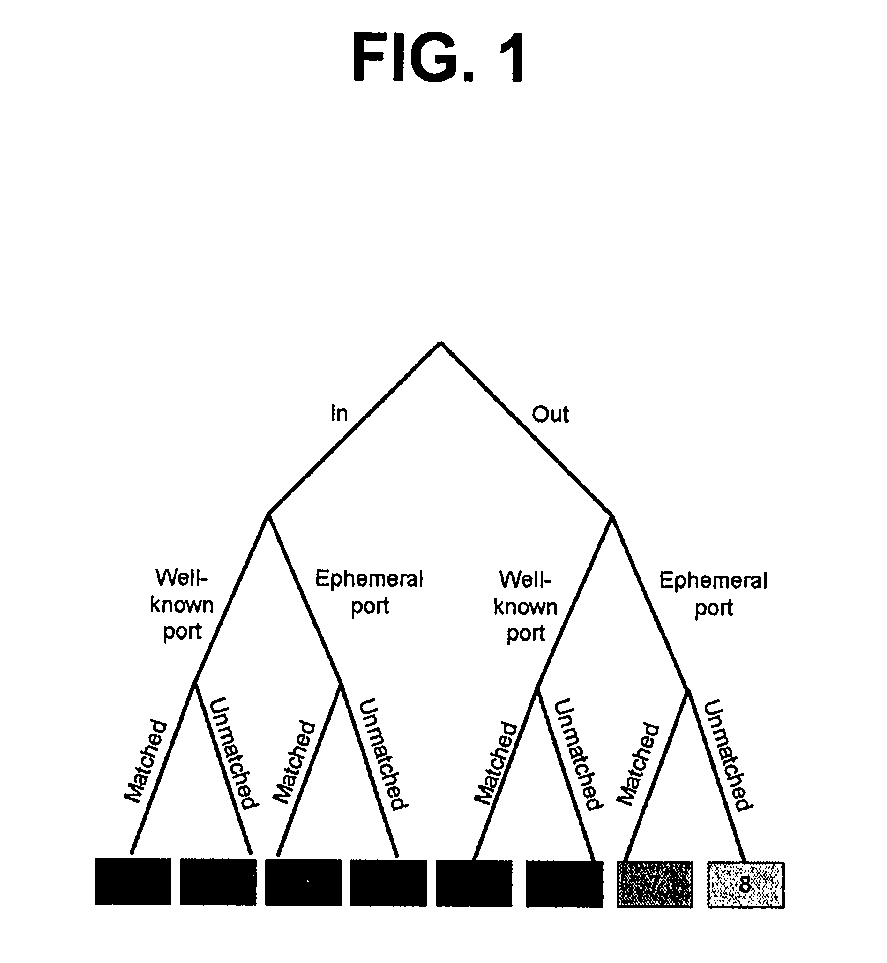
Patents
Literature
175results about How to "Increase safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
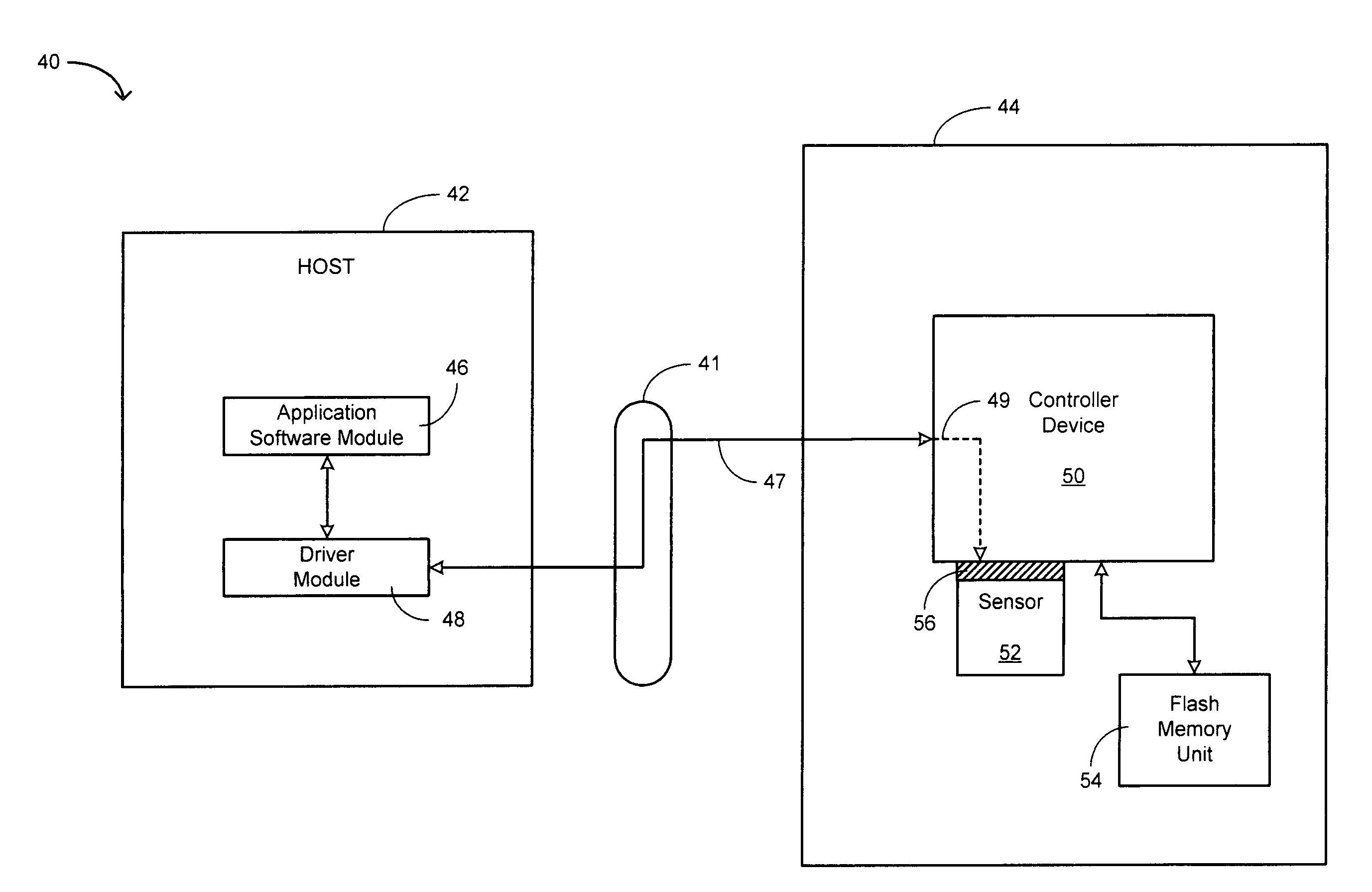
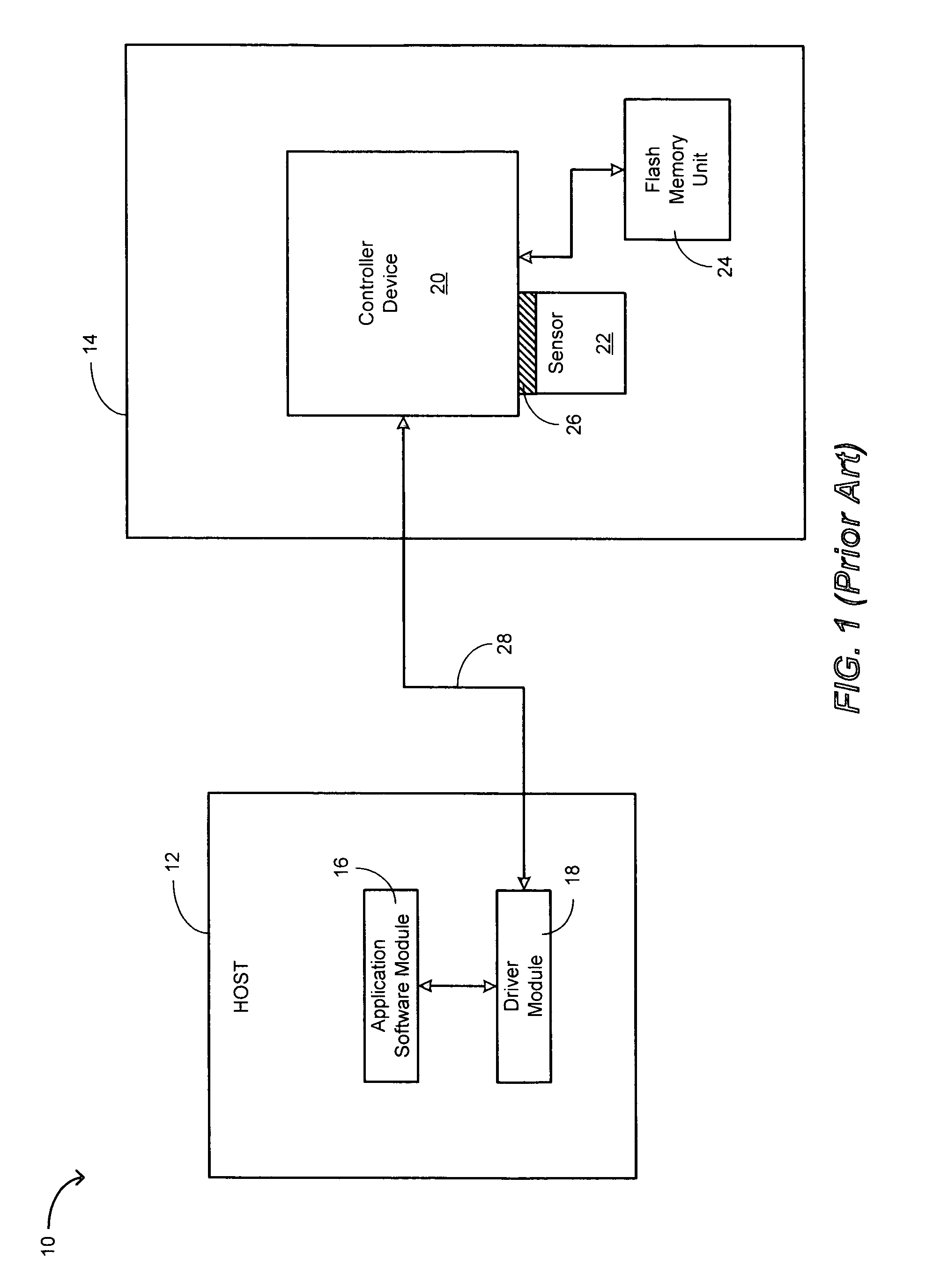
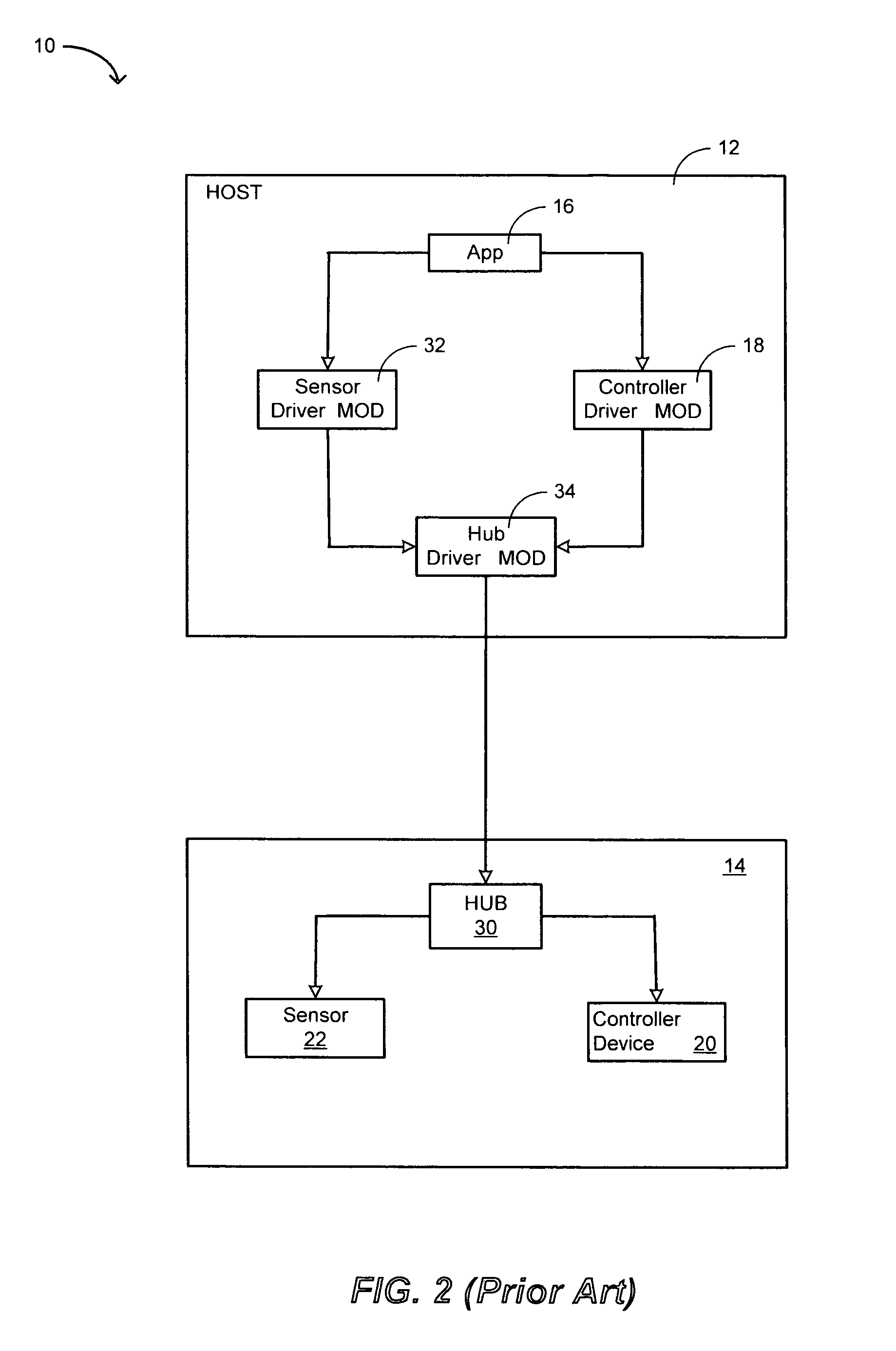
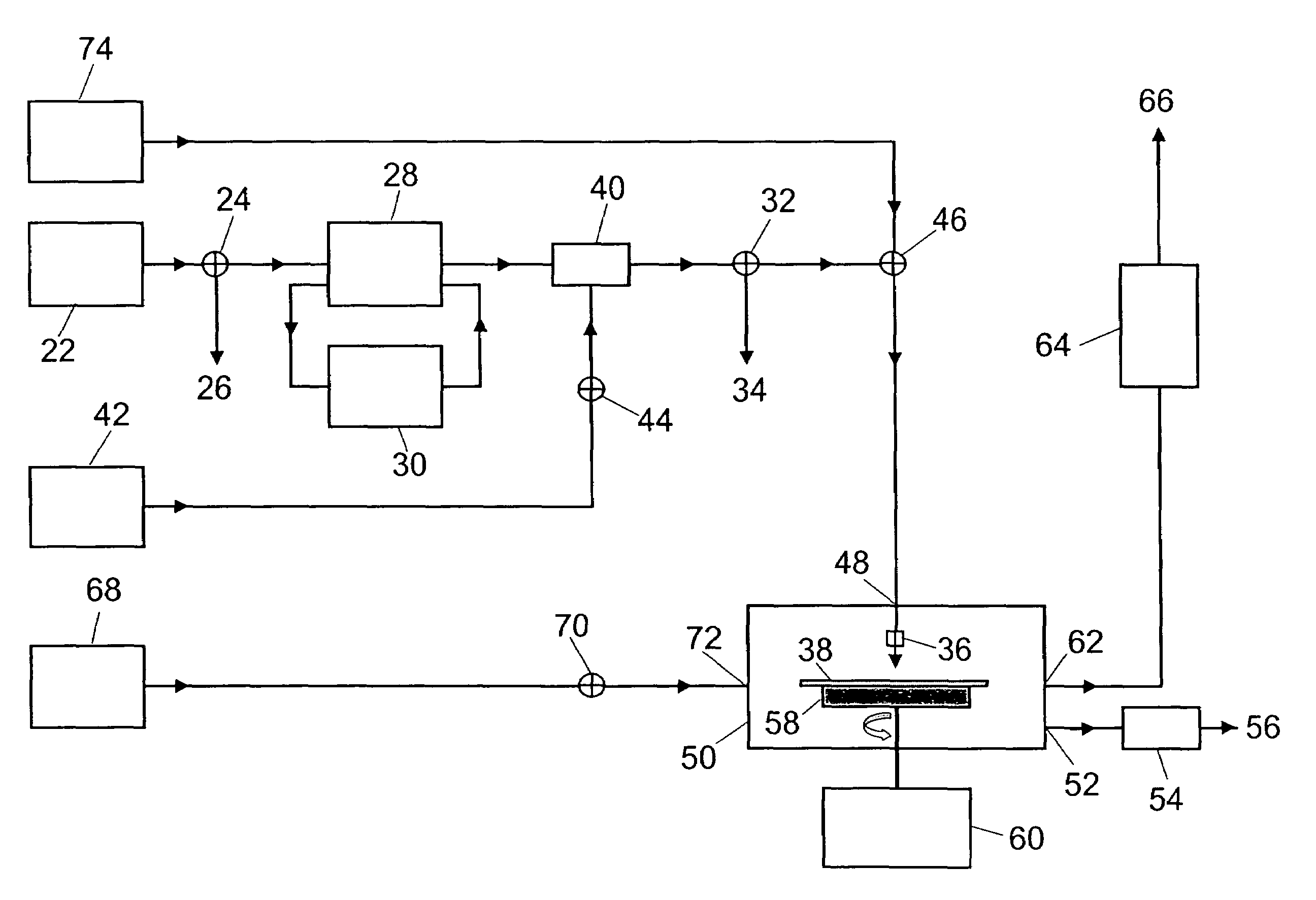
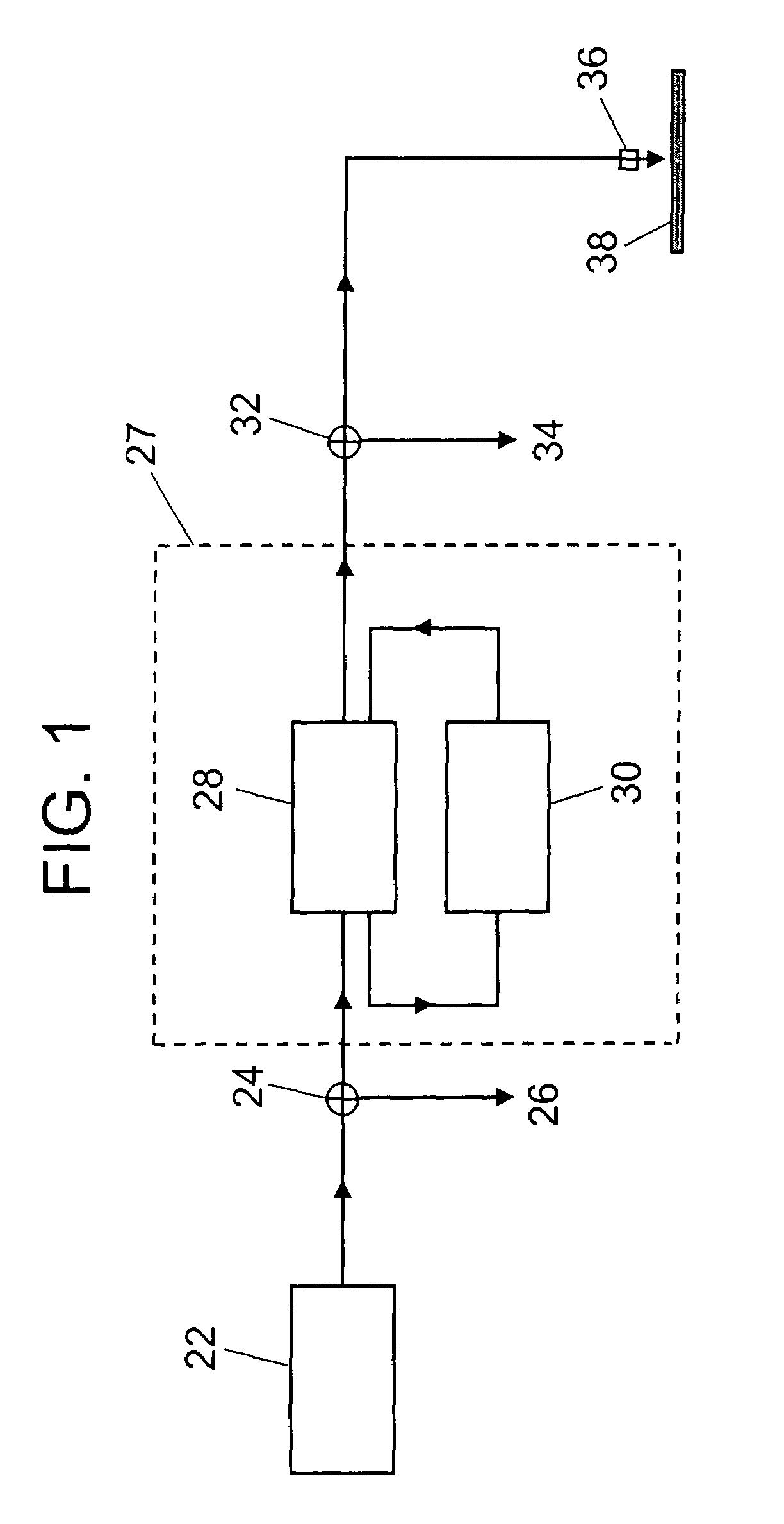
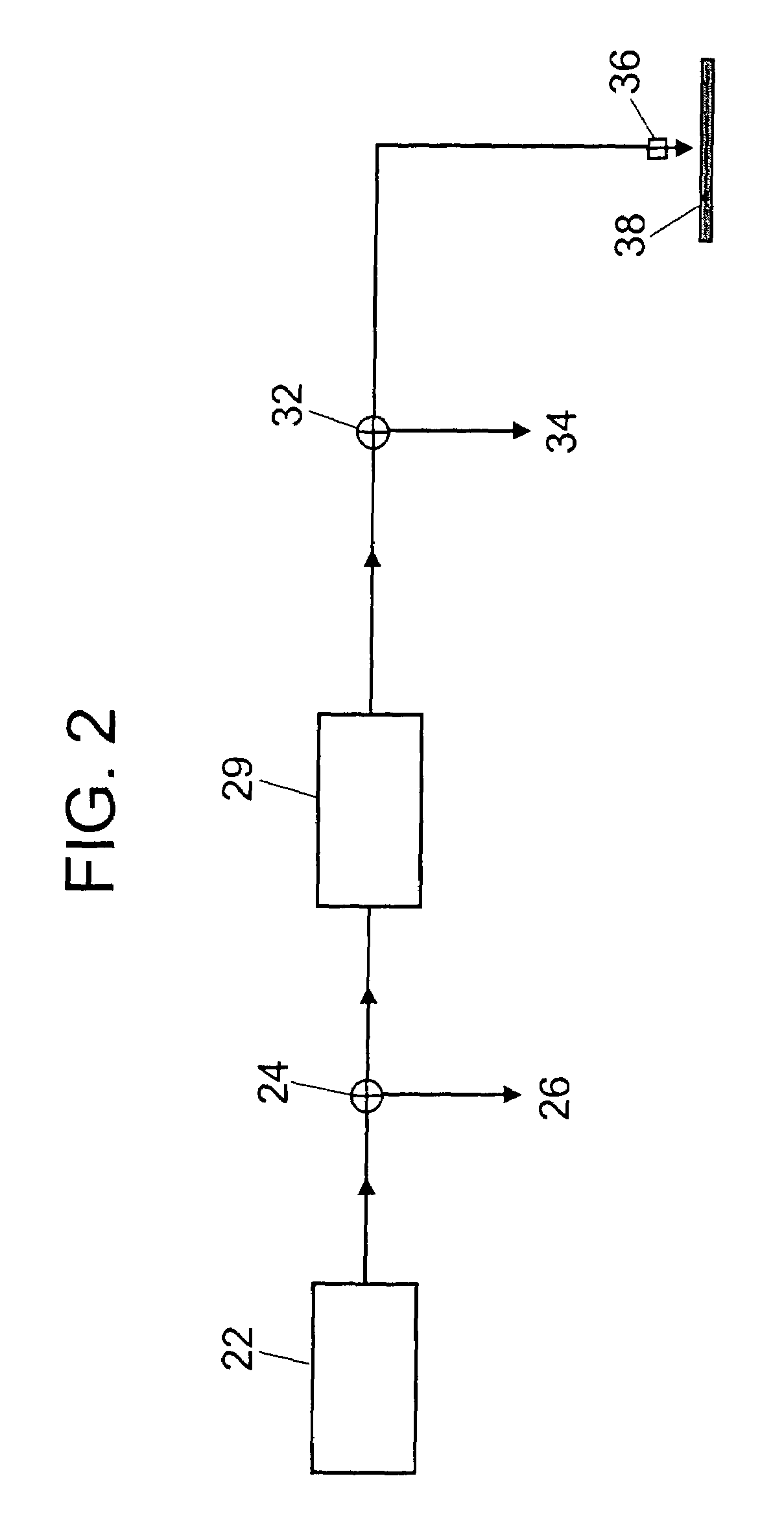
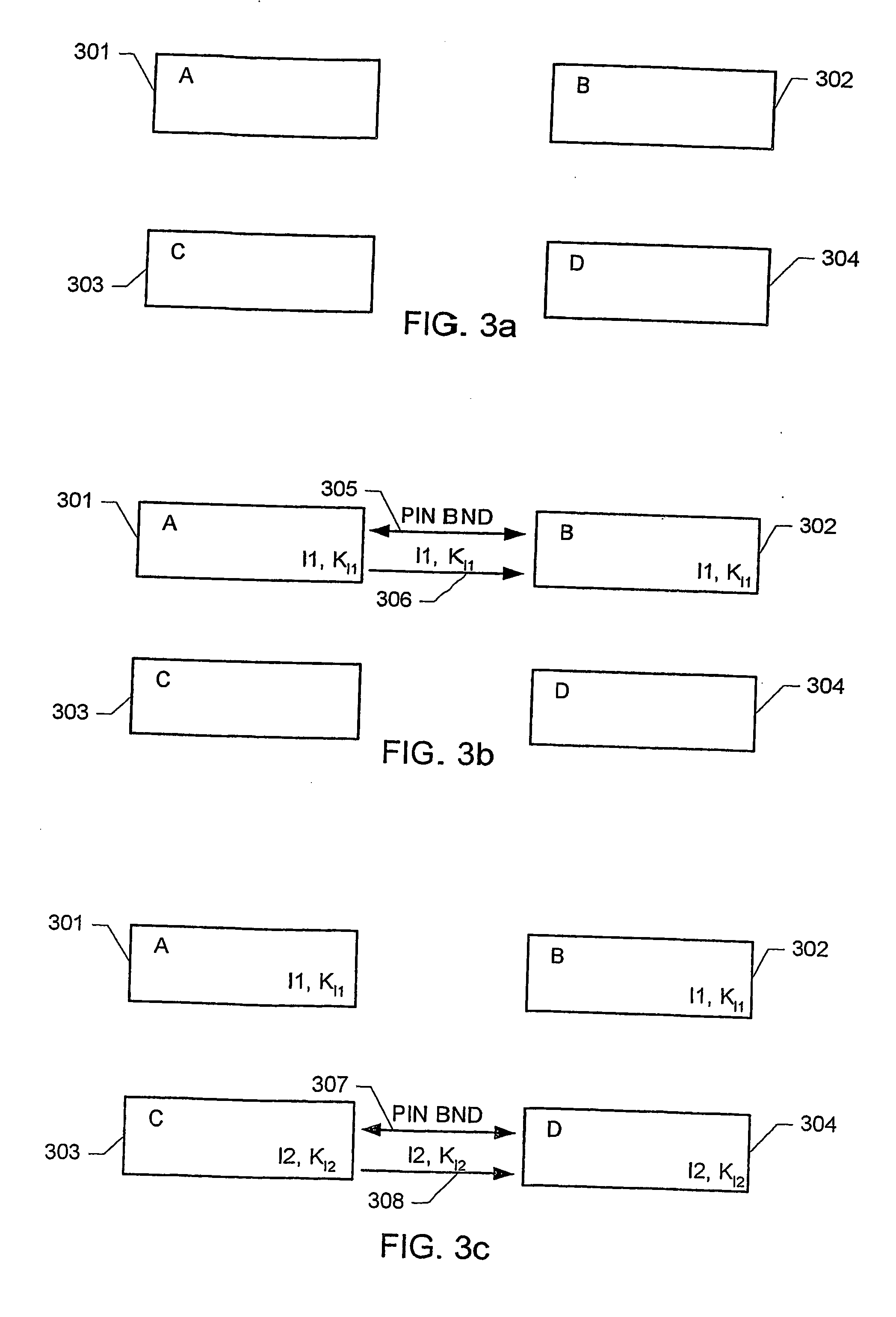
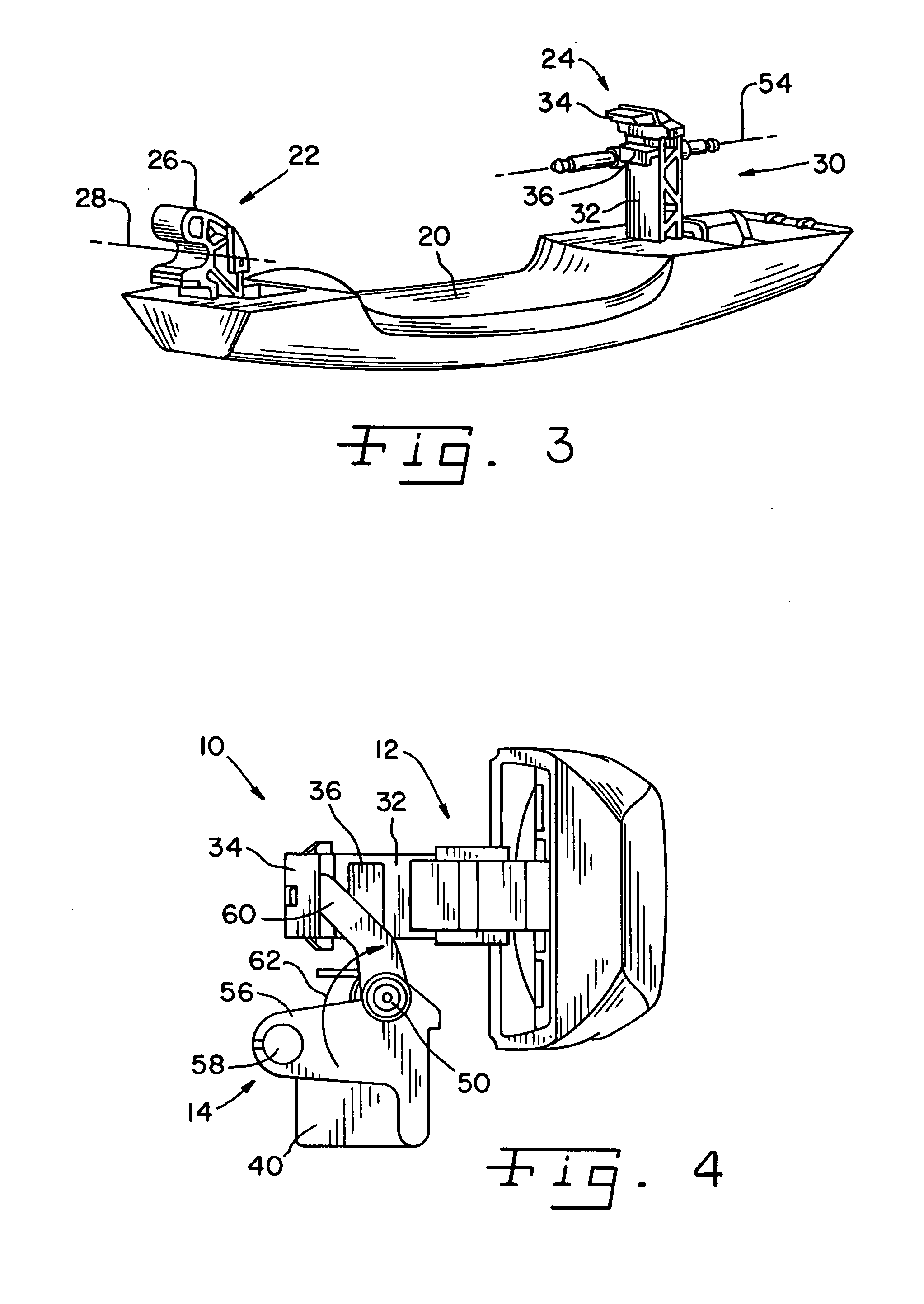
Direct secondary device interface by a host
ActiveUS7725628B1Increase safetyImprove securityInternal/peripheral component protectionDigital data authenticationApplication softwareSoftware modules
A storage system having a storage device in communication with a host and including one or more function devices for communicating with application software modules, in accordance with an embodiment of the present invention. Said application software modules issuing vendor specific commands to access said function devices, said function devices remaining unknown to said host and recognizing said vendor specific commands for acting thereupon, wherein said storage device causing said application software modules to access said function devices to increase the security of said storage device.
