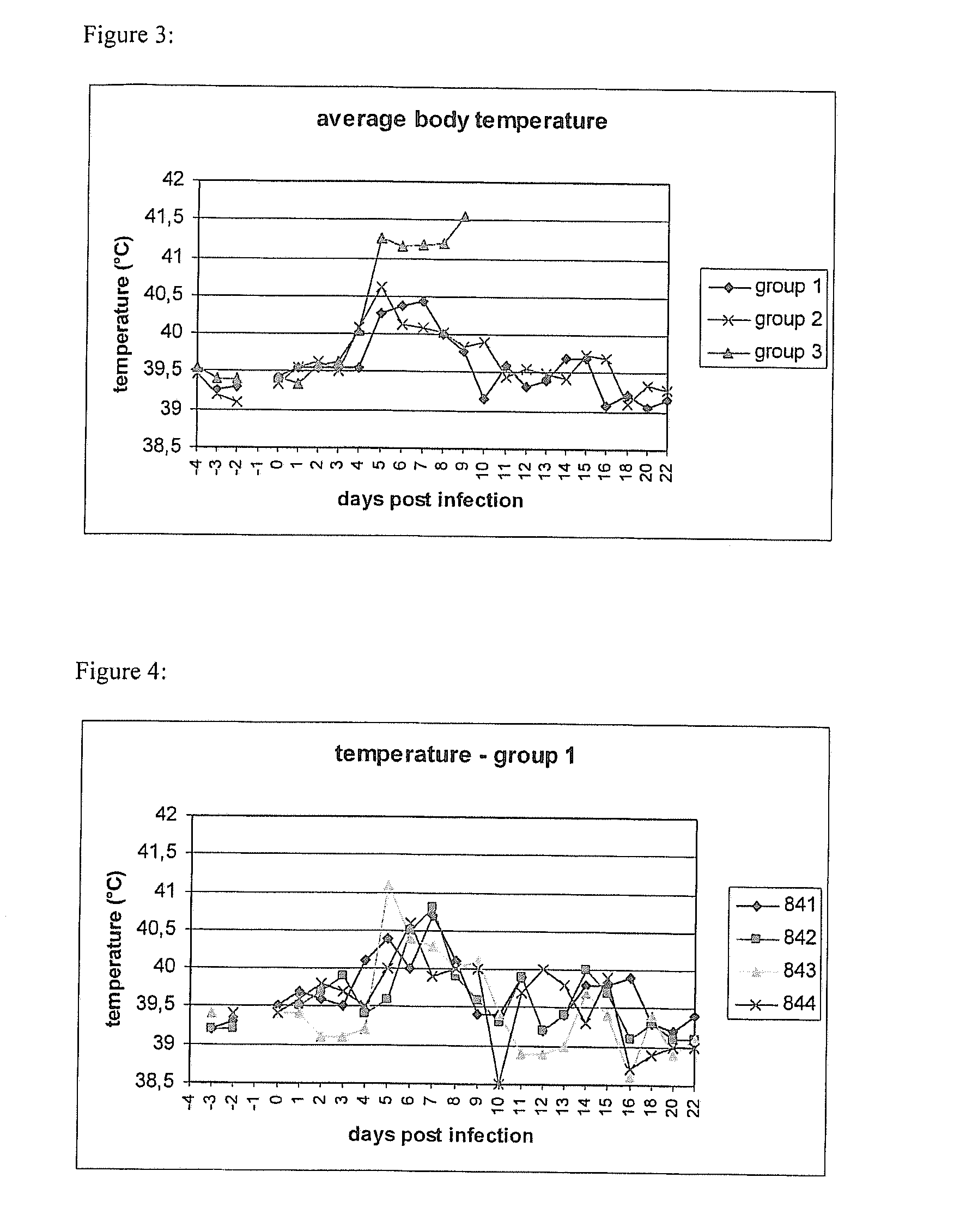
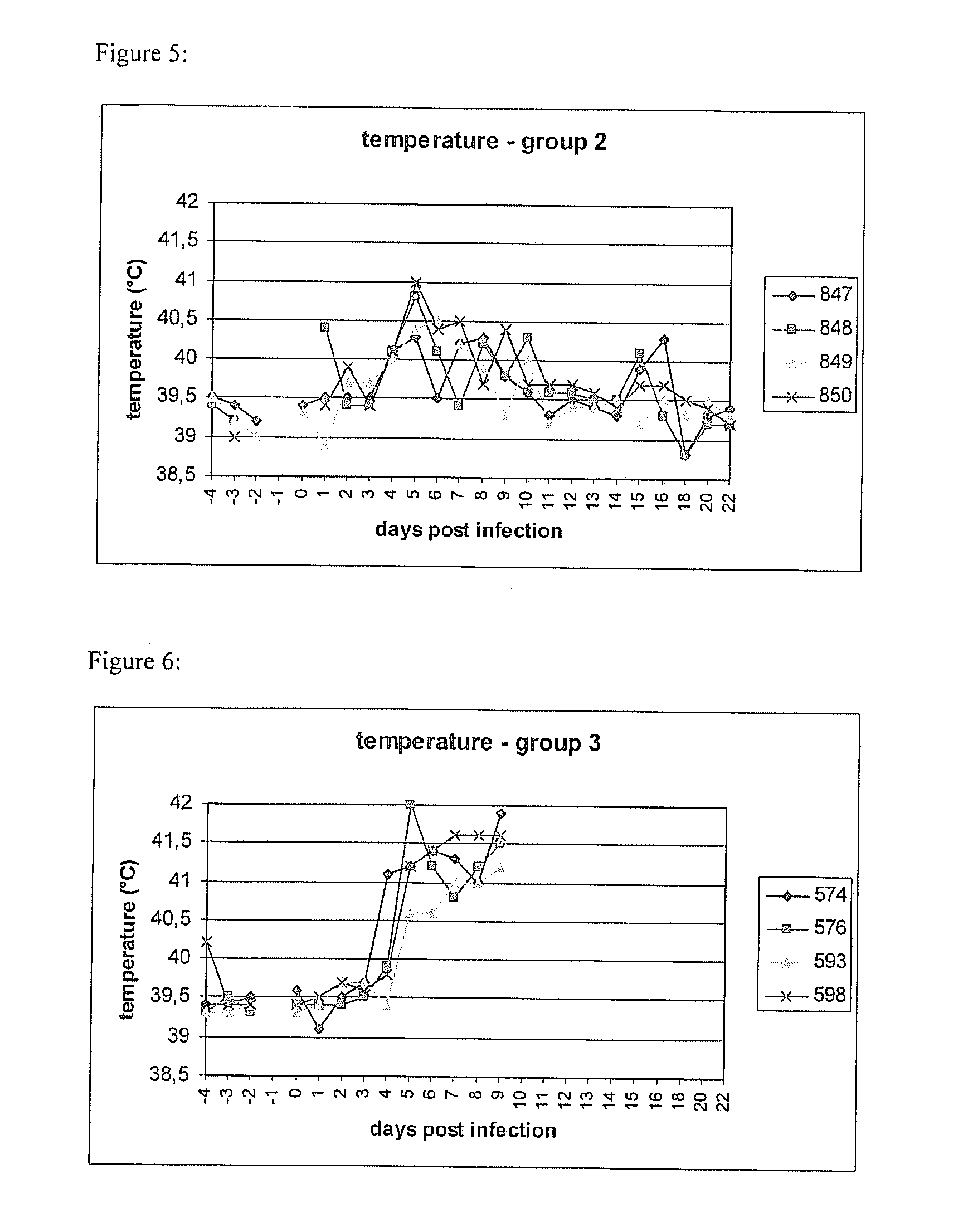
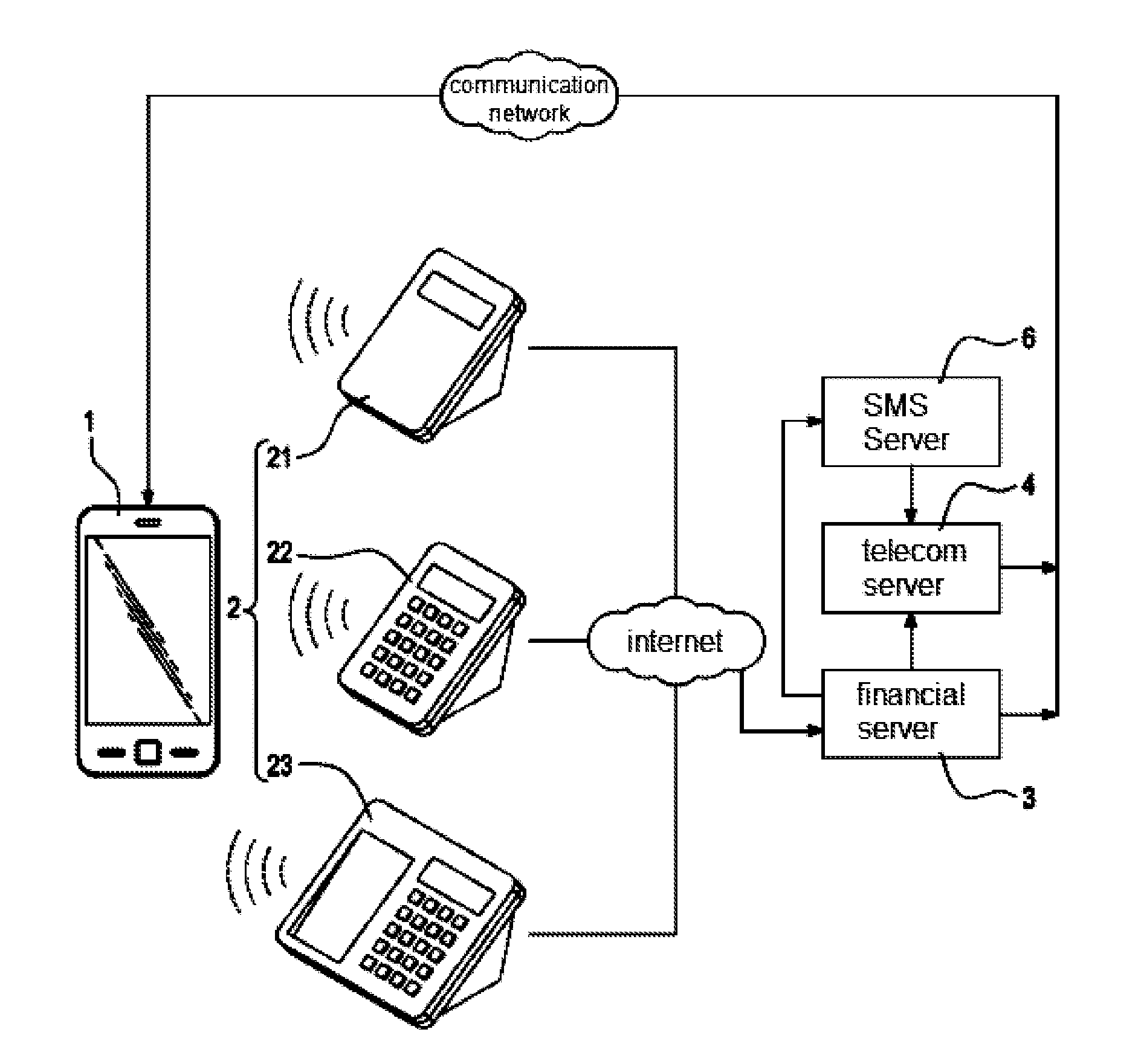
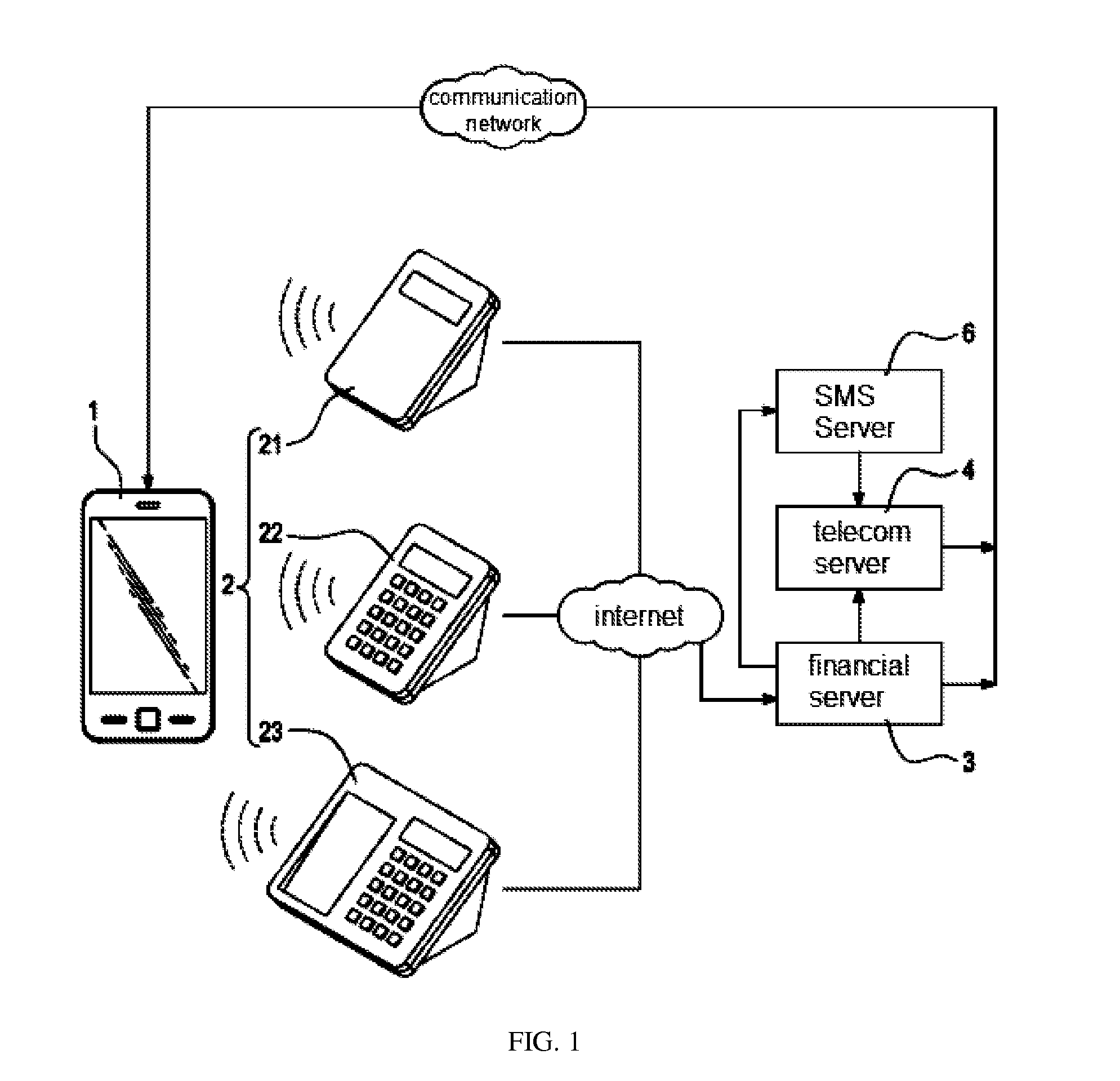
Patents
Literature
51results about How to "High level of security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
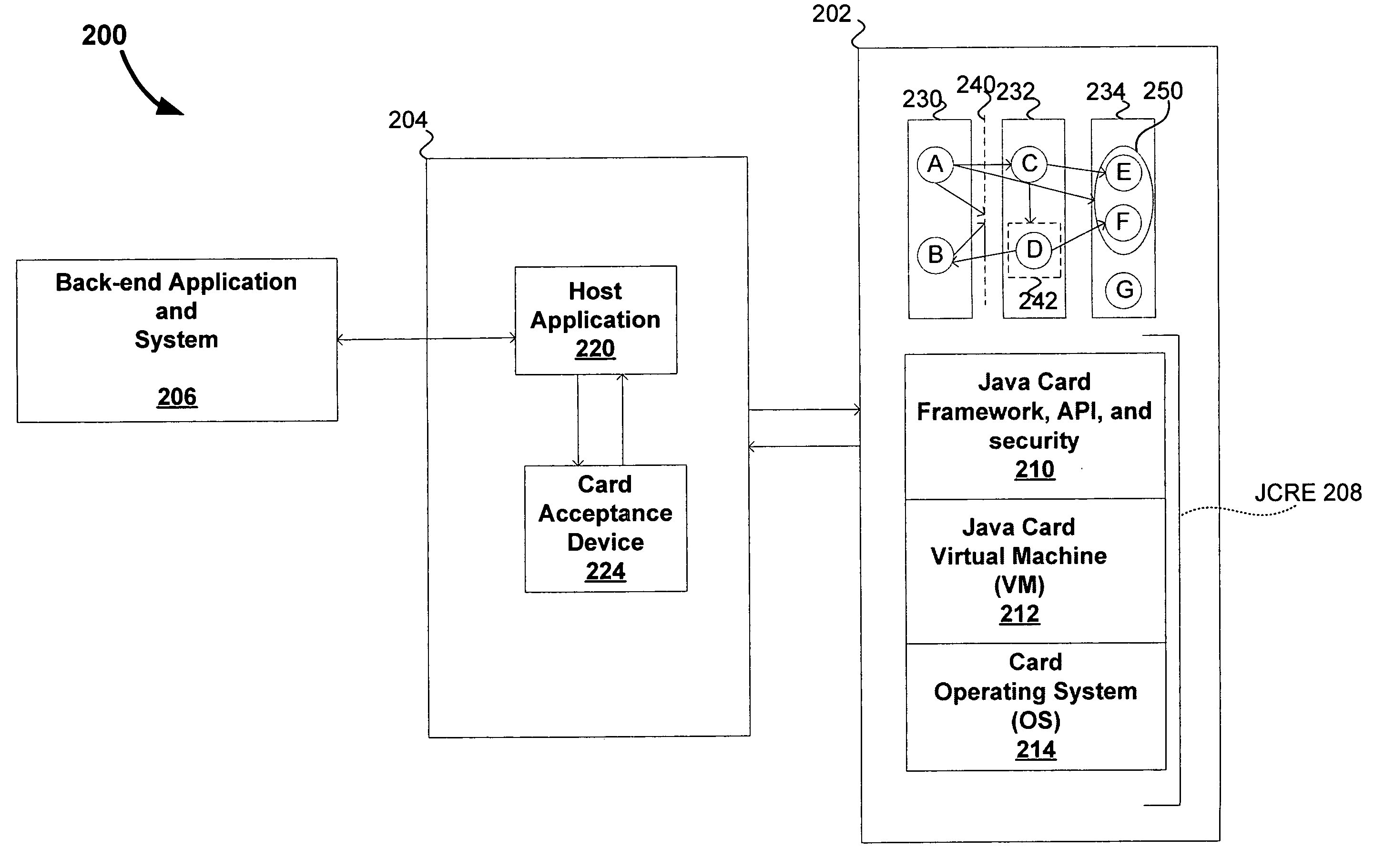
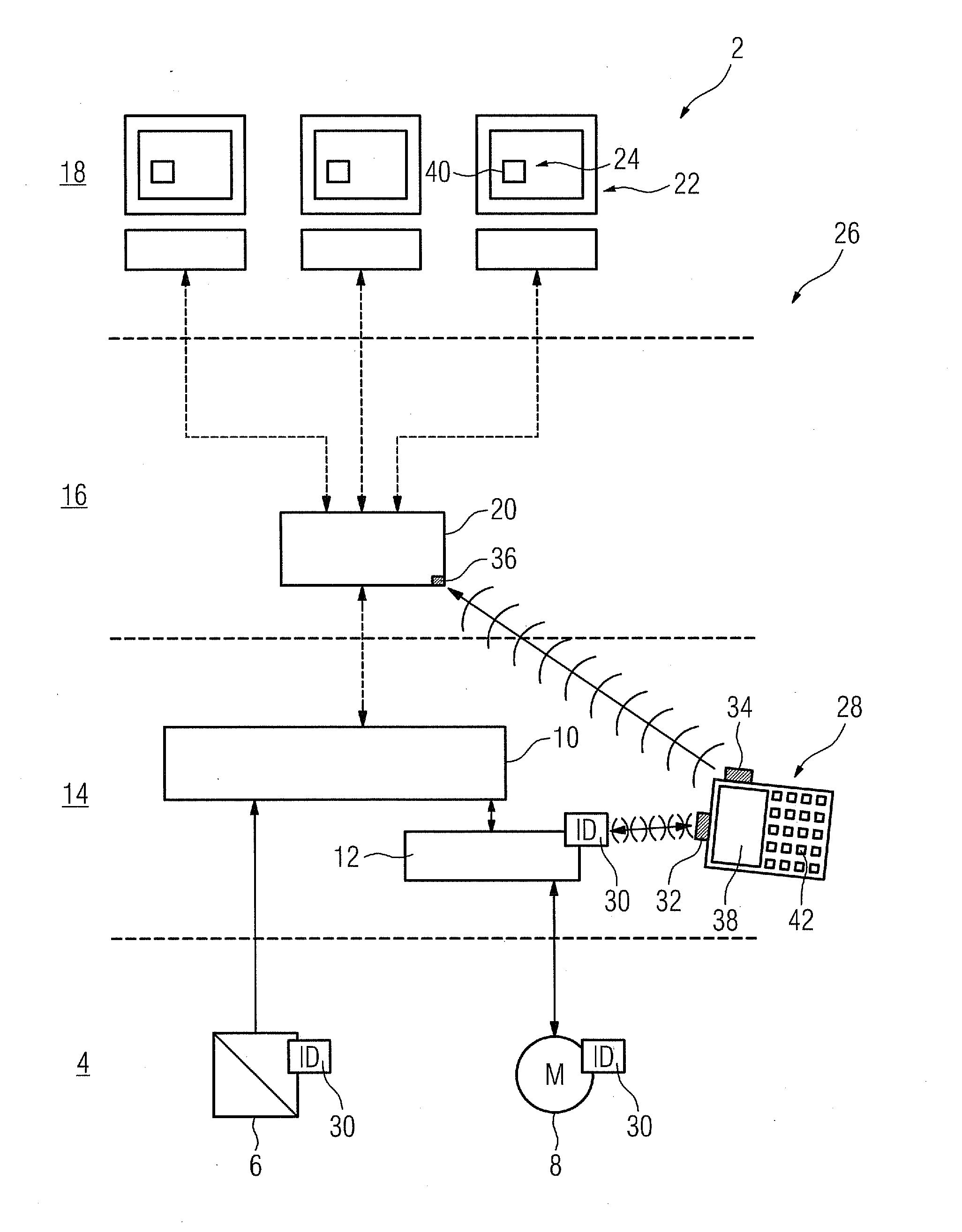
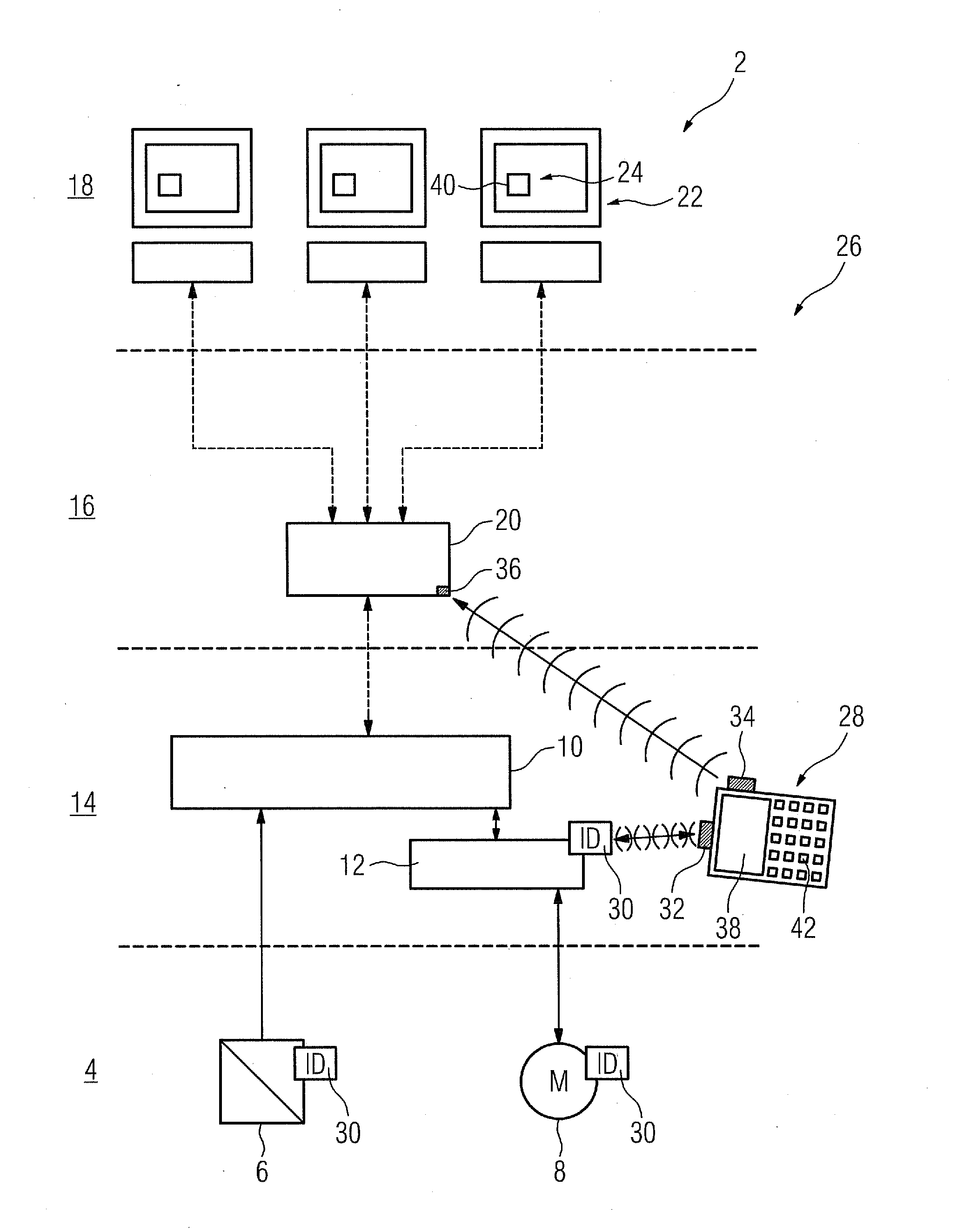
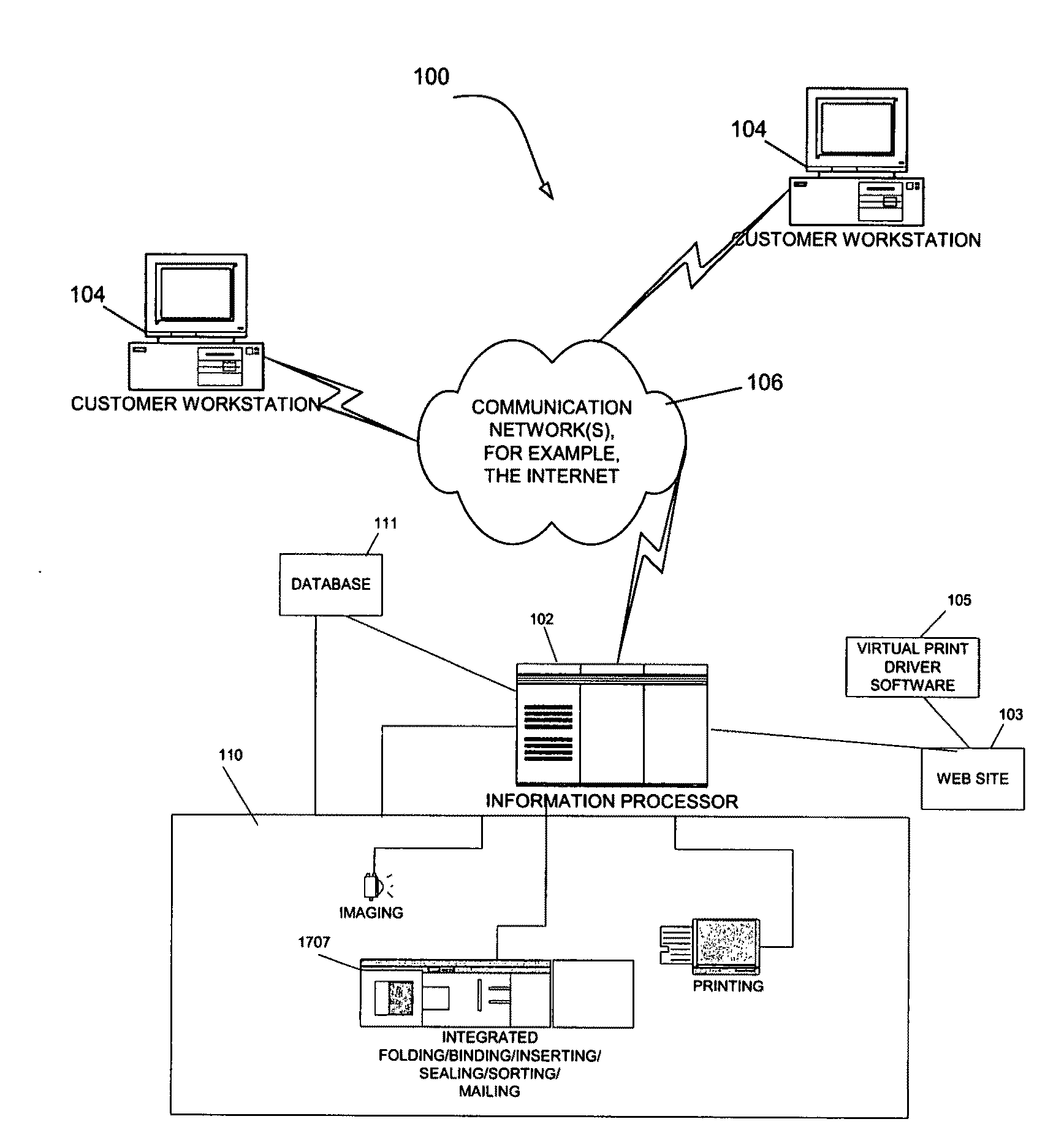
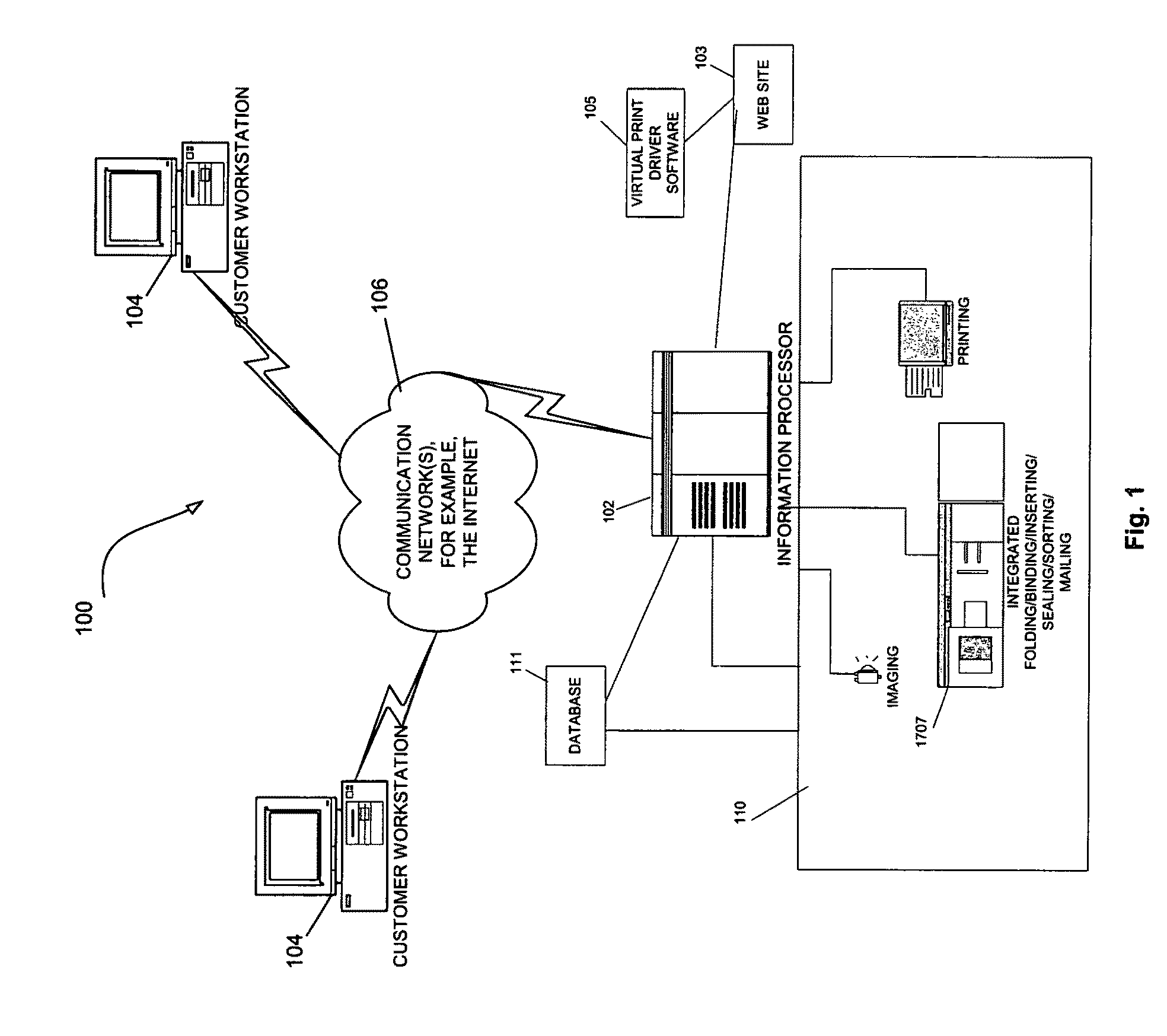
Framework for providing a configurable firewall for computing systems
ActiveUS20050149926A1Simpler to useHigh level of securitySpecific access rightsDigital data processing detailsSystem requirementsProcess rate
A configurable firewall for computing systems is disclosed. The configurable firewall provides a firewall control block that can be used as a mechanism to implement and control access privileges between various components of the computing environment. As such, the firewall control block can be used to determine whether one component (e.g., applet) can access another component in the computing environment. This allows a flexible environment where firewall boundaries can be configured in such a way that each applet can allow access to a desired set of other applets. In addition, the control block can be implemented using a variety of techniques that may be suitable for different system requirements (e.g., processing speed, memory). As such, the configurable firewall is useful for implementing security for various computing systems, especially those that operate with relatively limited processing power and / or provide highly specialized functionality (e.g., smart cards).
