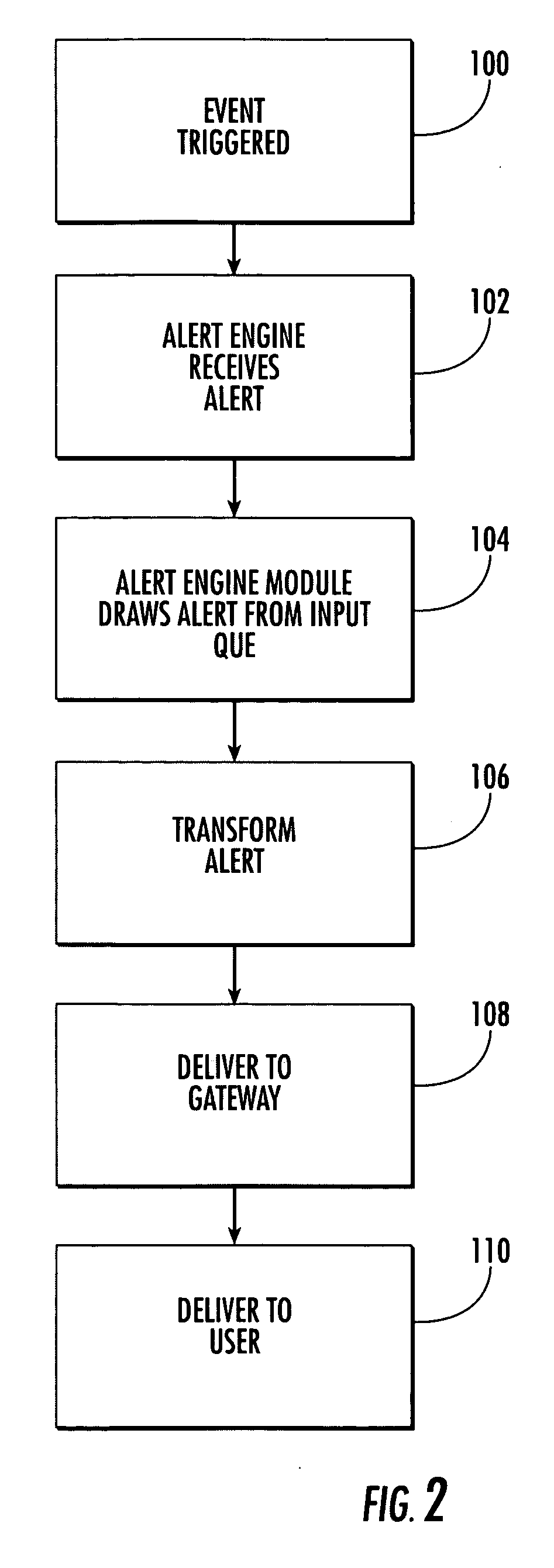
System and method for notifying users of an event using alerts
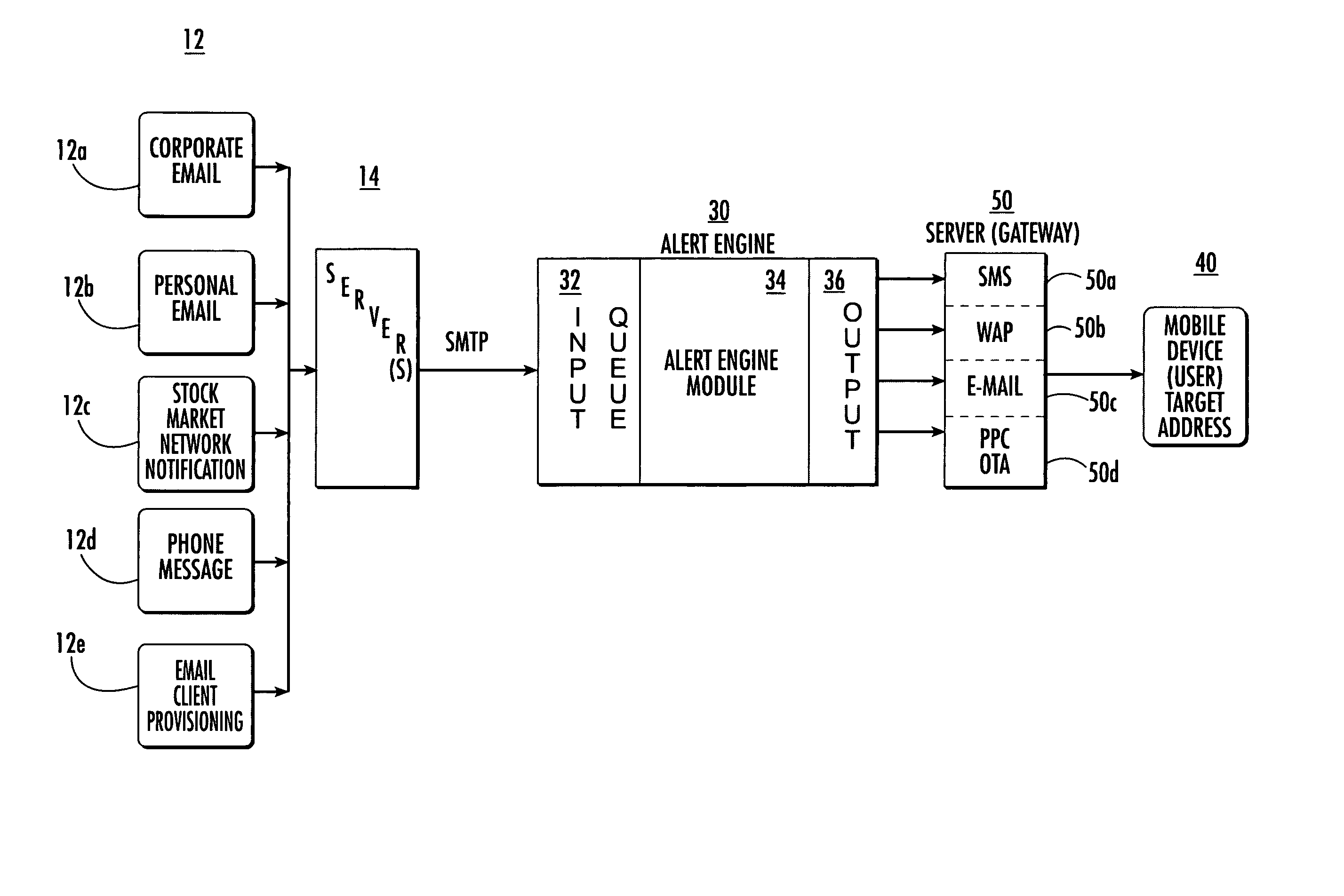
ActiveUS7162223B2Information formatSpecial service for subscribersComputer scienceSimple Mail Transfer Protocol
An alert engine module receives an alert for an event in a generic communications format and delivers an alert for the event to a target address in a communications format that is preferred by a user based on the alert content. The generic format can be an e-mail message, such as a Simple Mail Transfer Protocol (SMTP) message. The alert engine can be operative to transform the alert based on a header and / or format of a target address.
Owner:TEAMON SYST
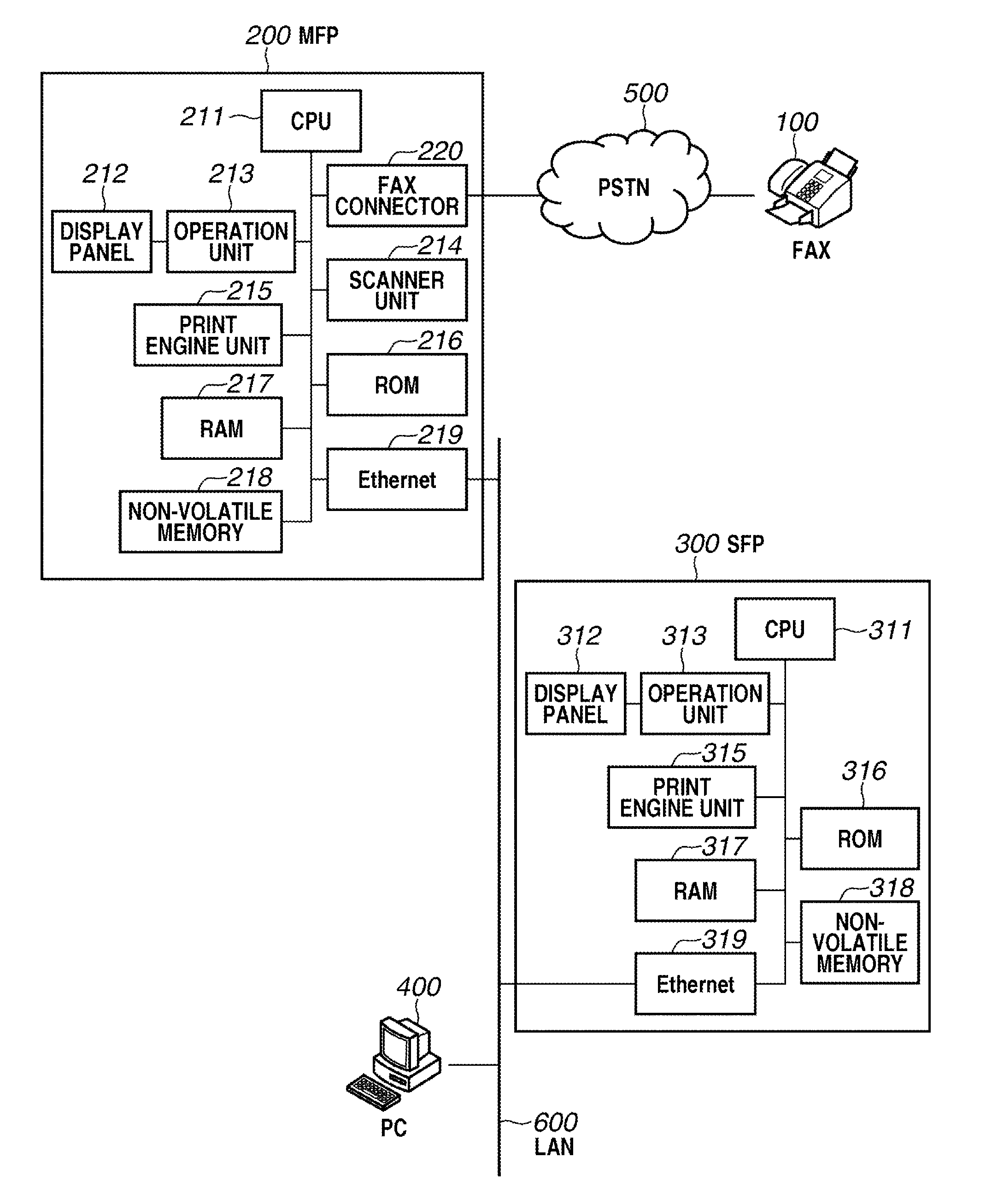
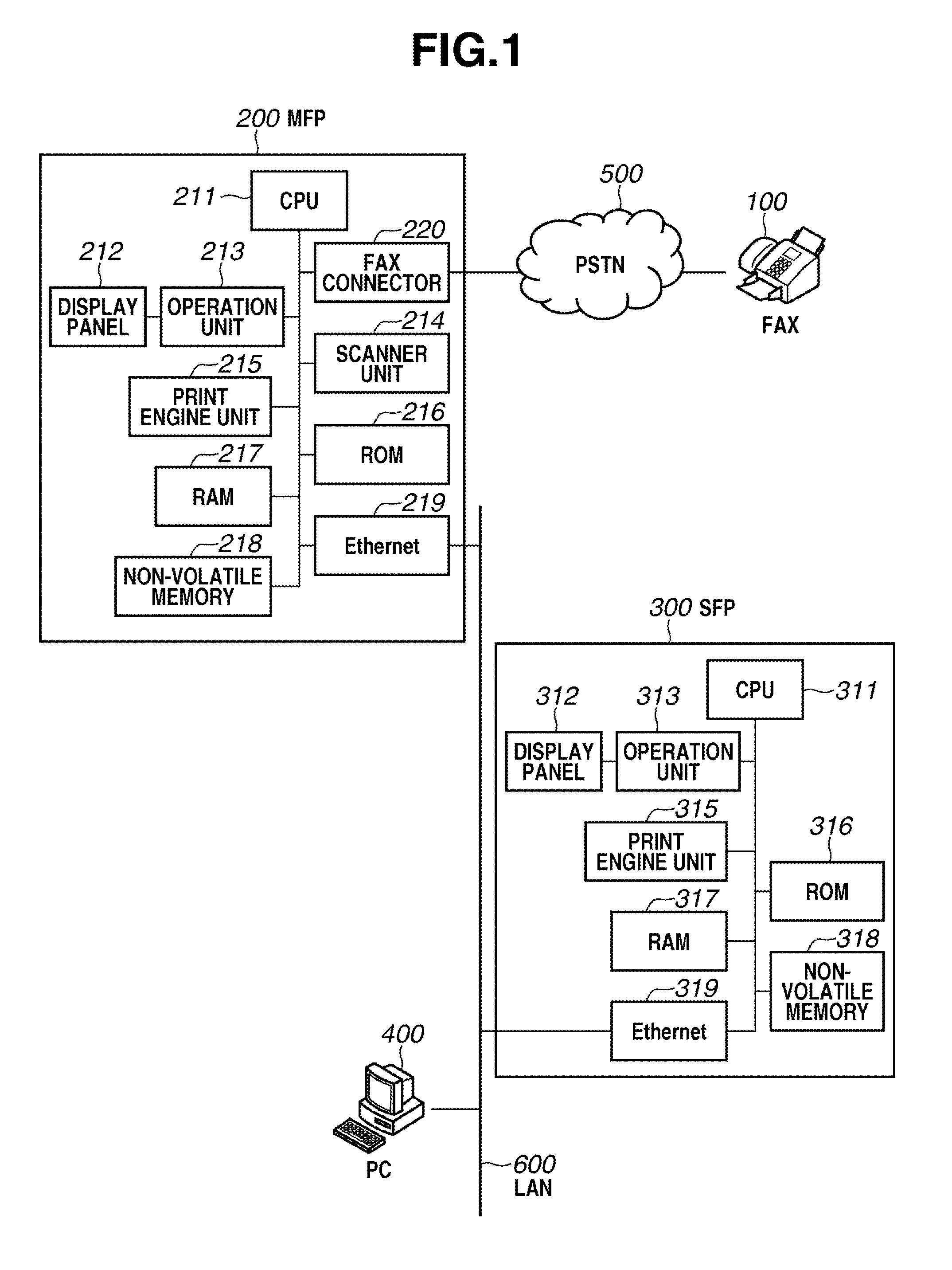
Image forming apparatus, image forming system, image forming system control method, and program
ActiveUS20120293836A1Visual presentation using printersPictoral communicationImage formationPage description language
An image forming apparatus includes a receiving unit configured to receive data via a network, a printing unit configured to print an image based on the data received from the receiving unit, and a control unit configured to control the receiving unit to refuse a data reception based on a simple mail transfer protocol (SMTP) when a toner remaining amount for the printing unit is less than a predetermined value, wherein the printing unit is configured to print, in the case that the receiving unit receives page description language (PDL) data, an image based on the received PDL data even if the toner remaining amount is less than the predetermined value.