Owner:MICRON TECH INC
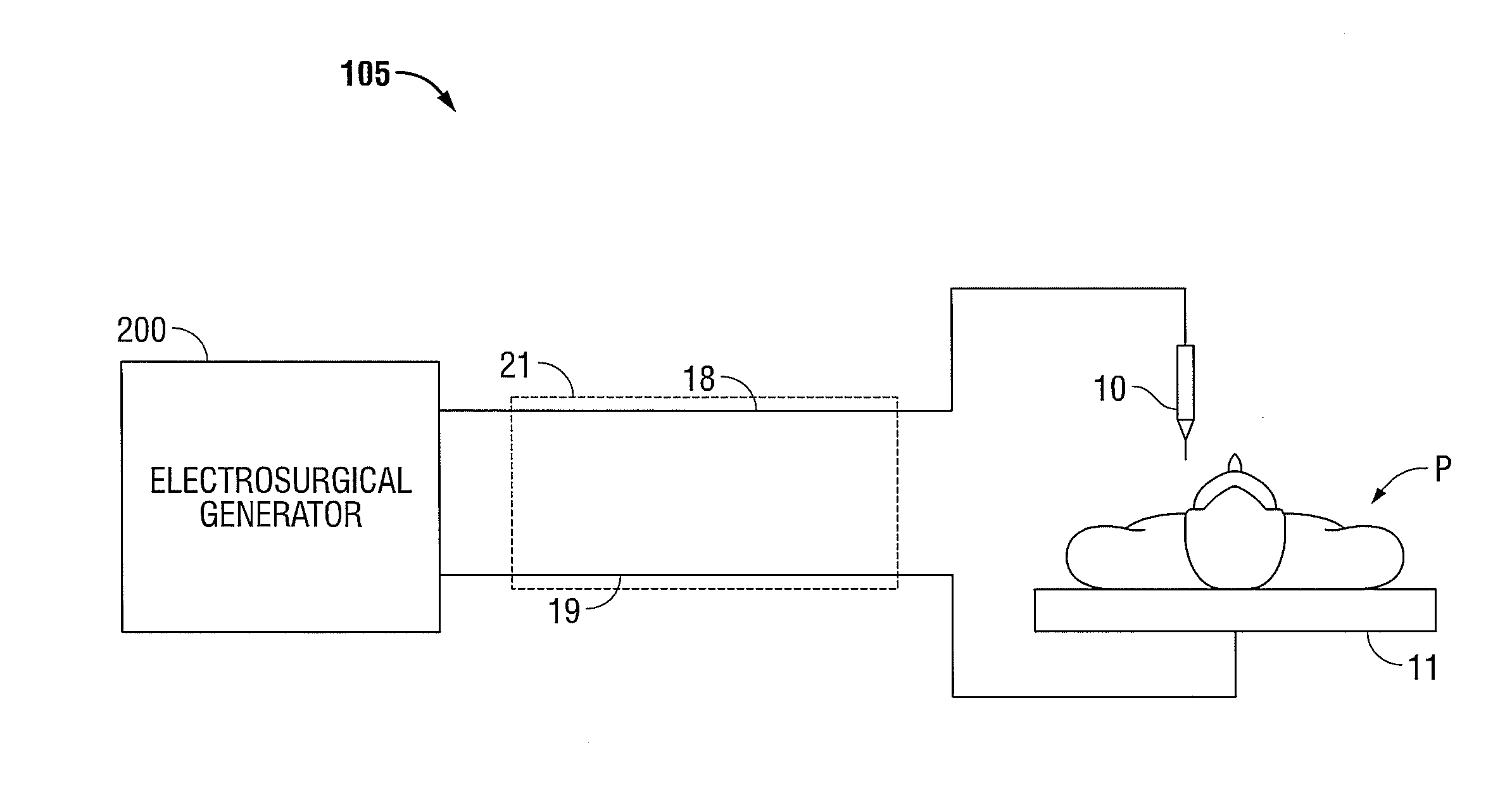
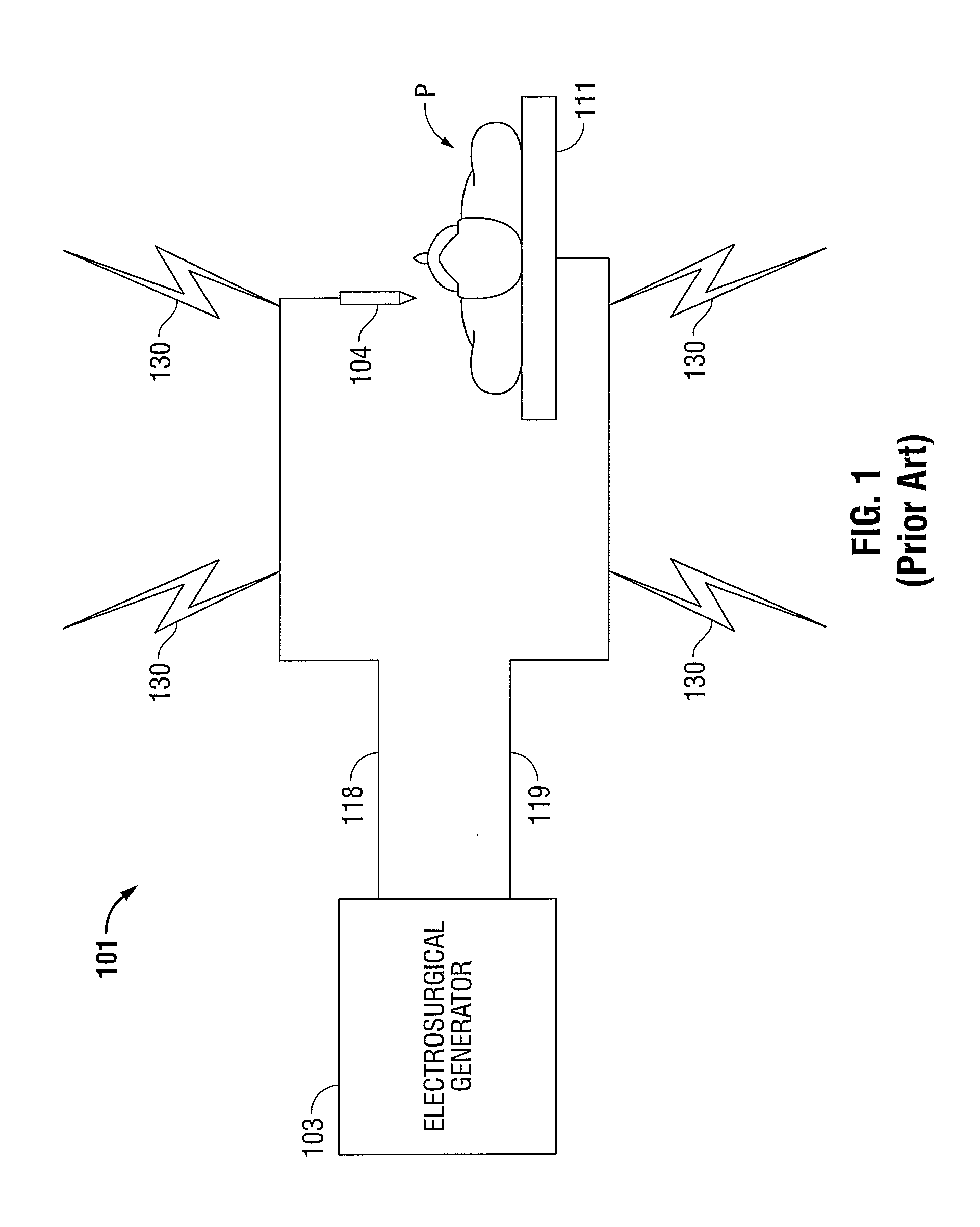
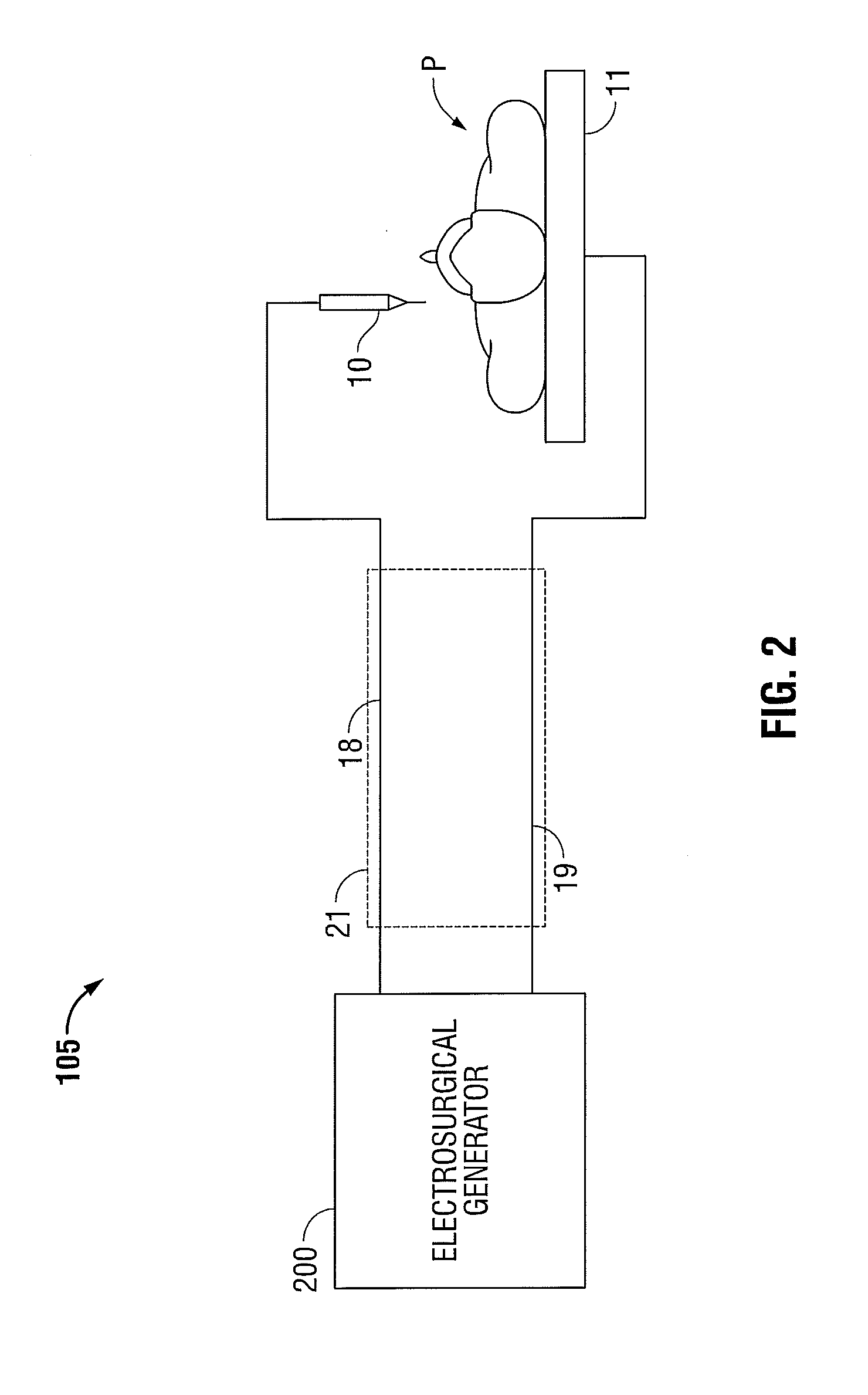
Electrosurgical Apparatus with Integrated Energy Sensing at Tissue Site
ActiveUS20130197503A1Increase safetyReduce coupleSurgical instruments for heatingSurgical forcepsRadio frequencyThermal conductivity
An electrosurgical system is disclosed. The system includes an electrosurgical instrument having at least one electrode configured as a first sensor for measuring a voltage drop therethrough and a temperature sensor for a thermal sensor configured to measure a temperature difference across the at least one electrode; and a generator including an output stage coupled to the at least one electrode, the output stage configured to generate radio frequency energy; and a controller configured to determine actual radio frequency current based on the voltage drop and electrical resistivity of the at least one electrode and radio frequency power based on the measured temperature difference and the thermal conductivity of the at least one electrode.
Owner:TYCO HEALTHCARE GRP LP
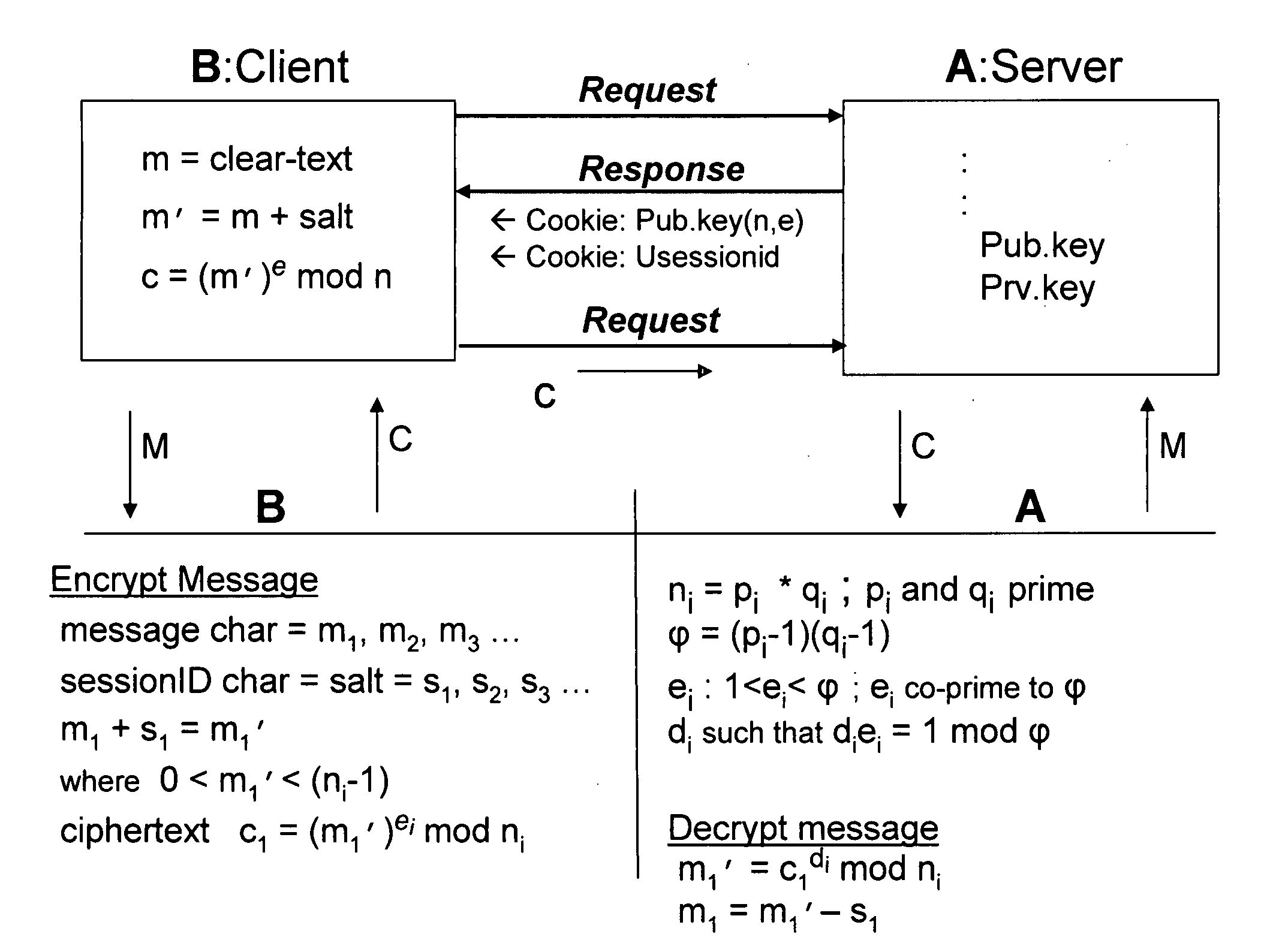
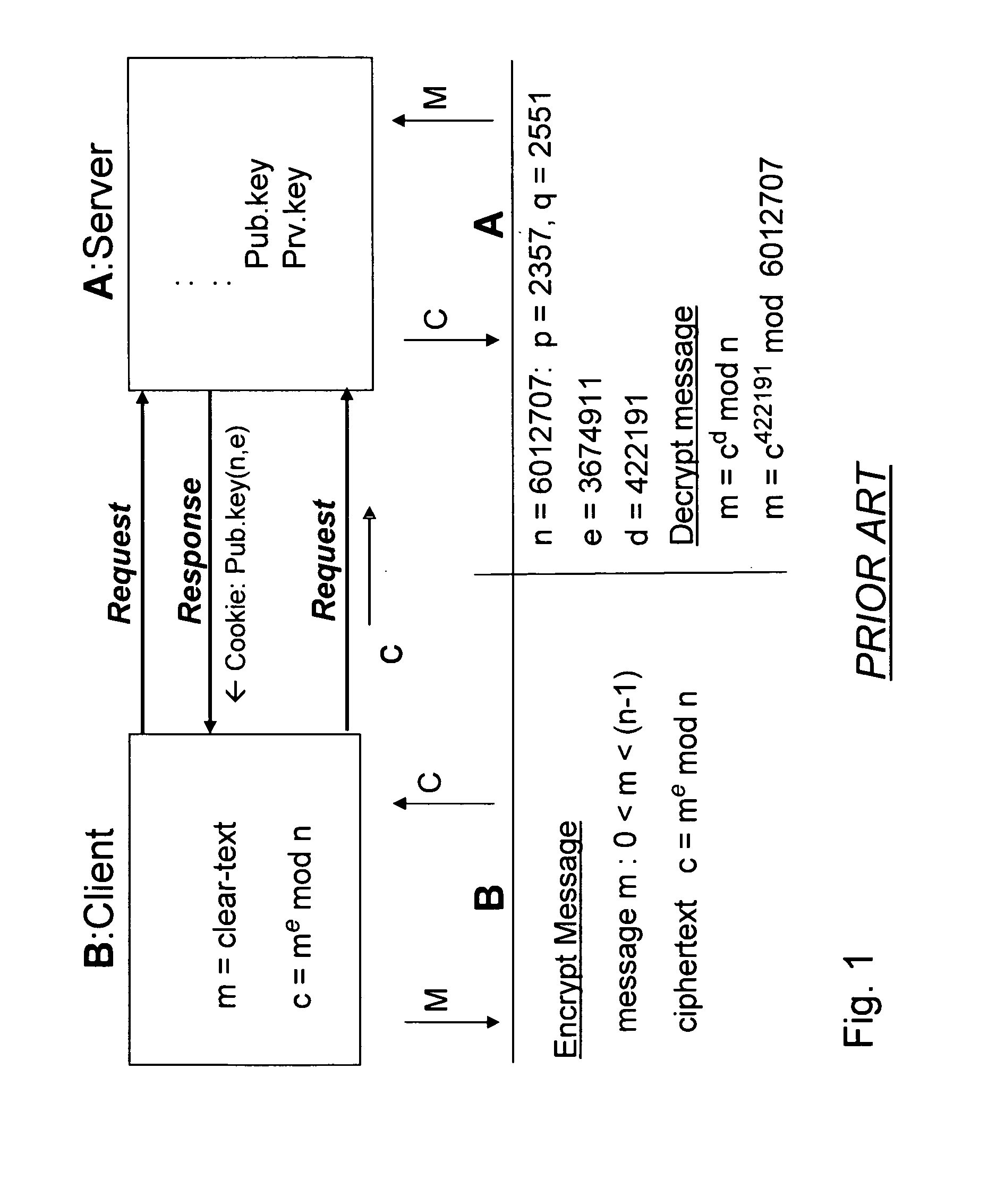
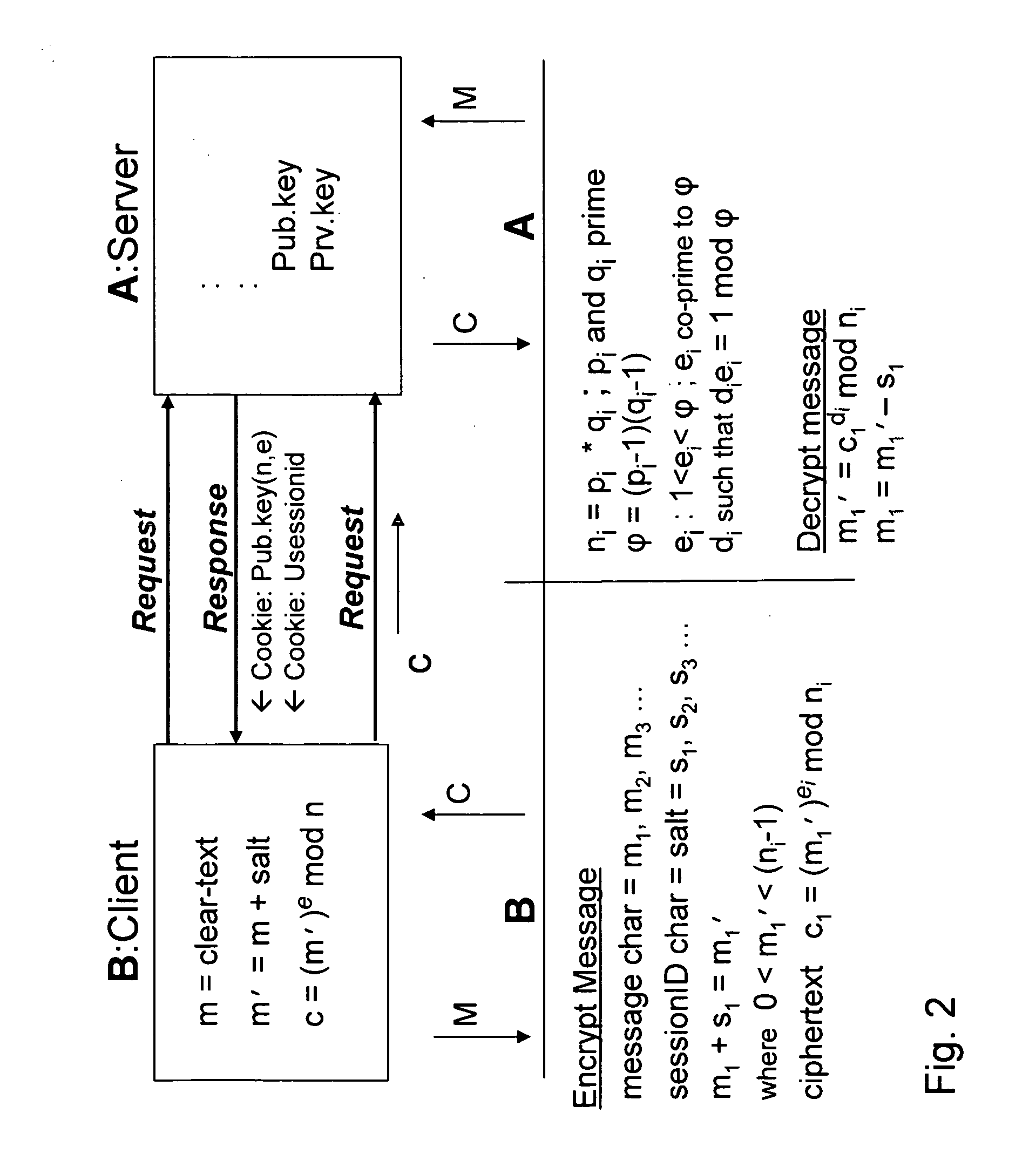
Bcencryption (BCE) - a public-key based method to encrypt a data stream
ActiveUS20070180230A1Increase safetyReduce loadData stream serial/continuous modificationUser identity/authority verificationClient-sideSession ID
A system and method for a web browser to convert an unencrypted character string into a cipher-text string combines a public-key encryption algorithm with a unique and constantly changing salt key. A private “server-key”, a public “client-key” and a server session ID are generated by the server, and the client-key and the session ID are sent to the browser with the code used to encrypt the message. The session-based string can be a randomly generated set of characters which changes between established user sessions and the salt key can be formed from the server session ID string. The server contains the matching code necessary to decrypt the stream using the private key.
Owner:KRONOS TECH SYST PARTNERSHIP
Print schedule control equipment, print schedule control method, and program therefor
InactiveUS20050243365A1Increase efficiencyIncrease safetyDigitally marking record carriersData processing applicationsProgram planningWorkflow
This invention aims at conducting a scheduling work of print processing efficiently. A device scheduler refers to print job composition information registered in step control information of the step “printer reservation” of other print job (other order) in a workflow information table, and a schedule information table. The device scheduler searches both other print jobs (proof print jobs and regular print jobs) that a to-be-registered proof print job having a processing time of the proof print job described above affects and other print jobs (proof print jobs and regular print jobs) that affect the to-be-registered proof print job. The device scheduler determines whether the to-be-registered proof print job can be registered in a schedule (there is no search result in Step 2017 described above). When the registration is not possible, the device scheduler informs an operator of the result that automatic scheduling is impossible.
Owner:CANON KK
Method and apparatus for treating a substrate with an ozone-solvent solution
InactiveUS6982006B1Increase safetyIncrease oxidation rateLighting and heating apparatusHollow article cleaningSolventAqueous solution
A general method and apparatus for treating materials at high speed comprises the steps of dissolving a relatively high concentration ozone gas in a solvent at a relatively low predetermined temperature T1 to form an ozone-solvent solution with a relatively high dissolved ozone concentration, and heating either the ozone-water solution or the material to be treated or both, the ozone-solvent solution and the material to be oxidized with a point-of-use heater to quickly increase the temperature to a predetermined higher temperature T2>T1, and applying the ozone-solvent solution to said material(s) whereby the heated ozone-water solution will have a much higher dissolved ozone concentration at said higher temperature, than could be achieved if the ozone gas was initially dissolved in water at said higher temperature.
