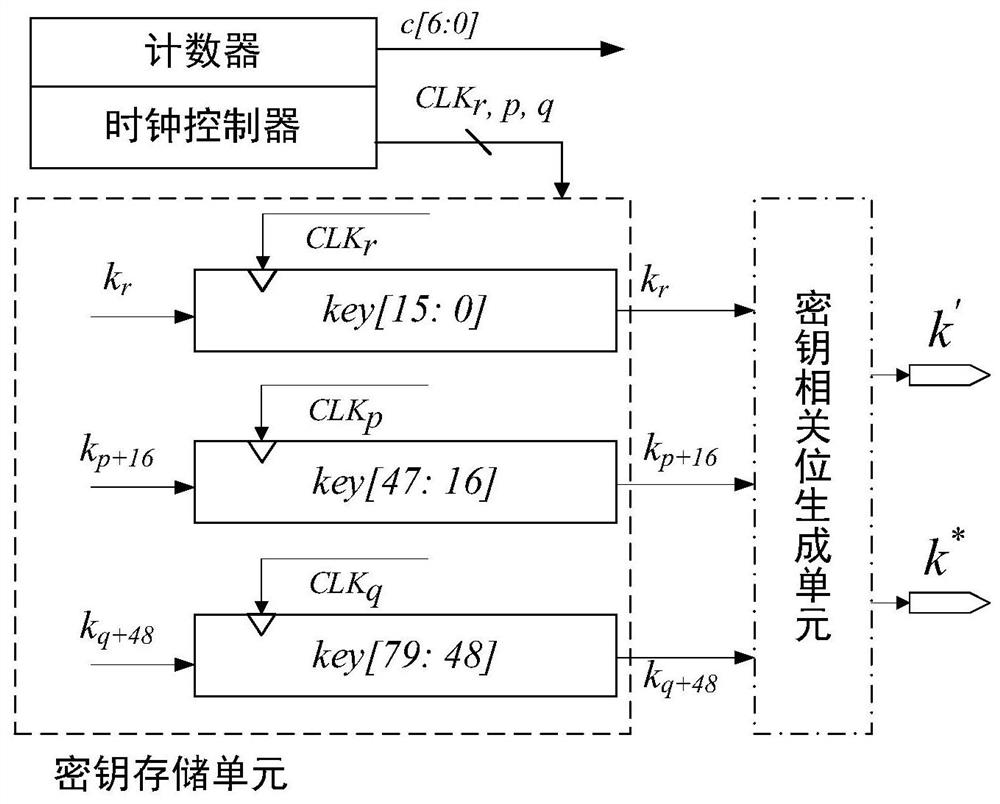
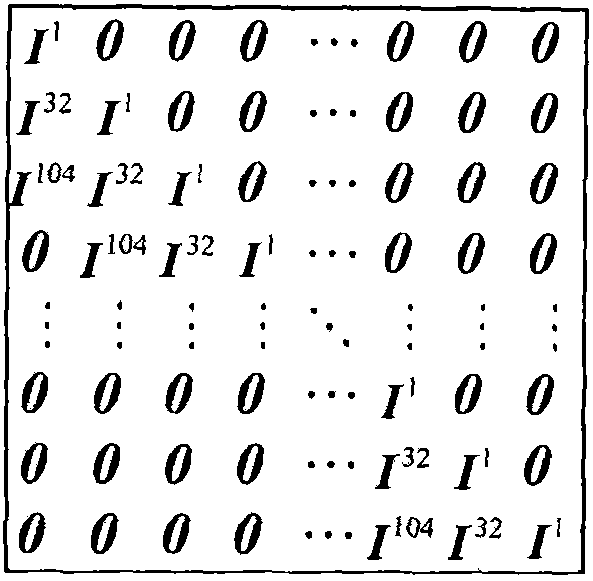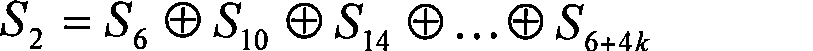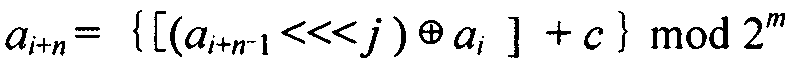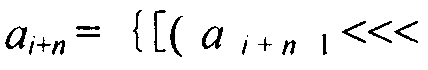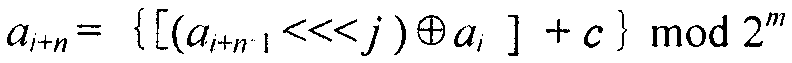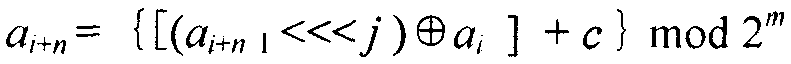Patents
Literature
33 results about "Nonlinear feedback shift register" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
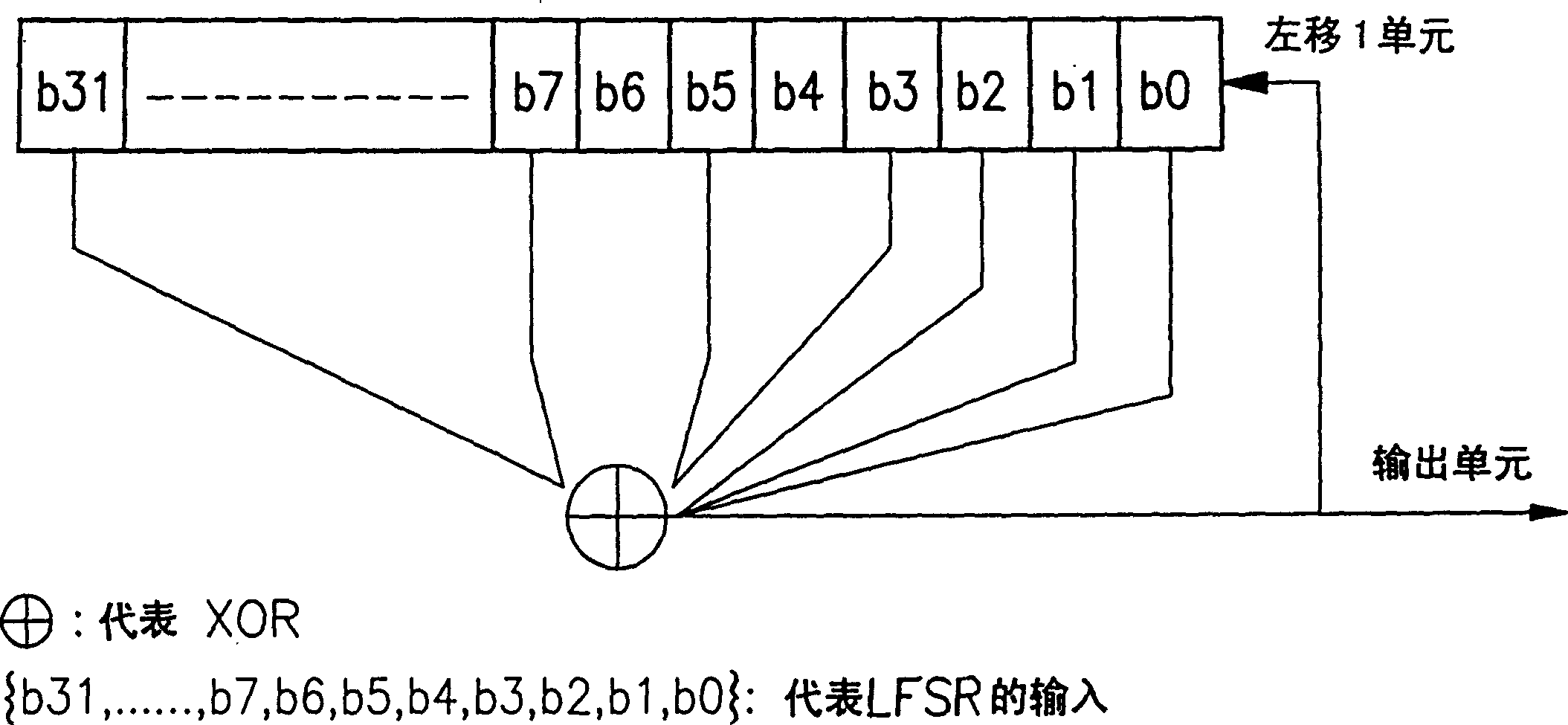
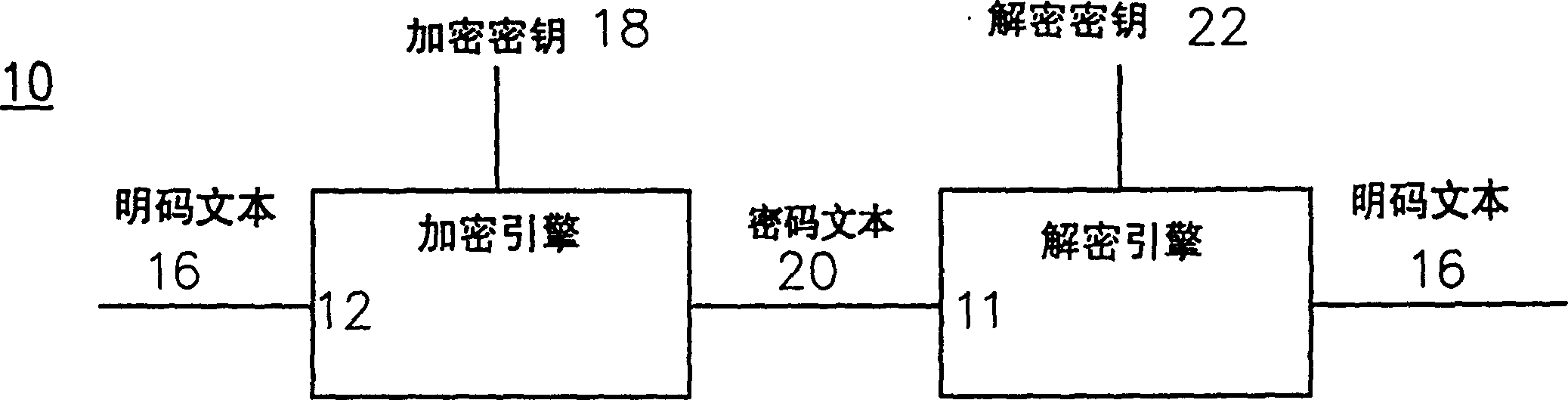
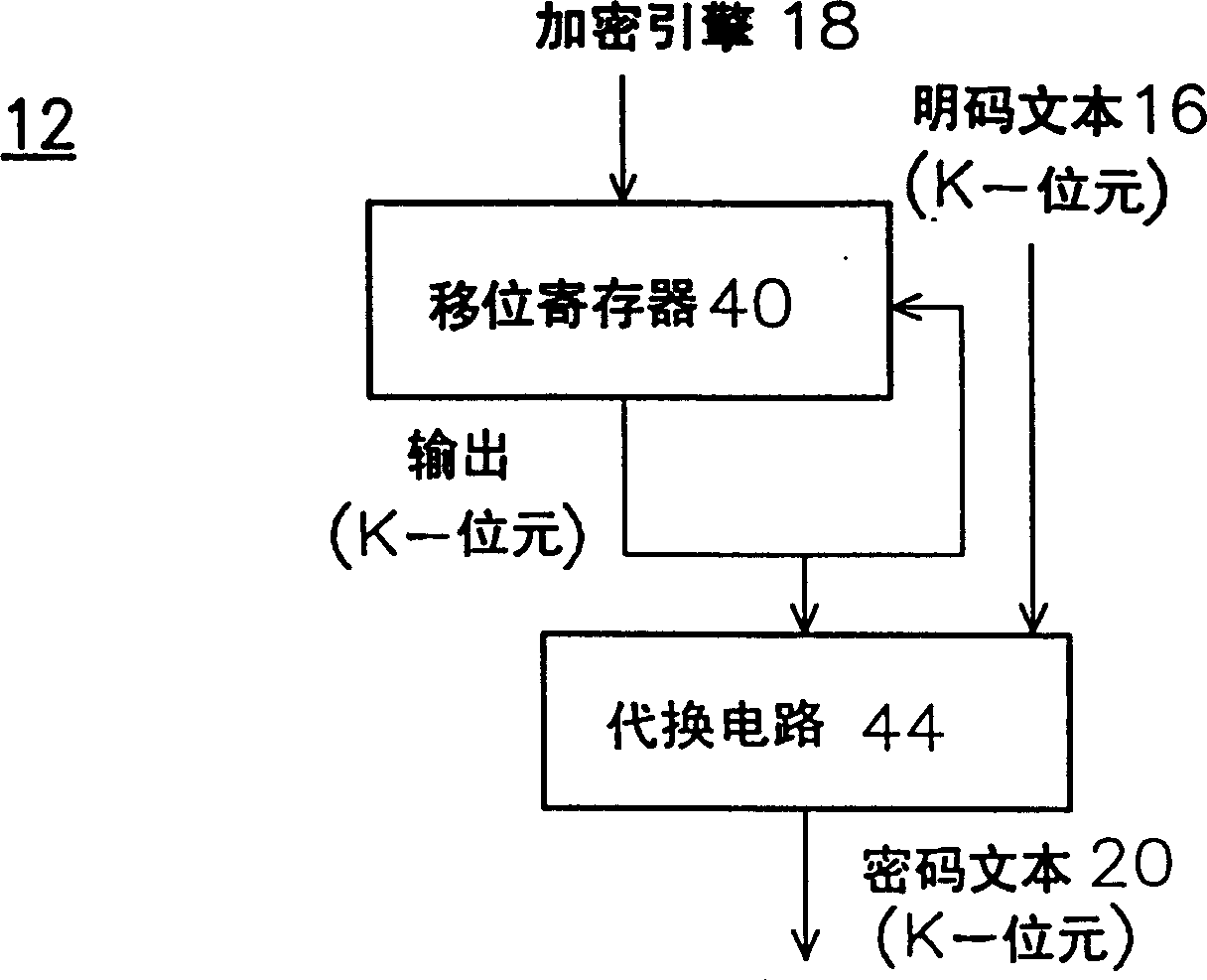
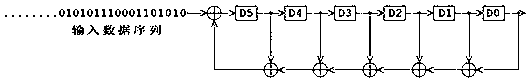
A nonlinear-feedback shift register (NLFSR) is a shift register whose input bit is a non-linear function of its previous state. For an n-bit shift register r its next state is defined as: rᵢ₊₁(b₀,b₁,b₂,…,bₙ₋₁)=rᵢ(b₁,b₂,…,f(b₀,b₁,b₂,…,bₙ₋₁)), where f is the non-linear feedback function.
Pseudo random number generation device and pseudo random number generation program
InactiveCN1914590ARandom number generatorsPulse generation with predetermined statistical distributionNonlinear feedback shift registerExclusive or
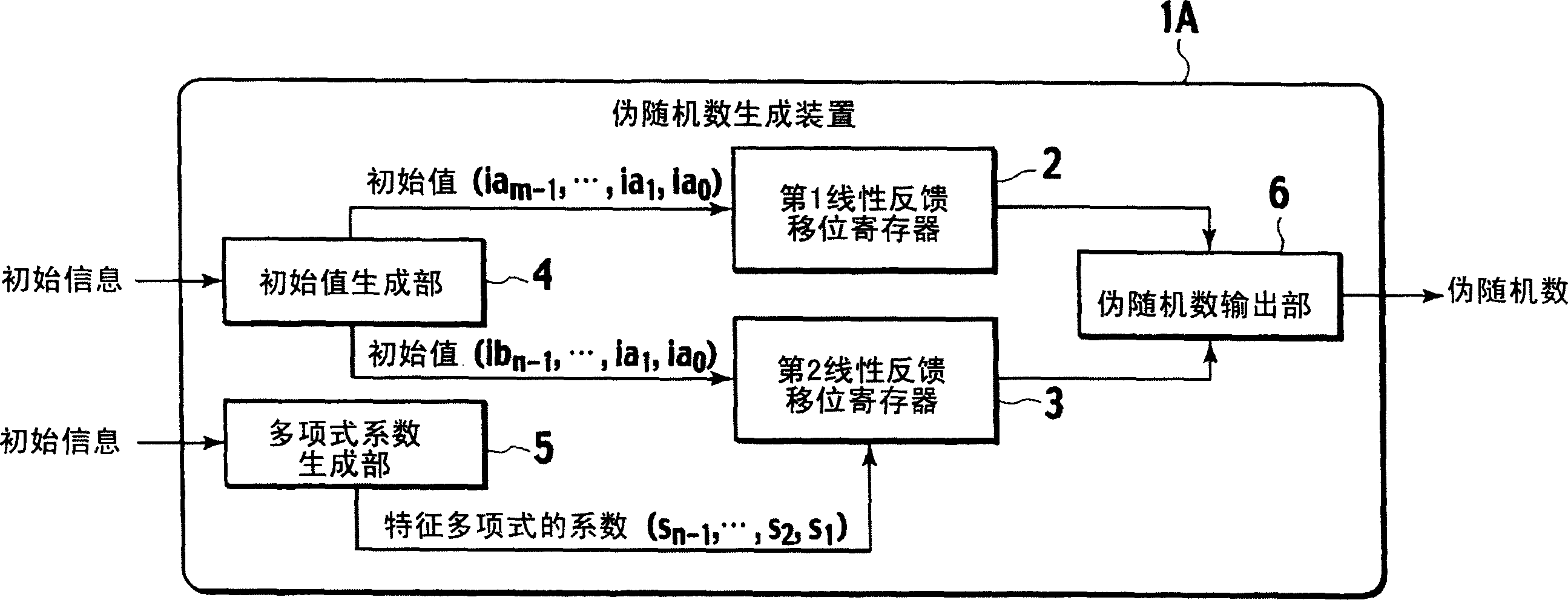
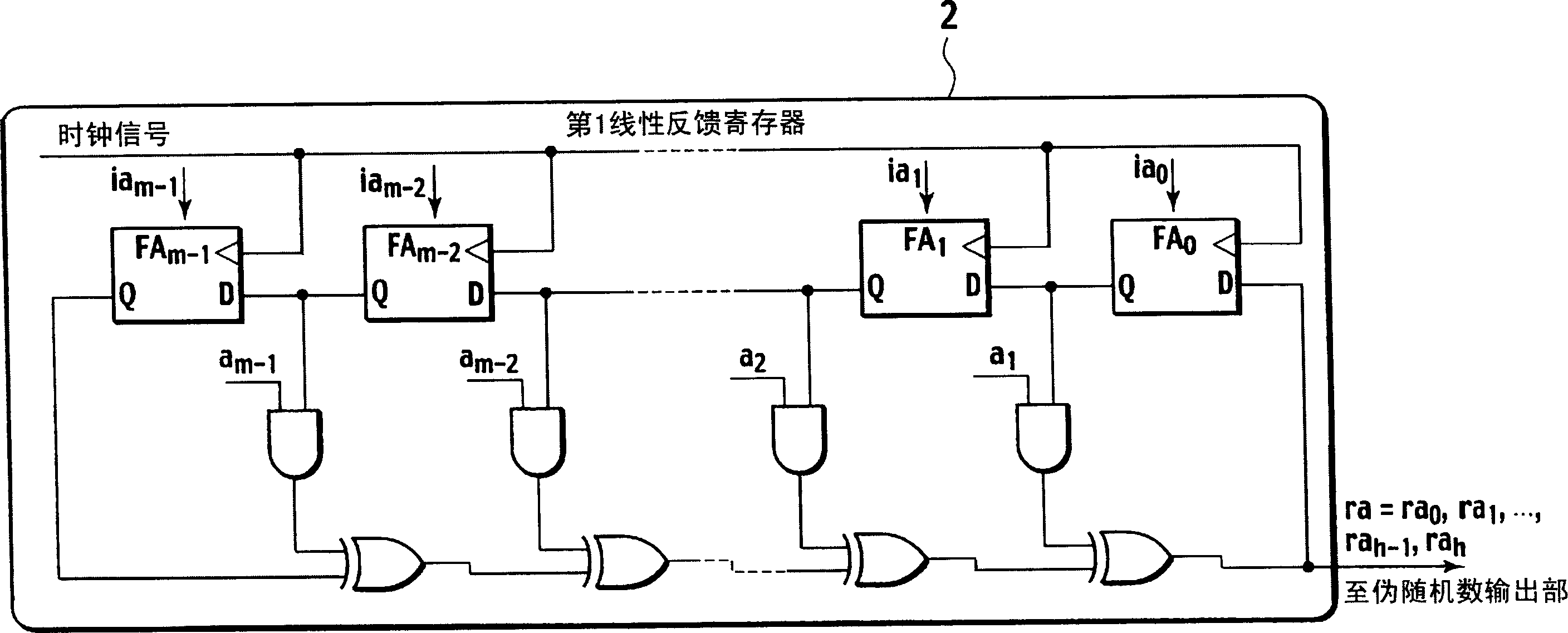
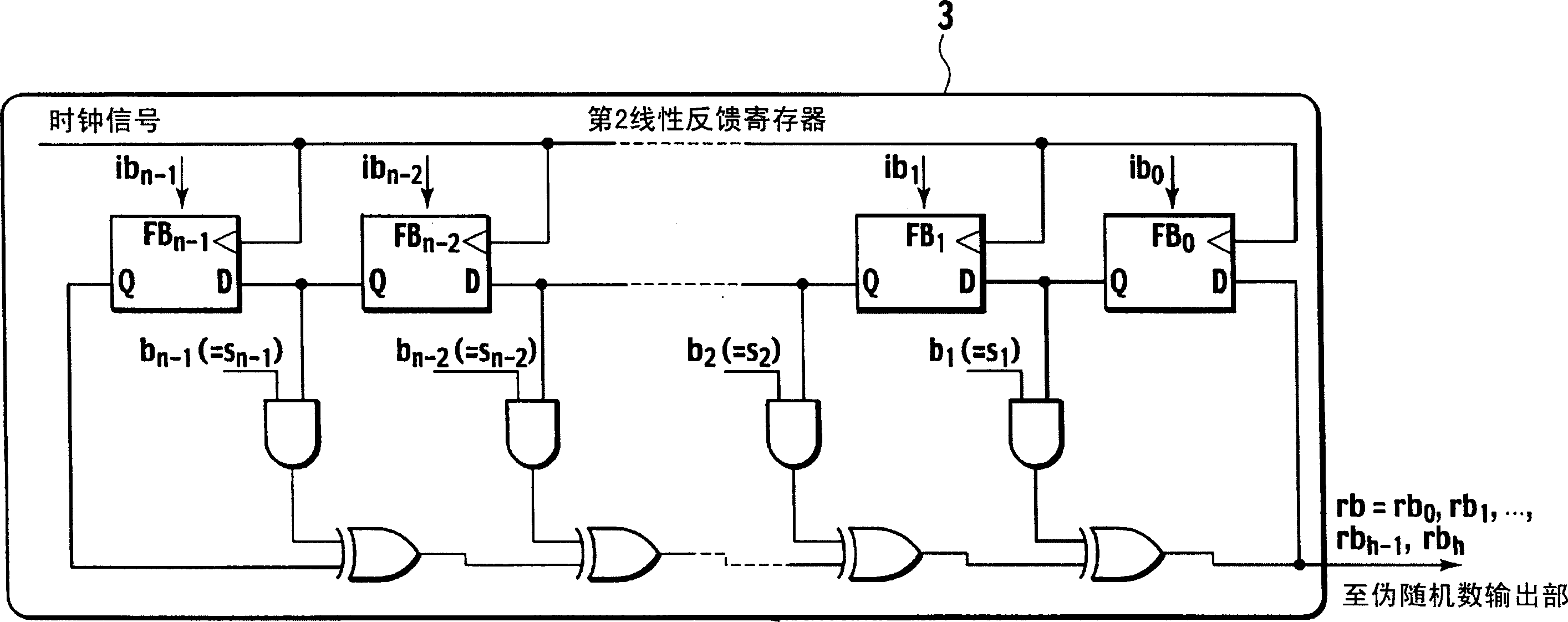
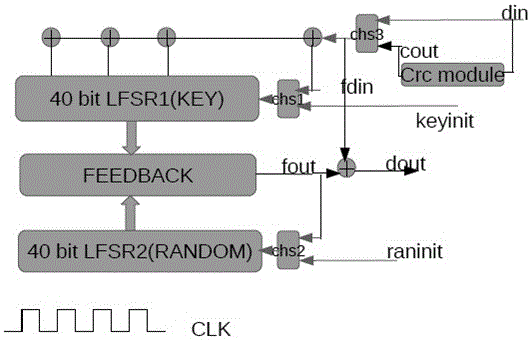
A pseudo random number generation device(1) includes a first linear feedback shift register(2), a second linear feedback shift register(3), an initial value generation unit(4), a polynomial coefficient generation unit(5), and a pseudo random number output unit(6). The initial value generation unit(4) generates an initial value and supplies it to the first linear feedback shift register(2) and the second linear feedback shift register(3). The polynomial coefficient generation unit(5) generates a characteristic polynomial coefficient and supplies it to the second feedback shift register(3). The pseudo random number output unit(6) generates a pseudo random number from the exclusive OR of each bit according to the bit string successively output from the first linear feedback shift register(2) and the second linear feedback shift register(3) and outputs it.
Owner:VICTOR CO OF JAPAN LTD
Encoder and encoding method for Quasic-low-density parity-check (QC-LDPC) codes in digital television terrestrial multimedia broadcasting (DTMB) system
InactiveCN102122963AError preventionError correction/detection using multiple parity bitsTelecommunicationsNonlinear feedback shift register
The invention relates to an encoding solution to three quasic-low-density parity-check (QC-LDPC) codes with different code rates in a digital television terrestrial multimedia broadcasting (DTMB) system. The encoding solution is characterized in that an encoder for the QC-LDPC codes in the system mainly comprises six parts, including a task scheduling module, a barrel shift accumulation circuit, a linear feedback shift register circuit, a convolution sum circuit, a modified shift register and accumulation circuit and an rearrangement splicing circuit.