Owner:ORACLE INT CORP
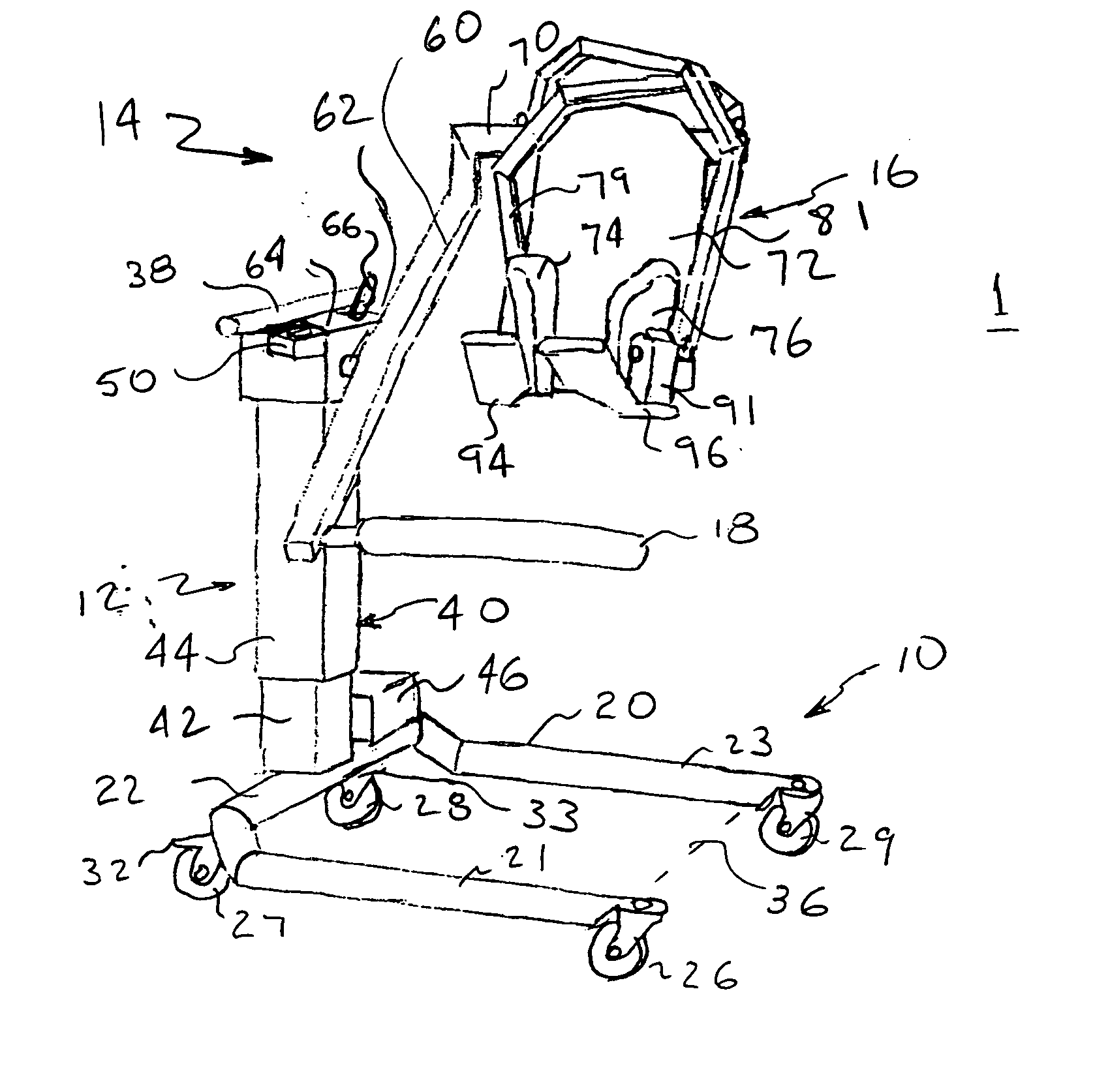
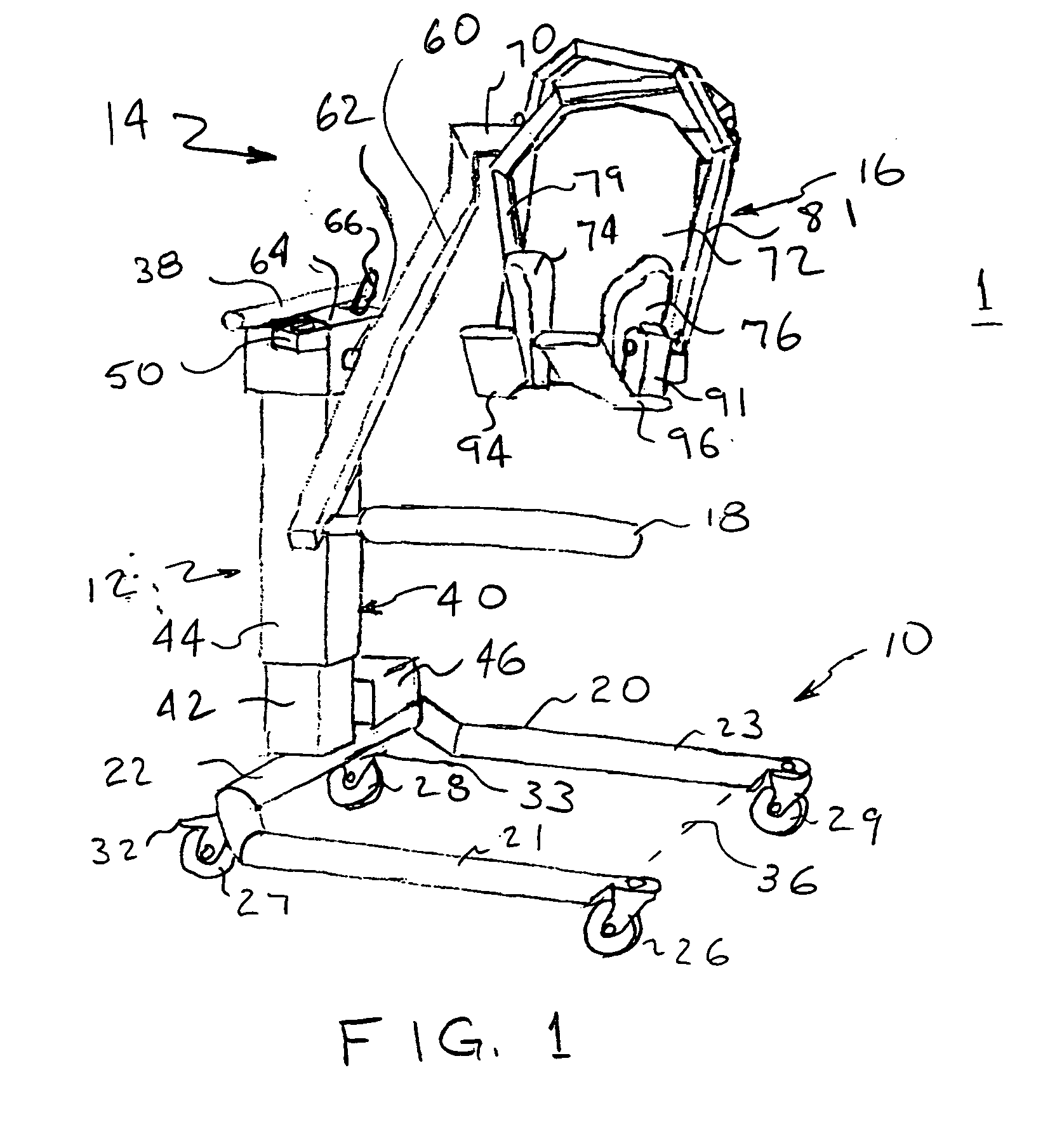
Patient lift and transfer device and method
InactiveUS20050217024A1Minimal manipulationHigh level of comfortWheelchairs/patient conveyanceNursing bedsHorizontal forceBariatric patient
In a lift and transfer device and method, a patient support assembly supported on a lift on a wheeled platform includes a main support arm pivoted to the lift. First and second transversely extending support arms respectively carrying a back support section and a leg support are cantilevered from the main support arm. The main support arm is positioned for lifting the patient from a bed. The main support arm is rotated from a first to a second angular position for lowering a patient to a wheelchair. First and second pivot arms each have an upper end pivotally supported to the back support section and a lower end having a torso grip pad positioned adjacent one side of the patient. Horizontal force applied by each torso grip pad and friction provide patient support. Further device forms are provided for bariatric patients and for use with other types of lifts.
Owner:AARESTAD JEROME K
System for selectively disabling cell phone text messaging function
InactiveUS20110294465A1High level of securityNeed for powerUnauthorised/fraudulent call preventionEavesdropping prevention circuitsEmbedded systemText messaging
A selective cell phone text messaging function disabling system prevents a vehicle occupant from text messaging while driving. Other occupants of the vehicle can text message using their cell phones. The driver's cell phone text messaging functionality is turned off by a signal broadcasting system as the driver enters the vehicle through the driver-side door. When the driver exits the vehicle through the driver-side door, the cell phone resumes its texting capability, preserving text messaging functionality while the driver is not operating the vehicle.
Owner:INSELBERG ERIC
Cell module
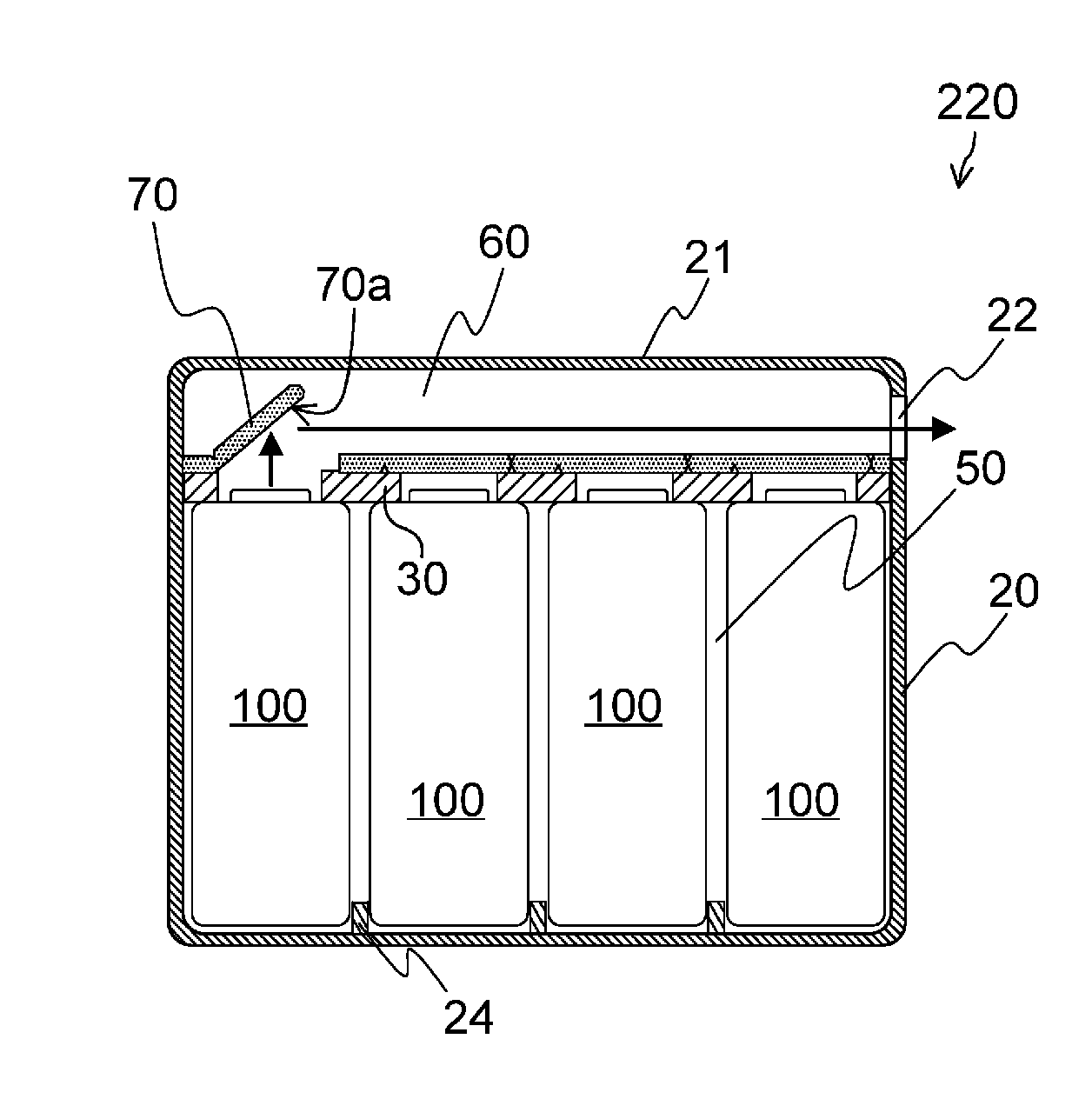
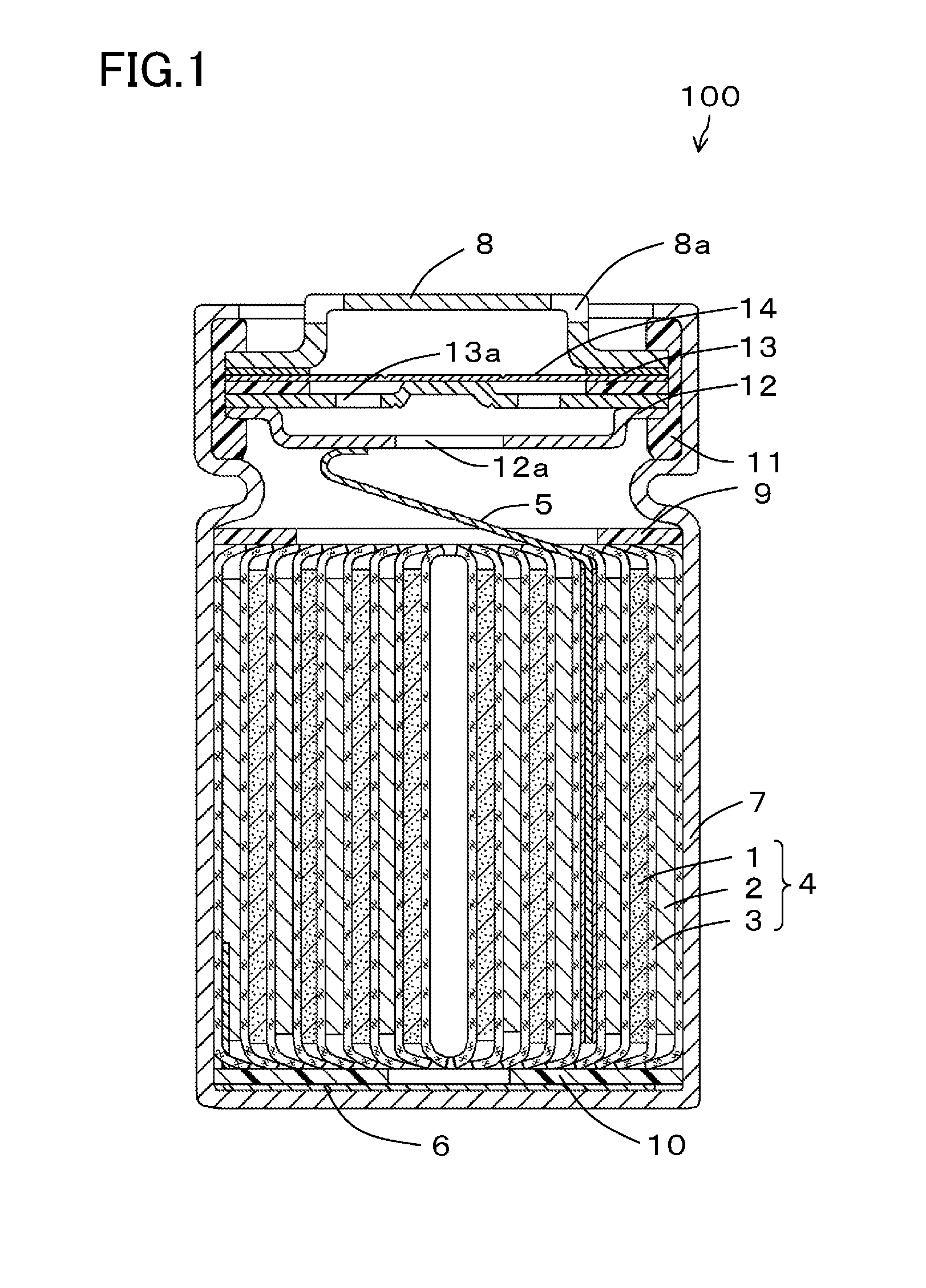
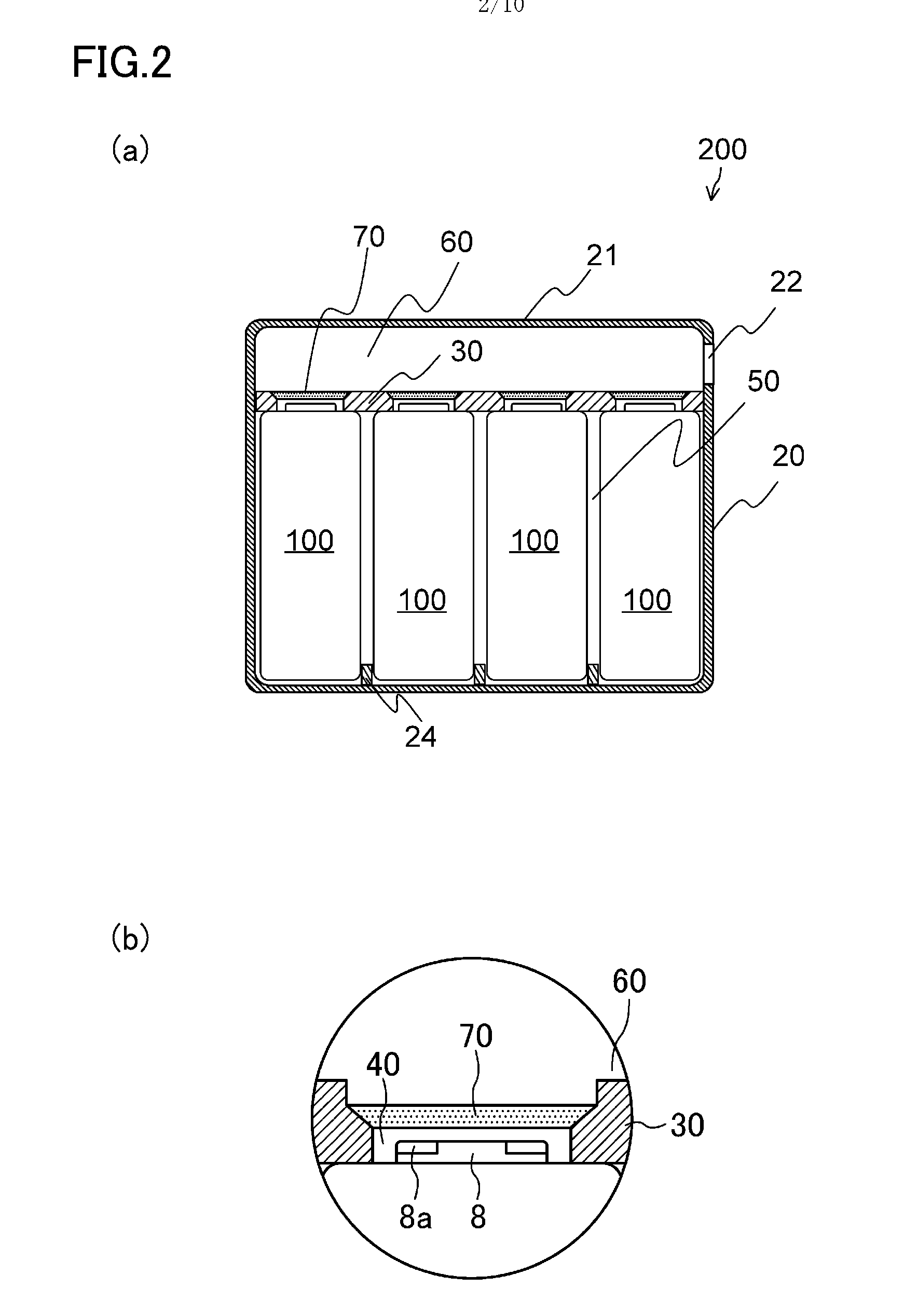
Batteries 100 are accommodated in a case 20, wherein the batteries 100 each include an opening portion 8a for releasing gas produced in an associated one of the batteries to outside the battery, the case 20 is partitioned into an accommodation section 50 configured to accommodate the batteries 100 and an exhaust passage 60 configured to expel the gas released from at least one of the opening portions 8a of the batteries 100 to outside the case 20, the opening portions 8a of the batteries 100 are allowed to communicate with the exhaust passage 60 through sealed connection passages 40, and a one-way open valve 70 which is configured to open only along a direction from the opening portion 8a of the battery 100 to the exhaust passage 60 is provided in an intermediate portion or at an end of each of the connection passages 40.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Device for signalling spatial separation or closeness beyond or within a predetermined limit
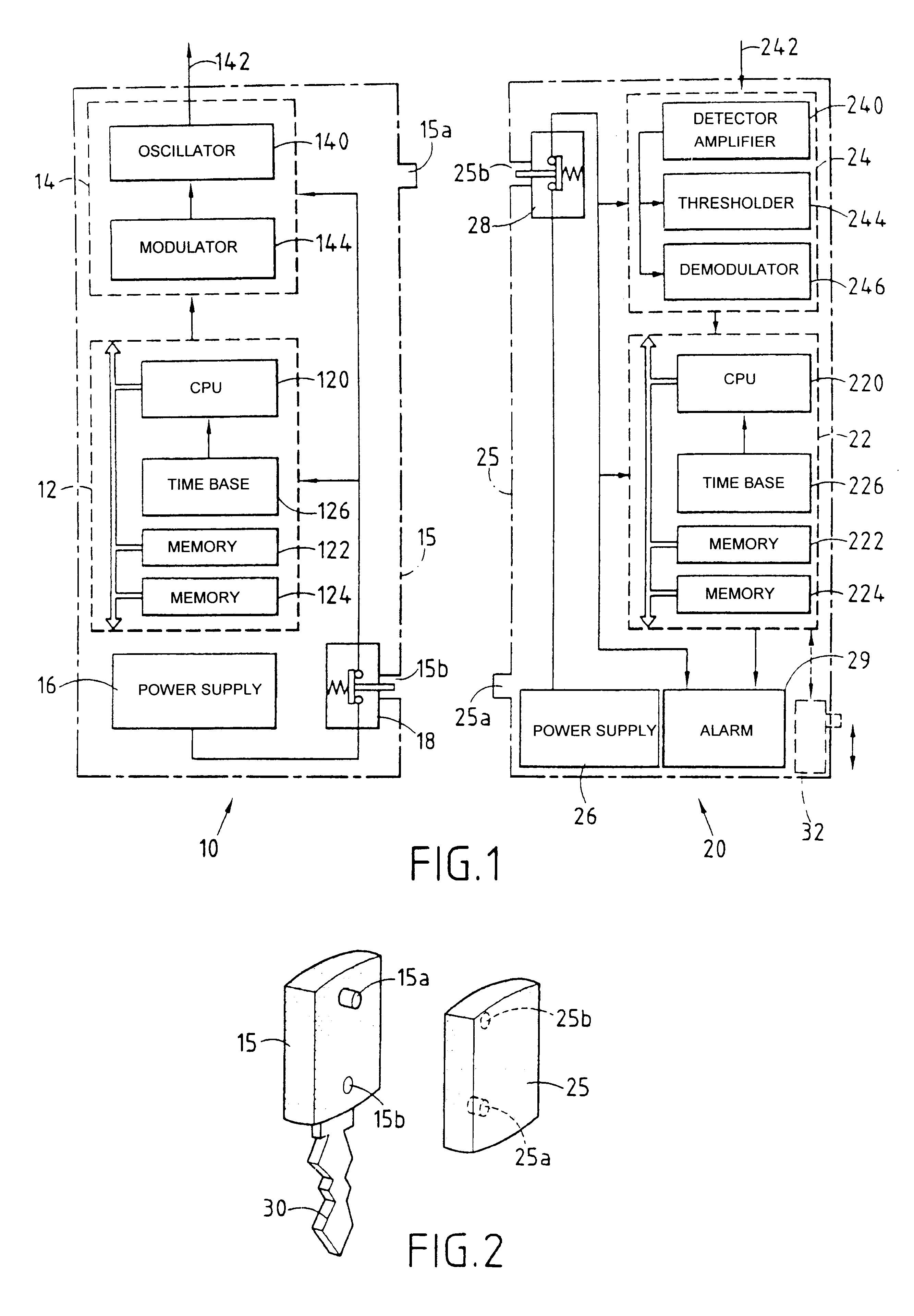
InactiveUS6472986B1High level of securityImprove security levelBurglar alarm by hand-portable articles removalRadio wave reradiation/reflectionEngineeringTransmitter
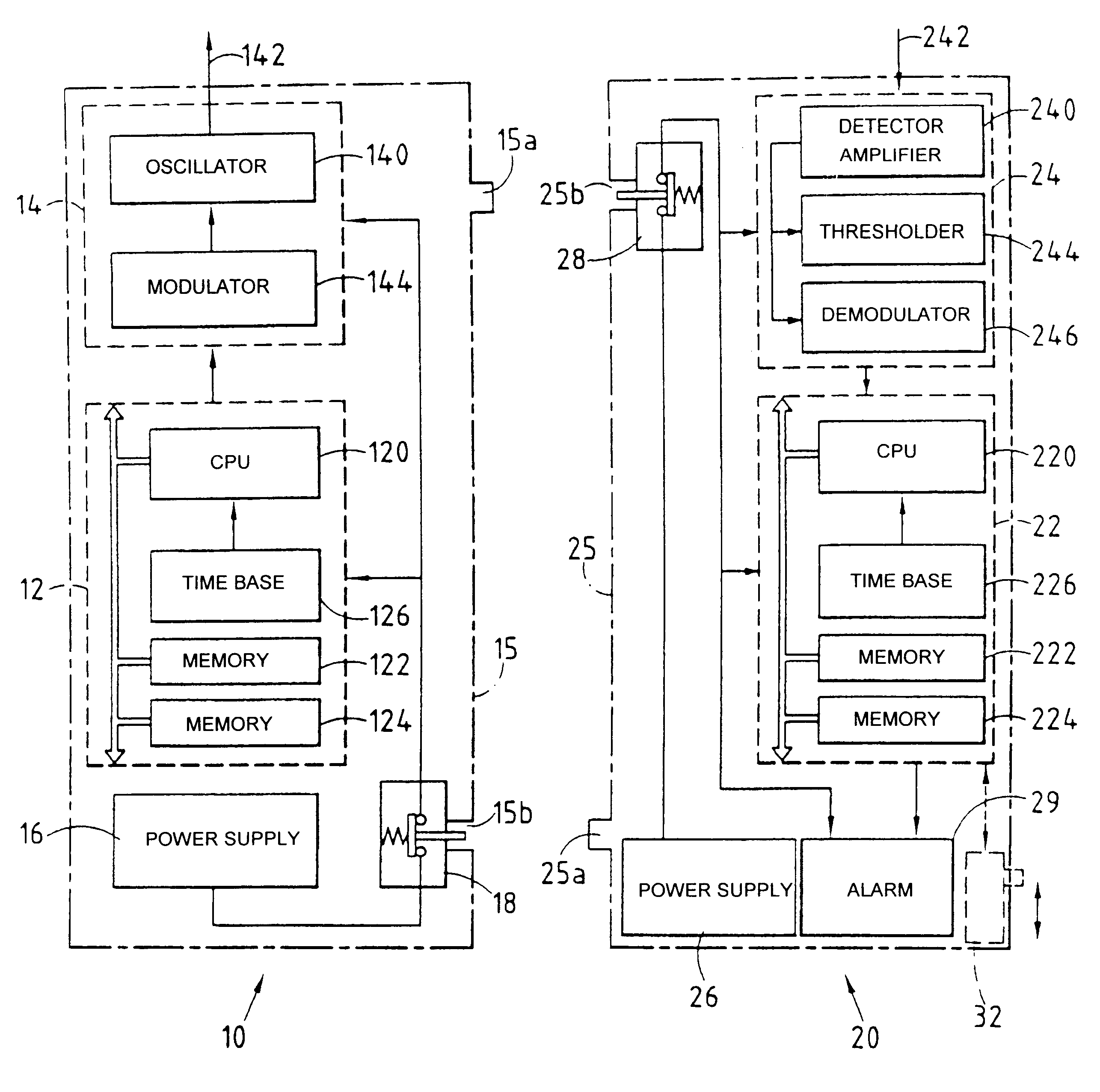
A first unit (10) comprises a first transmitter (12) for wireless transmission of a signal in the from of periodic frames comprising identity information encoded in varying form in each frame, and a second unit (20) comprises a first receiver (22) for receiving said signal and for causing an alarm (29) to operate in response to failure to receive or to recognize identity information. Means (16, 26, 15a, 25a, 15b, 25b) are provided for automatically deactivating at least one of the first and second units when they are physically close together, and for automatically activating said units when they are physically separate from each other.
