Patents
Literature
42results about How to "Slow process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
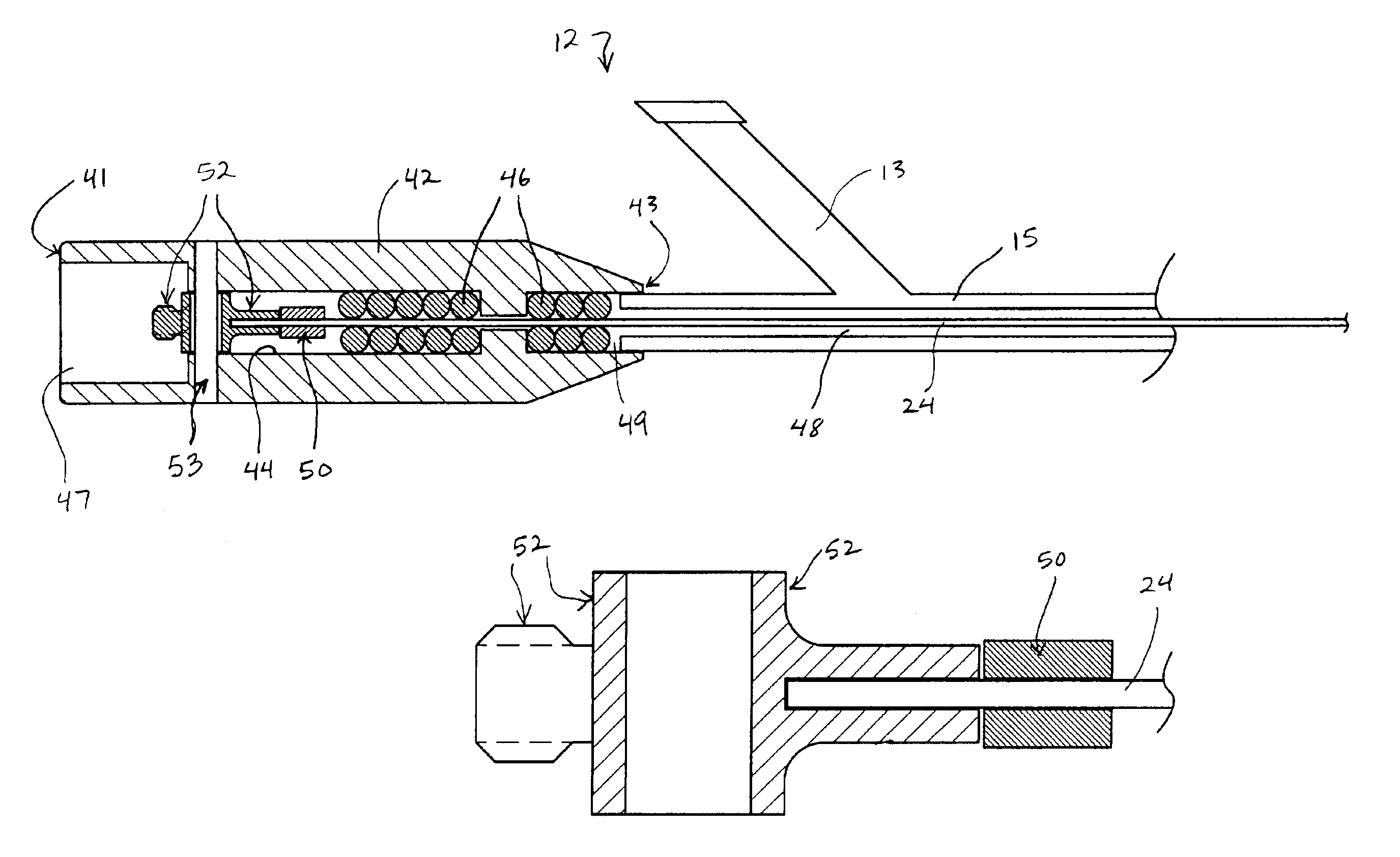
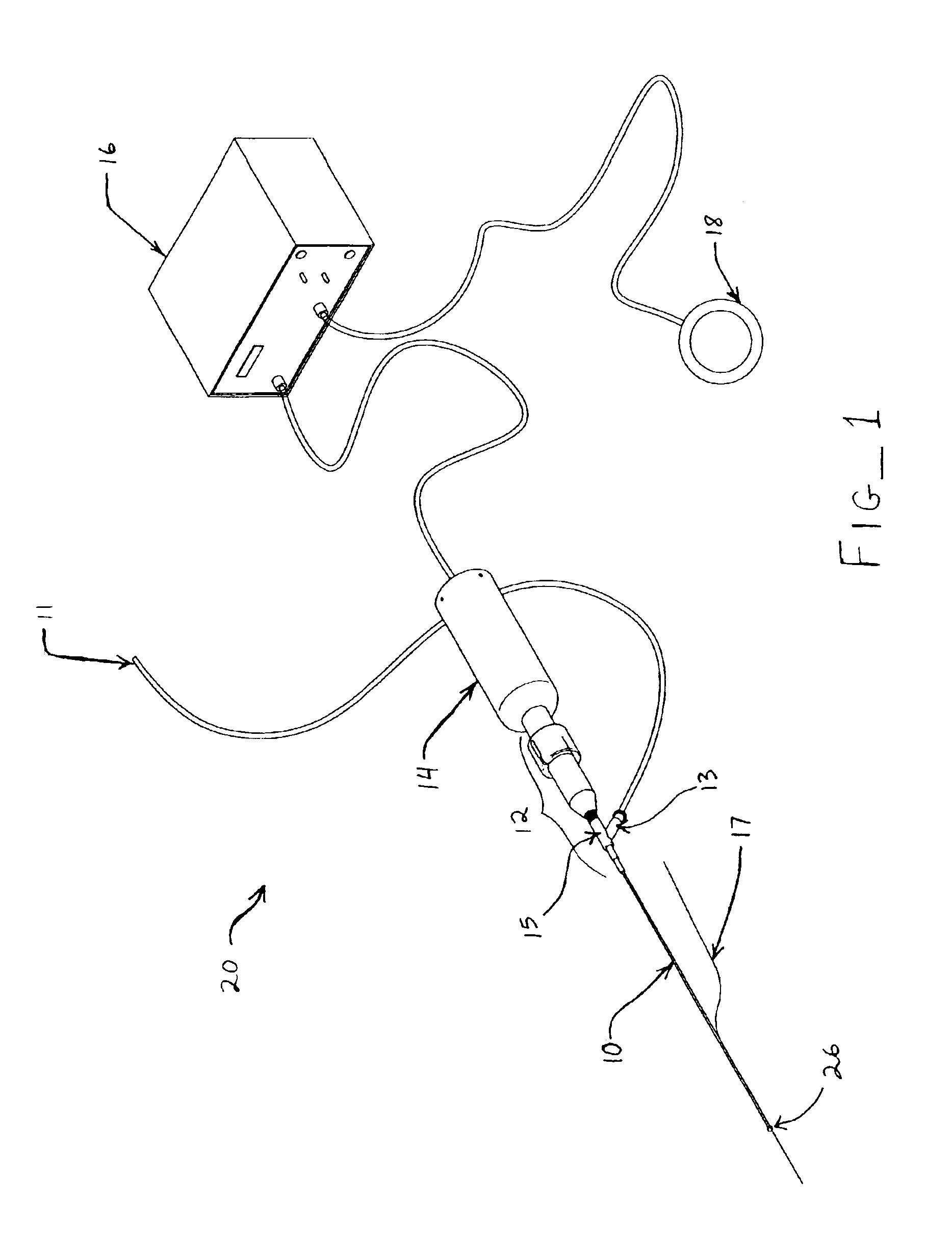
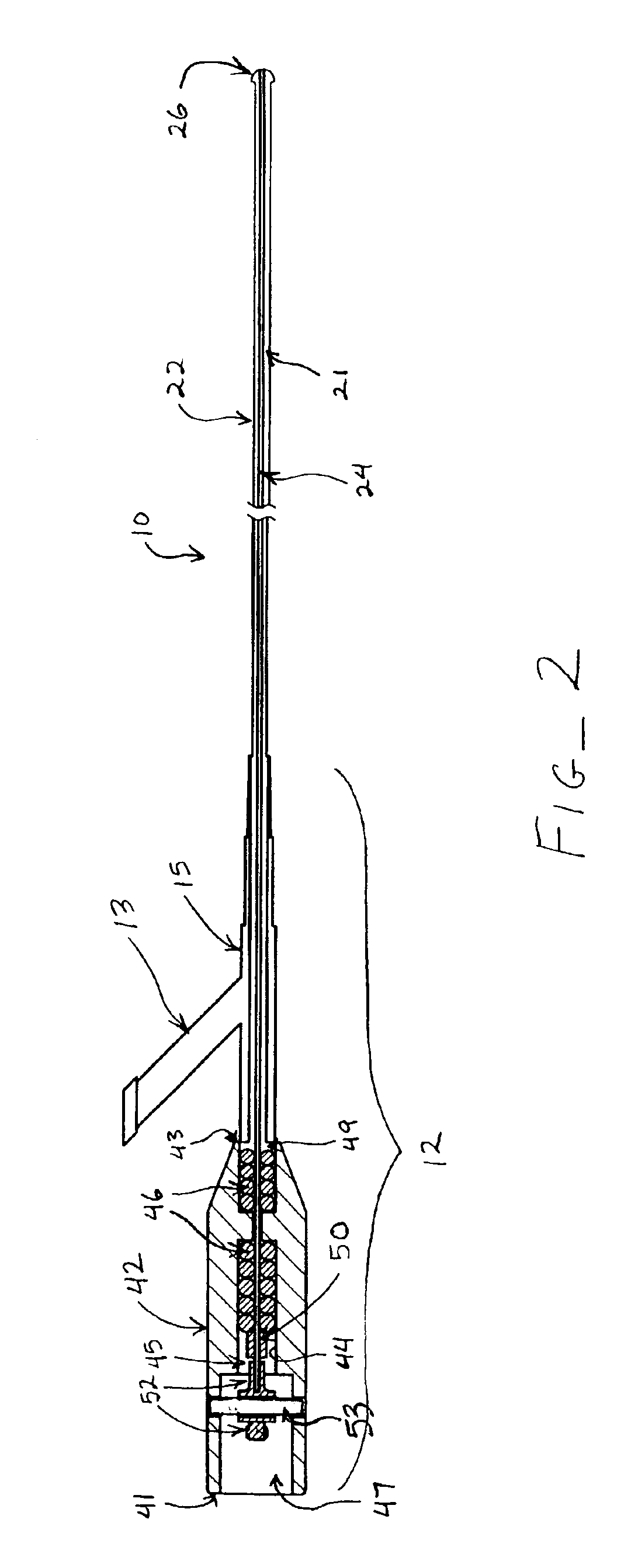
Ultrasound catheter apparatus
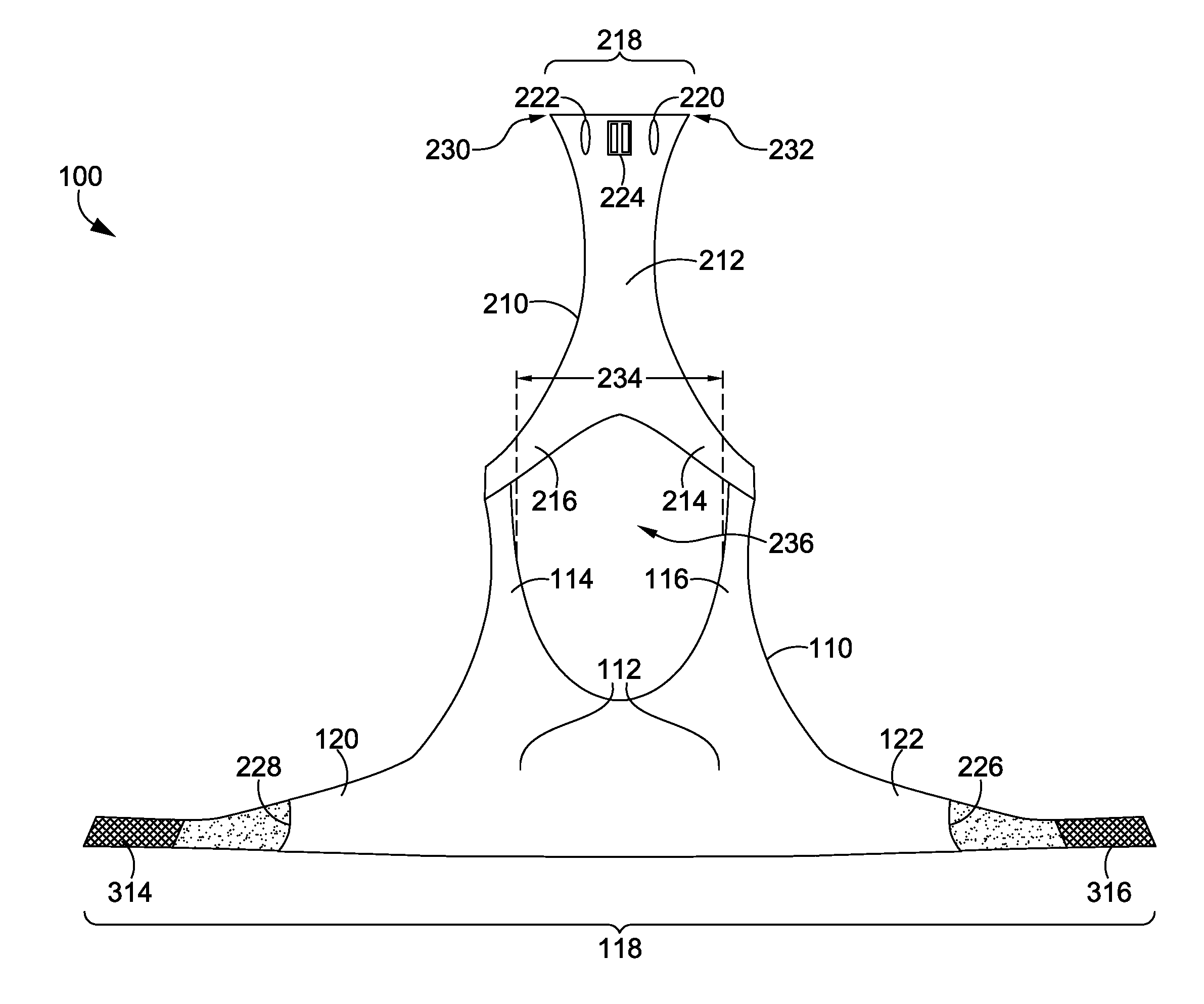
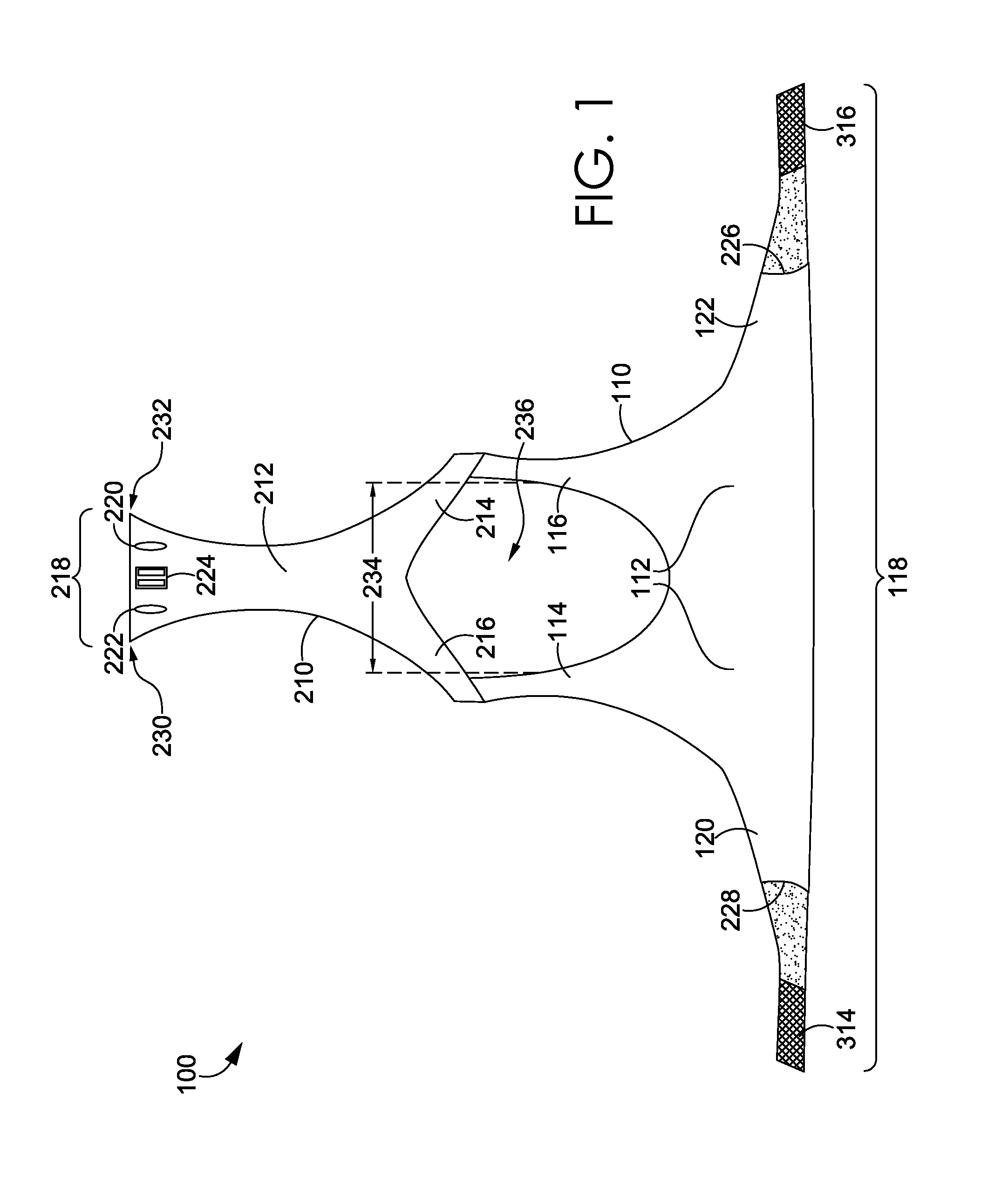
Ultrasound catheter devices and methods of the present invention generally provide for ablation and / or disruption of vascular occlusions. An ultrasound transmission member, such as a wire, transmits vibrational energy from an ultrasound transducer to a distal head of the catheter to disrupt vascular occlusions. At least one absorber member is disposed on or around the ultrasound transmission wire at a location adjacent the sonic connector of the catheter. The absorber member absorbs heat, vibrations, and / or the like from the ultrasound transmission wire at or near the area where the transmission wire is coupled with the sonic connector. The absorptive function typically slows the process of wear and tear on the transmission wire, thus extending the useful life of the ultrasound catheter.
Owner:FLOWCARDLA INC +1
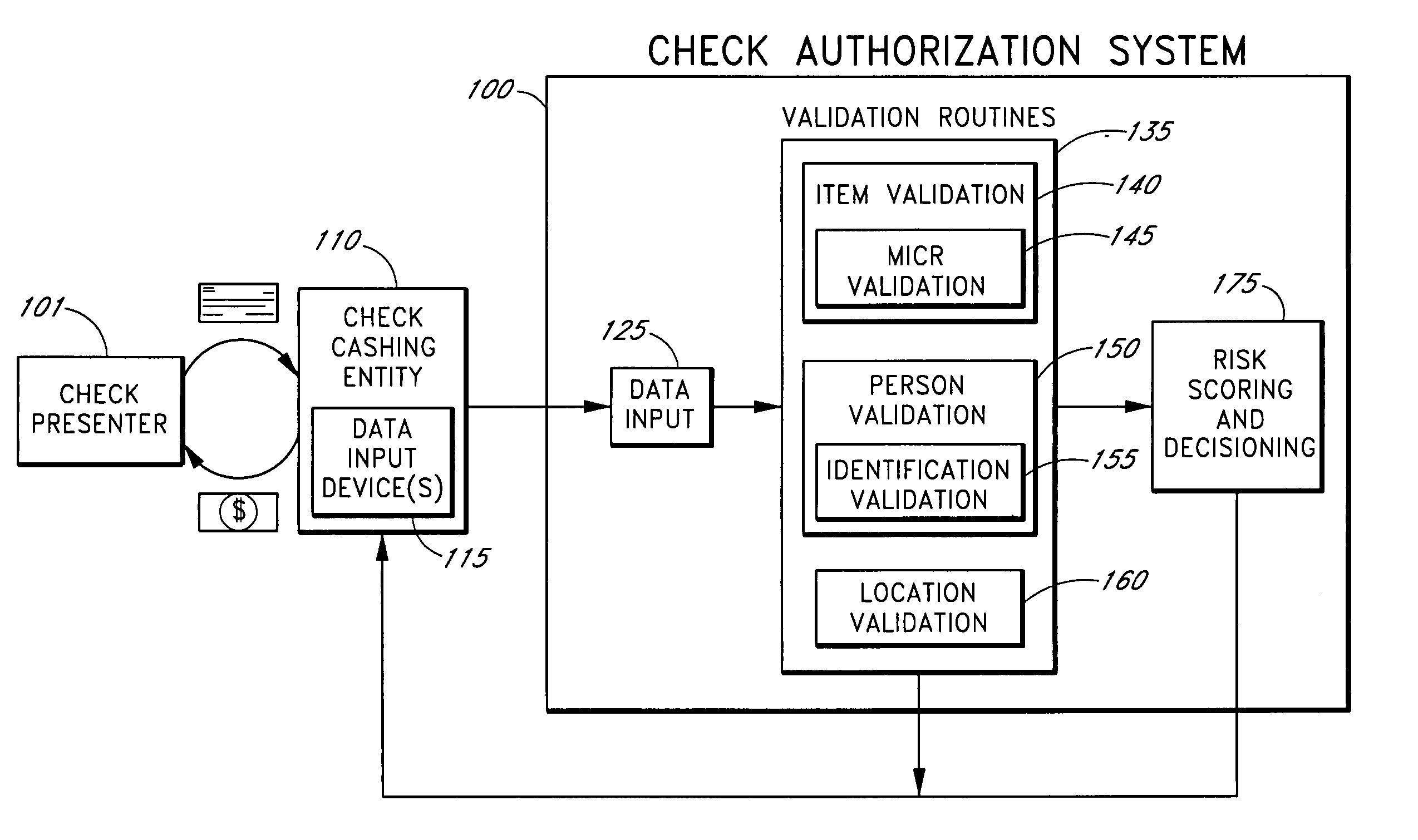
