Method and device for managing secret keys in wireless sensor network
A wireless sensor and key management technology, applied in wireless communication, network topology, security devices, etc., can solve the problems of reduced network security and inability to realize node authentication, and achieve protection security, good forward security, and good The effect of backward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0100] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0101] The key management method of the wireless sensor network of the present invention specifically includes the following steps:
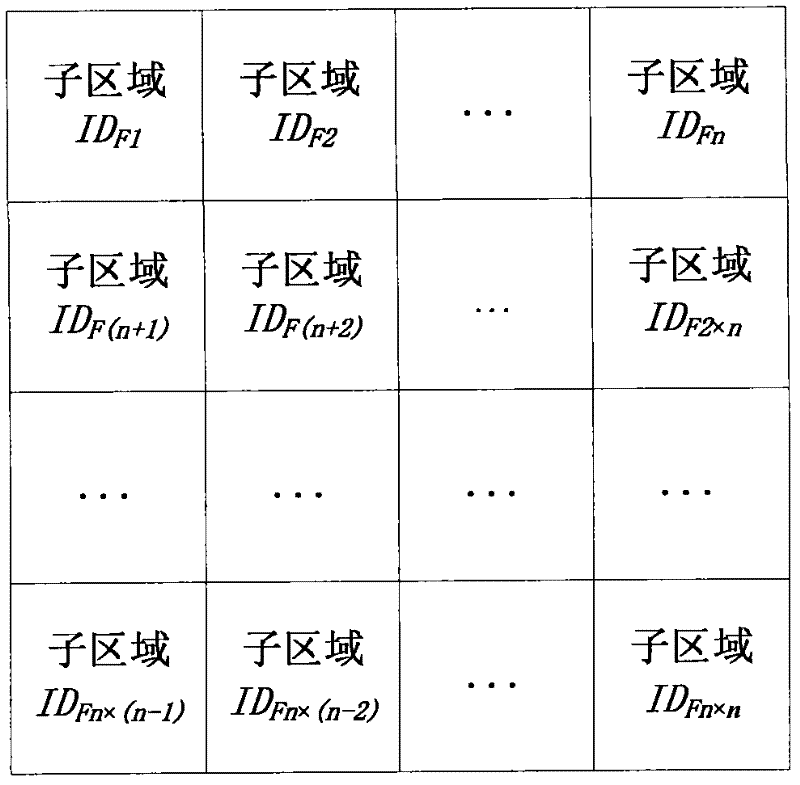
[0102] 1. Using node-based spatial location information to cluster sensor nodes, the WSN structure after clustering is as follows: Figure 4 As shown, the base station only communicates with the cluster head, and the cluster head communicates with the ordinary nodes in the cluster. The cluster heads cannot communicate directly. If the cluster heads need to communicate, a secure communication link must be established through the base station node. This structure can improve the security of WSN. If used as Figure 5 In the WSN structure shown, the nodes α, β, and ζ will have the communication keys of Zone 1 and Zone 2 at the same time. Once the hostile party captures these three nodes, the communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com