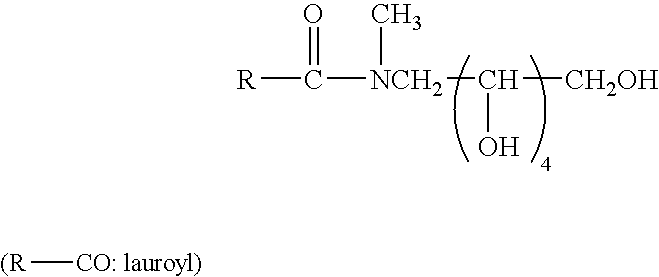
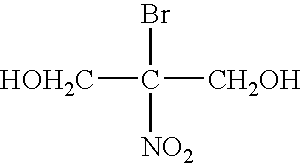Patents
Literature
124results about How to "High safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Firewall interface configuration and processes to enable bi-directional VoIP traversal communications
InactiveUS20040059942A1High safetyHigh performanceHardware monitoringMultiple digital computer combinationsData contentIp address
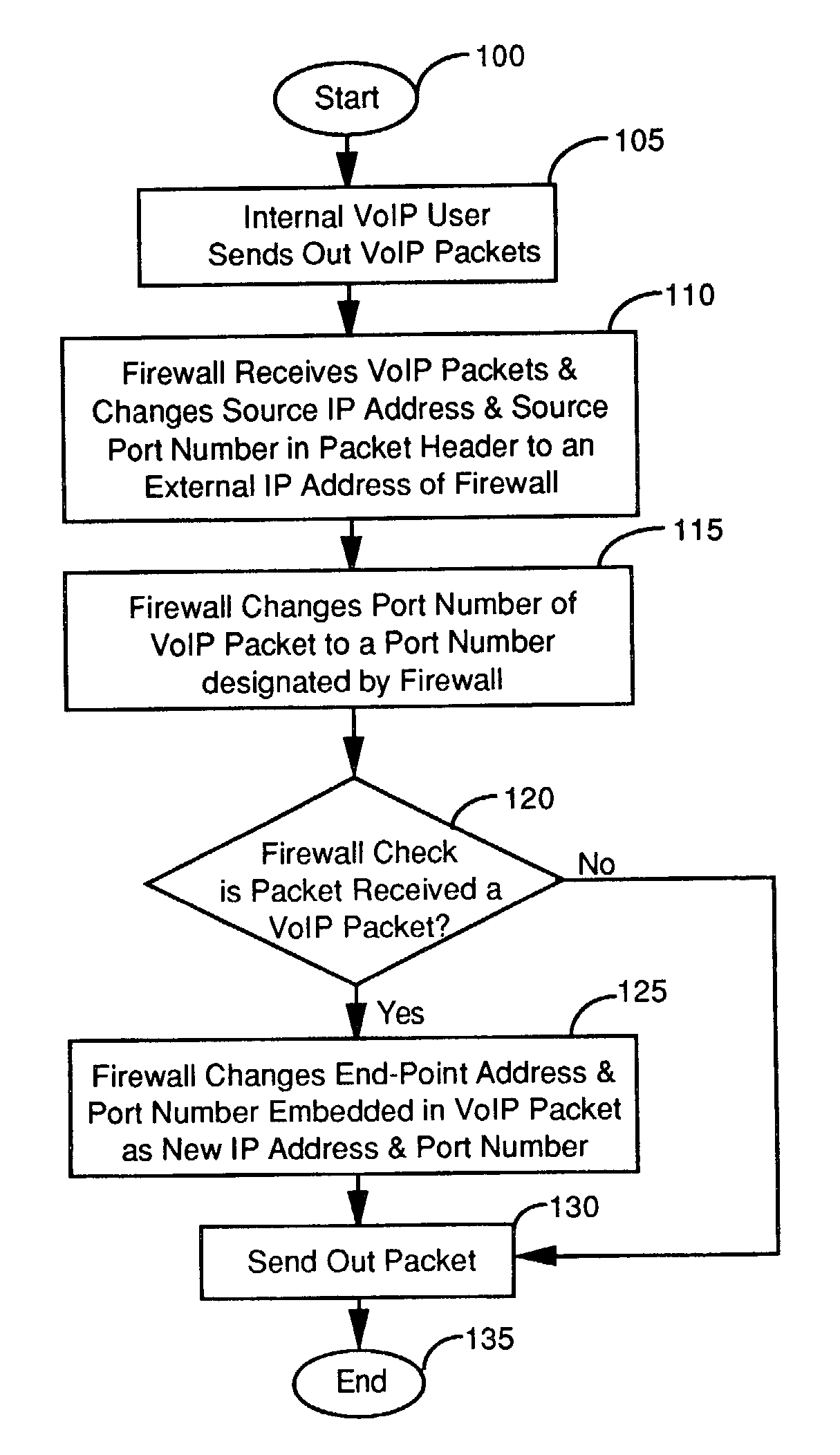
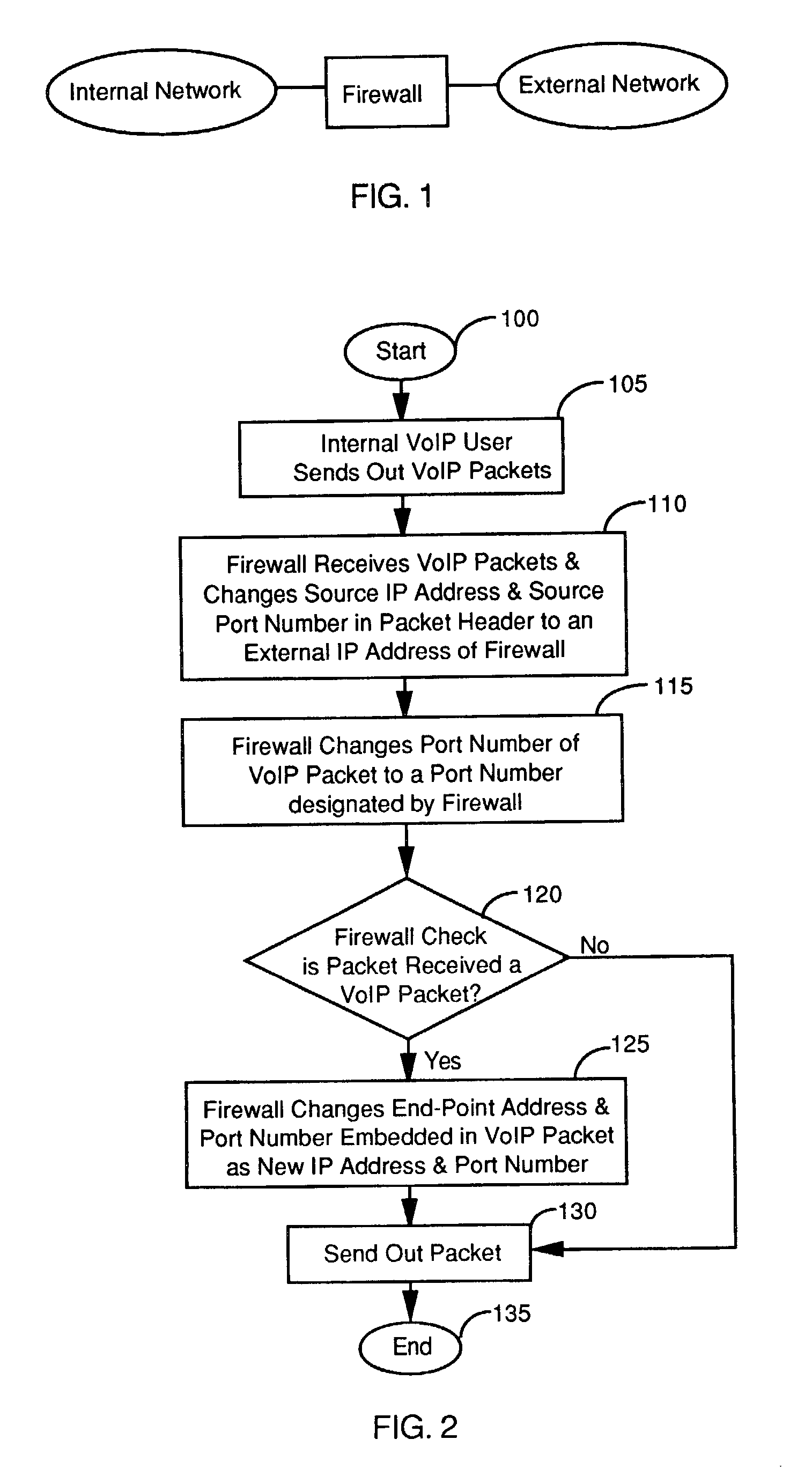
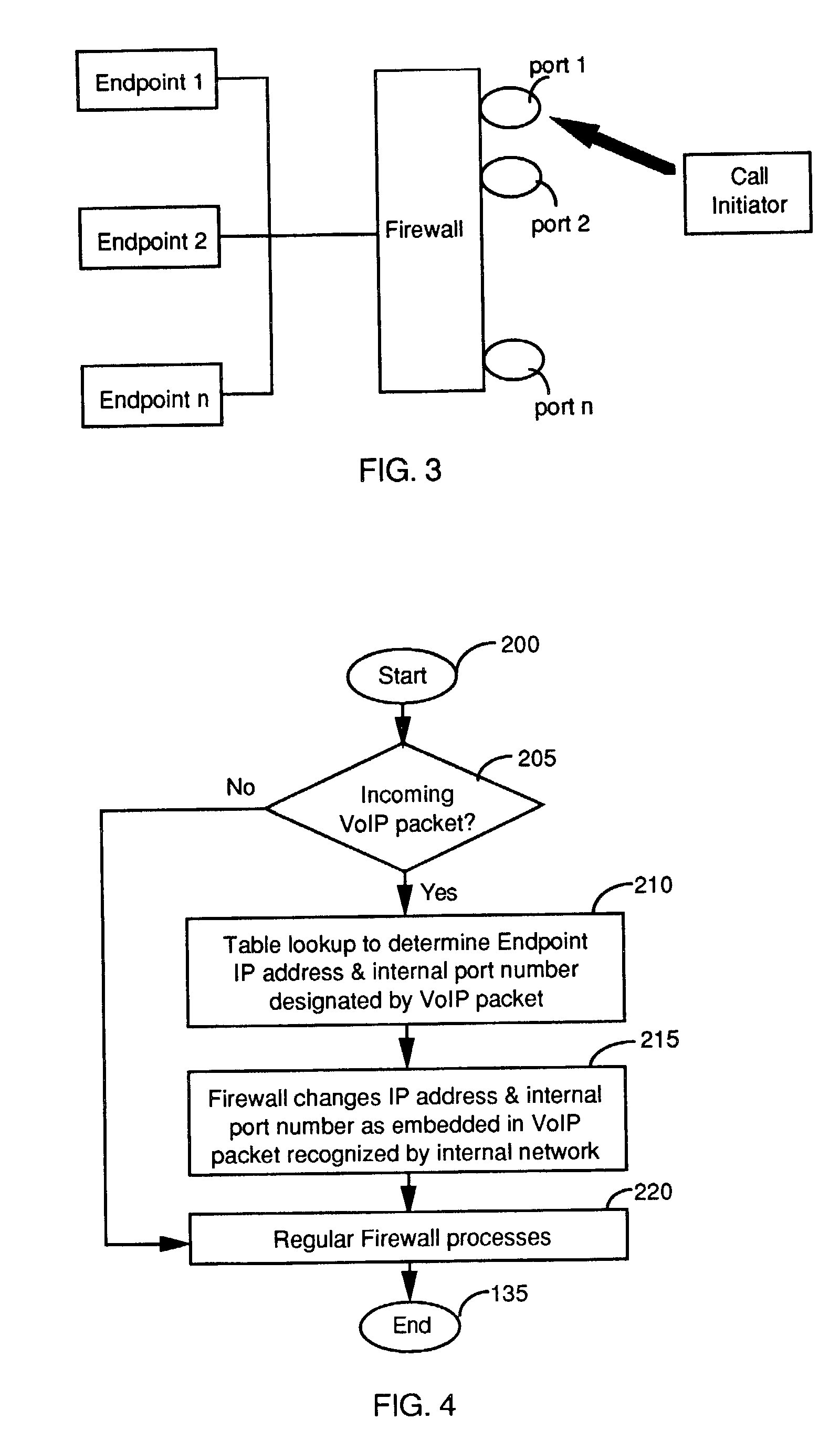
A firewall for interfaced between an internal and an external networks. The firewall includes a VoIP processor for detecting an outgoing VoIP packet sent from the internal network for changing data in a header of the VoIP packet and also changing data contents in the VoIP packet corresponding to data changed in the header to enable a bi-directional VoIP communication. In a preferred embodiment, the VoIP processor changes a source IP address and a port number in the header of the VoIP packet and also changes the data contents in the VoIP packet corresponding to the source IP address and the port number changed in the header to enable a bi-directional VoIP communication. In another preferred embodiment, the firewall further includes an external VoIP interface comprising a plurality of VoIP ports for receiving multiple incoming VoIP packets each designated with one of the VoIP ports. And, the VoIP processor further includes a VoIP port versus internal address table for identifying an internal address in the internal network for directing each of the incoming VoIP packets to the internal address identified.
Owner:FORTINET
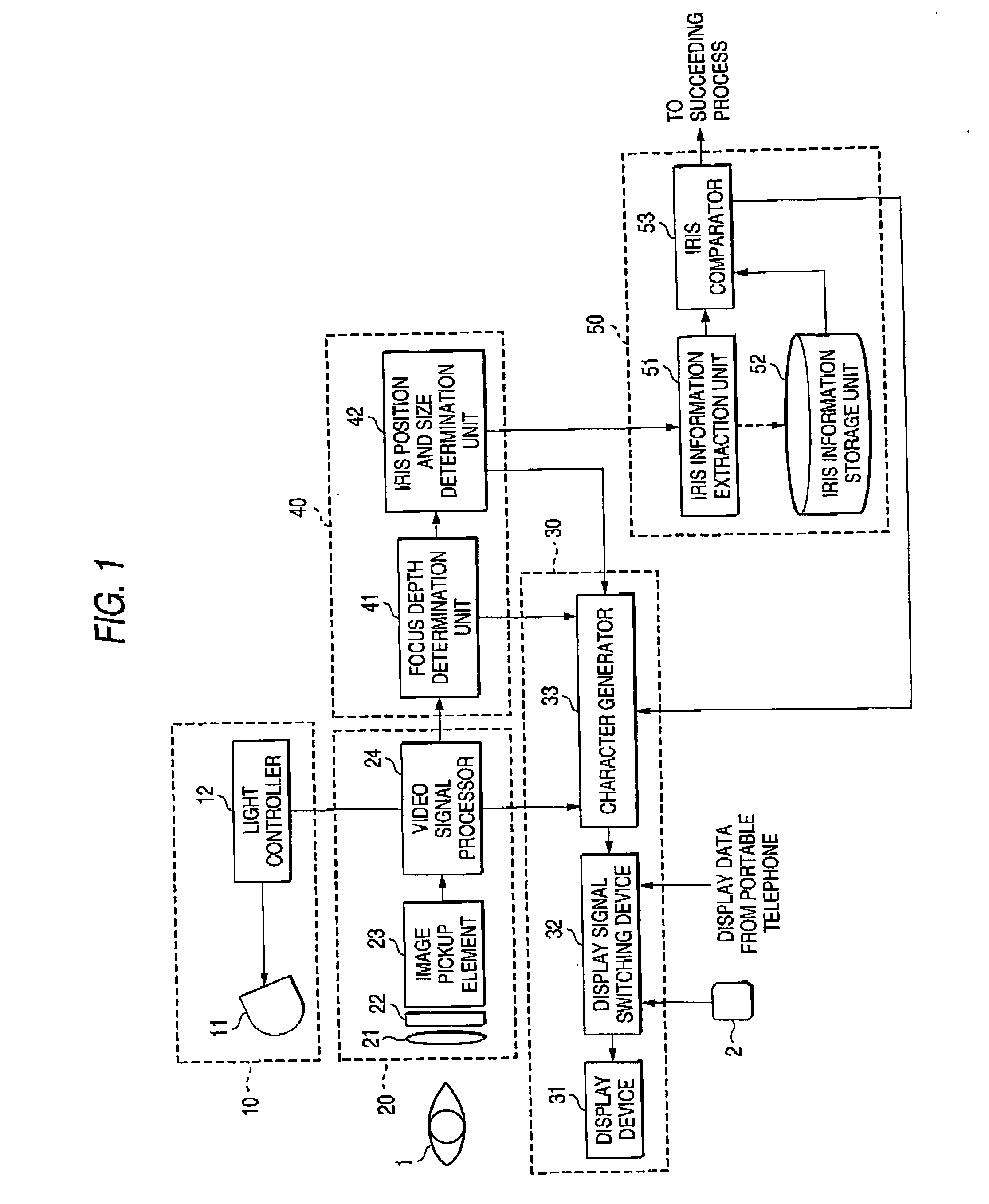
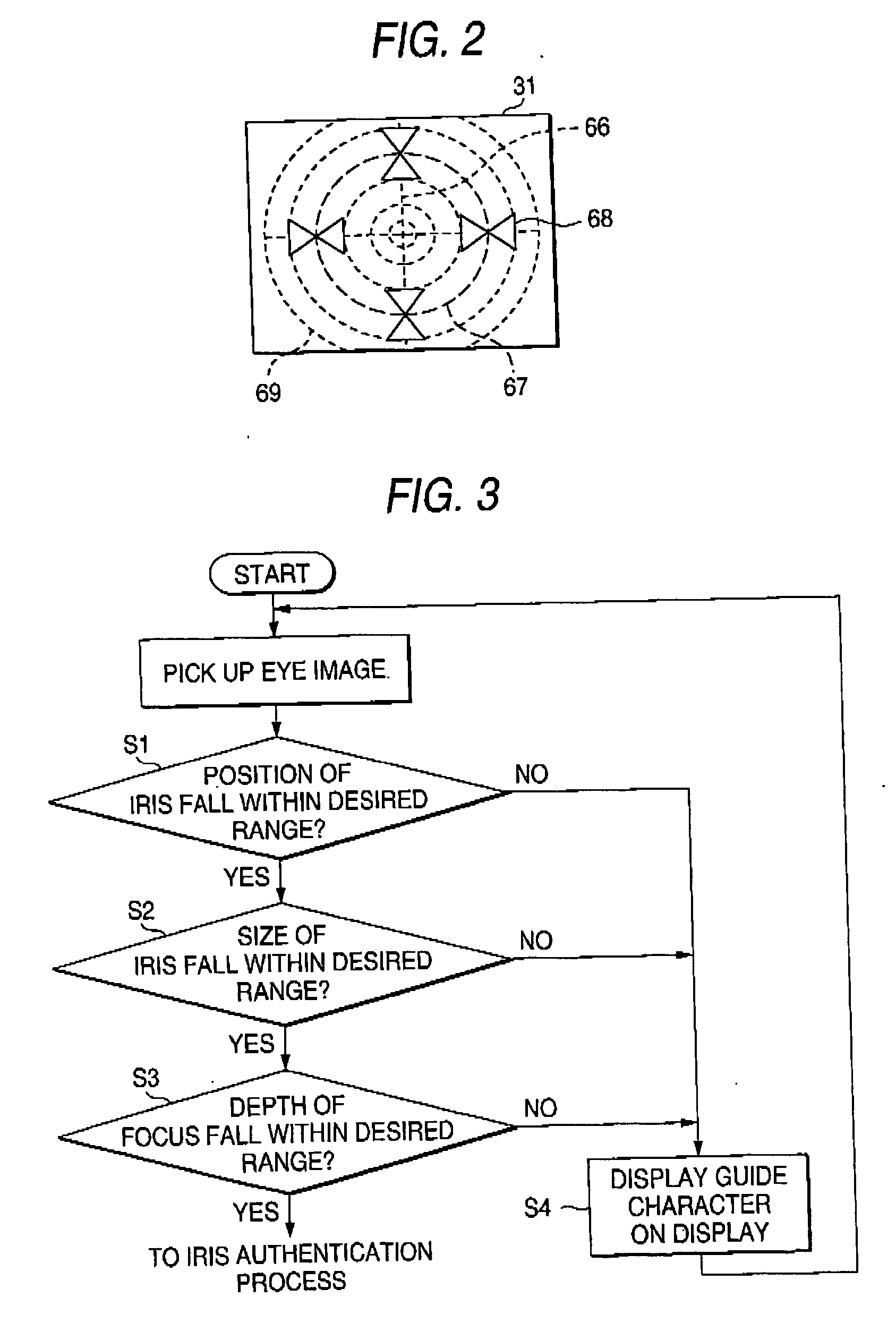
Eye image pickup apparatus, iris authentication apparatus and portable terminal device having iris authentication function
InactiveUS20060120707A1Reduce size and weightHigh safetyPrintersPerson identificationSurface plateIris image
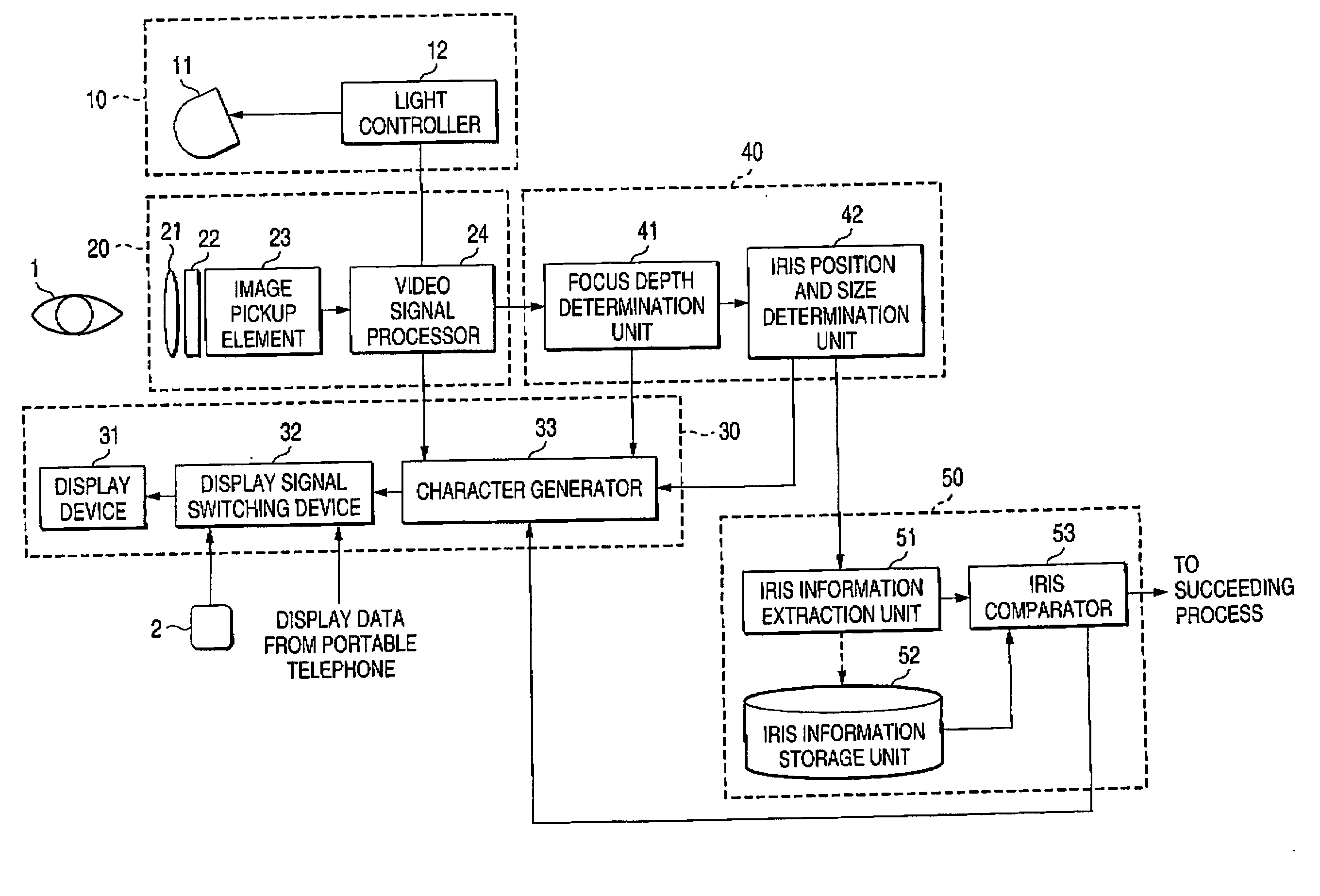
An iris authentication apparatus includes a camera for obtaining the image of an eye; a display panel arranged on the same plane as where the lens of the camera is arranged; and guide character generation means, wherein a guide character is displayed on a display panel, and the eye of a person to be authenticated who watches the guide character is guided. As a result, a satisfactory iris image can be obtained by the iris authentication apparatus of one camera type that does not have a zooming function, so that the iris authentication apparatus that can be mounted to a small body, such as a portable telephone, can be provided.
