Patents
Literature
168results about How to "Avoid Information Leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
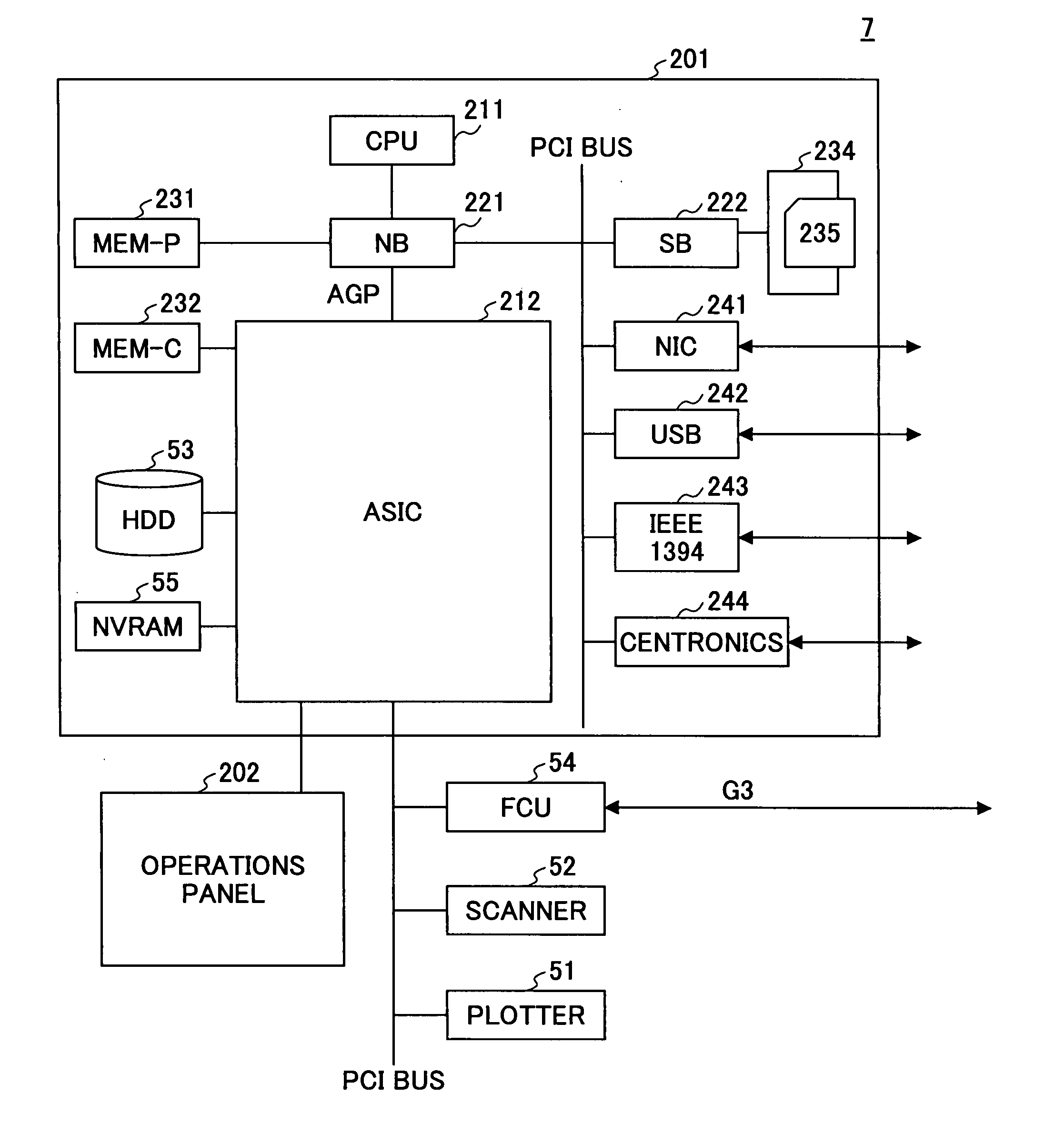
Document management system and method
InactiveUS20130218829A1Avoid lostAvoid Information LeakageDigital data information retrievalDigital data processing detailsData accessData content
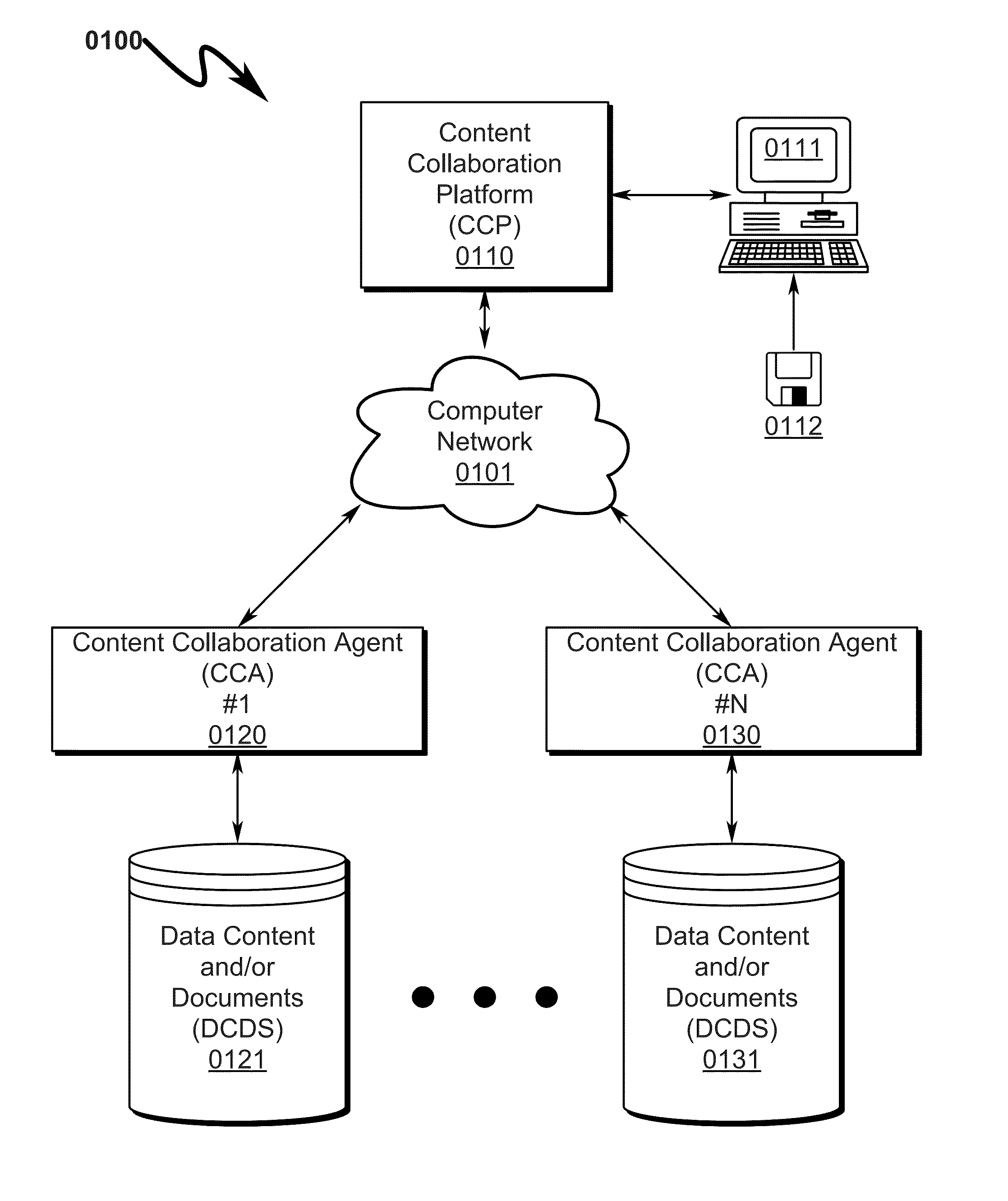
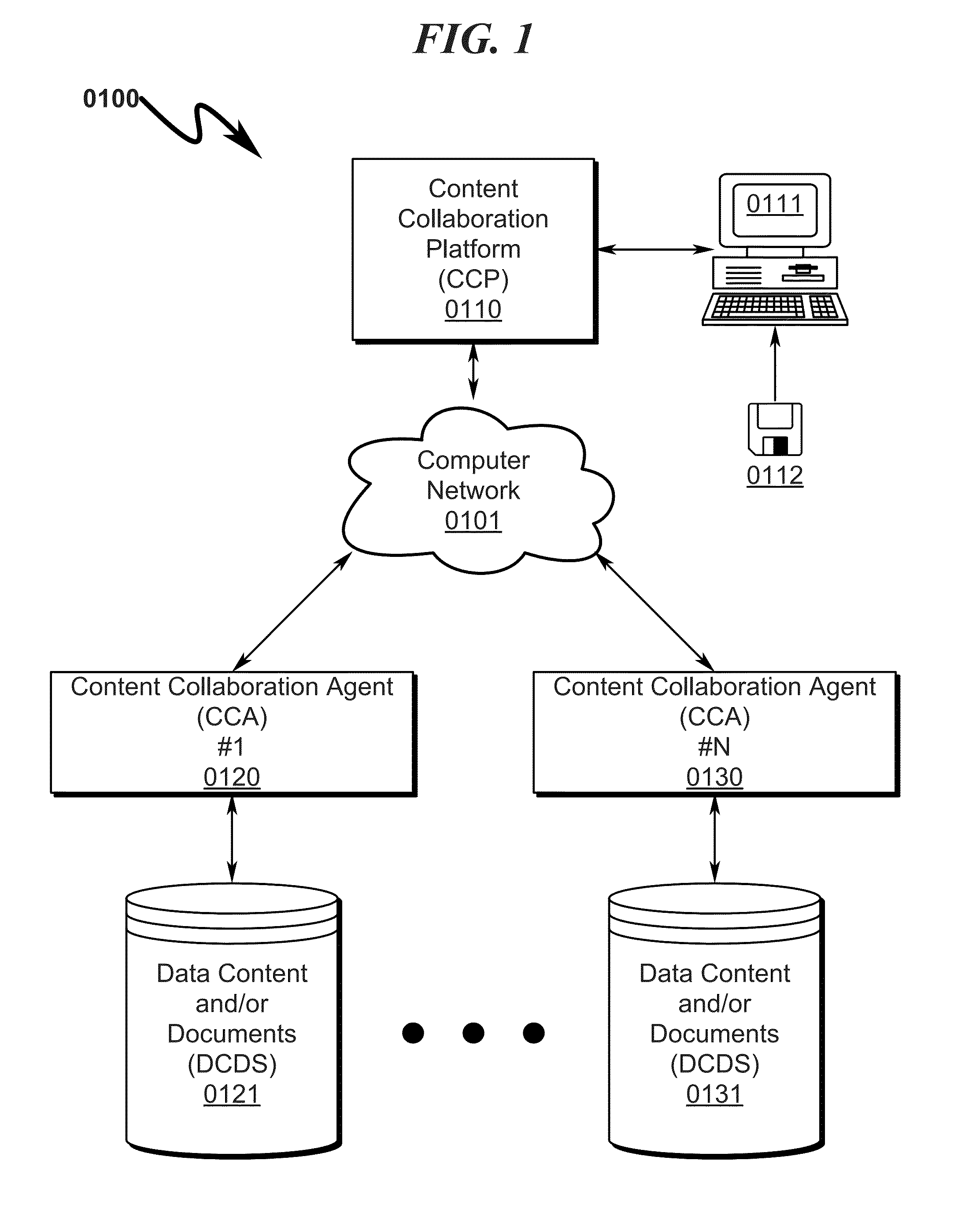
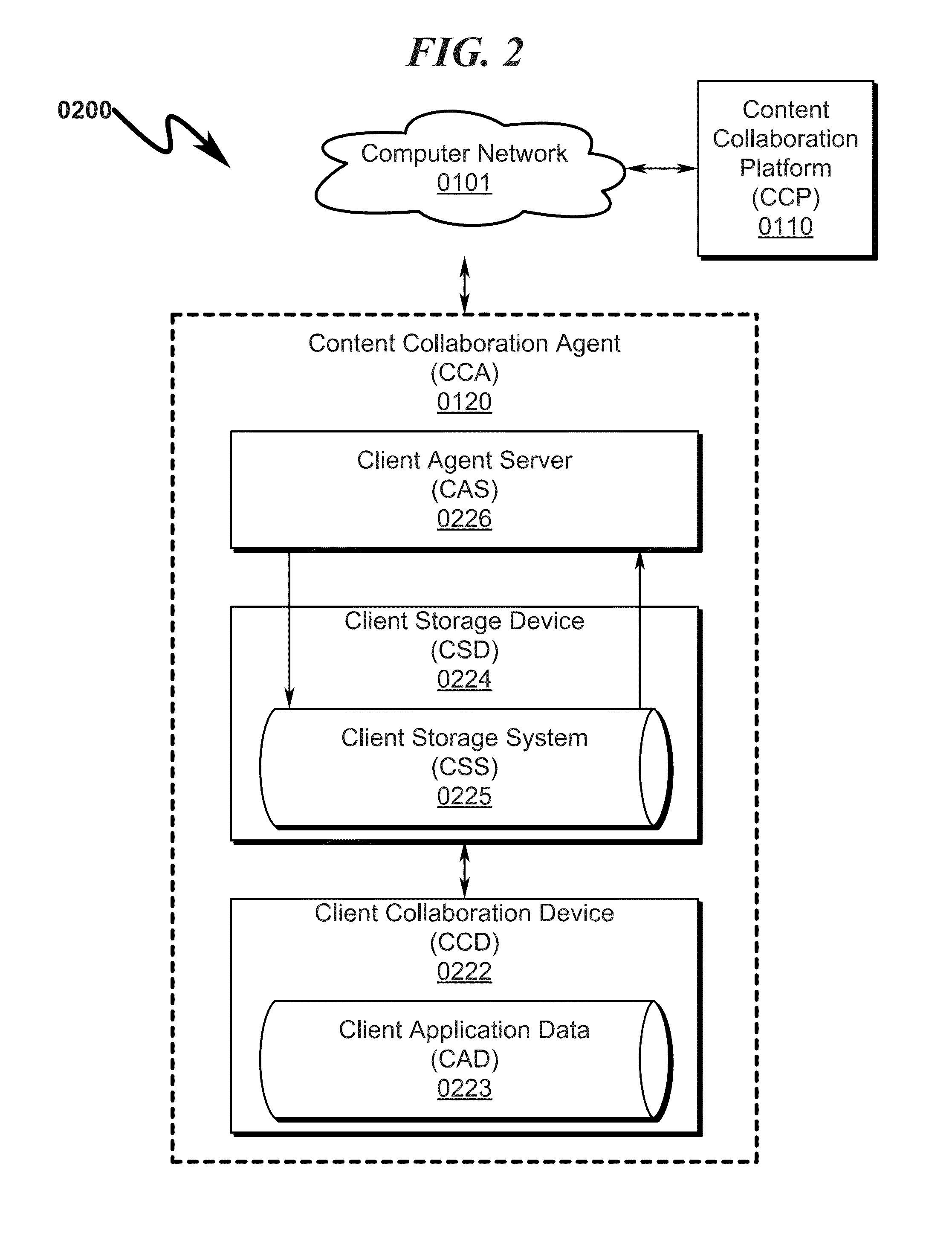
A document management system / method allowing coordinated synchronized modifications and secure, scalable, multi-level, and controlled access to Data Content and / or Documents (DCDS) over a computer network between multiple Content Owners and / or Reviewers (CORS) is disclosed. The system / method is configured to allow any number of CORS to share DCDS using a Content Collaboration Platform (CCP) while retaining complete DCDS integrity / retrieval control using a hierarchical Access Rights and Control List (ARCL) to prevent CORS from uncoordinated DCDS modification and prohibiting local maintenance of DCDS copies after the expiration of a CORS Data Access Session (DAS). Upon termination of a CORS DAS, the system synchronizes modifications to the DCDS and coordinates control information among various CORS to ensure proper return of the DCDS back to its original CORS owner and associated CORS storage location.
Owner:MARTINEZ DENEEN LIZETTE
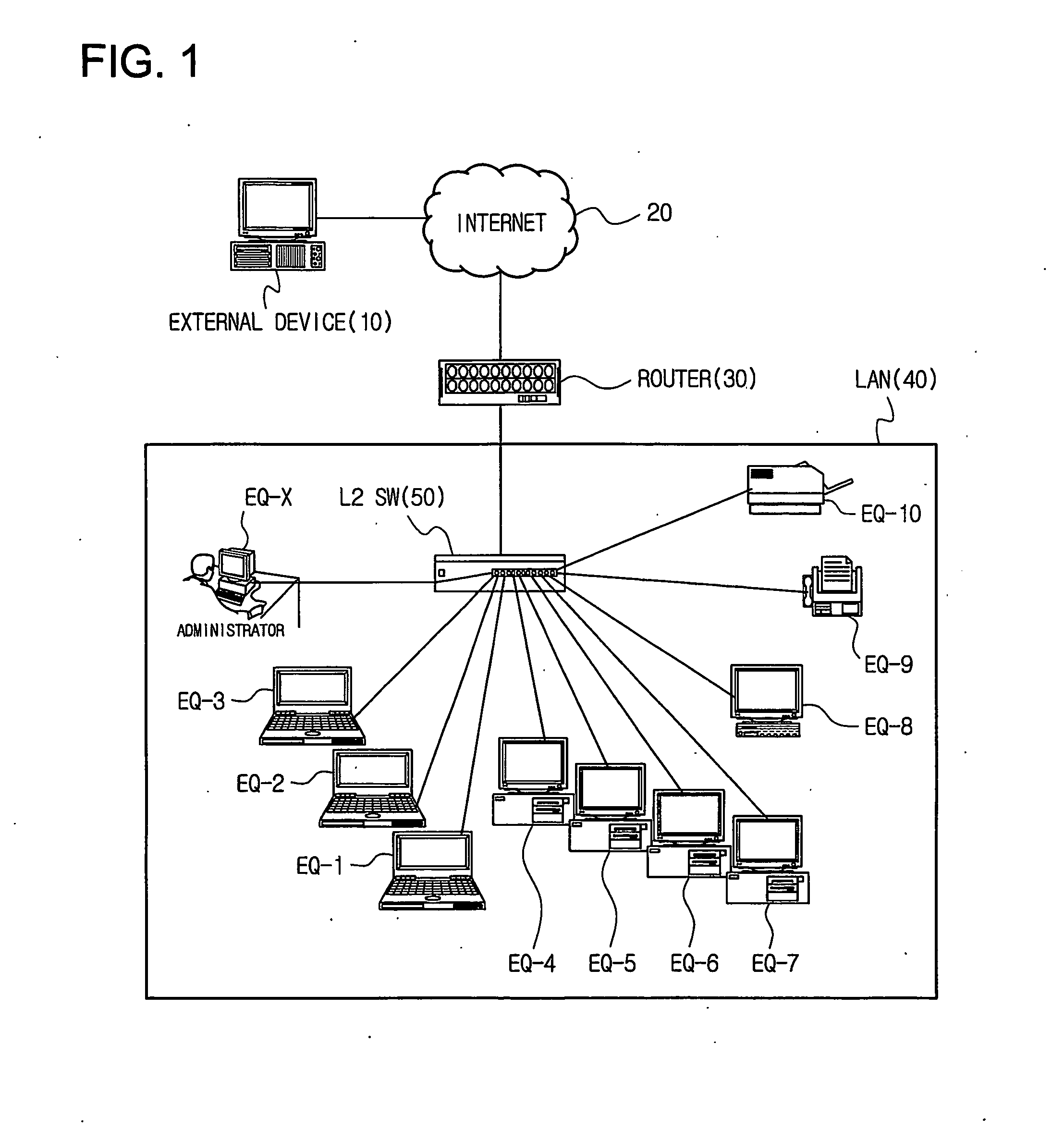
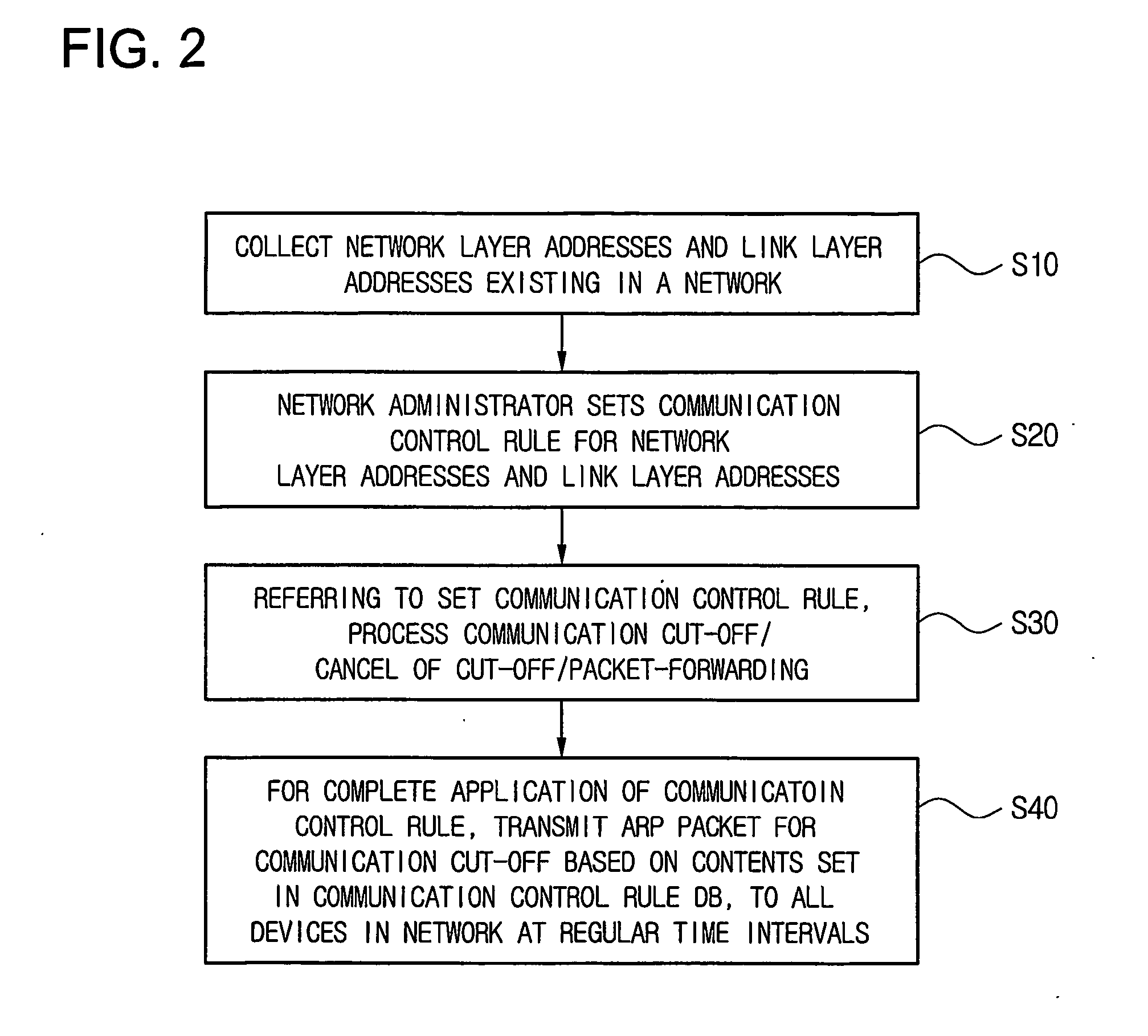
Method of controlling communication between devices in a network and apparatus for the same
InactiveUS20070064689A1Avoid collisionReduce communicationSpecial service provision for substationNetworks interconnectionAddress Resolution ProtocolVirtual firewall
Disclosed is a technology by which rules on communication permission or control are enforced to network internal devices such that an environment which looks as if to have a virtual firewall existing between network internal devices can be established. A communication control apparatus for this is located on the same level in the network as other devices are located. By using this communication control apparatus, an address resolution protocol (ARP) packet in which a data link layer address is manipulated is provided to devices that are the objects of communication cut-off, such that data packets transmitted by the communication cut-off object devices are transmitted to manipulated abnormal addresses. By doing so, communication with the communication cut-off object devices is cut off. For a device which is in a communication cut-off state although the device is not an object of communication cut-off any more, the communication control apparatus transmits an ARP packet including normal address information to the device such that the communication cut-off state is canceled.
Owner:INIMAX
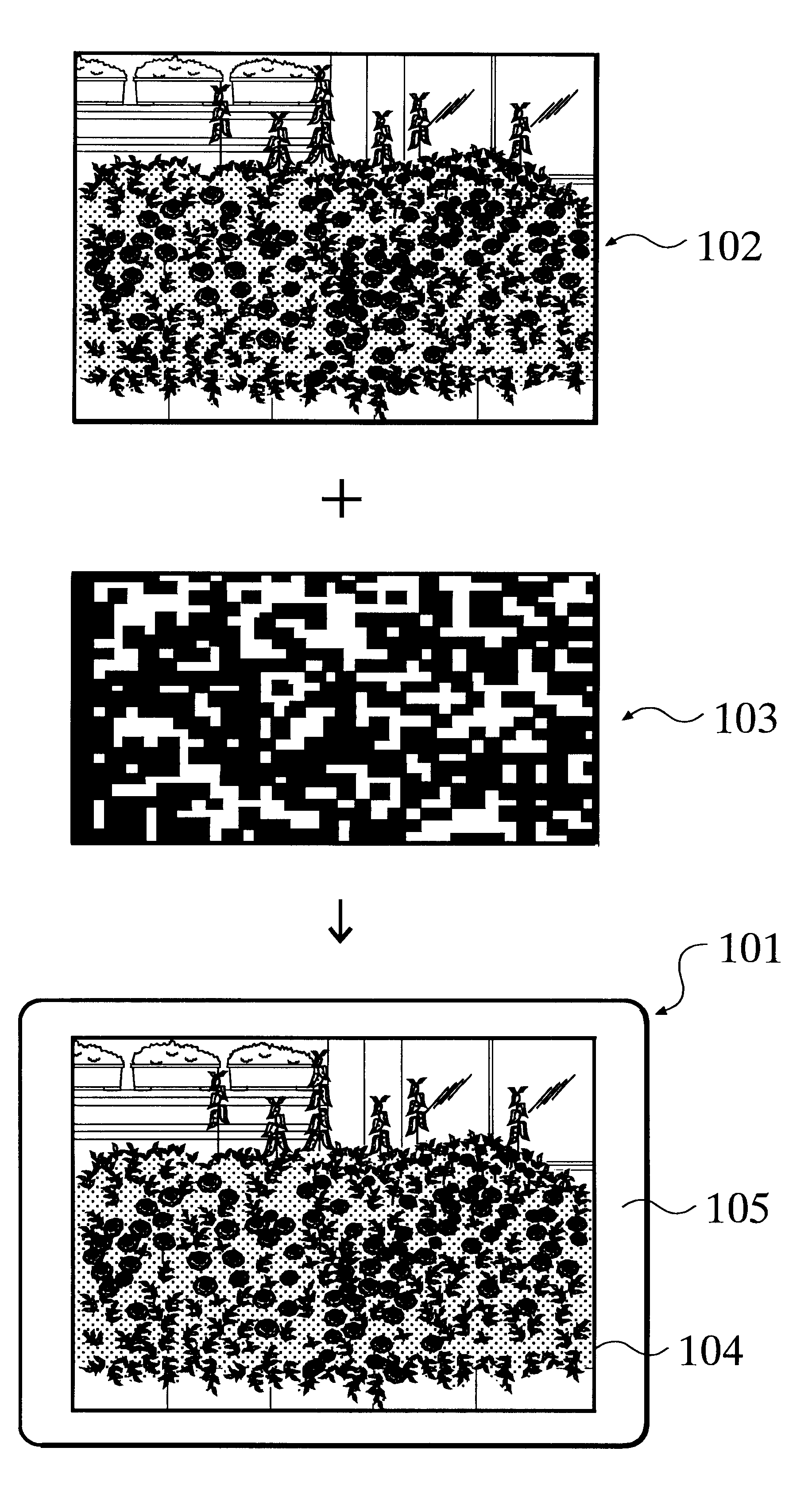
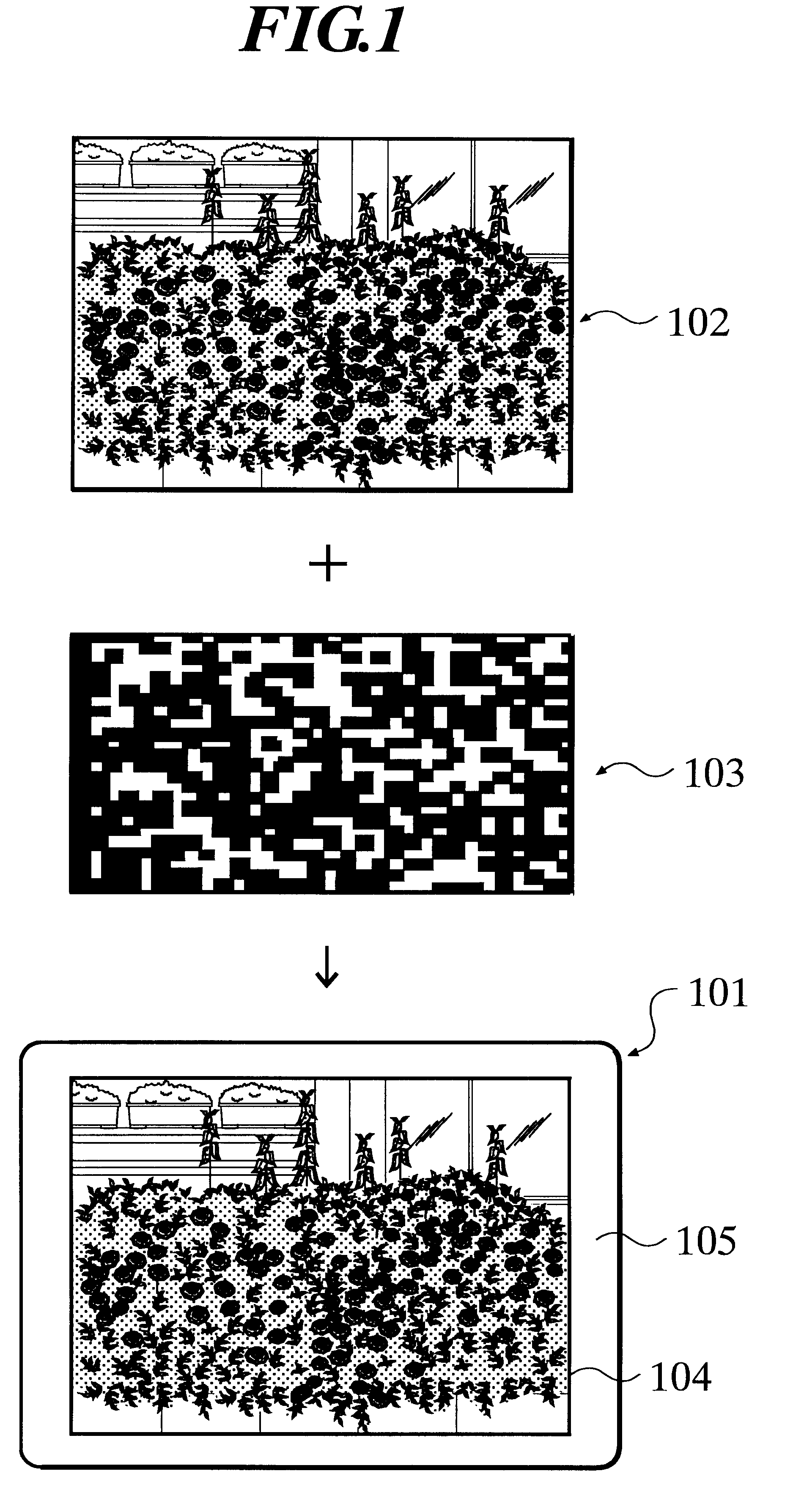
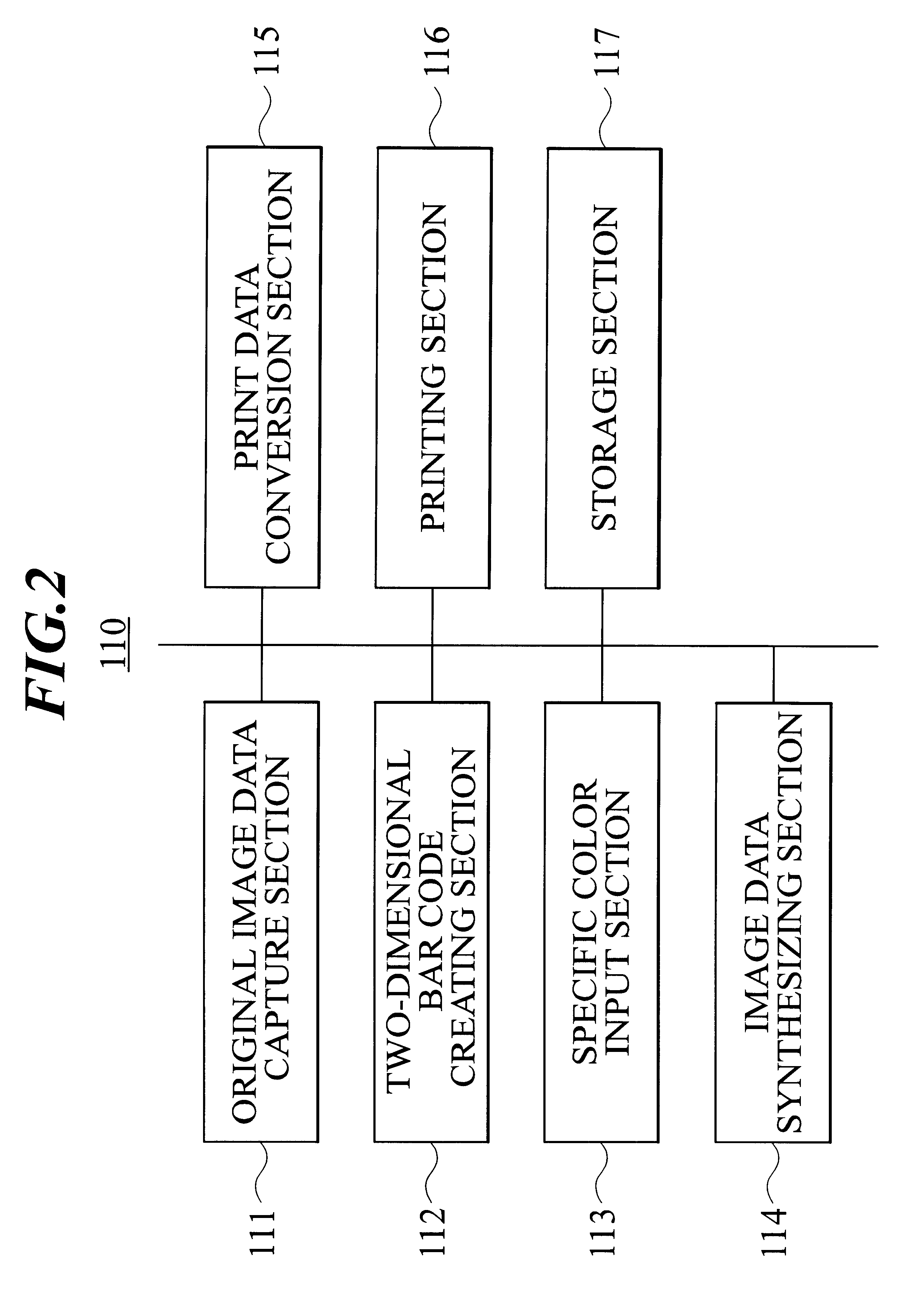
Information code product, manufacturing device and method for manufacturing the same, information code reading device, authentication system, authentication terminal, authentication server, and authentication method
InactiveUS6572025B1Improve securityAvoid Information LeakageCharacter and pattern recognitionPayment architectureComputer terminalAuthentication server
An information code product (101) comprising a body (105) having a code-including image (104) formed thereon which includes at least one unit of information codes (103) with one or more specific color, wherein the unit of information codes is adapted to be obtained by extracting an image with the specific color from the code-including image. A user is authenticated by an authentication system (301) which comprises an authentication terminal (302) for reading data included in the product (101) and an authentication server (303) which is interconnected to the authentication terminal through a network (304).