Owner:BOYERS DAVID G +1
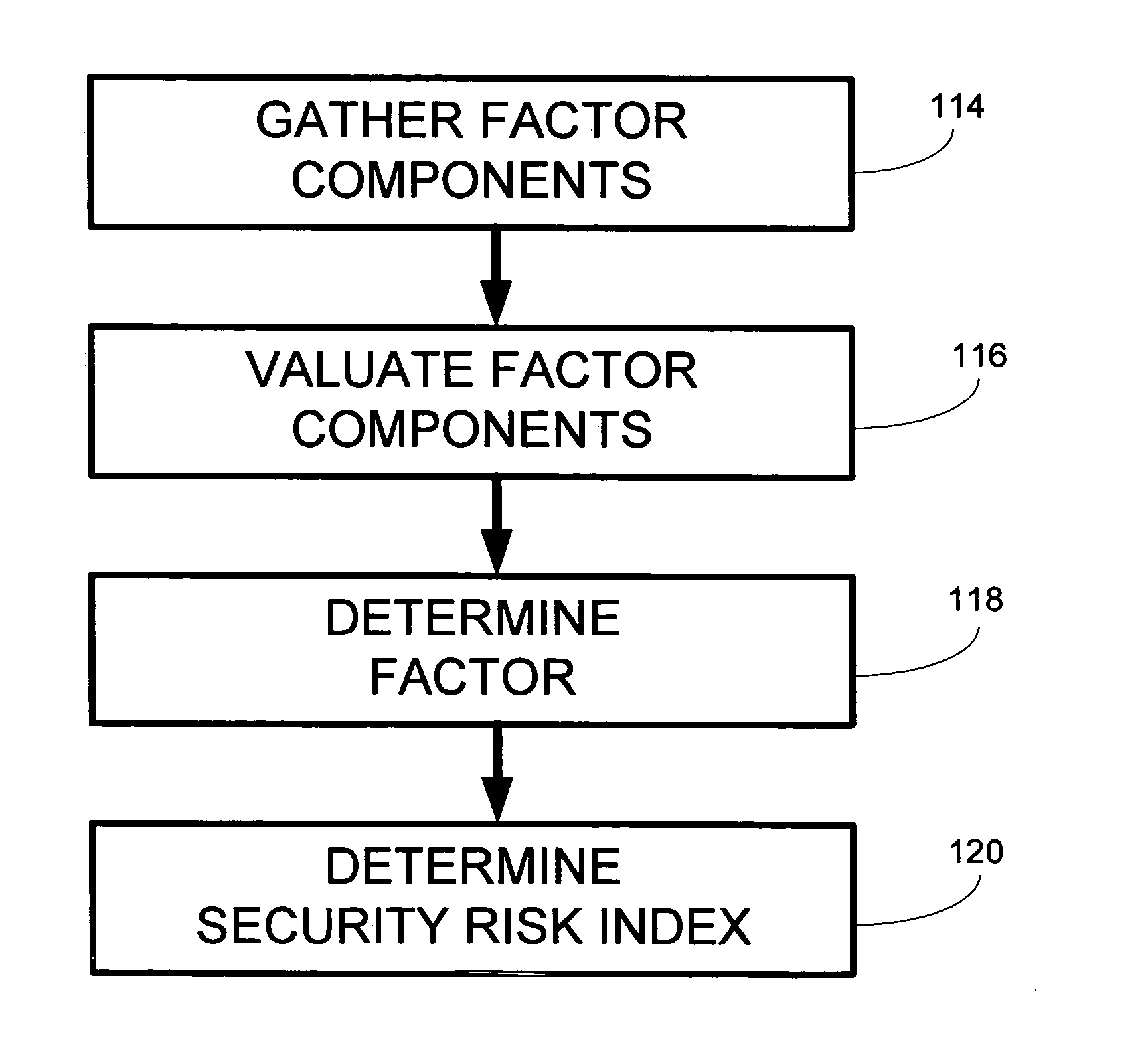
System and method for assessing risk to a collection of information resources
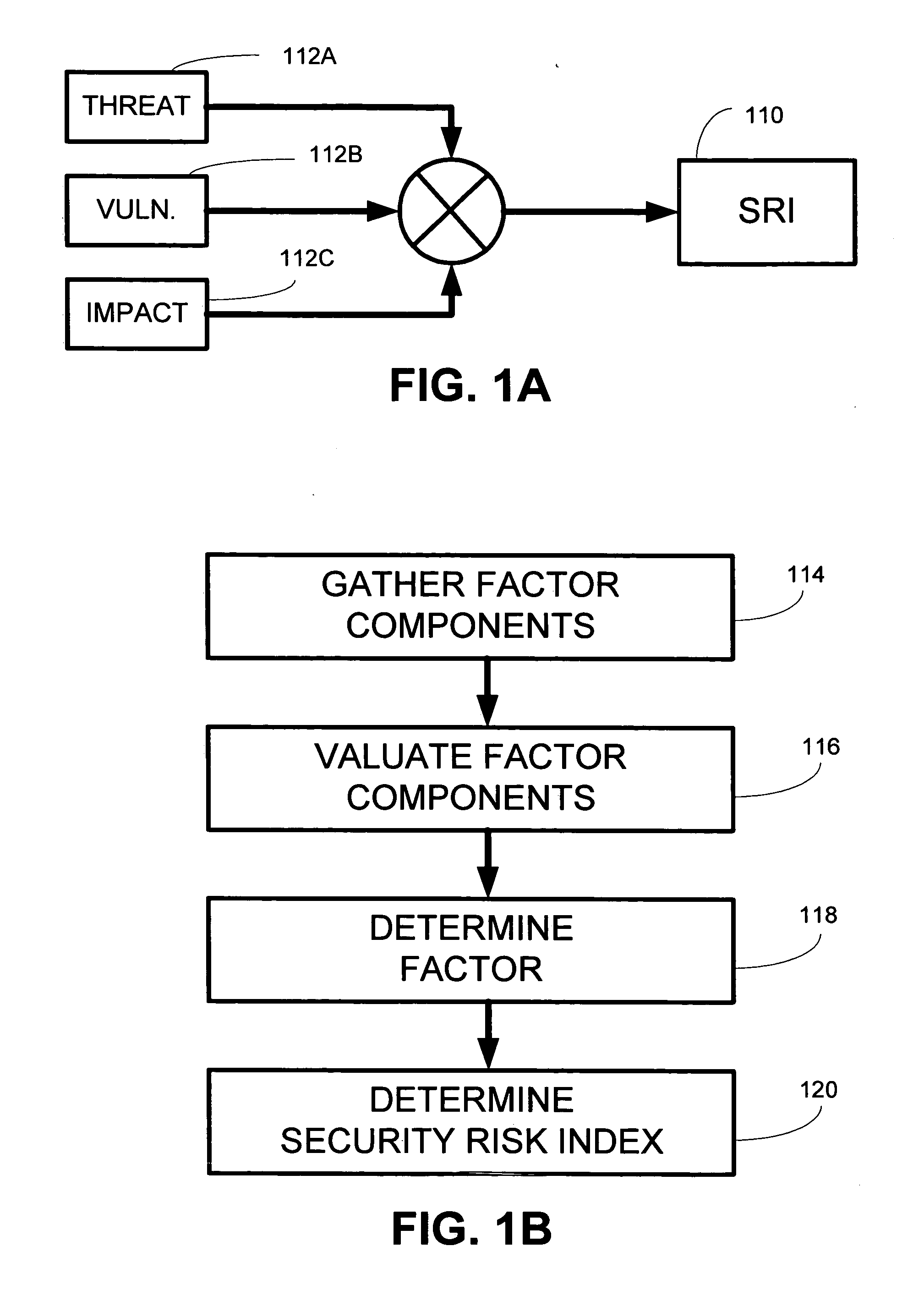
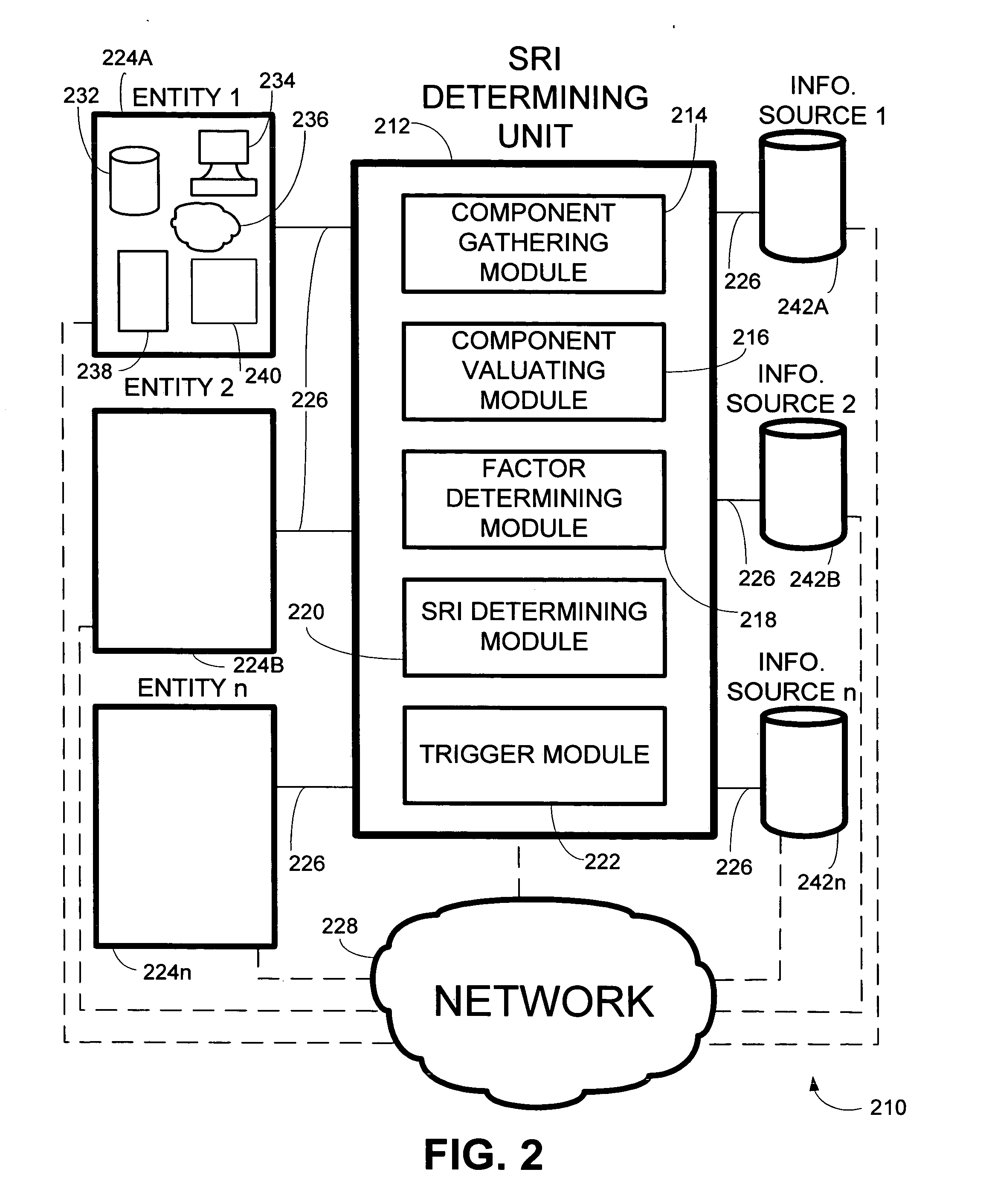
InactiveUS20050278786A1Increase safetyImprove securityMemory loss protectionError detection/correctionVulnerability factorComputer security
A system and method for assessing the risk to information resources that may include the generation and / or use of a security risk index. The security risk index may represent the security of information resources. The security risk index may be based on at least one factor. The at least one factor may be individually quantified. The at least one factor may include a threat factor associated with a rate or frequency of security events that threaten the security of the information resources, a vulnerability factor associated with a likelihood of a security event breaching the security of the information resources, an impact factor associated with an expected cost of a breach of the security of the information resources, or another type of factor. The security risk index of a subset of information resources including at least one resource may enable various comparisons and observations with respect to the security of the subset of information resources. The security risk index may be updated for a variety of reasons, such as, to be kept current, or for another reason.
Owner:VERIZON PATENT & LICENSING INC
Security in a communication network
InactiveUS20070055877A1Increase safetyLimit propagationUser identity/authority verificationConnection managementPeer communicationTelecommunications link
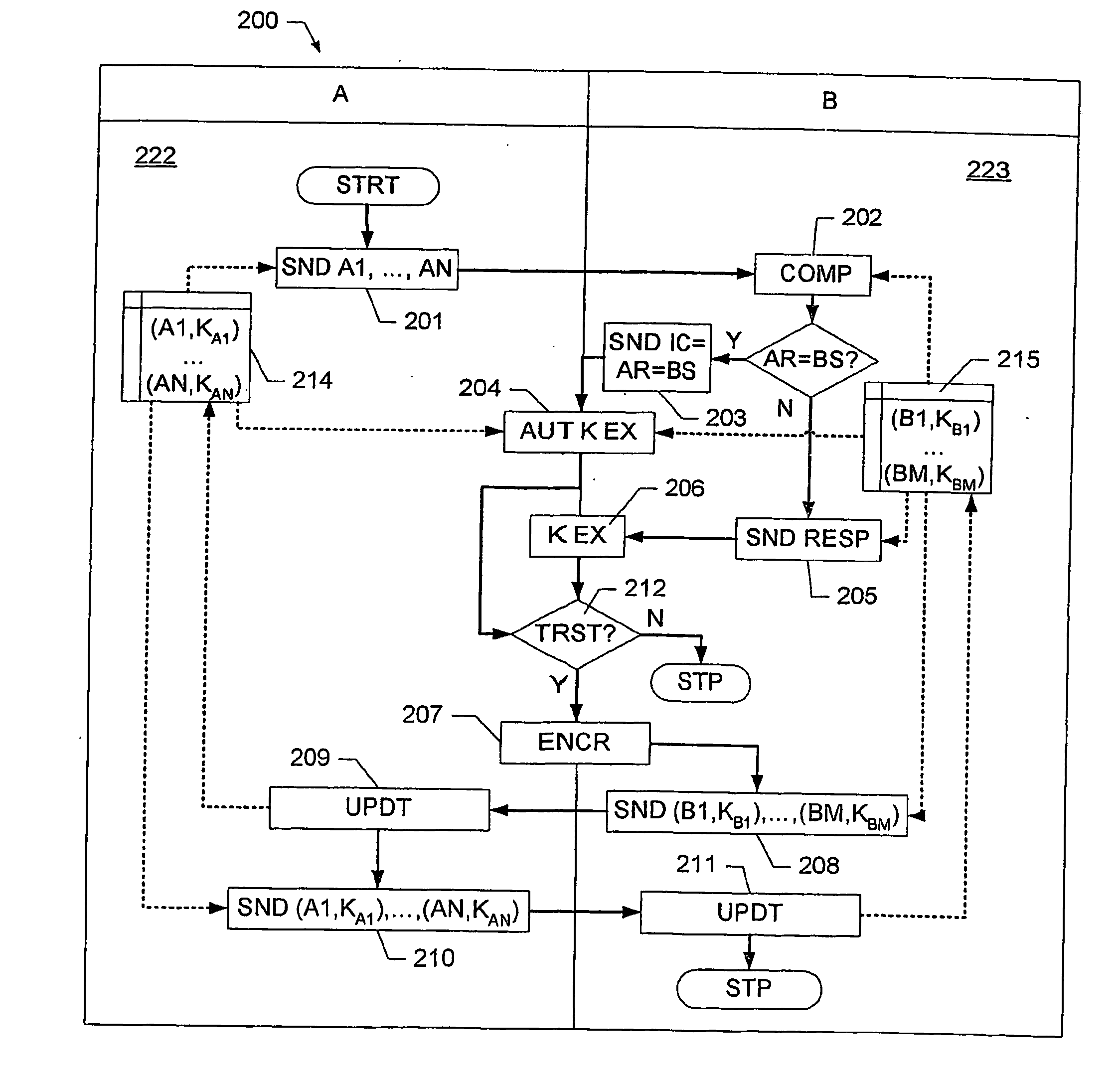
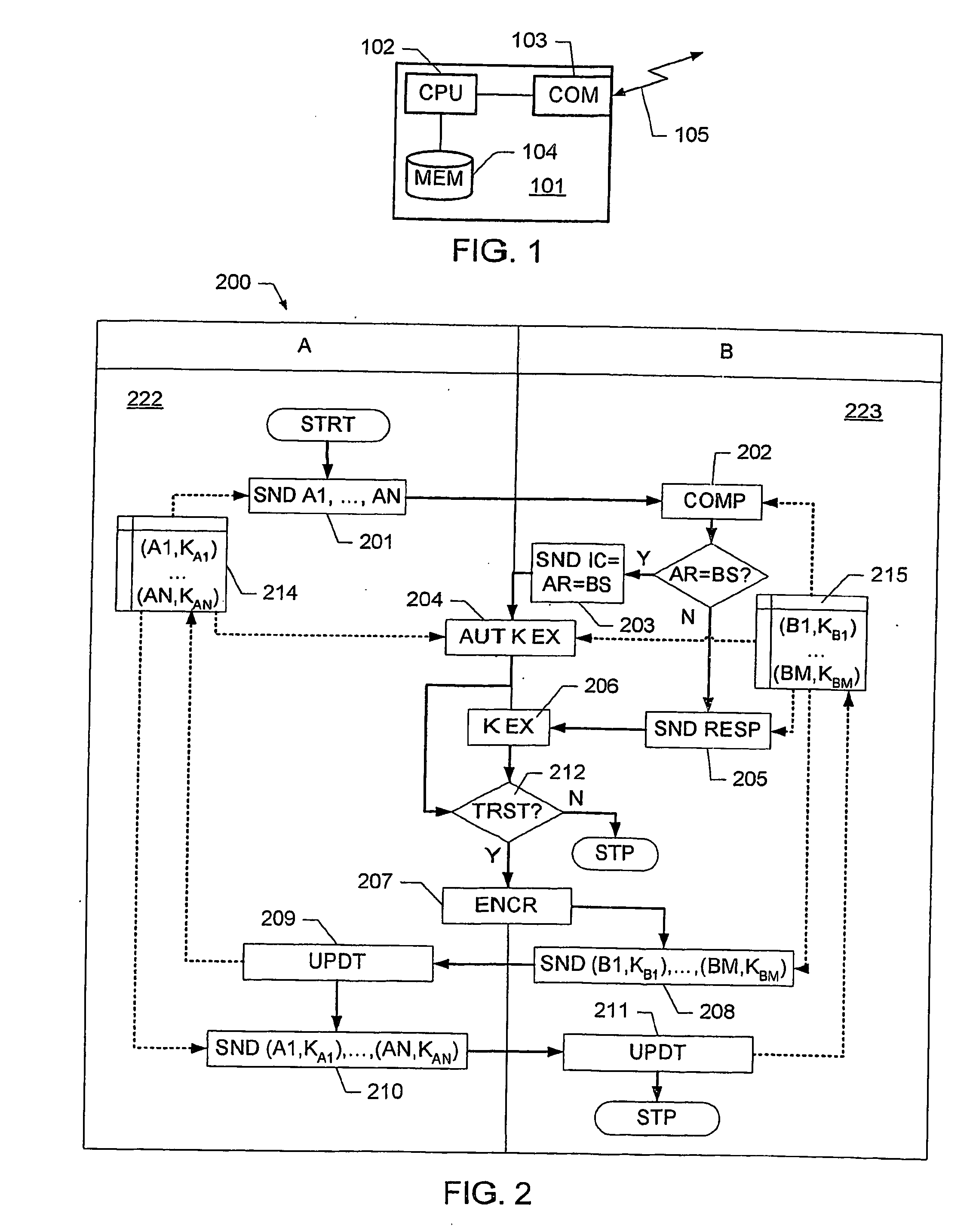
Disclosed is a method of establishing a secured peer-to-peer communication between two communications devices, each communications device having stored a respective set of previously established security associations with other communications devices. The method comprises determining whether the two communications devices have a common security association in their respective sets of established security associations; if the devices have determined a common security association, protecting the communications link between the two communications device based on the determined common security association; otherwise establishing a new security association between the two communications devices, and protecting the communications link based on the new security association; and extending the sets of previously established security associations of the two communications devices to the corresponding other exchanging corresponding key data.
Owner:TELEFON AB LM ERICSSON (PUBL)
Ticket management apparatus, a ticketing device and a data management system for cashless operation
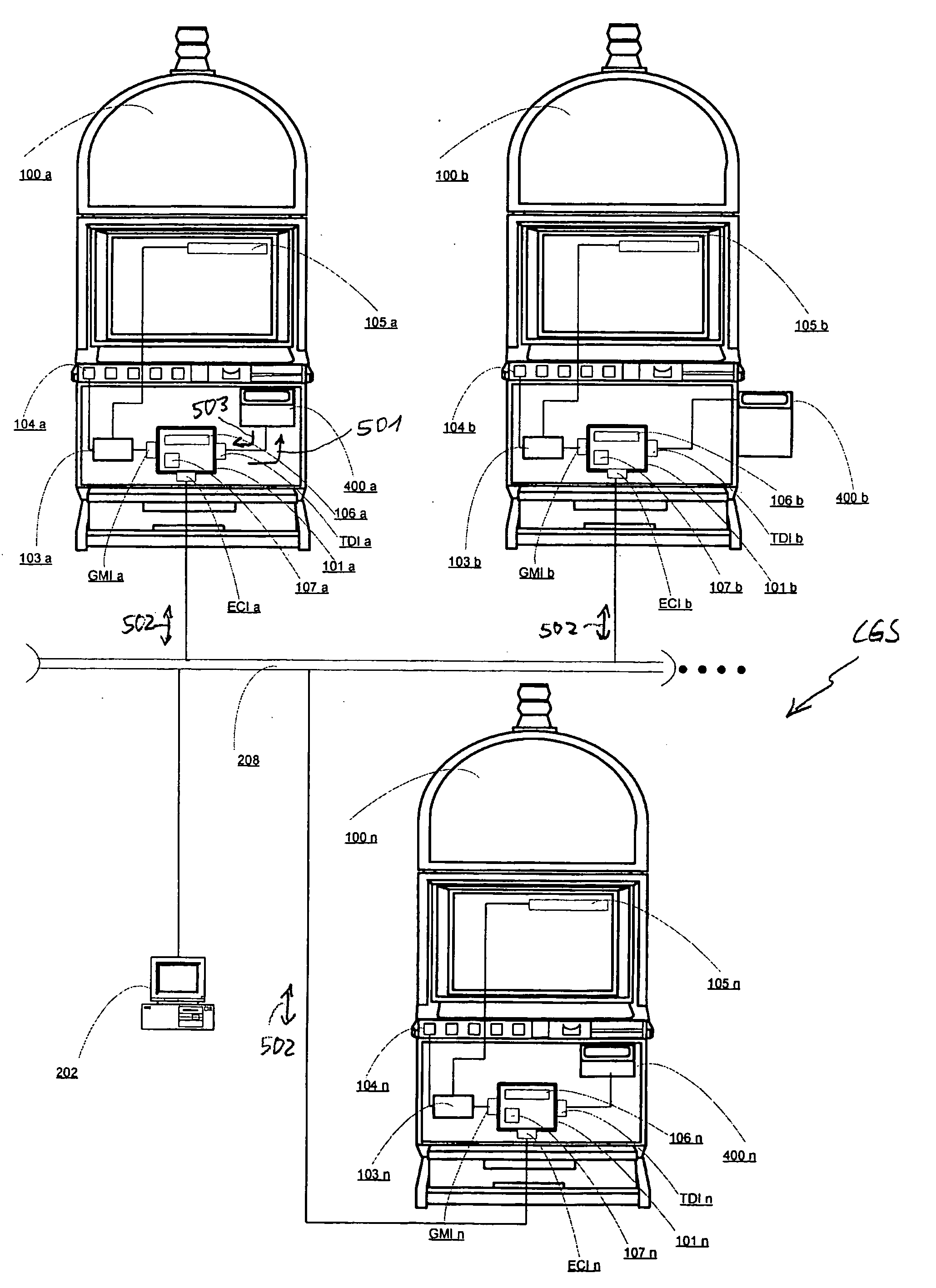
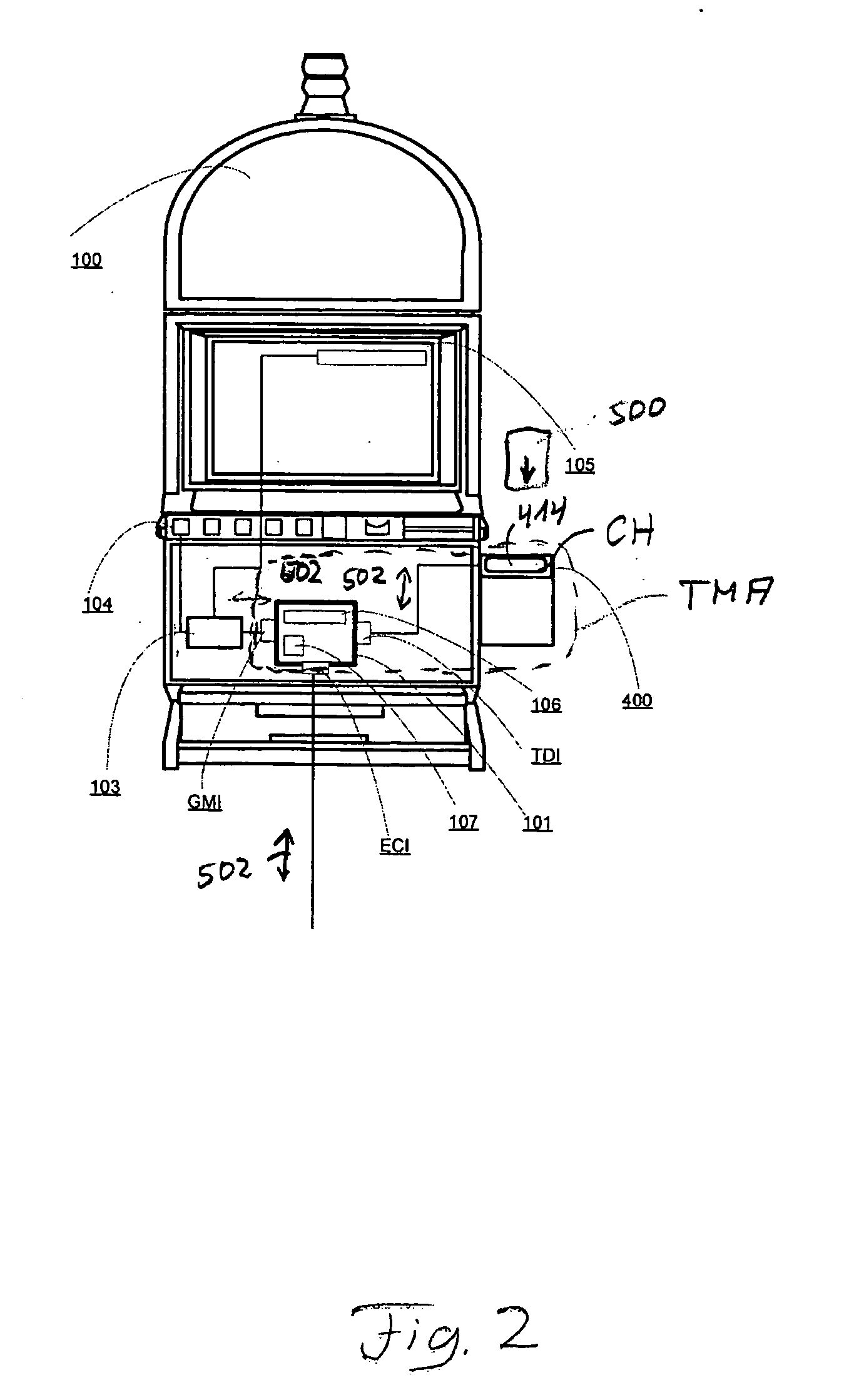
ActiveUS20060166732A1Increase safetyEasy to useApparatus for meter-controlled dispensingVideo gamesTicketMemory cell
The present invention relates to a ticket management apparatus (TMA) for cashless operation of gaming machines (100a-100n), comprising a ticketing device (400a-400n) for inputting and outputting tickets (500) containing gaming data (502) and at least one data management device (101a-101n). The data management device (101a-101n) includes a gaming machine interface (GMIa-GMIn) for exchanging gaming data (502) with a controller (103a-103n) of a gaming machine (100a-100n), a ticketing device interface (TDIa-TDIn) for exchanging gaming data (502) with that ticketing device (400a-400n), a processor unit (106a-106n), a memory unit (107a-107n) and an external communication interface (ECIa-ECIn) for exchanging gaming data (502) with one or more devices (208) external to that ticket management apparatus (TMA).
Owner:DR GAMING TECH +1
Method, network element, and system for providing security of a user session
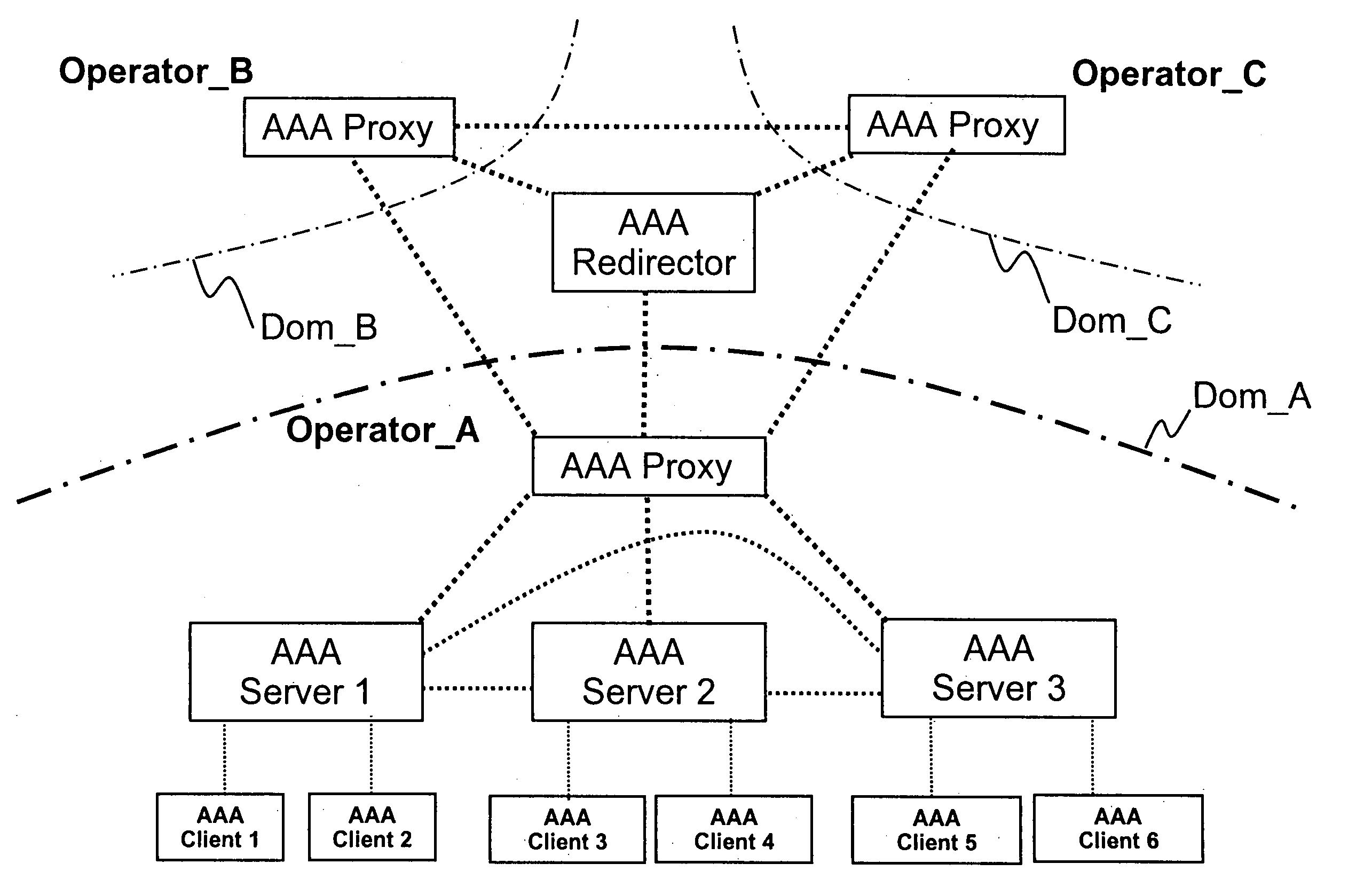
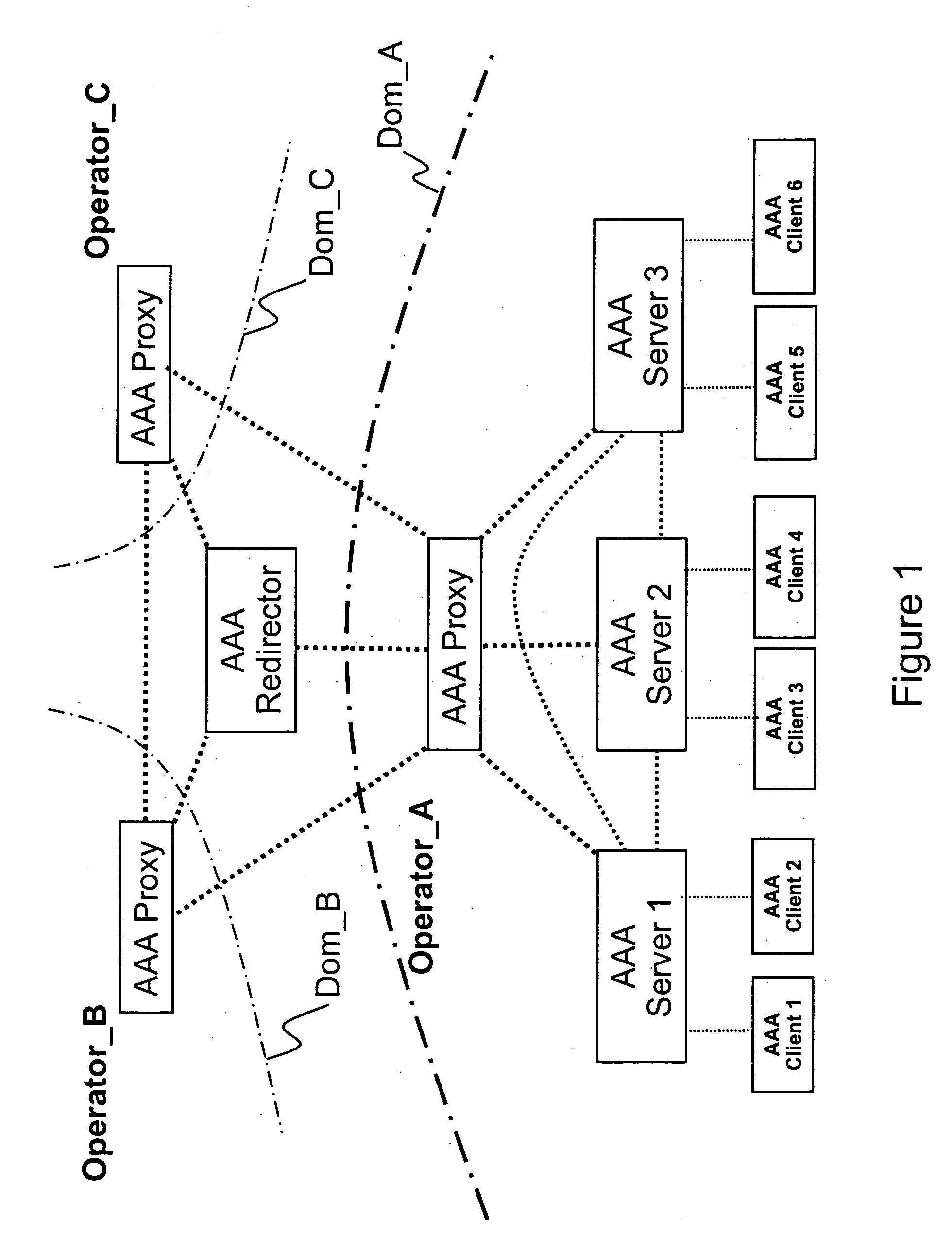
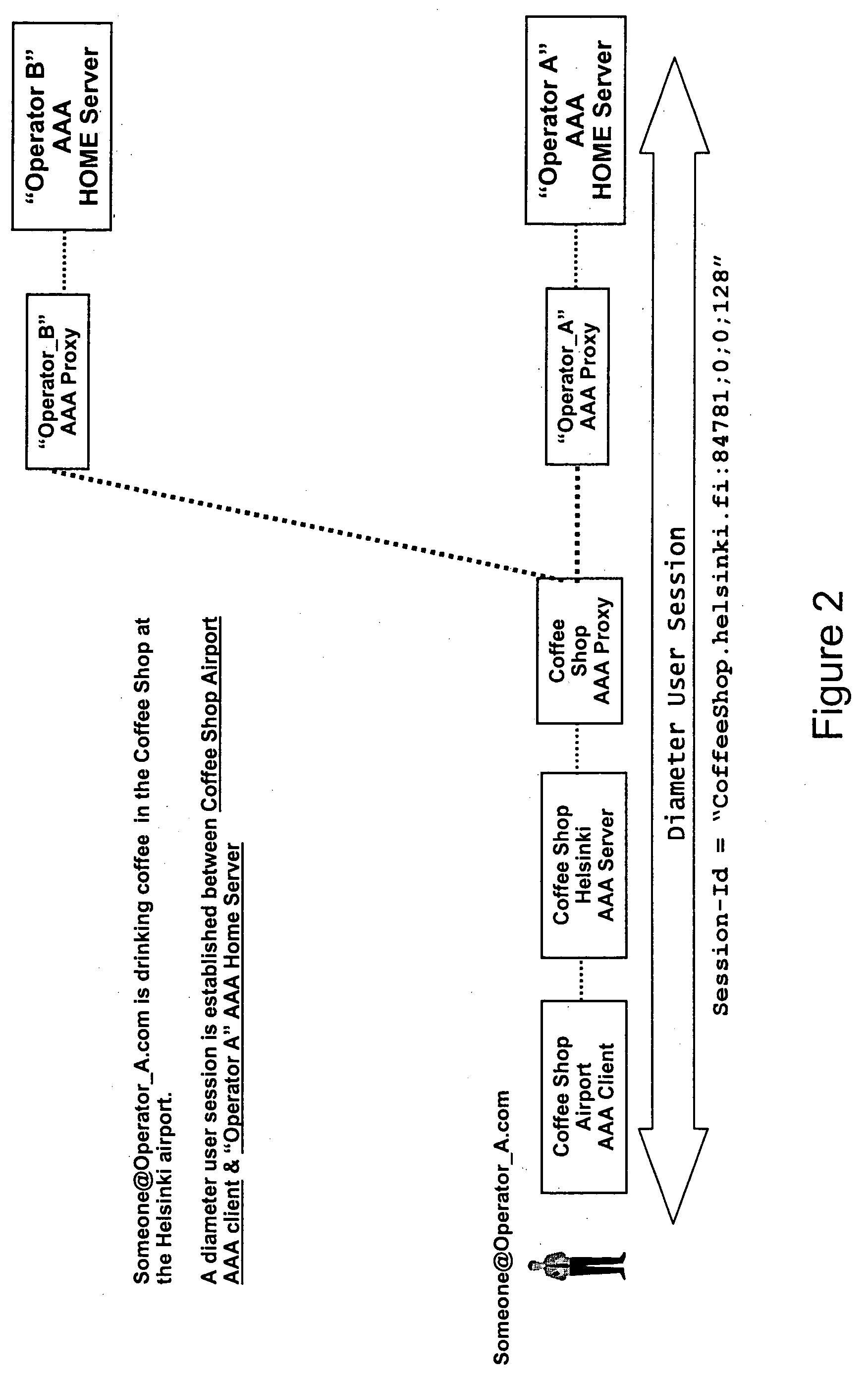
InactiveUS20050235065A1Increase safetyHigh safetyDigital computer detailsTransmissionClient-sideA domain
Methods, network elements, and a system for providing security of a session between a client of a domain of a network and a service node of said network are provided, which network consists of a plurality of domains, from which domain a user connected to said network via said client requests a service. The providing of security is based on analyzing a message, which is associated with said session and destined for said client, in terms of routing information. Such routing information may comprise an origin domain information of said message and a route information of said message, or an origin domain information of said message, which indicates a domain from which said message originates. The present invention is particularly advantageous for AAA sessions associated with authentication, authorization, and accounting functions and for usage of Diameter Base protocol.
