Capacity calling method, capacity calling request device, capacity calling platform and capacity calling system
A technology of invoking requests and capabilities, applied in the transmission system, electrical components, etc., can solve the problems of failing to meet the security requirements of capability development, failing to provide security, etc., to ensure security, improve security, and avoid information leakage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
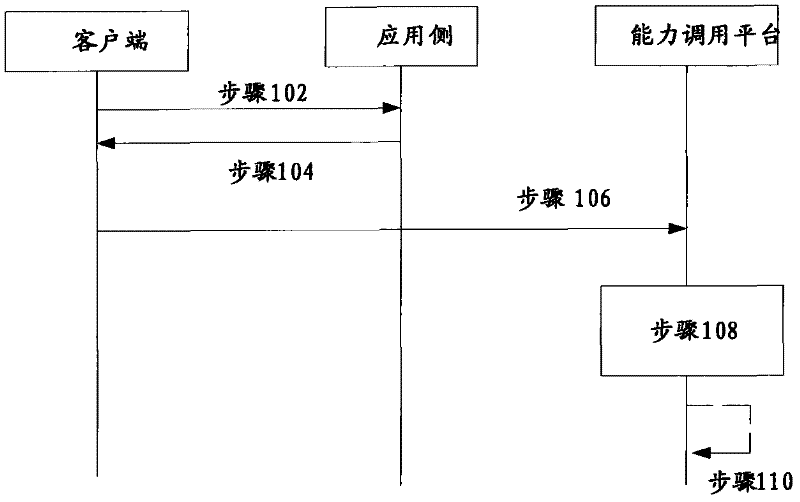
[0018] like figure 1 As shown, the embodiment of the capability call method of the present invention includes the following steps:
[0019] Step 102, the client sends a Token acquisition request to the application side;
[0020] Step 104, the application side generates a Token according to the Token acquisition request, and returns the Token to the client; details are as follows:
[0021] In order to ensure the confidentiality of the Token and avoid its unauthorized use, the Token can be customized during specific operations. The customized algorithm includes the Token generation function on the application side and the Token verification function on the server side (that is, the capability call platform side). And in the process of business use, the internal mechanism of Token is kept secret; the implementation mechanism is divided into five levels from bottom to top:
[0022] a. Standardized algorithm, the bottom layer is implemented by a standardized algorithm, such as th...
Embodiment 2
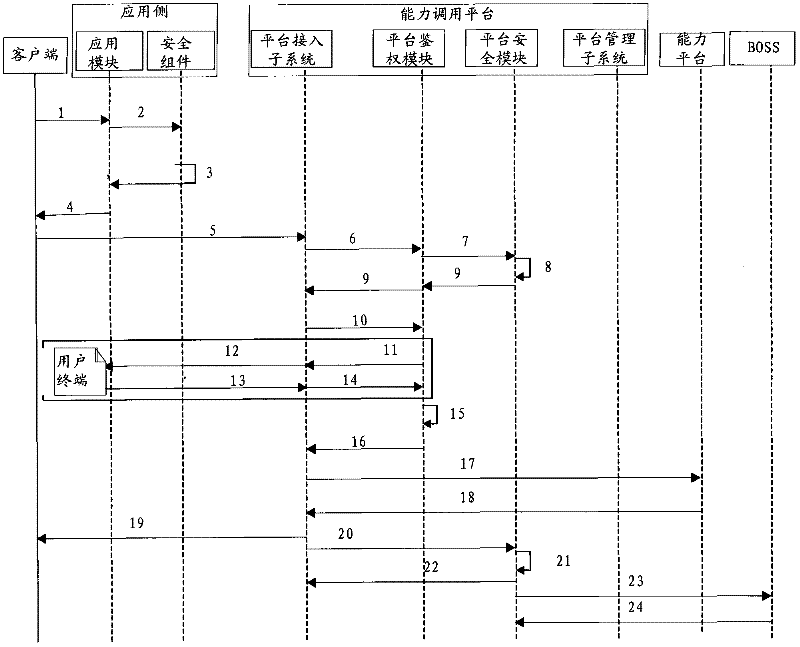
[0049] Such as figure 2 As shown, the detailed process of the capability calling method in this embodiment is as follows:
[0050] 1. The client, such as a web browser, sends a Token acquisition request to the application module on the application side, such as the web application module (the following steps are explained in terms of web applications, and should not be limitedly explained); those skilled in the art can understand, Here are various web applications, such as Ajax web applications;
[0051] 2. The Web application module forwards the request to the Web security component. During specific operations, the Web application module itself can confirm that the user identity is credible before forwarding the request;
[0052] 3. The Web security component generates a WebToken, and returns a response message including the WebToken to the Web application module; during specific operations, the response can also include the application identifier APPID and Counter;
[005...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com