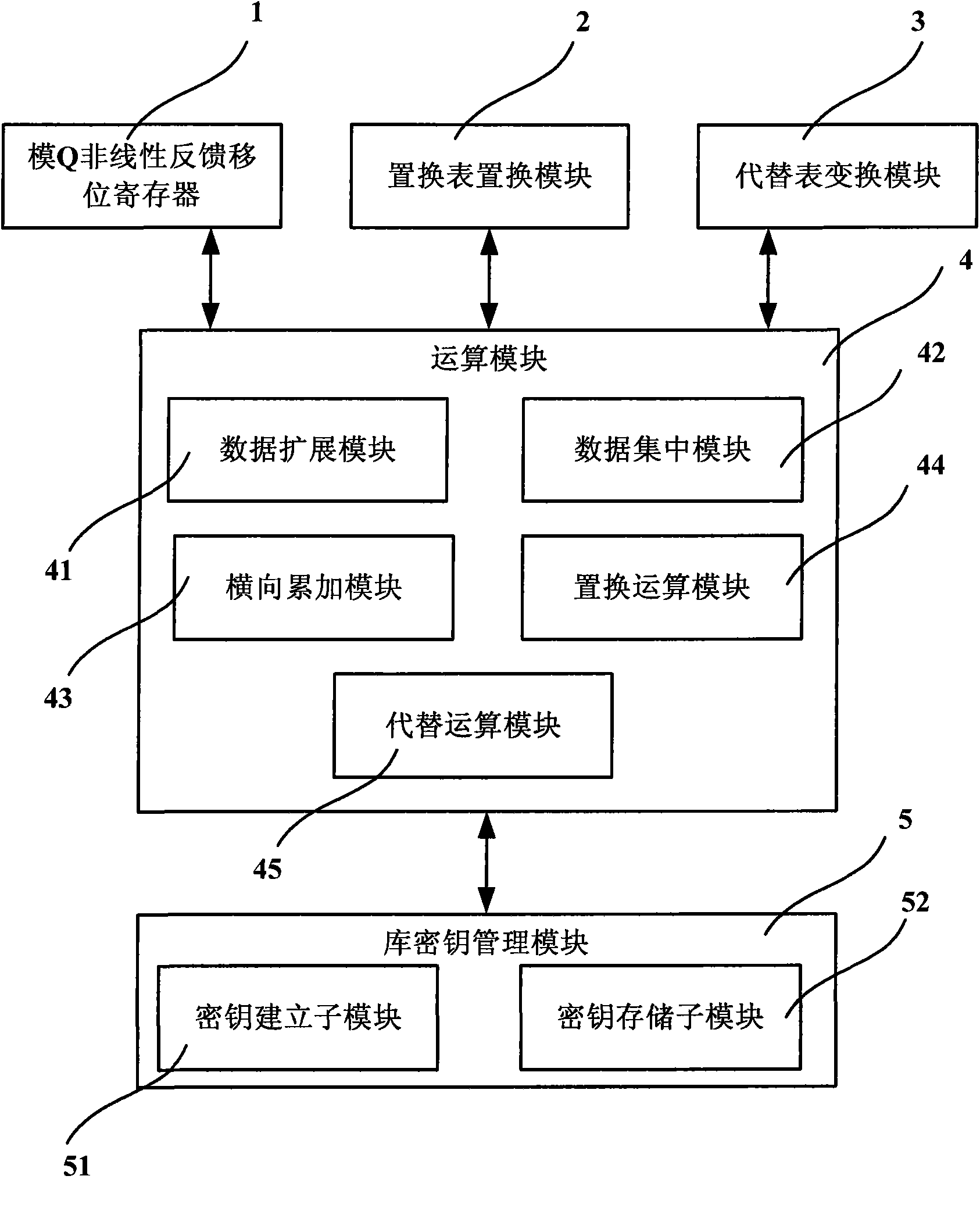
Database data encryption system and method thereof
A data encryption and database technology, applied in the field of information security, can solve problems such as invisible binary data, and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
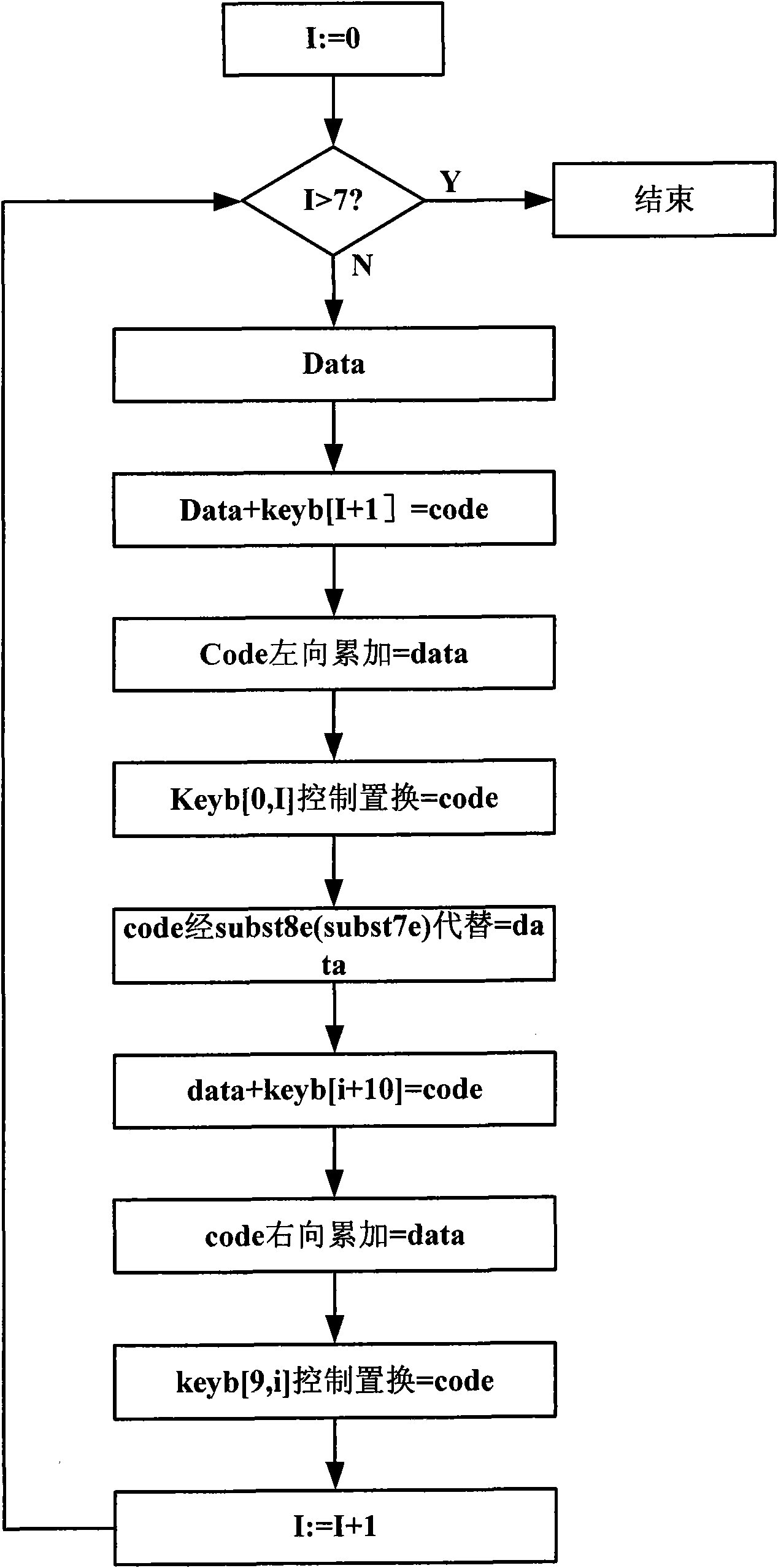
[0251] Embodiment 1: 8-bit unit code operation, 8-bit binary data is obtained after encryption
[0252] Given a key and data as follows:
[0253] Byte order [7][6][5][4][3][2][1][0]
[0254] Key variable key: 08 07 06 05 04 03 02 01
[0255] Given data:
[0256] Data length Data variable data
[0257] byte=1 01
[0258] byte=2 02 01
[0259] byte=3 03 02 01
[0260] byte=4 04 03 02 01
[0261] byte=8 08 07 06 05 04 03 02 01
[0262] in