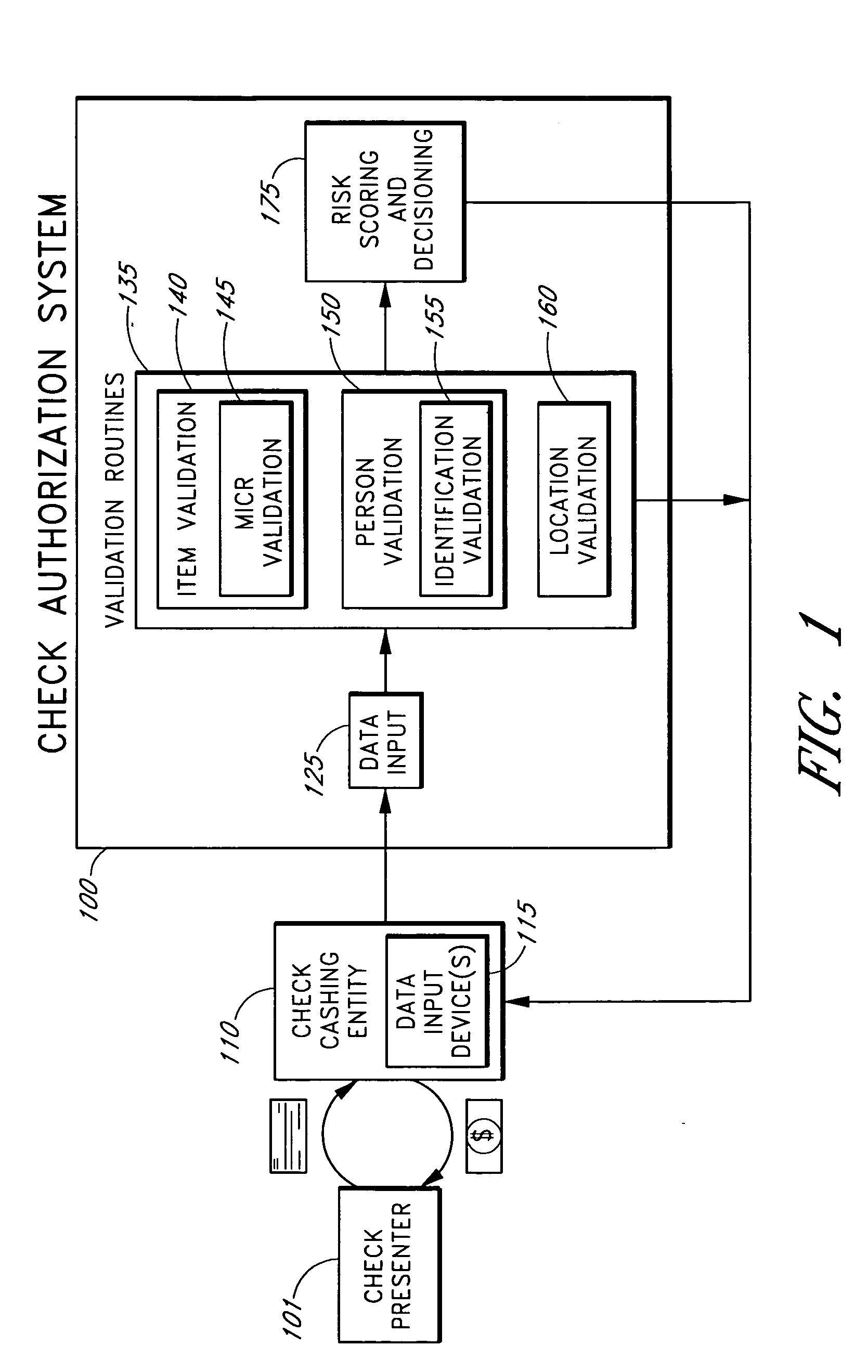
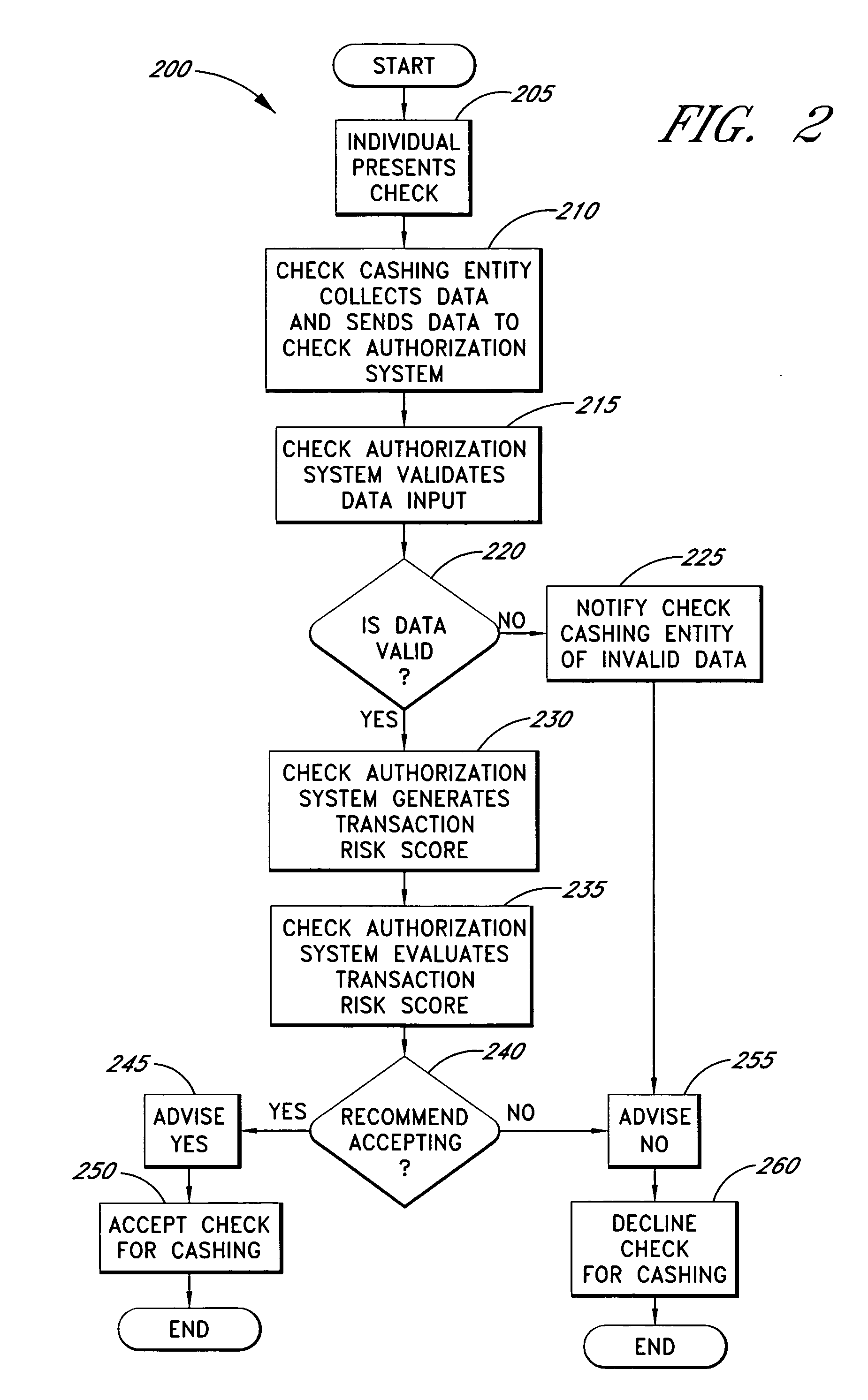
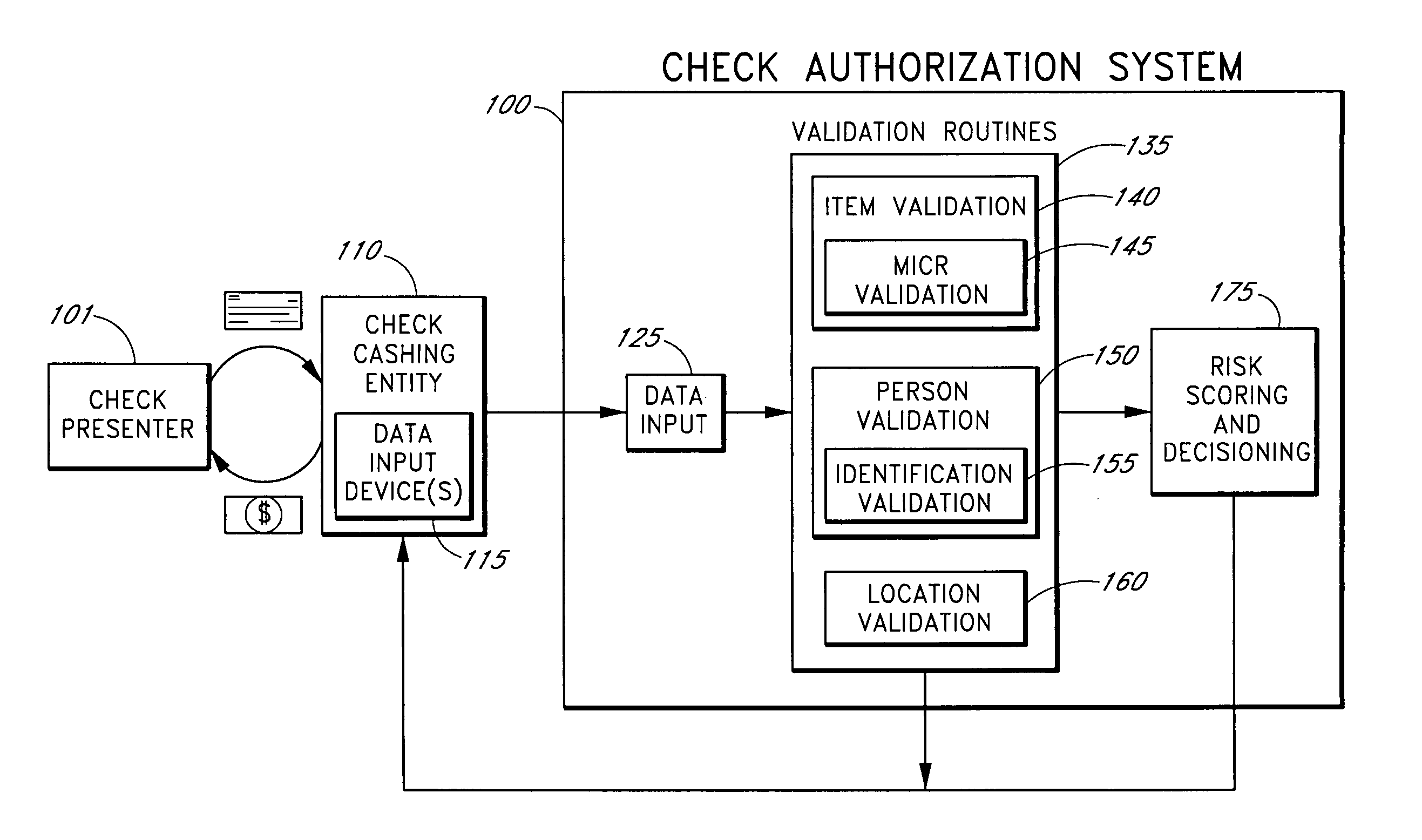
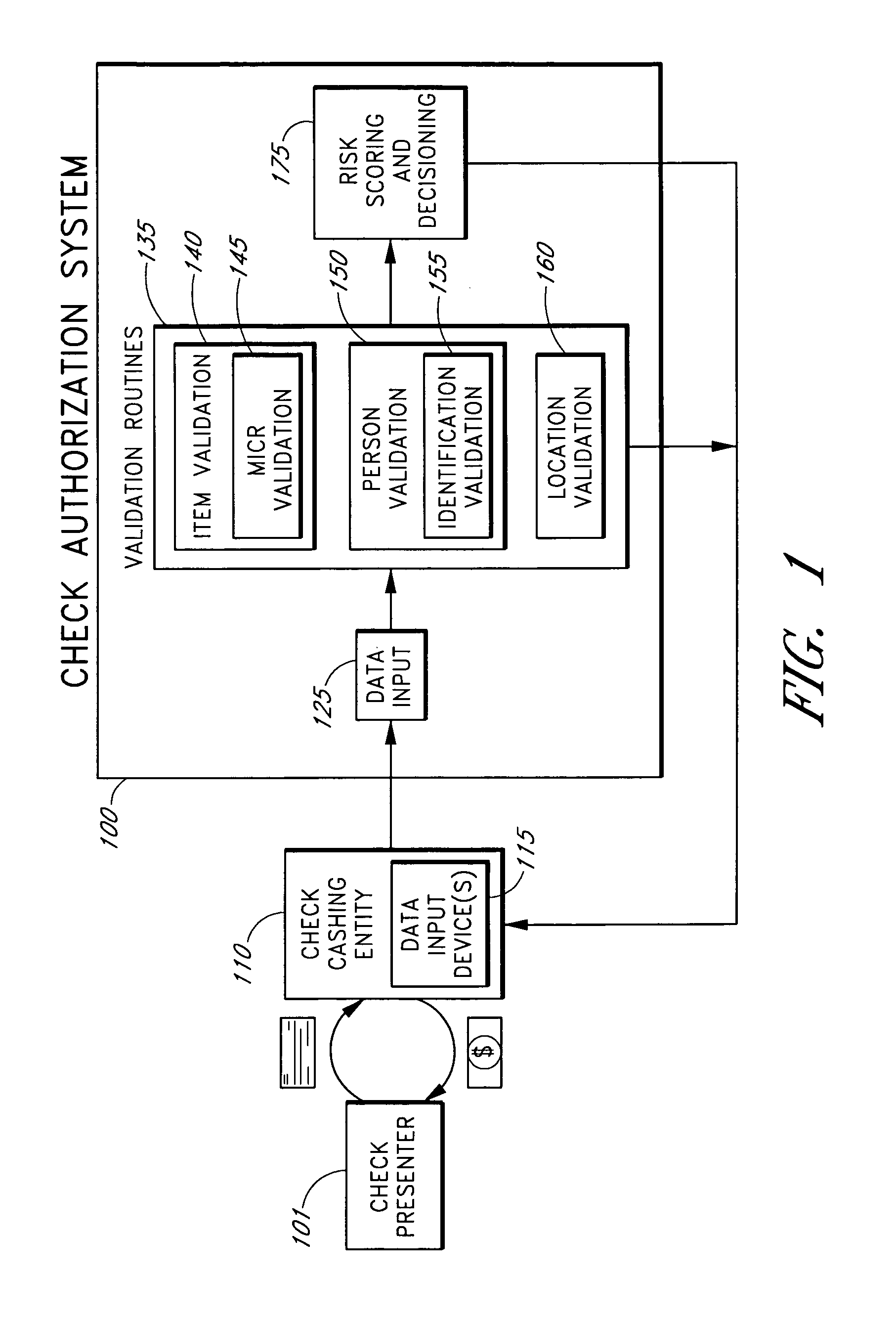
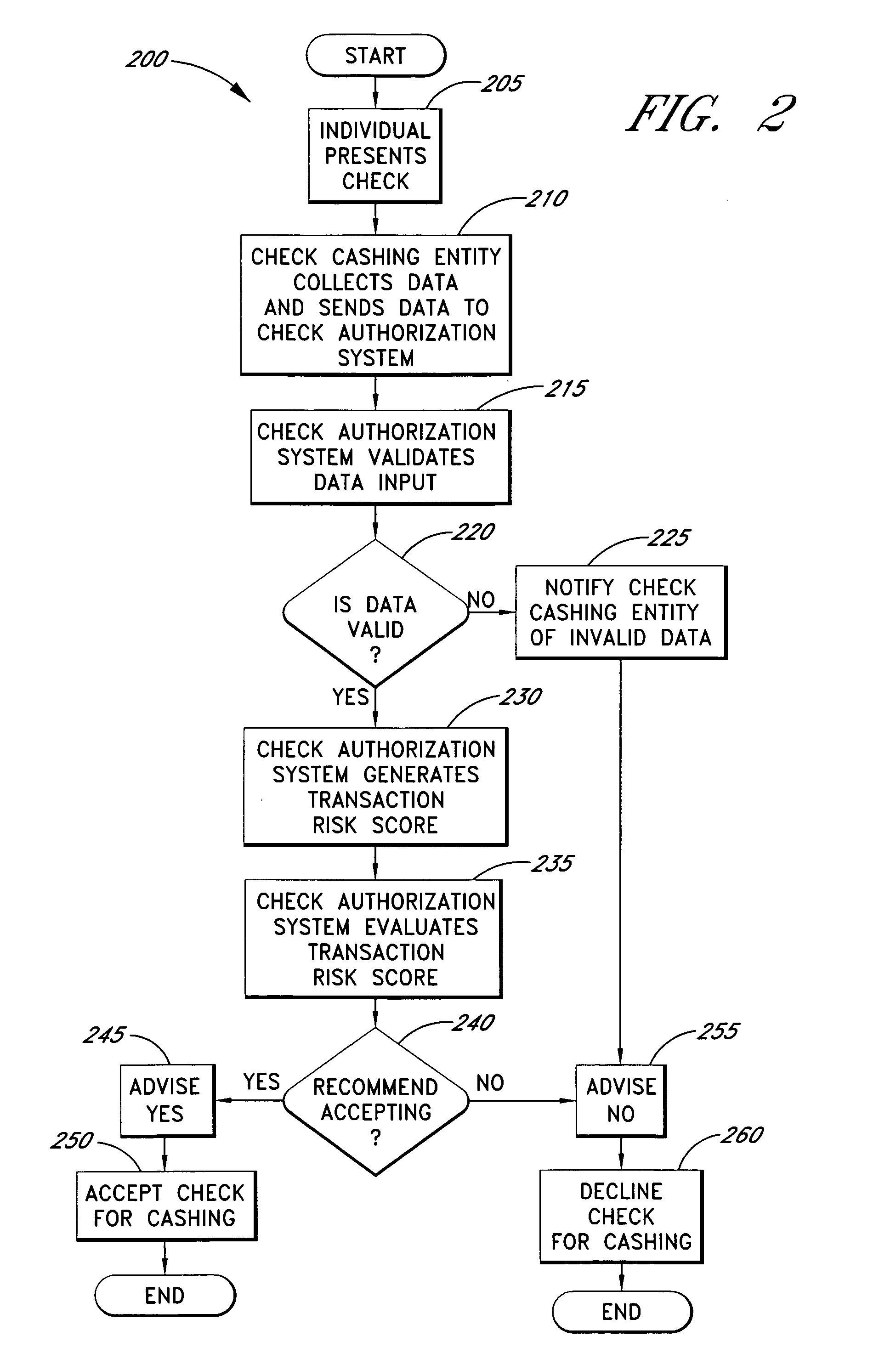
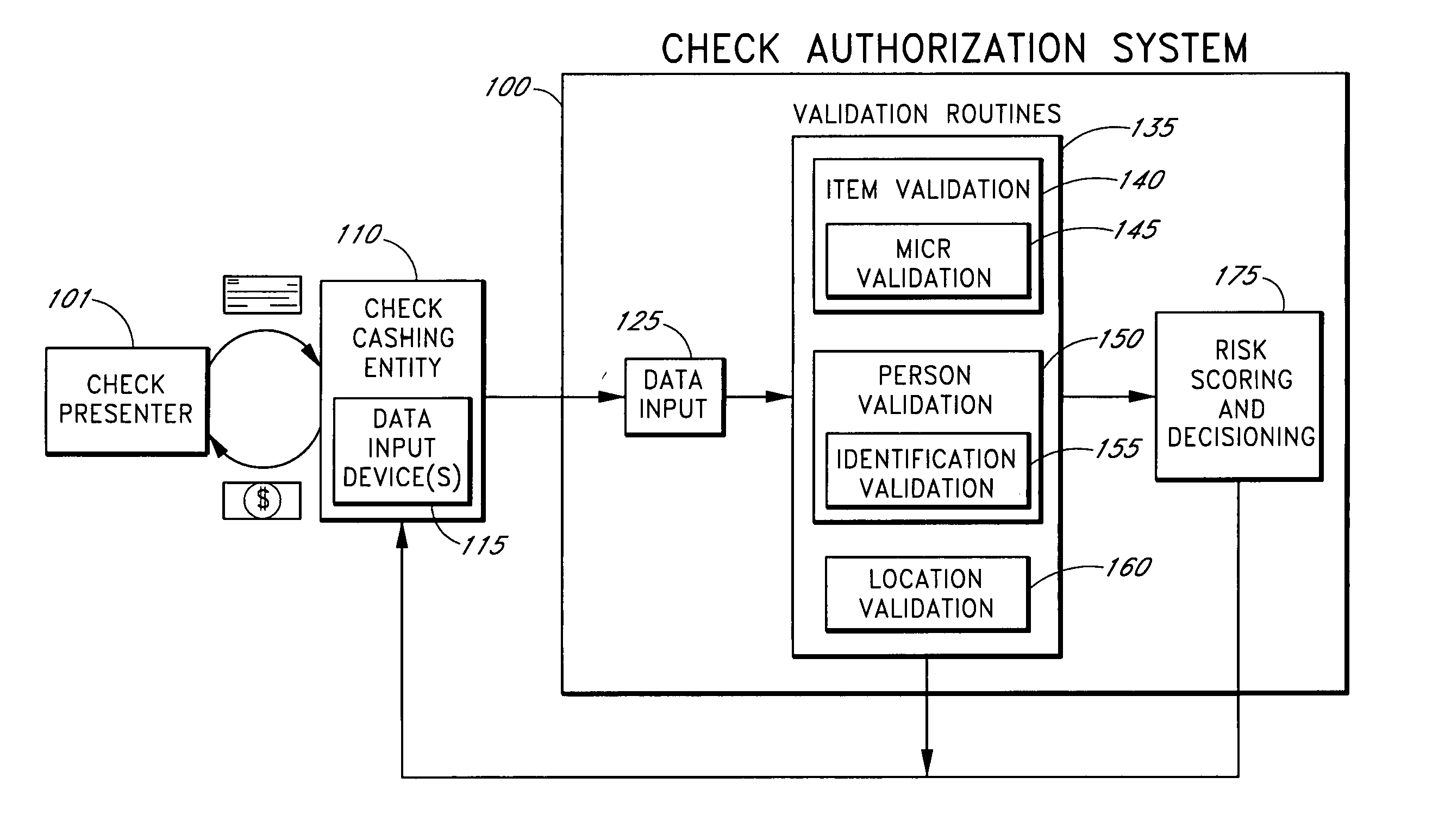
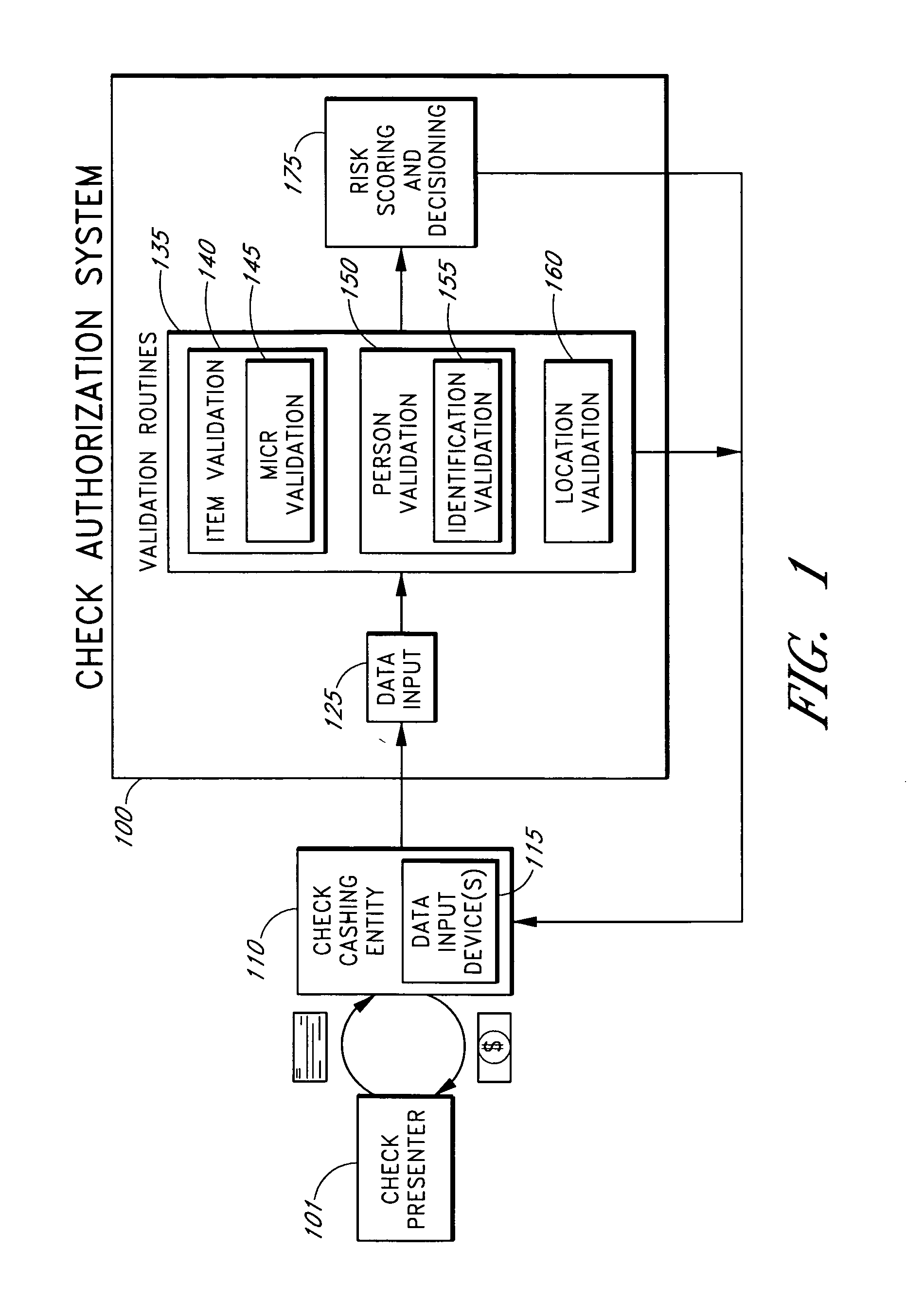
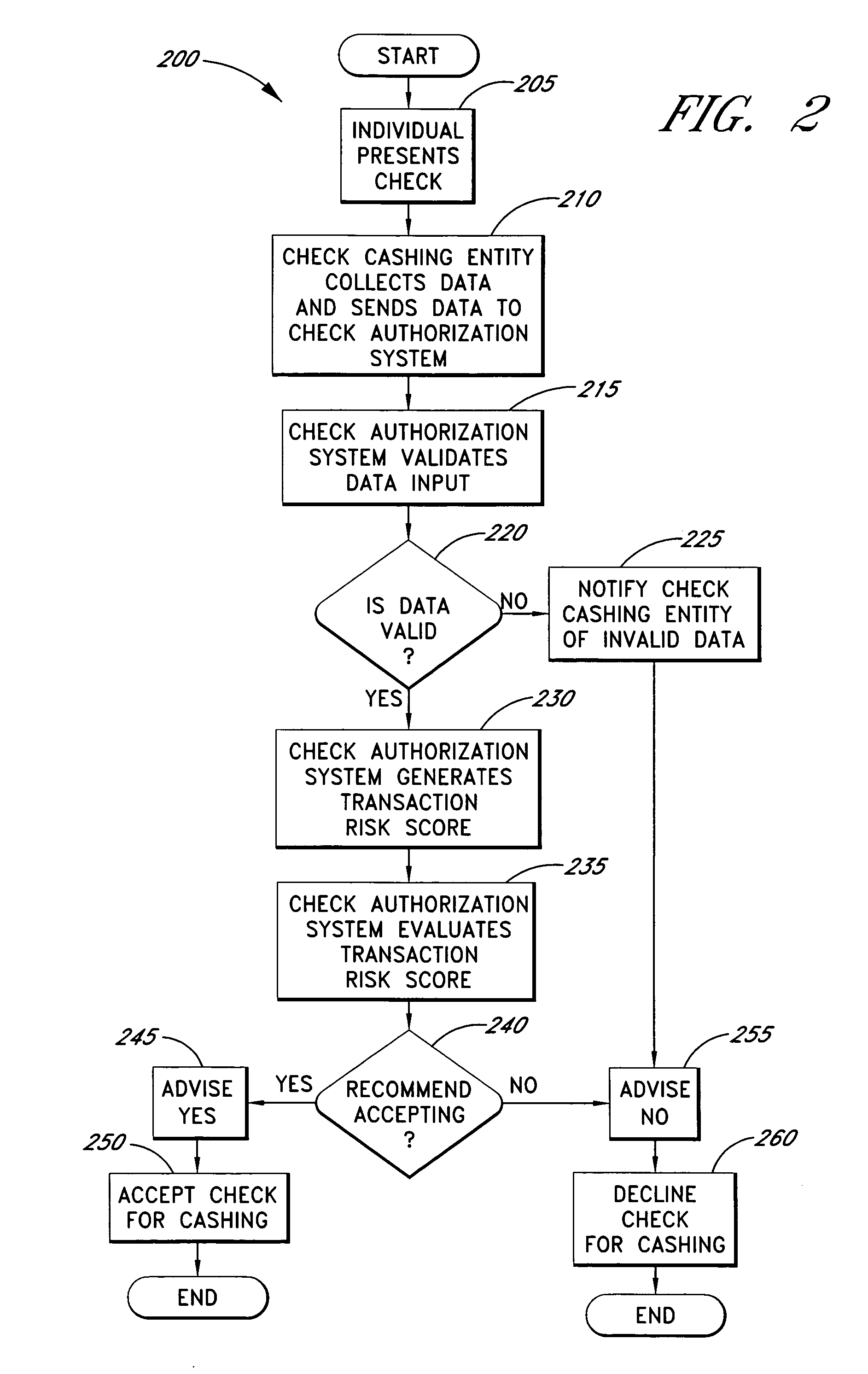
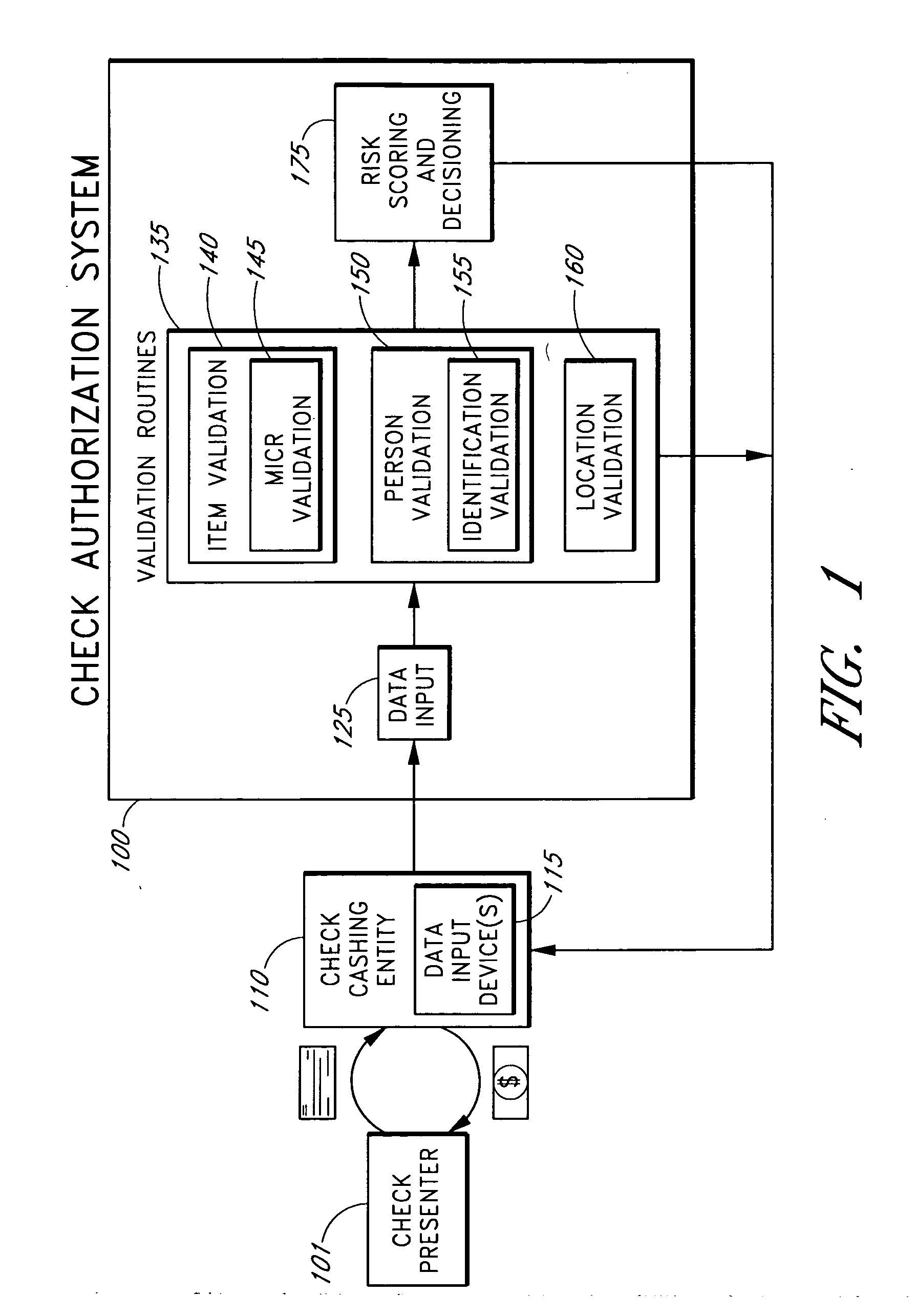
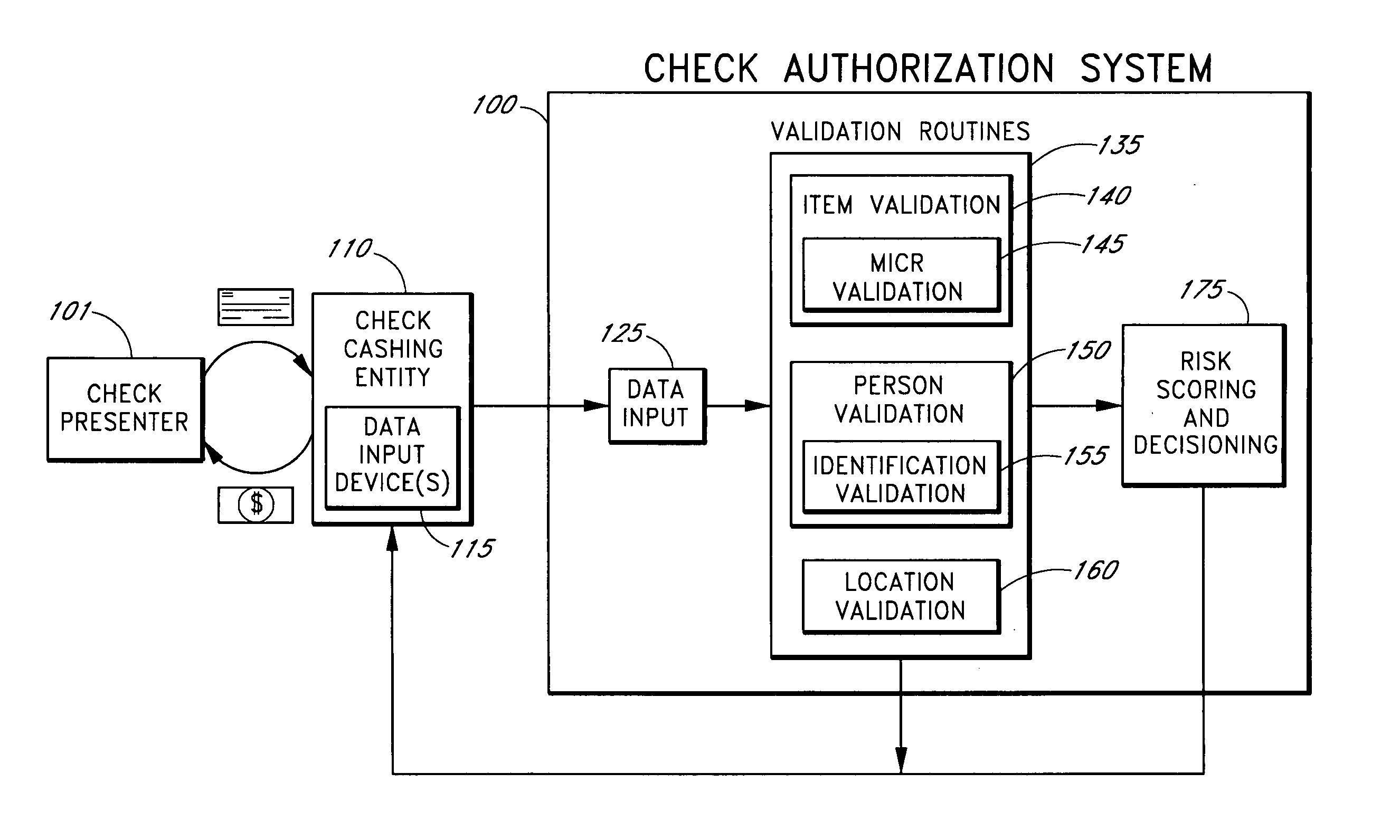
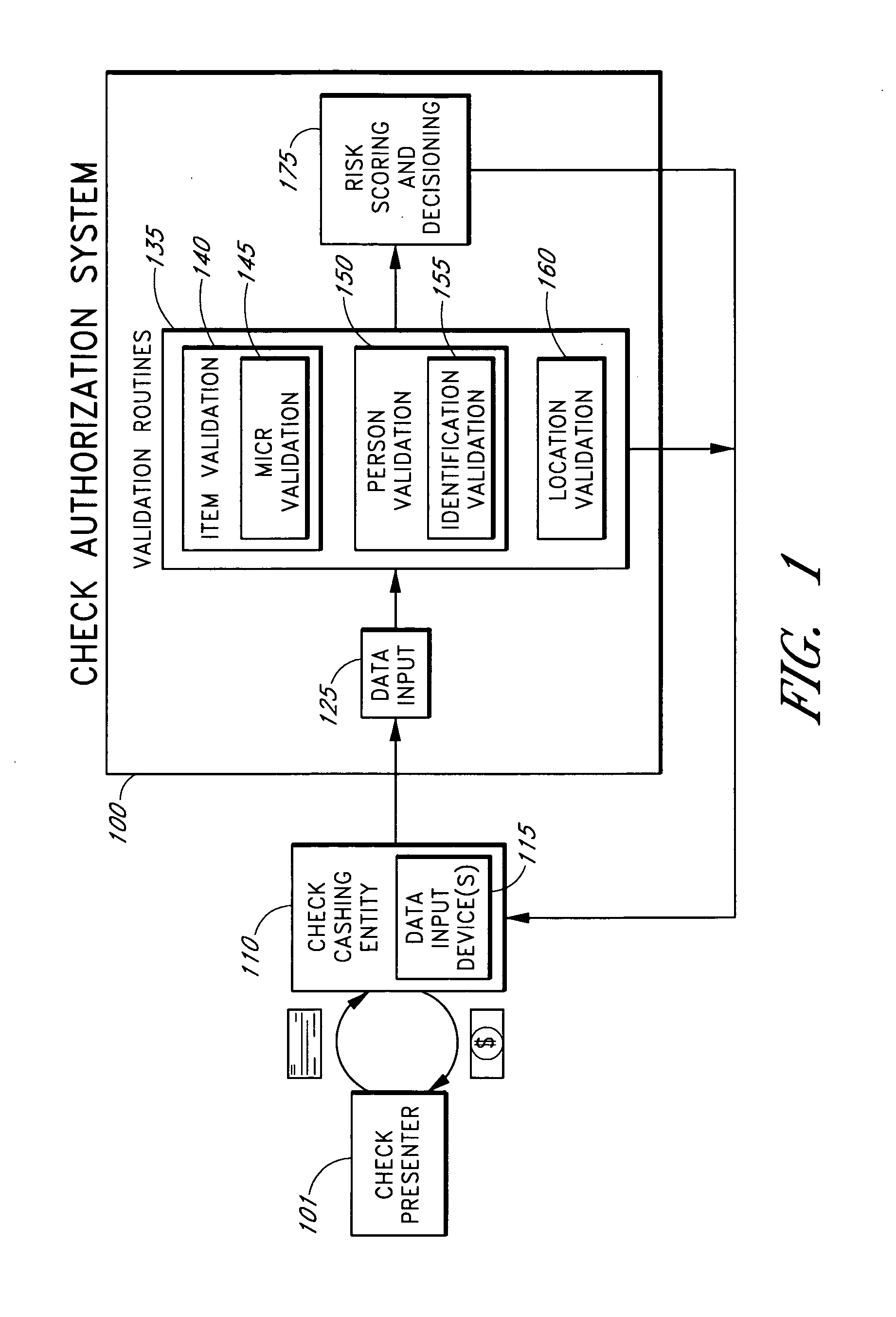
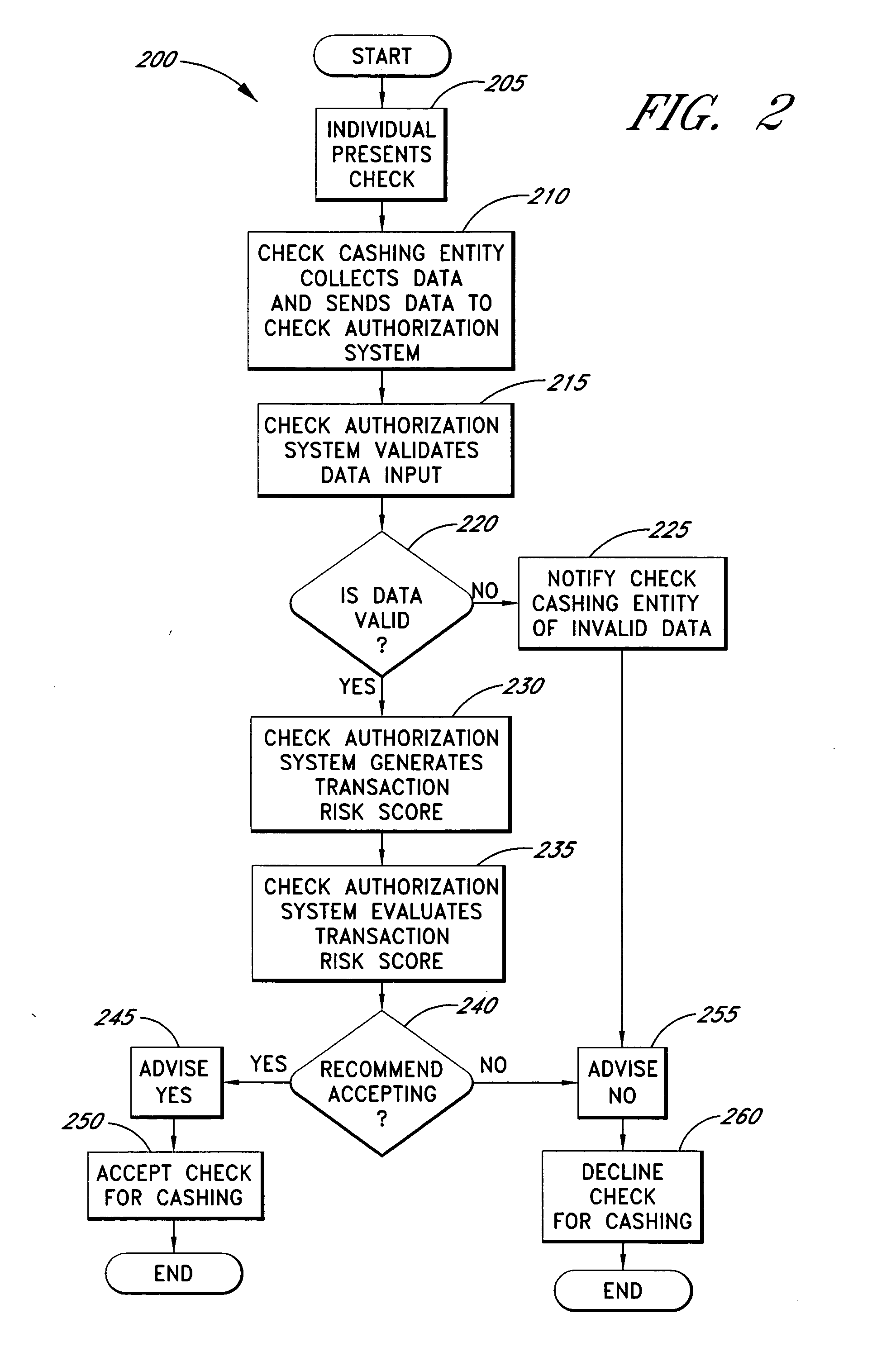
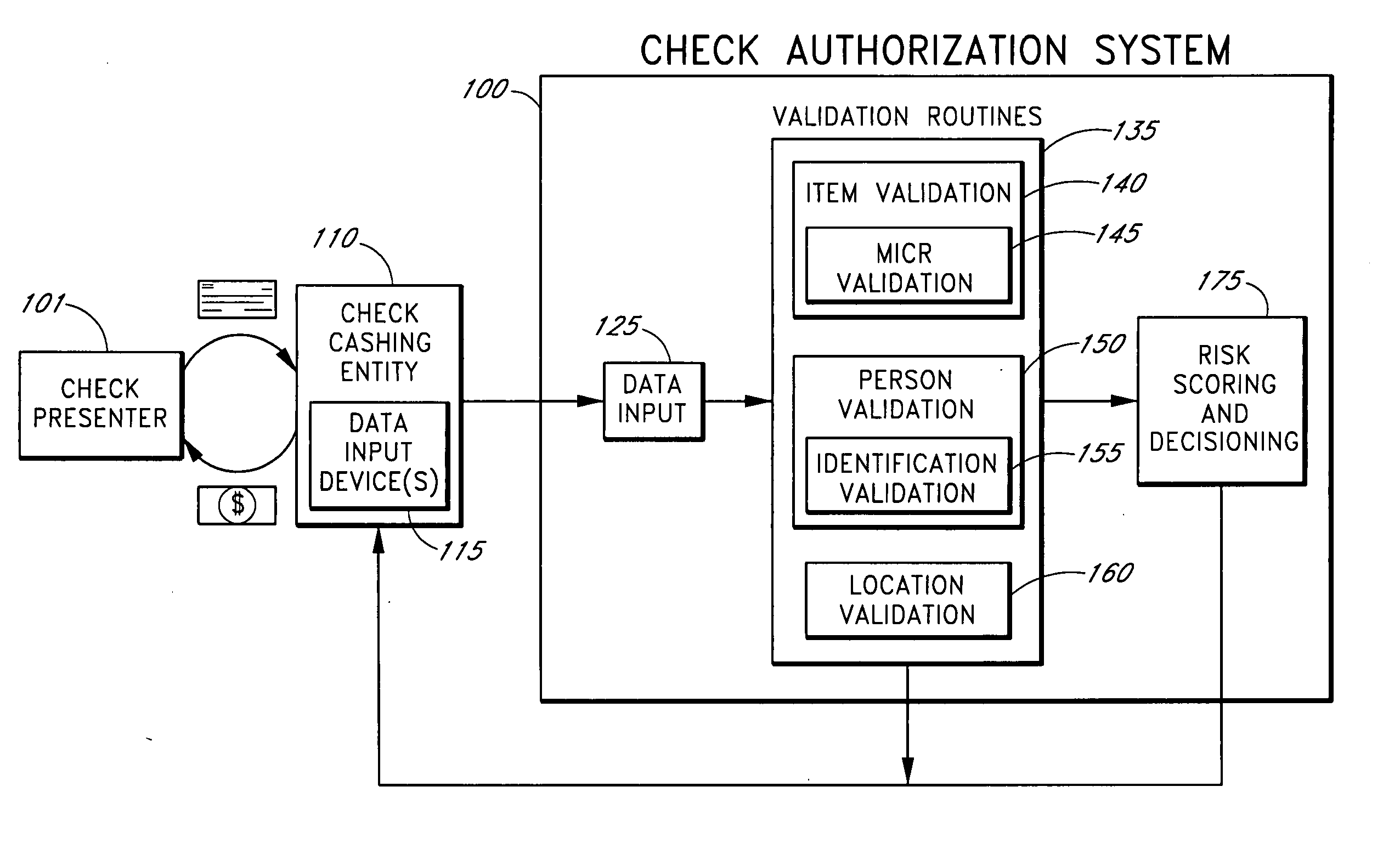
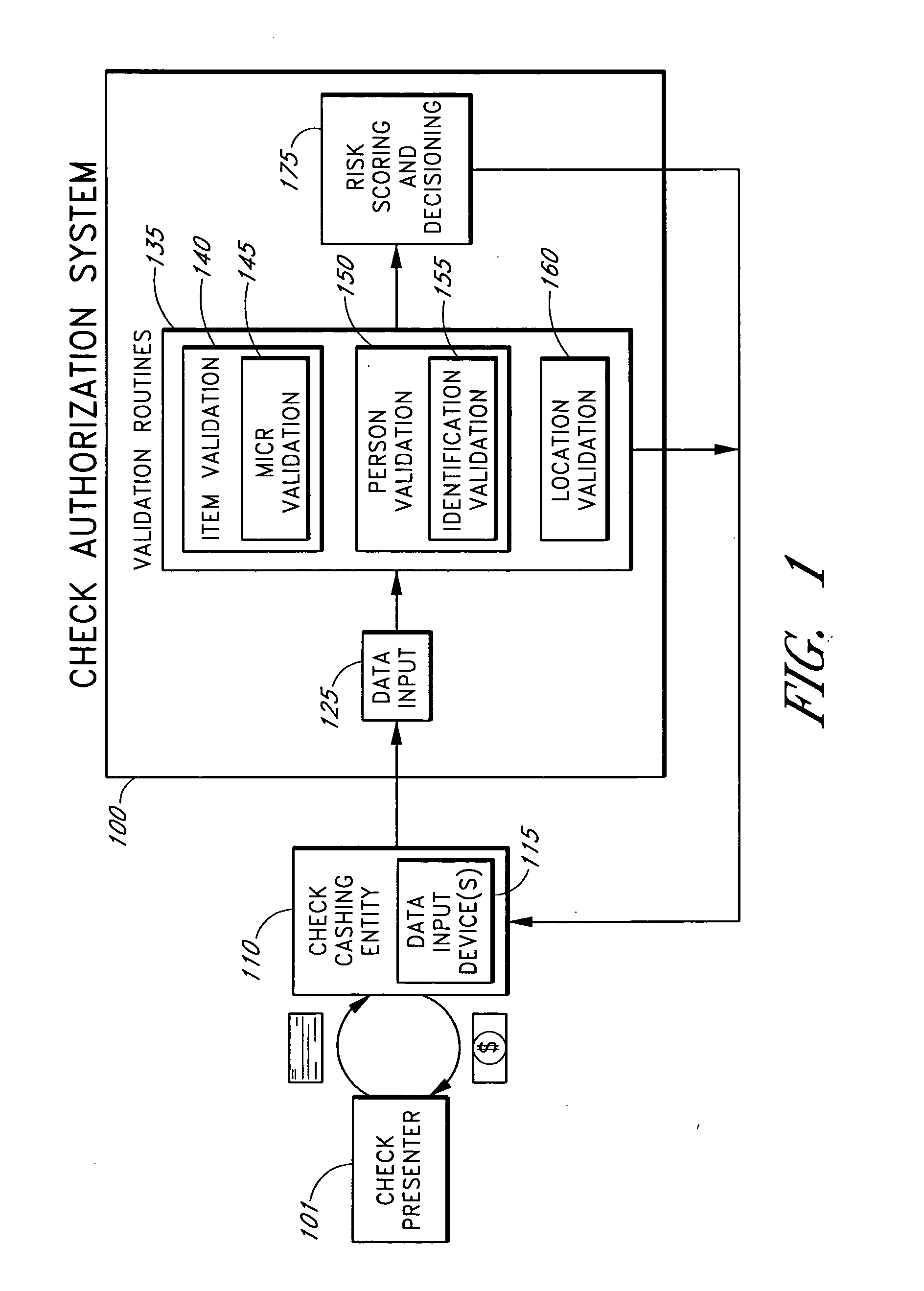
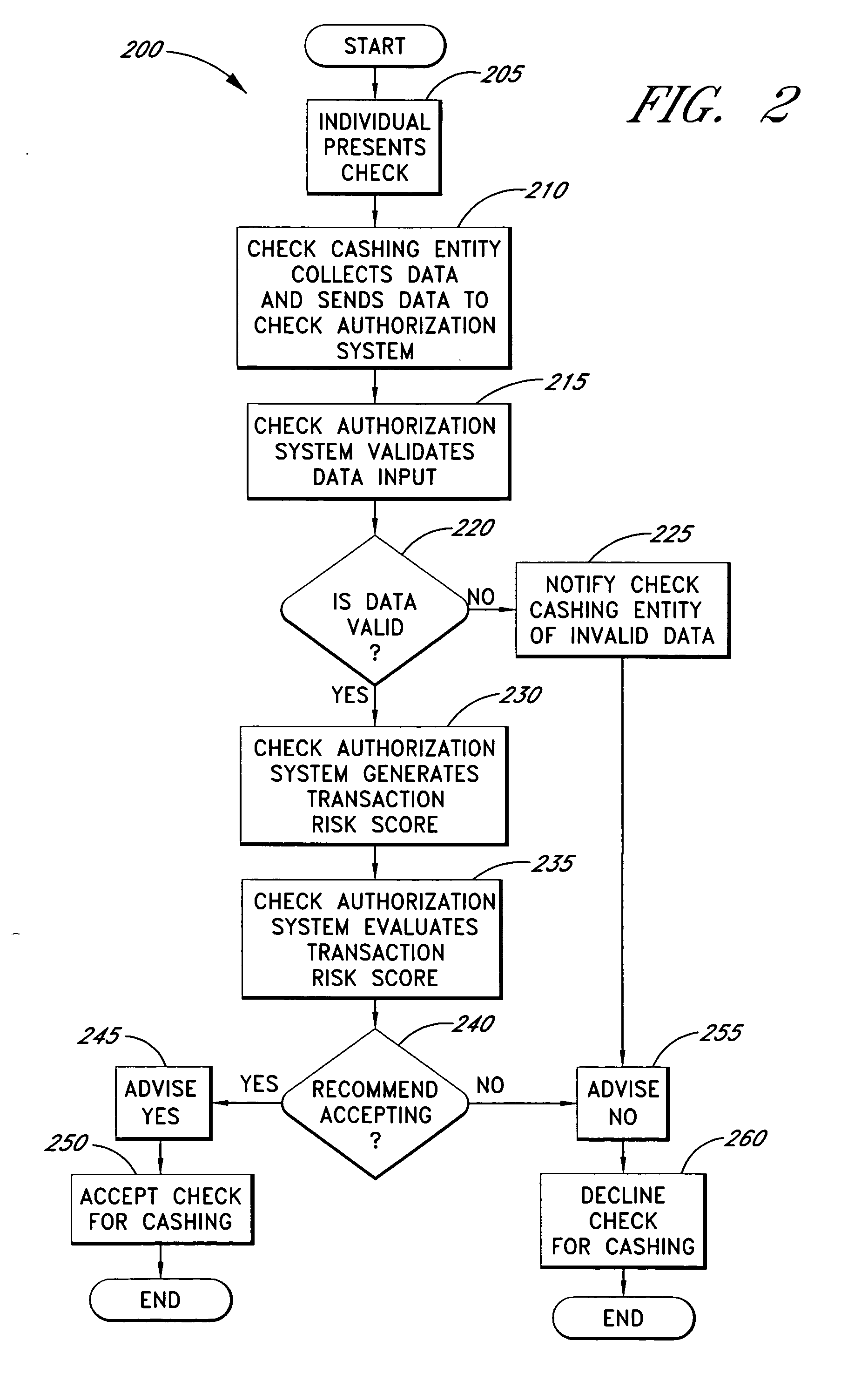
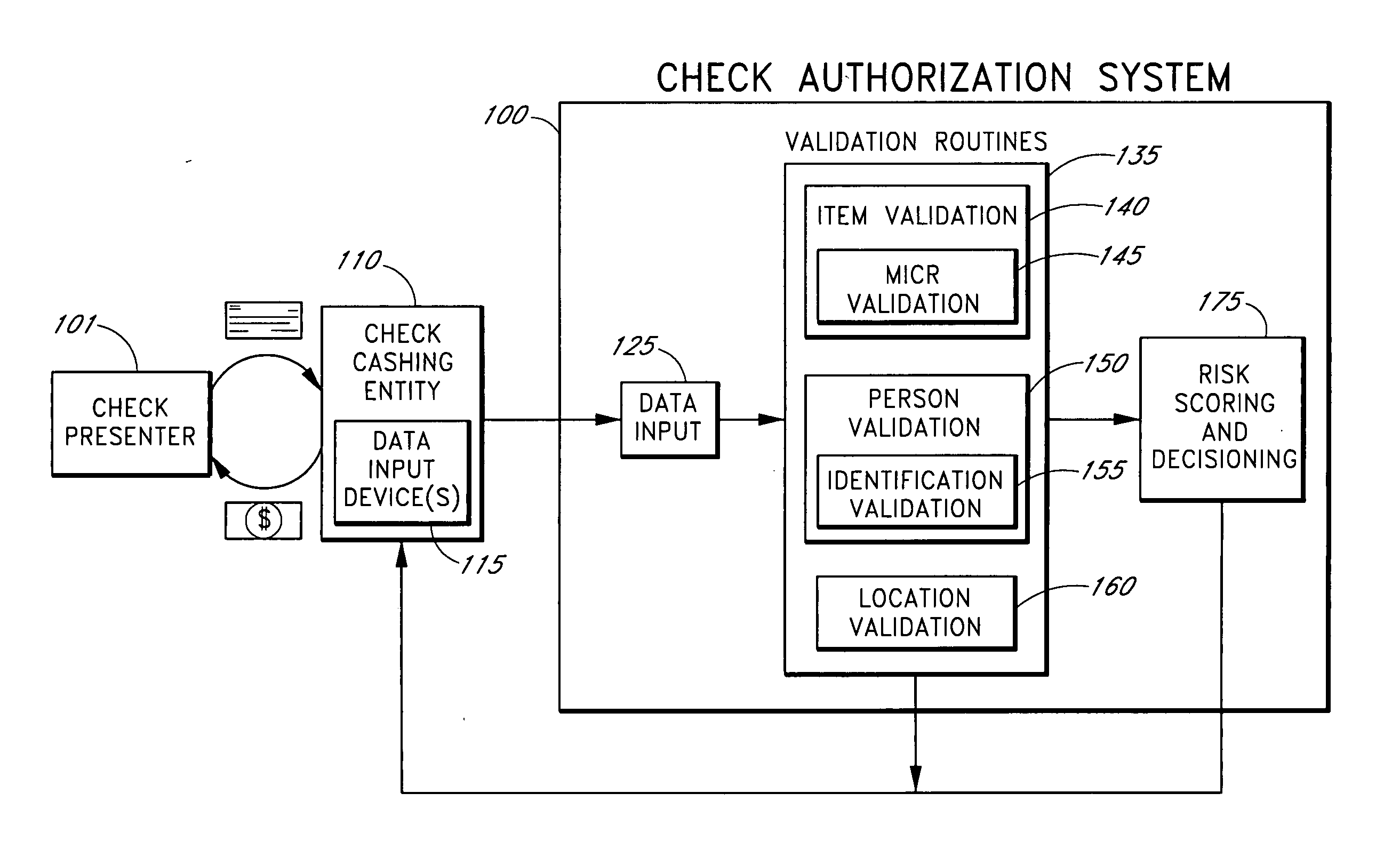
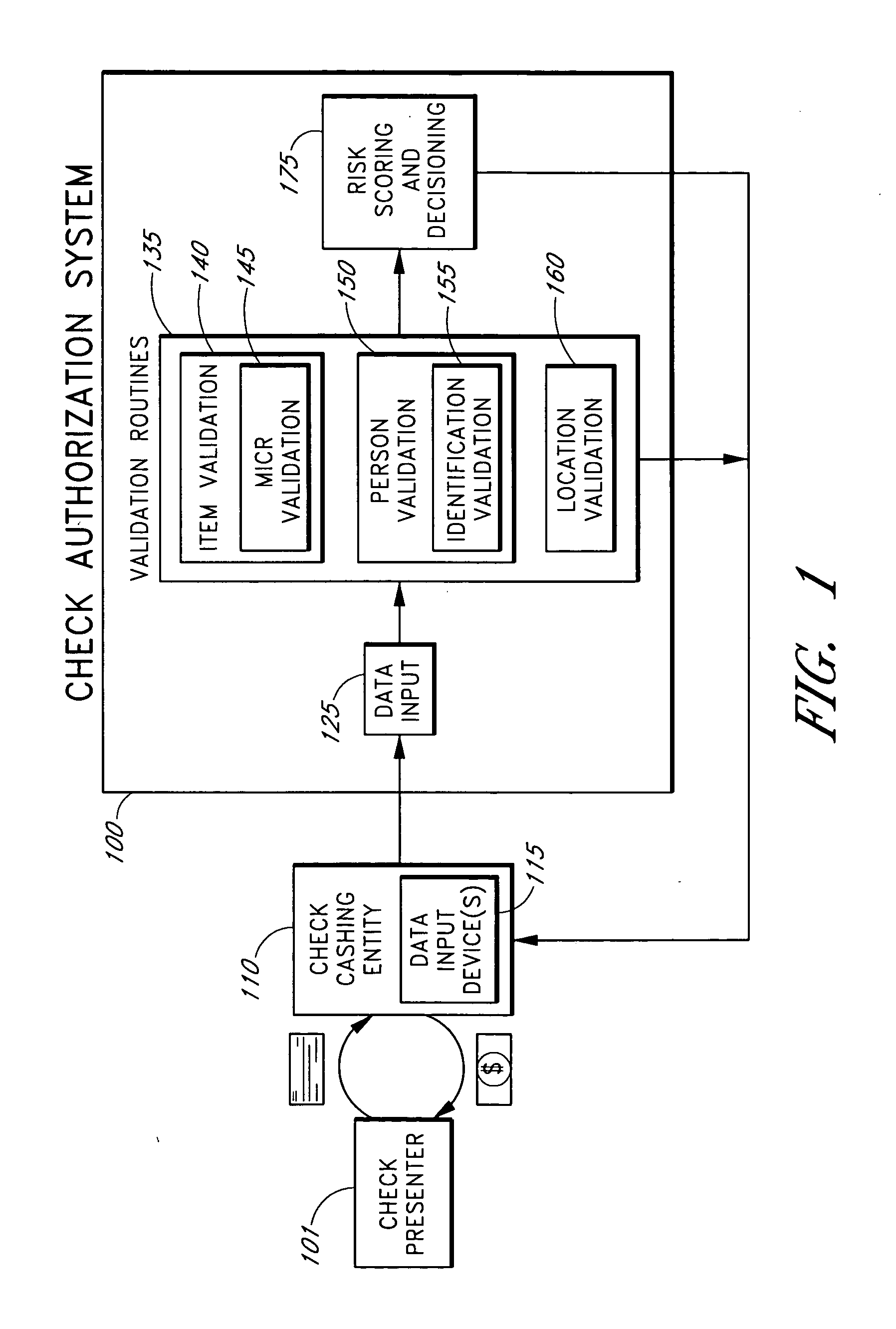
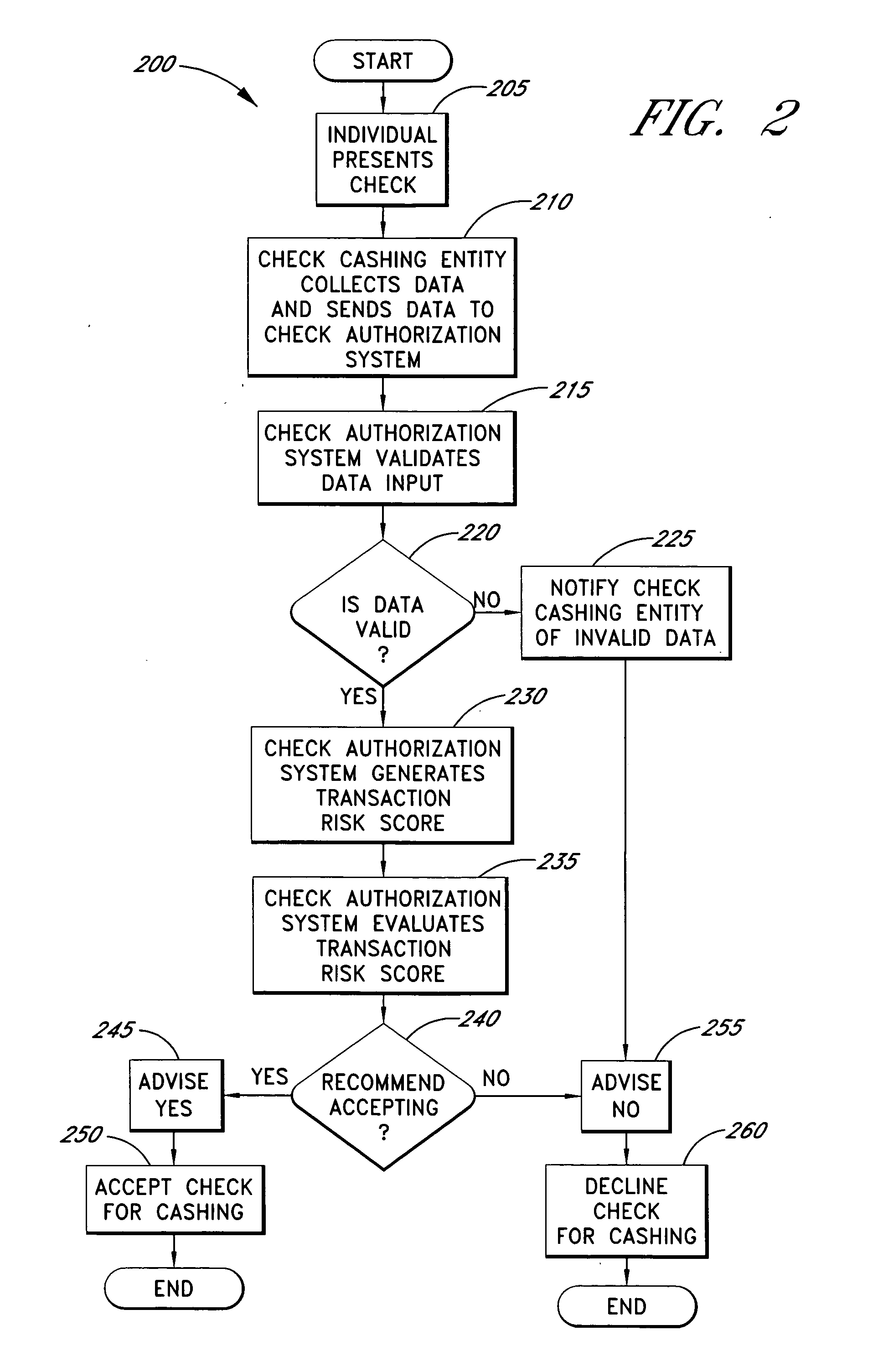
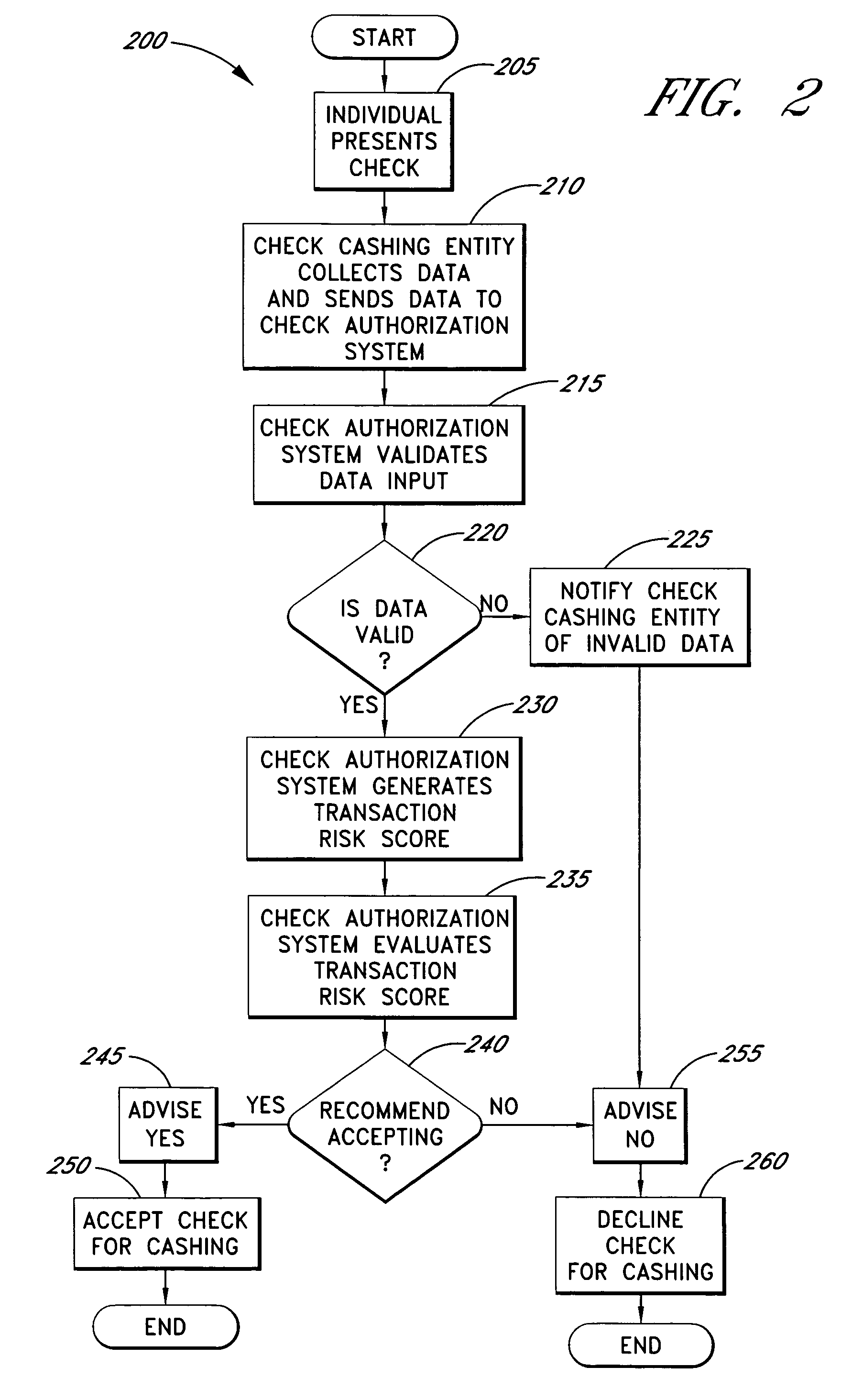
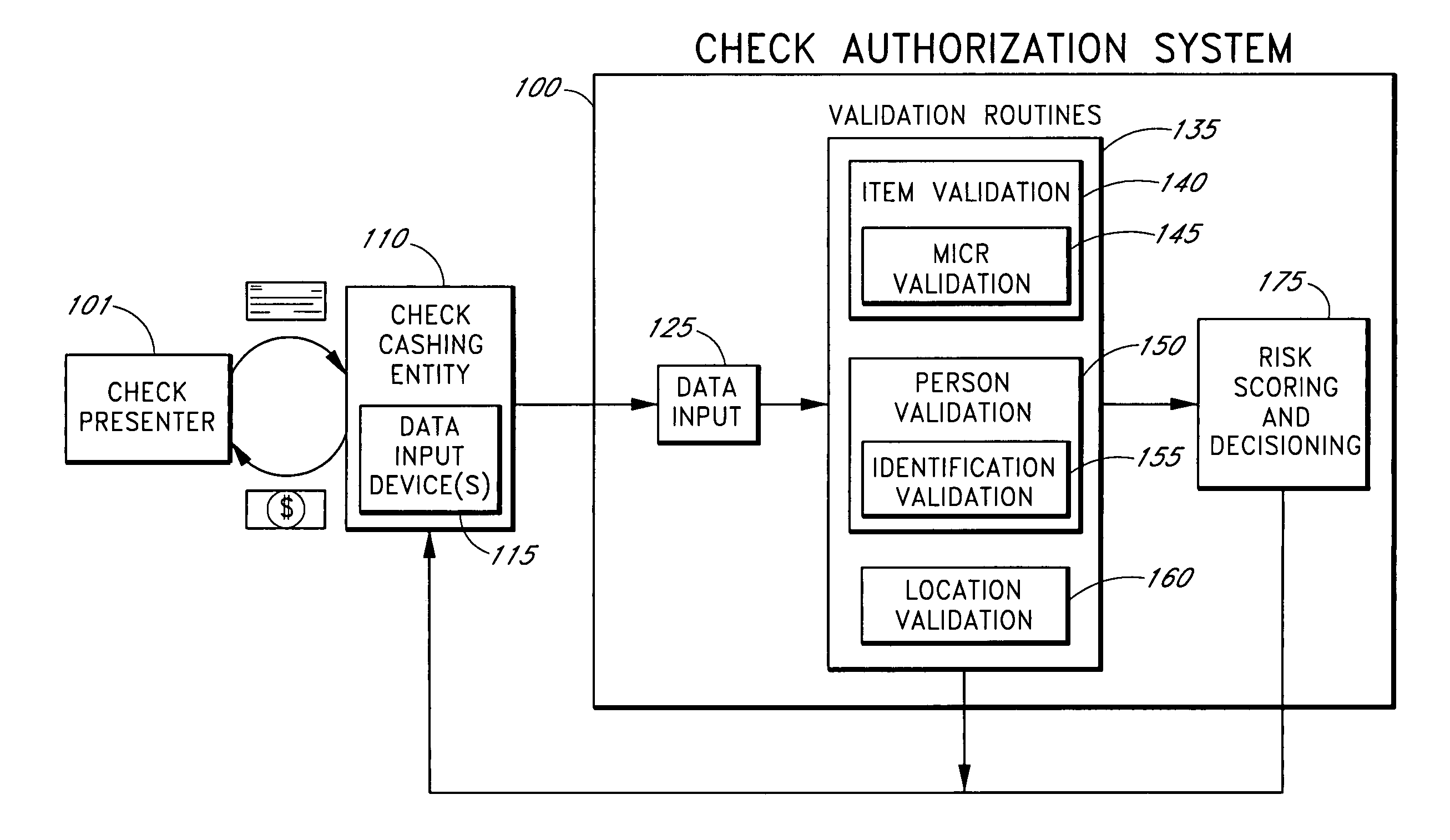
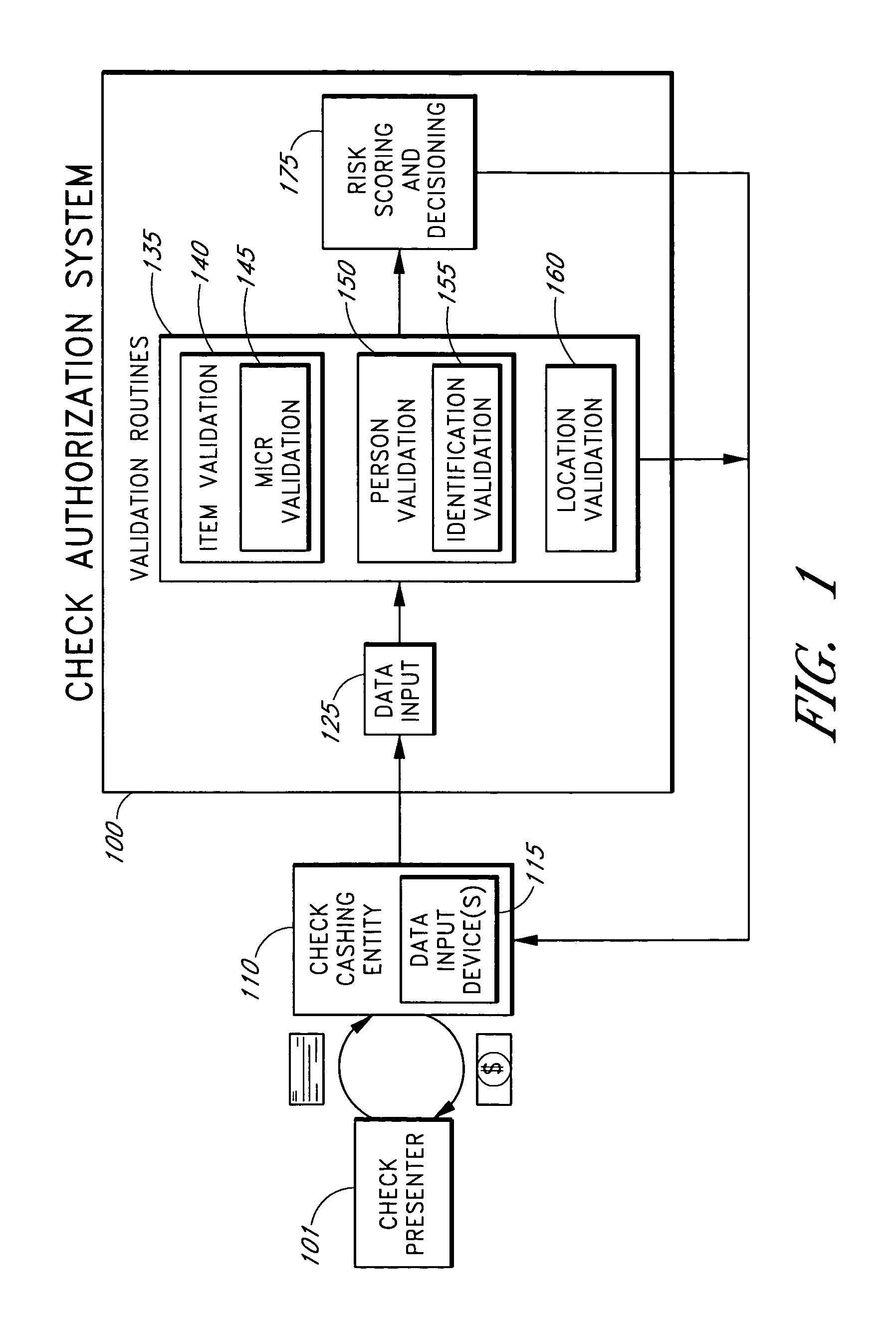
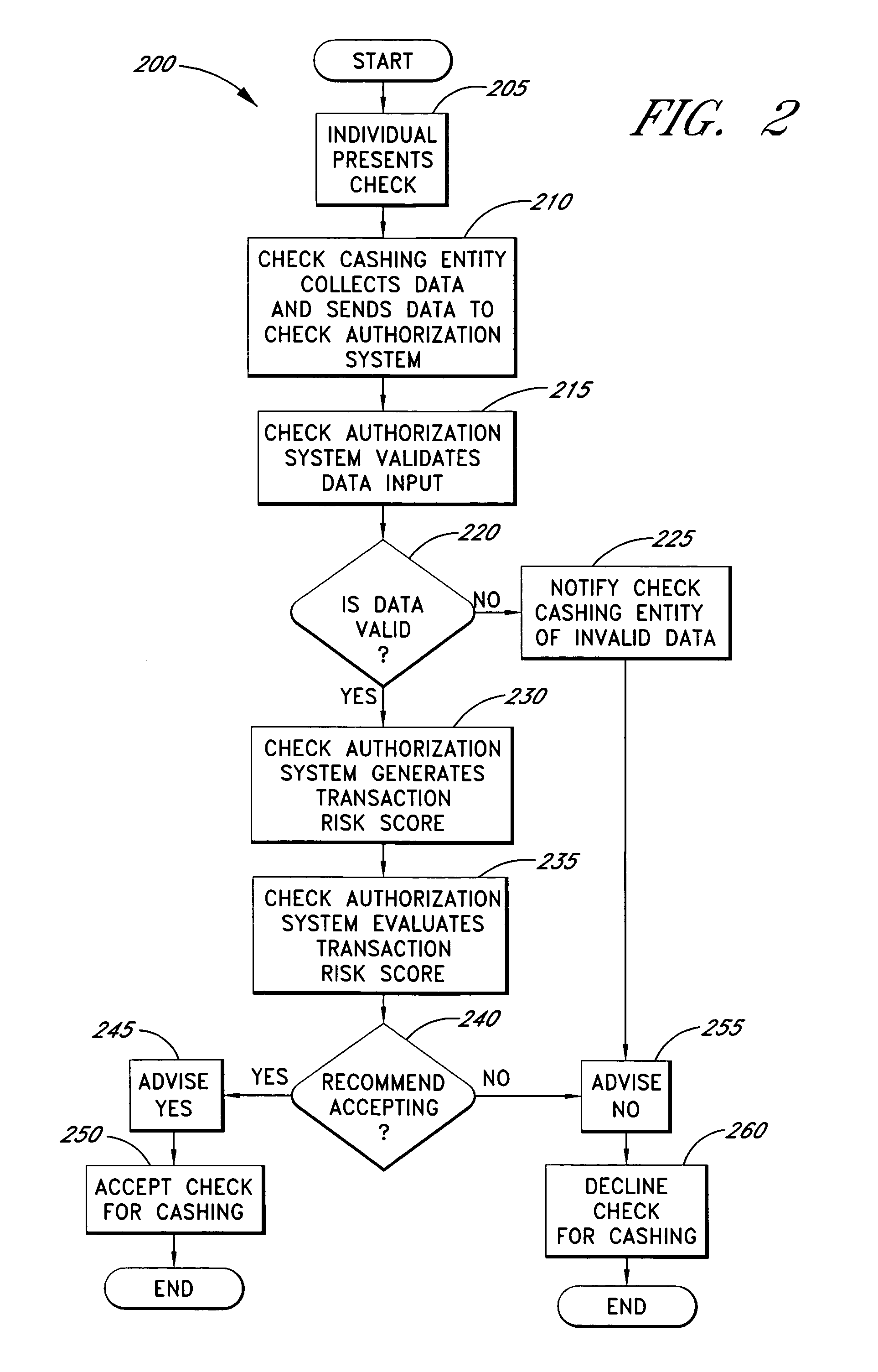
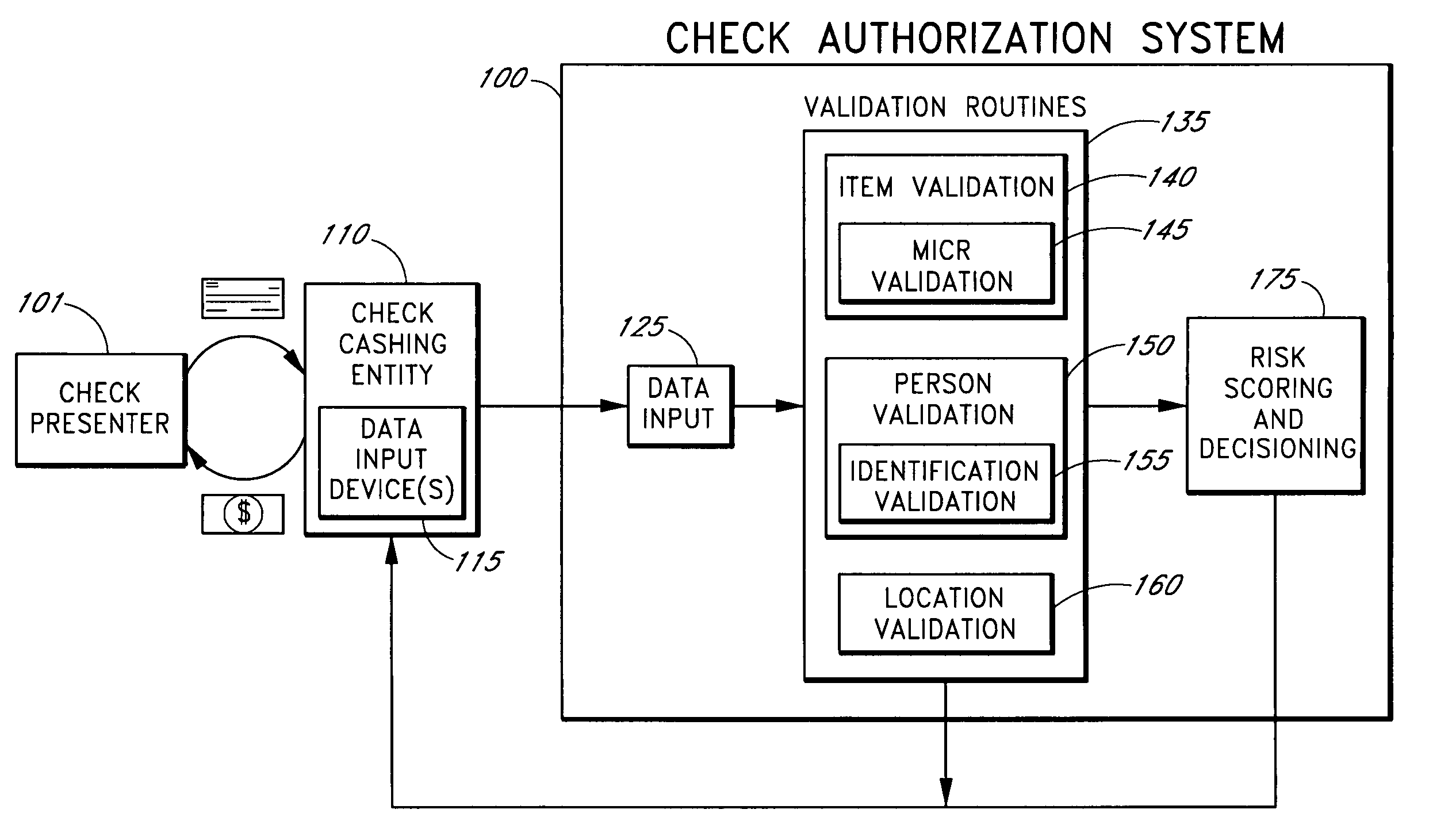
Systems and methods for obtaining authentication marks at a point of sale
InactiveUS20050125360A1Accurate descriptionSlow processPaper-money testing devicesPoint-of-sale network systemsBarcodeCheque
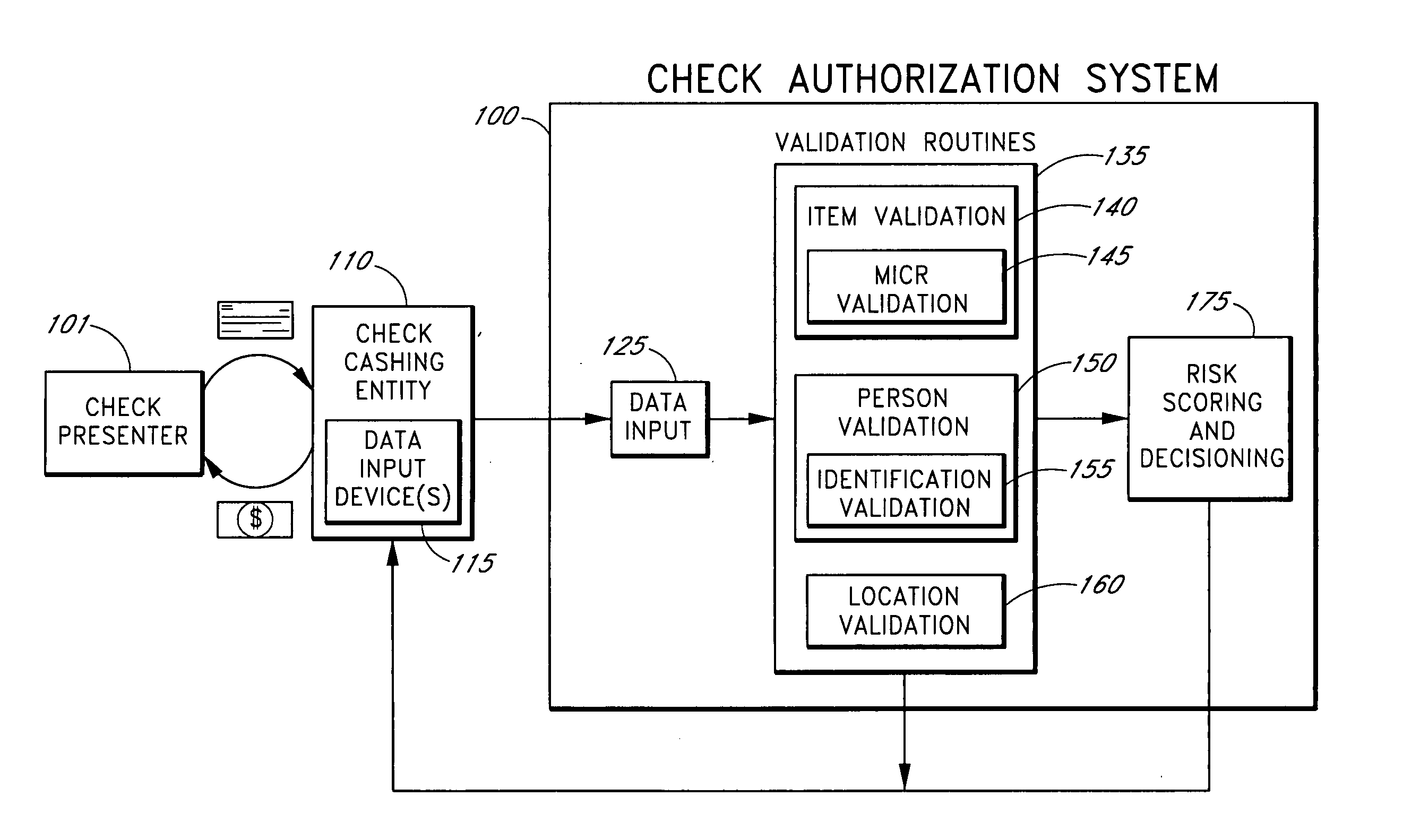
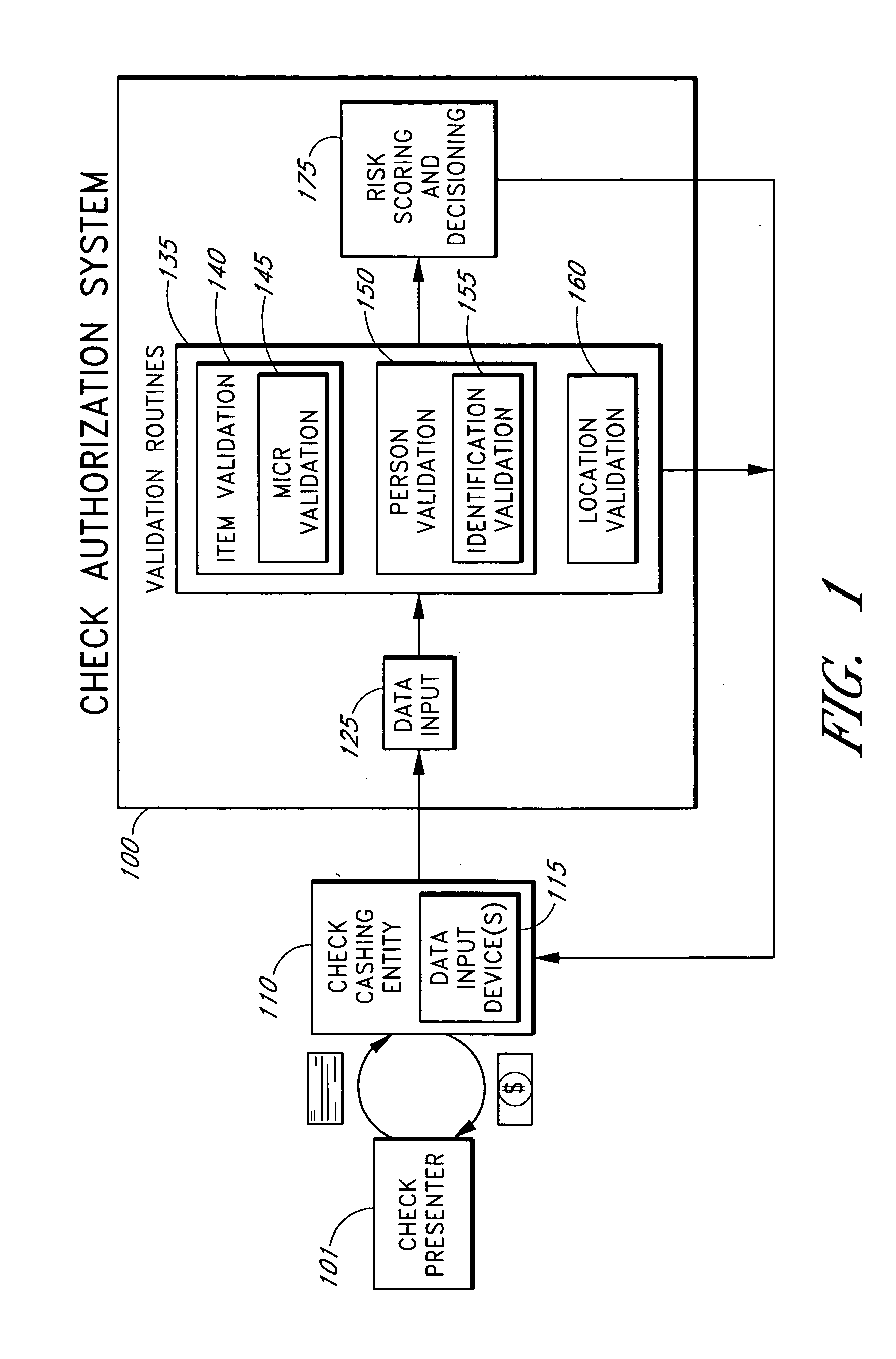