Owner:SORRIAUX PIERRE
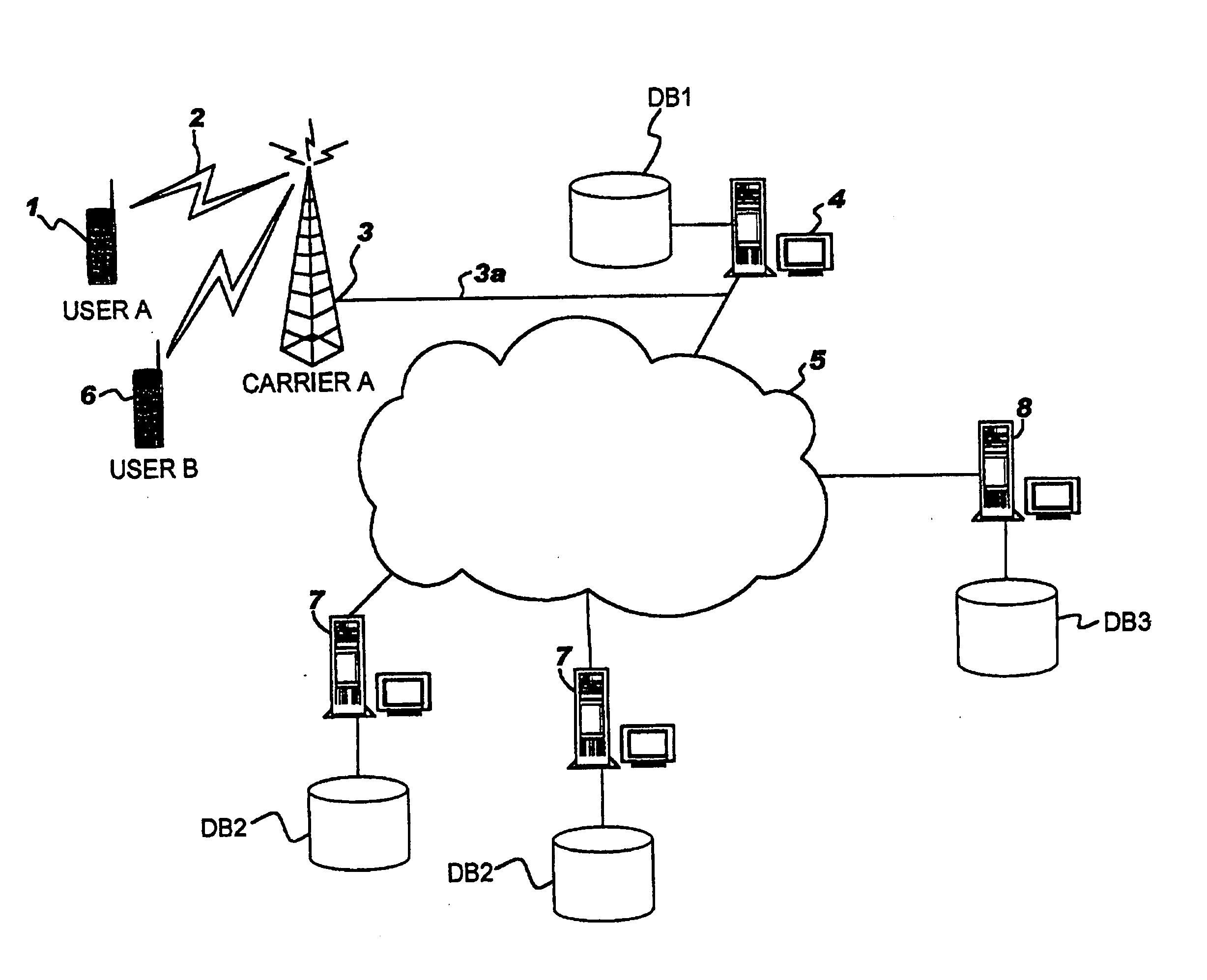
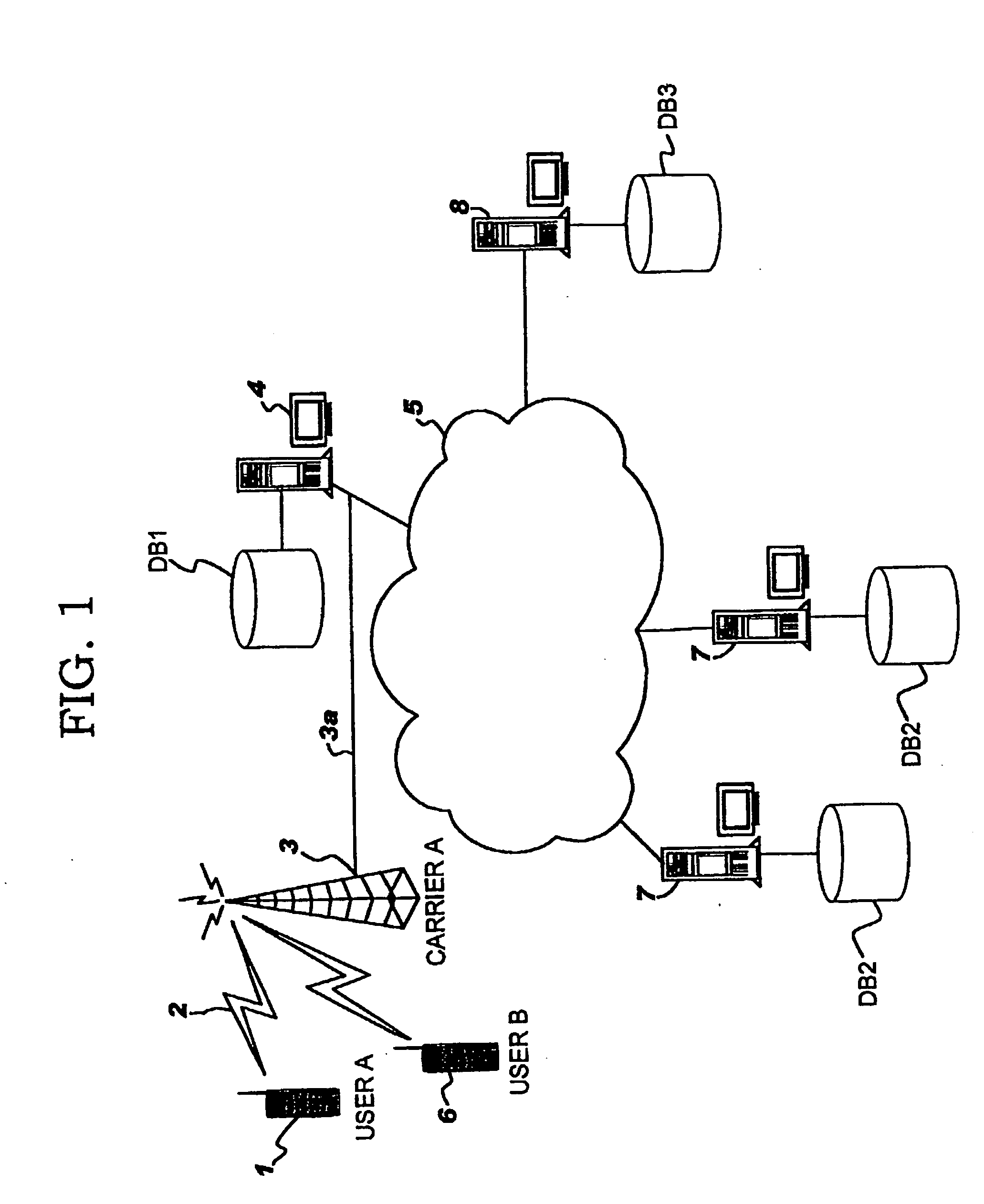
Secure communications
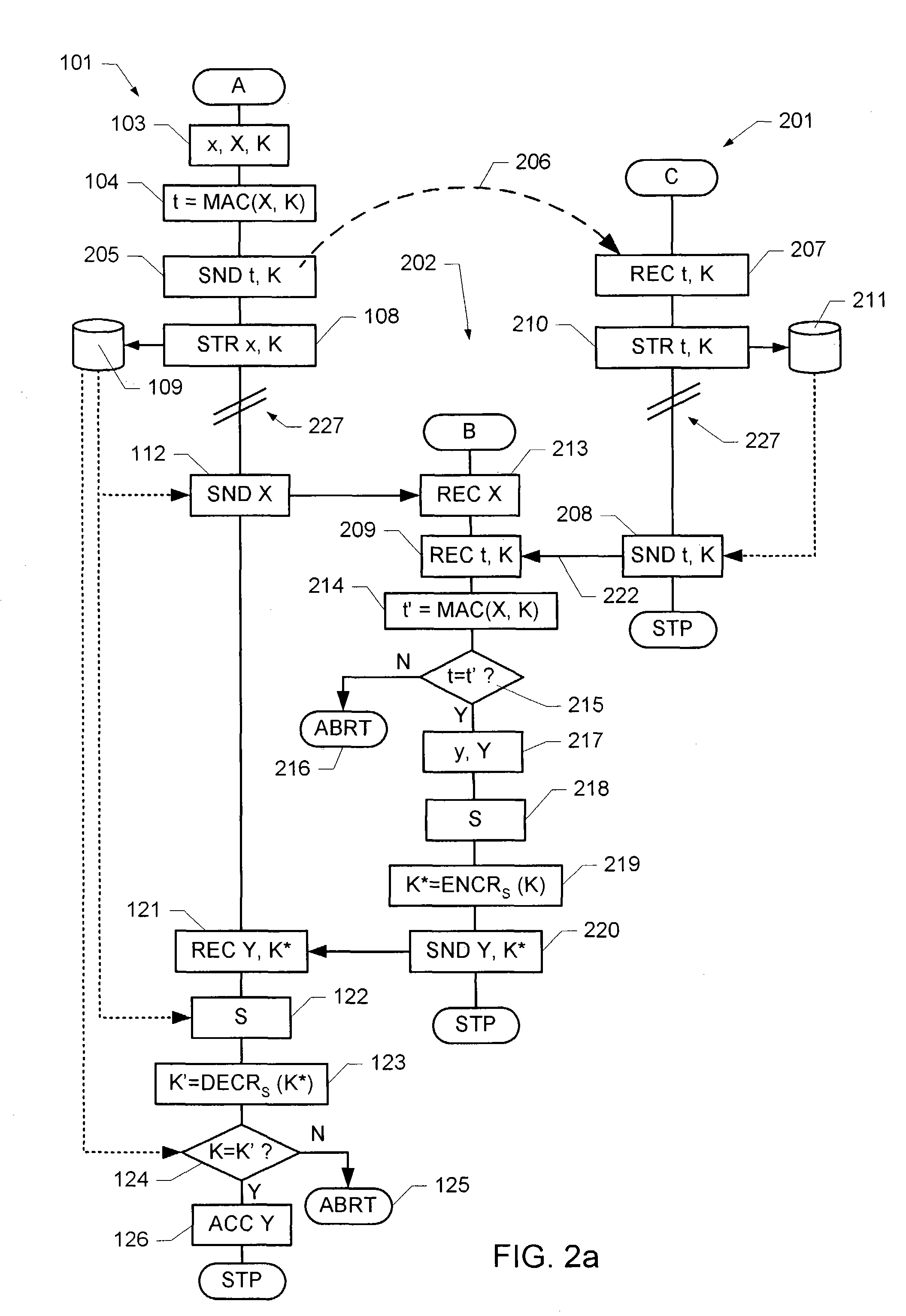
ActiveUS7284127B2High safetyHigh level of securityKey distribution for secure communicationPublic key for secure communicationSecure communicationComputer security
A method of providing secure communications between a first and a second communications unit comprising a key exchange between the communications units resulting in a shared secret key, the key exchange including a user interaction. The method includes the steps of providing, at least partly by means of a user interaction, a passcode to the first and second communications units; generating a first contribution to the shared secret key by the first communications unit and a second contribution to the shared secret key by the second communications unit, and transmitting each generated contribution to the corresponding other communications unit; authenticating the transmitted first and second contributions by the corresponding receiving communications unit based on at least the passcode; and establishing said shared secret key by each of the communications units from at least the corresponding received first or second contribution, only if the corresponding received contribution is authenticated successfully.
Owner:TELEFON AB LM ERICSSON (PUBL)
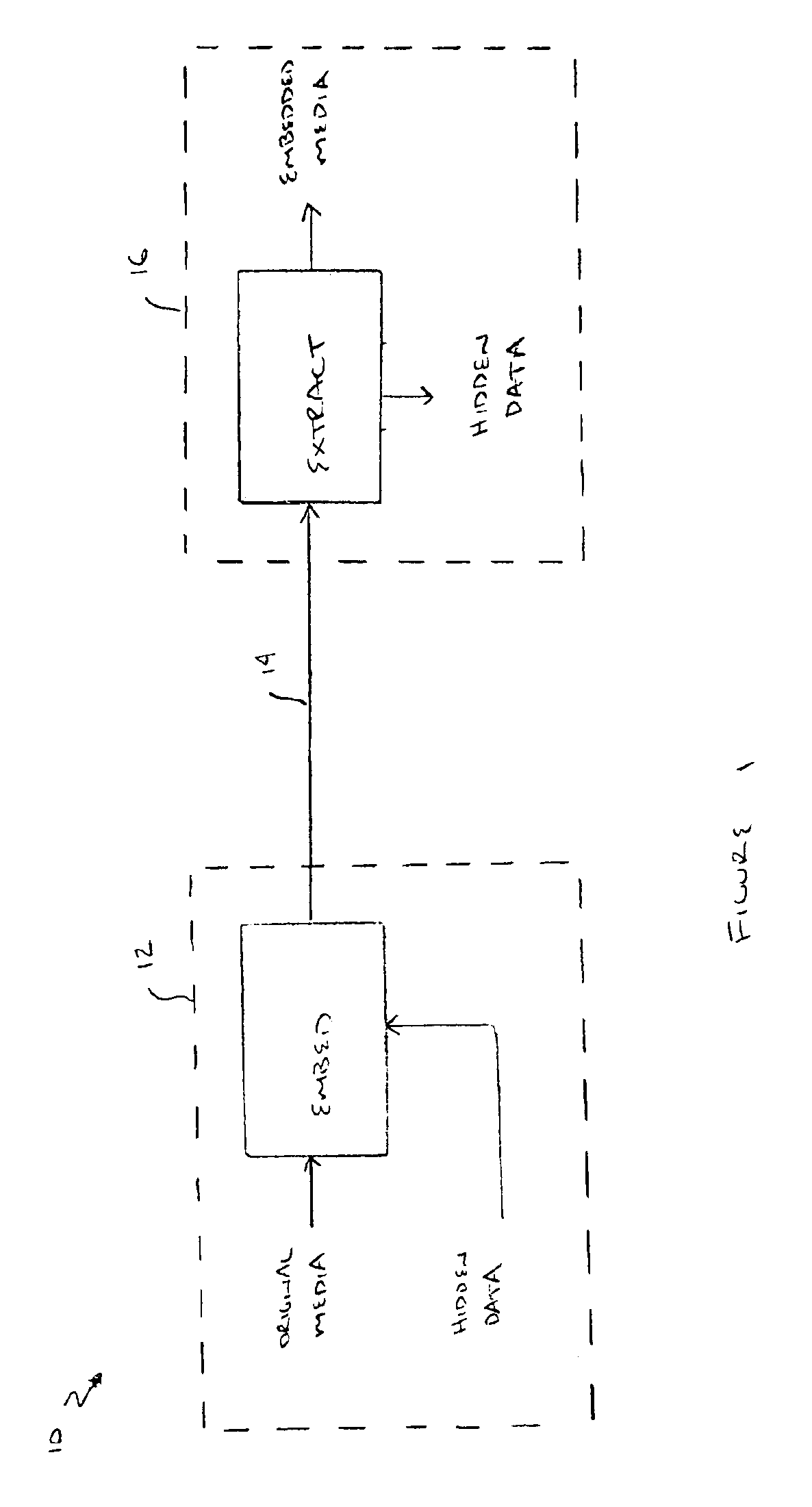
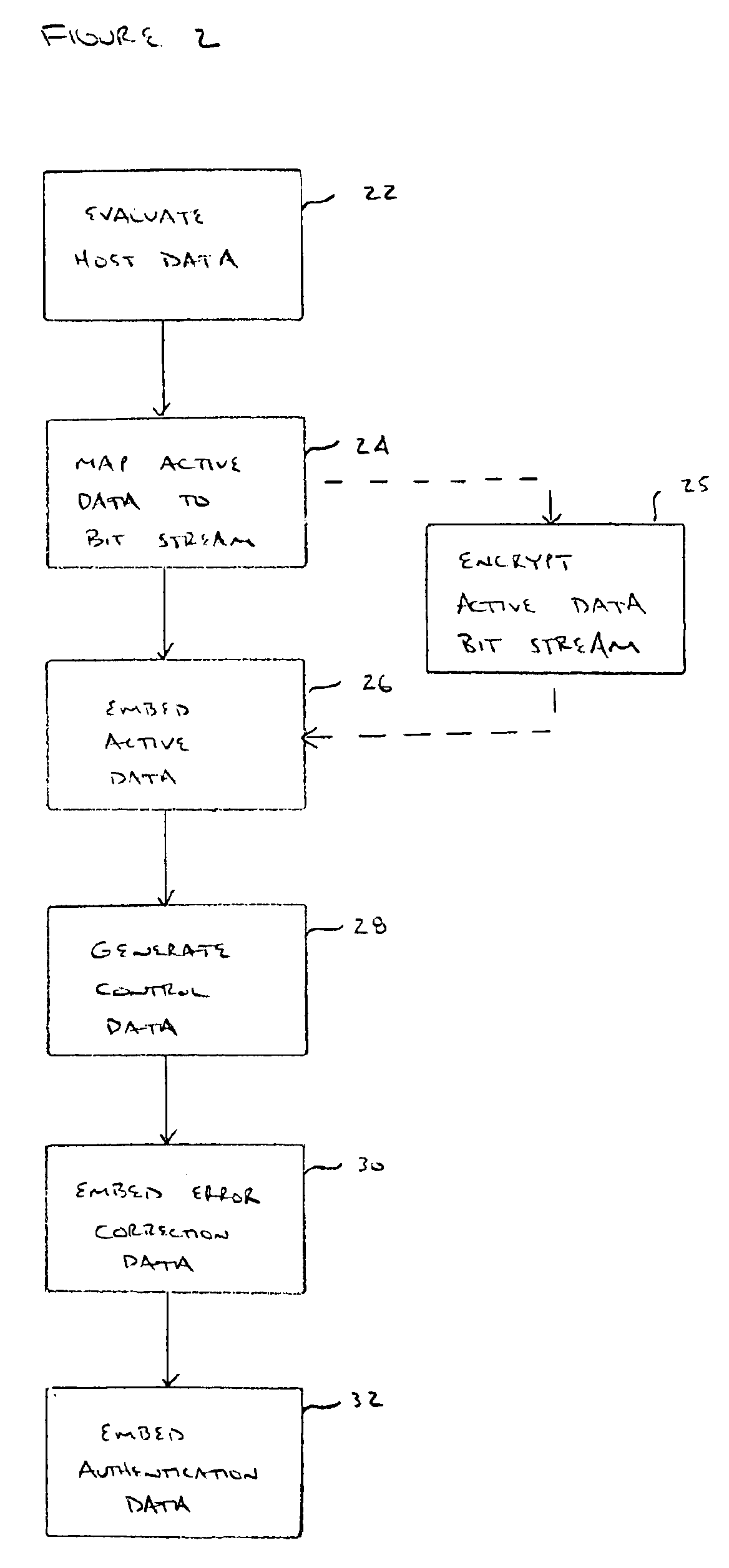
Active data hiding for secure electronic media distribution
InactiveUS6850910B1Improve renewability and controllability and interoperabilityHigh level of securityPulse modulation television signal transmissionRecord information storageDistribution systemActive data
A method is provided for distributing multimedia content in an electronic media distribution system. The method includes the steps of: (a) providing active hidden data, where the active hidden data includes a plurality of executable machine instructions; (b) embedding active hidden data into the host data stream, thereby forming an embedded data stream; (c) transmitting the embedded data stream from a content provider device to a player device; (d) extracting the active hidden data from the embedded data stream on the player device; and (e) executing the active hidden data on the player device.
Owner:PANASONIC CORP
Relay apparatus, communication system and relay method
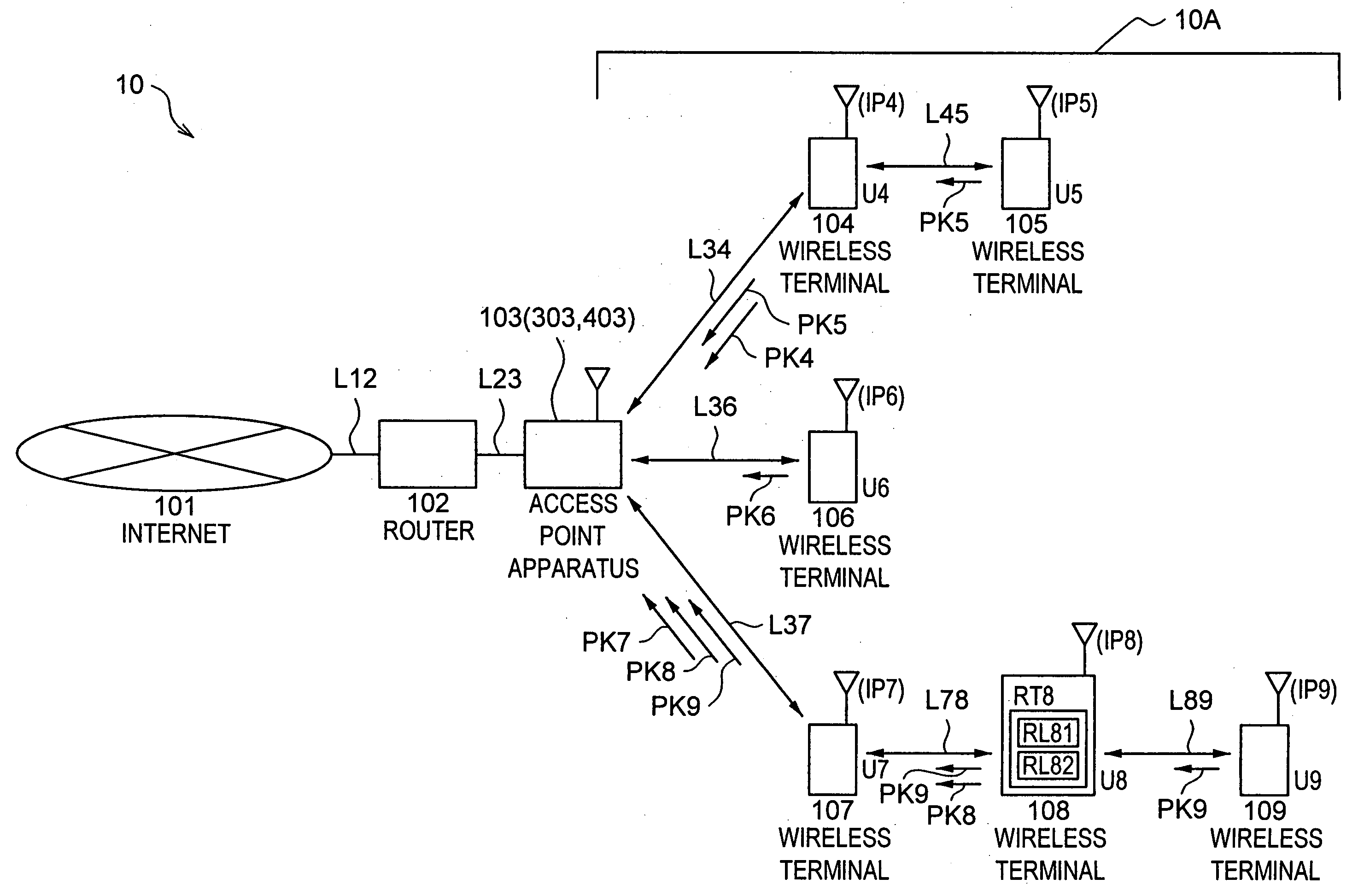
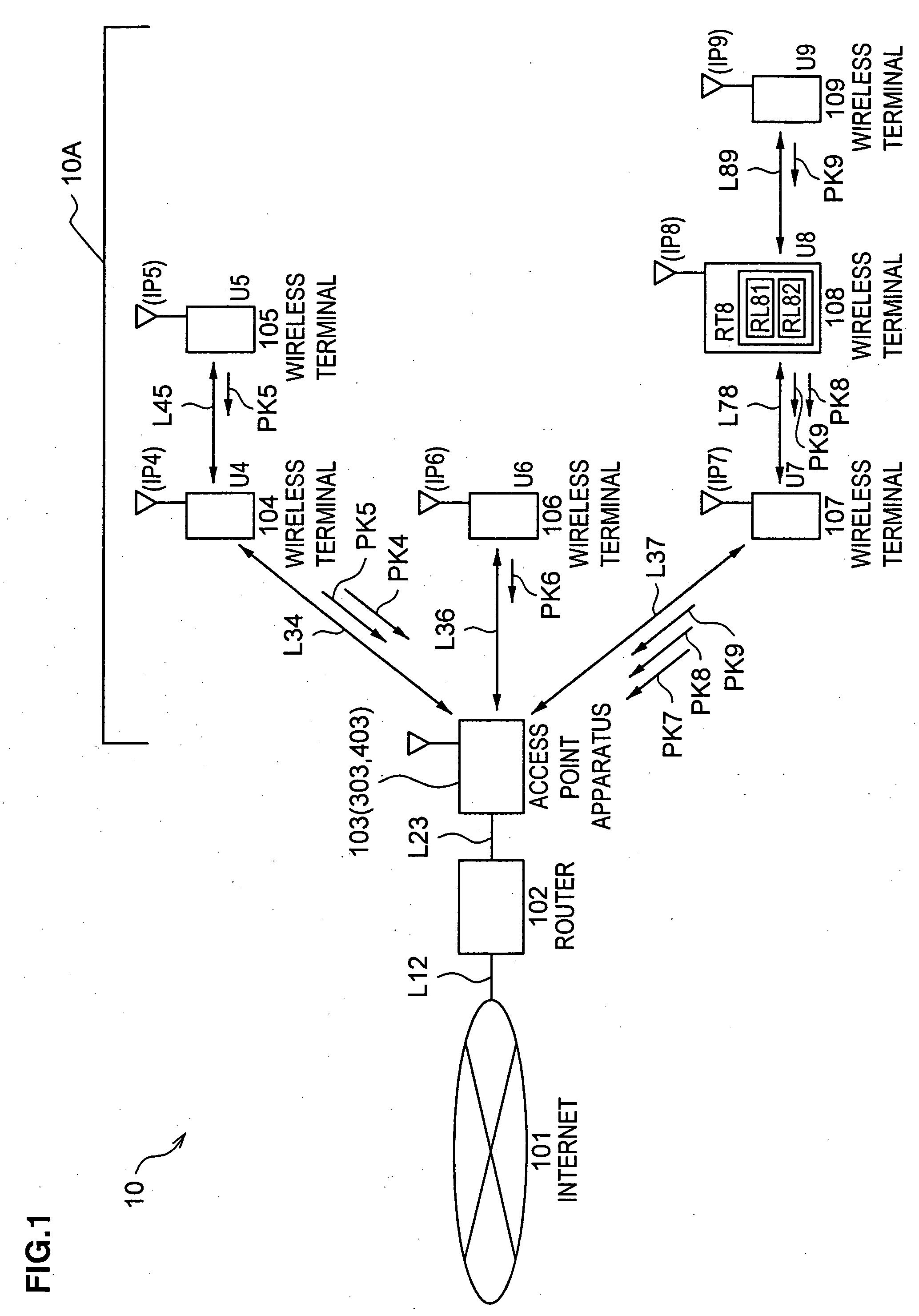
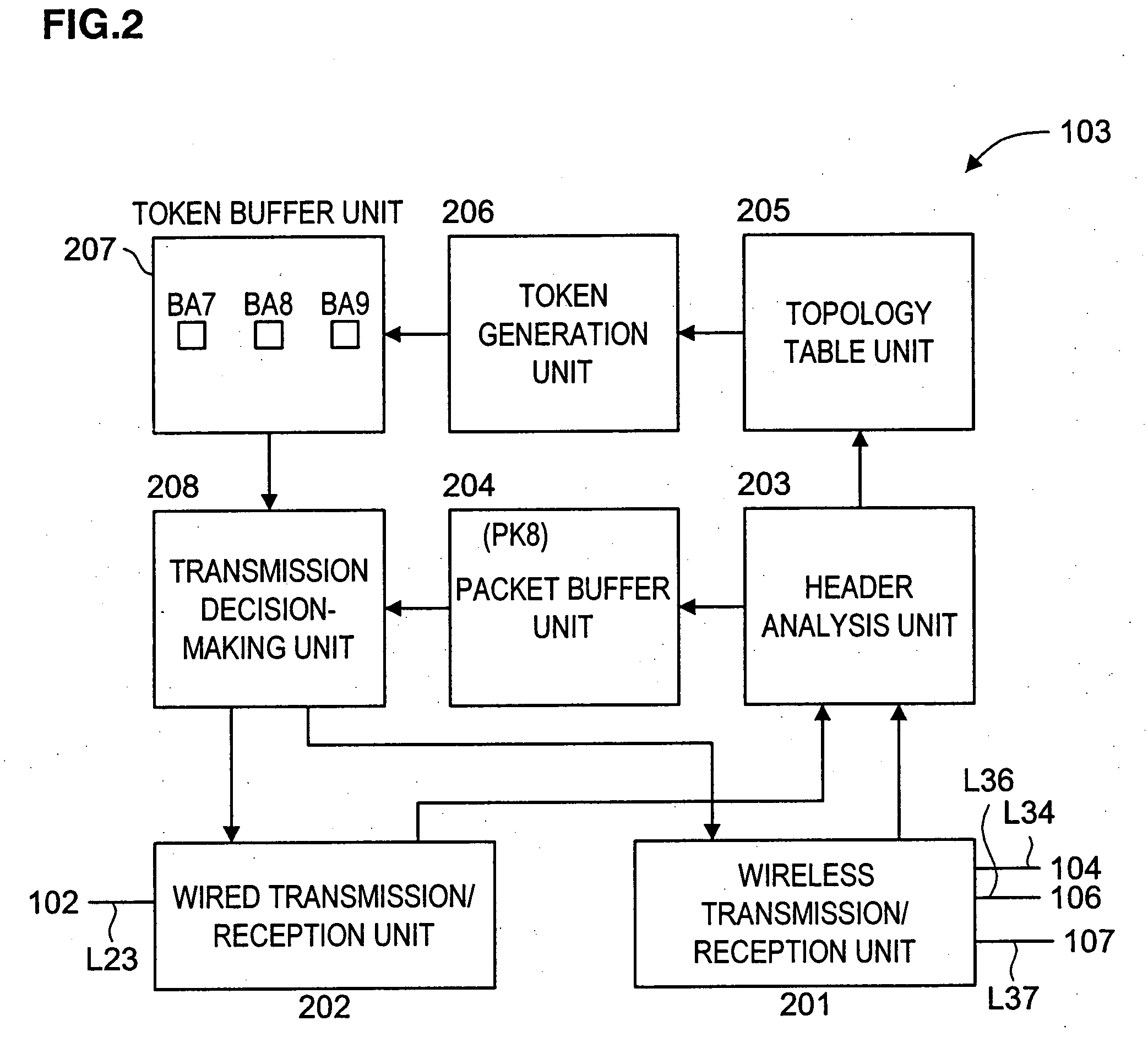
InactiveUS20050169206A1Good feasibilityHigh level of securityNetwork topologiesData switching by path configurationFrequency bandControl unit
A relay apparatus that handles dense traffic of unit data in a communication network constituted with a plurality of communication terminals each capable of sending or receiving unit data and relaying unit data transmitted by or to be received by another communication terminal, includes a band control unit that implements control so as to assign a specific communication band to a communication terminal engaged in unit data relay with priority over communication terminals not engaged in the unit data relay. The relay apparatus adopting the structure described above improves the feasibility and the level of security.