Owner:PANASONIC CORP
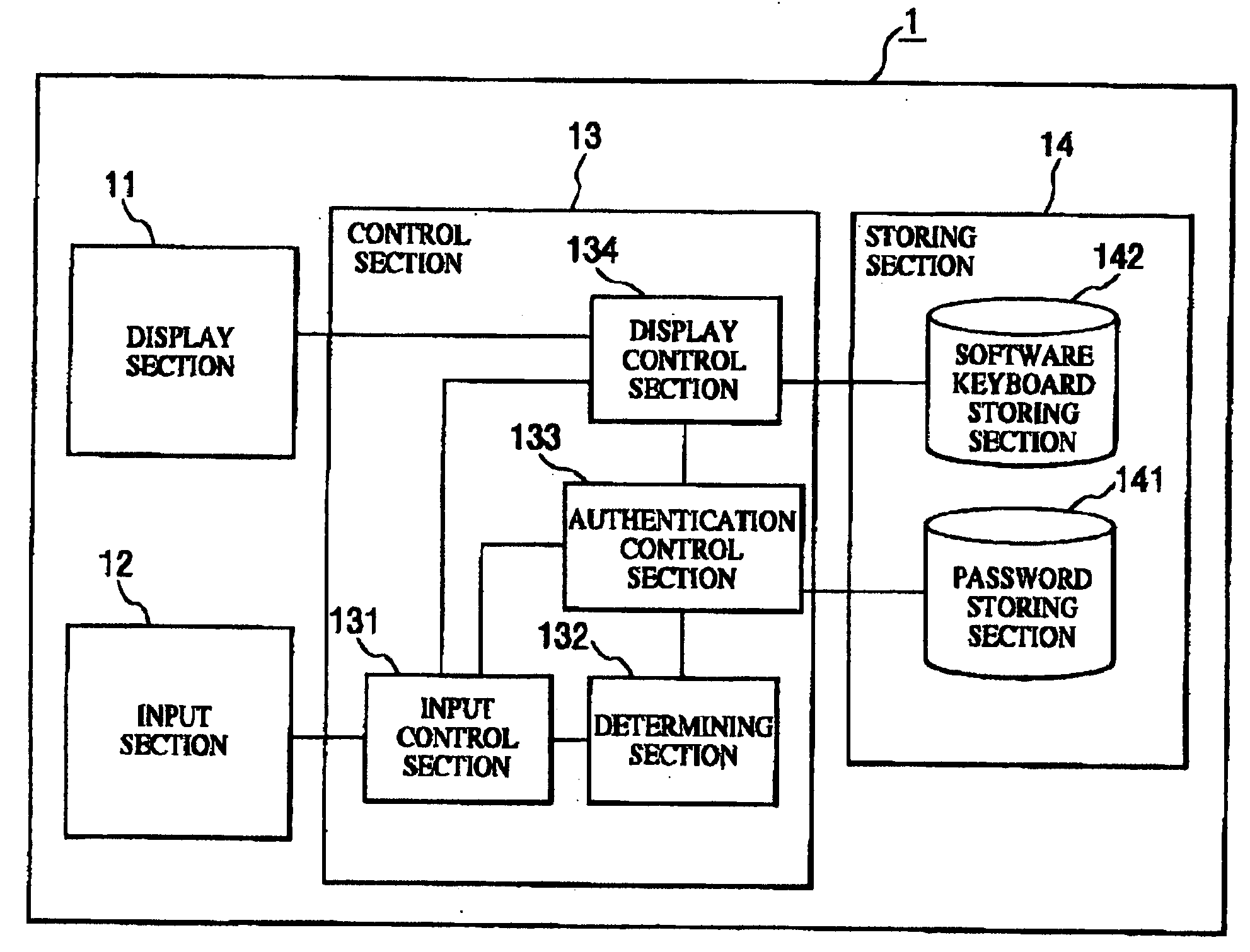
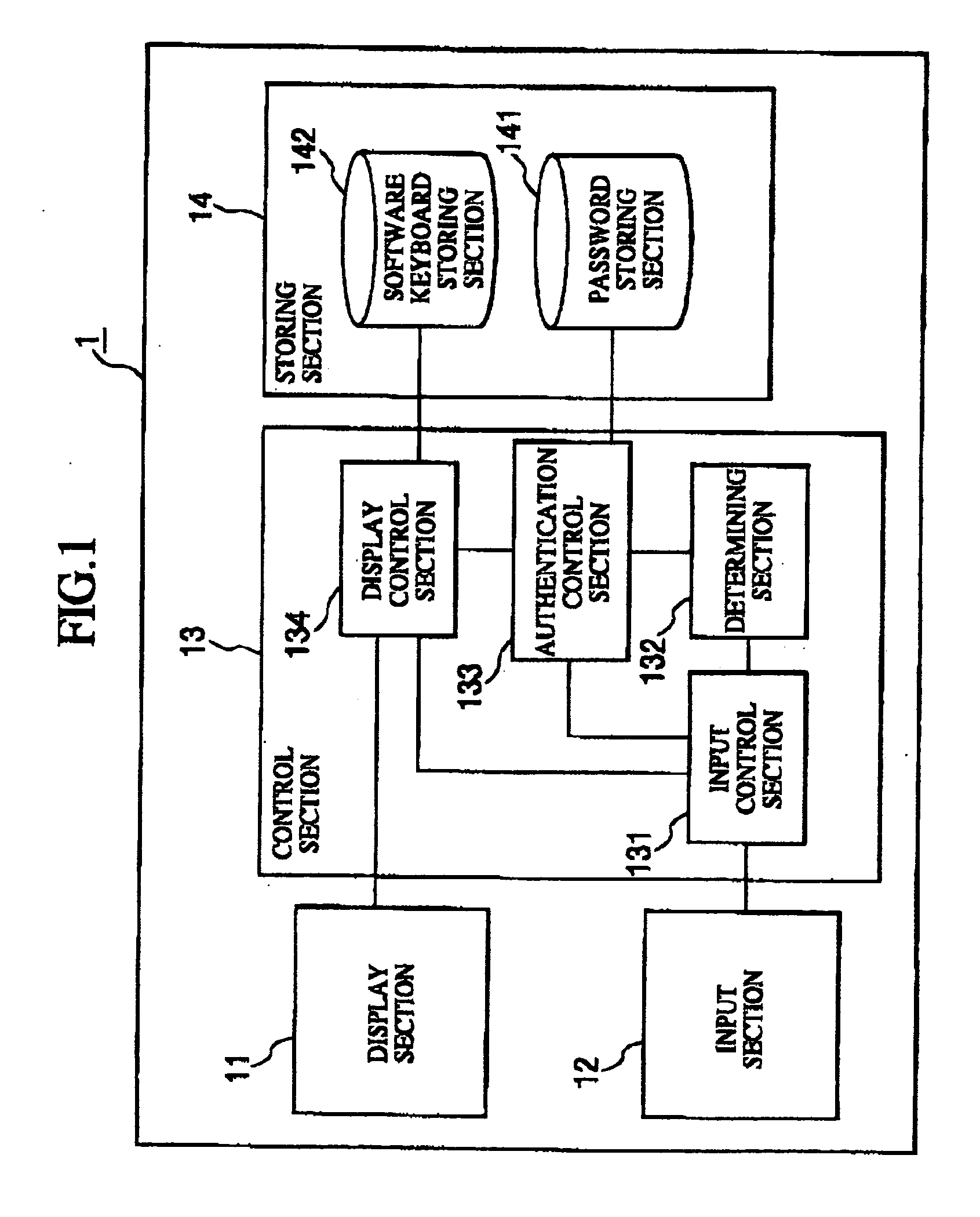
Password authenticating apparatus, method, and program
InactiveUS20050071637A1High safetyGood operationalityDigital data processing detailsUser identity/authority verificationPasswordCipher
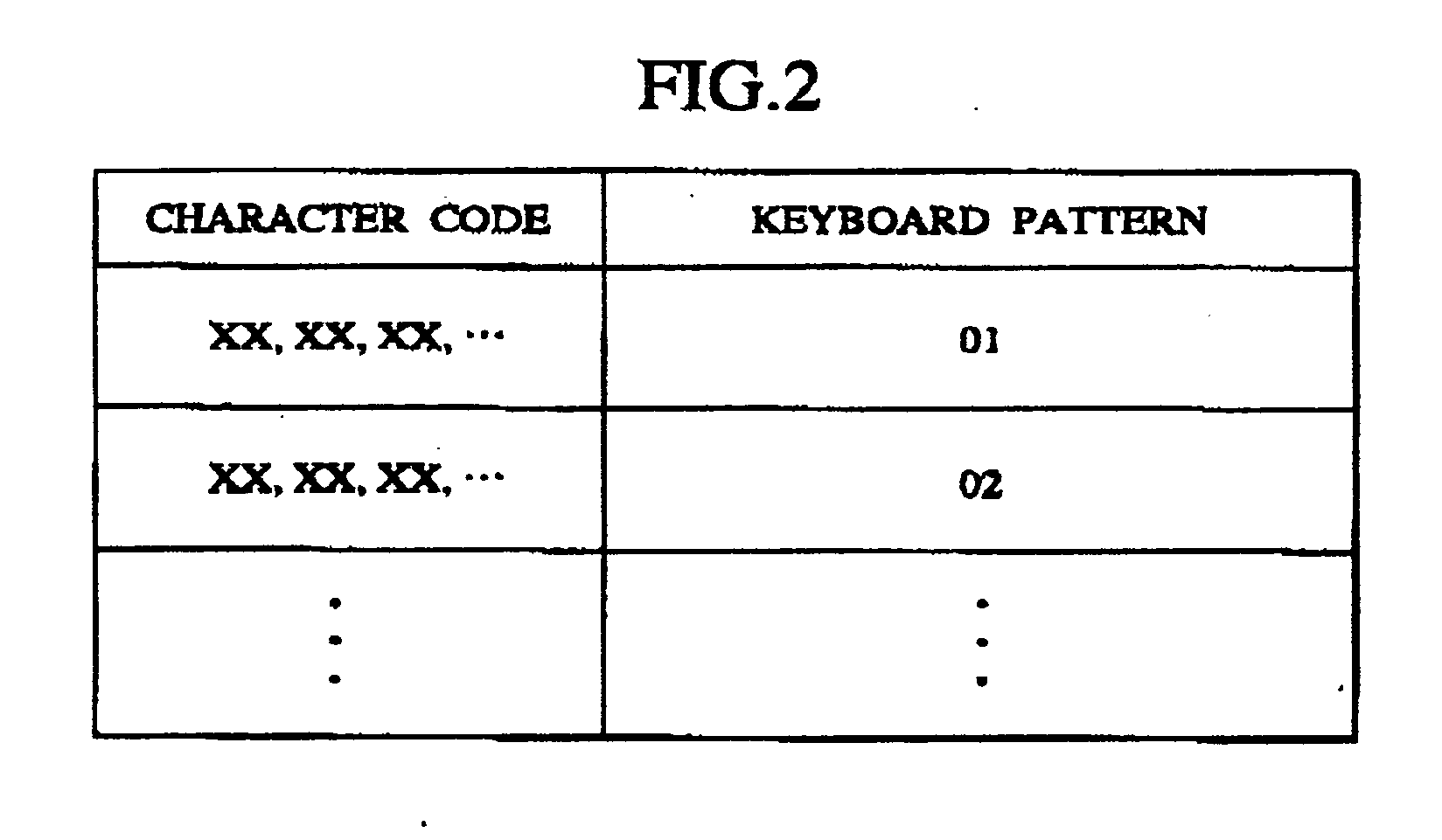
In a password authenticating apparatus, a control section displays an image of a keyboard including multiple character keys on a display section. An input section sends input data to the control section on reception of an input of a position on a display screen. In connection with the displayed keyboard, the control section specifies a character corresponding to the input position as an input character, checks the input character against a character that forms a registered password, determines whether the input character is correct, and holds a determination result. Then, after the input character is determined, a display is changed to an image of the keyboard for receiving a next character input. Then, in connection with all characters that form the password, authentication is determined as being OK when all held determination results are correct.
Owner:NEC CORP
Music distribution systems
InactiveUS7370016B1High safetyIncreased income baseFinanceComputer security arrangementsDistribution systemTime schedule
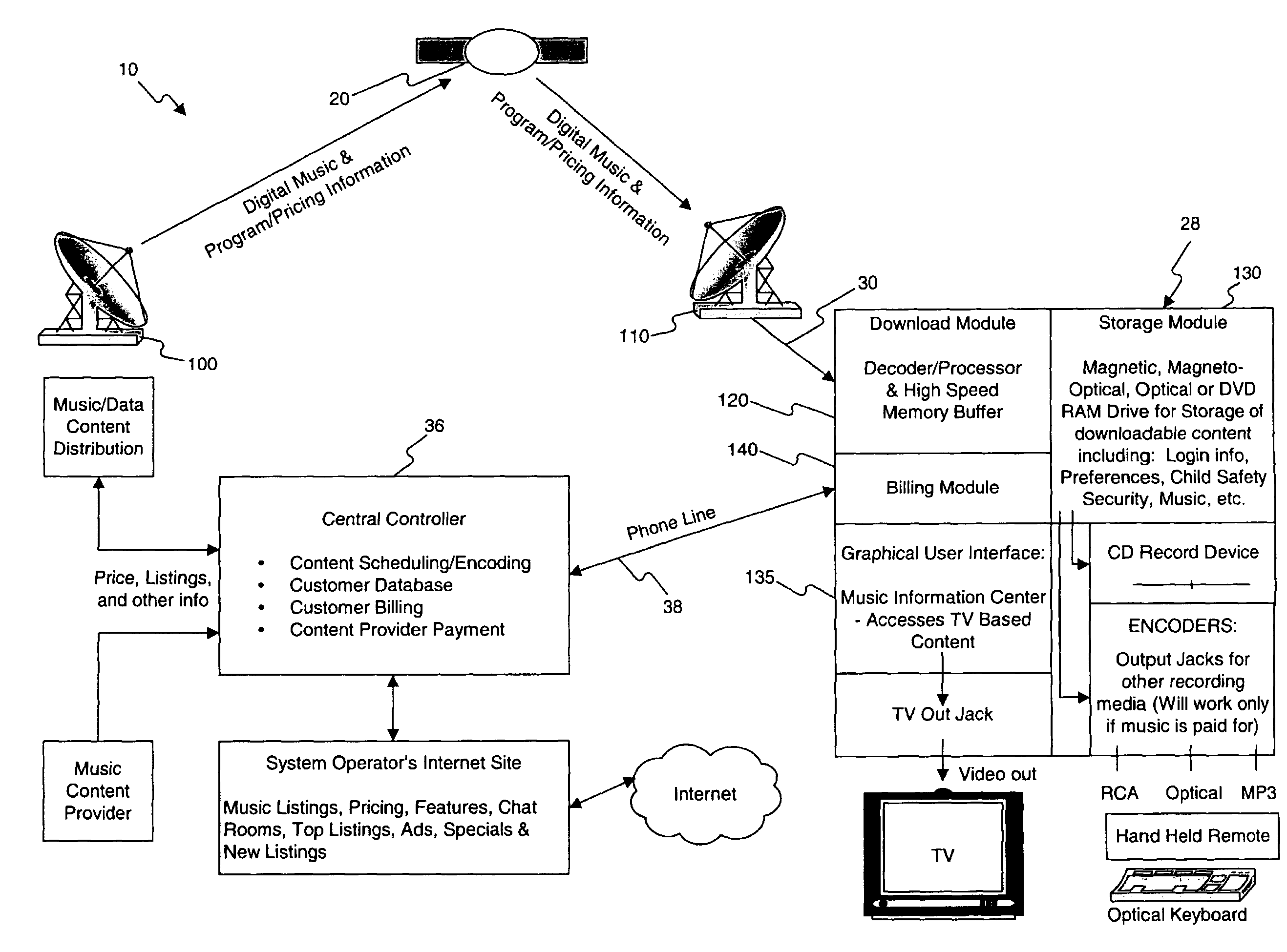
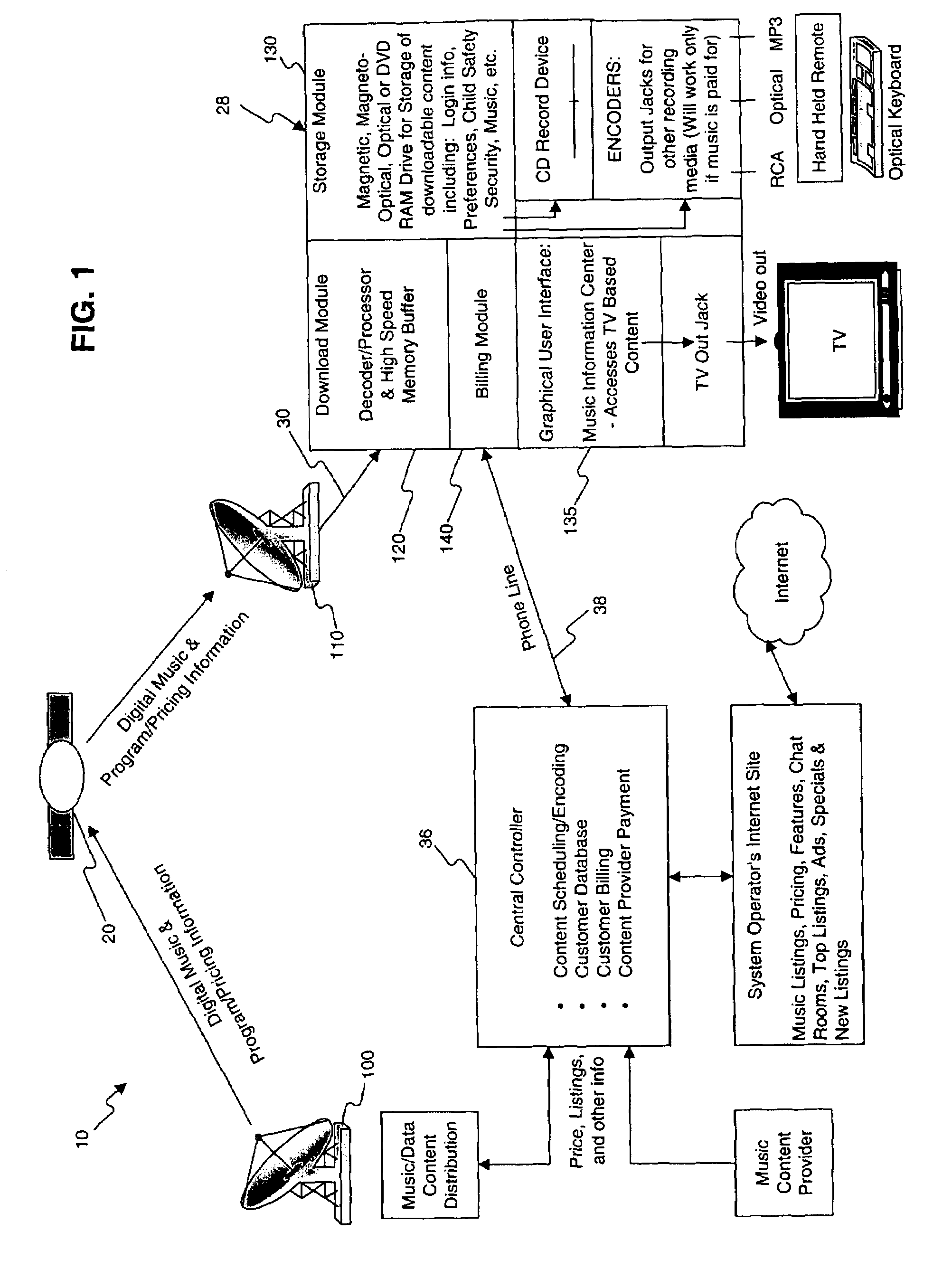
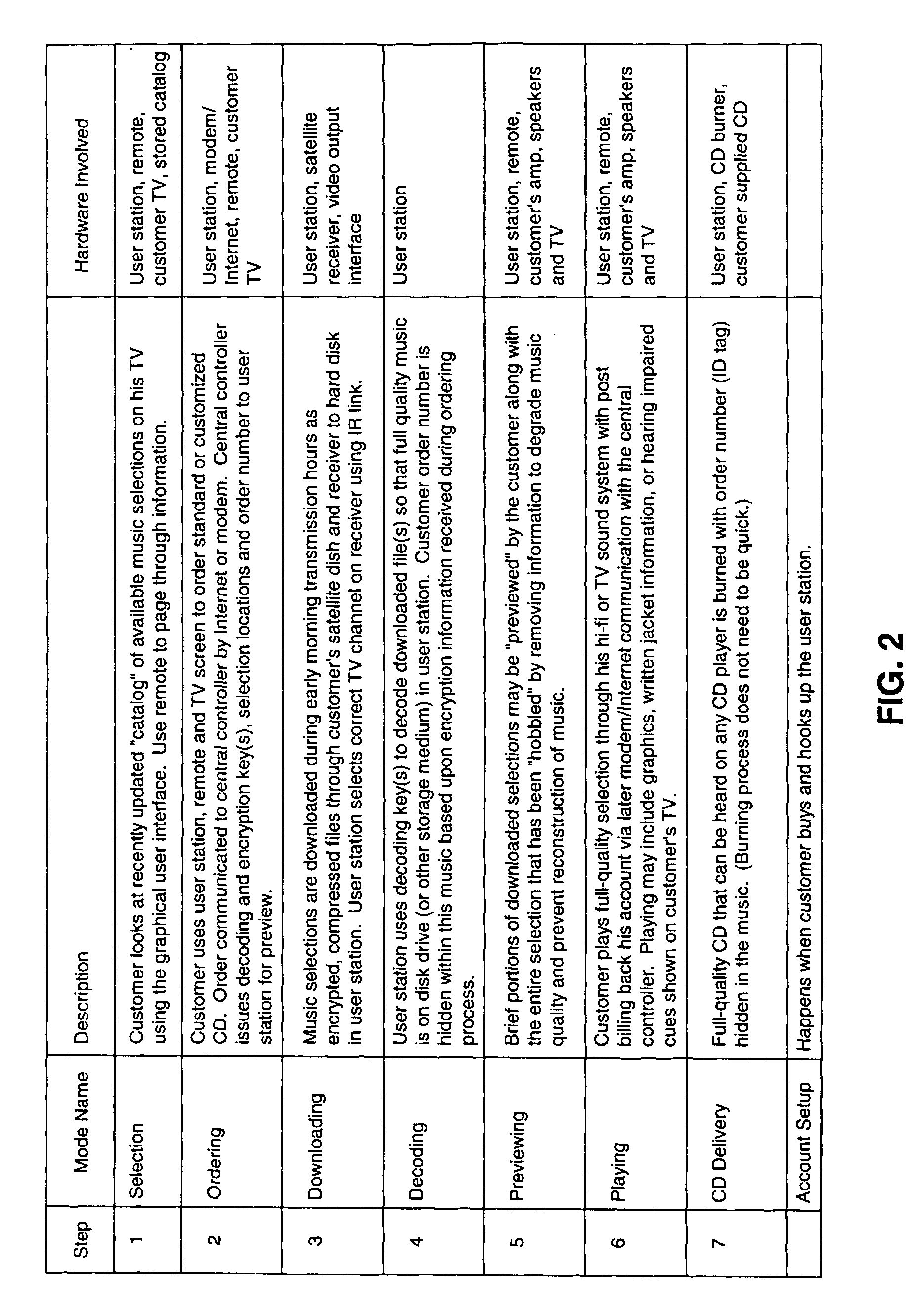
Music is blanket transmitted (for example, via satellite downlink transmission) to each customer's user station where selected music files are recorded. Customers preselect from a list of available music in advance using an interactive screen selector, and pay only for music that they choose to playback for their enjoyment. An antipiracy “ID tag” is woven into the recorded music so that any illegal copies therefrom may be traced to the purchase transaction. Music is transmitted on a fixed schedule or through an active scheduling process that monitors music requests from all or a subset of satellite receivers and adjust scheduling according to demand for various CD's. Receivers store selections that are likely to be preferred by a specific customer. In those instances where weather conditions, motion of atmospheric layers or dish obstructions result in data loss, the system downloads the next transmission of the requested CD and uses both transmissions to produce a “good copy”. In conjunction with the blanket transmission of more popular music, an automated CD manufacturing facility may be provided to manufacture CD's that are not frequently requested and distribute them by ground transportation.
Owner:WORLD THEATRE INC
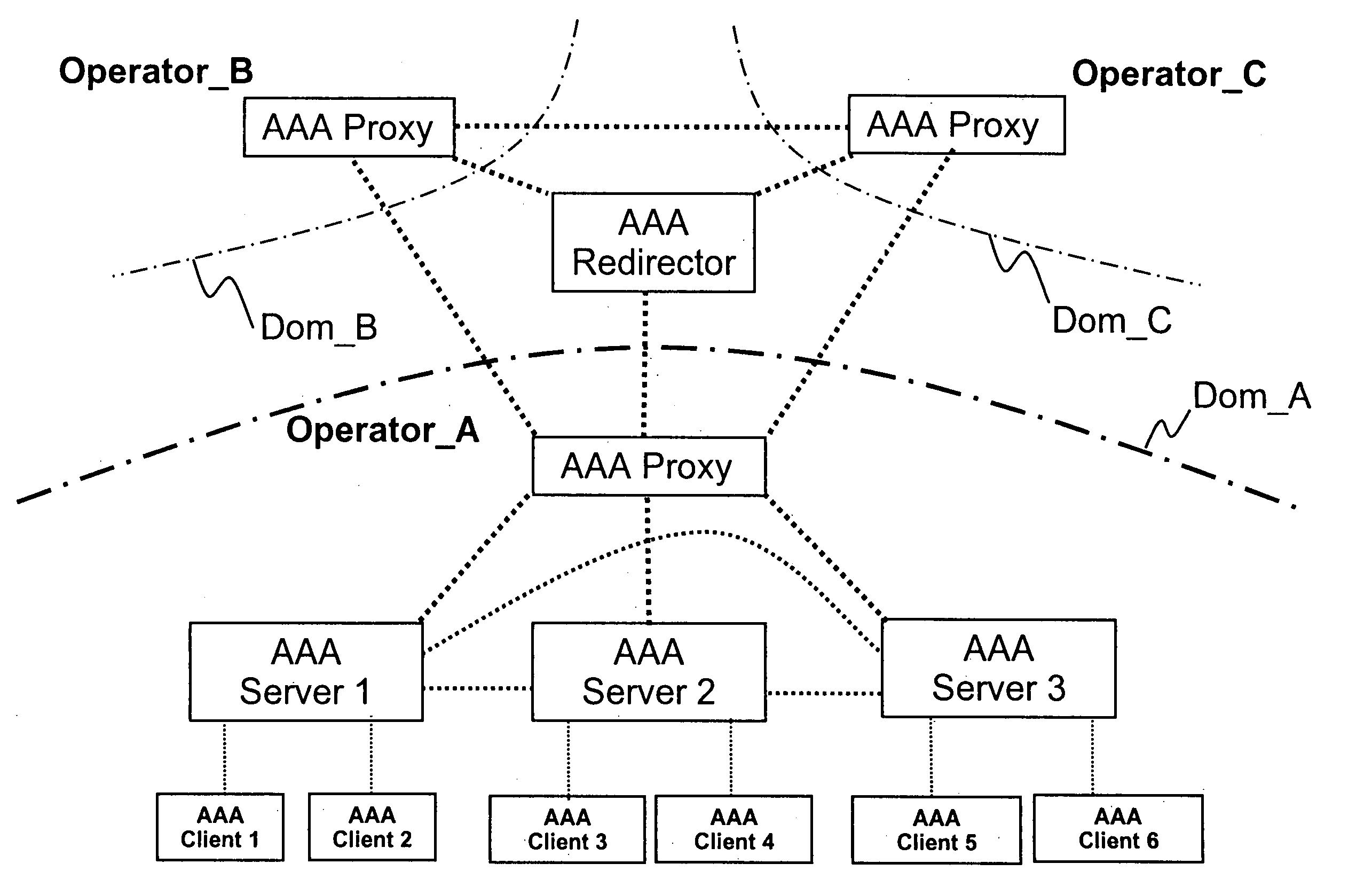
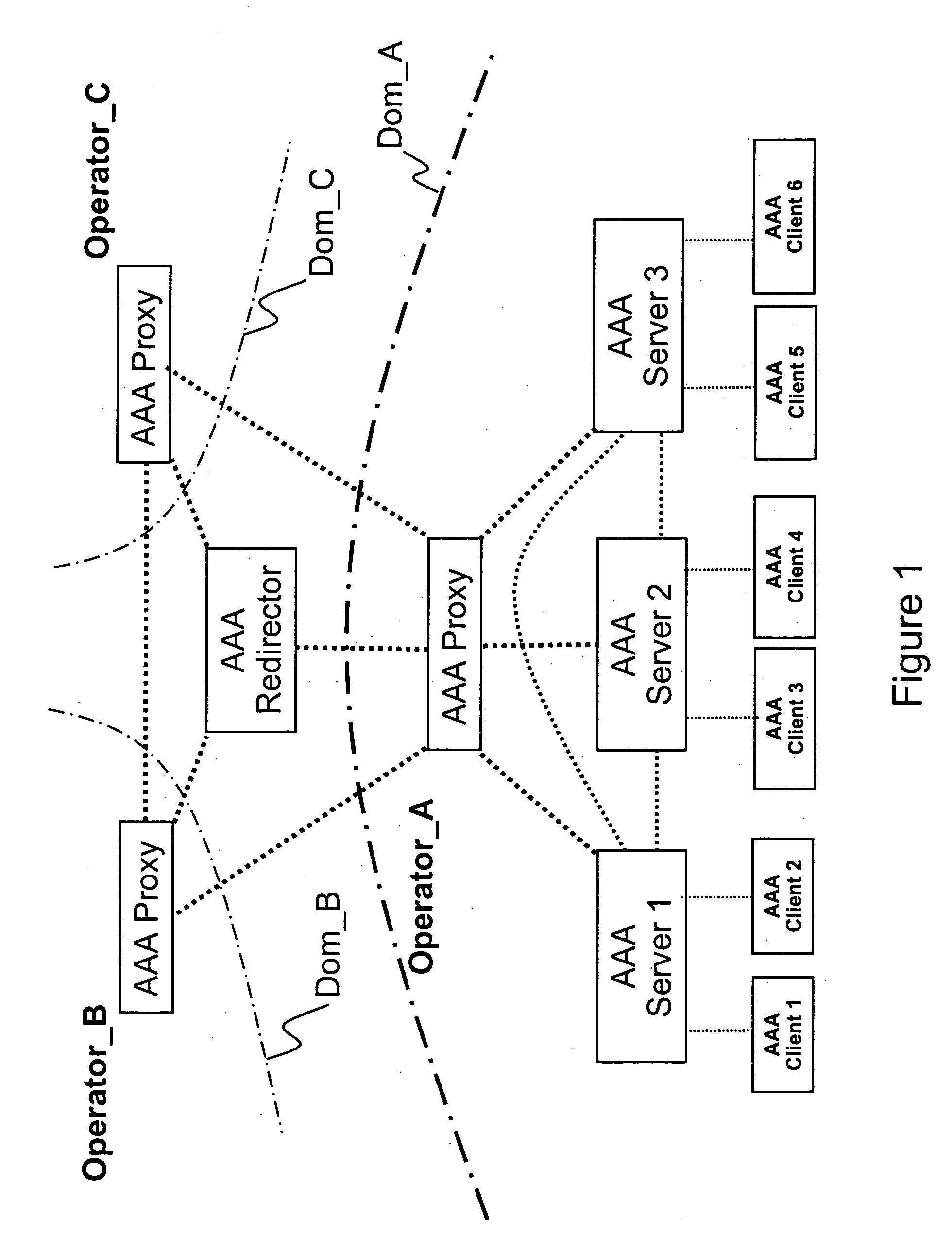
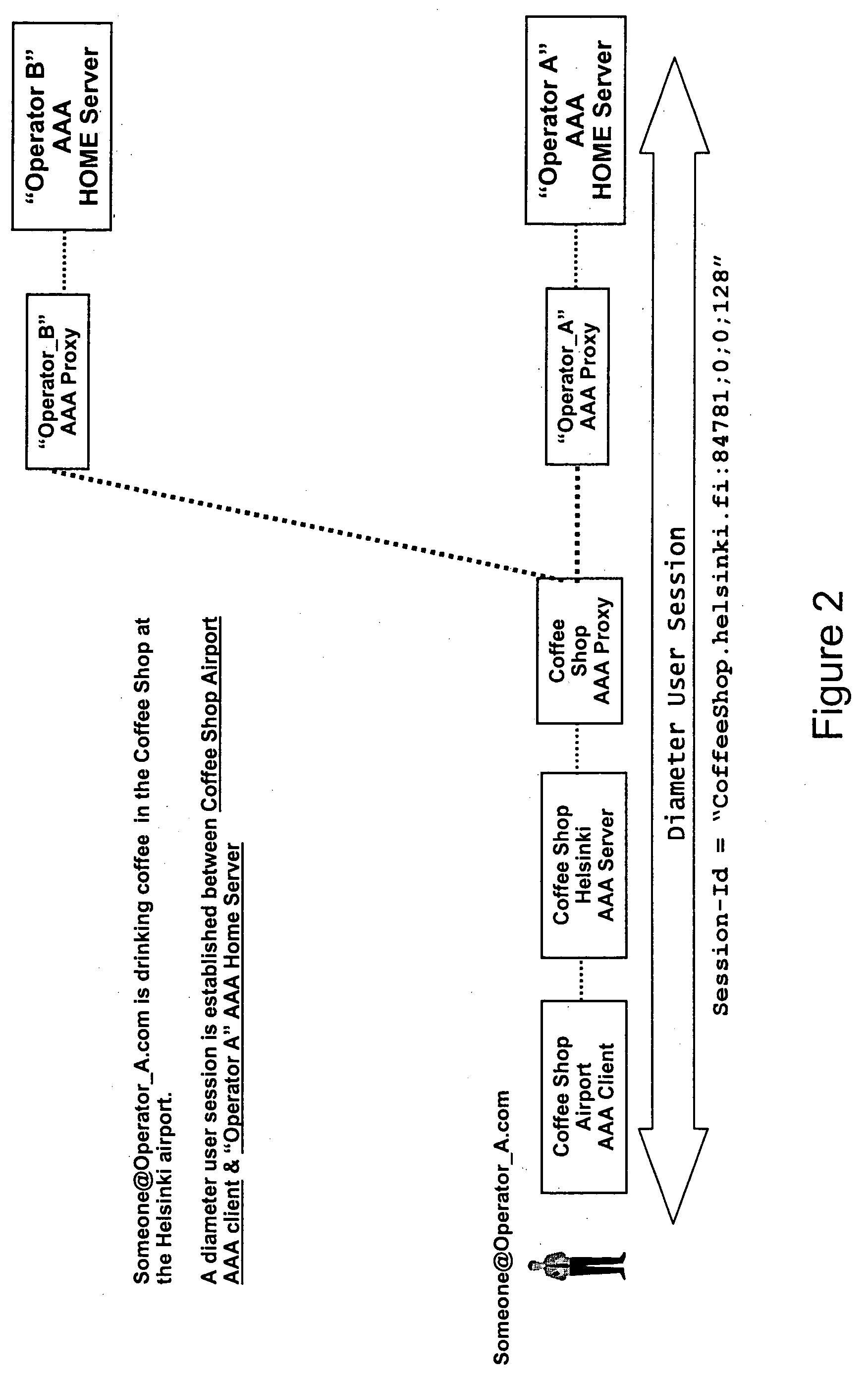
Method, network element, and system for providing security of a user session
InactiveUS20050235065A1Increase safetyHigh safetyDigital computer detailsTransmissionClient-sideA domain
Methods, network elements, and a system for providing security of a session between a client of a domain of a network and a service node of said network are provided, which network consists of a plurality of domains, from which domain a user connected to said network via said client requests a service. The providing of security is based on analyzing a message, which is associated with said session and destined for said client, in terms of routing information. Such routing information may comprise an origin domain information of said message and a route information of said message, or an origin domain information of said message, which indicates a domain from which said message originates. The present invention is particularly advantageous for AAA sessions associated with authentication, authorization, and accounting functions and for usage of Diameter Base protocol.