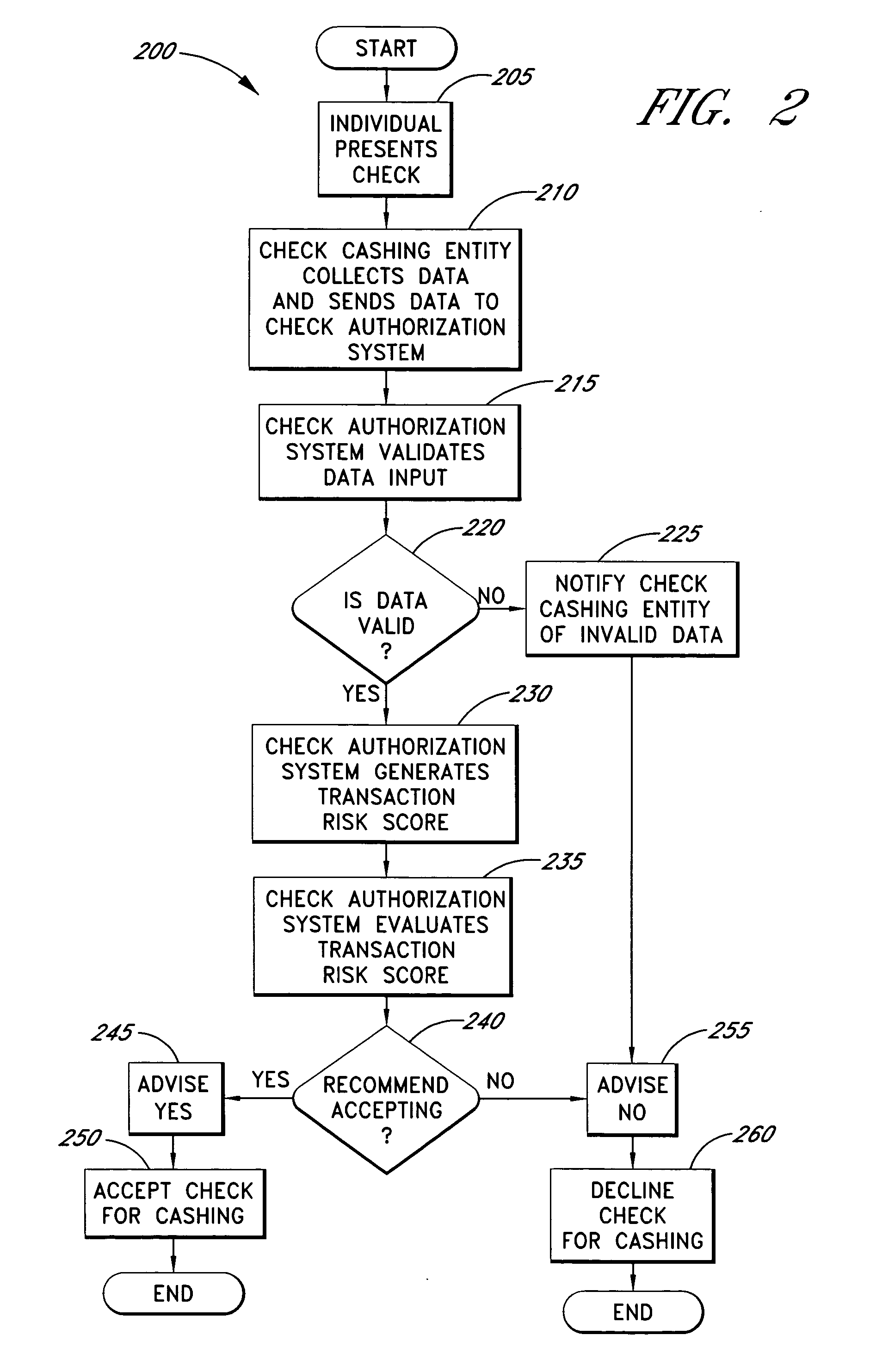
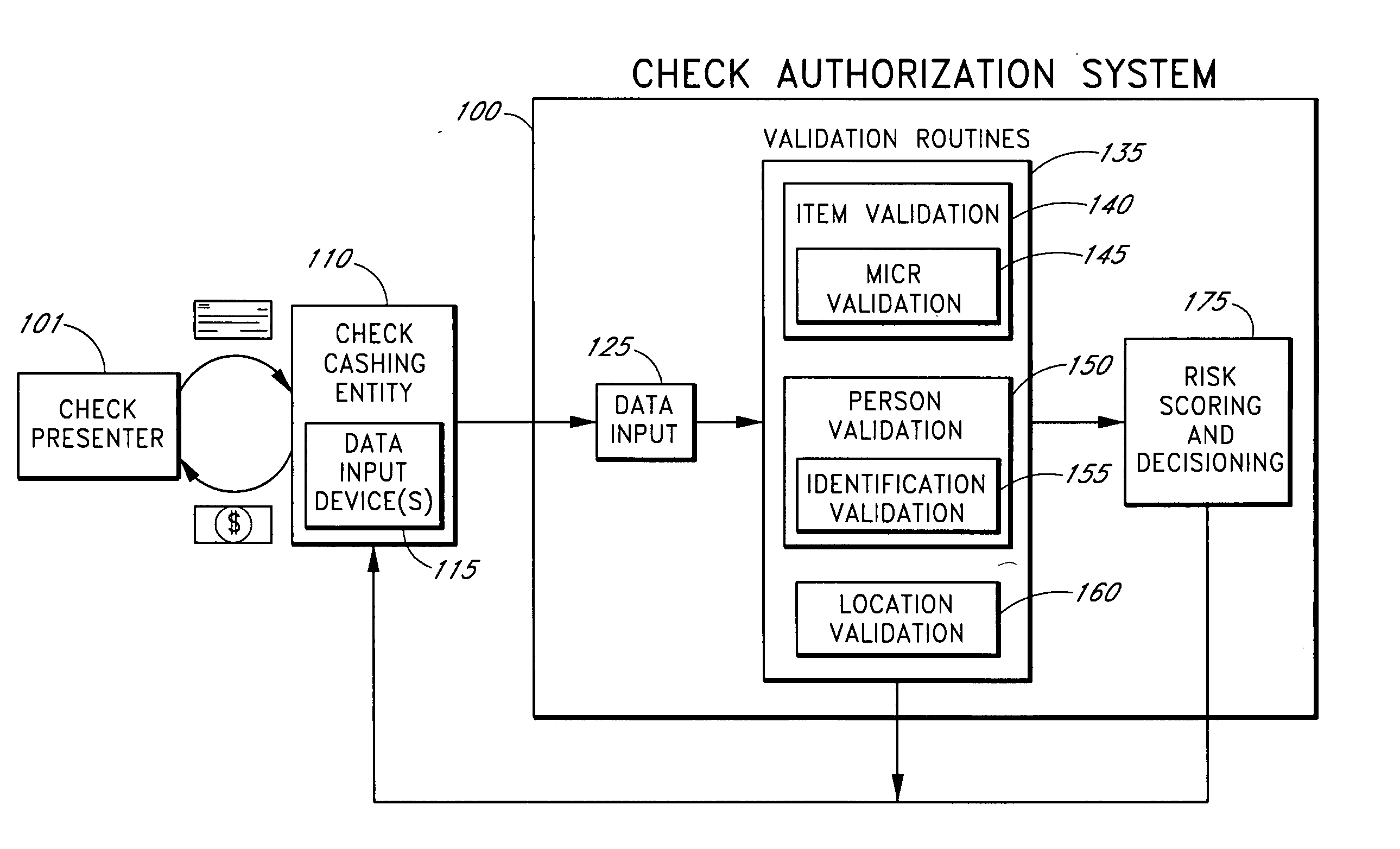
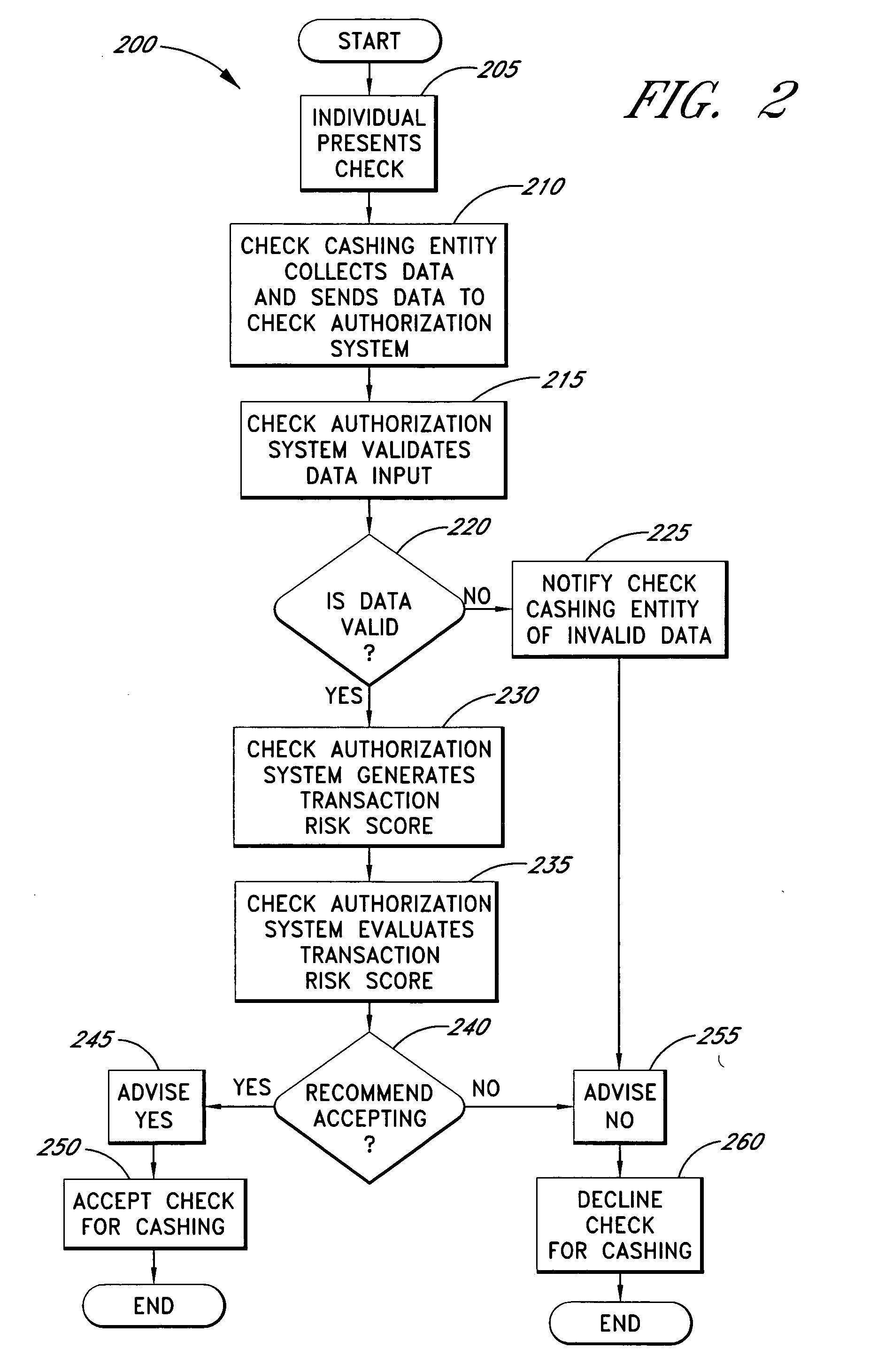
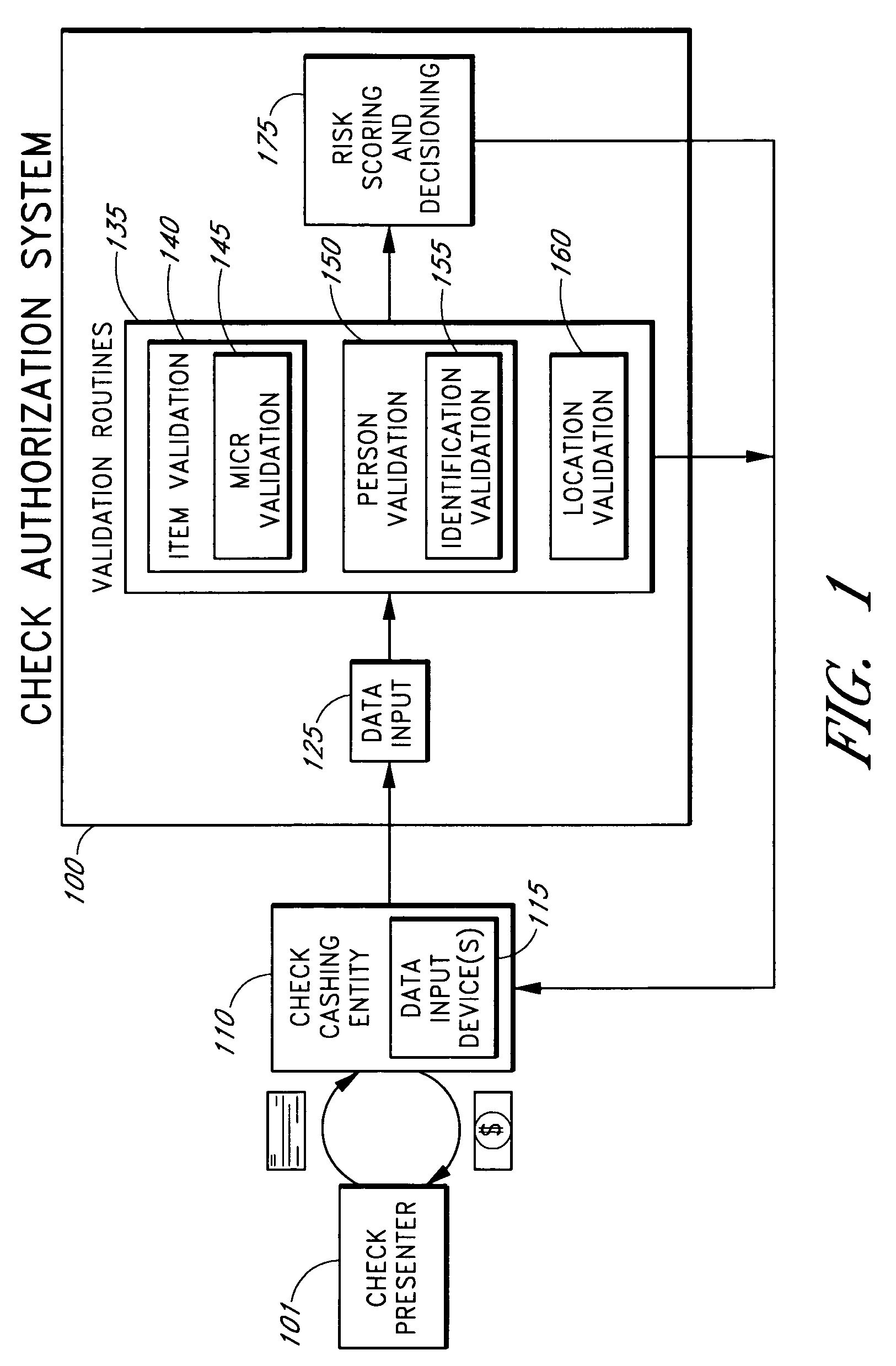
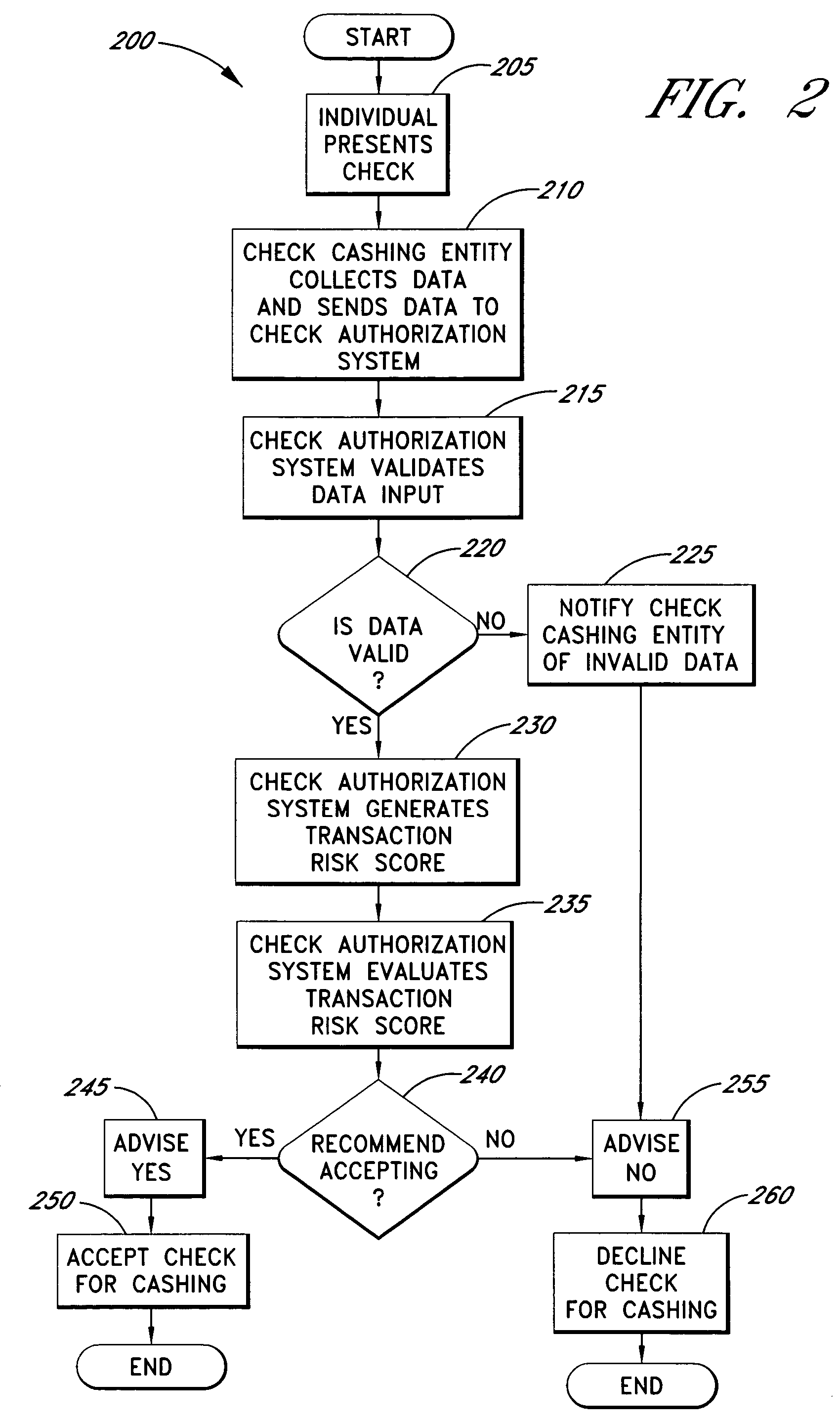
Systems and methods are described for using a point-of-sale device at a check-cashing entity to obtain information about one or more authenticating marks, such as watermarks, bar codes, background patterns, color schemes, insignia, security validation numbers, or the like, from a second-party check or other negotiable instrument presented for a proposed check-cashing transaction. In various embodiments, the authenticating mark information may be compared to stored information about expected configurations of authenticating marks as part of a risk assessment of the check. In various embodiments, the point-of-sale device transmits authenticating mark information to a check authorization system. The point-of-sale device may receive an accept / decline recommendation for the transaction from the check authorization system, based at least in part on the obtained authenticating mark information. The point-of-sale device may display a message about the recommendation to an operator of the device.
