Patents
Literature
817results about How to "Guaranteed growth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
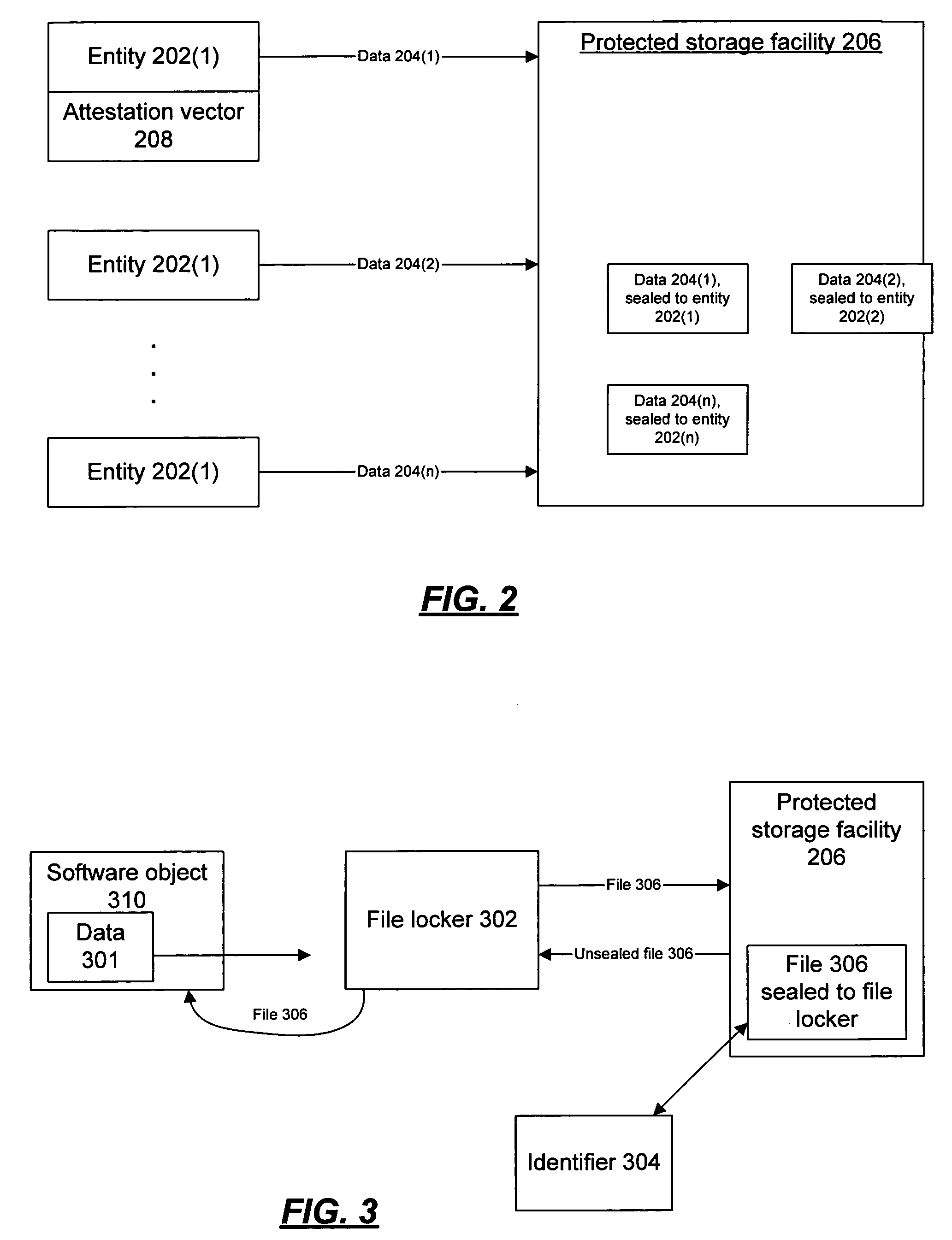
Distributed access to valuable and sensitive documents and data
InactiveUS20070220614A1Limiting exposure to identity theftImprove securityDigital data processing detailsUser identity/authority verificationPaper documentCharacter recognition
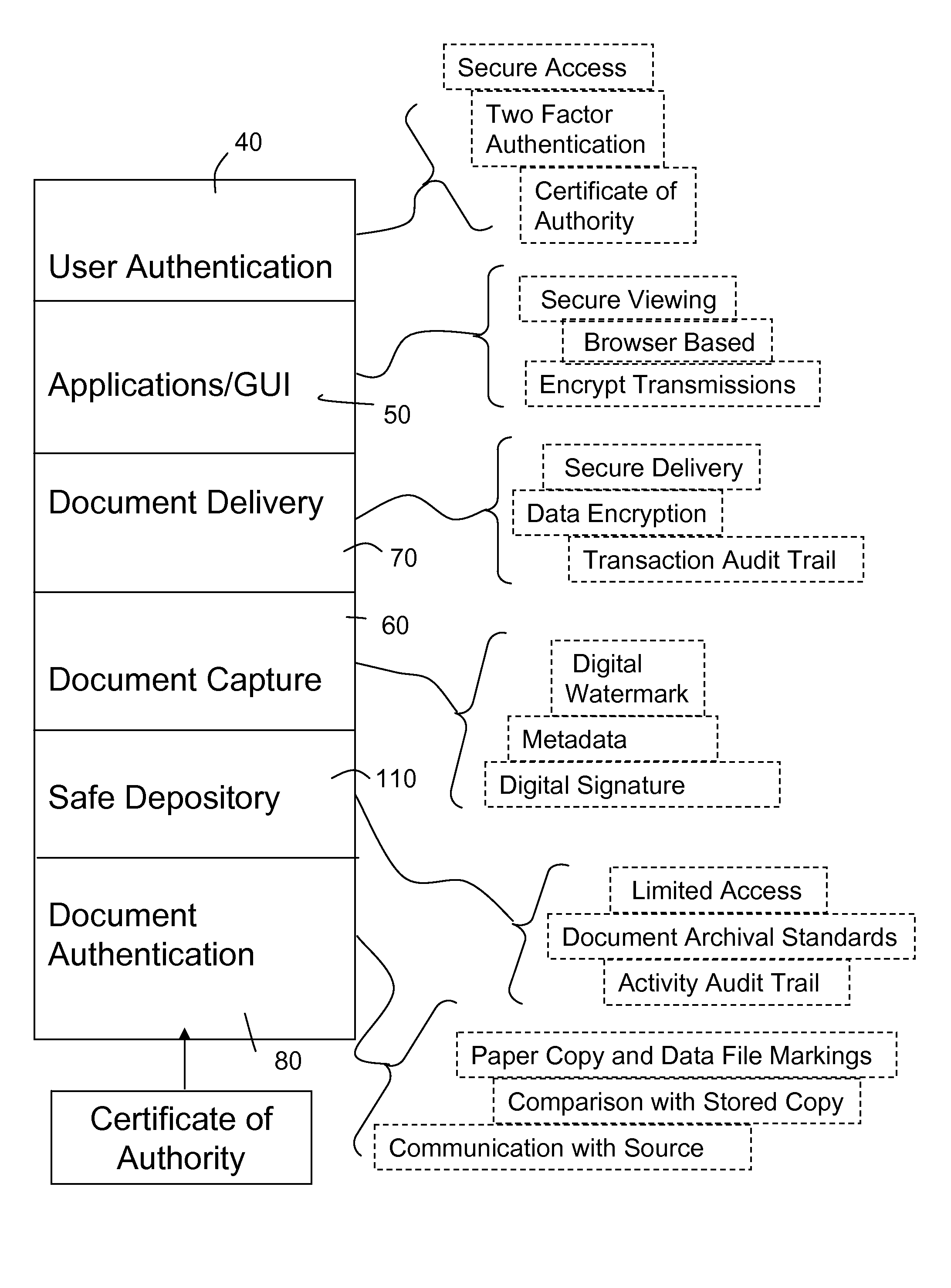
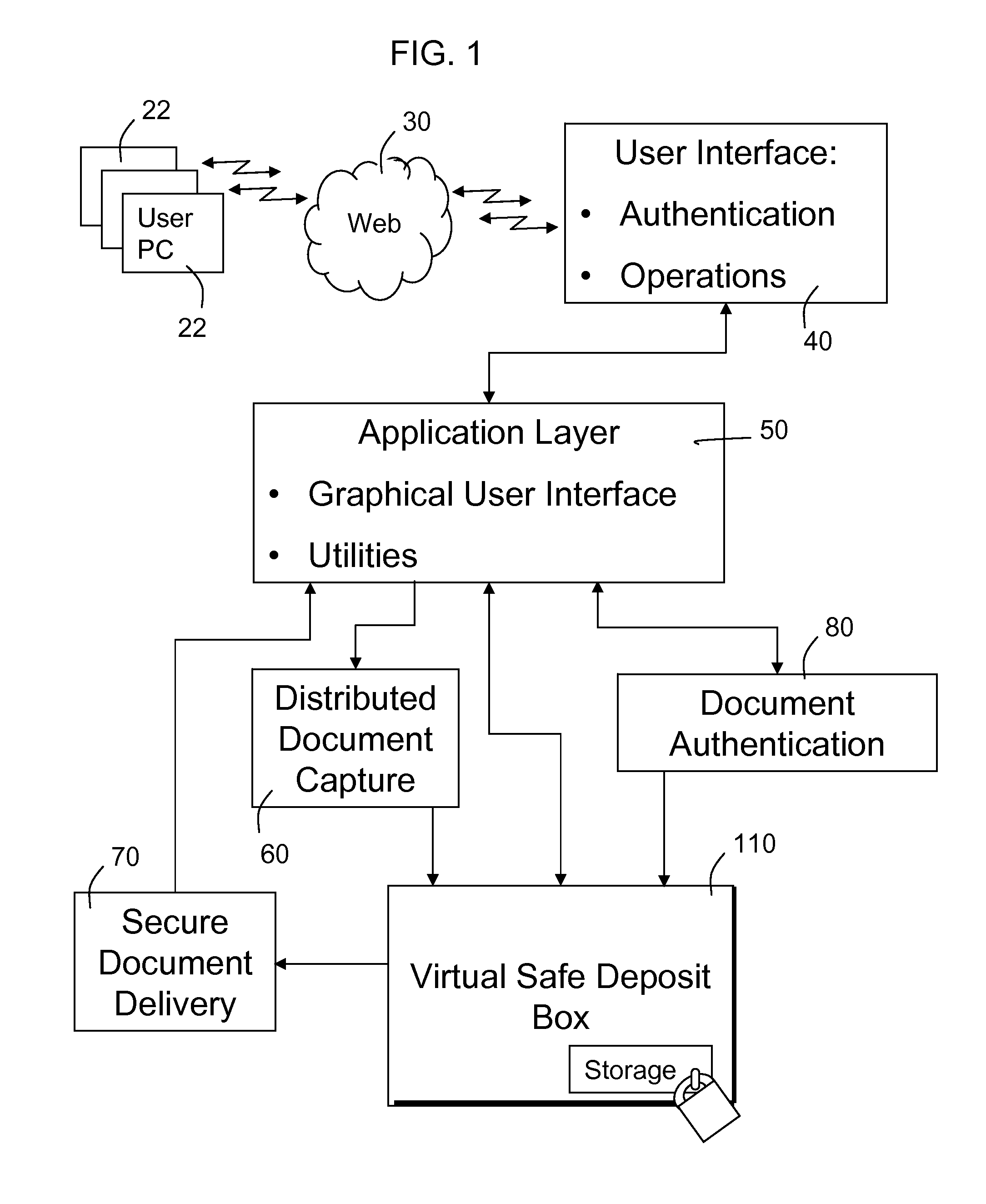
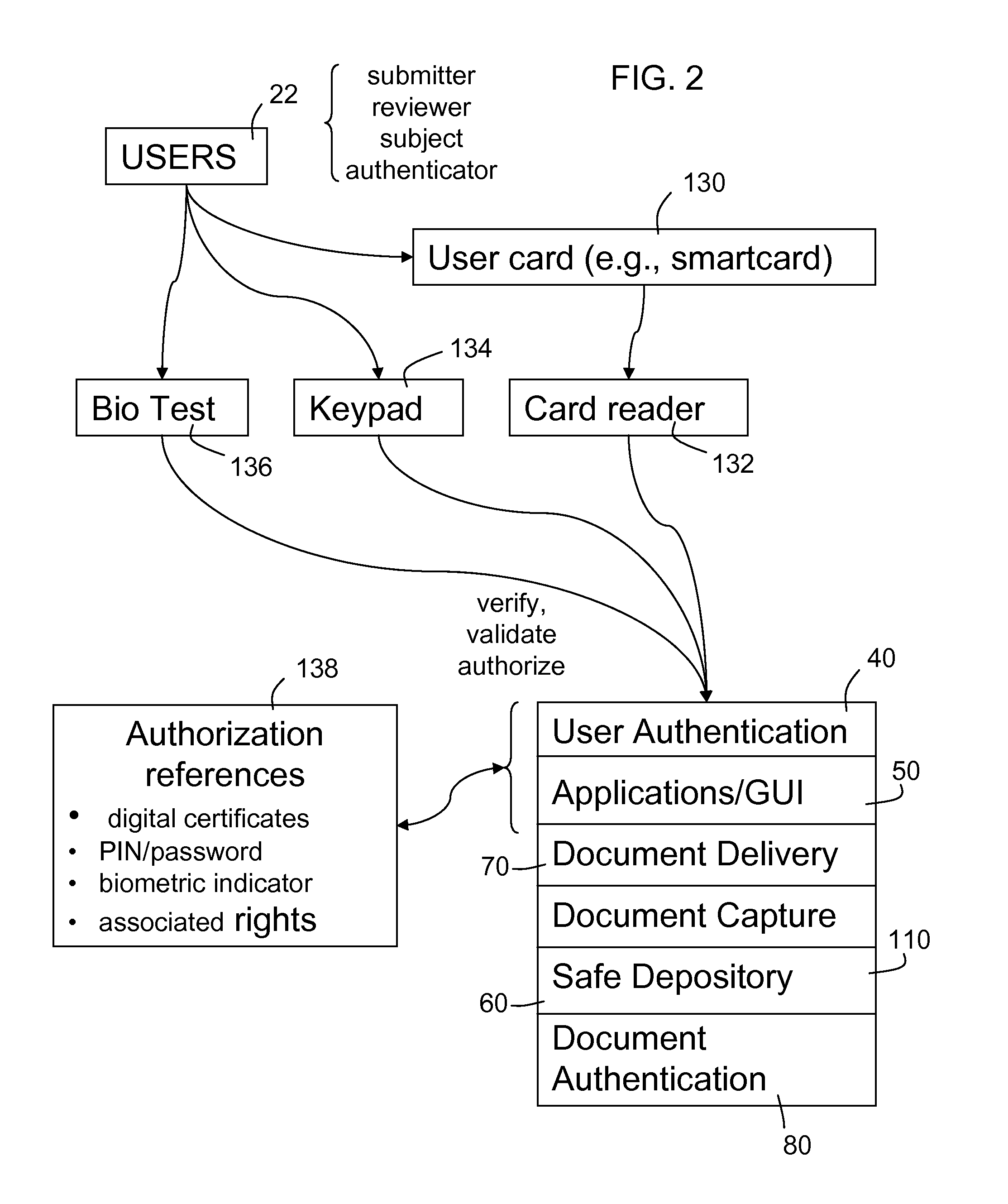
A method for providing access to documents and data files that are inherently valuable, and also documents that contain sensitive information, is configured with robust user identification and document control capabilities and facilitates document submission by, for or on behalf of a user who perhaps is the subject of the document. The document is processed, optionally character recognized and steganographically marked, and is stored in a fixed format together with descriptive identifiers and database indexing values to facilitate control and searching. The level of security encourages users to entrust documents to storage and the system is programmed to control disclosure of documents (or parts of them) according to the user's dictates. Correspondingly strict user identification and document controls apply to those who log on for purposes of document review or serve as authenticators. The result is a virtual safe depository for documents that enables documents to be reviewed when necessary with reduced risk of misuse, for example by inadvertent disclosure to identity thieves and others.
Owner:DOCUMENT ATM
Local secure service partitions for operating system security
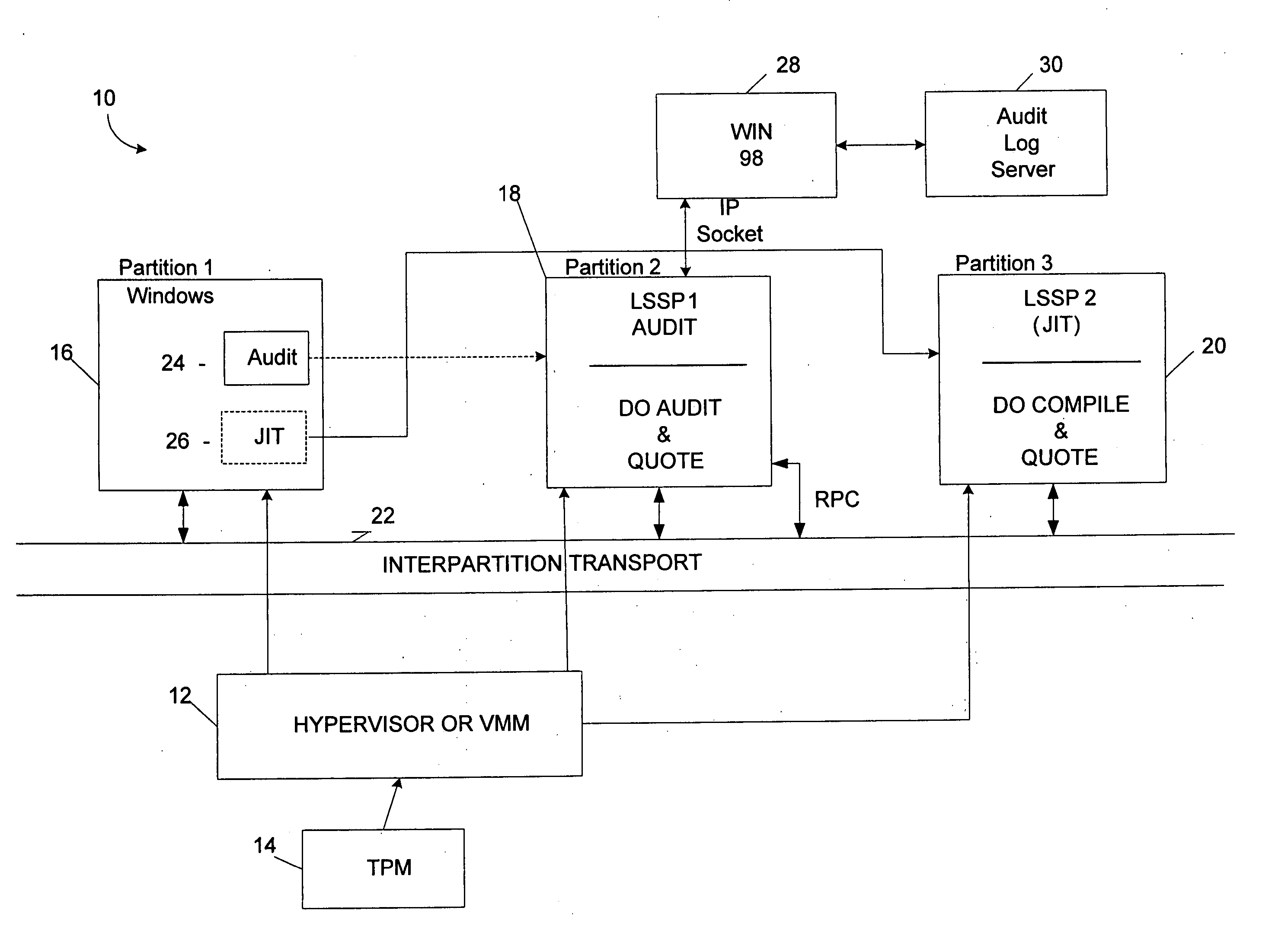
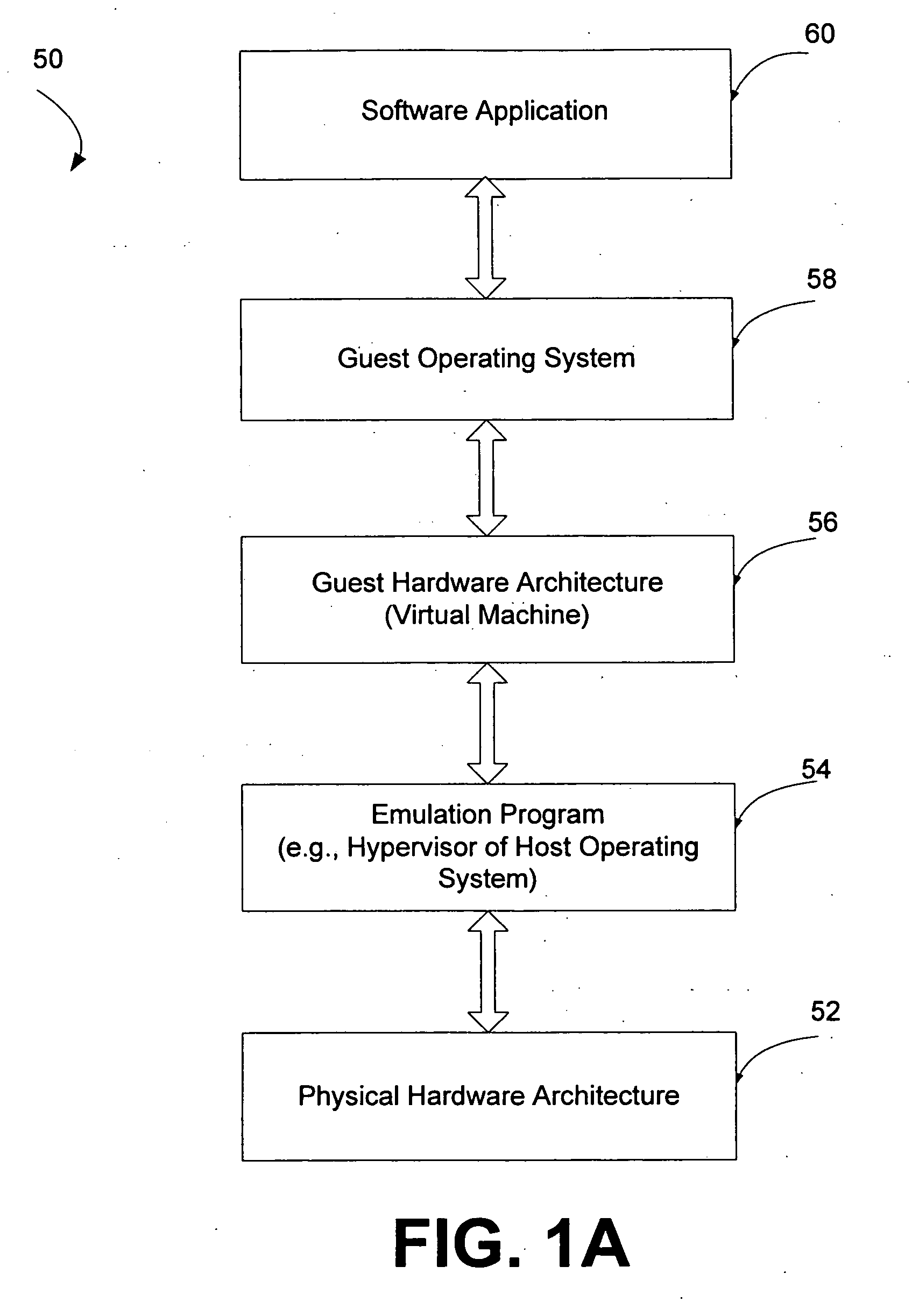
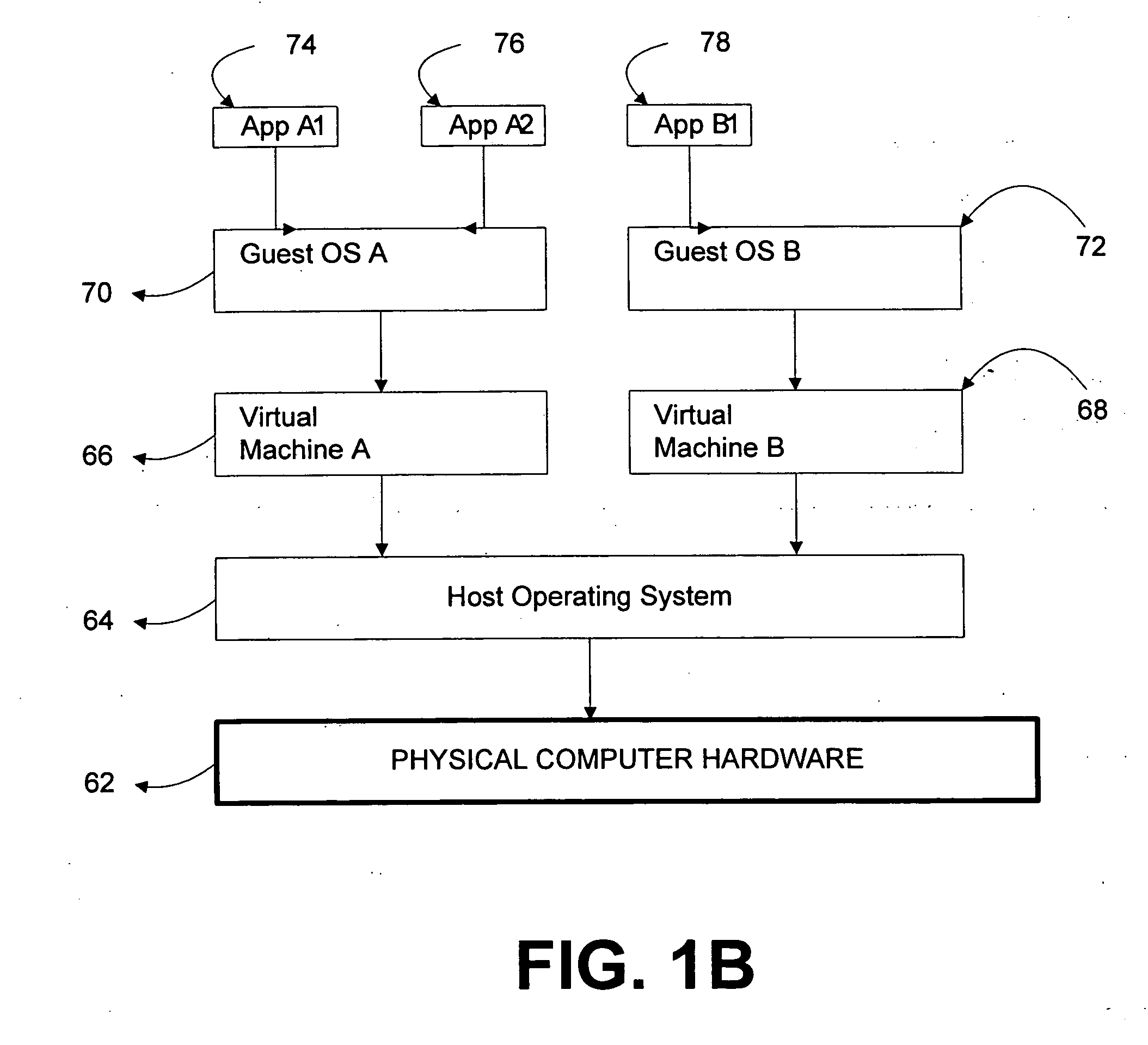
ActiveUS20060236127A1Guaranteed growthSmall sizeVolume/mass flow measurementUnauthorized memory use protectionOperational systemOperating system security
Systems and methods provide multiple partitions hosted on an isolation technology such as a hypervisor where at least one of the partitions, a local secure service partition (LSSP), provides security services to other partitions. The service partitions (LSSPs) host those high assurance services that require strict security isolation, where the service can be shared across partitions and accessed even when the user is not connected to a network. The LSSP also can certify the results of any computation using a key signed by a TPM attestation identity key (AIK), or other key held securely by the hypervisor or a service partition. The LSSPs may be configured to provide trusted audit logs, trusted security scans, trusted cryptographic services, trusted compilation and testing, trusted logon services, and the like.