Owner:JAPAN GAIN THE SUMMIT
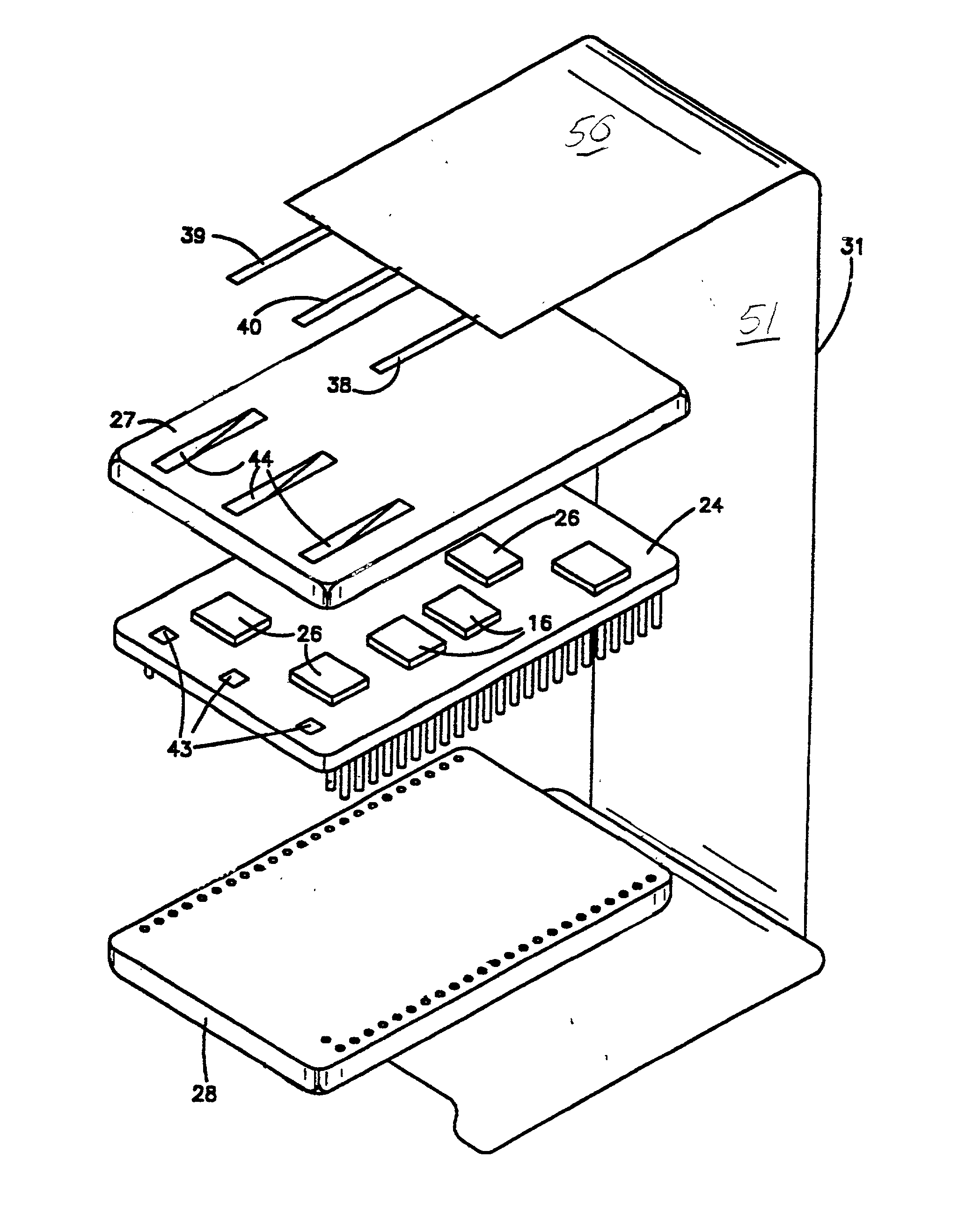
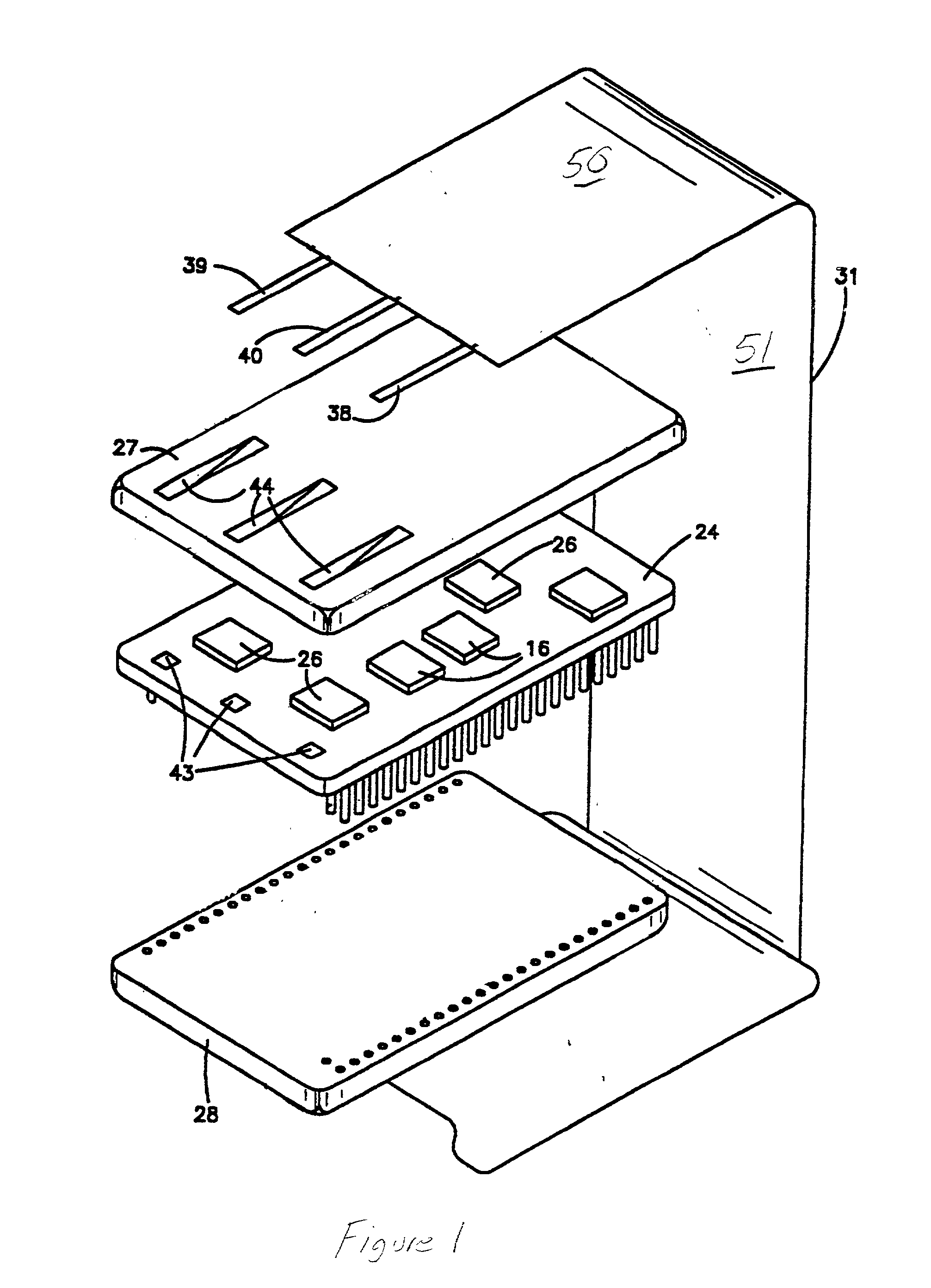
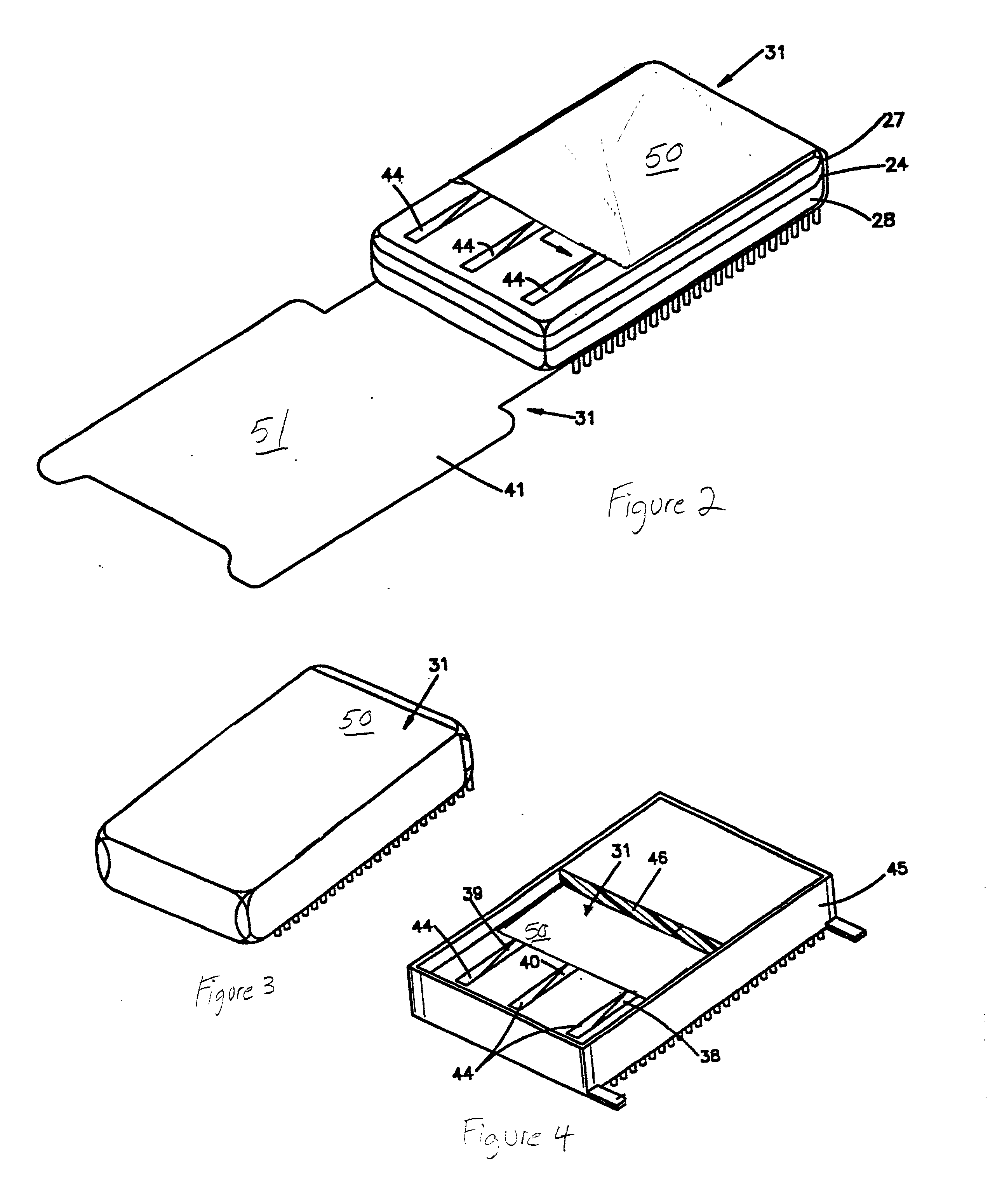
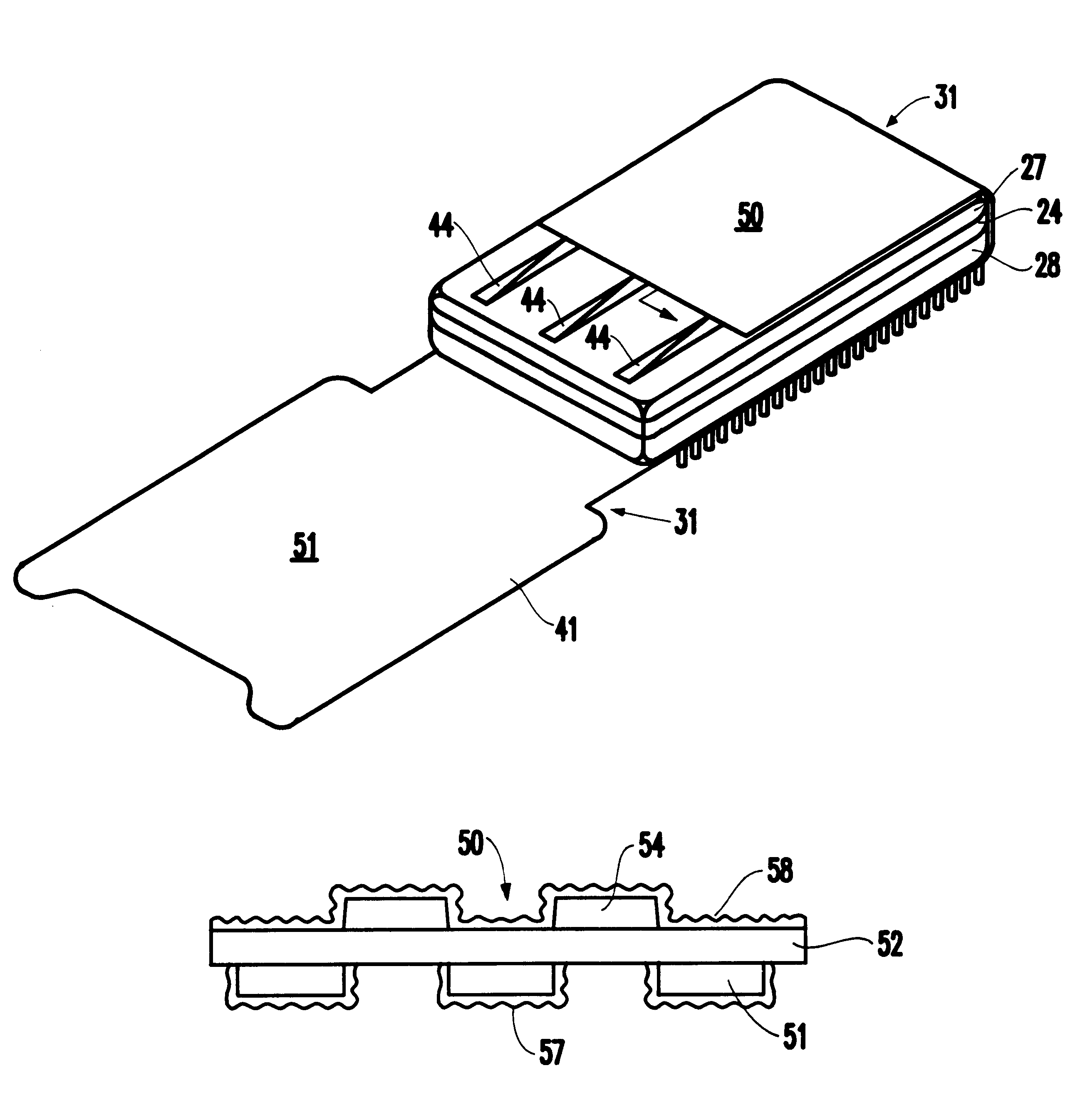
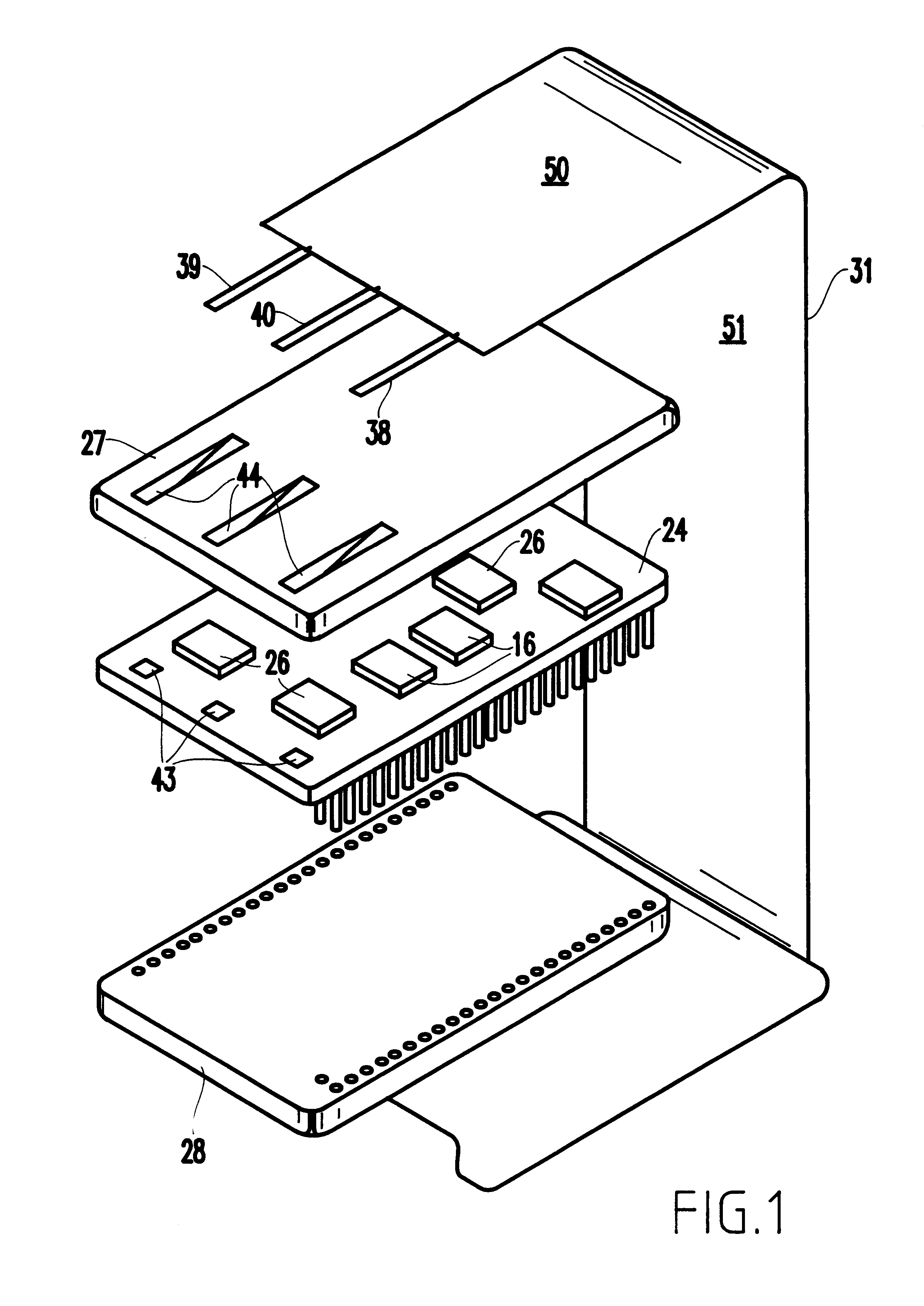
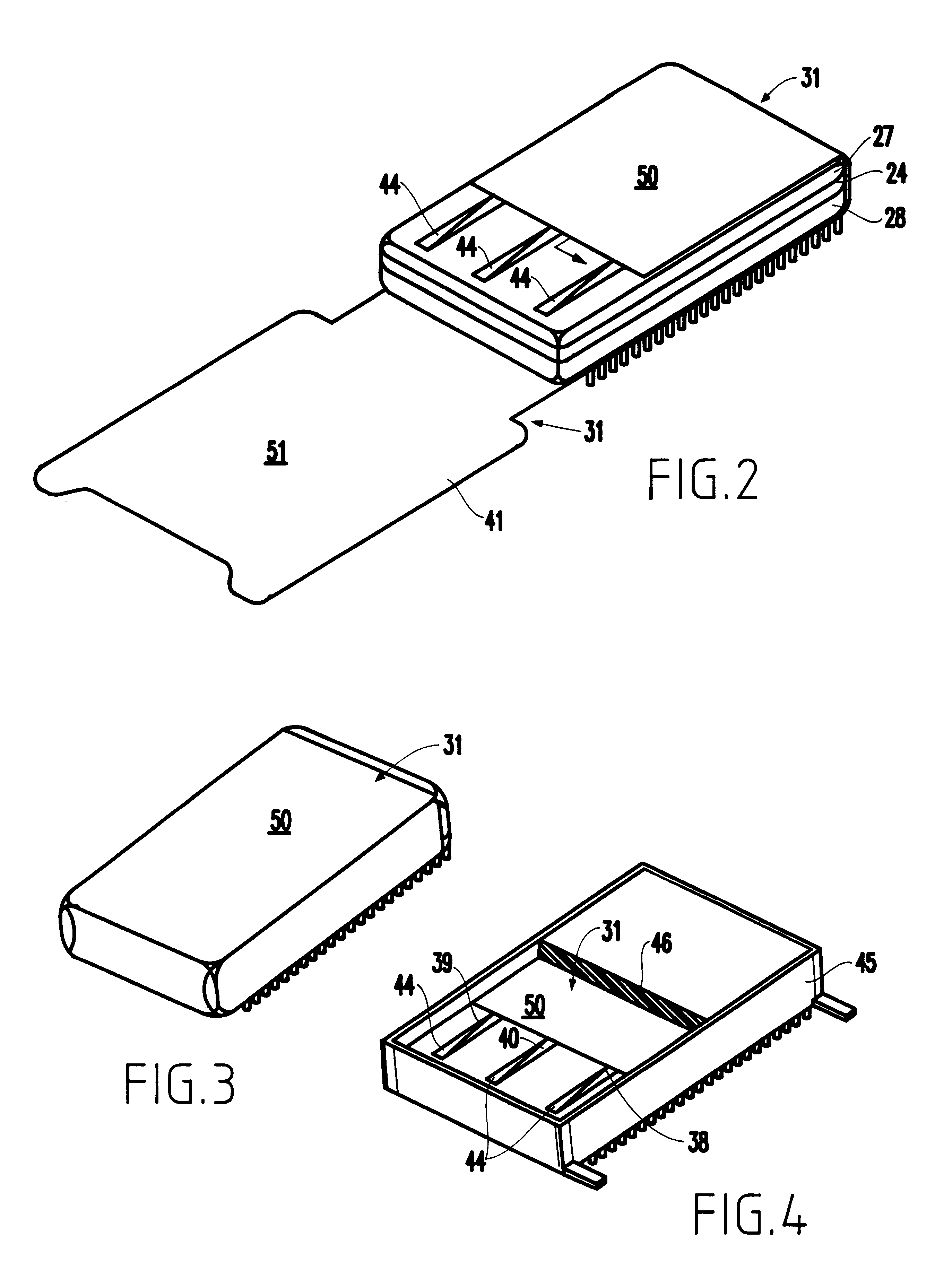
Tamper-responding encapsulated enclosure having flexible protective mesh structure
InactiveUS20020084090A1Sufficient protectionAvoid Information LeakageDigital data processing detailsSemiconductor/solid-state device detailsElectrically conductiveElectronic circuit
A structure and method for forming a tamper respondent electronic circuit enclosure that includes an integrated circuit structure, a mesh structure surrounding the integrated circuit structure, and a sealed enclosure surrounding the mesh structure. The mesh structure includes a layer of flexible dielectric having a first side and a second side, a screen-printed pattern of flexible electrically conductive first circuit lines forming a first resistor network on the first side, and a photo lithographically-formed pattern of flexible electrically conductive second circuit lines forming a second resistor network on the second side.
Owner:IBM CORP
Tamper-responding encapsulated enclosure having flexible protective mesh structure
InactiveUS6686539B2Avoid Information LeakageDigital data processing detailsSemiconductor/solid-state device detailsDielectricNetwork on
A structure and method for forming a tamper respondent electronic circuit enclosure that includes an integrated circuit structure, a mesh structure surrounding the integrated circuit structure, and a sealed enclosure surrounding the mesh structure. The mesh structure includes a layer of flexible dielectric having a first side and a second side, a screen-printed pattern of flexible electrically conductive first circuit lines forming a first resistor network on the first side, and a photo lithographically-formed pattern of flexible electrically conductive second circuit lines forming a second resistor network on the second side.
Owner:IBM CORP
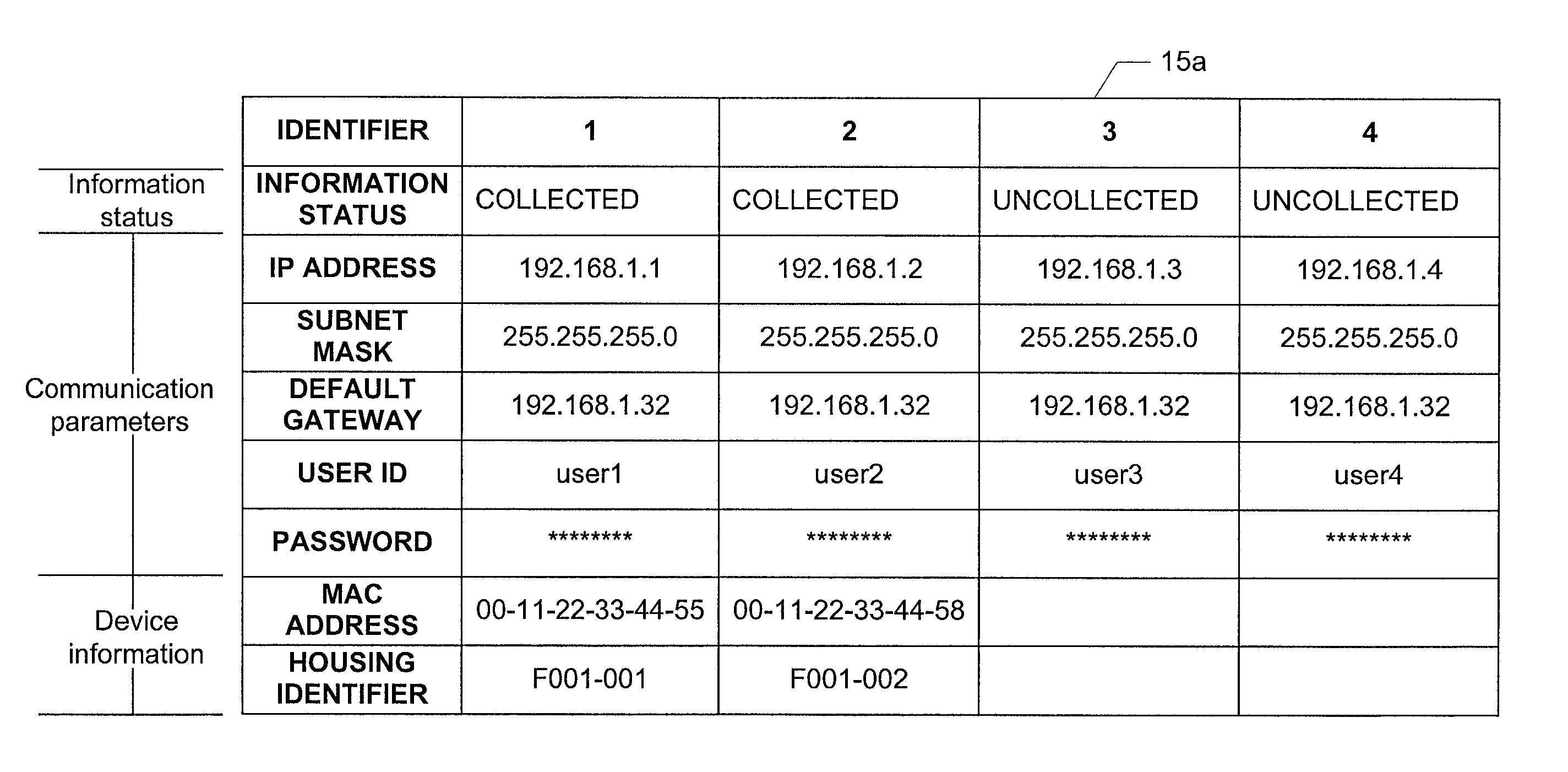
Management system and method for network devices using information recordable medium
InactiveUS20030041085A1Avoid Information LeakageDigital data processing detailsCo-operative working arrangementsComputer networkManagement system
There is provided a management system including a managed device connected to a network, and assigned network information that allows the managed device to communicate over the network, and a management device. The management device is connected to the network, and manages the managed device based on the network information and stores the network information in an information recordable medium. The management device has a drive unit which reads data from the information recordable medium, wherein the managed device is made accessible when the data read from the information recordable medium corresponds to the network information assigned to the managed device.