Owner:NOKIA CORP
Cathode active material powder for lithium secondary battery
ActiveUS20070099087A1Large volume capacity densityHigh safetyPositive electrodesCobalt compoundsComposite oxideCharge and discharge
It is to provide a cathode active material powder for a positive electrode for a lithium secondary battery, which has a large volume capacity density, high safety and excellent durability for charge and discharge cycles. A cathode active material powder for a lithium secondary battery characterized by comprising a first composite oxide powder represented by the formula (1) LipQxMyOzFa (wherein Q is Co or Mn, M is aluminum or an alkaline earth metal element or a transition metal element other than Q, provided that when Q is Co, 0.9≦p≦1.1, 0.980≦x≦1.000, 0≦y≦0.02, 1.9≦z≦2.1, x+y=1, and 0≦a≦0.02, and when Q is Mn, 1≦p≦1.3, x=2−y, 0≦y≦0.05, z=4, and a=0), having an average particle size D50 of from 5 to 30 μm, and having a compression breaking strength of at least 40 MPa; and a second composite oxide powder represented by the formula (2) LipNixCoyMnzNqOrFa (wherein N is aluminum or an alkaline earth metal element or a transition metal element other than Ni, Co and Mn, 0.9≦p≦1.1, 0.2≦x≦0.8, 0≦y≦0.4, 0≦z≦0.5, 0≦q≦0.05, 1.9≦r≦2.1, x+y+z+q=1, and 0≦a≦0.02), having an average particle size D50 of from 2 to 30 μm, and having a compression breaking strength less than 40 MPa; in a ratio (weight ratio) of the first composite oxide powder / the second composite oxide powder being from 95 / 5 to 30 / 70.
Owner:SUMITOMO CHEM CO LTD
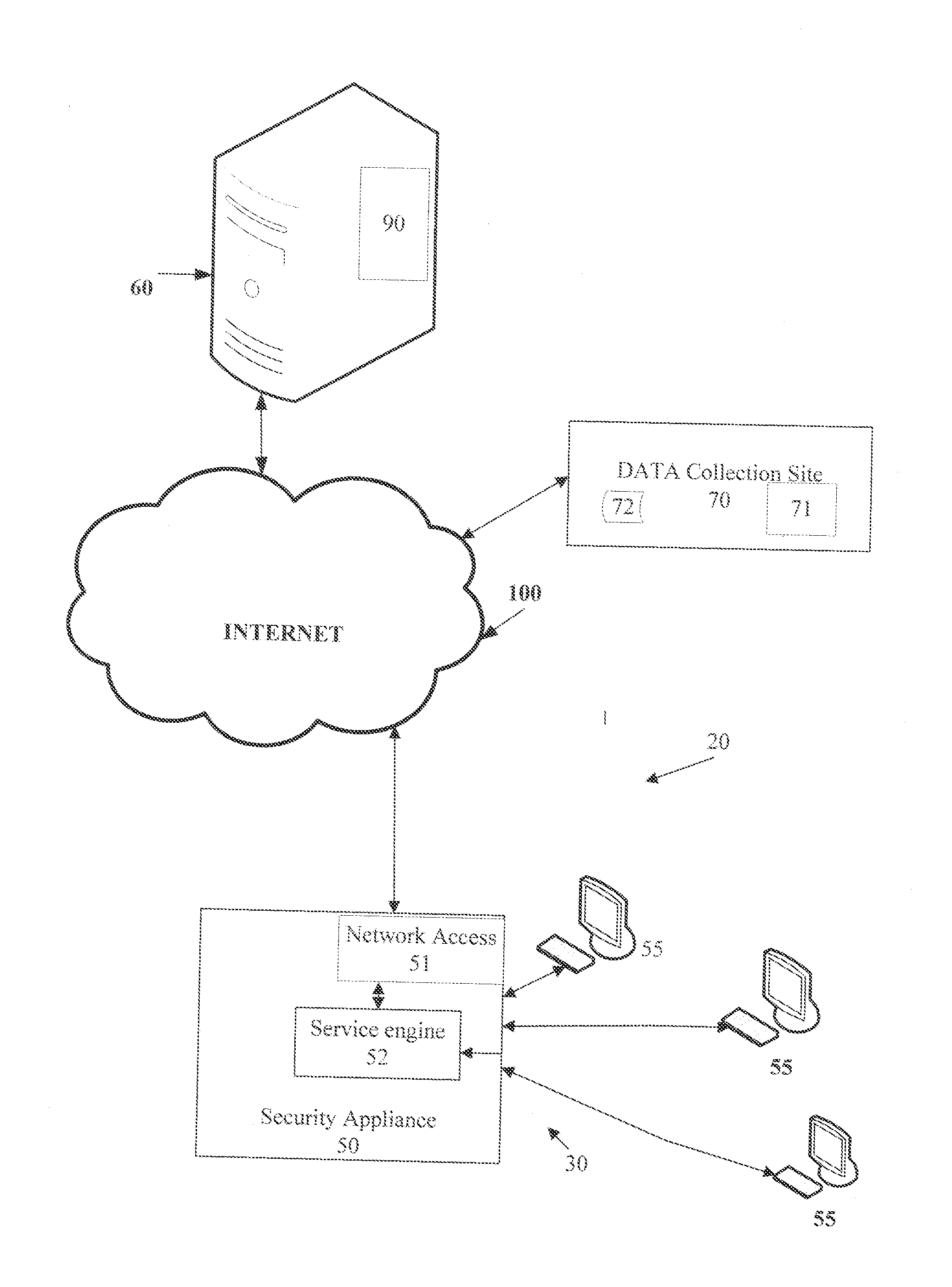
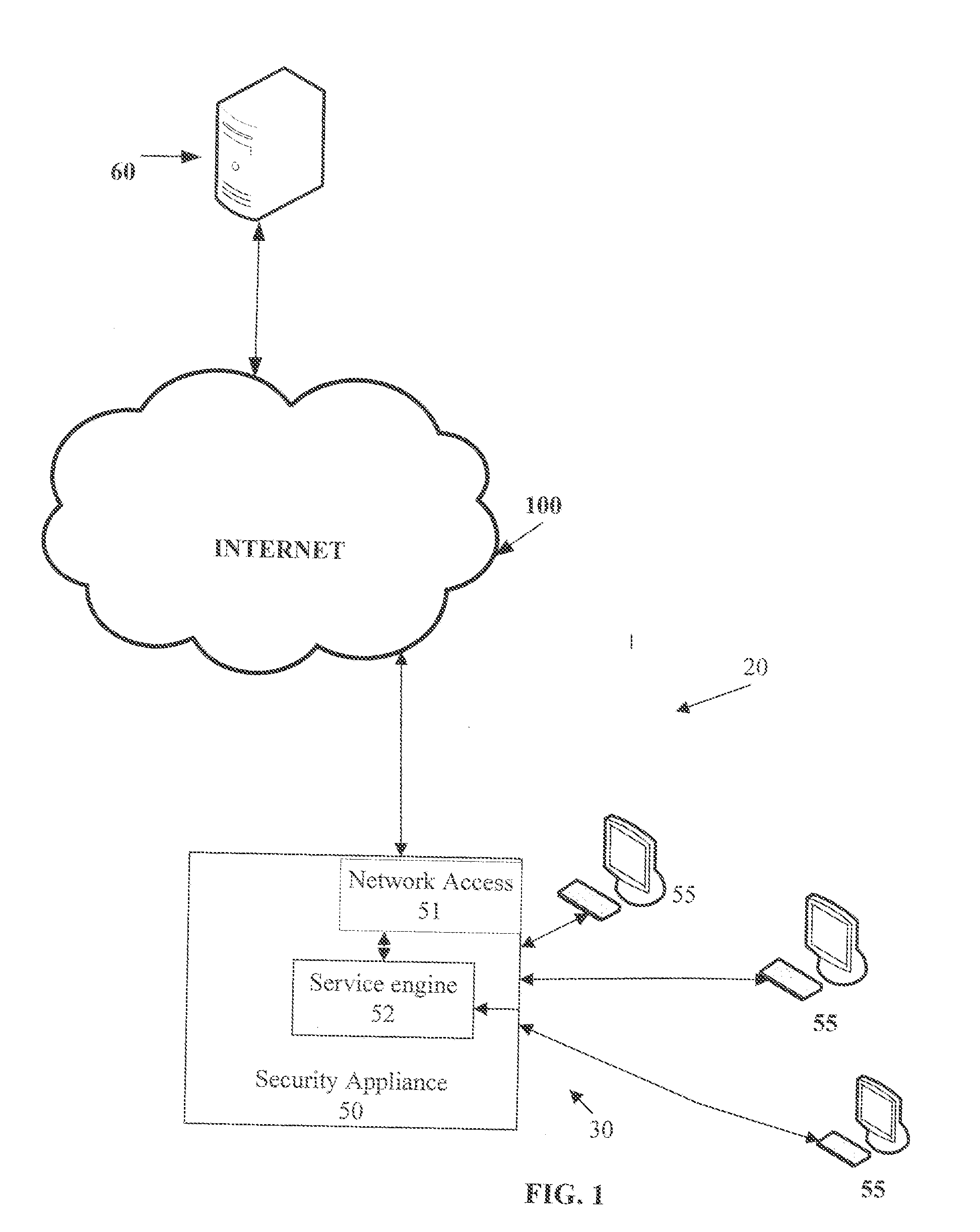
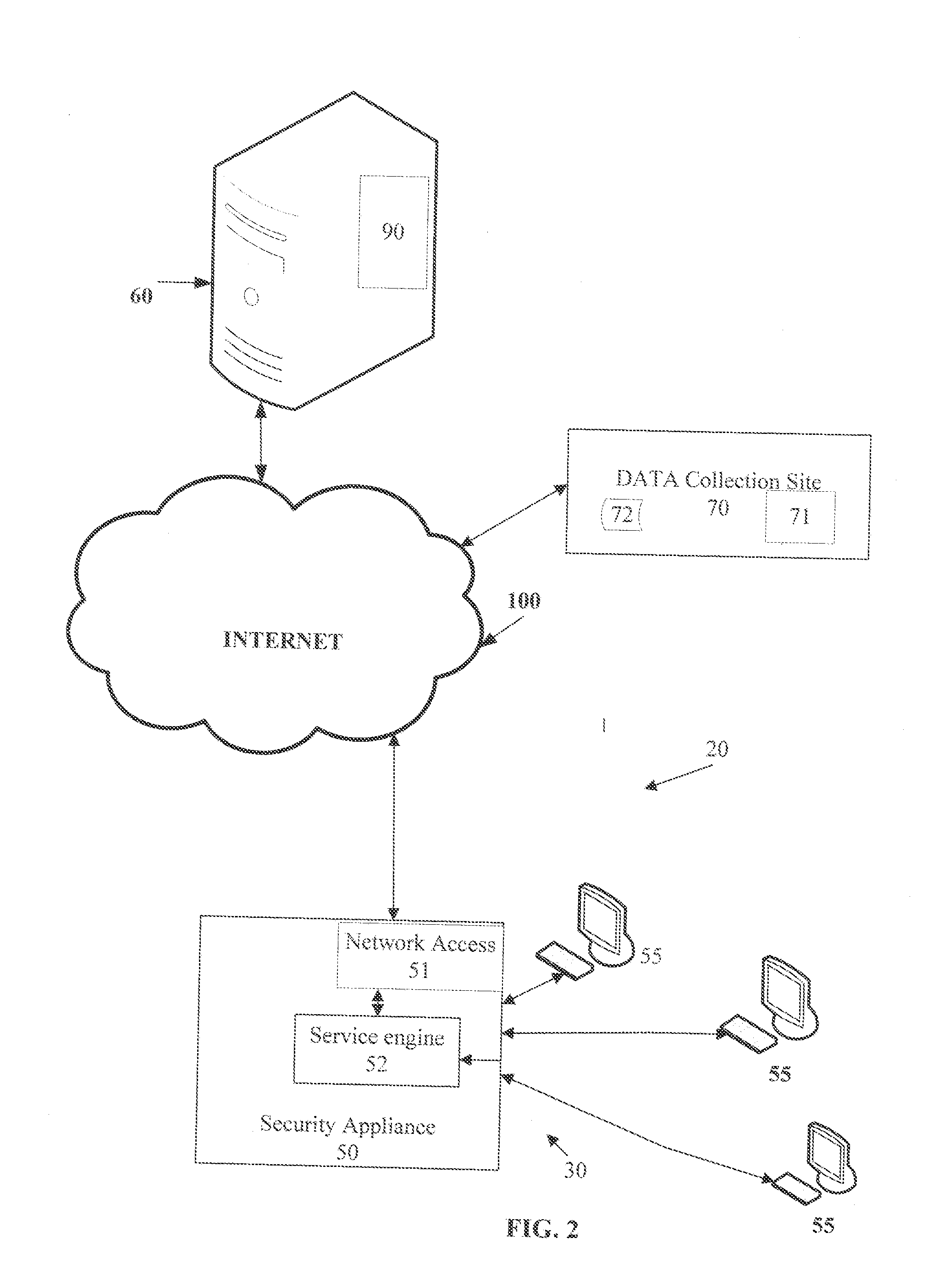
System And Method For Developing A Risk Profile For An Internet Service
ActiveUS20100269168A1High safetyDigital data processing detailsAnalogue secracy/subscription systemsResponse delayRunning time
A method and system for controlling access to an Internet resource is disclosed herein. When a request for an Internet resource, such as a Web site, is transmitted by an end-user of a LAN, a security appliance for the LAN analyzes a reputation index for the Internet resource before transmitting the request over the Internet. The reputation index is based on a reputation vector which includes a plurality of factors for the Internet resource such as country of domain registration, country of service hosting, country of an internet protocol address block, age of a domain registration, popularity rank, internet protocol address, number of hosts, to-level domain, a plurality of run-time behaviors, JavaScript block count, picture count, immediate redirect and response latency. If the reputation index for the Internet resource is at or above a threshold value established for the LAN, then access to the Internet resource is permitted. If the reputation index for the Internet resource is below a threshold value established for the LAN, then access to the Internet resource is denied.
Owner:WEBROOT INCORPORATED
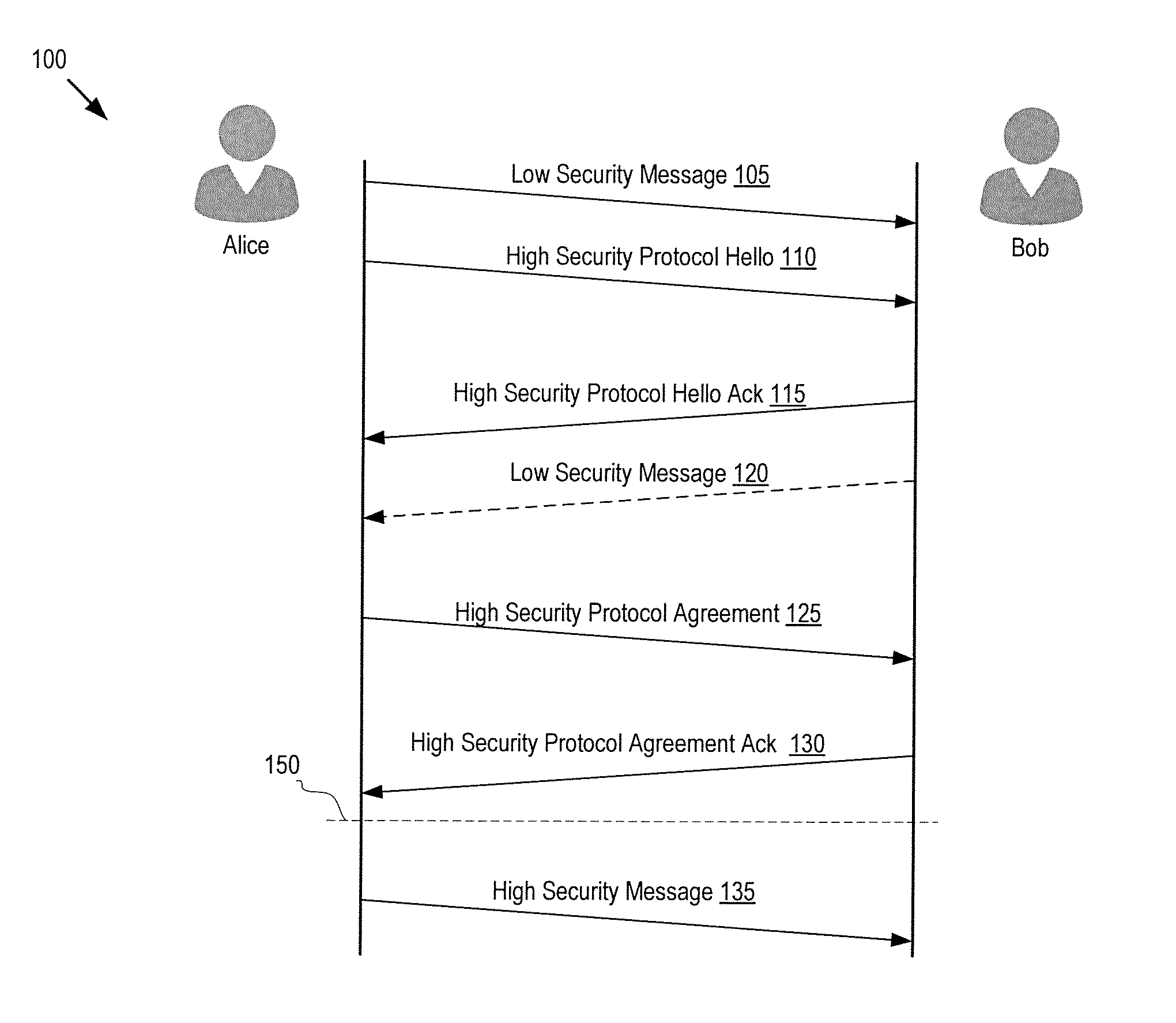
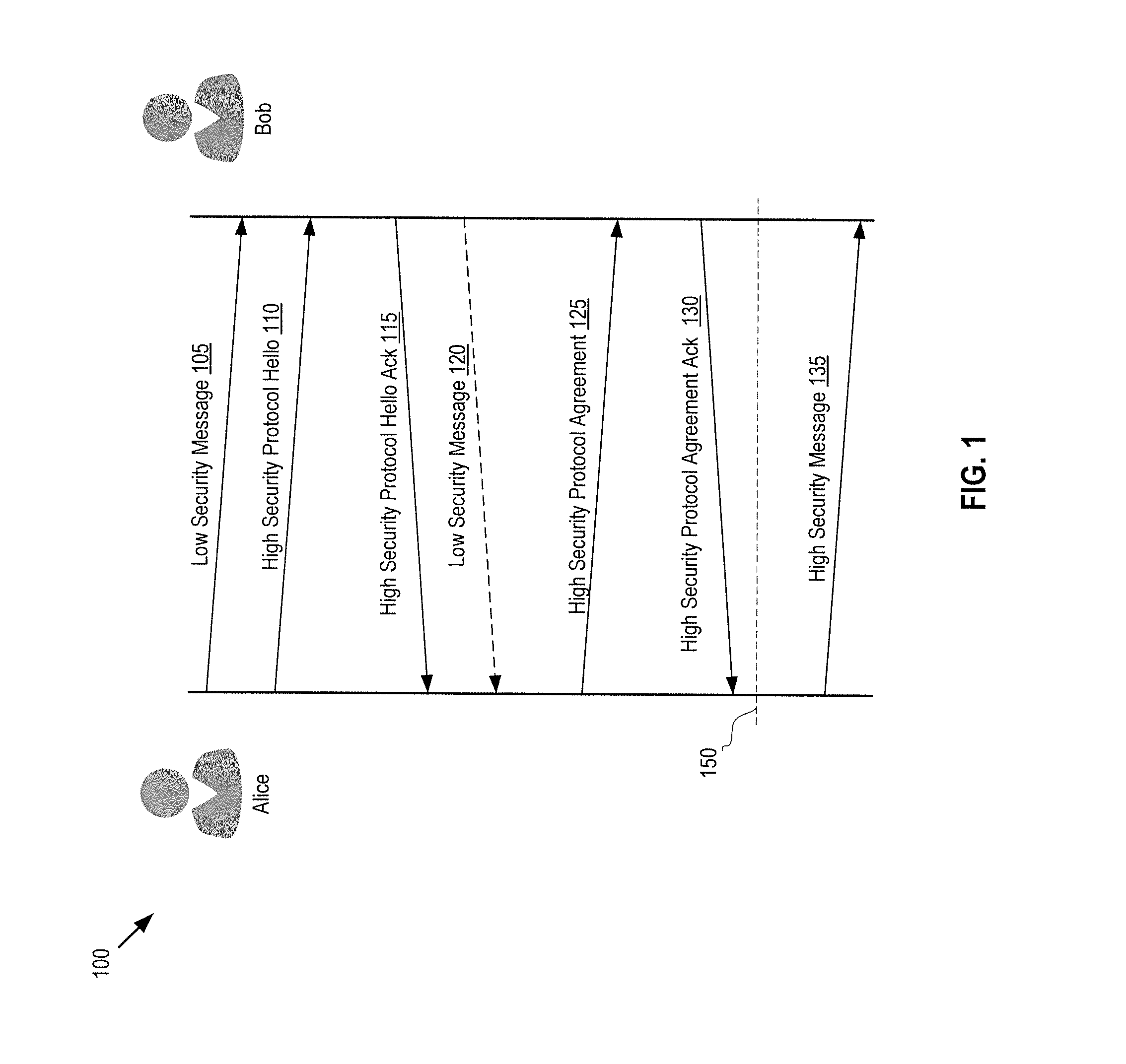
Efficient secure instant messaging
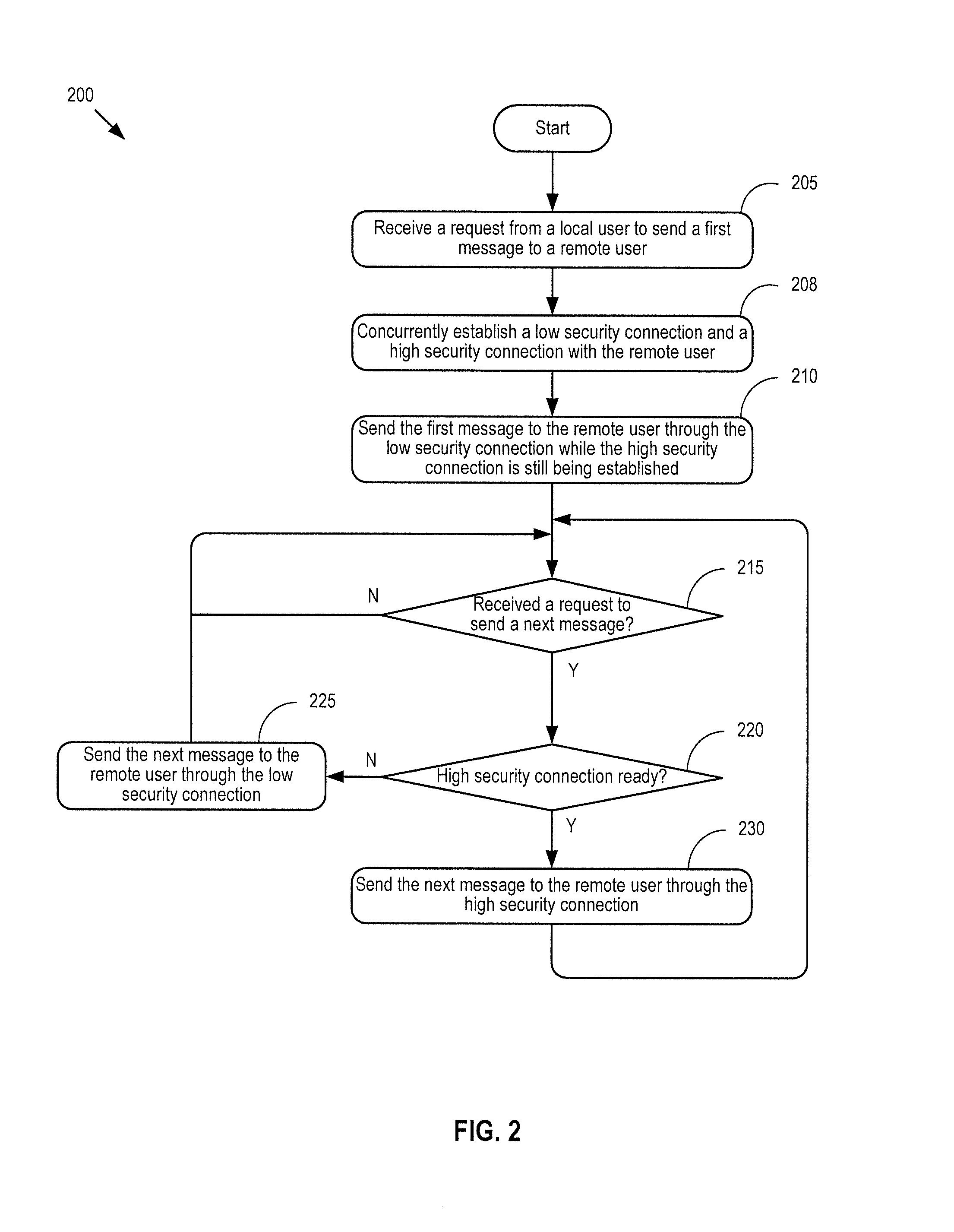
A method and apparatus of a device that enables a user to participate in a secure instant messaging session by starting with a low security connection before switching to a high security connection is described. The device concurrently establishes a low security connection and a high security connection with a remote participant of the secure instant messaging session. The device sends a first message to the remote participant through the low security connection while the high security connection is being established. The device further determines whether the high security connection is established. If the high security connection is established, the device can send a second message to the remote participant through the high security connection. If the high security connection is not yet established, the device can send the second message to the remote participant through the low security connection.
Owner:APPLE INC
Positive electrode active material for lithium secondary battery and process for producing the same
InactiveUS20060263690A1Large volume capacity densityHigh safetyElectrode manufacturing processesCobalt compoundsChemistryComposite oxide
A positive electrode active material for a lithium secondary battery containing a lithium-cobalt composite oxide, which has a large volume capacity density, has a high safety and is excellent in charge and discharge cyclic durability, and its production process, are provided. A lithium-cobalt composite oxide represented by the formula LipCoxMyOzFa (wherein M is a transition metal element other than Co or an alkaline earth metal element, 0.9≦p≦1.1, 0.980≦x≦1.000, 0≦y≦0.02, 1.9≦z≦2.1, x+y=1 and 0≦a≦0.02) and comprising a mixture containing substantially spherical hard first particles of lithium-cobalt composite oxide having such a sharp particle size distribution that the volume basis cumulative size D10 is at least 50% of the average particle size D50, and the volume basis cumulative size D90 is at most 150% of the average particle size D50, and second particles of lithium-cobalt composite oxide filling the space among the first particles, in a mass ratio of first particles / second particles of from 1 / 2 to 9 / 1, and process for producing the same.