Owner:NOKIA CORP
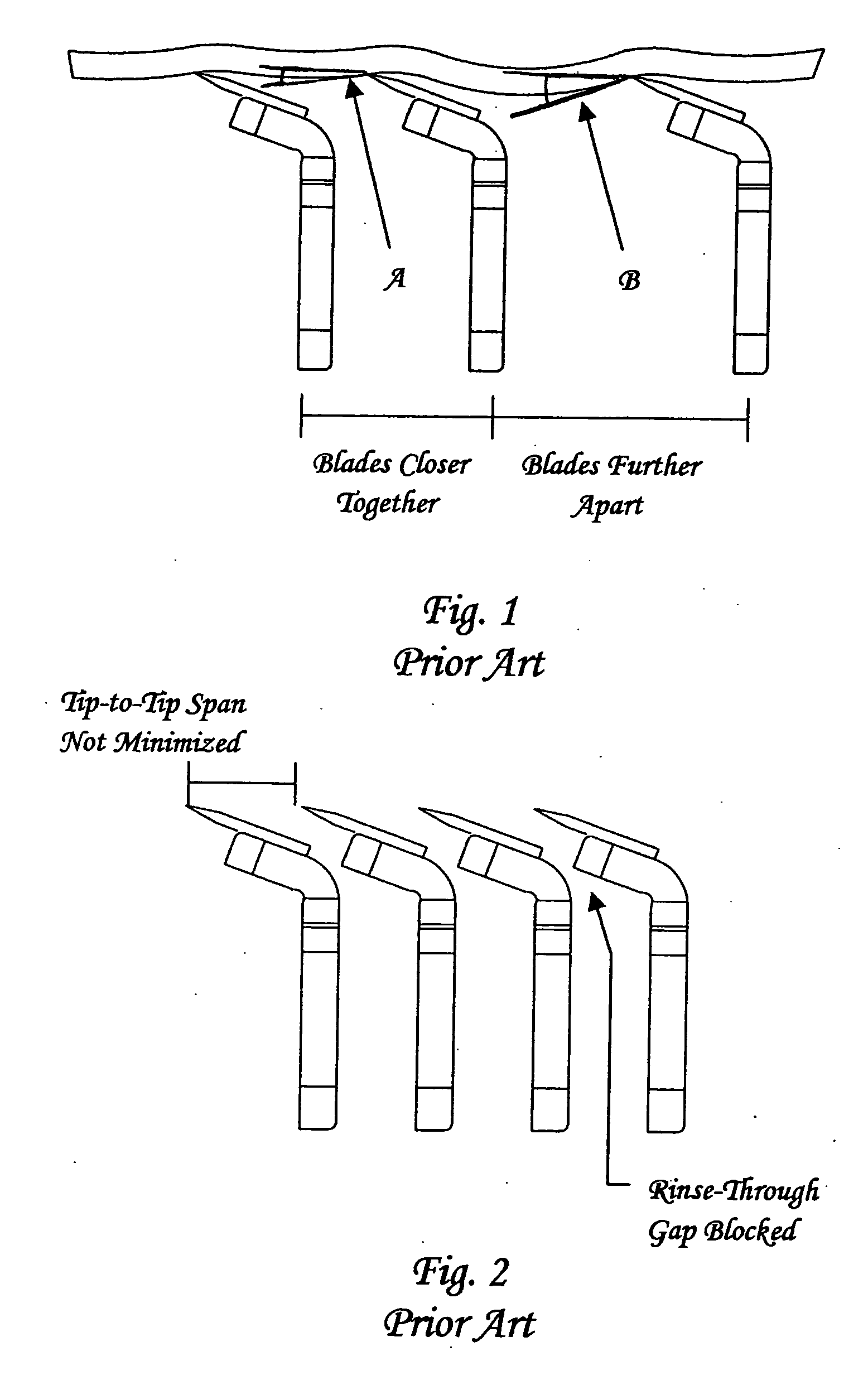
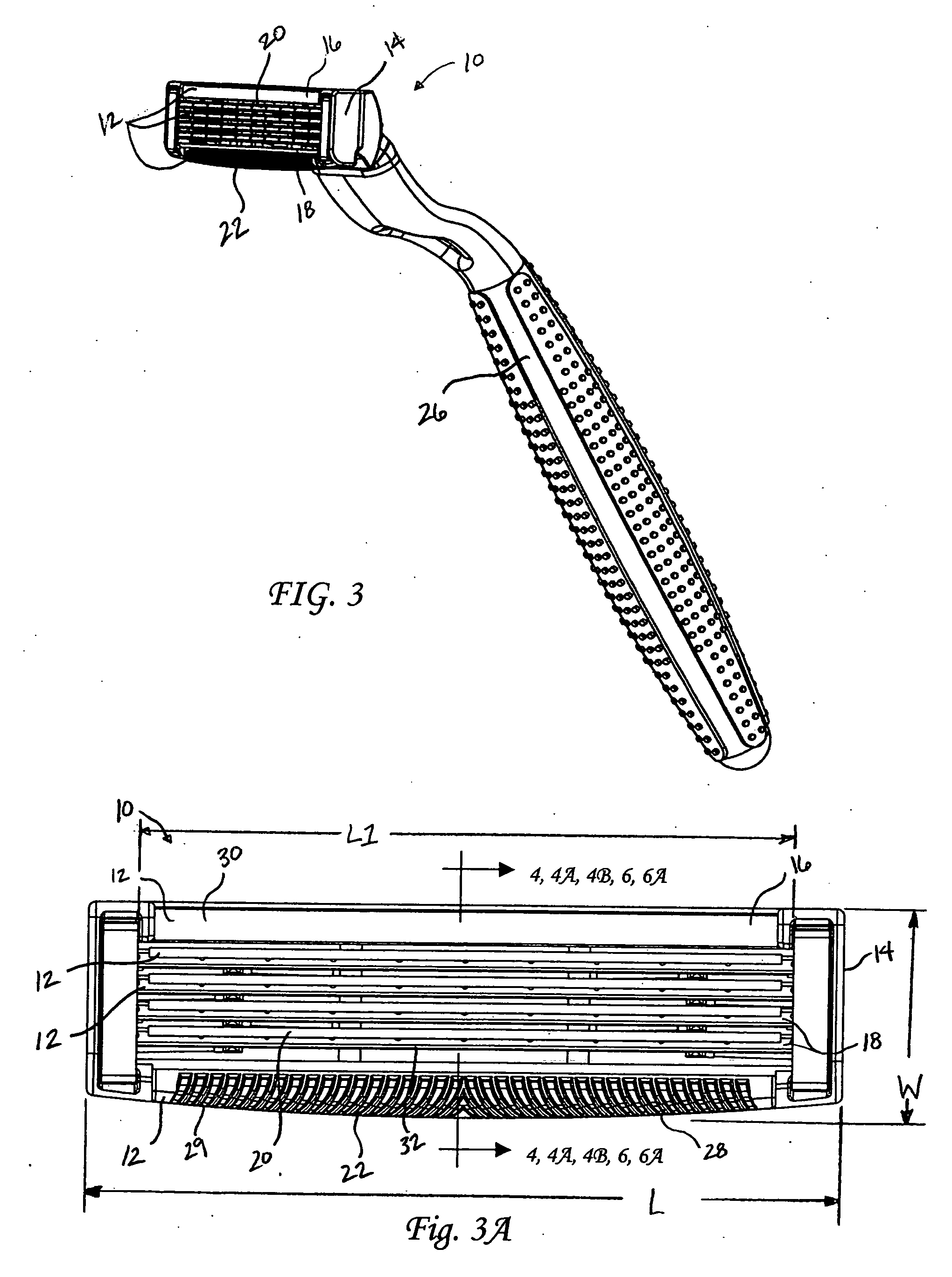
Inter-blade guard and method for manufacturing same
ActiveUS20060277759A1Increase safetyApparent advantageMetal working apparatusKnife bladesEngineering
According to the present invention, a razor cartridge includes a plurality of skin-engaging elements disposed on a frame. The skin engaging elements include at least two or more substantially blades having a sharpened cutting edge, a first inter-blade guard, and a cap. The two or more blades are disposed on the frame in parallel relation to one another. The first inter-blade guard is disposed on the frame between two (2) blades. A rinse-through gap extends across substantially the entire length of the frame between the first inter-blade guard and the blade aft the first inter-blade guard.
Owner:EDGEWELL PERSONAL CARE BRANDS LLC
Latchable container system
InactiveUS20070095848A1Increase efficiencyIncrease safetyPackage recyclingCapsMechanical engineeringEngineering
A latching system including both apparatus and methods addresses the need for a reusable latch that is identical on either side of a container opening, thereby facilitating container manufacture. Also disclosed are apparatus and methods for assuring the quality of latchable container enclosed contents and enhancing the safety of container users by providing an unopened condition assurance element such as a tab that is removable from a reusable container latch. A novel latching system with a split insertion clement on a first latch side and unitary receptor element on a second latch side is also disclosed. A preferred embodiment involves an elastically obstructed latch as used on a squeeze-openable container.
Owner:INT MOLDED PACKAGING CORP
Distributed secure data storage and transmission of streaming media content
InactiveUS20170048021A1Increase safetyHigh degree of safetyError preventionCode conversionDistributed securityMedia content
Disclosed is a method for the distributed storage and distribution of data. Original data is divided into fragments and erasure encoding is performed on it. The divided fragments are dispersedly stored on a plurality of storage mediums, preferably that are geographically remote from one another. When access to the data is requested, the fragments are transmitted through a network and reconstructed into the original data. In certain embodiments, the original data is media content which is steamed to a user from the distributed storage.
Owner:DATOMIA RES LABS OU
Data processing apparatus and method for correlation analysis
ActiveUS7065345B2Increase safetyPreserve integrityNear-field transmissionSpecial service for subscribersData processingCorrelation analysis
A data processing apparatus, a method and computer program product for comparing a first object associated with said data processing apparatus with a second object associated with a remote data processing apparatus, are provided. The data processing apparatus comprises an input device operable to accept a first and a second set of data associated with said first object. Said first set of data describes said first object, and said second set of data describes a third object. Additionally, the data processing apparatus includes a memory. Said memory is adapted to store said first and said second set of data. The data processing apparatus further comprises a receiver. Said receiver is adapted to obtain a first subset of a third and a fourth set of data, respectively, from said remote data processing apparatus. Said third and said fourth set of data is associated with said second object, and said third set of data describes said second object, and said fourth set of data describes a fourth object. It also includes a transmitter. Said transmitter is adapted to send a first subset of said first and said second set of data, respectively, to said remote data processing apparatus. Finally, the data processing apparatus comprises a processor. The processor is adapted to perform correlation analysis between said first subsets of said first and said fourth set of data, respectively, to obtain a first value of correlation between said first and said second object. The processor is further adapted to perform correlation analysis between said first subsets of said second and said third set of data, respectively, to obtain a second value of correlation between said first and said second object.
Owner:CARLTON STEPHEN J
Pressure responsive blowout latch
InactiveUS6866226B2Increase safetyIncreased strengthDoors/windowsAir-treatment apparatus arrangementsEngineeringSurface plate
Owner:HARTWELL
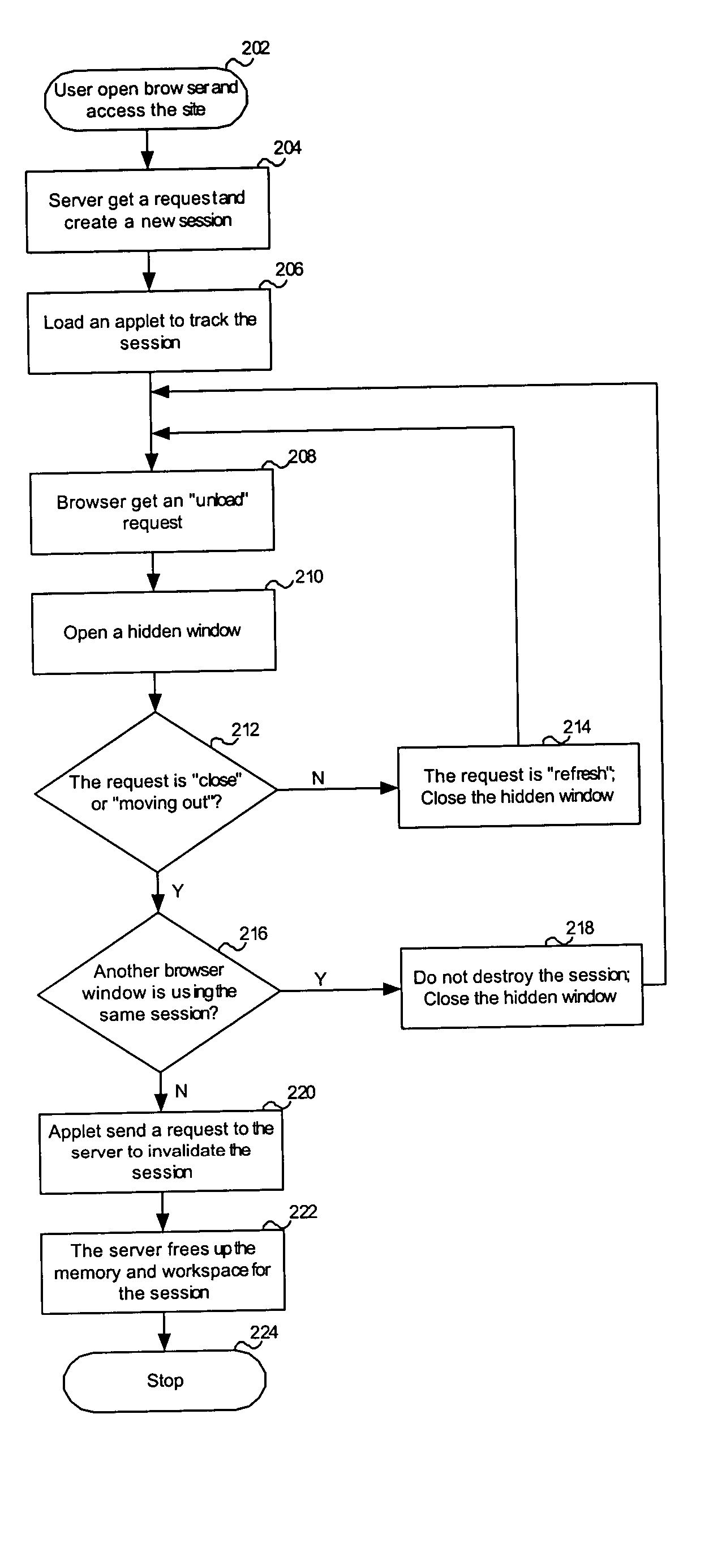
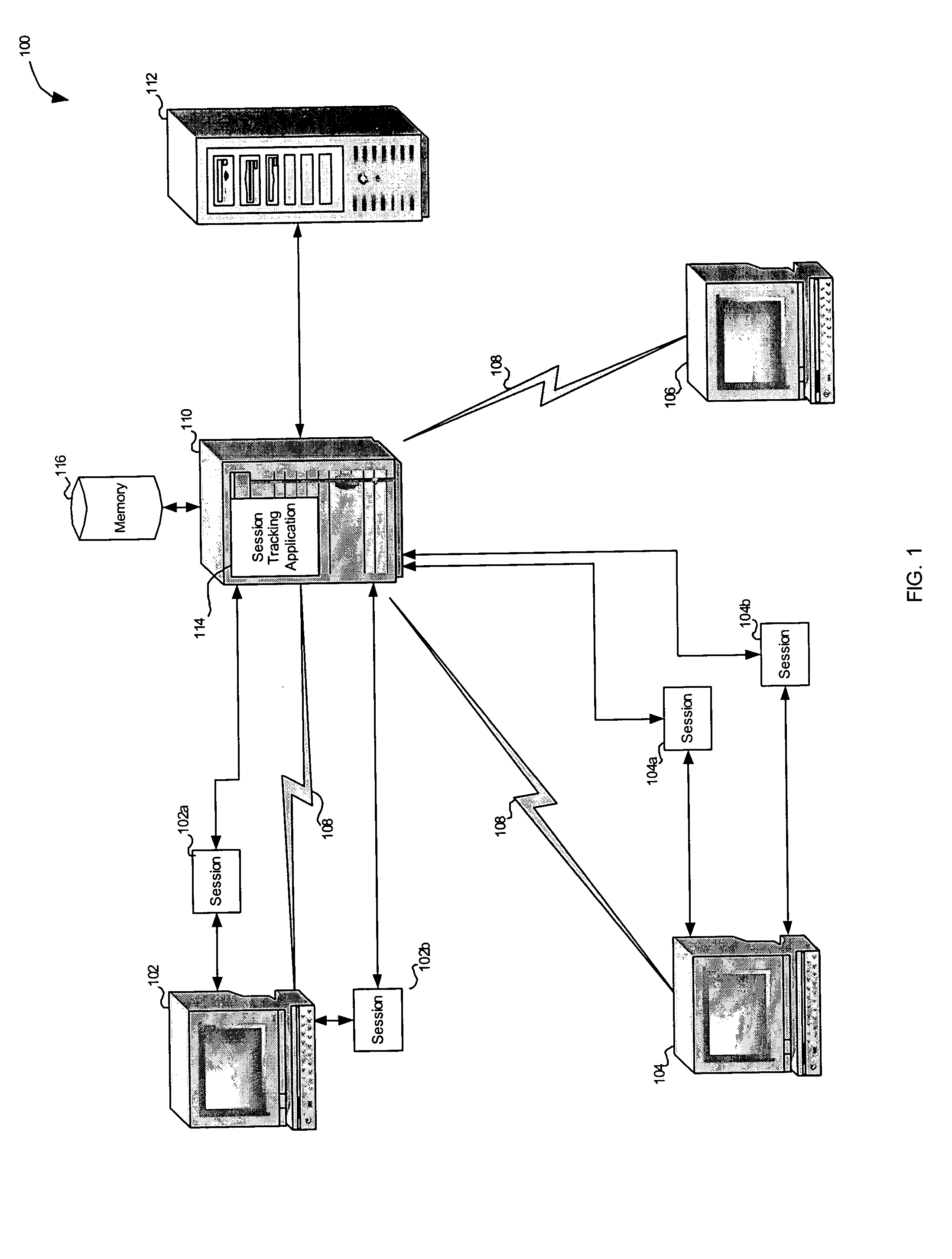
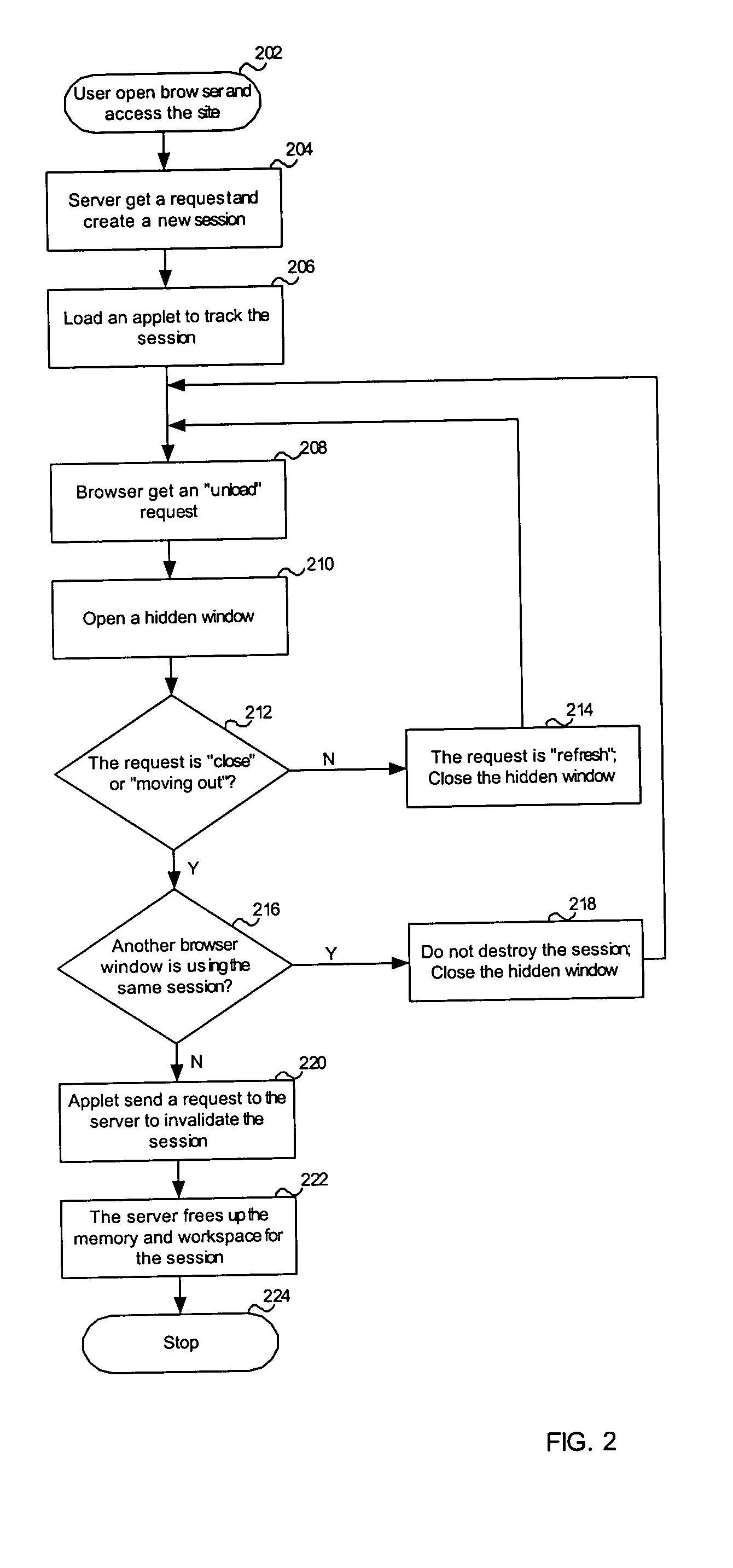
System and method for tracking web-based sessions
InactiveUS20050071464A1Increase safetyImprove securityMultiple digital computer combinationsSecuring communicationWeb serverApplication software
This invention is directed to a system and method for tracking sessions for web-based applications. The system and method comprise a browser disposed on an associated data terminal and having at least one browser window associated therewith. The browser is adapted to generate at least one interactive session with an associated web server. The system and method also comprises at least one session tracking application associated with an interactive session. The session tracking application includes monitoring means adapted for monitoring activity on the associated interactive session and testing means adapted for determining whether monitored activity includes an unload event. The session tracking application also includes termination means adapted for terminating the associated interactive session upon a determination of a selected unload event and notification means adapted for notifying the associated web server to close out the interactive session.