Owner:COMMUNICATION UNIVERSITY OF CHINA +2
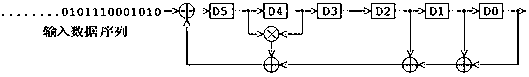
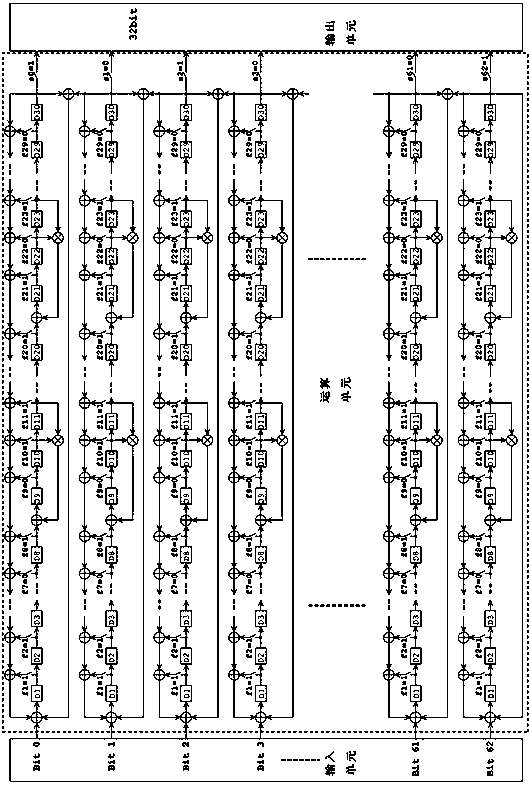
Non-linear feedback shift register
ActiveCN104238995ARandom number generatorsEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerAlgorithm
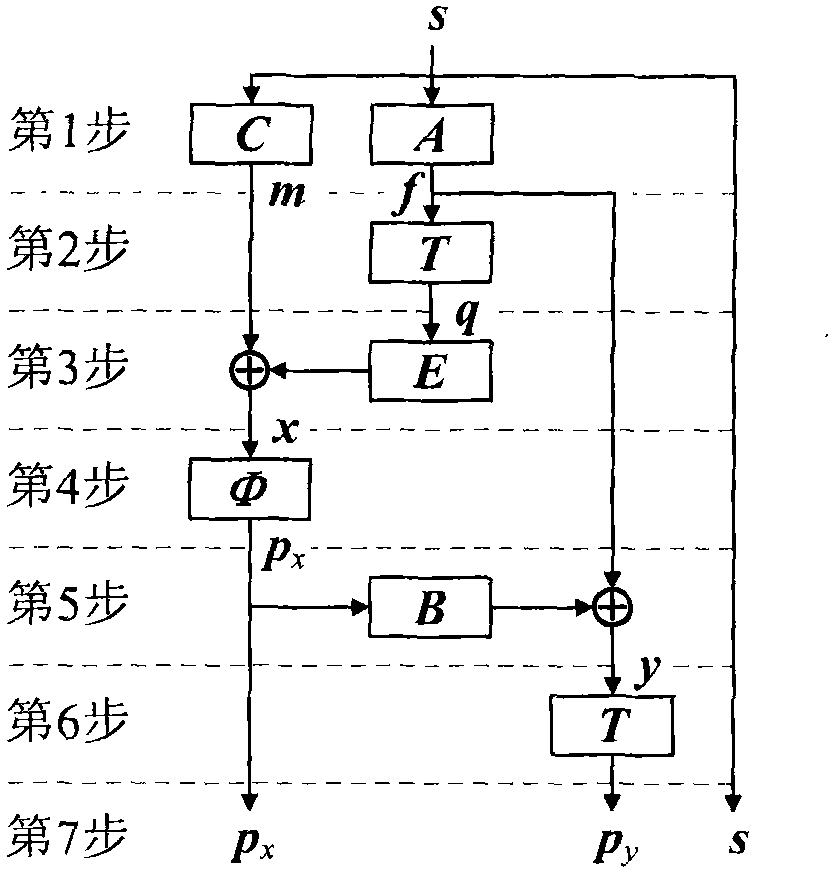
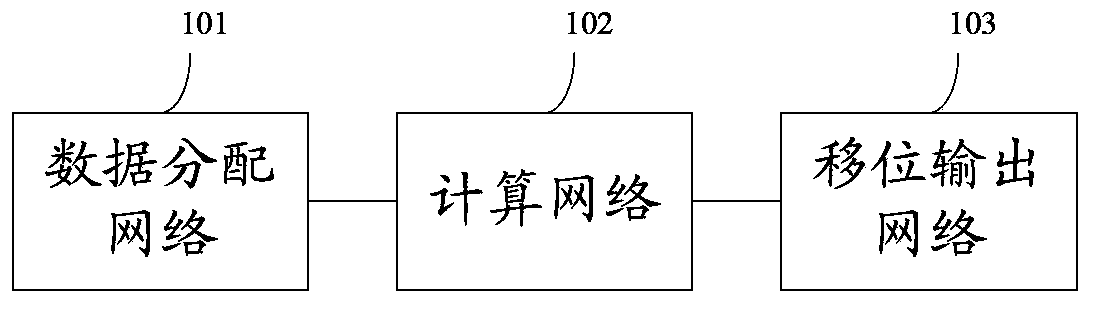
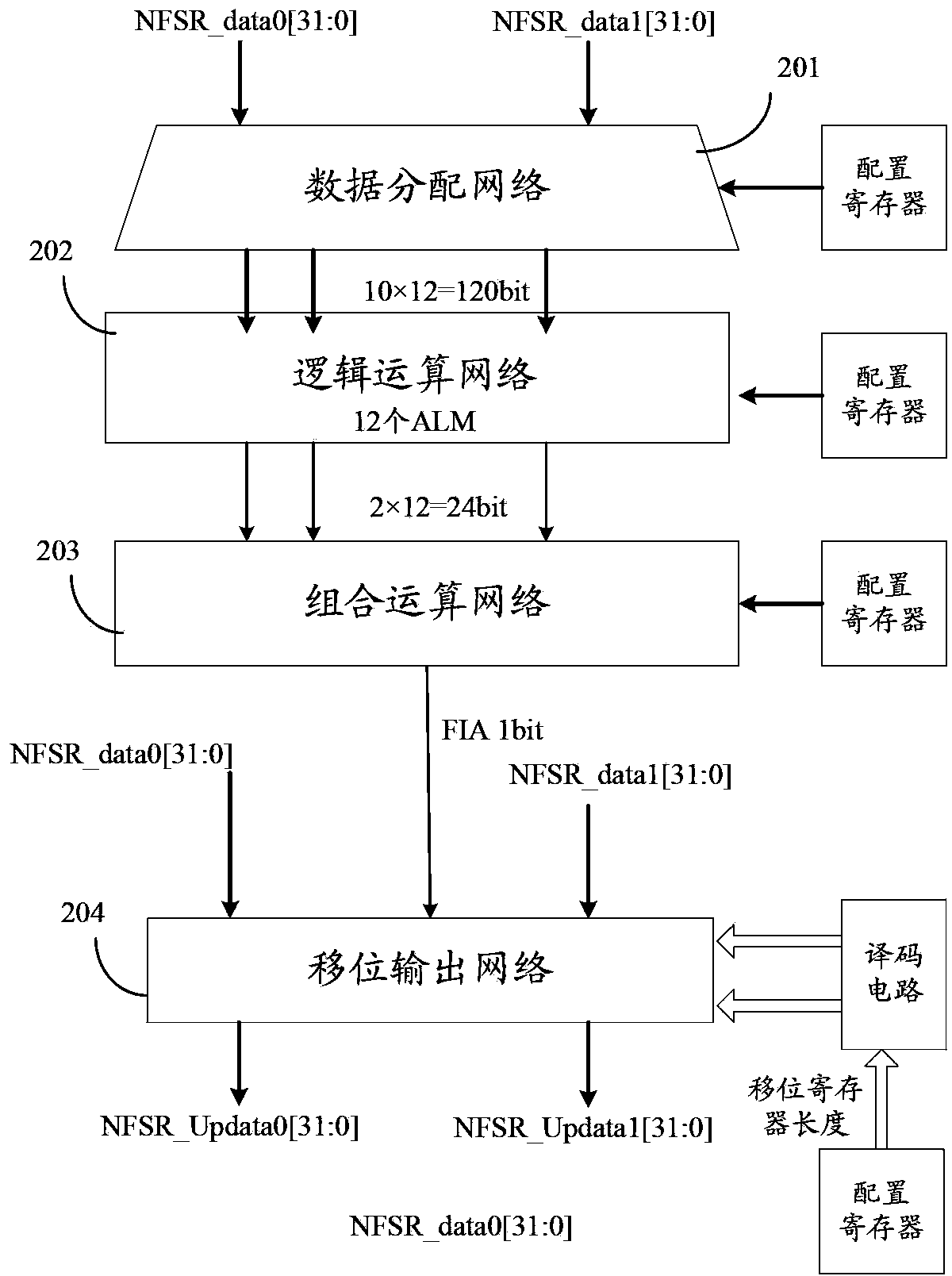
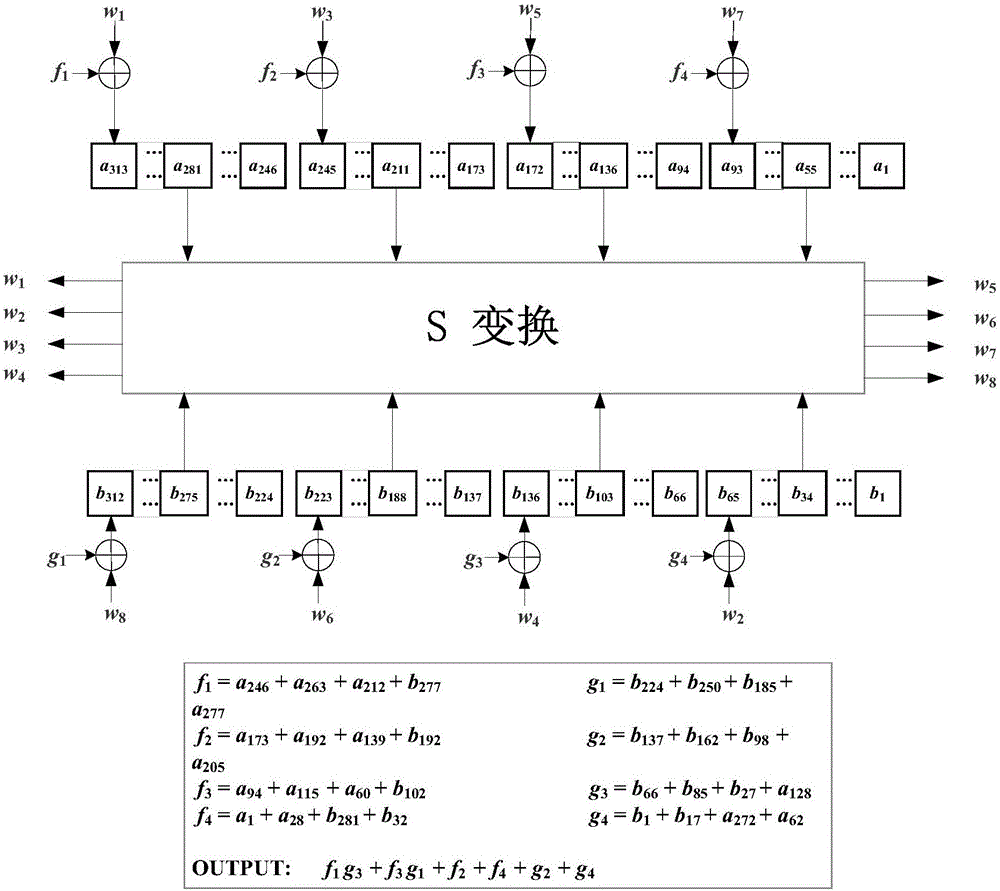
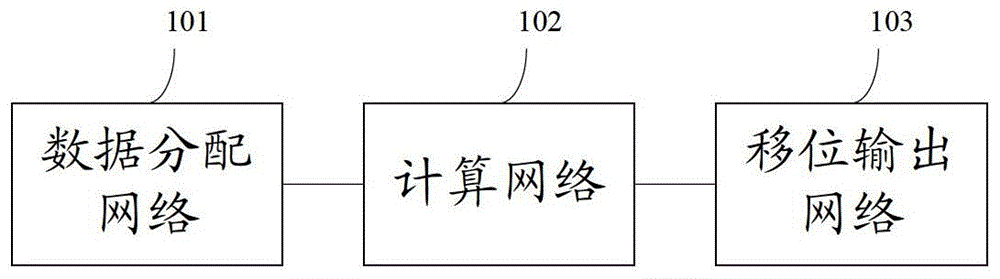
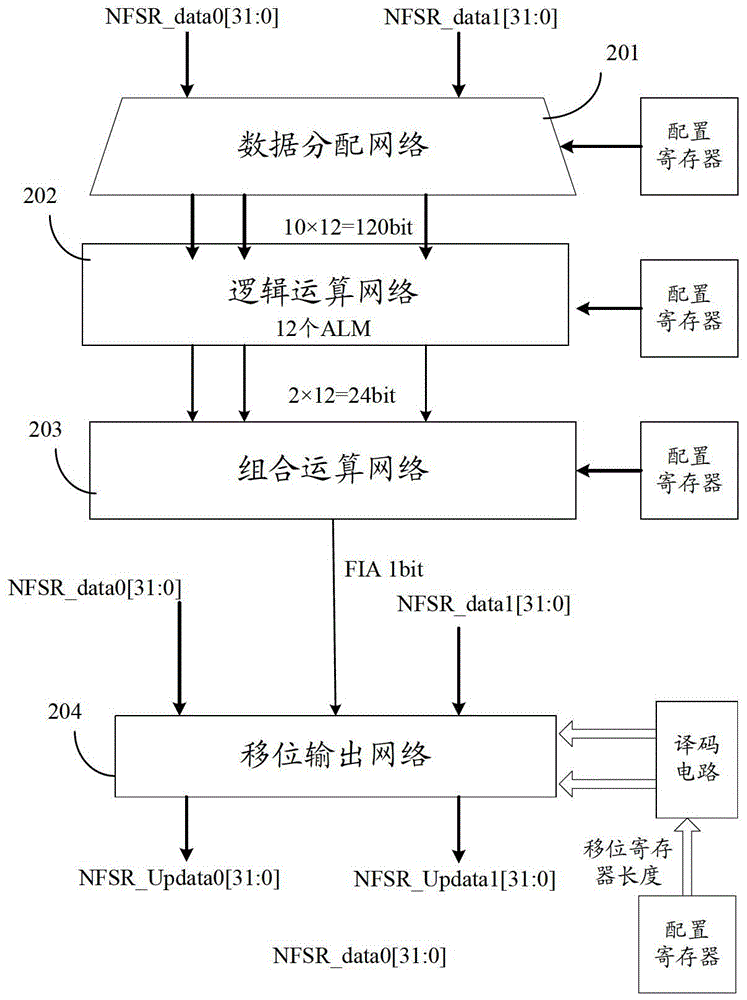
An embodiment of the invention provides a non-linear feedback shift register. A data distributing network selects variables from state values according to a logical operation function and outputs the variables; a calculating network performs logical conjunction operation and exclusive disjunction operation on the variables inputted by the data distributing network; non-linear feedback functions of a cryptographic algorithm can be converted into functions which only comprises logical conjunction and exclusive disjunction, the logical operation function for the data distributing network of the non-linear feedback shift register in an embodiment consists of logical conjunction operation and exclusive disjunction operation, and calculation carried out by the calculating network also consists of logical conjunction operation and exclusive disjunction operation, so that data can be selected and calculated according to different non-linear feedback functions. The non-linear feedback shift register is widely suitable for different cryptographic algorithms.
Owner:THE PLA INFORMATION ENG UNIV
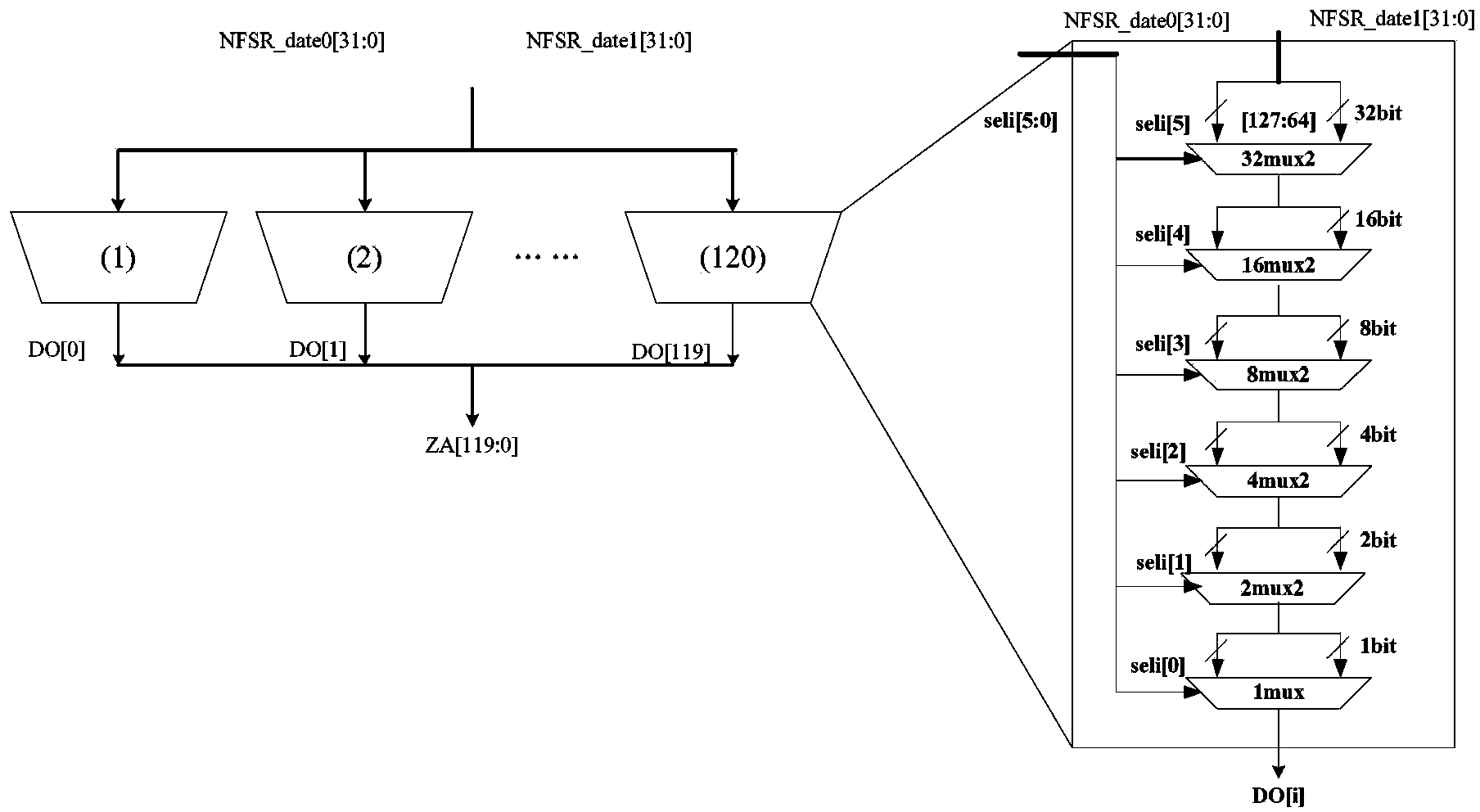
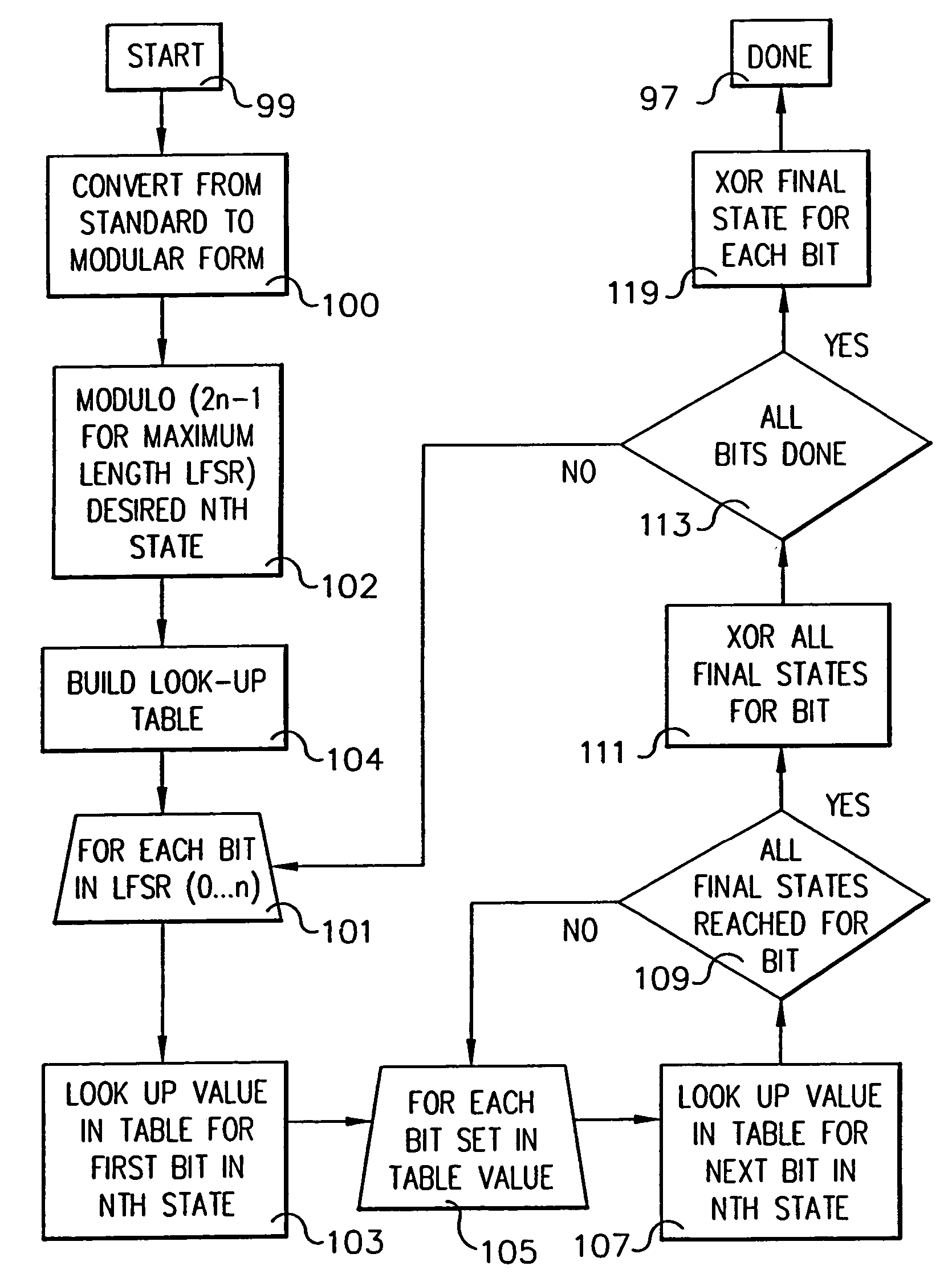
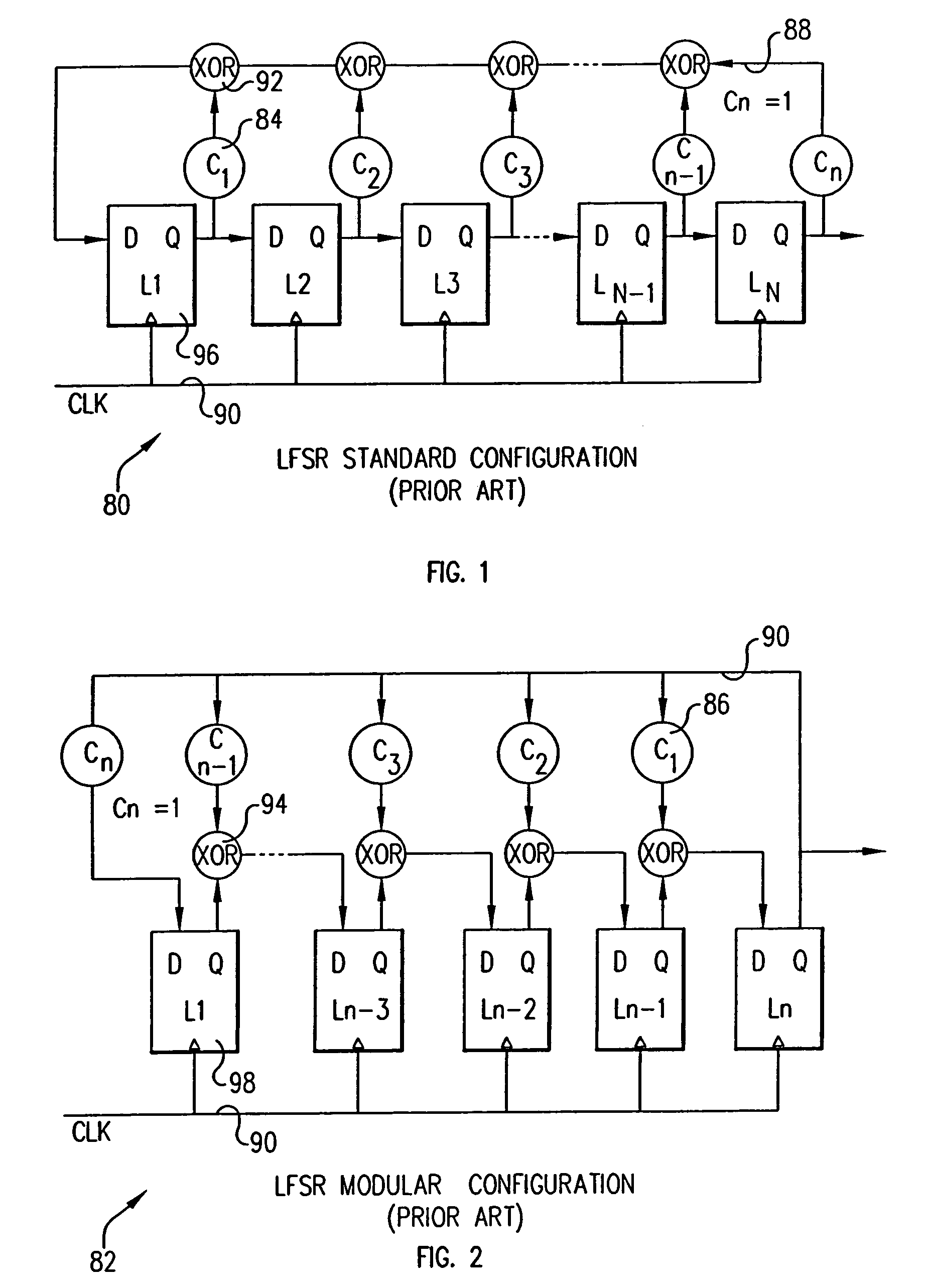
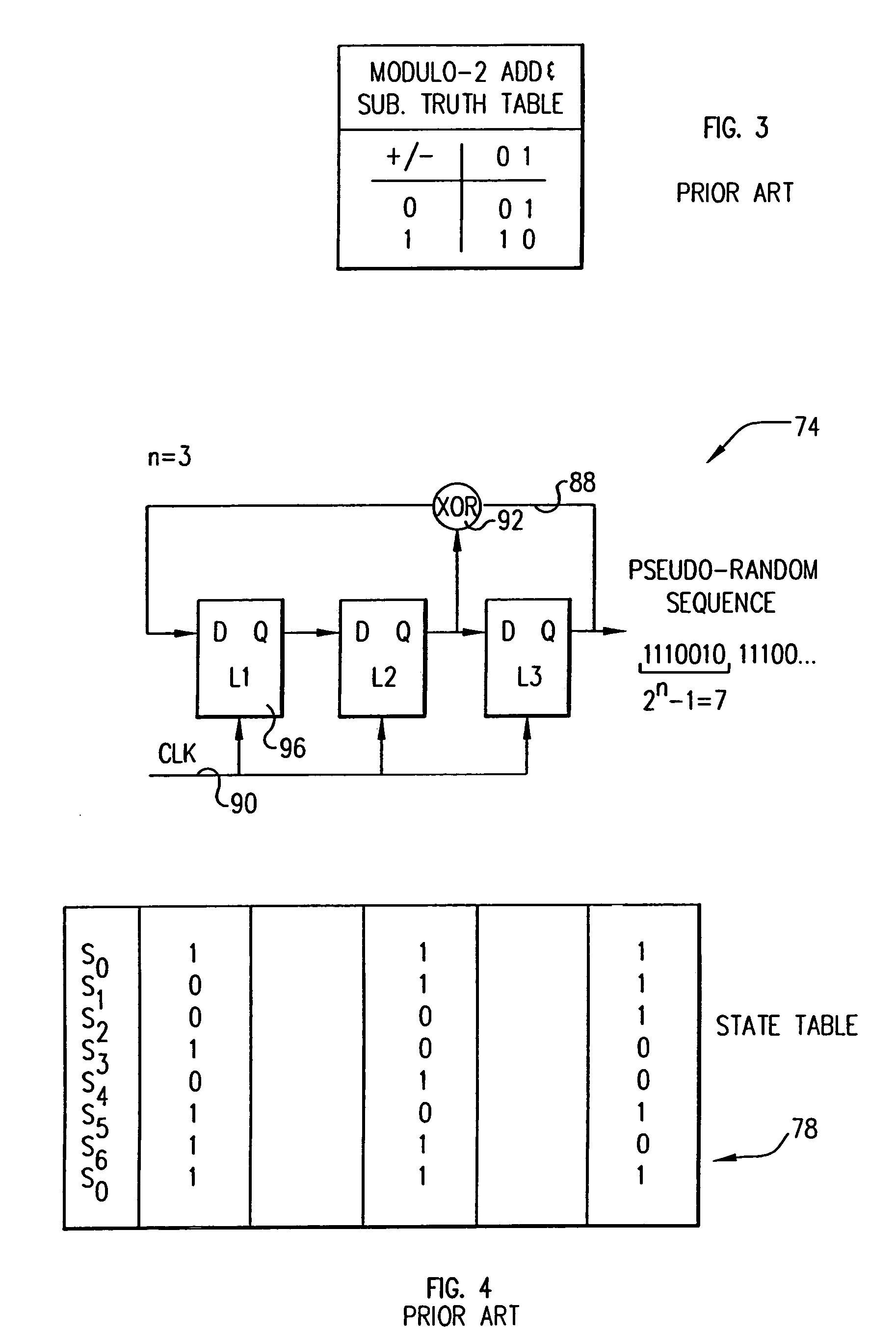
System and method for determining the Nth state of linear feedback shift registers
ActiveUS7340496B2Random number generatorsSecuring communicationNonlinear feedback shift registerProcessor register
Owner:GOOGLE LLC
Database data encryption system and method thereof
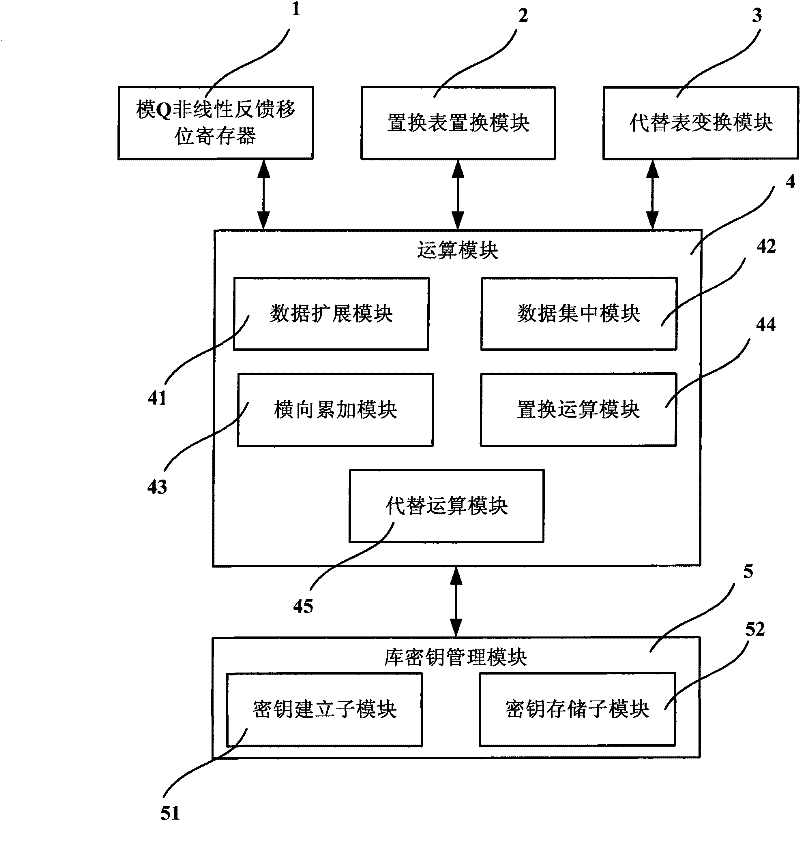
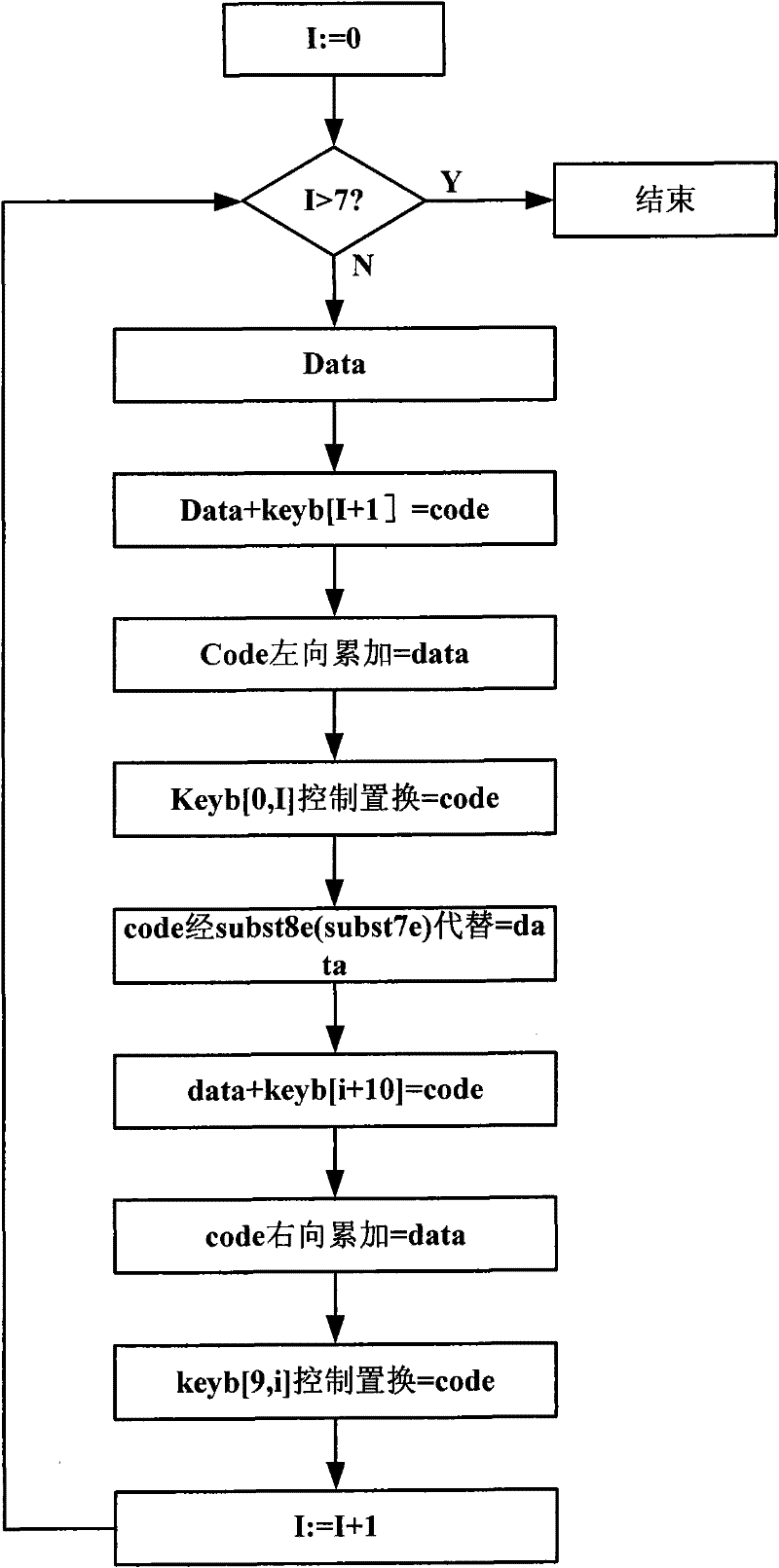
InactiveCN101571873ADoes not affect retrieval efficiencyProtection securityDigital data protectionSpecial data processing applicationsNonlinear feedback shift registerByte
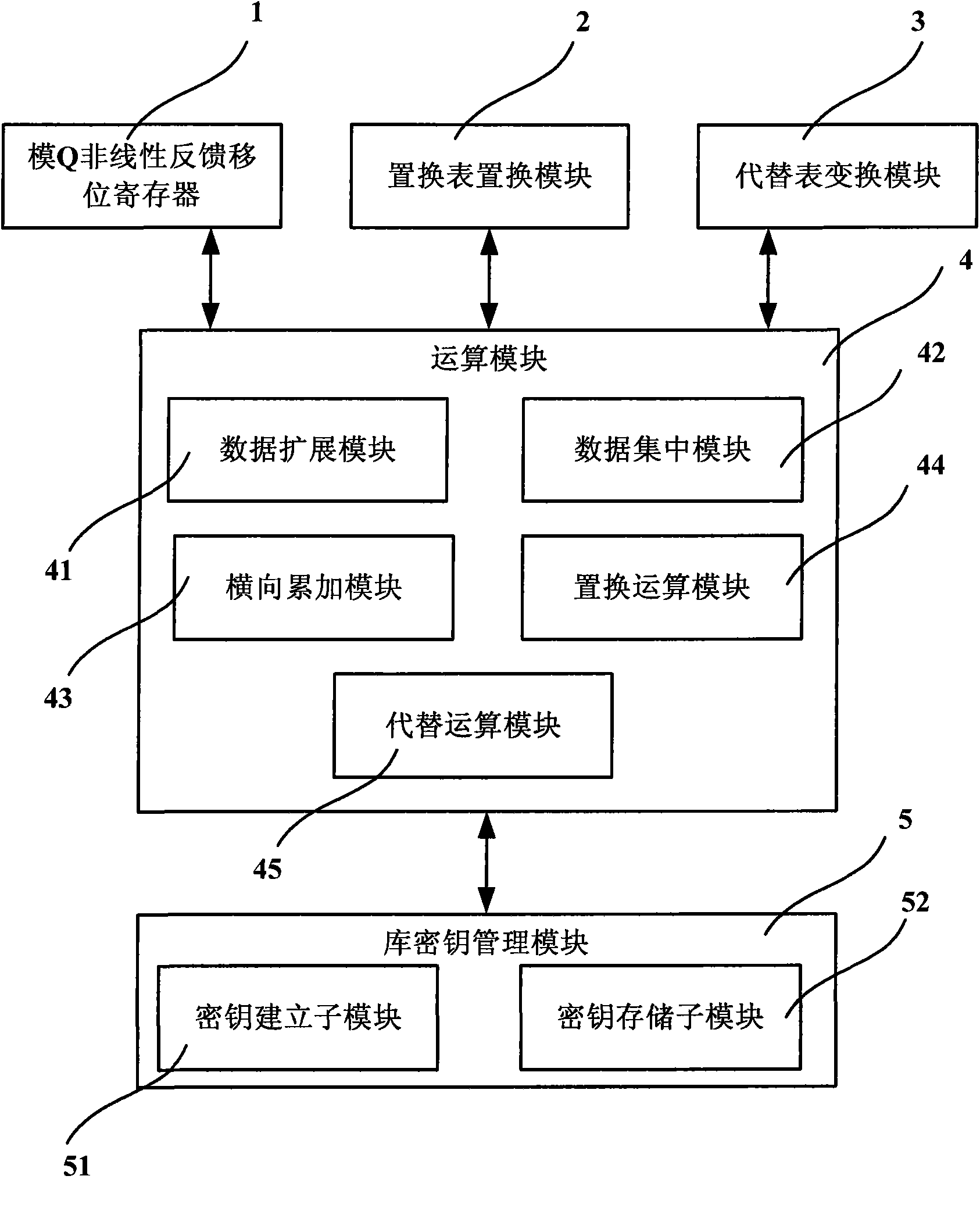
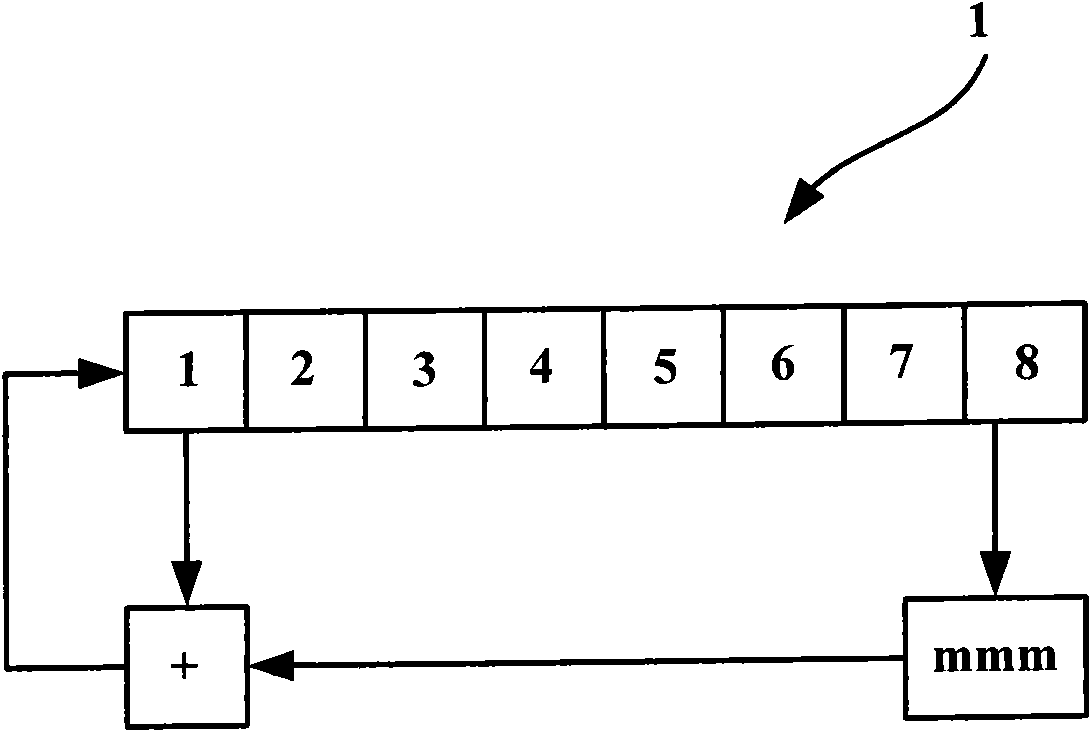