Owner:SEIMI CHEM CO LTD
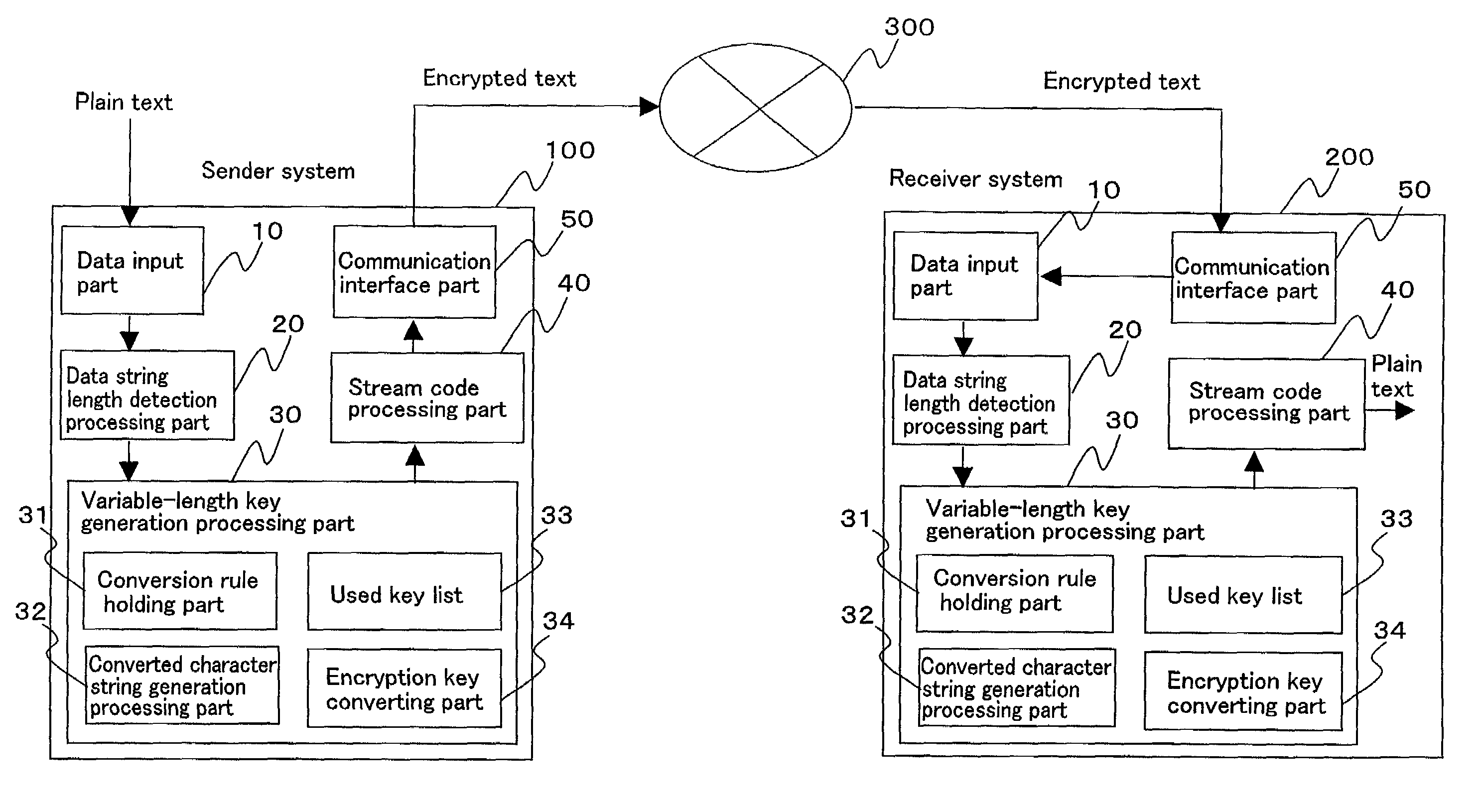
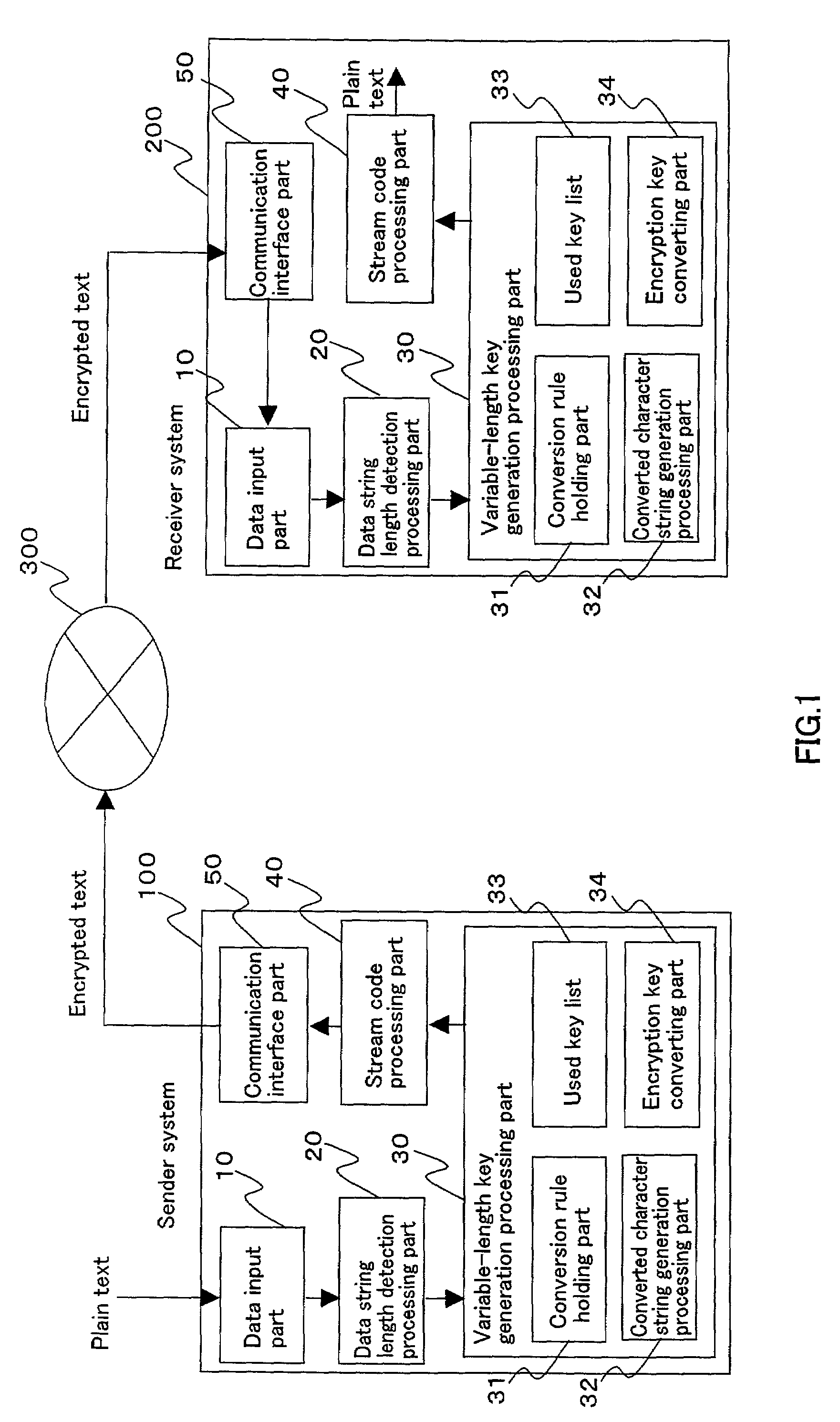
Variable-length key cryptosystem
InactiveUS7224795B2High safetyLow calculation costData stream serial/continuous modificationSecret communicationCryptosystemKey generation
A variable-length key cryptosystem is provided, in which the amount of parameters for generating a key to be shared is small, security is high, and calculation cost is small.The length of a plain text inputted from a data input part 10 is detected by a data string length detection processing part 20. A variable-length key generation processing part 30 generates an encryption key with a required arbitrary length, using an initial character string and a conversion rule, based on the length of a plain text. A conversion character string generation processing part 32 generates a converted character string from an initial character string by applying a conversion rule of increasing the length of a character string. Conversion is conducted until the length of a plain text is reached. An encryption key is not used twice. Therefore, an unused conversion character string is searched for, and a stream code processing part 40 generates an encrypted text by using a generated encrypted string. A receiver system 200 generates a converted character string from an initial character string by the same conversion, based on the length of an encrypted text, thereby obtaining the same encryption key.
Owner:FUJITSU LTD +1
Integrated circuit card
ActiveUS20060047971A1High safetyPrevent misuseAcutation objectsComputer security arrangementsIntegrated circuit cardFingerprint
Owner:SEIKO EPSON CORP
Optical watermark
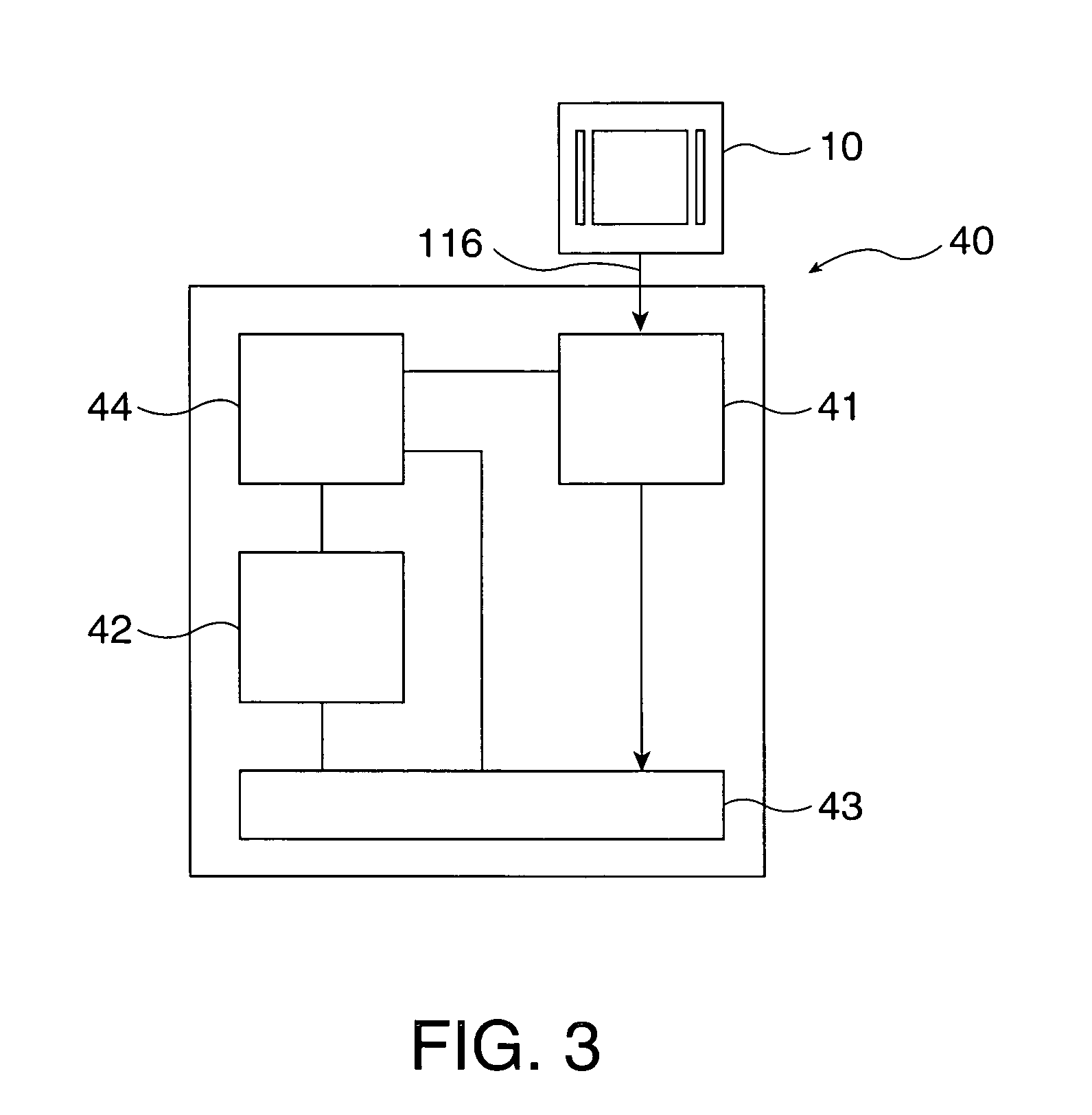
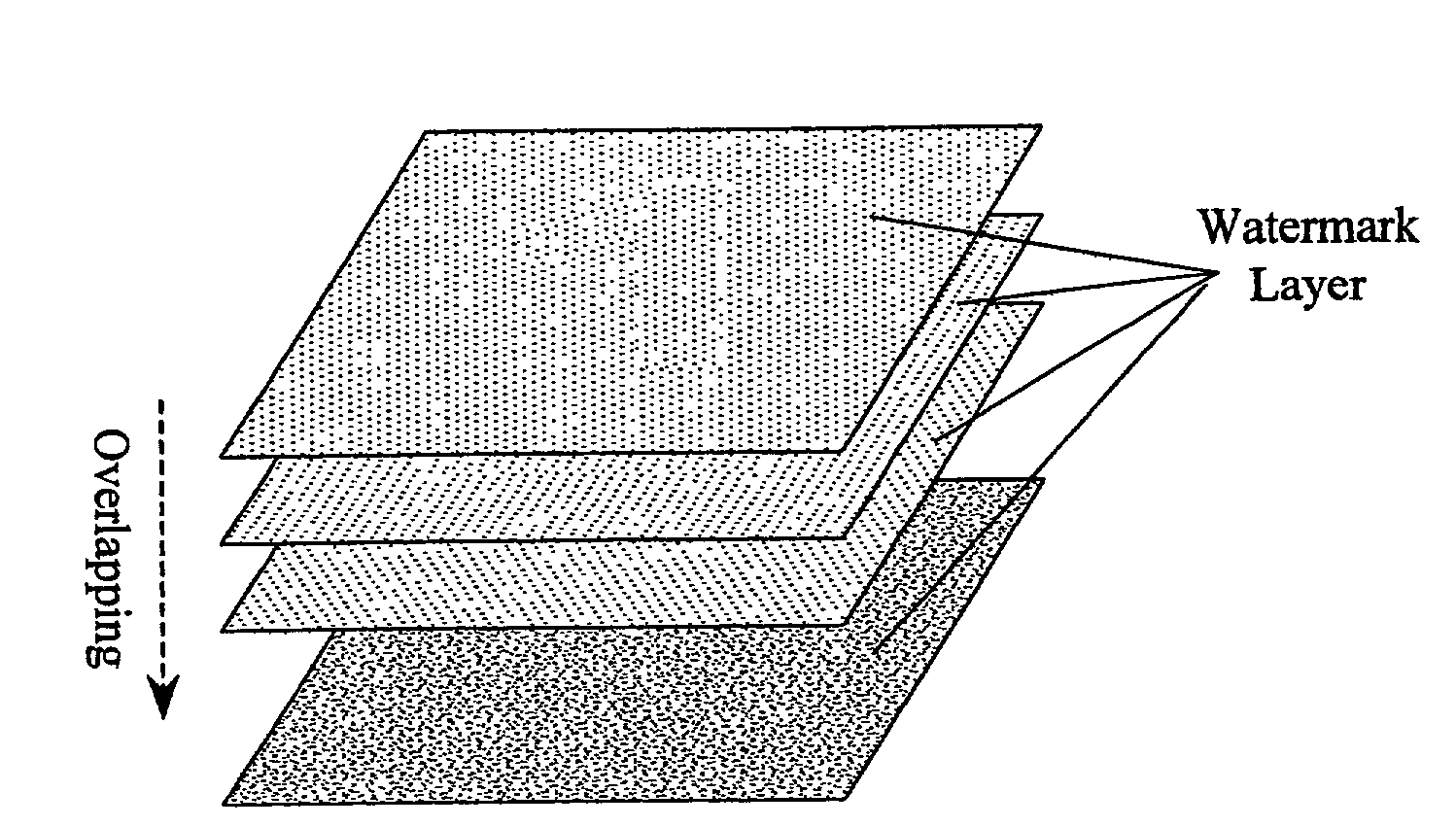
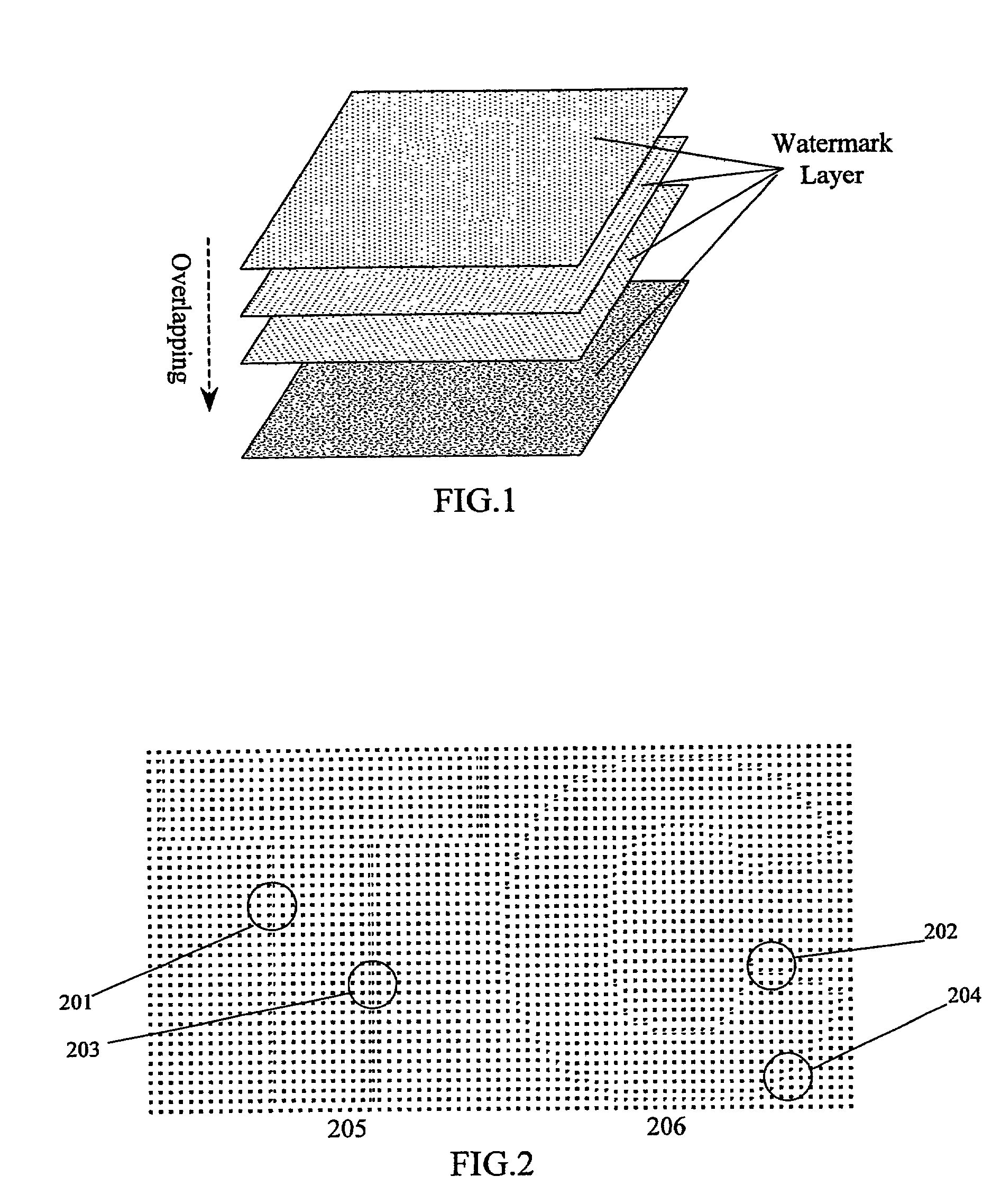
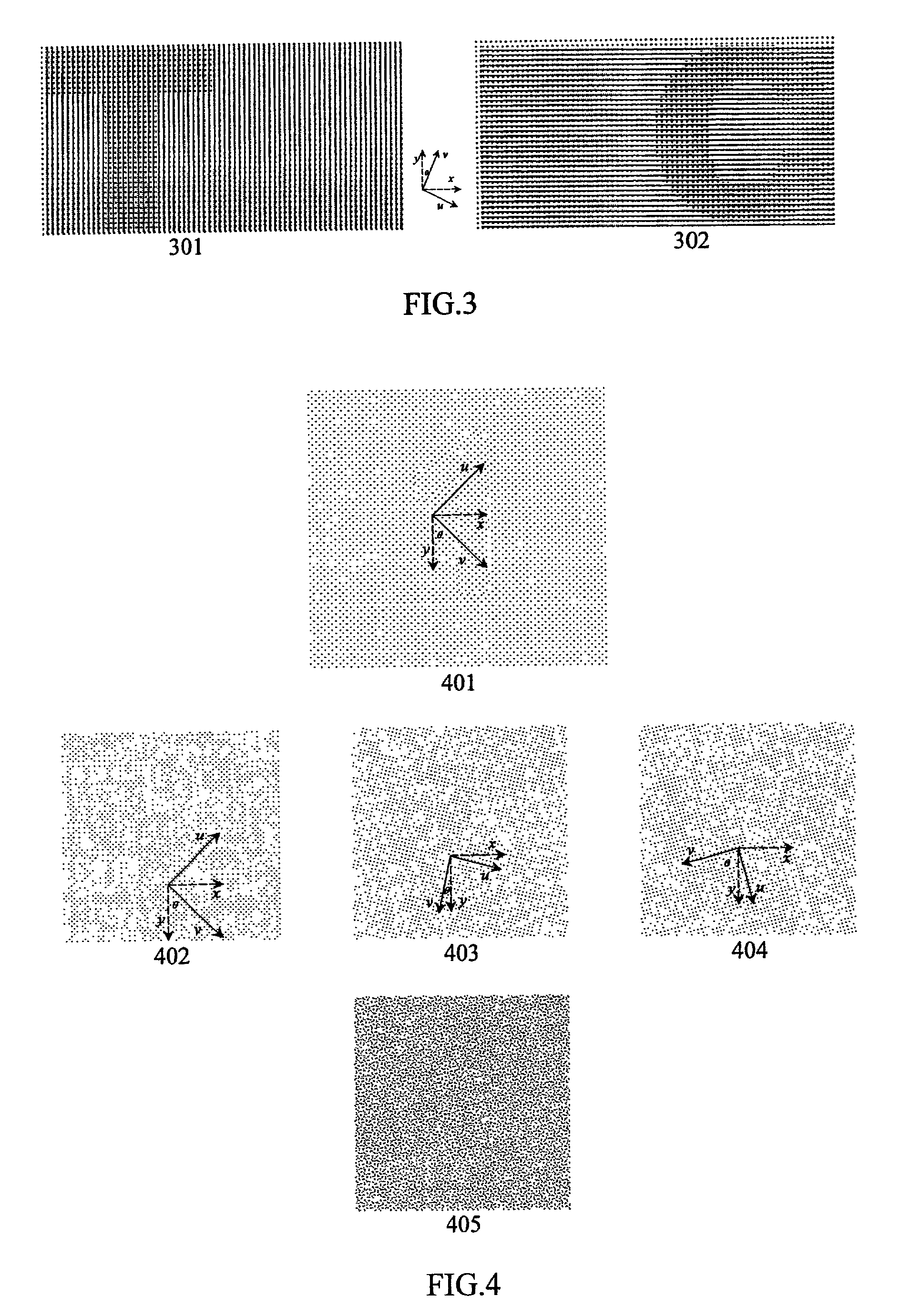
InactiveUS7366301B2Increase complicityHigh safetyOther printing matterDot-and-dash receiving apparatusLayered structureReverse engineering
A multiple-layered watermark is generated to be placed on document, to protect against counterfeiting and forgery. Hidden information embedded into each of the watermark's layers is only detectable by using a corresponding decoder. Because of the multiple-layered structure, it is difficult to reverse engineer the optical watermark. The generalized watermark structure significantly increases the “key space” of the decoder.
Owner:TRUSTCOPY PTE
Secure communications
ActiveUS7284127B2High safetyHigh level of securityKey distribution for secure communicationPublic key for secure communicationSecure communicationComputer security
A method of providing secure communications between a first and a second communications unit comprising a key exchange between the communications units resulting in a shared secret key, the key exchange including a user interaction. The method includes the steps of providing, at least partly by means of a user interaction, a passcode to the first and second communications units; generating a first contribution to the shared secret key by the first communications unit and a second contribution to the shared secret key by the second communications unit, and transmitting each generated contribution to the corresponding other communications unit; authenticating the transmitted first and second contributions by the corresponding receiving communications unit based on at least the passcode; and establishing said shared secret key by each of the communications units from at least the corresponding received first or second contribution, only if the corresponding received contribution is authenticated successfully.
Owner:TELEFON AB LM ERICSSON (PUBL)
Particulate positive electrode active material for a lithium secondary cell
InactiveUS20050019662A1High safetyHigh volume capacity densityFluoride preparationPositive electrodesChemistryHigh weight
A particulate positive electrode active material for a lithium secondary cell which satisfies high charge and discharge cyclic durability, high safety, high temperature storage properties, a high discharge average voltage, large current discharge properties, a high weight capacity density, a high volume capacity density, etc. in a well-balanced manner is provided. A particulate positive electrode active material for a lithium secondary cell, which is represented by the formula LipCoxMyOzFa (wherein M is at least one element selected from Groups 2 to 8, 13 and 14 of the Periodic Table, 0.9≦p≦1.1, 0.980≦x≦0.9999, 0.0001≦y≦0.02, 1.9≦z≦2.1, 0.9≦x+y≦1 and 0.0001≦a≦0.02), wherein fluorine atoms and element M are unevenly distributed on the particle surface, the atomic ratio of fluorine atoms to cobalt atoms (a / x) is from 0.0001 to 0.02, and in powder X-ray diffraction using CuKα-ray, the half value width of the angle of diffraction on (110) plane is from 0.06 to 0.13°, and the half value width of the angle of diffraction on (003) plane is from 0.05 to 0.12°.