Owner:FIRST DATA
Systems and methods for assessing the risk of a financial transaction using reconciliation information
InactiveUS20050125338A1Accurate descriptionSlow processFinancePayment architectureChequeFinancial transaction
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments using positive pay or other reconciliation information about a check presented for cashing. Positive pay information, which may be made available by a check issuer, provides a list of checks that have been, for example, issued and not yet cashed, already cashed, voided, stolen, and the like, thus providing an indication of whether the check issuer is willing to honor the checks. In various embodiments, positive pay information about a check may be expressed as a gradated positive pay risk score. In various embodiments, the positive pay risk score may be combined with risk scores that are descriptive of other aspects of the check cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the risk scores may be used to generate an accept / decline recommendation for the transaction as a whole.
Owner:FIRST DATA
Systems and methods for assessing the risk of a financial transaction using biometric information
ActiveUS20050125339A1Accurate descriptionAccurate transactionFinancePayment architectureConfidence metricFinancial transaction
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments by using biometric information obtained from an individual who presents a check or other negotiable instrument in a check-cashing transaction. In various embodiments, the obtained biometric information may be compared with stored biometric information in order to enhance confidence in the accurate identification of the check presenter. In various embodiments, a gradated biometric risk score, based at least in part on the comparison, may be generated for the check-cashing transaction. In various embodiments, the biometric risk score may be combined with risk scores that are descriptive of other aspects of the check-cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the risk scores may be used to generate an accept / decline recommendation for the transaction as a whole.
Owner:FIRST DATA
Systems and methods for assessing the risk of financial transaction using geographic-related information
InactiveUS20050125350A1Accurate descriptionSlow processComplete banking machinesFinancePosition dependentCheque
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments. The systems and methods make use of location-related information about an issuer of a second-party check being presented for cashing in order to better assess the legitimacy and cashability of the check. In various embodiments, information about the proximity of the check issuer to the check cashing location is used to enhance risk assessment of the check item. In various embodiments, location-based information about a check may be expressed as a gradated location-based risk score. In various embodiments, the location-based risk score may be combined with risk scores that are descriptive of other aspects of a check cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the risk scores may be used to generate an accept / decline recommendation for the transaction.
Owner:FIRST DATA
Systems and methods for obtaining payor information at a point of sale
InactiveUS20050125295A1Slow processKeep their service fees lowPaper-money testing devicesPoint-of-sale network systemsBank accountCheque
Systems and methods are described for using a point-of-sale device to obtain information about a payor of a second-party check or other negotiable instrument presented for a proposed check-cashing transaction. In various embodiments, a keyboard, touchscreen, voice input system or other input system is used to enter information about a payor of a second-party check, which may comprise, for example, payor name, payor bank account identifier, payor location information, and the like. The payor information may be used to determine the proximity of the payor to the location of the proposed check-cashing transaction. In various embodiments, the point-of-sale device transmits the payor information to a check authorization system for a risk assessment of the transaction. In some embodiments, the point-of-sale device may prompt an operator or a check presenter to enter payor information in response to a request from the check authorization system. In various embodiments, the point-of-sale device may receive an accept / decline recommendation for the transaction from the check authorization system, based at least in part on the obtained payor information.
Owner:FIRST DATA
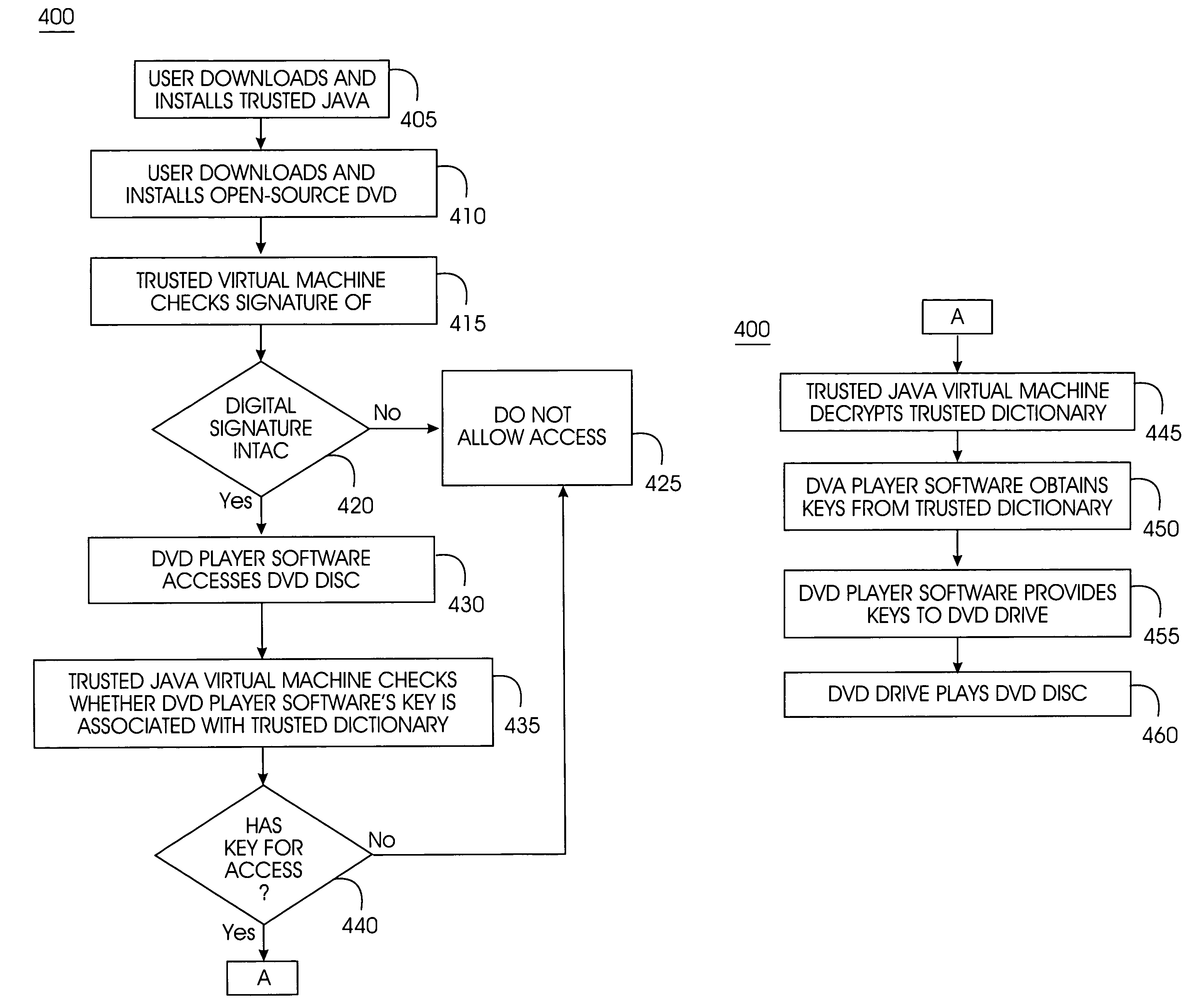
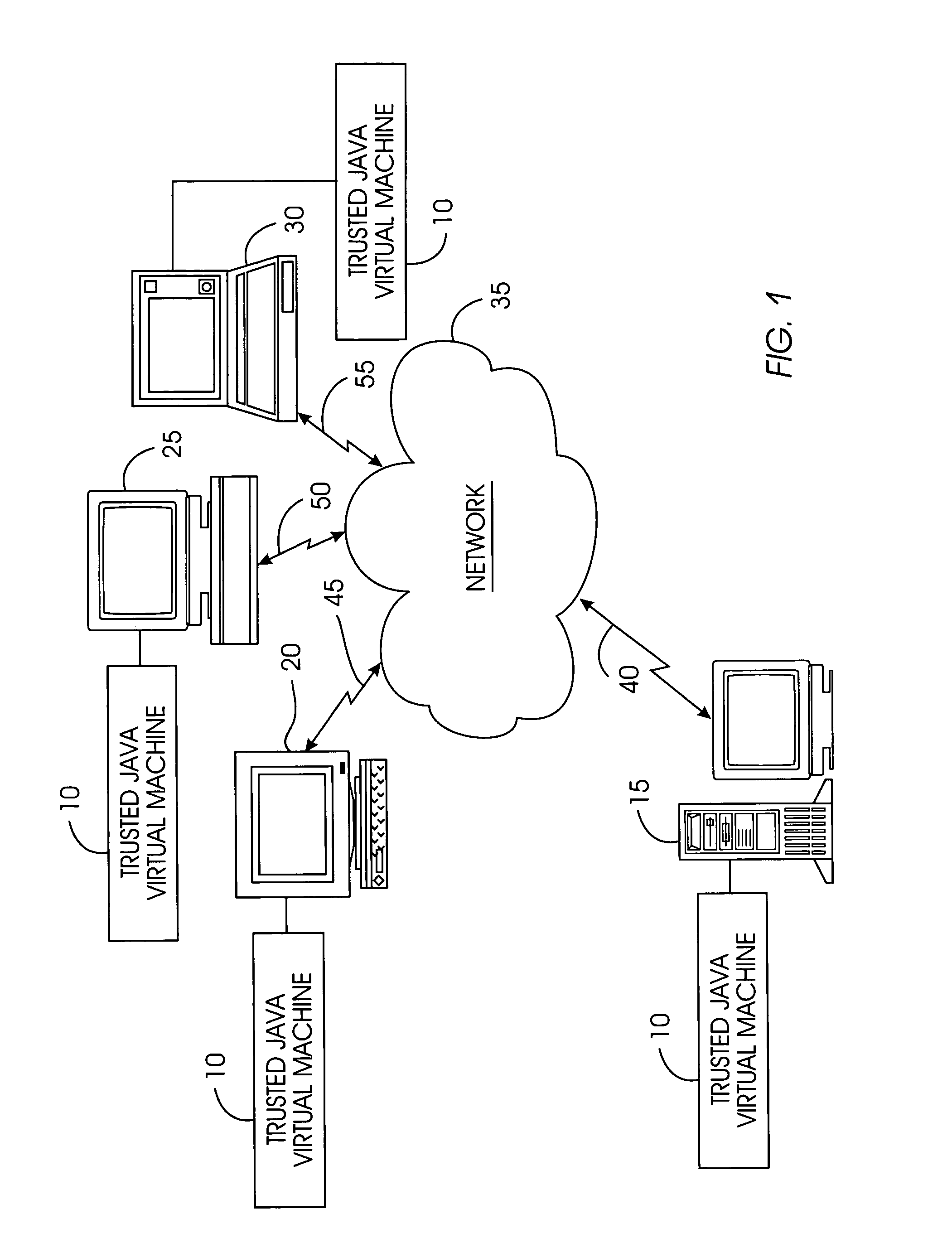
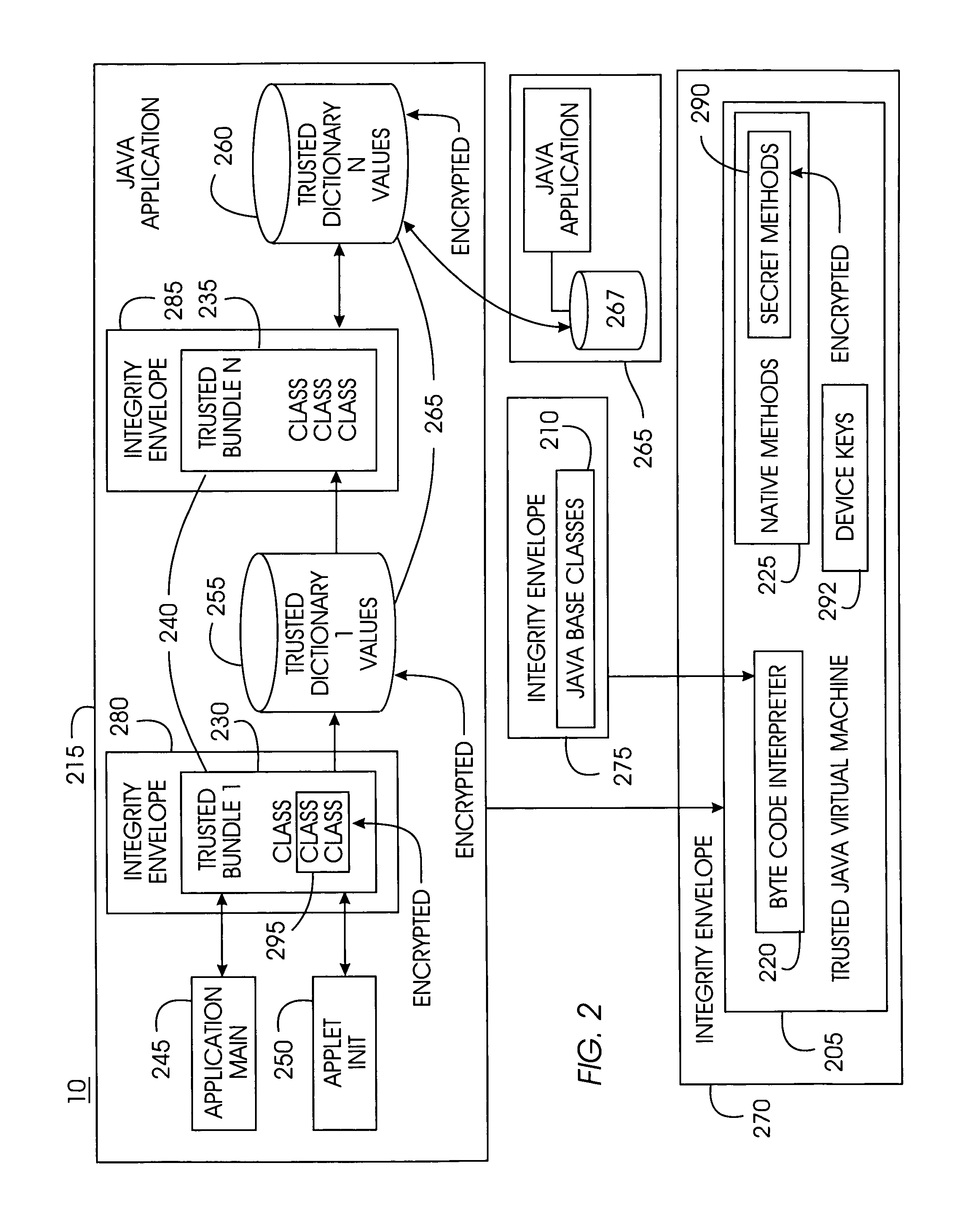
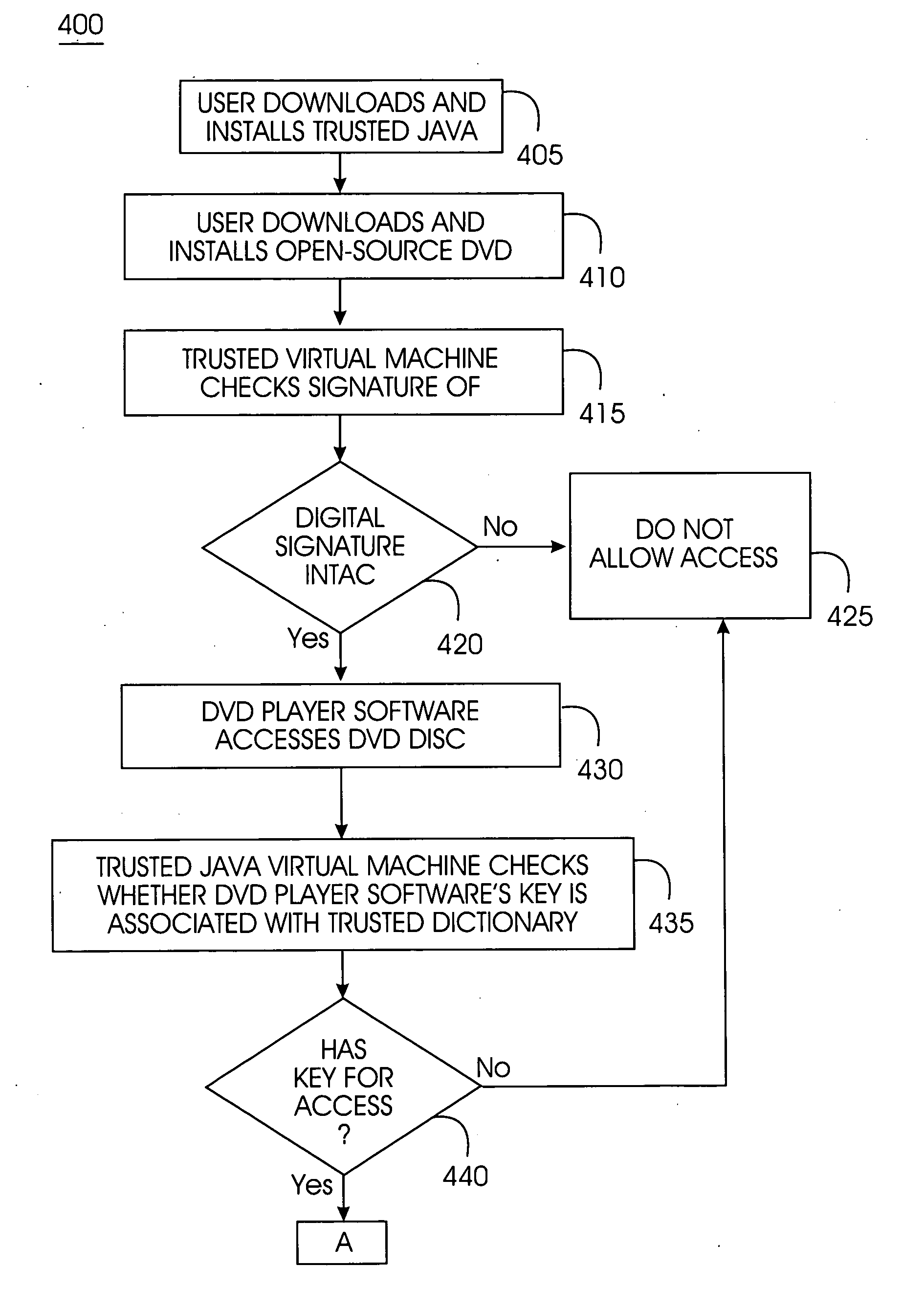
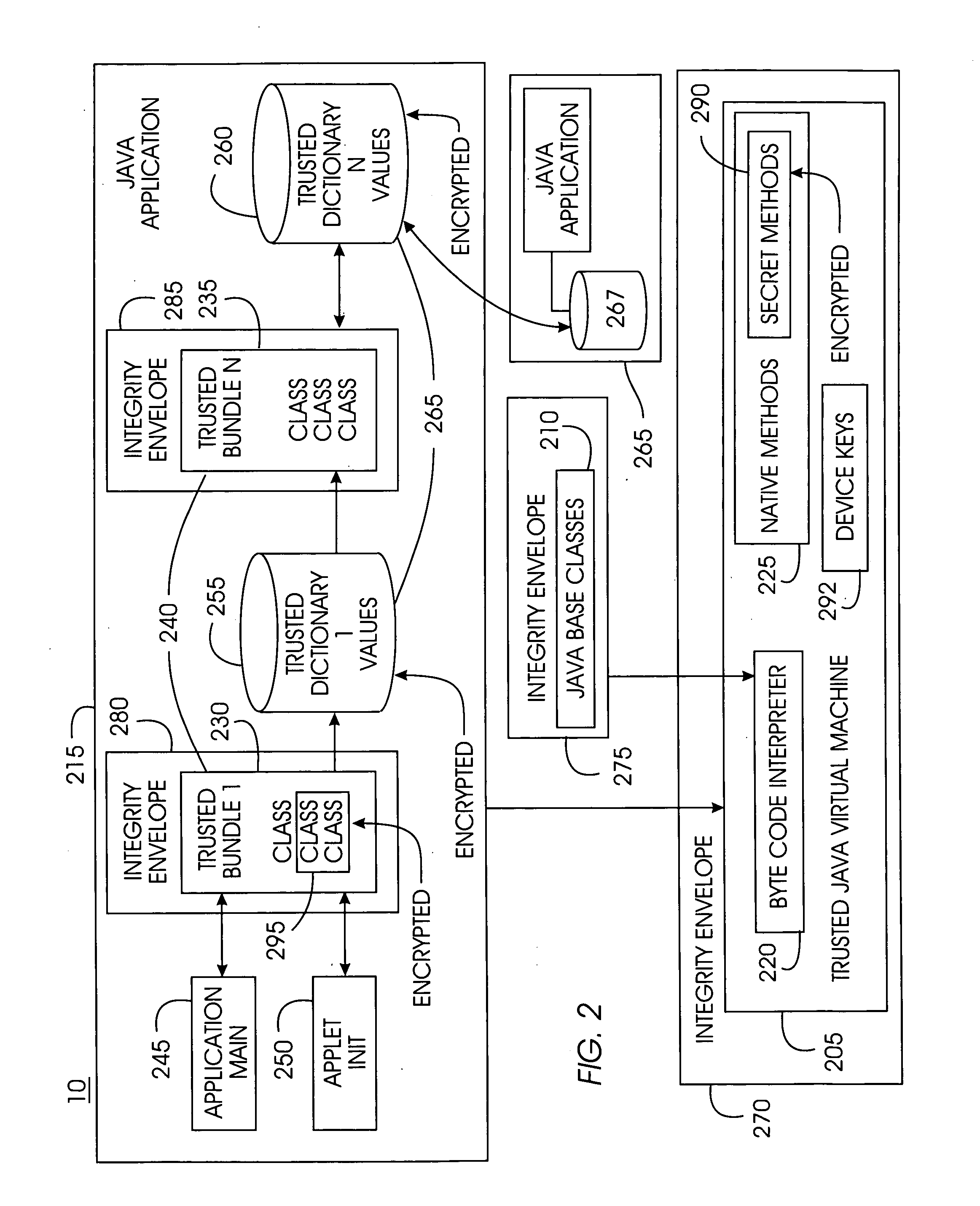
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
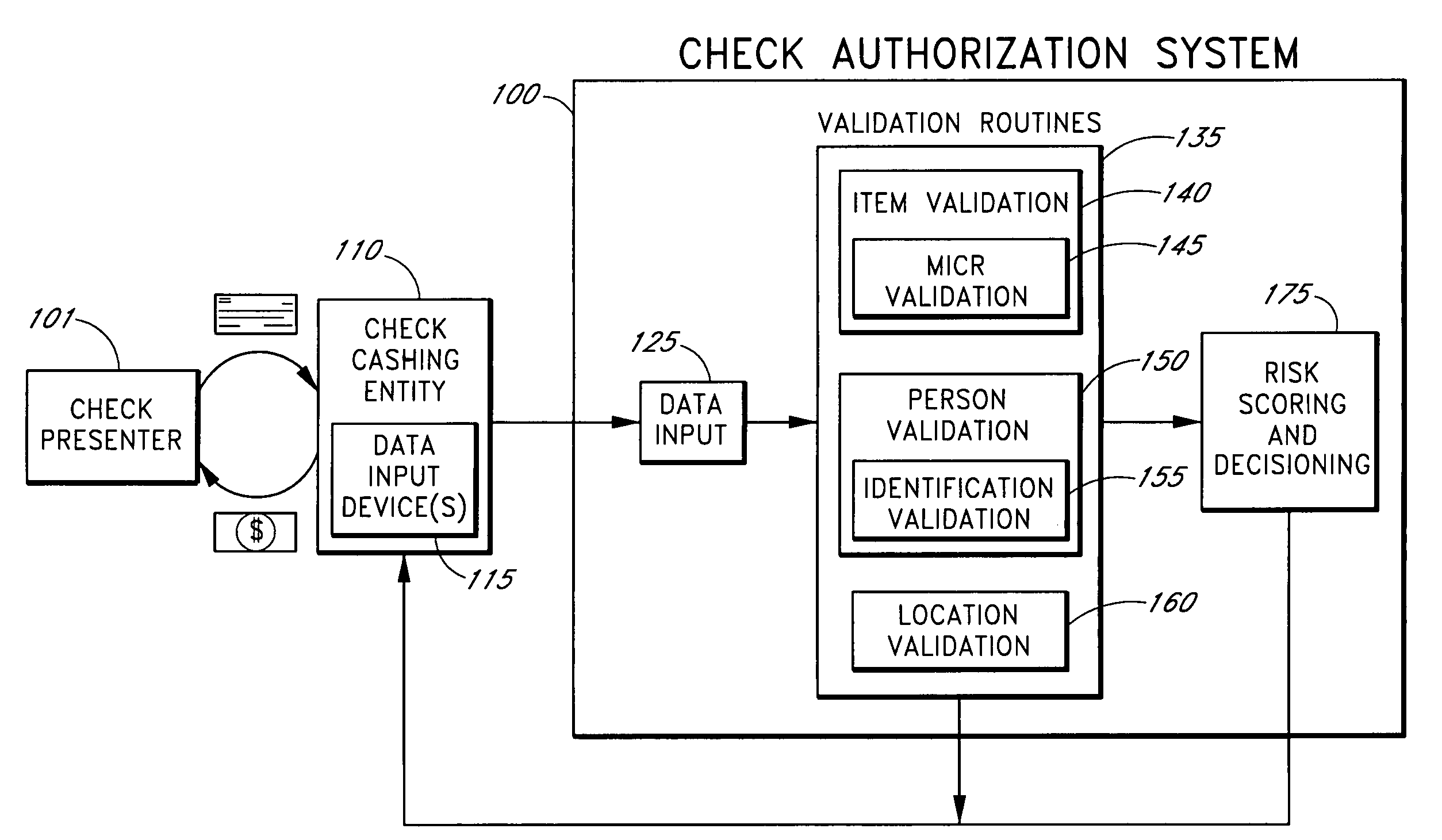
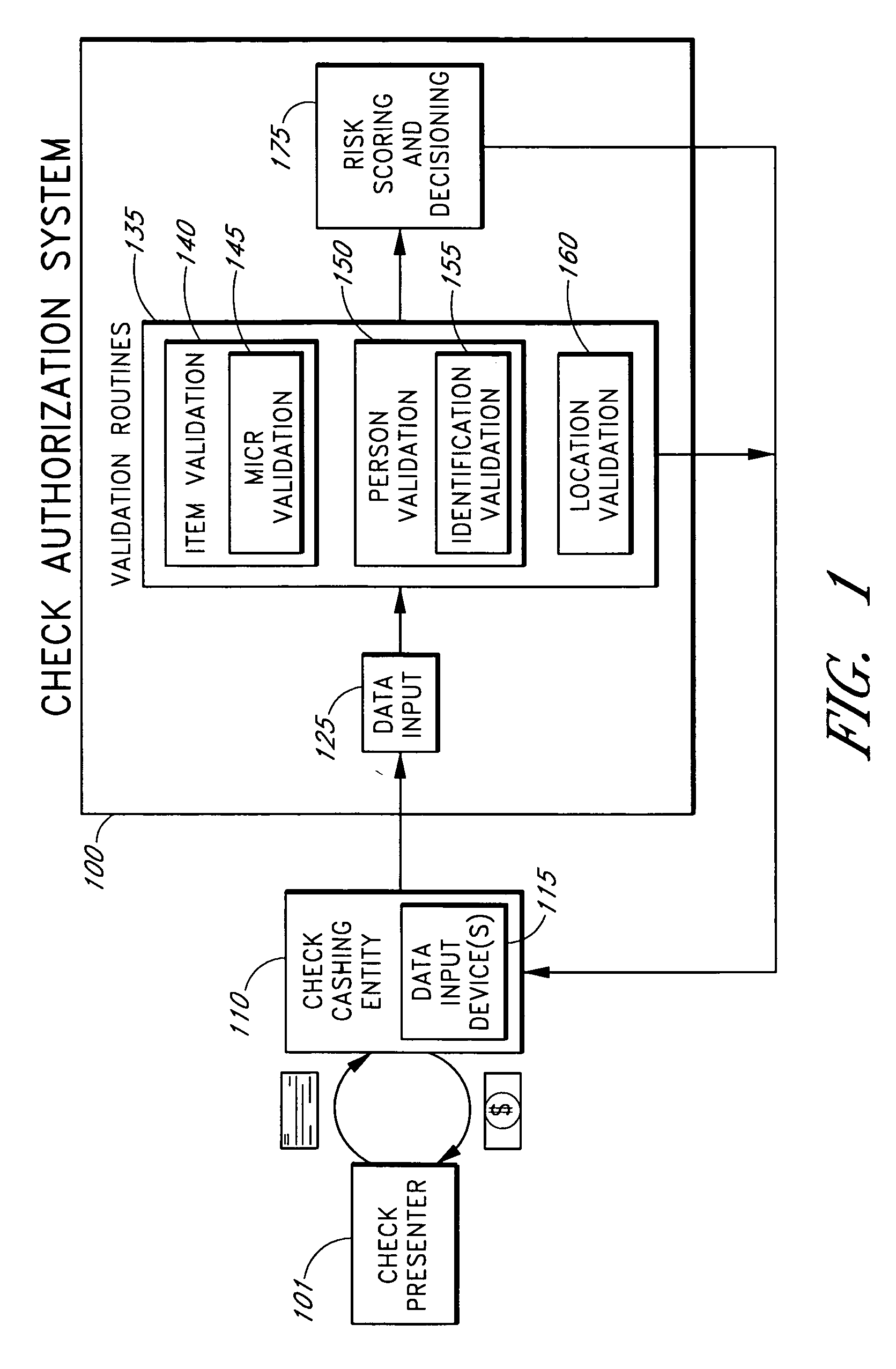
Systems and methods for identifying payor location based on transaction data
Systems and methods are described for building, maintaining, and using a repository of information about payors of second-party checks presented at a check-cashing entity for cashing. In various embodiments, the repository comprises stored information useful for determining the location of a payor of a second-party check. In one embodiment, information from the check that identifies an account on which the check is drawn, such as magnetic ink character recognition (MICR) line information from a paycheck, is used to access a repository of employer location information. In one embodiment, the payor location information is used to determine a proximity between the payor location and the check cashing entity location. In one embodiment, when a check is presented for which stored payor location information is not available, identifying information about the payor and / or the payor location is requested and is added to the repository.
Owner:FIRST DATA
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS20050114683A1Easy to processSatisfies needProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:IBM CORP
Systems and methods for obtaining biometric information at a point of sale
InactiveUS20050125296A1Accurate descriptionSlow processPaper-money testing devicesPoint-of-sale network systemsBiometric dataCheque
Systems and methods are described for using a point-of-sale device to obtain biometric information from an individual presenting a second-party check in association with a proposed check-cashing transaction. In various embodiments, a biometric sample is obtained from the check presenter and is compared to stored biometric data in order to enhance an assessment of the correct identification of the check presenter. In various embodiments, the biometric information, along with other transaction-related information, such as information about one or more authentication marks from the check, is transmitted to a check authorization system for a risk assessment of the transaction. In various embodiments, the point-of-sale device may receive an accept / decline recommendation from the check authorization system, based at least in part on the biometric information and may display a message about the recommendation to an operator of the point-of-sale device.
Owner:THE WESTERN UNION CO +1
Systems and methods for assessing the risk of a financial transaction using authenticating marks
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments. The systems and methods make use of information about authenticating marks, such as watermarks, bar codes, insignia, background patterns, and the like, from a check in order to better assess the legitimacy and cashability of the check. In various embodiments, information about an authenticating mark may be compared to stored information about an expected configuration for the authenticating mark. In various embodiments, a gradated risk score may be generated, based at least in part on the comparison. In various embodiments, the risk score may be combined with risk scores that are descriptive of other aspects of a check cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the transaction risk score may be used to generate an accept / decline recommendation for the transaction.