Owner:MICROSOFT TECH LICENSING LLC
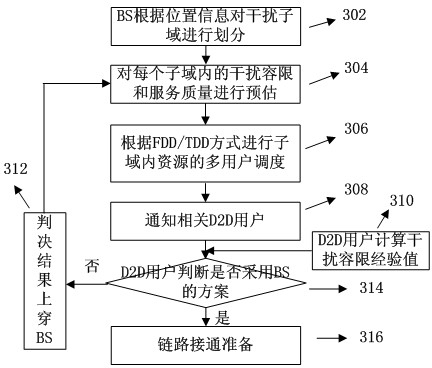
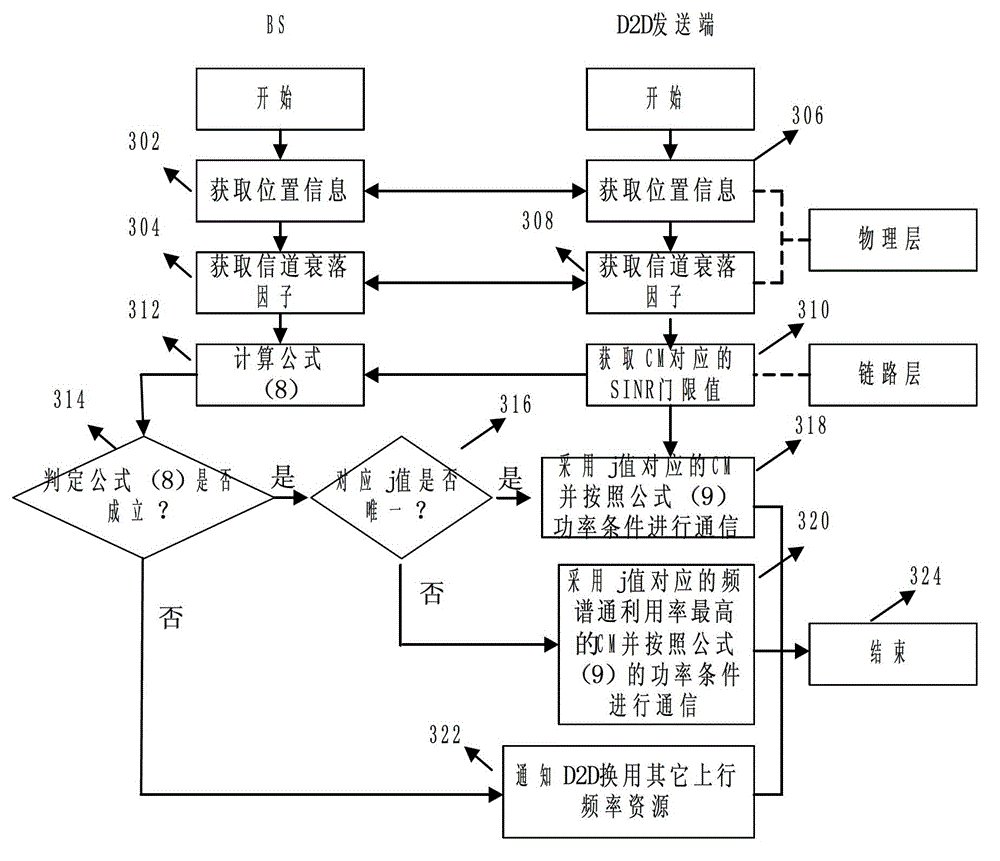
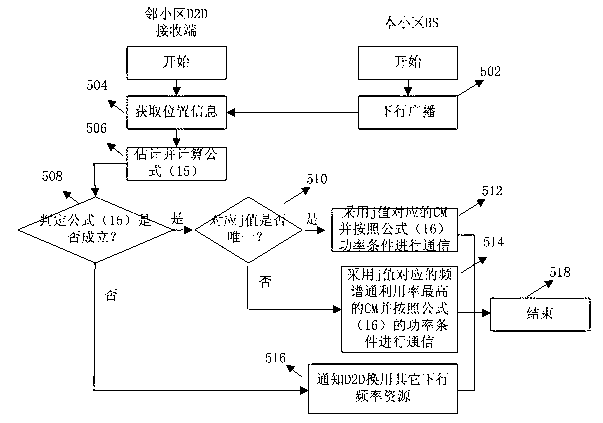
Base-station (BS)-combined direct-through terminal optimized resource allocation method in direct-through cellular system
ActiveCN102638893AImprove resource utilizationImprove effectivenessWireless communicationMultiplexingQuality of service
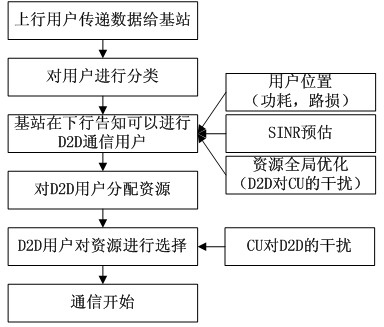
The invention provides a base-station (BS)-combined direct-through terminal optimized resource allocation method in a direct-through cellular system. In order not to interrupt the normal communication of traditional cellular subscriber links and obtain effective gain brought by device-to-device (D2D) direct-through technology, D2D subscribers are allowed to adopt a resource allocation manner that resources are selected by a D2D subscriber end when uplink and downlink resources of the cellular system are shared; at this time, the D2D subscribers only need to consider the interference to other cellular subscribers (CUs) arising from signals of the D2D subscribers; and meanwhile, a BS centralized-control manner is adopted to carry out resource allocation, the centralized-control advantage of a BS is exerted, a BS and D2D terminal combined optimization manner is fully utilized, and the advantages of the two allocation manners are exerted. The BS-combined direct-through terminal optimized resource allocation method in the direct-through cellular system has the advantages that the resource utilization ratio and availability of a coexistent system which is provided with the D2D direct-through technology are sufficiently improved, the multiplexing gain of the resources are maximally developed, the system capacity is increased, the service types are increased, and the quality of service is ensured; and many chances for resource multiplexing are developed under the condition of limited resources from a novel resource allocation viewing angle.
Owner:CERTUS NETWORK TECHNANJING
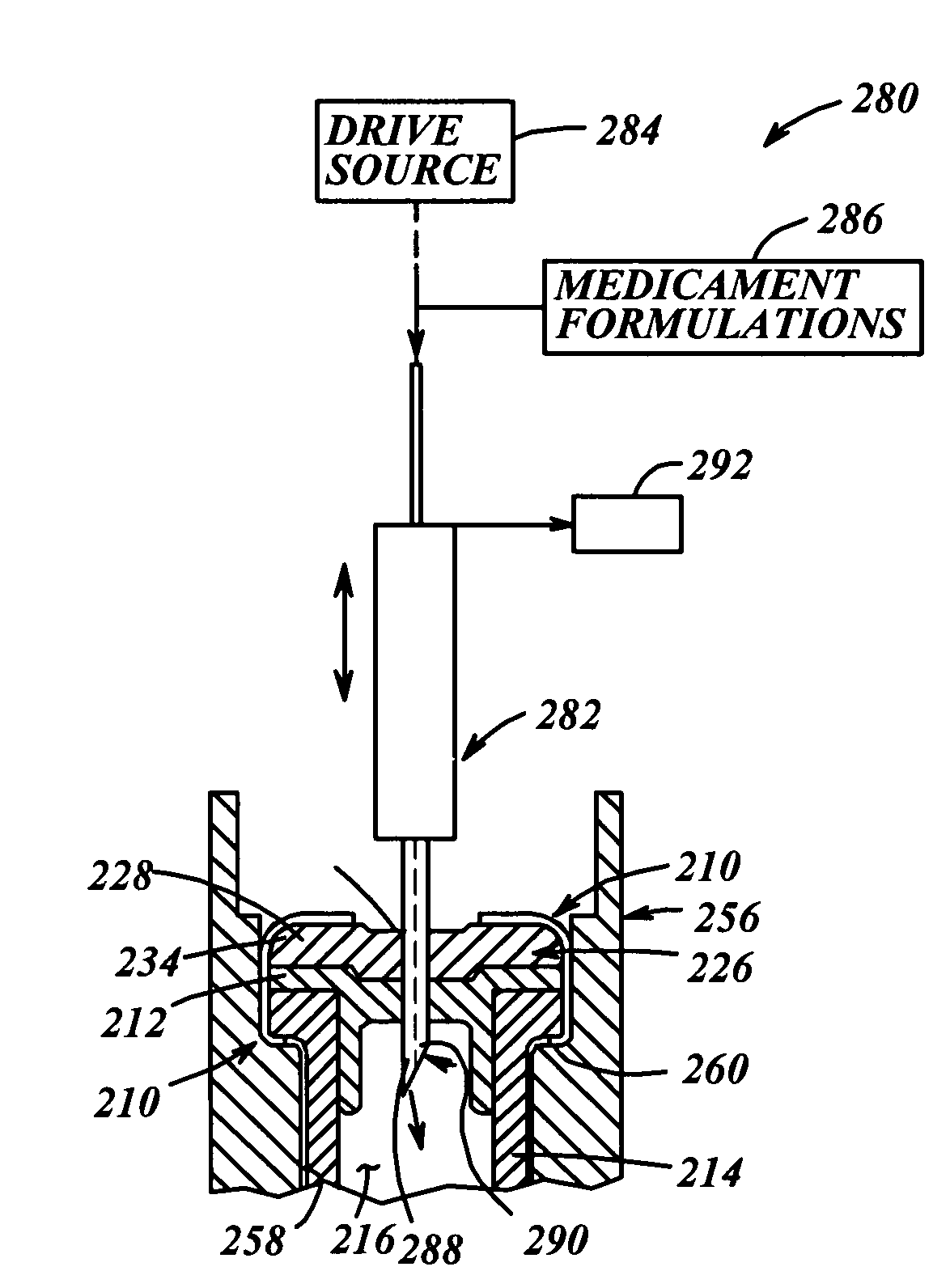
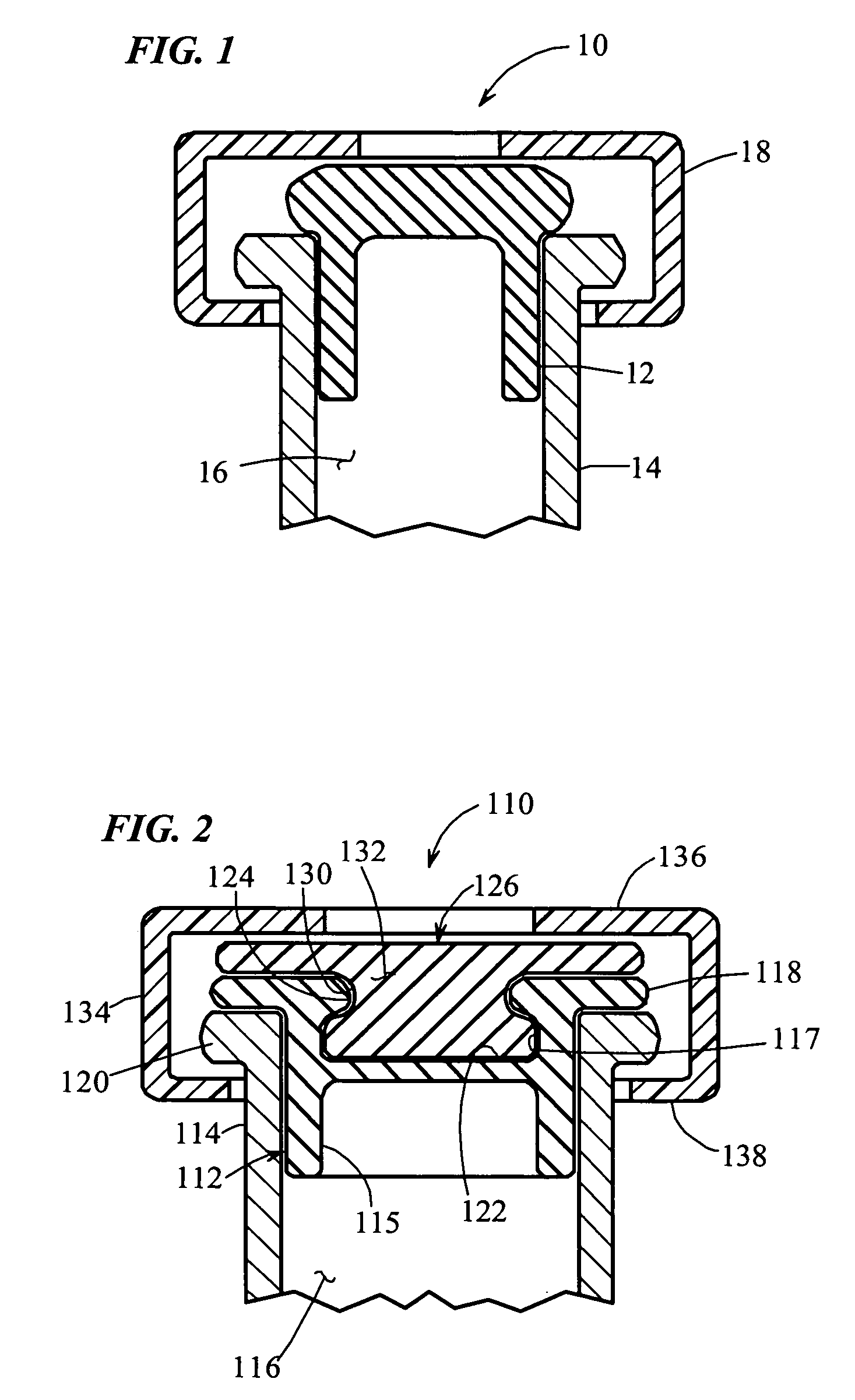
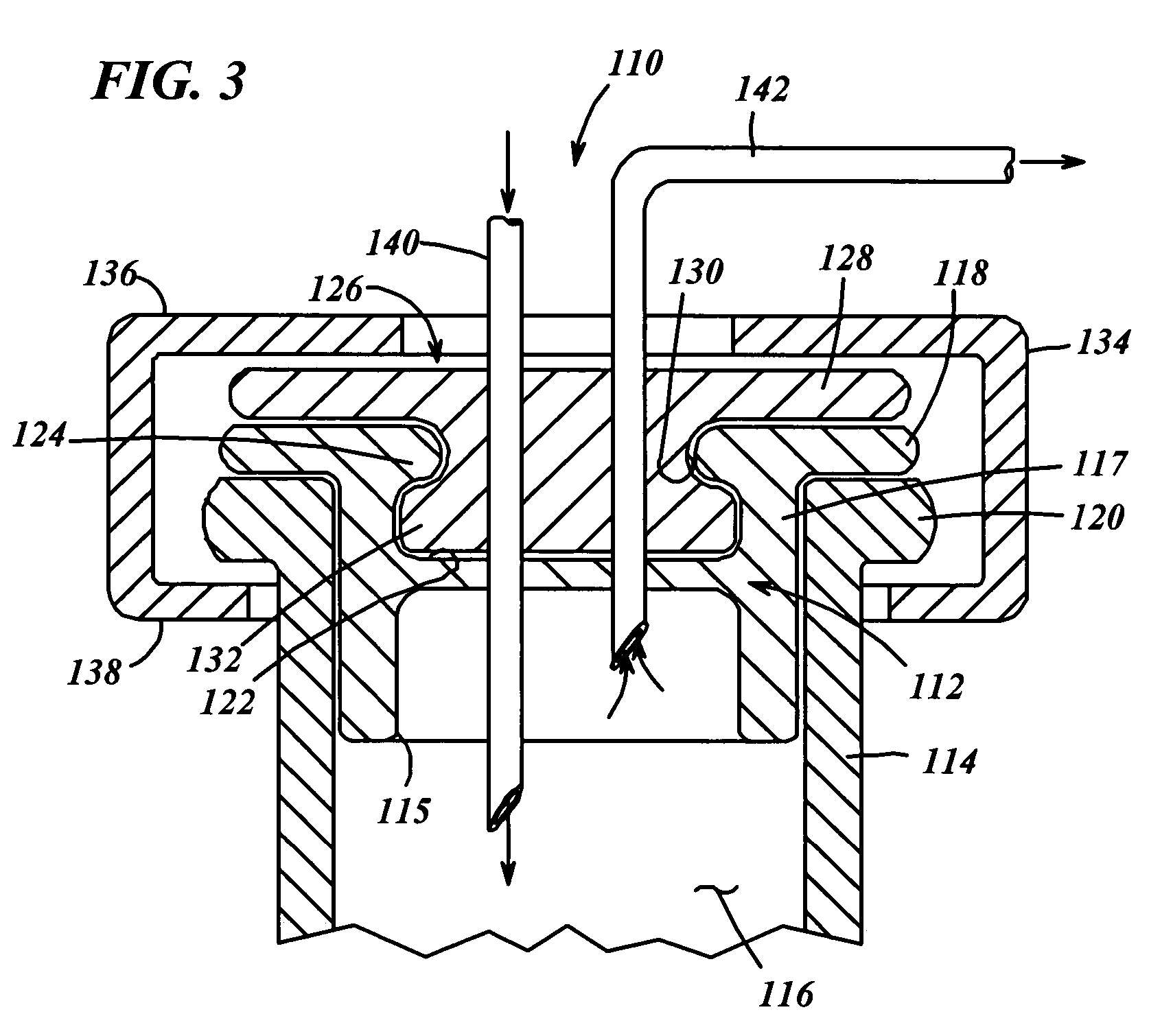
Medicament vial having a heat-sealable cap, and apparatus and method for filling the vial
InactiveUS7032631B2Stable environmentReduce frictionCapsCap application using vaccuumVialLow-density polyethylene
A resealable cap (110, 210) for a medicament vial (114, 214) has a base portion (112, 212) formed of vulcanized rubber or like material known for providing a stable environment for the medicament contained within the vial, and a resealable portion (126, 226) overlying the base portion. The resealable portion (126, 226) is made of low-density polyethylene or like material, and can be punctured by a needle or like injection member (140, 282) for dispensing medicament into the vial (114, 214). Prior to filling, the cap (110, 210) is assembled to the vial (114, 214) and the cap / vial assembly is sterilized. Then, a needle (140, 282) is inserted through the cap (110, 210) and medicament is introduced through the needle and into the vial. Upon withdrawal of the needle (140, 282), the penetrated region of the cap (248) is fused by laser (276) or direct heat sealing (264) to hermetically seal the needle hole (294) in the cap.
Owner:MEDINSTILL DEV
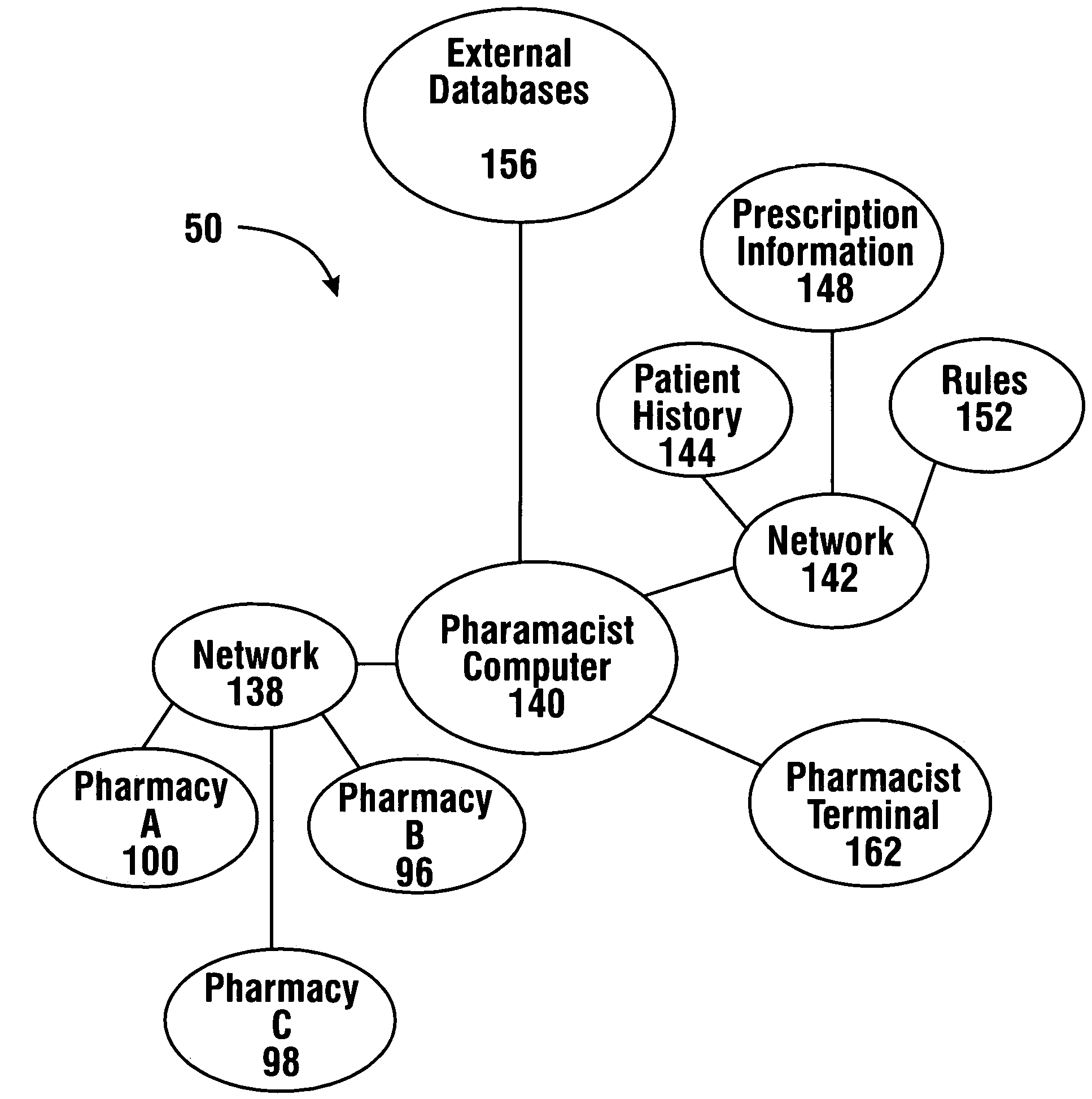
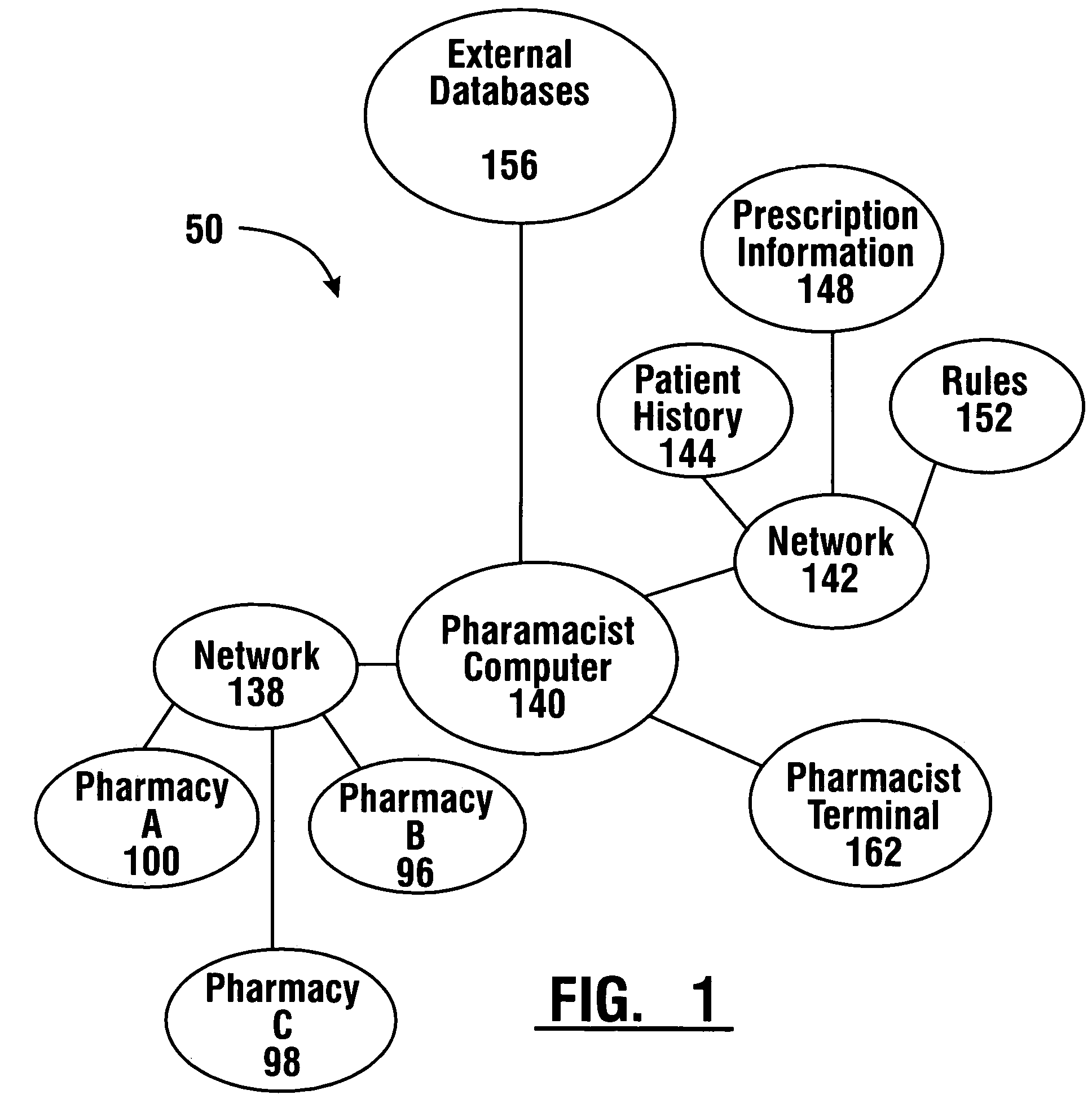
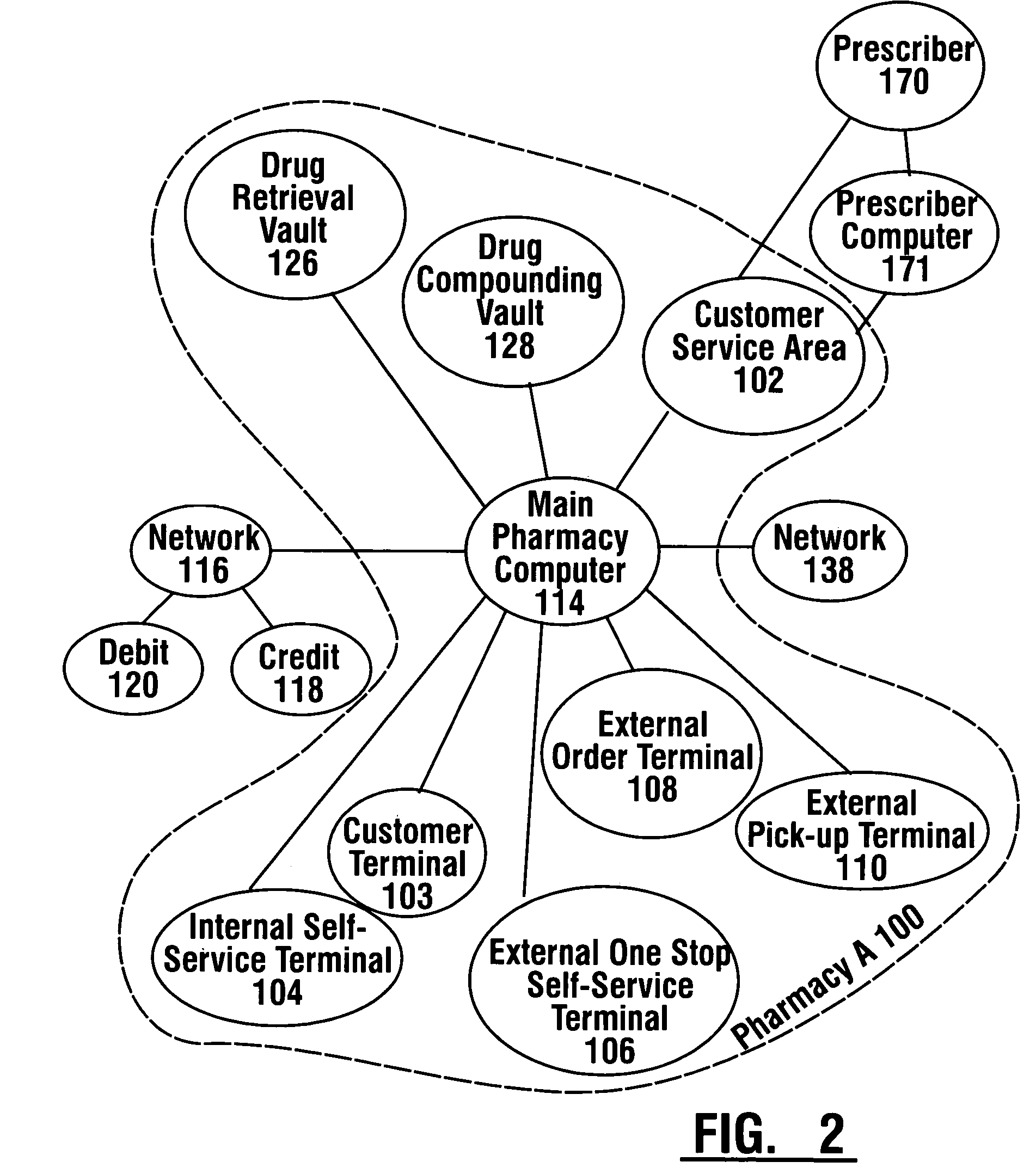
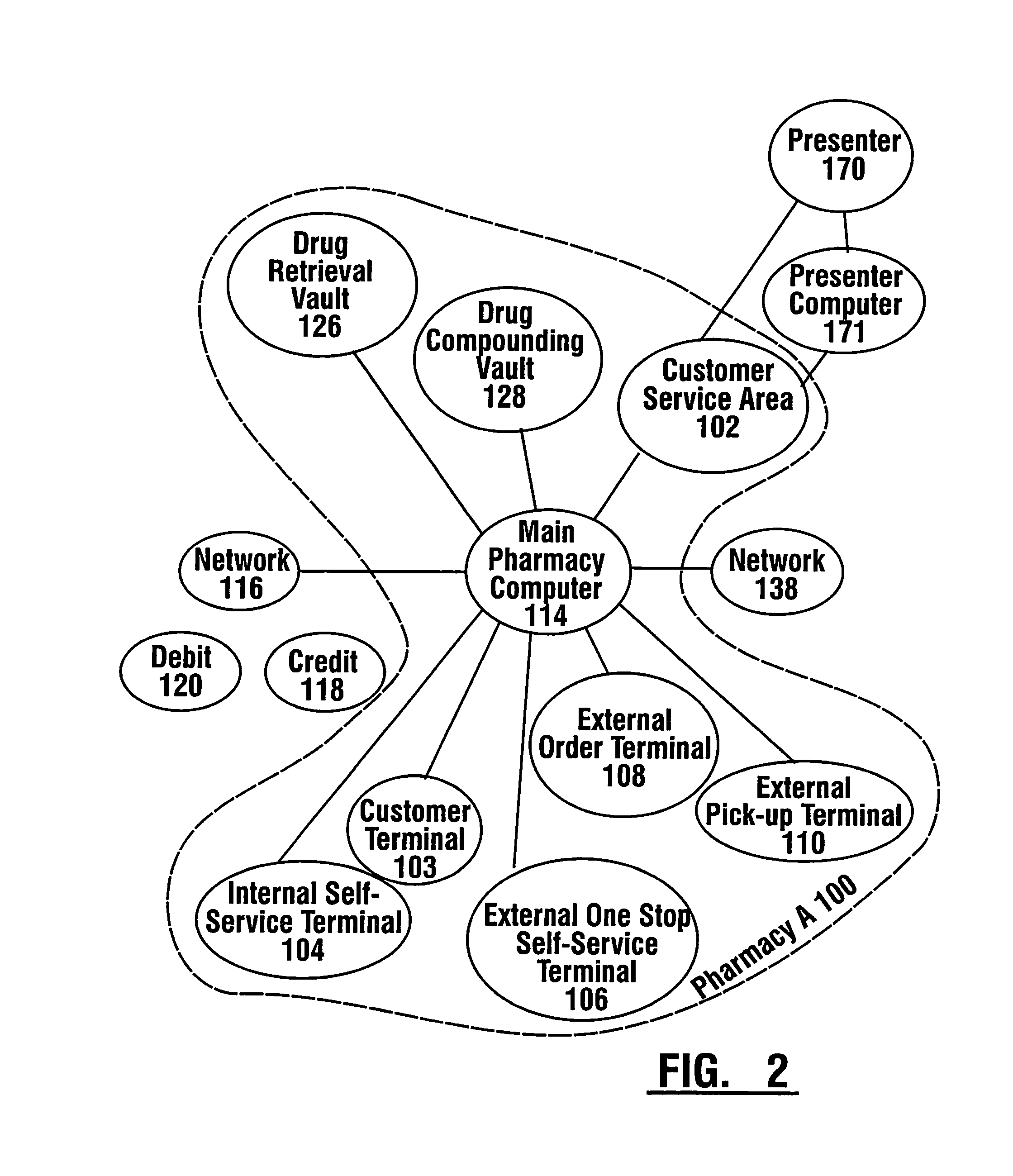
Pharmaceutical system in which pharmaceutical care is provided by a remote professional serving multiple pharmacies
InactiveUS7630788B1More accuracyGuaranteed growthFinanceDrug and medicationsElectronic networkDrugs preparations
A pharmaceutical system and method of operation in which a single remote professional provides pharmaceutical care and oversight of multiple local pharmacies. A control location is connected through an electronic network to one or more individual pharmacies, each of which may be located at a different physical site. Each individual pharmacy includes one or more drug preparation areas, and one or more self-service or staffed customer terminals. A drug preparation area includes a robot, which is adapted to prepare prescriptions or other items, and which is connected by a pneumatic delivery system to one or more customer terminals within the pharmacy.