Owner:ALLIED TELESIS
Information processing device, information processing system, and program
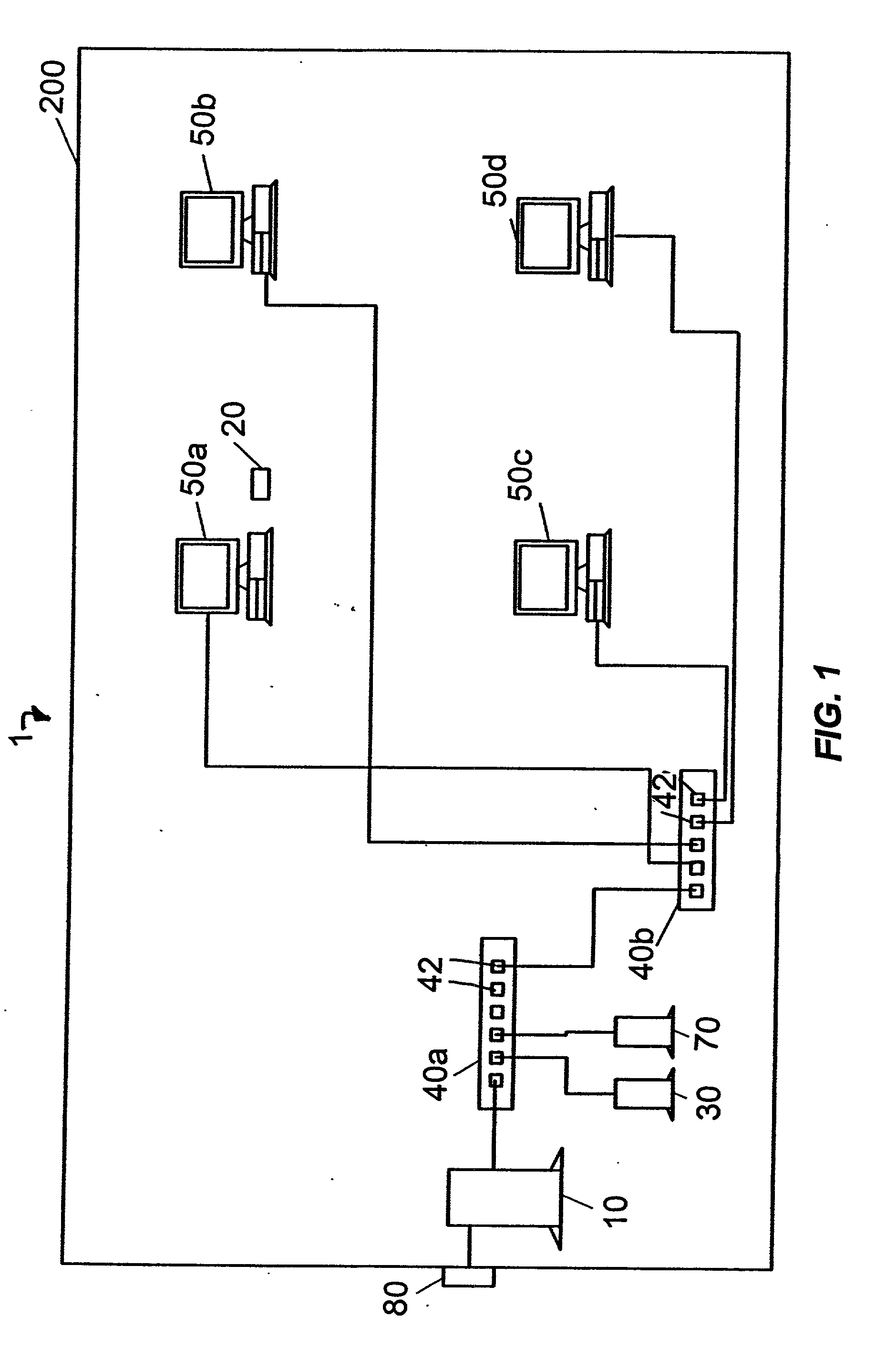
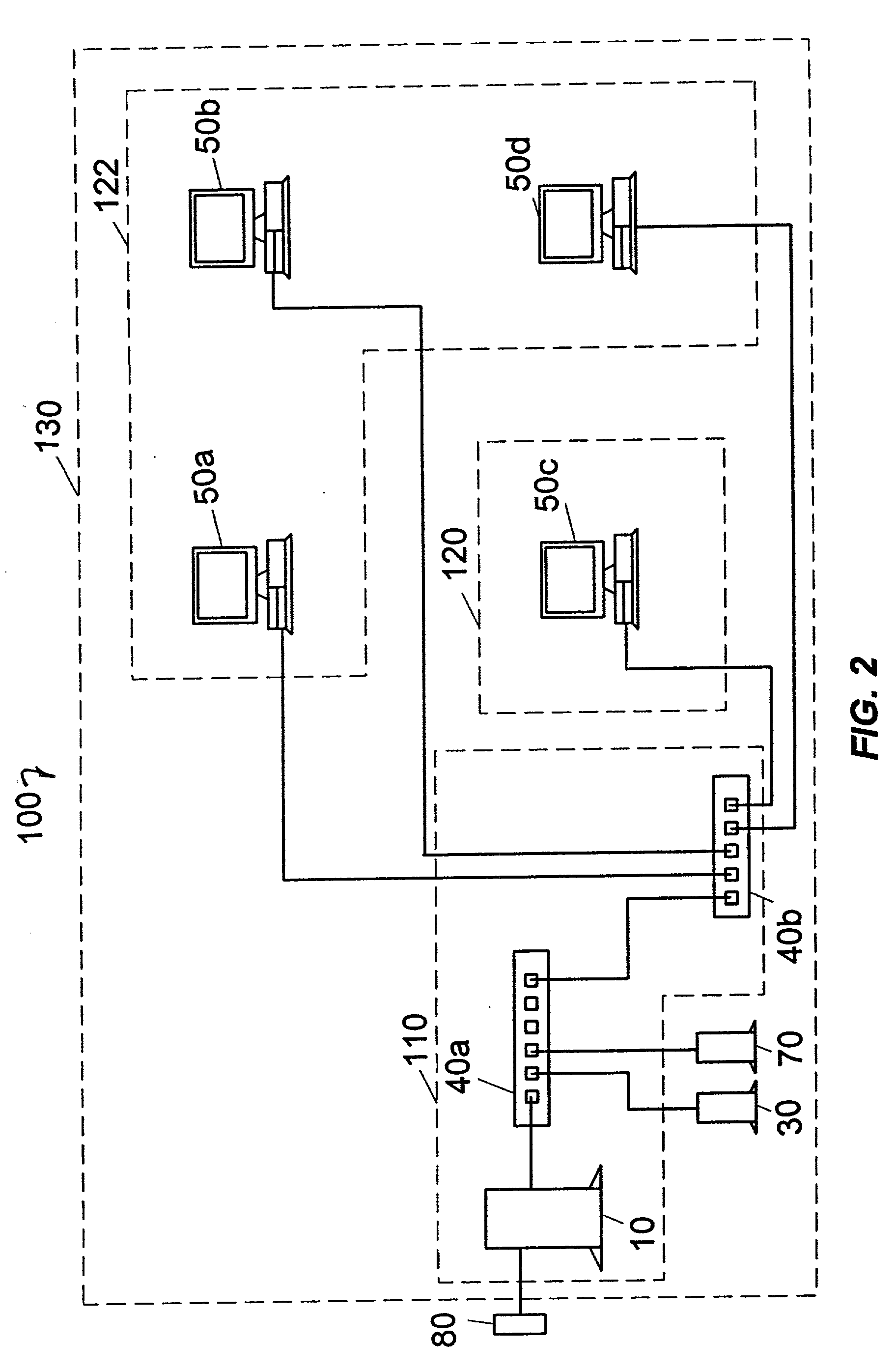
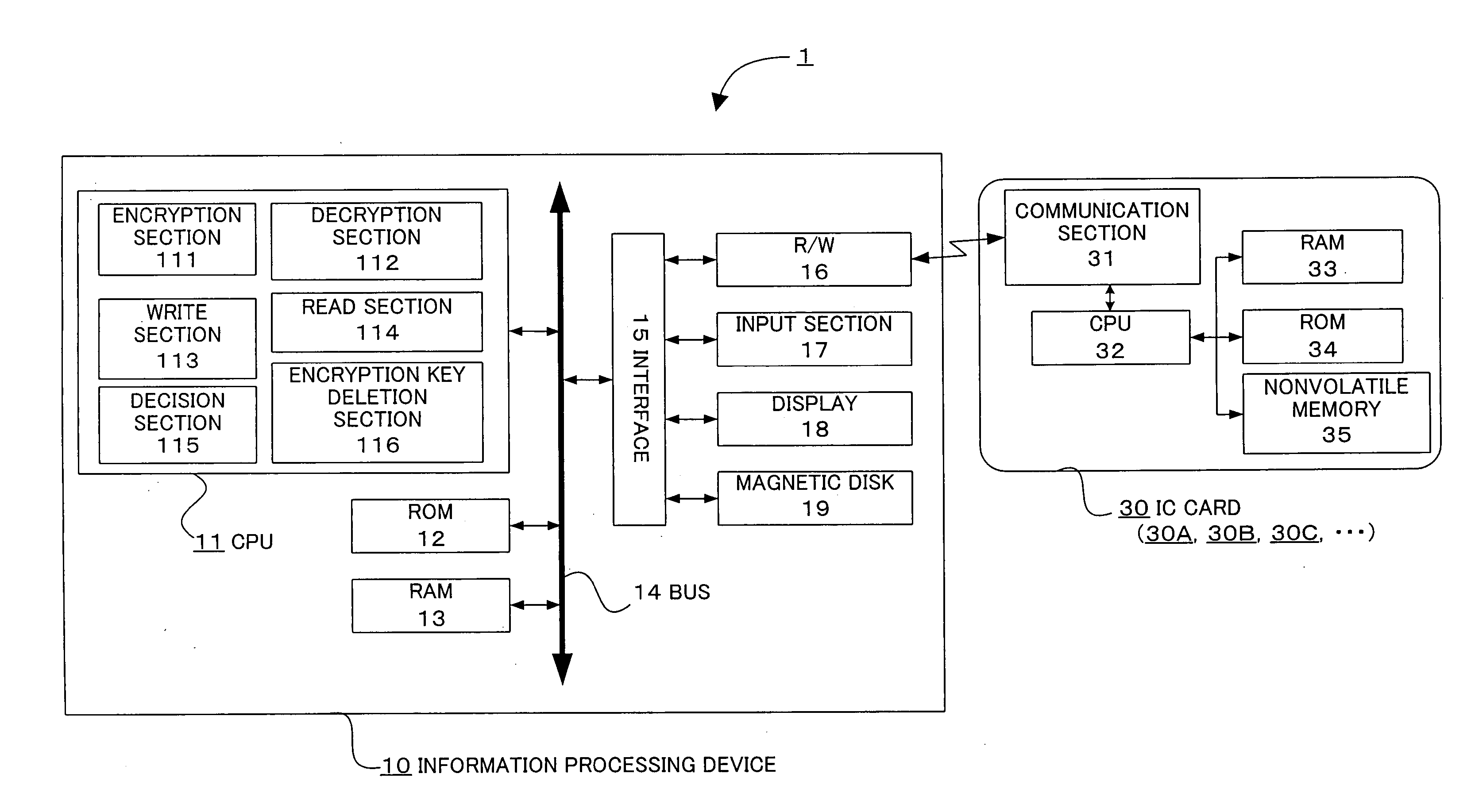
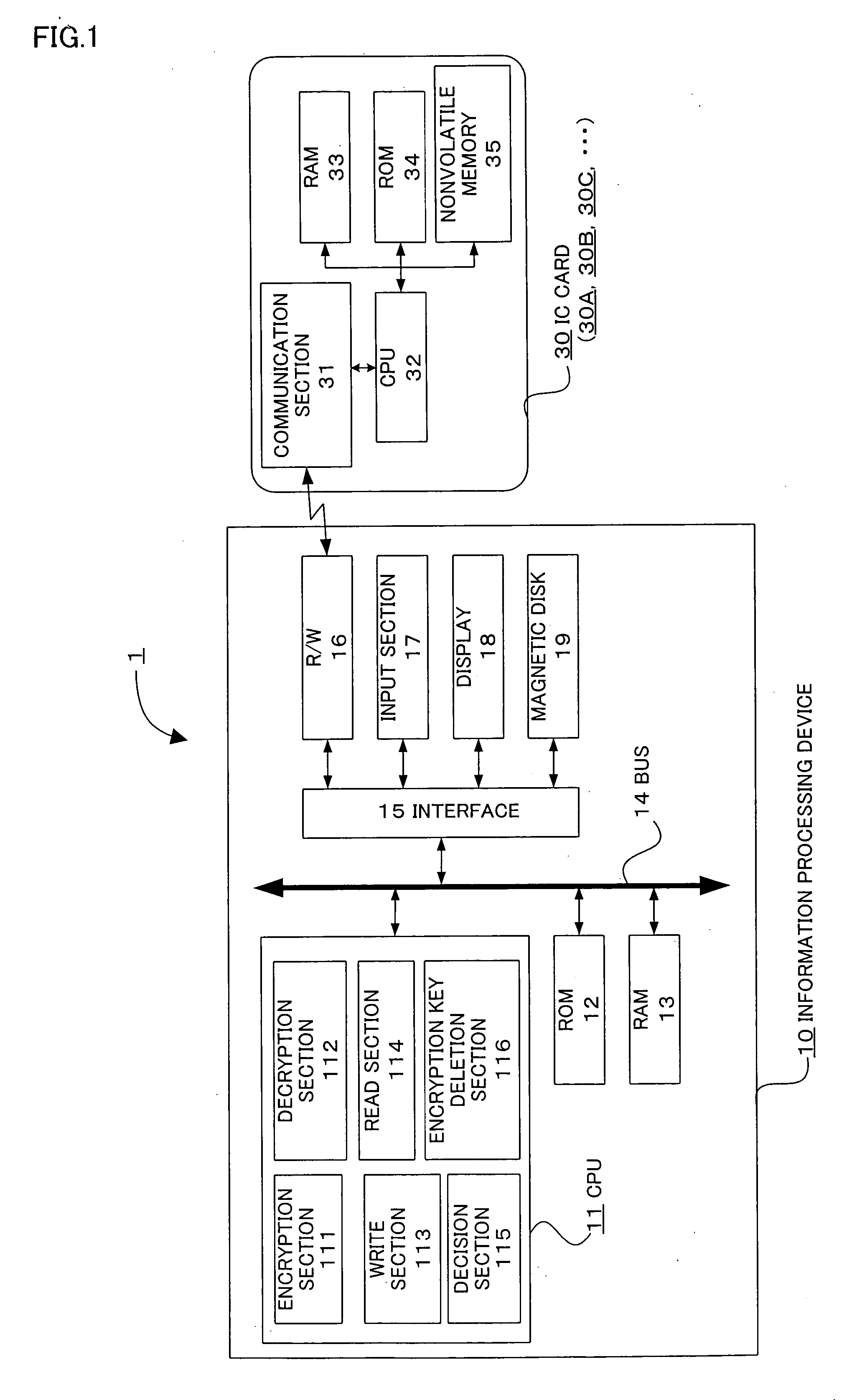
InactiveUS20060018484A1Eliminate the problemImprove securityKey distribution for secure communicationUnauthorized memory use protectionInformation processingPassword
The present invention provides an information processing device, an information processing system, and a program capable of improving security and convenience. An information processing system (1) includes an IC card (30) which stores an encryption key and a registered password and allows the encryption key to be read when the IC card (30) has authenticated the user as an authorized user based on the registered password, and an information processing device (10) which stores folder information in which the folder name, path, and hash value of the encryption key are associated, when a request to save data in the folder has been issued from the user, decides whether or not an encryption key corresponding to the folder is included in the encryption key read from the IC card (30) based on the folder information, encrypts the request target data using the corresponding encryption key when the information processing device (10) has decided “YES”, and stores the encrypted data.
Owner:DAI NIPPON PRINTING CO LTD
Image printing apparatus and display device and job processing method therefor
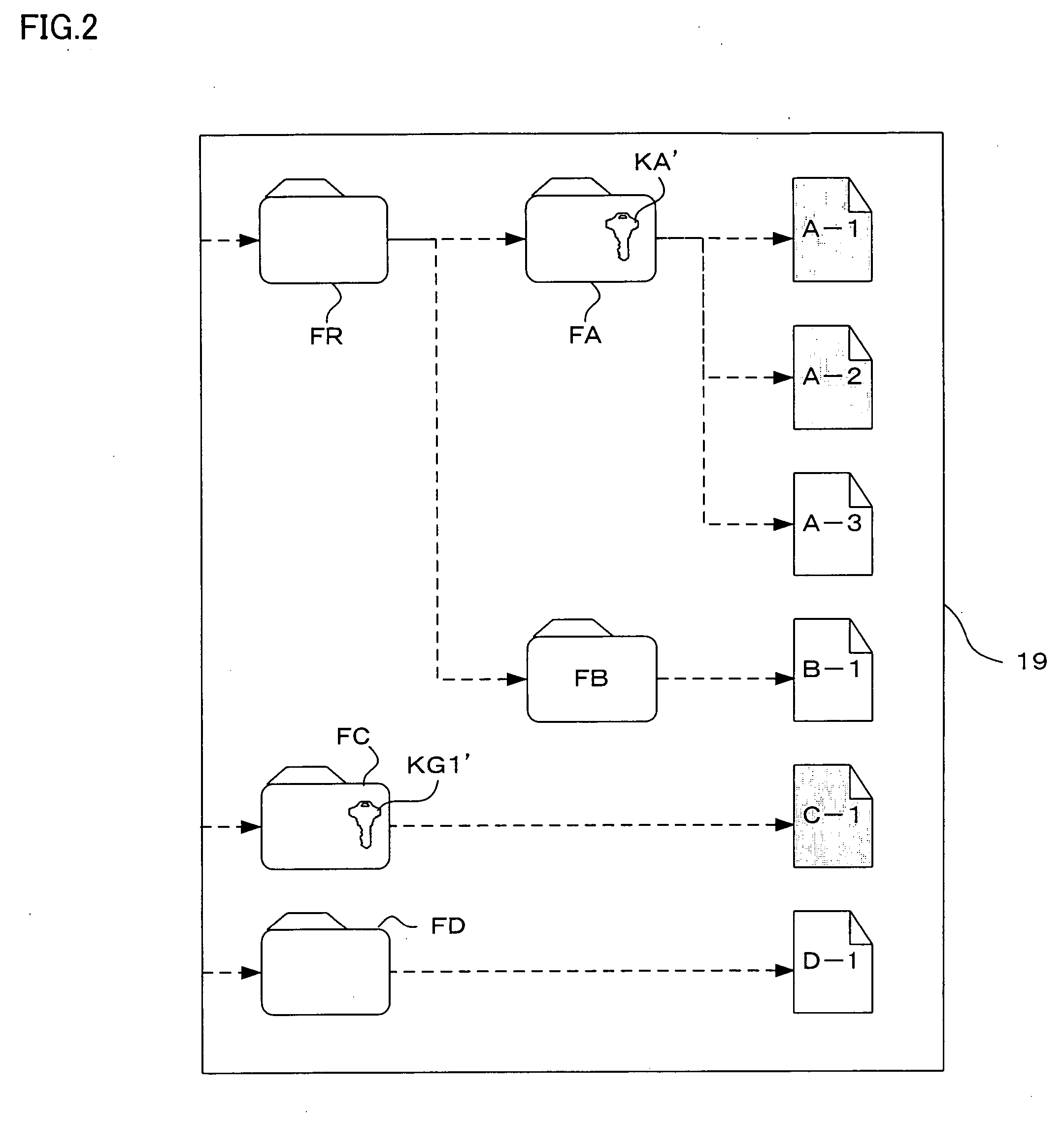
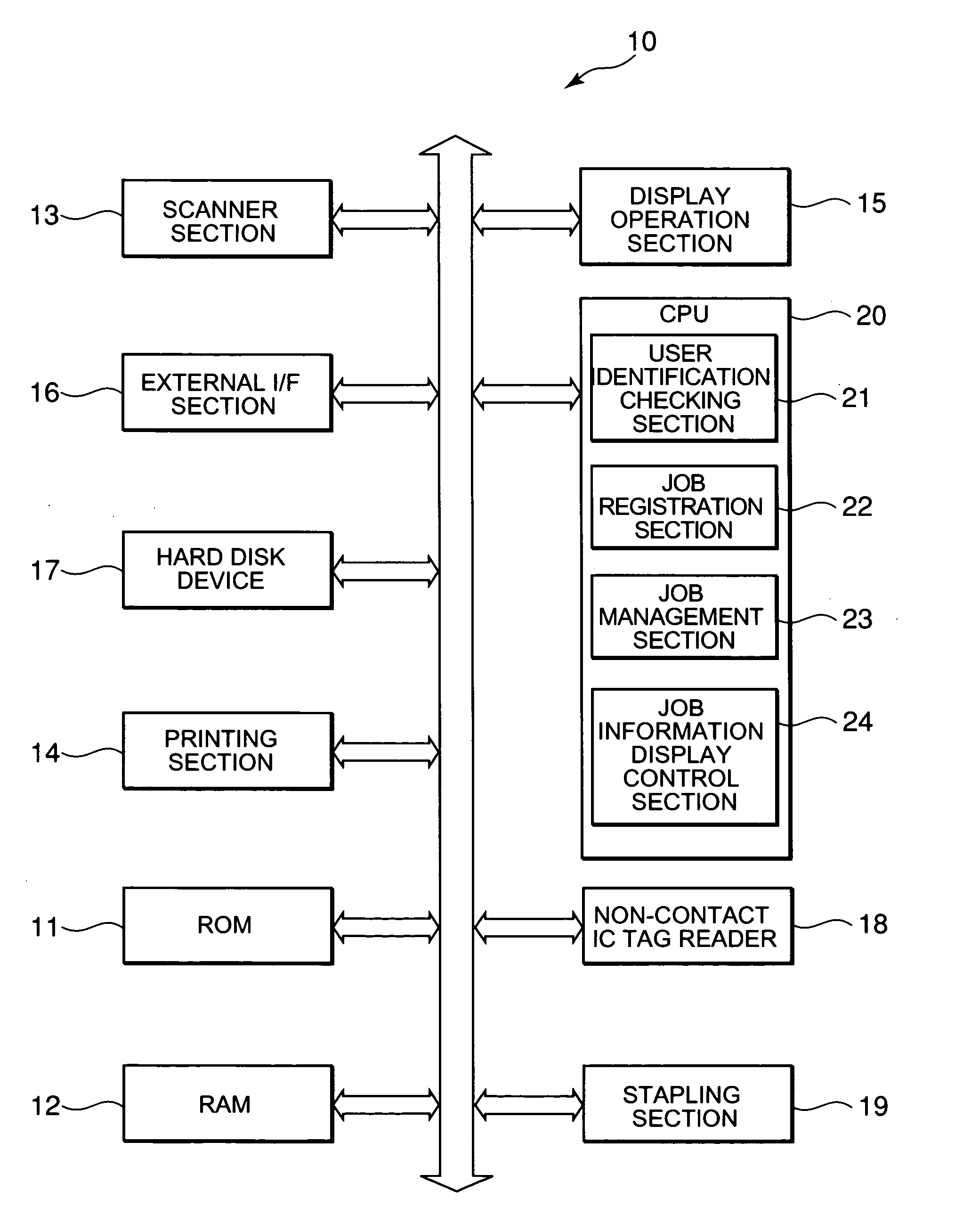
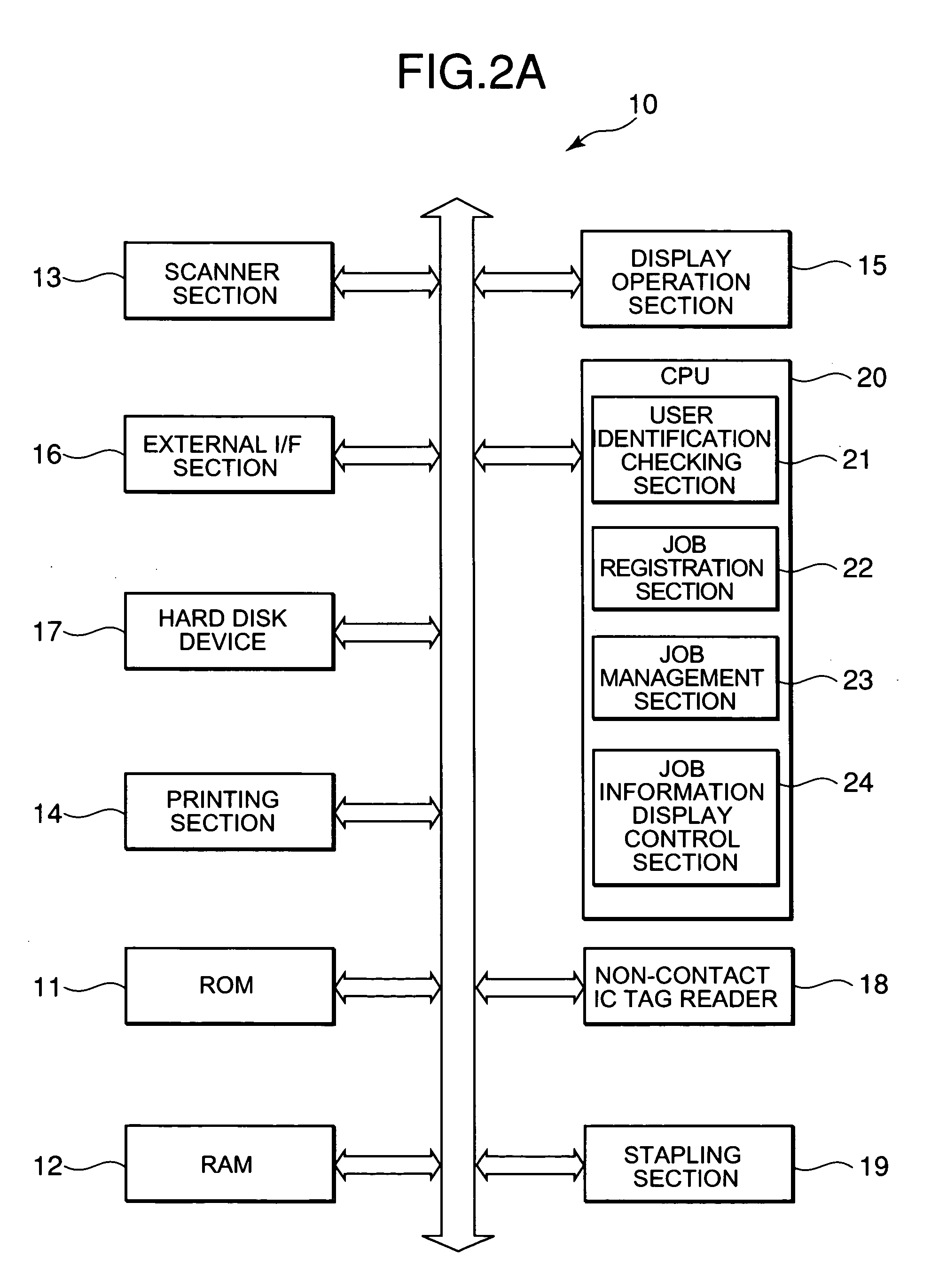
InactiveUS20060001898A1Ensure confidentialityImprove confidentialityDigital computer detailsVisual presentationConfidentialityDisplay device
There is provided an image printing apparatus which can ensure confidentiality by including an identification section which identifies whether or not a user who requests a job is present in a predetermined range from the image printing apparatus, a queue which stores the job and manages an execution of the job in stored order, a job registration section which registers the job at the end of the queue, and a job management section which suspends the start of execution of the job registered in the queue when the identification section does not recognize the presence of the user who requests the job, and permits the start of execution of the job registered in the queue when the identification section recognizes the presence of the user who manages the job. A display device and a job processing method are also provided.