Owner:OKI ELECTRIC IND CO LTD
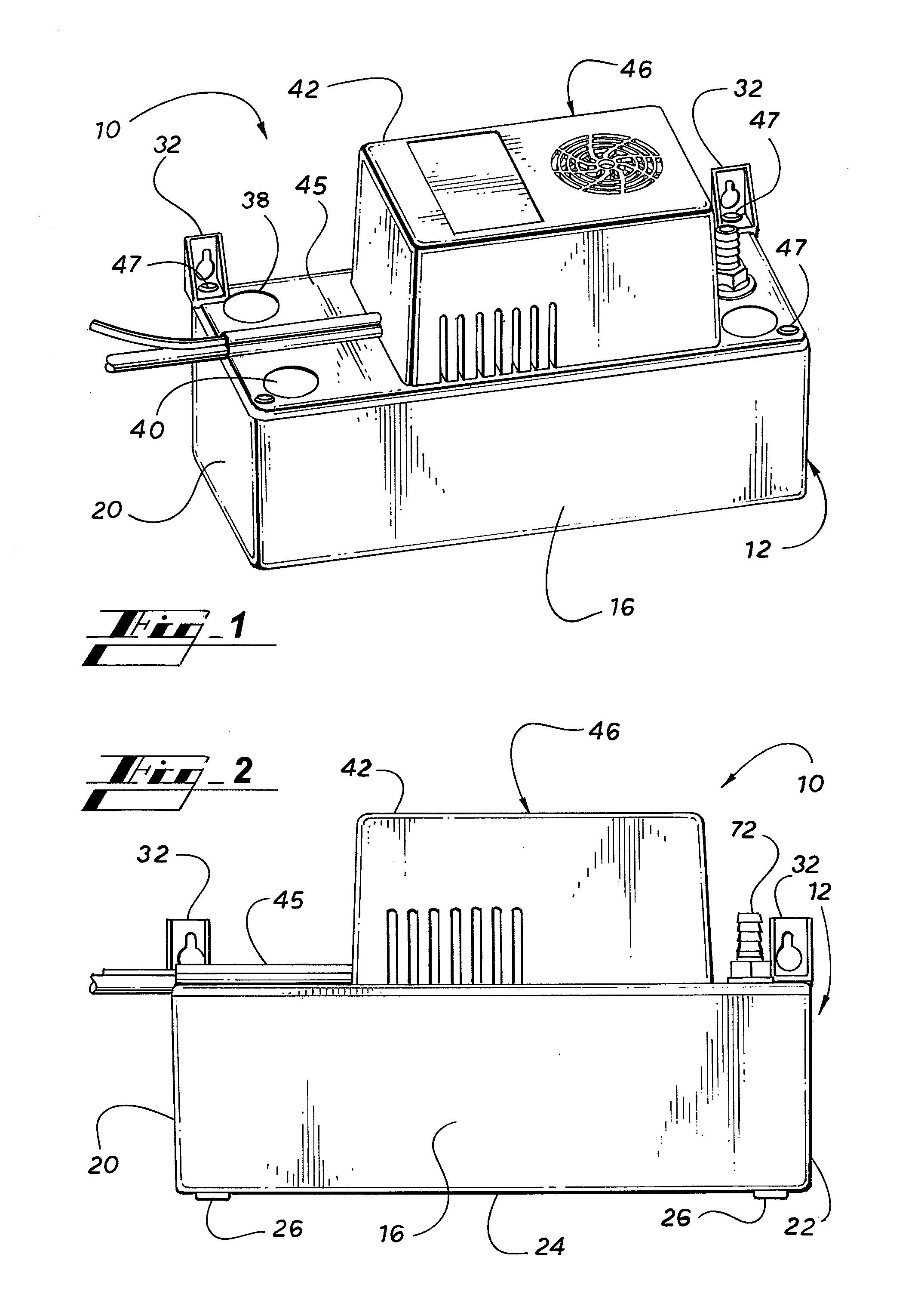
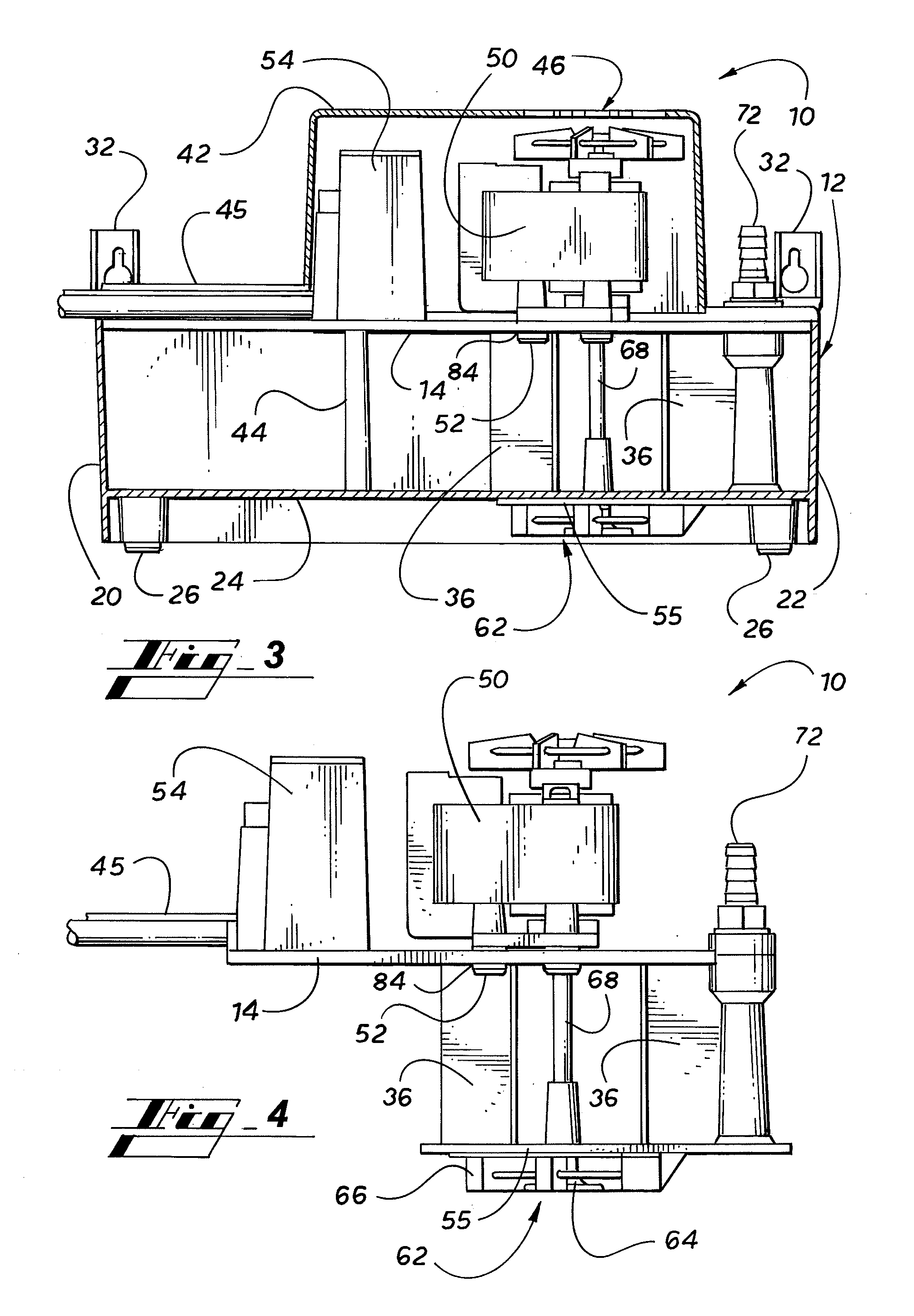
Condensate Pump
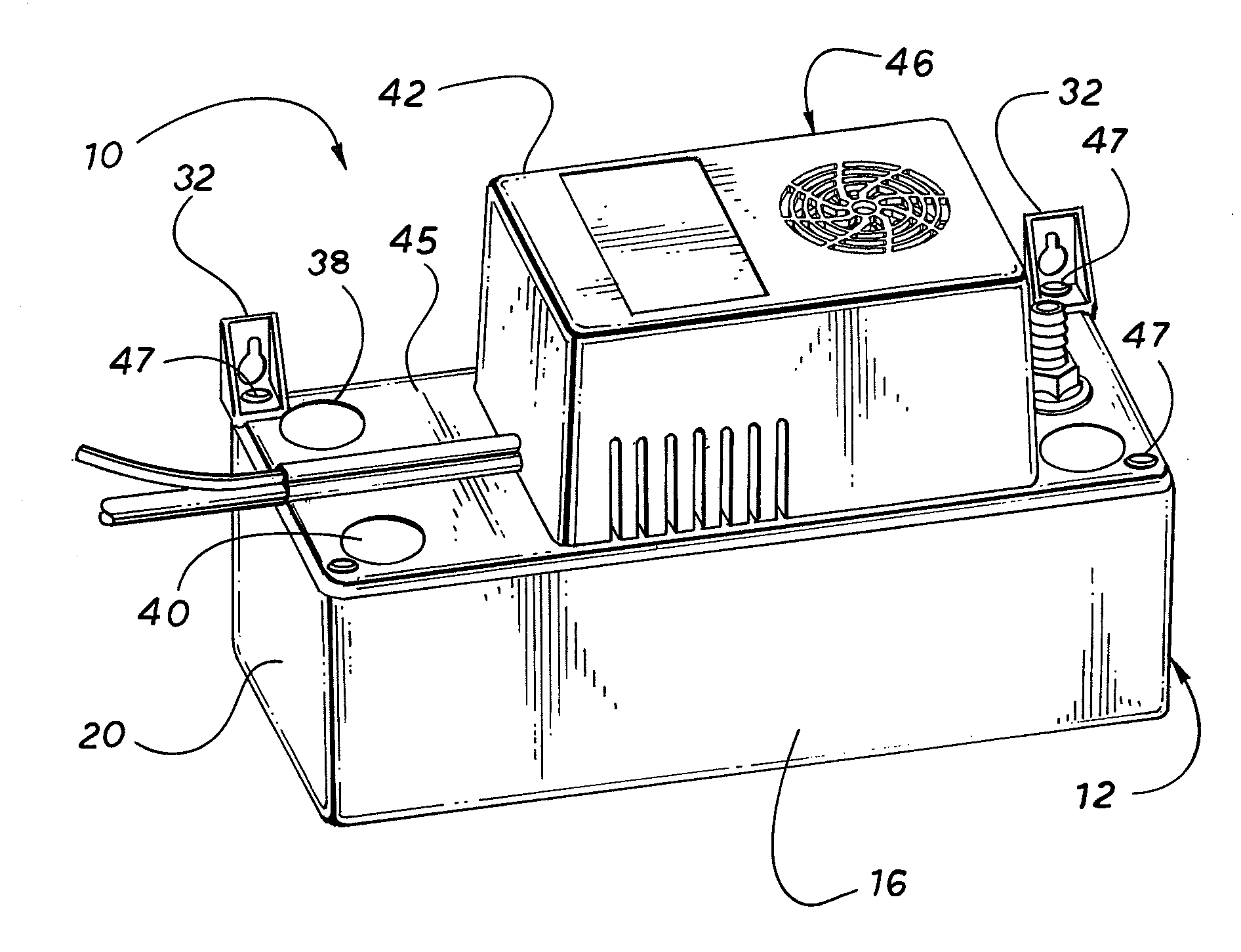
ActiveUS20110085917A1Low costHigh level of securityLighting and heating apparatusSpace heating and ventilation detailsImpellerHVAC
A condensate pump for an HVAC system includes a reservoir for collecting condensate water, a pump motor connected to an impeller pump for pumping the condensate water out of the reservoir, and a floatless pump controller. The floatless pump controller detects the water level in the reservoir and, based on the water level in the reservoir, controls the operation of the pump motor, and if necessary, sounds an alarm and shuts down the HVAC system. The floatless pump controller may employ an ultrasonic transducer or capacitance sensors to detect the level of condensate water in the reservoir.
Owner:DIVERSITECH
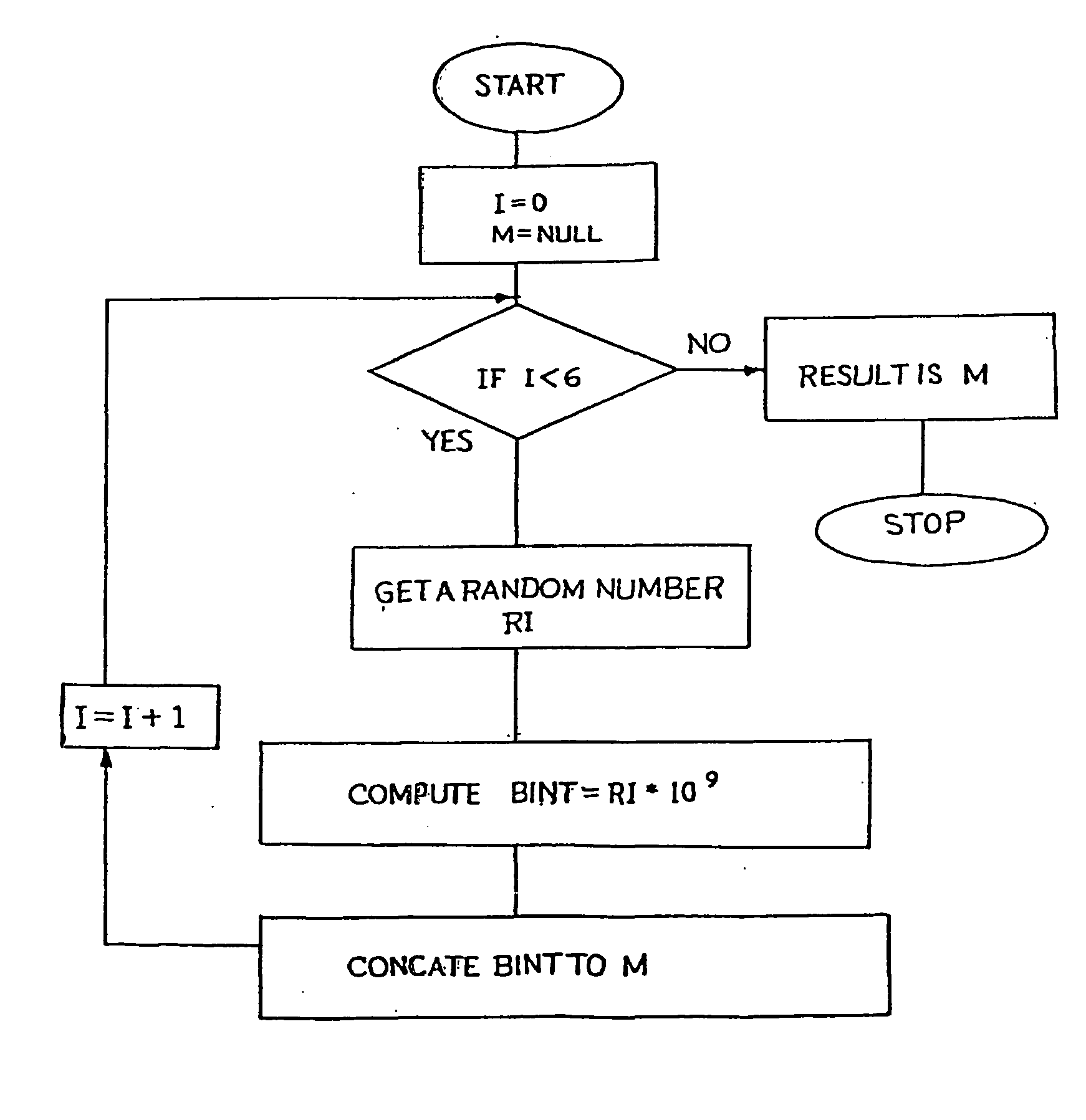
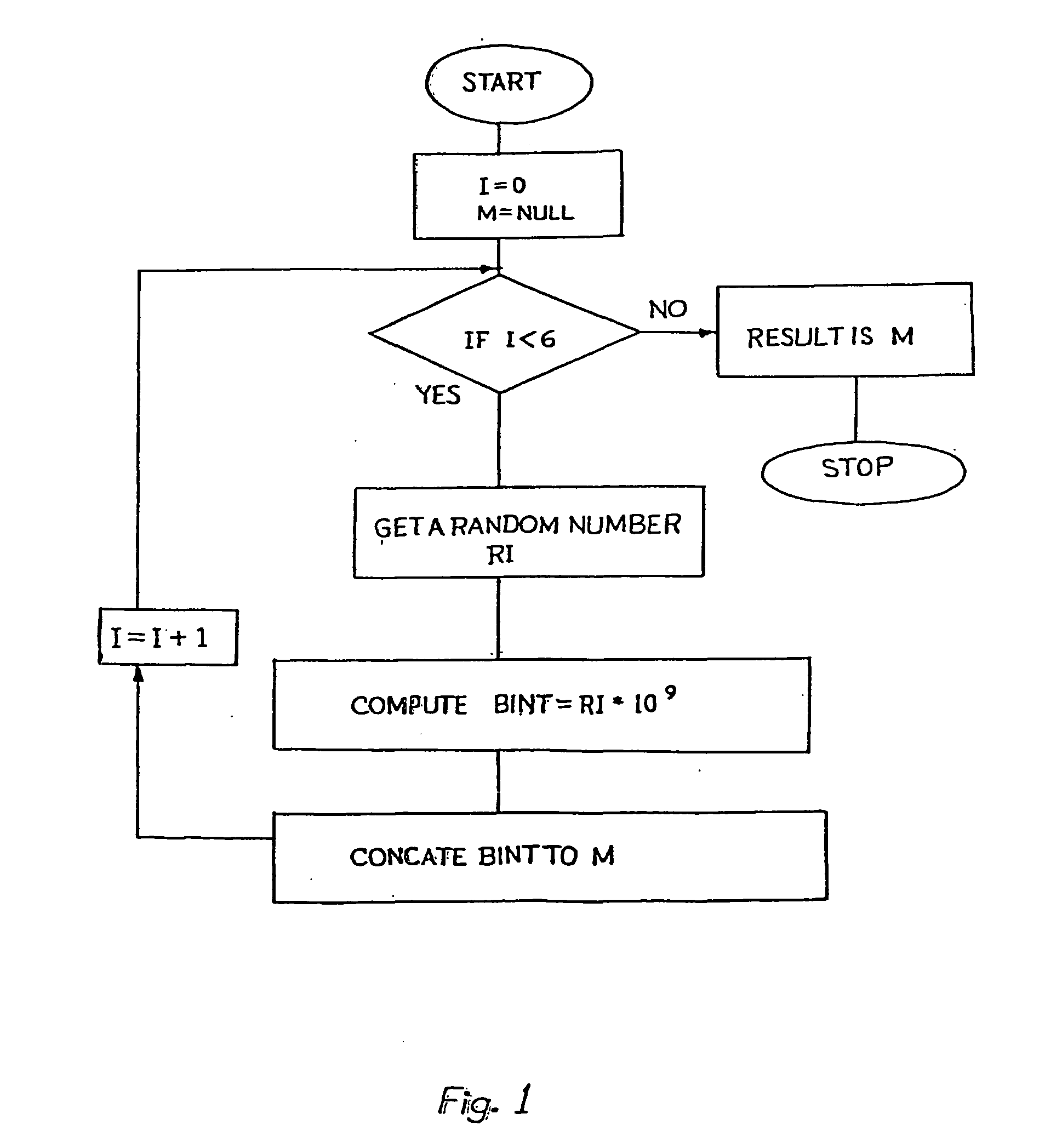
Method of elliptic curve encryption
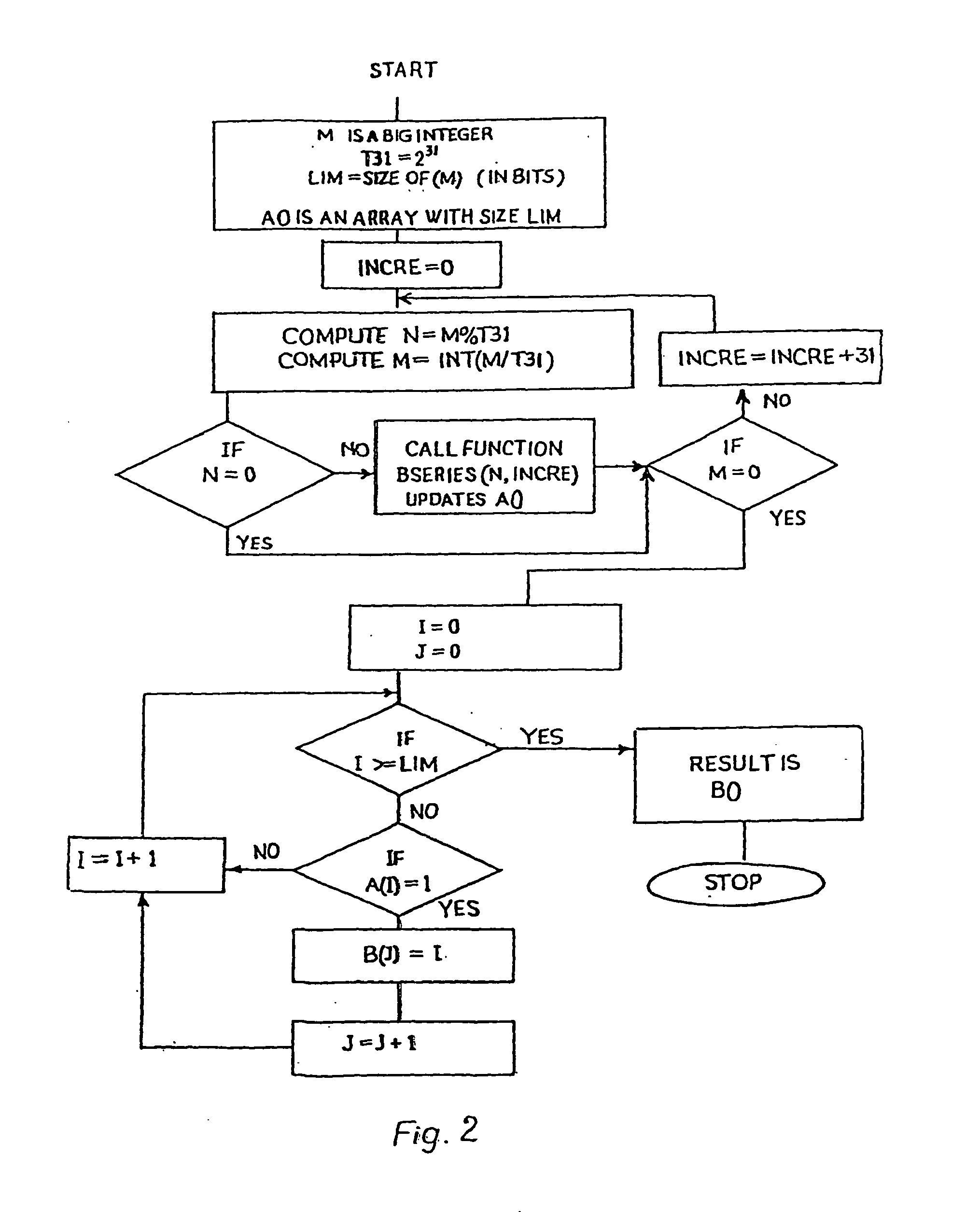
InactiveUS20060165231A1High level of securityOptimise multiplication timePublic key for secure communicationSecret communicationEllipseBit-length
A method of elliptic curve encryption includes, (a) selecting an elliptic curve Ep (a,b) of the form y2=x3+ax+b mod (p) wherein a and b are non-negative integers less than p satisfying the formula 4 a3+27b2 mod (p) not equal to 0; (b) generating a large 160 bit random number by a method of concatenation of a number of smaller random numbers; (c) generating a well hidden point G (x,y) on the elliptic curve Ep (a,b) by scalar multiplication of a point B (x,y) on the elliptic curve with a large random integer which further includes the steps: (i) converting the large random integer into a series of powers of 231; (ii) converting each coefficient of 231 obtained from above step into a binary series; (iii) multiplication of binary series obtained from steps (i) and (ii) above with the point B (x,y) on the elliptic curve; (d) generating a private key nA (of about >=160 bit length); (e) generating a public key PA (x,y) given by the formula PA (x,y)=(nA-G (x,y)) mod (p); (f) encrypting the input message MSG; (g) decrypting the ciphered text.