Owner:KK TOSHIBA +1
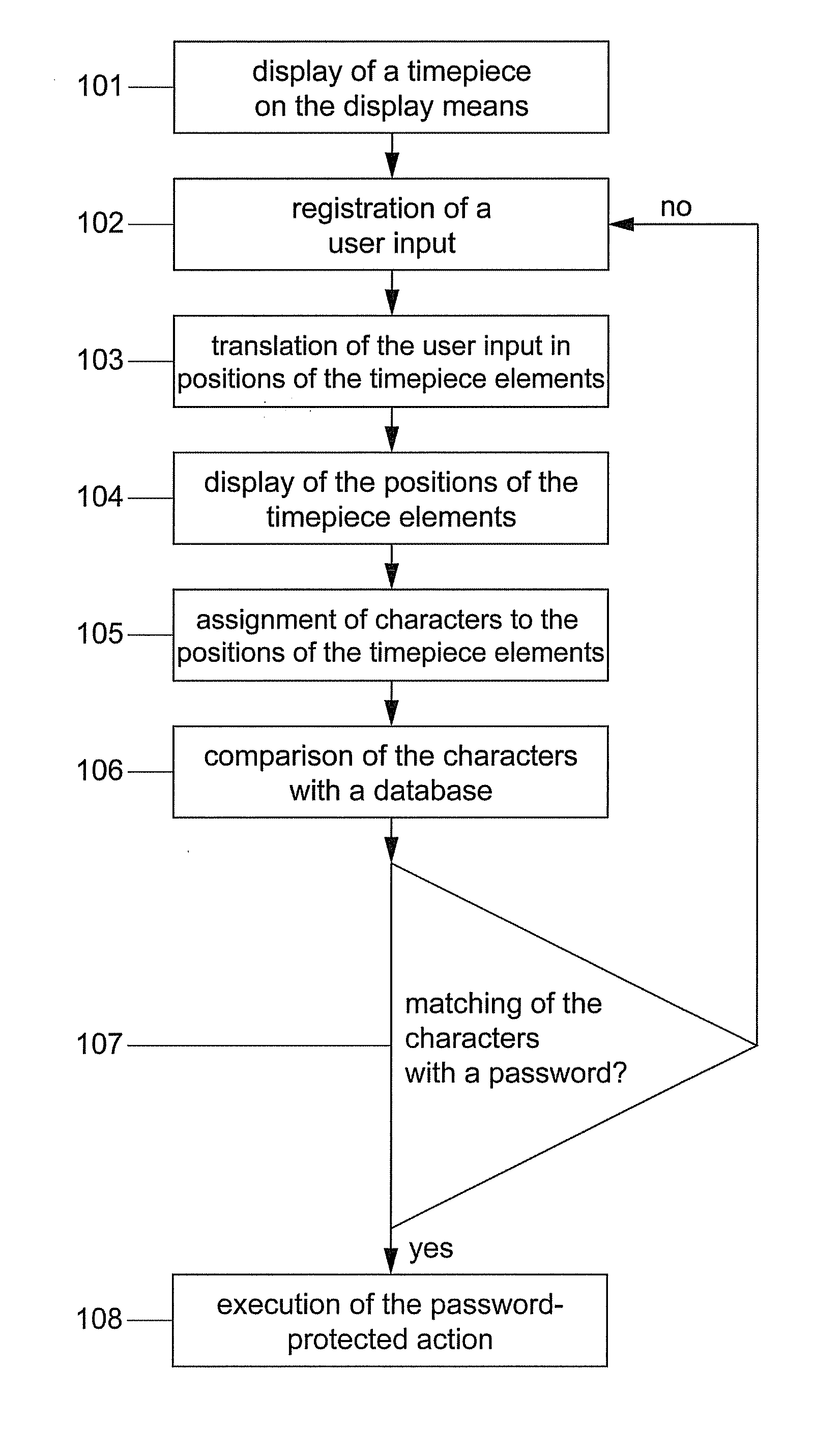
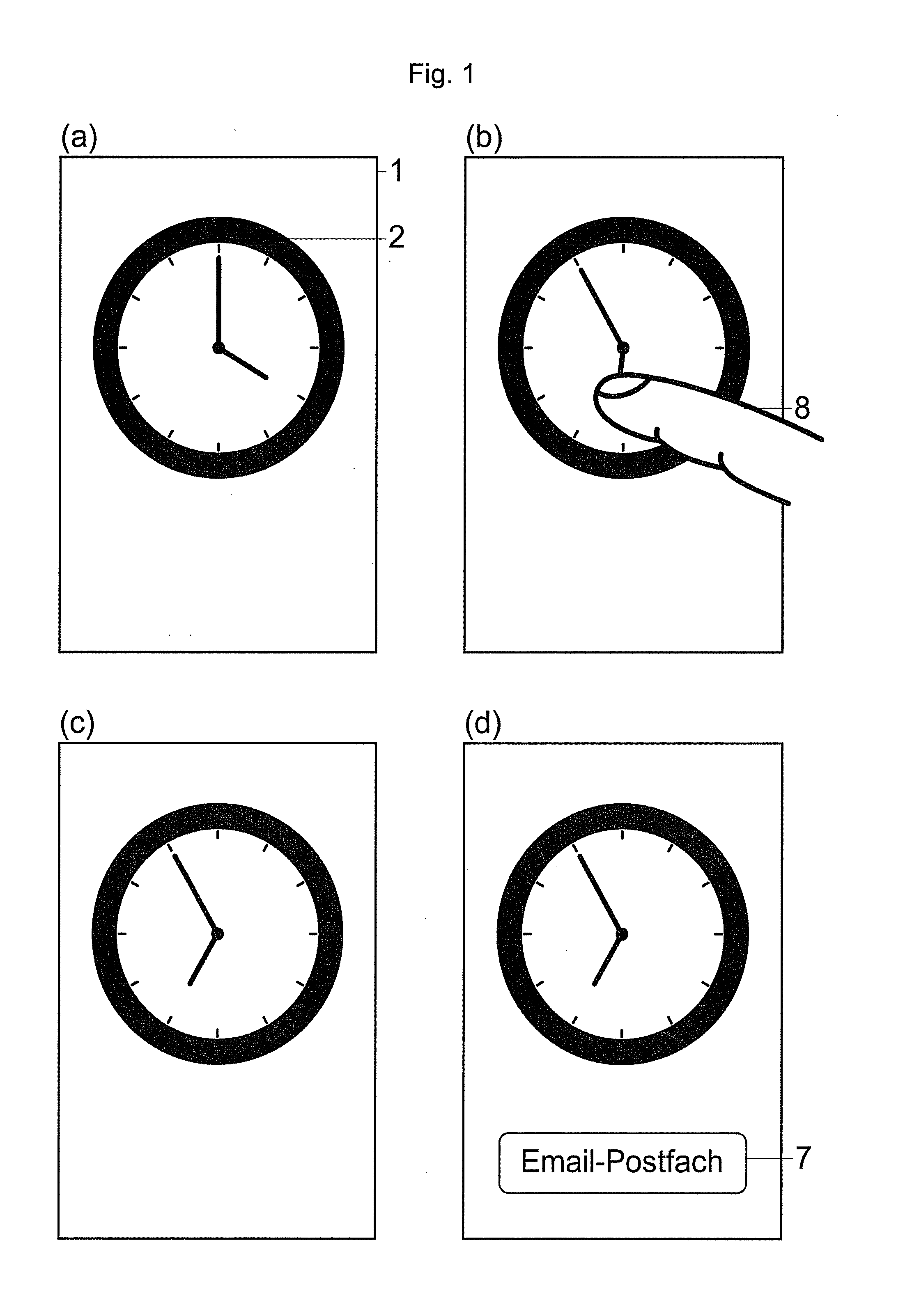
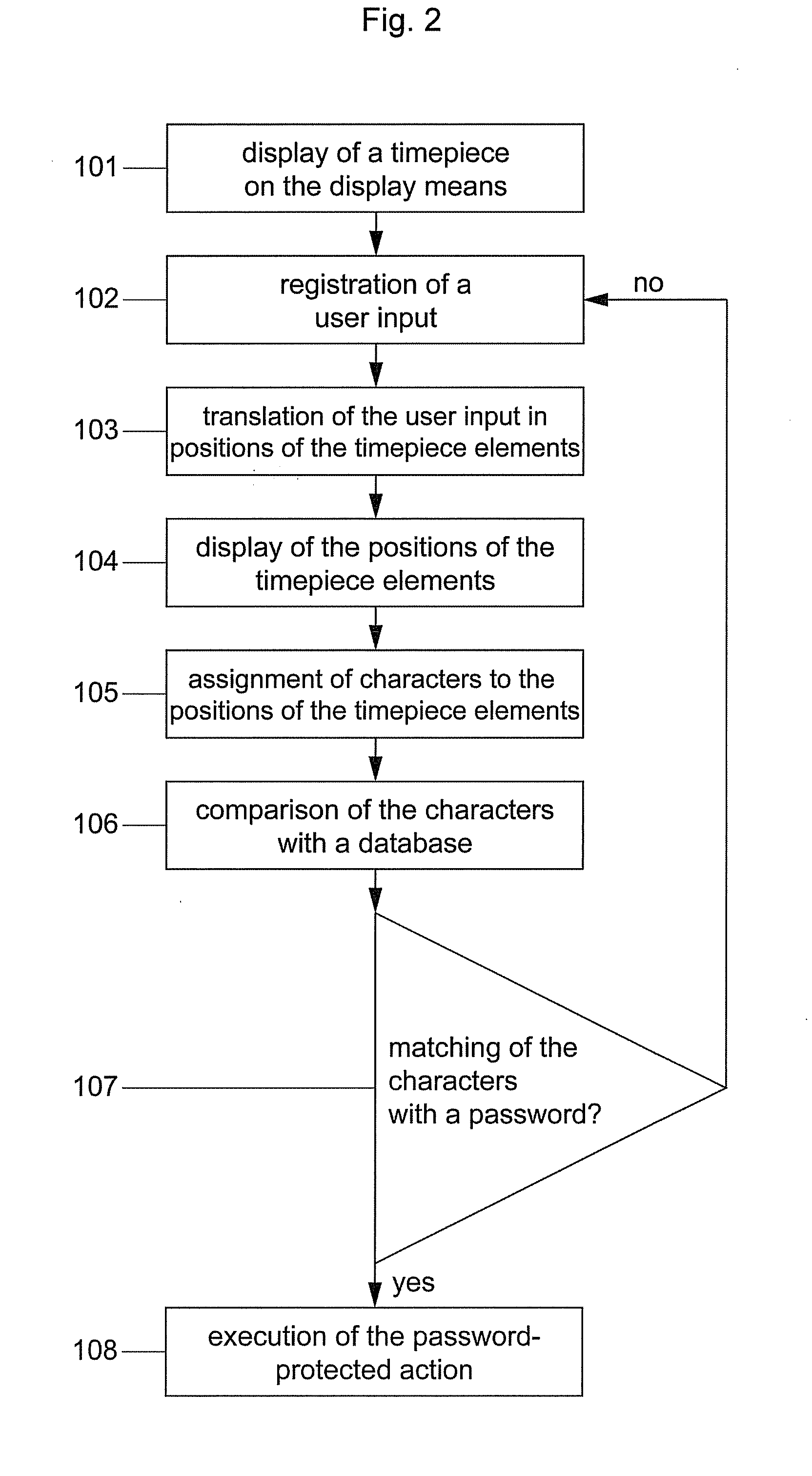
Method for entering a password and computer program (therefor)
InactiveUS20140047525A1Increase safetySignificant space savingDigital data processing detailsMultiple digital computer combinationsAlphanumericData processing
A method is provided for entering a password. The method includes: providing a display means which is coupled to a data processing means; displaying a timepiece with a first representation of a timepiece element on the display means, detecting a user input; and assigning an alphanumeric character of the password to the user input and the first representation of the timepiece element or a further representation of the timepiece element. In some instances, the first representation of the timepiece element is time dependent.
Owner:BONHOFF HANNES
Amusement park system
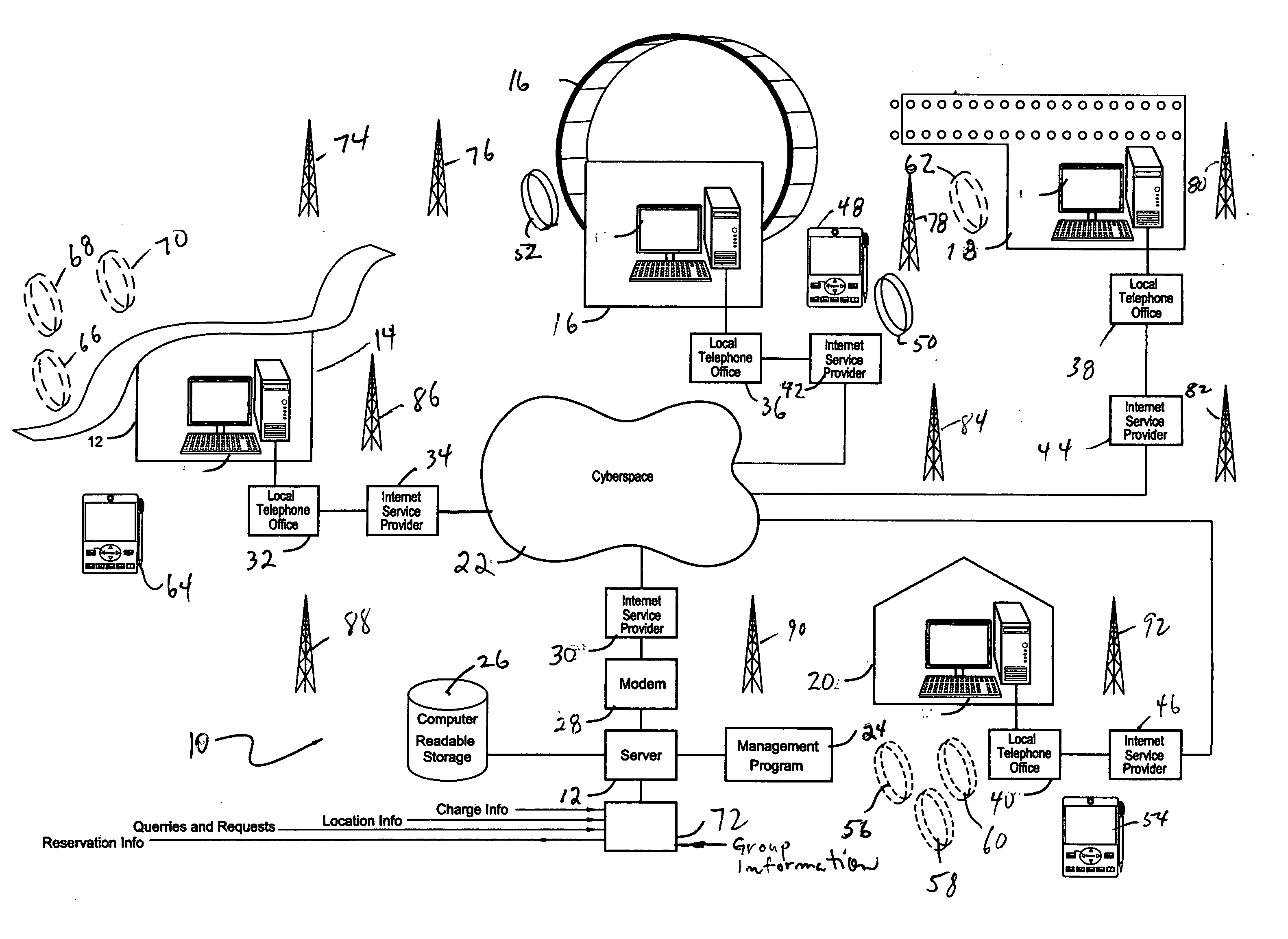
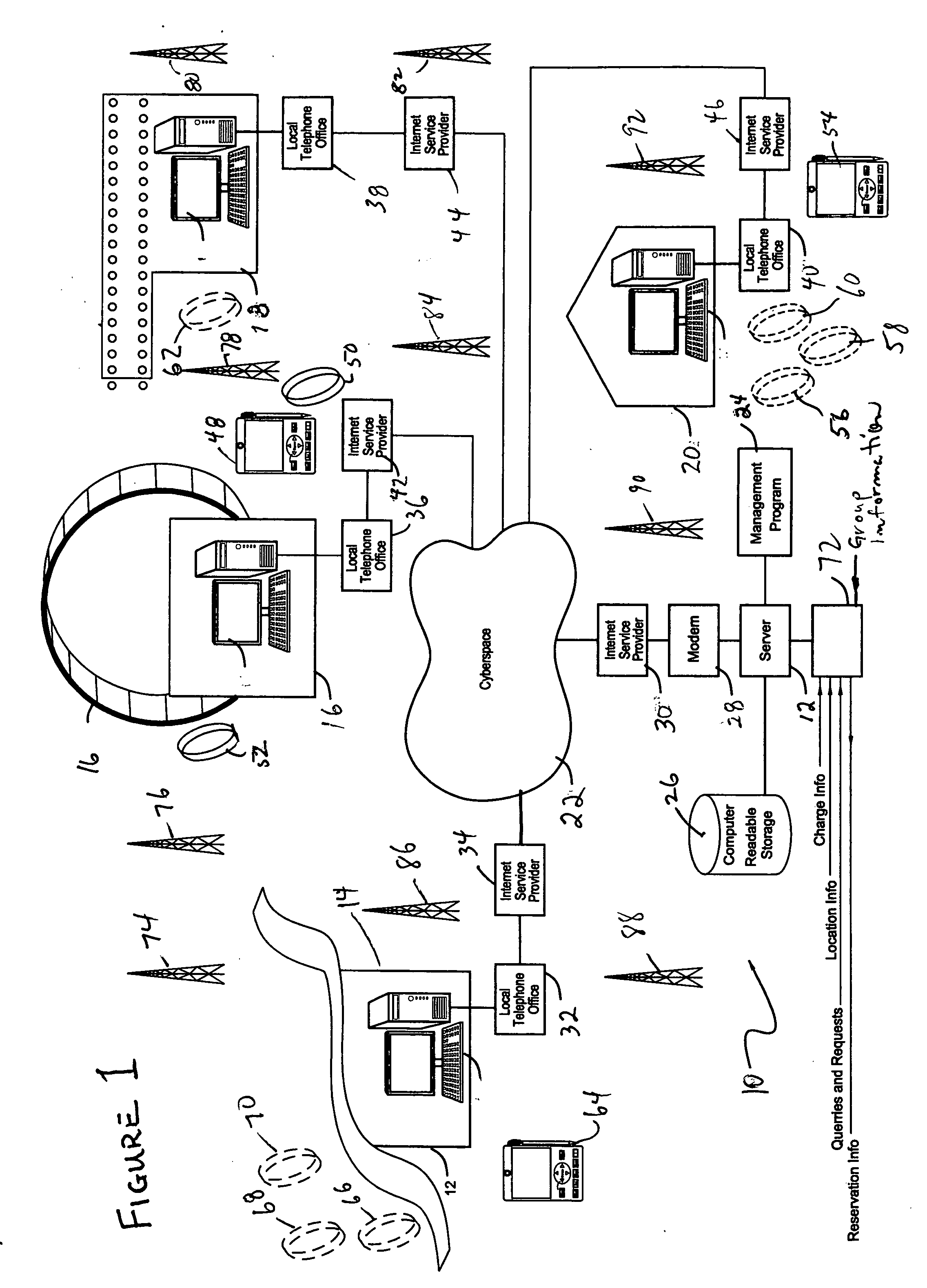
InactiveUS20050045710A1Increase safetyReduce traffic , confusion and stressCredit registering devices actuationChecking apparatusTransceiverEngineering
Owner:BURKE NICHOLAS
Hydraulic vehicle jack system
InactiveUS20060163551A1Increase safetyReduce maintenanceVehicle fittings for liftingVehicle cleaning apparatusAutomotive engineeringHydraulic pump
A hydraulic vehicle jack system that safely lifts vehicles without using the vehicle as a power source power source and without moving mechanical parts. The system comprises: (a) a hydraulic vehicle jack mounted to the chassis of a vehicle near one of its wheels; (b) a hydraulic pump system to provide pressurized fluid to the hydraulic vehicle jack; and (c) a control device to activate the hydraulic pump system. Also disclosed is a method for lifting a vehicle.
Owner:COENEN DUANE +1
Automobile door handle
ActiveUS20050161959A1Increase safetySimple modificationWing handlesConstruction fastening devicesArm movingDoor handle
An automobile door handle mechanism has a door handle with a handle arm and a latch lever with a lever arm moved by the handle in an unlatch direction to unlatch a door. The handle arm and lever arm overlap in the unlatch direction to restrict movement of the latch lever in the unlatch direction without movement of the handle.
Owner:ILLINOIS TOOL WORKS INC
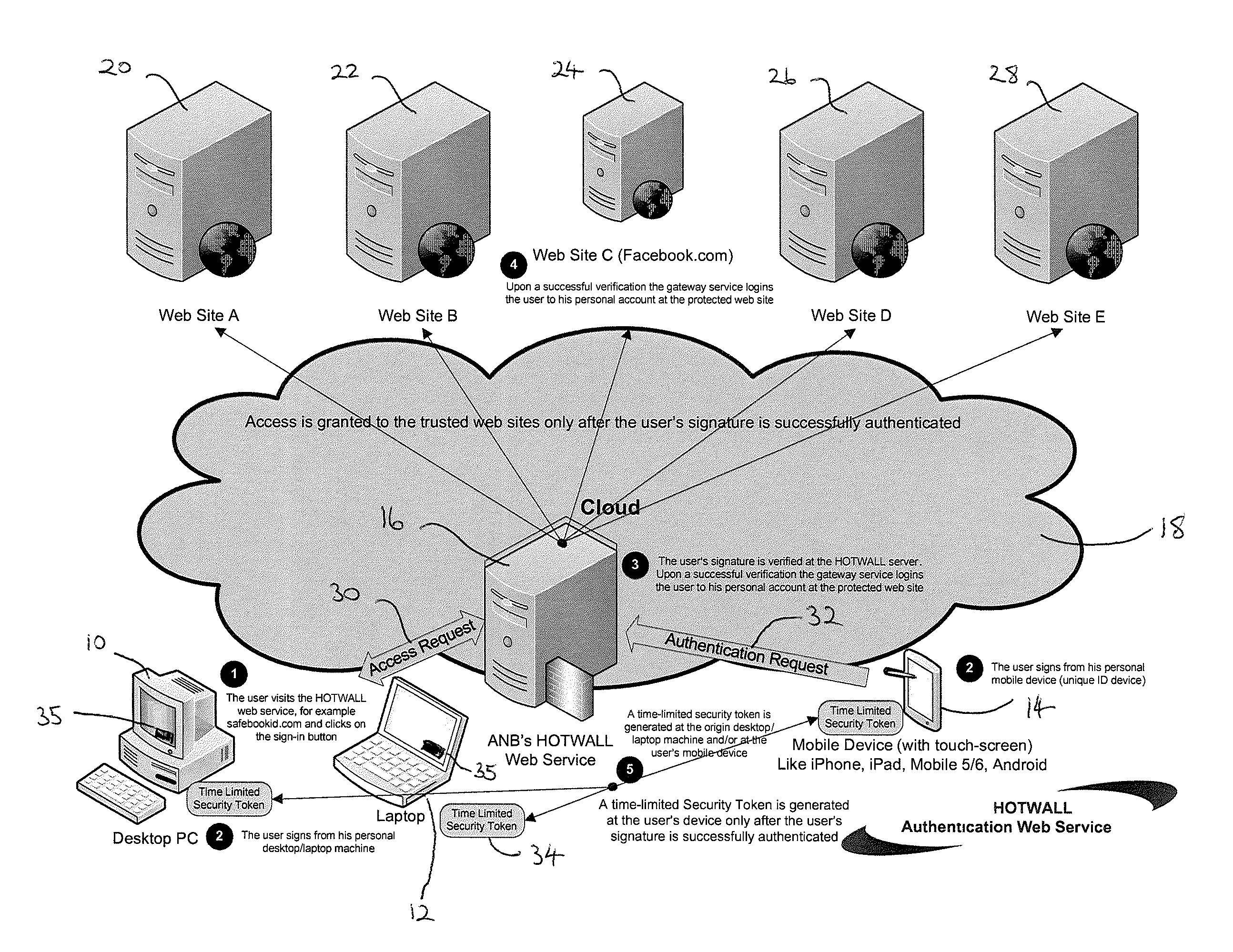
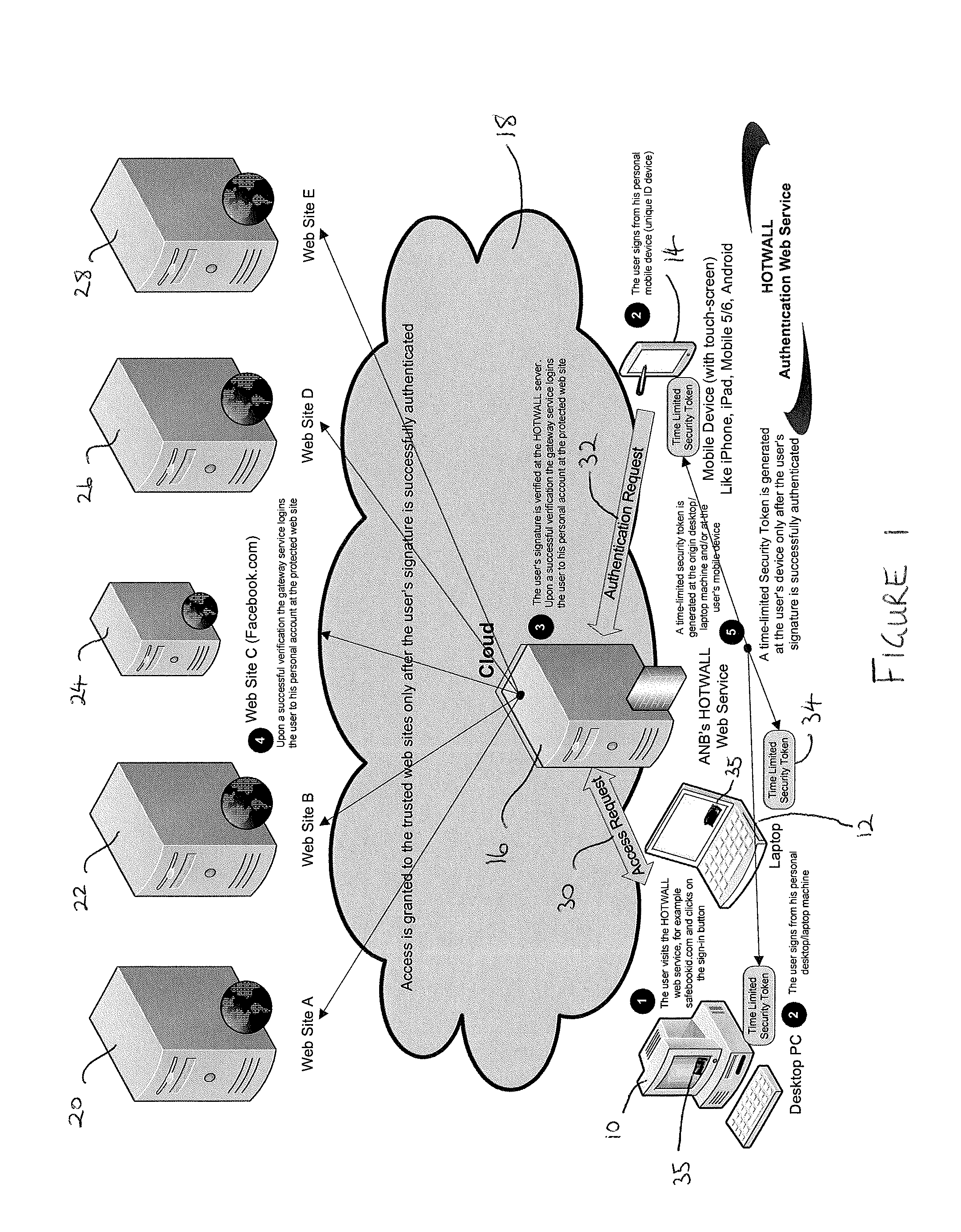
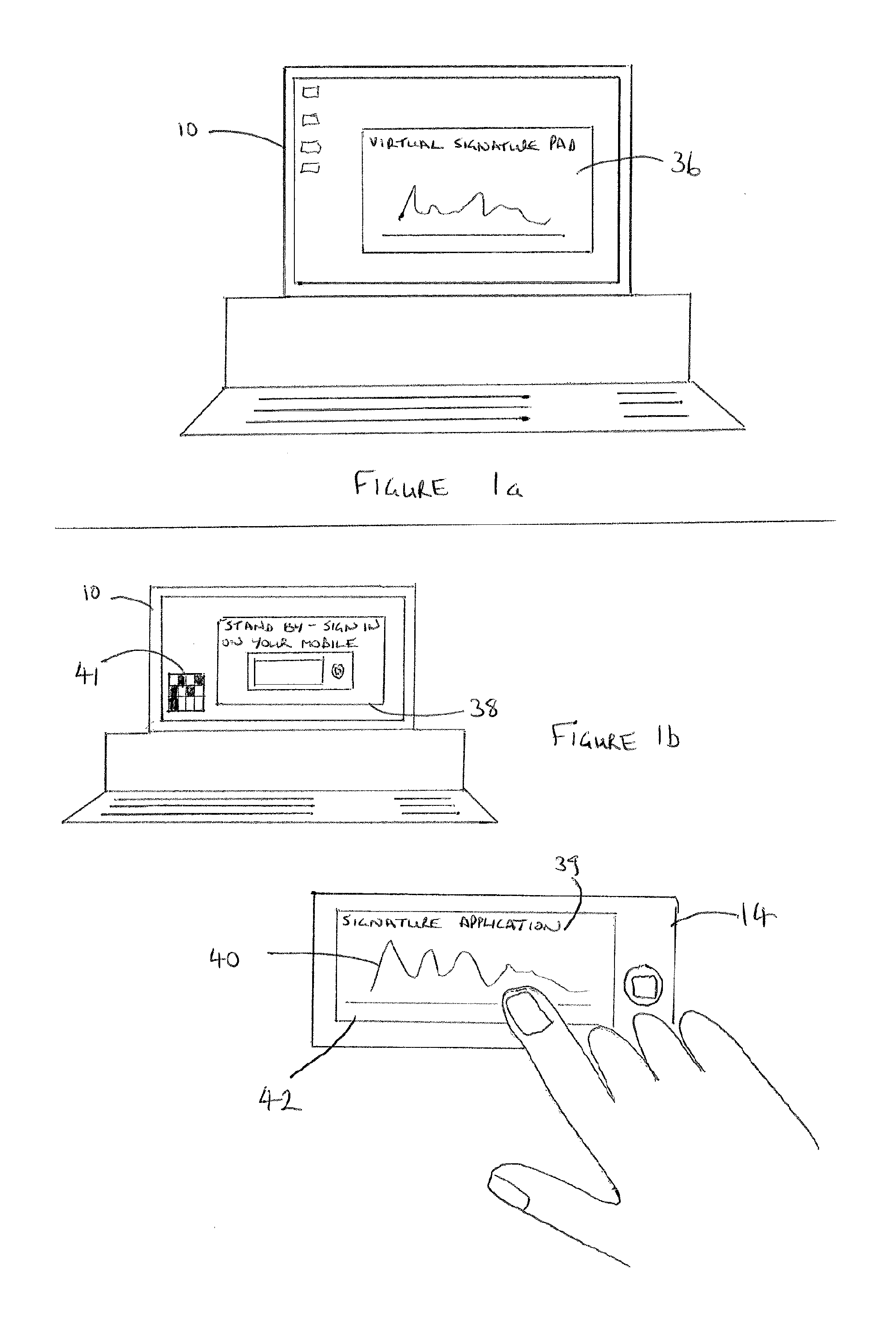
Identity verification
InactiveUS20130205380A1Increase safetyReduce chanceDigital data processing detailsMultiple digital computer combinationsAuthentication server
A method of verifying the identity of a user comprising: initiating (50) a sign-in request from a first computing device to an authentication server; receiving (58) an instruction from the authentication server to provide signature data from a second computing device; entering (64) signature data at the second computing device and sending the signature data to the authentication server; verifying (65) the signature data at the authentication server; notifying (66) the user that their identity has been verified on the basis of the data received from the second computing device.
