Patents
Literature
213results about How to "Improve tamper resistance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User public key address binding, searching and verifying method and system based on crypto currency open account book technology
ActiveCN104320262AImprove convenienceImprove securityUser identity/authority verificationPayment architectureDigital currencyDependability
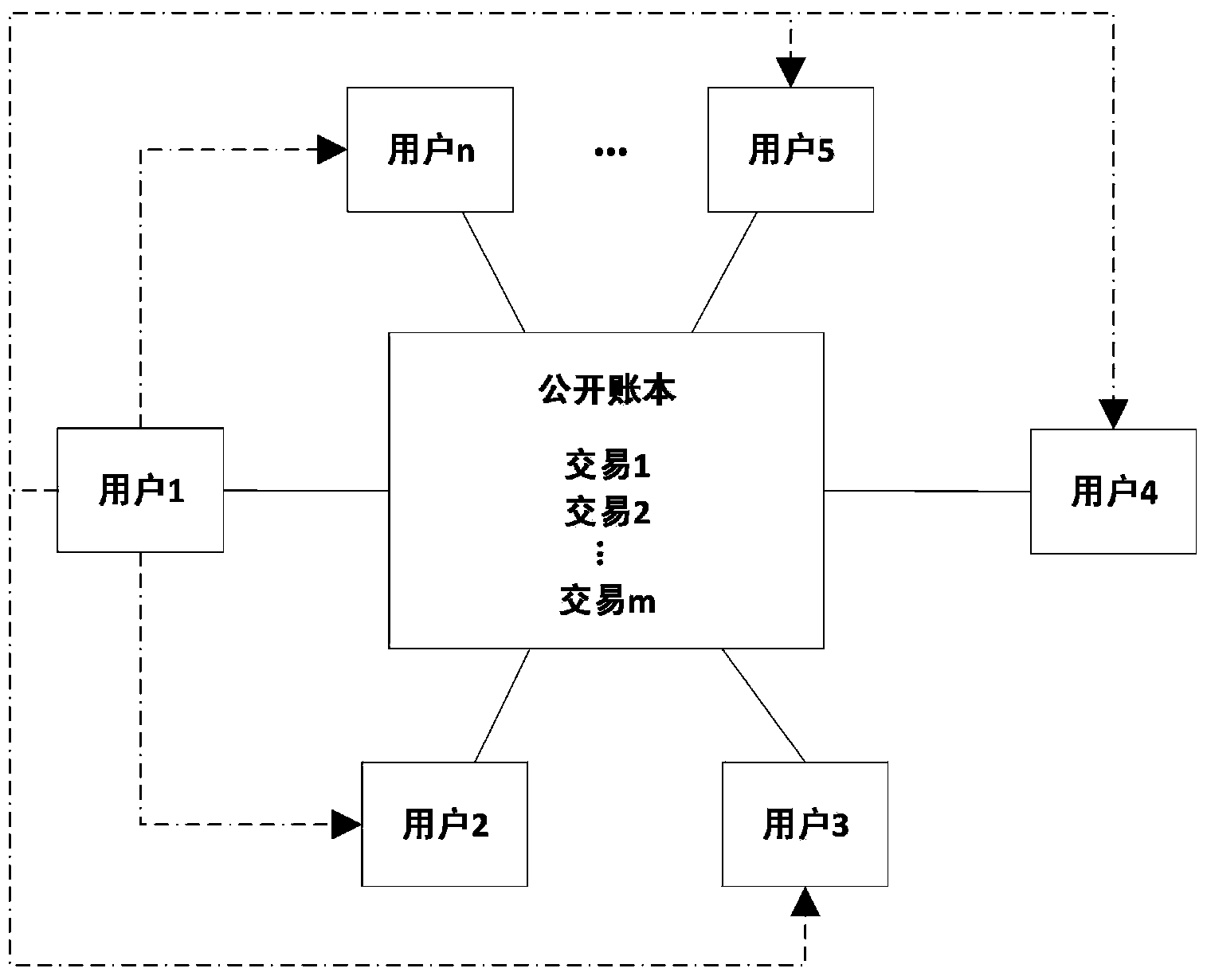
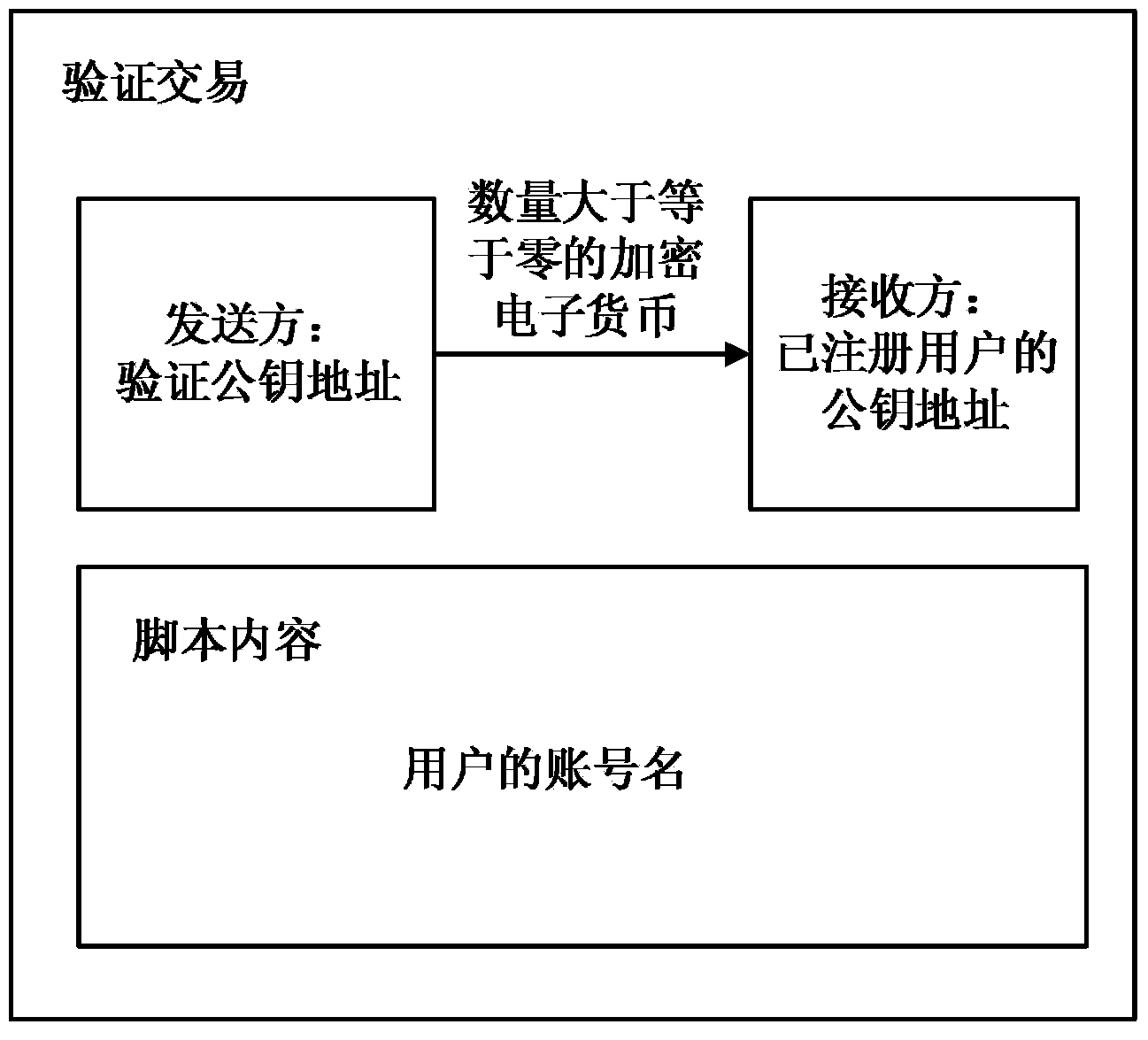
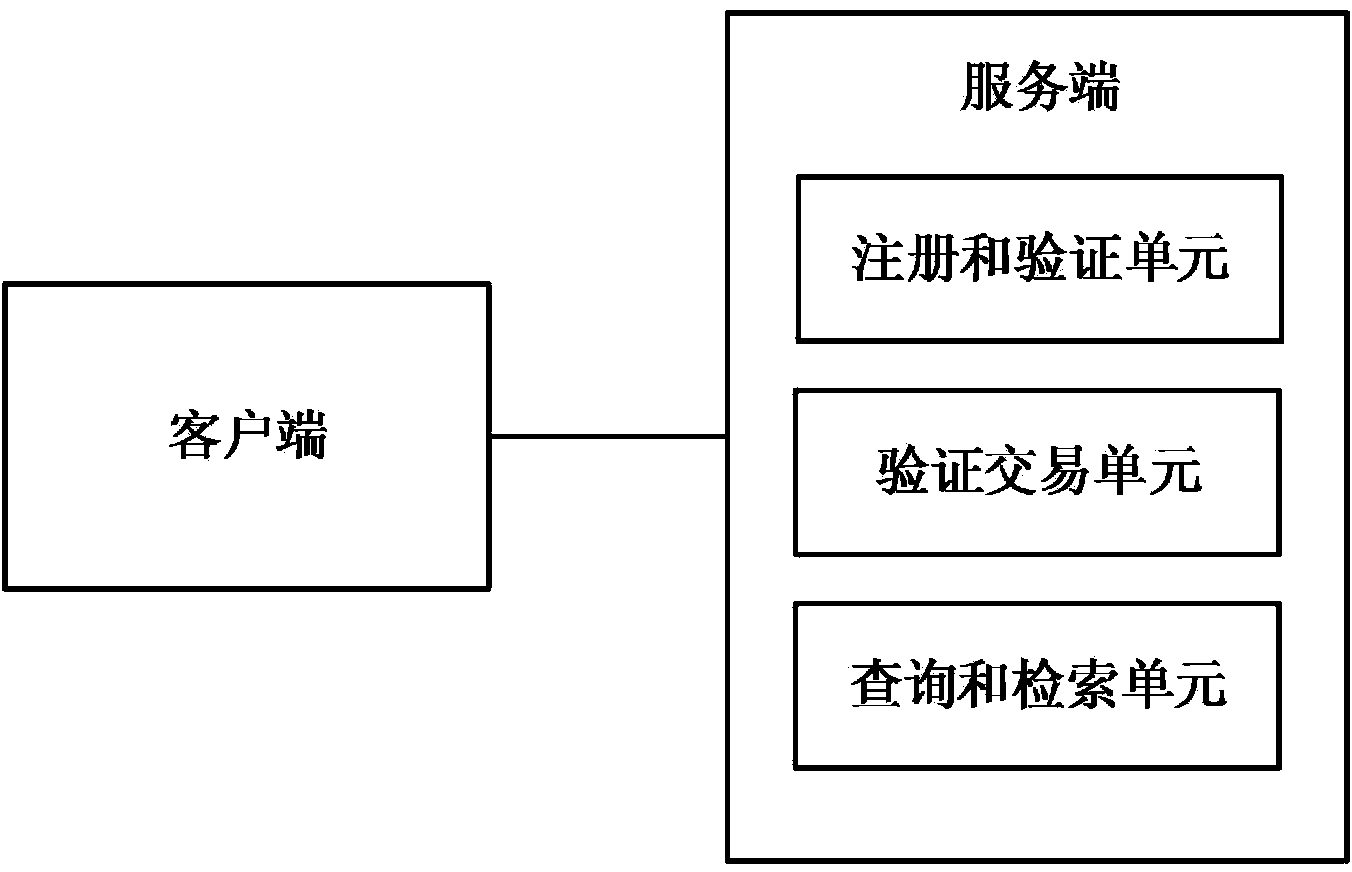
The invention discloses a user public key address binding, searching and verifying method and system based on the crypto currency open account book technology. The user public key address binding, searching and verifying method is characterized by comprising the following steps that (1) verification public key addresses are published to users in a crypto currency network; (2) an account name registration request of one user is received, and the public key address of the user is received; (3) crypto currency is sent to the public key address of the crypto currency of the registered user through a private key address corresponding to the verification public key address and used as a verification transaction, and it is set that additional information or script content of the verification transaction contains the account number of the user, wherein the amount of the crypto currency is greater than or equal to zero; (4) query requests from other users in the crypto currency network are received, and the public key address of the registered user is fed back according to the query requests. The user public key address binding, searching and verifying method and system can substantially improve the availability, convenience, safety and reliability of crypto currency transactions, and protect the users against economic losses caused by the situation that the public key addresses are tampered with and used illegally.
Owner:安徽中科晶格技术有限公司
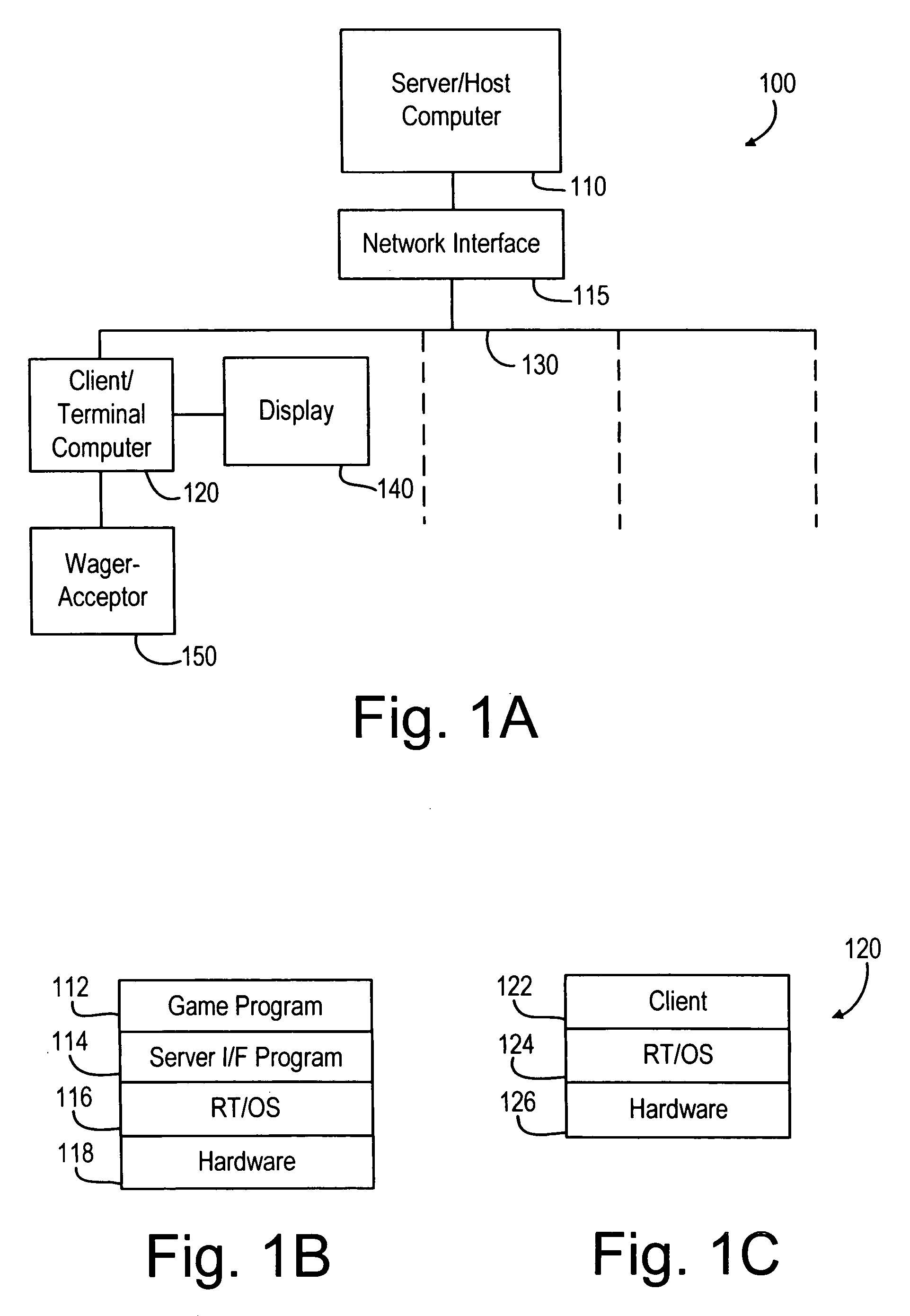
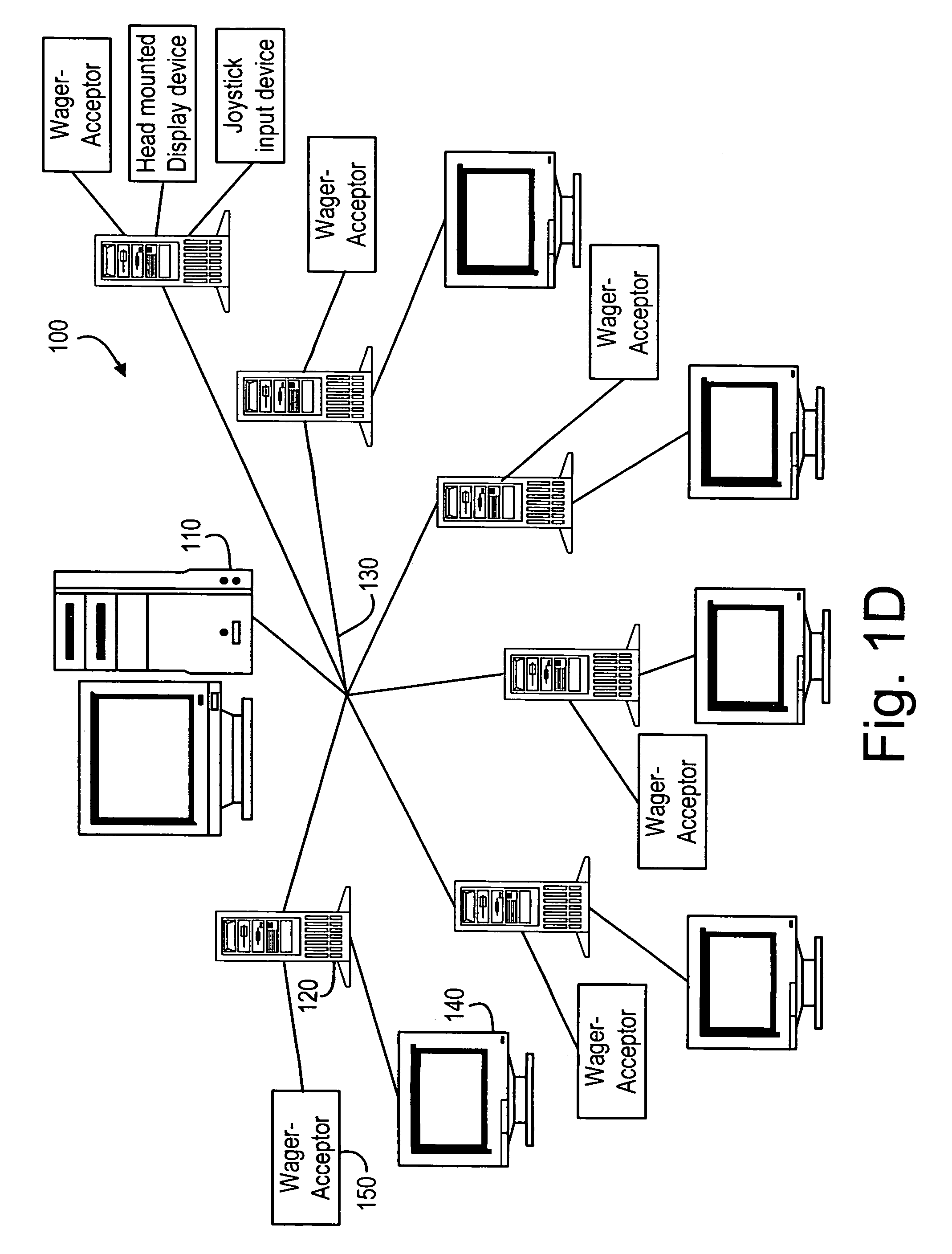
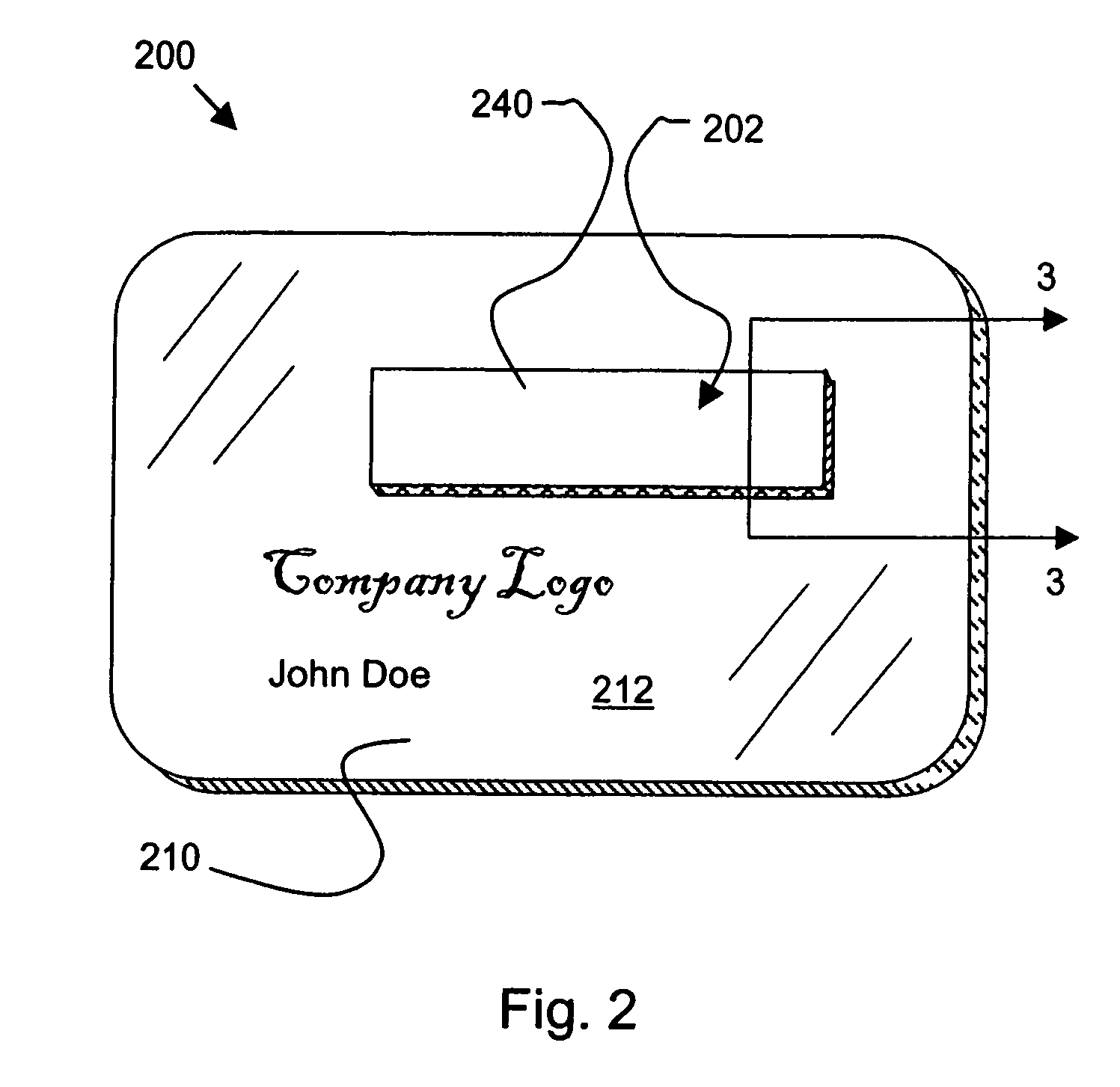
Slim terminal gaming system
InactiveUS7189161B1Improve tamper resistanceLow costData processing applicationsBoard gamesDisplay deviceComputer terminal
A computer gaming system and method of operation thereof are provided that both drastically reduce the cost of gaming stations and allow contemporaneous access to multiple game programs from a single gaming station. The computer gaming system of the present invention allows for transparent modifications and upgrades to the gaming programs by executing gaming programs on a server / host computer connected to a plurality of client / terminal computers via communication pathways. Each client / terminal computer comprises a client / terminal program that allows input and output streams of the gaming program executed on the server / host computer to be separated and redirected to the client / terminal computers. Since the gaming programs are executed entirely on the server / host computer, with only wagering input and display output operations being executed on the client / terminal computers, the cost of the hardware and software required for each client / terminal computer is greatly reduced. A patron of a client / terminal computer can access any of the gaming programs executed on the server / host computer. Modifications and upgrades of the gaming programs only need to be performed on the server / host computer. By using a stereo head-mounted display together with a joystick input device and wireless communication pathways, the present invention allows a patron to participate in a mobile gaming environment.
Owner:NEW MILLENIUM GAMING
Security label, secured article and method for making the label and article
InactiveUS20050230960A1Improve tamper resistanceReduces and minimizesStampsOther printing matterConfidentialityAdhesive
A tamper-resistant secure label, article and associated method. A label for overlying information comprises an adhesive layer for adhering the label to a substrate. The adhesive layer includes a structural adhesive that ensures that an initial removal precludes re-adhering using the adhesive layer. The label may further include an obscuring layer to selectively block visual access to the information and maintain the confidentiality of the information until the obscuring layer is removed.
