Safety control method and device for virtual machine mirror images
A technology of virtual machine mirroring and security control, applied in the field of cloud computing security, can solve problems such as insecurity and hidden dangers, and achieve the effect of preventing information leakage, preventing mirror deception, and ensuring legality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
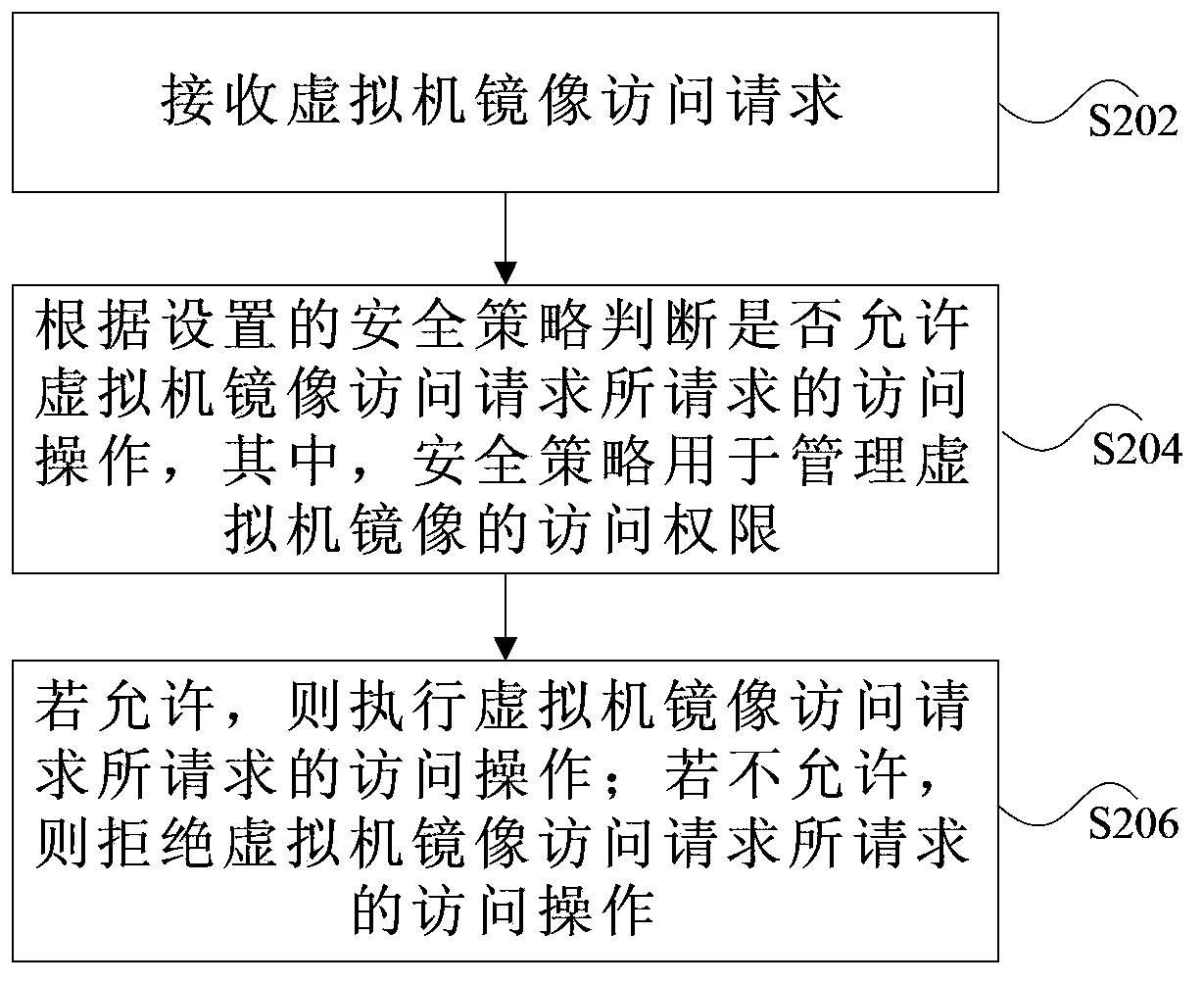
[0031] Such as figure 1 As shown, in this embodiment, the security control method of a virtual machine image may include the following steps:
[0032] S102. In the virtual machine system, a security policy is preset to protect the security of the virtual machine image during the entire life cycle; preferably, the above security policy may include but not limited to one of the following: during the running and dormancy stages of the virtual machine image , using an access control mechanism to prevent theft and modification; before the virtual machine image is started, a security check is used to prevent misconfiguration and deception of the pre-configured virtual machine image.
[0033] S104. During the running and dormant stages of the virtual machine image, an access control mechanism is adopted to prevent stealing and modification of the virtual machine image; before the virtual machine image is started, a security check is adopted to prevent misconfiguration and deception o...
Embodiment 2
[0067] Such as Figure 4 As shown, in this embodiment, the security control device for the virtual machine image may include:
[0068] 1) The setting unit 402 is used to pre-set security policies in the virtual machine system to protect the security of the virtual machine image during the entire life cycle; preferably, the above security policies may include but not limited to one of the following: During the running and dormant stages of the virtual machine image, an access control mechanism is adopted to prevent the theft and modification of the virtual machine image; before the virtual machine image is started, a security check is adopted to prevent misconfiguration and deception of the pre-configured virtual machine image.
[0069] 2) The control unit 404 is connected to the setting unit 402, and is used to adopt an access control mechanism during the running and dormant stages of the virtual machine image to prevent theft and modification; before the virtual machine image...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com