Owner:KONICA MINOLTA BUSINESS TECH INC
Isolated multi-network computer system and apparatus
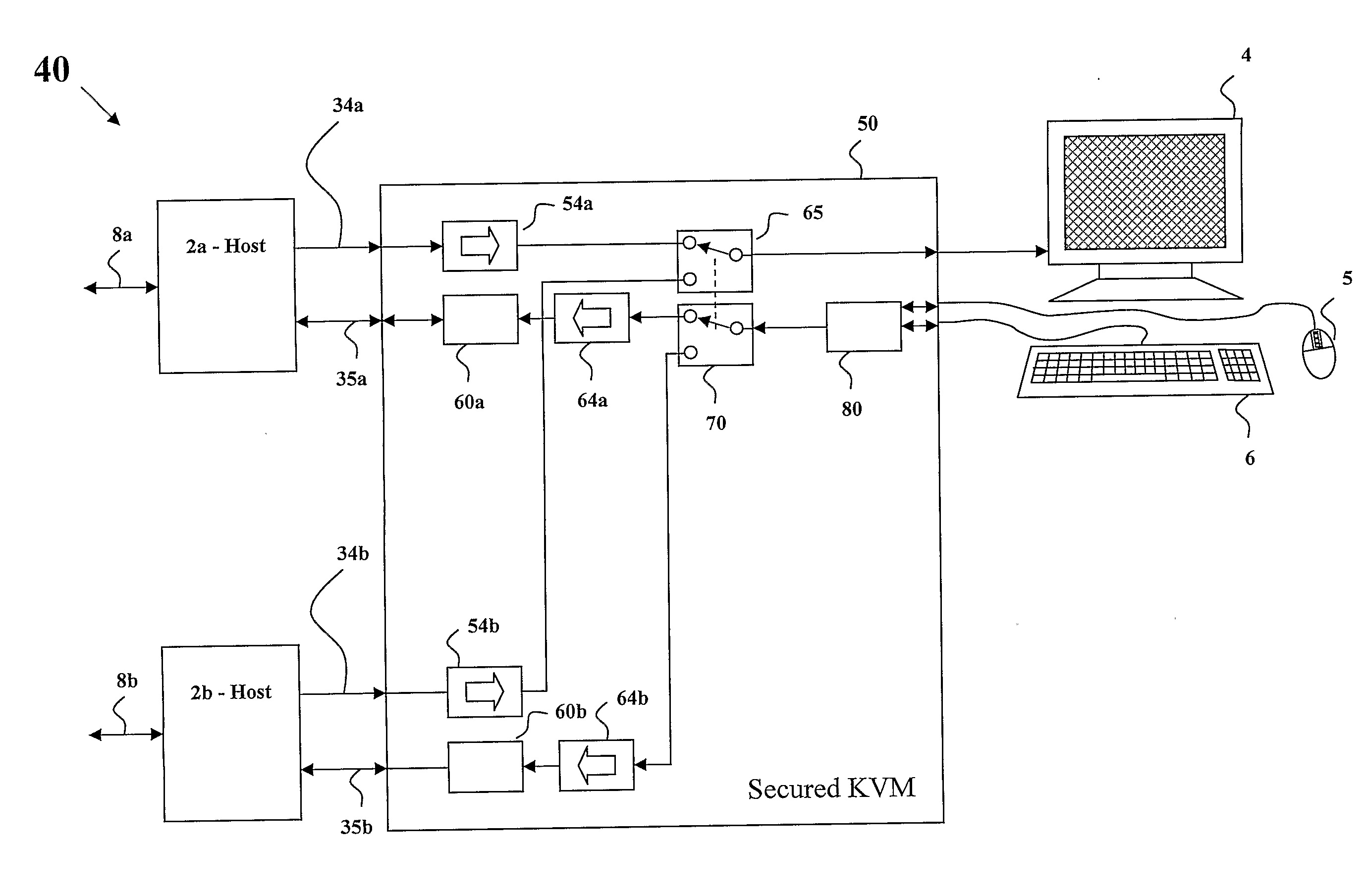
ActiveUS20110145451A1High levelAvoid Information LeakageStatic indicating devicesInternal/peripheral component protectionComputer hardwareDisplay device
Owner:HIGH SEC LABS LTD
Practical secrecy-preserving, verifiably correct and trustworthy auctions
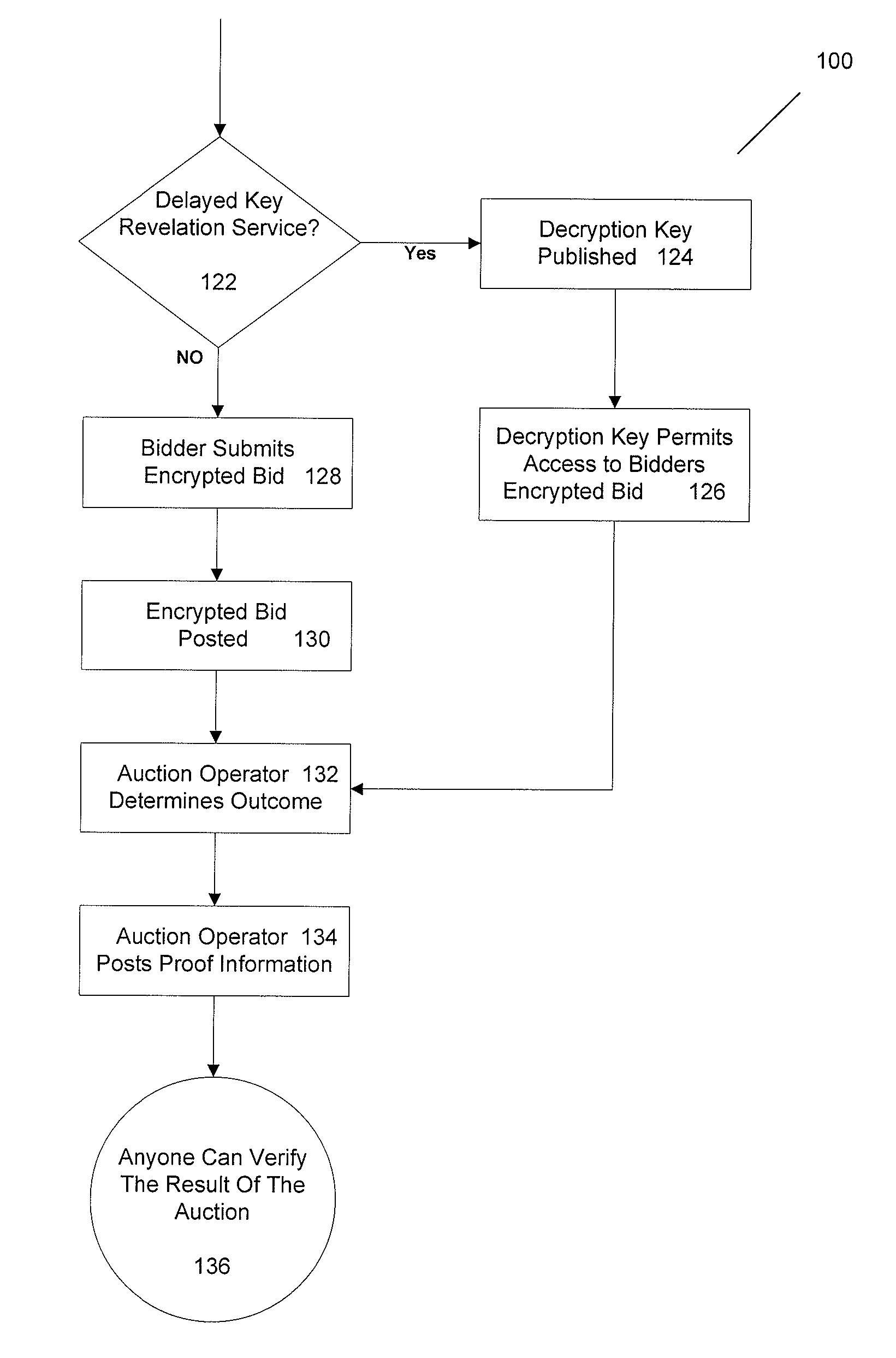
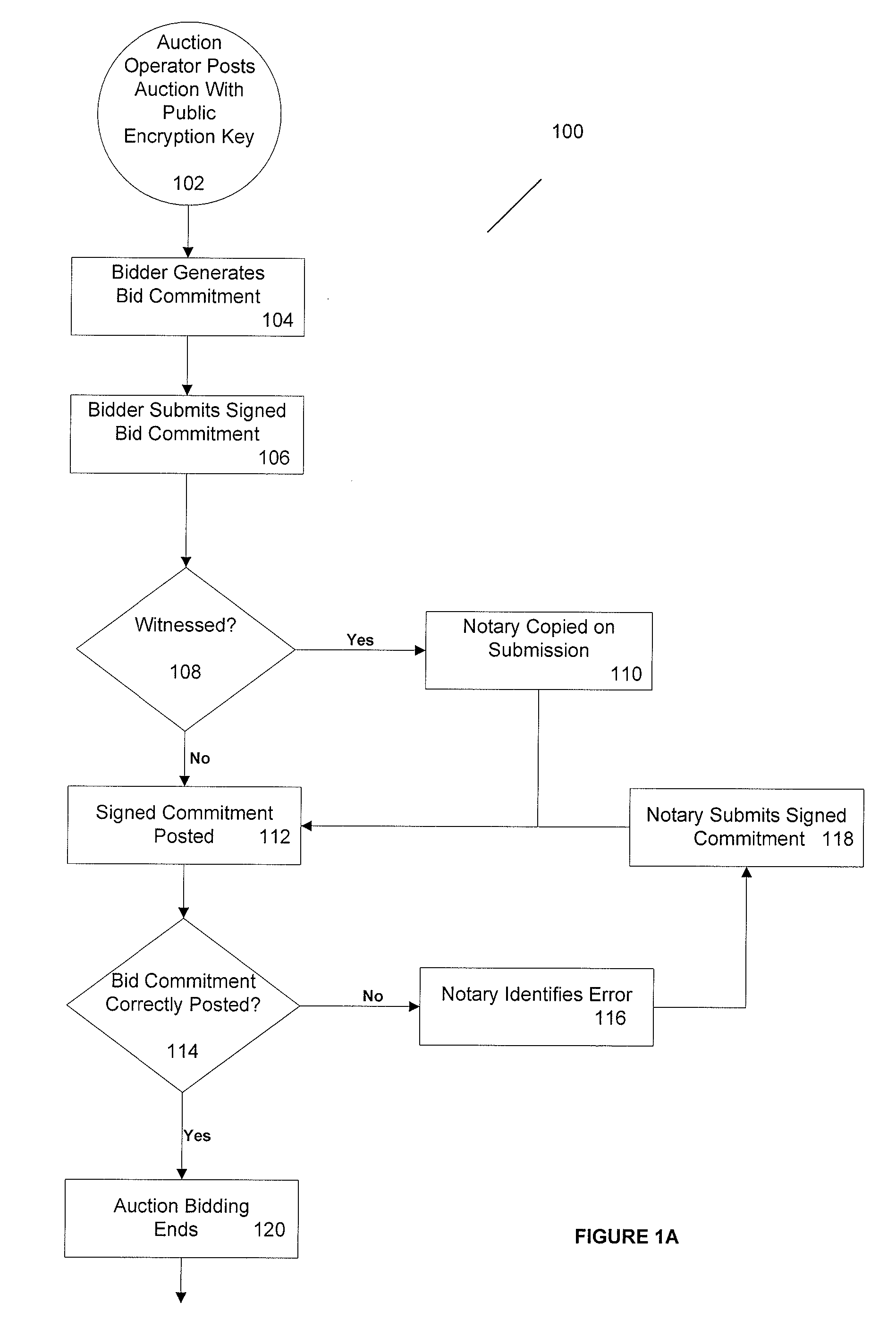
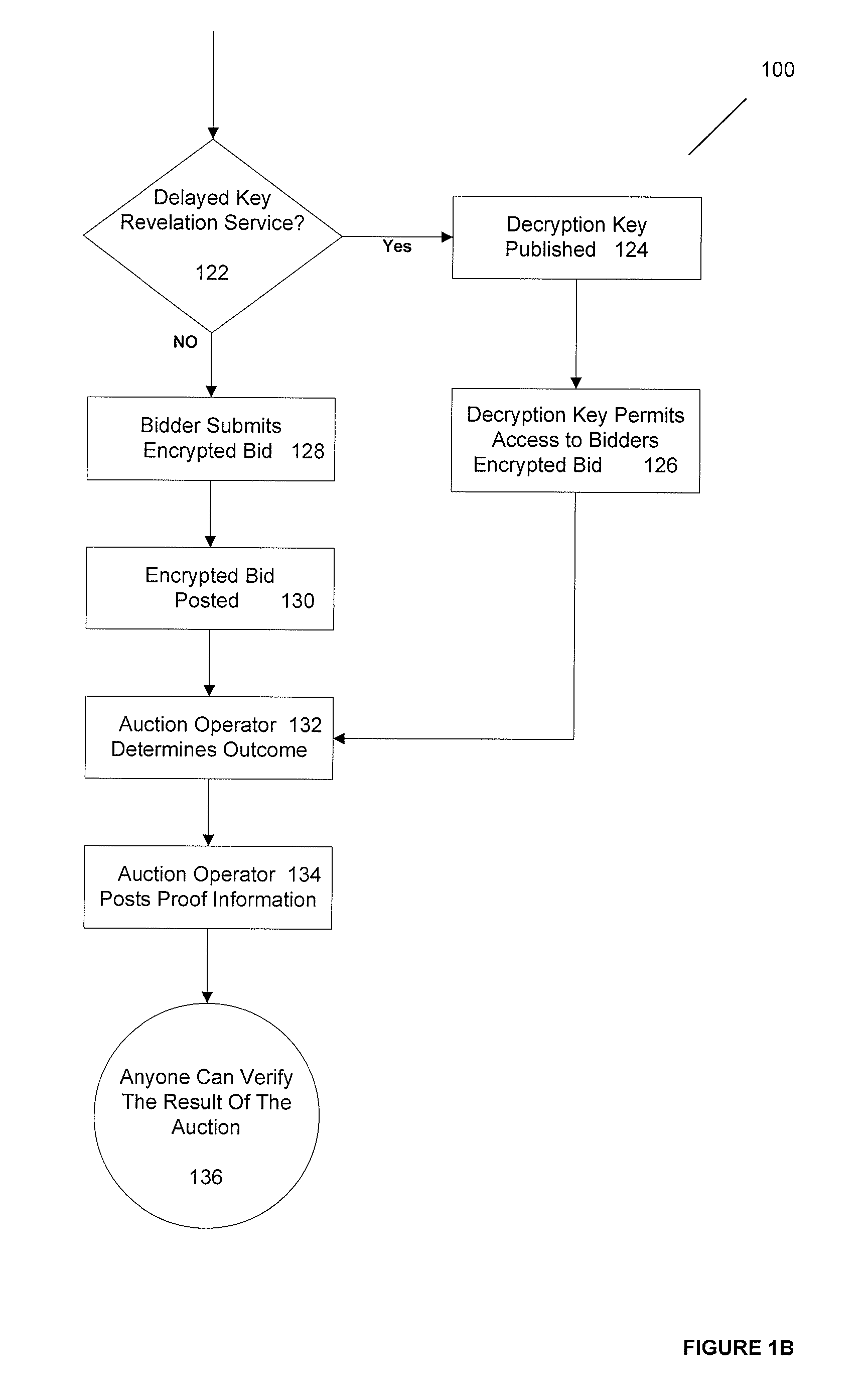
ActiveUS20090182667A1Ensure safetyImprove simplicityMultiple keys/algorithms usageUser identity/authority verificationCorrectness proofsTheoretical computer science
A system and method for conducting verifiably correct auctions that preserves the secrecy of the bids while providing for verifiable correctness and trustworthiness of the auction is disclosed. Some of the elements of the method and apparatus are that the auction operator accepts all bids submitted and follows the published rules of the auction. In one embodiment, the bids are maintained secret from the auctioneer and all bidders until the auction closes and no bidder is able to change or repudiate her bid. In another embodiment, the auction operator computes the auction results and publishes proofs of the results' correctness. In yet another embodiment, any party can check these proofs of correctness via publicly verifiable computations on encrypted bids.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
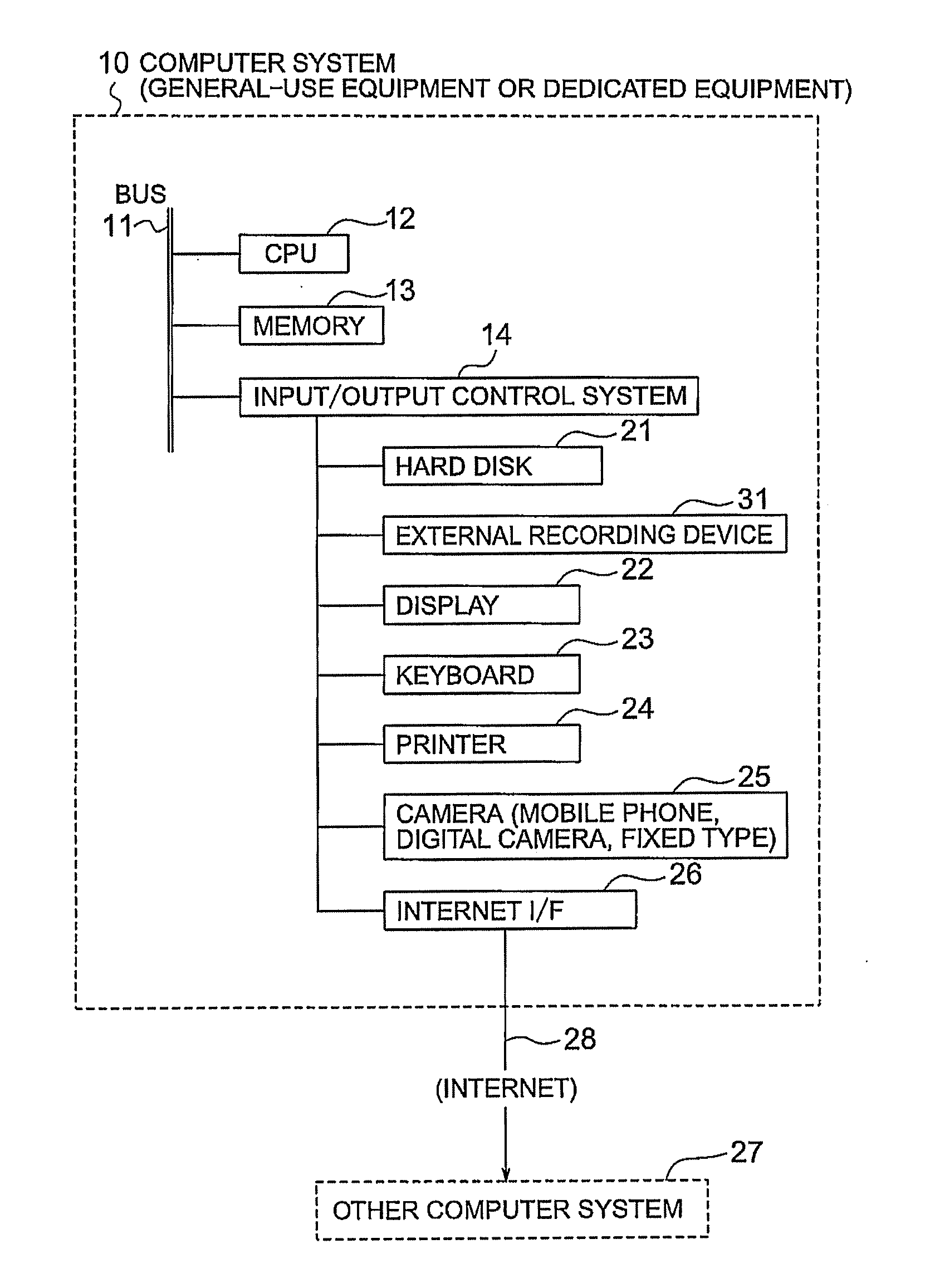
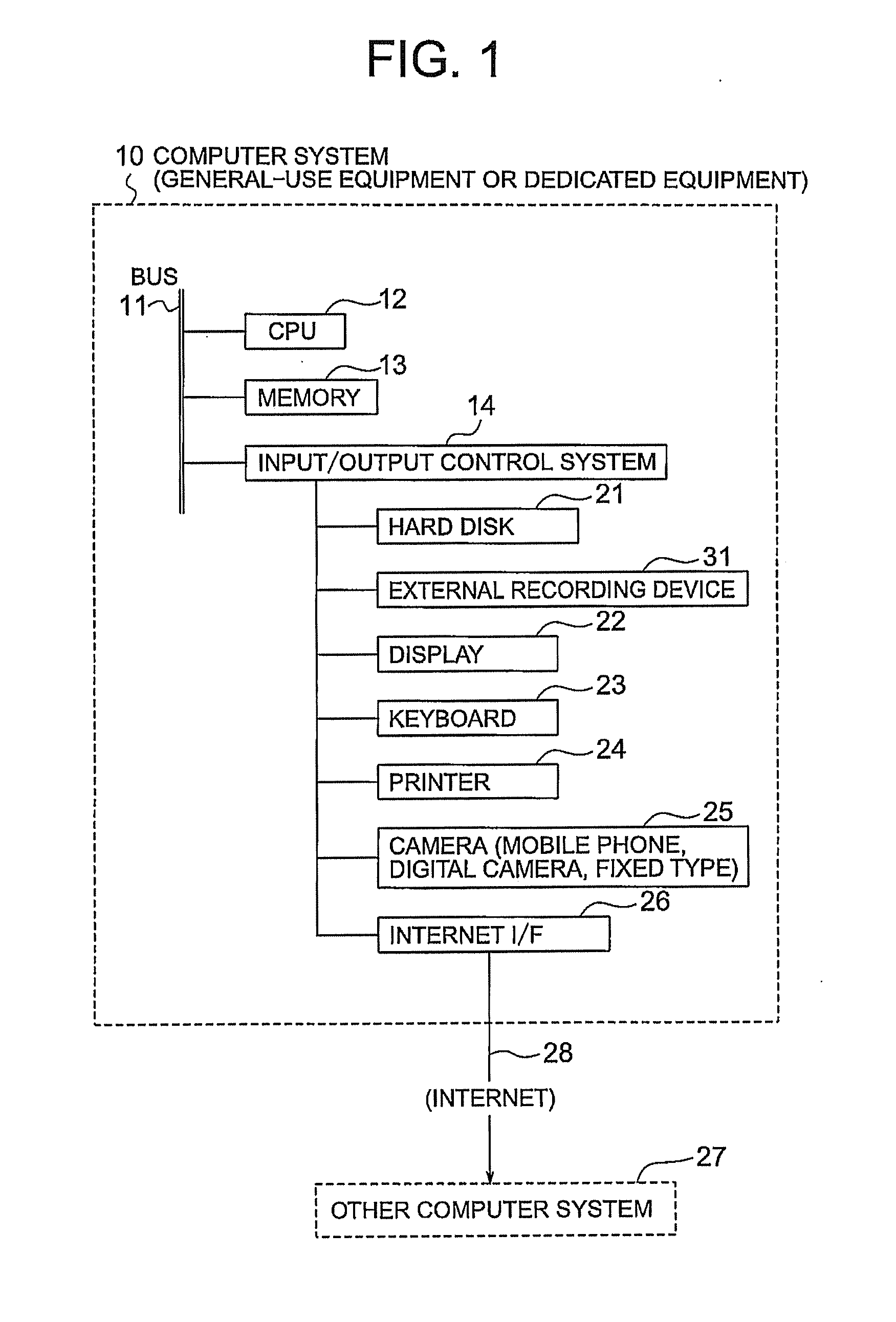
Information processing apparatus, information processing system, information processing method, storage medium, and program
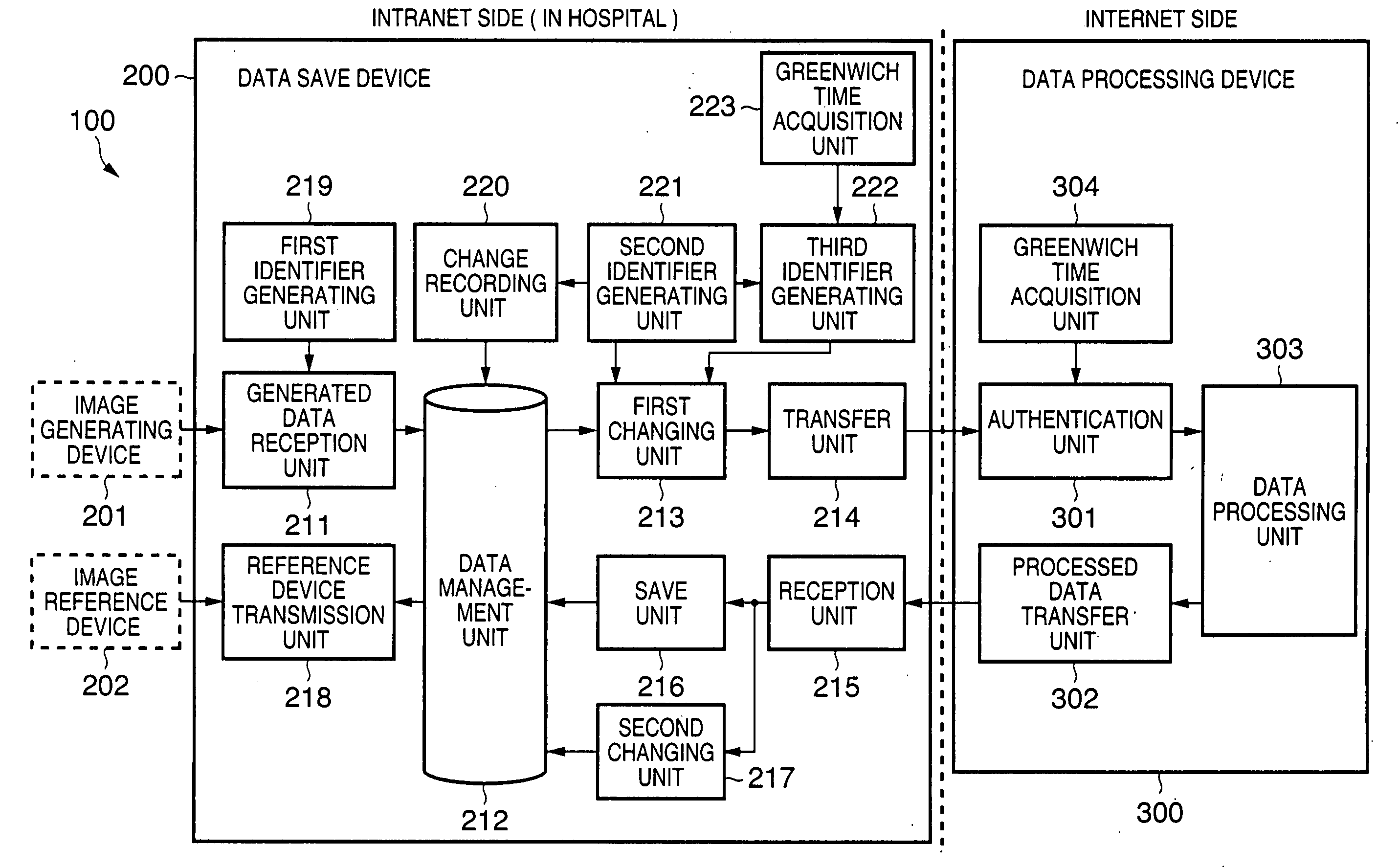
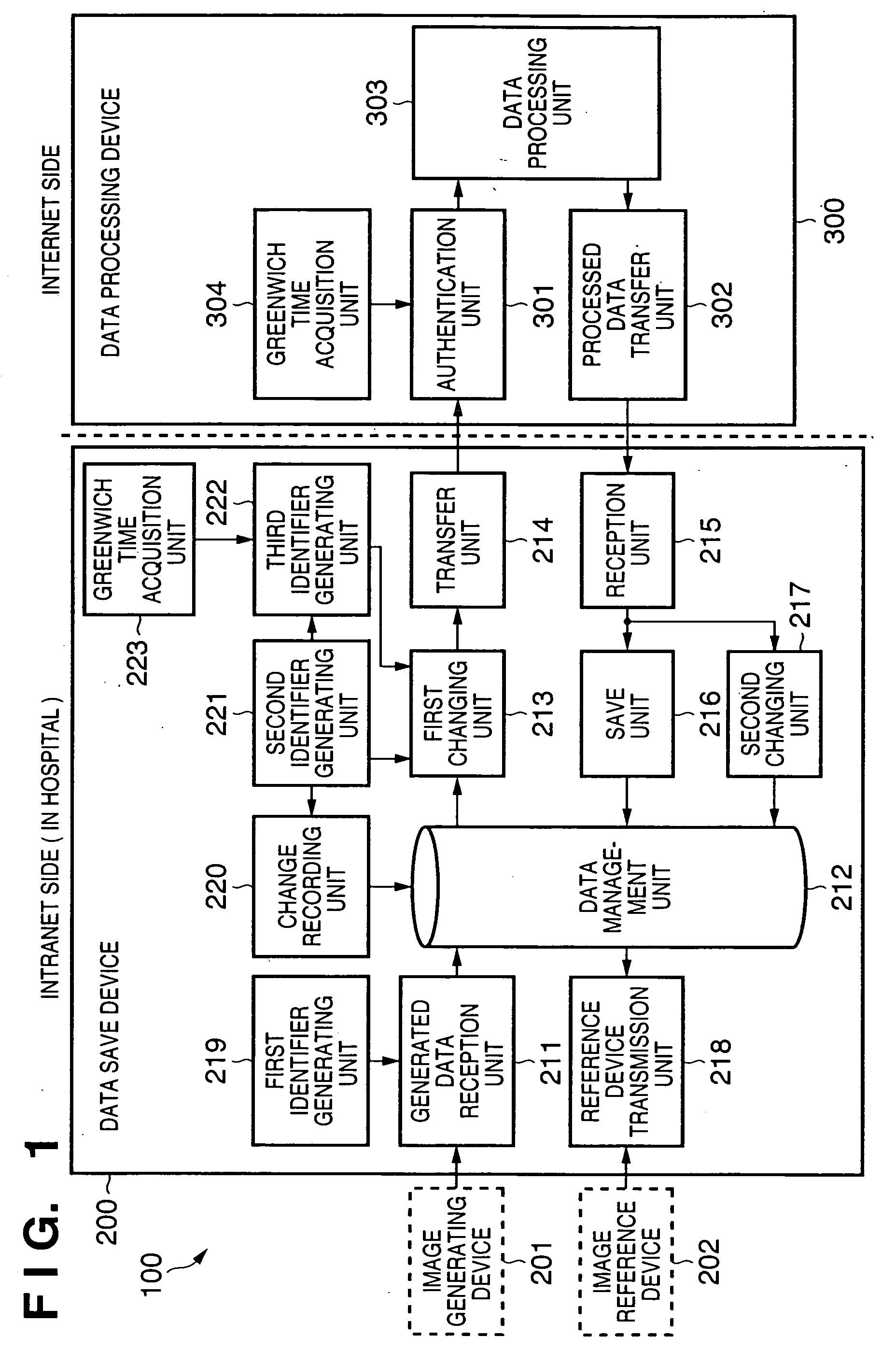
InactiveUS20050086720A1Inhibition of informationProtect informationUltrasonic/sonic/infrasonic diagnosticsDigital data processing detailsInformation processingManagement unit
In an information processing apparatus which transfers target information to an external data processing device to process the information, and saves the processed information, a data management unit stores second identification information corresponding to the target information in association with the target information to which first identification information is attached. The first changing unit deletes the first identification information from the target information and adds the corresponding second identification information to the target information in the data management unit. The transfer unit transfers the target information processed by the first changing unit to the external data processing device.