Owner:THE ADDITIONAL DIRECTOR IPR
Information processing device, program, and recording medium
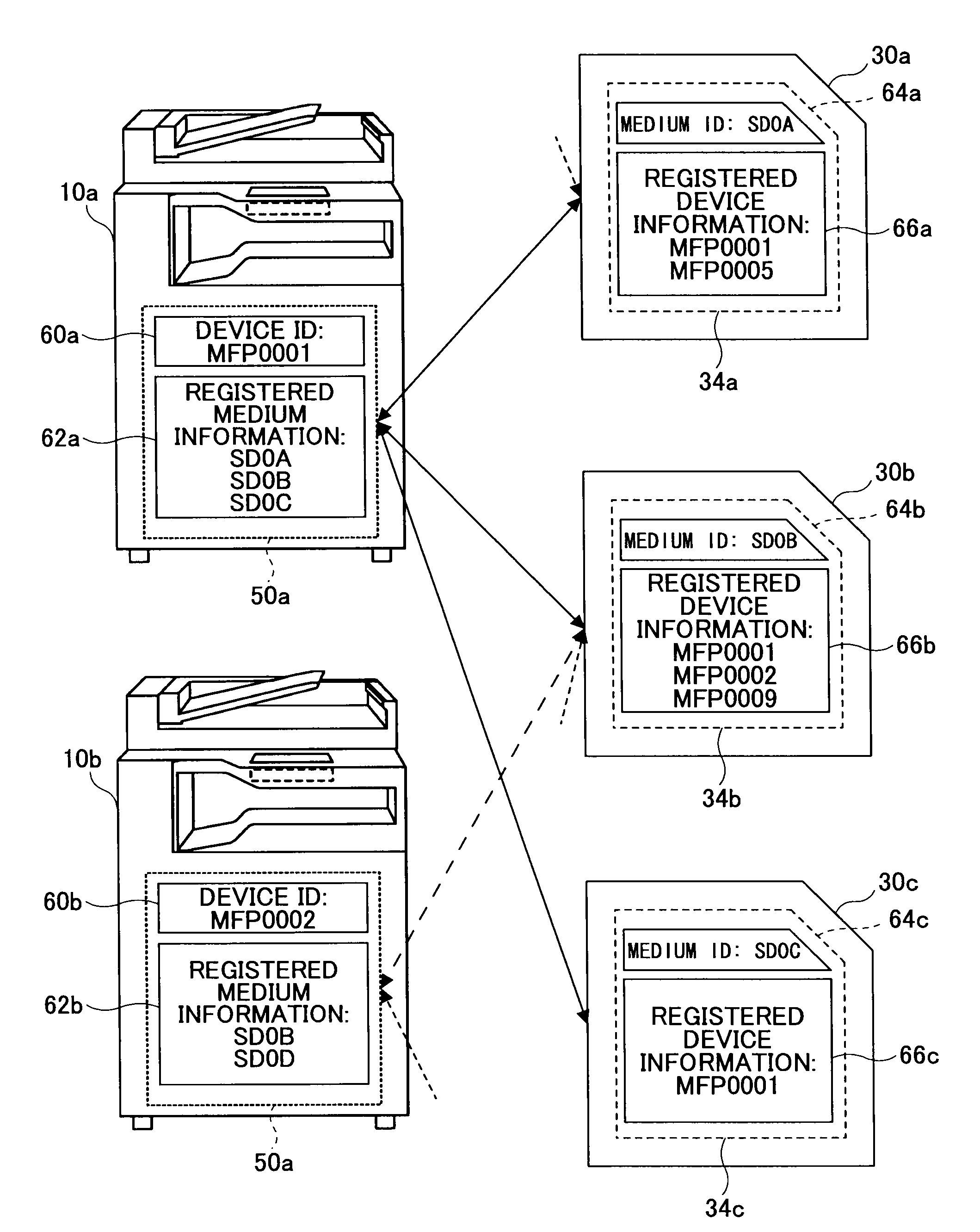
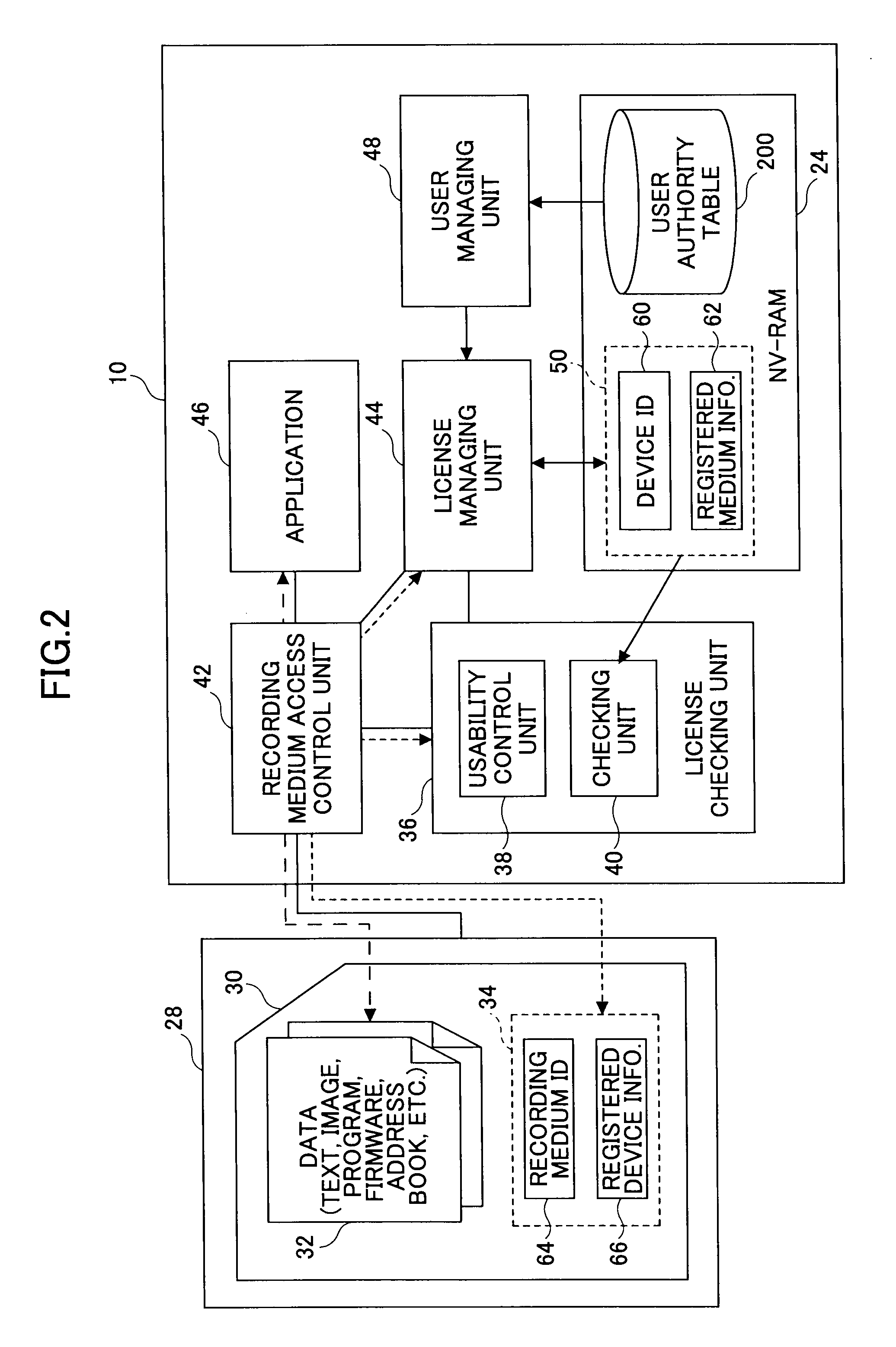
InactiveUS20080225337A1High level of securityImprove security levelDigital computer detailsVisual presentationStorage cellComputer hardware
An information processing device includes a storing unit in which registered medium information is stored, indicating a set of registered recording media uses, which uses are permitted by the information processing device. A checking unit checks usability of a removable recording medium attached to the information processing device by comparing the registered medium information with registered device information acquired from the recording medium attached to the information processing device and indicating a set of registered information processing devices, each of which permits use of the recording medium in the registered information processing device. A usability control unit manages use of the recording medium in the information processing device according to a result of the checking.
Owner:RICOH KK
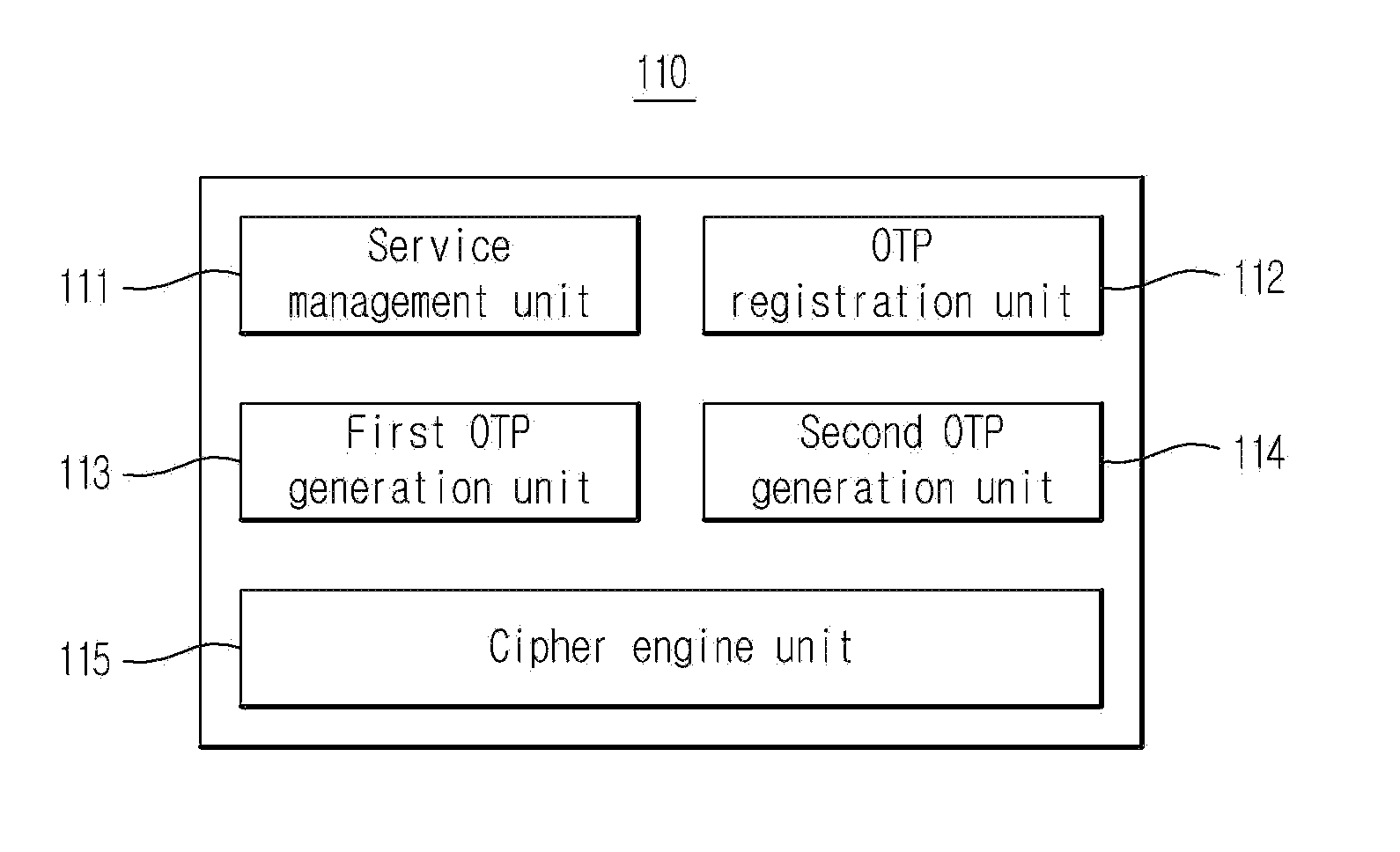
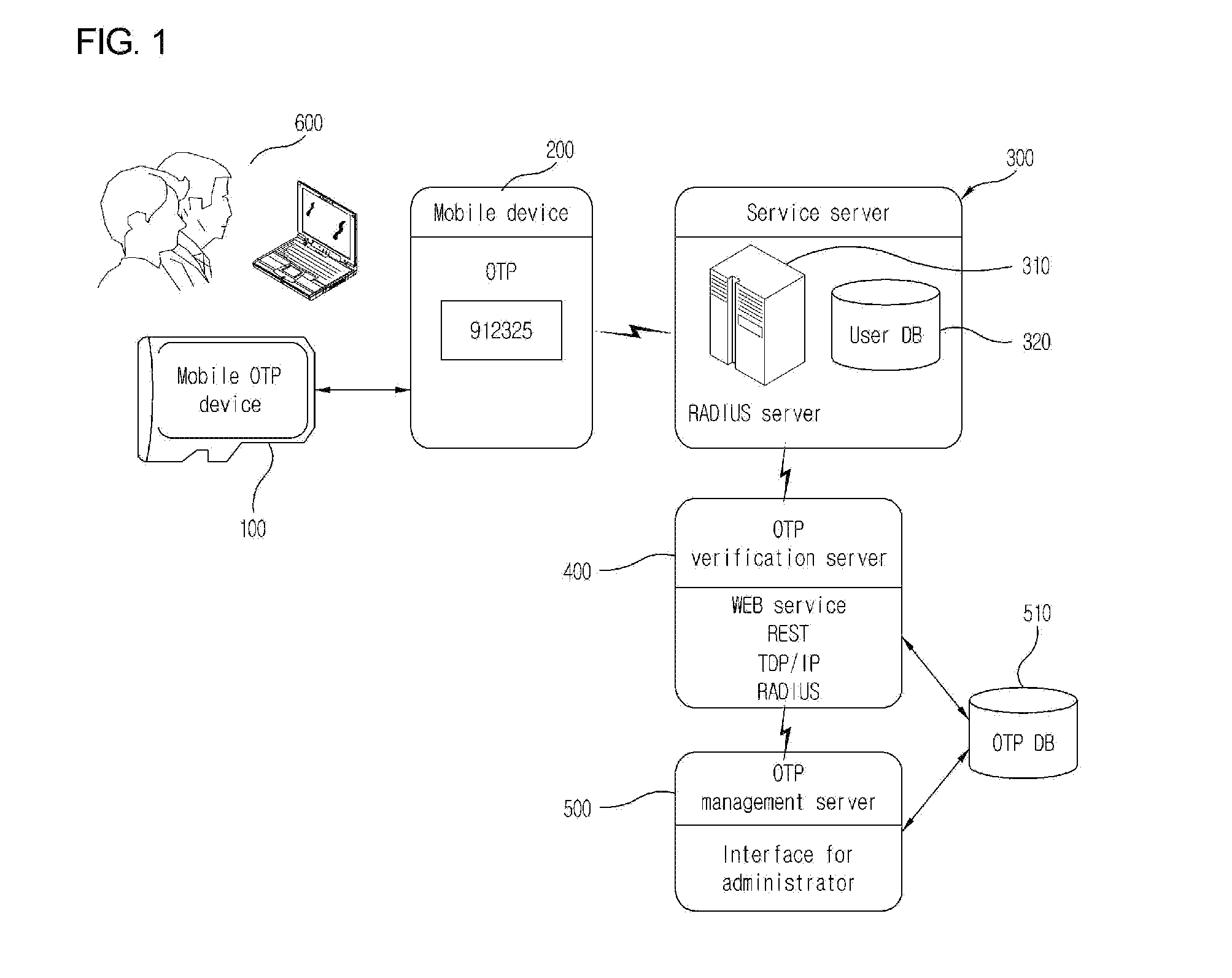
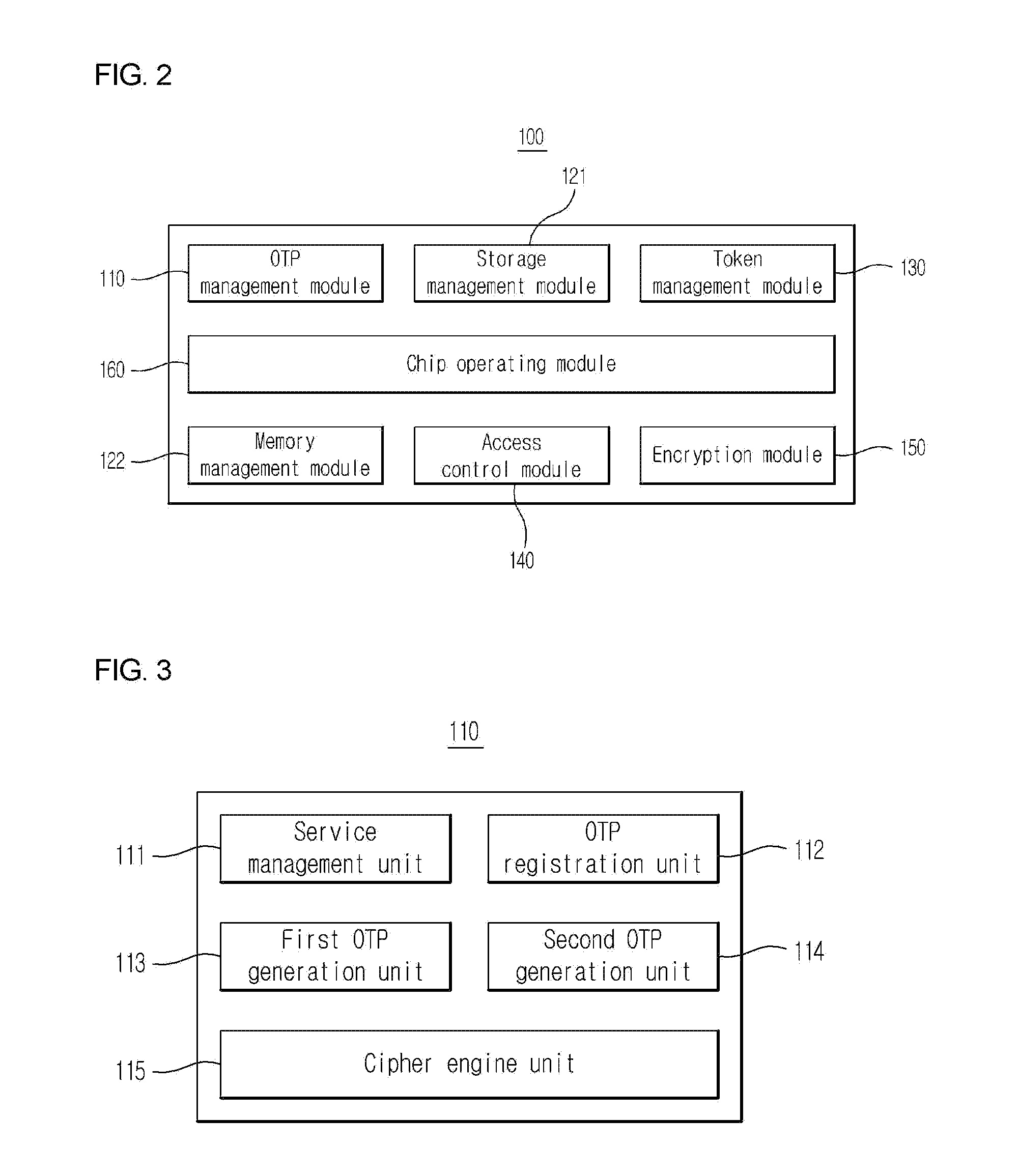
Mobile otp service providing system
InactiveUS20150132984A1High level of securityImprove security levelPayment architectureClamped/spring connectionsManagement functionsSecurity token
A mobile OTP system providing system is provided, in that it performs security token and OTP management functions, it generates an OTP having high security level in hardware by using a mobile OTP device for performing a security data storage function of encoding and decoding data during data storage, and it generates OTPs necessary for a plurality of services by using one mobile OTP device, thereby safely and easily utilizing it by means of the user.
Owner:SAFERZONE
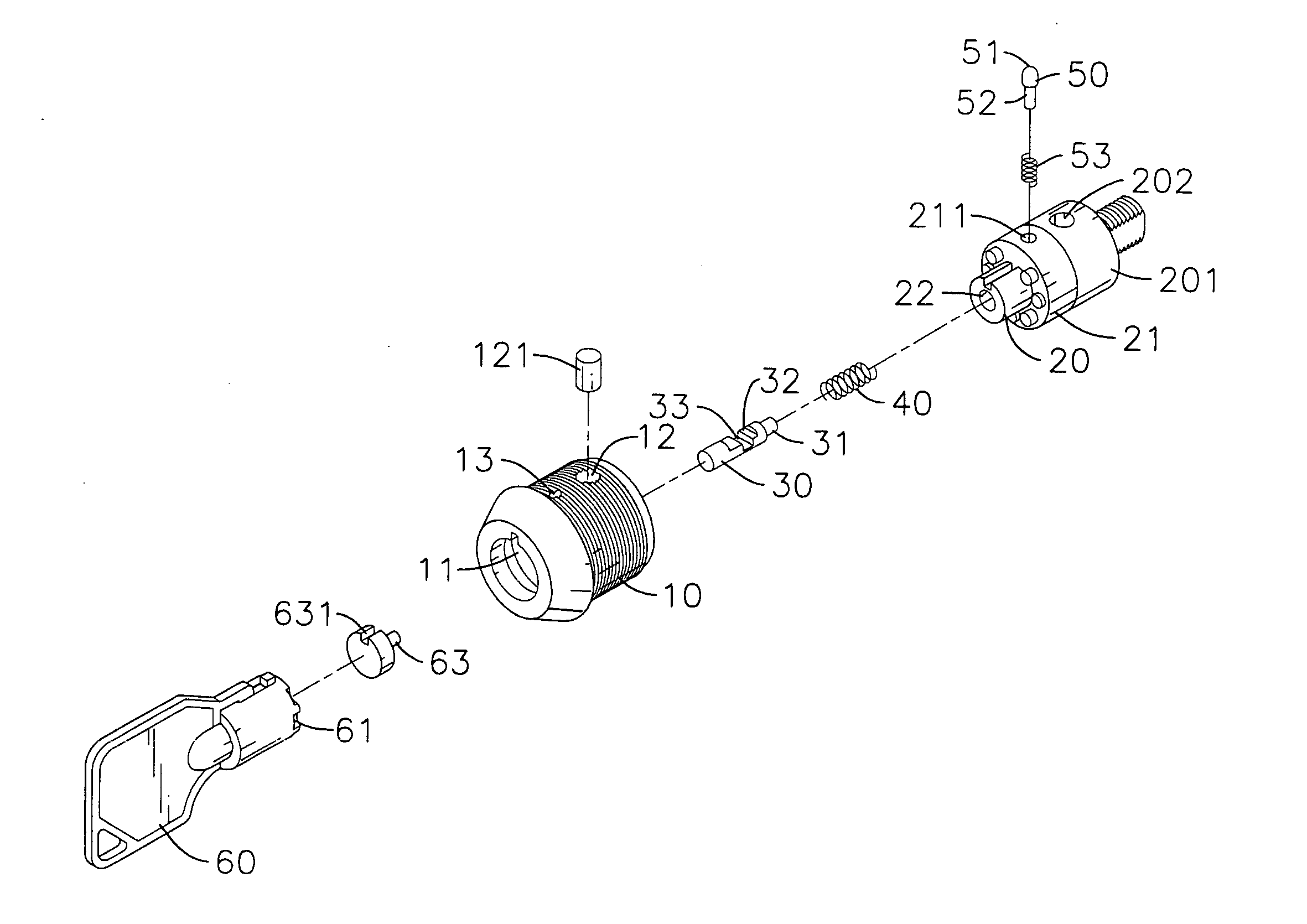
Cylinder lock
InactiveUS20060096344A1High level of securityImprove security levelKeysCylinder locksEngineeringHead parts
Owner:LIN GRACE
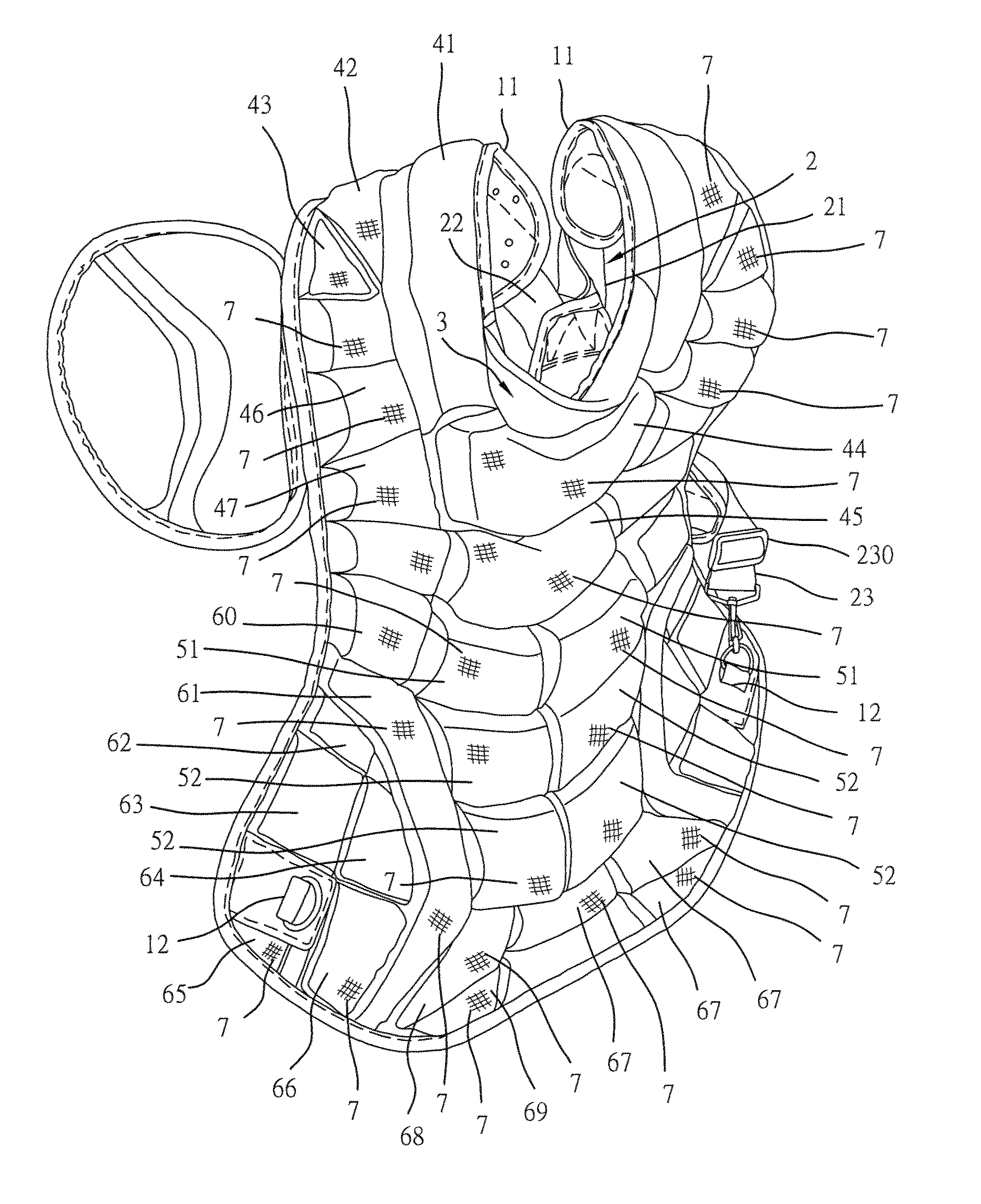
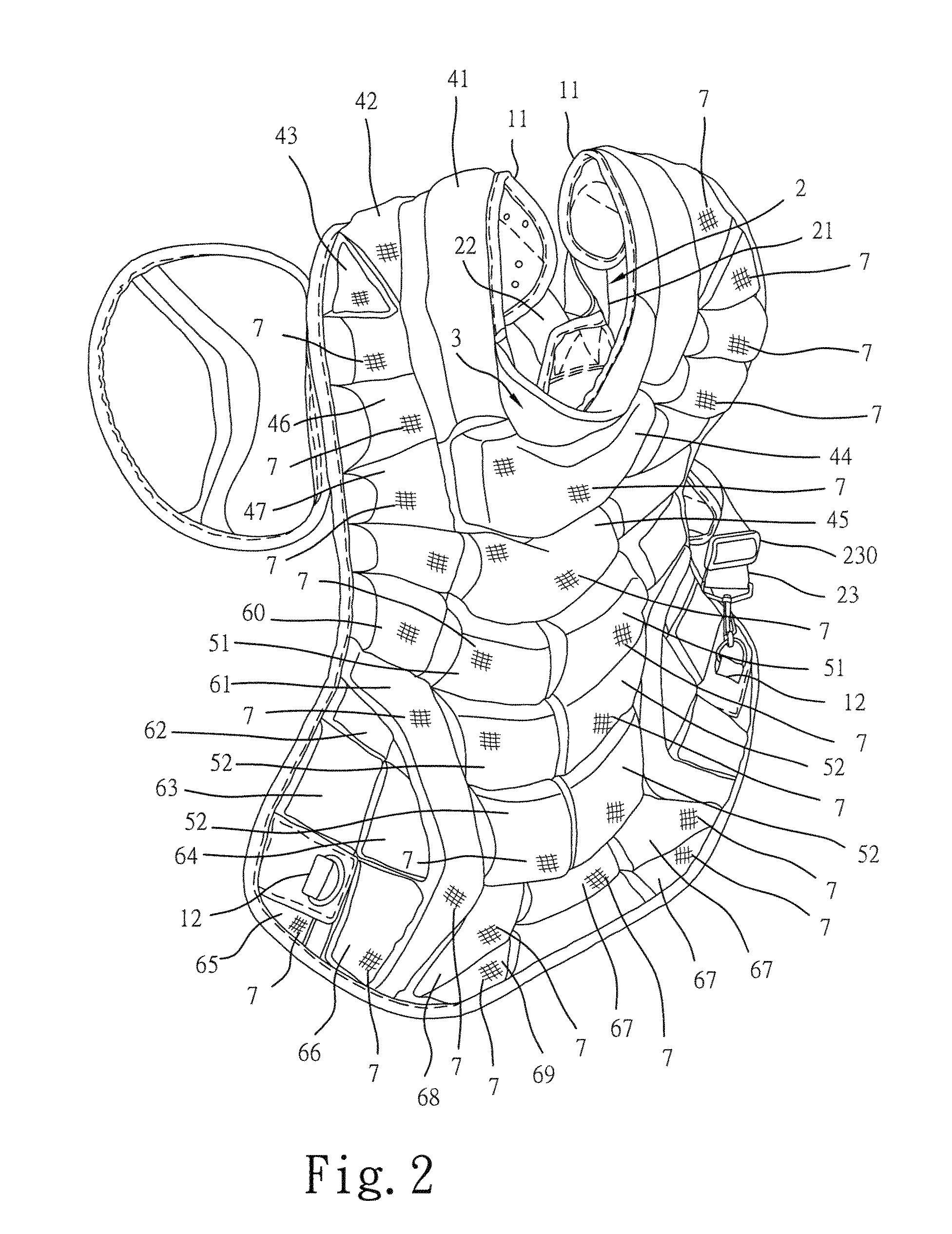
Chest protector for baseball game
ActiveUS7900283B1High level of securityEnhance effectChemical protectionHeat protectionBreathingCushion
A chest protector formed of a base, upper and lower shoulder straps, a neck pad, neck cushions, shoulder cushions, chest cushions, upper and lower abdomen cushions, lateral cushions, bottom cushions and breathing cloths. Each upper abdomen cushion is formed of an inner low bounce foam, an outer low bounce foam and an intermediate hard plastic board sandwiched in between the inner low bounce foam and outer low bounce foam. Each lower abdomen cushion is formed of an inner low bounce foam and an outer low bounce foam. The inner low bounce foam of each abdomen cushion is shorter and relatively softer than the associating outer low bounce form so that a buffer space is defined between the outer low bounce foam of each abdomen cushion and the base below the associating inner low bounce foam and the outer low bounce foams of the abdomen cushions are respectively held in a sloping status after stitching of the breathing cloths to the base.