Owner:AVERY DENNISON CORP
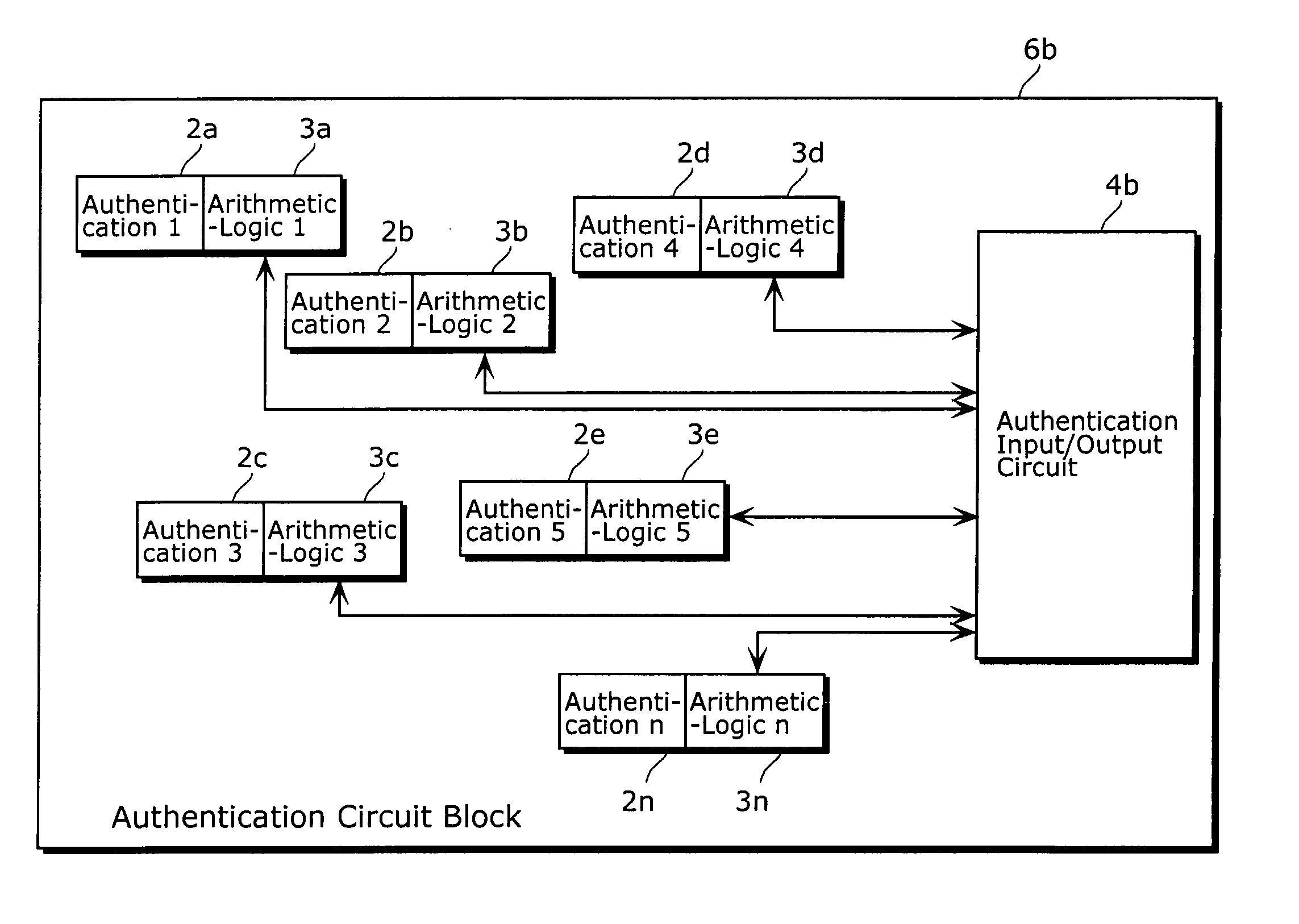
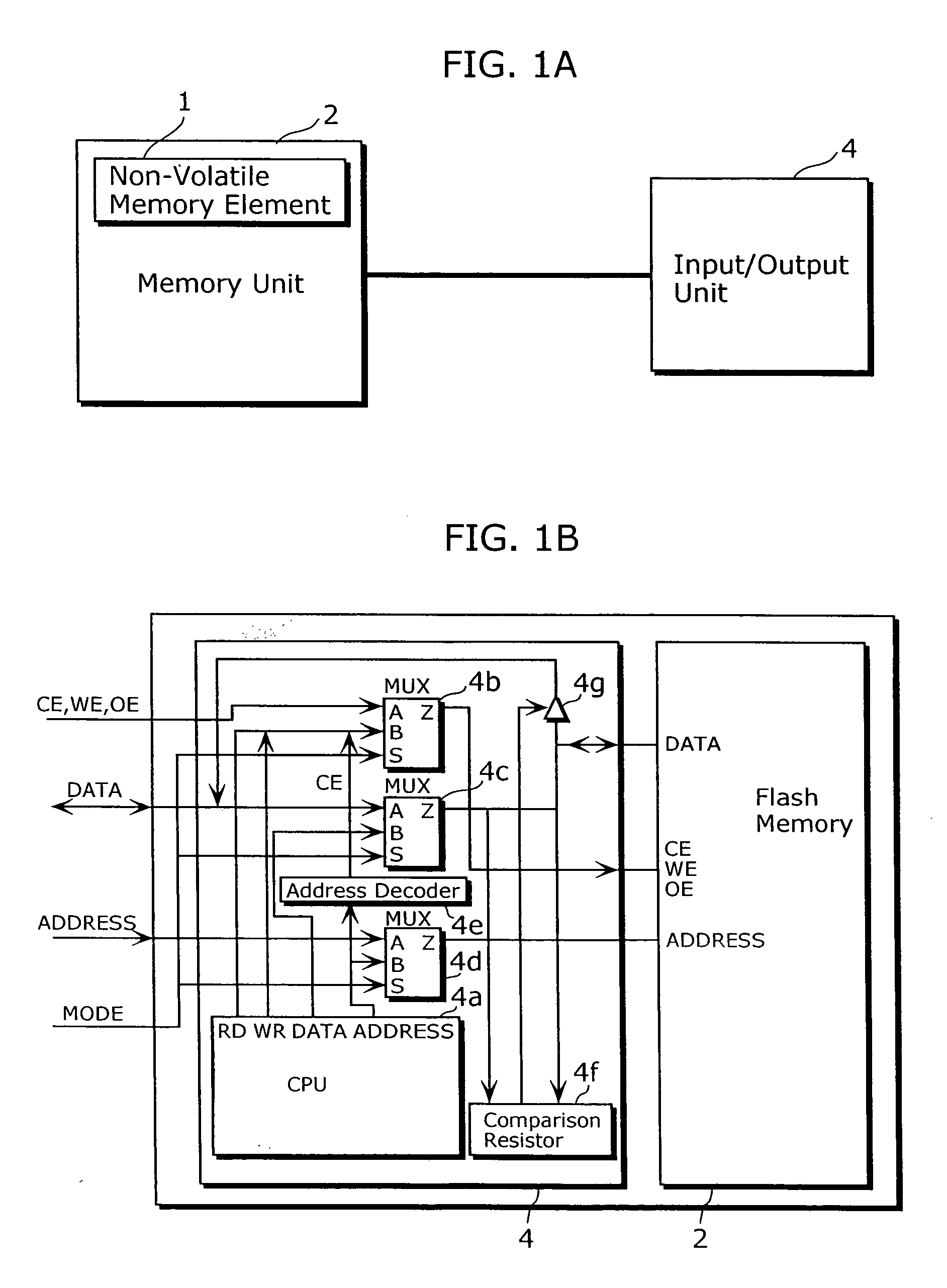
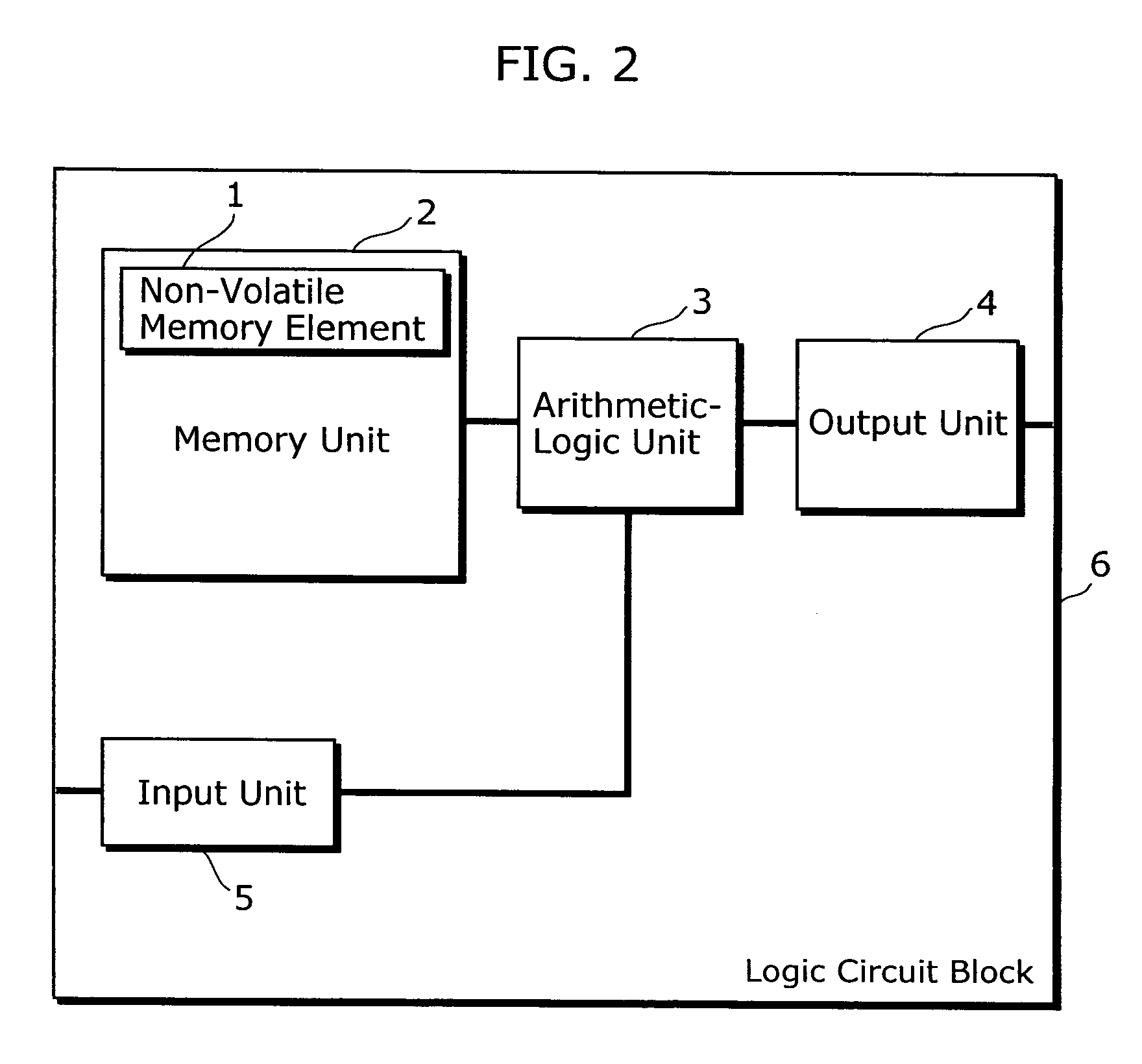
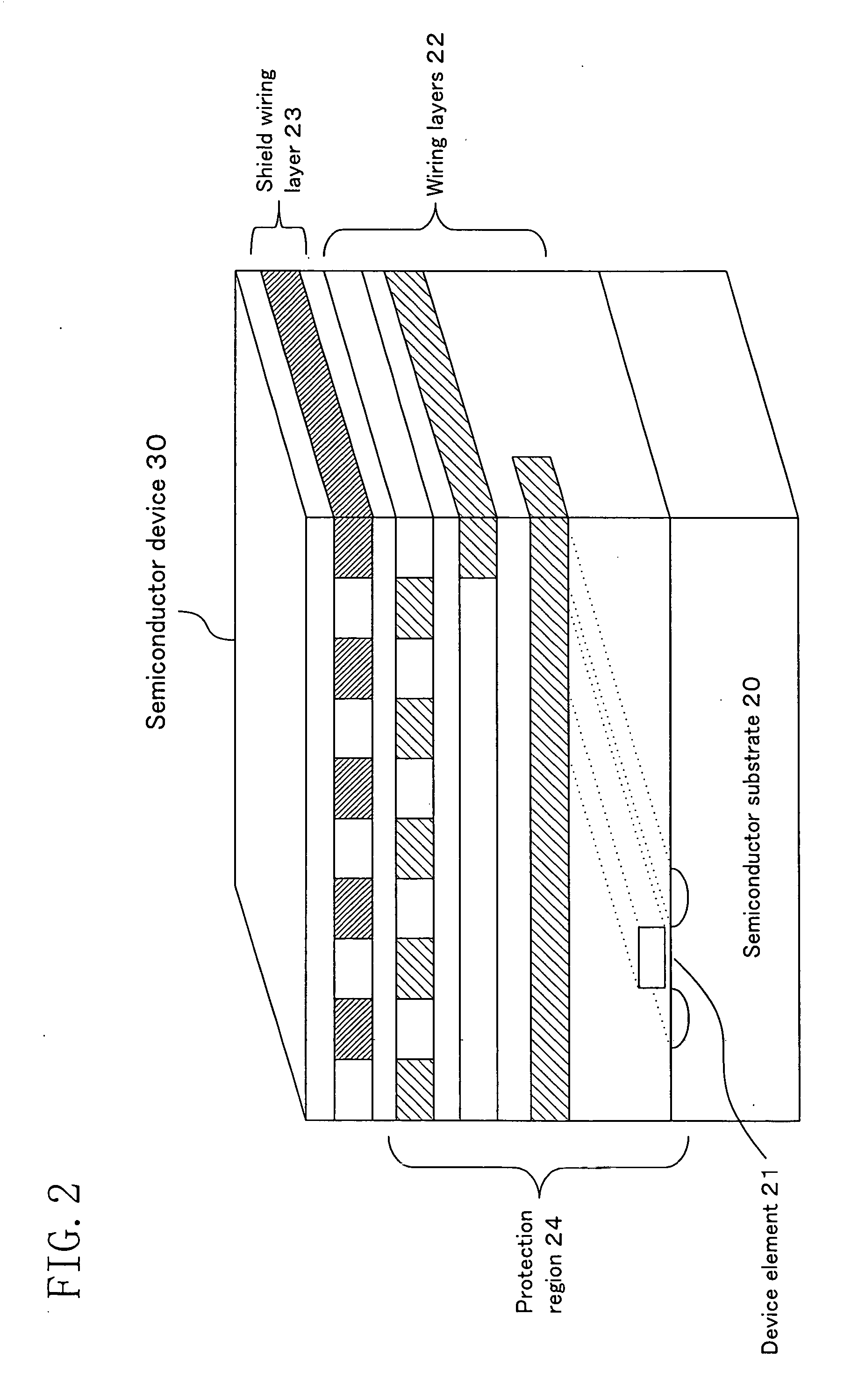
Semiconductor device
InactiveUS20060095975A1Reduce riskIncrease speedDigital data processing detailsUser identity/authority verificationArithmetic logic unitDevice material
A semiconductor device of the present invention includes: at least one of non-volatile memory unit operable to store data; at least one of an arithmetic-logic unit operable to perform an arithmetic-logic operation using data which is stored in the memory unit and data that is inputted from outside; and an output unit operable to output a result of arithmetic-logic operation performed by the arithmetic-logic unit; wherein the memory unit, the arithmetic-logic unit, and the output unit are included in a functional block, and an output line of each of the memory unit is connected only to one of at least one of the arithmetic-logic unit.
Owner:PANASONIC CORP