Owner:FIRST DATA
Systems and methods for assessing the risk of a financial transaction using biometric information
ActiveUS7398925B2Accurate descriptionAccurate transactionFinancePayment architectureConfidence metricCheque
Owner:FIRST DATA
Electronic bill presentment and payment system
InactiveUS20050060261A1Minimizing and eliminating opportunitySlow processFinanceBilling/invoicingAuthorizationElectronic network
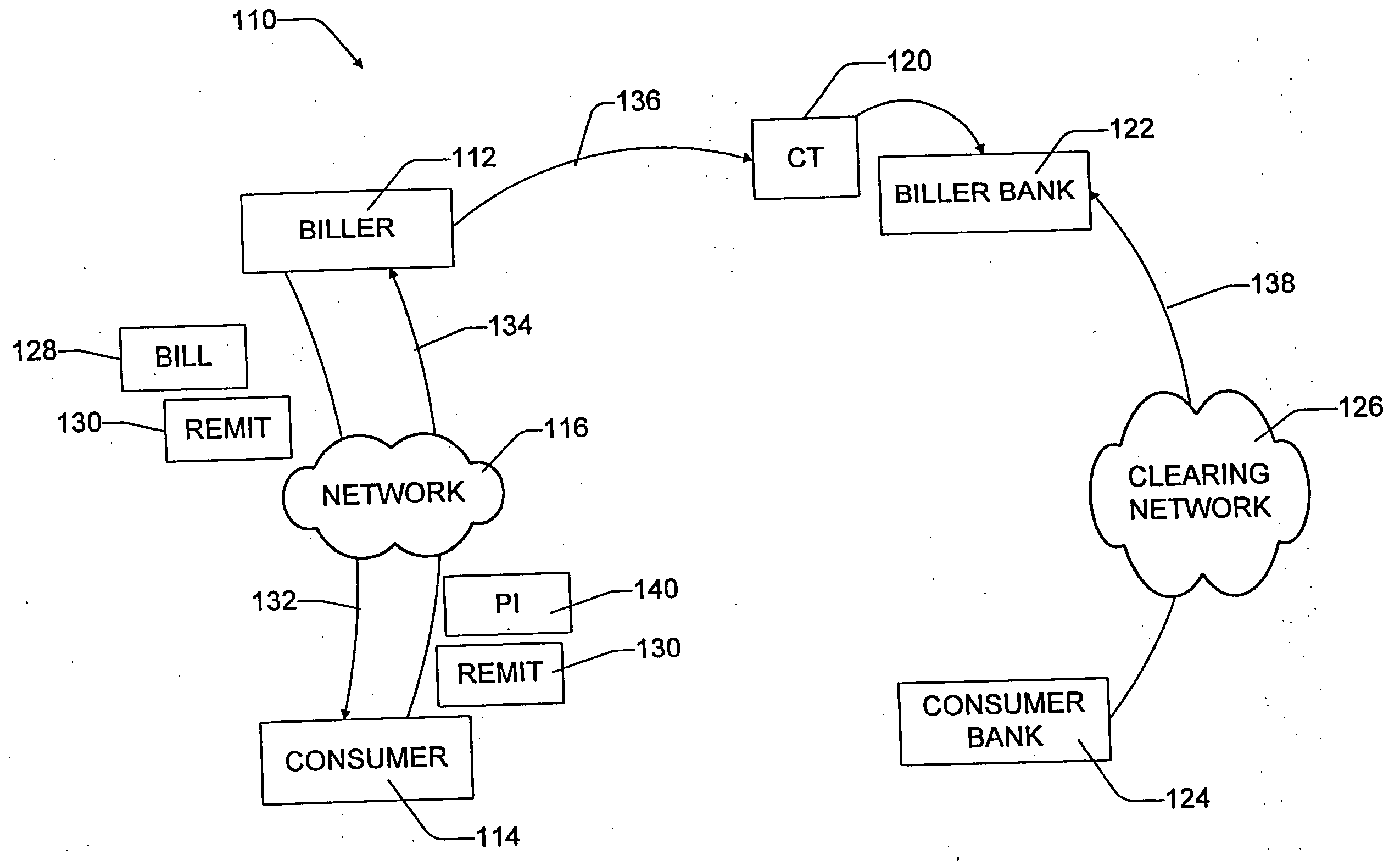
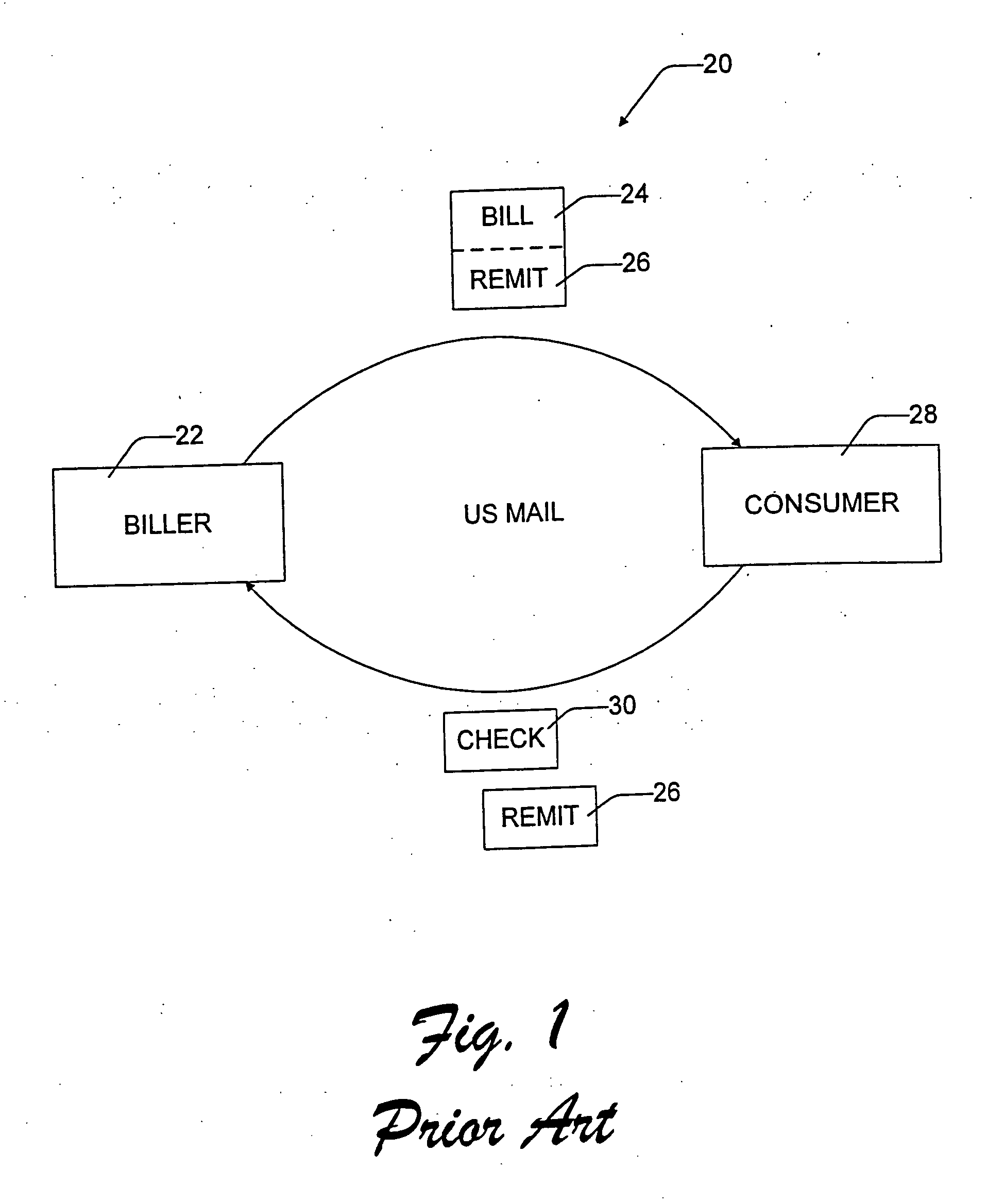
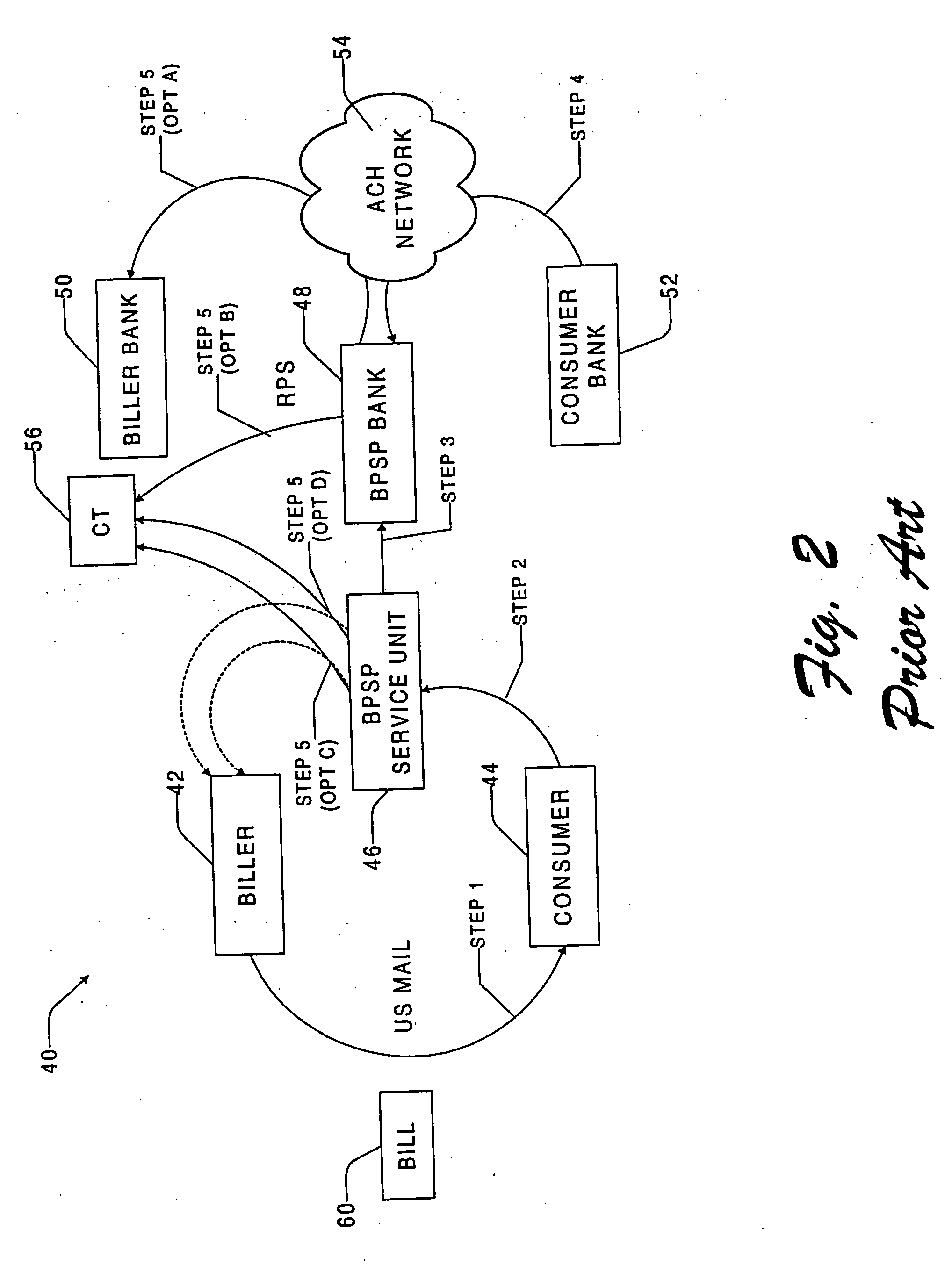
A bill presentment and payment remittance system is configured for use over an electronic network, such as the Internet. The bill presentment and payment remittance system allows the biller to create a bill and payment remittance information in a format specified by the biller. The biller submits the bill and associated payment remittance information by electronically transmitting it over the Internet to the consumer. The consumer authenticates that the bill did indeed come from the indicated biller. The bill is presented in a user interface which provides a line-by-line itemization of the bill, along with a predefined dispute reasons which the consumer can check to challenge particular items on the bill. The bill can then be automatically or manually adjusted to reflect any disputed amounts. Payment of the bill is preferably in the form of a “direct debit check” that is formed by the consumer software using the billing and remittance information provided in the bill to automatically name the biller as the payee. The consumer completely controls the payment authorization, specifying the amount to be paid (either partial or full), and the date for the payment to be made, and the account from which the money will be drawn. The electronic payment and any dispute criteria are associated with the payment remittance information. The payment instruction and remittance information are then transmitted in the biller prescribed format back over the Internet to the biller. In this manner, the payment remittance information is automatically returned directly to the biller in the format that the biller chooses, without intervention by the consumer. The biller executes the payment instructions sent to it electronically by the consumer by sending them onto the biller's bank.
Owner:MICROSOFT TECH LICENSING LLC
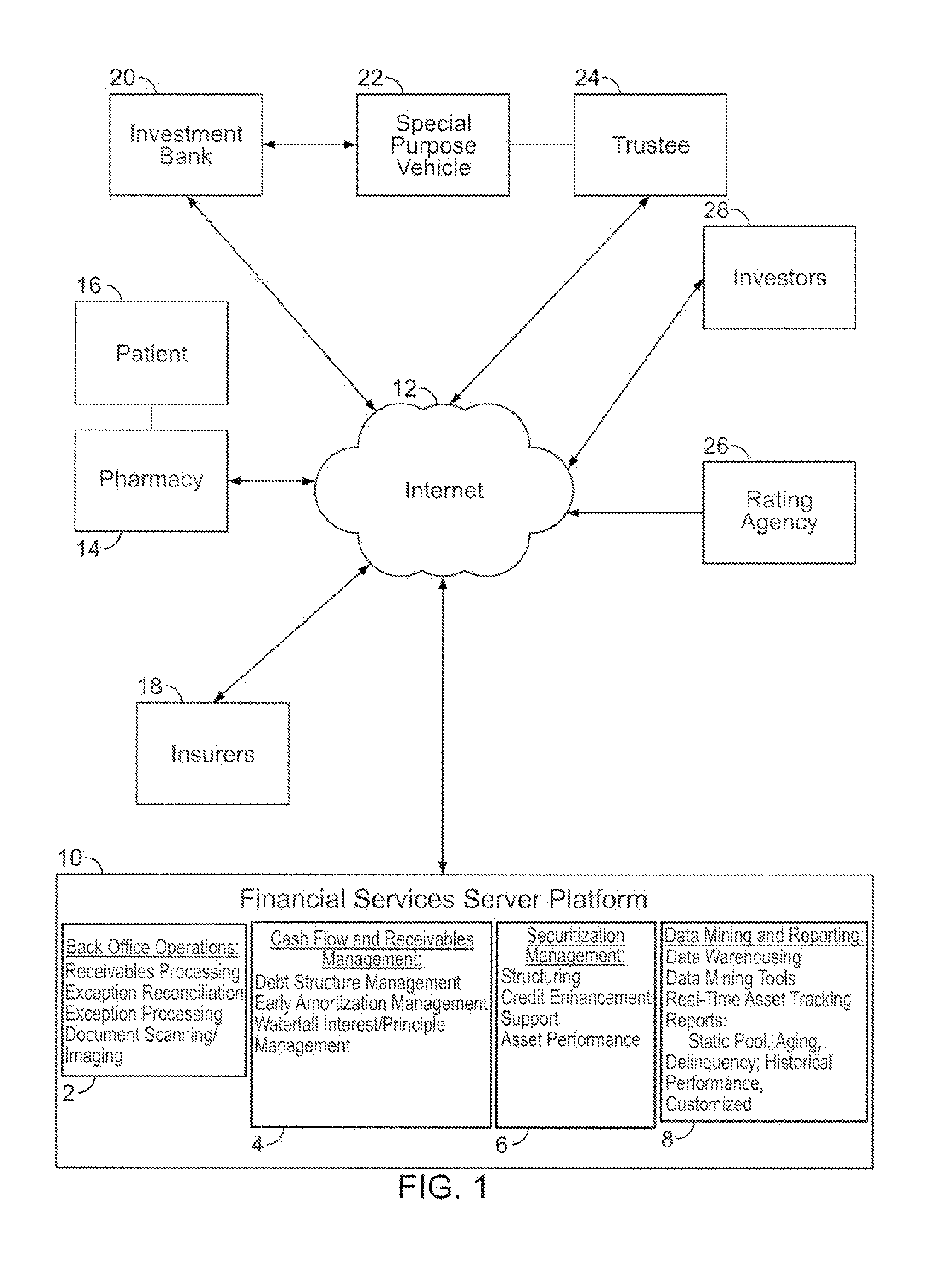
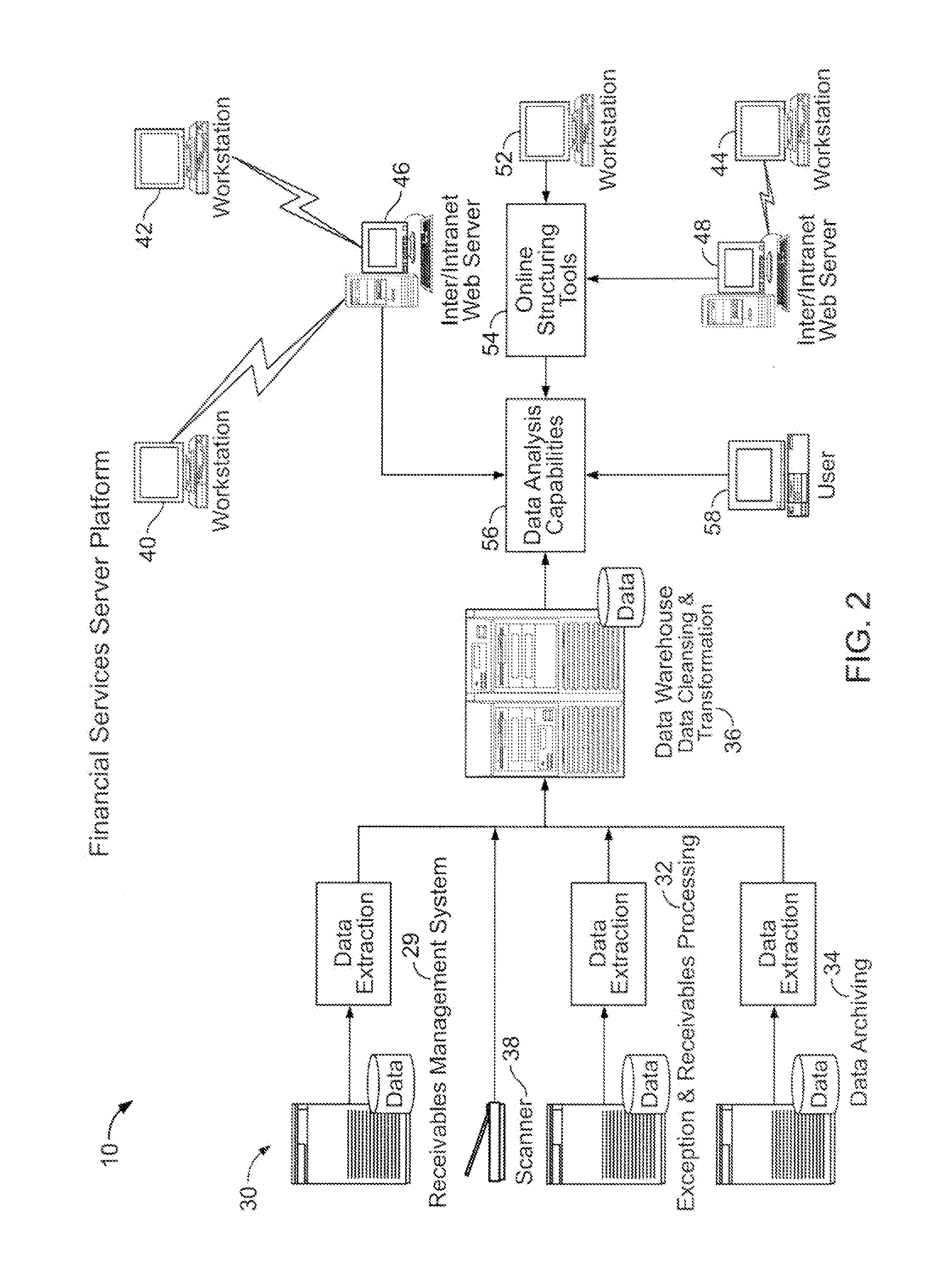
Segregation and management of financial assets by rules
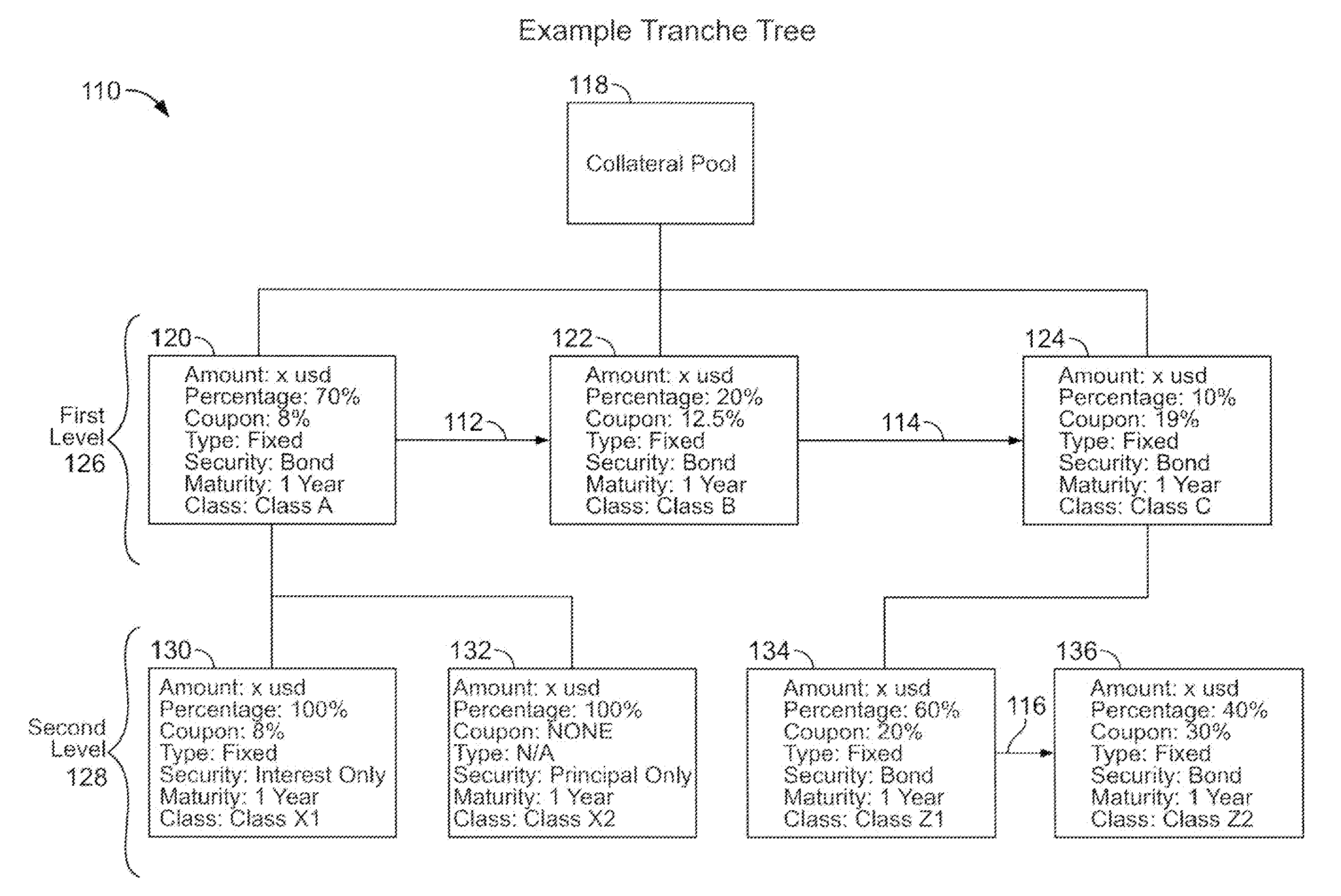
The invention supports the management of financial assets such as accounts receivable or mortgages. The invention provides a facility for a user to define rules to segregate assets into pools, define purchasing rules, capture real time information regarding transactions, reconcile payments and produce exception reports, define access rules for individual users to see information relating to pools of assets and individual assets within a pool, and provide customized reports and access to asset details over a network. Abstract representations of financial assets are used to obtain instances of defined financial-asset object classes to define pools of financial assets with common abstract characteristics. The invention uses a tree structured representation of asset classes for allocation of transactions to tranches and sub-tranches of assets within a pool. A user may define custom tranches and sub-tranches, as well as design pools of assets to an investment rating specification in advance.
Owner:TRANQUILMONEY
Systems and methods for assessing the risk of a financial transaction using authenticating marks
Systems and methods are described for better assessing risk associated with cashing second-party checks and other negotiable instruments. The systems and methods make use of information about authenticating marks, such as watermarks, bar codes, insignia, background patterns, and the like, from a check in order to better assess the legitimacy and cashability of the check. In various embodiments, information about an authenticating mark may be compared to stored information about an expected configuration for the authenticating mark. In various embodiments, a gradated risk score may be generated, based at least in part on the comparison. In various embodiments, the risk score may be combined with risk scores that are descriptive of other aspects of a check cashing transaction to calculate a risk score for the transaction as a whole. In some embodiments, the transaction risk score may be used to generate an accept / decline recommendation for the transaction.
Owner:FIRST DATA
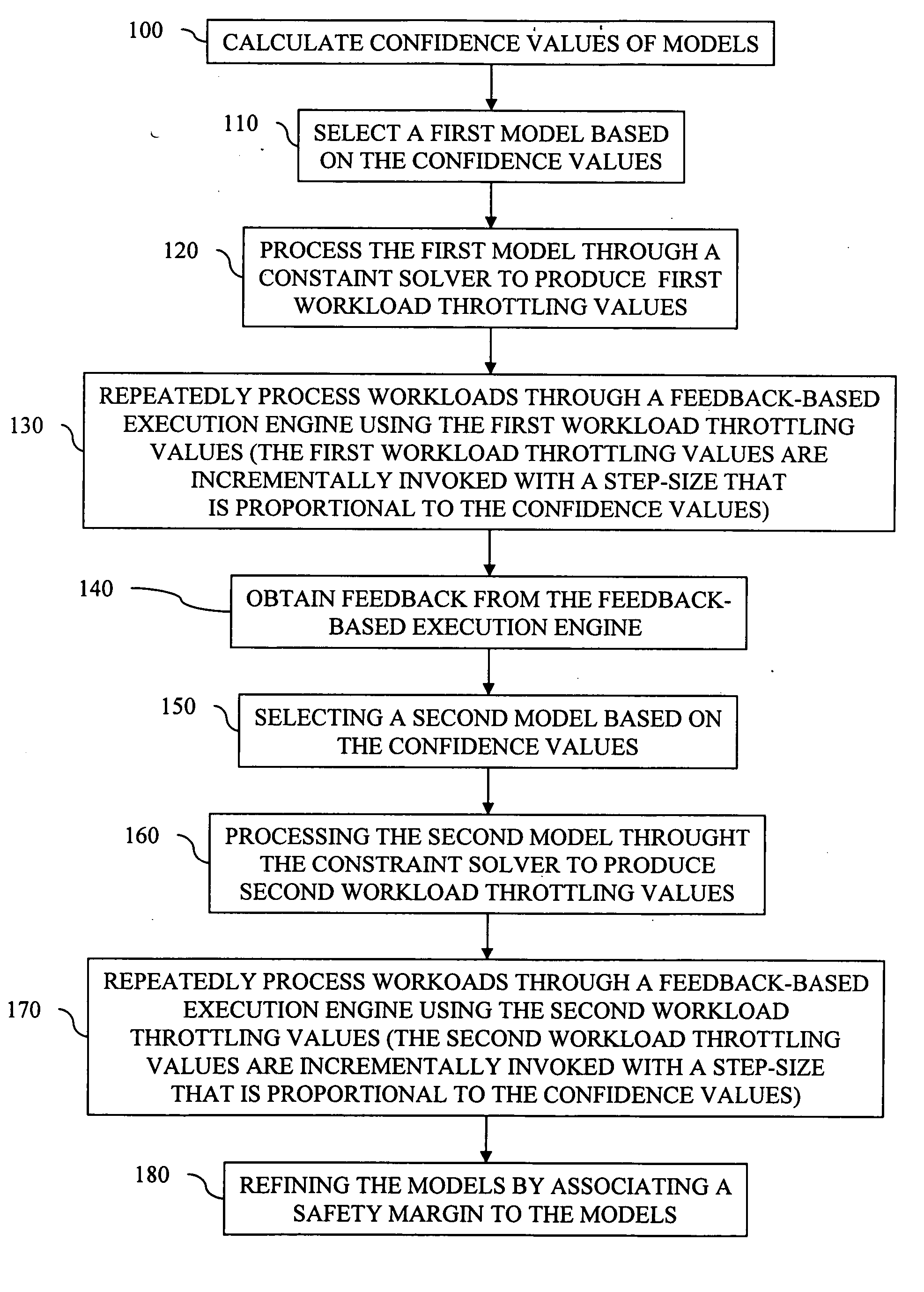
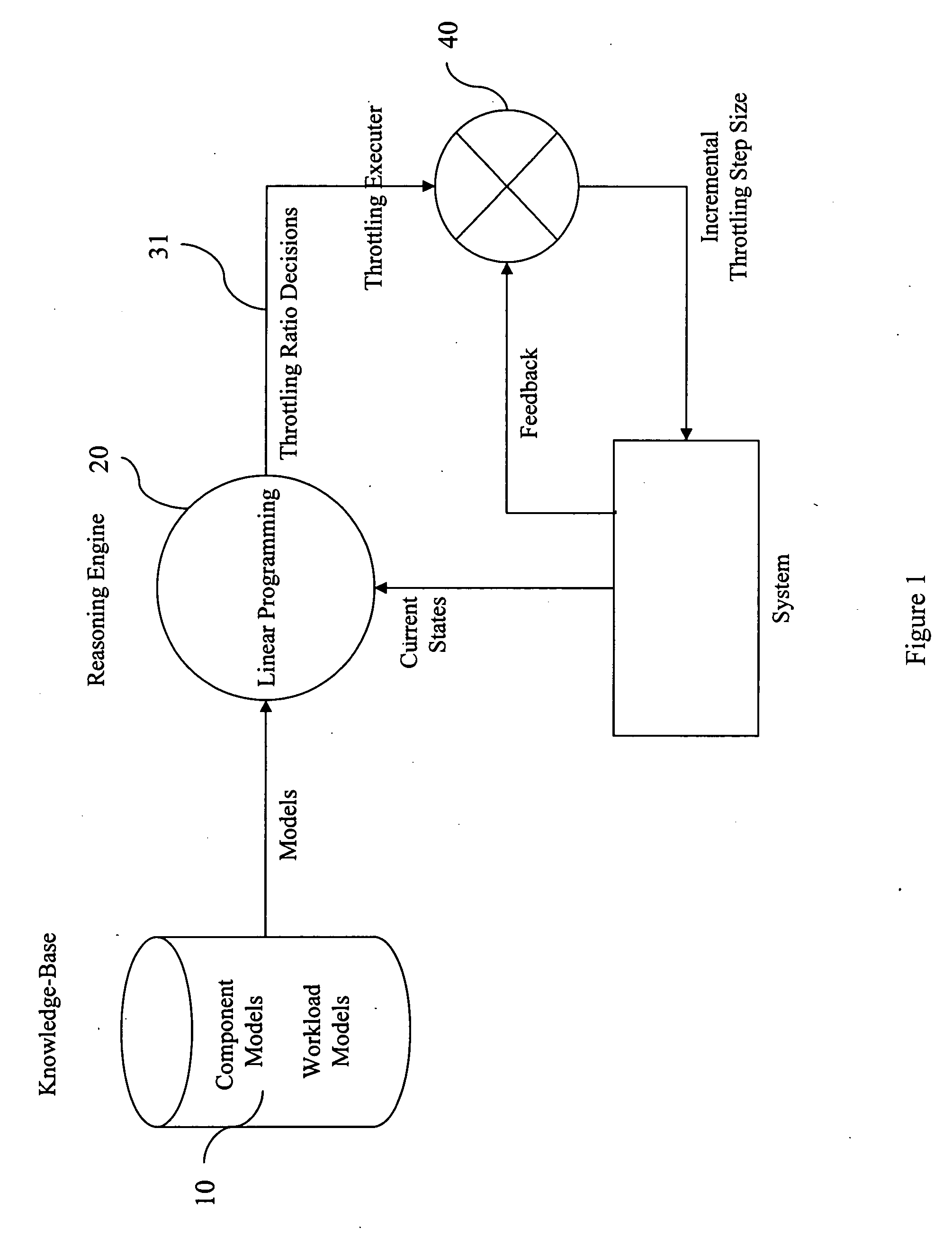
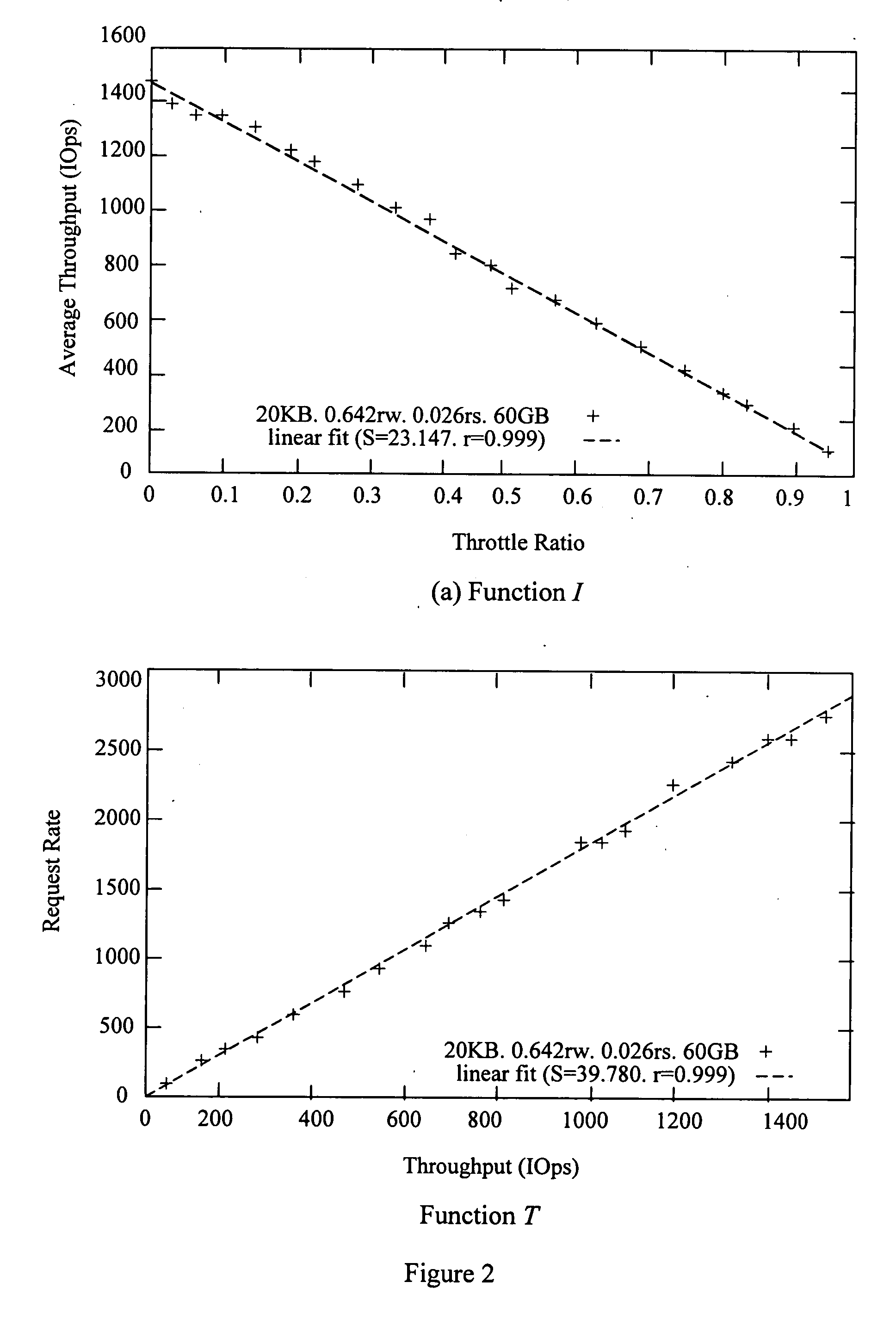
Self-modulation in a model-based automated management framework
InactiveUS20070088532A1Slow processHigh accuracySimulator controlDigital computer detailsComputational modelHybrid system
Embodiments herein present a method, system, computer program product, etc. for automated management using a hybrid of prediction models and feedback-based systems. The method begins by calculating confidence values of models. Next, the method selects a first model based on the confidence values and processes the first model through a constraint solver to produce first workload throttling values. Following this, workloads are repeatedly processed through a feedback-based execution engine, wherein the feedback-based execution engine is controlled by the first workload throttling values. The first workload throttling values are applied incrementally to the feedback-based execution engine, during repetitions of the processing of the workloads, with a step-size that is proportional to the confidence values. The processing of the workloads is repeated until an objective function is maximized, wherein the objective function specifies performance goals of the workloads.