Owner:ARTIFICIAL INTELLIGENCE RES GRP LTD
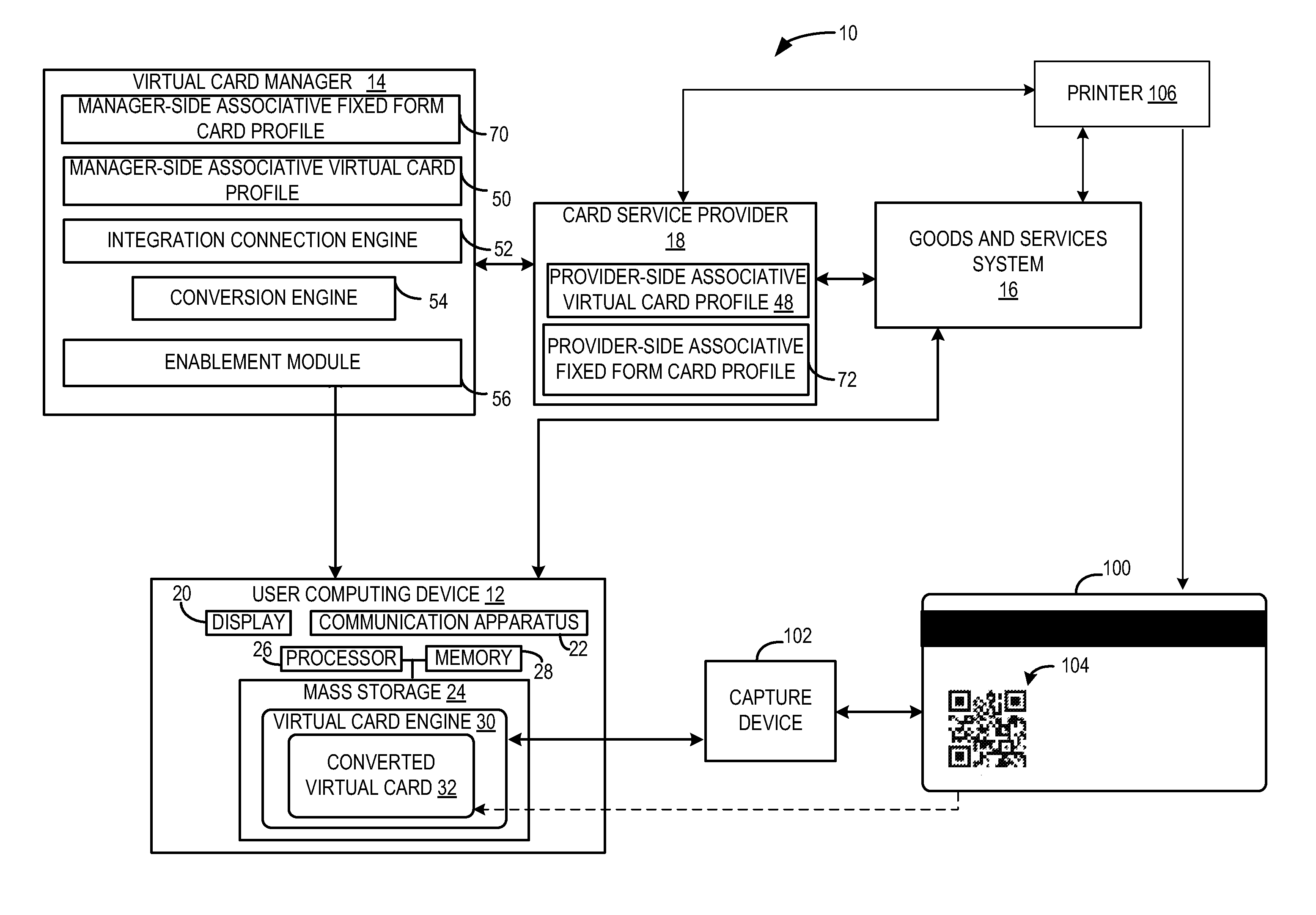
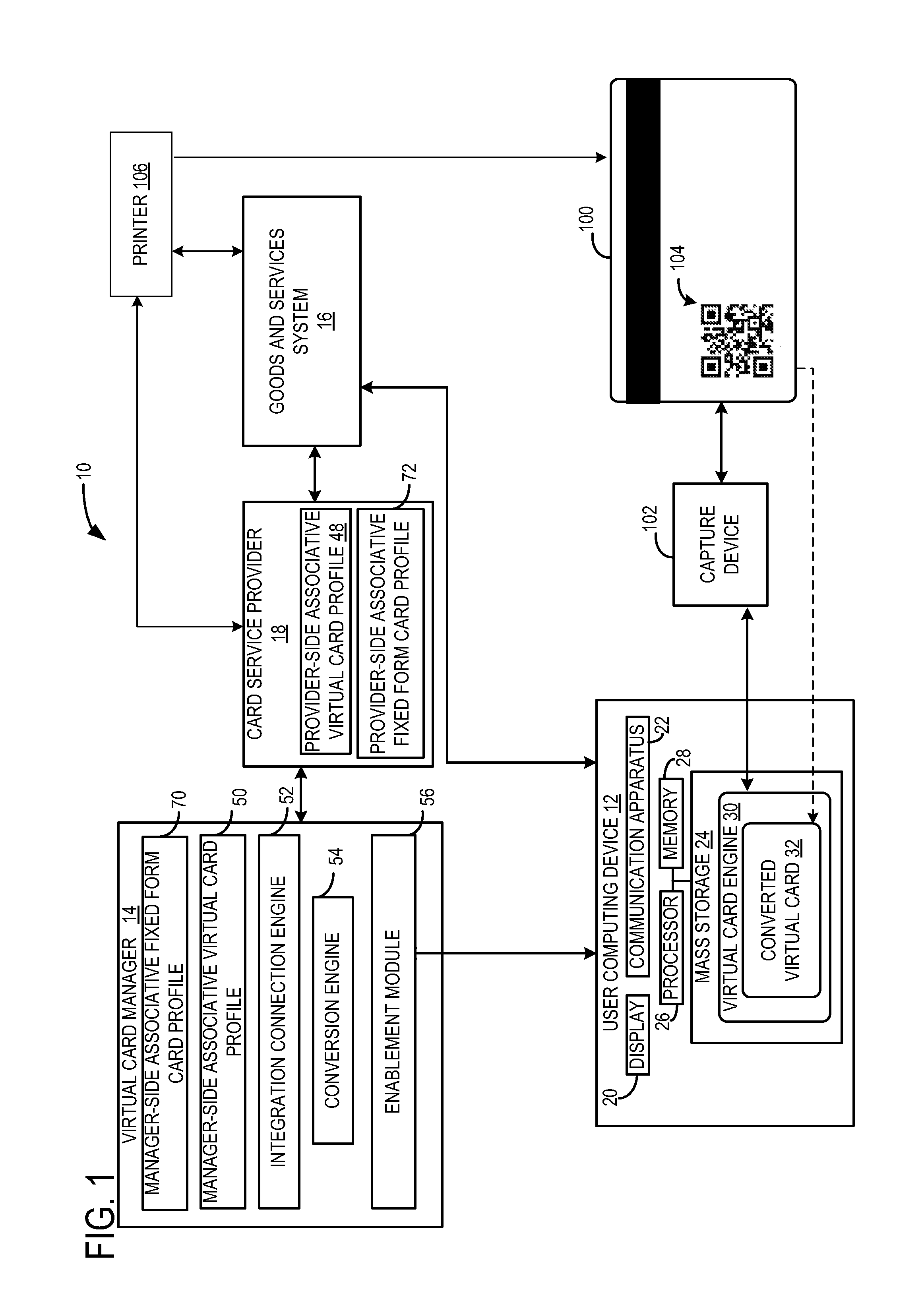
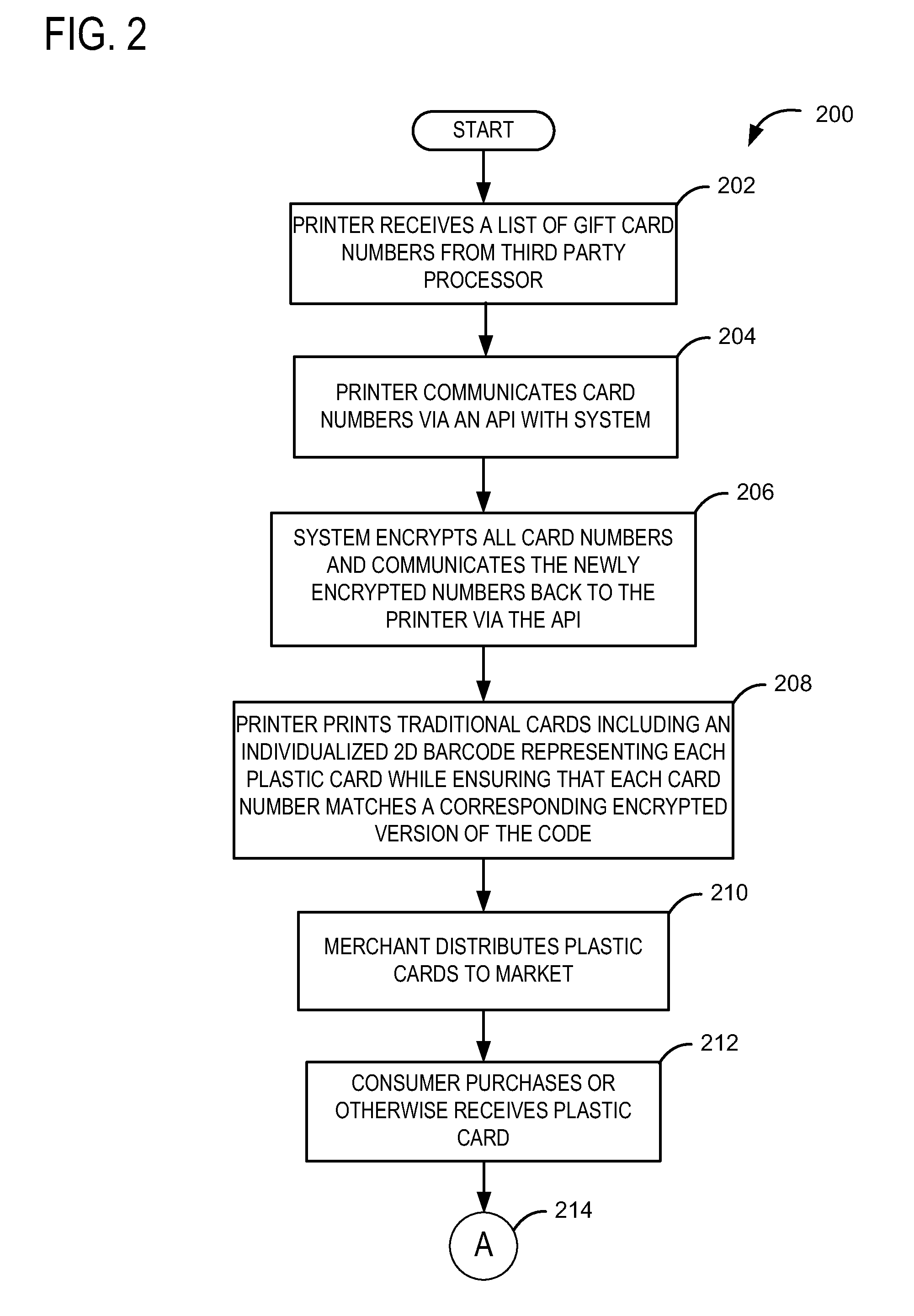
Systems and methods for fixed form card to virtual card communication
InactiveUS20120323787A1Decrease likelihoodIncrease safetyFinanceProtocol authorisationLarge capacityMass storage
System and methods for converting a fixed form card to a virtual card are disclosed herein. The system includes a virtual card manager and a user computing device communicatively coupled via a network. The virtual card manager may be configured to convert a fixed form card to a virtual card, and the user computing device may be configured to initiate a virtual card conversion request via a virtual card engine stored in mass storage and executable by a processor. As such, a stored value of the fixed form card may be transferred to the virtual card in a secure manner.
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
System and method for customer initiated payment transaction using customer's mobile device and card
ActiveUS20180204195A1Increase safetyPayment process become simplifyPayment circuitsProtocol authorisationPayment transactionDebit card
A system for a customer initiated payment transaction includes a mobile device of a customer, a merchant including merchant information and payment information, a multi-payment gateway, and a network. The mobile device includes a digital wallet, on which a customer may register one or more of a plurality of payment methods. Payment methods include credit card, debit card, virtual cards, cryptocurrency, and loyalty points.
Owner:KANG SOO HYANG
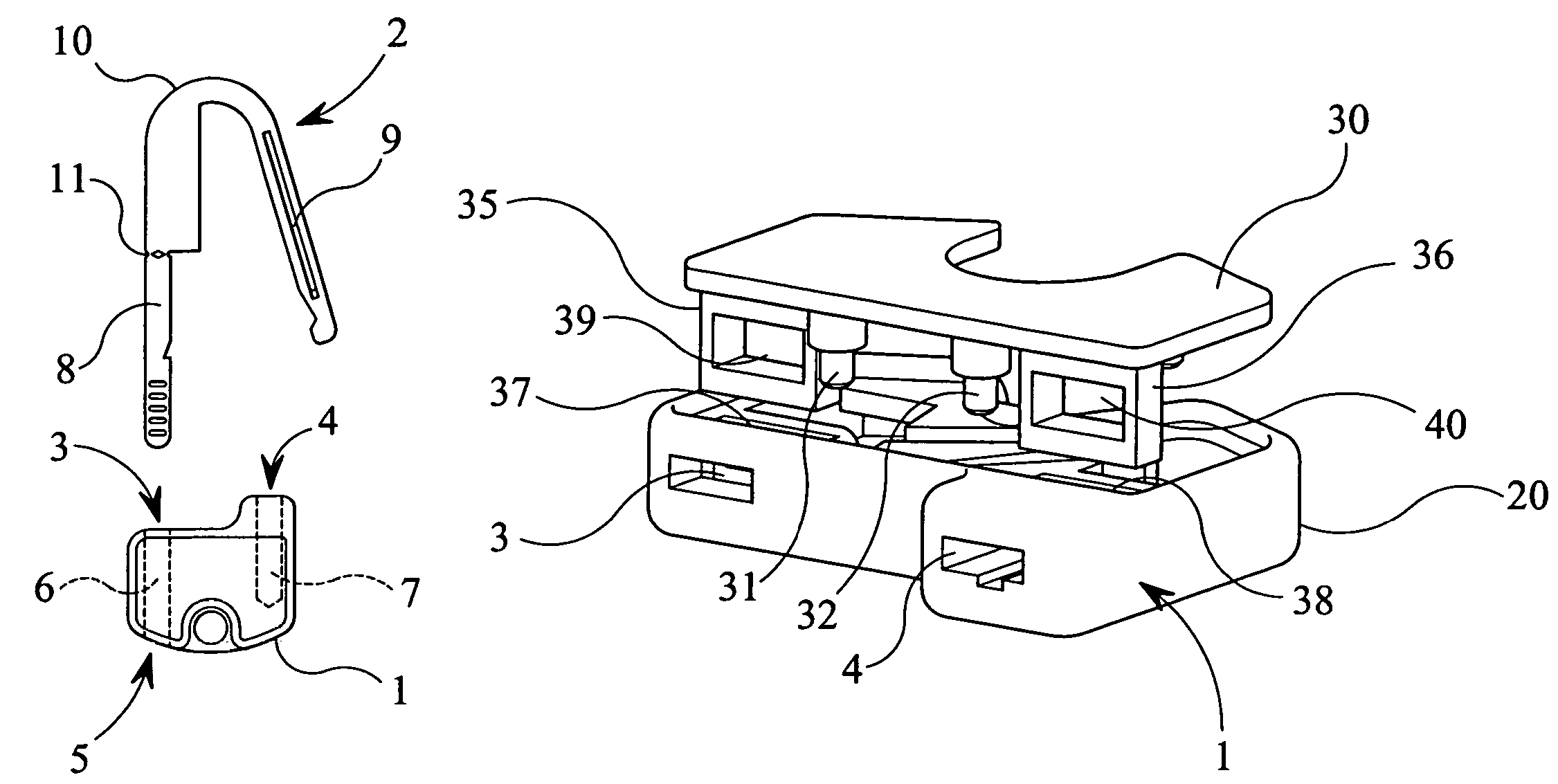
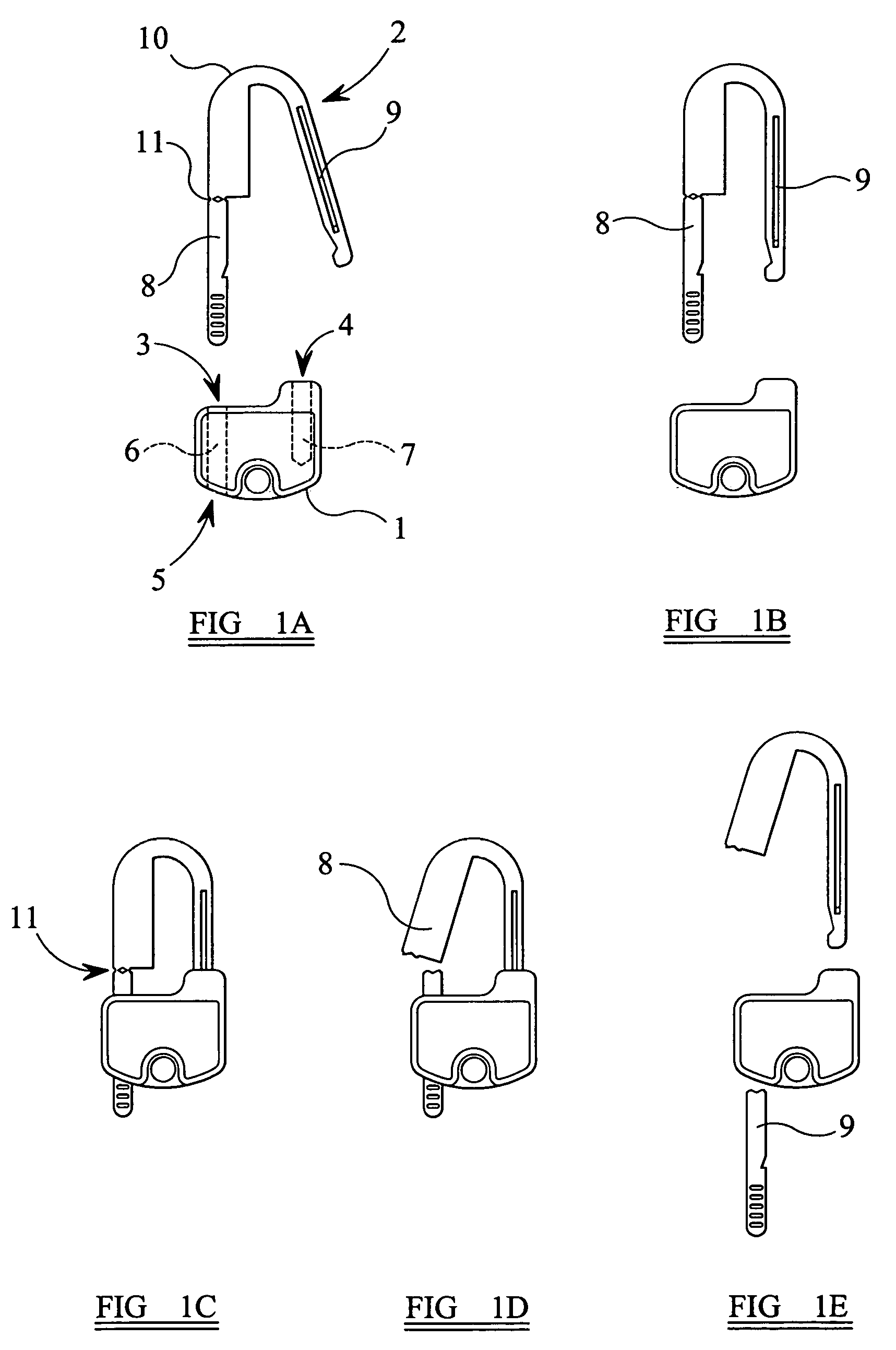
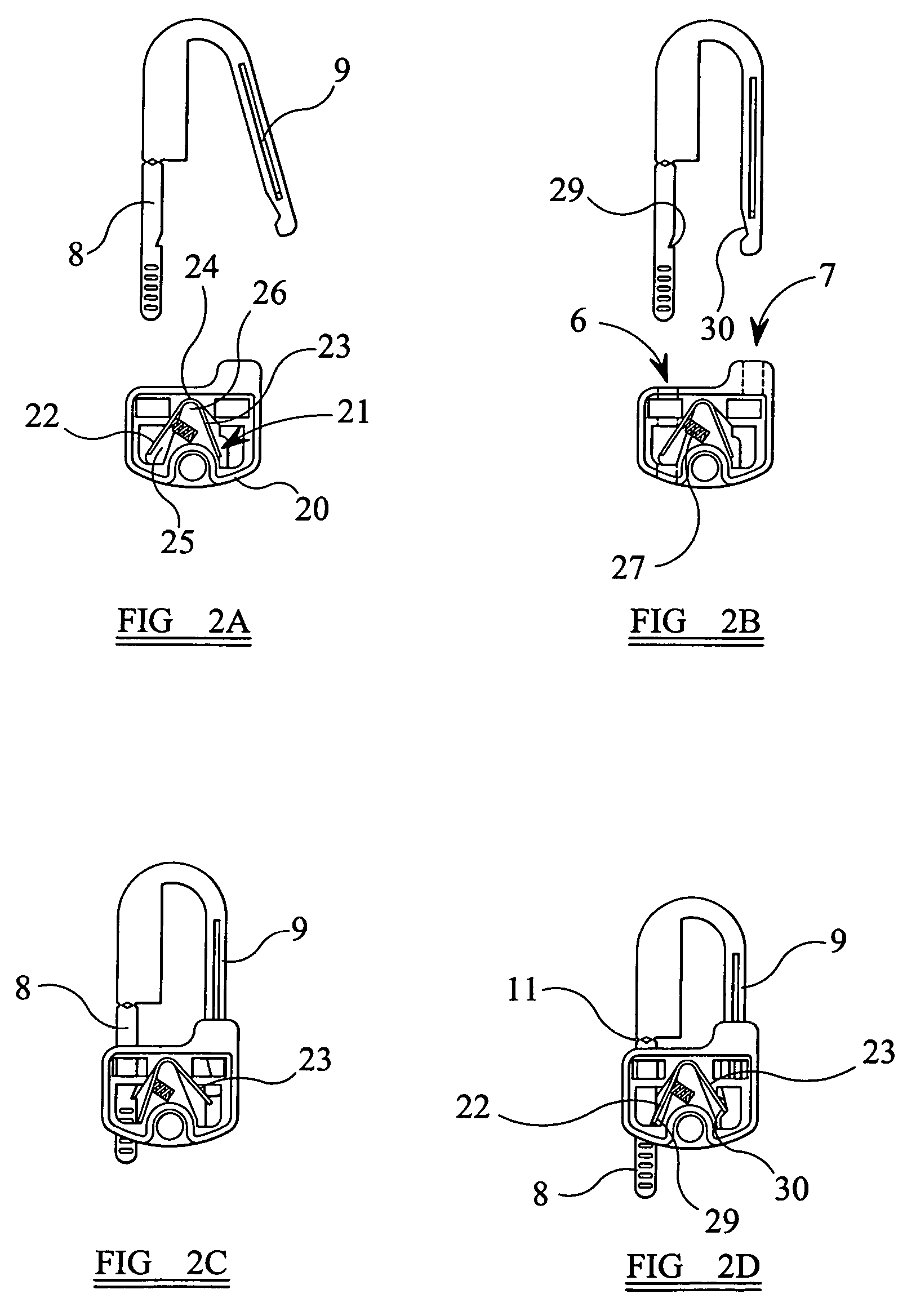
Security seal
A seal of the type includes a housing and a J- or U-shaped hasp, the housing having first and second openings to receive the legs of the hasp. The first opening communicating with a third opening of the housing to form a channel for a first leg of the hasp. A locking mechanism is provided within the housing which is biased to resist withdrawal of the first leg of the hasp through the first opening. The hasp being lockable within the housing such that it can only be removed by cutting of the first leg of the hasp. The legs of the hasp are substantially rigid and are connected together by a resilient hinge such that in a first, relaxed position the legs adopt a position in which they are not parallel, the legs being moveable to a second, parallel position against the resilient force of the hinge for insertion into the housing. The housing may be formed of a main body and a cover, the cover being sealed onto the body part, the cover having at least one protrusion which engages in a corresponding recess within the body part, and the protrusion having an aperture therethrough which in use receives one leg of the hasp.
Owner:ITW LTD
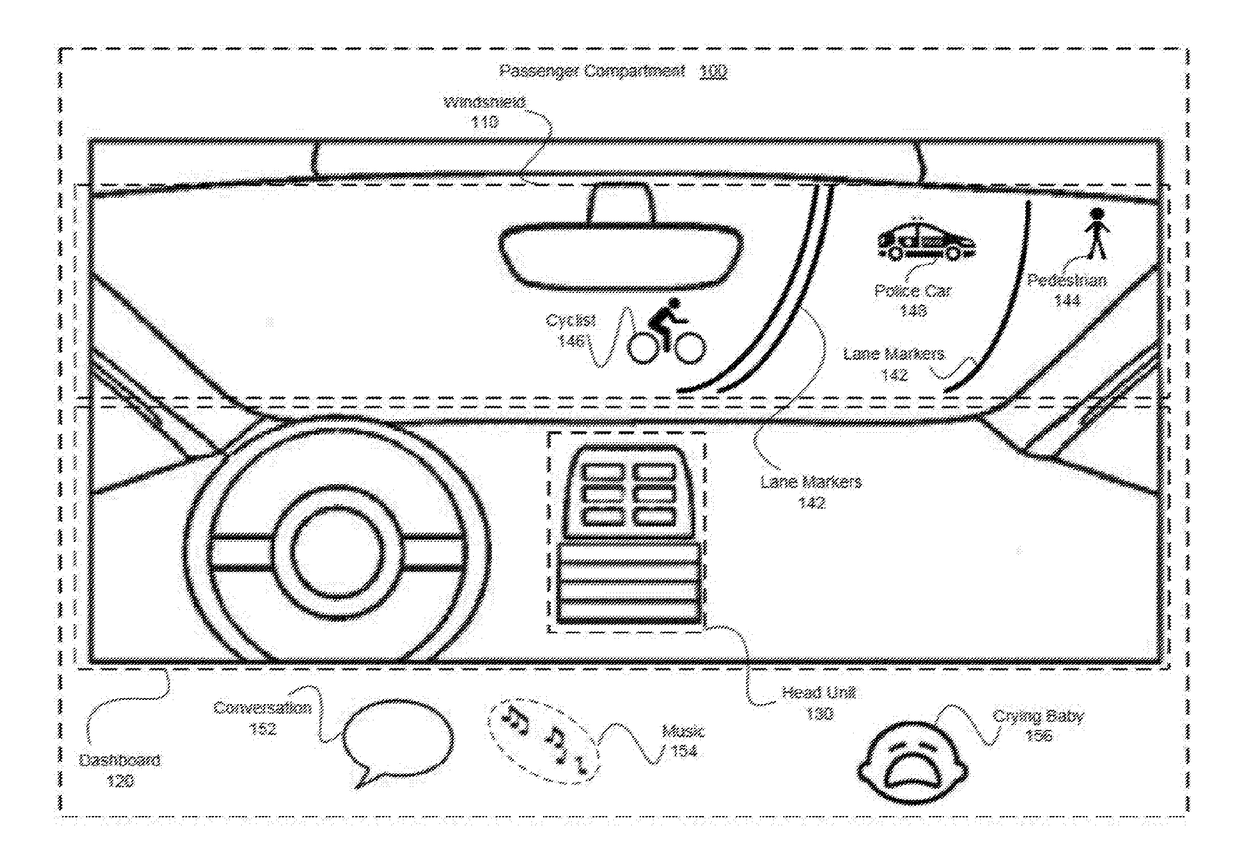
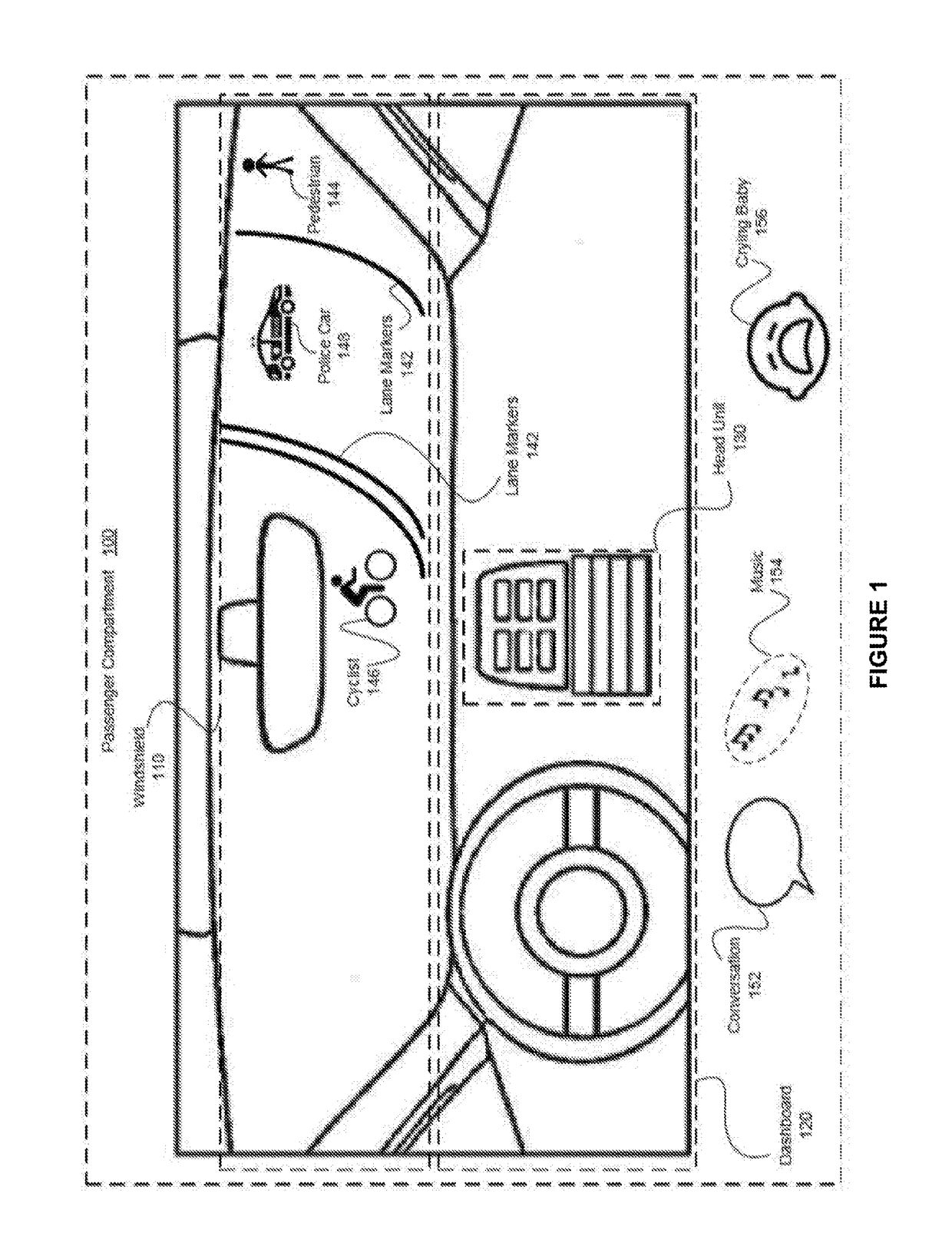
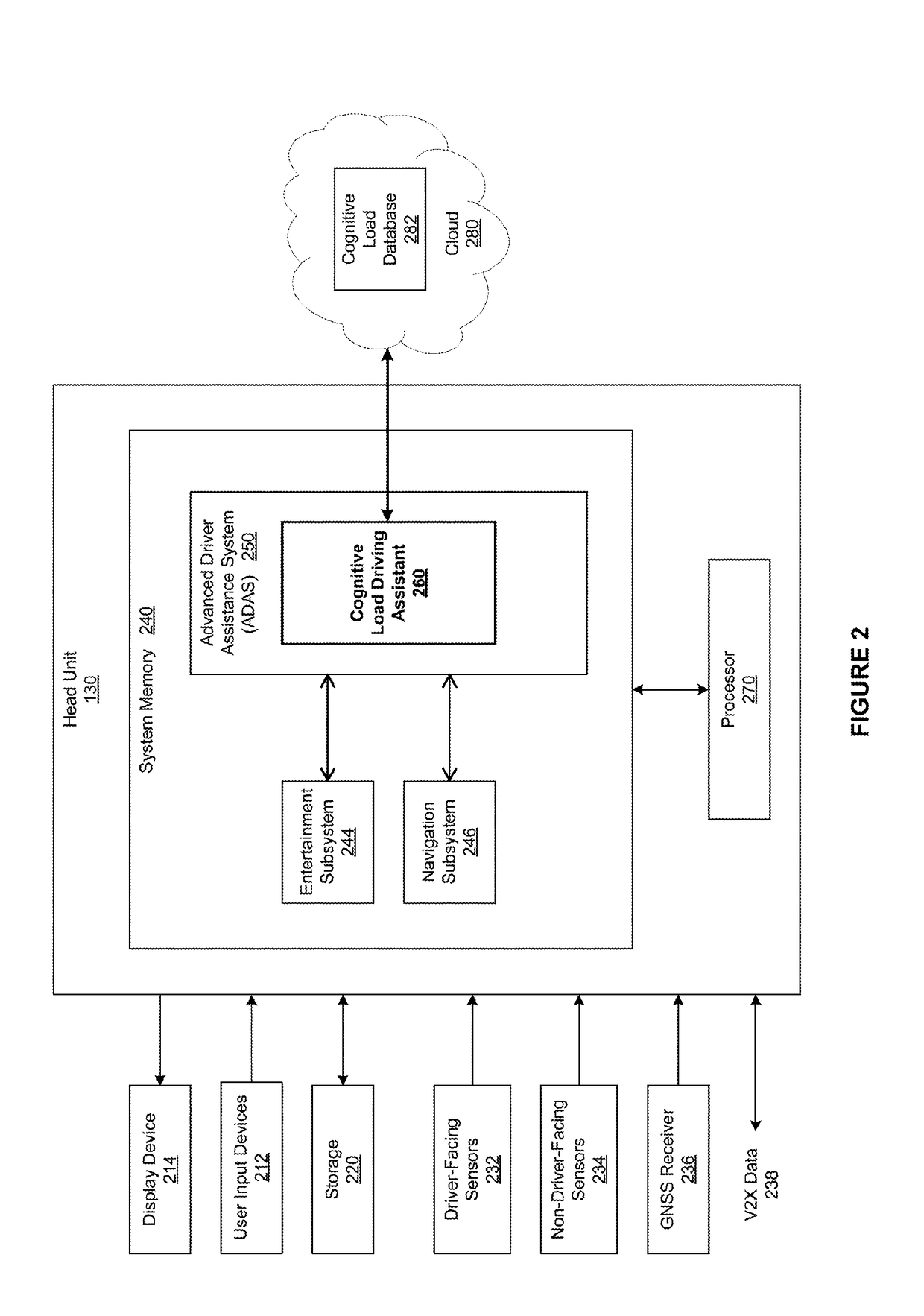
Cognitive load driving assistant
ActiveUS20180009442A1Increase safetyReduce complexityInstruments for road network navigationDetection of traffic movementDriver/operatorDriving safety
In one embodiment, a cognitive load driving assistant increases driving safety based on cognitive loads. In operation, the cognitive load driving assistant computes a current cognitive load of a driver based on sensor data. If the current cognitive load exceeds a threshold cognitive load, then the cognitive load driving assistant modifies the driving environment to reduce the cognitive load required to perform the primary driving task and / secondary task(s), such as texting via a cellular phone. The cognitive load driving assistant may modify the driving environment indirectly via sensory feedback to the driver or directly through reducing the complexity of the primary driving task and / or secondary tasks. In particular, if the driver is exhibiting elevated cognitive loads typically associated with distracted driving, then the cognitive load driving assistant modifies the driving environment to allow the driver to devote appropriate mental resources to the primary driving task, thereby increasing driving safety.