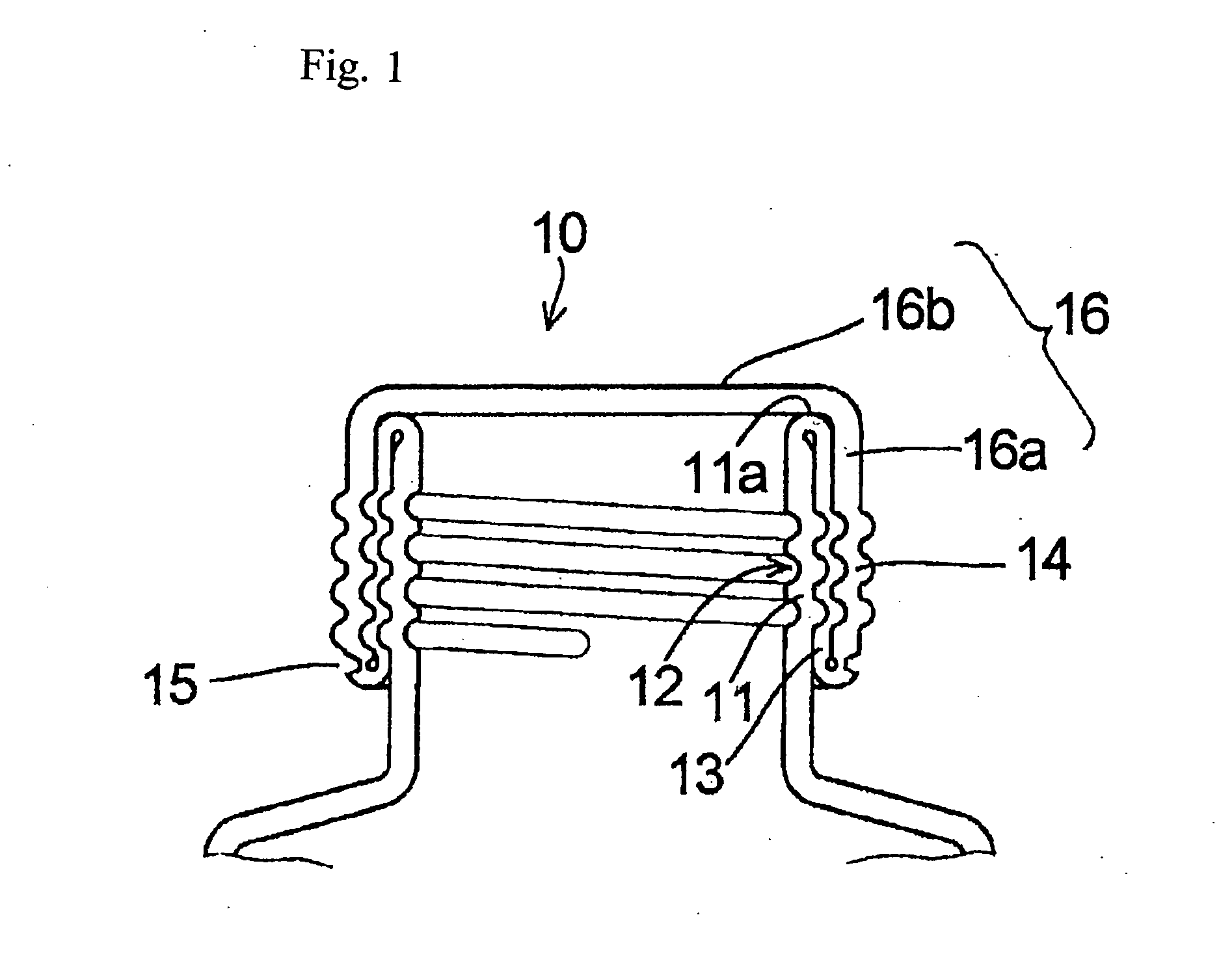
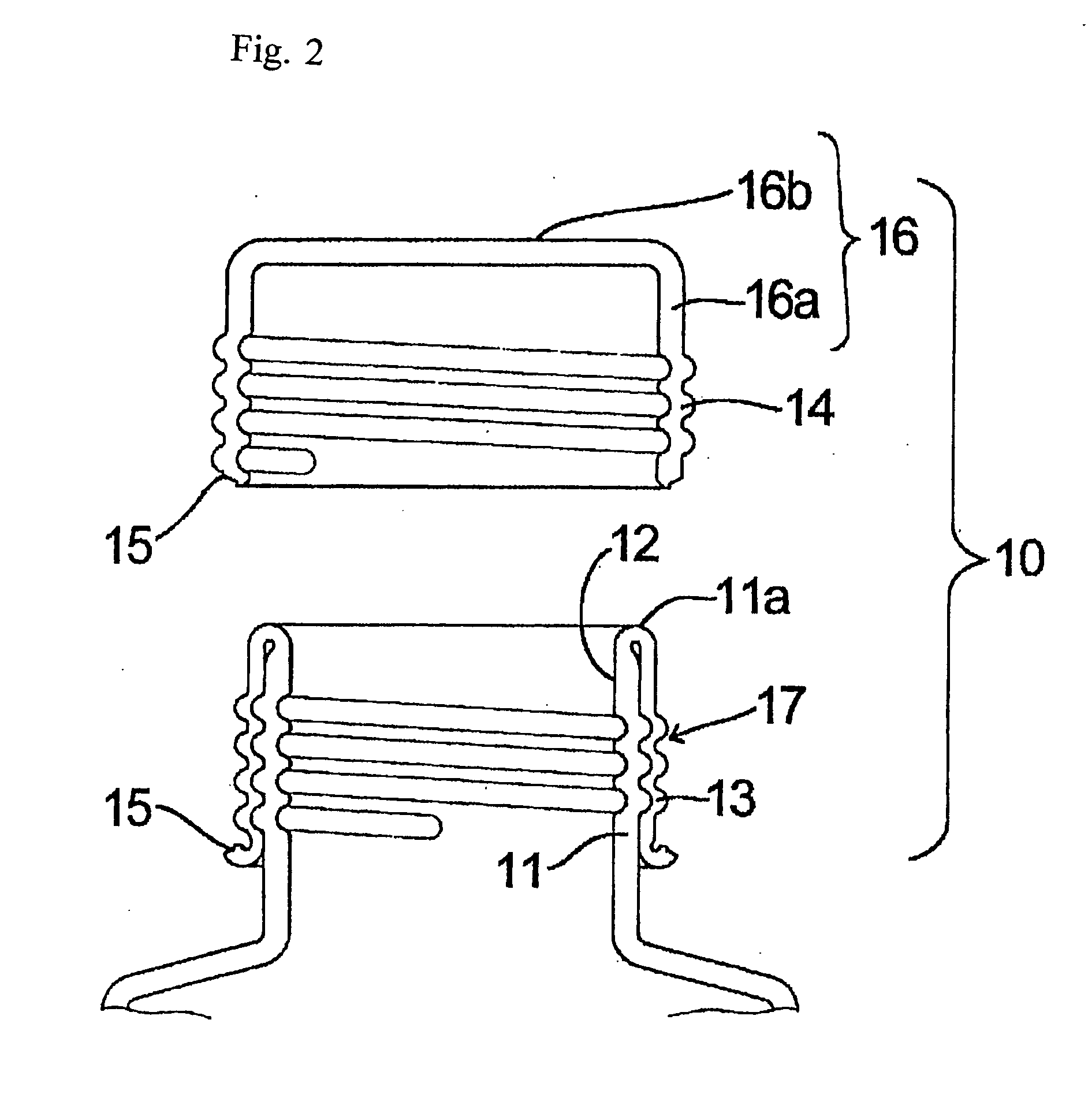
Dispensing Utensil
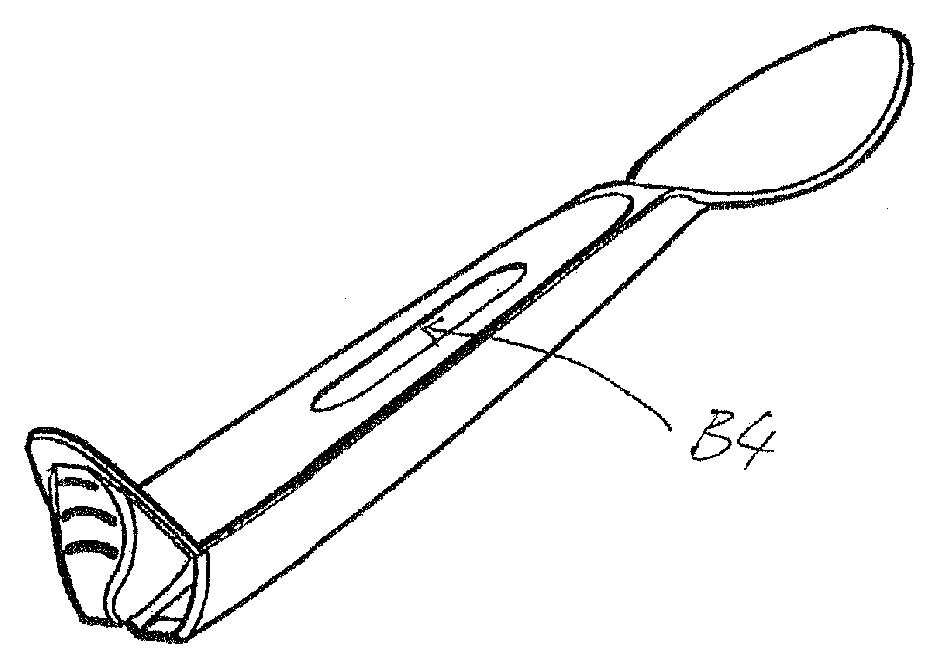
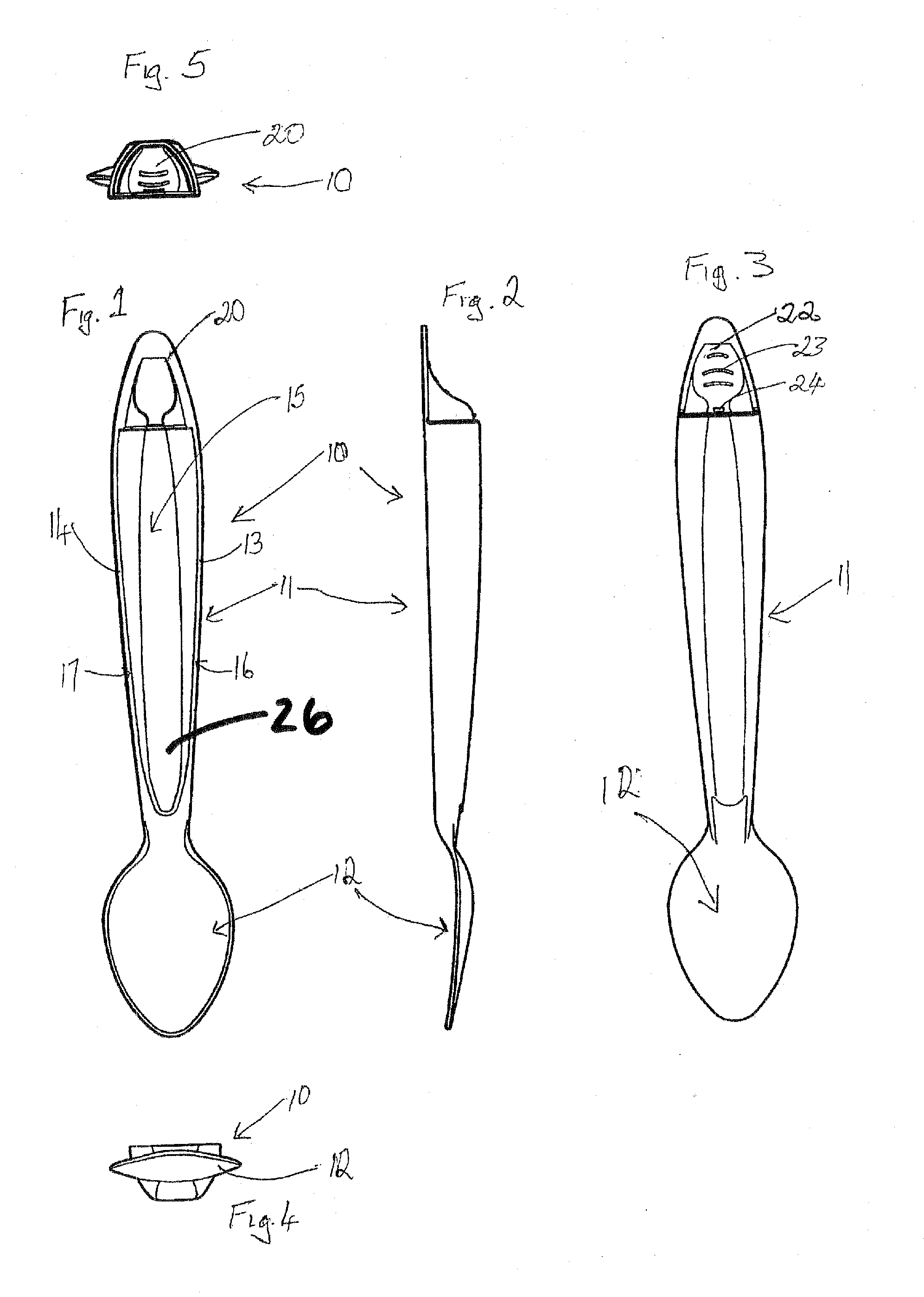
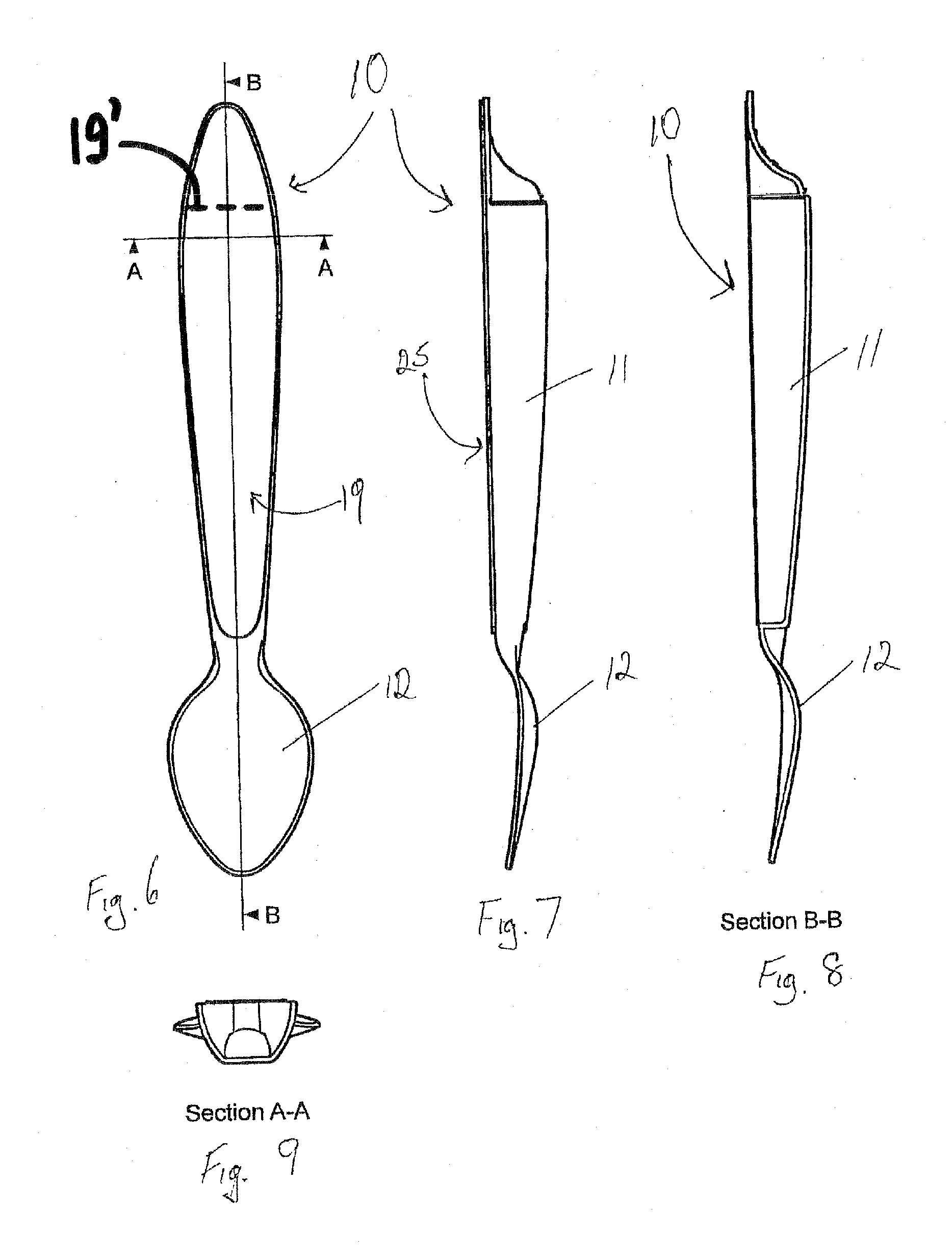
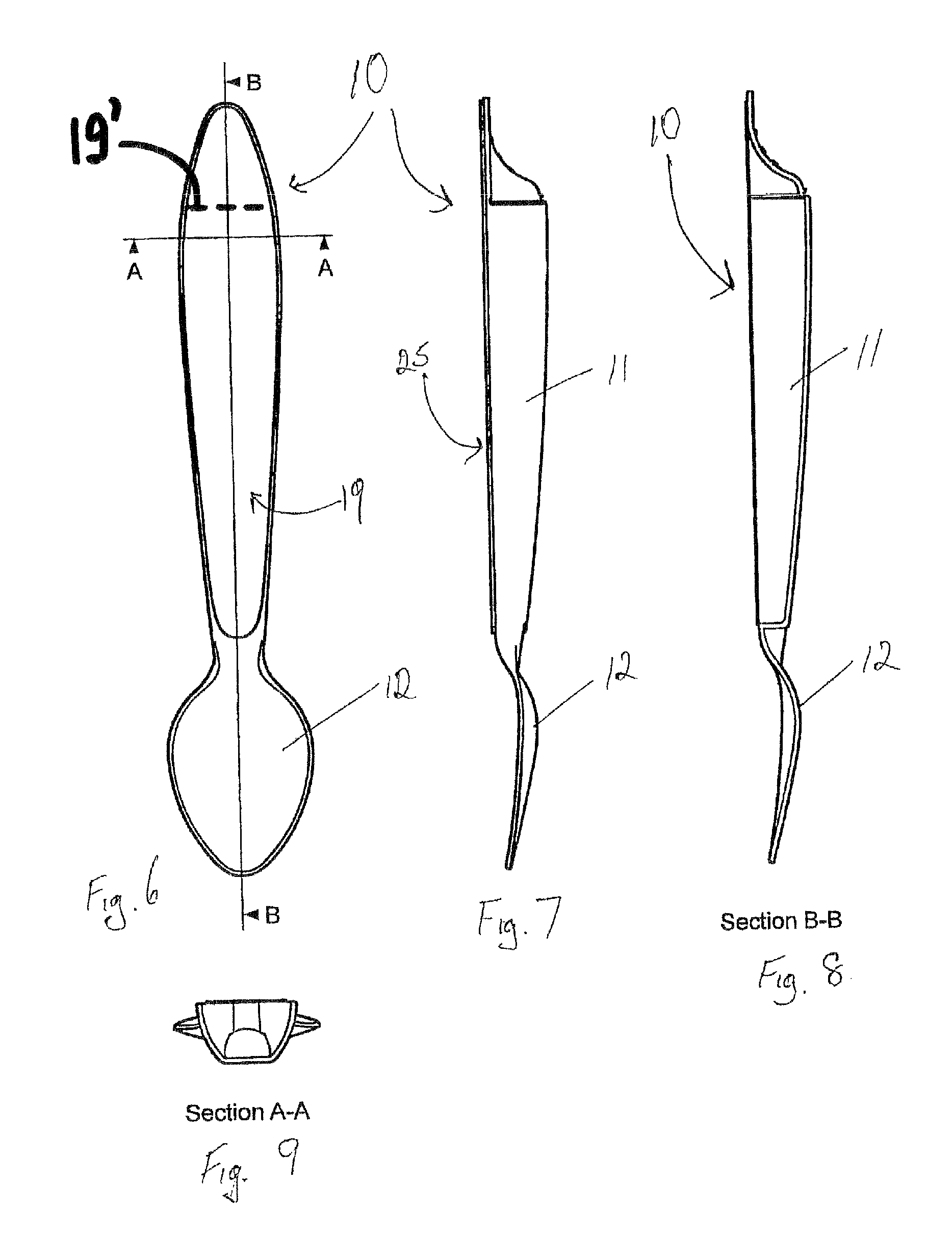
InactiveUS20080072432A1Easy to useReduce litteringSmall article dispensingPortable power-driven toolsMechanical engineeringEngineering
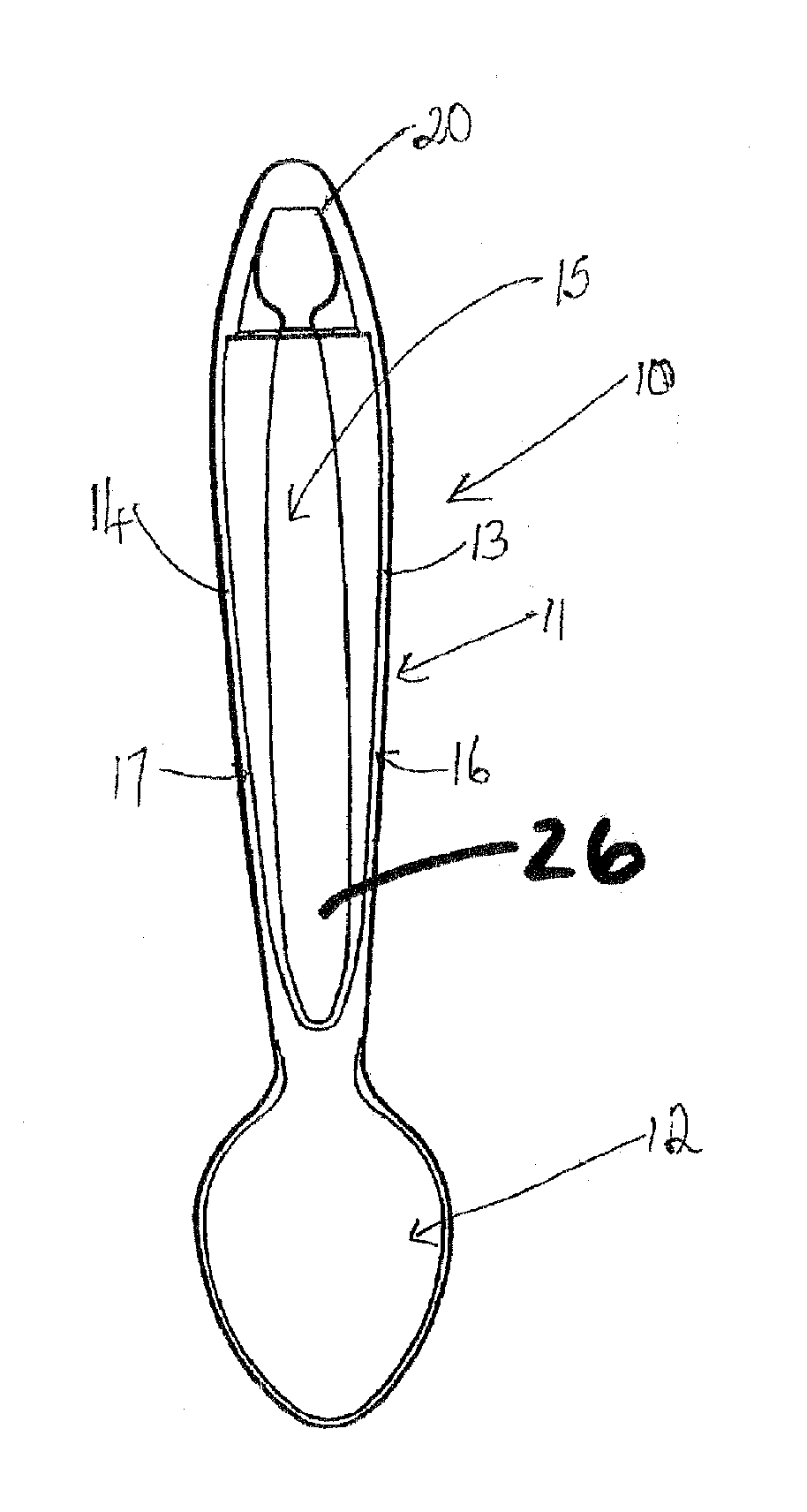
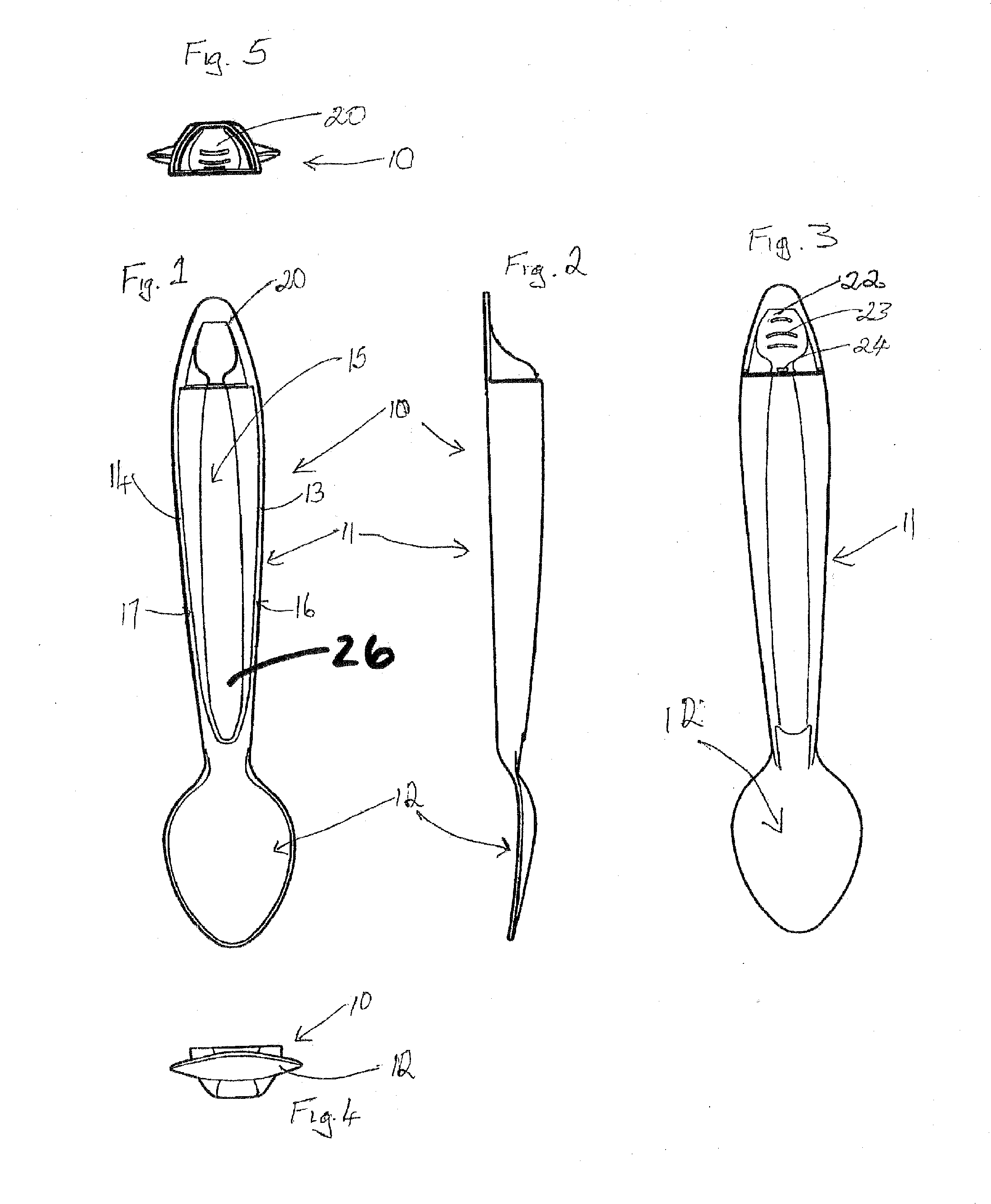
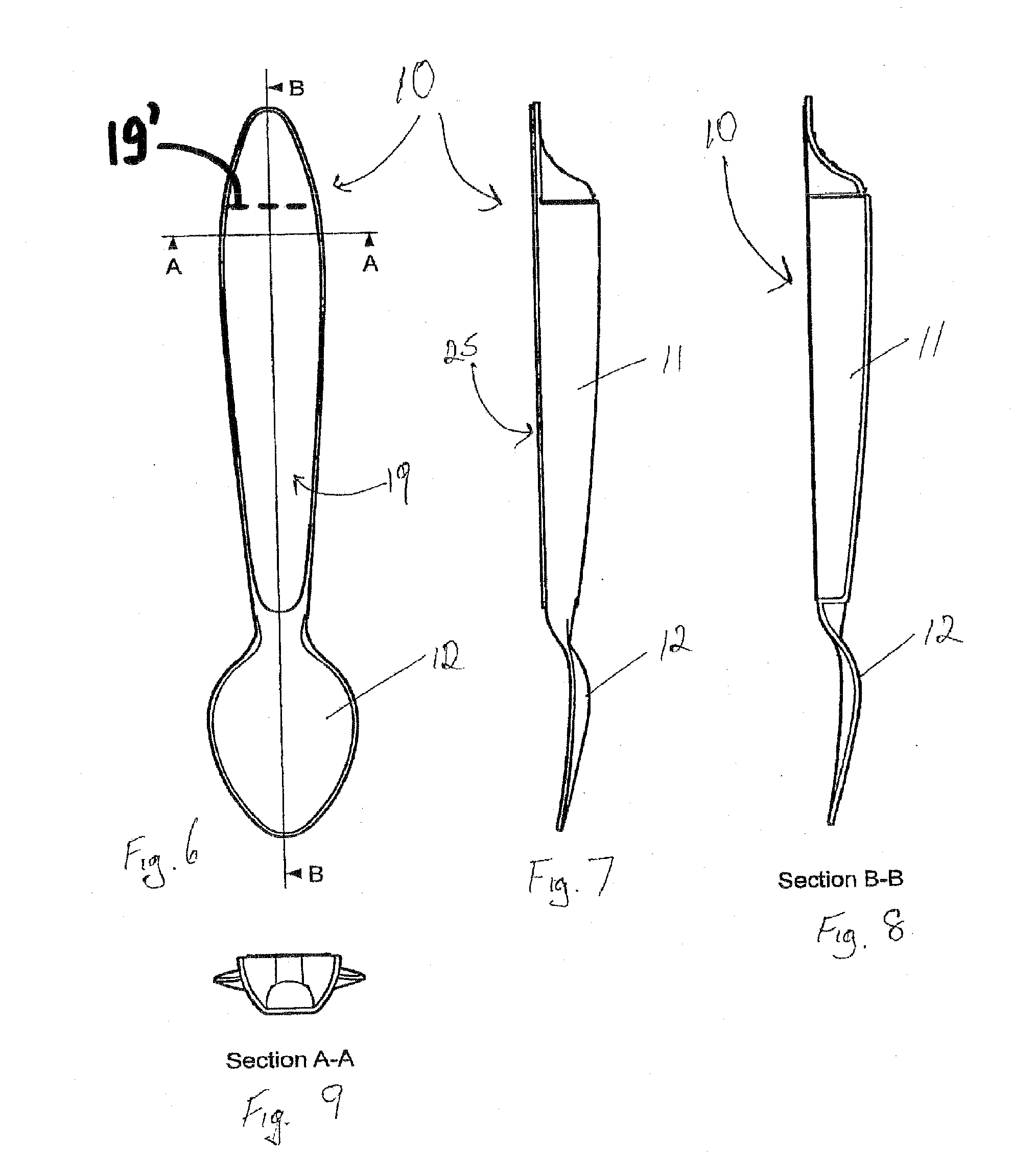
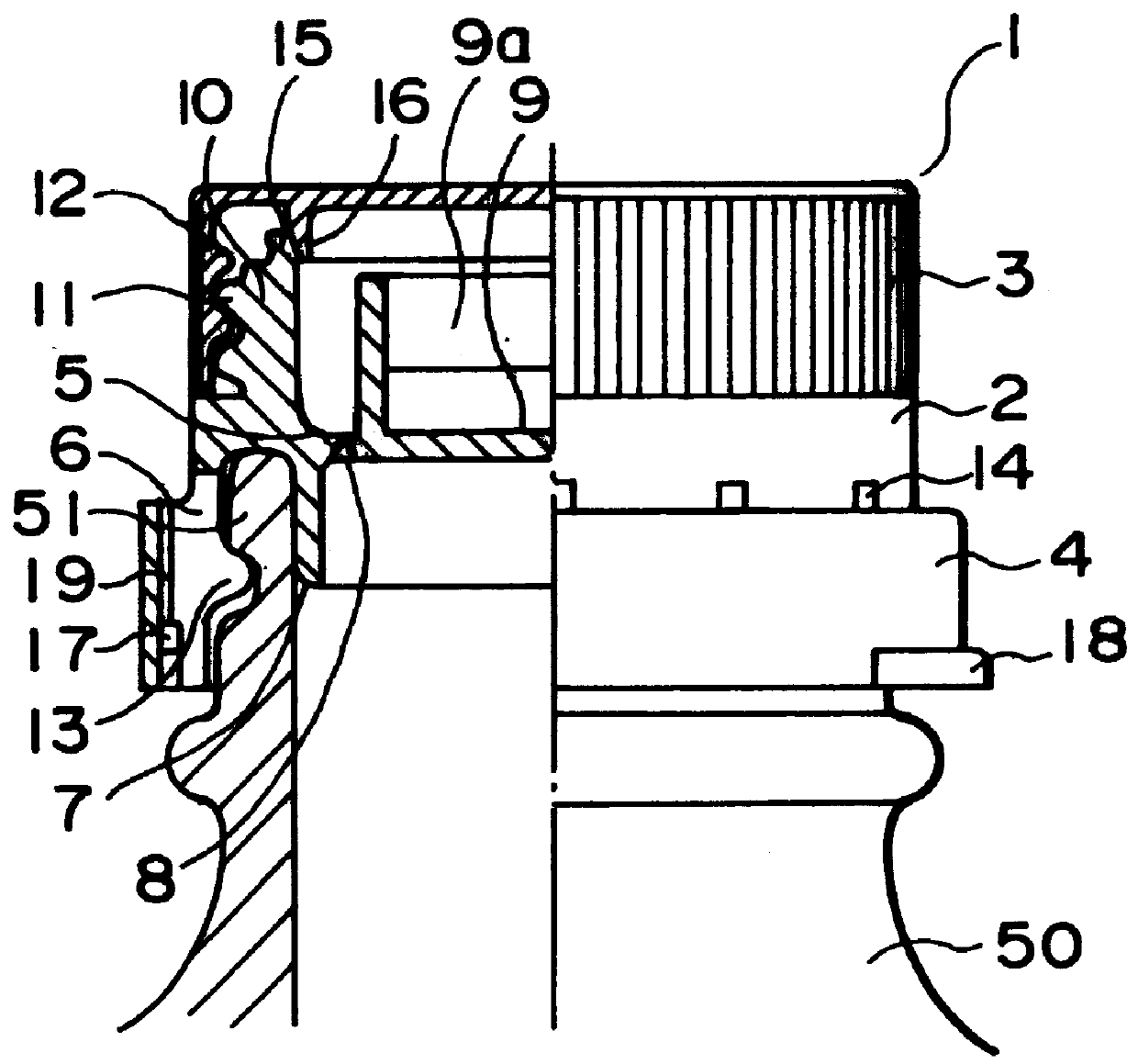
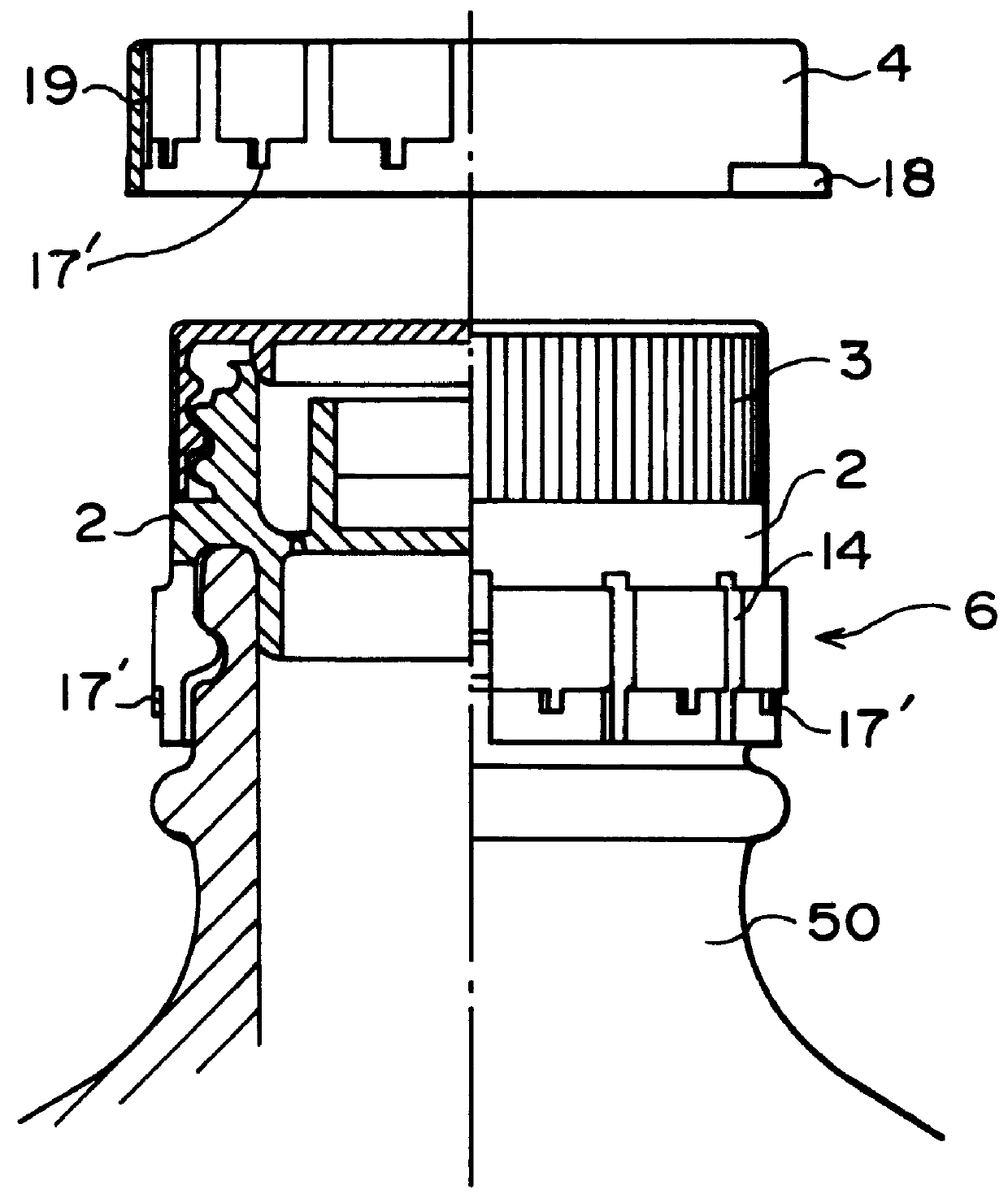
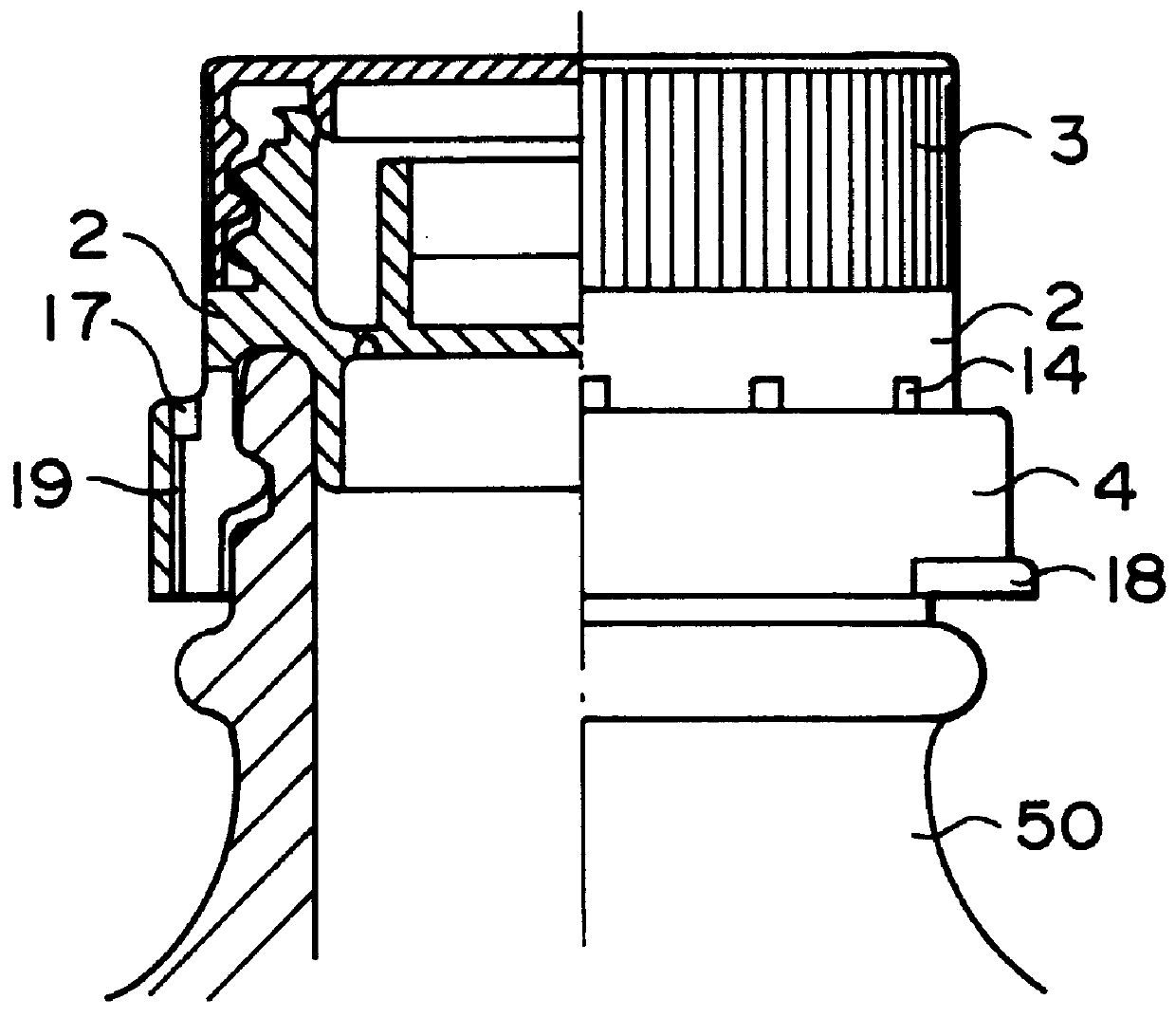
A dispensing utensil 10 comprising: a handle portion 11; an implement portion 12; a cavity 15 for storing dispensable contents, the cavity 15 defined by a first wall means 13, 14 and a second wall means 19 closing the cavity 15; characterised in that a first portion 20 of the first wall means 13, 14 is openable about a hinge formed by the second wall means 19, thereby allowing the contents to be dispensed.