Owner:DIEBOLD NIXDORF
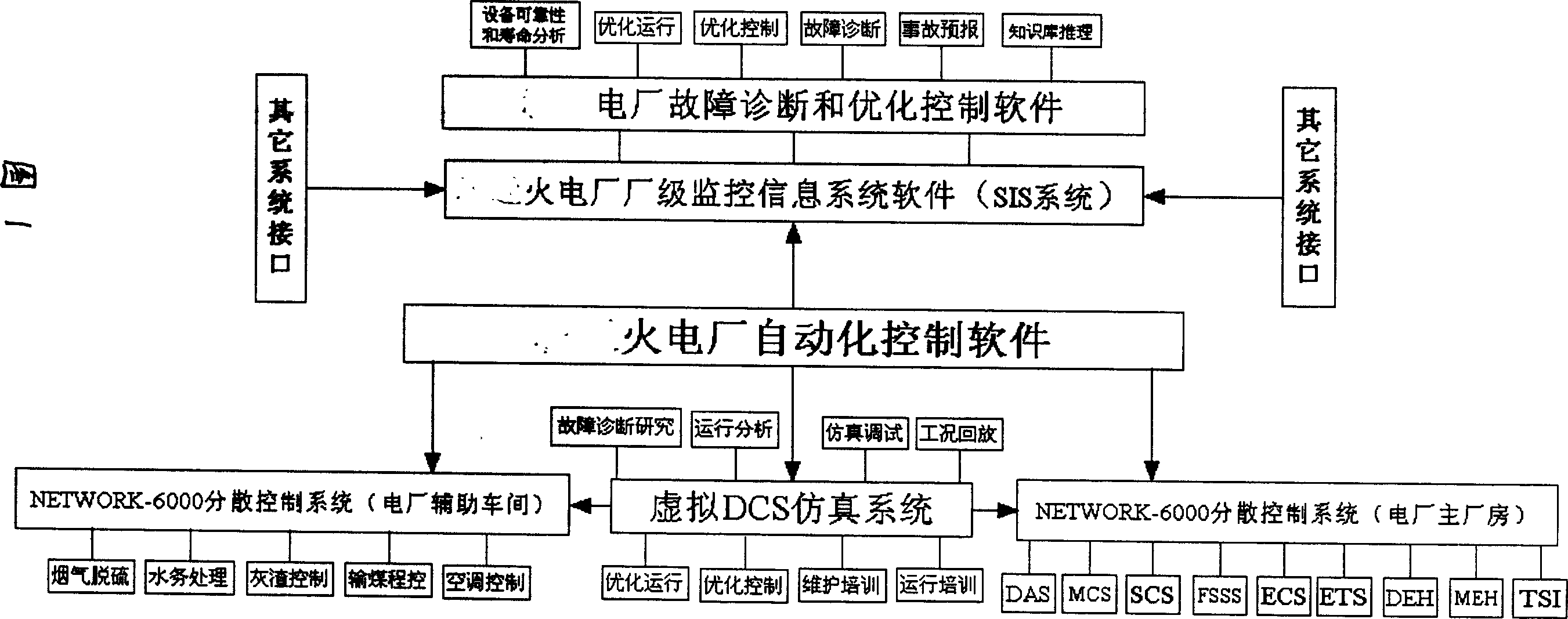
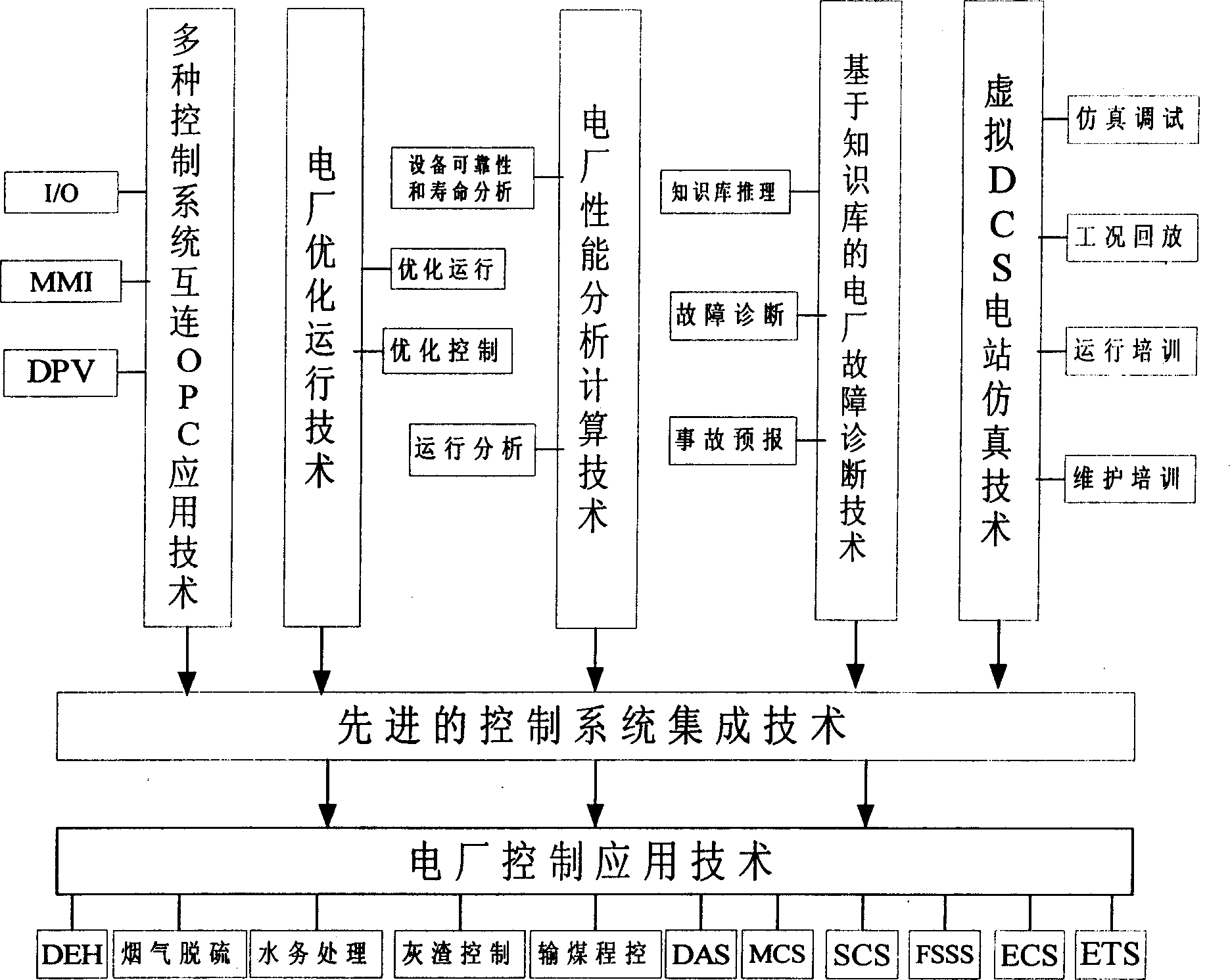
Automatic control system based on artificial intelligence for heat-engine plant
ActiveCN1694025ATake into account maturityGuaranteed growthComputer controlEnergy industryAutomatic controlPower station
The invention discloses a thermoelectric power station automatic control system based on artificial intelligence. It includes dispersible control system, virtual DCS simulation system, program controlling system, monitoring information system and malfunction diagnosing and optimizing controlling system; the dispersible control system is connected with the virtual DCS simulation system and program controlling system; the program controlling system process the operating parameters of every machine group transmitted by dispersible control system, and at the same time transmits data to monitoring information system to display, then transmits malfunction diagnosing and optimizing controlling system to have equipment state monitoring, malfunction diagnosing and forewarns. The invention gathers automatic control, optimizing operation, security monitoring and malfunction diagnosing and forecast. It can improves the automated management level of the thermoelectric power station operation, and enhances enterprises' benefit. It has great economic and applied value in the producing process automatic control of the thermoelectric power station.
Owner:南京科远智慧能源投资有限公司
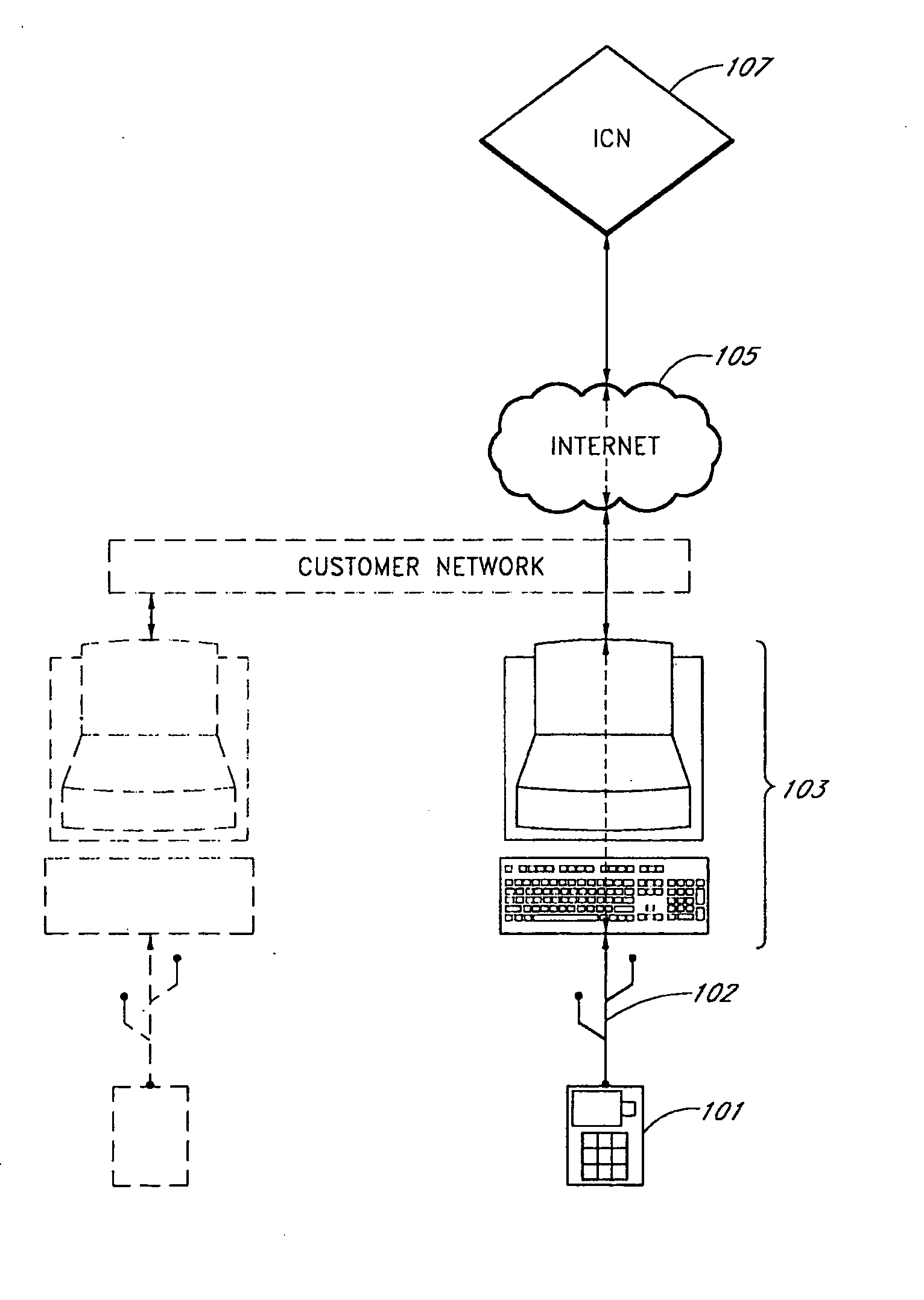
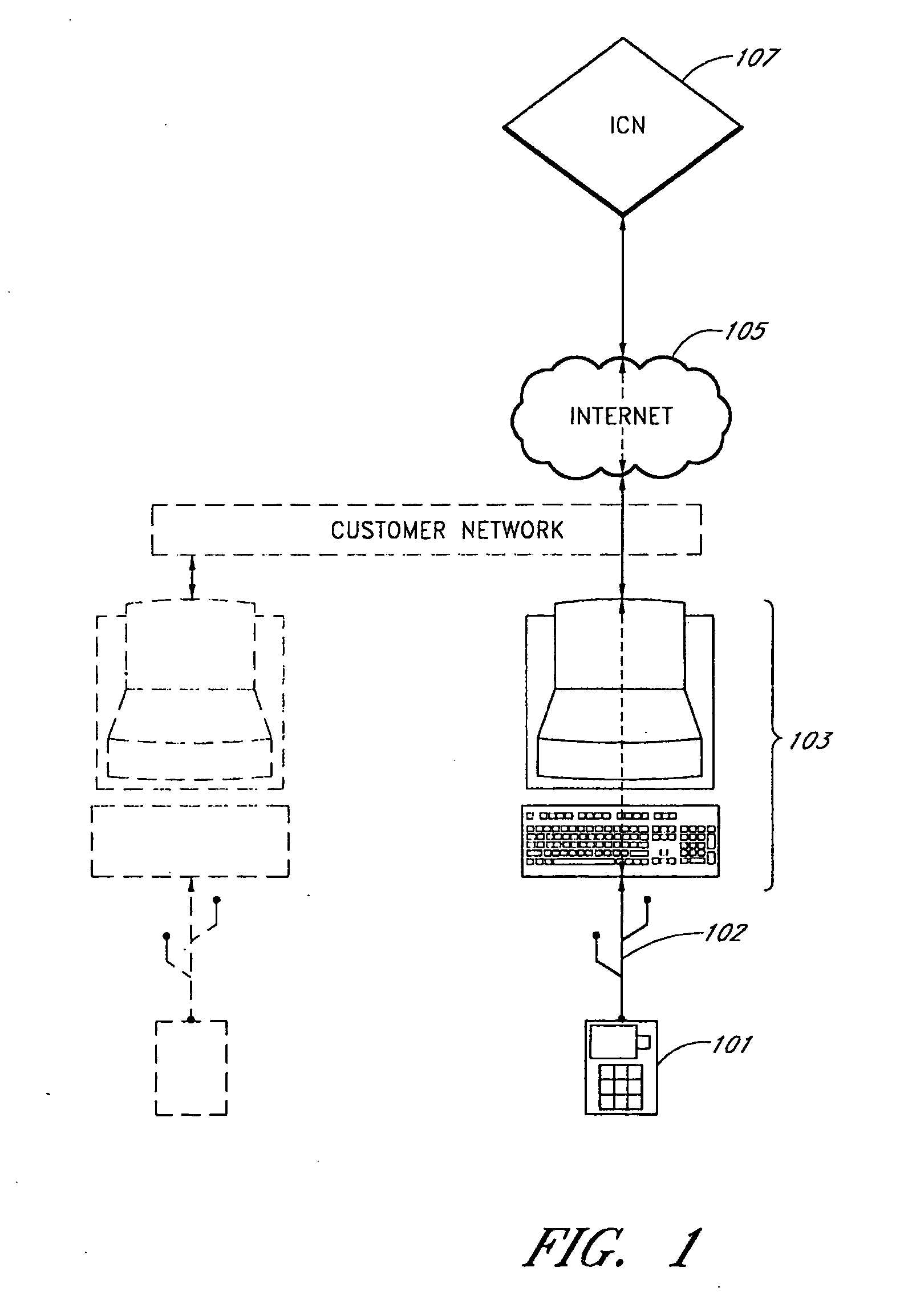
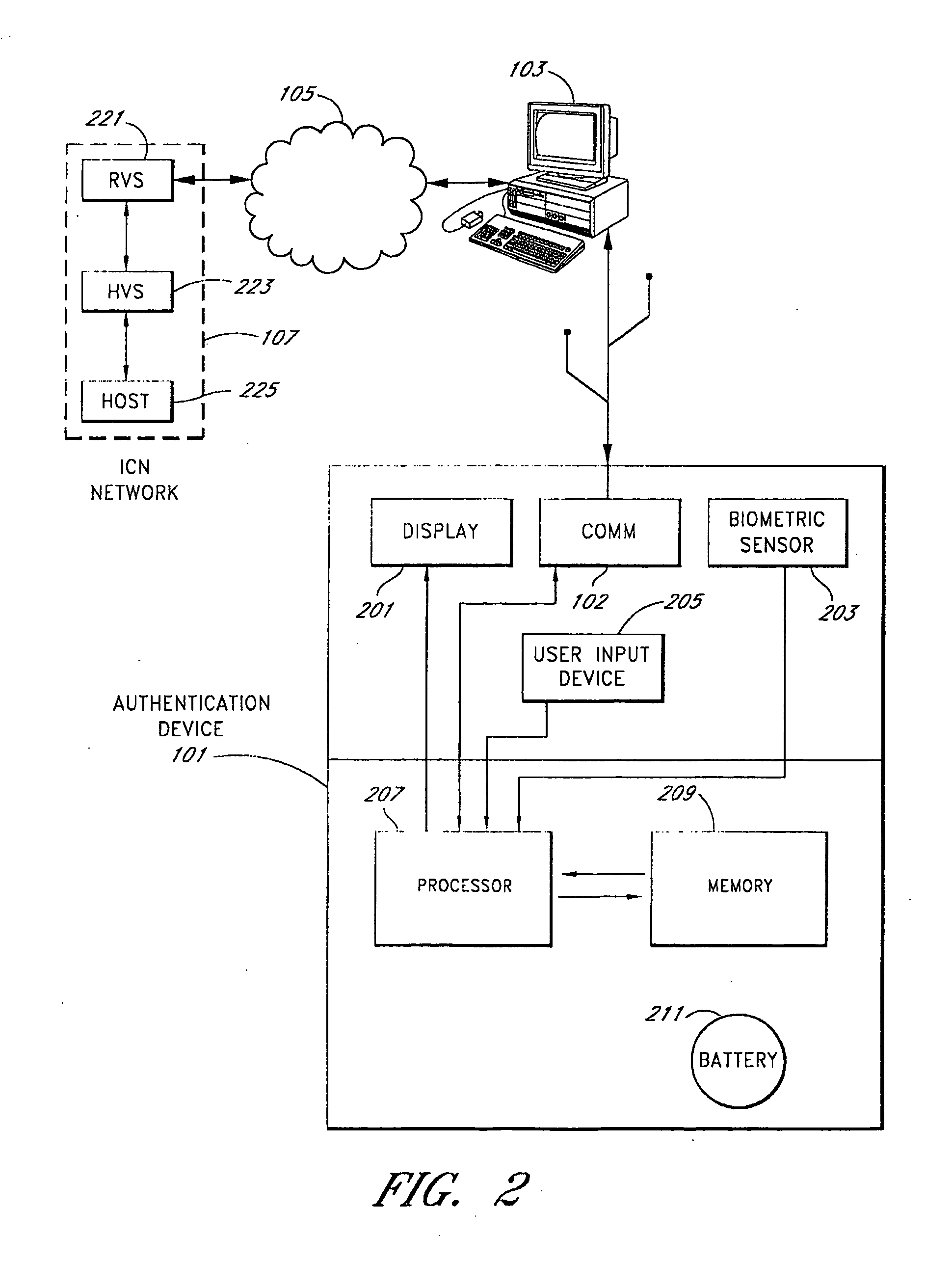
System and method for user identification and authentication
InactiveUS20070192601A1Improve security levelGuaranteed growthUser identity/authority verificationDigital data authenticationSecurity validationAuthorization
A user identification and authentication device provides a secure computing platform and a secure computing path for communication with a secure remote host. The device is coupled to an unsecure PC but provides for secure verification of a user's identity and authorization in participating in a transaction.
Owner:SPAIN JOHN D R +4
Needle penetrable and laser resealable lyophilization device and related method
InactiveUS20080039773A1Improve abilitiesGuaranteed growthDrying solid materials without heatSuction devicesBiomedical engineeringLaser source
A device and related method are provided for lyophilizing a substance within the device and storing therein the lyophilized substance. The device is penetrable by a needle for filling the device with the substance to be lyophilized, and a resulting needle hole in the device is laser resealable by transmitting thereon laser radiation from a laser source. The device defines a chamber for receiving therein the substance to be lyophilized. A needle penetrable and laser resealable portion of the device is pierceable with a needle to form a needle aperture therethrough to fill the chamber with the substance to be lyophilized through the needle, and is laser resealable to hermetically seal the needle aperture by applying laser radiation thereto. A filter is connectable in fluid communication between an interior and exterior of the chamber for permitting fluid to flow therethrough in a direction from the interior to the exterior of the chamber, and for substantially preventing contaminants from flowing therethrough in a direction from the exterior to the interior of the chamber.