[0263] byte: field length, byte=1, 2, 3, 4, 8 five kinds
[0264] i : operation of the i-th circle
[0265] key : the given key variable
[0266] data: plaintext data to be encrypted
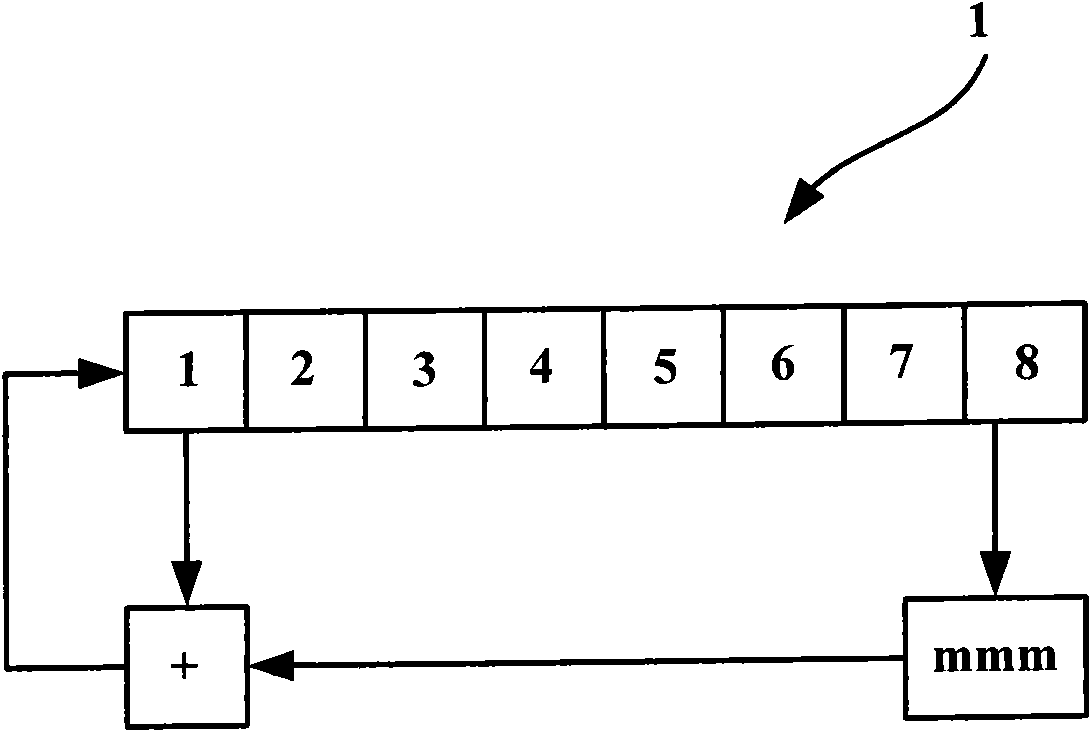
[0267] Step S11, from the given key key, use the modulo Q nonlinear feedback shift register 1 to perform feedback operation to obtain 18 groups of derived keys keyb;
[0268] [7] [6] [5] [4] [3] [2] [1] [0]
[0269] Set the given key key: 08 07 06 05 04 03 02 01
[0270] Then derive the key keyb[0]: 4C A4 7F 5D 08 18 94 B7
[027...
Embodiment 2
[0446] Embodiment two: 7 unit codes (7-bit) operation, the sign bit of each byte is reserved first, the binary code of 7-bit can still obtain the binary code of 7-bit after being encrypted, then the symbol of keeping Bits are restored to each byte, making it an 8-bit ASK code.
[0447] Given a key and data as follows:
[0448] [7][6][5][4][3][2][1][0]
[0449] Given key key: 08 07 06 05 04 03 02 01
[0450] Given data data:
[0451] byte=1 01
[0452] byte=2 02 01
[0453] byte=3 03 02 01
[0454] byte=4 04 03 02 01
[0455] byte=8 08 07 06 05 04 03 02 01
[0456] in
[0457] byte: packet length, byte=1, 2, 3, 4, 8 five kinds
[0458] i : operation of the i-th circle
[0459] key: given key
[0460] Step S21, using the modulo Q nonlinear feedback shift register 1 to perform a feedback operation from the original key key to obtain 18 groups of derived keys keyb;
[0461] [7][6][5][4][...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com