Owner:HARMAN INT IND INC
Wick holder magnetic retention means
The present invention relates to melting plate candles which employ heat conductive elements to distribute heat from a burning flame at a wick to a support plate for a solid fuel and to the body of said solid fuel, so as to more rapidly liquefy the solid fuel, such as paraffin wax, and to more uniformly and intensely heat such fuels to increase the efficiency of consumption thereof and to more rapidly release volatile materials contained within said fuels. The heat conductive support plate is configured so as to have a capillary pedestal upon the surface thereof, which magnetically engages a wick holder comprising a preferably consumable wick and heat conductive fins which conduct heat from a flame upon said wick to said support plate, said magnetic engagement of said wick holder preventing accidental removal thereof from said pedestal. The fuel may be provided in various forms, configured to cooperatively engage said wick holder and support plate, and may comprise various volatile materials. The capillary pedestal, in conjunction with the wick holder, causes rapid and complete flow of the liquefied fuel to said wick.
Owner:SC JOHNSON & SON INC
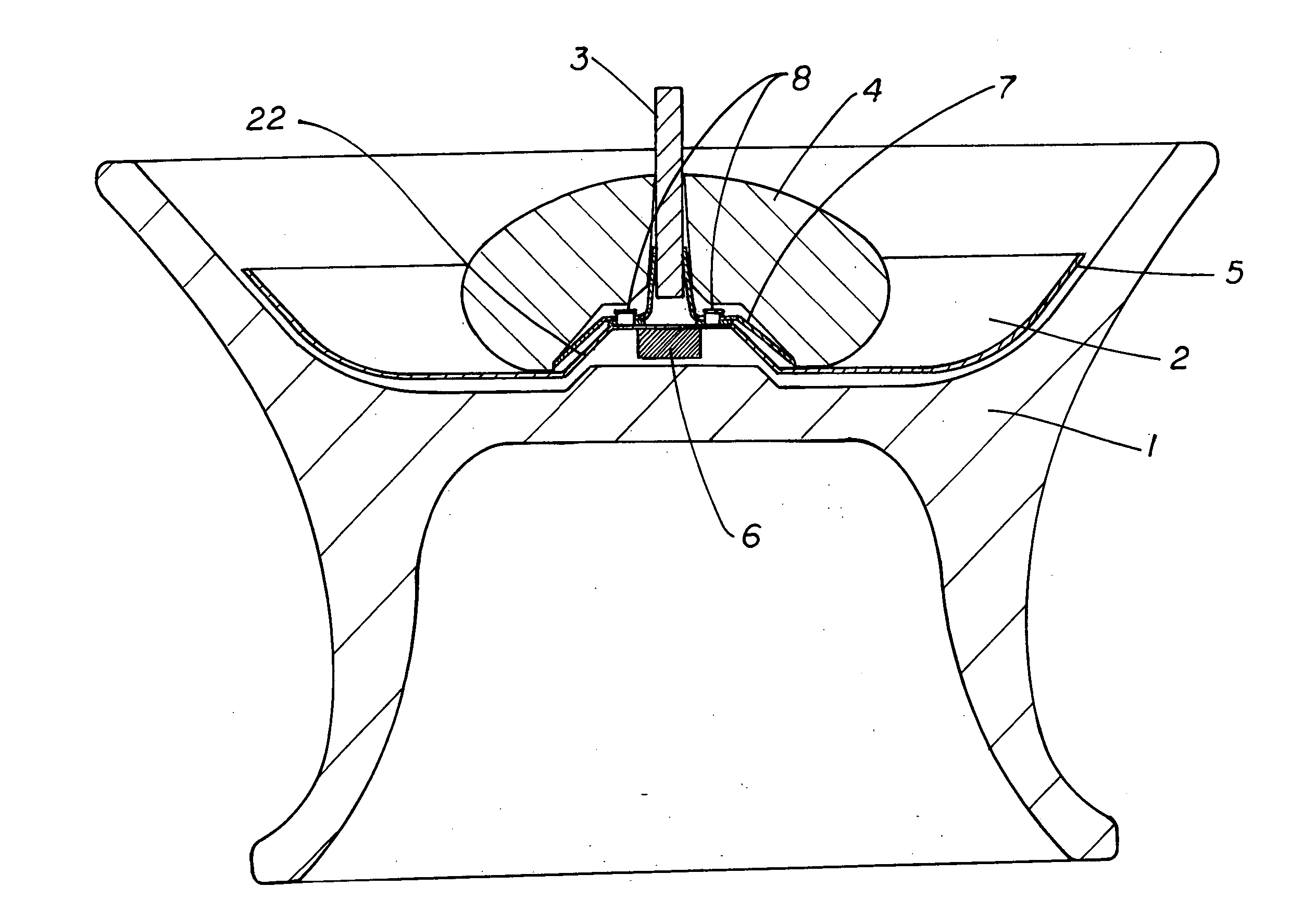
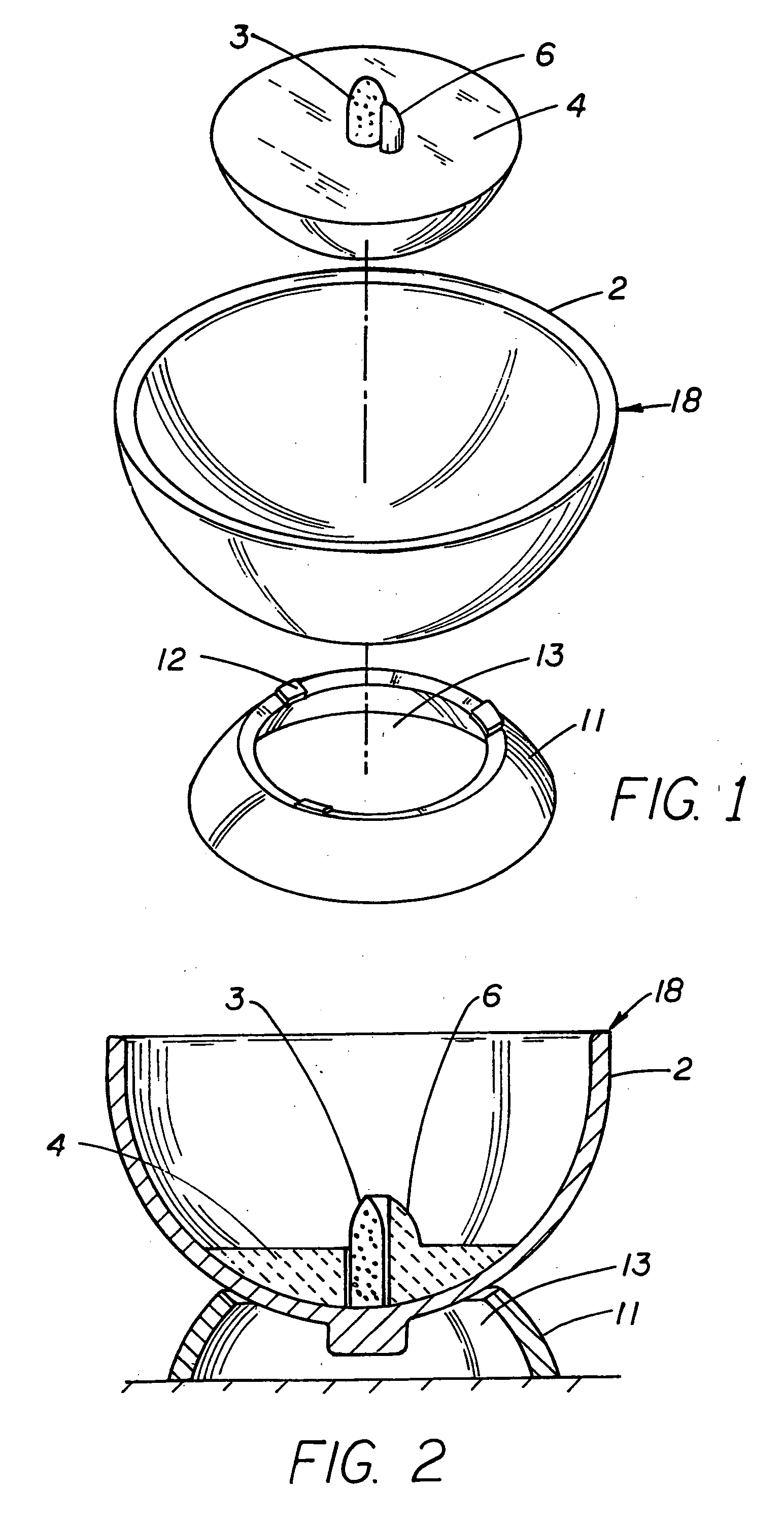
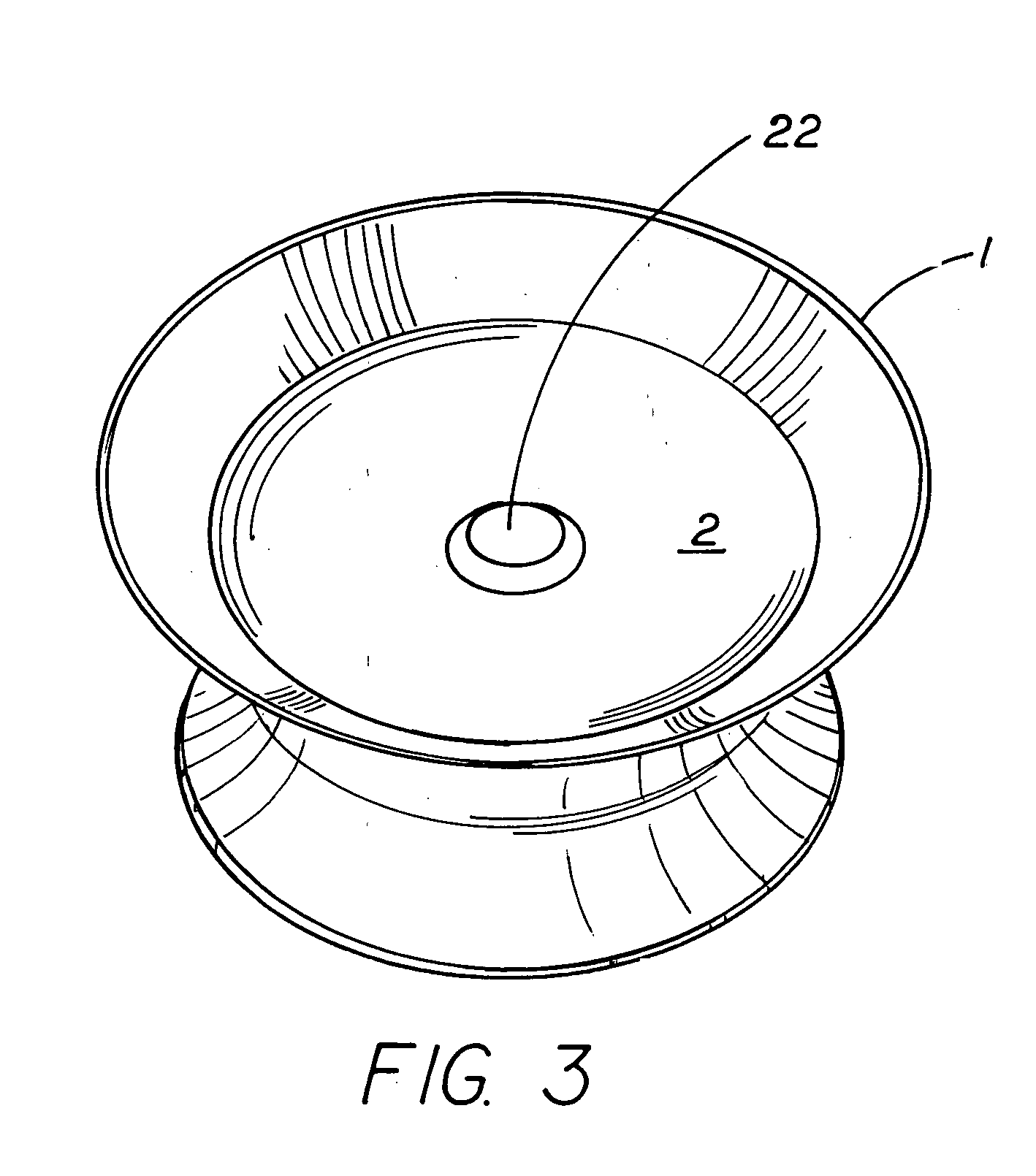
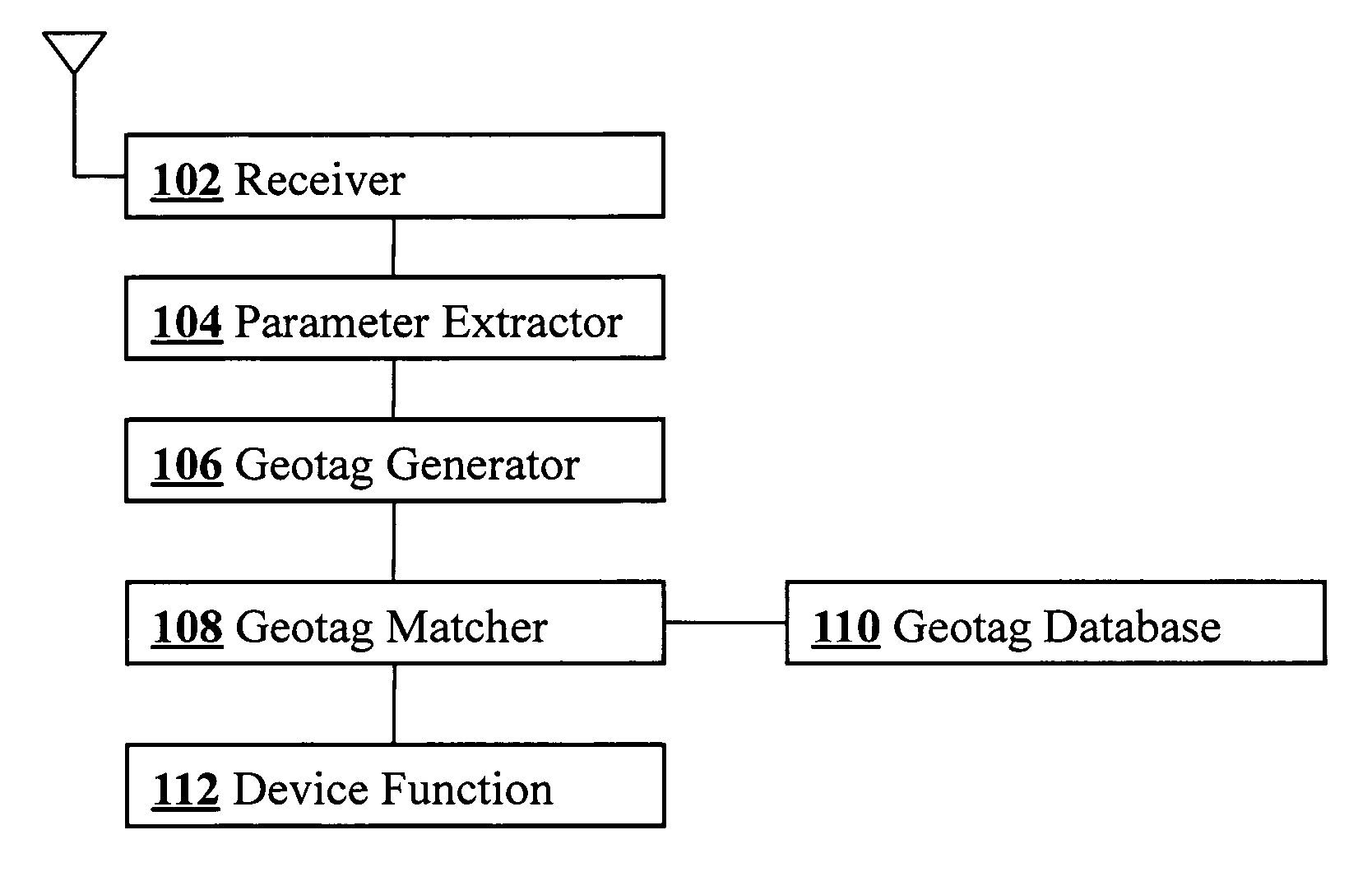
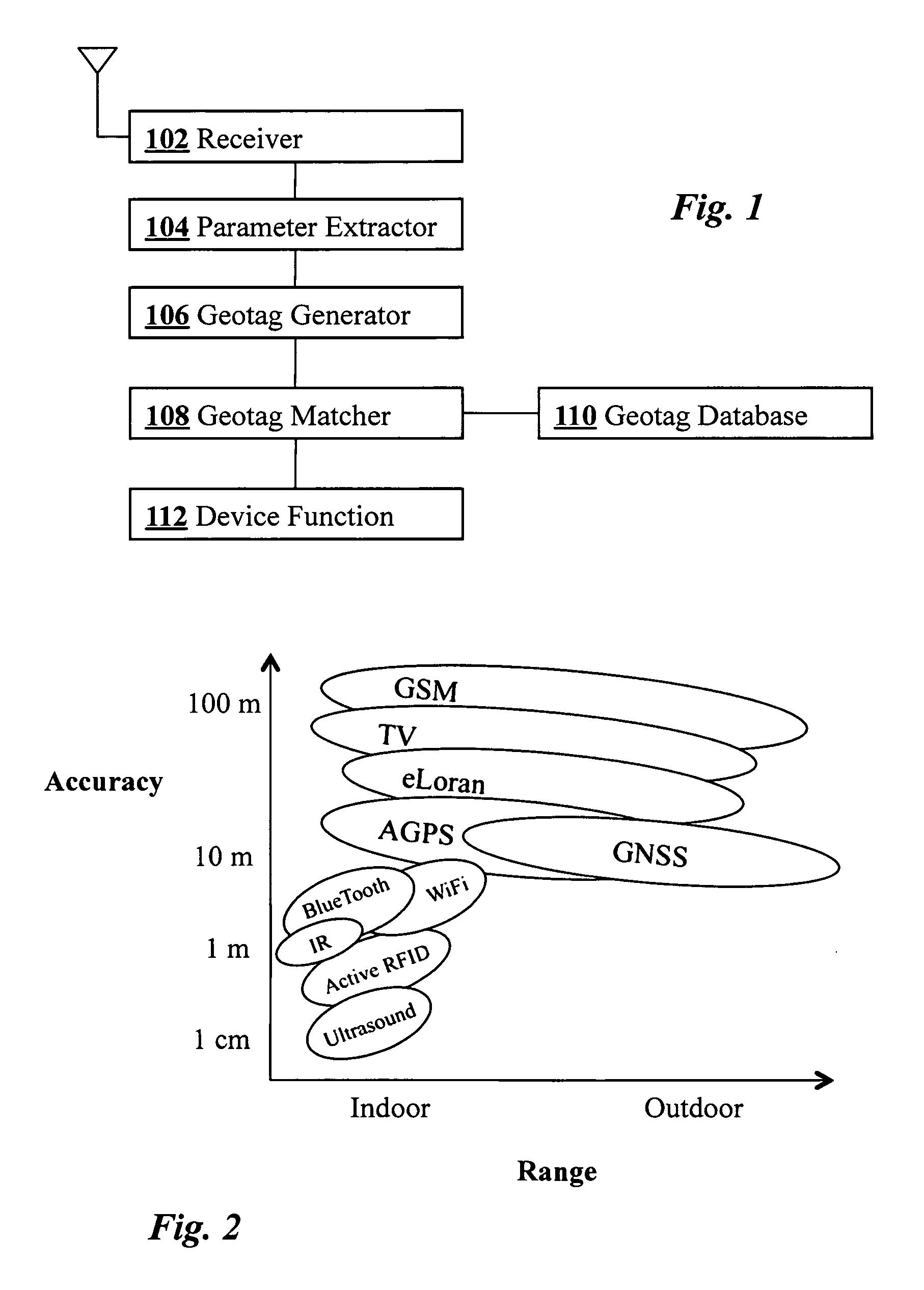
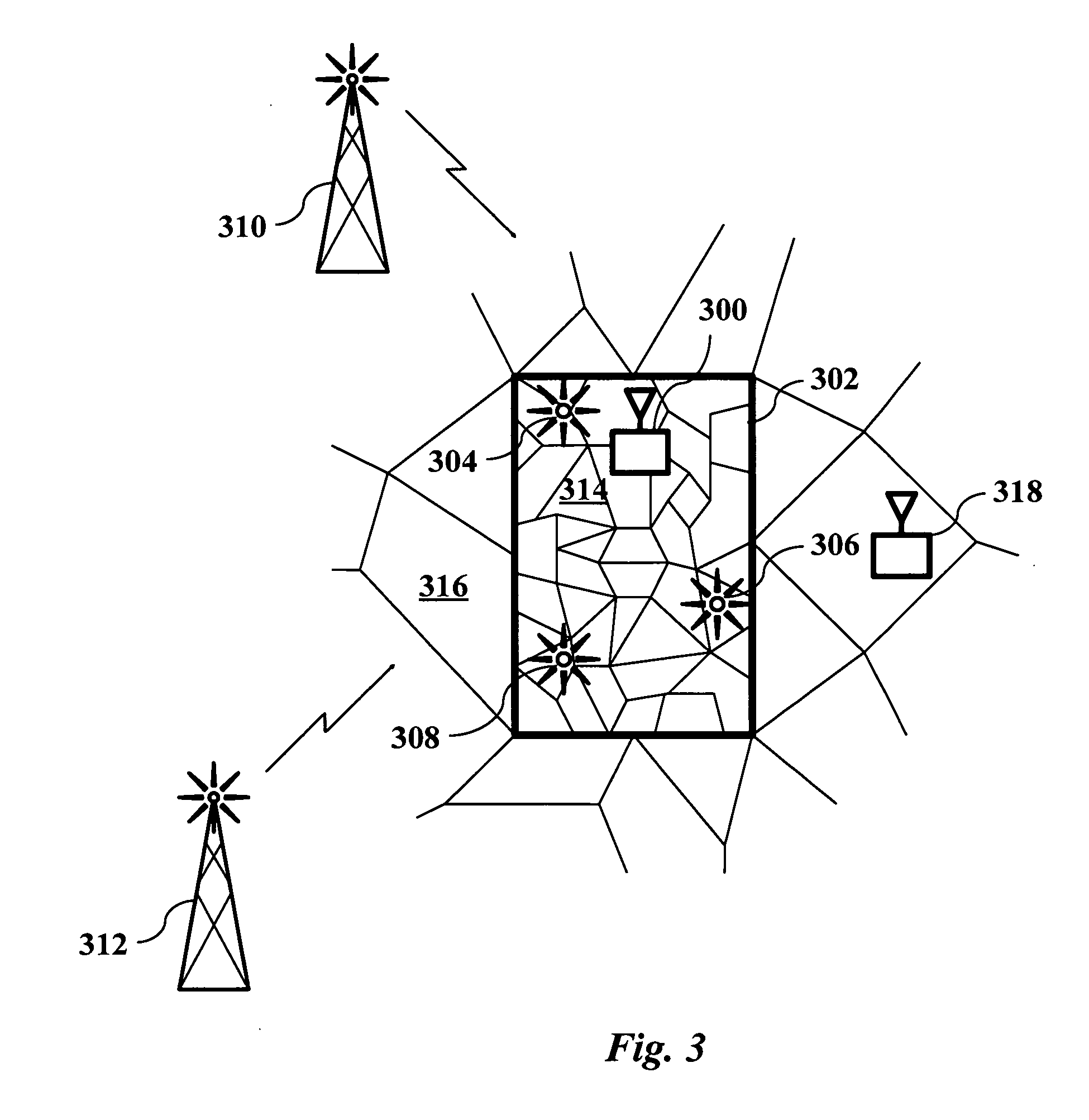
Geosecurity methods and devices using geotags derived from noisy location data from multiple sources
InactiveUS20110181470A1Increase safetyReduce ratePosition fixationSecret communicationLocation dataData science
In a geo-security system, a device receives RF signals from multiple distinct classes of RF communication systems and extracts location-dependent signal parameters. A current geotag is computed from the parameters by fuzzy extractors involving quantization of the parameters and Reed-Solomon decoding to provide a reproducible unique geotag. The current geotag is compared with a stored geotag, and a geo-secured function of the device is executed based on the result of the comparison. The use of multiple signal sources of different types, combined with special fuzzy extractors provides a robust geotag that allows both lower false rejection rate and lower false acceptance rate.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
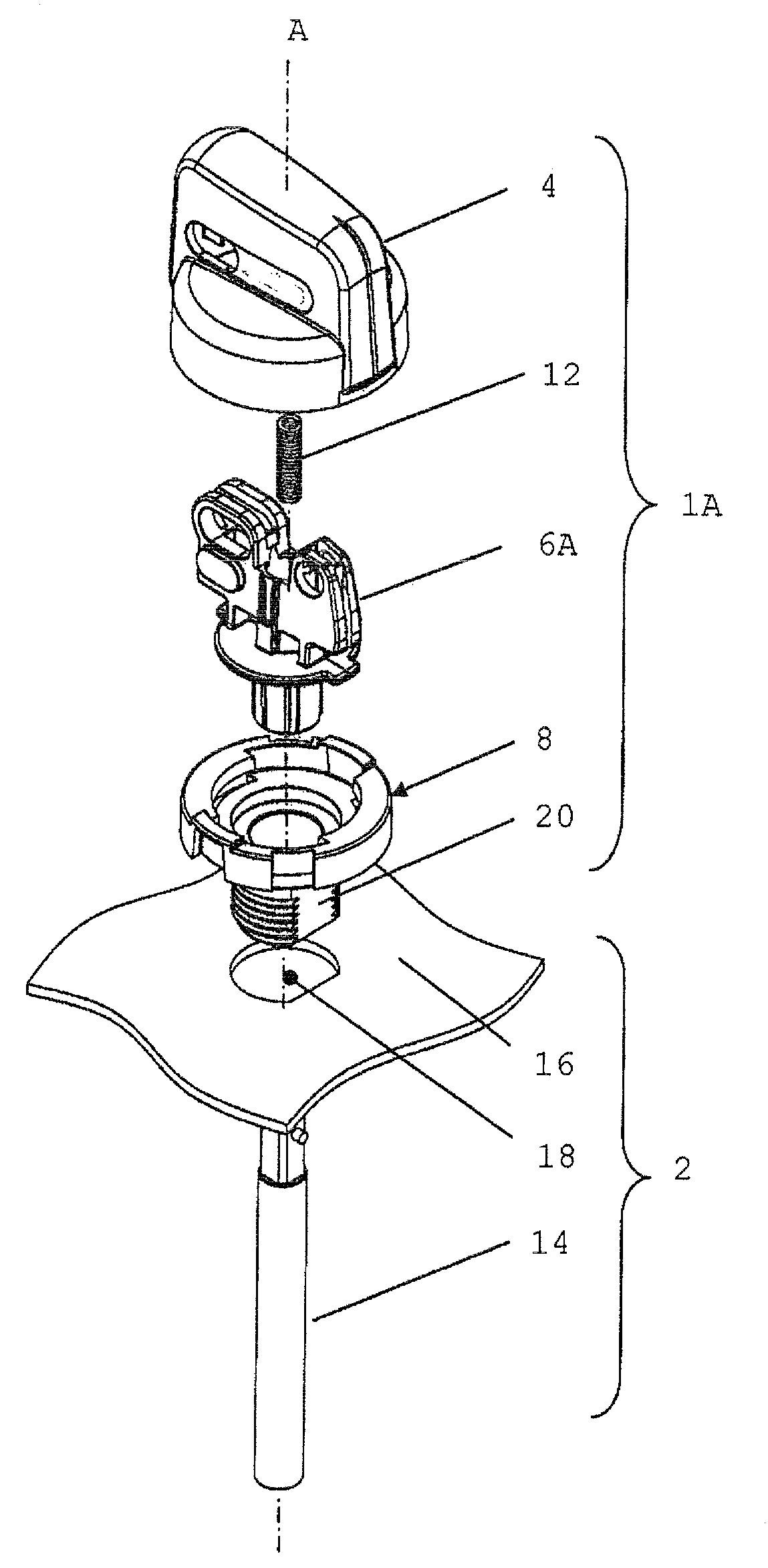
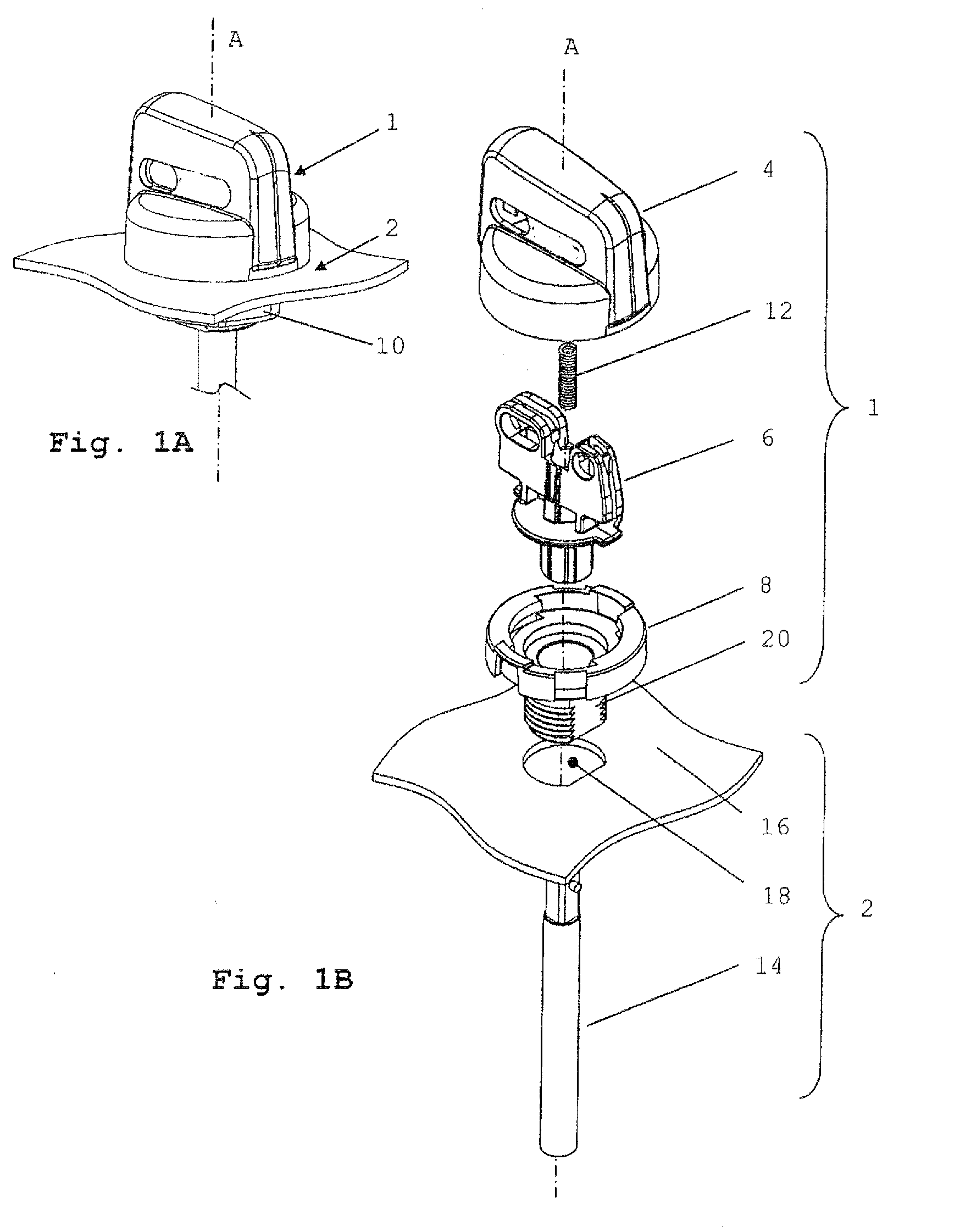
Safety Rotary Operator Assembly
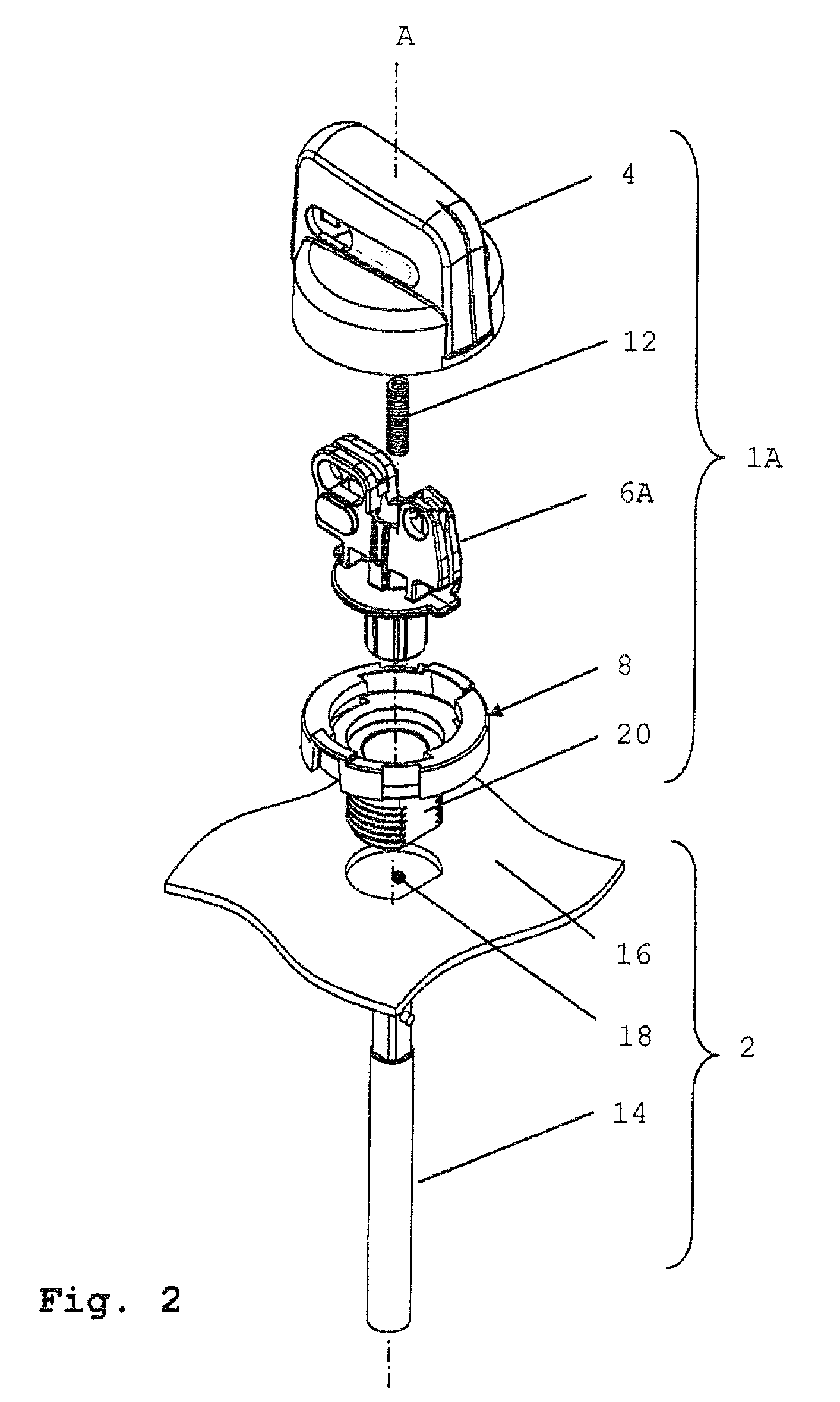
ActiveUS20100294632A1Operational safety be improveIncrease safetyControlling membersMechanical apparatusEngineeringMechanical engineering
A rotary operator assembly (1A) includes a grip member (4), a spindle member (6A), and an operator body member (8). The spindle member (6A) is attached to the operator body member (8), being rotatable with respect to the operator body member (8) about an operative axis of rotation (A). The grip member (4) is movably coupled to the spindle member (6A) and the operator body member (8) and is translatable between a first translational position and a second translational position with respect to the operator body member (8). The grip member (4) and the operator body member (8) include cooperating means for blocking rotation of the grip member (4) with respect to the operator body member (8) about the operative axis of rotation in the first position and for allowing rotation of the grip member (4) with respect to the operator body member (8) about the operative axis of rotation in the second position from a first angular position to a second angular position. The grip member (4) is configured to operably couple with the spindle member (6A) in at least the second translational position, and the grip member (4) comprises at least one portion cooperating with at least one portion of the spindle member (6A) for preventing translation of the grip member (4) between the first translational position and the second translational position in the first angular position.