Owner:MEDINSTILL DEV
Expanded stent and a method for producing same
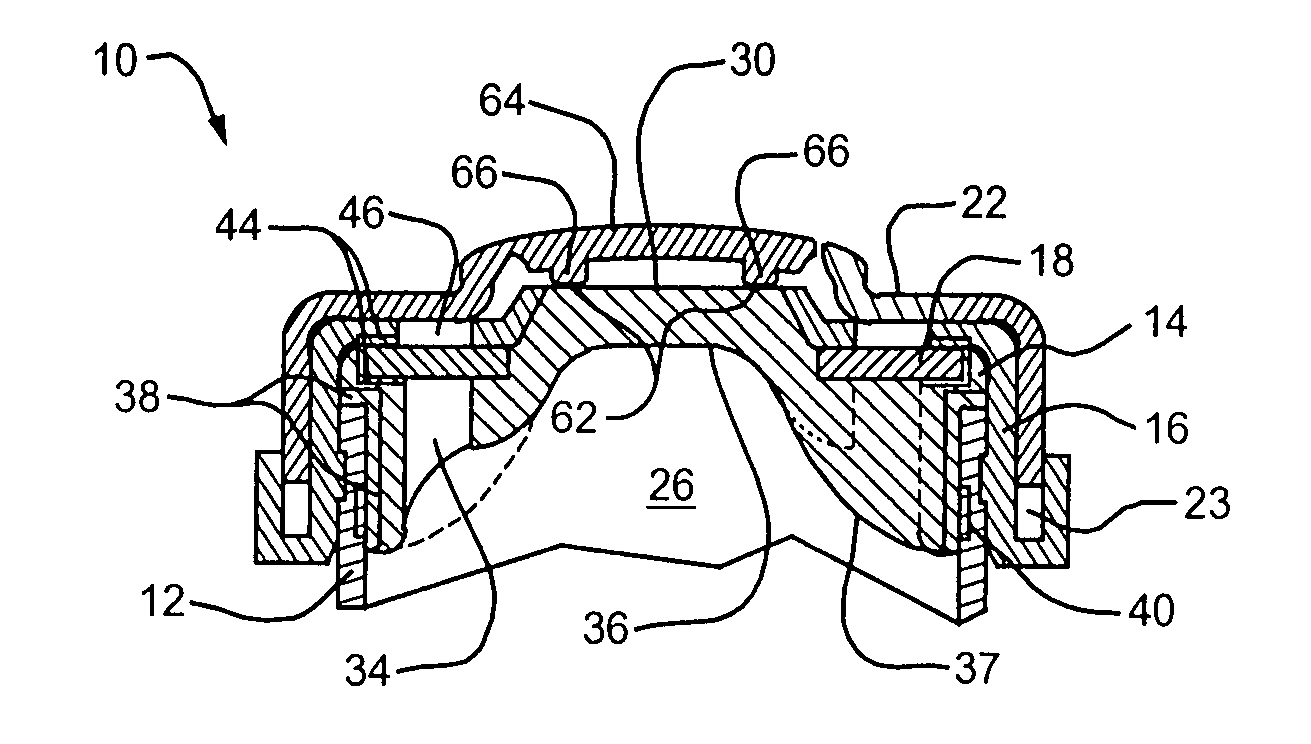
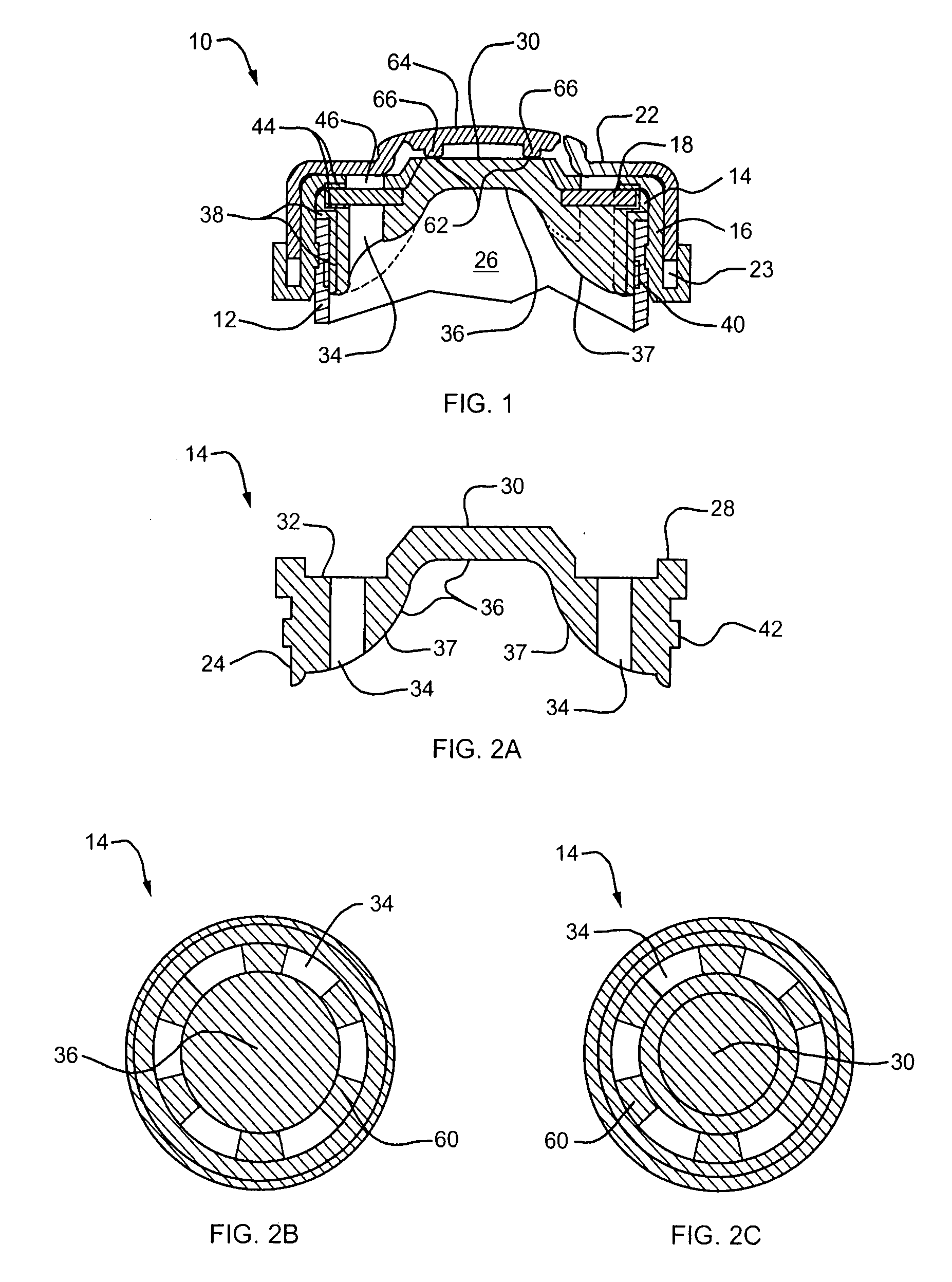
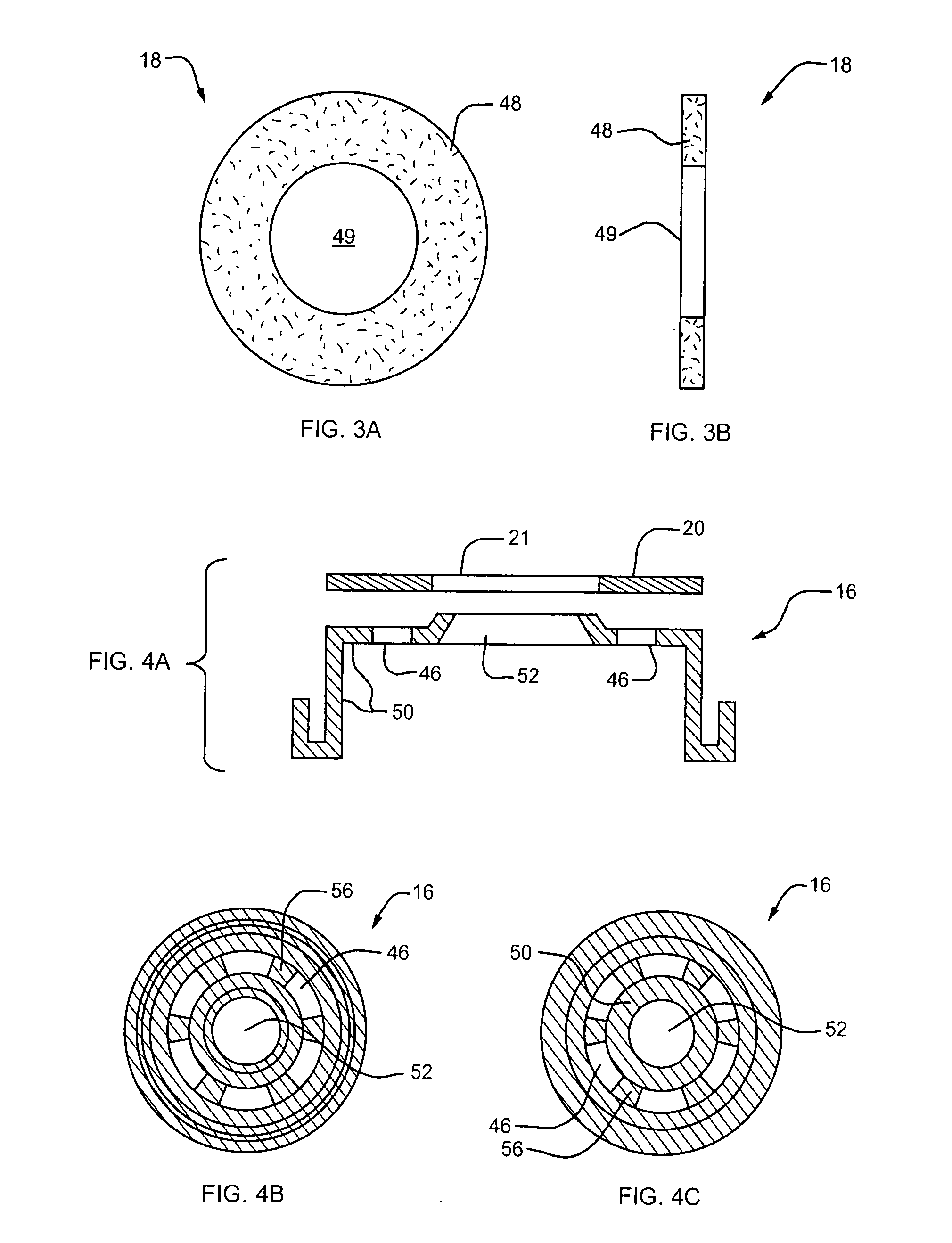
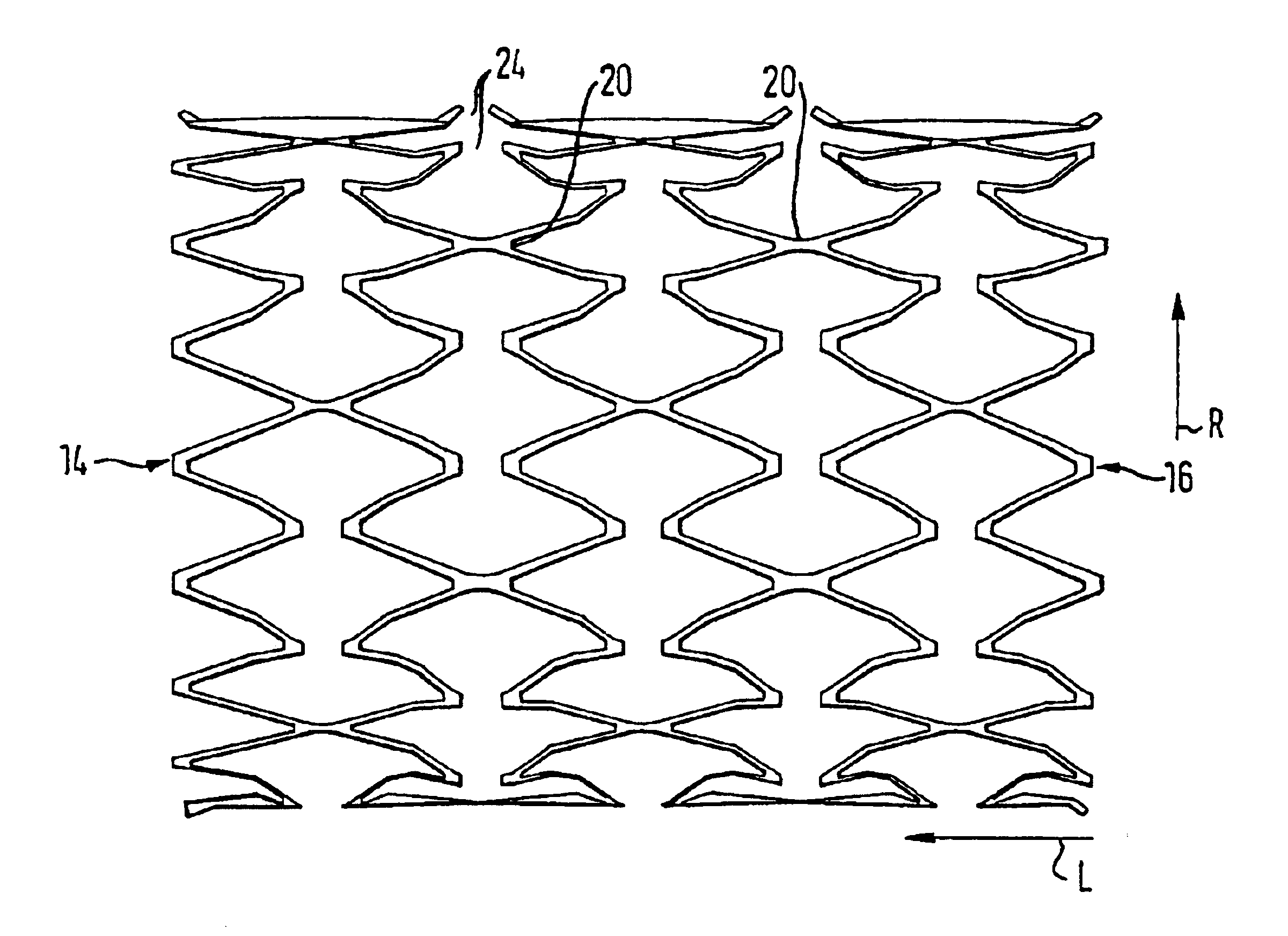
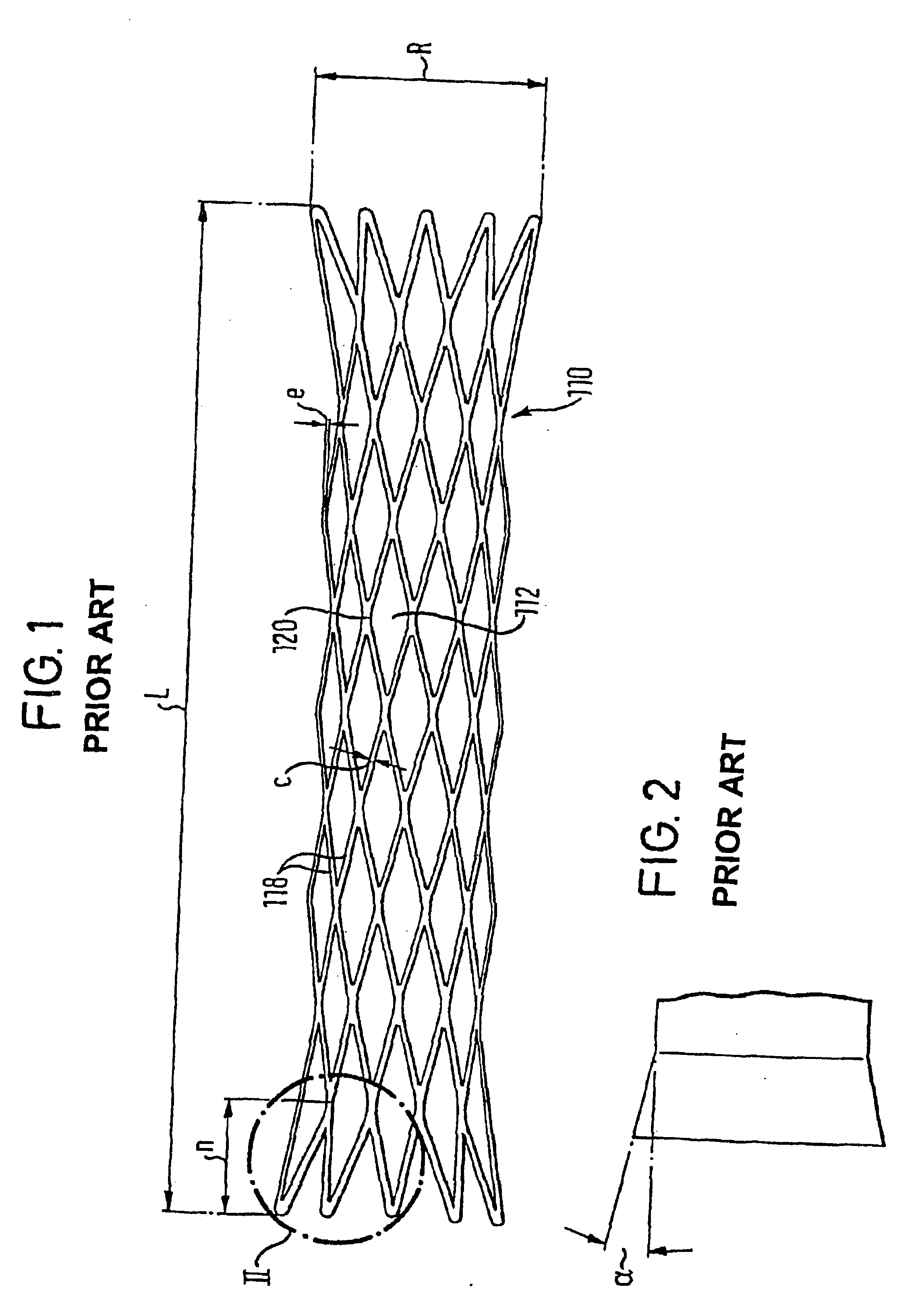
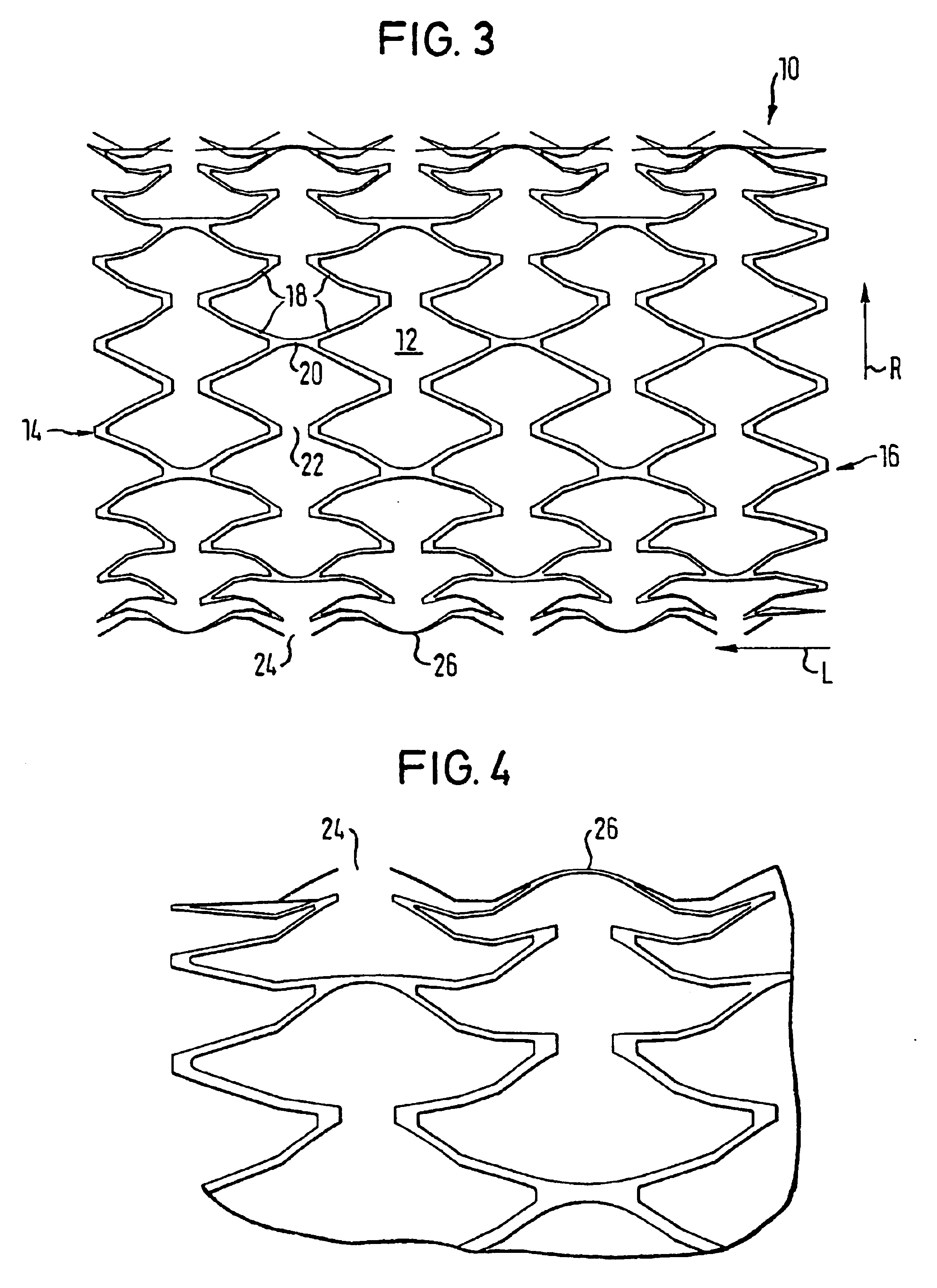
InactiveUS6911041B1Increase flexibilityIncrease anchorageStentsBlood vesselsInsertion stentWall segment
An expandable stent for insertion into a body lumen has a generally cylindrical lattice structure formed from wall segments that intersect and with some of the intersections being interrupted to enhance the flexibility of the stent. The wall segments associated with the interrupted portions are formed to have an outward flare such that when the stent is in a curved configuration, the wall segments will not project radially inwardly into the stent lumen, thereby avoiding obstruction to flow through the lumen.
Owner:ANGIOMED GMBH & CO MEDIZINTECHNIK KG
Systems controlled by data bearing records for maintaining inventory data
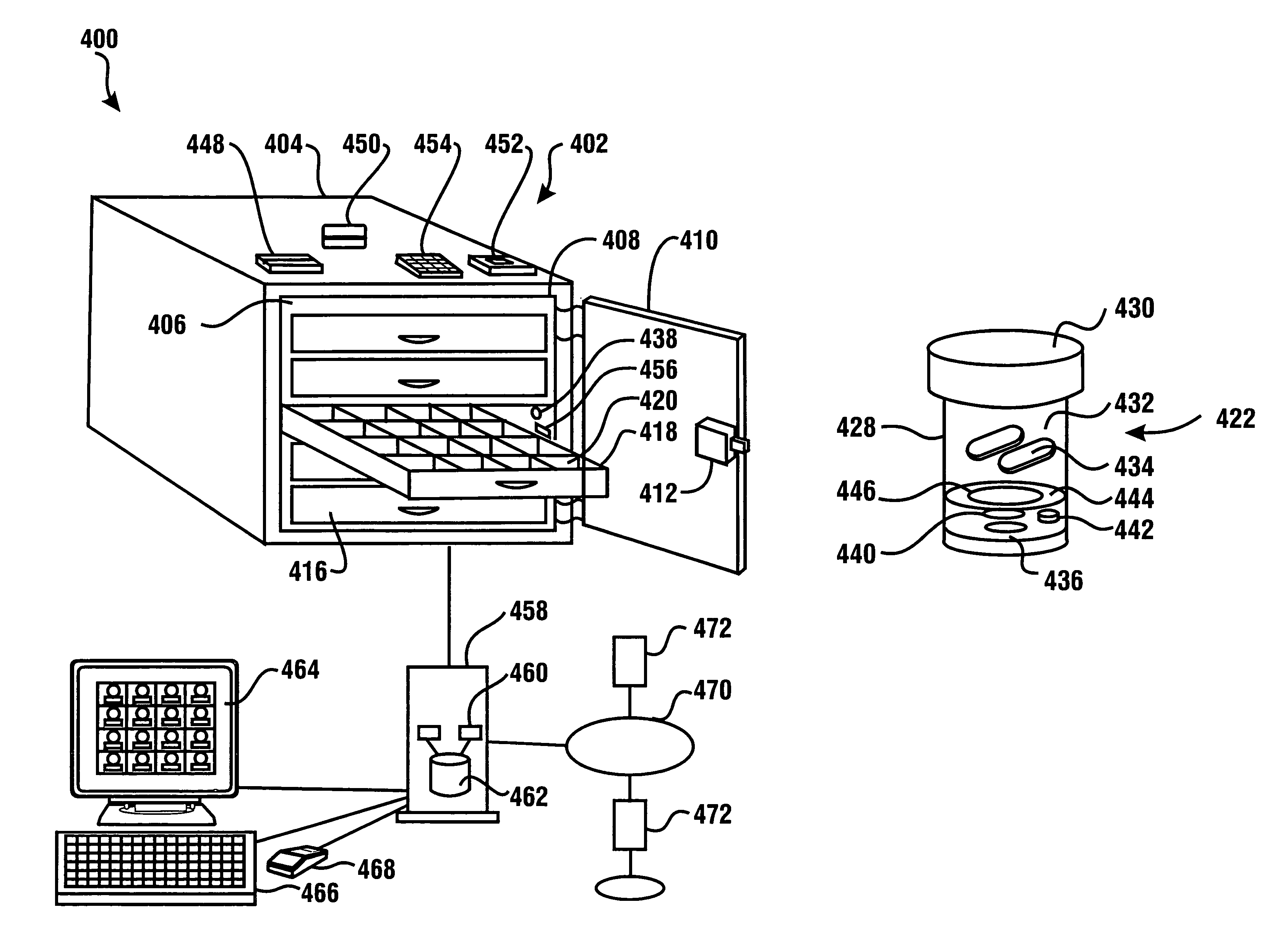
InactiveUS8342400B1More accuracyGuaranteed growthDrug and medicationsDigital data processing detailsDatabaseWireless transmitter
A registering and counting system operated in response to information included on data bearing records is used for maintaining inventory records related to narcotics items. Data corresponding to users is read through record reading devices (448, 452). Authorized users are allowed access to a narcotics vault (402). Narcotics holding containers (422) are removable from storage locations in drawers (416). Wireless transmitters on the containers operate in conjunction with wireless readers in the storage locations to enable a computer (458) to track the use of the narcotics items and operating parameters of the system.
Owner:DIEBOLD NIXDORF
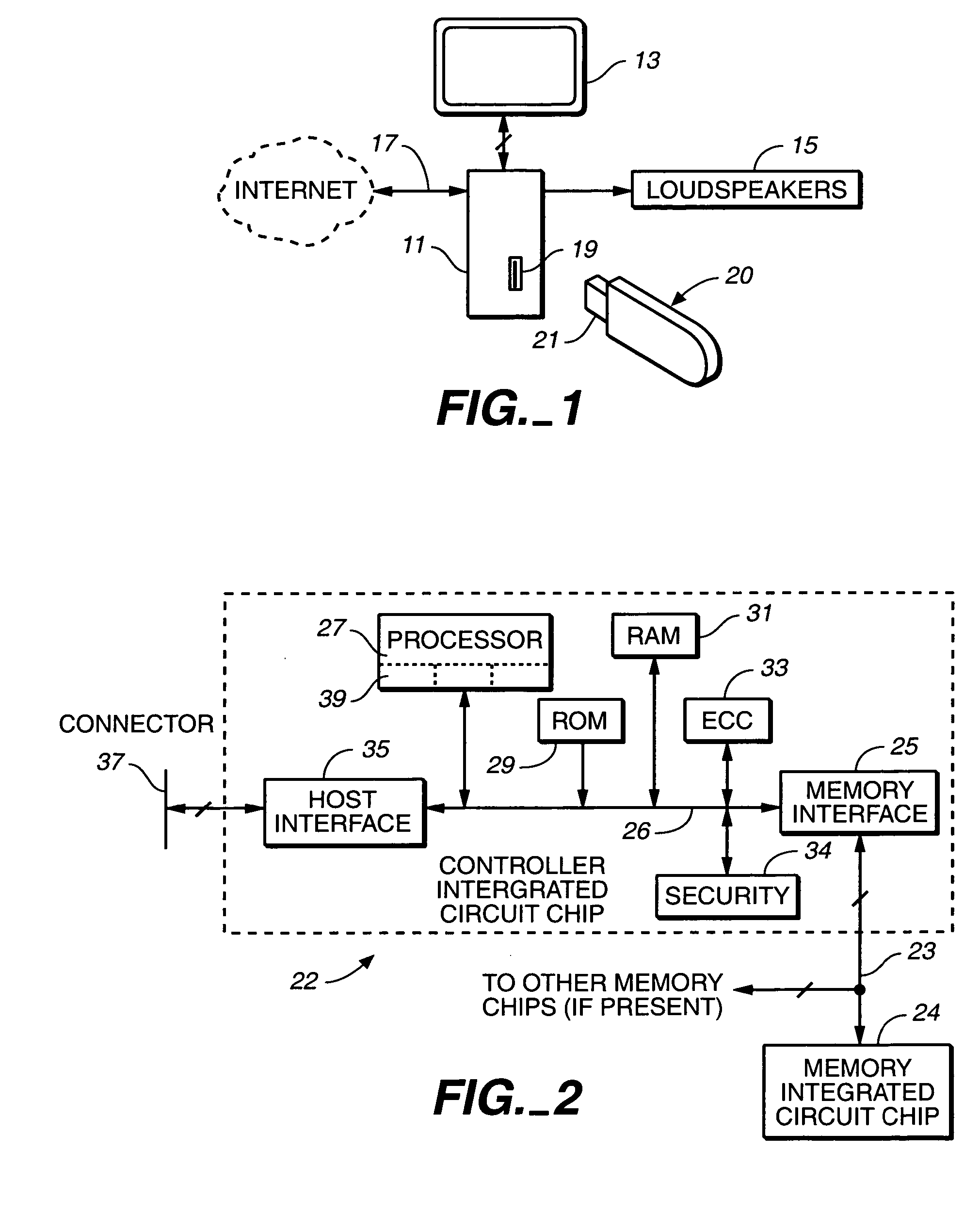
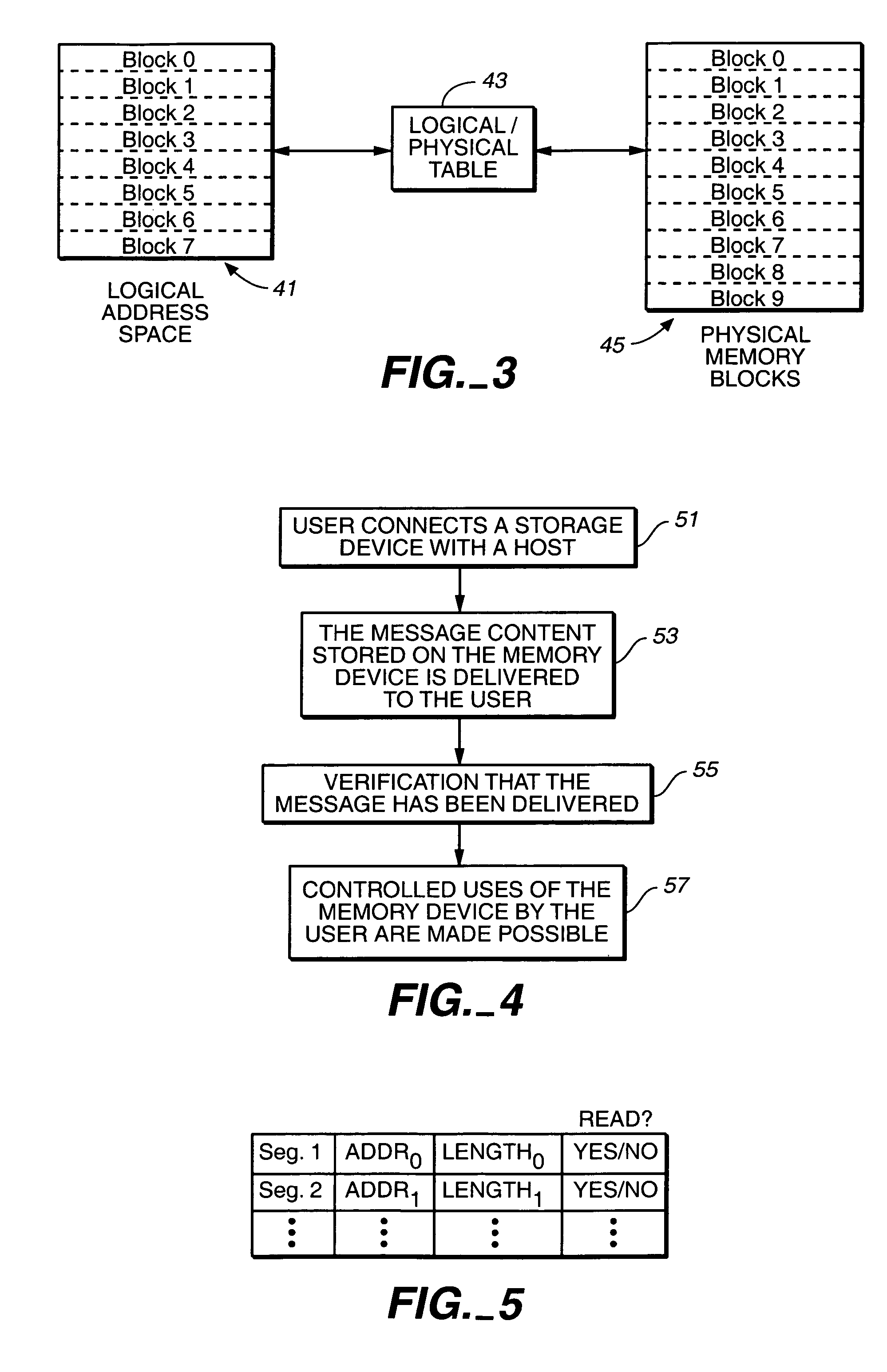
Delivery of a message to a user of a portable data storage device as a condition of its use
ActiveUS20060161749A1Increase valueValue maximizationDiscounts/incentivesAdvertisementsMessage passingData store
A memory card, flash memory drive or other removable re-programmable non-volatile memory device is configured so that at least part of the memory is not available for storage of user data until data of a message stored in the memory is at least read out by the user through a host device to which the memory device is connected. The message may be an advertisement, instructions on using the memory device, or the like, to which the user is at least exposed as a condition of having the full capacity of the memory card available thereafter for use by him or her.