Owner:SANDS INNOVATIONS
Container sealing structure, container with the sealing structure, and method of manufacturing the sealing structure
InactiveUS20050205575A1Easily breakableImprove tamper resistanceCapsThreaded caps applicationMechanical engineering
Owner:TOYO SEIKAN KAISHA LTD
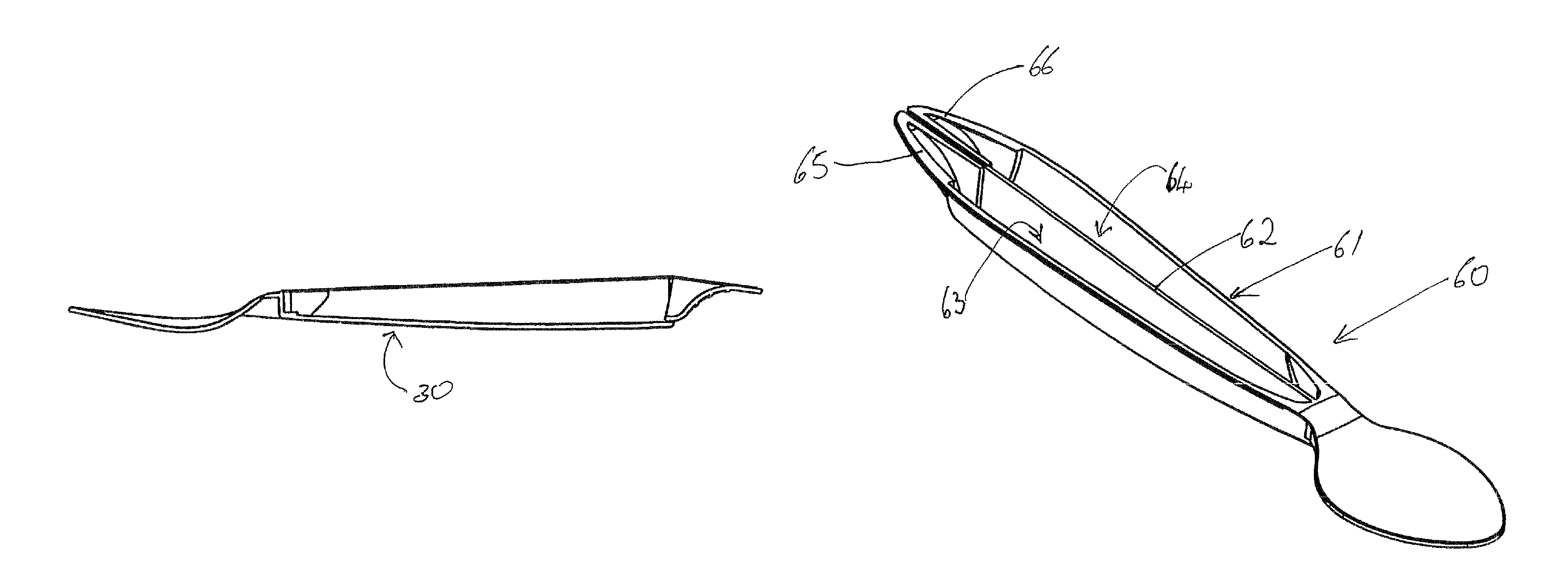
Dispensing utensil
InactiveUS8091242B2Easy to useReduce litteringSmall article dispensingContainer/bottle contructionEngineeringMechanical engineering
A dispensing utensil 10 comprising: a handle portion 11 having a first end portion and a second end portion and a frangible connection intermediate the first and second end portions; an implement portion 12; a cavity 15 for storing dispensable contents, the cavity 15 defined by a first wall means 13, 14 and a second wall means 19 closing the cavity 15; characterized in that a first portion 20 of the first wall means 13, 14 is openable about a hinge formed by the second wall means 19, thereby allowing the contents to be dispensed.
Owner:SANDS INNOVATIONS
Lock cylinder fixed type crossed-shaped mechanical antitheft lock matched with fingerprint lock
ActiveCN106368511APreserve unique propertiesImprove performance indicatorsBuilding locksIndividual entry/exit registersEngineeringCam
The invention discloses a lock cylinder fixed type cross-shaped mechanical antitheft lock matched with a fingerprint lock and relates to the field of antitheft locks. By means of the characteristic that the operation manner that a key can only be inserted and pulled and unlocking can be conducted as long as a handle is rotated of the mechanical antitheft lock is right the same as the operation manner of the fingerprint lock is utilized, the scheme of matched usage of the mechanical antitheft lock and the fingerprint lock is put forwards. A cam mechanism of a special structure and double clutches running independently are mainly adopted so that fingerprint recognition unlocking, key unlocking and locking operation can be completed through the same handle, wherein the cam mechanism is mainly composed of a torque limiter, a driven ring, a cam ring and a stirring wheel in a combined manner, engagement and disengagement of the auxiliary clutch are completed through key inserting and pulling, and the main clutch and the auxiliary clutch are relatively independent and do not interfere with each other; and therefore convenience of the fingerprint lock is maintained in the whole set of lock, and meanwhile the beneficial effects that technical opening, violent opening and damage are prevented, the handle can idle, and a main lock plunger, a spring bolt and a lock body are movably connected in an external hanging manner of the mechanical antitheft lock are achieved.
Owner:BEIHUA UNIV
Method of generating program, information processing device and microcomputer
InactiveUS20080271001A1Improve developmentAvoid attackInternal/peripheral component protectionProgram controlSyntaxTamper resistance
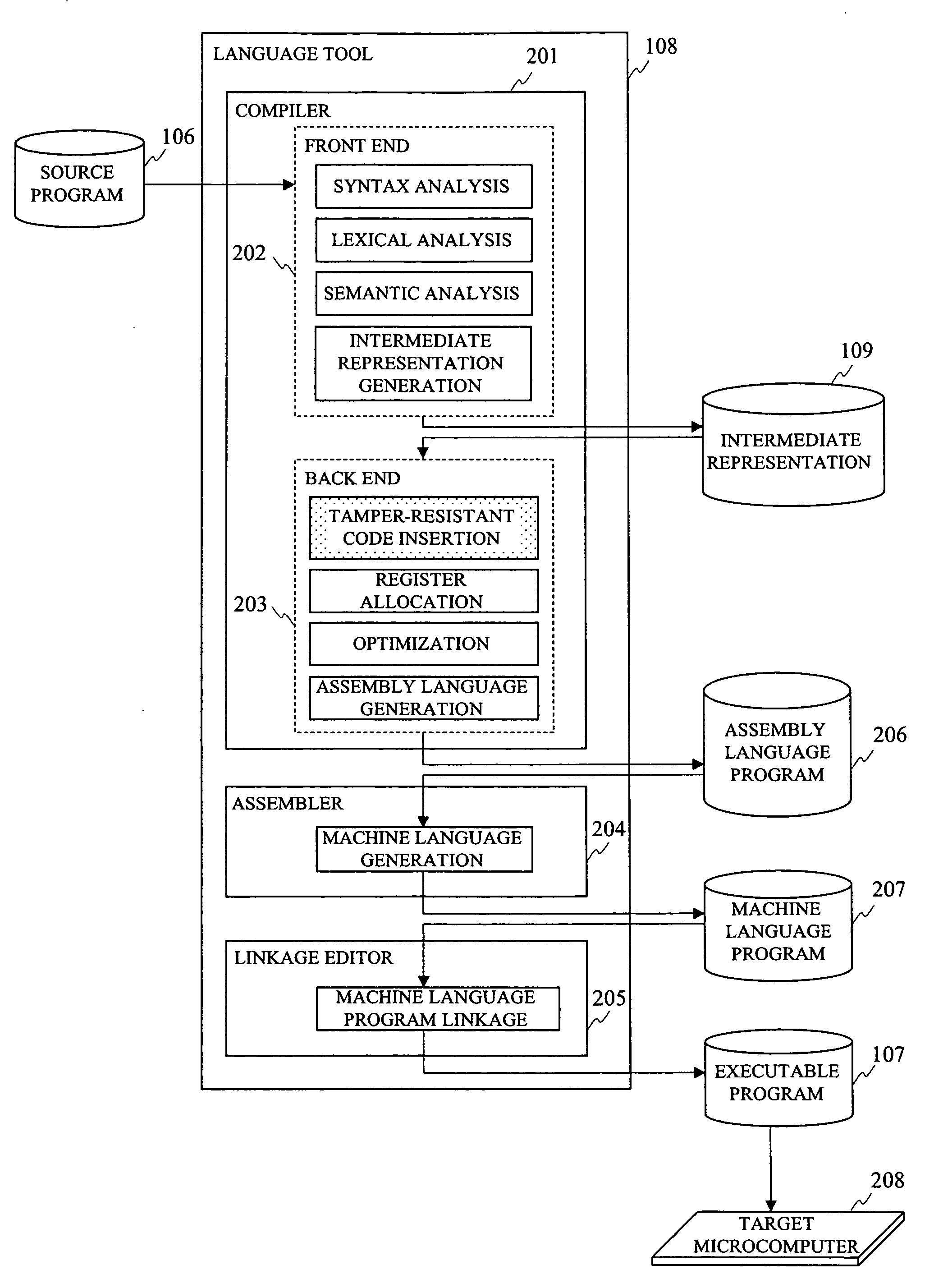
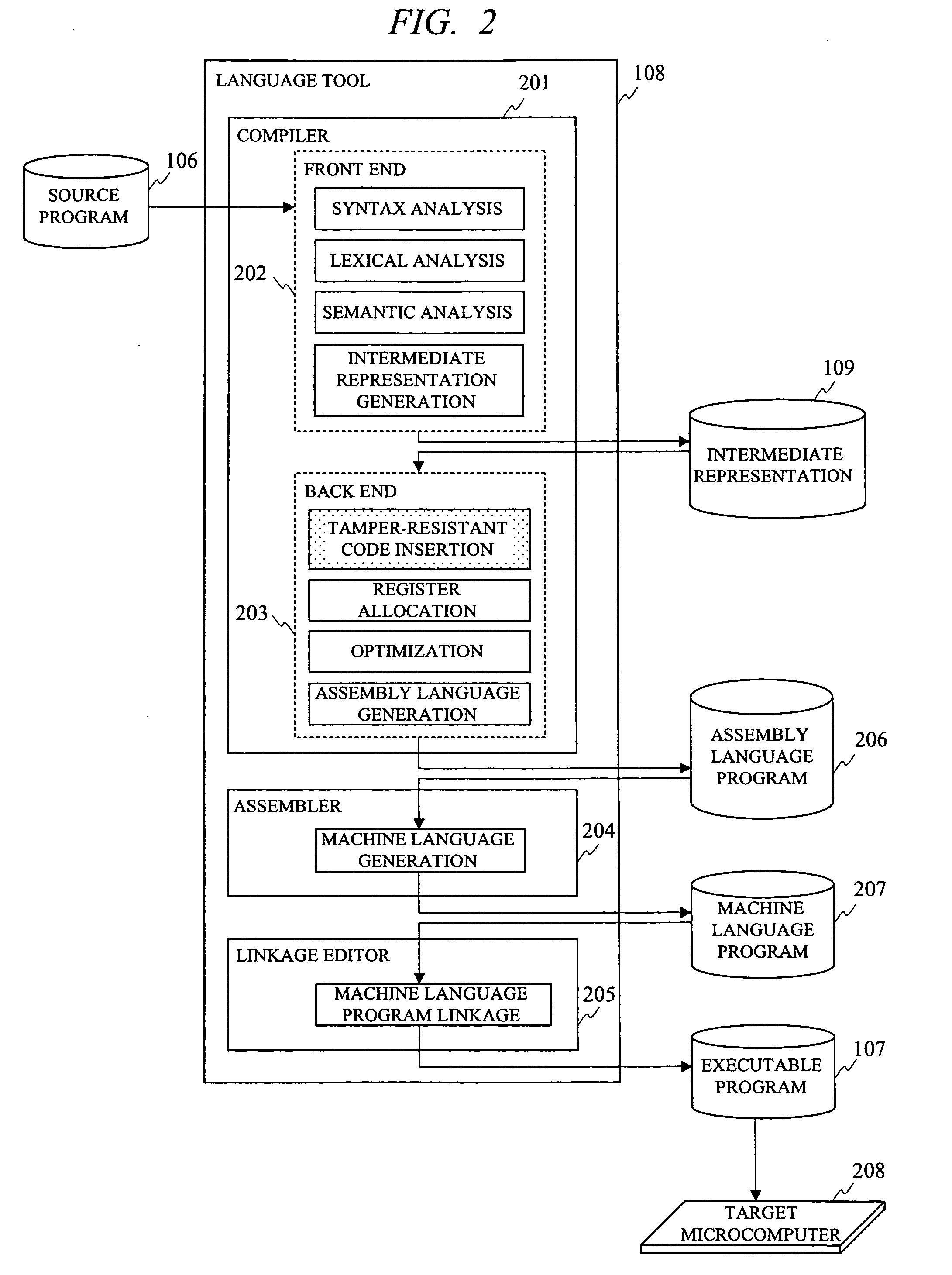
In programming in high-level language, a method of generating a program supporting external specifications for generating secure codes having high tamper-resistance and automatically generating an executable program having tamper-resistance with regard to a portion designated by a user is provided. A syntax analysis step, an intermediate representation generation step, a register allocation step, an optimization processing step, an assembly language generation step, a machine language generation step and a machine language program linkage step are executed. And between finish of reading of the source program and generating the executable program, a tamper-resistant code insertion step of automatically generating a code having tamper-resistance coping with unjust analysis of an operation content of the executable program is executed to the source program, the intermediate representation, the assembly language program or the machine language program based on an instruction of a user.