Owner:RACER SPORTING GOODS
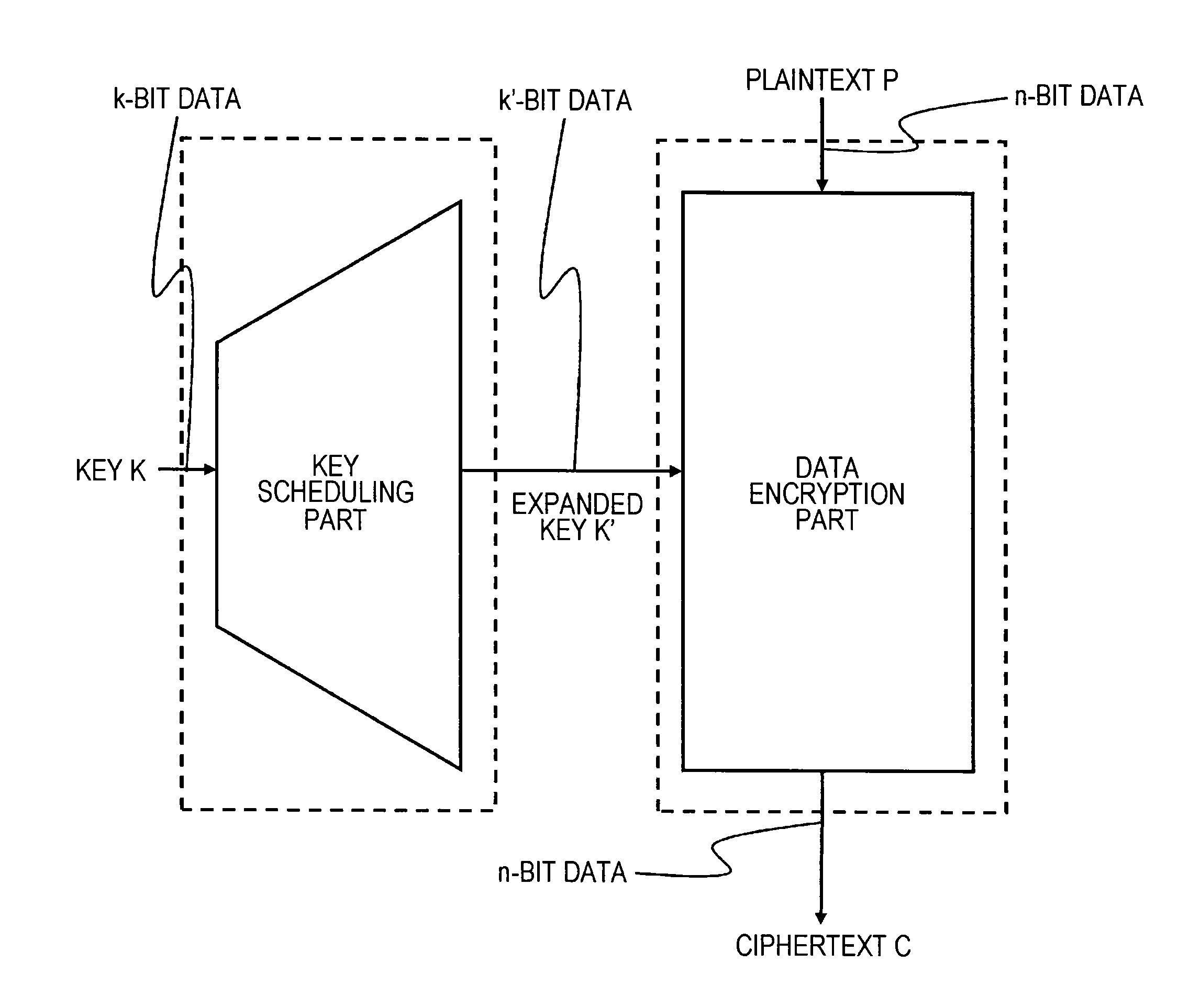
Encryption processing device, encryption processing method, and programme
ActiveUS20130343546A1High level of securityHigh level of resistanceKey distribution for secure communicationCryptographic attack countermeasuresData conversionRound function
An encryption processing device including an encryption processing part configured to divide configuration bits of data to be data processed into plural lines, and to input, and to repeatedly execute data conversion processing applying a round function to each line of data as a round calculation; and a key scheduling part configured to output round keys to a round calculation executing unit in the encryption processing part. The key scheduling part is a replacement type key scheduling part configured to generate plural round keys or round key configuration data by dividing a secret key stored beforehand into plural parts. The plural round keys are output to a round calculation executing unit sequentially executing in the encryption processing part such that a constant sequence is not repeated. The encryption processing configuration has a high level of security and a high level of resistance to repeated key attacks or other attacks.
Owner:SONY CORP
Wireless access for a mobile terminal to functional domains
ActiveUS20160095045A1High level of securityImprove securityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsReal-time computingWireless access point
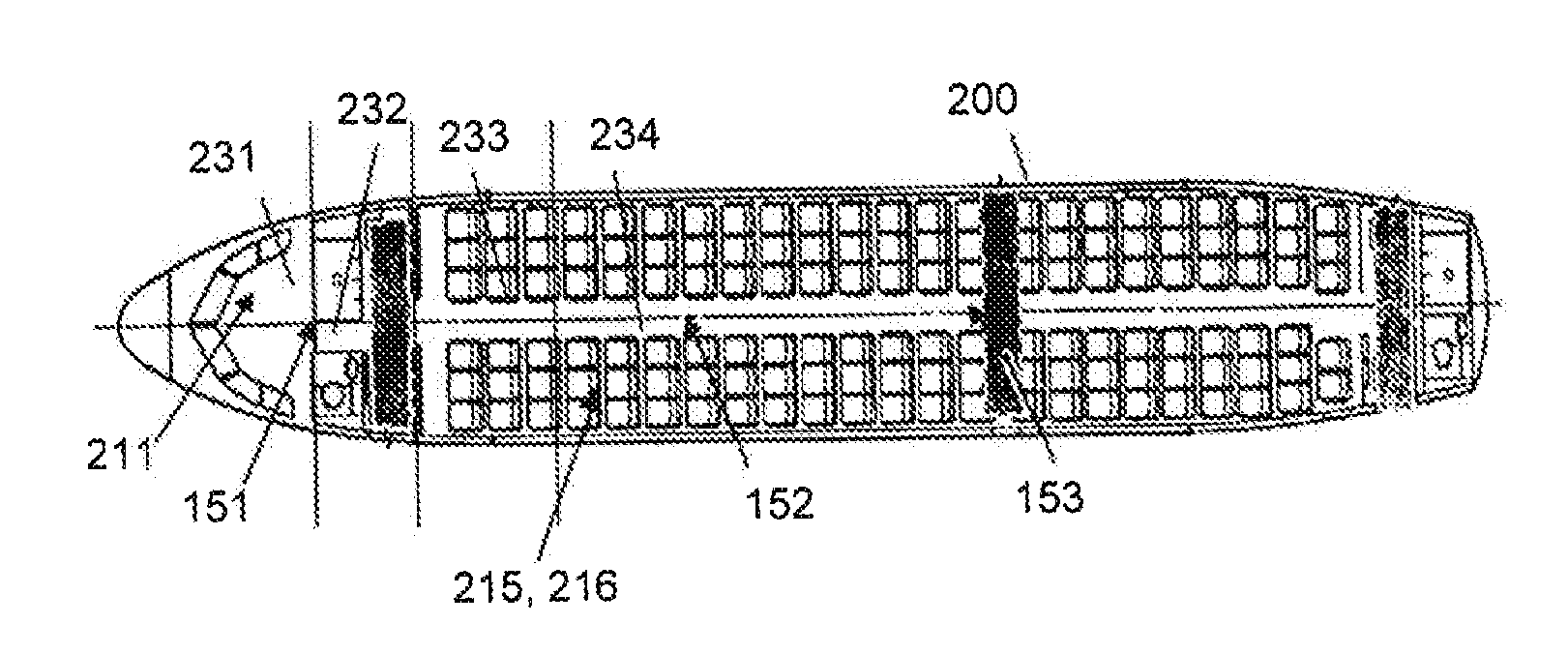
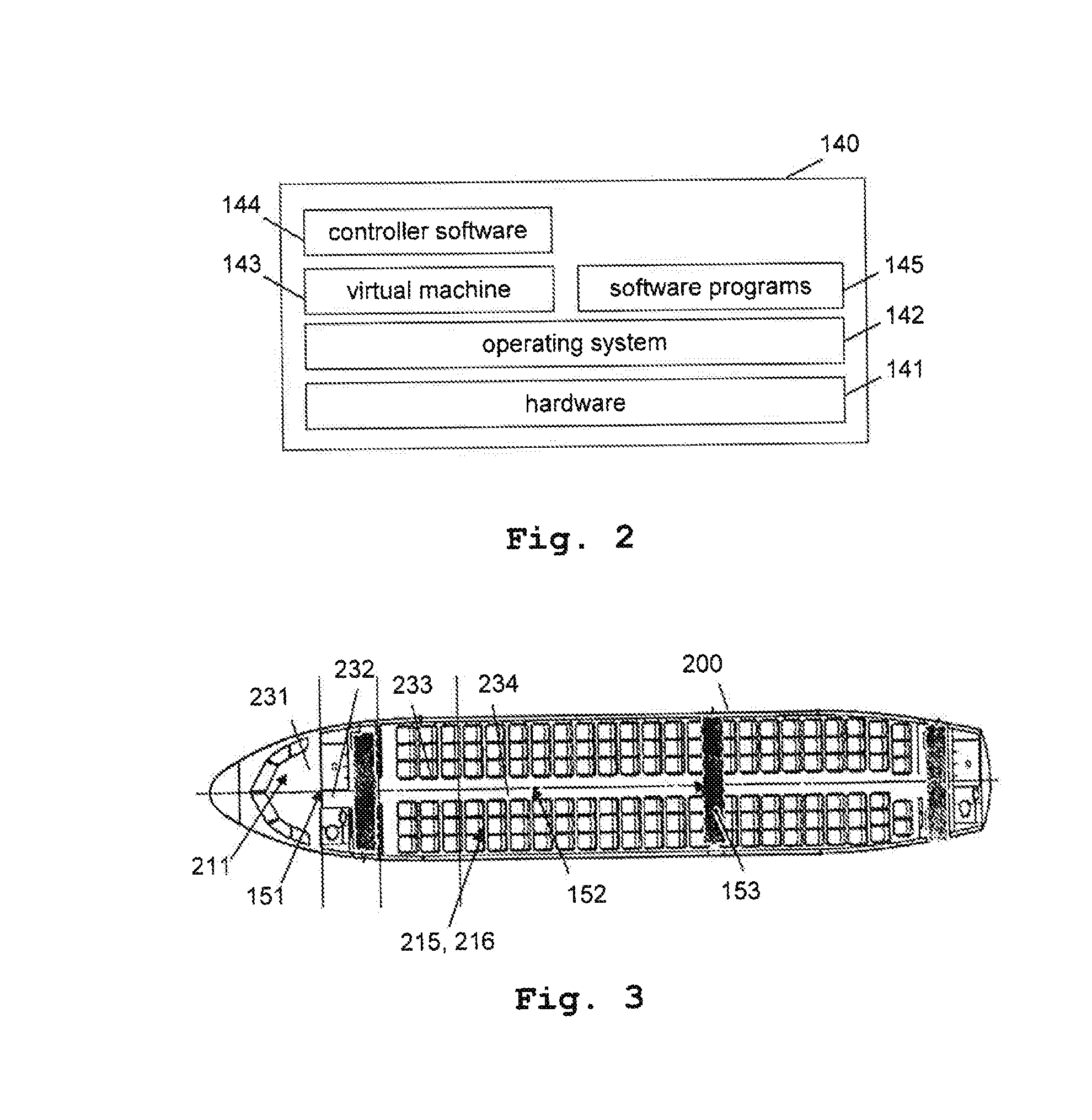
A system configured to be installed in an aircraft, the system comprising a first functional domain and a second functional domain. The first and second functional domains are configured to provide a first and service, respectively. The system further comprises a wireless access point configured to be externally managed by a controller and configured to communicate with a mobile terminal. The system comprises a controller configured to communicate with the wireless access point, the first and the second functional domains, configured to control the wireless access point and configured to control wireless access of the mobile terminal to the first and second functional domains. Further, the use of such a system in an aircraft, an aircraft comprising such a system and a method of controlling wireless access of a mobile terminal to a first functional domain and a second functional domain in an aircraft are disclosed.
Owner:AIRBUS OPERATIONS GMBH
Cryptoanalysis method and system
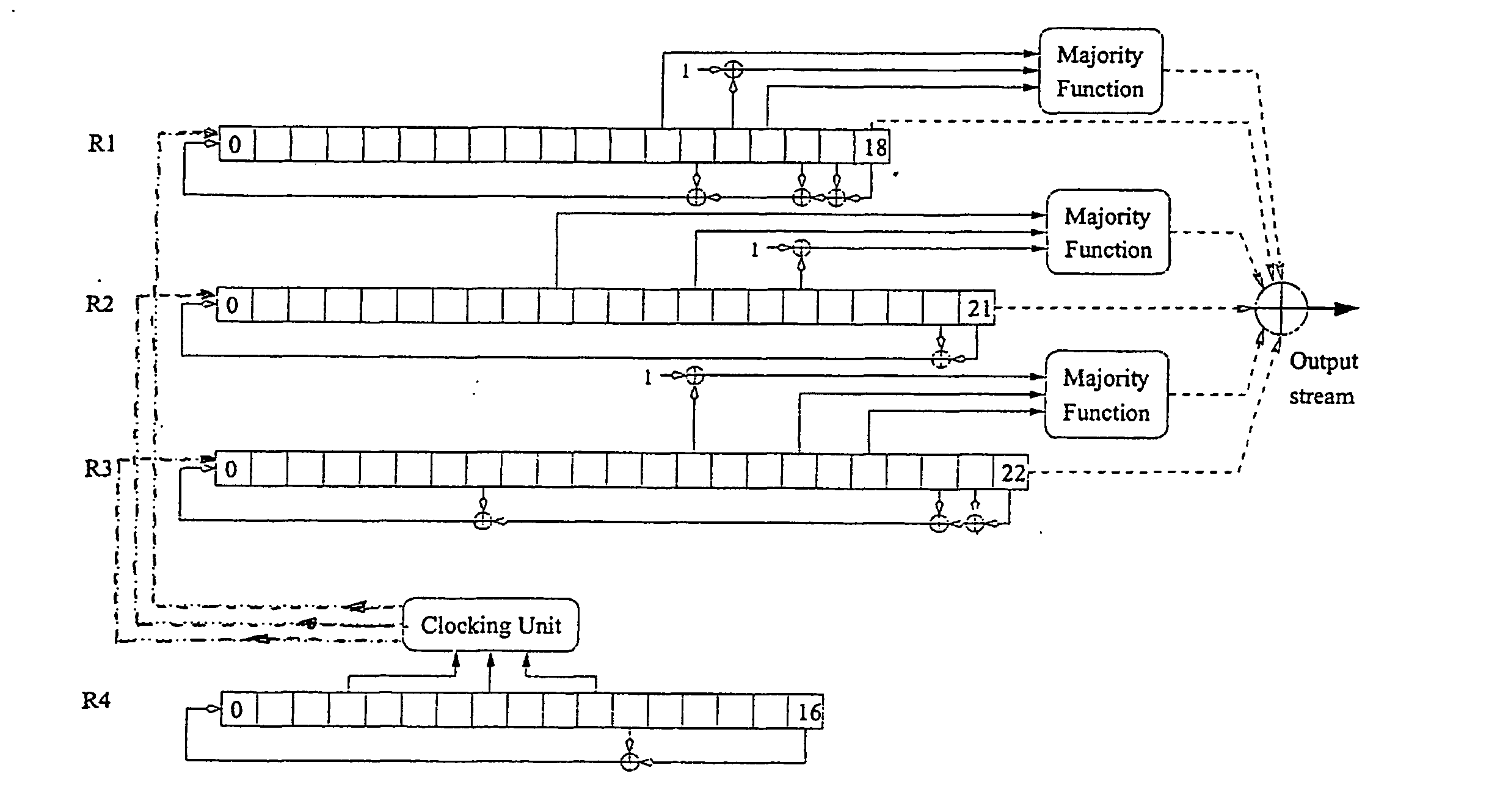
ActiveUS20070147621A1High level of securityImprove securityKey distribution for secure communicationMultiple keys/algorithms usageKnown-plaintext attackLinear cryptanalysis
A cryptanalysis method comprising: (A)Perfonning a ciphertext-only direct cryptanalysis of A5 / 1 and (B) Using results of Step (A) to facilitate the decryption and / or encryption of further communications that are consistent with encryption using the session key and / or decryption using the session key, wherein the cryptanalysis considers par t of the bits of the session key to have a known fixed value, and wherein the cryptanalysis finds the session key. An efficient known plaintext attack on A5 / 2 comprises trying all the possible values for R4o, and for each such value solving the linearized system of equations that describe the output; The solution of the equations gives the internai state of R1, R2, and R3; Together with R4, this pives the the full internai state which gives a suggestion for the key.
Owner:BARKAN ELAD
Information browsing system
InactiveUS20110081895A1High level of securityImprove security levelDigital data information retrievalSpecial service for subscribersMobile telephonyTransient storage
At the time when information stored in a server is browsed with the use of a mobile terminal, if the mobile phone is predicted to enter an out-of-service area, information that a user is going to browse is predicted and temporarily stored in the mobile terminal as cache. When the mobile phone is located in a service area at the time of a browse request, information corresponding to the request is acquired from the server, and when the mobile phone is located in an out-of-service area, the information is acquired from the information stored as cache and is displayed. The information stored as cache is deleted when the browsing is ended or when the mobile terminal enters a service area. Therefore, the user can browse desired information even in the out-of-service area with and high security level secured.
Owner:FUJIFILM CORP
Method and system for securing communications in a metering device
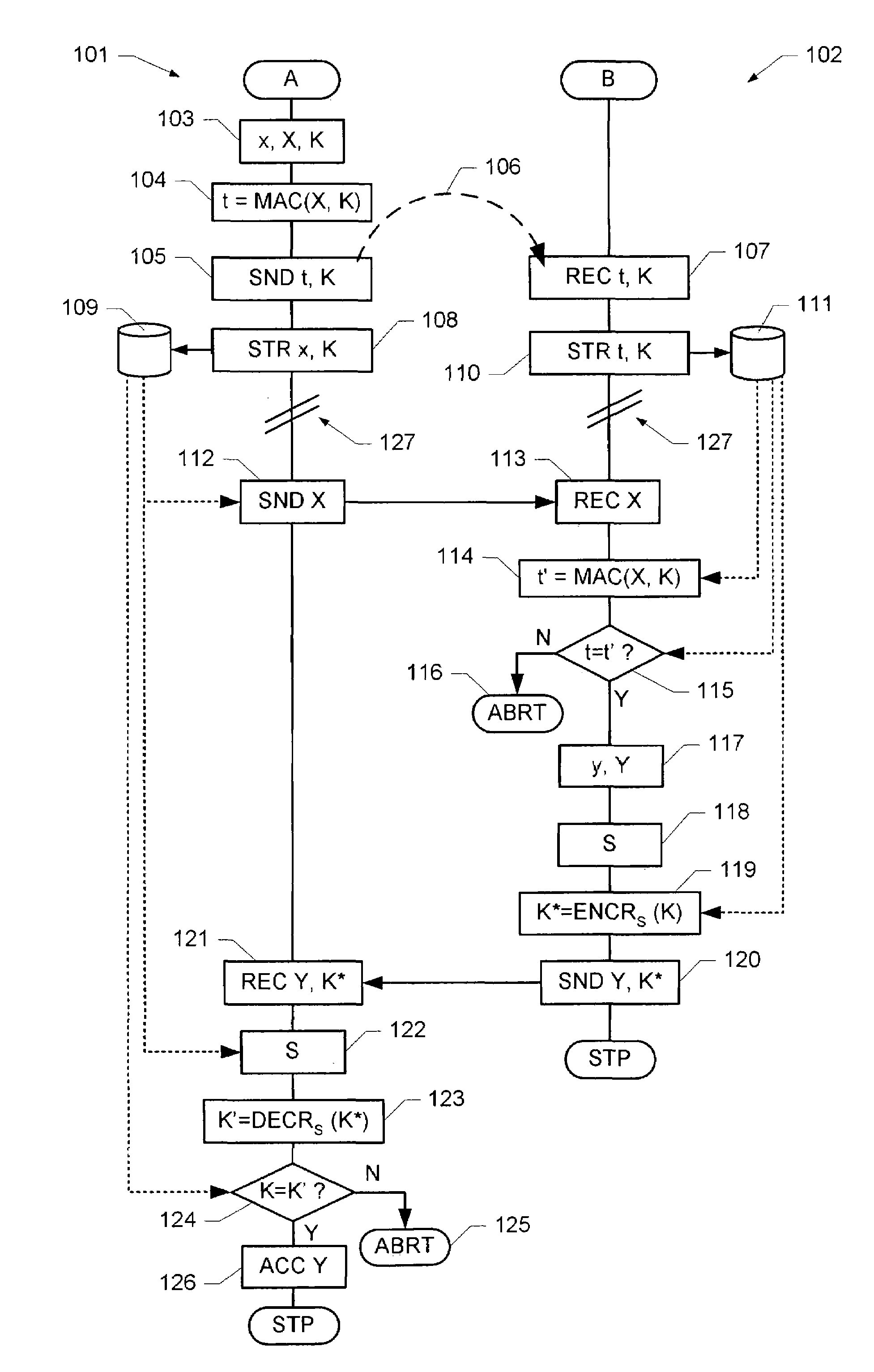
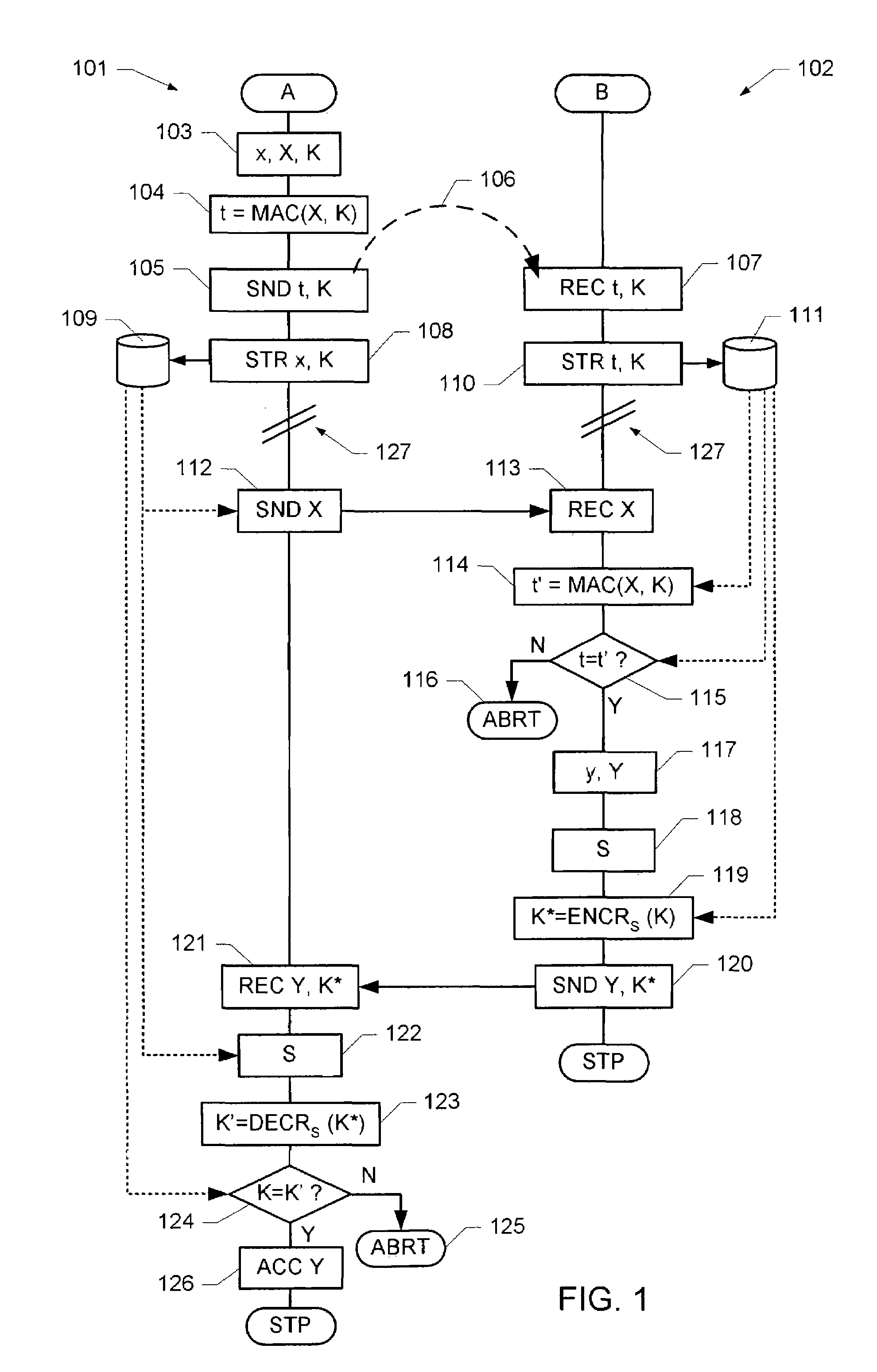
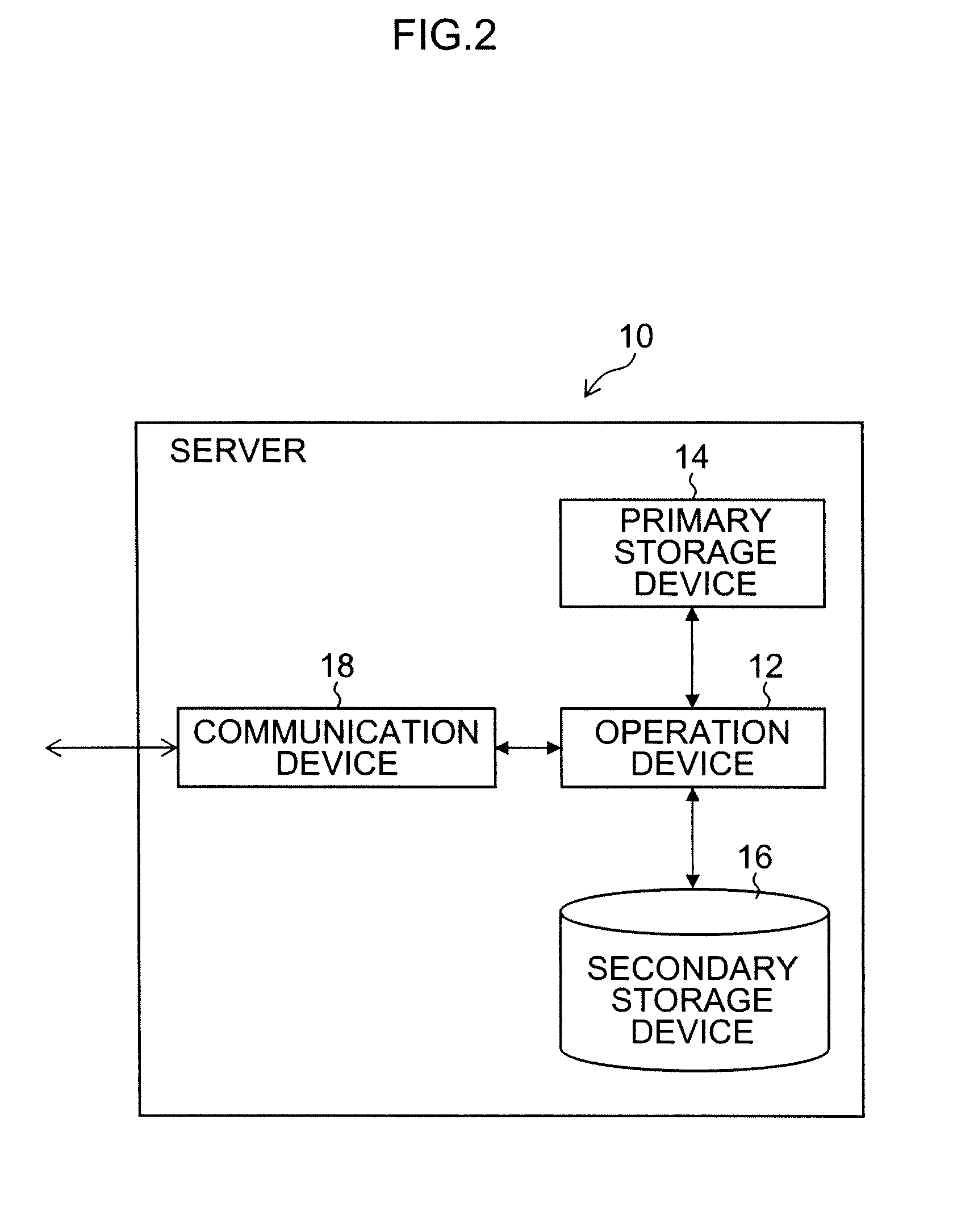
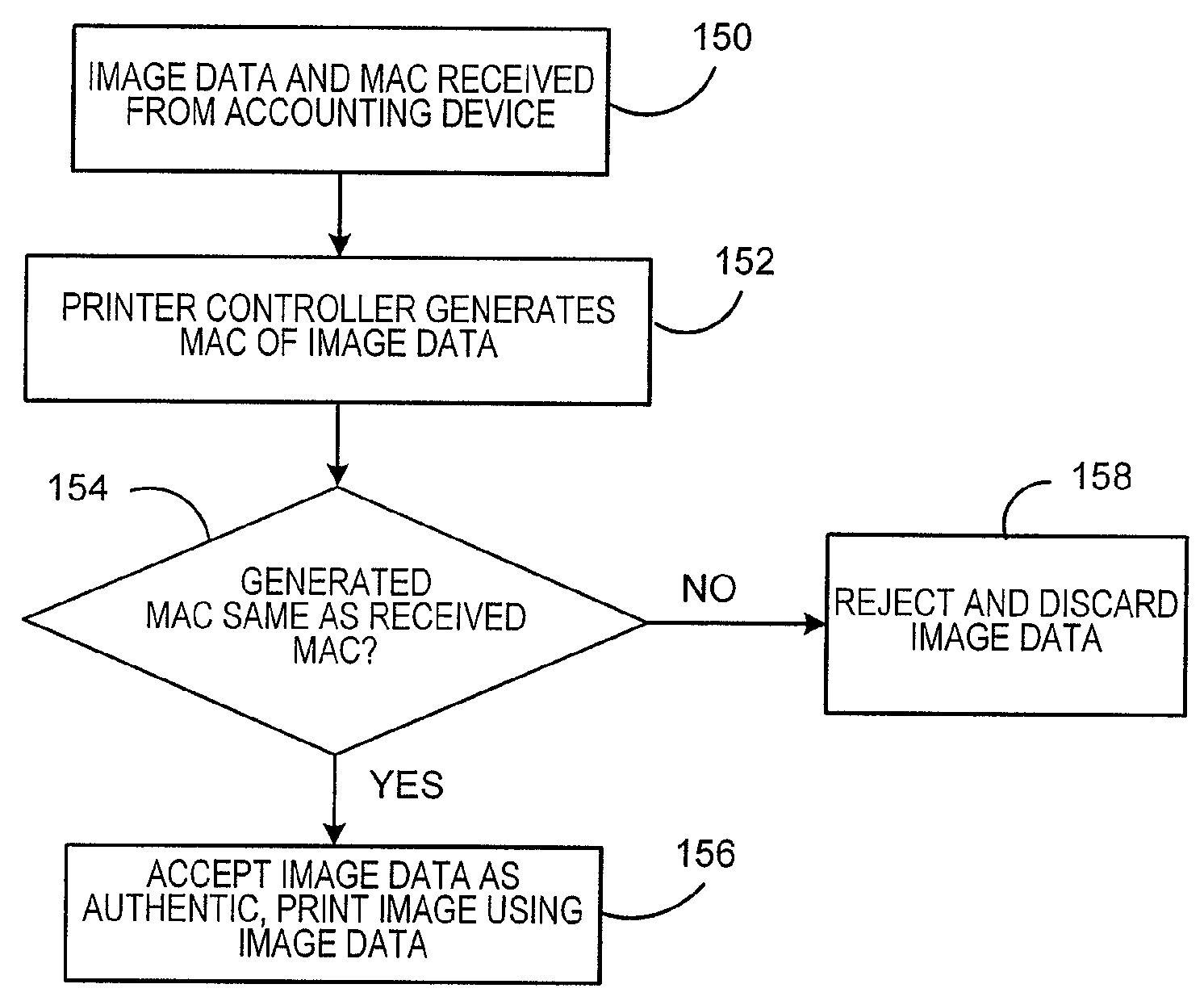
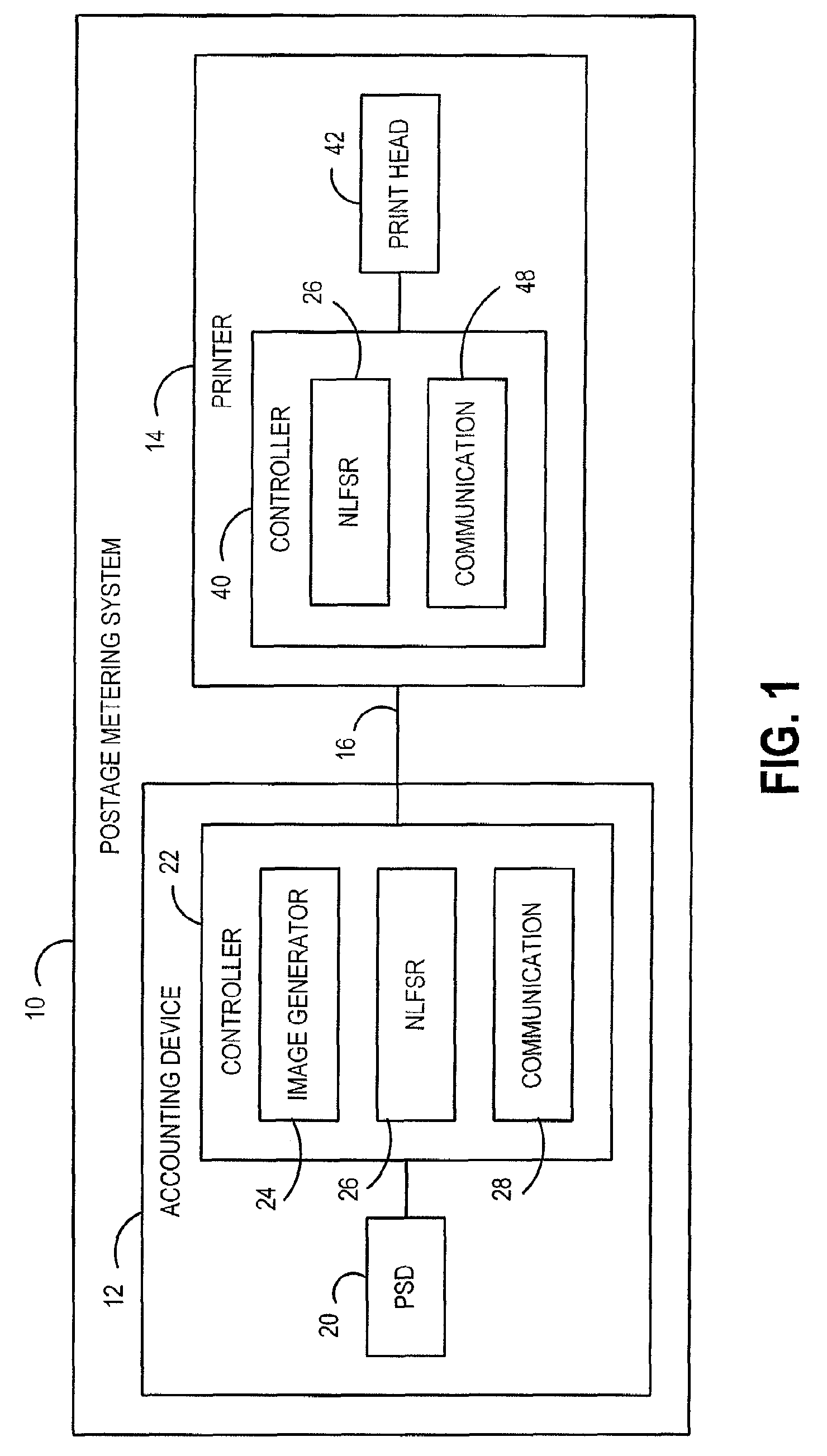
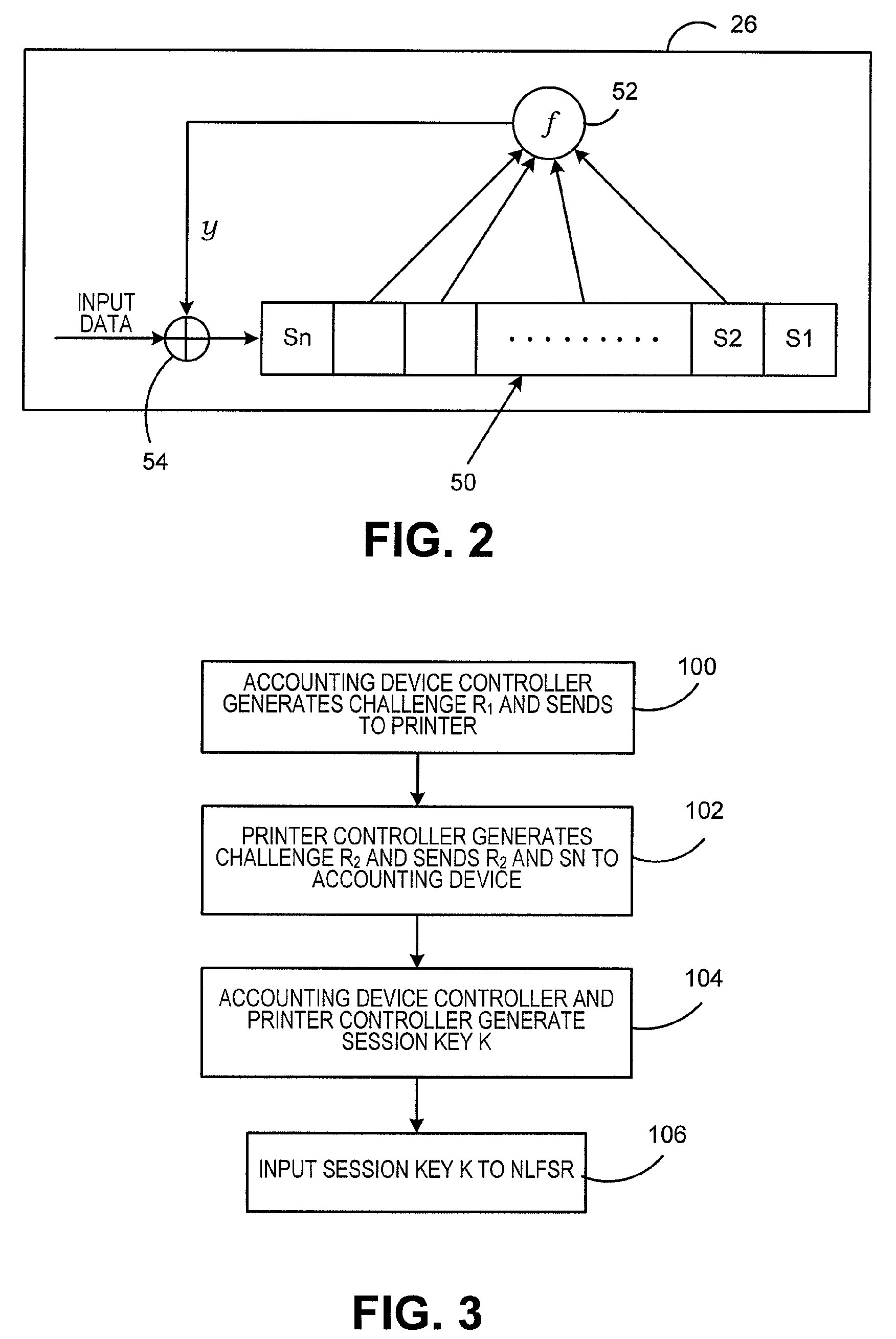
ActiveUS20100128872A1High level of securityReduce decreaseKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecure communicationTelecommunications link
A method and system for securing the communication link between the accounting device and printer of a metering system by authenticating the data being sent via the link utilizing a Nonlinear Feedback Shift Register (NLFSR) based system is provided. A NLFSR is provided in each of the accounting unit and printing unit of a metering system. The NLFSR in the accounting unit is utilized to generate a message authentication code (MAC) for the image data being sent from the accounting unit to the printing unit. The printing unit generates a corresponding MAC for the received image data using the NLFSR in the printing unit. The MAC generated by the printing unit is compared with the MAC generated by the accounting unit. If the MACs are similar, the image data is accepted as authentic and the printing unit will print the image corresponding to the image data.