Owner:SUMITOMO CHEM CO LTD
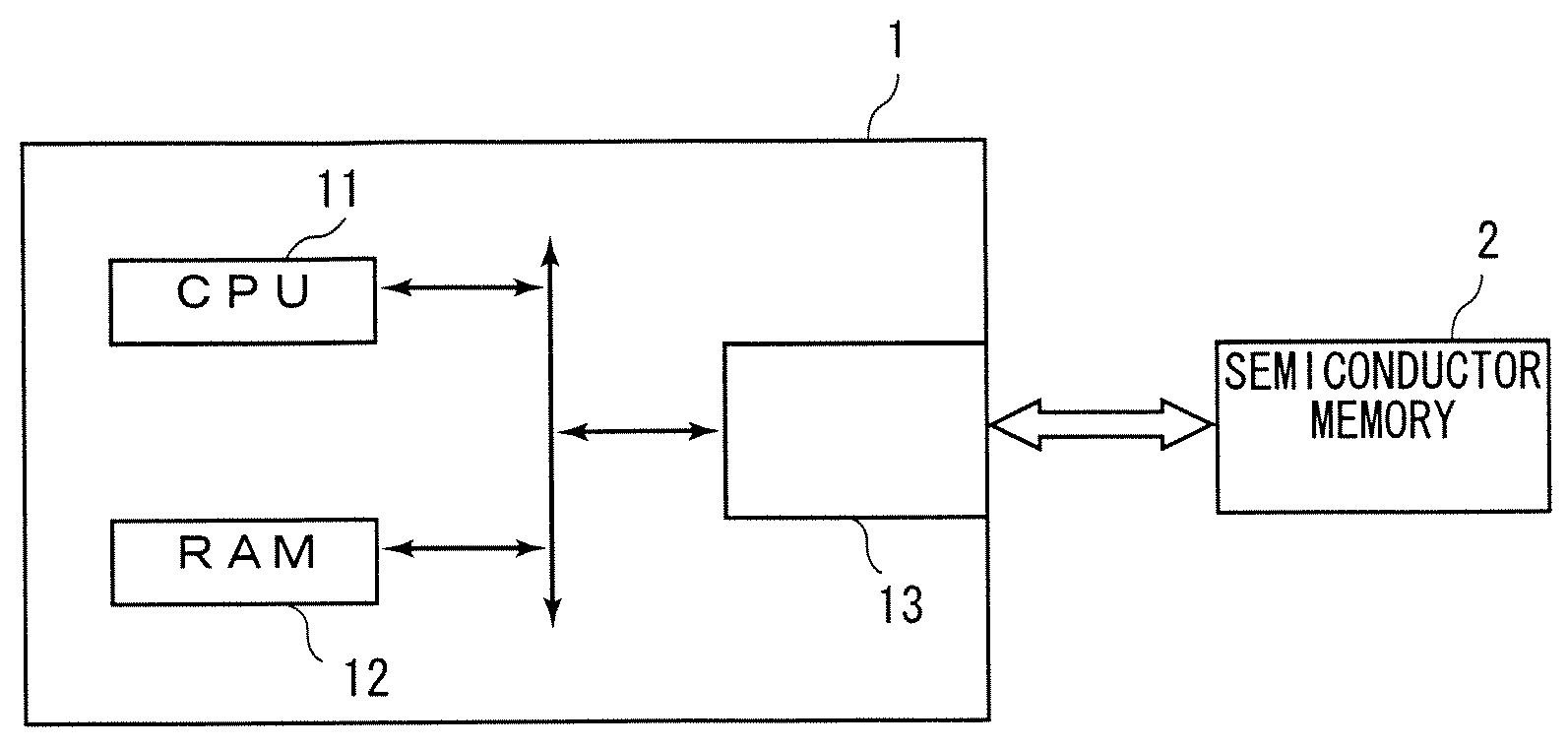
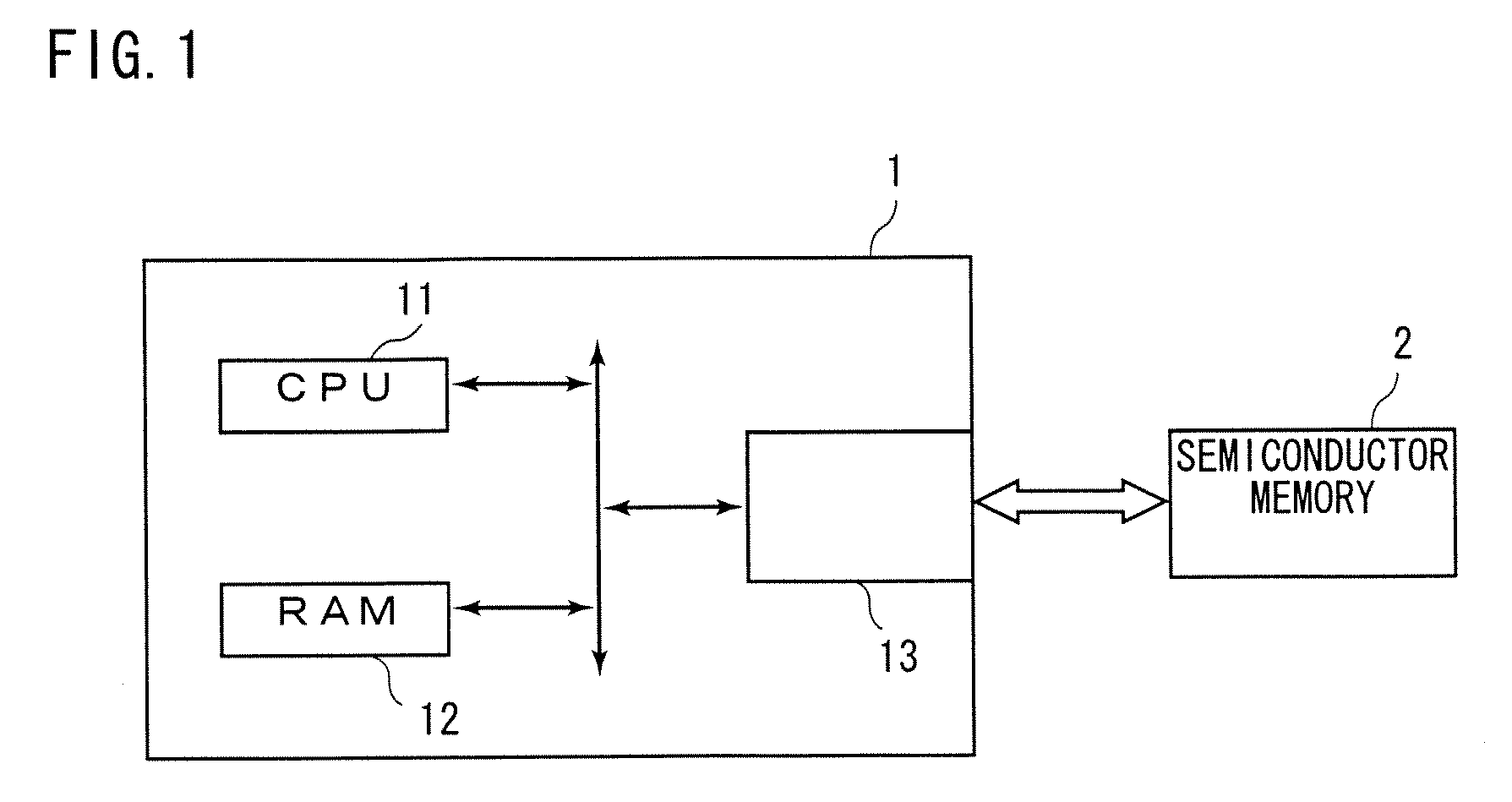
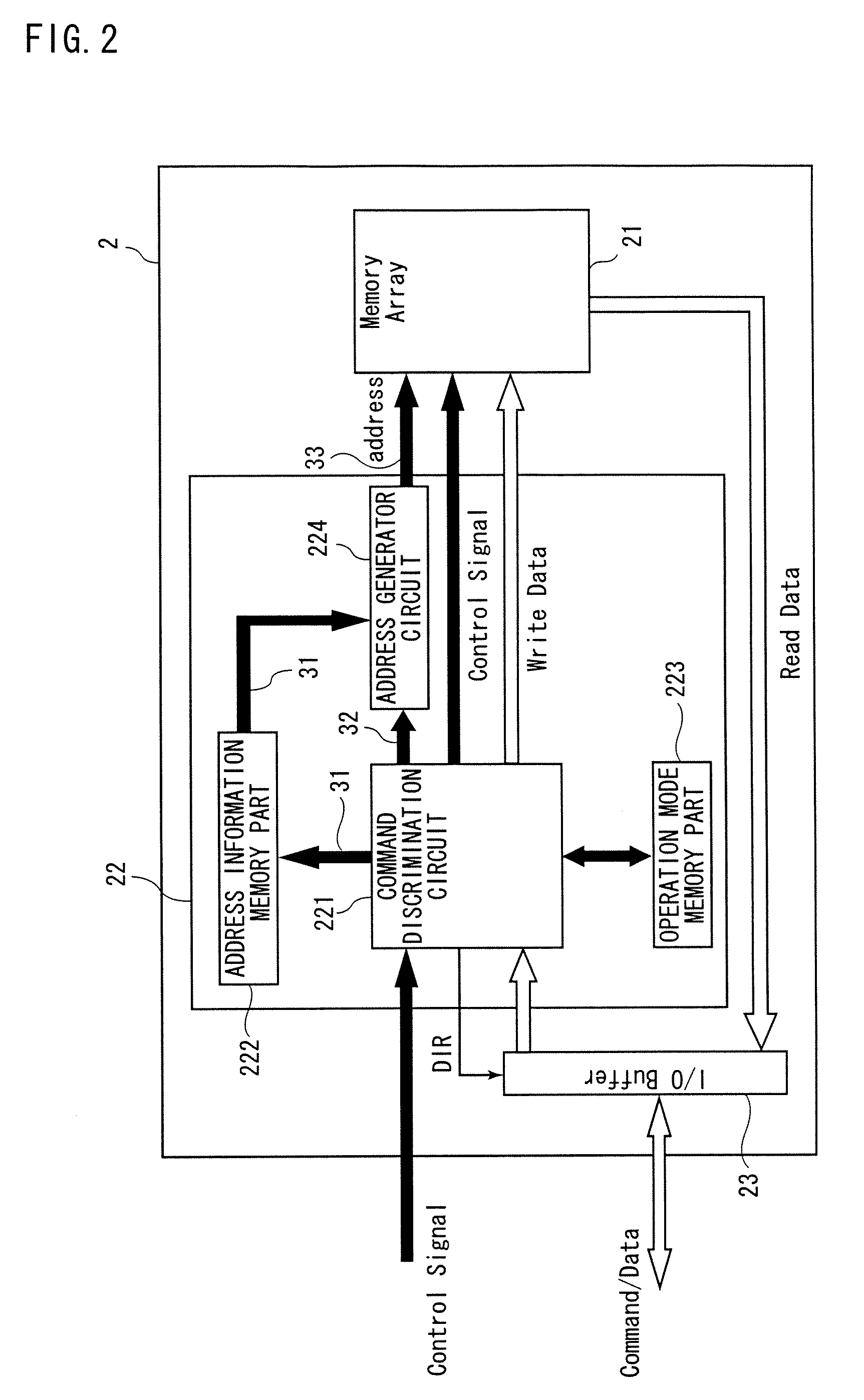
Semiconductor memory and data access method
InactiveUS20070192627A1High safetyImprove securityUser identity/authority verificationUnauthorized memory use protection4-bitSemiconductor memory
While a semiconductor memory operates in a first operation mode with high security, an encrypted command is inputted and then decoded to acquire the first address information. After the semiconductor memory comes into a second operation mode where the level of security is lower than that of the first operation mode, a command is inputted. Then, the second address information is acquired from the command. A control circuit in the semiconductor memory generates an address of 10 bits by using the first address information as a high-order 4 bits and the second address information as a low-order 6 bits and outputs the address to a memory array. With this operation, it becomes possible to read / write data from / to the memory array.
Owner:MEGACHIPS
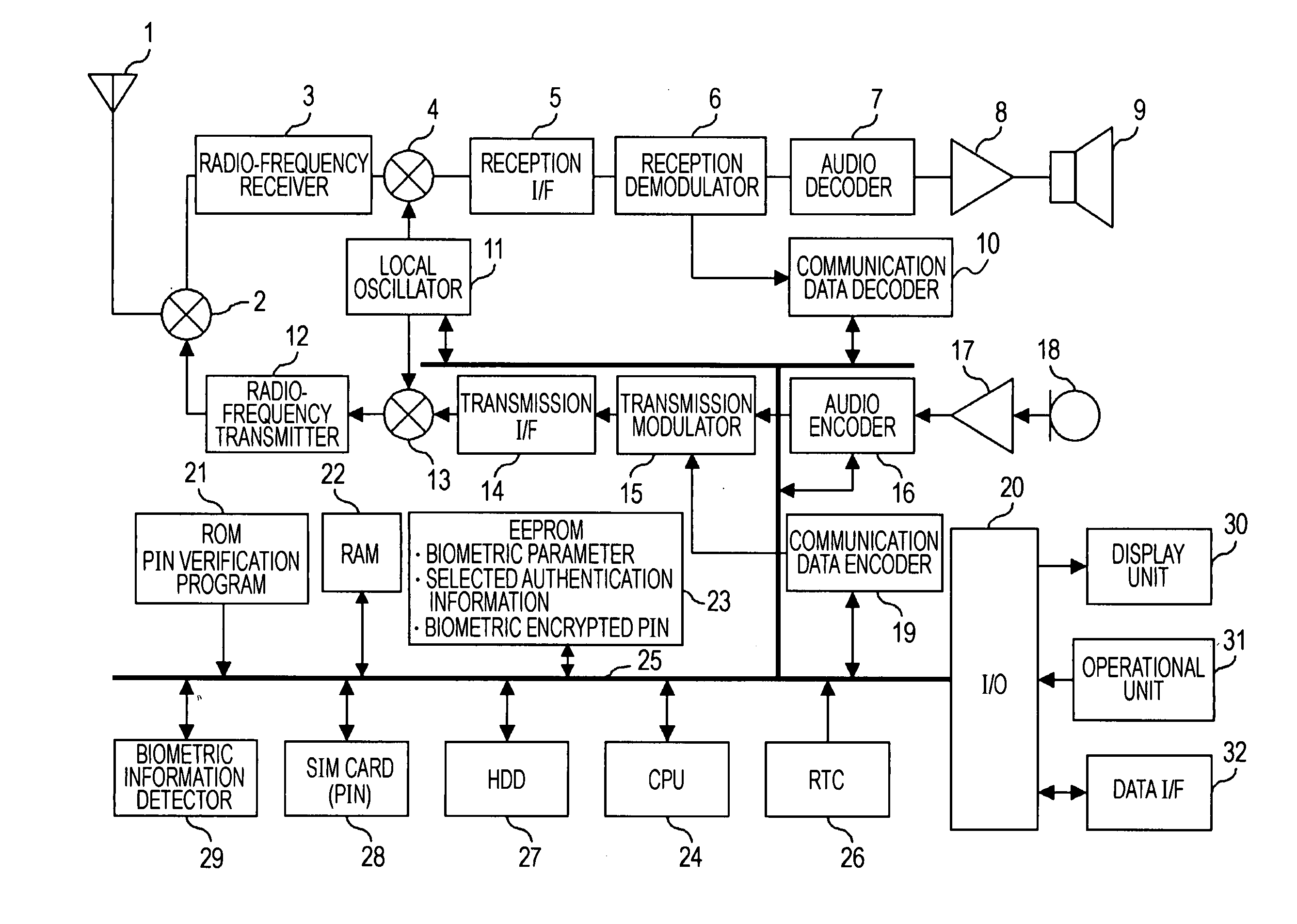
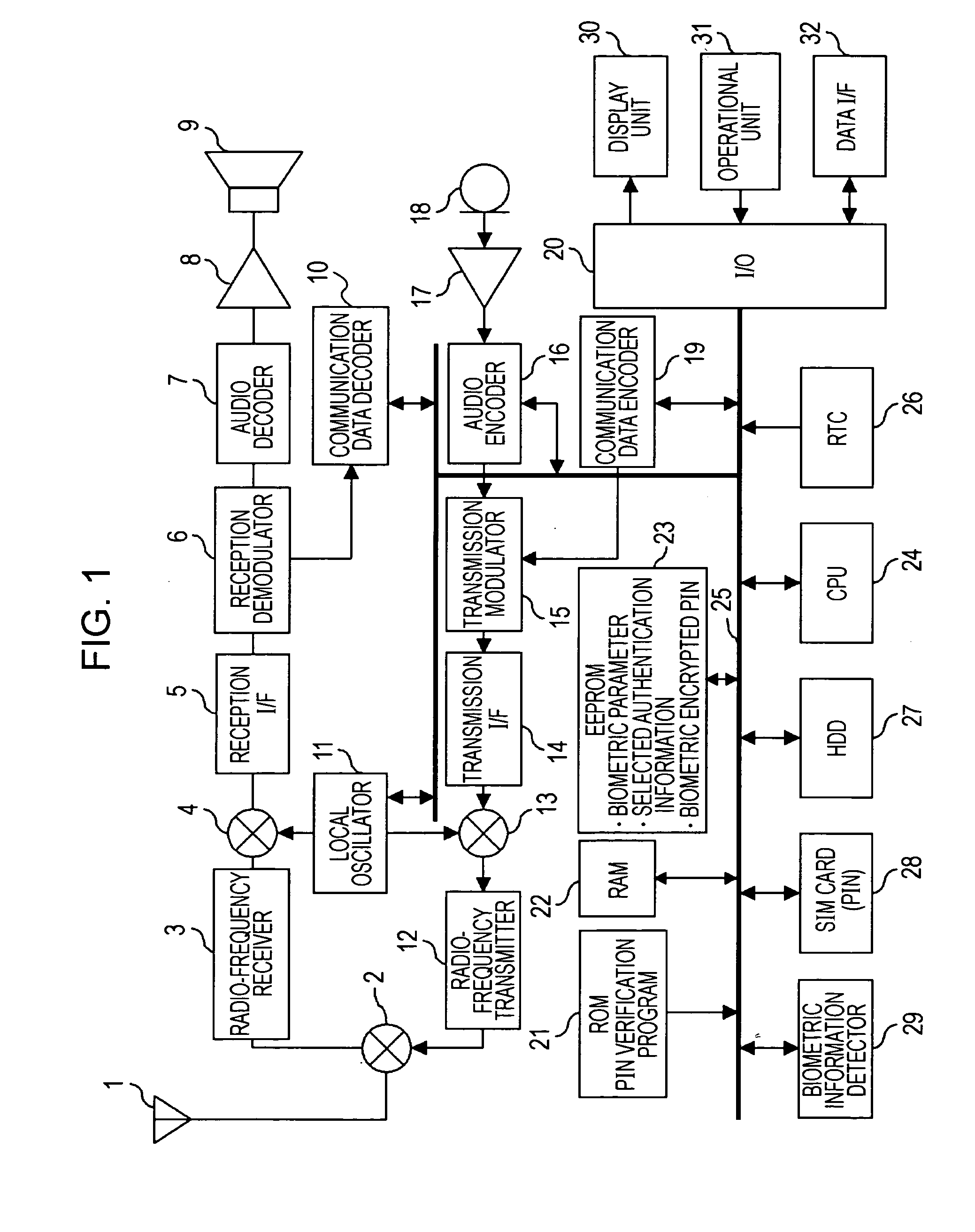
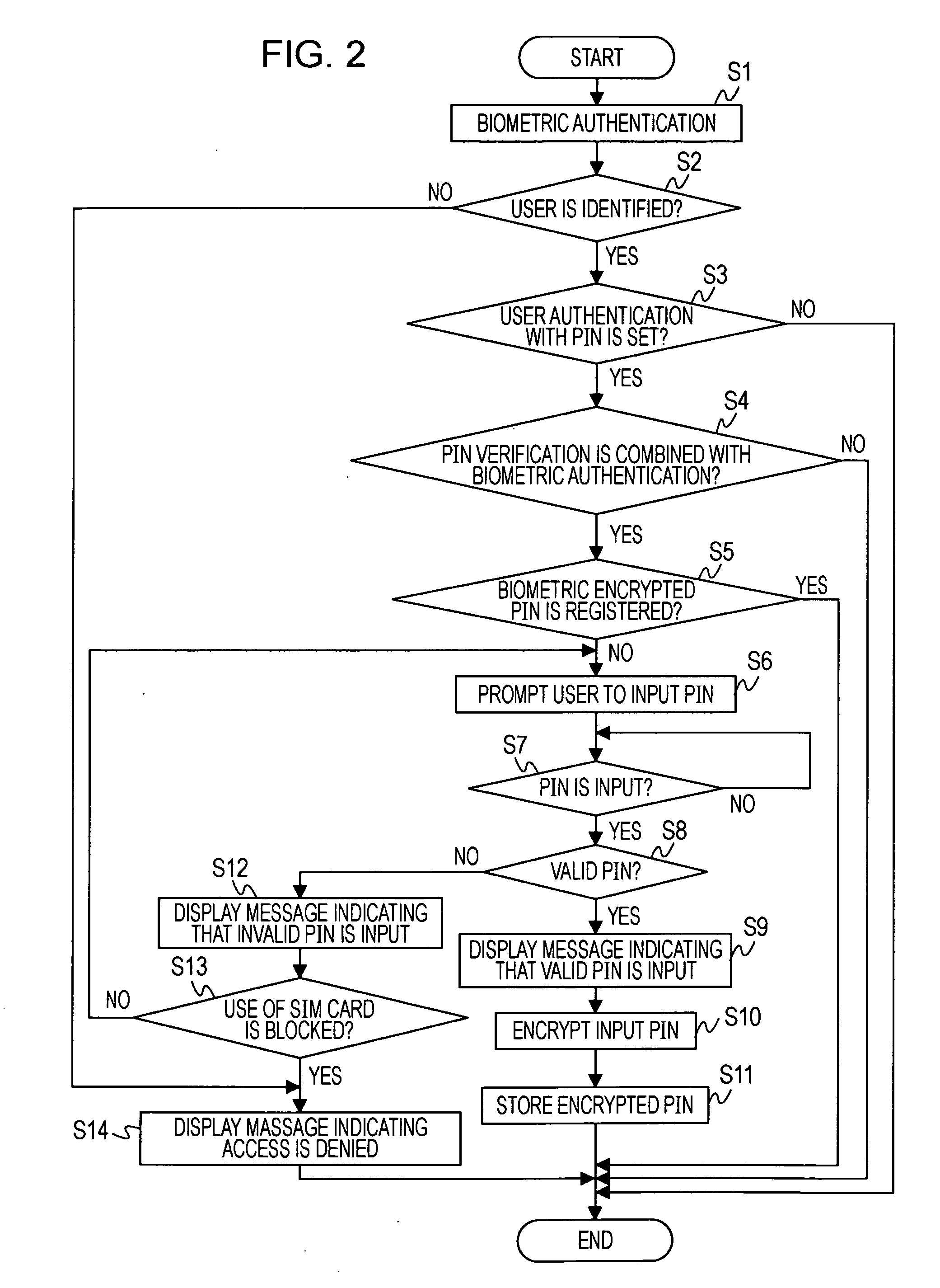
Mobil terminal device, personal identification number verification program, and method of verifying personal identification number
InactiveUS20070011466A1High safetyGreat convenienceUnauthorised/fraudulent call preventionDigital data processing detailsKey generationPersonal identification number
A mobile terminal device includes biometric information detecting means for detecting biometric information; encryption key generating means for generating an encryption key on the basis of the biometric information in registration; encrypting means for encrypting a predetermined personal identification number with the encryption key to generate a biometric encrypted personal identification number in the registration; encrypted personal-identification-number storing means for storing the biometric encrypted personal identification number in the registration; decryption key generating means for generating a decryption key on the basis of the detected biometric information in verification; decrypting means for decrypting the biometric encrypted personal identification number with the decryption key to reproduce the personal identification number in the verification; and personal identification number verifying means for comparing the reproduced personal identification number with the stored biometric encrypted personal identification number to perform the personal-identification-number verification.
Owner:SONY ERICSSON MOBILE COMM JAPAN INC
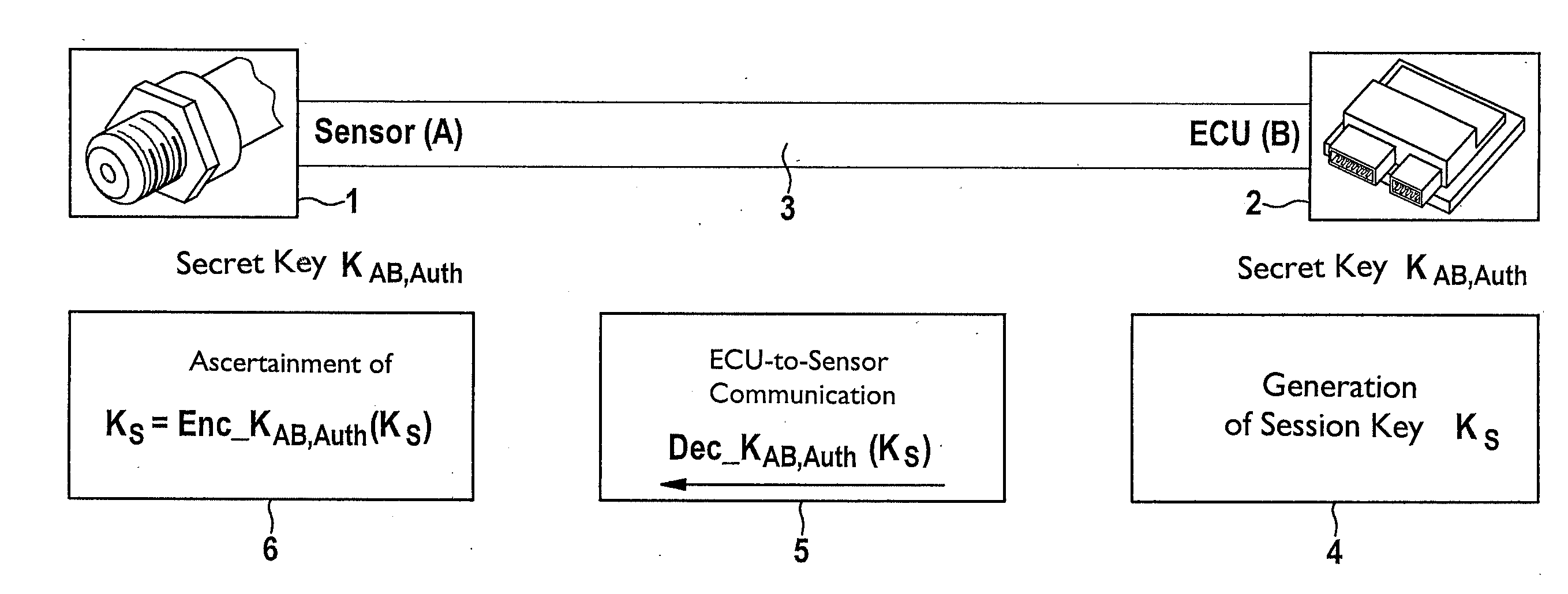
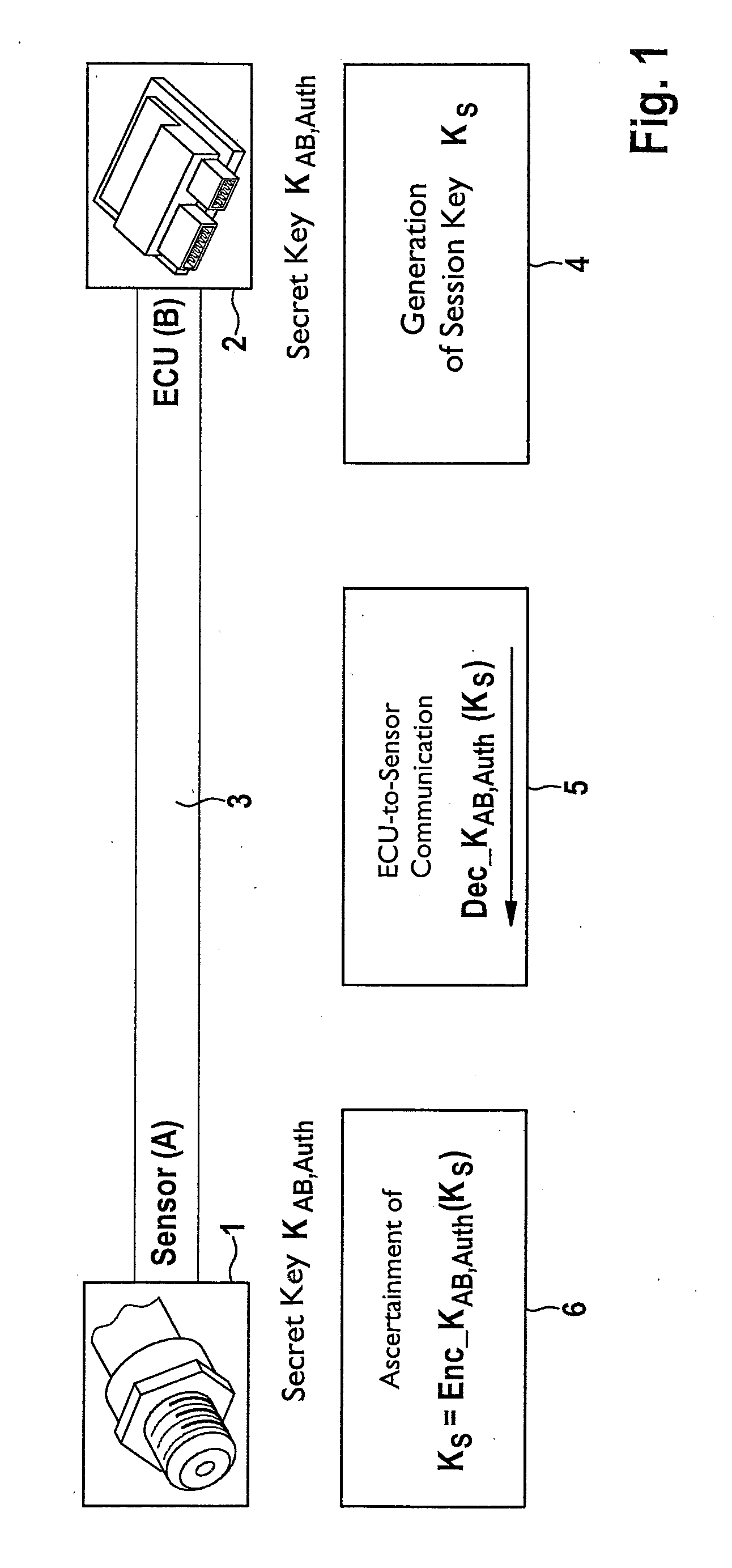
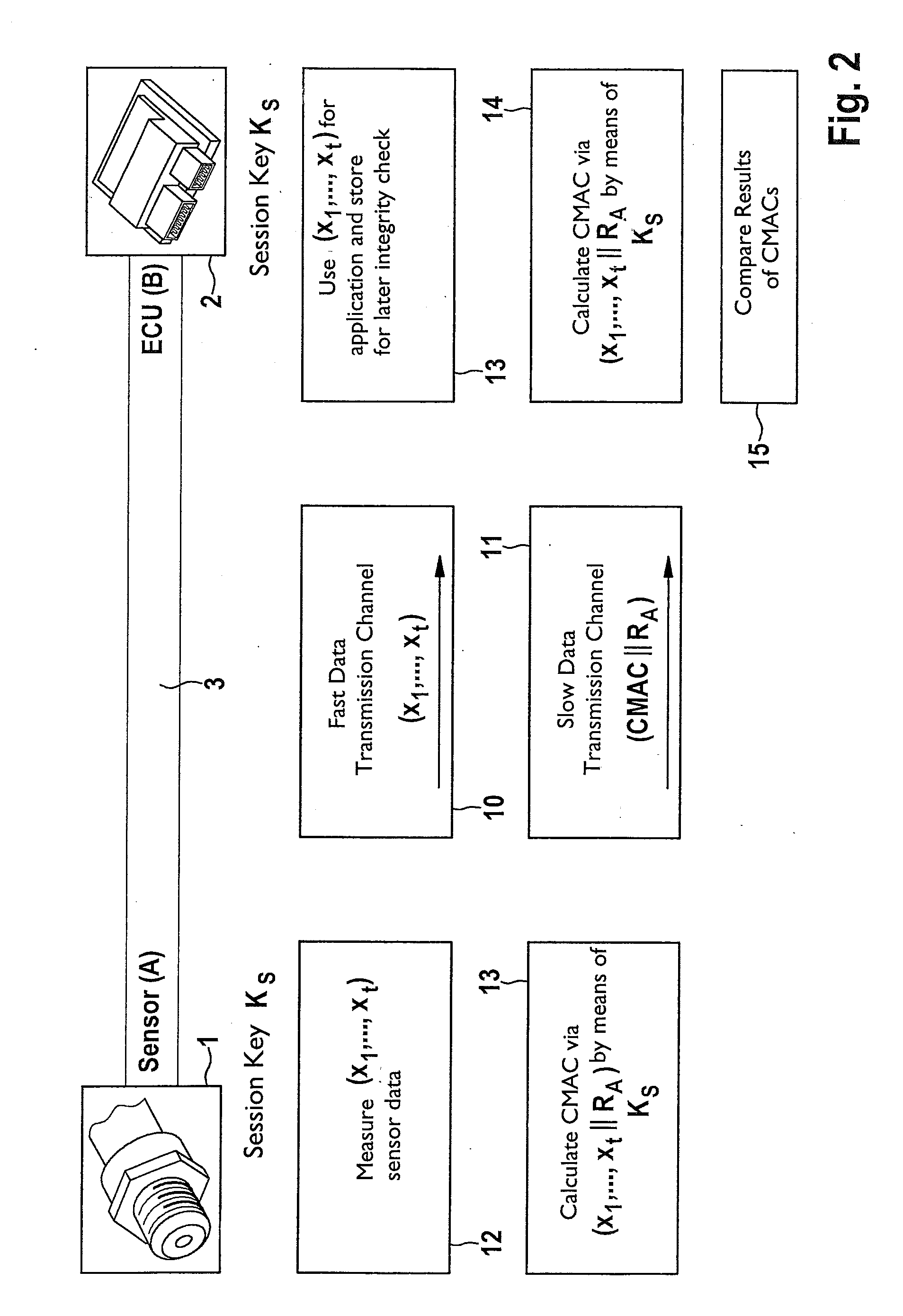
Method for recognizing a manipulation of a sensor and/or sensor data of the sensor
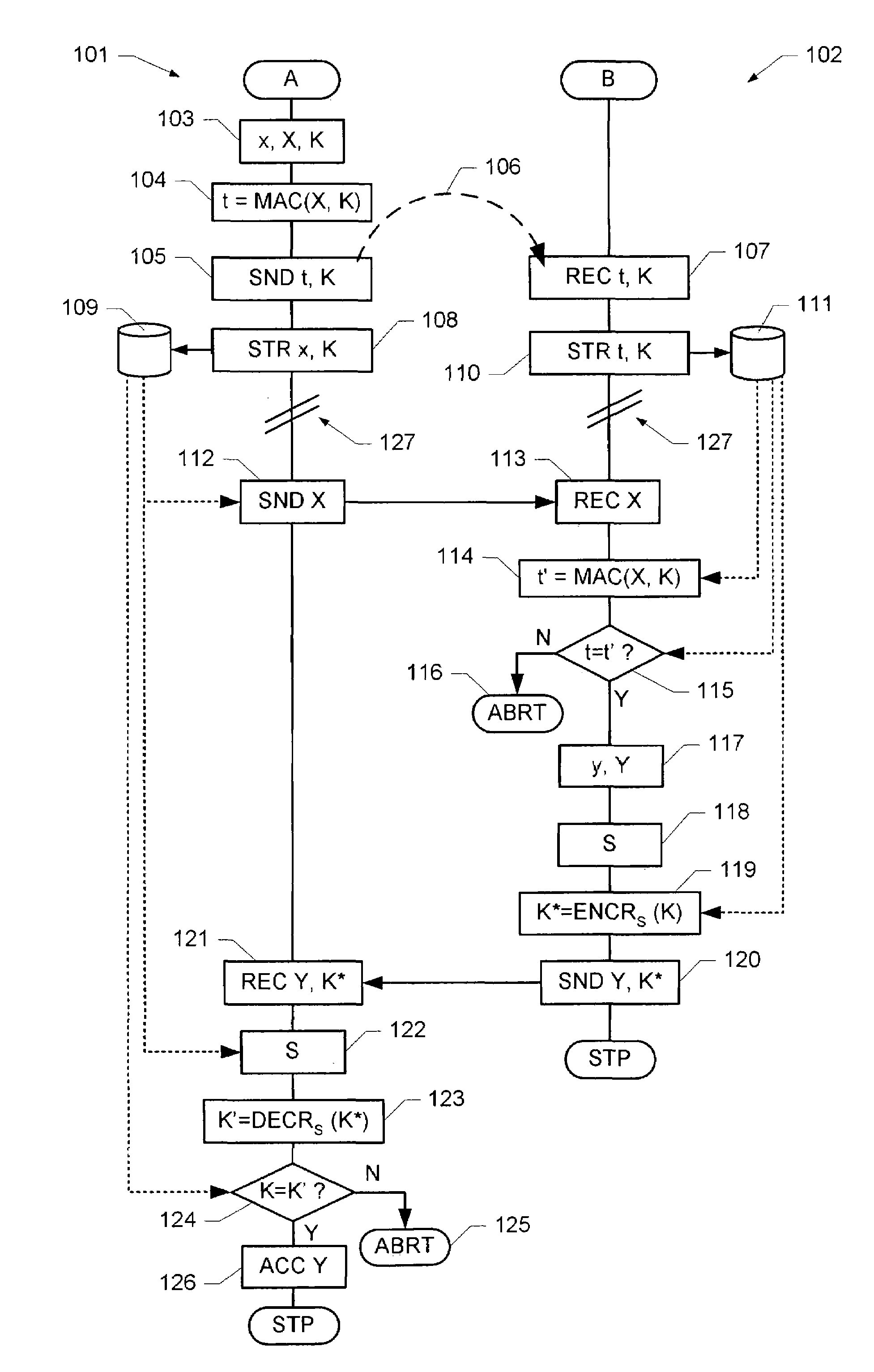
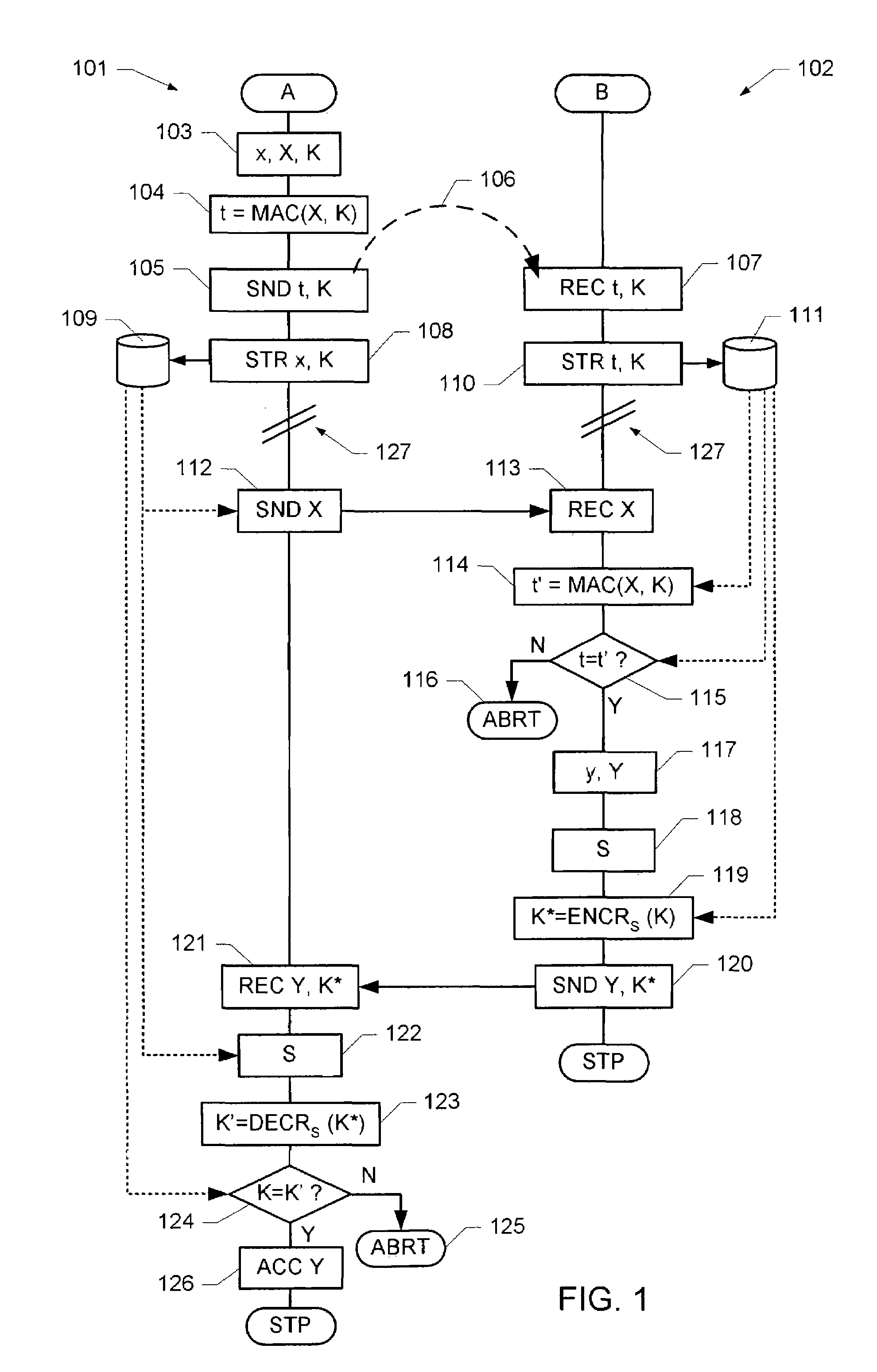
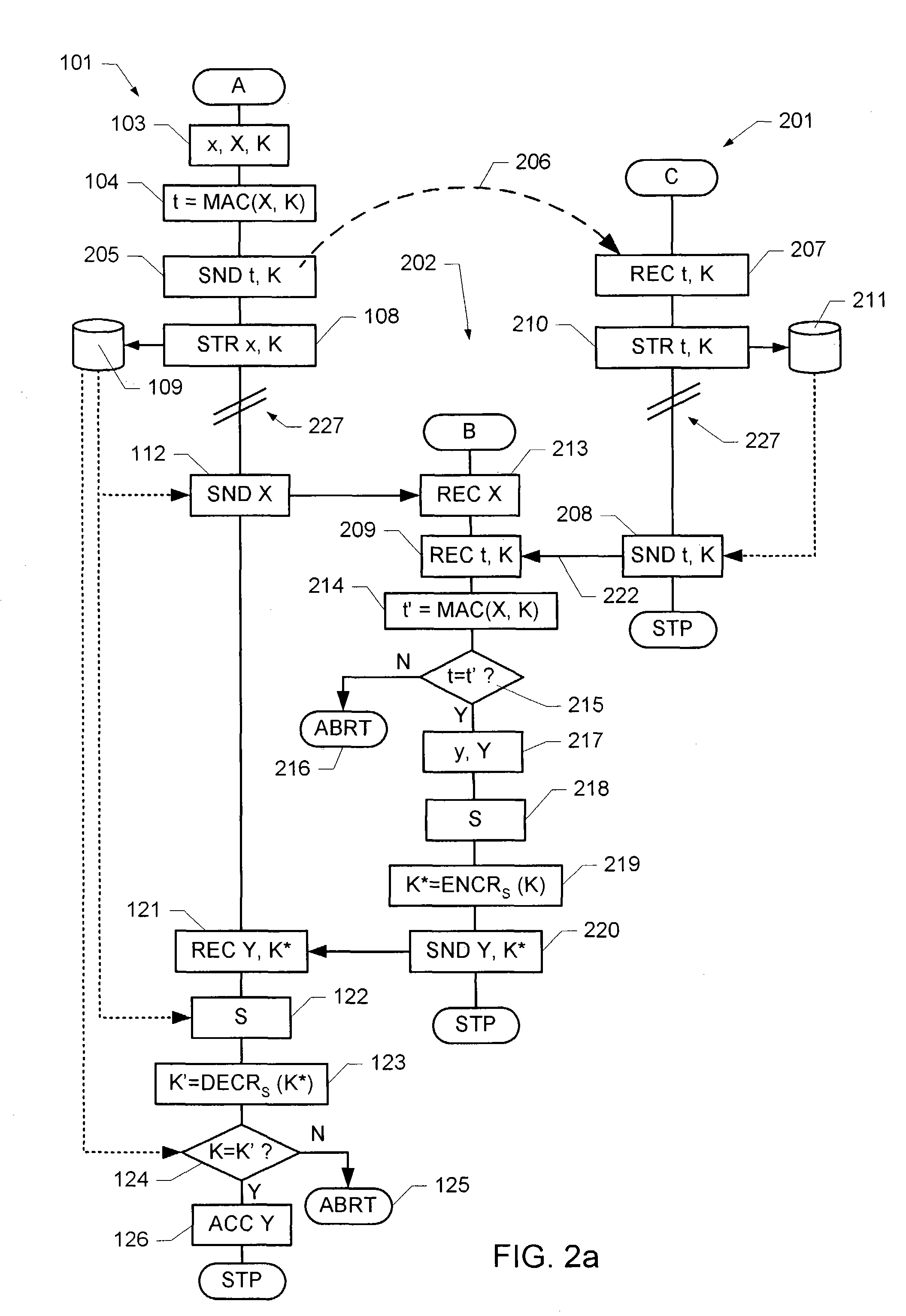