Owner:RENESAS ELECTRONICS CORP
Mobile terminal, circuit board, circuit board design aiding apparatus and method, design aiding program, and storage medium having stored therein design aiding program
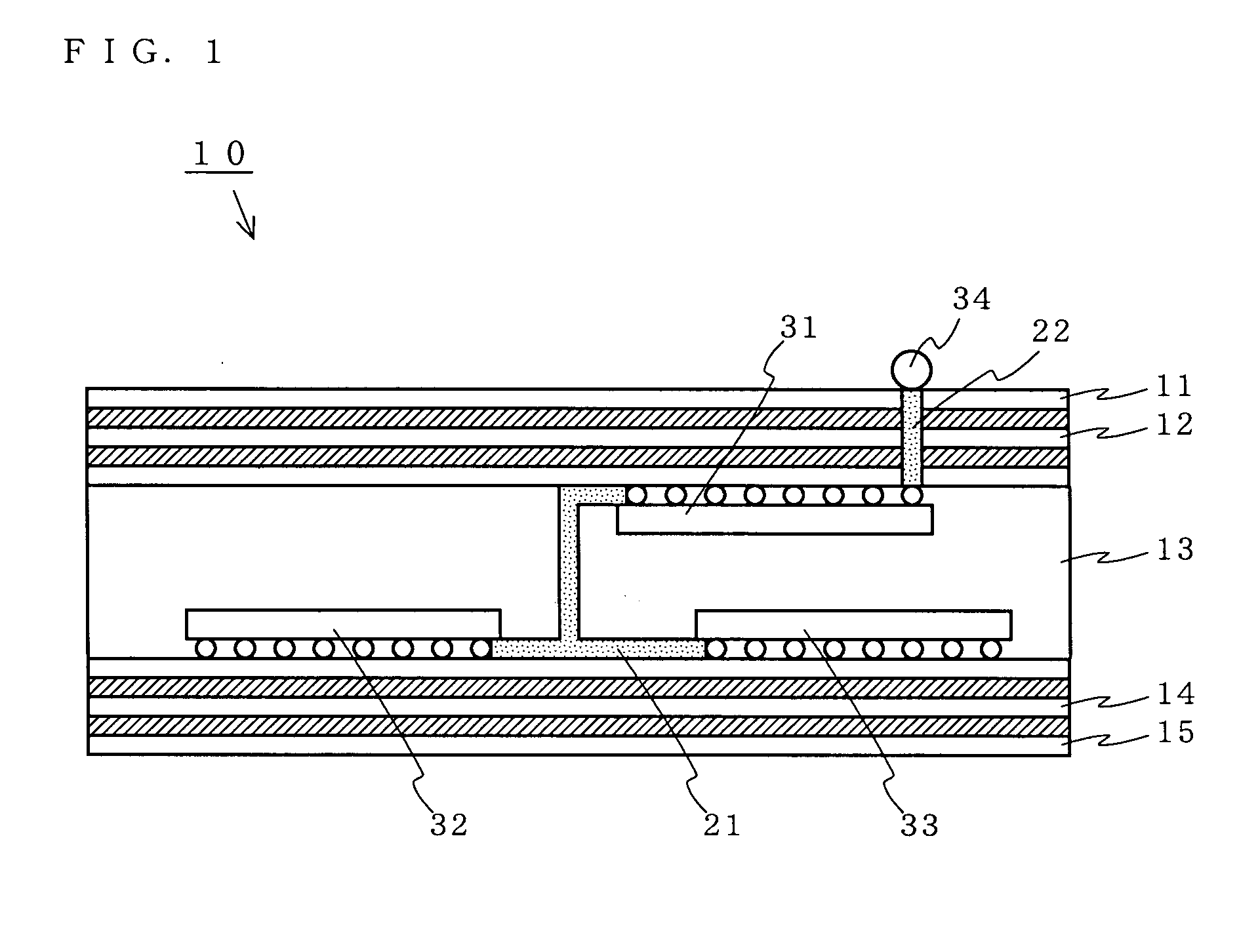
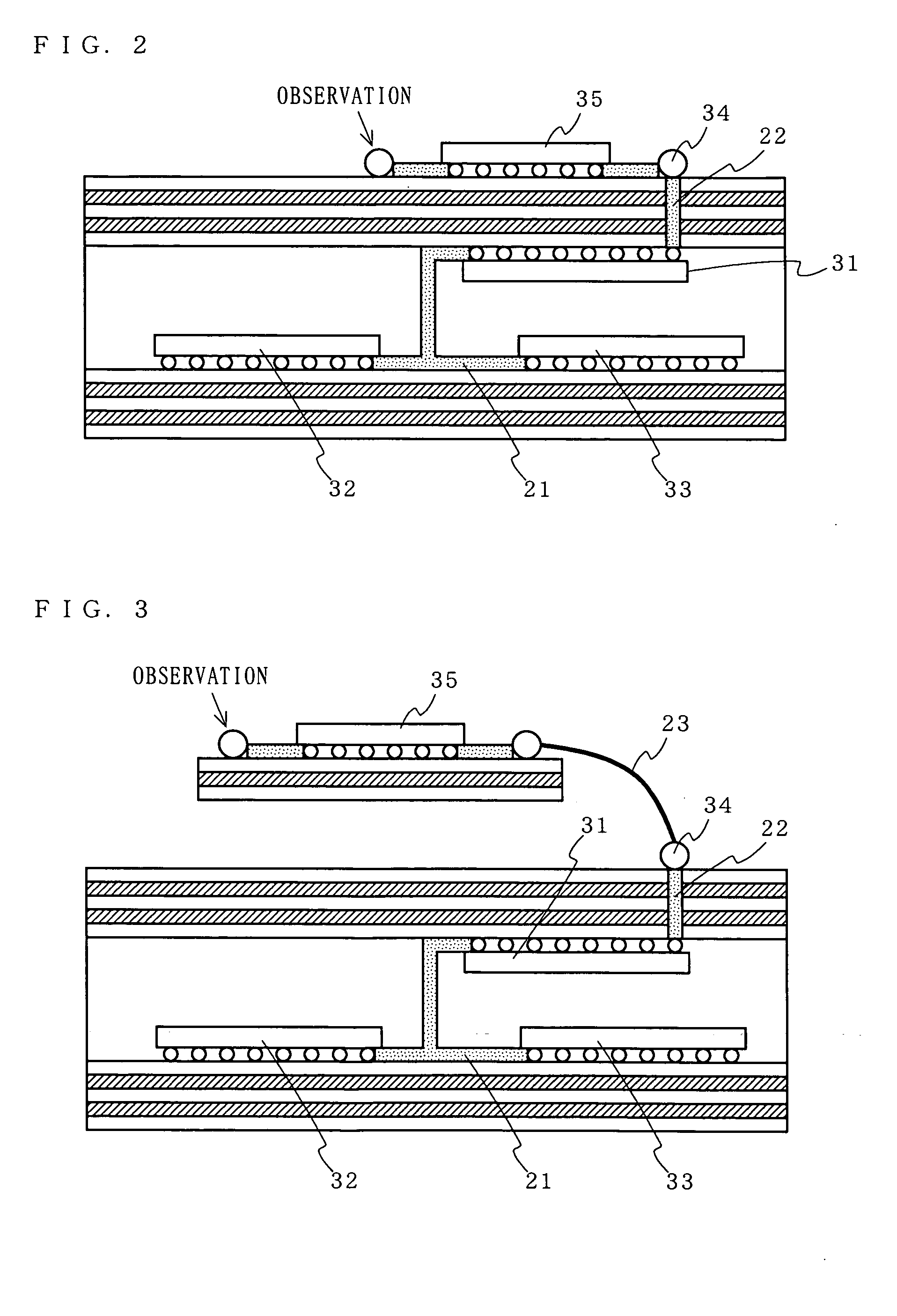
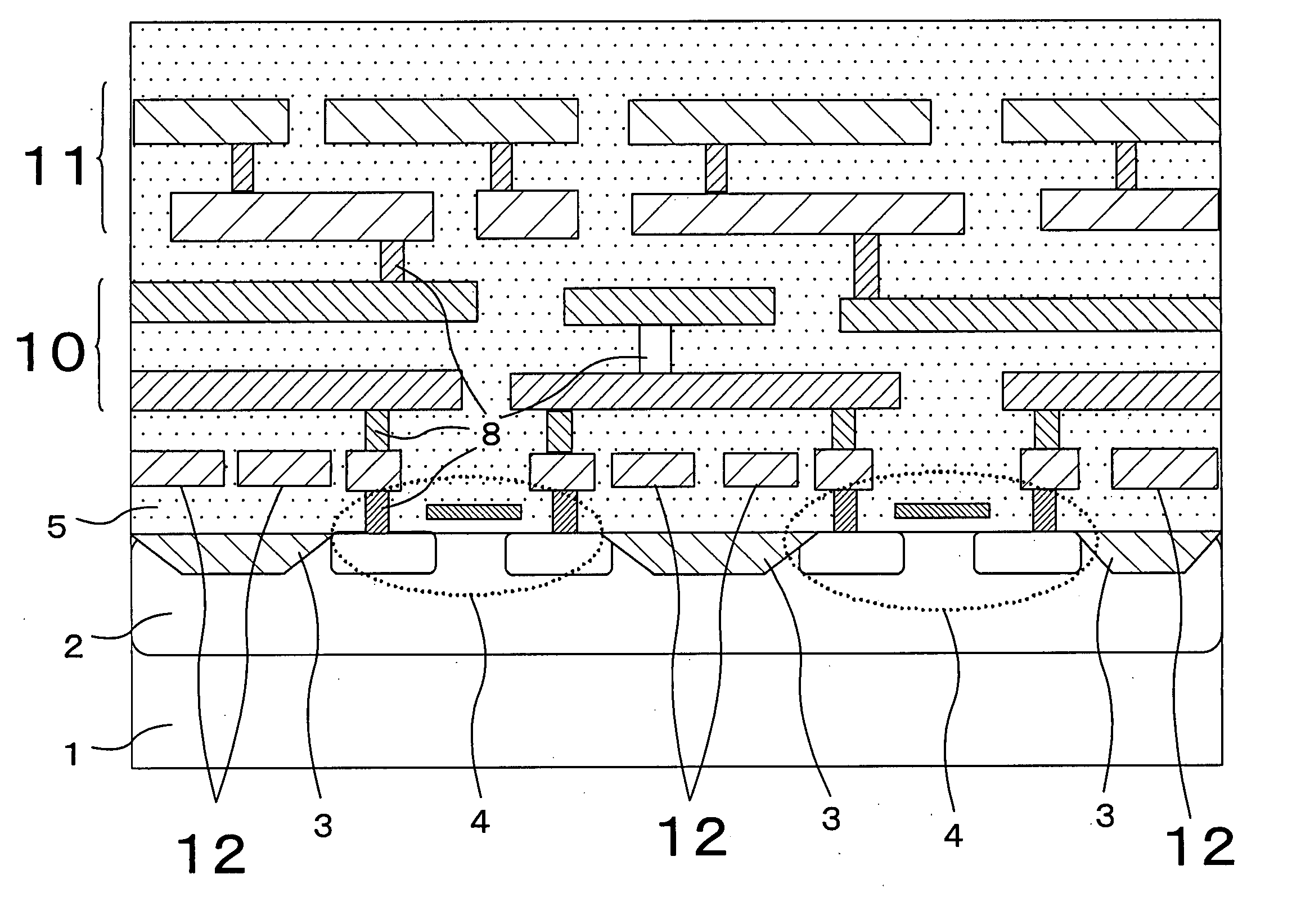
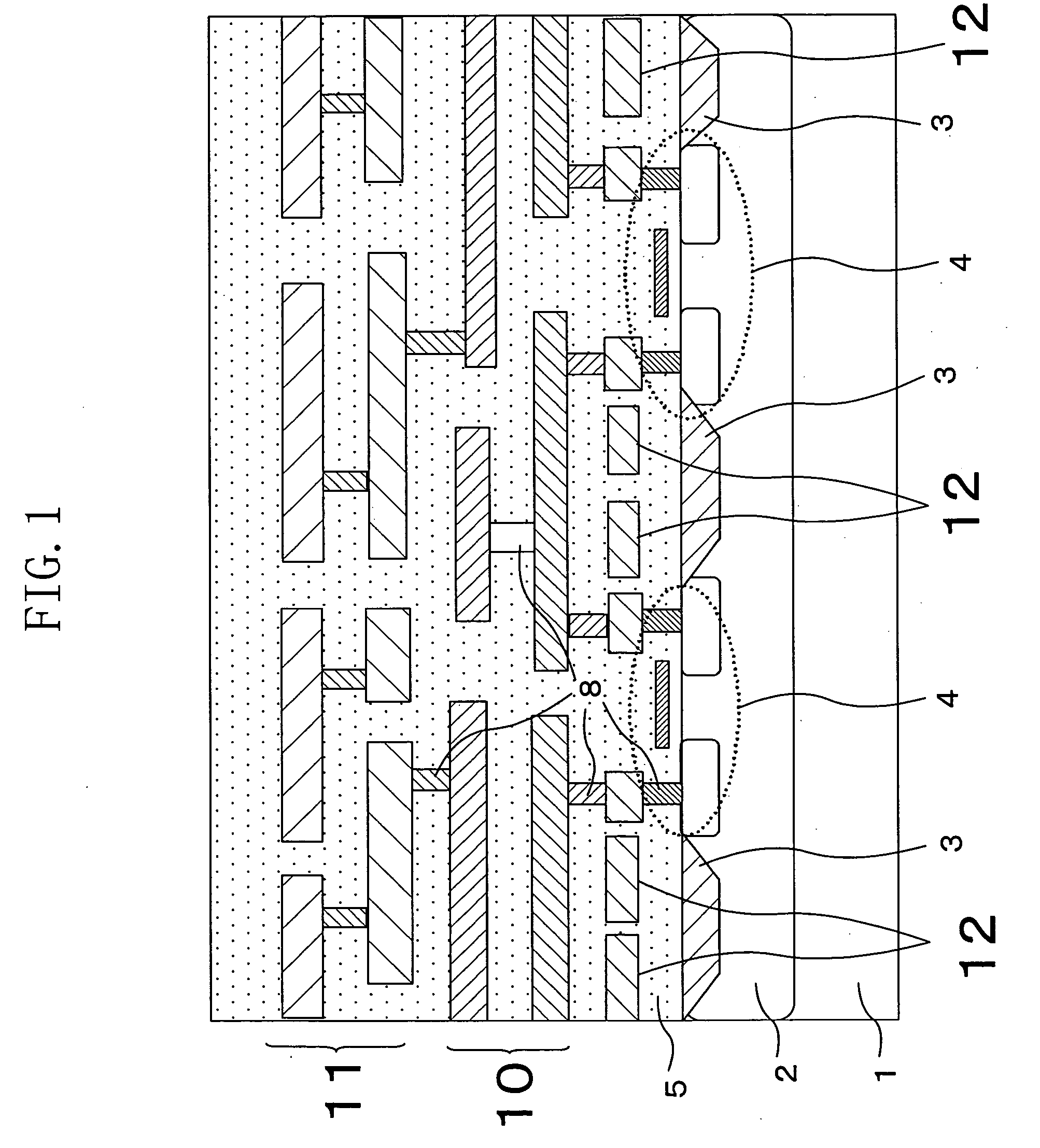
InactiveUS20050081049A1Improve tamper resistanceSolve the real problemSolid-state devicesAnalogue computers for electric apparatusThird partyTamper resistance
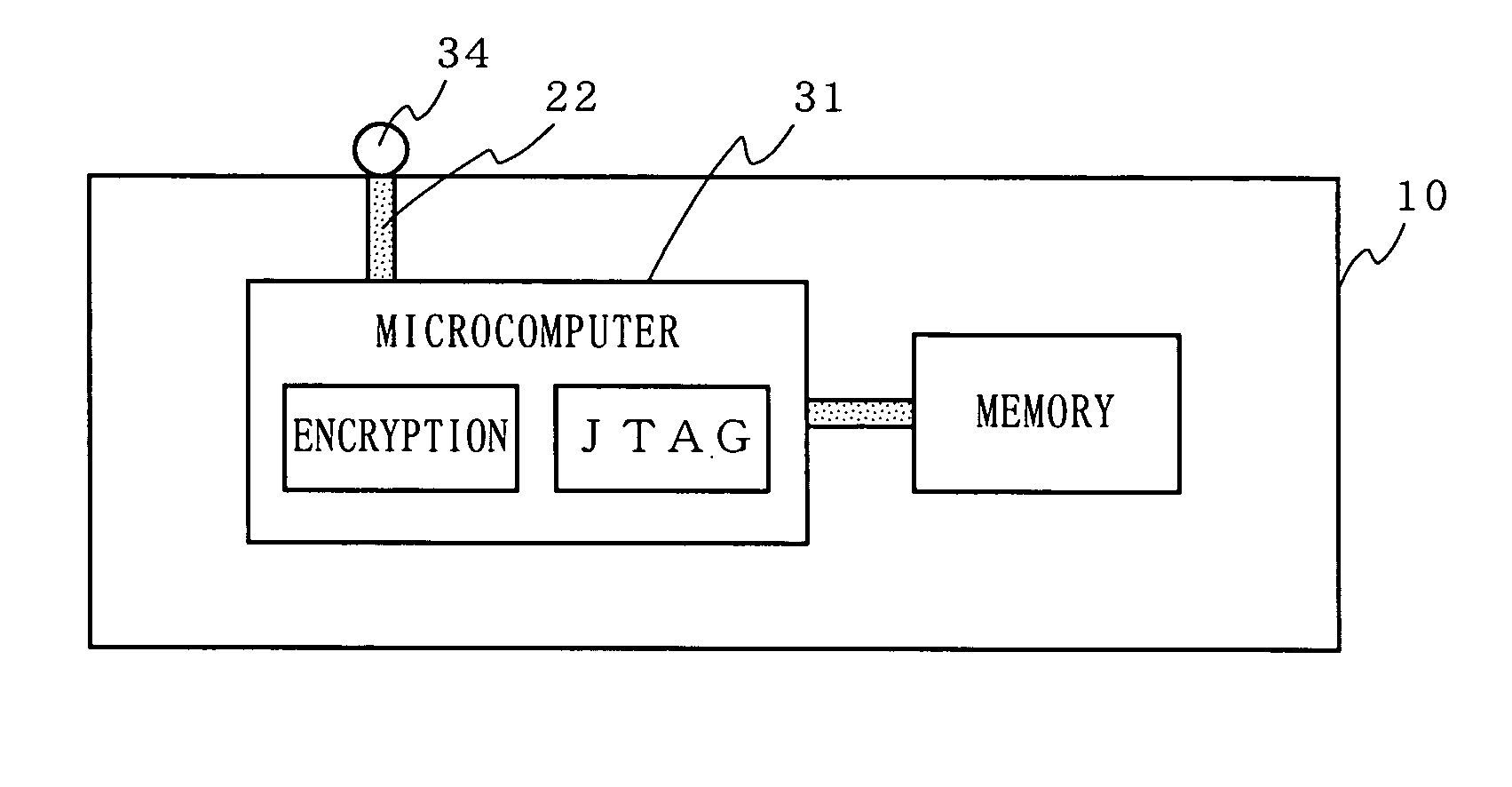
A circuit board is provided in which tamper resistance is improved by making probing by third parties difficult, while solving problems associated with the current techniques and manufacturing costs. A signal line through which a confidential signal requiring tamper resistance flows and components 32 and 33 connected to the signal line 21 by the terminals thereof, are laid out in a component-containing layer 13 of a circuit board 10. Only a confidential signal having been encrypted through a predetermined component 31 is outputted to an observation point 34 provided on a surface of the circuit board 10. External observation and control of the confidential signal is performed by decoding a cipher provided by the component 31 to the signal which appears at the observation point 34.
Owner:PANASONIC CORP
Tamper resistance of a digital data processing unit
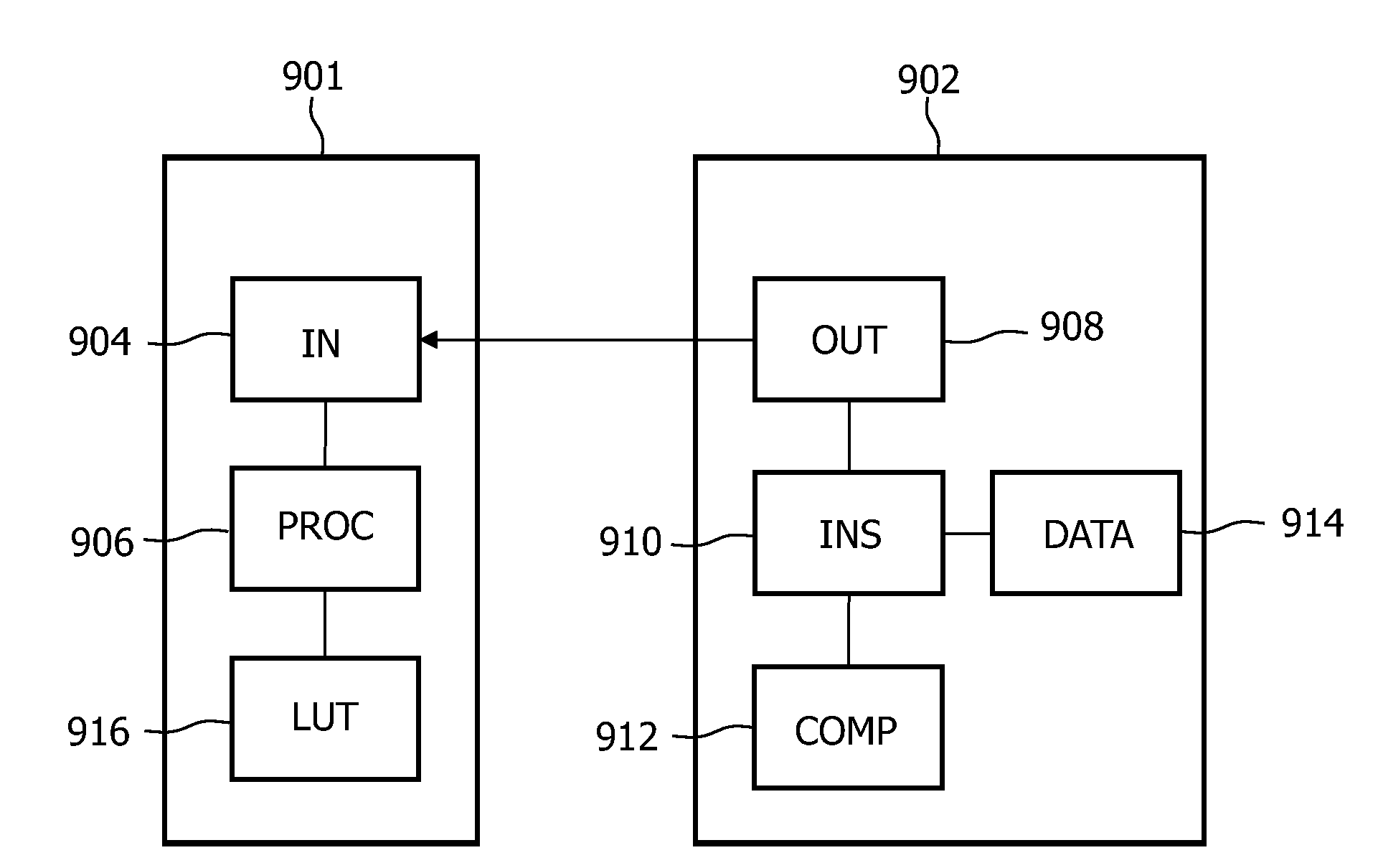
InactiveUS20090254759A1Efficient implementationImprove tamper resistanceEncryption apparatus with shift registers/memoriesVolume/mass flow measurementDigital dataTamper resistance
A system for increasing a tamper resistance of a digital data processing unit, comprises a first unit (901) comprising processing means (906) for processing the received digital data in dependence on values looked up in at least one look-up table (916) based on values in the received digital data. The system further comprises a second unit (902) comprising means (912) for computing at least one value for inclusion in the digital data causing the first unit (901) to look up at least one predetermined value in the look-up table (916) when processing the digital data. It comprises an inserter (910) for including the at least one value in the digital data, and an output (908) for transmitting the digital data to the first unit.
Owner:IRDETO ACCESS
Peer-to-peer network and node of a peer-to-peer network
ActiveUS20190089716A1Simple processImprove tamper resistanceSynchronisation receiversTime-division multiplexDistributed computingPeer-to-peer
The invention relates to a peer-to-peer network having at least one first node with a first clock module and part of a peer-to-peer application. Also included is at least one second node with a second clock module and part of the peer-to-peer application. At least one communication connection between the first node and the second node is establishable. The first node comprises at least one first synchronization clock module. The second node comprises at least one second synchronization clock module. At least the first synchronization clock module is configured to transmit at least one first synchronization clock message to the second synchronization clock module via the communication connection, the second synchronization clock module is configured to synchronize the clock signal of the second clock module to the clock signal of the first clock module based on synchronization information included in the first synchronization clock message.
Owner:INNOGY INNOVATION GMBH
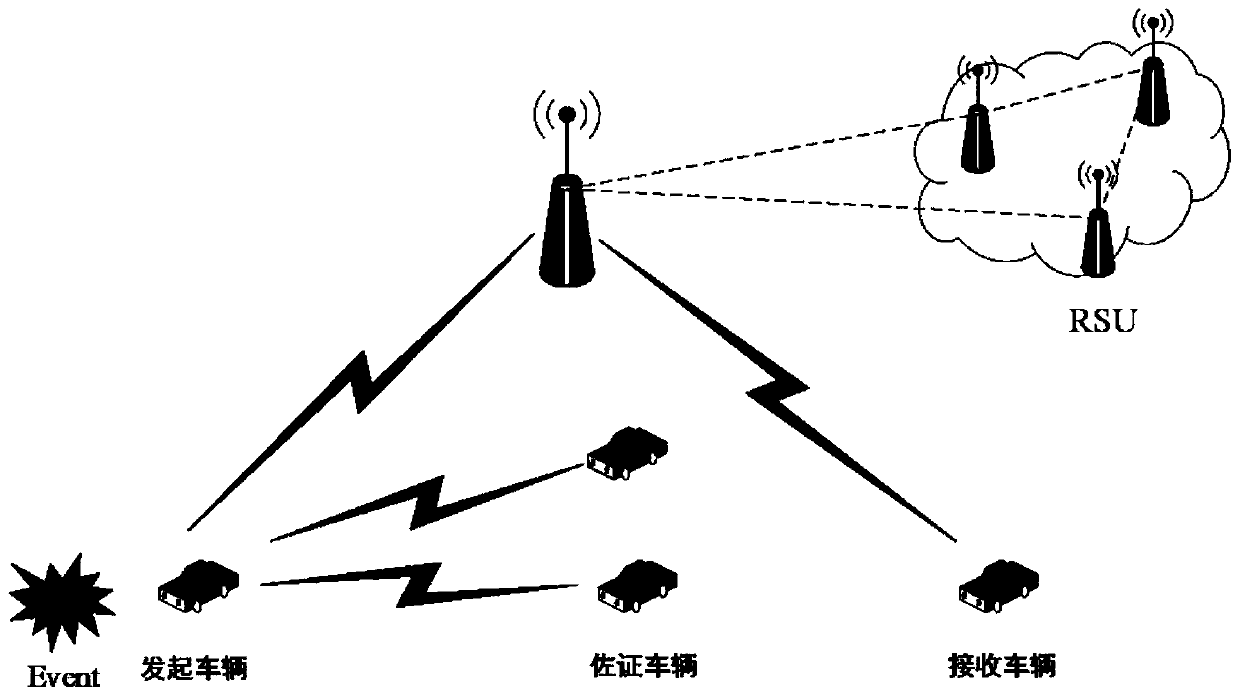
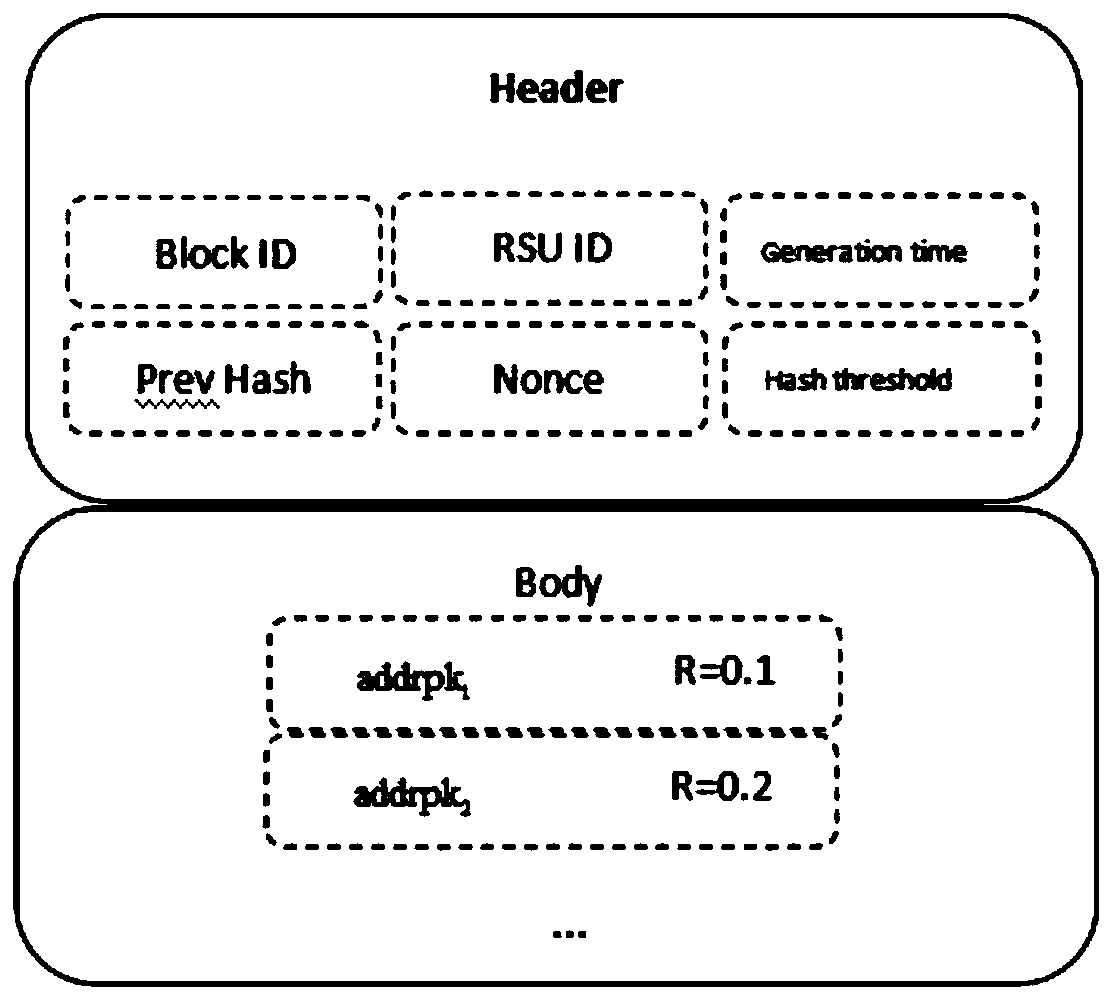
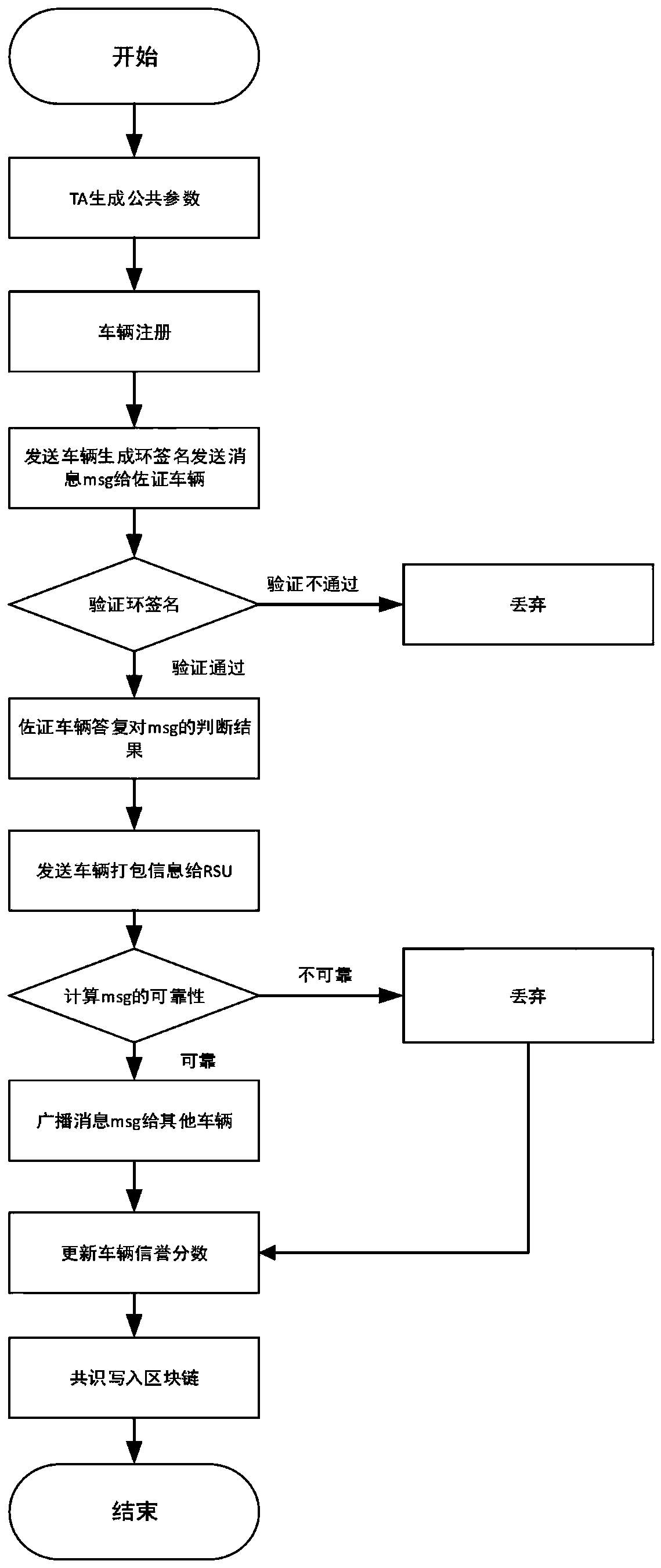
Internet of Vehicles privacy protection trust model based on block chain
ActiveCN110300107AAddress privacy concernsResolve trust issuesUser identity/authority verificationRing signaturePrivacy protection
The invention provides an Internet of Vehicles privacy protection trust model based on a block chain. Vehicles on the road generate and broadcast messages through the vehicle-mounted ad hoc network toshare surrounding traffic information so as to improve the traffic efficiency and safety. However, due to the untrusted network environment of the vehicle-mounted ad hoc network, the privacy of the vehicle is easy to expose, and whether the received message is reliable cannot be judged. The message is anonymously sent by the vehicle through the ring signature technology, so that the vehicle is prevented from being tracked by a malicious vehicle. Messages sent by the vehicle are evaluated and screened through a reputation evaluation mechanism based on the block chain technology, and forged information in the messages is filtered. Based on the characteristics of the block chain, it is guaranteed that the vehicle reputation is not maliciously tampered, real-time synchronous updating of the vehicle reputation is achieved, and the safety and usability of the vehicle-mounted ad hoc network are further improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
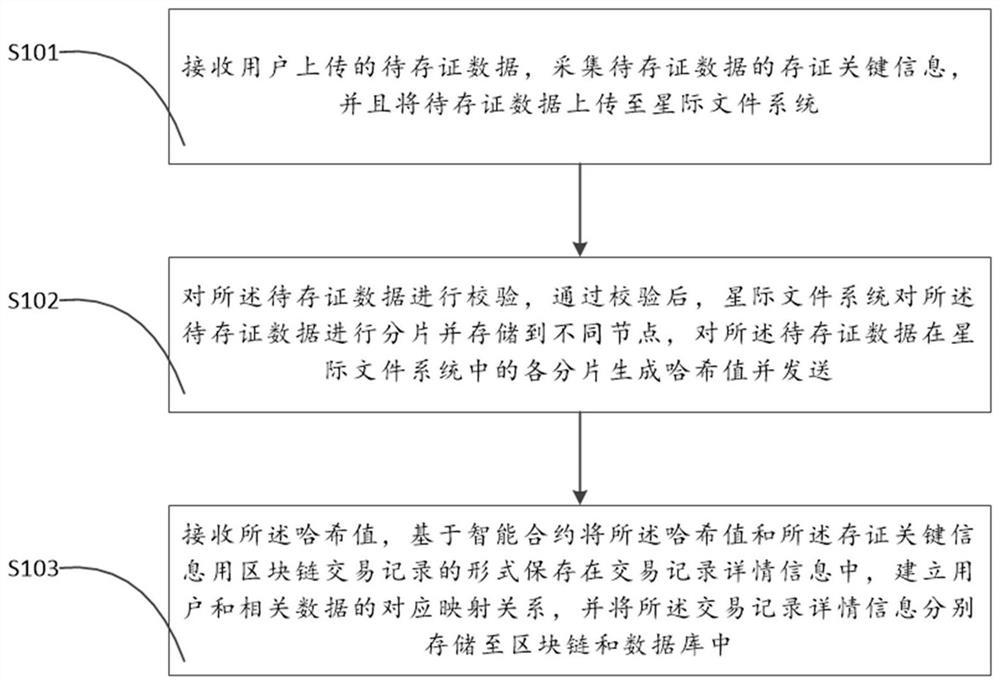
Data evidence storage method and system based on block chain and interstellar file system
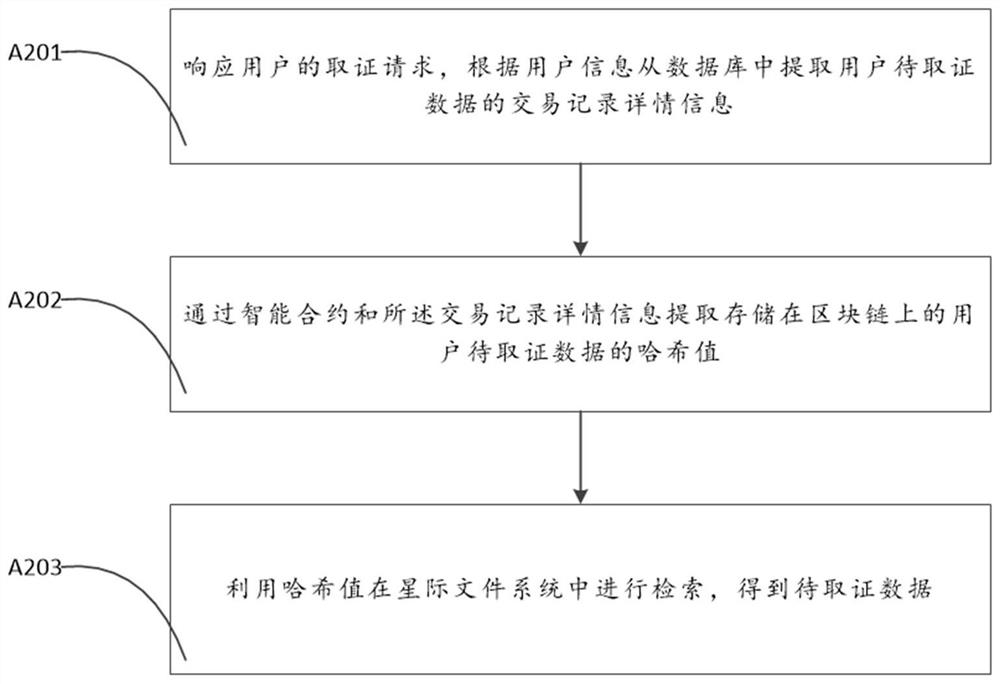
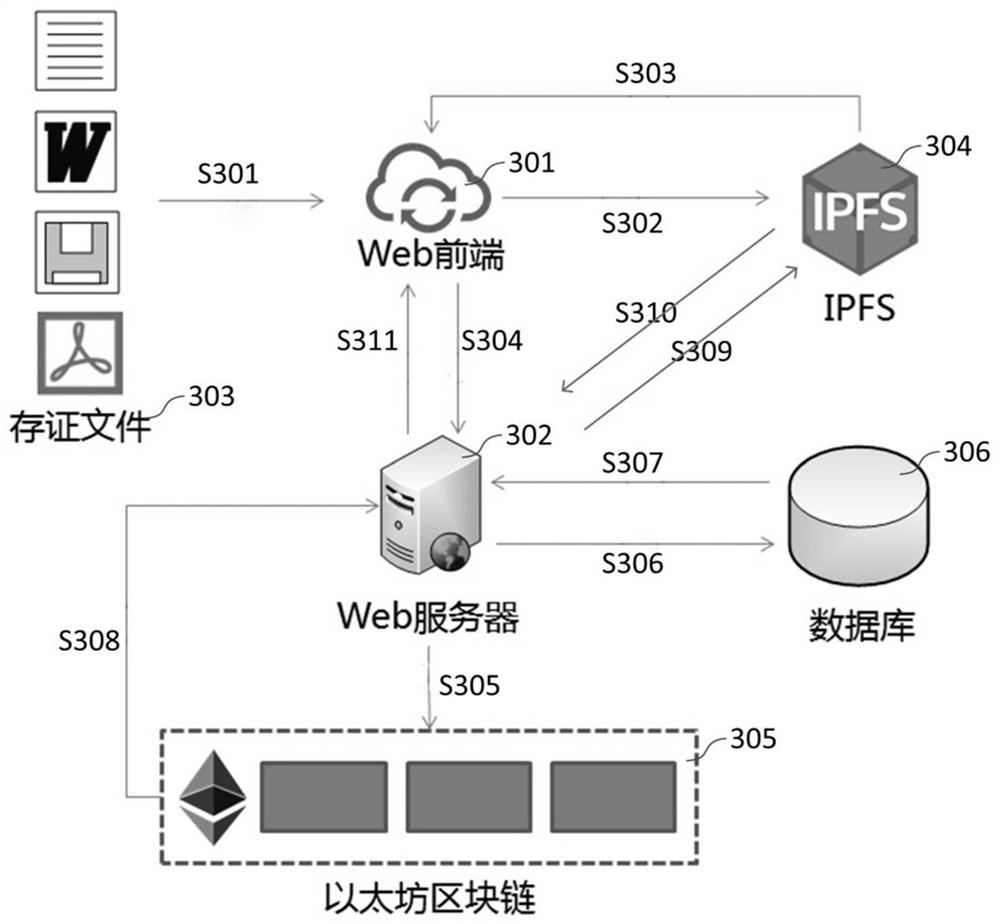
PendingCN112084164AEfficient searchGuaranteed validityDatabase distribution/replicationDigital data protectionFile systemData acquisition