Owner:GLOBALFOUNDRIES INC
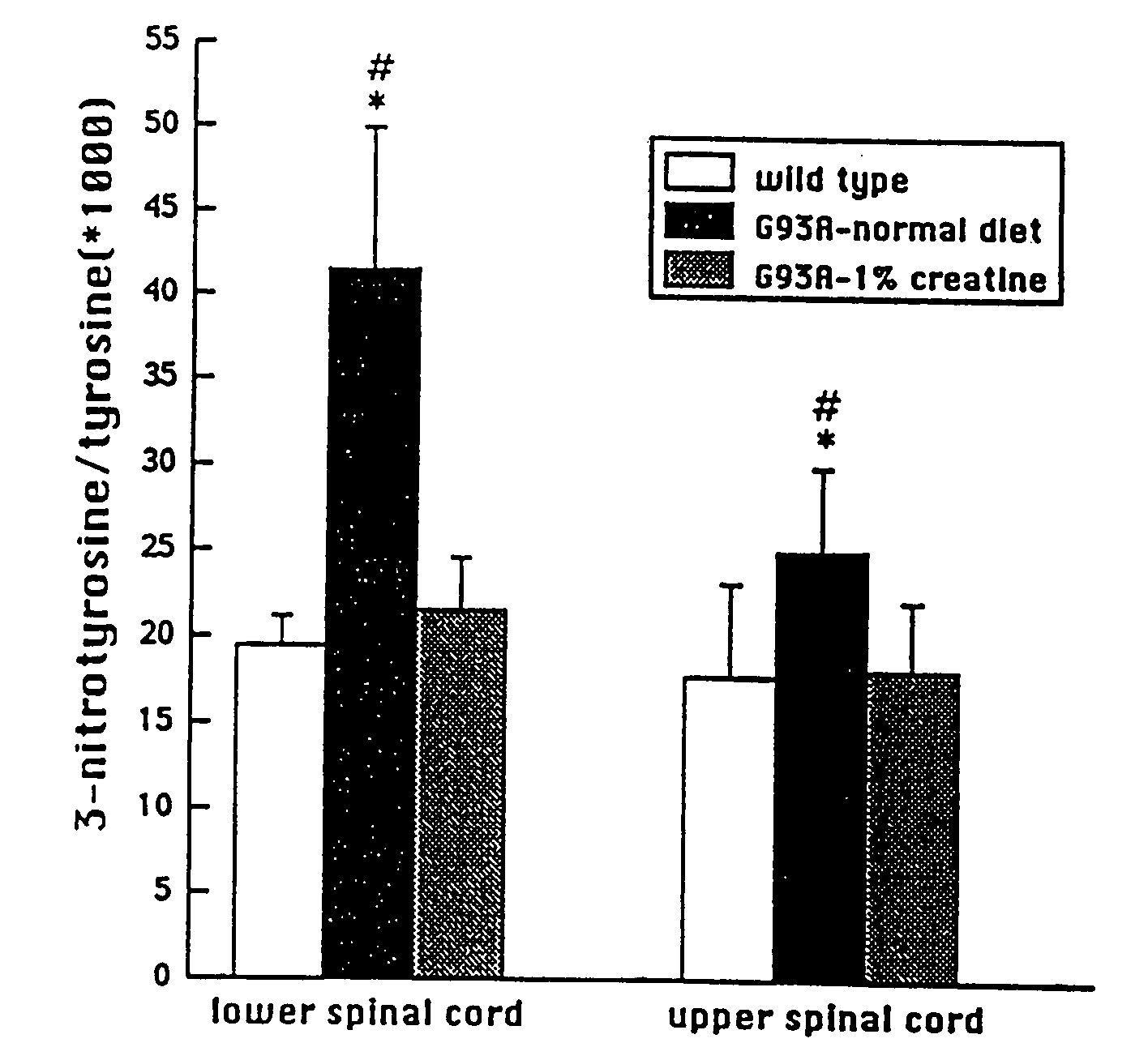
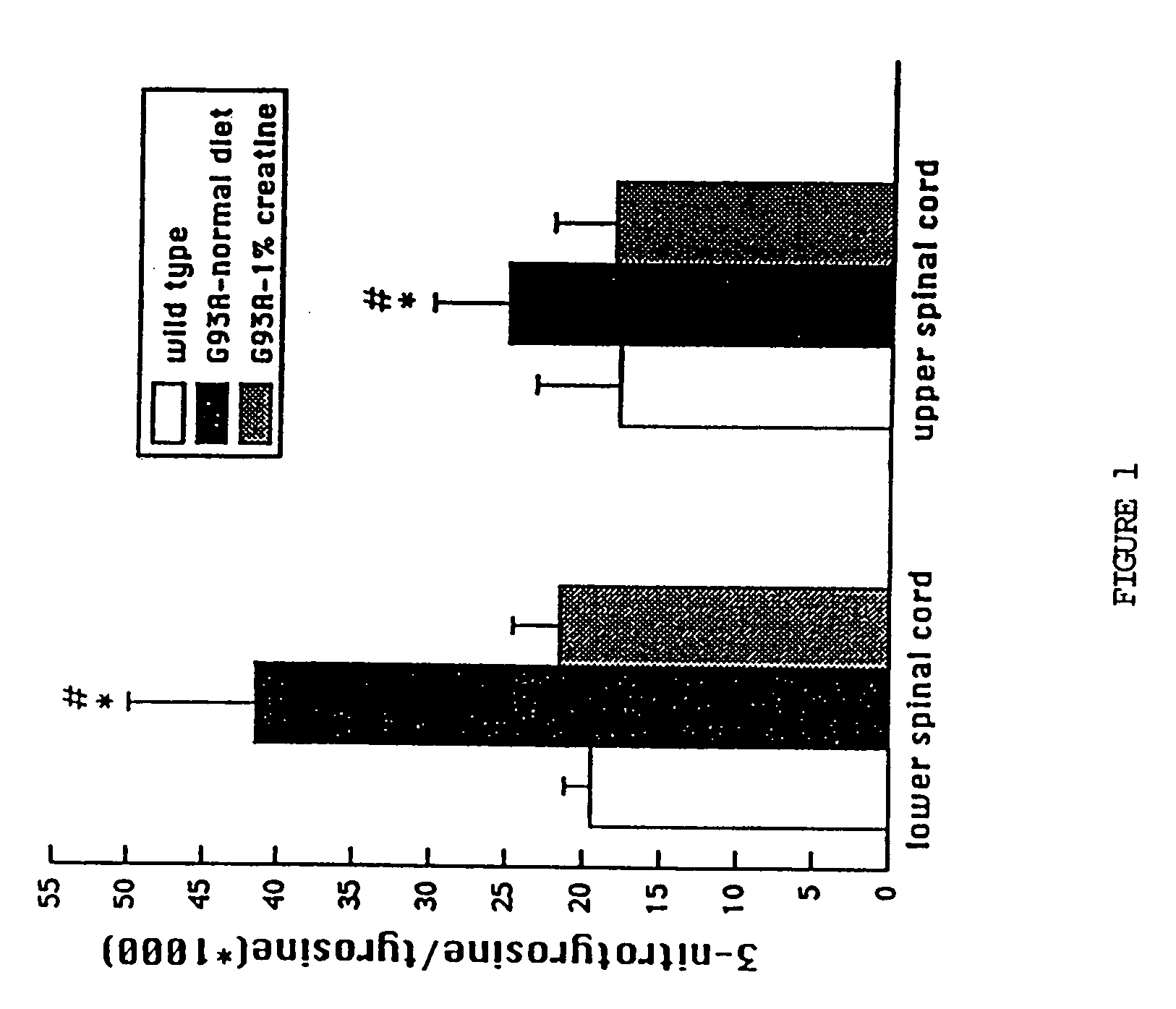
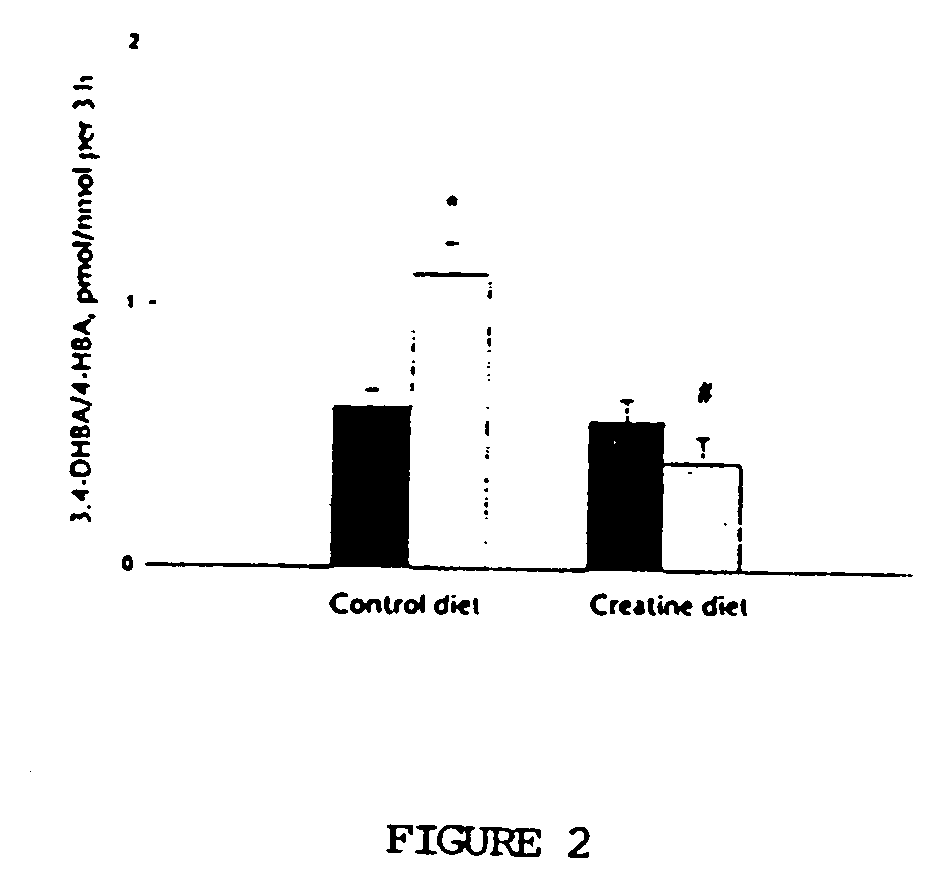
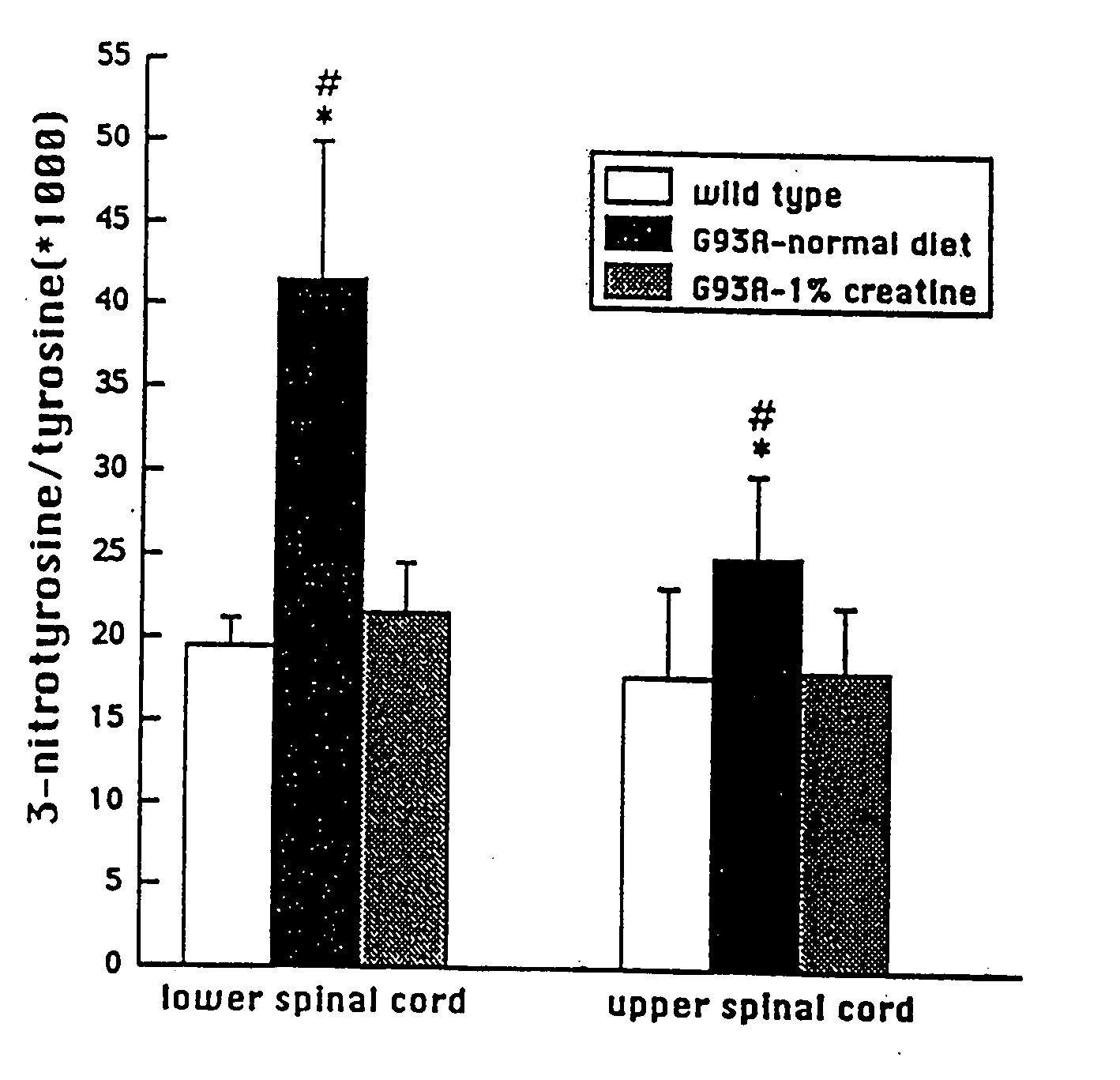
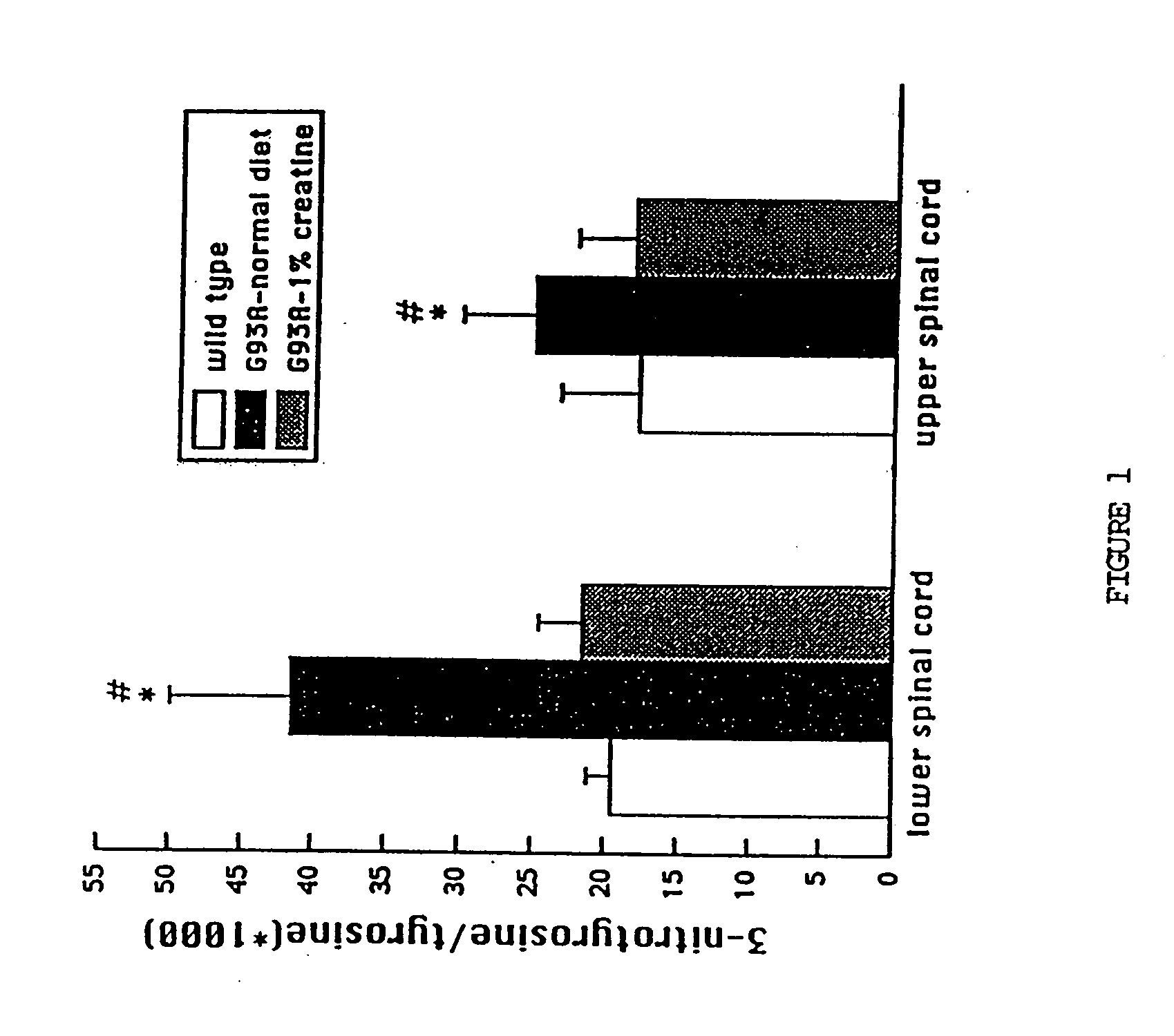
Use of creatine or creatine compounds for skin preservation
InactiveUS20050186158A1Slow processEasy to spreadCosmetic preparationsBiocideChemistryCompound (substance)
The present invention relates to the use of creatine compounds such as, for example, creatine, creatine phosphate or analogs of creatine, such as creatine-pyruvate, creatine-ascorbate, cyclocreatine, 3 guanidinopropionic acid, guanidinoacetate, homocyclocreatine, guanidino benzoates as energy generating systems and antioxidants for preservation of skin against adverse aging effects and damage secondary to insults such as harmful sun radiations, stress and fatigue. The creatine compounds which can be used in the present method include (1) creatine, creatine phosphate and analogs of these compounds which can act as substrates or substrate analogs for creatine kinase; (2) molecules that mimic the biological activity of creatine (3) molecules that modulate the creatine kinase system.
Owner:AVICENA GROUP
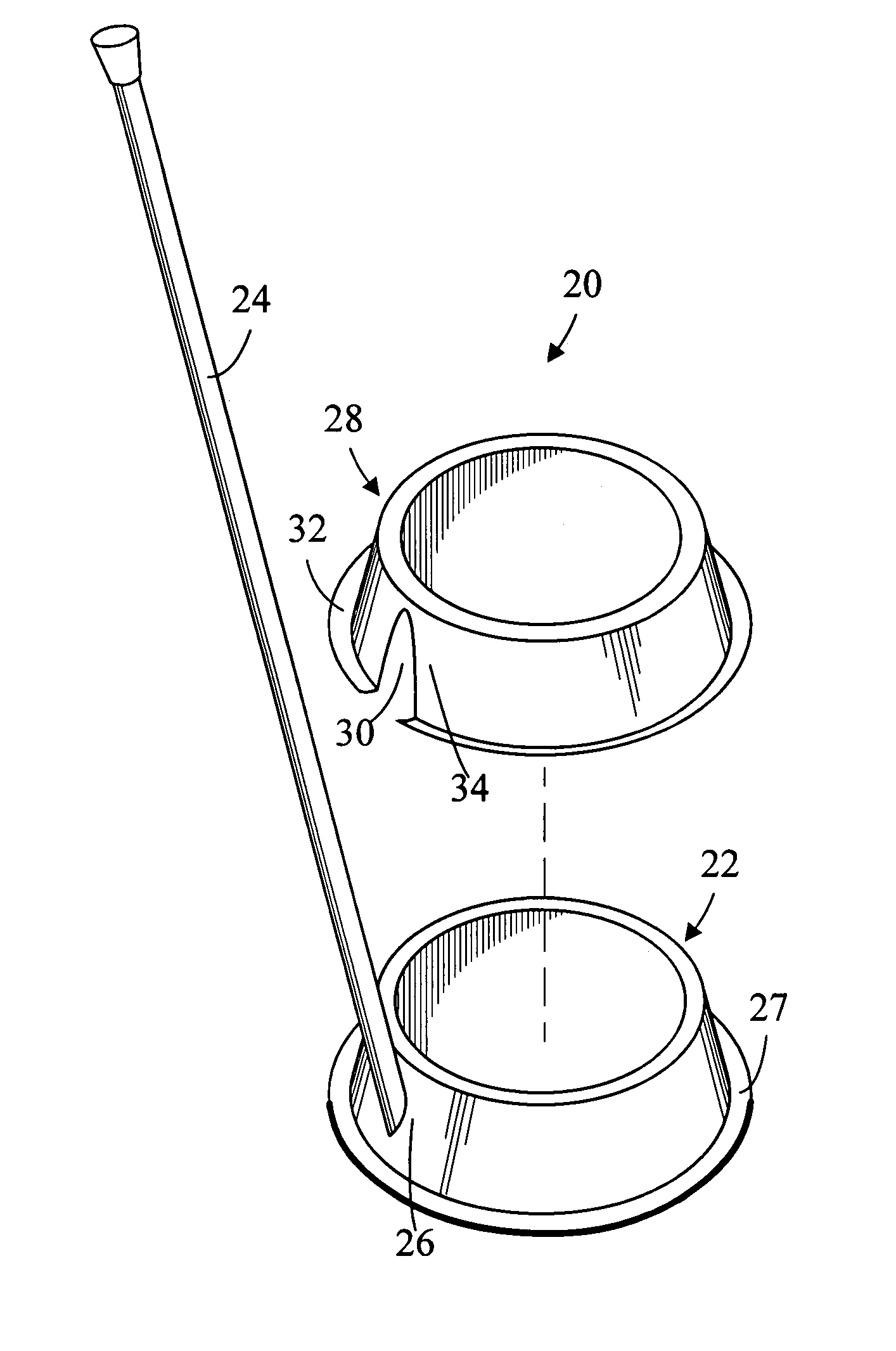
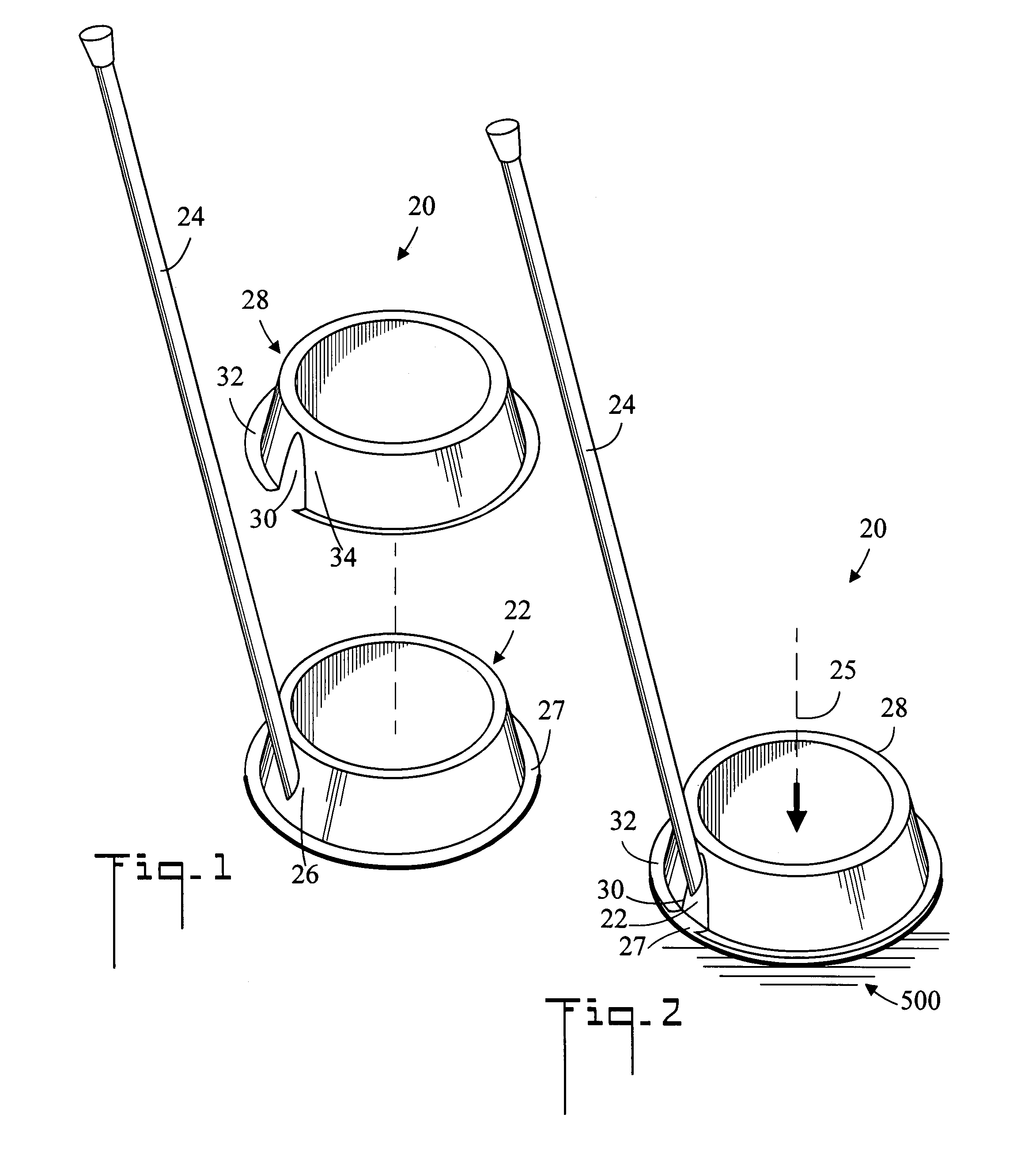
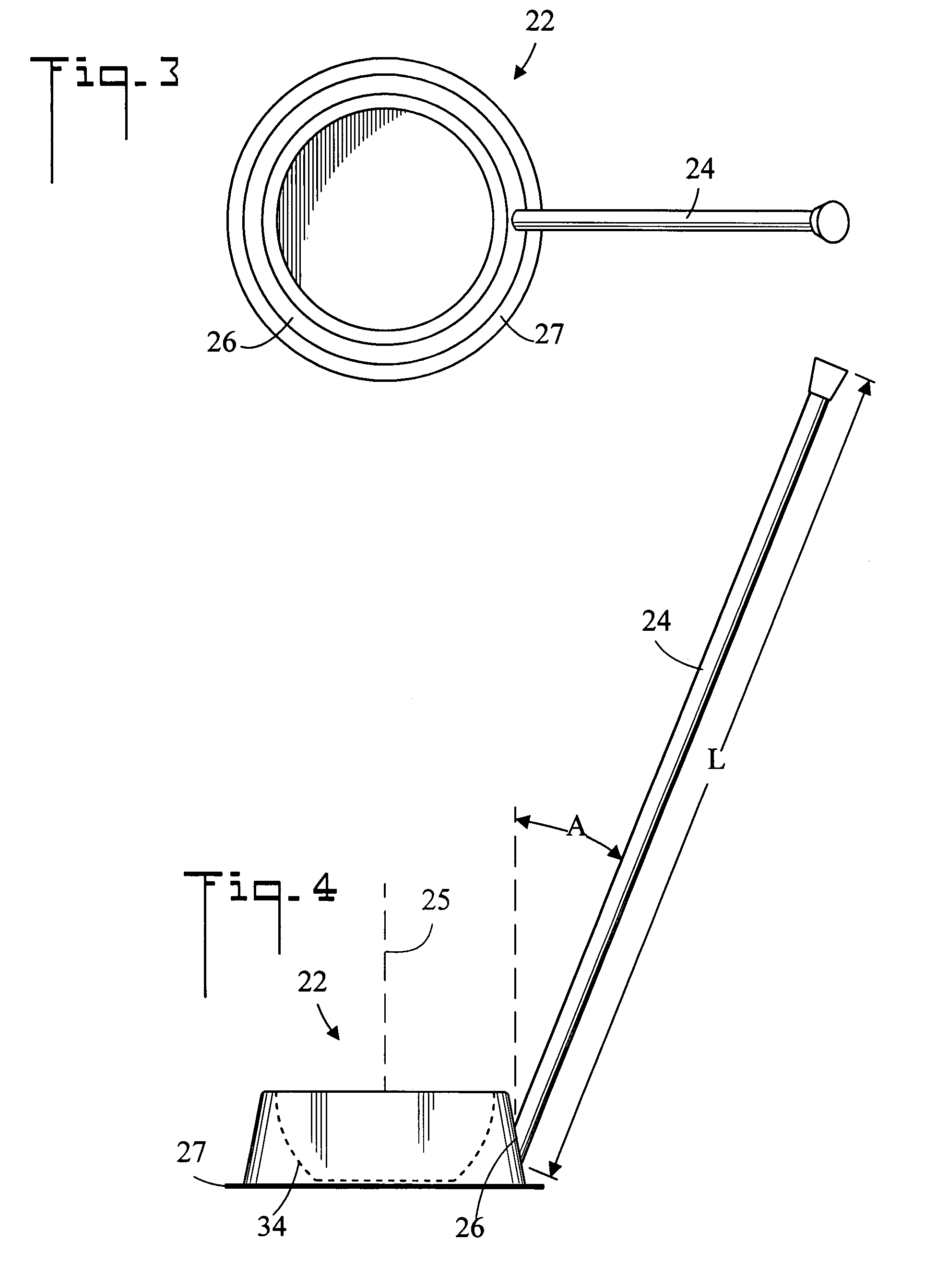
Pet feeding system and method of use
InactiveUS7320292B1Enhances clean up processSlow processAnimal feeding devicesAnimal housingEngineeringMechanical engineering
Owner:FERRANTELLI SALVATORE +1
Use of creatine or creatine compounds for skin preservation
InactiveUS20050186194A1Slow processEasy to spreadBiocideCosmetic preparationsChemistryCompound (substance)
The present invention relates to the use of creatine compounds such as, for example, creatine, creatine phosphate or analogs of creatine, such as creatine-pyruvate, creatine-ascorbate, cyclocreatine, 3 guanidinopropionic acid, guanidinoacetate, homocyclocreatine, guanidino benzoates as energy generating systems and antioxidants for preservation of skin against adverse aging effects and damage secondary to insults such as harmful sun radiations, stress and fatigue. The creatine compounds which can be used in the present method include (1) creatine, creatine phosphate and analogs of these compounds which can act as substrates or substrate analogs for creatine kinase; (2) molecules that mimic the biological activity of creatine (3) molecules that modulate the creatine kinase system.
Owner:AVICENA GROUP
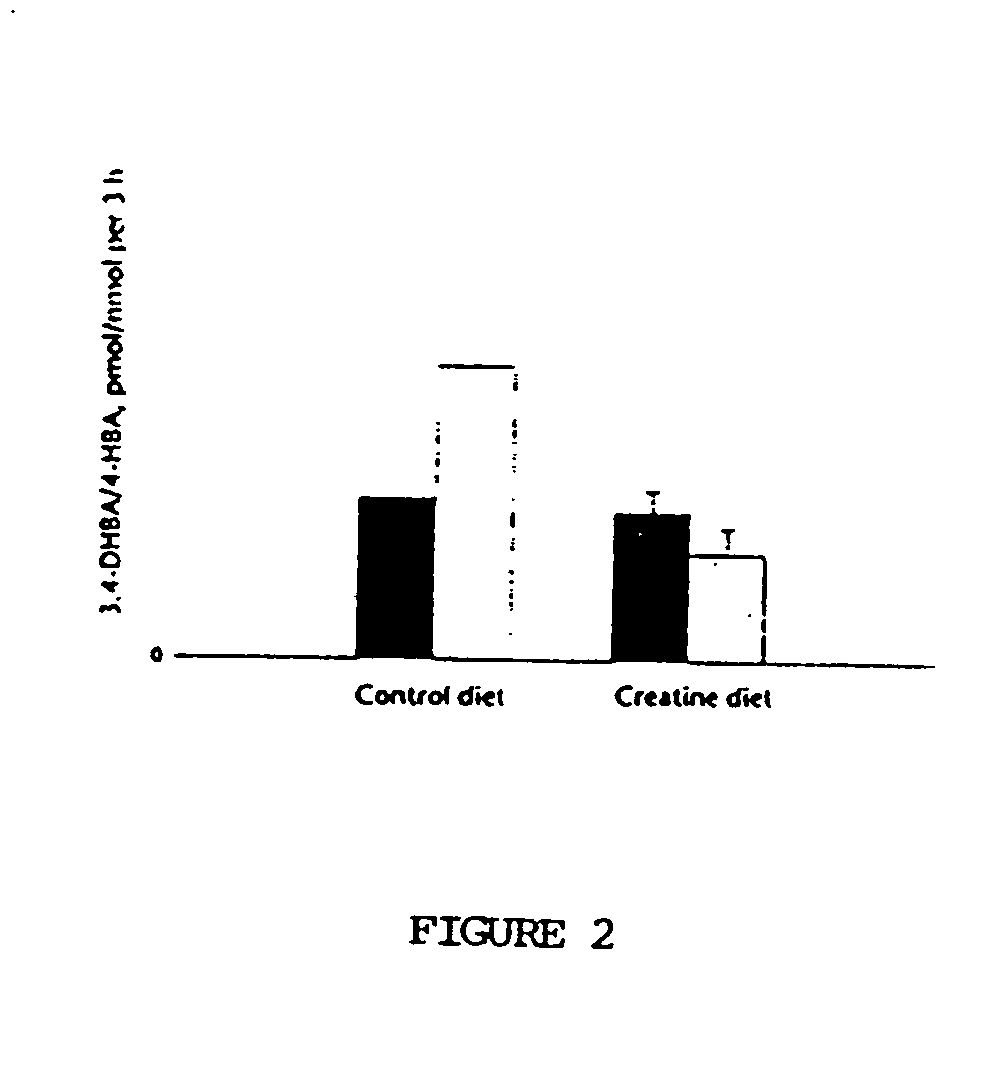
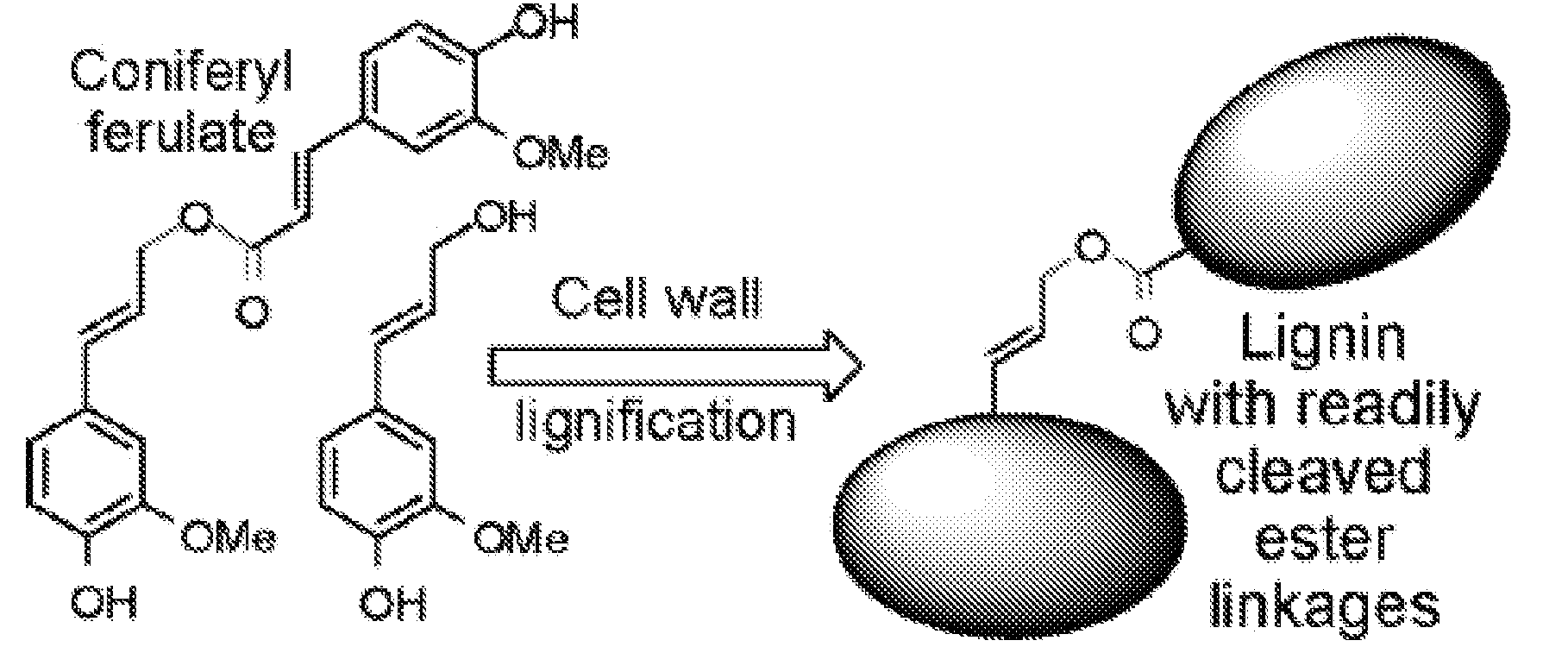
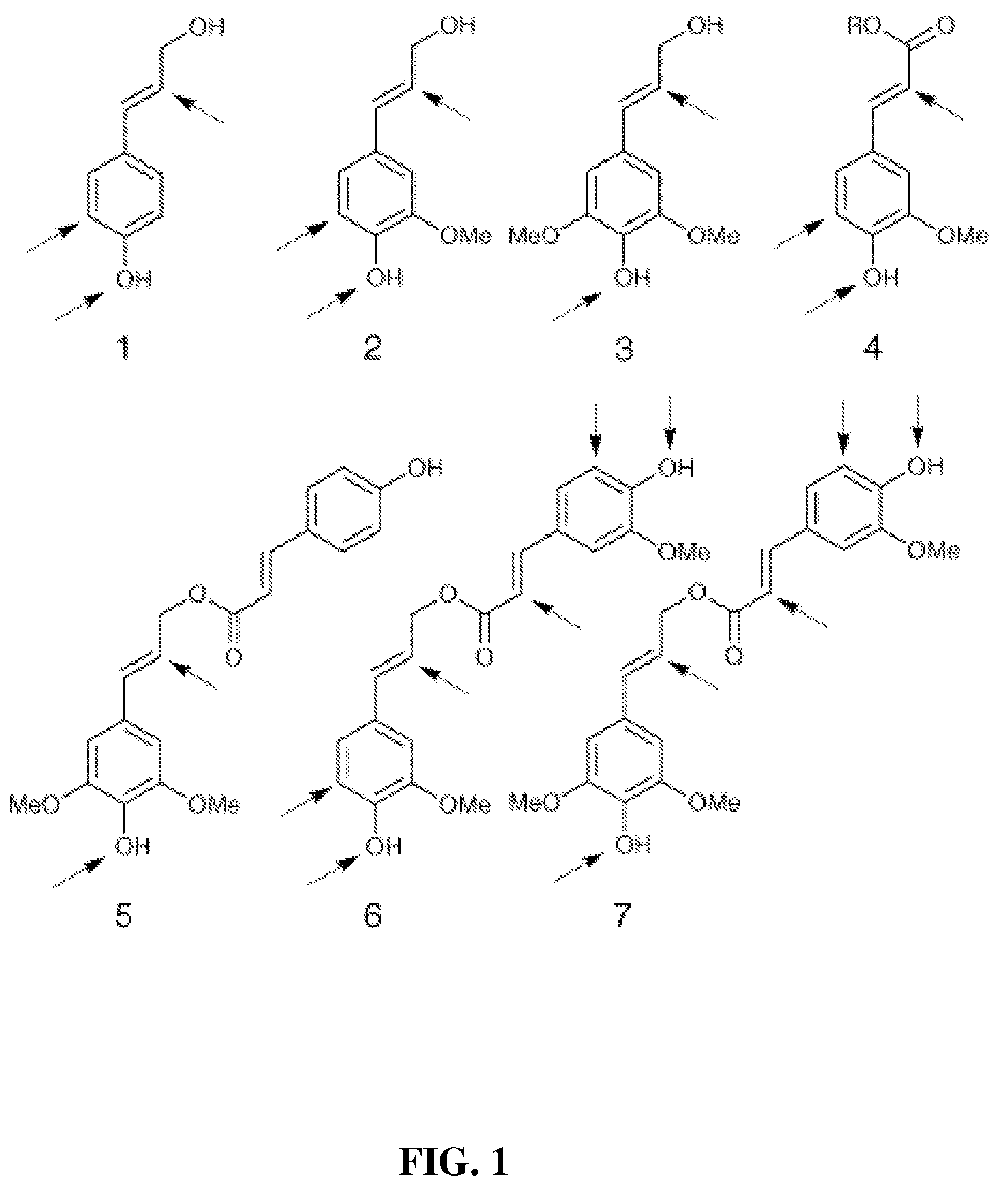
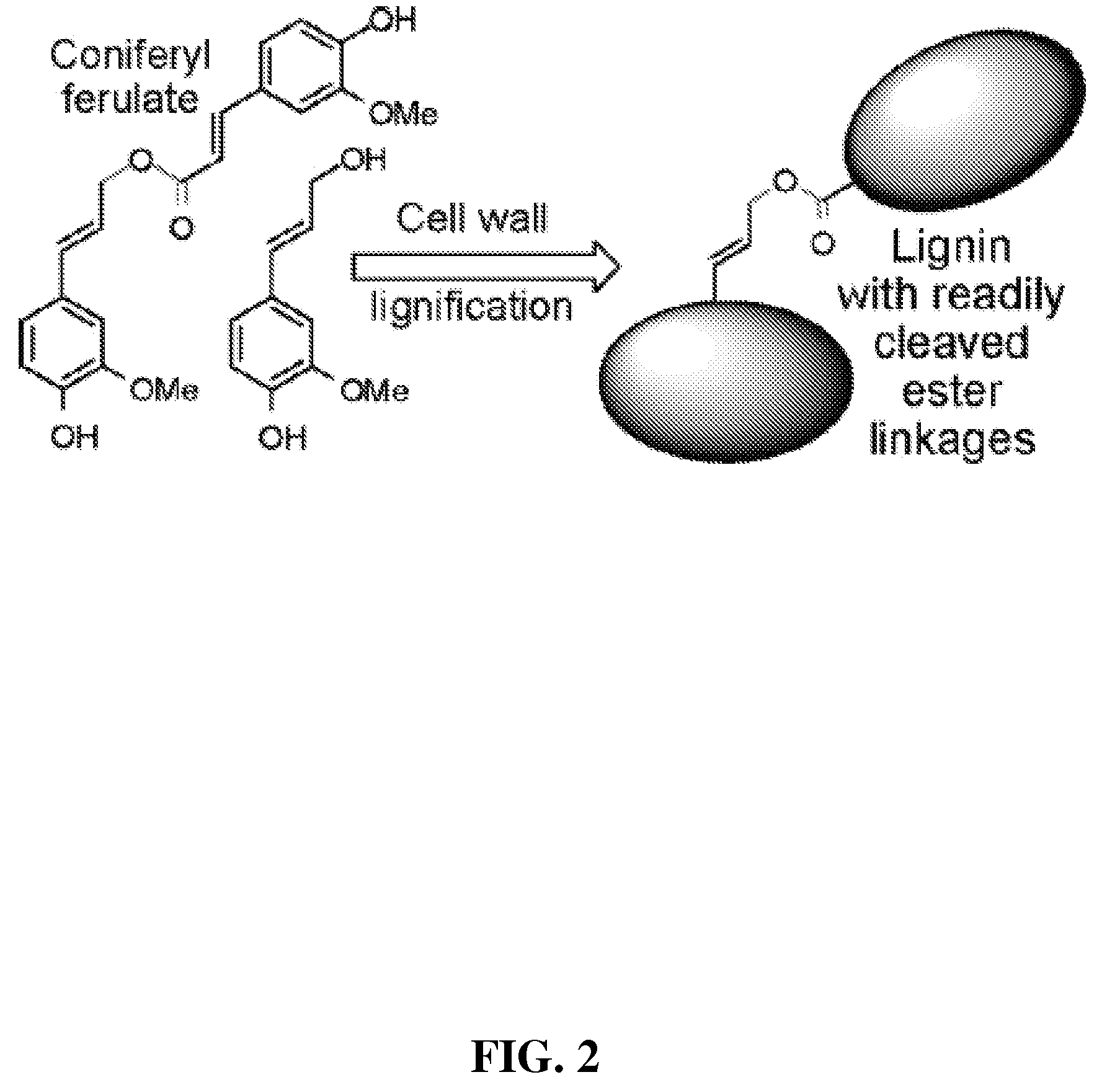
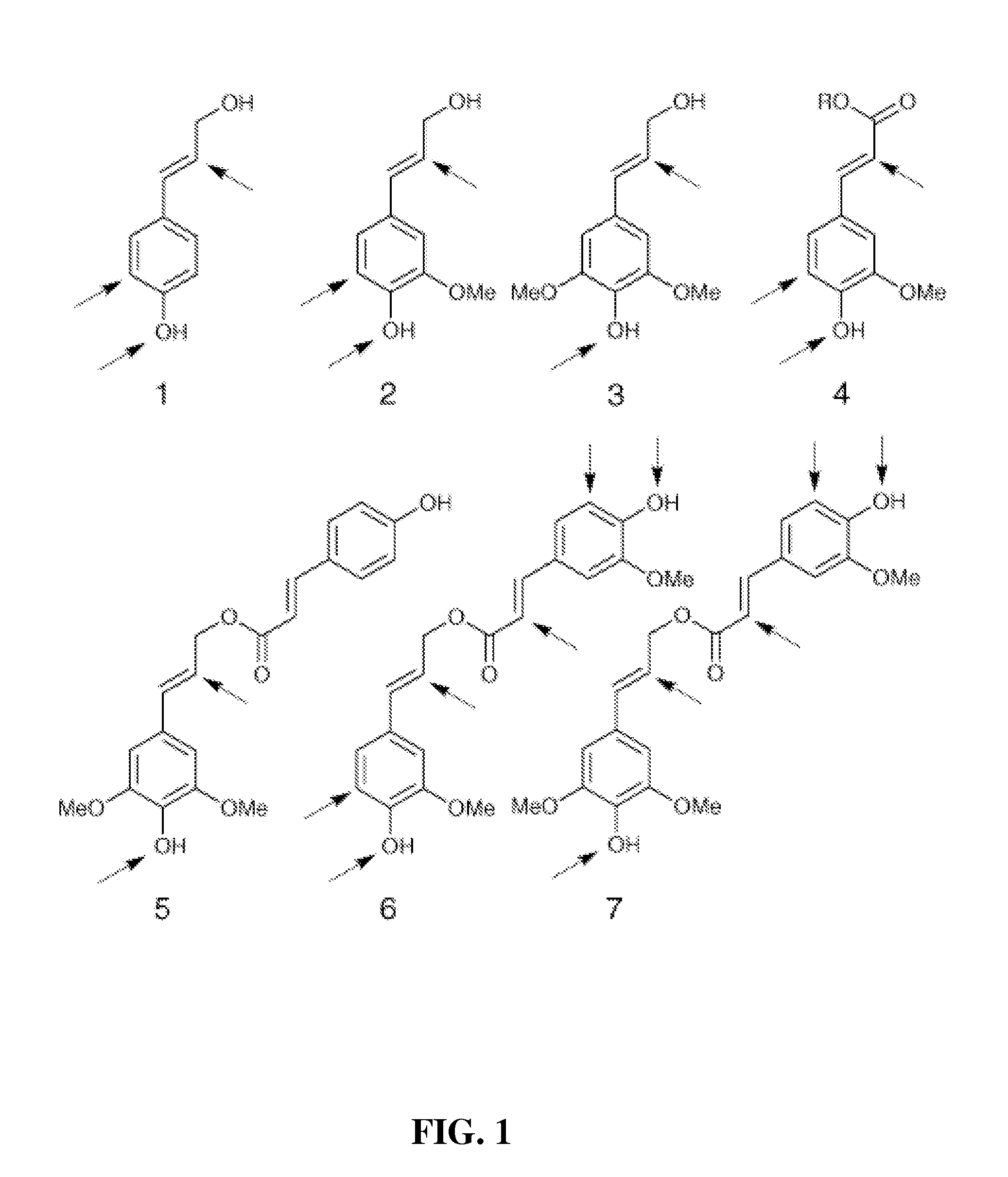
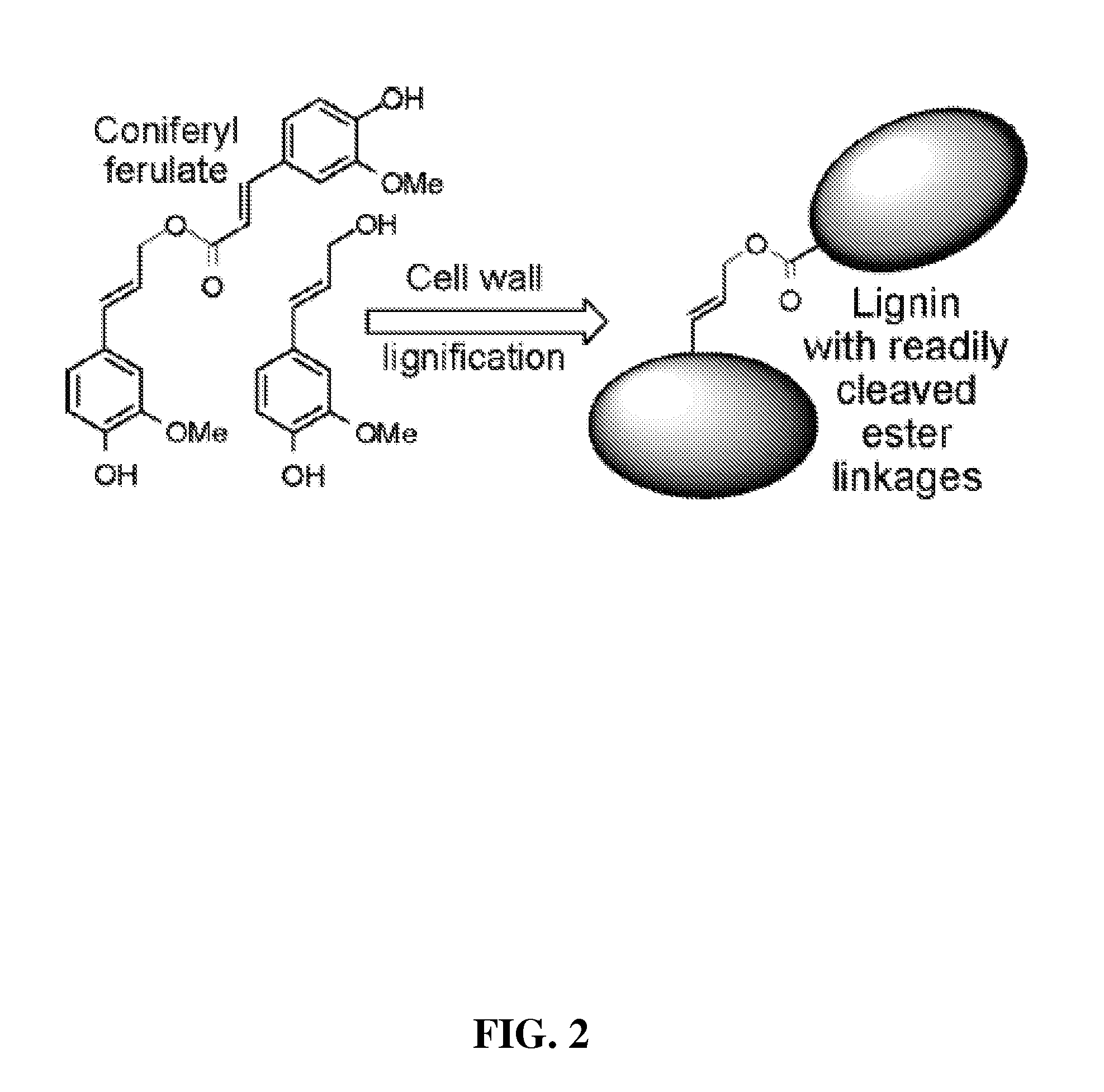
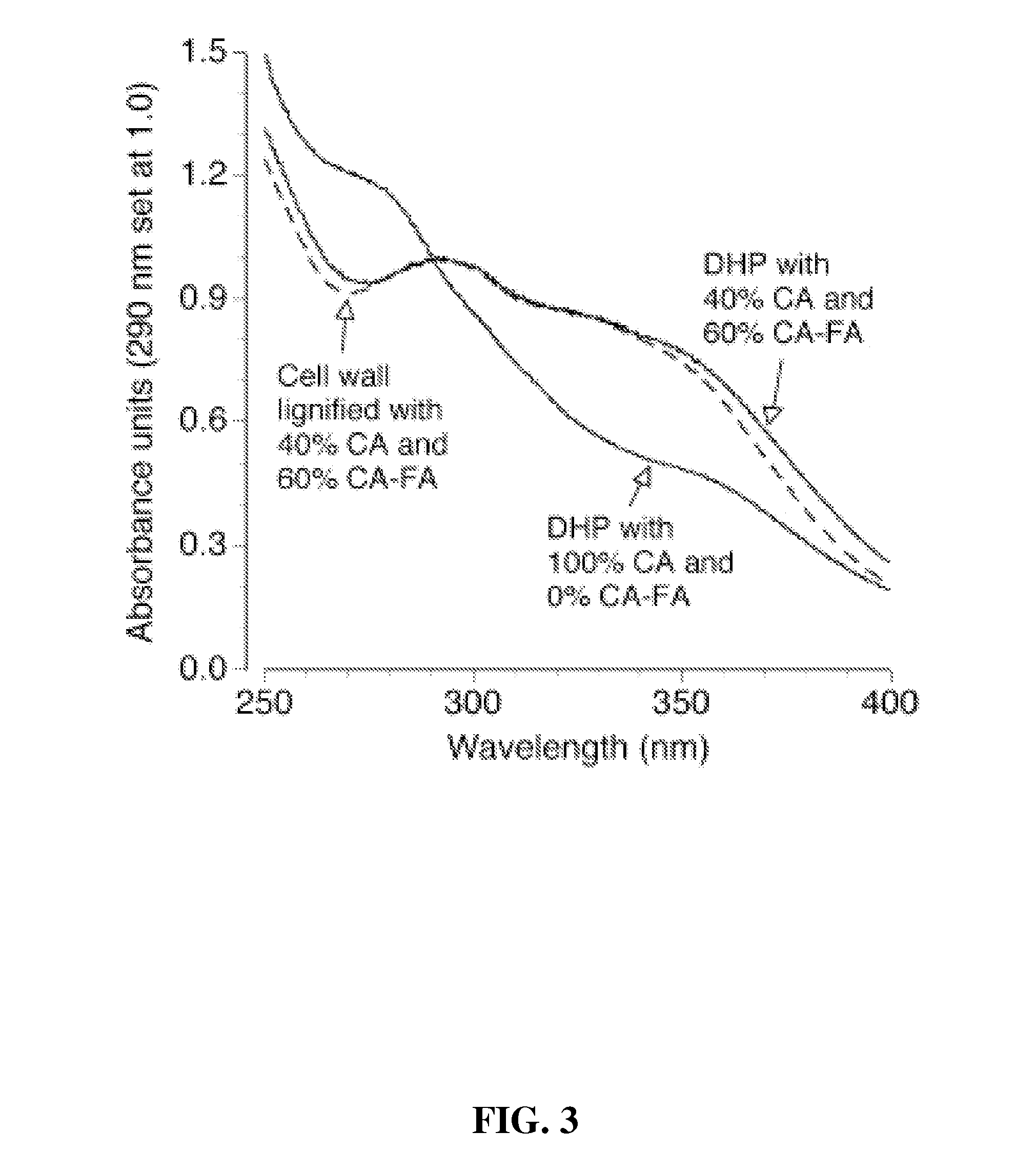
Method for modifying lignin structure using monolignol ferulate conjugates
ActiveUS8569465B2Limit enzyme accessImproves digestibility/fermentabilityMicroorganismsLignin derivativesPlant cellCell wall
Described is an isolated lignified plant cell wall including lignin, wherein the lignin includes a ferulate residue incorporated therein, such as from coniferyl ferulate and / or sinapyl ferulate. Also described is a method to make the isolated lignified plant cell wall, and the lignin produced by the method.