Owner:CANON KK
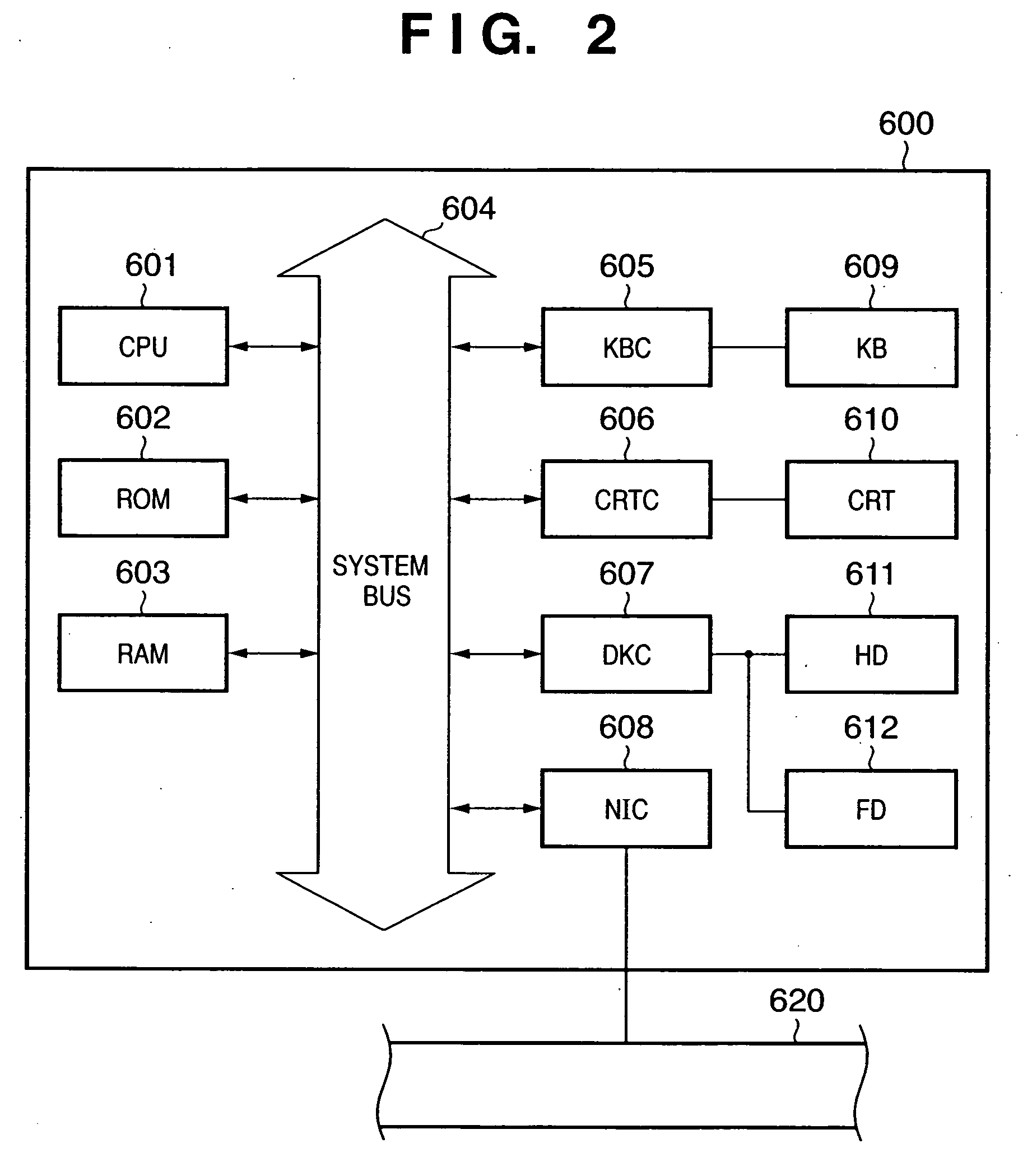
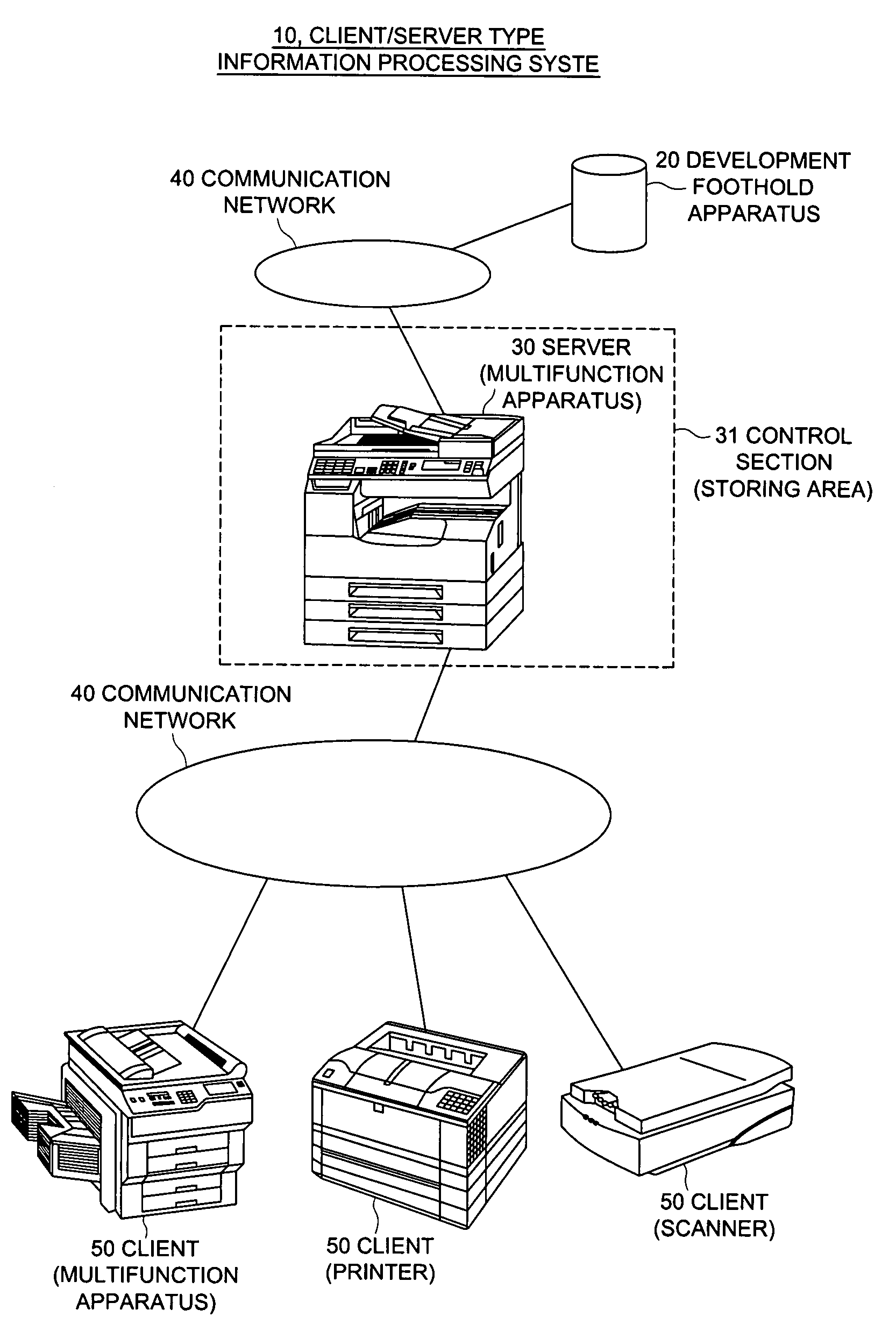
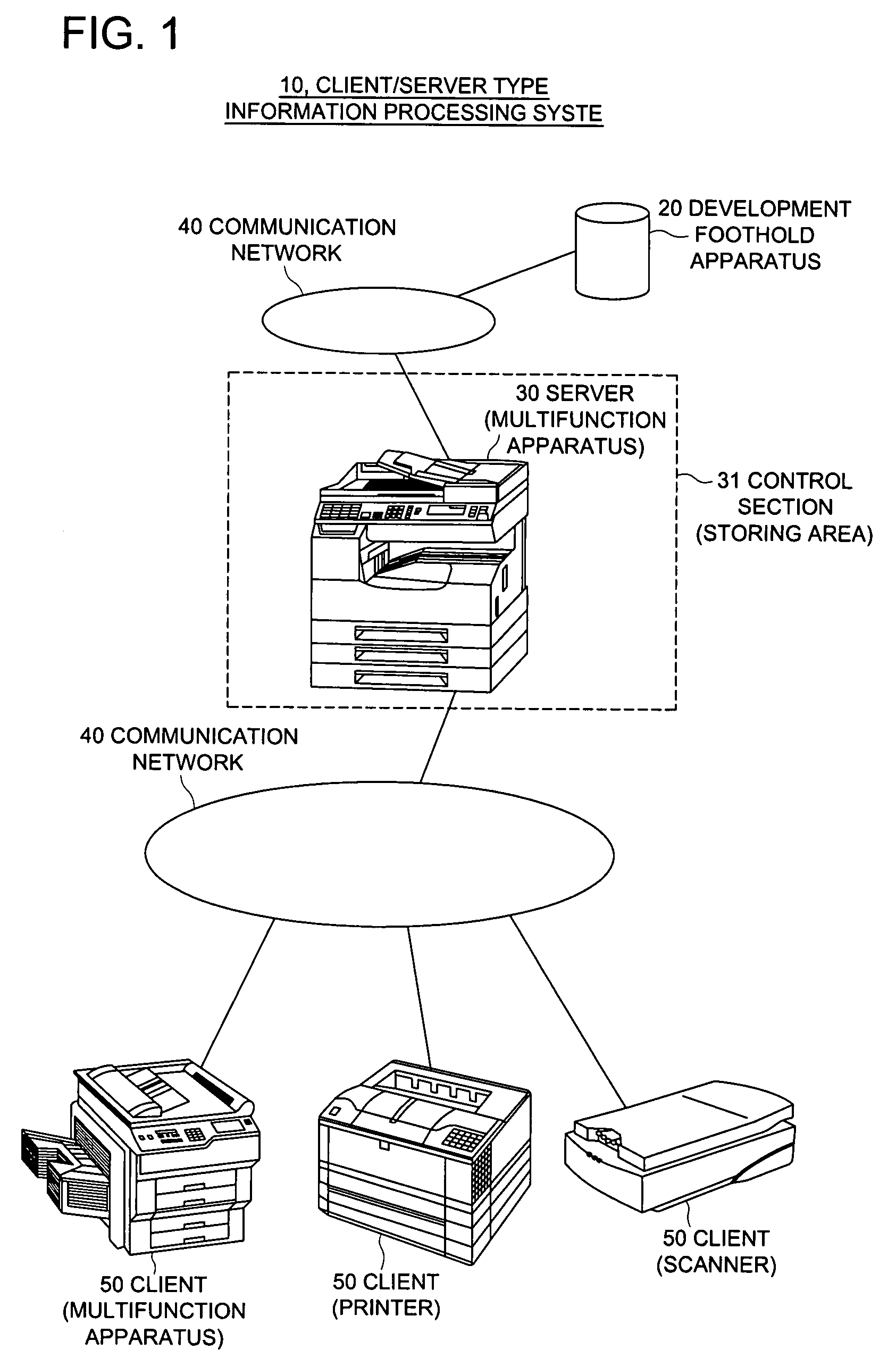
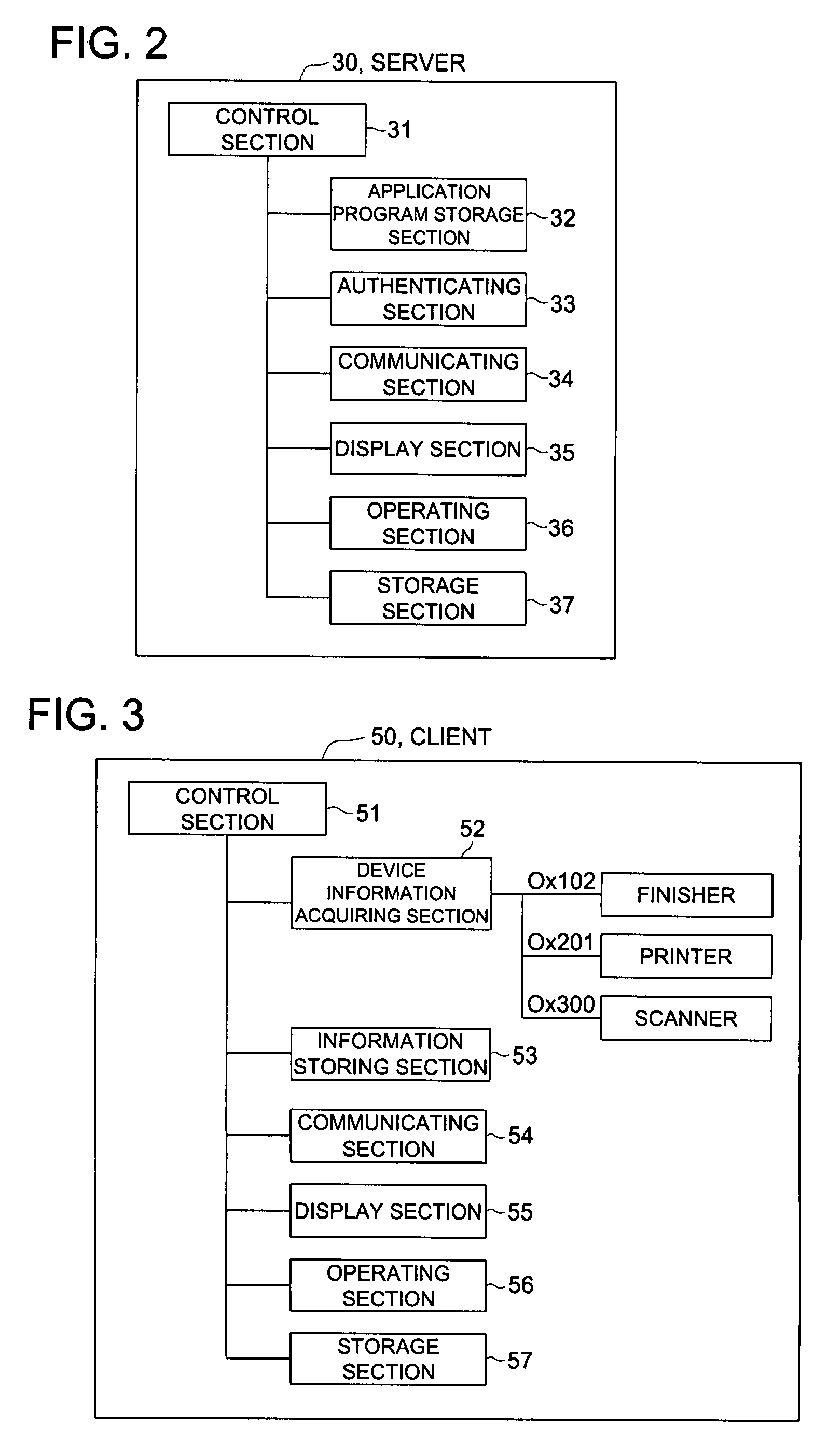
Image forming apparatus client/server type information processing system and information processing method
InactiveUS20080068643A1Avoid Information LeakageLow costDigital computer detailsDigital data protectionInformation processingImage formation
There is described an image forming apparatus that serves as a client in the client / server type information processing system. The apparatus includes a communicating section to communicate with the server; a device information acquiring section to acquire device information for specifying the device; an information storing section to store server information for specifying the server and client information for specifying the client itself; and a control section to transmit the device information, acquired by the device information acquiring section, and the client information, stored in the information storing section, to the server specified by the server information through the communicating section, in order to request the server to send an application program corresponding to the device information back to the client. When the control section receives the application program from the server, the control section develops the application program into the storage so as to make the device available.
Owner:KONICA MINOLTA BUSINESS TECH INC
Cryptographic processing of content
ActiveUS20100296649A1Efficient and convenientAvoid Information LeakageSecret communicationCryptographic attack countermeasuresComputer hardwareCryptographic protocol
A system for cryptographic processing of content comprises an input for receiving the content. A plurality of look-up tables represents a white-box implementation of a combined cryptographic and watermarking operation. The look-up tables represent processing steps of the combined cryptographic and watermarking operation and the look-up tables being arranged for being applied according to a predetermined look-up scheme. The look-up scheme prescribes that an output of a first look-up table of the plurality of look-up tables be used to generate an input of a second look-up table of the plurality of look-up tables. The combined cryptographic and watermarking operation comprises a cryptographic operation and a watermarking operation. A control module looks up values in the plurality of look-up tables in dependence on the received content and in accordance to the look-up scheme, thereby applying the combined cryptographic and watermarking operation to the content.
Owner:IRDETO ACCESS
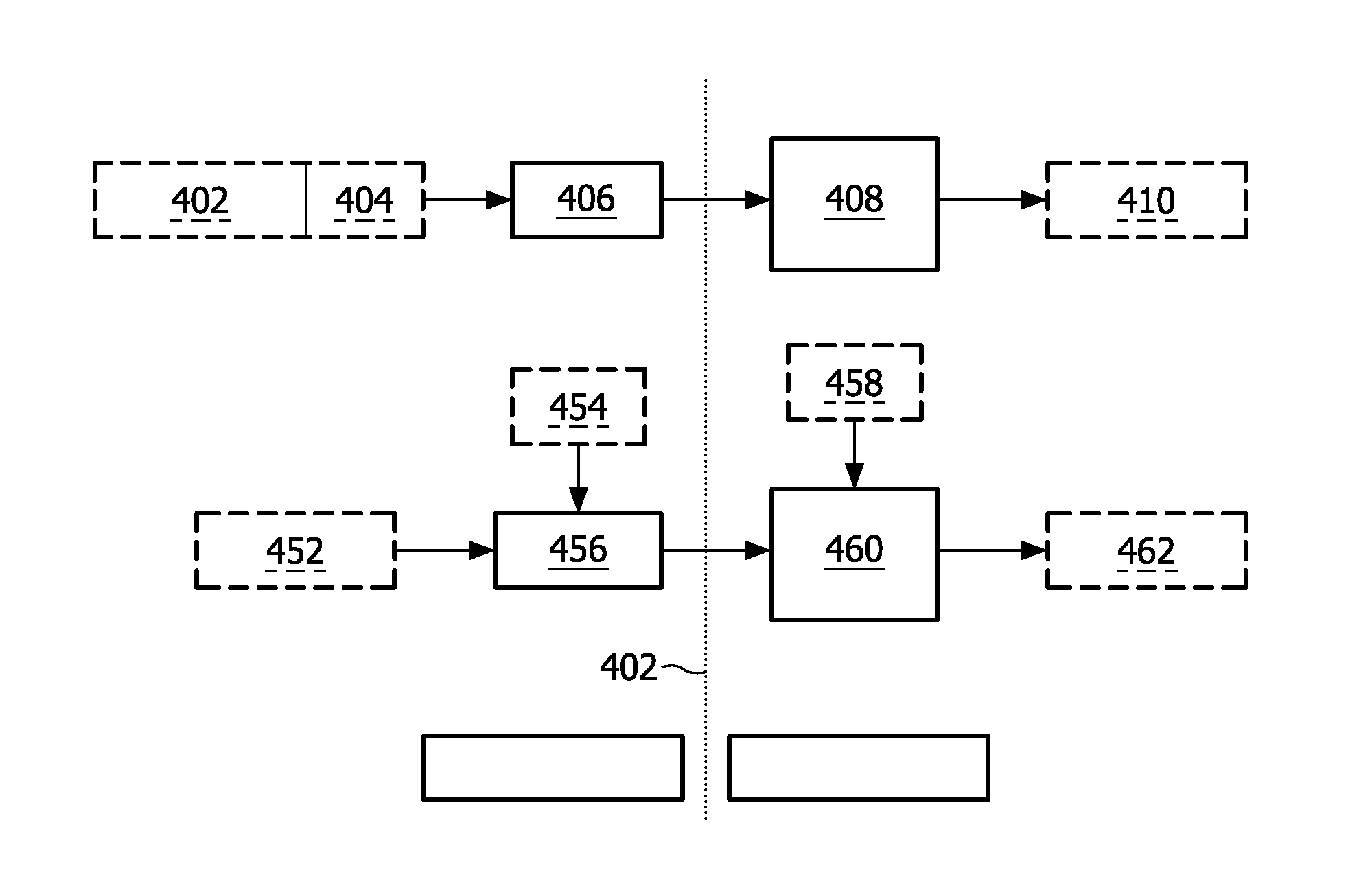
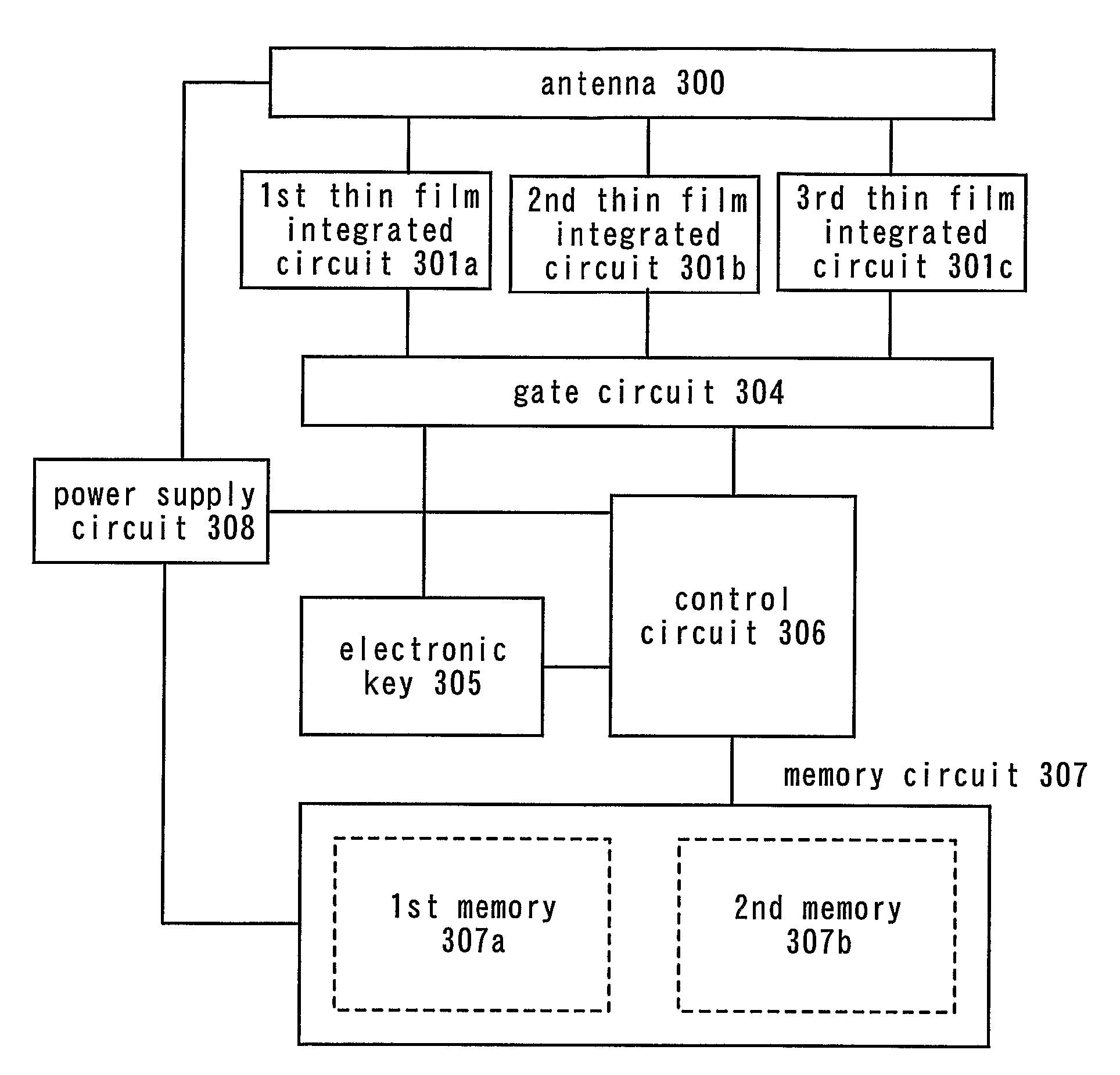
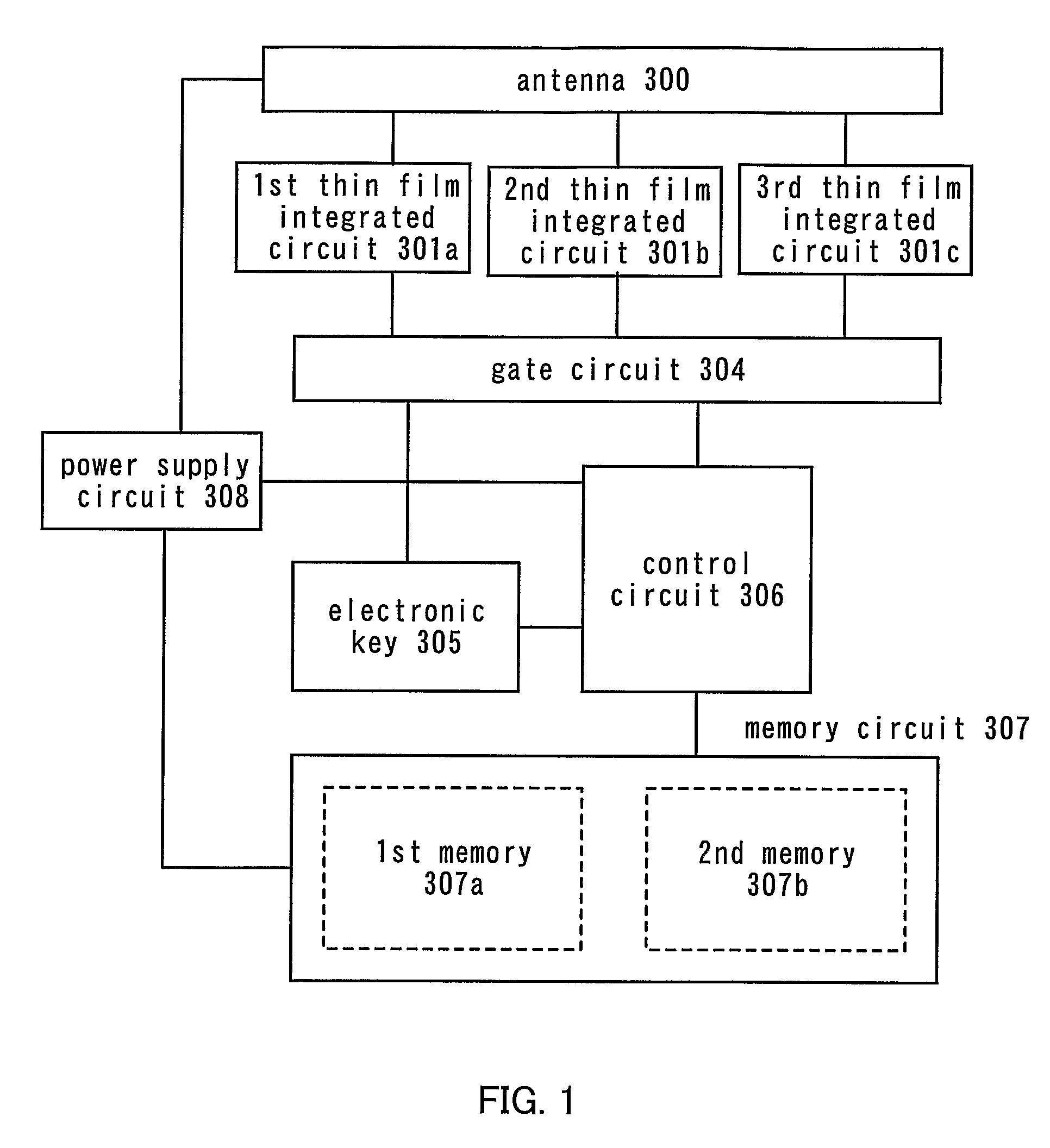
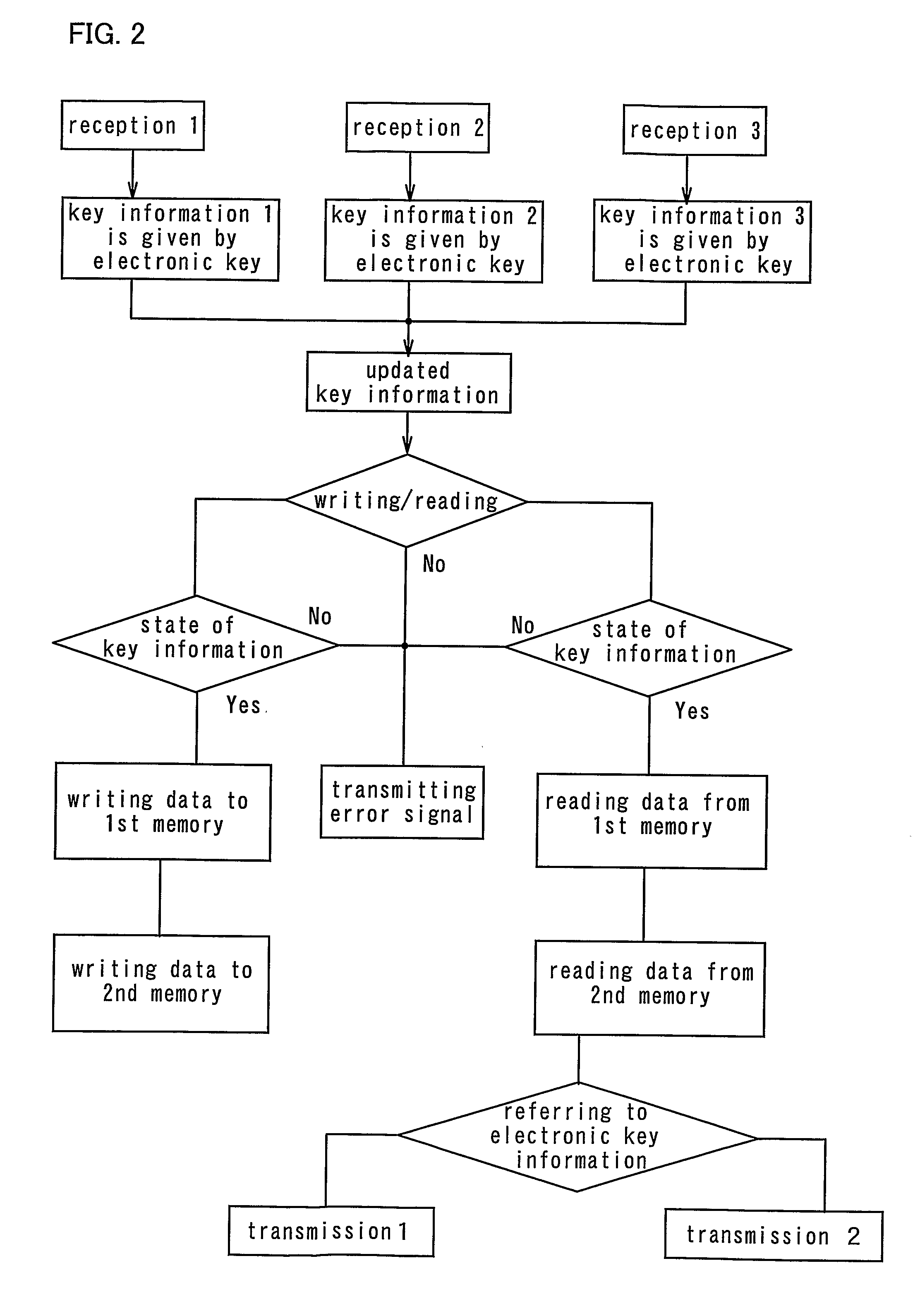
Thin Semiconductor Device And Operation Method Of Thin Semiconductor Device
InactiveUS20070273476A1Prevent forgeryImprove securityElectric signal transmission systemsDigital data processing detailsDevice materialSemiconductor
The present invention provides a thin semiconductor device in which its security such as prevention of counterfeit or information leakage is to be enhanced. One feature of the present invention is a thin semiconductor device in which a plurality of thin film integrated circuits are mounted and in which at least one integrated circuit is different from the other integrated circuits in any one of a specification, layout, frequency for transmission or reception, a memory, a communication means, a communication rule and the like. According to the present invention, a thin semiconductor device tag having the plurality of thin film integrated circuits communicates with a reader / writer and at least one of the thin film integrated circuits receives a signal to write information in a memory, and the information written in the memory determines which of the thin film integrated circuits communicates.
Owner:SEMICON ENERGY LAB CO LTD
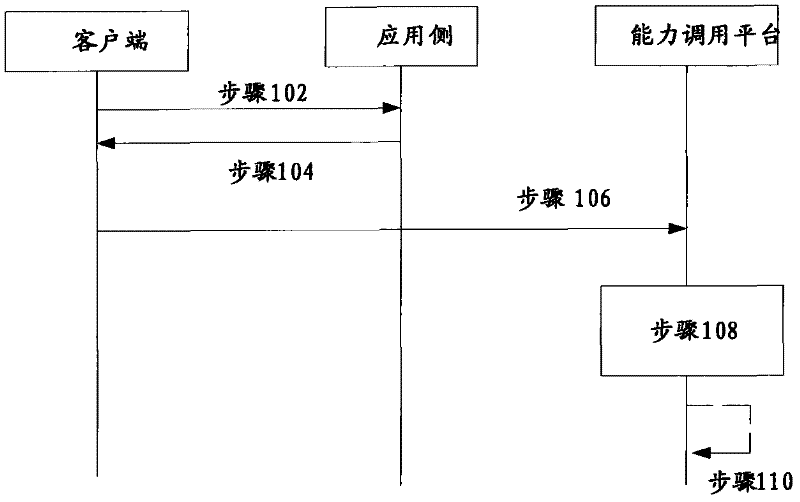
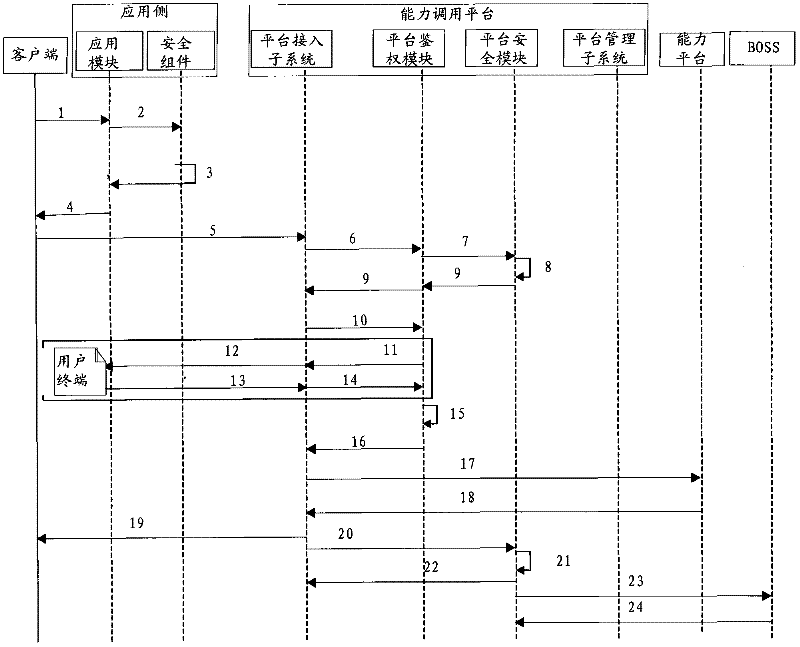
Capacity calling method, capacity calling request device, capacity calling platform and capacity calling system
ActiveCN102546532AImprove securityAvoid Information LeakageTransmissionClient-sideTelecommunications
The invention discloses a capacity calling method, a capacity calling request device, a capacity calling platform and a capacity calling system, wherein the capacity calling method includes: transmitting a token acquisition request to an application side by a client side, receiving a token returned from the application side, and generating and transmitting a capacity calling request including the token; and performing validation according to the capacity calling request and calling capacity for the client side after successful validation by the capacity calling platform. Safety of internet platform capacity opening is improved, and the defects of information leakage and low safety caused by operation through the application side are avoided.