Owner:SANDISK TECH LLC
Catheter assembly with segmented stabilization system
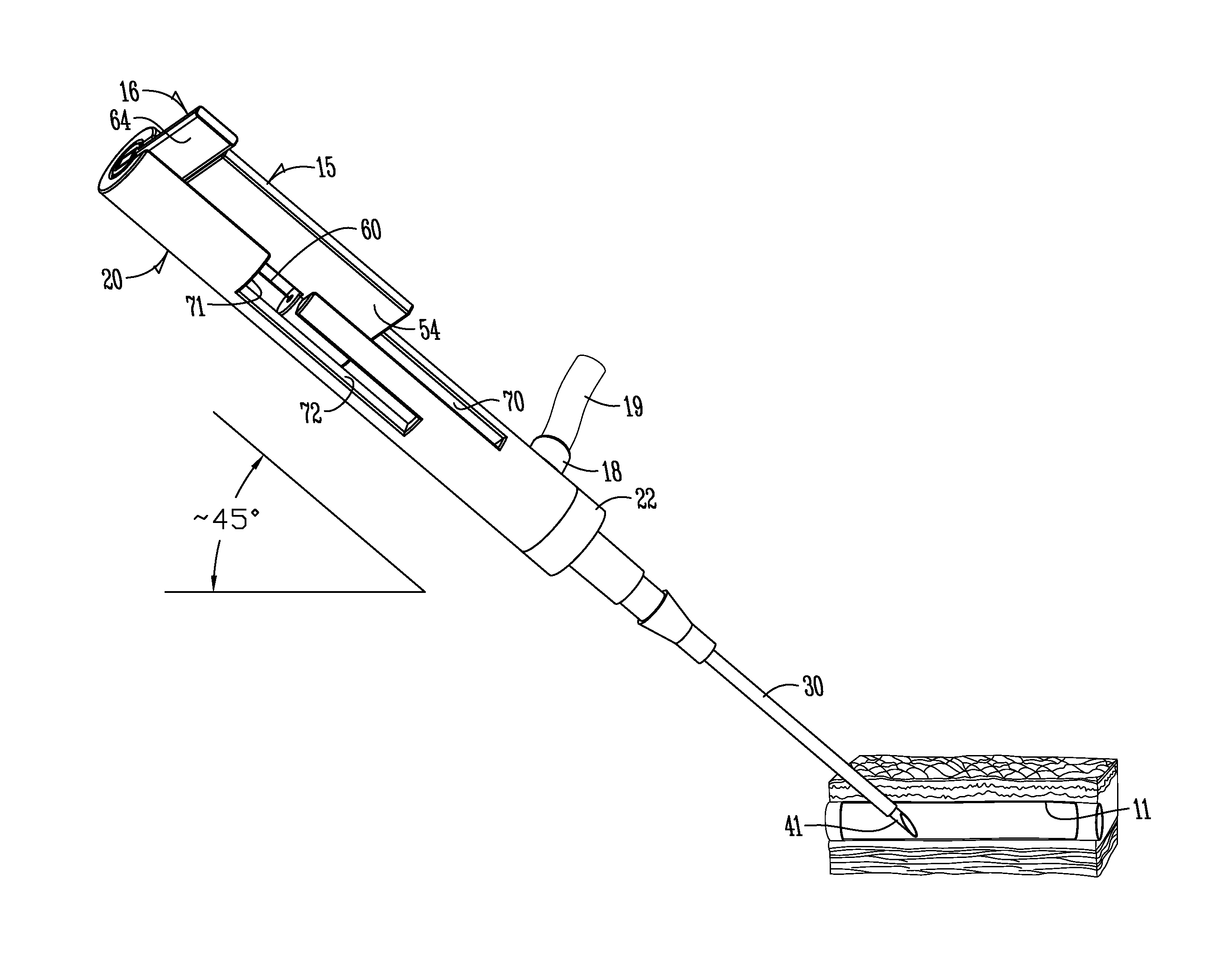
A catheter assembly with segmented or step-wise deployment stabilization system includes a base or handle, puncture needle extending from the handle, and a deployment mechanism or mechanisms to selectively extend from the distal end of the needle for first length a hollow stabilizing component and as a second step to a second further length a stabilizing guide wire element. The needle will gain sub-dermal access to the patient to the intended position for deployment of a catheter. Hollow stabilizing component provides for a first additional guide and support for a catheter sheath from the distal end of the needle. The stabilizing wire element provides additional length, guide and support for the catheter sheath. The hollow stabilizing component has some degree of flexibility as does the guide wire to minimize chance of damage to surrounding tissue. The user can feel resistance and have the opportunity to retract either component and attempt redeployment without a retraction of the puncture needle and a second poke of the patient's skin. In the example for peripheral venous catheterization, the system reduces the probability of blood vessel puncture. The deployment mechanism can have a guiding system which ensures the proper sequence of deployment.
Owner:TELEFLEX LIFE SCI LTD
High-elongation aluminum alloy material and preparation method thereof
ActiveCN101525709AHigh strengthImprove creep resistanceTemperature control deviceMetal rolling arrangementsRare-earth elementElectrical conductor
The invention relates to a high-elongation aluminum alloy material and a preparation method thereof. The high-elongation aluminum alloy material contains 0.30-1.20% of iron, 0.03-0.10% of silicon, 0.01-0.30% of rare earth elements, and aluminum and inevitable impurities in weight percentage. The aluminum alloy is made from materials according to a fusion casting process and half-annealing treatment. An aluminum alloy conductor made by the method has high elongation and good safety and stability in use.
Owner:ANHUI JOY SENSE CABLE
Practical secrecy-preserving, verifiably correct and trustworthy auctions
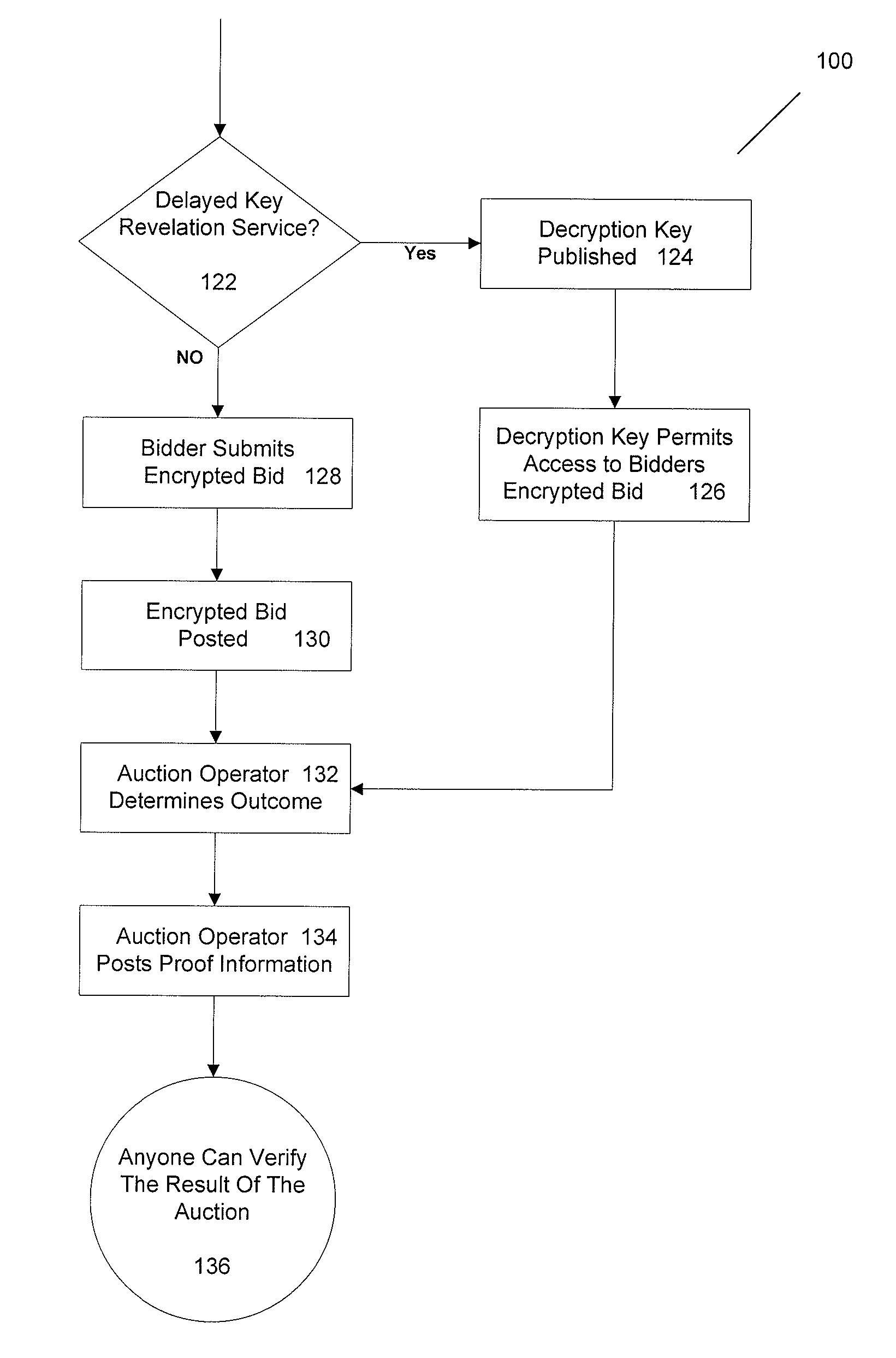
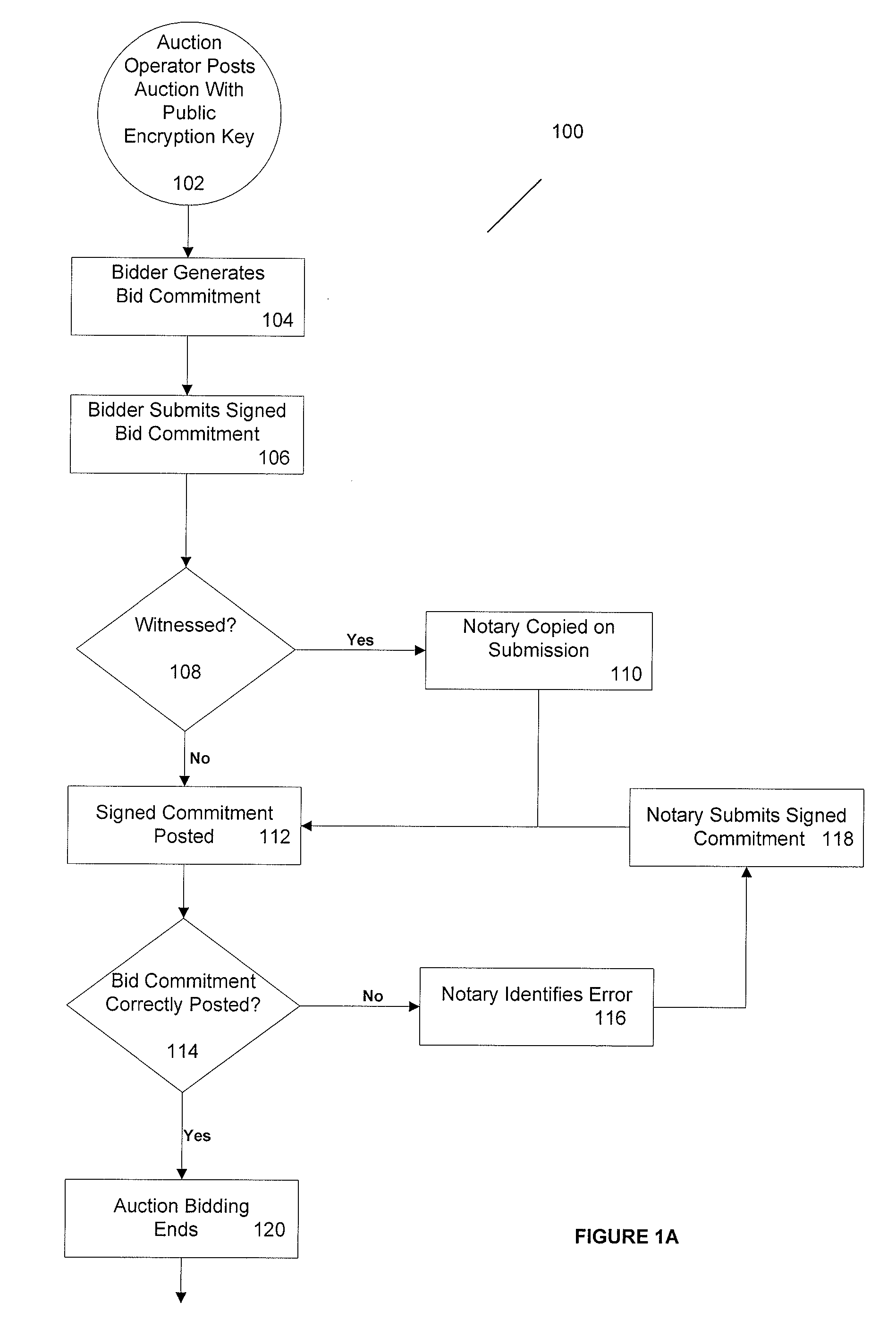
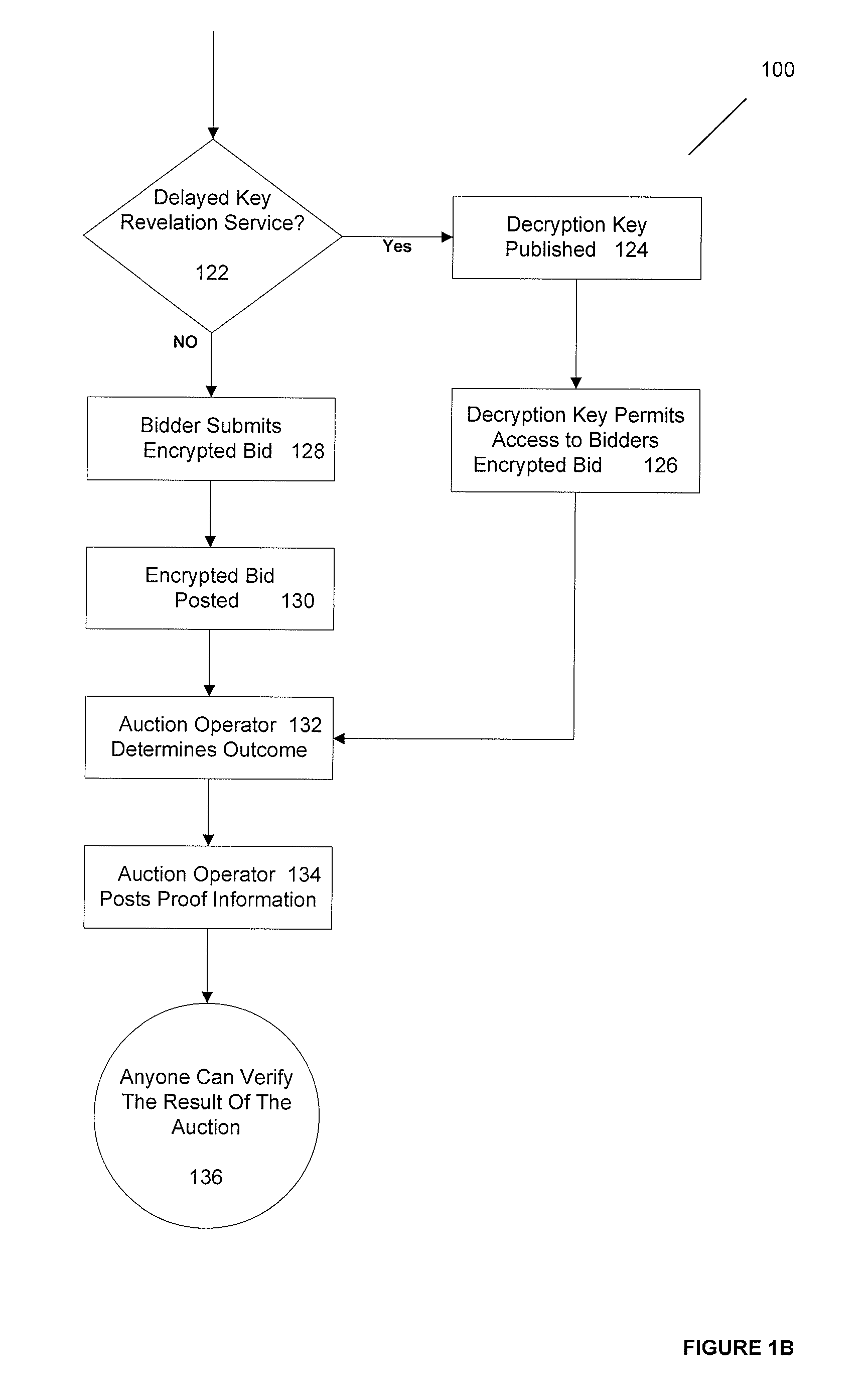
ActiveUS20090182667A1Ensure safetyImprove simplicityMultiple keys/algorithms usageUser identity/authority verificationCorrectness proofsTheoretical computer science
A system and method for conducting verifiably correct auctions that preserves the secrecy of the bids while providing for verifiable correctness and trustworthiness of the auction is disclosed. Some of the elements of the method and apparatus are that the auction operator accepts all bids submitted and follows the published rules of the auction. In one embodiment, the bids are maintained secret from the auctioneer and all bidders until the auction closes and no bidder is able to change or repudiate her bid. In another embodiment, the auction operator computes the auction results and publishes proofs of the results' correctness. In yet another embodiment, any party can check these proofs of correctness via publicly verifiable computations on encrypted bids.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
Location, identification and telemetry system using strobed signals at predetermined intervals
InactiveUS6222440B1Save powerAvailable bandwidthElectric signal transmission systemsDirection finders using radio wavesEngineeringWireless transmitter
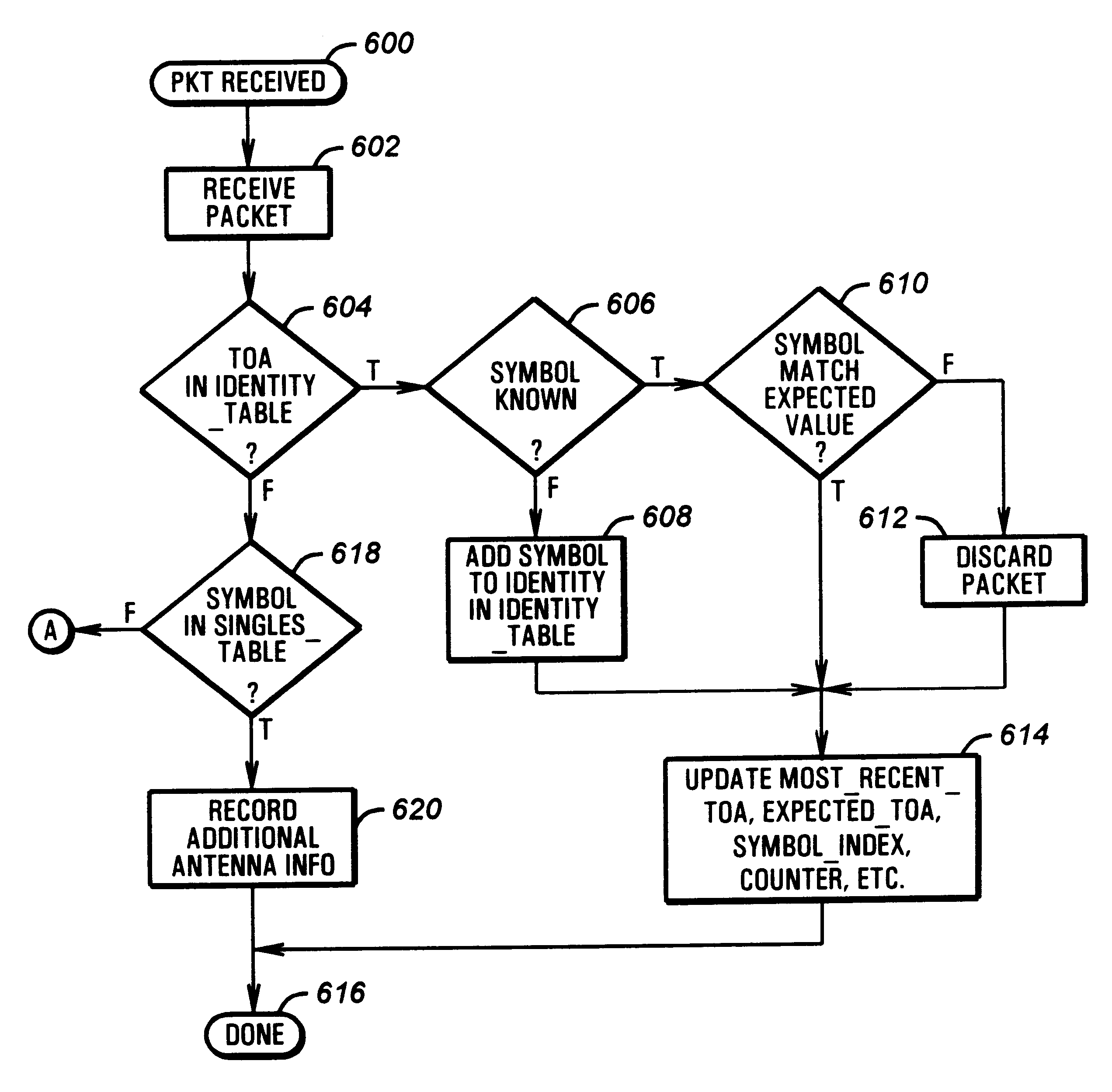
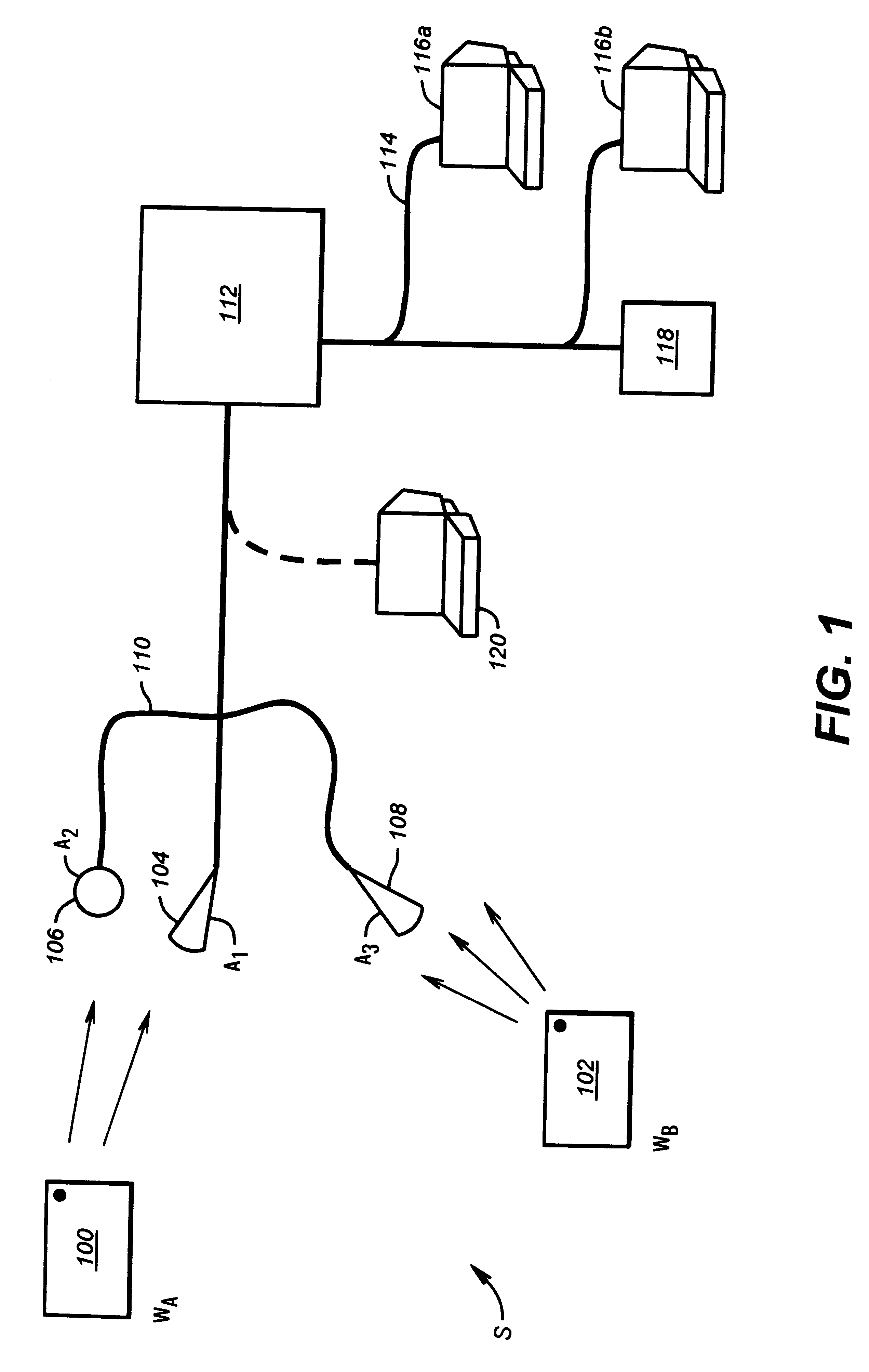
A tracking system is implemented according to the invention in which the identification data of a wireless transmitter is divided into multiple bursts. Instead of transmitting the entire identification in a single burst, the identification is split among bursts, so that it takes a period of time to uniquely identify a particular transmitter. However, the time between bursts falls under tight tolerance, so once a transmitter is identified, it can be further identified based on when it transmits as opposed to what it transmits. In this way, high tractability can be maintained without repeatedly transmitting the entire identification code of the transmitter.
Owner:FRESHLOC TECH
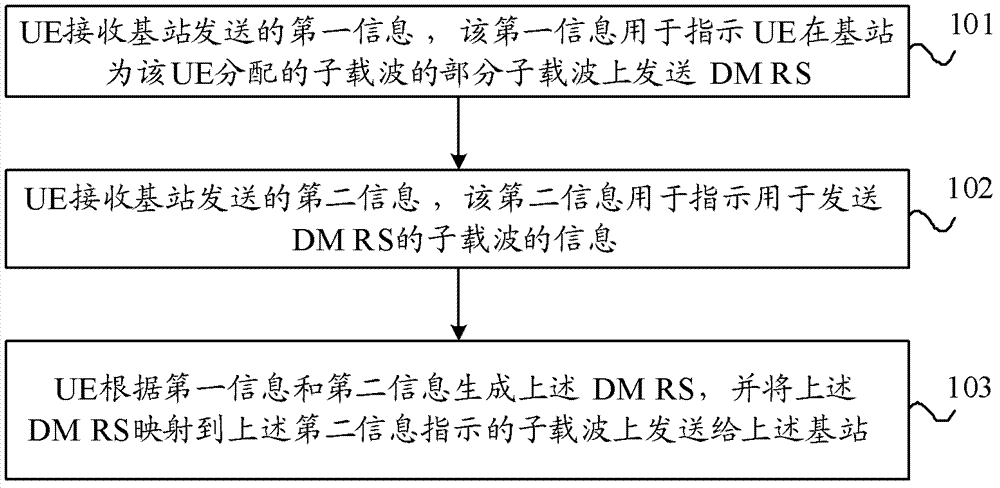
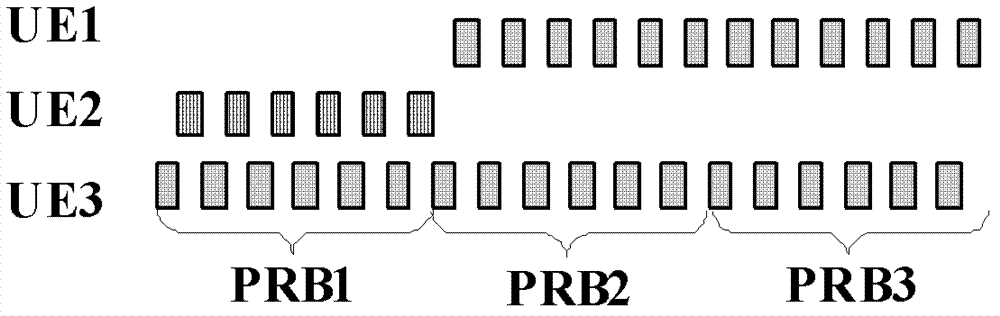
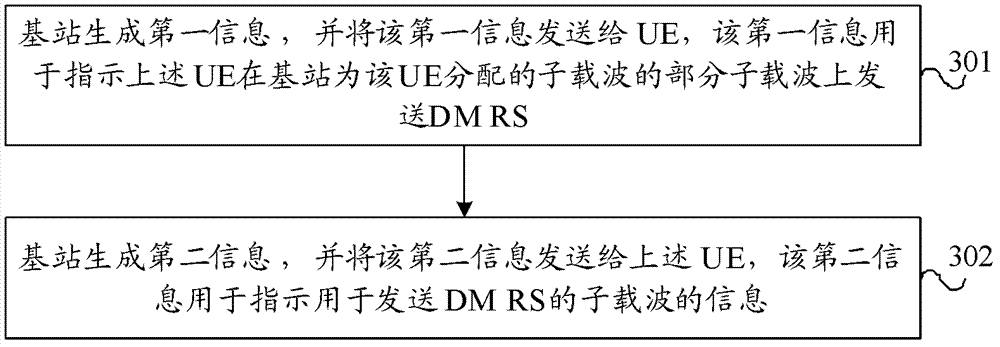
Transmission method of uplink reference signals and user equipment and base station
InactiveCN103096389AGuaranteed growthSite diversityNetwork traffic/resource managementSignal onCarrier signal
The invention provides a transmission method of uplink reference signals, user equipment and a base station. The transmission method of the uplink reference signals comprises the following steps: the user equipment receives first information transmitted by the base station, wherein the first information is used for indicating the user equipment to transmit demodulation reference signals on a part of subcarriers distributed by the user equipment on the base station; the user equipment receives second information transmitted by the base station, wherein the second information is used for indicating information used for transmitting information pf the subcarriers of demodulation reference signals; and the user equipment generates the demodulation reference signals according to the first information and the second information, maps the demodulation reference signals to the subcarriers indicated by the second information, and transmits the demodulation reference signals to the base station. According to the transmission method, orthogonality of the demodulation reference signals transmitted by the user equipment of different communities can be guaranteed, and gain brought by comp technology can be guaranteed.