Owner:WISCONSIN ALUMNI RES FOUND +1
Method for modifying lignin structure using monolignol ferulate conjugates
ActiveUS20110003978A1Limit enzyme accessImproves digestibility/fermentabilityMicroorganismsLignin derivativesSinapic acidMonolignol
Described is an isolated lignified plant cell wall including lignin, wherein the lignin includes a ferulate residue incorporated therein, such as from coniferyl ferulate and / or sinapyl ferulate. Also described is a method to make the isolated lignified plant cell wall, and the lignin produced by the method.
Owner:WISCONSIN ALUMNI RES FOUND +1
Systems and methods for identifying payor location based on transaction data
ActiveUS7783563B2Improve risk assessmentReduce riskFinanceMarketingInformation repositoryTransaction data
Systems and methods are described for building, maintaining, and using a repository of information about payors of second-party checks presented at a check-cashing entity for cashing. In various embodiments, the repository comprises stored information useful for determining the location of a payor of a second-party check. In one embodiment, information from the check that identifies an account on which the check is drawn, such as magnetic ink character recognition (MICR) line information from a paycheck, is used to access a repository of employer location information. In one embodiment, the payor location information is used to determine a proximity between the payor location and the check cashing entity location. In one embodiment, when a check is presented for which stored payor location information is not available, identifying information about the payor and / or the payor location is requested and is added to the repository.
Owner:FIRST DATA
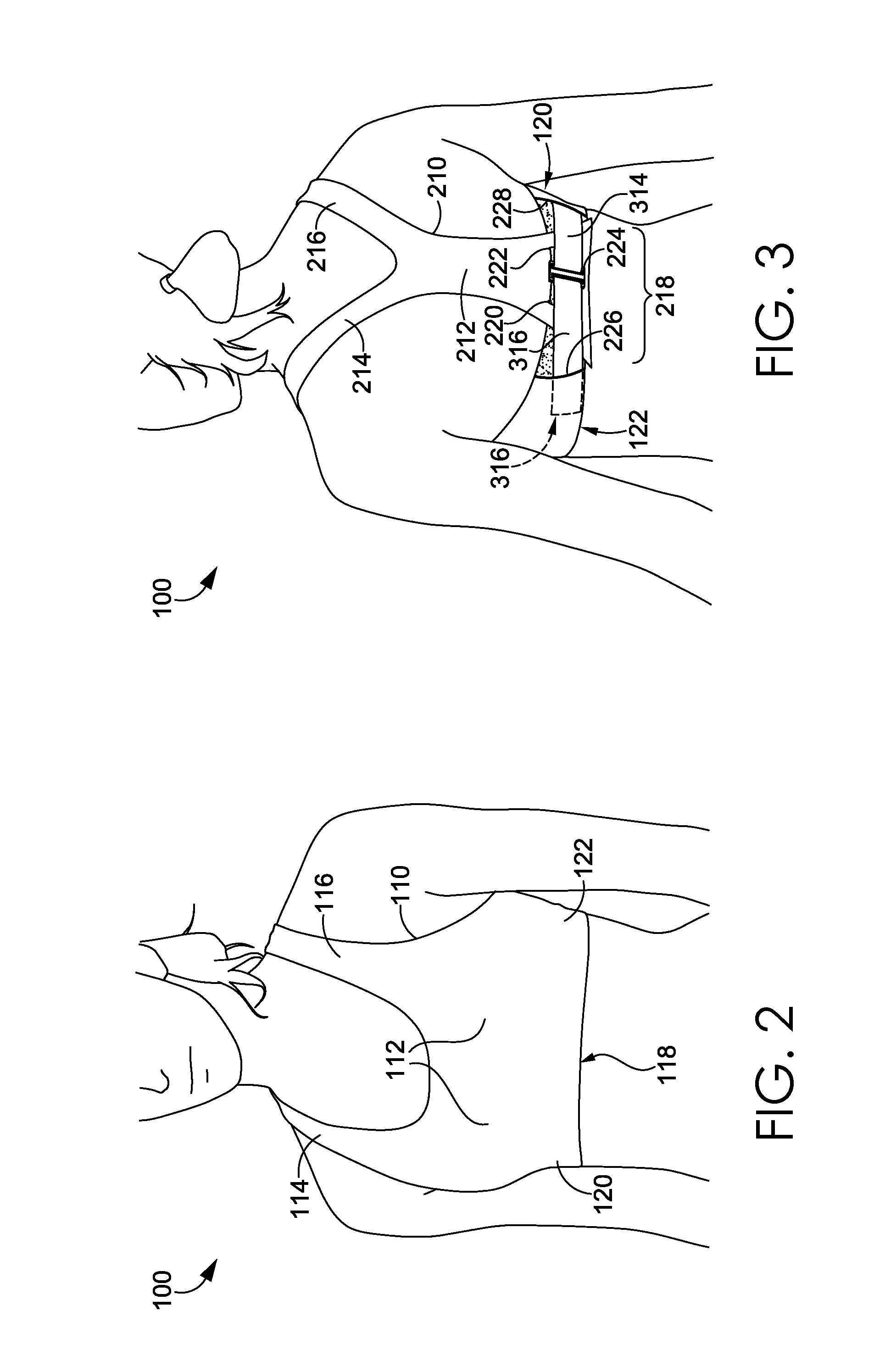
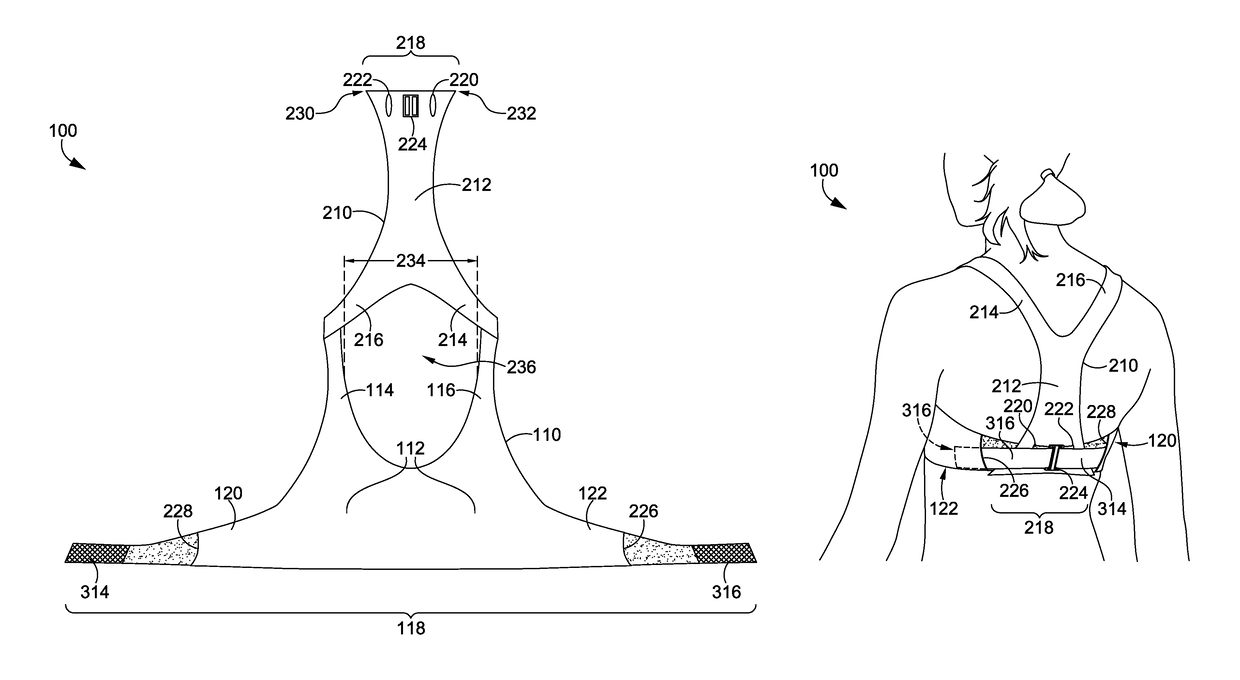
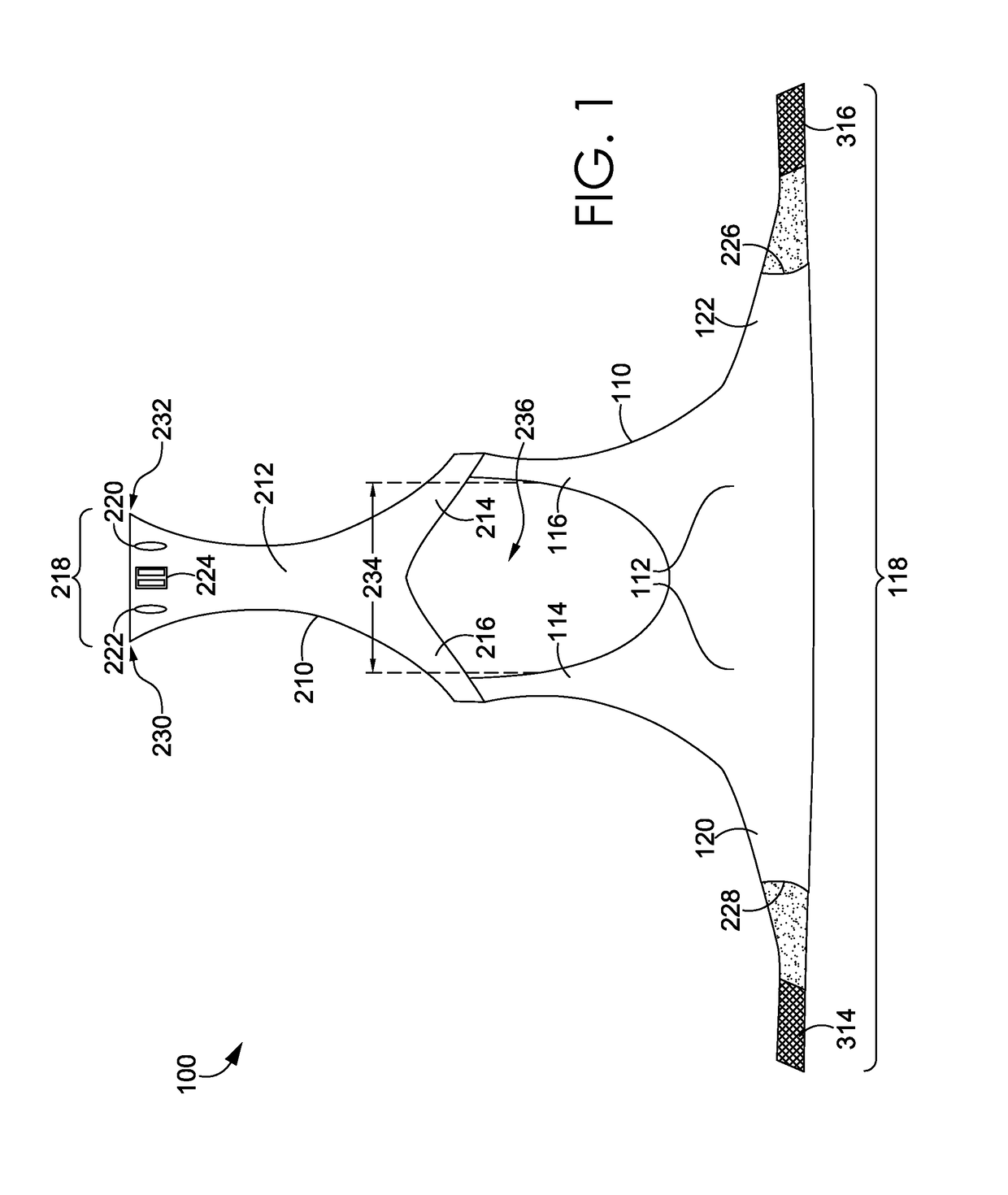
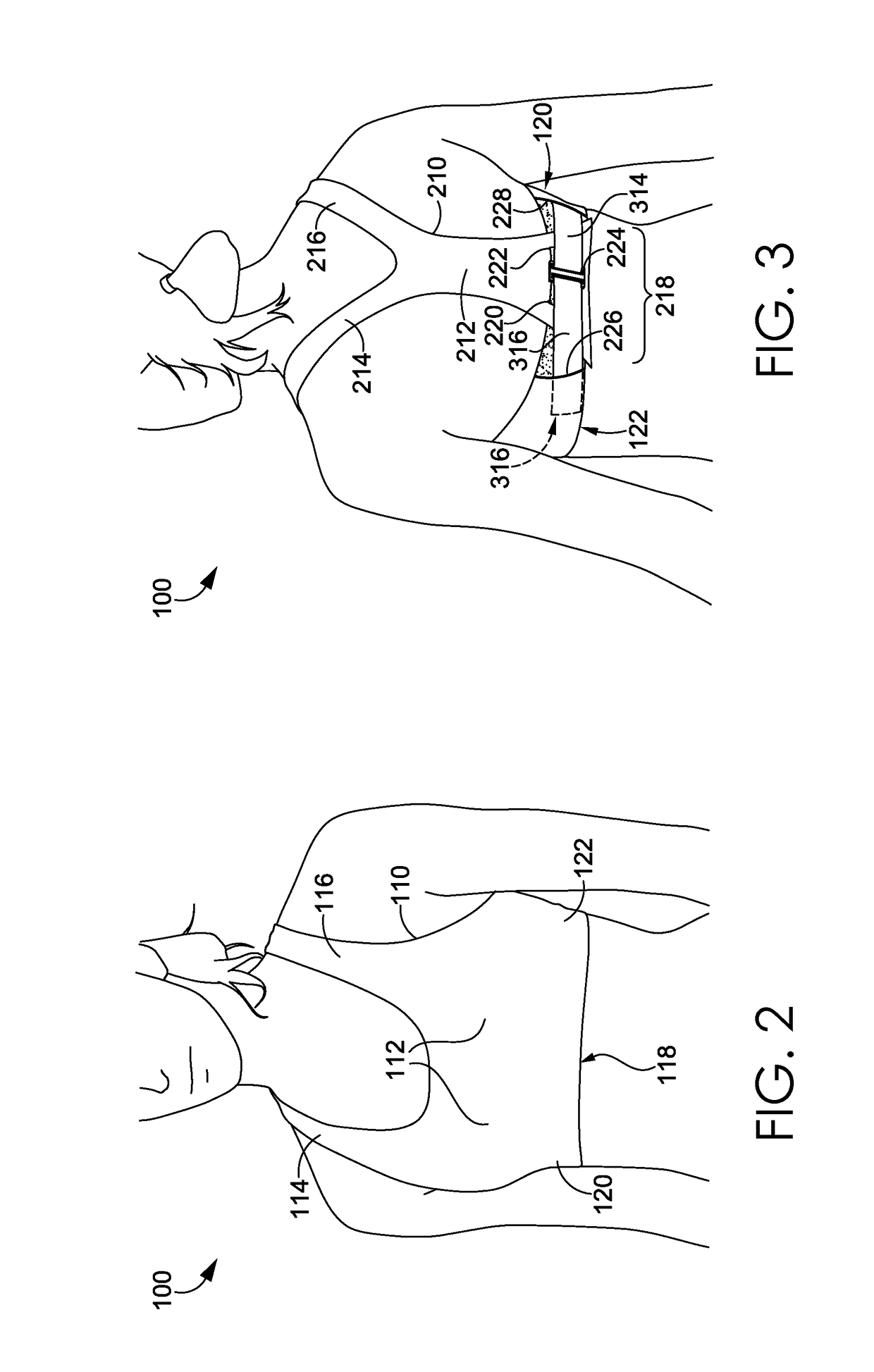
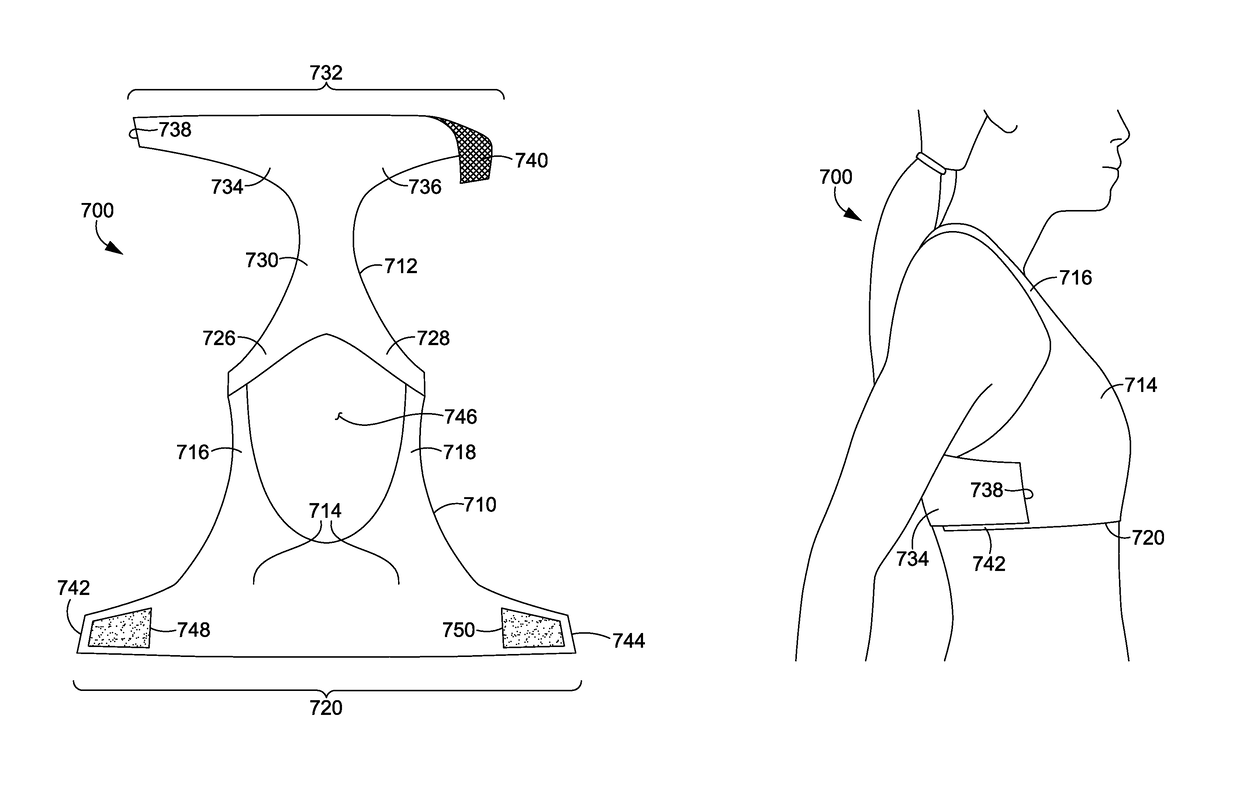
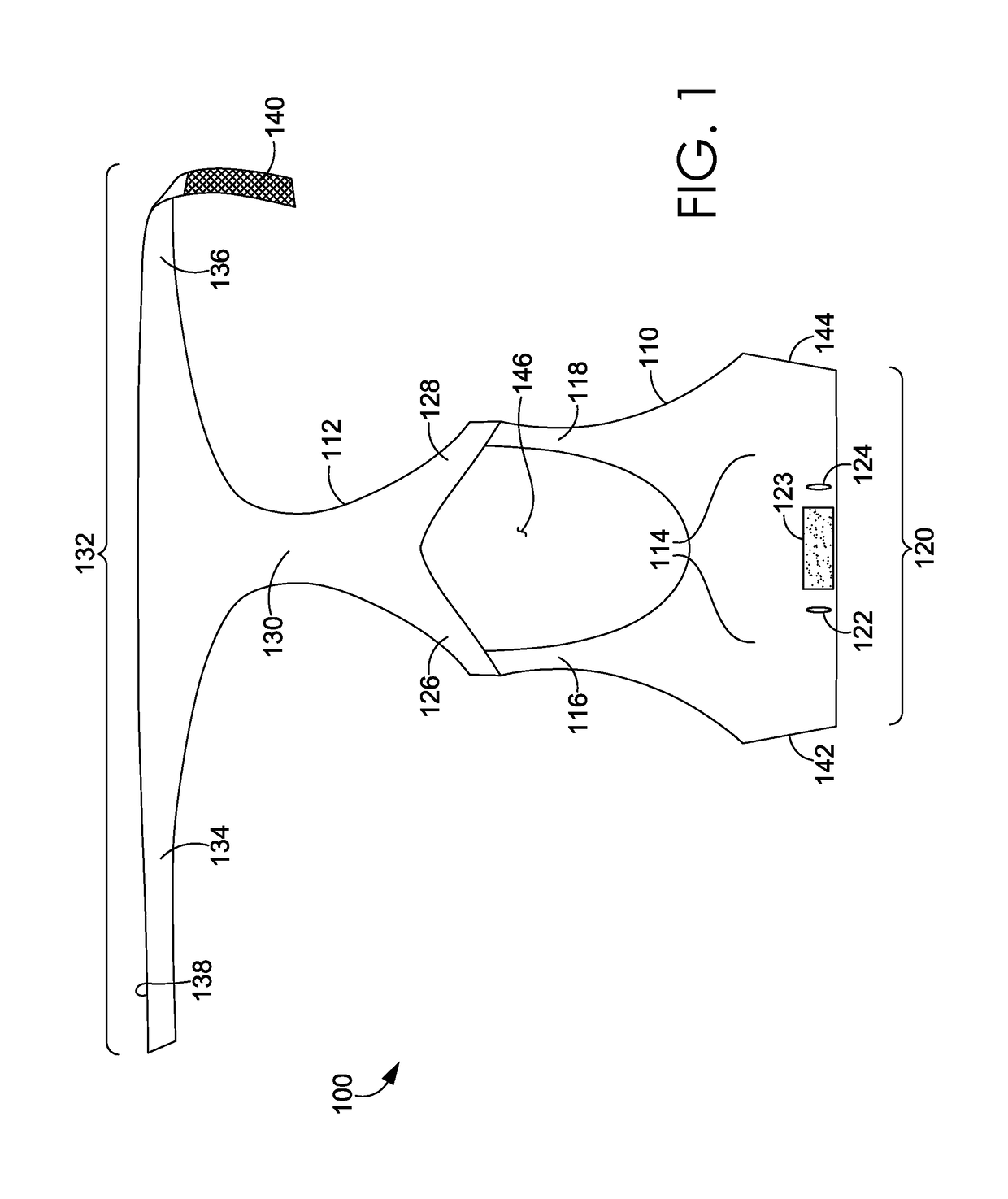
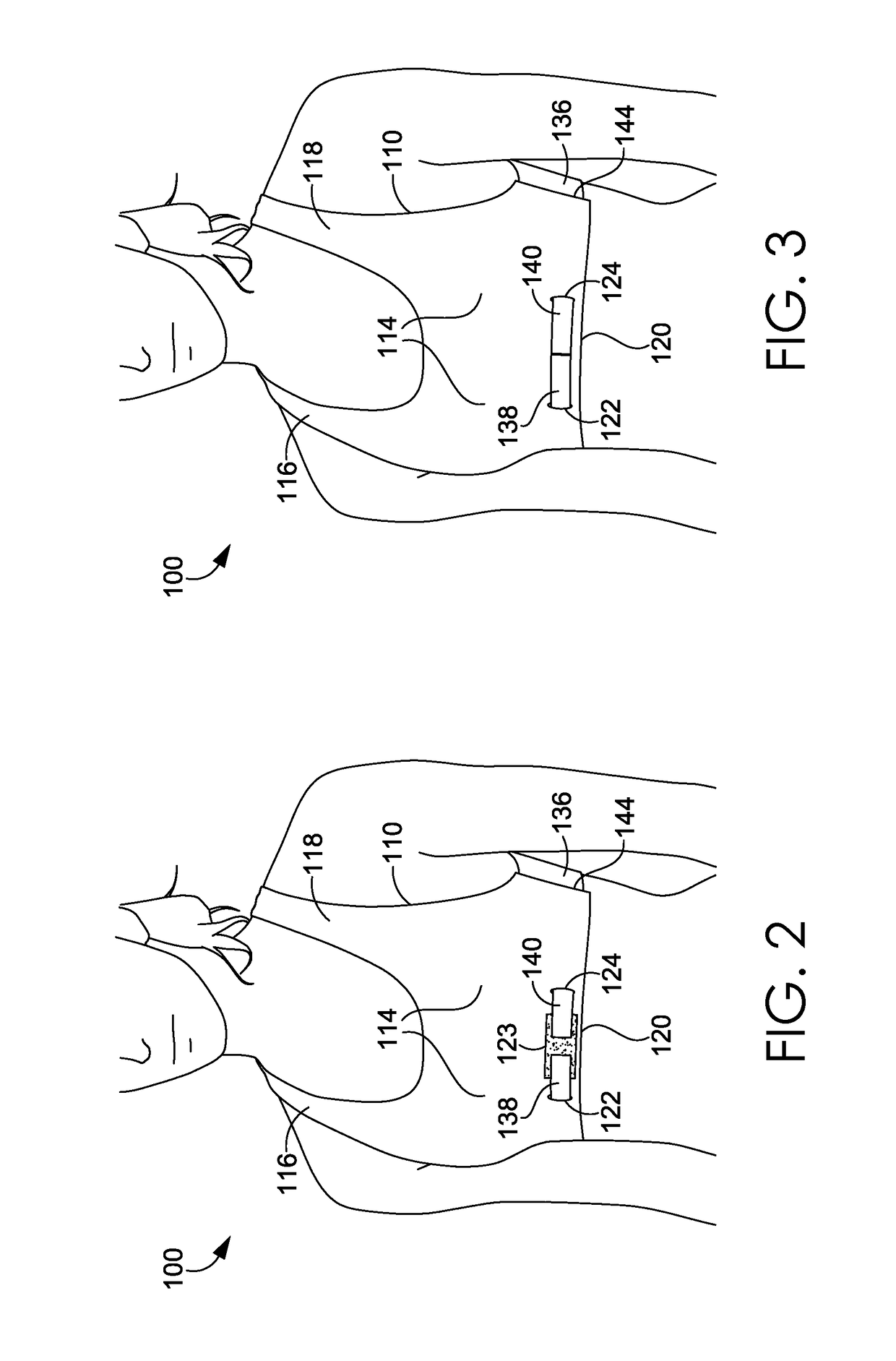
Wrap back bra
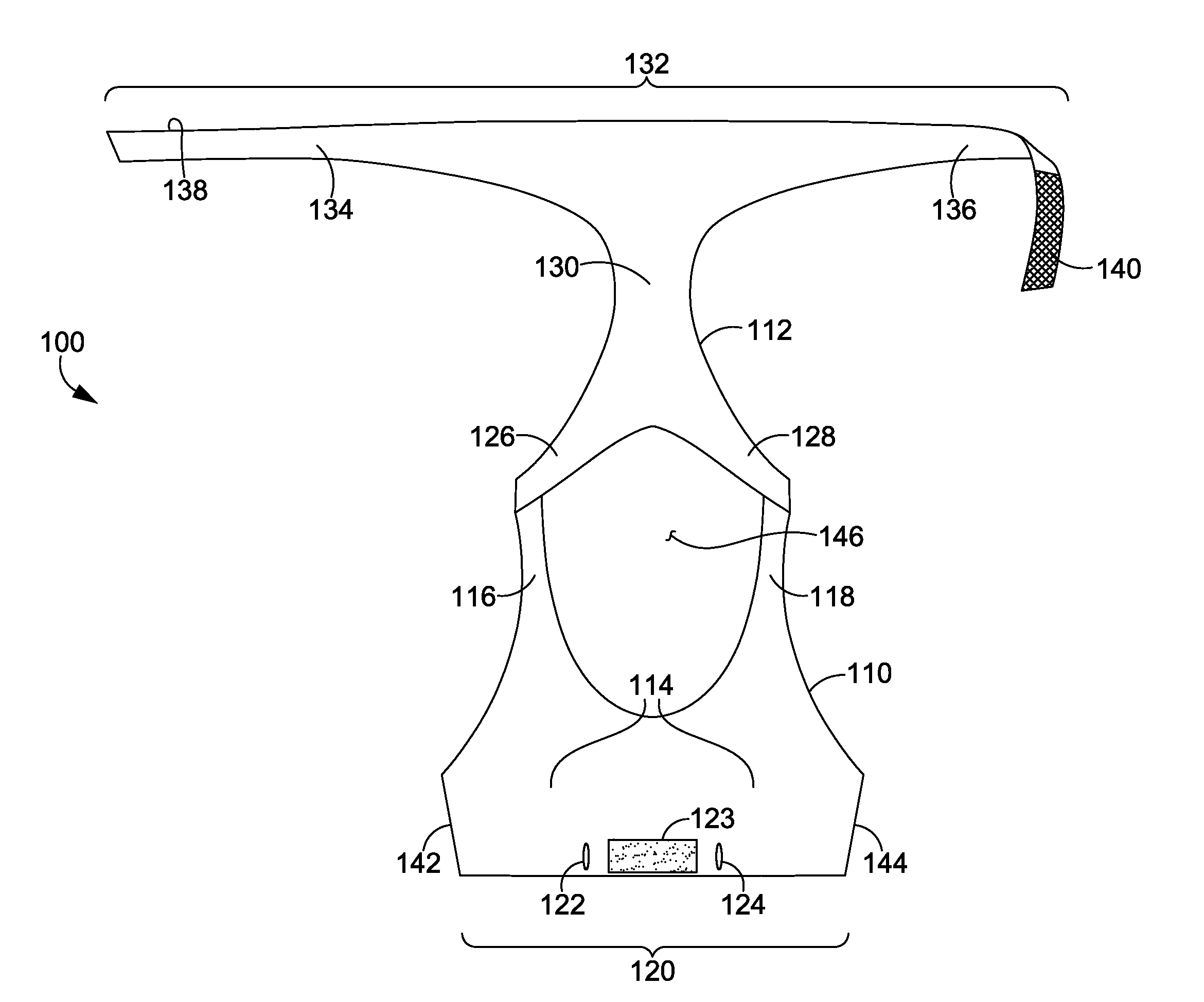
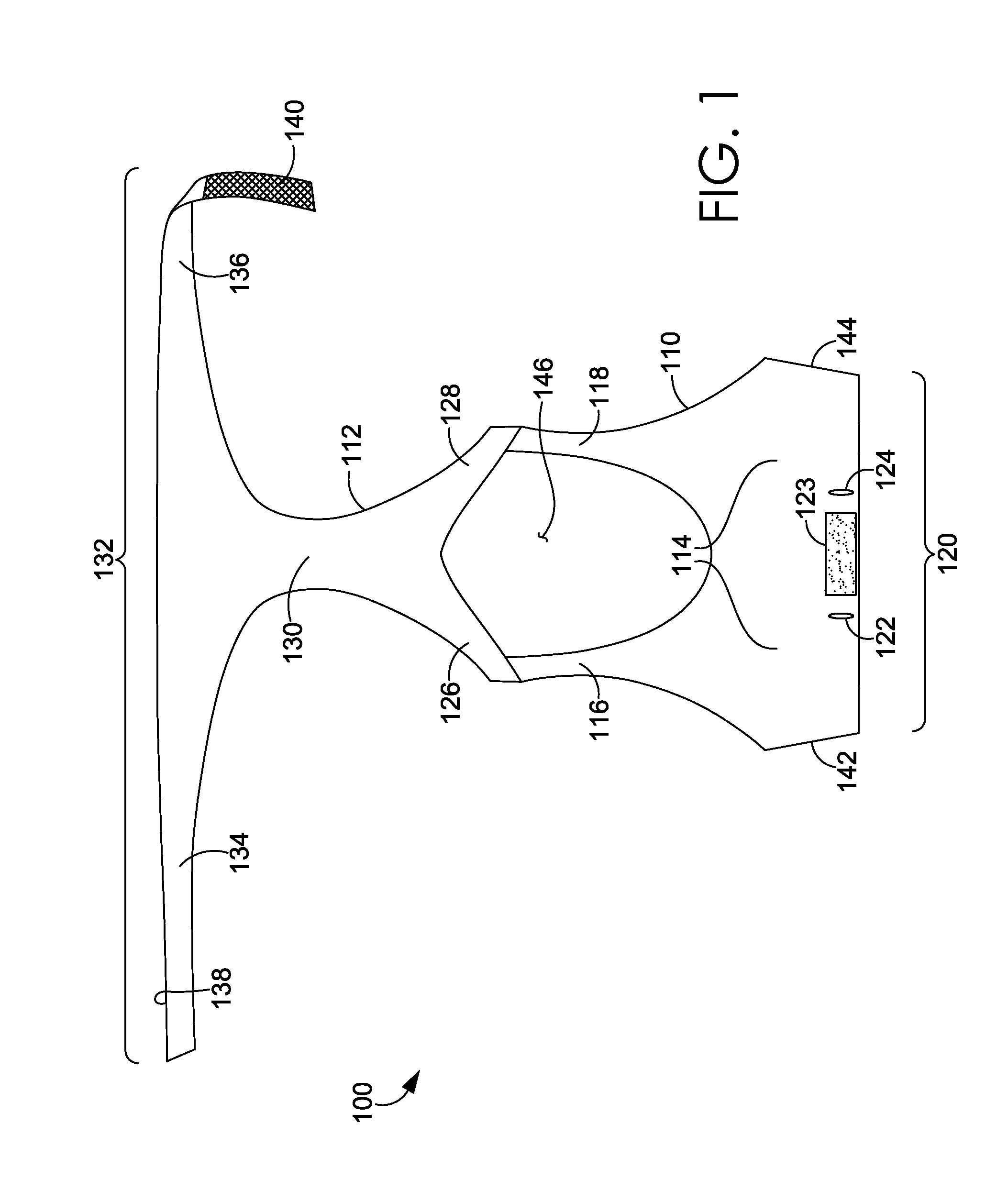
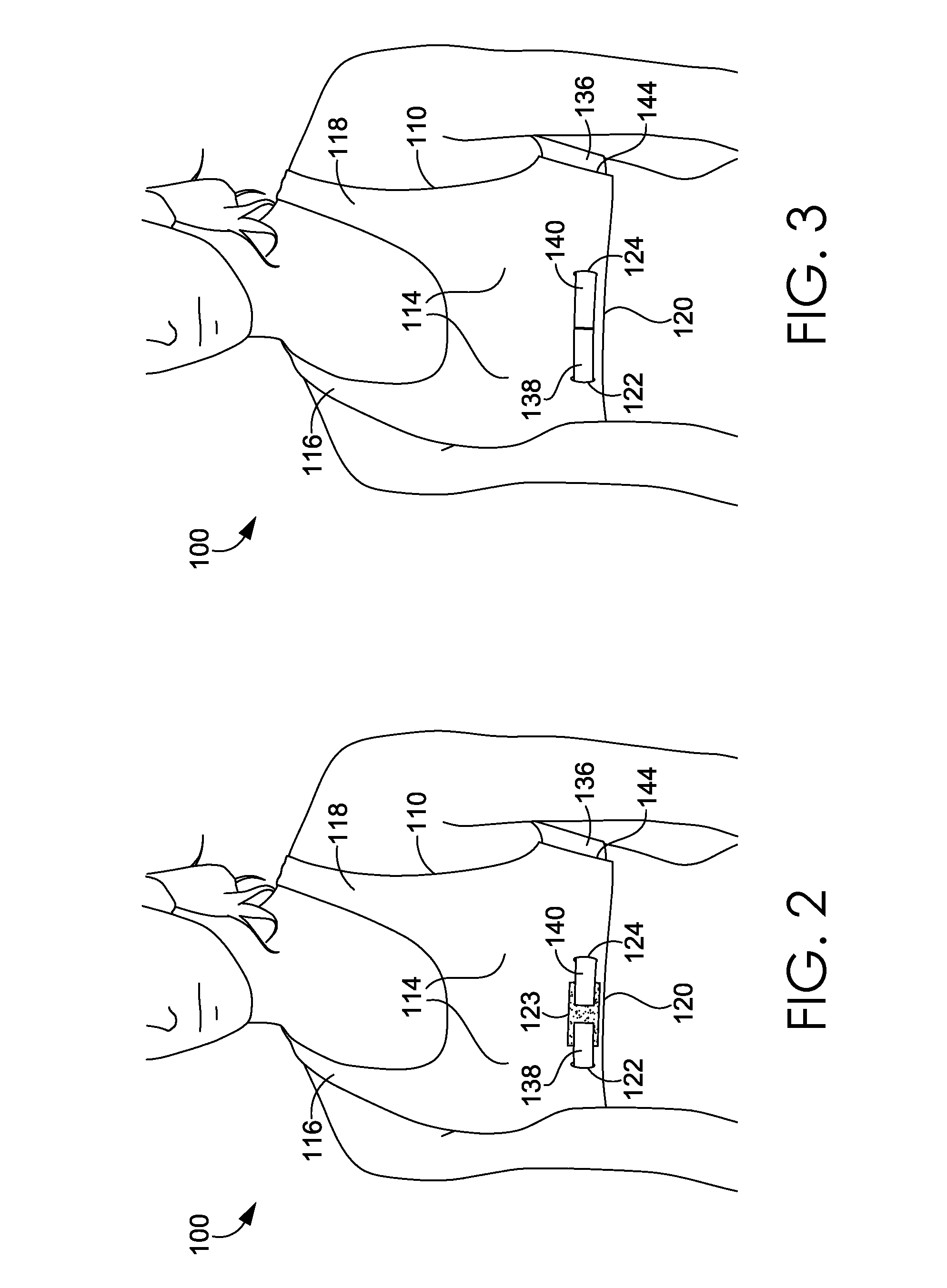
ActiveUS20160081398A1Easy to donIncrease girthBrassieresGarment fastenersPhysical medicine and rehabilitationEngineering
A sport bra having an adjustable underband tightening assembly is provided herein. The sport bra comprises a front portion having a pair of breast cups, a pair of shoulder straps, and a front underband segment comprising a first wing extending away from a first side of the front underband segment and terminating in a first free end and a second wing extending away from a second side of the front underband segment and terminating in a second free end. The sport bra further comprises a back portion having a central body portion, a pair of shoulder straps secured to the shoulder straps of the front portion, and a back underband segment unaffixed to the front underband segment in an un-worn configuration.