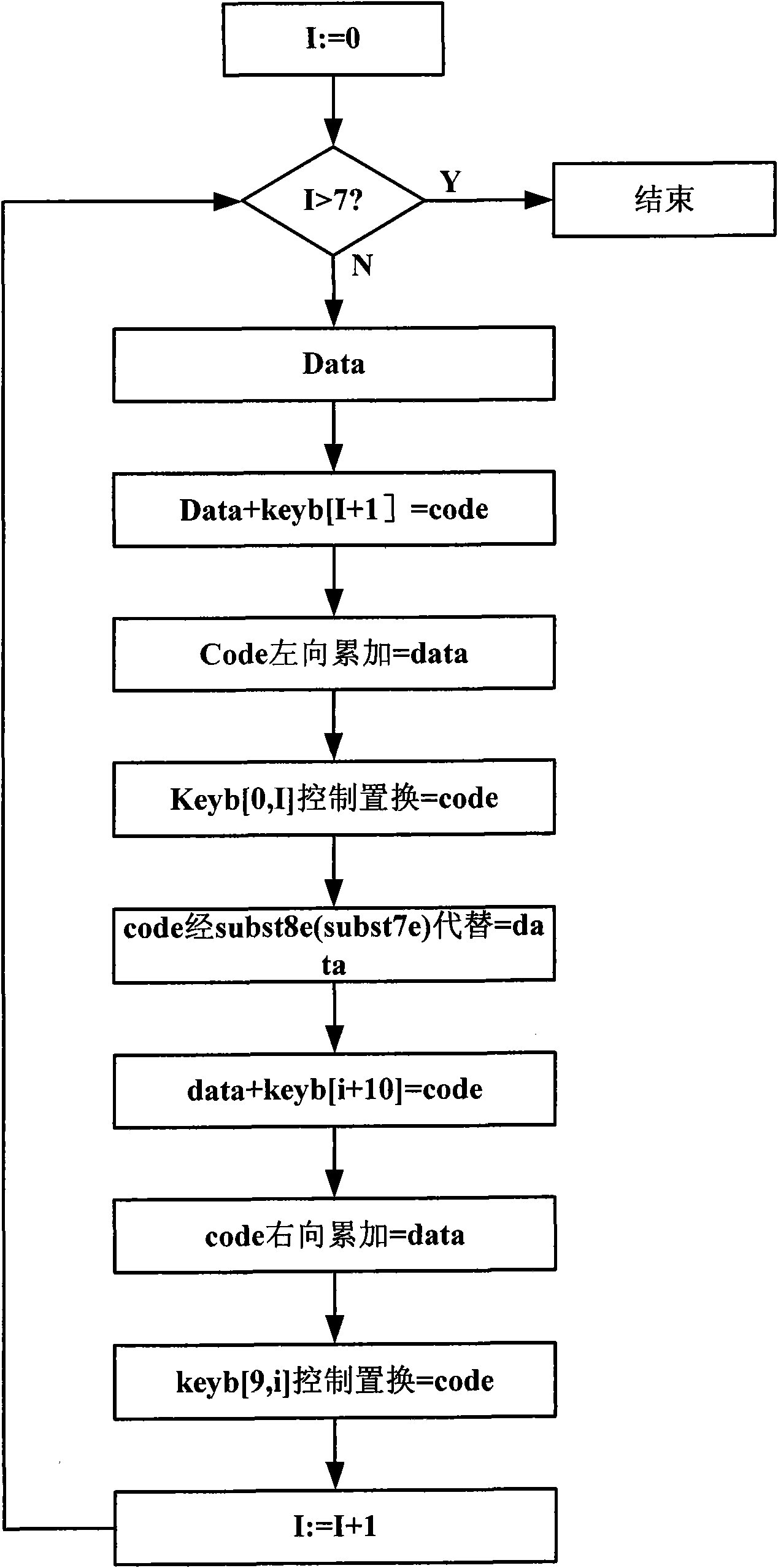
The invention discloses a database data encryption system and a method thereof. The system comprises a model Q nonlinear feedback shift register, a permutation table replacement module, a substitution transforming module and an operation module; wherein, the model Q nonlinear feedback shift register is used for nonlinear feedback by taking the specified key as initial value, the feedback value is replaced and converted by the preset substitution list to continuously generate derived keys with 18 states, and the generated derived keys are applied in encryption and decryption operation of all block ciphers; the permutation table replacement module is used for transforming by taking byte as unit; the substitution transforming module is used for replacing by taking byte as unit; the operation module is used for expanding or centralizing the data in a database according to the byte for lateral accumulating; under the indication of the derived keys which are replaced and transformed by the model Q nonlinear feedback shift register, replacement and substitution operation can be carried out, so that encryption and decryption of the data in the database can be completed. The invention can effectively protect the safety of the data in the database.
Owner:北京联合智华微电子科技有限公司
All-optical linear feedback shift register
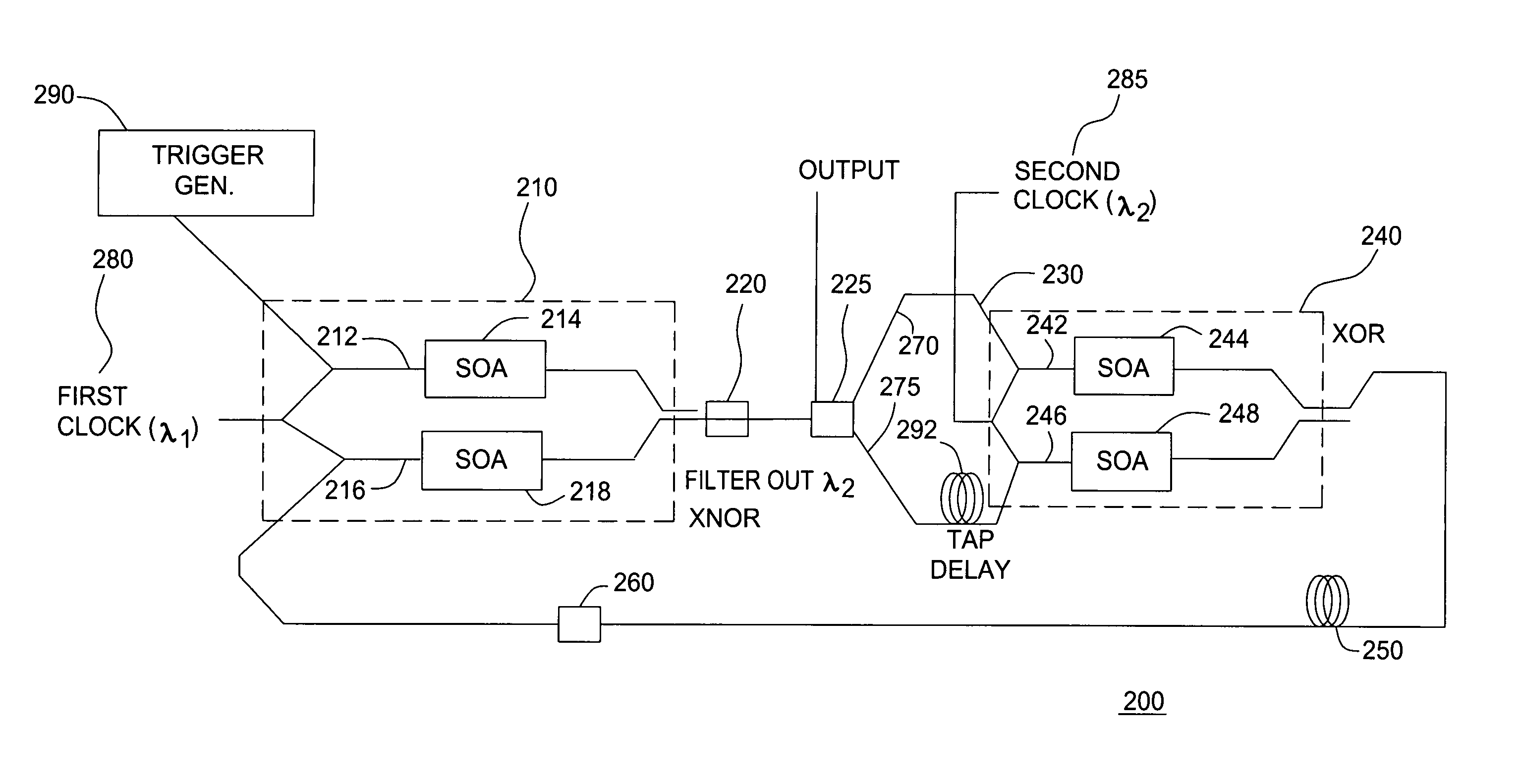
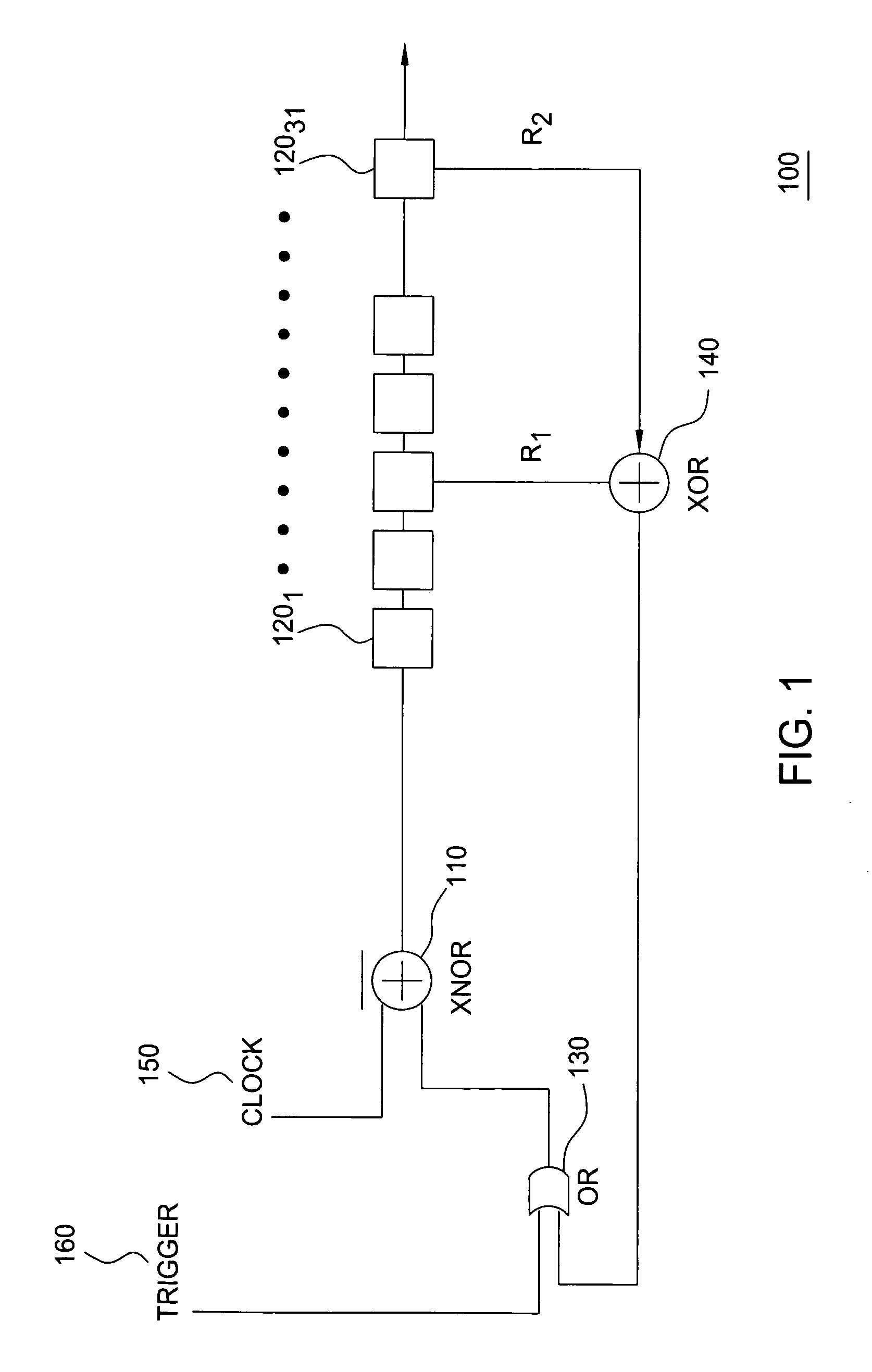
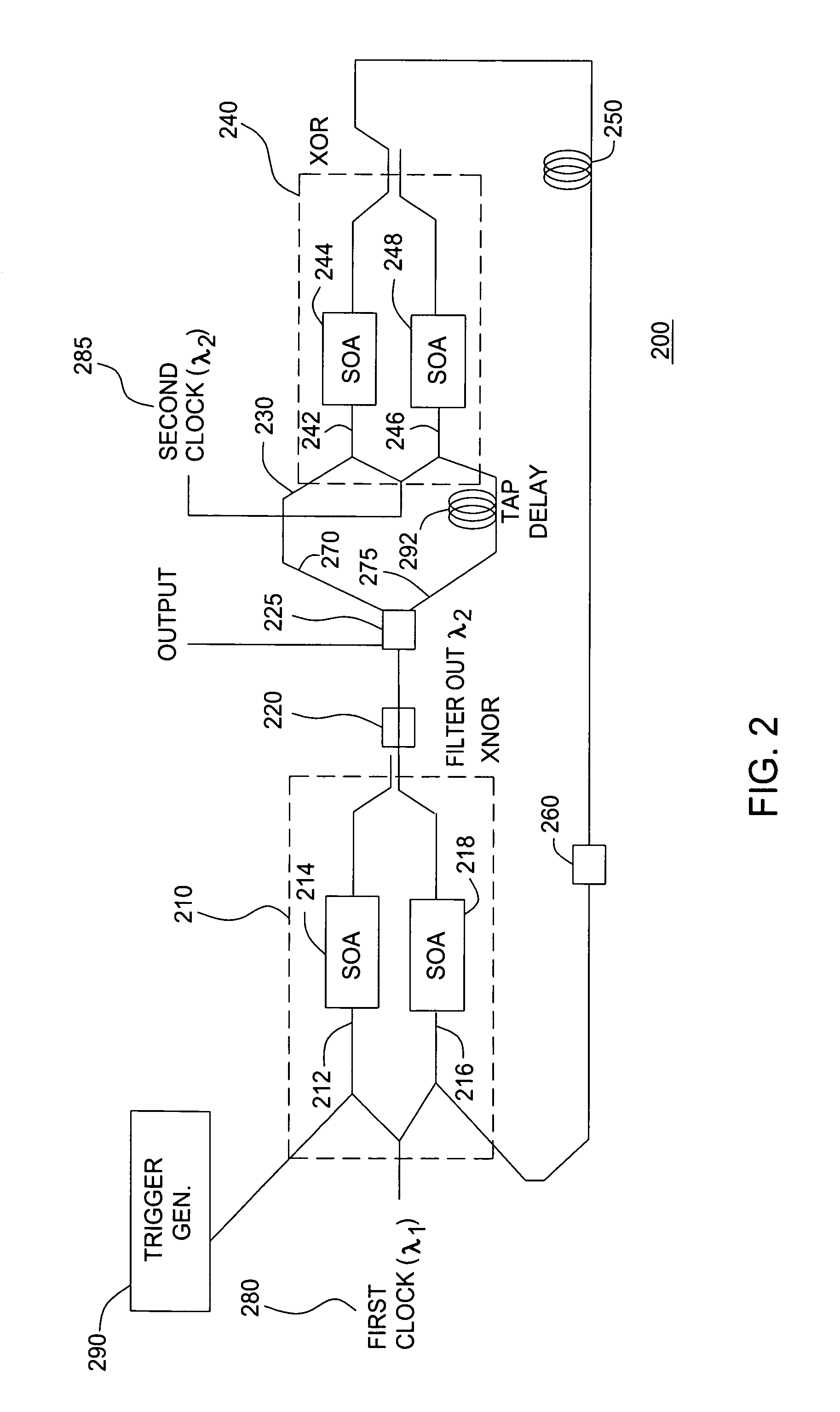
ActiveUS6952172B1Increase data rateElectric signal transmission systemsLaser detailsFeedback circuitsNonlinear element
An all-optical linear feedback circuit for use, for example, as a maximal length pseudo random bit sequence generator includes an all-optical logic circuit that is capable of generating 2N−1 bit maximal length pseudo random bit sequences on an optical channel at high data rates e.g. 80 Gbit / s. In the pseudo random bit sequence generator of the present invention, intensity-dependent phase modulation of at least one included semiconductor optical amplifier (SOA) is implemented. The maximum data rate is limited by the fast gain recovery time of the carriers in the SOA. An optical logic gate of the pseudo random bit sequence generator of the present invention may be constructed using various nonlinear elements that provide ultra-fast intensity-dependent phase modulation.