Owner:CANON KK
System and method for notifying users of an event using alerts
ActiveUS20050181836A1Information formatSpecial service for subscribersSimple Mail Transfer ProtocolReal-time computing
An alert engine module receives an alert for an event in a generic communications format and delivers an alert for the event to a target address in a communications format that is preferred by a user based on the alert content. The generic format can be an e-mail message, such as a Simple Mail Transfer Protocol (SMTP) message. The alert engine can be operative to transform the alert based on a header and / or format of a target address.
Owner:TEAMON SYST
System and method for delivering information via secure electronic messaging
InactiveUS20150326517A1Digital data information retrievalDigital data processing detailsMessage handlingEmail attachment
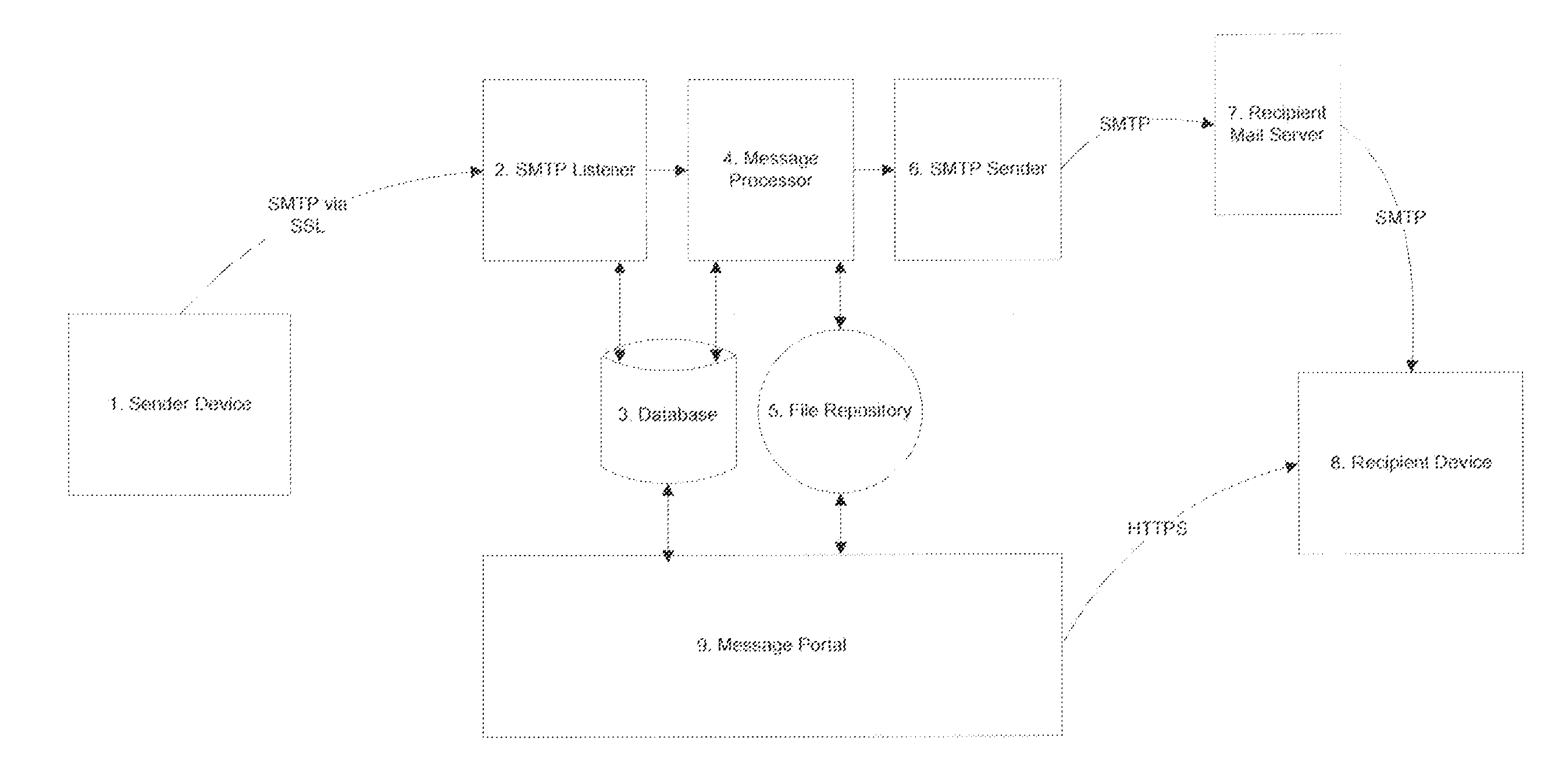
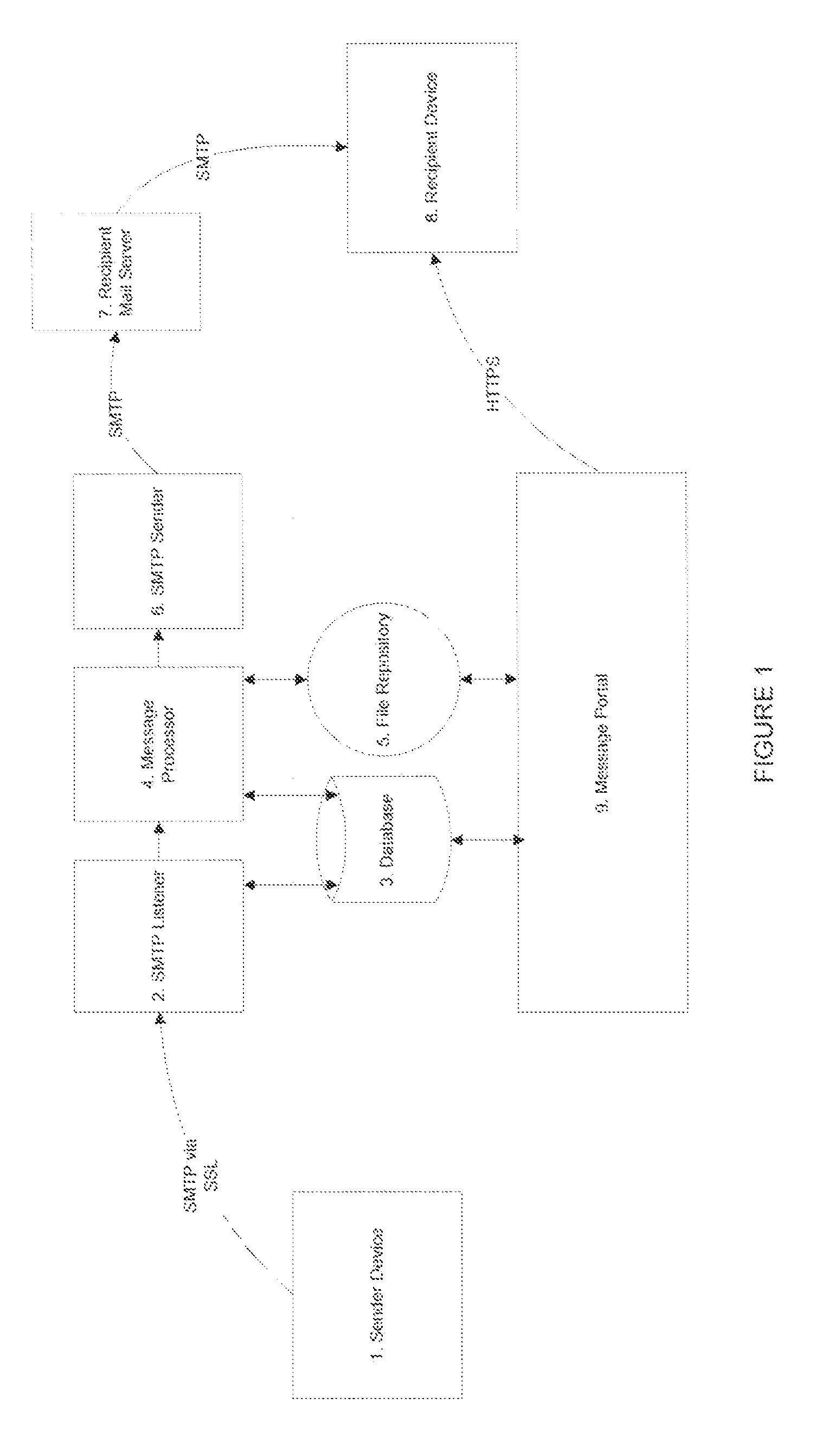
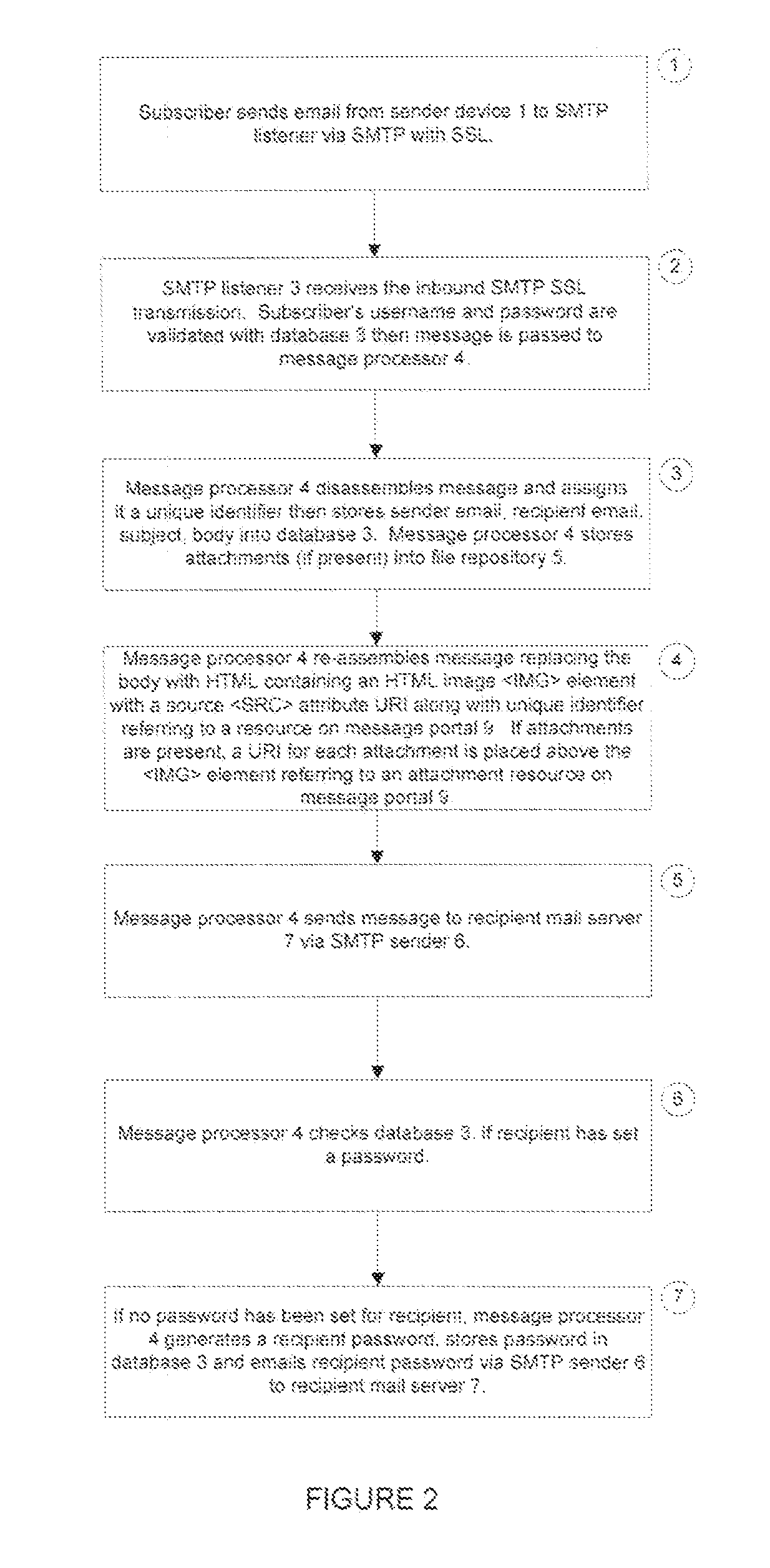
A computer-implemented system for delivering information comprising: a sender device with an email client for composing and sending an original email message to a Simple Mail Transfer Protocol (SMTP) listener server with encryption enabled; a message processor that extracts the message body payload from the email message, stores it in a database, and creates a new email message with a message body containing a reference to the message body of the original email message; a file repository for storage of attachments to the email message; and an SMTP sender that sends the new email message to a recipient mail server. The listener server assigns the message to the message processor, and the new email message contains links to the attachments residing in the file repository. A method utilizing the system described above.