A method comprises the steps: receiving to-be-stored data uploaded by a user, collecting storage key information of the to-be-stored data, and uploading the to-be-stored data to an interstellar file system; verifying the to-be-stored data by utilizing the interstellar file system, after the verification is passed, fragmenting the to-be-stored data by the interstellar file system, storing the fragmented to-be-stored data to different nodes, and generating a hash value for each fragment of the to-be-stored data in the interstellar file system; and storing the hash value and the evidence storagekey information in transaction record detail information in the form of a blockchain transaction record based on an intelligent contract, establishing a corresponding mapping relationship between theuser and related data, and respectively storing the transaction record detail information in a blockchain and a database. Through the decentration characteristic of the blockchain, and in combinationwith the distributed storage characteristic and encryption strength of the interstellar file system, higher tamper-proof capability is effectively realized.
Owner:厦门市美亚柏科信息安全研究所有限公司
Method and device for managing secret keys in wireless sensor network
InactiveCN102186170AImprove securityProtection securityNetwork topologiesSecurity arrangementSecure communicationWireless sensor networking
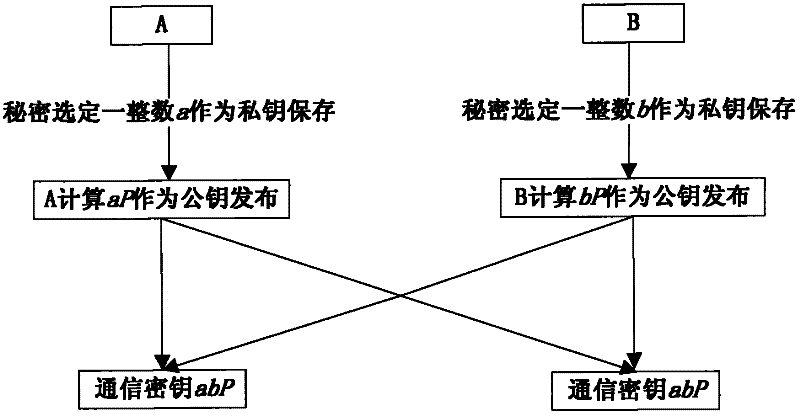
The invention discloses a method for managing secret keys in a wireless sensor network. The method comprises the following steps: 1. clustering the nodes of a sensor by adopting DECA (distributed energy-core algorithm) based on the spatial position information of the nodes, wherein a base station only communicates with cluster heads; the cluster heads communicate with the common nodes in the cluster; the cluster heads can not directly communicate with each other; and shared nodes do not exist among the clusters; and 2. during distributing the communication secret keys, adopting elliptic curve cryptography algorithm to encrypt and decrypt the wireless sensor network and carrying out communications among the nodes by utilizing a symmetric encryption method after establishing safe communication links. Dot multiplication of the elliptic curve cryptography algorithm is optimized by adopting a window sliding method to reduce the number of the continuous nonzero integers. By adopting the method, the safety of the wireless sensor network system can be remarkably improved. The invention also discloses a device for managing secret keys in the wireless sensor network. The device comprises a clustering module, a secret key management module and an elliptic curve cryptography algorithm optimization module.
Owner:BEIJING TOPSEC TECH
Dispensing Utensil
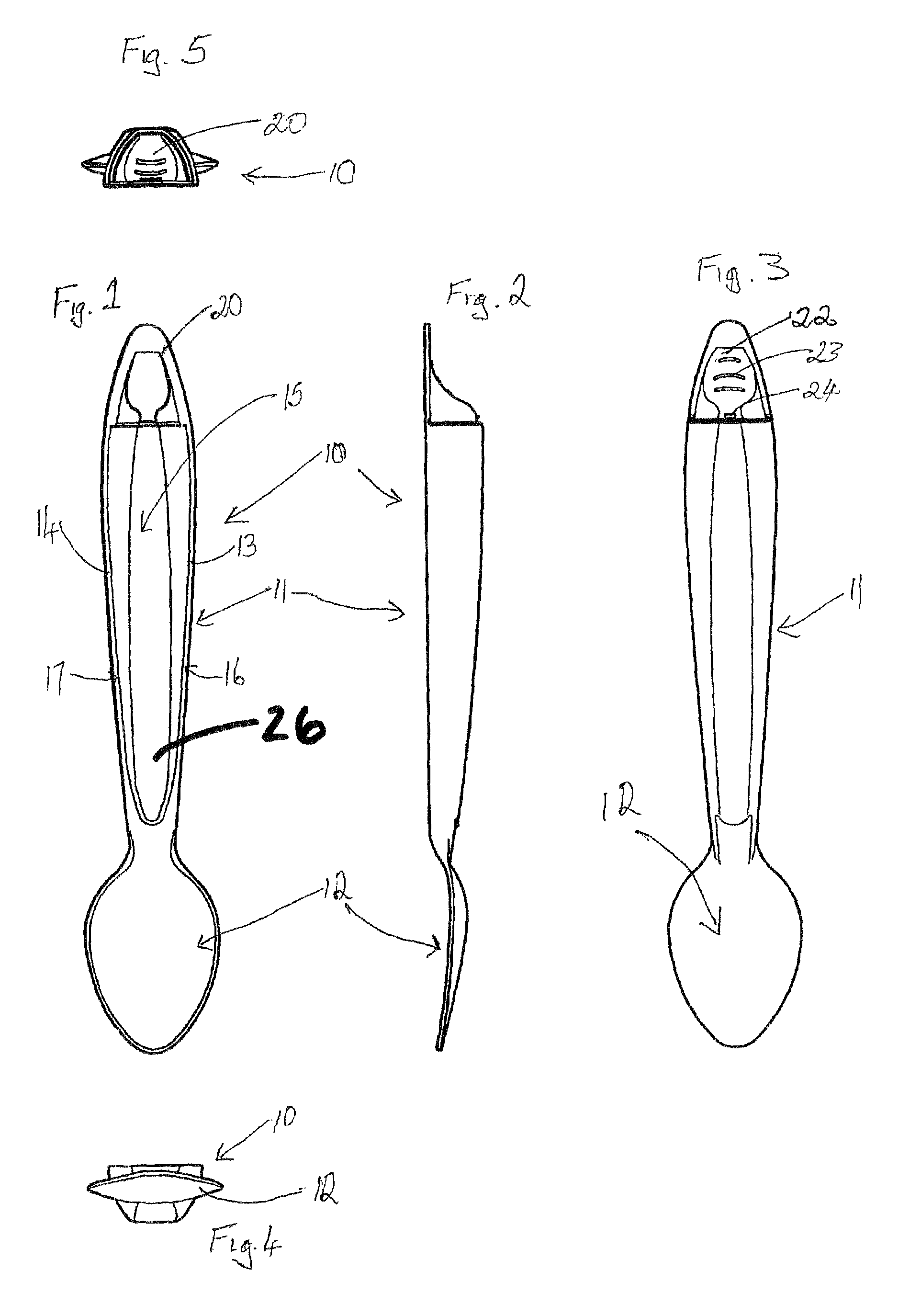
ActiveUS20110024462A1Easy to useReduce litteringSmall article dispensingOral administration deviceEngineeringMechanical engineering
A dispensing utensil 10 comprising: a handle portion 11; an implement portion 12; a cavity 15 for storing dispensable contents, the cavity 15 defined by a first wall means 13, 14 and a second wall means 19 closing the cavity 15; characterised in that a first portion 20 of the first wall means 13, 14 is openable about a hinge formed by the second wall means 19, thereby allowing the contents to be dispensed.
Owner:SANDS INNOVATIONS
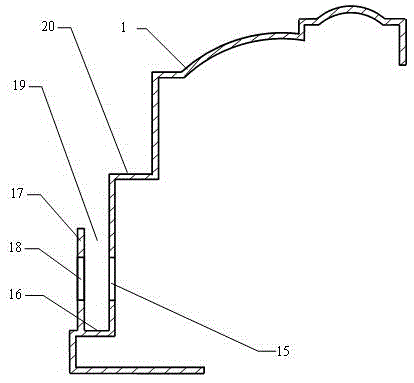
Tamper-resistant semiconductor device
ActiveUS20060180939A1Improve tamper resistanceSemiconductor/solid-state device detailsSolid-state devicesDevice materialIsolation layer
The semiconductor device of the present invention includes: first defensive wiring provided above a diffusion isolation layer formed in a substrate or a well, arranged at a minimum wiring pitch allowable in fabrication to cover the diffusion isolation layer; a plurality of signal wiring layers formed above the first defensive wiring; and means for applying a predetermined signal to the first defensive wiring and capturing a change in an electrical or physical property of the first defensive wiring.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
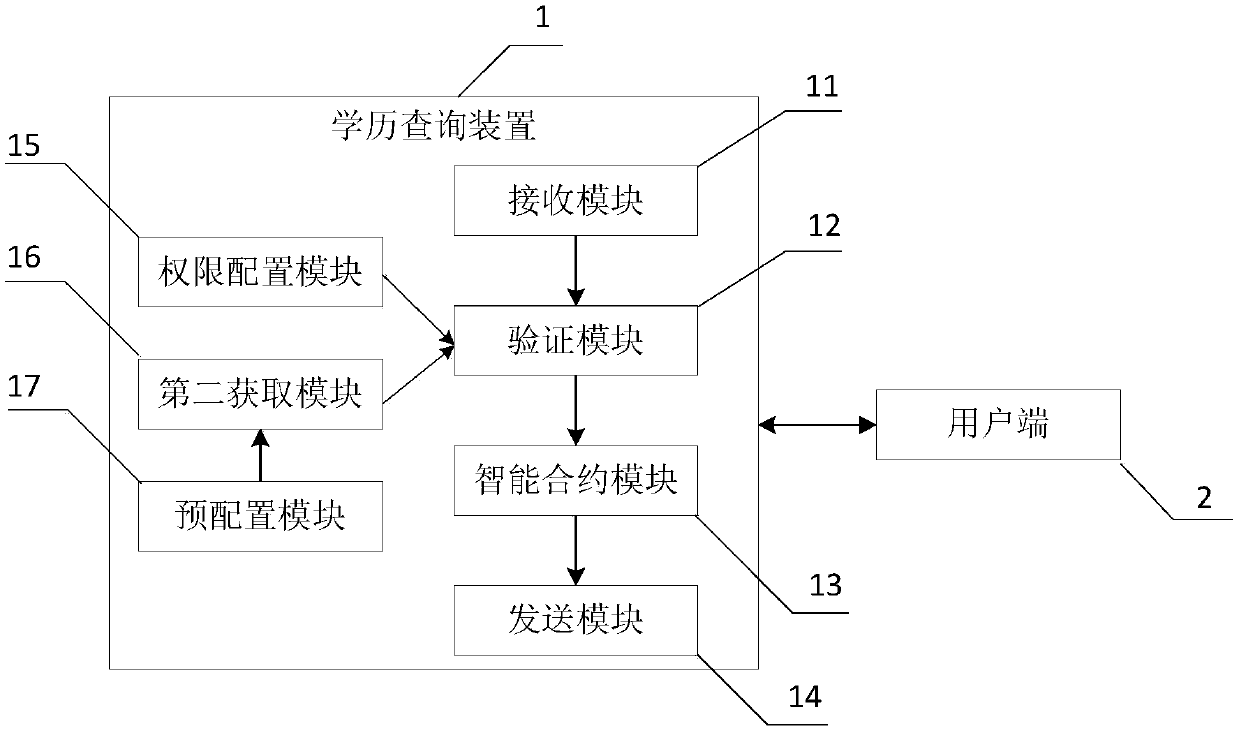
Blockchain-based academic diploma query method and device
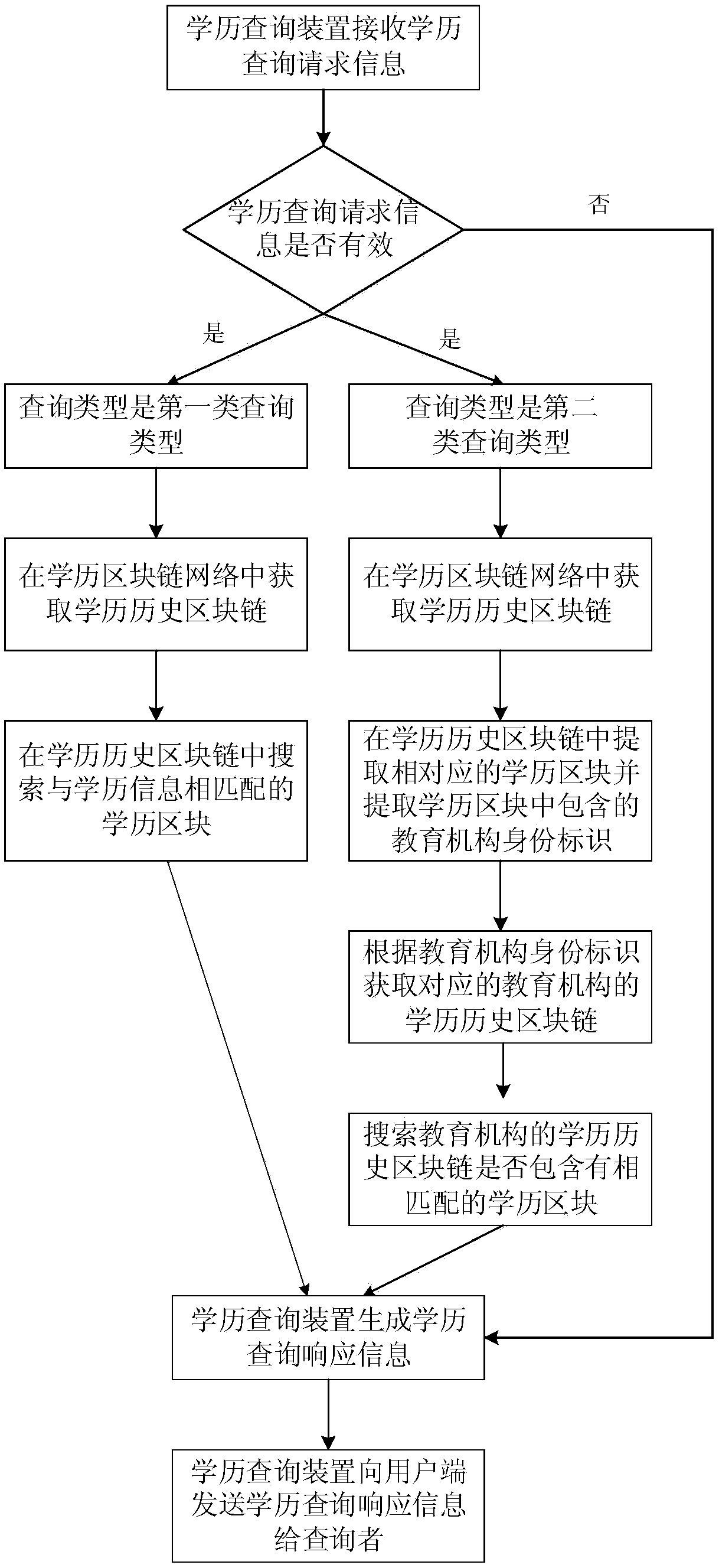
ActiveCN107943996AImprove tamper resistanceSolve the problem of low query efficiencyTransmissionSpecial data processing applicationsThe InternetComputer science
The invention relates to the technical field of the internet. The invention aims to provide a blockchain-based academic diploma query method and device. The academic diploma query method comprises thesteps that firstly, academic diploma query request information sent by a client is received by the academic diploma query device; secondly, the academic diploma query device verifies the validity ofthe academic diploma query request information; thirdly, the academic diploma query device acquires an academic diploma historical blockchain of an inquired person and / or generates academic diploma query response information; finally, the academic diploma query device sends the academic diploma query response information to the client. By means of the method, the problems that the academic diplomainformation tampering prevention capacity is poor, and academic diploma information query efficiency is low can be solved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
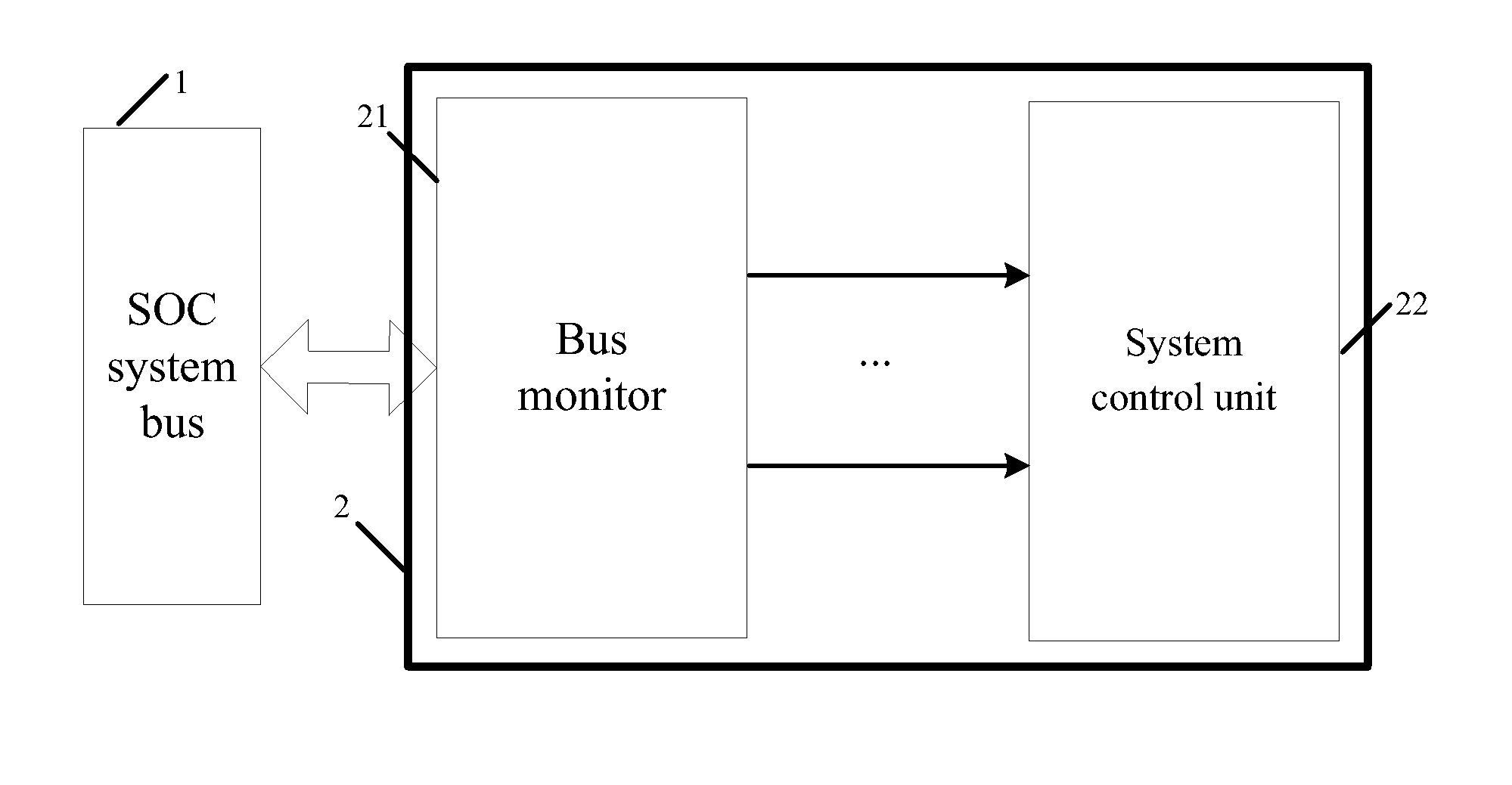
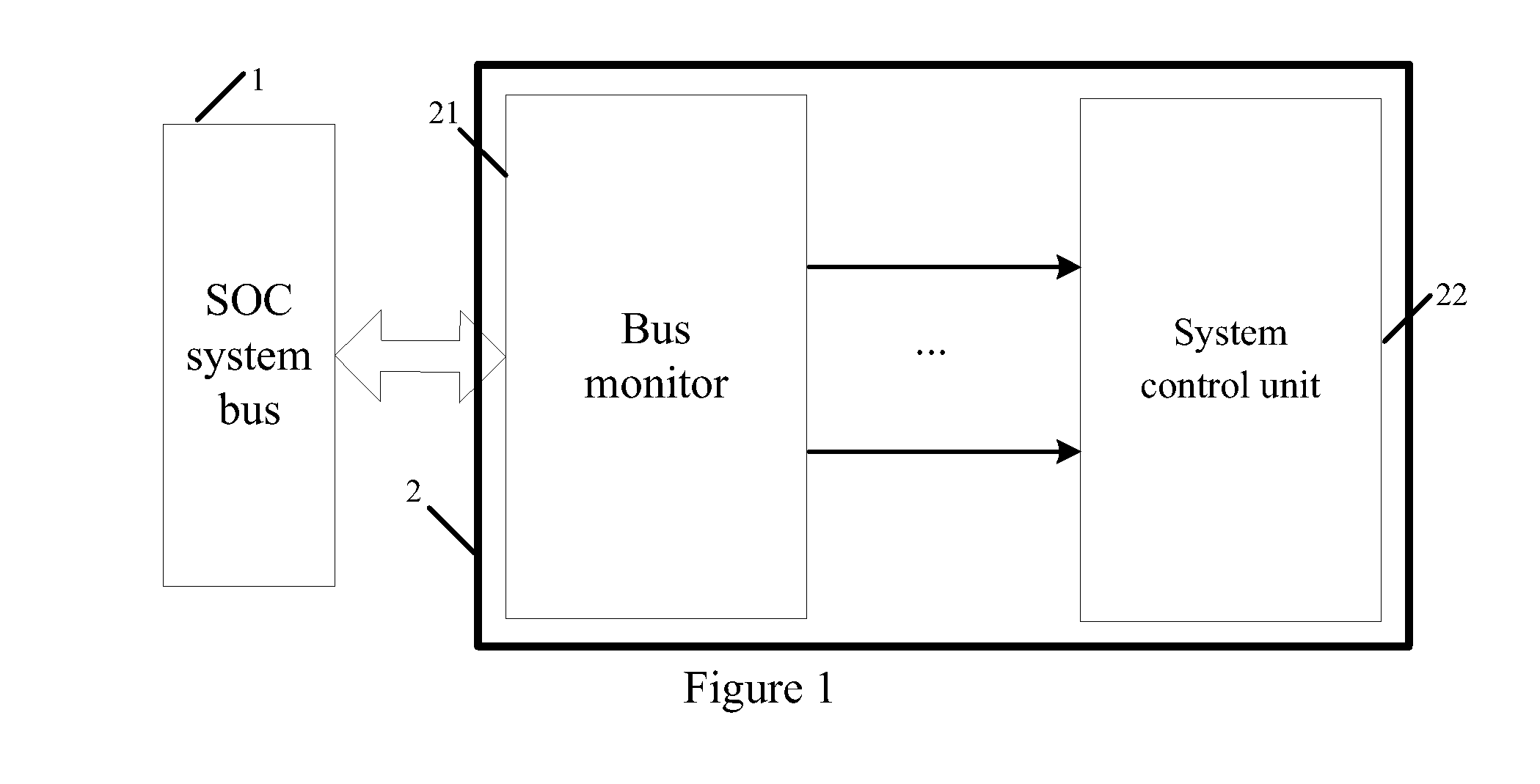
Bus monitor for enhancing soc system security and realization method thereof
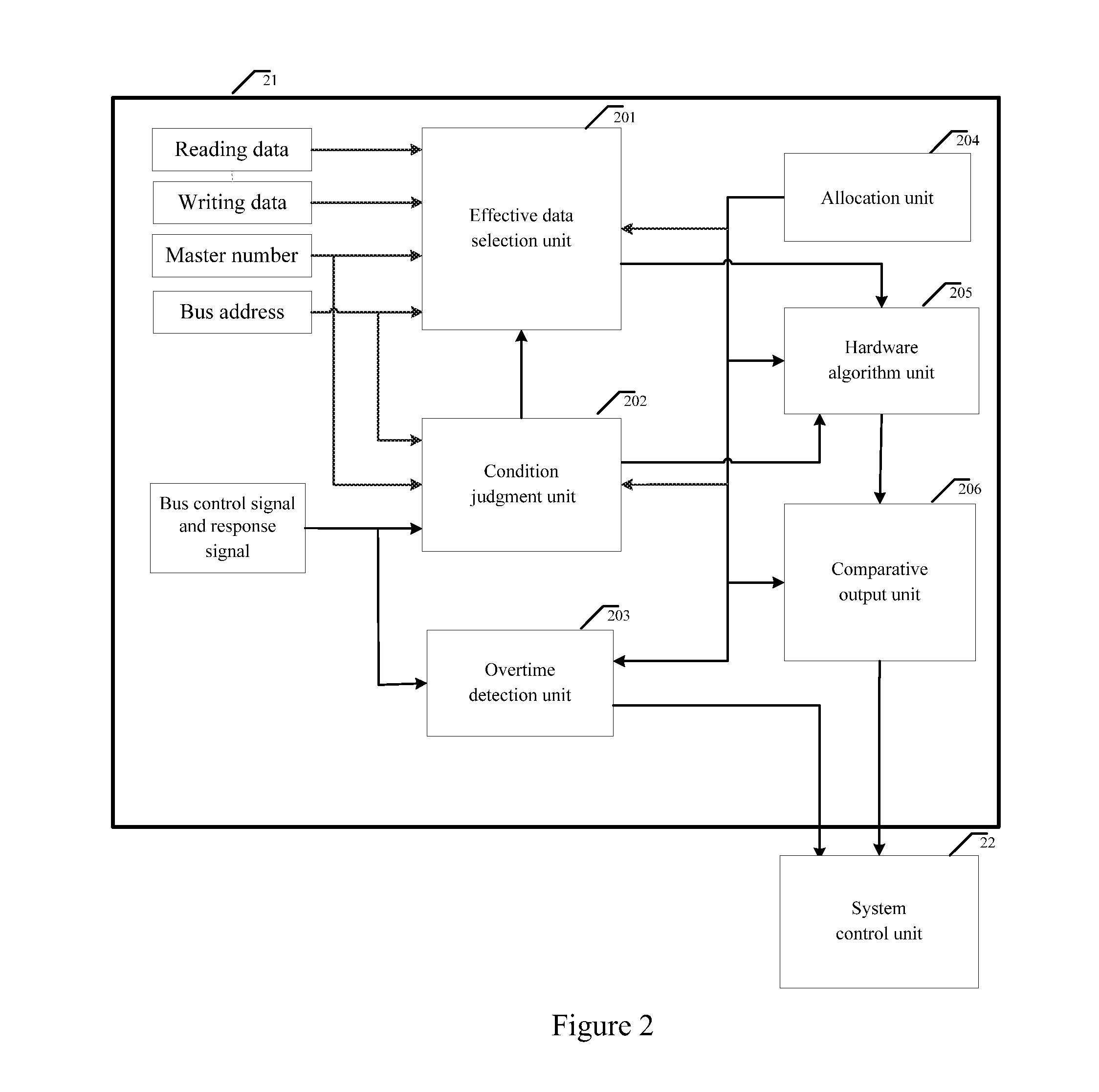
InactiveUS20130219452A1Improve information securityInformation leakageMemory loss protectionError detection/correctionClassified informationData selection
The present invention discloses a bus monitor for enhancing SOC system security and a realization method thereof. The bus monitor disposed between a system bus and a system control unit includes a configuration unit, a condition judgment unit, an effective data selection unit, a hardware algorithm unit and a comparative output unit. Without affecting the bus access efficiency, the present invention provides the method capable of immediately monitoring the bus behavior, and the detection system notices whether a particular bus access serial behavior is changed due to an accidental fault or intentional attacking fault. If the particular bus access serial behavior is changed, the present invention warns the system to adopt a suitable security measure to prevent the security hidden trouble and leakage of classified information due to the incorrect system security process.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Environmental parameter indicator for perishable goods