Owner:NIKE INC
Wrap back bra
ActiveUS9700081B2Girth of the sport bra to be increasedIncrease girthBrassieresGarment fastenersPhysical medicine and rehabilitationEngineering
Owner:NIKE INC
Wrap front bra
ActiveUS20160081399A1Easy to donIncrease girthBrassieresGarment fastenersEngineeringMechanical engineering
A sport bra having an adjustable underband tightening assembly is provided herein. The sport bra comprises a front portion having a pair of breast cups, a pair of shoulder straps, and a front underband segment having a first end and a second end. The sport bra further comprises a back portion having a central body portion, a pair of shoulder straps secured to the shoulder straps of the front portion, and a back underband segment comprising a first wing extending away from a first side of the back underband segment and terminating in a first end and a second wing extending away from a second side of the back underband segment and terminating in a second end. The first and second ends of the back underband segment are adapted to releasably and adjustably secured to the front underband segment in an as-worn configuration.
Owner:NIKE INC
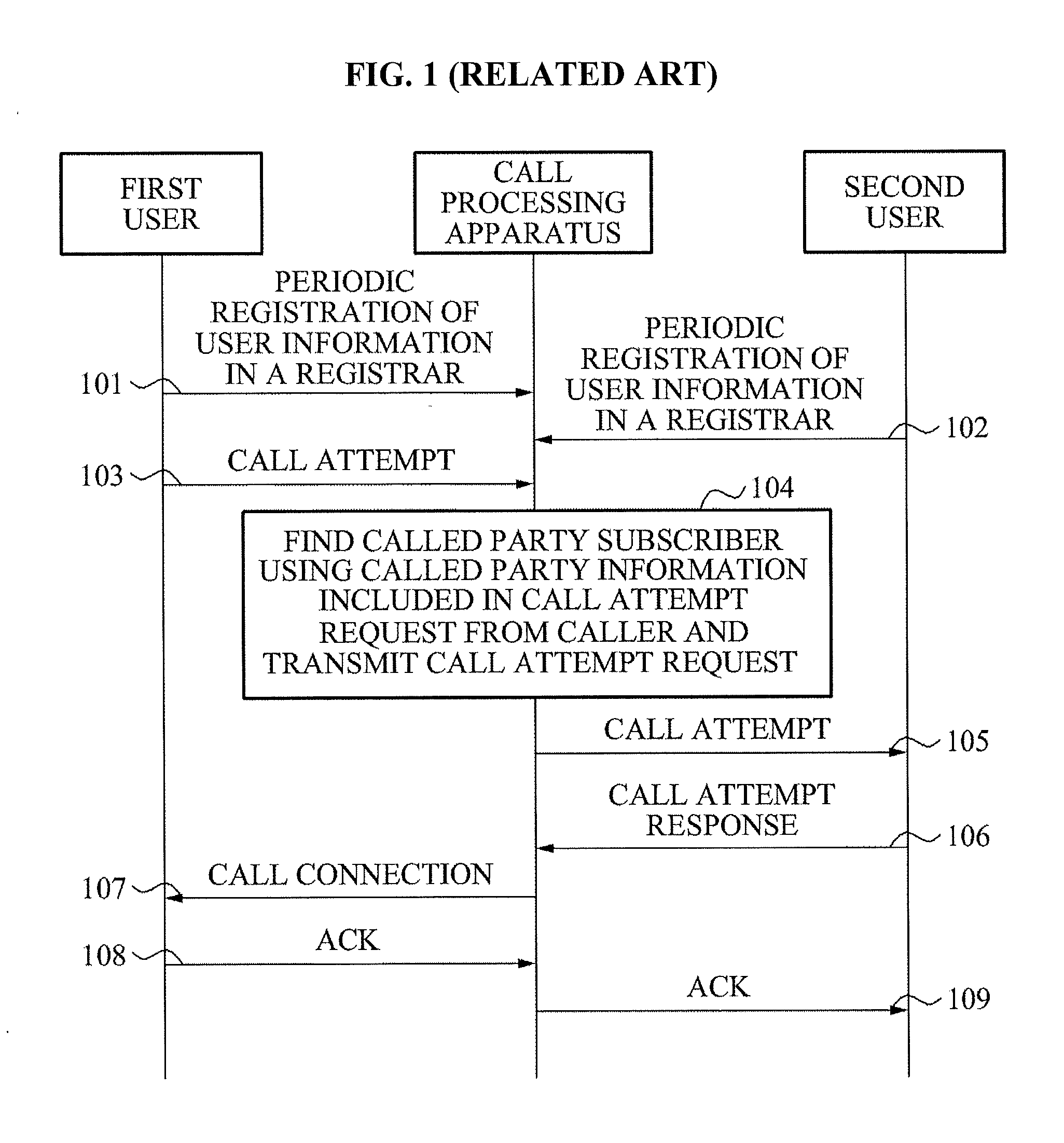
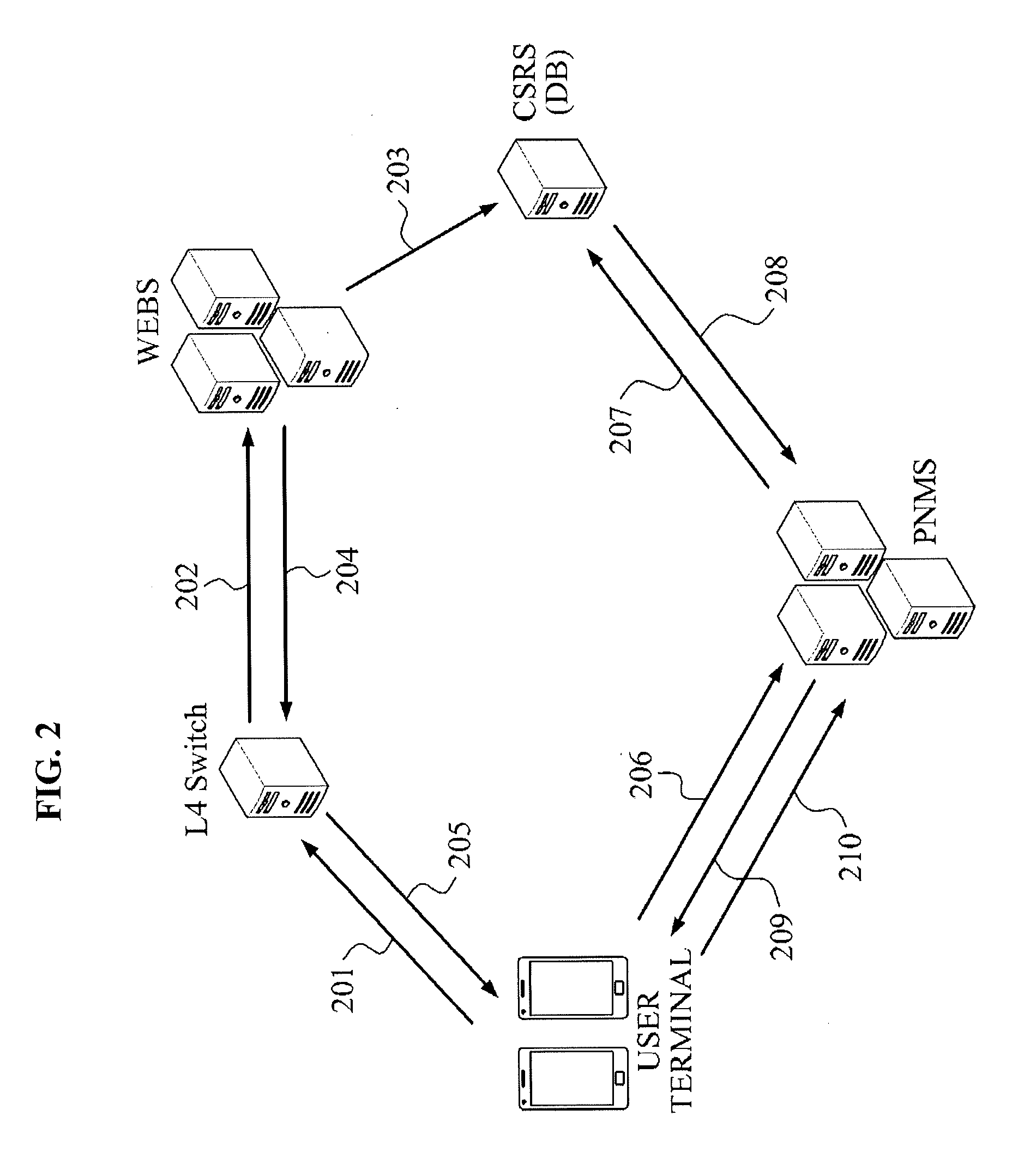
CALL CONNECTING METHOD AND SYSTEM BASED ON MOBILE VoIP
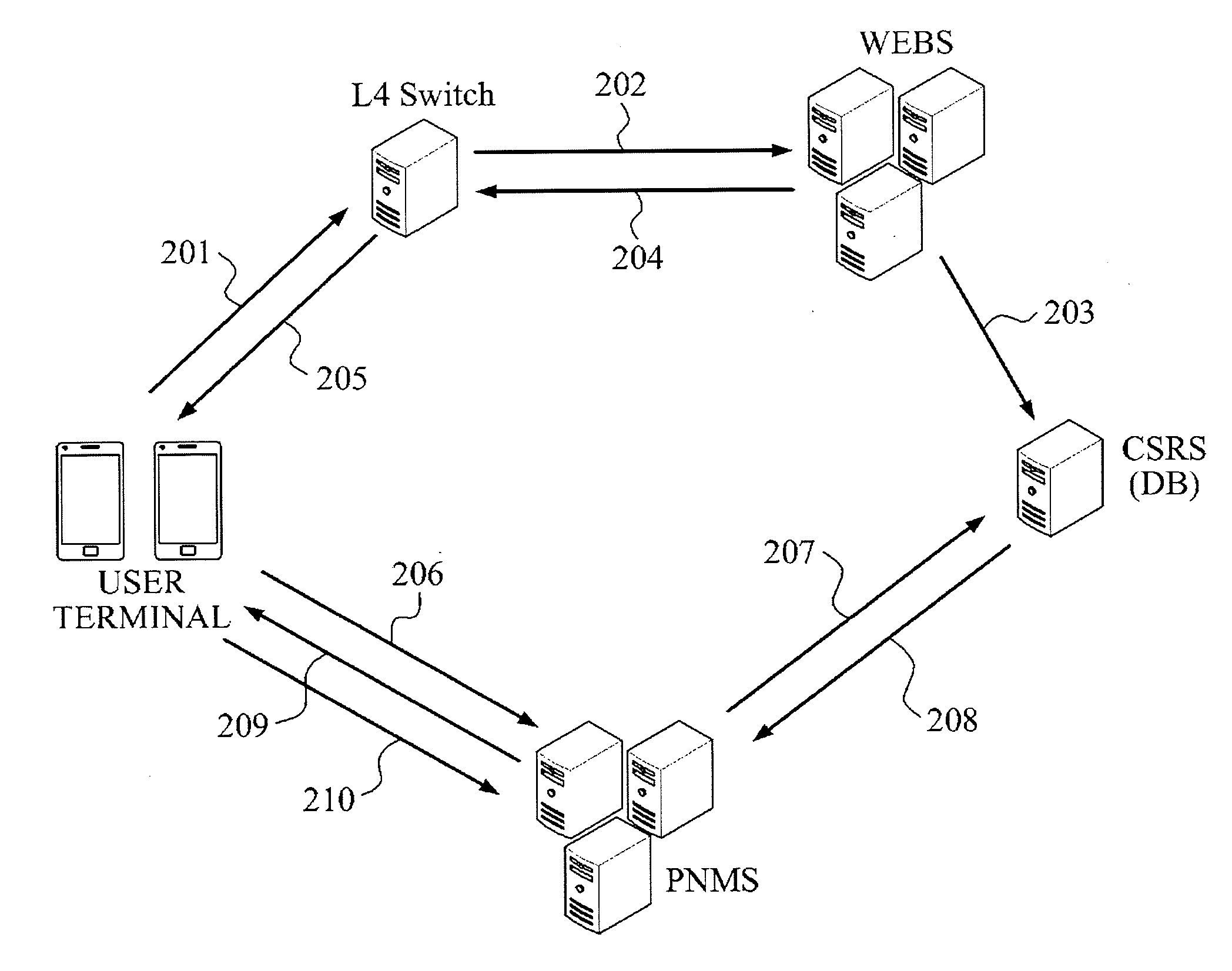
InactiveUS20130039223A1Easy to processIssue can be resolvedMultiplex system selection arrangementsSpecial service provision for substationTTEthernetInternet Protocol
Provided is a call connecting system and method based on mobile Voice over Internet Protocol (mVoIP). The method of connecting a call based on mVoIP performed in the system for connecting a call based on mVoIP including a subscriber server and a call processing apparatus may include the subscriber server receiving a call connection request to a second user terminal from a first user terminal and providing notification of the received call connection request to the second user terminal, the call processing apparatus receiving a call attempt message from the first user terminal, the call processing apparatus receiving a call waiting notification, providing notification of a ready state from the second user terminal, and the call processing apparatus establishing a call connection between the first user terminal and the second user terminal by transmitting the received call attempt message to the second user terminal.
Owner:XENER SYST
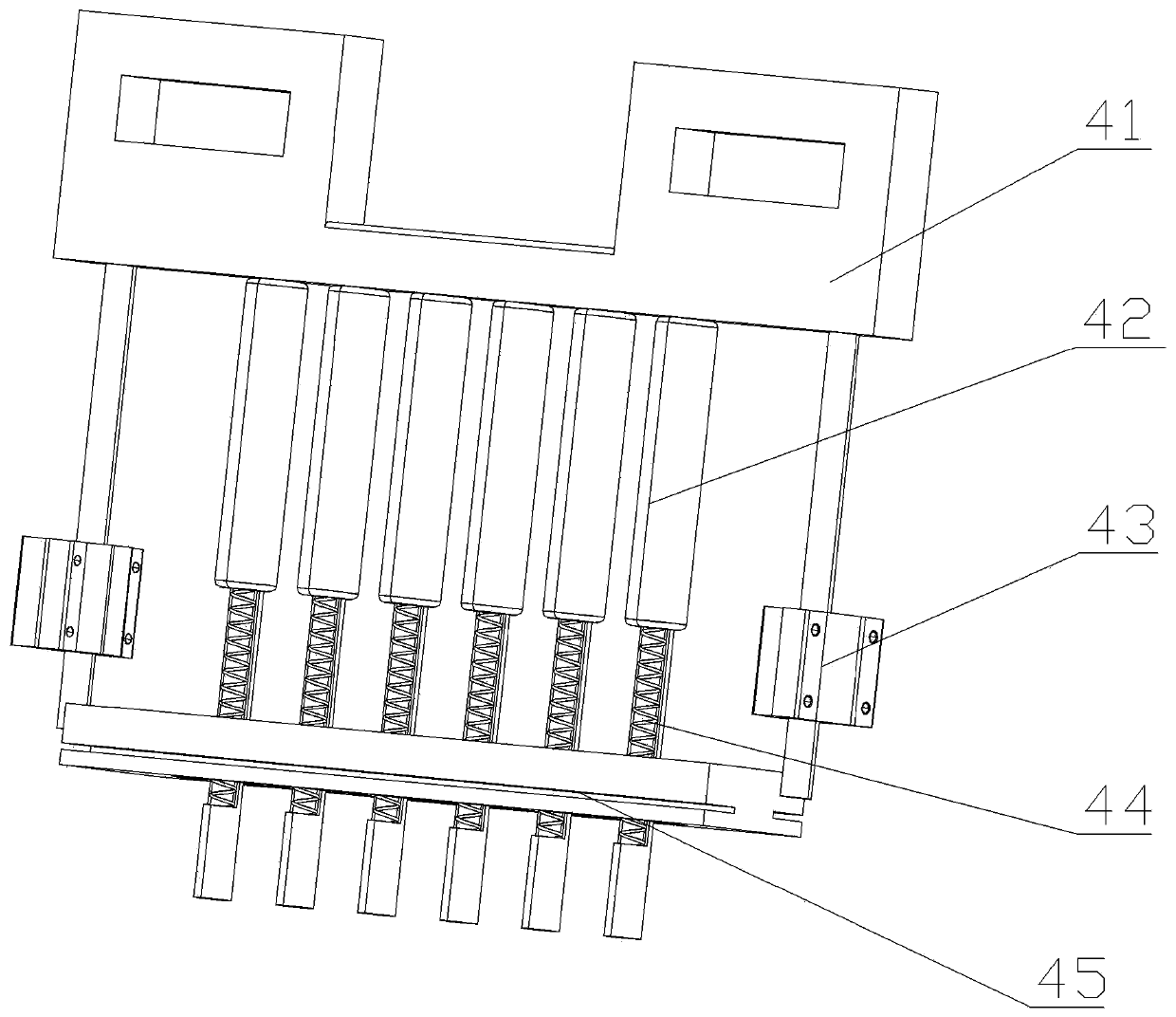
Sugarcoated fruit core-removing and stringing device
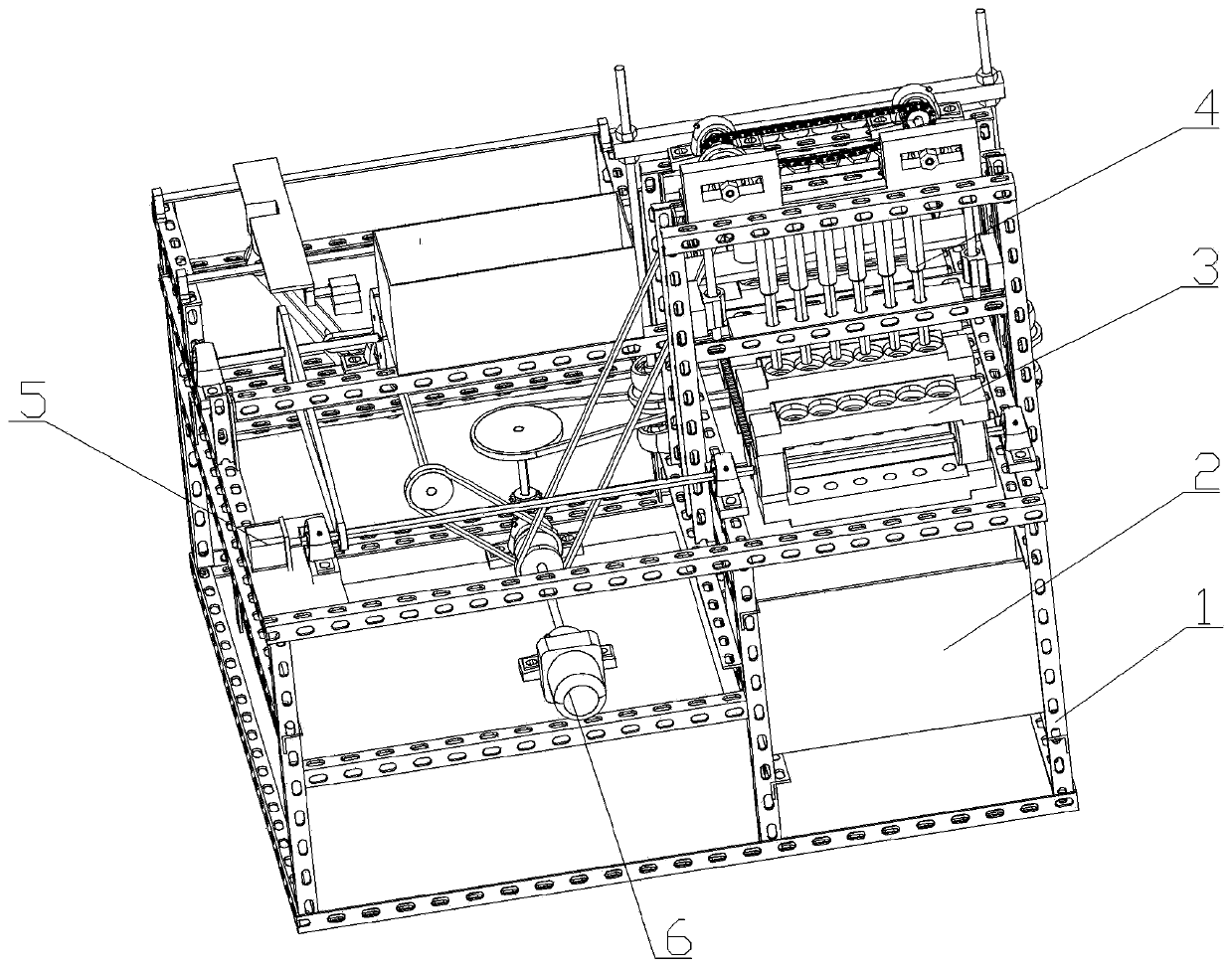
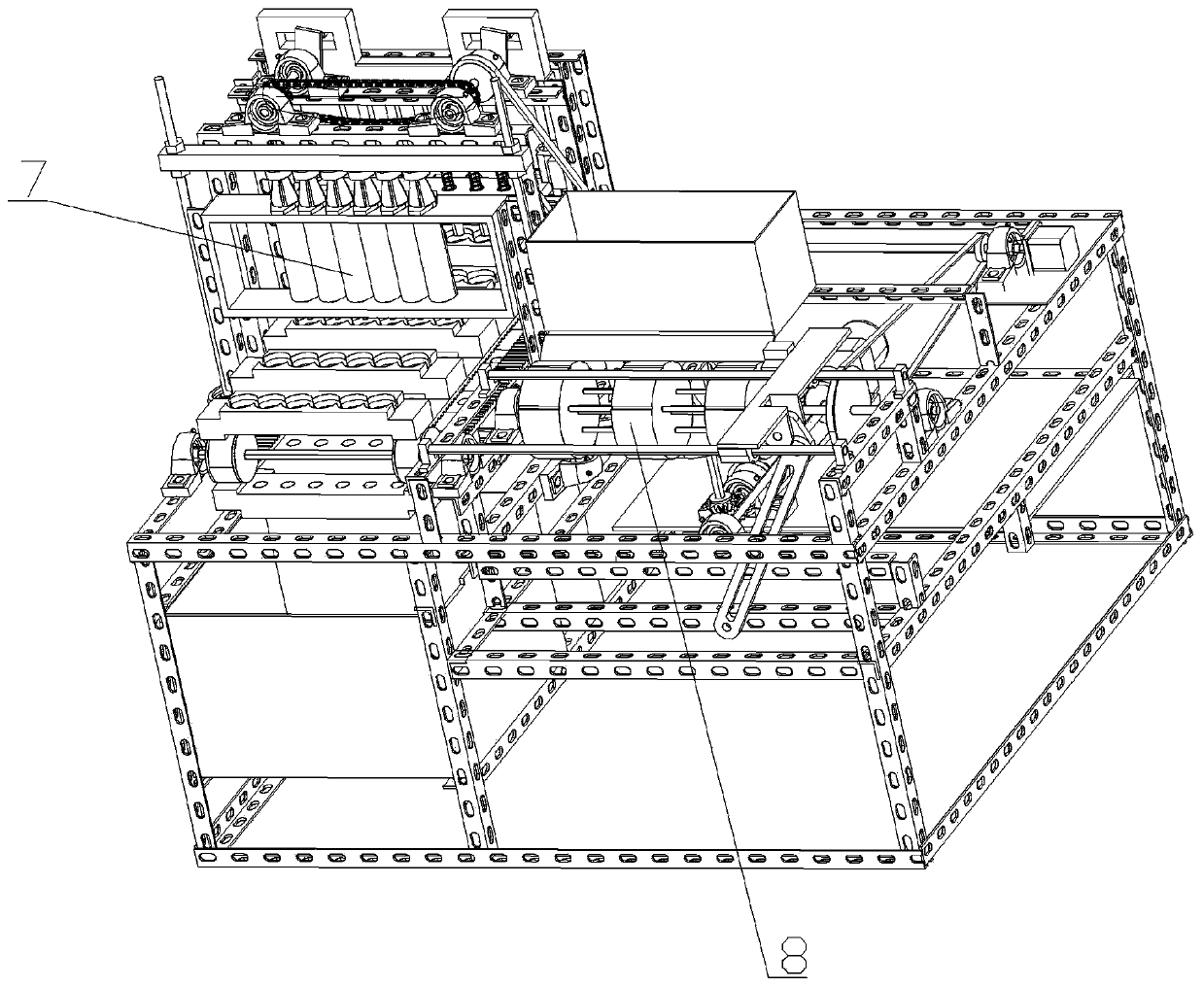
ActiveCN110403050AIncrease productivityPrecise positioningFruit stoningConfectioneryEngineeringMechanical engineering
The invention relates to the technical field of sugarcoated fruit manufacturing equipment, and in particular, relates to a sugarcoated fruit core-removing and stringing device. The sugarcoated fruit core-removing and stringing device comprises a frame, and a positioning conveying mechanism, a drilling and core-removing mechanism, a quantitative stuffing mechanism, a precise stringing mechanism anda driving mechanism arranged on the frame; the drilling and core-removing mechanism and the quantitative stuffing mechanism are arranged on the upper end of the positioning conveying mechanism from front to back successively, the precise stringing mechanism is arranged on one side of the positioning conveying mechanism and corresponds to the positioning conveying mechanism; the driving machine isarranged at one side of the positioning conveying mechanism and comprises a first driving mechanism and a second driving mechanism; the first driving mechanism is connected with the positioning conveying mechanism and the precise stringing mechanism; the second driving mechanism is connected with the drilling and core-removing mechanism and the quantitative stuffing mechanism. The sugarcoated fruit core-removing and stringing device realizes the integration of core removing, stuffing and stringing in the production process of sugarcoated fruits, greatly improves the working efficiency, reduces the production cost, and is suitable for promotion and application.
Owner:QINGDAO UNIV
Wrap front bra
ActiveUS9700082B2Girth of the sport bra to be increasedIncrease girthBrassieresGarment fastenersMechanical engineering
Owner:NIKE INC
Fire pump lifting equipment
The invention relates to a lifting device, in particular to a fire pump lifting device. The technical problem to be solved by the present invention is to provide a fire pump lifting device that is convenient for transportation. In order to solve the above technical problems, the present invention provides such a fire pump lifting equipment, which includes a base plate, wheels, push rods, slide rails, sliders, lifting devices, a second motor, etc.; There is a push rod on the left side, a slide rail on the rear side of the top of the bottom plate, a slide block is slidably connected to the top of the slide rail, a lifting device is provided on the top of the slide block, a second motor is provided on the front side of the slide block, and the output shaft of the second motor A second rotating shaft is connected, a gear is arranged at the front of the second rotating shaft, and a rack is arranged at the front of the bottom plate top. The present invention controls the left and right positions of the fire-fighting water pump through the clockwise rotation of the second motor, and adjusts the height of the fire-fighting water pump through the clockwise rotation of the first motor, which is very simple and fast, and the process is slow.
Owner:石媛瑗
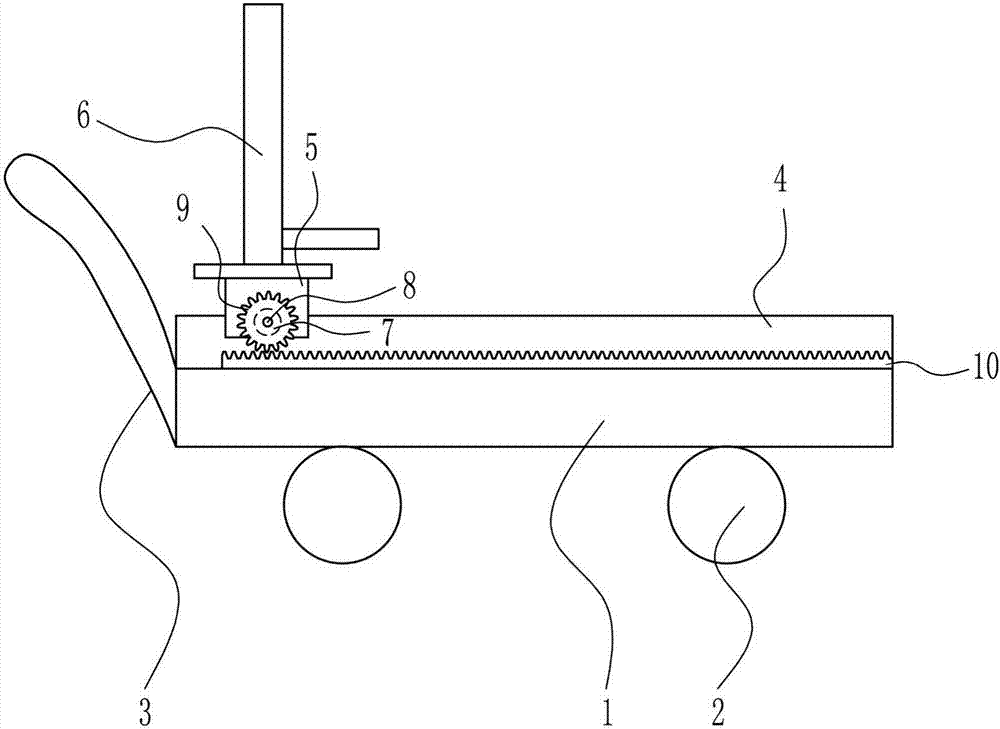
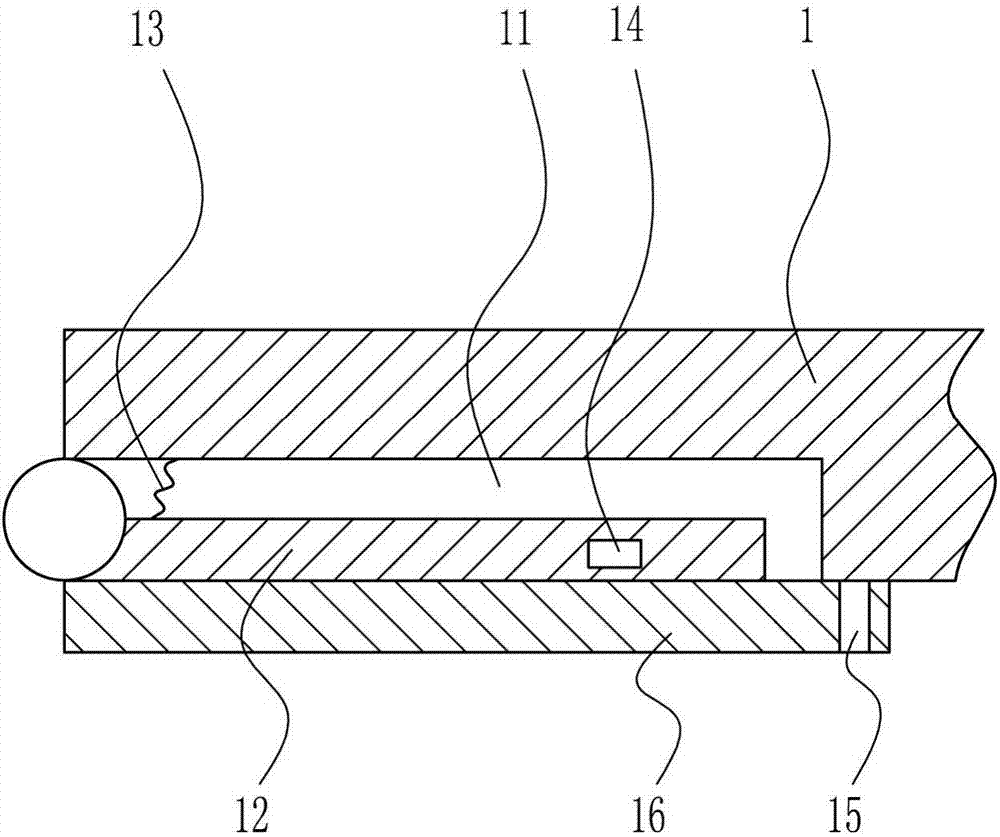
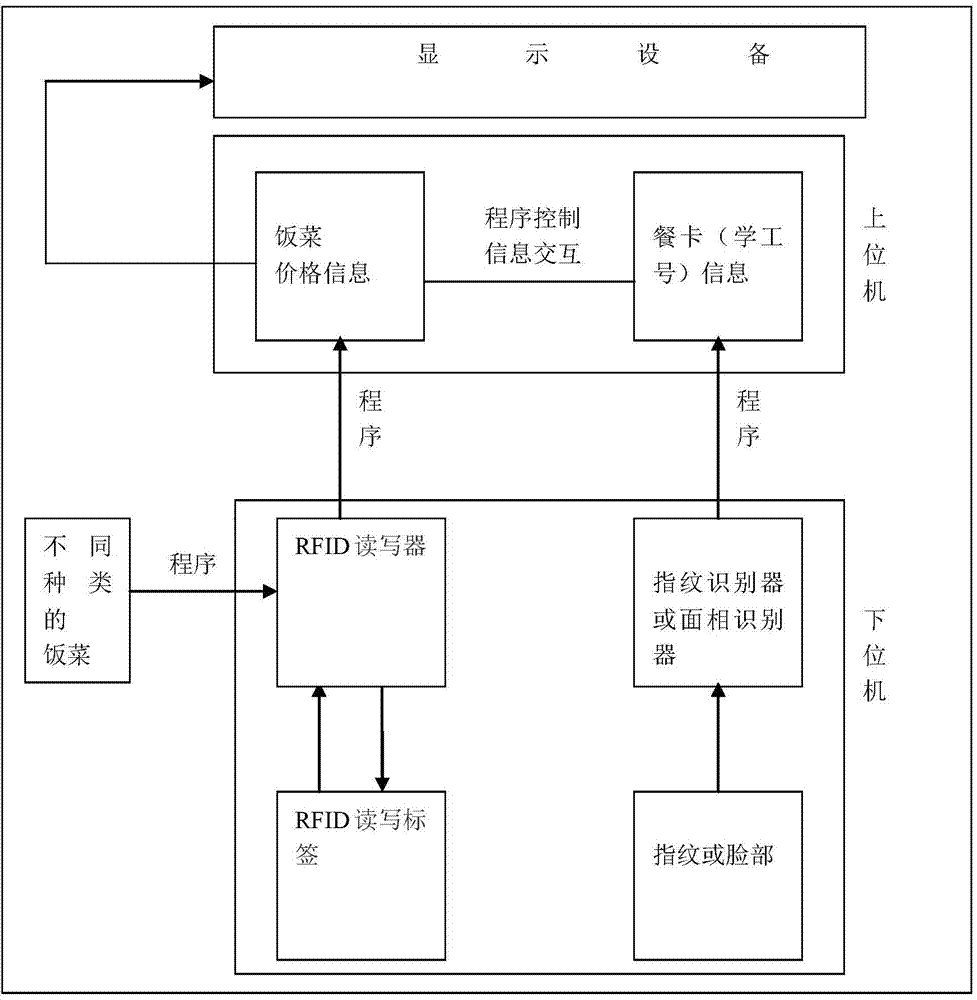
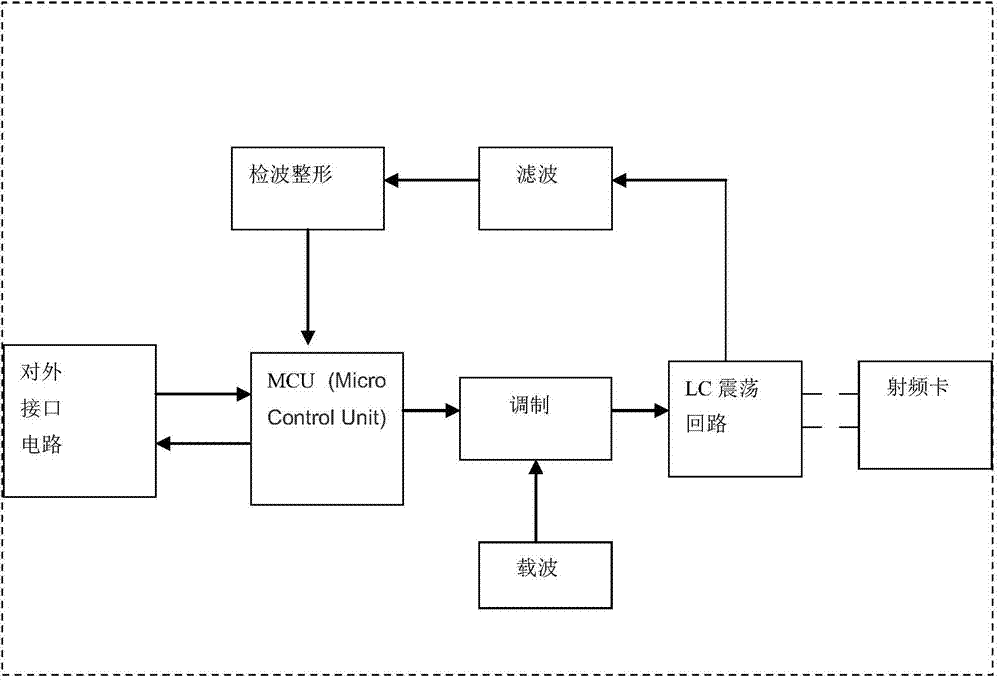
Dining room fee deduction system based on RFID and recognition technology
The invention provides a dining room fee deduction system based on an RFID and recognition technology. The system comprises an RFID reader-writer, a plurality of RFID reading-writing labels, a fingerprint identifier or a face image identifier, displaying equipment and a PC. The RFID reader-writer is connected with the PC and a power supply. The fingerprint identifier or the face image identifier is connected with the PC. The displaying equipment is connected with the PC. The RFID reading-writing labels are attached to tableware. A dining room fee deduction mode is upgraded and simplified, manual deduction cards are eliminated, and the functions of card reading through the reader-writer, fingerprint identifying or face identifying and automatic fee deduction are achieved. Fee deduction efficiency is improved, manual cost is saved, a dining environment is beautified, the benefit and the environment of a dining room are guaranteed through the reasonable fee deduction mode, and meanwhile the benefit of a customer is guaranteed.
Owner:FUJIAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com