Owner:MAILHIPPO INC
Sending and receiving electronic mail using group headers
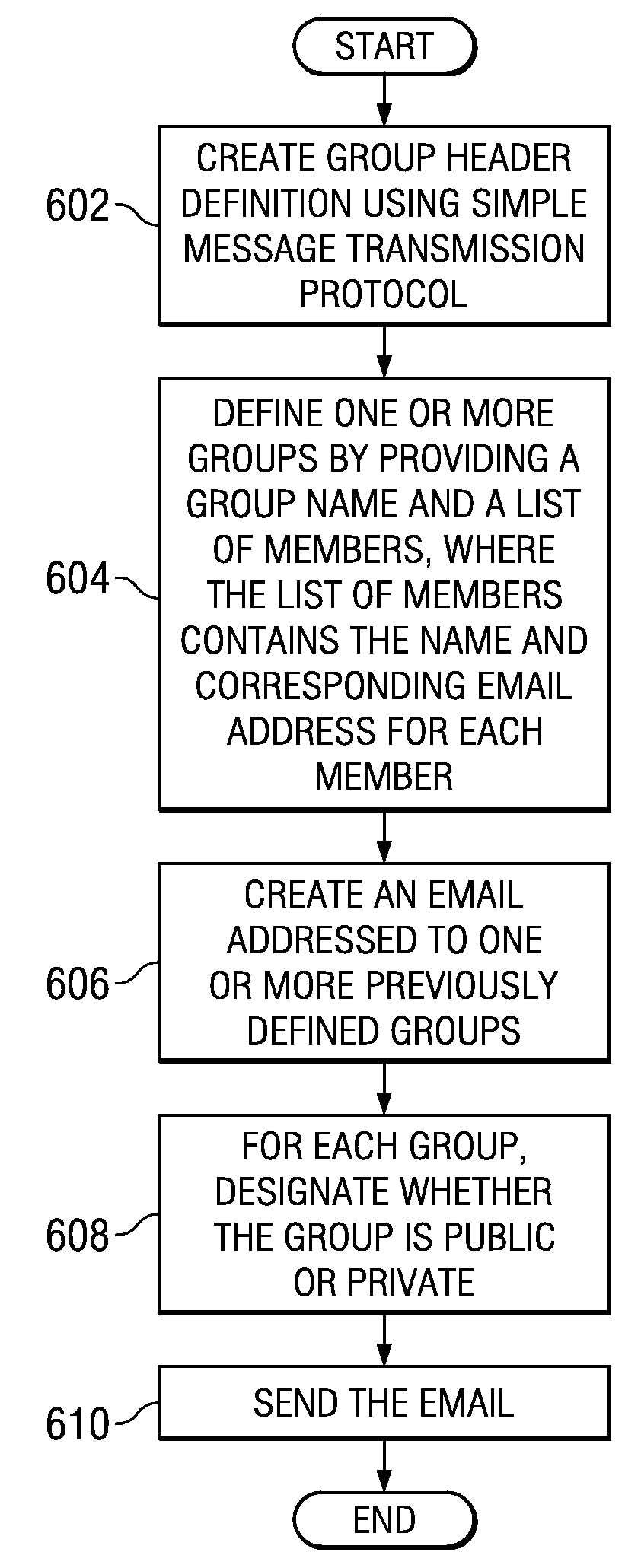
InactiveUS20080133669A1Multiple digital computer combinationsData switching networksTransmission protocolWorld Wide Web
A computer implemented method and apparatus for sending and receiving electronic mail messages. A group header is defined using simple mail transmission protocol. The group header provides information about a set of members of a group. The set of members of the group are one or more recipients of the electronic mail message. The group header is placed in the electronic mail message to form a completed electronic mail message addressed to the group. The completed electronic mail is sent to the group.
Owner:IBM CORP
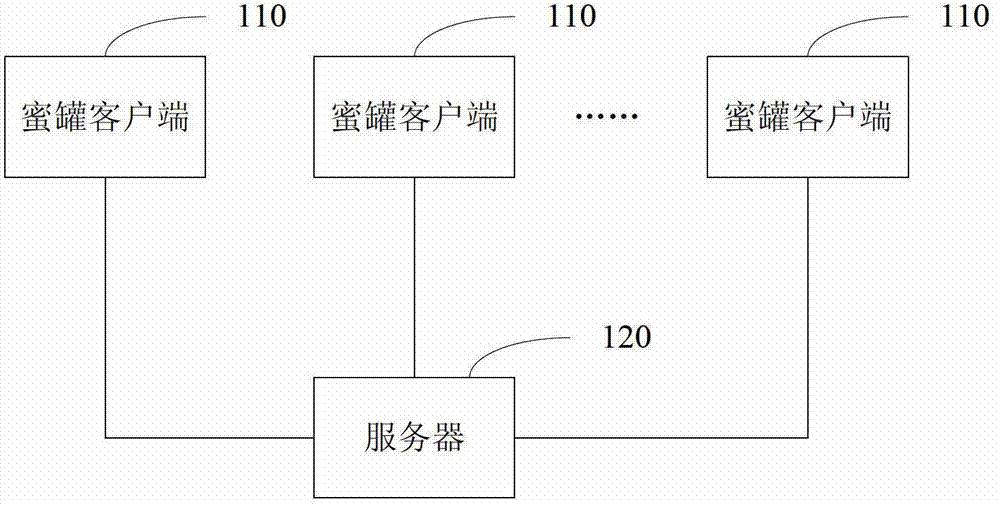
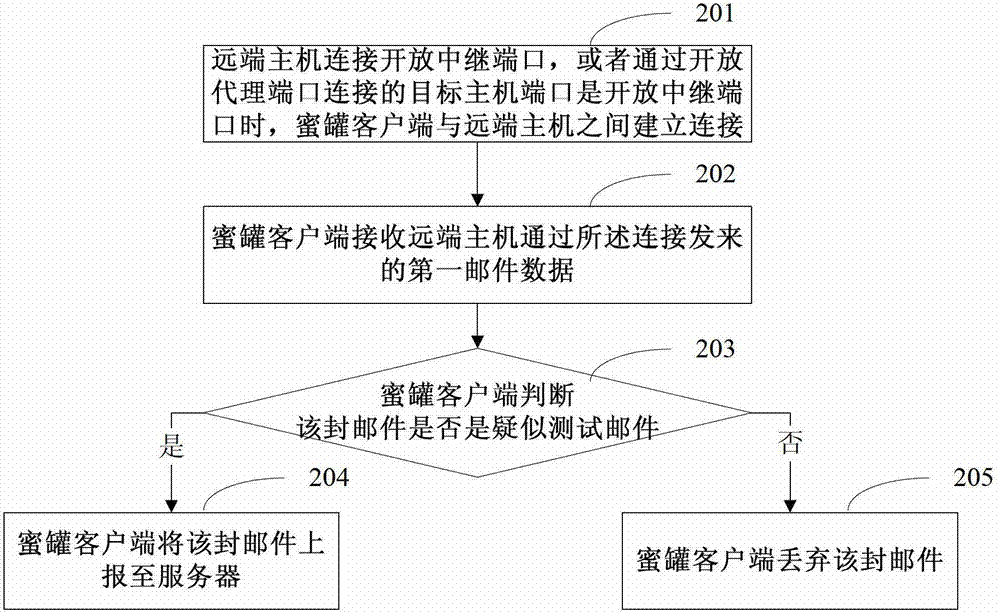
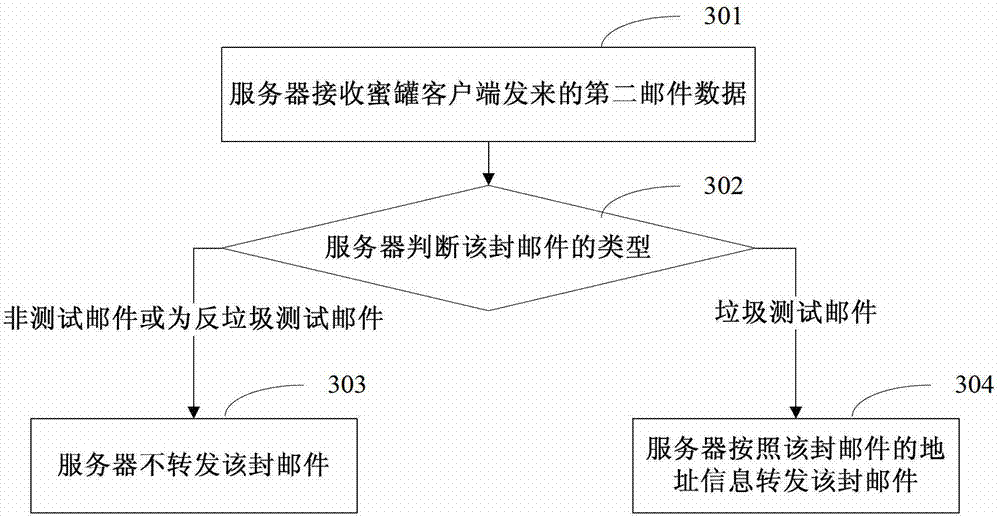
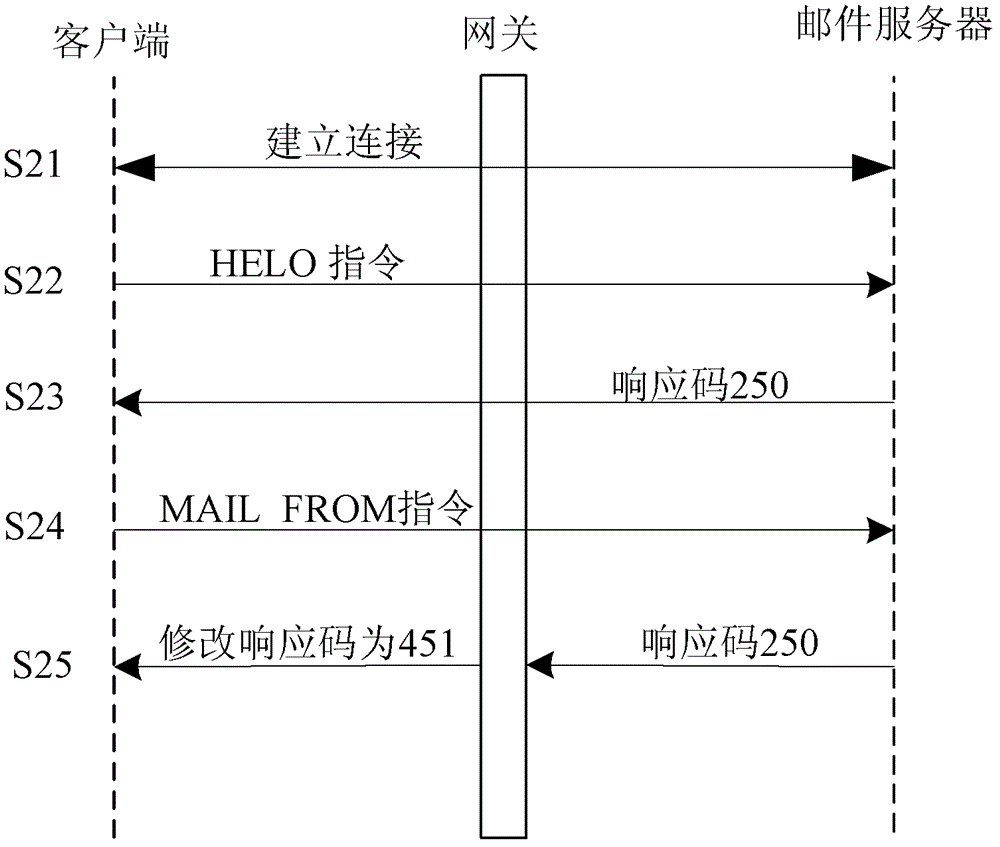
Method, device and system for processing mails
The embodiment of the invention discloses a method and a device for processing mails. The method comprises the following steps of enabling a remote host to connect with an open trunk port, or when a target host port connected by an open proxy port is an SMTP (simple mail transfer protocol) port, establishing the connection between the SMTP port and the remote host; receiving first mail data sent by the remote host through the connection; for each mail contained in the first mail data, judging whether the mail is a suspected test mail or not; if the mail is the suspected test mail, reporting the mail to a server, so on the premise of meeting the preset condition, the server can forward the mail; and if the mail is not the suspected test mail, discarding the mail. The method and the device have the advantages that the viscosity to a rubbish mail sender is ensured, and the abuse of a mail honeypot is avoided.
Owner:HUAWEI TECH CO LTD
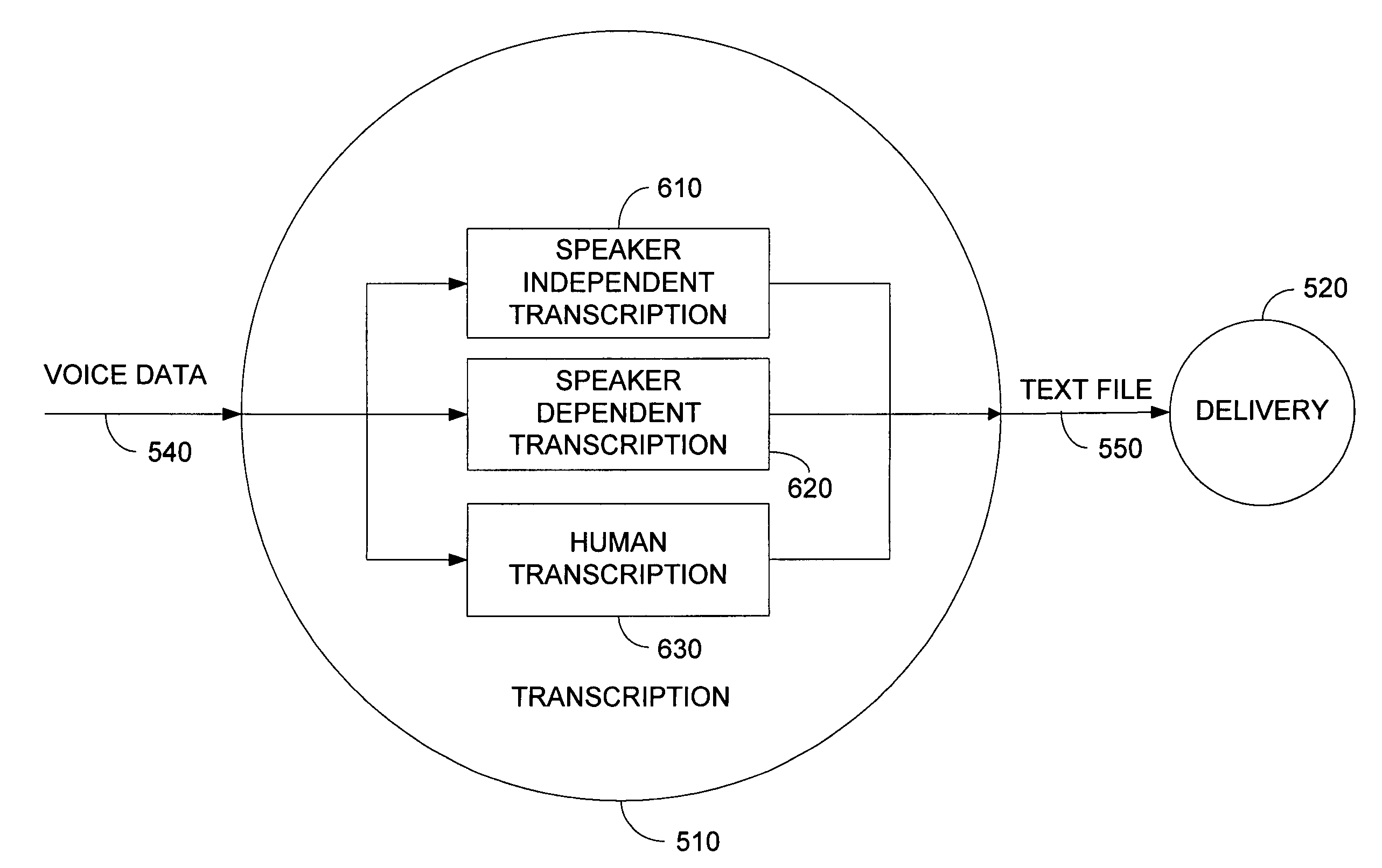
System and method for recording voice data and converting voice data to a text file
ActiveUS8265930B1Automatic call-answering/message-recording/conversation-recordingSpeech recognitionVoice communicationComputer software
The present invention relates to recording voice data using a voice communication device connected to a communication network and converting the voice data into a text file for delivery to a text communication device. In accordance with the present invention, the voice communication device may transfer the voice data in real-time or store the voice data on the device to be transmitted at a later time. Transcribing the voice data into a text file may be accomplished by automated computer software, either speaker-independent or speaker-dependent or by a human who transcribes the voice data into a text file. After transcribing the voice data into a text file, the text file may be delivered to a text communication device in a number of ways, such as email, file transfer protocol (FTP), or hypertext transfer protocol (HTTP).