Owner:PITNEY BOWES INC
Method for Isolating a Plant Device of an Industrial Plant
InactiveUS20100217409A1High level of securityImprove security levelProgramme controlSafety arrangmentsData inputCommunication unit
A method for isolating a plant device of an industrial plant, wherein at least one safety measure is implemented on the plant device in order for work to be done safely on the plant device is provided. Isolation information is communicated to a control and protection system using a data communication unit having a data input that receives data from the plant device. An interface between the data communication unit and a control and protection system of the industrial plant is used to transmit the isolation information from the data communication unit to the control and protection unit. A device for isolating a plant device of an industrial plant to carry out work on the plant device is also provided.
Owner:SIEMENS AG
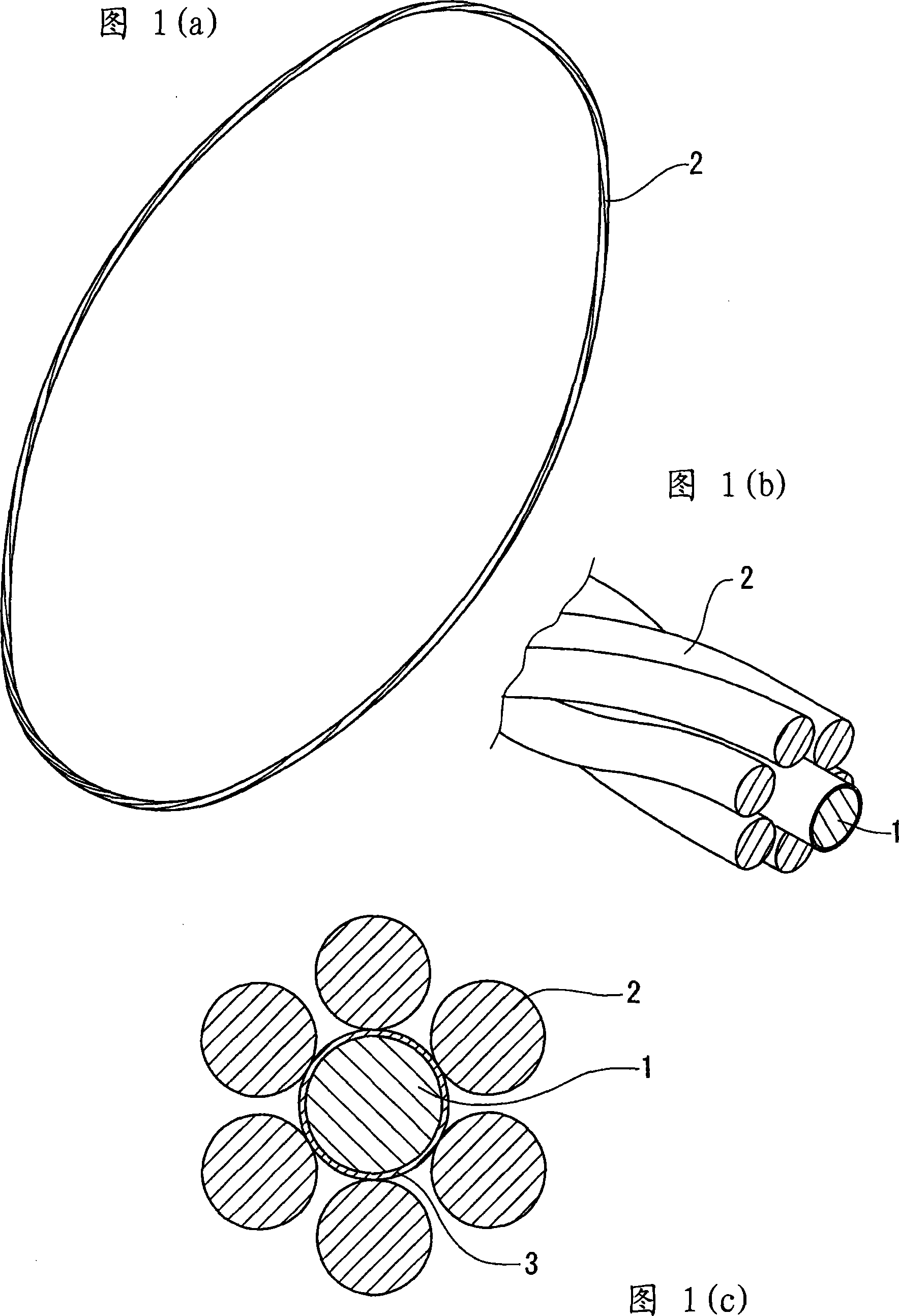
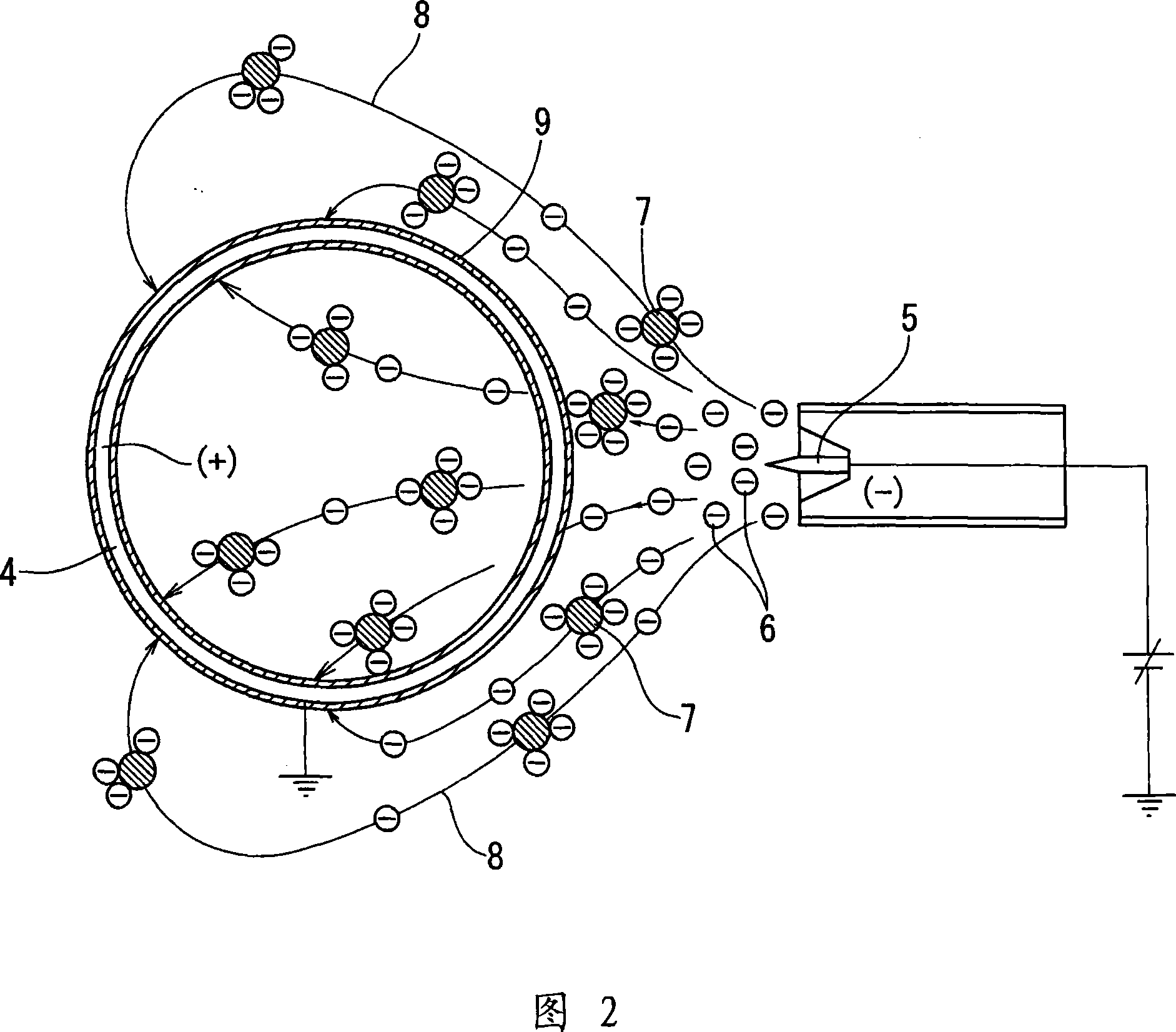
Annular concentric stranded bead cord and method for producing the same
An annular concentric stranded bead cord having an annular core, which cord is imparted with stable corrosion resistance over a long term at a low cost. The surface of a steel wire in an annular core (1) is applied with a corrosion-resistant paint and covered with a thick coating film (3) so that the surface of the steel wire is not exposed easily even if fretting takes place between the annular core (1) and a side wire (2), thereby ensuring stable corrosion resistance of the annular core (1) over a long term at a low cost.
Owner:SUMITOMO ELECTRIC IND LTD +1
Secure method for configuring internet of things (IOT) devices through wireless technologies
ActiveUS20200169886A1Improve usabilityHigh level of securityService provisioningNetwork topologiesSecure communicationComputer security
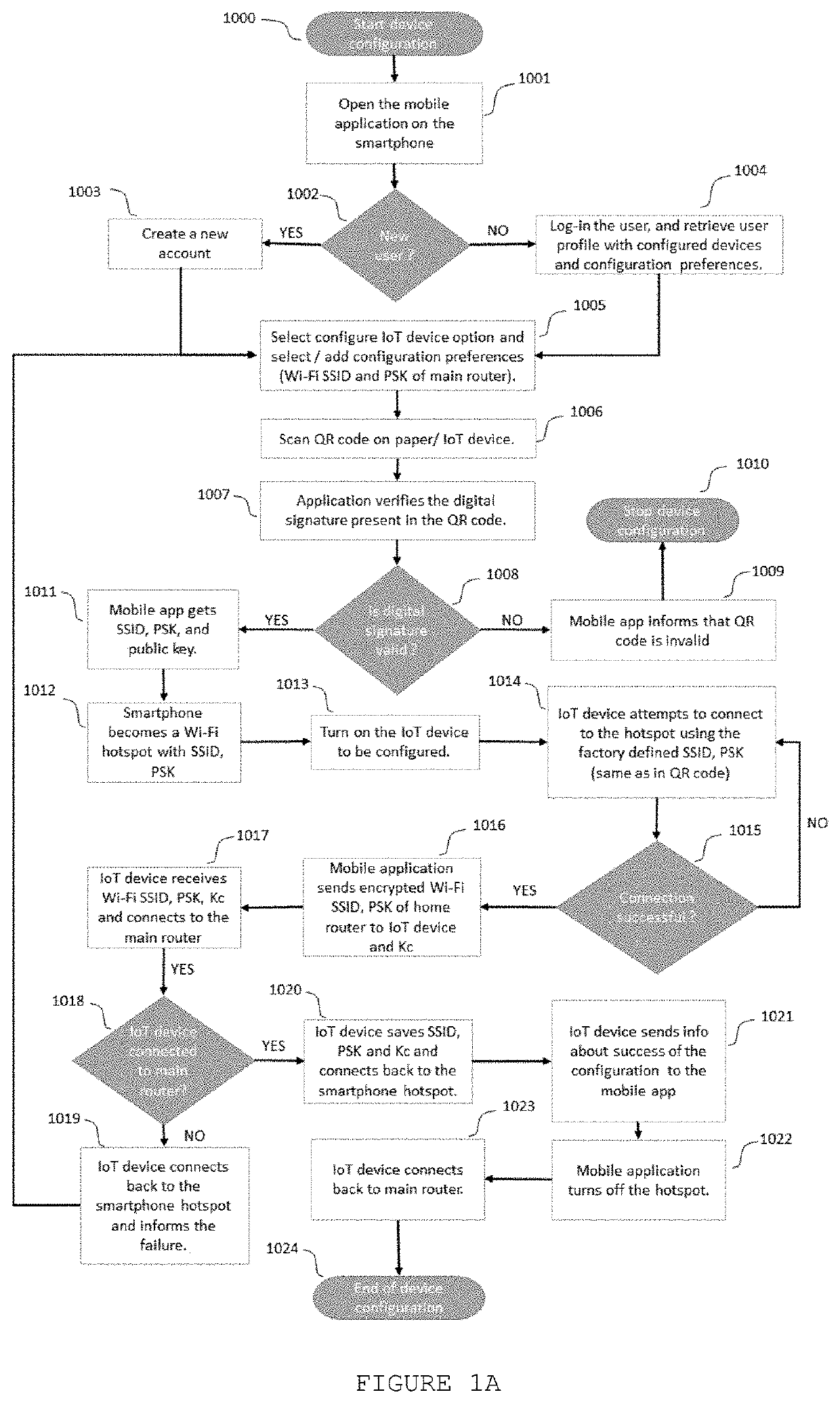
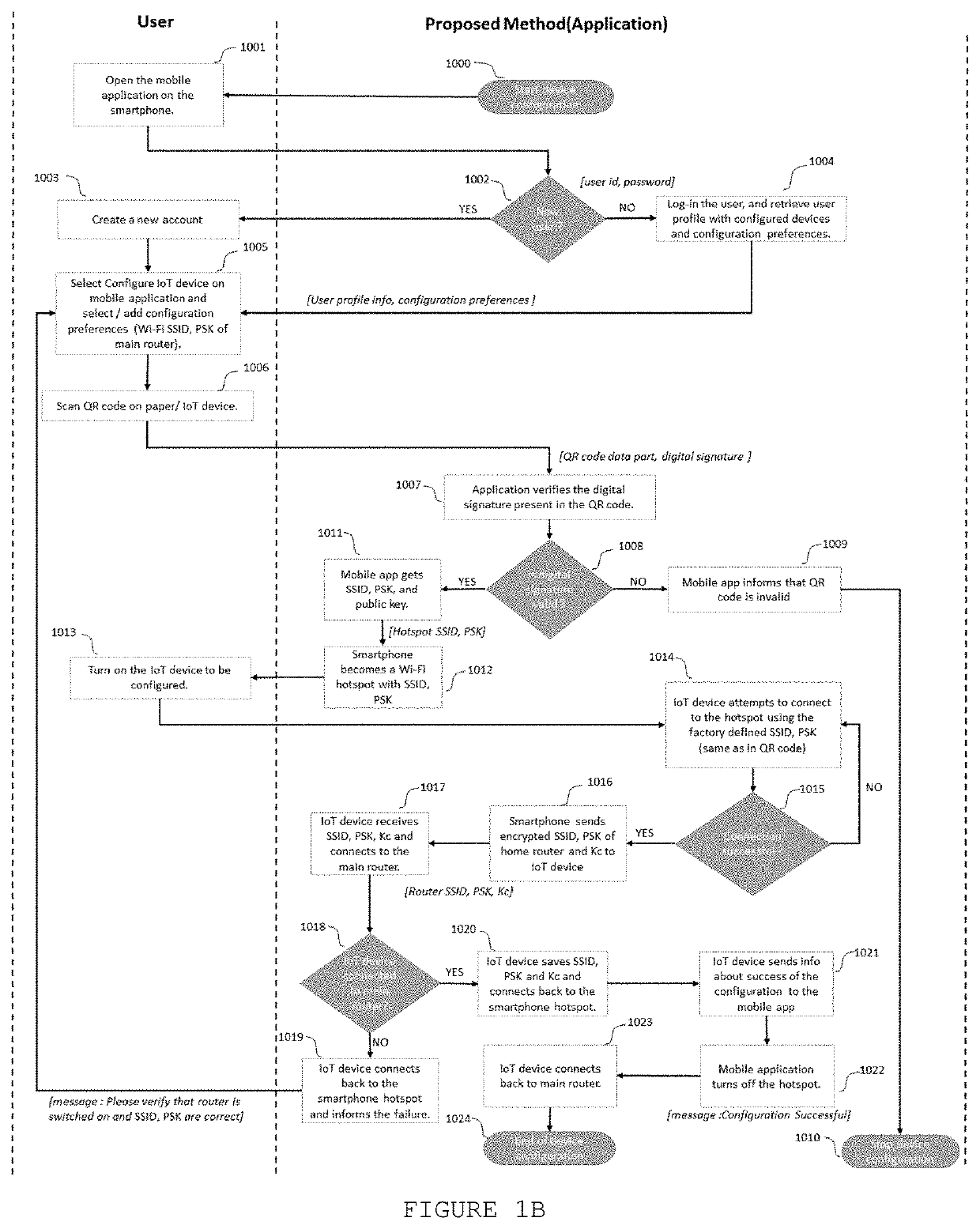
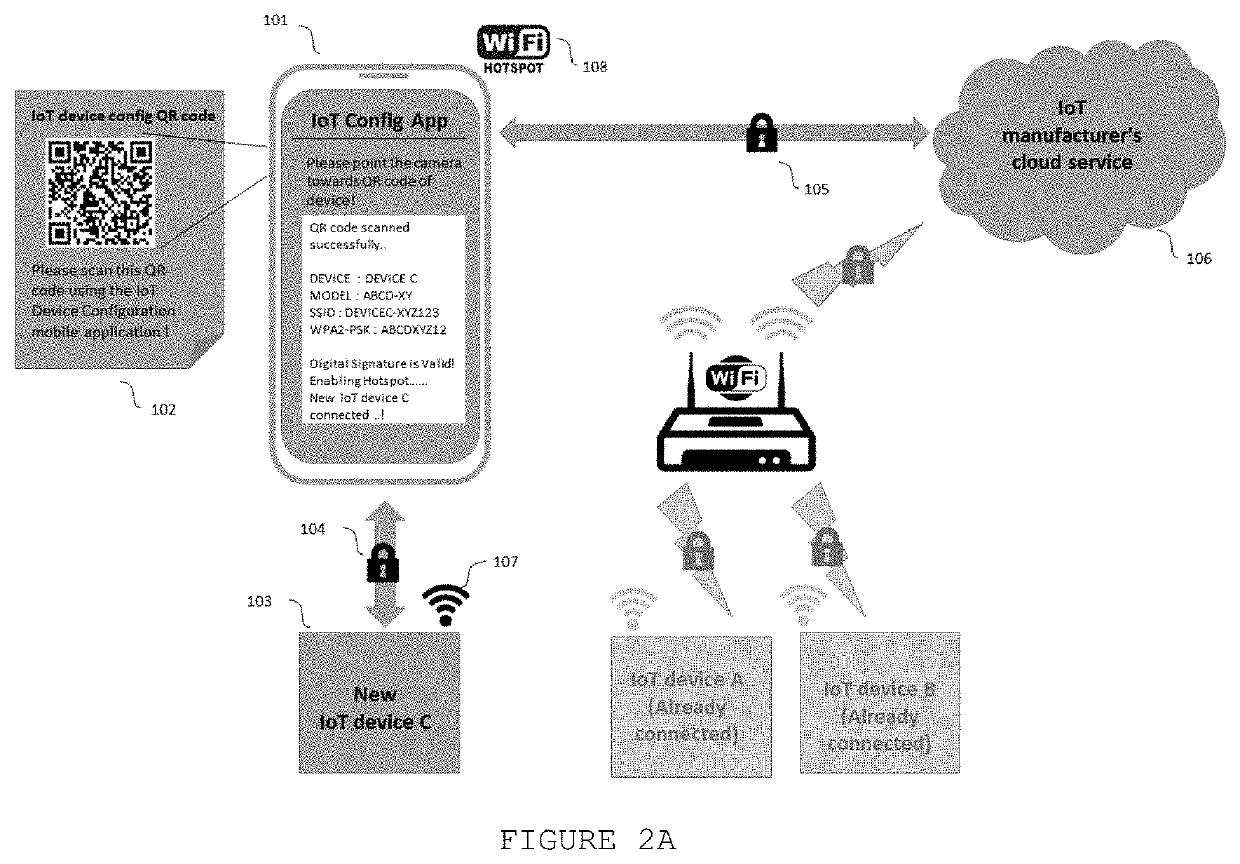
A method to configure a new IoT device using a smartphone with the IoT device configuration application / service installed. Once the user has added the configuration preferences after successful login to his account on the cloud service using secure communication channel (such as TLS), the user can scan the QR code printed on the device / paper shipped together with the device. After the QR code is scanned, the mobile application decodes the data contained in the QR code, verifies the digital signature, and automatically enables a Wi-Fi hotspot on the smartphone, based on the information retrieved from the QR code. Then, the mobile application informs the user to switch on the IoT device. Once the IoT device is turned on and boots completely, it connects to the hotspot on the smartphone using the default Wi-Fi SSID and PSK saved in its memory (the same as on the QR code).
Owner:SAMSUNG ELECTRONICSA AMAZONIA
Articulated open ring
InactiveUS7017368B2Easy to put inEasy to take offBraceletsClockwork casesEngineeringMechanical engineering
Owner:HARTCASE
Attenuated pestivirus
ActiveUS20110117126A1High level of securitySsRNA viruses positive-senseViral antigen ingredientsGlycoproteinImmunogenicity
The present invention relates to recombinant attenuated pestiviruses, in particular to recombinant attenuated CSFV, BVDV, or BDV, wherein said recombinant attenuated pestivirus does not produce a dimeric Ems glycoprotein. The present invention also relates to immunogenic compositions comprising such a pestivirus as well to a method of attenuating a pestivirus comprising the step of modifying the Ems glycoprotein by a deletion, insertion or substitution wherein such modification results in a non dimeric Ems glycoprotein.
Owner:BOEHRINGER LNGELHEIM VETMEDICA GMBH
Financial trade method and trade system using mobile device for the same
InactiveUS20120271764A1High level of securityAction faster and convenientFinancePayment architectureFinancial tradingApplication software
A financial trade method arranges a combo-chips card internally on a mobile device for trading. The mobile device selects one of the combo-chips card which combines a plurality of chip cards therein via an application program, and the mobile device progresses to swipe in a non-contact sensing mode. After sensing, the mobile device identifies for user thereon according to a request from a financial server, and the mobile device then transmits identification data to the financial server after identifying. Therefore, the financial server determines whether the trade is successful and completed after comparing with the identification data.