ActiveUS20140301550A1Simple and fastHigh safetyKey distribution for secure communicationData transmissionTransmission rate
A method for data transmission between a sensor and an electronic control and / or regulating unit (ECU), the transmitted sensor data (x1, . . . , xt) and the sensor being secured against a manipulation. The system provides a particularly simple, but very secure method for manipulation protection, the sensor data (x1, . . . , xt) being transmitted via a first logical data transmission channel at a first data transmission rate, and security data (MAC; CMAC) for securing the transmitted sensor data and / or the sensor being transmitted via a second logical data transmission channel at a second data transmission rate from the sensor to the ECU. At least once at the beginning of a data transmission session, a session key is transmitted from the ECU to the sensor via a third logical data transmission channel and received by the latter, the session key being used at least for the ongoing session to generate the security data.
Owner:ROBERT BOSCH GMBH
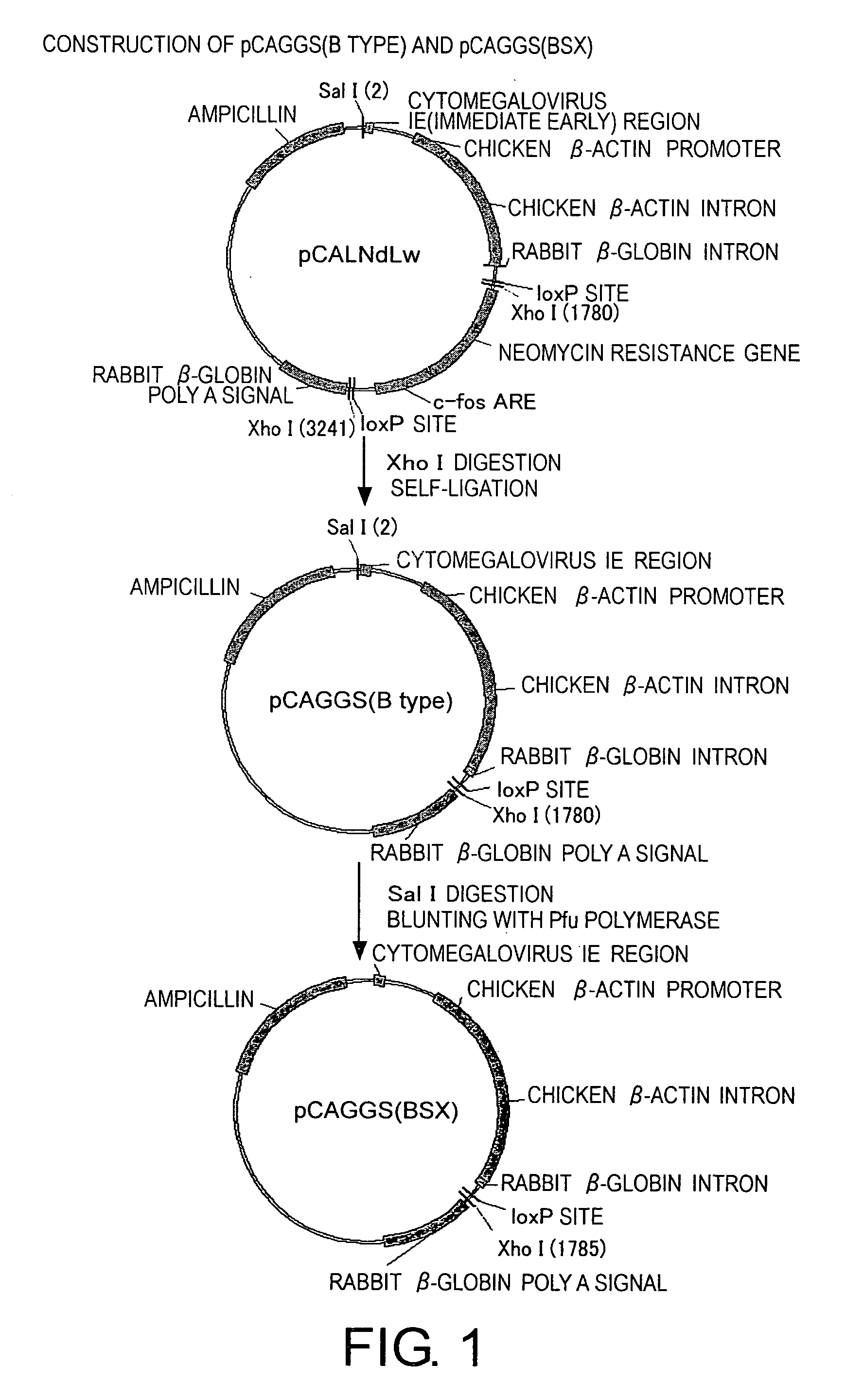
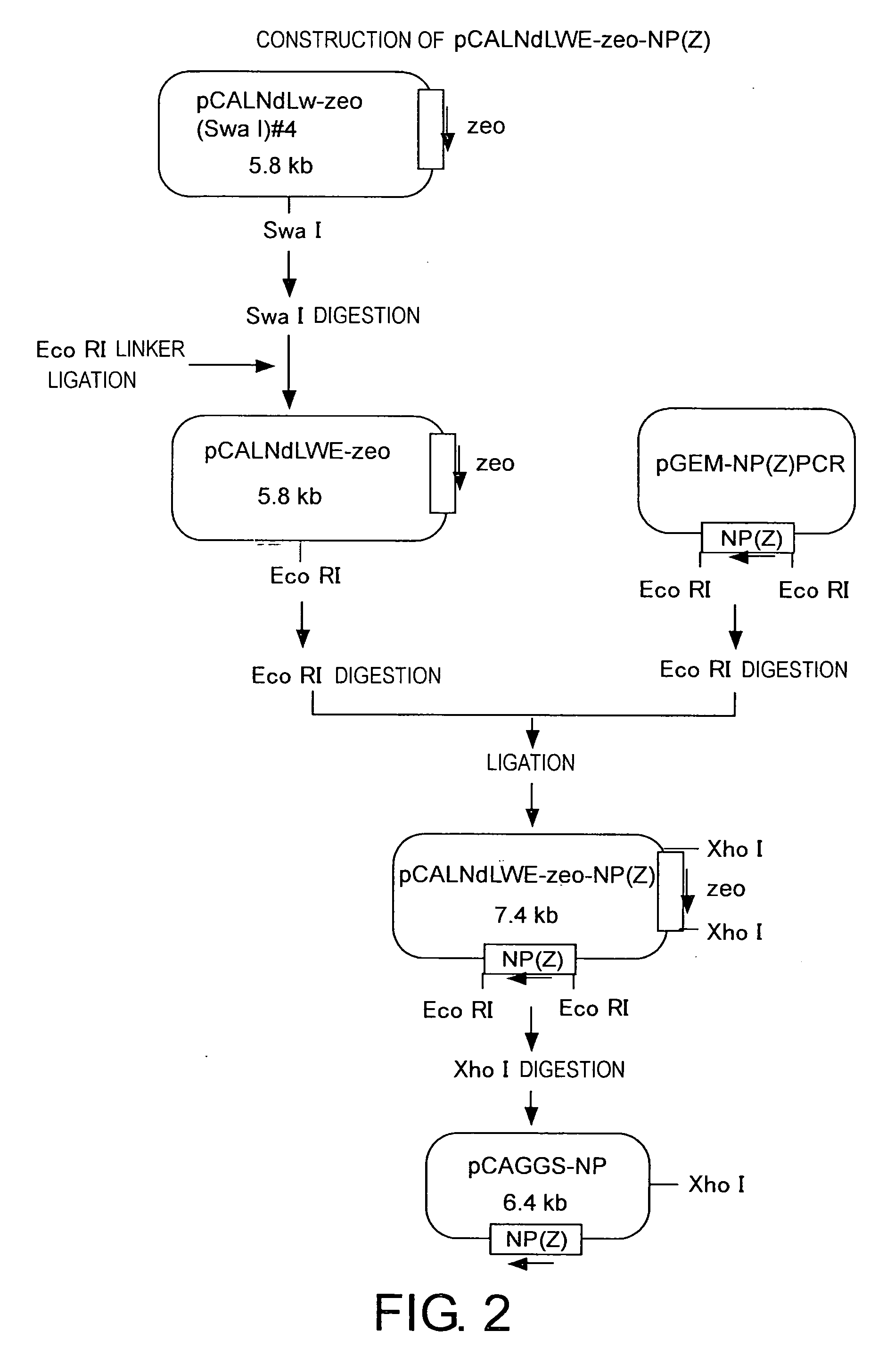
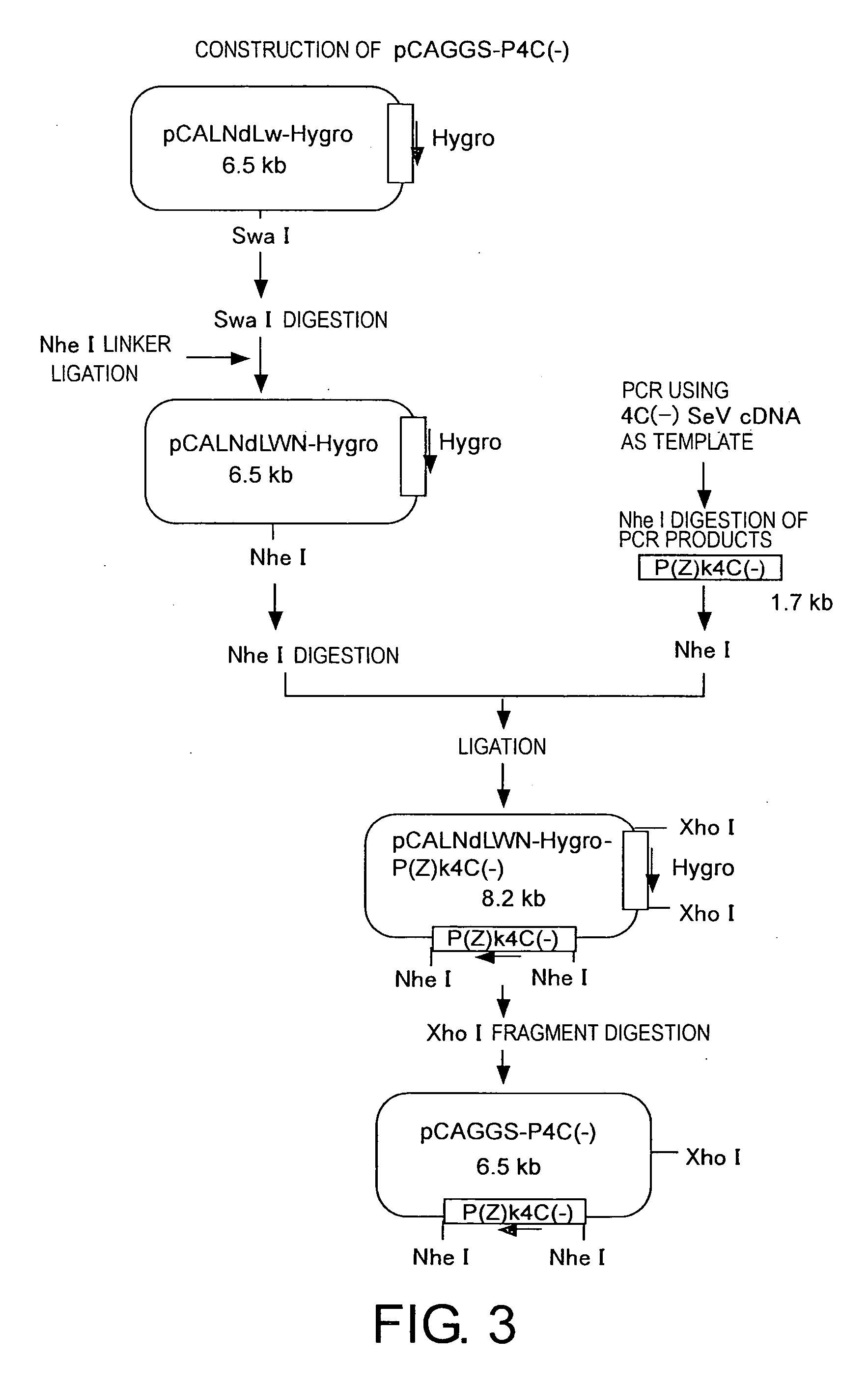
Methods for producing minus-strand rna viral vectors using hybrid promoter comprising cytomegalovirus enhancer and chicken beta-actin promoter
ActiveUS20070161110A1High safetyImprove securitySsRNA viruses positive-senseSugar derivativesCytomegalovirus diseaseActin
The present invention provides methods for producing a minus-strand RNA viral vector, which comprise using a promoter comprising a cytomegalovirus enhancer and a chicken β-actin promoter, to induce the transcription of the genome RNA of a minus-strand RNA viral vector and the expression of minus-strand RNA viral proteins that form a ribonucleoprotein with the genome RNA. The methods of the present invention enable high efficiency production of highly safe minus-strand RNA viral vectors. The methods of the present invention are particularly useful for producing minus-strand RNA viral vectors that are deficient in envelope-constituting protein genes.
Owner:DNAVEC RES
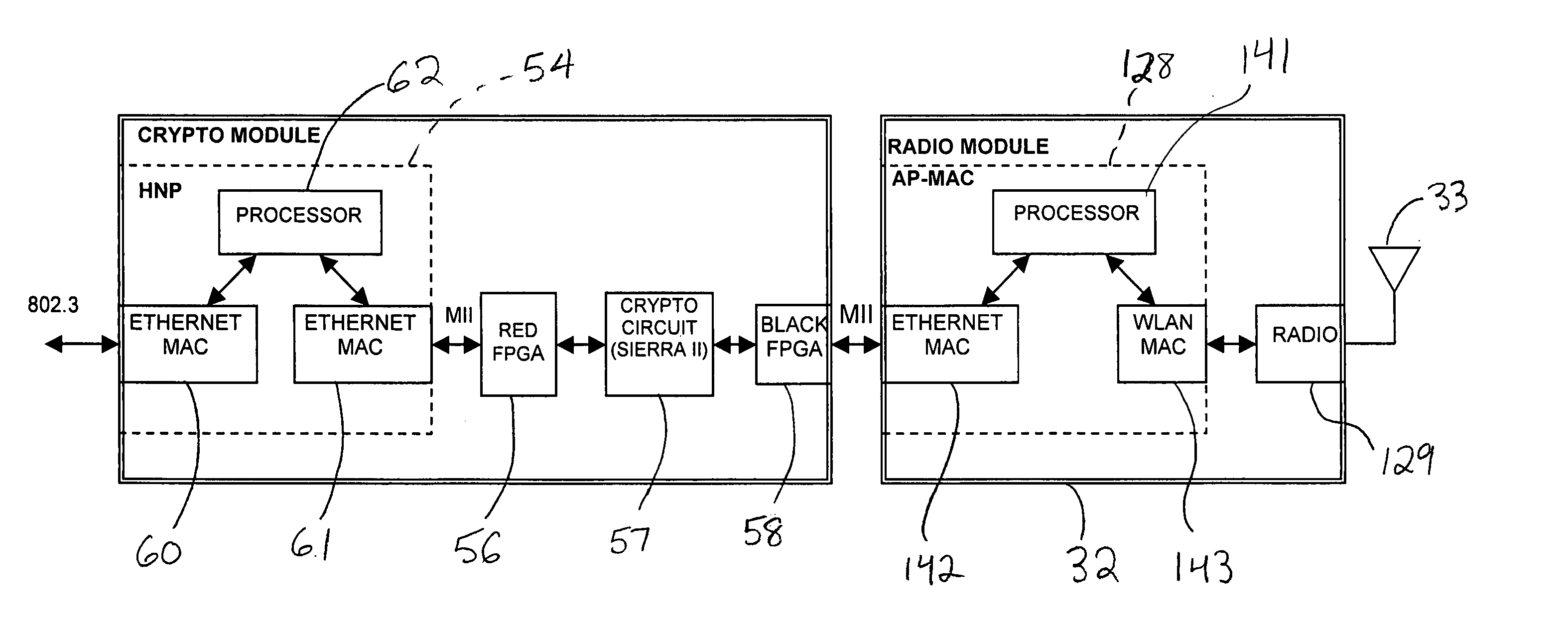
Modular cryptographic device providing enhanced interface protocol features and related methods
InactiveUS20050216726A1High safetyEasily adaptUser identity/authority verificationUnauthorized memory use protectionModularityNetwork communication
A cryptographic device may include a cryptographic module and a communications module coupled thereto. The cryptographic module may include a user network interface and a cryptographic processor coupled thereto. The communications module may include a network communications interface coupled to the cryptographic processor. The cryptographic processor may communicate with the user network interface using a predetermined protocol, and the cryptographic processor may also communicate with the network communications interface using the predetermined protocol.