Owner:T MOBILE INNOVATIONS LLC
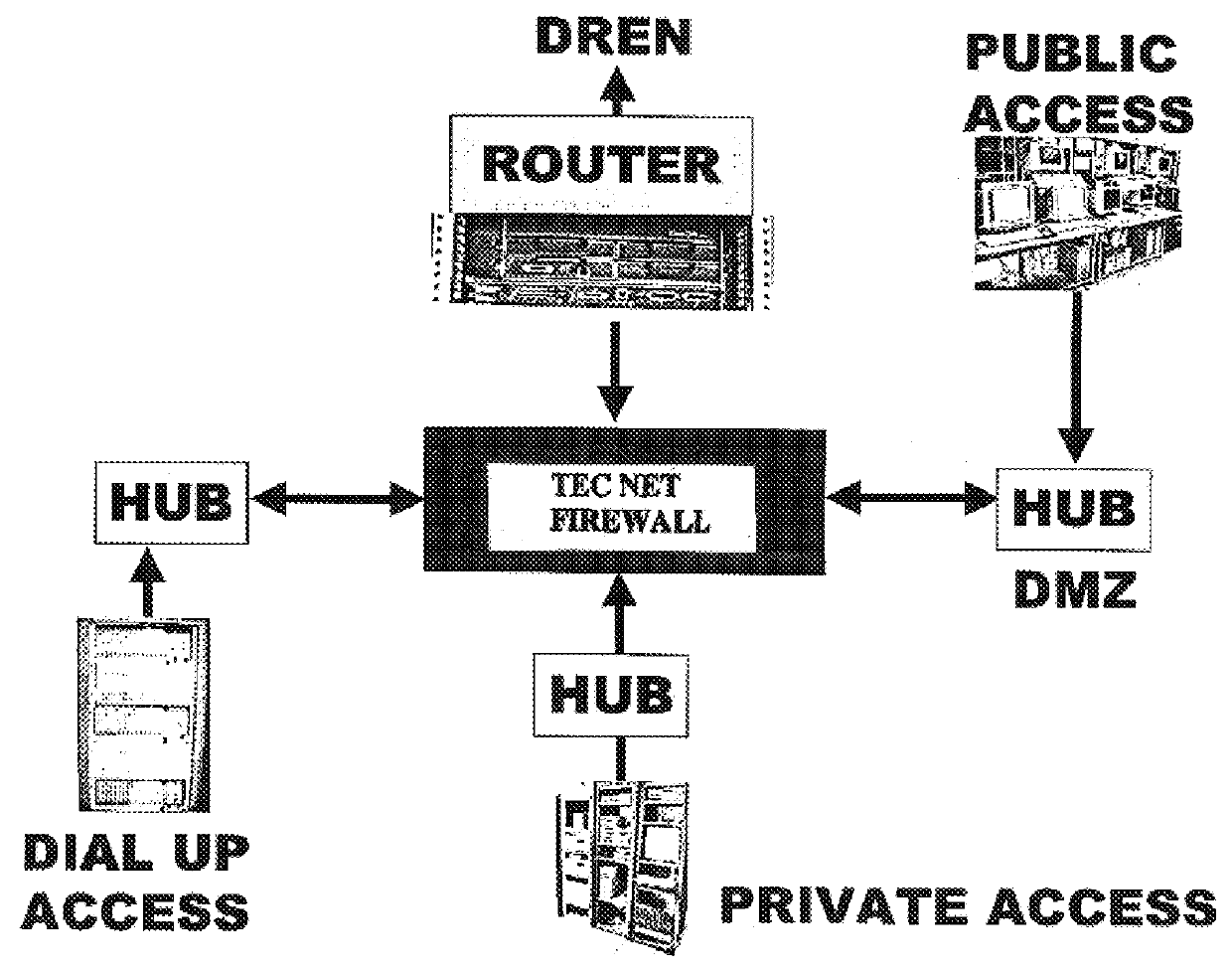
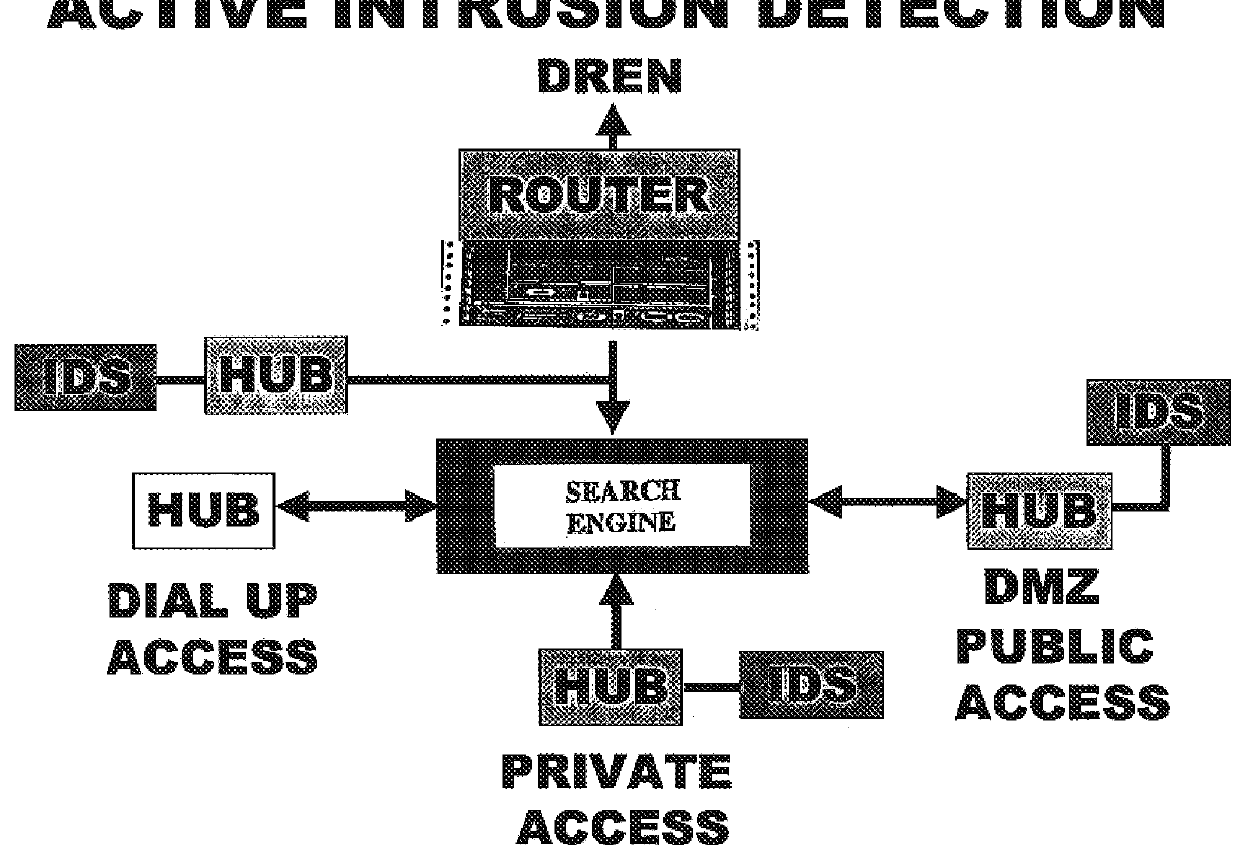
Test and evaluation community network (TECNET)
InactiveUSH2111H1Reduce riskWide accessSpecial service provision for substationMultiple digital computer combinationsUnixSimple Mail Transfer Protocol
Test and Evaluation Community Network (TECNET) is a set of software and safeguards that operates on a standard UNIX based computer to provide the following capabilities in a secure fashion via the World Wide Web operating over the Internet: Simple Mail Transfer Protocol (SMTP), Multimedia Internet Mail Extension (MIME) compliant electronic mail with many user features. Reflector configured bulletin board capabilities as a logical extension of the above electronic mail system for group sharing. Hierarchical file repositories allowing binary upload, copying, and download for Internet store and forward capability. Protected File Transfer Protocol (FTP) areas supplant the above file repository capability.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE +1
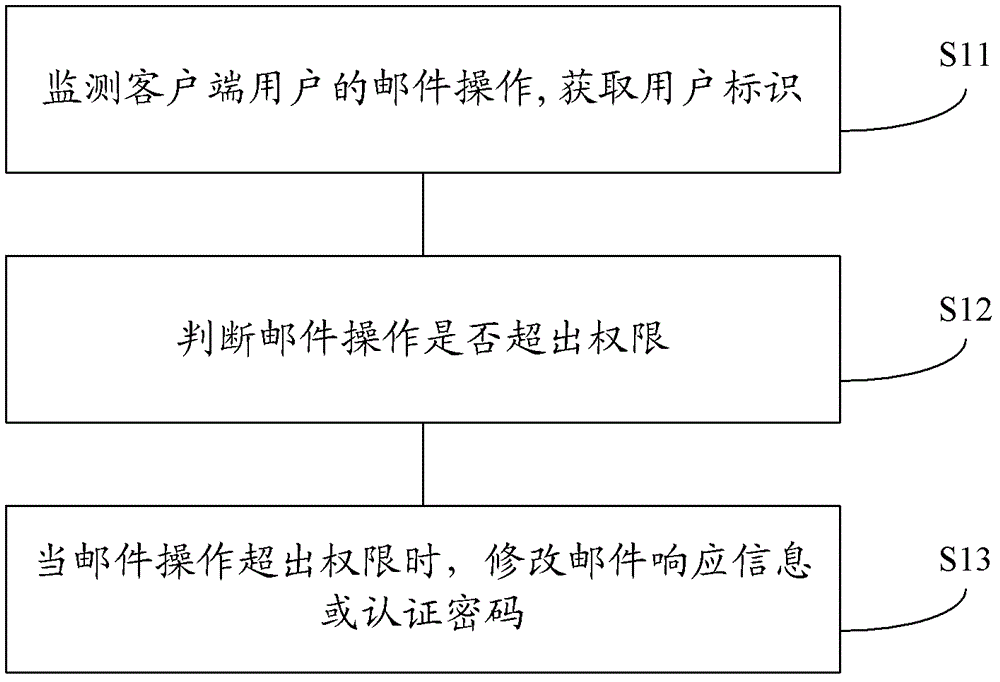
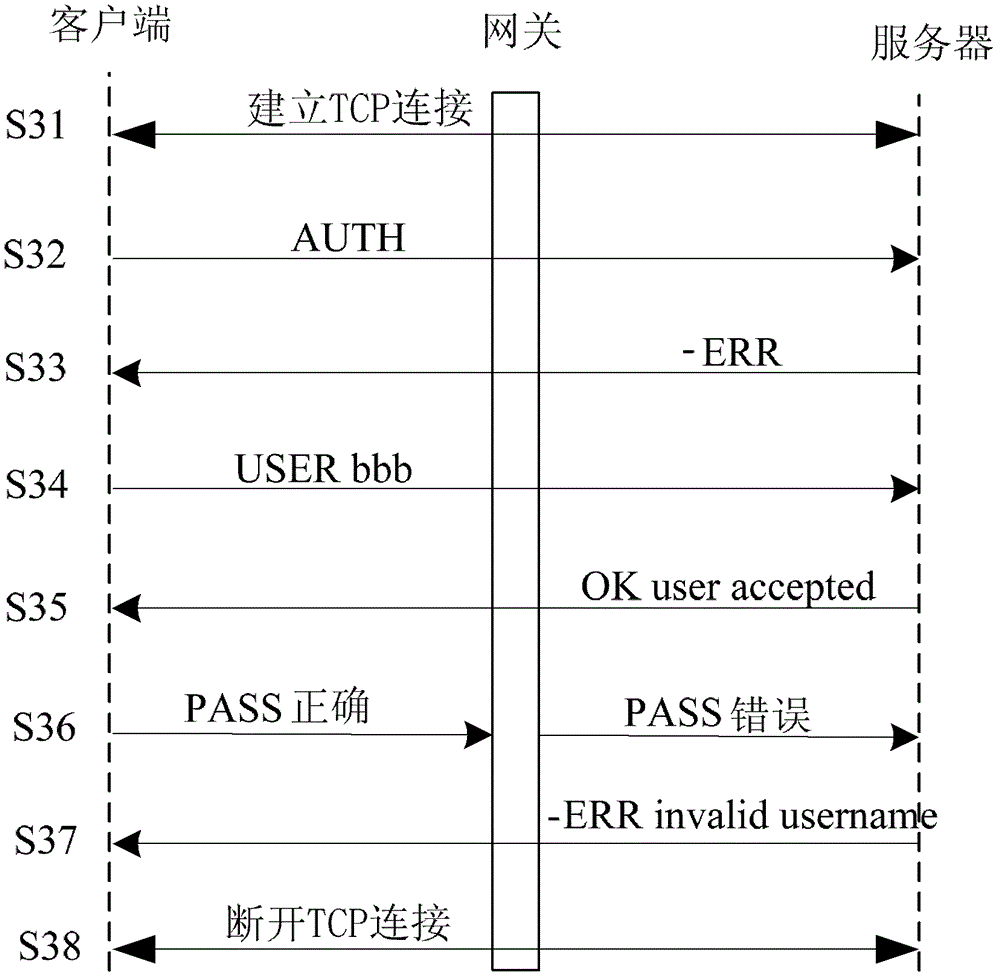
Method and device for blocking mail behavior and gateway
The invention discloses a method and a device for blocking a mail behavior and a gateway. The method for blocking the mail behavior comprises the following steps of: monitoring the mail operation of a client user; acquiring a user identifier in a simple mail transfer protocol (SMTP) instruction transmitted by a client of the user; judging whether the mail operation is out of right or not according to the user identifier and preset right corresponding to the user; and when the mail operation is out of the right, modifying mail response information or an authentication password, so that a mail server returns error information to the client, wherein the error information is used for instructing the client to abort the limited mail operation. According to the embodiment, the error information returned to the client is used for instructing the client to abort the limited mail operation, so that a limited user can be prevented from transmitting a mail. According to the method, a transmission control protocol (TCP) cannot be interrupted, so that the client cannot repeatedly establish connection, and the consumption of equipment is reduced.