Owner:EWAC HLDG
Method and device for recognizing unintended drive train responses of a motor vehicle having at least one drive unit
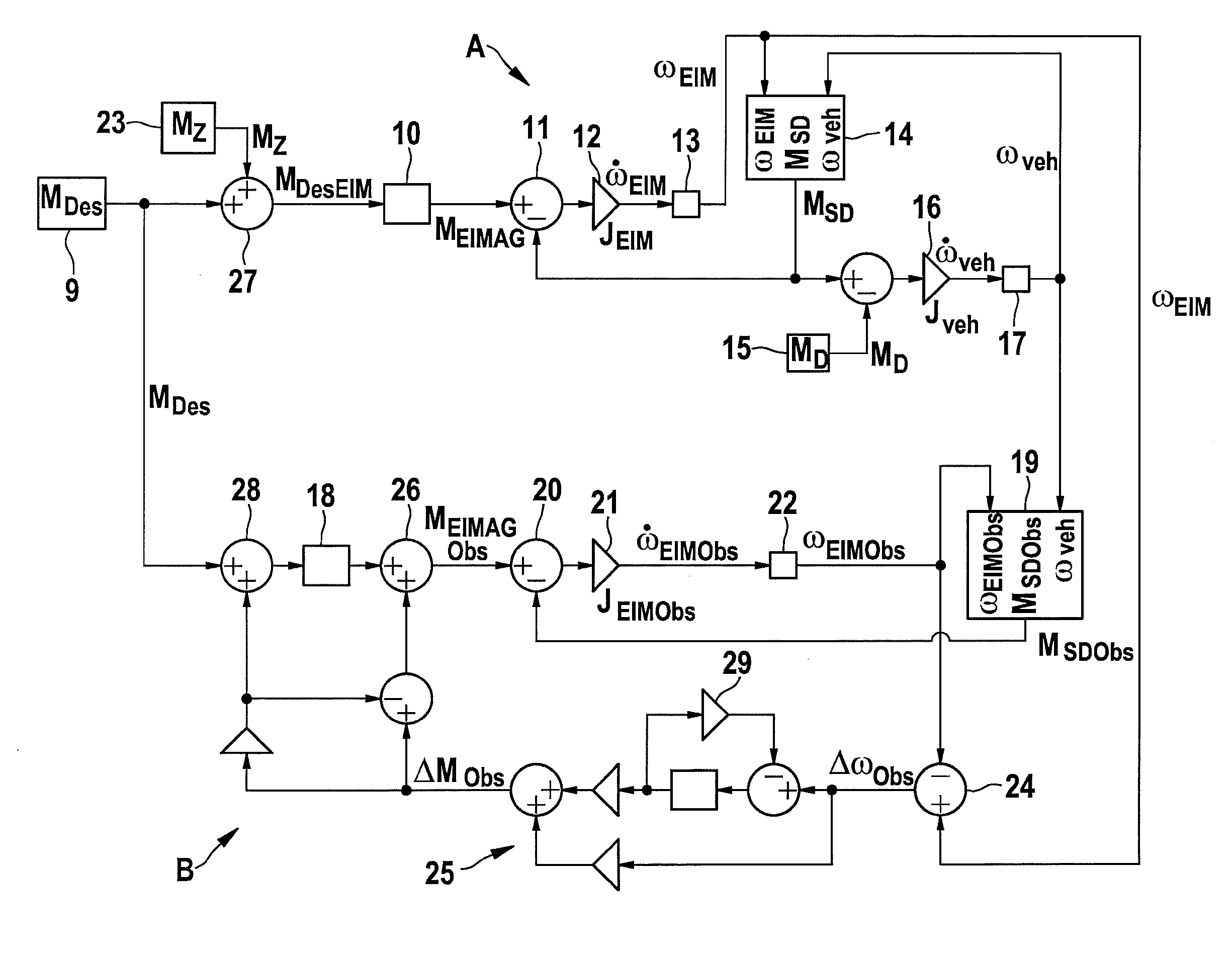
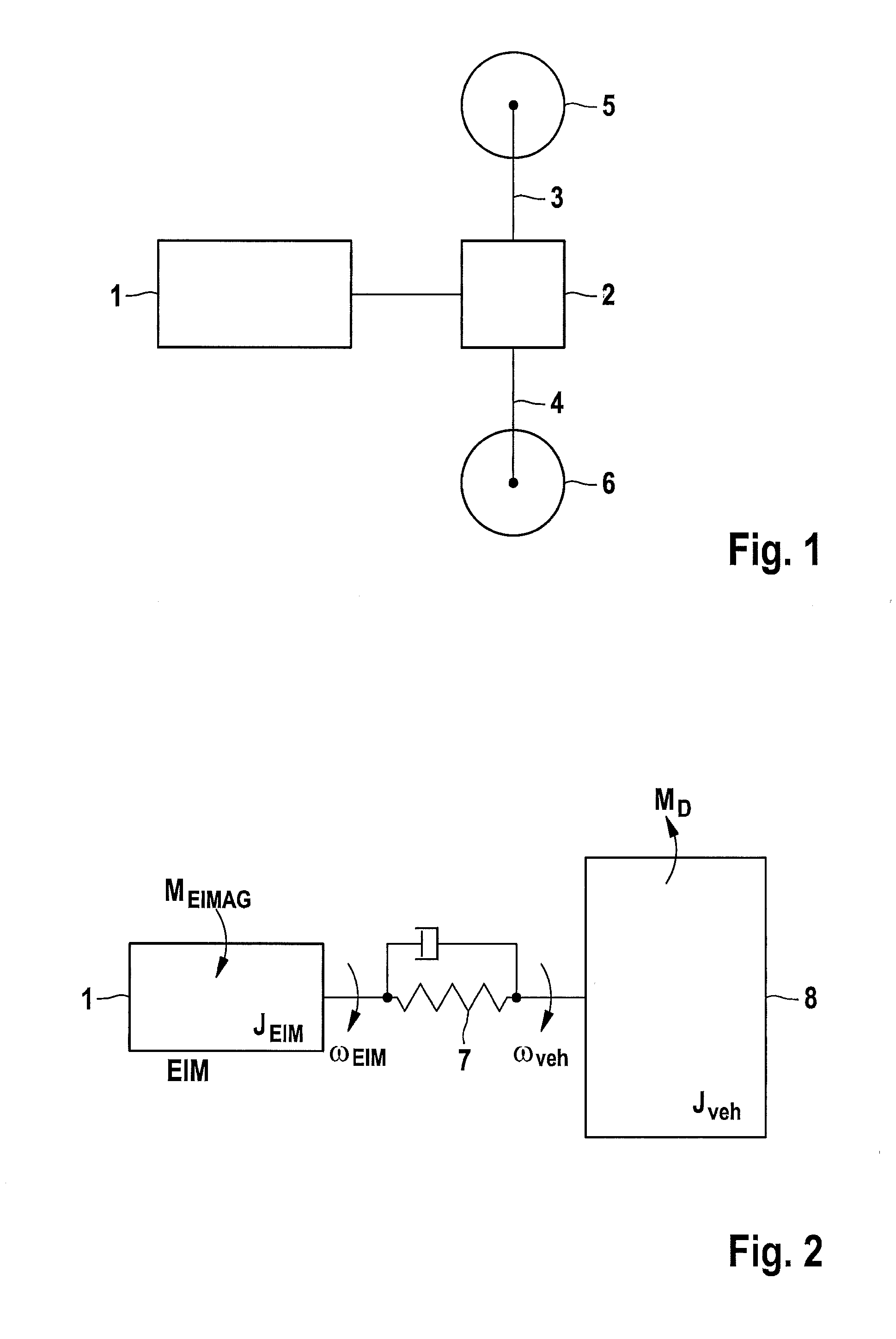
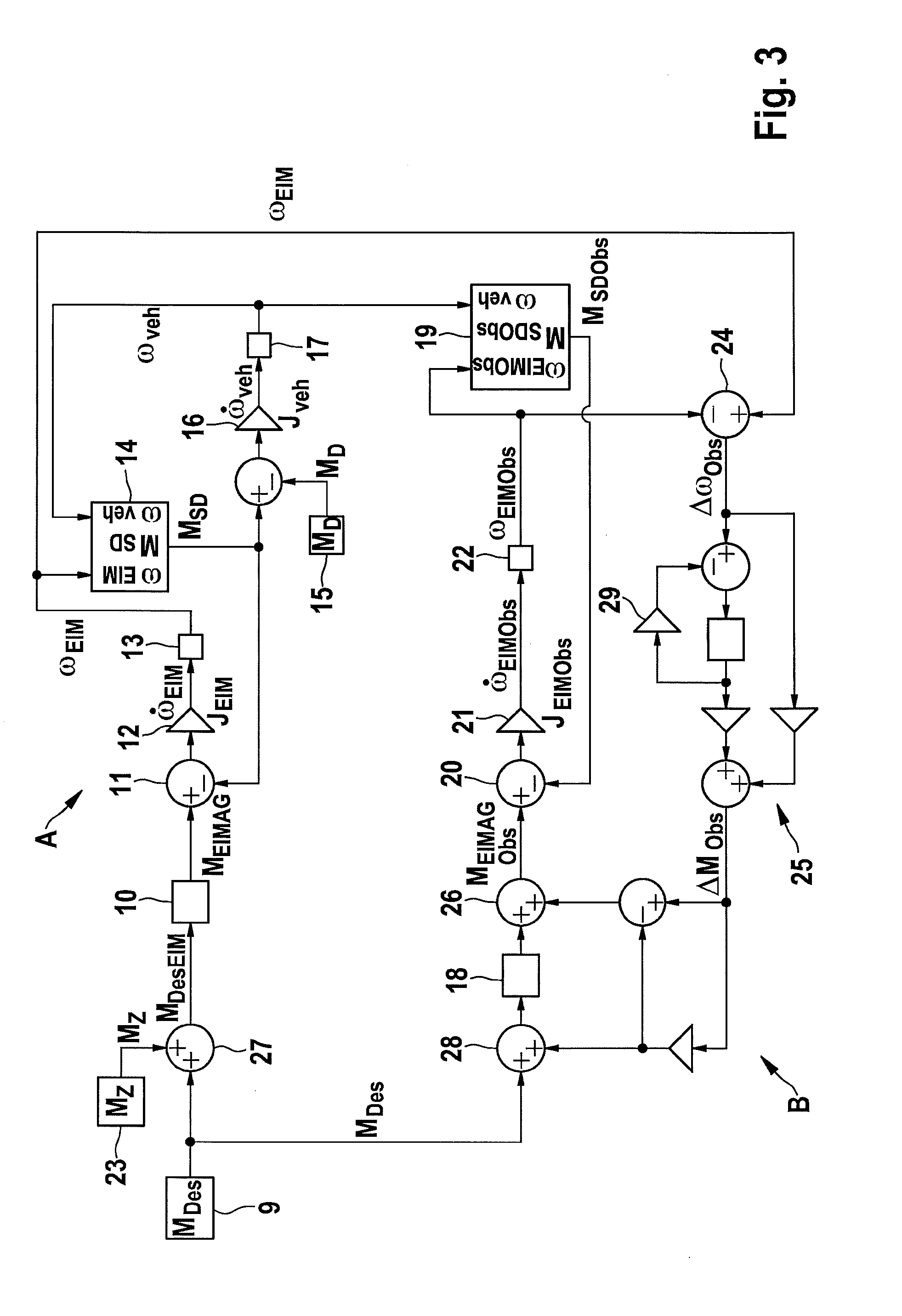
ActiveUS20130138290A1Increase safetyPrevent movementVehicle testingRegistering/indicating working of vehiclesDynamic modelsMotorized vehicle
A method for recognizing unintended drive train responses of a motor vehicle includes at least one drive unit, in which at least one input variable of the motor vehicle and / or of the drive unit is input into the drive train, and at least one output variable is measured at the motor vehicle and / or the drive unit. In order to recognize an unintended drive train response early, the at least one input variable is supplied to a dynamic model which at least partially simulates the drive train of the motor vehicle, the dynamic model determining, based on the at least one input variable, at least one model output variable which is compared to the at least one measured output variable, and an unintended drive train response being deduced if there is a difference between the measured output variable and the model output variable.
Owner:ROBERT BOSCH GMBH
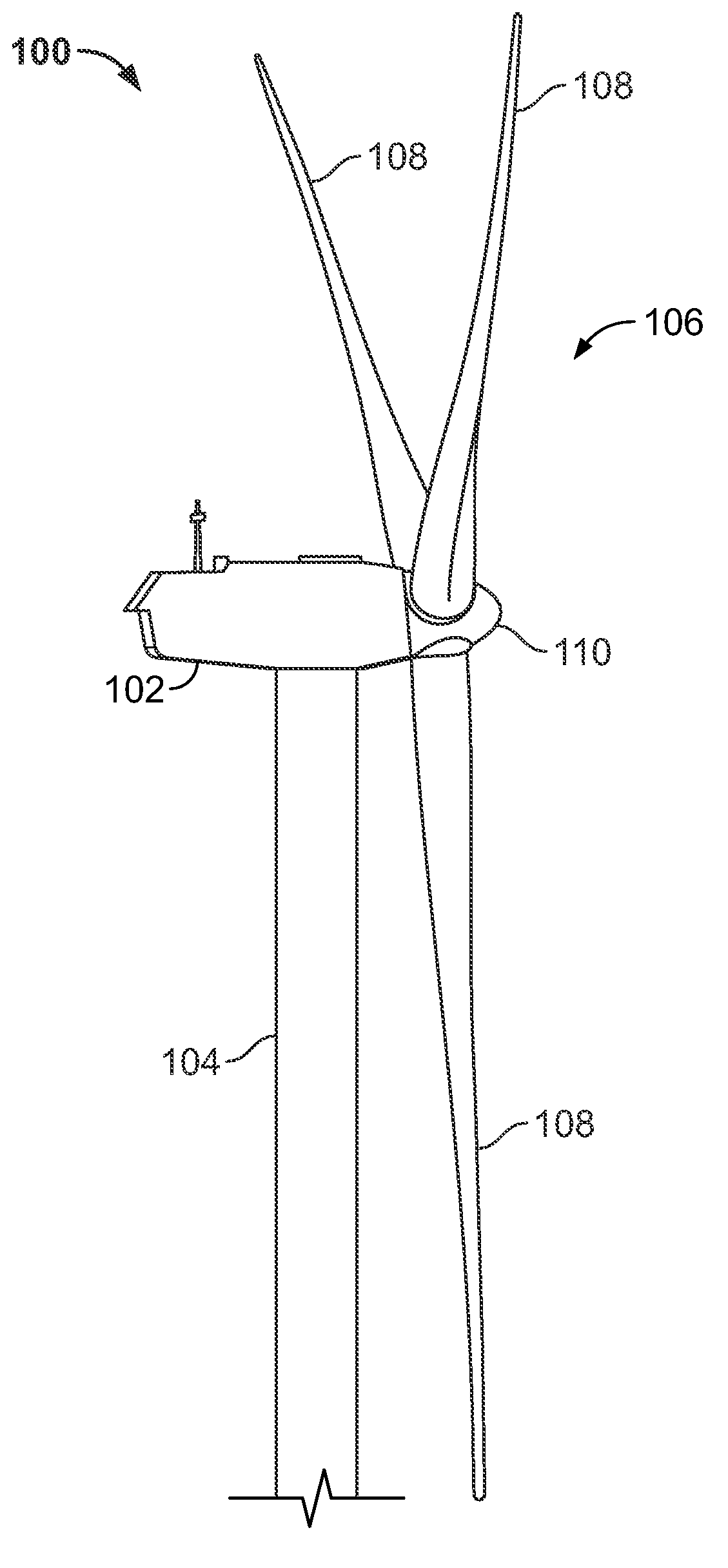
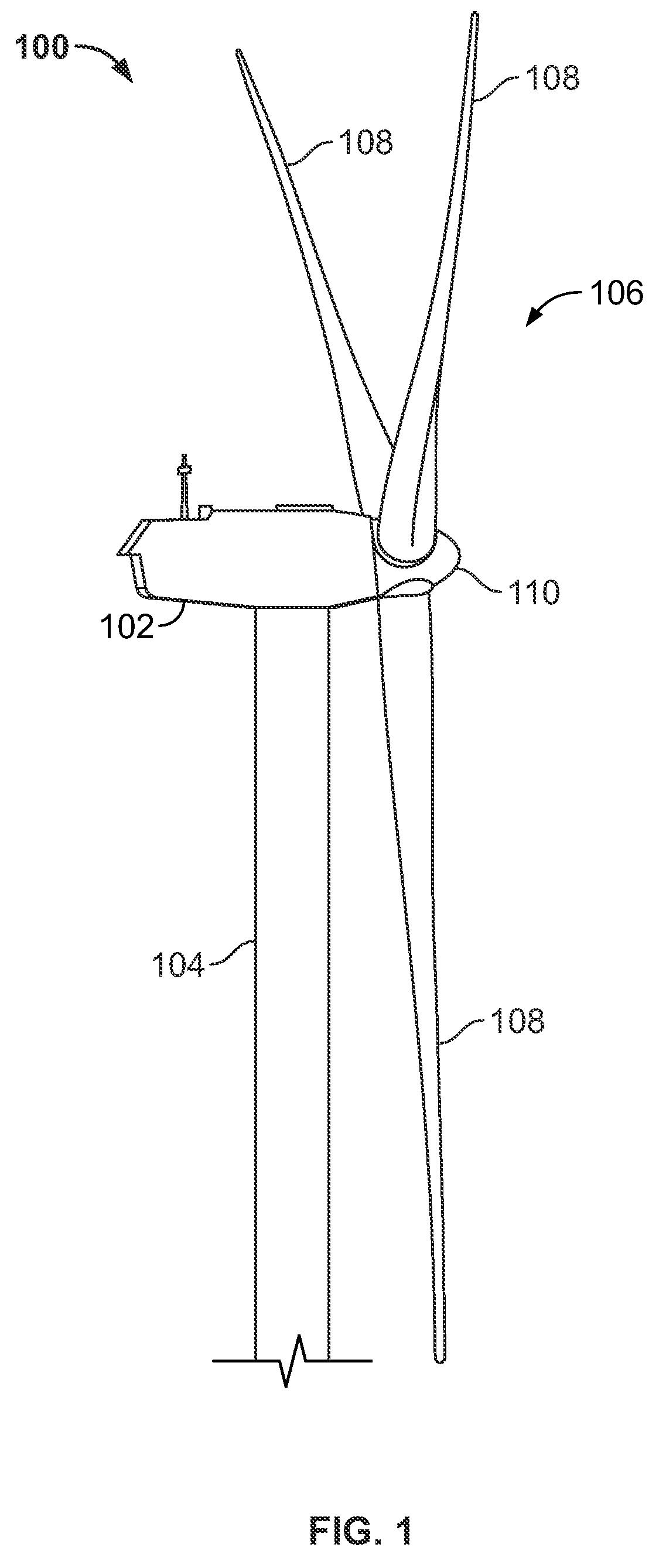
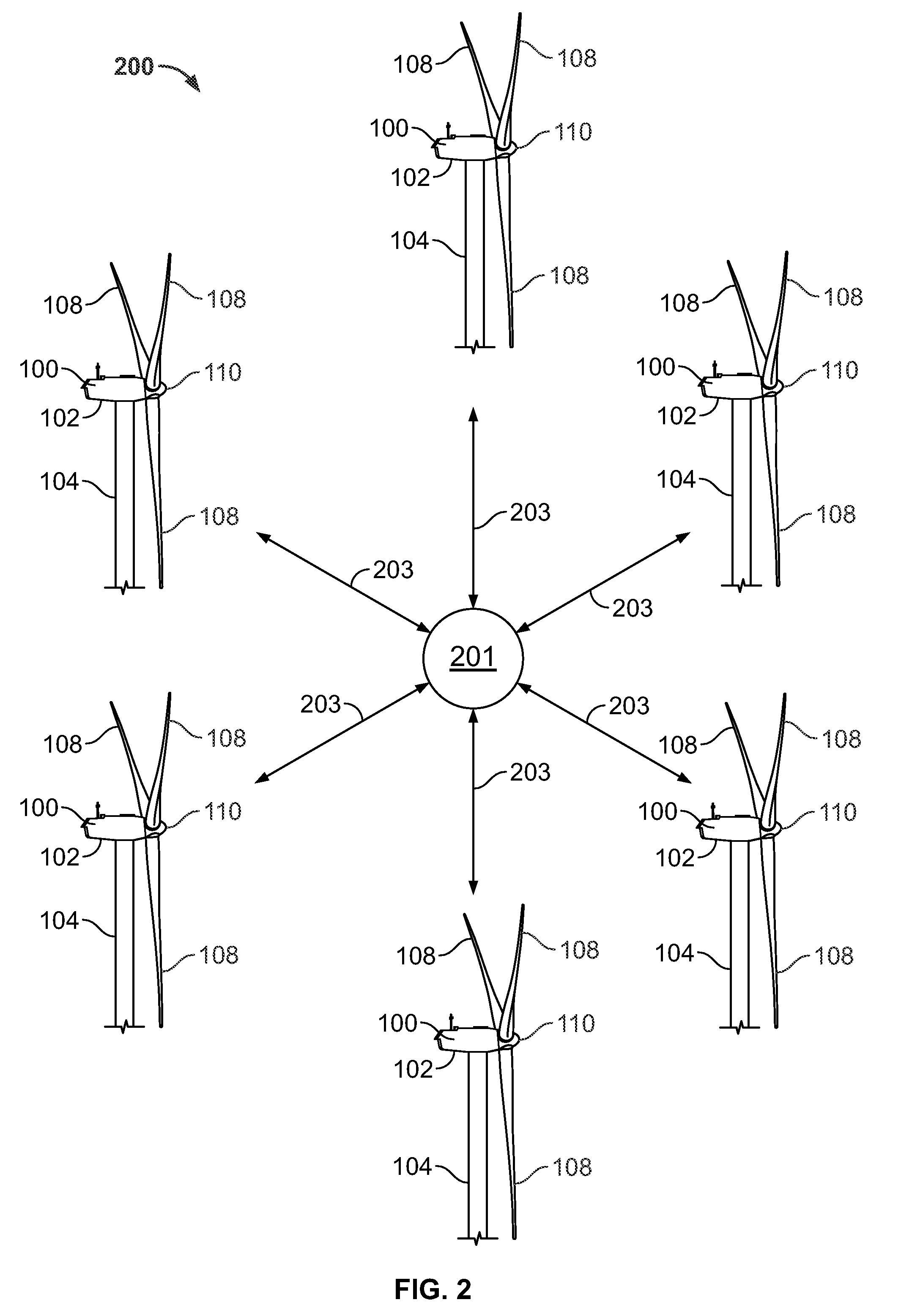
Wind turbine maintenance system
InactiveUS20090153656A1Increase safetyImprove securityColor television detailsClosed circuit television systemsAutomotive engineeringMaintenance system
A wind turbine monitoring system having a central monitoring device and one or more wind turbines. The central monitoring device is capable of receiving signals from one or more wind turbines. The wind turbines each include one or more cameras arranged and disposed to provide visual signals transmittable to the central monitoring device. The visual signals generated by the cameras provide sufficient information to the central monitoring device to determine whether maintenance to the wind turbine is required. A method for providing maintenance to a wind turbine is also disclosed.
Owner:GENERAL ELECTRIC CO
System and method for information assurance based on thermal analysis techniques
InactiveUS20090094618A1Improve performanceIncrease safetyDigital computer detailsTransmissionSafe systemNetwork security
Systems and methods for network security are disclosed. Embodiments of the present invention include a scalable, real-time solution to complement existing security systems and detect unusual activity. Embodiments of the present invention leverage the scale and complexity of networks and use the principles of statistical physics and thermodynamics to define thermal properties like entropy, temperature and energy for network states and changes in the properties as packets move through the network.
Owner:EQUILIBRIUM NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com