Owner:LGS INNOVATIONS
Test graph builder of integrated circuit
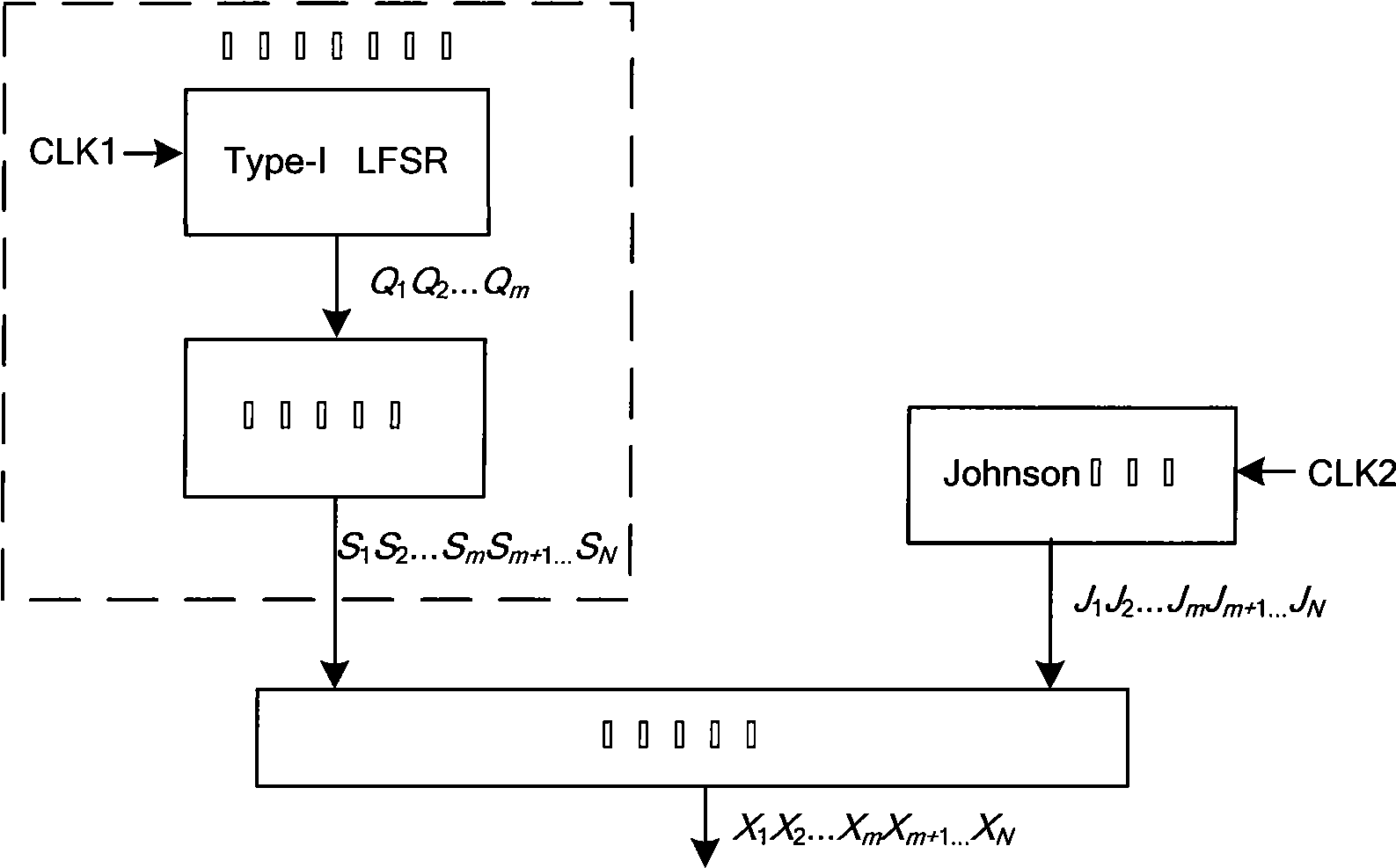
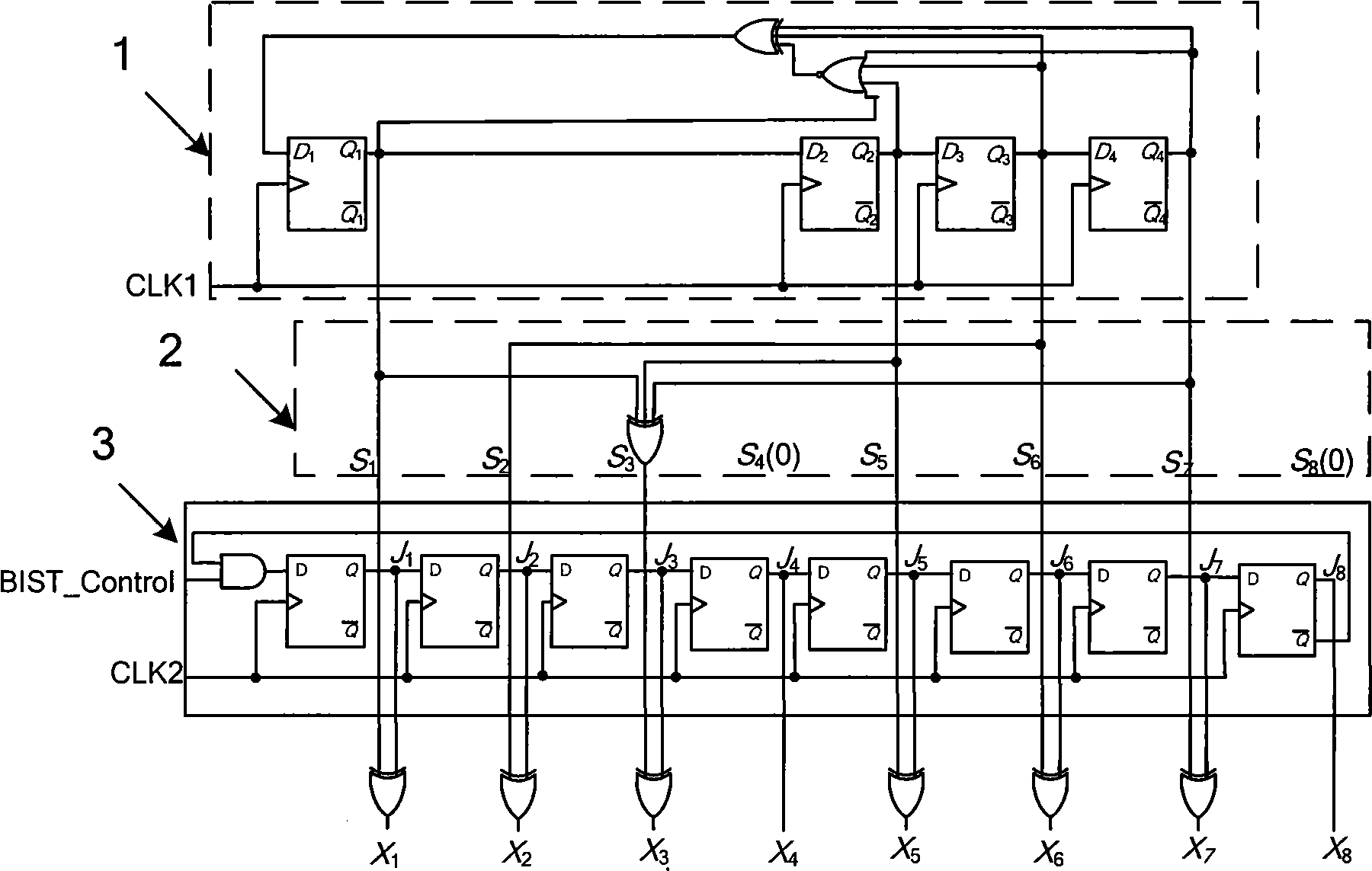
The invention relates to the field of integrated circuit testing and discloses a testing pattern generator of an integrated circuit, which consists of an I-typed linear feedback shift register, a decompressing circuit, a Johnson counter and an XOR gate network; wherein the I-typed linear feedback shift register has clock frequency of f1 and a generating sequence Q that is equal to (Q1Q2...Qm), and m is a natural number; the decompressing logic circuit has an output sequence S that is equal to (S1S2...SmSm+1...SN); the Johnson counter has a clock frequency of f2 and a generating sequence J that is equal to (J1J2...JmJm+1...JN), N is a natural number and N is more than m; the XOR gate network has an output sequence X that is equal to (X1X2...XmXm+1...XN) which is a output sequence of the testing pattern generator; and the clock frequency of the Johnson counter f2 is equal to 2 multiplied by N multiplied by f1; the I-typed linear feedback shift register, the decompressing circuit, the Johnson counter and the XOR gate network satisfy the following logic relation: (a) S equals to V multiplied by Q and (b) X equals to J XOR S.
Owner:XI AN JIAOTONG UNIV
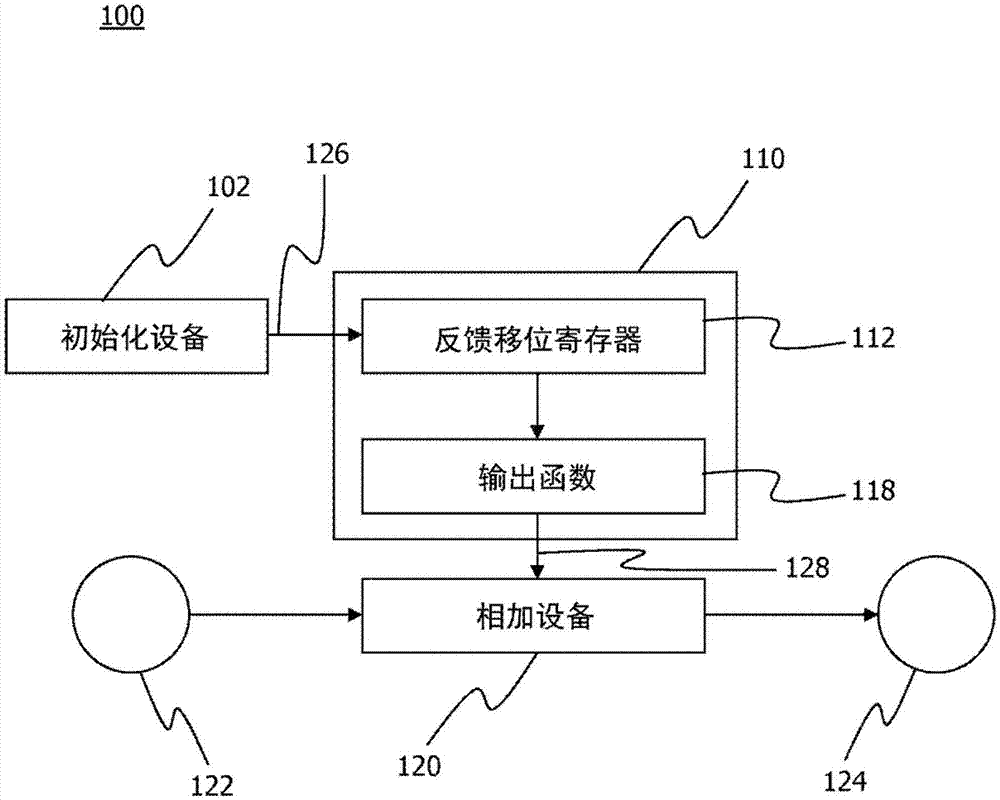
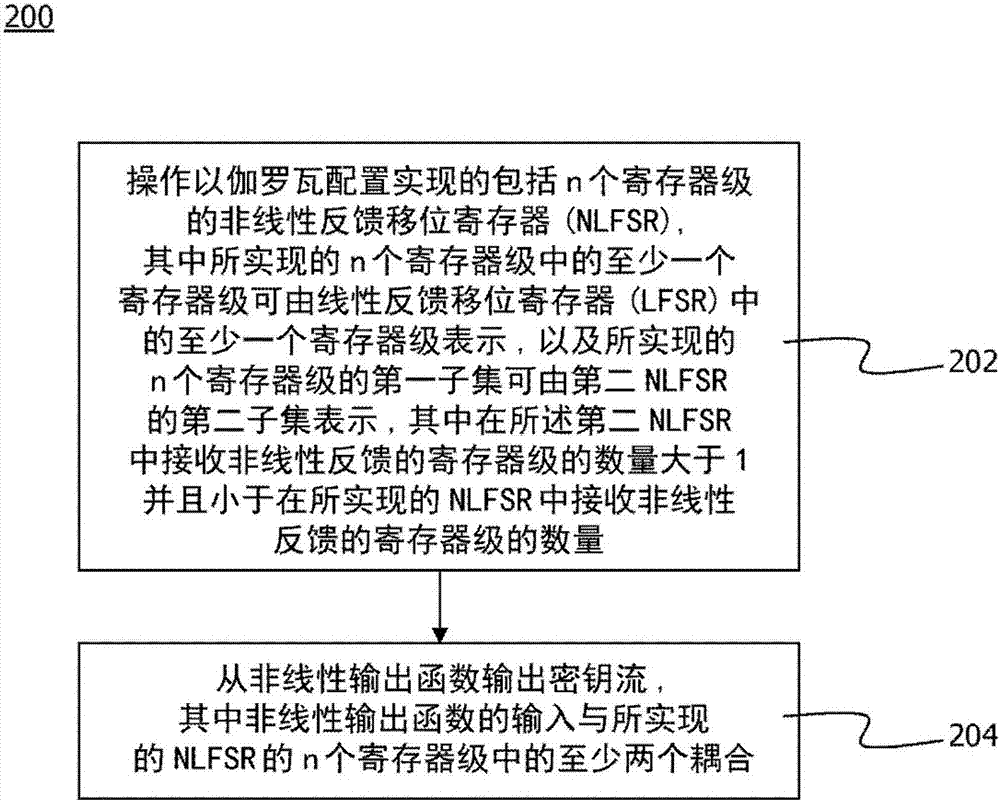
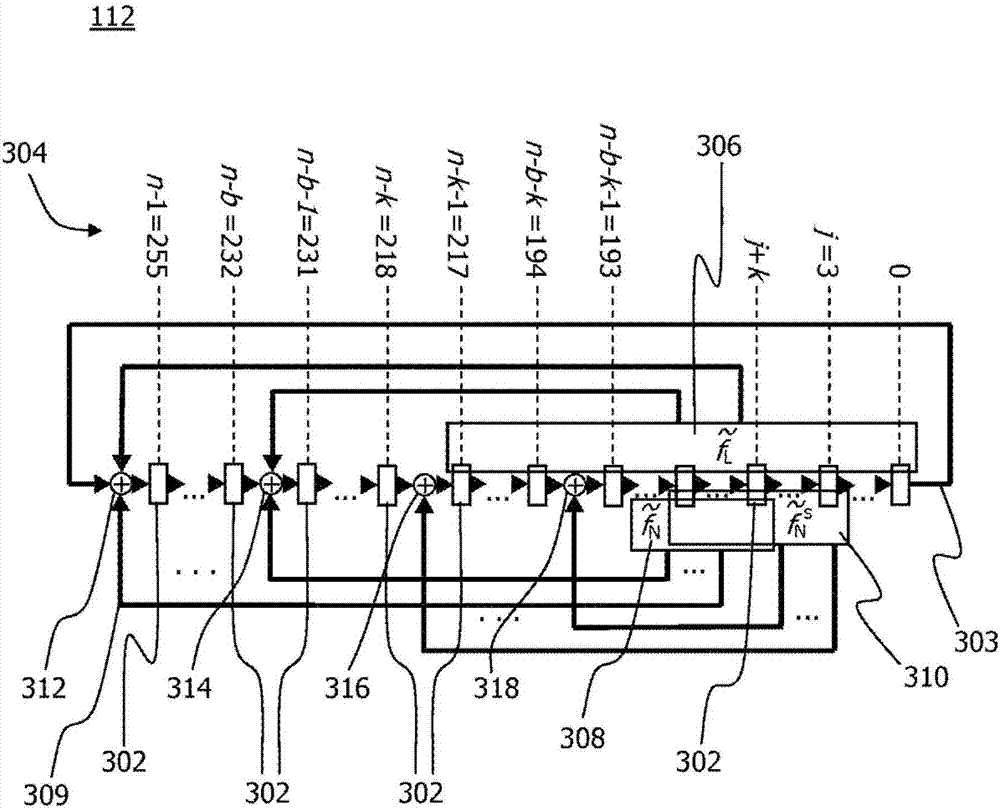
Stream ciphering technique
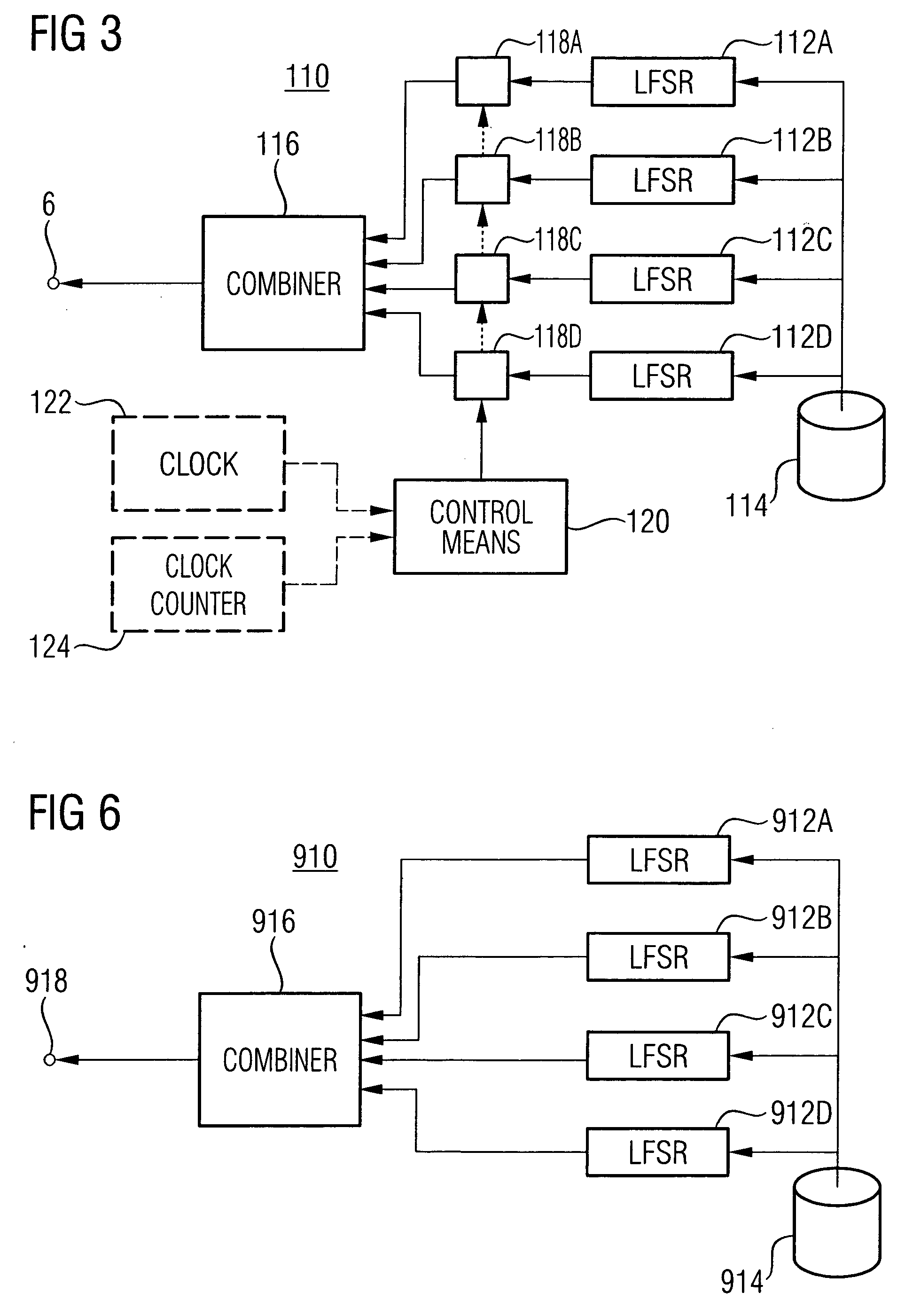
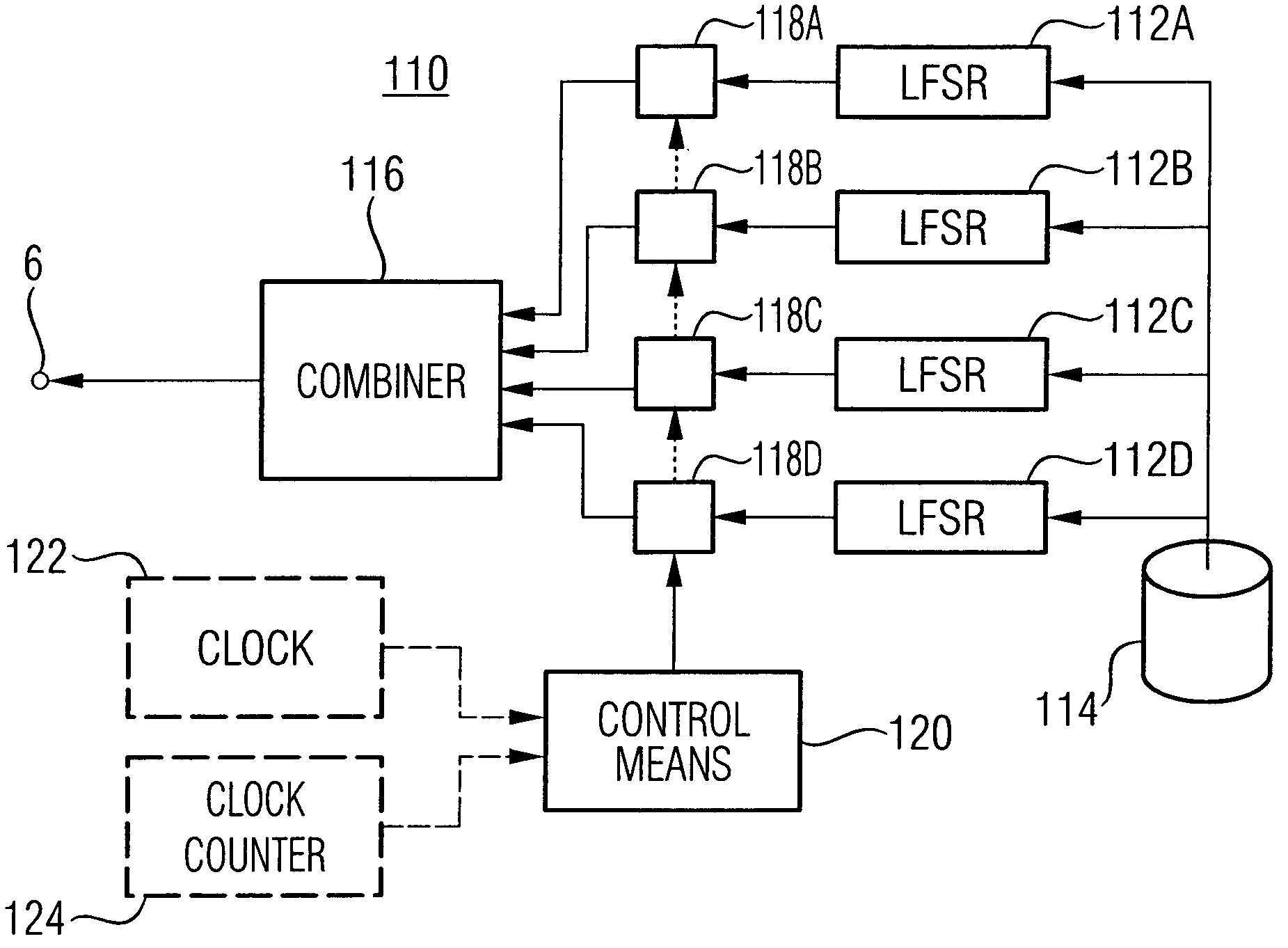
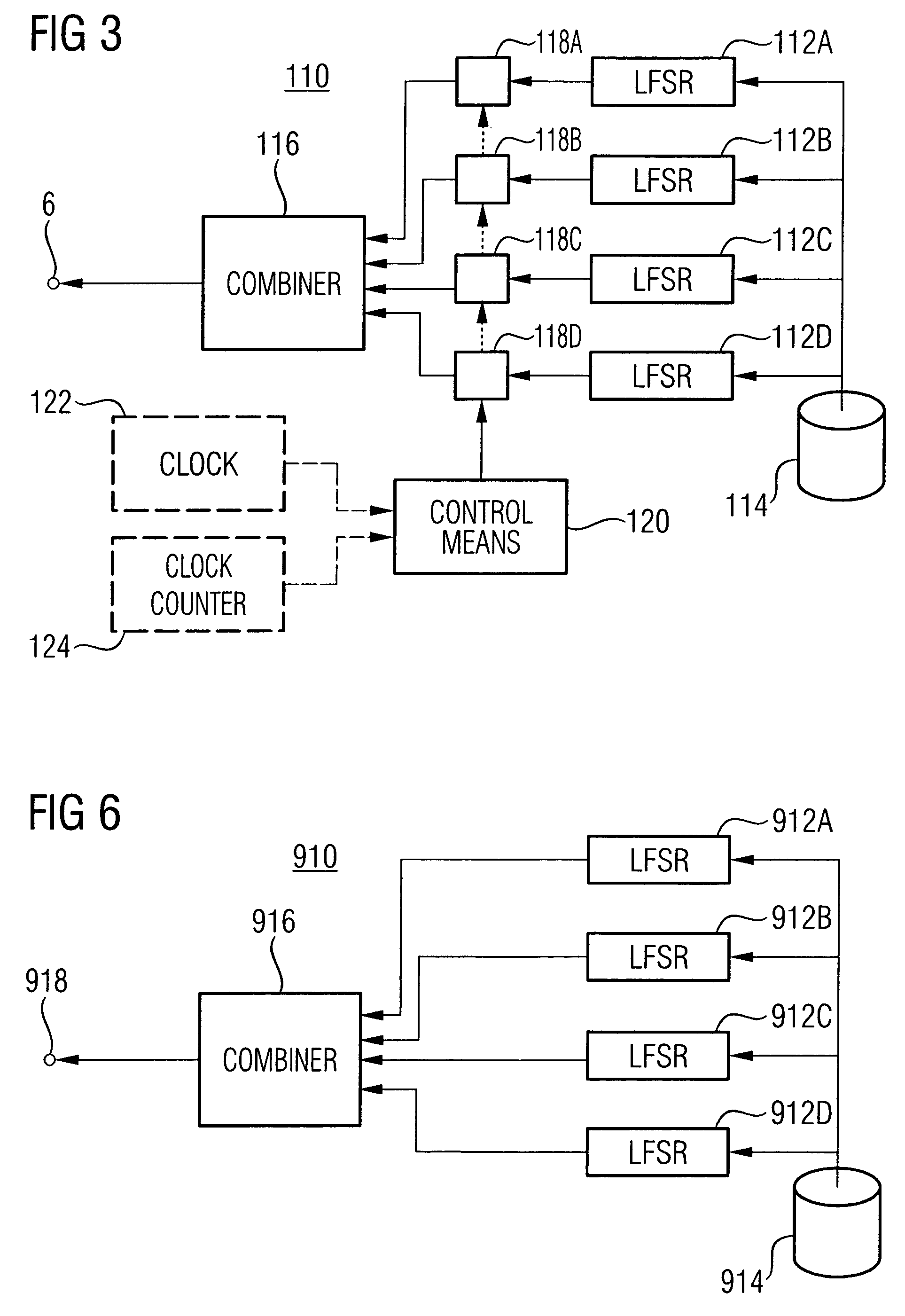
A technique for generating a keystream (128) for ciphering or deciphering a data stream (122) is provided. As to a method aspect of the technique, a nonlinear feedback shift register, NLFSR (112), including n register stages implemented in a Galois configuration is operated. At least one register stage of the implemented n register stages is representable by at least one register stage of a linear feedback shift register, LFSR. A first subset of the implemented n register stages is representable by a second subset of a second NLFSR. A number of register stages receiving a nonlinear feedback in the second NLFSR is greater than one and less than a number of register stages receiving a nonlinear feedback in the implemented NLFSR. The keystream (128) is outputted from a nonlinear output function (118). An input of the nonlinear output function (118) is coupled to at least two of the implemented n register stages of the NLFSR (112).