Owner:CHENGDU HUAWEI TECH
E-mail firewall
InactiveUS20070214353A1Easy to controlMultiple keys/algorithms usageData taking preventionContent managementDistributed computing
An e-mail firewall (105) applies policies to e-mail messages (204) between a first site and a plurality of second sites in accordance with a plurality of administrator selectable policies (216). The firewall comprises a simple mail transfer protocol (SMTP) relay (202) for causing the e-mail messages (204) to be transmitted between the first site and selected ones of the second sites. A plurality of policy managers (216) enforce-administrator selectable policies. The policies, such as encryption and decryption policies, comprise at least a first source / destination policy (218), at least a first content policy (202) and at least a first virus policy (224). The policies are characterized by a plurality of administrator selectable criteria (310), a plurality of administrator selectable exceptions (312) to the criteria and a plurality of administrator selectable actions (314, 316, 322) associated with the criteria and exceptions. The policy managers comprise an access manager (218) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the source / destination policy (218). The policy managers (216) further comprise a content manager (220) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the content policy (220), and a virus manager (224) for restriction transmission of e-mail messages (204) between the first site and the second sites in accordance with the virus policy (224).
Owner:AXWAY
Method and apparatus for meeting mail transmission
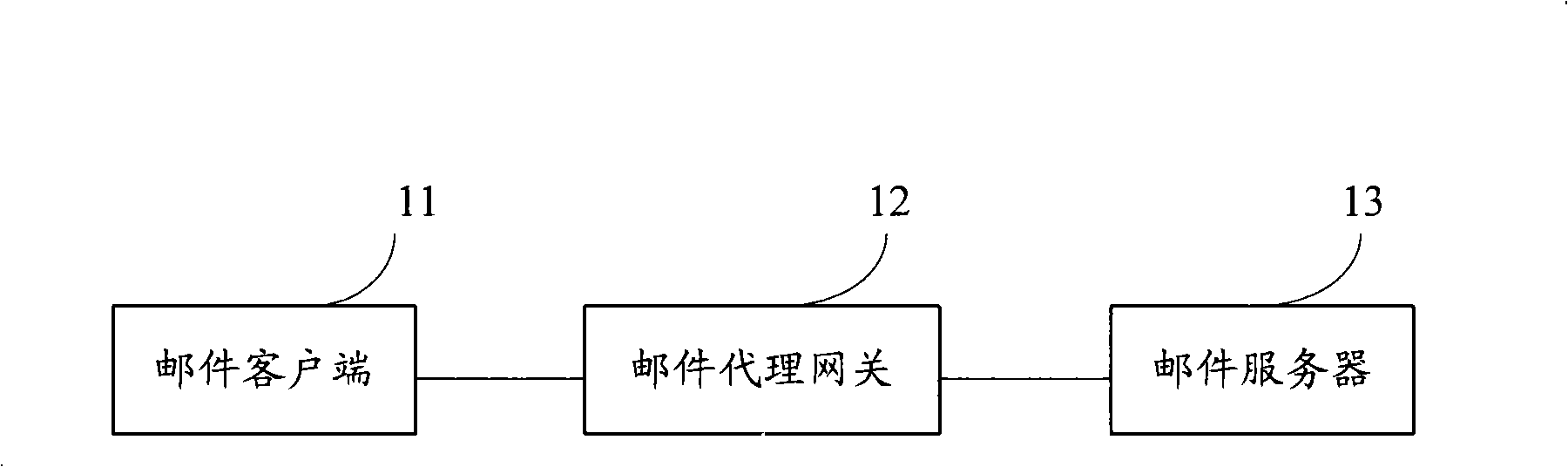
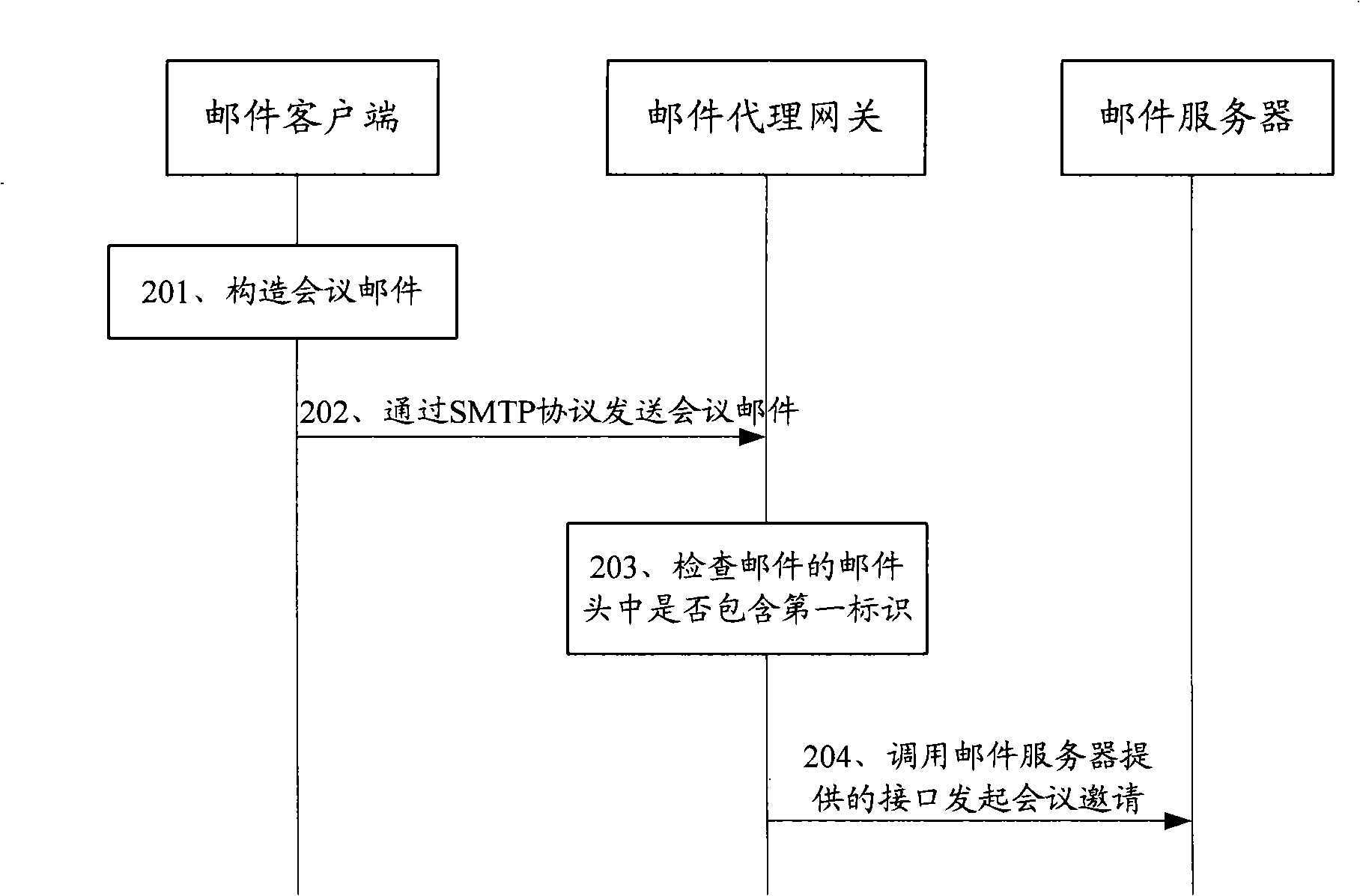
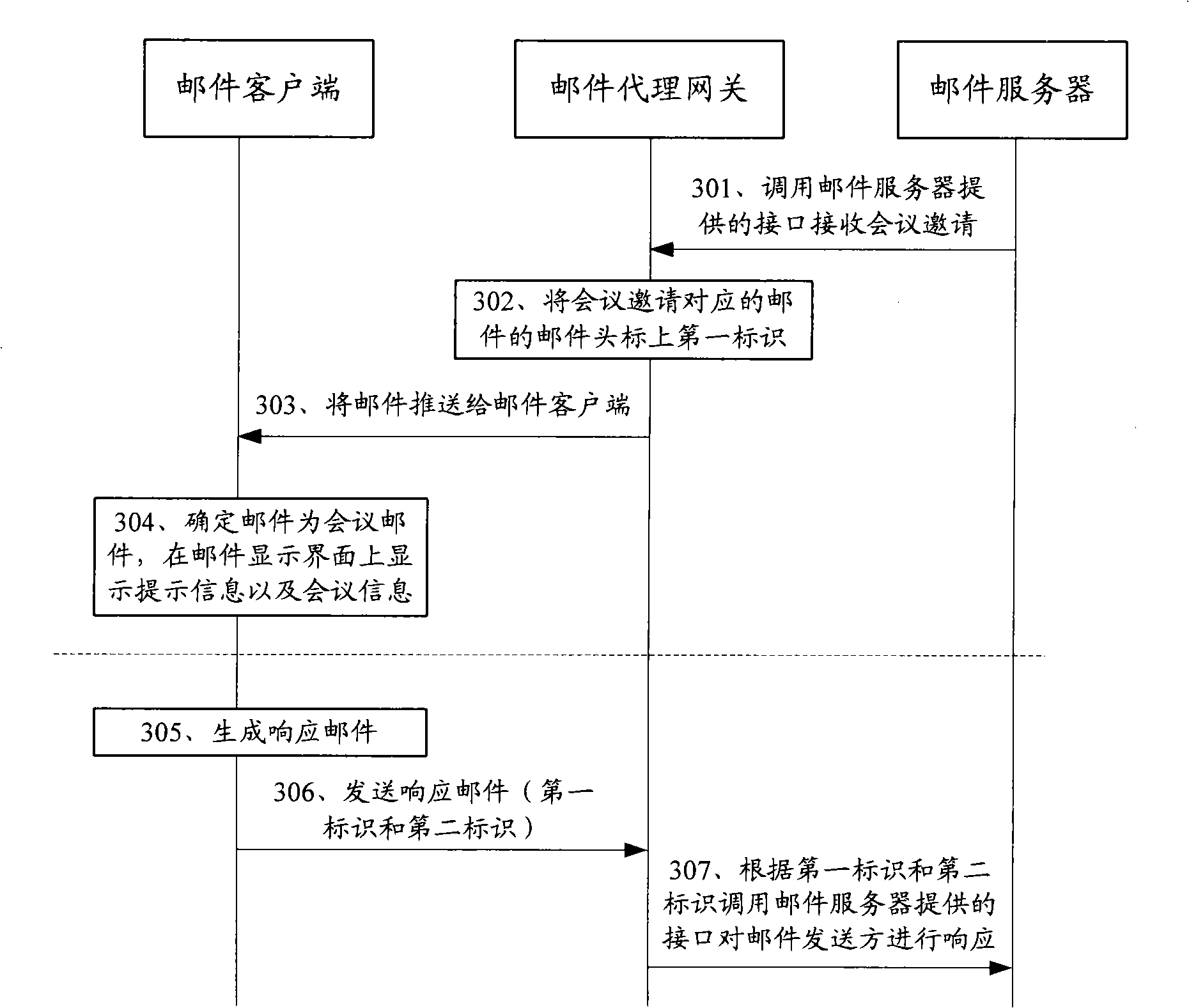
InactiveCN101340394ARealize transmissionEasy to useData switching networksClient-sideSimple Mail Transfer Protocol
The invention discloses a method and a device for the transmission of a meeting mail, the method comprises the steps as follows: a mail proxy gateway receives the mail which is sent by a mail client through a simple mail transfer protocol (SMTP), if a mail head of the mail contains a first identifier for identifying the meeting mail, an interface which is provided by a mail server is called to initiate meeting invitation; the mail proxy gateway calls the interface which is provided by the mail server to receive the meeting invitation, and the first identifier on the mail head of the mail which is corresponding to the meeting invitation is pushed back to the mail client. The utilization of the invention can conveniently realize the transmission of the meeting mail and other personal information.