InactiveUS20050021279A1Accurate expiry dataImprove quality controlThermometer detailsElectric/magnetic detection for well-loggingData interfaceComputer science
An electronic device is proposed for accompanying a perishable good during one period to monitor the exposure of the good to an environmental parameter, such as temperature. The device includes a data interface for receiving data representing the exposure of the good to the environmental parameter during an immediately preceding period. It further includes a sensor for measuring the environmental parameter. Also, the device includes a processor for using a relationship specific to the good (such an Arrhenius equation for that good) to compute a characteristic of the good at the end of the one period using the received data and the output of the sensor. The device further includes a memory for recording the output of the sensor. To economise on memory usage, data is stored at a faster rate during periods when the data is of most significant (e.g. it indicates a high temperature). A switch is provided for indicating that data should not be taken into account in the computation, during a short interval, in which for example the device may be being handled.
Owner:3M INNOVATIVE PROPERTIES CO
Cap separable from bottle at the time of disposal
InactiveUS6016931AImprove tamper resistanceEasy to disassembleCapsClosure using stoppersBottleBiomedical engineering
A cap comprises a cap body fitted and secured to the mouth of a container, an upper closure provided in the cap body, and a ring-like member which covers the outer surface of a skirt portion of the cap body. The ring-like member and the skirt portion are coupled together through breakable bridge portions. These two members are separated away from each other via cut surfaces but are intimately contacted to each other at the cut surfaces. The cap can be easily removed by hand from the mouth of the container, and can be separated from the container at the time of disposal.
Owner:JAPAN CROWN CORK CO LTD
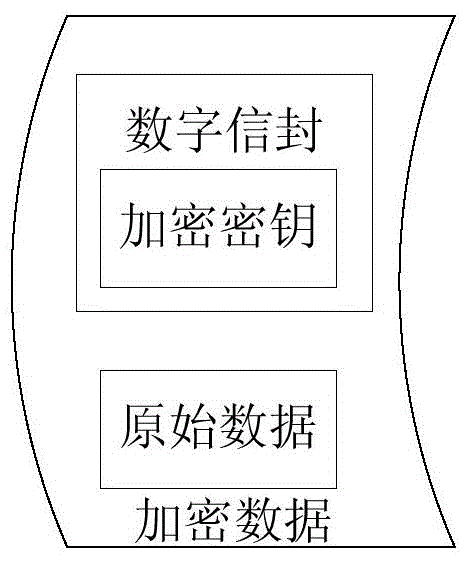
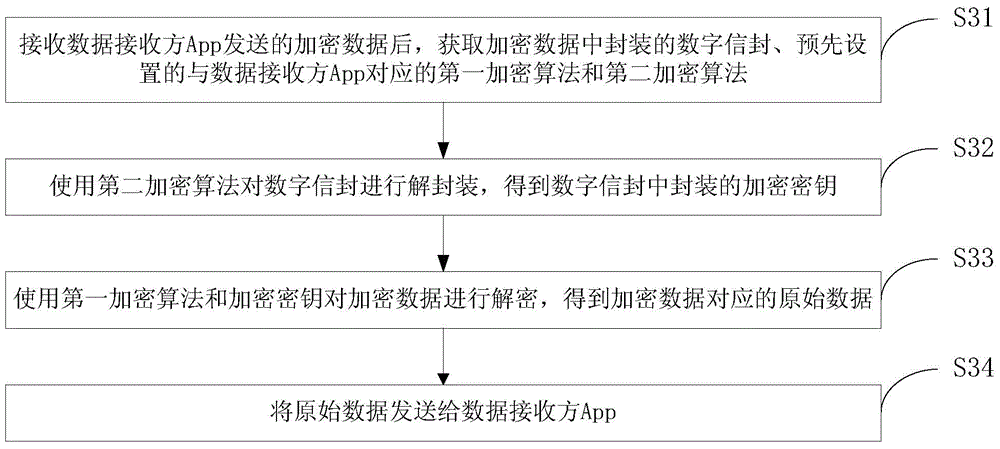
Data encryption method, data decryption method and devices
InactiveCN104580180AImprove securityImprove integrityMultiple keys/algorithms usageTamper resistanceComputer hardware
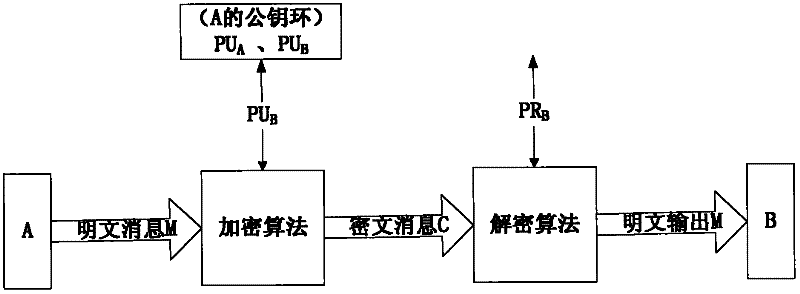
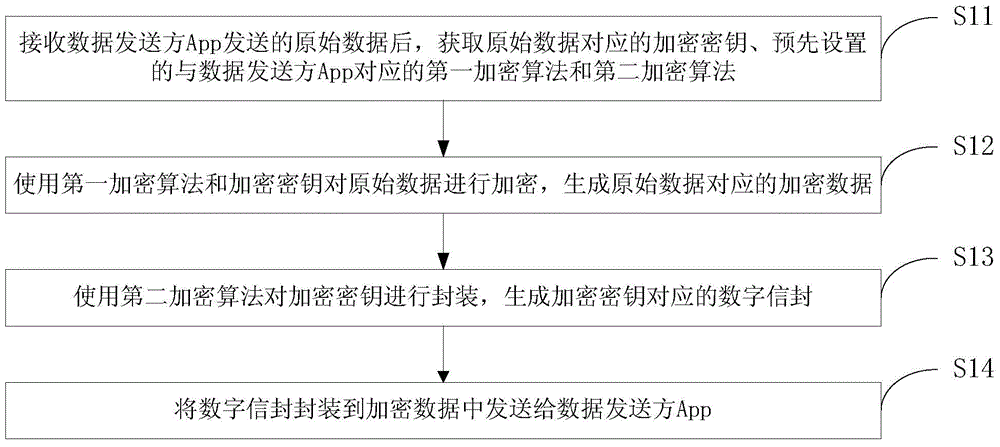
The embodiment of the invention discloses a data encryption method, a data decryption method, a data encryption device and a data decryption device. The data encryption method comprises the following steps: after receiving original data sent by a data sending party App (Application), acquiring an encryption key corresponding to the original data as well as a first encryption algorithm and a second encryption algorithm which are preset and correspond to the data sending party App; carrying out encryption on the original data by using the first encryption algorithm and the encryption key and generating encrypted data corresponding to the original data; packaging the encrypted data by using the second encryption algorithm and generating a digital envelope corresponding to the encryption key; packaging the digital envelope into the enciphered data to be sent to the data sending party App. According to the scheme, encrypted data interworking among multiple operation systems and among multiple Apps can be realized and safety, integrity and tamper resistance of the data are improved.
Owner:BEIJING BLUE POWER SOFTWARE
Double-insertion type antitheft door
ActiveCN105545183AImprove tamper resistanceImprove vandal resistanceBurglary protectionBuilding locksJambMechanical engineering
The invention discloses a double-insertion type antitheft door and relates to the field of antitheft safety doors. The double-insertion type antitheft door is mainly characterized in that an insertion lug is arranged at the position, corresponding to each doorframe insertion hole, of a doorframe buckled edge, an insertion lug gap is formed between each insertion lug and a doorframe, a double-insertion plate is arranged at the position, closely neighboring a door leaf side edge, inside the door leaf, the double-insertion plate is provided with liner plates in the mode that each liner plate corresponds to the corresponding insertion hole in the doorframe, a narrow-slit type insertion hole is formed between each liner plate and the double-insertion plate, the side edge of a panel inside the door leaf is provided with rectangular insertion holes in the mode that each rectangular insertion hole corresponds to the corresponding narrow-slit type insertion hole, the insertion lugs, the door leaf side edge, the double-insertion plate and the liner plates are each provided with an insertion hole in the mode of corresponding to the doorframe insertion holes, the five insertion holes which are correspondingly formed constitute a group, after the door leaf is closed, the insertion lugs are inserted into the rectangular insertion holes and the narrow-slit type insertion holes, the double-insertion plate is also inserted into the insertion lug gaps, the five insertion holes are all coaxial, lock tongues are inserted into the five concentric insertion holes correspondingly and used for locking the antitheft door, and the double-insertion type antitheft door is resistant to unclenching and damage.