Owner:TELEFON AB LM ERICSSON (PUBL)
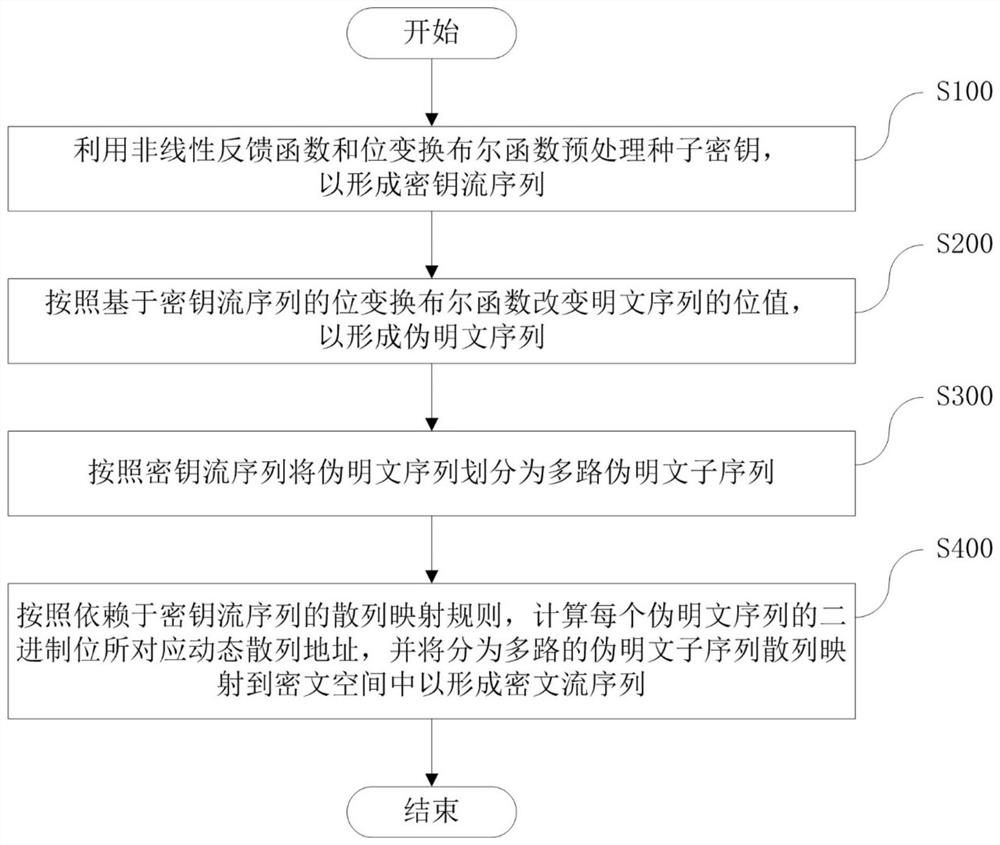
Encryption and decryption method and device based on zipper type dynamic hash and NLFSR
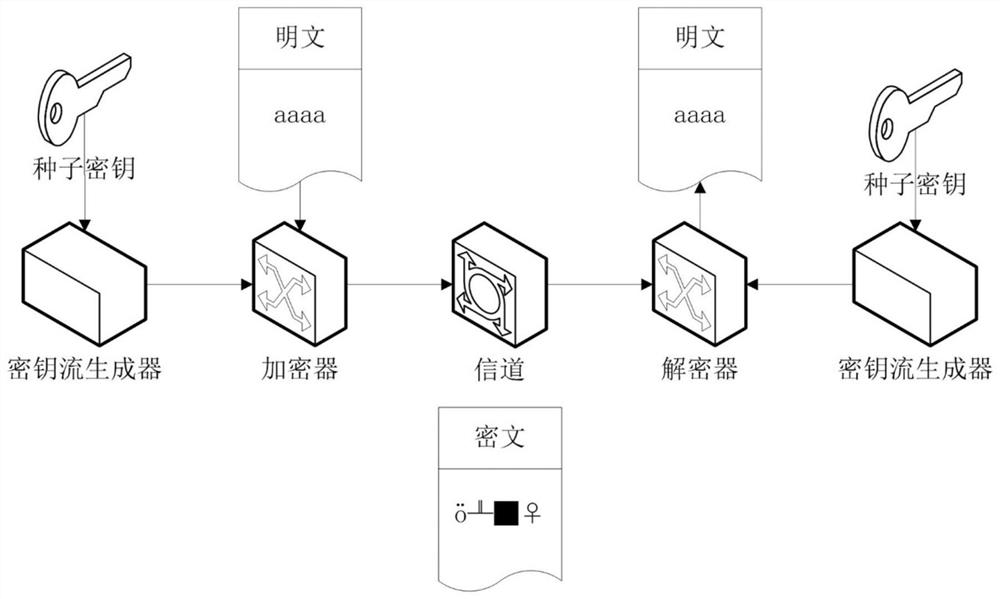
ActiveCN109981249AImprove uniformityLong cycleEncryption apparatus with shift registers/memoriesPlaintextShift register
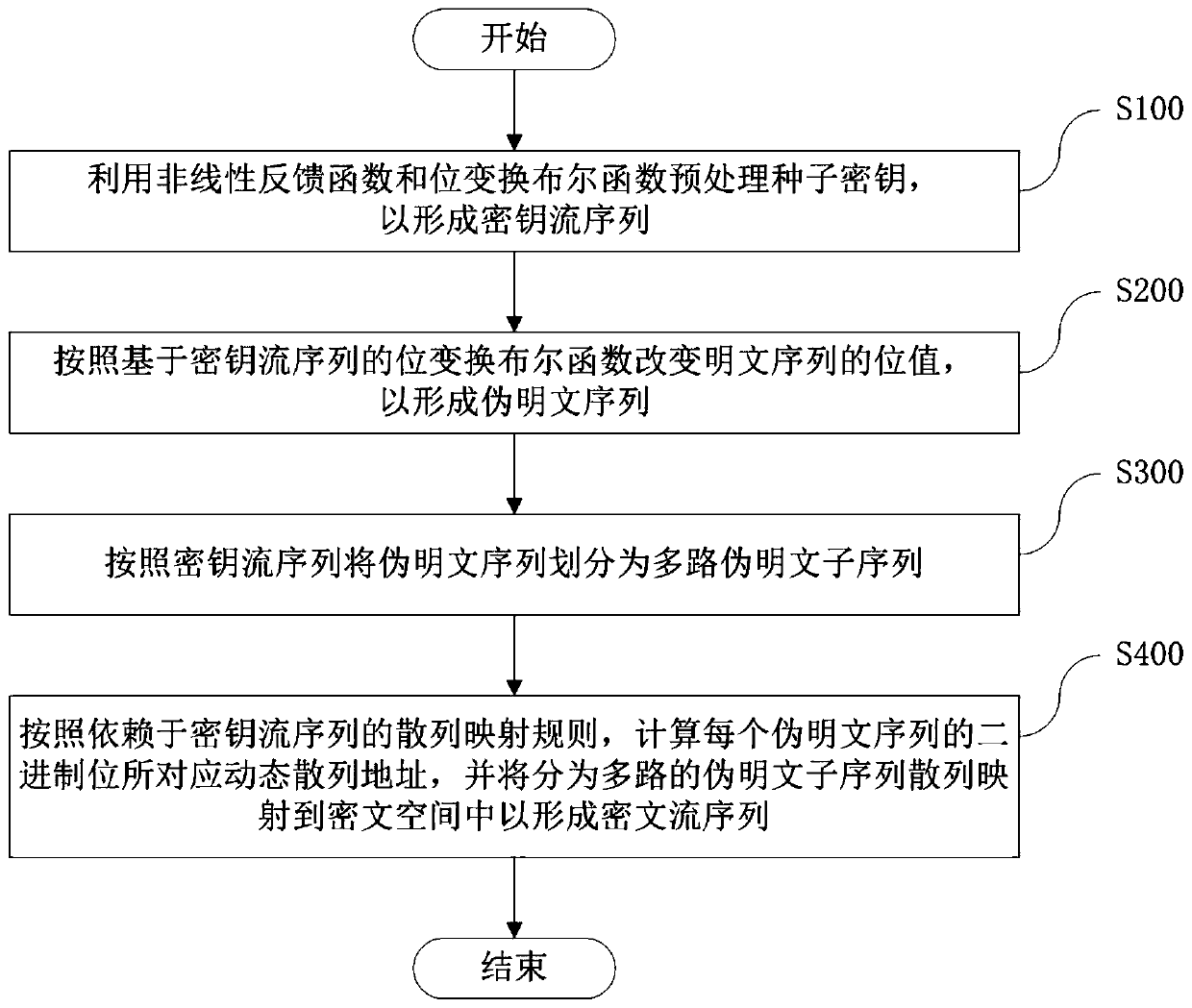
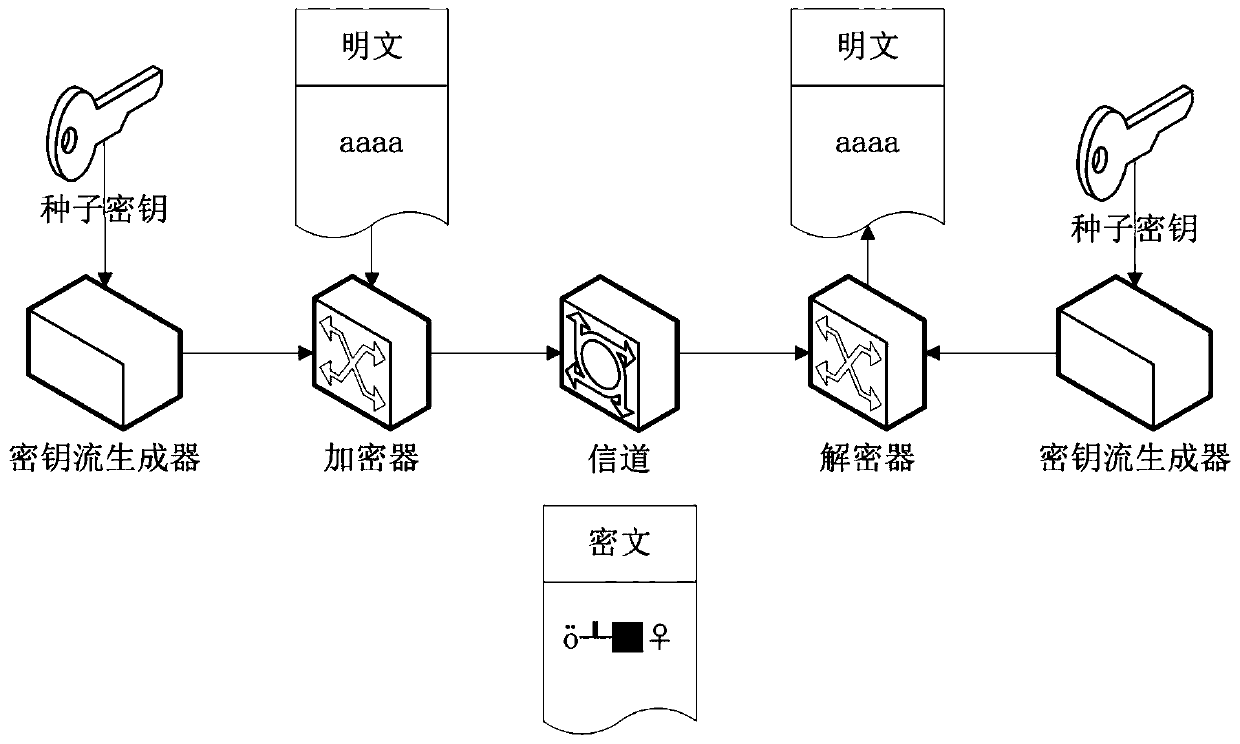
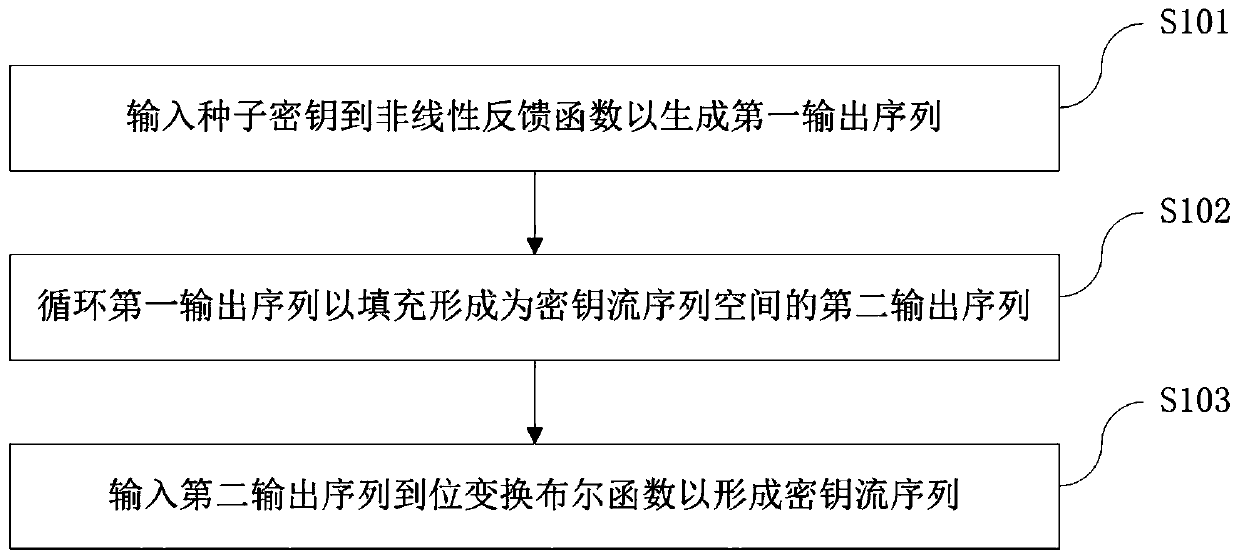
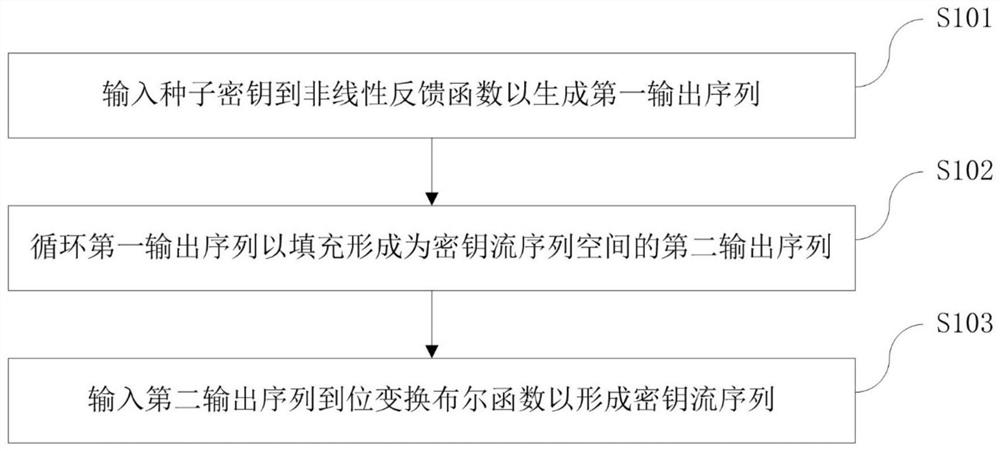
An encryption and decryption method based on zipper type dynamic hashes and NLFSRs comprises the following steps that a nonlinear feedback function and a bit transformation Boolean function are used for preprocessing a seed secret key to form a secret key stream sequence; changing the bit value of the plaintext sequence according to the bit transformation Boolean function based on the key stream sequence to form a pseudo plaintext sequence; dividing the pseudo-plaintext sequence into a plurality of paths of pseudo-plaintext subsequences according to the key stream sequence; and calculating a dynamic hash address corresponding to the binary bit of each pseudo plaintext sequence according to a hash mapping rule depending on the key stream sequence, and mapping the pseudo plaintext subsequence hashes which are divided into multiple paths into a ciphertext space to form the ciphertext stream sequence. The method has the beneficial effects that the key stream generator not only uses a nonlinear feedback shift register, but also introduces a bit transformation Boolean function, so that the key stream with longer period and better randomness is obtained; and through a plaintext bit transformation rule and a zipper type dynamic hash mapping rule, the decoding difficulty of the ciphertext stream sequence is improved.
Owner:ZHUHAI COLLEGE OF JILIN UNIV +1
Sequence cipher realization device and sequence cipher realization method thereof
ActiveCN106254062AFlexible deploymentImprove environmental applicabilityEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerCiphertext
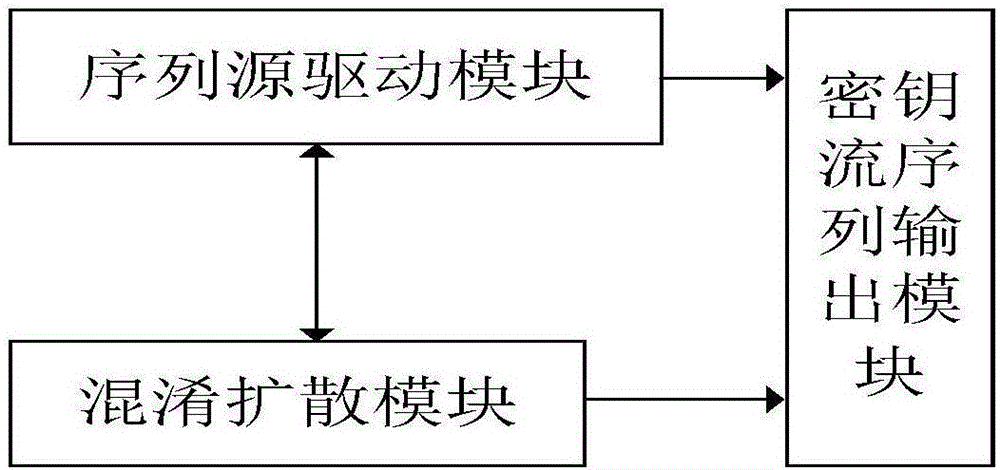
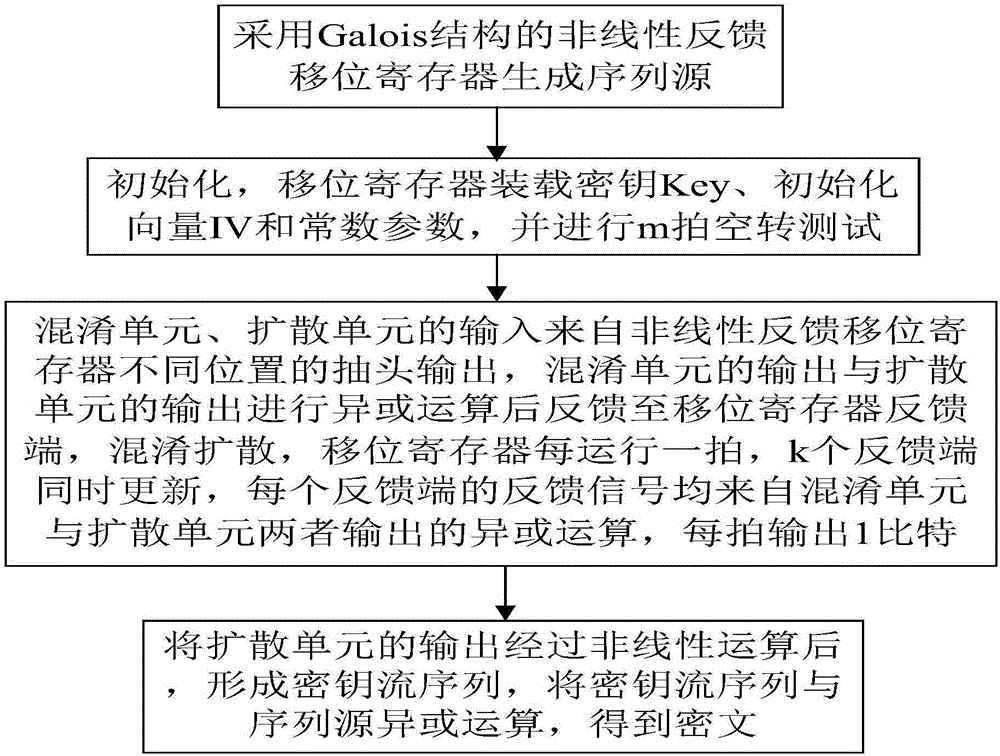
The invention relates to a sequence cipher realization device and a sequence cipher realization method thereof. The method comprises the following steps: firstly, generating a sequence source by adopting Galois-structure nonlinear feedback shift registers designed based on mixing and diffusion parts as a sequence source drive; and then, after the registers load keys, initialization vectors and constant parameters completely, carrying out idle operation for a certain number of beats, carrying out nonlinear operation on an output of the diffusion unit so that the output is taken as a key stream sequence, and carrying out exclusive or operation on the key stream sequence together with a plaintext sequence to form a ciphertext. According to the sequence cipher realization device and the sequence cipher realization method thereof disclosed by the invention, relatively less operation and hardware cost can be used; through combined use of the mixing unit and the diffusion unit, after multiple times of iterations, a pseudorandom sequence is output; according to hardware resource and speed requirements, the deployment and the implementation are flexible; and the requirements of communication for diverse networks and devices are met.
Owner:THE PLA INFORMATION ENG UNIV
Key bit stream generation
ActiveUS20050220297A1Improve securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerComputer science
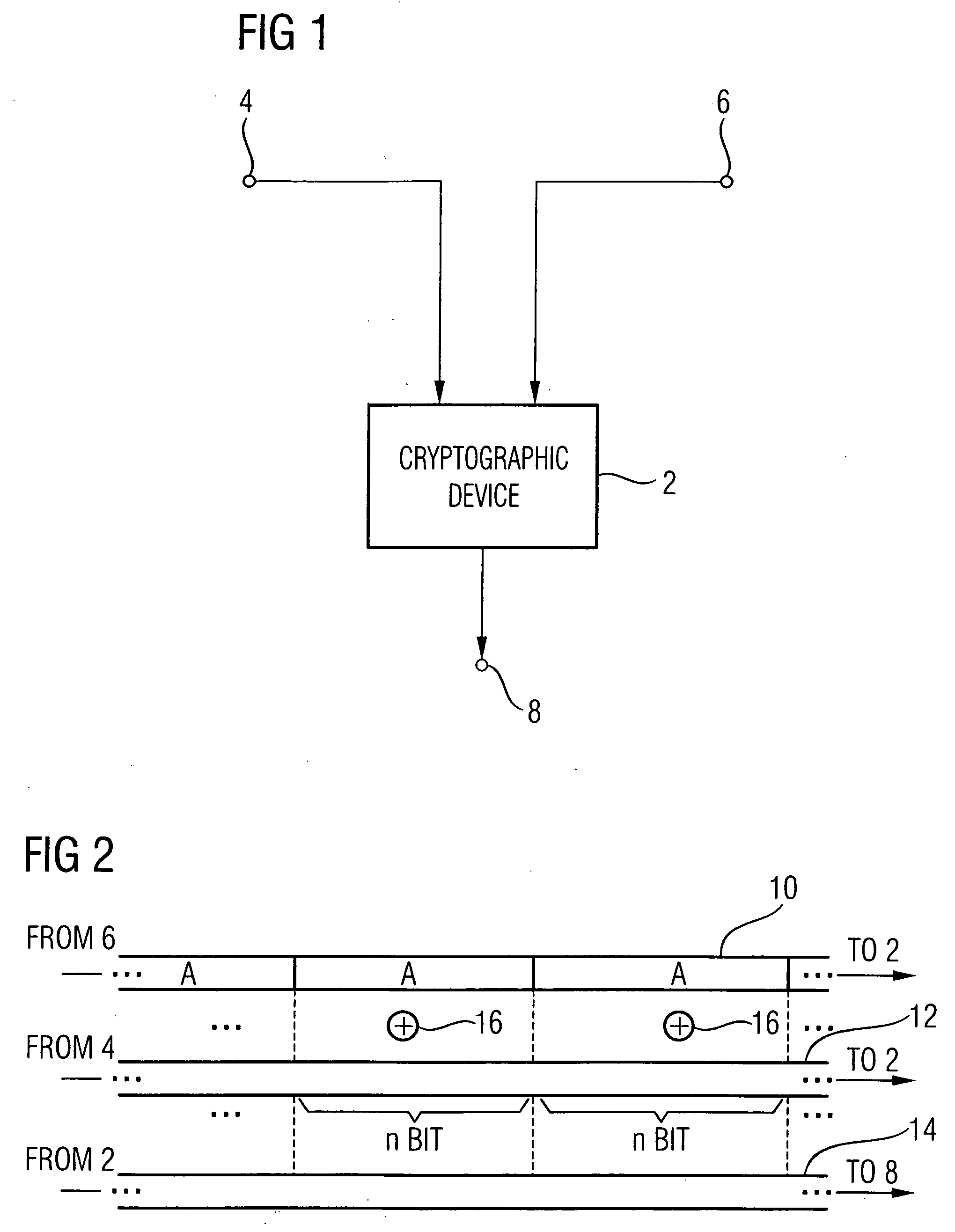
A bit sequence which is generated by a feedback shift register is decimated with a variable decimation value m (mε|N) in a predetermined manner which is known on the decryption side, i.e. in that every mth bit of the bit sequence is picked out from the bit sequence so as to obtain the key bit stream.