Owner:北京立通无限科技有限公司
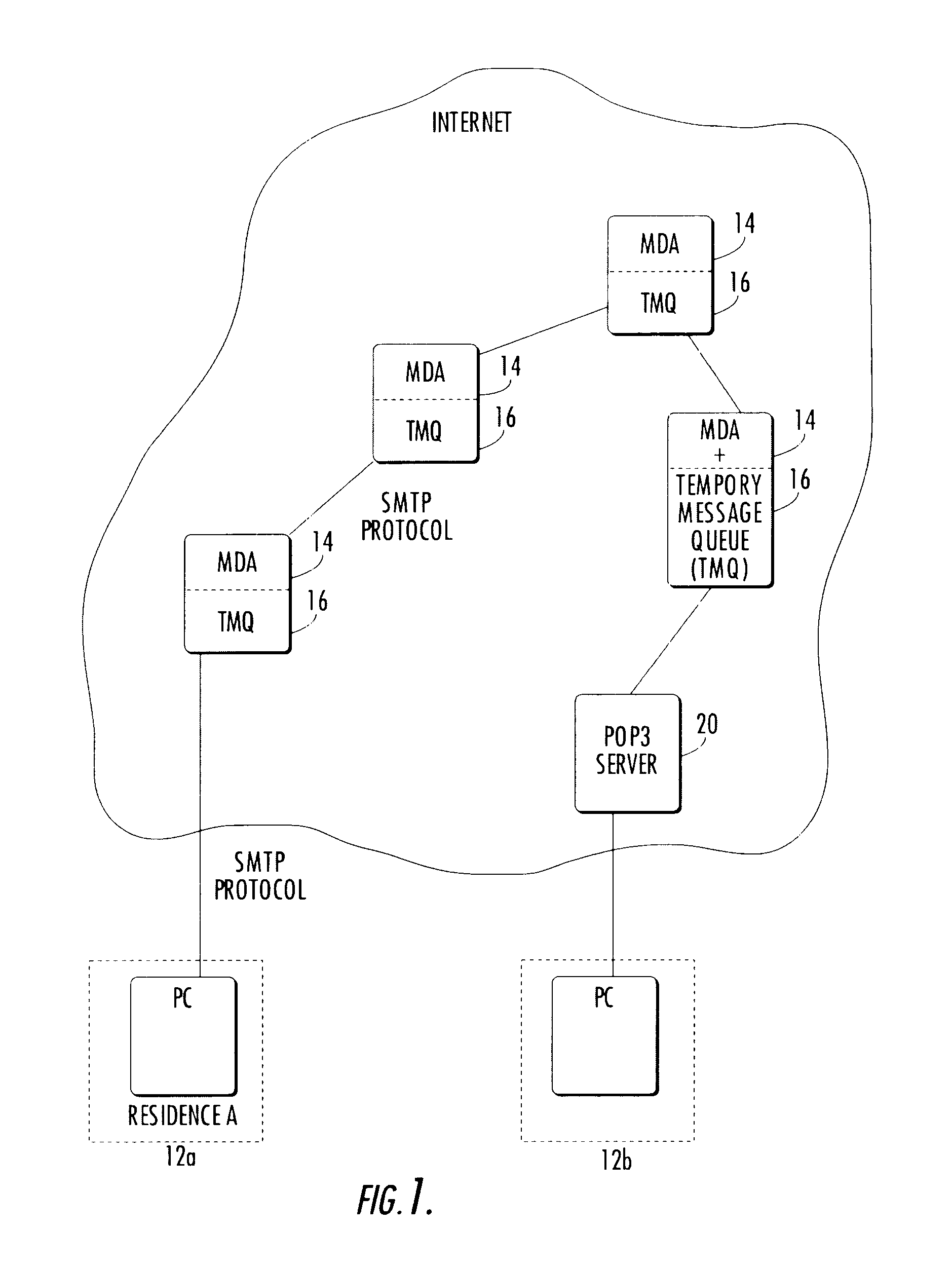
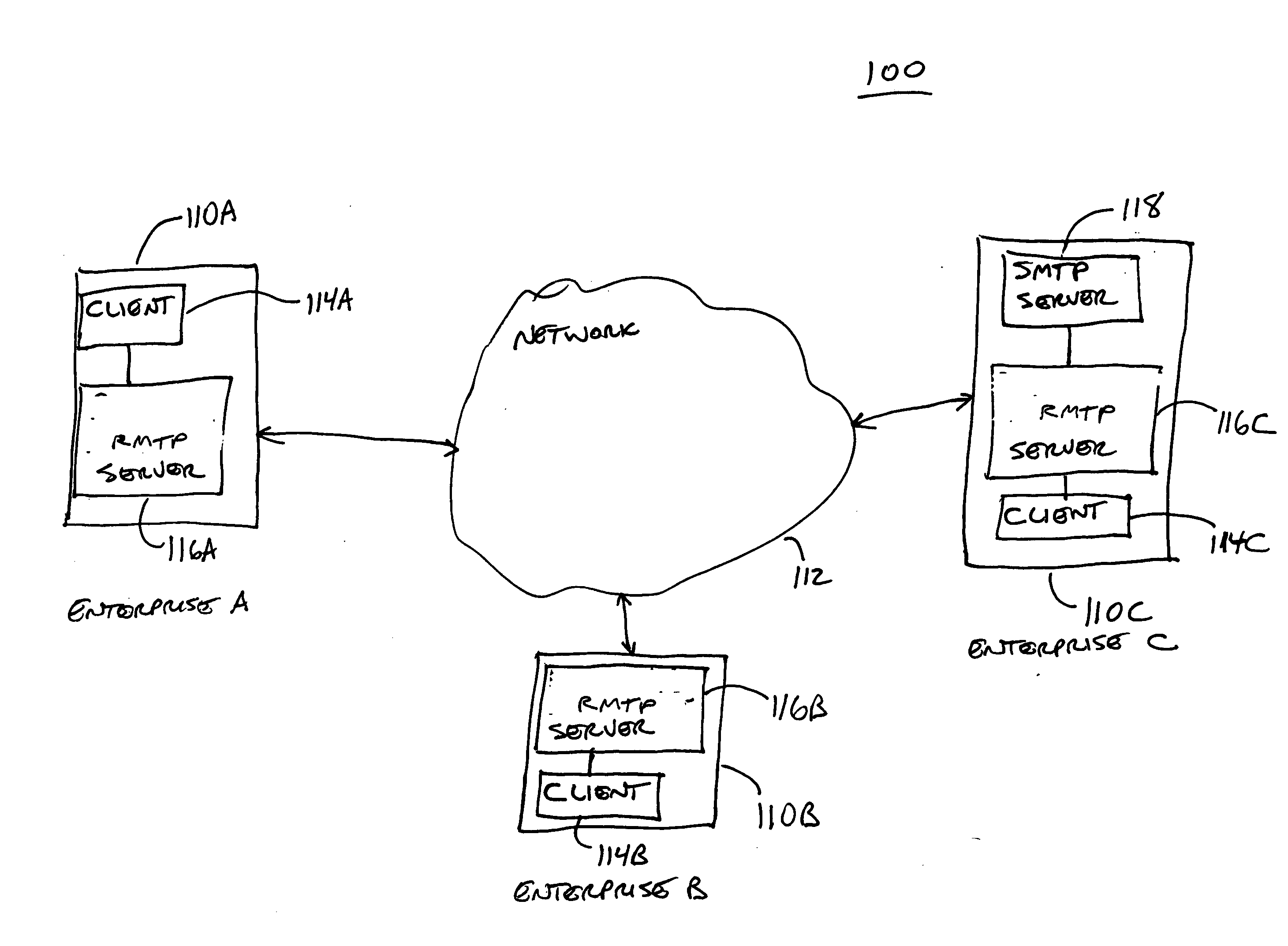
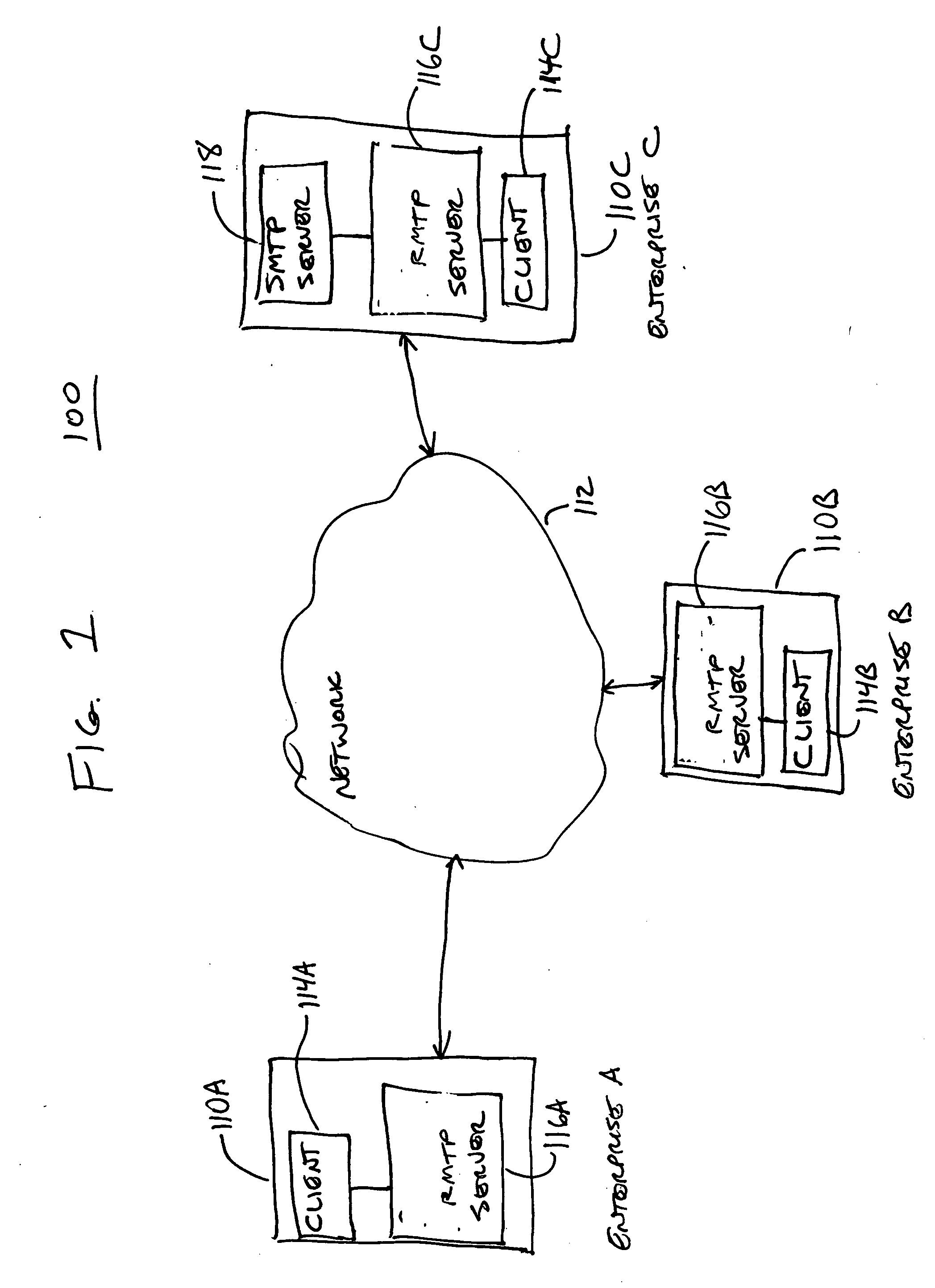
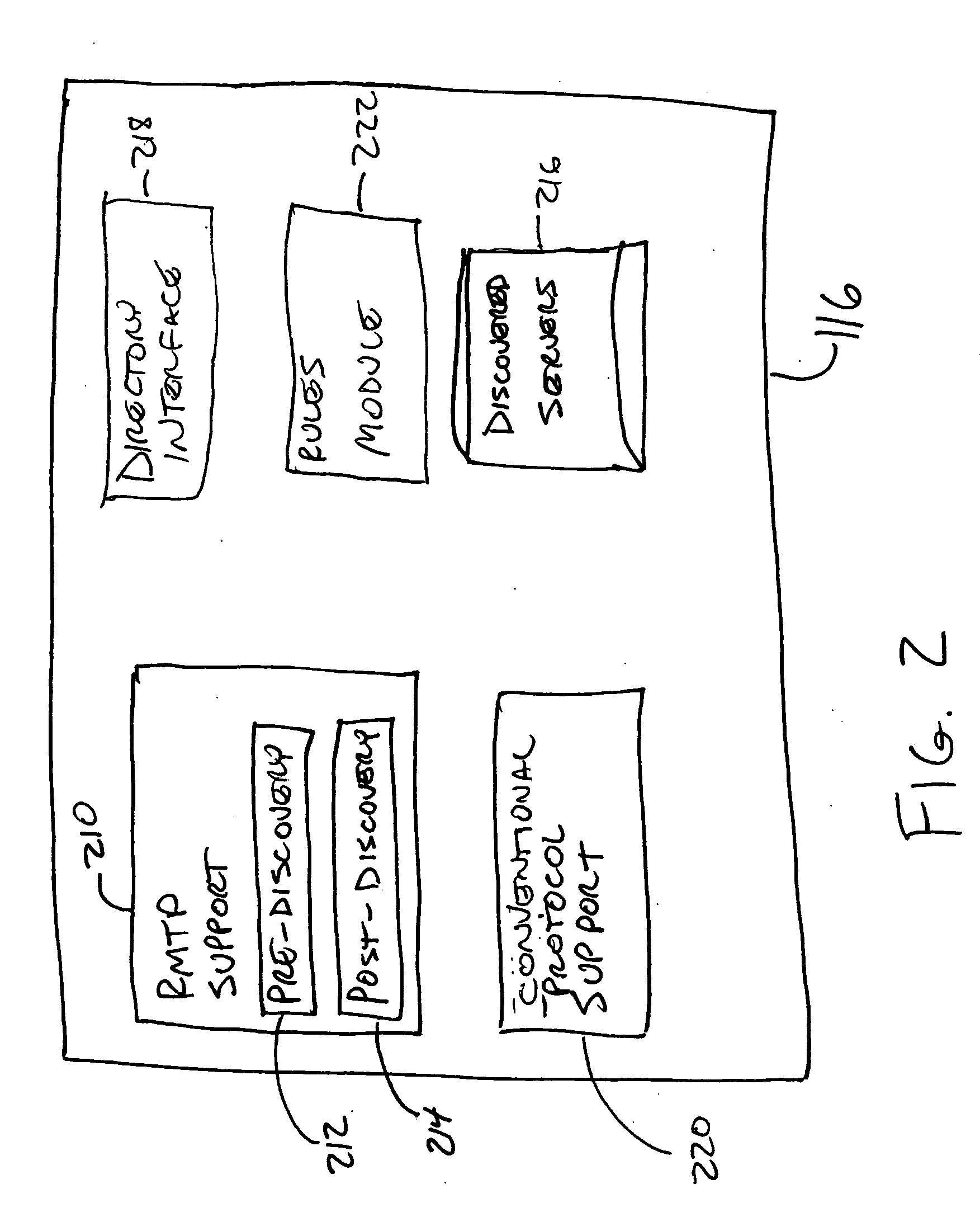
Messaging protocol discovery
A messaging server (116) supports a relational message transport protocol (RMTP). The RMTP server (116) discovers whether other messaging servers on a network (112) support the RMTP. In pre-discovery, the RMTP server (116) uses (320) simple mail transport protocol (SMTP) command lines to discover whether another messaging server supports RMTP. In post-discovery, the RMTP server (116) encodes the message with data that are recognized by a RMTP server and delivers (324) the data using a conventional protocol such as SMTP. A RMTP server (116) that receives the encoded message initiates (312) a RMTP connection with the sending server. The RMTP server (116) maintains a database of discovered servers (216) and provides a directory interface (218) that other RMTP servers can use to access the database.