Owner:BEIHUA UNIV
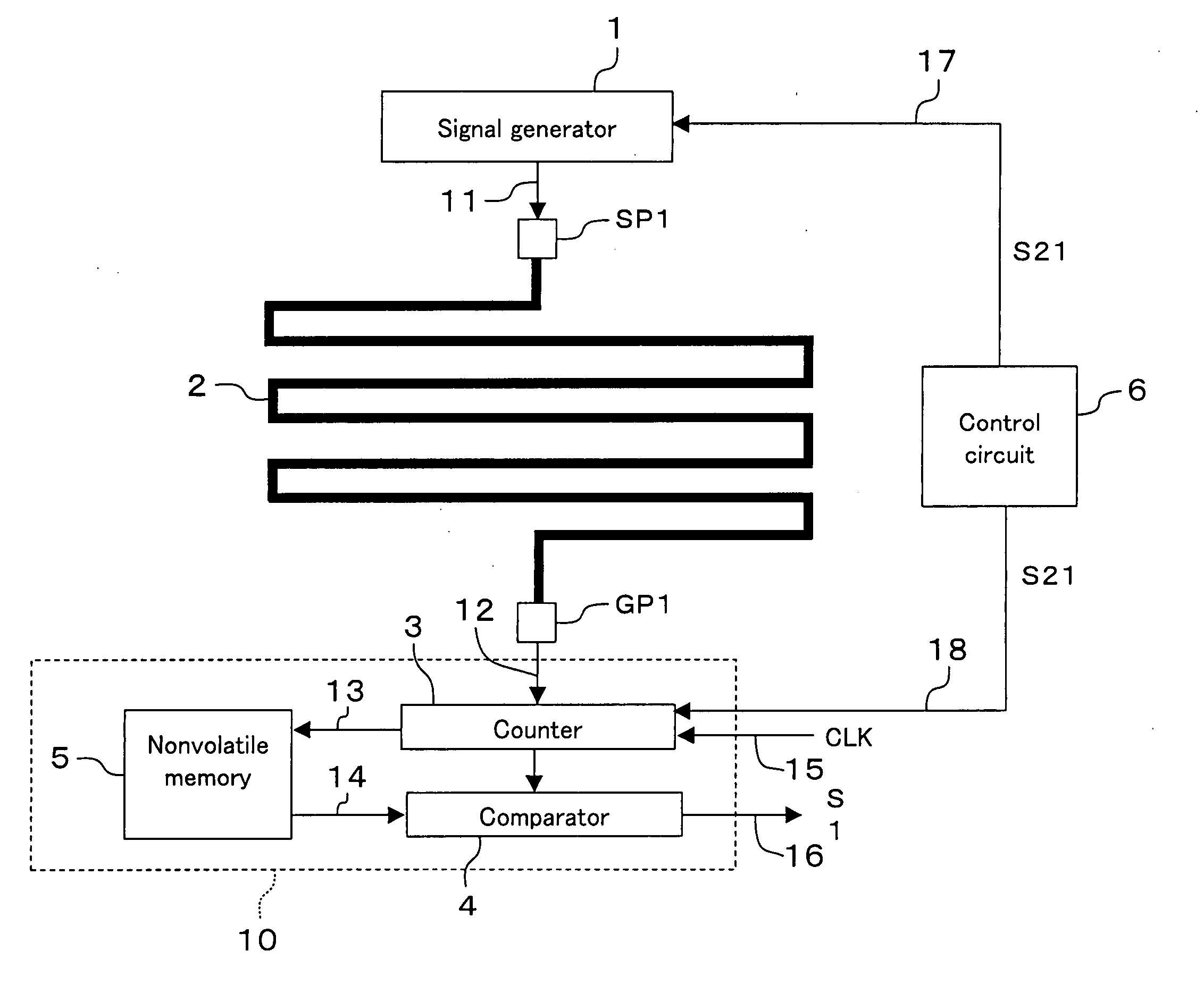
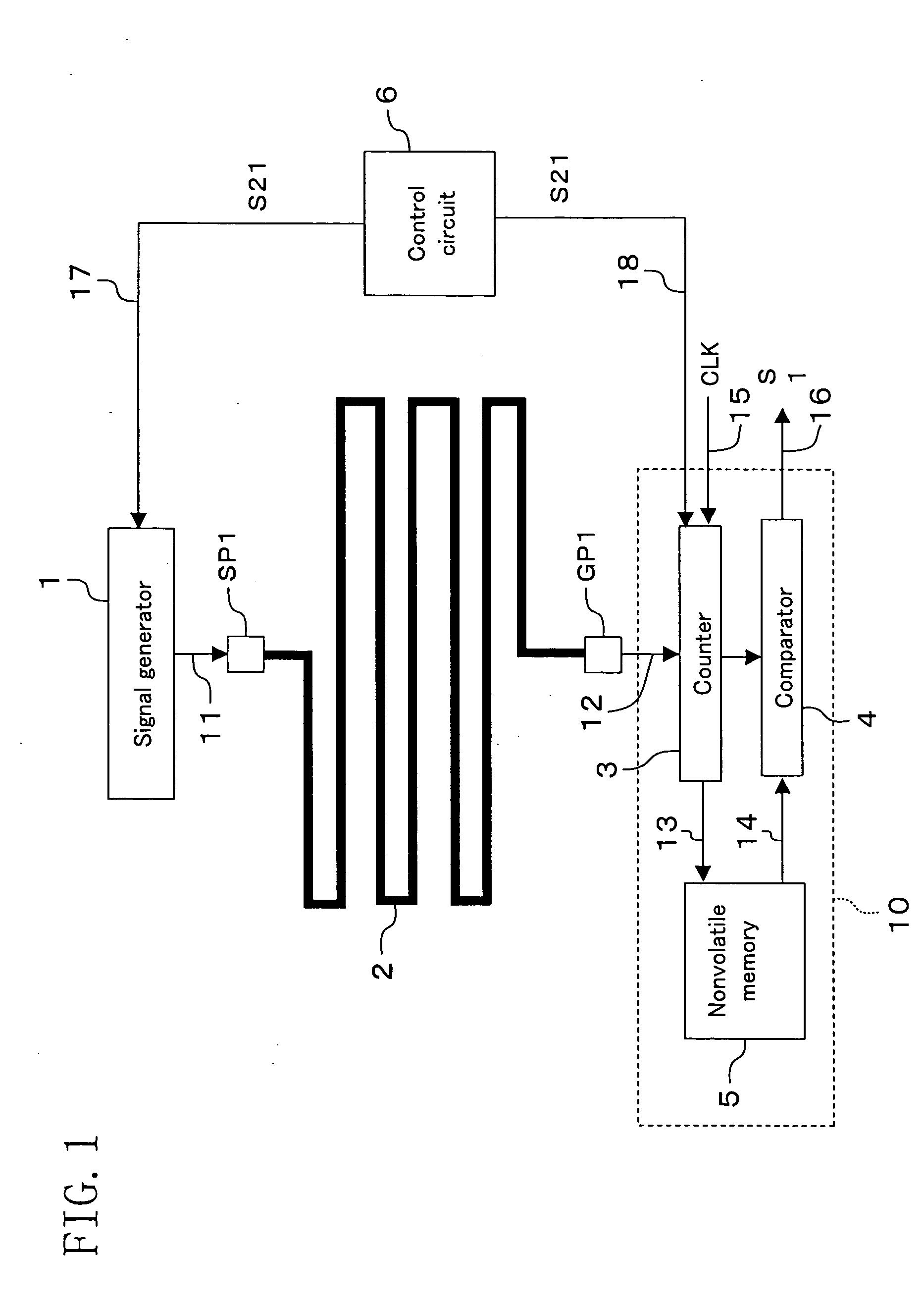
Protection circuit for semiconductor device and semiconductor device including the same
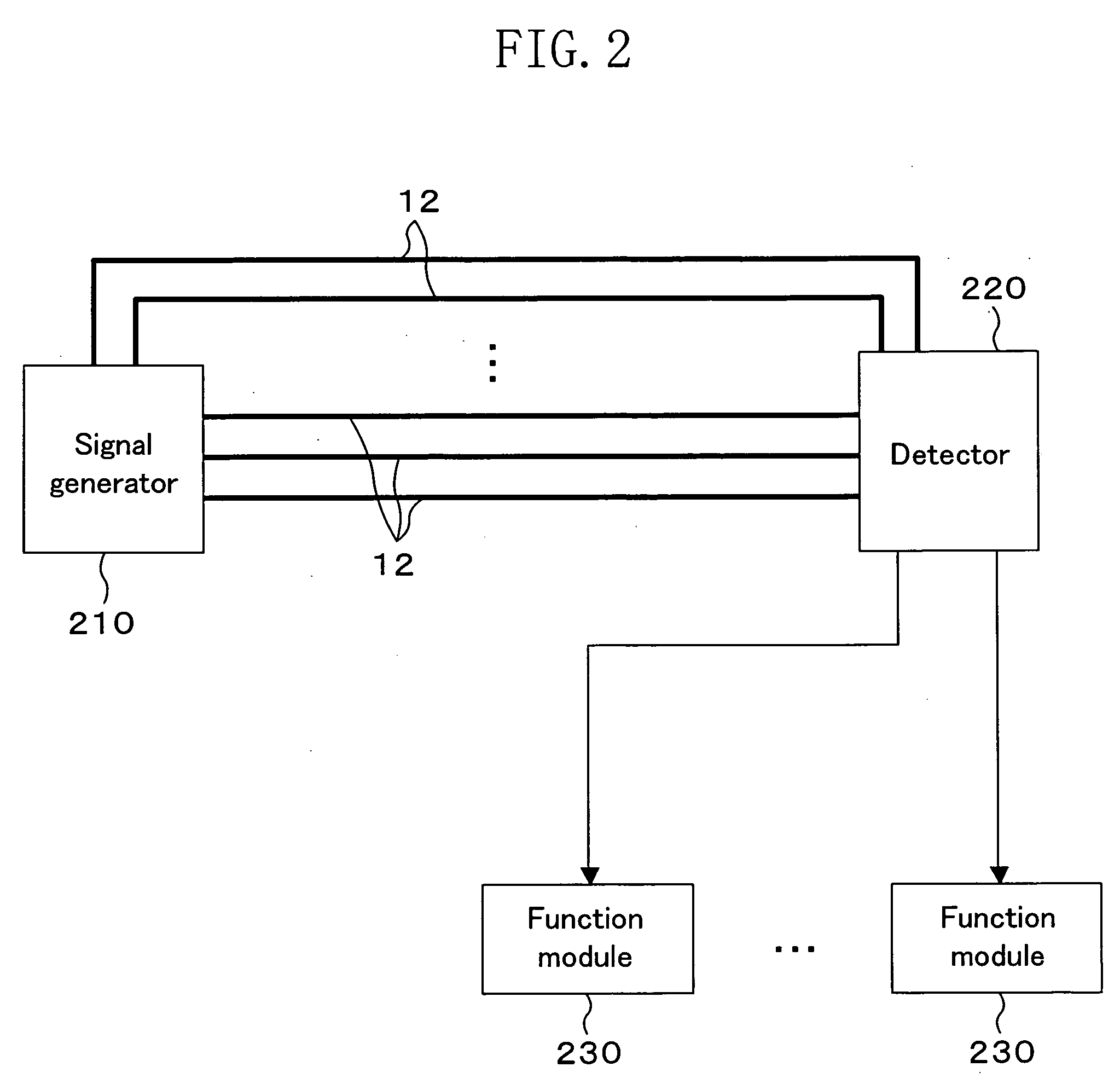
ActiveUS20050047047A1Improve tamper resistanceImproved confidentiality protection functionCircuit-breaking switches for excess currentsSemiconductor/solid-state device detailsEngineeringSignal generator
A protection circuit comprises: at least one shielded line arranged to cover an area to be protected over a semiconductor device, the at least one shielded line having only one route from a start point to an end point; a signal generator for applying a signal to the start point of the shielded line; a counter which starts measurement of time in response to application of the signal to the start point of the shielded line by the signal generator and which ends measurement of the time in response to arrival of the signal at the end point of the shielded line; and a comparator for comparing the time measured by the counter with a reference value to output a fraud detection signal according to a result of the comparison.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
Tamper-evident and/or tamper-resistant electronic components
InactiveUS7296299B2Reduce needReduce light intensitySemiconductor/solid-state device detailsVolume/mass flow measurementEngineeringElectronic component
A tamper-evident and / or tamper-resistant electronic module comprising an electronic component embedded in an encapsulant material and at least one thin sheet of frangible material contacting and overlying said encapsulant material and overlying said component, said sheet being sufficiently thin that it is likely to crack or break if an attempt is made to drill or cut through it with a laser drill.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
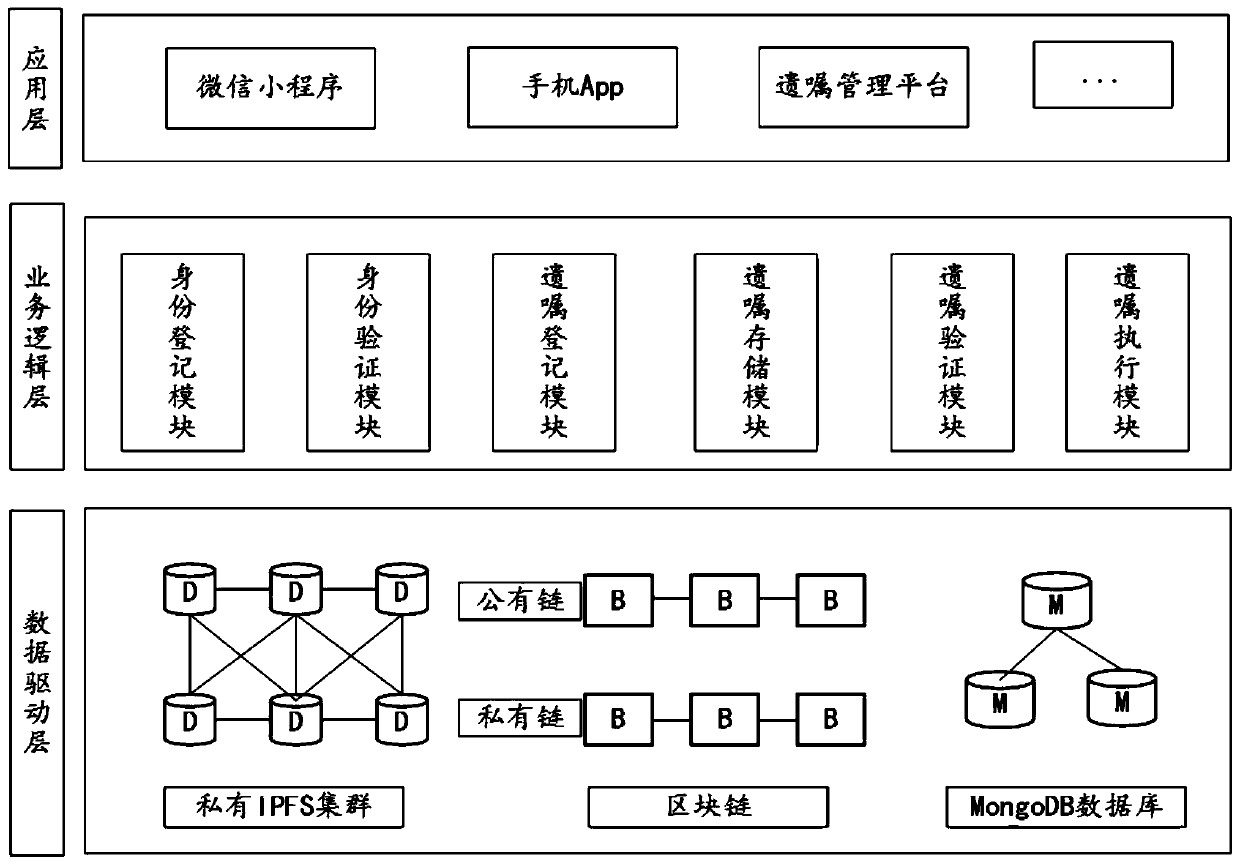
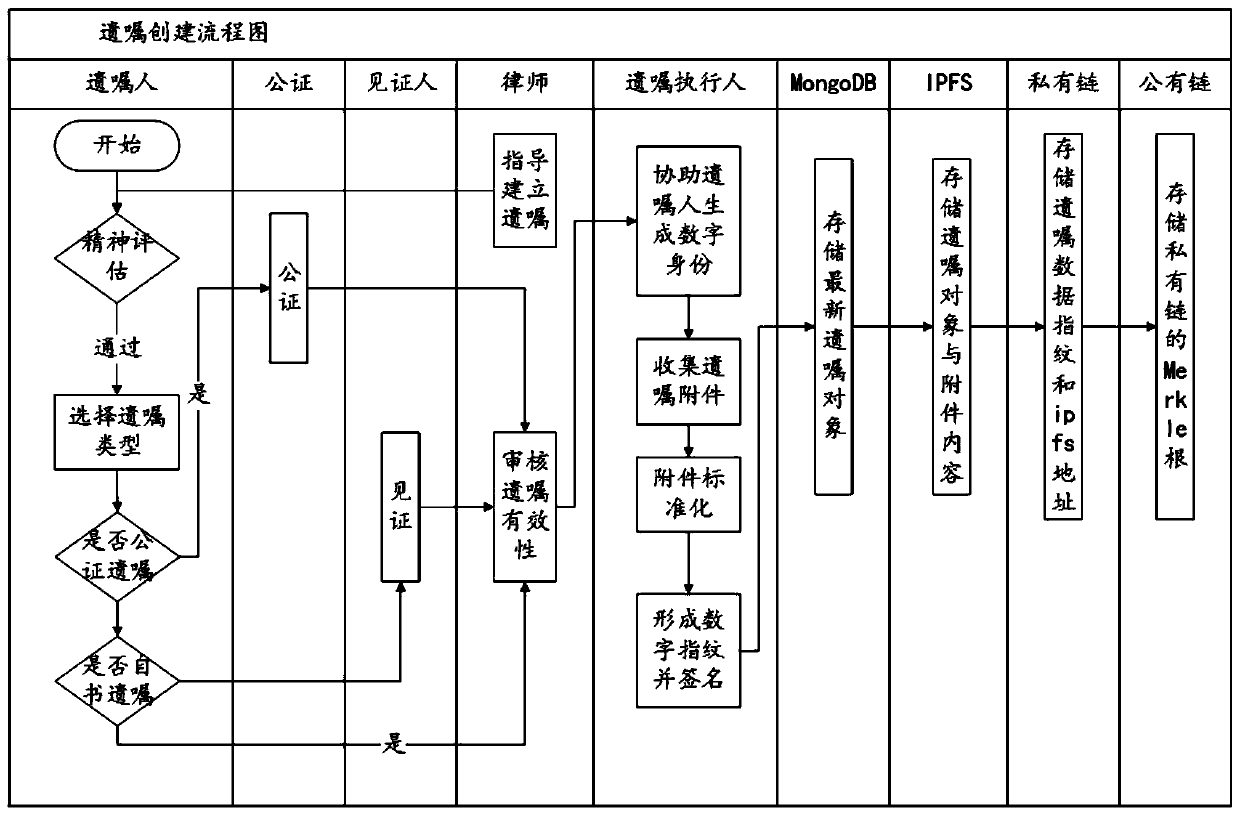
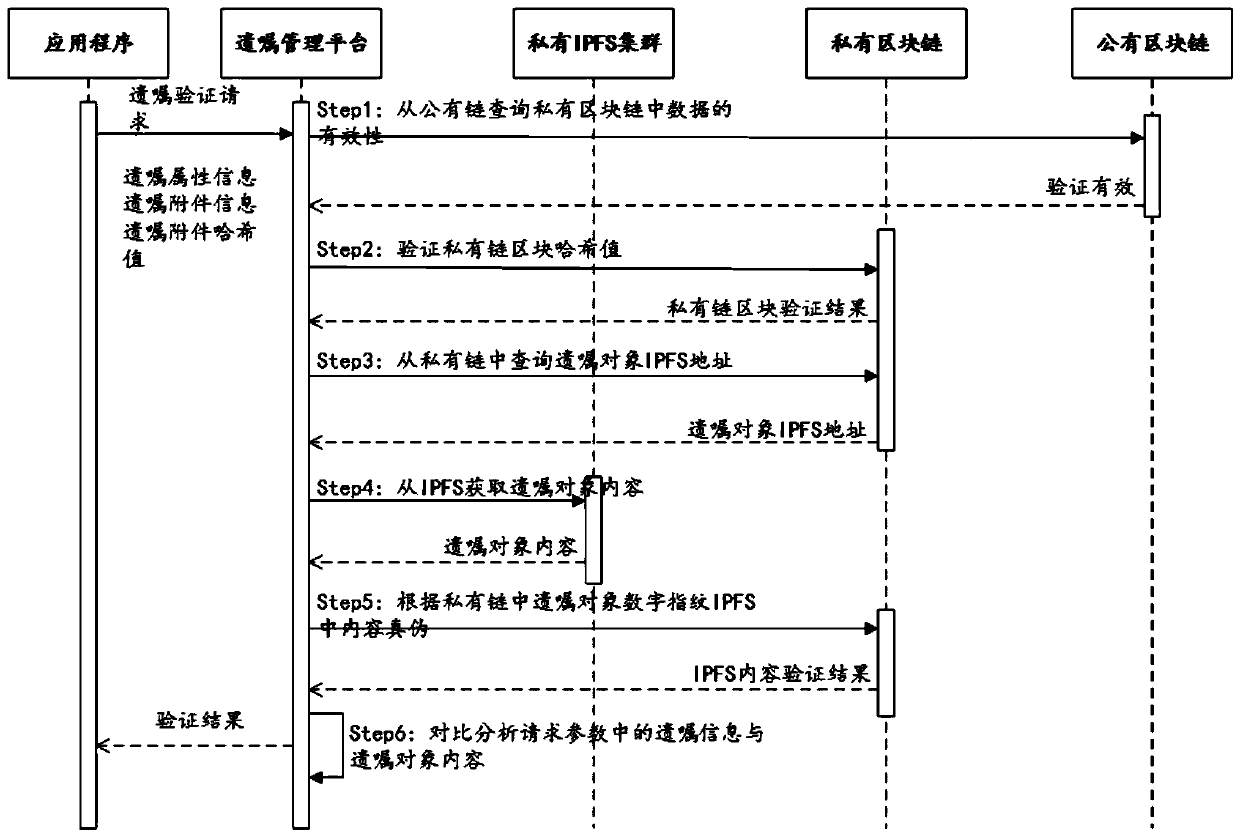
Testament management system and method based on block chain technology
PendingCN110287167ABest buildTrusted Will AppData processing applicationsUser identity/authority verificationData integrityData-driven
The invention relates to the technical field of data storage technologies and information security, in particular to a testament management system and method based on a block chain technology. The testament management system comprises a data driving layer, a business logic layer and an application layer, the data driving layer is used for providing the underlying technical support, the business logic layer is used for dividing the business scenes, and the application layer is used for providing the use interfaces. The testament management method is realized based on the testament management system. By the testament management system, the defects of a traditional testament management technology can be better overcome, and the data integrity of the testament customizing, storing, updating, verifying and other processes can be effectively guaranteed through the block chain technology.
Owner:安徽中科晶格技术有限公司
Electric energy meter theft prevention sealing structure
ActiveCN102254484AHigh strengthReduce intensityStampsTime integral measurementElectricityEngineering
The invention designs an electric energy meter theft prevention sealing structure which solves the technical problem of low productivity because the traditional electric energy meter seal is still manually operated. The electric energy meter theft prevention sealing structure comprises a meter shell and a meter body, wherein the meter shell is provided with a screw hole, and a screw is fixedly connected with the meter body after penetrating through the screw hole. The electric energy meter theft prevention sealing structure is characterized in that a seal cap with an outer folding edge at thelower part is arranged on the screw; a metal ring is sleeved outside the seal cap; the metal ring is abutted against the outer folding edge, and the outer wall is provided with a plurality of buckling pieces which are outwards inclined and opened to the upper part; the buckling pieces are circumferentially arranged; the inner wall of the surface shell arranged at the upper part of the screw hole is provided with an annular projection; and the buckling pieces are positioned at the lower part of the annular projection to form inversed buckling. The invention can visually find out damage traces and replace the damaged electric energy meter in time and has the advantages of good electricity theft prevention effect, high inversed buckling matching strength, good pickproof performance, convenience in processing, simplicity in sealing operation and high productivity.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Surface shape recognition sensor and method of manufacturing the same
InactiveUS6844744B2Improve tamper resistanceDeteriorate detectionResistance/reactance/impedencePerson identificationFingerprintTamper resistance
A surface shape recognition sensor of this invention has a surface protective film having a hydrophobic property on an insulating protective film which is made of an insulator and formed to cover a sensor electrode, and includes at least a ground electrode which is formed on the substrate such that the ground electrode is partly exposed on the surfaces of the insulating protective film and surface protective film so as to be insulated / isolated from the sensor electrode and come into contact with the surface of a detection target. This sensor prevents fingerprint residues from easily remaining and improves tamper resistance.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Block chain-based account password management method, device and apparatus and storage medium
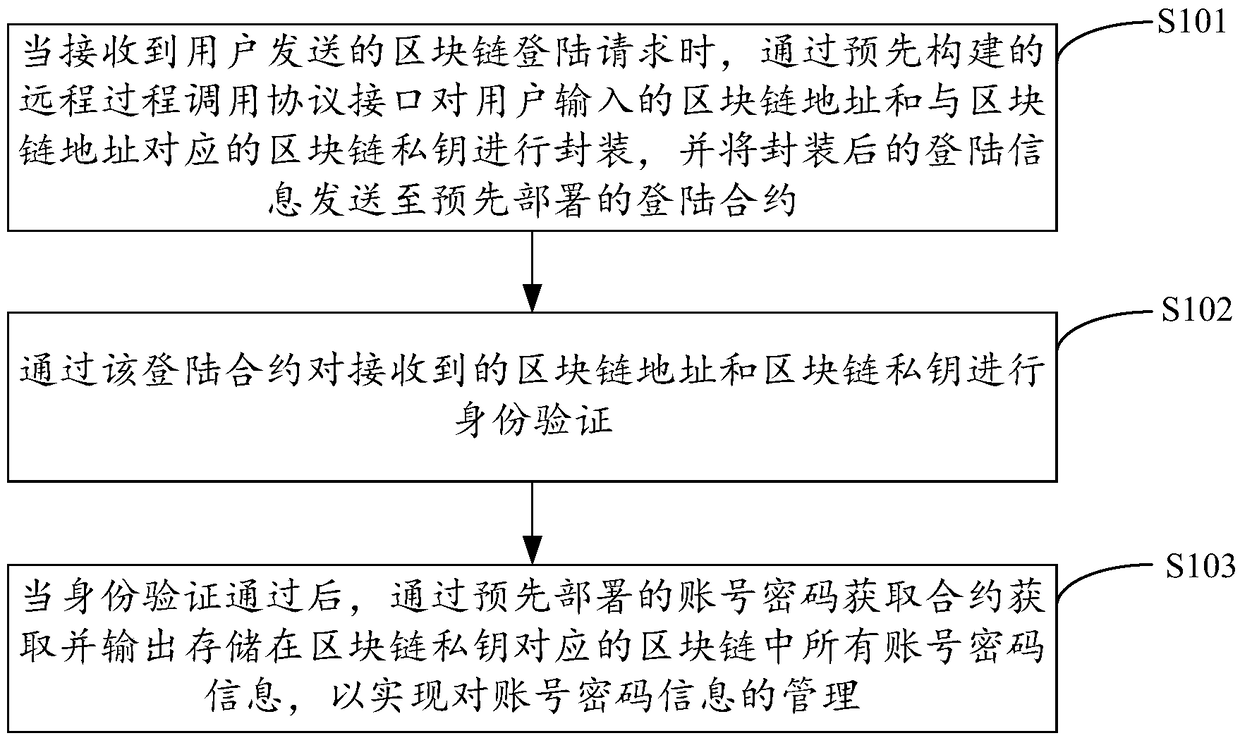
InactiveCN109359976AImprove loss preventionImprove tamper resistancePayment protocolsDigital data authenticationBlockchainOperational costs
The invention is applicable to the technical field of block chain, provides a block chain-based account password management method, device and apparatus and a storage medium. The method comprises: receiving a block chain login request sent by a user through a remote procedure call protocol interface, and encapsulatingthe block chain address and the block chain private key contained in the request, and then sending the encapsulated login information to the login contract; the chunk chain address and the chunk chain private key are authenticated by the login contract, When validation is passed,obtaining and outputting all account password information stored in the block chain corresponding to the block chain private key through the account password obtaining contract, so as to realize themanagement of account password information, Thus, a plurality of personal account password information of a user is managed by a block chain private key, the probability of preventing the account password from being lost, tampered with and stolen is improved, the security of the account password management based on the block chain is further improved, and the management cost and the operation costof the account password are reduced.
Owner:SHENZHEN UNIV
Cylindrical electronic password safe-deposit box
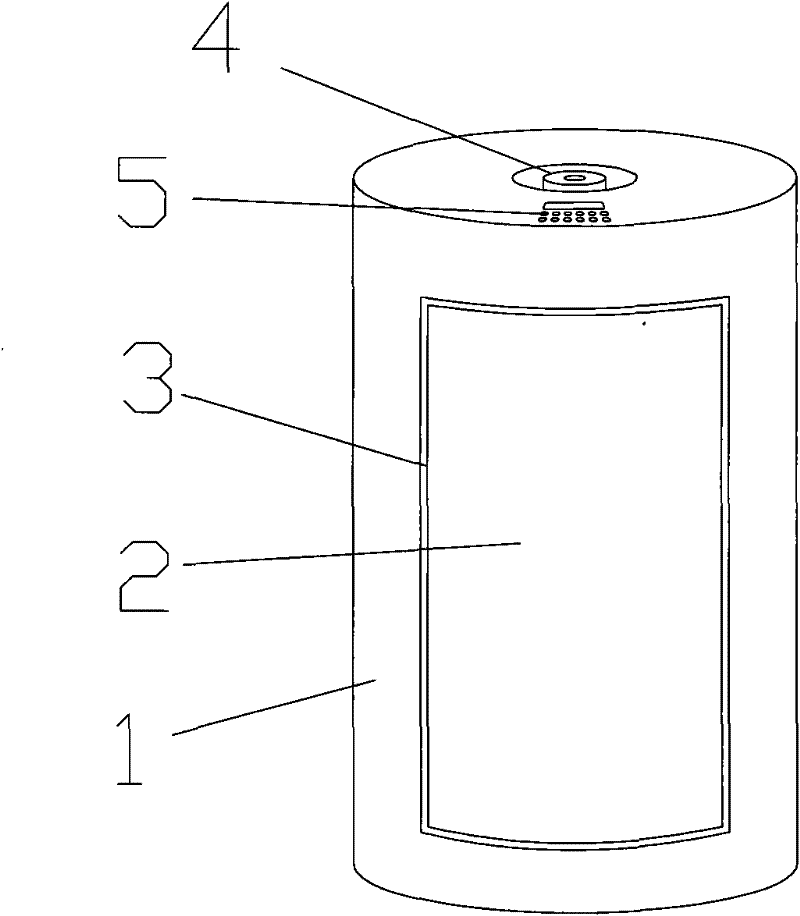
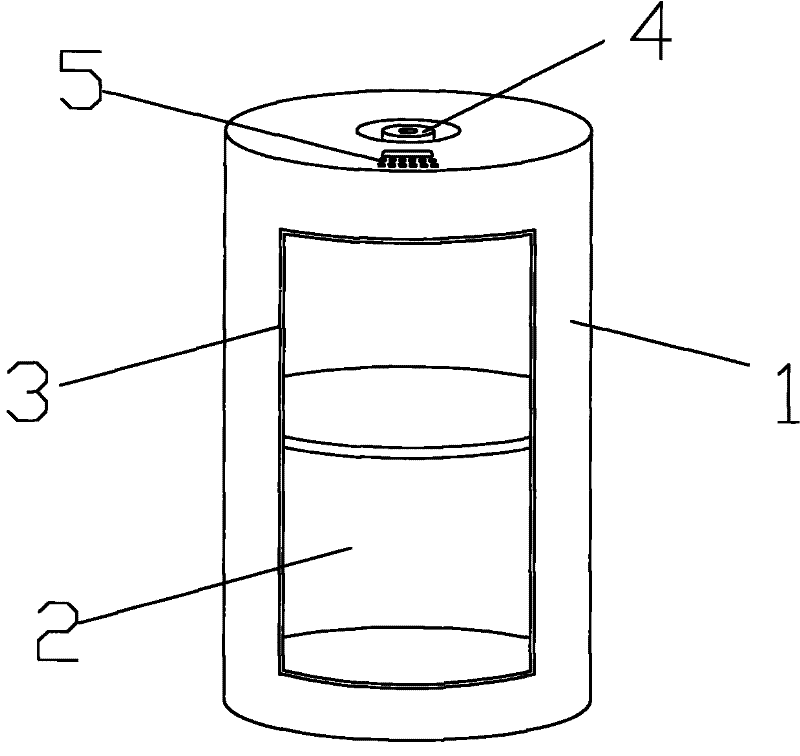
InactiveCN102454336AAchieve lockingEasy to operateNon-mechanical controlsElectric permutation locksKey pressingPassword
The invention discloses a cylindrical electronic password safe-deposit box, comprising a cylindrical outer box body and a cylindrical inner box body, wherein the inner box body can arranged in the outer box body in a relatively rotary way; based on the use state, the inner side faces of the outer box body and the inner box body are all provided with box doors equipped with gaps; the upper side face of the outer box body is provided with a turnplate; the turnplate can be rotated to make the box doors on the inner and outer box bodies in coincided and staggered states; the safe-deposit box is further provided with an electronic password lock and push buttons; the opening and closing of the electronic password lock can exactly make the turnplate into rotatable and locked states. The safe-deposit box has advantages of simple structure, convenient use, higher safety and reliability and higher aesthetic value.
Owner:陈海敏
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com