Owner:CHEN PING CHIEN
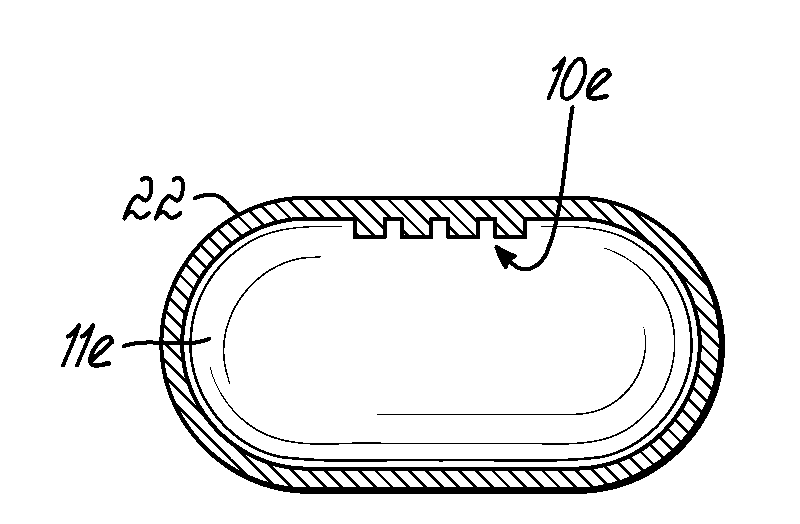
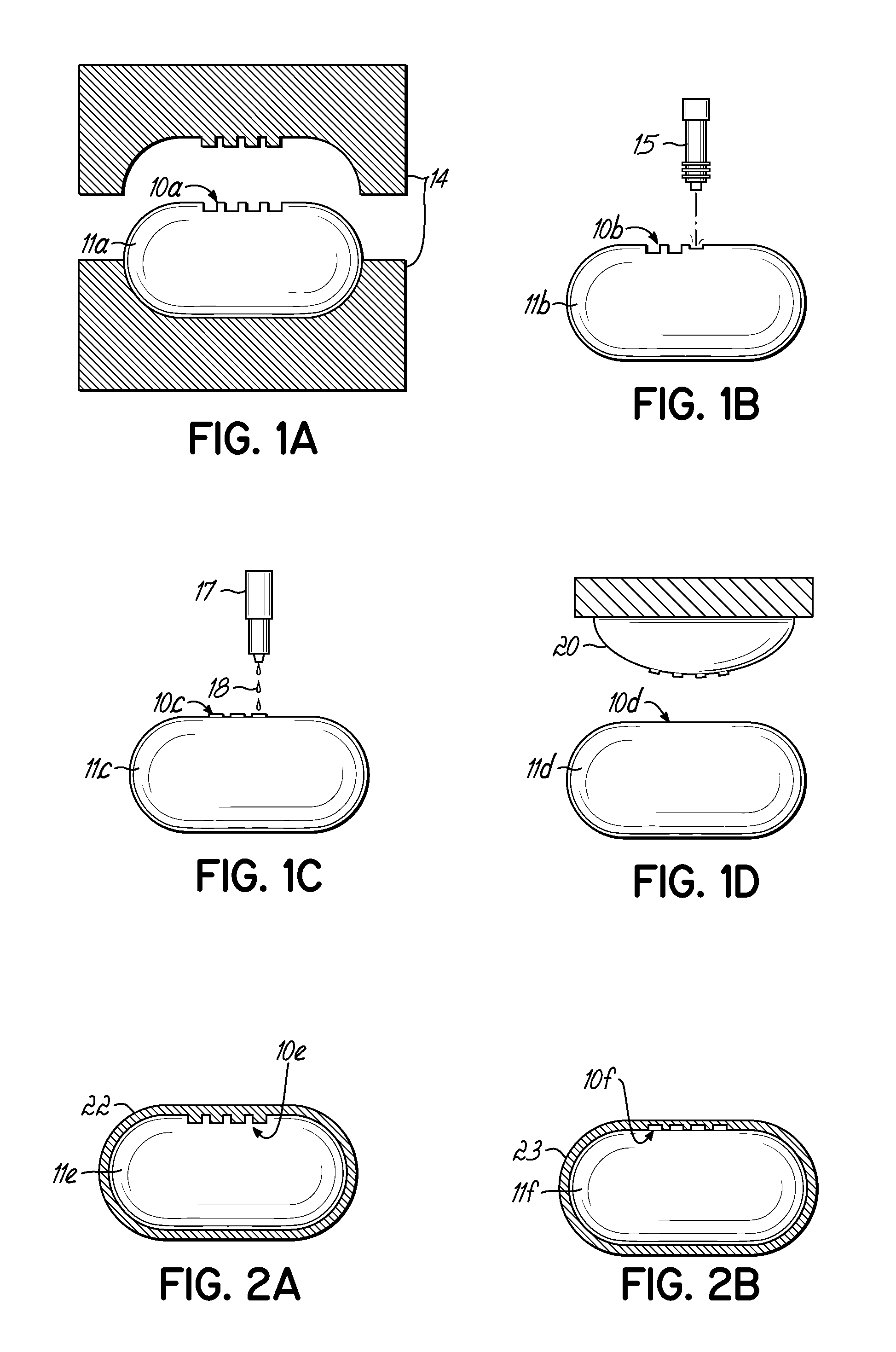
Pharmaceutical Moire Pill
InactiveUS20110256069A1High level of securityImprove security levelPharmaceutical product form changePretreated surfacesReduced susceptibilityDosage form
A pharmaceutical dosage form [11, 11g] has reduced susceptibility to counterfeiting, due to the forming directly thereon of a pattern or base layer [10, 10g] of a Moiré pair, wherein a Moiré effect is visually observable by looking through a revealing layer [12, 12g] positioned closely to and superimposed on the base layer [10, 10g]. The pattern fanned on the pharmaceutical dosage form [11, 11g] may be formed by embossing, oblation, inkjet printing, or tampon printing. The revealing layer [12, 12g] of the Moiré pair can be part of a blister package containing the pharmaceutical dosage form [11, 11g], so that the Moiré effect is observable while looking at the pharmaceutical dosage form [11, 11g] as it remains within the package.
Owner:I PROPERTY HLDG CORP
System and method for certifying and authenticating correspondence (II)
InactiveUS20100008481A1High level of integrityHigh level of securityTelephonic communicationComputer security arrangementsElectronic communicationMessage passing
A system and method are provided to monitor and control electronic communications. A processor is in operable communication with processor readable media, and a user interface is provided by the processor over a communication network that is operable to send, receive and report communications from a plurality of users. A database is provided on the processor readable media and accessible by the processor. A centralized messaging center is operable to receive from the processor the communications, to print the communications, to image the communications and to store the communications in a database.
Owner:GLOBALPEX
Method and system for presentation of content from one cellular phone to another through a computer network
InactiveUS20050032512A1High level of securityImprove usabilityInterconnection arrangementsAccounting/billing servicesMobile telephonyTelecommunications
A cellular phone issues a request for content from a server. The cellular requests and authorizes the content for use by another cellular phone. When the content is received by the second cellular phone, the first cellular phone is billed.
Owner:IBM CORP
Device authentication system
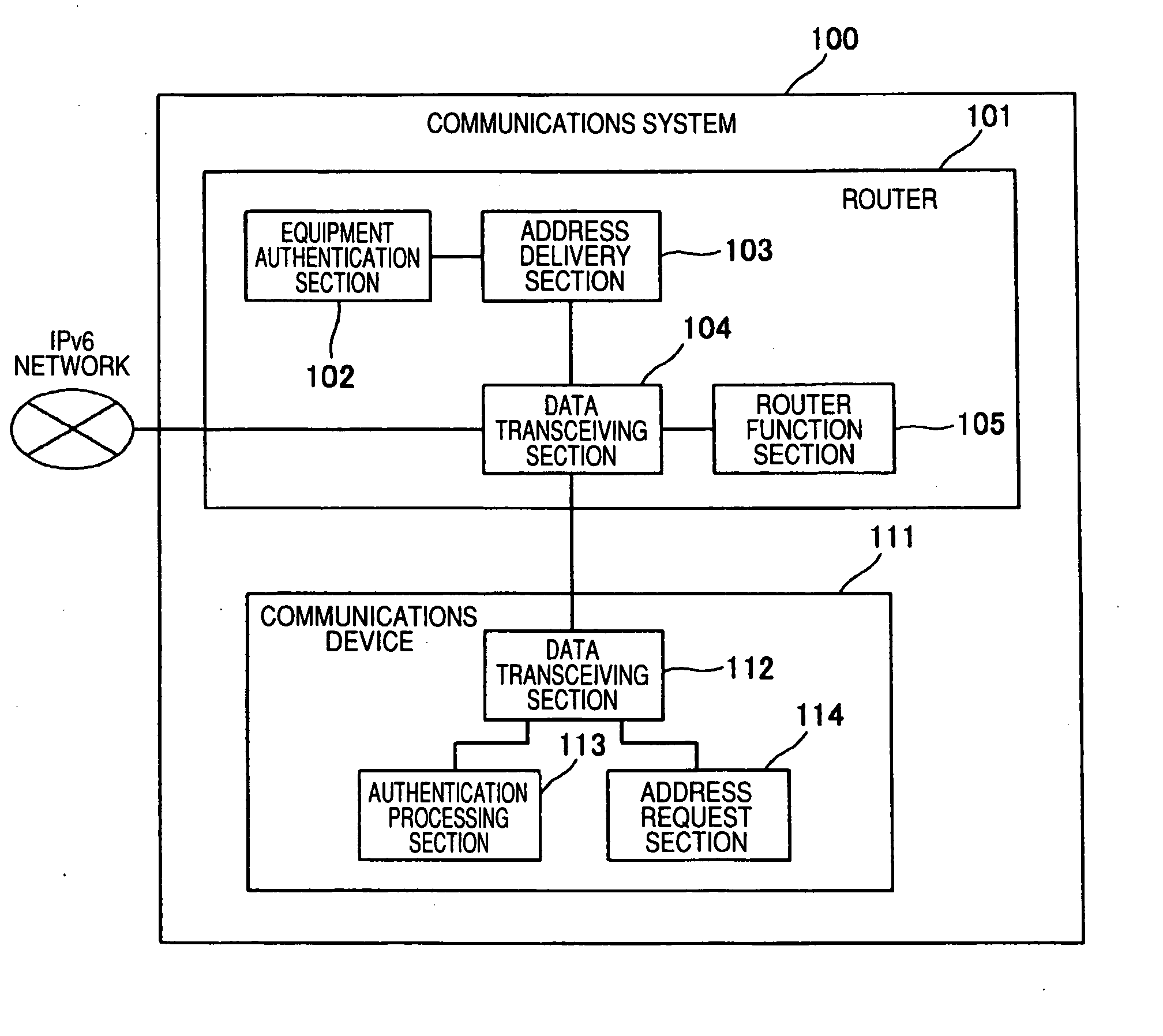
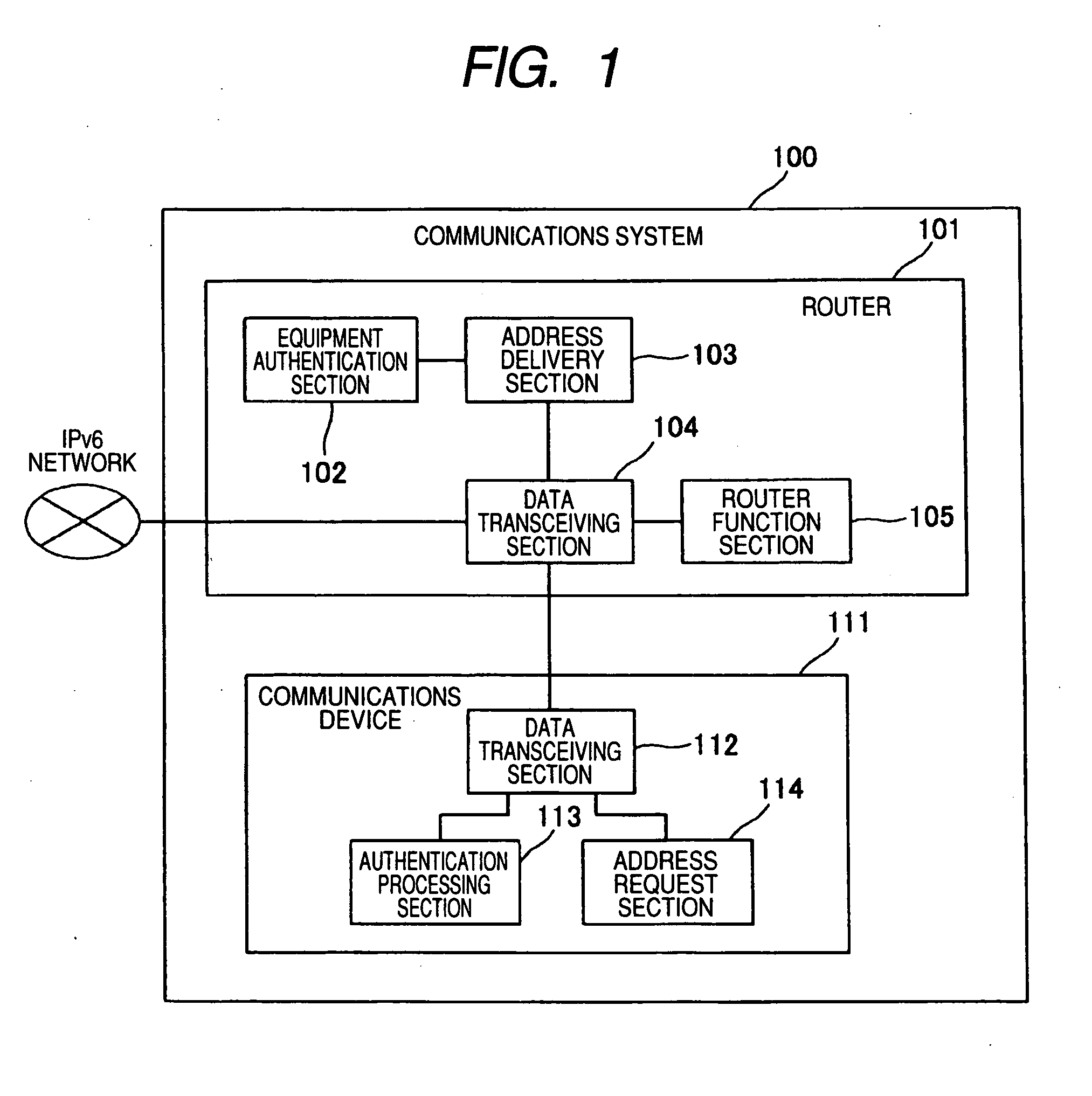
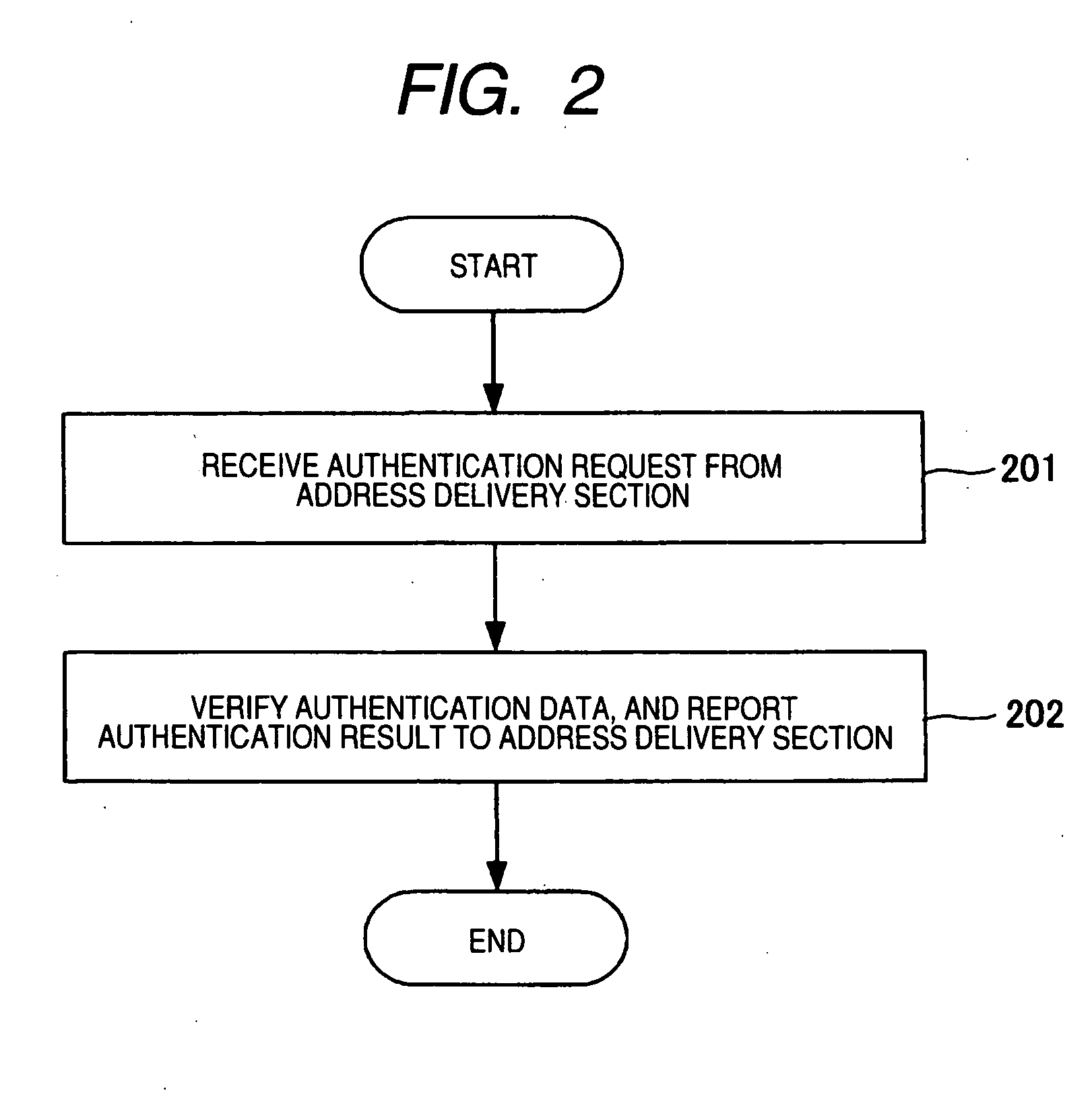
InactiveUS20070211729A1Lessen load imposeHigh level of securityData switching by path configurationNetwork connectionsAuthentication systemLink-local address
A high level of security is realized by imposing limitations on an unauthorized communications device in establishing connection to a network, without involvement of an increase in the burden of network equipment such as a router or a communications device constituting a network. An address delivery section 103 in a router 101 delivers a link local address in answer to an address request from a communications device 111, and requests the communications device 111 to transmit authentication data. An equipment authentication section 102 in the router 101 authenticates the communications device 111 on the basis of the authentication data transmitted from the communications device 111, and reports an authentication result to the address delivery section 103. When the communications device 111 has been authenticated, the address delivery section 103 delivers a global address or a site local address to the communications device 111.
Owner:PANASONIC CORP
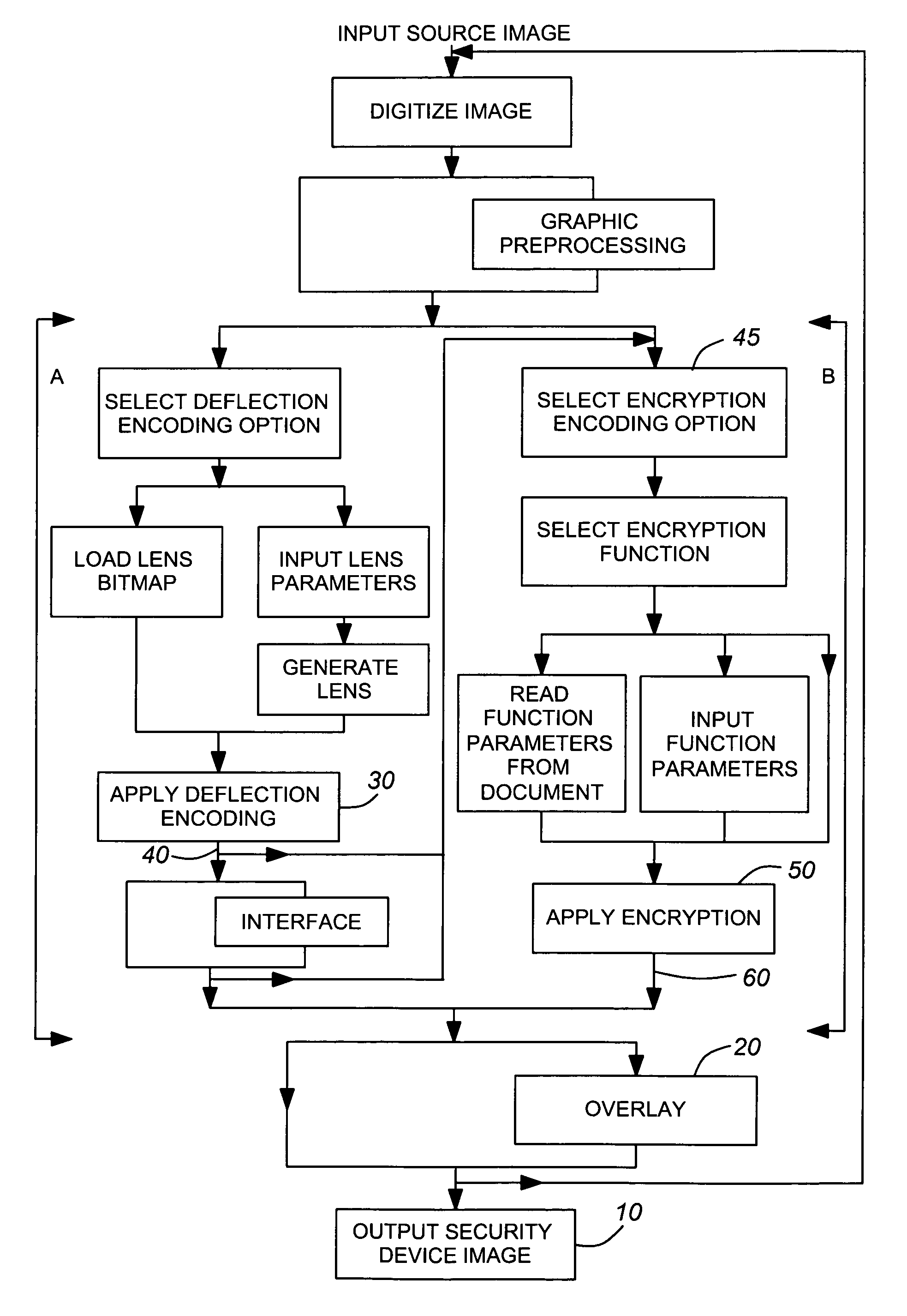
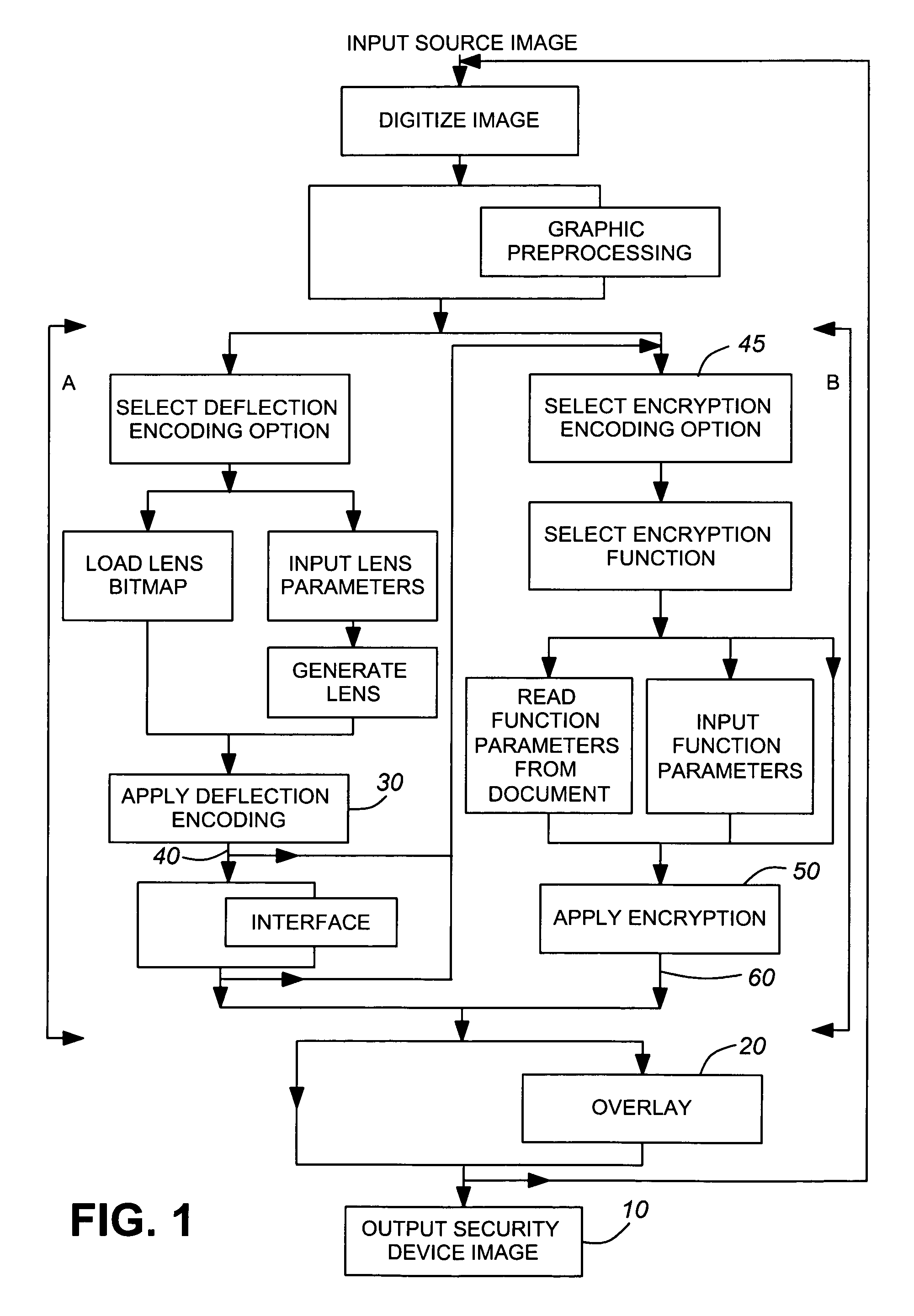
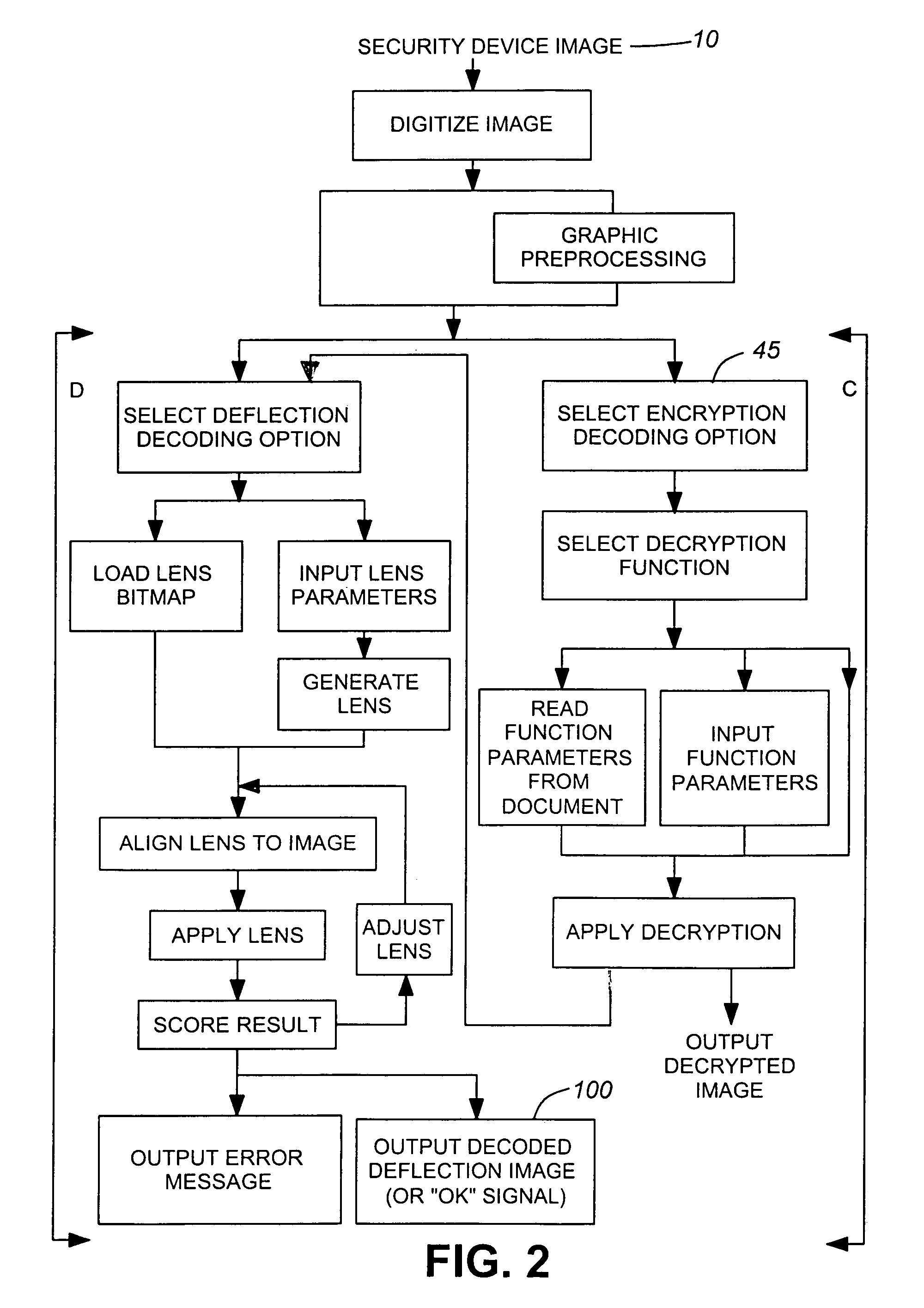
System for producing a printable security device image and detecting latent source image(s) therefrom
InactiveUS7046804B1High level of securityCoding/ciphering apparatusTransmissionCamera lensLenticular lens
An image encoding / decoding system and method for producing a computer-generated security device which can be printed onto a document, such as a passport, to secure the document against data alteration. Deflection encoding means comprises means for applying a selected software lens to a source image and producing a deflected image. Encryption encoding means comprises means for applying an encryption function to the deflected image or a source image and producing an encrypted image. Overlaying means is provided for overlaying the deflected and encrypted images and producing therefrom the security device image. The deflected image may be detected from the security device image both by means of a manual lenticular lens corresponding to the software lens applied to a printing of the security image and by means of computer decoding processing applying the software lens. However, the encrypted image may be detected from the security device image solely by means of computer decoding processing applying a decryption function corresponding to the encryption function.
Owner:CANADIAN BANK NOTE COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com