Owner:INFINEON TECH AG
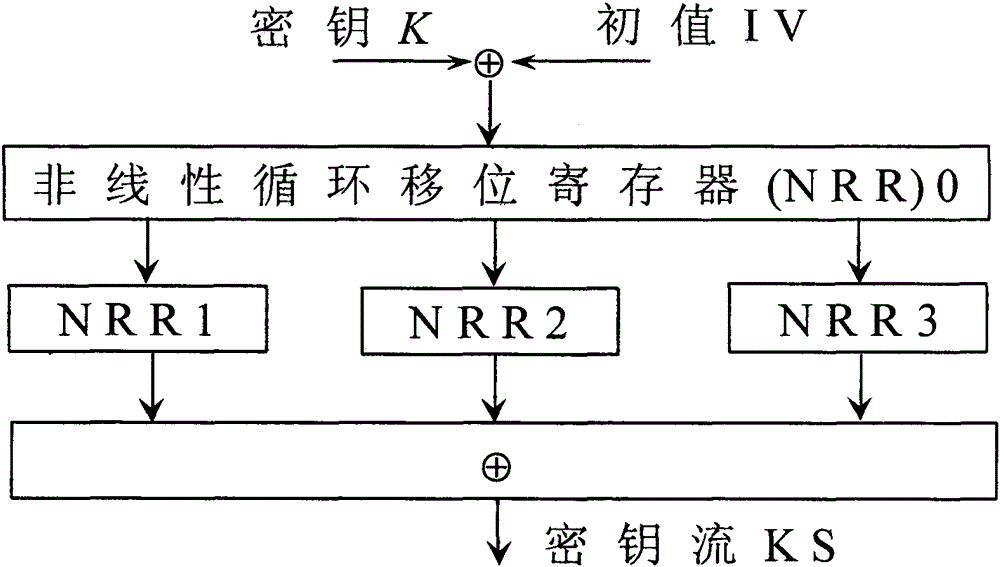
Lightweight stream cipher LSNRR based on non-linear cyclic shift register
InactiveCN105162579ALong cycleImprove securityEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerKey schedule
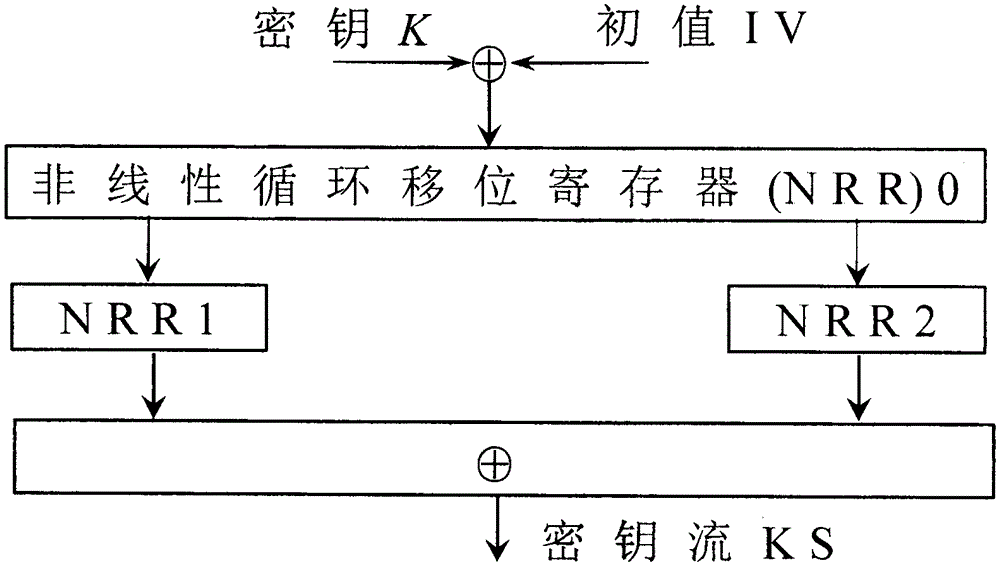
Shift registers are cipher components used for generating pseudo random sequences in the field of secret communication, comprising linear feedback shift registers LFSRs, non-linear feedback shift registers NLFSRs, and so on, wherein the maximum period T of the shift register is not greater than 2n. The feedback mode of an n-level non-linear cyclic shift register NRR refers to the following formula, in the formula, i>=0, n>=2, word length m is determined by the number of bits of a platform; <<<j represents ring shift left with j bits; a symbol referring to the description represents modular addition; c is an odd number within the range from 1 to 2<m>-1; initial values a<0>-a<n-1>of n inputted words are unlimited, and each word is an arbitrary m-digit number. When the word length is m bits, the period of the n-level non-linear cyclic shift register NRR is greater than (2<m>)<n>, i.e., the security of the n-level non-linear cyclic shift register NRR is better than the security of a traditional (non-)linear feedback shift register (N)LFSR, and the efficiency of the n-level non-linear cyclic shift register NRR is also better than the efficiency of a common (non-)linear feedback shift register (N)LFSR. The lightweight stream cipher LSNRR is designed through four non-linear cyclic shift registers NRRs, wherein the first NRR is used for secret key schedule, and modular addition is performed for outputs of the other three NRRs to generate a secret key stream of the LSNRR. The efficiency of the LSNRR is better than the efficiency of a common symmetric cipher, thus the LSNRR is suitable for the a resource-constrained environment and a resource-unconstrained environment, and is mainly used for data encryption and decryption.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Key bit stream generation
ActiveUS7764789B2Improve securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerComputer science
Owner:INFINEON TECH AG
Light-weight stream cipher technology LSNR2 based on nonlinear ring shift register
InactiveCN105553647ALong cycleImprove securityData stream serial/continuous modificationNonlinear feedback shift registerComputer science
Shift registers are cipher components used for generating pseudorandom sequences in the secret communication field and include linear feedback shift registers (LFSR), nonlinear feedback shift registers (NLFSR) and the like, and the maximum period T of the shift registers is smaller than or equal to 2n. The feedback mode of n stages of nonlinear ring shift registers (NRR) is shown in the specification, wherein i>=0, n>=2, the word length m is equal to the bit of a platform, <<<j represents ring shift left by j bits, the symbol in the specification represents modular addition, c is an odd number ranging from 1 to 2m-1, the initial values a0-an-1 of n input words are not limited, and each word has any m bits. When the word length is m bits, the period of the n stages of NRRs is larger than (2m)n, namely, the security is larger than that of traditional (N)LFSRs; the efficiency of the NRRs is also higher than that of common (N)LFSRs. The light-weight stream cipher LSNR2 is designed through 3 NRRs, wherein the first NRR is used for key scheduling, and output of the other two NRRs is subjected to modular addition to generate a key stream of the LSNR2. The efficiency of the LSNR2 is higher than that of common symmetric ciphers, and the LSNR2 is suitable for resource-constrained environments and is mainly used for encrypting and decrypting data in information systems.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Error detector, semiconductor device, and error detection method
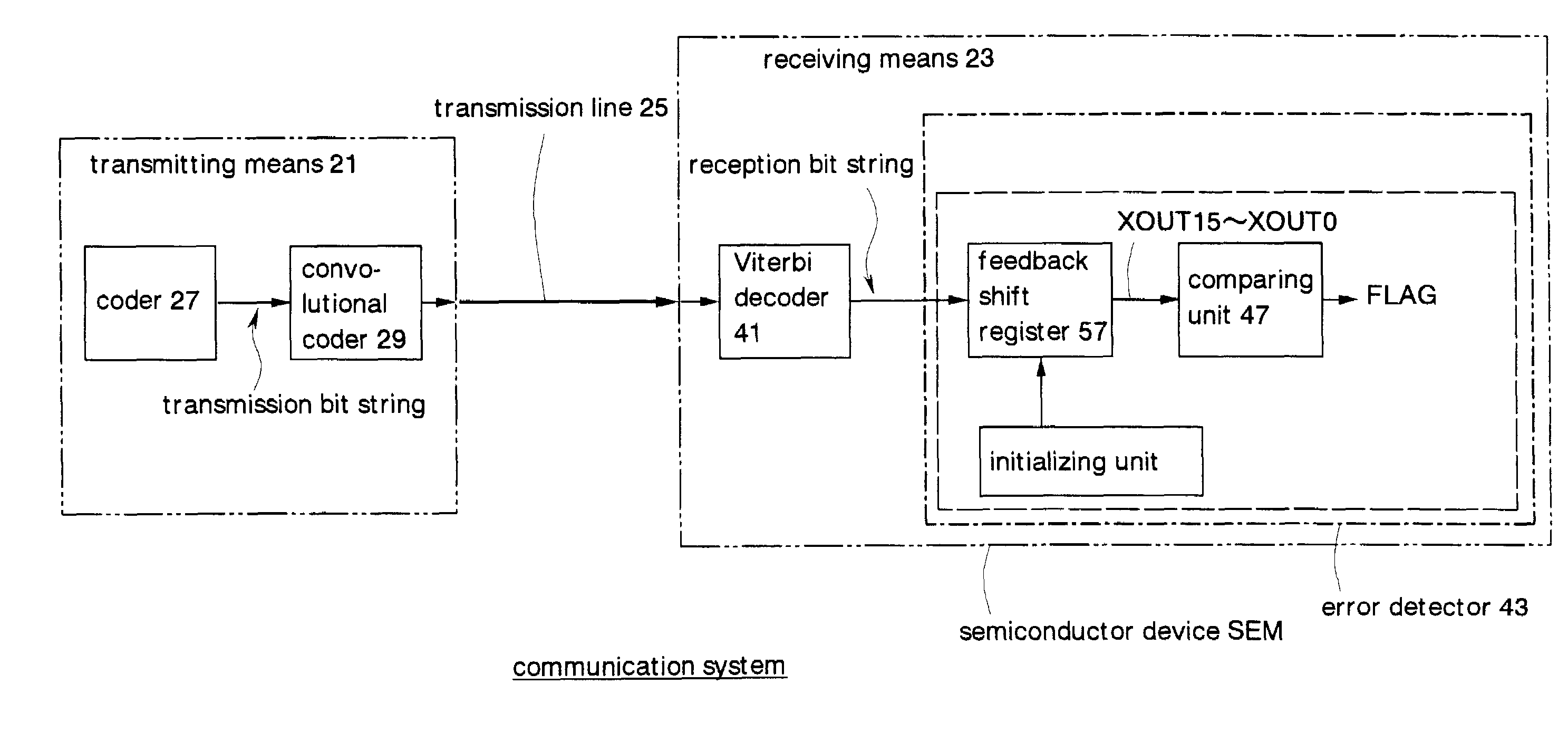
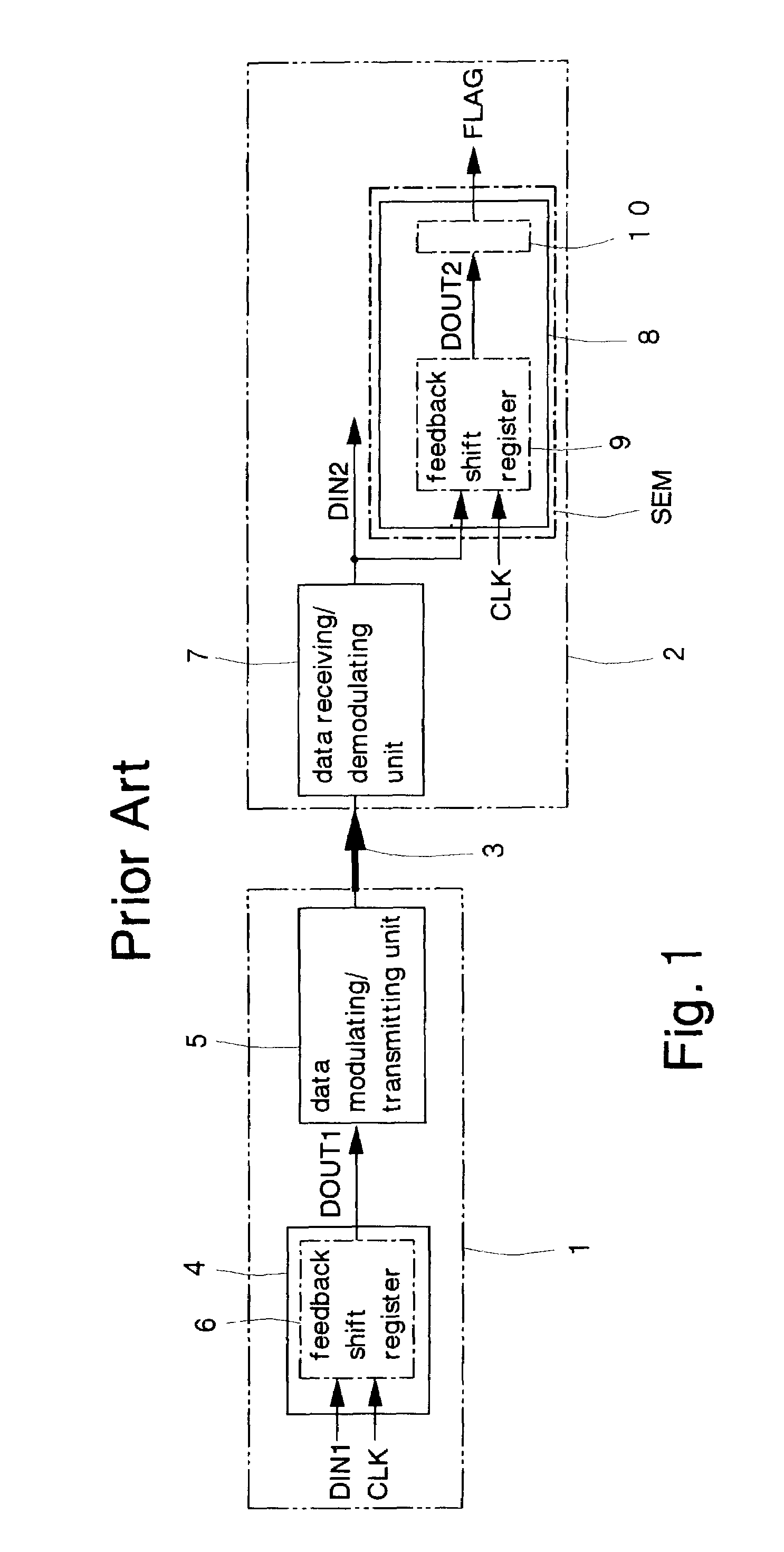
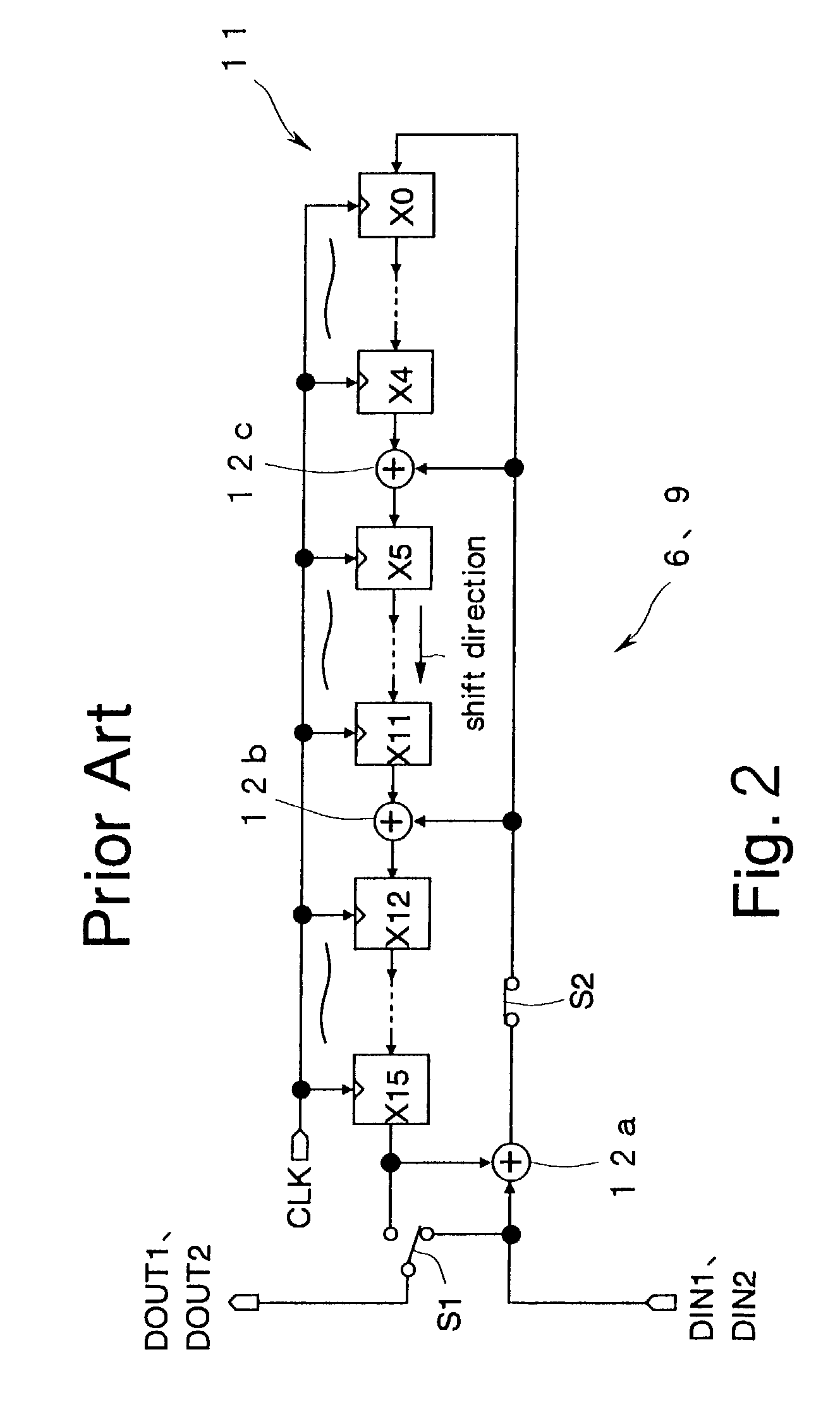
InactiveUS7032161B2Reduce processing timeProcessing time for error detection can be reducedError correction/detection using convolutional codesError preventionReverse orderNonlinear feedback shift register
An error detector at a receiver comprises a feedback shift register. A shift direction in the feedback shift register is opposite to a shift direction at a transmitter in generating a transmission bit string by using a specified generator polynomial. A reception bit string is inputted to the feedback shift register in reverse order to the transmission bit string was generated at the transmitter so that errors in the reception bit string is detected by obtaining the remainder. Another error detector at a receiver comprises first and second feedback shift registers. Respective shift directions in the first and second feedback shift registers are the same as and opposite to a shift direction at a transmitter in generating a transmission bit string. The reception bit string is inputted to the first feedback shift register in the same order in which the transmission bit string was generated, while the reception bit string is inputted to the second feedback shift register in reverse order to one which the transmission bit string was generated. Errors in the reception bit string are detected by comparing respective remainders obtained by the first and second feedback shift registers. This reduces the processing time required for the error detection and increases efficiency in detecting errors in transmitted data.
Owner:SOCIONEXT INC
A database data encryption system and method
InactiveCN101571873BDoes not affect retrieval efficiencyProtection securityDigital data protectionSpecial data processing applicationsNonlinear feedback shift registerTheoretical computer science
The invention discloses a database data encryption system and method. The system includes: a modulo Q nonlinear feedback shift register, which is used to perform nonlinear feedback with a given key as an initial value, and its feedback value is replaced by a preset Substitution and transformation of the table, which continuously generates 18 states of derived keys, which are used in the encryption and decryption operations of each circle of the block cipher; the replacement table replacement module is used for transformation in units of bytes; the substitution transformation module is used for transformation in units of bytes Replacement; the operation module is used to expand or concentrate the data in the database by bytes, perform horizontal accumulation, and perform replacement and replacement under the instruction of the derived key transformed by the modulo Q nonlinear feedback shift register Operation to complete the encryption and decryption of database data. It can effectively protect the security of data in the database.
Owner:北京联合智华微电子科技有限公司
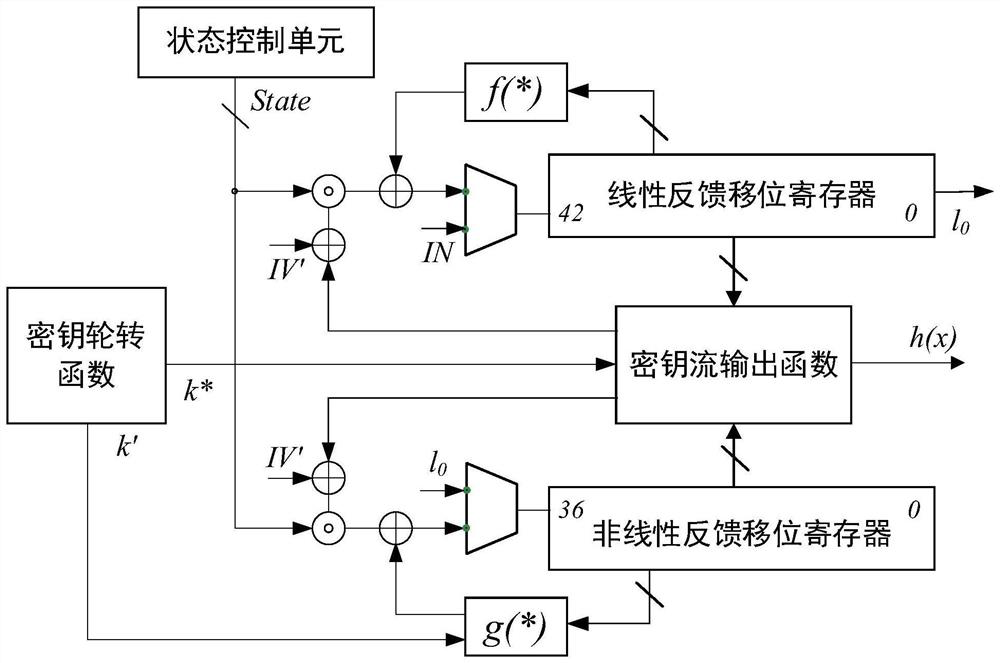
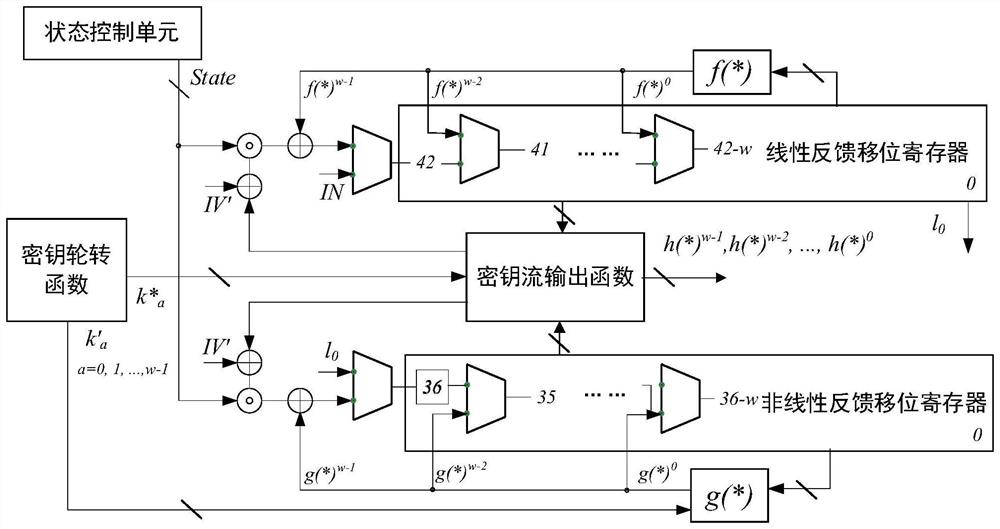
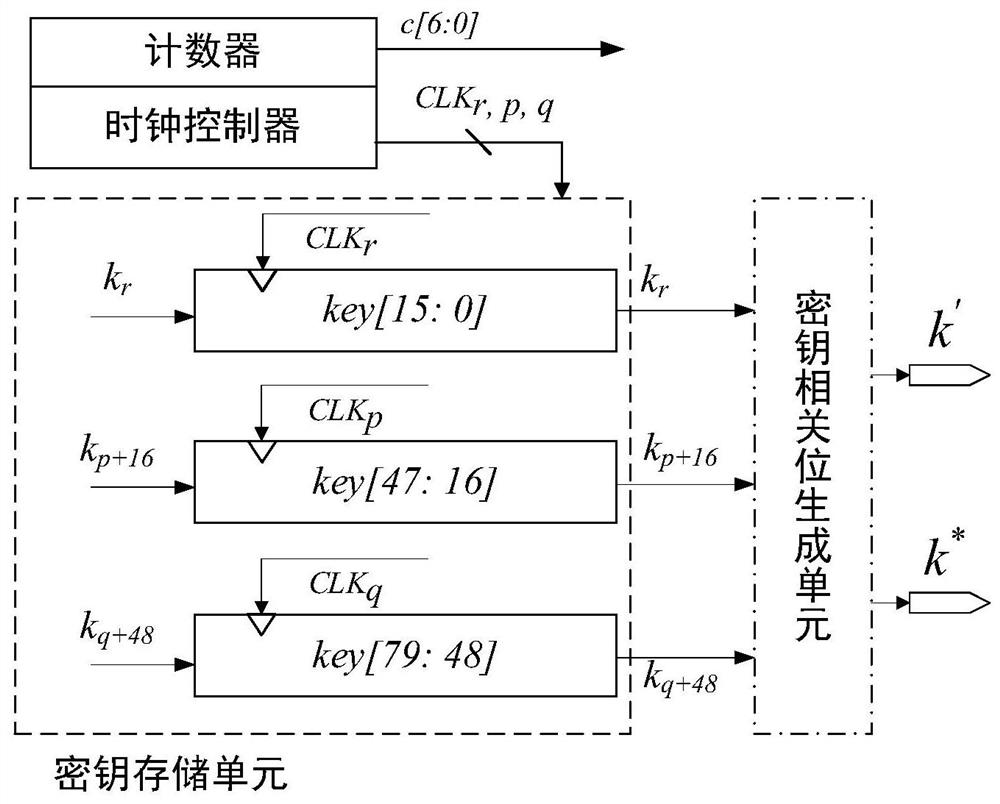
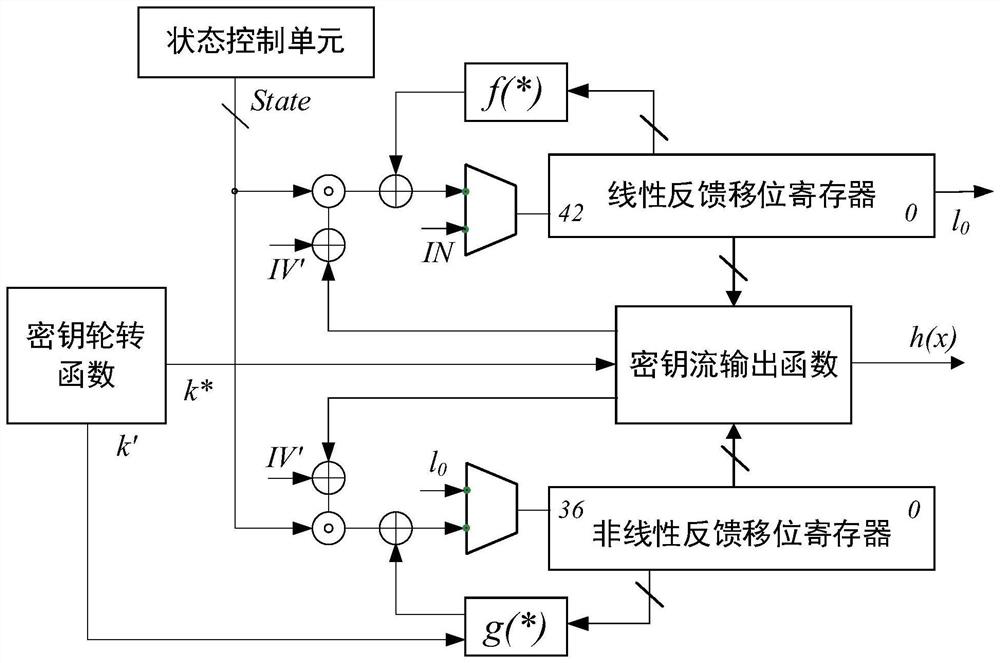
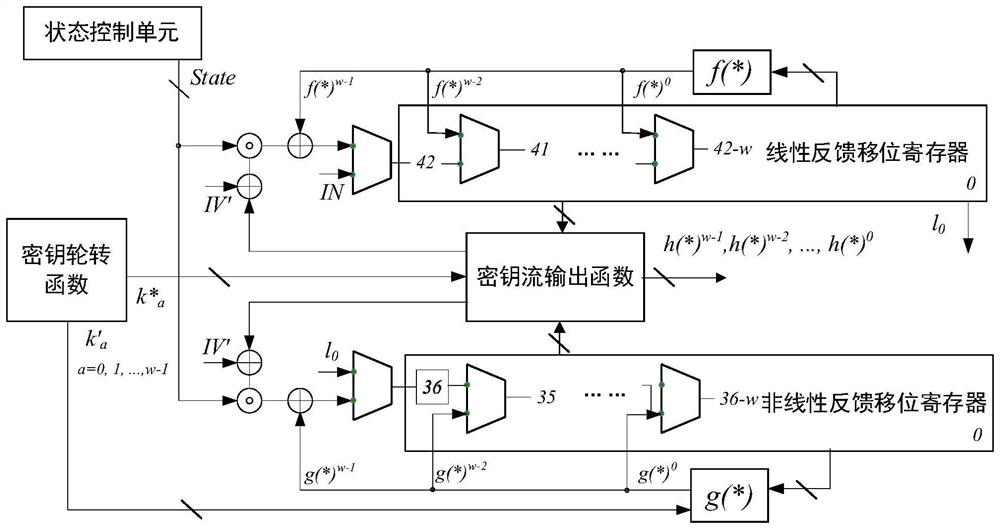
Hardware implementation device and method for Fruit-80 ultra-lightweight encryption algorithm
ActiveCN113612609AMeeting Compact Endpoint Security NeedsMeet security needsKey distribution for secure communicationAlgorithmNonlinear feedback shift register
The invention discloses a hardware implementation device and method for a Fruit-80 ultra-lightweight encryption algorithm. The hardware implementation device comprises a key rotation function, a nonlinear feedback shift register, a linear feedback shift register, a key stream output function and a state control unit. The key rotation function is used for providing two key correlation bits; each of the nonlinear feedback shift register and the linear feedback shift register comprises a nonlinear feedback function and a linear feedback function; the key stream output function extracts the internal states of the nonlinear feedback shift register and the linear feedback shift register in each round, and generates a key stream for encryption; and the state control unit is used for coordinating the state updating of the nonlinear feedback shift register and the linear feedback shift register in the password stage of the device. According to the hardware implementation device and method disclosed by the invention, the hardware resource occupation of the Fruit-80 ultra-lightweight sequence cipher can be reduced, and the throughput rate of the Fruit-80 ultra-lightweight sequence cipher can be improved to the greatest extent.
Owner:SHANDONG UNIV
Quantum random number post-processing device based on nonlinear feedback shift register
ActiveCN111258549AEasy to removeImprove uniformityQuantum computersRandom number generatorsAlgorithmNonlinear feedback shift register
The invention discloses a quantum random number post-processing device based on a nonlinear feedback shift register. The quantum random number post-processing device comprises an input unit, an arithmetic unit and an output unit, and the input unit comprises a plurality of bit input channels, and each channel inputs one bit of data into the arithmetic unit after passing through one clock. The quantum random number post-processing device has the beneficial effects that the classical randomness in the original data can be better removed by using the quantum random number processing algorithm ofthe non-linear feedback shift register, the quantum randomness is reserved, and the algorithm is better than an algorithm using a linear feedback shift register in the aspects of uniformity, unpredictability and the like of the final output data.
Owner:HENGTONG QASKY QUANTUM INFORMATION RES INST CO LTD +2
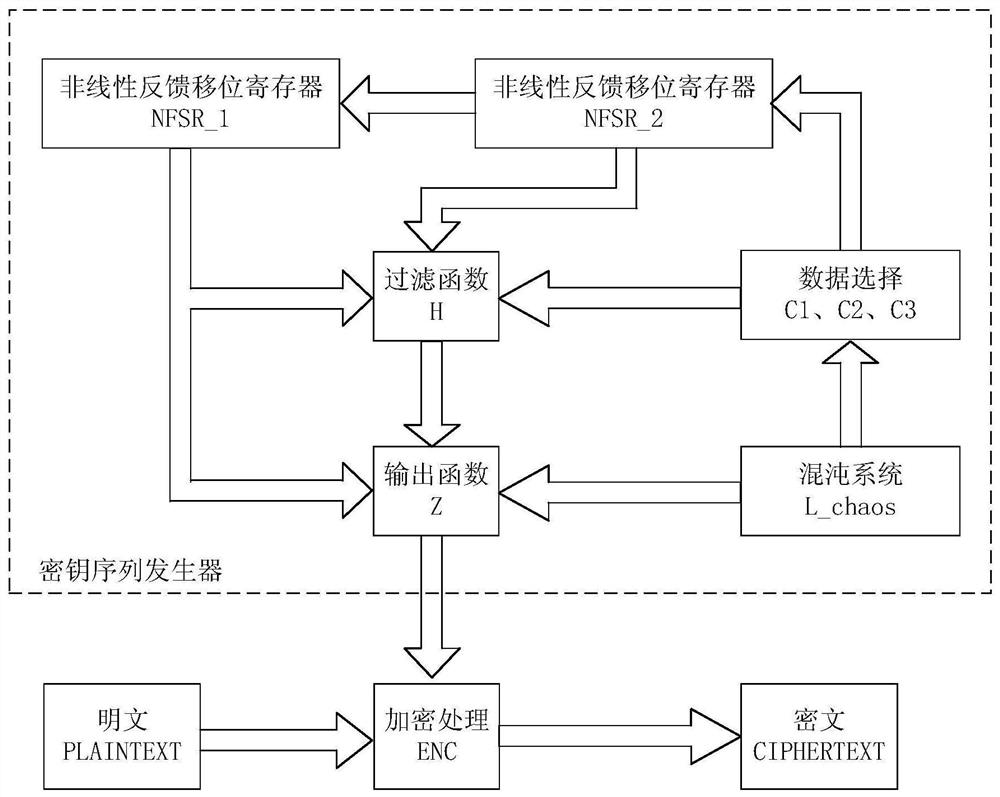
Lightweight key sequence generator based on chaotic system and FPGA
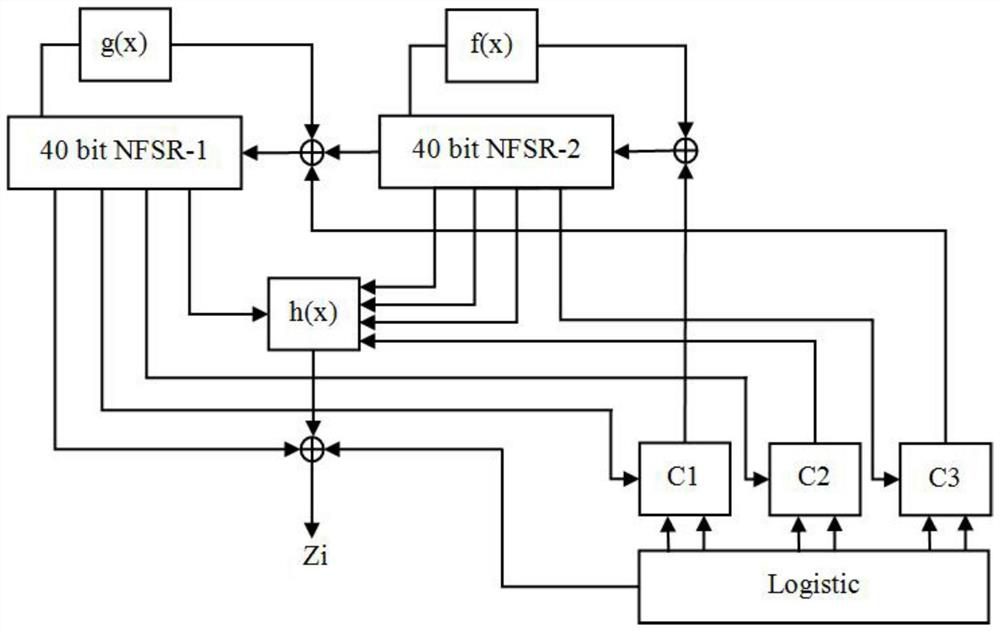
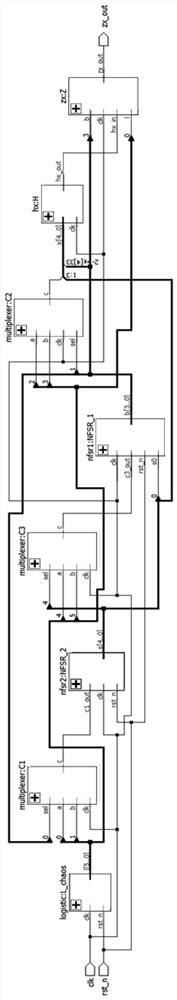
InactiveCN112260828AImprove bindingImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsNonlinear feedback shift registerData selection
The invention provides a lightweight key sequence generator based on a chaotic system and an FPGA, and solves the problem that the precision of the chaotic system is limited by hardware resources. Thelightweight key sequence generator comprises a sequence generator module based on a Logistic chaotic system, two nonlinear shift registers, three data selection modules, a filter function H module and an output function Z module. According to the lightweight key sequence generator, a Logistic chaotic sequence is digitalized and is combined with a nonlinear feedback shift register through a certain algorithm; the chaotic system and the non-linear feedback shift register are well combined, and the FPGA-based hardware implementation ensures the pseudo-randomness of the sequence and the securityof the system, enables the code scale to be smaller, and occupies less hardware resources.