Owner:HARRIS CORP
Identification Card and Method for the Production Thereof
InactiveUS20080296887A1Simply produceHigh safetyOther printing matterInformation cardsPaper sheetEngineering
Owner:LANDQUART
Electrode for secondary battery and secondary battery using same
ActiveUS20170309948A1Excellent in cycle characteristicHigh safetyPositive electrodesLi-accumulatorsElectrical batteryCarbon Nanohorn
A secondary battery which is highly safe even when it becomes in excessively high-temperature conditions and is excellent in cycle characteristics, and an electrode for a secondary battery are provided. The present invention relates to an electrode for a secondary battery comprising a maleimide compound and a conductive agent, wherein the conductive agent comprises at least one selected from carbon nanotube and carbon nanohorns.
Owner:NEC CORP
Freshness-keeping agents for plants
InactiveUS7345008B1High safetyFreshness of not is improvedDead plant preservationEdible seed preservationFungicideSugar alcohol
The present invention provides a freshness-keeping agent for plants, such as a harvested plant, demonstrating an effect of keeping the freshness without selecting a type among various plants such as a harvested plant and also having a high safety. That is, the present invention provides a freshness-keeping agent for plants, such as a harvested plant, comprising a sugar derivative- or sugar alcohol derivative-based surfactant (A) and at least one selected from the group consisting of a sugar (B), a plant hormone (C), an aging inhibitor (D), an aggregating agent for colloidal particles (E) and a germicide, fungicide and preservative (F), preferably in a specific ratio by weight.
Owner:KAO CORP
Positive electrode active material for non-aqueous electrolyte-based secondary battery and non-aqueous electrolyte-based secondary battery using the same
ActiveUS20070231694A1High capacityHigh safetyElectrode carriers/collectorsActive material electrodesComposite oxideOxide
The present invention provides a positive electrode active material for a non-aqueous electrolyte-based secondary battery, composed of a lithium / nickel composite oxide with high capacity, low cost and excellent heat stability, and a high safety non-aqueous electrolyte-based secondary battery. A positive electrode active material, comprising lithium / nickel composite oxide powders obtained by water washing fired powders having the following composition formula (1), followed by filtering and drying: LiNi1-aMaO2 (1) (wherein, M represents at least one kind of an element selected from transition metal elements other than Ni, group 2 elements, or group 13 elements; and “a” satisfies 0.01≦a≦0.5), characterized in that specific surface area of the lithium / nickel composite oxide powders after water washing is 0.3 to 2.0 m2 / g.
Owner:PANASONIC CORP +1
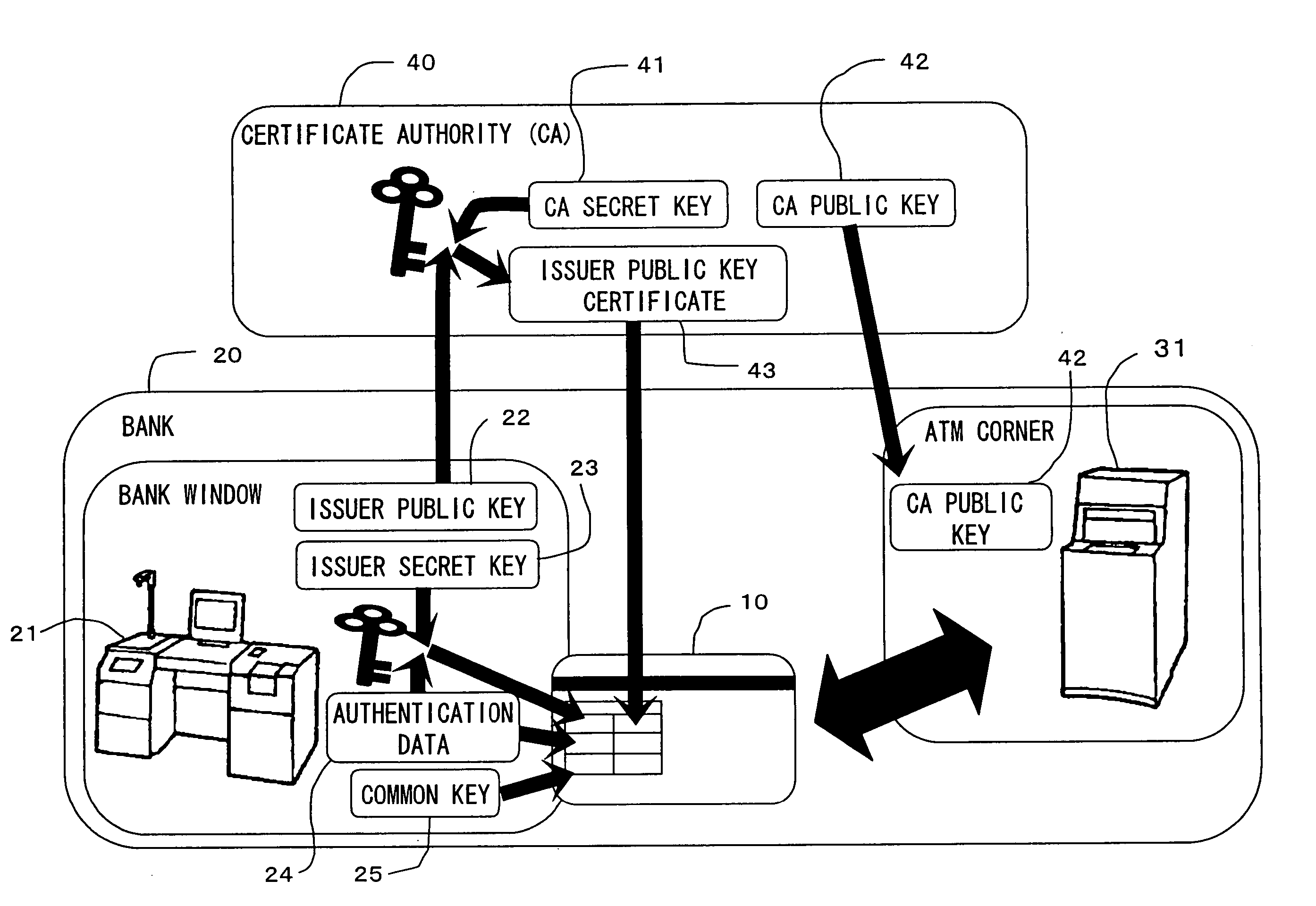
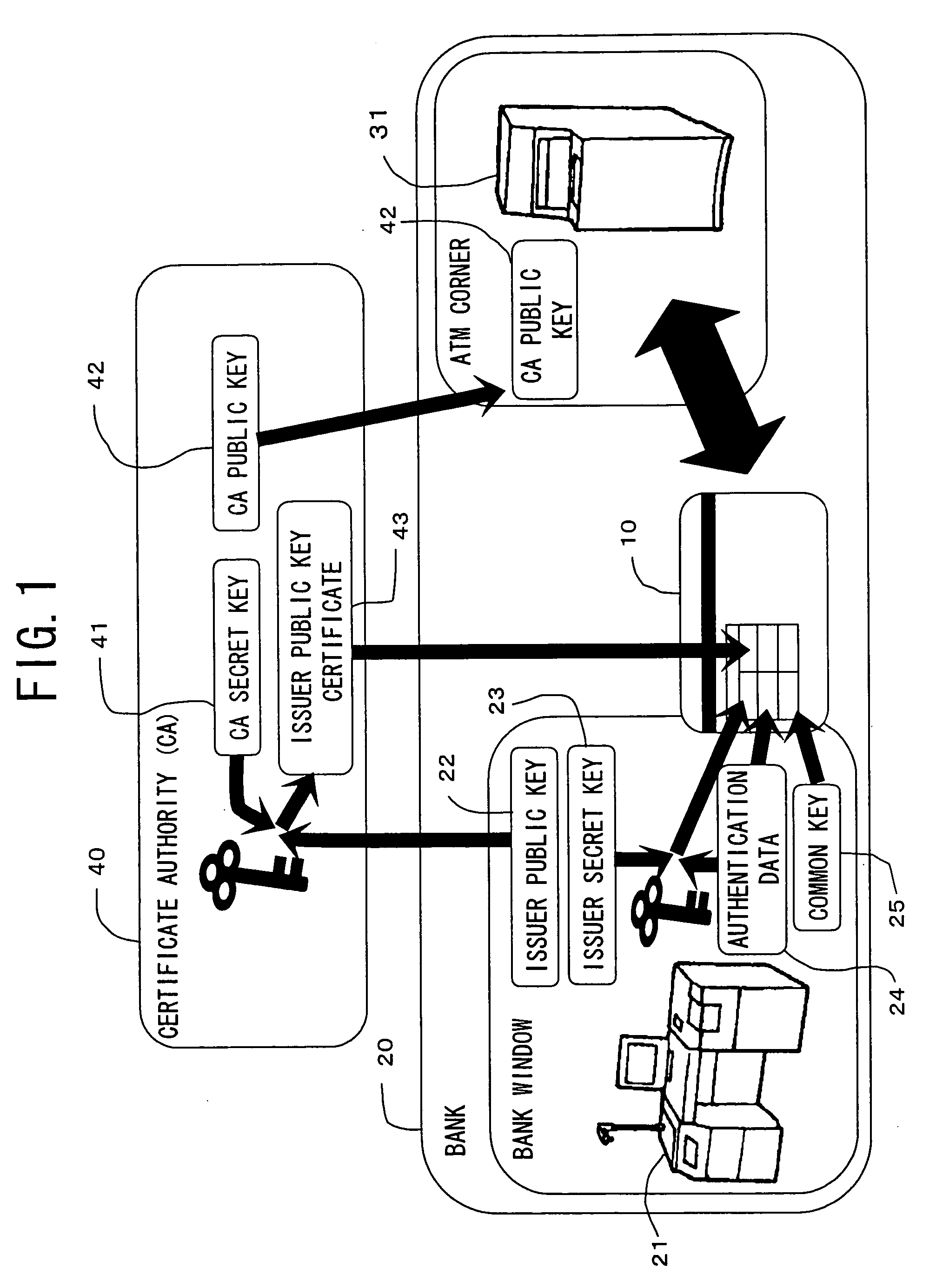
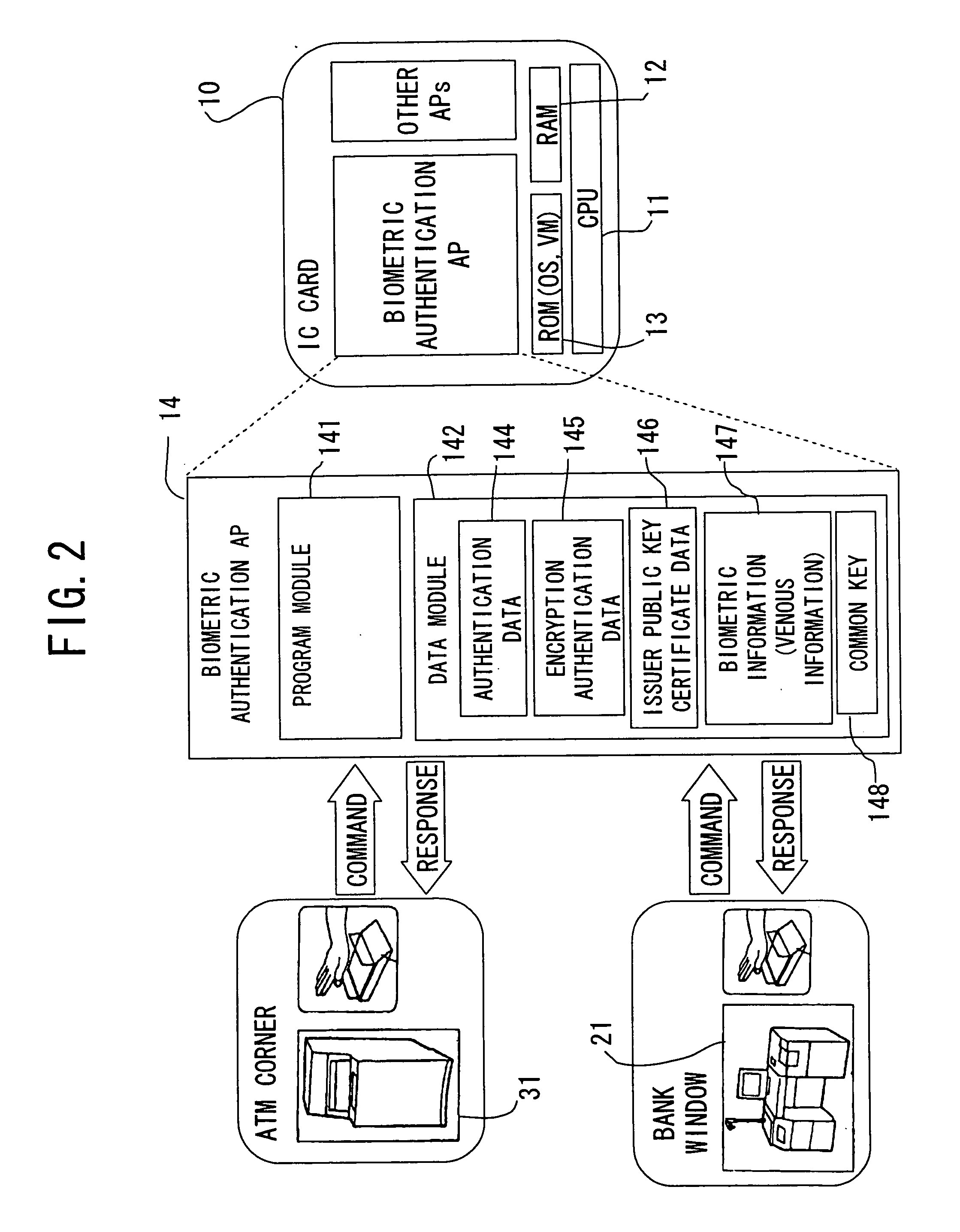
Biometric authentication device and terminal
InactiveUS20060080549A1High safetyImprove securityDigital data processing detailsAnalogue secracy/subscription systemsMutual authenticationCommon key
Owner:FUJITSU LTD +1
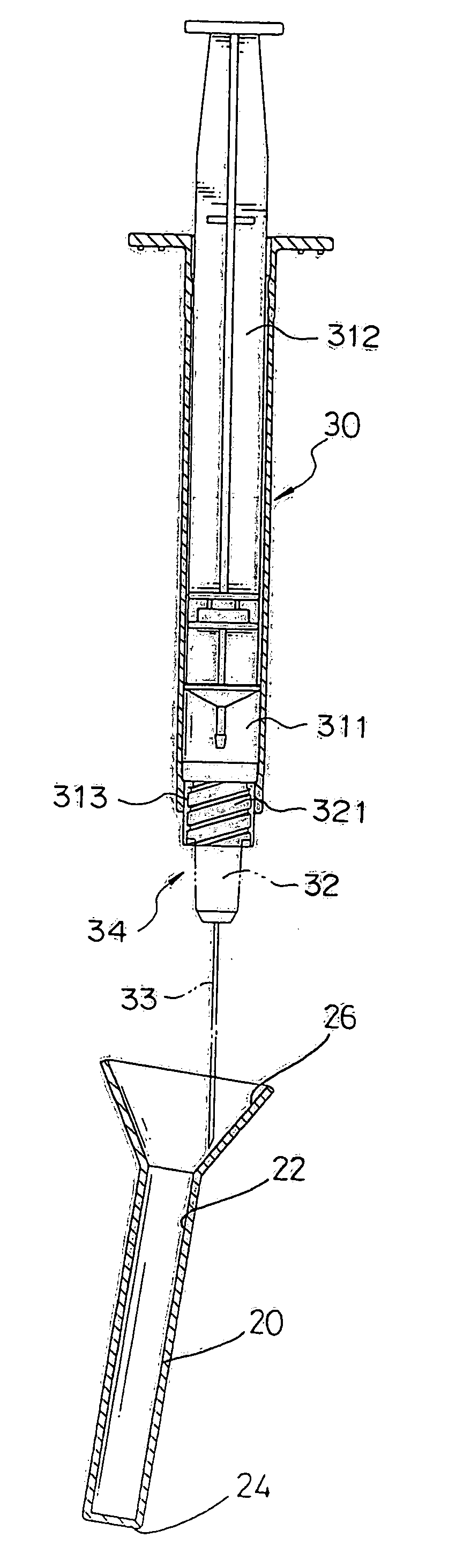
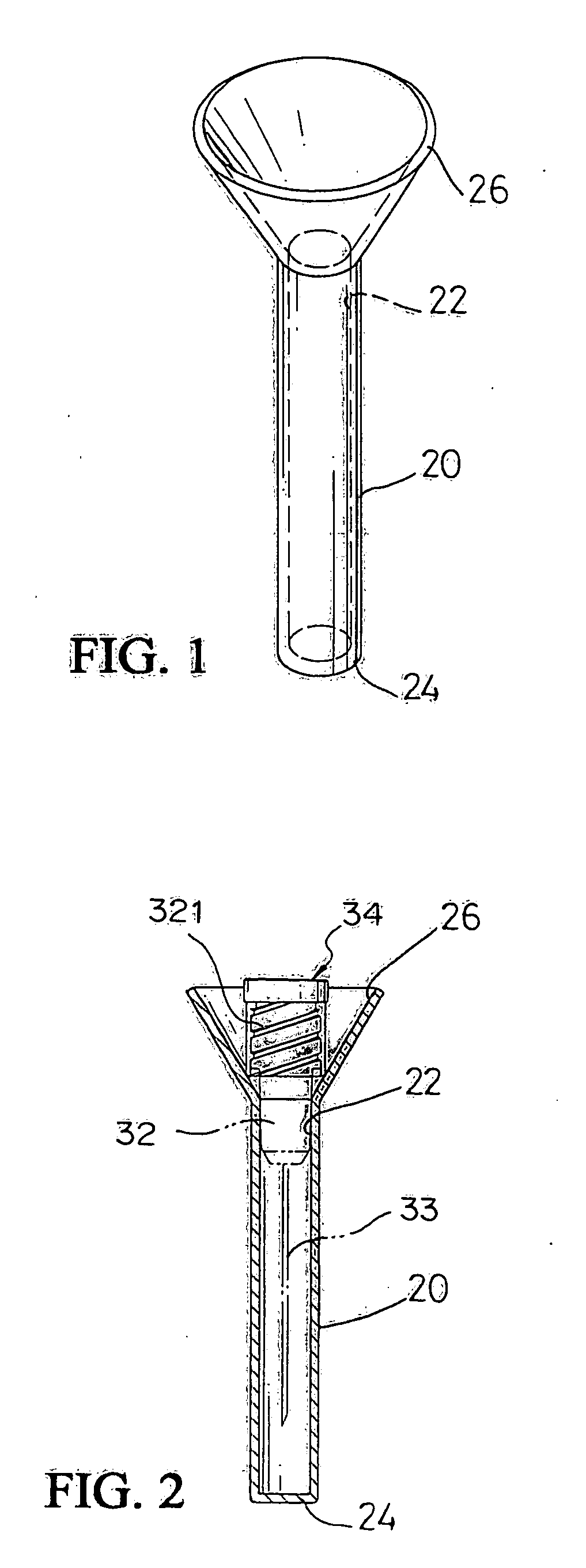
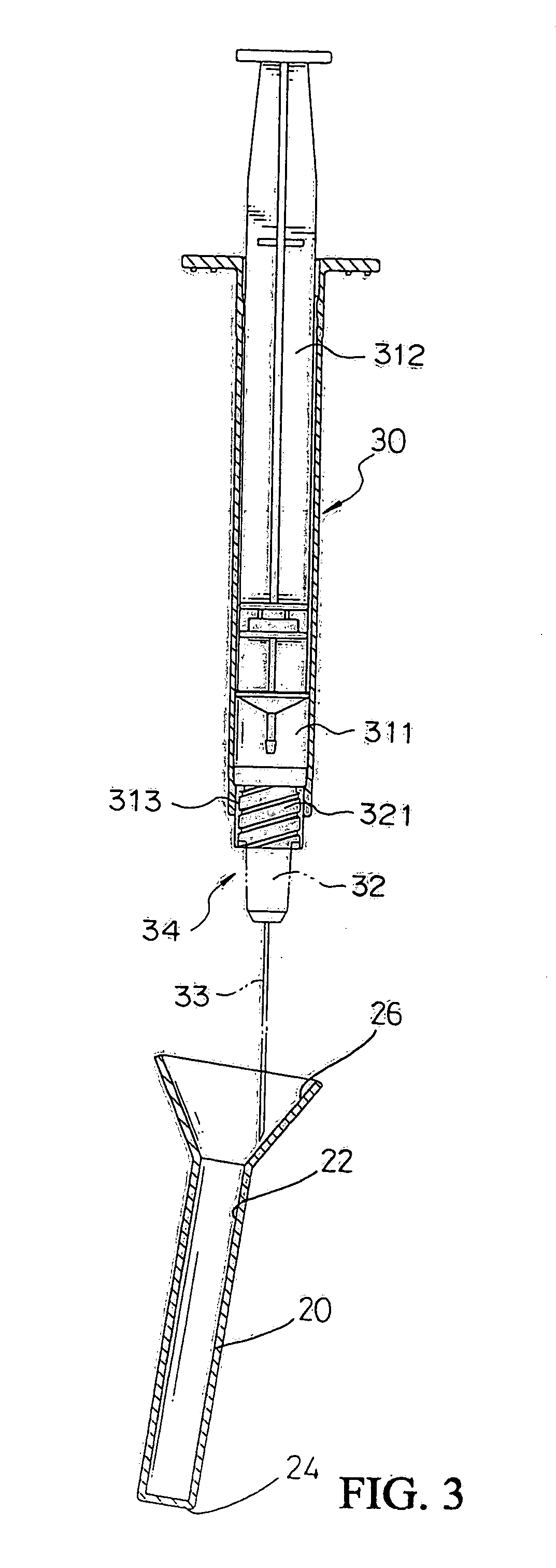
Safety cap of syringe needle head
Owner:LIN CHIH HSIUNG
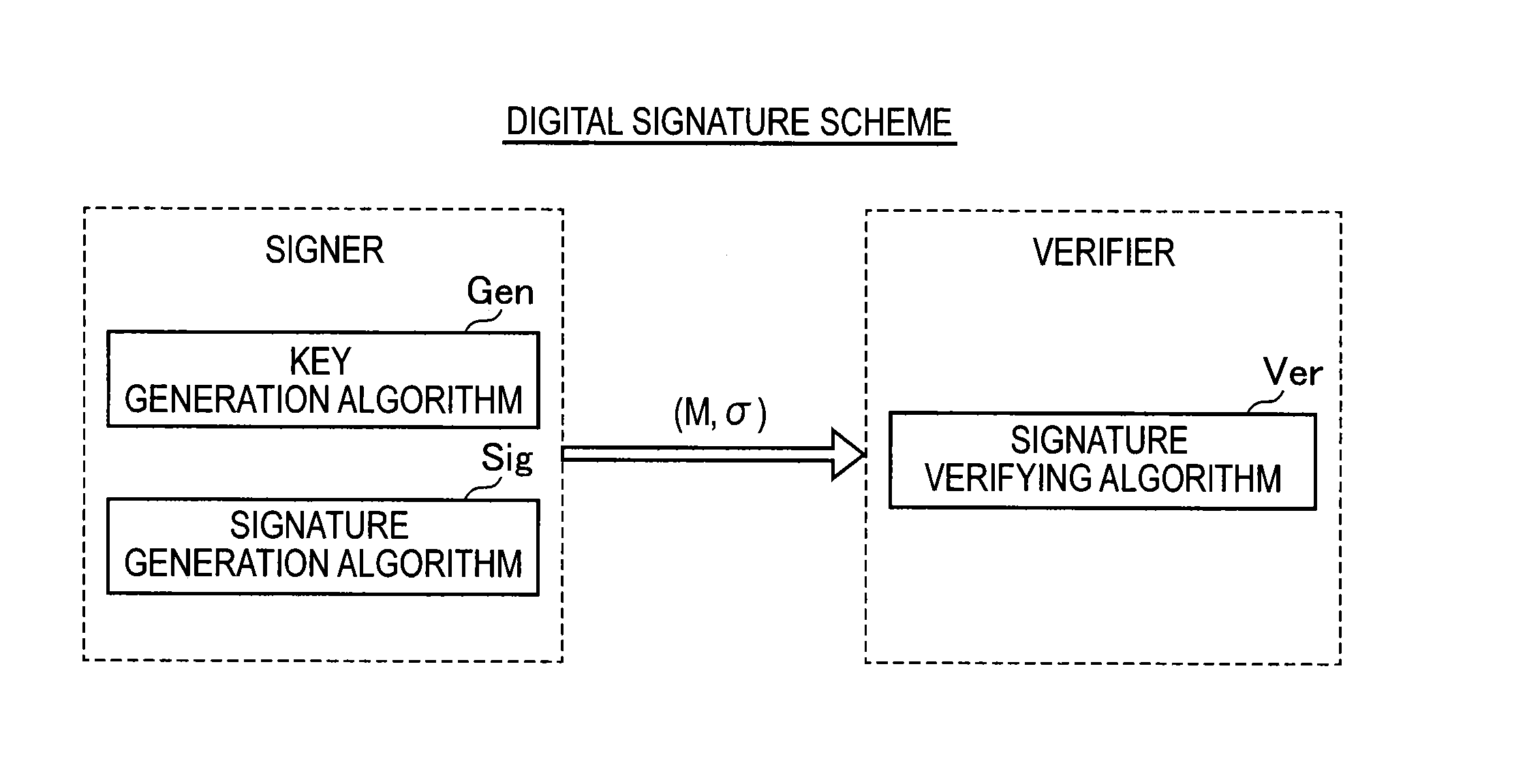
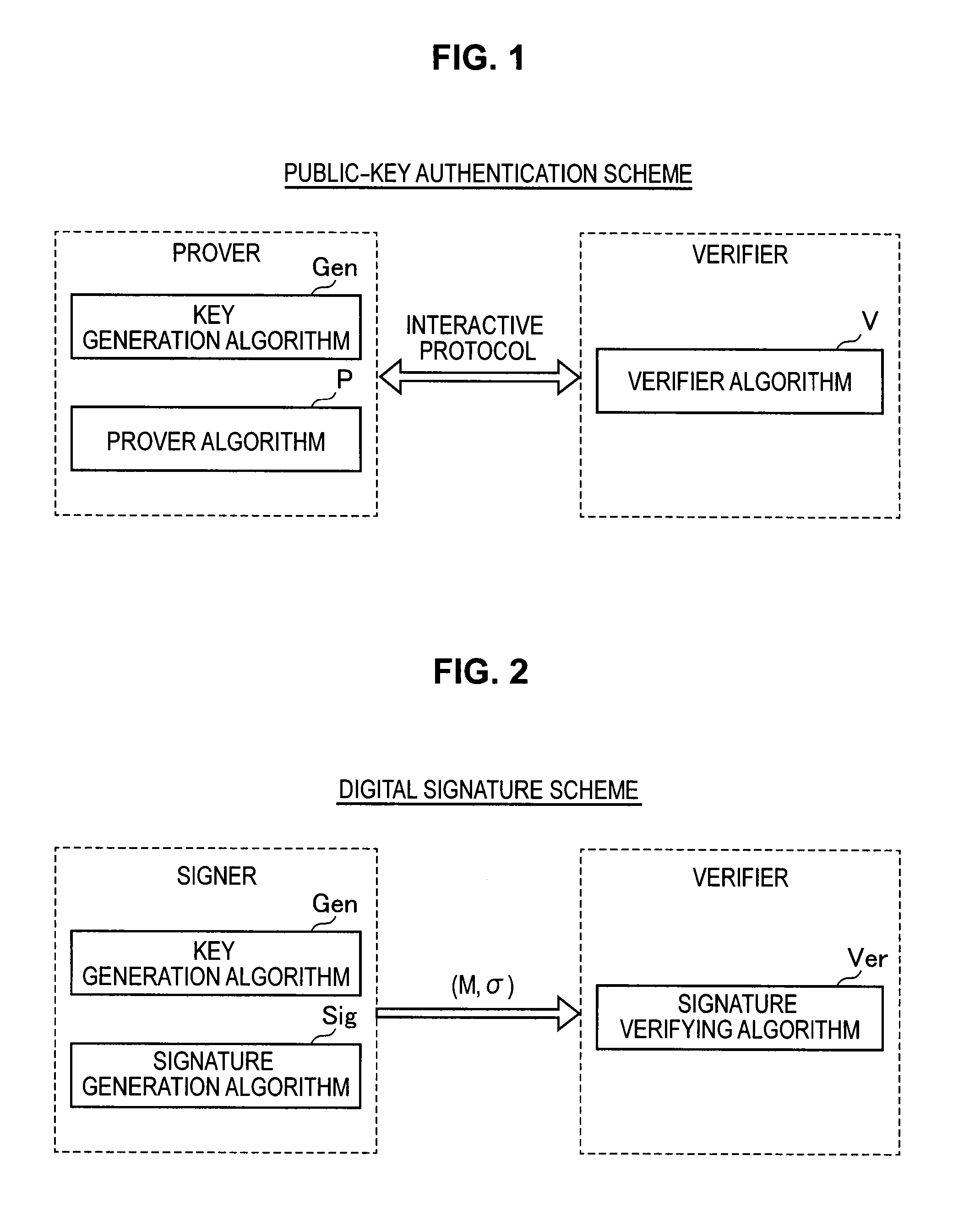
Signature verification apparatus, signature verification method, program, and recording medium
ActiveUS20140223193A1High safetySmall memoryUnauthorized memory use protectionHardware monitoringKey generationCommon key
A signature verification apparatus including a signature acquisition unit configured to acquire a digital signature including first information generated based on a pair of multi-order multivariate polynomials F=(f1, . . . , fm) defined in a ring K, a signature key s which is an element of a set Kn, and a document M and a plurality of pieces of second information for verifying that the first information is generated using the signature key s based on the data M, the pair of multi-order multivariate polynomials F, and vectors y=(f1(s), . . . , fm(s)), and a signature verification unit configured to verify legitimacy of the document M by confirming whether or not the first information is restorable using the plurality of pieces of second information included in the digital signature. The pair of multivariate polynomials F and the vectors y are public keys.