Owner:CHINA MOBILE COMM GRP CO LTD
Loudspeaker system
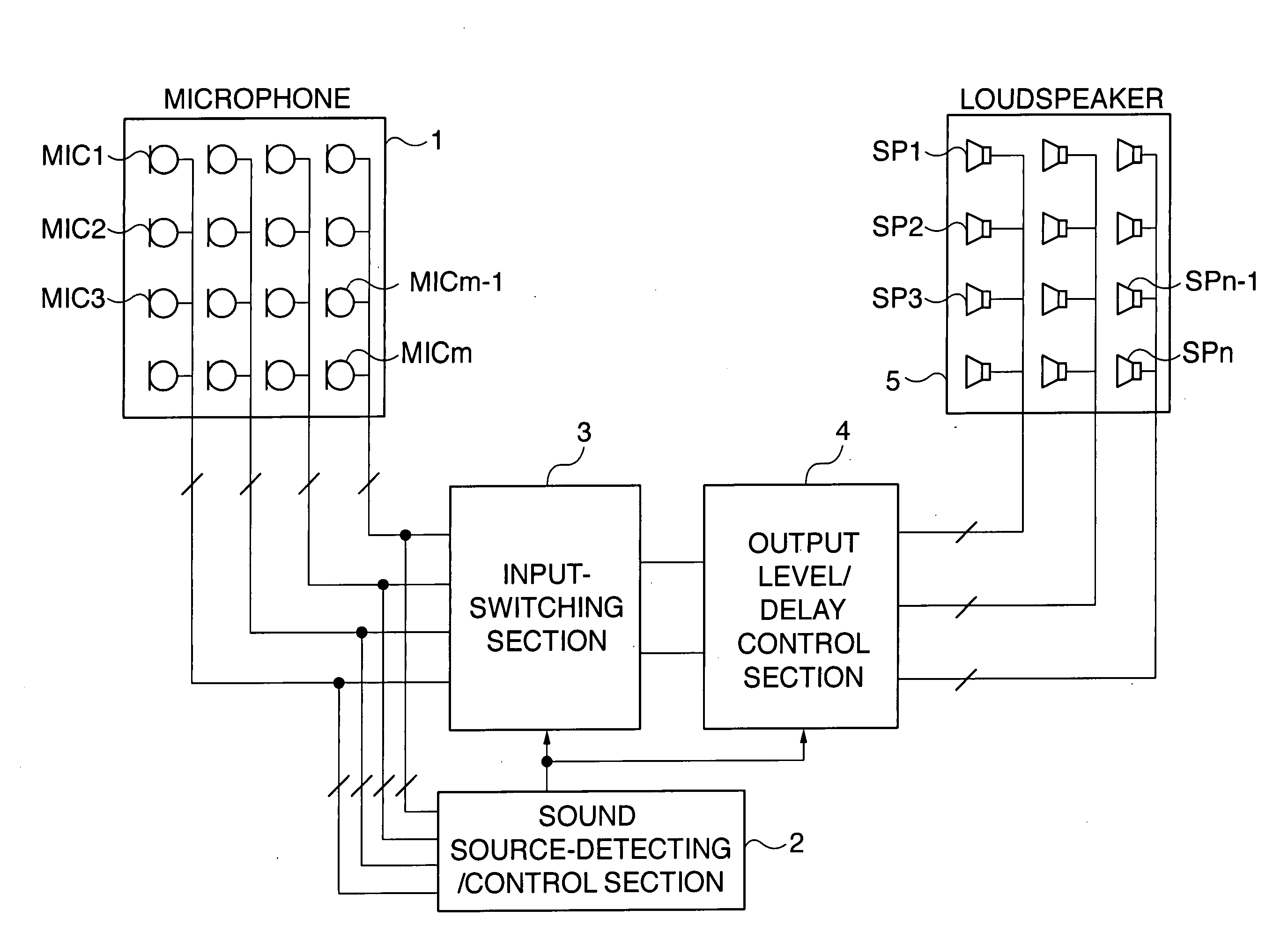
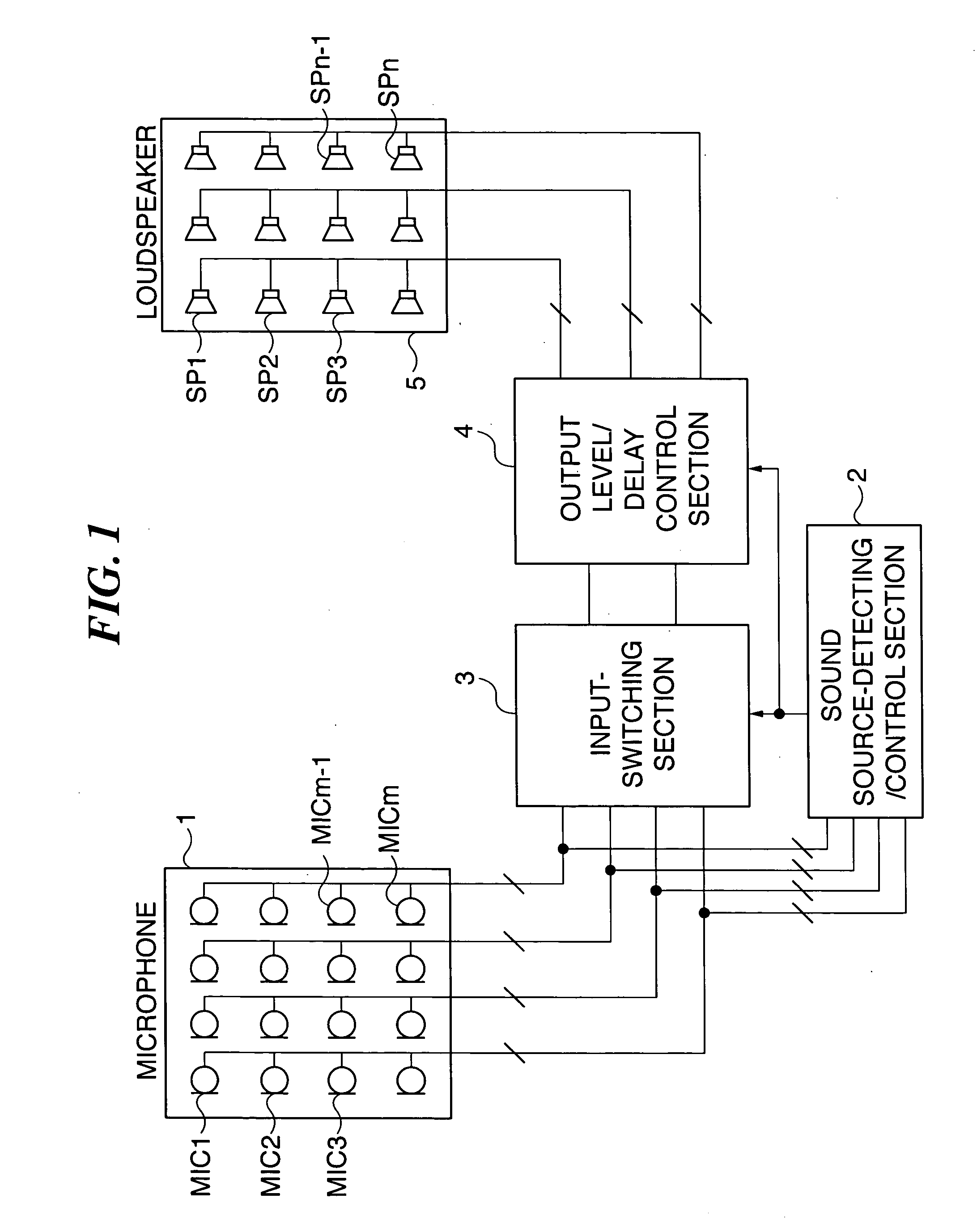
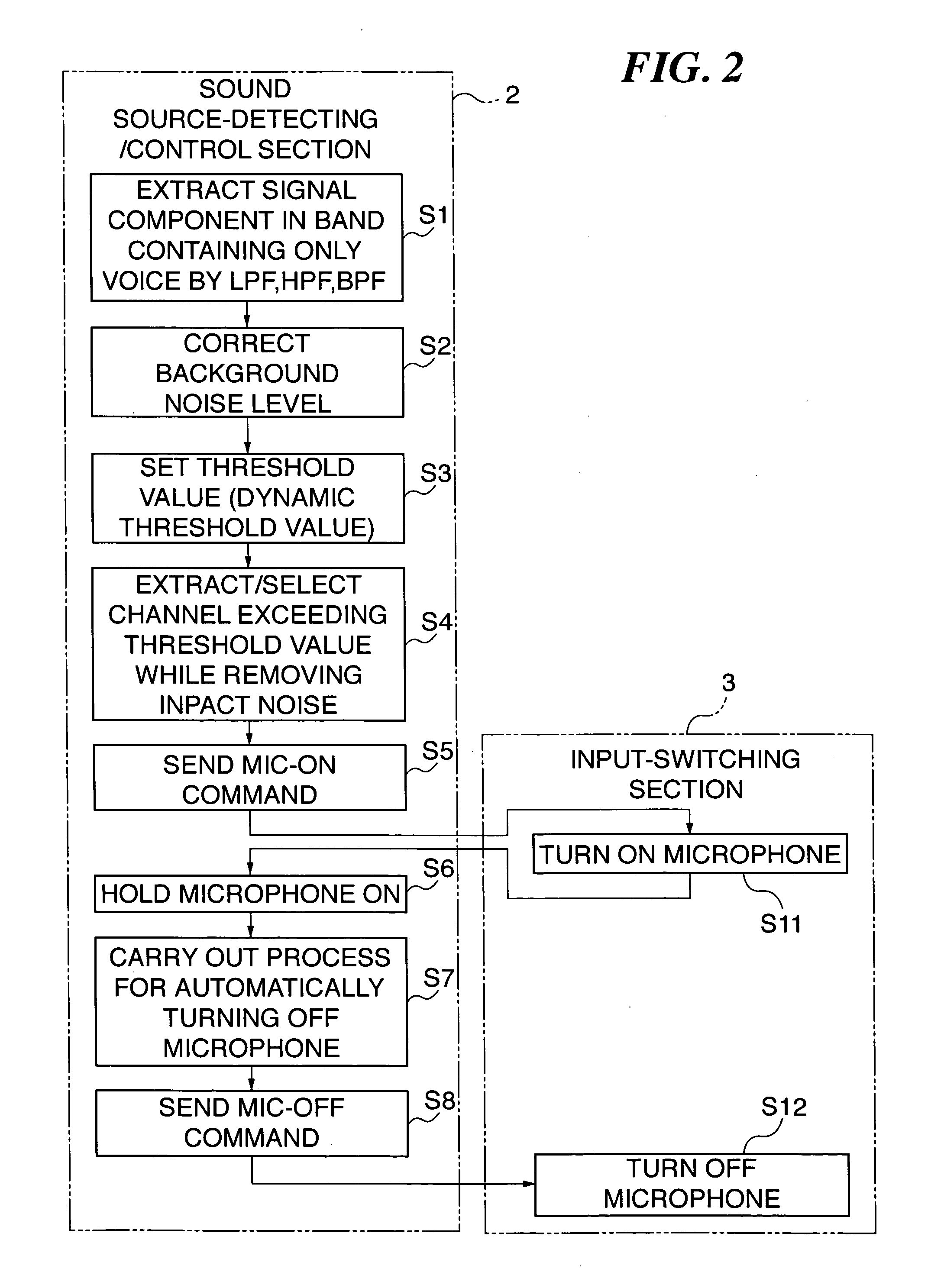
ActiveUS20070160240A1High-quality voice amplificationSuppress interferenceGain controlPublic address systemsTime segmentEngineering
A hands-free loudspeaker system which is capable of achieving high-quality voice amplification without requiring a human speaker to move to a microphone or a microphone to be moved to a human speaker. A microphone whose input level has continued to be above a threshold value for not shorter than a predetermined time period is detected, based on input signals from dispersedly arranged microphones. An input signal from the microphone is selected and outputted to each loudspeaker at an output level or with a delay time, according to a location of the loudspeaker. A preset lowest threshold level is initially set to the threshold value, and an input level of the microphone higher than the threshold value is newly set to the same, while when the input level is lower than the threshold value, a lower value is set to the same in a step-by-step manner.
Owner:YAMAHA CORP
Intelligent mobile phone anti-theft method and system
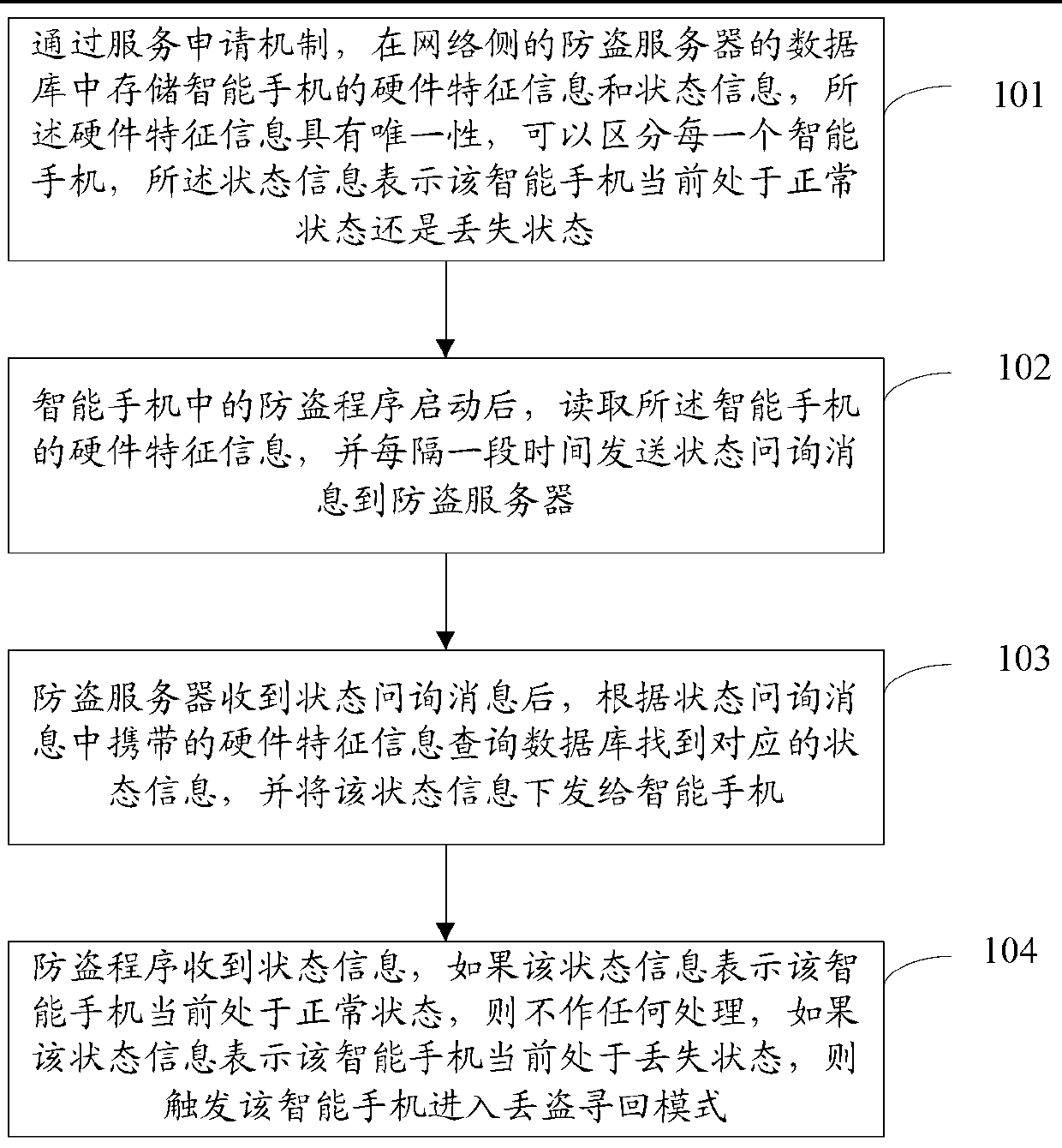
ActiveCN103347131AVarious meansMake up for the lossSubstation equipmentTransmissionComputer hardwareMobile phone
The invention discloses an intelligent mobile phone anti-theft method. Hardware feature information and state information of an intelligent mobile phone are stored in a database of an anti-theft server of a network side. The intelligent mobile phone anti-theft method comprises the steps that A, an anti-theft program in the intelligent mobile phone reads the hardware feature information of the intelligent mobile phone, and state inquiry information is sent to the anti-theft server at intervals; B, after the anti-theft server receives the state inquiry information, the database is inquired for finding corresponding state information according to the hardware feature information carried in the state inquiry information, and the state information is sent to the intelligent mobile phone; C, the anti-theft program receives the state information, if the state information represents that the intelligent mobile phone is in a normal state currently, no processing is conducted, and if the state information represents that the intelligent mobile phone is in a loss state currently, the intelligent mobile phone is triggered to enter a mode of finding the lost and stolen intelligent mobile phone .
Owner:张林
Information asset management system, log analysis server, log analysis program, and portable medium
InactiveUS8051204B2Avoid Information LeakagePrevent leakageDigital computer detailsResourcesCorrelation analysisData mining
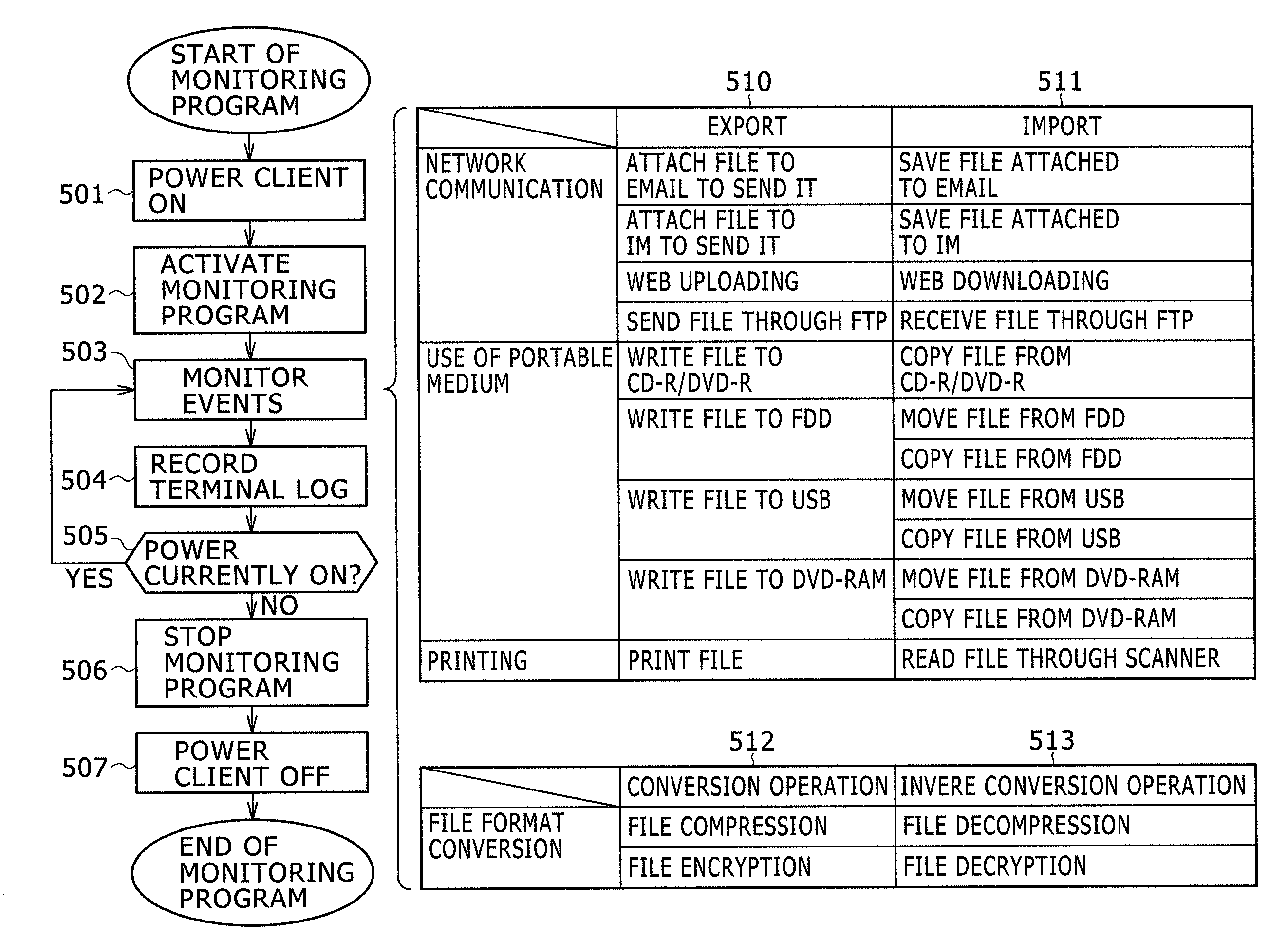
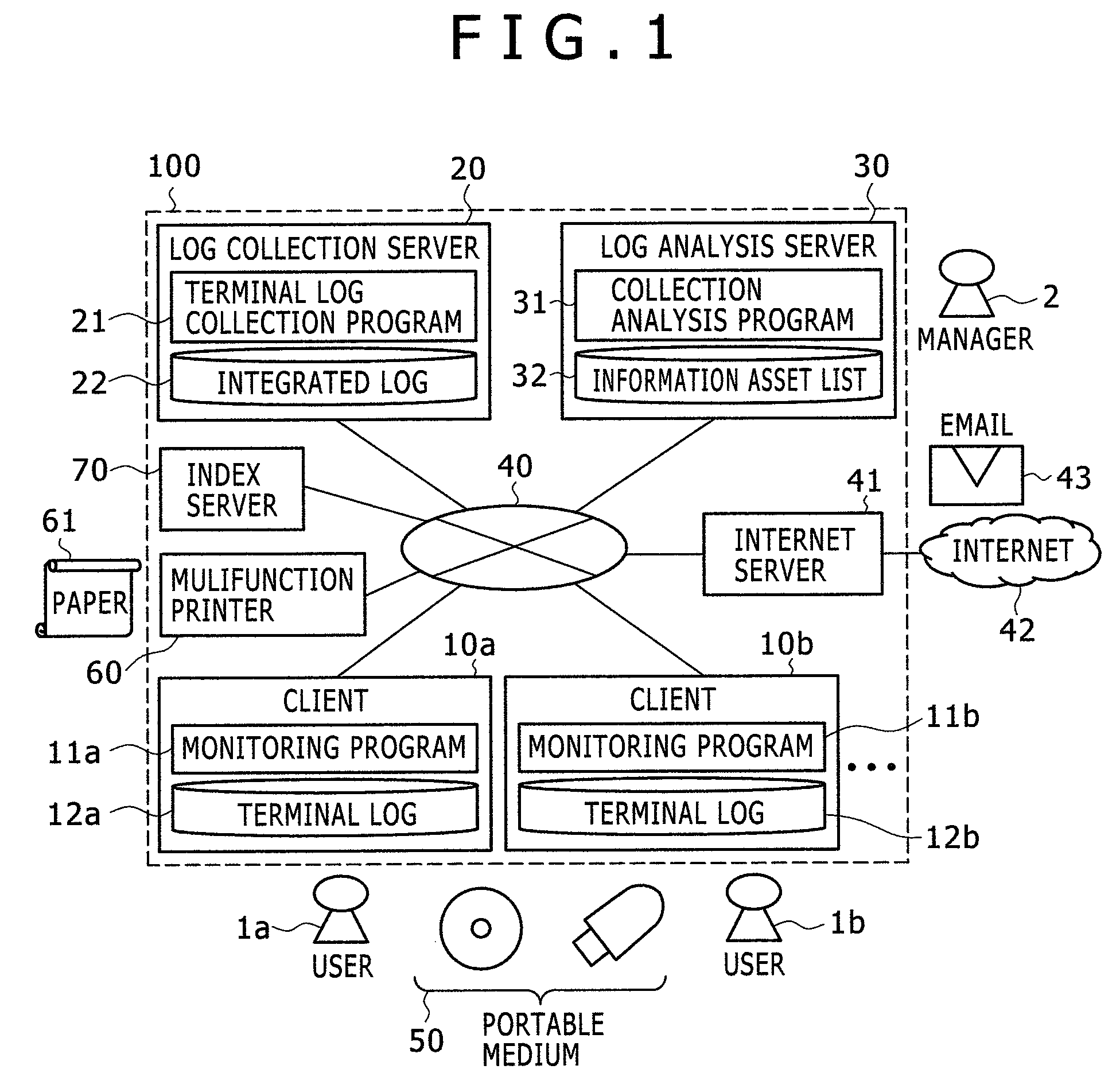
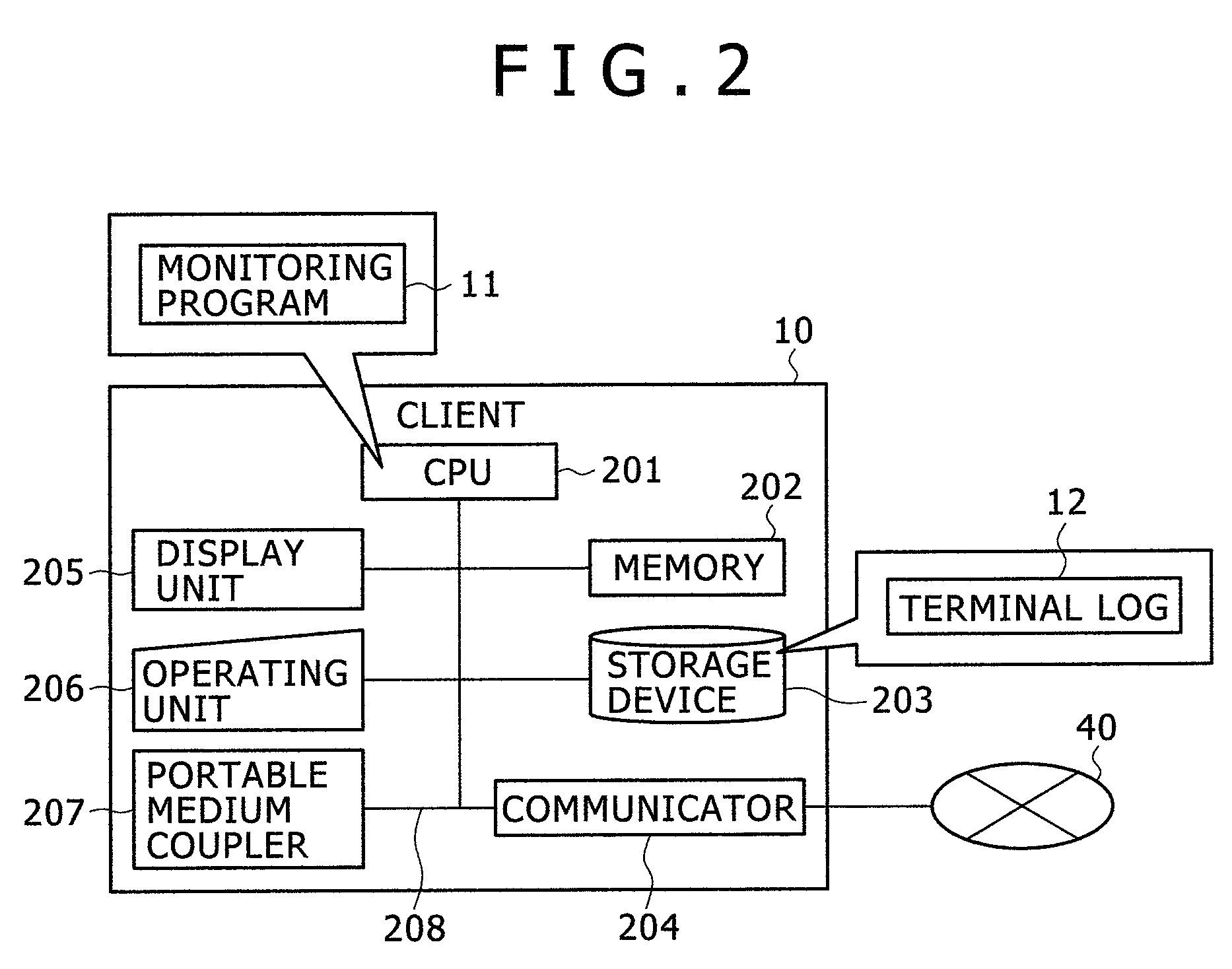
An information asset management system in a network environment includes a monitoring program 11 that monitors operation events performed by users and creates terminal logs 12, a terminal log collection program 21 that stores an integrated log 22 created by collecting the terminal logs 12, and a correlation analysis program 31 that analyzes the whereabouts of information assets using the integrated log 22. When the user exports an information asset from the network environment and when the user imports the information asset into the network environment, the monitoring program 11 monitors these export and import events including feature values of the information assets. The correlation analysis program 31 compares a pre-export feature value of each information asset with a post-import feature value of each information asset to determine whether the information assets are identical and reports a list of information assets in the organization.
Owner:HITACHI LTD
Mobile phone two-dimensional code safe use method based on information hiding
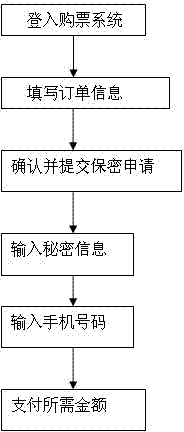
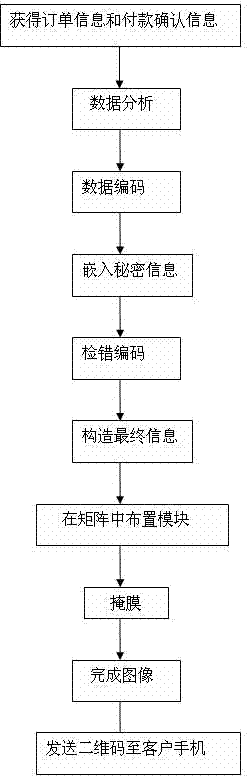
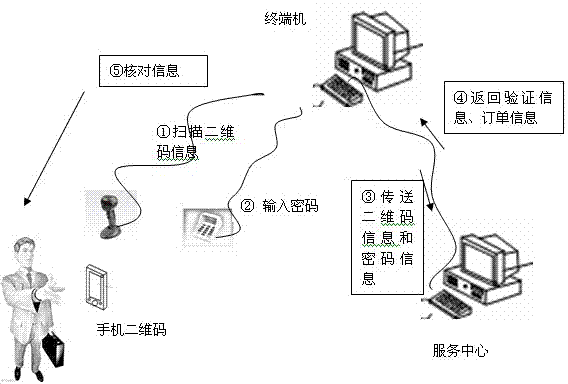
ActiveCN103415007AFix security issuesEnsure safetyRecord carriers used with machinesSecurity arrangementConfidentialityThe Internet
The invention discloses a mobile phone two-dimensional code safe use method based on information hiding. With the development of information technology and Internet technology, people pay more attention to the convenient and environmental-friendly two-dimensional code technology, and the use of the two-dimensional code is wider and wider. However, a traditional mobile phone two-dimensional code is lack of a necessary security mechanism, people can use a two-dimensional code as long as the people have the two-dimensional code, and the security of the private information of the user is invaded. The method is based on the information hiding technology, the cryptography theory and bar code technology are utilized, through a method of embedding user secret information in encoding and carrying out extraction, operation and comparison in decoding, the safe use problem of the mobile phone two-dimensional code is solved, the leakage and stealing of the information are prevented, and the integrity and confidentiality of the information are ensured. The method is simple and practical, with the gradual popularization of the Internet technology at the present age, and method plays an important role for the security of the information.
Owner:上海翰星电子科技有限公司
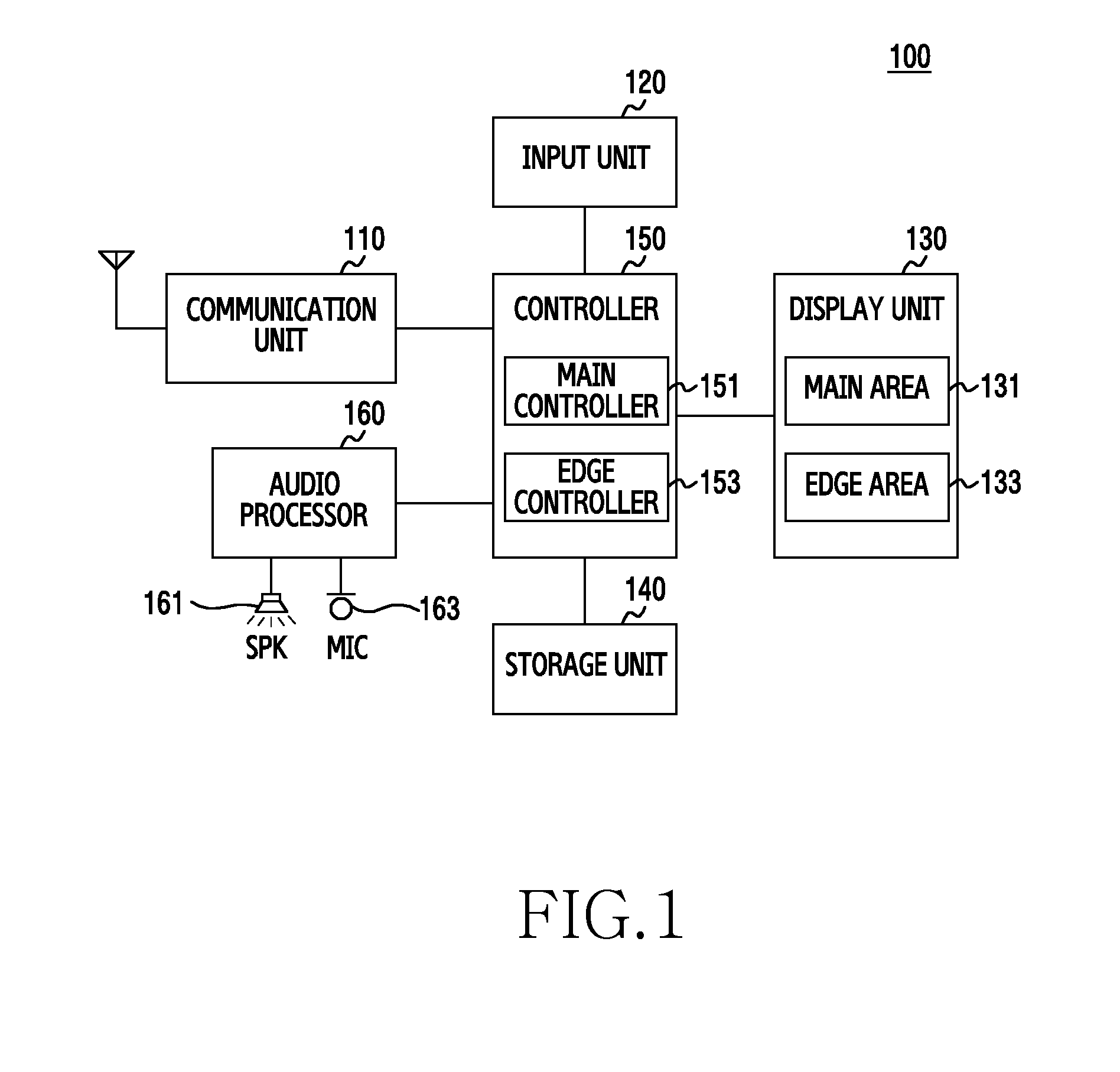
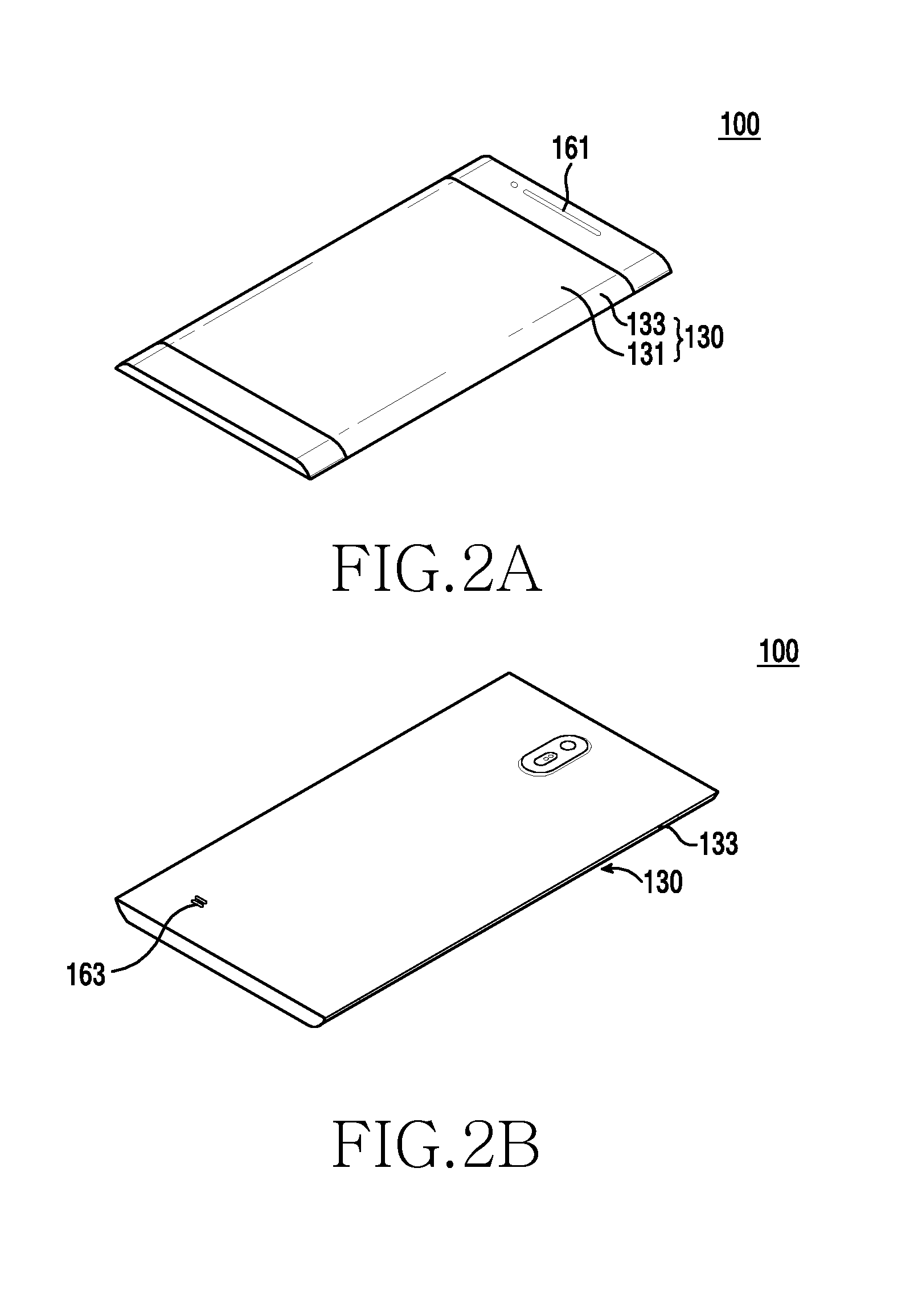
Electronic apparatus and operating method thereof
ActiveUS20160224299A1Avoid troubleEfficiently display informationCurrent supply arrangementsTelephone set constructionsDisplay deviceHuman–computer interaction
Owner:SAMSUNG ELECTRONICS CO LTD
Information management system, information management method and apparatus, and encryption method and program
ActiveUS20110154063A1Reduce loadAvoid Information LeakageUnauthorized memory use protectionHardware monitoringEngineeringData store
An information management system provided with an encrypting means for encrypting an original file to prepare an encrypted file, a data storage memory which stores the encrypted file, a decrypting means, a general memory, an information managing means for decrypting the encrypted file to an editable display file etc. and storing it in the general memory in a regular operational processing cycle, performing the required editing in the form of the display file etc., converting the display file etc. after editing to an encrypted file by the encrypting means, and storing this in the data storage memory, and an information management file which controls processing of or operations on the encrypted file by the information managing means. This standardizes information management at the different levels of an organization, managers, etc., enables secure protection and management of information contained in the different machinery and equipment, lightens the load of information management, prevents leakage of information, and preserves and protects files and prevents their destruction, tampering, and alteration.