Owner:HUAWEI TECH CO LTD
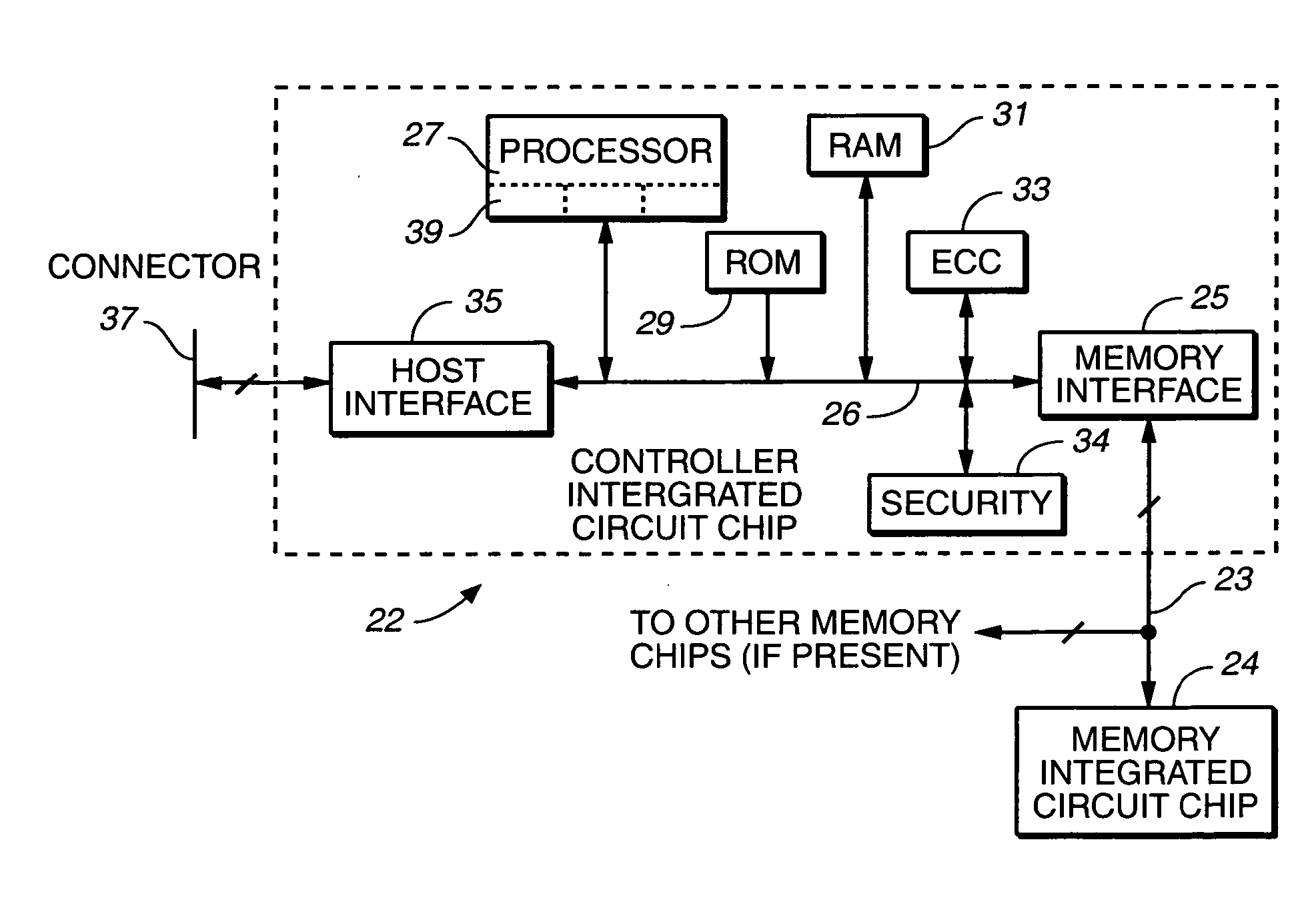
Secure virtual RAM
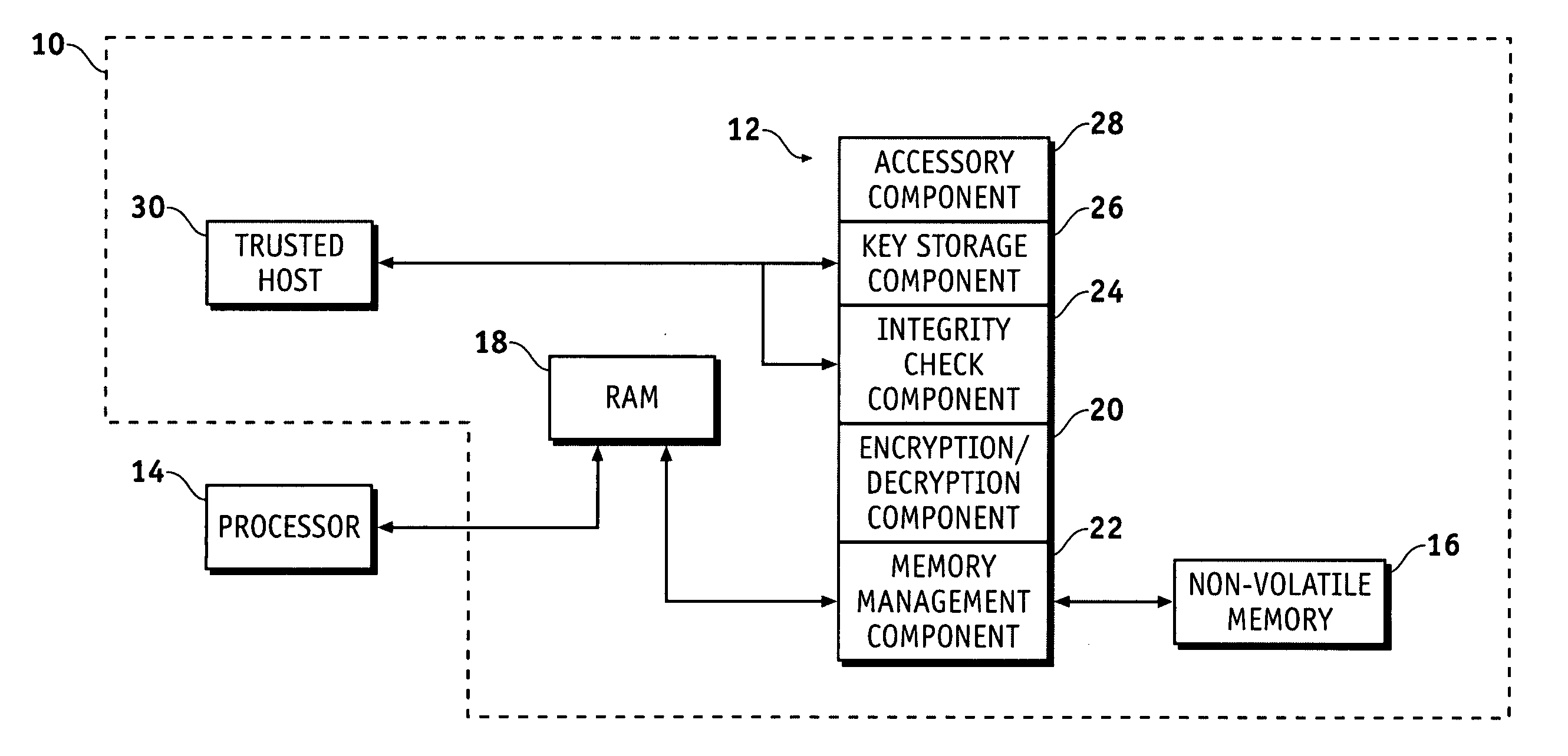
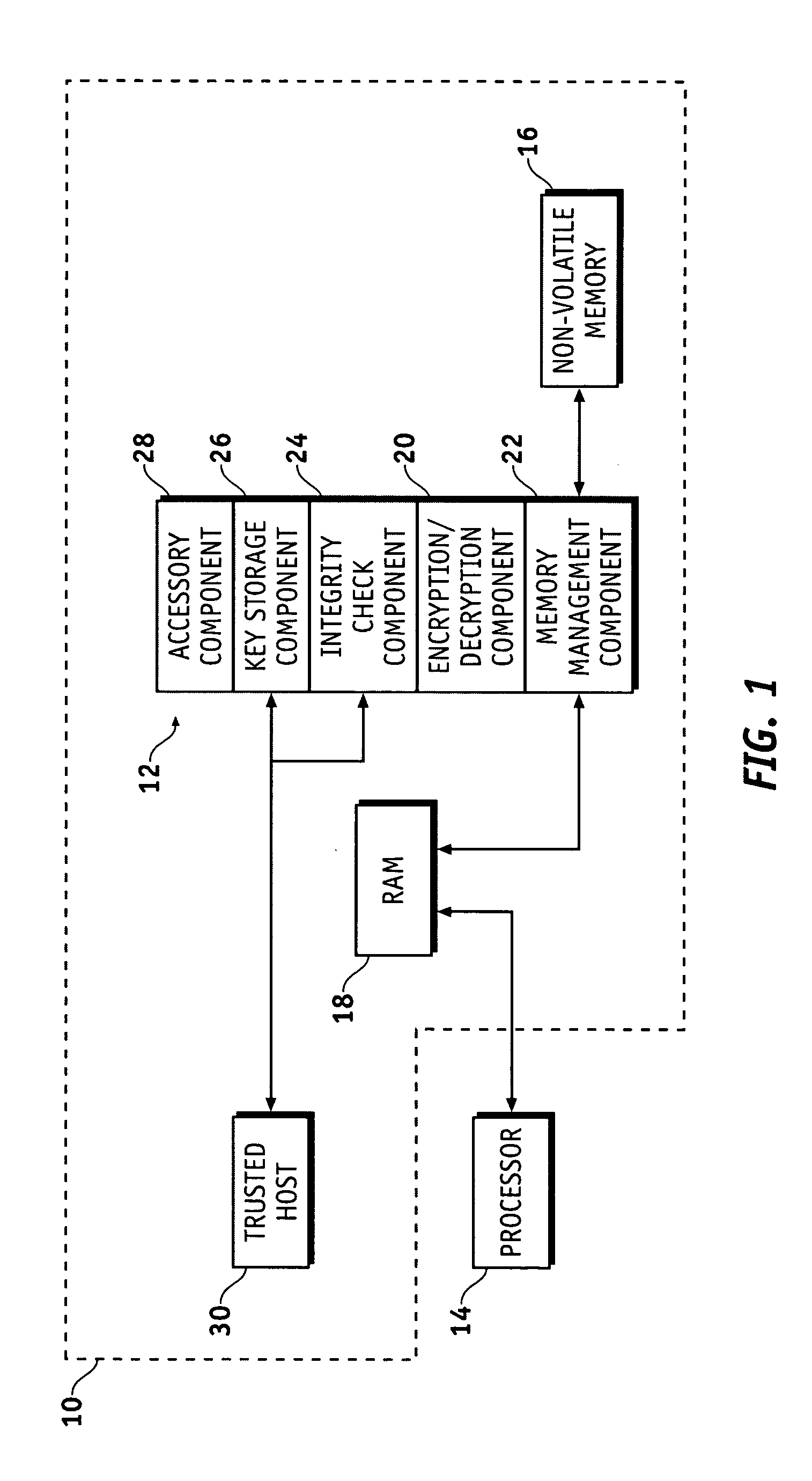
InactiveUS20080072070A1Guaranteed growthUnauthorized memory use protectionHardware monitoringKey storageNon-volatile memory
A secure virtual RAM securely transfers data within a device having a secure, non-volatile memory and a host. The secure virtual RAM includes a memory management component configured to direct the transfer of the data between the non-volatile memory and a processor, and an encryption / decryption component coupled to the memory management component and configured to decrypt the data provided to the processor and encrypt the data provided to the non-volatile memory. The secure virtual RAM further includes an integrity check component coupled to the encryption / decryption component and configured to monitor functional integrity, a key storage component coupled to the encryption / decryption component and configured to receive cryptographic keys and provide the cryptographic keys to the encryption / decryption component.
Owner:GENERAL DYNAMICS C4 SYSTEMS
Cigarette tipping paper water-based ink and preparation method
The invention discloses cigarette tipping paper water-based ink and a preparation method, belonging to the technical field of water-based ink. The water-based ink is characterized by consisting of the following raw materials in parts by weight: 50-60 parts of water-based emulsion resin oil, 10-20 parts of iron oxide pigment, 10-20 parts of de-ionized water and 0.5-1.0 part of one or more of auxiliary agents of defoaming agent, anti-sedimentation agent, leveling agent, wetting agent, antibacterial agent, wetting dispersant and surface tension agent. The cigarette tipping paper water-based ink has the advantages of small fineness, high drying speed, high consistency, low viscosity, good dispersion stability, no setting precipitate, no agglomeration, no toxicity, no residual peculiar smell, good wet leveling property, good color development, no brittle fracture at a low temperature, no edge folding during drying, good water resistance, full and clear print, stable color, smooth and glossy surface, good storage stability and wide application range to printing raw paper and printing speed; and the cigarette tipping paper water-based ink can be produced by the method.
Owner:义乌市伟航水性油墨有限公司
Method of Trading
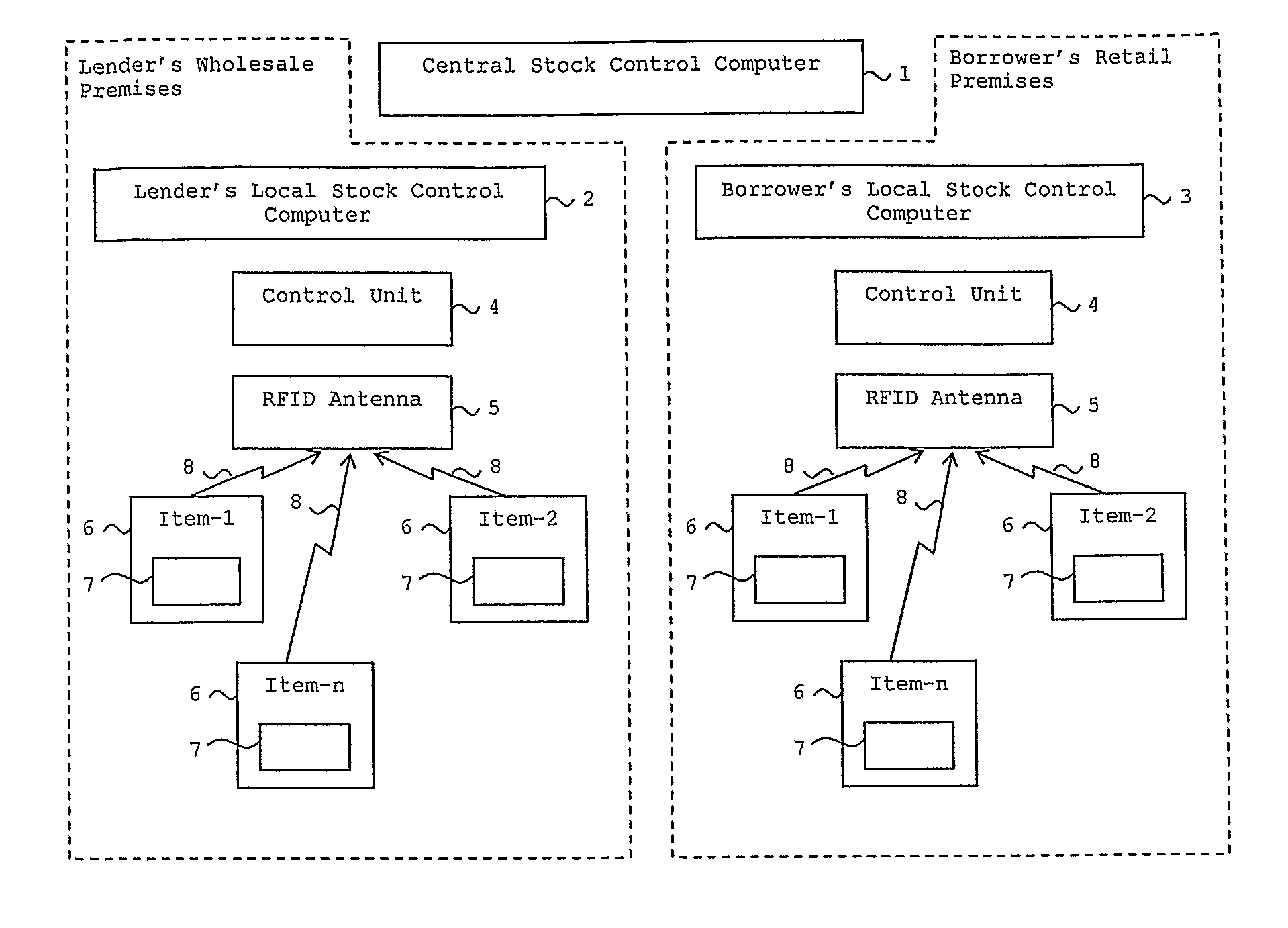
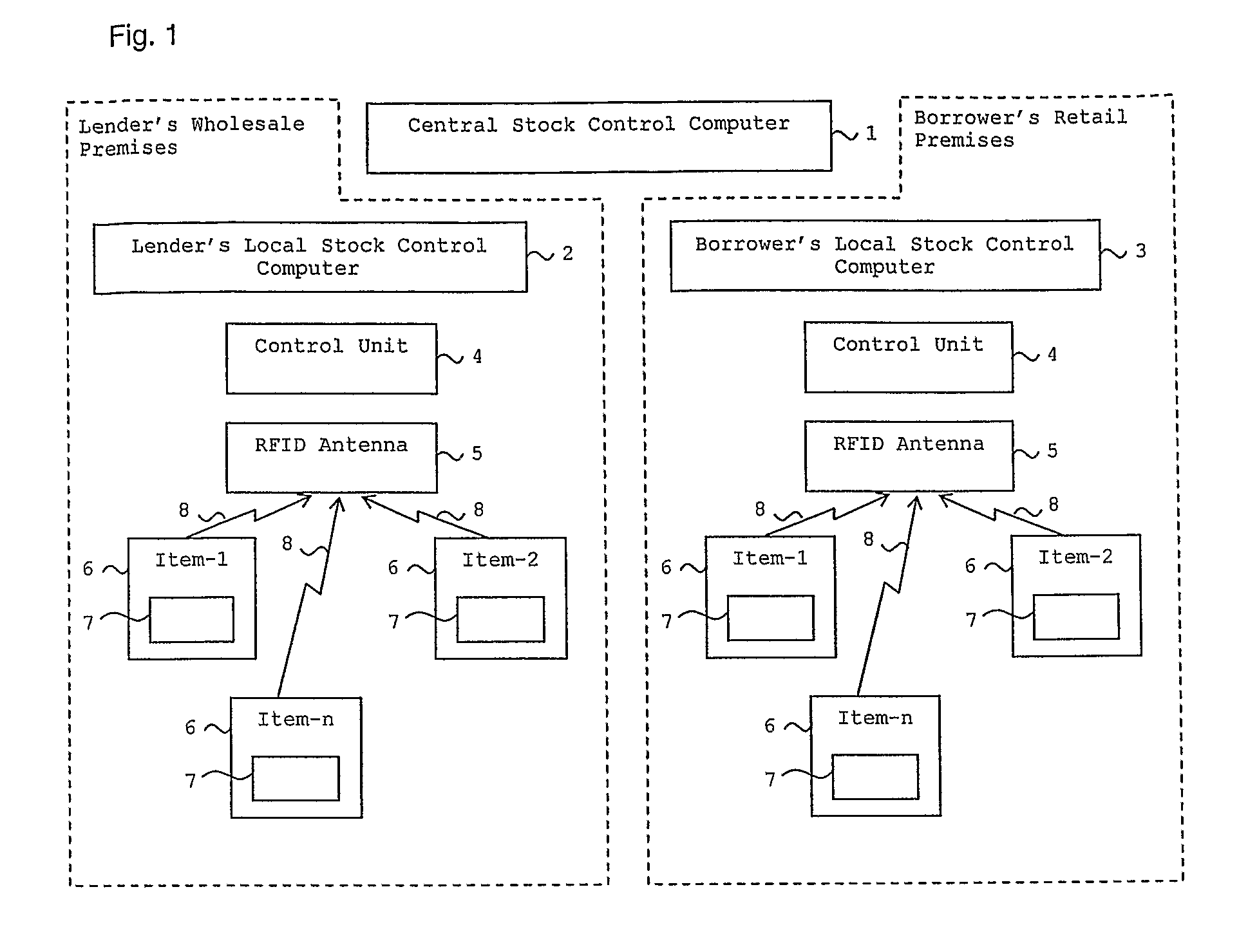
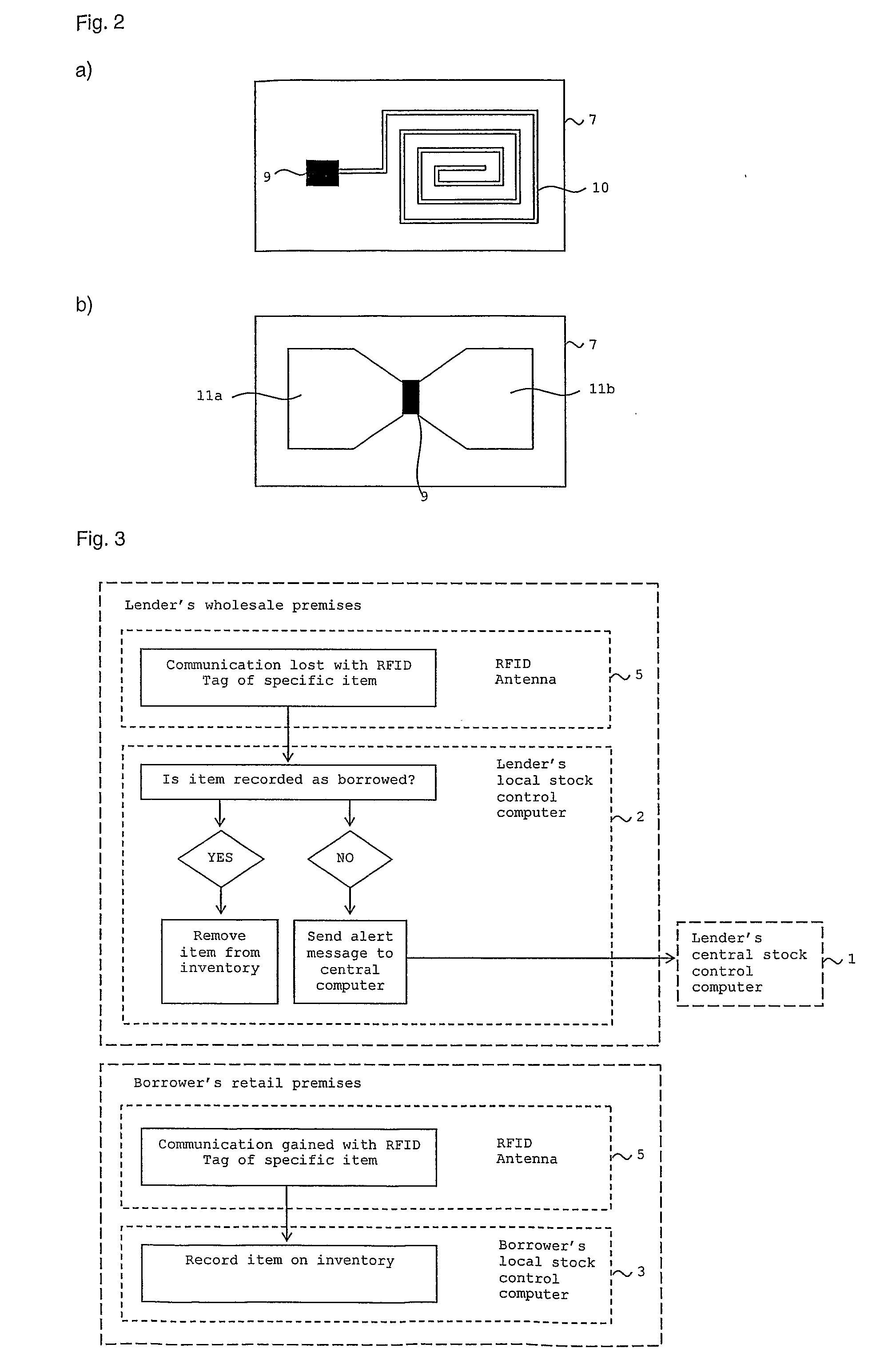
A method of borrowing an item from a lender to a borrower, in which the item has an RFID tracking device affixed thereto. While the item is in the possession of the borrower, the lender uses data transmitted from the RFID tracking device to monitor the item, to be assured of its location and security and optionally to compile an inventory of borrowed items. Whilst the item is in the possession of the borrower, the borrower may pay an interest payment to the lender agreed between the borrower and the lender and derived from the monetary value of the item. The borrower may sell the borrowed item to a third party for a price and pay the lender a sum agreed between the borrower and the lender and derived from a monetary value of the item when it is sold.