Owner:BLUSCE SOFTWARE CORP
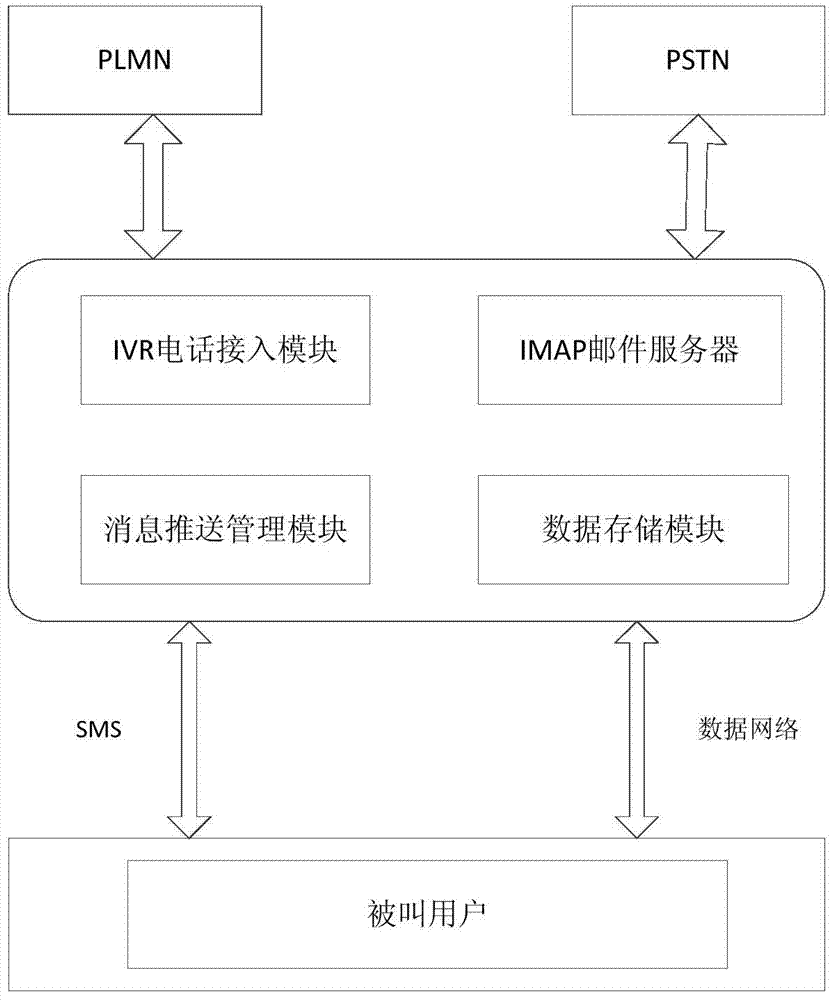
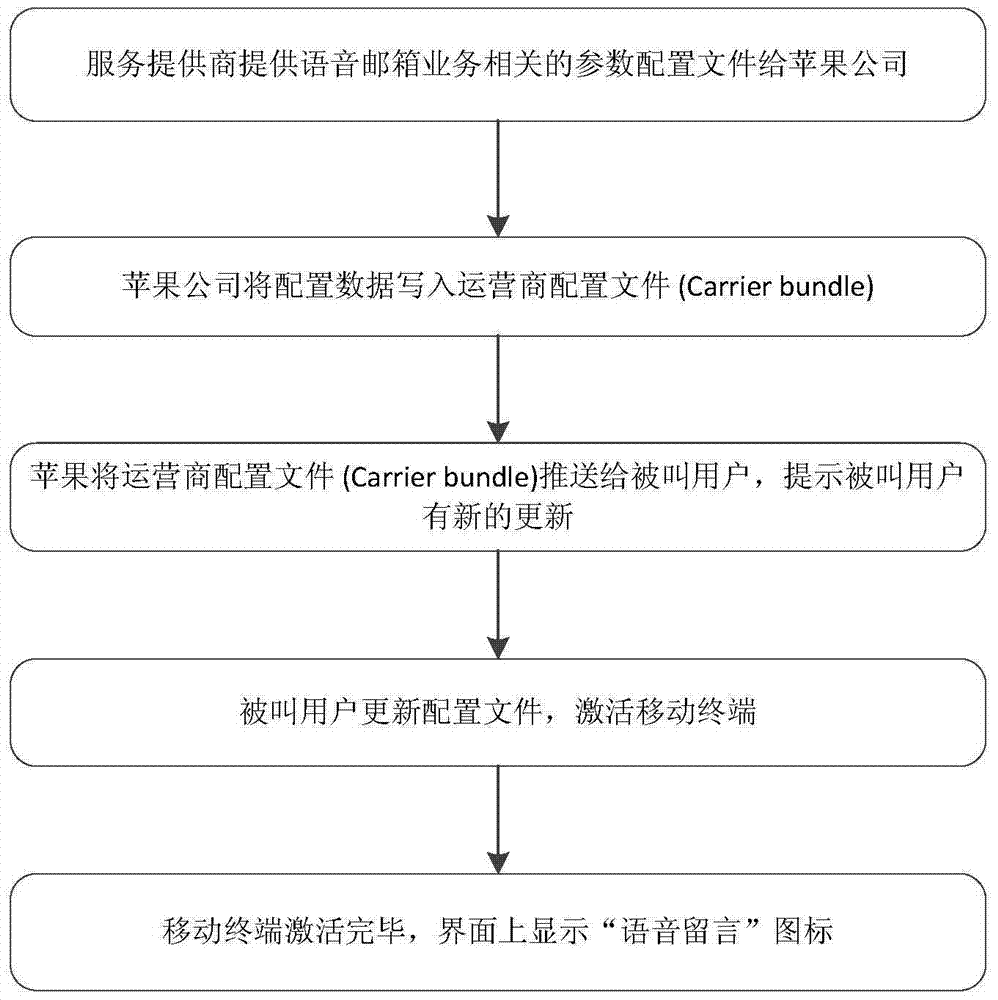
IOS (internetwork operating system) based visualization voice mailbox communication method and system
InactiveCN104243289ACommmunication supplementary servicesMessaging/mailboxes/announcementsMessage deliverySpeech sound
The invention relates to an IOS (internetwork operating system) based visualization voice mailbox communication method and system. The method includes: encapsulating a voice message given to a called party by a calling party into a voice mail through an IVR (interactive voice response) telephone access module and transferring the voice mail to an IMAP (internet mail access protocol) mail server by adopting an SMTP (simple mail transfer protocol) so as to allow the IMAP mail server to have the voice mailbox stored; when a new voice mail available to the called party is detected, a message delivery management module sends a SMS (short messaging service) message and an MWI (message waiting indication) message to the called party by adopting an SMS mode so as to enable the called party to be connected to the IMAP mail server through a voice mail access message in the MWI message and download the corresponding voice mail from the IMAP mail server, wherein the called party refers to a mobile terminal based on the IOS system. Under the condition that the method and the system conforms to related provisions of the Apple Inc and through reasonable and effective means of a technology, voice mailbox service can also be used in a China telecom operator network.
Owner:广州市讯飞樽鸿信息技术有限公司
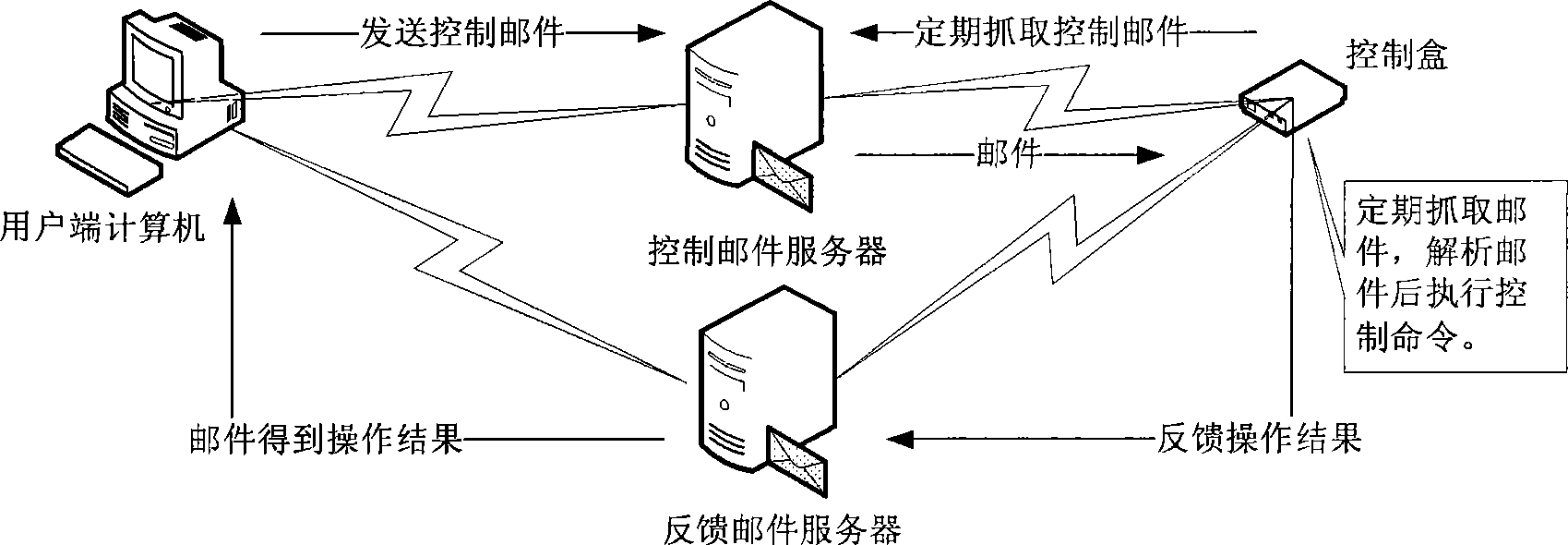
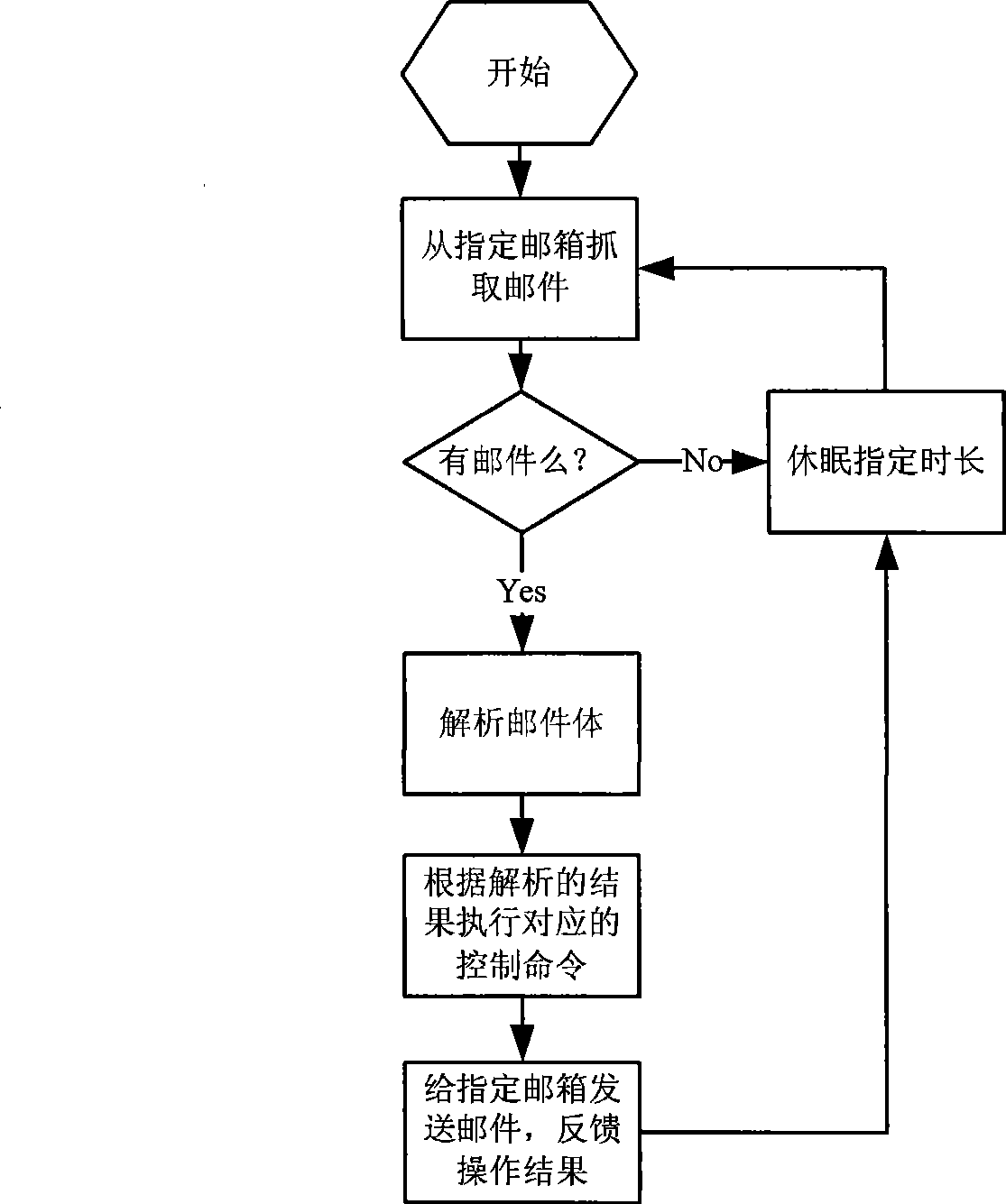
Remote control method and apparatus using internet terminal equipment
The invention relates to a method for carrying out remote control with an internet terminal device and a device thereof, and belongs to the computer technology field. The device comprises user-side computers which are interconnected via Internet cables, a mail server and a control box. The control box is provided with the Linux operating system and integrated with the FetchMail software and the simple mail transfer protocol (SMTP) client terminal. Compared with the prior art, the method and the device have the advantages of simple operation and good control stability and are applicable to the non-real-time control of the remote equipment crossing the wide-area network.