Owner:SONY CORP
Imaging device, biometric authentication device, electronic equipment
InactiveUS20120300989A1High safetyImprove securityColor television detailsClosed circuit television systemsMicrolensComputer vision
An imaging device that captures a vein pattern of a living body including a lens array having a plurality of microlenses and an imaging element that receives a light converged by the lens array, wherein the plurality of microlenses include a plurality of first microlenses and a plurality of second microlenses that have a focal distance longer than that of the plurality of first microlenses.
Owner:SEIKO EPSON CORP
Aroma diffuser with direct diffusion of essential oil and diffusing method thereof
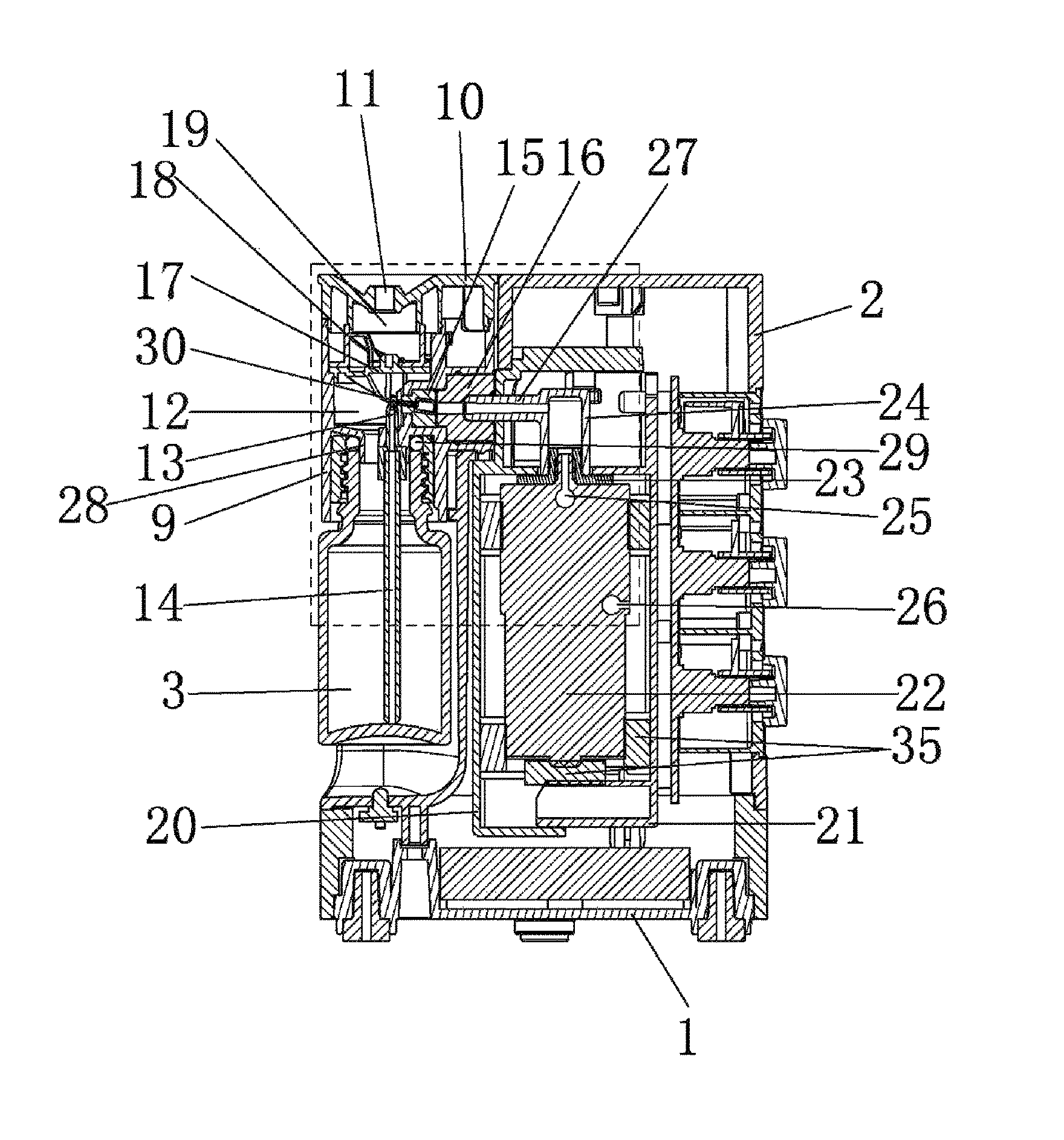
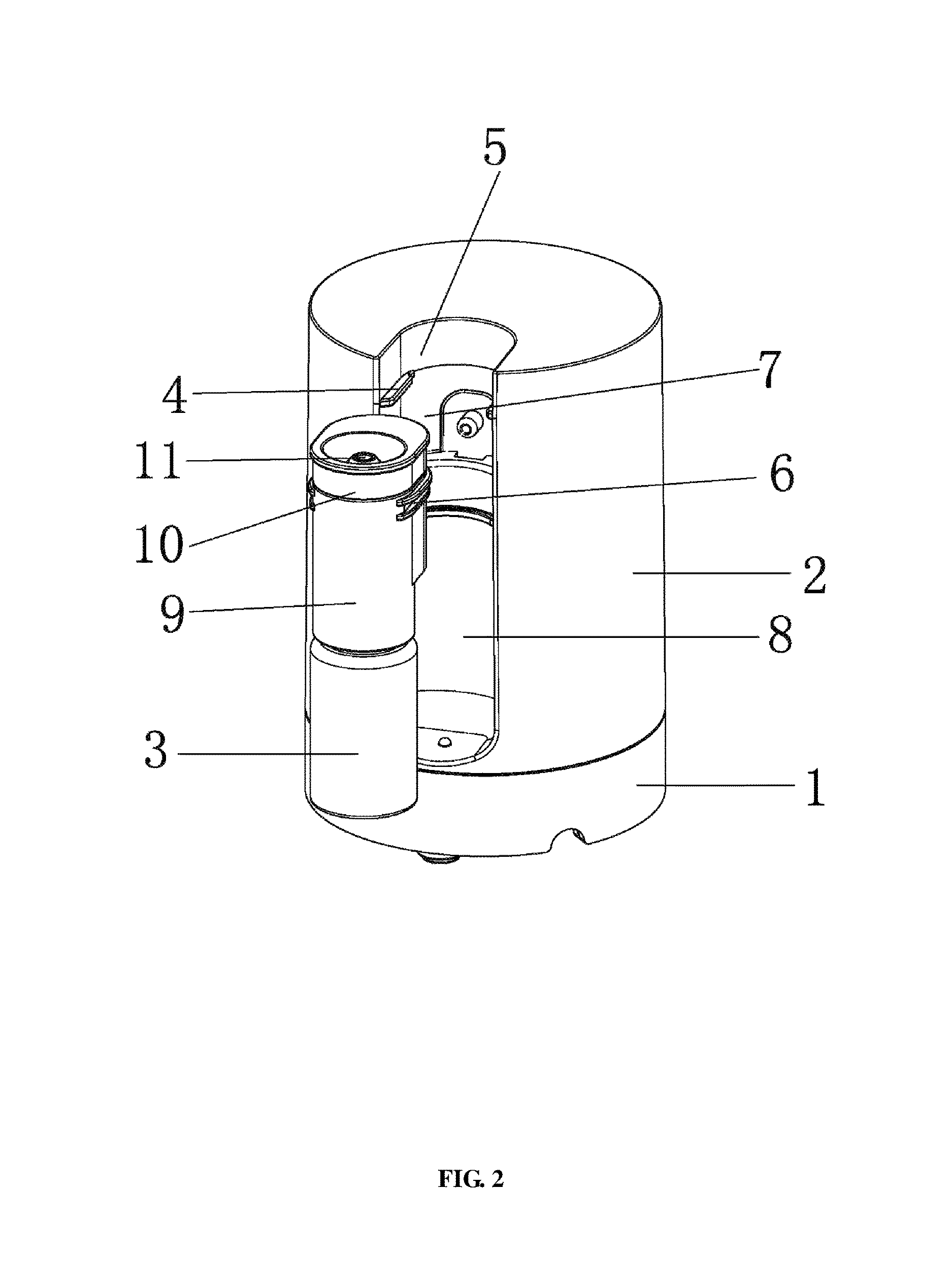
The present invention relates to an aroma diffuser with direct diffusion of essential oil, and an aroma diffusing method. The aroma diffuser comprises a base, a housing mounted on the base and an electric control element disposed on the housing. An essential oil bottle and a gasification element are also disposed on the housing, a pump element is disposed inside the housing and the open end of the essential oil bottle is connected to the lower end of the gasification element. The pump element is connected to the gasification element and the electric control element respectively and communicates with the gasification element. The gasified essential oil gas may be diffused to ambient air directly, rather than through the housing, the diffusion is fast, and the directly diffused essential oil does not need the dilution of water, greatly raising the efficiency of aromatherapy and meeting people's use requirements.
Owner:PUZHEN LIFE CO LTD
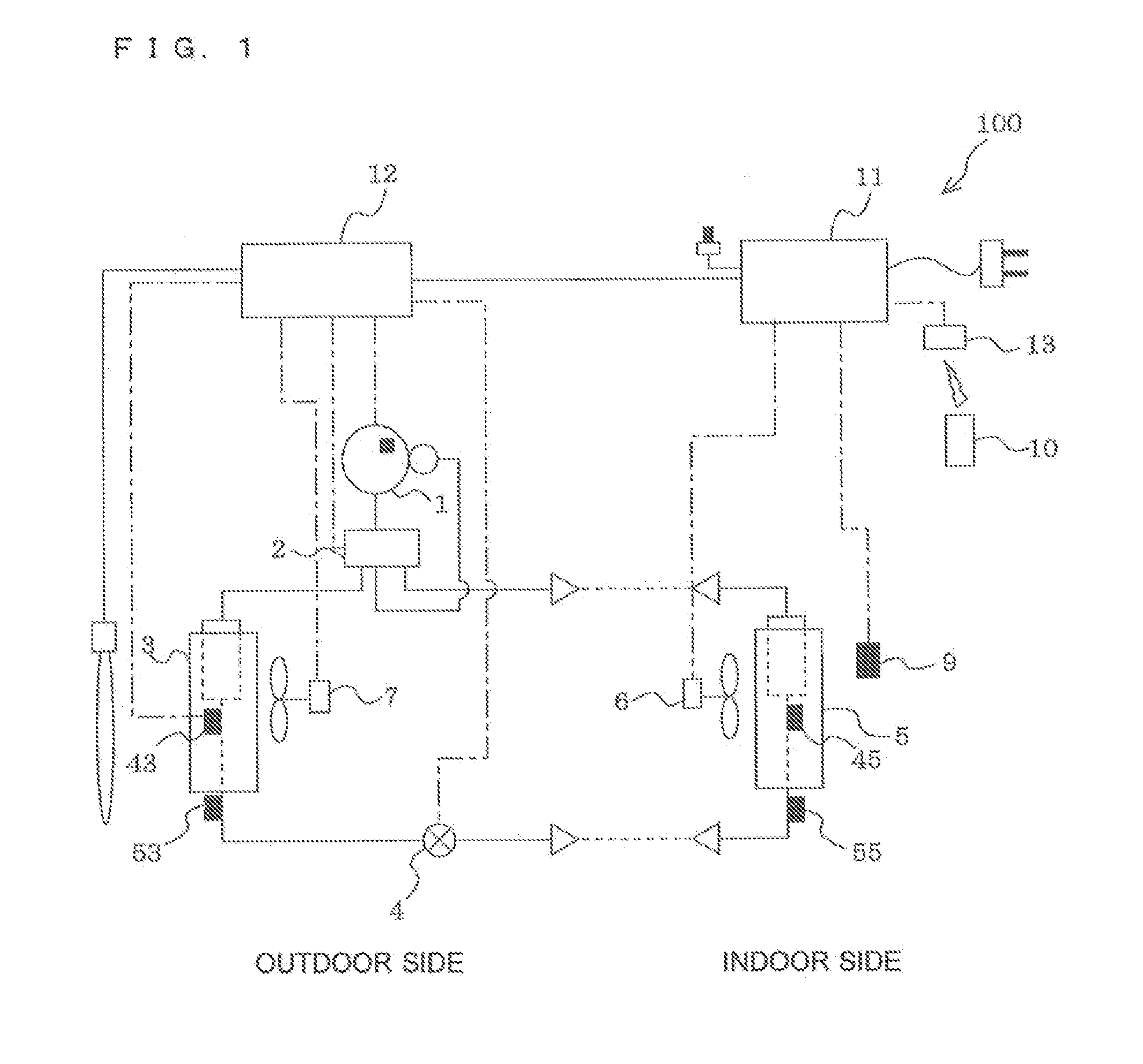
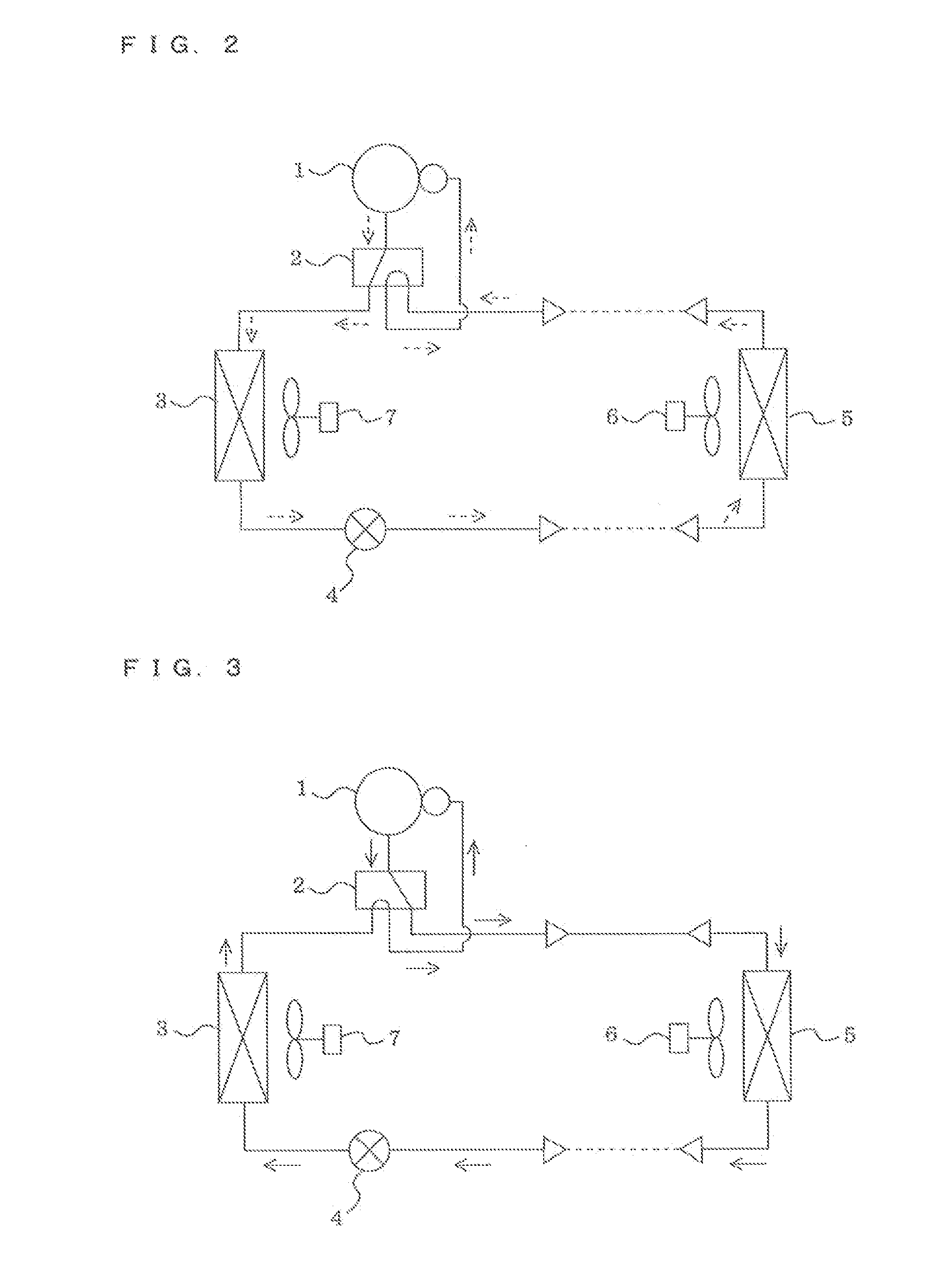
Outdoor unit and air-conditioning apparatus
ActiveUS20150075203A1Suppress freezingHigh safetyMechanical apparatusCondensate preventionRefrigerantElectricity
An outdoor unit includes a casing having a bottom plate and is configured such that at least a part thereof is made of metal, a compressor provided within the casing to compress a flammable refrigerant, an outdoor heat exchanger provided within the casing to exchange heat between the refrigerant and outside air, and an electric heater provided on an upper surface of the bottom plate. The power consumption of the electric heater is 250 W or less.
Owner:MITSUBISHI ELECTRIC CORP
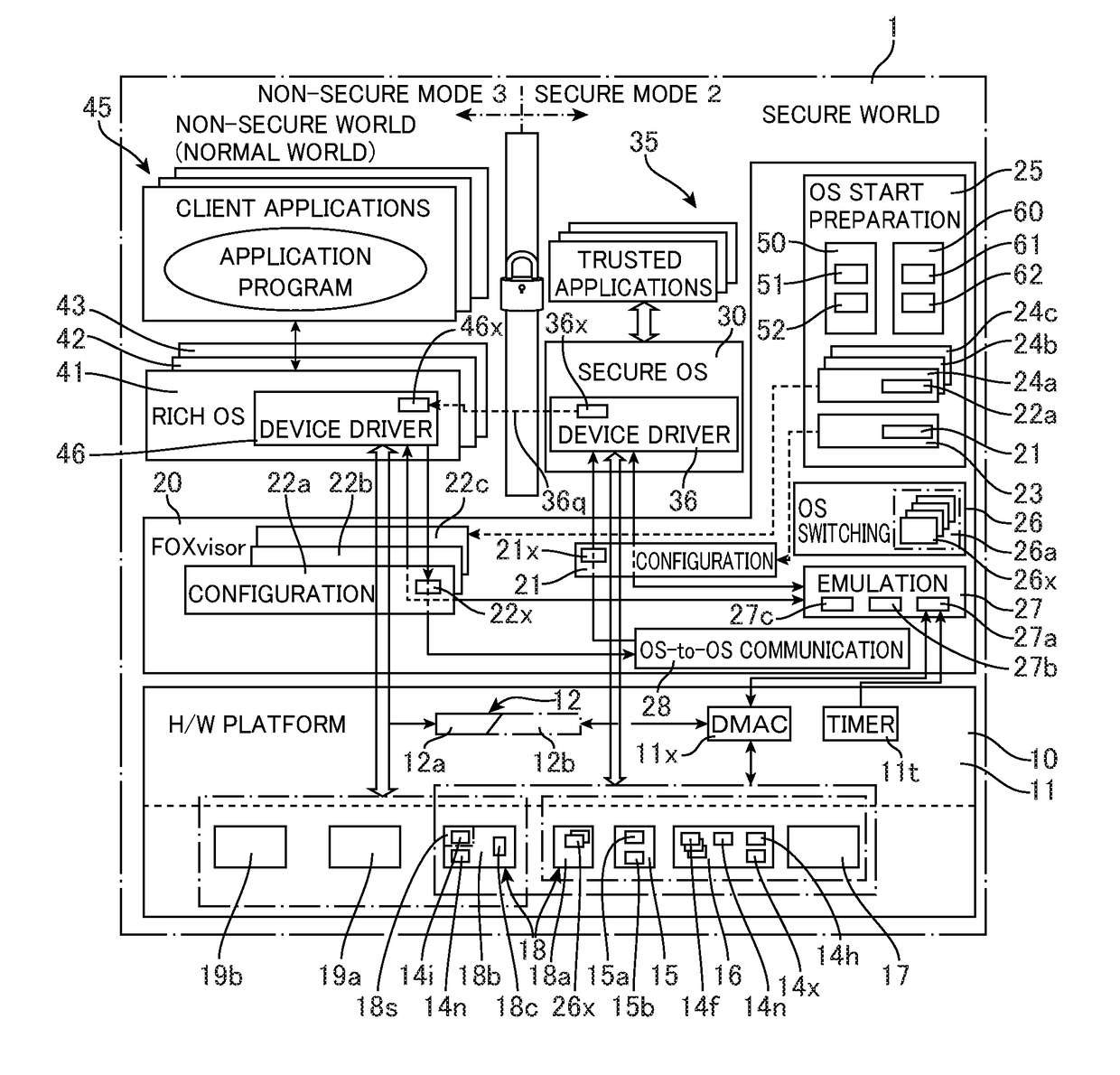
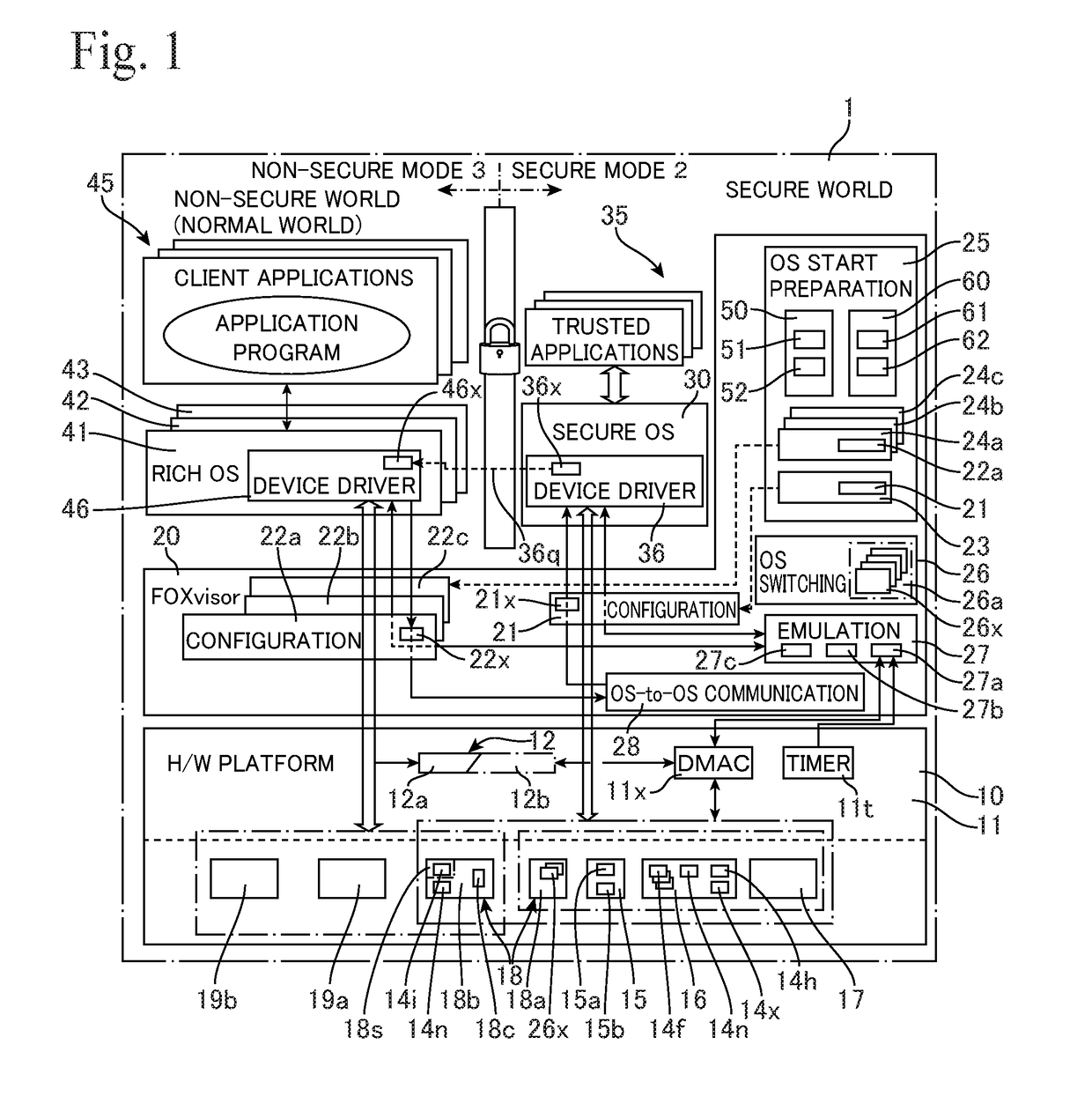
System including a hypervisor
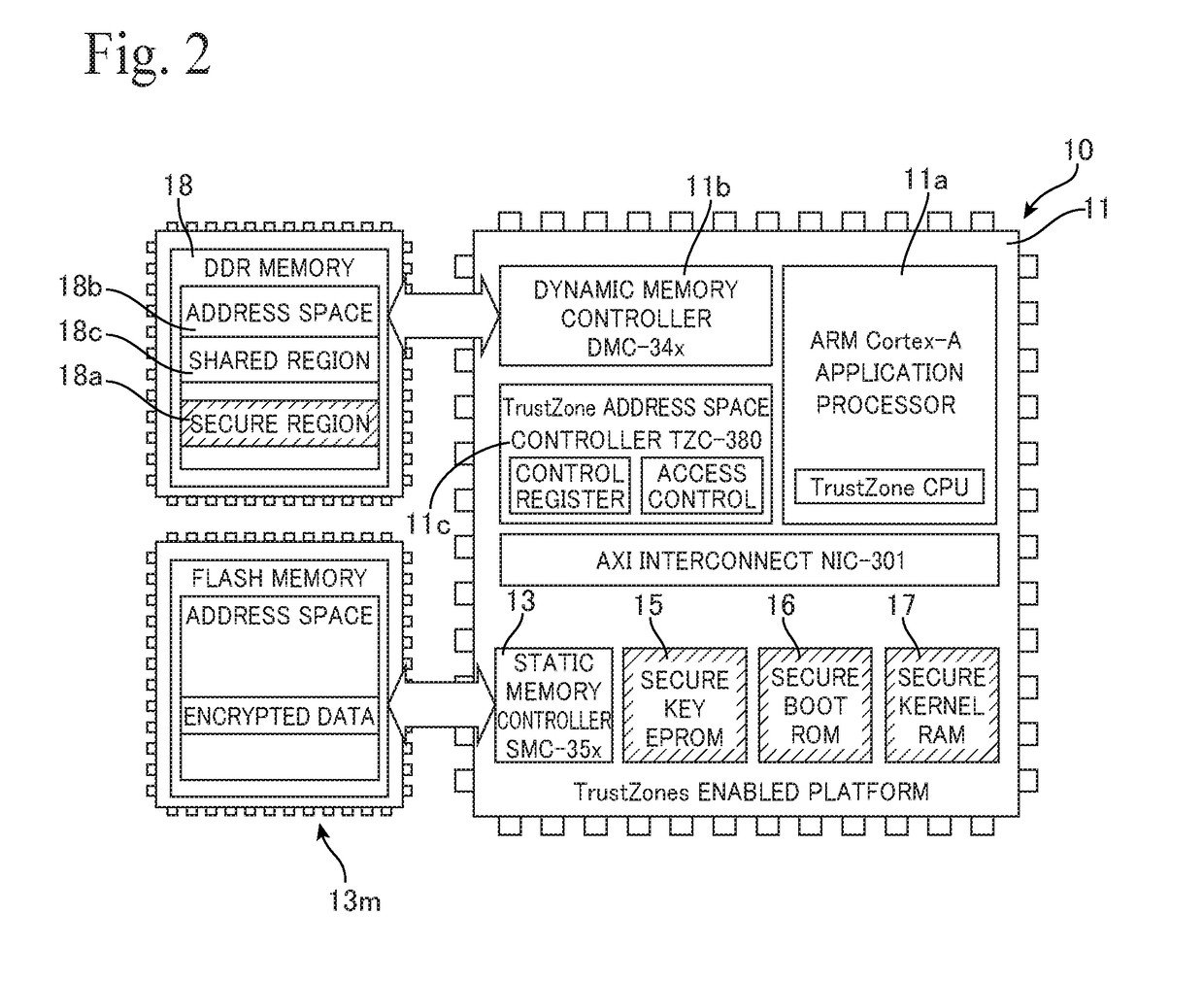
ActiveUS20180239896A1Reduce numberHigh safetyUnauthorized memory use protectionMultiprogramming arrangementsOperating systemHypervisor
There is provided a system (1) comprising: a processing unit (11) equipped with execution modes including a non-secure mode (3) in which access to a protected region of a memory is prohibited by a support function (12) and a secure mode (2) in which access to the protected region is permitted; and a hypervisor (20) which runs in the secure mode. The hypervisor includes: a first setting unit (23) for setting a first operation condition (21), which includes enabling a first OS (30) running in the secure mode to access the protected region and the unprotected region of the memory; and a second setting unit (24) for setting a second operation condition (22a), which includes enabling a second OS (41) running in the non-secure mode to access the unprotected region, using the support function to prevent the second OS (41) from accessing the secure region, and enabling a transition to the secure mode by accessing of the second OS to a first device shared with the first OS.
Owner:SEKISUI HOUSE KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com