Owner:THE JEWELRY STORE
Vending machine with elevator delivery of vended product to customer access
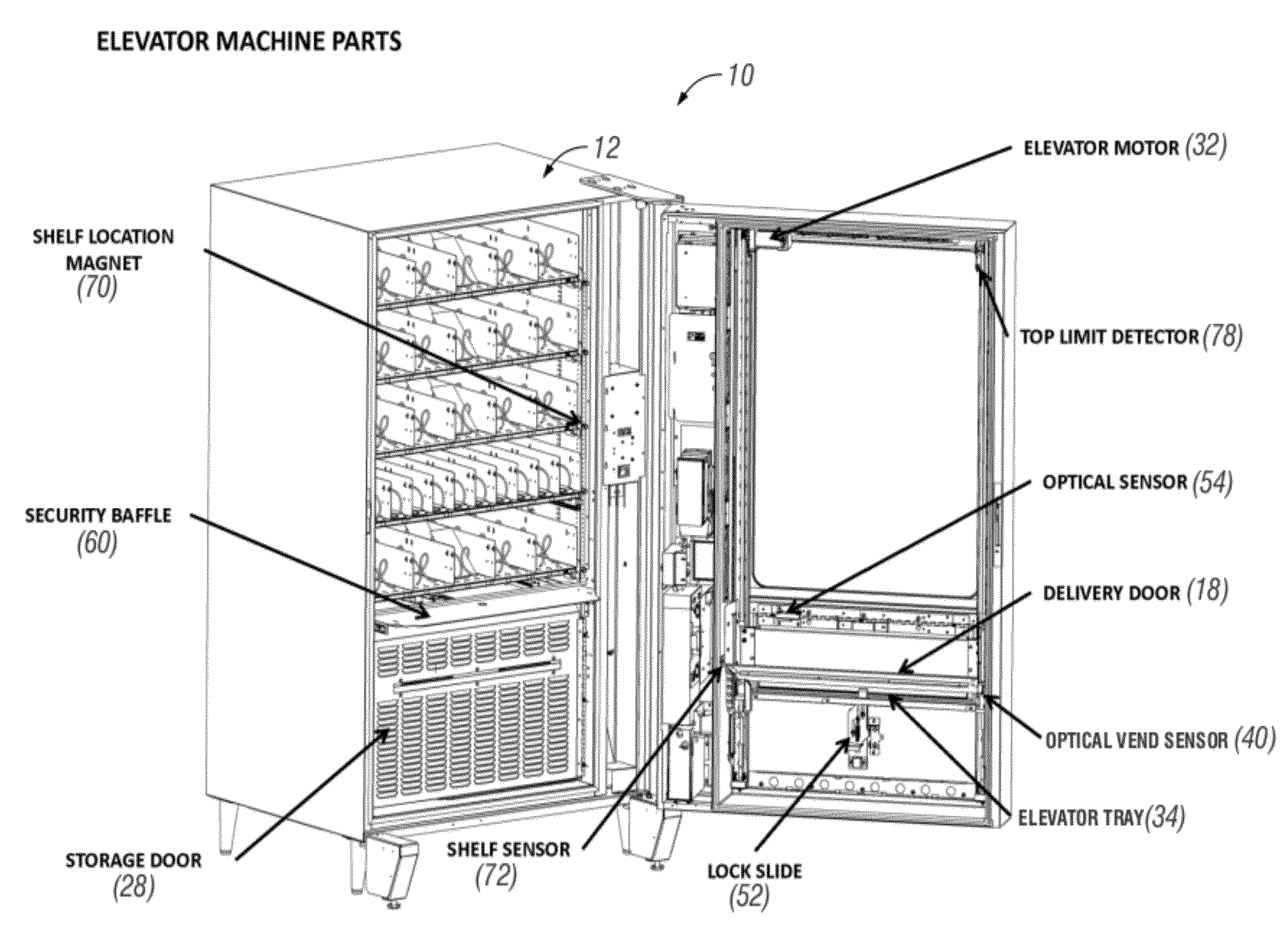
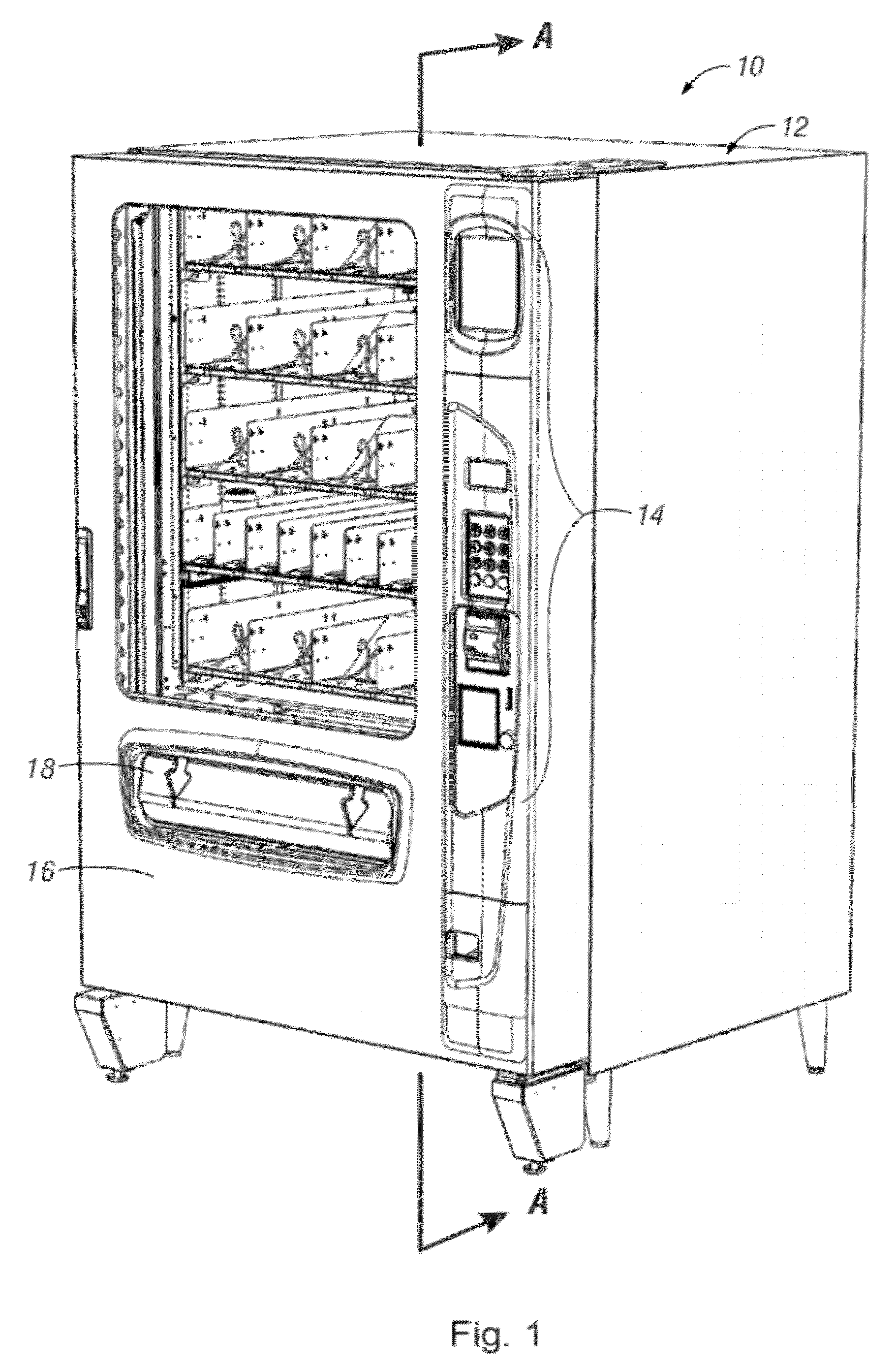
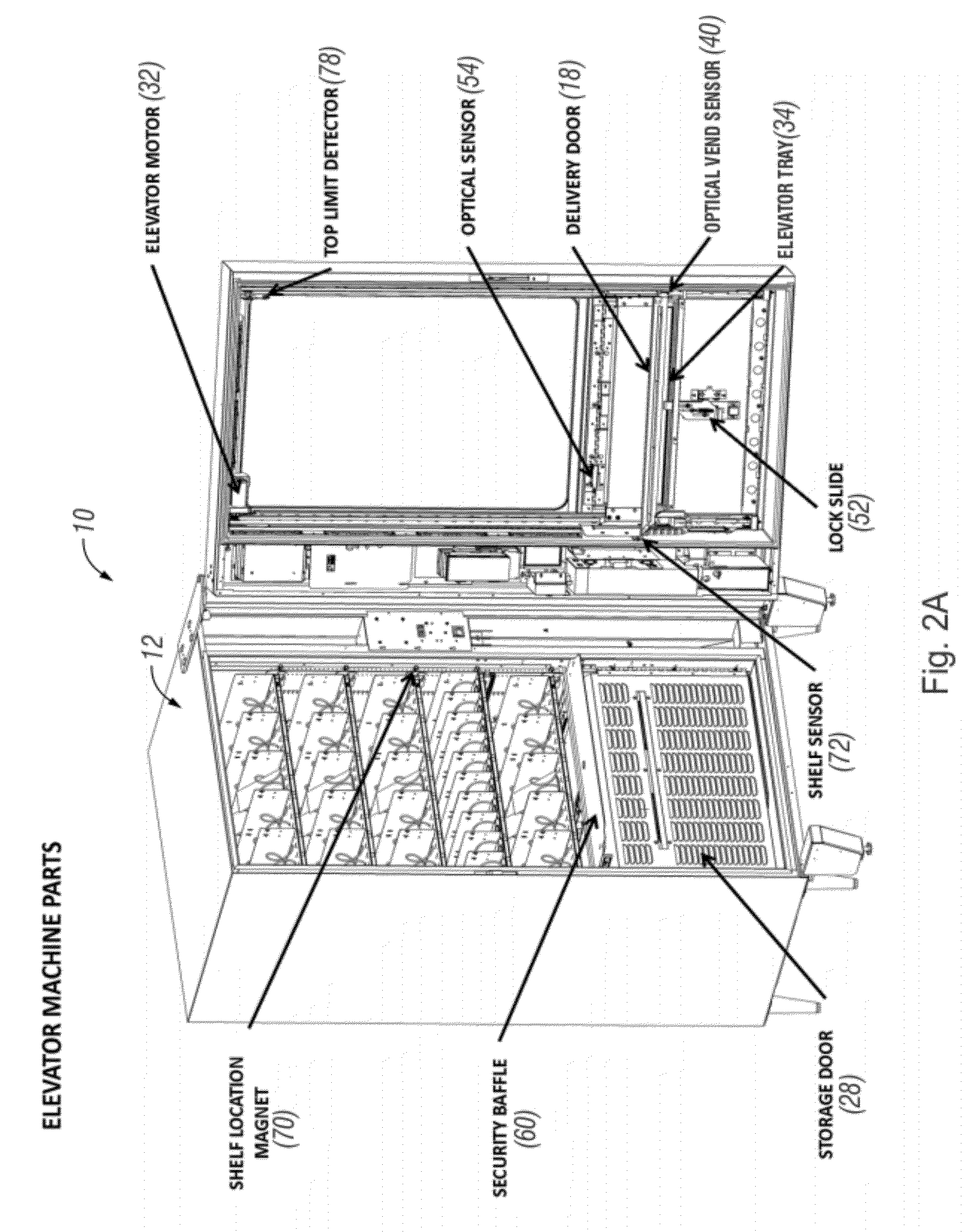
ActiveUS20120277904A1Easy accessImprove securityRacksDispensing apparatusEngineeringMechanical engineering
An automated vending or merchandizing machine includes an elevator sub-assembly which moves a dispensing bin or elevator tray vertically along the fronts of plural vertical levels of product dispensers in the vending machine. A controller tracks the vertical position of the elevator tray. This allows the controller to send the elevator tray to the vertical level of the dispenser of the product selected by a customer, at that level receive and confirm dispensing of the selected product into the elevator tray, and return the elevator tray holding the dispensed product down to a customer delivery or access door or opening in the vending machine that can below the vertical levels of dispensers. Features can include coordination of locking and unlocking of a customer access door and actuating an anti-cheat security baffle with the position of the elevator tray.
Owner:FAWN ENG
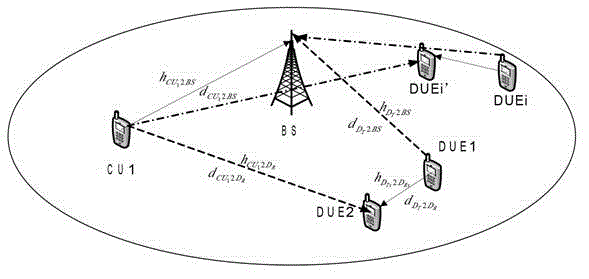
Cross layer design method of up resources of shared system by terminal direction connection technology
ActiveCN102883451AImprove resource utilizationImprove effectivenessWireless communicationPhysical layerHoneycomb
The invention relates to a cross layer design method of up resources of a shared system by the terminal direction connection technology. The method is used for conducting combined scheduling and optimization distribution on frequency, time, space and power resource by combining base stations, a D2D communication end physical layer, a link layer and a network layer. The method includes allowing D2D users to adopt the mode of simultaneously coordinating interference of the D2D client to a base state and interference of honeycomb users to the D2D client when the D2D users share up link resources of a honeycomb system to keep normal communication of a traditional user link and obtain effective gain brought by the D2D direction connection technology, and conducting cross layer resource distribution mode on the resources through the link self-adapting method. The cross layer design method is specifically applied to the following three scenes: 1) a single D2D communication pair and the honeycomb users coexist in a housing estate; 2) a plurality of D2D communication pairs and the honeycomb users coexist in the housing estate; and 3) a single D2D communication pair and the honeycomb users coexist between housing estates.
Owner:NANJING UNIV OF POSTS & TELECOMM
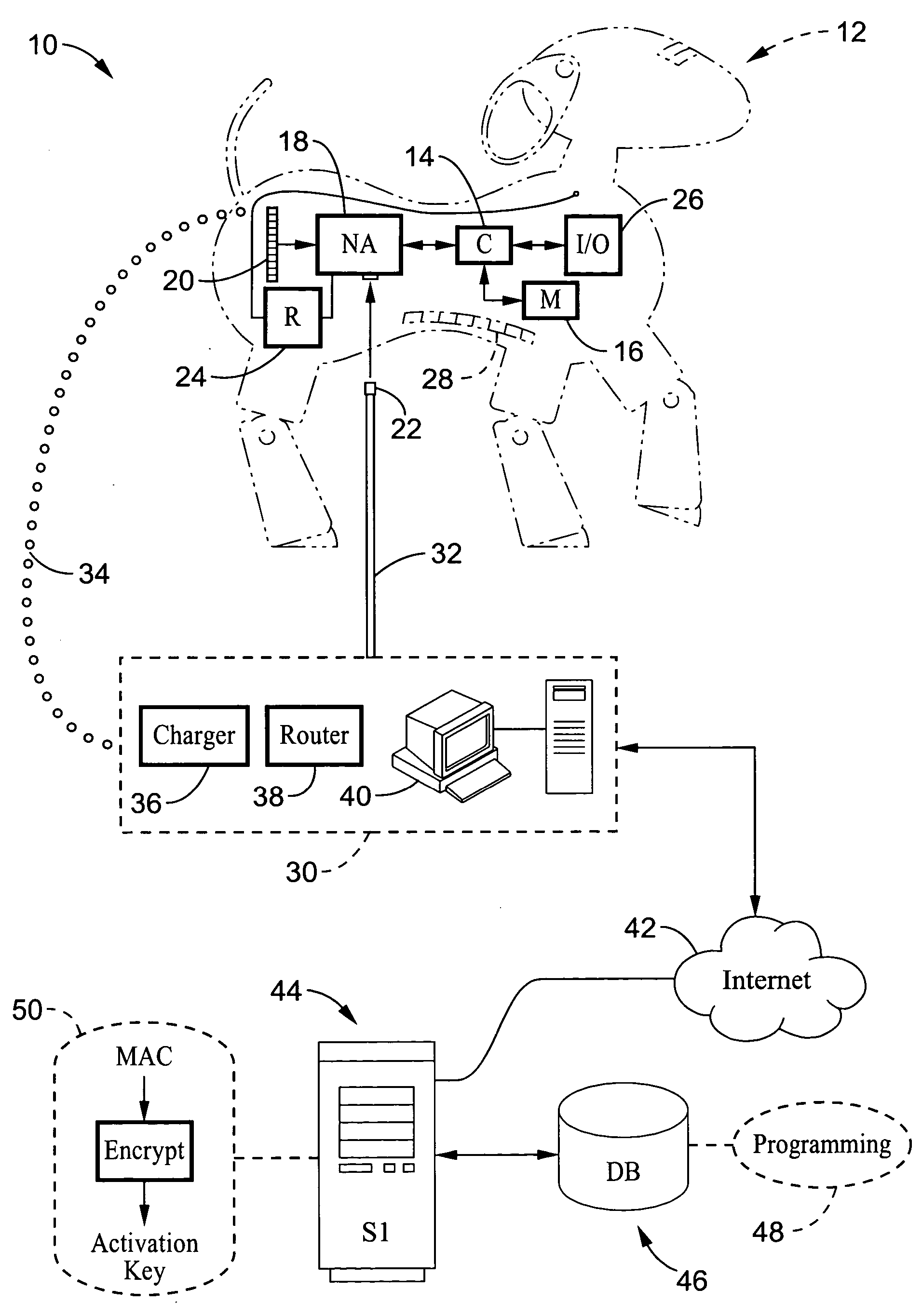
System and method of utilizing a MAC address based unlocking key
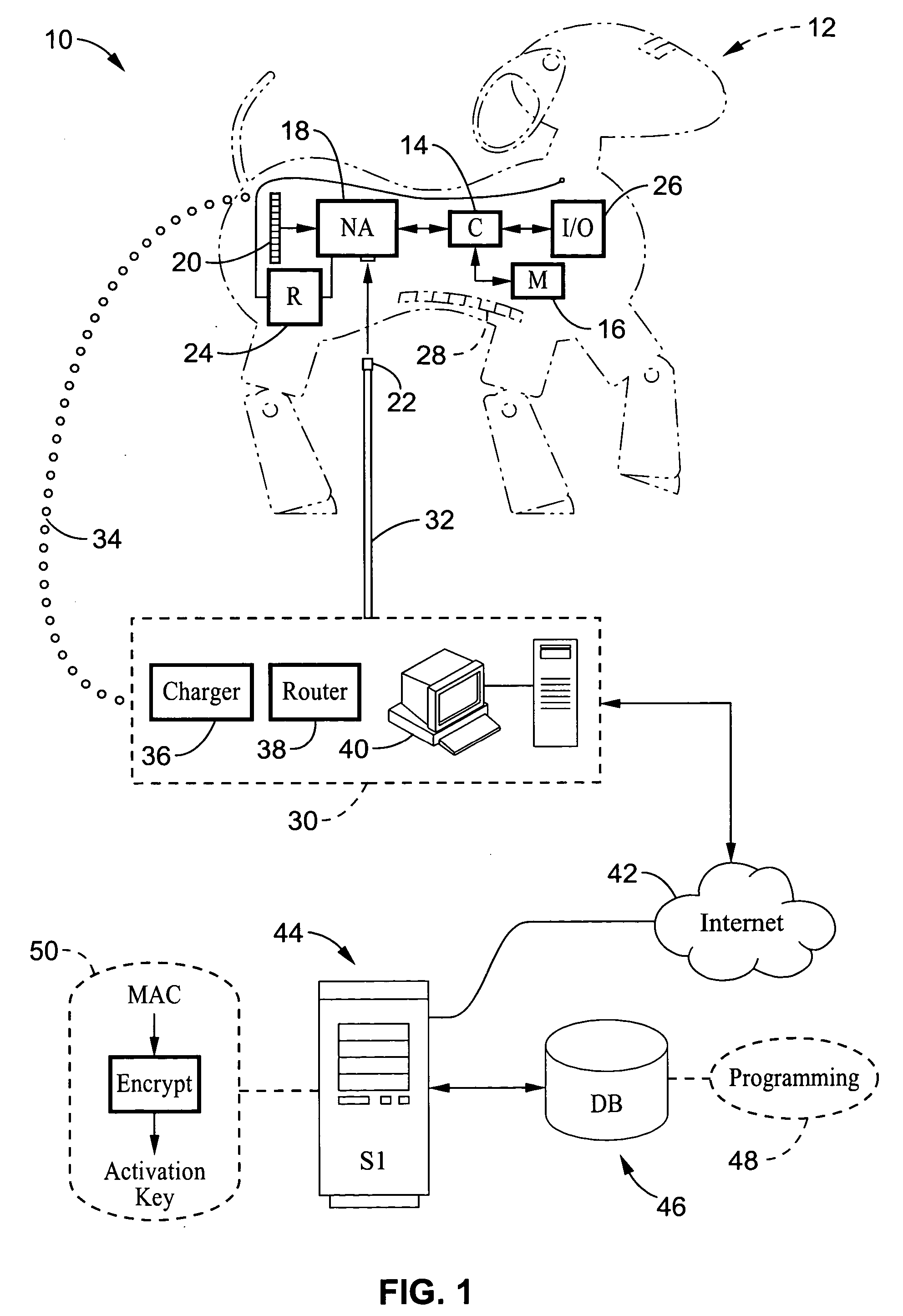
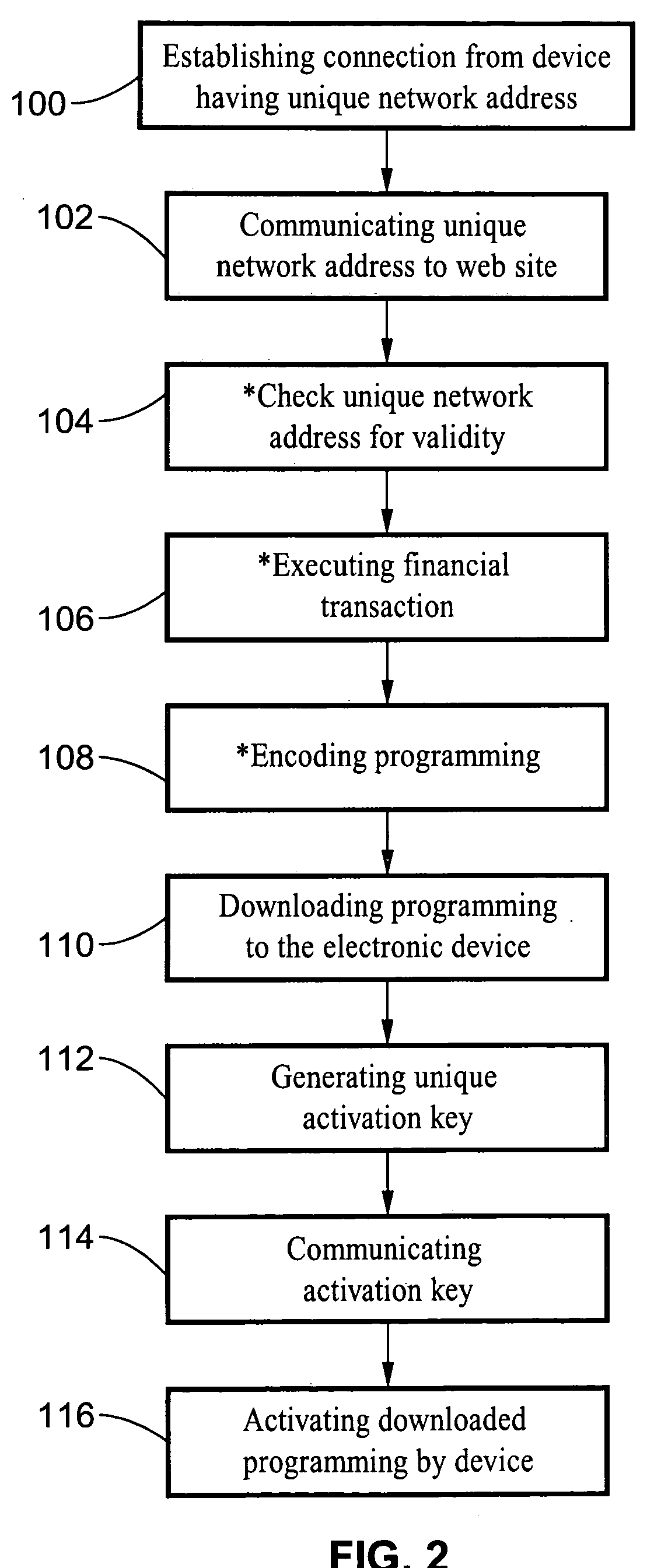
InactiveUS20060080464A1Inhibitory contentPrevent copyingComputer security arrangementsMultiple digital computer combinationsFinancial transactionNetwork address
A system and method are described for activating programming downloaded to electronic devices. The method involves the generation of an encrypted (or encoded) activation key which is produced in response to the network address (i.e. media access control (MAC) address) of the electronic device to which the download is directed. Programming can only be activated within the electronic device upon a match being detected between the activation key and the network address of the electronic device. Typically, the programming would be downloaded from a web site, such as from a manufacturer of the electronic device, in exchange for receipt of a payment preferably executed as an online financial transaction. The system and method prevent the copying of downloaded programs for a given electronic device for use by other users.
Owner:SONY CORP +1
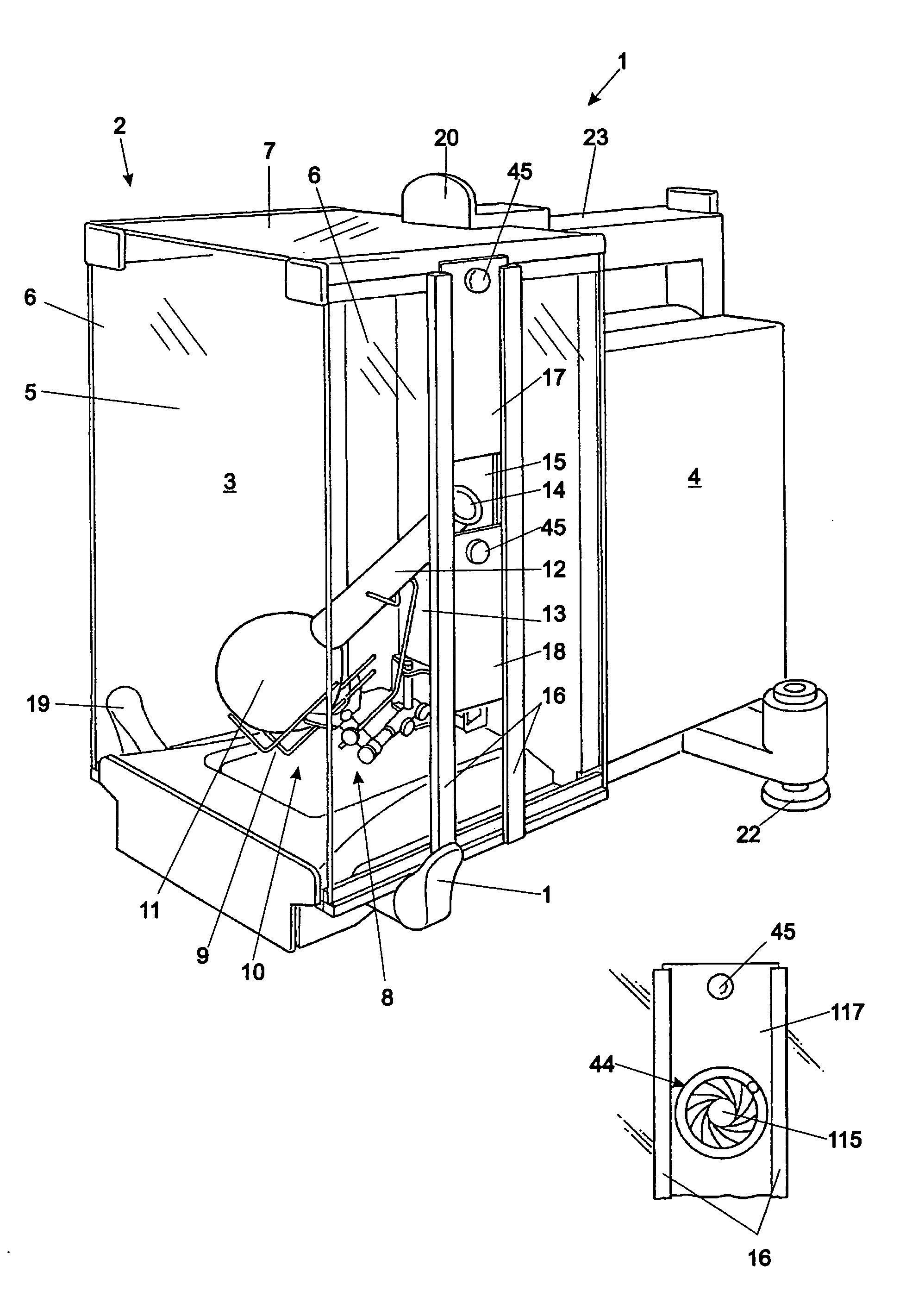
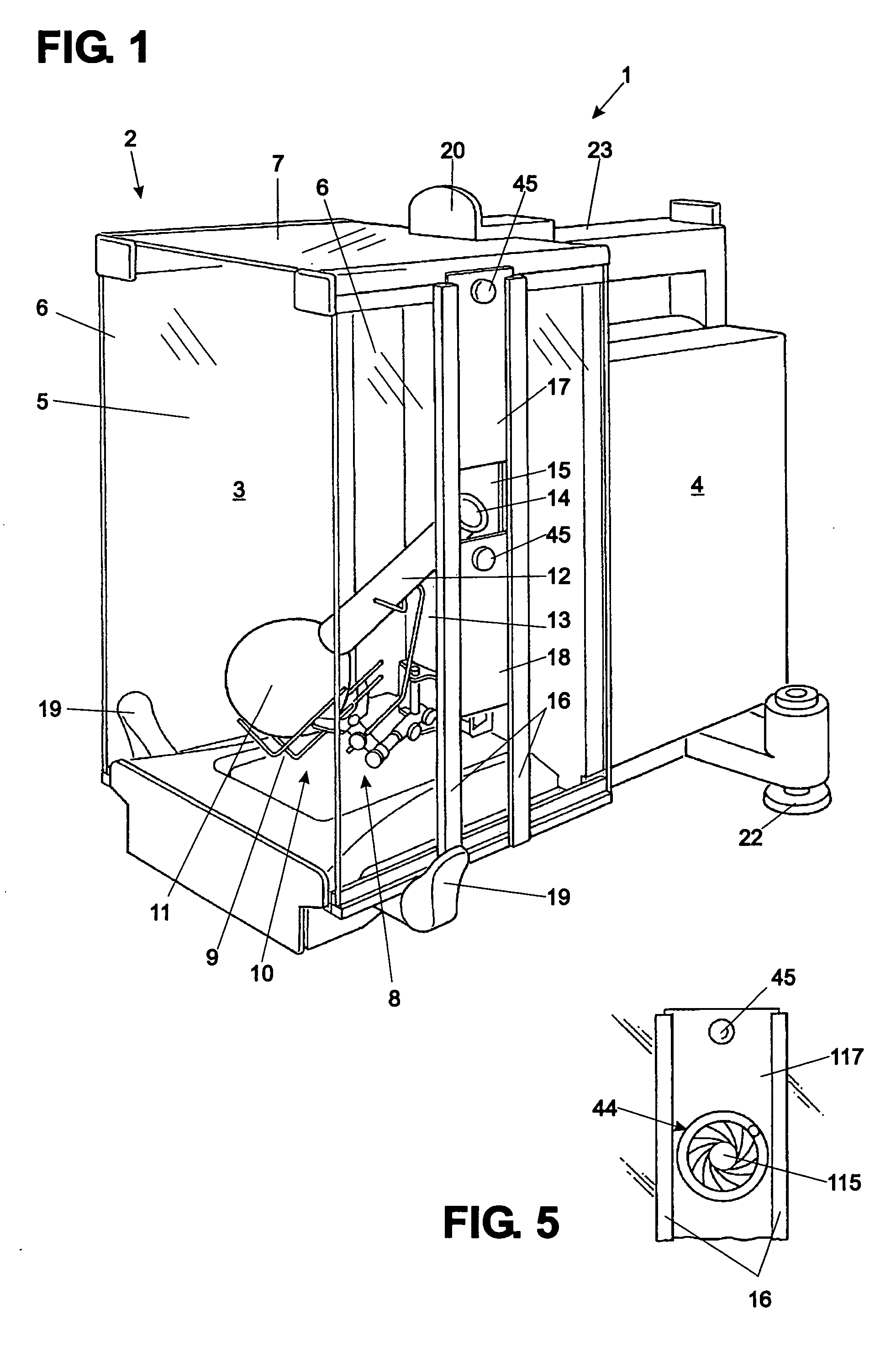
Balance with a draft shield
ActiveUS7227088B2Stable conditionEasy to measureShow cabinetsFurniture partsEngineeringMechanical engineering
Owner:METTLER TOLEDO GMBH
Al-Fe-Cu alloy material and preparation method thereof
The invention particularly relates to an Al-Fe-Cu alloy material and a preparation method thereof. The Al-Fe-Cu alloy material comprises the following components in percentage by weight: 0.20-1.30 wt% of Fe, 0.01-0.08 wt% of Cu, 0.06-0.15 wt% of Si, 0.02-0.10 wt% of rare-earth element and the balance of Al and unavoidable impurities. The aluminum alloy is prepared by casting and semi-annealing raw materials. When the aluminum alloy is prepared, the alloy material is semi-annealed, and thus, the adverse effects of stress on a conductor structure in the process of drawing and twisting are reduced, the electric conductivity reaches and even exceeds 61% of IACS (International Annealed Copper Standard) (the electric conductivity standard of an aluminum conductor for a general electrician is 61% of IACS), and the performances of elongation and the flexibility of the aluminum alloy are improved greatly by annealing. The performances of the elongation of a cable made of the aluminum alloy wire can reach 30%, the flexibility is 25% higher than that of a copper cable, and the resistivity maintains in a lower level.