Owner:TANI ELECTRONICS IND CO LTD
Instant communication message processing method and client
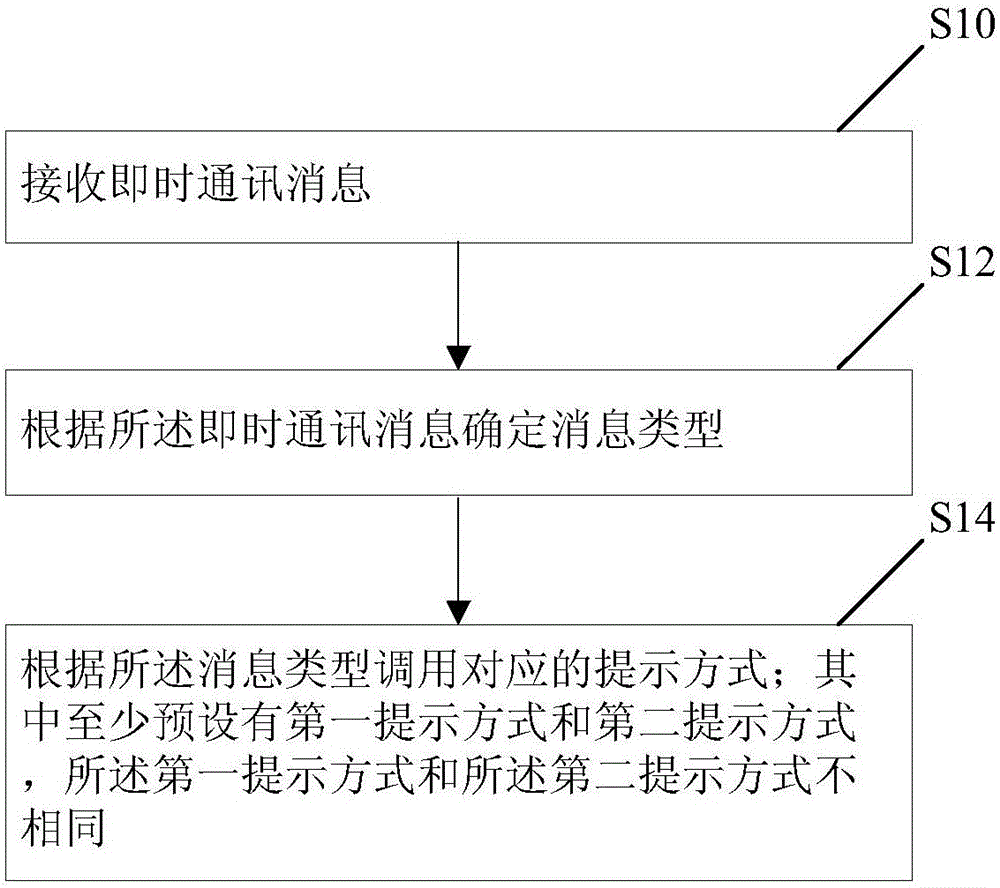
ActiveCN105119799AAvoid Information LeakagePrivacy Security GuaranteeDigital data protectionMessaging/mailboxes/announcementsClient-sideMessage type
The invention discloses an instant communication message processing method and a client. The method includes receiving instant communication messages, determining message types according to the instant communication messages, and calling corresponding notifying means according to the message types, wherein at least a first notifying means and a second notifying means are set in advance, and the first notifying means and the second notifying means are different. The instant communication message processing method and the client can give notification according to different types of instant communication messages.
Owner:ALIBABA GRP HLDG LTD
Image forming apparatus capable of managing configuration information of multiple modules
ActiveUS20070283253A1Increase safetySerious security vulnerabilityDigital computer detailsComputer security arrangementsMultiple applicationsInformation storage
An image forming apparatus is disclosed that includes multiple application modules configured to perform image processing including scanning, printing, and copying of an image; multiple service modules configured to perform an image forming operation and to control the image forming apparatus; a nonvolatile configuration information storage part configured to contain first configuration information of the application modules and the service modules; a configuration information comparison part configured to read second configuration information of the application modules and the service modules and compare the first configuration information and the second configuration information before starting the application modules and the service modules; and a notification part configured to notify the manager of the image forming apparatus of the difference between the first configuration information and the second configuration information in response to detection of the difference.
Owner:RICOH KK
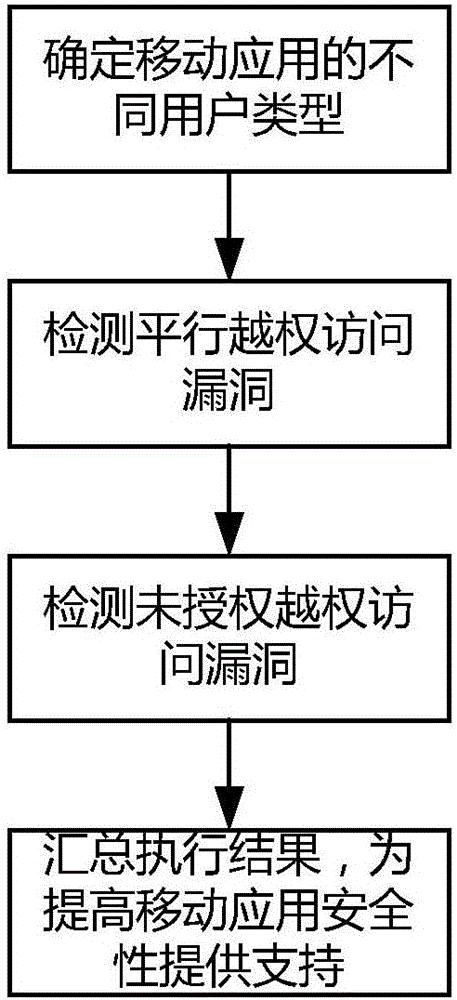
Method for detecting unauthorized access vulnerability of power mobile application
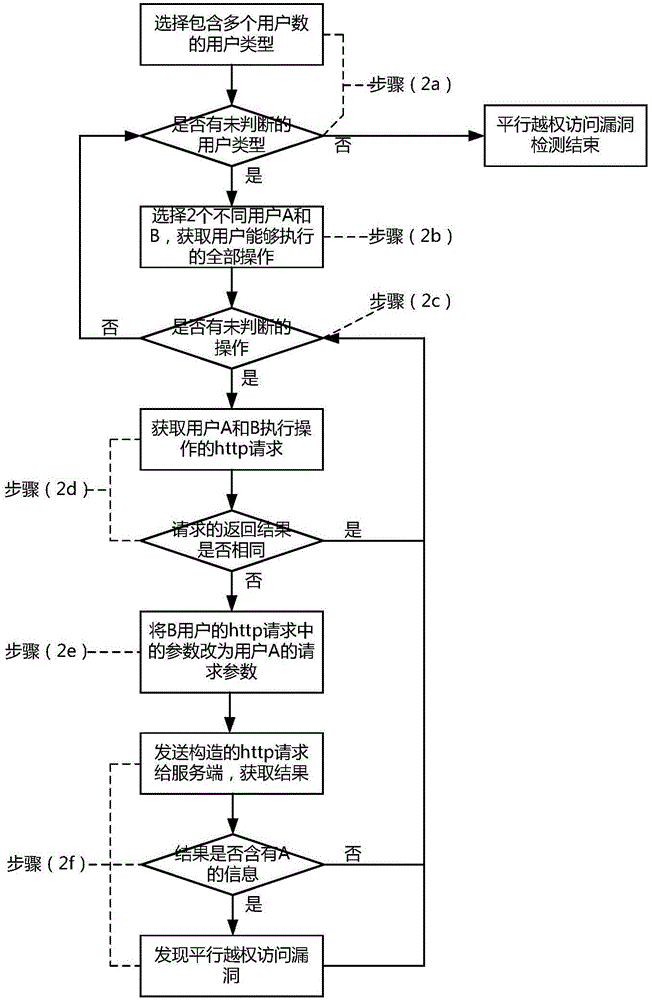
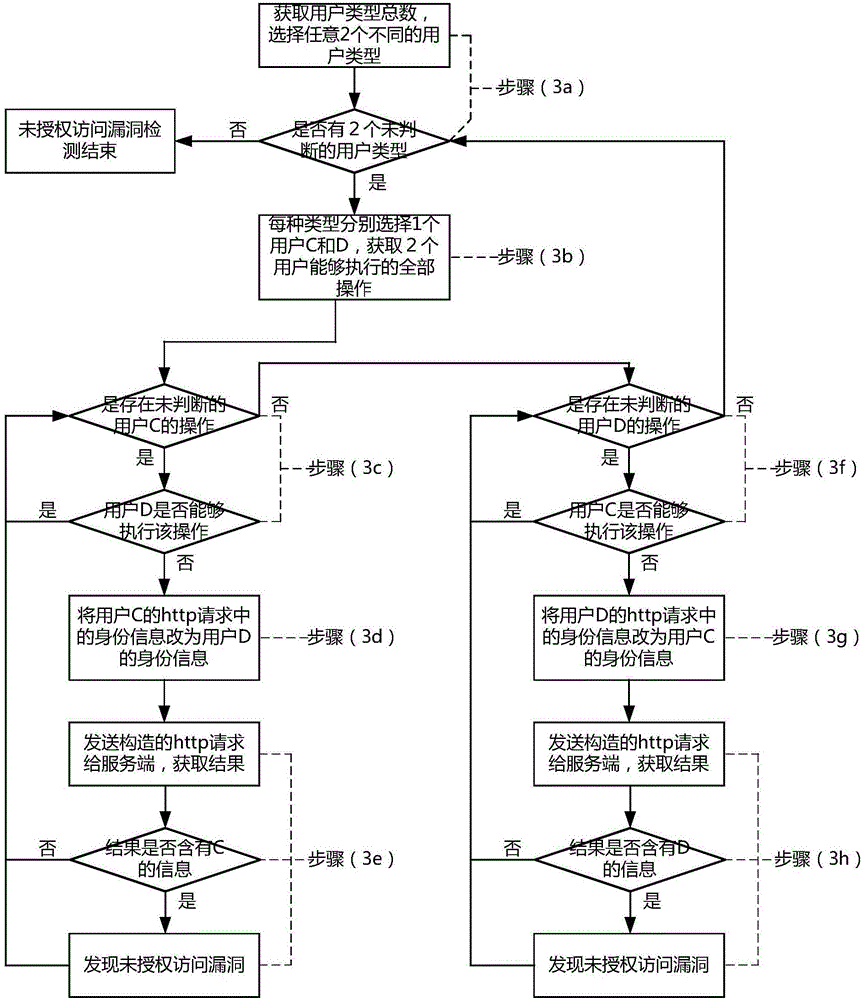
ActiveCN106713347AAvoid lostAvoid Information LeakagePlatform integrity maintainanceTransmissionElectric powerServer-side
The invention discloses a method for detecting an unauthorized access vulnerability of a power mobile application. The method comprises the steps of obtaining and storing all the user types of the mobile application and the user number corresponding to each user type; constructing http requests aiming at the same operation of different users in the same user type, modifying the http request of one user, sending the modified request to a server-side and analyzing an execution result to detect parallel unauthorized access vulnerabilities; constructing http requests of different users in different user types, modifying the http requests which can be executed by users in certain user types, but cannot be executed by users in other types, sending the modified requests to the server-side, and analyzing the execution results to detect the unauthorized access vulnerabilities; and comprehensively detecting the discovered vulnerabilities and finishing the unauthorized access vulnerability detection. The method for detecting the unauthorized access vulnerability of the power mobile application is used for performing safety assessment on the mobile application in an integrated testing stage and provides support for reducing the safety risk of the mobile application and improving the safety of the mobile application.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +1
Hardware cryptographic engine and encryption method
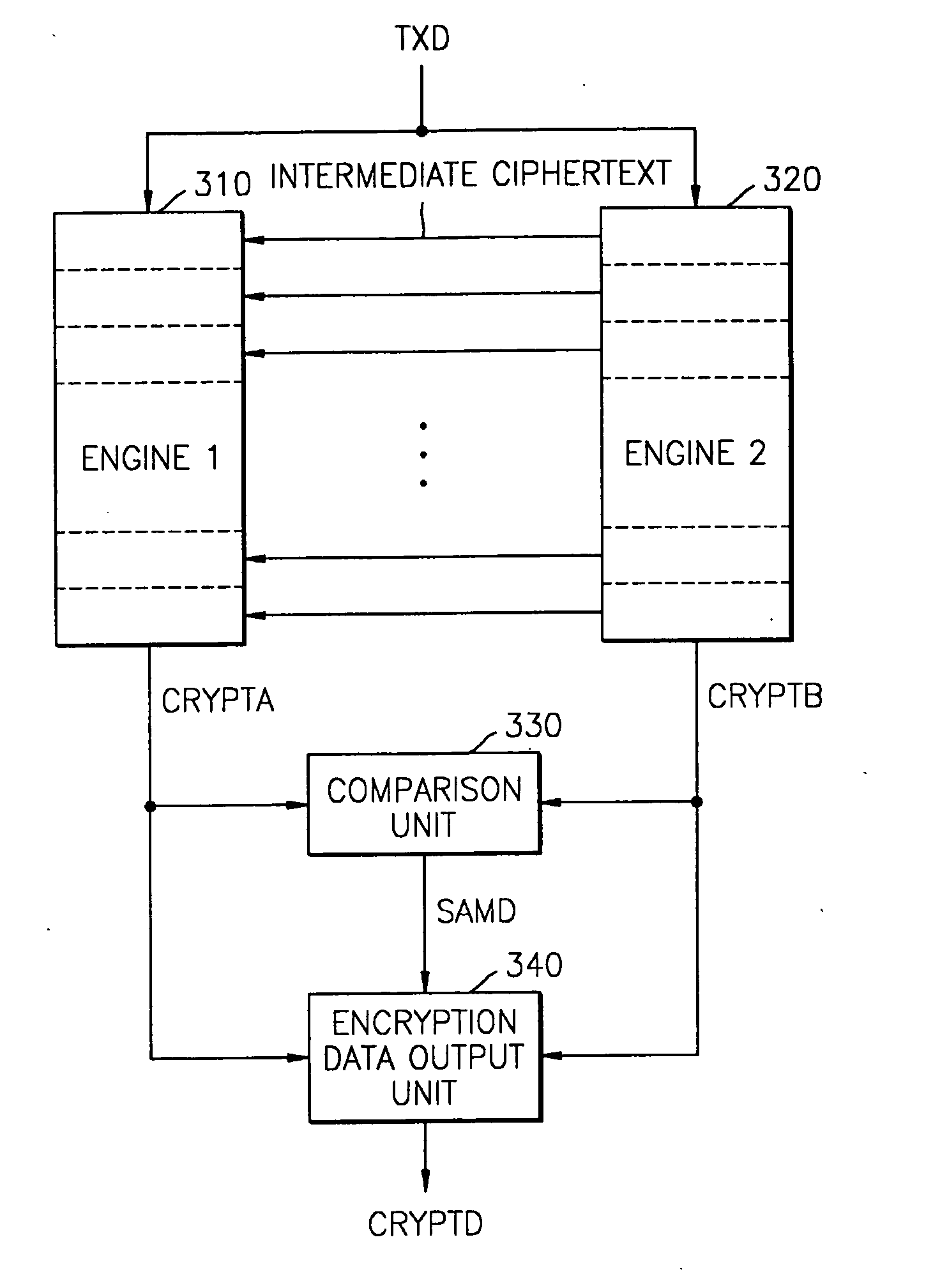
InactiveUS20050050340A1Prevent leakageIncrease computing speedEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionComputer hardwareCiphertext
A hardware cryptographic engine may include a plurality of ciphertext engines. A first ciphertext engine may receive a second intermediate ciphertext output from a second ciphertext engine, generate a first intermediate ciphertext, and use the first intermediate ciphertext to generate and output a first final ciphertext. The second ciphertext engine may output the second intermediate ciphertext, and use the second intermediate ciphertext to generate and output a second final ciphertext. A comparison unit may generate and output a control signal having a logic state depending on whether the first final ciphertext is the same as the second final ciphertext. An encryption data output unit may respond to the logic state of the output control signal, and output a final ciphertext when the first final ciphertext is the same as the second final ciphertext. A ciphertext engine may include plurality of round blocks, one of which may receive an odd number of intermediate ciphertext inputs, inclusive of an intermediate ciphertext from another ciphertext engine, to generate the respective intermediate ciphertext. A round block may include an encryption unit, a first logic operator, and a second logic operator that receives an intermediate ciphertext generated by the encryption unit and the intermediate ciphertext generated by the first logic operator.
Owner:SAMSUNG ELECTRONICS CO LTD
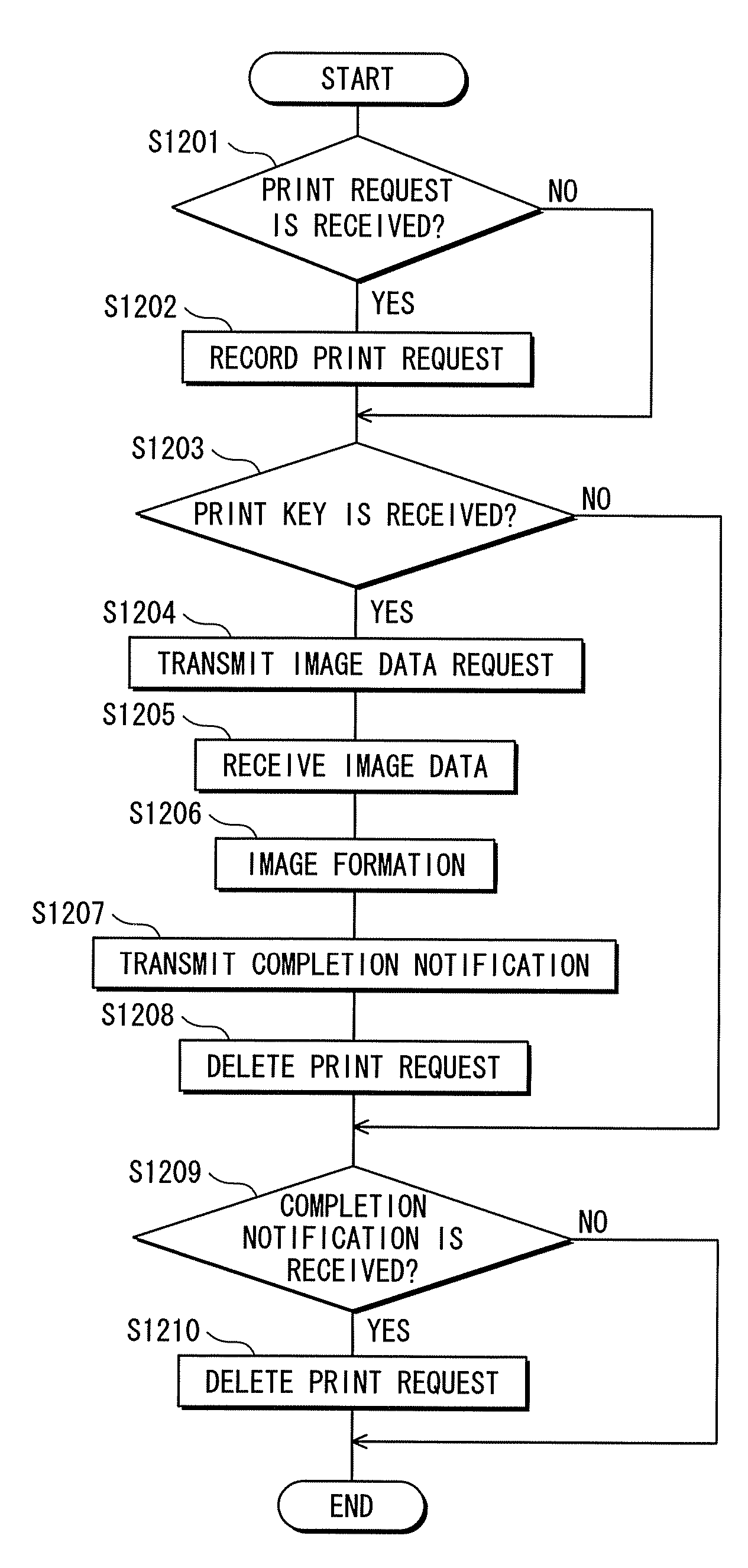
Image Processing System
ActiveUS20080291489A1Wasted storage areaPrevent confidentialityDigital computer detailsComputer security arrangementsImaging processingPersonal computer
After a print request is made from a personal computer to a multifunction peripheral, when a user who logs into the multifunction peripheral instructs an execution of the print request in the multifunction peripheral, the multifunction peripheral requests the personal computer to transmit image data. Then, the personal computer transmits the requested image data to the multifunction peripheral. The multifunction peripheral executes the printing using the received image data. When the printing is completed, the multifunction peripheral transmits a completion notification indicating that the printing is completed to the personal computer. When receiving the completion notification, the personal computer transmits a completion notification having the same content as the received completion notification to the multifunction peripheral.
Owner:KONICA MINOLTA BUSINESS TECH INC
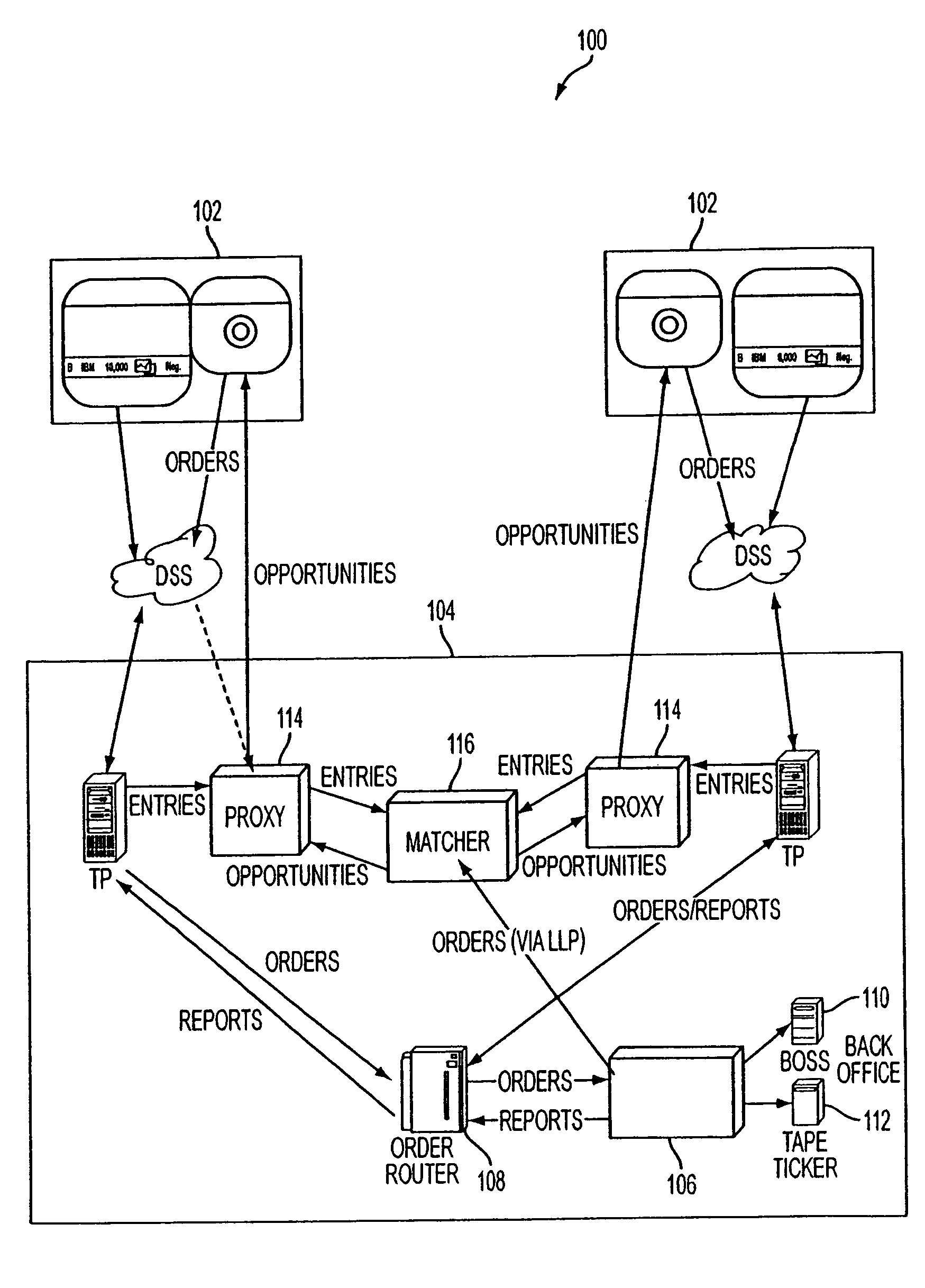
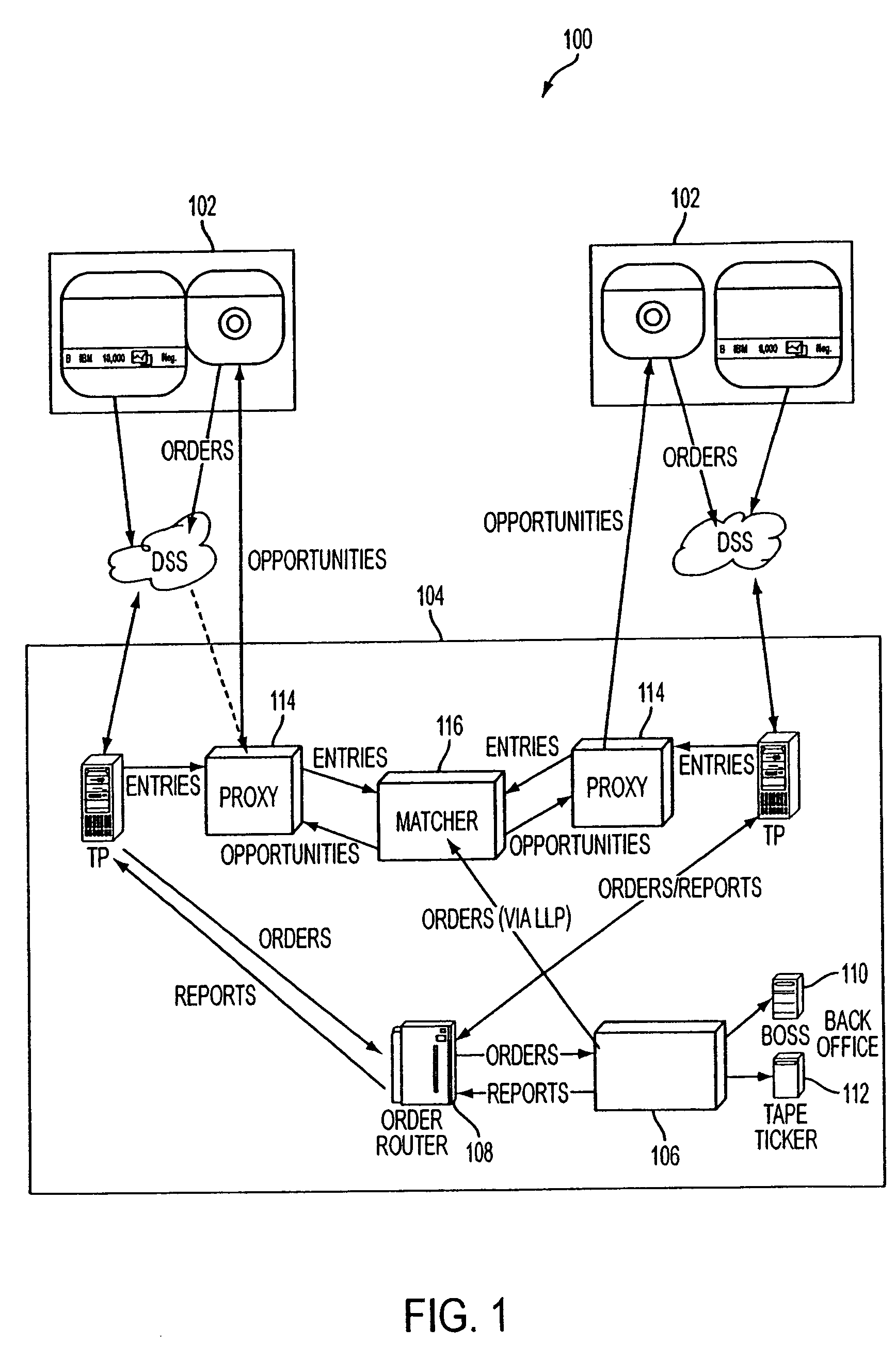
System and method for generating liquidity
A system for generating liquidity includes a plurality of client user interfaces and a matching system. Each client user interface includes a trading desktop which stores unexecuted trading positions. The matching system is coupled with the plurality of client user interfaces and configured to receive information about the unexecuted trading positions. The system can identify as a match one or more first indications of interest which can fulfill one or more second indications of interest, based upon the information about the unexecuted trading positions. For the identified matches, the system can provide a notification of the match and an invitation to execute the match to corresponding client user interfaces. When an invitation is accepted, the system forwards an order to an order execution system for execution.