Owner:HEILONGJIANG UNIV
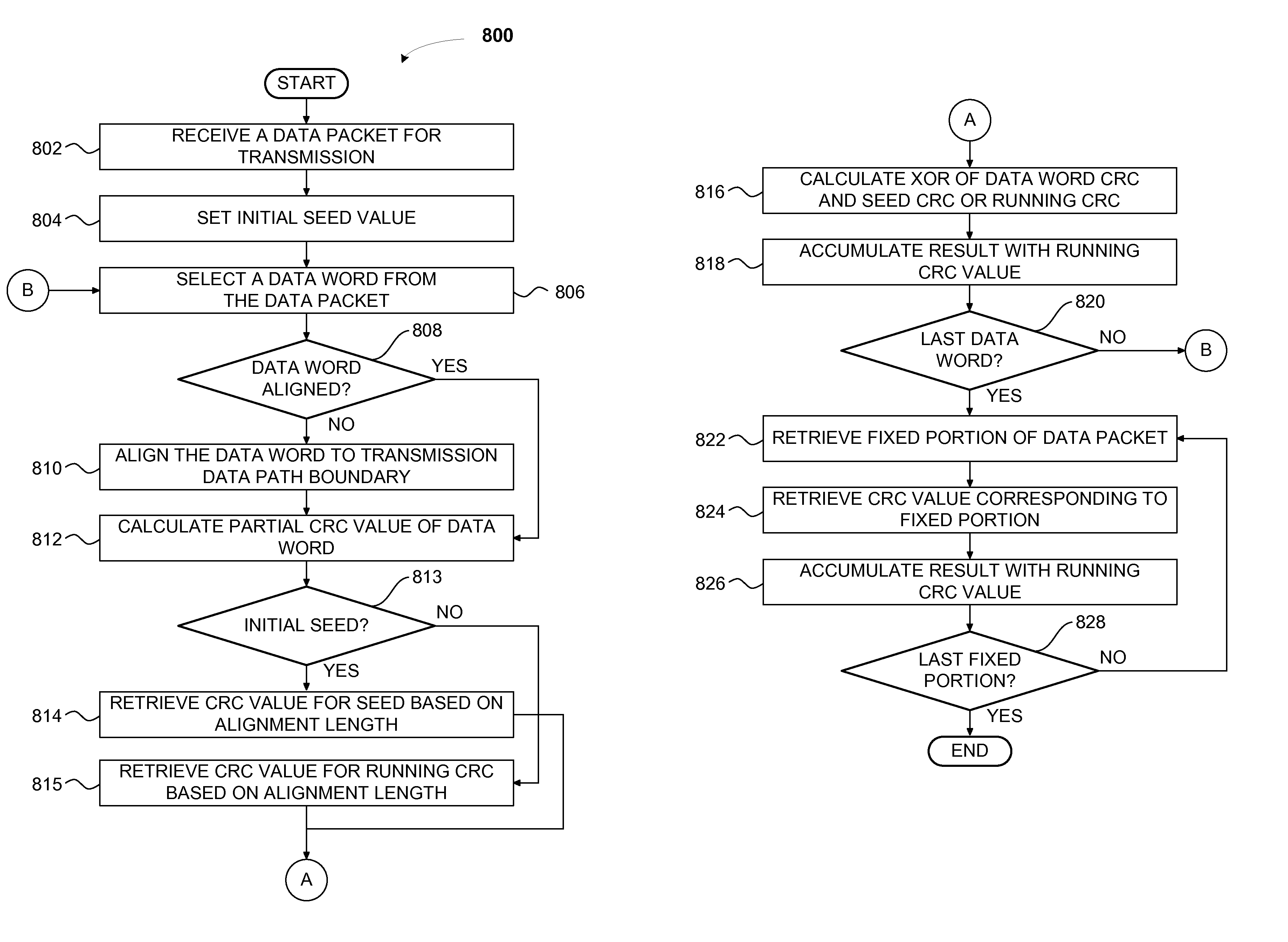
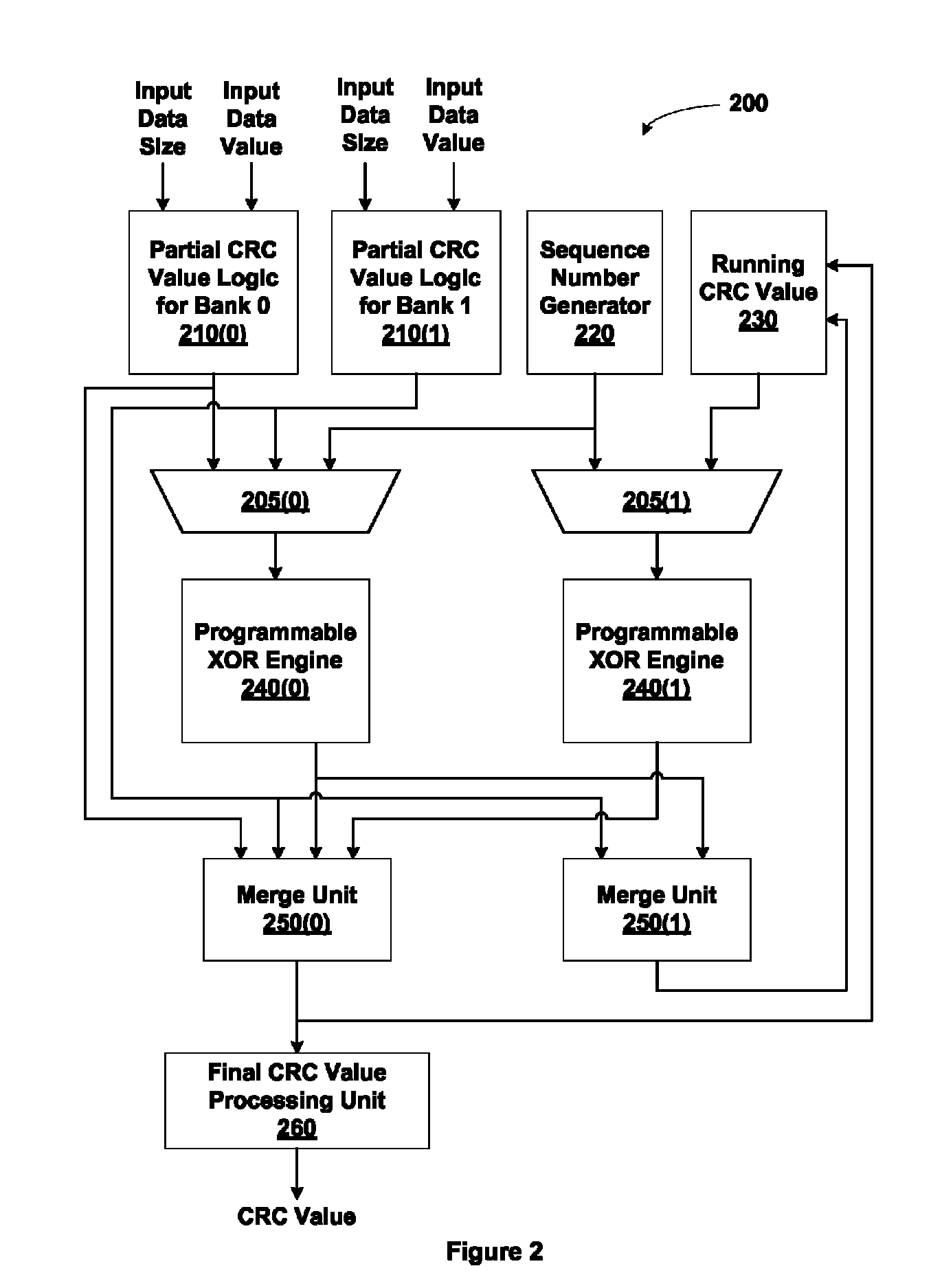
Cyclic redundancy check generation via distributed time multiplexed linear feedback shift registers
ActiveUS8726124B2Less surface areaLess powerCode conversionStatic storageNonlinear feedback shift registerTheoretical computer science
Cyclic redundancy check (CRC) values are efficiently calculated using an improved linear feedback shift register (LFSR) circuit. CRC value generation is separated into two sub-calculations, which are then combined to form a final CRC value. A programmable XOR engine performs logic functions via a table lookup rather than via a random logic circuit. LCRC and ECRC calculations are performed using a single shared LFSR circuit. Multiple links share the same CRC value generator. One advantage of the present invention is that CRC values are generated using smaller and fewer LFSR circuits relative to conventional circuit designs. As a result, a CRC value generator utilizing the disclosed techniques consumes less surface area of an integrated circuit and consumes less power, resulting in cooler operation.
Owner:NVIDIA CORP
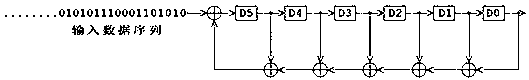
Nonlinear feedback shift register
PendingCN114270774ARandom number generatorsEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerControl engineering
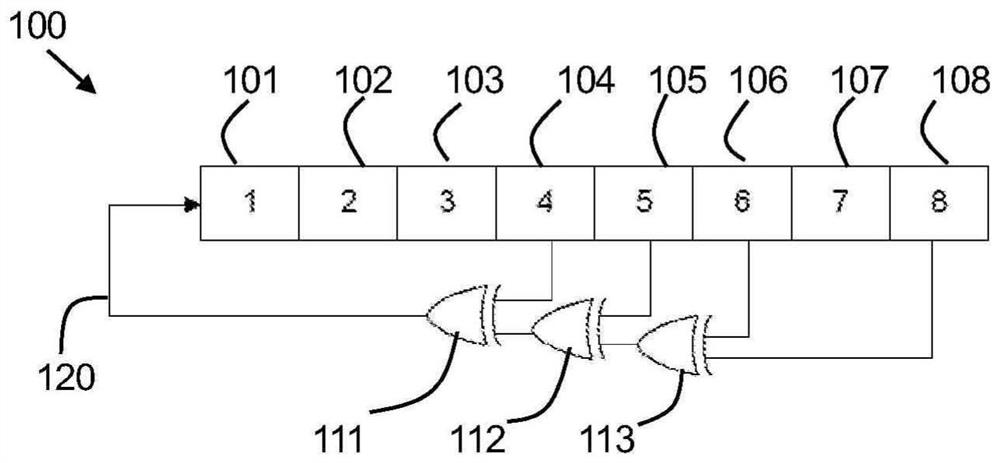
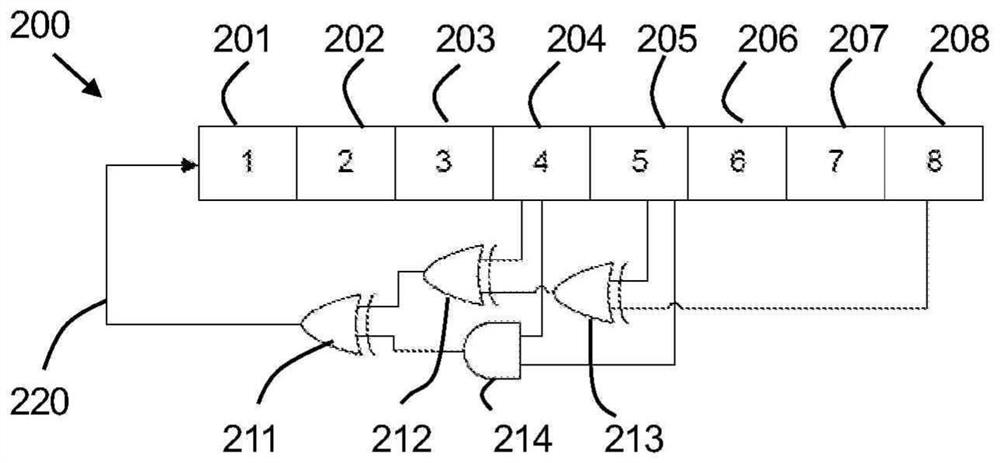
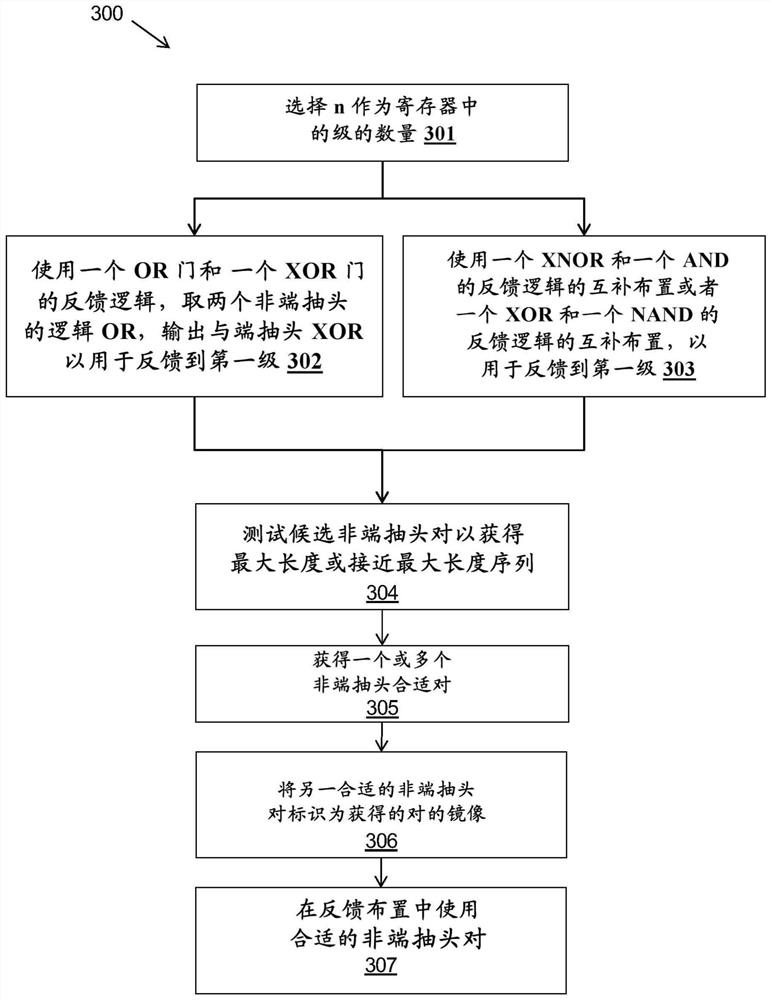
The invention provides a method and a system for generating n stages of pseudorandom sequences at least close to a maximum length using a non-linear feedback shift register (NLFSR), wherein the maximum length is 2n-1. The method comprises the following steps of: selecting n taps in the maximum-length linear feedback shift register, wherein n needs more than two taps; and for the selected n-level registers, generating a pseudorandom sequence by using a feedback logic operation of only the first logic gate and the second logic gate. The two suitable non-end taps are inputs for the first logic gate, the output of the first logic gate and the end tap are inputs for the second logic gate, and the output of the second logic gate serves as feedback to the first stage of the n-stage register.
Owner:IBM CORP
Linear feedback shift register, and method for selective encrpytion code and decryption code
InactiveCN1165131CIncrease transfer rateImprove system speedError preventionSecuring communicationNonlinear feedback shift registerParallel computing
The shift register used in system of providing enciphering code and deciphering code has one n-th order linear feedback shift register to provide polynomial coefficients and one memory to store calculation result with the polynomial coefficients of the linear feedback shift register and the received input sample. The memory has one input end to receive input sample and one output corresponding to the polynomial coefficients of the linear feedback shift register.
Owner:WINBOND ELECTRONICS CORP
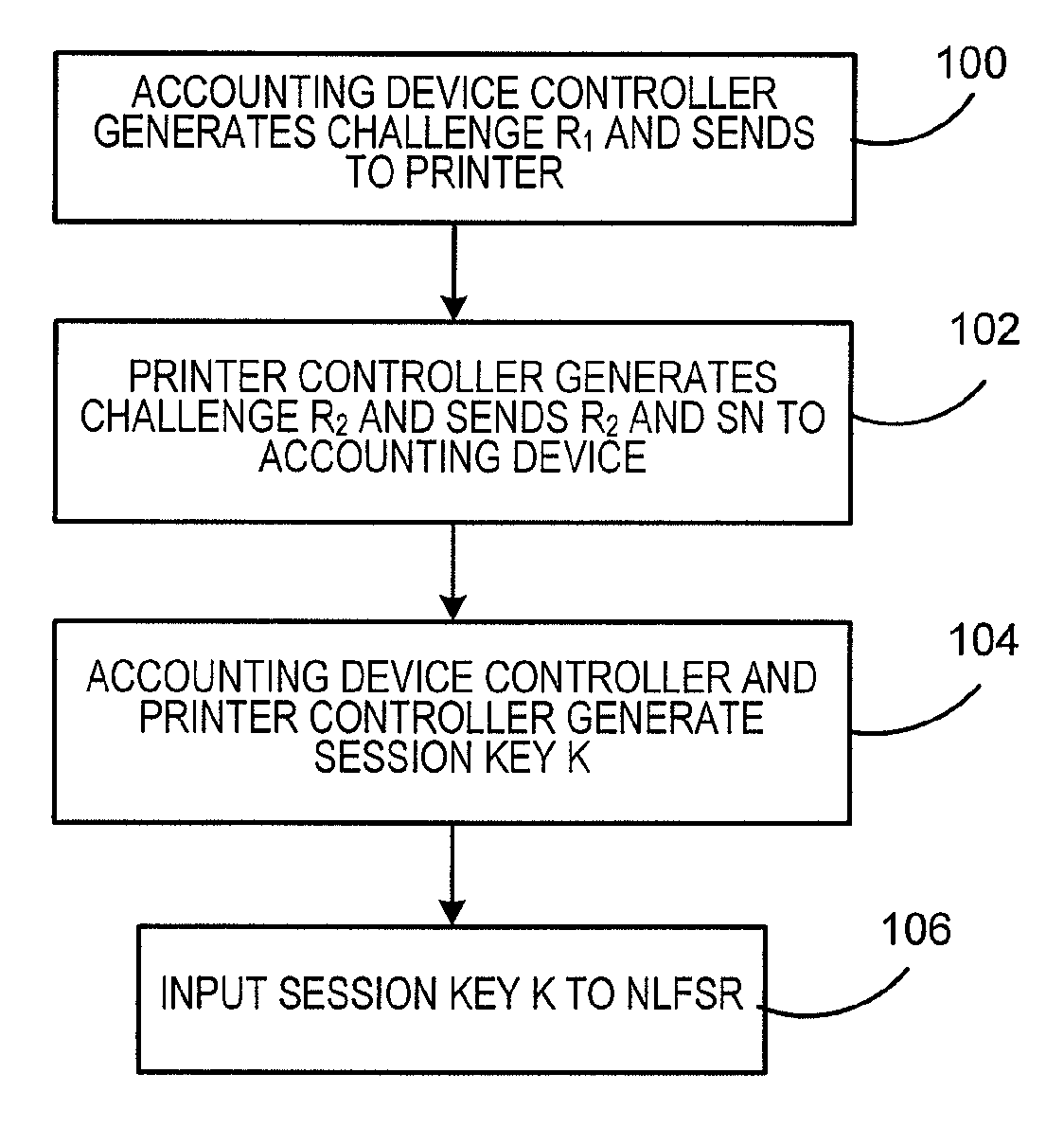
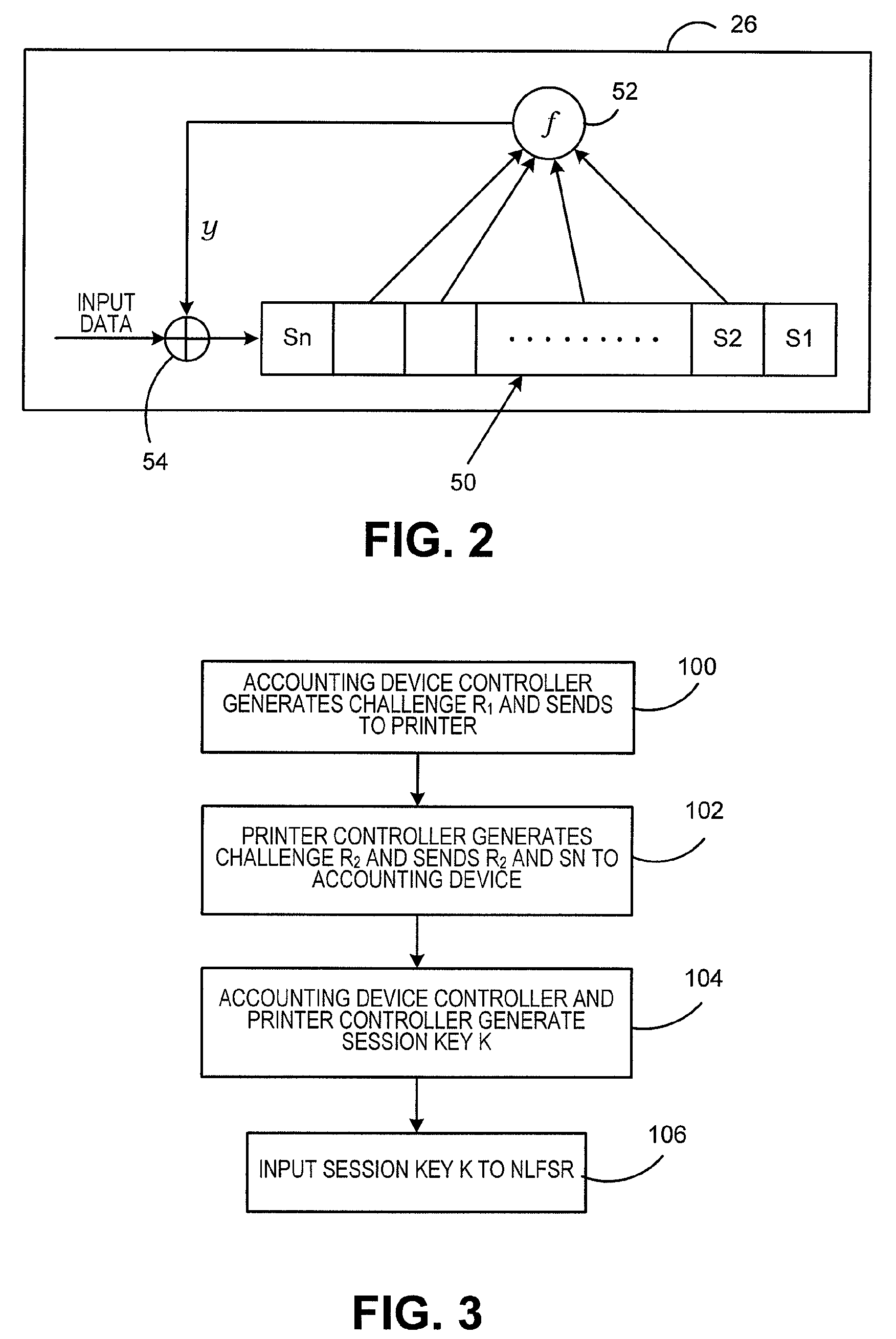
A Nonlinear Feedback Shift Register
ActiveCN104238995BRandom number generatorsEncryption apparatus with shift registers/memoriesNonlinear feedback shift registerLogical operations
An embodiment of the invention provides a non-linear feedback shift register. A data distributing network selects variables from state values according to a logical operation function and outputs the variables; a calculating network performs logical conjunction operation and exclusive disjunction operation on the variables inputted by the data distributing network; non-linear feedback functions of a cryptographic algorithm can be converted into functions which only comprises logical conjunction and exclusive disjunction, the logical operation function for the data distributing network of the non-linear feedback shift register in an embodiment consists of logical conjunction operation and exclusive disjunction operation, and calculation carried out by the calculating network also consists of logical conjunction operation and exclusive disjunction operation, so that data can be selected and calculated according to different non-linear feedback functions. The non-linear feedback shift register is widely suitable for different cryptographic algorithms.
Owner:THE PLA INFORMATION ENG UNIV
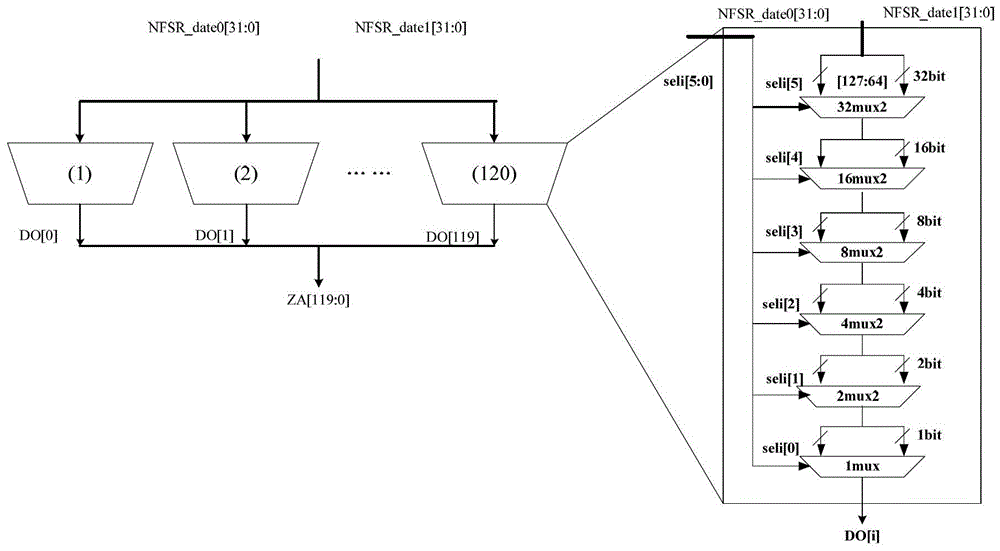
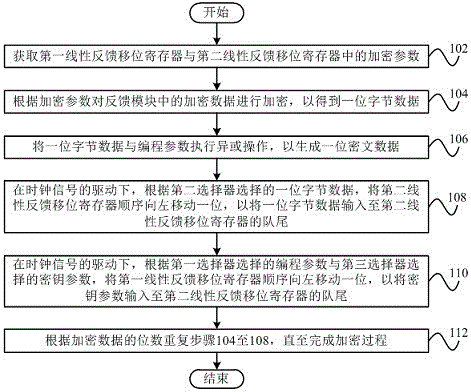
Encryption method and encryption device
InactiveCN106357385AEasy to implementHigh encryption strengthEncryption apparatus with shift registers/memoriesDuplex signal operationCiphertextNonlinear feedback shift register
The invention provides encryption and decryption algorithms and a data encryption device. A data encryption method comprises the following steps: acquiring encryption parameters in a first linear feedback shift register and a second linear feedback shift register; encrypting encryption data in a feedback module according to the encryption parameters to obtain single-bit byte data; executing xor operation on the single-bit byte data and programming parameters to generate single-bit encrypted data. With adoption of the method, the security of one-way data transmission of half-duplex low-frequency RFID is improved, and the method has the advantages of being high in encryption and decryption speed, easy to implement, high in encryption strength, good in security and wide in application, and is applicable to software and hardware.