Owner:TSINGHUA TONGFANG CO LTD
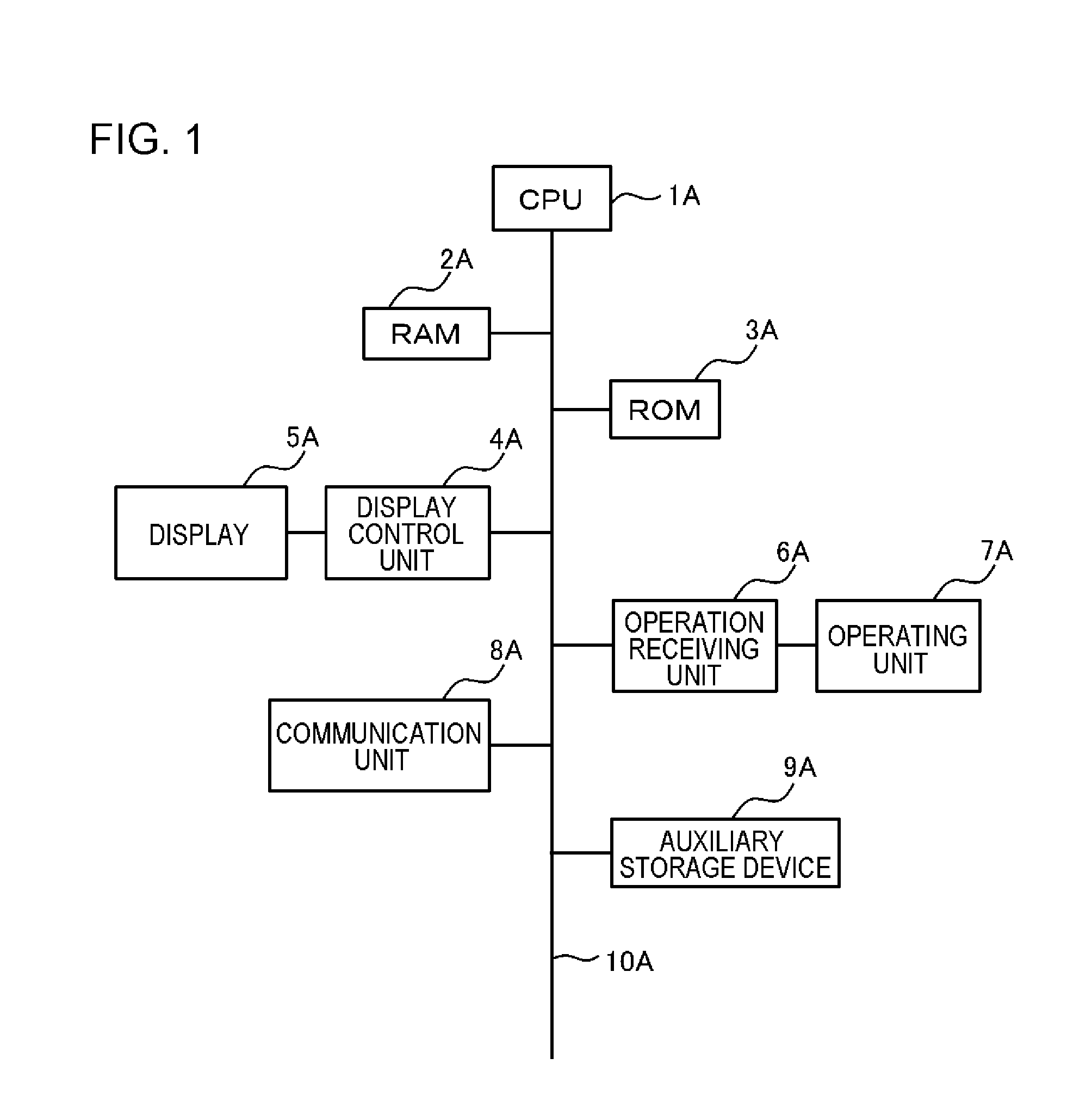
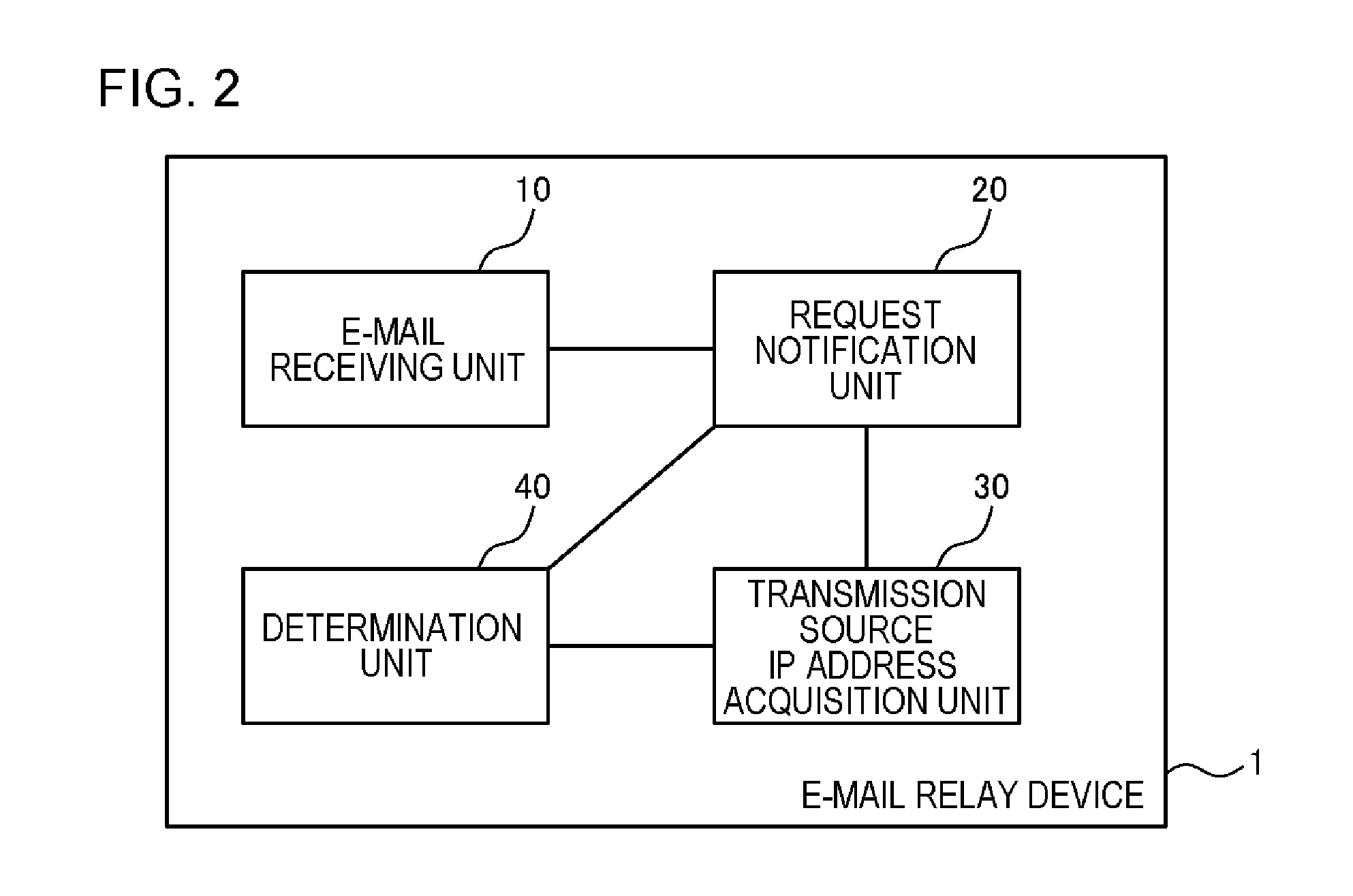
E-mail relay device, e-mail relay method, and non-transitory storage medium
ActiveUS20170019354A1Multiplex system selection arrangementsData switching networksEmail addressIp address
Provided is an e-mail relay device including: an e-mail receiving unit that acquires an e-mail to be delivered before the e-mail reaches a transmission destination, the e-mail being transmitted from a transmission source mailer through simple mail transfer protocol (SMTP); a request notification unit that transmits, after the e-mail receiving unit acquires the e-mail to be delivered, a notification e-mail for allowing communication with a predetermined authentication server through IP by using a transmission source e-mail address of the e-mail to be delivered as a destination; a transmission source IP address acquisition unit that acquires, in a case where the transmission source terminal communicates with the predetermined authentication server after the notification e-mail is transmitted, an IP address of a transmission source terminal contained in an IP header of an IP packet transmitted / received during the communication; and a determination unit that determines the reliability of the e-mail to be delivered based on the IP address of the transmission source terminal.
Owner:NEC CORP
News transmitting and receiving through tailered communication channel and program design model
InactiveCN1533117ADigital computer detailsFiling/rasping devicesComputer hardwareMessage passing architecture
Methods, systems, and computer program products for abstracting processing layers within a messaging infrastructure so that changes or enhancements can be made to the infrastructure while retaining existing functionality. Message transport implementations are abstracted within a message layer, allowing other layers within the infrastructure to interact with messages in a more generic fashion, largely independent of message transport. Transport examples include named pipes, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), etc. A channel layer above the message layer abstracts message exchange implementations, allowing other layers within the infrastructure to send and receive messages in a more generic fashion, largely independent of the message exchange semantics of a specific implementation. Message exchange examples include datagrams, dialogs, monologs, queues, and the like. Above the channel layer and message layer, a service layer abstracts the binding implementations that bind message exchange implementations to user code implementations.
Owner:MICROSOFT TECH LICENSING LLC
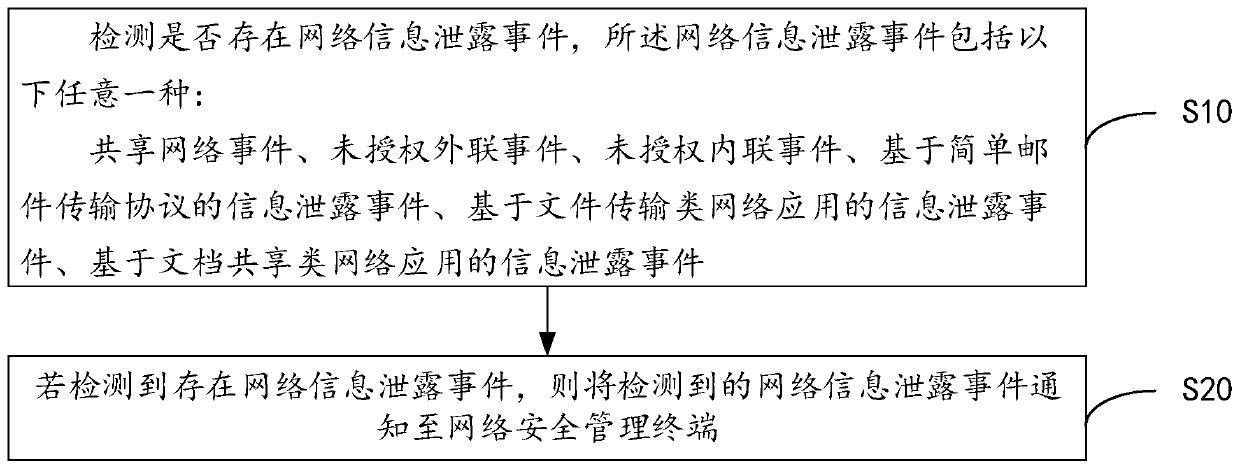
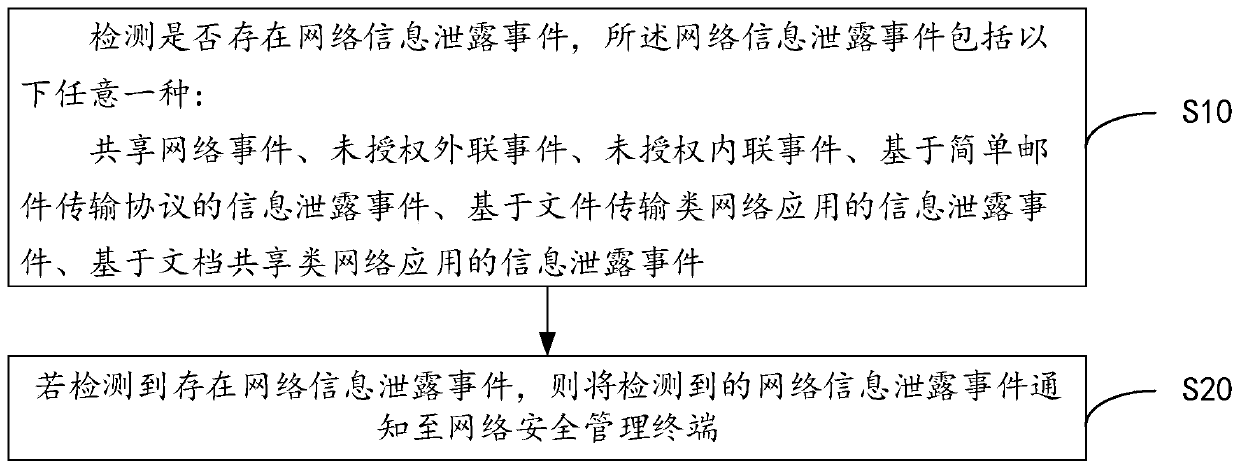
Network security monitoring method, computer equipment and computer readable storage medium
The invention discloses a network security monitoring method, computer equipment and a computer readable storage medium. Whether a shared network event, an unauthorized external connection event, an unauthorized internal connection event, an information leakage event based on a simple mail transmission protocol, an information leakage event based on a file transmission type network application andan information leakage event based on a document sharing type network application exist or not is detected, thus the network information leakage event recognition mode and method are perfected, the detected network information leakage events are notified to a network security management terminal, a user of the network security management terminal can process the network information leakage eventsin time, and harm caused by information leakage is reduced.
Owner:SURFILTER NETWORK TECH +1
Server-based service configuration system and approach
Network service providers are managed using a server-side configuration approach. According to an example embodiment of the present invention, a host network location includes two or more servers that automatically reconfigure their services in response to controller service settings corresponding to each server. Each server reads configuration information provided at a controller such as a domain name server (DNS), and in response, starts a network-based service corresponding to the configuration information. For instance, each of the two or more servers may be adapted to provide mail service via simple mail transfer protocol (SMTP) and web service via hyper text transfer protocol (HTTP). In this regard, when a DNS associates a first one of the servers with HTTP services and a second one of the servers with SMTP services, each server reconfigures its services accordingly, e.g., at a selected configuration time after startup or in response to an initiating event.
Owner:8X8 INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com