Owner:ITG SOFTWARE SOLUTIONS INC
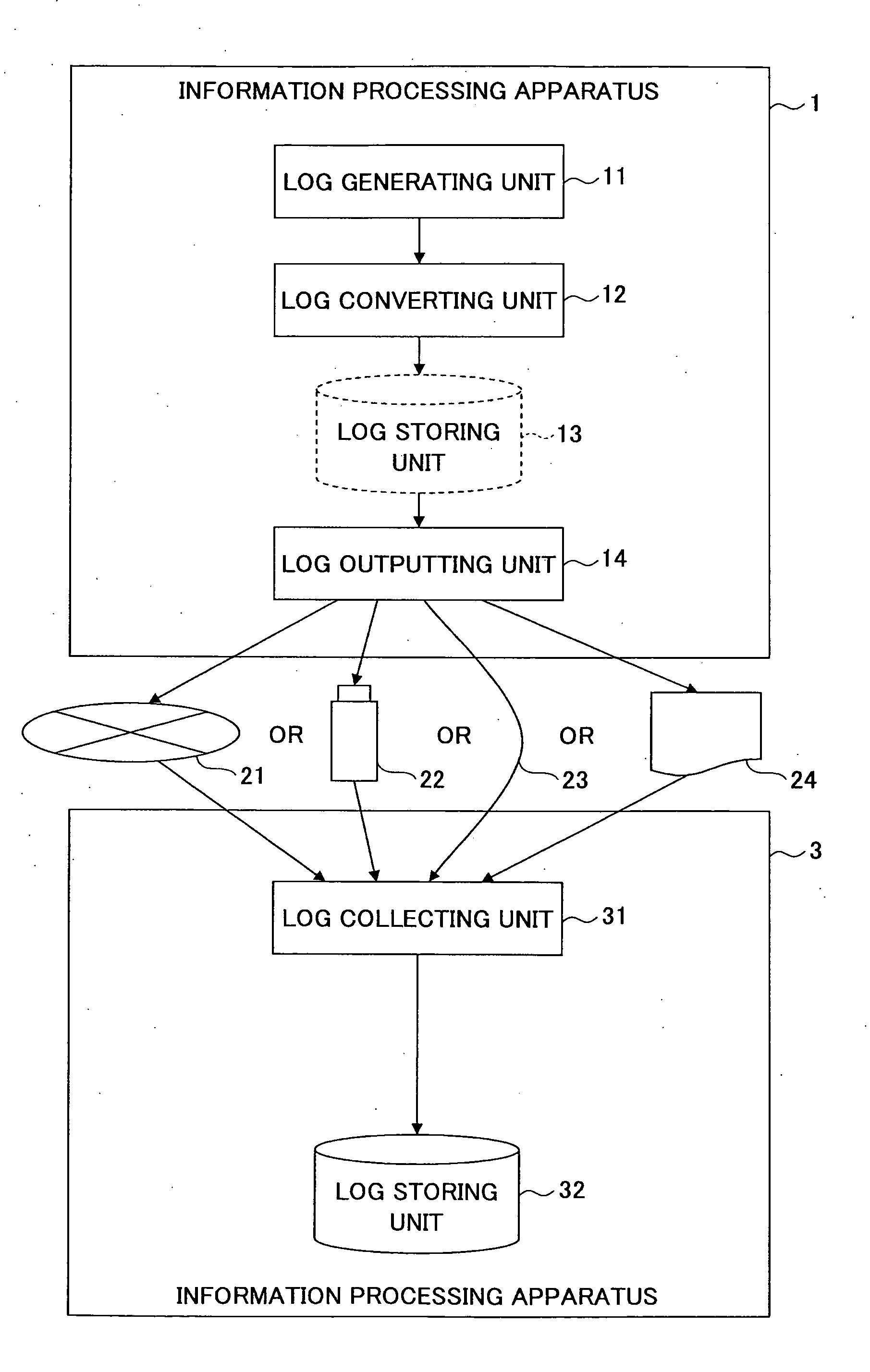
Information processing system
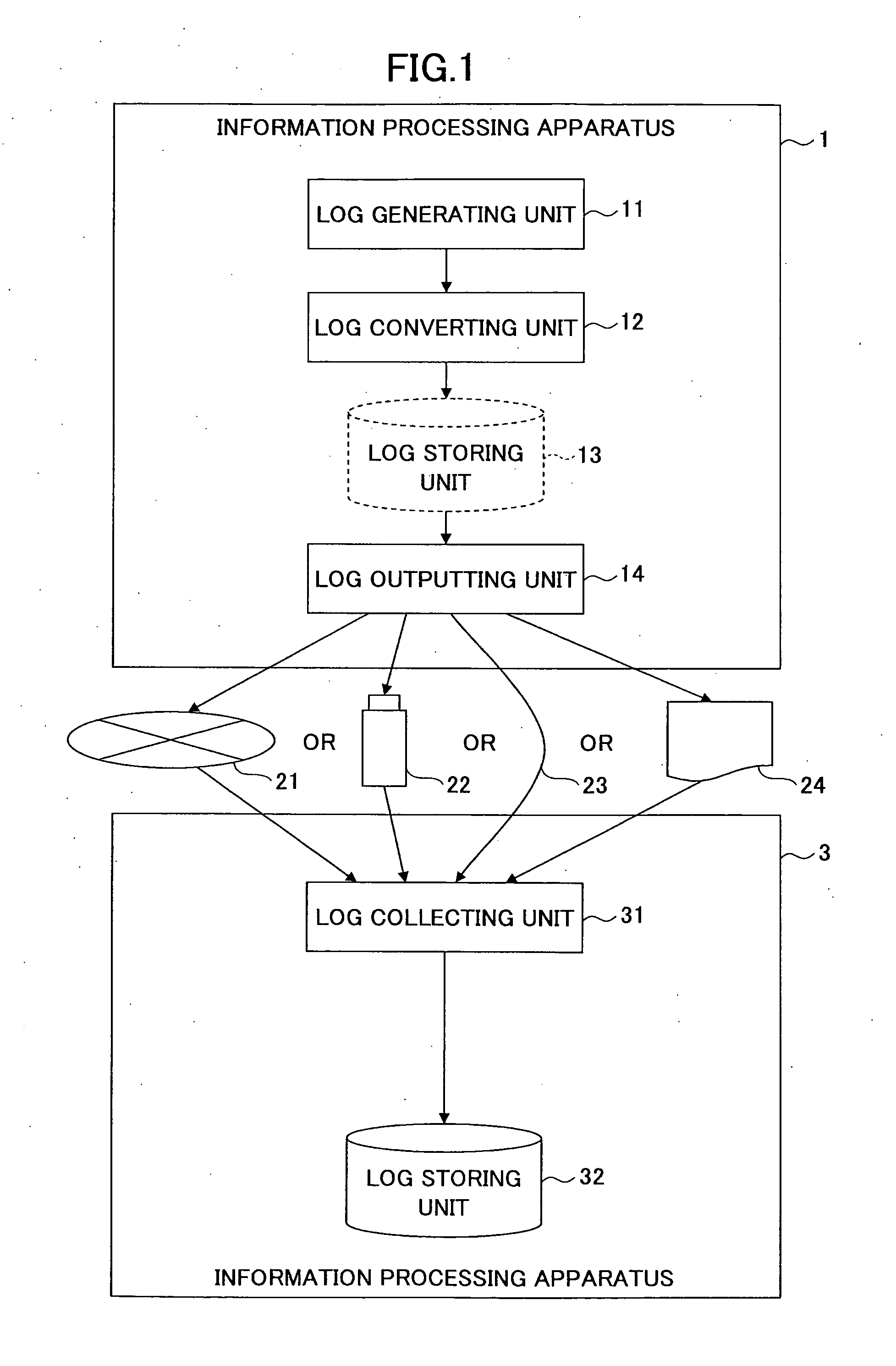
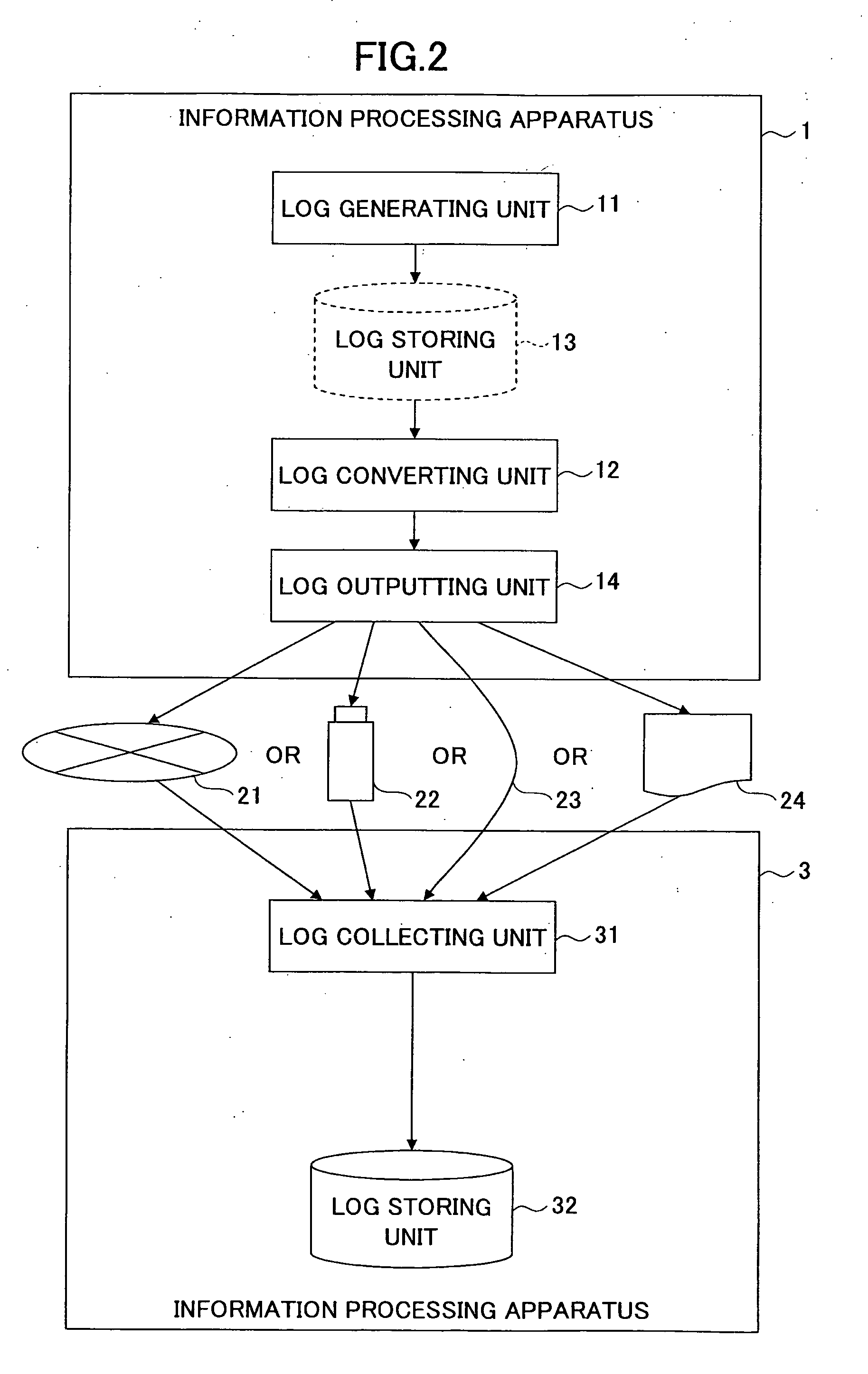
InactiveUS20110276541A1Avoid Information LeakageEliminate distractionsError detection/correctionDigital data processing detailsGenerating unitInformation handling system
An information processing system for recording operational information in a log includes a log generating unit configured to generate the log in such a manner that a conversion target character string included in the log is recognizable; a log converting unit configured to convert the conversion target character string to an irrecoverable and unique character string; a log outputting unit configured to output the log including the converted character string; and a log collecting unit configured to collect the output log.
Owner:RICOH KK
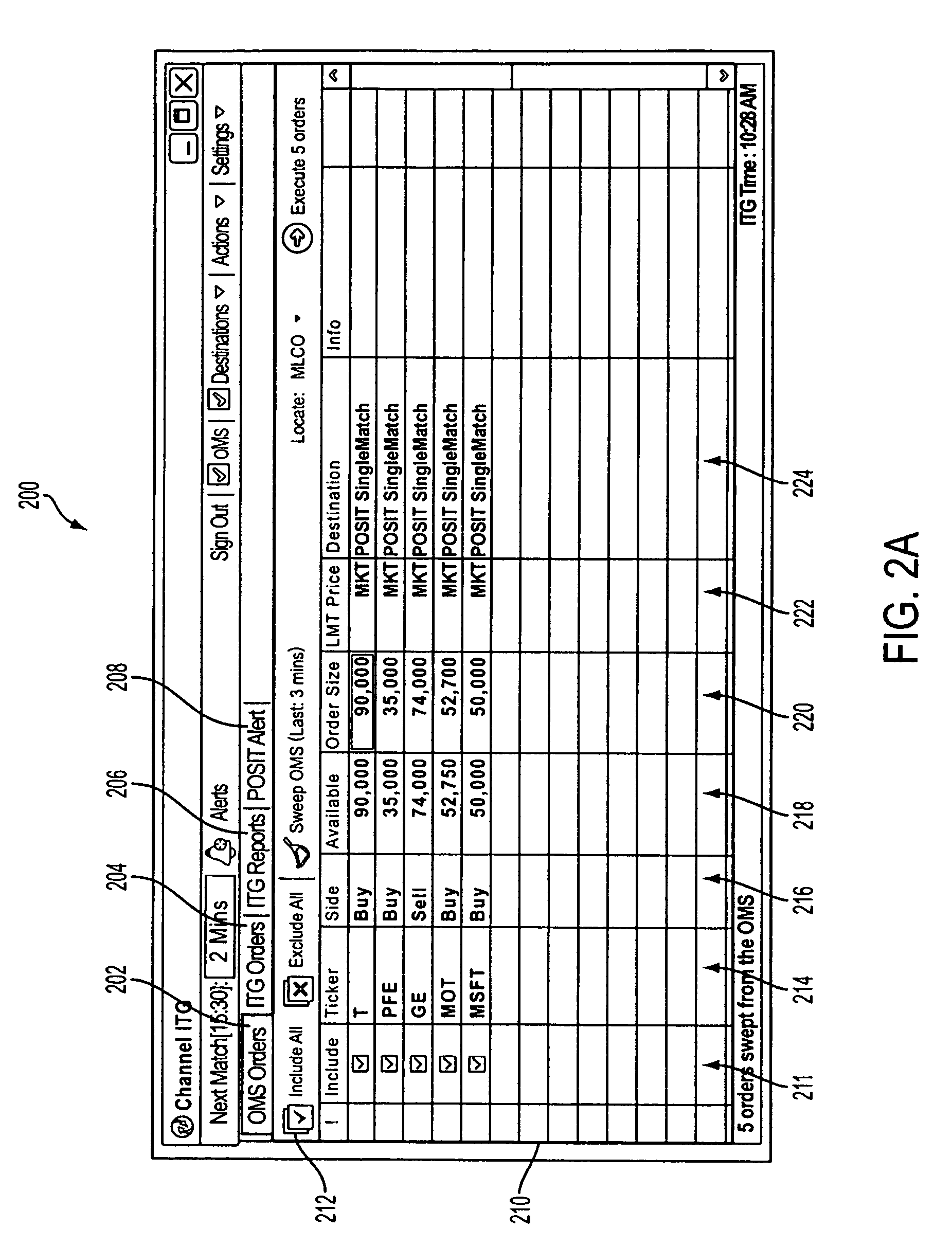
Printing Management Information Together with Image Data
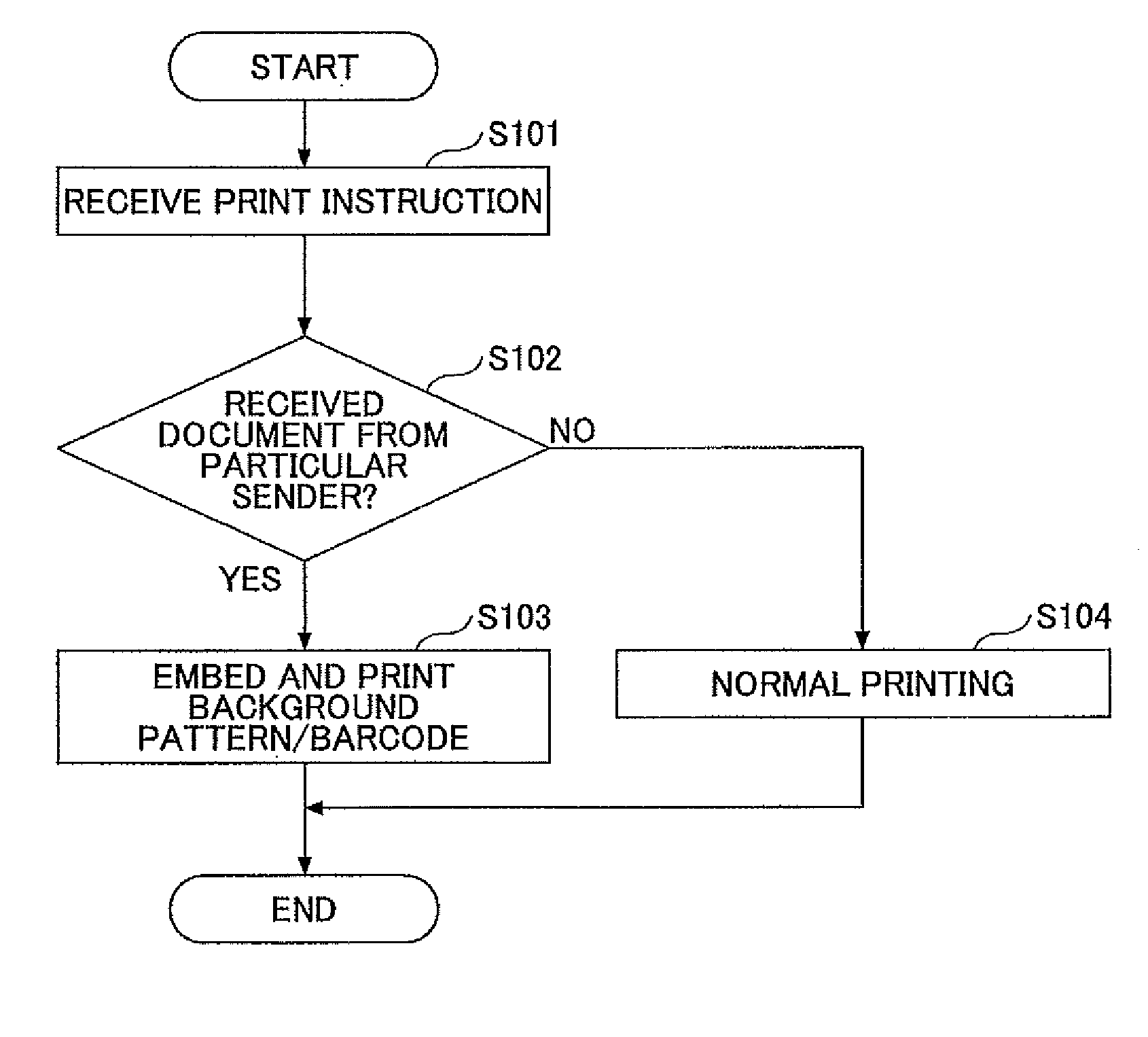
InactiveUS20090161141A1Shorten the timeSave effortDigital storageVisual presentationComputer graphics (images)Image formation
An image forming apparatus includes an image receiving unit configured to receive image data, a sender identifying unit configured to identify a sender of the received image data, a check unit configured to check whether the identified sender corresponds to a predetermined sender, a management information providing unit configured to provide management-purpose image data obtained by encoding management information for controlling at least one of a transmission operation for transmitting an image scanned from a printout and a copy operation for copying an image scanned from a printout, and a print unit configured to print the management-purpose image data together with the received image data in response to a check result by the check unit indicating that the identified sender corresponds to the predetermined sender.
Owner:RICOH KK
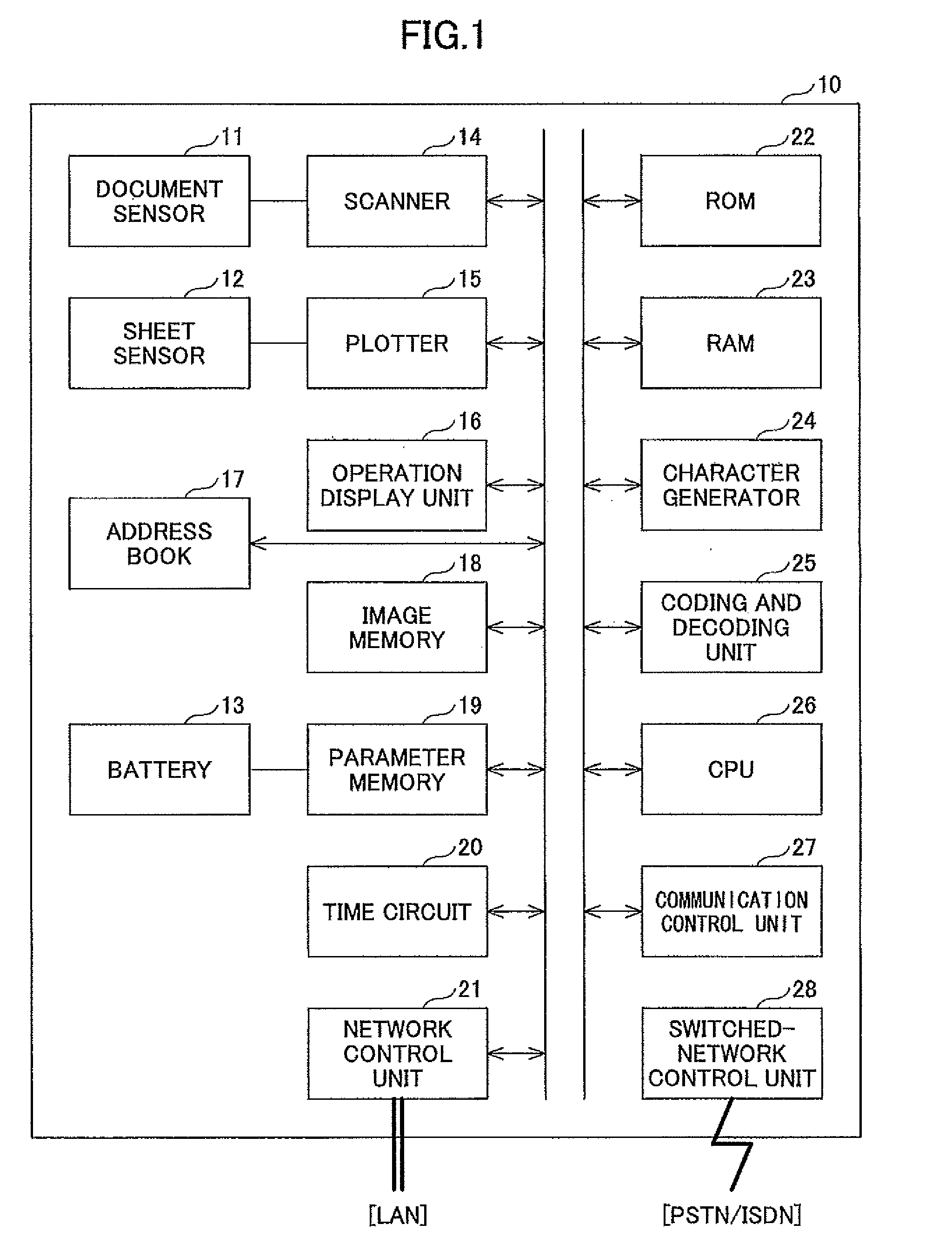
Facsimile apparatus, facsimile communication method, and facsimile communication system
ActiveUS20070247670A1Avoid nuisanceIncrease valuePictoral communicationDigital output to print unitsCommunications systemFacsimile transmission
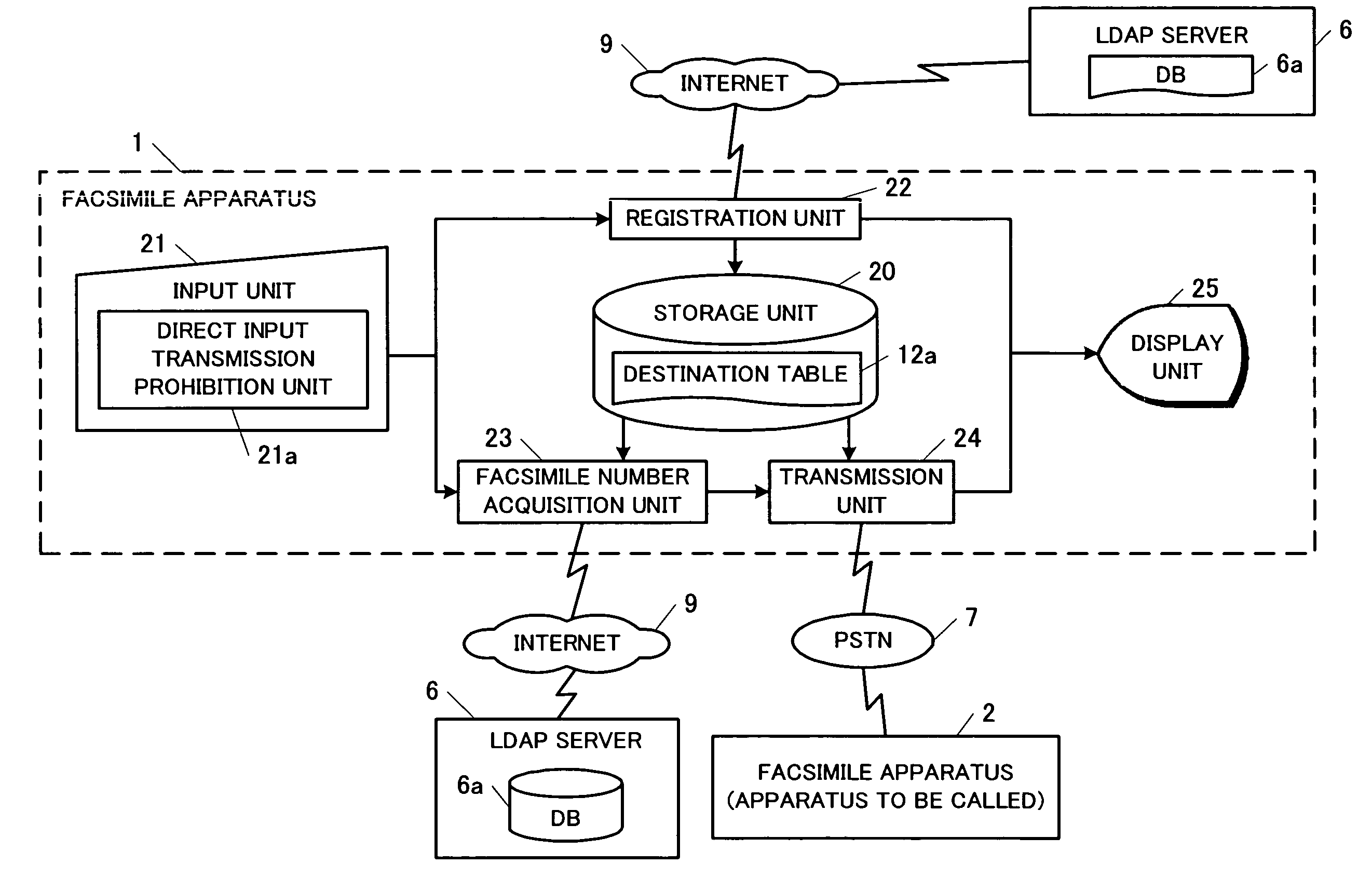
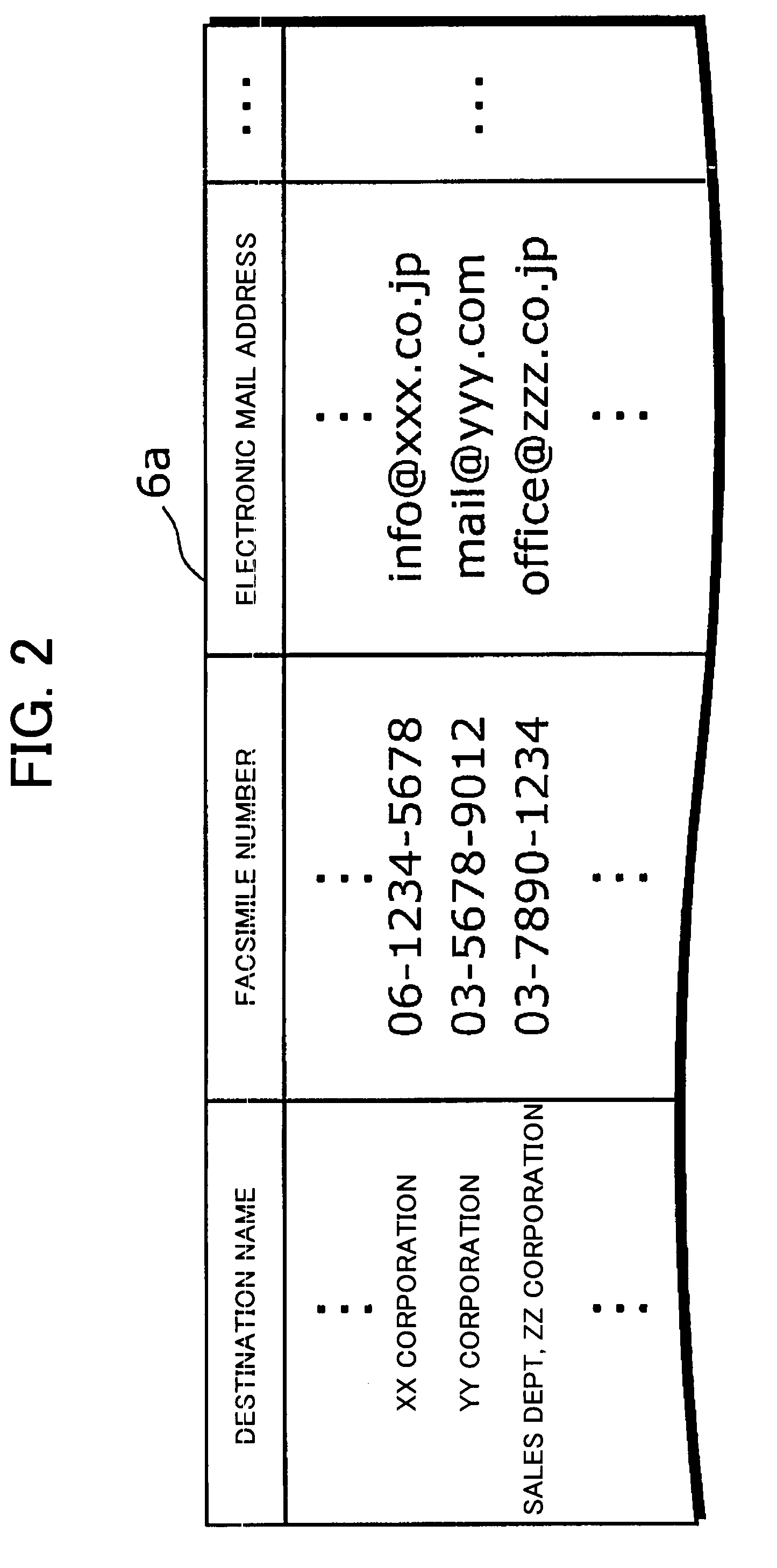
A facsimile apparatus 1 is provided, which can access a latest database 6a associating facsimile numbers and destination names. The apparatus includes a storage unit 20 for storing a destination table 12a in which button information such as one-touch dial buttons, facsimile numbers, and destination names are associated, an input unit 21 for accepting an instruction for one-touch facsimile transmission, a facsimile number acquisition unit 23 for identifying a destination name associated with the transmission instruction by referring to the destination table 12a and searching the database 6a using the destination name as a search key to acquire a facsimile number associated therewith, and a transmission unit 24 for determining whether the acquired facsimile number agrees with a facsimile number associated with a one-touch dial button accepted by the input unit 21 and executing facsimile transmission only when the numbers agree.
Owner:MURATA MASCH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com