Owner:BEIHAI YUNXIN ELECTRONICS TECH
Method and system for securing communications in a metering device
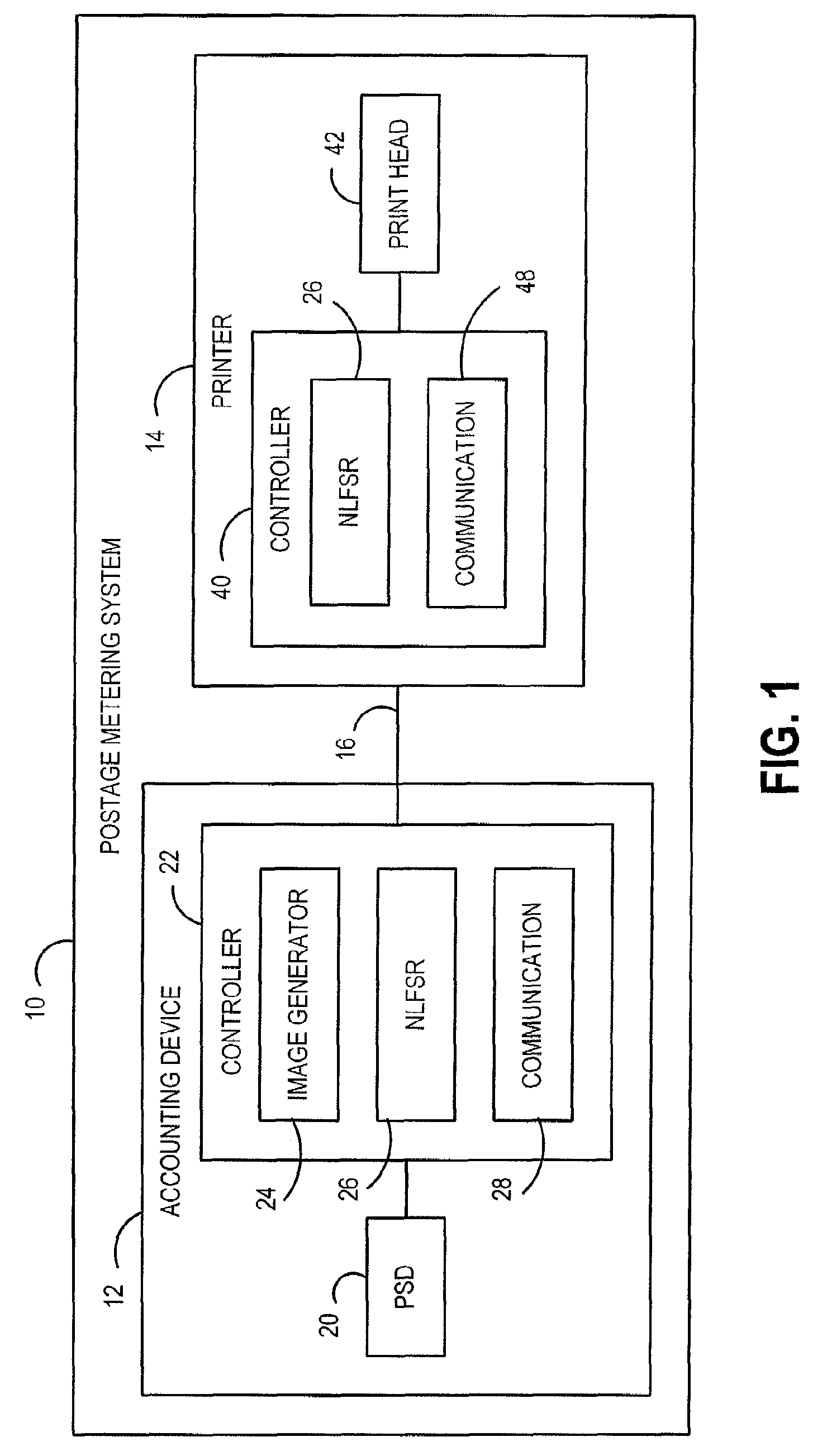
ActiveUS8208633B2Reduce decreaseImprove security levelUser identity/authority verificationOperator-supported drilling machinesSecure communicationShift register
A method and system for securing the communication link between the accounting device and printer of a metering system by authenticating the data being sent via the link utilizing a Nonlinear Feedback Shift Register (NLFSR) based system is provided. A NLFSR is provided in each of the accounting unit and printing unit of a metering system. The NLFSR in the accounting unit is utilized to generate a message authentication code (MAC) for the image data being sent from the accounting unit to the printing unit. The printing unit generates a corresponding MAC for the received image data using the NLFSR in the printing unit. The MAC generated by the printing unit is compared with the MAC generated by the accounting unit. If the MACs are similar, the image data is accepted as authentic and the printing unit will print the image corresponding to the image data.
Owner:PITNEY BOWES INC
Quantum random number post-processing device based on nonlinear feedback shift register
ActiveCN111258549BEasy to removeImprove uniformityQuantum computersRandom number generatorsAlgorithmNonlinear feedback shift register
The invention discloses a quantum random number post-processing device based on a nonlinear feedback shift register. The quantum random number post-processing device based on the nonlinear feedback shift register of the present invention includes: an input unit, an operation unit and an output unit; the input unit includes a plurality of bit input channels, each channel will send to One bit of data is input into the arithmetic unit. Beneficial effects of the present invention: the quantum random number processing algorithm using the nonlinear feedback shift register can better remove the classical randomness in the original data, retain the quantum randomness, and ensure the uniformity and unpredictability of the final output data In terms of performance and so on, it is better than the algorithm using linear feedback shift register.
Owner:HENGTONG QASKY QUANTUM INFORMATION RES INST CO LTD +2
A hardware implementation device and method of fruit-80 ultra-lightweight encryption algorithm
ActiveCN113612609BMeeting Compact Endpoint Security NeedsMeet security needsKey distribution for secure communicationComputer hardwareNonlinear feedback shift register
The invention discloses a hardware implementation device and method of Fruit-80 ultra-lightweight encryption algorithm, the hardware implementation device includes a key rotation function, a nonlinear feedback shift register, a linear feedback shift register, a key stream output function and State control unit; the key rotation function is used to provide two key-related bits; the nonlinear feedback shift register and the linear feedback shift register respectively contain a nonlinear feedback function and a linear feedback function; the key stream output function every round Extract the internal state of the nonlinear feedback shift register and the linear feedback shift register, and generate the key stream for encryption; the state control unit is used for the encryption stage of the device, and coordinates the states of the nonlinear feedback shift register and the linear feedback shift register renew. The hardware implementation device and method disclosed in the present invention can reduce the hardware resource occupation of the Fruit-80 ultra-lightweight serial cipher, and maximize its throughput rate.
Owner:SHANDONG UNIV
Shrinking key generator for parallel process
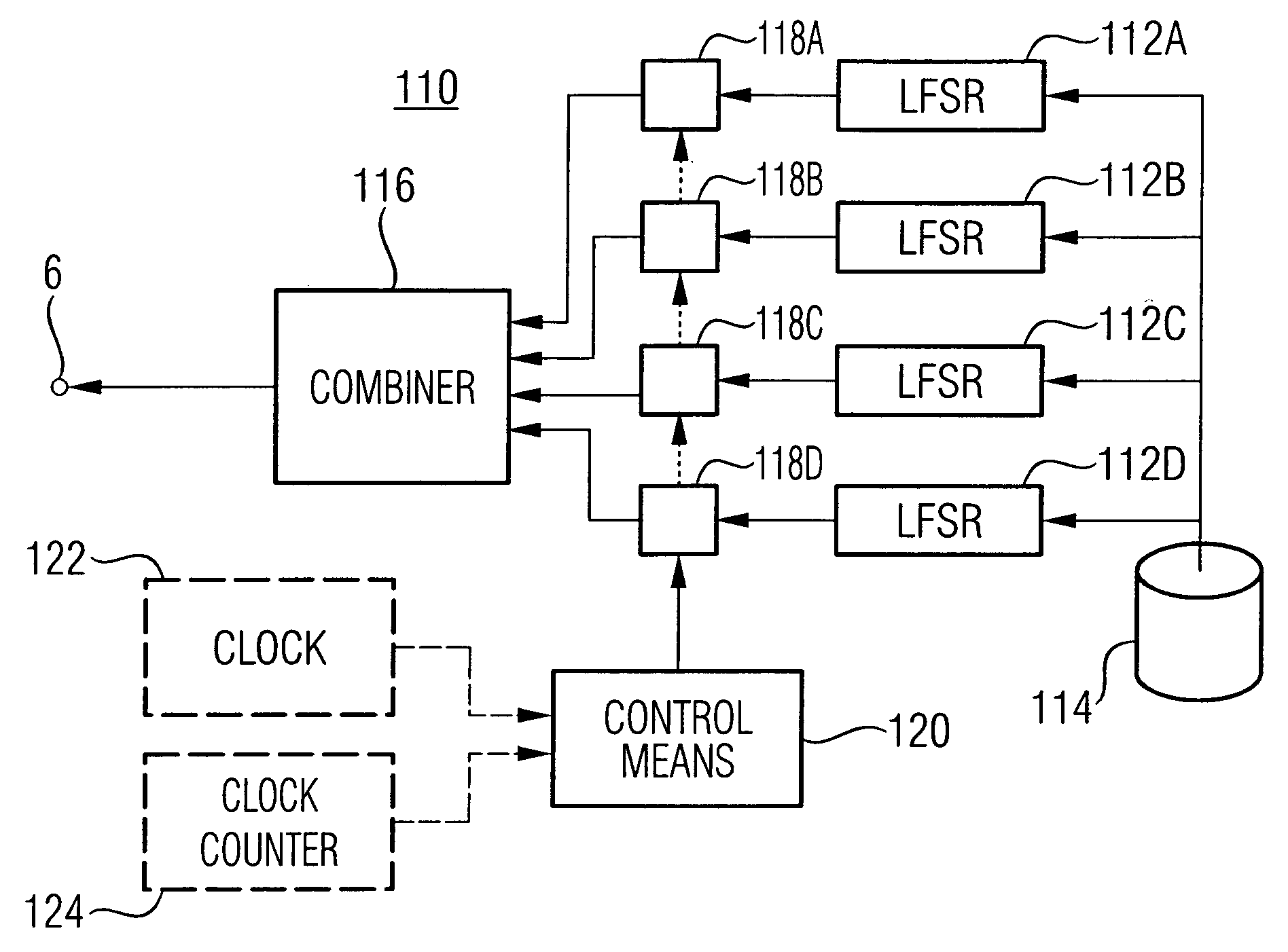
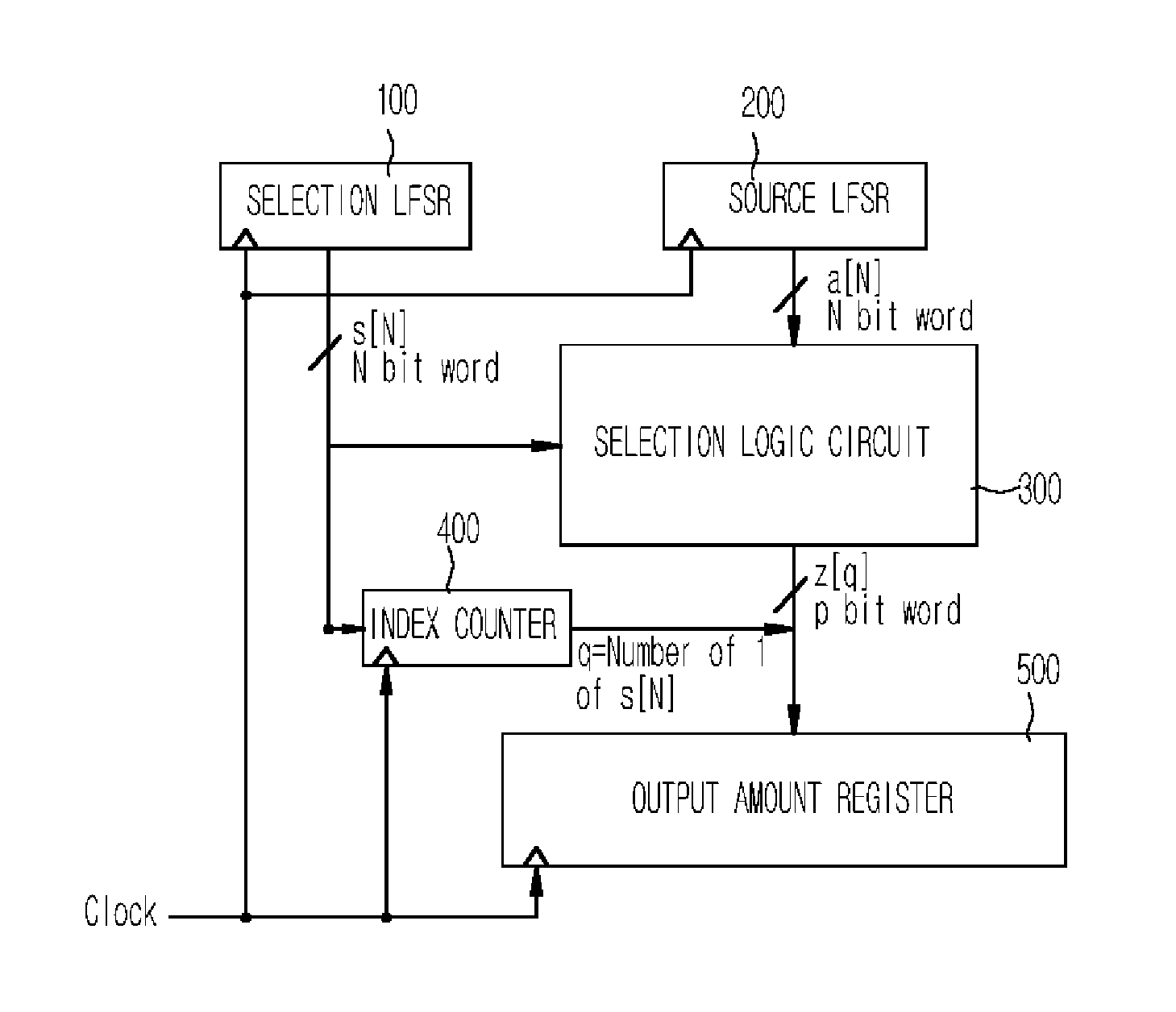
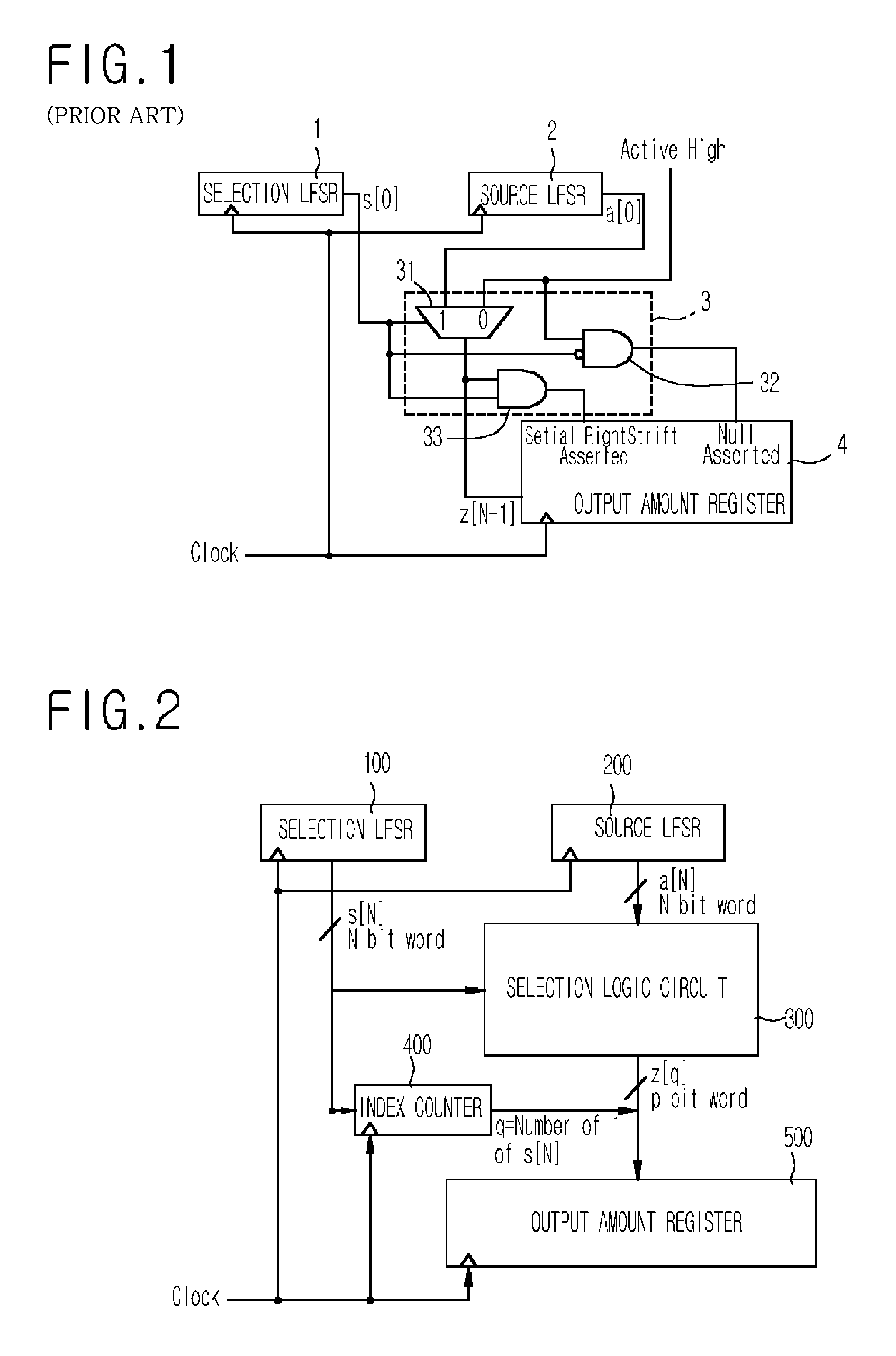
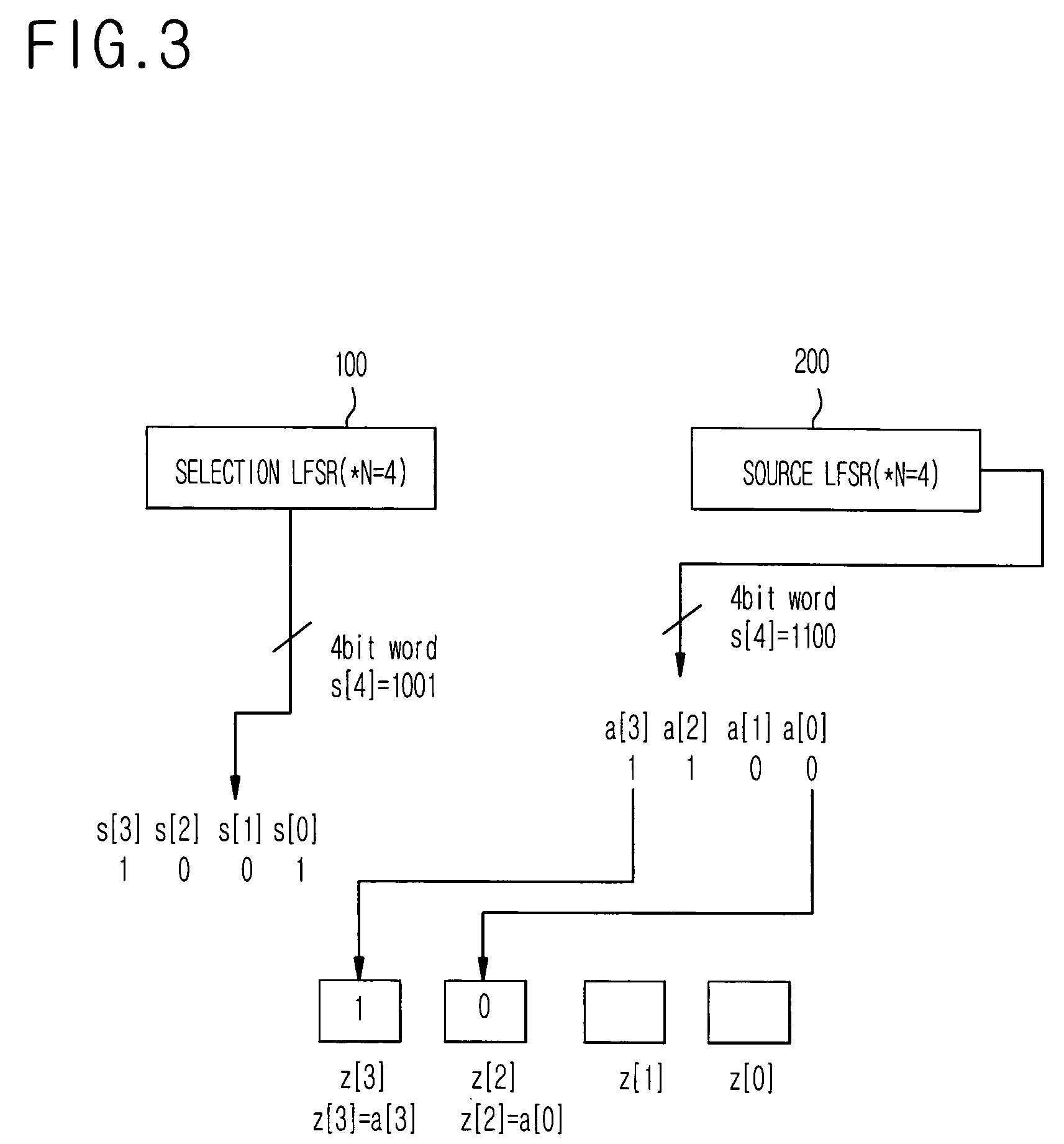
InactiveUS7742598B2Increasing speed of generationIncrease speedConcurrent instruction executionSecret communicationNonlinear feedback shift registerKey generator
A parallel processing shrinking key generator is provided. The parallel processing shrinking key generator includes: a selection linear feedback shift register (LFSR); a source LFSR; a selection logic circuit for selecting one of a source bit of the source LFSR and a predetermined input bit according to a selection bit of the selection LFSR; an index counter for assigning an index where output bits of the selection logic circuit are stored at a next clocking of a clock signal; and an output amount register for shifting an output bit of the selection logic circuit according to the assignment of the index counter.
Owner:ELECTRONICS & TELECOMM RES INST
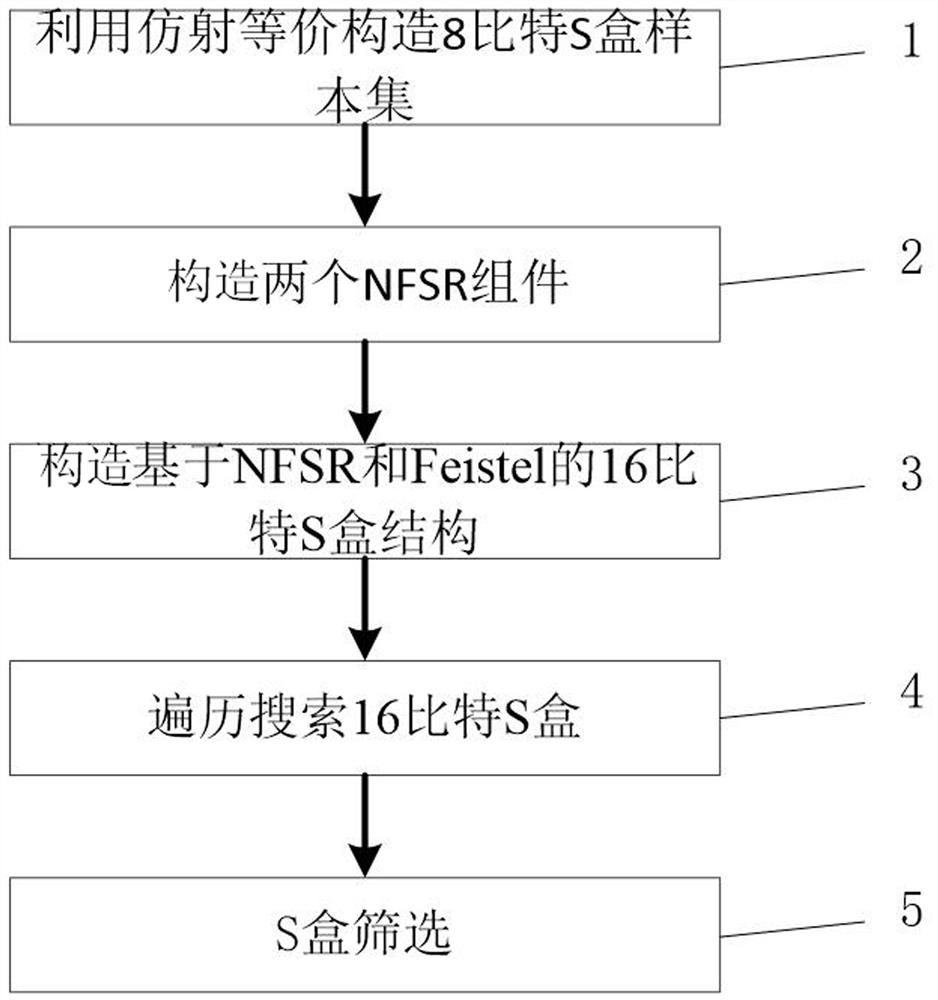
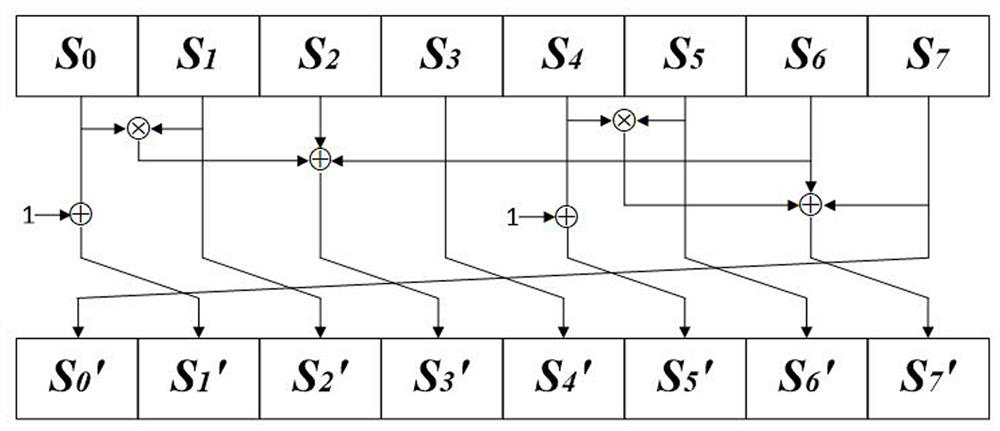
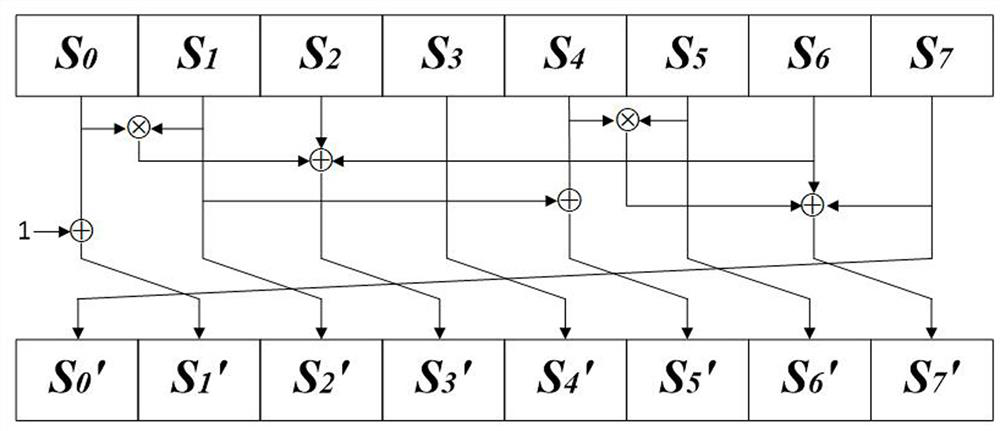
16-bit S box construction method based on NFSR and Feistel structure
ActiveCN113783684ASimple structureExcellent cryptographic propertiesEncryption apparatus with shift registers/memoriesS-boxNonlinear feedback shift register
The invention discloses a 16-bit S box construction method based on NFSR and an Feistel structure. The method comprises the following steps: constructing an 8-bit S box sample set; constructing two NFSR components by using an eight-stage nonlinear feedback shift register; combining the two constructed NFSR components with a Feistel structure, carrying out multi-round iteration based on the 8-bit password S box sample set, and carrying out output after iteration so as to construct a 16-bit password S box; and finally, testing the constructed 16-bit S box, performing screening according to difference uniformity, nonlinearity, algebraic times and signal-to-noise ratio in sequence, and screening out the 16-bit S box with better password property for outputting. The method is based on an NFSR and Feistel structure, an S box is used for replacing a round function, and the construction structure is simple; the 16-bit S box with better cryptographic properties can be constructed, and S box support with high security is provided for a block cipher algorithm.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Encryption and decryption method and device based on zipper type dynamic hash and nlfsr
ActiveCN109981249BImprove uniformityLong cycleEncryption apparatus with shift registers/memoriesHash functionCiphertext
An encryption and decryption method and device employing zipper-type dynamic hashing and NLFSR techniques. An encryption process comprises the following steps: using a nonlinear feedback function and a bit-manipulation Boolean function to pre-process a seed key, so as to form a keystream sequence; changing, according to the bit-manipulation Boolean function employing the keystream sequence, a bit value of a plaintext sequence, so as to form a pseudo-plaintext sequence; dividing, according to the keystream sequence, the pseudo-plaintext sequence into multiple pseudo-plaintext subsequences; and calculating, according to a hash mapping rule depending on the keystream sequence, a dynamic hash address corresponding to a binary bit of each respective pseudo-plaintext sequence, and mapping, by means of a hash function, the multiple pseudo-plaintext subsequences to a ciphertext space, so as to form a ciphertext stream sequence. The present application has the following beneficial effects: keystream generators, beside using nonlinear feedback shift registers, also use a bit-manipulation Boolean function so as to obtain keystreams having a longer period and improved randomness; moreover, bit-manipulation rules for plaintexts and mapping rules employing zipper-type dynamic hashing are used to increase the difficulty of decoding ciphertext stream sequences.
Owner:ZHUHAI COLLEGE OF JILIN UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com