Owner:安徽省惠尔电气有限公司
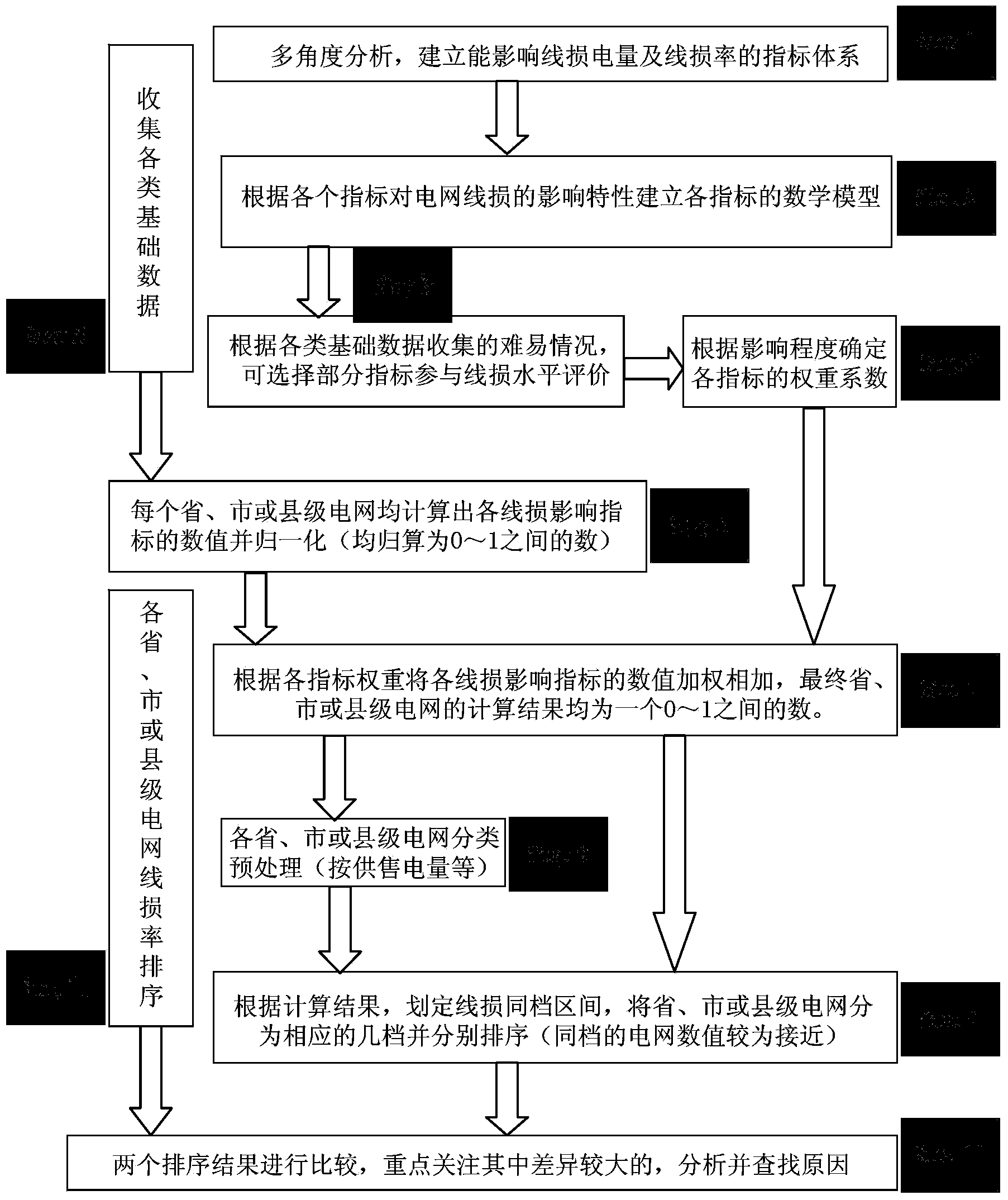
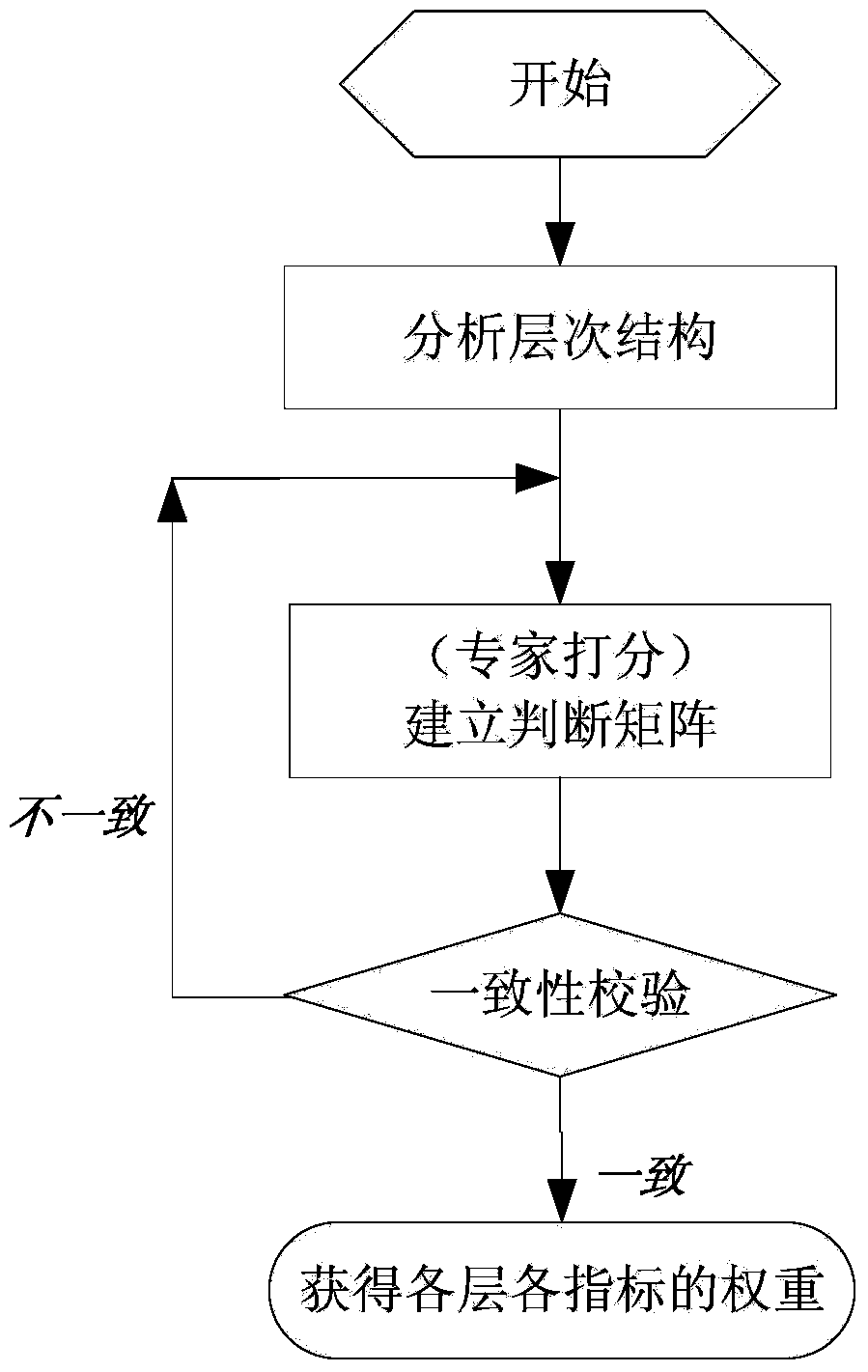
Line loss level evaluation method based on power grid characteristic difference
ActiveCN103942727AGuaranteed growthResourcesSystems intergating technologiesSingle indicatorNetwork structure
The invention relates to a line loss level evaluation method based on power grid characteristic difference. According to the method, line loss influence integrated factors such as the natural condition, the network structure, the power utilization structure and the power grid operating characteristics of each province or city or county are led in, an original single index only with the line loss rate numerical value size taken into account is changed into an index system which is composed of various indexes affecting line loss, considering the impact of all the indexes on the line loss rate, different weights are set, comprehensive calculation, analysis and evaluation are conducted, so that a scientific index system and evaluation criterion is established, and thus the advancement of the power grid line loss level evaluation method can be guaranteed. According to the line loss level evaluation method based on power grid characteristic difference, the traditional method that the line loss rate size is purely used for evaluating the line loss level before can be broken through, the quantitative evaluation method of the line loss level of a power grid at the same level is provided, the loss reduction potentiality of the power grid is exploited to the maximum degree, and thus the line loss management level of the power grid is improved.
Owner:STATE GRID CORP OF CHINA +2
Power distribution net box type transformer environmental parameters on-line monitoring system
ActiveCN103107597AReal-time online security monitoringSolve the problem of power supplyCircuit arrangementsInformation technology support systemTransformerData acquisition
The invention relates to a power distribution net box type transformer environmental parameters on-line monitoring system which includes the steps that aiming at any one of box-type transformer substations, the power distribution net box type transformer environmental parameters on-line monitoring system is provided with a plurality of sensors, wherein at least the temperature of a high pressure charged body in the environmental parameters of the box-type transformer substations, the high frequency partial discharge, the temperature and humidity in the box-type substation are monitored correspondingly by the sensors, and the monitored data of the various sensors are received and sent to a front-end data acquisition unit of a monitoring center based on a wired or wireless communication mode. The data processing server device of the monitoring center carries out the storage and processing analysis for the received data to generate a real-time dynamic monitoring curve and produces an audible and visual alarm when the monitored data exceed a set threshold value, and meanwhile the alarm information can notify attendants in the relevant areas in a text message form, so that the time of incident response is shortened and the economic loss is reduced.
Owner:SHANGHAI OUYI INTELLIGENT NETWORK +3
Method for tracking ground station through low earth orbit space-borne antenna
ActiveCN104332707AImprove forecast accuracyImprove on-orbit pointing accuracyAntennasNatural satelliteLow earth orbit
The invention provides a method for tracking a ground station through a low earth orbit space-borne antenna. The method comprises the following steps: 1) calculating UTC at the next pointing moment of the antenna; 2) calculating the number of transient satellite orbit at the next pointing moment of the antenna; 3) calculating the position of the satellite under a J2000 inertial coordinate system; 4) calculating the position of the ground station under the J2000 inertial coordinate system at the next pointing moment of the antenna; 5) calculating the opposite position vectors of the satellite and the ground station under the J2000 inertial coordinate system; 6) calculating the vector of the opposite position vectors of the satellite and the ground station under geo-center camber line; 7) calculating the vector of the opposite position vectors of the satellite and the ground station under the satellite orbit coordinate system; 8) calculating the vector of the opposite position vectors of the satellite and the ground station under a satellite body system; 9) calculating the vector of the opposite position vectors of the satellite and the ground station under an antenna coordinate system; 10) obtaining an antenna pointing angle, and driving the antenna to perform pointing tracking for the ground station.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
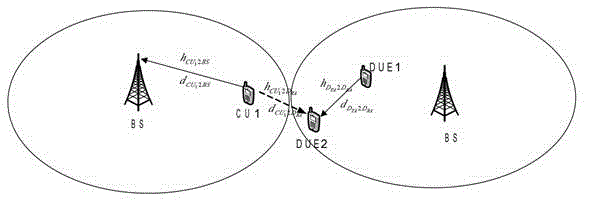
Cross-layer design method for downlink resources in D2D (device-to-device) technology sharing system
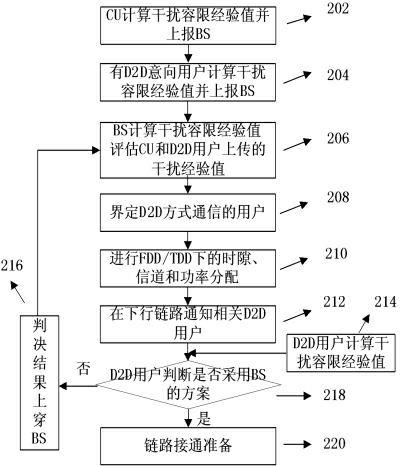
ActiveCN103024914AImprove resource utilizationImprove effectivenessWireless communicationCross layerWireless resources
The invention relates to a cross-layer design method for downlink resources in D2D (device-to-device) technology sharing system, in particular to a method and an algorithm for allocation and scheduling cross-layer resources in downlink resources of a cellular subscriber multiplexing cellular system with D2D terminals in an IMT-Advanced (international mobile telecommunications-advanced) system. A considered system model comprises an intra-cell application scenario and an inter-cell application scenario. D2D subscribers existing in a wireless cellular network system in the form of self-organization and cellular network subscribers co-exist in the form of underlay and share the same downlink radio resources (including channels, timeslot, power and space). Allocation and scheduling on the resources are discussed to solve the problems of interference coordination and suppression. The intra-cell application scenario and the inter-cell application scenario are considered respectively, common features of the different application scenarios are found, and personality factors of the different application scenarios are also considered. For characteristics of a D2D and cellular network system, the defects in existing resource allocation schemes are overcome and the resource-based cross-layer optimization, allocation and scheduling method is provided.
Owner:NANJING UNIV OF POSTS & TELECOMM
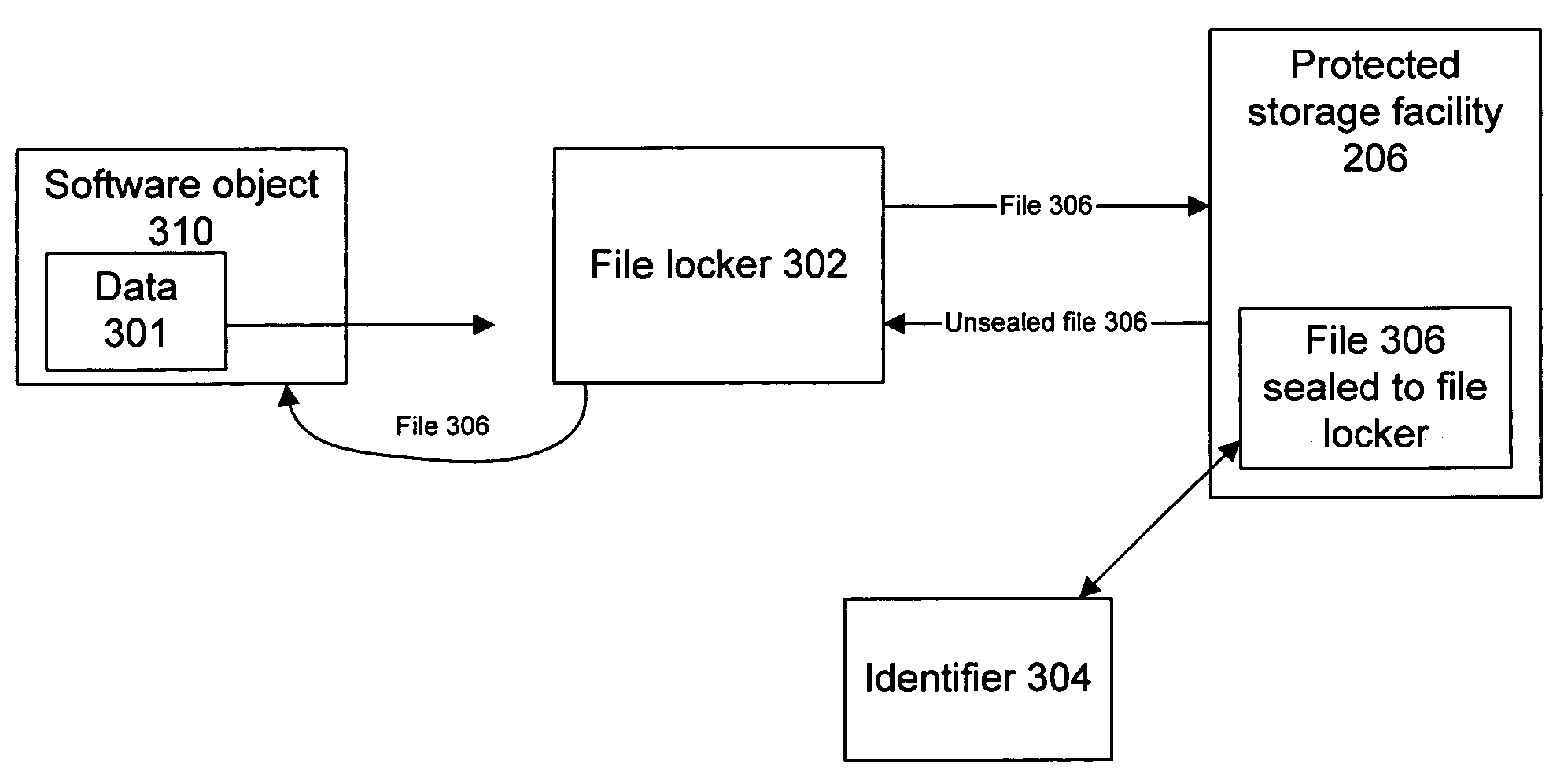
Fire locker and mechanisms for providing and using same
InactiveUS20050257048A1Low assuranceGuaranteed growthFlow mixersTransportation and packagingTrustworthinessSoftware
A file locker manages the storage and use of protected data for software objects. A protected environment maintains the cryptographic and isolative infrastructure to support sealing of data items for use by a trusted agent. The file locker uses the protected environment's sealing functionality to seal data items for the file locker's exclusive access. The file locker seals, to itself, files received from software objects, and provides those files upon request, and upon sufficient proof of the requestor's trustworthiness, authenticity, and / or identity. The file locker may be used to extend the protected environment's sealing functionality to legacy applications, without the legacy applications having to implement agents that can run in the protected environment and access the sealing functionality directly.
Owner:MICROSOFT TECH LICENSING LLC
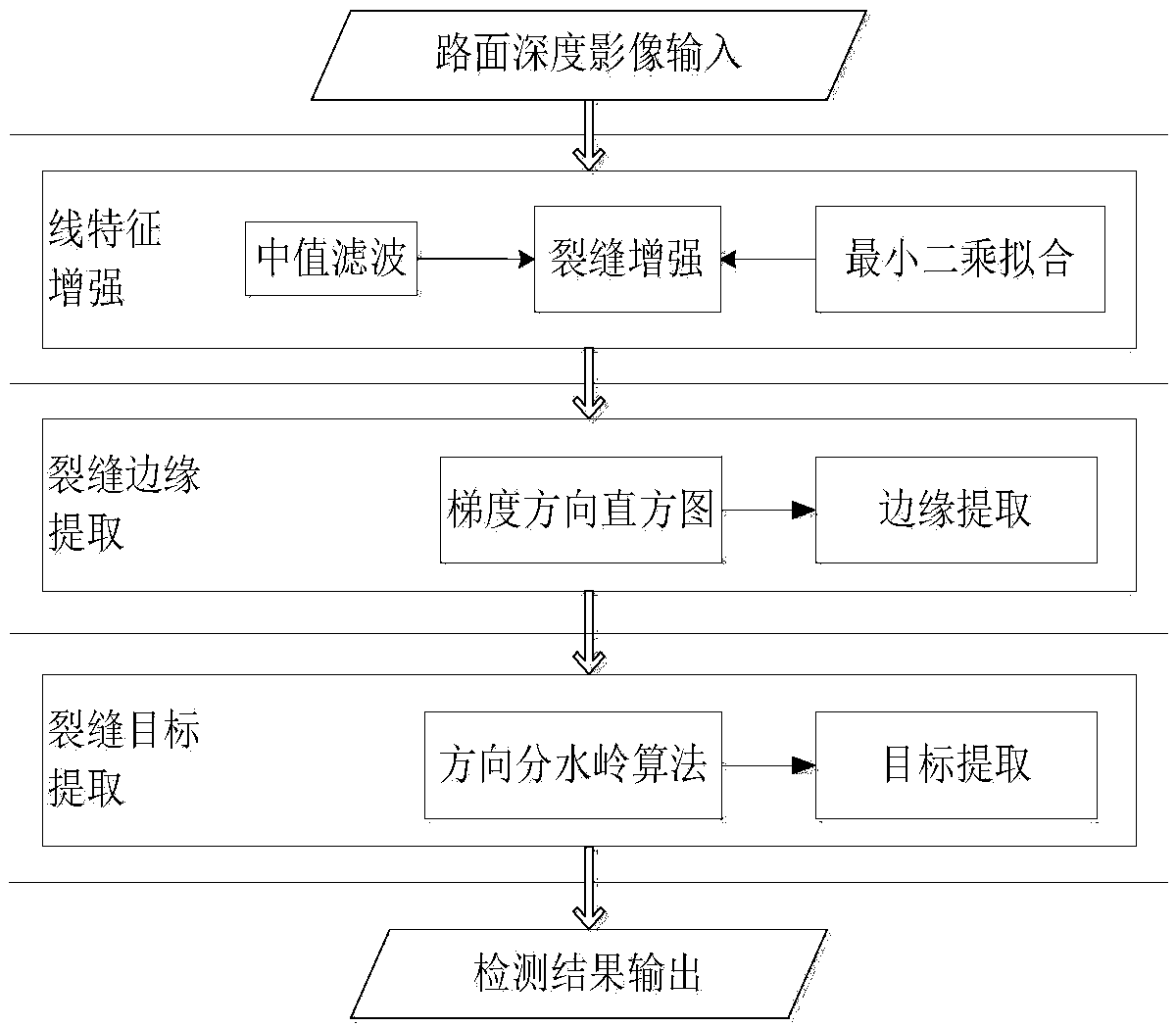
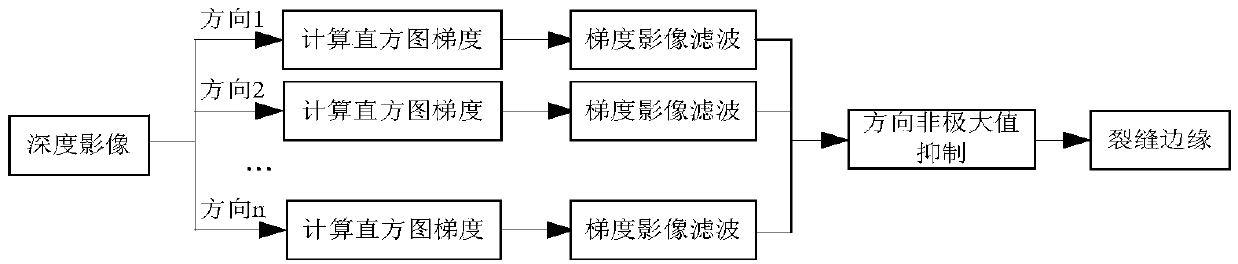
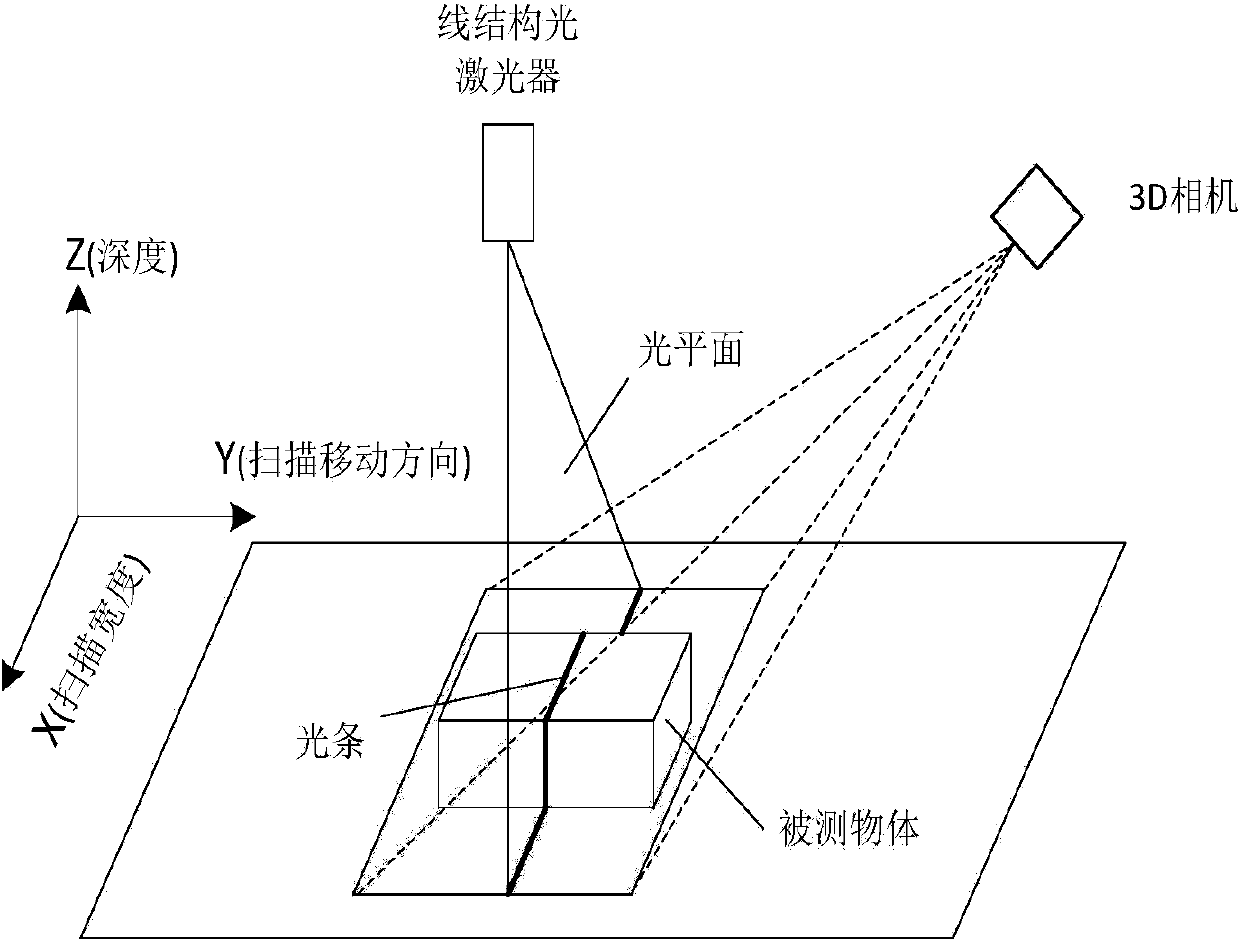
Crack detection method with image gradient direction histogram and watershed method conflated
ActiveCN104008553AGuaranteed growthSolve the puzzle of closure as a region targetImage enhancementImage analysis3d cameraImage gradient
The invention discloses a crack detection method with an image gradient direction histogram and watershed method conflated. The method includes the following steps that 1, the surface to be detected is illuminated by a light source of line structured light, light bar images of the surface to be measured is filmed through a 3D camera, the depth of each pixel point of the surface to be detected is obtained, the depth data are converted into grey level data, and a depth image of the surface to be detected is formed; 2, the gradients of the depth image in eight directions are worked out, and the gradient image of the surface to be detected is obtained; 3, the direction non-maximum suppression of the gradient image is worked out, and the edge image of the surface to be detected is obtained; 4, by adoption of watershed conversion, the connected domain of a crack is obtained, the boundaries of the connected domain are marked, and the closed boundaries of the crack are obtained.
Owner:WUHAN WUDA ZOYON SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com